New upstream version 3.11
Sophie Brun
4 years ago
| 6 | 6 | PIP_CACHE_DIR: "$CI_PROJECT_DIR/.cache/pip" |
| 7 | 7 | APT_CACHE_DIR: "$CI_PROJECT_DIR/apt-cache" |
| 8 | 8 | DEBIAN_FRONTEND: noninteractive |
| 9 | IMAGE_TAG: 'egrep -o "[0-9]\.([0-9]|[0-9][0-9])\.[0-9]" faraday/__init__.py' | |
| 9 | IMAGE_TAG: 'egrep -o "[0-9]\.([0-9]|[0-9][0-9])(\.[0-9])?" faraday/__init__.py' | |
| 10 | 10 | |
| 11 | 11 | ## ENV_VARS LIST |
| 12 | 12 | # FULL_TEST = Test all jobs |
| 55 | 55 | script: |
| 56 | 56 | - git config --global user.email "[email protected]" |
| 57 | 57 | - git config --global user.name "Mergerbot" |
| 58 | - python3 merge-conflict-detector.py | |
| 58 | - python3 scripts/merge-conflict-detector.py | |
| 59 | except: | |
| 60 | variables: | |
| 61 | - $BUILD_TEST | |
| 62 | ||
| 63 | build_and_push_to_cachix: | |
| 64 | tags: | |
| 65 | - faradaytests | |
| 66 | image: nixorg/nix | |
| 67 | stage: pre_testing | |
| 68 | script: | |
| 69 | - nix-env -if pypi2nixpkgs/nixpkgs.nix -A cachix | |
| 70 | - mkdir -p ~/.config/cachix | |
| 71 | - export USER=$(whoami) | |
| 72 | - echo "$CACHIX_CONFG" >~/.config/cachix/cachix.dhall | |
| 73 | - cachix use faradaysec | |
| 74 | - nix-build | cachix push faradaysec | |
| 59 | 75 | |
| 60 | 76 | pylint: |
| 61 | 77 | tags: |
| 62 | 78 | - faradaytests |
| 63 | image: registry.gitlab.com/faradaysec/integrationrepo | |
| 64 | stage: pre_testing | |
| 65 | script: | |
| 66 | - pip3 install virtualenv | |
| 67 | - virtualenv -p python3 faraday_venv | |
| 68 | - source faraday_venv/bin/activate | |
| 69 | - pip install --upgrade -r requirements.txt | |
| 70 | - python3 setup.py install | |
| 71 | # pylint slow issue https://github.com/PyCQA/pylint/issues/2765 | |
| 72 | - pip install pylint isort==4.3.4 | |
| 73 | - pylint --rcfile=.pylintrc faraday --ignore=faraday_venv | tee pylint.txt | |
| 79 | image: nixorg/nix | |
| 80 | stage: testing # This should be after build_and_push_to_cachix to improve performance | |
| 81 | script: | |
| 82 | - nix-env -if pypi2nixpkgs/nixpkgs.nix -A cachix | |
| 83 | - mkdir -p ~/.config/cachix | |
| 84 | - export USER=$(whoami) | |
| 85 | - echo "$CACHIX_CONFG" >~/.config/cachix/cachix.dhall | |
| 86 | - cachix use faradaysec | |
| 87 | - nix-shell --command "pylint --rcfile=.pylintrc faraday" | tee pylint.txt | |
| 88 | - nix-env -if pypi2nixpkgs/nixpkgs.nix -A gnused | |
| 74 | 89 | - score=$(sed -n 's/^Your code has been rated at \([-0-9.]*\)\/.*/\1/p' pylint.txt) |
| 75 | 90 | #- anybadge --label pylint --value=$score --file pylint.svg 4=red 6=orange 8=yellow 10=green |
| 76 | 91 | artifacts: |
| 81 | 96 | variables: |
| 82 | 97 | - $BUILD_TEST |
| 83 | 98 | |
| 84 | postgresql_test: | |
| 85 | image: registry.gitlab.com/faradaysec/integrationrepo | |
| 99 | .postgresql_test_base: | |
| 86 | 100 | tags: |
| 87 | 101 | - faradaytests |
| 88 | 102 | stage: testing |
| 89 | 103 | coverage: '/TOTAL\s+\d+\s+\d+\s+(\d+%)/' |
| 90 | 104 | script: |
| 105 | - nix-env -if pypi2nixpkgs/nixpkgs.nix -A cachix | |
| 106 | - mkdir -p ~/.config/cachix | |
| 107 | - export USER=$(whoami) | |
| 108 | - echo "$CACHIX_CONFG" >~/.config/cachix/cachix.dhall | |
| 109 | - cachix use faradaysec | |
| 110 | - "echo 'hosts: files dns' >/etc/nsswitch.conf" | |
| 91 | 111 | - export LC_ALL=C.UTF-8 |
| 92 | 112 | - export LANG=C.UTF-8 |
| 93 | - pip3 install virtualenv | |
| 94 | - virtualenv -p python3 faraday_venv | |
| 95 | - source faraday_venv/bin/activate | |
| 96 | - pip install pip -U | |
| 97 | - pip install --upgrade -r requirements.txt | |
| 98 | - python3 setup.py install | |
| 99 | - pip install --upgrade responses pytest-xdist pytest-cov | |
| 100 | - pip install --upgrade -r requirements_dev.txt | |
| 101 | 113 | - mkdir -p ~/.faraday/config |
| 102 | 114 | - cp tests/data/server.ini ~/.faraday/config |
| 103 | 115 | - mkdir run_from |
| 104 | - cd run_from && pytest ../tests -v --capture=sys --cov=../faraday/server --color=yes --disable-warnings --connection-string=postgresql+psycopg2://$POSTGRES_USER:$POSTGRES_PASSWORD@postgres/$POSTGRES_DB | |
| 116 | - nix-shell --command "cd run_from && pytest ../tests -v --capture=sys --cov=../faraday/server --color=yes --disable-warnings --connection-string=postgresql+psycopg2://$POSTGRES_USER:$POSTGRES_PASSWORD@postgres/$POSTGRES_DB" | |
| 105 | 117 | artifacts: |
| 106 | 118 | when: on_failure |
| 107 | 119 | paths: |
| 110 | 122 | variables: |
| 111 | 123 | - $BUILD_TEST |
| 112 | 124 | |
| 113 | sqlite_test: | |
| 114 | image: registry.gitlab.com/faradaysec/integrationrepo | |
| 125 | .sqlite_test_base: | |
| 115 | 126 | tags: |
| 116 | 127 | - faradaytests |
| 117 | 128 | stage: testing |
| 118 | 129 | coverage: '/TOTAL\s+\d+\s+\d+\s+(\d+%)/' |
| 119 | 130 | script: |
| 131 | - nix-env -if pypi2nixpkgs/nixpkgs.nix -A cachix | |
| 132 | - mkdir -p ~/.config/cachix | |
| 133 | - export USER=$(whoami) | |
| 134 | - echo "$CACHIX_CONFG" >~/.config/cachix/cachix.dhall | |
| 135 | - cachix use faradaysec | |
| 136 | - "echo 'hosts: files dns' >/etc/nsswitch.conf" | |
| 120 | 137 | - export LC_ALL=C.UTF-8 |
| 121 | 138 | - export LANG=C.UTF-8 |
| 122 | - pip3 install virtualenv | |
| 123 | - virtualenv -p python3 faraday_venv | |
| 124 | - source faraday_venv/bin/activate | |
| 125 | - pip install pip -U | |
| 126 | - pip install --upgrade -r requirements.txt | |
| 127 | - python3 setup.py install | |
| 128 | - pip install --upgrade responses pytest-xdist pytest-cov | |
| 129 | - pip install --upgrade -r requirements_dev.txt | |
| 130 | 139 | - mkdir -p ~/.faraday/config |
| 131 | 140 | - cp tests/data/server.ini ~/.faraday/config |
| 132 | 141 | - mkdir run_from |
| 133 | - cd run_from && pytest ../tests --capture=sys -v --cov=../faraday/server --color=yes --disable-warnings | |
| 142 | - nix-shell --command "cd run_from && pytest ../tests --capture=sys -v --cov=../faraday/server --color=yes --disable-warnings" | |
| 134 | 143 | artifacts: |
| 135 | 144 | when: on_failure |
| 136 | 145 | paths: |
| 138 | 147 | except: |
| 139 | 148 | variables: |
| 140 | 149 | - $BUILD_TEST |
| 150 | ||
| 151 | sqlite_test_3_7: | |
| 152 | extends: .sqlite_test_base | |
| 153 | image: nixorg/nix | |
| 154 | variables: | |
| 155 | PY_VERSION: python3.7 | |
| 156 | ||
| 157 | ||
| 158 | .sqlite_test_3_8: | |
| 159 | extends: .sqlite_test_base | |
| 160 | image: nixorg/nix | |
| 161 | variables: | |
| 162 | PY_VERSION: python3.8 | |
| 163 | ||
| 164 | ||
| 165 | postgresql_test_3_7: | |
| 166 | extends: .postgresql_test_base | |
| 167 | image: nixorg/nix | |
| 168 | variables: | |
| 169 | PY_VERSION: python3.7 | |
| 170 | ||
| 171 | ||
| 172 | .postgresql_test_3_8: | |
| 173 | extends: .postgresql_test_base | |
| 174 | image: nixorg/nix | |
| 175 | variables: | |
| 176 | PY_VERSION: python3.8 | |
| 141 | 177 | |
| 142 | 178 | |
| 143 | 179 | build_nix_python3: |
| 144 | 180 | image: nixorg/nix |
| 145 | 181 | stage: build_faraday |
| 146 | 182 | script: |
| 147 | - nix-channel --add https://nixos.org/channels/nixos-19.09 nixpkgs | |
| 148 | - nix-channel --update | |
| 149 | - nix-build buildpth.nix | |
| 150 | - nix-build '<nixpkgs>' -A gnome3.vte -o result-vte | |
| 151 | - nix-build '<nixpkgs>' -A gtk3 -o result-gtk | |
| 152 | - tar cf /py3.tar $(nix-store --query --requisites $(readlink result) $(readlink result-vte)) $(readlink result-gtk) | |
| 153 | - mkdir /opt | |
| 154 | - nix-env -i findutils | |
| 155 | - "nix-shell -p python37Packages.virtualenv --command 'virtualenv /opt/faraday'" | |
| 156 | # - cp result /opt/faraday/lib/python3.7/site-packages/nix.pth # This doesn't include dependencies of dependencies | |
| 157 | - 'for dir in $(nix-store -qR result); do if [[ -d "$dir/lib/python3.7/site-packages" ]]; then echo "$dir/lib/python3.7/site-packages" >>recursive.pth; fi; done' | |
| 158 | - mv recursive.pth /opt/faraday/lib/python3.7/site-packages/nix.pth | |
| 159 | - source /opt/faraday/bin/activate | |
| 160 | # - "nix-shell -p libxml2 libxslt zlib cairo gobject-introspection glib pkgconfig --run 'SOURCE_DATE_EPOCH=$(date +%s) /opt/faraday/bin/pip install -r requirements.txt'" | |
| 161 | - python setup.py install | |
| 162 | - pip install -r requirements.txt # This has to be below setup.py install | |
| 163 | - pip freeze | |
| 164 | - mv /opt/faraday/bin/faraday-client /opt/faraday/bin/_faraday_client_novte | |
| 165 | - 'nix-shell -p makeWrapper --command "makeWrapper /opt/faraday/bin/_faraday_client_novte /opt/faraday/bin/faraday-client --prefix GI_TYPELIB_PATH : $(find /nix/store -name "girepository-1.0" | tr "\n" ":")"' | |
| 166 | - 'nix-shell -p makeWrapper --command "makeWrapper /opt/faraday/bin/python /opt/faraday/bin/test --prefix GI_TYPELIB_PATH : $(find /nix/store -name "girepository-1.0" | tr "\n" ":")"' | |
| 167 | - nix-collect-garbage && /opt/faraday/bin/test -c "import gi;gi.require_version('Gtk', '3.0');gi.require_version('Vte', '2.91');from gi.repository import Gio, Gtk, GdkPixbuf, Vte, GLib, GObject, Gdk" # Test if GTK will work | |
| 183 | - nix-env -if pypi2nixpkgs/nixpkgs.nix -A cachix | |
| 184 | - mkdir -p ~/.config/cachix | |
| 185 | - export USER=$(whoami) | |
| 186 | - echo "$CACHIX_CONFG" >~/.config/cachix/cachix.dhall | |
| 187 | - cachix use faradaysec | |
| 188 | - nix-build | |
| 189 | - tar cf /py3.tar $(nix-store --query --requisites $(readlink result)) | |
| 190 | - mkdir -p /opt/faraday | |
| 191 | - cp -r $(readlink result)/* /opt/faraday | |
| 168 | 192 | - tar rvf /py3.tar /opt/faraday |
| 169 | 193 | - mv /py3.tar $CI_PROJECT_DIR |
| 170 | 194 | artifacts: |
| 218 | 242 | - cp -r /nix . |
| 219 | 243 | - mv ../../faraday-linux-installers-builder . |
| 220 | 244 | - cd faraday-linux-installers-builder |
| 245 | - git rev-parse HEAD | |
| 221 | 246 | - git clone https://github.com/jordansissel/fpm.git |
| 222 | 247 | - cd fpm |
| 223 | 248 | - git checkout d7b466787d17581bc723e474ecf6e18f48226031 |
| 228 | 253 | - sh faraday-linux-installers-builder/build.sh $(eval $IMAGE_TAG) server deb |
| 229 | 254 | - mv faraday-server_amd64.deb ../../faraday-server_amd64.deb |
| 230 | 255 | - sh faraday-linux-installers-builder/build.sh $(eval $IMAGE_TAG) client deb |
| 231 | - mv faraday-client_amd64.deb ../../faraday-client_amd64.deb | |
| 232 | 256 | dependencies: |
| 233 | 257 | - generate_build_file |
| 234 | 258 | - build_nix_python3 |
| 236 | 260 | name: 'faraday_$CI_COMMIT_REF_NAME.deb' |
| 237 | 261 | paths: |
| 238 | 262 | - "faraday-server_amd64.deb" |
| 239 | - "faraday-client_amd64.deb" | |
| 240 | 263 | expire_in: 15 days |
| 241 | 264 | only: |
| 242 | 265 | variables: |
| 248 | 271 | |
| 249 | 272 | |
| 250 | 273 | smoke_test_deb: |
| 251 | allow_failure: true | |
| 274 | allow_failure: false | |
| 252 | 275 | stage: distro_testing # TODO improve |
| 253 | 276 | image: ubuntu:18.04 |
| 254 | 277 | dependencies: |
| 305 | 328 | - cp -r /nix . |
| 306 | 329 | - mv ../../faraday-linux-installers-builder . |
| 307 | 330 | - cd faraday-linux-installers-builder |
| 331 | - git rev-parse HEAD | |
| 308 | 332 | - git clone https://github.com/jordansissel/fpm.git |
| 309 | 333 | - cd fpm |
| 310 | 334 | - git checkout d7b466787d17581bc723e474ecf6e18f48226031 |
| 315 | 339 | - sh faraday-linux-installers-builder/build.sh $(eval $IMAGE_TAG) server rpm |
| 316 | 340 | - mv faraday-server_amd64.rpm ../../faraday-server_amd64.rpm |
| 317 | 341 | - sh faraday-linux-installers-builder/build.sh $(eval $IMAGE_TAG) client rpm |
| 318 | - mv faraday-client_amd64.rpm ../../faraday-client_amd64.rpm | |
| 319 | 342 | dependencies: |
| 320 | 343 | - generate_build_file |
| 321 | 344 | - build_nix_python3 |
| 323 | 346 | name: 'faraday_$CI_COMMIT_REF_NAME.rpm' |
| 324 | 347 | paths: |
| 325 | 348 | - "faraday-server_amd64.rpm" |
| 326 | - "faraday-client_amd64.rpm" | |
| 327 | 349 | expire_in: 15 days |
| 328 | only: | |
| 329 | variables: | |
| 330 | - $CI_COMMIT_REF_NAME =~ /^.*\/(master)$/ | |
| 331 | - $CI_COMMIT_TAG | |
| 332 | - $BUILD_TEST | |
| 333 | - $FULL_TEST | |
| 334 | - $DAILY_TEST | |
| 335 | ||
| 336 | macos_pkg: | |
| 337 | tags: | |
| 338 | - macos | |
| 339 | stage: build | |
| 340 | allow_failure: true | |
| 341 | before_script: | |
| 342 | - echo 'export PATH="/usr/local/opt/openssl/bin:$PATH"' >> ~/.bash_profile | |
| 343 | - export LDFLAGS="-L/usr/local/opt/openssl/lib" | |
| 344 | - export CPPFLAGS="-I/usr/local/opt/openssl/include" | |
| 345 | - export PKG_CONFIG_PATH="/usr/local/opt/openssl/lib/pkgconfig" | |
| 346 | script: | |
| 347 | - pip3 install virtualenv | |
| 348 | - pip3 install virtualenv-tools3 | |
| 349 | - export PKG_CONFIG_PATH="${PKG_CONFIG_PATH}:/usr/local/opt/libffi/lib/pkgconfig" | |
| 350 | - mkdir build_installer | |
| 351 | - cp -a faraday.tar.gz build_installer/. | |
| 352 | - cd build_installer | |
| 353 | - /usr/bin/tar zxf faraday.tar.gz | |
| 354 | - cd faraday_copy | |
| 355 | - git clone [email protected]:faradaysec/faraday-linux-installers-builder.git | |
| 356 | - cd faraday-linux-installers-builder | |
| 357 | - git clone https://github.com/jordansissel/fpm.git | |
| 358 | - cd fpm | |
| 359 | - git checkout d7b466787d17581bc723e474ecf6e18f48226031 | |
| 360 | - git apply ../fpm-patchs/fpm.osx.patch | |
| 361 | - make gem | |
| 362 | - export GEM_HOME="$HOME/.gem" | |
| 363 | - export GEM_PATH=$HOME/.gem | |
| 364 | - export PATH=$PATH:$HOME/.gem/bin | |
| 365 | - gem install fpm-1.11.0.gem | |
| 366 | - cd ../../ | |
| 367 | - sh faraday-linux-installers-builder/build_osx.sh $(eval $IMAGE_TAG) server osxpkg | |
| 368 | - mv faraday-server_amd64.pkg ../../Faraday-server.pkg | |
| 369 | - sh faraday-linux-installers-builder/build_osx.sh $(eval $IMAGE_TAG) client osxpkg | |
| 370 | - mv faraday-client_amd64.pkg ../../Faraday-client.pkg | |
| 371 | - mv faraday-server_amd64.pkg ../../Faraday.pkg | |
| 372 | artifacts: | |
| 373 | name: "$CI_JOB_NAME-$CI_COMMIT_REF_NAME-binaries" | |
| 374 | paths: | |
| 375 | - Faraday-server.pkg | |
| 376 | - Faraday-client.pkg | |
| 377 | expire_in: 1 week | |
| 378 | 350 | only: |
| 379 | 351 | variables: |
| 380 | 352 | - $CI_COMMIT_REF_NAME =~ /^.*\/(master)$/ |
| 415 | 387 | variables: |
| 416 | 388 | - $CI_COMMIT_REF_NAME =~ /^.*\/(dev|master)$/ |
| 417 | 389 | - $INTEGRATION |
| 390 | except: | |
| 391 | variables: | |
| 392 | - $BUILD_TEST | |
| 89 | 89 | wrong-import-position, |
| 90 | 90 | old-style-class, |
| 91 | 91 | len-as-condition, |
| 92 | syntax-error, | |
| 93 | 92 | unrecognized-inline-option, |
| 94 | 93 | bad-option-value, |
| 95 | 94 | init-is-generator, |
| 96 | 95 | return-in-init, |
| 97 | function-redefined, | |
| 98 | 96 | not-in-loop, |
| 99 | 97 | return-outside-function, |
| 100 | 98 | yield-outside-function, |
| 247 | 245 | mixed-indentation, |
| 248 | 246 | lowercase-l-suffix, |
| 249 | 247 | deprecated-module, |
| 250 | relative-import, | |
| 251 | 248 | import-self, |
| 252 | 249 | misplaced-future, |
| 253 | 250 | fixme, |
| 254 | 251 | invalid-encoded-data, |
| 255 | global-variable-undefined, | |
| 256 | global-variable-not-assigned, | |
| 257 | global-at-module-level, | |
| 258 | unused-variable, | |
| 259 | 252 | unused-argument, |
| 260 | 253 | redefined-outer-name, |
| 261 | 254 | redefined-builtin, |
| 262 | 255 | redefine-in-handler, |
| 263 | 256 | undefined-loop-variable, |
| 264 | 257 | cell-var-from-loop, |
| 265 | bare-except, | |
| 266 | 258 | broad-except, |
| 267 | 259 | nonstandard-exception, |
| 268 | 260 | binary-op-exception, |
| 280 | 272 | invalid-format-index, |
| 281 | 273 | anomalous-backslash-in-string, |
| 282 | 274 | anomalous-unicode-escape-in-string, |
| 283 | bad-open-mode, | |
| 284 | boolean-datetime, | |
| 285 | 275 | redundant-unittest-assert, |
| 286 | 276 | deprecated-method, |
| 287 | 277 | bad-thread-instantiation, |
| 288 | shallow-copy-environ, | |
| 289 | unused-format-string-argument, | |
| 290 | global-statement, | |
| 291 | unused-import | |
| 278 | ||
| 292 | 279 | |
| 293 | 280 | # Enable the message, report, category or checker with the given id(s). You can |
| 294 | 281 | # either give multiple identifier separated by comma (,) or put this option |
| 19 | 19 | * Matias Ariel Ré Medina |
| 20 | 20 | * Matias Lang |
| 21 | 21 | * Micaela Ranea Sánchez |
| 22 | * Nicolas Rebagliati | |
| 23 | * Sebastian Brachi | |
| 22 | 24 | * Sebastian Kulesz |
| 23 | 25 | * Zoe Marino |
| 24 | 26 |
| 0 | Apr 22nd, 2020 |
| 0 | * Move GTK client to [another repository](https://github.com/infobyte/faraday-client) to improve release times. | |
| 1 | * Fix formula injection vulnerability when exporting vulnerability data to CSV. This was considered a low impact vulnerability. | |
| 2 | * Remove "--ssl" parameter. Read SSL information from the config file. | |
| 3 | * Add OpenAPI autogenerated documentation support | |
| 4 | * Show agent information in command history | |
| 5 | * Add bulk delete endpoint for hosts API | |
| 6 | * Add column with information to track agent execution data | |
| 7 | * Add tool attribute to vulnerability to avoid incorrectly showing "Web UI" as creator tool | |
| 8 | * Add sorting by target in credentials view | |
| 9 | * Add creator information when uploading reports or using de bulk create api | |
| 10 | * Add feature to disable rules in the searcher | |
| 11 | * Add API endpoint to export Faraday data to Metasploit XML format | |
| 12 | * Use run date instead of creation date when plugins report specifies it | |
| 13 | * Improve knowledge base UX | |
| 14 | * Improve workspace table and status report table UX. | |
| 15 | * Improve format of exported CSV to include more fields | |
| 16 | * Sort results in count API endpoint | |
| 17 | * Limit description width in knowledge base | |
| 18 | * Change log date format to ISO 8601 | |
| 19 | * Fix parsing server port config in server.ini | |
| 20 | * Fix bug when \_rev was send to the hosts API | |
| 21 | * Send JSON response when you get a 500 or 404 error | |
| 22 | * Fix bug parsing invalid data in NullToBlankString | |
| 23 | ||
| 24 | Changes in plugins (only available through Web UI, not in GTK client yet): | |
| 25 | ||
| 26 | New plugins: | |
| 27 | ||
| 28 | * Checkmarx | |
| 29 | * Faraday\_csv (output of exported Faraday csv) | |
| 30 | * Qualyswebapp | |
| 31 | * Whitesource | |
| 32 | ||
| 33 | Updated plugins: | |
| 34 | ||
| 35 | * Acunetix | |
| 36 | * AppScan | |
| 37 | * Arachni | |
| 38 | * Nessus | |
| 39 | * Netspaker | |
| 40 | * Netspaker cloud | |
| 41 | * Nexpose | |
| 42 | * Openvas | |
| 43 | * QualysGuard | |
| 44 | * Retina | |
| 45 | * W3af | |
| 46 | * WPScan | |
| 47 | * Webinspect | |
| 48 | * Zap |
| 7 | 7 | New features in the latest update |
| 8 | 8 | ===================================== |
| 9 | 9 | |
| 10 | ||
| 11 | 3.11 [Apr 22nd, 2020]: | |
| 12 | --- | |
| 13 | * Move GTK client to [another repository](https://github.com/infobyte/faraday-client) to improve release times. | |
| 14 | * Fix formula injection vulnerability when exporting vulnerability data to CSV. This was considered a low impact vulnerability. | |
| 15 | * Remove "--ssl" parameter. Read SSL information from the config file. | |
| 16 | * Add OpenAPI autogenerated documentation support | |
| 17 | * Show agent information in command history | |
| 18 | * Add bulk delete endpoint for hosts API | |
| 19 | * Add column with information to track agent execution data | |
| 20 | * Add tool attribute to vulnerability to avoid incorrectly showing "Web UI" as creator tool | |
| 21 | * Add sorting by target in credentials view | |
| 22 | * Add creator information when uploading reports or using de bulk create api | |
| 23 | * Add feature to disable rules in the searcher | |
| 24 | * Add API endpoint to export Faraday data to Metasploit XML format | |
| 25 | * Use run date instead of creation date when plugins report specifies it | |
| 26 | * Improve knowledge base UX | |
| 27 | * Improve workspace table and status report table UX. | |
| 28 | * Improve format of exported CSV to include more fields | |
| 29 | * Sort results in count API endpoint | |
| 30 | * Limit description width in knowledge base | |
| 31 | * Change log date format to ISO 8601 | |
| 32 | * Fix parsing server port config in server.ini | |
| 33 | * Fix bug when \_rev was send to the hosts API | |
| 34 | * Send JSON response when you get a 500 or 404 error | |
| 35 | * Fix bug parsing invalid data in NullToBlankString | |
| 36 | ||
| 37 | Changes in plugins (only available through Web UI, not in GTK client yet): | |
| 38 | ||
| 39 | New plugins: | |
| 40 | ||
| 41 | * Checkmarx | |
| 42 | * Faraday\_csv (output of exported Faraday csv) | |
| 43 | * Qualyswebapp | |
| 44 | * Whitesource | |
| 45 | ||
| 46 | Updated plugins: | |
| 47 | ||
| 48 | * Acunetix | |
| 49 | * AppScan | |
| 50 | * Arachni | |
| 51 | * Nessus | |
| 52 | * Netspaker | |
| 53 | * Netspaker cloud | |
| 54 | * Nexpose | |
| 55 | * Openvas | |
| 56 | * QualysGuard | |
| 57 | * Retina | |
| 58 | * W3af | |
| 59 | * WPScan | |
| 60 | * Webinspect | |
| 61 | * Zap | |
| 10 | 62 | |
| 11 | 63 | 3.10.2 [Jan 30th, 2020]: |
| 12 | 64 | --- |
| 0 | Change url route from / to /websockets |
| 3 | 3 | include faraday/config/default.xml |
| 4 | 4 | include faraday/server/default.ini |
| 5 | 5 | include requirements.txt |
| 6 | include requirements_dev.txt | |
| 7 | include requirements_server.txt | |
| 8 | include faraday/client/zsh/faraday.zsh | |
| 9 | include faraday/client/zsh/faraday-terminal.zsh | |
| 10 | include faraday/client/gui/gtk/menubar.xml | |
| 11 | recursive-include faraday/client/data * | |
| 12 | include faraday/client/plugins/port_mapper.txt |
| 5 | 5 | |
| 6 | 6 | Faraday was made to let you take advantage of the available tools in the community in a truly multiuser way. |
| 7 | 7 | |
| 8 | Faraday crunches the data you load into different visualizations that are useful to managers and pentesters alike. | |
| 9 | ||
| 10 | 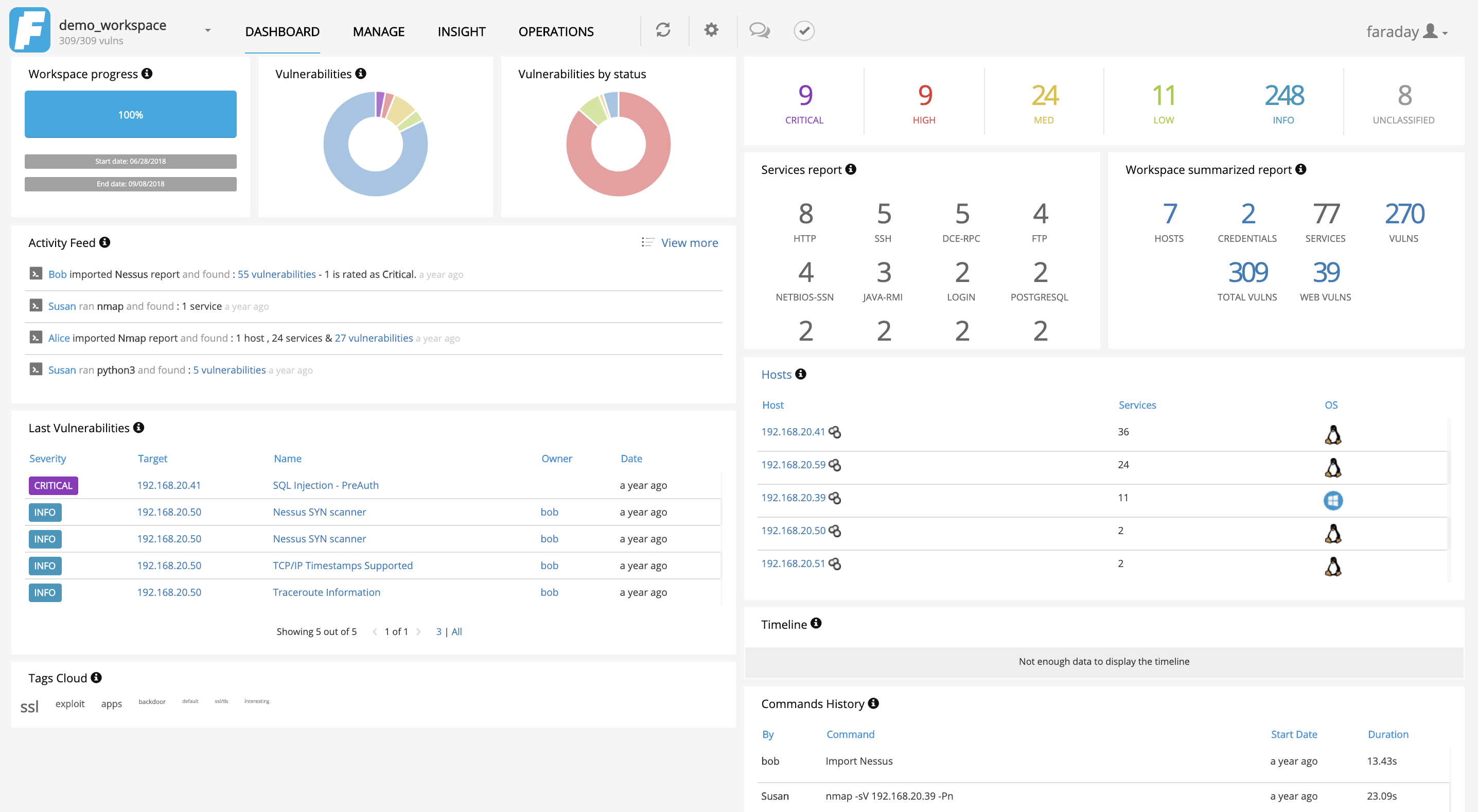 | |
| 11 | ||
| 8 | 12 | Designed for simplicity, users should notice no difference between their own terminal application and the one included in Faraday. Developed with a specialized set of functionalities, users improve their own work. Do you remember the last time you programmed without an IDE? What IDEs are to programming, Faraday is to pentesting. |
| 9 | 13 | |
| 10 | 14 |  |
| 11 | 15 | |
| 12 | Faraday crunches the data you load into different visualizations that are useful to managers and pentesters alike. | |
| 13 | ||
| 14 |  | |
| 15 | ||
| 16 | 16 | To read about the latest features check out the [release notes](https://github.com/infobyte/faraday/blob/master/RELEASE.md)! |
| 17 | 17 | |
| 18 | 18 | |
| 19 | # Installation | |
| 20 | ||
| 21 | Refer to the [releases page](https://github.com/infobyte/faraday/releases) for the latest pre-made installers for all supported operating systems. | |
| 22 | ||
| 23 | Check out our documentation for detailed information on how to install Faraday in all of our supported platforms: | |
| 24 | ||
| 25 |  | |
| 26 | ||
| 27 | To begin the installation process, check out our [Installation Wiki](https://github.com/infobyte/faraday/wiki/Install-Guide). | |
| 28 | ||
| 29 | ## Development | |
| 30 | ||
| 31 | You need Python 3.6+ and postgres to run the faraday server. | |
| 32 | ||
| 33 | If you want to develop for Faraday, please follow our [development setup for linux](https://github.com/infobyte/faraday/wiki/Development-setup) or [development setup for OSX](https://github.com/infobyte/faraday/wiki/Development-Installation-OSX). | |
| 34 | ||
| 19 | 35 | ## Quickstart |
| 20 | 36 | |
| 21 | Refer to the [releases page](https://github.com/infobyte/faraday/releases) for the latest pre-made installers for all supported operating systems. | |
| 22 | ||
| 23 | Check out our documentation for detailed information on how to install Faraday in all of our supported platforms: | |
| 24 | ||
| 25 |  | |
| 26 | ||
| 27 | To begin the installation process, check out our [Installation Wiki](https://github.com/infobyte/faraday/wiki/Installation-Community). | |
| 28 | ||
| 29 | ## Development | |
| 30 | ||
| 31 | You need Python 3.6+ and postgres to run the faraday server. | |
| 32 | ||
| 33 | ### Install OS Dependencies | |
| 34 | ||
| 35 | You need python 3.6+ and postgres. E.g. in Ubuntu | |
| 36 | ||
| 37 | ``` | |
| 38 | apt install postgresql python3.6 | |
| 39 | ``` | |
| 40 | ||
| 41 | Make sure postgres is up and running before the next steps. | |
| 42 | ||
| 43 | ||
| 44 | ||
| 45 | ### Install Python dependencies | |
| 46 | ||
| 47 | get the latest source | |
| 48 | ||
| 49 | ``` | |
| 50 | git clone https://github.com/infobyte/faraday | |
| 51 | ``` | |
| 52 | ||
| 53 | create a virtual environment and install Python dependencies. For example: | |
| 54 | ||
| 55 | ``` | |
| 56 | cd faraday | |
| 57 | python3 -m venv .venv | |
| 58 | source .venv/bin/activate | |
| 59 | python3 setup.py develop | |
| 60 | ||
| 61 | ``` | |
| 62 | ||
| 63 | ### Run the server | |
| 64 | ||
| 65 | In the virtual environment, initialize the faraday database: | |
| 37 | Once you installed faraday packages, you will need to initialize the faraday database: | |
| 66 | 38 | |
| 67 | 39 | ``` |
| 68 | 40 | sudo faraday-manage initdb |
| 69 | 41 | ``` |
| 70 | 42 | |
| 71 | This will give you a randomly generated password to log into the web UI. | |
| 72 | Now you can start the server | |
| 73 | ||
| 74 | ``` | |
| 75 | faraday-server | |
| 43 | This will give you a *randomly generated password* to log into the web UI. | |
| 44 | Now you can start the server with: | |
| 45 | ||
| 46 | ``` | |
| 47 | systemctl start faraday-server | |
| 76 | 48 | ``` |
| 77 | 49 | |
| 78 | 50 | In your browser, now you can go to localhost:5985 and login with "faraday" as username, and the password generated in the initdb step. |
| 80 | 52 | |
| 81 | 53 | ## New Features! |
| 82 | 54 | |
| 83 | All of Faraday's latest features and updates are always available on our [blog](http://blog.infobytesec.com/search/label/english). | |
| 55 | All of Faraday's latest features and updates are always available on our [blog](https://medium.com/faraday). | |
| 84 | 56 | There are new entries every few weeks, don't forget to check out our amazing new improvements on its latest entry! |
| 85 | 57 | |
| 58 | ## API | |
| 59 | ||
| 60 | This is a branch for a PoC of automatically generating the API documentation in the [OpenAPI/swagger](https://www.openapis.org/) format. | |
| 61 | To generate the API docs, for example, to use with swagger UI, run: | |
| 62 | ||
| 63 | ``` | |
| 64 | faraday-manage openapi-yaml | |
| 65 | ``` | |
| 66 | ||
| 86 | 67 | |
| 87 | 68 | ## Plugins list |
| 88 | 69 | |
| 94 | 75 | |
| 95 | 76 | [Read more about Plugins](http://github.com/infobyte/faraday/wiki/Plugin-List). |
| 96 | 77 | |
| 78 | Faraday plugins code can be found in [faraday-plugin repository](https://github.com/infobyte/faraday_plugins) | |
| 97 | 79 | |
| 98 | 80 | ## Features |
| 99 | 81 | |
| 100 | 82 | ### Workspaces |
| 101 | 83 | |
| 102 | 84 | Information is organized into various **Workspaces**. Each Workspace contains a pentest team's assignments and all the intel that is discovered. |
| 85 | ||
| 86 | ### Agents | |
| 87 | ||
| 88 | [Faraday Agents Dispatcher](https://github.com/infobyte/faraday_agent_dispatcher) helps user develop integrations with Faraday written in any language. | |
| 89 | Agents collects information from different network location using different tools. You can use [FaradaySEC](https://www.faradaysec.com) to orchestrate tool execution. | |
| 103 | 90 | |
| 104 | 91 | ### Conflicts |
| 105 | 92 | |
| 126 | 113 | |
| 127 | 114 | Read more about the [Faraday Plugin](https://github.com/infobyte/faraday/wiki/faraday-plugin). |
| 128 | 115 | |
| 129 | ### Notifications | |
| 130 | ||
| 131 | Updating objects on other Faraday instances result in notifications on your | |
| 132 | Faraday GTK Client. | |
| 133 | ||
| 134 | 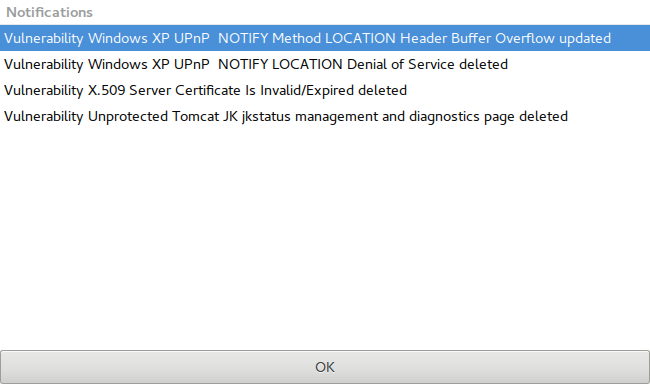 | |
| 135 | ||
| 136 | 116 | |
| 137 | 117 | ### CSV Exporting |
| 138 | 118 | |
| 141 | 121 | |
| 142 | 122 | ## Links |
| 143 | 123 | |
| 144 | * Homepage: https://www.faradaysec.com | |
| 145 | * User forum: https://forum.faradaysec.com | |
| 146 | * User's manual: https://github.com/infobyte/faraday/wiki | |
| 147 | * Download: [.tar.gz](https://github.com/infobyte/faraday/tarball/master) | |
| 124 | * Homepage: [FaradaySEC](https://www.faradaysec.com) | |
| 125 | * User forum: [Faraday Forum](https://forum.faradaysec.com) | |
| 126 | * User's manual: [Faraday Wiki](https://github.com/infobyte/faraday/wiki) or check our [support portal](https://support.faradaysec.com/portal/home) | |
| 127 | * Download: [Download .deb/.rpm from releases page](https://github.com/infobyte/faraday/releases) | |
| 148 | 128 | * Commits RSS feed: https://github.com/infobyte/faraday/commits/master.atom |
| 149 | * Issue tracker: https://github.com/infobyte/faraday/issues | |
| 150 | * Frequently Asked Questions (FAQ): https://github.com/infobyte/faraday/wiki/FAQ | |
| 151 | * Mailing list subscription: https://groups.google.com/forum/#!forum/faradaysec | |
| 129 | * Issue tracker: [Github issue tracker](https://github.com/infobyte/faraday/issues) | |
| 130 | * Frequently Asked Questions: [FaradaySEC FAQ](https://github.com/infobyte/faraday/wiki/FAQ) | |
| 152 | 131 | * Twitter: [@faradaysec](https://twitter.com/faradaysec) |
| 153 | 132 | * [Demos](https://github.com/infobyte/faraday/wiki/Demos) |
| 154 | 133 | * IRC: [ircs://irc.freenode.net/faraday-dev](ircs://irc.freenode.net/faraday-dev) [WebClient](https://webchat.freenode.net/?nick=wikiuser&channels=faraday-dev&prompt=1&uio=d4) |
| 155 | * Screenshots: https://github.com/infobyte/faraday/wiki/Screenshots | |
| 156 | * Send your ideas and suggestions here: [https://www.faradaysec.com/ideas](https://www.faradaysec.com/ideas) | |
| 157 | 134 | * Releases: [Faraday Releases](https://github.com/infobyte/faraday/releases/) |
| 158 | 135 | |
| 159 | 136 | ## Presentations |
| 162 | 139 | [2010](http://vimeo.com/16516987) - |
| 163 | 140 | [2014](https://www.youtube.com/watch?v=_j0T2S6Ppfo) - |
| 164 | 141 | [2017](http://blog.infobytesec.com/2017/10/ekoparty-2017-review_23.html) - |
| 165 | [2018](http://blog.infobytesec.com/2018/10/ekoparty-2018-review_18.html) | |
| 142 | [2018](http://blog.infobytesec.com/2018/10/ekoparty-2018-review_18.html) - | |
| 143 | [2019](https://medium.com/faraday/ekoparty-2019-review-abd1940ac8c6?source=collection_home---4------5-----------------------) | |
| 166 | 144 | |
| 167 | 145 | * Black Hat: |
| 168 | 146 | * USA : |
| 170 | 148 | [2015](https://www.blackhat.com/us-15/arsenal.html#faraday) - |
| 171 | 149 | [2016](https://www.blackhat.com/us-16/arsenal.html#faraday) - |
| 172 | 150 | [2017](https://www.blackhat.com/us-17/event-sponsors.html#faraday) - |
| 173 | [2018](https://www.blackhat.com/us-18/event-sponsors.html#faraday) | |
| 151 | [2018](https://www.blackhat.com/us-18/event-sponsors.html#faraday) - | |
| 152 | [2019](https://medium.com/faraday/another-year-at-las-vegas-with-faraday-21b0edcf8d6?source=collection_home---4------8-----------------------) | |
| 174 | 153 | |
| 175 | 154 | * Asia : |
| 176 | 155 | [2016](https://www.blackhat.com/asia-16/arsenal.html#faraday) - |
| 179 | 158 | |
| 180 | 159 | * Europe : |
| 181 | 160 | [2015](https://www.blackhat.com/eu-15/arsenal.html#faraday) - |
| 182 | [2016](https://www.blackhat.com/eu-16/arsenal.html#faraday) | |
| 161 | [2016](https://www.blackhat.com/eu-16/arsenal.html#faraday) - | |
| 162 | [2019](https://medium.com/faraday/the-end-of-the-year-is-always-jam-packed-it-is-a-period-for-looking-back-and-celebrating-the-road-fcf5cb007a3a) | |
| 183 | 163 | |
| 184 | 164 | * RSA USA : |
| 185 | 165 | [2015](https://www.rsaconference.com/events/us15/expo-sponsors/exhibitor-list/1782/infobyte-llc) |
| 205 | 185 | |
| 206 | 186 | |
| 207 | 187 | * PyConAr : |
| 208 | [2018](https://eventos.python.org.ar/events/pyconar2018/activity/75/) | |
| 188 | [2018](https://eventos.python.org.ar/events/pyconar2018/activity/75/) - | |
| 189 | [2019](https://eventos.python.org.ar/events/pyconar2019/activity/251/) | |
| 209 | 190 | |
| 210 | 191 | * 8.8 Chile : |
| 211 | 192 | [2018](http://blog.infobytesec.com/2018/11/chronicles-of-trip-to-santiago-88-review.html) |
| 7 | 7 | New features in the latest update |
| 8 | 8 | ===================================== |
| 9 | 9 | |
| 10 | ||
| 11 | 3.11 [Apr 22nd, 2020]: | |
| 12 | --- | |
| 13 | * Move GTK client to [another repository](https://github.com/infobyte/faraday-client) to improve release times. | |
| 14 | * Fix formula injection vulnerability when exporting vulnerability data to CSV. This was considered a low impact vulnerability. | |
| 15 | * Remove "--ssl" parameter. Read SSL information from the config file. | |
| 16 | * Add OpenAPI autogenerated documentation support | |
| 17 | * Show agent information in command history | |
| 18 | * Add bulk delete endpoint for hosts API | |
| 19 | * Add column with information to track agent execution data | |
| 20 | * Add tool attribute to vulnerability to avoid incorrectly showing "Web UI" as creator tool | |
| 21 | * Add sorting by target in credentials view | |
| 22 | * Add creator information when uploading reports or using de bulk create api | |
| 23 | * Add feature to disable rules in the searcher | |
| 24 | * Add API endpoint to export Faraday data to Metasploit XML format | |
| 25 | * Use run date instead of creation date when plugins report specifies it | |
| 26 | * Improve knowledge base UX | |
| 27 | * Improve workspace table and status report table UX. | |
| 28 | * Improve format of exported CSV to include more fields | |
| 29 | * Sort results in count API endpoint | |
| 30 | * Limit description width in knowledge base | |
| 31 | * Change log date format to ISO 8601 | |
| 32 | * Fix parsing server port config in server.ini | |
| 33 | * Fix bug when \_rev was send to the hosts API | |
| 34 | * Send JSON response when you get a 500 or 404 error | |
| 35 | * Fix bug parsing invalid data in NullToBlankString | |
| 36 | ||
| 37 | Changes in plugins (only available through Web UI, not in GTK client yet): | |
| 38 | ||
| 39 | New plugins: | |
| 40 | ||
| 41 | * Checkmarx | |
| 42 | * Faraday\_csv (output of exported Faraday csv) | |
| 43 | * Qualyswebapp | |
| 44 | * Whitesource | |
| 45 | ||
| 46 | Updated plugins: | |
| 47 | ||
| 48 | * Acunetix | |
| 49 | * AppScan | |
| 50 | * Arachni | |
| 51 | * Nessus | |
| 52 | * Netspaker | |
| 53 | * Netspaker cloud | |
| 54 | * Nexpose | |
| 55 | * Openvas | |
| 56 | * QualysGuard | |
| 57 | * Retina | |
| 58 | * W3af | |
| 59 | * WPScan | |
| 60 | * Webinspect | |
| 61 | * Zap | |
| 10 | 62 | |
| 11 | 63 | 3.10.2 [Jan 30th, 2020]: |
| 12 | 64 | --- |
| 0 | #!/usr/bin/env bash | |
| 1 | ||
| 2 | # Faraday Penetration Test IDE | |
| 3 | # Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | # See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | # Move files using the old files structure to the new one | |
| 7 | ||
| 8 | set -eu -o pipefail | |
| 9 | ||
| 10 | CLIENT_DIRS=(apis bin gui helpers managers model persistence plugins zsh) | |
| 11 | FARADAY_PACKAGE_DIRS=(client config server utils) | |
| 12 | ||
| 13 | DRY_RUN_PREFIX="" | |
| 14 | DRY_RUN_GIT_MV="" | |
| 15 | while getopts ":d" opt; do | |
| 16 | case $opt in | |
| 17 | d) | |
| 18 | DRY_RUN_PREFIX="echo " | |
| 19 | DRY_RUN_GIT_MV="-n" | |
| 20 | ;; | |
| 21 | \?) | |
| 22 | echo "Invalid option: -$OPTARG" >&2 | |
| 23 | exit 1 | |
| 24 | ;; | |
| 25 | esac | |
| 26 | done | |
| 27 | ||
| 28 | for dir in "${CLIENT_DIRS[@]}"; do | |
| 29 | if [[ -d "${dir}" ]]; then | |
| 30 | for subfile in $(find "${dir}" -type f); do | |
| 31 | $DRY_RUN_PREFIX mkdir -p "faraday/client/$(dirname "${subfile}")" | |
| 32 | git mv $DRY_RUN_GIT_MV -k "${subfile}" "faraday/client/${subfile}" | |
| 33 | done | |
| 34 | $DRY_RUN_PREFIX rmdir --ignore-fail-on-non-empty "${dir}" | |
| 35 | fi | |
| 36 | done | |
| 37 | ||
| 38 | ||
| 39 | for dir in "${FARADAY_PACKAGE_DIRS[@]}"; do | |
| 40 | if [[ -d "${dir}" ]]; then | |
| 41 | for subfile in $(find "${dir}" -type f); do | |
| 42 | $DRY_RUN_PREFIX mkdir -p "faraday/$(dirname "${subfile}")" | |
| 43 | git mv $DRY_RUN_GIT_MV -k "${subfile}" "faraday/${subfile}" | |
| 44 | done | |
| 45 | $DRY_RUN_PREFIX rmdir --ignore-fail-on-non-empty "${dir}" | |
| 46 | fi | |
| 47 | done | |
| 48 | ||
| 49 | ||
| 50 | if [[ -d test_cases ]]; then | |
| 51 | for subfile in $(find test_cases -type f); do | |
| 52 | $DRY_RUN_PREFIX mkdir -p "tests/$(dirname "${subfile}")" | |
| 53 | git mv $DRY_RUN_GIT_MV -k "${subfile}" "tests/${subfile#test_cases/}" | |
| 54 | done | |
| 55 | fi |
| 0 | CLIENT_IMPORTED="managers.mapper_manager model.api model.common model.controller model.guiapi model.log persistence.server.server plugins.controller" # I assume there are no "import ... as ..." | |
| 1 | OTHER_IMPORTED="server.config server.utils.logger server.web" # I assume there are no "import ... as ..." | |
| 2 | ||
| 3 | echo -n "This will mess most of the python files of the repo. Are you sure you have a clean git dir? (Type uppercase yes): " | |
| 4 | read ANSWER | |
| 5 | if [[ "$ANSWER" != "YES" ]] | |
| 6 | then | |
| 7 | exit 1 | |
| 8 | fi | |
| 9 | ||
| 10 | replace_occurences(){ | |
| 11 | CURRENT_MODULE_NAME=$1 | |
| 12 | TARGET_MODULE_NAME=$2 | |
| 13 | FILE=$3 | |
| 14 | echo $FILE | |
| 15 | sed -Ei "/$TARGET_MODULE_NAME/! s/\<$CURRENT_MODULE_NAME\>/$TARGET_MODULE_NAME/g" $FILE | |
| 16 | } | |
| 17 | ||
| 18 | for MODULE in $OTHER_IMPORTED | |
| 19 | do | |
| 20 | for FILE in $(git grep --name-only -E "^\s*import (faraday\.)?$MODULE") | |
| 21 | do | |
| 22 | replace_occurences $MODULE faraday.$MODULE $FILE | |
| 23 | done | |
| 24 | done | |
| 25 | ||
| 26 | for MODULE in $CLIENT_IMPORTED | |
| 27 | do | |
| 28 | for FILE in $(git grep --name-only -E "^\s*import (faraday\.)?$MODULE") | |
| 29 | do | |
| 30 | replace_occurences $MODULE faraday.client.$MODULE $FILE | |
| 31 | done | |
| 32 | done | |
| 33 |
| 0 | #!/usr/bin/env bash | |
| 1 | ||
| 2 | CLIENT_ROOTS="(apis|bin[^a]|data|gui|helpers|managers|model[^s]|persistence|plugins)" | |
| 3 | OTHER_ROOTS="(migrations|server|utils|config[^p]|reports)" | |
| 4 | ||
| 5 | if [[ "$1" ]] | |
| 6 | then | |
| 7 | FILES="$1" | |
| 8 | else | |
| 9 | FILES="$(git ls-files | egrep '\.py$')" | |
| 10 | fi | |
| 11 | ||
| 12 | echo -n "This will mess most of the python files of the repo. Are you sure you have a clean git dir? (Type uppercase yes): " | |
| 13 | read ANSWER | |
| 14 | if [[ "$ANSWER" != "YES" ]] | |
| 15 | then | |
| 16 | exit 1 | |
| 17 | fi | |
| 18 | ||
| 19 | for PYFILE in $FILES | |
| 20 | do | |
| 21 | echo $PYFILE | |
| 22 | sed -Ei "s/^(\s*)from $CLIENT_ROOTS/\1from faraday.client.\2/" $PYFILE | |
| 23 | sed -Ei "s/^(\s*)from $OTHER_ROOTS/\1from faraday.\2/" $PYFILE | |
| 24 | sed -Ei "/ as / { s/^(\s*)import $CLIENT_ROOTS/\1import faraday.client.\2/; }" $PYFILE | |
| 25 | sed -Ei "/ as / { s/^(\s*)import $OTHER_ROOTS/\1import faraday.\2/; }" $PYFILE | |
| 26 | sed -Ei "/__[a-z_]*version__/! s/^(\s*)from faraday import/\1from faraday.client.start_client import/" $PYFILE | |
| 27 | done | |
| 28 |
| 1 | 1 | |
| 2 | 2 | stdenv.mkDerivation { |
| 3 | 3 | name = "faraday-nix.pth"; |
| 4 | packages = with python37Packages; [virtualenv pip pyopenssl psycopg2 pillow pygobject3 pynacl matplotlib numpy lxml ldap autobahn gssapi setproctitle simplejson pycairo cffi cairocffi bcrypt twisted]; | |
| 4 | packages = with python37Packages; [virtualenv pip pyopenssl psycopg2 pgcli pillow pygobject3 pynacl matplotlib numpy lxml ldap autobahn gssapi setproctitle simplejson pycairo cffi cairocffi bcrypt twisted]; | |
| 5 | 5 | builder = ./buildpth.sh; |
| 6 | 6 | } |
| 0 | cwe,name,description,resolution,exploitation,references | |
| 1 | CWE-119,EN-Improper Restriction of Operations within the Bounds of a Memory Buffer (Type: Class),"The software performs operations on a memory buffer, but it can read from or write to a memory location that is outside of the intended boundary of the buffer. | |
| 2 | Certain languages allow direct addressing of memory locations and do not automatically ensure that these locations are valid for the memory buffer that is being referenced. This can cause read or write operations to be performed on memory locations that may be associated with other variables, data structures, or internal program data. | |
| 3 | As a result, an attacker may be able to execute arbitrary code, alter the intended control flow, read sensitive information, or cause the system to crash.",,high,"Writing Secure Code: Chapter 5, ""Public Enemy #1: The Buffer Overrun"" Page 127; Chapter 14, ""Prevent I18N Buffer Overruns"" Page 441 | |
| 4 | Using the Strsafe.h Functions: http://msdn.microsoft.com/en-us/library/ms647466.aspx | |
| 5 | Safe C String Library v1.0.3: http://www.zork.org/safestr/ | |
| 6 | Address Space Layout Randomization in Windows Vista: http://blogs.msdn.com/michael_howard/archive/2006/05/26/address-space-layout-randomization-in-windows-vista.aspx | |
| 7 | Limiting buffer overflows with ExecShield: http://www.redhat.com/magazine/009jul05/features/execshield/ | |
| 8 | PaX: http://en.wikipedia.org/wiki/PaX | |
| 9 | Understanding DEP as a mitigation technology part 1: http://blogs.technet.com/b/srd/archive/2009/06/12/understanding-dep-as-a-mitigation-technology-part-1.aspx | |
| 10 | The Art of Software Security Assessment: Chapter 5, ""Memory Corruption"", Page 167. | |
| 11 | The Art of Software Security Assessment: Chapter 5, ""Protection Mechanisms"", Page 189." | |
| 12 | CWE-123,EN-Write-what-where Condition (Type: Base),"Any condition where the attacker has the ability to write an arbitrary value to an arbitrary location, often as the result of a buffer overflow. | |
| 13 | A buffer overflow condition exists when a program attempts to put more data in a buffer than it can hold, or when a program attempts to put data in a memory area outside of the boundaries of a buffer. The simplest type of error, and the most common cause of buffer overflows, is the ""classic"" case in which the program copies the buffer without restricting how much is copied. Other variants exist, but the existence of a classic overflow strongly suggests that the programmer is not considering even the most basic of security protections.",,high,"24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89" | |
| 14 | CWE-129,EN-Improper Validation of Array Index (Type: Base),"The product uses untrusted input when calculating or using an array index, but the product does not validate or incorrectly validates the index to ensure the index references a valid position within the array. | |
| 15 | This typically occurs when the pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used. This may result in exposure of sensitive information or possibly a crash.",,high,"Writing Secure Code: Chapter 5, ""Array Indexing Errors"" Page 144 | |
| 16 | Top 25 Series - Rank 14 - Improper Validation of Array Index: http://blogs.sans.org/appsecstreetfighter/2010/03/12/top-25-series-rank-14-improper-validation-of-array-index/ | |
| 17 | Address Space Layout Randomization in Windows Vista: http://blogs.msdn.com/michael_howard/archive/2006/05/26/address-space-layout-randomization-in-windows-vista.aspx | |
| 18 | PaX: http://en.wikipedia.org/wiki/PaX | |
| 19 | Understanding DEP as a mitigation technology part 1: http://blogs.technet.com/b/srd/archive/2009/06/12/understanding-dep-as-a-mitigation-technology-part-1.aspx | |
| 20 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 21 | 24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89" | |
| 22 | CWE-194,EN-Unexpected Sign Extension (Type: Base),"The software performs an operation on a number that causes it to be sign extended when it is transformed into a larger data type. When the original number is negative, this can produce unexpected values that lead to resultant weaknesses. | |
| 23 | This can happen in signed and unsigned cases.",,high,"C Language Issues for Application Security: http://www.informit.com/articles/article.aspx?p=686170&seqNum=6 | |
| 24 | Integral Security: http://www.ddj.com/security/193501774" | |
| 25 | CWE-20,EN-Improper Input Validation (Type: Class),"The product does not validate or incorrectly validates input that can affect the control flow or data flow of a program. | |
| 26 | When software does not validate input properly, an attacker is able to craft the input in a form that is not expected by the rest of the application. This will lead to parts of the system receiving unintended input, which may result in altered control flow, arbitrary control of a resource, or arbitrary code execution.",,high,"Input Validation with ESAPI - Very Important: http://manicode.blogspot.com/2008/08/input-validation-with-esapi.html | |
| 27 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 28 | Hacking Exposed Web Applications, Second Edition: Input Validation Attacks | |
| 29 | Input validation or output filtering, which is better?: http://jeremiahgrossman.blogspot.com/2007/01/input-validation-or-output-filtering.html | |
| 30 | The importance of input validation: http://searchsoftwarequality.techtarget.com/tip/0,289483,sid92_gci1214373,00.html | |
| 31 | Writing Secure Code: Chapter 10, ""All Input Is Evil!"" Page 341" | |
| 32 | CWE-200,EN-Information Exposure (Type: Class),"An information exposure is the intentional or unintentional disclosure of information to an actor that is not explicitly authorized to have access to that information. | |
| 33 | The information either | |
| 34 | is regarded as sensitive within the product's own functionality, such as a private message; or | |
| 35 | provides information about the product or its environment that could be useful in an attack but is normally not available to the attacker, such as the installation path of a product that is remotely accessible. | |
| 36 | Many information exposures are resultant (e.g. PHP script error revealing the full path of the program), but they can also be primary (e.g. timing discrepancies in cryptography). There are many different types of problems that involve information exposures. Their severity can range widely depending on the type of information that is revealed.",,high,Mobile App Top 10 List: http://www.veracode.com/blog/2010/12/mobile-app-top-10-list/ | |
| 37 | CWE-209,EN-Information Exposure Through an Error Message (Type: Base),"The software generates an error message that includes sensitive information about its environment, users, or associated data. | |
| 38 | The sensitive information may be valuable information on its own (such as a password), or it may be useful for launching other, more deadly attacks. If an attack fails, an attacker may use error information provided by the server to launch another more focused attack. For example, an attempt to exploit a path traversal weakness (CWE-22) might yield the full pathname of the installed application. In turn, this could be used to select the proper number of "".."" sequences to navigate to the targeted file. An attack using SQL injection (CWE-89) might not initially succeed, but an error message could reveal the malformed query, which would expose query logic and possibly even passwords or other sensitive information used within the query.",,high,"Information Leakage: http://www.webappsec.org/projects/threat/classes/information_leakage.shtml | |
| 39 | Secure Programming with Static Analysis: Section 9.2, page 326. | |
| 40 | Writing Secure Code: Chapter 16, ""General Good Practices."" Page 415 | |
| 41 | 24 Deadly Sins of Software Security: ""Sin 11: Failure to Handle Errors Correctly."" Page 183 | |
| 42 | 24 Deadly Sins of Software Security: ""Sin 12: Information Leakage."" Page 191 | |
| 43 | Top 25 Series - Rank 16 - Information Exposure Through an Error Message: http://software-security.sans.org/blog/2010/03/17/top-25-series-rank-16-information-exposure-through-an-error-message | |
| 44 | The Art of Software Security Assessment: Chapter 3, ""Overly Verbose Error Messages"", Page 75." | |
| 45 | CWE-234,EN-Failure to Handle Missing Parameter (Type: Variant),"If too few arguments are sent to a function, the function will still pop the expected number of arguments from the stack. Potentially, a variable number of arguments could be exhausted in a function as well. | |
| 46 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,high, | |
| 47 | CWE-242,EN-Use of Inherently Dangerous Function (Type: Base),"The program calls a function that can never be guaranteed to work safely. | |
| 48 | Certain functions behave in dangerous ways regardless of how they are used. Functions in this category were often implemented without taking security concerns into account. The gets() function is unsafe because it does not perform bounds checking on the size of its input. An attacker can easily send arbitrarily-sized input to gets() and overflow the destination buffer. Similarly, the >> operator is unsafe to use when reading into a statically-allocated character array because it does not perform bounds checking on the size of its input. An attacker can easily send arbitrarily-sized input to the >> operator and overflow the destination buffer.",,high,"Herb Schildt's C++ Programming Cookbook: Chapter 5. Working with I/O | |
| 49 | Writing Secure Code: Chapter 5, ""gets and fgets"" Page 163" | |
| 50 | CWE-243,EN-Creation of chroot Jail Without Changing Working Directory (Type: Variant),"The program uses the chroot() system call to create a jail, but does not change the working directory afterward. This does not prevent access to files outside of the jail. | |
| 51 | Improper use of chroot() may allow attackers to escape from the chroot jail. The chroot() function call does not change the process's current working directory, so relative paths may still refer to file system resources outside of the chroot jail after chroot() has been called.",,high, | |
| 52 | CWE-268,EN-Privilege Chaining (Type: Base),"Two distinct privileges, roles, capabilities, or rights can be combined in a way that allows an entity to perform unsafe actions that would not be allowed without that combination. | |
| 53 | Just as neglecting to include functionality for the management of password aging is dangerous, so is allowing password aging to continue unchecked. Passwords must be given a maximum life span, after which a user is required to update with a new and different password.",,high,Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 54 | CWE-271,EN-Privilege Dropping / Lowering Errors (Type: Class),"The software does not drop privileges before passing control of a resource to an actor that does not have those privileges. | |
| 55 | In some contexts, a system executing with elevated permissions will hand off a process/file/etc. to another process or user. If the privileges of an entity are not reduced, then elevated privileges are spread throughout a system and possibly to an attacker.",,high,"24 Deadly Sins of Software Security: ""Sin 16: Executing Code With Too Much Privilege."" Page 243 | |
| 56 | The Art of Software Security Assessment: Chapter 9, ""Dropping Privileges Permanently"", Page 479." | |
| 57 | CWE-285,EN-Improper Authorization (Type: Class),"The software does not perform or incorrectly performs an authorization check when an actor attempts to access a resource or perform an action. | |
| 58 | Assuming a user with a given identity, authorization is the process of determining whether that user can access a given resource, based on the user's privileges and any permissions or other access-control specifications that apply to the resource. | |
| 59 | When access control checks are not applied consistently - or not at all - users are able to access data or perform actions that they should not be allowed to perform. This can lead to a wide range of problems, including information exposures, denial of service, and arbitrary code execution.",,high,"Role Based Access Control and Role Based Security: http://csrc.nist.gov/groups/SNS/rbac/ | |
| 60 | Writing Secure Code: Chapter 4, ""Authorization"" Page 114; Chapter 6, ""Determining Appropriate Access Control"" Page 171 | |
| 61 | Top 25 Series - Rank 5 - Improper Access Control (Authorization): http://blogs.sans.org/appsecstreetfighter/2010/03/04/top-25-series-rank-5-improper-access-control-authorization/ | |
| 62 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 63 | Authentication using JAAS: http://www.javaranch.com/journal/2008/04/authentication-using-JAAS.html | |
| 64 | The Art of Software Security Assessment: Chapter 2, ""Common Vulnerabilities of Authorization"", Page 39. | |
| 65 | The Art of Software Security Assessment: Chapter 11, ""ACL Inheritance"", Page 649." | |
| 66 | CWE-291,EN-Reliance on IP Address for Authentication (Type: Variant),"The software uses an IP address for authentication. | |
| 67 | IP addresses can be easily spoofed. Attackers can forge the source IP address of the packets they send, but response packets will return to the forged IP address. To see the response packets, the attacker has to sniff the traffic between the victim machine and the forged IP address. In order to accomplish the required sniffing, attackers typically attempt to locate themselves on the same subnet as the victim machine. Attackers may be able to circumvent this requirement by using source routing, but source routing is disabled across much of the Internet today. In summary, IP address verification can be a useful part of an authentication scheme, but it should not be the single factor required for authentication.",,high, | |
| 68 | CWE-292,EN-DEPRECATED (Duplicate): Trusting Self-reported DNS Name (Type: Variant),"This entry has been deprecated because it was a duplicate of CWE-350. All content has been transferred to CWE-350. | |
| 69 | IP addresses can be easily spoofed. Attackers can forge the source IP address of the packets they send, but response packets will return to the forged IP address. To see the response packets, the attacker has to sniff the traffic between the victim machine and the forged IP address. In order to accomplish the required sniffing, attackers typically attempt to locate themselves on the same subnet as the victim machine. Attackers may be able to circumvent this requirement by using source routing, but source routing is disabled across much of the Internet today. In summary, IP address verification can be a useful part of an authentication scheme, but it should not be the single factor required for authentication.",,high, | |
| 70 | CWE-293,EN-Using Referer Field for Authentication (Type: Variant),"The referer field in HTTP requests can be easily modified and, as such, is not a valid means of message integrity checking. | |
| 71 | IP addresses can be easily spoofed. Attackers can forge the source IP address of the packets they send, but response packets will return to the forged IP address. To see the response packets, the attacker has to sniff the traffic between the victim machine and the forged IP address. In order to accomplish the required sniffing, attackers typically attempt to locate themselves on the same subnet as the victim machine. Attackers may be able to circumvent this requirement by using source routing, but source routing is disabled across much of the Internet today. In summary, IP address verification can be a useful part of an authentication scheme, but it should not be the single factor required for authentication.",,high,"The Art of Software Security Assessment: Chapter 17, ""Referer Request Header"", Page 1030." | |
| 72 | CWE-294,EN-Authentication Bypass by Capture-replay (Type: Base),"A capture-replay flaw exists when the design of the software makes it possible for a malicious user to sniff network traffic and bypass authentication by replaying it to the server in question to the same effect as the original message (or with minor changes). | |
| 73 | Capture-replay attacks are common and can be difficult to defeat without cryptography. They are a subset of network injection attacks that rely on observing previously-sent valid commands, then changing them slightly if necessary and resending the same commands to the server.",,high, | |
| 74 | CWE-297,EN-Improper Validation of Certificate with Host Mismatch (Type: Variant),"The software communicates with a host that provides a certificate, but the software does not properly ensure that the certificate is actually associated with that host. | |
| 75 | Even if a certificate is well-formed, signed, and follows the chain of trust, it may simply be a valid certificate for a different site than the site that the software is interacting with. If the certificate's host-specific data is not properly checked - such as the Common Name (CN) in the Subject or the Subject Alternative Name (SAN) extension of an X.509 certificate - it may be possible for a redirection or spoofing attack to allow a malicious host with a valid certificate to provide data, impersonating a trusted host. In order to ensure data integrity, the certificate must be valid and it must pertain to the site that is being accessed. | |
| 76 | Even if the software attempts to check the hostname, it is still possible to incorrectly check the hostname. For example, attackers could create a certificate with a name that begins with a trusted name followed by a NUL byte, which could cause some string-based comparisons to only examine the portion that contains the trusted name.",,high,"The Most Dangerous Code in the World: Validating SSL Certificates in Non-Browser Software: http://www.cs.utexas.edu/~shmat/shmat_ccs12.pdf | |
| 77 | Why Eve and Mallory Love Android: An Analysis of Android SSL (In)Security: http://www2.dcsec.uni-hannover.de/files/android/p50-fahl.pdf | |
| 78 | Secure programming with the OpenSSL API, Part 2: Secure handshake: http://www.ibm.com/developerworks/library/l-openssl2/index.html | |
| 79 | An Introduction to OpenSSL Programming (Part I): http://www.rtfm.com/openssl-examples/part1.pdf | |
| 80 | 24 Deadly Sins of Software Security: ""Sin 23: Improper Use of PKI, Especially SSL."" Page 347" | |
| 81 | CWE-308,EN-Use of Single-factor Authentication (Type: Base),"The use of single-factor authentication can lead to unnecessary risk of compromise when compared with the benefits of a dual-factor authentication scheme. | |
| 82 | While the use of multiple authentication schemes is simply piling on more complexity on top of authentication, it is inestimably valuable to have such measures of redundancy. The use of weak, reused, and common passwords is rampant on the internet. Without the added protection of multiple authentication schemes, a single mistake can result in the compromise of an account. For this reason, if multiple schemes are possible and also easy to use, they should be implemented and required.",,high, | |
| 83 | CWE-321,EN-Use of Hard-coded Cryptographic Key (Type: Base),"The use of a hard-coded cryptographic key significantly increases the possibility that encrypted data may be recovered. | |
| 84 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 85 | The '...' manipulation is useful for bypassing some path traversal protection schemes. On some Windows systems, it is equivalent to ""..\.."" and might bypass checks that assume only two dots are valid. Incomplete filtering, such as removal of ""./"" sequences, can ultimately produce valid "".."" sequences due to a collapse into unsafe value (CWE-182).",,high, | |
| 86 | CWE-322,EN-Key Exchange without Entity Authentication (Type: Base),"The software performs a key exchange with an actor without verifying the identity of that actor. | |
| 87 | Performing a key exchange will preserve the integrity of the information sent between two entities, but this will not guarantee that the entities are who they claim they are. This may enable a set of ""man-in-the-middle"" attacks. Typically, this involves a victim client that contacts a malicious server that is impersonating a trusted server. If the client skips authentication or ignores an authentication failure, the malicious server may request authentication information from the user. The malicious server can then use this authentication information to log in to the trusted server using the victim's credentials, sniff traffic between the victim and trusted server, etc.",,high,"24 Deadly Sins of Software Security: ""Sin 23: Improper Use of PKI, Especially SSL."" Page 347 | |
| 88 | The Art of Software Security Assessment: Chapter 2, ""Untrustworthy Credentials"", Page 37." | |
| 89 | CWE-323,"EN-Reusing a Nonce, Key Pair in Encryption (Type: Base)","Nonces should be used for the present occasion and only once. | |
| 90 | Performing a key exchange will preserve the integrity of the information sent between two entities, but this will not guarantee that the entities are who they claim they are. This may enable a set of ""man-in-the-middle"" attacks. Typically, this involves a victim client that contacts a malicious server that is impersonating a trusted server. If the client skips authentication or ignores an authentication failure, the malicious server may request authentication information from the user. The malicious server can then use this authentication information to log in to the trusted server using the victim's credentials, sniff traffic between the victim and trusted server, etc.",,high, | |
| 91 | CWE-360,EN-Trust of System Event Data (Type: Base),"Security based on event locations are insecure and can be spoofed. | |
| 92 | Events are a messaging system which may provide control data to programs listening for events. Events often do not have any type of authentication framework to allow them to be verified from a trusted source. Any application, in Windows, on a given desktop can send a message to any window on the same desktop. There is no authentication framework for these messages. Therefore, any message can be used to manipulate any process on the desktop if the process does not check the validity and safeness of those messages.",,high, | |
| 93 | CWE-378,EN-Creation of Temporary File With Insecure Permissions (Type: Base),"Opening temporary files without appropriate measures or controls can leave the file, its contents and any function that it impacts vulnerable to attack. | |
| 94 | If the revocation status of a certificate is not checked before each action that requires privileges, the system may be subject to a race condition. If a certificate is revoked after the initial check, all subsequent actions taken with the owner of the revoked certificate will lose all benefits guaranteed by the certificate. In fact, it is almost certain that the use of a revoked certificate indicates malicious activity.",,high, | |
| 95 | CWE-416,EN-Use After Free (Type: Base),"Referencing memory after it has been freed can cause a program to crash, use unexpected values, or execute code. | |
| 96 | The use of previously-freed memory can have any number of adverse consequences, ranging from the corruption of valid data to the execution of arbitrary code, depending on the instantiation and timing of the flaw. The simplest way data corruption may occur involves the system's reuse of the freed memory. Use-after-free errors have two common and sometimes overlapping causes: | |
| 97 | Error conditions and other exceptional circumstances. | |
| 98 | Confusion over which part of the program is responsible for freeing the memory. | |
| 99 | In this scenario, the memory in question is allocated to another pointer validly at some point after it has been freed. The original pointer to the freed memory is used again and points to somewhere within the new allocation. As the data is changed, it corrupts the validly used memory; this induces undefined behavior in the process. | |
| 100 | If the newly allocated data chances to hold a class, in C++ for example, various function pointers may be scattered within the heap data. If one of these function pointers is overwritten with an address to valid shellcode, execution of arbitrary code can be achieved.",,high,"24 Deadly Sins of Software Security: ""Sin 8: C++ Catastrophes."" Page 143" | |
| 101 | CWE-457,EN-Use of Uninitialized Variable (Type: Variant),"The code uses a variable that has not been initialized, leading to unpredictable or unintended results. | |
| 102 | In some languages such as C and C++, stack variables are not initialized by default. They generally contain junk data with the contents of stack memory before the function was invoked. An attacker can sometimes control or read these contents. In other languages or conditions, a variable that is not explicitly initialized can be given a default value that has security implications, depending on the logic of the program. The presence of an uninitialized variable can sometimes indicate a typographic error in the code.",,high,"Exploiting Uninitialized Data: http://www.felinemenace.org/~mercy/papers/UBehavior/UBehavior.zip | |
| 103 | MS08-014 : The Case of the Uninitialized Stack Variable Vulnerability: http://blogs.technet.com/swi/archive/2008/03/11/the-case-of-the-uninitialized-stack-variable-vulnerability.aspx | |
| 104 | 24 Deadly Sins of Software Security: ""Sin 8: C++ Catastrophes."" Page 143 | |
| 105 | The Art of Software Security Assessment: Chapter 7, ""Variable Initialization"", Page 312." | |
| 106 | CWE-467,EN-Use of sizeof() on a Pointer Type (Type: Variant),"The code calls sizeof() on a malloced pointer type, which always returns the wordsize/8. This can produce an unexpected result if the programmer intended to determine how much memory has been allocated. | |
| 107 | Data-structure sentinels are often used to mark the structure of data. A common example of this is the null character at the end of strings or a special sentinel to mark the end of a linked list. It is dangerous to allow this type of control data to be easily accessible. Therefore, it is important to protect from the addition or modification of sentinels.",,high,EXP01-A. Do not take the sizeof a pointer to determine the size of a type: https://www.securecoding.cert.org/confluence/display/seccode/EXP01-A.+Do+not+take+the+sizeof+a+pointer+to+determine+the+size+of+a+type | |
| 108 | CWE-486,EN-Comparison of Classes by Name (Type: Variant),"The program compares classes by name, which can cause it to use the wrong class when multiple classes can have the same name. | |
| 109 | If the decision to trust the methods and data of an object is based on the name of a class, it is possible for malicious users to send objects of the same name as trusted classes and thereby gain the trust afforded to known classes and types.",,high, | |
| 110 | CWE-493,EN-Critical Public Variable Without Final Modifier (Type: Variant),"The product has a critical public variable that is not final, which allows the variable to be modified to contain unexpected values. | |
| 111 | If a field is non-final and public, it can be changed once the value is set by any function that has access to the class which contains the field. This could lead to a vulnerability if other parts of the program make assumptions about the contents of that field.",,high, | |
| 112 | CWE-499,EN-Serializable Class Containing Sensitive Data (Type: Variant),"The code contains a class with sensitive data, but the class does not explicitly deny serialization. The data can be accessed by serializing the class through another class. | |
| 113 | Serializable classes are effectively open classes since data cannot be hidden in them. Classes that do not explicitly deny serialization can be serialized by any other class, which can then in turn use the data stored inside it.",,high, | |
| 114 | CWE-500,EN-Public Static Field Not Marked Final (Type: Variant),"An object contains a public static field that is not marked final, which might allow it to be modified in unexpected ways. | |
| 115 | Public static variables can be read without an accessor and changed without a mutator by any classes in the application.",,high, | |
| 116 | CWE-515,EN-Covert Storage Channel (Type: Base),"A covert storage channel transfers information through the setting of bits by one program and the reading of those bits by another. What distinguishes this case from that of ordinary operation is that the bits are used to convey encoded information. | |
| 117 | Covert storage channels occur when out-of-band data is stored in messages for the purpose of memory reuse. Covert channels are frequently classified as either storage or timing channels. Examples would include using a file intended to hold only audit information to convey user passwords--using the name of a file or perhaps status bits associated with it that can be read by all users to signal the contents of the file. Steganography, concealing information in such a manner that no one but the intended recipient knows of the existence of the message, is a good example of a covert storage channel.",,high, | |
| 118 | CWE-639,EN-Authorization Bypass Through User-Controlled Key (Type: Base),"The system's authorization functionality does not prevent one user from gaining access to another user's data or record by modifying the key value identifying the data. | |
| 119 | Retrieval of a user record occurs in the system based on some key value that is under user control. The key would typically identify a user related record stored in the system and would be used to lookup that record for presentation to the user. It is likely that an attacker would have to be an authenticated user in the system. However, the authorization process would not properly check the data access operation to ensure that the authenticated user performing the operation has sufficient entitlements to perform the requested data access, hence bypassing any other authorization checks present in the system. One manifestation of this weakness would be if a system used sequential or otherwise easily guessable session ids that would allow one user to easily switch to another user's session and read/modify their data.",,high, | |
| 120 | CWE-640,EN-Weak Password Recovery Mechanism for Forgotten Password (Type: Base),"The software contains a mechanism for users to recover or change their passwords without knowing the original password, but the mechanism is weak. | |
| 121 | It is common for an application to have a mechanism that provides a means for a user to gain access to their account in the event they forget their password. Very often the password recovery mechanism is weak, which has the effect of making it more likely that it would be possible for a person other than the legitimate system user to gain access to that user's account. | |
| 122 | This weakness may be that the security question is too easy to guess or find an answer to (e.g. because it is too common). Or there might be an implementation weakness in the password recovery mechanism code that may for instance trick the system into e-mailing the new password to an e-mail account other than that of the user. There might be no throttling done on the rate of password resets so that a legitimate user can be denied service by an attacker if an attacker tries to recover their password in a rapid succession. The system may send the original password to the user rather than generating a new temporary password. In summary, password recovery functionality, if not carefully designed and implemented can often become the system's weakest link that can be misused in a way that would allow an attacker to gain unauthorized access to the system. Weak password recovery schemes completely undermine a strong password authentication scheme.",,high,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 123 | CWE-642,EN-External Control of Critical State Data (Type: Class),"The software stores security-critical state information about its users, or the software itself, in a location that is accessible to unauthorized actors. | |
| 124 | If an attacker can modify the state information without detection, then it could be used to perform unauthorized actions or access unexpected resources, since the application programmer does not expect that the state can be changed. | |
| 125 | State information can be stored in various locations such as a cookie, in a hidden web form field, input parameter or argument, an environment variable, a database record, within a settings file, etc. All of these locations have the potential to be modified by an attacker. When this state information is used to control security or determine resource usage, then it may create a vulnerability. For example, an application may perform authentication, then save the state in an ""authenticated=true"" cookie. An attacker may simply create this cookie in order to bypass the authentication.",,high,"Top 10 2007-Insecure Direct Object Reference: http://www.owasp.org/index.php/Top_10_2007-A4 | |
| 126 | HMAC: http://en.wikipedia.org/wiki/Hmac | |
| 127 | 24 Deadly Sins of Software Security: ""Sin 4: Use of Magic URLs, Predictable Cookies, and Hidden Form Fields."" Page 75" | |
| 128 | CWE-643,EN-Improper Neutralization of Data within XPath Expressions (XPath Injection) (Type: Base),"The software uses external input to dynamically construct an XPath expression used to retrieve data from an XML database, but it does not neutralize or incorrectly neutralizes that input. This allows an attacker to control the structure of the query. | |
| 129 | The net effect is that the attacker will have control over the information selected from the XML database and may use that ability to control application flow, modify logic, retrieve unauthorized data, or bypass important checks (e.g. authentication).",,high,"XPath Injection: http://www.webappsec.org/projects/threat/classes/xpath_injection.shtml | |
| 130 | The Art of Software Security Assessment: Chapter 17, ""XPath Injection"", Page 1070." | |
| 131 | CWE-644,EN-Improper Neutralization of HTTP Headers for Scripting Syntax (Type: Variant),"The application does not neutralize or incorrectly neutralizes web scripting syntax in HTTP headers that can be used by web browser components that can process raw headers, such as Flash. | |
| 132 | An attacker may be able to conduct cross-site scripting and other attacks against users who have these components enabled. | |
| 133 | If an application does not neutralize user controlled data being placed in the header of an HTTP response coming from the server, the header may contain a script that will get executed in the client's browser context, potentially resulting in a cross site scripting vulnerability or possibly an HTTP response splitting attack. It is important to carefully control data that is being placed both in HTTP response header and in the HTTP response body to ensure that no scripting syntax is present, taking various encodings into account.",,high, | |
| 134 | CWE-645,EN-Overly Restrictive Account Lockout Mechanism (Type: Base),"The software contains an account lockout protection mechanism, but the mechanism is too restrictive and can be triggered too easily. This allows attackers to deny service to legitimate users by causing their accounts to be locked out. | |
| 135 | Account lockout is a security feature often present in applications as a countermeasure to the brute force attack on the password based authentication mechanism of the system. After a certain number of failed login attempts, the users' account may be disabled for a certain period of time or until it is unlocked by an administrator. Other security events may also possibly trigger account lockout. However, an attacker may use this very security feature to deny service to legitimate system users. It is therefore important to ensure that the account lockout security mechanism is not overly restrictive.",,high, | |
| 136 | CWE-646,EN-Reliance on File Name or Extension of Externally-Supplied File (Type: Variant),"The software allows a file to be uploaded, but it relies on the file name or extension of the file to determine the appropriate behaviors. This could be used by attackers to cause the file to be misclassified and processed in a dangerous fashion. | |
| 137 | An application might use the file name or extension of of a user-supplied file to determine the proper course of action, such as selecting the correct process to which control should be passed, deciding what data should be made available, or what resources should be allocated. If the attacker can cause the code to misclassify the supplied file, then the wrong action could occur. For example, an attacker could supply a file that ends in a "".php.gif"" extension that appears to be a GIF image, but would be processed as PHP code. In extreme cases, code execution is possible, but the attacker could also cause exhaustion of resources, denial of service, exposure of debug or system data (including application source code), or being bound to a particular server side process. This weakness may be due to a vulnerability in any of the technologies used by the web and application servers, due to misconfiguration, or resultant from another flaw in the application itself.",,high, | |
| 138 | CWE-647,EN-Use of Non-Canonical URL Paths for Authorization Decisions (Type: Variant),"The software defines policy namespaces and makes authorization decisions based on the assumption that a URL is canonical. This can allow a non-canonical URL to bypass the authorization. | |
| 139 | If an application defines policy namespaces and makes authorization decisions based on the URL, but it does not require or convert to a canonical URL before making the authorization decision, then it opens the application to attack. For example, if the application only wants to allow access to http://www.example.com/mypage, then the attacker might be able to bypass this restriction using equivalent URLs such as: | |
| 140 | http://WWW.EXAMPLE.COM/mypage | |
| 141 | http://www.example.com/%6Dypage (alternate encoding) | |
| 142 | http://192.168.1.1/mypage (IP address) | |
| 143 | http://www.example.com/mypage/ (trailing /) | |
| 144 | http://www.example.com:80/mypage | |
| 145 | Therefore it is important to specify access control policy that is based on the path information in some canonical form with all alternate encodings rejected (which can be accomplished by a default deny rule).",,high, | |
| 146 | CWE-649,EN-Reliance on Obfuscation or Encryption of Security-Relevant Inputs without Integrity Checking (Type: Base),"The software uses obfuscation or encryption of inputs that should not be mutable by an external actor, but the software does not use integrity checks to detect if those inputs have been modified. | |
| 147 | When an application relies on obfuscation or incorrectly applied / weak encryption to protect client-controllable tokens or parameters, that may have an effect on the user state, system state, or some decision made on the server. Without protecting the tokens/parameters for integrity, the application is vulnerable to an attack where an adversary blindly traverses the space of possible values of the said token/parameter in order to attempt to gain an advantage. The goal of the attacker is to find another admissible value that will somehow elevate his or her privileges in the system, disclose information or change the behavior of the system in some way beneficial to the attacker. If the application does not protect these critical tokens/parameters for integrity, it will not be able to determine that these values have been tampered with. Measures that are used to protect data for confidentiality should not be relied upon to provide the integrity service.",,high, | |
| 148 | CWE-650,EN-Trusting HTTP Permission Methods on the Server Side (Type: Variant),"The server contains a protection mechanism that assumes that any URI that is accessed using HTTP GET will not cause a state change to the associated resource. This might allow attackers to bypass intended access restrictions and conduct resource modification and deletion attacks, since some applications allow GET to modify state. | |
| 149 | An application may disallow the HTTP requests to perform DELETE, PUT and POST operations on the resource representation, believing that it will be enough to prevent unintended resource alterations. Even though the HTTP GET specification requires that GET requests should not have side effects, there is nothing in the HTTP protocol itself that prevents the HTTP GET method from performing more than just query of the data. For instance, it is a common practice with REST based Web Services to have HTTP GET requests modifying resources on the server side. Whenever that happens however, the access control needs to be properly enforced in the application. No assumptions should be made that only HTTP DELETE, PUT, and POST methods have the power to alter the representation of the resource being accessed in the request.",,high, | |
| 150 | CWE-652,EN-Improper Neutralization of Data within XQuery Expressions (XQuery Injection) (Type: Base),"The software uses external input to dynamically construct an XQuery expression used to retrieve data from an XML database, but it does not neutralize or incorrectly neutralizes that input. This allows an attacker to control the structure of the query. | |
| 151 | The net effect is that the attacker will have control over the information selected from the XML database and may use that ability to control application flow, modify logic, retrieve unauthorized data, or bypass important checks (e.g. authentication).",,high, | |
| 152 | CWE-676,EN-Use of Potentially Dangerous Function (Type: Base),"The program invokes a potentially dangerous function that could introduce a vulnerability if it is used incorrectly, but the function can also be used safely. | |
| 153 | Typically, a product defines its control sphere within the code itself, or through configuration by the product's administrator. In some cases, an external party can change the definition of the control sphere. This is typically a resultant weakness.",,high,"Security Development Lifecycle (SDL) Banned Function Calls: http://msdn.microsoft.com/en-us/library/bb288454.aspx | |
| 154 | Writing Secure Code: Chapter 5, ""Safe String Handling"" Page 156, 160 | |
| 155 | The Art of Software Security Assessment: Chapter 8, ""C String Handling"", Page 388." | |
| 156 | CWE-682,EN-Incorrect Calculation (Type: Class),"The software performs a calculation that generates incorrect or unintended results that are later used in security-critical decisions or resource management.. | |
| 157 | When software performs a security-critical calculation incorrectly, it might lead to incorrect resource allocations, incorrect privilege assignments, or failed comparisons among other things. Many of the direct results of an incorrect calculation can lead to even larger problems such as failed protection mechanisms or even arbitrary code execution.",,high,"SafeInt: http://safeint.codeplex.com/ | |
| 158 | 24 Deadly Sins of Software Security: ""Sin 7: Integer Overflows."" Page 119 | |
| 159 | The Art of Software Security Assessment: Chapter 6, ""Signed Integer Boundaries"", Page 220." | |
| 160 | CWE-78,EN-Improper Neutralization of Special Elements used in an OS Command (OS Command Injection) (Type: Base),"The software constructs all or part of an OS command using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended OS command when it is sent to a downstream component.. | |
| 161 | This could allow attackers to execute unexpected, dangerous commands directly on the operating system. This weakness can lead to a vulnerability in environments in which the attacker does not have direct access to the operating system, such as in web applications. Alternately, if the weakness occurs in a privileged program, it could allow the attacker to specify commands that normally would not be accessible, or to call alternate commands with privileges that the attacker does not have. The problem is exacerbated if the compromised process does not follow the principle of least privilege, because the attacker-controlled commands may run with special system privileges that increases the amount of damage. | |
| 162 | There are at least two subtypes of OS command injection: | |
| 163 | The application intends to execute a single, fixed program that is under its own control. It intends to use externally-supplied inputs as arguments to that program. For example, the program might use system(""nslookup [HOSTNAME]"") to run nslookup and allow the user to supply a HOSTNAME, which is used as an argument. Attackers cannot prevent nslookup from executing. However, if the program does not remove command separators from the HOSTNAME argument, attackers could place the separators into the arguments, which allows them to execute their own program after nslookup has finished executing. | |
| 164 | The application accepts an input that it uses to fully select which program to run, as well as which commands to use. The application simply redirects this entire command to the operating system. For example, the program might use ""exec([COMMAND])"" to execute the [COMMAND] that was supplied by the user. If the COMMAND is under attacker control, then the attacker can execute arbitrary commands or programs. If the command is being executed using functions like exec() and CreateProcess(), the attacker might not be able to combine multiple commands together in the same line. | |
| 165 | From a weakness standpoint, these variants represent distinct programmer errors. In the first variant, the programmer clearly intends that input from untrusted parties will be part of the arguments in the command to be executed. In the second variant, the programmer does not intend for the command to be accessible to any untrusted party, but the programmer probably has not accounted for alternate ways in which malicious attackers can provide input.",,high,"Exploiting Software: How to Break Code | |
| 166 | Meta-Character Vulnerabilities: http://www.cs.purdue.edu/homes/cs390s/slides/week09.pdf | |
| 167 | OS Commanding: http://projects.webappsec.org/OS-Commanding | |
| 168 | The World Wide Web Security FAQ: http://www.w3.org/Security/Faq/wwwsf4.html | |
| 169 | Security Issues in Perl Scripts: http://www.cgisecurity.com/lib/sips.html | |
| 170 | 24 Deadly Sins of Software Security: ""Sin 10: Command Injection."" Page 171 | |
| 171 | Top 25 Series - Rank 9 - OS Command Injection: http://blogs.sans.org/appsecstreetfighter/2010/02/24/top-25-series-rank-9-os-command-injection/ | |
| 172 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 173 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 174 | The Art of Software Security Assessment: Chapter 8, ""Shell Metacharacters"", Page 425." | |
| 175 | CWE-784,EN-Reliance on Cookies without Validation and Integrity Checking in a Security Decision (Type: Variant),"The application uses a protection mechanism that relies on the existence or values of a cookie, but it does not properly ensure that the cookie is valid for the associated user. | |
| 176 | Attackers can easily modify cookies, within the browser or by implementing the client-side code outside of the browser. Attackers can bypass protection mechanisms such as authorization and authentication by modifying the cookie to contain an expected value.",,high,"Unforgivable Vulnerabilities: http://cve.mitre.org/docs/docs-2007/unforgivable.pdf | |
| 177 | Writing Secure Code: Chapter 13, ""Sensitive Data in Cookies and Fields"" Page 435" | |
| 178 | CWE-862,EN-Missing Authorization (Type: Class),"The software does not perform an authorization check when an actor attempts to access a resource or perform an action. | |
| 179 | Assuming a user with a given identity, authorization is the process of determining whether that user can access a given resource, based on the user's privileges and any permissions or other access-control specifications that apply to the resource. | |
| 180 | When access control checks are not applied, users are able to access data or perform actions that they should not be allowed to perform. This can lead to a wide range of problems, including information exposures, denial of service, and arbitrary code execution.",,high,"Role Based Access Control and Role Based Security: http://csrc.nist.gov/groups/SNS/rbac/ | |
| 181 | Writing Secure Code: Chapter 4, ""Authorization"" Page 114; Chapter 6, ""Determining Appropriate Access Control"" Page 171 | |
| 182 | Top 25 Series - Rank 5 - Improper Access Control (Authorization): http://blogs.sans.org/appsecstreetfighter/2010/03/04/top-25-series-rank-5-improper-access-control-authorization/ | |
| 183 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 184 | Authentication using JAAS: http://www.javaranch.com/journal/2008/04/authentication-using-JAAS.html | |
| 185 | The Art of Software Security Assessment: Chapter 2, ""Common Vulnerabilities of Authorization"", Page 39." | |
| 186 | CWE-863,EN-Incorrect Authorization (Type: Class),"The software performs an authorization check when an actor attempts to access a resource or perform an action, but it does not correctly perform the check. This allows attackers to bypass intended access restrictions. | |
| 187 | Assuming a user with a given identity, authorization is the process of determining whether that user can access a given resource, based on the user's privileges and any permissions or other access-control specifications that apply to the resource. | |
| 188 | When access control checks are incorrectly applied, users are able to access data or perform actions that they should not be allowed to perform. This can lead to a wide range of problems, including information exposures, denial of service, and arbitrary code execution.",,high,"Role Based Access Control and Role Based Security: http://csrc.nist.gov/groups/SNS/rbac/ | |
| 189 | Writing Secure Code: Chapter 4, ""Authorization"" Page 114; Chapter 6, ""Determining Appropriate Access Control"" Page 171 | |
| 190 | Top 25 Series - Rank 5 - Improper Access Control (Authorization): http://blogs.sans.org/appsecstreetfighter/2010/03/04/top-25-series-rank-5-improper-access-control-authorization/ | |
| 191 | Authentication using JAAS: http://www.javaranch.com/journal/2008/04/authentication-using-JAAS.html | |
| 192 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 193 | The Art of Software Security Assessment: Chapter 2, ""Common Vulnerabilities of Authorization"", Page 39." | |
| 194 | CWE-99,EN-Improper Control of Resource Identifiers (Resource Injection) (Type: Base),"The software receives input from an upstream component, but it does not restrict or incorrectly restricts the input before it is used as an identifier for a resource that may be outside the intended sphere of control. | |
| 195 | This may enable an attacker to access or modify otherwise protected system resources.",,high, | |
| 196 | CWE-120,EN-Buffer Copy without Checking Size of Input (Classic Buffer Overflow) (Type: Base),"The program copies an input buffer to an output buffer without verifying that the size of the input buffer is less than the size of the output buffer, leading to a buffer overflow. | |
| 197 | A buffer overflow condition exists when a program attempts to put more data in a buffer than it can hold, or when a program attempts to put data in a memory area outside of the boundaries of a buffer. The simplest type of error, and the most common cause of buffer overflows, is the ""classic"" case in which the program copies the buffer without restricting how much is copied. Other variants exist, but the existence of a classic overflow strongly suggests that the programmer is not considering even the most basic of security protections.",,high,"Writing Secure Code: Chapter 5, ""Public Enemy #1: The Buffer Overrun"" Page 127 | |
| 198 | 24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89 | |
| 199 | Using the Strsafe.h Functions: http://msdn.microsoft.com/en-us/library/ms647466.aspx | |
| 200 | Safe C String Library v1.0.3: http://www.zork.org/safestr/ | |
| 201 | Address Space Layout Randomization in Windows Vista: http://blogs.msdn.com/michael_howard/archive/2006/05/26/address-space-layout-randomization-in-windows-vista.aspx | |
| 202 | Limiting buffer overflows with ExecShield: http://www.redhat.com/magazine/009jul05/features/execshield/ | |
| 203 | PaX: http://en.wikipedia.org/wiki/PaX | |
| 204 | Top 25 Series - Rank 3 - Classic Buffer Overflow: http://software-security.sans.org/blog/2010/03/02/top-25-series-rank-3-classic-buffer-overflow/ | |
| 205 | Understanding DEP as a mitigation technology part 1: http://blogs.technet.com/b/srd/archive/2009/06/12/understanding-dep-as-a-mitigation-technology-part-1.aspx | |
| 206 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 207 | The Art of Software Security Assessment: Chapter 3, ""Nonexecutable Stack"", Page 76. | |
| 208 | The Art of Software Security Assessment: Chapter 5, ""Protection Mechanisms"", Page 189. | |
| 209 | The Art of Software Security Assessment: Chapter 8, ""C String Handling"", Page 388." | |
| 210 | CWE-122,EN-Heap-based Buffer Overflow (Type: Variant),"A heap overflow condition is a buffer overflow, where the buffer that can be overwritten is allocated in the heap portion of memory, generally meaning that the buffer was allocated using a routine such as malloc(). | |
| 211 | A buffer overflow condition exists when a program attempts to put more data in a buffer than it can hold, or when a program attempts to put data in a memory area outside of the boundaries of a buffer. The simplest type of error, and the most common cause of buffer overflows, is the ""classic"" case in which the program copies the buffer without restricting how much is copied. Other variants exist, but the existence of a classic overflow strongly suggests that the programmer is not considering even the most basic of security protections.",,high,"Writing Secure Code: Chapter 5, ""Heap Overruns"" Page 138 | |
| 212 | 24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89 | |
| 213 | The Art of Software Security Assessment: Chapter 3, ""Nonexecutable Stack"", Page 76. | |
| 214 | The Art of Software Security Assessment: Chapter 5, ""Protection Mechanisms"", Page 189." | |
| 215 | CWE-131,EN-Incorrect Calculation of Buffer Size (Type: Base),"The software does not correctly calculate the size to be used when allocating a buffer, which could lead to a buffer overflow. | |
| 216 | If an attacker can manipulate the length parameter associated with an input such that it is inconsistent with the actual length of the input, this can be leveraged to cause the target application to behave in unexpected, and possibly, malicious ways. One of the possible motives for doing so is to pass in arbitrarily large input to the application. Another possible motivation is the modification of application state by including invalid data for subsequent properties of the application. Such weaknesses commonly lead to attacks such as buffer overflows and execution of arbitrary code.",,high,"SafeInt: http://safeint.codeplex.com/ | |
| 217 | Top 25 Series - Rank 18 - Incorrect Calculation of Buffer Size: http://software-security.sans.org/blog/2010/03/19/top-25-series-rank-18-incorrect-calculation-of-buffer-size | |
| 218 | Address Space Layout Randomization in Windows Vista: http://blogs.msdn.com/michael_howard/archive/2006/05/26/address-space-layout-randomization-in-windows-vista.aspx | |
| 219 | Understanding DEP as a mitigation technology part 1: http://blogs.technet.com/b/srd/archive/2009/06/12/understanding-dep-as-a-mitigation-technology-part-1.aspx | |
| 220 | PaX: http://en.wikipedia.org/wiki/PaX | |
| 221 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 222 | Writing Secure Code: Chapter 20, ""Integer Overflows"" Page 620 | |
| 223 | 24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89 | |
| 224 | The Art of Software Security Assessment: Chapter 8, ""Incrementing Pointers Incorrectly"", Page 401." | |
| 225 | CWE-22,EN-Improper Limitation of a Pathname to a Restricted Directory (Path Traversal) (Type: Class),"The software uses external input to construct a pathname that is intended to identify a file or directory that is located underneath a restricted parent directory, but the software does not properly neutralize special elements within the pathname that can cause the pathname to resolve to a location that is outside of the restricted directory. | |
| 226 | Many file operations are intended to take place within a restricted directory. By using special elements such as "".."" and ""/"" separators, attackers can escape outside of the restricted location to access files or directories that are elsewhere on the system. One of the most common special elements is the ""../"" sequence, which in most modern operating systems is interpreted as the parent directory of the current location. This is referred to as relative path traversal. Path traversal also covers the use of absolute pathnames such as ""/usr/local/bin"", which may also be useful in accessing unexpected files. This is referred to as absolute path traversal. | |
| 227 | In many programming languages, the injection of a null byte (the 0 or NUL) may allow an attacker to truncate a generated filename to widen the scope of attack. For example, the software may add "".txt"" to any pathname, thus limiting the attacker to text files, but a null injection may effectively remove this restriction.",,high,"Writing Secure Code: Chapter 11, ""Directory Traversal and Using Parent Paths (..)"" Page 370 | |
| 228 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 229 | Testing for Path Traversal (OWASP-AZ-001): http://www.owasp.org/index.php/Testing_for_Path_Traversal_(OWASP-AZ-001) | |
| 230 | Top 25 Series - Rank 7 - Path Traversal: http://blogs.sans.org/appsecstreetfighter/2010/03/09/top-25-series-rank-7-path-traversal/ | |
| 231 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 232 | The Art of Software Security Assessment: Chapter 9, ""Filenames and Paths"", Page 503." | |
| 233 | CWE-311,EN-Missing Encryption of Sensitive Data (Type: Base),"The software does not encrypt sensitive or critical information before storage or transmission. | |
| 234 | The lack of proper data encryption passes up the guarantees of confidentiality, integrity, and accountability that properly implemented encryption conveys.",,high,"Writing Secure Code: Chapter 9, ""Protecting Secret Data"" Page 299 | |
| 235 | 24 Deadly Sins of Software Security: ""Sin 17: Failure to Protect Stored Data."" Page 253 | |
| 236 | Top 25 Series - Rank 10 - Missing Encryption of Sensitive Data: http://blogs.sans.org/appsecstreetfighter/2010/02/26/top-25-series-rank-10-missing-encryption-of-sensitive-data/ | |
| 237 | The Art of Software Security Assessment: Chapter 2, ""Common Vulnerabilities of Encryption"", Page 43. | |
| 238 | SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf" | |
| 239 | CWE-464,EN-Addition of Data Structure Sentinel (Type: Base),"The accidental addition of a data-structure sentinel can cause serious programming logic problems. | |
| 240 | Data-structure sentinels are often used to mark the structure of data. A common example of this is the null character at the end of strings or a special sentinel to mark the end of a linked list. It is dangerous to allow this type of control data to be easily accessible. Therefore, it is important to protect from the addition or modification of sentinels.",,high, | |
| 241 | CWE-67,EN-Improper Handling of Windows Device Names (Type: Variant),"The software constructs pathnames from user input, but it does not handle or incorrectly handles a pathname containing a Windows device name such as AUX or CON. This typically leads to denial of service or an information exposure when the application attempts to process the pathname as a regular file. | |
| 242 | Not properly handling virtual filenames (e.g. AUX, CON, PRN, COM1, LPT1) can result in different types of vulnerabilities. In some cases an attacker can request a device via injection of a virtual filename in a URL, which may cause an error that leads to a denial of service or an error page that reveals sensitive information. A software system that allows device names to bypass filtering runs the risk of an attacker injecting malicious code in a file with the name of a device.",,high,"Writing Secure Code | |
| 243 | The Art of Software Security Assessment: Chapter 11, ""Device Files"", Page 666." | |
| 244 | CWE-73,EN-External Control of File Name or Path (Type: Class),"The software allows user input to control or influence paths or file names that are used in filesystem operations. | |
| 245 | This could allow an attacker to access or modify system files or other files that are critical to the application. | |
| 246 | Path manipulation errors occur when the following two conditions are met: | |
| 247 | 1. An attacker can specify a path used in an operation on the filesystem. | |
| 248 | 2. By specifying the resource, the attacker gains a capability that would not otherwise be permitted. | |
| 249 | For example, the program may give the attacker the ability to overwrite the specified file or run with a configuration controlled by the attacker.",,high,OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 250 | CWE-76,EN-Improper Neutralization of Equivalent Special Elements (Type: Base),"The software properly neutralizes certain special elements, but it improperly neutralizes equivalent special elements. | |
| 251 | The software may have a fixed list of special characters it believes is complete. However, there may be alternate encodings, or representations that also have the same meaning. For example, the software may filter out a leading slash (/) to prevent absolute path names, but does not account for a tilde (~) followed by a user name, which on some *nix systems could be expanded to an absolute pathname. Alternately, the software might filter a dangerous ""-e"" command-line switch when calling an external program, but it might not account for ""--exec"" or other switches that have the same semantics.",,high, | |
| 252 | CWE-79,EN-Improper Neutralization of Input During Web Page Generation (Cross-site Scripting) (Type: Base),"The software does not neutralize or incorrectly neutralizes user-controllable input before it is placed in output that is used as a web page that is served to other users. | |
| 253 | Cross-site scripting (XSS) vulnerabilities occur when: | |
| 254 | 1. Untrusted data enters a web application, typically from a web request. | |
| 255 | 2. The web application dynamically generates a web page that contains this untrusted data. | |
| 256 | 3. During page generation, the application does not prevent the data from containing content that is executable by a web browser, such as JavaScript, HTML tags, HTML attributes, mouse events, Flash, ActiveX, etc. | |
| 257 | 4. A victim visits the generated web page through a web browser, which contains malicious script that was injected using the untrusted data. | |
| 258 | 5. Since the script comes from a web page that was sent by the web server, the victim's web browser executes the malicious script in the context of the web server's domain. | |
| 259 | 6. This effectively violates the intention of the web browser's same-origin policy, which states that scripts in one domain should not be able to access resources or run code in a different domain. | |
| 260 | There are three main kinds of XSS: | |
| 261 | The server reads data directly from the HTTP request and reflects it back in the HTTP response. Reflected XSS exploits occur when an attacker causes a victim to supply dangerous content to a vulnerable web application, which is then reflected back to the victim and executed by the web browser. The most common mechanism for delivering malicious content is to include it as a parameter in a URL that is posted publicly or e-mailed directly to the victim. URLs constructed in this manner constitute the core of many phishing schemes, whereby an attacker convinces a victim to visit a URL that refers to a vulnerable site. After the site reflects the attacker's content back to the victim, the content is executed by the victim's browser. | |
| 262 | The application stores dangerous data in a database, message forum, visitor log, or other trusted data store. At a later time, the dangerous data is subsequently read back into the application and included in dynamic content. From an attacker's perspective, the optimal place to inject malicious content is in an area that is displayed to either many users or particularly interesting users. Interesting users typically have elevated privileges in the application or interact with sensitive data that is valuable to the attacker. If one of these users executes malicious content, the attacker may be able to perform privileged operations on behalf of the user or gain access to sensitive data belonging to the user. For example, the attacker might inject XSS into a log message, which might not be handled properly when an administrator views the logs. | |
| 263 | In DOM-based XSS, the client performs the injection of XSS into the page; in the other types, the server performs the injection. DOM-based XSS generally involves server-controlled, trusted script that is sent to the client, such as Javascript that performs sanity checks on a form before the user submits it. If the server-supplied script processes user-supplied data and then injects it back into the web page (such as with dynamic HTML), then DOM-based XSS is possible. | |
| 264 | Once the malicious script is injected, the attacker can perform a variety of malicious activities. The attacker could transfer private information, such as cookies that may include session information, from the victim's machine to the attacker. The attacker could send malicious requests to a web site on behalf of the victim, which could be especially dangerous to the site if the victim has administrator privileges to manage that site. Phishing attacks could be used to emulate trusted web sites and trick the victim into entering a password, allowing the attacker to compromise the victim's account on that web site. Finally, the script could exploit a vulnerability in the web browser itself possibly taking over the victim's machine, sometimes referred to as ""drive-by hacking."" | |
| 265 | In many cases, the attack can be launched without the victim even being aware of it. Even with careful users, attackers frequently use a variety of methods to encode the malicious portion of the attack, such as URL encoding or Unicode, so the request looks less suspicious.",,high,"XSS Attacks | |
| 266 | 24 Deadly Sins of Software Security: ""Sin 2: Web-Server Related Vulnerabilities (XSS, XSRF, and Response Splitting)."" Page 31 | |
| 267 | 24 Deadly Sins of Software Security: ""Sin 3: Web-Client Related Vulnerabilities (XSS)."" Page 63 | |
| 268 | Cross-site scripting: http://en.wikipedia.org/wiki/Cross-site_scripting | |
| 269 | Writing Secure Code: Chapter 13, ""Web-Specific Input Issues"" Page 413 | |
| 270 | XSS (Cross Site Scripting) Cheat Sheet: http://ha.ckers.org/xss.html | |
| 271 | Mitigating Cross-site Scripting With HTTP-only Cookies: http://msdn.microsoft.com/en-us/library/ms533046.aspx | |
| 272 | Anti-XSS 3.0 Beta and CAT.NET Community Technology Preview now Live!: http://blogs.msdn.com/cisg/archive/2008/12/15/anti-xss-3-0-beta-and-cat-net-community-technology-preview-now-live.aspx | |
| 273 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 274 | XSS Defense HOWTO: http://blog.modsecurity.org/2008/07/do-you-know-how.html | |
| 275 | Web Application Firewall: http://www.owasp.org/index.php/Web_Application_Firewall | |
| 276 | Web Application Firewall Evaluation Criteria: http://www.webappsec.org/projects/wafec/v1/wasc-wafec-v1.0.html | |
| 277 | Firefox Implements httpOnly And is Vulnerable to XMLHTTPRequest | |
| 278 | XMLHttpRequest allows reading HTTPOnly cookies: https://bugzilla.mozilla.org/show_bug.cgi?id=380418 | |
| 279 | Apache Wicket: http://wicket.apache.org/ | |
| 280 | XSS (Cross Site Scripting) Prevention Cheat Sheet: http://www.owasp.org/index.php/XSS_(Cross_Site_Scripting)_Prevention_Cheat_Sheet | |
| 281 | DOM based XSS Prevention Cheat Sheet: http://www.owasp.org/index.php/DOM_based_XSS_Prevention_Cheat_Sheet | |
| 282 | Top 25 series - Rank 1 - Cross Site Scripting: http://blogs.sans.org/appsecstreetfighter/2010/02/22/top-25-series-rank-1-cross-site-scripting/ | |
| 283 | The Art of Software Security Assessment: Chapter 17, ""Cross Site Scripting"", Page 1071." | |
| 284 | CWE-80,EN-Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special characters such as ""<"", "">"", and ""&"" that could be interpreted as web-scripting elements when they are sent to a downstream component that processes web pages. | |
| 285 | This may allow such characters to be treated as control characters, which are executed client-side in the context of the user's session. Although this can be classified as an injection problem, the more pertinent issue is the improper conversion of such special characters to respective context-appropriate entities before displaying them to the user.",,high, | |
| 286 | CWE-98,EN-Improper Control of Filename for Include/Require Statement in PHP Program (PHP Remote File Inclusion) (Type: Base),"The PHP application receives input from an upstream component, but it does not restrict or incorrectly restricts the input before its usage in ""require,"" ""include,"" or similar functions. | |
| 287 | In certain versions and configurations of PHP, this can allow an attacker to specify a URL to a remote location from which the software will obtain the code to execute. In other cases in association with path traversal, the attacker can specify a local file that may contain executable statements that can be parsed by PHP.",,high,"Testing for Path Traversal (OWASP-AZ-001): http://www.owasp.org/index.php/Testing_for_Path_Traversal_(OWASP-AZ-001) | |
| 288 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 289 | A Study in Scarlet: http://www.cgisecurity.com/lib/studyinscarlet.txt | |
| 290 | Suhosin: http://www.hardened-php.net/suhosin/ | |
| 291 | Top 25 Series - Rank 13 - PHP File Inclusion: http://blogs.sans.org/appsecstreetfighter/2010/03/11/top-25-series-rank-13-php-file-inclusion/" | |
| 292 | CWE-188,EN-Reliance on Data/Memory Layout (Type: Base),"The software makes invalid assumptions about how protocol data or memory is organized at a lower level, resulting in unintended program behavior. | |
| 293 | For example, an attacker might succeed in authentication by providing a small password that matches the associated portion of the larger, correct password.",,low,"The Art of Software Security Assessment: Chapter 6, ""Structure Padding"", Page 284." | |
| 294 | CWE-197,EN-Numeric Truncation Error (Type: Base),"Truncation errors occur when a primitive is cast to a primitive of a smaller size and data is lost in the conversion. | |
| 295 | When a primitive is cast to a smaller primitive, the high order bits of the large value are lost in the conversion, potentially resulting in an unexpected value that is not equal to the original value. This value may be required as an index into a buffer, a loop iterator, or simply necessary state data. In any case, the value cannot be trusted and the system will be in an undefined state. While this method may be employed viably to isolate the low bits of a value, this usage is rare, and truncation usually implies that an implementation error has occurred.",,low,"The Art of Software Security Assessment: Chapter 6, ""Truncation"", Page 259." | |
| 296 | CWE-252,EN-Unchecked Return Value (Type: Base),"The software does not check the return value from a method or function, which can prevent it from detecting unexpected states and conditions. | |
| 297 | Two common programmer assumptions are ""this function call can never fail"" and ""it doesn't matter if this function call fails"". If an attacker can force the function to fail or otherwise return a value that is not expected, then the subsequent program logic could lead to a vulnerability, because the software is not in a state that the programmer assumes. For example, if the program calls a function to drop privileges but does not check the return code to ensure that privileges were successfully dropped, then the program will continue to operate with the higher privileges.",,low,"The Art of Software Security Assessment: Chapter 7, ""Program Building Blocks"" Page 341. | |
| 298 | Writing Secure Code: Chapter 20, ""Checking Returns"" Page 624 | |
| 299 | 24 Deadly Sins of Software Security: ""Sin 11: Failure to Handle Errors Correctly."" Page 183 | |
| 300 | ERR10-CPP. Check for error conditions: https://www.securecoding.cert.org/confluence/display/cplusplus/ERR10-CPP.+Check+for+error+conditions" | |
| 301 | CWE-253,EN-Incorrect Check of Function Return Value (Type: Base),"The software incorrectly checks a return value from a function, which prevents the software from detecting errors or exceptional conditions. | |
| 302 | Two common programmer assumptions are ""this function call can never fail"" and ""it doesn't matter if this function call fails"". If an attacker can force the function to fail or otherwise return a value that is not expected, then the subsequent program logic could lead to a vulnerability, because the software is not in a state that the programmer assumes. For example, if the program calls a function to drop privileges but does not check the return code to ensure that privileges were successfully dropped, then the program will continue to operate with the higher privileges.",,low,"The Art of Software Security Assessment: Chapter 7, ""Return Value Testing and Interpretation"", Page 340." | |
| 303 | CWE-296,EN-Improper Following of a Certificates Chain of Trust (Type: Base),"The software does not follow, or incorrectly follows, the chain of trust for a certificate back to a trusted root certificate, resulting in incorrect trust of any resource that is associated with that certificate. | |
| 304 | If a system does not follow the chain of trust of a certificate to a root server, the certificate loses all usefulness as a metric of trust. Essentially, the trust gained from a certificate is derived from a chain of trust -- with a reputable trusted entity at the end of that list. The end user must trust that reputable source, and this reputable source must vouch for the resource in question through the medium of the certificate. | |
| 305 | In some cases, this trust traverses several entities who vouch for one another. The entity trusted by the end user is at one end of this trust chain, while the certificate-wielding resource is at the other end of the chain. If the user receives a certificate at the end of one of these trust chains and then proceeds to check only that the first link in the chain, no real trust has been derived, since the entire chain must be traversed back to a trusted source to verify the certificate. | |
| 306 | There are several ways in which the chain of trust might be broken, including but not limited to: | |
| 307 | Any certificate in the chain is self-signed, unless it the root. | |
| 308 | Not every intermediate certificate is checked, starting from the original certificate all the way up to the root certificate. | |
| 309 | An intermediate, CA-signed certificate does not have the expected Basic Constraints or other important extensions. | |
| 310 | The root certificate has been compromised or authorized to the wrong party.",,low,"The Most Dangerous Code in the World: Validating SSL Certificates in Non-Browser Software: http://www.cs.utexas.edu/~shmat/shmat_ccs12.pdf | |
| 311 | 24 Deadly Sins of Software Security: ""Sin 23: Improper Use of PKI, Especially SSL."" Page 347" | |
| 312 | CWE-298,EN-Improper Validation of Certificate Expiration (Type: Variant),"A certificate expiration is not validated or is incorrectly validated, so trust may be assigned to certificates that have been abandoned due to age. | |
| 313 | When the expiration of a certificate is not taken into account, no trust has necessarily been conveyed through it. Therefore, the validity of the certificate cannot be verified and all benefit of the certificate is lost.",,low,"24 Deadly Sins of Software Security: ""Sin 23: Improper Use of PKI, Especially SSL."" Page 347" | |
| 314 | CWE-324,EN-Use of a Key Past its Expiration Date (Type: Base),"The product uses a cryptographic key or password past its expiration date, which diminishes its safety significantly by increasing the timing window for cracking attacks against that key. | |
| 315 | While the expiration of keys does not necessarily ensure that they are compromised, it is a significant concern that keys which remain in use for prolonged periods of time have a decreasing probability of integrity. For this reason, it is important to replace keys within a period of time proportional to their strength.",,low,"24 Deadly Sins of Software Security: ""Sin 23: Improper Use of PKI, Especially SSL."" Page 347" | |
| 316 | CWE-379,EN-Creation of Temporary File in Directory with Incorrect Permissions (Type: Base),"The software creates a temporary file in a directory whose permissions allow unintended actors to determine the file's existence or otherwise access that file. | |
| 317 | On some operating systems, the fact that the temporary file exists may be apparent to any user with sufficient privileges to access that directory. Since the file is visible, the application that is using the temporary file could be known. If one has access to list the processes on the system, the attacker has gained information about what the user is doing at that time. By correlating this with the applications the user is running, an attacker could potentially discover what a user's actions are. From this, higher levels of security could be breached.",,low,"The Art of Software Security Assessment: Chapter 9, ""Temporary Files"", Page 538." | |
| 318 | CWE-462,EN-Duplicate Key in Associative List (Alist) (Type: Base),"Duplicate keys in associative lists can lead to non-unique keys being mistaken for an error. | |
| 319 | A duplicate key entry -- if the alist is designed properly -- could be used as a constant time replace function. However, duplicate key entries could be inserted by mistake. Because of this ambiguity, duplicate key entries in an association list are not recommended and should not be allowed.",,low, | |
| 320 | CWE-479,EN-Signal Handler Use of a Non-reentrant Function (Type: Variant),"The program defines a signal handler that calls a non-reentrant function. | |
| 321 | Non-reentrant functions are functions that cannot safely be called, interrupted, and then recalled before the first call has finished without resulting in memory corruption. This can lead to an unexpected system state an unpredictable results with a variety of potential consequences depending on context, including denial of service and code execution. | |
| 322 | Many functions are not reentrant, but some of them can result in the corruption of memory if they are used in a signal handler. The function call syslog() is an example of this. In order to perform its functionality, it allocates a small amount of memory as ""scratch space."" If syslog() is suspended by a signal call and the signal handler calls syslog(), the memory used by both of these functions enters an undefined, and possibly, exploitable state. Implementations of malloc() and free() manage metadata in global structures in order to track which memory is allocated versus which memory is available, but they are non-reentrant. Simultaneous calls to these functions can cause corruption of the metadata.",,low,"The Art of Software Security Assessment: Chapter 13, ""Signal Vulnerabilities"", Page 791." | |
| 323 | CWE-480,EN-Use of Incorrect Operator (Type: Base),"The programmer accidentally uses the wrong operator, which changes the application logic in security-relevant ways. | |
| 324 | Non-reentrant functions are functions that cannot safely be called, interrupted, and then recalled before the first call has finished without resulting in memory corruption. This can lead to an unexpected system state an unpredictable results with a variety of potential consequences depending on context, including denial of service and code execution. | |
| 325 | Many functions are not reentrant, but some of them can result in the corruption of memory if they are used in a signal handler. The function call syslog() is an example of this. In order to perform its functionality, it allocates a small amount of memory as ""scratch space."" If syslog() is suspended by a signal call and the signal handler calls syslog(), the memory used by both of these functions enters an undefined, and possibly, exploitable state. Implementations of malloc() and free() manage metadata in global structures in order to track which memory is allocated versus which memory is available, but they are non-reentrant. Simultaneous calls to these functions can cause corruption of the metadata.",,low,"The Art of Software Security Assessment: Chapter 6, ""Typos"", Page 289." | |
| 326 | CWE-481,EN-Assigning instead of Comparing (Type: Variant),"The code uses an operator for assignment when the intention was to perform a comparison. | |
| 327 | In many languages the compare statement is very close in appearance to the assignment statement and are often confused. This bug is generally the result of a typo and usually causes obvious problems with program execution. If the comparison is in an if statement, the if statement will usually evaluate the value of the right-hand side of the predicate.",,low,"The Art of Software Security Assessment: Chapter 6, ""Typos"", Page 289." | |
| 328 | CWE-482,EN-Comparing instead of Assigning (Type: Variant),"The code uses an operator for comparison when the intention was to perform an assignment. | |
| 329 | In many languages, the compare statement is very close in appearance to the assignment statement; they are often confused.",,low,"The Art of Software Security Assessment: Chapter 6, ""Typos"", Page 289." | |
| 330 | CWE-483,EN-Incorrect Block Delimitation (Type: Variant),"The code does not explicitly delimit a block that is intended to contain 2 or more statements, creating a logic error. | |
| 331 | In some languages, braces (or other delimiters) are optional for blocks. When the delimiter is omitted, it is possible to insert a logic error in which a statement is thought to be in a block but is not. In some cases, the logic error can have security implications.",,low, | |
| 332 | CWE-641,EN-Improper Restriction of Names for Files and Other Resources (Type: Base),"The application constructs the name of a file or other resource using input from an upstream component, but does not restrict or incorrectly restricts the resulting name. | |
| 333 | This may produce resultant weaknesses. For instance, if the names of these resources contain scripting characters, it is possible that a script may get executed in the client's browser if the application ever displays the name of the resource on a dynamically generated web page. Alternately, if the resources are consumed by some application parser, a specially crafted name can exploit some vulnerability internal to the parser, potentially resulting in execution of arbitrary code on the server machine. The problems will vary based on the context of usage of such malformed resource names and whether vulnerabilities are present in or assumptions are made by the targeted technology that would make code execution possible.",,low, | |
| 334 | CWE-648,EN-Incorrect Use of Privileged APIs (Type: Base),"The application does not conform to the API requirements for a function call that requires extra privileges. This could allow attackers to gain privileges by causing the function to be called incorrectly. | |
| 335 | When an application contains certain functions that perform operations requiring an elevated level of privilege, the caller of a privileged API must be careful to: | |
| 336 | ensure that assumptions made by the APIs are valid, such as validity of arguments | |
| 337 | account for known weaknesses in the design/implementation of the API | |
| 338 | call the API from a safe context | |
| 339 | If the caller of the API does not follow these requirements, then it may allow a malicious user or process to elevate their privilege, hijack the process, or steal sensitive data. | |
| 340 | For instance, it is important to know if privileged APIs do not shed their privileges before returning to the caller or if the privileged function might make certain assumptions about the data, context or state information passed to it by the caller. It is important to always know when and how privileged APIs can be called in order to ensure that their elevated level of privilege cannot be exploited.",,low, | |
| 341 | CWE-762,EN-Mismatched Memory Management Routines (Type: Variant),"The application attempts to return a memory resource to the system, but it calls a release function that is not compatible with the function that was originally used to allocate that resource. | |
| 342 | This weakness can be generally described as mismatching memory management routines, such as: | |
| 343 | The memory was allocated on the stack (automatically), but it was deallocated using the memory management routine free() (CWE-590), which is intended for explicitly allocated heap memory. | |
| 344 | The memory was allocated explicitly using one set of memory management functions, and deallocated using a different set. For example, memory might be allocated with malloc() in C++ instead of the new operator, and then deallocated with the delete operator. | |
| 345 | When the memory management functions are mismatched, the consequences may be as severe as code execution, memory corruption, or program crash. Consequences and ease of exploit will vary depending on the implementation of the routines and the object being managed.",,low,"boost C++ Library Smart Pointers: http://www.boost.org/doc/libs/1_38_0/libs/smart_ptr/smart_ptr.htm | |
| 346 | Valgrind: http://valgrind.org/" | |
| 347 | CWE-783,EN-Operator Precedence Logic Error (Type: Variant),"The program uses an expression in which operator precedence causes incorrect logic to be used. | |
| 348 | While often just a bug, operator precedence logic errors can have serious consequences if they are used in security-critical code, such as making an authentication decision.",,low,"EXP00-C. Use parentheses for precedence of operation: https://www.securecoding.cert.org/confluence/display/seccode/EXP00-C.+Use+parentheses+for+precedence+of+operation | |
| 349 | The Art of Software Security Assessment: Chapter 6, ""Precedence"", Page 287." | |
| 350 | CWE-789,EN-Uncontrolled Memory Allocation (Type: Variant),"The product allocates memory based on an untrusted size value, but it does not validate or incorrectly validates the size, allowing arbitrary amounts of memory to be allocated. | |
| 351 | This typically occurs when a pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used. These problems may be resultant from missing sentinel values (CWE-463) or trusting a user-influenced input length variable.",,low,"The Art of Software Security Assessment: Chapter 10, ""Resource Limits"", Page 574." | |
| 352 | CWE-333,EN-Improper Handling of Insufficient Entropy in TRNG (Type: Variant),"True random number generators (TRNG) generally have a limited source of entropy and therefore can fail or block. | |
| 353 | The rate at which true random numbers can be generated is limited. It is important that one uses them only when they are needed for security.",,medium, | |
| 354 | CWE-367,EN-Time-of-check Time-of-use (TOCTOU) Race Condition (Type: Base),"The software checks the state of a resource before using that resource, but the resource's state can change between the check and the use in a way that invalidates the results of the check. This can cause the software to perform invalid actions when the resource is in an unexpected state. | |
| 355 | This weakness can be security-relevant when an attacker can influence the state of the resource between check and use. This can happen with shared resources such as files, memory, or even variables in multithreaded programs.",,medium,"Portably Solving File TOCTTOU Races with Hardness Amplification: http://www.usenix.org/events/fast08/tech/tsafrir.html | |
| 356 | 24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205 | |
| 357 | The Art of Software Security Assessment: Chapter 9, ""TOCTOU"", Page 527." | |
| 358 | CWE-404,EN-Improper Resource Shutdown or Release (Type: Base),"The program does not release or incorrectly releases a resource before it is made available for re-use. | |
| 359 | When a resource is created or allocated, the developer is responsible for properly releasing the resource as well as accounting for all potential paths of expiration or invalidation, such as a set period of time or revocation.",,medium,"24 Deadly Sins of Software Security: ""Sin 8: C++ Catastrophes."" Page 143" | |
| 360 | CWE-407,EN-Algorithmic Complexity (Type: Base),"An algorithm in a product has an inefficient worst-case computational complexity that may be detrimental to system performance and can be triggered by an attacker, typically using crafted manipulations that ensure that the worst case is being reached. | |
| 361 | In the absence of a policy to restrict asymmetric resource consumption, the application or system cannot distinguish between legitimate transmissions and traffic intended to serve as an amplifying attack on target systems. Systems can often be configured to restrict the amount of traffic sent out on behalf of a client, based on the client's origin or access level. This is usually defined in a resource allocation policy. In the absence of a mechanism to keep track of transmissions, the system or application can be easily abused to transmit asymmetrically greater traffic than the request or client should be permitted to.",,medium,Algorithmic Complexity Attacks: http://www.cs.rice.edu/~scrosby/hash/CrosbyWallach_UsenixSec2003/index.html | |
| 362 | CWE-415,EN-Double Free (Type: Variant),"The product calls free() twice on the same memory address, potentially leading to modification of unexpected memory locations. | |
| 363 | When a program calls free() twice with the same argument, the program's memory management data structures become corrupted. This corruption can cause the program to crash or, in some circumstances, cause two later calls to malloc() to return the same pointer. If malloc() returns the same value twice and the program later gives the attacker control over the data that is written into this doubly-allocated memory, the program becomes vulnerable to a buffer overflow attack.",,medium,"24 Deadly Sins of Software Security: ""Sin 8: C++ Catastrophes."" Page 143 | |
| 364 | The Art of Software Security Assessment: Chapter 7, ""Double Frees"", Page 379." | |
| 365 | CWE-59,EN-Improper Link Resolution Before File Access (Link Following) (Type: Base),"The software attempts to access a file based on the filename, but it does not properly prevent that filename from identifying a link or shortcut that resolves to an unintended resource. | |
| 366 | Some functions that offer security features supported by the OS are not available on all versions of the OS in common use. Likewise, functions are often deprecated or made obsolete for security reasons and should not be used.",,medium,"The Art of Software Security Assessment: Chapter 9, ""Symbolic Link Attacks"", Page 518." | |
| 367 | CWE-601,EN-URL Redirection to Untrusted Site (Open Redirect) (Type: Variant),"A web application accepts a user-controlled input that specifies a link to an external site, and uses that link in a Redirect. This simplifies phishing attacks. | |
| 368 | An http parameter may contain a URL value and could cause the web application to redirect the request to the specified URL. By modifying the URL value to a malicious site, an attacker may successfully launch a phishing scam and steal user credentials. Because the server name in the modified link is identical to the original site, phishing attempts have a more trustworthy appearance.",,medium,"Exploitable Redirects on the Web: Identification, Prevalence, and Defense: http://www.cs.indiana.edu/cgi-pub/cshue/research/woot08.pdf | |
| 369 | Open redirect vulnerabilities: definition and prevention: http://www.net-security.org/dl/insecure/INSECURE-Mag-17.pdf | |
| 370 | Top 25 Series - Rank 23 - Open Redirect: http://software-security.sans.org/blog/2010/03/25/top-25-series-rank-23-open-redirect | |
| 371 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI" | |
| 372 | CWE-749,EN-Exposed Dangerous Method or Function (Type: Base),"The software provides an Applications Programming Interface (API) or similar interface for interaction with external actors, but the interface includes a dangerous method or function that is not properly restricted. | |
| 373 | This weakness can lead to a wide variety of resultant weaknesses, depending on the behavior of the exposed method. It can apply to any number of technologies and approaches, such as ActiveX controls, Java functions, IOCTLs, and so on. | |
| 374 | The exposure can occur in a few different ways: | |
| 375 | 1) The function/method was never intended to be exposed to outside actors. | |
| 376 | 2) The function/method was only intended to be accessible to a limited set of actors, such as Internet-based access from a single web site.",,medium,"No description: http://msdn.microsoft.com/workshop/components/activex/safety.asp | |
| 377 | No description: http://msdn.microsoft.com/workshop/components/activex/security.asp" | |
| 378 | CWE-755,EN-Improper Handling of Exceptional Conditions (Type: Class),"The software does not handle or incorrectly handles an exceptional condition. | |
| 379 | The programmer may assume that certain events or conditions will never occur or do not need to be worried about, such as low memory conditions, lack of access to resources due to restrictive permissions, or misbehaving clients or components. However, attackers may intentionally trigger these unusual conditions, thus violating the programmer's assumptions, possibly introducing instability, incorrect behavior, or a vulnerability. | |
| 380 | Note that this entry is not exclusively about the use of exceptions and exception handling, which are mechanisms for both checking and handling unusual or unexpected conditions.",,medium, | |
| 381 | CWE-766,EN-Critical Variable Declared Public (Type: Variant),"The software declares a critical variable or field to be public when intended security policy requires it to be private. | |
| 382 | When software is operating in a concurrent environment and repeatedly unlocks a critical resource, the consequences will vary based on the type of lock, the lock's implementation, and the resource being protected. In some situations such as with semaphores, the resources are pooled and extra calls to unlock will increase the count for the number of available resources, likely resulting in a crash or unpredictable behavior when the system nears capacity.",,medium, | |
| 383 | CWE-767,EN-Access to Critical Private Variable via Public Method (Type: Variant),"The software defines a public method that reads or modifies a private variable. | |
| 384 | If an attacker modifies the variable to contain unexpected values, this could violate assumptions from other parts of the code. Additionally, if an attacker can read the private variable, it may expose sensitive information or make it easier to launch further attacks.",,medium, | |
| 385 | CWE-776,EN-Improper Restriction of Recursive Entity References in DTDs (XML Entity Expansion) (Type: Variant),"The software uses XML documents and allows their structure to be defined with a Document Type Definition (DTD), but it does not properly control the number of recursive definitions of entities. | |
| 386 | If the DTD contains a large number of nested or recursive entities, this can lead to explosive growth of data when parsed, causing a denial of service.",,medium,"Multiple vendors XML parser (and SOAP/WebServices server) Denial of Service attack using DTD: http://www.securityfocus.com/archive/1/303509 | |
| 387 | XML security: Preventing XML bombs: http://searchsoftwarequality.techtarget.com/expert/KnowledgebaseAnswer/0,289625,sid92_gci1168442,00.html?asrc=SS_CLA_302%20%20558&psrc=CLT_92# | |
| 388 | Dismantling an XML-Bomb: http://blog.didierstevens.com/2008/09/23/dismantling-an-xml-bomb/ | |
| 389 | XML Entity Expansion: http://projects.webappsec.org/XML-Entity-Expansion | |
| 390 | Tip: Configure SAX parsers for secure processing: http://www.ibm.com/developerworks/xml/library/x-tipcfsx.html | |
| 391 | XML Denial of Service Attacks and Defenses: http://msdn.microsoft.com/en-us/magazine/ee335713.aspx | |
| 392 | Preventing Entity Expansion Attacks in JAXB: http://blog.bdoughan.com/2011/03/preventing-entity-expansion-attacks-in.html" | |
| 393 | CWE-777,EN-Regular Expression without Anchors (Type: Variant),"The software uses a regular expression to perform neutralization, but the regular expression is not anchored and may allow malicious or malformed data to slip through. | |
| 394 | When performing tasks such as whitelist validation, data is examined and possibly modified to ensure that it is well-formed and adheres to a list of safe values. If the regular expression is not anchored, malicious or malformed data may be included before or after any string matching the regular expression. The type of malicious data that is allowed will depend on the context of the application and which anchors are omitted from the regular expression.",,medium, | |
| 395 | CWE-779,EN-Logging of Excessive Data (Type: Base),"The software logs too much information, making log files hard to process and possibly hindering recovery efforts or forensic analysis after an attack. | |
| 396 | While logging is a good practice in general, and very high levels of logging are appropriate for debugging stages of development, too much logging in a production environment might hinder a system administrator's ability to detect anomalous conditions. This can provide cover for an attacker while attempting to penetrate a system, clutter the audit trail for forensic analysis, or make it more difficult to debug problems in a production environment.",,medium, | |
| 397 | CWE-781,EN-Improper Address Validation in IOCTL with METHOD_NEITHER I/O Control Code (Type: Variant),"The software defines an IOCTL that uses METHOD_NEITHER for I/O, but it does not validate or incorrectly validates the addresses that are provided. | |
| 398 | When an IOCTL uses the METHOD_NEITHER option for I/O control, it is the responsibility of the IOCTL to validate the addresses that have been supplied to it. If validation is missing or incorrect, attackers can supply arbitrary memory addresses, leading to code execution or a denial of service.",,medium,"Exploiting Common Flaws in Drivers: http://reversemode.com/index.php?option=com_content&task=view&id=38&Itemid=1 | |
| 399 | Remote and Local Exploitation of Network Drivers: https://www.blackhat.com/presentations/bh-usa-07/Bulygin/Presentation/bh-usa-07-bulygin.pdf | |
| 400 | Windows driver vulnerabilities: the METHOD_NEITHER odyssey: http://www.net-security.org/dl/insecure/INSECURE-Mag-18.pdf | |
| 401 | Buffer Descriptions for I/O Control Codes: http://msdn.microsoft.com/en-us/library/ms795857.aspx | |
| 402 | Using Neither Buffered Nor Direct I/O: http://msdn.microsoft.com/en-us/library/cc264614.aspx | |
| 403 | Securing Device Objects: http://msdn.microsoft.com/en-us/library/ms794722.aspx | |
| 404 | No description: http://www.piotrbania.com/all/articles/ewdd.pdf" | |
| 405 | CWE-782,EN-Exposed IOCTL with Insufficient Access Control (Type: Variant),"The software implements an IOCTL with functionality that should be restricted, but it does not properly enforce access control for the IOCTL. | |
| 406 | When an IOCTL contains privileged functionality and is exposed unnecessarily, attackers may be able to access this functionality by invoking the IOCTL. Even if the functionality is benign, if the programmer has assumed that the IOCTL would only be accessed by a trusted process, there may be little or no validation of the incoming data, exposing weaknesses that would never be reachable if the attacker cannot call the IOCTL directly. | |
| 407 | The implementations of IOCTLs will differ between operating system types and versions, so the methods of attack and prevention may vary widely.",,medium,Securing Device Objects: http://msdn.microsoft.com/en-us/library/ms794722.aspx | |
| 408 | CWE-117,EN-Improper Output Neutralization for Logs (Type: Base),"The software does not neutralize or incorrectly neutralizes output that is written to logs. | |
| 409 | This can allow an attacker to forge log entries or inject malicious content into logs. | |
| 410 | Log forging vulnerabilities occur when: | |
| 411 | Data enters an application from an untrusted source. | |
| 412 | The data is written to an application or system log file.",,medium,"Exploiting Software: How to Break Code | |
| 413 | The night the log was forged: http://doc.novsu.ac.ru/oreilly/tcpip/puis/ch10_05.htm | |
| 414 | OWASP TOP 10: http://www.owasp.org/index.php/Top_10_2007" | |
| 415 | CWE-124,EN-Buffer Underwrite (Buffer Underflow) (Type: Base),"The software writes to a buffer using an index or pointer that references a memory location prior to the beginning of the buffer. | |
| 416 | This typically occurs when a pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used.",,medium,"Buffer UNDERFLOWS: What do you know about it?: http://seclists.org/vuln-dev/2004/Jan/0022.html | |
| 417 | 24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89" | |
| 418 | CWE-128,EN-Wrap-around Error (Type: Base),"Wrap around errors occur whenever a value is incremented past the maximum value for its type and therefore ""wraps around"" to a very small, negative, or undefined value. | |
| 419 | This typically occurs when the pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used. This may result in exposure of sensitive information or possibly a crash.",,medium,"24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89 | |
| 420 | The Art of Software Security Assessment: Chapter 6, ""Signed Integer Boundaries"", Page 220." | |
| 421 | CWE-170,EN-Improper Null Termination (Type: Base),"The software does not terminate or incorrectly terminates a string or array with a null character or equivalent terminator. | |
| 422 | Null termination errors frequently occur in two different ways. An off-by-one error could cause a null to be written out of bounds, leading to an overflow. Or, a program could use a strncpy() function call incorrectly, which prevents a null terminator from being added at all. Other scenarios are possible.",,medium, | |
| 423 | CWE-190,EN-Integer Overflow or Wraparound (Type: Base),"The software performs a calculation that can produce an integer overflow or wraparound, when the logic assumes that the resulting value will always be larger than the original value. This can introduce other weaknesses when the calculation is used for resource management or execution control. | |
| 424 | An integer overflow or wraparound occurs when an integer value is incremented to a value that is too large to store in the associated representation. When this occurs, the value may wrap to become a very small or negative number. While this may be intended behavior in circumstances that rely on wrapping, it can have security consequences if the wrap is unexpected. This is especially the case if the integer overflow can be triggered using user-supplied inputs. This becomes security-critical when the result is used to control looping, make a security decision, or determine the offset or size in behaviors such as memory allocation, copying, concatenation, etc.",,medium,"An overview of common programming security vulnerabilities and possible solutions: http://fort-knox.org/thesis.pdf | |
| 425 | Basic Integer Overflows: http://www.phrack.org/issues.html?issue=60&id=10#article | |
| 426 | Writing Secure Code: Chapter 20, ""Integer Overflows"" Page 620 | |
| 427 | 24 Deadly Sins of Software Security: ""Sin 7: Integer Overflows."" Page 119 | |
| 428 | SafeInt: http://safeint.codeplex.com/ | |
| 429 | Top 25 Series - Rank 17 - Integer Overflow Or Wraparound: http://software-security.sans.org/blog/2010/03/18/top-25-series-rank-17-integer-overflow-or-wraparound | |
| 430 | The Art of Software Security Assessment: Chapter 6, ""Signed Integer Boundaries"", Page 220." | |
| 431 | CWE-196,EN-Unsigned to Signed Conversion Error (Type: Variant),"An unsigned-to-signed conversion error takes place when a large unsigned primitive is used as a signed value. | |
| 432 | It is dangerous to rely on implicit casts between signed and unsigned numbers because the result can take on an unexpected value and violate assumptions made by the program.",,medium,"The Art of Software Security Assessment: Chapter 6, ""Type Conversions"", Page 223." | |
| 433 | CWE-202,EN-Exposure of Sensitive Data Through Data Queries (Type: Variant),"When trying to keep information confidential, an attacker can often infer some of the information by using statistics. | |
| 434 | In situations where data should not be tied to individual users, but a large number of users should be able to make queries that ""scrub"" the identity of users, it may be possible to get information about a user -- e.g., by specifying search terms that are known to be unique to that user.",,medium, | |
| 435 | CWE-250,EN-Execution with Unnecessary Privileges (Type: Class),"The software performs an operation at a privilege level that is higher than the minimum level required, which creates new weaknesses or amplifies the consequences of other weaknesses. | |
| 436 | New weaknesses can be exposed because running with extra privileges, such as root or Administrator, can disable the normal security checks being performed by the operating system or surrounding environment. Other pre-existing weaknesses can turn into security vulnerabilities if they occur while operating at raised privileges. | |
| 437 | Privilege management functions can behave in some less-than-obvious ways, and they have different quirks on different platforms. These inconsistencies are particularly pronounced if you are transitioning from one non-root user to another. Signal handlers and spawned processes run at the privilege of the owning process, so if a process is running as root when a signal fires or a sub-process is executed, the signal handler or sub-process will operate with root privileges.",,medium,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 438 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 439 | Writing Secure Code: Chapter 7, ""Running with Least Privilege"" Page 207 | |
| 440 | Federal Desktop Core Configuration: http://nvd.nist.gov/fdcc/index.cfm | |
| 441 | 24 Deadly Sins of Software Security: ""Sin 16: Executing Code With Too Much Privilege."" Page 243 | |
| 442 | The Art of Software Security Assessment: Chapter 9, ""Privilege Vulnerabilities"", Page 477." | |
| 443 | CWE-269,EN-Improper Privilege Management (Type: Base),"The software does not properly assign, modify, track, or check privileges for an actor, creating an unintended sphere of control for that actor. | |
| 444 | Just as neglecting to include functionality for the management of password aging is dangerous, so is allowing password aging to continue unchecked. Passwords must be given a maximum life span, after which a user is required to update with a new and different password.",,medium,"24 Deadly Sins of Software Security: ""Sin 16: Executing Code With Too Much Privilege."" Page 243 | |
| 445 | The Art of Software Security Assessment: Chapter 9, ""Dropping Privileges Permanently"", Page 479." | |
| 446 | CWE-273,EN-Improper Check for Dropped Privileges (Type: Base),"The software attempts to drop privileges but does not check or incorrectly checks to see if the drop succeeded. | |
| 447 | If the drop fails, the software will continue to run with the raised privileges, which might provide additional access to unprivileged users.",,medium, | |
| 448 | CWE-276,EN-Incorrect Default Permissions (Type: Variant),"The software, upon installation, sets incorrect permissions for an object that exposes it to an unintended actor. | |
| 449 | If the drop fails, the software will continue to run with the raised privileges, which might provide additional access to unprivileged users.",,medium,"The Art of Software Security Assessment: Chapter 3, ""Insecure Defaults"", Page 69." | |
| 450 | CWE-299,EN-Improper Check for Certificate Revocation (Type: Variant),"The software does not check or incorrectly checks the revocation status of a certificate, which may cause it to use a certificate that has been compromised. | |
| 451 | An improper check for certificate revocation is a far more serious flaw than related certificate failures. This is because the use of any revoked certificate is almost certainly malicious. The most common reason for certificate revocation is compromise of the system in question, with the result that no legitimate servers will be using a revoked certificate, unless they are sorely out of sync.",,medium,"24 Deadly Sins of Software Security: ""Sin 23: Improper Use of PKI, Especially SSL."" Page 347" | |
| 452 | CWE-301,EN-Reflection Attack in an Authentication Protocol (Type: Variant),"Simple authentication protocols are subject to reflection attacks if a malicious user can use the target machine to impersonate a trusted user. | |
| 453 | A mutual authentication protocol requires each party to respond to a random challenge by the other party by encrypting it with a pre-shared key. Often, however, such protocols employ the same pre-shared key for communication with a number of different entities. A malicious user or an attacker can easily compromise this protocol without possessing the correct key by employing a reflection attack on the protocol.",,medium,"The Art of Software Security Assessment: Chapter 2, ""Insufficient Validation"", Page 38." | |
| 454 | CWE-329,EN-Not Using a Random IV with CBC Mode (Type: Variant),"Not using a random initialization Vector (IV) with Cipher Block Chaining (CBC) Mode causes algorithms to be susceptible to dictionary attacks. | |
| 455 | This weakness is especially dangerous when the hash is used in security algorithms that require the one-way property to hold. For example, if an authentication system takes an incoming password and generates a hash, then compares the hash to another hash that it has stored in its authentication database, then the ability to create a collision could allow an attacker to provide an alternate password that produces the same target hash, bypassing authentication.",,medium,"The Art of Software Security Assessment: Chapter 2, ""Initialization Vectors"", Page 42." | |
| 456 | CWE-332,EN-Insufficient Entropy in PRNG (Type: Variant),"The lack of entropy available for, or used by, a Pseudo-Random Number Generator (PRNG) can be a stability and security threat. | |
| 457 | When software generates predictable values in a context requiring unpredictability, it may be possible for an attacker to guess the next value that will be generated, and use this guess to impersonate another user or access sensitive information.",,medium,SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 458 | CWE-338,EN-Use of Cryptographically Weak PRNG (Type: Base),"The product uses a Pseudo-Random Number Generator (PRNG) in a security context, but the PRNG is not cryptographically strong. | |
| 459 | The rate at which true random numbers can be generated is limited. It is important that one uses them only when they are needed for security.",,medium,"24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 460 | CWE-353,EN-Missing Support for Integrity Check (Type: Base),"The software uses a transmission protocol that does not include a mechanism for verifying the integrity of the data during transmission, such as a checksum. | |
| 461 | If integrity check values or ""checksums"" are omitted from a protocol, there is no way of determining if data has been corrupted in transmission. The lack of checksum functionality in a protocol removes the first application-level check of data that can be used. The end-to-end philosophy of checks states that integrity checks should be performed at the lowest level that they can be completely implemented. Excluding further sanity checks and input validation performed by applications, the protocol's checksum is the most important level of checksum, since it can be performed more completely than at any previous level and takes into account entire messages, as opposed to single packets.",,medium,"24 Deadly Sins of Software Security: ""Sin 15: Not Updating Easily."" Page 231" | |
| 462 | CWE-354,EN-Improper Validation of Integrity Check Value (Type: Base),"The software does not validate or incorrectly validates the integrity check values or ""checksums"" of a message. This may prevent it from detecting if the data has been modified or corrupted in transmission. | |
| 463 | Improper validation of checksums before use results in an unnecessary risk that can easily be mitigated. The protocol specification describes the algorithm used for calculating the checksum. It is then a simple matter of implementing the calculation and verifying that the calculated checksum and the received checksum match. Improper verification of the calculated checksum and the received checksum can lead to far greater consequences.",,medium, | |
| 464 | CWE-362,EN-Concurrent Execution using Shared Resource with Improper Synchronization (Race Condition) (Type: Class),"The program contains a code sequence that can run concurrently with other code, and the code sequence requires temporary, exclusive access to a shared resource, but a timing window exists in which the shared resource can be modified by another code sequence that is operating concurrently. | |
| 465 | This can have security implications when the expected synchronization is in security-critical code, such as recording whether a user is authenticated or modifying important state information that should not be influenced by an outsider. | |
| 466 | A race condition occurs within concurrent environments, and is effectively a property of a code sequence. Depending on the context, a code sequence may be in the form of a function call, a small number of instructions, a series of program invocations, etc. | |
| 467 | A race condition violates these properties, which are closely related: | |
| 468 | Exclusivity - the code sequence is given exclusive access to the shared resource, i.e., no other code sequence can modify properties of the shared resource before the original sequence has completed execution. | |
| 469 | Atomicity - the code sequence is behaviorally atomic, i.e., no other thread or process can concurrently execute the same sequence of instructions (or a subset) against the same resource. | |
| 470 | A race condition exists when an ""interfering code sequence"" can still access the shared resource, violating exclusivity. Programmers may assume that certain code sequences execute too quickly to be affected by an interfering code sequence; when they are not, this violates atomicity. For example, the single ""x++"" statement may appear atomic at the code layer, but it is actually non-atomic at the instruction layer, since it involves a read (the original value of x), followed by a computation (x+1), followed by a write (save the result to x). | |
| 471 | The interfering code sequence could be ""trusted"" or ""untrusted."" A trusted interfering code sequence occurs within the program; it cannot be modified by the attacker, and it can only be invoked indirectly. An untrusted interfering code sequence can be authored directly by the attacker, and typically it is external to the vulnerable program.",,medium,"24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205 | |
| 472 | volatile - Multithreaded Programmer's Best Friend: http://www.ddj.com/cpp/184403766 | |
| 473 | Thread-safe webapps using Spring: http://www.javalobby.org/articles/thread-safe/index.jsp | |
| 474 | Prevent race conditions: http://www.ibm.com/developerworks/library/l-sprace.html | |
| 475 | Race Conditions, Files, and Security Flaws; or the Tortoise and the Hare Redux: http://www.cs.ucdavis.edu/research/tech-reports/1995/CSE-95-9.pdf | |
| 476 | Secure Programming for Linux and Unix HOWTO: http://www.dwheeler.com/secure-programs/Secure-Programs-HOWTO/avoid-race.html | |
| 477 | Discovering and Exploiting Named Pipe Security Flaws for Fun and Profit: http://www.blakewatts.com/namedpipepaper.html | |
| 478 | On Race Vulnerabilities in Web Applications: http://security.dico.unimi.it/~roberto/pubs/dimva08-web.pdf | |
| 479 | Avoiding Race Conditions and Insecure File Operations: http://developer.apple.com/documentation/Security/Conceptual/SecureCodingGuide/Articles/RaceConditions.html | |
| 480 | Top 25 Series - Rank 25 - Race Conditions: http://blogs.sans.org/appsecstreetfighter/2010/03/26/top-25-series-rank-25-race-conditions/ | |
| 481 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html" | |
| 482 | CWE-364,EN-Signal Handler Race Condition (Type: Base),"The software uses a signal handler that introduces a race condition. | |
| 483 | Race conditions frequently occur in signal handlers, since signal handlers support asynchronous actions. These race conditions have a variety of root causes and symptoms. Attackers may be able to exploit a signal handler race condition to cause the software state to be corrupted, possibly leading to a denial of service or even code execution. | |
| 484 | These issues occur when non-reentrant functions, or state-sensitive actions occur in the signal handler, where they may be called at any time. These behaviors can violate assumptions being made by the ""regular"" code that is interrupted, or by other signal handlers that may also be invoked. If these functions are called at an inopportune moment - such as while a non-reentrant function is already running - memory corruption could occur that may be exploitable for code execution. Another signal race condition commonly found occurs when free is called within a signal handler, resulting in a double free and therefore a write-what-where condition. Even if a given pointer is set to NULL after it has been freed, a race condition still exists between the time the memory was freed and the pointer was set to NULL. This is especially problematic if the same signal handler has been set for more than one signal -- since it means that the signal handler itself may be reentered. | |
| 485 | There are several known behaviors related to signal handlers that have received the label of ""signal handler race condition"": | |
| 486 | Shared state (e.g. global data or static variables) that are accessible to both a signal handler and ""regular"" code | |
| 487 | Shared state between a signal handler and other signal handlers | |
| 488 | Use of non-reentrant functionality within a signal handler - which generally implies that shared state is being used. For example, malloc() and free() are non-reentrant because they may use global or static data structures for managing memory, and they are indirectly used by innocent-seeming functions such as syslog(); these functions could be exploited for memory corruption and, possibly, code execution. | |
| 489 | Association of the same signal handler function with multiple signals - which might imply shared state, since the same code and resources are accessed. For example, this can be a source of double-free and use-after-free weaknesses. | |
| 490 | Use of setjmp and longjmp, or other mechanisms that prevent a signal handler from returning control back to the original functionality | |
| 491 | While not technically a race condition, some signal handlers are designed to be called at most once, and being called more than once can introduce security problems, even when there are not any concurrent calls to the signal handler. This can be a source of double-free and use-after-free weaknesses. | |
| 492 | Signal handler vulnerabilities are often classified based on the absence of a specific protection mechanism, although this style of classification is discouraged in CWE because programmers often have a choice of several different mechanisms for addressing the weakness. Such protection mechanisms may preserve exclusivity of access to the shared resource, and behavioral atomicity for the relevant code: | |
| 493 | Avoiding shared state | |
| 494 | Using synchronization in the signal handler | |
| 495 | Using synchronization in the regular code | |
| 496 | Disabling or masking other signals, which provides atomicity (which effectively ensures exclusivity)",,medium,"Delivering Signals for Fun and Profit: http://lcamtuf.coredump.cx/signals.txt | |
| 497 | Race Condition: Signal Handling: http://www.fortify.com/vulncat/en/vulncat/cpp/race_condition_signal_handling.html | |
| 498 | 24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205 | |
| 499 | The Art of Software Security Assessment: Chapter 13, ""Signal Vulnerabilities"", Page 791." | |
| 500 | CWE-365,EN-Race Condition in Switch (Type: Base),"The code contains a switch statement in which the switched variable can be modified while the switch is still executing, resulting in unexpected behavior. | |
| 501 | Race conditions frequently occur in signal handlers, since signal handlers support asynchronous actions. These race conditions have a variety of root causes and symptoms. Attackers may be able to exploit a signal handler race condition to cause the software state to be corrupted, possibly leading to a denial of service or even code execution. | |
| 502 | These issues occur when non-reentrant functions, or state-sensitive actions occur in the signal handler, where they may be called at any time. These behaviors can violate assumptions being made by the ""regular"" code that is interrupted, or by other signal handlers that may also be invoked. If these functions are called at an inopportune moment - such as while a non-reentrant function is already running - memory corruption could occur that may be exploitable for code execution. Another signal race condition commonly found occurs when free is called within a signal handler, resulting in a double free and therefore a write-what-where condition. Even if a given pointer is set to NULL after it has been freed, a race condition still exists between the time the memory was freed and the pointer was set to NULL. This is especially problematic if the same signal handler has been set for more than one signal -- since it means that the signal handler itself may be reentered. | |
| 503 | There are several known behaviors related to signal handlers that have received the label of ""signal handler race condition"": | |
| 504 | Shared state (e.g. global data or static variables) that are accessible to both a signal handler and ""regular"" code | |
| 505 | Shared state between a signal handler and other signal handlers | |
| 506 | Use of non-reentrant functionality within a signal handler - which generally implies that shared state is being used. For example, malloc() and free() are non-reentrant because they may use global or static data structures for managing memory, and they are indirectly used by innocent-seeming functions such as syslog(); these functions could be exploited for memory corruption and, possibly, code execution. | |
| 507 | Association of the same signal handler function with multiple signals - which might imply shared state, since the same code and resources are accessed. For example, this can be a source of double-free and use-after-free weaknesses. | |
| 508 | Use of setjmp and longjmp, or other mechanisms that prevent a signal handler from returning control back to the original functionality | |
| 509 | While not technically a race condition, some signal handlers are designed to be called at most once, and being called more than once can introduce security problems, even when there are not any concurrent calls to the signal handler. This can be a source of double-free and use-after-free weaknesses. | |
| 510 | Signal handler vulnerabilities are often classified based on the absence of a specific protection mechanism, although this style of classification is discouraged in CWE because programmers often have a choice of several different mechanisms for addressing the weakness. Such protection mechanisms may preserve exclusivity of access to the shared resource, and behavioral atomicity for the relevant code: | |
| 511 | Avoiding shared state | |
| 512 | Using synchronization in the signal handler | |
| 513 | Using synchronization in the regular code | |
| 514 | Disabling or masking other signals, which provides atomicity (which effectively ensures exclusivity)",,medium,"24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205" | |
| 515 | CWE-366,EN-Race Condition within a Thread (Type: Base),"If two threads of execution use a resource simultaneously, there exists the possibility that resources may be used while invalid, in turn making the state of execution undefined. | |
| 516 | Race conditions frequently occur in signal handlers, since signal handlers support asynchronous actions. These race conditions have a variety of root causes and symptoms. Attackers may be able to exploit a signal handler race condition to cause the software state to be corrupted, possibly leading to a denial of service or even code execution. | |
| 517 | These issues occur when non-reentrant functions, or state-sensitive actions occur in the signal handler, where they may be called at any time. These behaviors can violate assumptions being made by the ""regular"" code that is interrupted, or by other signal handlers that may also be invoked. If these functions are called at an inopportune moment - such as while a non-reentrant function is already running - memory corruption could occur that may be exploitable for code execution. Another signal race condition commonly found occurs when free is called within a signal handler, resulting in a double free and therefore a write-what-where condition. Even if a given pointer is set to NULL after it has been freed, a race condition still exists between the time the memory was freed and the pointer was set to NULL. This is especially problematic if the same signal handler has been set for more than one signal -- since it means that the signal handler itself may be reentered. | |
| 518 | There are several known behaviors related to signal handlers that have received the label of ""signal handler race condition"": | |
| 519 | Shared state (e.g. global data or static variables) that are accessible to both a signal handler and ""regular"" code | |
| 520 | Shared state between a signal handler and other signal handlers | |
| 521 | Use of non-reentrant functionality within a signal handler - which generally implies that shared state is being used. For example, malloc() and free() are non-reentrant because they may use global or static data structures for managing memory, and they are indirectly used by innocent-seeming functions such as syslog(); these functions could be exploited for memory corruption and, possibly, code execution. | |
| 522 | Association of the same signal handler function with multiple signals - which might imply shared state, since the same code and resources are accessed. For example, this can be a source of double-free and use-after-free weaknesses. | |
| 523 | Use of setjmp and longjmp, or other mechanisms that prevent a signal handler from returning control back to the original functionality | |
| 524 | While not technically a race condition, some signal handlers are designed to be called at most once, and being called more than once can introduce security problems, even when there are not any concurrent calls to the signal handler. This can be a source of double-free and use-after-free weaknesses. | |
| 525 | Signal handler vulnerabilities are often classified based on the absence of a specific protection mechanism, although this style of classification is discouraged in CWE because programmers often have a choice of several different mechanisms for addressing the weakness. Such protection mechanisms may preserve exclusivity of access to the shared resource, and behavioral atomicity for the relevant code: | |
| 526 | Avoiding shared state | |
| 527 | Using synchronization in the signal handler | |
| 528 | Using synchronization in the regular code | |
| 529 | Disabling or masking other signals, which provides atomicity (which effectively ensures exclusivity)",,medium,"24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205 | |
| 530 | The Art of Software Security Assessment: Chapter 13, ""Race Conditions"", Page 759." | |
| 531 | CWE-369,EN-Divide By Zero (Type: Base),"The product divides a value by zero. | |
| 532 | This weakness typically occurs when an unexpected value is provided to the product, or if an error occurs that is not properly detected. It frequently occurs in calculations involving physical dimensions such as size, length, width, and height.",,medium,"No description: http://www.cprogramming.com/tutorial/exceptions.html | |
| 533 | No description: http://msdn.microsoft.com/en-us/library/ms173160(VS.80).aspx" | |
| 534 | CWE-370,EN-Missing Check for Certificate Revocation after Initial Check (Type: Base),"The software does not check the revocation status of a certificate after its initial revocation check, which can cause the software to perform privileged actions even after the certificate is revoked at a later time. | |
| 535 | If the revocation status of a certificate is not checked before each action that requires privileges, the system may be subject to a race condition. If a certificate is revoked after the initial check, all subsequent actions taken with the owner of the revoked certificate will lose all benefits guaranteed by the certificate. In fact, it is almost certain that the use of a revoked certificate indicates malicious activity.",,medium,"24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205" | |
| 536 | CWE-374,EN-Passing Mutable Objects to an Untrusted Method (Type: Base),"Sending non-cloned mutable data as an argument may result in that data being altered or deleted by the called function, thereby putting the calling function into an undefined state. | |
| 537 | If the revocation status of a certificate is not checked before each action that requires privileges, the system may be subject to a race condition. If a certificate is revoked after the initial check, all subsequent actions taken with the owner of the revoked certificate will lose all benefits guaranteed by the certificate. In fact, it is almost certain that the use of a revoked certificate indicates malicious activity.",,medium,"Does Java pass by reference or pass by value?: http://www.javaworld.com/javaworld/javaqa/2000-05/03-qa-0526-pass.html | |
| 538 | Java: The Complete Reference, J2SE 5th Edition" | |
| 539 | CWE-375,EN-Returning a Mutable Object to an Untrusted Caller (Type: Base),"Sending non-cloned mutable data as a return value may result in that data being altered or deleted by the calling function, thereby putting the class in an undefined state. | |
| 540 | If the revocation status of a certificate is not checked before each action that requires privileges, the system may be subject to a race condition. If a certificate is revoked after the initial check, all subsequent actions taken with the owner of the revoked certificate will lose all benefits guaranteed by the certificate. In fact, it is almost certain that the use of a revoked certificate indicates malicious activity.",,medium, | |
| 541 | CWE-385,EN-Covert Timing Channel (Type: Base),"Covert timing channels convey information by modulating some aspect of system behavior over time, so that the program receiving the information can observe system behavior and infer protected information. | |
| 542 | In some instances, knowing when data is transmitted between parties can provide a malicious user with privileged information. Also, externally monitoring the timing of operations can potentially reveal sensitive data. For example, a cryptographic operation can expose its internal state if the time it takes to perform the operation varies, based on the state. | |
| 543 | Covert channels are frequently classified as either storage or timing channels. Some examples of covert timing channels are the system's paging rate, the time a certain transaction requires to execute, and the time it takes to gain access to a shared bus.",,medium, | |
| 544 | CWE-390,EN-Detection of Error Condition Without Action (Type: Class),"The software detects a specific error, but takes no actions to handle the error. | |
| 545 | In some instances, knowing when data is transmitted between parties can provide a malicious user with privileged information. Also, externally monitoring the timing of operations can potentially reveal sensitive data. For example, a cryptographic operation can expose its internal state if the time it takes to perform the operation varies, based on the state. | |
| 546 | Covert channels are frequently classified as either storage or timing channels. Some examples of covert timing channels are the system's paging rate, the time a certain transaction requires to execute, and the time it takes to gain access to a shared bus.",,medium,"24 Deadly Sins of Software Security: ""Sin 11: Failure to Handle Errors Correctly."" Page 183" | |
| 547 | CWE-391,EN-Unchecked Error Condition (Type: Base),"Ignoring exceptions and other error conditions may allow an attacker to induce unexpected behavior unnoticed. | |
| 548 | In some instances, knowing when data is transmitted between parties can provide a malicious user with privileged information. Also, externally monitoring the timing of operations can potentially reveal sensitive data. For example, a cryptographic operation can expose its internal state if the time it takes to perform the operation varies, based on the state. | |
| 549 | Covert channels are frequently classified as either storage or timing channels. Some examples of covert timing channels are the system's paging rate, the time a certain transaction requires to execute, and the time it takes to gain access to a shared bus.",,medium, | |
| 550 | CWE-401,EN-Improper Release of Memory Before Removing Last Reference (Memory Leak) (Type: Base),"The software does not sufficiently track and release allocated memory after it has been used, which slowly consumes remaining memory. | |
| 551 | This is often triggered by improper handling of malformed data or unexpectedly interrupted sessions.",,medium,How to Break Software Security | |
| 552 | CWE-460,EN-Improper Cleanup on Thrown Exception (Type: Variant),"The product does not clean up its state or incorrectly cleans up its state when an exception is thrown, leading to unexpected state or control flow. | |
| 553 | In some languages such as C and C++, stack variables are not initialized by default. They generally contain junk data with the contents of stack memory before the function was invoked. An attacker can sometimes control or read these contents. In other languages or conditions, a variable that is not explicitly initialized can be given a default value that has security implications, depending on the logic of the program. The presence of an uninitialized variable can sometimes indicate a typographic error in the code.",,medium, | |
| 554 | CWE-468,EN-Incorrect Pointer Scaling (Type: Base),"In C and C++, one may often accidentally refer to the wrong memory due to the semantics of when math operations are implicitly scaled. | |
| 555 | Data-structure sentinels are often used to mark the structure of data. A common example of this is the null character at the end of strings or a special sentinel to mark the end of a linked list. It is dangerous to allow this type of control data to be easily accessible. Therefore, it is important to protect from the addition or modification of sentinels.",,medium,"The Art of Software Security Assessment: Chapter 6, ""Pointer Arithmetic"", Page 277." | |
| 556 | CWE-469,EN-Use of Pointer Subtraction to Determine Size (Type: Base),"The application subtracts one pointer from another in order to determine size, but this calculation can be incorrect if the pointers do not exist in the same memory chunk. | |
| 557 | Data-structure sentinels are often used to mark the structure of data. A common example of this is the null character at the end of strings or a special sentinel to mark the end of a linked list. It is dangerous to allow this type of control data to be easily accessible. Therefore, it is important to protect from the addition or modification of sentinels.",,medium, | |
| 558 | CWE-476,EN-NULL Pointer Dereference (Type: Base),"A NULL pointer dereference occurs when the application dereferences a pointer that it expects to be valid, but is NULL, typically causing a crash or exit. | |
| 559 | NULL pointer dereference issues can occur through a number of flaws, including race conditions, and simple programming omissions.",,medium, | |
| 560 | CWE-484,EN-Omitted Break Statement in Switch (Type: Base),"The program omits a break statement within a switch or similar construct, causing code associated with multiple conditions to execute. This can cause problems when the programmer only intended to execute code associated with one condition. | |
| 561 | This can lead to critical code executing in situations where it should not.",,medium,"The Art of Software Security Assessment: Chapter 7, ""Switch Statements"", Page 337." | |
| 562 | CWE-487,EN-Reliance on Package-level Scope (Type: Variant),"Java packages are not inherently closed; therefore, relying on them for code security is not a good practice. | |
| 563 | If the decision to trust the methods and data of an object is based on the name of a class, it is possible for malicious users to send objects of the same name as trusted classes and thereby gain the trust afforded to known classes and types.",,medium, | |
| 564 | CWE-492,EN-Use of Inner Class Containing Sensitive Data (Type: Variant),"Inner classes are translated into classes that are accessible at package scope and may expose code that the programmer intended to keep private to attackers. | |
| 565 | Data can ""bleed"" from one session to another through member variables of singleton objects, such as Servlets, and objects from a shared pool. | |
| 566 | In the case of Servlets, developers sometimes do not understand that, unless a Servlet implements the SingleThreadModel interface, the Servlet is a singleton; there is only one instance of the Servlet, and that single instance is used and re-used to handle multiple requests that are processed simultaneously by different threads. A common result is that developers use Servlet member fields in such a way that one user may inadvertently see another user's data. In other words, storing user data in Servlet member fields introduces a data access race condition.",,medium, | |
| 567 | CWE-494,EN-Download of Code Without Integrity Check (Type: Base),"The product downloads source code or an executable from a remote location and executes the code without sufficiently verifying the origin and integrity of the code. | |
| 568 | An attacker can execute malicious code by compromising the host server, performing DNS spoofing, or modifying the code in transit.",,medium,"Introduction to Code Signing: http://msdn.microsoft.com/en-us/library/ms537361(VS.85).aspx | |
| 569 | Authenticode: http://msdn.microsoft.com/en-us/library/ms537359(v=VS.85).aspx | |
| 570 | Code Signing Guide: http://developer.apple.com/documentation/Security/Conceptual/CodeSigningGuide/Introduction/chapter_1_section_1.html | |
| 571 | Secure Software Updates: Disappointments and New Challenges: http://prisms.cs.umass.edu/~kevinfu/papers/secureupdates-hotsec06.pdf | |
| 572 | 24 Deadly Sins of Software Security: ""Sin 18: The Sins of Mobile Code."" Page 267 | |
| 573 | Top 25 Series - Rank 20 - Download of Code Without Integrity Check: http://blogs.sans.org/appsecstreetfighter/2010/04/05/top-25-series-rank-20-download-code-integrity-check/ | |
| 574 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html" | |
| 575 | CWE-498,EN-Cloneable Class Containing Sensitive Information (Type: Variant),"The code contains a class with sensitive data, but the class is cloneable. The data can then be accessed by cloning the class. | |
| 576 | Cloneable classes are effectively open classes, since data cannot be hidden in them. Classes that do not explicitly deny cloning can be cloned by any other class without running the constructor.",,medium, | |
| 577 | CWE-502,EN-Deserialization of Untrusted Data (Type: Variant),"The application deserializes untrusted data without sufficiently verifying that the resulting data will be valid. | |
| 578 | It is often convenient to serialize objects for communication or to save them for later use. However, deserialized data or code can often be modified without using the provided accessor functions if it does not use cryptography to protect itself. Furthermore, any cryptography would still be client-side security -- which is a dangerous security assumption. | |
| 579 | Data that is untrusted can not be trusted to be well-formed.",,medium,"Unserializing user-supplied data, a bad idea: http://heine.familiedeelstra.com/security/unserialize | |
| 580 | Why Python Pickle is Insecure: http://nadiana.com/python-pickle-insecure" | |
| 581 | CWE-532,EN-Information Exposure Through Log Files (Type: Variant),"Information written to log files can be of a sensitive nature and give valuable guidance to an attacker or expose sensitive user information. | |
| 582 | While logging all information may be helpful during development stages, it is important that logging levels be set appropriately before a product ships so that sensitive user data and system information are not accidentally exposed to potential attackers.",,medium, | |
| 583 | CWE-602,EN-Client-Side Enforcement of Server-Side Security (Type: Base),"The software is composed of a server that relies on the client to implement a mechanism that is intended to protect the server. | |
| 584 | When the server relies on protection mechanisms placed on the client side, an attacker can modify the client-side behavior to bypass the protection mechanisms resulting in potentially unexpected interactions between the client and server. The consequences will vary, depending on what the mechanisms are trying to protect.",,medium,"Writing Secure Code: Chapter 23, ""Client-Side Security Is an Oxymoron"" Page 687" | |
| 585 | CWE-665,EN-Improper Initialization (Type: Base),"The software does not initialize or incorrectly initializes a resource, which might leave the resource in an unexpected state when it is accessed or used. | |
| 586 | This can have security implications when the associated resource is expected to have certain properties or values, such as a variable that determines whether a user has been authenticated or not.",,medium,"Exploiting Uninitialized Data: http://www.felinemenace.org/~mercy/papers/UBehavior/UBehavior.zip | |
| 587 | MS08-014 : The Case of the Uninitialized Stack Variable Vulnerability: http://blogs.technet.com/swi/archive/2008/03/11/the-case-of-the-uninitialized-stack-variable-vulnerability.aspx | |
| 588 | The Art of Software Security Assessment: Chapter 7, ""Variable Initialization"", Page 312." | |
| 589 | CWE-754,EN-Improper Check for Unusual or Exceptional Conditions (Type: Class),"The software does not check or improperly checks for unusual or exceptional conditions that are not expected to occur frequently during day to day operation of the software. | |
| 590 | The programmer may assume that certain events or conditions will never occur or do not need to be worried about, such as low memory conditions, lack of access to resources due to restrictive permissions, or misbehaving clients or components. However, attackers may intentionally trigger these unusual conditions, thus violating the programmer's assumptions, possibly introducing instability, incorrect behavior, or a vulnerability. | |
| 591 | Note that this entry is not exclusively about the use of exceptions and exception handling, which are mechanisms for both checking and handling unusual or unexpected conditions.",,medium,"The Art of Software Security Assessment: Chapter 7, ""Program Building Blocks"" Page 341 | |
| 592 | The Art of Software Security Assessment: Chapter 1, ""Exceptional Conditions,"" Page 22 | |
| 593 | 24 Deadly Sins of Software Security: ""Sin 11: Failure to Handle Errors Correctly."" Page 183 | |
| 594 | Top 25 Series - Rank 15 - Improper Check for Unusual or Exceptional Conditions: http://blogs.sans.org/appsecstreetfighter/2010/03/15/top-25-series-rank-15-improper-check-for-unusual-or-exceptional-conditions/" | |
| 595 | CWE-778,EN-Insufficient Logging (Type: Base),"When a security-critical event occurs, the software either does not record the event or omits important details about the event when logging it. | |
| 596 | When security-critical events are not logged properly, such as a failed login attempt, this can make malicious behavior more difficult to detect and may hinder forensic analysis after an attack succeeds.",,medium,"The Art of Software Security Assessment: Chapter 2, ""Accountability"", Page 40." | |
| 597 | CWE-780,EN-Use of RSA Algorithm without OAEP (Type: Variant),"The software uses the RSA algorithm but does not incorporate Optimal Asymmetric Encryption Padding (OAEP), which might weaken the encryption. | |
