Import upstream version 1.7.7
Kali Janitor
1 year, 5 months ago
| 0 | version: 2 | |
| 1 | updates: | |
| 2 | # Maintain dependencies for GitHub Actions | |
| 3 | - package-ecosystem: "github-actions" | |
| 4 | directory: "/" | |
| 5 | schedule: | |
| 6 | interval: "daily" |
| 45 | 45 | GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }} |
| 46 | 46 | with: |
| 47 | 47 | args: release --config .github/goreleaser.yml |
| 48 | - name: Set up QEMU | |
| 49 | uses: docker/setup-qemu-action@v1 | |
| 50 | - name: Set up Docker Buildx | |
| 51 | id: buildx | |
| 52 | uses: docker/setup-buildx-action@v1 | |
| 53 | - name: Login to DockerHub | |
| 54 | uses: docker/login-action@v1 | |
| 55 | with: | |
| 56 | username: ${{ secrets.DOCKERHUB_USERNAME }} | |
| 57 | password: ${{ secrets.DOCKERHUB_TOKEN }} | |
| 58 | - name: Docker meta | |
| 59 | id: docker_meta | |
| 60 | uses: crazy-max/ghaction-docker-meta@v1 | |
| 61 | with: | |
| 62 | images: jpillora/chisel | |
| 63 | tag-latest: true | |
| 64 | # Outputs: | |
| 65 | # jpillora/chisel:1.2.3 | |
| 66 | # jpillora/chisel:1.2 | |
| 67 | # jpillora/chisel:1 | |
| 68 | # jpillora/chisel:latest | |
| 69 | tag-semver: | | |
| 70 | {{version}} | |
| 71 | {{major}}.{{minor}} | |
| 72 | {{major}} | |
| 73 | - name: Build and push | |
| 74 | uses: docker/build-push-action@v2 | |
| 75 | with: | |
| 76 | context: . | |
| 77 | platforms: linux/amd64,linux/arm64,linux/ppc64le,linux/386,linux/arm/v7,linux/arm/v6 | |
| 78 | push: true | |
| 79 | tags: ${{ steps.docker_meta.outputs.tags }} | |
| 80 | labels: ${{ steps.docker_meta.outputs.labels }} |
| 0 | VERSION=$(shell git describe --abbrev=0 --tags) | |
| 1 | BUILD=$(shell git rev-parse HEAD) | |
| 2 | DIRBASE=./build | |
| 3 | DIR=${DIRBASE}/${VERSION}/${BUILD}/bin | |
| 4 | ||
| 5 | LDFLAGS=-ldflags "-s -w ${XBUILD} -buildid=${BUILD} -X github.com/jpillora/chisel/share.BuildVersion=${VERSION}" | |
| 6 | ||
| 7 | GOFILES=`go list ./...` | |
| 8 | GOFILESNOTEST=`go list ./... | grep -v test` | |
| 9 | ||
| 10 | # Make Directory to store executables | |
| 11 | $(shell mkdir -p ${DIR}) | |
| 12 | ||
| 13 | all: | |
| 14 | @goreleaser build --skip-validate --single-target --config .github/goreleaser.yml | |
| 15 | ||
| 16 | freebsd: lint | |
| 17 | env CGO_ENABLED=0 GOOS=freebsd GOARCH=amd64 go build -trimpath ${LDFLAGS} ${GCFLAGS} ${ASMFLAGS} -o ${DIR}/chisel-freebsd_amd64 . | |
| 18 | ||
| 19 | linux: lint | |
| 20 | env CGO_ENABLED=1 GOOS=linux GOARCH=amd64 go build -trimpath ${LDFLAGS} ${GCFLAGS} ${ASMFLAGS} -o ${DIR}/chisel-linux_amd64 . | |
| 21 | ||
| 22 | windows: lint | |