| 598 | Padding schemes are often used with cryptographic algorithms to make the plaintext less predictable and complicate attack efforts. The OAEP scheme is often used with RSA to nullify the impact of predictable common text.",,medium,"RSA Problem: http://people.csail.mit.edu/rivest/RivestKaliski-RSAProblem.pdf | |
| 599 | Optimal Asymmetric Encryption Padding: http://en.wikipedia.org/wiki/Optimal_Asymmetric_Encryption_Padding" | |
| 600 | CWE-908,EN-Use of Uninitialized Resource (Type: Base),"The software uses a resource that has not been properly initialized. | |
| 601 | This can have security implications when the associated resource is expected to have certain properties or values.",,medium,Exploiting Uninitialized Data: http://www.felinemenace.org/~mercy/papers/UBehavior/UBehavior.zip | |
| 602 | CWE-909,EN-Missing Initialization of Resource (Type: Base),"The software does not initialize a critical resource. | |
| 603 | Many resources require initialization before they can be properly used. If a resource is not initialized, it could contain unpredictable or expired data, or it could be initialized to defaults that are invalid. This can have security implications when the resource is expected to have certain properties or values.",,medium, | |
| 604 | CWE-910,EN-Use of Expired File Descriptor (Type: Base),"The software uses or accesses a file descriptor after it has been closed. | |
| 605 | After a file descriptor for a particular file or device has been released, it can be reused. The code might not write to the original file, since the reused file descriptor might reference a different file or device.",,medium, | |
| 606 | CWE-911,EN-Improper Update of Reference Count (Type: Base),"The software uses a reference count to manage a resource, but it does not update or incorrectly updates the reference count. | |
| 607 | Reference counts can be used when tracking how many objects contain a reference to a particular resource, such as in memory management or garbage collection. When the reference count reaches zero, the resource can be de-allocated or reused because there are no more objects that use it. If the reference count accidentally reaches zero, then the resource might be released too soon, even though it is still in use. If all objects no longer use the resource, but the reference count is not zero, then the resource might not ever be released.",,medium,Windows Kernel Reference Count Vulnerabilities - Case Study: http://j00ru.vexillium.org/dump/zn_slides.pdf | |
| 608 | CWE-94,EN-Improper Control of Generation of Code (Code Injection) (Type: Class),"The software constructs all or part of a code segment using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the syntax or behavior of the intended code segment. | |
| 609 | When software allows a user's input to contain code syntax, it might be possible for an attacker to craft the code in such a way that it will alter the intended control flow of the software. Such an alteration could lead to arbitrary code execution. | |
| 610 | Injection problems encompass a wide variety of issues -- all mitigated in very different ways. For this reason, the most effective way to discuss these weaknesses is to note the distinct features which classify them as injection weaknesses. The most important issue to note is that all injection problems share one thing in common -- i.e., they allow for the injection of control plane data into the user-controlled data plane. This means that the execution of the process may be altered by sending code in through legitimate data channels, using no other mechanism. While buffer overflows, and many other flaws, involve the use of some further issue to gain execution, injection problems need only for the data to be parsed. The most classic instantiations of this category of weakness are SQL injection and format string vulnerabilities.",,medium,"24 Deadly Sins of Software Security: ""Sin 3: Web-Client Related Vulnerabilities (XSS)."" Page 63" | |
| 611 | CWE-95,EN-Improper Neutralization of Directives in Dynamically Evaluated Code (Eval Injection) (Type: Base),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes code syntax before using the input in a dynamic evaluation call (e.g. ""eval""). | |
| 612 | This may allow an attacker to execute arbitrary code, or at least modify what code can be executed.",,medium,"No description: http://www.rubycentral.com/book/taint.html | |
| 613 | The Art of Software Security Assessment: Chapter 18, ""Inline Evaluation"", Page 1095." | |
| 614 | CWE-287,EN-Improper Authentication (Type: Class),"When an actor claims to have a given identity, the software does not prove or insufficiently proves that the claim is correct. | |
| 615 | Users can be assigned to the wrong group (class) of permissions resulting in unintended access rights to sensitive objects.",,high,"Weak Password Brings 'Happiness' to Twitter Hacker: http://www.wired.com/threatlevel/2009/01/professed-twitt/ | |
| 616 | Top 10 2007-Broken Authentication and Session Management: http://www.owasp.org/index.php/Top_10_2007-A7 | |
| 617 | Guide to Authentication: http://www.owasp.org/index.php/Guide_to_Authentication | |
| 618 | Authentication: http://msdn.microsoft.com/en-us/library/aa374735(VS.85).aspx | |
| 619 | Writing Secure Code: Chapter 4, ""Authentication"" Page 109" | |
| 620 | CWE-306,EN-Missing Authentication for Critical Function (Type: Variant),"The software does not perform any authentication for functionality that requires a provable user identity or consumes a significant amount of resources. | |
| 621 | Authentication techniques should follow the algorithms that define them exactly, otherwise authentication can be bypassed or more easily subjected to brute force attacks.",,high,"The Art of Software Security Assessment: Chapter 2, ""Common Vulnerabilities of Authentication,"" Page 36 | |
| 622 | Top 25 Series - Rank 19 - Missing Authentication for Critical Function: http://blogs.sans.org/appsecstreetfighter/2010/02/23/top-25-series-rank-19-missing-authentication-for-critical-function/ | |
| 623 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI" | |
| 624 | CWE-319,EN-Cleartext Transmission of Sensitive Information (Type: Base),"The software transmits sensitive or security-critical data in cleartext in a communication channel that can be sniffed by unauthorized actors. | |
| 625 | Many communication channels can be ""sniffed"" by attackers during data transmission. For example, network traffic can often be sniffed by any attacker who has access to a network interface. This significantly lowers the difficulty of exploitation by attackers.",,high,"Top 10 2007-Insecure Communications: http://www.owasp.org/index.php/Top_10_2007-A9 | |
| 626 | Writing Secure Code: Chapter 9, ""Protecting Secret Data"" Page 299 | |
| 627 | 24 Deadly Sins of Software Security: ""Sin 22: Failing to Protect Network Traffic."" Page 337 | |
| 628 | Mobile App Top 10 List: http://www.veracode.com/blog/2010/12/mobile-app-top-10-list/" | |
| 629 | CWE-327,EN-Use of a Broken or Risky Cryptographic Algorithm (Type: Base),"The use of a broken or risky cryptographic algorithm is an unnecessary risk that may result in the exposure of sensitive information. | |
| 630 | The use of a non-standard algorithm is dangerous because a determined attacker may be able to break the algorithm and compromise whatever data has been protected. Well-known techniques may exist to break the algorithm.",,high,"Applied Cryptography: http://www.schneier.com/book-applied.html | |
| 631 | Handbook of Applied Cryptography: http://www.cacr.math.uwaterloo.ca/hac/ | |
| 632 | Avoiding bogus encryption products: Snake Oil FAQ: http://www.faqs.org/faqs/cryptography-faq/snake-oil/ | |
| 633 | SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 634 | Microsoft Scraps Old Encryption in New Code: http://www.eweek.com/c/a/Security/Microsoft-Scraps-Old-Encryption-in-New-Code/ | |
| 635 | Writing Secure Code: Chapter 8, ""Cryptographic Foibles"" Page 259 | |
| 636 | 24 Deadly Sins of Software Security: ""Sin 21: Using the Wrong Cryptography."" Page 315 | |
| 637 | Top 25 Series - Rank 24 - Use of a Broken or Risky Cryptographic Algorithm: http://blogs.sans.org/appsecstreetfighter/2010/03/25/top-25-series-rank-24-use-of-a-broken-or-risky-cryptographic-algorithm/ | |
| 638 | The Art of Software Security Assessment: Chapter 2, ""Insufficient or Obsolete Encryption"", Page 44." | |
| 639 | CWE-330,EN-Use of Insufficiently Random Values (Type: Class),"The software may use insufficiently random numbers or values in a security context that depends on unpredictable numbers. | |
| 640 | When software generates predictable values in a context requiring unpredictability, it may be possible for an attacker to guess the next value that will be generated, and use this guess to impersonate another user or access sensitive information.",,high,"SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 641 | Building Secure Software: How to Avoid Security Problems the Right Way | |
| 642 | Writing Secure Code: Chapter 8, ""Using Poor Random Numbers"" Page 259 | |
| 643 | 24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 644 | CWE-400,EN-Uncontrolled Resource Consumption (Resource Exhaustion) (Type: Base),"The software does not properly restrict the size or amount of resources that are requested or influenced by an actor, which can be used to consume more resources than intended. | |
| 645 | Limited resources include memory, file system storage, database connection pool entries, or CPU. If an attacker can trigger the allocation of these limited resources, but the number or size of the resources is not controlled, then the attacker could cause a denial of service that consumes all available resources. This would prevent valid users from accessing the software, and it could potentially have an impact on the surrounding environment. For example, a memory exhaustion attack against an application could slow down the application as well as its host operating system. | |
| 646 | Resource exhaustion problems have at least two common causes: | |
| 647 | Error conditions and other exceptional circumstances | |
| 648 | Confusion over which part of the program is responsible for releasing the resource",,high,"Detection and Prediction of Resource-Exhaustion Vulnerabilities: http://homepages.di.fc.ul.pt/~nuno/PAPERS/ISSRE08.pdf | |
| 649 | Resource exhaustion: http://cr.yp.to/docs/resources.html | |
| 650 | Resource exhaustion: http://homes.cerias.purdue.edu/~pmeunier/secprog/sanitized/class1/6.resource%20exhaustion.ppt | |
| 651 | Writing Secure Code: Chapter 17, ""Protecting Against Denial of Service Attacks"" Page 517" | |
| 652 | CWE-434,EN-Unrestricted Upload of File with Dangerous Type (Type: Base),"The software allows the attacker to upload or transfer files of dangerous types that can be automatically processed within the product's environment. | |
| 653 | If code is stored in a file with an extension such as "".inc"" or "".pl"", and the web server does not have a handler for that extension, then the server will likely send the contents of the file directly to the requester without the pre-processing that was expected. When that file contains sensitive information such as database credentials, this may allow the attacker to compromise the application or associated components.",,high,"Dynamic File Uploads, Security and You: http://shsc.info/FileUploadSecurity | |
| 654 | 8 Basic Rules to Implement Secure File Uploads: http://blogs.sans.org/appsecstreetfighter/2009/12/28/8-basic-rules-to-implement-secure-file-uploads/ | |
| 655 | Top 25 Series - Rank 8 - Unrestricted Upload of Dangerous File Type: http://blogs.sans.org/appsecstreetfighter/2010/02/25/top-25-series-rank-8-unrestricted-upload-of-dangerous-file-type/ | |
| 656 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 657 | The Art of Software Security Assessment: Chapter 17, ""File Uploading"", Page 1068." | |
| 658 | CWE-64,EN-Windows Shortcut Following (.LNK) (Type: Variant),"The software, when opening a file or directory, does not sufficiently handle when the file is a Windows shortcut (.LNK) whose target is outside of the intended control sphere. This could allow an attacker to cause the software to operate on unauthorized files. | |
| 659 | The shortcut (file with the .lnk extension) can permit an attacker to read/write a file that they originally did not have permissions to access.",,high, | |
| 660 | CWE-681,EN-Incorrect Conversion between Numeric Types (Type: Base),"When converting from one data type to another, such as long to integer, data can be omitted or translated in a way that produces unexpected values. If the resulting values are used in a sensitive context, then dangerous behaviors may occur. | |
| 661 | Typically, a product defines its control sphere within the code itself, or through configuration by the product's administrator. In some cases, an external party can change the definition of the control sphere. This is typically a resultant weakness.",,high,"The Art of Software Security Assessment: Chapter 6, ""Type Conversions"", Page 223." | |
| 662 | CWE-732,EN-Incorrect Permission Assignment for Critical Resource (Type: Class),"The software specifies permissions for a security-critical resource in a way that allows that resource to be read or modified by unintended actors. | |
| 663 | When a resource is given a permissions setting that provides access to a wider range of actors than required, it could lead to the exposure of sensitive information, or the modification of that resource by unintended parties. This is especially dangerous when the resource is related to program configuration, execution or sensitive user data.",,high,"The Art of Software Security Assessment: Chapter 9, ""File Permissions."" Page 495. | |
| 664 | Building Secure Software: How to Avoid Security Problems the Right Way: Chapter 8, ""Access Control."" Page 194. | |
| 665 | Top 25 Series - Rank 21 - Incorrect Permission Assignment for Critical Response: http://software-security.sans.org/blog/2010/03/24/top-25-series-rank-21-incorrect-permission-assignment-for-critical-response | |
| 666 | Federal Desktop Core Configuration: http://nvd.nist.gov/fdcc/index.cfm" | |
| 667 | CWE-770,EN-Allocation of Resources Without Limits or Throttling (Type: Base),"The software allocates a reusable resource or group of resources on behalf of an actor without imposing any restrictions on how many resources can be allocated, in violation of the intended security policy for that actor. | |
| 668 | Command injection vulnerabilities typically occur when: | |
| 669 | 1. Data enters the application from an untrusted source. | |
| 670 | 2. The data is part of a string that is executed as a command by the application. | |
| 671 | 3. By executing the command, the application gives an attacker a privilege or capability that the attacker would not otherwise have.",,high,"Real-Life Example of a 'Business Logic Defect' (Screen Shots!): http://h30501.www3.hp.com/t5/Following-the-White-Rabbit-A/Real-Life-Example-of-a-Business-Logic-Defect-Screen-Shots/ba-p/22581 | |
| 672 | Detection and Prediction of Resource-Exhaustion Vulnerabilities: http://homepages.di.fc.ul.pt/~nuno/PAPERS/ISSRE08.pdf | |
| 673 | Resource exhaustion: http://cr.yp.to/docs/resources.html | |
| 674 | Resource exhaustion: http://homes.cerias.purdue.edu/~pmeunier/secprog/sanitized/class1/6.resource%20exhaustion.ppt | |
| 675 | Writing Secure Code: Chapter 17, ""Protecting Against Denial of Service Attacks"" Page 517 | |
| 676 | Top 25 Series - Rank 22 - Allocation of Resources Without Limits or Throttling: http://blogs.sans.org/appsecstreetfighter/2010/03/23/top-25-series-rank-22-allocation-of-resources-without-limits-or-throttling/ | |
| 677 | The Art of Software Security Assessment: Chapter 10, ""Resource Limits"", Page 574." | |
| 678 | CWE-771,EN-Missing Reference to Active Allocated Resource (Type: Base),"The software does not properly maintain a reference to a resource that has been allocated, which prevents the resource from being reclaimed. | |
| 679 | This does not necessarily apply in languages or frameworks that automatically perform garbage collection, since the removal of all references may act as a signal that the resource is ready to be reclaimed.",,high, | |
| 680 | CWE-772,EN-Missing Release of Resource after Effective Lifetime (Type: Base),"The software does not release a resource after its effective lifetime has ended, i.e., after the resource is no longer needed. | |
| 681 | When a resource is not released after use, it can allow attackers to cause a denial of service.",,high, | |
| 682 | CWE-773,EN-Missing Reference to Active File Descriptor or Handle (Type: Variant),"The software does not properly maintain references to a file descriptor or handle, which prevents that file descriptor/handle from being reclaimed. | |
| 683 | This can cause the software to consume all available file descriptors or handles, which can prevent other processes from performing critical file processing operations.",,high, | |
| 684 | CWE-774,EN-Allocation of File Descriptors or Handles Without Limits or Throttling (Type: Variant),"The software allocates file descriptors or handles on behalf of an actor without imposing any restrictions on how many descriptors can be allocated, in violation of the intended security policy for that actor. | |
| 685 | This can cause the software to consume all available file descriptors or handles, which can prevent other processes from performing critical file processing operations.",,high,"The Art of Software Security Assessment: Chapter 10, ""Resource Limits"", Page 574." | |
| 686 | CWE-775,EN-Missing Release of File Descriptor or Handle after Effective Lifetime (Type: Variant),"The software does not release a file descriptor or handle after its effective lifetime has ended, i.e., after the file descriptor/handle is no longer needed. | |
| 687 | When a file descriptor or handle is not released after use (typically by explicitly closing it), attackers can cause a denial of service by consuming all available file descriptors/handles, or otherwise preventing other system processes from obtaining their own file descriptors/handles.",,high,"The Art of Software Security Assessment: Chapter 10, ""File Descriptor Leaks"", Page 582." | |
| 688 | CWE-804,EN-Guessable CAPTCHA (Type: Base),"The software uses a CAPTCHA challenge, but the challenge can be guessed or automatically recognized by a non-human actor. | |
| 689 | An automated attacker could bypass the intended protection of the CAPTCHA challenge and perform actions at a higher frequency than humanly possible, such as launching spam attacks. | |
| 690 | There can be several different causes of a guessable CAPTCHA: | |
| 691 | An audio or visual image that does not have sufficient distortion from the unobfuscated source image. | |
| 692 | A question is generated that with a format that can be automatically recognized, such as a math question. | |
| 693 | A question for which the number of possible answers is limited, such as birth years or favorite sports teams. | |
| 694 | A general-knowledge or trivia question for which the answer can be accessed using a data base, such as country capitals or popular actors. | |
| 695 | Other data associated with the CAPTCHA may provide hints about its contents, such as an image whose filename contains the word that is used in the CAPTCHA.",,high,Insufficient Anti-automation: http://projects.webappsec.org/Insufficient+Anti-automation | |
| 696 | CWE-805,EN-Buffer Access with Incorrect Length Value (Type: Base),"The software uses a sequential operation to read or write a buffer, but it uses an incorrect length value that causes it to access memory that is outside of the bounds of the buffer. | |
| 697 | When the length value exceeds the size of the destination, a buffer overflow could occur.",,high,"Writing Secure Code: Chapter 6, ""Why ACLs Are Important"" Page 171 | |
| 698 | Address Space Layout Randomization in Windows Vista: http://blogs.msdn.com/michael_howard/archive/2006/05/26/address-space-layout-randomization-in-windows-vista.aspx | |
| 699 | Limiting buffer overflows with ExecShield: http://www.redhat.com/magazine/009jul05/features/execshield/ | |
| 700 | PaX: http://en.wikipedia.org/wiki/PaX | |
| 701 | Top 25 Series - Rank 12 - Buffer Access with Incorrect Length Value: http://blogs.sans.org/appsecstreetfighter/2010/03/11/top-25-series-rank-12-buffer-access-with-incorrect-length-value/ | |
| 702 | Safe C String Library v1.0.3: http://www.zork.org/safestr/ | |
| 703 | Using the Strsafe.h Functions: http://msdn.microsoft.com/en-us/library/ms647466.aspx | |
| 704 | Understanding DEP as a mitigation technology part 1: http://blogs.technet.com/b/srd/archive/2009/06/12/understanding-dep-as-a-mitigation-technology-part-1.aspx | |
| 705 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html" | |
| 706 | CWE-806,EN-Buffer Access Using Size of Source Buffer (Type: Variant),"The software uses the size of a source buffer when reading from or writing to a destination buffer, which may cause it to access memory that is outside of the bounds of the buffer. | |
| 707 | When the size of the destination is smaller than the size of the source, a buffer overflow could occur.",,high,"Using the Strsafe.h Functions: http://msdn.microsoft.com/en-us/library/ms647466.aspx | |
| 708 | Safe C String Library v1.0.3: http://www.zork.org/safestr/ | |
| 709 | Address Space Layout Randomization in Windows Vista: http://blogs.msdn.com/michael_howard/archive/2006/05/26/address-space-layout-randomization-in-windows-vista.aspx | |
| 710 | Limiting buffer overflows with ExecShield: http://www.redhat.com/magazine/009jul05/features/execshield/ | |
| 711 | PaX: http://en.wikipedia.org/wiki/PaX | |
| 712 | Understanding DEP as a mitigation technology part 1: http://blogs.technet.com/b/srd/archive/2009/06/12/understanding-dep-as-a-mitigation-technology-part-1.aspx" | |
| 713 | CWE-807,EN-Reliance on Untrusted Inputs in a Security Decision (Type: Base),"The application uses a protection mechanism that relies on the existence or values of an input, but the input can be modified by an untrusted actor in a way that bypasses the protection mechanism. | |
| 714 | Developers may assume that inputs such as cookies, environment variables, and hidden form fields cannot be modified. However, an attacker could change these inputs using customized clients or other attacks. This change might not be detected. When security decisions such as authentication and authorization are made based on the values of these inputs, attackers can bypass the security of the software. | |
| 715 | Without sufficient encryption, integrity checking, or other mechanism, any input that originates from an outsider cannot be trusted.",,high,"Top 25 Series - Rank 6 - Reliance on Untrusted Inputs in a Security Decision: http://blogs.sans.org/appsecstreetfighter/2010/03/05/top-25-series-rank-6-reliance-on-untrusted-inputs-in-a-security-decision/ | |
| 716 | HMAC: http://en.wikipedia.org/wiki/Hmac | |
| 717 | Understanding ASP.NET View State: http://msdn.microsoft.com/en-us/library/ms972976.aspx | |
| 718 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI" | |
| 719 | CWE-93,EN-Improper Neutralization of CRLF Sequences (CRLF Injection) (Type: Base),"The software uses CRLF (carriage return line feeds) as a special element, e.g. to separate lines or records, but it does not neutralize or incorrectly neutralizes CRLF sequences from inputs. | |
| 720 | Since an implicit intent does not specify a particular application to receive the data, any application can process the intent by using an Intent Filter for that intent. This can allow untrusted applications to obtain sensitive data.",,high,CRLF Injection: http://marc.info/?l=bugtraq&m=102088154213630&w=2 | |
| 721 | CWE-102,EN-Struts: Duplicate Validation Forms (Type: Variant),"The application uses multiple validation forms with the same name, which might cause the Struts Validator to validate a form that the programmer does not expect. | |
| 722 | If two validation forms have the same name, the Struts Validator arbitrarily chooses one of the forms to use for input validation and discards the other. This decision might not correspond to the programmer's expectations, possibly leading to resultant weaknesses. Moreover, it indicates that the validation logic is not up-to-date, and can indicate that other, more subtle validation errors are present.",,unclassified, | |
| 723 | CWE-103,EN-Struts: Incomplete validate() Method Definition (Type: Variant),"The application has a validator form that either does not define a validate() method, or defines a validate() method but does not call super.validate(). | |
| 724 | If you do not call super.validate(), the Validation Framework cannot check the contents of the form against a validation form. In other words, the validation framework will be disabled for the given form.",,unclassified, | |
| 725 | CWE-104,EN-Struts: Form Bean Does Not Extend Validation Class (Type: Variant),"If a form bean does not extend an ActionForm subclass of the Validator framework, it can expose the application to other weaknesses related to insufficient input validation. | |
| 726 | If you do not call super.validate(), the Validation Framework cannot check the contents of the form against a validation form. In other words, the validation framework will be disabled for the given form.",,unclassified, | |
| 727 | CWE-105,EN-Struts: Form Field Without Validator (Type: Variant),"The application has a form field that is not validated by a corresponding validation form, which can introduce other weaknesses related to insufficient input validation. | |
| 728 | If you do not call super.validate(), the Validation Framework cannot check the contents of the form against a validation form. In other words, the validation framework will be disabled for the given form.",,unclassified, | |
| 729 | CWE-106,EN-Struts: Plug-in Framework not in Use (Type: Variant),"When an application does not use an input validation framework such as the Struts Validator, there is a greater risk of introducing weaknesses related to insufficient input validation. | |
| 730 | If you do not call super.validate(), the Validation Framework cannot check the contents of the form against a validation form. In other words, the validation framework will be disabled for the given form.",,unclassified, | |
| 731 | CWE-107,EN-Struts: Unused Validation Form (Type: Variant),"An unused validation form indicates that validation logic is not up-to-date. | |
| 732 | It is easy for developers to forget to update validation logic when they remove or rename action form mappings. One indication that validation logic is not being properly maintained is the presence of an unused validation form.",,unclassified, | |
| 733 | CWE-108,EN-Struts: Unvalidated Action Form (Type: Variant),"Every Action Form must have a corresponding validation form. | |
| 734 | If a Struts Action Form Mapping specifies a form, it must have a validation form defined under the Struts Validator.",,unclassified, | |
| 735 | CWE-109,EN-Struts: Validator Turned Off (Type: Variant),"Automatic filtering via a Struts bean has been turned off, which disables the Struts Validator and custom validation logic. This exposes the application to other weaknesses related to insufficient input validation. | |
| 736 | If a Struts Action Form Mapping specifies a form, it must have a validation form defined under the Struts Validator.",,unclassified, | |
| 737 | CWE-11,EN-ASP.NET Misconfiguration: Creating Debug Binary (Type: Variant),"Debugging messages help attackers learn about the system and plan a form of attack. | |
| 738 | ASP .NET applications can be configured to produce debug binaries. These binaries give detailed debugging messages and should not be used in production environments. Debug binaries are meant to be used in a development or testing environment and can pose a security risk if they are deployed to production.",,unclassified, | |
| 739 | CWE-110,EN-Struts: Validator Without Form Field (Type: Variant),"Validation fields that do not appear in forms they are associated with indicate that the validation logic is out of date. | |
| 740 | It is easy for developers to forget to update validation logic when they make changes to an ActionForm class. One indication that validation logic is not being properly maintained is inconsistencies between the action form and the validation form.",,unclassified, | |
| 741 | CWE-111,EN-Direct Use of Unsafe JNI (Type: Base),"When a Java application uses the Java Native Interface (JNI) to call code written in another programming language, it can expose the application to weaknesses in that code, even if those weaknesses cannot occur in Java. | |
| 742 | Many safety features that programmers may take for granted simply do not apply for native code, so you must carefully review all such code for potential problems. The languages used to implement native code may be more susceptible to buffer overflows and other attacks. Native code is unprotected by the security features enforced by the runtime environment, such as strong typing and array bounds checking.",,unclassified,"Fortify Descriptions: http://vulncat.fortifysoftware.com | |
| 743 | The Java(TM) Tutorial: The Java Native Interface: http://java.sun.com/docs/books/tutorial/native1.1/" | |
| 744 | CWE-112,EN-Missing XML Validation (Type: Base),"The software accepts XML from an untrusted source but does not validate the XML against the proper schema. | |
| 745 | Most successful attacks begin with a violation of the programmer's assumptions. By accepting an XML document without validating it against a DTD or XML schema, the programmer leaves a door open for attackers to provide unexpected, unreasonable, or malicious input.",,unclassified, | |
| 746 | CWE-113,EN-Improper Neutralization of CRLF Sequences in HTTP Headers (HTTP Response Splitting) (Type: Base),"The software receives data from an upstream component, but does not neutralize or incorrectly neutralizes CR and LF characters before the data is included in outgoing HTTP headers. | |
| 747 | Including unvalidated data in an HTTP header allows an attacker to specify the entirety of the HTTP response rendered by the browser. When an HTTP request contains unexpected CR (carriage return, also given by %0d or \r) and LF (line feed, also given by %0a or \n) characters the server may respond with an output stream that is interpreted as two different HTTP responses (instead of one). An attacker can control the second response and mount attacks such as cross-site scripting and cache poisoning attacks. | |
| 748 | HTTP response splitting weaknesses may be present when: | |
| 749 | Data enters a web application through an untrusted source, most frequently an HTTP request. | |
| 750 | The data is included in an HTTP response header sent to a web user without being validated for malicious characters.",,unclassified,"OWASP TOP 10: http://www.owasp.org/index.php/Top_10_2007 | |
| 751 | 24 Deadly Sins of Software Security: ""Sin 2: Web-Server Related Vulnerabilities (XSS, XSRF, and Response Splitting)."" Page 31" | |
| 752 | CWE-114,EN-Process Control (Type: Base),"Executing commands or loading libraries from an untrusted source or in an untrusted environment can cause an application to execute malicious commands (and payloads) on behalf of an attacker. | |
| 753 | Process control vulnerabilities take two forms: 1. An attacker can change the command that the program executes: the attacker explicitly controls what the command is. 2. An attacker can change the environment in which the command executes: the attacker implicitly controls what the command means. Process control vulnerabilities of the first type occur when either data enters the application from an untrusted source and the data is used as part of a string representing a command that is executed by the application. By executing the command, the application gives an attacker a privilege or capability that the attacker would not otherwise have.",,unclassified, | |
| 754 | CWE-115,EN-Misinterpretation of Input (Type: Base),"The software misinterprets an input, whether from an attacker or another product, in a security-relevant fashion. | |
| 755 | Process control vulnerabilities take two forms: 1. An attacker can change the command that the program executes: the attacker explicitly controls what the command is. 2. An attacker can change the environment in which the command executes: the attacker implicitly controls what the command means. Process control vulnerabilities of the first type occur when either data enters the application from an untrusted source and the data is used as part of a string representing a command that is executed by the application. By executing the command, the application gives an attacker a privilege or capability that the attacker would not otherwise have.",,unclassified, | |
| 756 | CWE-118,EN-Improper Access of Indexable Resource (Range Error) (Type: Class),"The software does not restrict or incorrectly restricts operations within the boundaries of a resource that is accessed using an index or pointer, such as memory or files. | |
| 757 | This can allow an attacker to forge log entries or inject malicious content into logs. | |
| 758 | Log forging vulnerabilities occur when: | |
| 759 | Data enters an application from an untrusted source. | |
| 760 | The data is written to an application or system log file.",,unclassified, | |
| 761 | CWE-12,EN-ASP.NET Misconfiguration: Missing Custom Error Page (Type: Variant),"An ASP .NET application must enable custom error pages in order to prevent attackers from mining information from the framework's built-in responses. | |
| 762 | Certain languages allow direct addressing of memory locations and do not automatically ensure that these locations are valid for the memory buffer that is being referenced. This can cause read or write operations to be performed on memory locations that may be associated with other variables, data structures, or internal program data. | |
| 763 | As a result, an attacker may be able to execute arbitrary code, alter the intended control flow, read sensitive information, or cause the system to crash.",,unclassified,"19 Deadly Sins of Software Security | |
| 764 | ASP.NET Misconfiguration: Missing Custom Error Handling: http://www.owasp.org/index.php/ASP.NET_Misconfiguration:_Missing_Custom_Error_Handling" | |
| 765 | CWE-125,EN-Out-of-bounds Read (Type: Base),"The software reads data past the end, or before the beginning, of the intended buffer. | |
| 766 | This typically occurs when the pointer or its index is incremented or decremented to a position beyond the bounds of the buffer or when pointer arithmetic results in a position outside of the valid memory location to name a few. This may result in corruption of sensitive information, a crash, or code execution among other things.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89" | |
| 767 | CWE-126,EN-Buffer Over-read (Type: Variant),"The software reads from a buffer using buffer access mechanisms such as indexes or pointers that reference memory locations after the targeted buffer. | |
| 768 | This typically occurs when the pointer or its index is incremented to a position beyond the bounds of the buffer or when pointer arithmetic results in a position outside of the valid memory location to name a few. This may result in exposure of sensitive information or possibly a crash.",,unclassified, | |
| 769 | CWE-127,EN-Buffer Under-read (Type: Variant),"The software reads from a buffer using buffer access mechanisms such as indexes or pointers that reference memory locations prior to the targeted buffer. | |
| 770 | This typically occurs when the pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used. This may result in exposure of sensitive information or possibly a crash.",,unclassified, | |
| 771 | CWE-13,EN-ASP.NET Misconfiguration: Password in Configuration File (Type: Variant),"Storing a plaintext password in a configuration file allows anyone who can read the file access to the password-protected resource making them an easy target for attackers. | |
| 772 | This typically occurs when the pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used. This may result in exposure of sensitive information or possibly a crash.",,unclassified,"How To: Encrypt Configuration Sections in ASP.NET 2.0 Using DPAPI: http://msdn.microsoft.com/en-us/library/ms998280.aspx | |
| 773 | How To: Encrypt Configuration Sections in ASP.NET 2.0 Using RSA: http://msdn.microsoft.com/en-us/library/ms998283.aspx | |
| 774 | .NET Framework Developer's Guide - Securing Connection Strings: http://msdn.microsoft.com/en-us/library/89211k9b(VS.80).aspx" | |
| 775 | CWE-130,EN-Improper Handling of Length Parameter Inconsistency (Type: Variant),"The software parses a formatted message or structure, but it does not handle or incorrectly handles a length field that is inconsistent with the actual length of the associated data. | |
| 776 | If an attacker can manipulate the length parameter associated with an input such that it is inconsistent with the actual length of the input, this can be leveraged to cause the target application to behave in unexpected, and possibly, malicious ways. One of the possible motives for doing so is to pass in arbitrarily large input to the application. Another possible motivation is the modification of application state by including invalid data for subsequent properties of the application. Such weaknesses commonly lead to attacks such as buffer overflows and execution of arbitrary code.",,unclassified, | |
| 777 | CWE-132,EN-DEPRECATED (Duplicate): Miscalculated Null Termination (Type: Base),"This entry has been deprecated because it was a duplicate of CWE-170. All content has been transferred to CWE-170. | |
| 778 | If an attacker can manipulate the length parameter associated with an input such that it is inconsistent with the actual length of the input, this can be leveraged to cause the target application to behave in unexpected, and possibly, malicious ways. One of the possible motives for doing so is to pass in arbitrarily large input to the application. Another possible motivation is the modification of application state by including invalid data for subsequent properties of the application. Such weaknesses commonly lead to attacks such as buffer overflows and execution of arbitrary code.",,unclassified, | |
| 779 | CWE-135,EN-Incorrect Calculation of Multi-Byte String Length (Type: Base),"The software does not correctly calculate the length of strings that can contain wide or multi-byte characters. | |
| 780 | If an attacker can manipulate the length parameter associated with an input such that it is inconsistent with the actual length of the input, this can be leveraged to cause the target application to behave in unexpected, and possibly, malicious ways. One of the possible motives for doing so is to pass in arbitrarily large input to the application. Another possible motivation is the modification of application state by including invalid data for subsequent properties of the application. Such weaknesses commonly lead to attacks such as buffer overflows and execution of arbitrary code.",,unclassified,"Writing Secure Code: Chapter 5, ""Unicode and ANSI Buffer Size Mismatches"" Page 153" | |
| 781 | CWE-138,EN-Improper Neutralization of Special Elements (Type: Class),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as control elements or syntactic markers when they are sent to a downstream component. | |
| 782 | Most languages and protocols have their own special elements such as characters and reserved words. These special elements can carry control implications. If software does not prevent external control or influence over the inclusion of such special elements, the control flow of the program may be altered from what was intended. For example, both Unix and Windows interpret the symbol < (""less than"") as meaning ""read input from a file"".",,unclassified, | |
| 783 | CWE-14,EN-Compiler Removal of Code to Clear Buffers (Type: Base),"Sensitive memory is cleared according to the source code, but compiler optimizations leave the memory untouched when it is not read from again, aka ""dead store removal."" | |
| 784 | This compiler optimization error occurs when: | |
| 785 | 1. Secret data are stored in memory. | |
| 786 | 2. The secret data are scrubbed from memory by overwriting its contents. | |
| 787 | 3. The source code is compiled using an optimizing compiler, which identifies and removes the function that overwrites the contents as a dead store because the memory is not used subsequently.",,unclassified,"Writing Secure Code: Chapter 9, ""A Compiler Optimization Caveat"" Page 322 | |
| 788 | When scrubbing secrets in memory doesn't work: http://cert.uni-stuttgart.de/archive/bugtraq/2002/11/msg00046.html | |
| 789 | Some Bad News and Some Good News: http://msdn.microsoft.com/library/default.asp?url=/library/en-us/dncode/html/secure10102002.asp | |
| 790 | GNU GCC: Optimizer Removes Code Necessary for Security: http://www.derkeiler.com/Mailing-Lists/securityfocus/bugtraq/2002-11/0257.html" | |
| 791 | CWE-140,EN-Improper Neutralization of Delimiters (Type: Base),"The software does not neutralize or incorrectly neutralizes delimiters. | |
| 792 | This compiler optimization error occurs when: | |
| 793 | 1. Secret data are stored in memory. | |
| 794 | 2. The secret data are scrubbed from memory by overwriting its contents. | |
| 795 | 3. The source code is compiled using an optimizing compiler, which identifies and removes the function that overwrites the contents as a dead store because the memory is not used subsequently.",,unclassified, | |
| 796 | CWE-141,EN-Improper Neutralization of Parameter/Argument Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as parameter or argument delimiters when they are sent to a downstream component. | |
| 797 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Embedded Delimiters"", Page 408. | |
| 798 | The Art of Software Security Assessment: Chapter 10, ""IFS"", Page 604." | |
| 799 | CWE-142,EN-Improper Neutralization of Value Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as value delimiters when they are sent to a downstream component. | |
| 800 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Embedded Delimiters"", Page 408." | |
| 801 | CWE-143,EN-Improper Neutralization of Record Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as record delimiters when they are sent to a downstream component. | |
| 802 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Embedded Delimiters"", Page 408." | |
| 803 | CWE-144,EN-Improper Neutralization of Line Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as line delimiters when they are sent to a downstream component. | |
| 804 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Embedded Delimiters"", Page 408." | |
| 805 | CWE-145,EN-Improper Neutralization of Section Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as section delimiters when they are sent to a downstream component. | |
| 806 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions. | |
| 807 | One example of a section delimiter is the boundary string in a multipart MIME message. In many cases, doubled line delimiters can serve as a section delimiter.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Embedded Delimiters"", Page 408." | |
| 808 | CWE-146,EN-Improper Neutralization of Expression/Command Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as expression or command delimiters when they are sent to a downstream component. | |
| 809 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Embedded Delimiters"", Page 408." | |
| 810 | CWE-147,EN-Improper Neutralization of Input Terminators (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as input terminators when they are sent to a downstream component. | |
| 811 | For example, a ""."" in SMTP signifies the end of mail message data, whereas a null character can be used for the end of a string.",,unclassified, | |
| 812 | CWE-148,EN-Improper Neutralization of Input Leaders (Type: Variant),"The application does not properly handle when a leading character or sequence (""leader"") is missing or malformed, or if multiple leaders are used when only one should be allowed. | |
| 813 | For example, a ""."" in SMTP signifies the end of mail message data, whereas a null character can be used for the end of a string.",,unclassified, | |
| 814 | CWE-149,EN-Improper Neutralization of Quoting Syntax (Type: Variant),"Quotes injected into an application can be used to compromise a system. As data are parsed, an injected/absent/duplicate/malformed use of quotes may cause the process to take unexpected actions. | |
| 815 | For example, a ""."" in SMTP signifies the end of mail message data, whereas a null character can be used for the end of a string.",,unclassified, | |
| 816 | CWE-15,EN-External Control of System or Configuration Setting (Type: Base),"One or more system settings or configuration elements can be externally controlled by a user. | |
| 817 | Allowing external control of system settings can disrupt service or cause an application to behave in unexpected, and potentially malicious ways.",,unclassified, | |
| 818 | CWE-150,"EN-Improper Neutralization of Escape, Meta, or Control Sequences (Type: Variant)","The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as escape, meta, or control character sequences when they are sent to a downstream component. | |
| 819 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified, | |
| 820 | CWE-151,EN-Improper Neutralization of Comment Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as comment delimiters when they are sent to a downstream component. | |
| 821 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified, | |
| 822 | CWE-152,EN-Improper Neutralization of Macro Symbols (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as macro symbols when they are sent to a downstream component. | |
| 823 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified, | |
| 824 | CWE-153,EN-Improper Neutralization of Substitution Characters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as substitution characters when they are sent to a downstream component. | |
| 825 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified, | |
| 826 | CWE-154,EN-Improper Neutralization of Variable Name Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as variable name delimiters when they are sent to a downstream component. | |
| 827 | As data is parsed, an injected delimiter may cause the process to take unexpected actions that result in an attack. Example: ""$"" for an environment variable.",,unclassified, | |
| 828 | CWE-155,EN-Improper Neutralization of Wildcards or Matching Symbols (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as wildcards or matching symbols when they are sent to a downstream component. | |
| 829 | As data is parsed, an injected element may cause the process to take unexpected actions.",,unclassified, | |
| 830 | CWE-156,EN-Improper Neutralization of Whitespace (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as whitespace when they are sent to a downstream component. | |
| 831 | This can include space, tab, etc.",,unclassified, | |
| 832 | CWE-157,EN-Failure to Sanitize Paired Delimiters (Type: Variant),"The software does not properly handle the characters that are used to mark the beginning and ending of a group of entities, such as parentheses, brackets, and braces. | |
| 833 | This can include space, tab, etc.",,unclassified, | |
| 834 | CWE-158,EN-Improper Neutralization of Null Byte or NUL Character (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes NUL characters or null bytes when they are sent to a downstream component. | |
| 835 | As data is parsed, an injected NUL character or null byte may cause the software to believe the input is terminated earlier than it actually is, or otherwise cause the input to be misinterpreted. This could then be used to inject potentially dangerous input that occurs after the null byte or otherwise bypass validation routines and other protection mechanisms.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""NUL Character Injection"", Page 411." | |
| 836 | CWE-159,EN-Failure to Sanitize Special Element (Type: Class),"Weaknesses in this attack-focused category do not properly filter and interpret special elements in user-controlled input which could cause adverse effect on the software behavior and integrity. | |
| 837 | As data is parsed, an injected NUL character or null byte may cause the software to believe the input is terminated earlier than it actually is, or otherwise cause the input to be misinterpreted. This could then be used to inject potentially dangerous input that occurs after the null byte or otherwise bypass validation routines and other protection mechanisms.",,unclassified, | |
| 838 | CWE-160,EN-Improper Neutralization of Leading Special Elements (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes leading special elements that could be interpreted in unexpected ways when they are sent to a downstream component. | |
| 839 | As data is parsed, improperly handled leading special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 840 | CWE-161,EN-Improper Neutralization of Multiple Leading Special Elements (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes multiple leading special elements that could be interpreted in unexpected ways when they are sent to a downstream component. | |
| 841 | As data is parsed, improperly handled multiple leading special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 842 | CWE-162,EN-Improper Neutralization of Trailing Special Elements (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes trailing special elements that could be interpreted in unexpected ways when they are sent to a downstream component. | |
| 843 | As data is parsed, improperly handled trailing special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 844 | CWE-163,EN-Improper Neutralization of Multiple Trailing Special Elements (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes multiple trailing special elements that could be interpreted in unexpected ways when they are sent to a downstream component. | |
| 845 | As data is parsed, improperly handled multiple trailing special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 846 | CWE-164,EN-Improper Neutralization of Internal Special Elements (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes internal special elements that could be interpreted in unexpected ways when they are sent to a downstream component. | |
| 847 | As data is parsed, improperly handled internal special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 848 | CWE-165,EN-Improper Neutralization of Multiple Internal Special Elements (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes multiple internal special elements that could be interpreted in unexpected ways when they are sent to a downstream component. | |
| 849 | As data is parsed, improperly handled multiple internal special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 850 | CWE-166,EN-Improper Handling of Missing Special Element (Type: Base),"The software receives input from an upstream component, but it does not handle or incorrectly handles when an expected special element is missing. | |
| 851 | As data is parsed, improperly handled multiple internal special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 852 | CWE-167,EN-Improper Handling of Additional Special Element (Type: Base),"The software receives input from an upstream component, but it does not handle or incorrectly handles when an additional unexpected special element is missing. | |
| 853 | As data is parsed, improperly handled multiple internal special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 854 | CWE-168,EN-Improper Handling of Inconsistent Special Elements (Type: Base),"The software does not handle when an inconsistency exists between two or more special characters or reserved words. | |
| 855 | An example of this problem would be if paired characters appear in the wrong order, or if the special characters are not properly nested.",,unclassified, | |
| 856 | CWE-172,EN-Encoding Error (Type: Class),"The software does not properly encode or decode the data, resulting in unexpected values. | |
| 857 | Null termination errors frequently occur in two different ways. An off-by-one error could cause a null to be written out of bounds, leading to an overflow. Or, a program could use a strncpy() function call incorrectly, which prevents a null terminator from being added at all. Other scenarios are possible.",,unclassified, | |
| 858 | CWE-173,EN-Improper Handling of Alternate Encoding (Type: Variant),"The software does not properly handle when an input uses an alternate encoding that is valid for the control sphere to which the input is being sent. | |
| 859 | Null termination errors frequently occur in two different ways. An off-by-one error could cause a null to be written out of bounds, leading to an overflow. Or, a program could use a strncpy() function call incorrectly, which prevents a null terminator from being added at all. Other scenarios are possible.",,unclassified, | |
| 860 | CWE-174,EN-Double Decoding of the Same Data (Type: Variant),"The software decodes the same input twice, which can limit the effectiveness of any protection mechanism that occurs in between the decoding operations. | |
| 861 | Null termination errors frequently occur in two different ways. An off-by-one error could cause a null to be written out of bounds, leading to an overflow. Or, a program could use a strncpy() function call incorrectly, which prevents a null terminator from being added at all. Other scenarios are possible.",,unclassified, | |
| 862 | CWE-175,EN-Improper Handling of Mixed Encoding (Type: Variant),"The software does not properly handle when the same input uses several different (mixed) encodings. | |
| 863 | Null termination errors frequently occur in two different ways. An off-by-one error could cause a null to be written out of bounds, leading to an overflow. Or, a program could use a strncpy() function call incorrectly, which prevents a null terminator from being added at all. Other scenarios are possible.",,unclassified, | |
| 864 | CWE-176,EN-Improper Handling of Unicode Encoding (Type: Variant),"The software does not properly handle when an input contains Unicode encoding. | |
| 865 | Null termination errors frequently occur in two different ways. An off-by-one error could cause a null to be written out of bounds, leading to an overflow. Or, a program could use a strncpy() function call incorrectly, which prevents a null terminator from being added at all. Other scenarios are possible.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Character Sets and Unicode"", Page 446." | |
| 866 | CWE-177,EN-Improper Handling of URL Encoding (Hex Encoding) (Type: Variant),"The software does not properly handle when all or part of an input has been URL encoded. | |
| 867 | Null termination errors frequently occur in two different ways. An off-by-one error could cause a null to be written out of bounds, leading to an overflow. Or, a program could use a strncpy() function call incorrectly, which prevents a null terminator from being added at all. Other scenarios are possible.",,unclassified, | |
| 868 | CWE-178,EN-Improper Handling of Case Sensitivity (Type: Base),"The software does not properly account for differences in case sensitivity when accessing or determining the properties of a resource, leading to inconsistent results. | |
| 869 | Improperly handled case sensitive data can lead to several possible consequences, including: | |
| 870 | case-insensitive passwords reducing the size of the key space, making brute force attacks easier | |
| 871 | bypassing filters or access controls using alternate names | |
| 872 | multiple interpretation errors using alternate names.",,unclassified, | |
| 873 | CWE-179,EN-Incorrect Behavior Order: Early Validation (Type: Base),"The software validates input before applying protection mechanisms that modify the input, which could allow an attacker to bypass the validation via dangerous inputs that only arise after the modification. | |
| 874 | Software needs to validate data at the proper time, after data has been canonicalized and cleansed. Early validation is susceptible to various manipulations that result in dangerous inputs that are produced by canonicalization and cleansing.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Escaping Metacharacters"", Page 439." | |
| 875 | CWE-180,EN-Incorrect Behavior Order: Validate Before Canonicalize (Type: Base),"The software validates input before it is canonicalized, which prevents the software from detecting data that becomes invalid after the canonicalization step. | |
| 876 | This can be used by an attacker to bypass the validation and launch attacks that expose weaknesses that would otherwise be prevented, such as injection.",,unclassified, | |
| 877 | CWE-181,EN-Incorrect Behavior Order: Validate Before Filter (Type: Base),"The software validates data before it has been filtered, which prevents the software from detecting data that becomes invalid after the filtering step. | |
| 878 | This can be used by an attacker to bypass the validation and launch attacks that expose weaknesses that would otherwise be prevented, such as injection.",,unclassified, | |
| 879 | CWE-182,EN-Collapse of Data into Unsafe Value (Type: Base),"The software filters data in a way that causes it to be reduced or ""collapsed"" into an unsafe value that violates an expected security property. | |
| 880 | This can be used by an attacker to bypass the validation and launch attacks that expose weaknesses that would otherwise be prevented, such as injection.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Character Stripping Vulnerabilities"", Page 437." | |
| 881 | CWE-183,EN-Permissive Whitelist (Type: Base),"An application uses a ""whitelist"" of acceptable values, but the whitelist includes at least one unsafe value, leading to resultant weaknesses. | |
| 882 | This can be used by an attacker to bypass the validation and launch attacks that expose weaknesses that would otherwise be prevented, such as injection.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Eliminating Metacharacters"", Page 435." | |
| 883 | CWE-184,EN-Incomplete Blacklist (Type: Base),"An application uses a ""blacklist"" of prohibited values, but the blacklist is incomplete. | |
| 884 | If an incomplete blacklist is used as a security mechanism, then the software may allow unintended values to pass into the application logic.",,unclassified,"Exploiting Software: How to Break Code | |
| 885 | Blacklist defenses as a breeding ground for vulnerability variants: http://seclists.org/fulldisclosure/2006/Feb/0040.html | |
| 886 | The Art of Software Security Assessment: Chapter 8, ""Eliminating Metacharacters"", Page 435." | |
| 887 | CWE-185,EN-Incorrect Regular Expression (Type: Class),"The software specifies a regular expression in a way that causes data to be improperly matched or compared. | |
| 888 | When the regular expression is used in protection mechanisms such as filtering or validation, this may allow an attacker to bypass the intended restrictions on the incoming data.",,unclassified,"Writing Secure Code: Chapter 10, ""Using Regular Expressions for Checking Input"" Page 350" | |
| 889 | CWE-186,EN-Overly Restrictive Regular Expression (Type: Base),"A regular expression is overly restrictive, which prevents dangerous values from being detected. | |
| 890 | When the regular expression is used in protection mechanisms such as filtering or validation, this may allow an attacker to bypass the intended restrictions on the incoming data.",,unclassified, | |
| 891 | CWE-187,EN-Partial Comparison (Type: Base),"The software performs a comparison that only examines a portion of a factor before determining whether there is a match, such as a substring, leading to resultant weaknesses. | |
| 892 | For example, an attacker might succeed in authentication by providing a small password that matches the associated portion of the larger, correct password.",,unclassified, | |
| 893 | CWE-191,EN-Integer Underflow (Wrap or Wraparound) (Type: Base),"The product subtracts one value from another, such that the result is less than the minimum allowable integer value, which produces a value that is not equal to the correct result. | |
| 894 | This can happen in signed and unsigned cases.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 7: Integer Overflows."" Page 119" | |
| 895 | CWE-193,EN-Off-by-one Error (Type: Base),"A product calculates or uses an incorrect maximum or minimum value that is 1 more, or 1 less, than the correct value. | |
| 896 | This can happen in signed and unsigned cases.",,unclassified,"Third Generation Exploits: http://www.blackhat.com/presentations/bh-europe-01/halvar-flake/bh-europe-01-halvarflake.ppt | |
| 897 | Off-by-one errors: a brief explanation: http://marc.theaimsgroup.com/?l=secprog&m=108379742110553&w=2 | |
| 898 | The Frame Pointer Overwrite: http://kaizo.org/mirrors/phrack/phrack55/P55-08 | |
| 899 | Exploiting Software: How to Break Code (The buffer overflow chapter) | |
| 900 | 24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89 | |
| 901 | The Art of Software Security Assessment: Chapter 5, ""Off-by-One Errors"", Page 180." | |
| 902 | CWE-195,EN-Signed to Unsigned Conversion Error (Type: Variant),"A signed-to-unsigned conversion error takes place when a signed primitive is used as an unsigned value, usually as a size variable. | |
| 903 | It is dangerous to rely on implicit casts between signed and unsigned numbers because the result can take on an unexpected value and violate assumptions made by the program.",,unclassified,"The Art of Software Security Assessment: Chapter 6, ""Type Conversions"", Page 223." | |
| 904 | CWE-198,EN-Use of Incorrect Byte Ordering (Type: Base),"The software receives input from an upstream component, but it does not account for byte ordering (e.g. big-endian and little-endian) when processing the input, causing an incorrect number or value to be used. | |
| 905 | When a primitive is cast to a smaller primitive, the high order bits of the large value are lost in the conversion, potentially resulting in an unexpected value that is not equal to the original value. This value may be required as an index into a buffer, a loop iterator, or simply necessary state data. In any case, the value cannot be trusted and the system will be in an undefined state. While this method may be employed viably to isolate the low bits of a value, this usage is rare, and truncation usually implies that an implementation error has occurred.",,unclassified, | |
| 906 | CWE-201,EN-Information Exposure Through Sent Data (Type: Variant),"The accidental exposure of sensitive information through sent data refers to the transmission of data which are either sensitive in and of itself or useful in the further exploitation of the system through standard data channels. | |
| 907 | The information either | |
| 908 | is regarded as sensitive within the product's own functionality, such as a private message; or | |
| 909 | provides information about the product or its environment that could be useful in an attack but is normally not available to the attacker, such as the installation path of a product that is remotely accessible. | |
| 910 | Many information exposures are resultant (e.g. PHP script error revealing the full path of the program), but they can also be primary (e.g. timing discrepancies in cryptography). There are many different types of problems that involve information exposures. Their severity can range widely depending on the type of information that is revealed.",,unclassified, | |
| 911 | CWE-203,EN-Information Exposure Through Discrepancy (Type: Class),"The product behaves differently or sends different responses in a way that exposes security-relevant information about the state of the product, such as whether a particular operation was successful or not. | |
| 912 | In situations where data should not be tied to individual users, but a large number of users should be able to make queries that ""scrub"" the identity of users, it may be possible to get information about a user -- e.g., by specifying search terms that are known to be unique to that user.",,unclassified, | |
| 913 | CWE-204,EN-Response Discrepancy Information Exposure (Type: Base),"The software provides different responses to incoming requests in a way that allows an actor to determine system state information that is outside of that actor's control sphere. | |
| 914 | This issue frequently occurs during authentication, where a difference in failed-login messages could allow an attacker to determine if the username is valid or not. These exposures can be inadvertent (bug) or intentional (design).",,unclassified,"24 Deadly Sins of Software Security: ""Sin 12: Information Leakage."" Page 191" | |
| 915 | CWE-205,EN-Information Exposure Through Behavioral Discrepancy (Type: Base),"The product's actions indicate important differences based on (1) the internal state of the product or (2) differences from other products in the same class. | |
| 916 | For example, attacks such as OS fingerprinting rely heavily on both behavioral and response discrepancies.",,unclassified, | |
| 917 | CWE-206,EN-Information Exposure of Internal State Through Behavioral Inconsistency (Type: Variant),"Two separate operations in a product cause the product to behave differently in a way that is observable to an attacker and reveals security-relevant information about the internal state of the product, such as whether a particular operation was successful or not. | |
| 918 | For example, attacks such as OS fingerprinting rely heavily on both behavioral and response discrepancies.",,unclassified, | |
| 919 | CWE-207,EN-Information Exposure Through an External Behavioral Inconsistency (Type: Variant),"The product behaves differently than other products like it, in a way that is observable to an attacker and exposes security-relevant information about which product is being used. | |
| 920 | For example, attacks such as OS fingerprinting rely heavily on both behavioral and response discrepancies.",,unclassified, | |
| 921 | CWE-208,EN-Information Exposure Through Timing Discrepancy (Type: Base),"Two separate operations in a product require different amounts of time to complete, in a way that is observable to an actor and reveals security-relevant information about the state of the product, such as whether a particular operation was successful or not. | |
| 922 | For example, attacks such as OS fingerprinting rely heavily on both behavioral and response discrepancies.",,unclassified, | |
| 923 | CWE-210,EN-Information Exposure Through Self-generated Error Message (Type: Base),"The software identifies an error condition and creates its own diagnostic or error messages that contain sensitive information. | |
| 924 | The sensitive information may be valuable information on its own (such as a password), or it may be useful for launching other, more deadly attacks. If an attack fails, an attacker may use error information provided by the server to launch another more focused attack. For example, an attempt to exploit a path traversal weakness (CWE-22) might yield the full pathname of the installed application. In turn, this could be used to select the proper number of "".."" sequences to navigate to the targeted file. An attack using SQL injection (CWE-89) might not initially succeed, but an error message could reveal the malformed query, which would expose query logic and possibly even passwords or other sensitive information used within the query.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 12: Information Leakage."" Page 191 | |
| 925 | The Art of Software Security Assessment: Chapter 3, ""Overly Verbose Error Messages"", Page 75." | |
| 926 | CWE-211,EN-Information Exposure Through Externally-generated Error Message (Type: Base),"The software performs an operation that triggers an external diagnostic or error message that is not directly generated by the software, such as an error generated by the programming language interpreter that the software uses. The error can contain sensitive system information. | |
| 927 | The sensitive information may be valuable information on its own (such as a password), or it may be useful for launching other, more deadly attacks. If an attack fails, an attacker may use error information provided by the server to launch another more focused attack. For example, an attempt to exploit a path traversal weakness (CWE-22) might yield the full pathname of the installed application. In turn, this could be used to select the proper number of "".."" sequences to navigate to the targeted file. An attack using SQL injection (CWE-89) might not initially succeed, but an error message could reveal the malformed query, which would expose query logic and possibly even passwords or other sensitive information used within the query.",,unclassified, | |
| 928 | CWE-212,EN-Improper Cross-boundary Removal of Sensitive Data (Type: Base),"The software uses a resource that contains sensitive data, but it does not properly remove that data before it stores, transfers, or shares the resource with actors in another control sphere. | |
| 929 | Resources that may contain sensitive data include documents, packets, messages, databases, etc. While this data may be useful to an individual user or small set of users who share the resource, it may need to be removed before the resource can be shared outside of the trusted group. The process of removal is sometimes called cleansing or scrubbing. | |
| 930 | For example, software that is used for editing documents might not remove sensitive data such as reviewer comments or the local pathname where the document is stored. Or, a proxy might not remove an internal IP address from headers before making an outgoing request to an Internet site.",,unclassified, | |
| 931 | CWE-213,EN-Intentional Information Exposure (Type: Base),"A product's design or configuration explicitly requires the publication of information that could be regarded as sensitive by an administrator. | |
| 932 | Resources that may contain sensitive data include documents, packets, messages, databases, etc. While this data may be useful to an individual user or small set of users who share the resource, it may need to be removed before the resource can be shared outside of the trusted group. The process of removal is sometimes called cleansing or scrubbing. | |
| 933 | For example, software that is used for editing documents might not remove sensitive data such as reviewer comments or the local pathname where the document is stored. Or, a proxy might not remove an internal IP address from headers before making an outgoing request to an Internet site.",,unclassified, | |
| 934 | CWE-214,EN-Information Exposure Through Process Environment (Type: Variant),"A process is invoked with sensitive arguments, environment variables, or other elements that can be seen by other processes on the operating system. | |
| 935 | Many operating systems allow a user to list information about processes that are owned by other users. This information could include command line arguments or environment variable settings. When this data contains sensitive information such as credentials, it might allow other users to launch an attack against the software or related resources.",,unclassified, | |
| 936 | CWE-215,EN-Information Exposure Through Debug Information (Type: Variant),"The application contains debugging code that can expose sensitive information to untrusted parties. | |
| 937 | Many operating systems allow a user to list information about processes that are owned by other users. This information could include command line arguments or environment variable settings. When this data contains sensitive information such as credentials, it might allow other users to launch an attack against the software or related resources.",,unclassified, | |
| 938 | CWE-216,EN-Containment Errors (Container Errors) (Type: Class),"This tries to cover various problems in which improper data are included within a ""container."" | |
| 939 | Many operating systems allow a user to list information about processes that are owned by other users. This information could include command line arguments or environment variable settings. When this data contains sensitive information such as credentials, it might allow other users to launch an attack against the software or related resources.",,unclassified, | |
| 940 | CWE-217,EN-DEPRECATED: Failure to Protect Stored Data from Modification (Type: Base),"This weakness has been deprecated because it incorporated and confused multiple weaknesses. The issues formerly covered in this weakness can be found at CWE-766 and CWE-767. | |
| 941 | Many operating systems allow a user to list information about processes that are owned by other users. This information could include command line arguments or environment variable settings. When this data contains sensitive information such as credentials, it might allow other users to launch an attack against the software or related resources.",,unclassified, | |
| 942 | CWE-218,EN-DEPRECATED (Duplicate): Failure to provide confidentiality for stored data (Type: Base),"This weakness has been deprecated because it was a duplicate of CWE-493. All content has been transferred to CWE-493. | |
| 943 | Many operating systems allow a user to list information about processes that are owned by other users. This information could include command line arguments or environment variable settings. When this data contains sensitive information such as credentials, it might allow other users to launch an attack against the software or related resources.",,unclassified, | |
| 944 | CWE-219,EN-Sensitive Data Under Web Root (Type: Variant),"The application stores sensitive data under the web document root with insufficient access control, which might make it accessible to untrusted parties. | |
| 945 | Many operating systems allow a user to list information about processes that are owned by other users. This information could include command line arguments or environment variable settings. When this data contains sensitive information such as credentials, it might allow other users to launch an attack against the software or related resources.",,unclassified, | |
| 946 | CWE-220,EN-Sensitive Data Under FTP Root (Type: Variant),"The application stores sensitive data under the FTP document root with insufficient access control, which might make it accessible to untrusted parties. | |
| 947 | Many file operations are intended to take place within a restricted directory. By using special elements such as "".."" and ""/"" separators, attackers can escape outside of the restricted location to access files or directories that are elsewhere on the system. One of the most common special elements is the ""../"" sequence, which in most modern operating systems is interpreted as the parent directory of the current location. This is referred to as relative path traversal. Path traversal also covers the use of absolute pathnames such as ""/usr/local/bin"", which may also be useful in accessing unexpected files. This is referred to as absolute path traversal. | |
| 948 | In many programming languages, the injection of a null byte (the 0 or NUL) may allow an attacker to truncate a generated filename to widen the scope of attack. For example, the software may add "".txt"" to any pathname, thus limiting the attacker to text files, but a null injection may effectively remove this restriction.",,unclassified, | |
| 949 | CWE-221,EN-Information Loss or Omission (Type: Class),"The software does not record, or improperly records, security-relevant information that leads to an incorrect decision or hampers later analysis. | |
| 950 | This can be resultant, e.g. a buffer overflow might trigger a crash before the product can log the event.",,unclassified, | |
| 951 | CWE-222,EN-Truncation of Security-relevant Information (Type: Base),"The application truncates the display, recording, or processing of security-relevant information in a way that can obscure the source or nature of an attack. | |
| 952 | This can be resultant, e.g. a buffer overflow might trigger a crash before the product can log the event.",,unclassified, | |
| 953 | CWE-223,EN-Omission of Security-relevant Information (Type: Base),"The application does not record or display information that would be important for identifying the source or nature of an attack, or determining if an action is safe. | |
| 954 | This can be resultant, e.g. a buffer overflow might trigger a crash before the product can log the event.",,unclassified,"The Art of Software Security Assessment: Chapter 2, ""Accountability"", Page 40." | |
| 955 | CWE-224,EN-Obscured Security-relevant Information by Alternate Name (Type: Base),"The software records security-relevant information according to an alternate name of the affected entity, instead of the canonical name. | |
| 956 | This can be resultant, e.g. a buffer overflow might trigger a crash before the product can log the event.",,unclassified,Writing Secure Code | |
| 957 | CWE-225,EN-DEPRECATED (Duplicate): General Information Management Problems (Type: Base),"This weakness can be found at CWE-199. | |
| 958 | This can be resultant, e.g. a buffer overflow might trigger a crash before the product can log the event.",,unclassified, | |
| 959 | CWE-226,EN-Sensitive Information Uncleared Before Release (Type: Base),"The software does not fully clear previously used information in a data structure, file, or other resource, before making that resource available to a party in another control sphere. | |
| 960 | This typically results from new data that is not as long as the old data, which leaves portions of the old data still available. Equivalent errors can occur in other situations where the length of data is variable but the associated data structure is not. If memory is not cleared after use, it may allow unintended actors to read the data when the memory is reallocated.",,unclassified, | |
| 961 | CWE-227,EN-Improper Fulfillment of API Contract (API Abuse) (Type: Class),"The software uses an API in a manner contrary to its intended use. | |
| 962 | An API is a contract between a caller and a callee. The most common forms of API misuse occurs when the caller does not honor its end of this contract. For example, if a program does not call chdir() after calling chroot(), it violates the contract that specifies how to change the active root directory in a secure fashion. Another good example of library abuse is expecting the callee to return trustworthy DNS information to the caller. In this case, the caller misuses the callee API by making certain assumptions about its behavior (that the return value can be used for authentication purposes). One can also violate the caller-callee contract from the other side. For example, if a coder subclasses SecureRandom and returns a non-random value, the contract is violated.",,unclassified, | |
| 963 | CWE-228,EN-Improper Handling of Syntactically Invalid Structure (Type: Class),"The product does not handle or incorrectly handles input that is not syntactically well-formed with respect to the associated specification. | |
| 964 | An API is a contract between a caller and a callee. The most common forms of API misuse occurs when the caller does not honor its end of this contract. For example, if a program does not call chdir() after calling chroot(), it violates the contract that specifies how to change the active root directory in a secure fashion. Another good example of library abuse is expecting the callee to return trustworthy DNS information to the caller. In this case, the caller misuses the callee API by making certain assumptions about its behavior (that the return value can be used for authentication purposes). One can also violate the caller-callee contract from the other side. For example, if a coder subclasses SecureRandom and returns a non-random value, the contract is violated.",,unclassified, | |
| 965 | CWE-229,EN-Improper Handling of Values (Type: Base),"The software does not properly handle when the expected number of values for parameters, fields, or arguments is not provided in input, or if those values are undefined. | |
| 966 | An API is a contract between a caller and a callee. The most common forms of API misuse occurs when the caller does not honor its end of this contract. For example, if a program does not call chdir() after calling chroot(), it violates the contract that specifies how to change the active root directory in a secure fashion. Another good example of library abuse is expecting the callee to return trustworthy DNS information to the caller. In this case, the caller misuses the callee API by making certain assumptions about its behavior (that the return value can be used for authentication purposes). One can also violate the caller-callee contract from the other side. For example, if a coder subclasses SecureRandom and returns a non-random value, the contract is violated.",,unclassified, | |
| 967 | CWE-23,EN-Relative Path Traversal (Type: Base),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize sequences such as "".."" that can resolve to a location that is outside of that directory. | |
| 968 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified,"OWASP Attack listing: http://www.owasp.org/index.php/Relative_Path_Traversal | |
| 969 | The Art of Software Security Assessment: Chapter 9, ""Filenames and Paths"", Page 503." | |
| 970 | CWE-230,EN-Improper Handling of Missing Values (Type: Variant),"The software does not handle or incorrectly handles when a parameter, field, or argument name is specified, but the associated value is missing, i.e. it is empty, blank, or null. | |
| 971 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 972 | CWE-231,EN-Improper Handling of Extra Values (Type: Variant),"The software does not handle or incorrectly handles when more values are provided than expected. | |
| 973 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 974 | CWE-232,EN-Improper Handling of Undefined Values (Type: Variant),"The software does not handle or incorrectly handles when a value is not defined or supported for the associated parameter, field, or argument name. | |
| 975 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 976 | CWE-233,EN-Improper Handling of Parameters (Type: Base),"The software does not properly handle when the expected number of parameters, fields, or arguments is not provided in input, or if those parameters are undefined. | |
| 977 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 978 | CWE-235,EN-Improper Handling of Extra Parameters (Type: Variant),"The software does not handle or incorrectly handles when the number of parameters, fields, or arguments with the same name exceeds the expected amount. | |
| 979 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 980 | CWE-236,EN-Improper Handling of Undefined Parameters (Type: Variant),"The software does not handle or incorrectly handles when a particular parameter, field, or argument name is not defined or supported by the product. | |
| 981 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 982 | CWE-237,EN-Improper Handling of Structural Elements (Type: Base),"The software does not handle or incorrectly handles inputs that are related to complex structures. | |
| 983 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 984 | CWE-238,EN-Improper Handling of Incomplete Structural Elements (Type: Variant),"The software does not handle or incorrectly handles when a particular structural element is not completely specified. | |
| 985 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 986 | CWE-239,EN-Failure to Handle Incomplete Element (Type: Variant),"The software does not properly handle when a particular element is not completely specified. | |
| 987 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 988 | CWE-24,EN-Path Traversal: ../filedir (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize ""../"" sequences that can resolve to a location that is outside of that directory. | |
| 989 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 990 | The ""../"" manipulation is the canonical manipulation for operating systems that use ""/"" as directory separators, such as UNIX- and Linux-based systems. In some cases, it is useful for bypassing protection schemes in environments for which ""/"" is supported but not the primary separator, such as Windows, which uses ""\"" but can also accept ""/"".",,unclassified, | |
| 991 | CWE-240,EN-Improper Handling of Inconsistent Structural Elements (Type: Variant),"The software does not handle or incorrectly handles when two or more structural elements should be consistent, but are not. | |
| 992 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 993 | The ""../"" manipulation is the canonical manipulation for operating systems that use ""/"" as directory separators, such as UNIX- and Linux-based systems. In some cases, it is useful for bypassing protection schemes in environments for which ""/"" is supported but not the primary separator, such as Windows, which uses ""\"" but can also accept ""/"".",,unclassified, | |
| 994 | CWE-241,EN-Improper Handling of Unexpected Data Type (Type: Base),"The software does not handle or incorrectly handles when a particular element is not the expected type, e.g. it expects a digit (0-9) but is provided with a letter (A-Z). | |
| 995 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 996 | The ""../"" manipulation is the canonical manipulation for operating systems that use ""/"" as directory separators, such as UNIX- and Linux-based systems. In some cases, it is useful for bypassing protection schemes in environments for which ""/"" is supported but not the primary separator, such as Windows, which uses ""\"" but can also accept ""/"".",,unclassified, | |
| 997 | CWE-244,EN-Improper Clearing of Heap Memory Before Release (Heap Inspection) (Type: Variant),"Using realloc() to resize buffers that store sensitive information can leave the sensitive information exposed to attack, because it is not removed from memory. | |
| 998 | When sensitive data such as a password or an encryption key is not removed from memory, it could be exposed to an attacker using a ""heap inspection"" attack that reads the sensitive data using memory dumps or other methods. The realloc() function is commonly used to increase the size of a block of allocated memory. This operation often requires copying the contents of the old memory block into a new and larger block. This operation leaves the contents of the original block intact but inaccessible to the program, preventing the program from being able to scrub sensitive data from memory. If an attacker can later examine the contents of a memory dump, the sensitive data could be exposed.",,unclassified, | |
| 999 | CWE-245,EN-J2EE Bad Practices: Direct Management of Connections (Type: Variant),"The J2EE application directly manages connections, instead of using the container's connection management facilities. | |
| 1000 | When sensitive data such as a password or an encryption key is not removed from memory, it could be exposed to an attacker using a ""heap inspection"" attack that reads the sensitive data using memory dumps or other methods. The realloc() function is commonly used to increase the size of a block of allocated memory. This operation often requires copying the contents of the old memory block into a new and larger block. This operation leaves the contents of the original block intact but inaccessible to the program, preventing the program from being able to scrub sensitive data from memory. If an attacker can later examine the contents of a memory dump, the sensitive data could be exposed.",,unclassified, | |
| 1001 | CWE-246,EN-J2EE Bad Practices: Direct Use of Sockets (Type: Variant),"The J2EE application directly uses sockets instead of using framework method calls. | |
| 1002 | When sensitive data such as a password or an encryption key is not removed from memory, it could be exposed to an attacker using a ""heap inspection"" attack that reads the sensitive data using memory dumps or other methods. The realloc() function is commonly used to increase the size of a block of allocated memory. This operation often requires copying the contents of the old memory block into a new and larger block. This operation leaves the contents of the original block intact but inaccessible to the program, preventing the program from being able to scrub sensitive data from memory. If an attacker can later examine the contents of a memory dump, the sensitive data could be exposed.",,unclassified, | |
| 1003 | CWE-247,EN-DEPRECATED (Duplicate): Reliance on DNS Lookups in a Security Decision (Type: Base),"This entry has been deprecated because it was a duplicate of CWE-350. All content has been transferred to CWE-350. | |
| 1004 | When sensitive data such as a password or an encryption key is not removed from memory, it could be exposed to an attacker using a ""heap inspection"" attack that reads the sensitive data using memory dumps or other methods. The realloc() function is commonly used to increase the size of a block of allocated memory. This operation often requires copying the contents of the old memory block into a new and larger block. This operation leaves the contents of the original block intact but inaccessible to the program, preventing the program from being able to scrub sensitive data from memory. If an attacker can later examine the contents of a memory dump, the sensitive data could be exposed.",,unclassified, | |
| 1005 | CWE-248,EN-Uncaught Exception (Type: Base),"An exception is thrown from a function, but it is not caught. | |
| 1006 | When an exception is not caught, it may cause the program to crash or expose sensitive information.",,unclassified, | |
| 1007 | CWE-249,EN-DEPRECATED: Often Misused: Path Manipulation (Type: Variant),"This entry has been deprecated because of name confusion and an accidental combination of multiple weaknesses. Most of its content has been transferred to CWE-785. | |
| 1008 | When an exception is not caught, it may cause the program to crash or expose sensitive information.",,unclassified, | |
| 1009 | CWE-25,EN-Path Traversal: /../filedir (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize ""/../"" sequences that can resolve to a location that is outside of that directory. | |
| 1010 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1011 | Sometimes a program checks for ""../"" at the beginning of the input, so a ""/../"" can bypass that check.",,unclassified, | |
| 1012 | CWE-26,EN-Path Traversal: /dir/../filename (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize ""/dir/../filename"" sequences that can resolve to a location that is outside of that directory. | |
| 1013 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1014 | The '/dir/../filename' manipulation is useful for bypassing some path traversal protection schemes. Sometimes a program only checks for ""../"" at the beginning of the input, so a ""/../"" can bypass that check.",,unclassified, | |
| 1015 | CWE-260,EN-Password in Configuration File (Type: Variant),"The software stores a password in a configuration file that might be accessible to actors who do not know the password. | |
| 1016 | This can result in compromise of the system for which the password is used. An attacker could gain access to this file and learn the stored password or worse yet, change the password to one of their choosing.",,unclassified,Building Secure Software: How to Avoid Security Problems the Right Way | |
| 1017 | CWE-261,EN-Weak Cryptography for Passwords (Type: Variant),"Obscuring a password with a trivial encoding does not protect the password. | |
| 1018 | This can result in compromise of the system for which the password is used. An attacker could gain access to this file and learn the stored password or worse yet, change the password to one of their choosing.",,unclassified,"Building Secure Software: How to Avoid Security Problems the Right Way | |
| 1019 | 24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 1020 | CWE-266,EN-Incorrect Privilege Assignment (Type: Base),"A product incorrectly assigns a privilege to a particular actor, creating an unintended sphere of control for that actor. | |
| 1021 | Just as neglecting to include functionality for the management of password aging is dangerous, so is allowing password aging to continue unchecked. Passwords must be given a maximum life span, after which a user is required to update with a new and different password.",,unclassified,Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 1022 | CWE-267,EN-Privilege Defined With Unsafe Actions (Type: Base),"A particular privilege, role, capability, or right can be used to perform unsafe actions that were not intended, even when it is assigned to the correct entity. | |
| 1023 | Just as neglecting to include functionality for the management of password aging is dangerous, so is allowing password aging to continue unchecked. Passwords must be given a maximum life span, after which a user is required to update with a new and different password.",,unclassified,Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 1024 | CWE-27,EN-Path Traversal: dir/../../filename (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize multiple internal ""../"" sequences that can resolve to a location that is outside of that directory. | |
| 1025 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1026 | The 'directory/../../filename' manipulation is useful for bypassing some path traversal protection schemes. Sometimes a program only removes one ""../"" sequence, so multiple ""../"" can bypass that check. Alternately, this manipulation could be used to bypass a check for ""../"" at the beginning of the pathname, moving up more than one directory level.",,unclassified, | |
| 1027 | CWE-270,EN-Privilege Context Switching Error (Type: Base),"The software does not properly manage privileges while it is switching between different contexts that have different privileges or spheres of control. | |
| 1028 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1029 | The 'directory/../../filename' manipulation is useful for bypassing some path traversal protection schemes. Sometimes a program only removes one ""../"" sequence, so multiple ""../"" can bypass that check. Alternately, this manipulation could be used to bypass a check for ""../"" at the beginning of the pathname, moving up more than one directory level.",,unclassified,"Writing Secure Code: Chapter 7, ""Running with Least Privilege"" Page 207 | |
| 1030 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html" | |
| 1031 | CWE-272,EN-Least Privilege Violation (Type: Base),"The elevated privilege level required to perform operations such as chroot() should be dropped immediately after the operation is performed. | |
| 1032 | In some contexts, a system executing with elevated permissions will hand off a process/file/etc. to another process or user. If the privileges of an entity are not reduced, then elevated privileges are spread throughout a system and possibly to an attacker.",,unclassified, | |
| 1033 | CWE-274,EN-Improper Handling of Insufficient Privileges (Type: Base),"The software does not handle or incorrectly handles when it has insufficient privileges to perform an operation, leading to resultant weaknesses. | |
| 1034 | If the drop fails, the software will continue to run with the raised privileges, which might provide additional access to unprivileged users.",,unclassified, | |
| 1035 | CWE-277,EN-Insecure Inherited Permissions (Type: Variant),"A product defines a set of insecure permissions that are inherited by objects that are created by the program. | |
| 1036 | If the drop fails, the software will continue to run with the raised privileges, which might provide additional access to unprivileged users.",,unclassified, | |
| 1037 | CWE-278,EN-Insecure Preserved Inherited Permissions (Type: Variant),"A product inherits a set of insecure permissions for an object, e.g. when copying from an archive file, without user awareness or involvement. | |
| 1038 | If the drop fails, the software will continue to run with the raised privileges, which might provide additional access to unprivileged users.",,unclassified, | |
| 1039 | CWE-279,EN-Incorrect Execution-Assigned Permissions (Type: Variant),"While it is executing, the software sets the permissions of an object in a way that violates the intended permissions that have been specified by the user. | |
| 1040 | If the drop fails, the software will continue to run with the raised privileges, which might provide additional access to unprivileged users.",,unclassified, | |
| 1041 | CWE-28,EN-Path Traversal: ..\filedir (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize ""..\"" sequences that can resolve to a location that is outside of that directory. | |
| 1042 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1043 | The '..\' manipulation is the canonical manipulation for operating systems that use ""\"" as directory separators, such as Windows. However, it is also useful for bypassing path traversal protection schemes that only assume that the ""/"" separator is valid.",,unclassified, | |
| 1044 | CWE-280,EN-Improper Handling of Insufficient Permissions or Privileges (Type: Base),"The application does not handle or incorrectly handles when it has insufficient privileges to access resources or functionality as specified by their permissions. This may cause it to follow unexpected code paths that may leave the application in an invalid state. | |
| 1045 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1046 | The '..\' manipulation is the canonical manipulation for operating systems that use ""\"" as directory separators, such as Windows. However, it is also useful for bypassing path traversal protection schemes that only assume that the ""/"" separator is valid.",,unclassified, | |
| 1047 | CWE-281,EN-Improper Preservation of Permissions (Type: Base),"The software does not preserve permissions or incorrectly preserves permissions when copying, restoring, or sharing objects, which can cause them to have less restrictive permissions than intended. | |
| 1048 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1049 | The '..\' manipulation is the canonical manipulation for operating systems that use ""\"" as directory separators, such as Windows. However, it is also useful for bypassing path traversal protection schemes that only assume that the ""/"" separator is valid.",,unclassified, | |
| 1050 | CWE-282,EN-Improper Ownership Management (Type: Class),"The software assigns the wrong ownership, or does not properly verify the ownership, of an object or resource. | |
| 1051 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1052 | The '..\' manipulation is the canonical manipulation for operating systems that use ""\"" as directory separators, such as Windows. However, it is also useful for bypassing path traversal protection schemes that only assume that the ""/"" separator is valid.",,unclassified, | |
| 1053 | CWE-283,EN-Unverified Ownership (Type: Base),"The software does not properly verify that a critical resource is owned by the proper entity. | |
| 1054 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1055 | The '..\' manipulation is the canonical manipulation for operating systems that use ""\"" as directory separators, such as Windows. However, it is also useful for bypassing path traversal protection schemes that only assume that the ""/"" separator is valid.",,unclassified, | |
| 1056 | CWE-284,EN-Improper Access Control (Type: Class),"The software does not restrict or incorrectly restricts access to a resource from an unauthorized actor. | |
| 1057 | Access control involves the use of several protection mechanisms such as authentication (proving the identity of an actor) authorization (ensuring that a given actor can access a resource), and accountability (tracking of activities that were performed). When any mechanism is not applied or otherwise fails, attackers can compromise the security of the software by gaining privileges, reading sensitive information, executing commands, evading detection, etc. | |
| 1058 | There are two distinct behaviors that can introduce access control weaknesses: | |
| 1059 | Specification: incorrect privileges, permissions, ownership, etc. are explicitly specified for either the user or the resource (for example, setting a password file to be world-writable, or giving administrator capabilities to a guest user). This action could be performed by the program or the administrator. | |
| 1060 | Enforcement: the mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the user to specify their own privileges, or allowing a syntactically-incorrect ACL to produce insecure settings). This problem occurs within the program itself, in that it does not actually enforce the intended security policy that the administrator specifies.",,unclassified,"Writing Secure Code: Chapter 6, ""Determining Appropriate Access Control"" Page 171 | |
| 1061 | 24 Deadly Sins of Software Security: ""Sin 17: Failure to Protect Stored Data."" Page 253" | |
| 1062 | CWE-286,EN-Incorrect User Management (Type: Class),"The software does not properly manage a user within its environment. | |
| 1063 | Users can be assigned to the wrong group (class) of permissions resulting in unintended access rights to sensitive objects.",,unclassified, | |
| 1064 | CWE-288,EN-Authentication Bypass Using an Alternate Path or Channel (Type: Base),"A product requires authentication, but the product has an alternate path or channel that does not require authentication. | |
| 1065 | Users can be assigned to the wrong group (class) of permissions resulting in unintended access rights to sensitive objects.",,unclassified, | |
| 1066 | CWE-289,EN-Authentication Bypass by Alternate Name (Type: Variant),"The software performs authentication based on the name of a resource being accessed, or the name of the actor performing the access, but it does not properly check all possible names for that resource or actor. | |
| 1067 | Users can be assigned to the wrong group (class) of permissions resulting in unintended access rights to sensitive objects.",,unclassified, | |
| 1068 | CWE-29,EN-Path Traversal: \..\filename (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize '\..\filename' (leading backslash dot dot) sequences that can resolve to a location that is outside of that directory. | |
| 1069 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1070 | This is similar to CWE-25, except using ""\"" instead of ""/"". Sometimes a program checks for ""..\"" at the beginning of the input, so a ""\..\"" can bypass that check. It is also useful for bypassing path traversal protection schemes that only assume that the ""/"" separator is valid.",,unclassified, | |
| 1071 | CWE-290,EN-Authentication Bypass by Spoofing (Type: Base),"This attack-focused weakness is caused by improperly implemented authentication schemes that are subject to spoofing attacks. | |
| 1072 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1073 | This is similar to CWE-25, except using ""\"" instead of ""/"". Sometimes a program checks for ""..\"" at the beginning of the input, so a ""\..\"" can bypass that check. It is also useful for bypassing path traversal protection schemes that only assume that the ""/"" separator is valid.",,unclassified,"The Art of Software Security Assessment: Chapter 3, ""Spoofing and Identification"", Page 72." | |
| 1074 | CWE-295,EN-Improper Certificate Validation (Type: Base),"The software does not validate, or incorrectly validates, a certificate. | |
| 1075 | When a certificate is invalid or malicious, it might allow an attacker to spoof a trusted entity by using a man-in-the-middle (MITM) attack. The software might connect to a malicious host while believing it is a trusted host, or the software might be deceived into accepting spoofed data that appears to originate from a trusted host.",,unclassified,"Why Eve and Mallory Love Android: An Analysis of Android SSL (In)Security: http://www2.dcsec.uni-hannover.de/files/android/p50-fahl.pdf | |
| 1076 | Computer Security: Art and Science" | |
| 1077 | CWE-30,EN-Path Traversal: \dir\..\filename (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize '\dir\..\filename' (leading backslash dot dot) sequences that can resolve to a location that is outside of that directory. | |
| 1078 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1079 | This is similar to CWE-26, except using ""\"" instead of ""/"". The '\dir\..\filename' manipulation is useful for bypassing some path traversal protection schemes. Sometimes a program only checks for ""..\"" at the beginning of the input, so a ""\..\"" can bypass that check.",,unclassified, | |
| 1080 | CWE-300,EN-Channel Accessible by Non-Endpoint (Man-in-the-Middle) (Type: Class),"The product does not adequately verify the identity of actors at both ends of a communication channel, or does not adequately ensure the integrity of the channel, in a way that allows the channel to be accessed or influenced by an actor that is not an endpoint. | |
| 1081 | In order to establish secure communication between two parties, it is often important to adequately verify the identity of entities at each end of the communication channel. Inadequate or inconsistent verification may result in insufficient or incorrect identification of either communicating entity. This can have negative consequences such as misplaced trust in the entity at the other end of the channel. An attacker can leverage this by interposing between the communicating entities and masquerading as the original entity. In the absence of sufficient verification of identity, such an attacker can eavesdrop and potentially modify the communication between the original entities.",,unclassified,Computer Security: Art and Science | |
| 1082 | CWE-302,EN-Authentication Bypass by Assumed-Immutable Data (Type: Variant),"The authentication scheme or implementation uses key data elements that are assumed to be immutable, but can be controlled or modified by the attacker. | |
| 1083 | A mutual authentication protocol requires each party to respond to a random challenge by the other party by encrypting it with a pre-shared key. Often, however, such protocols employ the same pre-shared key for communication with a number of different entities. A malicious user or an attacker can easily compromise this protocol without possessing the correct key by employing a reflection attack on the protocol.",,unclassified, | |
| 1084 | CWE-303,EN-Incorrect Implementation of Authentication Algorithm (Type: Base),"The requirements for the software dictate the use of an established authentication algorithm, but the implementation of the algorithm is incorrect. | |
| 1085 | This incorrect implementation may allow authentication to be bypassed.",,unclassified, | |
| 1086 | CWE-304,EN-Missing Critical Step in Authentication (Type: Base),"The software implements an authentication technique, but it skips a step that weakens the technique. | |
| 1087 | Authentication techniques should follow the algorithms that define them exactly, otherwise authentication can be bypassed or more easily subjected to brute force attacks.",,unclassified, | |
| 1088 | CWE-305,EN-Authentication Bypass by Primary Weakness (Type: Base),"The authentication algorithm is sound, but the implemented mechanism can be bypassed as the result of a separate weakness that is primary to the authentication error. | |
| 1089 | Authentication techniques should follow the algorithms that define them exactly, otherwise authentication can be bypassed or more easily subjected to brute force attacks.",,unclassified, | |
| 1090 | CWE-307,EN-Improper Restriction of Excessive Authentication Attempts (Type: Base),"The software does not implement sufficient measures to prevent multiple failed authentication attempts within in a short time frame, making it more susceptible to brute force attacks. | |
| 1091 | Authentication techniques should follow the algorithms that define them exactly, otherwise authentication can be bypassed or more easily subjected to brute force attacks.",,unclassified,"Weak Password Brings 'Happiness' to Twitter Hacker: http://www.wired.com/threatlevel/2009/01/professed-twitt/ | |
| 1092 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI" | |
| 1093 | CWE-31,EN-Path Traversal: dir\..\..\filename (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize 'dir\..\..\filename' (multiple internal backslash dot dot) sequences that can resolve to a location that is outside of that directory. | |
| 1094 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1095 | The 'dir\..\..\filename' manipulation is useful for bypassing some path traversal protection schemes. Sometimes a program only removes one ""..\"" sequence, so multiple ""..\"" can bypass that check. Alternately, this manipulation could be used to bypass a check for ""..\"" at the beginning of the pathname, moving up more than one directory level.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1096 | CWE-312,EN-Cleartext Storage of Sensitive Information (Type: Base),"The application stores sensitive information in cleartext within a resource that might be accessible to another control sphere. | |
| 1097 | Because the information is stored in cleartext, attackers could potentially read it. Even if the information is encoded in a way that is not human-readable, certain techniques could determine which encoding is being used, then decode the information.",,unclassified,"Writing Secure Code: Chapter 9, ""Protecting Secret Data"" Page 299 | |
| 1098 | The Art of Software Security Assessment: Chapter 2, ""Common Vulnerabilities of Encryption"", Page 43. | |
| 1099 | Mobile App Top 10 List: http://www.veracode.com/blog/2010/12/mobile-app-top-10-list/" | |
| 1100 | CWE-313,EN-Cleartext Storage in a File or on Disk (Type: Variant),"The application stores sensitive information in cleartext in a file, or on disk. | |
| 1101 | The sensitive information could be read by attackers with access to the file, or with physical or administrator access to the raw disk. Even if the information is encoded in a way that is not human-readable, certain techniques could determine which encoding is being used, then decode the information.",,unclassified, | |
| 1102 | CWE-314,EN-Cleartext Storage in the Registry (Type: Variant),"The application stores sensitive information in cleartext in the registry. | |
| 1103 | Attackers can read the information by accessing the registry key. Even if the information is encoded in a way that is not human-readable, certain techniques could determine which encoding is being used, then decode the information.",,unclassified, | |
| 1104 | CWE-315,EN-Cleartext Storage of Sensitive Information in a Cookie (Type: Variant),"The application stores sensitive information in cleartext in a cookie. | |
| 1105 | Attackers can use widely-available tools to view the cookie and read the sensitive information. Even if the information is encoded in a way that is not human-readable, certain techniques could determine which encoding is being used, then decode the information.",,unclassified, | |
| 1106 | CWE-316,EN-Cleartext Storage of Sensitive Information in Memory (Type: Variant),"The application stores sensitive information in cleartext in memory. | |
| 1107 | The sensitive memory might be saved to disk, stored in a core dump, or remain uncleared if the application crashes, or if the programmer does not properly clear the memory before freeing it. | |
| 1108 | It could be argued that such problems are usually only exploitable by those with administrator privileges. However, swapping could cause the memory to be written to disk and leave it accessible to physical attack afterwards. Core dump files might have insecure permissions or be stored in archive files that are accessible to untrusted people. Or, uncleared sensitive memory might be inadvertently exposed to attackers due to another weakness.",,unclassified, | |
| 1109 | CWE-317,EN-Cleartext Storage of Sensitive Information in GUI (Type: Variant),"The application stores sensitive information in cleartext within the GUI. | |
| 1110 | An attacker can often obtain data from a GUI, even if hidden, by using an API to directly access GUI objects such as windows and menus. Even if the information is encoded in a way that is not human-readable, certain techniques could determine which encoding is being used, then decode the information.",,unclassified, | |
| 1111 | CWE-318,EN-Cleartext Storage of Sensitive Information in Executable (Type: Variant),"The application stores sensitive information in cleartext in an executable. | |
| 1112 | Attackers can reverse engineer binary code to obtain secret data. This is especially easy when the cleartext is plain ASCII. Even if the information is encoded in a way that is not human-readable, certain techniques could determine which encoding is being used, then decode the information.",,unclassified, | |
| 1113 | CWE-32,EN-Path Traversal: ... (Triple Dot) (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize '...' (triple dot) sequences that can resolve to a location that is outside of that directory. | |
| 1114 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1115 | The '...' manipulation is useful for bypassing some path traversal protection schemes. On some Windows systems, it is equivalent to ""..\.."" and might bypass checks that assume only two dots are valid. Incomplete filtering, such as removal of ""./"" sequences, can ultimately produce valid "".."" sequences due to a collapse into unsafe value (CWE-182).",,unclassified, | |
| 1116 | CWE-325,EN-Missing Required Cryptographic Step (Type: Base),"The software does not implement a required step in a cryptographic algorithm, resulting in weaker encryption than advertised by that algorithm. | |
| 1117 | Cryptographic implementations should follow the algorithms that define them exactly, otherwise encryption can be weaker than expected.",,unclassified, | |
| 1118 | CWE-326,EN-Inadequate Encryption Strength (Type: Class),"The software stores or transmits sensitive data using an encryption scheme that is theoretically sound, but is not strong enough for the level of protection required. | |
| 1119 | A weak encryption scheme can be subjected to brute force attacks that have a reasonable chance of succeeding using current attack methods and resources.",,unclassified,"Writing Secure Code: Chapter 8, ""Cryptographic Foibles"" Page 259 | |
| 1120 | 24 Deadly Sins of Software Security: ""Sin 21: Using the Wrong Cryptography."" Page 315" | |
| 1121 | CWE-328,EN-Reversible One-Way Hash (Type: Base),"The product uses a hashing algorithm that produces a hash value that can be used to determine the original input, or to find an input that can produce the same hash, more efficiently than brute force techniques. | |
| 1122 | This weakness is especially dangerous when the hash is used in security algorithms that require the one-way property to hold. For example, if an authentication system takes an incoming password and generates a hash, then compares the hash to another hash that it has stored in its authentication database, then the ability to create a collision could allow an attacker to provide an alternate password that produces the same target hash, bypassing authentication.",,unclassified,"MD5 considered harmful today: http://www.phreedom.org/research/rogue-ca/ | |
| 1123 | The Art of Software Security Assessment: Chapter 2, ""Common Vulnerabilities of Integrity"", Page 47. | |
| 1124 | RFC2898 - PKCS #5: Password-Based Cryptography Specification Version 2.0: http://tools.ietf.org/html/rfc2898 | |
| 1125 | How To Safely Store A Password: http://codahale.com/how-to-safely-store-a-password/ | |
| 1126 | Tarsnap - The scrypt key derivation function and encryption utility: http://www.tarsnap.com/scrypt.html | |
| 1127 | How Companies Can Beef Up Password Security (interview with Thomas H. Ptacek): http://krebsonsecurity.com/2012/06/how-companies-can-beef-up-password-security/ | |
| 1128 | Password security: past, present, future: http://www.openwall.com/presentations/PHDays2012-Password-Security/ | |
| 1129 | Our password hashing has no clothes: http://www.troyhunt.com/2012/06/our-password-hashing-has-no-clothes.html | |
| 1130 | Should we really use bcrypt/scrypt?: http://www.analyticalengine.net/2012/06/should-we-really-use-bcryptscrypt/" | |
| 1131 | CWE-33,EN-Path Traversal: .... (Multiple Dot) (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize '....' (multiple dot) sequences that can resolve to a location that is outside of that directory. | |
| 1132 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1133 | The '....' manipulation is useful for bypassing some path traversal protection schemes. On some Windows systems, it is equivalent to ""..\..\.."" and might bypass checks that assume only two dots are valid. Incomplete filtering, such as removal of ""./"" sequences, can ultimately produce valid "".."" sequences due to a collapse into unsafe value (CWE-182).",,unclassified, | |
| 1134 | CWE-331,EN-Insufficient Entropy (Type: Base),"The software uses an algorithm or scheme that produces insufficient entropy, leaving patterns or clusters of values that are more likely to occur than others. | |
| 1135 | When software generates predictable values in a context requiring unpredictability, it may be possible for an attacker to guess the next value that will be generated, and use this guess to impersonate another user or access sensitive information.",,unclassified,Building Secure Software: How to Avoid Security Problems the Right Way | |
| 1136 | CWE-334,EN-Small Space of Random Values (Type: Base),"The number of possible random values is smaller than needed by the product, making it more susceptible to brute force attacks. | |
| 1137 | The rate at which true random numbers can be generated is limited. It is important that one uses them only when they are needed for security.",,unclassified,"SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1138 | 24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1139 | CWE-335,EN-PRNG Seed Error (Type: Class),"A Pseudo-Random Number Generator (PRNG) uses seeds incorrectly. | |
| 1140 | The rate at which true random numbers can be generated is limited. It is important that one uses them only when they are needed for security.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1141 | CWE-336,EN-Same Seed in PRNG (Type: Base),"A PRNG uses the same seed each time the product is initialized. If an attacker can guess (or knows) the seed, then he/she may be able to determine the ""random"" number produced from the PRNG. | |
| 1142 | The rate at which true random numbers can be generated is limited. It is important that one uses them only when they are needed for security.",,unclassified,SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1143 | CWE-337,EN-Predictable Seed in PRNG (Type: Base),"A PRNG is initialized from a predictable seed, e.g. using process ID or system time. | |
| 1144 | The rate at which true random numbers can be generated is limited. It is important that one uses them only when they are needed for security.",,unclassified,"SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1145 | 24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1146 | CWE-339,EN-Small Seed Space in PRNG (Type: Base),"A PRNG uses a relatively small space of seeds. | |
| 1147 | The rate at which true random numbers can be generated is limited. It is important that one uses them only when they are needed for security.",,unclassified,SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1148 | CWE-34,EN-Path Traversal: ....// (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize '....//' (doubled dot dot slash) sequences that can resolve to a location that is outside of that directory. | |
| 1149 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1150 | The '....//' manipulation is useful for bypassing some path traversal protection schemes. If ""../"" is filtered in a sequential fashion, as done by some regular expression engines, then ""....//"" can collapse into the ""../"" unsafe value (CWE-182). It could also be useful when "".."" is removed, if the operating system treats ""//"" and ""/"" as equivalent.",,unclassified, | |
| 1151 | CWE-340,EN-Predictability Problems (Type: Class),"Weaknesses in this category are related to schemes that generate numbers or identifiers that are more predictable than required by the application. | |
| 1152 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1153 | The '....//' manipulation is useful for bypassing some path traversal protection schemes. If ""../"" is filtered in a sequential fashion, as done by some regular expression engines, then ""....//"" can collapse into the ""../"" unsafe value (CWE-182). It could also be useful when "".."" is removed, if the operating system treats ""//"" and ""/"" as equivalent.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1154 | CWE-341,EN-Predictable from Observable State (Type: Base),"A number or object is predictable based on observations that the attacker can make about the state of the system or network, such as time, process ID, etc. | |
| 1155 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1156 | The '....//' manipulation is useful for bypassing some path traversal protection schemes. If ""../"" is filtered in a sequential fashion, as done by some regular expression engines, then ""....//"" can collapse into the ""../"" unsafe value (CWE-182). It could also be useful when "".."" is removed, if the operating system treats ""//"" and ""/"" as equivalent.",,unclassified,"SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1157 | 24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1158 | CWE-342,EN-Predictable Exact Value from Previous Values (Type: Base),"An exact value or random number can be precisely predicted by observing previous values. | |
| 1159 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1160 | The '....//' manipulation is useful for bypassing some path traversal protection schemes. If ""../"" is filtered in a sequential fashion, as done by some regular expression engines, then ""....//"" can collapse into the ""../"" unsafe value (CWE-182). It could also be useful when "".."" is removed, if the operating system treats ""//"" and ""/"" as equivalent.",,unclassified,"SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1161 | 24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1162 | CWE-343,EN-Predictable Value Range from Previous Values (Type: Base),"The software's random number generator produces a series of values which, when observed, can be used to infer a relatively small range of possibilities for the next value that could be generated. | |
| 1163 | The output of a random number generator should not be predictable based on observations of previous values. In some cases, an attacker cannot predict the exact value that will be produced next, but can narrow down the possibilities significantly. This reduces the amount of effort to perform a brute force attack. For example, suppose the product generates random numbers between 1 and 100, but it always produces a larger value until it reaches 100. If the generator produces an 80, then the attacker knows that the next value will be somewhere between 81 and 100. Instead of 100 possibilities, the attacker only needs to consider 20.",,unclassified,"SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1164 | Strange Attractors and TCP/IP Sequence Number Analysis: http://www.bindview.com/Services/Razor/Papers/2001/tcpseq.cfm | |
| 1165 | 24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1166 | CWE-344,EN-Use of Invariant Value in Dynamically Changing Context (Type: Base),"The product uses a constant value, name, or reference, but this value can (or should) vary across different environments. | |
| 1167 | The output of a random number generator should not be predictable based on observations of previous values. In some cases, an attacker cannot predict the exact value that will be produced next, but can narrow down the possibilities significantly. This reduces the amount of effort to perform a brute force attack. For example, suppose the product generates random numbers between 1 and 100, but it always produces a larger value until it reaches 100. If the generator produces an 80, then the attacker knows that the next value will be somewhere between 81 and 100. Instead of 100 possibilities, the attacker only needs to consider 20.",,unclassified,SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1168 | CWE-345,EN-Insufficient Verification of Data Authenticity (Type: Class),"The software does not sufficiently verify the origin or authenticity of data, in a way that causes it to accept invalid data. | |
| 1169 | The output of a random number generator should not be predictable based on observations of previous values. In some cases, an attacker cannot predict the exact value that will be produced next, but can narrow down the possibilities significantly. This reduces the amount of effort to perform a brute force attack. For example, suppose the product generates random numbers between 1 and 100, but it always produces a larger value until it reaches 100. If the generator produces an 80, then the attacker knows that the next value will be somewhere between 81 and 100. Instead of 100 possibilities, the attacker only needs to consider 20.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 15: Not Updating Easily."" Page 231" | |
| 1170 | CWE-346,EN-Origin Validation Error (Type: Base),"The software does not properly verify that the source of data or communication is valid. | |
| 1171 | The output of a random number generator should not be predictable based on observations of previous values. In some cases, an attacker cannot predict the exact value that will be produced next, but can narrow down the possibilities significantly. This reduces the amount of effort to perform a brute force attack. For example, suppose the product generates random numbers between 1 and 100, but it always produces a larger value until it reaches 100. If the generator produces an 80, then the attacker knows that the next value will be somewhere between 81 and 100. Instead of 100 possibilities, the attacker only needs to consider 20.",,unclassified, | |
| 1172 | CWE-347,EN-Improper Verification of Cryptographic Signature (Type: Base),"The software does not verify, or incorrectly verifies, the cryptographic signature for data. | |
| 1173 | The output of a random number generator should not be predictable based on observations of previous values. In some cases, an attacker cannot predict the exact value that will be produced next, but can narrow down the possibilities significantly. This reduces the amount of effort to perform a brute force attack. For example, suppose the product generates random numbers between 1 and 100, but it always produces a larger value until it reaches 100. If the generator produces an 80, then the attacker knows that the next value will be somewhere between 81 and 100. Instead of 100 possibilities, the attacker only needs to consider 20.",,unclassified, | |
| 1174 | CWE-348,EN-Use of Less Trusted Source (Type: Base),"The software has two different sources of the same data or information, but it uses the source that has less support for verification, is less trusted, or is less resistant to attack. | |
| 1175 | The output of a random number generator should not be predictable based on observations of previous values. In some cases, an attacker cannot predict the exact value that will be produced next, but can narrow down the possibilities significantly. This reduces the amount of effort to perform a brute force attack. For example, suppose the product generates random numbers between 1 and 100, but it always produces a larger value until it reaches 100. If the generator produces an 80, then the attacker knows that the next value will be somewhere between 81 and 100. Instead of 100 possibilities, the attacker only needs to consider 20.",,unclassified, | |
| 1176 | CWE-349,EN-Acceptance of Extraneous Untrusted Data With Trusted Data (Type: Base),"The software, when processing trusted data, accepts any untrusted data that is also included with the trusted data, treating the untrusted data as if it were trusted. | |
| 1177 | The output of a random number generator should not be predictable based on observations of previous values. In some cases, an attacker cannot predict the exact value that will be produced next, but can narrow down the possibilities significantly. This reduces the amount of effort to perform a brute force attack. For example, suppose the product generates random numbers between 1 and 100, but it always produces a larger value until it reaches 100. If the generator produces an 80, then the attacker knows that the next value will be somewhere between 81 and 100. Instead of 100 possibilities, the attacker only needs to consider 20.",,unclassified, | |
| 1178 | CWE-35,EN-Path Traversal: .../...// (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize '.../...//' (doubled triple dot slash) sequences that can resolve to a location that is outside of that directory. | |
| 1179 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1180 | The '.../...//' manipulation is useful for bypassing some path traversal protection schemes. If ""../"" is filtered in a sequential fashion, as done by some regular expression engines, then "".../...//"" can collapse into the ""../"" unsafe value (CWE-182). Removing the first ""../"" yields ""....//""; the second removal yields ""../"". Depending on the algorithm, the software could be susceptible to CWE-34 but not CWE-35, or vice versa.",,unclassified, | |
| 1181 | CWE-350,EN-Reliance on Reverse DNS Resolution for a Security-Critical Action (Type: Variant),"The software performs reverse DNS resolution on an IP address to obtain the hostname and make a security decision, but it does not properly ensure that the IP address is truly associated with the hostname. | |
| 1182 | When the software performs a reverse DNS resolution for an IP address, if an attacker controls the server for that IP address, then the attacker can cause the server to return an arbitrary hostname. As a result, the attacker may be able to bypass authentication, cause the wrong hostname to be recorded in log files to hide activities, or perform other attacks. | |
| 1183 | Attackers can spoof DNS names by either (1) compromising a DNS server and modifying its records (sometimes called DNS cache poisoning), or (2) having legitimate control over a DNS server associated with their IP address. | |
| 1184 | Since DNS names can be easily spoofed or misreported, and it may be difficult for the software to detect if a trusted DNS server has not been compromised, they do not constitute a valid authentication mechanism.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 15: Not Updating Easily."" Page 231 | |
| 1185 | 24 Deadly Sins of Software Security: ""Sin 24: Trusting Network Name Resolution."" Page 361 | |
| 1186 | The Art of Software Security Assessment: Chapter 16, ""DNS Spoofing"", Page 1002." | |
| 1187 | CWE-351,EN-Insufficient Type Distinction (Type: Base),"The software does not properly distinguish between different types of elements in a way that leads to insecure behavior. | |
| 1188 | When the software performs a reverse DNS resolution for an IP address, if an attacker controls the server for that IP address, then the attacker can cause the server to return an arbitrary hostname. As a result, the attacker may be able to bypass authentication, cause the wrong hostname to be recorded in log files to hide activities, or perform other attacks. | |
| 1189 | Attackers can spoof DNS names by either (1) compromising a DNS server and modifying its records (sometimes called DNS cache poisoning), or (2) having legitimate control over a DNS server associated with their IP address. | |
| 1190 | Since DNS names can be easily spoofed or misreported, and it may be difficult for the software to detect if a trusted DNS server has not been compromised, they do not constitute a valid authentication mechanism.",,unclassified, | |
| 1191 | CWE-356,EN-Product UI does not Warn User of Unsafe Actions (Type: Base),"The software's user interface does not warn the user before undertaking an unsafe action on behalf of that user. This makes it easier for attackers to trick users into inflicting damage to their system. | |
| 1192 | Software systems should warn users that a potentially dangerous action may occur if the user proceeds. For example, if the user downloads a file from an unknown source and attempts to execute the file on their machine, then the application's GUI can indicate that the file is unsafe.",,unclassified, | |
| 1193 | CWE-357,EN-Insufficient UI Warning of Dangerous Operations (Type: Base),"The user interface provides a warning to a user regarding dangerous or sensitive operations, but the warning is not noticeable enough to warrant attention. | |
| 1194 | Software systems should warn users that a potentially dangerous action may occur if the user proceeds. For example, if the user downloads a file from an unknown source and attempts to execute the file on their machine, then the application's GUI can indicate that the file is unsafe.",,unclassified, | |
| 1195 | CWE-358,EN-Improperly Implemented Security Check for Standard (Type: Base),"The software does not implement or incorrectly implements one or more security-relevant checks as specified by the design of a standardized algorithm, protocol, or technique. | |
| 1196 | Software systems should warn users that a potentially dangerous action may occur if the user proceeds. For example, if the user downloads a file from an unknown source and attempts to execute the file on their machine, then the application's GUI can indicate that the file is unsafe.",,unclassified, | |
| 1197 | CWE-359,EN-Privacy Violation (Type: Class),"Mishandling private information, such as customer passwords or social security numbers, can compromise user privacy and is often illegal. | |
| 1198 | Software systems should warn users that a potentially dangerous action may occur if the user proceeds. For example, if the user downloads a file from an unknown source and attempts to execute the file on their machine, then the application's GUI can indicate that the file is unsafe.",,unclassified,"AOL man pleads guilty to selling 92m email addies: http://www.theregister.co.uk/2005/02/07/aol_email_theft/ | |
| 1199 | Safe Harbor Privacy Framework: http://www.export.gov/safeharbor/ | |
| 1200 | Financial Privacy: The Gramm-Leach Bliley Act (GLBA): http://www.ftc.gov/privacy/glbact/index.html | |
| 1201 | Health Insurance Portability and Accountability Act (HIPAA): http://www.hhs.gov/ocr/hipaa/ | |
| 1202 | California SB-1386: http://info.sen.ca.gov/pub/01-02/bill/sen/sb_1351-1400/sb_1386_bill_20020926_chaptered.html | |
| 1203 | SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1204 | Mobile App Top 10 List: http://www.veracode.com/blog/2010/12/mobile-app-top-10-list/" | |
| 1205 | CWE-36,EN-Absolute Path Traversal (Type: Base),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize absolute path sequences such as ""/abs/path"" that can resolve to a location that is outside of that directory. | |
| 1206 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified,"The Art of Software Security Assessment: Chapter 9, ""Filenames and Paths"", Page 503." | |
| 1207 | CWE-363,EN-Race Condition Enabling Link Following (Type: Base),"The software checks the status of a file or directory before accessing it, which produces a race condition in which the file can be replaced with a link before the access is performed, causing the software to access the wrong file. | |
| 1208 | While developers might expect that there is a very narrow time window between the time of check and time of use, there is still a race condition. An attacker could cause the software to slow down (e.g. with memory consumption), causing the time window to become larger. Alternately, in some situations, the attacker could win the race by performing a large number of attacks.",,unclassified,"The Art of Software Security Assessment: Chapter 9, ""Race Conditions"", Page 526." | |
| 1209 | CWE-368,EN-Context Switching Race Condition (Type: Base),"A product performs a series of non-atomic actions to switch between contexts that cross privilege or other security boundaries, but a race condition allows an attacker to modify or misrepresent the product's behavior during the switch. | |
| 1210 | This is commonly seen in web browser vulnerabilities in which the attacker can perform certain actions while the browser is transitioning from a trusted to an untrusted domain, or vice versa, and the browser performs the actions on one domain using the trust level and resources of the other domain.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205" | |
| 1211 | CWE-37,EN-Path Traversal: /absolute/pathname/here (Type: Variant),"A software system that accepts input in the form of a slash absolute path ('/absolute/pathname/here') without appropriate validation can allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1212 | This weakness typically occurs when an unexpected value is provided to the product, or if an error occurs that is not properly detected. It frequently occurs in calculations involving physical dimensions such as size, length, width, and height.",,unclassified, | |
| 1213 | CWE-372,EN-Incomplete Internal State Distinction (Type: Base),"The software does not properly determine which state it is in, causing it to assume it is in state X when in fact it is in state Y, causing it to perform incorrect operations in a security-relevant manner. | |
| 1214 | If the revocation status of a certificate is not checked before each action that requires privileges, the system may be subject to a race condition. If a certificate is revoked after the initial check, all subsequent actions taken with the owner of the revoked certificate will lose all benefits guaranteed by the certificate. In fact, it is almost certain that the use of a revoked certificate indicates malicious activity.",,unclassified, | |
| 1215 | CWE-373,EN-DEPRECATED: State Synchronization Error (Type: Base),"This entry was deprecated because it overlapped the same concepts as race condition (CWE-362) and Improper Synchronization (CWE-662). | |
| 1216 | If the revocation status of a certificate is not checked before each action that requires privileges, the system may be subject to a race condition. If a certificate is revoked after the initial check, all subsequent actions taken with the owner of the revoked certificate will lose all benefits guaranteed by the certificate. In fact, it is almost certain that the use of a revoked certificate indicates malicious activity.",,unclassified, | |
| 1217 | CWE-377,EN-Insecure Temporary File (Type: Base),"Creating and using insecure temporary files can leave application and system data vulnerable to attack. | |
| 1218 | If the revocation status of a certificate is not checked before each action that requires privileges, the system may be subject to a race condition. If a certificate is revoked after the initial check, all subsequent actions taken with the owner of the revoked certificate will lose all benefits guaranteed by the certificate. In fact, it is almost certain that the use of a revoked certificate indicates malicious activity.",,unclassified,"Writing Secure Code: Chapter 23, ""Creating Temporary Files Securely"" Page 682 | |
| 1219 | The Art of Software Security Assessment: Chapter 9, ""Temporary Files"", Page 538. | |
| 1220 | The Art of Software Security Assessment: Chapter 11, ""File Squatting"", Page 662." | |
| 1221 | CWE-38,EN-Path Traversal: \absolute\pathname\here (Type: Variant),"A software system that accepts input in the form of a backslash absolute path ('\absolute\pathname\here') without appropriate validation can allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1222 | On some operating systems, the fact that the temporary file exists may be apparent to any user with sufficient privileges to access that directory. Since the file is visible, the application that is using the temporary file could be known. If one has access to list the processes on the system, the attacker has gained information about what the user is doing at that time. By correlating this with the applications the user is running, an attacker could potentially discover what a user's actions are. From this, higher levels of security could be breached.",,unclassified, | |
| 1223 | CWE-382,EN-J2EE Bad Practices: Use of System.exit() (Type: Variant),"A J2EE application uses System.exit(), which also shuts down its container. | |
| 1224 | On some operating systems, the fact that the temporary file exists may be apparent to any user with sufficient privileges to access that directory. Since the file is visible, the application that is using the temporary file could be known. If one has access to list the processes on the system, the attacker has gained information about what the user is doing at that time. By correlating this with the applications the user is running, an attacker could potentially discover what a user's actions are. From this, higher levels of security could be breached.",,unclassified, | |
| 1225 | CWE-383,EN-J2EE Bad Practices: Direct Use of Threads (Type: Variant),"Thread management in a Web application is forbidden in some circumstances and is always highly error prone. | |
| 1226 | Thread management in a web application is forbidden by the J2EE standard in some circumstances and is always highly error prone. Managing threads is difficult and is likely to interfere in unpredictable ways with the behavior of the application container. Even without interfering with the container, thread management usually leads to bugs that are hard to detect and diagnose like deadlock, race conditions, and other synchronization errors.",,unclassified, | |
| 1227 | CWE-386,EN-Symbolic Name not Mapping to Correct Object (Type: Base),"A constant symbolic reference to an object is used, even though the reference can resolve to a different object over time. | |
| 1228 | In some instances, knowing when data is transmitted between parties can provide a malicious user with privileged information. Also, externally monitoring the timing of operations can potentially reveal sensitive data. For example, a cryptographic operation can expose its internal state if the time it takes to perform the operation varies, based on the state. | |
| 1229 | Covert channels are frequently classified as either storage or timing channels. Some examples of covert timing channels are the system's paging rate, the time a certain transaction requires to execute, and the time it takes to gain access to a shared bus.",,unclassified, | |
| 1230 | CWE-39,EN-Path Traversal: C:dirname (Type: Variant),"An attacker can inject a drive letter or Windows volume letter ('C:dirname') into a software system to potentially redirect access to an unintended location or arbitrary file. | |
| 1231 | In some instances, knowing when data is transmitted between parties can provide a malicious user with privileged information. Also, externally monitoring the timing of operations can potentially reveal sensitive data. For example, a cryptographic operation can expose its internal state if the time it takes to perform the operation varies, based on the state. | |
| 1232 | Covert channels are frequently classified as either storage or timing channels. Some examples of covert timing channels are the system's paging rate, the time a certain transaction requires to execute, and the time it takes to gain access to a shared bus.",,unclassified, | |
| 1233 | CWE-392,EN-Missing Report of Error Condition (Type: Base),"The software encounters an error but does not provide a status code or return value to indicate that an error has occurred. | |
| 1234 | In some instances, knowing when data is transmitted between parties can provide a malicious user with privileged information. Also, externally monitoring the timing of operations can potentially reveal sensitive data. For example, a cryptographic operation can expose its internal state if the time it takes to perform the operation varies, based on the state. | |
| 1235 | Covert channels are frequently classified as either storage or timing channels. Some examples of covert timing channels are the system's paging rate, the time a certain transaction requires to execute, and the time it takes to gain access to a shared bus.",,unclassified, | |
| 1236 | CWE-393,EN-Return of Wrong Status Code (Type: Base),"A function or operation returns an incorrect return value or status code that does not indicate an error, but causes the product to modify its behavior based on the incorrect result. | |
| 1237 | This can lead to unpredictable behavior. If the function is used to make security-critical decisions or provide security-critical information, then the wrong status code can cause the software to assume that an action is safe, even when it is not.",,unclassified, | |
| 1238 | CWE-394,EN-Unexpected Status Code or Return Value (Type: Base),"The software does not properly check when a function or operation returns a value that is legitimate for the function, but is not expected by the software. | |
| 1239 | This can lead to unpredictable behavior. If the function is used to make security-critical decisions or provide security-critical information, then the wrong status code can cause the software to assume that an action is safe, even when it is not.",,unclassified, | |
| 1240 | CWE-395,EN-Use of NullPointerException Catch to Detect NULL Pointer Dereference (Type: Base),"Catching NullPointerException should not be used as an alternative to programmatic checks to prevent dereferencing a null pointer. | |
| 1241 | This can lead to unpredictable behavior. If the function is used to make security-critical decisions or provide security-critical information, then the wrong status code can cause the software to assume that an action is safe, even when it is not.",,unclassified, | |
| 1242 | CWE-396,EN-Declaration of Catch for Generic Exception (Type: Base),"Catching overly broad exceptions promotes complex error handling code that is more likely to contain security vulnerabilities. | |
| 1243 | Multiple catch blocks can get ugly and repetitive, but ""condensing"" catch blocks by catching a high-level class like Exception can obscure exceptions that deserve special treatment or that should not be caught at this point in the program. Catching an overly broad exception essentially defeats the purpose of Java's typed exceptions, and can become particularly dangerous if the program grows and begins to throw new types of exceptions. The new exception types will not receive any attention.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 9: Catching Exceptions."" Page 157" | |
| 1244 | CWE-397,EN-Declaration of Throws for Generic Exception (Type: Base),"Throwing overly broad exceptions promotes complex error handling code that is more likely to contain security vulnerabilities. | |
| 1245 | Declaring a method to throw Exception or Throwable makes it difficult for callers to perform proper error handling and error recovery. Java's exception mechanism, for example, is set up to make it easy for callers to anticipate what can go wrong and write code to handle each specific exceptional circumstance. Declaring that a method throws a generic form of exception defeats this system.",,unclassified, | |
| 1246 | CWE-398,EN-Indicator of Poor Code Quality (Type: Class),"The code has features that do not directly introduce a weakness or vulnerability, but indicate that the product has not been carefully developed or maintained. | |
| 1247 | Programs are more likely to be secure when good development practices are followed. If a program is complex, difficult to maintain, not portable, or shows evidence of neglect, then there is a higher likelihood that weaknesses are buried in the code.",,unclassified, | |
| 1248 | CWE-40,EN-Path Traversal: \\UNC\share\name\ (Windows UNC Share) (Type: Variant),"An attacker can inject a Windows UNC share ('\\UNC\share\name') into a software system to potentially redirect access to an unintended location or arbitrary file. | |
| 1249 | Programs are more likely to be secure when good development practices are followed. If a program is complex, difficult to maintain, not portable, or shows evidence of neglect, then there is a higher likelihood that weaknesses are buried in the code.",,unclassified,"The Art of Software Security Assessment: Chapter 11, ""Filelike Objects"", Page 664." | |
| 1250 | CWE-402,EN-Transmission of Private Resources into a New Sphere (Resource Leak) (Type: Class),"The software makes resources available to untrusted parties when those resources are only intended to be accessed by the software. | |
| 1251 | This is often triggered by improper handling of malformed data or unexpectedly interrupted sessions.",,unclassified, | |
| 1252 | CWE-403,EN-Exposure of File Descriptor to Unintended Control Sphere (File Descriptor Leak) (Type: Base),"A process does not close sensitive file descriptors before invoking a child process, which allows the child to perform unauthorized I/O operations using those descriptors. | |
| 1253 | When a new process is forked or executed, the child process inherits any open file descriptors. When the child process has fewer privileges than the parent process, this might introduce a vulnerability if the child process can access the file descriptor but does not have the privileges to access the associated file.",,unclassified,"File descriptors and setuid applications: https://blogs.oracle.com/paulr/entry/file_descriptors_and_setuid_applications | |
| 1254 | Introduction to Secure Coding Guide: https://developer.apple.com/library/mac/#documentation/security/conceptual/SecureCodingGuide/Articles/AccessControl.html" | |
| 1255 | CWE-405,EN-Asymmetric Resource Consumption (Amplification) (Type: Class),"Software that does not appropriately monitor or control resource consumption can lead to adverse system performance. | |
| 1256 | This situation is amplified if the software allows malicious users or attackers to consume more resources than their access level permits. Exploiting such a weakness can lead to asymmetric resource consumption, aiding in amplification attacks against the system or the network.",,unclassified, | |
| 1257 | CWE-406,EN-Insufficient Control of Network Message Volume (Network Amplification) (Type: Base),"The software does not sufficiently monitor or control transmitted network traffic volume, so that an actor can cause the software to transmit more traffic than should be allowed for that actor. | |
| 1258 | In the absence of a policy to restrict asymmetric resource consumption, the application or system cannot distinguish between legitimate transmissions and traffic intended to serve as an amplifying attack on target systems. Systems can often be configured to restrict the amount of traffic sent out on behalf of a client, based on the client's origin or access level. This is usually defined in a resource allocation policy. In the absence of a mechanism to keep track of transmissions, the system or application can be easily abused to transmit asymmetrically greater traffic than the request or client should be permitted to.",,unclassified, | |
| 1259 | CWE-408,EN-Incorrect Behavior Order: Early Amplification (Type: Base),"The software allows an entity to perform a legitimate but expensive operation before authentication or authorization has taken place. | |
| 1260 | In the absence of a policy to restrict asymmetric resource consumption, the application or system cannot distinguish between legitimate transmissions and traffic intended to serve as an amplifying attack on target systems. Systems can often be configured to restrict the amount of traffic sent out on behalf of a client, based on the client's origin or access level. This is usually defined in a resource allocation policy. In the absence of a mechanism to keep track of transmissions, the system or application can be easily abused to transmit asymmetrically greater traffic than the request or client should be permitted to.",,unclassified, | |
| 1261 | CWE-409,EN-Improper Handling of Highly Compressed Data (Data Amplification) (Type: Base),"The software does not handle or incorrectly handles a compressed input with a very high compression ratio that produces a large output. | |
| 1262 | An example of data amplification is a ""decompression bomb,"" a small ZIP file that can produce a large amount of data when it is decompressed.",,unclassified, | |
| 1263 | CWE-41,EN-Improper Resolution of Path Equivalence (Type: Base),"The system or application is vulnerable to file system contents disclosure through path equivalence. Path equivalence involves the use of special characters in file and directory names. The associated manipulations are intended to generate multiple names for the same object. | |
| 1264 | Path equivalence is usually employed in order to circumvent access controls expressed using an incomplete set of file name or file path representations. This is different from path traversal, wherein the manipulations are performed to generate a name for a different object.",,unclassified, | |
| 1265 | CWE-410,EN-Insufficient Resource Pool (Type: Base),"The software's resource pool is not large enough to handle peak demand, which allows an attacker to prevent others from accessing the resource by using a (relatively) large number of requests for resources. | |
| 1266 | Frequently the consequence is a ""flood"" of connection or sessions.",,unclassified,"Writing Secure Code: Chapter 17, ""Protecting Against Denial of Service Attacks"" Page 517" | |
| 1267 | CWE-412,EN-Unrestricted Externally Accessible Lock (Type: Base),"The software properly checks for the existence of a lock, but the lock can be externally controlled or influenced by an actor that is outside of the intended sphere of control. | |
| 1268 | This prevents the software from acting on associated resources or performing other behaviors that are controlled by the presence of the lock. Relevant locks might include an exclusive lock or mutex, or modifying a shared resource that is treated as a lock. If the lock can be held for an indefinite period of time, then the denial of service could be permanent.",,unclassified, | |
| 1269 | CWE-413,EN-Improper Resource Locking (Type: Base),"The software does not lock or does not correctly lock a resource when the software must have exclusive access to the resource. | |
| 1270 | When a resource is not properly locked, an attacker could modify the resource while it is being operated on by the software. This might violate the software's assumption that the resource will not change, potentially leading to unexpected behaviors.",,unclassified, | |
| 1271 | CWE-414,EN-Missing Lock Check (Type: Base),"A product does not check to see if a lock is present before performing sensitive operations on a resource. | |
| 1272 | When a resource is not properly locked, an attacker could modify the resource while it is being operated on by the software. This might violate the software's assumption that the resource will not change, potentially leading to unexpected behaviors.",,unclassified, | |
| 1273 | CWE-419,EN-Unprotected Primary Channel (Type: Base),"The software uses a primary channel for administration or restricted functionality, but it does not properly protect the channel. | |
| 1274 | The use of previously-freed memory can have any number of adverse consequences, ranging from the corruption of valid data to the execution of arbitrary code, depending on the instantiation and timing of the flaw. The simplest way data corruption may occur involves the system's reuse of the freed memory. Use-after-free errors have two common and sometimes overlapping causes: | |
| 1275 | Error conditions and other exceptional circumstances. | |
| 1276 | Confusion over which part of the program is responsible for freeing the memory. | |
| 1277 | In this scenario, the memory in question is allocated to another pointer validly at some point after it has been freed. The original pointer to the freed memory is used again and points to somewhere within the new allocation. As the data is changed, it corrupts the validly used memory; this induces undefined behavior in the process. | |
| 1278 | If the newly allocated data chances to hold a class, in C++ for example, various function pointers may be scattered within the heap data. If one of these function pointers is overwritten with an address to valid shellcode, execution of arbitrary code can be achieved.",,unclassified, | |
| 1279 | CWE-42,EN-Path Equivalence: filename. (Trailing Dot) (Type: Variant),"A software system that accepts path input in the form of trailing dot ('filedir.') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1280 | The use of previously-freed memory can have any number of adverse consequences, ranging from the corruption of valid data to the execution of arbitrary code, depending on the instantiation and timing of the flaw. The simplest way data corruption may occur involves the system's reuse of the freed memory. Use-after-free errors have two common and sometimes overlapping causes: | |
| 1281 | Error conditions and other exceptional circumstances. | |
| 1282 | Confusion over which part of the program is responsible for freeing the memory. | |
| 1283 | In this scenario, the memory in question is allocated to another pointer validly at some point after it has been freed. The original pointer to the freed memory is used again and points to somewhere within the new allocation. As the data is changed, it corrupts the validly used memory; this induces undefined behavior in the process. | |
| 1284 | If the newly allocated data chances to hold a class, in C++ for example, various function pointers may be scattered within the heap data. If one of these function pointers is overwritten with an address to valid shellcode, execution of arbitrary code can be achieved.",,unclassified, | |
| 1285 | CWE-420,EN-Unprotected Alternate Channel (Type: Base),"The software protects a primary channel, but it does not use the same level of protection for an alternate channel. | |
| 1286 | The use of previously-freed memory can have any number of adverse consequences, ranging from the corruption of valid data to the execution of arbitrary code, depending on the instantiation and timing of the flaw. The simplest way data corruption may occur involves the system's reuse of the freed memory. Use-after-free errors have two common and sometimes overlapping causes: | |
| 1287 | Error conditions and other exceptional circumstances. | |
| 1288 | Confusion over which part of the program is responsible for freeing the memory. | |
| 1289 | In this scenario, the memory in question is allocated to another pointer validly at some point after it has been freed. The original pointer to the freed memory is used again and points to somewhere within the new allocation. As the data is changed, it corrupts the validly used memory; this induces undefined behavior in the process. | |
| 1290 | If the newly allocated data chances to hold a class, in C++ for example, various function pointers may be scattered within the heap data. If one of these function pointers is overwritten with an address to valid shellcode, execution of arbitrary code can be achieved.",,unclassified, | |
| 1291 | CWE-421,EN-Race Condition During Access to Alternate Channel (Type: Base),"The product opens an alternate channel to communicate with an authorized user, but the channel is accessible to other actors. | |
| 1292 | This creates a race condition that allows an attacker to access the channel before the authorized user does.",,unclassified,"Discovering and Exploiting Named Pipe Security Flaws for Fun and Profit: http://www.blakewatts.com/namedpipepaper.html | |
| 1293 | 24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205" | |
| 1294 | CWE-422,EN-Unprotected Windows Messaging Channel (Shatter) (Type: Variant),"The software does not properly verify the source of a message in the Windows Messaging System while running at elevated privileges, creating an alternate channel through which an attacker can directly send a message to the product. | |
| 1295 | This creates a race condition that allows an attacker to access the channel before the authorized user does.",,unclassified,"Exploiting design flaws in the Win32 API for privilege escalation. Or... Shatter Attacks - How to break Windows: http://web.archive.org/web/20060115174629/http://security.tombom.co.uk/shatter.html | |
| 1296 | The Art of Software Security Assessment: Chapter 2, ""Design Review."" Page 34. | |
| 1297 | The Art of Software Security Assessment: Chapter 12, ""Shatter Attacks"", Page 694." | |
| 1298 | CWE-423,EN-DEPRECATED (Duplicate): Proxied Trusted Channel (Type: Base),"This entry has been deprecated because it was a duplicate of CWE-441. All content has been transferred to CWE-441. | |
| 1299 | This creates a race condition that allows an attacker to access the channel before the authorized user does.",,unclassified, | |
| 1300 | CWE-424,EN-Improper Protection of Alternate Path (Type: Class),"The product does not sufficiently protect all possible paths that a user can take to access restricted functionality or resources. | |
| 1301 | This creates a race condition that allows an attacker to access the channel before the authorized user does.",,unclassified, | |
| 1302 | CWE-425,EN-Direct Request (Forced Browsing) (Type: Base),"The web application does not adequately enforce appropriate authorization on all restricted URLs, scripts, or files. | |
| 1303 | Web applications susceptible to direct request attacks often make the false assumption that such resources can only be reached through a given navigation path and so only apply authorization at certain points in the path.",,unclassified, | |
| 1304 | CWE-427,EN-Uncontrolled Search Path Element (Type: Base),"The product uses a fixed or controlled search path to find resources, but one or more locations in that path can be under the control of unintended actors. | |
| 1305 | Although this weakness can occur with any type of resource, it is frequently introduced when a product uses a directory search path to find executables or code libraries, but the path contains a directory that can be modified by an attacker, such as ""/tmp"" or the current working directory. | |
| 1306 | In Windows-based systems, when the LoadLibrary or LoadLibraryEx function is called with a DLL name that does not contain a fully qualified path, the function follows a search order that includes two path elements that might be uncontrolled: | |
| 1307 | the directory from which the program has been loaded | |
| 1308 | the current working directory. | |
| 1309 | In some cases, the attack can be conducted remotely, such as when SMB or WebDAV network shares are used. | |
| 1310 | In some Unix-based systems, a PATH might be created that contains an empty element, e.g. by splicing an empty variable into the PATH. This empty element can be interpreted as equivalent to the current working directory, which might be an untrusted search element.",,unclassified,"Double clicking on MS Office documents from Windows Explorer may execute arbitrary programs in some cases | |
| 1311 | ACROS Security: Remote Binary Planting in Apple iTunes for Windows (ASPR #2010-08-18-1) | |
| 1312 | Automatic Detection of Vulnerable Dynamic Component Loadings: http://www.cs.ucdavis.edu/research/tech-reports/2010/CSE-2010-2.pdf | |
| 1313 | Dynamic-Link Library Search Order: http://msdn.microsoft.com/en-us/library/ms682586%28v=VS.85%29.aspx | |
| 1314 | Dynamic-Link Library Security: http://msdn.microsoft.com/en-us/library/ff919712%28VS.85%29.aspx | |
| 1315 | An update on the DLL-preloading remote attack vector: http://blogs.technet.com/b/srd/archive/2010/08/23/an-update-on-the-dll-preloading-remote-attack-vector.aspx | |
| 1316 | Insecure Library Loading Could Allow Remote Code Execution: http://www.microsoft.com/technet/security/advisory/2269637.mspx | |
| 1317 | Application DLL Load Hijacking: http://blog.rapid7.com/?p=5325 | |
| 1318 | DLL Hijacking: Facts and Fiction: http://threatpost.com/en_us/blogs/dll-hijacking-facts-and-fiction-082610" | |
| 1319 | CWE-428,EN-Unquoted Search Path or Element (Type: Base),"The product uses a search path that contains an unquoted element, in which the element contains whitespace or other separators. This can cause the product to access resources in a parent path. | |
| 1320 | If a malicious individual has access to the file system, it is possible to elevate privileges by inserting such a file as ""C:\Program.exe"" to be run by a privileged program making use of WinExec.",,unclassified,"The Art of Software Security Assessment: Chapter 11, ""Process Loading"", Page 654." | |
| 1321 | CWE-43,EN-Path Equivalence: filename.... (Multiple Trailing Dot) (Type: Variant),"A software system that accepts path input in the form of multiple trailing dot ('filedir....') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1322 | If a malicious individual has access to the file system, it is possible to elevate privileges by inserting such a file as ""C:\Program.exe"" to be run by a privileged program making use of WinExec.",,unclassified, | |
| 1323 | CWE-430,EN-Deployment of Wrong Handler (Type: Base),"The wrong ""handler"" is assigned to process an object. | |
| 1324 | An example of deploying the wrong handler would be calling a servlet to reveal source code of a .JSP file, or automatically ""determining"" type of the object even if it is contradictory to an explicitly specified type.",,unclassified,"The Art of Software Security Assessment: Chapter 3, ""File Handlers"", Page 74." | |
| 1325 | CWE-431,EN-Missing Handler (Type: Base),"A handler is not available or implemented. | |
| 1326 | When an exception is thrown and not caught, the process has given up an opportunity to decide if a given failure or event is worth a change in execution.",,unclassified,"The Art of Software Security Assessment: Chapter 3, ""File Handlers"", Page 74." | |
| 1327 | CWE-432,EN-Dangerous Signal Handler not Disabled During Sensitive Operations (Type: Base),"The application uses a signal handler that shares state with other signal handlers, but it does not properly mask or prevent those signal handlers from being invoked while the original signal handler is still running. | |
| 1328 | During the execution of a signal handler, it can be interrupted by another handler when a different signal is sent. If the two handlers share state - such as global variables - then an attacker can corrupt the state by sending another signal before the first handler has completed execution.",,unclassified, | |
| 1329 | CWE-433,EN-Unparsed Raw Web Content Delivery (Type: Variant),"The software stores raw content or supporting code under the web document root with an extension that is not specifically handled by the server. | |
| 1330 | If code is stored in a file with an extension such as "".inc"" or "".pl"", and the web server does not have a handler for that extension, then the server will likely send the contents of the file directly to the requester without the pre-processing that was expected. When that file contains sensitive information such as database credentials, this may allow the attacker to compromise the application or associated components.",,unclassified,"The Art of Software Security Assessment: Chapter 3, ""File Handlers"", Page 74." | |
| 1331 | CWE-435,EN-Interaction Error (Type: Class),"An interaction error occurs when two entities work correctly when running independently, but they interact in unexpected ways when they are run together. | |
| 1332 | This could apply to products, systems, components, etc.",,unclassified, | |
| 1333 | CWE-436,EN-Interpretation Conflict (Type: Base),"Product A handles inputs or steps differently than Product B, which causes A to perform incorrect actions based on its perception of B's state. | |
| 1334 | This is generally found in proxies, firewalls, anti-virus software, and other intermediary devices that allow, deny, or modify traffic based on how the client or server is expected to behave.",,unclassified,"On Interpretation Conflict Vulnerabilities | |
| 1335 | Insertion, Evasion, and Denial of Service: Eluding Network Intrusion Detection: http://www.insecure.org/stf/secnet_ids/secnet_ids.pdf | |
| 1336 | 0x00 vs ASP file upload scripts: http://www.security-assessment.com/Whitepapers/0x00_vs_ASP_File_Uploads.pdf | |
| 1337 | Poison NULL byte | |
| 1338 | Re: Corsaire Security Advisory - Multiple vendor MIME RFC2047 encoding: http://marc.theaimsgroup.com/?l=bugtraq&m=109525864717484&w=2" | |
| 1339 | CWE-437,EN-Incomplete Model of Endpoint Features (Type: Base),"A product acts as an intermediary or monitor between two or more endpoints, but it does not have a complete model of an endpoint's features, behaviors, or state, potentially causing the product to perform incorrect actions based on this incomplete model. | |
| 1340 | This is generally found in proxies, firewalls, anti-virus software, and other intermediary devices that allow, deny, or modify traffic based on how the client or server is expected to behave.",,unclassified, | |
| 1341 | CWE-439,EN-Behavioral Change in New Version or Environment (Type: Base),"A's behavior or functionality changes with a new version of A, or a new environment, which is not known (or manageable) by B. | |
| 1342 | This is generally found in proxies, firewalls, anti-virus software, and other intermediary devices that allow, deny, or modify traffic based on how the client or server is expected to behave.",,unclassified, | |
| 1343 | CWE-44,EN-Path Equivalence: file.name (Internal Dot) (Type: Variant),"A software system that accepts path input in the form of internal dot ('file.ordir') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1344 | This is generally found in proxies, firewalls, anti-virus software, and other intermediary devices that allow, deny, or modify traffic based on how the client or server is expected to behave.",,unclassified, | |
| 1345 | CWE-440,EN-Expected Behavior Violation (Type: Base),"A feature, API, or function being used by a product behaves differently than the product expects. | |
| 1346 | This is generally found in proxies, firewalls, anti-virus software, and other intermediary devices that allow, deny, or modify traffic based on how the client or server is expected to behave.",,unclassified, | |
| 1347 | CWE-441,EN-Unintended Proxy or Intermediary (Confused Deputy) (Type: Class),"The software receives a request, message, or directive from an upstream component, but the software does not sufficiently preserve the original source of the request before forwarding the request to an external actor that is outside of the software's control sphere. This causes the software to appear to be the source of the request, leading it to act as a proxy or other intermediary between the upstream component and the external actor. | |
| 1348 | If an attacker cannot directly contact a target, but the software has access to the target, then the attacker can send a request to the software and have it be forwarded from the target. The request would appear to be coming from the software's system, not the attacker's system. As a result, the attacker can bypass access controls (such as firewalls) or hide the source of malicious requests, since the requests would not be coming directly from the attacker. | |
| 1349 | Since proxy functionality and message-forwarding often serve a legitimate purpose, this issue only becomes a vulnerability when: | |
| 1350 | The software runs with different privileges or on a different system, or otherwise has different levels of access than the upstream component; | |
| 1351 | The attacker is prevented from making the request directly to the target; and | |
| 1352 | The attacker can create a request that the proxy does not explicitly intend to be forwarded on the behalf of the requester. Such a request might point to an unexpected hostname, port number, or service. Or, the request might be sent to an allowed service, but the request could contain disallowed directives, commands, or resources.",,unclassified,The Confused Deputy (or why capabilities might have been invented): http://www.cap-lore.com/CapTheory/ConfusedDeputy.html | |
| 1353 | CWE-443,EN-DEPRECATED (Duplicate): HTTP response splitting (Type: Base),"This weakness can be found at CWE-113. | |
| 1354 | If an attacker cannot directly contact a target, but the software has access to the target, then the attacker can send a request to the software and have it be forwarded from the target. The request would appear to be coming from the software's system, not the attacker's system. As a result, the attacker can bypass access controls (such as firewalls) or hide the source of malicious requests, since the requests would not be coming directly from the attacker. | |
| 1355 | Since proxy functionality and message-forwarding often serve a legitimate purpose, this issue only becomes a vulnerability when: | |
| 1356 | The software runs with different privileges or on a different system, or otherwise has different levels of access than the upstream component; | |
| 1357 | The attacker is prevented from making the request directly to the target; and | |
| 1358 | The attacker can create a request that the proxy does not explicitly intend to be forwarded on the behalf of the requester. Such a request might point to an unexpected hostname, port number, or service. Or, the request might be sent to an allowed service, but the request could contain disallowed directives, commands, or resources.",,unclassified, | |
| 1359 | CWE-444,EN-Inconsistent Interpretation of HTTP Requests (HTTP Request Smuggling) (Type: Base),"When malformed or abnormal HTTP requests are interpreted by one or more entities in the data flow between the user and the web server, such as a proxy or firewall, they can be interpreted inconsistently, allowing the attacker to ""smuggle"" a request to one device without the other device being aware of it. | |
| 1360 | If an attacker cannot directly contact a target, but the software has access to the target, then the attacker can send a request to the software and have it be forwarded from the target. The request would appear to be coming from the software's system, not the attacker's system. As a result, the attacker can bypass access controls (such as firewalls) or hide the source of malicious requests, since the requests would not be coming directly from the attacker. | |
| 1361 | Since proxy functionality and message-forwarding often serve a legitimate purpose, this issue only becomes a vulnerability when: | |
| 1362 | The software runs with different privileges or on a different system, or otherwise has different levels of access than the upstream component; | |
| 1363 | The attacker is prevented from making the request directly to the target; and | |
| 1364 | The attacker can create a request that the proxy does not explicitly intend to be forwarded on the behalf of the requester. Such a request might point to an unexpected hostname, port number, or service. Or, the request might be sent to an allowed service, but the request could contain disallowed directives, commands, or resources.",,unclassified,HTTP Request Smuggling: http://www.cgisecurity.com/lib/HTTP-Request-Smuggling.pdf | |
| 1365 | CWE-446,EN-UI Discrepancy for Security Feature (Type: Base),"The user interface does not correctly enable or configure a security feature, but the interface provides feedback that causes the user to believe that the feature is in a secure state. | |
| 1366 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1367 | CWE-447,EN-Unimplemented or Unsupported Feature in UI (Type: Base),"A UI function for a security feature appears to be supported and gives feedback to the user that suggests that it is supported, but the underlying functionality is not implemented. | |
| 1368 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1369 | CWE-448,EN-Obsolete Feature in UI (Type: Base),"A UI function is obsolete and the product does not warn the user. | |
| 1370 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1371 | CWE-449,EN-The UI Performs the Wrong Action (Type: Base),"The UI performs the wrong action with respect to the user's request. | |
| 1372 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1373 | CWE-45,EN-Path Equivalence: file...name (Multiple Internal Dot) (Type: Variant),"A software system that accepts path input in the form of multiple internal dot ('file...dir') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1374 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1375 | CWE-450,EN-Multiple Interpretations of UI Input (Type: Base),"The UI has multiple interpretations of user input but does not prompt the user when it selects the less secure interpretation. | |
| 1376 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1377 | CWE-451,EN-UI Misrepresentation of Critical Information (Type: Base),"The UI does not properly represent critical information to the user, allowing the information - or its source - to be obscured or spoofed. This is often a component in phishing attacks. | |
| 1378 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1379 | CWE-453,EN-Insecure Default Variable Initialization (Type: Base),"The software, by default, initializes an internal variable with an insecure or less secure value than is possible. | |
| 1380 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1381 | CWE-454,EN-External Initialization of Trusted Variables or Data Stores (Type: Base),"The software initializes critical internal variables or data stores using inputs that can be modified by untrusted actors. | |
| 1382 | A software system should be reluctant to trust variables that have been initialized outside of its trust boundary, especially if they are initialized by users. They may have been initialized incorrectly. If an attacker can initialize the variable, then he/she can influence what the vulnerable system will do.",,unclassified, | |
| 1383 | CWE-455,EN-Non-exit on Failed Initialization (Type: Base),"The software does not exit or otherwise modify its operation when security-relevant errors occur during initialization, such as when a configuration file has a format error, which can cause the software to execute in a less secure fashion than intended by the administrator. | |
| 1384 | A software system should be reluctant to trust variables that have been initialized outside of its trust boundary, especially if they are initialized by users. They may have been initialized incorrectly. If an attacker can initialize the variable, then he/she can influence what the vulnerable system will do.",,unclassified, | |
| 1385 | CWE-456,EN-Missing Initialization of a Variable (Type: Base),"The software does not initialize critical variables, which causes the execution environment to use unexpected values. | |
| 1386 | A software system should be reluctant to trust variables that have been initialized outside of its trust boundary, especially if they are initialized by users. They may have been initialized incorrectly. If an attacker can initialize the variable, then he/she can influence what the vulnerable system will do.",,unclassified,"The Art of Software Security Assessment: Chapter 7, ""Variable Initialization"", Page 312." | |
| 1387 | CWE-458,EN-DEPRECATED: Incorrect Initialization (Type: Base),"This weakness has been deprecated because its name and description did not match. The description duplicated CWE-454, while the name suggested a more abstract initialization problem. Please refer to CWE-665 for the more abstract problem. | |
| 1388 | In some languages such as C and C++, stack variables are not initialized by default. They generally contain junk data with the contents of stack memory before the function was invoked. An attacker can sometimes control or read these contents. In other languages or conditions, a variable that is not explicitly initialized can be given a default value that has security implications, depending on the logic of the program. The presence of an uninitialized variable can sometimes indicate a typographic error in the code.",,unclassified, | |
| 1389 | CWE-459,EN-Incomplete Cleanup (Type: Base),"The software does not properly ""clean up"" and remove temporary or supporting resources after they have been used. | |
| 1390 | In some languages such as C and C++, stack variables are not initialized by default. They generally contain junk data with the contents of stack memory before the function was invoked. An attacker can sometimes control or read these contents. In other languages or conditions, a variable that is not explicitly initialized can be given a default value that has security implications, depending on the logic of the program. The presence of an uninitialized variable can sometimes indicate a typographic error in the code.",,unclassified, | |
| 1391 | CWE-46,EN-Path Equivalence: filename (Trailing Space) (Type: Variant),"A software system that accepts path input in the form of trailing space ('filedir ') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1392 | In some languages such as C and C++, stack variables are not initialized by default. They generally contain junk data with the contents of stack memory before the function was invoked. An attacker can sometimes control or read these contents. In other languages or conditions, a variable that is not explicitly initialized can be given a default value that has security implications, depending on the logic of the program. The presence of an uninitialized variable can sometimes indicate a typographic error in the code.",,unclassified, | |
| 1393 | CWE-463,EN-Deletion of Data Structure Sentinel (Type: Base),"The accidental deletion of a data-structure sentinel can cause serious programming logic problems. | |
| 1394 | Often times data-structure sentinels are used to mark structure of the data structure. A common example of this is the null character at the end of strings. Another common example is linked lists which may contain a sentinel to mark the end of the list. It is dangerous to allow this type of control data to be easily accessible. Therefore, it is important to protect from the deletion or modification outside of some wrapper interface which provides safety.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""NUL-Termination Problems"", Page 452." | |
| 1395 | CWE-466,EN-Return of Pointer Value Outside of Expected Range (Type: Base),"A function can return a pointer to memory that is outside of the buffer that the pointer is expected to reference. | |
| 1396 | Data-structure sentinels are often used to mark the structure of data. A common example of this is the null character at the end of strings or a special sentinel to mark the end of a linked list. It is dangerous to allow this type of control data to be easily accessible. Therefore, it is important to protect from the addition or modification of sentinels.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89" | |
| 1397 | CWE-47,EN-Path Equivalence: filename (Leading Space) (Type: Variant),"A software system that accepts path input in the form of leading space (' filedir') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1398 | Data-structure sentinels are often used to mark the structure of data. A common example of this is the null character at the end of strings or a special sentinel to mark the end of a linked list. It is dangerous to allow this type of control data to be easily accessible. Therefore, it is important to protect from the addition or modification of sentinels.",,unclassified, | |
| 1399 | CWE-470,EN-Use of Externally-Controlled Input to Select Classes or Code (Unsafe Reflection) (Type: Base),"The application uses external input with reflection to select which classes or code to use, but it does not sufficiently prevent the input from selecting improper classes or code. | |
| 1400 | If the application uses external inputs to determine which class to instantiate or which method to invoke, then an attacker could supply values to select unexpected classes or methods. If this occurs, then the attacker could create control flow paths that were not intended by the developer. These paths could bypass authentication or access control checks, or otherwise cause the application to behave in an unexpected manner. This situation becomes a doomsday scenario if the attacker can upload files into a location that appears on the application's classpath (CWE-427) or add new entries to the application's classpath (CWE-426). Under either of these conditions, the attacker can use reflection to introduce new, malicious behavior into the application.",,unclassified, | |
| 1401 | CWE-471,EN-Modification of Assumed-Immutable Data (MAID) (Type: Base),"The software does not properly protect an assumed-immutable element from being modified by an attacker. | |