| 23 | env CGO_ENABLED=1 GOOS=windows GOARCH=amd64 go build -trimpath ${LDFLAGS} ${GCFLAGS} ${ASMFLAGS} -o ${DIR}/chisel-windows_amd64 . | |
| 24 | ||
| 25 | darwin: | |
| 26 | env CGO_ENABLED=0 GOOS=darwin GOARCH=amd64 go build -trimpath ${LDFLAGS} ${GCFLAGS} ${ASMFLAGS} -o ${DIR}/chisel-darwin_amd64 . | |
| 27 | ||
| 28 | docker: | |
| 29 | @docker build . | |
| 30 | ||
| 31 | dep: ## Get the dependencies | |
| 32 | @go get -u github.com/goreleaser/goreleaser | |
| 33 | @go get -u github.com/boumenot/gocover-cobertura | |
| 34 | @go get -v -d ./... | |
| 35 | @go get -u all | |
| 36 | @go mod tidy | |
| 37 | ||
| 38 | lint: ## Lint the files | |
| 39 | @go fmt ${GOFILES} | |
| 40 | @go vet ${GOFILESNOTEST} | |
| 41 | ||
| 42 | test: ## Run unit tests | |
| 43 | @go test -coverprofile=${DIR}/coverage.out -race -short ${GOFILESNOTEST} | |
| 44 | @go tool cover -html=${DIR}/coverage.out -o ${DIR}/coverage.html | |
| 45 | @gocover-cobertura < ${DIR}/coverage.out > ${DIR}/coverage.xml | |
| 46 | ||
| 47 | release: lint test | |
| 48 | goreleaser release --config .github/goreleaser.yml | |
| 49 | ||
| 50 | clean: | |
| 51 | rm -rf ${DIRBASE}/* | |
| 52 | ||
| 53 | .PHONY: all freebsd linux windows docker dep lint test release clean⏎ |
| 0 | # chisel | |
| 0 | # Chisel | |
| 1 | 1 | |
| 2 | 2 | [](https://godoc.org/github.com/jpillora/chisel) [](https://github.com/jpillora/chisel/actions?workflow=CI) |
| 3 | 3 | |
| 5 | 5 | |
| 6 | 6 | 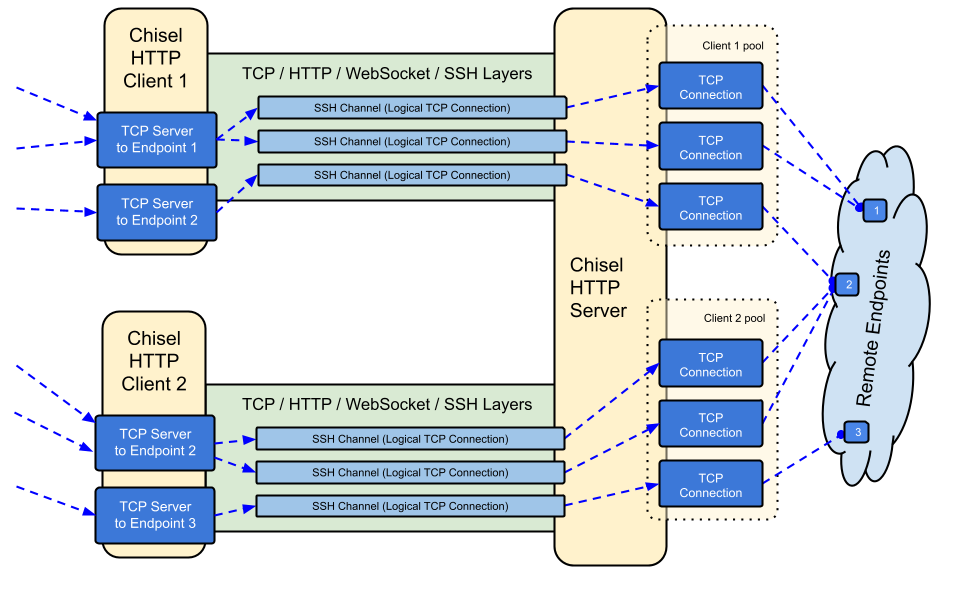 |
| 7 | 7 | |
| 8 | ### Features | |
| 8 | ## Table of Contents | |
| 9 | ||
| 10 | - [Features](#features) | |
| 11 | - [Install](#install) | |
| 12 | - [Demo](#demo) | |
| 13 | - [Usage](#usage) | |
| 14 | - [Contributing](#contributing) | |
| 15 | - [Changelog](#changelog) | |
| 16 | - [License](#license) | |
| 17 | ||
| 18 | ## Features | |
| 9 | 19 | |
| 10 | 20 | - Easy to use |
| 11 | 21 | - [Performant](./test/bench/perf.md)\* |
| 20 | 30 | - Clients optionally allow [SOCKS5](https://en.wikipedia.org/wiki/SOCKS) connections from a reversed port forward |
| 21 | 31 | - Client connections over stdio which supports `ssh -o ProxyCommand` providing SSH over HTTP |
| 22 | 32 | |
| 23 | ### Install | |
| 24 | ||
| 25 | **Binaries** | |
| 33 | ## Install | |
| 34 | ||
| 35 | ### Binaries | |
| 26 | 36 | |
| 27 | 37 | [](https://github.com/jpillora/chisel/releases) [](https://github.com/jpillora/chisel/releases) |
| 28 | 38 | |
| 29 | 39 | See [the latest release](https://github.com/jpillora/chisel/releases/latest) or download and install it now with `curl https://i.jpillora.com/chisel! | bash` |