| 1402 | If the application uses external inputs to determine which class to instantiate or which method to invoke, then an attacker could supply values to select unexpected classes or methods. If this occurs, then the attacker could create control flow paths that were not intended by the developer. These paths could bypass authentication or access control checks, or otherwise cause the application to behave in an unexpected manner. This situation becomes a doomsday scenario if the attacker can upload files into a location that appears on the application's classpath (CWE-427) or add new entries to the application's classpath (CWE-426). Under either of these conditions, the attacker can use reflection to introduce new, malicious behavior into the application.",,unclassified, | |
| 1403 | CWE-472,EN-External Control of Assumed-Immutable Web Parameter (Type: Base),"The web application does not sufficiently verify inputs that are assumed to be immutable but are actually externally controllable, such as hidden form fields. | |
| 1404 | If a web product does not properly protect assumed-immutable values from modification in hidden form fields, parameters, cookies, or URLs, this can lead to modification of critical data. Web applications often mistakenly make the assumption that data passed to the client in hidden fields or cookies is not susceptible to tampering. Improper validation of data that are user-controllable can lead to the application processing incorrect, and often malicious, input. | |
| 1405 | For example, custom cookies commonly store session data or persistent data across sessions. This kind of session data is normally involved in security related decisions on the server side, such as user authentication and access control. Thus, the cookies might contain sensitive data such as user credentials and privileges. This is a dangerous practice, as it can often lead to improper reliance on the value of the client-provided cookie by the server side application.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 4: Use of Magic URLs, Predictable Cookies, and Hidden Form Fields."" Page 75 | |
| 1406 | The Art of Software Security Assessment: Chapter 17, ""Embedding State in HTML and URLs"", Page 1032." | |
| 1407 | CWE-473,EN-PHP External Variable Modification (Type: Variant),"A PHP application does not properly protect against the modification of variables from external sources, such as query parameters or cookies. This can expose the application to numerous weaknesses that would not exist otherwise. | |
| 1408 | If a web product does not properly protect assumed-immutable values from modification in hidden form fields, parameters, cookies, or URLs, this can lead to modification of critical data. Web applications often mistakenly make the assumption that data passed to the client in hidden fields or cookies is not susceptible to tampering. Improper validation of data that are user-controllable can lead to the application processing incorrect, and often malicious, input. | |
| 1409 | For example, custom cookies commonly store session data or persistent data across sessions. This kind of session data is normally involved in security related decisions on the server side, such as user authentication and access control. Thus, the cookies might contain sensitive data such as user credentials and privileges. This is a dangerous practice, as it can often lead to improper reliance on the value of the client-provided cookie by the server side application.",,unclassified, | |
| 1410 | CWE-474,EN-Use of Function with Inconsistent Implementations (Type: Base),"The code uses a function that has inconsistent implementations across operating systems and versions, which might cause security-relevant portability problems. | |
| 1411 | If a web product does not properly protect assumed-immutable values from modification in hidden form fields, parameters, cookies, or URLs, this can lead to modification of critical data. Web applications often mistakenly make the assumption that data passed to the client in hidden fields or cookies is not susceptible to tampering. Improper validation of data that are user-controllable can lead to the application processing incorrect, and often malicious, input. | |
| 1412 | For example, custom cookies commonly store session data or persistent data across sessions. This kind of session data is normally involved in security related decisions on the server side, such as user authentication and access control. Thus, the cookies might contain sensitive data such as user credentials and privileges. This is a dangerous practice, as it can often lead to improper reliance on the value of the client-provided cookie by the server side application.",,unclassified, | |
| 1413 | CWE-475,EN-Undefined Behavior for Input to API (Type: Base),"The behavior of this function is undefined unless its control parameter is set to a specific value. | |
| 1414 | If a web product does not properly protect assumed-immutable values from modification in hidden form fields, parameters, cookies, or URLs, this can lead to modification of critical data. Web applications often mistakenly make the assumption that data passed to the client in hidden fields or cookies is not susceptible to tampering. Improper validation of data that are user-controllable can lead to the application processing incorrect, and often malicious, input. | |
| 1415 | For example, custom cookies commonly store session data or persistent data across sessions. This kind of session data is normally involved in security related decisions on the server side, such as user authentication and access control. Thus, the cookies might contain sensitive data such as user credentials and privileges. This is a dangerous practice, as it can often lead to improper reliance on the value of the client-provided cookie by the server side application.",,unclassified, | |
| 1416 | CWE-477,EN-Use of Obsolete Functions (Type: Base),"The code uses deprecated or obsolete functions, which suggests that the code has not been actively reviewed or maintained. | |
| 1417 | NULL pointer dereference issues can occur through a number of flaws, including race conditions, and simple programming omissions.",,unclassified, | |
| 1418 | CWE-478,EN-Missing Default Case in Switch Statement (Type: Variant),"The code does not have a default case in a switch statement, which might lead to complex logical errors and resultant weaknesses. | |
| 1419 | NULL pointer dereference issues can occur through a number of flaws, including race conditions, and simple programming omissions.",,unclassified,"The Art of Software Security Assessment: Chapter 7, ""Switch Statements"", Page 337." | |
| 1420 | CWE-48,EN-Path Equivalence: file name (Internal Whitespace) (Type: Variant),"A software system that accepts path input in the form of internal space ('file(SPACE)name') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1421 | Non-reentrant functions are functions that cannot safely be called, interrupted, and then recalled before the first call has finished without resulting in memory corruption. This can lead to an unexpected system state an unpredictable results with a variety of potential consequences depending on context, including denial of service and code execution. | |
| 1422 | Many functions are not reentrant, but some of them can result in the corruption of memory if they are used in a signal handler. The function call syslog() is an example of this. In order to perform its functionality, it allocates a small amount of memory as ""scratch space."" If syslog() is suspended by a signal call and the signal handler calls syslog(), the memory used by both of these functions enters an undefined, and possibly, exploitable state. Implementations of malloc() and free() manage metadata in global structures in order to track which memory is allocated versus which memory is available, but they are non-reentrant. Simultaneous calls to these functions can cause corruption of the metadata.",,unclassified, | |
| 1423 | CWE-485,EN-Insufficient Encapsulation (Type: Class),"The product does not sufficiently encapsulate critical data or functionality. | |
| 1424 | Encapsulation is about drawing strong boundaries. In a web browser that might mean ensuring that your mobile code cannot be abused by other mobile code. On the server it might mean differentiation between validated data and unvalidated data, between one user's data and another's, or between data users are allowed to see and data that they are not.",,unclassified, | |
| 1425 | CWE-488,EN-Exposure of Data Element to Wrong Session (Type: Variant),"The product does not sufficiently enforce boundaries between the states of different sessions, causing data to be provided to, or used by, the wrong session. | |
| 1426 | Data can ""bleed"" from one session to another through member variables of singleton objects, such as Servlets, and objects from a shared pool. | |
| 1427 | In the case of Servlets, developers sometimes do not understand that, unless a Servlet implements the SingleThreadModel interface, the Servlet is a singleton; there is only one instance of the Servlet, and that single instance is used and re-used to handle multiple requests that are processed simultaneously by different threads. A common result is that developers use Servlet member fields in such a way that one user may inadvertently see another user's data. In other words, storing user data in Servlet member fields introduces a data access race condition.",,unclassified, | |
| 1428 | CWE-489,EN-Leftover Debug Code (Type: Base),"The application can be deployed with active debugging code that can create unintended entry points. | |
| 1429 | Data can ""bleed"" from one session to another through member variables of singleton objects, such as Servlets, and objects from a shared pool. | |
| 1430 | In the case of Servlets, developers sometimes do not understand that, unless a Servlet implements the SingleThreadModel interface, the Servlet is a singleton; there is only one instance of the Servlet, and that single instance is used and re-used to handle multiple requests that are processed simultaneously by different threads. A common result is that developers use Servlet member fields in such a way that one user may inadvertently see another user's data. In other words, storing user data in Servlet member fields introduces a data access race condition.",,unclassified, | |
| 1431 | CWE-49,EN-Path Equivalence: filename/ (Trailing Slash) (Type: Variant),"A software system that accepts path input in the form of trailing slash ('filedir/') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1432 | Data can ""bleed"" from one session to another through member variables of singleton objects, such as Servlets, and objects from a shared pool. | |
| 1433 | In the case of Servlets, developers sometimes do not understand that, unless a Servlet implements the SingleThreadModel interface, the Servlet is a singleton; there is only one instance of the Servlet, and that single instance is used and re-used to handle multiple requests that are processed simultaneously by different threads. A common result is that developers use Servlet member fields in such a way that one user may inadvertently see another user's data. In other words, storing user data in Servlet member fields introduces a data access race condition.",,unclassified, | |
| 1434 | CWE-491,EN-Public cloneable() Method Without Final (Object Hijack) (Type: Variant),"A class has a cloneable() method that is not declared final, which allows an object to be created without calling the constructor. This can cause the object to be in an unexpected state. | |
| 1435 | Data can ""bleed"" from one session to another through member variables of singleton objects, such as Servlets, and objects from a shared pool. | |
| 1436 | In the case of Servlets, developers sometimes do not understand that, unless a Servlet implements the SingleThreadModel interface, the Servlet is a singleton; there is only one instance of the Servlet, and that single instance is used and re-used to handle multiple requests that are processed simultaneously by different threads. A common result is that developers use Servlet member fields in such a way that one user may inadvertently see another user's data. In other words, storing user data in Servlet member fields introduces a data access race condition.",,unclassified,"OWASP , Attack Category : Mobile code: object hijack: http://www.owasp.org/index.php/Mobile_code:_object_hijack" | |
| 1437 | CWE-495,EN-Private Array-Typed Field Returned From A Public Method (Type: Variant),"The product has a method that is declared public, but returns a reference to a private array, which could then be modified in unexpected ways. | |
| 1438 | An attacker can execute malicious code by compromising the host server, performing DNS spoofing, or modifying the code in transit.",,unclassified, | |
| 1439 | CWE-496,EN-Public Data Assigned to Private Array-Typed Field (Type: Variant),"Assigning public data to a private array is equivalent to giving public access to the array. | |
| 1440 | An attacker can execute malicious code by compromising the host server, performing DNS spoofing, or modifying the code in transit.",,unclassified, | |
| 1441 | CWE-497,EN-Exposure of System Data to an Unauthorized Control Sphere (Type: Variant),"Exposing system data or debugging information helps an adversary learn about the system and form an attack plan. | |
| 1442 | An information exposure occurs when system data or debugging information leaves the program through an output stream or logging function that makes it accessible to unauthorized parties. An attacker can also cause errors to occur by submitting unusual requests to the web application. The response to these errors can reveal detailed system information, deny service, cause security mechanisms to fail, and crash the server. An attacker can use error messages that reveal technologies, operating systems, and product versions to tune the attack against known vulnerabilities in these technologies. An application may use diagnostic methods that provide significant implementation details such as stack traces as part of its error handling mechanism.",,unclassified, | |
| 1443 | CWE-5,EN-J2EE Misconfiguration: Data Transmission Without Encryption (Type: Variant),"Information sent over a network can be compromised while in transit. An attacker may be able to read/modify the contents if the data are sent in plaintext or are weakly encrypted. | |
| 1444 | Serializable classes are effectively open classes since data cannot be hidden in them. Classes that do not explicitly deny serialization can be serialized by any other class, which can then in turn use the data stored inside it.",,unclassified, | |
| 1445 | CWE-50,EN-Path Equivalence: //multiple/leading/slash (Type: Variant),"A software system that accepts path input in the form of multiple leading slash ('//multiple/leading/slash') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1446 | Serializable classes are effectively open classes since data cannot be hidden in them. Classes that do not explicitly deny serialization can be serialized by any other class, which can then in turn use the data stored inside it.",,unclassified, | |
| 1447 | CWE-501,EN-Trust Boundary Violation (Type: Base),"The product mixes trusted and untrusted data in the same data structure or structured message. | |
| 1448 | By combining trusted and untrusted data in the same data structure, it becomes easier for programmers to mistakenly trust unvalidated data.",,unclassified, | |
| 1449 | CWE-506,EN-Embedded Malicious Code (Type: Class),"The application contains code that appears to be malicious in nature. | |
| 1450 | Malicious flaws have acquired colorful names, including Trojan horse, trapdoor, timebomb, and logic-bomb. A developer might insert malicious code with the intent to subvert the security of an application or its host system at some time in the future. It generally refers to a program that performs a useful service but exploits rights of the program's user in a way the user does not intend.",,unclassified, | |
| 1451 | CWE-507,EN-Trojan Horse (Type: Base),"The software appears to contain benign or useful functionality, but it also contains code that is hidden from normal operation that violates the intended security policy of the user or the system administrator. | |
| 1452 | Malicious flaws have acquired colorful names, including Trojan horse, trapdoor, timebomb, and logic-bomb. A developer might insert malicious code with the intent to subvert the security of an application or its host system at some time in the future. It generally refers to a program that performs a useful service but exploits rights of the program's user in a way the user does not intend.",,unclassified,"Writing Secure Code: Chapter 7, ""Viruses, Trojans, and Worms In a Nutshell"" Page 208" | |
| 1453 | CWE-508,EN-Non-Replicating Malicious Code (Type: Base),"Non-replicating malicious code only resides on the target system or software that is attacked; it does not attempt to spread to other systems. | |
| 1454 | Malicious flaws have acquired colorful names, including Trojan horse, trapdoor, timebomb, and logic-bomb. A developer might insert malicious code with the intent to subvert the security of an application or its host system at some time in the future. It generally refers to a program that performs a useful service but exploits rights of the program's user in a way the user does not intend.",,unclassified, | |
| 1455 | CWE-509,EN-Replicating Malicious Code (Virus or Worm) (Type: Base),"Replicating malicious code, including viruses and worms, will attempt to attack other systems once it has successfully compromised the target system or software. | |
| 1456 | Malicious flaws have acquired colorful names, including Trojan horse, trapdoor, timebomb, and logic-bomb. A developer might insert malicious code with the intent to subvert the security of an application or its host system at some time in the future. It generally refers to a program that performs a useful service but exploits rights of the program's user in a way the user does not intend.",,unclassified, | |
| 1457 | CWE-51,EN-Path Equivalence: /multiple//internal/slash (Type: Variant),"A software system that accepts path input in the form of multiple internal slash ('/multiple//internal/slash/') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1458 | Malicious flaws have acquired colorful names, including Trojan horse, trapdoor, timebomb, and logic-bomb. A developer might insert malicious code with the intent to subvert the security of an application or its host system at some time in the future. It generally refers to a program that performs a useful service but exploits rights of the program's user in a way the user does not intend.",,unclassified, | |
| 1459 | CWE-510,EN-Trapdoor (Type: Base),"A trapdoor is a hidden piece of code that responds to a special input, allowing its user access to resources without passing through the normal security enforcement mechanism. | |
| 1460 | Malicious flaws have acquired colorful names, including Trojan horse, trapdoor, timebomb, and logic-bomb. A developer might insert malicious code with the intent to subvert the security of an application or its host system at some time in the future. It generally refers to a program that performs a useful service but exploits rights of the program's user in a way the user does not intend.",,unclassified, | |
| 1461 | CWE-511,EN-Logic/Time Bomb (Type: Base),"The software contains code that is designed to disrupt the legitimate operation of the software (or its environment) when a certain time passes, or when a certain logical condition is met. | |
| 1462 | When the time bomb or logic bomb is detonated, it may perform a denial of service such as crashing the system, deleting critical data, or degrading system response time. This bomb might be placed within either a replicating or non-replicating Trojan horse.",,unclassified,Mobile App Top 10 List: http://www.veracode.com/blog/2010/12/mobile-app-top-10-list/ | |
| 1463 | CWE-512,EN-Spyware (Type: Base),"The software collects personally identifiable information about a human user or the user's activities, but the software accesses this information using other resources besides itself, and it does not require that user's explicit approval or direct input into the software. | |
| 1464 | ""Spyware"" is a commonly used term with many definitions and interpretations. In general, it is meant to software that collects information or installs functionality that human users might not allow if they were fully aware of the actions being taken by the software. For example, a user might expect that tax software would collect a social security number and include it when filing a tax return, but that same user would not expect gaming software to obtain the social security number from that tax software's data.",,unclassified, | |
| 1465 | CWE-514,EN-Covert Channel (Type: Class),"A covert channel is a path that can be used to transfer information in a way not intended by the system's designers. | |
| 1466 | Typically the system has not given authorization for the transmission and has no knowledge of its occurrence.",,unclassified, | |
| 1467 | CWE-516,EN-DEPRECATED (Duplicate): Covert Timing Channel (Type: Base),"This weakness can be found at CWE-385. | |
| 1468 | Covert storage channels occur when out-of-band data is stored in messages for the purpose of memory reuse. Covert channels are frequently classified as either storage or timing channels. Examples would include using a file intended to hold only audit information to convey user passwords--using the name of a file or perhaps status bits associated with it that can be read by all users to signal the contents of the file. Steganography, concealing information in such a manner that no one but the intended recipient knows of the existence of the message, is a good example of a covert storage channel.",,unclassified, | |
| 1469 | CWE-52,EN-Path Equivalence: /multiple/trailing/slash// (Type: Variant),"A software system that accepts path input in the form of multiple trailing slash ('/multiple/trailing/slash//') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1470 | Covert storage channels occur when out-of-band data is stored in messages for the purpose of memory reuse. Covert channels are frequently classified as either storage or timing channels. Examples would include using a file intended to hold only audit information to convey user passwords--using the name of a file or perhaps status bits associated with it that can be read by all users to signal the contents of the file. Steganography, concealing information in such a manner that no one but the intended recipient knows of the existence of the message, is a good example of a covert storage channel.",,unclassified, | |
| 1471 | CWE-520,EN-.NET Misconfiguration: Use of Impersonation (Type: Variant),"Allowing a .NET application to run at potentially escalated levels of access to the underlying operating and file systems can be dangerous and result in various forms of attacks. | |
| 1472 | Covert storage channels occur when out-of-band data is stored in messages for the purpose of memory reuse. Covert channels are frequently classified as either storage or timing channels. Examples would include using a file intended to hold only audit information to convey user passwords--using the name of a file or perhaps status bits associated with it that can be read by all users to signal the contents of the file. Steganography, concealing information in such a manner that no one but the intended recipient knows of the existence of the message, is a good example of a covert storage channel.",,unclassified, | |
| 1473 | CWE-521,EN-Weak Password Requirements (Type: Base),"The product does not require that users should have strong passwords, which makes it easier for attackers to compromise user accounts. | |
| 1474 | An authentication mechanism is only as strong as its credentials. For this reason, it is important to require users to have strong passwords. Lack of password complexity significantly reduces the search space when trying to guess user's passwords, making brute-force attacks easier.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 1475 | CWE-522,EN-Insufficiently Protected Credentials (Type: Base),"This weakness occurs when the application transmits or stores authentication credentials and uses an insecure method that is susceptible to unauthorized interception and/or retrieval. | |
| 1476 | An authentication mechanism is only as strong as its credentials. For this reason, it is important to require users to have strong passwords. Lack of password complexity significantly reduces the search space when trying to guess user's passwords, making brute-force attacks easier.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 1477 | CWE-523,EN-Unprotected Transport of Credentials (Type: Variant),"Login pages not using adequate measures to protect the user name and password while they are in transit from the client to the server. | |
| 1478 | An authentication mechanism is only as strong as its credentials. For this reason, it is important to require users to have strong passwords. Lack of password complexity significantly reduces the search space when trying to guess user's passwords, making brute-force attacks easier.",,unclassified, | |
| 1479 | CWE-524,EN-Information Exposure Through Caching (Type: Variant),"The application uses a cache to maintain a pool of objects, threads, connections, pages, or passwords to minimize the time it takes to access them or the resources to which they connect. If implemented improperly, these caches can allow access to unauthorized information or cause a denial of service vulnerability. | |
| 1480 | An authentication mechanism is only as strong as its credentials. For this reason, it is important to require users to have strong passwords. Lack of password complexity significantly reduces the search space when trying to guess user's passwords, making brute-force attacks easier.",,unclassified, | |
| 1481 | CWE-525,EN-Information Exposure Through Browser Caching (Type: Variant),"For each web page, the application should have an appropriate caching policy specifying the extent to which the page and its form fields should be cached. | |
| 1482 | An authentication mechanism is only as strong as its credentials. For this reason, it is important to require users to have strong passwords. Lack of password complexity significantly reduces the search space when trying to guess user's passwords, making brute-force attacks easier.",,unclassified, | |
| 1483 | CWE-526,EN-Information Exposure Through Environmental Variables (Type: Variant),"Environmental variables may contain sensitive information about a remote server. | |
| 1484 | An authentication mechanism is only as strong as its credentials. For this reason, it is important to require users to have strong passwords. Lack of password complexity significantly reduces the search space when trying to guess user's passwords, making brute-force attacks easier.",,unclassified, | |
| 1485 | CWE-527,EN-Exposure of CVS Repository to an Unauthorized Control Sphere (Type: Variant),"The product stores a CVS repository in a directory or other container that is accessible to actors outside of the intended control sphere. | |
| 1486 | Information contained within a CVS subdirectory on a web server or other server could be recovered by an attacker and used for malicious purposes. This information may include usernames, filenames, path root, and IP addresses.",,unclassified, | |
| 1487 | CWE-528,EN-Exposure of Core Dump File to an Unauthorized Control Sphere (Type: Variant),"The product generates a core dump file in a directory that is accessible to actors outside of the intended control sphere. | |
| 1488 | Information contained within a CVS subdirectory on a web server or other server could be recovered by an attacker and used for malicious purposes. This information may include usernames, filenames, path root, and IP addresses.",,unclassified, | |
| 1489 | CWE-529,EN-Exposure of Access Control List Files to an Unauthorized Control Sphere (Type: Variant),"The product stores access control list files in a directory or other container that is accessible to actors outside of the intended control sphere. | |
| 1490 | Exposure of these access control list files may give the attacker information about the configuration of the site or system. This information may then be used to bypass the intended security policy or identify trusted systems from which an attack can be launched.",,unclassified, | |
| 1491 | CWE-53,EN-Path Equivalence: \multiple\\internal\backslash (Type: Variant),"A software system that accepts path input in the form of multiple internal backslash ('\multiple\trailing\\slash') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1492 | Exposure of these access control list files may give the attacker information about the configuration of the site or system. This information may then be used to bypass the intended security policy or identify trusted systems from which an attack can be launched.",,unclassified, | |
| 1493 | CWE-530,EN-Exposure of Backup File to an Unauthorized Control Sphere (Type: Variant),"A backup file is stored in a directory that is accessible to actors outside of the intended control sphere. | |
| 1494 | Often, old files are renamed with an extension such as .~bk to distinguish them from production files. The source code for old files that have been renamed in this manner and left in the webroot can often be retrieved. This renaming may have been performed automatically by the web server, or manually by the administrator.",,unclassified, | |
| 1495 | CWE-531,EN-Information Exposure Through Test Code (Type: Variant),"Accessible test applications can pose a variety of security risks. Since developers or administrators rarely consider that someone besides themselves would even know about the existence of these applications, it is common for them to contain sensitive information or functions. | |
| 1496 | Often, old files are renamed with an extension such as .~bk to distinguish them from production files. The source code for old files that have been renamed in this manner and left in the webroot can often be retrieved. This renaming may have been performed automatically by the web server, or manually by the administrator.",,unclassified, | |
| 1497 | CWE-533,EN-Information Exposure Through Server Log Files (Type: Variant),"A server.log file was found. This can give information on whatever application left the file. Usually this can give full path names and system information, and sometimes usernames and passwords. | |
| 1498 | While logging all information may be helpful during development stages, it is important that logging levels be set appropriately before a product ships so that sensitive user data and system information are not accidentally exposed to potential attackers.",,unclassified, | |
| 1499 | CWE-534,EN-Information Exposure Through Debug Log Files (Type: Variant),"The application does not sufficiently restrict access to a log file that is used for debugging. | |
| 1500 | While logging all information may be helpful during development stages, it is important that logging levels be set appropriately before a product ships so that sensitive user data and system information are not accidentally exposed to potential attackers.",,unclassified, | |
| 1501 | CWE-535,EN-Information Exposure Through Shell Error Message (Type: Variant),"A command shell error message indicates that there exists an unhandled exception in the web application code. In many cases, an attacker can leverage the conditions that cause these errors in order to gain unauthorized access to the system. | |
| 1502 | While logging all information may be helpful during development stages, it is important that logging levels be set appropriately before a product ships so that sensitive user data and system information are not accidentally exposed to potential attackers.",,unclassified, | |
| 1503 | CWE-536,EN-Information Exposure Through Servlet Runtime Error Message (Type: Variant),"A servlet error message indicates that there exists an unhandled exception in your web application code and may provide useful information to an attacker. | |
| 1504 | While logging all information may be helpful during development stages, it is important that logging levels be set appropriately before a product ships so that sensitive user data and system information are not accidentally exposed to potential attackers.",,unclassified, | |
| 1505 | CWE-537,EN-Information Exposure Through Java Runtime Error Message (Type: Variant),"In many cases, an attacker can leverage the conditions that cause unhandled exception errors in order to gain unauthorized access to the system. | |
| 1506 | While logging all information may be helpful during development stages, it is important that logging levels be set appropriately before a product ships so that sensitive user data and system information are not accidentally exposed to potential attackers.",,unclassified, | |
| 1507 | CWE-538,EN-File and Directory Information Exposure (Type: Base),"The product stores sensitive information in files or directories that are accessible to actors outside of the intended control sphere. | |
| 1508 | While logging all information may be helpful during development stages, it is important that logging levels be set appropriately before a product ships so that sensitive user data and system information are not accidentally exposed to potential attackers.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 12: Information Leakage."" Page 191" | |
| 1509 | CWE-539,EN-Information Exposure Through Persistent Cookies (Type: Variant),"Persistent cookies are cookies that are stored on the browser's hard drive. This can cause security and privacy issues depending on the information stored in the cookie and how it is accessed. | |
| 1510 | Cookies are small bits of data that are sent by the web application but stored locally in the browser. This lets the application use the cookie to pass information between pages and store variable information. The web application controls what information is stored in a cookie and how it is used. Typical types of information stored in cookies are session Identifiers, personalization and customization information, and in rare cases even usernames to enable automated logins. There are two different types of cookies: session cookies and persistent cookies. Session cookies just live in the browser's memory, and are not stored anywhere, but persistent cookies are stored on the browser's hard drive.",,unclassified, | |
| 1511 | CWE-54,EN-Path Equivalence: filedir\ (Trailing Backslash) (Type: Variant),"A software system that accepts path input in the form of trailing backslash ('filedir\') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1512 | Cookies are small bits of data that are sent by the web application but stored locally in the browser. This lets the application use the cookie to pass information between pages and store variable information. The web application controls what information is stored in a cookie and how it is used. Typical types of information stored in cookies are session Identifiers, personalization and customization information, and in rare cases even usernames to enable automated logins. There are two different types of cookies: session cookies and persistent cookies. Session cookies just live in the browser's memory, and are not stored anywhere, but persistent cookies are stored on the browser's hard drive.",,unclassified, | |
| 1513 | CWE-540,EN-Information Exposure Through Source Code (Type: Variant),"Source code on a web server often contains sensitive information and should generally not be accessible to users. | |
| 1514 | There are situations where it is critical to remove source code from an area or server. For example, obtaining Perl source code on a system allows an attacker to understand the logic of the script and extract extremely useful information such as code bugs or logins and passwords.",,unclassified, | |
| 1515 | CWE-541,EN-Information Exposure Through Include Source Code (Type: Variant),"If an include file source is accessible, the file can contain usernames and passwords, as well as sensitive information pertaining to the application and system. | |
| 1516 | There are situations where it is critical to remove source code from an area or server. For example, obtaining Perl source code on a system allows an attacker to understand the logic of the script and extract extremely useful information such as code bugs or logins and passwords.",,unclassified, | |
| 1517 | CWE-542,EN-Information Exposure Through Cleanup Log Files (Type: Variant),"The application does not properly protect or delete a log file related to cleanup. | |
| 1518 | There are situations where it is critical to remove source code from an area or server. For example, obtaining Perl source code on a system allows an attacker to understand the logic of the script and extract extremely useful information such as code bugs or logins and passwords.",,unclassified, | |
| 1519 | CWE-543,EN-Use of Singleton Pattern Without Synchronization in a Multithreaded Context (Type: Variant),"The software uses the singleton pattern when creating a resource within a multithreaded environment. | |
| 1520 | The use of a singleton pattern may not be thread-safe.",,unclassified,Thread-Specifc Storage for C/C++: http://www.cs.wustl.edu/~schmidt/PDF/TSS-pattern.pdf | |
| 1521 | CWE-544,EN-Missing Standardized Error Handling Mechanism (Type: Base),"The software does not use a standardized method for handling errors throughout the code, which might introduce inconsistent error handling and resultant weaknesses. | |
| 1522 | If the application handles error messages individually, on a one-by-one basis, this is likely to result in inconsistent error handling. The causes of errors may be lost. Also, detailed information about the causes of an error may be unintentionally returned to the user.",,unclassified, | |
| 1523 | CWE-545,EN-Use of Dynamic Class Loading (Type: Variant),"Dynamically loaded code has the potential to be malicious. | |
| 1524 | If the application handles error messages individually, on a one-by-one basis, this is likely to result in inconsistent error handling. The causes of errors may be lost. Also, detailed information about the causes of an error may be unintentionally returned to the user.",,unclassified, | |
| 1525 | CWE-546,EN-Suspicious Comment (Type: Variant),"The code contains comments that suggest the presence of bugs, incomplete functionality, or weaknesses. | |
| 1526 | Many suspicious comments, such as BUG, HACK, FIXME, LATER, LATER2, TODO, in the code indicate missing security functionality and checking. Others indicate code problems that programmers should fix, such as hard-coded variables, error handling, not using stored procedures, and performance issues.",,unclassified, | |
| 1527 | CWE-547,"EN-Use of Hard-coded, Security-relevant Constants (Type: Variant)","The program uses hard-coded constants instead of symbolic names for security-critical values, which increases the likelihood of mistakes during code maintenance or security policy change. | |
| 1528 | If the developer does not find all occurrences of the hard-coded constants, an incorrect policy decision may be made if one of the constants is not changed. Making changes to these values will require code changes that may be difficult or impossible once the system is released to the field. In addition, these hard-coded values may become available to attackers if the code is ever disclosed.",,unclassified, | |
| 1529 | CWE-548,EN-Information Exposure Through Directory Listing (Type: Variant),"A directory listing is inappropriately exposed, yielding potentially sensitive information to attackers. | |
| 1530 | A directory listing provides an attacker with the complete index of all the resources located inside of the directory. The specific risks and consequences vary depending on which files are listed and accessible.",,unclassified, | |
| 1531 | CWE-549,EN-Missing Password Field Masking (Type: Variant),"The software does not mask passwords during entry, increasing the potential for attackers to observe and capture passwords. | |
| 1532 | A directory listing provides an attacker with the complete index of all the resources located inside of the directory. The specific risks and consequences vary depending on which files are listed and accessible.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 1533 | CWE-55,EN-Path Equivalence: /./ (Single Dot Directory) (Type: Variant),"A software system that accepts path input in the form of single dot directory exploit ('/./') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1534 | A directory listing provides an attacker with the complete index of all the resources located inside of the directory. The specific risks and consequences vary depending on which files are listed and accessible.",,unclassified, | |
| 1535 | CWE-550,EN-Information Exposure Through Server Error Message (Type: Variant),"Certain conditions, such as network failure, will cause a server error message to be displayed. | |
| 1536 | While error messages in and of themselves are not dangerous, per se, it is what an attacker can glean from them that might cause eventual problems.",,unclassified, | |
| 1537 | CWE-551,EN-Incorrect Behavior Order: Authorization Before Parsing and Canonicalization (Type: Base),"If a web server does not fully parse requested URLs before it examines them for authorization, it may be possible for an attacker to bypass authorization protection. | |
| 1538 | For instance, the character strings /./ and / both mean current directory. If /SomeDirectory is a protected directory and an attacker requests /./SomeDirectory, the attacker may be able to gain access to the resource if /./ is not converted to / before the authorization check is performed.",,unclassified, | |
| 1539 | CWE-552,EN-Files or Directories Accessible to External Parties (Type: Base),"Files or directories are accessible in the environment that should not be. | |
| 1540 | For instance, the character strings /./ and / both mean current directory. If /SomeDirectory is a protected directory and an attacker requests /./SomeDirectory, the attacker may be able to gain access to the resource if /./ is not converted to / before the authorization check is performed.",,unclassified, | |
| 1541 | CWE-553,EN-Command Shell in Externally Accessible Directory (Type: Variant),"A possible shell file exists in /cgi-bin/ or other accessible directories. This is extremely dangerous and can be used by an attacker to execute commands on the web server. | |
| 1542 | For instance, the character strings /./ and / both mean current directory. If /SomeDirectory is a protected directory and an attacker requests /./SomeDirectory, the attacker may be able to gain access to the resource if /./ is not converted to / before the authorization check is performed.",,unclassified, | |
| 1543 | CWE-554,EN-ASP.NET Misconfiguration: Not Using Input Validation Framework (Type: Variant),"The ASP.NET application does not use an input validation framework. | |
| 1544 | For instance, the character strings /./ and / both mean current directory. If /SomeDirectory is a protected directory and an attacker requests /./SomeDirectory, the attacker may be able to gain access to the resource if /./ is not converted to / before the authorization check is performed.",,unclassified, | |
| 1545 | CWE-555,EN-J2EE Misconfiguration: Plaintext Password in Configuration File (Type: Variant),"The J2EE application stores a plaintext password in a configuration file. | |
| 1546 | Storing a plaintext password in a configuration file allows anyone who can read the file to access the password-protected resource, making it an easy target for attackers.",,unclassified, | |
| 1547 | CWE-556,EN-ASP.NET Misconfiguration: Use of Identity Impersonation (Type: Variant),"Configuring an ASP.NET application to run with impersonated credentials may give the application unnecessary privileges. | |
| 1548 | The use of impersonated credentials allows an ASP.NET application to run with either the privileges of the client on whose behalf it is executing or with arbitrary privileges granted in its configuration.",,unclassified, | |
| 1549 | CWE-558,EN-Use of getlogin() in Multithreaded Application (Type: Variant),"The application uses the getlogin() function in a multithreaded context, potentially causing it to return incorrect values. | |
| 1550 | The getlogin() function returns a pointer to a string that contains the name of the user associated with the calling process. The function is not reentrant, meaning that if it is called from another process, the contents are not locked out and the value of the string can be changed by another process. This makes it very risky to use because the username can be changed by other processes, so the results of the function cannot be trusted.",,unclassified, | |
| 1551 | CWE-56,EN-Path Equivalence: filedir* (Wildcard) (Type: Variant),"A software system that accepts path input in the form of asterisk wildcard ('filedir*') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1552 | The getlogin() function returns a pointer to a string that contains the name of the user associated with the calling process. The function is not reentrant, meaning that if it is called from another process, the contents are not locked out and the value of the string can be changed by another process. This makes it very risky to use because the username can be changed by other processes, so the results of the function cannot be trusted.",,unclassified, | |
| 1553 | CWE-560,EN-Use of umask() with chmod-style Argument (Type: Variant),"The product calls umask() with an incorrect argument that is specified as if it is an argument to chmod(). | |
| 1554 | The getlogin() function returns a pointer to a string that contains the name of the user associated with the calling process. The function is not reentrant, meaning that if it is called from another process, the contents are not locked out and the value of the string can be changed by another process. This makes it very risky to use because the username can be changed by other processes, so the results of the function cannot be trusted.",,unclassified, | |
| 1555 | CWE-561,EN-Dead Code (Type: Variant),"The software contains dead code, which can never be executed. | |
| 1556 | Dead code is source code that can never be executed in a running program. The surrounding code makes it impossible for a section of code to ever be executed.",,unclassified, | |
| 1557 | CWE-562,EN-Return of Stack Variable Address (Type: Base),"A function returns the address of a stack variable, which will cause unintended program behavior, typically in the form of a crash. | |
| 1558 | Dead code is source code that can never be executed in a running program. The surrounding code makes it impossible for a section of code to ever be executed.",,unclassified, | |
| 1559 | CWE-563,EN-Unused Variable (Type: Variant),"The variable's value is assigned but never used, making it a dead store. | |
| 1560 | It is likely that the variable is simply vestigial, but it is also possible that the unused variable points out a bug.",,unclassified, | |
| 1561 | CWE-564,EN-SQL Injection: Hibernate (Type: Variant),"Using Hibernate to execute a dynamic SQL statement built with user-controlled input can allow an attacker to modify the statement's meaning or to execute arbitrary SQL commands. | |
| 1562 | It is likely that the variable is simply vestigial, but it is also possible that the unused variable points out a bug.",,unclassified, | |
| 1563 | CWE-565,EN-Reliance on Cookies without Validation and Integrity Checking (Type: Base),"The application relies on the existence or values of cookies when performing security-critical operations, but it does not properly ensure that the setting is valid for the associated user. | |
| 1564 | Attackers can easily modify cookies, within the browser or by implementing the client-side code outside of the browser. Reliance on cookies without detailed validation and integrity checking can allow attackers to bypass authentication, conduct injection attacks such as SQL injection and cross-site scripting, or otherwise modify inputs in unexpected ways.",,unclassified, | |
| 1565 | CWE-566,EN-Authorization Bypass Through User-Controlled SQL Primary Key (Type: Variant),"The software uses a database table that includes records that should not be accessible to an actor, but it executes a SQL statement with a primary key that can be controlled by that actor. | |
| 1566 | When a user can set a primary key to any value, then the user can modify the key to point to unauthorized records. | |
| 1567 | Database access control errors occur when: | |
| 1568 | Data enters a program from an untrusted source. | |
| 1569 | The data is used to specify the value of a primary key in a SQL query. | |
| 1570 | The untrusted source does not have the permissions to be able to access all rows in the associated table.",,unclassified, | |
| 1571 | CWE-567,EN-Unsynchronized Access to Shared Data in a Multithreaded Context (Type: Base),"The product does not properly synchronize shared data, such as static variables across threads, which can lead to undefined behavior and unpredictable data changes. | |
| 1572 | Within servlets, shared static variables are not protected from concurrent access, but servlets are multithreaded. This is a typical programming mistake in J2EE applications, since the multithreading is handled by the framework. When a shared variable can be influenced by an attacker, one thread could wind up modifying the variable to contain data that is not valid for a different thread that is also using the data within the variable. | |
| 1573 | Note that this weakness is not unique to servlets.",,unclassified, | |
| 1574 | CWE-568,EN-finalize() Method Without super.finalize() (Type: Variant),"The software contains a finalize() method that does not call super.finalize(). | |
| 1575 | The Java Language Specification states that it is a good practice for a finalize() method to call super.finalize().",,unclassified, | |
| 1576 | CWE-57,EN-Path Equivalence: fakedir/../realdir/filename (Type: Variant),"The software contains protection mechanisms to restrict access to 'realdir/filename', but it constructs pathnames using external input in the form of 'fakedir/../realdir/filename' that are not handled by those mechanisms. This allows attackers to perform unauthorized actions against the targeted file. | |
| 1577 | The Java Language Specification states that it is a good practice for a finalize() method to call super.finalize().",,unclassified, | |
| 1578 | CWE-570,EN-Expression is Always False (Type: Variant),"The software contains an expression that will always evaluate to false. | |
| 1579 | The Java Language Specification states that it is a good practice for a finalize() method to call super.finalize().",,unclassified, | |
| 1580 | CWE-571,EN-Expression is Always True (Type: Variant),"The software contains an expression that will always evaluate to true. | |
| 1581 | The Java Language Specification states that it is a good practice for a finalize() method to call super.finalize().",,unclassified, | |
| 1582 | CWE-572,EN-Call to Thread run() instead of start() (Type: Variant),"The program calls a thread's run() method instead of calling start(), which causes the code to run in the thread of the caller instead of the callee. | |
| 1583 | In most cases a direct call to a Thread object's run() method is a bug. The programmer intended to begin a new thread of control, but accidentally called run() instead of start(), so the run() method will execute in the caller's thread of control.",,unclassified, | |
| 1584 | CWE-573,EN-Improper Following of Specification by Caller (Type: Class),"The software does not follow or incorrectly follows the specifications as required by the implementation language, environment, framework, protocol, or platform. | |
| 1585 | When leveraging external functionality, such as an API, it is important that the caller does so in accordance with the requirements of the external functionality or else unintended behaviors may result, possibly leaving the system vulnerable to any number of exploits.",,unclassified, | |
| 1586 | CWE-574,EN-EJB Bad Practices: Use of Synchronization Primitives (Type: Variant),"The program violates the Enterprise JavaBeans (EJB) specification by using thread synchronization primitives. | |
| 1587 | The Enterprise JavaBeans specification requires that every bean provider follow a set of programming guidelines designed to ensure that the bean will be portable and behave consistently in any EJB container. In this case, the program violates the following EJB guideline: ""An enterprise bean must not use thread synchronization primitives to synchronize execution of multiple instances."" The specification justifies this requirement in the following way: ""This rule is required to ensure consistent runtime semantics because while some EJB containers may use a single JVM to execute all enterprise bean's instances, others may distribute the instances across multiple JVMs.""",,unclassified, | |
| 1588 | CWE-575,EN-EJB Bad Practices: Use of AWT Swing (Type: Variant),"The program violates the Enterprise JavaBeans (EJB) specification by using AWT/Swing. | |
| 1589 | The Enterprise JavaBeans specification requires that every bean provider follow a set of programming guidelines designed to ensure that the bean will be portable and behave consistently in any EJB container. In this case, the program violates the following EJB guideline: ""An enterprise bean must not use the AWT functionality to attempt to output information to a display, or to input information from a keyboard."" The specification justifies this requirement in the following way: ""Most servers do not allow direct interaction between an application program and a keyboard/display attached to the server system.""",,unclassified, | |
| 1590 | CWE-576,EN-EJB Bad Practices: Use of Java I/O (Type: Variant),"The program violates the Enterprise JavaBeans (EJB) specification by using the java.io package. | |
| 1591 | The Enterprise JavaBeans specification requires that every bean provider follow a set of programming guidelines designed to ensure that the bean will be portable and behave consistently in any EJB container. In this case, the program violates the following EJB guideline: ""An enterprise bean must not use the java.io package to attempt to access files and directories in the file system."" The specification justifies this requirement in the following way: ""The file system APIs are not well-suited for business components to access data. Business components should use a resource manager API, such as JDBC, to store data.""",,unclassified, | |
| 1592 | CWE-577,EN-EJB Bad Practices: Use of Sockets (Type: Variant),"The program violates the Enterprise JavaBeans (EJB) specification by using sockets. | |
| 1593 | The Enterprise JavaBeans specification requires that every bean provider follow a set of programming guidelines designed to ensure that the bean will be portable and behave consistently in any EJB container. In this case, the program violates the following EJB guideline: ""An enterprise bean must not attempt to listen on a socket, accept connections on a socket, or use a socket for multicast."" The specification justifies this requirement in the following way: ""The EJB architecture allows an enterprise bean instance to be a network socket client, but it does not allow it to be a network server. Allowing the instance to become a network server would conflict with the basic function of the enterprise bean-- to serve the EJB clients.""",,unclassified, | |
| 1594 | CWE-578,EN-EJB Bad Practices: Use of Class Loader (Type: Variant),"The program violates the Enterprise JavaBeans (EJB) specification by using the class loader. | |
| 1595 | The Enterprise JavaBeans specification requires that every bean provider follow a set of programming guidelines designed to ensure that the bean will be portable and behave consistently in any EJB container. In this case, the program violates the following EJB guideline: ""The enterprise bean must not attempt to create a class loader; obtain the current class loader; set the context class loader; set security manager; create a new security manager; stop the JVM; or change the input, output, and error streams."" The specification justifies this requirement in the following way: ""These functions are reserved for the EJB container. Allowing the enterprise bean to use these functions could compromise security and decrease the container's ability to properly manage the runtime environment.""",,unclassified, | |
| 1596 | CWE-579,EN-J2EE Bad Practices: Non-serializable Object Stored in Session (Type: Variant),"The application stores a non-serializable object as an HttpSession attribute, which can hurt reliability. | |
| 1597 | The Enterprise JavaBeans specification requires that every bean provider follow a set of programming guidelines designed to ensure that the bean will be portable and behave consistently in any EJB container. In this case, the program violates the following EJB guideline: ""The enterprise bean must not attempt to create a class loader; obtain the current class loader; set the context class loader; set security manager; create a new security manager; stop the JVM; or change the input, output, and error streams."" The specification justifies this requirement in the following way: ""These functions are reserved for the EJB container. Allowing the enterprise bean to use these functions could compromise security and decrease the container's ability to properly manage the runtime environment.""",,unclassified, | |
| 1598 | CWE-58,EN-Path Equivalence: Windows 8.3 Filename (Type: Variant),"The software contains a protection mechanism that restricts access to a long filename on a Windows operating system, but the software does not properly restrict access to the equivalent short ""8.3"" filename. | |
| 1599 | On later Windows operating systems, a file can have a ""long name"" and a short name that is compatible with older Windows file systems, with up to 8 characters in the filename and 3 characters for the extension. These ""8.3"" filenames, therefore, act as an alternate name for files with long names, so they are useful pathname equivalence manipulations.",,unclassified,"Writing Secure Code | |
| 1600 | The Art of Software Security Assessment: Chapter 11, ""DOS 8.3 Filenames"", Page 673." | |
| 1601 | CWE-580,EN-clone() Method Without super.clone() (Type: Variant),"The software contains a clone() method that does not call super.clone() to obtain the new object. | |
| 1602 | All implementations of clone() should obtain the new object by calling super.clone(). If a class does not follow this convention, a subclass's clone() method will return an object of the wrong type.",,unclassified, | |
| 1603 | CWE-581,EN-Object Model Violation: Just One of Equals and Hashcode Defined (Type: Base),"The software does not maintain equal hashcodes for equal objects. | |
| 1604 | Java objects are expected to obey a number of invariants related to equality. One of these invariants is that equal objects must have equal hashcodes. In other words, if a.equals(b) == true then a.hashCode() == b.hashCode().",,unclassified, | |
| 1605 | CWE-582,"EN-Array Declared Public, Final, and Static (Type: Variant)","The program declares an array public, final, and static, which is not sufficient to prevent the array's contents from being modified. | |
| 1606 | Because arrays are mutable objects, the final constraint requires that the array object itself be assigned only once, but makes no guarantees about the values of the array elements. Since the array is public, a malicious program can change the values stored in the array. As such, in most cases an array declared public, final and static is a bug.",,unclassified, | |
| 1607 | CWE-583,EN-finalize() Method Declared Public (Type: Variant),"The program violates secure coding principles for mobile code by declaring a finalize() method public. | |
| 1608 | A program should never call finalize explicitly, except to call super.finalize() inside an implementation of finalize(). In mobile code situations, the otherwise error prone practice of manual garbage collection can become a security threat if an attacker can maliciously invoke one of your finalize() methods because it is declared with public access.",,unclassified, | |
| 1609 | CWE-584,EN-Return Inside Finally Block (Type: Base),"The code has a return statement inside a finally block, which will cause any thrown exception in the try block to be discarded. | |
| 1610 | A program should never call finalize explicitly, except to call super.finalize() inside an implementation of finalize(). In mobile code situations, the otherwise error prone practice of manual garbage collection can become a security threat if an attacker can maliciously invoke one of your finalize() methods because it is declared with public access.",,unclassified, | |
| 1611 | CWE-585,EN-Empty Synchronized Block (Type: Variant),"The software contains an empty synchronized block. | |
| 1612 | An empty synchronized block does not actually accomplish any synchronization and may indicate a troubled section of code. An empty synchronized block can occur because code no longer needed within the synchronized block is commented out without removing the synchronized block.",,unclassified,Intrinsic Locks and Synchronization (in Java): http://java.sun.com/docs/books/tutorial/essential/concurrency/locksync.html | |
| 1613 | CWE-586,EN-Explicit Call to Finalize() (Type: Variant),"The software makes an explicit call to the finalize() method from outside the finalizer. | |
| 1614 | While the Java Language Specification allows an object's finalize() method to be called from outside the finalizer, doing so is usually a bad idea. For example, calling finalize() explicitly means that finalize() will be called more than once: the first time will be the explicit call and the last time will be the call that is made after the object is garbage collected.",,unclassified, | |
| 1615 | CWE-587,EN-Assignment of a Fixed Address to a Pointer (Type: Base),"The software sets a pointer to a specific address other than NULL or 0. | |
| 1616 | Using a fixed address is not portable because that address will probably not be valid in all environments or platforms.",,unclassified, | |
| 1617 | CWE-588,EN-Attempt to Access Child of a Non-structure Pointer (Type: Variant),"Casting a non-structure type to a structure type and accessing a field can lead to memory access errors or data corruption. | |
| 1618 | Using a fixed address is not portable because that address will probably not be valid in all environments or platforms.",,unclassified, | |
| 1619 | CWE-589,EN-Call to Non-ubiquitous API (Type: Variant),"The software uses an API function that does not exist on all versions of the target platform. This could cause portability problems or inconsistencies that allow denial of service or other consequences. | |
| 1620 | Some functions that offer security features supported by the OS are not available on all versions of the OS in common use. Likewise, functions are often deprecated or made obsolete for security reasons and should not be used.",,unclassified, | |
| 1621 | CWE-590,EN-Free of Memory not on the Heap (Type: Variant),"The application calls free() on a pointer to memory that was not allocated using associated heap allocation functions such as malloc(), calloc(), or realloc(). | |
| 1622 | When free() is called on an invalid pointer, the program's memory management data structures may become corrupted. This corruption can cause the program to crash or, in some circumstances, an attacker may be able to cause free() to operate on controllable memory locations to modify critical program variables or execute code.",,unclassified,Valgrind: http://valgrind.org/ | |
| 1623 | CWE-591,EN-Sensitive Data Storage in Improperly Locked Memory (Type: Variant),"The application stores sensitive data in memory that is not locked, or that has been incorrectly locked, which might cause the memory to be written to swap files on disk by the virtual memory manager. This can make the data more accessible to external actors. | |
| 1624 | On Windows systems the VirtualLock function can lock a page of memory to ensure that it will remain present in memory and not be swapped to disk. However, on older versions of Windows, such as 95, 98, or Me, the VirtualLock() function is only a stub and provides no protection. On POSIX systems the mlock() call ensures that a page will stay resident in memory but does not guarantee that the page will not appear in the swap. Therefore, it is unsuitable for use as a protection mechanism for sensitive data. Some platforms, in particular Linux, do make the guarantee that the page will not be swapped, but this is non-standard and is not portable. Calls to mlock() also require supervisor privilege. Return values for both of these calls must be checked to ensure that the lock operation was actually successful.",,unclassified, | |
| 1625 | CWE-592,EN-Authentication Bypass Issues (Type: Class),"The software does not properly perform authentication, allowing it to be bypassed through various methods. | |
| 1626 | On Windows systems the VirtualLock function can lock a page of memory to ensure that it will remain present in memory and not be swapped to disk. However, on older versions of Windows, such as 95, 98, or Me, the VirtualLock() function is only a stub and provides no protection. On POSIX systems the mlock() call ensures that a page will stay resident in memory but does not guarantee that the page will not appear in the swap. Therefore, it is unsuitable for use as a protection mechanism for sensitive data. Some platforms, in particular Linux, do make the guarantee that the page will not be swapped, but this is non-standard and is not portable. Calls to mlock() also require supervisor privilege. Return values for both of these calls must be checked to ensure that the lock operation was actually successful.",,unclassified,"The Art of Software Security Assessment: Chapter 2, ""Untrustworthy Credentials"", Page 37." | |
| 1627 | CWE-593,EN-Authentication Bypass: OpenSSL CTX Object Modified after SSL Objects are Created (Type: Variant),"The software modifies the SSL context after connection creation has begun. | |
| 1628 | If the program modifies the SSL_CTX object after creating SSL objects from it, there is the possibility that older SSL objects created from the original context could all be affected by that change.",,unclassified, | |
| 1629 | CWE-594,EN-J2EE Framework: Saving Unserializable Objects to Disk (Type: Variant),"When the J2EE container attempts to write unserializable objects to disk there is no guarantee that the process will complete successfully. | |
| 1630 | If the program modifies the SSL_CTX object after creating SSL objects from it, there is the possibility that older SSL objects created from the original context could all be affected by that change.",,unclassified, | |
| 1631 | CWE-595,EN-Comparison of Object References Instead of Object Contents (Type: Base),"The program compares object references instead of the contents of the objects themselves, preventing it from detecting equivalent objects. | |
| 1632 | If the program modifies the SSL_CTX object after creating SSL objects from it, there is the possibility that older SSL objects created from the original context could all be affected by that change.",,unclassified, | |
| 1633 | CWE-596,EN-Incorrect Semantic Object Comparison (Type: Base),"The software does not correctly compare two objects based on their conceptual content. | |
| 1634 | If the program modifies the SSL_CTX object after creating SSL objects from it, there is the possibility that older SSL objects created from the original context could all be affected by that change.",,unclassified, | |
| 1635 | CWE-597,EN-Use of Wrong Operator in String Comparison (Type: Variant),"The product uses the wrong operator when comparing a string, such as using ""=="" when the equals() method should be used instead. | |
| 1636 | In Java, using == or != to compare two strings for equality actually compares two objects for equality, not their values. Chances are good that the two references will never be equal. While this weakness often only affects program correctness, if the equality is used for a security decision, it could be leveraged to affect program security.",,unclassified,"The Art of Software Security Assessment: Chapter 6, ""Typos"", Page 289." | |
| 1637 | CWE-598,EN-Information Exposure Through Query Strings in GET Request (Type: Variant),"The web application uses the GET method to process requests that contain sensitive information, which can expose that information through the browser's history, Referers, web logs, and other sources. | |
| 1638 | In Java, using == or != to compare two strings for equality actually compares two objects for equality, not their values. Chances are good that the two references will never be equal. While this weakness often only affects program correctness, if the equality is used for a security decision, it could be leveraged to affect program security.",,unclassified, | |
| 1639 | CWE-599,EN-Missing Validation of OpenSSL Certificate (Type: Variant),"The software uses OpenSSL and trusts or uses a certificate without using the SSL_get_verify_result() function to ensure that the certificate satisfies all necessary security requirements. | |
| 1640 | This could allow an attacker to use an invalid certificate to claim to be a trusted host, use expired certificates, or conduct other attacks that could be detected if the certificate is properly validated.",,unclassified, | |
| 1641 | CWE-6,EN-J2EE Misconfiguration: Insufficient Session-ID Length (Type: Variant),"The J2EE application is configured to use an insufficient session ID length. | |
| 1642 | If an attacker can guess or steal a session ID, then he/she may be able to take over the user's session (called session hijacking). The number of possible session IDs increases with increased session ID length, making it more difficult to guess or steal a session ID.",,unclassified,No description: http://www.securiteam.com/securityreviews/5TP0F0UEVQ.html | |
| 1643 | CWE-600,EN-Uncaught Exception in Servlet (Type: Base),"The Servlet does not catch all exceptions, which may reveal sensitive debugging information. | |
| 1644 | When a Servlet throws an exception, the default error response the Servlet container sends back to the user typically includes debugging information. This information is of great value to an attacker. For example, a stack trace might show the attacker a malformed SQL query string, the type of database being used, and the version of the application container. This information enables the attacker to target known vulnerabilities in these components.",,unclassified, | |
| 1645 | CWE-603,EN-Use of Client-Side Authentication (Type: Base),"A client/server product performs authentication within client code but not in server code, allowing server-side authentication to be bypassed via a modified client that omits the authentication check. | |
| 1646 | Client-side authentication is extremely weak and may be breached easily. Any attacker may read the source code and reverse-engineer the authentication mechanism to access parts of the application which would otherwise be protected.",,unclassified,"The Art of Software Security Assessment: Chapter 2, ""Untrustworthy Credentials"", Page 37." | |
| 1647 | CWE-605,EN-Multiple Binds to the Same Port (Type: Base),"When multiple sockets are allowed to bind to the same port, other services on that port may be stolen or spoofed. | |
| 1648 | Client-side authentication is extremely weak and may be breached easily. Any attacker may read the source code and reverse-engineer the authentication mechanism to access parts of the application which would otherwise be protected.",,unclassified, | |
| 1649 | CWE-606,EN-Unchecked Input for Loop Condition (Type: Base),"The product does not properly check inputs that are used for loop conditions, potentially leading to a denial of service because of excessive looping. | |
| 1650 | Client-side authentication is extremely weak and may be breached easily. Any attacker may read the source code and reverse-engineer the authentication mechanism to access parts of the application which would otherwise be protected.",,unclassified,"The Art of Software Security Assessment: Chapter 7, ""Looping Constructs"", Page 327." | |
| 1651 | CWE-607,EN-Public Static Final Field References Mutable Object (Type: Variant),"A public or protected static final field references a mutable object, which allows the object to be changed by malicious code, or accidentally from another package. | |
| 1652 | Client-side authentication is extremely weak and may be breached easily. Any attacker may read the source code and reverse-engineer the authentication mechanism to access parts of the application which would otherwise be protected.",,unclassified, | |
| 1653 | CWE-608,EN-Struts: Non-private Field in ActionForm Class (Type: Variant),"An ActionForm class contains a field that has not been declared private, which can be accessed without using a setter or getter. | |
| 1654 | Client-side authentication is extremely weak and may be breached easily. Any attacker may read the source code and reverse-engineer the authentication mechanism to access parts of the application which would otherwise be protected.",,unclassified, | |
| 1655 | CWE-609,EN-Double-Checked Locking (Type: Base),"The program uses double-checked locking to access a resource without the overhead of explicit synchronization, but the locking is insufficient. | |
| 1656 | Double-checked locking refers to the situation where a programmer checks to see if a resource has been initialized, grabs a lock, checks again to see if the resource has been initialized, and then performs the initialization if it has not occurred yet. This should not be done, as is not guaranteed to work in all languages and on all architectures. In summary, other threads may not be operating inside the synchronous block and are not guaranteed to see the operations execute in the same order as they would appear inside the synchronous block.",,unclassified,"The ""Double-Checked Locking is Broken"" Declaration: http://www.cs.umd.edu/~pugh/java/memoryModel/DoubleCheckedLocking.html | |
| 1657 | JSR 133 (Java Memory Model) FAQ: http://www.cs.umd.edu/~pugh/java/memoryModel/jsr-133-faq.html#dcl | |
| 1658 | The Art of Software Security Assessment: Chapter 13, ""Threading Vulnerabilities"", Page 815." | |
| 1659 | CWE-610,EN-Externally Controlled Reference to a Resource in Another Sphere (Type: Class),"The product uses an externally controlled name or reference that resolves to a resource that is outside of the intended control sphere. | |
| 1660 | ",,unclassified, | |
| 1661 | CWE-611,EN-Improper Restriction of XML External Entity Reference (XXE) (Type: Variant),"The software processes an XML document that can contain XML entities with URIs that resolve to documents outside of the intended sphere of control, causing the product to embed incorrect documents into its output. | |
| 1662 | XML documents optionally contain a Document Type Definition (DTD), which, among other features, enables the definition of XML entities. It is possible to define an entity by providing a substitution string in the form of a URI. The XML parser can access the contents of this URI and embed these contents back into the XML document for further processing. | |
| 1663 | By submitting an XML file that defines an external entity with a file:// URI, an attacker can cause the processing application to read the contents of a local file. For example, a URI such as ""file:///c:/winnt/win.ini"" designates (in Windows) the file C:\Winnt\win.ini, or file:///etc/passwd designates the password file in Unix-based systems. Using URIs with other schemes such as http://, the attacker can force the application to make outgoing requests to servers that the attacker cannot reach directly, which can be used to bypass firewall restrictions or hide the source of attacks such as port scanning. | |
| 1664 | Once the content of the URI is read, it is fed back into the application that is processing the XML. This application may echo back the data (e.g. in an error message), thereby exposing the file contents.",,unclassified,"XML External Entity (XXE) Processing: https://www.owasp.org/index.php/XML_External_Entity_(XXE)_Processing | |
| 1665 | XML External Entity Attacks (XXE): https://www.owasp.org/images/5/5d/XML_Exteral_Entity_Attack.pdf | |
| 1666 | XXE (Xml eXternal Entity) Attack: http://www.securiteam.com/securitynews/6D0100A5PU.html | |
| 1667 | XML External Entities (XXE) Attack: http://projects.webappsec.org/w/page/13247003/XML%20External%20Entities | |
| 1668 | XML Denial of Service Attacks and Defenses: http://msdn.microsoft.com/en-us/magazine/ee335713.aspx | |
| 1669 | Preventing XXE in PHP: http://websec.io/2012/08/27/Preventing-XEE-in-PHP.html" | |
| 1670 | CWE-612,EN-Information Exposure Through Indexing of Private Data (Type: Variant),"The product performs an indexing routine against private documents, but does not sufficiently verify that the actors who can access the index also have the privileges to access the private documents. | |
| 1671 | When an indexing routine is applied against a group of private documents, and that index's results are available to outsiders who do not have access to those documents, then outsiders might be able to obtain sensitive information by conducting targeted searches. The risk is especially dangerous if search results include surrounding text that was not part of the search query. This issue can appear in search engines that are not configured (or implemented) to ignore critical files that should remain hidden; even without permissions to download these files directly, the remote user could read them.",,unclassified, | |
| 1672 | CWE-613,EN-Insufficient Session Expiration (Type: Base),"According to WASC, ""Insufficient Session Expiration is when a web site permits an attacker to reuse old session credentials or session IDs for authorization."" | |
| 1673 | When an indexing routine is applied against a group of private documents, and that index's results are available to outsiders who do not have access to those documents, then outsiders might be able to obtain sensitive information by conducting targeted searches. The risk is especially dangerous if search results include surrounding text that was not part of the search query. This issue can appear in search engines that are not configured (or implemented) to ignore critical files that should remain hidden; even without permissions to download these files directly, the remote user could read them.",,unclassified, | |
| 1674 | CWE-614,EN-Sensitive Cookie in HTTPS Session Without Secure Attribute (Type: Variant),"The Secure attribute for sensitive cookies in HTTPS sessions is not set, which could cause the user agent to send those cookies in plaintext over an HTTP session. | |
| 1675 | When an indexing routine is applied against a group of private documents, and that index's results are available to outsiders who do not have access to those documents, then outsiders might be able to obtain sensitive information by conducting targeted searches. The risk is especially dangerous if search results include surrounding text that was not part of the search query. This issue can appear in search engines that are not configured (or implemented) to ignore critical files that should remain hidden; even without permissions to download these files directly, the remote user could read them.",,unclassified, | |
| 1676 | CWE-615,EN-Information Exposure Through Comments (Type: Variant),"While adding general comments is very useful, some programmers tend to leave important data, such as: filenames related to the web application, old links or links which were not meant to be browsed by users, old code fragments, etc. | |
| 1677 | An attacker who finds these comments can map the application's structure and files, expose hidden parts of the site, and study the fragments of code to reverse engineer the application, which may help develop further attacks against the site.",,unclassified, | |
| 1678 | CWE-616,EN-Incomplete Identification of Uploaded File Variables (PHP) (Type: Variant),"The PHP application uses an old method for processing uploaded files by referencing the four global variables that are set for each file (e.g. $varname, $varname_size, $varname_name, $varname_type). These variables could be overwritten by attackers, causing the application to process unauthorized files. | |
| 1679 | These global variables could be overwritten by POST requests, cookies, or other methods of populating or overwriting these variables. This could be used to read or process arbitrary files by providing values such as ""/etc/passwd"".",,unclassified,"A Study in Scarlet - section 5, ""File Upload""" | |
| 1680 | CWE-617,EN-Reachable Assertion (Type: Variant),"The product contains an assert() or similar statement that can be triggered by an attacker, which leads to an application exit or other behavior that is more severe than necessary. | |
| 1681 | For example, if a server handles multiple simultaneous connections, and an assert() occurs in one single connection that causes all other connections to be dropped, this is a reachable assertion that leads to a denial of service.",,unclassified, | |
| 1682 | CWE-618,EN-Exposed Unsafe ActiveX Method (Type: Base),"An ActiveX control is intended for use in a web browser, but it exposes dangerous methods that perform actions that are outside of the browser's security model (e.g. the zone or domain). | |
| 1683 | ActiveX controls can exercise far greater control over the operating system than typical Java or javascript. Exposed methods can be subject to various vulnerabilities, depending on the implemented behaviors of those methods, and whether input validation is performed on the provided arguments. If there is no integrity checking or origin validation, this method could be invoked by attackers.",,unclassified,"No description: http://msdn.microsoft.com/workshop/components/activex/safety.asp | |
| 1684 | No description: http://msdn.microsoft.com/workshop/components/activex/security.asp | |
| 1685 | The Art of Software Security Assessment: Chapter 12, ""ActiveX Security"", Page 749." | |
| 1686 | CWE-619,EN-Dangling Database Cursor (Cursor Injection) (Type: Base),"If a database cursor is not closed properly, then it could become accessible to other users while retaining the same privileges that were originally assigned, leaving the cursor ""dangling."" | |
| 1687 | For example, an improper dangling cursor could arise from unhandled exceptions. The impact of the issue depends on the cursor's role, but SQL injection attacks are commonly possible.",,unclassified,"The Oracle Hacker's Handbook | |
| 1688 | Cursor Injection: http://www.databasesecurity.com/dbsec/cursor-injection.pdf" | |
| 1689 | CWE-62,EN-UNIX Hard Link (Type: Variant),"The software, when opening a file or directory, does not sufficiently account for when the name is associated with a hard link to a target that is outside of the intended control sphere. This could allow an attacker to cause the software to operate on unauthorized files. | |
| 1690 | Failure for a system to check for hard links can result in vulnerability to different types of attacks. For example, an attacker can escalate their privileges if a file used by a privileged program is replaced with a hard link to a sensitive file (e.g. /etc/passwd). When the process opens the file, the attacker can assume the privileges of that process.",,unclassified,"The Art of Software Security Assessment: Chapter 9, ""Hard Links"", Page 518." | |
| 1691 | CWE-620,EN-Unverified Password Change (Type: Variant),"When setting a new password for a user, the product does not require knowledge of the original password, or using another form of authentication. | |
| 1692 | This could be used by an attacker to change passwords for another user, thus gaining the privileges associated with that user.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 1693 | CWE-621,EN-Variable Extraction Error (Type: Base),"The product uses external input to determine the names of variables into which information is extracted, without verifying that the names of the specified variables are valid. This could cause the program to overwrite unintended variables. | |
| 1694 | For example, in PHP, calling extract() or import_request_variables() without the proper arguments could allow arbitrary global variables to be overwritten, including superglobals. Similar functionality might be possible in other interpreted languages, including custom languages.",,unclassified, | |
| 1695 | CWE-622,EN-Improper Validation of Function Hook Arguments (Type: Variant),"A product adds hooks to user-accessible API functions, but does not properly validate the arguments. This could lead to resultant vulnerabilities. | |
| 1696 | Such hooks can be used in defensive software that runs with privileges, such as anti-virus or firewall, which hooks kernel calls. When the arguments are not validated, they could be used to bypass the protection scheme or attack the product itself.",,unclassified, | |
| 1697 | CWE-623,EN-Unsafe ActiveX Control Marked Safe For Scripting (Type: Variant),"An ActiveX control is intended for restricted use, but it has been marked as safe-for-scripting. | |
| 1698 | This might allow attackers to use dangerous functionality via a web page that accesses the control, which can lead to different resultant vulnerabilities, depending on the control's behavior.",,unclassified,"No description: http://msdn.microsoft.com/workshop/components/activex/safety.asp | |
| 1699 | No description: http://msdn.microsoft.com/workshop/components/activex/security.asp | |
| 1700 | No description: http://support.microsoft.com/kb/240797 | |
| 1701 | Writing Secure Code: Chapter 16, ""What ActiveX Components Are Safe for Initialization and Safe for Scripting?"" Page 510 | |
| 1702 | The Art of Software Security Assessment: Chapter 12, ""ActiveX Security"", Page 749." | |
| 1703 | CWE-624,EN-Executable Regular Expression Error (Type: Base),"The product uses a regular expression that either (1) contains an executable component with user-controlled inputs, or (2) allows a user to enable execution by inserting pattern modifiers. | |
| 1704 | Case (2) is possible in the PHP preg_replace() function, and possibly in other languages when a user-controlled input is inserted into a string that is later parsed as a regular expression.",,unclassified, | |
| 1705 | CWE-625,EN-Permissive Regular Expression (Type: Base),"The product uses a regular expression that does not sufficiently restrict the set of allowed values. | |
| 1706 | This effectively causes the regexp to accept substrings that match the pattern, which produces a partial comparison to the target. In some cases, this can lead to other weaknesses. Common errors include: | |
| 1707 | not identifying the beginning and end of the target string | |
| 1708 | using wildcards instead of acceptable character ranges | |
| 1709 | others",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Character Stripping Vulnerabilities"", Page 437." | |
| 1710 | CWE-626,EN-Null Byte Interaction Error (Poison Null Byte) (Type: Variant),"The product does not properly handle null bytes or NUL characters when passing data between different representations or components. | |
| 1711 | A null byte (NUL character) can have different meanings across representations or languages. For example, it is a string terminator in standard C libraries, but Perl and PHP strings do not treat it as a terminator. When two representations are crossed - such as when Perl or PHP invokes underlying C functionality - this can produce an interaction error with unexpected results. Similar issues have been reported for ASP. Other interpreters written in C might also be affected.",,unclassified,"Poison NULL byte: http://insecure.org/news/P55-07.txt | |
| 1712 | 0x00 vs ASP file upload scripts: http://www.security-assessment.com/Whitepapers/0x00_vs_ASP_File_Uploads.pdf | |
| 1713 | ShAnKaR: multiple PHP application poison NULL byte vulnerability: http://seclists.org/fulldisclosure/2006/Sep/0185.html" | |
| 1714 | CWE-627,EN-Dynamic Variable Evaluation (Type: Base),"In a language where the user can influence the name of a variable at runtime, if the variable names are not controlled, an attacker can read or write to arbitrary variables, or access arbitrary functions. | |
| 1715 | The resultant vulnerabilities depend on the behavior of the application, both at the crossover point and in any control/data flow that is reachable by the related variables or functions.",,unclassified,"Dynamic Evaluation Vulnerabilities in PHP applications: http://seclists.org/fulldisclosure/2006/May/0035.html | |
| 1716 | A Study In Scarlet: Exploiting Common Vulnerabilities in PHP Applications: http://www.securereality.com.au/studyinscarlet.txt" | |
| 1717 | CWE-628,EN-Function Call with Incorrectly Specified Arguments (Type: Base),"The product calls a function, procedure, or routine with arguments that are not correctly specified, leading to always-incorrect behavior and resultant weaknesses. | |
| 1718 | There are multiple ways in which this weakness can be introduced, including: | |
| 1719 | the wrong variable or reference; | |
| 1720 | an incorrect number of arguments; | |
| 1721 | incorrect order of arguments; | |
| 1722 | wrong type of arguments; or | |
| 1723 | wrong value.",,unclassified, | |
| 1724 | CWE-636,EN-Not Failing Securely (Failing Open) (Type: Class),"When the product encounters an error condition or failure, its design requires it to fall back to a state that is less secure than other options that are available, such as selecting the weakest encryption algorithm or using the most permissive access control restrictions. | |
| 1725 | By entering a less secure state, the product inherits the weaknesses associated with that state, making it easier to compromise. At the least, it causes administrators to have a false sense of security. This weakness typically occurs as a result of wanting to ""fail functional"" to minimize administration and support costs, instead of ""failing safe.""",,unclassified,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1726 | Failing Securely: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/349.html" | |
| 1727 | CWE-637,EN-Unnecessary Complexity in Protection Mechanism (Not Using Economy of Mechanism) (Type: Class),"The software uses a more complex mechanism than necessary, which could lead to resultant weaknesses when the mechanism is not correctly understood, modeled, configured, implemented, or used. | |
| 1728 | Security mechanisms should be as simple as possible. Complex security mechanisms may engender partial implementations and compatibility problems, with resulting mismatches in assumptions and implemented security. A corollary of this principle is that data specifications should be as simple as possible, because complex data specifications result in complex validation code. Complex tasks and systems may also need to be guarded by complex security checks, so simple systems should be preferred.",,unclassified,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1729 | Economy of Mechanism: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/348.html" | |
| 1730 | CWE-638,EN-Not Using Complete Mediation (Type: Class),"The software does not perform access checks on a resource every time the resource is accessed by an entity, which can create resultant weaknesses if that entity's rights or privileges change over time. | |
| 1731 | ",,unclassified,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1732 | Complete Mediation: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/346.html" | |
| 1733 | CWE-65,EN-Windows Hard Link (Type: Variant),"The software, when opening a file or directory, does not sufficiently handle when the name is associated with a hard link to a target that is outside of the intended control sphere. This could allow an attacker to cause the software to operate on unauthorized files. | |
| 1734 | Failure for a system to check for hard links can result in vulnerability to different types of attacks. For example, an attacker can escalate their privileges if a file used by a privileged program is replaced with a hard link to a sensitive file (e.g. AUTOEXEC.BAT). When the process opens the file, the attacker can assume the privileges of that process, or prevent the program from accurately processing data.",,unclassified,"The Art of Software Security Assessment: Chapter 11, ""Links"", Page 676." | |
| 1735 | CWE-651,EN-Information Exposure Through WSDL File (Type: Variant),"The Web services architecture may require exposing a WSDL file that contains information on the publicly accessible services and how callers of these services should interact with them (e.g. what parameters they expect and what types they return). | |
| 1736 | An information exposure may occur if any of the following apply: | |
| 1737 | The WSDL file is accessible to a wider audience than intended. | |
| 1738 | The WSDL file contains information on the methods/services that should not be publicly accessible or information about deprecated methods. This problem is made more likely due to the WSDL often being automatically generated from the code. | |
| 1739 | Information in the WSDL file helps guess names/locations of methods/resources that should not be publicly accessible.",,unclassified, | |
| 1740 | CWE-653,EN-Insufficient Compartmentalization (Type: Base),"The product does not sufficiently compartmentalize functionality or processes that require different privilege levels, rights, or permissions. | |
| 1741 | When a weakness occurs in functionality that is accessible by lower-privileged users, then without strong boundaries, an attack might extend the scope of the damage to higher-privileged users.",,unclassified,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1742 | Separation of Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/357.html" | |
| 1743 | CWE-654,EN-Reliance on a Single Factor in a Security Decision (Type: Base),"A protection mechanism relies exclusively, or to a large extent, on the evaluation of a single condition or the integrity of a single object or entity in order to make a decision about granting access to restricted resources or functionality. | |
| 1744 | When a weakness occurs in functionality that is accessible by lower-privileged users, then without strong boundaries, an attack might extend the scope of the damage to higher-privileged users.",,unclassified,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1745 | Separation of Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/357.html" | |
| 1746 | CWE-655,EN-Insufficient Psychological Acceptability (Type: Base),"The software has a protection mechanism that is too difficult or inconvenient to use, encouraging non-malicious users to disable or bypass the mechanism, whether by accident or on purpose. | |
| 1747 | When a weakness occurs in functionality that is accessible by lower-privileged users, then without strong boundaries, an attack might extend the scope of the damage to higher-privileged users.",,unclassified,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1748 | Psychological Acceptability: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/354.html | |
| 1749 | Usability of Security: A Case Study: http://reports-archive.adm.cs.cmu.edu/anon/1998/CMU-CS-98-155.pdf | |
| 1750 | 24 Deadly Sins of Software Security: ""Sin 14: Poor Usability."" Page 217" | |
| 1751 | CWE-656,EN-Reliance on Security Through Obscurity (Type: Base),"The software uses a protection mechanism whose strength depends heavily on its obscurity, such that knowledge of its algorithms or key data is sufficient to defeat the mechanism. | |
| 1752 | This reliance on ""security through obscurity"" can produce resultant weaknesses if an attacker is able to reverse engineer the inner workings of the mechanism. Note that obscurity can be one small part of defense in depth, since it can create more work for an attacker; however, it is a significant risk if used as the primary means of protection.",,unclassified,"RFC: 793, TRANSMISSION CONTROL PROTOCOL: http://www.ietf.org/rfc/rfc0793.txt | |
| 1753 | The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1754 | Never Assuming that Your Secrets Are Safe: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/352.html" | |
| 1755 | CWE-657,EN-Violation of Secure Design Principles (Type: Class),"The product violates well-established principles for secure design. | |
| 1756 | This can introduce resultant weaknesses or make it easier for developers to introduce related weaknesses during implementation. Because code is centered around design, it can be resource-intensive to fix design problems.",,unclassified,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1757 | Design Principles: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/358.html" | |
| 1758 | CWE-66,EN-Improper Handling of File Names that Identify Virtual Resources (Type: Base),"The product does not handle or incorrectly handles a file name that identifies a ""virtual"" resource that is not directly specified within the directory that is associated with the file name, causing the product to perform file-based operations on a resource that is not a file. | |
| 1759 | Virtual file names are represented like normal file names, but they are effectively aliases for other resources that do not behave like normal files. Depending on their functionality, they could be alternate entities. They are not necessarily listed in directories.",,unclassified, | |
| 1760 | CWE-662,EN-Improper Synchronization (Type: Base),"The software attempts to use a shared resource in an exclusive manner, but does not prevent or incorrectly prevents use of the resource by another thread or process. | |
| 1761 | Virtual file names are represented like normal file names, but they are effectively aliases for other resources that do not behave like normal files. Depending on their functionality, they could be alternate entities. They are not necessarily listed in directories.",,unclassified, | |
| 1762 | CWE-663,EN-Use of a Non-reentrant Function in a Concurrent Context (Type: Base),"The software calls a non-reentrant function in a concurrent context in which a competing code sequence (e.g. thread or signal handler) may have an opportunity to call the same function or otherwise influence its state. | |
| 1763 | Virtual file names are represented like normal file names, but they are effectively aliases for other resources that do not behave like normal files. Depending on their functionality, they could be alternate entities. They are not necessarily listed in directories.",,unclassified,"Java Concurrency API: http://java.sun.com/j2se/1.5.0/docs/api/java/util/concurrent/locks/ReentrantLock.html | |
| 1764 | Use reentrant functions for safer signal handling: http://www.ibm.com/developerworks/linux/library/l-reent.html" | |
| 1765 | CWE-664,EN-Improper Control of a Resource Through its Lifetime (Type: Class),"The software does not maintain or incorrectly maintains control over a resource throughout its lifetime of creation, use, and release. | |
| 1766 | Resources often have explicit instructions on how to be created, used and destroyed. When software does not follow these instructions, it can lead to unexpected behaviors and potentially exploitable states. | |
| 1767 | Even without explicit instructions, various principles are expected to be adhered to, such as ""Do not use an object until after its creation is complete,"" or ""do not use an object after it has been slated for destruction.""",,unclassified, | |
| 1768 | CWE-666,EN-Operation on Resource in Wrong Phase of Lifetime (Type: Base),"The software performs an operation on a resource at the wrong phase of the resource's lifecycle, which can lead to unexpected behaviors. | |
| 1769 | When a developer wants to initialize, use or release a resource, it is important to follow the specifications outlined for how to operate on that resource and to ensure that the resource is in the expected state. In this case, the software wants to perform a normally valid operation, initialization, use or release, on a resource when it is in the incorrect phase of its lifetime.",,unclassified, | |
| 1770 | CWE-667,EN-Improper Locking (Type: Base),"The software does not properly acquire a lock on a resource, or it does not properly release a lock on a resource, leading to unexpected resource state changes and behaviors. | |
| 1771 | When a developer wants to initialize, use or release a resource, it is important to follow the specifications outlined for how to operate on that resource and to ensure that the resource is in the expected state. In this case, the software wants to perform a normally valid operation, initialization, use or release, on a resource when it is in the incorrect phase of its lifetime.",,unclassified, | |
| 1772 | CWE-668,EN-Exposure of Resource to Wrong Sphere (Type: Class),"The product exposes a resource to the wrong control sphere, providing unintended actors with inappropriate access to the resource. | |
| 1773 | Resources such as files and directories may be inadvertently exposed through mechanisms such as insecure permissions, or when a program accidentally operates on the wrong object. For example, a program may intend that private files can only be provided to a specific user. This effectively defines a control sphere that is intended to prevent attackers from accessing these private files. If the file permissions are insecure, then parties other than the user will be able to access those files. | |
| 1774 | A separate control sphere might effectively require that the user can only access the private files, but not any other files on the system. If the program does not ensure that the user is only requesting private files, then the user might be able to access other files on the system. | |
| 1775 | In either case, the end result is that a resource has been exposed to the wrong party.",,unclassified, | |
| 1776 | CWE-669,EN-Incorrect Resource Transfer Between Spheres (Type: Class),"The product does not properly transfer a resource/behavior to another sphere, or improperly imports a resource/behavior from another sphere, in a manner that provides unintended control over that resource. | |
| 1777 | Resources such as files and directories may be inadvertently exposed through mechanisms such as insecure permissions, or when a program accidentally operates on the wrong object. For example, a program may intend that private files can only be provided to a specific user. This effectively defines a control sphere that is intended to prevent attackers from accessing these private files. If the file permissions are insecure, then parties other than the user will be able to access those files. | |
| 1778 | A separate control sphere might effectively require that the user can only access the private files, but not any other files on the system. If the program does not ensure that the user is only requesting private files, then the user might be able to access other files on the system. | |
| 1779 | In either case, the end result is that a resource has been exposed to the wrong party.",,unclassified, | |
| 1780 | CWE-670,EN-Always-Incorrect Control Flow Implementation (Type: Class),"The code contains a control flow path that does not reflect the algorithm that the path is intended to implement, leading to incorrect behavior any time this path is navigated. | |
| 1781 | This weakness captures cases in which a particular code segment is always incorrect with respect to the algorithm that it is implementing. For example, if a C programmer intends to include multiple statements in a single block but does not include the enclosing braces (CWE-483), then the logic is always incorrect. This issue is in contrast to most weaknesses in which the code usually behaves correctly, except when it is externally manipulated in malicious ways.",,unclassified, | |
| 1782 | CWE-671,EN-Lack of Administrator Control over Security (Type: Class),"The product uses security features in a way that prevents the product's administrator from tailoring security settings to reflect the environment in which the product is being used. This introduces resultant weaknesses or prevents it from operating at a level of security that is desired by the administrator. | |
| 1783 | If the product's administrator does not have the ability to manage security-related decisions at all times, then protecting the product from outside threats - including the product's developer - can become impossible. For example, a hard-coded account name and password cannot be changed by the administrator, thus exposing that product to attacks that the administrator can not prevent.",,unclassified, | |
| 1784 | CWE-672,EN-Operation on a Resource after Expiration or Release (Type: Base),"The software uses, accesses, or otherwise operates on a resource after that resource has been expired, released, or revoked. | |
| 1785 | If the product's administrator does not have the ability to manage security-related decisions at all times, then protecting the product from outside threats - including the product's developer - can become impossible. For example, a hard-coded account name and password cannot be changed by the administrator, thus exposing that product to attacks that the administrator can not prevent.",,unclassified, | |
| 1786 | CWE-673,EN-External Influence of Sphere Definition (Type: Class),"The product does not prevent the definition of control spheres from external actors. | |
| 1787 | Typically, a product defines its control sphere within the code itself, or through configuration by the product's administrator. In some cases, an external party can change the definition of the control sphere. This is typically a resultant weakness.",,unclassified, | |
| 1788 | CWE-674,EN-Uncontrolled Recursion (Type: Base),"The product does not properly control the amount of recursion that takes place, which consumes excessive resources, such as allocated memory or the program stack. | |
| 1789 | Typically, a product defines its control sphere within the code itself, or through configuration by the product's administrator. In some cases, an external party can change the definition of the control sphere. This is typically a resultant weakness.",,unclassified, | |
| 1790 | CWE-675,EN-Duplicate Operations on Resource (Type: Class),"The product performs the same operation on a resource two or more times, when the operation should only be applied once. | |
| 1791 | Typically, a product defines its control sphere within the code itself, or through configuration by the product's administrator. In some cases, an external party can change the definition of the control sphere. This is typically a resultant weakness.",,unclassified, | |
| 1792 | CWE-683,EN-Function Call With Incorrect Order of Arguments (Type: Variant),"The software calls a function, procedure, or routine, but the caller specifies the arguments in an incorrect order, leading to resultant weaknesses. | |
| 1793 | While this weakness might be caught by the compiler in some languages, it can occur more frequently in cases in which the called function accepts variable numbers or types of arguments, such as format strings in C. It also can occur in languages or environments that do not enforce strong typing.",,unclassified, | |
| 1794 | CWE-684,EN-Incorrect Provision of Specified Functionality (Type: Base),"The code does not function according to its published specifications, potentially leading to incorrect usage. | |
| 1795 | When providing functionality to an external party, it is important that the software behaves in accordance with the details specified. When requirements of nuances are not documented, the functionality may produce unintended behaviors for the caller, possibly leading to an exploitable state.",,unclassified, | |
| 1796 | CWE-685,EN-Function Call With Incorrect Number of Arguments (Type: Variant),"The software calls a function, procedure, or routine, but the caller specifies too many arguments, or too few arguments, which may lead to undefined behavior and resultant weaknesses. | |
| 1797 | When providing functionality to an external party, it is important that the software behaves in accordance with the details specified. When requirements of nuances are not documented, the functionality may produce unintended behaviors for the caller, possibly leading to an exploitable state.",,unclassified, | |
| 1798 | CWE-686,EN-Function Call With Incorrect Argument Type (Type: Variant),"The software calls a function, procedure, or routine, but the caller specifies an argument that is the wrong data type, which may lead to resultant weaknesses. | |
| 1799 | This weakness is most likely to occur in loosely typed languages, or in strongly typed languages in which the types of variable arguments cannot be enforced at compilation time, or where there is implicit casting.",,unclassified, | |
| 1800 | CWE-687,EN-Function Call With Incorrectly Specified Argument Value (Type: Variant),"The software calls a function, procedure, or routine, but the caller specifies an argument that contains the wrong value, which may lead to resultant weaknesses. | |
| 1801 | This weakness is most likely to occur in loosely typed languages, or in strongly typed languages in which the types of variable arguments cannot be enforced at compilation time, or where there is implicit casting.",,unclassified, | |
| 1802 | CWE-688,EN-Function Call With Incorrect Variable or Reference as Argument (Type: Variant),"The software calls a function, procedure, or routine, but the caller specifies the wrong variable or reference as one of the arguments, which may lead to undefined behavior and resultant weaknesses. | |
| 1803 | This weakness is most likely to occur in loosely typed languages, or in strongly typed languages in which the types of variable arguments cannot be enforced at compilation time, or where there is implicit casting.",,unclassified, | |
| 1804 | CWE-69,EN-Improper Handling of Windows ::DATA Alternate Data Stream (Type: Variant),"The software does not properly prevent access to, or detect usage of, alternate data streams (ADS). | |
| 1805 | An attacker can use an ADS to hide information about a file (e.g. size, the name of the process) from a system or file browser tools such as Windows Explorer and 'dir' at the command line utility. Alternately, the attacker might be able to bypass intended access restrictions for the associated data fork.",,unclassified,"Windows NTFS Alternate Data Streams: http://www.securityfocus.com/infocus/1822 | |
| 1806 | Writing Secure Code" | |
| 1807 | CWE-691,EN-Insufficient Control Flow Management (Type: Class),"The code does not sufficiently manage its control flow during execution, creating conditions in which the control flow can be modified in unexpected ways. | |
| 1808 | An attacker can use an ADS to hide information about a file (e.g. size, the name of the process) from a system or file browser tools such as Windows Explorer and 'dir' at the command line utility. Alternately, the attacker might be able to bypass intended access restrictions for the associated data fork.",,unclassified, | |
| 1809 | CWE-693,EN-Protection Mechanism Failure (Type: Class),"The product does not use or incorrectly uses a protection mechanism that provides sufficient defense against directed attacks against the product. | |
| 1810 | This weakness covers three distinct situations. A ""missing"" protection mechanism occurs when the application does not define any mechanism against a certain class of attack. An ""insufficient"" protection mechanism might provide some defenses - for example, against the most common attacks - but it does not protect against everything that is intended. Finally, an ""ignored"" mechanism occurs when a mechanism is available and in active use within the product, but the developer has not applied it in some code path.",,unclassified, | |
| 1811 | CWE-694,EN-Use of Multiple Resources with Duplicate Identifier (Type: Base),"The software uses multiple resources that can have the same identifier, in a context in which unique identifiers are required. | |
| 1812 | If the software assumes that each resource has a unique identifier, the software could operate on the wrong resource if attackers can cause multiple resources to be associated with the same identifier.",,unclassified, | |
| 1813 | CWE-695,EN-Use of Low-Level Functionality (Type: Base),"The software uses low-level functionality that is explicitly prohibited by the framework or specification under which the software is supposed to operate. | |
| 1814 | The use of low-level functionality can violate the specification in unexpected ways that effectively disable built-in protection mechanisms, introduce exploitable inconsistencies, or otherwise expose the functionality to attack.",,unclassified, | |
| 1815 | CWE-696,EN-Incorrect Behavior Order (Type: Class),"The software performs multiple related behaviors, but the behaviors are performed in the wrong order in ways which may produce resultant weaknesses. | |
| 1816 | The use of low-level functionality can violate the specification in unexpected ways that effectively disable built-in protection mechanisms, introduce exploitable inconsistencies, or otherwise expose the functionality to attack.",,unclassified, | |
| 1817 | CWE-697,EN-Insufficient Comparison (Type: Class),"The software compares two entities in a security-relevant context, but the comparison is insufficient, which may lead to resultant weaknesses. | |
| 1818 | This weakness class covers several possibilities: | |
| 1819 | the comparison checks one factor incorrectly; | |
| 1820 | the comparison should consider multiple factors, but it does not check some of those factors at all.",,unclassified, | |
| 1821 | CWE-698,EN-Execution After Redirect (EAR) (Type: Base),"The web application sends a redirect to another location, but instead of exiting, it executes additional code. | |
| 1822 | This weakness class covers several possibilities: | |
| 1823 | the comparison checks one factor incorrectly; | |
| 1824 | the comparison should consider multiple factors, but it does not check some of those factors at all.",,unclassified,Fear the EAR: Discovering and Mitigating Execution After Redirect Vulnerabilities: http://cs.ucsb.edu/~bboe/public/pubs/fear-the-ear-ccs2011.pdf | |
| 1825 | CWE-7,EN-J2EE Misconfiguration: Missing Custom Error Page (Type: Variant),"The default error page of a web application should not display sensitive information about the software system. | |
| 1826 | A Web application must define a default error page for 4xx errors (e.g. 404), 5xx (e.g. 500) errors and catch java.lang.Throwable exceptions to prevent attackers from mining information from the application container's built-in error response.",,unclassified,19 Deadly Sins of Software Security | |
| 1827 | CWE-703,EN-Improper Check or Handling of Exceptional Conditions (Type: Class),"The software does not properly anticipate or handle exceptional conditions that rarely occur during normal operation of the software. | |
| 1828 | A Web application must define a default error page for 4xx errors (e.g. 404), 5xx (e.g. 500) errors and catch java.lang.Throwable exceptions to prevent attackers from mining information from the application container's built-in error response.",,unclassified,"A Taxonomy of Security Faults in the UNIX Operating System: http://ftp.cerias.purdue.edu/pub/papers/taimur-aslam/aslam-taxonomy-msthesis.pdf | |
| 1829 | Use of A Taxonomy of Security Faults: http://csrc.nist.gov/nissc/1996/papers/NISSC96/paper057/PAPER.PDF | |
| 1830 | 24 Deadly Sins of Software Security: ""Sin 8: C++ Catastrophes."" Page 143" | |
| 1831 | CWE-704,EN-Incorrect Type Conversion or Cast (Type: Class),"The software does not correctly convert an object, resource or structure from one type to a different type. | |
| 1832 | A Web application must define a default error page for 4xx errors (e.g. 404), 5xx (e.g. 500) errors and catch java.lang.Throwable exceptions to prevent attackers from mining information from the application container's built-in error response.",,unclassified, | |
| 1833 | CWE-705,EN-Incorrect Control Flow Scoping (Type: Class),"The software does not properly return control flow to the proper location after it has completed a task or detected an unusual condition. | |
| 1834 | A Web application must define a default error page for 4xx errors (e.g. 404), 5xx (e.g. 500) errors and catch java.lang.Throwable exceptions to prevent attackers from mining information from the application container's built-in error response.",,unclassified, | |
| 1835 | CWE-706,EN-Use of Incorrectly-Resolved Name or Reference (Type: Class),"The software uses a name or reference to access a resource, but the name/reference resolves to a resource that is outside of the intended control sphere. | |
| 1836 | A Web application must define a default error page for 4xx errors (e.g. 404), 5xx (e.g. 500) errors and catch java.lang.Throwable exceptions to prevent attackers from mining information from the application container's built-in error response.",,unclassified, | |
| 1837 | CWE-707,EN-Improper Enforcement of Message or Data Structure (Type: Class),"The software does not enforce or incorrectly enforces that structured messages or data are well-formed before being read from an upstream component or sent to a downstream component. | |
| 1838 | If a message is malformed it may cause the message to be incorrectly interpreted. | |
| 1839 | This weakness typically applies in cases where the product prepares a control message that another process must act on, such as a command or query, and malicious input that was intended as data, can enter the control plane instead. However, this weakness also applies to more general cases where there are not always control implications.",,unclassified, | |
| 1840 | CWE-708,EN-Incorrect Ownership Assignment (Type: Base),"The software assigns an owner to a resource, but the owner is outside of the intended control sphere. | |
| 1841 | This may allow the resource to be manipulated by actors outside of the intended control sphere.",,unclassified, | |
| 1842 | CWE-71,EN-Apple .DS_Store (Type: Variant),"Software operating in a MAC OS environment, where .DS_Store is in effect, must carefully manage hard links, otherwise an attacker may be able to leverage a hard link from .DS_Store to overwrite arbitrary files and gain privileges. | |
| 1843 | This may allow the resource to be manipulated by actors outside of the intended control sphere.",,unclassified, | |
| 1844 | CWE-710,EN-Coding Standards Violation (Type: Class),"The software does not follow certain coding rules for development, which can lead to resultant weaknesses or increase the severity of the associated vulnerabilities. | |
| 1845 | This may allow the resource to be manipulated by actors outside of the intended control sphere.",,unclassified, | |
| 1846 | CWE-72,EN-Improper Handling of Apple HFS+ Alternate Data Stream Path (Type: Variant),"The software does not properly handle special paths that may identify the data or resource fork of a file on the HFS+ file system. | |
| 1847 | If the software chooses actions to take based on the file name, then if an attacker provides the data or resource fork, the software may take unexpected actions. Further, if the software intends to restrict access to a file, then an attacker might still be able to bypass intended access restrictions by requesting the data or resource fork for that file.",,unclassified,No description: http://docs.info.apple.com/article.html?artnum=300422 | |
| 1848 | CWE-733,EN-Compiler Optimization Removal or Modification of Security-critical Code (Type: Base),"The developer builds a security-critical protection mechanism into the software but the compiler optimizes the program such that the mechanism is removed or modified. | |
| 1849 | When a resource is given a permissions setting that provides access to a wider range of actors than required, it could lead to the exposure of sensitive information, or the modification of that resource by unintended parties. This is especially dangerous when the resource is related to program configuration, execution or sensitive user data.",,unclassified,"Writing Secure Code: Chapter 9, ""A Compiler Optimization Caveat"" Page 322" | |
| 1850 | CWE-75,EN-Failure to Sanitize Special Elements into a Different Plane (Special Element Injection) (Type: Class),"The software does not adequately filter user-controlled input for special elements with control implications. | |
| 1851 | This weakness can lead to a wide variety of resultant weaknesses, depending on the behavior of the exposed method. It can apply to any number of technologies and approaches, such as ActiveX controls, Java functions, IOCTLs, and so on. | |
| 1852 | The exposure can occur in a few different ways: | |
| 1853 | 1) The function/method was never intended to be exposed to outside actors. | |
| 1854 | 2) The function/method was only intended to be accessible to a limited set of actors, such as Internet-based access from a single web site.",,unclassified, | |
| 1855 | CWE-756,EN-Missing Custom Error Page (Type: Class),"The software does not return custom error pages to the user, possibly exposing sensitive information. | |
| 1856 | The programmer may assume that certain events or conditions will never occur or do not need to be worried about, such as low memory conditions, lack of access to resources due to restrictive permissions, or misbehaving clients or components. However, attackers may intentionally trigger these unusual conditions, thus violating the programmer's assumptions, possibly introducing instability, incorrect behavior, or a vulnerability. | |
| 1857 | Note that this entry is not exclusively about the use of exceptions and exception handling, which are mechanisms for both checking and handling unusual or unexpected conditions.",,unclassified, | |
| 1858 | CWE-757,EN-Selection of Less-Secure Algorithm During Negotiation (Algorithm Downgrade) (Type: Class),"A protocol or its implementation supports interaction between multiple actors and allows those actors to negotiate which algorithm should be used as a protection mechanism such as encryption or authentication, but it does not select the strongest algorithm that is available to both parties. | |
| 1859 | When a security mechanism can be forced to downgrade to use a less secure algorithm, this can make it easier for attackers to compromise the software by exploiting weaker algorithm. The victim might not be aware that the less secure algorithm is being used. For example, if an attacker can force a communications channel to use cleartext instead of strongly-encrypted data, then the attacker could read the channel by sniffing, instead of going through extra effort of trying to decrypt the data using brute force techniques.",,unclassified, | |
| 1860 | CWE-758,"EN-Reliance on Undefined, Unspecified, or Implementation-Defined Behavior (Type: Class)","The software uses an API function, data structure, or other entity in a way that relies on properties that are not always guaranteed to hold for that entity. | |
| 1861 | This can lead to resultant weaknesses when the required properties change, such as when the software is ported to a different platform or if an interaction error (CWE-435) occurs.",,unclassified, | |
| 1862 | CWE-759,EN-Use of a One-Way Hash without a Salt (Type: Base),"The software uses a one-way cryptographic hash against an input that should not be reversible, such as a password, but the software does not also use a salt as part of the input. | |
| 1863 | This makes it easier for attackers to pre-compute the hash value using dictionary attack techniques such as rainbow tables. | |
| 1864 | It should be noted that, despite common perceptions, the use of a good salt with a hash does not sufficiently increase the effort for an attacker who is targeting an individual password, or who has a large amount of computing resources available, such as with cloud-based services or specialized, inexpensive hardware. Offline password cracking can still be effective if the hash function is not expensive to compute; many cryptographic functions are designed to be efficient and can be vulnerable to attacks using massive computing resources, even if the hash is cryptographically strong. The use of a salt only slightly increases the computing requirements for an attacker compared to other strategies such as adaptive hash functions. See CWE-916 for more details.",,unclassified,"bcrypt: http://bcrypt.sourceforge.net/ | |
| 1865 | Tarsnap - The scrypt key derivation function and encryption utility: http://www.tarsnap.com/scrypt.html | |
| 1866 | RFC2898 - PKCS #5: Password-Based Cryptography Specification Version 2.0: http://tools.ietf.org/html/rfc2898 | |
| 1867 | How Companies Can Beef Up Password Security (interview with Thomas H. Ptacek): http://krebsonsecurity.com/2012/06/how-companies-can-beef-up-password-security/ | |
| 1868 | Speed Hashing: http://www.codinghorror.com/blog/2012/04/speed-hashing.html | |
| 1869 | Password security: past, present, future: http://www.openwall.com/presentations/PHDays2012-Password-Security/ | |
| 1870 | Password Storage Cheat Sheet: https://www.owasp.org/index.php/Password_Storage_Cheat_Sheet | |
| 1871 | Enough With The Rainbow Tables: What You Need To Know About Secure Password Schemes: http://www.securityfocus.com/blogs/262 | |
| 1872 | The Importance of Being Canonical: http://erratasec.blogspot.com/2009/02/importance-of-being-canonical.html | |
| 1873 | Password Hashing: http://phpsec.org/articles/2005/password-hashing.html | |
| 1874 | Rainbow Hash Cracking: http://www.codinghorror.com/blog/archives/000949.html | |
| 1875 | Rainbow table: http://en.wikipedia.org/wiki/Rainbow_table | |
| 1876 | Writing Secure Code: Chapter 9, ""Creating a Salted Hash"" Page 302 | |
| 1877 | The Art of Software Security Assessment: Chapter 2, ""Salt Values"", Page 46. | |
| 1878 | How To Safely Store A Password: http://codahale.com/how-to-safely-store-a-password/ | |
| 1879 | Our password hashing has no clothes: http://www.troyhunt.com/2012/06/our-password-hashing-has-no-clothes.html | |
| 1880 | Should we really use bcrypt/scrypt?: http://www.analyticalengine.net/2012/06/should-we-really-use-bcryptscrypt/" | |
| 1881 | CWE-760,EN-Use of a One-Way Hash with a Predictable Salt (Type: Base),"The software uses a one-way cryptographic hash against an input that should not be reversible, such as a password, but the software uses a predictable salt as part of the input. | |
| 1882 | This makes it easier for attackers to pre-compute the hash value using dictionary attack techniques such as rainbow tables, effectively disabling the protection that an unpredictable salt would provide. | |
| 1883 | It should be noted that, despite common perceptions, the use of a good salt with a hash does not sufficiently increase the effort for an attacker who is targeting an individual password, or who has a large amount of computing resources available, such as with cloud-based services or specialized, inexpensive hardware. Offline password cracking can still be effective if the hash function is not expensive to compute; many cryptographic functions are designed to be efficient and can be vulnerable to attacks using massive computing resources, even if the hash is cryptographically strong. The use of a salt only slightly increases the computing requirements for an attacker compared to other strategies such as adaptive hash functions. See CWE-916 for more details.",,unclassified,"bcrypt: http://bcrypt.sourceforge.net/ | |
| 1884 | Tarsnap - The scrypt key derivation function and encryption utility: http://www.tarsnap.com/scrypt.html | |
| 1885 | RFC2898 - PKCS #5: Password-Based Cryptography Specification Version 2.0: http://tools.ietf.org/html/rfc2898 | |
| 1886 | How Companies Can Beef Up Password Security (interview with Thomas H. Ptacek): http://krebsonsecurity.com/2012/06/how-companies-can-beef-up-password-security/ | |
| 1887 | Speed Hashing: http://www.codinghorror.com/blog/2012/04/speed-hashing.html | |
| 1888 | Password security: past, present, future: http://www.openwall.com/presentations/PHDays2012-Password-Security/ | |
| 1889 | Password Storage Cheat Sheet: https://www.owasp.org/index.php/Password_Storage_Cheat_Sheet | |
| 1890 | Enough With The Rainbow Tables: What You Need To Know About Secure Password Schemes: http://www.securityfocus.com/blogs/262 | |
| 1891 | The Importance of Being Canonical: http://erratasec.blogspot.com/2009/02/importance-of-being-canonical.html | |
| 1892 | Password Hashing: http://phpsec.org/articles/2005/password-hashing.html | |
| 1893 | Rainbow Hash Cracking: http://www.codinghorror.com/blog/archives/000949.html | |
| 1894 | Rainbow table: http://en.wikipedia.org/wiki/Rainbow_table | |
| 1895 | Writing Secure Code: Chapter 9, ""Creating a Salted Hash"" Page 302 | |
| 1896 | The Art of Software Security Assessment: Chapter 2, ""Salt Values"", Page 46. | |
| 1897 | How To Safely Store A Password: http://codahale.com/how-to-safely-store-a-password/ | |
| 1898 | Our password hashing has no clothes: http://www.troyhunt.com/2012/06/our-password-hashing-has-no-clothes.html | |
| 1899 | Should we really use bcrypt/scrypt?: http://www.analyticalengine.net/2012/06/should-we-really-use-bcryptscrypt/" | |
| 1900 | CWE-761,EN-Free of Pointer not at Start of Buffer (Type: Variant),"The application calls free() on a pointer to a memory resource that was allocated on the heap, but the pointer is not at the start of the buffer. | |
| 1901 | This can cause the application to crash, or in some cases, modify critical program variables or execute code. | |
| 1902 | This weakness often occurs when the memory is allocated explicitly on the heap with one of the malloc() family functions and free() is called, but pointer arithmetic has caused the pointer to be in the interior or end of the buffer.",,unclassified,"boost C++ Library Smart Pointers: http://www.boost.org/doc/libs/1_38_0/libs/smart_ptr/smart_ptr.htm | |
| 1903 | Valgrind: http://valgrind.org/" | |
| 1904 | CWE-763,EN-Release of Invalid Pointer or Reference (Type: Base),"The application attempts to return a memory resource to the system, but calls the wrong release function or calls the appropriate release function incorrectly. | |
| 1905 | This weakness can take several forms, such as: | |
| 1906 | The memory was allocated, explicitly or implicitly, via one memory management method and deallocated using a different, non-compatible function (CWE-762). | |
| 1907 | The function calls or memory management routines chosen are appropriate, however they are used incorrectly, such as in CWE-761.",,unclassified,"boost C++ Library Smart Pointers: http://www.boost.org/doc/libs/1_38_0/libs/smart_ptr/smart_ptr.htm | |
| 1908 | Valgrind: http://valgrind.org/" | |
| 1909 | CWE-764,EN-Multiple Locks of a Critical Resource (Type: Variant),"The software locks a critical resource more times than intended, leading to an unexpected state in the system. | |
| 1910 | When software is operating in a concurrent environment and repeatedly locks a critical resource, the consequences will vary based on the type of lock, the lock's implementation, and the resource being protected. In some situations such as with semaphores, the resources are pooled and extra locking calls will reduce the size of the total available pool, possibly leading to degraded performance or a denial of service. If this can be triggered by an attacker, it will be similar to an unrestricted lock (CWE-412). In the context of a binary lock, it is likely that any duplicate locking attempts will never succeed since the lock is already held and progress may not be possible.",,unclassified, | |
| 1911 | CWE-765,EN-Multiple Unlocks of a Critical Resource (Type: Variant),"The software unlocks a critical resource more times than intended, leading to an unexpected state in the system. | |
| 1912 | When software is operating in a concurrent environment and repeatedly unlocks a critical resource, the consequences will vary based on the type of lock, the lock's implementation, and the resource being protected. In some situations such as with semaphores, the resources are pooled and extra calls to unlock will increase the count for the number of available resources, likely resulting in a crash or unpredictable behavior when the system nears capacity.",,unclassified, | |
| 1913 | CWE-785,EN-Use of Path Manipulation Function without Maximum-sized Buffer (Type: Variant),"The software invokes a function for normalizing paths or file names, but it provides an output buffer that is smaller than the maximum possible size, such as PATH_MAX. | |
| 1914 | Passing an inadequately-sized output buffer to a path manipulation function can result in a buffer overflow. Such functions include realpath(), readlink(), PathAppend(), and others.",,unclassified, | |
| 1915 | CWE-786,EN-Access of Memory Location Before Start of Buffer (Type: Base),"The software reads or writes to a buffer using an index or pointer that references a memory location prior to the beginning of the buffer. | |
| 1916 | This typically occurs when a pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used.",,unclassified, | |
| 1917 | CWE-787,EN-Out-of-bounds Write (Type: Base),"The software writes data past the end, or before the beginning, of the intended buffer. | |
| 1918 | This typically occurs when the pointer or its index is incremented or decremented to a position beyond the bounds of the buffer or when pointer arithmetic results in a position outside of the valid memory location to name a few. This may result in corruption of sensitive information, a crash, or code execution among other things.",,unclassified, | |
| 1919 | CWE-788,EN-Access of Memory Location After End of Buffer (Type: Base),"The software reads or writes to a buffer using an index or pointer that references a memory location after the end of the buffer. | |
| 1920 | This typically occurs when a pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used. These problems may be resultant from missing sentinel values (CWE-463) or trusting a user-influenced input length variable.",,unclassified, | |
| 1921 | CWE-790,EN-Improper Filtering of Special Elements (Type: Class),"The software receives data from an upstream component, but does not filter or incorrectly filters special elements before sending it to a downstream component. | |
| 1922 | Cross-site scripting (XSS) vulnerabilities occur when: | |
| 1923 | 1. Untrusted data enters a web application, typically from a web request. | |
| 1924 | 2. The web application dynamically generates a web page that contains this untrusted data. | |
| 1925 | 3. During page generation, the application does not prevent the data from containing content that is executable by a web browser, such as JavaScript, HTML tags, HTML attributes, mouse events, Flash, ActiveX, etc. | |
| 1926 | 4. A victim visits the generated web page through a web browser, which contains malicious script that was injected using the untrusted data. | |
| 1927 | 5. Since the script comes from a web page that was sent by the web server, the victim's web browser executes the malicious script in the context of the web server's domain. | |
| 1928 | 6. This effectively violates the intention of the web browser's same-origin policy, which states that scripts in one domain should not be able to access resources or run code in a different domain. | |
| 1929 | There are three main kinds of XSS: | |
| 1930 | The server reads data directly from the HTTP request and reflects it back in the HTTP response. Reflected XSS exploits occur when an attacker causes a victim to supply dangerous content to a vulnerable web application, which is then reflected back to the victim and executed by the web browser. The most common mechanism for delivering malicious content is to include it as a parameter in a URL that is posted publicly or e-mailed directly to the victim. URLs constructed in this manner constitute the core of many phishing schemes, whereby an attacker convinces a victim to visit a URL that refers to a vulnerable site. After the site reflects the attacker's content back to the victim, the content is executed by the victim's browser. | |
| 1931 | The application stores dangerous data in a database, message forum, visitor log, or other trusted data store. At a later time, the dangerous data is subsequently read back into the application and included in dynamic content. From an attacker's perspective, the optimal place to inject malicious content is in an area that is displayed to either many users or particularly interesting users. Interesting users typically have elevated privileges in the application or interact with sensitive data that is valuable to the attacker. If one of these users executes malicious content, the attacker may be able to perform privileged operations on behalf of the user or gain access to sensitive data belonging to the user. For example, the attacker might inject XSS into a log message, which might not be handled properly when an administrator views the logs. | |
| 1932 | In DOM-based XSS, the client performs the injection of XSS into the page; in the other types, the server performs the injection. DOM-based XSS generally involves server-controlled, trusted script that is sent to the client, such as Javascript that performs sanity checks on a form before the user submits it. If the server-supplied script processes user-supplied data and then injects it back into the web page (such as with dynamic HTML), then DOM-based XSS is possible. | |
| 1933 | Once the malicious script is injected, the attacker can perform a variety of malicious activities. The attacker could transfer private information, such as cookies that may include session information, from the victim's machine to the attacker. The attacker could send malicious requests to a web site on behalf of the victim, which could be especially dangerous to the site if the victim has administrator privileges to manage that site. Phishing attacks could be used to emulate trusted web sites and trick the victim into entering a password, allowing the attacker to compromise the victim's account on that web site. Finally, the script could exploit a vulnerability in the web browser itself possibly taking over the victim's machine, sometimes referred to as ""drive-by hacking."" | |
| 1934 | In many cases, the attack can be launched without the victim even being aware of it. Even with careful users, attackers frequently use a variety of methods to encode the malicious portion of the attack, such as URL encoding or Unicode, so the request looks less suspicious.",,unclassified, | |
| 1935 | CWE-791,EN-Incomplete Filtering of Special Elements (Type: Base),"The software receives data from an upstream component, but does not completely filter special elements before sending it to a downstream component. | |
| 1936 | Cross-site scripting (XSS) vulnerabilities occur when: | |
| 1937 | 1. Untrusted data enters a web application, typically from a web request. | |
| 1938 | 2. The web application dynamically generates a web page that contains this untrusted data. | |
| 1939 | 3. During page generation, the application does not prevent the data from containing content that is executable by a web browser, such as JavaScript, HTML tags, HTML attributes, mouse events, Flash, ActiveX, etc. | |
| 1940 | 4. A victim visits the generated web page through a web browser, which contains malicious script that was injected using the untrusted data. | |
| 1941 | 5. Since the script comes from a web page that was sent by the web server, the victim's web browser executes the malicious script in the context of the web server's domain. | |
| 1942 | 6. This effectively violates the intention of the web browser's same-origin policy, which states that scripts in one domain should not be able to access resources or run code in a different domain. | |
| 1943 | There are three main kinds of XSS: | |
| 1944 | The server reads data directly from the HTTP request and reflects it back in the HTTP response. Reflected XSS exploits occur when an attacker causes a victim to supply dangerous content to a vulnerable web application, which is then reflected back to the victim and executed by the web browser. The most common mechanism for delivering malicious content is to include it as a parameter in a URL that is posted publicly or e-mailed directly to the victim. URLs constructed in this manner constitute the core of many phishing schemes, whereby an attacker convinces a victim to visit a URL that refers to a vulnerable site. After the site reflects the attacker's content back to the victim, the content is executed by the victim's browser. | |
| 1945 | The application stores dangerous data in a database, message forum, visitor log, or other trusted data store. At a later time, the dangerous data is subsequently read back into the application and included in dynamic content. From an attacker's perspective, the optimal place to inject malicious content is in an area that is displayed to either many users or particularly interesting users. Interesting users typically have elevated privileges in the application or interact with sensitive data that is valuable to the attacker. If one of these users executes malicious content, the attacker may be able to perform privileged operations on behalf of the user or gain access to sensitive data belonging to the user. For example, the attacker might inject XSS into a log message, which might not be handled properly when an administrator views the logs. | |
| 1946 | In DOM-based XSS, the client performs the injection of XSS into the page; in the other types, the server performs the injection. DOM-based XSS generally involves server-controlled, trusted script that is sent to the client, such as Javascript that performs sanity checks on a form before the user submits it. If the server-supplied script processes user-supplied data and then injects it back into the web page (such as with dynamic HTML), then DOM-based XSS is possible. | |
| 1947 | Once the malicious script is injected, the attacker can perform a variety of malicious activities. The attacker could transfer private information, such as cookies that may include session information, from the victim's machine to the attacker. The attacker could send malicious requests to a web site on behalf of the victim, which could be especially dangerous to the site if the victim has administrator privileges to manage that site. Phishing attacks could be used to emulate trusted web sites and trick the victim into entering a password, allowing the attacker to compromise the victim's account on that web site. Finally, the script could exploit a vulnerability in the web browser itself possibly taking over the victim's machine, sometimes referred to as ""drive-by hacking."" | |
| 1948 | In many cases, the attack can be launched without the victim even being aware of it. Even with careful users, attackers frequently use a variety of methods to encode the malicious portion of the attack, such as URL encoding or Unicode, so the request looks less suspicious.",,unclassified, | |
| 1949 | CWE-792,EN-Incomplete Filtering of One or More Instances of Special Elements (Type: Variant),"The software receives data from an upstream component, but does not completely filter one or more instances of special elements before sending it to a downstream component. | |
| 1950 | Incomplete filtering of this nature involves either | |
| 1951 | only filtering a single instance of a special element when more exist, or | |
| 1952 | not filtering all instances or all elements where multiple special elements exist.",,unclassified, | |
| 1953 | CWE-793,EN-Only Filtering One Instance of a Special Element (Type: Variant),"The software receives data from an upstream component, but only filters a single instance of a special element before sending it to a downstream component. | |
| 1954 | Incomplete filtering of this nature may be location-dependent, as in only the first or last element is filtered.",,unclassified, | |
| 1955 | CWE-794,EN-Incomplete Filtering of Multiple Instances of Special Elements (Type: Variant),"The software receives data from an upstream component, but does not filter all instances of a special element before sending it to a downstream component. | |
| 1956 | Incomplete filtering of this nature may be applied to | |
| 1957 | sequential elements (special elements that appear next to each other) or | |
| 1958 | non-sequential elements (special elements that appear multiple times in different locations).",,unclassified, | |
| 1959 | CWE-795,EN-Only Filtering Special Elements at a Specified Location (Type: Base),"The software receives data from an upstream component, but only accounts for special elements at a specified location, thereby missing remaining special elements that may exist before sending it to a downstream component. | |
| 1960 | A filter might only account for instances of special elements when they occur: | |
| 1961 | relative to a marker (e.g. ""at the beginning/end of string; the second argument""), or | |
| 1962 | at an absolute position (e.g. ""byte number 10""). | |
| 1963 | This may leave special elements in the data that did not match the filter position, but still may be dangerous.",,unclassified, | |
| 1964 | CWE-796,EN-Only Filtering Special Elements Relative to a Marker (Type: Variant),"The software receives data from an upstream component, but only accounts for special elements positioned relative to a marker (e.g. ""at the beginning/end of a string; the second argument""), thereby missing remaining special elements that may exist before sending it to a downstream component. | |
| 1965 | A filter might only account for instances of special elements when they occur: | |
| 1966 | relative to a marker (e.g. ""at the beginning/end of string; the second argument""), or | |
| 1967 | at an absolute position (e.g. ""byte number 10""). | |
| 1968 | This may leave special elements in the data that did not match the filter position, but still may be dangerous.",,unclassified, | |
| 1969 | CWE-797,EN-Only Filtering Special Elements at an Absolute Position (Type: Variant),"The software receives data from an upstream component, but only accounts for special elements at an absolute position (e.g. ""byte number 10""), thereby missing remaining special elements that may exist before sending it to a downstream component. | |
| 1970 | A filter might only account for instances of special elements when they occur: | |
| 1971 | relative to a marker (e.g. ""at the beginning/end of string; the second argument""), or | |
| 1972 | at an absolute position (e.g. ""byte number 10""). | |
| 1973 | This may leave special elements in the data that did not match the filter position, but still may be dangerous.",,unclassified, | |
| 1974 | CWE-799,EN-Improper Control of Interaction Frequency (Type: Class),"The software does not properly limit the number or frequency of interactions that it has with an actor, such as the number of incoming requests. | |
| 1975 | This can allow the actor to perform actions more frequently than expected. The actor could be a human or an automated process such as a virus or bot. This could be used to cause a denial of service, compromise program logic (such as limiting humans to a single vote), or other consequences. For example, an authentication routine might not limit the number of times an attacker can guess a password. Or, a web site might conduct a poll but only expect humans to vote a maximum of once a day.",,unclassified,Insufficient Anti-automation: http://projects.webappsec.org/Insufficient+Anti-automation | |
| 1976 | CWE-8,EN-J2EE Misconfiguration: Entity Bean Declared Remote (Type: Variant),"When an application exposes a remote interface for an entity bean, it might also expose methods that get or set the bean's data. These methods could be leveraged to read sensitive information, or to change data in ways that violate the application's expectations, potentially leading to other vulnerabilities. | |
| 1977 | This can allow the actor to perform actions more frequently than expected. The actor could be a human or an automated process such as a virus or bot. This could be used to cause a denial of service, compromise program logic (such as limiting humans to a single vote), or other consequences. For example, an authentication routine might not limit the number of times an attacker can guess a password. Or, a web site might conduct a poll but only expect humans to vote a maximum of once a day.",,unclassified, | |
| 1978 | CWE-81,EN-Improper Neutralization of Script in an Error Message Web Page (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special characters that could be interpreted as web-scripting elements when they are sent to an error page. | |
| 1979 | Error pages may include customized 403 Forbidden or 404 Not Found pages. | |
| 1980 | When an attacker can trigger an error that contains unneutralized input, then cross-site scripting attacks may be possible.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 11: Failure to Handle Errors Correctly."" Page 183" | |
| 1981 | CWE-82,EN-Improper Neutralization of Script in Attributes of IMG Tags in a Web Page (Type: Variant),"The web application does not neutralize or incorrectly neutralizes scripting elements within attributes of HTML IMG tags, such as the src attribute. | |
| 1982 | Attackers can embed XSS exploits into the values for IMG attributes (e.g. SRC) that is streamed and then executed in a victim's browser. Note that when the page is loaded into a user's browsers, the exploit will automatically execute.",,unclassified, | |
| 1983 | CWE-820,EN-Missing Synchronization (Type: Base),"The software utilizes a shared resource in a concurrent manner but does not attempt to synchronize access to the resource. | |
| 1984 | If access to a shared resource is not synchronized, then the resource may not be in a state that is expected by the software. This might lead to unexpected or insecure behaviors, especially if an attacker can influence the shared resource.",,unclassified, | |
| 1985 | CWE-821,EN-Incorrect Synchronization (Type: Base),"The software utilizes a shared resource in a concurrent manner but it does not correctly synchronize access to the resource. | |
| 1986 | If access to a shared resource is not correctly synchronized, then the resource may not be in a state that is expected by the software. This might lead to unexpected or insecure behaviors, especially if an attacker can influence the shared resource.",,unclassified, | |
| 1987 | CWE-822,EN-Untrusted Pointer Dereference (Type: Base),"The program obtains a value from an untrusted source, converts this value to a pointer, and dereferences the resulting pointer. | |
| 1988 | An attacker can supply a pointer for memory locations that the program is not expecting. If the pointer is dereferenced for a write operation, the attack might allow modification of critical program state variables, cause a crash, or execute code. If the dereferencing operation is for a read, then the attack might allow reading of sensitive data, cause a crash, or set a program variable to an unexpected value (since the value will be read from an unexpected memory location). | |
| 1989 | There are several variants of this weakness, including but not necessarily limited to: | |
| 1990 | The untrusted value is directly invoked as a function call. | |
| 1991 | In OS kernels or drivers where there is a boundary between ""userland"" and privileged memory spaces, an untrusted pointer might enter through an API or system call (see CWE-781 for one such example). | |
| 1992 | Inadvertently accepting the value from an untrusted control sphere when it did not have to be accepted as input at all. This might occur when the code was originally developed to be run by a single user in a non-networked environment, and the code is then ported to or otherwise exposed to a networked environment.",,unclassified, | |
| 1993 | CWE-823,EN-Use of Out-of-range Pointer Offset (Type: Base),"The program performs pointer arithmetic on a valid pointer, but it uses an offset that can point outside of the intended range of valid memory locations for the resulting pointer. | |
| 1994 | While a pointer can contain a reference to any arbitrary memory location, a program typically only intends to use the pointer to access limited portions of memory, such as contiguous memory used to access an individual array. | |
| 1995 | Programs may use offsets in order to access fields or sub-elements stored within structured data. The offset might be out-of-range if it comes from an untrusted source, is the result of an incorrect calculation, or occurs because of another error. | |
| 1996 | If an attacker can control or influence the offset so that it points outside of the intended boundaries of the structure, then the attacker may be able to read or write to memory locations that are used elsewhere in the program. As a result, the attack might change the state of the software as accessed through program variables, cause a crash or instable behavior, and possibly lead to code execution.",,unclassified,"The Art of Software Security Assessment: Chapter 6, ""Pointer Arithmetic"", Page 277." | |
| 1997 | CWE-824,EN-Access of Uninitialized Pointer (Type: Base),"The program accesses or uses a pointer that has not been initialized. | |
| 1998 | If the pointer contains an uninitialized value, then the value might not point to a valid memory location. This could cause the program to read from or write to unexpected memory locations, leading to a denial of service. If the uninitialized pointer is used as a function call, then arbitrary functions could be invoked. If an attacker can influence the portion of uninitialized memory that is contained in the pointer, this weakness could be leveraged to execute code or perform other attacks. | |
| 1999 | Depending on memory layout, associated memory management behaviors, and program operation, the attacker might be able to influence the contents of the uninitialized pointer, thus gaining more fine-grained control of the memory location to be accessed.",,unclassified,"The Art of Software Security Assessment: Chapter 7, ""Variable Initialization"", Page 312." | |
| 2000 | CWE-825,EN-Expired Pointer Dereference (Type: Base),"The program dereferences a pointer that contains a location for memory that was previously valid, but is no longer valid. | |
| 2001 | When a program releases memory, but it maintains a pointer to that memory, then the memory might be re-allocated at a later time. If the original pointer is accessed to read or write data, then this could cause the program to read or modify data that is in use by a different function or process. Depending on how the newly-allocated memory is used, this could lead to a denial of service, information exposure, or code execution.",,unclassified, | |
| 2002 | CWE-826,EN-Premature Release of Resource During Expected Lifetime (Type: Base),"The program releases a resource that is still intended to be used by the program itself or another actor. | |
| 2003 | This weakness focuses on errors in which the program should not release a resource, but performs the release anyway. This is different than a weakness in which the program releases a resource at the appropriate time, but it maintains a reference to the resource, which it later accesses. For this weaknesses, the resource should still be valid upon the subsequent access. | |
| 2004 | When a program releases a resource that is still being used, it is possible that operations will still be taken on this resource, which may have been repurposed in the meantime, leading to issues similar to CWE-825. Consequences may include denial of service, information exposure, or code execution.",,unclassified, | |
| 2005 | CWE-827,EN-Improper Control of Document Type Definition (Type: Base),"The software does not restrict a reference to a Document Type Definition (DTD) to the intended control sphere. This might allow attackers to reference arbitrary DTDs, possibly causing the software to expose files, consume excessive system resources, or execute arbitrary http requests on behalf of the attacker. | |
| 2006 | As DTDs are processed, they might try to read or include files on the machine performing the parsing. If an attacker is able to control the DTD, then the attacker might be able to specify sensitive resources or requests or provide malicious content. | |
| 2007 | For example, the SOAP specification prohibits SOAP messages from containing DTDs.",,unclassified,Apache CXF Security Advisory (CVE-2010-2076): http://svn.apache.org/repos/asf/cxf/trunk/security/CVE-2010-2076.pdf | |
| 2008 | CWE-828,EN-Signal Handler with Functionality that is not Asynchronous-Safe (Type: Base),"The software defines a signal handler that contains code sequences that are not asynchronous-safe, i.e., the functionality is not reentrant, or it can be interrupted. | |
| 2009 | This can lead to an unexpected system state with a variety of potential consequences depending on context, including denial of service and code execution. | |
| 2010 | Signal handlers are typically intended to interrupt normal functionality of a program, or even other signals, in order to notify the process of an event. When a signal handler uses global or static variables, or invokes functions that ultimately depend on such state or its associated metadata, then it could corrupt system state that is being used by normal functionality. This could subject the program to race conditions or other weaknesses that allow an attacker to cause the program state to be corrupted. While denial of service is frequently the consequence, in some cases this weakness could be leveraged for code execution. | |
| 2011 | There are several different scenarios that introduce this issue: | |
| 2012 | Invocation of non-reentrant functions from within the handler. One example is malloc(), which modifies internal global variables as it manages memory. Very few functions are actually reentrant. | |
| 2013 | Code sequences (not necessarily function calls) contain non-atomic use of global variables, or associated metadata or structures, that can be accessed by other functionality of the program, including other signal handlers. Frequently, the same function is registered to handle multiple signals. | |
| 2014 | The signal handler function is intended to run at most one time, but instead it can be invoked multiple times. This could happen by repeated delivery of the same signal, or by delivery of different signals that have the same handler function (CWE-831). | |
| 2015 | Note that in some environments or contexts, it might be possible for the signal handler to be interrupted itself. | |
| 2016 | If both a signal handler and the normal behavior of the software have to operate on the same set of state variables, and a signal is received in the middle of the normal execution's modifications of those variables, the variables may be in an incorrect or corrupt state during signal handler execution, and possibly still incorrect or corrupt upon return.",,unclassified,"Delivering Signals for Fun and Profit: http://lcamtuf.coredump.cx/signals.txt | |
| 2017 | Race Condition: Signal Handling: http://www.fortify.com/vulncat/en/vulncat/cpp/race_condition_signal_handling.html" | |
| 2018 | CWE-829,EN-Inclusion of Functionality from Untrusted Control Sphere (Type: Class),"The software imports, requires, or includes executable functionality (such as a library) from a source that is outside of the intended control sphere. | |
| 2019 | When including third-party functionality, such as a web widget, library, or other source of functionality, the software must effectively trust that functionality. Without sufficient protection mechanisms, the functionality could be malicious in nature (either by coming from an untrusted source, being spoofed, or being modified in transit from a trusted source). The functionality might also contain its own weaknesses, or grant access to additional functionality and state information that should be kept private to the base system, such as system state information, sensitive application data, or the DOM of a web application. | |
| 2020 | This might lead to many different consequences depending on the included functionality, but some examples include injection of malware, information exposure by granting excessive privileges or permissions to the untrusted functionality, DOM-based XSS vulnerabilities, stealing user's cookies, or open redirect to malware (CWE-601).",,unclassified,"OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 2021 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html" | |
| 2022 | CWE-83,EN-Improper Neutralization of Script in Attributes in a Web Page (Type: Variant),"The software does not neutralize or incorrectly neutralizes ""javascript:"" or other URIs from dangerous attributes within tags, such as onmouseover, onload, onerror, or style. | |
| 2023 | When including third-party functionality, such as a web widget, library, or other source of functionality, the software must effectively trust that functionality. Without sufficient protection mechanisms, the functionality could be malicious in nature (either by coming from an untrusted source, being spoofed, or being modified in transit from a trusted source). The functionality might also contain its own weaknesses, or grant access to additional functionality and state information that should be kept private to the base system, such as system state information, sensitive application data, or the DOM of a web application. | |
| 2024 | This might lead to many different consequences depending on the included functionality, but some examples include injection of malware, information exposure by granting excessive privileges or permissions to the untrusted functionality, DOM-based XSS vulnerabilities, stealing user's cookies, or open redirect to malware (CWE-601).",,unclassified, | |
| 2025 | CWE-830,EN-Inclusion of Web Functionality from an Untrusted Source (Type: Base),"The software includes web functionality (such as a web widget) from another domain, which causes it to operate within the domain of the software, potentially granting total access and control of the software to the untrusted source. | |
| 2026 | Including third party functionality in a web-based environment is risky, especially if the source of the functionality is untrusted. | |
| 2027 | Even if the third party is a trusted source, the software may still be exposed to attacks and malicious behavior if that trusted source is compromised, or if the code is modified in transmission from the third party to the software. | |
| 2028 | This weakness is common in ""mashup"" development on the web, which may include source functionality from other domains. For example, Javascript-based web widgets may be inserted by using '<SCRIPT SRC=""http://other.domain.here"">' tags, which causes the code to run in the domain of the software, not the remote site from which the widget was loaded. As a result, the included code has access to the local DOM, including cookies and other data that the developer might not want the remote site to be able to access. | |
| 2029 | Such dependencies may be desirable, or even required, but sometimes programmers are not aware that a dependency exists.",,unclassified,Third-Party Web Widget Security FAQ: http://jeremiahgrossman.blogspot.com/2010/07/third-party-web-widget-security-faq.html | |
| 2030 | CWE-831,EN-Signal Handler Function Associated with Multiple Signals (Type: Base),"The software defines a function that is used as a handler for more than one signal. | |
| 2031 | While sometimes intentional and safe, when the same function is used to handle multiple signals, a race condition could occur if the function uses any state outside of its local declaration, such as global variables or non-reentrant functions, or has any side effects. | |
| 2032 | An attacker could send one signal that invokes the handler function; in many OSes, this will typically prevent the same signal from invoking the handler again, at least until the handler function has completed execution. However, the attacker could then send a different signal that is associated with the same handler function. This could interrupt the original handler function while it is still executing. If there is shared state, then the state could be corrupted. This can lead to a variety of potential consequences depending on context, including denial of service and code execution. | |
| 2033 | Another rarely-explored possibility arises when the signal handler is only designed to be executed once (if at all). By sending multiple signals, an attacker could invoke the function more than once. This may generate extra, unintended side effects. A race condition might not even be necessary; the attacker could send one signal, wait until it is handled, then send the other signal.",,unclassified,"Delivering Signals for Fun and Profit: http://lcamtuf.coredump.cx/signals.txt | |
| 2034 | Race Condition: Signal Handling: http://www.fortify.com/vulncat/en/vulncat/cpp/race_condition_signal_handling.html" | |
| 2035 | CWE-832,EN-Unlock of a Resource that is not Locked (Type: Base),"The software attempts to unlock a resource that is not locked. | |
| 2036 | Depending on the locking functionality, an unlock of a non-locked resource might cause memory corruption or other modification to the resource (or its associated metadata that is used for tracking locks).",,unclassified, | |
| 2037 | CWE-833,EN-Deadlock (Type: Base),"The software contains multiple threads or executable segments that are waiting for each other to release a necessary lock, resulting in deadlock. | |
| 2038 | Depending on the locking functionality, an unlock of a non-locked resource might cause memory corruption or other modification to the resource (or its associated metadata that is used for tracking locks).",,unclassified,"The Art of Software Security Assessment: Chapter 13, ""Synchronization Problems"" / ""Starvation and Deadlocks"", Page 760 | |
| 2039 | The Art of Software Security Assessment: Chapter 13, ""Starvation and Deadlocks"", Page 760. | |
| 2040 | Secure Coding in C and C++: Chapter 7, ""Concurrency"", section ""Mutual Exclusion and Deadlock"", Page 248." | |
| 2041 | CWE-834,EN-Excessive Iteration (Type: Base),"The software performs an iteration or loop without sufficiently limiting the number of times that the loop is executed. | |
| 2042 | If the iteration can be influenced by an attacker, this weakness could allow attackers to consume excessive resources such as CPU or memory. In many cases, a loop does not need to be infinite in order to cause enough resource consumption to adversely affect the software or its host system; it depends on the amount of resources consumed per iteration.",,unclassified,"The Art of Software Security Assessment: Chapter 7, ""Looping Constructs"", Page 327." | |
| 2043 | CWE-835,EN-Loop with Unreachable Exit Condition (Infinite Loop) (Type: Base),"The program contains an iteration or loop with an exit condition that cannot be reached, i.e., an infinite loop. | |
| 2044 | If the loop can be influenced by an attacker, this weakness could allow attackers to consume excessive resources such as CPU or memory.",,unclassified,"The Art of Software Security Assessment: Chapter 7, ""Looping Constructs"", Page 327." | |
| 2045 | CWE-836,EN-Use of Password Hash Instead of Password for Authentication (Type: Base),"The software records password hashes in a data store, receives a hash of a password from a client, and compares the supplied hash to the hash obtained from the data store. | |
| 2046 | Some authentication mechanisms rely on the client to generate the hash for a password, possibly to reduce load on the server or avoid sending the password across the network. However, when the client is used to generate the hash, an attacker can bypass the authentication by obtaining a copy of the hash, e.g. by using SQL injection to compromise a database of authentication credentials, or by exploiting an information exposure. The attacker could then use a modified client to replay the stolen hash without having knowledge of the original password. | |
| 2047 | As a result, the server-side comparison against a client-side hash does not provide any more security than the use of passwords without hashing.",,unclassified, | |
| 2048 | CWE-837,"EN-Improper Enforcement of a Single, Unique Action (Type: Base)","The software requires that an actor should only be able to perform an action once, or to have only one unique action, but the software does not enforce or improperly enforces this restriction. | |
| 2049 | In various applications, a user is only expected to perform a certain action once, such as voting, requesting a refund, or making a purchase. When this restriction is not enforced, sometimes this can have security implications. For example, in a voting application, an attacker could attempt to ""stuff the ballot box"" by voting multiple times. If these votes are counted separately, then the attacker could directly affect who wins the vote. This could have significant business impact depending on the purpose of the software.",,unclassified, | |
| 2050 | CWE-838,EN-Inappropriate Encoding for Output Context (Type: Base),"The software uses or specifies an encoding when generating output to a downstream component, but the specified encoding is not the same as the encoding that is expected by the downstream component. | |
| 2051 | This weakness can cause the downstream component to use a decoding method that produces different data than what the software intended to send. When the wrong encoding is used - even if closely related - the downstream component could decode the data incorrectly. This can have security consequences when the provided boundaries between control and data are inadvertently broken, because the resulting data could introduce control characters or special elements that were not sent by the software. The resulting data could then be used to bypass protection mechanisms such as input validation, and enable injection attacks. | |
| 2052 | While using output encoding is essential for ensuring that communications between components are accurate, the use of the wrong encoding - even if closely related - could cause the downstream component to misinterpret the output. | |
| 2053 | For example, HTML entity encoding is used for elements in the HTML body of a web page. However, a programmer might use entity encoding when generating output for that is used within an attribute of an HTML tag, which could contain functional Javascript that is not affected by the HTML encoding. | |
| 2054 | While web applications have received the most attention for this problem, this weakness could potentially apply to any type of software that uses a communications stream that could support multiple encodings.",,unclassified,"Injection-safe templating languages: http://manicode.blogspot.com/2010/06/injection-safe-templating-languages_30.html | |
| 2055 | Can we please stop saying that XSS is boring and easy to fix!: http://diniscruz.blogspot.com/2010/09/can-we-please-stop-saying-that-xss-is.html | |
| 2056 | Canoe: XSS prevention via context-aware output encoding: http://blog.ivanristic.com/2010/09/introducing-canoe-context-aware-output-encoding-for-xss-prevention.html | |
| 2057 | What is the Future of Automated XSS Defense Tools?: http://software-security.sans.org/downloads/appsec-2011-files/manico-appsec-future-tools.pdf | |
| 2058 | XSS Attacks: Preventing XSS Attacks | |
| 2059 | DOM based XSS Prevention Cheat Sheet: http://www.owasp.org/index.php/DOM_based_XSS_Prevention_Cheat_Sheet | |
| 2060 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI" | |
| 2061 | CWE-839,EN-Numeric Range Comparison Without Minimum Check (Type: Base),"The program checks a value to ensure that it does not exceed a maximum, but it does not verify that the value exceeds the minimum. | |
| 2062 | Some programs use signed integers or floats even when their values are only expected to be positive or 0. An input validation check might assume that the value is positive, and only check for the maximum value. If the value is negative, but the code assumes that the value is positive, this can produce an error. The error may have security consequences if the negative value is used for memory allocation, array access, buffer access, etc. Ultimately, the error could lead to a buffer overflow or other type of memory corruption. | |
| 2063 | The use of a negative number in a positive-only context could have security implications for other types of resources. For example, a shopping cart might check that the user is not requesting more than 10 items, but a request for -3 items could cause the application to calculate a negative price and credit the attacker's account.",,unclassified,"The Art of Software Security Assessment: Chapter 6, ""Type Conversion Vulnerabilities"" Page 246. | |
| 2064 | The Art of Software Security Assessment: Chapter 6, ""Comparisons"", Page 265." | |
| 2065 | CWE-84,EN-Improper Neutralization of Encoded URI Schemes in a Web Page (Type: Variant),"The web application improperly neutralizes user-controlled input for executable script disguised with URI encodings. | |
| 2066 | Some programs use signed integers or floats even when their values are only expected to be positive or 0. An input validation check might assume that the value is positive, and only check for the maximum value. If the value is negative, but the code assumes that the value is positive, this can produce an error. The error may have security consequences if the negative value is used for memory allocation, array access, buffer access, etc. Ultimately, the error could lead to a buffer overflow or other type of memory corruption. | |
| 2067 | The use of a negative number in a positive-only context could have security implications for other types of resources. For example, a shopping cart might check that the user is not requesting more than 10 items, but a request for -3 items could cause the application to calculate a negative price and credit the attacker's account.",,unclassified, | |
| 2068 | CWE-841,EN-Improper Enforcement of Behavioral Workflow (Type: Base),"The software supports a session in which more than one behavior must be performed by an actor, but it does not properly ensure that the actor performs the behaviors in the required sequence. | |
| 2069 | By performing actions in an unexpected order, or by omitting steps, an attacker could manipulate the business logic of the software or cause it to enter an invalid state. In some cases, this can also expose resultant weaknesses. | |
| 2070 | For example, a file-sharing protocol might require that an actor perform separate steps to provide a username, then a password, before being able to transfer files. If the file-sharing server accepts a password command followed by a transfer command, without any username being provided, the software might still perform the transfer. | |
| 2071 | Note that this is different than CWE-696, which focuses on when the software performs actions in the wrong sequence; this entry is closely related, but it is focused on ensuring that the actor performs actions in the correct sequence. | |
| 2072 | Workflow-related behaviors include: | |
| 2073 | Steps are performed in the expected order. | |
| 2074 | Required steps are not omitted. | |
| 2075 | Steps are not interrupted. | |
| 2076 | Steps are performed in a timely fashion.",,unclassified,"Business Logic Flaws and Yahoo Games: http://jeremiahgrossman.blogspot.com/2006/12/business-logic-flaws.html | |
| 2077 | Seven Business Logic Flaws That Put Your Website At Risk: http://www.whitehatsec.com/home/assets/WP_bizlogic092407.pdf | |
| 2078 | Business Logic Flaws: http://www.whitehatsec.com/home/solutions/BL_auction.html | |
| 2079 | Insufficient Process Validation: http://projects.webappsec.org/w/page/13246943/Insufficient-Process-Validation | |
| 2080 | Defying Logic: Theory, Design, and Implementation of Complex Systems for Testing Application Logic: http://www.slideshare.net/RafalLos/defying-logic-business-logic-testing-with-automation | |
| 2081 | Real-Life Example of a 'Business Logic Defect' (Screen Shots!): http://h30501.www3.hp.com/t5/Following-the-White-Rabbit-A/Real-Life-Example-of-a-Business-Logic-Defect-Screen-Shots/ba-p/22581 | |
| 2082 | Toward Automated Detection of Logic Vulnerabilities in Web Applications: http://www.usenix.org/events/sec10/tech/full_papers/Felmetsger.pdf | |
| 2083 | Designing a Framework Method for Secure Business Application Logic Integrity in e-Commerce Systems: http://ijns.femto.com.tw/contents/ijns-v12-n1/ijns-2011-v12-n1-p29-41.pdf" | |
| 2084 | CWE-842,EN-Placement of User into Incorrect Group (Type: Base),"The software or the administrator places a user into an incorrect group. | |
| 2085 | If the incorrect group has more access or privileges than the intended group, the user might be able to bypass intended security policy to access unexpected resources or perform unexpected actions. The access-control system might not be able to detect malicious usage of this group membership.",,unclassified, | |
| 2086 | CWE-843,EN-Access of Resource Using Incompatible Type (Type Confusion) (Type: Base),"The program allocates or initializes a resource such as a pointer, object, or variable using one type, but it later accesses that resource using a type that is incompatible with the original type. | |
| 2087 | When the program accesses the resource using an incompatible type, this could trigger logical errors because the resource does not have expected properties. In languages without memory safety, such as C and C++, type confusion can lead to out-of-bounds memory access. | |
| 2088 | While this weakness is frequently associated with unions when parsing data with many different embedded object types in C, it can be present in any application that can interpret the same variable or memory location in multiple ways. | |
| 2089 | This weakness is not unique to C and C++. For example, errors in PHP applications can be triggered by providing array parameters when scalars are expected, or vice versa. Languages such as Perl, which perform automatic conversion of a variable of one type when it is accessed as if it were another type, can also contain these issues.",,unclassified,"Attacking Interoperability: http://www.azimuthsecurity.com/resources/bh2009_dowd_smith_dewey.pdf | |
| 2090 | The Art of Software Security Assessment: Chapter 7, ""Type Confusion"", Page 319." | |
| 2091 | CWE-85,EN-Doubled Character XSS Manipulations (Type: Variant),"The web application does not filter user-controlled input for executable script disguised using doubling of the involved characters. | |
| 2092 | When the program accesses the resource using an incompatible type, this could trigger logical errors because the resource does not have expected properties. In languages without memory safety, such as C and C++, type confusion can lead to out-of-bounds memory access. | |
| 2093 | While this weakness is frequently associated with unions when parsing data with many different embedded object types in C, it can be present in any application that can interpret the same variable or memory location in multiple ways. | |
| 2094 | This weakness is not unique to C and C++. For example, errors in PHP applications can be triggered by providing array parameters when scalars are expected, or vice versa. Languages such as Perl, which perform automatic conversion of a variable of one type when it is accessed as if it were another type, can also contain these issues.",,unclassified, | |
| 2095 | CWE-86,EN-Improper Neutralization of Invalid Characters in Identifiers in Web Pages (Type: Variant),"The software does not neutralize or incorrectly neutralizes invalid characters or byte sequences in the middle of tag names, URI schemes, and other identifiers. | |
| 2096 | Some web browsers may remove these sequences, resulting in output that may have unintended control implications. For example, the software may attempt to remove a ""javascript:"" URI scheme, but a ""java%00script:"" URI may bypass this check and still be rendered as active javascript by some browsers, allowing XSS or other attacks.",,unclassified, | |
| 2097 | CWE-87,EN-Improper Neutralization of Alternate XSS Syntax (Type: Variant),"The software does not neutralize or incorrectly neutralizes user-controlled input for alternate script syntax. | |
| 2098 | Assuming a user with a given identity, authorization is the process of determining whether that user can access a given resource, based on the user's privileges and any permissions or other access-control specifications that apply to the resource. | |
| 2099 | When access control checks are incorrectly applied, users are able to access data or perform actions that they should not be allowed to perform. This can lead to a wide range of problems, including information exposures, denial of service, and arbitrary code execution.",,unclassified, | |
| 2100 | CWE-88,EN-Argument Injection or Modification (Type: Base),"The software does not sufficiently delimit the arguments being passed to a component in another control sphere, allowing alternate arguments to be provided, leading to potentially security-relevant changes. | |
| 2101 | Assuming a user with a given identity, authorization is the process of determining whether that user can access a given resource, based on the user's privileges and any permissions or other access-control specifications that apply to the resource. | |
| 2102 | When access control checks are incorrectly applied, users are able to access data or perform actions that they should not be allowed to perform. This can lead to a wide range of problems, including information exposures, denial of service, and arbitrary code execution.",,unclassified,"Argument injection issues: http://www.securityfocus.com/archive/1/archive/1/460089/100/100/threaded | |
| 2103 | The Art of Software Security Assessment: Chapter 10, ""The Argument Array"", Page 567." | |
| 2104 | CWE-9,EN-J2EE Misconfiguration: Weak Access Permissions for EJB Methods (Type: Variant),"If elevated access rights are assigned to EJB methods, then an attacker can take advantage of the permissions to exploit the software system. | |
| 2105 | Without sufficient removal or quoting of SQL syntax in user-controllable inputs, the generated SQL query can cause those inputs to be interpreted as SQL instead of ordinary user data. This can be used to alter query logic to bypass security checks, or to insert additional statements that modify the back-end database, possibly including execution of system commands. | |
| 2106 | SQL injection has become a common issue with database-driven web sites. The flaw is easily detected, and easily exploited, and as such, any site or software package with even a minimal user base is likely to be subject to an attempted attack of this kind. This flaw depends on the fact that SQL makes no real distinction between the control and data planes.",,unclassified, | |
| 2107 | CWE-90,EN-Improper Neutralization of Special Elements used in an LDAP Query (LDAP Injection) (Type: Base),"The software constructs all or part of an LDAP query using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended LDAP query when it is sent to a downstream component. | |
| 2108 | Without sufficient removal or quoting of SQL syntax in user-controllable inputs, the generated SQL query can cause those inputs to be interpreted as SQL instead of ordinary user data. This can be used to alter query logic to bypass security checks, or to insert additional statements that modify the back-end database, possibly including execution of system commands. | |
| 2109 | SQL injection has become a common issue with database-driven web sites. The flaw is easily detected, and easily exploited, and as such, any site or software package with even a minimal user base is likely to be subject to an attempted attack of this kind. This flaw depends on the fact that SQL makes no real distinction between the control and data planes.",,unclassified,Web Applications and LDAP Injection | |
| 2110 | CWE-91,EN-XML Injection (aka Blind XPath Injection) (Type: Base),"The software does not properly neutralize special elements that are used in XML, allowing attackers to modify the syntax, content, or commands of the XML before it is processed by an end system. | |
| 2111 | Within XML, special elements could include reserved words or characters such as ""<"", "">"", """""", and ""&"", which could then be used to add new data or modify XML syntax.",,unclassified,"Blind XPath Injection: http://www.modsecurity.org/archive/amit/blind-xpath-injection.pdf | |
| 2112 | The Art of Software Security Assessment: Chapter 17, ""XML Injection"", Page 1069." | |
| 2113 | CWE-912,EN-Hidden Functionality (Type: Class),"The software contains functionality that is not documented, not part of the specification, and not accessible through an interface or command sequence that is obvious to the software's users or administrators. | |
| 2114 | Hidden functionality can take many forms, such as intentionally malicious code, ""Easter Eggs"" that contain extraneous functionality such as games, developer-friendly shortcuts that reduce maintenance or support costs such as hard-coded accounts, etc. From a security perspective, even when the functionality is not intentionally malicious or damaging, it can increase the software's attack surface and expose additional weaknesses beyond what is already exposed by the intended functionality. Even if it is not easily accessible, the hidden functionality could be useful for attacks that modify the control flow of the application.",,unclassified, | |
| 2115 | CWE-913,EN-Improper Control of Dynamically-Managed Code Resources (Type: Class),"The software does not properly restrict reading from or writing to dynamically-managed code resources such as variables, objects, classes, attributes, functions, or executable instructions or statements. | |
| 2116 | Many languages offer powerful features that allow the programmer to dynamically create or modify existing code, or resources used by code such as variables and objects. While these features can offer significant flexibility and reduce development time, they can be extremely dangerous if attackers can directly influence these code resources in unexpected ways.",,unclassified, | |
| 2117 | CWE-914,EN-Improper Control of Dynamically-Identified Variables (Type: Base),"The software does not properly restrict reading from or writing to dynamically-identified variables. | |
| 2118 | Many languages offer powerful features that allow the programmer to access arbitrary variables that are specified by an input string. While these features can offer significant flexibility and reduce development time, they can be extremely dangerous if attackers can modify unintended variables that have security implications.",,unclassified, | |
| 2119 | CWE-915,EN-Improperly Controlled Modification of Dynamically-Determined Object Attributes (Type: Base),"The software receives input from an upstream component that specifies multiple attributes, properties, or fields that are to be initialized or updated in an object, but it does not properly control which attributes can be modified. | |
| 2120 | If the object contains attributes that were only intended for internal use, then their unexpected modification could lead to a vulnerability. | |
| 2121 | This weakness is sometimes known by the language-specific mechanisms that make it possible, such as mass assignment, autobinding, or object injection.",,unclassified,"Shocking News in PHP Exploitation: http://www.suspekt.org/downloads/POC2009-ShockingNewsInPHPExploitation.pdf | |
| 2122 | ""Two Security Vulnerabilities in the Spring Framework's MVC"" pdf (from 2008): http://blog.diniscruz.com/2011/07/two-security-vulnerabilities-in-spring.html | |
| 2123 | Two Security Vulnerabilities in the Spring Framework's MVC: http://o2platform.files.wordpress.com/2011/07/ounce_springframework_vulnerabilities.pdf | |
| 2124 | Best Practices for ASP.NET MVC: http://blogs.msdn.com/b/aspnetue/archive/2010/09/17/second_2d00_post.aspx | |
| 2125 | Mass assignment in Rails applications: http://blog.mhartl.com/2008/09/21/mass-assignment-in-rails-applications/ | |
| 2126 | Secure your Rails apps!: http://pragtob.wordpress.com/2012/03/06/secure-your-rails-apps/ | |
| 2127 | Ruby On Rails Security Guide: http://guides.rubyonrails.org/security.html#mass-assignment | |
| 2128 | Mass Assignment Vulnerability in ASP.NET MVC: http://freshbrewedcode.com/joshbush/2012/03/05/mass-assignment-aspnet-mvc/ | |
| 2129 | 6 Ways To Avoid Mass Assignment in ASP.NET MVC: http://odetocode.com/blogs/scott/archive/2012/03/11/complete-guide-to-mass-assignment-in-asp-net-mvc.aspx | |
| 2130 | PHP Object Injection: https://www.owasp.org/index.php/PHP_Object_Injection | |
| 2131 | Unserializing user-supplied data, a bad idea: http://heine.familiedeelstra.com/security/unserialize | |
| 2132 | Why Python Pickle is Insecure: http://nadiana.com/python-pickle-insecure" | |
| 2133 | CWE-916,EN-Use of Password Hash With Insufficient Computational Effort (Type: Base),"The software generates a hash for a password, but it uses a scheme that does not provide a sufficient level of computational effort that would make password cracking attacks infeasible or expensive. | |
| 2134 | Many password storage mechanisms compute a hash and store the hash, instead of storing the original password in plaintext. In this design, authentication involves accepting an incoming password, computing its hash, and comparing it to the stored hash. | |
| 2135 | Many hash algorithms are designed to execute quickly with minimal overhead, even cryptographic hashes. However, this efficiency is a problem for password storage, because it can reduce an attacker's workload for brute-force password cracking. If an attacker can obtain the hashes through some other method (such as SQL injection on a database that stores hashes), then the attacker can store the hashes offline and use various techniques to crack the passwords by computing hashes efficiently. Without a built-in workload, modern attacks can compute large numbers of hashes, or even exhaust the entire space of all possible passwords, within a very short amount of time, using massively-parallel computing (such as cloud computing) and GPU, ASIC, or FPGA hardware. In such a scenario, an efficient hash algorithm helps the attacker. | |
| 2136 | There are several properties of a hash scheme that are relevant to its strength against an offline, massively-parallel attack: | |
| 2137 | The amount of CPU time required to compute the hash (""stretching"") | |
| 2138 | The amount of memory required to compute the hash (""memory-hard"" operations) | |
| 2139 | Including a random value, along with the password, as input to the hash computation (""salting"") | |
| 2140 | Given a hash, there is no known way of determining a password that produces this hash value, other than by guessing possible passwords (""one-way"" hashing) | |
| 2141 | Relative to the number of all possible hashes that can be generated by the scheme, there is a low likelihood of producing the same hash for multiple different inputs (""collision resistance"") | |
| 2142 | Note that the security requirements for the software may vary depending on the environment and the value of the passwords. Different schemes might not provide all of these properties, yet may still provide sufficient security for the environment. Conversely, a solution might be very strong in preserving one property, which still being very weak for an attack against another property, or it might not be able to significantly reduce the efficiency of a massively-parallel attack.",,unclassified,"bcrypt: http://bcrypt.sourceforge.net/ | |
| 2143 | Tarsnap - The scrypt key derivation function and encryption utility: http://www.tarsnap.com/scrypt.html | |
| 2144 | RFC2898 - PKCS #5: Password-Based Cryptography Specification Version 2.0: http://tools.ietf.org/html/rfc2898 | |
| 2145 | How Companies Can Beef Up Password Security (interview with Thomas H. Ptacek): http://krebsonsecurity.com/2012/06/how-companies-can-beef-up-password-security/ | |
| 2146 | Speed Hashing: http://www.codinghorror.com/blog/2012/04/speed-hashing.html | |
| 2147 | Password security: past, present, future: http://www.openwall.com/presentations/PHDays2012-Password-Security/ | |
| 2148 | Password Storage Cheat Sheet: https://www.owasp.org/index.php/Password_Storage_Cheat_Sheet | |
| 2149 | Enough With The Rainbow Tables: What You Need To Know About Secure Password Schemes: http://www.securityfocus.com/blogs/262 | |
| 2150 | How To Safely Store A Password: http://codahale.com/how-to-safely-store-a-password/ | |
| 2151 | Password hashing at scale: http://www.openwall.com/presentations/YaC2012-Password-Hashing-At-Scale/ | |
| 2152 | New developments in password hashing: ROM-port-hard functions: http://www.openwall.com/presentations/ZeroNights2012-New-In-Password-Hashing/ | |
| 2153 | The Importance of Being Canonical: http://erratasec.blogspot.com/2009/02/importance-of-being-canonical.html | |
| 2154 | Our password hashing has no clothes: http://www.troyhunt.com/2012/06/our-password-hashing-has-no-clothes.html | |
| 2155 | Should we really use bcrypt/scrypt?: http://www.analyticalengine.net/2012/06/should-we-really-use-bcryptscrypt/" | |
| 2156 | CWE-917,EN-Improper Neutralization of Special Elements used in an Expression Language Statement (Expression Language Injection) (Type: Base),"The software constructs all or part of an expression language (EL) statement in a Java Server Page (JSP) using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended EL statement before it is executed. | |
| 2157 | Many password storage mechanisms compute a hash and store the hash, instead of storing the original password in plaintext. In this design, authentication involves accepting an incoming password, computing its hash, and comparing it to the stored hash. | |
| 2158 | Many hash algorithms are designed to execute quickly with minimal overhead, even cryptographic hashes. However, this efficiency is a problem for password storage, because it can reduce an attacker's workload for brute-force password cracking. If an attacker can obtain the hashes through some other method (such as SQL injection on a database that stores hashes), then the attacker can store the hashes offline and use various techniques to crack the passwords by computing hashes efficiently. Without a built-in workload, modern attacks can compute large numbers of hashes, or even exhaust the entire space of all possible passwords, within a very short amount of time, using massively-parallel computing (such as cloud computing) and GPU, ASIC, or FPGA hardware. In such a scenario, an efficient hash algorithm helps the attacker. | |
| 2159 | There are several properties of a hash scheme that are relevant to its strength against an offline, massively-parallel attack: | |
| 2160 | The amount of CPU time required to compute the hash (""stretching"") | |
| 2161 | The amount of memory required to compute the hash (""memory-hard"" operations) | |
| 2162 | Including a random value, along with the password, as input to the hash computation (""salting"") | |
| 2163 | Given a hash, there is no known way of determining a password that produces this hash value, other than by guessing possible passwords (""one-way"" hashing) | |
| 2164 | Relative to the number of all possible hashes that can be generated by the scheme, there is a low likelihood of producing the same hash for multiple different inputs (""collision resistance"") | |
| 2165 | Note that the security requirements for the software may vary depending on the environment and the value of the passwords. Different schemes might not provide all of these properties, yet may still provide sufficient security for the environment. Conversely, a solution might be very strong in preserving one property, which still being very weak for an attack against another property, or it might not be able to significantly reduce the efficiency of a massively-parallel attack.",,unclassified,"Expression Language Injection: http://www.mindedsecurity.com/fileshare/ExpressionLanguageInjection.pdf | |
| 2166 | Remote Code with Expression Language Injection: http://danamodio.com/application-security/discoveries/spring-remote-code-with-expression-language-injection/" | |
| 2167 | CWE-918,EN-Server-Side Request Forgery (SSRF) (Type: Base),"The web server receives a URL or similar request from an upstream component and retrieves the contents of this URL, but it does not sufficiently ensure that the request is being sent to the expected destination. | |
| 2168 | By providing URLs to unexpected hosts or ports, attackers can make it appear that the server is sending the request, possibly bypassing access controls such as firewalls that prevent the attackers from accessing the URLs directly. The server can be used as a proxy to conduct port scanning of hosts in internal networks, use other URLs such as that can access documents on the system (using file://), or use other protocols such as gopher:// or tftp://, which may provide greater control over the contents of requests.",,unclassified,"SSRF vs. Business-critical applications: XXE tunneling in SAP: https://media.blackhat.com/bh-us-12/Briefings/Polyakov/BH_US_12_Polyakov_SSRF_Business_Slides.pdf | |
| 2169 | SSRF vs. Business-critical Applications. Part 1: XXE Tunnelling in SAP NetWeaver: http://erpscan.com/wp-content/uploads/2012/08/SSRF-vs-Businness-critical-applications-whitepaper.pdf | |
| 2170 | Cross Site Port Attacks - XSPA - Part 1: http://www.riyazwalikar.com/2012/11/cross-site-port-attacks-xspa-part-1.html | |
| 2171 | Cross Site Port Attacks - XSPA - Part 2: http://www.riyazwalikar.com/2012/11/cross-site-port-attacks-xspa-part-2.html | |
| 2172 | Cross Site Port Attacks - XSPA - Part 3: http://www.riyazwalikar.com/2012/11/cross-site-port-attacks-xspa-part-3.html | |
| 2173 | SSRF attacks and sockets: smorgasbord of vulnerabilities: http://www.slideshare.net/d0znpp/ssrf-attacks-and-sockets-smorgasbord-of-vulnerabilities | |
| 2174 | SSRF bible. Cheatsheet: https://docs.google.com/document/d/1v1TkWZtrhzRLy0bYXBcdLUedXGb9njTNIJXa3u9akHM/edit?pli=1# | |
| 2175 | Web Portals: Gateway To Information, Or A Hole In Our Perimeter Defenses: http://www.shmoocon.org/2008/presentations/Web%20portals,%20gateway%20to%20information.ppt" | |
| 2176 | CWE-92,EN-DEPRECATED: Improper Sanitization of Custom Special Characters (Type: Base),"This entry has been deprecated. It originally came from PLOVER, which sometimes defined ""other"" and ""miscellaneous"" categories in order to satisfy exhaustiveness requirements for taxonomies. Within the context of CWE, the use of a more abstract entry is preferred in mapping situations. CWE-75 is a more appropriate mapping. | |
| 2177 | By providing URLs to unexpected hosts or ports, attackers can make it appear that the server is sending the request, possibly bypassing access controls such as firewalls that prevent the attackers from accessing the URLs directly. The server can be used as a proxy to conduct port scanning of hosts in internal networks, use other URLs such as that can access documents on the system (using file://), or use other protocols such as gopher:// or tftp://, which may provide greater control over the contents of requests.",,unclassified, | |
| 2178 | CWE-920,EN-Improper Restriction of Power Consumption (Type: Base),"The software operates in an environment in which power is a limited resource that cannot be automatically replenished, but the software does not properly restrict the amount of power that its operation consumes. | |
| 2179 | In environments such as embedded or mobile devices, power can be a limited resource such as a battery, which cannot be automatically replenished by the software itself, and the device might not always be directly attached to a reliable power source. If the software uses too much power too quickly, then this could cause the device (and subsequently, the software) to stop functioning until power is restored, or increase the financial burden on the device owner because of increased power costs. | |
| 2180 | Normal operation of an application will consume power. However, in some cases, an attacker could cause the application to consume more power than intended, using components such as: | |
| 2181 | Display | |
| 2182 | CPU | |
| 2183 | Disk I/O | |
| 2184 | GPS | |
| 2185 | Sound | |
| 2186 | Microphone | |
| 2187 | USB interface",,unclassified, | |
| 2188 | CWE-921,EN-Storage of Sensitive Data in a Mechanism without Access Control (Type: Base),"The software stores sensitive information in a file system or device that does not have built-in access control. | |
| 2189 | While many modern file systems or devices utilize some form of access control in order to restrict access to data, not all storage mechanisms have this capability. For example, memory cards, floppy disks, CDs, and USB devices are typically made accessible to any user within the system. This can become a problem when sensitive data is stored in these mechanisms in a multi-user environment, because anybody on the system can read or write this data. | |
| 2190 | On Android devices, external storage is typically globally readable and writable by other applications on the device. External storage may also be easily accessible through the mobile device's USB connection or physically accessible through the device's memory card port.",,unclassified,Security Tips: http://developer.android.com/training/articles/security-tips.html#StoringData | |
| 2191 | CWE-922,EN-Insecure Storage of Sensitive Information (Type: Class),"The software stores sensitive information without properly limiting read or write access by unauthorized actors. | |
| 2192 | If read access is not properly restricted, then attackers can steal the sensitive information. If write access is not properly restricted, then attackers can modify and possibly delete the data, causing incorrect results and possibly a denial of service.",,unclassified, | |
| 2193 | CWE-923,EN-Improper Authentication of Endpoint in a Communication Channel (Type: Class),"The software establishes a communication channel to (or from) an endpoint for privileged or protected operations, but it does not properly authenticate the endpoint to ensure it is associated with the identity of the intended actor. | |
| 2194 | Attackers might be able to spoof the intended endpoint from a different system or process, thus gaining the same level of access as the intended endpoint. | |
| 2195 | While this issue frequently involves authentication between network-based clients and servers, other types of communication channels and endpoints can have this weakness.",,unclassified, | |
| 2196 | CWE-924,EN-Improper Enforcement of Message Integrity During Transmission in a Communication Channel (Type: Class),"The software establishes a communication channel with an endpoint and receives a message from that endpoint, but it does not sufficiently ensure that the message was not modified during transmission. | |
| 2197 | A man-in-the-middle (MITM) attacker might be able to modify the message and spoof the endpoint.",,unclassified, | |
| 2198 | CWE-925,EN-Improper Verification of Intent by Broadcast Receiver (Type: Variant),"The Android application uses a Broadcast Receiver that receives an Intent but does not properly verify that the Intent came from an authorized source, e.g. by checking the action string. | |
| 2199 | Certain types of Intents, identified by action string, can only be broadcast by the operating system itself, not by third-party applications. However, when an application declares the ability for a component to receive broadcast messages, in most cases a malicious application can send an Intent with a non-reserved action string to that receiving component.",,unclassified, | |
| 2200 | CWE-926,EN-Improper Restriction of Content Provider Export to Other Applications (Type: Variant),"The Android application uses a Content Provider that does not properly restrict which applications can access the data that is offered by the Content Provider. | |
| 2201 | Android's Content Provider mechanism can be used to share data with other applications or internally within the same application. If access to the Content Provider is not restricted to only the expected applications, then malicious applications might be able to access the sensitive data. | |
| 2202 | This weakness could be expressed in several different ways: | |
| 2203 | The Content Provider is only intended for internal use by the application, and thus does not need to be exported. | |
| 2204 | In Android before 4.2, the Content Provider is automatically exported unless it has been explicitly declared as NOT exported. | |
| 2205 | The Content Provider is intended for external use by some applications, but it does not properly limit access, e.g. by exporting with excessive permissions.",,unclassified,No description: http://developer.android.com/training/articles/security-tips.html#ContentProviders | |
| 2206 | CWE-927,EN-Use of Implicit Intent for Sensitive Communication (Type: Variant),"The Android application uses an implicit intent for transmitting sensitive data to other applications. | |
| 2207 | Since an implicit intent does not specify a particular application to receive the data, any application can process the intent by using an Intent Filter for that intent. This can allow untrusted applications to obtain sensitive data.",,unclassified,"Analyzing Inter-Application Communication in Android: http://www.cs.berkeley.edu/~afelt/intentsecurity-mobisys.pdf | |
| 2208 | Security Tips: http://developer.android.com/training/articles/security-tips.html#ContentProviders" | |
| 2209 | CWE-96,EN-Improper Neutralization of Directives in Statically Saved Code (Static Code Injection) (Type: Base),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes code syntax before inserting the input into an executable resource, such as a library, configuration file, or template. | |
| 2210 | This may allow an attacker to execute arbitrary code, or at least modify what code can be executed.",,unclassified, | |
| 2211 | CWE-97,EN-Improper Neutralization of Server-Side Includes (SSI) Within a Web Page (Type: Variant),"The software generates a web page, but does not neutralize or incorrectly neutralizes user-controllable input that could be interpreted as a server-side include (SSI) directive. | |
| 2212 | This may allow an attacker to execute arbitrary code, or at least modify what code can be executed.",,unclassified, | |
| 2213 | CWE-116,EN-Improper Encoding or Escaping of Output (Type: Class),"The software prepares a structured message for communication with another component, but encoding or escaping of the data is either missing or done incorrectly. As a result, the intended structure of the message is not preserved. | |
| 2214 | Improper encoding or escaping can allow attackers to change the commands that are sent to another component, inserting malicious commands instead. | |
| 2215 | Most software follows a certain protocol that uses structured messages for communication between components, such as queries or commands. These structured messages can contain raw data interspersed with metadata or control information. For example, ""GET /index.html HTTP/1.1"" is a structured message containing a command (""GET"") with a single argument (""/index.html"") and metadata about which protocol version is being used (""HTTP/1.1""). | |
| 2216 | If an application uses attacker-supplied inputs to construct a structured message without properly encoding or escaping, then the attacker could insert special characters that will cause the data to be interpreted as control information or metadata. Consequently, the component that receives the output will perform the wrong operations, or otherwise interpret the data incorrectly.",,high,"OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 2217 | Input validation or output filtering, which is better?: http://jeremiahgrossman.blogspot.com/2007/01/input-validation-or-output-filtering.html | |
| 2218 | Output Sanitization: http://www.analyticalengine.net/archives/58 | |
| 2219 | Sanitizing user data: How and where to do it: http://www.diovo.com/2008/09/sanitizing-user-data-how-and-where-to-do-it/ | |
| 2220 | Input validation or output filtering, which is better?: http://jeremiahgrossman.blogspot.com/2007/01/input-validation-or-output-filtering.html | |
| 2221 | Input Validation - Not That Important: http://manicode.blogspot.com/2008/08/input-validation-not-that-important.html | |
| 2222 | Preventing XSS with Correct Output Encoding: http://phed.org/2008/05/19/preventing-xss-with-correct-output-encoding/ | |
| 2223 | Writing Secure Code: Chapter 11, ""Canonical Representation Issues"" Page 363" | |
| 2224 | CWE-121,EN-Stack-based Buffer Overflow (Type: Variant),"A stack-based buffer overflow condition is a condition where the buffer being overwritten is allocated on the stack (i.e., is a local variable or, rarely, a parameter to a function). | |
| 2225 | A buffer overflow condition exists when a program attempts to put more data in a buffer than it can hold, or when a program attempts to put data in a memory area outside of the boundaries of a buffer. The simplest type of error, and the most common cause of buffer overflows, is the ""classic"" case in which the program copies the buffer without restricting how much is copied. Other variants exist, but the existence of a classic overflow strongly suggests that the programmer is not considering even the most basic of security protections.",,high,"Writing Secure Code: Chapter 5, ""Stack Overruns"" Page 129 | |
| 2226 | 24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89 | |
| 2227 | The Art of Software Security Assessment: Chapter 3, ""Nonexecutable Stack"", Page 76. | |
| 2228 | The Art of Software Security Assessment: Chapter 5, ""Protection Mechanisms"", Page 189." | |
| 2229 | CWE-134,EN-Uncontrolled Format String (Type: Base),"The software uses externally-controlled format strings in printf-style functions, which can lead to buffer overflows or data representation problems. | |
| 2230 | If an attacker can manipulate the length parameter associated with an input such that it is inconsistent with the actual length of the input, this can be leveraged to cause the target application to behave in unexpected, and possibly, malicious ways. One of the possible motives for doing so is to pass in arbitrarily large input to the application. Another possible motivation is the modification of application state by including invalid data for subsequent properties of the application. Such weaknesses commonly lead to attacks such as buffer overflows and execution of arbitrary code.",,high,"Format String Vulnerabilities in Perl Programs: http://www.securityfocus.com/archive/1/418460/30/0/threaded | |
| 2231 | Programming Language Format String Vulnerabilities: http://www.ddj.com/dept/security/197002914 | |
| 2232 | Format String Attacks: http://www.thenewsh.com/~newsham/format-string-attacks.pdf | |
| 2233 | Writing Secure Code: Chapter 5, ""Format String Bugs"" Page 147 | |
| 2234 | 24 Deadly Sins of Software Security: ""Sin 6: Format String Problems."" Page 109 | |
| 2235 | The Art of Software Security Assessment: Chapter 8, ""C Format Strings"", Page 422." | |
| 2236 | CWE-256,EN-Plaintext Storage of a Password (Type: Variant),"Storing a password in plaintext may result in a system compromise. | |
| 2237 | Two common programmer assumptions are ""this function call can never fail"" and ""it doesn't matter if this function call fails"". If an attacker can force the function to fail or otherwise return a value that is not expected, then the subsequent program logic could lead to a vulnerability, because the software is not in a state that the programmer assumes. For example, if the program calls a function to drop privileges but does not check the return code to ensure that privileges were successfully dropped, then the program will continue to operate with the higher privileges.",,high,Building Secure Software: How to Avoid Security Problems the Right Way | |
| 2238 | CWE-257,EN-Storing Passwords in a Recoverable Format (Type: Base),"The storage of passwords in a recoverable format makes them subject to password reuse attacks by malicious users. If a system administrator can recover a password directly, or use a brute force search on the available information, the administrator can use the password on other accounts. | |
| 2239 | Two common programmer assumptions are ""this function call can never fail"" and ""it doesn't matter if this function call fails"". If an attacker can force the function to fail or otherwise return a value that is not expected, then the subsequent program logic could lead to a vulnerability, because the software is not in a state that the programmer assumes. For example, if the program calls a function to drop privileges but does not check the return code to ensure that privileges were successfully dropped, then the program will continue to operate with the higher privileges.",,high, | |
| 2240 | CWE-258,EN-Empty Password in Configuration File (Type: Variant),"Using an empty string as a password is insecure. | |
| 2241 | Two common programmer assumptions are ""this function call can never fail"" and ""it doesn't matter if this function call fails"". If an attacker can force the function to fail or otherwise return a value that is not expected, then the subsequent program logic could lead to a vulnerability, because the software is not in a state that the programmer assumes. For example, if the program calls a function to drop privileges but does not check the return code to ensure that privileges were successfully dropped, then the program will continue to operate with the higher privileges.",,high,Building Secure Software: How to Avoid Security Problems the Right Way | |
| 2242 | CWE-259,EN-Use of Hard-coded Password (Type: Base),"The software contains a hard-coded password, which it uses for its own inbound authentication or for outbound communication to external components. | |
| 2243 | A hard-coded password typically leads to a significant authentication failure that can be difficult for the system administrator to detect. Once detected, it can be difficult to fix, so the administrator may be forced into disabling the product entirely. There are two main variations: | |
| 2244 | Inbound: the software contains an authentication mechanism that checks for a hard-coded password. | |
| 2245 | Outbound: the software connects to another system or component, and it contains hard-coded password for connecting to that component. | |
| 2246 | In the Inbound variant, a default administration account is created, and a simple password is hard-coded into the product and associated with that account. This hard-coded password is the same for each installation of the product, and it usually cannot be changed or disabled by system administrators without manually modifying the program, or otherwise patching the software. If the password is ever discovered or published (a common occurrence on the Internet), then anybody with knowledge of this password can access the product. Finally, since all installations of the software will have the same password, even across different organizations, this enables massive attacks such as worms to take place. | |
| 2247 | The Outbound variant applies to front-end systems that authenticate with a back-end service. The back-end service may require a fixed password which can be easily discovered. The programmer may simply hard-code those back-end credentials into the front-end software. Any user of that program may be able to extract the password. Client-side systems with hard-coded passwords pose even more of a threat, since the extraction of a password from a binary is usually very simple.",,high,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 2248 | CWE-309,EN-Use of Password System for Primary Authentication (Type: Base),"The use of password systems as the primary means of authentication may be subject to several flaws or shortcomings, each reducing the effectiveness of the mechanism. | |
| 2249 | While the use of multiple authentication schemes is simply piling on more complexity on top of authentication, it is inestimably valuable to have such measures of redundancy. The use of weak, reused, and common passwords is rampant on the internet. Without the added protection of multiple authentication schemes, a single mistake can result in the compromise of an account. For this reason, if multiple schemes are possible and also easy to use, they should be implemented and required.",,high, | |
| 2250 | CWE-74,EN-Improper Neutralization of Special Elements in Output Used by a Downstream Component (Injection) (Type: Class),"The software constructs all or part of a command, data structure, or record using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify how it is parsed or interpreted when it is sent to a downstream component. | |
| 2251 | Software has certain assumptions about what constitutes data and control respectively. It is the lack of verification of these assumptions for user-controlled input that leads to injection problems. Injection problems encompass a wide variety of issues -- all mitigated in very different ways and usually attempted in order to alter the control flow of the process. For this reason, the most effective way to discuss these weaknesses is to note the distinct features which classify them as injection weaknesses. The most important issue to note is that all injection problems share one thing in common -- i.e., they allow for the injection of control plane data into the user-controlled data plane. This means that the execution of the process may be altered by sending code in through legitimate data channels, using no other mechanism. While buffer overflows, and many other flaws, involve the use of some further issue to gain execution, injection problems need only for the data to be parsed. The most classic instantiations of this category of weakness are SQL injection and format string vulnerabilities.",,high, | |
| 2252 | CWE-77,EN-Improper Neutralization of Special Elements used in a Command (Command Injection) (Type: Class),"The software constructs all or part of a command using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended command when it is sent to a downstream component. | |
| 2253 | Command injection vulnerabilities typically occur when: | |
| 2254 | 1. Data enters the application from an untrusted source. | |
| 2255 | 2. The data is part of a string that is executed as a command by the application. | |
| 2256 | 3. By executing the command, the application gives an attacker a privilege or capability that the attacker would not otherwise have.",,high,"Exploiting Software: How to Break Code | |
| 2257 | 24 Deadly Sins of Software Security: ""Sin 10: Command Injection."" Page 171" | |
| 2258 | CWE-798,EN-Use of Hard-coded Credentials (Type: Base),"The software contains hard-coded credentials, such as a password or cryptographic key, which it uses for its own inbound authentication, outbound communication to external components, or encryption of internal data. | |
| 2259 | Hard-coded credentials typically create a significant hole that allows an attacker to bypass the authentication that has been configured by the software administrator. This hole might be difficult for the system administrator to detect. Even if detected, it can be difficult to fix, so the administrator may be forced into disabling the product entirely. There are two main variations: | |
| 2260 | Inbound: the software contains an authentication mechanism that checks the input credentials against a hard-coded set of credentials. | |
| 2261 | Outbound: the software connects to another system or component, and it contains hard-coded credentials for connecting to that component. | |
| 2262 | In the Inbound variant, a default administration account is created, and a simple password is hard-coded into the product and associated with that account. This hard-coded password is the same for each installation of the product, and it usually cannot be changed or disabled by system administrators without manually modifying the program, or otherwise patching the software. If the password is ever discovered or published (a common occurrence on the Internet), then anybody with knowledge of this password can access the product. Finally, since all installations of the software will have the same password, even across different organizations, this enables massive attacks such as worms to take place. | |
| 2263 | The Outbound variant applies to front-end systems that authenticate with a back-end service. The back-end service may require a fixed password which can be easily discovered. The programmer may simply hard-code those back-end credentials into the front-end software. Any user of that program may be able to extract the password. Client-side systems with hard-coded passwords pose even more of a threat, since the extraction of a password from a binary is usually very simple.",,high,"Writing Secure Code: Chapter 8, ""Key Management Issues"" Page 272 | |
| 2264 | Top 25 Series - Rank 11 - Hardcoded Credentials: http://blogs.sans.org/appsecstreetfighter/2010/03/10/top-25-series-rank-11-hardcoded-credentials/ | |
| 2265 | Mobile App Top 10 List: http://www.veracode.com/blog/2010/12/mobile-app-top-10-list/" | |
| 2266 | CWE-89,EN-Improper Neutralization of Special Elements used in an SQL Command (SQL Injection) (Type: Base),"The software constructs all or part of an SQL command using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended SQL command when it is sent to a downstream component. | |
| 2267 | Without sufficient removal or quoting of SQL syntax in user-controllable inputs, the generated SQL query can cause those inputs to be interpreted as SQL instead of ordinary user data. This can be used to alter query logic to bypass security checks, or to insert additional statements that modify the back-end database, possibly including execution of system commands. | |
| 2268 | SQL injection has become a common issue with database-driven web sites. The flaw is easily detected, and easily exploited, and as such, any site or software package with even a minimal user base is likely to be subject to an attempted attack of this kind. This flaw depends on the fact that SQL makes no real distinction between the control and data planes.",,high,"24 Deadly Sins of Software Security: ""Sin 1: SQL Injection."" Page 3 | |
| 2269 | Writing Secure Code: Chapter 12, ""Database Input Issues"" Page 397 | |
| 2270 | SQL Injection Prevention Cheat Sheet: http://www.owasp.org/index.php/SQL_Injection_Prevention_Cheat_Sheet | |
| 2271 | SQL Injection Attacks by Example: http://www.unixwiz.net/techtips/sql-injection.html | |
| 2272 | SQL Injection Cheat Sheet: http://ferruh.mavituna.com/sql-injection-cheatsheet-oku/ | |
| 2273 | The Database Hacker's Handbook: Defending Database Servers | |
| 2274 | The Oracle Hacker's Handbook: Hacking and Defending Oracle | |
| 2275 | SQL Injection: http://msdn.microsoft.com/en-us/library/ms161953.aspx | |
| 2276 | SQL Injection Attack: http://blogs.technet.com/swi/archive/2008/05/29/sql-injection-attack.aspx | |
| 2277 | Giving SQL Injection the Respect it Deserves: http://blogs.msdn.com/sdl/archive/2008/05/15/giving-sql-injection-the-respect-it-deserves.aspx | |
| 2278 | Top 25 Series - Rank 2 - SQL Injection: http://blogs.sans.org/appsecstreetfighter/2010/03/01/top-25-series-rank-2-sql-injection/ | |
| 2279 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 2280 | The Art of Software Security Assessment: Chapter 8, ""SQL Queries"", Page 431. | |
| 2281 | The Art of Software Security Assessment: Chapter 17, ""SQL Injection"", Page 1061." | |
| 2282 | CWE-262,EN-Not Using Password Aging (Type: Variant),"If no mechanism is in place for managing password aging, users will have no incentive to update passwords in a timely manner. | |
| 2283 | This can result in compromise of the system for which the password is used. An attacker could gain access to this file and learn the stored password or worse yet, change the password to one of their choosing.",,low,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 2284 | CWE-263,EN-Password Aging with Long Expiration (Type: Base),"Allowing password aging to occur unchecked can result in the possibility of diminished password integrity. | |
| 2285 | Just as neglecting to include functionality for the management of password aging is dangerous, so is allowing password aging to continue unchecked. Passwords must be given a maximum life span, after which a user is required to update with a new and different password.",,low,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 2286 | CWE-768,ES-Incorrect Short Circuit Evaluation (Type: Variant),"The software contains a conditional statement with multiple logical expressions in which one of the non-leading expressions may produce side effects. This may lead to an unexpected state in the program after the execution of the conditional, because short-circuiting logic may prevent the side effects from occurring. | |
| 2287 | ","Usage of short circuit evaluation, though well-defined in the C standard, may alter control flow in a way that introduces logic errors that are difficult to detect, possibly causing errors later during the software's execution. If an attacker can discover such an inconsistency, it may be exploitable to gain arbitrary control over a system. | |
| 2288 | If the first condition of an ""or"" statement is assumed to be true under normal circumstances, or if the first condition of an ""and"" statement is assumed to be false, then any subsequent conditional may contain its own logic errors that are not detected during code review or testing. | |
| 2289 | Finally, the usage of short circuit evaluation may decrease the maintainability of the code.",low, | |
| 2290 | ,Metadatos,"250+ Archivos conteniendo metadatos: Usuarios, Carpetas, fechas de edicion y modificacion, software usado, Direccion de impresoras locales | |
| 2291 | ","Datos privados son revelados a traves de los metadatos de documentos hosteados en el dominio (PDF, WORD). Datos como nombres de usuario, versiones de sistemas operativos, versiones de software utilizados, fechas y horas de cada modificacion del documento, direcciones de red de impresoras, etc. Se recomienda limpiar de metadatos documentos que luego seran publicados en internet",unclassified, | |
| 2292 | ,ES-Session Cookie without Secure flag set,"La cookie no tiene la marca de ""Secure"". Esto instruye al navegador que dicha cookie puede ser solo accedida por canales SSL. | |
| 2293 | ",Si es posible se deberia habilitar la flag Secure para esta cookie,low, | |
| 2294 | ,ES-Session Cookie without HttpOnly flag Set,"La cookie de sesion no esta marcada como HTTPOnly, cuando una cookie es marcada de esta manera da instruccion al navegador que esa cookie puede ser accedida solamente por el servdor y no por script del lado del cliente. Es una importante proteccion de seguridad para las cookies de sesion | |
| 2295 | ",Si es posible se deberia habilitar la flag HTTPOnly para esta cookie,low, | |
| 2296 | ,ES-Apache httpd Remote Denial of Service,"* Alerta generada por el flag del servidor: ver: 2.2.15 * | |
| 2297 | Se ha detectado un problema en las versiones de apache 1.3.0, 2.0.x hasta 2.0.64 y 2.2.X hasta 2.2.19 que mediante una herramienta automatizada un atacante usand una moderada cantidad de request puede causar un uso significativo de memoria y CPU en el servidor. Datos: http://seclists.org/fulldisclosure/2011/Aug/175. | |
| 2298 | ",Actualizar version de apache,medium, | |
| 2299 | ,ES-Robots.txt,"Robots.txt revela directorios sensibles. Un atacante busca directamente robots.txt para encontrar puntos desde donde comenzar su ataque. | |
| 2300 | ","Es conveniente manejar nombres de directorios que no describan el contenido, en especial en directorios sensibles. Por ejemplo en lugar de /setup o /app_data llamar al directorio /Dir_Code1. De esta manera no revelar a un atacante que clase de informacion contiene un directorio, que se intenta ocultar de los buscadores (mediante robots.txt) | |
| 2301 | Otra practica que se me ocurre es la utilizacion de parametros. Por ejemplo: | |
| 2302 | Disallow: /*AB/$ | |
| 2303 | Esto desactivará cualquier carpeta que termine con ""AB"" por ejemplo /sourceAB/. Evitando pasar cualquier dato a un atacante y centralizando las carpetas sensibles y ocultandolas simplemente colocando ""AB"" al final.",informational, | |
| 2304 | ,ES-Typical Login Web,"Archivo de Login nombrado de manera ""comun"". | |
| 2305 | ",Esto facilita a los robots de ataque encontrar paginas sensibles. Se recomienda no usar nombres estandard para paginas de login.,unclassified, | |
| 2306 | ,ES-Credentials en Texto Plano,"Las Credenciales de usuario son trasmitidas por un canal sin cifrar y puede ser interceptada. | |
| 2307 | ",Es altamente recomendable que las paginas de login se fuerzen a usar SSL (https),medium, | |
| 2308 | ,ES-Parametro __VIEWSTATE sin encriptar,"El parametro ""__VIEWSTATE"" no esta encriptado. Para reducir las posibilidades que alguien intercepte informacion guardada en ViewState es bueno encriptarlo. | |
| 2309 | ","Se recomienda encriptar el parametro ""__VIEWSTATE"", para hacer esto se debe setear el tipo de validacion a 3DES. Editar Web.Config y agregar la siguiente linea bajo <system.web> | |
| 2310 | <machineKey validation=""3DES""/>",unclassified, | |
| 2311 | ,ES-Insecure Captcha,"La resolucion del Captcha esta incluida en el mismo codigo: | |
| 2312 | ||
| 2313 | <img id=""ctl01_mainContent_imgCaptcha"" src=""http://test-www.bancofalabella.com.co/Data/Sites/1/ImgTemp/ImageFormat_THHvB.png"" | |
| 2314 | style=""border-width:0px;"" /> | |
| 2315 | ||
| 2316 | Siendo la respuesta THHvB | |
| 2317 | ||
| 2318 | Facilitando la manera de automatizar un script para atacar el form | |
| 2319 | ",Se recomienda implementar un sistema de Captcha que la resolucion no se incluya en el codigo.,unclassified, | |
| 2320 | ,"ES-Mensaje de error de la aplicacion | |
| 2321 | (Application error message)","El server responde con mensajes de error internos que no deberián mostrarse, facilitando de esta manera informacion que puede ser sensible o util para un atacante. Pudiendo de esta manera obtener datos para mejorar su vector de ataque | |
| 2322 | ","Se recomienda deshabilitar los mensajes de error, para no proporcionar información de la tecnología o software implementado. | |
| 2323 | ||
| 2324 | ",low, | |
| 2325 | ,ES-Apache httpOnly Cookie Disclosure,"El servidor Apache version 2.2.X hasta la 2.2.21 no restringe correctamente la informacion mostrada en la contrsuccion del error "" Bad Request "" (aka 400) permitiendo a un atacante obtener los parametros de HTTPOnly. | |
| 2326 | Datos: http://fd.the-wildcat.de/apache_e36a9cf46c.php | |
| 2327 | ",Actualizar el apache. La version 2.2.22 es la primer version que soluciona este problema.,medium, | |
| 2328 | ,ES-Input de Contraseña con Autocompletar,"Un form de login con autocompletar sugiere un problema de seguridad, sobretodo para los usuarios que utilizan el servicio desde computadoras publicas. | |
| 2329 | ","Se recomienta establecer el input con Autocomplete OFF: | |
| 2330 | <INPUT TYPE=""password"" AUTOCOMPLETE=""off"">",low, | |
| 2331 | ,ES-Archivos de Backup,"Los archivos de Backup pueden contener codigo fuente de script, archivos de configuracion u otra informacion sensible que puede ayudar a un atacante a conocer el servidor y preparar ataques mas avanzados o especificos. | |
| 2332 | ",Remover el/los archivo(s) si no son requeridos en el servidor en produccion. Como un paso adicional es recomendado implementar una politica de seguridad para no permitir la creacion de archivos de backup en directorios accesibles desde la web.,unclassified, | |
| 2333 | ,ES-Possible sensitive directories,"Un posible directorio sensible fue encotnrado. Este directorio no esta directamente linkeado en el servidor Web.Se chekeo usando nombres comunes para directorios de configuracion, backups, bajadas de bases de datos, paginas de administracion, archivos temporales, etc. Usar nombres comunes de directorios para almacenar este tipo de informacion facilita a usuarios maliciosos buscar archivos sensibles. | |
| 2334 | ","Se recomienda llamar a estos directorios de manera no estandard, por ejemplo: | |
| 2335 | config-->c0nfig05 | |
| 2336 | backup-->b4ccup | |
| 2337 | Aunque es aun mas recomendabl, de ser posible, no dejar directorios de backup, configuracion, etc accesibles directamente desde la web",unclassified, | |
| 2338 | ,ES-Slow HTTP Denial of Service Attack,"Los ataques conocidos como ""Slowloris"" y ""Slow HTTP POST DoS"" se basan en el hecho de que el protocolo HTTP, por diseño, requiere que las consultas esten completamente recividas por el servidor antes de poder ser procesadas. Si la consulta HTTP no esta completa, o si la tranferencia es muy lenta, el servidor mantiene recursos ocupados esperando el resto de la informacion. Si el servidor mantiene demasiados recursos ocupados, esto crea una denegacion de servicio. | |
| 2339 | ",Es importante establecer los tiempos de espera del servidor. Se adjunta link de recomendacion para evitar este tipo de ataques: https://community.qualys.com/blogs/securitylabs/2011/11/02/how-to-protect-against-slow-http-attacks,medium, | |
| 2340 | ,ES-Clickjacking,"No se encuentra ningún tipo de impedimento para evitar que la web sea embebida dentro de un iframe. Esta restricción es importante ya que un atacante podría engañar a un usuario autenticado a realizar operaciones mediante un engaño llamado Clickjacking donde la víctima se le presenta una web, posiblemente con algun juego, utilizando algunos engaños de interfaz la victima podria ser engañada a aprobar una venta. Ref:http://javascript.info/tutorial/clickjacking | |
| 2341 | ","Todos los browsers modernos son capaces de interpretar los valores seteados en X-Frame-Options, si los mismos son incluidos en el Header del servidor.",low, | |
| 2342 | ,"ES-XSS Cross Site Scripting | |
| 2343 | (Secuencias de comandos en sitios cruzados)","Es posible injectar tags html y código javascript malicioso, por una falta en la comprobación de los datos ingresados en los parameros. De esta forma, un atacante podría ejecutar código que le permita obtener las cookies del usuario atacado, y de esa forma, tomar control de su cuenta. | |
| 2344 | ","Recomendamos filtrar todos los parámetros en búsqueda de posibles injecciones, y escapar todos los datos de entrada que se vayan a mostrar en la respuesta.",high, | |
| 2345 | ,ES-SSL 2.0 Obsolete Protocol,"El servicio remoto encripta el trafico utilizando una version obsoleta del protocolo SSL con errores y debilidades conocidas. Un atacante puede explotar estas vulneravilidades y conducir a un ataque de ""man in the middle"" o desencriptar la comunicaciones entre el servicio afectado y los clientes. | |
| 2346 | ",Se recomienda desactivar SSL 2.0 y usar SSL 3.0 o TLS 1.0 en su lugar.,high, | |
| 2347 | ,"ES-OPTIONS method is enabled | |
| 2348 | (Metodo OPTIONS activado)","El metodo HTTP OPTIONS esta activado en el servidor. El metodo OPTIONS provee una lista de los metodos que son soportados por el servidor web. El metodo OPTIONS puede exponer informasion sensible que puede ayudar a un usuario malicioso a preparar ataques mas avanzados | |
| 2349 | ",Es recomendado desactivar el metodo OPTIONS en un servidor en produccion.,low, | |
| 2350 | ,ES-TLS1/SSLv3 Renegotiation Vulnerability,"Una vulnerabilidad en la manera que el protocol SSL and TLS acepta pedidos renegociaciones pueden permitir a un atacante inyectar texto plano en ect plaintext into an application protocol stream. This could result in a situation where the attacker may be able to issue commands to the server that appear to be coming from a legitimate source. This issue affects SSL version 3.0 and newer and TLS version 1.0 and newer. | |
| 2351 | A remote, unauthenticated attacker may be able to inject an arbitrary amount of chosen plaintext into the beginning of the application protocol stream. This could allow and attacker to issue HTTP requests, or take action impersonating the user, among other consequences. | |
| 2352 | ",http://www.g-sec.lu/practicaltls.pdf,unclassified, | |
| 2353 | ,ES-File Inclusion,"Es posible que un atacante remoto incluya un archivo de recursos locales o remotos y / o la ejecución de código de script arbitrario con los privilegios del servidor web. | |
| 2354 | ","Editar el código fuente para asegurarse de que la entrada esté correctamente validada. Cuando es posible, se recomienda hacer una lista de nombres de archivos aceptados y restringir la entrada a la lista. | |
| 2355 | ||
| 2356 | En PHP, la opción allow_url_fopen normalmente permite a un programador para abrir, incluir o utilizan de alguna manera un archivo remoto a través de una URL en lugar de una ruta de archivo local. Se recomienda desactivar esta opción de php.ini.",unclassified, | |
| 2357 | CWE-319,"ES-Credenciales enviadas por un canal en texto plano | |
| 2358 | (User Credentials Sent in Clear Text)","Las credenciales de usuario se transmiten sobre un canal sin cifrar. Esta información siempre debe ser transferida a través de un canal cifrado (HTTPS) para evitar ser interceptados por usuarios maliciosos. | |
| 2359 | ||
| 2360 | Una tercera persona puede ser capaz de leer las credenciales de usuario mediante la interceptación de una conexión no cifrada de HTTP. | |
| 2361 | ","Debido que las credenciales del usuario son considerados información confidencial, siempre debe ser transferido al servidor a través de una conexión segura (HTTPS).",medium, | |
| 2362 | ,ES-URL Redirection,"Este script es vulnerable a los ataques de redireccion por URL | |
| 2363 | ||
| 2364 | La redireccion por URL es comunmente usado para pishing y suplantacion de identidad, ya que confunde al usuario a que sitio esta ingresando realmente. Un atacante puede redireccionar una visita desde un sitio valido hasta un servidor preparado por el, para poder hacer ataques como por ejemplo de pishin o distribucion de malware. | |
| 2365 | ","El script debe filtrar los sitios destinos del redirect, manteniendolo siempre dentro de los dominios validos.",unclassified, | |
| 2366 | ,ES-Apache Server Status Enabled,"Server Status es una opcion de debug que muestra informacion sensible del servidor, como numero de peticiones, url de las peticiones, uso de memoria, threads, etc | |
| 2367 | ","Es recomendable desactivar esta opcion en servidores en produccion, o de ser necesaria la utilizacion de la misma, securizar la carpeta con contraseña o renombrarla para que no sea de facil ubicacion",unclassified, | |
| 2368 | ,ES-Microsoft IIS tilde directory enumeration,"Es posible detectar nombres cortos de archivosy directorios cuyo nombrado sea en formato 8.3 en Windows usando vectores en varias versiones de Microsoft IIS. For instance, it is possible to detect all short-names of "".aspx"" files as they have 4 letters in their extensions. This can be a major issue especially for the .Net websites which are vulnerable to direct URL access as an attacker can find important files and folders that they are not normally visible. | |
| 2369 | ",There is a way to disable Windows 8.3 short name creation.You can create a registry key named NtfsDisable8dot3NameCreation in HKLMSYSTEMCurrentControlSetControlFileSystem and set it to 1. That should disable short names creation. Refer to this Microsoft TechNet article to read more about the solution.,unclassified, | |
| 2370 | ,ES-SQL Injection,"Debido al incorrecto filtrado de parámetros es posible ejecutar comandos SQL en la base de datos situada en el servidor mediante manipulación de parámetros. Un atacante podría utilizar esta técnica para extraer/modificar/eliminar el contenido de la base de datos, el único limitante son los privilegios del usuario utilizado por la web application aunque en muchos casos es posible, gracias a una inyeccion de SQL, es posible catapultar un acceso al sistema operativo. | |
| 2371 | ","Se debe modificar la aplicación para filtrar caracteres en los campos de input antes de ser enviados como consulta al servidor de base de datos. | |
| 2372 | Es importante que se sigan buenas prácticas de programación, en todos los sitios desarrollados, y sobre todos los parámetros, y no solo sobre aquellos que sean vulnerables actualmente. | |
| 2373 | Guía de cómo evitar estos ataques (en inglés): https://www.owasp.org/index.php/Guide_to_SQL_Injection",high, | |
| 2374 | ,ES-ASP.NET debugging enabled,"El modo depuracion de ASP.NET esta activado en el servidor. Es recomendado desactivar este modo en servidores en produccion. Por defecto en la instalacion de IIS este modo esta desactivado, si fue activado para diagnosticar errores es conveniente luego desactivarlo. | |
| 2375 | ","Es posible que el modo debug muestre datos sensibles del servidor. | |
| 2376 | Mas informacion de como desactivar el modo debug: | |
| 2377 | http://support.microsoft.com/default.aspx?scid=kb;es-us;815157",unclassified, | |
| 2378 | ,ES-Unicode tranfsormation Issues,"La pagina es vulnerable a varias tranformaciones de Unicode como ""Best-Fit Mappings"", ""Overlong byte sequences"" y ""Ill-formed sequences"". | |
| 2379 | Best-Fit Mappings ocurre cuando el caracter X es tranformado por un totalmente diferente caracter Y. En general, best-fit mappings occure cuando el caracter es transcodeado entre Unicode y otro encodificado. | |
| 2380 | ||
| 2381 | ************************************ | |
| 2382 | ||
| 2383 | ""Overlong byte sequences"" (no la forma corta) - UTF-8 allows for different representations of characters that also have a shorter form. For security reasons, a UTF-8 decoder must not accept UTF-8 sequences that are longer than necessary to encode a character. For example, the character U+000A (line feed) must be accepted from a UTF-8 stream only in the form 0x0A, but not in any of the following five possible overlong forms: | |
| 2384 | 0xC0 0x8A | |
| 2385 | 0xE0 0x80 0x8A | |
| 2386 | 0xF0 0x80 0x80 0x8A | |
| 2387 | 0xF8 0x80 0x80 0x80 0x8A | |
| 2388 | 0xFC 0x80 0x80 0x80 0x80 0x8A | |
| 2389 | ||
| 2390 | Ill-Formed Subsequences As REQUIRED by UNICODE 3.0, and noted in the Unicode Technical Report #36, if a leading byte is followed by an invalid successor byte, then it should NOT consume it. | |
| 2391 | ||
| 2392 | ||
| 2393 | Software vulnerabilities arise when Best-Fit mappings occur. For example, characters can be manipulated to bypass string handling filters, such as cross-site scripting (XSS) or SQL Injection filters, WAF's, and IDS devices. Overlong UTF-8 sequence could be abused to bypass UTF-8 substring tests that look only for the shortest possible encoding. | |
| 2394 | ","Se debe identificar el origen de esta tranformacion Unicode y reparar el problema. Se deja links a paginas con informacion: | |
| 2395 | Links with more information: | |
| 2396 | http://www.blackhat.com/presentations/bh-usa-09/WEBER/BHUSA09-Weber-UnicodeSecurityPreview-PAPER.pdf | |
| 2397 | http://www.cl.cam.ac.uk/~mgk25/unicode.html | |
| 2398 | http://sirdarckcat.blogspot.ro/2009/10/couple-of-unicode-issues-on-php-and.html | |
| 2399 | http://www.unicode.org/reports/tr36/",unclassified, | |
| 2400 | ,"ES-File Upload XSS | |
| 2401 | (Subida dearchivo de secuencias de comandos de sitios curzados)","El Script es vulnerable a XSS (Cross-site scripting). La aplicacion permite la carga de archivos y se subio un archivo conteniendo lenguaje HTML. Cuando este tipo de archivos es permitido en la carga, Lugo se pueden ejecutar o linkear, mostrando codigo o acciones malociosas en dicha web. | |
| 2402 | ||
| 2403 | Usuarios maliciosos pueden inyectar: JavaScript, VBScript, ActiveX, HTML o Flash en esta aplicacion vulnerable y engañar a un usuario para obtener informacion de el, tambien se puede robar datos de la sesion, asi como las cookies de la misma. Dependiendo del codigo que se pueda ejecutar, tambien se puede ganar acceso al wevidor web, archivos de configuracion o hasta ejecucion de binarios en el sistema operativo host. | |
| 2404 | ","Se deben restringir los tipos de archivos aceptados en el sistema de Carga: chekear la extension y solo aceptar ciertos tipos de archivos. Se recomienda una Whitelist en lugar de Un blacklist (es mejor especificar listado unico de extensiones permitidas, sobre un listado de denegadas). Tambien se debe chekear doble extensiones como .php.png. Chekear archivos sin nombre como "".htaccess"" (en ASP.NET, se debe chekear archivos de configuracion como web.config). Cambiar los permisos sobre la carpeta upload (de carga) para que los archivos no puedan ser ejecutados ahi. Si es posible, renombre los archivos que son subidos al servidor. | |
| 2405 | Links con mas informacion: | |
| 2406 | https://www.owasp.org/index.php/Unrestricted_File_Upload | |
| 2407 | https://www.owasp.org/index.php/Testing_for_Stored_Cross_site_scripting_(OWASP-DV-002)",unclassified, | |
| 2408 | ,ES-jQuery cross site scripting,"Esta pagina esta usando una version obsoleta de jQuery la cual es vulnerable a Cross Site Scripting. Muchos sitios estan utilisando la seleccion de elementos usando location.hash lo que permite la ejecucion de scripts en la pagina. El problema fue solucionado en la vercion jQuery 1.6.3 o superior. | |
| 2409 | Usuarios malociosos pueden inyectar JavaScript, VBScript, ActiveX, HTML o Flash en la aplicacion vulnerable, pudiendo asi engañar a un usuario para sacarle informacion sensible. | |
| 2410 | ","Update to the latest version of jQuery. | |
| 2411 | More info: http://ma.la/jquery_xss/ | |
| 2412 | http://blog.jquery.com/2011/09/01/jquery-1-6-3-released/",unclassified, | |
| 2413 | ,ES-Host Header Attack,"Un atacante puede manipular el header Host y causar que la aplicacion se comporte de maneras inesperadas. Programadores aveces creen en el header host y programas el codigo basado en el: (_SERVER[""HTTP_HOST""] in PHP). Esto tambien se refleja en portales como joombla o wordpress donde los plugins y ejecucion de script, ejemplos: | |
| 2414 | ||
| 2415 | <link href=""http://_SERVER['HOST']"" (Joomla) | |
| 2416 | ||
| 2417 | ...haciendo un apend de keys secretas y tokens: | |
| 2418 | <a href=""http://_SERVER['HOST']?token=topsecret""> (Django, Gallery y otros) | |
| 2419 | ....e importante directamente scripts: | |
| 2420 | <script src=""http://_SERVER['HOST']/misc/jquery.js?v=1.4.4""> (Various) | |
| 2421 | ","La aplicacion web deberia usar una variable ""SERVER_NAME"" en lugar de basarse en le Host header.",high, | |
| 2422 | ,ES-Login Page password-guessing attack,"Un problema común con el que se encuentran los programadores web son los ataques de fuerza bruta de logins. Un ataque de fuerza bruta es un intento de adivinar la contraseña por sistemáticamente probar todas las posibles combinaciones de números, letras y símbolos hasta descubrir la convencional correcta. Este ataque se mejora utilizando diccionarios con palabras comunes y combinaciones de las mismas | |
| 2423 | ||
| 2424 | Esta pagina de Login no tiene ninguna protección contra este ataque ya que se probaron 20 logins inválidos y el servidor no bloqueo el acceso para seguir intentando. Tampoco dispone de ninguna protección para evitar los intentos de login automáticos (como un captcha). | |
| 2425 | ","Es recomendable implementar algun tipo de bloqueo de intentos de login tras un numero de fallos en los intentos. | |
| 2426 | Mas información: | |
| 2427 | https://www.owasp.org/index.php/Blocking_Brute_Force_Attacks",unclassified, | |
| 2428 | ,ES-Error page web server version disclosure (Pagina de error mostrando version de servidor ),"Pidiendo una pagina que no existe el servidor responde con un error. En esta pagina de error se encuentran datos que contienen version del servidor web y/o modulos activados en este. Dicha informacion puede ser usada para mejorar las tacticas del atacante sabiendo a que se enfrenta | |
| 2429 | ",Se debe configurar paginas de error customizadas evitando mostrar esta informacion.,low, | |
| 2430 | ,ES-Weak SSL,"El servidor esta utiizando un cifrado SSL dèbil. | |
| 2431 | ||
| 2432 | Weak SSL ciphers (SSL2 on port 443): | |
| 2433 | ||
| 2434 | SSL2_CK_RC4_128_EXPORT40_WITH_MD5 - Low strength | |
| 2435 | SSL2_CK_RC2_128_CBC_EXPORT40_WITH_MD5 - Low strength | |
| 2436 | SSL2_CK_DES_64_CBC_WITH_MD5 - Low strength | |
| 2437 | ||
| 2438 | Weak SSL ciphers (SSL3 on port 443): | |
| 2439 | ||
| 2440 | SSL3_CK_RSA_RC4_40_MD5 - Low strength | |
| 2441 | SSL3_CK_RSA_RC2_40_MD5 - Low strength | |
| 2442 | SSL3_CK_RSA_DES_40_CBC_SHA - Low strength | |
| 2443 | SSL3_CK_RSA_DES_64_CBC_SHA - Low strength | |
| 2444 | SSL3_CK_EDH_RSA_DES_40_CBC_SHA - Low strength | |
| 2445 | SSL3_CK_EDH_RSA_DES_64_CBC_SHA - Low strength | |
| 2446 | ||
| 2447 | Weak SSL ciphers (TLS1 on port 443): | |
| 2448 | ||
| 2449 | TLS1_CK_RSA_EXPORT_WITH_RC4_40_MD5 - Low strength | |
| 2450 | TLS1_CK_RSA_EXPORT_WITH_RC2_CBC_40_MD5 - Low strength | |
| 2451 | TLS1_CK_RSA_EXPORT_WITH_DES40_CBC_SHA - Low strength | |
| 2452 | TLS1_CK_RSA_WITH_DES_CBC_SHA - Low strength | |
| 2453 | TLS1_CK_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA - Low strength | |
| 2454 | TLS1_CK_DHE_RSA_WITH_DES_CBC_SHA - Low strength | |
| 2455 | ",Reconfigurar el servidor para encriptado mas fuerte.,unclassified, | |
| 2456 | ,ES-CRIME SSL/TLS attack,"Compression Ratio Info-leak Made Easy (CRIME) es un exploit contra las cookies secretas del servidor sobre conexiones usando protocolos HTTPS y SPDY que tambien esten usando compresion de datos. Cuando se recupera el contenido de la cookie de autentificacion, permite a un atacante robar la sesion, permitiendo iniciar otros ataques. | |
| 2457 | ||
| 2458 | CRIME es un ataque del lado cliente, pero el servidor puede proteger al cliente rechazando la combinacion de estas opciones. Para CRIME, la debilidad es la compresion Deflate. | |
| 2459 | ","CRIME puede ser combatido previniendo el uso de compresion, tanto del lado del cliente, desactivando la compresion de las peticiones HTTPS, o del lado del servidor previniendo el uso de compresion de datos en las transacciones que utilicen el protocolo TLS. | |
| 2460 | ||
| 2461 | Referencias WEB. | |
| 2462 | http://blogs.cisco.com/security/breach-crime-and-blackhat/ | |
| 2463 | http://en.wikipedia.org/wiki/CRIME_(security_exploit) | |
| 2464 | http://isecpartners.com/blog/2012/september/details-on-the-crime-attack.aspx",high, | |
| 2465 | ,ES-Transaccion Insegura de HTTPS a HTTP en el form POST,"La pagina segura (https) contiene un form que realiza el post sobre una pagina insegura (http). Esto puede confundir al usuario y hacerle creer que su datos son enviados encriptados cuando en realidad no. | |
| 2466 | ",El destino del FORM debe apuntar a una pagina segura (https),unclassified, | |
| 2467 | ,ES-Trace Method is Enabled (Metodo TRACE activado),"El metodo Trace esta habilitado en el servidor. En precencia de otras vulnerabilidades cross-domain en los navegadores web, informacion sensible del campo header puede ser leida desde cualquier dominio que soporte metodo HTTP TRACE. | |
| 2468 | ||
| 2469 | Un atacante poria abusar de la funcionabilidad HTTP TRACE para ganar acceso a la informacion de los headers HTTP como las cookies y datos de autenticacion. | |
| 2470 | ","Se recomienda desactivar el metodo TRACE en el servidor web. | |
| 2471 | ||
| 2472 | Referencias WEB: | |
| 2473 | http://www.w3.org/Protocols/rfc2616/rfc2616-sec9.html | |
| 2474 | http://www.cgisecurity.com/lib/WH-WhitePaper_XST_ebook.pdf",low, | |
| 2475 | ,ES-Public Key SSL < 2048 bits (Certificado de llave Publica SSL menor de 2048 Bits),"El certificado SSL usado por el servidor contiene una llave publica de menos de 2048 bits de largo | |
| 2476 | ||
| 2477 | Los nuevos estandares de de la Industria de Certificados para SSL (SSL Certificates Industry) seteados por Certification Authority/Browser (CA/B) Forum requiere que los certificados expedidos despues de enero 1 del 2014. Deben ser al menos de 2048-bit largo. Con el incremento del poder de procesamiento de las computadoras, cualquier certificado menor de 2048-bit es riesgoso de ser comprometido por personas mal intecionadas con poder de procesamiento. | |
| 2478 | ","Si se tiene cualquier certificado de 1024-bito certificados con menos de 2048-bit de largo, sera necesario que se migre a 2048-bit. | |
| 2479 | ||
| 2480 | New Standard: https://www.cabforum.org/wp-content/uploads/Baseline_Requirements_V1.pdf",unclassified, | |
| 2481 | ,ES-Ruby on Rails CookieStore session cookie persistence,"Ruby on Rails contiene un fallo en su diseño que podria permitir a atacantes facilitar el acceso a las aplicaciones. El problema esta en mecanicsmo de la CookieStore en guardar la cookie en el lado del cliente, mientras no guarda la entrada correspondiente en el lado del servidor. Cuando la aplicacion termina la sesion, Ruby on Rails no tiene manera de trackear esto y verdaderamente invalidad la cookie con la configuracion por defecto. Esto significa que persiste ""de por vida"" y puede ser usada para acceder a aplicaciones inclusive cuando se piensa que se termino la sesion. | |
| 2482 | ","Actualmente, no se conocen actualizaciones o parches para corregir esta vulnerabilidad. Si es posible migrar temporalmente implementando un sistema de autenticacion mas seguro (e.g. ActiveRecordStore).",unclassified, | |
| 2483 | ,EN-Metadatos,"250+ Archivos conteniendo metadatos: Usuarios, Carpetas, fechas de edicion y modificacion, software usado, Direccion de impresoras locales | |
| 2484 | ","Datos privados son revelados a traves de los metadatos de documentos hosteados en el dominio (PDF, WORD). Datos como nombres de usuario, versiones de sistemas operativos, versiones de software utilizados, fechas y horas de cada modificacion del documento, direcciones de red de impresoras, etc. Se recomienda limpiar de metadatos documentos que luego seran publicados en internet",unclassified, | |
| 2485 | ,EN-Session Cookie without Secure flag set,"This cookie does not have the Secure flag set. When a cookie is set with the Secure flag, it instructs the browser that the cookie can only be accessed over secure SSL channels. This is an important security protection for session cookies. | |
| 2486 | ","If possible, you should set the Secure flag for this cookie.",low, | |
| 2487 | ,EN-Session Cookie without HttpOnly flag Set,"This cookie does not have the HTTPOnly flag set. When a cookie is set with the HTTPOnly flag, it instructs the browser that the cookie can only be accessed by the server and not by client-side scripts. This is an important security protection for session cookies. | |
| 2488 | ","If possible, you should set the HTTPOnly flag for this cookie.",low, | |
| 2489 | ,EN-Apache httpd Remote Denial of Service,"* Alerta generada por el flag del servidor: ver: 2.2.15 * | |
| 2490 | Se ha detectado un problema en las versiones de apache 1.3.0, 2.0.x hasta 2.0.64 y 2.2.X hasta 2.2.19 que mediante una herramienta automatizada un atacante usand una moderada cantidad de request puede causar un uso significativo de memoria y CPU en el servidor. Datos: http://seclists.org/fulldisclosure/2011/Aug/175. | |
| 2491 | ",Actualizar version de apache,unclassified, | |
| 2492 | ,EN-Robots.txt,"Robots.txt revela directorios sensibles. Un atacante busca directamente robots.txt para encontrar puntos desde donde comenzar su ataque. | |
| 2493 | ","Es conveniente manejar nombres de directorios que no describan el contenido, en especial en directorios sensibles. Por ejemplo en lugar de /setup o /app_data llamar al directorio /Dir_Code1. De esta manera no revelar a un atacante que clase de informacion contiene un directorio, que se intenta ocultar de los buscadores (mediante robots.txt) | |
| 2494 | Otra practica que se me ocurre es la utilizacion de parametros. Por ejemplo: | |
| 2495 | Disallow: /*AB/$ | |
| 2496 | Esto desactivará cualquier carpeta que termine con ""AB"" por ejemplo /sourceAB/. Evitando pasar cualquier dato a un atacante y centralizando las carpetas sensibles y ocultandolas simplemente colocando ""AB"" al final.",unclassified, | |
| 2497 | ,EN-Typical Login Web,"Archivo de Login nombrado de manera ""comun"". | |
| 2498 | ",Esto facilita a los robots de ataque encontrar paginas sensibles. Se recomienda no usar nombres estandard para paginas de login.,unclassified, | |
| 2499 | ,EN-Credentials in Plain Text,"La pagina de login viaja sobre texto plano | |
| 2500 | ",Es altamente recomendable que las paginas de login se fuerzen a usar SSL (https),medium, | |
| 2501 | ,EN-Unencrypted __VIEWSTATE parameter,"El parametro ""__VIEWSTATE"" no esta encriptado. Para reducir las posibilidades que alguien intercepte informacion guardada en ViewState es bueno encriptarlo. | |
| 2502 | ","Se recomienda encriptar el parametro ""__VIEWSTATE"", para hacer esto se debe setear el tipo de validacion a 3DES. Editar Web.Config y agregar la siguiente linea bajo <system.web> | |
| 2503 | <machineKey validation=""3DES""/>",unclassified, | |
| 2504 | ,EN-Insecure Captcha,"La resolucion del Captcha esta incluida en el mismo codigo: | |
| 2505 | ||
| 2506 | <img id=""ctl01_mainContent_imgCaptcha"" src=""http://test-www.bancofalabella.com.co/Data/Sites/1/ImgTemp/ImageFormat_THHvB.png"" | |
| 2507 | style=""border-width:0px;"" /> | |
| 2508 | ||
| 2509 | Siendo la respuesta THHvB | |
| 2510 | ||
| 2511 | Facilitando la manera de automatizar un script para atacar el form | |
| 2512 | ",Se recomienda implementar un sistema de Captcha que la resolucion no se incluya en el codigo.,unclassified, | |
| 2513 | ,EN-Application error message,"This page contains an error/warning message that may disclose sensitive information.The message can also contain the location of the file that produced the unhandled exception. | |
| 2514 | ||
| 2515 | The error messages may disclose sensitive information. This information can be used to launch further attacks. | |
| 2516 | ",Review the source code for this script. The application need to show generic errors.,unclassified, | |
| 2517 | ,EN-Apache httpOnly Cookie Disclosure,"El servidor Apache version 2.2.X hasta la 2.2.21 no restringe correctamente la informacion mostrada en la contrsuccion del error "" Bad Request "" (aka 400) permitiendo a un atacante obtener los parametros de HTTPOnly. | |
| 2518 | Datos: http://fd.the-wildcat.de/apache_e36a9cf46c.php | |
| 2519 | ",Actualizar el apache. La version 2.2.22 es la primer version que soluciona este problema.,unclassified, | |
| 2520 | ,EN-Input Password with Autocomplete Enable,"Autocomplete allows the browser to predict the value. When a user starts to type in a field, the browser should display options to fill in the field, based on earlier typed values. If an attacker gain access to a computer its possible of get credentials back. | |
| 2521 | ","You should include the attribute Autocomplete OFF: | |
| 2522 | <INPUT TYPE=""password"" AUTOCOMPLETE=""off"">",low, | |
| 2523 | ,Backup FilesEN-,"Backup files can contain script sources, configuration files or other sensitive information that may help an malicious user to prepare more advanced attacks | |
| 2524 | ","Remove the file(s) if they are not required on your website. As an additional step, it is recommended to implement a security policy within your organization to disallow creation of backup files in directories accessible from the web.",unclassified, | |
| 2525 | ,EN-Sesintive directory,"A possible sensitive directory has been found. This directory is not directly linked from the website.This check looks for common sensitive resources like backup directories, database dumps, administration pages, temporary directories. Each one of these directories could help an attacker to learn more about his target. | |
| 2526 | ",,unclassified, | |
| 2527 | ,EN-Slow HTTP Denial of Service Attack,"Slowloris and Slow HTTP POST DoS attacks rely on the fact that the HTTP protocol, by design, requires requests to be completely received by the server before they are processed. If an HTTP request is not complete, or if the transfer rate is very low, the server keeps its resources busy waiting for the rest of the data. If the server keeps too many resources busy, this creates a denial of service. | |
| 2528 | ",It's important to configure the timout values on the Webserver. Here is a link to a guide on how to prevent this kind of attack: https://community.qualys.com/blogs/securitylabs/2011/11/02/how-to-protect-against-slow-http-attacks,medium, | |
| 2529 | ,EN-Clickjacking,"It might be possible for a web page controlled by an attacker to load the content of this response within an iframe on the attacker's page. This may enable a ""clickjacking"" attack, in which the attacker's page overlays the target application's interface with a different interface provided by the attacker. By inducing victim users to perform actions such as mouse clicks and keystrokes, the attacker can cause them to unwittingly carry out actions within the application that is being targeted. This technique allows the attacker to circumvent defenses against cross-site request forgery, and may result in unauthorized actions. Ref:http://javascript.info/tutorial/clickjacking | |
| 2530 | ","To effectively prevent framing attacks, the application should return a response header with the name X-Frame-Options and the value DENY to prevent framing altogether, or the value SAMEORIGIN to allow framing only by pages on the same origin as the response itself.",low, | |
| 2531 | ,EN-OPTIONS method is enabled,"HTTP OPTIONS method is enabled on this web server. The OPTIONS method provides a list of the methods that are supported by the web server, it represents a request for information about the communication options available on the request/response chain identified by the Request-URI. | |
| 2532 | The OPTIONS method may expose sensitive information that may help an malicious user to prepare more advanced attacks. | |
| 2533 | ",It's recommended to disable OPTIONS Method on the web server.,low, | |
| 2534 | ,EN-TLS1/SSLv3 Renegotiation Vulnerability,"A vulnerability in the way SSL and TLS protocols allow renegotiation requests may allow an attacker to inject plaintext into an application protocol stream. This could result in a situation where the attacker may be able to issue commands to the server that appear to be coming from a legitimate source. This issue affects SSL version 3.0 and newer and TLS version 1.0 and newer. | |
| 2535 | A remote, unauthenticated attacker may be able to inject an arbitrary amount of chosen plaintext into the beginning of the application protocol stream. This could allow and attacker to issue HTTP requests, or take action impersonating the user, among other consequences. | |
| 2536 | ",http://www.g-sec.lu/practicaltls.pdf,unclassified, | |
| 2537 | ,EN-Email address found,"One or more email addresses have been found on this page. The majority of spam comes from email addresses harvested off the internet. The spam-bots (also known as email harvesters and email extractors) are programs that scour the internet looking for email addresses on any website they come across. Spambot programs look for strings like [email protected] and then record any addresses found. | |
| 2538 | ",,unclassified, | |
| 2539 | ,EN-File Inclusion,"It is possible for a remote attacker to include a file from local or remote resources and/or execute arbitrary script code with the privileges of the webserver. | |
| 2540 | ","Edit the source code to ensure that input is properly validated. Where is possible, it is recommended to make a list of accepted filenames and restrict the input to that list. | |
| 2541 | ||
| 2542 | For PHP, the option allow_url_fopen would normally allow a programmer to open, include or otherwise use a remote file using a URL rather than a local file path. It is recommended to disable this option from php.ini.",unclassified, | |
| 2543 | ,EN-User Credentials Sent in Clear Text,"Vulnerability description | |
| 2544 | User credentials are transmitted over an unencrypted channel. This information should always be transferred via an encrypted channel (HTTPS) to avoid being intercepted by malicious users. | |
| 2545 | ||
| 2546 | The impact of this vulnerability | |
| 2547 | A third party may be able to read the user credentials by intercepting an unencrypted HTTP connection. | |
| 2548 | ","Because user credentials are considered sensitive information, should always be transferred to the server over an encrypted connection (HTTPS).",unclassified, | |
| 2549 | ,EN-URL Redirection,"This script is possibly vulnerable to URL redirection attacks. | |
| 2550 | ||
| 2551 | URL redirection is sometimes used as a part of phishing attacks that confuse visitors about which web site they are visiting. | |
| 2552 | ||
| 2553 | The impact of this vulnerability | |
| 2554 | A remote attacker can redirect users from your website to a specified URL. This problem may assist an attacker to conduct phishing attacks, trojan distribution, spammers. | |
| 2555 | ",Your script should properly sanitize user input.,unclassified, | |
| 2556 | ,EN-Microsoft IIS tilde directory enumeration,"It is possible to detect short names of files and directories which have an 8.3 file naming scheme equivalent in Windows by using some vectors in several versions of Microsoft IIS. For instance, it is possible to detect all short-names of "".aspx"" files as they have 4 letters in their extensions. This can be a major issue especially for the .Net websites which are vulnerable to direct URL access as an attacker can find important files and folders that they are not normally visible. | |
| 2557 | ",There is a way to disable Windows 8.3 short name creation.You can create a registry key named NtfsDisable8dot3NameCreation in HKLMSYSTEMCurrentControlSetControlFileSystem and set it to 1. That should disable short names creation. Refer to this Microsoft TechNet article to read more about the solution.,unclassified, | |
| 2558 | ,EN-SQL Injection,"SQL injection is a vulnerability that allows an attacker to alter back-end SQL statements by manipulating the user input. An SQL injection occurs when web applications accept user input that is directly placed into a SQL statement and doesn't properly filter out dangerous characters. | |
| 2559 | ||
| 2560 | This is one of the most common application layer attacks currently being used on the Internet. Despite the fact that it is relatively easy to protect against, there is a large number of web applications vulnerable. | |
| 2561 | ||
| 2562 | An attacker may execute arbitrary SQL statements on the vulnerable system. This may compromise the integrity of your database and/or expose sensitive information. | |
| 2563 | ||
| 2564 | Depending on the back-end database in use, SQL injection vulnerabilities lead to varying levels of data/system access for the attacker. It may be possible to not only manipulate existing queries, but to UNION in arbitrary data, use sub selects, or append additional queries. In some cases, it may be possible to read in or write out to files, or to execute shell commands on the underlying operating system. | |
| 2565 | ||
| 2566 | Certain SQL Servers such as Microsoft SQL Server contain stored and extended procedures (database server functions). If an attacker can obtain access to these procedures it may be possible to compromise the entire machine. | |
| 2567 | ","Your script should filter metacharacters from user input. | |
| 2568 | Check detailed information for more information about fixing this vulnerability. | |
| 2569 | Detailed information",unclassified, | |
| 2570 | ,EN-ASP.NET debugging enabled,"ASP.NET debugging is enabled on this application. It is recommended to disable debug mode before deploying a production application. By default, debugging is disabled, and although debugging is frequently enabled to troubleshoot a problem, it is also frequently not disabled again after the problem is resolved. | |
| 2571 | ","It may be possible to disclose sensitive information about the web sever the ASP.NET application. | |
| 2572 | More information on how to fix it: | |
| 2573 | http://support.microsoft.com/default.aspx?scid=kb;en-us;815157",unclassified, | |
| 2574 | ,EN-Unicode tranformation Issues,"This page is vulnerable to various Unicode transformation issues such as Best-Fit Mappings, Overlong byte sequences, Ill-formed sequences. | |
| 2575 | Best-Fit Mappings occurs when a character X gets transformed to an entirely different character Y. In general, best-fit mappings occur when characters are transcoded between Unicode and another encoding. | |
| 2576 | ||
| 2577 | Overlong byte sequences (non-shortest form) - UTF-8 allows for different representations of characters that also have a shorter form. For security reasons, a UTF-8 decoder must not accept UTF-8 sequences that are longer than necessary to encode a character. For example, the character U+000A (line feed) must be accepted from a UTF-8 stream only in the form 0x0A, but not in any of the following five possible overlong forms: | |
| 2578 | 0xC0 0x8A | |
| 2579 | 0xE0 0x80 0x8A | |
| 2580 | 0xF0 0x80 0x80 0x8A | |
| 2581 | 0xF8 0x80 0x80 0x80 0x8A | |
| 2582 | 0xFC 0x80 0x80 0x80 0x80 0x8A | |
| 2583 | ||
| 2584 | Ill-Formed Subsequences As REQUIRED by UNICODE 3.0, and noted in the Unicode Technical Report #36, if a leading byte is followed by an invalid successor byte, then it should NOT consume it. | |
| 2585 | ||
| 2586 | ||
| 2587 | Software vulnerabilities arise when Best-Fit mappings occur. For example, characters can be manipulated to bypass string handling filters, such as cross-site scripting (XSS) or SQL Injection filters, WAF's, and IDS devices. Overlong UTF-8 sequence could be abused to bypass UTF-8 substring tests that look only for the shortest possible encoding. | |
| 2588 | ","Identiy the source of these Unicode transformation issues and fix them. Consult the web references bellow for more information. | |
| 2589 | Links with more information: | |
| 2590 | http://www.blackhat.com/presentations/bh-usa-09/WEBER/BHUSA09-Weber-UnicodeSecurityPreview-PAPER.pdf | |
| 2591 | http://www.cl.cam.ac.uk/~mgk25/unicode.html | |
| 2592 | http://sirdarckcat.blogspot.ro/2009/10/couple-of-unicode-issues-on-php-and.html | |
| 2593 | http://www.unicode.org/reports/tr36/",unclassified, | |
| 2594 | ,EN-File Upload XSS,"This script is possibly vulnerable to XSS (Cross-site scripting). The web application allows file upload and Acunetix WVS was able to upload a file containing HTML content. When HTML files are allowed, XSS payload can be injected in the file uploaded. Check Attack details for more information about this attack. | |
| 2595 | ||
| 2596 | Malicious users may inject JavaScript, VBScript, ActiveX, HTML or Flash into a vulnerable application to fool a user in order to gather data from them. An attacker can steal the session cookie and take over the account, impersonating the user. It is also possible to modify the content of the page presented to the user. | |
| 2597 | ","Restrict file types accepted for upload: check the file extension and only allow certain files to be uploaded. Use a whitelist approach instead of a blacklist. Check for double extensions such as .php.png. Check for files without a filename like .htaccess (on ASP.NET, check for configuration files like web.config). Change the permissions on the upload folder so the files within it are not executable. If possible, rename the files that are uploaded. | |
| 2598 | ||
| 2599 | https://www.owasp.org/index.php/Unrestricted_File_Upload | |
| 2600 | https://www.owasp.org/index.php/Testing_for_Stored_Cross_site_scripting_(OWASP-DV-002)",unclassified, | |
| 2601 | ,EN-Possible virtual host found,"Virtual hosting is a method for hosting multiple domain names (with separate handling of each name) on a single server (or pool of servers). This allows one server to share its resources, such as memory and processor cycles, without requiring all services provided to use the same host name. | |
| 2602 | ||
| 2603 | This web server is responding differently when the Host header is manipulated and various common virtual hosts are tested. This could indicate there is a Virtual Host present. | |
| 2604 | ",Consult the virtual host configuration and check if this virtual host should be publicly accessible,unclassified, | |
| 2605 | ,EN-Host header attack,"An attacker can manipulate the Host header as seen by the web application and cause the application to behave in unexpected ways. | |
| 2606 | Developers often resort to the exceedingly untrustworthy HTTP Host header (_SERVER[""HTTP_HOST""] in PHP). | |
| 2607 | Even otherwise-secure applications trust this value enough to write it to the page without HTML-encoding it with code equivalent to: | |
| 2608 | ||
| 2609 | <link href=""http://_SERVER['HOST']"" (Joomla) | |
| 2610 | ...and append secret keys and tokens to links containing it: | |
| 2611 | ||
| 2612 | <a href=""http://_SERVER['HOST']?token=topsecret""> (Django, Gallery, others) | |
| 2613 | ....and even directly import scripts from it: | |
| 2614 | ||
| 2615 | <script src=""http://_SERVER['HOST']/misc/jquery.js?v=1.4.4""> (Various) | |
| 2616 | ||
| 2617 | Host header *********evilhostDx5oMrAd.com was reflected inside a A tag (href attribute). | |
| 2618 | ","The web application should use the SERVER_NAME instead of the Host header. It should also create a dummy vhost that catches all requests with unrecognized Host headers. This can also be done under Nginx by specifying a non-wildcard SERVER_NAME, and under Apache by using a non-wildcard serverName and turning the UseCanonicalName directive on. Consult references for detailed information.",unclassified, | |
| 2619 | ,EN-jQuery cross site scripting,"This page is using an older version of jQuery that is vulnerable to a Cross Site Scripting vulnerability. Many sites are using to select elements using location.hash that allows someone to inject script into the page. This problem was fixed in jQuery 1.6.3 and up. | |
| 2620 | Malicious users may inject JavaScript, VBScript, ActiveX, HTML or Flash into a vulnerable application to fool a user in order to gather data from them. An attacker can steal the session cookie and take over the account, impersonating the user. It is also possible to modify the content of the page presented to the user. | |
| 2621 | ","Update to the latest version of jQuery. | |
| 2622 | More info: http://ma.la/jquery_xss/ | |
| 2623 | http://blog.jquery.com/2011/09/01/jquery-1-6-3-released/",unclassified, | |
| 2624 | ,EN-Login Page password-guessing attack,"A common threat web developers face is a password-guessing attack known as a brute force attack. A brute-force attack is an attempt to discover a password by systematically trying every possible combination of letters, numbers, and symbols until you discover the one correct combination that works. | |
| 2625 | ||
| 2626 | This login page doesn't have any protection against password-guessing attacks (brute force attacks). It's recommended to implement some type of account lockout after a defined number of incorrect password attempts. Consult Web references for more information about fixing this problem. | |
| 2627 | ||
| 2628 | The scanner tested 10 invalid credentials and no account lockout was detected. | |
| 2629 | ","It's recommended to implement some type of account lockout after a defined number of incorrect password attempts. | |
| 2630 | More info: | |
| 2631 | https://www.owasp.org/index.php/Blocking_Brute_Force_Attacks",unclassified, | |
| 2632 | ,EN-Error page web server version disclosure,"By requesting a page that doesn't exist, an error page was returned. This error page contains the web server version number and a list of modules enabled on this server. This information can be used to conduct further attacks. Possible sensitive information disclosure. | |
| 2633 | ","If you are using Apache, you can setup a custom 404 page by following the instructions provided in the References section.",unclassified, | |
| 2634 | ,EN-SSL weak ciphers,"The remote host supports the use of SSL ciphers that offer either weak encryption or no encryption at all. | |
| 2635 | This vulnerability affects Server. | |
| 2636 | ",Reconfigure the affected application to avoid use of weak ciphers.,unclassified, | |
| 2637 | ,EN-CRIME SSL/TLS attack,"Compression Ratio Info-leak Made Easy (CRIME) is a security exploit against secret web cookies over connections using the HTTPS and SPDY protocols that also use data compression. When used to recover the content of secret authentication cookies, it allows an attacker to perform session hijacking on an authenticated web session, allowing the launching of further attacks. | |
| 2638 | ||
| 2639 | CRIME is a client-side attack, but the server can protect the client by refusing to use the feature combinations which can be attacked. For CRIME, the weakness is Deflate compression. This alert is issued if the server accepts Deflate compression. | |
| 2640 | ||
| 2641 | An attacker can perform session hijacking on an authenticated web session, allowing the launching of further attacks. | |
| 2642 | ","CRIME can be defeated by preventing the use of compression, either at the client end, by the browser disabling the compression of HTTPS requests, or by the website preventing the use of data compression on such transactions using the protocol negotiation features of the TLS protocol. As detailed in The Transport Layer Security (TLS) Protocol Version 1.2, the client sends a list of compression algorithms in its ClientHello message, and the server picks one of them and sends it back in its ServerHello message. The server can only choose a compression method the client has offered, so if the client only offers 'none' (no compression), the data will not be compressed. Similarly, since 'no compression' must be allowed by all TLS clients, a server can always refuse to use compression. | |
| 2643 | ||
| 2644 | Web references | |
| 2645 | http://en.wikipedia.org/wiki/CRIME_(security_exploit) | |
| 2646 | http://isecpartners.com/blog/2012/september/details-on-the-crime-attack.aspx",unclassified, | |
| 2647 | ,EN-Insecure transition from HTTPS to HTTP in form post,"This secure (https) page contains a form that is posting to an insecure (http) page. This could confuse users who may think their data is encrypted when in fact it's not. | |
| 2648 | Impact: Possible information disclosure. | |
| 2649 | ",The form target should point to a secure (https) page.,unclassified, | |
| 2650 | ,EN-TRACE method is enabled,"HTTP TRACE method is enabled on this web server. In the presence of other cross-domain vulnerabilities in web browsers, sensitive header information could be read from any domains that support the HTTP TRACE method. | |
| 2651 | ||
| 2652 | Attackers may abuse HTTP TRACE functionality to gain access to information in HTTP headers such as cookies and authentication data. | |
| 2653 | ","Disable TRACE Method on the web server. | |
| 2654 | ||
| 2655 | Web references | |
| 2656 | http://www.w3.org/Protocols/rfc2616/rfc2616-sec9.html | |
| 2657 | http://www.cgisecurity.com/lib/WH-WhitePaper_XST_ebook.pdf",unclassified, | |
| 2658 | ,EN-SSL certificate public key less than 2048 bit,"The product does not sufficiently filter code (control-plane) syntax from user-controlled input (data plane) when that input is used within code that the product generates.When software allows a user's input to contain code syntax, it might be possible for an attacker to craft the code in such a way that it will alter the intended control flow of the software. Such an alteration could lead to arbitrary code execution | |
| 2659 | ","If you have any 1024-bit certificates or certificates with less than 2048-bit key length, you will need to migrate to 2048-bit key length. | |
| 2660 | ||
| 2661 | New Standard: https://www.cabforum.org/wp-content/uploads/Baseline_Requirements_V1.pdf",unclassified, | |
| 2662 | ,EN-Ruby on Rails CookieStore session cookie persistence,"Debido que las credenciales del usuario son considerados información confidencial, siempre debe ser transferido al servidor a través de una conexión segura (HTTPS). | |
| 2663 | ","Currently, there are no known upgrades or patches to correct this vulnerability. It is possible to temporarily mitigate the flaw by implementing the following workaround: switch to a more secure authentication management systems (e.g. ActiveRecordStore).",unclassified, | |
| 2664 | ,EN-Remote Code Execution - ms_08_067 netapi,"The product does not sufficiently filter code (control-plane) syntax from user-controlled input (data plane) when that input is used within code that the product generates.When software allows a user's input to contain code syntax, it might be possible for an attacker to craft the code in such a way that it will alter the intended control flow of the software. Such an alteration could lead to arbitrary code execution | |
| 2665 | ",,high, | |
| 2666 | ,EN-Windows Print Spooler Components Vulnerability - MS13-001,"The software performs operations on a memory buffer, but it can read from or write to a memory location that is outside of the intended boundary of the buffer.Certain languages allow direct addressing of memory locations and do not automatically ensure that these locations are valid for the memory buffer that is being referenced. This can cause read or write operations to be performed on memory locations that may be associated with other variables, data structures, or internal program data. | |
| 2667 | Certain languages allow direct addressing of memory locations and do not automatically ensure that these locations are valid for the memory buffer that is being referenced. This can cause read or write operations to be performed on memory locations that may be associated with other variables, data structures, or internal program data. | |
| 2668 | As a result, an attacker may be able to execute arbitrary code, alter the intended control flow, read sensitive information, or cause the system to crash.",,high, | |
| 2669 | ,ES-Credenciales Repetidas,"Existen multiples credeciales repetidas para un mismo acceso. | |
| 2670 | Tener credenciales repetidas de un mismo servidor o acceso, posibilita a un atacante tener mayor impacto, pues utilizando un mismo password puede ingresar a distintos servicios o áreas",Evitar utilizar mismas credenciales en distintos servicios,high, | |
| 2671 | ,ES-Ftp Anonimo,"Es servicio de FTP posee el usuario : anonymous | |
| 2672 | Los servidores FTP anónimos ofrecen sus servicios libremente a todos los usuarios, permiten acceder a sus archivos sin necesidad de tener un 'USER ID' o una cuenta de usuario. Es la manera más cómoda fuera del servicio web de permitir que todo el mundo tenga acceso a cierta información sin que para ello el administrador de un sistema tenga que crear una cuenta para cada usuario. | |
| 2673 | ||
| 2674 | Si un servidor posee servicio 'FTP anonymous' solamente con teclear la palabra «anonymous», cuando pregunte por tu usuario tendrás acceso a ese sistema. No se necesita ninguna contraseña preestablecida, aunque tendrás que introducir una sólo para ese momento, normalmente se suele utilizar la dirección de correo electrónico propia.",Evitar usuario anonimo,medium, | |
| 2675 | ,ES-Credenciales débiles Tomcat,"Se detectaron credenciales por defecto en servidores Tomcat, ejecutándose con privilegios elevados. | |
| 2676 | Un atacante que intente loguearse con una lista de usuarios por defecto podría comprometer el servicio. | |
| 2677 | En este caso en particular el usuario “admin” es muy común en servidores Tomcat, y cuenta con privilegios para ejecutar código, por lo que debe ser protegido con una contraseña fuerte. | |
| 2678 | ",Aplicar una política de seguridad al servidor que obligue el uso de contraseñas de acuerdo con las políticas de seguridad interna.,high, | |
| 2679 | ,ES-Wpad Spoofing,"En los ambientes Windows ante una falla a resolver un nombre de host, | |
| 2680 | realizan una segunda búsqueda utilizando NetBios. La naturaleza de este | |
| 2681 | pedido realizado utilizando broadcast es inseguro si no se tienen | |
| 2682 | recaudos. | |
| 2683 | ||
| 2684 | Un atacante podría utilizar esta vulnerabilidad para | |
| 2685 | registrar el dominio WPAD en netbios con el fin de redirigir y modificar | |
| 2686 | el tráfico de las workstations con las que comparte el segmento de red. | |
| 2687 | Este ataque podría derivar en la captura de credenciales o hashes que | |
| 2688 | le brinden acceso a sistemas críticos. | |
| 2689 | ","Deshabilitar la configuración automática de proxy en los equipos | |
| 2690 | windows, y registrar el nombre de domino wpad, para que ningún equipo de | |
| 2691 | la red pueda impersonarlo.",high, | |
| 2692 | ,ES-Servicio de Telnet,"Las credenciales de usuario se transmiten sobre un canal sin cifrar (servicio telnet). | |
| 2693 | Un atacante capaz de interceptar el tráfico entre los hosts y el usuario remoto, será capaz de obtener las credenciales utilizadas. | |
| 2694 | ","Reemplazar los servicios que permiten el envío de credenciales en texto plano, por aquellos que lo hacen de forma cifrada. En este caso, existen diferentes alternativas para reemplazar los servicios de administración remota, como por ejemplo ssh o rdp.",medium, | |
| 2695 | ,ES-Tokens cacheados,"Fue posible impersonar diferentes usuarios de dominio, incluido un administrador de dominio, a través de los tokens de acceso cacheados en el servidor. | |
| 2696 | ","No existe un parche para resolver este tipo de situaciones, ya que los tokens de acceso son propios de la arquitectura de Windows. Sin embargo es posible implementar algunas medidas a nivel operativo para mitigar en gran parte el impacto del cacheo de tokens. Recomendamos: | |
| 2697 | > Asegurarse que usuarios con altos privilegios (especialmente administradores) tengan una cuenta específica para tareas de administración y otra para loguearse en sus sistemas. | |
| 2698 | > Ejecutar aquellas tareas que requieran mayores privilegios utilizando la aplicación “RunAs”. | |
| 2699 | > Asegurarse que los Domain Admins sólo sean utilizados para administrar el dominio. Crear diferentes cuentas de dominio y asignarle autorización administrativa solo para la unidad de negocio correspondiente. | |
| 2700 | > Asegurarse que las cuentas administrativas de ambientes de desarrollo y test sean diferentes a las de los sistemas críticos de producción. | |
| 2701 | > Ejecutar los servicios necesarios para el correcto funcionamiento de la unidad de negocio en un equipo diferente al Controlador de Dominio. | |
| 2702 | > Utilizar la opción de Active Directory “Account is sensitive and cannot be delegated” (sólo aplica a los logueos interactivos, pero ayuda a reforzar la seguridad de la cuenta). | |
| 2703 | ||
| 2704 | Referencias: | |
| 2705 | http://carnal0wnage.attackresearch.com/2008/05/token-passing-with-incognito-part-2.html | |
| 2706 | http://pentestmonkey.net/uncategorized/from-local-admin-to-domain-admin | |
| 2707 | http://www.offensive-security.com/metasploit-unleashed/Fun_With_Incognito",high, | |
| 2708 | ,ES-Denegacion de Servicios(DOS),"un ataque de denegación de servicios, también llamado ataque DoS (de las siglas en inglés Denial of Service) o DDoS (de Distributed Denial of Service), es un ataque a un sistema de computadoras o red que causa que un servicio o recurso sea inaccesible a los usuarios legítimos. Normalmente provoca la pérdida de la conectividad de la red por el consumo del ancho de banda de la red de la víctima o sobrecarga de los recursos computacionales del sistema de la víctima | |
| 2709 | ",La forma de prevenirlo: https://www.owasp.org/index.php/Denial_of_Service,high, | |
| 2710 | ,ES-Revelacion de Informacion (Information Disclosure),"Se puede obtener una información sensible del usuario. Esto podría ayudar a un atacante a tener control de una base de datos ó permitirle escalar hacia otro vector de ataque. | |
| 2711 | ","Determinar si esta información debería ser accesible desde la red, sin estar protegida por credenciales.",medium, | |
| 2712 | ,ES-Sitio sin Informar," | |
| 2713 | ",/reclamaciones/home/index. ,unclassified, | |
| 2714 | ,ES-Listado de Directorios,"Muestra directorios que no deberian ser publicos | |
| 2715 | ",Evitar que dichos directorios sean publicos,medium, | |
| 2716 | ,ES-Shell,"Una shell es parte de codigo programado en (PHP,Python,Ruby,etc) que una vez que es subido al host victima, puede ser utilizado para subir, bajar, borrar archivos. | |
| 2717 | ","Evitar entradas que posibiliten subir imagenes o codigo al servidor, sin ser adecuadamente controlado",unclassified, | |
| 2718 | ,ES-Path Disclosure,"Permite ver la ruta a archivos u aplicaciones que no deberian ser mostradas | |
| 2719 | ","Puede solucionarse desactivando los mensajes de error : | |
| 2720 | En PHP modificando el archivo php.ini ( display_errors = 'off' ) | |
| 2721 | En Apache modificando el archivo httpd.conf ( php_flag display_errors off)",unclassified, | |
| 2722 | ,ES-File Upload,"Es posible subir código o imagenes sin ser fitradas adecuadamente. | |
| 2723 | ",Evitar campos para subir archivos que no sean correctamente filtrados,unclassified, | |
| 2724 | ,ES-Metodo Put habilitado (Put File Allow),"Sube, carga o realiza un upload de un recurso especificado (archivo), es el camino más eficiente para subir archivos a un servidor. | |
| 2725 | ","Evitar que el metodo PUT se encuentre con libre acceso a cualquier tipo de usuario, restringir acceso.",unclassified, | |
| 2726 | ,ES-Leer Archivos (Read files)," | |
| 2727 | ",,unclassified, | |
| 2728 | ,ES-Usuarios por defecto(default users),"Se debe evitar utilizar usuarios y contraseñas por defecto, pues el sistema puede quedar suseptible a un ataque de fuerza bruta o de diccionario. | |
| 2729 | ",Cambiar usuarios y contraseñas de acuerdo a las politicas de la empresa,unclassified, | |
| 2730 | ,ES-Sslstrip Attack,"Dado que la página no esta utilizando https para proteger sus credenciales, el panel de ingreso esta implementedo mediante http, y no https, es posible modificar los recursos obtenidos, si el atacante logra intereceptar la comunicación entre ambos sitios. | |
| 2731 | ","Cargar todos los recursos a través de https, para los recursos externos recomendamos incluir los mismo de la siguiente manera src=""//dominio.com/recurso.js"" de esta manera el navegador automaticamete incluye el protocolo http o https segun la conexion inicial que genera.",high, | |
| 2732 | ,ES-Enumerar Usuarios," | |
| 2733 | ",,medium, | |
| 2734 | ,ES-Login User HTTP,"Las credenciales de usuario y contraseña, viajan en texto plano con lo cual un atacante podría obtener dichas credenciales para un posterior acceso | |
| 2735 | ",Utilizar HTTPS para autenticar usuarios,medium, | |
| 2736 | ,ES-Falta de Control de Acceso,"Se puede acceder a parte del sitio sin una sesion valida | |
| 2737 | ",Validar correctamente la sesiones del sitio verifiquen que el usuario poseen una sesion valida,medium, | |
| 2738 | ,ES-Cookie Reutilization,"La cookie puede ser modificada y reutilizada para hacer nuevas consultas o impersonar usuarios | |
| 2739 | ",Evitar ,medium, | |
| 2740 | ,ES-Credenciales Debiles md5,"Se detecto que dentro del request se envía el nombre de usuario y la contraseña hasheada. Si bien la contraseña utiliza una funcion de md5, lo hace sin salt para protegerla. | |
| 2741 | Con lo cual un atacante que la intercepte, puede decifrar el md5 para luego obtener la contraseña en texto plano junto con el usuario para acceder al sistema. | |
| 2742 | ","Aplicar una política de seguridad al servidor que obligue el uso de contraseñas de acuerdo con las políticas de seguridad interna. | |
| 2743 | Se recomienda un cifrado mas robusto con la funcion salt",high, | |
| 2744 | ,ES-CSRF,"Un ataque CSRF fuerza al navegador web validado de una víctima a enviar una petición a una aplicación web vulnerable, la cual entonces realiza la acción elegida a través de la víctima. Al contrario que en los ataques XSS, los cuales explotan la confianza que un usuario tiene en un sitio en particular, el cross site request forgery explota la confianza que un sitio tiene en un usuario en particular. | |
| 2745 | ","Recomendamos la imprementacion de un feature anti-csrf con el fin de autenticar todoslos request,en particual aquellas peticiones sensibles como por ejemplo el cambiode contraseñas y asignacion de roles (dar permisos de administrador a un usuario). El framework de ASP.net cuenta con este feature llamado viewstate (https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)_Prevention_Cheat_Sheet#Viewstate_.28ASP.NET.29)",medium, | |
| 2746 | ,ES-SSL weak ciphers (Cifrado debil),"El servidor remoto soporta el uso de SSL pero ofrece una encriptacion debil | |
| 2747 | ",Reconfigurar el servidor web con un nivel de encriptacion mayor,medium, | |
| 2748 | ,EN-Android Debugging Activated,"The Application has enabled Debugging in it's manifiest. This feature allows an attacker to debug native code and sensitive information could be retrived using this vector | |
| 2749 | ",Set to false debuging features in production releases,unclassified, | |
| 2750 | ,EN-Flash Crossdomain policy,"The application publishes a Flash cross-domain policy which allows access from any domain. | |
| 2751 | ",The policy must include the domains which are allowed by the Flash cross-domain policy,medium, | |
| 2752 | ,EN-Session Token in URL,"The Session token is included in the URL. This could leak the session token | |
| 2753 | ",Session tokens should only be included using safe channels,medium, | |
| 2754 | ,ES-Token de Session en URL,"Información sensible dentro de las URLs puede ser guardado en distintas lugares, por ejemplo en la información del navegador del usuario, en el webserver, o en cualquier proxy o reverse proxy. Las URLs se pueden ver en las pantallas, puede ser guardadas como favoritos o pueden ser enviada entre los usuarios. Esta información puede ser obtenida también como referer, en el histórico de la ultima pagina desde donde se ingresa a otra pagina. Guardar la sesiones en las URLs incrementa que esa información sea captura por un atacante para luego impersonarse como un usuario valido. | |
| 2755 | ",La aplicación debería utilizar otros mecanismos para el envió de las sessiones como cookies o campos ocultos enviados a traves de métodos de POST ,medium, | |
| 2756 | ,ES-Autenticacion sin HTTPS,"La aplicación web no utiliza HTTPS para la autenticación de usuarios al sistema. Las credenciales de usuario y contraseña, viajan en texto plano con lo cual un atacante podría obtener dichas credenciales para un posterior acceso | |
| 2757 | ",Siempre utilizar HTTPS para autenticar usuarios,high, | |
| 2758 | ,Es-Version Obsoleta / Desactualizada,"El servidor se encuentra utilizando una versión de Apache Tomcat MUY desactualizada (Apache Tomcat/4.1.31), la cual es vulnerable a multiples vulnerabilidades publicas. Actualmente la ultima versión estable es la 8.0.9 | |
| 2759 | ","Recomendación actualizar y desactivar los mensajes de error del servidor, que puedan brindar información extra a un atacante",medium, | |
| 2760 | ,ES-Numero de Tarjeta en Texto Plano,"La respuesta del servidor, contiene el numero de tarjeta de crédito y otra información sensible que debería evitarse enviar en texto plano. | |
| 2761 | ",Utilizar HTTPS en todo el sitio en donde la información sensible pueda ser expuesta.,high, | |
| 2762 | ,ES-Server Version Discloure,"El servidor web responde con la version del sistema facilitando a un atacante saber contra que se enfrenta | |
| 2763 | ","Filtrar en las respuestas del servidor, cualquier dato que demuestre la version del servidor y del sistema operativo del mismo",low, | |
| 2764 | ,EN-Insecure crossdomain.xml file,"The browser security model normally prevents web content from one domain from accessing data from another domain. This is commonly known as the ""same origin policy"". URL policy files grant cross-domain permissions for reading data. They permit operations that are not permitted by default. The URL policy file is located, by default, in the root directory of the target server, with the name crossdomain.xml (for example, at www.example.com/crossdomain.xml). | |
| 2765 | ||
| 2766 | When a domain is specified in crossdomain.xml file, the site declares that it is willing to allow the operators of any servers in that domain to obtain any document on the server where the policy file resides. The crossdomain.xml file deployed on this website opens the server to all domains (use of a single asterisk ""*"" as a pure wildcard is supported) like so: | |
| 2767 | <cross-domain-policy> | |
| 2768 | <allow-access-from domain=""*"" /> | |
| 2769 | </cross-domain-policy> | |
| 2770 | This practice is suitable for public servers, but should not be used for sites located behind a firewall because it could permit access to protected areas. It should not be used for sites that require authentication in the form of passwords or cookies. Sites that use the common practice of authentication based on cookies to access private or user-specific data should be especially careful when using cross-domain policy files. | |
| 2771 | ||
| 2772 | Using an insecure cross-domain policy file could expose your site to various attacks. | |
| 2773 | ","Carefully evaluate which sites will be allowed to make cross-domain calls. Consider network topology and any authentication mechanisms that will be affected by the configuration or implementation of the cross-domain policy. | |
| 2774 | ",medium, | |
| 2775 | ,ES-Archivo crossdomain.xml inseguro,"El modelo de seguridad del navegador normalmente previene el contenido web de ser accedido desde otro dominio. Esto comunmente es conocido como ""same origin policy"" (""politica del mismo origen""). Lo politica de archivos URL garantiza acceso cross-dominio para leer datos. Permiten operaciones que no son permitidas por defecto. La politica de acceso de archivo URL esta localizado, por defecto, en el directorio raiz del servidor destino, con el nombre crossdomain.xml (por ejemplo en www.ejemplo.com/crossdomain.xml). | |
| 2776 | ||
| 2777 | Cuando un dominio es especificado en el archivo crossdomain.xml, el sitio declara que esta dispuesto a dar acceso a operadores de cualqueir server en ese dominio para obtener cualquier documento donde la regla reside. El archivo crossdomain.xml desplegado en este servidor web abre el servidor a todos los dominios (uso de un unico asterisco ""*"" de comodin es soportado) Como por ejemplo: | |
| 2778 | <cross-domain-policy> | |
| 2779 | <allow-access-from domain=""*"" /> | |
| 2780 | </cross-domain-policy> | |
| 2781 | ||
| 2782 | Esta practica es correcta para servidores publicos, pero no deberia ser usada en servidores que se encuentran tras un firewall porque puede permitir acceso a areas protejidas. No deberia ser usada para sitios que requieren autenticacion en forma de contraseñas o cookies. | |
| 2783 | ","Detenidamente evaluar que sitios deben tener permitido el acceso cross-dominio. Considerar la topologia de red y todos los mecanismos de autenticacion afectados por la configuracion o implementacion de la politica cross-domain. | |
| 2784 | ",medium, | |
| 2785 | ,EN-BREACH attack,"This web application is potentially vulnerable to the BREACH attack. | |
| 2786 | An attacker with the ability to: | |
| 2787 | Inject partial chosen plaintext into a victim's requests | |
| 2788 | Measure the size of encrypted traffic | |
| 2789 | can leverage information leaked by compression to recover targeted parts of the plaintext. | |
| 2790 | ||
| 2791 | BREACH (Browser Reconnaissance & Exfiltration via Adaptive Compression of Hypertext) is a category of vulnerabilities and not a specific instance affecting a specific piece of software. To be vulnerable, a web application must: | |
| 2792 | ||
| 2793 | Be served from a server that uses HTTP-level compression | |
| 2794 | Reflect user-input in HTTP response bodies | |
| 2795 | Reflect a secret (such as a CSRF token) in HTTP response bodies | |
| 2796 | ||
| 2797 | ||
| 2798 | This alert was issued because the following conditions were met: | |
| 2799 | The page content is served via HTTPS | |
| 2800 | The server is using HTTP-level compression | |
| 2801 | URL encoded GET input next was reflected into the HTTP response body. | |
| 2802 | HTTP response body contains a secret named csrfmiddlewaretoken | |
| 2803 | ","The mitigations are ordered by effectiveness (not by their practicality - as this may differ from one application to another). | |
| 2804 | ||
| 2805 | Disabling HTTP compression | |
| 2806 | Separating secrets from user input | |
| 2807 | Randomizing secrets per request | |
| 2808 | Masking secrets (effectively randomizing by XORing with a random secret per request) | |
| 2809 | Protecting vulnerable pages with CSRF | |
| 2810 | Length hiding (by adding random number of bytes to the responses) | |
| 2811 | Rate-limiting the requests | |
| 2812 | ||
| 2813 | More information http://breachattack.com/",unclassified, | |
| 2814 | ,ES-Archivos de backup en servidor de producción,"La aplicación web tiene multiples archivos de buckup disponibles para ser descargados, los cuales brindan información de la tecnología que se utiliza en el sitio, así como código fuente de las aplicaciones, nombres de usuarios, rutas de acceso y multiple información sensible del mismo. | |
| 2815 | ","Es recomendable aplicar buenas politicas deprotección de información sensible, evitando exponer buckups y otra información del sitio web",high, | |
| 2816 | ,ES-Exposición de información a través del listado de directorios,"Estos directorios no deberian estar publicos, pues exponen información sensible del tipo de tecnología utilizada, código de programación, información sobre rutas de acceso a distintos lugares, particularmente en este caso podemos listar toda la información del servidor sin ningun tipo de restricción | |
| 2817 | ",Siempre evitar que se puedan listar directorios de manera externa y sin permisos,high, | |
| 2818 | ,ES-Archivos con información sensible,"Es posible acceder a archivos con información sensible, podemos ver el ""log error"" y dentro de este rutas de acceso, nombres de usuario, etc . Con lo cual un atacante con tiempo podría intentar obtener credeciales de un servicio ssh, ftp,o similar para luego crackearlo. | |
| 2819 | ||
| 2820 | ",Evitar exponer toda información sensible del sistema,high, | |
| 2821 | ,ES-Revelación de IP interno,"La aplicación expone ip/s interno, con lo cual si por algun vector de ataque un atacante logra acceder al servidor o servicio podría continuar la explotación por dicho vector | |
| 2822 | ",Evitar exponer toda información sensible y privada del sistemadel sistema,low, | |
| 2823 | ,ES-Archivos e información de desarollo en ambientes productivos,"Podemos ver código de programacion, con ejemplos concretos del funcionamiento interno y | |
| 2824 | de la lógica utilizada a la hora de programar, dejando en evidencia | |
| 2825 | informacion como nombres de usuarios, email, dni, telefonos, etc | |
| 2826 | ",Evitar exponer toda información sensible y privada del sistemadel sistema,high, | |
| 2827 | ,ES-Sentencias SQL sin Prepared Statement,"Se detecto que se utilizan una mala implementacion de sentencias SQL concatenando las variables manualmente pudiendo un atacante realizar ataques de SQL Injection | |
| 2828 | ","Utilizar para la sentencia de SQL Prepared Statement | |
| 2829 | Reference: | |
| 2830 | https://www.owasp.org/index.php/Query_Parameterization_Cheat_Sheet#Prepared_Statement_Examples",high, | |
| 2831 | ,ES-Mysql lectura y escritura de archivos,"Es posible utilizar mysql server para la lectura y escritura de archivos en el servidor | |
| 2832 | ","Seguir los siguientes lineamientos para el hardening de Mysql Server | |
| 2833 | https://www.owasp.org/index.php/Testing_for_MySQL#Read_from_a_File",high, | |
| 2834 | ,ES-Servidor productivo y desarrollo,"Por lo que pudimos observar este servidor sirve tanto para produccion como desarrollo, contiene muchisima informacion y pruebas que deberian ser eliminadas. | |
| 2835 | ","Eliminar el contenido de desarrollo, dejar solo lo necesario para el entorno productivo",high, | |
| 2836 | ,EN-Internal IP Address Disclosure,"A string matching an internal IPv4 address was found on this page. This may disclose information about the IP addressing scheme of the internal network. This information can be used to conduct further attacks. | |
| 2837 | ",Prevent this information from being displayed to the user,low, | |
| 2838 | ,ES-Internal IP Address Disclosure,"Una cadena coincidente con una direccion interna de IPv4 fue encontrada en esta pagina. Esto lleva a divulgar informacion sensible acerca del esquema de la red interna. Esta informacion puede ser usada para generar ataques especificos. | |
| 2839 | ",Se recomienda prevenir que esta informacion sea mostrada al usuario,low, | |
| 2840 | ,EN-ASP.NET MAC disabled,"By default, the serialized value is signed by the server to prevent tampering by the user; however, this behavior can be disabled by setting the Page.EnableViewStateMac property to false. If this is done, then an attacker can modify the contents of the ViewState and cause arbitrary data to be deserialized and processed by the server. If the ViewState contains any items that are critical to the server's processing of the request, then this may result in a security exposure. | |
| 2841 | ",Set the Page.EnableViewStateMac property to true on any pages where the ViewState is not currently signed.,low, | |
| 2842 | ,ES-Cisco ASA Error,"El Cisco ASA es vulnerable a un Information Leak (CVE-2014-3392), un atacante podria obtener credenciales em base a un error. | |
| 2843 | ",Actualizar a la ultima version del firmware del CISCO ASA,high, | |
| 2844 | ,ES-Listado de directorios,"Evitar listar directorios, muchas veces a partir de aqui se pueden realizar distintos vectores de ataques, por claves almacenadas en archivos ocultos o por tener acceso a archivos de configuracion. | |
| 2845 | ","Evitar listar directorios, es recomendable que se desabiliten o se resguarden con algun tipo de autenticacion.",low, | |
| 2846 | ,EN-Cifrado Debil (SSL weak ciphers),"El host remoto es compatible con el uso de sistemas de cifrado SSL que ofrecen ya sea cifrado debil o sin cifrado en absoluto. | |
| 2847 | Esta vulnerabilidad afecta Server. | |
| 2848 | ",Vuelva a configurar la aplicacion afectada para evitar el uso de cifrados debiles.,medium, | |
| 2849 | ,EN-Privilege Escalation,"This happens when an attacker has already done reconnaissance and successfully compromised a system by gaining access to a low-level account. In this phase, an attacker wants to have a strong grip on the system and seeks ways to heighten the privileges, either to study the system further or perform an attack.","Change passwords of administrative accounts regularly and enforce strong password policy (e.g. ensure that local administrator accounts have complex, unique passwords across all systems).",medium,https://www.owasp.org/index.php/Testing_for_Privilege_escalation_(OTG-AUTHZ-003) | |
| 2850 | ,EN-Default Credentials,"It was detected that the system has default credentials to access the administration console. These credentials can be obtained from internet sites, for example: technology forums, system manuals, among others.",It is recommended to change all system passwords by default and adapt them to a secure password policy. It is also recommended that all default system accounts be renamed and their passwords changed.,critical,https://www.owasp.org/index.php/Testing_for_default_credentials_(OTG-AUTHN-002) |
| 0 | cwe,name,description,resolution,exploitation,references | |
| 1 | CWE-119,Improper Restriction of Operations within the Bounds of a Memory Buffer (Type: Class),"The software performs operations on a memory buffer, but it can read from or write to a memory location that is outside of the intended boundary of the buffer. | |
| 2 | Certain languages allow direct addressing of memory locations and do not automatically ensure that these locations are valid for the memory buffer that is being referenced. This can cause read or write operations to be performed on memory locations that may be associated with other variables, data structures, or internal program data. | |
| 3 | As a result, an attacker may be able to execute arbitrary code, alter the intended control flow, read sensitive information, or cause the system to crash.",,high,"Writing Secure Code: Chapter 5, ""Public Enemy #1: The Buffer Overrun"" Page 127; Chapter 14, ""Prevent I18N Buffer Overruns"" Page 441 | |
| 4 | Using the Strsafe.h Functions: http://msdn.microsoft.com/en-us/library/ms647466.aspx | |
| 5 | Safe C String Library v1.0.3: http://www.zork.org/safestr/ | |
| 6 | Address Space Layout Randomization in Windows Vista: http://blogs.msdn.com/michael_howard/archive/2006/05/26/address-space-layout-randomization-in-windows-vista.aspx | |
| 7 | Limiting buffer overflows with ExecShield: http://www.redhat.com/magazine/009jul05/features/execshield/ | |
| 8 | PaX: http://en.wikipedia.org/wiki/PaX | |
| 9 | Understanding DEP as a mitigation technology part 1: http://blogs.technet.com/b/srd/archive/2009/06/12/understanding-dep-as-a-mitigation-technology-part-1.aspx | |
| 10 | The Art of Software Security Assessment: Chapter 5, ""Memory Corruption"", Page 167. | |
| 11 | The Art of Software Security Assessment: Chapter 5, ""Protection Mechanisms"", Page 189." | |
| 12 | CWE-123,Write-what-where Condition (Type: Base),"Any condition where the attacker has the ability to write an arbitrary value to an arbitrary location, often as the result of a buffer overflow. | |
| 13 | A buffer overflow condition exists when a program attempts to put more data in a buffer than it can hold, or when a program attempts to put data in a memory area outside of the boundaries of a buffer. The simplest type of error, and the most common cause of buffer overflows, is the ""classic"" case in which the program copies the buffer without restricting how much is copied. Other variants exist, but the existence of a classic overflow strongly suggests that the programmer is not considering even the most basic of security protections.",,high,"24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89" | |
| 14 | CWE-129,Improper Validation of Array Index (Type: Base),"The product uses untrusted input when calculating or using an array index, but the product does not validate or incorrectly validates the index to ensure the index references a valid position within the array. | |
| 15 | This typically occurs when the pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used. This may result in exposure of sensitive information or possibly a crash.",,high,"Writing Secure Code: Chapter 5, ""Array Indexing Errors"" Page 144 | |
| 16 | Top 25 Series - Rank 14 - Improper Validation of Array Index: http://blogs.sans.org/appsecstreetfighter/2010/03/12/top-25-series-rank-14-improper-validation-of-array-index/ | |
| 17 | Address Space Layout Randomization in Windows Vista: http://blogs.msdn.com/michael_howard/archive/2006/05/26/address-space-layout-randomization-in-windows-vista.aspx | |
| 18 | PaX: http://en.wikipedia.org/wiki/PaX | |
| 19 | Understanding DEP as a mitigation technology part 1: http://blogs.technet.com/b/srd/archive/2009/06/12/understanding-dep-as-a-mitigation-technology-part-1.aspx | |
| 20 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 21 | 24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89" | |
| 22 | CWE-194,Unexpected Sign Extension (Type: Base),"The software performs an operation on a number that causes it to be sign extended when it is transformed into a larger data type. When the original number is negative, this can produce unexpected values that lead to resultant weaknesses. | |
| 23 | This can happen in signed and unsigned cases.",,high,"C Language Issues for Application Security: http://www.informit.com/articles/article.aspx?p=686170&seqNum=6 | |
| 24 | Integral Security: http://www.ddj.com/security/193501774" | |
| 25 | CWE-20,Improper Input Validation (Type: Class),"The product does not validate or incorrectly validates input that can affect the control flow or data flow of a program. | |
| 26 | When software does not validate input properly, an attacker is able to craft the input in a form that is not expected by the rest of the application. This will lead to parts of the system receiving unintended input, which may result in altered control flow, arbitrary control of a resource, or arbitrary code execution.",,high,"Input Validation with ESAPI - Very Important: http://manicode.blogspot.com/2008/08/input-validation-with-esapi.html | |
| 27 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 28 | Hacking Exposed Web Applications, Second Edition: Input Validation Attacks | |
| 29 | Input validation or output filtering, which is better?: http://jeremiahgrossman.blogspot.com/2007/01/input-validation-or-output-filtering.html | |
| 30 | The importance of input validation: http://searchsoftwarequality.techtarget.com/tip/0,289483,sid92_gci1214373,00.html | |
| 31 | Writing Secure Code: Chapter 10, ""All Input Is Evil!"" Page 341" | |
| 32 | CWE-200,Information Exposure (Type: Class),"An information exposure is the intentional or unintentional disclosure of information to an actor that is not explicitly authorized to have access to that information. | |
| 33 | The information either | |
| 34 | is regarded as sensitive within the product's own functionality, such as a private message; or | |
| 35 | provides information about the product or its environment that could be useful in an attack but is normally not available to the attacker, such as the installation path of a product that is remotely accessible. | |
| 36 | Many information exposures are resultant (e.g. PHP script error revealing the full path of the program), but they can also be primary (e.g. timing discrepancies in cryptography). There are many different types of problems that involve information exposures. Their severity can range widely depending on the type of information that is revealed.",,high,Mobile App Top 10 List: http://www.veracode.com/blog/2010/12/mobile-app-top-10-list/ | |
| 37 | CWE-209,Information Exposure Through an Error Message (Type: Base),"The software generates an error message that includes sensitive information about its environment, users, or associated data. | |
| 38 | The sensitive information may be valuable information on its own (such as a password), or it may be useful for launching other, more deadly attacks. If an attack fails, an attacker may use error information provided by the server to launch another more focused attack. For example, an attempt to exploit a path traversal weakness (CWE-22) might yield the full pathname of the installed application. In turn, this could be used to select the proper number of "".."" sequences to navigate to the targeted file. An attack using SQL injection (CWE-89) might not initially succeed, but an error message could reveal the malformed query, which would expose query logic and possibly even passwords or other sensitive information used within the query.",,high,"Information Leakage: http://www.webappsec.org/projects/threat/classes/information_leakage.shtml | |
| 39 | Secure Programming with Static Analysis: Section 9.2, page 326. | |
| 40 | Writing Secure Code: Chapter 16, ""General Good Practices."" Page 415 | |
| 41 | 24 Deadly Sins of Software Security: ""Sin 11: Failure to Handle Errors Correctly."" Page 183 | |
| 42 | 24 Deadly Sins of Software Security: ""Sin 12: Information Leakage."" Page 191 | |
| 43 | Top 25 Series - Rank 16 - Information Exposure Through an Error Message: http://software-security.sans.org/blog/2010/03/17/top-25-series-rank-16-information-exposure-through-an-error-message | |
| 44 | The Art of Software Security Assessment: Chapter 3, ""Overly Verbose Error Messages"", Page 75." | |
| 45 | CWE-234,Failure to Handle Missing Parameter (Type: Variant),"If too few arguments are sent to a function, the function will still pop the expected number of arguments from the stack. Potentially, a variable number of arguments could be exhausted in a function as well. | |
| 46 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,high, | |
| 47 | CWE-242,Use of Inherently Dangerous Function (Type: Base),"The program calls a function that can never be guaranteed to work safely. | |
| 48 | Certain functions behave in dangerous ways regardless of how they are used. Functions in this category were often implemented without taking security concerns into account. The gets() function is unsafe because it does not perform bounds checking on the size of its input. An attacker can easily send arbitrarily-sized input to gets() and overflow the destination buffer. Similarly, the >> operator is unsafe to use when reading into a statically-allocated character array because it does not perform bounds checking on the size of its input. An attacker can easily send arbitrarily-sized input to the >> operator and overflow the destination buffer.",,high,"Herb Schildt's C++ Programming Cookbook: Chapter 5. Working with I/O | |
| 49 | Writing Secure Code: Chapter 5, ""gets and fgets"" Page 163" | |
| 50 | CWE-243,Creation of chroot Jail Without Changing Working Directory (Type: Variant),"The program uses the chroot() system call to create a jail, but does not change the working directory afterward. This does not prevent access to files outside of the jail. | |
| 51 | Improper use of chroot() may allow attackers to escape from the chroot jail. The chroot() function call does not change the process's current working directory, so relative paths may still refer to file system resources outside of the chroot jail after chroot() has been called.",,high, | |
| 52 | CWE-268,Privilege Chaining (Type: Base),"Two distinct privileges, roles, capabilities, or rights can be combined in a way that allows an entity to perform unsafe actions that would not be allowed without that combination. | |
| 53 | Just as neglecting to include functionality for the management of password aging is dangerous, so is allowing password aging to continue unchecked. Passwords must be given a maximum life span, after which a user is required to update with a new and different password.",,high,Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 54 | CWE-271,Privilege Dropping / Lowering Errors (Type: Class),"The software does not drop privileges before passing control of a resource to an actor that does not have those privileges. | |
| 55 | In some contexts, a system executing with elevated permissions will hand off a process/file/etc. to another process or user. If the privileges of an entity are not reduced, then elevated privileges are spread throughout a system and possibly to an attacker.",,high,"24 Deadly Sins of Software Security: ""Sin 16: Executing Code With Too Much Privilege."" Page 243 | |
| 56 | The Art of Software Security Assessment: Chapter 9, ""Dropping Privileges Permanently"", Page 479." | |
| 57 | CWE-285,Improper Authorization (Type: Class),"The software does not perform or incorrectly performs an authorization check when an actor attempts to access a resource or perform an action. | |
| 58 | Assuming a user with a given identity, authorization is the process of determining whether that user can access a given resource, based on the user's privileges and any permissions or other access-control specifications that apply to the resource. | |
| 59 | When access control checks are not applied consistently - or not at all - users are able to access data or perform actions that they should not be allowed to perform. This can lead to a wide range of problems, including information exposures, denial of service, and arbitrary code execution.",,high,"Role Based Access Control and Role Based Security: http://csrc.nist.gov/groups/SNS/rbac/ | |
| 60 | Writing Secure Code: Chapter 4, ""Authorization"" Page 114; Chapter 6, ""Determining Appropriate Access Control"" Page 171 | |
| 61 | Top 25 Series - Rank 5 - Improper Access Control (Authorization): http://blogs.sans.org/appsecstreetfighter/2010/03/04/top-25-series-rank-5-improper-access-control-authorization/ | |
| 62 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 63 | Authentication using JAAS: http://www.javaranch.com/journal/2008/04/authentication-using-JAAS.html | |
| 64 | The Art of Software Security Assessment: Chapter 2, ""Common Vulnerabilities of Authorization"", Page 39. | |
| 65 | The Art of Software Security Assessment: Chapter 11, ""ACL Inheritance"", Page 649." | |
| 66 | CWE-291,Reliance on IP Address for Authentication (Type: Variant),"The software uses an IP address for authentication. | |
| 67 | IP addresses can be easily spoofed. Attackers can forge the source IP address of the packets they send, but response packets will return to the forged IP address. To see the response packets, the attacker has to sniff the traffic between the victim machine and the forged IP address. In order to accomplish the required sniffing, attackers typically attempt to locate themselves on the same subnet as the victim machine. Attackers may be able to circumvent this requirement by using source routing, but source routing is disabled across much of the Internet today. In summary, IP address verification can be a useful part of an authentication scheme, but it should not be the single factor required for authentication.",,high, | |
| 68 | CWE-292,DEPRECATED (Duplicate): Trusting Self-reported DNS Name (Type: Variant),"This entry has been deprecated because it was a duplicate of CWE-350. All content has been transferred to CWE-350. | |
| 69 | IP addresses can be easily spoofed. Attackers can forge the source IP address of the packets they send, but response packets will return to the forged IP address. To see the response packets, the attacker has to sniff the traffic between the victim machine and the forged IP address. In order to accomplish the required sniffing, attackers typically attempt to locate themselves on the same subnet as the victim machine. Attackers may be able to circumvent this requirement by using source routing, but source routing is disabled across much of the Internet today. In summary, IP address verification can be a useful part of an authentication scheme, but it should not be the single factor required for authentication.",,high, | |
| 70 | CWE-293,Using Referer Field for Authentication (Type: Variant),"The referer field in HTTP requests can be easily modified and, as such, is not a valid means of message integrity checking. | |
| 71 | IP addresses can be easily spoofed. Attackers can forge the source IP address of the packets they send, but response packets will return to the forged IP address. To see the response packets, the attacker has to sniff the traffic between the victim machine and the forged IP address. In order to accomplish the required sniffing, attackers typically attempt to locate themselves on the same subnet as the victim machine. Attackers may be able to circumvent this requirement by using source routing, but source routing is disabled across much of the Internet today. In summary, IP address verification can be a useful part of an authentication scheme, but it should not be the single factor required for authentication.",,high,"The Art of Software Security Assessment: Chapter 17, ""Referer Request Header"", Page 1030." | |
| 72 | CWE-294,Authentication Bypass by Capture-replay (Type: Base),"A capture-replay flaw exists when the design of the software makes it possible for a malicious user to sniff network traffic and bypass authentication by replaying it to the server in question to the same effect as the original message (or with minor changes). | |
| 73 | Capture-replay attacks are common and can be difficult to defeat without cryptography. They are a subset of network injection attacks that rely on observing previously-sent valid commands, then changing them slightly if necessary and resending the same commands to the server.",,high, | |
| 74 | CWE-297,Improper Validation of Certificate with Host Mismatch (Type: Variant),"The software communicates with a host that provides a certificate, but the software does not properly ensure that the certificate is actually associated with that host. | |
| 75 | Even if a certificate is well-formed, signed, and follows the chain of trust, it may simply be a valid certificate for a different site than the site that the software is interacting with. If the certificate's host-specific data is not properly checked - such as the Common Name (CN) in the Subject or the Subject Alternative Name (SAN) extension of an X.509 certificate - it may be possible for a redirection or spoofing attack to allow a malicious host with a valid certificate to provide data, impersonating a trusted host. In order to ensure data integrity, the certificate must be valid and it must pertain to the site that is being accessed. | |
| 76 | Even if the software attempts to check the hostname, it is still possible to incorrectly check the hostname. For example, attackers could create a certificate with a name that begins with a trusted name followed by a NUL byte, which could cause some string-based comparisons to only examine the portion that contains the trusted name.",,high,"The Most Dangerous Code in the World: Validating SSL Certificates in Non-Browser Software: http://www.cs.utexas.edu/~shmat/shmat_ccs12.pdf | |
| 77 | Why Eve and Mallory Love Android: An Analysis of Android SSL (In)Security: http://www2.dcsec.uni-hannover.de/files/android/p50-fahl.pdf | |
| 78 | Secure programming with the OpenSSL API, Part 2: Secure handshake: http://www.ibm.com/developerworks/library/l-openssl2/index.html | |
| 79 | An Introduction to OpenSSL Programming (Part I): http://www.rtfm.com/openssl-examples/part1.pdf | |
| 80 | 24 Deadly Sins of Software Security: ""Sin 23: Improper Use of PKI, Especially SSL."" Page 347" | |
| 81 | CWE-308,Use of Single-factor Authentication (Type: Base),"The use of single-factor authentication can lead to unnecessary risk of compromise when compared with the benefits of a dual-factor authentication scheme. | |
| 82 | While the use of multiple authentication schemes is simply piling on more complexity on top of authentication, it is inestimably valuable to have such measures of redundancy. The use of weak, reused, and common passwords is rampant on the internet. Without the added protection of multiple authentication schemes, a single mistake can result in the compromise of an account. For this reason, if multiple schemes are possible and also easy to use, they should be implemented and required.",,high, | |
| 83 | CWE-321,Use of Hard-coded Cryptographic Key (Type: Base),"The use of a hard-coded cryptographic key significantly increases the possibility that encrypted data may be recovered. | |
| 84 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 85 | The '...' manipulation is useful for bypassing some path traversal protection schemes. On some Windows systems, it is equivalent to ""..\.."" and might bypass checks that assume only two dots are valid. Incomplete filtering, such as removal of ""./"" sequences, can ultimately produce valid "".."" sequences due to a collapse into unsafe value (CWE-182).",,high, | |
| 86 | CWE-322,Key Exchange without Entity Authentication (Type: Base),"The software performs a key exchange with an actor without verifying the identity of that actor. | |
| 87 | Performing a key exchange will preserve the integrity of the information sent between two entities, but this will not guarantee that the entities are who they claim they are. This may enable a set of ""man-in-the-middle"" attacks. Typically, this involves a victim client that contacts a malicious server that is impersonating a trusted server. If the client skips authentication or ignores an authentication failure, the malicious server may request authentication information from the user. The malicious server can then use this authentication information to log in to the trusted server using the victim's credentials, sniff traffic between the victim and trusted server, etc.",,high,"24 Deadly Sins of Software Security: ""Sin 23: Improper Use of PKI, Especially SSL."" Page 347 | |
| 88 | The Art of Software Security Assessment: Chapter 2, ""Untrustworthy Credentials"", Page 37." | |
| 89 | CWE-323,"Reusing a Nonce, Key Pair in Encryption (Type: Base)","Nonces should be used for the present occasion and only once. | |
| 90 | Performing a key exchange will preserve the integrity of the information sent between two entities, but this will not guarantee that the entities are who they claim they are. This may enable a set of ""man-in-the-middle"" attacks. Typically, this involves a victim client that contacts a malicious server that is impersonating a trusted server. If the client skips authentication or ignores an authentication failure, the malicious server may request authentication information from the user. The malicious server can then use this authentication information to log in to the trusted server using the victim's credentials, sniff traffic between the victim and trusted server, etc.",,high, | |
| 91 | CWE-360,Trust of System Event Data (Type: Base),"Security based on event locations are insecure and can be spoofed. | |
| 92 | Events are a messaging system which may provide control data to programs listening for events. Events often do not have any type of authentication framework to allow them to be verified from a trusted source. Any application, in Windows, on a given desktop can send a message to any window on the same desktop. There is no authentication framework for these messages. Therefore, any message can be used to manipulate any process on the desktop if the process does not check the validity and safeness of those messages.",,high, | |
| 93 | CWE-378,Creation of Temporary File With Insecure Permissions (Type: Base),"Opening temporary files without appropriate measures or controls can leave the file, its contents and any function that it impacts vulnerable to attack. | |
| 94 | If the revocation status of a certificate is not checked before each action that requires privileges, the system may be subject to a race condition. If a certificate is revoked after the initial check, all subsequent actions taken with the owner of the revoked certificate will lose all benefits guaranteed by the certificate. In fact, it is almost certain that the use of a revoked certificate indicates malicious activity.",,high, | |
| 95 | CWE-416,Use After Free (Type: Base),"Referencing memory after it has been freed can cause a program to crash, use unexpected values, or execute code. | |
| 96 | The use of previously-freed memory can have any number of adverse consequences, ranging from the corruption of valid data to the execution of arbitrary code, depending on the instantiation and timing of the flaw. The simplest way data corruption may occur involves the system's reuse of the freed memory. Use-after-free errors have two common and sometimes overlapping causes: | |
| 97 | Error conditions and other exceptional circumstances. | |
| 98 | Confusion over which part of the program is responsible for freeing the memory. | |
| 99 | In this scenario, the memory in question is allocated to another pointer validly at some point after it has been freed. The original pointer to the freed memory is used again and points to somewhere within the new allocation. As the data is changed, it corrupts the validly used memory; this induces undefined behavior in the process. | |
| 100 | If the newly allocated data chances to hold a class, in C++ for example, various function pointers may be scattered within the heap data. If one of these function pointers is overwritten with an address to valid shellcode, execution of arbitrary code can be achieved.",,high,"24 Deadly Sins of Software Security: ""Sin 8: C++ Catastrophes."" Page 143" | |
| 101 | CWE-457,Use of Uninitialized Variable (Type: Variant),"The code uses a variable that has not been initialized, leading to unpredictable or unintended results. | |
| 102 | In some languages such as C and C++, stack variables are not initialized by default. They generally contain junk data with the contents of stack memory before the function was invoked. An attacker can sometimes control or read these contents. In other languages or conditions, a variable that is not explicitly initialized can be given a default value that has security implications, depending on the logic of the program. The presence of an uninitialized variable can sometimes indicate a typographic error in the code.",,high,"Exploiting Uninitialized Data: http://www.felinemenace.org/~mercy/papers/UBehavior/UBehavior.zip | |
| 103 | MS08-014 : The Case of the Uninitialized Stack Variable Vulnerability: http://blogs.technet.com/swi/archive/2008/03/11/the-case-of-the-uninitialized-stack-variable-vulnerability.aspx | |
| 104 | 24 Deadly Sins of Software Security: ""Sin 8: C++ Catastrophes."" Page 143 | |
| 105 | The Art of Software Security Assessment: Chapter 7, ""Variable Initialization"", Page 312." | |
| 106 | CWE-467,Use of sizeof() on a Pointer Type (Type: Variant),"The code calls sizeof() on a malloced pointer type, which always returns the wordsize/8. This can produce an unexpected result if the programmer intended to determine how much memory has been allocated. | |
| 107 | Data-structure sentinels are often used to mark the structure of data. A common example of this is the null character at the end of strings or a special sentinel to mark the end of a linked list. It is dangerous to allow this type of control data to be easily accessible. Therefore, it is important to protect from the addition or modification of sentinels.",,high,EXP01-A. Do not take the sizeof a pointer to determine the size of a type: https://www.securecoding.cert.org/confluence/display/seccode/EXP01-A.+Do+not+take+the+sizeof+a+pointer+to+determine+the+size+of+a+type | |
| 108 | CWE-486,Comparison of Classes by Name (Type: Variant),"The program compares classes by name, which can cause it to use the wrong class when multiple classes can have the same name. | |
| 109 | If the decision to trust the methods and data of an object is based on the name of a class, it is possible for malicious users to send objects of the same name as trusted classes and thereby gain the trust afforded to known classes and types.",,high, | |
| 110 | CWE-493,Critical Public Variable Without Final Modifier (Type: Variant),"The product has a critical public variable that is not final, which allows the variable to be modified to contain unexpected values. | |
| 111 | If a field is non-final and public, it can be changed once the value is set by any function that has access to the class which contains the field. This could lead to a vulnerability if other parts of the program make assumptions about the contents of that field.",,high, | |
| 112 | CWE-499,Serializable Class Containing Sensitive Data (Type: Variant),"The code contains a class with sensitive data, but the class does not explicitly deny serialization. The data can be accessed by serializing the class through another class. | |
| 113 | Serializable classes are effectively open classes since data cannot be hidden in them. Classes that do not explicitly deny serialization can be serialized by any other class, which can then in turn use the data stored inside it.",,high, | |
| 114 | CWE-500,Public Static Field Not Marked Final (Type: Variant),"An object contains a public static field that is not marked final, which might allow it to be modified in unexpected ways. | |
| 115 | Public static variables can be read without an accessor and changed without a mutator by any classes in the application.",,high, | |
| 116 | CWE-515,Covert Storage Channel (Type: Base),"A covert storage channel transfers information through the setting of bits by one program and the reading of those bits by another. What distinguishes this case from that of ordinary operation is that the bits are used to convey encoded information. | |
| 117 | Covert storage channels occur when out-of-band data is stored in messages for the purpose of memory reuse. Covert channels are frequently classified as either storage or timing channels. Examples would include using a file intended to hold only audit information to convey user passwords--using the name of a file or perhaps status bits associated with it that can be read by all users to signal the contents of the file. Steganography, concealing information in such a manner that no one but the intended recipient knows of the existence of the message, is a good example of a covert storage channel.",,high, | |
| 118 | CWE-639,Authorization Bypass Through User-Controlled Key (Type: Base),"The system's authorization functionality does not prevent one user from gaining access to another user's data or record by modifying the key value identifying the data. | |
| 119 | Retrieval of a user record occurs in the system based on some key value that is under user control. The key would typically identify a user related record stored in the system and would be used to lookup that record for presentation to the user. It is likely that an attacker would have to be an authenticated user in the system. However, the authorization process would not properly check the data access operation to ensure that the authenticated user performing the operation has sufficient entitlements to perform the requested data access, hence bypassing any other authorization checks present in the system. One manifestation of this weakness would be if a system used sequential or otherwise easily guessable session ids that would allow one user to easily switch to another user's session and read/modify their data.",,high, | |
| 120 | CWE-640,Weak Password Recovery Mechanism for Forgotten Password (Type: Base),"The software contains a mechanism for users to recover or change their passwords without knowing the original password, but the mechanism is weak. | |
| 121 | It is common for an application to have a mechanism that provides a means for a user to gain access to their account in the event they forget their password. Very often the password recovery mechanism is weak, which has the effect of making it more likely that it would be possible for a person other than the legitimate system user to gain access to that user's account. | |
| 122 | This weakness may be that the security question is too easy to guess or find an answer to (e.g. because it is too common). Or there might be an implementation weakness in the password recovery mechanism code that may for instance trick the system into e-mailing the new password to an e-mail account other than that of the user. There might be no throttling done on the rate of password resets so that a legitimate user can be denied service by an attacker if an attacker tries to recover their password in a rapid succession. The system may send the original password to the user rather than generating a new temporary password. In summary, password recovery functionality, if not carefully designed and implemented can often become the system's weakest link that can be misused in a way that would allow an attacker to gain unauthorized access to the system. Weak password recovery schemes completely undermine a strong password authentication scheme.",,high,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 123 | CWE-642,External Control of Critical State Data (Type: Class),"The software stores security-critical state information about its users, or the software itself, in a location that is accessible to unauthorized actors. | |
| 124 | If an attacker can modify the state information without detection, then it could be used to perform unauthorized actions or access unexpected resources, since the application programmer does not expect that the state can be changed. | |
| 125 | State information can be stored in various locations such as a cookie, in a hidden web form field, input parameter or argument, an environment variable, a database record, within a settings file, etc. All of these locations have the potential to be modified by an attacker. When this state information is used to control security or determine resource usage, then it may create a vulnerability. For example, an application may perform authentication, then save the state in an ""authenticated=true"" cookie. An attacker may simply create this cookie in order to bypass the authentication.",,high,"Top 10 2007-Insecure Direct Object Reference: http://www.owasp.org/index.php/Top_10_2007-A4 | |
| 126 | HMAC: http://en.wikipedia.org/wiki/Hmac | |
| 127 | 24 Deadly Sins of Software Security: ""Sin 4: Use of Magic URLs, Predictable Cookies, and Hidden Form Fields."" Page 75" | |
| 128 | CWE-643,Improper Neutralization of Data within XPath Expressions (XPath Injection) (Type: Base),"The software uses external input to dynamically construct an XPath expression used to retrieve data from an XML database, but it does not neutralize or incorrectly neutralizes that input. This allows an attacker to control the structure of the query. | |
| 129 | The net effect is that the attacker will have control over the information selected from the XML database and may use that ability to control application flow, modify logic, retrieve unauthorized data, or bypass important checks (e.g. authentication).",,high,"XPath Injection: http://www.webappsec.org/projects/threat/classes/xpath_injection.shtml | |
| 130 | The Art of Software Security Assessment: Chapter 17, ""XPath Injection"", Page 1070." | |
| 131 | CWE-644,Improper Neutralization of HTTP Headers for Scripting Syntax (Type: Variant),"The application does not neutralize or incorrectly neutralizes web scripting syntax in HTTP headers that can be used by web browser components that can process raw headers, such as Flash. | |
| 132 | An attacker may be able to conduct cross-site scripting and other attacks against users who have these components enabled. | |
| 133 | If an application does not neutralize user controlled data being placed in the header of an HTTP response coming from the server, the header may contain a script that will get executed in the client's browser context, potentially resulting in a cross site scripting vulnerability or possibly an HTTP response splitting attack. It is important to carefully control data that is being placed both in HTTP response header and in the HTTP response body to ensure that no scripting syntax is present, taking various encodings into account.",,high, | |
| 134 | CWE-645,Overly Restrictive Account Lockout Mechanism (Type: Base),"The software contains an account lockout protection mechanism, but the mechanism is too restrictive and can be triggered too easily. This allows attackers to deny service to legitimate users by causing their accounts to be locked out. | |
| 135 | Account lockout is a security feature often present in applications as a countermeasure to the brute force attack on the password based authentication mechanism of the system. After a certain number of failed login attempts, the users' account may be disabled for a certain period of time or until it is unlocked by an administrator. Other security events may also possibly trigger account lockout. However, an attacker may use this very security feature to deny service to legitimate system users. It is therefore important to ensure that the account lockout security mechanism is not overly restrictive.",,high, | |
| 136 | CWE-646,Reliance on File Name or Extension of Externally-Supplied File (Type: Variant),"The software allows a file to be uploaded, but it relies on the file name or extension of the file to determine the appropriate behaviors. This could be used by attackers to cause the file to be misclassified and processed in a dangerous fashion. | |
| 137 | An application might use the file name or extension of of a user-supplied file to determine the proper course of action, such as selecting the correct process to which control should be passed, deciding what data should be made available, or what resources should be allocated. If the attacker can cause the code to misclassify the supplied file, then the wrong action could occur. For example, an attacker could supply a file that ends in a "".php.gif"" extension that appears to be a GIF image, but would be processed as PHP code. In extreme cases, code execution is possible, but the attacker could also cause exhaustion of resources, denial of service, exposure of debug or system data (including application source code), or being bound to a particular server side process. This weakness may be due to a vulnerability in any of the technologies used by the web and application servers, due to misconfiguration, or resultant from another flaw in the application itself.",,high, | |
| 138 | CWE-647,Use of Non-Canonical URL Paths for Authorization Decisions (Type: Variant),"The software defines policy namespaces and makes authorization decisions based on the assumption that a URL is canonical. This can allow a non-canonical URL to bypass the authorization. | |
| 139 | If an application defines policy namespaces and makes authorization decisions based on the URL, but it does not require or convert to a canonical URL before making the authorization decision, then it opens the application to attack. For example, if the application only wants to allow access to http://www.example.com/mypage, then the attacker might be able to bypass this restriction using equivalent URLs such as: | |
| 140 | http://WWW.EXAMPLE.COM/mypage | |
| 141 | http://www.example.com/%6Dypage (alternate encoding) | |
| 142 | http://192.168.1.1/mypage (IP address) | |
| 143 | http://www.example.com/mypage/ (trailing /) | |
| 144 | http://www.example.com:80/mypage | |
| 145 | Therefore it is important to specify access control policy that is based on the path information in some canonical form with all alternate encodings rejected (which can be accomplished by a default deny rule).",,high, | |
| 146 | CWE-649,Reliance on Obfuscation or Encryption of Security-Relevant Inputs without Integrity Checking (Type: Base),"The software uses obfuscation or encryption of inputs that should not be mutable by an external actor, but the software does not use integrity checks to detect if those inputs have been modified. | |
| 147 | When an application relies on obfuscation or incorrectly applied / weak encryption to protect client-controllable tokens or parameters, that may have an effect on the user state, system state, or some decision made on the server. Without protecting the tokens/parameters for integrity, the application is vulnerable to an attack where an adversary blindly traverses the space of possible values of the said token/parameter in order to attempt to gain an advantage. The goal of the attacker is to find another admissible value that will somehow elevate his or her privileges in the system, disclose information or change the behavior of the system in some way beneficial to the attacker. If the application does not protect these critical tokens/parameters for integrity, it will not be able to determine that these values have been tampered with. Measures that are used to protect data for confidentiality should not be relied upon to provide the integrity service.",,high, | |
| 148 | CWE-650,Trusting HTTP Permission Methods on the Server Side (Type: Variant),"The server contains a protection mechanism that assumes that any URI that is accessed using HTTP GET will not cause a state change to the associated resource. This might allow attackers to bypass intended access restrictions and conduct resource modification and deletion attacks, since some applications allow GET to modify state. | |
| 149 | An application may disallow the HTTP requests to perform DELETE, PUT and POST operations on the resource representation, believing that it will be enough to prevent unintended resource alterations. Even though the HTTP GET specification requires that GET requests should not have side effects, there is nothing in the HTTP protocol itself that prevents the HTTP GET method from performing more than just query of the data. For instance, it is a common practice with REST based Web Services to have HTTP GET requests modifying resources on the server side. Whenever that happens however, the access control needs to be properly enforced in the application. No assumptions should be made that only HTTP DELETE, PUT, and POST methods have the power to alter the representation of the resource being accessed in the request.",,high, | |
| 150 | CWE-652,Improper Neutralization of Data within XQuery Expressions (XQuery Injection) (Type: Base),"The software uses external input to dynamically construct an XQuery expression used to retrieve data from an XML database, but it does not neutralize or incorrectly neutralizes that input. This allows an attacker to control the structure of the query. | |
| 151 | The net effect is that the attacker will have control over the information selected from the XML database and may use that ability to control application flow, modify logic, retrieve unauthorized data, or bypass important checks (e.g. authentication).",,high, | |
| 152 | CWE-676,Use of Potentially Dangerous Function (Type: Base),"The program invokes a potentially dangerous function that could introduce a vulnerability if it is used incorrectly, but the function can also be used safely. | |
| 153 | Typically, a product defines its control sphere within the code itself, or through configuration by the product's administrator. In some cases, an external party can change the definition of the control sphere. This is typically a resultant weakness.",,high,"Security Development Lifecycle (SDL) Banned Function Calls: http://msdn.microsoft.com/en-us/library/bb288454.aspx | |
| 154 | Writing Secure Code: Chapter 5, ""Safe String Handling"" Page 156, 160 | |
| 155 | The Art of Software Security Assessment: Chapter 8, ""C String Handling"", Page 388." | |
| 156 | CWE-682,Incorrect Calculation (Type: Class),"The software performs a calculation that generates incorrect or unintended results that are later used in security-critical decisions or resource management.. | |
| 157 | When software performs a security-critical calculation incorrectly, it might lead to incorrect resource allocations, incorrect privilege assignments, or failed comparisons among other things. Many of the direct results of an incorrect calculation can lead to even larger problems such as failed protection mechanisms or even arbitrary code execution.",,high,"SafeInt: http://safeint.codeplex.com/ | |
| 158 | 24 Deadly Sins of Software Security: ""Sin 7: Integer Overflows."" Page 119 | |
| 159 | The Art of Software Security Assessment: Chapter 6, ""Signed Integer Boundaries"", Page 220." | |
| 160 | CWE-78,Improper Neutralization of Special Elements used in an OS Command (OS Command Injection) (Type: Base),"The software constructs all or part of an OS command using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended OS command when it is sent to a downstream component.. | |
| 161 | This could allow attackers to execute unexpected, dangerous commands directly on the operating system. This weakness can lead to a vulnerability in environments in which the attacker does not have direct access to the operating system, such as in web applications. Alternately, if the weakness occurs in a privileged program, it could allow the attacker to specify commands that normally would not be accessible, or to call alternate commands with privileges that the attacker does not have. The problem is exacerbated if the compromised process does not follow the principle of least privilege, because the attacker-controlled commands may run with special system privileges that increases the amount of damage. | |
| 162 | There are at least two subtypes of OS command injection: | |
| 163 | The application intends to execute a single, fixed program that is under its own control. It intends to use externally-supplied inputs as arguments to that program. For example, the program might use system(""nslookup [HOSTNAME]"") to run nslookup and allow the user to supply a HOSTNAME, which is used as an argument. Attackers cannot prevent nslookup from executing. However, if the program does not remove command separators from the HOSTNAME argument, attackers could place the separators into the arguments, which allows them to execute their own program after nslookup has finished executing. | |
| 164 | The application accepts an input that it uses to fully select which program to run, as well as which commands to use. The application simply redirects this entire command to the operating system. For example, the program might use ""exec([COMMAND])"" to execute the [COMMAND] that was supplied by the user. If the COMMAND is under attacker control, then the attacker can execute arbitrary commands or programs. If the command is being executed using functions like exec() and CreateProcess(), the attacker might not be able to combine multiple commands together in the same line. | |
| 165 | From a weakness standpoint, these variants represent distinct programmer errors. In the first variant, the programmer clearly intends that input from untrusted parties will be part of the arguments in the command to be executed. In the second variant, the programmer does not intend for the command to be accessible to any untrusted party, but the programmer probably has not accounted for alternate ways in which malicious attackers can provide input.",,high,"Exploiting Software: How to Break Code | |
| 166 | Meta-Character Vulnerabilities: http://www.cs.purdue.edu/homes/cs390s/slides/week09.pdf | |
| 167 | OS Commanding: http://projects.webappsec.org/OS-Commanding | |
| 168 | The World Wide Web Security FAQ: http://www.w3.org/Security/Faq/wwwsf4.html | |
| 169 | Security Issues in Perl Scripts: http://www.cgisecurity.com/lib/sips.html | |
| 170 | 24 Deadly Sins of Software Security: ""Sin 10: Command Injection."" Page 171 | |
| 171 | Top 25 Series - Rank 9 - OS Command Injection: http://blogs.sans.org/appsecstreetfighter/2010/02/24/top-25-series-rank-9-os-command-injection/ | |
| 172 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 173 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 174 | The Art of Software Security Assessment: Chapter 8, ""Shell Metacharacters"", Page 425." | |
| 175 | CWE-784,Reliance on Cookies without Validation and Integrity Checking in a Security Decision (Type: Variant),"The application uses a protection mechanism that relies on the existence or values of a cookie, but it does not properly ensure that the cookie is valid for the associated user. | |
| 176 | Attackers can easily modify cookies, within the browser or by implementing the client-side code outside of the browser. Attackers can bypass protection mechanisms such as authorization and authentication by modifying the cookie to contain an expected value.",,high,"Unforgivable Vulnerabilities: http://cve.mitre.org/docs/docs-2007/unforgivable.pdf | |
| 177 | Writing Secure Code: Chapter 13, ""Sensitive Data in Cookies and Fields"" Page 435" | |
| 178 | CWE-862,Missing Authorization (Type: Class),"The software does not perform an authorization check when an actor attempts to access a resource or perform an action. | |
| 179 | Assuming a user with a given identity, authorization is the process of determining whether that user can access a given resource, based on the user's privileges and any permissions or other access-control specifications that apply to the resource. | |
| 180 | When access control checks are not applied, users are able to access data or perform actions that they should not be allowed to perform. This can lead to a wide range of problems, including information exposures, denial of service, and arbitrary code execution.",,high,"Role Based Access Control and Role Based Security: http://csrc.nist.gov/groups/SNS/rbac/ | |
| 181 | Writing Secure Code: Chapter 4, ""Authorization"" Page 114; Chapter 6, ""Determining Appropriate Access Control"" Page 171 | |
| 182 | Top 25 Series - Rank 5 - Improper Access Control (Authorization): http://blogs.sans.org/appsecstreetfighter/2010/03/04/top-25-series-rank-5-improper-access-control-authorization/ | |
| 183 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 184 | Authentication using JAAS: http://www.javaranch.com/journal/2008/04/authentication-using-JAAS.html | |
| 185 | The Art of Software Security Assessment: Chapter 2, ""Common Vulnerabilities of Authorization"", Page 39." | |
| 186 | CWE-863,Incorrect Authorization (Type: Class),"The software performs an authorization check when an actor attempts to access a resource or perform an action, but it does not correctly perform the check. This allows attackers to bypass intended access restrictions. | |
| 187 | Assuming a user with a given identity, authorization is the process of determining whether that user can access a given resource, based on the user's privileges and any permissions or other access-control specifications that apply to the resource. | |
| 188 | When access control checks are incorrectly applied, users are able to access data or perform actions that they should not be allowed to perform. This can lead to a wide range of problems, including information exposures, denial of service, and arbitrary code execution.",,high,"Role Based Access Control and Role Based Security: http://csrc.nist.gov/groups/SNS/rbac/ | |
| 189 | Writing Secure Code: Chapter 4, ""Authorization"" Page 114; Chapter 6, ""Determining Appropriate Access Control"" Page 171 | |
| 190 | Top 25 Series - Rank 5 - Improper Access Control (Authorization): http://blogs.sans.org/appsecstreetfighter/2010/03/04/top-25-series-rank-5-improper-access-control-authorization/ | |
| 191 | Authentication using JAAS: http://www.javaranch.com/journal/2008/04/authentication-using-JAAS.html | |
| 192 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 193 | The Art of Software Security Assessment: Chapter 2, ""Common Vulnerabilities of Authorization"", Page 39." | |
| 194 | CWE-99,Improper Control of Resource Identifiers (Resource Injection) (Type: Base),"The software receives input from an upstream component, but it does not restrict or incorrectly restricts the input before it is used as an identifier for a resource that may be outside the intended sphere of control. | |
| 195 | This may enable an attacker to access or modify otherwise protected system resources.",,high, | |
| 196 | CWE-120,Buffer Copy without Checking Size of Input (Classic Buffer Overflow) (Type: Base),"The program copies an input buffer to an output buffer without verifying that the size of the input buffer is less than the size of the output buffer, leading to a buffer overflow. | |
| 197 | A buffer overflow condition exists when a program attempts to put more data in a buffer than it can hold, or when a program attempts to put data in a memory area outside of the boundaries of a buffer. The simplest type of error, and the most common cause of buffer overflows, is the ""classic"" case in which the program copies the buffer without restricting how much is copied. Other variants exist, but the existence of a classic overflow strongly suggests that the programmer is not considering even the most basic of security protections.",,high,"Writing Secure Code: Chapter 5, ""Public Enemy #1: The Buffer Overrun"" Page 127 | |
| 198 | 24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89 | |
| 199 | Using the Strsafe.h Functions: http://msdn.microsoft.com/en-us/library/ms647466.aspx | |
| 200 | Safe C String Library v1.0.3: http://www.zork.org/safestr/ | |
| 201 | Address Space Layout Randomization in Windows Vista: http://blogs.msdn.com/michael_howard/archive/2006/05/26/address-space-layout-randomization-in-windows-vista.aspx | |
| 202 | Limiting buffer overflows with ExecShield: http://www.redhat.com/magazine/009jul05/features/execshield/ | |
| 203 | PaX: http://en.wikipedia.org/wiki/PaX | |
| 204 | Top 25 Series - Rank 3 - Classic Buffer Overflow: http://software-security.sans.org/blog/2010/03/02/top-25-series-rank-3-classic-buffer-overflow/ | |
| 205 | Understanding DEP as a mitigation technology part 1: http://blogs.technet.com/b/srd/archive/2009/06/12/understanding-dep-as-a-mitigation-technology-part-1.aspx | |
| 206 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 207 | The Art of Software Security Assessment: Chapter 3, ""Nonexecutable Stack"", Page 76. | |
| 208 | The Art of Software Security Assessment: Chapter 5, ""Protection Mechanisms"", Page 189. | |
| 209 | The Art of Software Security Assessment: Chapter 8, ""C String Handling"", Page 388." | |
| 210 | CWE-122,Heap-based Buffer Overflow (Type: Variant),"A heap overflow condition is a buffer overflow, where the buffer that can be overwritten is allocated in the heap portion of memory, generally meaning that the buffer was allocated using a routine such as malloc(). | |
| 211 | A buffer overflow condition exists when a program attempts to put more data in a buffer than it can hold, or when a program attempts to put data in a memory area outside of the boundaries of a buffer. The simplest type of error, and the most common cause of buffer overflows, is the ""classic"" case in which the program copies the buffer without restricting how much is copied. Other variants exist, but the existence of a classic overflow strongly suggests that the programmer is not considering even the most basic of security protections.",,high,"Writing Secure Code: Chapter 5, ""Heap Overruns"" Page 138 | |
| 212 | 24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89 | |
| 213 | The Art of Software Security Assessment: Chapter 3, ""Nonexecutable Stack"", Page 76. | |
| 214 | The Art of Software Security Assessment: Chapter 5, ""Protection Mechanisms"", Page 189." | |
| 215 | CWE-131,Incorrect Calculation of Buffer Size (Type: Base),"The software does not correctly calculate the size to be used when allocating a buffer, which could lead to a buffer overflow. | |
| 216 | If an attacker can manipulate the length parameter associated with an input such that it is inconsistent with the actual length of the input, this can be leveraged to cause the target application to behave in unexpected, and possibly, malicious ways. One of the possible motives for doing so is to pass in arbitrarily large input to the application. Another possible motivation is the modification of application state by including invalid data for subsequent properties of the application. Such weaknesses commonly lead to attacks such as buffer overflows and execution of arbitrary code.",,high,"SafeInt: http://safeint.codeplex.com/ | |
| 217 | Top 25 Series - Rank 18 - Incorrect Calculation of Buffer Size: http://software-security.sans.org/blog/2010/03/19/top-25-series-rank-18-incorrect-calculation-of-buffer-size | |
| 218 | Address Space Layout Randomization in Windows Vista: http://blogs.msdn.com/michael_howard/archive/2006/05/26/address-space-layout-randomization-in-windows-vista.aspx | |
| 219 | Understanding DEP as a mitigation technology part 1: http://blogs.technet.com/b/srd/archive/2009/06/12/understanding-dep-as-a-mitigation-technology-part-1.aspx | |
| 220 | PaX: http://en.wikipedia.org/wiki/PaX | |
| 221 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 222 | Writing Secure Code: Chapter 20, ""Integer Overflows"" Page 620 | |
| 223 | 24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89 | |
| 224 | The Art of Software Security Assessment: Chapter 8, ""Incrementing Pointers Incorrectly"", Page 401." | |
| 225 | CWE-22,Improper Limitation of a Pathname to a Restricted Directory (Path Traversal) (Type: Class),"The software uses external input to construct a pathname that is intended to identify a file or directory that is located underneath a restricted parent directory, but the software does not properly neutralize special elements within the pathname that can cause the pathname to resolve to a location that is outside of the restricted directory. | |
| 226 | Many file operations are intended to take place within a restricted directory. By using special elements such as "".."" and ""/"" separators, attackers can escape outside of the restricted location to access files or directories that are elsewhere on the system. One of the most common special elements is the ""../"" sequence, which in most modern operating systems is interpreted as the parent directory of the current location. This is referred to as relative path traversal. Path traversal also covers the use of absolute pathnames such as ""/usr/local/bin"", which may also be useful in accessing unexpected files. This is referred to as absolute path traversal. | |
| 227 | In many programming languages, the injection of a null byte (the 0 or NUL) may allow an attacker to truncate a generated filename to widen the scope of attack. For example, the software may add "".txt"" to any pathname, thus limiting the attacker to text files, but a null injection may effectively remove this restriction.",,high,"Writing Secure Code: Chapter 11, ""Directory Traversal and Using Parent Paths (..)"" Page 370 | |
| 228 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 229 | Testing for Path Traversal (OWASP-AZ-001): http://www.owasp.org/index.php/Testing_for_Path_Traversal_(OWASP-AZ-001) | |
| 230 | Top 25 Series - Rank 7 - Path Traversal: http://blogs.sans.org/appsecstreetfighter/2010/03/09/top-25-series-rank-7-path-traversal/ | |
| 231 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 232 | The Art of Software Security Assessment: Chapter 9, ""Filenames and Paths"", Page 503." | |
| 233 | CWE-311,Missing Encryption of Sensitive Data (Type: Base),"The software does not encrypt sensitive or critical information before storage or transmission. | |
| 234 | The lack of proper data encryption passes up the guarantees of confidentiality, integrity, and accountability that properly implemented encryption conveys.",,high,"Writing Secure Code: Chapter 9, ""Protecting Secret Data"" Page 299 | |
| 235 | 24 Deadly Sins of Software Security: ""Sin 17: Failure to Protect Stored Data."" Page 253 | |
| 236 | Top 25 Series - Rank 10 - Missing Encryption of Sensitive Data: http://blogs.sans.org/appsecstreetfighter/2010/02/26/top-25-series-rank-10-missing-encryption-of-sensitive-data/ | |
| 237 | The Art of Software Security Assessment: Chapter 2, ""Common Vulnerabilities of Encryption"", Page 43. | |
| 238 | SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf" | |
| 239 | CWE-464,Addition of Data Structure Sentinel (Type: Base),"The accidental addition of a data-structure sentinel can cause serious programming logic problems. | |
| 240 | Data-structure sentinels are often used to mark the structure of data. A common example of this is the null character at the end of strings or a special sentinel to mark the end of a linked list. It is dangerous to allow this type of control data to be easily accessible. Therefore, it is important to protect from the addition or modification of sentinels.",,high, | |
| 241 | CWE-67,Improper Handling of Windows Device Names (Type: Variant),"The software constructs pathnames from user input, but it does not handle or incorrectly handles a pathname containing a Windows device name such as AUX or CON. This typically leads to denial of service or an information exposure when the application attempts to process the pathname as a regular file. | |
| 242 | Not properly handling virtual filenames (e.g. AUX, CON, PRN, COM1, LPT1) can result in different types of vulnerabilities. In some cases an attacker can request a device via injection of a virtual filename in a URL, which may cause an error that leads to a denial of service or an error page that reveals sensitive information. A software system that allows device names to bypass filtering runs the risk of an attacker injecting malicious code in a file with the name of a device.",,high,"Writing Secure Code | |
| 243 | The Art of Software Security Assessment: Chapter 11, ""Device Files"", Page 666." | |
| 244 | CWE-73,External Control of File Name or Path (Type: Class),"The software allows user input to control or influence paths or file names that are used in filesystem operations. | |
| 245 | This could allow an attacker to access or modify system files or other files that are critical to the application. | |
| 246 | Path manipulation errors occur when the following two conditions are met: | |
| 247 | 1. An attacker can specify a path used in an operation on the filesystem. | |
| 248 | 2. By specifying the resource, the attacker gains a capability that would not otherwise be permitted. | |
| 249 | For example, the program may give the attacker the ability to overwrite the specified file or run with a configuration controlled by the attacker.",,high,OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 250 | CWE-76,Improper Neutralization of Equivalent Special Elements (Type: Base),"The software properly neutralizes certain special elements, but it improperly neutralizes equivalent special elements. | |
| 251 | The software may have a fixed list of special characters it believes is complete. However, there may be alternate encodings, or representations that also have the same meaning. For example, the software may filter out a leading slash (/) to prevent absolute path names, but does not account for a tilde (~) followed by a user name, which on some *nix systems could be expanded to an absolute pathname. Alternately, the software might filter a dangerous ""-e"" command-line switch when calling an external program, but it might not account for ""--exec"" or other switches that have the same semantics.",,high, | |
| 252 | CWE-79,Improper Neutralization of Input During Web Page Generation (Cross-site Scripting) (Type: Base),"The software does not neutralize or incorrectly neutralizes user-controllable input before it is placed in output that is used as a web page that is served to other users. | |
| 253 | Cross-site scripting (XSS) vulnerabilities occur when: | |
| 254 | 1. Untrusted data enters a web application, typically from a web request. | |
| 255 | 2. The web application dynamically generates a web page that contains this untrusted data. | |