| 30 | 40 | |
| 31 | **Docker** | |
| 41 | ### Docker | |
| 32 | 42 | |
| 33 | 43 | [](https://hub.docker.com/r/jpillora/chisel/) [](https://microbadger.com/images/jpillora/chisel) |
| 34 | 44 | |
| 36 | 46 | docker run --rm -it jpillora/chisel --help |
| 37 | 47 | ``` |
| 38 | 48 | |
| 39 | **Source** | |
| 49 | ### Fedora | |
| 50 | ||
| 51 | The package is maintained by the Fedora community. If you encounter issues related to the usage of the RPM, please use this [issue tracker](https://bugzilla.redhat.com/buglist.cgi?bug_status=NEW&bug_status=ASSIGNED&classification=Fedora&component=chisel&list_id=11614537&product=Fedora&product=Fedora%20EPEL). | |
| 52 | ||
| 53 | ```sh | |
| 54 | sudo dnf -y install chisel | |
| 55 | ``` | |
| 56 | ||
| 57 | ### Source | |
| 40 | 58 | |
| 41 | 59 | ```sh |
| 42 | 60 | $ go get -v github.com/jpillora/chisel |
| 43 | 61 | ``` |
| 44 | 62 | |
| 45 | ### Demo | |
| 63 | ## Demo | |
| 46 | 64 | |
| 47 | 65 | A [demo app](https://chisel-demo.herokuapp.com) on Heroku is running this `chisel server`: |
| 48 | 66 | |
| 61 | 79 | |
| 62 | 80 | and then visit [localhost:3000](http://localhost:3000/), we should see a directory listing. Also, if we visit the [demo app](https://chisel-demo.herokuapp.com) in the browser we should hit the server's default proxy and see a copy of [example.com](http://example.com). |
| 63 | 81 | |
| 64 | ### Usage | |
| 82 | ## Usage | |
| 65 | 83 | |
| 66 | 84 | <!-- render these help texts by hand, |
| 67 | 85 | or use https://github.com/jpillora/md-tmpl |
| 356 | 374 | 4. Now you have an encrypted, authenticated SOCKS5 connection over HTTP |
| 357 | 375 | |
| 358 | 376 | |
| 359 | ### Caveats | |
| 377 | #### Caveats | |
| 360 | 378 | |
| 361 | 379 | Since WebSockets support is required: |
| 362 | 380 | |
| 366 | 384 | - Openshift has full support though connections are only accepted on ports 8443 and 8080 |
| 367 | 385 | - Google App Engine has **no** support (Track this on [their repo](https://code.google.com/p/googleappengine/issues/detail?id=2535)) |
| 368 | 386 | |
| 369 | ### Contributing | |
| 387 | ## Contributing | |
| 370 | 388 | |
| 371 | 389 | - http://golang.org/doc/code.html |
| 372 | 390 | - http://golang.org/doc/effective_go.html |
| 374 | 392 | - `github.com/jpillora/chisel/server` contains the server package |
| 375 | 393 | - `github.com/jpillora/chisel/client` contains the client package |
| 376 | 394 | |
| 377 | ### Changelog | |
| 395 | ## Changelog | |
| 378 | 396 | |
| 379 | 397 | - `1.0` - Initial release |
| 380 | 398 | - `1.1` - Replaced simple symmetric encryption for ECDSA SSH |
| 384 | 402 | - `1.5` - Added reverse SOCKS support (by @aus) |
| 385 | 403 | - `1.6` - Added client stdio support (by @BoleynSu) |
| 386 | 404 | - `1.7` - Added UDP support |
| 405 | ||
| 406 | ## License | |
| 407 | ||
| 408 | [MIT](https://github.com/jpillora/chisel/blob/master/LICENSE) © Jaime Pillora⏎ | |
| 175 | 175 | } |
| 176 | 176 | //prepare client tunnel |
| 177 | 177 | client.tunnel = tunnel.New(tunnel.Config{ |
| 178 | Logger: client.Logger, | |
| 179 | Inbound: true, //client always accepts inbound | |
| 180 | Outbound: hasReverse, | |
| 181 | Socks: hasReverse && hasSocks, | |
| 178 | Logger: client.Logger, | |
| 179 | Inbound: true, //client always accepts inbound | |
| 180 | Outbound: hasReverse, | |
| 181 | Socks: hasReverse && hasSocks, | |
| 182 | KeepAlive: client.config.KeepAlive, | |
| 182 | 183 | }) |
| 183 | 184 | return client, nil |
| 184 | 185 | } |
| 0 | # Reverse Tunneling | |
| 1 | ||
| 2 | > **Use Case**: Host a website on your Raspberry Pi without opening ports on your router. | |
| 3 | ||
| 4 | This guide will show you how to use an internet-facing server (for example, a cloud VPS) as a relay to bounce down TCP traffic on port 80 to your Raspberry Pi. | |
| 5 | ||
| 6 | ## Chisel CLI | |
| 7 | ||
| 8 | ### Server | |
| 9 | ||
| 10 | Setup a relay server on the VPS to bounce down TCP traffic on port 80: | |
| 11 | ||
| 12 | ```bash | |
| 13 | #!/bin/bash | |
| 14 | ||
| 15 | # ⬇️ Start Chisel server in Reverse mode | |
| 16 | chisel server --reverse \ | |
| 17 | ||
| 18 | # ⬇️ Use the include users.json as an authfile | |
| 19 | --authfile="./users.json" \ | |
| 20 | ``` | |
| 21 | ||
| 22 | The corresponding `authfile` might look like this: | |
| 23 | ||
| 24 | ```json | |
| 25 | { | |
| 26 | "foo:bar": ["0.0.0.0:80"] | |
| 27 | } | |
| 28 | ``` | |
| 29 | ||
| 30 | ### Client | |
| 31 | ||
| 32 | Setup a chisel client to receive bounced-down traffic and forward it to the webserver running on the Pi: | |
| 33 | ||
| 34 | ```bash | |
| 35 | #!/bin/bash | |
| 36 | ||
| 37 | chisel client \ | |
| 38 | ||
| 39 | # ⬇️ Authenticates user "foo" with password "bar" | |
| 40 | --auth="foo:bar" \ | |
| 41 | ||
| 42 | # ⬇️ Connects to chisel relay server example.com | |
| 43 | # listening on the default ("fallback") port, 8080 | |
| 44 | example.com \ | |
| 45 | ||
| 46 | # ⬇️ Reverse tunnels port 80 on the relay server to | |
| 47 | # port 80 on your Pi. | |
| 48 | R:80:localhost:80 | |
| 49 | ``` | |
| 50 | ||
| 51 | --- | |
| 52 | ||
| 53 | ## Chisel Container | |
| 54 | ||
| 55 | This guide makes use of Docker and Docker compose to accomplish the same task as the above guide. | |