| 256 | 3. During page generation, the application does not prevent the data from containing content that is executable by a web browser, such as JavaScript, HTML tags, HTML attributes, mouse events, Flash, ActiveX, etc. | |
| 257 | 4. A victim visits the generated web page through a web browser, which contains malicious script that was injected using the untrusted data. | |
| 258 | 5. Since the script comes from a web page that was sent by the web server, the victim's web browser executes the malicious script in the context of the web server's domain. | |
| 259 | 6. This effectively violates the intention of the web browser's same-origin policy, which states that scripts in one domain should not be able to access resources or run code in a different domain. | |
| 260 | There are three main kinds of XSS: | |
| 261 | The server reads data directly from the HTTP request and reflects it back in the HTTP response. Reflected XSS exploits occur when an attacker causes a victim to supply dangerous content to a vulnerable web application, which is then reflected back to the victim and executed by the web browser. The most common mechanism for delivering malicious content is to include it as a parameter in a URL that is posted publicly or e-mailed directly to the victim. URLs constructed in this manner constitute the core of many phishing schemes, whereby an attacker convinces a victim to visit a URL that refers to a vulnerable site. After the site reflects the attacker's content back to the victim, the content is executed by the victim's browser. | |
| 262 | The application stores dangerous data in a database, message forum, visitor log, or other trusted data store. At a later time, the dangerous data is subsequently read back into the application and included in dynamic content. From an attacker's perspective, the optimal place to inject malicious content is in an area that is displayed to either many users or particularly interesting users. Interesting users typically have elevated privileges in the application or interact with sensitive data that is valuable to the attacker. If one of these users executes malicious content, the attacker may be able to perform privileged operations on behalf of the user or gain access to sensitive data belonging to the user. For example, the attacker might inject XSS into a log message, which might not be handled properly when an administrator views the logs. | |
| 263 | In DOM-based XSS, the client performs the injection of XSS into the page; in the other types, the server performs the injection. DOM-based XSS generally involves server-controlled, trusted script that is sent to the client, such as Javascript that performs sanity checks on a form before the user submits it. If the server-supplied script processes user-supplied data and then injects it back into the web page (such as with dynamic HTML), then DOM-based XSS is possible. | |
| 264 | Once the malicious script is injected, the attacker can perform a variety of malicious activities. The attacker could transfer private information, such as cookies that may include session information, from the victim's machine to the attacker. The attacker could send malicious requests to a web site on behalf of the victim, which could be especially dangerous to the site if the victim has administrator privileges to manage that site. Phishing attacks could be used to emulate trusted web sites and trick the victim into entering a password, allowing the attacker to compromise the victim's account on that web site. Finally, the script could exploit a vulnerability in the web browser itself possibly taking over the victim's machine, sometimes referred to as ""drive-by hacking."" | |
| 265 | In many cases, the attack can be launched without the victim even being aware of it. Even with careful users, attackers frequently use a variety of methods to encode the malicious portion of the attack, such as URL encoding or Unicode, so the request looks less suspicious.",,high,"XSS Attacks | |
| 266 | 24 Deadly Sins of Software Security: ""Sin 2: Web-Server Related Vulnerabilities (XSS, XSRF, and Response Splitting)."" Page 31 | |
| 267 | 24 Deadly Sins of Software Security: ""Sin 3: Web-Client Related Vulnerabilities (XSS)."" Page 63 | |
| 268 | Cross-site scripting: http://en.wikipedia.org/wiki/Cross-site_scripting | |
| 269 | Writing Secure Code: Chapter 13, ""Web-Specific Input Issues"" Page 413 | |
| 270 | XSS (Cross Site Scripting) Cheat Sheet: http://ha.ckers.org/xss.html | |
| 271 | Mitigating Cross-site Scripting With HTTP-only Cookies: http://msdn.microsoft.com/en-us/library/ms533046.aspx | |
| 272 | Anti-XSS 3.0 Beta and CAT.NET Community Technology Preview now Live!: http://blogs.msdn.com/cisg/archive/2008/12/15/anti-xss-3-0-beta-and-cat-net-community-technology-preview-now-live.aspx | |
| 273 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 274 | XSS Defense HOWTO: http://blog.modsecurity.org/2008/07/do-you-know-how.html | |
| 275 | Web Application Firewall: http://www.owasp.org/index.php/Web_Application_Firewall | |
| 276 | Web Application Firewall Evaluation Criteria: http://www.webappsec.org/projects/wafec/v1/wasc-wafec-v1.0.html | |
| 277 | Firefox Implements httpOnly And is Vulnerable to XMLHTTPRequest | |
| 278 | XMLHttpRequest allows reading HTTPOnly cookies: https://bugzilla.mozilla.org/show_bug.cgi?id=380418 | |
| 279 | Apache Wicket: http://wicket.apache.org/ | |
| 280 | XSS (Cross Site Scripting) Prevention Cheat Sheet: http://www.owasp.org/index.php/XSS_(Cross_Site_Scripting)_Prevention_Cheat_Sheet | |
| 281 | DOM based XSS Prevention Cheat Sheet: http://www.owasp.org/index.php/DOM_based_XSS_Prevention_Cheat_Sheet | |
| 282 | Top 25 series - Rank 1 - Cross Site Scripting: http://blogs.sans.org/appsecstreetfighter/2010/02/22/top-25-series-rank-1-cross-site-scripting/ | |
| 283 | The Art of Software Security Assessment: Chapter 17, ""Cross Site Scripting"", Page 1071." | |
| 284 | CWE-80,Improper Neutralization of Script-Related HTML Tags in a Web Page (Basic XSS) (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special characters such as ""<"", "">"", and ""&"" that could be interpreted as web-scripting elements when they are sent to a downstream component that processes web pages. | |
| 285 | This may allow such characters to be treated as control characters, which are executed client-side in the context of the user's session. Although this can be classified as an injection problem, the more pertinent issue is the improper conversion of such special characters to respective context-appropriate entities before displaying them to the user.",,high, | |
| 286 | CWE-98,Improper Control of Filename for Include/Require Statement in PHP Program (PHP Remote File Inclusion) (Type: Base),"The PHP application receives input from an upstream component, but it does not restrict or incorrectly restricts the input before its usage in ""require,"" ""include,"" or similar functions. | |
| 287 | In certain versions and configurations of PHP, this can allow an attacker to specify a URL to a remote location from which the software will obtain the code to execute. In other cases in association with path traversal, the attacker can specify a local file that may contain executable statements that can be parsed by PHP.",,high,"Testing for Path Traversal (OWASP-AZ-001): http://www.owasp.org/index.php/Testing_for_Path_Traversal_(OWASP-AZ-001) | |
| 288 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 289 | A Study in Scarlet: http://www.cgisecurity.com/lib/studyinscarlet.txt | |
| 290 | Suhosin: http://www.hardened-php.net/suhosin/ | |
| 291 | Top 25 Series - Rank 13 - PHP File Inclusion: http://blogs.sans.org/appsecstreetfighter/2010/03/11/top-25-series-rank-13-php-file-inclusion/" | |
| 292 | CWE-188,Reliance on Data/Memory Layout (Type: Base),"The software makes invalid assumptions about how protocol data or memory is organized at a lower level, resulting in unintended program behavior. | |
| 293 | For example, an attacker might succeed in authentication by providing a small password that matches the associated portion of the larger, correct password.",,low,"The Art of Software Security Assessment: Chapter 6, ""Structure Padding"", Page 284." | |
| 294 | CWE-197,Numeric Truncation Error (Type: Base),"Truncation errors occur when a primitive is cast to a primitive of a smaller size and data is lost in the conversion. | |
| 295 | When a primitive is cast to a smaller primitive, the high order bits of the large value are lost in the conversion, potentially resulting in an unexpected value that is not equal to the original value. This value may be required as an index into a buffer, a loop iterator, or simply necessary state data. In any case, the value cannot be trusted and the system will be in an undefined state. While this method may be employed viably to isolate the low bits of a value, this usage is rare, and truncation usually implies that an implementation error has occurred.",,low,"The Art of Software Security Assessment: Chapter 6, ""Truncation"", Page 259." | |
| 296 | CWE-252,Unchecked Return Value (Type: Base),"The software does not check the return value from a method or function, which can prevent it from detecting unexpected states and conditions. | |
| 297 | Two common programmer assumptions are ""this function call can never fail"" and ""it doesn't matter if this function call fails"". If an attacker can force the function to fail or otherwise return a value that is not expected, then the subsequent program logic could lead to a vulnerability, because the software is not in a state that the programmer assumes. For example, if the program calls a function to drop privileges but does not check the return code to ensure that privileges were successfully dropped, then the program will continue to operate with the higher privileges.",,low,"The Art of Software Security Assessment: Chapter 7, ""Program Building Blocks"" Page 341. | |
| 298 | Writing Secure Code: Chapter 20, ""Checking Returns"" Page 624 | |
| 299 | 24 Deadly Sins of Software Security: ""Sin 11: Failure to Handle Errors Correctly."" Page 183 | |
| 300 | ERR10-CPP. Check for error conditions: https://www.securecoding.cert.org/confluence/display/cplusplus/ERR10-CPP.+Check+for+error+conditions" | |
| 301 | CWE-253,Incorrect Check of Function Return Value (Type: Base),"The software incorrectly checks a return value from a function, which prevents the software from detecting errors or exceptional conditions. | |
| 302 | Two common programmer assumptions are ""this function call can never fail"" and ""it doesn't matter if this function call fails"". If an attacker can force the function to fail or otherwise return a value that is not expected, then the subsequent program logic could lead to a vulnerability, because the software is not in a state that the programmer assumes. For example, if the program calls a function to drop privileges but does not check the return code to ensure that privileges were successfully dropped, then the program will continue to operate with the higher privileges.",,low,"The Art of Software Security Assessment: Chapter 7, ""Return Value Testing and Interpretation"", Page 340." | |
| 303 | CWE-296,Improper Following of a Certificates Chain of Trust (Type: Base),"The software does not follow, or incorrectly follows, the chain of trust for a certificate back to a trusted root certificate, resulting in incorrect trust of any resource that is associated with that certificate. | |
| 304 | If a system does not follow the chain of trust of a certificate to a root server, the certificate loses all usefulness as a metric of trust. Essentially, the trust gained from a certificate is derived from a chain of trust -- with a reputable trusted entity at the end of that list. The end user must trust that reputable source, and this reputable source must vouch for the resource in question through the medium of the certificate. | |
| 305 | In some cases, this trust traverses several entities who vouch for one another. The entity trusted by the end user is at one end of this trust chain, while the certificate-wielding resource is at the other end of the chain. If the user receives a certificate at the end of one of these trust chains and then proceeds to check only that the first link in the chain, no real trust has been derived, since the entire chain must be traversed back to a trusted source to verify the certificate. | |
| 306 | There are several ways in which the chain of trust might be broken, including but not limited to: | |
| 307 | Any certificate in the chain is self-signed, unless it the root. | |
| 308 | Not every intermediate certificate is checked, starting from the original certificate all the way up to the root certificate. | |
| 309 | An intermediate, CA-signed certificate does not have the expected Basic Constraints or other important extensions. | |
| 310 | The root certificate has been compromised or authorized to the wrong party.",,low,"The Most Dangerous Code in the World: Validating SSL Certificates in Non-Browser Software: http://www.cs.utexas.edu/~shmat/shmat_ccs12.pdf | |
| 311 | 24 Deadly Sins of Software Security: ""Sin 23: Improper Use of PKI, Especially SSL."" Page 347" | |
| 312 | CWE-298,Improper Validation of Certificate Expiration (Type: Variant),"A certificate expiration is not validated or is incorrectly validated, so trust may be assigned to certificates that have been abandoned due to age. | |
| 313 | When the expiration of a certificate is not taken into account, no trust has necessarily been conveyed through it. Therefore, the validity of the certificate cannot be verified and all benefit of the certificate is lost.",,low,"24 Deadly Sins of Software Security: ""Sin 23: Improper Use of PKI, Especially SSL."" Page 347" | |
| 314 | CWE-324,Use of a Key Past its Expiration Date (Type: Base),"The product uses a cryptographic key or password past its expiration date, which diminishes its safety significantly by increasing the timing window for cracking attacks against that key. | |
| 315 | While the expiration of keys does not necessarily ensure that they are compromised, it is a significant concern that keys which remain in use for prolonged periods of time have a decreasing probability of integrity. For this reason, it is important to replace keys within a period of time proportional to their strength.",,low,"24 Deadly Sins of Software Security: ""Sin 23: Improper Use of PKI, Especially SSL."" Page 347" | |
| 316 | CWE-379,Creation of Temporary File in Directory with Incorrect Permissions (Type: Base),"The software creates a temporary file in a directory whose permissions allow unintended actors to determine the file's existence or otherwise access that file. | |
| 317 | On some operating systems, the fact that the temporary file exists may be apparent to any user with sufficient privileges to access that directory. Since the file is visible, the application that is using the temporary file could be known. If one has access to list the processes on the system, the attacker has gained information about what the user is doing at that time. By correlating this with the applications the user is running, an attacker could potentially discover what a user's actions are. From this, higher levels of security could be breached.",,low,"The Art of Software Security Assessment: Chapter 9, ""Temporary Files"", Page 538." | |
| 318 | CWE-462,Duplicate Key in Associative List (Alist) (Type: Base),"Duplicate keys in associative lists can lead to non-unique keys being mistaken for an error. | |
| 319 | A duplicate key entry -- if the alist is designed properly -- could be used as a constant time replace function. However, duplicate key entries could be inserted by mistake. Because of this ambiguity, duplicate key entries in an association list are not recommended and should not be allowed.",,low, | |
| 320 | CWE-479,Signal Handler Use of a Non-reentrant Function (Type: Variant),"The program defines a signal handler that calls a non-reentrant function. | |
| 321 | Non-reentrant functions are functions that cannot safely be called, interrupted, and then recalled before the first call has finished without resulting in memory corruption. This can lead to an unexpected system state an unpredictable results with a variety of potential consequences depending on context, including denial of service and code execution. | |
| 322 | Many functions are not reentrant, but some of them can result in the corruption of memory if they are used in a signal handler. The function call syslog() is an example of this. In order to perform its functionality, it allocates a small amount of memory as ""scratch space."" If syslog() is suspended by a signal call and the signal handler calls syslog(), the memory used by both of these functions enters an undefined, and possibly, exploitable state. Implementations of malloc() and free() manage metadata in global structures in order to track which memory is allocated versus which memory is available, but they are non-reentrant. Simultaneous calls to these functions can cause corruption of the metadata.",,low,"The Art of Software Security Assessment: Chapter 13, ""Signal Vulnerabilities"", Page 791." | |
| 323 | CWE-480,Use of Incorrect Operator (Type: Base),"The programmer accidentally uses the wrong operator, which changes the application logic in security-relevant ways. | |
| 324 | Non-reentrant functions are functions that cannot safely be called, interrupted, and then recalled before the first call has finished without resulting in memory corruption. This can lead to an unexpected system state an unpredictable results with a variety of potential consequences depending on context, including denial of service and code execution. | |
| 325 | Many functions are not reentrant, but some of them can result in the corruption of memory if they are used in a signal handler. The function call syslog() is an example of this. In order to perform its functionality, it allocates a small amount of memory as ""scratch space."" If syslog() is suspended by a signal call and the signal handler calls syslog(), the memory used by both of these functions enters an undefined, and possibly, exploitable state. Implementations of malloc() and free() manage metadata in global structures in order to track which memory is allocated versus which memory is available, but they are non-reentrant. Simultaneous calls to these functions can cause corruption of the metadata.",,low,"The Art of Software Security Assessment: Chapter 6, ""Typos"", Page 289." | |
| 326 | CWE-481,Assigning instead of Comparing (Type: Variant),"The code uses an operator for assignment when the intention was to perform a comparison. | |
| 327 | In many languages the compare statement is very close in appearance to the assignment statement and are often confused. This bug is generally the result of a typo and usually causes obvious problems with program execution. If the comparison is in an if statement, the if statement will usually evaluate the value of the right-hand side of the predicate.",,low,"The Art of Software Security Assessment: Chapter 6, ""Typos"", Page 289." | |
| 328 | CWE-482,Comparing instead of Assigning (Type: Variant),"The code uses an operator for comparison when the intention was to perform an assignment. | |
| 329 | In many languages, the compare statement is very close in appearance to the assignment statement; they are often confused.",,low,"The Art of Software Security Assessment: Chapter 6, ""Typos"", Page 289." | |
| 330 | CWE-483,Incorrect Block Delimitation (Type: Variant),"The code does not explicitly delimit a block that is intended to contain 2 or more statements, creating a logic error. | |
| 331 | In some languages, braces (or other delimiters) are optional for blocks. When the delimiter is omitted, it is possible to insert a logic error in which a statement is thought to be in a block but is not. In some cases, the logic error can have security implications.",,low, | |
| 332 | CWE-641,Improper Restriction of Names for Files and Other Resources (Type: Base),"The application constructs the name of a file or other resource using input from an upstream component, but does not restrict or incorrectly restricts the resulting name. | |
| 333 | This may produce resultant weaknesses. For instance, if the names of these resources contain scripting characters, it is possible that a script may get executed in the client's browser if the application ever displays the name of the resource on a dynamically generated web page. Alternately, if the resources are consumed by some application parser, a specially crafted name can exploit some vulnerability internal to the parser, potentially resulting in execution of arbitrary code on the server machine. The problems will vary based on the context of usage of such malformed resource names and whether vulnerabilities are present in or assumptions are made by the targeted technology that would make code execution possible.",,low, | |
| 334 | CWE-648,Incorrect Use of Privileged APIs (Type: Base),"The application does not conform to the API requirements for a function call that requires extra privileges. This could allow attackers to gain privileges by causing the function to be called incorrectly. | |
| 335 | When an application contains certain functions that perform operations requiring an elevated level of privilege, the caller of a privileged API must be careful to: | |
| 336 | ensure that assumptions made by the APIs are valid, such as validity of arguments | |
| 337 | account for known weaknesses in the design/implementation of the API | |
| 338 | call the API from a safe context | |
| 339 | If the caller of the API does not follow these requirements, then it may allow a malicious user or process to elevate their privilege, hijack the process, or steal sensitive data. | |
| 340 | For instance, it is important to know if privileged APIs do not shed their privileges before returning to the caller or if the privileged function might make certain assumptions about the data, context or state information passed to it by the caller. It is important to always know when and how privileged APIs can be called in order to ensure that their elevated level of privilege cannot be exploited.",,low, | |
| 341 | CWE-762,Mismatched Memory Management Routines (Type: Variant),"The application attempts to return a memory resource to the system, but it calls a release function that is not compatible with the function that was originally used to allocate that resource. | |
| 342 | This weakness can be generally described as mismatching memory management routines, such as: | |
| 343 | The memory was allocated on the stack (automatically), but it was deallocated using the memory management routine free() (CWE-590), which is intended for explicitly allocated heap memory. | |
| 344 | The memory was allocated explicitly using one set of memory management functions, and deallocated using a different set. For example, memory might be allocated with malloc() in C++ instead of the new operator, and then deallocated with the delete operator. | |
| 345 | When the memory management functions are mismatched, the consequences may be as severe as code execution, memory corruption, or program crash. Consequences and ease of exploit will vary depending on the implementation of the routines and the object being managed.",,low,"boost C++ Library Smart Pointers: http://www.boost.org/doc/libs/1_38_0/libs/smart_ptr/smart_ptr.htm | |
| 346 | Valgrind: http://valgrind.org/" | |
| 347 | CWE-783,Operator Precedence Logic Error (Type: Variant),"The program uses an expression in which operator precedence causes incorrect logic to be used. | |
| 348 | While often just a bug, operator precedence logic errors can have serious consequences if they are used in security-critical code, such as making an authentication decision.",,low,"EXP00-C. Use parentheses for precedence of operation: https://www.securecoding.cert.org/confluence/display/seccode/EXP00-C.+Use+parentheses+for+precedence+of+operation | |
| 349 | The Art of Software Security Assessment: Chapter 6, ""Precedence"", Page 287." | |
| 350 | CWE-789,Uncontrolled Memory Allocation (Type: Variant),"The product allocates memory based on an untrusted size value, but it does not validate or incorrectly validates the size, allowing arbitrary amounts of memory to be allocated. | |
| 351 | This typically occurs when a pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used. These problems may be resultant from missing sentinel values (CWE-463) or trusting a user-influenced input length variable.",,low,"The Art of Software Security Assessment: Chapter 10, ""Resource Limits"", Page 574." | |
| 352 | CWE-333,Improper Handling of Insufficient Entropy in TRNG (Type: Variant),"True random number generators (TRNG) generally have a limited source of entropy and therefore can fail or block. | |
| 353 | The rate at which true random numbers can be generated is limited. It is important that one uses them only when they are needed for security.",,medium, | |
| 354 | CWE-367,Time-of-check Time-of-use (TOCTOU) Race Condition (Type: Base),"The software checks the state of a resource before using that resource, but the resource's state can change between the check and the use in a way that invalidates the results of the check. This can cause the software to perform invalid actions when the resource is in an unexpected state. | |
| 355 | This weakness can be security-relevant when an attacker can influence the state of the resource between check and use. This can happen with shared resources such as files, memory, or even variables in multithreaded programs.",,medium,"Portably Solving File TOCTTOU Races with Hardness Amplification: http://www.usenix.org/events/fast08/tech/tsafrir.html | |
| 356 | 24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205 | |
| 357 | The Art of Software Security Assessment: Chapter 9, ""TOCTOU"", Page 527." | |
| 358 | CWE-404,Improper Resource Shutdown or Release (Type: Base),"The program does not release or incorrectly releases a resource before it is made available for re-use. | |
| 359 | When a resource is created or allocated, the developer is responsible for properly releasing the resource as well as accounting for all potential paths of expiration or invalidation, such as a set period of time or revocation.",,medium,"24 Deadly Sins of Software Security: ""Sin 8: C++ Catastrophes."" Page 143" | |
| 360 | CWE-407,Algorithmic Complexity (Type: Base),"An algorithm in a product has an inefficient worst-case computational complexity that may be detrimental to system performance and can be triggered by an attacker, typically using crafted manipulations that ensure that the worst case is being reached. | |
| 361 | In the absence of a policy to restrict asymmetric resource consumption, the application or system cannot distinguish between legitimate transmissions and traffic intended to serve as an amplifying attack on target systems. Systems can often be configured to restrict the amount of traffic sent out on behalf of a client, based on the client's origin or access level. This is usually defined in a resource allocation policy. In the absence of a mechanism to keep track of transmissions, the system or application can be easily abused to transmit asymmetrically greater traffic than the request or client should be permitted to.",,medium,Algorithmic Complexity Attacks: http://www.cs.rice.edu/~scrosby/hash/CrosbyWallach_UsenixSec2003/index.html | |
| 362 | CWE-415,Double Free (Type: Variant),"The product calls free() twice on the same memory address, potentially leading to modification of unexpected memory locations. | |
| 363 | When a program calls free() twice with the same argument, the program's memory management data structures become corrupted. This corruption can cause the program to crash or, in some circumstances, cause two later calls to malloc() to return the same pointer. If malloc() returns the same value twice and the program later gives the attacker control over the data that is written into this doubly-allocated memory, the program becomes vulnerable to a buffer overflow attack.",,medium,"24 Deadly Sins of Software Security: ""Sin 8: C++ Catastrophes."" Page 143 | |
| 364 | The Art of Software Security Assessment: Chapter 7, ""Double Frees"", Page 379." | |
| 365 | CWE-59,Improper Link Resolution Before File Access (Link Following) (Type: Base),"The software attempts to access a file based on the filename, but it does not properly prevent that filename from identifying a link or shortcut that resolves to an unintended resource. | |
| 366 | Some functions that offer security features supported by the OS are not available on all versions of the OS in common use. Likewise, functions are often deprecated or made obsolete for security reasons and should not be used.",,medium,"The Art of Software Security Assessment: Chapter 9, ""Symbolic Link Attacks"", Page 518." | |
| 367 | CWE-601,URL Redirection to Untrusted Site (Open Redirect) (Type: Variant),"A web application accepts a user-controlled input that specifies a link to an external site, and uses that link in a Redirect. This simplifies phishing attacks. | |
| 368 | An http parameter may contain a URL value and could cause the web application to redirect the request to the specified URL. By modifying the URL value to a malicious site, an attacker may successfully launch a phishing scam and steal user credentials. Because the server name in the modified link is identical to the original site, phishing attempts have a more trustworthy appearance.",,medium,"Exploitable Redirects on the Web: Identification, Prevalence, and Defense: http://www.cs.indiana.edu/cgi-pub/cshue/research/woot08.pdf | |
| 369 | Open redirect vulnerabilities: definition and prevention: http://www.net-security.org/dl/insecure/INSECURE-Mag-17.pdf | |
| 370 | Top 25 Series - Rank 23 - Open Redirect: http://software-security.sans.org/blog/2010/03/25/top-25-series-rank-23-open-redirect | |
| 371 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI" | |
| 372 | CWE-749,Exposed Dangerous Method or Function (Type: Base),"The software provides an Applications Programming Interface (API) or similar interface for interaction with external actors, but the interface includes a dangerous method or function that is not properly restricted. | |
| 373 | This weakness can lead to a wide variety of resultant weaknesses, depending on the behavior of the exposed method. It can apply to any number of technologies and approaches, such as ActiveX controls, Java functions, IOCTLs, and so on. | |
| 374 | The exposure can occur in a few different ways: | |
| 375 | 1) The function/method was never intended to be exposed to outside actors. | |
| 376 | 2) The function/method was only intended to be accessible to a limited set of actors, such as Internet-based access from a single web site.",,medium,"No description: http://msdn.microsoft.com/workshop/components/activex/safety.asp | |
| 377 | No description: http://msdn.microsoft.com/workshop/components/activex/security.asp" | |
| 378 | CWE-755,Improper Handling of Exceptional Conditions (Type: Class),"The software does not handle or incorrectly handles an exceptional condition. | |
| 379 | The programmer may assume that certain events or conditions will never occur or do not need to be worried about, such as low memory conditions, lack of access to resources due to restrictive permissions, or misbehaving clients or components. However, attackers may intentionally trigger these unusual conditions, thus violating the programmer's assumptions, possibly introducing instability, incorrect behavior, or a vulnerability. | |
| 380 | Note that this entry is not exclusively about the use of exceptions and exception handling, which are mechanisms for both checking and handling unusual or unexpected conditions.",,medium, | |
| 381 | CWE-766,Critical Variable Declared Public (Type: Variant),"The software declares a critical variable or field to be public when intended security policy requires it to be private. | |
| 382 | When software is operating in a concurrent environment and repeatedly unlocks a critical resource, the consequences will vary based on the type of lock, the lock's implementation, and the resource being protected. In some situations such as with semaphores, the resources are pooled and extra calls to unlock will increase the count for the number of available resources, likely resulting in a crash or unpredictable behavior when the system nears capacity.",,medium, | |
| 383 | CWE-767,Access to Critical Private Variable via Public Method (Type: Variant),"The software defines a public method that reads or modifies a private variable. | |
| 384 | If an attacker modifies the variable to contain unexpected values, this could violate assumptions from other parts of the code. Additionally, if an attacker can read the private variable, it may expose sensitive information or make it easier to launch further attacks.",,medium, | |
| 385 | CWE-776,Improper Restriction of Recursive Entity References in DTDs (XML Entity Expansion) (Type: Variant),"The software uses XML documents and allows their structure to be defined with a Document Type Definition (DTD), but it does not properly control the number of recursive definitions of entities. | |
| 386 | If the DTD contains a large number of nested or recursive entities, this can lead to explosive growth of data when parsed, causing a denial of service.",,medium,"Multiple vendors XML parser (and SOAP/WebServices server) Denial of Service attack using DTD: http://www.securityfocus.com/archive/1/303509 | |
| 387 | XML security: Preventing XML bombs: http://searchsoftwarequality.techtarget.com/expert/KnowledgebaseAnswer/0,289625,sid92_gci1168442,00.html?asrc=SS_CLA_302%20%20558&psrc=CLT_92# | |
| 388 | Dismantling an XML-Bomb: http://blog.didierstevens.com/2008/09/23/dismantling-an-xml-bomb/ | |
| 389 | XML Entity Expansion: http://projects.webappsec.org/XML-Entity-Expansion | |
| 390 | Tip: Configure SAX parsers for secure processing: http://www.ibm.com/developerworks/xml/library/x-tipcfsx.html | |
| 391 | XML Denial of Service Attacks and Defenses: http://msdn.microsoft.com/en-us/magazine/ee335713.aspx | |
| 392 | Preventing Entity Expansion Attacks in JAXB: http://blog.bdoughan.com/2011/03/preventing-entity-expansion-attacks-in.html" | |
| 393 | CWE-777,Regular Expression without Anchors (Type: Variant),"The software uses a regular expression to perform neutralization, but the regular expression is not anchored and may allow malicious or malformed data to slip through. | |
| 394 | When performing tasks such as whitelist validation, data is examined and possibly modified to ensure that it is well-formed and adheres to a list of safe values. If the regular expression is not anchored, malicious or malformed data may be included before or after any string matching the regular expression. The type of malicious data that is allowed will depend on the context of the application and which anchors are omitted from the regular expression.",,medium, | |
| 395 | CWE-779,Logging of Excessive Data (Type: Base),"The software logs too much information, making log files hard to process and possibly hindering recovery efforts or forensic analysis after an attack. | |
| 396 | While logging is a good practice in general, and very high levels of logging are appropriate for debugging stages of development, too much logging in a production environment might hinder a system administrator's ability to detect anomalous conditions. This can provide cover for an attacker while attempting to penetrate a system, clutter the audit trail for forensic analysis, or make it more difficult to debug problems in a production environment.",,medium, | |
| 397 | CWE-781,Improper Address Validation in IOCTL with METHOD_NEITHER I/O Control Code (Type: Variant),"The software defines an IOCTL that uses METHOD_NEITHER for I/O, but it does not validate or incorrectly validates the addresses that are provided. | |
| 398 | When an IOCTL uses the METHOD_NEITHER option for I/O control, it is the responsibility of the IOCTL to validate the addresses that have been supplied to it. If validation is missing or incorrect, attackers can supply arbitrary memory addresses, leading to code execution or a denial of service.",,medium,"Exploiting Common Flaws in Drivers: http://reversemode.com/index.php?option=com_content&task=view&id=38&Itemid=1 | |
| 399 | Remote and Local Exploitation of Network Drivers: https://www.blackhat.com/presentations/bh-usa-07/Bulygin/Presentation/bh-usa-07-bulygin.pdf | |
| 400 | Windows driver vulnerabilities: the METHOD_NEITHER odyssey: http://www.net-security.org/dl/insecure/INSECURE-Mag-18.pdf | |
| 401 | Buffer Descriptions for I/O Control Codes: http://msdn.microsoft.com/en-us/library/ms795857.aspx | |
| 402 | Using Neither Buffered Nor Direct I/O: http://msdn.microsoft.com/en-us/library/cc264614.aspx | |
| 403 | Securing Device Objects: http://msdn.microsoft.com/en-us/library/ms794722.aspx | |
| 404 | No description: http://www.piotrbania.com/all/articles/ewdd.pdf" | |
| 405 | CWE-782,Exposed IOCTL with Insufficient Access Control (Type: Variant),"The software implements an IOCTL with functionality that should be restricted, but it does not properly enforce access control for the IOCTL. | |
| 406 | When an IOCTL contains privileged functionality and is exposed unnecessarily, attackers may be able to access this functionality by invoking the IOCTL. Even if the functionality is benign, if the programmer has assumed that the IOCTL would only be accessed by a trusted process, there may be little or no validation of the incoming data, exposing weaknesses that would never be reachable if the attacker cannot call the IOCTL directly. | |
| 407 | The implementations of IOCTLs will differ between operating system types and versions, so the methods of attack and prevention may vary widely.",,medium,Securing Device Objects: http://msdn.microsoft.com/en-us/library/ms794722.aspx | |
| 408 | CWE-117,Improper Output Neutralization for Logs (Type: Base),"The software does not neutralize or incorrectly neutralizes output that is written to logs. | |
| 409 | This can allow an attacker to forge log entries or inject malicious content into logs. | |
| 410 | Log forging vulnerabilities occur when: | |
| 411 | Data enters an application from an untrusted source. | |
| 412 | The data is written to an application or system log file.",,medium,"Exploiting Software: How to Break Code | |
| 413 | The night the log was forged: http://doc.novsu.ac.ru/oreilly/tcpip/puis/ch10_05.htm | |
| 414 | OWASP TOP 10: http://www.owasp.org/index.php/Top_10_2007" | |
| 415 | CWE-124,Buffer Underwrite (Buffer Underflow) (Type: Base),"The software writes to a buffer using an index or pointer that references a memory location prior to the beginning of the buffer. | |
| 416 | This typically occurs when a pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used.",,medium,"Buffer UNDERFLOWS: What do you know about it?: http://seclists.org/vuln-dev/2004/Jan/0022.html | |
| 417 | 24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89" | |
| 418 | CWE-128,Wrap-around Error (Type: Base),"Wrap around errors occur whenever a value is incremented past the maximum value for its type and therefore ""wraps around"" to a very small, negative, or undefined value. | |
| 419 | This typically occurs when the pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used. This may result in exposure of sensitive information or possibly a crash.",,medium,"24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89 | |
| 420 | The Art of Software Security Assessment: Chapter 6, ""Signed Integer Boundaries"", Page 220." | |
| 421 | CWE-170,Improper Null Termination (Type: Base),"The software does not terminate or incorrectly terminates a string or array with a null character or equivalent terminator. | |
| 422 | Null termination errors frequently occur in two different ways. An off-by-one error could cause a null to be written out of bounds, leading to an overflow. Or, a program could use a strncpy() function call incorrectly, which prevents a null terminator from being added at all. Other scenarios are possible.",,medium, | |
| 423 | CWE-190,Integer Overflow or Wraparound (Type: Base),"The software performs a calculation that can produce an integer overflow or wraparound, when the logic assumes that the resulting value will always be larger than the original value. This can introduce other weaknesses when the calculation is used for resource management or execution control. | |
| 424 | An integer overflow or wraparound occurs when an integer value is incremented to a value that is too large to store in the associated representation. When this occurs, the value may wrap to become a very small or negative number. While this may be intended behavior in circumstances that rely on wrapping, it can have security consequences if the wrap is unexpected. This is especially the case if the integer overflow can be triggered using user-supplied inputs. This becomes security-critical when the result is used to control looping, make a security decision, or determine the offset or size in behaviors such as memory allocation, copying, concatenation, etc.",,medium,"An overview of common programming security vulnerabilities and possible solutions: http://fort-knox.org/thesis.pdf | |
| 425 | Basic Integer Overflows: http://www.phrack.org/issues.html?issue=60&id=10#article | |
| 426 | Writing Secure Code: Chapter 20, ""Integer Overflows"" Page 620 | |
| 427 | 24 Deadly Sins of Software Security: ""Sin 7: Integer Overflows."" Page 119 | |
| 428 | SafeInt: http://safeint.codeplex.com/ | |
| 429 | Top 25 Series - Rank 17 - Integer Overflow Or Wraparound: http://software-security.sans.org/blog/2010/03/18/top-25-series-rank-17-integer-overflow-or-wraparound | |
| 430 | The Art of Software Security Assessment: Chapter 6, ""Signed Integer Boundaries"", Page 220." | |
| 431 | CWE-196,Unsigned to Signed Conversion Error (Type: Variant),"An unsigned-to-signed conversion error takes place when a large unsigned primitive is used as a signed value. | |
| 432 | It is dangerous to rely on implicit casts between signed and unsigned numbers because the result can take on an unexpected value and violate assumptions made by the program.",,medium,"The Art of Software Security Assessment: Chapter 6, ""Type Conversions"", Page 223." | |
| 433 | CWE-202,Exposure of Sensitive Data Through Data Queries (Type: Variant),"When trying to keep information confidential, an attacker can often infer some of the information by using statistics. | |
| 434 | In situations where data should not be tied to individual users, but a large number of users should be able to make queries that ""scrub"" the identity of users, it may be possible to get information about a user -- e.g., by specifying search terms that are known to be unique to that user.",,medium, | |
| 435 | CWE-250,Execution with Unnecessary Privileges (Type: Class),"The software performs an operation at a privilege level that is higher than the minimum level required, which creates new weaknesses or amplifies the consequences of other weaknesses. | |
| 436 | New weaknesses can be exposed because running with extra privileges, such as root or Administrator, can disable the normal security checks being performed by the operating system or surrounding environment. Other pre-existing weaknesses can turn into security vulnerabilities if they occur while operating at raised privileges. | |
| 437 | Privilege management functions can behave in some less-than-obvious ways, and they have different quirks on different platforms. These inconsistencies are particularly pronounced if you are transitioning from one non-root user to another. Signal handlers and spawned processes run at the privilege of the owning process, so if a process is running as root when a signal fires or a sub-process is executed, the signal handler or sub-process will operate with root privileges.",,medium,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 438 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 439 | Writing Secure Code: Chapter 7, ""Running with Least Privilege"" Page 207 | |
| 440 | Federal Desktop Core Configuration: http://nvd.nist.gov/fdcc/index.cfm | |
| 441 | 24 Deadly Sins of Software Security: ""Sin 16: Executing Code With Too Much Privilege."" Page 243 | |
| 442 | The Art of Software Security Assessment: Chapter 9, ""Privilege Vulnerabilities"", Page 477." | |
| 443 | CWE-269,Improper Privilege Management (Type: Base),"The software does not properly assign, modify, track, or check privileges for an actor, creating an unintended sphere of control for that actor. | |
| 444 | Just as neglecting to include functionality for the management of password aging is dangerous, so is allowing password aging to continue unchecked. Passwords must be given a maximum life span, after which a user is required to update with a new and different password.",,medium,"24 Deadly Sins of Software Security: ""Sin 16: Executing Code With Too Much Privilege."" Page 243 | |
| 445 | The Art of Software Security Assessment: Chapter 9, ""Dropping Privileges Permanently"", Page 479." | |
| 446 | CWE-273,Improper Check for Dropped Privileges (Type: Base),"The software attempts to drop privileges but does not check or incorrectly checks to see if the drop succeeded. | |
| 447 | If the drop fails, the software will continue to run with the raised privileges, which might provide additional access to unprivileged users.",,medium, | |
| 448 | CWE-276,Incorrect Default Permissions (Type: Variant),"The software, upon installation, sets incorrect permissions for an object that exposes it to an unintended actor. | |
| 449 | If the drop fails, the software will continue to run with the raised privileges, which might provide additional access to unprivileged users.",,medium,"The Art of Software Security Assessment: Chapter 3, ""Insecure Defaults"", Page 69." | |
| 450 | CWE-299,Improper Check for Certificate Revocation (Type: Variant),"The software does not check or incorrectly checks the revocation status of a certificate, which may cause it to use a certificate that has been compromised. | |
| 451 | An improper check for certificate revocation is a far more serious flaw than related certificate failures. This is because the use of any revoked certificate is almost certainly malicious. The most common reason for certificate revocation is compromise of the system in question, with the result that no legitimate servers will be using a revoked certificate, unless they are sorely out of sync.",,medium,"24 Deadly Sins of Software Security: ""Sin 23: Improper Use of PKI, Especially SSL."" Page 347" | |
| 452 | CWE-301,Reflection Attack in an Authentication Protocol (Type: Variant),"Simple authentication protocols are subject to reflection attacks if a malicious user can use the target machine to impersonate a trusted user. | |
| 453 | A mutual authentication protocol requires each party to respond to a random challenge by the other party by encrypting it with a pre-shared key. Often, however, such protocols employ the same pre-shared key for communication with a number of different entities. A malicious user or an attacker can easily compromise this protocol without possessing the correct key by employing a reflection attack on the protocol.",,medium,"The Art of Software Security Assessment: Chapter 2, ""Insufficient Validation"", Page 38." | |
| 454 | CWE-329,Not Using a Random IV with CBC Mode (Type: Variant),"Not using a random initialization Vector (IV) with Cipher Block Chaining (CBC) Mode causes algorithms to be susceptible to dictionary attacks. | |
| 455 | This weakness is especially dangerous when the hash is used in security algorithms that require the one-way property to hold. For example, if an authentication system takes an incoming password and generates a hash, then compares the hash to another hash that it has stored in its authentication database, then the ability to create a collision could allow an attacker to provide an alternate password that produces the same target hash, bypassing authentication.",,medium,"The Art of Software Security Assessment: Chapter 2, ""Initialization Vectors"", Page 42." | |
| 456 | CWE-332,Insufficient Entropy in PRNG (Type: Variant),"The lack of entropy available for, or used by, a Pseudo-Random Number Generator (PRNG) can be a stability and security threat. | |
| 457 | When software generates predictable values in a context requiring unpredictability, it may be possible for an attacker to guess the next value that will be generated, and use this guess to impersonate another user or access sensitive information.",,medium,SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 458 | CWE-338,Use of Cryptographically Weak PRNG (Type: Base),"The product uses a Pseudo-Random Number Generator (PRNG) in a security context, but the PRNG is not cryptographically strong. | |
| 459 | The rate at which true random numbers can be generated is limited. It is important that one uses them only when they are needed for security.",,medium,"24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 460 | CWE-353,Missing Support for Integrity Check (Type: Base),"The software uses a transmission protocol that does not include a mechanism for verifying the integrity of the data during transmission, such as a checksum. | |
| 461 | If integrity check values or ""checksums"" are omitted from a protocol, there is no way of determining if data has been corrupted in transmission. The lack of checksum functionality in a protocol removes the first application-level check of data that can be used. The end-to-end philosophy of checks states that integrity checks should be performed at the lowest level that they can be completely implemented. Excluding further sanity checks and input validation performed by applications, the protocol's checksum is the most important level of checksum, since it can be performed more completely than at any previous level and takes into account entire messages, as opposed to single packets.",,medium,"24 Deadly Sins of Software Security: ""Sin 15: Not Updating Easily."" Page 231" | |
| 462 | CWE-354,Improper Validation of Integrity Check Value (Type: Base),"The software does not validate or incorrectly validates the integrity check values or ""checksums"" of a message. This may prevent it from detecting if the data has been modified or corrupted in transmission. | |
| 463 | Improper validation of checksums before use results in an unnecessary risk that can easily be mitigated. The protocol specification describes the algorithm used for calculating the checksum. It is then a simple matter of implementing the calculation and verifying that the calculated checksum and the received checksum match. Improper verification of the calculated checksum and the received checksum can lead to far greater consequences.",,medium, | |
| 464 | CWE-362,Concurrent Execution using Shared Resource with Improper Synchronization (Race Condition) (Type: Class),"The program contains a code sequence that can run concurrently with other code, and the code sequence requires temporary, exclusive access to a shared resource, but a timing window exists in which the shared resource can be modified by another code sequence that is operating concurrently. | |
| 465 | This can have security implications when the expected synchronization is in security-critical code, such as recording whether a user is authenticated or modifying important state information that should not be influenced by an outsider. | |
| 466 | A race condition occurs within concurrent environments, and is effectively a property of a code sequence. Depending on the context, a code sequence may be in the form of a function call, a small number of instructions, a series of program invocations, etc. | |
| 467 | A race condition violates these properties, which are closely related: | |
| 468 | Exclusivity - the code sequence is given exclusive access to the shared resource, i.e., no other code sequence can modify properties of the shared resource before the original sequence has completed execution. | |
| 469 | Atomicity - the code sequence is behaviorally atomic, i.e., no other thread or process can concurrently execute the same sequence of instructions (or a subset) against the same resource. | |
| 470 | A race condition exists when an ""interfering code sequence"" can still access the shared resource, violating exclusivity. Programmers may assume that certain code sequences execute too quickly to be affected by an interfering code sequence; when they are not, this violates atomicity. For example, the single ""x++"" statement may appear atomic at the code layer, but it is actually non-atomic at the instruction layer, since it involves a read (the original value of x), followed by a computation (x+1), followed by a write (save the result to x). | |
| 471 | The interfering code sequence could be ""trusted"" or ""untrusted."" A trusted interfering code sequence occurs within the program; it cannot be modified by the attacker, and it can only be invoked indirectly. An untrusted interfering code sequence can be authored directly by the attacker, and typically it is external to the vulnerable program.",,medium,"24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205 | |
| 472 | volatile - Multithreaded Programmer's Best Friend: http://www.ddj.com/cpp/184403766 | |
| 473 | Thread-safe webapps using Spring: http://www.javalobby.org/articles/thread-safe/index.jsp | |
| 474 | Prevent race conditions: http://www.ibm.com/developerworks/library/l-sprace.html | |
| 475 | Race Conditions, Files, and Security Flaws; or the Tortoise and the Hare Redux: http://www.cs.ucdavis.edu/research/tech-reports/1995/CSE-95-9.pdf | |
| 476 | Secure Programming for Linux and Unix HOWTO: http://www.dwheeler.com/secure-programs/Secure-Programs-HOWTO/avoid-race.html | |
| 477 | Discovering and Exploiting Named Pipe Security Flaws for Fun and Profit: http://www.blakewatts.com/namedpipepaper.html | |
| 478 | On Race Vulnerabilities in Web Applications: http://security.dico.unimi.it/~roberto/pubs/dimva08-web.pdf | |
| 479 | Avoiding Race Conditions and Insecure File Operations: http://developer.apple.com/documentation/Security/Conceptual/SecureCodingGuide/Articles/RaceConditions.html | |
| 480 | Top 25 Series - Rank 25 - Race Conditions: http://blogs.sans.org/appsecstreetfighter/2010/03/26/top-25-series-rank-25-race-conditions/ | |
| 481 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html" | |
| 482 | CWE-364,Signal Handler Race Condition (Type: Base),"The software uses a signal handler that introduces a race condition. | |
| 483 | Race conditions frequently occur in signal handlers, since signal handlers support asynchronous actions. These race conditions have a variety of root causes and symptoms. Attackers may be able to exploit a signal handler race condition to cause the software state to be corrupted, possibly leading to a denial of service or even code execution. | |
| 484 | These issues occur when non-reentrant functions, or state-sensitive actions occur in the signal handler, where they may be called at any time. These behaviors can violate assumptions being made by the ""regular"" code that is interrupted, or by other signal handlers that may also be invoked. If these functions are called at an inopportune moment - such as while a non-reentrant function is already running - memory corruption could occur that may be exploitable for code execution. Another signal race condition commonly found occurs when free is called within a signal handler, resulting in a double free and therefore a write-what-where condition. Even if a given pointer is set to NULL after it has been freed, a race condition still exists between the time the memory was freed and the pointer was set to NULL. This is especially problematic if the same signal handler has been set for more than one signal -- since it means that the signal handler itself may be reentered. | |
| 485 | There are several known behaviors related to signal handlers that have received the label of ""signal handler race condition"": | |
| 486 | Shared state (e.g. global data or static variables) that are accessible to both a signal handler and ""regular"" code | |
| 487 | Shared state between a signal handler and other signal handlers | |
| 488 | Use of non-reentrant functionality within a signal handler - which generally implies that shared state is being used. For example, malloc() and free() are non-reentrant because they may use global or static data structures for managing memory, and they are indirectly used by innocent-seeming functions such as syslog(); these functions could be exploited for memory corruption and, possibly, code execution. | |
| 489 | Association of the same signal handler function with multiple signals - which might imply shared state, since the same code and resources are accessed. For example, this can be a source of double-free and use-after-free weaknesses. | |
| 490 | Use of setjmp and longjmp, or other mechanisms that prevent a signal handler from returning control back to the original functionality | |
| 491 | While not technically a race condition, some signal handlers are designed to be called at most once, and being called more than once can introduce security problems, even when there are not any concurrent calls to the signal handler. This can be a source of double-free and use-after-free weaknesses. | |
| 492 | Signal handler vulnerabilities are often classified based on the absence of a specific protection mechanism, although this style of classification is discouraged in CWE because programmers often have a choice of several different mechanisms for addressing the weakness. Such protection mechanisms may preserve exclusivity of access to the shared resource, and behavioral atomicity for the relevant code: | |
| 493 | Avoiding shared state | |
| 494 | Using synchronization in the signal handler | |
| 495 | Using synchronization in the regular code | |
| 496 | Disabling or masking other signals, which provides atomicity (which effectively ensures exclusivity)",,medium,"Delivering Signals for Fun and Profit: http://lcamtuf.coredump.cx/signals.txt | |
| 497 | Race Condition: Signal Handling: http://www.fortify.com/vulncat/en/vulncat/cpp/race_condition_signal_handling.html | |
| 498 | 24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205 | |
| 499 | The Art of Software Security Assessment: Chapter 13, ""Signal Vulnerabilities"", Page 791." | |
| 500 | CWE-365,Race Condition in Switch (Type: Base),"The code contains a switch statement in which the switched variable can be modified while the switch is still executing, resulting in unexpected behavior. | |
| 501 | Race conditions frequently occur in signal handlers, since signal handlers support asynchronous actions. These race conditions have a variety of root causes and symptoms. Attackers may be able to exploit a signal handler race condition to cause the software state to be corrupted, possibly leading to a denial of service or even code execution. | |
| 502 | These issues occur when non-reentrant functions, or state-sensitive actions occur in the signal handler, where they may be called at any time. These behaviors can violate assumptions being made by the ""regular"" code that is interrupted, or by other signal handlers that may also be invoked. If these functions are called at an inopportune moment - such as while a non-reentrant function is already running - memory corruption could occur that may be exploitable for code execution. Another signal race condition commonly found occurs when free is called within a signal handler, resulting in a double free and therefore a write-what-where condition. Even if a given pointer is set to NULL after it has been freed, a race condition still exists between the time the memory was freed and the pointer was set to NULL. This is especially problematic if the same signal handler has been set for more than one signal -- since it means that the signal handler itself may be reentered. | |
| 503 | There are several known behaviors related to signal handlers that have received the label of ""signal handler race condition"": | |
| 504 | Shared state (e.g. global data or static variables) that are accessible to both a signal handler and ""regular"" code | |
| 505 | Shared state between a signal handler and other signal handlers | |
| 506 | Use of non-reentrant functionality within a signal handler - which generally implies that shared state is being used. For example, malloc() and free() are non-reentrant because they may use global or static data structures for managing memory, and they are indirectly used by innocent-seeming functions such as syslog(); these functions could be exploited for memory corruption and, possibly, code execution. | |
| 507 | Association of the same signal handler function with multiple signals - which might imply shared state, since the same code and resources are accessed. For example, this can be a source of double-free and use-after-free weaknesses. | |
| 508 | Use of setjmp and longjmp, or other mechanisms that prevent a signal handler from returning control back to the original functionality | |
| 509 | While not technically a race condition, some signal handlers are designed to be called at most once, and being called more than once can introduce security problems, even when there are not any concurrent calls to the signal handler. This can be a source of double-free and use-after-free weaknesses. | |
| 510 | Signal handler vulnerabilities are often classified based on the absence of a specific protection mechanism, although this style of classification is discouraged in CWE because programmers often have a choice of several different mechanisms for addressing the weakness. Such protection mechanisms may preserve exclusivity of access to the shared resource, and behavioral atomicity for the relevant code: | |
| 511 | Avoiding shared state | |
| 512 | Using synchronization in the signal handler | |
| 513 | Using synchronization in the regular code | |
| 514 | Disabling or masking other signals, which provides atomicity (which effectively ensures exclusivity)",,medium,"24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205" | |
| 515 | CWE-366,Race Condition within a Thread (Type: Base),"If two threads of execution use a resource simultaneously, there exists the possibility that resources may be used while invalid, in turn making the state of execution undefined. | |
| 516 | Race conditions frequently occur in signal handlers, since signal handlers support asynchronous actions. These race conditions have a variety of root causes and symptoms. Attackers may be able to exploit a signal handler race condition to cause the software state to be corrupted, possibly leading to a denial of service or even code execution. | |
| 517 | These issues occur when non-reentrant functions, or state-sensitive actions occur in the signal handler, where they may be called at any time. These behaviors can violate assumptions being made by the ""regular"" code that is interrupted, or by other signal handlers that may also be invoked. If these functions are called at an inopportune moment - such as while a non-reentrant function is already running - memory corruption could occur that may be exploitable for code execution. Another signal race condition commonly found occurs when free is called within a signal handler, resulting in a double free and therefore a write-what-where condition. Even if a given pointer is set to NULL after it has been freed, a race condition still exists between the time the memory was freed and the pointer was set to NULL. This is especially problematic if the same signal handler has been set for more than one signal -- since it means that the signal handler itself may be reentered. | |
| 518 | There are several known behaviors related to signal handlers that have received the label of ""signal handler race condition"": | |
| 519 | Shared state (e.g. global data or static variables) that are accessible to both a signal handler and ""regular"" code | |
| 520 | Shared state between a signal handler and other signal handlers | |
| 521 | Use of non-reentrant functionality within a signal handler - which generally implies that shared state is being used. For example, malloc() and free() are non-reentrant because they may use global or static data structures for managing memory, and they are indirectly used by innocent-seeming functions such as syslog(); these functions could be exploited for memory corruption and, possibly, code execution. | |
| 522 | Association of the same signal handler function with multiple signals - which might imply shared state, since the same code and resources are accessed. For example, this can be a source of double-free and use-after-free weaknesses. | |
| 523 | Use of setjmp and longjmp, or other mechanisms that prevent a signal handler from returning control back to the original functionality | |
| 524 | While not technically a race condition, some signal handlers are designed to be called at most once, and being called more than once can introduce security problems, even when there are not any concurrent calls to the signal handler. This can be a source of double-free and use-after-free weaknesses. | |
| 525 | Signal handler vulnerabilities are often classified based on the absence of a specific protection mechanism, although this style of classification is discouraged in CWE because programmers often have a choice of several different mechanisms for addressing the weakness. Such protection mechanisms may preserve exclusivity of access to the shared resource, and behavioral atomicity for the relevant code: | |
| 526 | Avoiding shared state | |
| 527 | Using synchronization in the signal handler | |
| 528 | Using synchronization in the regular code | |
| 529 | Disabling or masking other signals, which provides atomicity (which effectively ensures exclusivity)",,medium,"24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205 | |
| 530 | The Art of Software Security Assessment: Chapter 13, ""Race Conditions"", Page 759." | |
| 531 | CWE-369,Divide By Zero (Type: Base),"The product divides a value by zero. | |
| 532 | This weakness typically occurs when an unexpected value is provided to the product, or if an error occurs that is not properly detected. It frequently occurs in calculations involving physical dimensions such as size, length, width, and height.",,medium,"No description: http://www.cprogramming.com/tutorial/exceptions.html | |
| 533 | No description: http://msdn.microsoft.com/en-us/library/ms173160(VS.80).aspx" | |
| 534 | CWE-370,Missing Check for Certificate Revocation after Initial Check (Type: Base),"The software does not check the revocation status of a certificate after its initial revocation check, which can cause the software to perform privileged actions even after the certificate is revoked at a later time. | |
| 535 | If the revocation status of a certificate is not checked before each action that requires privileges, the system may be subject to a race condition. If a certificate is revoked after the initial check, all subsequent actions taken with the owner of the revoked certificate will lose all benefits guaranteed by the certificate. In fact, it is almost certain that the use of a revoked certificate indicates malicious activity.",,medium,"24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205" | |
| 536 | CWE-374,Passing Mutable Objects to an Untrusted Method (Type: Base),"Sending non-cloned mutable data as an argument may result in that data being altered or deleted by the called function, thereby putting the calling function into an undefined state. | |
| 537 | If the revocation status of a certificate is not checked before each action that requires privileges, the system may be subject to a race condition. If a certificate is revoked after the initial check, all subsequent actions taken with the owner of the revoked certificate will lose all benefits guaranteed by the certificate. In fact, it is almost certain that the use of a revoked certificate indicates malicious activity.",,medium,"Does Java pass by reference or pass by value?: http://www.javaworld.com/javaworld/javaqa/2000-05/03-qa-0526-pass.html | |
| 538 | Java: The Complete Reference, J2SE 5th Edition" | |
| 539 | CWE-375,Returning a Mutable Object to an Untrusted Caller (Type: Base),"Sending non-cloned mutable data as a return value may result in that data being altered or deleted by the calling function, thereby putting the class in an undefined state. | |
| 540 | If the revocation status of a certificate is not checked before each action that requires privileges, the system may be subject to a race condition. If a certificate is revoked after the initial check, all subsequent actions taken with the owner of the revoked certificate will lose all benefits guaranteed by the certificate. In fact, it is almost certain that the use of a revoked certificate indicates malicious activity.",,medium, | |
| 541 | CWE-385,Covert Timing Channel (Type: Base),"Covert timing channels convey information by modulating some aspect of system behavior over time, so that the program receiving the information can observe system behavior and infer protected information. | |
| 542 | In some instances, knowing when data is transmitted between parties can provide a malicious user with privileged information. Also, externally monitoring the timing of operations can potentially reveal sensitive data. For example, a cryptographic operation can expose its internal state if the time it takes to perform the operation varies, based on the state. | |
| 543 | Covert channels are frequently classified as either storage or timing channels. Some examples of covert timing channels are the system's paging rate, the time a certain transaction requires to execute, and the time it takes to gain access to a shared bus.",,medium, | |
| 544 | CWE-390,Detection of Error Condition Without Action (Type: Class),"The software detects a specific error, but takes no actions to handle the error. | |
| 545 | In some instances, knowing when data is transmitted between parties can provide a malicious user with privileged information. Also, externally monitoring the timing of operations can potentially reveal sensitive data. For example, a cryptographic operation can expose its internal state if the time it takes to perform the operation varies, based on the state. | |
| 546 | Covert channels are frequently classified as either storage or timing channels. Some examples of covert timing channels are the system's paging rate, the time a certain transaction requires to execute, and the time it takes to gain access to a shared bus.",,medium,"24 Deadly Sins of Software Security: ""Sin 11: Failure to Handle Errors Correctly."" Page 183" | |
| 547 | CWE-391,Unchecked Error Condition (Type: Base),"Ignoring exceptions and other error conditions may allow an attacker to induce unexpected behavior unnoticed. | |
| 548 | In some instances, knowing when data is transmitted between parties can provide a malicious user with privileged information. Also, externally monitoring the timing of operations can potentially reveal sensitive data. For example, a cryptographic operation can expose its internal state if the time it takes to perform the operation varies, based on the state. | |
| 549 | Covert channels are frequently classified as either storage or timing channels. Some examples of covert timing channels are the system's paging rate, the time a certain transaction requires to execute, and the time it takes to gain access to a shared bus.",,medium, | |
| 550 | CWE-401,Improper Release of Memory Before Removing Last Reference (Memory Leak) (Type: Base),"The software does not sufficiently track and release allocated memory after it has been used, which slowly consumes remaining memory. | |
| 551 | This is often triggered by improper handling of malformed data or unexpectedly interrupted sessions.",,medium,How to Break Software Security | |
| 552 | CWE-460,Improper Cleanup on Thrown Exception (Type: Variant),"The product does not clean up its state or incorrectly cleans up its state when an exception is thrown, leading to unexpected state or control flow. | |
| 553 | In some languages such as C and C++, stack variables are not initialized by default. They generally contain junk data with the contents of stack memory before the function was invoked. An attacker can sometimes control or read these contents. In other languages or conditions, a variable that is not explicitly initialized can be given a default value that has security implications, depending on the logic of the program. The presence of an uninitialized variable can sometimes indicate a typographic error in the code.",,medium, | |
| 554 | CWE-468,Incorrect Pointer Scaling (Type: Base),"In C and C++, one may often accidentally refer to the wrong memory due to the semantics of when math operations are implicitly scaled. | |
| 555 | Data-structure sentinels are often used to mark the structure of data. A common example of this is the null character at the end of strings or a special sentinel to mark the end of a linked list. It is dangerous to allow this type of control data to be easily accessible. Therefore, it is important to protect from the addition or modification of sentinels.",,medium,"The Art of Software Security Assessment: Chapter 6, ""Pointer Arithmetic"", Page 277." | |
| 556 | CWE-469,Use of Pointer Subtraction to Determine Size (Type: Base),"The application subtracts one pointer from another in order to determine size, but this calculation can be incorrect if the pointers do not exist in the same memory chunk. | |
| 557 | Data-structure sentinels are often used to mark the structure of data. A common example of this is the null character at the end of strings or a special sentinel to mark the end of a linked list. It is dangerous to allow this type of control data to be easily accessible. Therefore, it is important to protect from the addition or modification of sentinels.",,medium, | |
| 558 | CWE-476,NULL Pointer Dereference (Type: Base),"A NULL pointer dereference occurs when the application dereferences a pointer that it expects to be valid, but is NULL, typically causing a crash or exit. | |
| 559 | NULL pointer dereference issues can occur through a number of flaws, including race conditions, and simple programming omissions.",,medium, | |
| 560 | CWE-484,Omitted Break Statement in Switch (Type: Base),"The program omits a break statement within a switch or similar construct, causing code associated with multiple conditions to execute. This can cause problems when the programmer only intended to execute code associated with one condition. | |
| 561 | This can lead to critical code executing in situations where it should not.",,medium,"The Art of Software Security Assessment: Chapter 7, ""Switch Statements"", Page 337." | |
| 562 | CWE-487,Reliance on Package-level Scope (Type: Variant),"Java packages are not inherently closed; therefore, relying on them for code security is not a good practice. | |
| 563 | If the decision to trust the methods and data of an object is based on the name of a class, it is possible for malicious users to send objects of the same name as trusted classes and thereby gain the trust afforded to known classes and types.",,medium, | |
| 564 | CWE-492,Use of Inner Class Containing Sensitive Data (Type: Variant),"Inner classes are translated into classes that are accessible at package scope and may expose code that the programmer intended to keep private to attackers. | |
| 565 | Data can ""bleed"" from one session to another through member variables of singleton objects, such as Servlets, and objects from a shared pool. | |
| 566 | In the case of Servlets, developers sometimes do not understand that, unless a Servlet implements the SingleThreadModel interface, the Servlet is a singleton; there is only one instance of the Servlet, and that single instance is used and re-used to handle multiple requests that are processed simultaneously by different threads. A common result is that developers use Servlet member fields in such a way that one user may inadvertently see another user's data. In other words, storing user data in Servlet member fields introduces a data access race condition.",,medium, | |
| 567 | CWE-494,Download of Code Without Integrity Check (Type: Base),"The product downloads source code or an executable from a remote location and executes the code without sufficiently verifying the origin and integrity of the code. | |
| 568 | An attacker can execute malicious code by compromising the host server, performing DNS spoofing, or modifying the code in transit.",,medium,"Introduction to Code Signing: http://msdn.microsoft.com/en-us/library/ms537361(VS.85).aspx | |
| 569 | Authenticode: http://msdn.microsoft.com/en-us/library/ms537359(v=VS.85).aspx | |
| 570 | Code Signing Guide: http://developer.apple.com/documentation/Security/Conceptual/CodeSigningGuide/Introduction/chapter_1_section_1.html | |
| 571 | Secure Software Updates: Disappointments and New Challenges: http://prisms.cs.umass.edu/~kevinfu/papers/secureupdates-hotsec06.pdf | |
| 572 | 24 Deadly Sins of Software Security: ""Sin 18: The Sins of Mobile Code."" Page 267 | |
| 573 | Top 25 Series - Rank 20 - Download of Code Without Integrity Check: http://blogs.sans.org/appsecstreetfighter/2010/04/05/top-25-series-rank-20-download-code-integrity-check/ | |
| 574 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html" | |
| 575 | CWE-498,Cloneable Class Containing Sensitive Information (Type: Variant),"The code contains a class with sensitive data, but the class is cloneable. The data can then be accessed by cloning the class. | |
| 576 | Cloneable classes are effectively open classes, since data cannot be hidden in them. Classes that do not explicitly deny cloning can be cloned by any other class without running the constructor.",,medium, | |
| 577 | CWE-502,Deserialization of Untrusted Data (Type: Variant),"The application deserializes untrusted data without sufficiently verifying that the resulting data will be valid. | |
| 578 | It is often convenient to serialize objects for communication or to save them for later use. However, deserialized data or code can often be modified without using the provided accessor functions if it does not use cryptography to protect itself. Furthermore, any cryptography would still be client-side security -- which is a dangerous security assumption. | |
| 579 | Data that is untrusted can not be trusted to be well-formed.",,medium,"Unserializing user-supplied data, a bad idea: http://heine.familiedeelstra.com/security/unserialize | |
| 580 | Why Python Pickle is Insecure: http://nadiana.com/python-pickle-insecure" | |
| 581 | CWE-532,Information Exposure Through Log Files (Type: Variant),"Information written to log files can be of a sensitive nature and give valuable guidance to an attacker or expose sensitive user information. | |
| 582 | While logging all information may be helpful during development stages, it is important that logging levels be set appropriately before a product ships so that sensitive user data and system information are not accidentally exposed to potential attackers.",,medium, | |
| 583 | CWE-602,Client-Side Enforcement of Server-Side Security (Type: Base),"The software is composed of a server that relies on the client to implement a mechanism that is intended to protect the server. | |
| 584 | When the server relies on protection mechanisms placed on the client side, an attacker can modify the client-side behavior to bypass the protection mechanisms resulting in potentially unexpected interactions between the client and server. The consequences will vary, depending on what the mechanisms are trying to protect.",,medium,"Writing Secure Code: Chapter 23, ""Client-Side Security Is an Oxymoron"" Page 687" | |
| 585 | CWE-665,Improper Initialization (Type: Base),"The software does not initialize or incorrectly initializes a resource, which might leave the resource in an unexpected state when it is accessed or used. | |
| 586 | This can have security implications when the associated resource is expected to have certain properties or values, such as a variable that determines whether a user has been authenticated or not.",,medium,"Exploiting Uninitialized Data: http://www.felinemenace.org/~mercy/papers/UBehavior/UBehavior.zip | |
| 587 | MS08-014 : The Case of the Uninitialized Stack Variable Vulnerability: http://blogs.technet.com/swi/archive/2008/03/11/the-case-of-the-uninitialized-stack-variable-vulnerability.aspx | |
| 588 | The Art of Software Security Assessment: Chapter 7, ""Variable Initialization"", Page 312." | |
| 589 | CWE-754,Improper Check for Unusual or Exceptional Conditions (Type: Class),"The software does not check or improperly checks for unusual or exceptional conditions that are not expected to occur frequently during day to day operation of the software. | |
| 590 | The programmer may assume that certain events or conditions will never occur or do not need to be worried about, such as low memory conditions, lack of access to resources due to restrictive permissions, or misbehaving clients or components. However, attackers may intentionally trigger these unusual conditions, thus violating the programmer's assumptions, possibly introducing instability, incorrect behavior, or a vulnerability. | |
| 591 | Note that this entry is not exclusively about the use of exceptions and exception handling, which are mechanisms for both checking and handling unusual or unexpected conditions.",,medium,"The Art of Software Security Assessment: Chapter 7, ""Program Building Blocks"" Page 341 | |
| 592 | The Art of Software Security Assessment: Chapter 1, ""Exceptional Conditions,"" Page 22 | |
| 593 | 24 Deadly Sins of Software Security: ""Sin 11: Failure to Handle Errors Correctly."" Page 183 | |
| 594 | Top 25 Series - Rank 15 - Improper Check for Unusual or Exceptional Conditions: http://blogs.sans.org/appsecstreetfighter/2010/03/15/top-25-series-rank-15-improper-check-for-unusual-or-exceptional-conditions/" | |
| 595 | CWE-778,Insufficient Logging (Type: Base),"When a security-critical event occurs, the software either does not record the event or omits important details about the event when logging it. | |
| 596 | When security-critical events are not logged properly, such as a failed login attempt, this can make malicious behavior more difficult to detect and may hinder forensic analysis after an attack succeeds.",,medium,"The Art of Software Security Assessment: Chapter 2, ""Accountability"", Page 40." | |
| 597 | CWE-780,Use of RSA Algorithm without OAEP (Type: Variant),"The software uses the RSA algorithm but does not incorporate Optimal Asymmetric Encryption Padding (OAEP), which might weaken the encryption. | |
| 598 | Padding schemes are often used with cryptographic algorithms to make the plaintext less predictable and complicate attack efforts. The OAEP scheme is often used with RSA to nullify the impact of predictable common text.",,medium,"RSA Problem: http://people.csail.mit.edu/rivest/RivestKaliski-RSAProblem.pdf | |
| 599 | Optimal Asymmetric Encryption Padding: http://en.wikipedia.org/wiki/Optimal_Asymmetric_Encryption_Padding" | |
| 600 | CWE-908,Use of Uninitialized Resource (Type: Base),"The software uses a resource that has not been properly initialized. | |
| 601 | This can have security implications when the associated resource is expected to have certain properties or values.",,medium,Exploiting Uninitialized Data: http://www.felinemenace.org/~mercy/papers/UBehavior/UBehavior.zip | |
| 602 | CWE-909,Missing Initialization of Resource (Type: Base),"The software does not initialize a critical resource. | |
| 603 | Many resources require initialization before they can be properly used. If a resource is not initialized, it could contain unpredictable or expired data, or it could be initialized to defaults that are invalid. This can have security implications when the resource is expected to have certain properties or values.",,medium, | |
| 604 | CWE-910,Use of Expired File Descriptor (Type: Base),"The software uses or accesses a file descriptor after it has been closed. | |
| 605 | After a file descriptor for a particular file or device has been released, it can be reused. The code might not write to the original file, since the reused file descriptor might reference a different file or device.",,medium, | |
| 606 | CWE-911,Improper Update of Reference Count (Type: Base),"The software uses a reference count to manage a resource, but it does not update or incorrectly updates the reference count. | |
| 607 | Reference counts can be used when tracking how many objects contain a reference to a particular resource, such as in memory management or garbage collection. When the reference count reaches zero, the resource can be de-allocated or reused because there are no more objects that use it. If the reference count accidentally reaches zero, then the resource might be released too soon, even though it is still in use. If all objects no longer use the resource, but the reference count is not zero, then the resource might not ever be released.",,medium,Windows Kernel Reference Count Vulnerabilities - Case Study: http://j00ru.vexillium.org/dump/zn_slides.pdf | |
| 608 | CWE-94,Improper Control of Generation of Code (Code Injection) (Type: Class),"The software constructs all or part of a code segment using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the syntax or behavior of the intended code segment. | |
| 609 | When software allows a user's input to contain code syntax, it might be possible for an attacker to craft the code in such a way that it will alter the intended control flow of the software. Such an alteration could lead to arbitrary code execution. | |
| 610 | Injection problems encompass a wide variety of issues -- all mitigated in very different ways. For this reason, the most effective way to discuss these weaknesses is to note the distinct features which classify them as injection weaknesses. The most important issue to note is that all injection problems share one thing in common -- i.e., they allow for the injection of control plane data into the user-controlled data plane. This means that the execution of the process may be altered by sending code in through legitimate data channels, using no other mechanism. While buffer overflows, and many other flaws, involve the use of some further issue to gain execution, injection problems need only for the data to be parsed. The most classic instantiations of this category of weakness are SQL injection and format string vulnerabilities.",,medium,"24 Deadly Sins of Software Security: ""Sin 3: Web-Client Related Vulnerabilities (XSS)."" Page 63" | |
| 611 | CWE-95,Improper Neutralization of Directives in Dynamically Evaluated Code (Eval Injection) (Type: Base),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes code syntax before using the input in a dynamic evaluation call (e.g. ""eval""). | |
| 612 | This may allow an attacker to execute arbitrary code, or at least modify what code can be executed.",,medium,"No description: http://www.rubycentral.com/book/taint.html | |
| 613 | The Art of Software Security Assessment: Chapter 18, ""Inline Evaluation"", Page 1095." | |
| 614 | CWE-287,Improper Authentication (Type: Class),"When an actor claims to have a given identity, the software does not prove or insufficiently proves that the claim is correct. | |
| 615 | Users can be assigned to the wrong group (class) of permissions resulting in unintended access rights to sensitive objects.",,high,"Weak Password Brings 'Happiness' to Twitter Hacker: http://www.wired.com/threatlevel/2009/01/professed-twitt/ | |
| 616 | Top 10 2007-Broken Authentication and Session Management: http://www.owasp.org/index.php/Top_10_2007-A7 | |
| 617 | Guide to Authentication: http://www.owasp.org/index.php/Guide_to_Authentication | |
| 618 | Authentication: http://msdn.microsoft.com/en-us/library/aa374735(VS.85).aspx | |
| 619 | Writing Secure Code: Chapter 4, ""Authentication"" Page 109" | |
| 620 | CWE-306,Missing Authentication for Critical Function (Type: Variant),"The software does not perform any authentication for functionality that requires a provable user identity or consumes a significant amount of resources. | |
| 621 | Authentication techniques should follow the algorithms that define them exactly, otherwise authentication can be bypassed or more easily subjected to brute force attacks.",,high,"The Art of Software Security Assessment: Chapter 2, ""Common Vulnerabilities of Authentication,"" Page 36 | |
| 622 | Top 25 Series - Rank 19 - Missing Authentication for Critical Function: http://blogs.sans.org/appsecstreetfighter/2010/02/23/top-25-series-rank-19-missing-authentication-for-critical-function/ | |
| 623 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI" | |
| 624 | CWE-319,Cleartext Transmission of Sensitive Information (Type: Base),"The software transmits sensitive or security-critical data in cleartext in a communication channel that can be sniffed by unauthorized actors. | |
| 625 | Many communication channels can be ""sniffed"" by attackers during data transmission. For example, network traffic can often be sniffed by any attacker who has access to a network interface. This significantly lowers the difficulty of exploitation by attackers.",,high,"Top 10 2007-Insecure Communications: http://www.owasp.org/index.php/Top_10_2007-A9 | |
| 626 | Writing Secure Code: Chapter 9, ""Protecting Secret Data"" Page 299 | |
| 627 | 24 Deadly Sins of Software Security: ""Sin 22: Failing to Protect Network Traffic."" Page 337 | |
| 628 | Mobile App Top 10 List: http://www.veracode.com/blog/2010/12/mobile-app-top-10-list/" | |
| 629 | CWE-327,Use of a Broken or Risky Cryptographic Algorithm (Type: Base),"The use of a broken or risky cryptographic algorithm is an unnecessary risk that may result in the exposure of sensitive information. | |
| 630 | The use of a non-standard algorithm is dangerous because a determined attacker may be able to break the algorithm and compromise whatever data has been protected. Well-known techniques may exist to break the algorithm.",,high,"Applied Cryptography: http://www.schneier.com/book-applied.html | |
| 631 | Handbook of Applied Cryptography: http://www.cacr.math.uwaterloo.ca/hac/ | |
| 632 | Avoiding bogus encryption products: Snake Oil FAQ: http://www.faqs.org/faqs/cryptography-faq/snake-oil/ | |
| 633 | SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 634 | Microsoft Scraps Old Encryption in New Code: http://www.eweek.com/c/a/Security/Microsoft-Scraps-Old-Encryption-in-New-Code/ | |
| 635 | Writing Secure Code: Chapter 8, ""Cryptographic Foibles"" Page 259 | |
| 636 | 24 Deadly Sins of Software Security: ""Sin 21: Using the Wrong Cryptography."" Page 315 | |
| 637 | Top 25 Series - Rank 24 - Use of a Broken or Risky Cryptographic Algorithm: http://blogs.sans.org/appsecstreetfighter/2010/03/25/top-25-series-rank-24-use-of-a-broken-or-risky-cryptographic-algorithm/ | |
| 638 | The Art of Software Security Assessment: Chapter 2, ""Insufficient or Obsolete Encryption"", Page 44." | |
| 639 | CWE-330,Use of Insufficiently Random Values (Type: Class),"The software may use insufficiently random numbers or values in a security context that depends on unpredictable numbers. | |
| 640 | When software generates predictable values in a context requiring unpredictability, it may be possible for an attacker to guess the next value that will be generated, and use this guess to impersonate another user or access sensitive information.",,high,"SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 641 | Building Secure Software: How to Avoid Security Problems the Right Way | |
| 642 | Writing Secure Code: Chapter 8, ""Using Poor Random Numbers"" Page 259 | |
| 643 | 24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 644 | CWE-400,Uncontrolled Resource Consumption (Resource Exhaustion) (Type: Base),"The software does not properly restrict the size or amount of resources that are requested or influenced by an actor, which can be used to consume more resources than intended. | |
| 645 | Limited resources include memory, file system storage, database connection pool entries, or CPU. If an attacker can trigger the allocation of these limited resources, but the number or size of the resources is not controlled, then the attacker could cause a denial of service that consumes all available resources. This would prevent valid users from accessing the software, and it could potentially have an impact on the surrounding environment. For example, a memory exhaustion attack against an application could slow down the application as well as its host operating system. | |
| 646 | Resource exhaustion problems have at least two common causes: | |
| 647 | Error conditions and other exceptional circumstances | |
| 648 | Confusion over which part of the program is responsible for releasing the resource",,high,"Detection and Prediction of Resource-Exhaustion Vulnerabilities: http://homepages.di.fc.ul.pt/~nuno/PAPERS/ISSRE08.pdf | |
| 649 | Resource exhaustion: http://cr.yp.to/docs/resources.html | |
| 650 | Resource exhaustion: http://homes.cerias.purdue.edu/~pmeunier/secprog/sanitized/class1/6.resource%20exhaustion.ppt | |
| 651 | Writing Secure Code: Chapter 17, ""Protecting Against Denial of Service Attacks"" Page 517" | |
| 652 | CWE-434,Unrestricted Upload of File with Dangerous Type (Type: Base),"The software allows the attacker to upload or transfer files of dangerous types that can be automatically processed within the product's environment. | |
| 653 | If code is stored in a file with an extension such as "".inc"" or "".pl"", and the web server does not have a handler for that extension, then the server will likely send the contents of the file directly to the requester without the pre-processing that was expected. When that file contains sensitive information such as database credentials, this may allow the attacker to compromise the application or associated components.",,high,"Dynamic File Uploads, Security and You: http://shsc.info/FileUploadSecurity | |
| 654 | 8 Basic Rules to Implement Secure File Uploads: http://blogs.sans.org/appsecstreetfighter/2009/12/28/8-basic-rules-to-implement-secure-file-uploads/ | |
| 655 | Top 25 Series - Rank 8 - Unrestricted Upload of Dangerous File Type: http://blogs.sans.org/appsecstreetfighter/2010/02/25/top-25-series-rank-8-unrestricted-upload-of-dangerous-file-type/ | |
| 656 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 657 | The Art of Software Security Assessment: Chapter 17, ""File Uploading"", Page 1068." | |
| 658 | CWE-64,Windows Shortcut Following (.LNK) (Type: Variant),"The software, when opening a file or directory, does not sufficiently handle when the file is a Windows shortcut (.LNK) whose target is outside of the intended control sphere. This could allow an attacker to cause the software to operate on unauthorized files. | |
| 659 | The shortcut (file with the .lnk extension) can permit an attacker to read/write a file that they originally did not have permissions to access.",,high, | |
| 660 | CWE-681,Incorrect Conversion between Numeric Types (Type: Base),"When converting from one data type to another, such as long to integer, data can be omitted or translated in a way that produces unexpected values. If the resulting values are used in a sensitive context, then dangerous behaviors may occur. | |
| 661 | Typically, a product defines its control sphere within the code itself, or through configuration by the product's administrator. In some cases, an external party can change the definition of the control sphere. This is typically a resultant weakness.",,high,"The Art of Software Security Assessment: Chapter 6, ""Type Conversions"", Page 223." | |
| 662 | CWE-732,Incorrect Permission Assignment for Critical Resource (Type: Class),"The software specifies permissions for a security-critical resource in a way that allows that resource to be read or modified by unintended actors. | |
| 663 | When a resource is given a permissions setting that provides access to a wider range of actors than required, it could lead to the exposure of sensitive information, or the modification of that resource by unintended parties. This is especially dangerous when the resource is related to program configuration, execution or sensitive user data.",,high,"The Art of Software Security Assessment: Chapter 9, ""File Permissions."" Page 495. | |
| 664 | Building Secure Software: How to Avoid Security Problems the Right Way: Chapter 8, ""Access Control."" Page 194. | |
| 665 | Top 25 Series - Rank 21 - Incorrect Permission Assignment for Critical Response: http://software-security.sans.org/blog/2010/03/24/top-25-series-rank-21-incorrect-permission-assignment-for-critical-response | |
| 666 | Federal Desktop Core Configuration: http://nvd.nist.gov/fdcc/index.cfm" | |
| 667 | CWE-770,Allocation of Resources Without Limits or Throttling (Type: Base),"The software allocates a reusable resource or group of resources on behalf of an actor without imposing any restrictions on how many resources can be allocated, in violation of the intended security policy for that actor. | |
| 668 | Command injection vulnerabilities typically occur when: | |
| 669 | 1. Data enters the application from an untrusted source. | |
| 670 | 2. The data is part of a string that is executed as a command by the application. | |
| 671 | 3. By executing the command, the application gives an attacker a privilege or capability that the attacker would not otherwise have.",,high,"Real-Life Example of a 'Business Logic Defect' (Screen Shots!): http://h30501.www3.hp.com/t5/Following-the-White-Rabbit-A/Real-Life-Example-of-a-Business-Logic-Defect-Screen-Shots/ba-p/22581 | |
| 672 | Detection and Prediction of Resource-Exhaustion Vulnerabilities: http://homepages.di.fc.ul.pt/~nuno/PAPERS/ISSRE08.pdf | |
| 673 | Resource exhaustion: http://cr.yp.to/docs/resources.html | |
| 674 | Resource exhaustion: http://homes.cerias.purdue.edu/~pmeunier/secprog/sanitized/class1/6.resource%20exhaustion.ppt | |
| 675 | Writing Secure Code: Chapter 17, ""Protecting Against Denial of Service Attacks"" Page 517 | |
| 676 | Top 25 Series - Rank 22 - Allocation of Resources Without Limits or Throttling: http://blogs.sans.org/appsecstreetfighter/2010/03/23/top-25-series-rank-22-allocation-of-resources-without-limits-or-throttling/ | |
| 677 | The Art of Software Security Assessment: Chapter 10, ""Resource Limits"", Page 574." | |
| 678 | CWE-771,Missing Reference to Active Allocated Resource (Type: Base),"The software does not properly maintain a reference to a resource that has been allocated, which prevents the resource from being reclaimed. | |
| 679 | This does not necessarily apply in languages or frameworks that automatically perform garbage collection, since the removal of all references may act as a signal that the resource is ready to be reclaimed.",,high, | |
| 680 | CWE-772,Missing Release of Resource after Effective Lifetime (Type: Base),"The software does not release a resource after its effective lifetime has ended, i.e., after the resource is no longer needed. | |
| 681 | When a resource is not released after use, it can allow attackers to cause a denial of service.",,high, | |
| 682 | CWE-773,Missing Reference to Active File Descriptor or Handle (Type: Variant),"The software does not properly maintain references to a file descriptor or handle, which prevents that file descriptor/handle from being reclaimed. | |
| 683 | This can cause the software to consume all available file descriptors or handles, which can prevent other processes from performing critical file processing operations.",,high, | |
| 684 | CWE-774,Allocation of File Descriptors or Handles Without Limits or Throttling (Type: Variant),"The software allocates file descriptors or handles on behalf of an actor without imposing any restrictions on how many descriptors can be allocated, in violation of the intended security policy for that actor. | |
| 685 | This can cause the software to consume all available file descriptors or handles, which can prevent other processes from performing critical file processing operations.",,high,"The Art of Software Security Assessment: Chapter 10, ""Resource Limits"", Page 574." | |
| 686 | CWE-775,Missing Release of File Descriptor or Handle after Effective Lifetime (Type: Variant),"The software does not release a file descriptor or handle after its effective lifetime has ended, i.e., after the file descriptor/handle is no longer needed. | |
| 687 | When a file descriptor or handle is not released after use (typically by explicitly closing it), attackers can cause a denial of service by consuming all available file descriptors/handles, or otherwise preventing other system processes from obtaining their own file descriptors/handles.",,high,"The Art of Software Security Assessment: Chapter 10, ""File Descriptor Leaks"", Page 582." | |
| 688 | CWE-804,Guessable CAPTCHA (Type: Base),"The software uses a CAPTCHA challenge, but the challenge can be guessed or automatically recognized by a non-human actor. | |
| 689 | An automated attacker could bypass the intended protection of the CAPTCHA challenge and perform actions at a higher frequency than humanly possible, such as launching spam attacks. | |
| 690 | There can be several different causes of a guessable CAPTCHA: | |
| 691 | An audio or visual image that does not have sufficient distortion from the unobfuscated source image. | |
| 692 | A question is generated that with a format that can be automatically recognized, such as a math question. | |
| 693 | A question for which the number of possible answers is limited, such as birth years or favorite sports teams. | |
| 694 | A general-knowledge or trivia question for which the answer can be accessed using a data base, such as country capitals or popular actors. | |
| 695 | Other data associated with the CAPTCHA may provide hints about its contents, such as an image whose filename contains the word that is used in the CAPTCHA.",,high,Insufficient Anti-automation: http://projects.webappsec.org/Insufficient+Anti-automation | |
| 696 | CWE-805,Buffer Access with Incorrect Length Value (Type: Base),"The software uses a sequential operation to read or write a buffer, but it uses an incorrect length value that causes it to access memory that is outside of the bounds of the buffer. | |
| 697 | When the length value exceeds the size of the destination, a buffer overflow could occur.",,high,"Writing Secure Code: Chapter 6, ""Why ACLs Are Important"" Page 171 | |
| 698 | Address Space Layout Randomization in Windows Vista: http://blogs.msdn.com/michael_howard/archive/2006/05/26/address-space-layout-randomization-in-windows-vista.aspx | |
| 699 | Limiting buffer overflows with ExecShield: http://www.redhat.com/magazine/009jul05/features/execshield/ | |
| 700 | PaX: http://en.wikipedia.org/wiki/PaX | |
| 701 | Top 25 Series - Rank 12 - Buffer Access with Incorrect Length Value: http://blogs.sans.org/appsecstreetfighter/2010/03/11/top-25-series-rank-12-buffer-access-with-incorrect-length-value/ | |
| 702 | Safe C String Library v1.0.3: http://www.zork.org/safestr/ | |
| 703 | Using the Strsafe.h Functions: http://msdn.microsoft.com/en-us/library/ms647466.aspx | |
| 704 | Understanding DEP as a mitigation technology part 1: http://blogs.technet.com/b/srd/archive/2009/06/12/understanding-dep-as-a-mitigation-technology-part-1.aspx | |
| 705 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html" | |
| 706 | CWE-806,Buffer Access Using Size of Source Buffer (Type: Variant),"The software uses the size of a source buffer when reading from or writing to a destination buffer, which may cause it to access memory that is outside of the bounds of the buffer. | |
| 707 | When the size of the destination is smaller than the size of the source, a buffer overflow could occur.",,high,"Using the Strsafe.h Functions: http://msdn.microsoft.com/en-us/library/ms647466.aspx | |
| 708 | Safe C String Library v1.0.3: http://www.zork.org/safestr/ | |
| 709 | Address Space Layout Randomization in Windows Vista: http://blogs.msdn.com/michael_howard/archive/2006/05/26/address-space-layout-randomization-in-windows-vista.aspx | |
| 710 | Limiting buffer overflows with ExecShield: http://www.redhat.com/magazine/009jul05/features/execshield/ | |
| 711 | PaX: http://en.wikipedia.org/wiki/PaX | |
| 712 | Understanding DEP as a mitigation technology part 1: http://blogs.technet.com/b/srd/archive/2009/06/12/understanding-dep-as-a-mitigation-technology-part-1.aspx" | |
| 713 | CWE-807,Reliance on Untrusted Inputs in a Security Decision (Type: Base),"The application uses a protection mechanism that relies on the existence or values of an input, but the input can be modified by an untrusted actor in a way that bypasses the protection mechanism. | |
| 714 | Developers may assume that inputs such as cookies, environment variables, and hidden form fields cannot be modified. However, an attacker could change these inputs using customized clients or other attacks. This change might not be detected. When security decisions such as authentication and authorization are made based on the values of these inputs, attackers can bypass the security of the software. | |
| 715 | Without sufficient encryption, integrity checking, or other mechanism, any input that originates from an outsider cannot be trusted.",,high,"Top 25 Series - Rank 6 - Reliance on Untrusted Inputs in a Security Decision: http://blogs.sans.org/appsecstreetfighter/2010/03/05/top-25-series-rank-6-reliance-on-untrusted-inputs-in-a-security-decision/ | |
| 716 | HMAC: http://en.wikipedia.org/wiki/Hmac | |
| 717 | Understanding ASP.NET View State: http://msdn.microsoft.com/en-us/library/ms972976.aspx | |
| 718 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI" | |
| 719 | CWE-93,Improper Neutralization of CRLF Sequences (CRLF Injection) (Type: Base),"The software uses CRLF (carriage return line feeds) as a special element, e.g. to separate lines or records, but it does not neutralize or incorrectly neutralizes CRLF sequences from inputs. | |
| 720 | Since an implicit intent does not specify a particular application to receive the data, any application can process the intent by using an Intent Filter for that intent. This can allow untrusted applications to obtain sensitive data.",,high,CRLF Injection: http://marc.info/?l=bugtraq&m=102088154213630&w=2 | |
| 721 | CWE-102,Struts: Duplicate Validation Forms (Type: Variant),"The application uses multiple validation forms with the same name, which might cause the Struts Validator to validate a form that the programmer does not expect. | |
| 722 | If two validation forms have the same name, the Struts Validator arbitrarily chooses one of the forms to use for input validation and discards the other. This decision might not correspond to the programmer's expectations, possibly leading to resultant weaknesses. Moreover, it indicates that the validation logic is not up-to-date, and can indicate that other, more subtle validation errors are present.",,unclassified, | |
| 723 | CWE-103,Struts: Incomplete validate() Method Definition (Type: Variant),"The application has a validator form that either does not define a validate() method, or defines a validate() method but does not call super.validate(). | |
| 724 | If you do not call super.validate(), the Validation Framework cannot check the contents of the form against a validation form. In other words, the validation framework will be disabled for the given form.",,unclassified, | |
| 725 | CWE-104,Struts: Form Bean Does Not Extend Validation Class (Type: Variant),"If a form bean does not extend an ActionForm subclass of the Validator framework, it can expose the application to other weaknesses related to insufficient input validation. | |
| 726 | If you do not call super.validate(), the Validation Framework cannot check the contents of the form against a validation form. In other words, the validation framework will be disabled for the given form.",,unclassified, | |
| 727 | CWE-105,Struts: Form Field Without Validator (Type: Variant),"The application has a form field that is not validated by a corresponding validation form, which can introduce other weaknesses related to insufficient input validation. | |
| 728 | If you do not call super.validate(), the Validation Framework cannot check the contents of the form against a validation form. In other words, the validation framework will be disabled for the given form.",,unclassified, | |
| 729 | CWE-106,Struts: Plug-in Framework not in Use (Type: Variant),"When an application does not use an input validation framework such as the Struts Validator, there is a greater risk of introducing weaknesses related to insufficient input validation. | |
| 730 | If you do not call super.validate(), the Validation Framework cannot check the contents of the form against a validation form. In other words, the validation framework will be disabled for the given form.",,unclassified, | |
| 731 | CWE-107,Struts: Unused Validation Form (Type: Variant),"An unused validation form indicates that validation logic is not up-to-date. | |
| 732 | It is easy for developers to forget to update validation logic when they remove or rename action form mappings. One indication that validation logic is not being properly maintained is the presence of an unused validation form.",,unclassified, | |
| 733 | CWE-108,Struts: Unvalidated Action Form (Type: Variant),"Every Action Form must have a corresponding validation form. | |
| 734 | If a Struts Action Form Mapping specifies a form, it must have a validation form defined under the Struts Validator.",,unclassified, | |
| 735 | CWE-109,Struts: Validator Turned Off (Type: Variant),"Automatic filtering via a Struts bean has been turned off, which disables the Struts Validator and custom validation logic. This exposes the application to other weaknesses related to insufficient input validation. | |
| 736 | If a Struts Action Form Mapping specifies a form, it must have a validation form defined under the Struts Validator.",,unclassified, | |
| 737 | CWE-11,ASP.NET Misconfiguration: Creating Debug Binary (Type: Variant),"Debugging messages help attackers learn about the system and plan a form of attack. | |
| 738 | ASP .NET applications can be configured to produce debug binaries. These binaries give detailed debugging messages and should not be used in production environments. Debug binaries are meant to be used in a development or testing environment and can pose a security risk if they are deployed to production.",,unclassified, | |
| 739 | CWE-110,Struts: Validator Without Form Field (Type: Variant),"Validation fields that do not appear in forms they are associated with indicate that the validation logic is out of date. | |
| 740 | It is easy for developers to forget to update validation logic when they make changes to an ActionForm class. One indication that validation logic is not being properly maintained is inconsistencies between the action form and the validation form.",,unclassified, | |
| 741 | CWE-111,Direct Use of Unsafe JNI (Type: Base),"When a Java application uses the Java Native Interface (JNI) to call code written in another programming language, it can expose the application to weaknesses in that code, even if those weaknesses cannot occur in Java. | |
| 742 | Many safety features that programmers may take for granted simply do not apply for native code, so you must carefully review all such code for potential problems. The languages used to implement native code may be more susceptible to buffer overflows and other attacks. Native code is unprotected by the security features enforced by the runtime environment, such as strong typing and array bounds checking.",,unclassified,"Fortify Descriptions: http://vulncat.fortifysoftware.com | |
| 743 | The Java(TM) Tutorial: The Java Native Interface: http://java.sun.com/docs/books/tutorial/native1.1/" | |
| 744 | CWE-112,Missing XML Validation (Type: Base),"The software accepts XML from an untrusted source but does not validate the XML against the proper schema. | |
| 745 | Most successful attacks begin with a violation of the programmer's assumptions. By accepting an XML document without validating it against a DTD or XML schema, the programmer leaves a door open for attackers to provide unexpected, unreasonable, or malicious input.",,unclassified, | |
| 746 | CWE-113,Improper Neutralization of CRLF Sequences in HTTP Headers (HTTP Response Splitting) (Type: Base),"The software receives data from an upstream component, but does not neutralize or incorrectly neutralizes CR and LF characters before the data is included in outgoing HTTP headers. | |
| 747 | Including unvalidated data in an HTTP header allows an attacker to specify the entirety of the HTTP response rendered by the browser. When an HTTP request contains unexpected CR (carriage return, also given by %0d or \r) and LF (line feed, also given by %0a or \n) characters the server may respond with an output stream that is interpreted as two different HTTP responses (instead of one). An attacker can control the second response and mount attacks such as cross-site scripting and cache poisoning attacks. | |
| 748 | HTTP response splitting weaknesses may be present when: | |
| 749 | Data enters a web application through an untrusted source, most frequently an HTTP request. | |
| 750 | The data is included in an HTTP response header sent to a web user without being validated for malicious characters.",,unclassified,"OWASP TOP 10: http://www.owasp.org/index.php/Top_10_2007 | |
| 751 | 24 Deadly Sins of Software Security: ""Sin 2: Web-Server Related Vulnerabilities (XSS, XSRF, and Response Splitting)."" Page 31" | |
| 752 | CWE-114,Process Control (Type: Base),"Executing commands or loading libraries from an untrusted source or in an untrusted environment can cause an application to execute malicious commands (and payloads) on behalf of an attacker. | |
| 753 | Process control vulnerabilities take two forms: 1. An attacker can change the command that the program executes: the attacker explicitly controls what the command is. 2. An attacker can change the environment in which the command executes: the attacker implicitly controls what the command means. Process control vulnerabilities of the first type occur when either data enters the application from an untrusted source and the data is used as part of a string representing a command that is executed by the application. By executing the command, the application gives an attacker a privilege or capability that the attacker would not otherwise have.",,unclassified, | |
| 754 | CWE-115,Misinterpretation of Input (Type: Base),"The software misinterprets an input, whether from an attacker or another product, in a security-relevant fashion. | |
| 755 | Process control vulnerabilities take two forms: 1. An attacker can change the command that the program executes: the attacker explicitly controls what the command is. 2. An attacker can change the environment in which the command executes: the attacker implicitly controls what the command means. Process control vulnerabilities of the first type occur when either data enters the application from an untrusted source and the data is used as part of a string representing a command that is executed by the application. By executing the command, the application gives an attacker a privilege or capability that the attacker would not otherwise have.",,unclassified, | |
| 756 | CWE-118,Improper Access of Indexable Resource (Range Error) (Type: Class),"The software does not restrict or incorrectly restricts operations within the boundaries of a resource that is accessed using an index or pointer, such as memory or files. | |
| 757 | This can allow an attacker to forge log entries or inject malicious content into logs. | |
| 758 | Log forging vulnerabilities occur when: | |
| 759 | Data enters an application from an untrusted source. | |
| 760 | The data is written to an application or system log file.",,unclassified, | |
| 761 | CWE-12,ASP.NET Misconfiguration: Missing Custom Error Page (Type: Variant),"An ASP .NET application must enable custom error pages in order to prevent attackers from mining information from the framework's built-in responses. | |
| 762 | Certain languages allow direct addressing of memory locations and do not automatically ensure that these locations are valid for the memory buffer that is being referenced. This can cause read or write operations to be performed on memory locations that may be associated with other variables, data structures, or internal program data. | |
| 763 | As a result, an attacker may be able to execute arbitrary code, alter the intended control flow, read sensitive information, or cause the system to crash.",,unclassified,"19 Deadly Sins of Software Security | |
| 764 | ASP.NET Misconfiguration: Missing Custom Error Handling: http://www.owasp.org/index.php/ASP.NET_Misconfiguration:_Missing_Custom_Error_Handling" | |
| 765 | CWE-125,Out-of-bounds Read (Type: Base),"The software reads data past the end, or before the beginning, of the intended buffer. | |
| 766 | This typically occurs when the pointer or its index is incremented or decremented to a position beyond the bounds of the buffer or when pointer arithmetic results in a position outside of the valid memory location to name a few. This may result in corruption of sensitive information, a crash, or code execution among other things.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89" | |
| 767 | CWE-126,Buffer Over-read (Type: Variant),"The software reads from a buffer using buffer access mechanisms such as indexes or pointers that reference memory locations after the targeted buffer. | |
| 768 | This typically occurs when the pointer or its index is incremented to a position beyond the bounds of the buffer or when pointer arithmetic results in a position outside of the valid memory location to name a few. This may result in exposure of sensitive information or possibly a crash.",,unclassified, | |
| 769 | CWE-127,Buffer Under-read (Type: Variant),"The software reads from a buffer using buffer access mechanisms such as indexes or pointers that reference memory locations prior to the targeted buffer. | |
| 770 | This typically occurs when the pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used. This may result in exposure of sensitive information or possibly a crash.",,unclassified, | |
| 771 | CWE-13,ASP.NET Misconfiguration: Password in Configuration File (Type: Variant),"Storing a plaintext password in a configuration file allows anyone who can read the file access to the password-protected resource making them an easy target for attackers. | |
| 772 | This typically occurs when the pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used. This may result in exposure of sensitive information or possibly a crash.",,unclassified,"How To: Encrypt Configuration Sections in ASP.NET 2.0 Using DPAPI: http://msdn.microsoft.com/en-us/library/ms998280.aspx | |
| 773 | How To: Encrypt Configuration Sections in ASP.NET 2.0 Using RSA: http://msdn.microsoft.com/en-us/library/ms998283.aspx | |
| 774 | .NET Framework Developer's Guide - Securing Connection Strings: http://msdn.microsoft.com/en-us/library/89211k9b(VS.80).aspx" | |
| 775 | CWE-130,Improper Handling of Length Parameter Inconsistency (Type: Variant),"The software parses a formatted message or structure, but it does not handle or incorrectly handles a length field that is inconsistent with the actual length of the associated data. | |
| 776 | If an attacker can manipulate the length parameter associated with an input such that it is inconsistent with the actual length of the input, this can be leveraged to cause the target application to behave in unexpected, and possibly, malicious ways. One of the possible motives for doing so is to pass in arbitrarily large input to the application. Another possible motivation is the modification of application state by including invalid data for subsequent properties of the application. Such weaknesses commonly lead to attacks such as buffer overflows and execution of arbitrary code.",,unclassified, | |
| 777 | CWE-132,DEPRECATED (Duplicate): Miscalculated Null Termination (Type: Base),"This entry has been deprecated because it was a duplicate of CWE-170. All content has been transferred to CWE-170. | |
| 778 | If an attacker can manipulate the length parameter associated with an input such that it is inconsistent with the actual length of the input, this can be leveraged to cause the target application to behave in unexpected, and possibly, malicious ways. One of the possible motives for doing so is to pass in arbitrarily large input to the application. Another possible motivation is the modification of application state by including invalid data for subsequent properties of the application. Such weaknesses commonly lead to attacks such as buffer overflows and execution of arbitrary code.",,unclassified, | |
| 779 | CWE-135,Incorrect Calculation of Multi-Byte String Length (Type: Base),"The software does not correctly calculate the length of strings that can contain wide or multi-byte characters. | |
| 780 | If an attacker can manipulate the length parameter associated with an input such that it is inconsistent with the actual length of the input, this can be leveraged to cause the target application to behave in unexpected, and possibly, malicious ways. One of the possible motives for doing so is to pass in arbitrarily large input to the application. Another possible motivation is the modification of application state by including invalid data for subsequent properties of the application. Such weaknesses commonly lead to attacks such as buffer overflows and execution of arbitrary code.",,unclassified,"Writing Secure Code: Chapter 5, ""Unicode and ANSI Buffer Size Mismatches"" Page 153" | |
| 781 | CWE-138,Improper Neutralization of Special Elements (Type: Class),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as control elements or syntactic markers when they are sent to a downstream component. | |
| 782 | Most languages and protocols have their own special elements such as characters and reserved words. These special elements can carry control implications. If software does not prevent external control or influence over the inclusion of such special elements, the control flow of the program may be altered from what was intended. For example, both Unix and Windows interpret the symbol < (""less than"") as meaning ""read input from a file"".",,unclassified, | |
| 783 | CWE-14,Compiler Removal of Code to Clear Buffers (Type: Base),"Sensitive memory is cleared according to the source code, but compiler optimizations leave the memory untouched when it is not read from again, aka ""dead store removal."" | |
| 784 | This compiler optimization error occurs when: | |
| 785 | 1. Secret data are stored in memory. | |
| 786 | 2. The secret data are scrubbed from memory by overwriting its contents. | |
| 787 | 3. The source code is compiled using an optimizing compiler, which identifies and removes the function that overwrites the contents as a dead store because the memory is not used subsequently.",,unclassified,"Writing Secure Code: Chapter 9, ""A Compiler Optimization Caveat"" Page 322 | |
| 788 | When scrubbing secrets in memory doesn't work: http://cert.uni-stuttgart.de/archive/bugtraq/2002/11/msg00046.html | |
| 789 | Some Bad News and Some Good News: http://msdn.microsoft.com/library/default.asp?url=/library/en-us/dncode/html/secure10102002.asp | |
| 790 | GNU GCC: Optimizer Removes Code Necessary for Security: http://www.derkeiler.com/Mailing-Lists/securityfocus/bugtraq/2002-11/0257.html" | |
| 791 | CWE-140,Improper Neutralization of Delimiters (Type: Base),"The software does not neutralize or incorrectly neutralizes delimiters. | |
| 792 | This compiler optimization error occurs when: | |
| 793 | 1. Secret data are stored in memory. | |
| 794 | 2. The secret data are scrubbed from memory by overwriting its contents. | |
| 795 | 3. The source code is compiled using an optimizing compiler, which identifies and removes the function that overwrites the contents as a dead store because the memory is not used subsequently.",,unclassified, | |
| 796 | CWE-141,Improper Neutralization of Parameter/Argument Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as parameter or argument delimiters when they are sent to a downstream component. | |
| 797 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Embedded Delimiters"", Page 408. | |
| 798 | The Art of Software Security Assessment: Chapter 10, ""IFS"", Page 604." | |
| 799 | CWE-142,Improper Neutralization of Value Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as value delimiters when they are sent to a downstream component. | |
| 800 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Embedded Delimiters"", Page 408." | |
| 801 | CWE-143,Improper Neutralization of Record Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as record delimiters when they are sent to a downstream component. | |
| 802 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Embedded Delimiters"", Page 408." | |
| 803 | CWE-144,Improper Neutralization of Line Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as line delimiters when they are sent to a downstream component. | |
| 804 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Embedded Delimiters"", Page 408." | |
| 805 | CWE-145,Improper Neutralization of Section Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as section delimiters when they are sent to a downstream component. | |
| 806 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions. | |
| 807 | One example of a section delimiter is the boundary string in a multipart MIME message. In many cases, doubled line delimiters can serve as a section delimiter.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Embedded Delimiters"", Page 408." | |
| 808 | CWE-146,Improper Neutralization of Expression/Command Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as expression or command delimiters when they are sent to a downstream component. | |
| 809 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Embedded Delimiters"", Page 408." | |
| 810 | CWE-147,Improper Neutralization of Input Terminators (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as input terminators when they are sent to a downstream component. | |
| 811 | For example, a ""."" in SMTP signifies the end of mail message data, whereas a null character can be used for the end of a string.",,unclassified, | |
| 812 | CWE-148,Improper Neutralization of Input Leaders (Type: Variant),"The application does not properly handle when a leading character or sequence (""leader"") is missing or malformed, or if multiple leaders are used when only one should be allowed. | |
| 813 | For example, a ""."" in SMTP signifies the end of mail message data, whereas a null character can be used for the end of a string.",,unclassified, | |
| 814 | CWE-149,Improper Neutralization of Quoting Syntax (Type: Variant),"Quotes injected into an application can be used to compromise a system. As data are parsed, an injected/absent/duplicate/malformed use of quotes may cause the process to take unexpected actions. | |
| 815 | For example, a ""."" in SMTP signifies the end of mail message data, whereas a null character can be used for the end of a string.",,unclassified, | |
| 816 | CWE-15,External Control of System or Configuration Setting (Type: Base),"One or more system settings or configuration elements can be externally controlled by a user. | |
| 817 | Allowing external control of system settings can disrupt service or cause an application to behave in unexpected, and potentially malicious ways.",,unclassified, | |
| 818 | CWE-150,"Improper Neutralization of Escape, Meta, or Control Sequences (Type: Variant)","The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as escape, meta, or control character sequences when they are sent to a downstream component. | |
| 819 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified, | |
| 820 | CWE-151,Improper Neutralization of Comment Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as comment delimiters when they are sent to a downstream component. | |
| 821 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified, | |
| 822 | CWE-152,Improper Neutralization of Macro Symbols (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as macro symbols when they are sent to a downstream component. | |
| 823 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified, | |
| 824 | CWE-153,Improper Neutralization of Substitution Characters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as substitution characters when they are sent to a downstream component. | |
| 825 | As data is parsed, an injected/absent/malformed delimiter may cause the process to take unexpected actions.",,unclassified, | |
| 826 | CWE-154,Improper Neutralization of Variable Name Delimiters (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as variable name delimiters when they are sent to a downstream component. | |
| 827 | As data is parsed, an injected delimiter may cause the process to take unexpected actions that result in an attack. Example: ""$"" for an environment variable.",,unclassified, | |
| 828 | CWE-155,Improper Neutralization of Wildcards or Matching Symbols (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as wildcards or matching symbols when they are sent to a downstream component. | |
| 829 | As data is parsed, an injected element may cause the process to take unexpected actions.",,unclassified, | |
| 830 | CWE-156,Improper Neutralization of Whitespace (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could be interpreted as whitespace when they are sent to a downstream component. | |
| 831 | This can include space, tab, etc.",,unclassified, | |
| 832 | CWE-157,Failure to Sanitize Paired Delimiters (Type: Variant),"The software does not properly handle the characters that are used to mark the beginning and ending of a group of entities, such as parentheses, brackets, and braces. | |
| 833 | This can include space, tab, etc.",,unclassified, | |
| 834 | CWE-158,Improper Neutralization of Null Byte or NUL Character (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes NUL characters or null bytes when they are sent to a downstream component. | |
| 835 | As data is parsed, an injected NUL character or null byte may cause the software to believe the input is terminated earlier than it actually is, or otherwise cause the input to be misinterpreted. This could then be used to inject potentially dangerous input that occurs after the null byte or otherwise bypass validation routines and other protection mechanisms.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""NUL Character Injection"", Page 411." | |
| 836 | CWE-159,Failure to Sanitize Special Element (Type: Class),"Weaknesses in this attack-focused category do not properly filter and interpret special elements in user-controlled input which could cause adverse effect on the software behavior and integrity. | |
| 837 | As data is parsed, an injected NUL character or null byte may cause the software to believe the input is terminated earlier than it actually is, or otherwise cause the input to be misinterpreted. This could then be used to inject potentially dangerous input that occurs after the null byte or otherwise bypass validation routines and other protection mechanisms.",,unclassified, | |
| 838 | CWE-160,Improper Neutralization of Leading Special Elements (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes leading special elements that could be interpreted in unexpected ways when they are sent to a downstream component. | |
| 839 | As data is parsed, improperly handled leading special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 840 | CWE-161,Improper Neutralization of Multiple Leading Special Elements (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes multiple leading special elements that could be interpreted in unexpected ways when they are sent to a downstream component. | |
| 841 | As data is parsed, improperly handled multiple leading special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 842 | CWE-162,Improper Neutralization of Trailing Special Elements (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes trailing special elements that could be interpreted in unexpected ways when they are sent to a downstream component. | |
| 843 | As data is parsed, improperly handled trailing special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 844 | CWE-163,Improper Neutralization of Multiple Trailing Special Elements (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes multiple trailing special elements that could be interpreted in unexpected ways when they are sent to a downstream component. | |
| 845 | As data is parsed, improperly handled multiple trailing special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 846 | CWE-164,Improper Neutralization of Internal Special Elements (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes internal special elements that could be interpreted in unexpected ways when they are sent to a downstream component. | |
| 847 | As data is parsed, improperly handled internal special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 848 | CWE-165,Improper Neutralization of Multiple Internal Special Elements (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes multiple internal special elements that could be interpreted in unexpected ways when they are sent to a downstream component. | |
| 849 | As data is parsed, improperly handled multiple internal special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 850 | CWE-166,Improper Handling of Missing Special Element (Type: Base),"The software receives input from an upstream component, but it does not handle or incorrectly handles when an expected special element is missing. | |
| 851 | As data is parsed, improperly handled multiple internal special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 852 | CWE-167,Improper Handling of Additional Special Element (Type: Base),"The software receives input from an upstream component, but it does not handle or incorrectly handles when an additional unexpected special element is missing. | |
| 853 | As data is parsed, improperly handled multiple internal special elements may cause the process to take unexpected actions that result in an attack.",,unclassified, | |
| 854 | CWE-168,Improper Handling of Inconsistent Special Elements (Type: Base),"The software does not handle when an inconsistency exists between two or more special characters or reserved words. | |
| 855 | An example of this problem would be if paired characters appear in the wrong order, or if the special characters are not properly nested.",,unclassified, | |
| 856 | CWE-172,Encoding Error (Type: Class),"The software does not properly encode or decode the data, resulting in unexpected values. | |
| 857 | Null termination errors frequently occur in two different ways. An off-by-one error could cause a null to be written out of bounds, leading to an overflow. Or, a program could use a strncpy() function call incorrectly, which prevents a null terminator from being added at all. Other scenarios are possible.",,unclassified, | |
| 858 | CWE-173,Improper Handling of Alternate Encoding (Type: Variant),"The software does not properly handle when an input uses an alternate encoding that is valid for the control sphere to which the input is being sent. | |
| 859 | Null termination errors frequently occur in two different ways. An off-by-one error could cause a null to be written out of bounds, leading to an overflow. Or, a program could use a strncpy() function call incorrectly, which prevents a null terminator from being added at all. Other scenarios are possible.",,unclassified, | |
| 860 | CWE-174,Double Decoding of the Same Data (Type: Variant),"The software decodes the same input twice, which can limit the effectiveness of any protection mechanism that occurs in between the decoding operations. | |
| 861 | Null termination errors frequently occur in two different ways. An off-by-one error could cause a null to be written out of bounds, leading to an overflow. Or, a program could use a strncpy() function call incorrectly, which prevents a null terminator from being added at all. Other scenarios are possible.",,unclassified, | |
| 862 | CWE-175,Improper Handling of Mixed Encoding (Type: Variant),"The software does not properly handle when the same input uses several different (mixed) encodings. | |
| 863 | Null termination errors frequently occur in two different ways. An off-by-one error could cause a null to be written out of bounds, leading to an overflow. Or, a program could use a strncpy() function call incorrectly, which prevents a null terminator from being added at all. Other scenarios are possible.",,unclassified, | |
| 864 | CWE-176,Improper Handling of Unicode Encoding (Type: Variant),"The software does not properly handle when an input contains Unicode encoding. | |
| 865 | Null termination errors frequently occur in two different ways. An off-by-one error could cause a null to be written out of bounds, leading to an overflow. Or, a program could use a strncpy() function call incorrectly, which prevents a null terminator from being added at all. Other scenarios are possible.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Character Sets and Unicode"", Page 446." | |
| 866 | CWE-177,Improper Handling of URL Encoding (Hex Encoding) (Type: Variant),"The software does not properly handle when all or part of an input has been URL encoded. | |
| 867 | Null termination errors frequently occur in two different ways. An off-by-one error could cause a null to be written out of bounds, leading to an overflow. Or, a program could use a strncpy() function call incorrectly, which prevents a null terminator from being added at all. Other scenarios are possible.",,unclassified, | |
| 868 | CWE-178,Improper Handling of Case Sensitivity (Type: Base),"The software does not properly account for differences in case sensitivity when accessing or determining the properties of a resource, leading to inconsistent results. | |
| 869 | Improperly handled case sensitive data can lead to several possible consequences, including: | |
| 870 | case-insensitive passwords reducing the size of the key space, making brute force attacks easier | |
| 871 | bypassing filters or access controls using alternate names | |
| 872 | multiple interpretation errors using alternate names.",,unclassified, | |
| 873 | CWE-179,Incorrect Behavior Order: Early Validation (Type: Base),"The software validates input before applying protection mechanisms that modify the input, which could allow an attacker to bypass the validation via dangerous inputs that only arise after the modification. | |
| 874 | Software needs to validate data at the proper time, after data has been canonicalized and cleansed. Early validation is susceptible to various manipulations that result in dangerous inputs that are produced by canonicalization and cleansing.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Escaping Metacharacters"", Page 439." | |
| 875 | CWE-180,Incorrect Behavior Order: Validate Before Canonicalize (Type: Base),"The software validates input before it is canonicalized, which prevents the software from detecting data that becomes invalid after the canonicalization step. | |
| 876 | This can be used by an attacker to bypass the validation and launch attacks that expose weaknesses that would otherwise be prevented, such as injection.",,unclassified, | |
| 877 | CWE-181,Incorrect Behavior Order: Validate Before Filter (Type: Base),"The software validates data before it has been filtered, which prevents the software from detecting data that becomes invalid after the filtering step. | |
| 878 | This can be used by an attacker to bypass the validation and launch attacks that expose weaknesses that would otherwise be prevented, such as injection.",,unclassified, | |
| 879 | CWE-182,Collapse of Data into Unsafe Value (Type: Base),"The software filters data in a way that causes it to be reduced or ""collapsed"" into an unsafe value that violates an expected security property. | |
| 880 | This can be used by an attacker to bypass the validation and launch attacks that expose weaknesses that would otherwise be prevented, such as injection.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Character Stripping Vulnerabilities"", Page 437." | |
| 881 | CWE-183,Permissive Whitelist (Type: Base),"An application uses a ""whitelist"" of acceptable values, but the whitelist includes at least one unsafe value, leading to resultant weaknesses. | |
| 882 | This can be used by an attacker to bypass the validation and launch attacks that expose weaknesses that would otherwise be prevented, such as injection.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Eliminating Metacharacters"", Page 435." | |
| 883 | CWE-184,Incomplete Blacklist (Type: Base),"An application uses a ""blacklist"" of prohibited values, but the blacklist is incomplete. | |
| 884 | If an incomplete blacklist is used as a security mechanism, then the software may allow unintended values to pass into the application logic.",,unclassified,"Exploiting Software: How to Break Code | |
| 885 | Blacklist defenses as a breeding ground for vulnerability variants: http://seclists.org/fulldisclosure/2006/Feb/0040.html | |
| 886 | The Art of Software Security Assessment: Chapter 8, ""Eliminating Metacharacters"", Page 435." | |
| 887 | CWE-185,Incorrect Regular Expression (Type: Class),"The software specifies a regular expression in a way that causes data to be improperly matched or compared. | |
| 888 | When the regular expression is used in protection mechanisms such as filtering or validation, this may allow an attacker to bypass the intended restrictions on the incoming data.",,unclassified,"Writing Secure Code: Chapter 10, ""Using Regular Expressions for Checking Input"" Page 350" | |
| 889 | CWE-186,Overly Restrictive Regular Expression (Type: Base),"A regular expression is overly restrictive, which prevents dangerous values from being detected. | |
| 890 | When the regular expression is used in protection mechanisms such as filtering or validation, this may allow an attacker to bypass the intended restrictions on the incoming data.",,unclassified, | |
| 891 | CWE-187,Partial Comparison (Type: Base),"The software performs a comparison that only examines a portion of a factor before determining whether there is a match, such as a substring, leading to resultant weaknesses. | |
| 892 | For example, an attacker might succeed in authentication by providing a small password that matches the associated portion of the larger, correct password.",,unclassified, | |
| 893 | CWE-191,Integer Underflow (Wrap or Wraparound) (Type: Base),"The product subtracts one value from another, such that the result is less than the minimum allowable integer value, which produces a value that is not equal to the correct result. | |
| 894 | This can happen in signed and unsigned cases.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 7: Integer Overflows."" Page 119" | |
| 895 | CWE-193,Off-by-one Error (Type: Base),"A product calculates or uses an incorrect maximum or minimum value that is 1 more, or 1 less, than the correct value. | |
| 896 | This can happen in signed and unsigned cases.",,unclassified,"Third Generation Exploits: http://www.blackhat.com/presentations/bh-europe-01/halvar-flake/bh-europe-01-halvarflake.ppt | |
| 897 | Off-by-one errors: a brief explanation: http://marc.theaimsgroup.com/?l=secprog&m=108379742110553&w=2 | |
| 898 | The Frame Pointer Overwrite: http://kaizo.org/mirrors/phrack/phrack55/P55-08 | |
| 899 | Exploiting Software: How to Break Code (The buffer overflow chapter) | |
| 900 | 24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89 | |
| 901 | The Art of Software Security Assessment: Chapter 5, ""Off-by-One Errors"", Page 180." | |
| 902 | CWE-195,Signed to Unsigned Conversion Error (Type: Variant),"A signed-to-unsigned conversion error takes place when a signed primitive is used as an unsigned value, usually as a size variable. | |
| 903 | It is dangerous to rely on implicit casts between signed and unsigned numbers because the result can take on an unexpected value and violate assumptions made by the program.",,unclassified,"The Art of Software Security Assessment: Chapter 6, ""Type Conversions"", Page 223." | |
| 904 | CWE-198,Use of Incorrect Byte Ordering (Type: Base),"The software receives input from an upstream component, but it does not account for byte ordering (e.g. big-endian and little-endian) when processing the input, causing an incorrect number or value to be used. | |
| 905 | When a primitive is cast to a smaller primitive, the high order bits of the large value are lost in the conversion, potentially resulting in an unexpected value that is not equal to the original value. This value may be required as an index into a buffer, a loop iterator, or simply necessary state data. In any case, the value cannot be trusted and the system will be in an undefined state. While this method may be employed viably to isolate the low bits of a value, this usage is rare, and truncation usually implies that an implementation error has occurred.",,unclassified, | |
| 906 | CWE-201,Information Exposure Through Sent Data (Type: Variant),"The accidental exposure of sensitive information through sent data refers to the transmission of data which are either sensitive in and of itself or useful in the further exploitation of the system through standard data channels. | |
| 907 | The information either | |
| 908 | is regarded as sensitive within the product's own functionality, such as a private message; or | |
| 909 | provides information about the product or its environment that could be useful in an attack but is normally not available to the attacker, such as the installation path of a product that is remotely accessible. | |
| 910 | Many information exposures are resultant (e.g. PHP script error revealing the full path of the program), but they can also be primary (e.g. timing discrepancies in cryptography). There are many different types of problems that involve information exposures. Their severity can range widely depending on the type of information that is revealed.",,unclassified, | |
| 911 | CWE-203,Information Exposure Through Discrepancy (Type: Class),"The product behaves differently or sends different responses in a way that exposes security-relevant information about the state of the product, such as whether a particular operation was successful or not. | |
| 912 | In situations where data should not be tied to individual users, but a large number of users should be able to make queries that ""scrub"" the identity of users, it may be possible to get information about a user -- e.g., by specifying search terms that are known to be unique to that user.",,unclassified, | |
| 913 | CWE-204,Response Discrepancy Information Exposure (Type: Base),"The software provides different responses to incoming requests in a way that allows an actor to determine system state information that is outside of that actor's control sphere. | |
| 914 | This issue frequently occurs during authentication, where a difference in failed-login messages could allow an attacker to determine if the username is valid or not. These exposures can be inadvertent (bug) or intentional (design).",,unclassified,"24 Deadly Sins of Software Security: ""Sin 12: Information Leakage."" Page 191" | |
| 915 | CWE-205,Information Exposure Through Behavioral Discrepancy (Type: Base),"The product's actions indicate important differences based on (1) the internal state of the product or (2) differences from other products in the same class. | |
| 916 | For example, attacks such as OS fingerprinting rely heavily on both behavioral and response discrepancies.",,unclassified, | |
| 917 | CWE-206,Information Exposure of Internal State Through Behavioral Inconsistency (Type: Variant),"Two separate operations in a product cause the product to behave differently in a way that is observable to an attacker and reveals security-relevant information about the internal state of the product, such as whether a particular operation was successful or not. | |
| 918 | For example, attacks such as OS fingerprinting rely heavily on both behavioral and response discrepancies.",,unclassified, | |
| 919 | CWE-207,Information Exposure Through an External Behavioral Inconsistency (Type: Variant),"The product behaves differently than other products like it, in a way that is observable to an attacker and exposes security-relevant information about which product is being used. | |
| 920 | For example, attacks such as OS fingerprinting rely heavily on both behavioral and response discrepancies.",,unclassified, | |
| 921 | CWE-208,Information Exposure Through Timing Discrepancy (Type: Base),"Two separate operations in a product require different amounts of time to complete, in a way that is observable to an actor and reveals security-relevant information about the state of the product, such as whether a particular operation was successful or not. | |
| 922 | For example, attacks such as OS fingerprinting rely heavily on both behavioral and response discrepancies.",,unclassified, | |
| 923 | CWE-210,Information Exposure Through Self-generated Error Message (Type: Base),"The software identifies an error condition and creates its own diagnostic or error messages that contain sensitive information. | |
| 924 | The sensitive information may be valuable information on its own (such as a password), or it may be useful for launching other, more deadly attacks. If an attack fails, an attacker may use error information provided by the server to launch another more focused attack. For example, an attempt to exploit a path traversal weakness (CWE-22) might yield the full pathname of the installed application. In turn, this could be used to select the proper number of "".."" sequences to navigate to the targeted file. An attack using SQL injection (CWE-89) might not initially succeed, but an error message could reveal the malformed query, which would expose query logic and possibly even passwords or other sensitive information used within the query.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 12: Information Leakage."" Page 191 | |
| 925 | The Art of Software Security Assessment: Chapter 3, ""Overly Verbose Error Messages"", Page 75." | |
| 926 | CWE-211,Information Exposure Through Externally-generated Error Message (Type: Base),"The software performs an operation that triggers an external diagnostic or error message that is not directly generated by the software, such as an error generated by the programming language interpreter that the software uses. The error can contain sensitive system information. | |
| 927 | The sensitive information may be valuable information on its own (such as a password), or it may be useful for launching other, more deadly attacks. If an attack fails, an attacker may use error information provided by the server to launch another more focused attack. For example, an attempt to exploit a path traversal weakness (CWE-22) might yield the full pathname of the installed application. In turn, this could be used to select the proper number of "".."" sequences to navigate to the targeted file. An attack using SQL injection (CWE-89) might not initially succeed, but an error message could reveal the malformed query, which would expose query logic and possibly even passwords or other sensitive information used within the query.",,unclassified, | |
| 928 | CWE-212,Improper Cross-boundary Removal of Sensitive Data (Type: Base),"The software uses a resource that contains sensitive data, but it does not properly remove that data before it stores, transfers, or shares the resource with actors in another control sphere. | |
| 929 | Resources that may contain sensitive data include documents, packets, messages, databases, etc. While this data may be useful to an individual user or small set of users who share the resource, it may need to be removed before the resource can be shared outside of the trusted group. The process of removal is sometimes called cleansing or scrubbing. | |
| 930 | For example, software that is used for editing documents might not remove sensitive data such as reviewer comments or the local pathname where the document is stored. Or, a proxy might not remove an internal IP address from headers before making an outgoing request to an Internet site.",,unclassified, | |
| 931 | CWE-213,Intentional Information Exposure (Type: Base),"A product's design or configuration explicitly requires the publication of information that could be regarded as sensitive by an administrator. | |
| 932 | Resources that may contain sensitive data include documents, packets, messages, databases, etc. While this data may be useful to an individual user or small set of users who share the resource, it may need to be removed before the resource can be shared outside of the trusted group. The process of removal is sometimes called cleansing or scrubbing. | |
| 933 | For example, software that is used for editing documents might not remove sensitive data such as reviewer comments or the local pathname where the document is stored. Or, a proxy might not remove an internal IP address from headers before making an outgoing request to an Internet site.",,unclassified, | |
| 934 | CWE-214,Information Exposure Through Process Environment (Type: Variant),"A process is invoked with sensitive arguments, environment variables, or other elements that can be seen by other processes on the operating system. | |
| 935 | Many operating systems allow a user to list information about processes that are owned by other users. This information could include command line arguments or environment variable settings. When this data contains sensitive information such as credentials, it might allow other users to launch an attack against the software or related resources.",,unclassified, | |
| 936 | CWE-215,Information Exposure Through Debug Information (Type: Variant),"The application contains debugging code that can expose sensitive information to untrusted parties. | |
| 937 | Many operating systems allow a user to list information about processes that are owned by other users. This information could include command line arguments or environment variable settings. When this data contains sensitive information such as credentials, it might allow other users to launch an attack against the software or related resources.",,unclassified, | |
| 938 | CWE-216,Containment Errors (Container Errors) (Type: Class),"This tries to cover various problems in which improper data are included within a ""container."" | |
| 939 | Many operating systems allow a user to list information about processes that are owned by other users. This information could include command line arguments or environment variable settings. When this data contains sensitive information such as credentials, it might allow other users to launch an attack against the software or related resources.",,unclassified, | |
| 940 | CWE-217,DEPRECATED: Failure to Protect Stored Data from Modification (Type: Base),"This weakness has been deprecated because it incorporated and confused multiple weaknesses. The issues formerly covered in this weakness can be found at CWE-766 and CWE-767. | |
| 941 | Many operating systems allow a user to list information about processes that are owned by other users. This information could include command line arguments or environment variable settings. When this data contains sensitive information such as credentials, it might allow other users to launch an attack against the software or related resources.",,unclassified, | |
| 942 | CWE-218,DEPRECATED (Duplicate): Failure to provide confidentiality for stored data (Type: Base),"This weakness has been deprecated because it was a duplicate of CWE-493. All content has been transferred to CWE-493. | |
| 943 | Many operating systems allow a user to list information about processes that are owned by other users. This information could include command line arguments or environment variable settings. When this data contains sensitive information such as credentials, it might allow other users to launch an attack against the software or related resources.",,unclassified, | |
| 944 | CWE-219,Sensitive Data Under Web Root (Type: Variant),"The application stores sensitive data under the web document root with insufficient access control, which might make it accessible to untrusted parties. | |
| 945 | Many operating systems allow a user to list information about processes that are owned by other users. This information could include command line arguments or environment variable settings. When this data contains sensitive information such as credentials, it might allow other users to launch an attack against the software or related resources.",,unclassified, | |
| 946 | CWE-220,Sensitive Data Under FTP Root (Type: Variant),"The application stores sensitive data under the FTP document root with insufficient access control, which might make it accessible to untrusted parties. | |
| 947 | Many file operations are intended to take place within a restricted directory. By using special elements such as "".."" and ""/"" separators, attackers can escape outside of the restricted location to access files or directories that are elsewhere on the system. One of the most common special elements is the ""../"" sequence, which in most modern operating systems is interpreted as the parent directory of the current location. This is referred to as relative path traversal. Path traversal also covers the use of absolute pathnames such as ""/usr/local/bin"", which may also be useful in accessing unexpected files. This is referred to as absolute path traversal. | |
| 948 | In many programming languages, the injection of a null byte (the 0 or NUL) may allow an attacker to truncate a generated filename to widen the scope of attack. For example, the software may add "".txt"" to any pathname, thus limiting the attacker to text files, but a null injection may effectively remove this restriction.",,unclassified, | |
| 949 | CWE-221,Information Loss or Omission (Type: Class),"The software does not record, or improperly records, security-relevant information that leads to an incorrect decision or hampers later analysis. | |
| 950 | This can be resultant, e.g. a buffer overflow might trigger a crash before the product can log the event.",,unclassified, | |
| 951 | CWE-222,Truncation of Security-relevant Information (Type: Base),"The application truncates the display, recording, or processing of security-relevant information in a way that can obscure the source or nature of an attack. | |
| 952 | This can be resultant, e.g. a buffer overflow might trigger a crash before the product can log the event.",,unclassified, | |
| 953 | CWE-223,Omission of Security-relevant Information (Type: Base),"The application does not record or display information that would be important for identifying the source or nature of an attack, or determining if an action is safe. | |
| 954 | This can be resultant, e.g. a buffer overflow might trigger a crash before the product can log the event.",,unclassified,"The Art of Software Security Assessment: Chapter 2, ""Accountability"", Page 40." | |
| 955 | CWE-224,Obscured Security-relevant Information by Alternate Name (Type: Base),"The software records security-relevant information according to an alternate name of the affected entity, instead of the canonical name. | |
| 956 | This can be resultant, e.g. a buffer overflow might trigger a crash before the product can log the event.",,unclassified,Writing Secure Code | |
| 957 | CWE-225,DEPRECATED (Duplicate): General Information Management Problems (Type: Base),"This weakness can be found at CWE-199. | |
| 958 | This can be resultant, e.g. a buffer overflow might trigger a crash before the product can log the event.",,unclassified, | |
| 959 | CWE-226,Sensitive Information Uncleared Before Release (Type: Base),"The software does not fully clear previously used information in a data structure, file, or other resource, before making that resource available to a party in another control sphere. | |
| 960 | This typically results from new data that is not as long as the old data, which leaves portions of the old data still available. Equivalent errors can occur in other situations where the length of data is variable but the associated data structure is not. If memory is not cleared after use, it may allow unintended actors to read the data when the memory is reallocated.",,unclassified, | |
| 961 | CWE-227,Improper Fulfillment of API Contract (API Abuse) (Type: Class),"The software uses an API in a manner contrary to its intended use. | |
| 962 | An API is a contract between a caller and a callee. The most common forms of API misuse occurs when the caller does not honor its end of this contract. For example, if a program does not call chdir() after calling chroot(), it violates the contract that specifies how to change the active root directory in a secure fashion. Another good example of library abuse is expecting the callee to return trustworthy DNS information to the caller. In this case, the caller misuses the callee API by making certain assumptions about its behavior (that the return value can be used for authentication purposes). One can also violate the caller-callee contract from the other side. For example, if a coder subclasses SecureRandom and returns a non-random value, the contract is violated.",,unclassified, | |
| 963 | CWE-228,Improper Handling of Syntactically Invalid Structure (Type: Class),"The product does not handle or incorrectly handles input that is not syntactically well-formed with respect to the associated specification. | |
| 964 | An API is a contract between a caller and a callee. The most common forms of API misuse occurs when the caller does not honor its end of this contract. For example, if a program does not call chdir() after calling chroot(), it violates the contract that specifies how to change the active root directory in a secure fashion. Another good example of library abuse is expecting the callee to return trustworthy DNS information to the caller. In this case, the caller misuses the callee API by making certain assumptions about its behavior (that the return value can be used for authentication purposes). One can also violate the caller-callee contract from the other side. For example, if a coder subclasses SecureRandom and returns a non-random value, the contract is violated.",,unclassified, | |
| 965 | CWE-229,Improper Handling of Values (Type: Base),"The software does not properly handle when the expected number of values for parameters, fields, or arguments is not provided in input, or if those values are undefined. | |
| 966 | An API is a contract between a caller and a callee. The most common forms of API misuse occurs when the caller does not honor its end of this contract. For example, if a program does not call chdir() after calling chroot(), it violates the contract that specifies how to change the active root directory in a secure fashion. Another good example of library abuse is expecting the callee to return trustworthy DNS information to the caller. In this case, the caller misuses the callee API by making certain assumptions about its behavior (that the return value can be used for authentication purposes). One can also violate the caller-callee contract from the other side. For example, if a coder subclasses SecureRandom and returns a non-random value, the contract is violated.",,unclassified, | |
| 967 | CWE-23,Relative Path Traversal (Type: Base),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize sequences such as "".."" that can resolve to a location that is outside of that directory. | |
| 968 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified,"OWASP Attack listing: http://www.owasp.org/index.php/Relative_Path_Traversal | |
| 969 | The Art of Software Security Assessment: Chapter 9, ""Filenames and Paths"", Page 503." | |
| 970 | CWE-230,Improper Handling of Missing Values (Type: Variant),"The software does not handle or incorrectly handles when a parameter, field, or argument name is specified, but the associated value is missing, i.e. it is empty, blank, or null. | |
| 971 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 972 | CWE-231,Improper Handling of Extra Values (Type: Variant),"The software does not handle or incorrectly handles when more values are provided than expected. | |
| 973 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 974 | CWE-232,Improper Handling of Undefined Values (Type: Variant),"The software does not handle or incorrectly handles when a value is not defined or supported for the associated parameter, field, or argument name. | |
| 975 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 976 | CWE-233,Improper Handling of Parameters (Type: Base),"The software does not properly handle when the expected number of parameters, fields, or arguments is not provided in input, or if those parameters are undefined. | |
| 977 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 978 | CWE-235,Improper Handling of Extra Parameters (Type: Variant),"The software does not handle or incorrectly handles when the number of parameters, fields, or arguments with the same name exceeds the expected amount. | |
| 979 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 980 | CWE-236,Improper Handling of Undefined Parameters (Type: Variant),"The software does not handle or incorrectly handles when a particular parameter, field, or argument name is not defined or supported by the product. | |
| 981 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 982 | CWE-237,Improper Handling of Structural Elements (Type: Base),"The software does not handle or incorrectly handles inputs that are related to complex structures. | |
| 983 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 984 | CWE-238,Improper Handling of Incomplete Structural Elements (Type: Variant),"The software does not handle or incorrectly handles when a particular structural element is not completely specified. | |
| 985 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 986 | CWE-239,Failure to Handle Incomplete Element (Type: Variant),"The software does not properly handle when a particular element is not completely specified. | |
| 987 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified, | |
| 988 | CWE-24,Path Traversal: ../filedir (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize ""../"" sequences that can resolve to a location that is outside of that directory. | |
| 989 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 990 | The ""../"" manipulation is the canonical manipulation for operating systems that use ""/"" as directory separators, such as UNIX- and Linux-based systems. In some cases, it is useful for bypassing protection schemes in environments for which ""/"" is supported but not the primary separator, such as Windows, which uses ""\"" but can also accept ""/"".",,unclassified, | |
| 991 | CWE-240,Improper Handling of Inconsistent Structural Elements (Type: Variant),"The software does not handle or incorrectly handles when two or more structural elements should be consistent, but are not. | |
| 992 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 993 | The ""../"" manipulation is the canonical manipulation for operating systems that use ""/"" as directory separators, such as UNIX- and Linux-based systems. In some cases, it is useful for bypassing protection schemes in environments for which ""/"" is supported but not the primary separator, such as Windows, which uses ""\"" but can also accept ""/"".",,unclassified, | |
| 994 | CWE-241,Improper Handling of Unexpected Data Type (Type: Base),"The software does not handle or incorrectly handles when a particular element is not the expected type, e.g. it expects a digit (0-9) but is provided with a letter (A-Z). | |
| 995 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 996 | The ""../"" manipulation is the canonical manipulation for operating systems that use ""/"" as directory separators, such as UNIX- and Linux-based systems. In some cases, it is useful for bypassing protection schemes in environments for which ""/"" is supported but not the primary separator, such as Windows, which uses ""\"" but can also accept ""/"".",,unclassified, | |
| 997 | CWE-244,Improper Clearing of Heap Memory Before Release (Heap Inspection) (Type: Variant),"Using realloc() to resize buffers that store sensitive information can leave the sensitive information exposed to attack, because it is not removed from memory. | |
| 998 | When sensitive data such as a password or an encryption key is not removed from memory, it could be exposed to an attacker using a ""heap inspection"" attack that reads the sensitive data using memory dumps or other methods. The realloc() function is commonly used to increase the size of a block of allocated memory. This operation often requires copying the contents of the old memory block into a new and larger block. This operation leaves the contents of the original block intact but inaccessible to the program, preventing the program from being able to scrub sensitive data from memory. If an attacker can later examine the contents of a memory dump, the sensitive data could be exposed.",,unclassified, | |
| 999 | CWE-245,J2EE Bad Practices: Direct Management of Connections (Type: Variant),"The J2EE application directly manages connections, instead of using the container's connection management facilities. | |
| 1000 | When sensitive data such as a password or an encryption key is not removed from memory, it could be exposed to an attacker using a ""heap inspection"" attack that reads the sensitive data using memory dumps or other methods. The realloc() function is commonly used to increase the size of a block of allocated memory. This operation often requires copying the contents of the old memory block into a new and larger block. This operation leaves the contents of the original block intact but inaccessible to the program, preventing the program from being able to scrub sensitive data from memory. If an attacker can later examine the contents of a memory dump, the sensitive data could be exposed.",,unclassified, | |
| 1001 | CWE-246,J2EE Bad Practices: Direct Use of Sockets (Type: Variant),"The J2EE application directly uses sockets instead of using framework method calls. | |
| 1002 | When sensitive data such as a password or an encryption key is not removed from memory, it could be exposed to an attacker using a ""heap inspection"" attack that reads the sensitive data using memory dumps or other methods. The realloc() function is commonly used to increase the size of a block of allocated memory. This operation often requires copying the contents of the old memory block into a new and larger block. This operation leaves the contents of the original block intact but inaccessible to the program, preventing the program from being able to scrub sensitive data from memory. If an attacker can later examine the contents of a memory dump, the sensitive data could be exposed.",,unclassified, | |
| 1003 | CWE-247,DEPRECATED (Duplicate): Reliance on DNS Lookups in a Security Decision (Type: Base),"This entry has been deprecated because it was a duplicate of CWE-350. All content has been transferred to CWE-350. | |
| 1004 | When sensitive data such as a password or an encryption key is not removed from memory, it could be exposed to an attacker using a ""heap inspection"" attack that reads the sensitive data using memory dumps or other methods. The realloc() function is commonly used to increase the size of a block of allocated memory. This operation often requires copying the contents of the old memory block into a new and larger block. This operation leaves the contents of the original block intact but inaccessible to the program, preventing the program from being able to scrub sensitive data from memory. If an attacker can later examine the contents of a memory dump, the sensitive data could be exposed.",,unclassified, | |
| 1005 | CWE-248,Uncaught Exception (Type: Base),"An exception is thrown from a function, but it is not caught. | |
| 1006 | When an exception is not caught, it may cause the program to crash or expose sensitive information.",,unclassified, | |
| 1007 | CWE-249,DEPRECATED: Often Misused: Path Manipulation (Type: Variant),"This entry has been deprecated because of name confusion and an accidental combination of multiple weaknesses. Most of its content has been transferred to CWE-785. | |
| 1008 | When an exception is not caught, it may cause the program to crash or expose sensitive information.",,unclassified, | |
| 1009 | CWE-25,Path Traversal: /../filedir (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize ""/../"" sequences that can resolve to a location that is outside of that directory. | |
| 1010 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1011 | Sometimes a program checks for ""../"" at the beginning of the input, so a ""/../"" can bypass that check.",,unclassified, | |
| 1012 | CWE-26,Path Traversal: /dir/../filename (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize ""/dir/../filename"" sequences that can resolve to a location that is outside of that directory. | |
| 1013 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1014 | The '/dir/../filename' manipulation is useful for bypassing some path traversal protection schemes. Sometimes a program only checks for ""../"" at the beginning of the input, so a ""/../"" can bypass that check.",,unclassified, | |
| 1015 | CWE-260,Password in Configuration File (Type: Variant),"The software stores a password in a configuration file that might be accessible to actors who do not know the password. | |
| 1016 | This can result in compromise of the system for which the password is used. An attacker could gain access to this file and learn the stored password or worse yet, change the password to one of their choosing.",,unclassified,Building Secure Software: How to Avoid Security Problems the Right Way | |
| 1017 | CWE-261,Weak Cryptography for Passwords (Type: Variant),"Obscuring a password with a trivial encoding does not protect the password. | |
| 1018 | This can result in compromise of the system for which the password is used. An attacker could gain access to this file and learn the stored password or worse yet, change the password to one of their choosing.",,unclassified,"Building Secure Software: How to Avoid Security Problems the Right Way | |
| 1019 | 24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 1020 | CWE-266,Incorrect Privilege Assignment (Type: Base),"A product incorrectly assigns a privilege to a particular actor, creating an unintended sphere of control for that actor. | |
| 1021 | Just as neglecting to include functionality for the management of password aging is dangerous, so is allowing password aging to continue unchecked. Passwords must be given a maximum life span, after which a user is required to update with a new and different password.",,unclassified,Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 1022 | CWE-267,Privilege Defined With Unsafe Actions (Type: Base),"A particular privilege, role, capability, or right can be used to perform unsafe actions that were not intended, even when it is assigned to the correct entity. | |
| 1023 | Just as neglecting to include functionality for the management of password aging is dangerous, so is allowing password aging to continue unchecked. Passwords must be given a maximum life span, after which a user is required to update with a new and different password.",,unclassified,Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 1024 | CWE-27,Path Traversal: dir/../../filename (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize multiple internal ""../"" sequences that can resolve to a location that is outside of that directory. | |
| 1025 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1026 | The 'directory/../../filename' manipulation is useful for bypassing some path traversal protection schemes. Sometimes a program only removes one ""../"" sequence, so multiple ""../"" can bypass that check. Alternately, this manipulation could be used to bypass a check for ""../"" at the beginning of the pathname, moving up more than one directory level.",,unclassified, | |
| 1027 | CWE-270,Privilege Context Switching Error (Type: Base),"The software does not properly manage privileges while it is switching between different contexts that have different privileges or spheres of control. | |
| 1028 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1029 | The 'directory/../../filename' manipulation is useful for bypassing some path traversal protection schemes. Sometimes a program only removes one ""../"" sequence, so multiple ""../"" can bypass that check. Alternately, this manipulation could be used to bypass a check for ""../"" at the beginning of the pathname, moving up more than one directory level.",,unclassified,"Writing Secure Code: Chapter 7, ""Running with Least Privilege"" Page 207 | |
| 1030 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html" | |
| 1031 | CWE-272,Least Privilege Violation (Type: Base),"The elevated privilege level required to perform operations such as chroot() should be dropped immediately after the operation is performed. | |
| 1032 | In some contexts, a system executing with elevated permissions will hand off a process/file/etc. to another process or user. If the privileges of an entity are not reduced, then elevated privileges are spread throughout a system and possibly to an attacker.",,unclassified, | |
| 1033 | CWE-274,Improper Handling of Insufficient Privileges (Type: Base),"The software does not handle or incorrectly handles when it has insufficient privileges to perform an operation, leading to resultant weaknesses. | |
| 1034 | If the drop fails, the software will continue to run with the raised privileges, which might provide additional access to unprivileged users.",,unclassified, | |
| 1035 | CWE-277,Insecure Inherited Permissions (Type: Variant),"A product defines a set of insecure permissions that are inherited by objects that are created by the program. | |
| 1036 | If the drop fails, the software will continue to run with the raised privileges, which might provide additional access to unprivileged users.",,unclassified, | |
| 1037 | CWE-278,Insecure Preserved Inherited Permissions (Type: Variant),"A product inherits a set of insecure permissions for an object, e.g. when copying from an archive file, without user awareness or involvement. | |
| 1038 | If the drop fails, the software will continue to run with the raised privileges, which might provide additional access to unprivileged users.",,unclassified, | |
| 1039 | CWE-279,Incorrect Execution-Assigned Permissions (Type: Variant),"While it is executing, the software sets the permissions of an object in a way that violates the intended permissions that have been specified by the user. | |
| 1040 | If the drop fails, the software will continue to run with the raised privileges, which might provide additional access to unprivileged users.",,unclassified, | |
| 1041 | CWE-28,Path Traversal: ..\filedir (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize ""..\"" sequences that can resolve to a location that is outside of that directory. | |
| 1042 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1043 | The '..\' manipulation is the canonical manipulation for operating systems that use ""\"" as directory separators, such as Windows. However, it is also useful for bypassing path traversal protection schemes that only assume that the ""/"" separator is valid.",,unclassified, | |
| 1044 | CWE-280,Improper Handling of Insufficient Permissions or Privileges (Type: Base),"The application does not handle or incorrectly handles when it has insufficient privileges to access resources or functionality as specified by their permissions. This may cause it to follow unexpected code paths that may leave the application in an invalid state. | |
| 1045 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1046 | The '..\' manipulation is the canonical manipulation for operating systems that use ""\"" as directory separators, such as Windows. However, it is also useful for bypassing path traversal protection schemes that only assume that the ""/"" separator is valid.",,unclassified, | |
| 1047 | CWE-281,Improper Preservation of Permissions (Type: Base),"The software does not preserve permissions or incorrectly preserves permissions when copying, restoring, or sharing objects, which can cause them to have less restrictive permissions than intended. | |
| 1048 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1049 | The '..\' manipulation is the canonical manipulation for operating systems that use ""\"" as directory separators, such as Windows. However, it is also useful for bypassing path traversal protection schemes that only assume that the ""/"" separator is valid.",,unclassified, | |
| 1050 | CWE-282,Improper Ownership Management (Type: Class),"The software assigns the wrong ownership, or does not properly verify the ownership, of an object or resource. | |
| 1051 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1052 | The '..\' manipulation is the canonical manipulation for operating systems that use ""\"" as directory separators, such as Windows. However, it is also useful for bypassing path traversal protection schemes that only assume that the ""/"" separator is valid.",,unclassified, | |
| 1053 | CWE-283,Unverified Ownership (Type: Base),"The software does not properly verify that a critical resource is owned by the proper entity. | |
| 1054 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1055 | The '..\' manipulation is the canonical manipulation for operating systems that use ""\"" as directory separators, such as Windows. However, it is also useful for bypassing path traversal protection schemes that only assume that the ""/"" separator is valid.",,unclassified, | |
| 1056 | CWE-284,Improper Access Control (Type: Class),"The software does not restrict or incorrectly restricts access to a resource from an unauthorized actor. | |
| 1057 | Access control involves the use of several protection mechanisms such as authentication (proving the identity of an actor) authorization (ensuring that a given actor can access a resource), and accountability (tracking of activities that were performed). When any mechanism is not applied or otherwise fails, attackers can compromise the security of the software by gaining privileges, reading sensitive information, executing commands, evading detection, etc. | |
| 1058 | There are two distinct behaviors that can introduce access control weaknesses: | |
| 1059 | Specification: incorrect privileges, permissions, ownership, etc. are explicitly specified for either the user or the resource (for example, setting a password file to be world-writable, or giving administrator capabilities to a guest user). This action could be performed by the program or the administrator. | |
| 1060 | Enforcement: the mechanism contains errors that prevent it from properly enforcing the specified access control requirements (e.g., allowing the user to specify their own privileges, or allowing a syntactically-incorrect ACL to produce insecure settings). This problem occurs within the program itself, in that it does not actually enforce the intended security policy that the administrator specifies.",,unclassified,"Writing Secure Code: Chapter 6, ""Determining Appropriate Access Control"" Page 171 | |
| 1061 | 24 Deadly Sins of Software Security: ""Sin 17: Failure to Protect Stored Data."" Page 253" | |
| 1062 | CWE-286,Incorrect User Management (Type: Class),"The software does not properly manage a user within its environment. | |
| 1063 | Users can be assigned to the wrong group (class) of permissions resulting in unintended access rights to sensitive objects.",,unclassified, | |
| 1064 | CWE-288,Authentication Bypass Using an Alternate Path or Channel (Type: Base),"A product requires authentication, but the product has an alternate path or channel that does not require authentication. | |
| 1065 | Users can be assigned to the wrong group (class) of permissions resulting in unintended access rights to sensitive objects.",,unclassified, | |
| 1066 | CWE-289,Authentication Bypass by Alternate Name (Type: Variant),"The software performs authentication based on the name of a resource being accessed, or the name of the actor performing the access, but it does not properly check all possible names for that resource or actor. | |
| 1067 | Users can be assigned to the wrong group (class) of permissions resulting in unintended access rights to sensitive objects.",,unclassified, | |
| 1068 | CWE-29,Path Traversal: \..\filename (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize '\..\filename' (leading backslash dot dot) sequences that can resolve to a location that is outside of that directory. | |
| 1069 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1070 | This is similar to CWE-25, except using ""\"" instead of ""/"". Sometimes a program checks for ""..\"" at the beginning of the input, so a ""\..\"" can bypass that check. It is also useful for bypassing path traversal protection schemes that only assume that the ""/"" separator is valid.",,unclassified, | |
| 1071 | CWE-290,Authentication Bypass by Spoofing (Type: Base),"This attack-focused weakness is caused by improperly implemented authentication schemes that are subject to spoofing attacks. | |
| 1072 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1073 | This is similar to CWE-25, except using ""\"" instead of ""/"". Sometimes a program checks for ""..\"" at the beginning of the input, so a ""\..\"" can bypass that check. It is also useful for bypassing path traversal protection schemes that only assume that the ""/"" separator is valid.",,unclassified,"The Art of Software Security Assessment: Chapter 3, ""Spoofing and Identification"", Page 72." | |
| 1074 | CWE-295,Improper Certificate Validation (Type: Base),"The software does not validate, or incorrectly validates, a certificate. | |
| 1075 | When a certificate is invalid or malicious, it might allow an attacker to spoof a trusted entity by using a man-in-the-middle (MITM) attack. The software might connect to a malicious host while believing it is a trusted host, or the software might be deceived into accepting spoofed data that appears to originate from a trusted host.",,unclassified,"Why Eve and Mallory Love Android: An Analysis of Android SSL (In)Security: http://www2.dcsec.uni-hannover.de/files/android/p50-fahl.pdf | |
| 1076 | Computer Security: Art and Science" | |
| 1077 | CWE-30,Path Traversal: \dir\..\filename (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize '\dir\..\filename' (leading backslash dot dot) sequences that can resolve to a location that is outside of that directory. | |
| 1078 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1079 | This is similar to CWE-26, except using ""\"" instead of ""/"". The '\dir\..\filename' manipulation is useful for bypassing some path traversal protection schemes. Sometimes a program only checks for ""..\"" at the beginning of the input, so a ""\..\"" can bypass that check.",,unclassified, | |
| 1080 | CWE-300,Channel Accessible by Non-Endpoint (Man-in-the-Middle) (Type: Class),"The product does not adequately verify the identity of actors at both ends of a communication channel, or does not adequately ensure the integrity of the channel, in a way that allows the channel to be accessed or influenced by an actor that is not an endpoint. | |
| 1081 | In order to establish secure communication between two parties, it is often important to adequately verify the identity of entities at each end of the communication channel. Inadequate or inconsistent verification may result in insufficient or incorrect identification of either communicating entity. This can have negative consequences such as misplaced trust in the entity at the other end of the channel. An attacker can leverage this by interposing between the communicating entities and masquerading as the original entity. In the absence of sufficient verification of identity, such an attacker can eavesdrop and potentially modify the communication between the original entities.",,unclassified,Computer Security: Art and Science | |
| 1082 | CWE-302,Authentication Bypass by Assumed-Immutable Data (Type: Variant),"The authentication scheme or implementation uses key data elements that are assumed to be immutable, but can be controlled or modified by the attacker. | |
| 1083 | A mutual authentication protocol requires each party to respond to a random challenge by the other party by encrypting it with a pre-shared key. Often, however, such protocols employ the same pre-shared key for communication with a number of different entities. A malicious user or an attacker can easily compromise this protocol without possessing the correct key by employing a reflection attack on the protocol.",,unclassified, | |
| 1084 | CWE-303,Incorrect Implementation of Authentication Algorithm (Type: Base),"The requirements for the software dictate the use of an established authentication algorithm, but the implementation of the algorithm is incorrect. | |
| 1085 | This incorrect implementation may allow authentication to be bypassed.",,unclassified, | |
| 1086 | CWE-304,Missing Critical Step in Authentication (Type: Base),"The software implements an authentication technique, but it skips a step that weakens the technique. | |
| 1087 | Authentication techniques should follow the algorithms that define them exactly, otherwise authentication can be bypassed or more easily subjected to brute force attacks.",,unclassified, | |
| 1088 | CWE-305,Authentication Bypass by Primary Weakness (Type: Base),"The authentication algorithm is sound, but the implemented mechanism can be bypassed as the result of a separate weakness that is primary to the authentication error. | |
| 1089 | Authentication techniques should follow the algorithms that define them exactly, otherwise authentication can be bypassed or more easily subjected to brute force attacks.",,unclassified, | |
| 1090 | CWE-307,Improper Restriction of Excessive Authentication Attempts (Type: Base),"The software does not implement sufficient measures to prevent multiple failed authentication attempts within in a short time frame, making it more susceptible to brute force attacks. | |
| 1091 | Authentication techniques should follow the algorithms that define them exactly, otherwise authentication can be bypassed or more easily subjected to brute force attacks.",,unclassified,"Weak Password Brings 'Happiness' to Twitter Hacker: http://www.wired.com/threatlevel/2009/01/professed-twitt/ | |
| 1092 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI" | |
| 1093 | CWE-31,Path Traversal: dir\..\..\filename (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize 'dir\..\..\filename' (multiple internal backslash dot dot) sequences that can resolve to a location that is outside of that directory. | |
| 1094 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1095 | The 'dir\..\..\filename' manipulation is useful for bypassing some path traversal protection schemes. Sometimes a program only removes one ""..\"" sequence, so multiple ""..\"" can bypass that check. Alternately, this manipulation could be used to bypass a check for ""..\"" at the beginning of the pathname, moving up more than one directory level.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1096 | CWE-312,Cleartext Storage of Sensitive Information (Type: Base),"The application stores sensitive information in cleartext within a resource that might be accessible to another control sphere. | |
| 1097 | Because the information is stored in cleartext, attackers could potentially read it. Even if the information is encoded in a way that is not human-readable, certain techniques could determine which encoding is being used, then decode the information.",,unclassified,"Writing Secure Code: Chapter 9, ""Protecting Secret Data"" Page 299 | |
| 1098 | The Art of Software Security Assessment: Chapter 2, ""Common Vulnerabilities of Encryption"", Page 43. | |
| 1099 | Mobile App Top 10 List: http://www.veracode.com/blog/2010/12/mobile-app-top-10-list/" | |
| 1100 | CWE-313,Cleartext Storage in a File or on Disk (Type: Variant),"The application stores sensitive information in cleartext in a file, or on disk. | |
| 1101 | The sensitive information could be read by attackers with access to the file, or with physical or administrator access to the raw disk. Even if the information is encoded in a way that is not human-readable, certain techniques could determine which encoding is being used, then decode the information.",,unclassified, | |
| 1102 | CWE-314,Cleartext Storage in the Registry (Type: Variant),"The application stores sensitive information in cleartext in the registry. | |
| 1103 | Attackers can read the information by accessing the registry key. Even if the information is encoded in a way that is not human-readable, certain techniques could determine which encoding is being used, then decode the information.",,unclassified, | |
| 1104 | CWE-315,Cleartext Storage of Sensitive Information in a Cookie (Type: Variant),"The application stores sensitive information in cleartext in a cookie. | |
| 1105 | Attackers can use widely-available tools to view the cookie and read the sensitive information. Even if the information is encoded in a way that is not human-readable, certain techniques could determine which encoding is being used, then decode the information.",,unclassified, | |
| 1106 | CWE-316,Cleartext Storage of Sensitive Information in Memory (Type: Variant),"The application stores sensitive information in cleartext in memory. | |
| 1107 | The sensitive memory might be saved to disk, stored in a core dump, or remain uncleared if the application crashes, or if the programmer does not properly clear the memory before freeing it. | |
| 1108 | It could be argued that such problems are usually only exploitable by those with administrator privileges. However, swapping could cause the memory to be written to disk and leave it accessible to physical attack afterwards. Core dump files might have insecure permissions or be stored in archive files that are accessible to untrusted people. Or, uncleared sensitive memory might be inadvertently exposed to attackers due to another weakness.",,unclassified, | |
| 1109 | CWE-317,Cleartext Storage of Sensitive Information in GUI (Type: Variant),"The application stores sensitive information in cleartext within the GUI. | |
| 1110 | An attacker can often obtain data from a GUI, even if hidden, by using an API to directly access GUI objects such as windows and menus. Even if the information is encoded in a way that is not human-readable, certain techniques could determine which encoding is being used, then decode the information.",,unclassified, | |
| 1111 | CWE-318,Cleartext Storage of Sensitive Information in Executable (Type: Variant),"The application stores sensitive information in cleartext in an executable. | |
| 1112 | Attackers can reverse engineer binary code to obtain secret data. This is especially easy when the cleartext is plain ASCII. Even if the information is encoded in a way that is not human-readable, certain techniques could determine which encoding is being used, then decode the information.",,unclassified, | |
| 1113 | CWE-32,Path Traversal: ... (Triple Dot) (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize '...' (triple dot) sequences that can resolve to a location that is outside of that directory. | |
| 1114 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1115 | The '...' manipulation is useful for bypassing some path traversal protection schemes. On some Windows systems, it is equivalent to ""..\.."" and might bypass checks that assume only two dots are valid. Incomplete filtering, such as removal of ""./"" sequences, can ultimately produce valid "".."" sequences due to a collapse into unsafe value (CWE-182).",,unclassified, | |
| 1116 | CWE-325,Missing Required Cryptographic Step (Type: Base),"The software does not implement a required step in a cryptographic algorithm, resulting in weaker encryption than advertised by that algorithm. | |
| 1117 | Cryptographic implementations should follow the algorithms that define them exactly, otherwise encryption can be weaker than expected.",,unclassified, | |
| 1118 | CWE-326,Inadequate Encryption Strength (Type: Class),"The software stores or transmits sensitive data using an encryption scheme that is theoretically sound, but is not strong enough for the level of protection required. | |
| 1119 | A weak encryption scheme can be subjected to brute force attacks that have a reasonable chance of succeeding using current attack methods and resources.",,unclassified,"Writing Secure Code: Chapter 8, ""Cryptographic Foibles"" Page 259 | |
| 1120 | 24 Deadly Sins of Software Security: ""Sin 21: Using the Wrong Cryptography."" Page 315" | |
| 1121 | CWE-328,Reversible One-Way Hash (Type: Base),"The product uses a hashing algorithm that produces a hash value that can be used to determine the original input, or to find an input that can produce the same hash, more efficiently than brute force techniques. | |
| 1122 | This weakness is especially dangerous when the hash is used in security algorithms that require the one-way property to hold. For example, if an authentication system takes an incoming password and generates a hash, then compares the hash to another hash that it has stored in its authentication database, then the ability to create a collision could allow an attacker to provide an alternate password that produces the same target hash, bypassing authentication.",,unclassified,"MD5 considered harmful today: http://www.phreedom.org/research/rogue-ca/ | |
| 1123 | The Art of Software Security Assessment: Chapter 2, ""Common Vulnerabilities of Integrity"", Page 47. | |
| 1124 | RFC2898 - PKCS #5: Password-Based Cryptography Specification Version 2.0: http://tools.ietf.org/html/rfc2898 | |
| 1125 | How To Safely Store A Password: http://codahale.com/how-to-safely-store-a-password/ | |
| 1126 | Tarsnap - The scrypt key derivation function and encryption utility: http://www.tarsnap.com/scrypt.html | |
| 1127 | How Companies Can Beef Up Password Security (interview with Thomas H. Ptacek): http://krebsonsecurity.com/2012/06/how-companies-can-beef-up-password-security/ | |
| 1128 | Password security: past, present, future: http://www.openwall.com/presentations/PHDays2012-Password-Security/ | |
| 1129 | Our password hashing has no clothes: http://www.troyhunt.com/2012/06/our-password-hashing-has-no-clothes.html | |
| 1130 | Should we really use bcrypt/scrypt?: http://www.analyticalengine.net/2012/06/should-we-really-use-bcryptscrypt/" | |
| 1131 | CWE-33,Path Traversal: .... (Multiple Dot) (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize '....' (multiple dot) sequences that can resolve to a location that is outside of that directory. | |
| 1132 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1133 | The '....' manipulation is useful for bypassing some path traversal protection schemes. On some Windows systems, it is equivalent to ""..\..\.."" and might bypass checks that assume only two dots are valid. Incomplete filtering, such as removal of ""./"" sequences, can ultimately produce valid "".."" sequences due to a collapse into unsafe value (CWE-182).",,unclassified, | |
| 1134 | CWE-331,Insufficient Entropy (Type: Base),"The software uses an algorithm or scheme that produces insufficient entropy, leaving patterns or clusters of values that are more likely to occur than others. | |
| 1135 | When software generates predictable values in a context requiring unpredictability, it may be possible for an attacker to guess the next value that will be generated, and use this guess to impersonate another user or access sensitive information.",,unclassified,Building Secure Software: How to Avoid Security Problems the Right Way | |
| 1136 | CWE-334,Small Space of Random Values (Type: Base),"The number of possible random values is smaller than needed by the product, making it more susceptible to brute force attacks. | |
| 1137 | The rate at which true random numbers can be generated is limited. It is important that one uses them only when they are needed for security.",,unclassified,"SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1138 | 24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1139 | CWE-335,PRNG Seed Error (Type: Class),"A Pseudo-Random Number Generator (PRNG) uses seeds incorrectly. | |
| 1140 | The rate at which true random numbers can be generated is limited. It is important that one uses them only when they are needed for security.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1141 | CWE-336,Same Seed in PRNG (Type: Base),"A PRNG uses the same seed each time the product is initialized. If an attacker can guess (or knows) the seed, then he/she may be able to determine the ""random"" number produced from the PRNG. | |
| 1142 | The rate at which true random numbers can be generated is limited. It is important that one uses them only when they are needed for security.",,unclassified,SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1143 | CWE-337,Predictable Seed in PRNG (Type: Base),"A PRNG is initialized from a predictable seed, e.g. using process ID or system time. | |
| 1144 | The rate at which true random numbers can be generated is limited. It is important that one uses them only when they are needed for security.",,unclassified,"SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1145 | 24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1146 | CWE-339,Small Seed Space in PRNG (Type: Base),"A PRNG uses a relatively small space of seeds. | |
| 1147 | The rate at which true random numbers can be generated is limited. It is important that one uses them only when they are needed for security.",,unclassified,SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1148 | CWE-34,Path Traversal: ....// (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize '....//' (doubled dot dot slash) sequences that can resolve to a location that is outside of that directory. | |
| 1149 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1150 | The '....//' manipulation is useful for bypassing some path traversal protection schemes. If ""../"" is filtered in a sequential fashion, as done by some regular expression engines, then ""....//"" can collapse into the ""../"" unsafe value (CWE-182). It could also be useful when "".."" is removed, if the operating system treats ""//"" and ""/"" as equivalent.",,unclassified, | |
| 1151 | CWE-340,Predictability Problems (Type: Class),"Weaknesses in this category are related to schemes that generate numbers or identifiers that are more predictable than required by the application. | |
| 1152 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1153 | The '....//' manipulation is useful for bypassing some path traversal protection schemes. If ""../"" is filtered in a sequential fashion, as done by some regular expression engines, then ""....//"" can collapse into the ""../"" unsafe value (CWE-182). It could also be useful when "".."" is removed, if the operating system treats ""//"" and ""/"" as equivalent.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1154 | CWE-341,Predictable from Observable State (Type: Base),"A number or object is predictable based on observations that the attacker can make about the state of the system or network, such as time, process ID, etc. | |
| 1155 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1156 | The '....//' manipulation is useful for bypassing some path traversal protection schemes. If ""../"" is filtered in a sequential fashion, as done by some regular expression engines, then ""....//"" can collapse into the ""../"" unsafe value (CWE-182). It could also be useful when "".."" is removed, if the operating system treats ""//"" and ""/"" as equivalent.",,unclassified,"SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1157 | 24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1158 | CWE-342,Predictable Exact Value from Previous Values (Type: Base),"An exact value or random number can be precisely predicted by observing previous values. | |
| 1159 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1160 | The '....//' manipulation is useful for bypassing some path traversal protection schemes. If ""../"" is filtered in a sequential fashion, as done by some regular expression engines, then ""....//"" can collapse into the ""../"" unsafe value (CWE-182). It could also be useful when "".."" is removed, if the operating system treats ""//"" and ""/"" as equivalent.",,unclassified,"SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1161 | 24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1162 | CWE-343,Predictable Value Range from Previous Values (Type: Base),"The software's random number generator produces a series of values which, when observed, can be used to infer a relatively small range of possibilities for the next value that could be generated. | |
| 1163 | The output of a random number generator should not be predictable based on observations of previous values. In some cases, an attacker cannot predict the exact value that will be produced next, but can narrow down the possibilities significantly. This reduces the amount of effort to perform a brute force attack. For example, suppose the product generates random numbers between 1 and 100, but it always produces a larger value until it reaches 100. If the generator produces an 80, then the attacker knows that the next value will be somewhere between 81 and 100. Instead of 100 possibilities, the attacker only needs to consider 20.",,unclassified,"SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1164 | Strange Attractors and TCP/IP Sequence Number Analysis: http://www.bindview.com/Services/Razor/Papers/2001/tcpseq.cfm | |
| 1165 | 24 Deadly Sins of Software Security: ""Sin 20: Weak Random Numbers."" Page 299" | |
| 1166 | CWE-344,Use of Invariant Value in Dynamically Changing Context (Type: Base),"The product uses a constant value, name, or reference, but this value can (or should) vary across different environments. | |
| 1167 | The output of a random number generator should not be predictable based on observations of previous values. In some cases, an attacker cannot predict the exact value that will be produced next, but can narrow down the possibilities significantly. This reduces the amount of effort to perform a brute force attack. For example, suppose the product generates random numbers between 1 and 100, but it always produces a larger value until it reaches 100. If the generator produces an 80, then the attacker knows that the next value will be somewhere between 81 and 100. Instead of 100 possibilities, the attacker only needs to consider 20.",,unclassified,SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1168 | CWE-345,Insufficient Verification of Data Authenticity (Type: Class),"The software does not sufficiently verify the origin or authenticity of data, in a way that causes it to accept invalid data. | |
| 1169 | The output of a random number generator should not be predictable based on observations of previous values. In some cases, an attacker cannot predict the exact value that will be produced next, but can narrow down the possibilities significantly. This reduces the amount of effort to perform a brute force attack. For example, suppose the product generates random numbers between 1 and 100, but it always produces a larger value until it reaches 100. If the generator produces an 80, then the attacker knows that the next value will be somewhere between 81 and 100. Instead of 100 possibilities, the attacker only needs to consider 20.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 15: Not Updating Easily."" Page 231" | |
| 1170 | CWE-346,Origin Validation Error (Type: Base),"The software does not properly verify that the source of data or communication is valid. | |
| 1171 | The output of a random number generator should not be predictable based on observations of previous values. In some cases, an attacker cannot predict the exact value that will be produced next, but can narrow down the possibilities significantly. This reduces the amount of effort to perform a brute force attack. For example, suppose the product generates random numbers between 1 and 100, but it always produces a larger value until it reaches 100. If the generator produces an 80, then the attacker knows that the next value will be somewhere between 81 and 100. Instead of 100 possibilities, the attacker only needs to consider 20.",,unclassified, | |
| 1172 | CWE-347,Improper Verification of Cryptographic Signature (Type: Base),"The software does not verify, or incorrectly verifies, the cryptographic signature for data. | |
| 1173 | The output of a random number generator should not be predictable based on observations of previous values. In some cases, an attacker cannot predict the exact value that will be produced next, but can narrow down the possibilities significantly. This reduces the amount of effort to perform a brute force attack. For example, suppose the product generates random numbers between 1 and 100, but it always produces a larger value until it reaches 100. If the generator produces an 80, then the attacker knows that the next value will be somewhere between 81 and 100. Instead of 100 possibilities, the attacker only needs to consider 20.",,unclassified, | |
| 1174 | CWE-348,Use of Less Trusted Source (Type: Base),"The software has two different sources of the same data or information, but it uses the source that has less support for verification, is less trusted, or is less resistant to attack. | |
| 1175 | The output of a random number generator should not be predictable based on observations of previous values. In some cases, an attacker cannot predict the exact value that will be produced next, but can narrow down the possibilities significantly. This reduces the amount of effort to perform a brute force attack. For example, suppose the product generates random numbers between 1 and 100, but it always produces a larger value until it reaches 100. If the generator produces an 80, then the attacker knows that the next value will be somewhere between 81 and 100. Instead of 100 possibilities, the attacker only needs to consider 20.",,unclassified, | |
| 1176 | CWE-349,Acceptance of Extraneous Untrusted Data With Trusted Data (Type: Base),"The software, when processing trusted data, accepts any untrusted data that is also included with the trusted data, treating the untrusted data as if it were trusted. | |
| 1177 | The output of a random number generator should not be predictable based on observations of previous values. In some cases, an attacker cannot predict the exact value that will be produced next, but can narrow down the possibilities significantly. This reduces the amount of effort to perform a brute force attack. For example, suppose the product generates random numbers between 1 and 100, but it always produces a larger value until it reaches 100. If the generator produces an 80, then the attacker knows that the next value will be somewhere between 81 and 100. Instead of 100 possibilities, the attacker only needs to consider 20.",,unclassified, | |
| 1178 | CWE-35,Path Traversal: .../...// (Type: Variant),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize '.../...//' (doubled triple dot slash) sequences that can resolve to a location that is outside of that directory. | |
| 1179 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory. | |
| 1180 | The '.../...//' manipulation is useful for bypassing some path traversal protection schemes. If ""../"" is filtered in a sequential fashion, as done by some regular expression engines, then "".../...//"" can collapse into the ""../"" unsafe value (CWE-182). Removing the first ""../"" yields ""....//""; the second removal yields ""../"". Depending on the algorithm, the software could be susceptible to CWE-34 but not CWE-35, or vice versa.",,unclassified, | |
| 1181 | CWE-350,Reliance on Reverse DNS Resolution for a Security-Critical Action (Type: Variant),"The software performs reverse DNS resolution on an IP address to obtain the hostname and make a security decision, but it does not properly ensure that the IP address is truly associated with the hostname. | |
| 1182 | When the software performs a reverse DNS resolution for an IP address, if an attacker controls the server for that IP address, then the attacker can cause the server to return an arbitrary hostname. As a result, the attacker may be able to bypass authentication, cause the wrong hostname to be recorded in log files to hide activities, or perform other attacks. | |
| 1183 | Attackers can spoof DNS names by either (1) compromising a DNS server and modifying its records (sometimes called DNS cache poisoning), or (2) having legitimate control over a DNS server associated with their IP address. | |
| 1184 | Since DNS names can be easily spoofed or misreported, and it may be difficult for the software to detect if a trusted DNS server has not been compromised, they do not constitute a valid authentication mechanism.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 15: Not Updating Easily."" Page 231 | |
| 1185 | 24 Deadly Sins of Software Security: ""Sin 24: Trusting Network Name Resolution."" Page 361 | |
| 1186 | The Art of Software Security Assessment: Chapter 16, ""DNS Spoofing"", Page 1002." | |
| 1187 | CWE-351,Insufficient Type Distinction (Type: Base),"The software does not properly distinguish between different types of elements in a way that leads to insecure behavior. | |
| 1188 | When the software performs a reverse DNS resolution for an IP address, if an attacker controls the server for that IP address, then the attacker can cause the server to return an arbitrary hostname. As a result, the attacker may be able to bypass authentication, cause the wrong hostname to be recorded in log files to hide activities, or perform other attacks. | |
| 1189 | Attackers can spoof DNS names by either (1) compromising a DNS server and modifying its records (sometimes called DNS cache poisoning), or (2) having legitimate control over a DNS server associated with their IP address. | |
| 1190 | Since DNS names can be easily spoofed or misreported, and it may be difficult for the software to detect if a trusted DNS server has not been compromised, they do not constitute a valid authentication mechanism.",,unclassified, | |
| 1191 | CWE-356,Product UI does not Warn User of Unsafe Actions (Type: Base),"The software's user interface does not warn the user before undertaking an unsafe action on behalf of that user. This makes it easier for attackers to trick users into inflicting damage to their system. | |
| 1192 | Software systems should warn users that a potentially dangerous action may occur if the user proceeds. For example, if the user downloads a file from an unknown source and attempts to execute the file on their machine, then the application's GUI can indicate that the file is unsafe.",,unclassified, | |
| 1193 | CWE-357,Insufficient UI Warning of Dangerous Operations (Type: Base),"The user interface provides a warning to a user regarding dangerous or sensitive operations, but the warning is not noticeable enough to warrant attention. | |
| 1194 | Software systems should warn users that a potentially dangerous action may occur if the user proceeds. For example, if the user downloads a file from an unknown source and attempts to execute the file on their machine, then the application's GUI can indicate that the file is unsafe.",,unclassified, | |
| 1195 | CWE-358,Improperly Implemented Security Check for Standard (Type: Base),"The software does not implement or incorrectly implements one or more security-relevant checks as specified by the design of a standardized algorithm, protocol, or technique. | |
| 1196 | Software systems should warn users that a potentially dangerous action may occur if the user proceeds. For example, if the user downloads a file from an unknown source and attempts to execute the file on their machine, then the application's GUI can indicate that the file is unsafe.",,unclassified, | |
| 1197 | CWE-359,Privacy Violation (Type: Class),"Mishandling private information, such as customer passwords or social security numbers, can compromise user privacy and is often illegal. | |
| 1198 | Software systems should warn users that a potentially dangerous action may occur if the user proceeds. For example, if the user downloads a file from an unknown source and attempts to execute the file on their machine, then the application's GUI can indicate that the file is unsafe.",,unclassified,"AOL man pleads guilty to selling 92m email addies: http://www.theregister.co.uk/2005/02/07/aol_email_theft/ | |
| 1199 | Safe Harbor Privacy Framework: http://www.export.gov/safeharbor/ | |
| 1200 | Financial Privacy: The Gramm-Leach Bliley Act (GLBA): http://www.ftc.gov/privacy/glbact/index.html | |
| 1201 | Health Insurance Portability and Accountability Act (HIPAA): http://www.hhs.gov/ocr/hipaa/ | |
| 1202 | California SB-1386: http://info.sen.ca.gov/pub/01-02/bill/sen/sb_1351-1400/sb_1386_bill_20020926_chaptered.html | |
| 1203 | SECURITY REQUIREMENTS FOR CRYPTOGRAPHIC MODULES: http://csrc.nist.gov/publications/fips/fips140-2/fips1402.pdf | |
| 1204 | Mobile App Top 10 List: http://www.veracode.com/blog/2010/12/mobile-app-top-10-list/" | |
| 1205 | CWE-36,Absolute Path Traversal (Type: Base),"The software uses external input to construct a pathname that should be within a restricted directory, but it does not properly neutralize absolute path sequences such as ""/abs/path"" that can resolve to a location that is outside of that directory. | |
| 1206 | This allows attackers to traverse the file system to access files or directories that are outside of the restricted directory.",,unclassified,"The Art of Software Security Assessment: Chapter 9, ""Filenames and Paths"", Page 503." | |
| 1207 | CWE-363,Race Condition Enabling Link Following (Type: Base),"The software checks the status of a file or directory before accessing it, which produces a race condition in which the file can be replaced with a link before the access is performed, causing the software to access the wrong file. | |
| 1208 | While developers might expect that there is a very narrow time window between the time of check and time of use, there is still a race condition. An attacker could cause the software to slow down (e.g. with memory consumption), causing the time window to become larger. Alternately, in some situations, the attacker could win the race by performing a large number of attacks.",,unclassified,"The Art of Software Security Assessment: Chapter 9, ""Race Conditions"", Page 526." | |
| 1209 | CWE-368,Context Switching Race Condition (Type: Base),"A product performs a series of non-atomic actions to switch between contexts that cross privilege or other security boundaries, but a race condition allows an attacker to modify or misrepresent the product's behavior during the switch. | |
| 1210 | This is commonly seen in web browser vulnerabilities in which the attacker can perform certain actions while the browser is transitioning from a trusted to an untrusted domain, or vice versa, and the browser performs the actions on one domain using the trust level and resources of the other domain.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205" | |
| 1211 | CWE-37,Path Traversal: /absolute/pathname/here (Type: Variant),"A software system that accepts input in the form of a slash absolute path ('/absolute/pathname/here') without appropriate validation can allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1212 | This weakness typically occurs when an unexpected value is provided to the product, or if an error occurs that is not properly detected. It frequently occurs in calculations involving physical dimensions such as size, length, width, and height.",,unclassified, | |
| 1213 | CWE-372,Incomplete Internal State Distinction (Type: Base),"The software does not properly determine which state it is in, causing it to assume it is in state X when in fact it is in state Y, causing it to perform incorrect operations in a security-relevant manner. | |
| 1214 | If the revocation status of a certificate is not checked before each action that requires privileges, the system may be subject to a race condition. If a certificate is revoked after the initial check, all subsequent actions taken with the owner of the revoked certificate will lose all benefits guaranteed by the certificate. In fact, it is almost certain that the use of a revoked certificate indicates malicious activity.",,unclassified, | |
| 1215 | CWE-373,DEPRECATED: State Synchronization Error (Type: Base),"This entry was deprecated because it overlapped the same concepts as race condition (CWE-362) and Improper Synchronization (CWE-662). | |
| 1216 | If the revocation status of a certificate is not checked before each action that requires privileges, the system may be subject to a race condition. If a certificate is revoked after the initial check, all subsequent actions taken with the owner of the revoked certificate will lose all benefits guaranteed by the certificate. In fact, it is almost certain that the use of a revoked certificate indicates malicious activity.",,unclassified, | |
| 1217 | CWE-377,Insecure Temporary File (Type: Base),"Creating and using insecure temporary files can leave application and system data vulnerable to attack. | |
| 1218 | If the revocation status of a certificate is not checked before each action that requires privileges, the system may be subject to a race condition. If a certificate is revoked after the initial check, all subsequent actions taken with the owner of the revoked certificate will lose all benefits guaranteed by the certificate. In fact, it is almost certain that the use of a revoked certificate indicates malicious activity.",,unclassified,"Writing Secure Code: Chapter 23, ""Creating Temporary Files Securely"" Page 682 | |
| 1219 | The Art of Software Security Assessment: Chapter 9, ""Temporary Files"", Page 538. | |
| 1220 | The Art of Software Security Assessment: Chapter 11, ""File Squatting"", Page 662." | |
| 1221 | CWE-38,Path Traversal: \absolute\pathname\here (Type: Variant),"A software system that accepts input in the form of a backslash absolute path ('\absolute\pathname\here') without appropriate validation can allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1222 | On some operating systems, the fact that the temporary file exists may be apparent to any user with sufficient privileges to access that directory. Since the file is visible, the application that is using the temporary file could be known. If one has access to list the processes on the system, the attacker has gained information about what the user is doing at that time. By correlating this with the applications the user is running, an attacker could potentially discover what a user's actions are. From this, higher levels of security could be breached.",,unclassified, | |
| 1223 | CWE-382,J2EE Bad Practices: Use of System.exit() (Type: Variant),"A J2EE application uses System.exit(), which also shuts down its container. | |
| 1224 | On some operating systems, the fact that the temporary file exists may be apparent to any user with sufficient privileges to access that directory. Since the file is visible, the application that is using the temporary file could be known. If one has access to list the processes on the system, the attacker has gained information about what the user is doing at that time. By correlating this with the applications the user is running, an attacker could potentially discover what a user's actions are. From this, higher levels of security could be breached.",,unclassified, | |
| 1225 | CWE-383,J2EE Bad Practices: Direct Use of Threads (Type: Variant),"Thread management in a Web application is forbidden in some circumstances and is always highly error prone. | |
| 1226 | Thread management in a web application is forbidden by the J2EE standard in some circumstances and is always highly error prone. Managing threads is difficult and is likely to interfere in unpredictable ways with the behavior of the application container. Even without interfering with the container, thread management usually leads to bugs that are hard to detect and diagnose like deadlock, race conditions, and other synchronization errors.",,unclassified, | |
| 1227 | CWE-386,Symbolic Name not Mapping to Correct Object (Type: Base),"A constant symbolic reference to an object is used, even though the reference can resolve to a different object over time. | |
| 1228 | In some instances, knowing when data is transmitted between parties can provide a malicious user with privileged information. Also, externally monitoring the timing of operations can potentially reveal sensitive data. For example, a cryptographic operation can expose its internal state if the time it takes to perform the operation varies, based on the state. | |
| 1229 | Covert channels are frequently classified as either storage or timing channels. Some examples of covert timing channels are the system's paging rate, the time a certain transaction requires to execute, and the time it takes to gain access to a shared bus.",,unclassified, | |
| 1230 | CWE-39,Path Traversal: C:dirname (Type: Variant),"An attacker can inject a drive letter or Windows volume letter ('C:dirname') into a software system to potentially redirect access to an unintended location or arbitrary file. | |
| 1231 | In some instances, knowing when data is transmitted between parties can provide a malicious user with privileged information. Also, externally monitoring the timing of operations can potentially reveal sensitive data. For example, a cryptographic operation can expose its internal state if the time it takes to perform the operation varies, based on the state. | |
| 1232 | Covert channels are frequently classified as either storage or timing channels. Some examples of covert timing channels are the system's paging rate, the time a certain transaction requires to execute, and the time it takes to gain access to a shared bus.",,unclassified, | |
| 1233 | CWE-392,Missing Report of Error Condition (Type: Base),"The software encounters an error but does not provide a status code or return value to indicate that an error has occurred. | |
| 1234 | In some instances, knowing when data is transmitted between parties can provide a malicious user with privileged information. Also, externally monitoring the timing of operations can potentially reveal sensitive data. For example, a cryptographic operation can expose its internal state if the time it takes to perform the operation varies, based on the state. | |
| 1235 | Covert channels are frequently classified as either storage or timing channels. Some examples of covert timing channels are the system's paging rate, the time a certain transaction requires to execute, and the time it takes to gain access to a shared bus.",,unclassified, | |
| 1236 | CWE-393,Return of Wrong Status Code (Type: Base),"A function or operation returns an incorrect return value or status code that does not indicate an error, but causes the product to modify its behavior based on the incorrect result. | |
| 1237 | This can lead to unpredictable behavior. If the function is used to make security-critical decisions or provide security-critical information, then the wrong status code can cause the software to assume that an action is safe, even when it is not.",,unclassified, | |
| 1238 | CWE-394,Unexpected Status Code or Return Value (Type: Base),"The software does not properly check when a function or operation returns a value that is legitimate for the function, but is not expected by the software. | |
| 1239 | This can lead to unpredictable behavior. If the function is used to make security-critical decisions or provide security-critical information, then the wrong status code can cause the software to assume that an action is safe, even when it is not.",,unclassified, | |
| 1240 | CWE-395,Use of NullPointerException Catch to Detect NULL Pointer Dereference (Type: Base),"Catching NullPointerException should not be used as an alternative to programmatic checks to prevent dereferencing a null pointer. | |
| 1241 | This can lead to unpredictable behavior. If the function is used to make security-critical decisions or provide security-critical information, then the wrong status code can cause the software to assume that an action is safe, even when it is not.",,unclassified, | |
| 1242 | CWE-396,Declaration of Catch for Generic Exception (Type: Base),"Catching overly broad exceptions promotes complex error handling code that is more likely to contain security vulnerabilities. | |
| 1243 | Multiple catch blocks can get ugly and repetitive, but ""condensing"" catch blocks by catching a high-level class like Exception can obscure exceptions that deserve special treatment or that should not be caught at this point in the program. Catching an overly broad exception essentially defeats the purpose of Java's typed exceptions, and can become particularly dangerous if the program grows and begins to throw new types of exceptions. The new exception types will not receive any attention.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 9: Catching Exceptions."" Page 157" | |
| 1244 | CWE-397,Declaration of Throws for Generic Exception (Type: Base),"Throwing overly broad exceptions promotes complex error handling code that is more likely to contain security vulnerabilities. | |
| 1245 | Declaring a method to throw Exception or Throwable makes it difficult for callers to perform proper error handling and error recovery. Java's exception mechanism, for example, is set up to make it easy for callers to anticipate what can go wrong and write code to handle each specific exceptional circumstance. Declaring that a method throws a generic form of exception defeats this system.",,unclassified, | |
| 1246 | CWE-398,Indicator of Poor Code Quality (Type: Class),"The code has features that do not directly introduce a weakness or vulnerability, but indicate that the product has not been carefully developed or maintained. | |
| 1247 | Programs are more likely to be secure when good development practices are followed. If a program is complex, difficult to maintain, not portable, or shows evidence of neglect, then there is a higher likelihood that weaknesses are buried in the code.",,unclassified, | |
| 1248 | CWE-40,Path Traversal: \\UNC\share\name\ (Windows UNC Share) (Type: Variant),"An attacker can inject a Windows UNC share ('\\UNC\share\name') into a software system to potentially redirect access to an unintended location or arbitrary file. | |
| 1249 | Programs are more likely to be secure when good development practices are followed. If a program is complex, difficult to maintain, not portable, or shows evidence of neglect, then there is a higher likelihood that weaknesses are buried in the code.",,unclassified,"The Art of Software Security Assessment: Chapter 11, ""Filelike Objects"", Page 664." | |
| 1250 | CWE-402,Transmission of Private Resources into a New Sphere (Resource Leak) (Type: Class),"The software makes resources available to untrusted parties when those resources are only intended to be accessed by the software. | |
| 1251 | This is often triggered by improper handling of malformed data or unexpectedly interrupted sessions.",,unclassified, | |
| 1252 | CWE-403,Exposure of File Descriptor to Unintended Control Sphere (File Descriptor Leak) (Type: Base),"A process does not close sensitive file descriptors before invoking a child process, which allows the child to perform unauthorized I/O operations using those descriptors. | |
| 1253 | When a new process is forked or executed, the child process inherits any open file descriptors. When the child process has fewer privileges than the parent process, this might introduce a vulnerability if the child process can access the file descriptor but does not have the privileges to access the associated file.",,unclassified,"File descriptors and setuid applications: https://blogs.oracle.com/paulr/entry/file_descriptors_and_setuid_applications | |
| 1254 | Introduction to Secure Coding Guide: https://developer.apple.com/library/mac/#documentation/security/conceptual/SecureCodingGuide/Articles/AccessControl.html" | |
| 1255 | CWE-405,Asymmetric Resource Consumption (Amplification) (Type: Class),"Software that does not appropriately monitor or control resource consumption can lead to adverse system performance. | |
| 1256 | This situation is amplified if the software allows malicious users or attackers to consume more resources than their access level permits. Exploiting such a weakness can lead to asymmetric resource consumption, aiding in amplification attacks against the system or the network.",,unclassified, | |
| 1257 | CWE-406,Insufficient Control of Network Message Volume (Network Amplification) (Type: Base),"The software does not sufficiently monitor or control transmitted network traffic volume, so that an actor can cause the software to transmit more traffic than should be allowed for that actor. | |
| 1258 | In the absence of a policy to restrict asymmetric resource consumption, the application or system cannot distinguish between legitimate transmissions and traffic intended to serve as an amplifying attack on target systems. Systems can often be configured to restrict the amount of traffic sent out on behalf of a client, based on the client's origin or access level. This is usually defined in a resource allocation policy. In the absence of a mechanism to keep track of transmissions, the system or application can be easily abused to transmit asymmetrically greater traffic than the request or client should be permitted to.",,unclassified, | |
| 1259 | CWE-408,Incorrect Behavior Order: Early Amplification (Type: Base),"The software allows an entity to perform a legitimate but expensive operation before authentication or authorization has taken place. | |
| 1260 | In the absence of a policy to restrict asymmetric resource consumption, the application or system cannot distinguish between legitimate transmissions and traffic intended to serve as an amplifying attack on target systems. Systems can often be configured to restrict the amount of traffic sent out on behalf of a client, based on the client's origin or access level. This is usually defined in a resource allocation policy. In the absence of a mechanism to keep track of transmissions, the system or application can be easily abused to transmit asymmetrically greater traffic than the request or client should be permitted to.",,unclassified, | |
| 1261 | CWE-409,Improper Handling of Highly Compressed Data (Data Amplification) (Type: Base),"The software does not handle or incorrectly handles a compressed input with a very high compression ratio that produces a large output. | |
| 1262 | An example of data amplification is a ""decompression bomb,"" a small ZIP file that can produce a large amount of data when it is decompressed.",,unclassified, | |
| 1263 | CWE-41,Improper Resolution of Path Equivalence (Type: Base),"The system or application is vulnerable to file system contents disclosure through path equivalence. Path equivalence involves the use of special characters in file and directory names. The associated manipulations are intended to generate multiple names for the same object. | |
| 1264 | Path equivalence is usually employed in order to circumvent access controls expressed using an incomplete set of file name or file path representations. This is different from path traversal, wherein the manipulations are performed to generate a name for a different object.",,unclassified, | |
| 1265 | CWE-410,Insufficient Resource Pool (Type: Base),"The software's resource pool is not large enough to handle peak demand, which allows an attacker to prevent others from accessing the resource by using a (relatively) large number of requests for resources. | |
| 1266 | Frequently the consequence is a ""flood"" of connection or sessions.",,unclassified,"Writing Secure Code: Chapter 17, ""Protecting Against Denial of Service Attacks"" Page 517" | |
| 1267 | CWE-412,Unrestricted Externally Accessible Lock (Type: Base),"The software properly checks for the existence of a lock, but the lock can be externally controlled or influenced by an actor that is outside of the intended sphere of control. | |
| 1268 | This prevents the software from acting on associated resources or performing other behaviors that are controlled by the presence of the lock. Relevant locks might include an exclusive lock or mutex, or modifying a shared resource that is treated as a lock. If the lock can be held for an indefinite period of time, then the denial of service could be permanent.",,unclassified, | |
| 1269 | CWE-413,Improper Resource Locking (Type: Base),"The software does not lock or does not correctly lock a resource when the software must have exclusive access to the resource. | |
| 1270 | When a resource is not properly locked, an attacker could modify the resource while it is being operated on by the software. This might violate the software's assumption that the resource will not change, potentially leading to unexpected behaviors.",,unclassified, | |
| 1271 | CWE-414,Missing Lock Check (Type: Base),"A product does not check to see if a lock is present before performing sensitive operations on a resource. | |
| 1272 | When a resource is not properly locked, an attacker could modify the resource while it is being operated on by the software. This might violate the software's assumption that the resource will not change, potentially leading to unexpected behaviors.",,unclassified, | |
| 1273 | CWE-419,Unprotected Primary Channel (Type: Base),"The software uses a primary channel for administration or restricted functionality, but it does not properly protect the channel. | |
| 1274 | The use of previously-freed memory can have any number of adverse consequences, ranging from the corruption of valid data to the execution of arbitrary code, depending on the instantiation and timing of the flaw. The simplest way data corruption may occur involves the system's reuse of the freed memory. Use-after-free errors have two common and sometimes overlapping causes: | |
| 1275 | Error conditions and other exceptional circumstances. | |
| 1276 | Confusion over which part of the program is responsible for freeing the memory. | |
| 1277 | In this scenario, the memory in question is allocated to another pointer validly at some point after it has been freed. The original pointer to the freed memory is used again and points to somewhere within the new allocation. As the data is changed, it corrupts the validly used memory; this induces undefined behavior in the process. | |
| 1278 | If the newly allocated data chances to hold a class, in C++ for example, various function pointers may be scattered within the heap data. If one of these function pointers is overwritten with an address to valid shellcode, execution of arbitrary code can be achieved.",,unclassified, | |
| 1279 | CWE-42,Path Equivalence: filename. (Trailing Dot) (Type: Variant),"A software system that accepts path input in the form of trailing dot ('filedir.') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1280 | The use of previously-freed memory can have any number of adverse consequences, ranging from the corruption of valid data to the execution of arbitrary code, depending on the instantiation and timing of the flaw. The simplest way data corruption may occur involves the system's reuse of the freed memory. Use-after-free errors have two common and sometimes overlapping causes: | |
| 1281 | Error conditions and other exceptional circumstances. | |
| 1282 | Confusion over which part of the program is responsible for freeing the memory. | |
| 1283 | In this scenario, the memory in question is allocated to another pointer validly at some point after it has been freed. The original pointer to the freed memory is used again and points to somewhere within the new allocation. As the data is changed, it corrupts the validly used memory; this induces undefined behavior in the process. | |
| 1284 | If the newly allocated data chances to hold a class, in C++ for example, various function pointers may be scattered within the heap data. If one of these function pointers is overwritten with an address to valid shellcode, execution of arbitrary code can be achieved.",,unclassified, | |
| 1285 | CWE-420,Unprotected Alternate Channel (Type: Base),"The software protects a primary channel, but it does not use the same level of protection for an alternate channel. | |
| 1286 | The use of previously-freed memory can have any number of adverse consequences, ranging from the corruption of valid data to the execution of arbitrary code, depending on the instantiation and timing of the flaw. The simplest way data corruption may occur involves the system's reuse of the freed memory. Use-after-free errors have two common and sometimes overlapping causes: | |
| 1287 | Error conditions and other exceptional circumstances. | |
| 1288 | Confusion over which part of the program is responsible for freeing the memory. | |
| 1289 | In this scenario, the memory in question is allocated to another pointer validly at some point after it has been freed. The original pointer to the freed memory is used again and points to somewhere within the new allocation. As the data is changed, it corrupts the validly used memory; this induces undefined behavior in the process. | |
| 1290 | If the newly allocated data chances to hold a class, in C++ for example, various function pointers may be scattered within the heap data. If one of these function pointers is overwritten with an address to valid shellcode, execution of arbitrary code can be achieved.",,unclassified, | |
| 1291 | CWE-421,Race Condition During Access to Alternate Channel (Type: Base),"The product opens an alternate channel to communicate with an authorized user, but the channel is accessible to other actors. | |
| 1292 | This creates a race condition that allows an attacker to access the channel before the authorized user does.",,unclassified,"Discovering and Exploiting Named Pipe Security Flaws for Fun and Profit: http://www.blakewatts.com/namedpipepaper.html | |
| 1293 | 24 Deadly Sins of Software Security: ""Sin 13: Race Conditions."" Page 205" | |
| 1294 | CWE-422,Unprotected Windows Messaging Channel (Shatter) (Type: Variant),"The software does not properly verify the source of a message in the Windows Messaging System while running at elevated privileges, creating an alternate channel through which an attacker can directly send a message to the product. | |
| 1295 | This creates a race condition that allows an attacker to access the channel before the authorized user does.",,unclassified,"Exploiting design flaws in the Win32 API for privilege escalation. Or... Shatter Attacks - How to break Windows: http://web.archive.org/web/20060115174629/http://security.tombom.co.uk/shatter.html | |
| 1296 | The Art of Software Security Assessment: Chapter 2, ""Design Review."" Page 34. | |
| 1297 | The Art of Software Security Assessment: Chapter 12, ""Shatter Attacks"", Page 694." | |
| 1298 | CWE-423,DEPRECATED (Duplicate): Proxied Trusted Channel (Type: Base),"This entry has been deprecated because it was a duplicate of CWE-441. All content has been transferred to CWE-441. | |
| 1299 | This creates a race condition that allows an attacker to access the channel before the authorized user does.",,unclassified, | |
| 1300 | CWE-424,Improper Protection of Alternate Path (Type: Class),"The product does not sufficiently protect all possible paths that a user can take to access restricted functionality or resources. | |
| 1301 | This creates a race condition that allows an attacker to access the channel before the authorized user does.",,unclassified, | |
| 1302 | CWE-425,Direct Request (Forced Browsing) (Type: Base),"The web application does not adequately enforce appropriate authorization on all restricted URLs, scripts, or files. | |
| 1303 | Web applications susceptible to direct request attacks often make the false assumption that such resources can only be reached through a given navigation path and so only apply authorization at certain points in the path.",,unclassified, | |
| 1304 | CWE-427,Uncontrolled Search Path Element (Type: Base),"The product uses a fixed or controlled search path to find resources, but one or more locations in that path can be under the control of unintended actors. | |
| 1305 | Although this weakness can occur with any type of resource, it is frequently introduced when a product uses a directory search path to find executables or code libraries, but the path contains a directory that can be modified by an attacker, such as ""/tmp"" or the current working directory. | |
| 1306 | In Windows-based systems, when the LoadLibrary or LoadLibraryEx function is called with a DLL name that does not contain a fully qualified path, the function follows a search order that includes two path elements that might be uncontrolled: | |
| 1307 | the directory from which the program has been loaded | |
| 1308 | the current working directory. | |
| 1309 | In some cases, the attack can be conducted remotely, such as when SMB or WebDAV network shares are used. | |
| 1310 | In some Unix-based systems, a PATH might be created that contains an empty element, e.g. by splicing an empty variable into the PATH. This empty element can be interpreted as equivalent to the current working directory, which might be an untrusted search element.",,unclassified,"Double clicking on MS Office documents from Windows Explorer may execute arbitrary programs in some cases | |
| 1311 | ACROS Security: Remote Binary Planting in Apple iTunes for Windows (ASPR #2010-08-18-1) | |
| 1312 | Automatic Detection of Vulnerable Dynamic Component Loadings: http://www.cs.ucdavis.edu/research/tech-reports/2010/CSE-2010-2.pdf | |
| 1313 | Dynamic-Link Library Search Order: http://msdn.microsoft.com/en-us/library/ms682586%28v=VS.85%29.aspx | |
| 1314 | Dynamic-Link Library Security: http://msdn.microsoft.com/en-us/library/ff919712%28VS.85%29.aspx | |
| 1315 | An update on the DLL-preloading remote attack vector: http://blogs.technet.com/b/srd/archive/2010/08/23/an-update-on-the-dll-preloading-remote-attack-vector.aspx | |
| 1316 | Insecure Library Loading Could Allow Remote Code Execution: http://www.microsoft.com/technet/security/advisory/2269637.mspx | |
| 1317 | Application DLL Load Hijacking: http://blog.rapid7.com/?p=5325 | |
| 1318 | DLL Hijacking: Facts and Fiction: http://threatpost.com/en_us/blogs/dll-hijacking-facts-and-fiction-082610" | |
| 1319 | CWE-428,Unquoted Search Path or Element (Type: Base),"The product uses a search path that contains an unquoted element, in which the element contains whitespace or other separators. This can cause the product to access resources in a parent path. | |
| 1320 | If a malicious individual has access to the file system, it is possible to elevate privileges by inserting such a file as ""C:\Program.exe"" to be run by a privileged program making use of WinExec.",,unclassified,"The Art of Software Security Assessment: Chapter 11, ""Process Loading"", Page 654." | |
| 1321 | CWE-43,Path Equivalence: filename.... (Multiple Trailing Dot) (Type: Variant),"A software system that accepts path input in the form of multiple trailing dot ('filedir....') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1322 | If a malicious individual has access to the file system, it is possible to elevate privileges by inserting such a file as ""C:\Program.exe"" to be run by a privileged program making use of WinExec.",,unclassified, | |
| 1323 | CWE-430,Deployment of Wrong Handler (Type: Base),"The wrong ""handler"" is assigned to process an object. | |
| 1324 | An example of deploying the wrong handler would be calling a servlet to reveal source code of a .JSP file, or automatically ""determining"" type of the object even if it is contradictory to an explicitly specified type.",,unclassified,"The Art of Software Security Assessment: Chapter 3, ""File Handlers"", Page 74." | |
| 1325 | CWE-431,Missing Handler (Type: Base),"A handler is not available or implemented. | |
| 1326 | When an exception is thrown and not caught, the process has given up an opportunity to decide if a given failure or event is worth a change in execution.",,unclassified,"The Art of Software Security Assessment: Chapter 3, ""File Handlers"", Page 74." | |
| 1327 | CWE-432,Dangerous Signal Handler not Disabled During Sensitive Operations (Type: Base),"The application uses a signal handler that shares state with other signal handlers, but it does not properly mask or prevent those signal handlers from being invoked while the original signal handler is still running. | |
| 1328 | During the execution of a signal handler, it can be interrupted by another handler when a different signal is sent. If the two handlers share state - such as global variables - then an attacker can corrupt the state by sending another signal before the first handler has completed execution.",,unclassified, | |
| 1329 | CWE-433,Unparsed Raw Web Content Delivery (Type: Variant),"The software stores raw content or supporting code under the web document root with an extension that is not specifically handled by the server. | |
| 1330 | If code is stored in a file with an extension such as "".inc"" or "".pl"", and the web server does not have a handler for that extension, then the server will likely send the contents of the file directly to the requester without the pre-processing that was expected. When that file contains sensitive information such as database credentials, this may allow the attacker to compromise the application or associated components.",,unclassified,"The Art of Software Security Assessment: Chapter 3, ""File Handlers"", Page 74." | |
| 1331 | CWE-435,Interaction Error (Type: Class),"An interaction error occurs when two entities work correctly when running independently, but they interact in unexpected ways when they are run together. | |
| 1332 | This could apply to products, systems, components, etc.",,unclassified, | |
| 1333 | CWE-436,Interpretation Conflict (Type: Base),"Product A handles inputs or steps differently than Product B, which causes A to perform incorrect actions based on its perception of B's state. | |
| 1334 | This is generally found in proxies, firewalls, anti-virus software, and other intermediary devices that allow, deny, or modify traffic based on how the client or server is expected to behave.",,unclassified,"On Interpretation Conflict Vulnerabilities | |
| 1335 | Insertion, Evasion, and Denial of Service: Eluding Network Intrusion Detection: http://www.insecure.org/stf/secnet_ids/secnet_ids.pdf | |
| 1336 | 0x00 vs ASP file upload scripts: http://www.security-assessment.com/Whitepapers/0x00_vs_ASP_File_Uploads.pdf | |
| 1337 | Poison NULL byte | |
| 1338 | Re: Corsaire Security Advisory - Multiple vendor MIME RFC2047 encoding: http://marc.theaimsgroup.com/?l=bugtraq&m=109525864717484&w=2" | |
| 1339 | CWE-437,Incomplete Model of Endpoint Features (Type: Base),"A product acts as an intermediary or monitor between two or more endpoints, but it does not have a complete model of an endpoint's features, behaviors, or state, potentially causing the product to perform incorrect actions based on this incomplete model. | |
| 1340 | This is generally found in proxies, firewalls, anti-virus software, and other intermediary devices that allow, deny, or modify traffic based on how the client or server is expected to behave.",,unclassified, | |
| 1341 | CWE-439,Behavioral Change in New Version or Environment (Type: Base),"A's behavior or functionality changes with a new version of A, or a new environment, which is not known (or manageable) by B. | |
| 1342 | This is generally found in proxies, firewalls, anti-virus software, and other intermediary devices that allow, deny, or modify traffic based on how the client or server is expected to behave.",,unclassified, | |
| 1343 | CWE-44,Path Equivalence: file.name (Internal Dot) (Type: Variant),"A software system that accepts path input in the form of internal dot ('file.ordir') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1344 | This is generally found in proxies, firewalls, anti-virus software, and other intermediary devices that allow, deny, or modify traffic based on how the client or server is expected to behave.",,unclassified, | |
| 1345 | CWE-440,Expected Behavior Violation (Type: Base),"A feature, API, or function being used by a product behaves differently than the product expects. | |
| 1346 | This is generally found in proxies, firewalls, anti-virus software, and other intermediary devices that allow, deny, or modify traffic based on how the client or server is expected to behave.",,unclassified, | |
| 1347 | CWE-441,Unintended Proxy or Intermediary (Confused Deputy) (Type: Class),"The software receives a request, message, or directive from an upstream component, but the software does not sufficiently preserve the original source of the request before forwarding the request to an external actor that is outside of the software's control sphere. This causes the software to appear to be the source of the request, leading it to act as a proxy or other intermediary between the upstream component and the external actor. | |
| 1348 | If an attacker cannot directly contact a target, but the software has access to the target, then the attacker can send a request to the software and have it be forwarded from the target. The request would appear to be coming from the software's system, not the attacker's system. As a result, the attacker can bypass access controls (such as firewalls) or hide the source of malicious requests, since the requests would not be coming directly from the attacker. | |
| 1349 | Since proxy functionality and message-forwarding often serve a legitimate purpose, this issue only becomes a vulnerability when: | |
| 1350 | The software runs with different privileges or on a different system, or otherwise has different levels of access than the upstream component; | |
| 1351 | The attacker is prevented from making the request directly to the target; and | |
| 1352 | The attacker can create a request that the proxy does not explicitly intend to be forwarded on the behalf of the requester. Such a request might point to an unexpected hostname, port number, or service. Or, the request might be sent to an allowed service, but the request could contain disallowed directives, commands, or resources.",,unclassified,The Confused Deputy (or why capabilities might have been invented): http://www.cap-lore.com/CapTheory/ConfusedDeputy.html | |
| 1353 | CWE-443,DEPRECATED (Duplicate): HTTP response splitting (Type: Base),"This weakness can be found at CWE-113. | |
| 1354 | If an attacker cannot directly contact a target, but the software has access to the target, then the attacker can send a request to the software and have it be forwarded from the target. The request would appear to be coming from the software's system, not the attacker's system. As a result, the attacker can bypass access controls (such as firewalls) or hide the source of malicious requests, since the requests would not be coming directly from the attacker. | |
| 1355 | Since proxy functionality and message-forwarding often serve a legitimate purpose, this issue only becomes a vulnerability when: | |
| 1356 | The software runs with different privileges or on a different system, or otherwise has different levels of access than the upstream component; | |
| 1357 | The attacker is prevented from making the request directly to the target; and | |
| 1358 | The attacker can create a request that the proxy does not explicitly intend to be forwarded on the behalf of the requester. Such a request might point to an unexpected hostname, port number, or service. Or, the request might be sent to an allowed service, but the request could contain disallowed directives, commands, or resources.",,unclassified, | |
| 1359 | CWE-444,Inconsistent Interpretation of HTTP Requests (HTTP Request Smuggling) (Type: Base),"When malformed or abnormal HTTP requests are interpreted by one or more entities in the data flow between the user and the web server, such as a proxy or firewall, they can be interpreted inconsistently, allowing the attacker to ""smuggle"" a request to one device without the other device being aware of it. | |
| 1360 | If an attacker cannot directly contact a target, but the software has access to the target, then the attacker can send a request to the software and have it be forwarded from the target. The request would appear to be coming from the software's system, not the attacker's system. As a result, the attacker can bypass access controls (such as firewalls) or hide the source of malicious requests, since the requests would not be coming directly from the attacker. | |
| 1361 | Since proxy functionality and message-forwarding often serve a legitimate purpose, this issue only becomes a vulnerability when: | |
| 1362 | The software runs with different privileges or on a different system, or otherwise has different levels of access than the upstream component; | |
| 1363 | The attacker is prevented from making the request directly to the target; and | |
| 1364 | The attacker can create a request that the proxy does not explicitly intend to be forwarded on the behalf of the requester. Such a request might point to an unexpected hostname, port number, or service. Or, the request might be sent to an allowed service, but the request could contain disallowed directives, commands, or resources.",,unclassified,HTTP Request Smuggling: http://www.cgisecurity.com/lib/HTTP-Request-Smuggling.pdf | |
| 1365 | CWE-446,UI Discrepancy for Security Feature (Type: Base),"The user interface does not correctly enable or configure a security feature, but the interface provides feedback that causes the user to believe that the feature is in a secure state. | |
| 1366 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1367 | CWE-447,Unimplemented or Unsupported Feature in UI (Type: Base),"A UI function for a security feature appears to be supported and gives feedback to the user that suggests that it is supported, but the underlying functionality is not implemented. | |
| 1368 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1369 | CWE-448,Obsolete Feature in UI (Type: Base),"A UI function is obsolete and the product does not warn the user. | |
| 1370 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1371 | CWE-449,The UI Performs the Wrong Action (Type: Base),"The UI performs the wrong action with respect to the user's request. | |
| 1372 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1373 | CWE-45,Path Equivalence: file...name (Multiple Internal Dot) (Type: Variant),"A software system that accepts path input in the form of multiple internal dot ('file...dir') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1374 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1375 | CWE-450,Multiple Interpretations of UI Input (Type: Base),"The UI has multiple interpretations of user input but does not prompt the user when it selects the less secure interpretation. | |
| 1376 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1377 | CWE-451,UI Misrepresentation of Critical Information (Type: Base),"The UI does not properly represent critical information to the user, allowing the information - or its source - to be obscured or spoofed. This is often a component in phishing attacks. | |
| 1378 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1379 | CWE-453,Insecure Default Variable Initialization (Type: Base),"The software, by default, initializes an internal variable with an insecure or less secure value than is possible. | |
| 1380 | When the user interface does not properly reflect what the user asks of it, then it can lead the user into a false sense of security. For example, the user might check a box to enable a security option to enable encrypted communications, but the software does not actually enable the encryption. Alternately, the user might provide a ""restrict ALL'"" access control rule, but the software only implements ""restrict SOME"".",,unclassified, | |
| 1381 | CWE-454,External Initialization of Trusted Variables or Data Stores (Type: Base),"The software initializes critical internal variables or data stores using inputs that can be modified by untrusted actors. | |
| 1382 | A software system should be reluctant to trust variables that have been initialized outside of its trust boundary, especially if they are initialized by users. They may have been initialized incorrectly. If an attacker can initialize the variable, then he/she can influence what the vulnerable system will do.",,unclassified, | |
| 1383 | CWE-455,Non-exit on Failed Initialization (Type: Base),"The software does not exit or otherwise modify its operation when security-relevant errors occur during initialization, such as when a configuration file has a format error, which can cause the software to execute in a less secure fashion than intended by the administrator. | |
| 1384 | A software system should be reluctant to trust variables that have been initialized outside of its trust boundary, especially if they are initialized by users. They may have been initialized incorrectly. If an attacker can initialize the variable, then he/she can influence what the vulnerable system will do.",,unclassified, | |
| 1385 | CWE-456,Missing Initialization of a Variable (Type: Base),"The software does not initialize critical variables, which causes the execution environment to use unexpected values. | |
| 1386 | A software system should be reluctant to trust variables that have been initialized outside of its trust boundary, especially if they are initialized by users. They may have been initialized incorrectly. If an attacker can initialize the variable, then he/she can influence what the vulnerable system will do.",,unclassified,"The Art of Software Security Assessment: Chapter 7, ""Variable Initialization"", Page 312." | |
| 1387 | CWE-458,DEPRECATED: Incorrect Initialization (Type: Base),"This weakness has been deprecated because its name and description did not match. The description duplicated CWE-454, while the name suggested a more abstract initialization problem. Please refer to CWE-665 for the more abstract problem. | |
| 1388 | In some languages such as C and C++, stack variables are not initialized by default. They generally contain junk data with the contents of stack memory before the function was invoked. An attacker can sometimes control or read these contents. In other languages or conditions, a variable that is not explicitly initialized can be given a default value that has security implications, depending on the logic of the program. The presence of an uninitialized variable can sometimes indicate a typographic error in the code.",,unclassified, | |
| 1389 | CWE-459,Incomplete Cleanup (Type: Base),"The software does not properly ""clean up"" and remove temporary or supporting resources after they have been used. | |
| 1390 | In some languages such as C and C++, stack variables are not initialized by default. They generally contain junk data with the contents of stack memory before the function was invoked. An attacker can sometimes control or read these contents. In other languages or conditions, a variable that is not explicitly initialized can be given a default value that has security implications, depending on the logic of the program. The presence of an uninitialized variable can sometimes indicate a typographic error in the code.",,unclassified, | |
| 1391 | CWE-46,Path Equivalence: filename (Trailing Space) (Type: Variant),"A software system that accepts path input in the form of trailing space ('filedir ') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1392 | In some languages such as C and C++, stack variables are not initialized by default. They generally contain junk data with the contents of stack memory before the function was invoked. An attacker can sometimes control or read these contents. In other languages or conditions, a variable that is not explicitly initialized can be given a default value that has security implications, depending on the logic of the program. The presence of an uninitialized variable can sometimes indicate a typographic error in the code.",,unclassified, | |
| 1393 | CWE-463,Deletion of Data Structure Sentinel (Type: Base),"The accidental deletion of a data-structure sentinel can cause serious programming logic problems. | |
| 1394 | Often times data-structure sentinels are used to mark structure of the data structure. A common example of this is the null character at the end of strings. Another common example is linked lists which may contain a sentinel to mark the end of the list. It is dangerous to allow this type of control data to be easily accessible. Therefore, it is important to protect from the deletion or modification outside of some wrapper interface which provides safety.",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""NUL-Termination Problems"", Page 452." | |
| 1395 | CWE-466,Return of Pointer Value Outside of Expected Range (Type: Base),"A function can return a pointer to memory that is outside of the buffer that the pointer is expected to reference. | |
| 1396 | Data-structure sentinels are often used to mark the structure of data. A common example of this is the null character at the end of strings or a special sentinel to mark the end of a linked list. It is dangerous to allow this type of control data to be easily accessible. Therefore, it is important to protect from the addition or modification of sentinels.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89" | |
| 1397 | CWE-47,Path Equivalence: filename (Leading Space) (Type: Variant),"A software system that accepts path input in the form of leading space (' filedir') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1398 | Data-structure sentinels are often used to mark the structure of data. A common example of this is the null character at the end of strings or a special sentinel to mark the end of a linked list. It is dangerous to allow this type of control data to be easily accessible. Therefore, it is important to protect from the addition or modification of sentinels.",,unclassified, | |
| 1399 | CWE-470,Use of Externally-Controlled Input to Select Classes or Code (Unsafe Reflection) (Type: Base),"The application uses external input with reflection to select which classes or code to use, but it does not sufficiently prevent the input from selecting improper classes or code. | |
| 1400 | If the application uses external inputs to determine which class to instantiate or which method to invoke, then an attacker could supply values to select unexpected classes or methods. If this occurs, then the attacker could create control flow paths that were not intended by the developer. These paths could bypass authentication or access control checks, or otherwise cause the application to behave in an unexpected manner. This situation becomes a doomsday scenario if the attacker can upload files into a location that appears on the application's classpath (CWE-427) or add new entries to the application's classpath (CWE-426). Under either of these conditions, the attacker can use reflection to introduce new, malicious behavior into the application.",,unclassified, | |
| 1401 | CWE-471,Modification of Assumed-Immutable Data (MAID) (Type: Base),"The software does not properly protect an assumed-immutable element from being modified by an attacker. | |
| 1402 | If the application uses external inputs to determine which class to instantiate or which method to invoke, then an attacker could supply values to select unexpected classes or methods. If this occurs, then the attacker could create control flow paths that were not intended by the developer. These paths could bypass authentication or access control checks, or otherwise cause the application to behave in an unexpected manner. This situation becomes a doomsday scenario if the attacker can upload files into a location that appears on the application's classpath (CWE-427) or add new entries to the application's classpath (CWE-426). Under either of these conditions, the attacker can use reflection to introduce new, malicious behavior into the application.",,unclassified, | |
| 1403 | CWE-472,External Control of Assumed-Immutable Web Parameter (Type: Base),"The web application does not sufficiently verify inputs that are assumed to be immutable but are actually externally controllable, such as hidden form fields. | |
| 1404 | If a web product does not properly protect assumed-immutable values from modification in hidden form fields, parameters, cookies, or URLs, this can lead to modification of critical data. Web applications often mistakenly make the assumption that data passed to the client in hidden fields or cookies is not susceptible to tampering. Improper validation of data that are user-controllable can lead to the application processing incorrect, and often malicious, input. | |
| 1405 | For example, custom cookies commonly store session data or persistent data across sessions. This kind of session data is normally involved in security related decisions on the server side, such as user authentication and access control. Thus, the cookies might contain sensitive data such as user credentials and privileges. This is a dangerous practice, as it can often lead to improper reliance on the value of the client-provided cookie by the server side application.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 4: Use of Magic URLs, Predictable Cookies, and Hidden Form Fields."" Page 75 | |
| 1406 | The Art of Software Security Assessment: Chapter 17, ""Embedding State in HTML and URLs"", Page 1032." | |
| 1407 | CWE-473,PHP External Variable Modification (Type: Variant),"A PHP application does not properly protect against the modification of variables from external sources, such as query parameters or cookies. This can expose the application to numerous weaknesses that would not exist otherwise. | |
| 1408 | If a web product does not properly protect assumed-immutable values from modification in hidden form fields, parameters, cookies, or URLs, this can lead to modification of critical data. Web applications often mistakenly make the assumption that data passed to the client in hidden fields or cookies is not susceptible to tampering. Improper validation of data that are user-controllable can lead to the application processing incorrect, and often malicious, input. | |
| 1409 | For example, custom cookies commonly store session data or persistent data across sessions. This kind of session data is normally involved in security related decisions on the server side, such as user authentication and access control. Thus, the cookies might contain sensitive data such as user credentials and privileges. This is a dangerous practice, as it can often lead to improper reliance on the value of the client-provided cookie by the server side application.",,unclassified, | |
| 1410 | CWE-474,Use of Function with Inconsistent Implementations (Type: Base),"The code uses a function that has inconsistent implementations across operating systems and versions, which might cause security-relevant portability problems. | |
| 1411 | If a web product does not properly protect assumed-immutable values from modification in hidden form fields, parameters, cookies, or URLs, this can lead to modification of critical data. Web applications often mistakenly make the assumption that data passed to the client in hidden fields or cookies is not susceptible to tampering. Improper validation of data that are user-controllable can lead to the application processing incorrect, and often malicious, input. | |
| 1412 | For example, custom cookies commonly store session data or persistent data across sessions. This kind of session data is normally involved in security related decisions on the server side, such as user authentication and access control. Thus, the cookies might contain sensitive data such as user credentials and privileges. This is a dangerous practice, as it can often lead to improper reliance on the value of the client-provided cookie by the server side application.",,unclassified, | |
| 1413 | CWE-475,Undefined Behavior for Input to API (Type: Base),"The behavior of this function is undefined unless its control parameter is set to a specific value. | |
| 1414 | If a web product does not properly protect assumed-immutable values from modification in hidden form fields, parameters, cookies, or URLs, this can lead to modification of critical data. Web applications often mistakenly make the assumption that data passed to the client in hidden fields or cookies is not susceptible to tampering. Improper validation of data that are user-controllable can lead to the application processing incorrect, and often malicious, input. | |
| 1415 | For example, custom cookies commonly store session data or persistent data across sessions. This kind of session data is normally involved in security related decisions on the server side, such as user authentication and access control. Thus, the cookies might contain sensitive data such as user credentials and privileges. This is a dangerous practice, as it can often lead to improper reliance on the value of the client-provided cookie by the server side application.",,unclassified, | |
| 1416 | CWE-477,Use of Obsolete Functions (Type: Base),"The code uses deprecated or obsolete functions, which suggests that the code has not been actively reviewed or maintained. | |
| 1417 | NULL pointer dereference issues can occur through a number of flaws, including race conditions, and simple programming omissions.",,unclassified, | |
| 1418 | CWE-478,Missing Default Case in Switch Statement (Type: Variant),"The code does not have a default case in a switch statement, which might lead to complex logical errors and resultant weaknesses. | |
| 1419 | NULL pointer dereference issues can occur through a number of flaws, including race conditions, and simple programming omissions.",,unclassified,"The Art of Software Security Assessment: Chapter 7, ""Switch Statements"", Page 337." | |
| 1420 | CWE-48,Path Equivalence: file name (Internal Whitespace) (Type: Variant),"A software system that accepts path input in the form of internal space ('file(SPACE)name') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1421 | Non-reentrant functions are functions that cannot safely be called, interrupted, and then recalled before the first call has finished without resulting in memory corruption. This can lead to an unexpected system state an unpredictable results with a variety of potential consequences depending on context, including denial of service and code execution. | |
| 1422 | Many functions are not reentrant, but some of them can result in the corruption of memory if they are used in a signal handler. The function call syslog() is an example of this. In order to perform its functionality, it allocates a small amount of memory as ""scratch space."" If syslog() is suspended by a signal call and the signal handler calls syslog(), the memory used by both of these functions enters an undefined, and possibly, exploitable state. Implementations of malloc() and free() manage metadata in global structures in order to track which memory is allocated versus which memory is available, but they are non-reentrant. Simultaneous calls to these functions can cause corruption of the metadata.",,unclassified, | |
| 1423 | CWE-485,Insufficient Encapsulation (Type: Class),"The product does not sufficiently encapsulate critical data or functionality. | |
| 1424 | Encapsulation is about drawing strong boundaries. In a web browser that might mean ensuring that your mobile code cannot be abused by other mobile code. On the server it might mean differentiation between validated data and unvalidated data, between one user's data and another's, or between data users are allowed to see and data that they are not.",,unclassified, | |
| 1425 | CWE-488,Exposure of Data Element to Wrong Session (Type: Variant),"The product does not sufficiently enforce boundaries between the states of different sessions, causing data to be provided to, or used by, the wrong session. | |
| 1426 | Data can ""bleed"" from one session to another through member variables of singleton objects, such as Servlets, and objects from a shared pool. | |
| 1427 | In the case of Servlets, developers sometimes do not understand that, unless a Servlet implements the SingleThreadModel interface, the Servlet is a singleton; there is only one instance of the Servlet, and that single instance is used and re-used to handle multiple requests that are processed simultaneously by different threads. A common result is that developers use Servlet member fields in such a way that one user may inadvertently see another user's data. In other words, storing user data in Servlet member fields introduces a data access race condition.",,unclassified, | |
| 1428 | CWE-489,Leftover Debug Code (Type: Base),"The application can be deployed with active debugging code that can create unintended entry points. | |
| 1429 | Data can ""bleed"" from one session to another through member variables of singleton objects, such as Servlets, and objects from a shared pool. | |
| 1430 | In the case of Servlets, developers sometimes do not understand that, unless a Servlet implements the SingleThreadModel interface, the Servlet is a singleton; there is only one instance of the Servlet, and that single instance is used and re-used to handle multiple requests that are processed simultaneously by different threads. A common result is that developers use Servlet member fields in such a way that one user may inadvertently see another user's data. In other words, storing user data in Servlet member fields introduces a data access race condition.",,unclassified, | |
| 1431 | CWE-49,Path Equivalence: filename/ (Trailing Slash) (Type: Variant),"A software system that accepts path input in the form of trailing slash ('filedir/') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1432 | Data can ""bleed"" from one session to another through member variables of singleton objects, such as Servlets, and objects from a shared pool. | |
| 1433 | In the case of Servlets, developers sometimes do not understand that, unless a Servlet implements the SingleThreadModel interface, the Servlet is a singleton; there is only one instance of the Servlet, and that single instance is used and re-used to handle multiple requests that are processed simultaneously by different threads. A common result is that developers use Servlet member fields in such a way that one user may inadvertently see another user's data. In other words, storing user data in Servlet member fields introduces a data access race condition.",,unclassified, | |
| 1434 | CWE-491,Public cloneable() Method Without Final (Object Hijack) (Type: Variant),"A class has a cloneable() method that is not declared final, which allows an object to be created without calling the constructor. This can cause the object to be in an unexpected state. | |
| 1435 | Data can ""bleed"" from one session to another through member variables of singleton objects, such as Servlets, and objects from a shared pool. | |
| 1436 | In the case of Servlets, developers sometimes do not understand that, unless a Servlet implements the SingleThreadModel interface, the Servlet is a singleton; there is only one instance of the Servlet, and that single instance is used and re-used to handle multiple requests that are processed simultaneously by different threads. A common result is that developers use Servlet member fields in such a way that one user may inadvertently see another user's data. In other words, storing user data in Servlet member fields introduces a data access race condition.",,unclassified,"OWASP , Attack Category : Mobile code: object hijack: http://www.owasp.org/index.php/Mobile_code:_object_hijack" | |
| 1437 | CWE-495,Private Array-Typed Field Returned From A Public Method (Type: Variant),"The product has a method that is declared public, but returns a reference to a private array, which could then be modified in unexpected ways. | |
| 1438 | An attacker can execute malicious code by compromising the host server, performing DNS spoofing, or modifying the code in transit.",,unclassified, | |
| 1439 | CWE-496,Public Data Assigned to Private Array-Typed Field (Type: Variant),"Assigning public data to a private array is equivalent to giving public access to the array. | |
| 1440 | An attacker can execute malicious code by compromising the host server, performing DNS spoofing, or modifying the code in transit.",,unclassified, | |
| 1441 | CWE-497,Exposure of System Data to an Unauthorized Control Sphere (Type: Variant),"Exposing system data or debugging information helps an adversary learn about the system and form an attack plan. | |
| 1442 | An information exposure occurs when system data or debugging information leaves the program through an output stream or logging function that makes it accessible to unauthorized parties. An attacker can also cause errors to occur by submitting unusual requests to the web application. The response to these errors can reveal detailed system information, deny service, cause security mechanisms to fail, and crash the server. An attacker can use error messages that reveal technologies, operating systems, and product versions to tune the attack against known vulnerabilities in these technologies. An application may use diagnostic methods that provide significant implementation details such as stack traces as part of its error handling mechanism.",,unclassified, | |
| 1443 | CWE-5,J2EE Misconfiguration: Data Transmission Without Encryption (Type: Variant),"Information sent over a network can be compromised while in transit. An attacker may be able to read/modify the contents if the data are sent in plaintext or are weakly encrypted. | |
| 1444 | Serializable classes are effectively open classes since data cannot be hidden in them. Classes that do not explicitly deny serialization can be serialized by any other class, which can then in turn use the data stored inside it.",,unclassified, | |
| 1445 | CWE-50,Path Equivalence: //multiple/leading/slash (Type: Variant),"A software system that accepts path input in the form of multiple leading slash ('//multiple/leading/slash') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1446 | Serializable classes are effectively open classes since data cannot be hidden in them. Classes that do not explicitly deny serialization can be serialized by any other class, which can then in turn use the data stored inside it.",,unclassified, | |
| 1447 | CWE-501,Trust Boundary Violation (Type: Base),"The product mixes trusted and untrusted data in the same data structure or structured message. | |
| 1448 | By combining trusted and untrusted data in the same data structure, it becomes easier for programmers to mistakenly trust unvalidated data.",,unclassified, | |
| 1449 | CWE-506,Embedded Malicious Code (Type: Class),"The application contains code that appears to be malicious in nature. | |
| 1450 | Malicious flaws have acquired colorful names, including Trojan horse, trapdoor, timebomb, and logic-bomb. A developer might insert malicious code with the intent to subvert the security of an application or its host system at some time in the future. It generally refers to a program that performs a useful service but exploits rights of the program's user in a way the user does not intend.",,unclassified, | |
| 1451 | CWE-507,Trojan Horse (Type: Base),"The software appears to contain benign or useful functionality, but it also contains code that is hidden from normal operation that violates the intended security policy of the user or the system administrator. | |
| 1452 | Malicious flaws have acquired colorful names, including Trojan horse, trapdoor, timebomb, and logic-bomb. A developer might insert malicious code with the intent to subvert the security of an application or its host system at some time in the future. It generally refers to a program that performs a useful service but exploits rights of the program's user in a way the user does not intend.",,unclassified,"Writing Secure Code: Chapter 7, ""Viruses, Trojans, and Worms In a Nutshell"" Page 208" | |
| 1453 | CWE-508,Non-Replicating Malicious Code (Type: Base),"Non-replicating malicious code only resides on the target system or software that is attacked; it does not attempt to spread to other systems. | |
| 1454 | Malicious flaws have acquired colorful names, including Trojan horse, trapdoor, timebomb, and logic-bomb. A developer might insert malicious code with the intent to subvert the security of an application or its host system at some time in the future. It generally refers to a program that performs a useful service but exploits rights of the program's user in a way the user does not intend.",,unclassified, | |
| 1455 | CWE-509,Replicating Malicious Code (Virus or Worm) (Type: Base),"Replicating malicious code, including viruses and worms, will attempt to attack other systems once it has successfully compromised the target system or software. | |
| 1456 | Malicious flaws have acquired colorful names, including Trojan horse, trapdoor, timebomb, and logic-bomb. A developer might insert malicious code with the intent to subvert the security of an application or its host system at some time in the future. It generally refers to a program that performs a useful service but exploits rights of the program's user in a way the user does not intend.",,unclassified, | |
| 1457 | CWE-51,Path Equivalence: /multiple//internal/slash (Type: Variant),"A software system that accepts path input in the form of multiple internal slash ('/multiple//internal/slash/') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1458 | Malicious flaws have acquired colorful names, including Trojan horse, trapdoor, timebomb, and logic-bomb. A developer might insert malicious code with the intent to subvert the security of an application or its host system at some time in the future. It generally refers to a program that performs a useful service but exploits rights of the program's user in a way the user does not intend.",,unclassified, | |
| 1459 | CWE-510,Trapdoor (Type: Base),"A trapdoor is a hidden piece of code that responds to a special input, allowing its user access to resources without passing through the normal security enforcement mechanism. | |
| 1460 | Malicious flaws have acquired colorful names, including Trojan horse, trapdoor, timebomb, and logic-bomb. A developer might insert malicious code with the intent to subvert the security of an application or its host system at some time in the future. It generally refers to a program that performs a useful service but exploits rights of the program's user in a way the user does not intend.",,unclassified, | |
| 1461 | CWE-511,Logic/Time Bomb (Type: Base),"The software contains code that is designed to disrupt the legitimate operation of the software (or its environment) when a certain time passes, or when a certain logical condition is met. | |
| 1462 | When the time bomb or logic bomb is detonated, it may perform a denial of service such as crashing the system, deleting critical data, or degrading system response time. This bomb might be placed within either a replicating or non-replicating Trojan horse.",,unclassified,Mobile App Top 10 List: http://www.veracode.com/blog/2010/12/mobile-app-top-10-list/ | |
| 1463 | CWE-512,Spyware (Type: Base),"The software collects personally identifiable information about a human user or the user's activities, but the software accesses this information using other resources besides itself, and it does not require that user's explicit approval or direct input into the software. | |
| 1464 | ""Spyware"" is a commonly used term with many definitions and interpretations. In general, it is meant to software that collects information or installs functionality that human users might not allow if they were fully aware of the actions being taken by the software. For example, a user might expect that tax software would collect a social security number and include it when filing a tax return, but that same user would not expect gaming software to obtain the social security number from that tax software's data.",,unclassified, | |
| 1465 | CWE-514,Covert Channel (Type: Class),"A covert channel is a path that can be used to transfer information in a way not intended by the system's designers. | |
| 1466 | Typically the system has not given authorization for the transmission and has no knowledge of its occurrence.",,unclassified, | |
| 1467 | CWE-516,DEPRECATED (Duplicate): Covert Timing Channel (Type: Base),"This weakness can be found at CWE-385. | |
| 1468 | Covert storage channels occur when out-of-band data is stored in messages for the purpose of memory reuse. Covert channels are frequently classified as either storage or timing channels. Examples would include using a file intended to hold only audit information to convey user passwords--using the name of a file or perhaps status bits associated with it that can be read by all users to signal the contents of the file. Steganography, concealing information in such a manner that no one but the intended recipient knows of the existence of the message, is a good example of a covert storage channel.",,unclassified, | |
| 1469 | CWE-52,Path Equivalence: /multiple/trailing/slash// (Type: Variant),"A software system that accepts path input in the form of multiple trailing slash ('/multiple/trailing/slash//') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1470 | Covert storage channels occur when out-of-band data is stored in messages for the purpose of memory reuse. Covert channels are frequently classified as either storage or timing channels. Examples would include using a file intended to hold only audit information to convey user passwords--using the name of a file or perhaps status bits associated with it that can be read by all users to signal the contents of the file. Steganography, concealing information in such a manner that no one but the intended recipient knows of the existence of the message, is a good example of a covert storage channel.",,unclassified, | |
| 1471 | CWE-520,.NET Misconfiguration: Use of Impersonation (Type: Variant),"Allowing a .NET application to run at potentially escalated levels of access to the underlying operating and file systems can be dangerous and result in various forms of attacks. | |
| 1472 | Covert storage channels occur when out-of-band data is stored in messages for the purpose of memory reuse. Covert channels are frequently classified as either storage or timing channels. Examples would include using a file intended to hold only audit information to convey user passwords--using the name of a file or perhaps status bits associated with it that can be read by all users to signal the contents of the file. Steganography, concealing information in such a manner that no one but the intended recipient knows of the existence of the message, is a good example of a covert storage channel.",,unclassified, | |
| 1473 | CWE-521,Weak Password Requirements (Type: Base),"The product does not require that users should have strong passwords, which makes it easier for attackers to compromise user accounts. | |
| 1474 | An authentication mechanism is only as strong as its credentials. For this reason, it is important to require users to have strong passwords. Lack of password complexity significantly reduces the search space when trying to guess user's passwords, making brute-force attacks easier.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 1475 | CWE-522,Insufficiently Protected Credentials (Type: Base),"This weakness occurs when the application transmits or stores authentication credentials and uses an insecure method that is susceptible to unauthorized interception and/or retrieval. | |
| 1476 | An authentication mechanism is only as strong as its credentials. For this reason, it is important to require users to have strong passwords. Lack of password complexity significantly reduces the search space when trying to guess user's passwords, making brute-force attacks easier.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 1477 | CWE-523,Unprotected Transport of Credentials (Type: Variant),"Login pages not using adequate measures to protect the user name and password while they are in transit from the client to the server. | |
| 1478 | An authentication mechanism is only as strong as its credentials. For this reason, it is important to require users to have strong passwords. Lack of password complexity significantly reduces the search space when trying to guess user's passwords, making brute-force attacks easier.",,unclassified, | |
| 1479 | CWE-524,Information Exposure Through Caching (Type: Variant),"The application uses a cache to maintain a pool of objects, threads, connections, pages, or passwords to minimize the time it takes to access them or the resources to which they connect. If implemented improperly, these caches can allow access to unauthorized information or cause a denial of service vulnerability. | |
| 1480 | An authentication mechanism is only as strong as its credentials. For this reason, it is important to require users to have strong passwords. Lack of password complexity significantly reduces the search space when trying to guess user's passwords, making brute-force attacks easier.",,unclassified, | |
| 1481 | CWE-525,Information Exposure Through Browser Caching (Type: Variant),"For each web page, the application should have an appropriate caching policy specifying the extent to which the page and its form fields should be cached. | |
| 1482 | An authentication mechanism is only as strong as its credentials. For this reason, it is important to require users to have strong passwords. Lack of password complexity significantly reduces the search space when trying to guess user's passwords, making brute-force attacks easier.",,unclassified, | |
| 1483 | CWE-526,Information Exposure Through Environmental Variables (Type: Variant),"Environmental variables may contain sensitive information about a remote server. | |
| 1484 | An authentication mechanism is only as strong as its credentials. For this reason, it is important to require users to have strong passwords. Lack of password complexity significantly reduces the search space when trying to guess user's passwords, making brute-force attacks easier.",,unclassified, | |
| 1485 | CWE-527,Exposure of CVS Repository to an Unauthorized Control Sphere (Type: Variant),"The product stores a CVS repository in a directory or other container that is accessible to actors outside of the intended control sphere. | |
| 1486 | Information contained within a CVS subdirectory on a web server or other server could be recovered by an attacker and used for malicious purposes. This information may include usernames, filenames, path root, and IP addresses.",,unclassified, | |
| 1487 | CWE-528,Exposure of Core Dump File to an Unauthorized Control Sphere (Type: Variant),"The product generates a core dump file in a directory that is accessible to actors outside of the intended control sphere. | |
| 1488 | Information contained within a CVS subdirectory on a web server or other server could be recovered by an attacker and used for malicious purposes. This information may include usernames, filenames, path root, and IP addresses.",,unclassified, | |
| 1489 | CWE-529,Exposure of Access Control List Files to an Unauthorized Control Sphere (Type: Variant),"The product stores access control list files in a directory or other container that is accessible to actors outside of the intended control sphere. | |
| 1490 | Exposure of these access control list files may give the attacker information about the configuration of the site or system. This information may then be used to bypass the intended security policy or identify trusted systems from which an attack can be launched.",,unclassified, | |
| 1491 | CWE-53,Path Equivalence: \multiple\\internal\backslash (Type: Variant),"A software system that accepts path input in the form of multiple internal backslash ('\multiple\trailing\\slash') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1492 | Exposure of these access control list files may give the attacker information about the configuration of the site or system. This information may then be used to bypass the intended security policy or identify trusted systems from which an attack can be launched.",,unclassified, | |
| 1493 | CWE-530,Exposure of Backup File to an Unauthorized Control Sphere (Type: Variant),"A backup file is stored in a directory that is accessible to actors outside of the intended control sphere. | |
| 1494 | Often, old files are renamed with an extension such as .~bk to distinguish them from production files. The source code for old files that have been renamed in this manner and left in the webroot can often be retrieved. This renaming may have been performed automatically by the web server, or manually by the administrator.",,unclassified, | |
| 1495 | CWE-531,Information Exposure Through Test Code (Type: Variant),"Accessible test applications can pose a variety of security risks. Since developers or administrators rarely consider that someone besides themselves would even know about the existence of these applications, it is common for them to contain sensitive information or functions. | |
| 1496 | Often, old files are renamed with an extension such as .~bk to distinguish them from production files. The source code for old files that have been renamed in this manner and left in the webroot can often be retrieved. This renaming may have been performed automatically by the web server, or manually by the administrator.",,unclassified, | |
| 1497 | CWE-533,Information Exposure Through Server Log Files (Type: Variant),"A server.log file was found. This can give information on whatever application left the file. Usually this can give full path names and system information, and sometimes usernames and passwords. | |
| 1498 | While logging all information may be helpful during development stages, it is important that logging levels be set appropriately before a product ships so that sensitive user data and system information are not accidentally exposed to potential attackers.",,unclassified, | |
| 1499 | CWE-534,Information Exposure Through Debug Log Files (Type: Variant),"The application does not sufficiently restrict access to a log file that is used for debugging. | |
| 1500 | While logging all information may be helpful during development stages, it is important that logging levels be set appropriately before a product ships so that sensitive user data and system information are not accidentally exposed to potential attackers.",,unclassified, | |
| 1501 | CWE-535,Information Exposure Through Shell Error Message (Type: Variant),"A command shell error message indicates that there exists an unhandled exception in the web application code. In many cases, an attacker can leverage the conditions that cause these errors in order to gain unauthorized access to the system. | |
| 1502 | While logging all information may be helpful during development stages, it is important that logging levels be set appropriately before a product ships so that sensitive user data and system information are not accidentally exposed to potential attackers.",,unclassified, | |
| 1503 | CWE-536,Information Exposure Through Servlet Runtime Error Message (Type: Variant),"A servlet error message indicates that there exists an unhandled exception in your web application code and may provide useful information to an attacker. | |
| 1504 | While logging all information may be helpful during development stages, it is important that logging levels be set appropriately before a product ships so that sensitive user data and system information are not accidentally exposed to potential attackers.",,unclassified, | |
| 1505 | CWE-537,Information Exposure Through Java Runtime Error Message (Type: Variant),"In many cases, an attacker can leverage the conditions that cause unhandled exception errors in order to gain unauthorized access to the system. | |
| 1506 | While logging all information may be helpful during development stages, it is important that logging levels be set appropriately before a product ships so that sensitive user data and system information are not accidentally exposed to potential attackers.",,unclassified, | |
| 1507 | CWE-538,File and Directory Information Exposure (Type: Base),"The product stores sensitive information in files or directories that are accessible to actors outside of the intended control sphere. | |
| 1508 | While logging all information may be helpful during development stages, it is important that logging levels be set appropriately before a product ships so that sensitive user data and system information are not accidentally exposed to potential attackers.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 12: Information Leakage."" Page 191" | |
| 1509 | CWE-539,Information Exposure Through Persistent Cookies (Type: Variant),"Persistent cookies are cookies that are stored on the browser's hard drive. This can cause security and privacy issues depending on the information stored in the cookie and how it is accessed. | |
| 1510 | Cookies are small bits of data that are sent by the web application but stored locally in the browser. This lets the application use the cookie to pass information between pages and store variable information. The web application controls what information is stored in a cookie and how it is used. Typical types of information stored in cookies are session Identifiers, personalization and customization information, and in rare cases even usernames to enable automated logins. There are two different types of cookies: session cookies and persistent cookies. Session cookies just live in the browser's memory, and are not stored anywhere, but persistent cookies are stored on the browser's hard drive.",,unclassified, | |
| 1511 | CWE-54,Path Equivalence: filedir\ (Trailing Backslash) (Type: Variant),"A software system that accepts path input in the form of trailing backslash ('filedir\') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1512 | Cookies are small bits of data that are sent by the web application but stored locally in the browser. This lets the application use the cookie to pass information between pages and store variable information. The web application controls what information is stored in a cookie and how it is used. Typical types of information stored in cookies are session Identifiers, personalization and customization information, and in rare cases even usernames to enable automated logins. There are two different types of cookies: session cookies and persistent cookies. Session cookies just live in the browser's memory, and are not stored anywhere, but persistent cookies are stored on the browser's hard drive.",,unclassified, | |
| 1513 | CWE-540,Information Exposure Through Source Code (Type: Variant),"Source code on a web server often contains sensitive information and should generally not be accessible to users. | |
| 1514 | There are situations where it is critical to remove source code from an area or server. For example, obtaining Perl source code on a system allows an attacker to understand the logic of the script and extract extremely useful information such as code bugs or logins and passwords.",,unclassified, | |
| 1515 | CWE-541,Information Exposure Through Include Source Code (Type: Variant),"If an include file source is accessible, the file can contain usernames and passwords, as well as sensitive information pertaining to the application and system. | |
| 1516 | There are situations where it is critical to remove source code from an area or server. For example, obtaining Perl source code on a system allows an attacker to understand the logic of the script and extract extremely useful information such as code bugs or logins and passwords.",,unclassified, | |
| 1517 | CWE-542,Information Exposure Through Cleanup Log Files (Type: Variant),"The application does not properly protect or delete a log file related to cleanup. | |
| 1518 | There are situations where it is critical to remove source code from an area or server. For example, obtaining Perl source code on a system allows an attacker to understand the logic of the script and extract extremely useful information such as code bugs or logins and passwords.",,unclassified, | |
| 1519 | CWE-543,Use of Singleton Pattern Without Synchronization in a Multithreaded Context (Type: Variant),"The software uses the singleton pattern when creating a resource within a multithreaded environment. | |
| 1520 | The use of a singleton pattern may not be thread-safe.",,unclassified,Thread-Specifc Storage for C/C++: http://www.cs.wustl.edu/~schmidt/PDF/TSS-pattern.pdf | |
| 1521 | CWE-544,Missing Standardized Error Handling Mechanism (Type: Base),"The software does not use a standardized method for handling errors throughout the code, which might introduce inconsistent error handling and resultant weaknesses. | |
| 1522 | If the application handles error messages individually, on a one-by-one basis, this is likely to result in inconsistent error handling. The causes of errors may be lost. Also, detailed information about the causes of an error may be unintentionally returned to the user.",,unclassified, | |
| 1523 | CWE-545,Use of Dynamic Class Loading (Type: Variant),"Dynamically loaded code has the potential to be malicious. | |
| 1524 | If the application handles error messages individually, on a one-by-one basis, this is likely to result in inconsistent error handling. The causes of errors may be lost. Also, detailed information about the causes of an error may be unintentionally returned to the user.",,unclassified, | |
| 1525 | CWE-546,Suspicious Comment (Type: Variant),"The code contains comments that suggest the presence of bugs, incomplete functionality, or weaknesses. | |
| 1526 | Many suspicious comments, such as BUG, HACK, FIXME, LATER, LATER2, TODO, in the code indicate missing security functionality and checking. Others indicate code problems that programmers should fix, such as hard-coded variables, error handling, not using stored procedures, and performance issues.",,unclassified, | |
| 1527 | CWE-547,"Use of Hard-coded, Security-relevant Constants (Type: Variant)","The program uses hard-coded constants instead of symbolic names for security-critical values, which increases the likelihood of mistakes during code maintenance or security policy change. | |
| 1528 | If the developer does not find all occurrences of the hard-coded constants, an incorrect policy decision may be made if one of the constants is not changed. Making changes to these values will require code changes that may be difficult or impossible once the system is released to the field. In addition, these hard-coded values may become available to attackers if the code is ever disclosed.",,unclassified, | |
| 1529 | CWE-548,Information Exposure Through Directory Listing (Type: Variant),"A directory listing is inappropriately exposed, yielding potentially sensitive information to attackers. | |
| 1530 | A directory listing provides an attacker with the complete index of all the resources located inside of the directory. The specific risks and consequences vary depending on which files are listed and accessible.",,unclassified, | |
| 1531 | CWE-549,Missing Password Field Masking (Type: Variant),"The software does not mask passwords during entry, increasing the potential for attackers to observe and capture passwords. | |
| 1532 | A directory listing provides an attacker with the complete index of all the resources located inside of the directory. The specific risks and consequences vary depending on which files are listed and accessible.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 1533 | CWE-55,Path Equivalence: /./ (Single Dot Directory) (Type: Variant),"A software system that accepts path input in the form of single dot directory exploit ('/./') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1534 | A directory listing provides an attacker with the complete index of all the resources located inside of the directory. The specific risks and consequences vary depending on which files are listed and accessible.",,unclassified, | |
| 1535 | CWE-550,Information Exposure Through Server Error Message (Type: Variant),"Certain conditions, such as network failure, will cause a server error message to be displayed. | |
| 1536 | While error messages in and of themselves are not dangerous, per se, it is what an attacker can glean from them that might cause eventual problems.",,unclassified, | |
| 1537 | CWE-551,Incorrect Behavior Order: Authorization Before Parsing and Canonicalization (Type: Base),"If a web server does not fully parse requested URLs before it examines them for authorization, it may be possible for an attacker to bypass authorization protection. | |
| 1538 | For instance, the character strings /./ and / both mean current directory. If /SomeDirectory is a protected directory and an attacker requests /./SomeDirectory, the attacker may be able to gain access to the resource if /./ is not converted to / before the authorization check is performed.",,unclassified, | |
| 1539 | CWE-552,Files or Directories Accessible to External Parties (Type: Base),"Files or directories are accessible in the environment that should not be. | |
| 1540 | For instance, the character strings /./ and / both mean current directory. If /SomeDirectory is a protected directory and an attacker requests /./SomeDirectory, the attacker may be able to gain access to the resource if /./ is not converted to / before the authorization check is performed.",,unclassified, | |
| 1541 | CWE-553,Command Shell in Externally Accessible Directory (Type: Variant),"A possible shell file exists in /cgi-bin/ or other accessible directories. This is extremely dangerous and can be used by an attacker to execute commands on the web server. | |
| 1542 | For instance, the character strings /./ and / both mean current directory. If /SomeDirectory is a protected directory and an attacker requests /./SomeDirectory, the attacker may be able to gain access to the resource if /./ is not converted to / before the authorization check is performed.",,unclassified, | |
| 1543 | CWE-554,ASP.NET Misconfiguration: Not Using Input Validation Framework (Type: Variant),"The ASP.NET application does not use an input validation framework. | |
| 1544 | For instance, the character strings /./ and / both mean current directory. If /SomeDirectory is a protected directory and an attacker requests /./SomeDirectory, the attacker may be able to gain access to the resource if /./ is not converted to / before the authorization check is performed.",,unclassified, | |
| 1545 | CWE-555,J2EE Misconfiguration: Plaintext Password in Configuration File (Type: Variant),"The J2EE application stores a plaintext password in a configuration file. | |
| 1546 | Storing a plaintext password in a configuration file allows anyone who can read the file to access the password-protected resource, making it an easy target for attackers.",,unclassified, | |
| 1547 | CWE-556,ASP.NET Misconfiguration: Use of Identity Impersonation (Type: Variant),"Configuring an ASP.NET application to run with impersonated credentials may give the application unnecessary privileges. | |
| 1548 | The use of impersonated credentials allows an ASP.NET application to run with either the privileges of the client on whose behalf it is executing or with arbitrary privileges granted in its configuration.",,unclassified, | |
| 1549 | CWE-558,Use of getlogin() in Multithreaded Application (Type: Variant),"The application uses the getlogin() function in a multithreaded context, potentially causing it to return incorrect values. | |
| 1550 | The getlogin() function returns a pointer to a string that contains the name of the user associated with the calling process. The function is not reentrant, meaning that if it is called from another process, the contents are not locked out and the value of the string can be changed by another process. This makes it very risky to use because the username can be changed by other processes, so the results of the function cannot be trusted.",,unclassified, | |
| 1551 | CWE-56,Path Equivalence: filedir* (Wildcard) (Type: Variant),"A software system that accepts path input in the form of asterisk wildcard ('filedir*') without appropriate validation can lead to ambiguous path resolution and allow an attacker to traverse the file system to unintended locations or access arbitrary files. | |
| 1552 | The getlogin() function returns a pointer to a string that contains the name of the user associated with the calling process. The function is not reentrant, meaning that if it is called from another process, the contents are not locked out and the value of the string can be changed by another process. This makes it very risky to use because the username can be changed by other processes, so the results of the function cannot be trusted.",,unclassified, | |
| 1553 | CWE-560,Use of umask() with chmod-style Argument (Type: Variant),"The product calls umask() with an incorrect argument that is specified as if it is an argument to chmod(). | |
| 1554 | The getlogin() function returns a pointer to a string that contains the name of the user associated with the calling process. The function is not reentrant, meaning that if it is called from another process, the contents are not locked out and the value of the string can be changed by another process. This makes it very risky to use because the username can be changed by other processes, so the results of the function cannot be trusted.",,unclassified, | |
| 1555 | CWE-561,Dead Code (Type: Variant),"The software contains dead code, which can never be executed. | |
| 1556 | Dead code is source code that can never be executed in a running program. The surrounding code makes it impossible for a section of code to ever be executed.",,unclassified, | |
| 1557 | CWE-562,Return of Stack Variable Address (Type: Base),"A function returns the address of a stack variable, which will cause unintended program behavior, typically in the form of a crash. | |
| 1558 | Dead code is source code that can never be executed in a running program. The surrounding code makes it impossible for a section of code to ever be executed.",,unclassified, | |
| 1559 | CWE-563,Unused Variable (Type: Variant),"The variable's value is assigned but never used, making it a dead store. | |
| 1560 | It is likely that the variable is simply vestigial, but it is also possible that the unused variable points out a bug.",,unclassified, | |
| 1561 | CWE-564,SQL Injection: Hibernate (Type: Variant),"Using Hibernate to execute a dynamic SQL statement built with user-controlled input can allow an attacker to modify the statement's meaning or to execute arbitrary SQL commands. | |
| 1562 | It is likely that the variable is simply vestigial, but it is also possible that the unused variable points out a bug.",,unclassified, | |
| 1563 | CWE-565,Reliance on Cookies without Validation and Integrity Checking (Type: Base),"The application relies on the existence or values of cookies when performing security-critical operations, but it does not properly ensure that the setting is valid for the associated user. | |
| 1564 | Attackers can easily modify cookies, within the browser or by implementing the client-side code outside of the browser. Reliance on cookies without detailed validation and integrity checking can allow attackers to bypass authentication, conduct injection attacks such as SQL injection and cross-site scripting, or otherwise modify inputs in unexpected ways.",,unclassified, | |
| 1565 | CWE-566,Authorization Bypass Through User-Controlled SQL Primary Key (Type: Variant),"The software uses a database table that includes records that should not be accessible to an actor, but it executes a SQL statement with a primary key that can be controlled by that actor. | |
| 1566 | When a user can set a primary key to any value, then the user can modify the key to point to unauthorized records. | |
| 1567 | Database access control errors occur when: | |
| 1568 | Data enters a program from an untrusted source. | |
| 1569 | The data is used to specify the value of a primary key in a SQL query. | |
| 1570 | The untrusted source does not have the permissions to be able to access all rows in the associated table.",,unclassified, | |
| 1571 | CWE-567,Unsynchronized Access to Shared Data in a Multithreaded Context (Type: Base),"The product does not properly synchronize shared data, such as static variables across threads, which can lead to undefined behavior and unpredictable data changes. | |
| 1572 | Within servlets, shared static variables are not protected from concurrent access, but servlets are multithreaded. This is a typical programming mistake in J2EE applications, since the multithreading is handled by the framework. When a shared variable can be influenced by an attacker, one thread could wind up modifying the variable to contain data that is not valid for a different thread that is also using the data within the variable. | |
| 1573 | Note that this weakness is not unique to servlets.",,unclassified, | |
| 1574 | CWE-568,finalize() Method Without super.finalize() (Type: Variant),"The software contains a finalize() method that does not call super.finalize(). | |
| 1575 | The Java Language Specification states that it is a good practice for a finalize() method to call super.finalize().",,unclassified, | |
| 1576 | CWE-57,Path Equivalence: fakedir/../realdir/filename (Type: Variant),"The software contains protection mechanisms to restrict access to 'realdir/filename', but it constructs pathnames using external input in the form of 'fakedir/../realdir/filename' that are not handled by those mechanisms. This allows attackers to perform unauthorized actions against the targeted file. | |
| 1577 | The Java Language Specification states that it is a good practice for a finalize() method to call super.finalize().",,unclassified, | |
| 1578 | CWE-570,Expression is Always False (Type: Variant),"The software contains an expression that will always evaluate to false. | |
| 1579 | The Java Language Specification states that it is a good practice for a finalize() method to call super.finalize().",,unclassified, | |
| 1580 | CWE-571,Expression is Always True (Type: Variant),"The software contains an expression that will always evaluate to true. | |
| 1581 | The Java Language Specification states that it is a good practice for a finalize() method to call super.finalize().",,unclassified, | |
| 1582 | CWE-572,Call to Thread run() instead of start() (Type: Variant),"The program calls a thread's run() method instead of calling start(), which causes the code to run in the thread of the caller instead of the callee. | |
| 1583 | In most cases a direct call to a Thread object's run() method is a bug. The programmer intended to begin a new thread of control, but accidentally called run() instead of start(), so the run() method will execute in the caller's thread of control.",,unclassified, | |
| 1584 | CWE-573,Improper Following of Specification by Caller (Type: Class),"The software does not follow or incorrectly follows the specifications as required by the implementation language, environment, framework, protocol, or platform. | |
| 1585 | When leveraging external functionality, such as an API, it is important that the caller does so in accordance with the requirements of the external functionality or else unintended behaviors may result, possibly leaving the system vulnerable to any number of exploits.",,unclassified, | |
| 1586 | CWE-574,EJB Bad Practices: Use of Synchronization Primitives (Type: Variant),"The program violates the Enterprise JavaBeans (EJB) specification by using thread synchronization primitives. | |
| 1587 | The Enterprise JavaBeans specification requires that every bean provider follow a set of programming guidelines designed to ensure that the bean will be portable and behave consistently in any EJB container. In this case, the program violates the following EJB guideline: ""An enterprise bean must not use thread synchronization primitives to synchronize execution of multiple instances."" The specification justifies this requirement in the following way: ""This rule is required to ensure consistent runtime semantics because while some EJB containers may use a single JVM to execute all enterprise bean's instances, others may distribute the instances across multiple JVMs.""",,unclassified, | |
| 1588 | CWE-575,EJB Bad Practices: Use of AWT Swing (Type: Variant),"The program violates the Enterprise JavaBeans (EJB) specification by using AWT/Swing. | |
| 1589 | The Enterprise JavaBeans specification requires that every bean provider follow a set of programming guidelines designed to ensure that the bean will be portable and behave consistently in any EJB container. In this case, the program violates the following EJB guideline: ""An enterprise bean must not use the AWT functionality to attempt to output information to a display, or to input information from a keyboard."" The specification justifies this requirement in the following way: ""Most servers do not allow direct interaction between an application program and a keyboard/display attached to the server system.""",,unclassified, | |
| 1590 | CWE-576,EJB Bad Practices: Use of Java I/O (Type: Variant),"The program violates the Enterprise JavaBeans (EJB) specification by using the java.io package. | |
| 1591 | The Enterprise JavaBeans specification requires that every bean provider follow a set of programming guidelines designed to ensure that the bean will be portable and behave consistently in any EJB container. In this case, the program violates the following EJB guideline: ""An enterprise bean must not use the java.io package to attempt to access files and directories in the file system."" The specification justifies this requirement in the following way: ""The file system APIs are not well-suited for business components to access data. Business components should use a resource manager API, such as JDBC, to store data.""",,unclassified, | |
| 1592 | CWE-577,EJB Bad Practices: Use of Sockets (Type: Variant),"The program violates the Enterprise JavaBeans (EJB) specification by using sockets. | |
| 1593 | The Enterprise JavaBeans specification requires that every bean provider follow a set of programming guidelines designed to ensure that the bean will be portable and behave consistently in any EJB container. In this case, the program violates the following EJB guideline: ""An enterprise bean must not attempt to listen on a socket, accept connections on a socket, or use a socket for multicast."" The specification justifies this requirement in the following way: ""The EJB architecture allows an enterprise bean instance to be a network socket client, but it does not allow it to be a network server. Allowing the instance to become a network server would conflict with the basic function of the enterprise bean-- to serve the EJB clients.""",,unclassified, | |
| 1594 | CWE-578,EJB Bad Practices: Use of Class Loader (Type: Variant),"The program violates the Enterprise JavaBeans (EJB) specification by using the class loader. | |
| 1595 | The Enterprise JavaBeans specification requires that every bean provider follow a set of programming guidelines designed to ensure that the bean will be portable and behave consistently in any EJB container. In this case, the program violates the following EJB guideline: ""The enterprise bean must not attempt to create a class loader; obtain the current class loader; set the context class loader; set security manager; create a new security manager; stop the JVM; or change the input, output, and error streams."" The specification justifies this requirement in the following way: ""These functions are reserved for the EJB container. Allowing the enterprise bean to use these functions could compromise security and decrease the container's ability to properly manage the runtime environment.""",,unclassified, | |
| 1596 | CWE-579,J2EE Bad Practices: Non-serializable Object Stored in Session (Type: Variant),"The application stores a non-serializable object as an HttpSession attribute, which can hurt reliability. | |
| 1597 | The Enterprise JavaBeans specification requires that every bean provider follow a set of programming guidelines designed to ensure that the bean will be portable and behave consistently in any EJB container. In this case, the program violates the following EJB guideline: ""The enterprise bean must not attempt to create a class loader; obtain the current class loader; set the context class loader; set security manager; create a new security manager; stop the JVM; or change the input, output, and error streams."" The specification justifies this requirement in the following way: ""These functions are reserved for the EJB container. Allowing the enterprise bean to use these functions could compromise security and decrease the container's ability to properly manage the runtime environment.""",,unclassified, | |
| 1598 | CWE-58,Path Equivalence: Windows 8.3 Filename (Type: Variant),"The software contains a protection mechanism that restricts access to a long filename on a Windows operating system, but the software does not properly restrict access to the equivalent short ""8.3"" filename. | |
| 1599 | On later Windows operating systems, a file can have a ""long name"" and a short name that is compatible with older Windows file systems, with up to 8 characters in the filename and 3 characters for the extension. These ""8.3"" filenames, therefore, act as an alternate name for files with long names, so they are useful pathname equivalence manipulations.",,unclassified,"Writing Secure Code | |
| 1600 | The Art of Software Security Assessment: Chapter 11, ""DOS 8.3 Filenames"", Page 673." | |
| 1601 | CWE-580,clone() Method Without super.clone() (Type: Variant),"The software contains a clone() method that does not call super.clone() to obtain the new object. | |
| 1602 | All implementations of clone() should obtain the new object by calling super.clone(). If a class does not follow this convention, a subclass's clone() method will return an object of the wrong type.",,unclassified, | |
| 1603 | CWE-581,Object Model Violation: Just One of Equals and Hashcode Defined (Type: Base),"The software does not maintain equal hashcodes for equal objects. | |
| 1604 | Java objects are expected to obey a number of invariants related to equality. One of these invariants is that equal objects must have equal hashcodes. In other words, if a.equals(b) == true then a.hashCode() == b.hashCode().",,unclassified, | |
| 1605 | CWE-582,"Array Declared Public, Final, and Static (Type: Variant)","The program declares an array public, final, and static, which is not sufficient to prevent the array's contents from being modified. | |
| 1606 | Because arrays are mutable objects, the final constraint requires that the array object itself be assigned only once, but makes no guarantees about the values of the array elements. Since the array is public, a malicious program can change the values stored in the array. As such, in most cases an array declared public, final and static is a bug.",,unclassified, | |
| 1607 | CWE-583,finalize() Method Declared Public (Type: Variant),"The program violates secure coding principles for mobile code by declaring a finalize() method public. | |
| 1608 | A program should never call finalize explicitly, except to call super.finalize() inside an implementation of finalize(). In mobile code situations, the otherwise error prone practice of manual garbage collection can become a security threat if an attacker can maliciously invoke one of your finalize() methods because it is declared with public access.",,unclassified, | |
| 1609 | CWE-584,Return Inside Finally Block (Type: Base),"The code has a return statement inside a finally block, which will cause any thrown exception in the try block to be discarded. | |
| 1610 | A program should never call finalize explicitly, except to call super.finalize() inside an implementation of finalize(). In mobile code situations, the otherwise error prone practice of manual garbage collection can become a security threat if an attacker can maliciously invoke one of your finalize() methods because it is declared with public access.",,unclassified, | |
| 1611 | CWE-585,Empty Synchronized Block (Type: Variant),"The software contains an empty synchronized block. | |
| 1612 | An empty synchronized block does not actually accomplish any synchronization and may indicate a troubled section of code. An empty synchronized block can occur because code no longer needed within the synchronized block is commented out without removing the synchronized block.",,unclassified,Intrinsic Locks and Synchronization (in Java): http://java.sun.com/docs/books/tutorial/essential/concurrency/locksync.html | |
| 1613 | CWE-586,Explicit Call to Finalize() (Type: Variant),"The software makes an explicit call to the finalize() method from outside the finalizer. | |
| 1614 | While the Java Language Specification allows an object's finalize() method to be called from outside the finalizer, doing so is usually a bad idea. For example, calling finalize() explicitly means that finalize() will be called more than once: the first time will be the explicit call and the last time will be the call that is made after the object is garbage collected.",,unclassified, | |
| 1615 | CWE-587,Assignment of a Fixed Address to a Pointer (Type: Base),"The software sets a pointer to a specific address other than NULL or 0. | |
| 1616 | Using a fixed address is not portable because that address will probably not be valid in all environments or platforms.",,unclassified, | |
| 1617 | CWE-588,Attempt to Access Child of a Non-structure Pointer (Type: Variant),"Casting a non-structure type to a structure type and accessing a field can lead to memory access errors or data corruption. | |
| 1618 | Using a fixed address is not portable because that address will probably not be valid in all environments or platforms.",,unclassified, | |
| 1619 | CWE-589,Call to Non-ubiquitous API (Type: Variant),"The software uses an API function that does not exist on all versions of the target platform. This could cause portability problems or inconsistencies that allow denial of service or other consequences. | |
| 1620 | Some functions that offer security features supported by the OS are not available on all versions of the OS in common use. Likewise, functions are often deprecated or made obsolete for security reasons and should not be used.",,unclassified, | |
| 1621 | CWE-590,Free of Memory not on the Heap (Type: Variant),"The application calls free() on a pointer to memory that was not allocated using associated heap allocation functions such as malloc(), calloc(), or realloc(). | |
| 1622 | When free() is called on an invalid pointer, the program's memory management data structures may become corrupted. This corruption can cause the program to crash or, in some circumstances, an attacker may be able to cause free() to operate on controllable memory locations to modify critical program variables or execute code.",,unclassified,Valgrind: http://valgrind.org/ | |
| 1623 | CWE-591,Sensitive Data Storage in Improperly Locked Memory (Type: Variant),"The application stores sensitive data in memory that is not locked, or that has been incorrectly locked, which might cause the memory to be written to swap files on disk by the virtual memory manager. This can make the data more accessible to external actors. | |
| 1624 | On Windows systems the VirtualLock function can lock a page of memory to ensure that it will remain present in memory and not be swapped to disk. However, on older versions of Windows, such as 95, 98, or Me, the VirtualLock() function is only a stub and provides no protection. On POSIX systems the mlock() call ensures that a page will stay resident in memory but does not guarantee that the page will not appear in the swap. Therefore, it is unsuitable for use as a protection mechanism for sensitive data. Some platforms, in particular Linux, do make the guarantee that the page will not be swapped, but this is non-standard and is not portable. Calls to mlock() also require supervisor privilege. Return values for both of these calls must be checked to ensure that the lock operation was actually successful.",,unclassified, | |
| 1625 | CWE-592,Authentication Bypass Issues (Type: Class),"The software does not properly perform authentication, allowing it to be bypassed through various methods. | |
| 1626 | On Windows systems the VirtualLock function can lock a page of memory to ensure that it will remain present in memory and not be swapped to disk. However, on older versions of Windows, such as 95, 98, or Me, the VirtualLock() function is only a stub and provides no protection. On POSIX systems the mlock() call ensures that a page will stay resident in memory but does not guarantee that the page will not appear in the swap. Therefore, it is unsuitable for use as a protection mechanism for sensitive data. Some platforms, in particular Linux, do make the guarantee that the page will not be swapped, but this is non-standard and is not portable. Calls to mlock() also require supervisor privilege. Return values for both of these calls must be checked to ensure that the lock operation was actually successful.",,unclassified,"The Art of Software Security Assessment: Chapter 2, ""Untrustworthy Credentials"", Page 37." | |
| 1627 | CWE-593,Authentication Bypass: OpenSSL CTX Object Modified after SSL Objects are Created (Type: Variant),"The software modifies the SSL context after connection creation has begun. | |
| 1628 | If the program modifies the SSL_CTX object after creating SSL objects from it, there is the possibility that older SSL objects created from the original context could all be affected by that change.",,unclassified, | |
| 1629 | CWE-594,J2EE Framework: Saving Unserializable Objects to Disk (Type: Variant),"When the J2EE container attempts to write unserializable objects to disk there is no guarantee that the process will complete successfully. | |
| 1630 | If the program modifies the SSL_CTX object after creating SSL objects from it, there is the possibility that older SSL objects created from the original context could all be affected by that change.",,unclassified, | |
| 1631 | CWE-595,Comparison of Object References Instead of Object Contents (Type: Base),"The program compares object references instead of the contents of the objects themselves, preventing it from detecting equivalent objects. | |
| 1632 | If the program modifies the SSL_CTX object after creating SSL objects from it, there is the possibility that older SSL objects created from the original context could all be affected by that change.",,unclassified, | |
| 1633 | CWE-596,Incorrect Semantic Object Comparison (Type: Base),"The software does not correctly compare two objects based on their conceptual content. | |
| 1634 | If the program modifies the SSL_CTX object after creating SSL objects from it, there is the possibility that older SSL objects created from the original context could all be affected by that change.",,unclassified, | |
| 1635 | CWE-597,Use of Wrong Operator in String Comparison (Type: Variant),"The product uses the wrong operator when comparing a string, such as using ""=="" when the equals() method should be used instead. | |
| 1636 | In Java, using == or != to compare two strings for equality actually compares two objects for equality, not their values. Chances are good that the two references will never be equal. While this weakness often only affects program correctness, if the equality is used for a security decision, it could be leveraged to affect program security.",,unclassified,"The Art of Software Security Assessment: Chapter 6, ""Typos"", Page 289." | |
| 1637 | CWE-598,Information Exposure Through Query Strings in GET Request (Type: Variant),"The web application uses the GET method to process requests that contain sensitive information, which can expose that information through the browser's history, Referers, web logs, and other sources. | |
| 1638 | In Java, using == or != to compare two strings for equality actually compares two objects for equality, not their values. Chances are good that the two references will never be equal. While this weakness often only affects program correctness, if the equality is used for a security decision, it could be leveraged to affect program security.",,unclassified, | |
| 1639 | CWE-599,Missing Validation of OpenSSL Certificate (Type: Variant),"The software uses OpenSSL and trusts or uses a certificate without using the SSL_get_verify_result() function to ensure that the certificate satisfies all necessary security requirements. | |
| 1640 | This could allow an attacker to use an invalid certificate to claim to be a trusted host, use expired certificates, or conduct other attacks that could be detected if the certificate is properly validated.",,unclassified, | |
| 1641 | CWE-6,J2EE Misconfiguration: Insufficient Session-ID Length (Type: Variant),"The J2EE application is configured to use an insufficient session ID length. | |
| 1642 | If an attacker can guess or steal a session ID, then he/she may be able to take over the user's session (called session hijacking). The number of possible session IDs increases with increased session ID length, making it more difficult to guess or steal a session ID.",,unclassified,No description: http://www.securiteam.com/securityreviews/5TP0F0UEVQ.html | |
| 1643 | CWE-600,Uncaught Exception in Servlet (Type: Base),"The Servlet does not catch all exceptions, which may reveal sensitive debugging information. | |
| 1644 | When a Servlet throws an exception, the default error response the Servlet container sends back to the user typically includes debugging information. This information is of great value to an attacker. For example, a stack trace might show the attacker a malformed SQL query string, the type of database being used, and the version of the application container. This information enables the attacker to target known vulnerabilities in these components.",,unclassified, | |
| 1645 | CWE-603,Use of Client-Side Authentication (Type: Base),"A client/server product performs authentication within client code but not in server code, allowing server-side authentication to be bypassed via a modified client that omits the authentication check. | |
| 1646 | Client-side authentication is extremely weak and may be breached easily. Any attacker may read the source code and reverse-engineer the authentication mechanism to access parts of the application which would otherwise be protected.",,unclassified,"The Art of Software Security Assessment: Chapter 2, ""Untrustworthy Credentials"", Page 37." | |
| 1647 | CWE-605,Multiple Binds to the Same Port (Type: Base),"When multiple sockets are allowed to bind to the same port, other services on that port may be stolen or spoofed. | |
| 1648 | Client-side authentication is extremely weak and may be breached easily. Any attacker may read the source code and reverse-engineer the authentication mechanism to access parts of the application which would otherwise be protected.",,unclassified, | |
| 1649 | CWE-606,Unchecked Input for Loop Condition (Type: Base),"The product does not properly check inputs that are used for loop conditions, potentially leading to a denial of service because of excessive looping. | |
| 1650 | Client-side authentication is extremely weak and may be breached easily. Any attacker may read the source code and reverse-engineer the authentication mechanism to access parts of the application which would otherwise be protected.",,unclassified,"The Art of Software Security Assessment: Chapter 7, ""Looping Constructs"", Page 327." | |
| 1651 | CWE-607,Public Static Final Field References Mutable Object (Type: Variant),"A public or protected static final field references a mutable object, which allows the object to be changed by malicious code, or accidentally from another package. | |
| 1652 | Client-side authentication is extremely weak and may be breached easily. Any attacker may read the source code and reverse-engineer the authentication mechanism to access parts of the application which would otherwise be protected.",,unclassified, | |
| 1653 | CWE-608,Struts: Non-private Field in ActionForm Class (Type: Variant),"An ActionForm class contains a field that has not been declared private, which can be accessed without using a setter or getter. | |
| 1654 | Client-side authentication is extremely weak and may be breached easily. Any attacker may read the source code and reverse-engineer the authentication mechanism to access parts of the application which would otherwise be protected.",,unclassified, | |
| 1655 | CWE-609,Double-Checked Locking (Type: Base),"The program uses double-checked locking to access a resource without the overhead of explicit synchronization, but the locking is insufficient. | |
| 1656 | Double-checked locking refers to the situation where a programmer checks to see if a resource has been initialized, grabs a lock, checks again to see if the resource has been initialized, and then performs the initialization if it has not occurred yet. This should not be done, as is not guaranteed to work in all languages and on all architectures. In summary, other threads may not be operating inside the synchronous block and are not guaranteed to see the operations execute in the same order as they would appear inside the synchronous block.",,unclassified,"The ""Double-Checked Locking is Broken"" Declaration: http://www.cs.umd.edu/~pugh/java/memoryModel/DoubleCheckedLocking.html | |
| 1657 | JSR 133 (Java Memory Model) FAQ: http://www.cs.umd.edu/~pugh/java/memoryModel/jsr-133-faq.html#dcl | |
| 1658 | The Art of Software Security Assessment: Chapter 13, ""Threading Vulnerabilities"", Page 815." | |
| 1659 | CWE-610,Externally Controlled Reference to a Resource in Another Sphere (Type: Class),"The product uses an externally controlled name or reference that resolves to a resource that is outside of the intended control sphere. | |
| 1660 | ",,unclassified, | |
| 1661 | CWE-611,Improper Restriction of XML External Entity Reference (XXE) (Type: Variant),"The software processes an XML document that can contain XML entities with URIs that resolve to documents outside of the intended sphere of control, causing the product to embed incorrect documents into its output. | |
| 1662 | XML documents optionally contain a Document Type Definition (DTD), which, among other features, enables the definition of XML entities. It is possible to define an entity by providing a substitution string in the form of a URI. The XML parser can access the contents of this URI and embed these contents back into the XML document for further processing. | |
| 1663 | By submitting an XML file that defines an external entity with a file:// URI, an attacker can cause the processing application to read the contents of a local file. For example, a URI such as ""file:///c:/winnt/win.ini"" designates (in Windows) the file C:\Winnt\win.ini, or file:///etc/passwd designates the password file in Unix-based systems. Using URIs with other schemes such as http://, the attacker can force the application to make outgoing requests to servers that the attacker cannot reach directly, which can be used to bypass firewall restrictions or hide the source of attacks such as port scanning. | |
| 1664 | Once the content of the URI is read, it is fed back into the application that is processing the XML. This application may echo back the data (e.g. in an error message), thereby exposing the file contents.",,unclassified,"XML External Entity (XXE) Processing: https://www.owasp.org/index.php/XML_External_Entity_(XXE)_Processing | |
| 1665 | XML External Entity Attacks (XXE): https://www.owasp.org/images/5/5d/XML_Exteral_Entity_Attack.pdf | |
| 1666 | XXE (Xml eXternal Entity) Attack: http://www.securiteam.com/securitynews/6D0100A5PU.html | |
| 1667 | XML External Entities (XXE) Attack: http://projects.webappsec.org/w/page/13247003/XML%20External%20Entities | |
| 1668 | XML Denial of Service Attacks and Defenses: http://msdn.microsoft.com/en-us/magazine/ee335713.aspx | |
| 1669 | Preventing XXE in PHP: http://websec.io/2012/08/27/Preventing-XEE-in-PHP.html" | |
| 1670 | CWE-612,Information Exposure Through Indexing of Private Data (Type: Variant),"The product performs an indexing routine against private documents, but does not sufficiently verify that the actors who can access the index also have the privileges to access the private documents. | |
| 1671 | When an indexing routine is applied against a group of private documents, and that index's results are available to outsiders who do not have access to those documents, then outsiders might be able to obtain sensitive information by conducting targeted searches. The risk is especially dangerous if search results include surrounding text that was not part of the search query. This issue can appear in search engines that are not configured (or implemented) to ignore critical files that should remain hidden; even without permissions to download these files directly, the remote user could read them.",,unclassified, | |
| 1672 | CWE-613,Insufficient Session Expiration (Type: Base),"According to WASC, ""Insufficient Session Expiration is when a web site permits an attacker to reuse old session credentials or session IDs for authorization."" | |
| 1673 | When an indexing routine is applied against a group of private documents, and that index's results are available to outsiders who do not have access to those documents, then outsiders might be able to obtain sensitive information by conducting targeted searches. The risk is especially dangerous if search results include surrounding text that was not part of the search query. This issue can appear in search engines that are not configured (or implemented) to ignore critical files that should remain hidden; even without permissions to download these files directly, the remote user could read them.",,unclassified, | |
| 1674 | CWE-614,Sensitive Cookie in HTTPS Session Without Secure Attribute (Type: Variant),"The Secure attribute for sensitive cookies in HTTPS sessions is not set, which could cause the user agent to send those cookies in plaintext over an HTTP session. | |
| 1675 | When an indexing routine is applied against a group of private documents, and that index's results are available to outsiders who do not have access to those documents, then outsiders might be able to obtain sensitive information by conducting targeted searches. The risk is especially dangerous if search results include surrounding text that was not part of the search query. This issue can appear in search engines that are not configured (or implemented) to ignore critical files that should remain hidden; even without permissions to download these files directly, the remote user could read them.",,unclassified, | |
| 1676 | CWE-615,Information Exposure Through Comments (Type: Variant),"While adding general comments is very useful, some programmers tend to leave important data, such as: filenames related to the web application, old links or links which were not meant to be browsed by users, old code fragments, etc. | |
| 1677 | An attacker who finds these comments can map the application's structure and files, expose hidden parts of the site, and study the fragments of code to reverse engineer the application, which may help develop further attacks against the site.",,unclassified, | |
| 1678 | CWE-616,Incomplete Identification of Uploaded File Variables (PHP) (Type: Variant),"The PHP application uses an old method for processing uploaded files by referencing the four global variables that are set for each file (e.g. $varname, $varname_size, $varname_name, $varname_type). These variables could be overwritten by attackers, causing the application to process unauthorized files. | |
| 1679 | These global variables could be overwritten by POST requests, cookies, or other methods of populating or overwriting these variables. This could be used to read or process arbitrary files by providing values such as ""/etc/passwd"".",,unclassified,"A Study in Scarlet - section 5, ""File Upload""" | |
| 1680 | CWE-617,Reachable Assertion (Type: Variant),"The product contains an assert() or similar statement that can be triggered by an attacker, which leads to an application exit or other behavior that is more severe than necessary. | |
| 1681 | For example, if a server handles multiple simultaneous connections, and an assert() occurs in one single connection that causes all other connections to be dropped, this is a reachable assertion that leads to a denial of service.",,unclassified, | |
| 1682 | CWE-618,Exposed Unsafe ActiveX Method (Type: Base),"An ActiveX control is intended for use in a web browser, but it exposes dangerous methods that perform actions that are outside of the browser's security model (e.g. the zone or domain). | |
| 1683 | ActiveX controls can exercise far greater control over the operating system than typical Java or javascript. Exposed methods can be subject to various vulnerabilities, depending on the implemented behaviors of those methods, and whether input validation is performed on the provided arguments. If there is no integrity checking or origin validation, this method could be invoked by attackers.",,unclassified,"No description: http://msdn.microsoft.com/workshop/components/activex/safety.asp | |
| 1684 | No description: http://msdn.microsoft.com/workshop/components/activex/security.asp | |
| 1685 | The Art of Software Security Assessment: Chapter 12, ""ActiveX Security"", Page 749." | |
| 1686 | CWE-619,Dangling Database Cursor (Cursor Injection) (Type: Base),"If a database cursor is not closed properly, then it could become accessible to other users while retaining the same privileges that were originally assigned, leaving the cursor ""dangling."" | |
| 1687 | For example, an improper dangling cursor could arise from unhandled exceptions. The impact of the issue depends on the cursor's role, but SQL injection attacks are commonly possible.",,unclassified,"The Oracle Hacker's Handbook | |
| 1688 | Cursor Injection: http://www.databasesecurity.com/dbsec/cursor-injection.pdf" | |
| 1689 | CWE-62,UNIX Hard Link (Type: Variant),"The software, when opening a file or directory, does not sufficiently account for when the name is associated with a hard link to a target that is outside of the intended control sphere. This could allow an attacker to cause the software to operate on unauthorized files. | |
| 1690 | Failure for a system to check for hard links can result in vulnerability to different types of attacks. For example, an attacker can escalate their privileges if a file used by a privileged program is replaced with a hard link to a sensitive file (e.g. /etc/passwd). When the process opens the file, the attacker can assume the privileges of that process.",,unclassified,"The Art of Software Security Assessment: Chapter 9, ""Hard Links"", Page 518." | |
| 1691 | CWE-620,Unverified Password Change (Type: Variant),"When setting a new password for a user, the product does not require knowledge of the original password, or using another form of authentication. | |
| 1692 | This could be used by an attacker to change passwords for another user, thus gaining the privileges associated with that user.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 1693 | CWE-621,Variable Extraction Error (Type: Base),"The product uses external input to determine the names of variables into which information is extracted, without verifying that the names of the specified variables are valid. This could cause the program to overwrite unintended variables. | |
| 1694 | For example, in PHP, calling extract() or import_request_variables() without the proper arguments could allow arbitrary global variables to be overwritten, including superglobals. Similar functionality might be possible in other interpreted languages, including custom languages.",,unclassified, | |
| 1695 | CWE-622,Improper Validation of Function Hook Arguments (Type: Variant),"A product adds hooks to user-accessible API functions, but does not properly validate the arguments. This could lead to resultant vulnerabilities. | |
| 1696 | Such hooks can be used in defensive software that runs with privileges, such as anti-virus or firewall, which hooks kernel calls. When the arguments are not validated, they could be used to bypass the protection scheme or attack the product itself.",,unclassified, | |
| 1697 | CWE-623,Unsafe ActiveX Control Marked Safe For Scripting (Type: Variant),"An ActiveX control is intended for restricted use, but it has been marked as safe-for-scripting. | |
| 1698 | This might allow attackers to use dangerous functionality via a web page that accesses the control, which can lead to different resultant vulnerabilities, depending on the control's behavior.",,unclassified,"No description: http://msdn.microsoft.com/workshop/components/activex/safety.asp | |
| 1699 | No description: http://msdn.microsoft.com/workshop/components/activex/security.asp | |
| 1700 | No description: http://support.microsoft.com/kb/240797 | |
| 1701 | Writing Secure Code: Chapter 16, ""What ActiveX Components Are Safe for Initialization and Safe for Scripting?"" Page 510 | |
| 1702 | The Art of Software Security Assessment: Chapter 12, ""ActiveX Security"", Page 749." | |
| 1703 | CWE-624,Executable Regular Expression Error (Type: Base),"The product uses a regular expression that either (1) contains an executable component with user-controlled inputs, or (2) allows a user to enable execution by inserting pattern modifiers. | |
| 1704 | Case (2) is possible in the PHP preg_replace() function, and possibly in other languages when a user-controlled input is inserted into a string that is later parsed as a regular expression.",,unclassified, | |
| 1705 | CWE-625,Permissive Regular Expression (Type: Base),"The product uses a regular expression that does not sufficiently restrict the set of allowed values. | |
| 1706 | This effectively causes the regexp to accept substrings that match the pattern, which produces a partial comparison to the target. In some cases, this can lead to other weaknesses. Common errors include: | |
| 1707 | not identifying the beginning and end of the target string | |
| 1708 | using wildcards instead of acceptable character ranges | |
| 1709 | others",,unclassified,"The Art of Software Security Assessment: Chapter 8, ""Character Stripping Vulnerabilities"", Page 437." | |
| 1710 | CWE-626,Null Byte Interaction Error (Poison Null Byte) (Type: Variant),"The product does not properly handle null bytes or NUL characters when passing data between different representations or components. | |
| 1711 | A null byte (NUL character) can have different meanings across representations or languages. For example, it is a string terminator in standard C libraries, but Perl and PHP strings do not treat it as a terminator. When two representations are crossed - such as when Perl or PHP invokes underlying C functionality - this can produce an interaction error with unexpected results. Similar issues have been reported for ASP. Other interpreters written in C might also be affected.",,unclassified,"Poison NULL byte: http://insecure.org/news/P55-07.txt | |
| 1712 | 0x00 vs ASP file upload scripts: http://www.security-assessment.com/Whitepapers/0x00_vs_ASP_File_Uploads.pdf | |
| 1713 | ShAnKaR: multiple PHP application poison NULL byte vulnerability: http://seclists.org/fulldisclosure/2006/Sep/0185.html" | |
| 1714 | CWE-627,Dynamic Variable Evaluation (Type: Base),"In a language where the user can influence the name of a variable at runtime, if the variable names are not controlled, an attacker can read or write to arbitrary variables, or access arbitrary functions. | |
| 1715 | The resultant vulnerabilities depend on the behavior of the application, both at the crossover point and in any control/data flow that is reachable by the related variables or functions.",,unclassified,"Dynamic Evaluation Vulnerabilities in PHP applications: http://seclists.org/fulldisclosure/2006/May/0035.html | |
| 1716 | A Study In Scarlet: Exploiting Common Vulnerabilities in PHP Applications: http://www.securereality.com.au/studyinscarlet.txt" | |
| 1717 | CWE-628,Function Call with Incorrectly Specified Arguments (Type: Base),"The product calls a function, procedure, or routine with arguments that are not correctly specified, leading to always-incorrect behavior and resultant weaknesses. | |
| 1718 | There are multiple ways in which this weakness can be introduced, including: | |
| 1719 | the wrong variable or reference; | |
| 1720 | an incorrect number of arguments; | |
| 1721 | incorrect order of arguments; | |
| 1722 | wrong type of arguments; or | |
| 1723 | wrong value.",,unclassified, | |
| 1724 | CWE-636,Not Failing Securely (Failing Open) (Type: Class),"When the product encounters an error condition or failure, its design requires it to fall back to a state that is less secure than other options that are available, such as selecting the weakest encryption algorithm or using the most permissive access control restrictions. | |
| 1725 | By entering a less secure state, the product inherits the weaknesses associated with that state, making it easier to compromise. At the least, it causes administrators to have a false sense of security. This weakness typically occurs as a result of wanting to ""fail functional"" to minimize administration and support costs, instead of ""failing safe.""",,unclassified,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1726 | Failing Securely: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/349.html" | |
| 1727 | CWE-637,Unnecessary Complexity in Protection Mechanism (Not Using Economy of Mechanism) (Type: Class),"The software uses a more complex mechanism than necessary, which could lead to resultant weaknesses when the mechanism is not correctly understood, modeled, configured, implemented, or used. | |
| 1728 | Security mechanisms should be as simple as possible. Complex security mechanisms may engender partial implementations and compatibility problems, with resulting mismatches in assumptions and implemented security. A corollary of this principle is that data specifications should be as simple as possible, because complex data specifications result in complex validation code. Complex tasks and systems may also need to be guarded by complex security checks, so simple systems should be preferred.",,unclassified,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1729 | Economy of Mechanism: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/348.html" | |
| 1730 | CWE-638,Not Using Complete Mediation (Type: Class),"The software does not perform access checks on a resource every time the resource is accessed by an entity, which can create resultant weaknesses if that entity's rights or privileges change over time. | |
| 1731 | ",,unclassified,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1732 | Complete Mediation: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/346.html" | |
| 1733 | CWE-65,Windows Hard Link (Type: Variant),"The software, when opening a file or directory, does not sufficiently handle when the name is associated with a hard link to a target that is outside of the intended control sphere. This could allow an attacker to cause the software to operate on unauthorized files. | |
| 1734 | Failure for a system to check for hard links can result in vulnerability to different types of attacks. For example, an attacker can escalate their privileges if a file used by a privileged program is replaced with a hard link to a sensitive file (e.g. AUTOEXEC.BAT). When the process opens the file, the attacker can assume the privileges of that process, or prevent the program from accurately processing data.",,unclassified,"The Art of Software Security Assessment: Chapter 11, ""Links"", Page 676." | |
| 1735 | CWE-651,Information Exposure Through WSDL File (Type: Variant),"The Web services architecture may require exposing a WSDL file that contains information on the publicly accessible services and how callers of these services should interact with them (e.g. what parameters they expect and what types they return). | |
| 1736 | An information exposure may occur if any of the following apply: | |
| 1737 | The WSDL file is accessible to a wider audience than intended. | |
| 1738 | The WSDL file contains information on the methods/services that should not be publicly accessible or information about deprecated methods. This problem is made more likely due to the WSDL often being automatically generated from the code. | |
| 1739 | Information in the WSDL file helps guess names/locations of methods/resources that should not be publicly accessible.",,unclassified, | |
| 1740 | CWE-653,Insufficient Compartmentalization (Type: Base),"The product does not sufficiently compartmentalize functionality or processes that require different privilege levels, rights, or permissions. | |
| 1741 | When a weakness occurs in functionality that is accessible by lower-privileged users, then without strong boundaries, an attack might extend the scope of the damage to higher-privileged users.",,unclassified,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1742 | Separation of Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/357.html" | |
| 1743 | CWE-654,Reliance on a Single Factor in a Security Decision (Type: Base),"A protection mechanism relies exclusively, or to a large extent, on the evaluation of a single condition or the integrity of a single object or entity in order to make a decision about granting access to restricted resources or functionality. | |
| 1744 | When a weakness occurs in functionality that is accessible by lower-privileged users, then without strong boundaries, an attack might extend the scope of the damage to higher-privileged users.",,unclassified,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1745 | Separation of Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/357.html" | |
| 1746 | CWE-655,Insufficient Psychological Acceptability (Type: Base),"The software has a protection mechanism that is too difficult or inconvenient to use, encouraging non-malicious users to disable or bypass the mechanism, whether by accident or on purpose. | |
| 1747 | When a weakness occurs in functionality that is accessible by lower-privileged users, then without strong boundaries, an attack might extend the scope of the damage to higher-privileged users.",,unclassified,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1748 | Psychological Acceptability: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/354.html | |
| 1749 | Usability of Security: A Case Study: http://reports-archive.adm.cs.cmu.edu/anon/1998/CMU-CS-98-155.pdf | |
| 1750 | 24 Deadly Sins of Software Security: ""Sin 14: Poor Usability."" Page 217" | |
| 1751 | CWE-656,Reliance on Security Through Obscurity (Type: Base),"The software uses a protection mechanism whose strength depends heavily on its obscurity, such that knowledge of its algorithms or key data is sufficient to defeat the mechanism. | |
| 1752 | This reliance on ""security through obscurity"" can produce resultant weaknesses if an attacker is able to reverse engineer the inner workings of the mechanism. Note that obscurity can be one small part of defense in depth, since it can create more work for an attacker; however, it is a significant risk if used as the primary means of protection.",,unclassified,"RFC: 793, TRANSMISSION CONTROL PROTOCOL: http://www.ietf.org/rfc/rfc0793.txt | |
| 1753 | The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1754 | Never Assuming that Your Secrets Are Safe: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/352.html" | |
| 1755 | CWE-657,Violation of Secure Design Principles (Type: Class),"The product violates well-established principles for secure design. | |
| 1756 | This can introduce resultant weaknesses or make it easier for developers to introduce related weaknesses during implementation. Because code is centered around design, it can be resource-intensive to fix design problems.",,unclassified,"The Protection of Information in Computer Systems: http://web.mit.edu/Saltzer/www/publications/protection/ | |
| 1757 | Design Principles: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/358.html" | |
| 1758 | CWE-66,Improper Handling of File Names that Identify Virtual Resources (Type: Base),"The product does not handle or incorrectly handles a file name that identifies a ""virtual"" resource that is not directly specified within the directory that is associated with the file name, causing the product to perform file-based operations on a resource that is not a file. | |
| 1759 | Virtual file names are represented like normal file names, but they are effectively aliases for other resources that do not behave like normal files. Depending on their functionality, they could be alternate entities. They are not necessarily listed in directories.",,unclassified, | |
| 1760 | CWE-662,Improper Synchronization (Type: Base),"The software attempts to use a shared resource in an exclusive manner, but does not prevent or incorrectly prevents use of the resource by another thread or process. | |
| 1761 | Virtual file names are represented like normal file names, but they are effectively aliases for other resources that do not behave like normal files. Depending on their functionality, they could be alternate entities. They are not necessarily listed in directories.",,unclassified, | |
| 1762 | CWE-663,Use of a Non-reentrant Function in a Concurrent Context (Type: Base),"The software calls a non-reentrant function in a concurrent context in which a competing code sequence (e.g. thread or signal handler) may have an opportunity to call the same function or otherwise influence its state. | |
| 1763 | Virtual file names are represented like normal file names, but they are effectively aliases for other resources that do not behave like normal files. Depending on their functionality, they could be alternate entities. They are not necessarily listed in directories.",,unclassified,"Java Concurrency API: http://java.sun.com/j2se/1.5.0/docs/api/java/util/concurrent/locks/ReentrantLock.html | |
| 1764 | Use reentrant functions for safer signal handling: http://www.ibm.com/developerworks/linux/library/l-reent.html" | |
| 1765 | CWE-664,Improper Control of a Resource Through its Lifetime (Type: Class),"The software does not maintain or incorrectly maintains control over a resource throughout its lifetime of creation, use, and release. | |
| 1766 | Resources often have explicit instructions on how to be created, used and destroyed. When software does not follow these instructions, it can lead to unexpected behaviors and potentially exploitable states. | |
| 1767 | Even without explicit instructions, various principles are expected to be adhered to, such as ""Do not use an object until after its creation is complete,"" or ""do not use an object after it has been slated for destruction.""",,unclassified, | |
| 1768 | CWE-666,Operation on Resource in Wrong Phase of Lifetime (Type: Base),"The software performs an operation on a resource at the wrong phase of the resource's lifecycle, which can lead to unexpected behaviors. | |
| 1769 | When a developer wants to initialize, use or release a resource, it is important to follow the specifications outlined for how to operate on that resource and to ensure that the resource is in the expected state. In this case, the software wants to perform a normally valid operation, initialization, use or release, on a resource when it is in the incorrect phase of its lifetime.",,unclassified, | |
| 1770 | CWE-667,Improper Locking (Type: Base),"The software does not properly acquire a lock on a resource, or it does not properly release a lock on a resource, leading to unexpected resource state changes and behaviors. | |
| 1771 | When a developer wants to initialize, use or release a resource, it is important to follow the specifications outlined for how to operate on that resource and to ensure that the resource is in the expected state. In this case, the software wants to perform a normally valid operation, initialization, use or release, on a resource when it is in the incorrect phase of its lifetime.",,unclassified, | |
| 1772 | CWE-668,Exposure of Resource to Wrong Sphere (Type: Class),"The product exposes a resource to the wrong control sphere, providing unintended actors with inappropriate access to the resource. | |
| 1773 | Resources such as files and directories may be inadvertently exposed through mechanisms such as insecure permissions, or when a program accidentally operates on the wrong object. For example, a program may intend that private files can only be provided to a specific user. This effectively defines a control sphere that is intended to prevent attackers from accessing these private files. If the file permissions are insecure, then parties other than the user will be able to access those files. | |
| 1774 | A separate control sphere might effectively require that the user can only access the private files, but not any other files on the system. If the program does not ensure that the user is only requesting private files, then the user might be able to access other files on the system. | |
| 1775 | In either case, the end result is that a resource has been exposed to the wrong party.",,unclassified, | |
| 1776 | CWE-669,Incorrect Resource Transfer Between Spheres (Type: Class),"The product does not properly transfer a resource/behavior to another sphere, or improperly imports a resource/behavior from another sphere, in a manner that provides unintended control over that resource. | |