| 56 | ### Server | |
| 57 | ||
| 58 | Setup a relay server on the VPS to bounce down TCP traffic on port 80: | |
| 59 | ||
| 60 | ```yaml | |
| 61 | version: '3' | |
| 62 | ||
| 63 | services: | |
| 64 | chisel: | |
| 65 | image: jpillora/chisel | |
| 66 | restart: unless-stopped | |
| 67 | container_name: chisel | |
| 68 | # ⬇️ Pass CLI arguments one at a time in an array, as required by Docker compose. | |
| 69 | command: | |
| 70 | - 'server' | |
| 71 | # ⬇️ Use the --key=value syntax, since Docker compose doesn't parse whitespace well. | |
| 72 | - '--authfile=/users.json' | |
| 73 | - '--reverse' | |
| 74 | # ⬇️ Mount the authfile as a Docker volume | |
| 75 | volumes: | |
| 76 | - './users.json:/users.json' | |
| 77 | # ⬇️ Give the container unrestricted access to the Docker host's network | |
| 78 | network_mode: host | |
| 79 | ``` | |
| 80 | ||
| 81 | The `authfile` (`users.json`) remains the same as in the non-containerized version - shown again with the username `foo` and password `bar`. | |
| 82 | ||
| 83 | ```json | |
| 84 | { | |
| 85 | "foo:bar": ["0.0.0.0:80"] | |
| 86 | } | |
| 87 | ``` | |
| 88 | ||
| 89 | ### Client | |
| 90 | ||
| 91 | Setup an instance of the Chisel client on the Pi to receive relayed TCP traffic and feed it to the web server: | |
| 92 | ||
| 93 | ```yaml | |
| 94 | version: '3' | |
| 95 | ||
| 96 | services: | |
| 97 | chisel: | |
| 98 | # ⬇️ Delay starting Chisel server until the web server container is started. | |
| 99 | depends_on: | |
| 100 | - webserver | |
| 101 | image: jpillora/chisel | |
| 102 | restart: unless-stopped | |
| 103 | container_name: 'chisel' | |
| 104 | command: | |
| 105 | - 'client' | |
| 106 | # ⬇️ Use username `foo` and password `bar` to authenticate with Chisel server. | |
| 107 | - '--auth=foo:bar' | |
| 108 | # ⬇️ Domain & port of Chisel server. Port defaults to 8080 on server, but must be manually set on client. | |
| 109 | - 'proxy.example.com:8080' | |
| 110 | # ⬇️ Reverse tunnel traffic from the chisel server to the web server container, identified in Docker using DNS by its service name `webserver`. | |
| 111 | - 'R:80:webserver:80' | |
| 112 | networks: | |
| 113 | - internal | |
| 114 | # ⬇️ Basic Nginx webserver for demo purposes. | |
| 115 | webserver: | |
| 116 | image: nginx | |
| 117 | restart: unless-stopped | |
| 118 | container_name: nginx | |
| 119 | networks: | |
| 120 | - internal | |
| 121 | ||
| 122 | # ⬇️ Make use of a Docker network called `internal`. | |
| 123 | networks: | |
| 124 | internal: | |
| 125 | ``` |
| 11 | 11 | github.com/jpillora/requestlog v1.0.0 |
| 12 | 12 | github.com/jpillora/sizestr v1.0.0 |
| 13 | 13 | github.com/tomasen/realip v0.0.0-20180522021738-f0c99a92ddce // indirect |
| 14 | golang.org/x/crypto v0.0.0-20200709230013-948cd5f35899 | |
| 15 | golang.org/x/net v0.0.0-20200707034311-ab3426394381 | |
| 16 | golang.org/x/sync v0.0.0-20200625203802-6e8e738ad208 | |
| 17 | golang.org/x/sys v0.0.0-20200625212154-ddb9806d33ae // indirect | |
| 14 | golang.org/x/crypto v0.0.0-20210616213533-5ff15b29337e | |
| 15 | golang.org/x/net v0.0.0-20210614182718-04defd469f4e | |
| 16 | golang.org/x/sync v0.0.0-20210220032951-036812b2e83c | |
| 17 | golang.org/x/sys v0.0.0-20210630005230-0f9fa26af87c // indirect | |
| 18 | golang.org/x/term v0.0.0-20210615171337-6886f2dfbf5b // indirect | |
| 18 | 19 | ) |
| 15 | 15 | github.com/jpillora/sizestr v1.0.0/go.mod h1:bUhLv4ctkknatr6gR42qPxirmd5+ds1u7mzD+MZ33f0= |
| 16 | 16 | github.com/tomasen/realip v0.0.0-20180522021738-f0c99a92ddce h1:fb190+cK2Xz/dvi9Hv8eCYJYvIGUTN2/KLq1pT6CjEc= |
| 17 | 17 | github.com/tomasen/realip v0.0.0-20180522021738-f0c99a92ddce/go.mod h1:o8v6yHRoik09Xen7gje4m9ERNah1d1PPsVq1VEx9vE4= |
| 18 | golang.org/x/crypto v0.0.0-20190308221718-c2843e01d9a2/go.mod h1:djNgcEr1/C05ACkg1iLfiJU5Ep61QUkGW8qpdssI0+w= | |
| 19 | golang.org/x/crypto v0.0.0-20200622213623-75b288015ac9/go.mod h1:LzIPMQfyMNhhGPhUkYOs5KpL4U8rLKemX1yGLhDgUto= | |
| 20 | golang.org/x/crypto v0.0.0-20200709230013-948cd5f35899 h1:DZhuSZLsGlFL4CmhA8BcRA0mnthyA/nZ00AqCUo7vHg= | |
| 21 | golang.org/x/crypto v0.0.0-20200709230013-948cd5f35899/go.mod h1:LzIPMQfyMNhhGPhUkYOs5KpL4U8rLKemX1yGLhDgUto= | |
| 22 | golang.org/x/net v0.0.0-20190404232315-eb5bcb51f2a3/go.mod h1:t9HGtf8HONx5eT2rtn7q6eTqICYqUVnKs3thJo3Qplg= | |
| 23 | golang.org/x/net v0.0.0-20200707034311-ab3426394381 h1:VXak5I6aEWmAXeQjA+QSZzlgNrpq9mjcfDemuexIKsU= | |
| 24 | golang.org/x/net v0.0.0-20200707034311-ab3426394381/go.mod h1:/O7V0waA8r7cgGh81Ro3o1hOxt32SMVPicZroKQ2sZA= | |
| 25 | golang.org/x/sync v0.0.0-20200625203802-6e8e738ad208 h1:qwRHBd0NqMbJxfbotnDhm2ByMI1Shq4Y6oRJo21SGJA= | |
| 26 | golang.org/x/sync v0.0.0-20200625203802-6e8e738ad208/go.mod h1:RxMgew5VJxzue5/jJTE5uejpjVlOe/izrB70Jof72aM= | |
| 27 | golang.org/x/sys v0.0.0-20190215142949-d0b11bdaac8a/go.mod h1:STP8DvDyc/dI5b8T5hshtkjS+E42TnysNCUPdjciGhY= | |
| 28 | golang.org/x/sys v0.0.0-20190412213103-97732733099d/go.mod h1:h1NjWce9XRLGQEsW7wpKNCjG9DtNlClVuFLEZdDNbEs= | |
| 18 | golang.org/x/crypto v0.0.0-20210616213533-5ff15b29337e h1:gsTQYXdTw2Gq7RBsWvlQ91b+aEQ6bXFUngBGuR8sPpI= | |