| 1777 | Resources such as files and directories may be inadvertently exposed through mechanisms such as insecure permissions, or when a program accidentally operates on the wrong object. For example, a program may intend that private files can only be provided to a specific user. This effectively defines a control sphere that is intended to prevent attackers from accessing these private files. If the file permissions are insecure, then parties other than the user will be able to access those files. | |
| 1778 | A separate control sphere might effectively require that the user can only access the private files, but not any other files on the system. If the program does not ensure that the user is only requesting private files, then the user might be able to access other files on the system. | |
| 1779 | In either case, the end result is that a resource has been exposed to the wrong party.",,unclassified, | |
| 1780 | CWE-670,Always-Incorrect Control Flow Implementation (Type: Class),"The code contains a control flow path that does not reflect the algorithm that the path is intended to implement, leading to incorrect behavior any time this path is navigated. | |
| 1781 | This weakness captures cases in which a particular code segment is always incorrect with respect to the algorithm that it is implementing. For example, if a C programmer intends to include multiple statements in a single block but does not include the enclosing braces (CWE-483), then the logic is always incorrect. This issue is in contrast to most weaknesses in which the code usually behaves correctly, except when it is externally manipulated in malicious ways.",,unclassified, | |
| 1782 | CWE-671,Lack of Administrator Control over Security (Type: Class),"The product uses security features in a way that prevents the product's administrator from tailoring security settings to reflect the environment in which the product is being used. This introduces resultant weaknesses or prevents it from operating at a level of security that is desired by the administrator. | |
| 1783 | If the product's administrator does not have the ability to manage security-related decisions at all times, then protecting the product from outside threats - including the product's developer - can become impossible. For example, a hard-coded account name and password cannot be changed by the administrator, thus exposing that product to attacks that the administrator can not prevent.",,unclassified, | |
| 1784 | CWE-672,Operation on a Resource after Expiration or Release (Type: Base),"The software uses, accesses, or otherwise operates on a resource after that resource has been expired, released, or revoked. | |
| 1785 | If the product's administrator does not have the ability to manage security-related decisions at all times, then protecting the product from outside threats - including the product's developer - can become impossible. For example, a hard-coded account name and password cannot be changed by the administrator, thus exposing that product to attacks that the administrator can not prevent.",,unclassified, | |
| 1786 | CWE-673,External Influence of Sphere Definition (Type: Class),"The product does not prevent the definition of control spheres from external actors. | |
| 1787 | Typically, a product defines its control sphere within the code itself, or through configuration by the product's administrator. In some cases, an external party can change the definition of the control sphere. This is typically a resultant weakness.",,unclassified, | |
| 1788 | CWE-674,Uncontrolled Recursion (Type: Base),"The product does not properly control the amount of recursion that takes place, which consumes excessive resources, such as allocated memory or the program stack. | |
| 1789 | Typically, a product defines its control sphere within the code itself, or through configuration by the product's administrator. In some cases, an external party can change the definition of the control sphere. This is typically a resultant weakness.",,unclassified, | |
| 1790 | CWE-675,Duplicate Operations on Resource (Type: Class),"The product performs the same operation on a resource two or more times, when the operation should only be applied once. | |
| 1791 | Typically, a product defines its control sphere within the code itself, or through configuration by the product's administrator. In some cases, an external party can change the definition of the control sphere. This is typically a resultant weakness.",,unclassified, | |
| 1792 | CWE-683,Function Call With Incorrect Order of Arguments (Type: Variant),"The software calls a function, procedure, or routine, but the caller specifies the arguments in an incorrect order, leading to resultant weaknesses. | |
| 1793 | While this weakness might be caught by the compiler in some languages, it can occur more frequently in cases in which the called function accepts variable numbers or types of arguments, such as format strings in C. It also can occur in languages or environments that do not enforce strong typing.",,unclassified, | |
| 1794 | CWE-684,Incorrect Provision of Specified Functionality (Type: Base),"The code does not function according to its published specifications, potentially leading to incorrect usage. | |
| 1795 | When providing functionality to an external party, it is important that the software behaves in accordance with the details specified. When requirements of nuances are not documented, the functionality may produce unintended behaviors for the caller, possibly leading to an exploitable state.",,unclassified, | |
| 1796 | CWE-685,Function Call With Incorrect Number of Arguments (Type: Variant),"The software calls a function, procedure, or routine, but the caller specifies too many arguments, or too few arguments, which may lead to undefined behavior and resultant weaknesses. | |
| 1797 | When providing functionality to an external party, it is important that the software behaves in accordance with the details specified. When requirements of nuances are not documented, the functionality may produce unintended behaviors for the caller, possibly leading to an exploitable state.",,unclassified, | |
| 1798 | CWE-686,Function Call With Incorrect Argument Type (Type: Variant),"The software calls a function, procedure, or routine, but the caller specifies an argument that is the wrong data type, which may lead to resultant weaknesses. | |
| 1799 | This weakness is most likely to occur in loosely typed languages, or in strongly typed languages in which the types of variable arguments cannot be enforced at compilation time, or where there is implicit casting.",,unclassified, | |
| 1800 | CWE-687,Function Call With Incorrectly Specified Argument Value (Type: Variant),"The software calls a function, procedure, or routine, but the caller specifies an argument that contains the wrong value, which may lead to resultant weaknesses. | |
| 1801 | This weakness is most likely to occur in loosely typed languages, or in strongly typed languages in which the types of variable arguments cannot be enforced at compilation time, or where there is implicit casting.",,unclassified, | |
| 1802 | CWE-688,Function Call With Incorrect Variable or Reference as Argument (Type: Variant),"The software calls a function, procedure, or routine, but the caller specifies the wrong variable or reference as one of the arguments, which may lead to undefined behavior and resultant weaknesses. | |
| 1803 | This weakness is most likely to occur in loosely typed languages, or in strongly typed languages in which the types of variable arguments cannot be enforced at compilation time, or where there is implicit casting.",,unclassified, | |
| 1804 | CWE-69,Improper Handling of Windows ::DATA Alternate Data Stream (Type: Variant),"The software does not properly prevent access to, or detect usage of, alternate data streams (ADS). | |
| 1805 | An attacker can use an ADS to hide information about a file (e.g. size, the name of the process) from a system or file browser tools such as Windows Explorer and 'dir' at the command line utility. Alternately, the attacker might be able to bypass intended access restrictions for the associated data fork.",,unclassified,"Windows NTFS Alternate Data Streams: http://www.securityfocus.com/infocus/1822 | |
| 1806 | Writing Secure Code" | |
| 1807 | CWE-691,Insufficient Control Flow Management (Type: Class),"The code does not sufficiently manage its control flow during execution, creating conditions in which the control flow can be modified in unexpected ways. | |
| 1808 | An attacker can use an ADS to hide information about a file (e.g. size, the name of the process) from a system or file browser tools such as Windows Explorer and 'dir' at the command line utility. Alternately, the attacker might be able to bypass intended access restrictions for the associated data fork.",,unclassified, | |
| 1809 | CWE-693,Protection Mechanism Failure (Type: Class),"The product does not use or incorrectly uses a protection mechanism that provides sufficient defense against directed attacks against the product. | |
| 1810 | This weakness covers three distinct situations. A ""missing"" protection mechanism occurs when the application does not define any mechanism against a certain class of attack. An ""insufficient"" protection mechanism might provide some defenses - for example, against the most common attacks - but it does not protect against everything that is intended. Finally, an ""ignored"" mechanism occurs when a mechanism is available and in active use within the product, but the developer has not applied it in some code path.",,unclassified, | |
| 1811 | CWE-694,Use of Multiple Resources with Duplicate Identifier (Type: Base),"The software uses multiple resources that can have the same identifier, in a context in which unique identifiers are required. | |
| 1812 | If the software assumes that each resource has a unique identifier, the software could operate on the wrong resource if attackers can cause multiple resources to be associated with the same identifier.",,unclassified, | |
| 1813 | CWE-695,Use of Low-Level Functionality (Type: Base),"The software uses low-level functionality that is explicitly prohibited by the framework or specification under which the software is supposed to operate. | |
| 1814 | The use of low-level functionality can violate the specification in unexpected ways that effectively disable built-in protection mechanisms, introduce exploitable inconsistencies, or otherwise expose the functionality to attack.",,unclassified, | |
| 1815 | CWE-696,Incorrect Behavior Order (Type: Class),"The software performs multiple related behaviors, but the behaviors are performed in the wrong order in ways which may produce resultant weaknesses. | |
| 1816 | The use of low-level functionality can violate the specification in unexpected ways that effectively disable built-in protection mechanisms, introduce exploitable inconsistencies, or otherwise expose the functionality to attack.",,unclassified, | |
| 1817 | CWE-697,Insufficient Comparison (Type: Class),"The software compares two entities in a security-relevant context, but the comparison is insufficient, which may lead to resultant weaknesses. | |
| 1818 | This weakness class covers several possibilities: | |
| 1819 | the comparison checks one factor incorrectly; | |
| 1820 | the comparison should consider multiple factors, but it does not check some of those factors at all.",,unclassified, | |
| 1821 | CWE-698,Execution After Redirect (EAR) (Type: Base),"The web application sends a redirect to another location, but instead of exiting, it executes additional code. | |
| 1822 | This weakness class covers several possibilities: | |
| 1823 | the comparison checks one factor incorrectly; | |
| 1824 | the comparison should consider multiple factors, but it does not check some of those factors at all.",,unclassified,Fear the EAR: Discovering and Mitigating Execution After Redirect Vulnerabilities: http://cs.ucsb.edu/~bboe/public/pubs/fear-the-ear-ccs2011.pdf | |
| 1825 | CWE-7,J2EE Misconfiguration: Missing Custom Error Page (Type: Variant),"The default error page of a web application should not display sensitive information about the software system. | |
| 1826 | A Web application must define a default error page for 4xx errors (e.g. 404), 5xx (e.g. 500) errors and catch java.lang.Throwable exceptions to prevent attackers from mining information from the application container's built-in error response.",,unclassified,19 Deadly Sins of Software Security | |
| 1827 | CWE-703,Improper Check or Handling of Exceptional Conditions (Type: Class),"The software does not properly anticipate or handle exceptional conditions that rarely occur during normal operation of the software. | |
| 1828 | A Web application must define a default error page for 4xx errors (e.g. 404), 5xx (e.g. 500) errors and catch java.lang.Throwable exceptions to prevent attackers from mining information from the application container's built-in error response.",,unclassified,"A Taxonomy of Security Faults in the UNIX Operating System: http://ftp.cerias.purdue.edu/pub/papers/taimur-aslam/aslam-taxonomy-msthesis.pdf | |
| 1829 | Use of A Taxonomy of Security Faults: http://csrc.nist.gov/nissc/1996/papers/NISSC96/paper057/PAPER.PDF | |
| 1830 | 24 Deadly Sins of Software Security: ""Sin 8: C++ Catastrophes."" Page 143" | |
| 1831 | CWE-704,Incorrect Type Conversion or Cast (Type: Class),"The software does not correctly convert an object, resource or structure from one type to a different type. | |
| 1832 | A Web application must define a default error page for 4xx errors (e.g. 404), 5xx (e.g. 500) errors and catch java.lang.Throwable exceptions to prevent attackers from mining information from the application container's built-in error response.",,unclassified, | |
| 1833 | CWE-705,Incorrect Control Flow Scoping (Type: Class),"The software does not properly return control flow to the proper location after it has completed a task or detected an unusual condition. | |
| 1834 | A Web application must define a default error page for 4xx errors (e.g. 404), 5xx (e.g. 500) errors and catch java.lang.Throwable exceptions to prevent attackers from mining information from the application container's built-in error response.",,unclassified, | |
| 1835 | CWE-706,Use of Incorrectly-Resolved Name or Reference (Type: Class),"The software uses a name or reference to access a resource, but the name/reference resolves to a resource that is outside of the intended control sphere. | |
| 1836 | A Web application must define a default error page for 4xx errors (e.g. 404), 5xx (e.g. 500) errors and catch java.lang.Throwable exceptions to prevent attackers from mining information from the application container's built-in error response.",,unclassified, | |
| 1837 | CWE-707,Improper Enforcement of Message or Data Structure (Type: Class),"The software does not enforce or incorrectly enforces that structured messages or data are well-formed before being read from an upstream component or sent to a downstream component. | |
| 1838 | If a message is malformed it may cause the message to be incorrectly interpreted. | |
| 1839 | This weakness typically applies in cases where the product prepares a control message that another process must act on, such as a command or query, and malicious input that was intended as data, can enter the control plane instead. However, this weakness also applies to more general cases where there are not always control implications.",,unclassified, | |
| 1840 | CWE-708,Incorrect Ownership Assignment (Type: Base),"The software assigns an owner to a resource, but the owner is outside of the intended control sphere. | |
| 1841 | This may allow the resource to be manipulated by actors outside of the intended control sphere.",,unclassified, | |
| 1842 | CWE-71,Apple .DS_Store (Type: Variant),"Software operating in a MAC OS environment, where .DS_Store is in effect, must carefully manage hard links, otherwise an attacker may be able to leverage a hard link from .DS_Store to overwrite arbitrary files and gain privileges. | |
| 1843 | This may allow the resource to be manipulated by actors outside of the intended control sphere.",,unclassified, | |
| 1844 | CWE-710,Coding Standards Violation (Type: Class),"The software does not follow certain coding rules for development, which can lead to resultant weaknesses or increase the severity of the associated vulnerabilities. | |
| 1845 | This may allow the resource to be manipulated by actors outside of the intended control sphere.",,unclassified, | |
| 1846 | CWE-72,Improper Handling of Apple HFS+ Alternate Data Stream Path (Type: Variant),"The software does not properly handle special paths that may identify the data or resource fork of a file on the HFS+ file system. | |
| 1847 | If the software chooses actions to take based on the file name, then if an attacker provides the data or resource fork, the software may take unexpected actions. Further, if the software intends to restrict access to a file, then an attacker might still be able to bypass intended access restrictions by requesting the data or resource fork for that file.",,unclassified,No description: http://docs.info.apple.com/article.html?artnum=300422 | |
| 1848 | CWE-733,Compiler Optimization Removal or Modification of Security-critical Code (Type: Base),"The developer builds a security-critical protection mechanism into the software but the compiler optimizes the program such that the mechanism is removed or modified. | |
| 1849 | When a resource is given a permissions setting that provides access to a wider range of actors than required, it could lead to the exposure of sensitive information, or the modification of that resource by unintended parties. This is especially dangerous when the resource is related to program configuration, execution or sensitive user data.",,unclassified,"Writing Secure Code: Chapter 9, ""A Compiler Optimization Caveat"" Page 322" | |
| 1850 | CWE-75,Failure to Sanitize Special Elements into a Different Plane (Special Element Injection) (Type: Class),"The software does not adequately filter user-controlled input for special elements with control implications. | |
| 1851 | This weakness can lead to a wide variety of resultant weaknesses, depending on the behavior of the exposed method. It can apply to any number of technologies and approaches, such as ActiveX controls, Java functions, IOCTLs, and so on. | |
| 1852 | The exposure can occur in a few different ways: | |
| 1853 | 1) The function/method was never intended to be exposed to outside actors. | |
| 1854 | 2) The function/method was only intended to be accessible to a limited set of actors, such as Internet-based access from a single web site.",,unclassified, | |
| 1855 | CWE-756,Missing Custom Error Page (Type: Class),"The software does not return custom error pages to the user, possibly exposing sensitive information. | |
| 1856 | The programmer may assume that certain events or conditions will never occur or do not need to be worried about, such as low memory conditions, lack of access to resources due to restrictive permissions, or misbehaving clients or components. However, attackers may intentionally trigger these unusual conditions, thus violating the programmer's assumptions, possibly introducing instability, incorrect behavior, or a vulnerability. | |
| 1857 | Note that this entry is not exclusively about the use of exceptions and exception handling, which are mechanisms for both checking and handling unusual or unexpected conditions.",,unclassified, | |
| 1858 | CWE-757,Selection of Less-Secure Algorithm During Negotiation (Algorithm Downgrade) (Type: Class),"A protocol or its implementation supports interaction between multiple actors and allows those actors to negotiate which algorithm should be used as a protection mechanism such as encryption or authentication, but it does not select the strongest algorithm that is available to both parties. | |
| 1859 | When a security mechanism can be forced to downgrade to use a less secure algorithm, this can make it easier for attackers to compromise the software by exploiting weaker algorithm. The victim might not be aware that the less secure algorithm is being used. For example, if an attacker can force a communications channel to use cleartext instead of strongly-encrypted data, then the attacker could read the channel by sniffing, instead of going through extra effort of trying to decrypt the data using brute force techniques.",,unclassified, | |
| 1860 | CWE-758,"Reliance on Undefined, Unspecified, or Implementation-Defined Behavior (Type: Class)","The software uses an API function, data structure, or other entity in a way that relies on properties that are not always guaranteed to hold for that entity. | |
| 1861 | This can lead to resultant weaknesses when the required properties change, such as when the software is ported to a different platform or if an interaction error (CWE-435) occurs.",,unclassified, | |
| 1862 | CWE-759,Use of a One-Way Hash without a Salt (Type: Base),"The software uses a one-way cryptographic hash against an input that should not be reversible, such as a password, but the software does not also use a salt as part of the input. | |
| 1863 | This makes it easier for attackers to pre-compute the hash value using dictionary attack techniques such as rainbow tables. | |
| 1864 | It should be noted that, despite common perceptions, the use of a good salt with a hash does not sufficiently increase the effort for an attacker who is targeting an individual password, or who has a large amount of computing resources available, such as with cloud-based services or specialized, inexpensive hardware. Offline password cracking can still be effective if the hash function is not expensive to compute; many cryptographic functions are designed to be efficient and can be vulnerable to attacks using massive computing resources, even if the hash is cryptographically strong. The use of a salt only slightly increases the computing requirements for an attacker compared to other strategies such as adaptive hash functions. See CWE-916 for more details.",,unclassified,"bcrypt: http://bcrypt.sourceforge.net/ | |
| 1865 | Tarsnap - The scrypt key derivation function and encryption utility: http://www.tarsnap.com/scrypt.html | |
| 1866 | RFC2898 - PKCS #5: Password-Based Cryptography Specification Version 2.0: http://tools.ietf.org/html/rfc2898 | |
| 1867 | How Companies Can Beef Up Password Security (interview with Thomas H. Ptacek): http://krebsonsecurity.com/2012/06/how-companies-can-beef-up-password-security/ | |
| 1868 | Speed Hashing: http://www.codinghorror.com/blog/2012/04/speed-hashing.html | |
| 1869 | Password security: past, present, future: http://www.openwall.com/presentations/PHDays2012-Password-Security/ | |
| 1870 | Password Storage Cheat Sheet: https://www.owasp.org/index.php/Password_Storage_Cheat_Sheet | |
| 1871 | Enough With The Rainbow Tables: What You Need To Know About Secure Password Schemes: http://www.securityfocus.com/blogs/262 | |
| 1872 | The Importance of Being Canonical: http://erratasec.blogspot.com/2009/02/importance-of-being-canonical.html | |
| 1873 | Password Hashing: http://phpsec.org/articles/2005/password-hashing.html | |
| 1874 | Rainbow Hash Cracking: http://www.codinghorror.com/blog/archives/000949.html | |
| 1875 | Rainbow table: http://en.wikipedia.org/wiki/Rainbow_table | |
| 1876 | Writing Secure Code: Chapter 9, ""Creating a Salted Hash"" Page 302 | |
| 1877 | The Art of Software Security Assessment: Chapter 2, ""Salt Values"", Page 46. | |
| 1878 | How To Safely Store A Password: http://codahale.com/how-to-safely-store-a-password/ | |
| 1879 | Our password hashing has no clothes: http://www.troyhunt.com/2012/06/our-password-hashing-has-no-clothes.html | |
| 1880 | Should we really use bcrypt/scrypt?: http://www.analyticalengine.net/2012/06/should-we-really-use-bcryptscrypt/" | |
| 1881 | CWE-760,Use of a One-Way Hash with a Predictable Salt (Type: Base),"The software uses a one-way cryptographic hash against an input that should not be reversible, such as a password, but the software uses a predictable salt as part of the input. | |
| 1882 | This makes it easier for attackers to pre-compute the hash value using dictionary attack techniques such as rainbow tables, effectively disabling the protection that an unpredictable salt would provide. | |
| 1883 | It should be noted that, despite common perceptions, the use of a good salt with a hash does not sufficiently increase the effort for an attacker who is targeting an individual password, or who has a large amount of computing resources available, such as with cloud-based services or specialized, inexpensive hardware. Offline password cracking can still be effective if the hash function is not expensive to compute; many cryptographic functions are designed to be efficient and can be vulnerable to attacks using massive computing resources, even if the hash is cryptographically strong. The use of a salt only slightly increases the computing requirements for an attacker compared to other strategies such as adaptive hash functions. See CWE-916 for more details.",,unclassified,"bcrypt: http://bcrypt.sourceforge.net/ | |
| 1884 | Tarsnap - The scrypt key derivation function and encryption utility: http://www.tarsnap.com/scrypt.html | |
| 1885 | RFC2898 - PKCS #5: Password-Based Cryptography Specification Version 2.0: http://tools.ietf.org/html/rfc2898 | |
| 1886 | How Companies Can Beef Up Password Security (interview with Thomas H. Ptacek): http://krebsonsecurity.com/2012/06/how-companies-can-beef-up-password-security/ | |
| 1887 | Speed Hashing: http://www.codinghorror.com/blog/2012/04/speed-hashing.html | |
| 1888 | Password security: past, present, future: http://www.openwall.com/presentations/PHDays2012-Password-Security/ | |
| 1889 | Password Storage Cheat Sheet: https://www.owasp.org/index.php/Password_Storage_Cheat_Sheet | |
| 1890 | Enough With The Rainbow Tables: What You Need To Know About Secure Password Schemes: http://www.securityfocus.com/blogs/262 | |
| 1891 | The Importance of Being Canonical: http://erratasec.blogspot.com/2009/02/importance-of-being-canonical.html | |
| 1892 | Password Hashing: http://phpsec.org/articles/2005/password-hashing.html | |
| 1893 | Rainbow Hash Cracking: http://www.codinghorror.com/blog/archives/000949.html | |
| 1894 | Rainbow table: http://en.wikipedia.org/wiki/Rainbow_table | |
| 1895 | Writing Secure Code: Chapter 9, ""Creating a Salted Hash"" Page 302 | |
| 1896 | The Art of Software Security Assessment: Chapter 2, ""Salt Values"", Page 46. | |
| 1897 | How To Safely Store A Password: http://codahale.com/how-to-safely-store-a-password/ | |
| 1898 | Our password hashing has no clothes: http://www.troyhunt.com/2012/06/our-password-hashing-has-no-clothes.html | |
| 1899 | Should we really use bcrypt/scrypt?: http://www.analyticalengine.net/2012/06/should-we-really-use-bcryptscrypt/" | |
| 1900 | CWE-761,Free of Pointer not at Start of Buffer (Type: Variant),"The application calls free() on a pointer to a memory resource that was allocated on the heap, but the pointer is not at the start of the buffer. | |
| 1901 | This can cause the application to crash, or in some cases, modify critical program variables or execute code. | |
| 1902 | This weakness often occurs when the memory is allocated explicitly on the heap with one of the malloc() family functions and free() is called, but pointer arithmetic has caused the pointer to be in the interior or end of the buffer.",,unclassified,"boost C++ Library Smart Pointers: http://www.boost.org/doc/libs/1_38_0/libs/smart_ptr/smart_ptr.htm | |
| 1903 | Valgrind: http://valgrind.org/" | |
| 1904 | CWE-763,Release of Invalid Pointer or Reference (Type: Base),"The application attempts to return a memory resource to the system, but calls the wrong release function or calls the appropriate release function incorrectly. | |
| 1905 | This weakness can take several forms, such as: | |
| 1906 | The memory was allocated, explicitly or implicitly, via one memory management method and deallocated using a different, non-compatible function (CWE-762). | |
| 1907 | The function calls or memory management routines chosen are appropriate, however they are used incorrectly, such as in CWE-761.",,unclassified,"boost C++ Library Smart Pointers: http://www.boost.org/doc/libs/1_38_0/libs/smart_ptr/smart_ptr.htm | |
| 1908 | Valgrind: http://valgrind.org/" | |
| 1909 | CWE-764,Multiple Locks of a Critical Resource (Type: Variant),"The software locks a critical resource more times than intended, leading to an unexpected state in the system. | |
| 1910 | When software is operating in a concurrent environment and repeatedly locks a critical resource, the consequences will vary based on the type of lock, the lock's implementation, and the resource being protected. In some situations such as with semaphores, the resources are pooled and extra locking calls will reduce the size of the total available pool, possibly leading to degraded performance or a denial of service. If this can be triggered by an attacker, it will be similar to an unrestricted lock (CWE-412). In the context of a binary lock, it is likely that any duplicate locking attempts will never succeed since the lock is already held and progress may not be possible.",,unclassified, | |
| 1911 | CWE-765,Multiple Unlocks of a Critical Resource (Type: Variant),"The software unlocks a critical resource more times than intended, leading to an unexpected state in the system. | |
| 1912 | When software is operating in a concurrent environment and repeatedly unlocks a critical resource, the consequences will vary based on the type of lock, the lock's implementation, and the resource being protected. In some situations such as with semaphores, the resources are pooled and extra calls to unlock will increase the count for the number of available resources, likely resulting in a crash or unpredictable behavior when the system nears capacity.",,unclassified, | |
| 1913 | CWE-785,Use of Path Manipulation Function without Maximum-sized Buffer (Type: Variant),"The software invokes a function for normalizing paths or file names, but it provides an output buffer that is smaller than the maximum possible size, such as PATH_MAX. | |
| 1914 | Passing an inadequately-sized output buffer to a path manipulation function can result in a buffer overflow. Such functions include realpath(), readlink(), PathAppend(), and others.",,unclassified, | |
| 1915 | CWE-786,Access of Memory Location Before Start of Buffer (Type: Base),"The software reads or writes to a buffer using an index or pointer that references a memory location prior to the beginning of the buffer. | |
| 1916 | This typically occurs when a pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used.",,unclassified, | |
| 1917 | CWE-787,Out-of-bounds Write (Type: Base),"The software writes data past the end, or before the beginning, of the intended buffer. | |
| 1918 | This typically occurs when the pointer or its index is incremented or decremented to a position beyond the bounds of the buffer or when pointer arithmetic results in a position outside of the valid memory location to name a few. This may result in corruption of sensitive information, a crash, or code execution among other things.",,unclassified, | |
| 1919 | CWE-788,Access of Memory Location After End of Buffer (Type: Base),"The software reads or writes to a buffer using an index or pointer that references a memory location after the end of the buffer. | |
| 1920 | This typically occurs when a pointer or its index is decremented to a position before the buffer, when pointer arithmetic results in a position before the beginning of the valid memory location, or when a negative index is used. These problems may be resultant from missing sentinel values (CWE-463) or trusting a user-influenced input length variable.",,unclassified, | |
| 1921 | CWE-790,Improper Filtering of Special Elements (Type: Class),"The software receives data from an upstream component, but does not filter or incorrectly filters special elements before sending it to a downstream component. | |
| 1922 | Cross-site scripting (XSS) vulnerabilities occur when: | |
| 1923 | 1. Untrusted data enters a web application, typically from a web request. | |
| 1924 | 2. The web application dynamically generates a web page that contains this untrusted data. | |
| 1925 | 3. During page generation, the application does not prevent the data from containing content that is executable by a web browser, such as JavaScript, HTML tags, HTML attributes, mouse events, Flash, ActiveX, etc. | |
| 1926 | 4. A victim visits the generated web page through a web browser, which contains malicious script that was injected using the untrusted data. | |
| 1927 | 5. Since the script comes from a web page that was sent by the web server, the victim's web browser executes the malicious script in the context of the web server's domain. | |
| 1928 | 6. This effectively violates the intention of the web browser's same-origin policy, which states that scripts in one domain should not be able to access resources or run code in a different domain. | |
| 1929 | There are three main kinds of XSS: | |
| 1930 | The server reads data directly from the HTTP request and reflects it back in the HTTP response. Reflected XSS exploits occur when an attacker causes a victim to supply dangerous content to a vulnerable web application, which is then reflected back to the victim and executed by the web browser. The most common mechanism for delivering malicious content is to include it as a parameter in a URL that is posted publicly or e-mailed directly to the victim. URLs constructed in this manner constitute the core of many phishing schemes, whereby an attacker convinces a victim to visit a URL that refers to a vulnerable site. After the site reflects the attacker's content back to the victim, the content is executed by the victim's browser. | |
| 1931 | The application stores dangerous data in a database, message forum, visitor log, or other trusted data store. At a later time, the dangerous data is subsequently read back into the application and included in dynamic content. From an attacker's perspective, the optimal place to inject malicious content is in an area that is displayed to either many users or particularly interesting users. Interesting users typically have elevated privileges in the application or interact with sensitive data that is valuable to the attacker. If one of these users executes malicious content, the attacker may be able to perform privileged operations on behalf of the user or gain access to sensitive data belonging to the user. For example, the attacker might inject XSS into a log message, which might not be handled properly when an administrator views the logs. | |
| 1932 | In DOM-based XSS, the client performs the injection of XSS into the page; in the other types, the server performs the injection. DOM-based XSS generally involves server-controlled, trusted script that is sent to the client, such as Javascript that performs sanity checks on a form before the user submits it. If the server-supplied script processes user-supplied data and then injects it back into the web page (such as with dynamic HTML), then DOM-based XSS is possible. | |
| 1933 | Once the malicious script is injected, the attacker can perform a variety of malicious activities. The attacker could transfer private information, such as cookies that may include session information, from the victim's machine to the attacker. The attacker could send malicious requests to a web site on behalf of the victim, which could be especially dangerous to the site if the victim has administrator privileges to manage that site. Phishing attacks could be used to emulate trusted web sites and trick the victim into entering a password, allowing the attacker to compromise the victim's account on that web site. Finally, the script could exploit a vulnerability in the web browser itself possibly taking over the victim's machine, sometimes referred to as ""drive-by hacking."" | |
| 1934 | In many cases, the attack can be launched without the victim even being aware of it. Even with careful users, attackers frequently use a variety of methods to encode the malicious portion of the attack, such as URL encoding or Unicode, so the request looks less suspicious.",,unclassified, | |
| 1935 | CWE-791,Incomplete Filtering of Special Elements (Type: Base),"The software receives data from an upstream component, but does not completely filter special elements before sending it to a downstream component. | |
| 1936 | Cross-site scripting (XSS) vulnerabilities occur when: | |
| 1937 | 1. Untrusted data enters a web application, typically from a web request. | |
| 1938 | 2. The web application dynamically generates a web page that contains this untrusted data. | |
| 1939 | 3. During page generation, the application does not prevent the data from containing content that is executable by a web browser, such as JavaScript, HTML tags, HTML attributes, mouse events, Flash, ActiveX, etc. | |
| 1940 | 4. A victim visits the generated web page through a web browser, which contains malicious script that was injected using the untrusted data. | |
| 1941 | 5. Since the script comes from a web page that was sent by the web server, the victim's web browser executes the malicious script in the context of the web server's domain. | |
| 1942 | 6. This effectively violates the intention of the web browser's same-origin policy, which states that scripts in one domain should not be able to access resources or run code in a different domain. | |
| 1943 | There are three main kinds of XSS: | |
| 1944 | The server reads data directly from the HTTP request and reflects it back in the HTTP response. Reflected XSS exploits occur when an attacker causes a victim to supply dangerous content to a vulnerable web application, which is then reflected back to the victim and executed by the web browser. The most common mechanism for delivering malicious content is to include it as a parameter in a URL that is posted publicly or e-mailed directly to the victim. URLs constructed in this manner constitute the core of many phishing schemes, whereby an attacker convinces a victim to visit a URL that refers to a vulnerable site. After the site reflects the attacker's content back to the victim, the content is executed by the victim's browser. | |
| 1945 | The application stores dangerous data in a database, message forum, visitor log, or other trusted data store. At a later time, the dangerous data is subsequently read back into the application and included in dynamic content. From an attacker's perspective, the optimal place to inject malicious content is in an area that is displayed to either many users or particularly interesting users. Interesting users typically have elevated privileges in the application or interact with sensitive data that is valuable to the attacker. If one of these users executes malicious content, the attacker may be able to perform privileged operations on behalf of the user or gain access to sensitive data belonging to the user. For example, the attacker might inject XSS into a log message, which might not be handled properly when an administrator views the logs. | |
| 1946 | In DOM-based XSS, the client performs the injection of XSS into the page; in the other types, the server performs the injection. DOM-based XSS generally involves server-controlled, trusted script that is sent to the client, such as Javascript that performs sanity checks on a form before the user submits it. If the server-supplied script processes user-supplied data and then injects it back into the web page (such as with dynamic HTML), then DOM-based XSS is possible. | |
| 1947 | Once the malicious script is injected, the attacker can perform a variety of malicious activities. The attacker could transfer private information, such as cookies that may include session information, from the victim's machine to the attacker. The attacker could send malicious requests to a web site on behalf of the victim, which could be especially dangerous to the site if the victim has administrator privileges to manage that site. Phishing attacks could be used to emulate trusted web sites and trick the victim into entering a password, allowing the attacker to compromise the victim's account on that web site. Finally, the script could exploit a vulnerability in the web browser itself possibly taking over the victim's machine, sometimes referred to as ""drive-by hacking."" | |
| 1948 | In many cases, the attack can be launched without the victim even being aware of it. Even with careful users, attackers frequently use a variety of methods to encode the malicious portion of the attack, such as URL encoding or Unicode, so the request looks less suspicious.",,unclassified, | |
| 1949 | CWE-792,Incomplete Filtering of One or More Instances of Special Elements (Type: Variant),"The software receives data from an upstream component, but does not completely filter one or more instances of special elements before sending it to a downstream component. | |
| 1950 | Incomplete filtering of this nature involves either | |
| 1951 | only filtering a single instance of a special element when more exist, or | |
| 1952 | not filtering all instances or all elements where multiple special elements exist.",,unclassified, | |
| 1953 | CWE-793,Only Filtering One Instance of a Special Element (Type: Variant),"The software receives data from an upstream component, but only filters a single instance of a special element before sending it to a downstream component. | |
| 1954 | Incomplete filtering of this nature may be location-dependent, as in only the first or last element is filtered.",,unclassified, | |
| 1955 | CWE-794,Incomplete Filtering of Multiple Instances of Special Elements (Type: Variant),"The software receives data from an upstream component, but does not filter all instances of a special element before sending it to a downstream component. | |
| 1956 | Incomplete filtering of this nature may be applied to | |
| 1957 | sequential elements (special elements that appear next to each other) or | |
| 1958 | non-sequential elements (special elements that appear multiple times in different locations).",,unclassified, | |
| 1959 | CWE-795,Only Filtering Special Elements at a Specified Location (Type: Base),"The software receives data from an upstream component, but only accounts for special elements at a specified location, thereby missing remaining special elements that may exist before sending it to a downstream component. | |
| 1960 | A filter might only account for instances of special elements when they occur: | |
| 1961 | relative to a marker (e.g. ""at the beginning/end of string; the second argument""), or | |
| 1962 | at an absolute position (e.g. ""byte number 10""). | |
| 1963 | This may leave special elements in the data that did not match the filter position, but still may be dangerous.",,unclassified, | |
| 1964 | CWE-796,Only Filtering Special Elements Relative to a Marker (Type: Variant),"The software receives data from an upstream component, but only accounts for special elements positioned relative to a marker (e.g. ""at the beginning/end of a string; the second argument""), thereby missing remaining special elements that may exist before sending it to a downstream component. | |
| 1965 | A filter might only account for instances of special elements when they occur: | |
| 1966 | relative to a marker (e.g. ""at the beginning/end of string; the second argument""), or | |
| 1967 | at an absolute position (e.g. ""byte number 10""). | |
| 1968 | This may leave special elements in the data that did not match the filter position, but still may be dangerous.",,unclassified, | |
| 1969 | CWE-797,Only Filtering Special Elements at an Absolute Position (Type: Variant),"The software receives data from an upstream component, but only accounts for special elements at an absolute position (e.g. ""byte number 10""), thereby missing remaining special elements that may exist before sending it to a downstream component. | |
| 1970 | A filter might only account for instances of special elements when they occur: | |
| 1971 | relative to a marker (e.g. ""at the beginning/end of string; the second argument""), or | |
| 1972 | at an absolute position (e.g. ""byte number 10""). | |
| 1973 | This may leave special elements in the data that did not match the filter position, but still may be dangerous.",,unclassified, | |
| 1974 | CWE-799,Improper Control of Interaction Frequency (Type: Class),"The software does not properly limit the number or frequency of interactions that it has with an actor, such as the number of incoming requests. | |
| 1975 | This can allow the actor to perform actions more frequently than expected. The actor could be a human or an automated process such as a virus or bot. This could be used to cause a denial of service, compromise program logic (such as limiting humans to a single vote), or other consequences. For example, an authentication routine might not limit the number of times an attacker can guess a password. Or, a web site might conduct a poll but only expect humans to vote a maximum of once a day.",,unclassified,Insufficient Anti-automation: http://projects.webappsec.org/Insufficient+Anti-automation | |
| 1976 | CWE-8,J2EE Misconfiguration: Entity Bean Declared Remote (Type: Variant),"When an application exposes a remote interface for an entity bean, it might also expose methods that get or set the bean's data. These methods could be leveraged to read sensitive information, or to change data in ways that violate the application's expectations, potentially leading to other vulnerabilities. | |
| 1977 | This can allow the actor to perform actions more frequently than expected. The actor could be a human or an automated process such as a virus or bot. This could be used to cause a denial of service, compromise program logic (such as limiting humans to a single vote), or other consequences. For example, an authentication routine might not limit the number of times an attacker can guess a password. Or, a web site might conduct a poll but only expect humans to vote a maximum of once a day.",,unclassified, | |
| 1978 | CWE-81,Improper Neutralization of Script in an Error Message Web Page (Type: Variant),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes special characters that could be interpreted as web-scripting elements when they are sent to an error page. | |
| 1979 | Error pages may include customized 403 Forbidden or 404 Not Found pages. | |
| 1980 | When an attacker can trigger an error that contains unneutralized input, then cross-site scripting attacks may be possible.",,unclassified,"24 Deadly Sins of Software Security: ""Sin 11: Failure to Handle Errors Correctly."" Page 183" | |
| 1981 | CWE-82,Improper Neutralization of Script in Attributes of IMG Tags in a Web Page (Type: Variant),"The web application does not neutralize or incorrectly neutralizes scripting elements within attributes of HTML IMG tags, such as the src attribute. | |
| 1982 | Attackers can embed XSS exploits into the values for IMG attributes (e.g. SRC) that is streamed and then executed in a victim's browser. Note that when the page is loaded into a user's browsers, the exploit will automatically execute.",,unclassified, | |
| 1983 | CWE-820,Missing Synchronization (Type: Base),"The software utilizes a shared resource in a concurrent manner but does not attempt to synchronize access to the resource. | |
| 1984 | If access to a shared resource is not synchronized, then the resource may not be in a state that is expected by the software. This might lead to unexpected or insecure behaviors, especially if an attacker can influence the shared resource.",,unclassified, | |
| 1985 | CWE-821,Incorrect Synchronization (Type: Base),"The software utilizes a shared resource in a concurrent manner but it does not correctly synchronize access to the resource. | |
| 1986 | If access to a shared resource is not correctly synchronized, then the resource may not be in a state that is expected by the software. This might lead to unexpected or insecure behaviors, especially if an attacker can influence the shared resource.",,unclassified, | |
| 1987 | CWE-822,Untrusted Pointer Dereference (Type: Base),"The program obtains a value from an untrusted source, converts this value to a pointer, and dereferences the resulting pointer. | |
| 1988 | An attacker can supply a pointer for memory locations that the program is not expecting. If the pointer is dereferenced for a write operation, the attack might allow modification of critical program state variables, cause a crash, or execute code. If the dereferencing operation is for a read, then the attack might allow reading of sensitive data, cause a crash, or set a program variable to an unexpected value (since the value will be read from an unexpected memory location). | |
| 1989 | There are several variants of this weakness, including but not necessarily limited to: | |
| 1990 | The untrusted value is directly invoked as a function call. | |
| 1991 | In OS kernels or drivers where there is a boundary between ""userland"" and privileged memory spaces, an untrusted pointer might enter through an API or system call (see CWE-781 for one such example). | |
| 1992 | Inadvertently accepting the value from an untrusted control sphere when it did not have to be accepted as input at all. This might occur when the code was originally developed to be run by a single user in a non-networked environment, and the code is then ported to or otherwise exposed to a networked environment.",,unclassified, | |
| 1993 | CWE-823,Use of Out-of-range Pointer Offset (Type: Base),"The program performs pointer arithmetic on a valid pointer, but it uses an offset that can point outside of the intended range of valid memory locations for the resulting pointer. | |
| 1994 | While a pointer can contain a reference to any arbitrary memory location, a program typically only intends to use the pointer to access limited portions of memory, such as contiguous memory used to access an individual array. | |
| 1995 | Programs may use offsets in order to access fields or sub-elements stored within structured data. The offset might be out-of-range if it comes from an untrusted source, is the result of an incorrect calculation, or occurs because of another error. | |
| 1996 | If an attacker can control or influence the offset so that it points outside of the intended boundaries of the structure, then the attacker may be able to read or write to memory locations that are used elsewhere in the program. As a result, the attack might change the state of the software as accessed through program variables, cause a crash or instable behavior, and possibly lead to code execution.",,unclassified,"The Art of Software Security Assessment: Chapter 6, ""Pointer Arithmetic"", Page 277." | |
| 1997 | CWE-824,Access of Uninitialized Pointer (Type: Base),"The program accesses or uses a pointer that has not been initialized. | |
| 1998 | If the pointer contains an uninitialized value, then the value might not point to a valid memory location. This could cause the program to read from or write to unexpected memory locations, leading to a denial of service. If the uninitialized pointer is used as a function call, then arbitrary functions could be invoked. If an attacker can influence the portion of uninitialized memory that is contained in the pointer, this weakness could be leveraged to execute code or perform other attacks. | |
| 1999 | Depending on memory layout, associated memory management behaviors, and program operation, the attacker might be able to influence the contents of the uninitialized pointer, thus gaining more fine-grained control of the memory location to be accessed.",,unclassified,"The Art of Software Security Assessment: Chapter 7, ""Variable Initialization"", Page 312." | |
| 2000 | CWE-825,Expired Pointer Dereference (Type: Base),"The program dereferences a pointer that contains a location for memory that was previously valid, but is no longer valid. | |
| 2001 | When a program releases memory, but it maintains a pointer to that memory, then the memory might be re-allocated at a later time. If the original pointer is accessed to read or write data, then this could cause the program to read or modify data that is in use by a different function or process. Depending on how the newly-allocated memory is used, this could lead to a denial of service, information exposure, or code execution.",,unclassified, | |
| 2002 | CWE-826,Premature Release of Resource During Expected Lifetime (Type: Base),"The program releases a resource that is still intended to be used by the program itself or another actor. | |
| 2003 | This weakness focuses on errors in which the program should not release a resource, but performs the release anyway. This is different than a weakness in which the program releases a resource at the appropriate time, but it maintains a reference to the resource, which it later accesses. For this weaknesses, the resource should still be valid upon the subsequent access. | |
| 2004 | When a program releases a resource that is still being used, it is possible that operations will still be taken on this resource, which may have been repurposed in the meantime, leading to issues similar to CWE-825. Consequences may include denial of service, information exposure, or code execution.",,unclassified, | |
| 2005 | CWE-827,Improper Control of Document Type Definition (Type: Base),"The software does not restrict a reference to a Document Type Definition (DTD) to the intended control sphere. This might allow attackers to reference arbitrary DTDs, possibly causing the software to expose files, consume excessive system resources, or execute arbitrary http requests on behalf of the attacker. | |
| 2006 | As DTDs are processed, they might try to read or include files on the machine performing the parsing. If an attacker is able to control the DTD, then the attacker might be able to specify sensitive resources or requests or provide malicious content. | |
| 2007 | For example, the SOAP specification prohibits SOAP messages from containing DTDs.",,unclassified,Apache CXF Security Advisory (CVE-2010-2076): http://svn.apache.org/repos/asf/cxf/trunk/security/CVE-2010-2076.pdf | |
| 2008 | CWE-828,Signal Handler with Functionality that is not Asynchronous-Safe (Type: Base),"The software defines a signal handler that contains code sequences that are not asynchronous-safe, i.e., the functionality is not reentrant, or it can be interrupted. | |
| 2009 | This can lead to an unexpected system state with a variety of potential consequences depending on context, including denial of service and code execution. | |
| 2010 | Signal handlers are typically intended to interrupt normal functionality of a program, or even other signals, in order to notify the process of an event. When a signal handler uses global or static variables, or invokes functions that ultimately depend on such state or its associated metadata, then it could corrupt system state that is being used by normal functionality. This could subject the program to race conditions or other weaknesses that allow an attacker to cause the program state to be corrupted. While denial of service is frequently the consequence, in some cases this weakness could be leveraged for code execution. | |
| 2011 | There are several different scenarios that introduce this issue: | |
| 2012 | Invocation of non-reentrant functions from within the handler. One example is malloc(), which modifies internal global variables as it manages memory. Very few functions are actually reentrant. | |
| 2013 | Code sequences (not necessarily function calls) contain non-atomic use of global variables, or associated metadata or structures, that can be accessed by other functionality of the program, including other signal handlers. Frequently, the same function is registered to handle multiple signals. | |
| 2014 | The signal handler function is intended to run at most one time, but instead it can be invoked multiple times. This could happen by repeated delivery of the same signal, or by delivery of different signals that have the same handler function (CWE-831). | |
| 2015 | Note that in some environments or contexts, it might be possible for the signal handler to be interrupted itself. | |
| 2016 | If both a signal handler and the normal behavior of the software have to operate on the same set of state variables, and a signal is received in the middle of the normal execution's modifications of those variables, the variables may be in an incorrect or corrupt state during signal handler execution, and possibly still incorrect or corrupt upon return.",,unclassified,"Delivering Signals for Fun and Profit: http://lcamtuf.coredump.cx/signals.txt | |
| 2017 | Race Condition: Signal Handling: http://www.fortify.com/vulncat/en/vulncat/cpp/race_condition_signal_handling.html" | |
| 2018 | CWE-829,Inclusion of Functionality from Untrusted Control Sphere (Type: Class),"The software imports, requires, or includes executable functionality (such as a library) from a source that is outside of the intended control sphere. | |
| 2019 | When including third-party functionality, such as a web widget, library, or other source of functionality, the software must effectively trust that functionality. Without sufficient protection mechanisms, the functionality could be malicious in nature (either by coming from an untrusted source, being spoofed, or being modified in transit from a trusted source). The functionality might also contain its own weaknesses, or grant access to additional functionality and state information that should be kept private to the base system, such as system state information, sensitive application data, or the DOM of a web application. | |
| 2020 | This might lead to many different consequences depending on the included functionality, but some examples include injection of malware, information exposure by granting excessive privileges or permissions to the untrusted functionality, DOM-based XSS vulnerabilities, stealing user's cookies, or open redirect to malware (CWE-601).",,unclassified,"OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 2021 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html" | |
| 2022 | CWE-83,Improper Neutralization of Script in Attributes in a Web Page (Type: Variant),"The software does not neutralize or incorrectly neutralizes ""javascript:"" or other URIs from dangerous attributes within tags, such as onmouseover, onload, onerror, or style. | |
| 2023 | When including third-party functionality, such as a web widget, library, or other source of functionality, the software must effectively trust that functionality. Without sufficient protection mechanisms, the functionality could be malicious in nature (either by coming from an untrusted source, being spoofed, or being modified in transit from a trusted source). The functionality might also contain its own weaknesses, or grant access to additional functionality and state information that should be kept private to the base system, such as system state information, sensitive application data, or the DOM of a web application. | |
| 2024 | This might lead to many different consequences depending on the included functionality, but some examples include injection of malware, information exposure by granting excessive privileges or permissions to the untrusted functionality, DOM-based XSS vulnerabilities, stealing user's cookies, or open redirect to malware (CWE-601).",,unclassified, | |
| 2025 | CWE-830,Inclusion of Web Functionality from an Untrusted Source (Type: Base),"The software includes web functionality (such as a web widget) from another domain, which causes it to operate within the domain of the software, potentially granting total access and control of the software to the untrusted source. | |
| 2026 | Including third party functionality in a web-based environment is risky, especially if the source of the functionality is untrusted. | |
| 2027 | Even if the third party is a trusted source, the software may still be exposed to attacks and malicious behavior if that trusted source is compromised, or if the code is modified in transmission from the third party to the software. | |
| 2028 | This weakness is common in ""mashup"" development on the web, which may include source functionality from other domains. For example, Javascript-based web widgets may be inserted by using '<SCRIPT SRC=""http://other.domain.here"">' tags, which causes the code to run in the domain of the software, not the remote site from which the widget was loaded. As a result, the included code has access to the local DOM, including cookies and other data that the developer might not want the remote site to be able to access. | |
| 2029 | Such dependencies may be desirable, or even required, but sometimes programmers are not aware that a dependency exists.",,unclassified,Third-Party Web Widget Security FAQ: http://jeremiahgrossman.blogspot.com/2010/07/third-party-web-widget-security-faq.html | |
| 2030 | CWE-831,Signal Handler Function Associated with Multiple Signals (Type: Base),"The software defines a function that is used as a handler for more than one signal. | |
| 2031 | While sometimes intentional and safe, when the same function is used to handle multiple signals, a race condition could occur if the function uses any state outside of its local declaration, such as global variables or non-reentrant functions, or has any side effects. | |
| 2032 | An attacker could send one signal that invokes the handler function; in many OSes, this will typically prevent the same signal from invoking the handler again, at least until the handler function has completed execution. However, the attacker could then send a different signal that is associated with the same handler function. This could interrupt the original handler function while it is still executing. If there is shared state, then the state could be corrupted. This can lead to a variety of potential consequences depending on context, including denial of service and code execution. | |
| 2033 | Another rarely-explored possibility arises when the signal handler is only designed to be executed once (if at all). By sending multiple signals, an attacker could invoke the function more than once. This may generate extra, unintended side effects. A race condition might not even be necessary; the attacker could send one signal, wait until it is handled, then send the other signal.",,unclassified,"Delivering Signals for Fun and Profit: http://lcamtuf.coredump.cx/signals.txt | |
| 2034 | Race Condition: Signal Handling: http://www.fortify.com/vulncat/en/vulncat/cpp/race_condition_signal_handling.html" | |
| 2035 | CWE-832,Unlock of a Resource that is not Locked (Type: Base),"The software attempts to unlock a resource that is not locked. | |
| 2036 | Depending on the locking functionality, an unlock of a non-locked resource might cause memory corruption or other modification to the resource (or its associated metadata that is used for tracking locks).",,unclassified, | |
| 2037 | CWE-833,Deadlock (Type: Base),"The software contains multiple threads or executable segments that are waiting for each other to release a necessary lock, resulting in deadlock. | |
| 2038 | Depending on the locking functionality, an unlock of a non-locked resource might cause memory corruption or other modification to the resource (or its associated metadata that is used for tracking locks).",,unclassified,"The Art of Software Security Assessment: Chapter 13, ""Synchronization Problems"" / ""Starvation and Deadlocks"", Page 760 | |
| 2039 | The Art of Software Security Assessment: Chapter 13, ""Starvation and Deadlocks"", Page 760. | |
| 2040 | Secure Coding in C and C++: Chapter 7, ""Concurrency"", section ""Mutual Exclusion and Deadlock"", Page 248." | |
| 2041 | CWE-834,Excessive Iteration (Type: Base),"The software performs an iteration or loop without sufficiently limiting the number of times that the loop is executed. | |
| 2042 | If the iteration can be influenced by an attacker, this weakness could allow attackers to consume excessive resources such as CPU or memory. In many cases, a loop does not need to be infinite in order to cause enough resource consumption to adversely affect the software or its host system; it depends on the amount of resources consumed per iteration.",,unclassified,"The Art of Software Security Assessment: Chapter 7, ""Looping Constructs"", Page 327." | |
| 2043 | CWE-835,Loop with Unreachable Exit Condition (Infinite Loop) (Type: Base),"The program contains an iteration or loop with an exit condition that cannot be reached, i.e., an infinite loop. | |
| 2044 | If the loop can be influenced by an attacker, this weakness could allow attackers to consume excessive resources such as CPU or memory.",,unclassified,"The Art of Software Security Assessment: Chapter 7, ""Looping Constructs"", Page 327." | |
| 2045 | CWE-836,Use of Password Hash Instead of Password for Authentication (Type: Base),"The software records password hashes in a data store, receives a hash of a password from a client, and compares the supplied hash to the hash obtained from the data store. | |
| 2046 | Some authentication mechanisms rely on the client to generate the hash for a password, possibly to reduce load on the server or avoid sending the password across the network. However, when the client is used to generate the hash, an attacker can bypass the authentication by obtaining a copy of the hash, e.g. by using SQL injection to compromise a database of authentication credentials, or by exploiting an information exposure. The attacker could then use a modified client to replay the stolen hash without having knowledge of the original password. | |
| 2047 | As a result, the server-side comparison against a client-side hash does not provide any more security than the use of passwords without hashing.",,unclassified, | |
| 2048 | CWE-837,"Improper Enforcement of a Single, Unique Action (Type: Base)","The software requires that an actor should only be able to perform an action once, or to have only one unique action, but the software does not enforce or improperly enforces this restriction. | |
| 2049 | In various applications, a user is only expected to perform a certain action once, such as voting, requesting a refund, or making a purchase. When this restriction is not enforced, sometimes this can have security implications. For example, in a voting application, an attacker could attempt to ""stuff the ballot box"" by voting multiple times. If these votes are counted separately, then the attacker could directly affect who wins the vote. This could have significant business impact depending on the purpose of the software.",,unclassified, | |
| 2050 | CWE-838,Inappropriate Encoding for Output Context (Type: Base),"The software uses or specifies an encoding when generating output to a downstream component, but the specified encoding is not the same as the encoding that is expected by the downstream component. | |
| 2051 | This weakness can cause the downstream component to use a decoding method that produces different data than what the software intended to send. When the wrong encoding is used - even if closely related - the downstream component could decode the data incorrectly. This can have security consequences when the provided boundaries between control and data are inadvertently broken, because the resulting data could introduce control characters or special elements that were not sent by the software. The resulting data could then be used to bypass protection mechanisms such as input validation, and enable injection attacks. | |
| 2052 | While using output encoding is essential for ensuring that communications between components are accurate, the use of the wrong encoding - even if closely related - could cause the downstream component to misinterpret the output. | |
| 2053 | For example, HTML entity encoding is used for elements in the HTML body of a web page. However, a programmer might use entity encoding when generating output for that is used within an attribute of an HTML tag, which could contain functional Javascript that is not affected by the HTML encoding. | |
| 2054 | While web applications have received the most attention for this problem, this weakness could potentially apply to any type of software that uses a communications stream that could support multiple encodings.",,unclassified,"Injection-safe templating languages: http://manicode.blogspot.com/2010/06/injection-safe-templating-languages_30.html | |
| 2055 | Can we please stop saying that XSS is boring and easy to fix!: http://diniscruz.blogspot.com/2010/09/can-we-please-stop-saying-that-xss-is.html | |
| 2056 | Canoe: XSS prevention via context-aware output encoding: http://blog.ivanristic.com/2010/09/introducing-canoe-context-aware-output-encoding-for-xss-prevention.html | |
| 2057 | What is the Future of Automated XSS Defense Tools?: http://software-security.sans.org/downloads/appsec-2011-files/manico-appsec-future-tools.pdf | |
| 2058 | XSS Attacks: Preventing XSS Attacks | |
| 2059 | DOM based XSS Prevention Cheat Sheet: http://www.owasp.org/index.php/DOM_based_XSS_Prevention_Cheat_Sheet | |
| 2060 | OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI" | |
| 2061 | CWE-839,Numeric Range Comparison Without Minimum Check (Type: Base),"The program checks a value to ensure that it does not exceed a maximum, but it does not verify that the value exceeds the minimum. | |
| 2062 | Some programs use signed integers or floats even when their values are only expected to be positive or 0. An input validation check might assume that the value is positive, and only check for the maximum value. If the value is negative, but the code assumes that the value is positive, this can produce an error. The error may have security consequences if the negative value is used for memory allocation, array access, buffer access, etc. Ultimately, the error could lead to a buffer overflow or other type of memory corruption. | |
| 2063 | The use of a negative number in a positive-only context could have security implications for other types of resources. For example, a shopping cart might check that the user is not requesting more than 10 items, but a request for -3 items could cause the application to calculate a negative price and credit the attacker's account.",,unclassified,"The Art of Software Security Assessment: Chapter 6, ""Type Conversion Vulnerabilities"" Page 246. | |
| 2064 | The Art of Software Security Assessment: Chapter 6, ""Comparisons"", Page 265." | |
| 2065 | CWE-84,Improper Neutralization of Encoded URI Schemes in a Web Page (Type: Variant),"The web application improperly neutralizes user-controlled input for executable script disguised with URI encodings. | |
| 2066 | Some programs use signed integers or floats even when their values are only expected to be positive or 0. An input validation check might assume that the value is positive, and only check for the maximum value. If the value is negative, but the code assumes that the value is positive, this can produce an error. The error may have security consequences if the negative value is used for memory allocation, array access, buffer access, etc. Ultimately, the error could lead to a buffer overflow or other type of memory corruption. | |
| 2067 | The use of a negative number in a positive-only context could have security implications for other types of resources. For example, a shopping cart might check that the user is not requesting more than 10 items, but a request for -3 items could cause the application to calculate a negative price and credit the attacker's account.",,unclassified, | |
| 2068 | CWE-841,Improper Enforcement of Behavioral Workflow (Type: Base),"The software supports a session in which more than one behavior must be performed by an actor, but it does not properly ensure that the actor performs the behaviors in the required sequence. | |
| 2069 | By performing actions in an unexpected order, or by omitting steps, an attacker could manipulate the business logic of the software or cause it to enter an invalid state. In some cases, this can also expose resultant weaknesses. | |
| 2070 | For example, a file-sharing protocol might require that an actor perform separate steps to provide a username, then a password, before being able to transfer files. If the file-sharing server accepts a password command followed by a transfer command, without any username being provided, the software might still perform the transfer. | |
| 2071 | Note that this is different than CWE-696, which focuses on when the software performs actions in the wrong sequence; this entry is closely related, but it is focused on ensuring that the actor performs actions in the correct sequence. | |
| 2072 | Workflow-related behaviors include: | |
| 2073 | Steps are performed in the expected order. | |
| 2074 | Required steps are not omitted. | |
| 2075 | Steps are not interrupted. | |
| 2076 | Steps are performed in a timely fashion.",,unclassified,"Business Logic Flaws and Yahoo Games: http://jeremiahgrossman.blogspot.com/2006/12/business-logic-flaws.html | |
| 2077 | Seven Business Logic Flaws That Put Your Website At Risk: http://www.whitehatsec.com/home/assets/WP_bizlogic092407.pdf | |
| 2078 | Business Logic Flaws: http://www.whitehatsec.com/home/solutions/BL_auction.html | |
| 2079 | Insufficient Process Validation: http://projects.webappsec.org/w/page/13246943/Insufficient-Process-Validation | |
| 2080 | Defying Logic: Theory, Design, and Implementation of Complex Systems for Testing Application Logic: http://www.slideshare.net/RafalLos/defying-logic-business-logic-testing-with-automation | |
| 2081 | Real-Life Example of a 'Business Logic Defect' (Screen Shots!): http://h30501.www3.hp.com/t5/Following-the-White-Rabbit-A/Real-Life-Example-of-a-Business-Logic-Defect-Screen-Shots/ba-p/22581 | |
| 2082 | Toward Automated Detection of Logic Vulnerabilities in Web Applications: http://www.usenix.org/events/sec10/tech/full_papers/Felmetsger.pdf | |
| 2083 | Designing a Framework Method for Secure Business Application Logic Integrity in e-Commerce Systems: http://ijns.femto.com.tw/contents/ijns-v12-n1/ijns-2011-v12-n1-p29-41.pdf" | |
| 2084 | CWE-842,Placement of User into Incorrect Group (Type: Base),"The software or the administrator places a user into an incorrect group. | |
| 2085 | If the incorrect group has more access or privileges than the intended group, the user might be able to bypass intended security policy to access unexpected resources or perform unexpected actions. The access-control system might not be able to detect malicious usage of this group membership.",,unclassified, | |
| 2086 | CWE-843,Access of Resource Using Incompatible Type (Type Confusion) (Type: Base),"The program allocates or initializes a resource such as a pointer, object, or variable using one type, but it later accesses that resource using a type that is incompatible with the original type. | |
| 2087 | When the program accesses the resource using an incompatible type, this could trigger logical errors because the resource does not have expected properties. In languages without memory safety, such as C and C++, type confusion can lead to out-of-bounds memory access. | |
| 2088 | While this weakness is frequently associated with unions when parsing data with many different embedded object types in C, it can be present in any application that can interpret the same variable or memory location in multiple ways. | |
| 2089 | This weakness is not unique to C and C++. For example, errors in PHP applications can be triggered by providing array parameters when scalars are expected, or vice versa. Languages such as Perl, which perform automatic conversion of a variable of one type when it is accessed as if it were another type, can also contain these issues.",,unclassified,"Attacking Interoperability: http://www.azimuthsecurity.com/resources/bh2009_dowd_smith_dewey.pdf | |
| 2090 | The Art of Software Security Assessment: Chapter 7, ""Type Confusion"", Page 319." | |
| 2091 | CWE-85,Doubled Character XSS Manipulations (Type: Variant),"The web application does not filter user-controlled input for executable script disguised using doubling of the involved characters. | |
| 2092 | When the program accesses the resource using an incompatible type, this could trigger logical errors because the resource does not have expected properties. In languages without memory safety, such as C and C++, type confusion can lead to out-of-bounds memory access. | |
| 2093 | While this weakness is frequently associated with unions when parsing data with many different embedded object types in C, it can be present in any application that can interpret the same variable or memory location in multiple ways. | |
| 2094 | This weakness is not unique to C and C++. For example, errors in PHP applications can be triggered by providing array parameters when scalars are expected, or vice versa. Languages such as Perl, which perform automatic conversion of a variable of one type when it is accessed as if it were another type, can also contain these issues.",,unclassified, | |
| 2095 | CWE-86,Improper Neutralization of Invalid Characters in Identifiers in Web Pages (Type: Variant),"The software does not neutralize or incorrectly neutralizes invalid characters or byte sequences in the middle of tag names, URI schemes, and other identifiers. | |
| 2096 | Some web browsers may remove these sequences, resulting in output that may have unintended control implications. For example, the software may attempt to remove a ""javascript:"" URI scheme, but a ""java%00script:"" URI may bypass this check and still be rendered as active javascript by some browsers, allowing XSS or other attacks.",,unclassified, | |
| 2097 | CWE-87,Improper Neutralization of Alternate XSS Syntax (Type: Variant),"The software does not neutralize or incorrectly neutralizes user-controlled input for alternate script syntax. | |
| 2098 | Assuming a user with a given identity, authorization is the process of determining whether that user can access a given resource, based on the user's privileges and any permissions or other access-control specifications that apply to the resource. | |
| 2099 | When access control checks are incorrectly applied, users are able to access data or perform actions that they should not be allowed to perform. This can lead to a wide range of problems, including information exposures, denial of service, and arbitrary code execution.",,unclassified, | |
| 2100 | CWE-88,Argument Injection or Modification (Type: Base),"The software does not sufficiently delimit the arguments being passed to a component in another control sphere, allowing alternate arguments to be provided, leading to potentially security-relevant changes. | |
| 2101 | Assuming a user with a given identity, authorization is the process of determining whether that user can access a given resource, based on the user's privileges and any permissions or other access-control specifications that apply to the resource. | |
| 2102 | When access control checks are incorrectly applied, users are able to access data or perform actions that they should not be allowed to perform. This can lead to a wide range of problems, including information exposures, denial of service, and arbitrary code execution.",,unclassified,"Argument injection issues: http://www.securityfocus.com/archive/1/archive/1/460089/100/100/threaded | |
| 2103 | The Art of Software Security Assessment: Chapter 10, ""The Argument Array"", Page 567." | |
| 2104 | CWE-9,J2EE Misconfiguration: Weak Access Permissions for EJB Methods (Type: Variant),"If elevated access rights are assigned to EJB methods, then an attacker can take advantage of the permissions to exploit the software system. | |
| 2105 | Without sufficient removal or quoting of SQL syntax in user-controllable inputs, the generated SQL query can cause those inputs to be interpreted as SQL instead of ordinary user data. This can be used to alter query logic to bypass security checks, or to insert additional statements that modify the back-end database, possibly including execution of system commands. | |
| 2106 | SQL injection has become a common issue with database-driven web sites. The flaw is easily detected, and easily exploited, and as such, any site or software package with even a minimal user base is likely to be subject to an attempted attack of this kind. This flaw depends on the fact that SQL makes no real distinction between the control and data planes.",,unclassified, | |
| 2107 | CWE-90,Improper Neutralization of Special Elements used in an LDAP Query (LDAP Injection) (Type: Base),"The software constructs all or part of an LDAP query using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended LDAP query when it is sent to a downstream component. | |
| 2108 | Without sufficient removal or quoting of SQL syntax in user-controllable inputs, the generated SQL query can cause those inputs to be interpreted as SQL instead of ordinary user data. This can be used to alter query logic to bypass security checks, or to insert additional statements that modify the back-end database, possibly including execution of system commands. | |
| 2109 | SQL injection has become a common issue with database-driven web sites. The flaw is easily detected, and easily exploited, and as such, any site or software package with even a minimal user base is likely to be subject to an attempted attack of this kind. This flaw depends on the fact that SQL makes no real distinction between the control and data planes.",,unclassified,Web Applications and LDAP Injection | |
| 2110 | CWE-91,XML Injection (aka Blind XPath Injection) (Type: Base),"The software does not properly neutralize special elements that are used in XML, allowing attackers to modify the syntax, content, or commands of the XML before it is processed by an end system. | |
| 2111 | Within XML, special elements could include reserved words or characters such as ""<"", "">"", """""", and ""&"", which could then be used to add new data or modify XML syntax.",,unclassified,"Blind XPath Injection: http://www.modsecurity.org/archive/amit/blind-xpath-injection.pdf | |
| 2112 | The Art of Software Security Assessment: Chapter 17, ""XML Injection"", Page 1069." | |
| 2113 | CWE-912,Hidden Functionality (Type: Class),"The software contains functionality that is not documented, not part of the specification, and not accessible through an interface or command sequence that is obvious to the software's users or administrators. | |
| 2114 | Hidden functionality can take many forms, such as intentionally malicious code, ""Easter Eggs"" that contain extraneous functionality such as games, developer-friendly shortcuts that reduce maintenance or support costs such as hard-coded accounts, etc. From a security perspective, even when the functionality is not intentionally malicious or damaging, it can increase the software's attack surface and expose additional weaknesses beyond what is already exposed by the intended functionality. Even if it is not easily accessible, the hidden functionality could be useful for attacks that modify the control flow of the application.",,unclassified, | |
| 2115 | CWE-913,Improper Control of Dynamically-Managed Code Resources (Type: Class),"The software does not properly restrict reading from or writing to dynamically-managed code resources such as variables, objects, classes, attributes, functions, or executable instructions or statements. | |
| 2116 | Many languages offer powerful features that allow the programmer to dynamically create or modify existing code, or resources used by code such as variables and objects. While these features can offer significant flexibility and reduce development time, they can be extremely dangerous if attackers can directly influence these code resources in unexpected ways.",,unclassified, | |
| 2117 | CWE-914,Improper Control of Dynamically-Identified Variables (Type: Base),"The software does not properly restrict reading from or writing to dynamically-identified variables. | |
| 2118 | Many languages offer powerful features that allow the programmer to access arbitrary variables that are specified by an input string. While these features can offer significant flexibility and reduce development time, they can be extremely dangerous if attackers can modify unintended variables that have security implications.",,unclassified, | |
| 2119 | CWE-915,Improperly Controlled Modification of Dynamically-Determined Object Attributes (Type: Base),"The software receives input from an upstream component that specifies multiple attributes, properties, or fields that are to be initialized or updated in an object, but it does not properly control which attributes can be modified. | |
| 2120 | If the object contains attributes that were only intended for internal use, then their unexpected modification could lead to a vulnerability. | |
| 2121 | This weakness is sometimes known by the language-specific mechanisms that make it possible, such as mass assignment, autobinding, or object injection.",,unclassified,"Shocking News in PHP Exploitation: http://www.suspekt.org/downloads/POC2009-ShockingNewsInPHPExploitation.pdf | |
| 2122 | ""Two Security Vulnerabilities in the Spring Framework's MVC"" pdf (from 2008): http://blog.diniscruz.com/2011/07/two-security-vulnerabilities-in-spring.html | |
| 2123 | Two Security Vulnerabilities in the Spring Framework's MVC: http://o2platform.files.wordpress.com/2011/07/ounce_springframework_vulnerabilities.pdf | |
| 2124 | Best Practices for ASP.NET MVC: http://blogs.msdn.com/b/aspnetue/archive/2010/09/17/second_2d00_post.aspx | |
| 2125 | Mass assignment in Rails applications: http://blog.mhartl.com/2008/09/21/mass-assignment-in-rails-applications/ | |
| 2126 | Secure your Rails apps!: http://pragtob.wordpress.com/2012/03/06/secure-your-rails-apps/ | |
| 2127 | Ruby On Rails Security Guide: http://guides.rubyonrails.org/security.html#mass-assignment | |
| 2128 | Mass Assignment Vulnerability in ASP.NET MVC: http://freshbrewedcode.com/joshbush/2012/03/05/mass-assignment-aspnet-mvc/ | |
| 2129 | 6 Ways To Avoid Mass Assignment in ASP.NET MVC: http://odetocode.com/blogs/scott/archive/2012/03/11/complete-guide-to-mass-assignment-in-asp-net-mvc.aspx | |
| 2130 | PHP Object Injection: https://www.owasp.org/index.php/PHP_Object_Injection | |
| 2131 | Unserializing user-supplied data, a bad idea: http://heine.familiedeelstra.com/security/unserialize | |
| 2132 | Why Python Pickle is Insecure: http://nadiana.com/python-pickle-insecure" | |
| 2133 | CWE-916,Use of Password Hash With Insufficient Computational Effort (Type: Base),"The software generates a hash for a password, but it uses a scheme that does not provide a sufficient level of computational effort that would make password cracking attacks infeasible or expensive. | |
| 2134 | Many password storage mechanisms compute a hash and store the hash, instead of storing the original password in plaintext. In this design, authentication involves accepting an incoming password, computing its hash, and comparing it to the stored hash. | |
| 2135 | Many hash algorithms are designed to execute quickly with minimal overhead, even cryptographic hashes. However, this efficiency is a problem for password storage, because it can reduce an attacker's workload for brute-force password cracking. If an attacker can obtain the hashes through some other method (such as SQL injection on a database that stores hashes), then the attacker can store the hashes offline and use various techniques to crack the passwords by computing hashes efficiently. Without a built-in workload, modern attacks can compute large numbers of hashes, or even exhaust the entire space of all possible passwords, within a very short amount of time, using massively-parallel computing (such as cloud computing) and GPU, ASIC, or FPGA hardware. In such a scenario, an efficient hash algorithm helps the attacker. | |
| 2136 | There are several properties of a hash scheme that are relevant to its strength against an offline, massively-parallel attack: | |
| 2137 | The amount of CPU time required to compute the hash (""stretching"") | |
| 2138 | The amount of memory required to compute the hash (""memory-hard"" operations) | |
| 2139 | Including a random value, along with the password, as input to the hash computation (""salting"") | |
| 2140 | Given a hash, there is no known way of determining a password that produces this hash value, other than by guessing possible passwords (""one-way"" hashing) | |
| 2141 | Relative to the number of all possible hashes that can be generated by the scheme, there is a low likelihood of producing the same hash for multiple different inputs (""collision resistance"") | |
| 2142 | Note that the security requirements for the software may vary depending on the environment and the value of the passwords. Different schemes might not provide all of these properties, yet may still provide sufficient security for the environment. Conversely, a solution might be very strong in preserving one property, which still being very weak for an attack against another property, or it might not be able to significantly reduce the efficiency of a massively-parallel attack.",,unclassified,"bcrypt: http://bcrypt.sourceforge.net/ | |
| 2143 | Tarsnap - The scrypt key derivation function and encryption utility: http://www.tarsnap.com/scrypt.html | |
| 2144 | RFC2898 - PKCS #5: Password-Based Cryptography Specification Version 2.0: http://tools.ietf.org/html/rfc2898 | |
| 2145 | How Companies Can Beef Up Password Security (interview with Thomas H. Ptacek): http://krebsonsecurity.com/2012/06/how-companies-can-beef-up-password-security/ | |
| 2146 | Speed Hashing: http://www.codinghorror.com/blog/2012/04/speed-hashing.html | |
| 2147 | Password security: past, present, future: http://www.openwall.com/presentations/PHDays2012-Password-Security/ | |
| 2148 | Password Storage Cheat Sheet: https://www.owasp.org/index.php/Password_Storage_Cheat_Sheet | |
| 2149 | Enough With The Rainbow Tables: What You Need To Know About Secure Password Schemes: http://www.securityfocus.com/blogs/262 | |
| 2150 | How To Safely Store A Password: http://codahale.com/how-to-safely-store-a-password/ | |
| 2151 | Password hashing at scale: http://www.openwall.com/presentations/YaC2012-Password-Hashing-At-Scale/ | |
| 2152 | New developments in password hashing: ROM-port-hard functions: http://www.openwall.com/presentations/ZeroNights2012-New-In-Password-Hashing/ | |
| 2153 | The Importance of Being Canonical: http://erratasec.blogspot.com/2009/02/importance-of-being-canonical.html | |
| 2154 | Our password hashing has no clothes: http://www.troyhunt.com/2012/06/our-password-hashing-has-no-clothes.html | |
| 2155 | Should we really use bcrypt/scrypt?: http://www.analyticalengine.net/2012/06/should-we-really-use-bcryptscrypt/" | |
| 2156 | CWE-917,Improper Neutralization of Special Elements used in an Expression Language Statement (Expression Language Injection) (Type: Base),"The software constructs all or part of an expression language (EL) statement in a Java Server Page (JSP) using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended EL statement before it is executed. | |
| 2157 | Many password storage mechanisms compute a hash and store the hash, instead of storing the original password in plaintext. In this design, authentication involves accepting an incoming password, computing its hash, and comparing it to the stored hash. | |
| 2158 | Many hash algorithms are designed to execute quickly with minimal overhead, even cryptographic hashes. However, this efficiency is a problem for password storage, because it can reduce an attacker's workload for brute-force password cracking. If an attacker can obtain the hashes through some other method (such as SQL injection on a database that stores hashes), then the attacker can store the hashes offline and use various techniques to crack the passwords by computing hashes efficiently. Without a built-in workload, modern attacks can compute large numbers of hashes, or even exhaust the entire space of all possible passwords, within a very short amount of time, using massively-parallel computing (such as cloud computing) and GPU, ASIC, or FPGA hardware. In such a scenario, an efficient hash algorithm helps the attacker. | |
| 2159 | There are several properties of a hash scheme that are relevant to its strength against an offline, massively-parallel attack: | |
| 2160 | The amount of CPU time required to compute the hash (""stretching"") | |
| 2161 | The amount of memory required to compute the hash (""memory-hard"" operations) | |
| 2162 | Including a random value, along with the password, as input to the hash computation (""salting"") | |
| 2163 | Given a hash, there is no known way of determining a password that produces this hash value, other than by guessing possible passwords (""one-way"" hashing) | |
| 2164 | Relative to the number of all possible hashes that can be generated by the scheme, there is a low likelihood of producing the same hash for multiple different inputs (""collision resistance"") | |
| 2165 | Note that the security requirements for the software may vary depending on the environment and the value of the passwords. Different schemes might not provide all of these properties, yet may still provide sufficient security for the environment. Conversely, a solution might be very strong in preserving one property, which still being very weak for an attack against another property, or it might not be able to significantly reduce the efficiency of a massively-parallel attack.",,unclassified,"Expression Language Injection: http://www.mindedsecurity.com/fileshare/ExpressionLanguageInjection.pdf | |
| 2166 | Remote Code with Expression Language Injection: http://danamodio.com/application-security/discoveries/spring-remote-code-with-expression-language-injection/" | |
| 2167 | CWE-918,Server-Side Request Forgery (SSRF) (Type: Base),"The web server receives a URL or similar request from an upstream component and retrieves the contents of this URL, but it does not sufficiently ensure that the request is being sent to the expected destination. | |
| 2168 | By providing URLs to unexpected hosts or ports, attackers can make it appear that the server is sending the request, possibly bypassing access controls such as firewalls that prevent the attackers from accessing the URLs directly. The server can be used as a proxy to conduct port scanning of hosts in internal networks, use other URLs such as that can access documents on the system (using file://), or use other protocols such as gopher:// or tftp://, which may provide greater control over the contents of requests.",,unclassified,"SSRF vs. Business-critical applications: XXE tunneling in SAP: https://media.blackhat.com/bh-us-12/Briefings/Polyakov/BH_US_12_Polyakov_SSRF_Business_Slides.pdf | |
| 2169 | SSRF vs. Business-critical Applications. Part 1: XXE Tunnelling in SAP NetWeaver: http://erpscan.com/wp-content/uploads/2012/08/SSRF-vs-Businness-critical-applications-whitepaper.pdf | |
| 2170 | Cross Site Port Attacks - XSPA - Part 1: http://www.riyazwalikar.com/2012/11/cross-site-port-attacks-xspa-part-1.html | |
| 2171 | Cross Site Port Attacks - XSPA - Part 2: http://www.riyazwalikar.com/2012/11/cross-site-port-attacks-xspa-part-2.html | |
| 2172 | Cross Site Port Attacks - XSPA - Part 3: http://www.riyazwalikar.com/2012/11/cross-site-port-attacks-xspa-part-3.html | |
| 2173 | SSRF attacks and sockets: smorgasbord of vulnerabilities: http://www.slideshare.net/d0znpp/ssrf-attacks-and-sockets-smorgasbord-of-vulnerabilities | |
| 2174 | SSRF bible. Cheatsheet: https://docs.google.com/document/d/1v1TkWZtrhzRLy0bYXBcdLUedXGb9njTNIJXa3u9akHM/edit?pli=1# | |
| 2175 | Web Portals: Gateway To Information, Or A Hole In Our Perimeter Defenses: http://www.shmoocon.org/2008/presentations/Web%20portals,%20gateway%20to%20information.ppt" | |
| 2176 | CWE-92,DEPRECATED: Improper Sanitization of Custom Special Characters (Type: Base),"This entry has been deprecated. It originally came from PLOVER, which sometimes defined ""other"" and ""miscellaneous"" categories in order to satisfy exhaustiveness requirements for taxonomies. Within the context of CWE, the use of a more abstract entry is preferred in mapping situations. CWE-75 is a more appropriate mapping. | |
| 2177 | By providing URLs to unexpected hosts or ports, attackers can make it appear that the server is sending the request, possibly bypassing access controls such as firewalls that prevent the attackers from accessing the URLs directly. The server can be used as a proxy to conduct port scanning of hosts in internal networks, use other URLs such as that can access documents on the system (using file://), or use other protocols such as gopher:// or tftp://, which may provide greater control over the contents of requests.",,unclassified, | |
| 2178 | CWE-920,Improper Restriction of Power Consumption (Type: Base),"The software operates in an environment in which power is a limited resource that cannot be automatically replenished, but the software does not properly restrict the amount of power that its operation consumes. | |
| 2179 | In environments such as embedded or mobile devices, power can be a limited resource such as a battery, which cannot be automatically replenished by the software itself, and the device might not always be directly attached to a reliable power source. If the software uses too much power too quickly, then this could cause the device (and subsequently, the software) to stop functioning until power is restored, or increase the financial burden on the device owner because of increased power costs. | |
| 2180 | Normal operation of an application will consume power. However, in some cases, an attacker could cause the application to consume more power than intended, using components such as: | |
| 2181 | Display | |
| 2182 | CPU | |
| 2183 | Disk I/O | |
| 2184 | GPS | |
| 2185 | Sound | |
| 2186 | Microphone | |
| 2187 | USB interface",,unclassified, | |
| 2188 | CWE-921,Storage of Sensitive Data in a Mechanism without Access Control (Type: Base),"The software stores sensitive information in a file system or device that does not have built-in access control. | |
| 2189 | While many modern file systems or devices utilize some form of access control in order to restrict access to data, not all storage mechanisms have this capability. For example, memory cards, floppy disks, CDs, and USB devices are typically made accessible to any user within the system. This can become a problem when sensitive data is stored in these mechanisms in a multi-user environment, because anybody on the system can read or write this data. | |
| 2190 | On Android devices, external storage is typically globally readable and writable by other applications on the device. External storage may also be easily accessible through the mobile device's USB connection or physically accessible through the device's memory card port.",,unclassified,Security Tips: http://developer.android.com/training/articles/security-tips.html#StoringData | |
| 2191 | CWE-922,Insecure Storage of Sensitive Information (Type: Class),"The software stores sensitive information without properly limiting read or write access by unauthorized actors. | |
| 2192 | If read access is not properly restricted, then attackers can steal the sensitive information. If write access is not properly restricted, then attackers can modify and possibly delete the data, causing incorrect results and possibly a denial of service.",,unclassified, | |
| 2193 | CWE-923,Improper Authentication of Endpoint in a Communication Channel (Type: Class),"The software establishes a communication channel to (or from) an endpoint for privileged or protected operations, but it does not properly authenticate the endpoint to ensure it is associated with the identity of the intended actor. | |
| 2194 | Attackers might be able to spoof the intended endpoint from a different system or process, thus gaining the same level of access as the intended endpoint. | |
| 2195 | While this issue frequently involves authentication between network-based clients and servers, other types of communication channels and endpoints can have this weakness.",,unclassified, | |
| 2196 | CWE-924,Improper Enforcement of Message Integrity During Transmission in a Communication Channel (Type: Class),"The software establishes a communication channel with an endpoint and receives a message from that endpoint, but it does not sufficiently ensure that the message was not modified during transmission. | |
| 2197 | A man-in-the-middle (MITM) attacker might be able to modify the message and spoof the endpoint.",,unclassified, | |
| 2198 | CWE-925,Improper Verification of Intent by Broadcast Receiver (Type: Variant),"The Android application uses a Broadcast Receiver that receives an Intent but does not properly verify that the Intent came from an authorized source, e.g. by checking the action string. | |
| 2199 | Certain types of Intents, identified by action string, can only be broadcast by the operating system itself, not by third-party applications. However, when an application declares the ability for a component to receive broadcast messages, in most cases a malicious application can send an Intent with a non-reserved action string to that receiving component.",,unclassified, | |
| 2200 | CWE-926,Improper Restriction of Content Provider Export to Other Applications (Type: Variant),"The Android application uses a Content Provider that does not properly restrict which applications can access the data that is offered by the Content Provider. | |
| 2201 | Android's Content Provider mechanism can be used to share data with other applications or internally within the same application. If access to the Content Provider is not restricted to only the expected applications, then malicious applications might be able to access the sensitive data. | |
| 2202 | This weakness could be expressed in several different ways: | |
| 2203 | The Content Provider is only intended for internal use by the application, and thus does not need to be exported. | |
| 2204 | In Android before 4.2, the Content Provider is automatically exported unless it has been explicitly declared as NOT exported. | |
| 2205 | The Content Provider is intended for external use by some applications, but it does not properly limit access, e.g. by exporting with excessive permissions.",,unclassified,No description: http://developer.android.com/training/articles/security-tips.html#ContentProviders | |
| 2206 | CWE-927,Use of Implicit Intent for Sensitive Communication (Type: Variant),"The Android application uses an implicit intent for transmitting sensitive data to other applications. | |
| 2207 | Since an implicit intent does not specify a particular application to receive the data, any application can process the intent by using an Intent Filter for that intent. This can allow untrusted applications to obtain sensitive data.",,unclassified,"Analyzing Inter-Application Communication in Android: http://www.cs.berkeley.edu/~afelt/intentsecurity-mobisys.pdf | |
| 2208 | Security Tips: http://developer.android.com/training/articles/security-tips.html#ContentProviders" | |
| 2209 | CWE-96,Improper Neutralization of Directives in Statically Saved Code (Static Code Injection) (Type: Base),"The software receives input from an upstream component, but it does not neutralize or incorrectly neutralizes code syntax before inserting the input into an executable resource, such as a library, configuration file, or template. | |
| 2210 | This may allow an attacker to execute arbitrary code, or at least modify what code can be executed.",,unclassified, | |
| 2211 | CWE-97,Improper Neutralization of Server-Side Includes (SSI) Within a Web Page (Type: Variant),"The software generates a web page, but does not neutralize or incorrectly neutralizes user-controllable input that could be interpreted as a server-side include (SSI) directive. | |
| 2212 | This may allow an attacker to execute arbitrary code, or at least modify what code can be executed.",,unclassified, | |
| 2213 | CWE-116,Improper Encoding or Escaping of Output (Type: Class),"The software prepares a structured message for communication with another component, but encoding or escaping of the data is either missing or done incorrectly. As a result, the intended structure of the message is not preserved. | |
| 2214 | Improper encoding or escaping can allow attackers to change the commands that are sent to another component, inserting malicious commands instead. | |
| 2215 | Most software follows a certain protocol that uses structured messages for communication between components, such as queries or commands. These structured messages can contain raw data interspersed with metadata or control information. For example, ""GET /index.html HTTP/1.1"" is a structured message containing a command (""GET"") with a single argument (""/index.html"") and metadata about which protocol version is being used (""HTTP/1.1""). | |
| 2216 | If an application uses attacker-supplied inputs to construct a structured message without properly encoding or escaping, then the attacker could insert special characters that will cause the data to be interpreted as control information or metadata. Consequently, the component that receives the output will perform the wrong operations, or otherwise interpret the data incorrectly.",,high,"OWASP Enterprise Security API (ESAPI) Project: http://www.owasp.org/index.php/ESAPI | |
| 2217 | Input validation or output filtering, which is better?: http://jeremiahgrossman.blogspot.com/2007/01/input-validation-or-output-filtering.html | |
| 2218 | Output Sanitization: http://www.analyticalengine.net/archives/58 | |
| 2219 | Sanitizing user data: How and where to do it: http://www.diovo.com/2008/09/sanitizing-user-data-how-and-where-to-do-it/ | |
| 2220 | Input validation or output filtering, which is better?: http://jeremiahgrossman.blogspot.com/2007/01/input-validation-or-output-filtering.html | |
| 2221 | Input Validation - Not That Important: http://manicode.blogspot.com/2008/08/input-validation-not-that-important.html | |
| 2222 | Preventing XSS with Correct Output Encoding: http://phed.org/2008/05/19/preventing-xss-with-correct-output-encoding/ | |
| 2223 | Writing Secure Code: Chapter 11, ""Canonical Representation Issues"" Page 363" | |
| 2224 | CWE-121,Stack-based Buffer Overflow (Type: Variant),"A stack-based buffer overflow condition is a condition where the buffer being overwritten is allocated on the stack (i.e., is a local variable or, rarely, a parameter to a function). | |
| 2225 | A buffer overflow condition exists when a program attempts to put more data in a buffer than it can hold, or when a program attempts to put data in a memory area outside of the boundaries of a buffer. The simplest type of error, and the most common cause of buffer overflows, is the ""classic"" case in which the program copies the buffer without restricting how much is copied. Other variants exist, but the existence of a classic overflow strongly suggests that the programmer is not considering even the most basic of security protections.",,high,"Writing Secure Code: Chapter 5, ""Stack Overruns"" Page 129 | |
| 2226 | 24 Deadly Sins of Software Security: ""Sin 5: Buffer Overruns."" Page 89 | |
| 2227 | The Art of Software Security Assessment: Chapter 3, ""Nonexecutable Stack"", Page 76. | |
| 2228 | The Art of Software Security Assessment: Chapter 5, ""Protection Mechanisms"", Page 189." | |
| 2229 | CWE-134,Uncontrolled Format String (Type: Base),"The software uses externally-controlled format strings in printf-style functions, which can lead to buffer overflows or data representation problems. | |
| 2230 | If an attacker can manipulate the length parameter associated with an input such that it is inconsistent with the actual length of the input, this can be leveraged to cause the target application to behave in unexpected, and possibly, malicious ways. One of the possible motives for doing so is to pass in arbitrarily large input to the application. Another possible motivation is the modification of application state by including invalid data for subsequent properties of the application. Such weaknesses commonly lead to attacks such as buffer overflows and execution of arbitrary code.",,high,"Format String Vulnerabilities in Perl Programs: http://www.securityfocus.com/archive/1/418460/30/0/threaded | |
| 2231 | Programming Language Format String Vulnerabilities: http://www.ddj.com/dept/security/197002914 | |
| 2232 | Format String Attacks: http://www.thenewsh.com/~newsham/format-string-attacks.pdf | |
| 2233 | Writing Secure Code: Chapter 5, ""Format String Bugs"" Page 147 | |
| 2234 | 24 Deadly Sins of Software Security: ""Sin 6: Format String Problems."" Page 109 | |
| 2235 | The Art of Software Security Assessment: Chapter 8, ""C Format Strings"", Page 422." | |
| 2236 | CWE-256,Plaintext Storage of a Password (Type: Variant),"Storing a password in plaintext may result in a system compromise. | |
| 2237 | Two common programmer assumptions are ""this function call can never fail"" and ""it doesn't matter if this function call fails"". If an attacker can force the function to fail or otherwise return a value that is not expected, then the subsequent program logic could lead to a vulnerability, because the software is not in a state that the programmer assumes. For example, if the program calls a function to drop privileges but does not check the return code to ensure that privileges were successfully dropped, then the program will continue to operate with the higher privileges.",,high,Building Secure Software: How to Avoid Security Problems the Right Way | |
| 2238 | CWE-257,Storing Passwords in a Recoverable Format (Type: Base),"The storage of passwords in a recoverable format makes them subject to password reuse attacks by malicious users. If a system administrator can recover a password directly, or use a brute force search on the available information, the administrator can use the password on other accounts. | |
| 2239 | Two common programmer assumptions are ""this function call can never fail"" and ""it doesn't matter if this function call fails"". If an attacker can force the function to fail or otherwise return a value that is not expected, then the subsequent program logic could lead to a vulnerability, because the software is not in a state that the programmer assumes. For example, if the program calls a function to drop privileges but does not check the return code to ensure that privileges were successfully dropped, then the program will continue to operate with the higher privileges.",,high, | |
| 2240 | CWE-258,Empty Password in Configuration File (Type: Variant),"Using an empty string as a password is insecure. | |
| 2241 | Two common programmer assumptions are ""this function call can never fail"" and ""it doesn't matter if this function call fails"". If an attacker can force the function to fail or otherwise return a value that is not expected, then the subsequent program logic could lead to a vulnerability, because the software is not in a state that the programmer assumes. For example, if the program calls a function to drop privileges but does not check the return code to ensure that privileges were successfully dropped, then the program will continue to operate with the higher privileges.",,high,Building Secure Software: How to Avoid Security Problems the Right Way | |
| 2242 | CWE-259,Use of Hard-coded Password (Type: Base),"The software contains a hard-coded password, which it uses for its own inbound authentication or for outbound communication to external components. | |
| 2243 | A hard-coded password typically leads to a significant authentication failure that can be difficult for the system administrator to detect. Once detected, it can be difficult to fix, so the administrator may be forced into disabling the product entirely. There are two main variations: | |
| 2244 | Inbound: the software contains an authentication mechanism that checks for a hard-coded password. | |
| 2245 | Outbound: the software connects to another system or component, and it contains hard-coded password for connecting to that component. | |
| 2246 | In the Inbound variant, a default administration account is created, and a simple password is hard-coded into the product and associated with that account. This hard-coded password is the same for each installation of the product, and it usually cannot be changed or disabled by system administrators without manually modifying the program, or otherwise patching the software. If the password is ever discovered or published (a common occurrence on the Internet), then anybody with knowledge of this password can access the product. Finally, since all installations of the software will have the same password, even across different organizations, this enables massive attacks such as worms to take place. | |
| 2247 | The Outbound variant applies to front-end systems that authenticate with a back-end service. The back-end service may require a fixed password which can be easily discovered. The programmer may simply hard-code those back-end credentials into the front-end software. Any user of that program may be able to extract the password. Client-side systems with hard-coded passwords pose even more of a threat, since the extraction of a password from a binary is usually very simple.",,high,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 2248 | CWE-309,Use of Password System for Primary Authentication (Type: Base),"The use of password systems as the primary means of authentication may be subject to several flaws or shortcomings, each reducing the effectiveness of the mechanism. | |
| 2249 | While the use of multiple authentication schemes is simply piling on more complexity on top of authentication, it is inestimably valuable to have such measures of redundancy. The use of weak, reused, and common passwords is rampant on the internet. Without the added protection of multiple authentication schemes, a single mistake can result in the compromise of an account. For this reason, if multiple schemes are possible and also easy to use, they should be implemented and required.",,high, | |
| 2250 | CWE-74,Improper Neutralization of Special Elements in Output Used by a Downstream Component (Injection) (Type: Class),"The software constructs all or part of a command, data structure, or record using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify how it is parsed or interpreted when it is sent to a downstream component. | |
| 2251 | Software has certain assumptions about what constitutes data and control respectively. It is the lack of verification of these assumptions for user-controlled input that leads to injection problems. Injection problems encompass a wide variety of issues -- all mitigated in very different ways and usually attempted in order to alter the control flow of the process. For this reason, the most effective way to discuss these weaknesses is to note the distinct features which classify them as injection weaknesses. The most important issue to note is that all injection problems share one thing in common -- i.e., they allow for the injection of control plane data into the user-controlled data plane. This means that the execution of the process may be altered by sending code in through legitimate data channels, using no other mechanism. While buffer overflows, and many other flaws, involve the use of some further issue to gain execution, injection problems need only for the data to be parsed. The most classic instantiations of this category of weakness are SQL injection and format string vulnerabilities.",,high, | |
| 2252 | CWE-77,Improper Neutralization of Special Elements used in a Command (Command Injection) (Type: Class),"The software constructs all or part of a command using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended command when it is sent to a downstream component. | |
| 2253 | Command injection vulnerabilities typically occur when: | |
| 2254 | 1. Data enters the application from an untrusted source. | |
| 2255 | 2. The data is part of a string that is executed as a command by the application. | |
| 2256 | 3. By executing the command, the application gives an attacker a privilege or capability that the attacker would not otherwise have.",,high,"Exploiting Software: How to Break Code | |
| 2257 | 24 Deadly Sins of Software Security: ""Sin 10: Command Injection."" Page 171" | |
| 2258 | CWE-798,Use of Hard-coded Credentials (Type: Base),"The software contains hard-coded credentials, such as a password or cryptographic key, which it uses for its own inbound authentication, outbound communication to external components, or encryption of internal data. | |
| 2259 | Hard-coded credentials typically create a significant hole that allows an attacker to bypass the authentication that has been configured by the software administrator. This hole might be difficult for the system administrator to detect. Even if detected, it can be difficult to fix, so the administrator may be forced into disabling the product entirely. There are two main variations: | |
| 2260 | Inbound: the software contains an authentication mechanism that checks the input credentials against a hard-coded set of credentials. | |
| 2261 | Outbound: the software connects to another system or component, and it contains hard-coded credentials for connecting to that component. | |
| 2262 | In the Inbound variant, a default administration account is created, and a simple password is hard-coded into the product and associated with that account. This hard-coded password is the same for each installation of the product, and it usually cannot be changed or disabled by system administrators without manually modifying the program, or otherwise patching the software. If the password is ever discovered or published (a common occurrence on the Internet), then anybody with knowledge of this password can access the product. Finally, since all installations of the software will have the same password, even across different organizations, this enables massive attacks such as worms to take place. | |
| 2263 | The Outbound variant applies to front-end systems that authenticate with a back-end service. The back-end service may require a fixed password which can be easily discovered. The programmer may simply hard-code those back-end credentials into the front-end software. Any user of that program may be able to extract the password. Client-side systems with hard-coded passwords pose even more of a threat, since the extraction of a password from a binary is usually very simple.",,high,"Writing Secure Code: Chapter 8, ""Key Management Issues"" Page 272 | |
| 2264 | Top 25 Series - Rank 11 - Hardcoded Credentials: http://blogs.sans.org/appsecstreetfighter/2010/03/10/top-25-series-rank-11-hardcoded-credentials/ | |
| 2265 | Mobile App Top 10 List: http://www.veracode.com/blog/2010/12/mobile-app-top-10-list/" | |
| 2266 | CWE-89,Improper Neutralization of Special Elements used in an SQL Command (SQL Injection) (Type: Base),"The software constructs all or part of an SQL command using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended SQL command when it is sent to a downstream component. | |
| 2267 | Without sufficient removal or quoting of SQL syntax in user-controllable inputs, the generated SQL query can cause those inputs to be interpreted as SQL instead of ordinary user data. This can be used to alter query logic to bypass security checks, or to insert additional statements that modify the back-end database, possibly including execution of system commands. | |
| 2268 | SQL injection has become a common issue with database-driven web sites. The flaw is easily detected, and easily exploited, and as such, any site or software package with even a minimal user base is likely to be subject to an attempted attack of this kind. This flaw depends on the fact that SQL makes no real distinction between the control and data planes.",,high,"24 Deadly Sins of Software Security: ""Sin 1: SQL Injection."" Page 3 | |
| 2269 | Writing Secure Code: Chapter 12, ""Database Input Issues"" Page 397 | |
| 2270 | SQL Injection Prevention Cheat Sheet: http://www.owasp.org/index.php/SQL_Injection_Prevention_Cheat_Sheet | |
| 2271 | SQL Injection Attacks by Example: http://www.unixwiz.net/techtips/sql-injection.html | |
| 2272 | SQL Injection Cheat Sheet: http://ferruh.mavituna.com/sql-injection-cheatsheet-oku/ | |
| 2273 | The Database Hacker's Handbook: Defending Database Servers | |
| 2274 | The Oracle Hacker's Handbook: Hacking and Defending Oracle | |
| 2275 | SQL Injection: http://msdn.microsoft.com/en-us/library/ms161953.aspx | |
| 2276 | SQL Injection Attack: http://blogs.technet.com/swi/archive/2008/05/29/sql-injection-attack.aspx | |
| 2277 | Giving SQL Injection the Respect it Deserves: http://blogs.msdn.com/sdl/archive/2008/05/15/giving-sql-injection-the-respect-it-deserves.aspx | |
| 2278 | Top 25 Series - Rank 2 - SQL Injection: http://blogs.sans.org/appsecstreetfighter/2010/03/01/top-25-series-rank-2-sql-injection/ | |
| 2279 | Least Privilege: https://buildsecurityin.us-cert.gov/daisy/bsi/articles/knowledge/principles/351.html | |
| 2280 | The Art of Software Security Assessment: Chapter 8, ""SQL Queries"", Page 431. | |
| 2281 | The Art of Software Security Assessment: Chapter 17, ""SQL Injection"", Page 1061." | |
| 2282 | CWE-262,Not Using Password Aging (Type: Variant),"If no mechanism is in place for managing password aging, users will have no incentive to update passwords in a timely manner. | |
| 2283 | This can result in compromise of the system for which the password is used. An attacker could gain access to this file and learn the stored password or worse yet, change the password to one of their choosing.",,low,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 2284 | CWE-263,Password Aging with Long Expiration (Type: Base),"Allowing password aging to occur unchecked can result in the possibility of diminished password integrity. | |
| 2285 | Just as neglecting to include functionality for the management of password aging is dangerous, so is allowing password aging to continue unchecked. Passwords must be given a maximum life span, after which a user is required to update with a new and different password.",,low,"24 Deadly Sins of Software Security: ""Sin 19: Use of Weak Password-Based Systems."" Page 279" | |
| 2286 | ,Session Cookie without Secure flag set,"This cookie does not have the Secure flag set. When a cookie is set with the Secure flag, it instructs the browser that the cookie can only be accessed over secure SSL channels. This is an important security protection for session cookies. | |
| 2287 | ","If possible, you should set the Secure flag for this cookie.",low, | |
| 2288 | ,Session Cookie without HttpOnly flag Set,"This cookie does not have the HTTPOnly flag set. When a cookie is set with the HTTPOnly flag, it instructs the browser that the cookie can only be accessed by the server and not by client-side scripts. This is an important security protection for session cookies. | |
| 2289 | ","If possible, you should set the HTTPOnly flag for this cookie.",low, | |
| 2290 | ,Application error message,"This page contains an error/warning message that may disclose sensitive information.The message can also contain the location of the file that produced the unhandled exception. | |
| 2291 | ||
| 2292 | The error messages may disclose sensitive information. This information can be used to launch further attacks. | |
| 2293 | ",Review the source code for this script. The application need to show generic errors.,unclassified, | |
| 2294 | ,Apache httpOnly Cookie Disclosure,"El servidor Apache version 2.2.X hasta la 2.2.21 no restringe correctamente la informacion mostrada en la contrsuccion del error "" Bad Request "" (aka 400) permitiendo a un atacante obtener los parametros de HTTPOnly. | |
| 2295 | Datos: http://fd.the-wildcat.de/apache_e36a9cf46c.php | |
| 2296 | ",Actualizar el apache. La version 2.2.22 es la primer version que soluciona este problema.,unclassified, | |
| 2297 | ,Input Password with Autocomplete Enable,"Autocomplete allows the browser to predict the value. When a user starts to type in a field, the browser should display options to fill in the field, based on earlier typed values. If an attacker gain access to a computer its possible of get credentials back. | |
| 2298 | ","You should include the attribute Autocomplete OFF: | |
| 2299 | <INPUT TYPE=""password"" AUTOCOMPLETE=""off"">",low, | |
| 2300 | ,Backup Files,"Backup files can contain script sources, configuration files or other sensitive information that may help an malicious user to prepare more advanced attacks | |
| 2301 | ","Remove the file(s) if they are not required on your website. As an additional step, it is recommended to implement a security policy within your organization to disallow creation of backup files in directories accessible from the web.",unclassified, | |
| 2302 | ,Sesintive directory,"A possible sensitive directory has been found. This directory is not directly linked from the website.This check looks for common sensitive resources like backup directories, database dumps, administration pages, temporary directories. Each one of these directories could help an attacker to learn more about his target. | |
| 2303 | ",,unclassified, | |
| 2304 | ,Slow HTTP Denial of Service Attack,"Slowloris and Slow HTTP POST DoS attacks rely on the fact that the HTTP protocol, by design, requires requests to be completely received by the server before they are processed. If an HTTP request is not complete, or if the transfer rate is very low, the server keeps its resources busy waiting for the rest of the data. If the server keeps too many resources busy, this creates a denial of service. | |
| 2305 | ",It's important to configure the timout values on the Webserver. Here is a link to a guide on how to prevent this kind of attack: https://community.qualys.com/blogs/securitylabs/2011/11/02/how-to-protect-against-slow-http-attacks,medium, | |
| 2306 | ,Clickjacking,"It might be possible for a web page controlled by an attacker to load the content of this response within an iframe on the attacker's page. This may enable a ""clickjacking"" attack, in which the attacker's page overlays the target application's interface with a different interface provided by the attacker. By inducing victim users to perform actions such as mouse clicks and keystrokes, the attacker can cause them to unwittingly carry out actions within the application that is being targeted. This technique allows the attacker to circumvent defenses against cross-site request forgery, and may result in unauthorized actions. Ref:http://javascript.info/tutorial/clickjacking | |
| 2307 | ","To effectively prevent framing attacks, the application should return a response header with the name X-Frame-Options and the value DENY to prevent framing altogether, or the value SAMEORIGIN to allow framing only by pages on the same origin as the response itself.",low, | |
| 2308 | ,OPTIONS method is enabled,"HTTP OPTIONS method is enabled on this web server. The OPTIONS method provides a list of the methods that are supported by the web server, it represents a request for information about the communication options available on the request/response chain identified by the Request-URI. | |
| 2309 | The OPTIONS method may expose sensitive information that may help an malicious user to prepare more advanced attacks. | |
| 2310 | ",It's recommended to disable OPTIONS Method on the web server.,low, | |
| 2311 | ,TLS1/SSLv3 Renegotiation Vulnerability,"A vulnerability in the way SSL and TLS protocols allow renegotiation requests may allow an attacker to inject plaintext into an application protocol stream. This could result in a situation where the attacker may be able to issue commands to the server that appear to be coming from a legitimate source. This issue affects SSL version 3.0 and newer and TLS version 1.0 and newer. | |
| 2312 | A remote, unauthenticated attacker may be able to inject an arbitrary amount of chosen plaintext into the beginning of the application protocol stream. This could allow and attacker to issue HTTP requests, or take action impersonating the user, among other consequences. | |
| 2313 | ",http://www.g-sec.lu/practicaltls.pdf,unclassified, | |
| 2314 | ,Email address found,"One or more email addresses have been found on this page. The majority of spam comes from email addresses harvested off the internet. The spam-bots (also known as email harvesters and email extractors) are programs that scour the internet looking for email addresses on any website they come across. Spambot programs look for strings like [email protected] and then record any addresses found. | |
| 2315 | ",,unclassified, | |
| 2316 | ,File Inclusion,"It is possible for a remote attacker to include a file from local or remote resources and/or execute arbitrary script code with the privileges of the webserver. | |
| 2317 | ","Edit the source code to ensure that input is properly validated. Where is possible, it is recommended to make a list of accepted filenames and restrict the input to that list. | |
| 2318 | ||
| 2319 | For PHP, the option allow_url_fopen would normally allow a programmer to open, include or otherwise use a remote file using a URL rather than a local file path. It is recommended to disable this option from php.ini.",unclassified, | |
| 2320 | ,User Credentials Sent in Clear Text,"Vulnerability description | |
| 2321 | User credentials are transmitted over an unencrypted channel. This information should always be transferred via an encrypted channel (HTTPS) to avoid being intercepted by malicious users. | |
| 2322 | ||
| 2323 | The impact of this vulnerability | |
| 2324 | A third party may be able to read the user credentials by intercepting an unencrypted HTTP connection. | |
| 2325 | ","Because user credentials are considered sensitive information, should always be transferred to the server over an encrypted connection (HTTPS).",unclassified, | |
| 2326 | ,URL Redirection,"This script is possibly vulnerable to URL redirection attacks. | |
| 2327 | ||
| 2328 | URL redirection is sometimes used as a part of phishing attacks that confuse visitors about which web site they are visiting. | |
| 2329 | ||
| 2330 | The impact of this vulnerability | |
| 2331 | A remote attacker can redirect users from your website to a specified URL. This problem may assist an attacker to conduct phishing attacks, trojan distribution, spammers. | |
| 2332 | ",Your script should properly sanitize user input.,unclassified, | |
| 2333 | ,Microsoft IIS tilde directory enumeration,"It is possible to detect short names of files and directories which have an 8.3 file naming scheme equivalent in Windows by using some vectors in several versions of Microsoft IIS. For instance, it is possible to detect all short-names of "".aspx"" files as they have 4 letters in their extensions. This can be a major issue especially for the .Net websites which are vulnerable to direct URL access as an attacker can find important files and folders that they are not normally visible. | |
| 2334 | ",There is a way to disable Windows 8.3 short name creation.You can create a registry key named NtfsDisable8dot3NameCreation in HKLMSYSTEMCurrentControlSetControlFileSystem and set it to 1. That should disable short names creation. Refer to this Microsoft TechNet article to read more about the solution.,unclassified, | |
| 2335 | ,SQL Injection,"SQL injection is a vulnerability that allows an attacker to alter back-end SQL statements by manipulating the user input. An SQL injection occurs when web applications accept user input that is directly placed into a SQL statement and doesn't properly filter out dangerous characters. | |
| 2336 | ||
| 2337 | This is one of the most common application layer attacks currently being used on the Internet. Despite the fact that it is relatively easy to protect against, there is a large number of web applications vulnerable. | |
| 2338 | ||
| 2339 | An attacker may execute arbitrary SQL statements on the vulnerable system. This may compromise the integrity of your database and/or expose sensitive information. | |
| 2340 | ||
| 2341 | Depending on the back-end database in use, SQL injection vulnerabilities lead to varying levels of data/system access for the attacker. It may be possible to not only manipulate existing queries, but to UNION in arbitrary data, use sub selects, or append additional queries. In some cases, it may be possible to read in or write out to files, or to execute shell commands on the underlying operating system. | |
| 2342 | ||
| 2343 | Certain SQL Servers such as Microsoft SQL Server contain stored and extended procedures (database server functions). If an attacker can obtain access to these procedures it may be possible to compromise the entire machine. | |
| 2344 | ","Your script should filter metacharacters from user input. | |
| 2345 | Check detailed information for more information about fixing this vulnerability. | |
| 2346 | Detailed information",unclassified, | |
| 2347 | ,ASP.NET debugging enabled,"ASP.NET debugging is enabled on this application. It is recommended to disable debug mode before deploying a production application. By default, debugging is disabled, and although debugging is frequently enabled to troubleshoot a problem, it is also frequently not disabled again after the problem is resolved. | |
| 2348 | ","It may be possible to disclose sensitive information about the web sever the ASP.NET application. | |
| 2349 | More information on how to fix it: | |
| 2350 | http://support.microsoft.com/default.aspx?scid=kb;en-us;815157",unclassified, | |
| 2351 | ,Unicode tranformation Issues,"This page is vulnerable to various Unicode transformation issues such as Best-Fit Mappings, Overlong byte sequences, Ill-formed sequences. | |
| 2352 | Best-Fit Mappings occurs when a character X gets transformed to an entirely different character Y. In general, best-fit mappings occur when characters are transcoded between Unicode and another encoding. | |
| 2353 | ||
| 2354 | Overlong byte sequences (non-shortest form) - UTF-8 allows for different representations of characters that also have a shorter form. For security reasons, a UTF-8 decoder must not accept UTF-8 sequences that are longer than necessary to encode a character. For example, the character U+000A (line feed) must be accepted from a UTF-8 stream only in the form 0x0A, but not in any of the following five possible overlong forms: | |
| 2355 | 0xC0 0x8A | |
| 2356 | 0xE0 0x80 0x8A | |
| 2357 | 0xF0 0x80 0x80 0x8A | |
| 2358 | 0xF8 0x80 0x80 0x80 0x8A | |
| 2359 | 0xFC 0x80 0x80 0x80 0x80 0x8A | |
| 2360 | ||
| 2361 | Ill-Formed Subsequences As REQUIRED by UNICODE 3.0, and noted in the Unicode Technical Report #36, if a leading byte is followed by an invalid successor byte, then it should NOT consume it. | |
| 2362 | ||
| 2363 | ||
| 2364 | Software vulnerabilities arise when Best-Fit mappings occur. For example, characters can be manipulated to bypass string handling filters, such as cross-site scripting (XSS) or SQL Injection filters, WAF's, and IDS devices. Overlong UTF-8 sequence could be abused to bypass UTF-8 substring tests that look only for the shortest possible encoding. | |
| 2365 | ","Identiy the source of these Unicode transformation issues and fix them. Consult the web references bellow for more information. | |
| 2366 | Links with more information: | |
| 2367 | http://www.blackhat.com/presentations/bh-usa-09/WEBER/BHUSA09-Weber-UnicodeSecurityPreview-PAPER.pdf | |
| 2368 | http://www.cl.cam.ac.uk/~mgk25/unicode.html | |
| 2369 | http://sirdarckcat.blogspot.ro/2009/10/couple-of-unicode-issues-on-php-and.html | |
| 2370 | http://www.unicode.org/reports/tr36/",unclassified, | |
| 2371 | ,File Upload XSS,"This script is possibly vulnerable to XSS (Cross-site scripting). The web application allows file upload and Acunetix WVS was able to upload a file containing HTML content. When HTML files are allowed, XSS payload can be injected in the file uploaded. Check Attack details for more information about this attack. | |
| 2372 | ||
| 2373 | Malicious users may inject JavaScript, VBScript, ActiveX, HTML or Flash into a vulnerable application to fool a user in order to gather data from them. An attacker can steal the session cookie and take over the account, impersonating the user. It is also possible to modify the content of the page presented to the user. | |
| 2374 | ","Restrict file types accepted for upload: check the file extension and only allow certain files to be uploaded. Use a whitelist approach instead of a blacklist. Check for double extensions such as .php.png. Check for files without a filename like .htaccess (on ASP.NET, check for configuration files like web.config). Change the permissions on the upload folder so the files within it are not executable. If possible, rename the files that are uploaded. | |
| 2375 | ||
| 2376 | https://www.owasp.org/index.php/Unrestricted_File_Upload | |
| 2377 | https://www.owasp.org/index.php/Testing_for_Stored_Cross_site_scripting_(OWASP-DV-002)",unclassified, | |
| 2378 | ,Possible virtual host found,"Virtual hosting is a method for hosting multiple domain names (with separate handling of each name) on a single server (or pool of servers). This allows one server to share its resources, such as memory and processor cycles, without requiring all services provided to use the same host name. | |
| 2379 | ||
| 2380 | This web server is responding differently when the Host header is manipulated and various common virtual hosts are tested. This could indicate there is a Virtual Host present. | |
| 2381 | ",Consult the virtual host configuration and check if this virtual host should be publicly accessible,unclassified, | |
| 2382 | ,Host header attack,"An attacker can manipulate the Host header as seen by the web application and cause the application to behave in unexpected ways. | |
| 2383 | Developers often resort to the exceedingly untrustworthy HTTP Host header (_SERVER[""HTTP_HOST""] in PHP). | |
| 2384 | Even otherwise-secure applications trust this value enough to write it to the page without HTML-encoding it with code equivalent to: | |
| 2385 | ||
| 2386 | <link href=""http://_SERVER['HOST']"" (Joomla) | |
| 2387 | ...and append secret keys and tokens to links containing it: | |
| 2388 | ||
| 2389 | <a href=""http://_SERVER['HOST']?token=topsecret""> (Django, Gallery, others) | |
| 2390 | ....and even directly import scripts from it: | |
| 2391 | ||
| 2392 | <script src=""http://_SERVER['HOST']/misc/jquery.js?v=1.4.4""> (Various) | |
| 2393 | ||
| 2394 | Host header *********evilhostDx5oMrAd.com was reflected inside a A tag (href attribute). | |
| 2395 | ","The web application should use the SERVER_NAME instead of the Host header. It should also create a dummy vhost that catches all requests with unrecognized Host headers. This can also be done under Nginx by specifying a non-wildcard SERVER_NAME, and under Apache by using a non-wildcard serverName and turning the UseCanonicalName directive on. Consult references for detailed information.",unclassified, | |
| 2396 | ,jQuery cross site scripting,"This page is using an older version of jQuery that is vulnerable to a Cross Site Scripting vulnerability. Many sites are using to select elements using location.hash that allows someone to inject script into the page. This problem was fixed in jQuery 1.6.3 and up. | |
| 2397 | Malicious users may inject JavaScript, VBScript, ActiveX, HTML or Flash into a vulnerable application to fool a user in order to gather data from them. An attacker can steal the session cookie and take over the account, impersonating the user. It is also possible to modify the content of the page presented to the user. | |
| 2398 | ","Update to the latest version of jQuery. | |
| 2399 | More info: http://ma.la/jquery_xss/ | |
| 2400 | http://blog.jquery.com/2011/09/01/jquery-1-6-3-released/",unclassified, | |
| 2401 | ,Login Page password-guessing attack,"A common threat web developers face is a password-guessing attack known as a brute force attack. A brute-force attack is an attempt to discover a password by systematically trying every possible combination of letters, numbers, and symbols until you discover the one correct combination that works. | |
| 2402 | ||
| 2403 | This login page doesn't have any protection against password-guessing attacks (brute force attacks). It's recommended to implement some type of account lockout after a defined number of incorrect password attempts. Consult Web references for more information about fixing this problem. | |
| 2404 | ||
| 2405 | The scanner tested 10 invalid credentials and no account lockout was detected. | |
| 2406 | ","It's recommended to implement some type of account lockout after a defined number of incorrect password attempts. | |
| 2407 | More info: | |
| 2408 | https://www.owasp.org/index.php/Blocking_Brute_Force_Attacks",unclassified, | |
| 2409 | ,Error page web server version disclosure,"By requesting a page that doesn't exist, an error page was returned. This error page contains the web server version number and a list of modules enabled on this server. This information can be used to conduct further attacks. Possible sensitive information disclosure. | |
| 2410 | ","If you are using Apache, you can setup a custom 404 page by following the instructions provided in the References section.",unclassified, | |
| 2411 | ,SSL weak ciphers,"The remote host supports the use of SSL ciphers that offer either weak encryption or no encryption at all. | |
| 2412 | This vulnerability affects Server. | |
| 2413 | ",Reconfigure the affected application to avoid use of weak ciphers.,unclassified, | |
| 2414 | ,CRIME SSL/TLS attack,"Compression Ratio Info-leak Made Easy (CRIME) is a security exploit against secret web cookies over connections using the HTTPS and SPDY protocols that also use data compression. When used to recover the content of secret authentication cookies, it allows an attacker to perform session hijacking on an authenticated web session, allowing the launching of further attacks. | |
| 2415 | ||
| 2416 | CRIME is a client-side attack, but the server can protect the client by refusing to use the feature combinations which can be attacked. For CRIME, the weakness is Deflate compression. This alert is issued if the server accepts Deflate compression. | |
| 2417 | ||
| 2418 | An attacker can perform session hijacking on an authenticated web session, allowing the launching of further attacks. | |
| 2419 | ","CRIME can be defeated by preventing the use of compression, either at the client end, by the browser disabling the compression of HTTPS requests, or by the website preventing the use of data compression on such transactions using the protocol negotiation features of the TLS protocol. As detailed in The Transport Layer Security (TLS) Protocol Version 1.2, the client sends a list of compression algorithms in its ClientHello message, and the server picks one of them and sends it back in its ServerHello message. The server can only choose a compression method the client has offered, so if the client only offers 'none' (no compression), the data will not be compressed. Similarly, since 'no compression' must be allowed by all TLS clients, a server can always refuse to use compression. | |
| 2420 | ||
| 2421 | Web references | |
| 2422 | http://en.wikipedia.org/wiki/CRIME_(security_exploit) | |
| 2423 | http://isecpartners.com/blog/2012/september/details-on-the-crime-attack.aspx",unclassified, | |
| 2424 | ,Insecure transition from HTTPS to HTTP in form post,"This secure (https) page contains a form that is posting to an insecure (http) page. This could confuse users who may think their data is encrypted when in fact it's not. | |
| 2425 | Impact: Possible information disclosure. | |
| 2426 | ",The form target should point to a secure (https) page.,unclassified, | |
| 2427 | ,TRACE method is enabled,"HTTP TRACE method is enabled on this web server. In the presence of other cross-domain vulnerabilities in web browsers, sensitive header information could be read from any domains that support the HTTP TRACE method. | |
| 2428 | ||
| 2429 | Attackers may abuse HTTP TRACE functionality to gain access to information in HTTP headers such as cookies and authentication data. | |
| 2430 | ","Disable TRACE Method on the web server. | |
| 2431 | ||
| 2432 | Web references | |
| 2433 | http://www.w3.org/Protocols/rfc2616/rfc2616-sec9.html | |
| 2434 | http://www.cgisecurity.com/lib/WH-WhitePaper_XST_ebook.pdf",unclassified, | |
| 2435 | ,SSL certificate public key less than 2048 bit,"The product does not sufficiently filter code (control-plane) syntax from user-controlled input (data plane) when that input is used within code that the product generates.When software allows a user's input to contain code syntax, it might be possible for an attacker to craft the code in such a way that it will alter the intended control flow of the software. Such an alteration could lead to arbitrary code execution | |
| 2436 | ","If you have any 1024-bit certificates or certificates with less than 2048-bit key length, you will need to migrate to 2048-bit key length. | |
| 2437 | ||
| 2438 | New Standard: https://www.cabforum.org/wp-content/uploads/Baseline_Requirements_V1.pdf",unclassified, | |
| 2439 | ,Ruby on Rails CookieStore session cookie persistence,"Debido que las credenciales del usuario son considerados información confidencial, siempre debe ser transferido al servidor a través de una conexión segura (HTTPS). | |
| 2440 | ","Currently, there are no known upgrades or patches to correct this vulnerability. It is possible to temporarily mitigate the flaw by implementing the following workaround: switch to a more secure authentication management systems (e.g. ActiveRecordStore).",unclassified, | |
| 2441 | ,Remote Code Execution - ms_08_067 netapi,"The product does not sufficiently filter code (control-plane) syntax from user-controlled input (data plane) when that input is used within code that the product generates.When software allows a user's input to contain code syntax, it might be possible for an attacker to craft the code in such a way that it will alter the intended control flow of the software. Such an alteration could lead to arbitrary code execution | |
| 2442 | ",,high, | |
| 2443 | ,Windows Print Spooler Components Vulnerability - MS13-001,"The software performs operations on a memory buffer, but it can read from or write to a memory location that is outside of the intended boundary of the buffer.Certain languages allow direct addressing of memory locations and do not automatically ensure that these locations are valid for the memory buffer that is being referenced. This can cause read or write operations to be performed on memory locations that may be associated with other variables, data structures, or internal program data. | |
| 2444 | Certain languages allow direct addressing of memory locations and do not automatically ensure that these locations are valid for the memory buffer that is being referenced. This can cause read or write operations to be performed on memory locations that may be associated with other variables, data structures, or internal program data. | |
| 2445 | As a result, an attacker may be able to execute arbitrary code, alter the intended control flow, read sensitive information, or cause the system to crash.",,high, | |
| 2446 | ,Android Debugging Activated,"The Application has enabled Debugging in it's manifiest. This feature allows an attacker to debug native code and sensitive information could be retrived using this vector | |
| 2447 | ",Set to false debuging features in production releases,unclassified, | |
| 2448 | ,Flash Crossdomain policy,"The application publishes a Flash cross-domain policy which allows access from any domain. | |
| 2449 | ",The policy must include the domains which are allowed by the Flash cross-domain policy,medium, | |
| 2450 | ,Session Token in URL,"The Session token is included in the URL. This could leak the session token | |
| 2451 | ",Session tokens should only be included using safe channels,medium, | |
| 2452 | ,Insecure crossdomain.xml file,"The browser security model normally prevents web content from one domain from accessing data from another domain. This is commonly known as the ""same origin policy"". URL policy files grant cross-domain permissions for reading data. They permit operations that are not permitted by default. The URL policy file is located, by default, in the root directory of the target server, with the name crossdomain.xml (for example, at www.example.com/crossdomain.xml). | |
| 2453 | ||
| 2454 | When a domain is specified in crossdomain.xml file, the site declares that it is willing to allow the operators of any servers in that domain to obtain any document on the server where the policy file resides. The crossdomain.xml file deployed on this website opens the server to all domains (use of a single asterisk ""*"" as a pure wildcard is supported) like so: | |
| 2455 | <cross-domain-policy> | |
| 2456 | <allow-access-from domain=""*"" /> | |
| 2457 | </cross-domain-policy> | |
| 2458 | This practice is suitable for public servers, but should not be used for sites located behind a firewall because it could permit access to protected areas. It should not be used for sites that require authentication in the form of passwords or cookies. Sites that use the common practice of authentication based on cookies to access private or user-specific data should be especially careful when using cross-domain policy files. | |
| 2459 | ||
| 2460 | Using an insecure cross-domain policy file could expose your site to various attacks. | |
| 2461 | ","Carefully evaluate which sites will be allowed to make cross-domain calls. Consider network topology and any authentication mechanisms that will be affected by the configuration or implementation of the cross-domain policy. | |
| 2462 | ",medium, | |
| 2463 | ,BREACH attack,"This web application is potentially vulnerable to the BREACH attack. | |
| 2464 | An attacker with the ability to: | |
| 2465 | Inject partial chosen plaintext into a victim's requests | |
| 2466 | Measure the size of encrypted traffic | |
| 2467 | can leverage information leaked by compression to recover targeted parts of the plaintext. | |
| 2468 | ||
| 2469 | BREACH (Browser Reconnaissance & Exfiltration via Adaptive Compression of Hypertext) is a category of vulnerabilities and not a specific instance affecting a specific piece of software. To be vulnerable, a web application must: | |
| 2470 | ||
| 2471 | Be served from a server that uses HTTP-level compression | |
| 2472 | Reflect user-input in HTTP response bodies | |
| 2473 | Reflect a secret (such as a CSRF token) in HTTP response bodies | |
| 2474 | ||
| 2475 | ||
| 2476 | This alert was issued because the following conditions were met: | |
| 2477 | The page content is served via HTTPS | |
| 2478 | The server is using HTTP-level compression | |
| 2479 | URL encoded GET input next was reflected into the HTTP response body. | |
| 2480 | HTTP response body contains a secret named csrfmiddlewaretoken | |
| 2481 | ","The mitigations are ordered by effectiveness (not by their practicality - as this may differ from one application to another). | |
| 2482 | ||
| 2483 | Disabling HTTP compression | |
| 2484 | Separating secrets from user input | |
| 2485 | Randomizing secrets per request | |
| 2486 | Masking secrets (effectively randomizing by XORing with a random secret per request) | |
| 2487 | Protecting vulnerable pages with CSRF | |
| 2488 | Length hiding (by adding random number of bytes to the responses) | |
| 2489 | Rate-limiting the requests | |
| 2490 | ||
| 2491 | More information http://breachattack.com/",unclassified, | |
| 2492 | ,Internal IP Address Disclosure,"A string matching an internal IPv4 address was found on this page. This may disclose information about the IP addressing scheme of the internal network. This information can be used to conduct further attacks. | |
| 2493 | ",Prevent this information from being displayed to the user,low, | |
| 2494 | ,ASP.NET MAC disabled,"By default, the serialized value is signed by the server to prevent tampering by the user; however, this behavior can be disabled by setting the Page.EnableViewStateMac property to false. If this is done, then an attacker can modify the contents of the ViewState and cause arbitrary data to be deserialized and processed by the server. If the ViewState contains any items that are critical to the server's processing of the request, then this may result in a security exposure. | |
| 2495 | ",Set the Page.EnableViewStateMac property to true on any pages where the ViewState is not currently signed.,low, | |
| 2496 | ,Privilege Escalation,"This happens when an attacker has already done reconnaissance and successfully compromised a system by gaining access to a low-level account. In this phase, an attacker wants to have a strong grip on the system and seeks ways to heighten the privileges, either to study the system further or perform an attack.","Change passwords of administrative accounts regularly and enforce strong password policy (e.g. ensure that local administrator accounts have complex, unique passwords across all systems).",medium,https://www.owasp.org/index.php/Testing_for_Privilege_escalation_(OTG-AUTHZ-003) | |
| 2497 | ,Default Credentials,"It was detected that the system has default credentials to access the administration console. These credentials can be obtained from internet sites, for example: technology forums, system manuals, among others.",It is recommended to change all system passwords by default and adapt them to a secure password policy. It is also recommended that all default system accounts be renamed and their passwords changed.,critical,https://www.owasp.org/index.php/Testing_for_default_credentials_(OTG-AUTHN-002) |
| 0 | cwe,name,description,resolution,exploitation,references | |
| 1 | ,Metadatos,"250+ Archivos conteniendo metadatos: usuarios, carpetas, fechas de edición y modificación, software usado, dirección de impresoras locales. | |
| 2 | ","Datos privados son revelados a través de los metadatos de documentos hosteados en el dominio (PDF, WORD). Datos como nombres de usuario, versiones de sistemas operativos, versiones de software utilizados, fechas y horas de cada modificación del documento, direcciones de red de impresoras, etc. Se recomienda limpiar de metadatos documentos que luego serán publicados en internet.",unclassified, | |
| 3 | ,Session Cookie without Secure flag set,"La cookie no tiene la marca de ""Secure"". Esto instruye al navegador que dicha cookie puede ser solo accedida por canales SSL. | |
| 4 | ",Si es posible se debería habilitar el flag Secure para esta cookie.,low, | |
| 5 | ,Session Cookie without HttpOnly flag Set,"La cookie de sesion no esta marcada como HTTPOnly, cuando una cookie es marcada de esta manera da instruccion al navegador que esa cookie puede ser accedida solamente por el servdor y no por script del lado del cliente. Es una importante proteccion de seguridad para las cookies de sesion | |
| 6 | ",Si es posible se debería habilitar la flag HTTPOnly para esta cookie.,low, | |
| 7 | ,Apache httpd Remote Denial of Service,"* Alerta generada por el flag del servidor: ver: 2.2.15 * | |
| 8 | Se ha detectado un problema en las versiones de apache 1.3.0, 2.0.x hasta 2.0.64 y 2.2.X hasta 2.2.19 que mediante una herramienta automatizada un atacante usando una moderada cantidad de requests puede causar un uso significativo de memoria y CPU en el servidor. Datos: http://seclists.org/fulldisclosure/2011/Aug/175. | |
| 9 | ",Actualizar versión de Apache,medium, | |
| 10 | ,Robots.txt,"Robots.txt revela directorios sensibles. Un atacante busca directamente robots.txt para encontrar puntos desde donde comenzar su ataque. | |
| 11 | ","Es conveniente manejar nombres de directorios que no describan el contenido, en especial en directorios sensibles. Por ejemplo en lugar de /setup o /app_data llamar al directorio /Dir_Code1. De esta manera no revelar a un atacante que clase de información contiene un directorio, que se intenta ocultar de los buscadores (mediante robots.txt). | |
| 12 | Otra practica que se me ocurre es la utilización de parámetros. Por ejemplo: | |
| 13 | Disallow: /*AB/$ | |
| 14 | Esto desactivará cualquier carpeta que termine con ""AB"", por ejemplo: /sourceAB/. Evitando pasar cualquier dato a un atacante y centralizando las carpetas sensibles y ocultándolas simplemente colocando ""AB"" al final.",informational, | |
| 15 | ,Credenciales en Texto Plano,"Las credenciales de usuario son trasmitidas por un canal sin cifrar y pueden ser interceptadas. | |
| 16 | ",Es altamente recomendable que las páginas de login se fuerzen a usar SSL (https).,medium, | |
| 17 | ,Parametro __VIEWSTATE sin encriptar,"El parámetro ""__VIEWSTATE"" no esta encriptado. Para reducir las posibilidades de que alguien intercepte información guardada en ViewState, es bueno encriptarlo. | |
| 18 | ","Se recomienda encriptar el parámetro ""__VIEWSTATE"", para hacer esto se debe setear el tipo de validación a 3DES. Editar Web.Config y agregar la siguiente línea bajo <system.web> | |
| 19 | <machineKey validation=""3DES""/>",unclassified, | |
| 20 | ,Insecure Captcha,"La resolucion del Captcha esta incluida en el mismo codigo: | |
| 21 | ||
| 22 | <img id=""ctl01_mainContent_imgCaptcha"" src=""http://test-www.bancofalabella.com.co/Data/Sites/1/ImgTemp/ImageFormat_THHvB.png"" | |
| 23 | style=""border-width:0px;"" /> | |
| 24 | ||
| 25 | Siendo la respuesta THHvB | |
| 26 | ||
| 27 | Facilitando la manera de automatizar un script para atacar el form. | |
| 28 | ",Se recomienda implementar un sistema de Captcha que la resolución no se incluya en el código.,unclassified, | |
| 29 | ,"Mensaje de error de la aplicación | |
| 30 | (Application error message)","El server responde con mensajes de error internos que no deberían mostrarse, facilitando de esta manera información que puede ser sensible o útil para un atacante. Pudiendo de esta manera obtener datos para mejorar su vector de ataque. | |
| 31 | ","Se recomienda deshabilitar los mensajes de error, para no proporcionar información de la tecnología o software implementado. | |
| 32 | ||
| 33 | ",low, | |
| 34 | ,Apache httpOnly Cookie Disclosure,"El servidor Apache desde la versión 2.2.X hasta la 2.2.21 no restringe correctamente la información mostrada en la construcción del error "" Bad Request "" (aka 400) permitiendo a un atacante obtener los parámetros de HTTPOnly. | |
| 35 | Datos: http://fd.the-wildcat.de/apache_e36a9cf46c.php | |
| 36 | ",Actualizar el Apache. La versión 2.2.22 es la primera versión que soluciona este problema.,medium, | |
| 37 | ,Input de Contraseña con Autocompletar,"Un form de login con autocompletar sugiere un problema de seguridad, sobretodo para los usuarios que utilizan el servicio desde computadoras públicas. | |
| 38 | ","Se recomienta establecer el input con Autocomplete OFF: | |
| 39 | <INPUT TYPE=""password"" AUTOCOMPLETE=""off"">",low, | |
| 40 | ,Archivos de Backup,"Los archivos de Backup pueden contener código fuente de script, archivos de configuración u otra información sensible que puede ayudar a un atacante a conocer el servidor y preparar ataques más avanzados o específicos. | |
| 41 | ","Remover el/los archivo(s) si no son requeridos en el servidor en producción. Como un paso adicional, es recomendado implementar una política de seguridad para no permitir la creación de archivos de Backup en directorios accesibles desde la web.",unclassified, | |
| 42 | ,Possible sensitive directories,"Un posible directorio sensible fue encontrado. Este directorio no esta directamente linkeado en el servidor Web. Se chequeó usando nombres comunes para directorios de configuración, backups, bajadas de bases de datos, páginas de administración, archivos temporales, etc. Usar nombres comunes de directorios para almacenar este tipo de información facilita a usuarios maliciosos buscar archivos sensibles. | |
| 43 | ","Se recomienda llamar a estos directorios de manera no estándar, por ejemplo: | |
| 44 | config-->c0nfig05 | |
| 45 | backup-->b4ccup | |
| 46 | Aunque es aun más recomendable, de ser posible, no dejar directorios de backup, configuración, etc, accesibles directamente desde la web.",unclassified, | |
| 47 | ,Slow HTTP Denial of Service Attack,"Los ataques conocidos como ""Slowloris"" y ""Slow HTTP POST DoS"" se basan en el hecho de que el protocolo HTTP, por diseño, requiere que las consultas esten completamente recividas por el servidor antes de poder ser procesadas. Si la consulta HTTP no esta completa, o si la tranferencia es muy lenta, el servidor mantiene recursos ocupados esperando el resto de la informacion. Si el servidor mantiene demasiados recursos ocupados, esto crea una denegacion de servicio. | |
| 48 | ",Es importante establecer los tiempos de espera del servidor. Se adjunta link de recomendacion para evitar este tipo de ataques: https://community.qualys.com/blogs/securitylabs/2011/11/02/how-to-protect-against-slow-http-attacks,medium, | |
| 49 | ,Clickjacking,"No se encuentra ningún tipo de impedimento para evitar que la web sea embebida dentro de un iframe. Esta restricción es importante ya que un atacante podría engañar a un usuario autenticado a realizar operaciones mediante un engaño llamado Clickjacking donde a la víctima se le presenta una web, posiblemente con algún juego, y utilizando algunos engaños de interfaz la víctima podria ser engañada para aprobar una venta. Ref:http://javascript.info/tutorial/clickjacking | |
| 50 | ","Todos los browsers modernos son capaces de interpretar los valores seteados en X-Frame-Options, si los mismos son incluidos en el Header del servidor.",low, | |
| 51 | ,"XSS Cross Site Scripting | |
| 52 | (Secuencias de comandos en sitios cruzados)","Es posible inyectar tags de html y código javascript malicioso, por una falta en la comprobación de los datos ingresados en los parámetros. De esta forma, un atacante podría ejecutar código que le permita obtener las cookies del usuario atacado, y de esa forma, tomar control de su cuenta. | |
| 53 | ","Recomendamos filtrar todos los parámetros en búsqueda de posibles inyecciones, y escapar todos los datos de entrada que se vayan a mostrar en la respuesta.",high, | |
| 54 | ,SSL 2.0 Obsolete Protocol,"El servicio remoto encripta el tráfico utilizando una versión obsoleta del protocolo SSL con errores y debilidades conocidas. Un atacante puede explotar estas vulnerabilidades y conducir a un ataque de ""man in the middle"" o desencriptar la comunicaciones entre el servicio afectado y los clientes. | |
| 55 | ",Se recomienda desactivar SSL 2.0 y usar SSL 3.0 o TLS 1.0 en su lugar.,high, | |
| 56 | ,Metodo OPTIONS activado,"El metodo HTTP OPTIONS está activado en el servidor. El metodo OPTIONS provee una lista de los métodos que son soportados por el servidor web. El método OPTIONS puede exponer información sensible que puede ayudar a un usuario malicioso a preparar ataques más avanzados. | |
| 57 | ",Es recomendado desactivar el método OPTIONS en un servidor en producción.,low, | |
| 58 | ,TLS1/SSLv3 Renegotiation Vulnerability,"Una vulnerabilidad, en la manera que los protocolos SSL y TLS aceptan pedidos de renegociaciones, puede permitir a un atacante inyectar texto plano en un flujo de protocolo de aplicación. Esto puede resultar en una situación donde el atacante puede enviar comandos al servidor que parecieran venir desde una fuente legítima. Este problema afecta la versión 3.0 (y más nuevas) de SSL y la versión 1.0 (y más nuevas) de TLS. | |
| 59 | Un atacante remoto y sin estar autenticado puede inyectar una cantidad arbitraria de textos planos al comienzo del flujo de protocolo de aplicación. Esto permitiría al atacante enviar requests de HTTP o hacerse pasar por un usuario, entre otras consecuencias. | |
| 60 | ",http://www.g-sec.lu/practicaltls.pdf,unclassified, | |
| 61 | ,File Inclusion,"Es posible que un atacante remoto incluya un archivo de recursos locales o remotos y / o la ejecución de código de script arbitrario con los privilegios del servidor web. | |
| 62 | ","Editar el código fuente para asegurarse de que la entrada esté correctamente validada. Cuando es posible, se recomienda hacer una lista de nombres de archivos aceptados y restringir la entrada a la lista. | |
| 63 | ||
| 64 | En PHP, la opción allow_url_fopen normalmente permite a un programador para abrir, incluir o utilizan de alguna manera un archivo remoto a través de una URL en lugar de una ruta de archivo local. Se recomienda desactivar esta opción de php.ini.",unclassified, | |
| 65 | CWE-319,Credenciales enviadas por un canal en texto plano,"Las credenciales de usuario se transmiten sobre un canal sin cifrar. Esta información siempre debe ser transferida a través de un canal cifrado (HTTPS) para evitar ser interceptados por usuarios maliciosos. | |
| 66 | ||
| 67 | Una tercera persona puede ser capaz de leer las credenciales de usuario mediante la interceptación de una conexión no cifrada de HTTP. | |
| 68 | ","Debido que las credenciales del usuario son considerados información confidencial, siempre debe ser transferido al servidor a través de una conexión segura (HTTPS).",medium, | |
| 69 | ,URL Redirection,"Este script es vulnerable a los ataques de redirección por URL | |
| 70 | ||
| 71 | La redirección por URL es comúnmente usado para phishing y suplantación de identidad, ya que confunde al usuario a que sitio está ingresando realmente. Un atacante puede redireccionar una visita desde un sitio válido hasta un servidor preparado por el, para poder hacer ataques como por ejemplo de phishing o distribución de malware. | |
| 72 | ","El script debe filtrar los sitios destinos del redirect, manteniéndolo siempre dentro de los dominios válidos.",unclassified, | |
| 73 | ,Apache Server Status Enabled,"Server Status es una opción de debug que muestra información sensible del servidor, como número de peticiones, url de las peticiones, uso de memoria, threads, etc. | |
| 74 | ","Es recomendable desactivar esta opción en servidores en producción, o de ser necesaria la utilización de la misma, securizar la carpeta con contraseña o renombrarla para que no sea de fácil ubicación.",unclassified, | |
| 75 | ,Microsoft IIS tilde directory enumeration,"Es posible detectar nombres cortos de archivos y directorios cuyo nombrado sea en formato 8.3 en Windows usando vectores en varias versiones de Microsoft IIS. Por ejemplo, es posible detectar todos los nombres cortos de los archivos “.aspx” ya que tienen 4 letras en las extensiones. Esto puede ser un problema mayor, especialmente para los sitios web .Net los cuales son vulnerables al acceso directo a la URL ya que un atacante puede encontrar archivos y carpetas importantes que normalmente no están visibles. | |
| 76 | ",Hay una manera de deshabilitar la creación del nombre corto de Windows 8.3. Puede crear una clave de registro llamada NtfsDisable8dot3NameCreation en HKLMSYSTEMCurrentControlSetControlFileSystem y establecerlo en 1. Eso debería deshabilitar la creación de nombres cortos. Consulte este artículo de Microsoft TechNet para leer más sobre la solución.,unclassified, | |
| 77 | ,SQL Injection,"Debido al incorrecto filtrado de parámetros es posible ejecutar comandos SQL en la base de datos situada en el servidor mediante manipulación de parámetros. Un atacante podría utilizar esta técnica para extraer/modificar/eliminar el contenido de la base de datos, el único limitante son los privilegios del usuario utilizado por la aplicación web aunque en muchos casos es posible, gracias a una inyección de SQL, catapultar un acceso al sistema operativo. | |
| 78 | ","Se debe modificar la aplicación para filtrar caracteres en los campos de input antes de ser enviados como consulta al servidor de base de datos. | |
| 79 | Es importante que se sigan buenas prácticas de programación, en todos los sitios desarrollados, y sobre todos los parámetros, y no solo sobre aquellos que sean vulnerables actualmente. | |
| 80 | Guía de cómo evitar estos ataques (en inglés): https://www.owasp.org/index.php/Guide_to_SQL_Injection",high, | |
| 81 | ,ASP.NET debugging enabled,"El modo depuración de ASP.NET está activado en el servidor. Es recomendado desactivar este modo en servidores en producción. Por defecto, en la instalación de IIS este modo está desactivado, si fue activado para diagnosticar errores es conveniente luego desactivarlo. | |
| 82 | ","Es posible que el modo debug muestre datos sensibles del servidor. | |
| 83 | Más información de como desactivar el modo debug: | |
| 84 | http://support.microsoft.com/default.aspx?scid=kb;es-us;815157",unclassified, | |
| 85 | ,Unicode transformation Issues,"La página es vulnerable a varias transformaciones de Unicode como ""Best-Fit Mappings"", ""Overlong byte sequences"" y ""Ill-formed sequences"". | |
| 86 | ||
| 87 | “Best-Fit Mappings” ocurre cuando el caracter X es transformado por un caracter Y totalmente diferente. En general, best-fit mappings occure cuando el caracter es transcodeado entre Unicode y otro encodificado. | |
| 88 | ||
| 89 | ""Overlong byte sequences"" (no la forma corta) - UTF-8 permite diferentes representaciones de caracteres que también tienen una forma más corta. Por razones de seguridad, un decodificador UTF-8 no debe aceptar secuencias UTF-8 que sean más largas de lo necesario para codificar un carácter. Por ejemplo, el carácter U + 000A (salto de línea) debe aceptarse desde un flujo UTF-8 solo en la forma 0x0A, pero no en ninguna de las siguientes cinco posibles formas prolongadas: | |
| 90 | 0xC0 0x8A | |
| 91 | 0xE0 0x80 0x8A | |
| 92 | 0xF0 0x80 0x80 0x8A | |
| 93 | 0xF8 0x80 0x80 0x80 0x8A | |
| 94 | 0xFC 0x80 0x80 0x80 0x80 0x8A | |
| 95 | ||
| 96 | “Ill-Formed Subsequences” Como lo REQUIERE UNICODE 3.0, y se indica en el Informe Técnico Unicode # 36, si un byte inicial es seguido por un byte sucesor no válido, entonces NO debe consumirlo. | |
| 97 | ||
| 98 | ||
| 99 | Las vulnerabilidades del software surgen cuando se producen las asignaciones Best-Fit. Por ejemplo, los caracteres se pueden manipular para omitir los filtros de manejo de cadenas, como los scripts entre sitios (XSS) o los filtros de inyección SQL, los dispositivos WAF y los dispositivos IDS. Podría abusarse de una secuencia UTF-8 excesiva para omitir las pruebas de subcadenas UTF-8 que buscan solo la codificación más corta posible.","Se debe identificar el origen de esta tranformación Unicode y reparar el problema. Se deja links a páginas con información: | |
| 100 | ||
| 101 | http://www.blackhat.com/presentations/bh-usa-09/WEBER/BHUSA09-Weber-UnicodeSecurityPreview-PAPER.pdf | |
| 102 | http://www.cl.cam.ac.uk/~mgk25/unicode.html | |
| 103 | http://sirdarckcat.blogspot.ro/2009/10/couple-of-unicode-issues-on-php-and.html | |
| 104 | http://www.unicode.org/reports/tr36/",unclassified, | |
| 105 | ,"File Upload XSS | |
| 106 | (Subida de archivo de secuencias de comandos de sitios cruzados)","El Script es vulnerable a XSS (Cross-site scripting). La aplicación permite la carga de archivos y se subió un archivo conteniendo lenguaje HTML. Cuando este tipo de archivos es permitido en la carga, luego se pueden ejecutar o linkear, mostrando código o acciones maliciosas en dicha web. | |
| 107 | ||
| 108 | Usuarios maliciosos pueden inyectar: JavaScript, VBScript, ActiveX, HTML o Flash en esta aplicación vulnerable y engañar a un usuario para obtener información de el, tambien se puede robar datos de la sesión, así como las cookies de la misma. Dependiendo del código que se pueda ejecutar, tambien se puede ganar acceso al servidor web, archivos de configuración o hasta ejecución de binarios en el sistema operativo host. | |
| 109 | ","Se deben restringir los tipos de archivos aceptados en el sistema de Carga: chequear la extensión y solo aceptar ciertos tipos de archivos. Se recomienda una Whitelist en lugar de una Blacklist (es mejor especificar un listado único de extensiones permitidas, sobre un listado de denegadas). También se debe chequear doble extensiones como .php.png. Chequear archivos sin nombre como "".htaccess"" (en ASP.NET, se debe chequear archivos de configuración como web.config). Cambiar los permisos sobre la carpeta upload (de carga) para que los archivos no puedan ser ejecutados ahí. Si es posible, renombre los archivos que son subidos al servidor. | |
| 110 | Links con mas información: | |
| 111 | https://www.owasp.org/index.php/Unrestricted_File_Upload | |
| 112 | https://www.owasp.org/index.php/Testing_for_Stored_Cross_site_scripting_(OWASP-DV-002)",unclassified, | |
| 113 | ,jQuery cross site scripting,"Esta página esta usando una versión obsoleta de jQuery la cual es vulnerable a Cross Site Scripting. Muchos sitios estan utilizando la selección de elementos usando location.hash lo que permite la ejecución de scripts en la página. El problema fue solucionado en la versión jQuery 1.6.3 o superior. | |
| 114 | Usuarios malíciosos pueden inyectar JavaScript, VBScript, ActiveX, HTML o Flash en la aplicación vulnerable, pudiendo asi engañar a un usuario para sacarle información sensible. | |
| 115 | ","Update to the latest version of jQuery. | |
| 116 | More info: | |
| 117 | http://ma.la/jquery_xss/ | |
| 118 | http://blog.jquery.com/2011/09/01/jquery-1-6-3-released/",unclassified, | |
| 119 | ,Host Header Attack,"Un atacante puede manipular el header Host y causar que la aplicación se comporte de maneras inesperadas. Los programadores a veces creen en el header host y programan el código basado en el: (_SERVER[""HTTP_HOST""] in PHP). Esto tambien se refleja en portales como Joomla o Wordpress en los plugins y ejecución de script, ejemplos: | |
| 120 | ||
| 121 | <link href=""http://_SERVER['HOST']"" (Joomla) | |
| 122 | ||
| 123 | ...haciendo un apend de keys secretas y tokens: | |
| 124 | <a href=""http://_SERVER['HOST']?token=topsecret""> (Django, Gallery y otros) | |
| 125 | ....e importante directamente scripts: | |
| 126 | <script src=""http://_SERVER['HOST']/misc/jquery.js?v=1.4.4""> (Various) | |
| 127 | ","La aplicación web debería usar una variable ""SERVER_NAME"" en lugar de basarse en el Host header.",high, | |
| 128 | ,Login Page password-guessing attack,"Un problema común con el que se encuentran los programadores web son los ataques de fuerza bruta de logins. Un ataque de fuerza bruta es un intento de adivinar la contraseña por sistemáticamente probar todas las posibles combinaciones de números, letras y símbolos hasta descubrir la combinación correcta. Este ataque se mejora utilizando diccionarios con palabras comunes y combinaciones de las mismas. | |
| 129 | ||
| 130 | Esta página de Login no tiene ninguna protección contra este ataque ya que se probaron 20 logins inválidos y el servidor no bloqueó el acceso para seguir intentando. Tampoco dispone de ninguna protección para evitar los intentos de login automáticos (como un captcha). | |
| 131 | ","Es recomendable implementar algun tipo de bloqueo de intentos de login tras un número de fallos en los intentos. | |
| 132 | Más información: | |
| 133 | https://www.owasp.org/index.php/Blocking_Brute_Force_Attacks",unclassified, | |
| 134 | ,Error page web server version disclosure (Pagina de error mostrando version de servidor ),"Pidiendo una página que no existe, el servidor responde con un error. En esta página de error se encuentran datos que contienen la versión del servidor web y/o módulos activados en este. Dicha información puede ser usada para mejorar las tácticas del atacante sabiendo a que se enfrenta. | |
| 135 | ",Se debe configurar paginas de error customizadas evitando mostrar esta información.,low, | |
| 136 | ,Weak SSL,"El servidor está utiizando un cifrado SSL débil. | |
| 137 | ||
| 138 | Weak SSL ciphers (SSL2 on port 443): | |
| 139 | ||
| 140 | SSL2_CK_RC4_128_EXPORT40_WITH_MD5 - Low strength | |
| 141 | SSL2_CK_RC2_128_CBC_EXPORT40_WITH_MD5 - Low strength | |
| 142 | SSL2_CK_DES_64_CBC_WITH_MD5 - Low strength | |
| 143 | ||
| 144 | Weak SSL ciphers (SSL3 on port 443): | |
| 145 | ||
| 146 | SSL3_CK_RSA_RC4_40_MD5 - Low strength | |
| 147 | SSL3_CK_RSA_RC2_40_MD5 - Low strength | |
| 148 | SSL3_CK_RSA_DES_40_CBC_SHA - Low strength | |
| 149 | SSL3_CK_RSA_DES_64_CBC_SHA - Low strength | |
| 150 | SSL3_CK_EDH_RSA_DES_40_CBC_SHA - Low strength | |
| 151 | SSL3_CK_EDH_RSA_DES_64_CBC_SHA - Low strength | |
| 152 | ||
| 153 | Weak SSL ciphers (TLS1 on port 443): | |
| 154 | ||
| 155 | TLS1_CK_RSA_EXPORT_WITH_RC4_40_MD5 - Low strength | |
| 156 | TLS1_CK_RSA_EXPORT_WITH_RC2_CBC_40_MD5 - Low strength | |
| 157 | TLS1_CK_RSA_EXPORT_WITH_DES40_CBC_SHA - Low strength | |
| 158 | TLS1_CK_RSA_WITH_DES_CBC_SHA - Low strength | |
| 159 | TLS1_CK_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA - Low strength | |
| 160 | TLS1_CK_DHE_RSA_WITH_DES_CBC_SHA - Low strength | |
| 161 | ",Reconfigurar el servidor para un encriptado más fuerte.,unclassified, | |
| 162 | ,CRIME SSL/TLS attack,"Compression Ratio Info-leak Made Easy (CRIME) es un exploit contra las cookies secretas del servidor sobre conexiones usando protocolos HTTPS y SPDY que también estén usando compresión de datos. Cuando se recupera el contenido de la cookie de autentificación, permite a un atacante robar la sesión, permitiendo iniciar otros ataques. | |
| 163 | ||
| 164 | CRIME es un ataque del lado cliente, pero el servidor puede proteger al cliente rechazando la combinación de estas opciones. Para CRIME, la debilidad es la compresión Deflate. | |
| 165 | ","CRIME puede ser combatido previniendo el uso de compresión, tanto del lado del cliente, desactivando la compresión de las peticiones HTTPS, o del lado del servidor previniendo el uso de compresión de datos en las transacciones que utilicen el protocolo TLS. | |
| 166 | ||
| 167 | Referencias WEB: | |
| 168 | http://blogs.cisco.com/security/breach-crime-and-blackhat/ | |
| 169 | http://en.wikipedia.org/wiki/CRIME_(security_exploit) | |
| 170 | http://isecpartners.com/blog/2012/september/details-on-the-crime-attack.aspx",high, | |
| 171 | ,Transacción Insegura de HTTPS a HTTP en el form POST,"La página segura (https) contiene un form que realiza el post sobre una página insegura (http). Esto puede confundir al usuario y hacerle creer que su datos son enviados encriptados cuando en realidad no. | |
| 172 | ",El destino del FORM debe apuntar a una página segura (https).,unclassified, | |
| 173 | ,Trace Method is Enabled (Método TRACE activado),"El método Trace está habilitado en el servidor. En presencia de otras vulnerabilidades cross-domain en los navegadores web, información sensible del campo header puede ser leída desde cualquier dominio que soporte método HTTP TRACE. | |
| 174 | ||
| 175 | Un atacante podría abusar de la funcionalidad HTTP TRACE para ganar acceso a la información de los headers HTTP como las cookies y datos de autenticación. | |
| 176 | ","Se recomienda desactivar el método TRACE en el servidor web. | |
| 177 | ||
| 178 | Referencias WEB: | |
| 179 | http://www.w3.org/Protocols/rfc2616/rfc2616-sec9.html | |
| 180 | http://www.cgisecurity.com/lib/WH-WhitePaper_XST_ebook.pdf",low, | |
| 181 | ,Public Key SSL < 2048 bits (Certificado de llave pública SSL menor de 2048 Bits),"El certificado SSL usado por el servidor contiene una llave pública de menos de 2048 bits de largo. | |
| 182 | ||
| 183 | Los nuevos estándares de la Industria de Certificados para SSL (SSL Certificates Industry) seteados por Certification Authority/Browser (CA/B) Forum requiere que los certificados expedidos después de enero 1 del 2014. Deben ser al menos de 2048-bit largo. Con el incremento del poder de procesamiento de las computadoras, cualquier certificado menor de 2048-bit es riesgoso de ser comprometido por personas mal intencionadas con poder de procesamiento. | |
| 184 | ","Si se tiene cualquier certificado de 1024-bit o certificados con menos de 2048-bit de largo, será necesario que se migre a 2048-bit. | |
| 185 | ||
| 186 | Nuevo estándar: https://www.cabforum.org/wp-content/uploads/Baseline_Requirements_V1.pdf",unclassified, | |
| 187 | ,Ruby on Rails CookieStore session cookie persistence,"Ruby on Rails contiene un fallo en su diseño que podría permitir a atacantes facilitar el acceso a las aplicaciones. El problema está en el mecanismo de la CookieStore en guardar la cookie en el lado del cliente, mientras no guarda la entrada correspondiente en el lado del servidor. Cuando la aplicación termina la sesión, Ruby on Rails no tiene manera de trackear esto y verdaderamente invalida la cookie con la configuración por defecto. Esto significa que persiste ""de por vida"" y puede ser usada para acceder a aplicaciones inclusive cuando se piensa que se terminó la sesión. | |
| 188 | ","Actualmente, no se conocen actualizaciones o parches para corregir esta vulnerabilidad. Si es posible migrar temporalmente implementando un sistema de autenticación más seguro (e.g. ActiveRecordStore).",unclassified, | |
| 189 | ,Typical Login Web,"Archivo de Login nombrado de manera ""común"". | |
| 190 | ",Esto facilita a los robots de ataque encontrar páginas sensibles. Se recomienda no usar nombres estándar para páginas de login.,unclassified, | |
| 191 | ,Credentials in Plain Text,"La página de login viaja sobre texto plano | |
| 192 | ",Es altamente recomendable que las páginas de login se fuercen a usar SSL (https),medium, | |
| 193 | ,Unencrypted __VIEWSTATE parameter,"El parámetro ""__VIEWSTATE"" no está encriptado. Para reducir las posibilidades que alguien intercepte información guardada en ViewState es bueno encriptarlo. | |
| 194 | ","Se recomienda encriptar el parámetro ""__VIEWSTATE"", para hacer esto se debe setear el tipo de validación a 3DES. Editar Web.Config y agregar la siguiente línea bajo <system.web> | |
| 195 | <machineKey validation=""3DES""/>",unclassified, | |
| 196 | ,Credenciales Repetidas,"Existen múltiples credenciales repetidas para un mismo acceso. | |
| 197 | Tener credenciales repetidas de un mismo servidor o acceso, posibilita a un atacante tener mayor impacto, pues utilizando un mismo password puede ingresar a distintos servicios o áreas",Evitar utilizar mismas credenciales en distintos servicios.,high, | |
| 198 | ,FTP Anónimo,"El servicio de FTP posee el usuario : anonymous | |
| 199 | Los servidores FTP anónimos ofrecen sus servicios libremente a todos los usuarios, permiten acceder a sus archivos sin necesidad de tener un 'USER ID' o una cuenta de usuario. Es la manera más cómoda fuera del servicio web de permitir que todo el mundo tenga acceso a cierta información sin que para ello el administrador de un sistema tenga que crear una cuenta para cada usuario. | |
| 200 | ||
| 201 | Si un servidor posee servicio 'FTP anonymous' solamente con teclear la palabra «anonymous», cuando pregunte por tu usuario tendrás acceso a ese sistema. No se necesita ninguna contraseña preestablecida, aunque tendrás que introducir una sólo para ese momento, normalmente se suele utilizar la dirección de correo electrónico propia.",Evitar usuario anónimo.,medium, | |
| 202 | ,Credenciales débiles Tomcat,"Se detectaron credenciales por defecto en servidores Tomcat, ejecutándose con privilegios elevados. | |
| 203 | Un atacante que intente loguearse con una lista de usuarios por defecto podría comprometer el servicio. | |
| 204 | En este caso en particular el usuario “admin” es muy común en servidores Tomcat, y cuenta con privilegios para ejecutar código, por lo que debe ser protegido con una contraseña fuerte. | |
| 205 | ",Aplicar una política de seguridad al servidor que obligue el uso de contraseñas de acuerdo con las políticas de seguridad interna.,high, | |
| 206 | ,Wpad Spoofing,"Los ambientes Windows, ante una falla a resolver un nombre de host, | |
| 207 | realizan una segunda búsqueda utilizando NetBios. La naturaleza de este | |
| 208 | pedido realizado utilizando broadcast, es inseguro si no se tienen | |
| 209 | recaudos. | |
| 210 | ||
| 211 | Un atacante podría utilizar esta vulnerabilidad para | |
| 212 | registrar el dominio WPAD en NetBios con el fin de redirigir y modificar | |
| 213 | el tráfico de las workstations con las que comparte el segmento de red. | |
| 214 | Este ataque podría derivar en la captura de credenciales o hashes que | |
| 215 | le brinden acceso a sistemas críticos. | |
| 216 | ","Deshabilitar la configuración automática de proxy en los equipos | |
| 217 | Windows, y registrar el nombre de dominio WPAD, para que ningún equipo de | |
| 218 | la red pueda impersonarlo.",high, | |
| 219 | ,Servicio de Telnet,"Las credenciales de usuario se transmiten sobre un canal sin cifrar (servicio Telnet). | |
| 220 | Un atacante capaz de interceptar el tráfico entre los hosts y el usuario remoto, será capaz de obtener las credenciales utilizadas. | |
| 221 | ","Reemplazar los servicios que permiten el envío de credenciales en texto plano, por aquellos que lo hacen de forma cifrada. En este caso, existen diferentes alternativas para reemplazar los servicios de administración remota, como por ejemplo: SSH o RDP.",medium, | |