| 19 | golang.org/x/crypto v0.0.0-20210616213533-5ff15b29337e/go.mod h1:GvvjBRRGRdwPK5ydBHafDWAxML/pGHZbMvKqRZ5+Abc= | |
| 20 | golang.org/x/net v0.0.0-20210226172049-e18ecbb05110/go.mod h1:m0MpNAwzfU5UDzcl9v0D8zg8gWTRqZa9RBIspLL5mdg= | |
| 21 | golang.org/x/net v0.0.0-20210614182718-04defd469f4e h1:XpT3nA5TvE525Ne3hInMh6+GETgn27Zfm9dxsThnX2Q= | |
| 22 | golang.org/x/net v0.0.0-20210614182718-04defd469f4e/go.mod h1:9nx3DQGgdP8bBQD5qxJ1jj9UTztislL4KSBs9R2vV5Y= | |
| 23 | golang.org/x/sync v0.0.0-20210220032951-036812b2e83c h1:5KslGYwFpkhGh+Q16bwMP3cOontH8FOep7tGV86Y7SQ= | |
| 24 | golang.org/x/sync v0.0.0-20210220032951-036812b2e83c/go.mod h1:RxMgew5VJxzue5/jJTE5uejpjVlOe/izrB70Jof72aM= | |
| 29 | 25 | golang.org/x/sys v0.0.0-20191005200804-aed5e4c7ecf9/go.mod h1:h1NjWce9XRLGQEsW7wpKNCjG9DtNlClVuFLEZdDNbEs= |
| 30 | golang.org/x/sys v0.0.0-20200323222414-85ca7c5b95cd/go.mod h1:h1NjWce9XRLGQEsW7wpKNCjG9DtNlClVuFLEZdDNbEs= | |
| 31 | golang.org/x/sys v0.0.0-20200625212154-ddb9806d33ae h1:Ih9Yo4hSPImZOpfGuA4bR/ORKTAbhZo2AbWNRCnevdo= | |
| 32 | golang.org/x/sys v0.0.0-20200625212154-ddb9806d33ae/go.mod h1:h1NjWce9XRLGQEsW7wpKNCjG9DtNlClVuFLEZdDNbEs= | |
| 33 | golang.org/x/text v0.3.0 h1:g61tztE5qeGQ89tm6NTjjM9VPIm088od1l6aSorWRWg= | |
| 34 | golang.org/x/text v0.3.0/go.mod h1:NqM8EUOU14njkJ3fqMW+pc6Ldnwhi/IjpwHt7yyuwOQ= | |
| 26 | golang.org/x/sys v0.0.0-20201119102817-f84b799fce68/go.mod h1:h1NjWce9XRLGQEsW7wpKNCjG9DtNlClVuFLEZdDNbEs= | |
| 27 | golang.org/x/sys v0.0.0-20210423082822-04245dca01da/go.mod h1:h1NjWce9XRLGQEsW7wpKNCjG9DtNlClVuFLEZdDNbEs= | |
| 28 | golang.org/x/sys v0.0.0-20210615035016-665e8c7367d1/go.mod h1:oPkhp1MJrh7nUepCBck5+mAzfO9JrbApNNgaTdGDITg= | |
| 29 | golang.org/x/sys v0.0.0-20210630005230-0f9fa26af87c h1:F1jZWGFhYfh0Ci55sIpILtKKK8p3i2/krTr0H1rg74I= | |
| 30 | golang.org/x/sys v0.0.0-20210630005230-0f9fa26af87c/go.mod h1:oPkhp1MJrh7nUepCBck5+mAzfO9JrbApNNgaTdGDITg= | |
| 31 | golang.org/x/term v0.0.0-20201126162022-7de9c90e9dd1/go.mod h1:bj7SfCRtBDWHUb9snDiAeCFNEtKQo2Wmx5Cou7ajbmo= | |
| 32 | golang.org/x/term v0.0.0-20210615171337-6886f2dfbf5b h1:9zKuko04nR4gjZ4+DNjHqRlAJqbJETHwiNKDqTfOjfE= | |
| 33 | golang.org/x/term v0.0.0-20210615171337-6886f2dfbf5b/go.mod h1:jbD1KX2456YbFQfuXm/mYQcufACuNUgVhRMnK/tPxf8= | |
| 34 | golang.org/x/text v0.3.3/go.mod h1:5Zoc/QRtKVWzQhOtBMvqHzDpF6irO9z98xDceosuGiQ= | |
| 35 | golang.org/x/text v0.3.6 h1:aRYxNxv6iGQlyVaZmk6ZgYEDa+Jg18DxebPSrd6bg1M= | |
| 36 | golang.org/x/text v0.3.6/go.mod h1:5Zoc/QRtKVWzQhOtBMvqHzDpF6irO9z98xDceosuGiQ= | |
| 37 | golang.org/x/tools v0.0.0-20180917221912-90fa682c2a6e/go.mod h1:n7NCudcB/nEzxVGmLbDWY5pfWTLqBcC2KZ6jyYvM4mQ= |