| 222 | ,Tokens cacheados,"Fue posible impersonar diferentes usuarios de dominio, incluido un administrador de dominio, a través de los tokens de acceso cacheados en el servidor. | |
| 223 | ","No existe un parche para resolver este tipo de situaciones, ya que los tokens de acceso son propios de la arquitectura de Windows. Sin embargo es posible implementar algunas medidas a nivel operativo para mitigar en gran parte el impacto del cacheo de tokens. Recomendamos: | |
| 224 | > Asegurarse que usuarios con altos privilegios (especialmente administradores) tengan una cuenta específica para tareas de administración y otra para loguearse en sus sistemas. | |
| 225 | > Ejecutar aquellas tareas que requieran mayores privilegios utilizando la aplicación “RunAs”. | |
| 226 | > Asegurarse que los Domain Admins sólo sean utilizados para administrar el dominio. Crear diferentes cuentas de dominio y asignarle autorización administrativa solo para la unidad de negocio correspondiente. | |
| 227 | > Asegurarse que las cuentas administrativas de ambientes de desarrollo y test sean diferentes a las de los sistemas críticos de producción. | |
| 228 | > Ejecutar los servicios necesarios para el correcto funcionamiento de la unidad de negocio en un equipo diferente al Controlador de Dominio. | |
| 229 | > Utilizar la opción de Active Directory “Account is sensitive and cannot be delegated” (sólo aplica a los logueos interactivos, pero ayuda a reforzar la seguridad de la cuenta). | |
| 230 | ||
| 231 | Referencias: | |
| 232 | http://carnal0wnage.attackresearch.com/2008/05/token-passing-with-incognito-part-2.html | |
| 233 | http://pentestmonkey.net/uncategorized/from-local-admin-to-domain-admin | |
| 234 | http://www.offensive-security.com/metasploit-unleashed/Fun_With_Incognito",high, | |
| 235 | ,Denegación de Servicios(DOS),"Un ataque de denegación de servicios, también llamado ataque DoS (de las siglas en inglés Denial of Service) o DDoS (de Distributed Denial of Service), es un ataque a un sistema de computadoras o red que causa que un servicio o recurso sea inaccesible a los usuarios legítimos. Normalmente provoca la pérdida de la conectividad de la red por el consumo del ancho de banda de la red de la víctima o sobrecarga de los recursos computacionales del sistema de la víctima | |
| 236 | ",La forma de prevenirlo: https://www.owasp.org/index.php/Denial_of_Service,high, | |
| 237 | ,Revelación de Información (Information Disclosure),"Se puede obtener una información sensible del usuario. Esto podría ayudar a un atacante a tener control de una base de datos ó permitirle escalar hacia otro vector de ataque. | |
| 238 | ","Determinar si esta información debería ser accesible desde la red, sin estar protegida por credenciales.",medium, | |
| 239 | ,Sitio sin Informar," | |
| 240 | ",/reclamaciones/home/index. ,unclassified, | |
| 241 | ,Listado de Directorios,"Muestra directorios que no deberian ser públicos | |
| 242 | ",Evitar que dichos directorios sean públicos,medium, | |
| 243 | ,Shell,"Una shell es parte de código programado en (PHP,Python,Ruby,etc) que una vez que es subido al host victima, puede ser utilizado para subir, bajar, borrar archivos. | |
| 244 | ","Evitar entradas que posibiliten subir imágenes o código al servidor, sin ser adecuadamente controladas.",unclassified, | |
| 245 | ,Path Disclosure,"Permite ver la ruta a archivos u aplicaciones que no deberían ser mostradas | |
| 246 | ","Puede solucionarse desactivando los mensajes de error : | |
| 247 | En PHP modificando el archivo php.ini ( display_errors = 'off' ) | |
| 248 | En Apache modificando el archivo httpd.conf ( php_flag display_errors off)",unclassified, | |
| 249 | ,File Upload,"Es posible subir código o imágenes sin ser fitradas adecuadamente. | |
| 250 | ",Evitar campos para subir archivos que no sean correctamente filtrados,unclassified, | |
| 251 | ,Metodo Put habilitado (Put File Allow),"Sube, carga o realiza un upload de un recurso especificado (archivo), es el camino más eficiente para subir archivos a un servidor. | |
| 252 | ","Evitar que el metodo PUT se encuentre con libre acceso a cualquier tipo de usuario, restringir acceso.",unclassified, | |
| 253 | ,Leer Archivos (Read files)," | |
| 254 | ",,unclassified, | |
| 255 | ,Usuarios por defecto (default users),"Se debe evitar utilizar usuarios y contraseñas por defecto, pues el sistema puede quedar susceptible a un ataque de fuerza bruta o de diccionario. | |
| 256 | ",Cambiar usuarios y contraseñas de acuerdo a las políticas de la empresa,unclassified, | |
| 257 | ,SSLstrip Attack,"Dado que la página no esta utilizando https para proteger sus credenciales, el panel de ingreso está implementado mediante http, y no https, es posible modificar los recursos obtenidos, si el atacante logra intereceptar la comunicación entre ambos sitios. | |
| 258 | ","Cargar todos los recursos a través de HTTPS, para los recursos externos recomendamos incluir los mismos de la siguiente manera: src=""//dominio.com/recurso.js"" de esta manera el navegador automáticamete incluye el protocolo HTTP o HTTPS segun la conexion inicial que genera.",high, | |
| 259 | ,Enumerar Usuarios," | |
| 260 | ",,medium, | |
| 261 | ,Login User HTTP,"Las credenciales de usuario y contraseña, viajan en texto plano con lo cual un atacante podría obtener dichas credenciales para un posterior acceso | |
| 262 | ",Utilizar HTTPS para autenticar usuarios,medium, | |
| 263 | ,Falta de Control de Acceso,"Se puede acceder a una parte del sitio sin una sesión válida. | |
| 264 | ",Validar correctamente la sesiones del sitio verificando que el usuario posee una sesión válida,medium, | |
| 265 | ,Cookie Reutilization,"La cookie puede ser modificada y reutilizada para hacer nuevas consultas o impersonar usuarios. | |
| 266 | ",Evitar ,medium, | |
| 267 | ,Credenciales Débiles md5,"Se detecto que dentro del request se envía el nombre de usuario y la contraseña hasheada. Si bien la contraseña utiliza una función de md5, lo hace sin salt para protegerla. Con lo cual un atacante que la intercepte, puede descifrar el md5 para luego obtener la contraseña en texto plano junto con el usuario para acceder al sistema. | |
| 268 | ","Aplicar una política de seguridad al servidor que obligue el uso de contraseñas de acuerdo con las políticas de seguridad interna. | |
| 269 | Se recomienda un cifrado más robusto con la función salt.",high, | |
| 270 | ,CSRF,"Un ataque CSRF fuerza al navegador web validado de una víctima a enviar una petición a una aplicación web vulnerable, la cual entonces realiza la acción elegida a través de la víctima. Al contrario que en los ataques XSS, los cuales explotan la confianza que un usuario tiene en un sitio en particular, el cross site request forgery explota la confianza que un sitio tiene en un usuario en particular. | |
| 271 | ","Recomendamos la imprementación de un feature anti-csrf con el fin de autenticar todos los request, en particular aquellas peticiones sensibles, como por ejemplo: el cambio de contraseñas y asignación de roles (dar permisos de administrador a un usuario). El framework de ASP.net cuenta con este feature llamado viewstate (https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF)_Prevention_Cheat_Sheet#Viewstate_.28ASP.NET.29)",medium, | |
| 272 | ,SSL weak ciphers (Cifrado débil),"El servidor remoto soporta el uso de SSL pero ofrece una encriptación débil | |
| 273 | ",Reconfigurar el servidor web con un nivel de encriptación mayor,medium, | |
| 274 | ,Token de Session en URL,"Información sensible dentro de las URLs puede ser guardado en distintas lugares, por ejemplo en la información del navegador del usuario, en el webserver, o en cualquier proxy o reverse proxy. Las URLs se pueden ver en las pantallas, pueden ser guardadas como favoritos o pueden ser enviadas entre los usuarios. Esta información puede ser obtenida también como referer, en el histórico de la última página desde donde se ingresa a otra página. Guardar la sesiones en las URLs incrementa que esa información sea capturada por un atacante para luego impersonarse como un usuario válido. | |
| 275 | ",La aplicación debería utilizar otros mecanismos para el envío de las sessiones como cookies o campos ocultos enviados a traves de métodos de POST ,medium, | |
| 276 | ,Autenticación sin HTTPS,"La aplicación web no utiliza HTTPS para la autenticación de usuarios al sistema. Las credenciales de usuario y contraseña, viajan en texto plano con lo cual un atacante podría obtener dichas credenciales para un posterior acceso. | |
| 277 | ",Siempre utilizar HTTPS para autenticar usuarios,high, | |
| 278 | ,Es-Version Obsoleta / Desactualizada,"El servidor se encuentra utilizando una versión de Apache Tomcat MUY desactualizada (Apache Tomcat/4.1.31), la cual es vulnerable a múltiples vulnerabilidades públicas. Actualmente la ultima versión estable es la 8.0.9 | |
| 279 | ","Recomendación: actualizar y desactivar los mensajes de error del servidor, que puedan brindar información extra a un atacante",medium, | |
| 280 | ,Número de Tarjeta en Texto Plano,"La respuesta del servidor, contiene el número de tarjeta de crédito y otra información sensible que debería evitarse enviar en texto plano. | |
| 281 | ",Utilizar HTTPS en todo el sitio en donde la información sensible pueda ser expuesta.,high, | |
| 282 | ,Server Version Discloure,"El servidor web responde con la versión del sistema facilitando a un atacante saber contra que se enfrenta | |
| 283 | ","Filtrar en las respuestas del servidor, cualquier dato que muestre la versión del servidor y del sistema operativo del mismo",low, | |
| 284 | ,Archivo crossdomain.xml inseguro,"El modelo de seguridad del navegador normalmente previene el contenido web de ser accedido desde otro dominio. Esto comunmente es conocido como ""same origin policy"" (""política del mismo origen""). La política de archivos URL garantiza acceso cross-dominio para leer datos. Permiten operaciones que no son permitidas por defecto. La política de acceso de archivo URL esta localizado, por defecto, en el directorio raíz del servidor destino, con el nombre crossdomain.xml (por ejemplo en www.ejemplo.com/crossdomain.xml). | |
| 285 | ||
| 286 | Cuando un dominio es especificado en el archivo crossdomain.xml, el sitio declara que está dispuesto a dar acceso a operadores de cualqueir server en ese dominio para obtener cualquier documento donde la regla reside. El archivo crossdomain.xml desplegado en este servidor web abre el servidor a todos los dominios (uso de un único asterisco ""*"" de comodín es soportado), por ejemplo: | |
| 287 | <cross-domain-policy> | |
| 288 | <allow-access-from domain=""*"" /> | |
| 289 | </cross-domain-policy> | |
| 290 | ||
| 291 | Esta práctica es correcta para servidores públicos, pero no debería ser usada en servidores que se encuentran tras un firewall porque puede permitir acceso a áreas protegidas. No debería ser usada para sitios que requieren autenticación en forma de contraseñas o cookies. | |
| 292 | ","Evaluar detenidamente qué sitios deben tener permitido el acceso cross-dominio. Considerar la topología de red y todos los mecanismos de autenticación afectados por la configuración o implementación de la política cross-domain. | |
| 293 | ",medium, | |
| 294 | ,Archivos de backup en servidor de producción,"La aplicación web tiene múltiples archivos de backup disponibles para ser descargados, los cuales brindan información de la tecnología que se utiliza en el sitio, así como código fuente de las aplicaciones, nombres de usuarios, rutas de acceso y múltiple información sensible del mismo. | |
| 295 | ","Es recomendable aplicar buenas políticas de protección de información sensible, evitando exponer backups y otra información del sitio web",high, | |
| 296 | ,Exposición de información a través del listado de directorios,"Estos directorios no deberían estar públicos, pues exponen información sensible del tipo de tecnología utilizada, código de programación, información sobre rutas de acceso a distintos lugares, particularmente en este caso podemos listar toda la información del servidor sin ningun tipo de restricción | |
| 297 | ",Siempre evitar que se puedan listar directorios de manera externa y sin permisos,high, | |
| 298 | ,Archivos con información sensible,"Es posible acceder a archivos con información sensible, podemos ver el ""log error"" y dentro de este: rutas de acceso, nombres de usuario, etc. Con lo cual un atacante con tiempo podría intentar obtener credenciales de un servicio SSH, FTP, o similar para luego crackearlo. | |
| 299 | ||
| 300 | ",Evitar exponer toda información sensible del sistema,high, | |
| 301 | ,Revelación de IP interno,"La aplicación expone ip/s interno, con lo cual, si por algún vector de ataque un atacante logra acceder al servidor o servicio, podría continuar la explotación por dicho vector | |
| 302 | ",Evitar exponer toda información sensible y privada del sistema ,low, | |
| 303 | ,Archivos e información de desarollo en ambientes productivos,"Podemos ver código de programación, con ejemplos concretos del funcionamiento interno y | |
| 304 | de la lógica utilizada a la hora de programar, dejando en evidencia | |
| 305 | información como nombres de usuarios, email, dni, teléfonos, etc. | |
| 306 | ",Evitar exponer toda información sensible y privada del sistema,high, | |
| 307 | ,Sentencias SQL sin Prepared Statement,"Se detectó que se utiliza una mala implementación de sentencias SQL concatenando las variables manualmente pudiendo un atacante realizar ataques de SQL Injection | |
| 308 | ","Utilizar, para la sentencia de SQL, Prepared Statement. | |
| 309 | Referencia: | |
| 310 | https://www.owasp.org/index.php/Query_Parameterization_Cheat_Sheet#Prepared_Statement_Examples",high, | |
| 311 | ,MySQL: lectura y escritura de archivos,"Es posible utilizar MySQL server para la lectura y escritura de archivos en el servidor | |
| 312 | ","Seguir los siguientes lineamientos para el hardening de MySQL Server: | |
| 313 | https://www.owasp.org/index.php/Testing_for_MySQL#Read_from_a_File",high, | |
| 314 | ,Servidor productivo y desarrollo,"Por lo que pudimos observar, este servidor sirve tanto para producción como desarrollo, por lo tanto contiene muchísima información y pruebas que deberían ser eliminadas. | |
| 315 | ","Eliminar el contenido de desarrollo, dejar solo lo necesario para el entorno productivo",high, | |
| 316 | ,Internal IP Address Disclosure,"Una cadena coincidente con una dirección interna de IPv4 fue encontrada en esta página. Esto lleva a divulgar información sensible acerca del esquema de la red interna. Esta información puede ser usada para generar ataques específicos. | |
| 317 | ",Se recomienda prevenir que esta información sea mostrada al usuario,low, | |
| 318 | ,Cisco ASA Error,"El Cisco ASA es vulnerable a un Information Leak (CVE-2014-3392), un atacante podría obtener credenciales en base a un error. | |
| 319 | ",Actualizar a la última versión del firmware del CISCO ASA,high, | |
| 320 | ,Listado de directorios,"Evitar listar directorios. Muchas veces a partir de aquí, se pueden realizar distintos vectores de ataques, por claves almacenadas en archivos ocultos o por tener acceso a archivos de configuración. | |
| 321 | ",Evitar listar directorios. Es recomendable que se deshabiliten o se resguarden con algún tipo de autenticación.,low, | |
| 322 | ,Privilege Escalation,"Esto sucede cuando un atacante ya ha hecho un reconocimiento y ha comprometido con éxito un sistema al obtener acceso a una cuenta de bajo nivel. En esta fase, un atacante quiere tener un fuerte control sobre el sistema y busca formas de aumentar los privilegios, ya sea para estudiar más el sistema o realizar un ataque.","Cambiar las contraseñas de las cuentas administrativas con regularidad y aplicar una política de contraseñas seguras (por ejemplo, asegurarse de que las cuentas de los administradores locales tengan contraseñas complejas y únicas en todos los sistemas). | |
| 323 | ||
| 324 | Referencia: | |
| 325 | https://www.owasp.org/index.php/Testing_for_Privilege_escalation_(OTG-AUTHZ-003) | |
| 326 | ",medium, | |
| 327 | ,Default Credentials,"Se detectó que el sistema posee credenciales por defecto para acceder a la consola de administración. Estas credenciales pueden ser obtenidas desde sitios de internet, por ejemplo: foros de tecnología, manuales del sistema, entre otros.","Se recomienda cambiar todas las contraseñas por defecto del sistema y adaptarlas a una política de contraseñas seguras. También es recomendable que todas las cuentas por defecto del sistema sean renombradas y sus contraseñas cambiadas. | |
| 328 | ||
| 329 | Referencia: | |
| 330 | https://www.owasp.org/index.php/Testing_for_default_credentials_(OTG-AUTHN-002) | |
| 331 | ",critical, |
| 0 | # Faraday Penetration Test IDE | |
| 1 | # Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 2 | # See the file 'doc/LICENSE' for the license information | |
| 3 | from __future__ import absolute_import | |
| 4 | import csv | |
| 5 | import click | |
| 6 | from collections import OrderedDict | |
| 7 | ||
| 8 | ||
| 9 | MAPPED_VULN_SEVERITY = OrderedDict([ | |
| 10 | ('critical', 'critical'), | |
| 11 | ('high', 'high'), | |
| 12 | ('med', 'medium'), | |
| 13 | ('low', 'low'), | |
| 14 | ('info', 'informational'), | |
| 15 | ('unclassified', 'unclassified'), | |
| 16 | ('unknown', 'unclassified'), | |
| 17 | ]) | |
| 18 | ||
| 19 | ||
| 20 | @click.command() | |
| 21 | @click.argument('input_csv', type=click.File(mode='r+')) | |
| 22 | @click.option('-o', '--output', help="Write to a new file instead of " | |
| 23 | "overwritting the input file", type=click.File(mode='w')) | |
| 24 | @click.pass_context | |
| 25 | def fix_severities(ctx, input_csv, output): | |
| 26 | """Ensures the severity/exploitation of a vuln templace CSV has | |
| 27 | valid values. If not, it will use the most appropiate value""" | |
| 28 | if output is None: | |
| 29 | if not click.confirm(click.style( | |
| 30 | "WARNING: you didn't specify the --output option, so " | |
| 31 | "the input file will be overwritten. Are you sure you " | |
| 32 | "want to do this?", fg='red', bold=True)): | |
| 33 | ctx.abort() | |
| 34 | reader = csv.DictReader(input_csv) | |
| 35 | rows = [fix_row(row) for row in reader] | |
| 36 | ||
| 37 | fieldnames = ['cwe', 'name', 'description', 'resolution', 'exploitation', | |
| 38 | 'references'] | |
| 39 | if output is None: | |
| 40 | input_csv.seek(0) | |
| 41 | output = input_csv | |
| 42 | writer = csv.DictWriter(output, fieldnames=fieldnames) | |
| 43 | writer.writeheader() | |
| 44 | for row in rows: | |
| 45 | writer.writerow(row) | |
| 46 | ||
| 47 | ||
| 48 | def fix_row(row): | |
| 49 | old_severity = row.get('exploitation', 'unclassified') | |
| 50 | new_severity = 'unclassified' | |
| 51 | for (key, value) in MAPPED_VULN_SEVERITY.items(): | |
| 52 | if key in old_severity.lower(): | |
| 53 | new_severity = value | |
| 54 | break | |
| 55 | else: | |
| 56 | if old_severity: | |
| 57 | click.echo(click.style( | |
| 58 | 'Unknown severity: "{}" found in vulnerability template named ' | |
| 59 | '"{}"'.format(old_severity, row.get('name')), | |
| 60 | fg='yellow'), err=True, color='yellow') | |
| 61 | row['exploitation'] = new_severity | |
| 62 | return row | |
| 63 | ||
| 64 | ||
| 65 | if __name__ == "__main__": | |
| 66 | fix_severities() | |
| 67 | # I'm Py3⏎ |
| 0 | faraday (2.3.0-deb) saucy; urgency=medium | |
| 1 | ||
| 2 | * Initial deb package | |
| 3 | ||
| 4 | -- Sebastian Kulesz <[email protected]> Fri, 16 Dec 2016 09:29:58 +0100⏎ |
| 0 | Source: faraday | |
| 1 | Section: python | |
| 2 | Priority: optional | |
| 3 | Maintainer: Sebastian Kulesz <[email protected]> | |
| 4 | Build-Depends: debhelper (>= 9), dh-systemd | |
| 5 | Standards-Version: 3.9.8 | |
| 6 | Homepage: http://faradaysec.com | |
| 7 | Vcs-Git: https://github.com/infobyte/faraday.git | |
| 8 | Vcs-Browser: https://github.com/infobyte/faraday | |
| 9 | ||
| 10 | Package: faraday | |
| 11 | Architecture: all | |
| 12 | Depends: faraday-server (= ${binary:Version}), faraday-client (= ${binary:Version}) | |
| 13 | Description: Collaborative Penetration Test IDE | |
| 14 | Faraday introduces a new concept (IPE) Integrated Penetration-Test Environment | |
| 15 | a multiuser Penetration test IDE. Designed for distribution, indexation and | |
| 16 | analysis of the generated data during the process of a security audit. | |
| 17 | . | |
| 18 | This is a metapackage which will install the Faraday client and server. | |
| 19 | ||
| 20 | Package: faraday-server | |
| 21 | Architecture: all | |
| 22 | Depends: python, | |
| 23 | ipython, | |
| 24 | python-couchdbkit, | |
| 25 | python-mockito, | |
| 26 | python-whoosh, | |
| 27 | python-argparse, | |
| 28 | python-ipy, | |
| 29 | python-requests (>= 2.7.0), | |
| 30 | python-tornado, | |
| 31 | python-flask (>= 0.10.1), | |
| 32 | python-colorama, | |
| 33 | python-psycopg2, | |
| 34 | python-sip, | |
| 35 | zsh, | |
| 36 | python-twisted, | |
| 37 | python-sqlalchemy, | |
| 38 | python-openssl, | |
| 39 | couchdb (>=1.6.0) | couchdb (>=1.4.0), | |
| 40 | python-pip | |
| 41 | Description: Collaborative Penetration Test IDE | |
| 42 | Faraday introduces a new concept (IPE) Integrated Penetration-Test Environment | |
| 43 | a multiuser Penetration test IDE. Designed for distribution, indexation and | |
| 44 | analysis of the generated data during the process of a security audit. | |
| 45 | . | |
| 46 | This package includes the Faraday server. | |
| 47 | ||
| 48 | Package: faraday-client | |
| 49 | Architecture: all | |
| 50 | Depends: python, | |
| 51 | ipython, | |
| 52 | python-couchdbkit, | |
| 53 | python-mockito, | |
| 54 | python-whoosh, | |
| 55 | python-argparse, | |
| 56 | python-ipy, | |
| 57 | python-requests (>= 2.7.0), | |
| 58 | python-tornado, | |
| 59 | python-flask (>= 0.10.1), | |
| 60 | python-colorama, | |
| 61 | python-psycopg2, | |
| 62 | python-sip, | |
| 63 | zsh, | |
| 64 | python-twisted, | |
| 65 | python-sqlalchemy, | |
| 66 | python-openssl, | |
| 67 | curl, | |
| 68 | gir1.2-gtk-3.0, | |
| 69 | gir1.2-vte-2.90 | gir1.2-vte-2.91, | |
| 70 | python-gobject, | |
| 71 | zsh, | |
| 72 | python-pip | |
| 73 | Description: Collaborative Penetration Test IDE | |
| 74 | Faraday introduces a new concept (IPE) Integrated Penetration-Test Environment | |
| 75 | a multiuser Penetration test IDE. Designed for distribution, indexation and | |
| 76 | analysis of the generated data during the process of a security audit. | |
| 77 | . | |
| 78 | This package includes the Faraday client. |
| 0 | Format: http://www.debian.org/doc/packaging-manuals/copyright-format/1.0/ | |
| 1 | Upstream-Name: faraday | |
| 2 | Source: https://github.com/infobyte/faraday | |
| 3 | ||
| 4 | Files: * | |
| 5 | Copyright: 2013-2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | License: GPL-3 | |
| 7 | ||
| 8 | Files: gui/qt3/pyqonsole/widget.py shell/core/ca.py shell/core/helpers.py | |
| 9 | shell/core/qt3/pty_.py shell/core/history.py shell/core/screen.py | |
| 10 | shell/controller/qt3/procctrl.py shell/controller/qt3/emulation.py | |
| 11 | shell/controller/qt3/session.py shell/controller/qt3/keytrans.py | |
| 12 | shell/controller/qt3/emuVt102.py | |
| 13 | Copyright: 2003 LOGILAB S.A. (Paris, FRANCE) | |
| 14 | 2005-2006 LOGILAB S.A. (Paris, FRANCE) | |
| 15 | 2005-2006 CEA Grenoble | |
| 16 | License: CECILL-2 | |
| 17 | ||
| 18 | Files: views/reports/_attachments/script/jquery-1.11.2.js | |
| 19 | views/reports/_attachments/script/jquery.ui.tabs.min.js | |
| 20 | Copyright: 2005, 2014 jQuery Foundation, Inc. and other contributors | |
| 21 | License: MIT | |
| 22 | ||
| 23 | Files: views/reports/_attachments/script/angular-cookies.js | |
| 24 | views/reports/_attachments/script/angular.js | |
| 25 | views/reports/_attachments/script/angular.min.js | |
| 26 | views/reports/_attachments/script/angular.mocks.js | |
| 27 | Copyright: 2010-2015 Google, Inc. http://angularjs.org | |
| 28 | License: MIT | |
| 29 | ||
| 30 | Files: views/reports/_attachments/script/jquery.qtip.js | |
| 31 | Copyright: 2014 Craig Michael Thompson | |
| 32 | License: MIT | |
| 33 | ||
| 34 | Files: views/reports/_attachments/script/ZeroClipboard.min.js | |
| 35 | Copyright: 2014 Jon Rohan, James M. Greene | |
| 36 | License: MIT | |
| 37 | ||
| 38 | Files: plugins/repo/sshdefaultscan/plugin.py | |
| 39 | plugins/repo/peepingtom/plugin.py | |
| 40 | Copyright: 2015 Andres Tarantini <[email protected]> | |
| 41 | License: MIT | |
| 42 | ||
| 43 | Files: views/reports/_attachments/script/cryptojs-sha1.js | |
| 44 | Copyright: 2009-2013 by Jeff Mott | |
| 45 | License: BSD-3-clause | |
| 46 | ||
| 47 | Files: plugins/repo/nessus/dotnessus_v2.py plugins/repo/nessus/pynessus.py | |
| 48 | Copyright: 2010 Dustin Seibel | |
| 49 | License: GPL-2+ | |
| 50 | ||
| 51 | Files: scripts/cscan/plugin/carbonator/carbonator.py | |
| 52 | Copyright: Blake Cornell, CTO, Integris Security LLC | |
| 53 | License: GPL-2 | |
| 54 | ||
| 55 | Files: views/reports/_attachments/script/Chart.js | |
| 56 | Copyright: 2014 Nick Downie | |
| 57 | License: MIT | |
| 58 | ||
| 59 | Files: views/reports/_attachments/script/couch.js | |
| 60 | License: Apache-2.0 | |
| 61 | Licensed under the Apache License, Version 2.0 (the "License"); | |
| 62 | you may not use this file except in compliance with the License. | |
| 63 | You may obtain a copy of the License at | |
| 64 | . | |
| 65 | http://www.apache.org/licenses/LICENSE-2.0 | |
| 66 | . | |
| 67 | Unless required by applicable law or agreed to in writing, software | |
| 68 | distributed under the License is distributed on an "AS IS" BASIS, | |
| 69 | WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. | |
| 70 | See the License for the specific language governing permissions and | |
| 71 | limitations under the License. | |
| 72 | . | |
| 73 | On Debian systems, the complete text of the Apache 2 License can be found in | |
| 74 | "/usr/share/common-licenses/Apache-2.0". | |
| 75 | ||
| 76 | Files: plugins/repo/fruitywifi/fruitywifi.py | |
| 77 | Copyright: 2016 xtr4nge [email protected] | |
| 78 | License: GPL-3+ | |
| 79 | ||
| 80 | Files: server/www/script/anguilar-ui-notification.min.css | |
| 81 | server/www/script/angular-ui-notification.min.js | |
| 82 | Copyright: 2014 Alexey Avramchik | |
| 83 | License: MIT | |
| 84 | ||
| 85 | Files: debian/* | |
| 86 | Copyright: 2014-2015 Sophie Brun <[email protected]> | |
| 87 | License: GPL-3 | |
| 88 | ||
| 89 | License: GPL-3 | |
| 90 | This package is free software; you can redistribute it and/or modify | |
| 91 | it under the terms of the GNU General Public License as published by | |
| 92 | the Free Software Foundation, version 3. | |
| 93 | . | |
| 94 | This package is distributed in the hope that it will be useful, | |
| 95 | but WITHOUT ANY WARRANTY; without even the implied warranty of | |
| 96 | MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |
| 97 | GNU General Public License for more details. | |
| 98 | . | |
| 99 | You should have received a copy of the GNU General Public License | |
| 100 | along with this program. If not, see <http://www.gnu.org/licenses/> | |
| 101 | . | |
| 102 | On Debian systems, the complete text of the GNU General | |
| 103 | Public License version 3 can be found in "/usr/share/common-licenses/GPL-3". | |
| 104 | ||
| 105 | License: GPL-3+ | |
| 106 | This package is free software; you can redistribute it and/or modify | |
| 107 | it under the terms of the GNU General Public License as published by | |
| 108 | the Free Software Foundation, either version 3 of the license, or | |
| 109 | (at your option) any later version. | |
| 110 | . | |
| 111 | This package is distributed in the hope that it will be useful, | |
| 112 | but WITHOUT ANY WARRANTY; without even the implied warranty of | |
| 113 | MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |
| 114 | GNU General Public License for more details. | |
| 115 | . | |
| 116 | You should have received a copy of the GNU General Public License | |
| 117 | along with this program. If not, see <http://www.gnu.org/licenses/> | |
| 118 | . | |
| 119 | On Debian systems, the complete text of the GNU General | |
| 120 | Public License version 3 can be found in "/usr/share/common-licenses/GPL-3". | |
| 121 | ||
| 122 | License: MIT | |
| 123 | Permission is hereby granted, free of charge, to any person obtaining a copy | |
| 124 | of this software and associated documentation files (the "Software"), to deal | |
| 125 | in the Software without restriction, including without limitation the rights | |
| 126 | to use, copy, modify, merge, publish, distribute, sublicense, and/or sell | |
| 127 | copies of the Software, and to permit persons to whom the Software is | |
| 128 | furnished to do so, subject to the following conditions: | |
| 129 | . | |
| 130 | The above copyright notice and this permission notice shall be included in | |
| 131 | all copies or substantial portions of the Software. | |
| 132 | . | |
| 133 | THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR | |
| 134 | IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, | |
| 135 | FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE | |
| 136 | AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER | |
| 137 | LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, | |
| 138 | OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN | |
| 139 | THE SOFTWARE. | |
| 140 | ||
| 141 | License: BSD-3-clause | |
| 142 | All rights reserved. | |
| 143 | . | |
| 144 | Redistribution and use in source and binary forms, with or without | |
| 145 | modification, are permitted provided that the following conditions are met: | |
| 146 | . | |
| 147 | 1. Redistributions of source code must retain the above copyright notice, | |
| 148 | this list of conditions and the following disclaimer. | |
| 149 | . | |
| 150 | 2. Redistributions in binary form must reproduce the above copyright | |
| 151 | notice, this list of conditions and the following disclaimer in the | |
| 152 | documentation and/or other materials provided with the distribution. | |
| 153 | . | |
| 154 | 3. Neither the name of the copyright holder nor the names of its | |
| 155 | contributors may be used to endorse or promote products derived from this | |
| 156 | software without specific prior written permission. | |
| 157 | . | |
| 158 | THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS | |
| 159 | IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, | |
| 160 | THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR | |
| 161 | PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT HOLDER OR | |
| 162 | CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, | |
| 163 | EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, | |
| 164 | PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR | |
| 165 | PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF | |
| 166 | LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING | |
| 167 | NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS | |
| 168 | SOFTWARE, EVEN IF ADVISED OF THE POSSIBILITY OF SUCH DAMAGE. | |
| 169 | ||
| 170 | License: GPL-2+ | |
| 171 | This package is free software; you can redistribute it and/or modify | |
| 172 | it under the terms of the GNU General Public License as published by | |
| 173 | the Free Software Foundation; either version 2 of the License, or | |
| 174 | (at your option) any later version. | |
| 175 | . | |
| 176 | This package is distributed in the hope that it will be useful, | |
| 177 | but WITHOUT ANY WARRANTY; without even the implied warranty of | |
| 178 | MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |
| 179 | GNU General Public License for more details. | |
| 180 | . | |
| 181 | You should have received a copy of the GNU General Public License | |
| 182 | along with this program. If not, see <http://www.gnu.org/licenses/>. | |
| 183 | . | |
| 184 | On Debian systems, the complete text of the GNU General Public | |
| 185 | License version 2 can be found in "/usr/share/common-licenses/GPL-2". | |
| 186 | ||
| 187 | License: GPL-2 | |
| 188 | This package is free software; you can redistribute it and/or modify | |
| 189 | it under the terms of the GNU General Public License version 2 as published by | |
| 190 | the Free Software Foundation. | |
| 191 | . | |
| 192 | This package is distributed in the hope that it will be useful, | |
| 193 | but WITHOUT ANY WARRANTY; without even the implied warranty of | |
| 194 | MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |
| 195 | GNU General Public License for more details. | |
| 196 | . | |
| 197 | You should have received a copy of the GNU General Public License | |
| 198 | along with this program. If not, see <http://www.gnu.org/licenses/>. | |
| 199 | . | |
| 200 | On Debian systems, the complete text of the GNU General Public | |
| 201 | License version 2 can be found in "/usr/share/common-licenses/GPL-2". | |
| 202 | ||
| 203 | License: CECILL-2 | |
| 204 | This Agreement is a Free Software license agreement that is the result | |
| 205 | of discussions between its authors in order to ensure compliance with | |
| 206 | the two main principles guiding its drafting: | |
| 207 | . | |
| 208 | * firstly, compliance with the principles governing the distribution | |
| 209 | of Free Software: access to source code, broad rights granted to | |
| 210 | users, | |
| 211 | * secondly, the election of a governing law, French law, with which | |
| 212 | it is conformant, both as regards the law of torts and | |
| 213 | intellectual property law, and the protection that it offers to | |
| 214 | both authors and holders of the economic rights over software. | |
| 215 | . | |
| 216 | The authors of the CeCILL (for Ce[a] C[nrs] I[nria] L[ogiciel] L[ibre]) | |
| 217 | license are: | |
| 218 | . | |
| 219 | Commissariat à l'Energie Atomique - CEA, a public scientific, technical | |
| 220 | and industrial research establishment, having its principal place of | |
| 221 | business at 25 rue Leblanc, immeuble Le Ponant D, 75015 Paris, France. | |
| 222 | . | |
| 223 | Centre National de la Recherche Scientifique - CNRS, a public scientific | |
| 224 | and technological establishment, having its principal place of business | |
| 225 | at 3 rue Michel-Ange, 75794 Paris cedex 16, France. | |
| 226 | . | |
| 227 | Institut National de Recherche en Informatique et en Automatique - | |
| 228 | INRIA, a public scientific and technological establishment, having its | |
| 229 | principal place of business at Domaine de Voluceau, Rocquencourt, BP | |
| 230 | 105, 78153 Le Chesnay cedex, France. | |
| 231 | . | |
| 232 | Preamble | |
| 233 | . | |
| 234 | The purpose of this Free Software license agreement is to grant users | |
| 235 | the right to modify and redistribute the software governed by this | |
| 236 | license within the framework of an open source distribution model. | |
| 237 | . | |
| 238 | The exercising of these rights is conditional upon certain obligations | |
| 239 | for users so as to preserve this status for all subsequent | |
| 240 | redistributions. | |
| 241 | . | |
| 242 | In consideration of access to the source code and the rights to copy, | |
| 243 | modify and redistribute granted by the license, users are provided only | |
| 244 | with a limited warranty and the software's author, the holder of the | |
| 245 | economic rights, and the successive licensors only have limited liability. | |
| 246 | . | |
| 247 | In this respect, the risks associated with loading, using, modifying | |
| 248 | and/or developing or reproducing the software by the user are brought to | |
| 249 | the user's attention, given its Free Software status, which may make it | |
| 250 | complicated to use, with the result that its use is reserved for | |
| 251 | developers and experienced professionals having in-depth computer | |
| 252 | knowledge. Users are therefore encouraged to load and test the | |
| 253 | suitability of the software as regards their requirements in conditions | |
| 254 | enabling the security of their systems and/or data to be ensured and, | |
| 255 | more generally, to use and operate it in the same conditions of | |
| 256 | security. This Agreement may be freely reproduced and published, | |
| 257 | provided it is not altered, and that no provisions are either added or | |
| 258 | removed herefrom. | |
| 259 | . | |
| 260 | This Agreement may apply to any or all software for which the holder of | |
| 261 | the economic rights decides to submit the use thereof to its provisions. | |
| 262 | . | |
| 263 | Article 1 - DEFINITIONS | |
| 264 | . | |
| 265 | For the purpose of this Agreement, when the following expressions | |
| 266 | commence with a capital letter, they shall have the following meaning: | |
| 267 | . | |
| 268 | Agreement: means this license agreement, and its possible subsequent | |
| 269 | versions and annexes. | |
| 270 | . | |
| 271 | Software: means the software in its Object Code and/or Source Code form | |
| 272 | and, where applicable, its documentation, "as is" when the Licensee | |
| 273 | accepts the Agreement. | |
| 274 | . | |
| 275 | Initial Software: means the Software in its Source Code and possibly its | |
| 276 | Object Code form and, where applicable, its documentation, "as is" when | |
| 277 | it is first distributed under the terms and conditions of the Agreement. | |
| 278 | . | |
| 279 | Modified Software: means the Software modified by at least one | |
| 280 | Contribution. | |
| 281 | . | |
| 282 | Source Code: means all the Software's instructions and program lines to | |
| 283 | which access is required so as to modify the Software. | |
| 284 | . | |
| 285 | Object Code: means the binary files originating from the compilation of | |
| 286 | the Source Code. | |
| 287 | . | |
| 288 | Holder: means the holder(s) of the economic rights over the Initial | |
| 289 | Software. | |
| 290 | . | |
| 291 | Licensee: means the Software user(s) having accepted the Agreement. | |
| 292 | . | |
| 293 | Contributor: means a Licensee having made at least one Contribution. | |
| 294 | . | |
| 295 | Licensor: means the Holder, or any other individual or legal entity, who | |
| 296 | distributes the Software under the Agreement. | |
| 297 | . | |
| 298 | Contribution: means any or all modifications, corrections, translations, | |
| 299 | adaptations and/or new functions integrated into the Software by any or | |
| 300 | all Contributors, as well as any or all Internal Modules. | |
| 301 | . | |
| 302 | Module: means a set of sources files including their documentation that | |
| 303 | enables supplementary functions or services in addition to those offered | |
| 304 | by the Software. | |
| 305 | . | |
| 306 | External Module: means any or all Modules, not derived from the | |
| 307 | Software, so that this Module and the Software run in separate address | |
| 308 | spaces, with one calling the other when they are run. | |
| 309 | . | |
| 310 | Internal Module: means any or all Module, connected to the Software so | |
| 311 | that they both execute in the same address space. | |
| 312 | . | |
| 313 | GNU GPL: means the GNU General Public License version 2 or any | |
| 314 | subsequent version, as published by the Free Software Foundation Inc. | |
| 315 | . | |
| 316 | Parties: mean both the Licensee and the Licensor. | |
| 317 | . | |
| 318 | These expressions may be used both in singular and plural form. | |
| 319 | . | |
| 320 | Article 2 - PURPOSE | |
| 321 | . | |
| 322 | The purpose of the Agreement is the grant by the Licensor to the | |
| 323 | Licensee of a non-exclusive, transferable and worldwide license for the | |
| 324 | Software as set forth in Article 5 hereinafter for the whole term of the | |
| 325 | protection granted by the rights over said Software. | |
| 326 | . | |
| 327 | Article 3 - ACCEPTANCE | |
| 328 | 3.1 The Licensee shall be deemed as having accepted the terms and | |
| 329 | conditions of this Agreement upon the occurrence of the first of the | |
| 330 | following events: | |
| 331 | . | |
| 332 | * (i) loading the Software by any or all means, notably, by | |
| 333 | downloading from a remote server, or by loading from a physical | |
| 334 | medium; | |
| 335 | * (ii) the first time the Licensee exercises any of the rights | |
| 336 | granted hereunder. | |
| 337 | . | |
| 338 | 3.2 One copy of the Agreement, containing a notice relating to the | |
| 339 | characteristics of the Software, to the limited warranty, and to the | |
| 340 | fact that its use is restricted to experienced users has been provided | |
| 341 | to the Licensee prior to its acceptance as set forth in Article 3.1 | |
| 342 | hereinabove, and the Licensee hereby acknowledges that it has read and | |
| 343 | understood it. | |
| 344 | . | |
| 345 | Article 4 - EFFECTIVE DATE AND TERM | |
| 346 | . | |
| 347 | 4.1 EFFECTIVE DATE | |
| 348 | . | |
| 349 | The Agreement shall become effective on the date when it is accepted by | |
| 350 | the Licensee as set forth in Article 3.1. | |
| 351 | . | |
| 352 | 4.2 TERM | |
| 353 | . | |
| 354 | The Agreement shall remain in force for the entire legal term of | |
| 355 | protection of the economic rights over the Software. | |
| 356 | . | |
| 357 | Article 5 - SCOPE OF RIGHTS GRANTED | |
| 358 | . | |
| 359 | The Licensor hereby grants to the Licensee, who accepts, the following | |
| 360 | rights over the Software for any or all use, and for the term of the | |
| 361 | Agreement, on the basis of the terms and conditions set forth hereinafter. | |
| 362 | . | |
| 363 | Besides, if the Licensor owns or comes to own one or more patents | |
| 364 | protecting all or part of the functions of the Software or of its | |
| 365 | components, the Licensor undertakes not to enforce the rights granted by | |
| 366 | these patents against successive Licensees using, exploiting or | |
| 367 | modifying the Software. If these patents are transferred, the Licensor | |
| 368 | undertakes to have the transferees subscribe to the obligations set | |
| 369 | forth in this paragraph. | |
| 370 | . | |
| 371 | 5.1 RIGHT OF USE | |
| 372 | . | |
| 373 | The Licensee is authorized to use the Software, without any limitation | |
| 374 | as to its fields of application, with it being hereinafter specified | |
| 375 | that this comprises: | |
| 376 | . | |
| 377 | 1. permanent or temporary reproduction of all or part of the Software | |
| 378 | by any or all means and in any or all form. | |
| 379 | . | |
| 380 | 2. loading, displaying, running, or storing the Software on any or | |
| 381 | all medium. | |
| 382 | . | |
| 383 | 3. entitlement to observe, study or test its operation so as to | |
| 384 | determine the ideas and principles behind any or all constituent | |
| 385 | elements of said Software. This shall apply when the Licensee | |
| 386 | carries out any or all loading, displaying, running, transmission | |
| 387 | or storage operation as regards the Software, that it is entitled | |
| 388 | to carry out hereunder. | |
| 389 | . | |
| 390 | 5.2 ENTITLEMENT TO MAKE CONTRIBUTIONS | |
| 391 | . | |
| 392 | The right to make Contributions includes the right to translate, adapt, | |
| 393 | arrange, or make any or all modifications to the Software, and the right | |
| 394 | to reproduce the resulting software. | |
| 395 | . | |
| 396 | The Licensee is authorized to make any or all Contributions to the | |
| 397 | Software provided that it includes an explicit notice that it is the | |
| 398 | author of said Contribution and indicates the date of the creation | |
| 399 | thereof. | |
| 400 | . | |
| 401 | 5.3 RIGHT OF DISTRIBUTION | |
| 402 | . | |
| 403 | In particular, the right of distribution includes the right to publish, | |
| 404 | transmit and communicate the Software to the general public on any or | |
| 405 | all medium, and by any or all means, and the right to market, either in | |
| 406 | consideration of a fee, or free of charge, one or more copies of the | |
| 407 | Software by any means. | |
| 408 | . | |
| 409 | The Licensee is further authorized to distribute copies of the modified | |
| 410 | or unmodified Software to third parties according to the terms and | |
| 411 | conditions set forth hereinafter. | |
| 412 | . | |
| 413 | 5.3.1 DISTRIBUTION OF SOFTWARE WITHOUT MODIFICATION | |
| 414 | . | |
| 415 | The Licensee is authorized to distribute true copies of the Software in | |
| 416 | Source Code or Object Code form, provided that said distribution | |
| 417 | complies with all the provisions of the Agreement and is accompanied by: | |
| 418 | . | |
| 419 | 1. a copy of the Agreement, | |
| 420 | . | |
| 421 | 2. a notice relating to the limitation of both the Licensor's | |
| 422 | warranty and liability as set forth in Articles 8 and 9, | |
| 423 | . | |
| 424 | and that, in the event that only the Object Code of the Software is | |
| 425 | redistributed, the Licensee allows future Licensees unhindered access to | |
| 426 | the full Source Code of the Software by indicating how to access it, it | |
| 427 | being understood that the additional cost of acquiring the Source Code | |
| 428 | shall not exceed the cost of transferring the data. | |
| 429 | . | |
| 430 | 5.3.2 DISTRIBUTION OF MODIFIED SOFTWARE | |
| 431 | . | |
| 432 | When the Licensee makes a Contribution to the Software, the terms and | |
| 433 | conditions for the distribution of the resulting Modified Software | |
| 434 | become subject to all the provisions of this Agreement. | |
| 435 | . | |
| 436 | The Licensee is authorized to distribute the Modified Software, in | |
| 437 | source code or object code form, provided that said distribution | |
| 438 | complies with all the provisions of the Agreement and is accompanied by: | |
| 439 | . | |
| 440 | 1. a copy of the Agreement, | |
| 441 | . | |
| 442 | 2. a notice relating to the limitation of both the Licensor's | |
| 443 | warranty and liability as set forth in Articles 8 and 9, | |
| 444 | . | |
| 445 | and that, in the event that only the object code of the Modified | |
| 446 | Software is redistributed, the Licensee allows future Licensees | |
| 447 | unhindered access to the full source code of the Modified Software by | |
| 448 | indicating how to access it, it being understood that the additional | |
| 449 | cost of acquiring the source code shall not exceed the cost of | |
| 450 | transferring the data. | |
| 451 | . | |
| 452 | 5.3.3 DISTRIBUTION OF EXTERNAL MODULES | |
| 453 | . | |
| 454 | When the Licensee has developed an External Module, the terms and | |
| 455 | conditions of this Agreement do not apply to said External Module, that | |
| 456 | may be distributed under a separate license agreement. | |
| 457 | . | |
| 458 | 5.3.4 COMPATIBILITY WITH THE GNU GPL | |
| 459 | . | |
| 460 | The Licensee can include a code that is subject to the provisions of one | |
| 461 | of the versions of the GNU GPL in the Modified or unmodified Software, | |
| 462 | and distribute that entire code under the terms of the same version of | |
| 463 | the GNU GPL. | |
| 464 | . | |
| 465 | The Licensee can include the Modified or unmodified Software in a code | |
| 466 | that is subject to the provisions of one of the versions of the GNU GPL, | |
| 467 | and distribute that entire code under the terms of the same version of | |
| 468 | the GNU GPL. | |
| 469 | . | |
| 470 | Article 6 - INTELLECTUAL PROPERTY | |
| 471 | . | |
| 472 | 6.1 OVER THE INITIAL SOFTWARE | |
| 473 | . | |
| 474 | The Holder owns the economic rights over the Initial Software. Any or | |
| 475 | all use of the Initial Software is subject to compliance with the terms | |
| 476 | and conditions under which the Holder has elected to distribute its work | |
| 477 | and no one shall be entitled to modify the terms and conditions for the | |
| 478 | distribution of said Initial Software. | |
| 479 | . | |
| 480 | The Holder undertakes that the Initial Software will remain ruled at | |
| 481 | least by this Agreement, for the duration set forth in Article 4.2. | |
| 482 | . | |
| 483 | 6.2 OVER THE CONTRIBUTIONS | |
| 484 | . | |
| 485 | The Licensee who develops a Contribution is the owner of the | |
| 486 | intellectual property rights over this Contribution as defined by | |
| 487 | applicable law. | |
| 488 | . | |
| 489 | 6.3 OVER THE EXTERNAL MODULES | |
| 490 | . | |
| 491 | The Licensee who develops an External Module is the owner of the | |
| 492 | intellectual property rights over this External Module as defined by | |
| 493 | applicable law and is free to choose the type of agreement that shall | |
| 494 | govern its distribution. | |
| 495 | . | |
| 496 | 6.4 JOINT PROVISIONS | |
| 497 | . | |
| 498 | The Licensee expressly undertakes: | |
| 499 | . | |
| 500 | 1. not to remove, or modify, in any manner, the intellectual property | |
| 501 | notices attached to the Software; | |
| 502 | . | |
| 503 | 2. to reproduce said notices, in an identical manner, in the copies | |
| 504 | of the Software modified or not. | |
| 505 | . | |
| 506 | The Licensee undertakes not to directly or indirectly infringe the | |
| 507 | intellectual property rights of the Holder and/or Contributors on the | |
| 508 | Software and to take, where applicable, vis-à-vis its staff, any and all | |
| 509 | measures required to ensure respect of said intellectual property rights | |
| 510 | of the Holder and/or Contributors. | |
| 511 | . | |
| 512 | Article 7 - RELATED SERVICES | |
| 513 | . | |
| 514 | 7.1 Under no circumstances shall the Agreement oblige the Licensor to | |
| 515 | provide technical assistance or maintenance services for the Software. | |
| 516 | . | |
| 517 | However, the Licensor is entitled to offer this type of services. The | |
| 518 | terms and conditions of such technical assistance, and/or such | |
| 519 | maintenance, shall be set forth in a separate instrument. Only the | |
| 520 | Licensor offering said maintenance and/or technical assistance services | |
| 521 | shall incur liability therefor. | |
| 522 | . | |
| 523 | 7.2 Similarly, any Licensor is entitled to offer to its licensees, under | |
| 524 | its sole responsibility, a warranty, that shall only be binding upon | |
| 525 | itself, for the redistribution of the Software and/or the Modified | |
| 526 | Software, under terms and conditions that it is free to decide. Said | |
| 527 | warranty, and the financial terms and conditions of its application, | |
| 528 | shall be subject of a separate instrument executed between the Licensor | |
| 529 | and the Licensee. | |
| 530 | . | |
| 531 | Article 8 - LIABILITY | |
| 532 | . | |
| 533 | 8.1 Subject to the provisions of Article 8.2, the Licensee shall be | |
| 534 | entitled to claim compensation for any direct loss it may have suffered | |
| 535 | from the Software as a result of a fault on the part of the relevant | |
| 536 | Licensor, subject to providing evidence thereof. | |
| 537 | . | |
| 538 | 8.2 The Licensor's liability is limited to the commitments made under | |
| 539 | this Agreement and shall not be incurred as a result of in particular: | |
| 540 | (i) loss due the Licensee's total or partial failure to fulfill its | |
| 541 | obligations, (ii) direct or consequential loss that is suffered by the | |
| 542 | Licensee due to the use or performance of the Software, and (iii) more | |
| 543 | generally, any consequential loss. In particular the Parties expressly | |
| 544 | agree that any or all pecuniary or business loss (i.e. loss of data, | |
| 545 | loss of profits, operating loss, loss of customers or orders, | |
| 546 | opportunity cost, any disturbance to business activities) or any or all | |
| 547 | legal proceedings instituted against the Licensee by a third party, | |
| 548 | shall constitute consequential loss and shall not provide entitlement to | |
| 549 | any or all compensation from the Licensor. | |
| 550 | . | |
| 551 | Article 9 - WARRANTY | |
| 552 | . | |
| 553 | 9.1 The Licensee acknowledges that the scientific and technical | |
| 554 | state-of-the-art when the Software was distributed did not enable all | |
| 555 | possible uses to be tested and verified, nor for the presence of | |
| 556 | possible defects to be detected. In this respect, the Licensee's | |
| 557 | attention has been drawn to the risks associated with loading, using, | |
| 558 | modifying and/or developing and reproducing the Software which are | |
| 559 | reserved for experienced users. | |
| 560 | . | |
| 561 | The Licensee shall be responsible for verifying, by any or all means, | |
| 562 | the suitability of the product for its requirements, its good working | |
| 563 | order, and for ensuring that it shall not cause damage to either persons | |
| 564 | or properties. | |
| 565 | . | |
| 566 | 9.2 The Licensor hereby represents, in good faith, that it is entitled | |
| 567 | to grant all the rights over the Software (including in particular the | |
| 568 | rights set forth in Article 5). | |
| 569 | . | |
| 570 | 9.3 The Licensee acknowledges that the Software is supplied "as is" by | |
| 571 | the Licensor without any other express or tacit warranty, other than | |
| 572 | that provided for in Article 9.2 and, in particular, without any warranty | |
| 573 | as to its commercial value, its secured, safe, innovative or relevant | |
| 574 | nature. | |
| 575 | . | |
| 576 | Specifically, the Licensor does not warrant that the Software is free | |
| 577 | from any error, that it will operate without interruption, that it will | |
| 578 | be compatible with the Licensee's own equipment and software | |
| 579 | configuration, nor that it will meet the Licensee's requirements. | |
| 580 | . | |
| 581 | 9.4 The Licensor does not either expressly or tacitly warrant that the | |
| 582 | Software does not infringe any third party intellectual property right | |
| 583 | relating to a patent, software or any other property right. Therefore, | |
| 584 | the Licensor disclaims any and all liability towards the Licensee | |
| 585 | arising out of any or all proceedings for infringement that may be | |
| 586 | instituted in respect of the use, modification and redistribution of the | |
| 587 | Software. Nevertheless, should such proceedings be instituted against | |
| 588 | the Licensee, the Licensor shall provide it with technical and legal | |
| 589 | assistance for its defense. Such technical and legal assistance shall be | |
| 590 | decided on a case-by-case basis between the relevant Licensor and the | |
| 591 | Licensee pursuant to a memorandum of understanding. The Licensor | |
| 592 | disclaims any and all liability as regards the Licensee's use of the | |
| 593 | name of the Software. No warranty is given as regards the existence of | |
| 594 | prior rights over the name of the Software or as regards the existence | |
| 595 | of a trademark. | |
| 596 | . | |
| 597 | Article 10 - TERMINATION | |
| 598 | . | |
| 599 | 10.1 In the event of a breach by the Licensee of its obligations | |
| 600 | hereunder, the Licensor may automatically terminate this Agreement | |
| 601 | thirty (30) days after notice has been sent to the Licensee and has | |
| 602 | remained ineffective. | |
| 603 | . | |
| 604 | 10.2 A Licensee whose Agreement is terminated shall no longer be | |
| 605 | authorized to use, modify or distribute the Software. However, any | |
| 606 | licenses that it may have granted prior to termination of the Agreement | |
| 607 | shall remain valid subject to their having been granted in compliance | |
| 608 | with the terms and conditions hereof. | |
| 609 | . | |
| 610 | Article 11 - MISCELLANEOUS | |
| 611 | . | |
| 612 | 11.1 EXCUSABLE EVENTS | |
| 613 | . | |
| 614 | Neither Party shall be liable for any or all delay, or failure to | |
| 615 | perform the Agreement, that may be attributable to an event of force | |
| 616 | majeure, an act of God or an outside cause, such as defective | |
| 617 | functioning or interruptions of the electricity or telecommunications | |
| 618 | networks, network paralysis following a virus attack, intervention by | |
| 619 | government authorities, natural disasters, water damage, earthquakes, | |
| 620 | fire, explosions, strikes and labor unrest, war, etc. | |
| 621 | . | |
| 622 | 11.2 Any failure by either Party, on one or more occasions, to invoke | |
| 623 | one or more of the provisions hereof, shall under no circumstances be | |
| 624 | interpreted as being a waiver by the interested Party of its right to | |
| 625 | invoke said provision(s) subsequently. | |
| 626 | . | |
| 627 | 11.3 The Agreement cancels and replaces any or all previous agreements, | |
| 628 | whether written or oral, between the Parties and having the same | |
| 629 | purpose, and constitutes the entirety of the agreement between said | |
| 630 | Parties concerning said purpose. No supplement or modification to the | |
| 631 | terms and conditions hereof shall be effective as between the Parties | |
| 632 | unless it is made in writing and signed by their duly authorized | |
| 633 | representatives. | |
| 634 | . | |
| 635 | 11.4 In the event that one or more of the provisions hereof were to | |
| 636 | conflict with a current or future applicable act or legislative text, | |
| 637 | said act or legislative text shall prevail, and the Parties shall make | |
| 638 | the necessary amendments so as to comply with said act or legislative | |
| 639 | text. All other provisions shall remain effective. Similarly, invalidity | |
| 640 | of a provision of the Agreement, for any reason whatsoever, shall not | |
| 641 | cause the Agreement as a whole to be invalid. | |
| 642 | . | |
| 643 | 11.5 LANGUAGE | |
| 644 | . | |
| 645 | The Agreement is drafted in both French and English and both versions | |
| 646 | are deemed authentic. | |
| 647 | . | |
| 648 | Article 12 - NEW VERSIONS OF THE AGREEMENT | |
| 649 | . | |
| 650 | 12.1 Any person is authorized to duplicate and distribute copies of this | |
| 651 | Agreement. | |
| 652 | . | |
| 653 | 12.2 So as to ensure coherence, the wording of this Agreement is | |
| 654 | protected and may only be modified by the authors of the License, who | |
| 655 | reserve the right to periodically publish updates or new versions of the | |
| 656 | Agreement, each with a separate number. These subsequent versions may | |
| 657 | address new issues encountered by Free Software. | |
| 658 | . | |
| 659 | 12.3 Any Software distributed under a given version of the Agreement may | |
| 660 | only be subsequently distributed under the same version of the Agreement | |
| 661 | or a subsequent version, subject to the provisions of Article 5.3.4. | |
| 662 | . | |
| 663 | Article 13 - GOVERNING LAW AND JURISDICTION | |
| 664 | . | |
| 665 | 13.1 The Agreement is governed by French law. The Parties agree to | |
| 666 | endeavor to seek an amicable solution to any disagreements or disputes | |
| 667 | that may arise during the performance of the Agreement. | |
| 668 | . | |
| 669 | 13.2 Failing an amicable solution within two (2) months as from their | |
| 670 | occurrence, and unless emergency proceedings are necessary, the | |
| 671 | disagreements or disputes shall be referred to the Paris Courts having | |
| 672 | jurisdiction, by the more diligent Party. | |
| 673 | . | |
| 674 | Version 2.0 dated 2006-09-05. |
| 0 | apis/ opt/faraday/client | |
| 1 | backup/ opt/faraday/client | |
| 2 | bin/ opt/faraday/client | |
| 3 | config/ opt/faraday/client | |
| 4 | controllers/ opt/faraday/client | |
| 5 | data/ opt/faraday/client | |
| 6 | exporters/ opt/faraday/client | |
| 7 | gui/ opt/faraday/client | |
| 8 | helpers/ opt/faraday/client | |
| 9 | managers/ opt/faraday/client | |
| 10 | model/ opt/faraday/client | |
| 11 | persistence/ opt/faraday/client | |
| 12 | plugins/ opt/faraday/client | |
| 13 | scripts/ opt/faraday/client | |
| 14 | server/ opt/faraday/client | |
| 15 | test_cases/ opt/faraday/client | |
| 16 | tests_web/ opt/faraday/client | |
| 17 | updates/ opt/faraday/client | |
| 18 | utils/ opt/faraday/client | |
| 19 | views/ opt/faraday/client | |
| 20 | zsh/ opt/faraday/client | |
| 21 | *.py opt/faraday/client | |
| 22 | VERSION opt/faraday/client/ | |
| 23 | requirements.txt opt/faraday/client | |
| 24 | faraday-terminal.zsh opt/faraday/client | |
| 25 | debian/helper-script/faraday usr/bin/ | |
| 26 | debian/faraday.desktop usr/share/applications | |
| 27 | data/images/icons/faraday_icon.png usr/share/icons/hicolor/48x48/apps⏎ |
| 0 | apis/ opt/faraday/server/ | |
| 1 | backup/ opt/faraday/server/ | |
| 2 | bin/ opt/faraday/server/ | |
| 3 | config/ opt/faraday/server/ | |
| 4 | controllers/ opt/faraday/server/ | |
| 5 | data/ opt/faraday/server/ | |
| 6 | exporters/ opt/faraday/server/ | |
| 7 | gui/ opt/faraday/server/ | |
| 8 | helpers/ opt/faraday/server/ | |
| 9 | managers/ opt/faraday/server/ | |
| 10 | model/ opt/faraday/server/ | |
| 11 | persistence/ opt/faraday/server/ | |
| 12 | plugins/ opt/faraday/server/ | |
| 13 | scripts/ opt/faraday/server/ | |
| 14 | server/ opt/faraday/server/ | |
| 15 | test_cases/ opt/faraday/server/ | |
| 16 | tests_web/ opt/faraday/server/ | |
| 17 | updates/ opt/faraday/server/ | |
| 18 | utils/ opt/faraday/server/ | |
| 19 | views/ opt/faraday/server/ | |
| 20 | zsh/ opt/faraday/server/ | |
| 21 | *.py opt/faraday/server/ | |
| 22 | VERSION opt/faraday/server/ | |
| 23 | requirements_server.txt opt/faraday/server | |
| 24 | debian/helper-script/faraday-server usr/bin/ |
| 0 | #!/bin/sh | |
| 1 | ||
| 2 | set -e | |
| 3 | ||
| 4 | if [ "$1" = "configure" ]; then | |
| 5 | chmod 777 /opt/faraday/server/server/www/config/ | |
| 6 | chmod 777 /opt/faraday/server/server/ | |
| 7 | chmod 777 /opt/faraday/server/server/workspaces | |
| 8 | fi |
| 0 | [Unit] | |
| 1 | Description=Faraday Server | |
| 2 | Requires=couchdb.service | |
| 3 | After=couchdb.service | |
| 4 | ||
| 5 | [Service] | |
| 6 | Type=simple | |
| 7 | ExecStart=/opt/faraday/server/faraday-server.py --nodeps | |
| 8 | ||
| 9 | [Install] | |
| 10 | WantedBy=multi-user.target |
| 0 | [Desktop Entry] | |
| 1 | Encoding=UTF-8 | |
| 2 | Version=1.0 | |
| 3 | Name=Faraday | |
| 4 | Comment=Collaborative Penetration Test IDE | |
| 5 | Exec=faraday | |
| 6 | Type=Application | |
| 7 | Icon=/usr/share/icons/hicolor/48x48/apps/faraday_icon.png | |
| 8 | Terminal=false | |
| 9 | Categories=Development; |
| 0 | #!/usr/bin/make -f | |
| 1 | ||
| 2 | UNAME_M = $(shell uname -m) | |
| 3 | ||
| 4 | %: | |
| 5 | dh $@ | |
| 6 | ||
| 7 | override_dh_installchangelogs: | |
| 8 | dh_installchangelogs RELEASE.md |
| 0 | openapi: "3.0.0" | |
| 1 | info: | |
| 2 | version: 1.0.0 | |
| 3 | title: Faraday API | |
| 4 | license: | |
| 5 | name: GPLv3 | |
| 6 | servers: | |
| 7 | - url: https://cloud.faradaysec.com | |
| 8 | ||
| 9 | paths: | |
| 10 | /ws: | |
| 11 | get: | |
| 12 | summary: List all workspaces | |
| 13 | responses: | |
| 14 | '200': | |
| 15 | description: An array of workspaces | |
| 16 | content: | |
| 17 | application/json: | |
| 18 | schema: | |
| 19 | $ref: "#/components/schemas/Workspace" | |
| 20 | components: | |
| 21 | schemas: | |
| 22 | Workspace: | |
| 23 | type: object | |
| 24 | required: | |
| 25 | - _id | |
| 26 | - name | |
| 27 | properties: | |
| 28 | id: | |
| 29 | type: integer | |
| 30 | format: int64 | |
| 31 | name: | |
| 32 | type: string | |
| 33 | tag: | |
| 34 | type: string |
| 1 | 1 | # Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) |
| 2 | 2 | # See the file 'doc/LICENSE' for the license information |
| 3 | 3 | |
| 4 | __version__ = '3.10.2' | |
| 4 | __version__ = '3.11' | |
| 5 | 5 | __license_version__ = __version__ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | import socket | |
| 7 | import threading | |
| 8 | import logging | |
| 9 | import base64 | |
| 10 | ||
| 11 | from flask import Flask, request, jsonify | |
| 12 | from tornado.wsgi import WSGIContainer # pylint: disable=import-error | |
| 13 | from tornado.httpserver import HTTPServer # pylint: disable=import-error | |
| 14 | from tornado.ioloop import IOLoop # pylint: disable=import-error | |
| 15 | from tornado import gen # pylint: disable=import-error | |
| 16 | ||
| 17 | from faraday.client.model.visitor import VulnsLookupVisitor | |
| 18 | ||
| 19 | from faraday.config.configuration import getInstanceConfiguration | |
| 20 | CONF = getInstanceConfiguration() | |
| 21 | ||
| 22 | ||
| 23 | _plugin_controller_api = None | |
| 24 | _http_server = None | |
| 25 | ioloop_instance = None | |
| 26 | def startServer(): | |
| 27 | global _http_server | |
| 28 | global ioloop_instance | |
| 29 | if _http_server is not None: | |
| 30 | ioloop_instance.start() | |
| 31 | ||
| 32 | ||
| 33 | def stopServer(): | |
| 34 | global _http_server | |
| 35 | global ioloop_instance | |
| 36 | if _http_server is not None: | |
| 37 | # Code taken from https://github.com/tornadoweb/tornado/issues/1791#issuecomment-409258371 | |
| 38 | async def shutdown(): | |
| 39 | _http_server.stop() | |
| 40 | await gen.sleep(1) | |
| 41 | ioloop_instance.stop() | |
| 42 | ioloop_instance.add_callback_from_signal(shutdown) | |
| 43 | ||
| 44 | ||
| 45 | def startAPIs(plugin_controller, model_controller, hostname, port): | |
| 46 | global _rest_controllers | |
| 47 | global _http_server | |
| 48 | global ioloop_instance | |
| 49 | _rest_controllers = [PluginControllerAPI(plugin_controller), ModelControllerAPI(model_controller)] | |
| 50 | ||
| 51 | app = Flask('APISController') | |
| 52 | ||
| 53 | ioloop_instance = IOLoop.current() | |
| 54 | _http_server = HTTPServer(WSGIContainer(app)) | |
| 55 | hostnames = [hostname] | |
| 56 | ||
| 57 | #Fixed hostname bug | |
| 58 | if hostname == "localhost": | |
| 59 | hostnames.append("127.0.0.1") | |
| 60 | ||
| 61 | listening = False | |
| 62 | for hostname in hostnames: | |
| 63 | try: | |
| 64 | _http_server.listen(port, address=hostname) | |
| 65 | logging.getLogger(__name__).info( | |
| 66 | "REST API server configured on %s" % str( | |
| 67 | CONF.getApiRestfulConInfo())) | |
| 68 | listening = True | |
| 69 | CONF.setApiConInfoHost(hostname) | |
| 70 | CONF.saveConfig() | |
| 71 | break | |
| 72 | except socket.error as exception: | |
| 73 | continue | |
| 74 | if not listening: | |
| 75 | raise RuntimeError("Port already in use") | |
| 76 | ||
| 77 | routes = [r for c in _rest_controllers for r in c.getRoutes()] | |
| 78 | ||
| 79 | for route in routes: | |
| 80 | app.add_url_rule(route.path, view_func=route.view_func, methods=route.methods) | |
| 81 | ||
| 82 | logging.getLogger("tornado.access").addHandler(logging.getLogger(__name__)) | |
| 83 | logging.getLogger("tornado.access").propagate = False | |
| 84 | threading.Thread(target=startServer, name='restapi-server').start() | |
| 85 | ||
| 86 | ||
| 87 | class RESTApi: | |
| 88 | """ Abstract class for REST Controllers | |
| 89 | All REST Controllers should extend this class | |
| 90 | in order to get published""" | |
| 91 | ||
| 92 | def getRoutes(self): | |
| 93 | raise NotImplementedError('Abstract Class') | |
| 94 | ||
| 95 | def badRequest(self, message): | |
| 96 | error = 400 | |
| 97 | return jsonify(error=error, | |
| 98 | message=message) | |
| 99 | ||
| 100 | def noContent(self, message): | |
| 101 | code = 204 | |
| 102 | return jsonify(code=code, | |
| 103 | message=message) | |
| 104 | ||
| 105 | def ok(self, message): | |
| 106 | code = 200 | |
| 107 | return jsonify(code=code, | |
| 108 | message=message) | |
| 109 | ||
| 110 | ||
| 111 | class ModelControllerAPI(RESTApi): | |
| 112 | def __init__(self, model_controller): | |
| 113 | self.controller = model_controller | |
| 114 | ||
| 115 | def getRoutes(self): | |
| 116 | routes = [] | |
| 117 | ||
| 118 | routes.append(Route(path='/model/interface', | |
| 119 | view_func=self.createInterface, | |
| 120 | methods=['PUT'])) | |
| 121 | ||
| 122 | routes.append(Route(path='/model/edit/vulns', | |
| 123 | view_func=self.postEditVulns, | |
| 124 | methods=['POST'])) | |
| 125 | ||
| 126 | routes.append(Route(path='/model/del/vulns', | |
| 127 | view_func=self.deleteVuln, | |
| 128 | methods=['DELETE'])) | |
| 129 | ||
| 130 | routes.append(Route(path='/model/host', | |
| 131 | view_func=self.createHost, | |
| 132 | methods=['PUT'])) | |
| 133 | ||
| 134 | routes.append(Route(path='/model/webvulns', | |
| 135 | view_func=self.listWebVulns, | |
| 136 | methods=['GET'])) | |
| 137 | ||
| 138 | routes.append(Route(path='/model/service', | |
| 139 | view_func=self.createService, | |
| 140 | methods=['PUT'])) | |
| 141 | ||
| 142 | routes.append(Route(path='/model/vuln', | |
| 143 | view_func=self.createVuln, | |
| 144 | methods=['PUT'])) | |
| 145 | ||
| 146 | routes.append(Route(path='/model/vulnweb', | |
| 147 | view_func=self.createVulnWeb, | |
| 148 | methods=['PUT'])) | |
| 149 | ||
| 150 | routes.append(Route(path='/model/note', | |
| 151 | view_func=self.createNote, | |
| 152 | methods=['PUT'])) | |
| 153 | ||
| 154 | routes.append(Route(path='/model/cred', | |
| 155 | view_func=self.createCred, | |
| 156 | methods=['PUT'])) | |
| 157 | ||
| 158 | routes.append(Route(path='/status/check', | |
| 159 | view_func=self.statusCheck, | |
| 160 | methods=['GET'])) | |
| 161 | ||
| 162 | ||
| 163 | return routes | |
| 164 | ||
| 165 | def listWebVulns(self): | |
| 166 | vulns = self.controller.getWebVulns() | |
| 167 | j = [{'request': v.request, 'website': v.website, 'path': v.path, 'name': v.name, | |
| 168 | 'desc': v.desc, 'severity': v.severity, 'resolution': v.resolution} for v in vulns] | |
| 169 | return self.ok(j) | |
| 170 | ||
| 171 | def deleteVuln(self): | |
| 172 | json_data = request.get_json() | |
| 173 | # validate mandatory: | |
| 174 | if not 'vulnid' in json_data: | |
| 175 | return self.badRequest("vulid is mandatory") | |
| 176 | if not 'hostid' in json_data: | |
| 177 | return self.badRequest("hostid is mandatory") | |
| 178 | ||
| 179 | vulnid = json_data['vulnid'] | |
| 180 | hostid = json_data['hostid'] | |
| 181 | ||
| 182 | host = self.controller.getHost(hostid) | |
| 183 | if not host: | |
| 184 | return self.badRequest("no plugin available for cmd") | |
| 185 | ||
| 186 | visitor = VulnsLookupVisitor(vulnid) | |
| 187 | host.accept(visitor) | |
| 188 | ||
| 189 | if not visitor.vulns: | |
| 190 | return self.noContent('No vuls matched criteria') | |
| 191 | ||
| 192 | # forward to controller | |
| 193 | for vuln, parents in zip(visitor.vulns, visitor.parents): | |
| 194 | last_parent = parents[0] | |
| 195 | self.controller.delVulnSYNC(last_parent, vuln.getID()) | |
| 196 | ||
| 197 | return self.ok("output successfully sent to plugin") | |
| 198 | ||
| 199 | ||
| 200 | def postEditVulns(self): | |
| 201 | json_data = request.get_json() | |
| 202 | # validate mandatory: | |
| 203 | if not 'vulnid' in json_data: | |
| 204 | return self.badRequest("vulid is mandatory") | |
| 205 | if not 'hostid' in json_data: | |
| 206 | return self.badRequest("hostid is mandatory") | |
| 207 | ||
| 208 | vulnid = json_data['vulnid'] | |
| 209 | hostid = json_data['hostid'] | |
| 210 | ||
| 211 | host = self.controller.getHost(hostid) | |
| 212 | if not host: | |
| 213 | return self.badRequest("no plugin available for cmd") | |
| 214 | ||
| 215 | visitor = VulnsLookupVisitor(vulnid) | |
| 216 | host.accept(visitor) | |
| 217 | ||
| 218 | if not visitor.vulns: | |
| 219 | return self.noContent('No vuls matched criteria') | |
| 220 | ||
| 221 | name = json_data.get('name', None) | |
| 222 | desc = json_data.get('desc', None) | |
| 223 | severity = json_data.get('severity', None) | |
| 224 | resolution = json_data.get('resolution', None) | |
| 225 | refs = json_data.get('refs', None) | |
| 226 | ||
| 227 | # forward to controller | |
| 228 | for vuln in visitor.vulns: | |
| 229 | self.controller.editVulnSYNC(vuln, name, desc, severity, resolution, refs) | |
| 230 | ||
| 231 | return self.ok("output successfully sent to plugin") | |
| 232 | ||
| 233 | def _create(self, creation_callback, params): | |
| 234 | data = request.get_json() | |
| 235 | if not 'name' in data: | |
| 236 | return self.badRequest("name is mandatory") | |
| 237 | ||
| 238 | kwargs = {} | |
| 239 | for param in params: | |
| 240 | kwargs[param] = data.get(param, None) | |
| 241 | obj = creation_callback(**kwargs) | |
| 242 | ||
| 243 | if obj: | |
| 244 | return jsonify(code=200, | |
| 245 | id=obj.getID()) | |
| 246 | return self.badRequest("Object cannot be created") | |
| 247 | ||
| 248 | def createHost(self): | |
| 249 | return self._create( | |
| 250 | self.controller.newHost, | |
| 251 | ['name', 'os']) | |
| 252 | ||
| 253 | def createInterface(self): | |
| 254 | return jsonify( | |
| 255 | code=200, | |
| 256 | id=request.get_json().get("parent_id")) | |
| 257 | ||
| 258 | def createService(self): | |
| 259 | return self._create( | |
| 260 | self.controller.newService, | |
| 261 | ['name', 'protocol', 'ports', 'status', | |
| 262 | 'version', 'description', 'parent_id']) | |
| 263 | ||
| 264 | def createVuln(self): | |
| 265 | return self._create( | |
| 266 | self.controller.newVuln, | |
| 267 | ['name', 'desc', 'ref', 'severity', 'resolution', 'parent_id']) | |
| 268 | ||
| 269 | def createVulnWeb(self): | |
| 270 | return self._create( | |
| 271 | self.controller.newVulnWeb, | |
| 272 | ['name', 'desc', 'ref', 'severity', 'resolution', 'website', | |
| 273 | 'path', 'request', 'response', 'method', 'pname', | |
| 274 | 'params', 'query', 'category', 'parent_id']) | |
| 275 | ||
| 276 | def createNote(self): | |
| 277 | return jsonify(code=200) | |
| 278 | ||
| 279 | def createCred(self): | |
| 280 | return self._create( | |
| 281 | self.controller.newCred, | |
| 282 | ['username', 'password', 'parent_id']) | |
| 283 | ||
| 284 | def statusCheck(self): | |
| 285 | return self.ok("Faraday API Status: OK") | |
| 286 | ||
| 287 | ||
| 288 | class PluginControllerAPI(RESTApi): | |
| 289 | def __init__(self, plugin_controller): | |
| 290 | self.plugin_controller = plugin_controller | |
| 291 | ||
| 292 | def getRoutes(self): | |
| 293 | routes = [] | |
| 294 | routes.append(Route(path='/cmd/input', | |
| 295 | view_func=self.postCmdInput, | |
| 296 | methods=['POST'])) | |
| 297 | routes.append(Route(path='/cmd/output', | |
| 298 | view_func=self.postCmdOutput, | |
| 299 | methods=['POST'])) | |
| 300 | routes.append(Route(path='/cmd/active-plugins', | |
| 301 | view_func=self.clearActivePlugins, | |
| 302 | methods=['DELETE'])) | |
| 303 | return routes | |
| 304 | ||
| 305 | def pluginAvailable(self, plugin, cmd): | |
| 306 | code = 200 | |
| 307 | return jsonify(code=code, | |
| 308 | cmd=cmd, | |
| 309 | plugin=plugin) | |
| 310 | ||
| 311 | def postCmdInput(self): | |
| 312 | json_data = request.get_json() | |
| 313 | if 'cmd' in json_data.keys(): | |
| 314 | if 'pid' in json_data.keys(): | |
| 315 | if 'pwd' in json_data.keys(): | |
| 316 | try: | |
| 317 | cmd = base64.b64decode(json_data.get('cmd')).decode() | |
| 318 | pwd = base64.b64decode(json_data.get('pwd')).decode() | |
| 319 | except: | |
| 320 | cmd = '' | |
| 321 | pwd = '' | |
| 322 | pid = json_data.get('pid') | |
| 323 | plugin, new_cmd = self.plugin_controller.\ | |
| 324 | processCommandInput(pid, cmd, pwd) | |
| 325 | if plugin: | |
| 326 | return self.pluginAvailable(plugin, new_cmd) | |
| 327 | else: | |
| 328 | return self.noContent("no plugin available for cmd") | |
| 329 | else: | |
| 330 | return self.badRequest("pwd parameter not sent") | |
| 331 | else: | |
| 332 | return self.badRequest("pid parameter not sent") | |
| 333 | else: | |
| 334 | return self.badRequest("cmd parameter not sent") | |
| 335 | ||
| 336 | ||
| 337 | ||
| 338 | def postCmdOutput(self): | |
| 339 | json_data = request.get_json() | |
| 340 | if 'pid' in json_data.keys(): | |
| 341 | if 'output' in json_data.keys(): | |
| 342 | if 'exit_code' in json_data.keys(): | |
| 343 | pid = json_data.get('pid') | |
| 344 | output = base64.b64decode(json_data.get('output')) | |
| 345 | exit_code = json_data.get('exit_code') | |
| 346 | if self.plugin_controller.onCommandFinished( | |
| 347 | pid, exit_code, output): | |
| 348 | return self.ok("output successfully sent to plugin") | |
| 349 | return self.badRequest( | |
| 350 | "output received but no active plugin") | |
| 351 | return self.badRequest("exit_code parameter not sent") | |
| 352 | return self.badRequest("output parameter not sent") | |
| 353 | return self.badRequest("pid parameter not sent") | |
| 354 | ||
| 355 | def clearActivePlugins(self): | |
| 356 | self.plugin_controller.clearActivePlugins() | |
| 357 | return self.ok("active plugins cleared") | |
| 358 | ||
| 359 | ||
| 360 | class Route: | |
| 361 | """ Route class, abstracts information about: | |
| 362 | path, handler and methods """ | |
| 363 | def __init__(self, **kwargs): | |
| 364 | for k, v in kwargs.items(): | |
| 365 | setattr(self, k, v) | |
| 366 | ||
| 367 | ||
| 368 | # I'm Py3 |
| 0 | #!/usr/bin/env python | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | """ | |
| 7 | import requests | |
| 8 | import json | |
| 9 | import base64 | |
| 10 | ||
| 11 | ||
| 12 | class RestApiClient: | |
| 13 | def __init__(self, hostname, port): | |
| 14 | self.hostname = hostname | |
| 15 | self.port = port | |
| 16 | self.url = f"http://{self.hostname}:{self.port}/" | |
| 17 | self.headers = {'Content-type': 'application/json', 'Accept': 'application/json'} | |
| 18 | ||
| 19 | ||
| 20 | class ModelRestApiClient(RestApiClient): | |
| 21 | def __init__(self, hostname, port): | |
| 22 | super(ModelRestApiClient, self).__init__(hostname, port) | |
| 23 | ||
| 24 | def _create(self, obj_class_url, **kwargs): | |
| 25 | url = f"{self.url}model/{obj_class_url}" | |
| 26 | data = {} | |
| 27 | for k, v in kwargs.items(): | |
| 28 | data[k] = v | |
| 29 | obj_id = None | |
| 30 | try: | |
| 31 | response = requests.put( | |
| 32 | url, data=json.dumps(data), | |
| 33 | headers=self.headers) | |
| 34 | if response.status_code == 200: | |
| 35 | json_response = response.json() | |
| 36 | obj_id = json_response.get('id') | |
| 37 | except: | |
| 38 | pass | |
| 39 | return obj_id | |
| 40 | ||
| 41 | def createHost(self, name, os): | |
| 42 | return self._create("host", name=name, os=os) | |
| 43 | ||
| 44 | def createInterface(self, name, mac, ipv4_address, ipv4_mask, | |
| 45 | ipv4_gateway, ipv4_dns, ipv6_address, ipv6_prefix, | |
| 46 | ipv6_gateway, ipv6_dns, network_segment, | |
| 47 | hostname_resolution, parent_id): | |
| 48 | return self._create( | |
| 49 | "interface", name=name, mac=mac, ipv4_address=ipv4_address, | |
| 50 | ipv4_mask=ipv4_mask, ipv4_gateway=ipv4_gateway, ipv4_dns=ipv4_dns, | |
| 51 | ipv6_address=ipv6_address, ipv6_prefix=ipv6_prefix, | |
| 52 | ipv6_gateway=ipv6_gateway, ipv6_dns=ipv6_dns, | |
| 53 | network_segment=network_segment, | |
| 54 | hostname_resolution=hostname_resolution, | |
| 55 | parent_id=parent_id) | |
| 56 | ||
| 57 | def createService(self, name, protocol, ports, status, version, | |
| 58 | description, parent_id): | |
| 59 | return self._create( | |
| 60 | "service", name=name, protocol=protocol, ports=ports, | |
| 61 | status=status, version=version, description=description, | |
| 62 | parent_id=parent_id) | |
| 63 | ||
| 64 | def createVuln(self, name, desc, ref, severity, resolution, parent_id): | |
| 65 | return self._create( | |
| 66 | "vuln", name=name, desc=desc, ref=ref, severity=severity, | |
| 67 | resolution=resolution, parent_id=parent_id) | |
| 68 | ||
| 69 | def createVulnWeb(self, name, desc, ref, severity, resolution, website, path, | |
| 70 | request, response, method, pname, params, query, category, | |
| 71 | parent_id): | |
| 72 | return self._create( | |
| 73 | "vulnweb", name=name, desc=desc, ref=ref, severity=severity, | |
| 74 | resolution=resolution, website=website, path=path, request=request, | |
| 75 | response=response, method=method, pname=pname, params=params, query=query, | |
| 76 | category=category, parent_id=parent_id) | |
| 77 | ||
| 78 | def createNote(self, name, text, parent_id): | |
| 79 | return self._create("note", name=name, text=text, parent_id=parent_id) | |
| 80 | ||
| 81 | def createCred(self, username, password, parent_id): | |
| 82 | return self._create( | |
| 83 | "cred", username=username, password=password, parent_id=parent_id) | |
| 84 | ||
| 85 | ||
| 86 | class PluginControllerAPIClient: | |
| 87 | def __init__(self, hostname, port): | |
| 88 | self.hostname = hostname | |
| 89 | self.port = port | |
| 90 | self.url_input = "http://%s:%d/cmd/input" % (self.hostname, self.port) | |
| 91 | self.url_output = "http://%s:%d/cmd/output" % (self.hostname, self.port) | |
| 92 | self.url_active_plugins = "http://%s:%d/cmd/active-plugins" % (self.hostname, self.port) | |
| 93 | self.headers = {'Content-type': 'application/json', 'Accept': 'application/json'} | |
| 94 | ||
| 95 | def send_cmd(self, cmd): | |
| 96 | data = {"cmd": cmd} | |
| 97 | new_cmd = cmd | |
| 98 | output_file = None | |
| 99 | try: | |
| 100 | response = requests.post(self.url_input, | |
| 101 | data=json.dumps(data), | |
| 102 | headers=self.headers) | |
| 103 | ||
| 104 | if response.status_code == 200: | |
| 105 | json_response = response.json() | |
| 106 | if "cmd" in json_response.keys(): | |
| 107 | if json_response.get("cmd") is not None: | |
| 108 | new_cmd = json_response.get("cmd") | |
| 109 | if "custom_output_file" in json_response.keys(): | |
| 110 | output_file = json_response.get("custom_output_file") | |
| 111 | except: | |
| 112 | new_cmd = cmd | |
| 113 | finally: | |
| 114 | return new_cmd, output_file | |
| 115 | ||
| 116 | def send_output(self, cmd, output_file=None): | |
| 117 | # output_file could be None, when there is | |
| 118 | # no output to send | |
| 119 | output = "" | |
| 120 | if output_file: | |
| 121 | output_file = open(output_file) | |
| 122 | output = base64.b64encode(output_file.read()) | |
| 123 | data = {"cmd": cmd, "output": output} | |
| 124 | response = requests.post(self.url_output, | |
| 125 | data=json.dumps(data), | |
| 126 | headers=self.headers) | |
| 127 | if response.status_code != 200: | |
| 128 | return False | |
| 129 | return True | |
| 130 | ||
| 131 | ||
| 132 | # I'm Py3 |
| 0 | # Faraday Penetration Test IDE | |
| 1 | # Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 2 | # See the file 'doc/LICENSE' for the license information | |
| 3 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | import requests | |
| 6 | from tqdm import tqdm | |
| 7 | from dateutil import parser | |
| 8 | from datetime import datetime | |
| 9 | ||
| 10 | from faraday.client.persistence.server import models | |
| 11 | ||
| 12 | ||
| 13 | __description__ = 'Closes vulns from the current workspace if a certain time has passed' | |
| 14 | __prettyname__ = 'Close vulns if a certain time has passed' | |
| 15 | ||
| 16 | ||
| 17 | def get_vulns_from_workspace(session, url, workspace): | |
| 18 | vulns = session.get('{url}/_api/v2/ws/{ws_name}/vulns/'\ | |
| 19 | .format(url=url, ws_name=workspace)) | |
| 20 | ||
| 21 | return vulns.json() | |
| 22 | ||
| 23 | ||
| 24 | def close_vulns(session, url, workspace, vulns, duration_time): | |
| 25 | vuln_closed_count = 0 | |
| 26 | vulnerabilities = vulns['vulnerabilities'] | |
| 27 | with tqdm(total=len(vulnerabilities)) as progress_bar: | |
| 28 | for vuln in vulnerabilities: | |
| 29 | create_time = vuln['value']['metadata']['create_time'] | |
| 30 | ||
| 31 | # Convert date | |
| 32 | # create_time[:-6] -> date without timezone | |
| 33 | creation_date = parser.parse(create_time[:-6]) | |
| 34 | elapsed_time = datetime.now() - creation_date | |
| 35 | ||
| 36 | # If elapsed time since creation is greater than duration time, the vuln will be closed | |
| 37 | if elapsed_time.total_seconds() > duration_time and vuln['value']['status'] != 'closed': | |
| 38 | vuln['value']['status'] = 'closed' | |
| 39 | close = session.put('{url}/_api/v2/ws/{ws_name}/vulns/{vuln_id}/'\ | |
| 40 | .format(url=url, | |
| 41 | ws_name=workspace, | |
| 42 | vuln_id=vuln['id'] | |
| 43 | ), | |
| 44 | json=vuln['value'] | |
| 45 | ) | |
| 46 | vuln_closed_count += 1 | |
| 47 | progress_bar.update(1) | |
| 48 | ||
| 49 | return vuln_closed_count | |
| 50 | ||
| 51 | ||
| 52 | def main(workspace='', args=None, parser=None): | |
| 53 | parser.add_argument('--vuln_duration', | |
| 54 | help='Duration time of a vulnerability (in seconds)', | |
| 55 | required=True) | |
| 56 | vuln_duration = parser.parse_args(args).vuln_duration | |
| 57 | ||
| 58 | s = requests.Session() | |
| 59 | ||
| 60 | url = models.server.SERVER_URL | |
| 61 | data = { | |
| 62 | "email": models.server.AUTH_USER, | |
| 63 | "password": models.server.AUTH_PASS | |
| 64 | } | |
| 65 | login_response = s.post('{url}/_api/login'.format(url=url), data=data) | |
| 66 | ||
| 67 | vulns = get_vulns_from_workspace(s, url, workspace) | |
| 68 | vulns_closed = close_vulns(s, url, workspace, vulns, float(vuln_duration)) | |
| 69 | ||
| 70 | print("[+] {count} vulnerabilities closed in workspace '{ws}'".format(count=vulns_closed, ws=workspace)) | |
| 71 | return 0, None | |
| 72 | ||
| 73 | ||
| 74 | # I'm Py3 |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | from __future__ import print_function | |
| 9 | from faraday.client.persistence.server.server_io_exceptions import ResourceDoesNotExist | |
| 10 | from faraday.client.persistence.server import models | |
| 11 | from faraday.utils.user_input import query_yes_no | |
| 12 | ||
| 13 | __description__ = 'Changes Vulns Status (to closed)' | |
| 14 | __prettyname__ = 'Change Vulns Status (to closed)' | |
| 15 | ||
| 16 | def main(workspace='', args=None, parser=None): | |
| 17 | ||
| 18 | parser.add_argument('-y', '--yes', action="store_true") | |
| 19 | parsed_args = parser.parse_args(args) | |
| 20 | ||
| 21 | try: | |
| 22 | vulns = models.get_all_vulns(workspace) | |
| 23 | except ResourceDoesNotExist: | |
| 24 | print ("Invalid workspace name: ", workspace) | |
| 25 | return 1, None | |
| 26 | ||
| 27 | if not parsed_args.yes: | |
| 28 | if not query_yes_no("Are you sure you want to change the status to closed of all the vulns in workspace %s" % workspace, default='no'): | |
| 29 | return 1, None | |
| 30 | ||
| 31 | count = 0 | |
| 32 | for vuln in vulns: | |
| 33 | old_status = vuln.status | |
| 34 | ||
| 35 | # Valid status | |
| 36 | if vuln.status != "closed": | |
| 37 | ||
| 38 | vuln.status = "closed" | |
| 39 | count += 1 | |
| 40 | ||
| 41 | if vuln.class_signature == "Vulnerability": | |
| 42 | models.update_vuln(workspace, vuln) | |
| 43 | ||
| 44 | elif vuln.class_signature == "VulnerabilityWeb": | |
| 45 | models.update_vuln_web(workspace, vuln) | |
| 46 | ||
| 47 | print (vuln.name, ": Status changed from", old_status,"to closed successfully") | |
| 48 | ||
| 49 | print ("End of process:", count, "vulnerabilities changed to closed") | |
| 50 | return 0, None | |
| 51 | ||
| 52 | ||
| 53 | # I'm Py3 |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | from __future__ import print_function | |
| 9 | ||
| 10 | from faraday.client.model.common import factory | |
| 11 | from faraday.client.persistence.server import models | |
| 12 | ||
| 13 | __description__ = 'Creates new credentials' | |
| 14 | __prettyname__ = 'Create Credentials' | |
| 15 | ||
| 16 | ||
| 17 | def main(workspace='', args=None, parser=None): | |
| 18 | parser.add_argument('parent', help='Parent ID') | |
| 19 | parser.add_argument('name', help='Credential Name') | |
| 20 | parser.add_argument('username', help='Username') | |
| 21 | parser.add_argument('password', help='Password') | |
| 22 | ||
| 23 | parser.add_argument('--parent_type', | |
| 24 | help='Vulnerability severity', | |
| 25 | choices=['Host', 'Service'], | |
| 26 | default='unclassified') | |
| 27 | ||
| 28 | parser.add_argument('--dry-run', action='store_true', help='Do not touch the database. Only print the object ID') | |
| 29 | parsed_args = parser.parse_args(args) | |
| 30 | ||
| 31 | params = { | |
| 32 | 'username': parsed_args.username, | |
| 33 | } | |
| 34 | ||
| 35 | if parsed_args.parent_type == 'Host': | |
| 36 | params.update({'host_id': parsed_args.parent}) | |
| 37 | elif parsed_args.parent_type == 'Service': | |
| 38 | params.update({'service_id': parsed_args.parent}) | |
| 39 | else: | |
| 40 | raise UserWarning('Credential only allow Host or Service as parent_type') | |
| 41 | ||
| 42 | obj = factory.createModelObject(models.Credential.class_signature, | |
| 43 | parsed_args.name, | |
| 44 | workspace, | |
| 45 | username=parsed_args.username, | |
| 46 | password=parsed_args.password, | |
| 47 | parent_type=parsed_args.parent_type, | |
| 48 | parent=parsed_args.parent | |
| 49 | ) | |
| 50 | ||
| 51 | old = models.get_credential(workspace, **params) | |
| 52 | ||
| 53 | if old is None: | |
| 54 | if not parsed_args.dry_run: | |
| 55 | models.create_credential(workspace, obj) | |
| 56 | old = models.get_credential(workspace, **params) | |
| 57 | else: | |
| 58 | print("A credential with ID %s already exists!" % old.getID()) | |
| 59 | return 2, None | |
| 60 | ||
| 61 | return 0, old.getID() | |
| 62 | ||
| 63 | ||
| 64 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.model.common import factory | |
| 6 | from faraday.client.persistence.server import models | |
| 7 | ||
| 8 | __description__ = 'Creates a new host in current workspace' | |
| 9 | __prettyname__ = 'Create Host' | |
| 10 | ||
| 11 | ||
| 12 | def main(workspace='', args=None, parser=None): | |
| 13 | parser.add_argument('ip', help='Host IP') | |
| 14 | parser.add_argument('os', help='OS') | |
| 15 | ||
| 16 | parser.add_argument('mac', help='Interface MAC Address') | |
| 17 | ||
| 18 | parser.add_argument('--gateway', help='IPV4 or IPV6 Gateway', default='0.0.0.0') | |
| 19 | ||
| 20 | parser.add_argument('--netsegment', help='Network Segment', default='') | |
| 21 | ||
| 22 | ||
| 23 | parser.add_argument('--dry-run', action='store_true', help='Do not touch the database. Only print the object ID') | |
| 24 | ||
| 25 | parsed_args = parser.parse_args(args) | |
| 26 | ||
| 27 | params = { | |
| 28 | 'ip': parsed_args.ip, | |
| 29 | } | |
| 30 | ||
| 31 | obj_host = factory.createModelObject(models.Host.class_signature, | |
| 32 | parsed_args.ip, | |
| 33 | workspace, | |
| 34 | os=parsed_args.os, | |
| 35 | mac=parsed_args.mac, | |
| 36 | network_segment=parsed_args.netsegment, | |
| 37 | parent_id=None) | |
| 38 | ||
| 39 | ||
| 40 | old_host = models.get_host(workspace, **params) | |
| 41 | ||
| 42 | if old_host is None: | |
| 43 | if not parsed_args.dry_run: | |
| 44 | models.create_host(workspace, obj_host) | |
| 45 | old_host = models.get_host(workspace, **params) | |
| 46 | else: | |
| 47 | return 0, None | |
| 48 | else: | |
| 49 | print("A host with ID %s already exists!" % old_host.getID()) | |
| 50 | return 2, None | |
| 51 | ||
| 52 | return 0, old_host.getID() | |
| 53 | ||
| 54 | ||
| 55 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.model.common import factory | |
| 6 | from faraday.client.persistence.server import models | |
| 7 | ||
| 8 | __description__ = 'Creates a new service in a specified interface' | |
| 9 | __prettyname__ = 'Create Service' | |
| 10 | ||
| 11 | ||
| 12 | def main(workspace='', args=None, parser=None): | |
| 13 | parser.add_argument('host_id', help='Service Parent Host ID') | |
| 14 | parser.add_argument('name', help='Service Name') | |
| 15 | parser.add_argument('ports', help='Service ports, as a comma separated list') | |
| 16 | parser.add_argument('--protocol', help='Service protocol', default='tcp') | |
| 17 | parser.add_argument('--status', help='Service status', default='open') | |
| 18 | parser.add_argument('--version', help='Service version', default='unknown') | |
| 19 | parser.add_argument('--description', help='Service description', default='') | |
| 20 | ||
| 21 | parser.add_argument('--dry-run', action='store_true', help='Do not touch the database. Only print the object ID') | |
| 22 | ||
| 23 | parsed_args = parser.parse_args(args) | |
| 24 | ||
| 25 | ports = list(filter(None, parsed_args.ports.split(','))) | |
| 26 | res_ids = [] #new service or old services ids affected by the command | |
| 27 | for port in ports: | |
| 28 | params = { | |
| 29 | 'name': parsed_args.name, | |
| 30 | 'port': port, | |
| 31 | 'protocol': parsed_args.protocol, | |
| 32 | 'host_id': parsed_args.host_id | |
| 33 | } | |
| 34 | ||
| 35 | obj = factory.createModelObject(models.Service.class_signature, | |
| 36 | parsed_args.name, | |
| 37 | workspace, | |
| 38 | protocol=parsed_args.protocol, | |
| 39 | ports=[port], | |
| 40 | status=parsed_args.status, | |
| 41 | version=parsed_args.version, | |
| 42 | description=parsed_args.description, | |
| 43 | parent_id=parsed_args.host_id | |
| 44 | ) | |
| 45 | ||
| 46 | old = models.get_service(workspace, **params) | |
| 47 | ||
| 48 | if old is None: | |
| 49 | if not parsed_args.dry_run: | |
| 50 | models.create_service(workspace, obj) | |
| 51 | old = models.get_service(workspace, **params) | |
| 52 | else: | |
| 53 | print("A service with ID %s already exists!" % old.getID()) | |
| 54 | ||
| 55 | res_ids.append(old.getID()) | |
| 56 | ||
| 57 | return 0, res_ids | |
| 58 | ||
| 59 | ||
| 60 | # I'm Py3 |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | from __future__ import print_function | |
| 9 | ||
| 10 | from faraday.client.model.common import factory | |
| 11 | from faraday.client.persistence.server import models | |
| 12 | from faraday.client.persistence.server.server_io_exceptions import ( | |
| 13 | CantCommunicateWithServerError, | |
| 14 | ConflictInDatabase | |
| 15 | ) | |
| 16 | ||
| 17 | __description__ = 'Creates a new vulnerability' | |
| 18 | __prettyname__ = 'Create Vulnerability' | |
| 19 | ||
| 20 | ||
| 21 | def main(workspace='', args=None, parser=None): | |
| 22 | parser.add_argument('parent_type', | |
| 23 | choices=['Host', 'Service']) | |
| 24 | parser.add_argument('parent', help='Parent ID') | |
| 25 | parser.add_argument('name', help='Vulnerability Name') | |
| 26 | ||
| 27 | parser.add_argument('--reference', help='Vulnerability reference', default='') # Fixme | |
| 28 | parser.add_argument('--severity', | |
| 29 | help='Vulnerability severity', | |
| 30 | choices=['critical', 'high', 'med', 'low', 'info', 'unclassified'], | |
| 31 | default='unclassified') | |
| 32 | ||
| 33 | parser.add_argument('--resolution', help='Resolution', default='') | |
| 34 | parser.add_argument('--confirmed', help='Is the vulnerability confirmed', | |
| 35 | choices=['true', 'false'], | |
| 36 | default='false') | |
| 37 | parser.add_argument('--description', help='Vulnerability description', default='') | |
| 38 | ||
| 39 | parsed_args = parser.parse_args(args) | |
| 40 | ||
| 41 | obj = factory.createModelObject(models.Vuln.class_signature, | |
| 42 | parsed_args.name, | |
| 43 | workspace, | |
| 44 | ref=parsed_args.reference, | |
| 45 | severity=parsed_args.severity, | |
| 46 | resolution=parsed_args.resolution, | |
| 47 | confirmed=(parsed_args.confirmed == 'true'), | |
| 48 | desc=parsed_args.description, | |
| 49 | parent_id=parsed_args.parent, | |
| 50 | parent_type=parsed_args.parent_type.capitalize() | |
| 51 | ) | |
| 52 | params = { | |
| 53 | 'name': parsed_args.name, | |
| 54 | 'description': parsed_args.description, | |
| 55 | 'parent_type': parsed_args.parent_type.capitalize(), | |
| 56 | 'parent': parsed_args.parent, | |
| 57 | } | |
| 58 | ||
| 59 | try: | |
| 60 | models.create_vuln(workspace, obj) | |
| 61 | except ConflictInDatabase as ex: | |
| 62 | if ex.answer.status_code == 409: | |
| 63 | try: | |
| 64 | old_id = ex.answer.json()['object']['_id'] | |
| 65 | except KeyError: | |
| 66 | print("Vulnerability already exists. Couldn't fetch ID") | |
| 67 | return 2, None | |
| 68 | else: | |
| 69 | print("A vulnerability with ID %s already exists!" % old_id) | |
| 70 | return 2, None | |
| 71 | else: | |
| 72 | print("Unknown error while creating the vulnerability") | |
| 73 | return 2, None | |
| 74 | except CantCommunicateWithServerError as ex: | |
| 75 | print("Error while creating vulnerability:", ex.response.text) | |
| 76 | return 2, None | |
| 77 | ||
| 78 | new = models.get_vulns( | |
| 79 | workspace, | |
| 80 | **params | |
| 81 | ) | |
| 82 | ||
| 83 | return 0, new[0].getID() | |
| 84 | ||
| 85 | ||
| 86 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.model.common import factory | |
| 6 | from faraday.client.persistence.server import models | |
| 7 | ||
| 8 | __description__ = 'Creates a new website vulnerability in a specified service' | |
| 9 | __prettyname__ = 'Create Website Vulnerability' | |
| 10 | ||
| 11 | ||
| 12 | def main(workspace='', args=None, parser=None): | |
| 13 | parser.add_argument('service', help='Parent service ID') | |
| 14 | parser.add_argument('name', help='Vulnerability name') | |
| 15 | parser.add_argument('--reference', help='Vulnerability reference', default='') # Fixme | |
| 16 | ||
| 17 | parser.add_argument('--severity', | |
| 18 | help='Vulnerability severity', | |
| 19 | choices=['critical', 'high', 'med', 'low', 'info', 'unclassified'], | |
| 20 | default='unclassified') | |
| 21 | ||
| 22 | parser.add_argument('--resolution', help='Resolution', default='') | |
| 23 | parser.add_argument('--description', help='Vulnerability description', default='') | |
| 24 | ||
| 25 | parser.add_argument('--website', help='Website', default='') | |
| 26 | parser.add_argument('--path', help='Path', default='') | |
| 27 | parser.add_argument('--request', help='Request', default='') | |
| 28 | parser.add_argument('--response', help='Response', default='') | |
| 29 | parser.add_argument('--method', help='Method', default='') | |
| 30 | parser.add_argument('--pname', help='pname', default='') # FIXME | |
| 31 | parser.add_argument('--params', help='Parameters', default='') | |
| 32 | parser.add_argument('--query', help='Query', default='') | |
| 33 | parser.add_argument('--category', help='Category', default='') | |
| 34 | ||
| 35 | parser.add_argument('--confirmed', help='Is the vulnerability confirmed', | |
| 36 | choices=['true', 'false'], | |
| 37 | default='false') | |
| 38 | ||
| 39 | parser.add_argument('--dry-run', action='store_true', help='Do not touch the database. Only print the object ID') | |
| 40 | ||
| 41 | parsed_args = parser.parse_args(args) | |
| 42 | ||
| 43 | params = { | |
| 44 | 'name': parsed_args.name, | |
| 45 | 'description': parsed_args.description, | |
| 46 | 'service_id': parsed_args.service, | |
| 47 | 'method': parsed_args.method, | |
| 48 | 'parameter_name': parsed_args.params, | |
| 49 | 'path': parsed_args.path, | |
| 50 | 'website': parsed_args.website, | |
| 51 | } | |
| 52 | ||
| 53 | obj = factory.createModelObject(models.VulnWeb.class_signature, parsed_args.name, workspace, | |
| 54 | desc=parsed_args.description, | |
| 55 | ref=parsed_args.reference, | |
| 56 | severity=parsed_args.severity, | |
| 57 | resolution=parsed_args.resolution, | |
| 58 | ||
| 59 | website=parsed_args.website, | |
| 60 | path=parsed_args.path, | |
| 61 | request=parsed_args.request, | |
| 62 | response=parsed_args.response, | |
| 63 | method=parsed_args.method, | |
| 64 | pname=parsed_args.pname, | |
| 65 | params=parsed_args.params, | |
| 66 | query=parsed_args.query, | |
| 67 | category=parsed_args.category, | |
| 68 | ||
| 69 | confirmed=(parsed_args.confirmed == 'true'), | |
| 70 | parent_id=parsed_args.service, | |
| 71 | parent_type='Service' | |
| 72 | ) | |
| 73 | ||
| 74 | old = models.get_web_vuln(workspace, **params) | |
| 75 | ||
| 76 | if old is None: | |
| 77 | if not parsed_args.dry_run: | |
| 78 | models.create_vuln_web(workspace, obj) | |
| 79 | old = models.get_web_vuln(workspace, **params) | |
| 80 | else: | |
| 81 | print("A web vulnerability with ID %s already exists!" % old.getID()) | |
| 82 | return 2, None | |
| 83 | ||
| 84 | return 0, old.getID() | |
| 85 | ||
| 86 | ||
| 87 | # I'm Py3 |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | """ | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | """ | |
| 8 | from __future__ import absolute_import | |
| 9 | from __future__ import print_function | |
| 10 | ||
| 11 | from builtins import input | |
| 12 | ||
| 13 | from faraday.client.persistence.server import models | |
| 14 | ||
| 15 | __description__ = 'Deletes all stored hosts' | |
| 16 | __prettyname__ = 'Delete All Hosts' | |
| 17 | ||
| 18 | ||
| 19 | def main(workspace='', args=None, parser=None): | |
| 20 | parser.add_argument('-y', '--yes', action="store_true") | |
| 21 | parsed_args = parser.parse_args(args) | |
| 22 | if not parsed_args.yes: | |
| 23 | msg = ("Are you sure you want to delete all hosts in the " | |
| 24 | "workspace {}? This action can't be undone [y/n] ".format( | |
| 25 | workspace)) | |
| 26 | if input(msg) not in ('y', 'yes'): | |
| 27 | return 1, None | |
| 28 | for host in models.get_hosts(workspace): | |
| 29 | print('Delete Host:' + host.name) | |
| 30 | models.delete_host(workspace, host.id) | |
| 31 | return 0, None | |
| 32 | ||
| 33 | ||
| 34 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.persistence.server import models | |
| 6 | from faraday.utils.user_input import query_yes_no | |
| 7 | ||
| 8 | __description__ = 'Deletes all services with a non open port' | |
| 9 | __prettyname__ = 'Delete All Service Closed' | |
| 10 | ||
| 11 | ||
| 12 | def main(workspace='', args=None, parser=None): | |
| 13 | parser.add_argument('-y', '--yes', action="store_true") | |
| 14 | parsed_args = parser.parse_args(args) | |
| 15 | if not parsed_args.yes: | |
| 16 | ||
| 17 | if not query_yes_no("Are you sure you want to delete all closed services in the " | |
| 18 | "workspace %s" % workspace, default='no'): | |
| 19 | return 1, None | |
| 20 | ||
| 21 | for service in models.get_services(workspace): | |
| 22 | if service.status != 'open' and service.status != 'opened': | |
| 23 | print('Deleted service: ' + service.name) | |
| 24 | models.delete_service(workspace, service.id) | |
| 25 | return 0, None | |
| 26 | ||
| 27 | ||
| 28 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from __future__ import absolute_import | |
| 6 | from __future__ import print_function | |
| 7 | from builtins import input | |
| 8 | ||
| 9 | import re | |
| 10 | from faraday.client.persistence.server import models | |
| 11 | ||
| 12 | __description__ = "Delete all vulnerabilities matched with regex" | |
| 13 | __prettyname__ = "Delete all vulnerabilities with (...)" | |
| 14 | ||
| 15 | ||
| 16 | def main(workspace='', args=None, parser=None): | |
| 17 | default_regex = ( | |
| 18 | r"ssl\-cert|ssl\-date|Traceroute Information|TCP\/IP Timestamps Supported" | |
| 19 | r"|OS Identification|Common Platform Enumeration") | |
| 20 | parser.add_argument('-y', '--yes', action="store_true") | |
| 21 | parser.add_argument('-r', '--regex', default=default_regex) | |
| 22 | parsed_args = parser.parse_args(args) | |
| 23 | if not parsed_args.yes: | |
| 24 | msg = ("Are you sure you want to delete all vulnerabilities " | |
| 25 | "matching the regex {} in the worspace {}? " | |
| 26 | "This action can't be undone [y/n] ".format( | |
| 27 | parsed_args.regex, workspace)) | |
| 28 | if input(msg) not in ('y', 'yes'): | |
| 29 | return 1, None | |
| 30 | ||
| 31 | for vuln in models.get_all_vulns(workspace): | |
| 32 | if re.findall(parsed_args.regex, vuln.name, ) != []: | |
| 33 | print("Delete Vuln: " + vuln.name) | |
| 34 | models.delete_vuln(workspace, vuln.id) | |
| 35 | return 0, None | |
| 36 | ||
| 37 | ||
| 38 | # I'm Py3 |
| 0 | #!/usr/bin/env python | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | """ | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2018 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | """ | |
| 8 | from __future__ import absolute_import | |
| 9 | from __future__ import print_function | |
| 10 | ||
| 11 | from builtins import input | |
| 12 | import os | |
| 13 | import sys | |
| 14 | import base64 | |
| 15 | import shlex | |
| 16 | import time | |
| 17 | import re | |
| 18 | import requests | |
| 19 | ||
| 20 | ||
| 21 | from subprocess import Popen, PIPE, call | |
| 22 | from faraday.client.persistence.server import models, server | |
| 23 | from faraday.client.persistence.server.server import SERVER_URL | |
| 24 | ||
| 25 | __description__ = 'Script to perform a brute force attack on different services in a workspace' | |
| 26 | __prettyname__ = 'FBrute' | |
| 27 | ||
| 28 | SUPPORTED_SERVICES = ["asterisk", "cisco", "cisco-enable", "cvs", "firebird", "ftp", "ftps", "http", | |
| 29 | "https", "http-proxy", "icq", "imap", "imaps", "irc", "ldap2", "ldap3", | |
| 30 | "mssql", "mysql", "nntp", "oracle-listener", "oracle-sid", "pcanywhere", | |
| 31 | "pcnfs", "pop3", "pop3s", "postgres", "rdp", "redis", "rexec", "rlogin", | |
| 32 | "rsh", "rtsp", "s7-300", "sip", "smb", "smtp", "smtps", "smtp-enum", "snmp", | |
| 33 | "socks5", "ssh", "sshkey", "svn", "teamspeak", "telnet" | |
| 34 | "telnets", "vmauthd", "vnc", "xmpp"] | |
| 35 | ||
| 36 | PID = os.getpid() | |
| 37 | ||
| 38 | def check_hydra(): | |
| 39 | p = Popen(["which", "hydra"], stdout=PIPE) | |
| 40 | p.communicate()[0] | |
| 41 | return p.returncode == 0 | |
| 42 | ||
| 43 | ||
| 44 | def add_output(output): | |
| 45 | pwd = os.getcwd() | |
| 46 | data = {"cmd" : base64.b64encode(output), "pid" : PID, "pwd" : base64.b64encode(pwd)} | |
| 47 | requests.post("http://localhost:9977/cmd/input", json=data) | |
| 48 | ||
| 49 | ||
| 50 | def send_output(output): | |
| 51 | output = base64.b64encode(open(output, "r").read()) | |
| 52 | data = {"exit_code" : 0, "pid" : PID, "output" : output} | |
| 53 | requests.post("http://localhost:9977/cmd/output", json=data) | |
| 54 | ||
| 55 | ||
| 56 | def search_hosts_by_service(workspace, b_service): | |
| 57 | output = "" | |
| 58 | all_hosts = list(models.get_hosts(workspace)) | |
| 59 | all_services = list(models.get_services(workspace)) | |
| 60 | for host in all_hosts: | |
| 61 | for service in all_services: | |
| 62 | id_service_host = service.parent_id | |
| 63 | if host.id == id_service_host and service.name == b_service: | |
| 64 | output += host.name + "\n" | |
| 65 | break | |
| 66 | return output | |
| 67 | ||
| 68 | ||
| 69 | def total_credentials(workspace): | |
| 70 | json_creds = server._get( | |
| 71 | SERVER_URL + "/_api/v2/ws/%s/credential" % workspace) | |
| 72 | ||
| 73 | return len(json_creds["rows"]) | |
| 74 | ||
| 75 | ||
| 76 | def get_credentials(workspace, key): | |
| 77 | credentials = "" | |
| 78 | ||
| 79 | json_creds = server._get( | |
| 80 | SERVER_URL + "/_api/v2/ws/%s/credential" % workspace) | |
| 81 | ||
| 82 | if len(json_creds["rows"]) > 0: | |
| 83 | ||
| 84 | for c in json_creds["rows"]: | |
| 85 | credentials += c["value"][key] + "\n" | |
| 86 | return credentials | |
| 87 | ||
| 88 | else: | |
| 89 | sys.exit("No credentials were found on faraday") | |
| 90 | ||
| 91 | ||
| 92 | def show_table_services(workspace): | |
| 93 | ||
| 94 | services = [] | |
| 95 | table = "" | |
| 96 | ||
| 97 | j_parsed = server._get( | |
| 98 | SERVER_URL + "/_api/v2/ws/%s/services/count?group_by=name" % workspace) | |
| 99 | ||
| 100 | if len(j_parsed["groups"]) > 0: | |
| 101 | ||
| 102 | table += "Number\tService\tCount\n" | |
| 103 | table += "------\t-------\t------\n" | |
| 104 | ||
| 105 | for l in j_parsed["groups"]: | |
| 106 | if l["name"] in SUPPORTED_SERVICES: | |
| 107 | services.append(l["name"]) | |
| 108 | table += "[" + str(services.index(l["name"])) + "]\t" | |
| 109 | table += l["name"] + "\t" + str(l["count"]) + "\n" | |
| 110 | return table, services | |
| 111 | ||
| 112 | else: | |
| 113 | sys.exit("No services availables") | |
| 114 | ||
| 115 | ||
| 116 | def input_index(text, leng): | |
| 117 | while 1: | |
| 118 | ||
| 119 | stdin = input(text+"[0-"+str(leng-1)+"/q]: ") | |
| 120 | ||
| 121 | if re.search("[0-9]", stdin) is not None: | |
| 122 | ||
| 123 | if int(stdin) > leng-1 or int(stdin) < 0: | |
| 124 | continue | |
| 125 | return stdin | |
| 126 | ||
| 127 | elif stdin == "q": | |
| 128 | sys.exit(1) | |
| 129 | ||
| 130 | else: | |
| 131 | continue | |
| 132 | ||
| 133 | ||
| 134 | def show_options(workspace): | |
| 135 | ||
| 136 | user_define_dictionary = False | |
| 137 | usernames_dic_path = None | |
| 138 | passwords_dic_path = None | |
| 139 | user_faraday = None | |
| 140 | passwd_faraday = None | |
| 141 | ||
| 142 | # Muestro los servicios en el workspace soportados por hydra, en formato tabla | |
| 143 | table_services, services = show_table_services(workspace) | |
| 144 | print(table_services) | |
| 145 | ||
| 146 | service = int(input_index("What service do you want to bruteforce?", len(services))) | |
| 147 | ||
| 148 | # Verifico si el usuario quiere armar un diccionario con las credenciales | |
| 149 | # guardadas en faraday o si quiere utilizar uno propio | |
| 150 | print("\n[0] Choose a dictionary") | |
| 151 | print("[1] Create dictionary from Faraday (based in credentials stored in Faraday)\n") | |
| 152 | ||
| 153 | dictionary = int(input_index("Options ", 2)) | |
| 154 | ||
| 155 | #Le pido el path de el user dic y el password dic | |
| 156 | if dictionary == 0: | |
| 157 | usernames_dic_path = input("Usernames file: ") | |
| 158 | passwords_dic_path = input("Passwords file: ") | |
| 159 | user_define_dictionary = True | |
| 160 | ||
| 161 | else: | |
| 162 | ||
| 163 | print("\n[*] Obtaining credentials from the workspace %s" % workspace) | |
| 164 | ||
| 165 | user_faraday = save_targets(get_credentials(workspace, "username")) | |
| 166 | passwd_faraday = save_targets(get_credentials(workspace, "password")) | |
| 167 | ||
| 168 | print("[*] Credentials found: %s" % total_credentials(workspace)) | |
| 169 | print("\nUsername\t\tPassword") | |
| 170 | print("--------\t\t--------") | |
| 171 | ||
| 172 | for user, passw in zip( | |
| 173 | open(user_faraday, "r"), open(passwd_faraday, "r")): | |
| 174 | ||
| 175 | print("%s\t\t%s" % (user.strip(), passw.strip())) | |
| 176 | ||
| 177 | ||
| 178 | return service, services, user_define_dictionary, user_faraday, passwd_faraday, usernames_dic_path, passwords_dic_path | |
| 179 | ||
| 180 | ||
| 181 | def save_targets(output): | |
| 182 | ||
| 183 | dicc = "/tmp/targets_"+str(time.time()) | |
| 184 | ||
| 185 | f = open(dicc, "w") | |
| 186 | f.write(output) | |
| 187 | f.close() | |
| 188 | ||
| 189 | return dicc | |
| 190 | ||
| 191 | ||
| 192 | def main(workspace='', args=None, parser=None): | |
| 193 | ||
| 194 | print("\nThis script needs to be run inside from Faraday GTK.\n") | |
| 195 | if check_hydra(): | |
| 196 | ||
| 197 | service, services, user_define_dictionary, user_faraday, passwd_faraday, usernames_dic_path, passwords_dic_path = show_options(workspace) | |
| 198 | ||
| 199 | b_service = services[service] | |
| 200 | output = search_hosts_by_service(workspace, b_service) | |
| 201 | targets = save_targets(output) | |
| 202 | ||
| 203 | hydra_output = "/tmp/hydra_output-%s.txt" % time.time() | |
| 204 | ||
| 205 | print("Running Hydra, please wait to finish the bruteforce...\n") | |
| 206 | ||
| 207 | if user_define_dictionary: | |
| 208 | ||
| 209 | hydra_command1 = "hydra -L {0} -P {1} -e sr -M {2} -V -q {3} -o {4}".format( | |
| 210 | usernames_dic_path, | |
| 211 | passwords_dic_path, | |
| 212 | targets, | |
| 213 | b_service, | |
| 214 | hydra_output) | |
| 215 | ||
| 216 | add_output(hydra_command1) | |
| 217 | call(shlex.split(hydra_command1)) | |
| 218 | ||
| 219 | else: | |
| 220 | hydra_command2 = "hydra -L {0} -P {1} -e sr -M {2} -V -q {3} -o {4}".format( | |
| 221 | user_faraday, | |
| 222 | passwd_faraday, | |
| 223 | targets, | |
| 224 | b_service, | |
| 225 | hydra_output) | |
| 226 | ||
| 227 | add_output(hydra_command2) | |
| 228 | call(shlex.split(hydra_command2)) | |
| 229 | ||
| 230 | print("Processing information found in Faraday...\n") | |
| 231 | send_output(hydra_output) | |
| 232 | ||
| 233 | return None, None | |
| 234 | ||
| 235 | else: | |
| 236 | sys.exit("Hydra is not installed on the system. Install hydra to continue execution") | |
| 237 | return None, None | |
| 238 | ||
| 239 | ||
| 240 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from past.builtins import cmp | |
| 6 | ||
| 7 | import functools | |
| 8 | ||
| 9 | from colorama import Fore | |
| 10 | import sys | |
| 11 | ||
| 12 | from faraday.client.persistence.server import models | |
| 13 | ||
| 14 | __description__ = 'Filter services by port or service name' | |
| 15 | __prettyname__ = 'Filter services' | |
| 16 | ||
| 17 | SERVICES = { | |
| 18 | 'http': [80, 443, 8080, 8443], | |
| 19 | 'ftp': [21], | |
| 20 | 'ssh': [22], | |
| 21 | 'telnet': [23], | |
| 22 | 'smtp': [25], | |
| 23 | 'domain': [53], | |
| 24 | 'pop3': [110, 995], | |
| 25 | 'imap': [143, 993], | |
| 26 | 'vnc': [5900], | |
| 27 | } | |
| 28 | ||
| 29 | # FIXME Update when persistence API changes | |
| 30 | COLUMNS = { | |
| 31 | 'host': lambda service, workspace: models.get_host(workspace, service.getParent()).name, | |
| 32 | 'host_os': lambda service, workspace: models.get_host(workspace, service.getParent()).os, | |
| 33 | 'service': lambda service, workspace: service.name, | |
| 34 | 'ports': lambda service, workspace: str(service.ports[0]), | |
| 35 | 'protocol': lambda service, workspace: service.protocol, | |
| 36 | 'status': lambda service, workspace: service.status, | |
| 37 | } | |
| 38 | ||
| 39 | ||
| 40 | def main(workspace='', args=None, parser=None): | |
| 41 | parser.add_argument('-p', type=int, nargs='+', metavar='port', help='List of ports to filter', default=[]) | |
| 42 | parser.add_argument('services', nargs='*', help='List of service names', default=[]) | |
| 43 | parser.add_argument('--columns', help='Comma separated list of columns to show.', | |
| 44 | default="host,service,ports,protocol,status,host_os", choices=list(COLUMNS.keys())) | |
| 45 | ||
| 46 | parser.add_argument('--status', help='Comma separated list of status to filter for.') | |
| 47 | ||
| 48 | parser.add_argument('-a', help='Show additional information, like ports filtered and column headers.', | |
| 49 | action='store_true', dest='additional_info') | |
| 50 | ||
| 51 | parser.add_argument('-f', help='Do not apply any filter. Print every host.', | |
| 52 | action='store_true', dest='no_filter') | |
| 53 | ||
| 54 | parser.add_argument('-s', '--sorted', help='Print the list sorted IP..', action='store_true') | |
| 55 | ||
| 56 | parsed_args = parser.parse_args(args) | |
| 57 | ||
| 58 | port_list = parsed_args.p | |
| 59 | ||
| 60 | for service in parsed_args.services: | |
| 61 | if service in SERVICES: | |
| 62 | port_list += SERVICES[service] | |
| 63 | else: | |
| 64 | sys.stderr.write(Fore.YELLOW + | |
| 65 | "WARNING: Service definition not found. [%s]\n" % service + | |
| 66 | Fore.RESET) | |
| 67 | ||
| 68 | if not port_list and not parsed_args.no_filter: | |
| 69 | print("Empty filter set.") | |
| 70 | return 1, None | |
| 71 | ||
| 72 | if parsed_args.additional_info and not parsed_args.no_filter: | |
| 73 | print('Filtering services for ports: ' + ', '.join(map(str, sorted(port_list)))) | |
| 74 | ||
| 75 | columns = list(filter(None, parsed_args.columns.split(','))) | |
| 76 | ||
| 77 | status_filter = None | |
| 78 | ||
| 79 | if parsed_args.status is not None: | |
| 80 | status_filter = list(filter(None, parsed_args.status.split(','))) | |
| 81 | ||
| 82 | lines = [] | |
| 83 | ||
| 84 | for service in models.get_services(workspace): | |
| 85 | for port in service.ports: | |
| 86 | if port in port_list or parsed_args.no_filter: | |
| 87 | ||
| 88 | if not parsed_args.no_filter and status_filter is not None and not service.status in status_filter: | |
| 89 | continue | |
| 90 | ||
| 91 | column_data = [] | |
| 92 | ||
| 93 | for column in columns: | |
| 94 | column_data += [COLUMNS[column](service, workspace)] | |
| 95 | ||
| 96 | lines += [column_data] | |
| 97 | ||
| 98 | if not lines: | |
| 99 | print("No services running on that port found.") | |
| 100 | return 0, None | |
| 101 | ||
| 102 | col_width = max(len(word) for row in lines for word in row) + 2 | |
| 103 | ||
| 104 | if parsed_args.additional_info: | |
| 105 | print(''.join(col.ljust(col_width) for col in columns)) | |
| 106 | print('-' * (col_width * len(columns))) | |
| 107 | ||
| 108 | if parsed_args.sorted: | |
| 109 | # Compare lines using the first column (IP) | |
| 110 | for row in sorted(lines, key=functools.cmp_to_key(lambda l1, l2: cmp(l1[0], l2[0]))): # passed from py2 to py2/3, TODO check | |
| 111 | print("".join(word.ljust(col_width) for word in row)) | |
| 112 | else: | |
| 113 | for row in lines: | |
| 114 | print("".join(word.ljust(col_width) for word in row)) | |
| 115 | ||
| 116 | return 0, None | |
| 117 | ||
| 118 | ||
| 119 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from builtins import input | |
| 6 | ||
| 7 | import os | |
| 8 | import sys | |
| 9 | import imp | |
| 10 | import shlex | |
| 11 | import atexit | |
| 12 | import signal | |
| 13 | import inspect | |
| 14 | import argparse | |
| 15 | import readline | |
| 16 | from queue import Queue | |
| 17 | ||
| 18 | from faraday.client.plugins import fplugin_utils | |
| 19 | ||
| 20 | from colorama import Fore | |
| 21 | from faraday.config.configuration import getInstanceConfiguration | |
| 22 | from faraday.client.managers.mapper_manager import MapperManager | |
| 23 | from faraday.client.model.controller import ModelController | |
| 24 | from faraday.client.persistence.server.server import login_user | |
| 25 | ||
| 26 | CONF = getInstanceConfiguration() | |
| 27 | ||
| 28 | plugins = None | |
| 29 | ||
| 30 | ||
| 31 | class RawDescriptionAndDefaultsHelpFormatter(argparse.RawDescriptionHelpFormatter, | |
| 32 | argparse.ArgumentDefaultsHelpFormatter): | |
| 33 | pass | |
| 34 | ||
| 35 | ||
| 36 | # Call signature corresponding to a function defined as: | |
| 37 | # def main(workspace='', args=[], parser = None): | |
| 38 | CURRENT_MAIN_ARGSPEC = inspect.ArgSpec(args=['workspace', 'args', 'parser'], varargs=None, keywords=None, | |
| 39 | defaults=('', None, None)) | |
| 40 | ||
| 41 | FPLUGIN_INTERACTIVE_LAST_TOKEN = '$last' | |
| 42 | ||
| 43 | ||
| 44 | def signal_handler(signal, frame): | |
| 45 | print('Bye Bye!') | |
| 46 | os._exit(0) | |
| 47 | ||
| 48 | ||
| 49 | def dispatch(args, unknown, user_help, username, password): | |
| 50 | session_cookie = login_user(args.url, username, password) | |
| 51 | if not session_cookie: | |
| 52 | raise UserWarning('Invalid credentials!') | |
| 53 | ||
| 54 | CONF.setDBUser(username) | |
| 55 | CONF.setDBSessionCookies(session_cookie) | |
| 56 | ||
| 57 | if '--' in unknown: | |
| 58 | unknown.remove('--') | |
| 59 | ||
| 60 | # We need the ModelController to register all available models | |
| 61 | mappers_manager = MapperManager() | |
| 62 | pending_actions = Queue() | |
| 63 | model_controller = ModelController(mappers_manager, pending_actions) | |
| 64 | ||
| 65 | if not args.command: | |
| 66 | print(user_help) | |
| 67 | if not args.interactive: | |
| 68 | sys.exit(1) | |
| 69 | ||
| 70 | if args.command not in list(plugins.keys()): | |
| 71 | sys.stderr.write(Fore.RED + | |
| 72 | ("ERROR: Plugin %s not found.\n" % args.command) + | |
| 73 | Fore.RESET) | |
| 74 | if args.interactive: | |
| 75 | return None | |
| 76 | else: | |
| 77 | sys.exit(1) | |
| 78 | ||
| 79 | from faraday import client # pylint:disable=import-outside-toplevel | |
| 80 | faraday_directory = os.path.dirname(os.path.realpath(os.path.join(client.__file__))) | |
| 81 | ||
| 82 | plugin_path = os.path.join(faraday_directory, "bin/", args.command + '.py') | |
| 83 | # Get filename and import this | |
| 84 | module_fplugin = imp.load_source('module_fplugin', plugin_path) | |
| 85 | module_fplugin.models.server.FARADAY_UP = False | |
| 86 | module_fplugin.models.server.SERVER_URL = args.url | |
| 87 | module_fplugin.models.server.AUTH_USER = username | |
| 88 | module_fplugin.models.server.AUTH_PASS = password | |
| 89 | ||
| 90 | call_main = getattr(module_fplugin, 'main', None) | |
| 91 | ||
| 92 | if call_main is None: | |
| 93 | sys.stderr.write(Fore.RED + "ERROR: Main function not found.\n" + Fore.RESET) | |
| 94 | if args.interactive: | |
| 95 | return None | |
| 96 | else: | |
| 97 | sys.exit(1) | |
| 98 | ||
| 99 | # Inspect the main function imported from the plugin and decide the best calling option | |
| 100 | main_argspec = inspect.getargspec(call_main) | |
| 101 | ||
| 102 | if main_argspec != CURRENT_MAIN_ARGSPEC: | |
| 103 | # Function argspec does not match current API. | |
| 104 | # Warn the user and call with original parameteres. | |
| 105 | sys.stderr.write(Fore.YELLOW + | |
| 106 | "WARNING: Plugin does not follow current call signature. Please update it! [%s.py]\n" % args.command + | |
| 107 | Fore.RESET) | |
| 108 | ||
| 109 | obj_id = None | |
| 110 | ||
| 111 | if {'args', 'parser'} <= set(main_argspec.args): | |
| 112 | # Function accepts args and parser arguments | |
| 113 | ||
| 114 | new_parser = argparse.ArgumentParser(description=plugins[args.command]['description'], | |
| 115 | prog="fplugin %s" % args.command, | |
| 116 | formatter_class=RawDescriptionAndDefaultsHelpFormatter) | |
| 117 | ||
| 118 | ret, obj_id = call_main(workspace=args.workspace, args=unknown, parser=new_parser) | |
| 119 | ||
| 120 | if obj_id is not None: | |
| 121 | print(obj_id) | |
| 122 | else: | |
| 123 | # Use old API to call plugin | |
| 124 | sys.stderr.write(Fore.YELLOW + | |
| 125 | "WARNING: Call with arguments and parser not supported.\n" + | |
| 126 | Fore.RESET) | |
| 127 | ret = call_main(workspace=args.workspace) | |
| 128 | ||
| 129 | if ret is None: | |
| 130 | ret = 0 | |
| 131 | ||
| 132 | if args.interactive: | |
| 133 | # print ('code = %d' % ret) | |
| 134 | return obj_id | |
| 135 | else: | |
| 136 | sys.exit(ret) | |
| 137 | ||
| 138 | ||
| 139 | def main(): | |
| 140 | global plugins | |
| 141 | ||
| 142 | signal.signal(signal.SIGINT, signal_handler) | |
| 143 | ||
| 144 | description = ('Using our plugin you can do different actions in the command line\n' | |
| 145 | 'and interact with Faraday. Faraday comes with some presets for bulk\n' | |
| 146 | 'actions such as object removal, get object information, etc.\n' | |
| 147 | 'Any parameter not recognized by fplugin, or everything after -- will be passed on \n' | |
| 148 | 'to the called script.\n') | |
| 149 | ||
| 150 | epilog = 'Available scripts:\n' | |
| 151 | ||
| 152 | plugins = fplugin_utils.get_available_plugins() | |
| 153 | ||
| 154 | for plugin in sorted(plugins.keys()): | |
| 155 | epilog += '\t- %s: %s\n' % (plugin, plugins[plugin]['description']) | |
| 156 | ||
| 157 | parser = argparse.ArgumentParser(description=description, | |
| 158 | epilog=epilog, | |
| 159 | formatter_class=RawDescriptionAndDefaultsHelpFormatter) | |
| 160 | ||
| 161 | group = parser.add_mutually_exclusive_group() | |
| 162 | ||
| 163 | group.add_argument('command', nargs='?', help='Command to execute. Example: ./fplugin getAllIps') | |
| 164 | group.add_argument('-i', '--interactive', action='store_true', help='Run in interactive mode') | |
| 165 | ||
| 166 | parser.add_argument( | |
| 167 | '-w', | |
| 168 | '--workspace', | |
| 169 | help='Workspace to use', | |
| 170 | default=CONF.getLastWorkspace()) | |
| 171 | ||
| 172 | parser.add_argument( | |
| 173 | '-u', | |
| 174 | '--url', | |
| 175 | help='Faraday Server URL. Example: http://localhost:5985', | |
| 176 | default='http://localhost:5985') | |
| 177 | ||
| 178 | parser.add_argument( | |
| 179 | '--username', | |
| 180 | required=True) | |
| 181 | ||
| 182 | parser.add_argument( | |
| 183 | '--password', | |
| 184 | required=True) | |
| 185 | ||
| 186 | # Only parse known args. Unknown ones will be passed on the the called script | |
| 187 | args, unknown = parser.parse_known_args() | |
| 188 | ||
| 189 | # print("""\nTo login please provide your valid DB Credentials.\n""") | |
| 190 | # username = raw_input('Username: ') | |
| 191 | # password = getpass.getpass('Password: ') | |
| 192 | ||
| 193 | if not args.interactive: | |
| 194 | dispatch(args, unknown, parser.format_help(), args.username, args.password) | |
| 195 | else: | |
| 196 | ||
| 197 | # print ("Loading command history...") | |
| 198 | histfile = os.path.join(CONF.getDataPath(), ".faraday_hist") | |
| 199 | readline.parse_and_bind('tab: complete') | |
| 200 | atexit.register(readline.write_history_file, histfile) | |
| 201 | ||
| 202 | try: | |
| 203 | readline.read_history_file(histfile) | |
| 204 | # default history len is -1 (infinite), which may grow unruly | |
| 205 | readline.set_history_length(1000) | |
| 206 | except IOError: | |
| 207 | pass | |
| 208 | ||
| 209 | print("Welcome to interactive Faraday!") | |
| 210 | print("Press CTRL-D or run 'exit' to quit interactive mode.") | |
| 211 | last_id = None | |
| 212 | ||
| 213 | while True: | |
| 214 | try: | |
| 215 | line = input("> ") | |
| 216 | ||
| 217 | if line.strip() == 'exit': | |
| 218 | os._exit(0) | |
| 219 | ||
| 220 | # Split line read from stdin into argv | |
| 221 | new_args = shlex.split(line) | |
| 222 | new_args += ['--username', args.username, '--password', args.password] | |
| 223 | ||
| 224 | if '-i' in new_args or '--interactive' in new_args: | |
| 225 | print('Already in interactive mode!') | |
| 226 | continue | |
| 227 | ||
| 228 | if 'h' in new_args or 'help' in new_args: | |
| 229 | parser.print_help() | |
| 230 | continue | |
| 231 | ||
| 232 | if FPLUGIN_INTERACTIVE_LAST_TOKEN in new_args: | |
| 233 | i = new_args.index(FPLUGIN_INTERACTIVE_LAST_TOKEN) | |
| 234 | new_args[i] = last_id or '' | |
| 235 | ||
| 236 | parsed_args, new_unknown = parser.parse_known_args(new_args) | |
| 237 | parsed_args.interactive = True | |
| 238 | ||
| 239 | last_id = dispatch(parsed_args, new_unknown, parser.format_help(), args.username, args.password) or last_id | |
| 240 | # print '$last = %s' % last_id | |
| 241 | except (EOFError, KeyboardInterrupt): | |
| 242 | print('Bye Bye!') | |
| 243 | sys.exit(0) | |
| 244 | except SystemExit: | |
| 245 | pass | |
| 246 | ||
| 247 | ||
| 248 | if __name__ == '__main__': | |
| 249 | main() | |
| 250 | ||
| 251 | ||
| 252 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | import re | |
| 6 | from faraday.client.persistence.server import models | |
| 7 | ||
| 8 | __description__ = "Get all scanned interfaces" | |
| 9 | __prettyname__ = "Get All IPs Interfaces" | |
| 10 | ||
| 11 | ||
| 12 | def main(workspace='', args=None, parser=None): | |
| 13 | ip_regex = re.compile("^\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}$") | |
| 14 | not_matching_count = 0 | |
| 15 | for host in models.get_hosts(workspace): | |
| 16 | if re.match(ip_regex, host.ip): | |
| 17 | print(host.ip) | |
| 18 | else: | |
| 19 | not_matching_count += 1 | |
| 20 | if not_matching_count: | |
| 21 | print('Hosts that has invalid ip addresses {0}'.format(not_matching_count)) | |
| 22 | ||
| 23 | return 0, None | |
| 24 | ||
| 25 | ||
| 26 | # I'm Py3 |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | from __future__ import print_function | |
| 9 | ||
| 10 | import json | |
| 11 | ||
| 12 | import requests | |
| 13 | ||
| 14 | from faraday.client.persistence.server import models | |
| 15 | ||
| 16 | __description__ = 'Get Vulns filtered by Severity and change Severity based in CWE' | |
| 17 | __prettyname__ = 'Get Severity By CWE' | |
| 18 | ||
| 19 | SEVERITY_OPTIONS = ('unclassified', 'info', 'low', 'med', 'high', 'critical', 'all') | |
| 20 | ||
| 21 | ||
| 22 | def getCweData(couch_url): | |
| 23 | # Get elements from cwe DB in couchdb | |
| 24 | headers = {'Content-Type': 'application/json'} | |
| 25 | ||
| 26 | payload = { | |
| 27 | 'map': | |
| 28 | 'function(doc) { if(doc.severity && doc.name){' | |
| 29 | 'emit(doc.name, doc.severity); }}' | |
| 30 | } | |
| 31 | ||
| 32 | r = requests.post( | |
| 33 | couch_url + '/cwe/_temp_view', | |
| 34 | headers=headers, | |
| 35 | data=json.dumps(payload) | |
| 36 | ) | |
| 37 | ||
| 38 | response_code = r.status_code | |
| 39 | ||
| 40 | if response_code == 200: | |
| 41 | ||
| 42 | data = r.json()['rows'] | |
| 43 | dict = {} | |
| 44 | ||
| 45 | for item in data: | |
| 46 | ||
| 47 | value = item['value'] | |
| 48 | if value == 'informational': | |
| 49 | value = 'info' | |
| 50 | ||
| 51 | dict.update({item['key']: value}) | |
| 52 | ||
| 53 | if dict == {}: | |
| 54 | return None | |
| 55 | else: | |
| 56 | print('Get CWE data: OK\n') | |
| 57 | return dict | |
| 58 | ||
| 59 | elif response_code == 401: | |
| 60 | print('Autorization required, make sure to add user:pwd to Couch URI') | |
| 61 | else: | |
| 62 | print('Error couchDB: ' + str(response_code) + str(r.text)) | |
| 63 | ||
| 64 | ||
| 65 | def checkSeverity(vuln, cwe_dict, severity_choose, workspace, couch_url): | |
| 66 | severity_dict = { | |
| 67 | 'unclassified': 0, | |
| 68 | 'info': 1, | |
| 69 | 'low': 2, | |
| 70 | 'med': 3, | |
| 71 | 'high': 4, | |
| 72 | 'critical': 5, | |
| 73 | 'all': 100 | |
| 74 | } | |
| 75 | ||
| 76 | if vuln._name in cwe_dict and severity_dict[vuln.severity] <= severity_dict[severity_choose]: | |
| 77 | ||
| 78 | print('Change: ' + vuln._name + ' to ' + cwe_dict[vuln._name]) | |
| 79 | ||
| 80 | # Get object Vuln | |
| 81 | response = requests.get( | |
| 82 | models.server.SERVER_URL + '/' + workspace + '/' + str(vuln._id) | |
| 83 | ) | |
| 84 | vulnWeb = response.json() | |
| 85 | ||
| 86 | # Change severity | |
| 87 | vulnWeb['severity'] = cwe_dict[vuln._name] | |
| 88 | ||
| 89 | # Put changes... | |
| 90 | headers = {'Content-Type': 'application/json'} | |
| 91 | update = requests.put( | |
| 92 | couch_url + '/' + workspace + '/' + vuln._id, | |
| 93 | headers=headers, | |
| 94 | data=json.dumps(vulnWeb) | |
| 95 | ) | |
| 96 | ||
| 97 | if update.status_code == 200 or update.status_code == 201: | |
| 98 | print('Change OK\n') | |
| 99 | else: | |
| 100 | print('Error in update Vulnerability, status code: ' + str(update.status_code)) | |
| 101 | print(update.text) | |
| 102 | ||
| 103 | ||
| 104 | def main(workspace='', args=None, parser=None): | |
| 105 | parser.add_argument('severity', nargs='?', help='Filter by Severity (<=)', default="info", choices=SEVERITY_OPTIONS) | |
| 106 | parser.add_argument('--couchdb', nargs='?', help='CouchDB URL', default="http://faraday:faraday@localhost:5984") | |
| 107 | ||
| 108 | parsed_args = parser.parse_args(args) | |
| 109 | ||
| 110 | cwe = getCweData(parsed_args.couchdb) | |
| 111 | ||
| 112 | if cwe is None: | |
| 113 | print('CWE DB not downloaded....EXIT') | |
| 114 | return 2, None | |
| 115 | ||
| 116 | for host in models.get_hosts(workspace): | |
| 117 | for v in host.getVulns(): | |
| 118 | checkSeverity(v, cwe, parsed_args.severity, workspace, parsed_args.couchdb) | |
| 119 | ||
| 120 | for i in host.getAllInterfaces(): | |
| 121 | for s in i.getAllServices(): | |
| 122 | for v in s.getVulns(): | |
| 123 | checkSeverity(v, cwe, parsed_args.severity, workspace, parsed_args.couchdb) | |
| 124 | ||
| 125 | return 0, None | |
| 126 | ||
| 127 | ||
| 128 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2017 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file "doc/LICENSE" for the license information | |
| 4 | """ | |
| 5 | import csv | |
| 6 | from time import mktime | |
| 7 | from datetime import datetime | |
| 8 | from faraday.client.persistence.server import models | |
| 9 | from faraday.client.persistence.server.server_io_exceptions import ConflictInDatabase, CantCommunicateWithServerError | |
| 10 | ||
| 11 | WORKSPACE = "" | |
| 12 | __description__ = "Import Faraday objects from CSV file" | |
| 13 | __prettyname__ = "Import objects from CSV" | |
| 14 | ||
| 15 | VULN_SEVERITIES = ["info", "low", "med", "high", "critical"] | |
| 16 | VULN_STATUS = ["opened", "closed", "re-opened", "risk-accepted"] | |
| 17 | SERVICE_STATUS = ["open", "filtered", "close"] | |
| 18 | ||
| 19 | ||
| 20 | def parse_register(register): | |
| 21 | ||
| 22 | host = parse_host(register) | |
| 23 | service = parse_service(register) | |
| 24 | vulnerability = parse_vulnerability(register) | |
| 25 | vulnerability_web = parse_vulnerability_web(register) | |
| 26 | ||
| 27 | return host, service, vulnerability, vulnerability_web | |
| 28 | ||
| 29 | ||
| 30 | def transform_dict_to_object(columns, register): | |
| 31 | ||
| 32 | """ | |
| 33 | Iterate over all columns and create a new obj with default data | |
| 34 | and values with the real key for Faraday objects. | |
| 35 | """ | |
| 36 | ||
| 37 | obj = {} | |
| 38 | ||
| 39 | for key, val in columns.items(): | |
| 40 | ||
| 41 | # Default data | |
| 42 | value = {val : ""} | |
| 43 | ||
| 44 | if val == "service_id": | |
| 45 | value["parent"] = register["service_id"] | |
| 46 | ||
| 47 | if val in ["owned", "confirmed"]: | |
| 48 | value[val] = False | |
| 49 | ||
| 50 | elif val in ["ports", "hostnames", "refs", "policyviolations"]: | |
| 51 | value[val] = [] | |
| 52 | ||
| 53 | elif key == "service_status": | |
| 54 | value[val] = "open" | |
| 55 | ||
| 56 | elif key in ["vulnerability_status", "vulnerability_web_status"]: | |
| 57 | value[val] = "opened" | |
| 58 | ||
| 59 | elif key in ["vulnerability_severity", "vulnerability_web_severity"]: | |
| 60 | value[val] = "info" | |
| 61 | ||
| 62 | # Copy data to new object | |
| 63 | if key in register: | |
| 64 | ||
| 65 | if val == "host_name": | |
| 66 | value[val] = register['interface_ipv4_address'] or register['interface_ipv6_address'] | |
| 67 | ||
| 68 | if val == "ports": | |
| 69 | value[val] = [register[key]] | |
| 70 | ||
| 71 | elif val in ["owned", "confirmed"]: | |
| 72 | if register[key] == "true": | |
| 73 | value[val] = True | |
| 74 | ||
| 75 | elif val == "desc": | |
| 76 | value["description"] = register[key] | |
| 77 | value["desc"] = register[key] | |
| 78 | ||
| 79 | elif val in ["refs", "hostnames", "policyviolations"]: | |
| 80 | value[val] = register[key].split(",") | |
| 81 | ||
| 82 | elif key == "service_status": | |
| 83 | if register[key].lower() in SERVICE_STATUS: | |
| 84 | value[val] = register[key] | |
| 85 | ||
| 86 | elif key in ["vulnerability_status", "vulnerability_web_status"]: | |
| 87 | if register[key].lower() in VULN_STATUS: | |
| 88 | value[val] = register[key] | |
| 89 | ||
| 90 | elif key in ["vulnerability_severity", "vulnerability_web_severity"]: | |
| 91 | if register[key].lower() == 'informational': | |
| 92 | register[key] = 'info' | |
| 93 | if register[key].lower() == 'medium': | |
| 94 | register[key] = 'med' | |
| 95 | if register[key].lower() in VULN_SEVERITIES: | |
| 96 | value[val] = register[key] | |
| 97 | else: | |
| 98 | value[val] = register[key] | |
| 99 | ||
| 100 | # Append new value to new object. | |
| 101 | obj.update(value) | |
| 102 | ||
| 103 | # Check if obj is Invalid, return None | |
| 104 | for key, val in obj.items(): | |
| 105 | if val not in [[""], [], "", False, "info", "opened", "open"]: | |
| 106 | return obj | |
| 107 | ||
| 108 | return None | |
| 109 | ||
| 110 | ||
| 111 | def parse_host(register): | |
| 112 | ||
| 113 | columns = { | |
| 114 | "host_name" : "name", | |
| 115 | "host_description" : "description", | |
| 116 | "host_owned" : "owned", #boolean | |
| 117 | "host_os" : "os" | |
| 118 | } | |
| 119 | ||
| 120 | obj = transform_dict_to_object(columns, register) | |
| 121 | if obj is None: | |
| 122 | return None | |
| 123 | host = models.Host(obj, WORKSPACE) | |
| 124 | ||
| 125 | try: | |
| 126 | ||
| 127 | date = register.get("host_metadata_create_time") | |
| 128 | if date is not None: | |
| 129 | datetime_object = datetime.strptime(date, "%m/%d/%Y") | |
| 130 | host._metadata.create_time = mktime(datetime_object.timetuple()) | |
| 131 | except Exception: | |
| 132 | print("Invalid date", host.name) | |
| 133 | ||
| 134 | return host | |
| 135 | ||
| 136 | ||
| 137 | def parse_service(register): | |
| 138 | ||
| 139 | columns = { | |
| 140 | "service_name" : "name", | |
| 141 | "service_description" : "description", | |
| 142 | "service_owned" : "owned", #boolean | |
| 143 | "service_port" : "ports", #list | |
| 144 | "service_protocol": "protocol", | |
| 145 | "service_version" : "version", | |
| 146 | "service_status" : "status" | |
| 147 | } | |
| 148 | ||
| 149 | obj = transform_dict_to_object(columns, register) | |
| 150 | if obj is None: | |
| 151 | return None | |
| 152 | service = models.Service(obj, WORKSPACE) | |
| 153 | return service | |
| 154 | ||
| 155 | ||
| 156 | def parse_vulnerability(register): | |
| 157 | ||
| 158 | columns = { | |
| 159 | "vulnerability_name" : "name", | |
| 160 | "vulnerability_desc" : "desc", | |
| 161 | "vulnerability_data" : "data", | |
| 162 | "vulnerability_severity" : "severity", | |
| 163 | "vulnerability_refs" : "refs", #list | |
| 164 | "vulnerability_confirmed" : "confirmed", #boolean | |
| 165 | "vulnerability_resolution" : "resolution", | |
| 166 | "vulnerability_status" : "status", | |
| 167 | "vulnerability_policyviolations" : "policyviolations" #list | |
| 168 | ||
| 169 | } | |
| 170 | ||
| 171 | obj = transform_dict_to_object(columns, register) | |
| 172 | if obj is None: | |
| 173 | return None | |
| 174 | vulnerability = models.Vuln(obj, WORKSPACE) | |
| 175 | ||
| 176 | try: | |
| 177 | ||
| 178 | date = register.get("vulnerability_metadata_create_time") | |
| 179 | if date is not None: | |
| 180 | datetime_object = datetime.strptime(date, "%m/%d/%Y") | |
| 181 | vulnerability._metadata.create_time = mktime(datetime_object.timetuple()) | |
| 182 | except Exception: | |
| 183 | print("Invalid date", vulnerability.name) | |
| 184 | ||
| 185 | return vulnerability | |
| 186 | ||
| 187 | ||
| 188 | def parse_vulnerability_web(register): | |
| 189 | ||
| 190 | columns = { | |
| 191 | "vulnerability_web_name" : "name", | |
| 192 | "vulnerability_web_desc" : "desc", | |
| 193 | "vulnerability_web_data" : "data", | |
| 194 | "vulnerability_web_severity" : "severity", | |
| 195 | "vulnerability_web_refs" : "refs", #list | |
| 196 | "vulnerability_web_confirmed" : "confirmed", #boolean | |
| 197 | "vulnerability_web_status" : "status", | |
| 198 | "vulnerability_web_website" : "website", | |
| 199 | "vulnerability_web_request" : "request", | |
| 200 | "vulnerability_web_response" : "response", | |
| 201 | "vulnerability_web_method" : "method", | |
| 202 | "vulnerability_web_pname" : "pname", | |
| 203 | "vulnerability_web_params" : "params", | |
| 204 | "vulnerability_web_query" : "query", | |
| 205 | "vulnerability_web_resolution" : "resolution", | |
| 206 | "vulnerability_web_policyviolations" : "policyviolations", #list | |
| 207 | "vulnerability_web_path" : "path" | |
| 208 | } | |
| 209 | ||
| 210 | obj = transform_dict_to_object(columns, register) | |
| 211 | if obj is None: | |
| 212 | return None | |
| 213 | vulnerability_web = models.VulnWeb(obj, WORKSPACE) | |
| 214 | ||
| 215 | try: | |
| 216 | date = register.get("vulnerability_web_metadata_create_time") | |
| 217 | if date is not None: | |
| 218 | datetime_object = datetime.strptime(date, "%m/%d/%Y") | |
| 219 | vulnerability_web._metadata.create_time = mktime(datetime_object.timetuple()) | |
| 220 | except Exception: | |
| 221 | print("Invalid date", vulnerability_web.name) | |
| 222 | ||
| 223 | return vulnerability_web | |
| 224 | ||
| 225 | ||
| 226 | def main(workspace="", args=None, parser=None): | |
| 227 | ||
| 228 | WORKSPACE = workspace | |
| 229 | ||
| 230 | parser.add_argument("--csv", help="Csv file to import") | |
| 231 | parsed_args = parser.parse_args(args) | |
| 232 | ||
| 233 | if not parsed_args.csv: | |
| 234 | print("Error: Give a CSV file to import with --csv") | |
| 235 | return 2, None | |
| 236 | ||
| 237 | try: | |
| 238 | file_csv = open(parsed_args.csv, "r") | |
| 239 | except: | |
| 240 | print("Error: Unreadeable CSV file, check the path") | |
| 241 | raise | |
| 242 | ||
| 243 | counter = 0 | |
| 244 | csv_reader = csv.DictReader(file_csv, delimiter=",", quotechar='"') | |
| 245 | for register in csv_reader: | |
| 246 | try: | |
| 247 | host, service, vulnerability, vulnerability_web = parse_register(register) | |
| 248 | ||
| 249 | # Set all IDs and create objects | |
| 250 | if host is not None: | |
| 251 | old_host = models.get_host(WORKSPACE, ip=host.getName()) | |
| 252 | if not old_host: | |
| 253 | ||
| 254 | counter += 1 | |
| 255 | ||
| 256 | print("New host: " + host.getName()) | |
| 257 | try: | |
| 258 | models.create_host(WORKSPACE, host) | |
| 259 | except Exception as ex: | |
| 260 | print(ex) | |
| 261 | host = models.get_host(WORKSPACE, ip=host.getName()) | |
| 262 | ||
| 263 | if service is not None: | |
| 264 | service.setParent(host.getID()) | |
| 265 | service_params = { | |
| 266 | 'name': service.getName(), | |
| 267 | 'port': service.getPorts()[0], | |
| 268 | 'protocol': service.getProtocol(), | |
| 269 | 'host_id': service.getParent() | |
| 270 | } | |
| 271 | old_service = models.get_service(WORKSPACE, **service_params) | |
| 272 | if not old_service: | |
| 273 | ||
| 274 | counter += 1 | |
| 275 | print("New service: " + service.getName()) | |
| 276 | models.create_service(WORKSPACE, service) | |
| 277 | service = models.get_service(WORKSPACE, **service_params) | |
| 278 | ||
| 279 | # Check if Service exist, then create the vuln with parent Service. | |
| 280 | # If not exist the Service, create the vuln with parent Host. | |
| 281 | if vulnerability is not None: | |
| 282 | if host and not service: | |
| 283 | parent_type = 'Host' | |
| 284 | parent_id = host.getID() | |
| 285 | if host and service: | |
| 286 | parent_type = 'Service' | |
| 287 | parent_id = service.getID() | |
| 288 | vulnerability.setParent(parent_id) | |
| 289 | vulnerability.setParentType(parent_type) | |
| 290 | ||
| 291 | vuln_params = { | |
| 292 | 'name': vulnerability.getName(), | |
| 293 | 'description': vulnerability.getDescription(), | |
| 294 | 'parent_type': parent_type, | |
| 295 | 'parent': parent_id, | |
| 296 | } | |
| 297 | ||
| 298 | if not models.get_vuln(WORKSPACE, **vuln_params): | |
| 299 | counter += 1 | |
| 300 | print("New vulnerability: " + vulnerability.getName()) | |
| 301 | models.create_vuln(WORKSPACE, vulnerability) | |
| 302 | ||
| 303 | elif vulnerability_web is not None: | |
| 304 | ||
| 305 | vuln_web_params = { | |
| 306 | 'name': vulnerability_web.getName(), | |
| 307 | 'description': vulnerability_web.getDescription(), | |
| 308 | 'parent': service.getID(), | |
| 309 | 'parent_type': 'Service', | |
| 310 | 'method': vulnerability_web.getMethod(), | |
| 311 | 'parameter_name': vulnerability_web.getParams(), | |
| 312 | 'path': vulnerability_web.getPath(), | |
| 313 | 'website': vulnerability_web.getWebsite(), | |
| 314 | } | |
| 315 | vulnerability_web.setParent(service.getID()) | |
| 316 | if not models.get_web_vuln(WORKSPACE, **vuln_web_params): | |
| 317 | ||
| 318 | counter += 1 | |
| 319 | print("New web vulnerability: " + vulnerability_web.getName()) | |
| 320 | models.create_vuln_web(WORKSPACE, vulnerability_web) | |
| 321 | except ConflictInDatabase: | |
| 322 | print('Conflict in Database, skiping csv row') | |
| 323 | except CantCommunicateWithServerError as ex: | |
| 324 | print(register) | |
| 325 | print('Error', ex) | |
| 326 | print("[*]", counter, "new Faraday objects created.") | |
| 327 | file_csv.close() | |
| 328 | return 0, None | |
| 329 | ||
| 330 | ||
| 331 | # I'm Py3 |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | """ | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | """ | |
| 8 | import os | |
| 9 | ||
| 10 | from faraday.client.model.common import factory | |
| 11 | from faraday.client.persistence.server import models | |
| 12 | ||
| 13 | PCAP_IMPORTED = False | |
| 14 | ||
| 15 | try: | |
| 16 | from pcapfile import savefile | |
| 17 | import pcapfile | |
| 18 | PCAP_IMPORTED = True | |
| 19 | except ImportError: | |
| 20 | pass | |
| 21 | ||
| 22 | ||
| 23 | __description__ = 'Import every host found in a PCAP file for further scanning' | |
| 24 | __prettyname__ = 'Import PCAP' | |
| 25 | ||
| 26 | ||
| 27 | def main(workspace='', args=None, parser=None): | |
| 28 | ||
| 29 | if not PCAP_IMPORTED: | |
| 30 | print('capfile not found, please install it to use this plugin.' | |
| 31 | ' You can do it executing pip2 install pcapfile in a shell.') | |
| 32 | return 1, None | |
| 33 | ||
| 34 | parser.add_argument('-s', '--source', nargs='*', help='Filter packets by source') | |
| 35 | parser.add_argument('-d', '--dest', nargs='*', help='Filter packets by destination') | |
| 36 | ||
| 37 | parser.add_argument('--dry-run', action='store_true', help='Do not touch the database. Only print the object ID') | |
| 38 | ||
| 39 | parser.add_argument('-v', '--verbose', action='store_true', help='Verbose output from the pcapfile library.') | |
| 40 | parser.add_argument('pcap', help='Path to the PCAP file') | |
| 41 | ||
| 42 | parsed_args = parser.parse_args(args) | |
| 43 | ||
| 44 | if not os.path.isfile(parsed_args.pcap): | |
| 45 | print("pcap file not found: " % parsed_args.pcap) | |
| 46 | return 2, None | |
| 47 | ||
| 48 | testcap = open(parsed_args.pcap, 'rb') | |
| 49 | ||
| 50 | try: | |
| 51 | capfile = savefile.load_savefile(testcap, layers=2, verbose=parsed_args.verbose) | |
| 52 | except pcapfile.Error: | |
| 53 | print("Invalid pcap file") | |
| 54 | return 3, None | |
| 55 | ||
| 56 | print('pcap file loaded. Parsing packets...') | |
| 57 | ||
| 58 | # Set() to store already added hosts. This will save an enormous amount of time by not querying the database | |
| 59 | # for hosts we already know are in Faraday | |
| 60 | added = set() | |
| 61 | ||
| 62 | for packet in capfile.packets: | |
| 63 | ||
| 64 | if packet.packet.type != 2048: | |
| 65 | continue | |
| 66 | ||
| 67 | src = packet.packet.payload.src | |
| 68 | dst = packet.packet.payload.dst | |
| 69 | ||
| 70 | if parsed_args.source and not src in parsed_args.source: | |
| 71 | continue | |
| 72 | ||
| 73 | if parsed_args.dest and not dst in parsed_args.dest: | |
| 74 | continue | |
| 75 | ||
| 76 | if src not in added: | |
| 77 | ||
| 78 | # Lets save additional queries for this IP, it will already be on the database anyway! | |
| 79 | added.add(packet.packet.payload.src) | |
| 80 | ||
| 81 | # Parsing of source field | |
| 82 | obj = factory.createModelObject(models.Host.class_signature, src, | |
| 83 | workspace, os=None, parent_id=None) | |
| 84 | ||
| 85 | old = models.get_host(workspace, obj.getID()) | |
| 86 | ||
| 87 | if old is None: | |
| 88 | if not parsed_args.dry_run: | |
| 89 | models.create_host(workspace, obj) | |
| 90 | print('%s\t%s' % (src, obj.getID())) | |
| 91 | ||
| 92 | if dst not in added: | |
| 93 | ||
| 94 | # Lets save additional queries for this IP, it will already be on the database anyway! | |
| 95 | added.add(packet.packet.payload.dst) | |
| 96 | ||
| 97 | # Parsing of destination field | |
| 98 | obj = factory.createModelObject(models.Host.class_signature, dst, | |
| 99 | workspace, os=None, parent_id=None) | |
| 100 | ||
| 101 | old = models.get_host(workspace, obj.getID()) | |
| 102 | ||
| 103 | if old is None: | |
| 104 | if not parsed_args.dry_run: | |
| 105 | models.create_host(workspace, obj) | |
| 106 | print('%s\t%s' % (dst, obj.getID())) | |
| 107 | ||
| 108 | return 0, None | |
| 109 | ||
| 110 | ||
| 111 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.persistence.server import models | |
| 6 | ||
| 7 | __description__ = 'Get all stored credentials' | |
| 8 | __prettyname__ = 'List Credentials' | |
| 9 | ||
| 10 | ||
| 11 | def main(workspace='', args=None, parser=None): | |
| 12 | parsed_args = parser.parse_args(args) | |
| 13 | ||
| 14 | for credential in models.get_credentials(workspace): | |
| 15 | print(credential.username + ' : ' + credential.password) | |
| 16 | return 0, None | |
| 17 | ||
| 18 | ||
| 19 | # I'm Py3 |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | from __future__ import print_function | |
| 9 | ||
| 10 | from faraday.client.persistence.server import models | |
| 11 | ||
| 12 | __description__ = 'List hosts' | |
| 13 | __prettyname__ = 'List Hosts' | |
| 14 | ||
| 15 | ||
| 16 | def main(workspace='', args=None, parser=None): | |
| 17 | parser.add_argument('os_filter', nargs='*', help='List of OSs to filter for', default=[]) | |
| 18 | ||
| 19 | parsed_args = parser.parse_args(args) | |
| 20 | ||
| 21 | for host in models.get_hosts(workspace): | |
| 22 | ||
| 23 | if not parsed_args.os_filter or (parsed_args.os_filter and host.os in parsed_args.os_filter): | |
| 24 | print('%s\t%s' % (host.name, host.os)) | |
| 25 | ||
| 26 | return 0, None | |
| 27 | ||
| 28 | ||
| 29 | # I'm Py3 |
| 0 | #!/usr/bin/env python3 | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | """ | |
| 6 | from __future__ import absolute_import | |
| 7 | from __future__ import print_function | |
| 8 | ||
| 9 | from faraday.client.persistence.server import models | |
| 10 | ||
| 11 | __description__ = 'List all scanned IPs' | |
| 12 | __prettyname__ = 'Get All IPs' | |
| 13 | ||
| 14 | ||
| 15 | def main(workspace='', args=None, parser=None): | |
| 16 | parser.add_argument('-s', '--sorted', help='Print a sorted list of IPs.', action='store_true') | |
| 17 | ||
| 18 | parsed_args = parser.parse_args(args) | |
| 19 | ||
| 20 | ips = [] | |
| 21 | ||
| 22 | for host in models.get_hosts(workspace): | |
| 23 | ||
| 24 | if parsed_args.sorted: | |
| 25 | ips += [host.name] | |
| 26 | else: | |
| 27 | print(host.name) | |
| 28 | ||
| 29 | if parsed_args.sorted: | |
| 30 | print('\n'.join(sorted(ips))) | |
| 31 | ||
| 32 | return 0, None | |
| 33 | ||
| 34 | ||
| 35 | # I'm Py3 |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | """ | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | """ | |
| 8 | from __future__ import absolute_import | |
| 9 | from __future__ import print_function | |
| 10 | ||
| 11 | __description__ = 'Lists all scanned OSs' | |
| 12 | __prettyname__ = 'Get All OSs' | |
| 13 | ||
| 14 | from faraday.client.persistence.server import models | |
| 15 | ||
| 16 | ||
| 17 | def main(workspace='', args=None, parser=None): | |
| 18 | parser.add_argument('-q', '--unique', help='Group OSs and print the total amount of hosts.', action='store_true') | |
| 19 | ||
| 20 | parsed_args = parser.parse_args(args) | |
| 21 | ||
| 22 | host_count = {} | |
| 23 | ||
| 24 | for host in models.get_hosts(workspace): | |
| 25 | ||
| 26 | if parsed_args.unique: | |
| 27 | if host.os in host_count: | |
| 28 | host_count[host.os] += 1 | |
| 29 | else: | |
| 30 | host_count[host.os] = 1 | |
| 31 | ||
| 32 | else: | |
| 33 | print(host.os) | |
| 34 | ||
| 35 | if parsed_args.unique: | |
| 36 | for host, count in host_count.items(): | |
| 37 | print('%s\t(%d)' % (host, count)) | |
| 38 | ||
| 39 | return 0, None | |
| 40 | ||
| 41 | ||
| 42 | # I'm Py3 |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | from __future__ import print_function | |
| 9 | import os | |
| 10 | import sys | |
| 11 | from faraday.client.persistence.server.server_io_exceptions import ResourceDoesNotExist | |
| 12 | from faraday.client.persistence.server import models | |
| 13 | ||
| 14 | __description__ = 'Takes a Screenshot of the ip:ports of a given protocol' | |
| 15 | __prettyname__ = 'Screenshot_server' | |
| 16 | ||
| 17 | ||
| 18 | def screenshot(path, protocol, ip, port): | |
| 19 | try: | |
| 20 | from selenium import webdriver # pylint:disable=import-outside-toplevel | |
| 21 | except ImportError: | |
| 22 | print("Missing dependencies: (selenium). " | |
| 23 | "Install it with pip install selenium. ") | |
| 24 | sys.exit(1) | |
| 25 | driver = webdriver.PhantomJS() | |
| 26 | driver.set_window_size(1024, 768) # set the window size that you need | |
| 27 | driver.set_page_load_timeout(5) | |
| 28 | try: | |
| 29 | driver.get(protocol + "://" + ip + ":" + port + "/") | |
| 30 | driver.get_screenshot_as_file(os.path.join(path, ip + "_" + port + ".png")) | |
| 31 | except Exception: | |
| 32 | print("Coudn't connect") | |
| 33 | finally: | |
| 34 | driver.quit() | |
| 35 | ||
| 36 | return 0 | |
| 37 | ||
| 38 | ||
| 39 | def main(workspace='', args=None, parser=None): | |
| 40 | parser.add_argument('protocol', help="Desired protocol", default="") | |
| 41 | parser.add_argument('--path', help="Saves the Image in a given path", default=".") | |
| 42 | parsed_args = parser.parse_args(args) | |
| 43 | ||
| 44 | protocols = parsed_args.protocol.split(",") | |
| 45 | path = parsed_args.path | |
| 46 | ||
| 47 | for protocol in protocols: | |
| 48 | ||
| 49 | if not os.path.exists(path): | |
| 50 | print("Invalid Path") | |
| 51 | sys.exit() | |
| 52 | ||
| 53 | try: | |
| 54 | services = models.get_services(workspace) | |
| 55 | except ResourceDoesNotExist: | |
| 56 | print("Invalid workspace name: ", workspace) | |
| 57 | return 1, None | |
| 58 | ||
| 59 | for service in services: | |
| 60 | service_protocol = service.protocol.lower() | |
| 61 | ||
| 62 | if service_protocol == protocol: | |
| 63 | port = str(service.ports[0]) | |
| 64 | ||
| 65 | interface_id = ".".join(service.id.split(".")[:2]) | |
| 66 | interface = models.get_interface(workspace, interface_id) | |
| 67 | ip = interface.ipv4["address"] | |
| 68 | ||
| 69 | print(protocol + "://" + ip + ":" + port) | |
| 70 | screenshot(path, protocol, ip, port) | |
| 71 | return 0, None | |
| 72 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | ||
| 7 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | """ | |
| 9 | This module contains the definition of all the CustomEvent's used | |
| 10 | in the application. | |
| 11 | These events are needed to communicate secondary threads with the GUI. | |
| 12 | ||
| 13 | """ | |
| 14 | ||
| 15 | import time | |
| 16 | ||
| 17 | LOGEVENT_ID = 3131 | |
| 18 | SHOWDIALOG_ID = 3132 | |
| 19 | SHOWPOPUP_ID = 3133 | |
| 20 | EXCEPTION_ID = 3134 | |
| 21 | RENAMEHOSTSROOT_ID = 3135 | |
| 22 | CLEARHOSTS_ID = 3136 | |
| 23 | DIFFHOSTS_ID = 3137 | |
| 24 | SYNCFAILED_ID = 3138 | |
| 25 | CONFLICTS_ID = 3139 | |
| 26 | WORKSPACE_CHANGED = 3140 | |
| 27 | CONFLICT_UPDATE = 3141 | |
| 28 | RESOLVECONFLICTS_ID = 3142 | |
| 29 | ADDHOST = 4100 | |
| 30 | DELHOST = 4101 | |
| 31 | EDITHOST = 4102 | |
| 32 | CHANGEFROMINSTANCE = 5100 | |
| 33 | CONNECTION_REFUSED = 42424 | |
| 34 | WORKSPACE_PROBLEM = 24242 | |
| 35 | ADDOBJECT = 7777 | |
| 36 | DELETEOBJECT = 8888 | |
| 37 | UPDATEOBJECT = 9999 | |
| 38 | ||
| 39 | class CustomEvent: | |
| 40 | def __init__(self, type): | |
| 41 | self._type = type | |
| 42 | self._time = time.time() | |
| 43 | ||
| 44 | def type(self): | |
| 45 | return self._type | |
| 46 | ||
| 47 | def time(self): | |
| 48 | return self._time | |
| 49 | ||
| 50 | ||
| 51 | class LogCustomEvent(CustomEvent): | |
| 52 | def __init__(self, text): | |
| 53 | CustomEvent.__init__(self, LOGEVENT_ID) | |
| 54 | self.text = text | |
| 55 | ||
| 56 | ||
| 57 | class ShowDialogCustomEvent(CustomEvent): | |
| 58 | def __init__(self, text, level): | |
| 59 | CustomEvent.__init__(self, SHOWDIALOG_ID) | |
| 60 | self.text = text | |
| 61 | self.level = level | |
| 62 | ||
| 63 | ||
| 64 | class ShowPopupCustomEvent(CustomEvent): | |
| 65 | def __init__(self, text): | |
| 66 | CustomEvent.__init__(self, SHOWPOPUP_ID) | |
| 67 | self.text = text | |
| 68 | self.level = "INFORMATION" | |
| 69 | ||
| 70 | ||
| 71 | class ShowExceptionCustomEvent(CustomEvent): | |
| 72 | def __init__(self, text, callback, error_name=None): | |
| 73 | CustomEvent.__init__(self, EXCEPTION_ID) | |
| 74 | self.text = text | |
| 75 | self.exception_objects = [None, text] | |
| 76 | self.callback = callback | |
| 77 | if error_name is not None: | |
| 78 | self.error_name = error_name | |
| 79 | ||
| 80 | # this is probably a bad name for the class | |
| 81 | # maybe ConnectionRefusedCustomEven would've been better | |
| 82 | class ShowExceptionConnectionRefusedCustomEvent(CustomEvent): | |
| 83 | def __init__(self, problem=None): | |
| 84 | CustomEvent.__init__(self, CONNECTION_REFUSED) | |
| 85 | self.problem = problem | |
| 86 | ||
| 87 | class WorkspaceProblemCustomEvent(CustomEvent): | |
| 88 | def __init__(self, problem=None): | |
| 89 | CustomEvent.__init__(self, WORKSPACE_PROBLEM) | |
| 90 | self.problem = problem | |
| 91 | ||
| 92 | ||
| 93 | class RenameHostsRootCustomEvent(CustomEvent): | |
| 94 | def __init__(self, name): | |
| 95 | CustomEvent.__init__(self, RENAMEHOSTSROOT_ID) | |
| 96 | self.name = name | |
| 97 | ||
| 98 | ||
| 99 | class WorkspaceChangedCustomEvent(CustomEvent): | |
| 100 | def __init__(self, workspace): | |
| 101 | CustomEvent.__init__(self, WORKSPACE_CHANGED) | |
| 102 | self.workspace = workspace | |
| 103 | ||
| 104 | ||
| 105 | class ConflictUpdatedCustomEvent(CustomEvent): | |
| 106 | def __init__(self, nconflicts): | |
| 107 | CustomEvent.__init__(self, CONFLICT_UPDATE) | |
| 108 | self.nconflicts = nconflicts | |
| 109 | ||
| 110 | ||
| 111 | class DiffHostsCustomEvent(CustomEvent): | |
| 112 | def __init__(self, old_host, new_host): | |
| 113 | CustomEvent.__init__(self, DIFFHOSTS_ID) | |
| 114 | self.new_host = new_host | |
| 115 | self.old_host = old_host | |
| 116 | ||
| 117 | ||
| 118 | class ResolveConflictsCustomEvent(CustomEvent): | |
| 119 | def __init__(self, conflicts): | |
| 120 | CustomEvent.__init__(self, RESOLVECONFLICTS_ID) | |
| 121 | self.conflicts = conflicts | |
| 122 | ||
| 123 | ||
| 124 | class ClearHostsCustomEvent(CustomEvent): | |
| 125 | def __init__(self): | |
| 126 | CustomEvent.__init__(self, CLEARHOSTS_ID) | |
| 127 | ||
| 128 | ||
| 129 | class AddHostCustomEvent(CustomEvent): | |
| 130 | def __init__(self, host): | |
| 131 | CustomEvent.__init__(self, ADDHOST) | |
| 132 | self.host = host | |
| 133 | ||
| 134 | ||
| 135 | class EditHostCustomEvent(CustomEvent): | |
| 136 | def __init__(self, host): | |
| 137 | CustomEvent.__init__(self, EDITHOST) | |
| 138 | self.host = host | |
| 139 | ||
| 140 | ||
| 141 | class DeleteHostCustomEvent(CustomEvent): | |
| 142 | def __init__(self, host_id): | |
| 143 | CustomEvent.__init__(self, DELHOST) | |
| 144 | self.host_id = host_id | |
| 145 | ||
| 146 | ||
| 147 | class ChangeFromInstanceCustomEvent(CustomEvent): | |
| 148 | def __init__(self, action, object_id, object_type, object_name): | |
| 149 | CustomEvent.__init__(self, CHANGEFROMINSTANCE) | |
| 150 | self.object_id = object_id | |
| 151 | self.object_type = object_type | |
| 152 | self.object_name = object_name | |
| 153 | self.action = action | |
| 154 | ||
| 155 | def __str__(self): | |
| 156 | action_msg = { | |
| 157 | 'UPDATE': 'updated', | |
| 158 | 'CREATE': 'created', | |
| 159 | 'DELETE': 'deleted', | |
| 160 | } | |
| 161 | return "The {0} {1} was {2}".format(self.object_type, | |
| 162 | self.object_name, | |
| 163 | action_msg[self.action]) | |
| 164 | ||
| 165 | class AddObjectCustomEvent(CustomEvent): | |
| 166 | def __init__(self, new_obj): | |
| 167 | CustomEvent.__init__(self, ADDOBJECT) | |
| 168 | self.new_obj = new_obj | |
| 169 | ||
| 170 | class DeleteObjectCustomEvent(CustomEvent): | |
| 171 | def __init__(self, obj_id, obj_type): | |
| 172 | CustomEvent.__init__(self, DELETEOBJECT) | |
| 173 | self.obj_id = obj_id | |
| 174 | self.obj_type = obj_type | |
| 175 | ||
| 176 | class UpdateObjectCustomEvent(CustomEvent): | |
| 177 | def __init__(self, obj): | |
| 178 | CustomEvent.__init__(self, UPDATEOBJECT) | |
| 179 | self.obj = obj | |
| 180 | ||
| 181 | ||
| 182 | # I'm Py3 |
| 0 | # Faraday Penetration Test IDE | |
| 1 | # Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 2 | # See the file 'doc/LICENSE' for the license information | |
| 3 | ||
| 4 | # I'm Py3⏎ |
| 0 | #!/usr/bin/python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | ||
| 7 | """ | |
| 8 | from __future__ import absolute_import | |
| 9 | from __future__ import print_function | |
| 10 | from past.builtins import basestring | |
| 11 | ||
| 12 | import os | |
| 13 | import sys | |
| 14 | import threading | |
| 15 | import traceback | |
| 16 | ||
| 17 | import webbrowser | |
| 18 | import logging | |
| 19 | ||
| 20 | try: | |
| 21 | import gi | |
| 22 | except ImportError as e: | |
| 23 | print ("You are missing Gobject Instrospection. Please install " | |
| 24 | "version 3.14 or above (recommended) or 3.12") | |
| 25 | sys.exit(1) | |
| 26 | ||
| 27 | try: | |
| 28 | gi.require_version('Gtk', '3.0') | |
| 29 | except ValueError: | |
| 30 | print ("WARNING: You don't seem to have installed the recommended version" | |
| 31 | " of GTK. You can still use the program, but we recommend you" | |
| 32 | " check your install of GTK+3") | |
| 33 | ||
| 34 | try: | |
| 35 | gi.require_version('Vte', '2.91') | |
| 36 | except ValueError: | |
| 37 | gi.require_version('Vte', '2.90') | |
| 38 | ||
| 39 | try: | |
| 40 | # there are several imports not needed here, but they're needed in other | |
| 41 | # modules. this just checks for every dependence when starting the app | |
| 42 | from gi.repository import Gio, Gtk, GdkPixbuf, Vte, GLib, GObject, Gdk | |
| 43 | except ImportError as e: | |
| 44 | print ("You are missing some of the required dependencies. " | |
| 45 | "Check that you have GTK+3 and Vte installed.") | |
| 46 | sys.exit(1) | |
| 47 | ||
| 48 | import faraday.client.model.guiapi | |
| 49 | import faraday.client.model.api | |
| 50 | import faraday.client.model.log | |
| 51 | ||
| 52 | from faraday.client.gui.gui_app import FaradayUi | |
| 53 | ||
| 54 | from faraday.config.configuration import getInstanceConfiguration | |
| 55 | from faraday.server.utils.logger import get_logger | |
| 56 | from faraday.client.gui.gtk.appwindow import AppWindow | |
| 57 | ||
| 58 | from faraday.client.persistence.server.server import is_authenticated, check_faraday_version, Unauthorized | |
| 59 | ||
| 60 | from faraday.client.gui.gtk.server import ServerIO | |
| 61 | from faraday.client.gui.gtk.dialogs import aboutDialog | |
| 62 | from faraday.client.gui.gtk.dialogs import ConflictsDialog | |
| 63 | from faraday.client.gui.gtk.dialogs import ForceChooseWorkspaceDialog | |
| 64 | from faraday.client.gui.gtk.dialogs import ForceNewWorkspaceDialog | |
| 65 | from faraday.client.gui.gtk.dialogs import ForcePreferenceWindowDialog | |
| 66 | from faraday.client.gui.gtk.dialogs import HostInfoDialog | |
| 67 | from faraday.client.gui.gtk.dialogs import ImportantErrorDialog | |
| 68 | from faraday.client.gui.gtk.dialogs import ForceLoginDialog | |
| 69 | from faraday.client.gui.gtk.dialogs import NewWorkspaceDialog | |
| 70 | from faraday.client.gui.gtk.dialogs import NotificationsDialog | |
| 71 | from faraday.client.gui.gtk.dialogs import PluginOptionsDialog | |
| 72 | from faraday.client.gui.gtk.dialogs import PreferenceWindowDialog | |
| 73 | from faraday.client.gui.gtk.dialogs import FaradayPluginsDialog | |
| 74 | from faraday.client.gui.gtk.dialogs import errorDialog | |
| 75 | ||
| 76 | from faraday.client.gui.gtk.mainwidgets import Sidebar | |
| 77 | from faraday.client.gui.gtk.mainwidgets import WorkspaceSidebar | |
| 78 | from faraday.client.gui.gtk.mainwidgets import HostsSidebar | |
| 79 | from faraday.client.gui.gtk.mainwidgets import ConsoleLog | |
| 80 | from faraday.client.gui.gtk.mainwidgets import Terminal | |
| 81 | from faraday.client.gui.gtk.mainwidgets import Statusbar | |
| 82 | ||
| 83 | from faraday.client.gui.loghandler import GUIHandler | |
| 84 | from faraday.server.utils.logger import add_handler | |
| 85 | from faraday.client.start_client import FARADAY_CLIENT_BASE | |
| 86 | from faraday.utils.common import checkSSL | |
| 87 | ||
| 88 | from faraday.client.plugins import fplugin_utils | |
| 89 | ||
| 90 | CONF = getInstanceConfiguration() | |
| 91 | ||
| 92 | logger = logging.getLogger(__name__) | |
| 93 | ||
| 94 | ||
| 95 | class GuiApp(Gtk.Application, FaradayUi): | |
| 96 | """ | |
| 97 | Creates the application and has the necesary callbacks to FaradayUi | |
| 98 | As far as the GUI goes, this handles only the menu, everything is else is | |
| 99 | appWindow's resposibility. All logic by the main window should be done | |
| 100 | here. Some of the logic on the dialogs is implemented in the dialogs own | |
| 101 | class. Some dialogs are shown by the appwindow to handle errors coming | |
| 102 | from other threads outside GTK's. | |
| 103 | ||
| 104 | Please respect the following structure: | |
| 105 | TOP: __init__ | |
| 106 | UPPER-MIDDLE: all logic mostly not inherited fom Gtk.Application | |
| 107 | LOWER-MIDDLE: all do_ starting, gtk related methods | |
| 108 | BOTTOM: all on_ starting, dialog opener methods | |
| 109 | ||
| 110 | """ | |
| 111 | ||
| 112 | def __init__(self, model_controller, plugin_manager, workspace_manager, | |
| 113 | plugin_controller): | |
| 114 | """Does not do much. Most of the initialization work is actually | |
| 115 | done by the run() method, as specified in FaradayUi.""" | |
| 116 | ||
| 117 | FaradayUi.__init__(self, | |
| 118 | model_controller, | |
| 119 | plugin_manager, | |
| 120 | workspace_manager, | |
| 121 | plugin_controller) | |
| 122 | ||
| 123 | Gtk.Application.__init__(self, application_id="org.infobyte.faraday", | |
| 124 | flags=Gio.ApplicationFlags.FLAGS_NONE) | |
| 125 | ||
| 126 | self.lost_connection_dialog_raised = None | |
| 127 | self.workspace_dialogs_raised = None | |
| 128 | self.loading_dialog_raised = None | |
| 129 | self.icons = os.path.join(FARADAY_CLIENT_BASE, "data", "images", "icons") | |
| 130 | faraday_icon = os.path.join(self.icons, "faraday_icon.png") | |
| 131 | self.icon = GdkPixbuf.Pixbuf.new_from_file_at_scale(faraday_icon, 16, | |
| 132 | 16, False) | |
| 133 | self.window = None | |
| 134 | self.model_controller = model_controller | |
| 135 | ||
| 136 | @property | |
| 137 | def active_ws_name(self): | |
| 138 | active_workspace = self.get_active_workspace() | |
| 139 | ||
| 140 | if active_workspace: | |
| 141 | return active_workspace.name | |
| 142 | return "" | |
| 143 | ||
| 144 | def get_active_workspace(self): | |
| 145 | """Return the currently active workspace""" | |
| 146 | return self.workspace_manager.getActiveWorkspace() | |
| 147 | ||
| 148 | def getMainWindow(self): | |
| 149 | """Useless mostly, but guiapi uses this method to access the main | |
| 150 | window.""" | |
| 151 | return self.window | |
| 152 | ||
| 153 | def createWorkspace(self, name, description=""): | |
| 154 | """Uses the instance of workspace manager passed into __init__ to | |
| 155 | get all the workspaces names and see if they don't clash with | |
| 156 | the one the user wrote. If everything's fine, it saves the new | |
| 157 | workspace and returns True. If something went wrong, return False""" | |
| 158 | ||
| 159 | if name in self.workspace_manager.getWorkspacesNames(): | |
| 160 | error_str = "A workspace with name %s already exists" % name | |
| 161 | faraday.client.model.api.log(error_str, "ERROR") | |
| 162 | errorDialog(self.window, error_str) | |
| 163 | creation_ok = False | |
| 164 | else: | |
| 165 | faraday.client.model.api.log("Creating workspace '%s'" % name) | |
| 166 | faraday.client.model.api.devlog("Looking for the delegation class") | |
| 167 | manager = self.getWorkspaceManager() | |
| 168 | try: | |
| 169 | name = manager.createWorkspace(name, description) | |
| 170 | self.change_workspace(name) | |
| 171 | creation_ok = True | |
| 172 | except Exception as e: | |
| 173 | faraday.client.model.guiapi.notification_center.showDialog(str(e)) | |
| 174 | creation_ok = False | |
| 175 | ||
| 176 | return creation_ok | |
| 177 | ||
| 178 | def remove_workspace(self, button, ws_name): | |
| 179 | """Removes a workspace. If the workspace deleted is currently active, | |
| 180 | a signal will be incoming vis postUpdates() and force the user to | |
| 181 | select another workspace.""" | |
| 182 | try: | |
| 183 | faraday.client.model.api.log("Removing Workspace: %s" % ws_name) | |
| 184 | self.getWorkspaceManager().removeWorkspace(ws_name) | |
| 185 | self.ws_sidebar.clear_sidebar() | |
| 186 | self.ws_sidebar.refresh_sidebar() | |
| 187 | except Exception as ex: | |
| 188 | traceback_str = traceback.format_exc() | |
| 189 | faraday.client.model.api.log("An exception was captured while deleting " | |
| 190 | "workspace %s\n%s" % (ws_name, traceback_str), | |
| 191 | "ERROR") | |
| 192 | ||
| 193 | available_workspaces = self.serverIO.get_workspaces_names() | |
| 194 | if available_workspaces: | |
| 195 | self.select_last_workspace_in_list(available_workspaces) | |
| 196 | else: | |
| 197 | self.handle_no_active_workspace() | |
| 198 | ||
| 199 | def lost_db_connection(self, explanatory_message=None, | |
| 200 | handle_connection_lost=None, | |
| 201 | connect_to_a_different_couch=None): | |
| 202 | """Creates a simple dialog with an error message to inform the user | |
| 203 | some kind of problem has happened and the connection was lost. | |
| 204 | ||
| 205 | Returns whether the login dialog should be shown or not | |
| 206 | """ | |
| 207 | ||
| 208 | # NOTE: if we start faraday without CouchDB, both the signal coming | |
| 209 | # from CouchDB manager AND our test in do_activate will try | |
| 210 | # to raise the dialog. This avoids more than one dialog to be raised. | |
| 211 | if self.lost_connection_dialog_raised: | |
| 212 | return False | |
| 213 | ||
| 214 | def do_nothing_on_key_stroke(event, key): | |
| 215 | """Do nothing except return True""" | |
| 216 | return True | |
| 217 | ||
| 218 | self.lost_connection_dialog_raised = True | |
| 219 | ||
| 220 | if explanatory_message and isinstance(explanatory_message, basestring): | |
| 221 | explanation = "\n The specific error was: " + explanatory_message | |
| 222 | else: | |
| 223 | explanation = "" | |
| 224 | ||
| 225 | dialog = Gtk.MessageDialog(self.window, 0, | |
| 226 | Gtk.MessageType.ERROR, | |
| 227 | Gtk.ButtonsType.NONE, | |
| 228 | "The client can't connect to Faraday Server. " | |
| 229 | "You can try to reconnect to the last URL " | |
| 230 | "you set up, change it or exit Faraday " | |
| 231 | "until you fix the problem. \n" | |
| 232 | "For more information about Faraday Server " | |
| 233 | "please refer to the Faraday Github Wiki. \n " | |
| 234 | + explanation) | |
| 235 | ||
| 236 | dialog.set_deletable(False) | |
| 237 | ||
| 238 | dialog.set_modal(True) | |
| 239 | dialog.connect("key_press_event", do_nothing_on_key_stroke) | |
| 240 | ||
| 241 | retry_button = dialog.add_button("Retry connection?", 42) | |
| 242 | retry_button.connect("clicked", handle_connection_lost, dialog) | |
| 243 | ||
| 244 | change_couch_url = dialog.add_button("Change server IP?", 43) | |
| 245 | change_couch_url.connect("clicked", connect_to_a_different_couch, dialog) | |
| 246 | ||
| 247 | cancel_button = dialog.add_button("Exit Faraday", 0) | |
| 248 | cancel_button.connect("clicked", self.on_quit) | |
| 249 | ||
| 250 | if hasattr(self, 'force_new_workspace_dialog'): | |
| 251 | # The dialog to create a new workspace is open. Lets close it | |
| 252 | new_workspace_dialog = getattr(self, 'force_new_workspace_dialog') | |
| 253 | ||
| 254 | new_workspace_dialog.destroy() | |
| 255 | setattr(self, 'force_new_workspace_dialog', None) | |
| 256 | ||
| 257 | response = dialog.run() | |
| 258 | if response == Gtk.ResponseType.DELETE_EVENT: | |
| 259 | GObject.idle_add(self.exit_faraday_without_confirm) | |
| 260 | elif response in [0, 42, 43]: | |
| 261 | return False | |
| 262 | ||
| 263 | return True | |
| 264 | ||
| 265 | def handle_no_active_workspace(self): | |
| 266 | """If there's been a problem opening a workspace or for some reason | |
| 267 | we suddenly find our selves without one, force the user | |
| 268 | to select one if possible, or if not, to create one. | |
| 269 | """ | |
| 270 | ||
| 271 | def change_flag(widget): | |
| 272 | self.workspace_dialogs_raised = not self.workspace_dialogs_raised | |
| 273 | ||
| 274 | if self.workspace_dialogs_raised: | |
| 275 | return False | |
| 276 | ||
| 277 | if self.serverIO.server_info() is None: | |
| 278 | # make sure it is not because we're not connected to Couch | |
| 279 | # there's another whole strategy for that. | |
| 280 | return False | |
| 281 | ||
| 282 | self.workspace_dialogs_raised = True | |
| 283 | self.ws_sidebar.refresh_sidebar() | |
| 284 | ||
| 285 | available_workspaces = self.serverIO.get_workspaces_names() | |
| 286 | workspace_model = self.ws_sidebar.workspace_model | |
| 287 | ||
| 288 | if available_workspaces: | |
| 289 | dialog = ForceChooseWorkspaceDialog(self.window, | |
| 290 | workspace_model, | |
| 291 | self.change_workspace) | |
| 292 | else: | |
| 293 | dialog = ForceNewWorkspaceDialog(self.window, | |
| 294 | self.createWorkspace, | |
| 295 | self.workspace_manager, | |
| 296 | self.ws_sidebar, | |
| 297 | self.exit_faraday) | |
| 298 | self.force_new_workspace_dialog = dialog | |
| 299 | ||
| 300 | dialog.connect("destroy", change_flag) | |
| 301 | dialog.show_all() | |
| 302 | ||
| 303 | def select_active_workspace(self): | |
| 304 | """Selects on the sidebar the currently active workspace.""" | |
| 305 | self.ws_sidebar.select_ws_by_name(self.active_ws_name) | |
| 306 | ||
| 307 | def select_last_workspace_in_list(self, ws_names_list): | |
| 308 | self.ws_sidebar.select_ws_by_name(ws_names_list[-1]) | |
| 309 | ||
| 310 | def exit_faraday(self, button=None, parent=None): | |
| 311 | """A simple exit which will ask for confirmation.""" | |
| 312 | if not self.window.do_delete_event(parent): | |
| 313 | if parent is not None: | |
| 314 | GObject.idle_add(parent.destroy) | |
| 315 | GObject.idle_add(self.window.destroy) | |
| 316 | ||
| 317 | def exit_faraday_without_confirm(self, widget=None): | |
| 318 | """Exits faraday without confirm. Used as a middle-man between | |
| 319 | connect callbacks (which will send the widget as an argument and | |
| 320 | self.window.destroy, which takes none. | |
| 321 | """ | |
| 322 | logger.error("Faraday exited because you didn't connect to a valid Faraday Server.") | |
| 323 | GObject.idle_add(self.window.destroy) | |
| 324 | GObject.idle_add(self.on_quit) | |
| 325 | ||
| 326 | def force_change_couch_url(self, button=None, dialog=None): | |
| 327 | """Forces the user to change the couch URL. You **will** ended up | |
| 328 | connected to CouchDB or you will exit my application, cowboy. | |
| 329 | """ | |
| 330 | ||
| 331 | # destroy the ugly dialog that got us here | |
| 332 | if dialog is not None: | |
| 333 | dialog.destroy() | |
| 334 | ||
| 335 | preference_window = ForcePreferenceWindowDialog(self.reload_workspaces, | |
| 336 | self.connect_to_couch, | |
| 337 | self.window, | |
| 338 | self.exit_faraday) | |
| 339 | ||
| 340 | preference_window.run() | |
| 341 | ||
| 342 | def connect_to_couch(self, server_url, parent=None): | |
| 343 | """Tries to connect to a CouchDB on a specified Couch URI. | |
| 344 | Returns the success status of the operation, False for not successful, | |
| 345 | True for successful | |
| 346 | """ | |
| 347 | if parent is None: | |
| 348 | parent = self.window | |
| 349 | ||
| 350 | if not self.serverIO.check_server_url(server_url): | |
| 351 | errorDialog(parent, "Could not connect to Faraday Server.", | |
| 352 | ("Are you sure it is running and that you can " | |
| 353 | "connect to it? \n Make sure your username and " | |
| 354 | "password are still valid.")) | |
| 355 | success = False | |
| 356 | elif server_url.startswith("https://"): | |
| 357 | if not checkSSL(server_url): | |
| 358 | errorDialog(self.window, | |
| 359 | "The SSL certificate validation has failed") | |
| 360 | success = False | |
| 361 | else: | |
| 362 | try: | |
| 363 | check_faraday_version() | |
| 364 | except RuntimeError: | |
| 365 | errorDialog(parent, | |
| 366 | "The server ir running a different Faraday version then the " | |
| 367 | "client you are runnung. Version numbers must match!") | |
| 368 | success = False | |
| 369 | return success | |
| 370 | CONF.setAPIUrl(server_url) | |
| 371 | CONF.saveConfig() | |
| 372 | self.reload_workspaces() | |
| 373 | self.open_last_workspace() | |
| 374 | success = True | |
| 375 | self.lost_connection_dialog_raised = False | |
| 376 | return success | |
| 377 | ||
| 378 | def handle_connection_lost(self, button=None, dialog=None): | |
| 379 | """Tries to connect to Couch using the same URI""" | |
| 380 | couch_uri = CONF.getServerURI() | |
| 381 | if self.connect_to_couch(couch_uri, parent=dialog): | |
| 382 | reconnected = True | |
| 383 | if dialog is not None: | |
| 384 | dialog.destroy() | |
| 385 | self.open_last_workspace() | |
| 386 | self.lost_connection_dialog_raised = False | |
| 387 | else: | |
| 388 | reconnected = False | |
| 389 | return reconnected | |
| 390 | ||
| 391 | def update_counts(self): | |
| 392 | """Returns the counts of hosts, services and vulns on the current | |
| 393 | workspace.""" | |
| 394 | hosts, services, vulns = self.serverIO.get_workspace_numbers() | |
| 395 | return hosts, services, vulns | |
| 396 | ||
| 397 | def show_host_info(self, host_id): | |
| 398 | """Looks up the host selected in the HostSidebar by id and shows | |
| 399 | its information on the HostInfoDialog. | |
| 400 | ||
| 401 | Return True if everything went OK, False if there was a problem | |
| 402 | looking for the host.""" | |
| 403 | active_workspace = self.get_active_workspace() | |
| 404 | ||
| 405 | if active_workspace: | |
| 406 | current_ws_name = active_workspace.name | |
| 407 | else: | |
| 408 | current_ws_name = "" | |
| 409 | ||
| 410 | host = self.serverIO.get_host(host_id) | |
| 411 | if not host: | |
| 412 | self.show_normal_error("The host you clicked isn't accessible. " | |
| 413 | "This is most probably due to an internal " | |
| 414 | "error.") | |
| 415 | return False | |
| 416 | ||
| 417 | info_window = HostInfoDialog(self.window, current_ws_name, host) | |
| 418 | info_window.show_all() | |
| 419 | return True | |
| 420 | ||
| 421 | def reload_workspaces_no_connection(self): | |
| 422 | """Very similar to reload_workspaces, but doesn't resource the | |
| 423 | workspace_manager to avoid asking for information to a database | |
| 424 | we can't access.""" | |
| 425 | self.ws_sidebar.clear_sidebar() | |
| 426 | ||
| 427 | def reload_workspaces(self): | |
| 428 | """Close workspace, resources the workspaces available, | |
| 429 | clears the sidebar of the old workspaces and injects all the new ones | |
| 430 | in there too""" | |
| 431 | self.ws_sidebar.clear_sidebar() | |
| 432 | self.ws_sidebar.refresh_sidebar() | |
| 433 | ||
| 434 | def delete_notifications(self): | |
| 435 | """Clear the notifications model of all info, also send a signal | |
| 436 | to get the notification label to 0 on the main window's button | |
| 437 | """ | |
| 438 | self.notificationsModel.clear() | |
| 439 | GObject.idle_add(self.statusbar.set_default_notif_label) | |
| 440 | ||
| 441 | def change_workspace(self, workspace_name): | |
| 442 | """Changes workspace in a separate thread. Emits a signal | |
| 443 | to present a 'Loading workspace' dialog while Faraday processes | |
| 444 | the change. If there are conflict present in the workspace, it will | |
| 445 | show a warning before changing the workspaces.""" | |
| 446 | ||
| 447 | def loading_workspace(action): | |
| 448 | """Function to be called via GObject.idle_add by the background | |
| 449 | process. Preconditions: show must have been called before destroy | |
| 450 | can be called. | |
| 451 | """ | |
| 452 | ||
| 453 | if action == "show" and not self.loading_dialog_raised: | |
| 454 | message_string = ("Loading workspace {0}. Please wait. \n" | |
| 455 | "To cancel, press Alt+F4 or a similar shorcut." | |
| 456 | .format(workspace_name)) | |
| 457 | ||
| 458 | self.loading_dialog_raised = True | |
| 459 | self.loading_dialog = Gtk.MessageDialog(self.window, 0, | |
| 460 | Gtk.MessageType.INFO, | |
| 461 | Gtk.ButtonsType.NONE, | |
| 462 | message_string) | |
| 463 | ||
| 464 | self.loading_dialog.set_modal(True) | |
| 465 | ||
| 466 | # on every key stroke just return true, wont allow user | |
| 467 | # to press scape | |
| 468 | self.loading_dialog.connect("key_press_event", | |
| 469 | lambda _, __: True) | |
| 470 | ||
| 471 | self.loading_dialog.connect("delete_event", | |
| 472 | lambda _, __: self.handle_no_active_workspace()) | |
| 473 | ||
| 474 | self.loading_dialog.show_all() | |
| 475 | ||
| 476 | if action == "destroy": | |
| 477 | self.loading_dialog.destroy() | |
| 478 | self.loading_dialog_raised = False | |
| 479 | ||
| 480 | def background_process(): | |
| 481 | """Change workspace. This function runs on a separated thread | |
| 482 | created by the parent function. DO NOT call any Gtk methods | |
| 483 | withing its scope, except by emiting signals to the window | |
| 484 | """ | |
| 485 | GObject.idle_add(loading_workspace, 'show') | |
| 486 | try: | |
| 487 | ws = self.openWorkspace(workspace_name) | |
| 488 | GObject.idle_add(CONF.setLastWorkspace, ws.name) | |
| 489 | GObject.idle_add(CONF.saveConfig) | |
| 490 | except Exception as e: | |
| 491 | GObject.idle_add(self.handle_no_active_workspace) | |
| 492 | get_logger("GTK").error(e) | |
| 493 | ||
| 494 | GObject.idle_add(loading_workspace, 'destroy') | |
| 495 | return True | |
| 496 | ||
| 497 | self.ws_sidebar.select_ws_by_name(workspace_name) | |
| 498 | if self.statusbar.conflict_button_label_int > 0: | |
| 499 | response = self.window.show_conflicts_warning() | |
| 500 | if response == Gtk.ResponseType.NO: | |
| 501 | self.select_active_workspace() | |
| 502 | return False | |
| 503 | ||
| 504 | thread = threading.Thread(target=background_process, name='background_process') | |
| 505 | thread.daemon = True | |
| 506 | thread.start() | |
| 507 | ||
| 508 | def open_workspace_from_args(self): | |
| 509 | """Opens the workspace specified in the arguemnts, if possible. | |
| 510 | Return True if args.workspace is set, False if not.""" | |
| 511 | if self.args.workspace: | |
| 512 | workspace_name = self.args.workspace | |
| 513 | self.change_workspace(workspace_name) | |
| 514 | return True | |
| 515 | else: | |
| 516 | return False | |
| 517 | ||
| 518 | def open_last_workspace(self): | |
| 519 | """Tries to open the last workspace the user had opened. Return | |
| 520 | None.""" | |
| 521 | workspace_name = CONF.getLastWorkspace() | |
| 522 | self.change_workspace(workspace_name) | |
| 523 | ||
| 524 | def run(self, args): | |
| 525 | """First method to run, as defined by FaradayUi. This method is | |
| 526 | mandatory""" | |
| 527 | self.args = args | |
| 528 | Gtk.Application.run(self) | |
| 529 | ||
| 530 | ########################################################################## | |
| 531 | # NOTE: uninteresting part below. do not touch unless you have a very # | |
| 532 | # good reason, or you want to connect a new button on the toolbar, # | |
| 533 | # or, maybe most probably, you wanna register a new signal on # | |
| 534 | # postEvent(). # | |
| 535 | # Remember! -- even the best advice must sometimes not be heeded. # | |
| 536 | ########################################################################## | |
| 537 | ||
| 538 | def postEvent(self, _, event): | |
| 539 | """Handles the events from gui/customevents. The second | |
| 540 | argument is the 'receiver', but as this was made for QT3 it is now | |
| 541 | deprecated and we must manually set the receiver until the | |
| 542 | events module is updated. | |
| 543 | ||
| 544 | DO NOT, AND I REPEAT, DO NOT REDRAW *ANYTHING* FROM THE GUI | |
| 545 | FROM HERE. If you must do it, you should to it sing GObject.idle_add, | |
| 546 | a misterious function with outdated documentation. Good luck.""" | |
| 547 | ||
| 548 | def new_log_event(): | |
| 549 | GObject.idle_add(self.console_log.customEvent, event.text) | |
| 550 | ||
| 551 | def new_conflict_event(): | |
| 552 | GObject.idle_add(self.statusbar.update_conflict_button_label, | |
| 553 | event.nconflicts) | |
| 554 | ||
| 555 | def new_notification_event(): | |
| 556 | self.notificationsModel.prepend([str(event)]) | |
| 557 | GObject.idle_add(self.statusbar.inc_notif_button_label) | |
| 558 | host_count, service_count, vuln_count = self.update_counts() | |
| 559 | GObject.idle_add(self.statusbar.update_ws_info, host_count, | |
| 560 | service_count, vuln_count) | |
| 561 | ||
| 562 | def workspace_changed_event(): | |
| 563 | self.serverIO.active_workspace = event.workspace.name | |
| 564 | host_count, service_count, vuln_count = self.update_counts() | |
| 565 | total_host_amount = self.serverIO.get_hosts_number() | |
| 566 | first_host_page = self.serverIO.get_hosts(page='1', page_size='20', | |
| 567 | sort='vulns', sort_dir='desc') | |
| 568 | ||
| 569 | total_host_amount = self.serverIO.get_workspace_numbers()[0] | |
| 570 | GObject.idle_add(self.statusbar.set_workspace_label, event.workspace.name) | |
| 571 | GObject.idle_add(self.hosts_sidebar.reset_model_after_workspace_changed, | |
| 572 | first_host_page, total_host_amount) | |
| 573 | GObject.idle_add(self.statusbar.update_ws_info, host_count, | |
| 574 | service_count, vuln_count) | |
| 575 | GObject.idle_add(self.statusbar.set_default_conflict_label) | |
| 576 | GObject.idle_add(self.statusbar.set_default_conflict_label) | |
| 577 | GObject.idle_add(self.select_active_workspace) | |
| 578 | ||
| 579 | def normal_error_event(): | |
| 580 | GObject.idle_add(self.show_normal_error, event.text) | |
| 581 | ||
| 582 | def important_error_event(): | |
| 583 | GObject.idle_add(self.show_important_error, event) | |
| 584 | ||
| 585 | def lost_connection_to_server_event(): | |
| 586 | GObject.idle_add(self.lost_db_connection, event.problem, | |
| 587 | self.handle_connection_lost, | |
| 588 | self.force_change_couch_url) | |
| 589 | GObject.idle_add(self.reload_workspaces_no_connection) | |
| 590 | ||
| 591 | def workspace_not_accessible_event(): | |
| 592 | GObject.idle_add(self.handle_no_active_workspace) | |
| 593 | ||
| 594 | def add_object(): | |
| 595 | if event.new_obj: | |
| 596 | GObject.idle_add(self.hosts_sidebar.add_object, event.new_obj) | |
| 597 | host_count, service_count, vuln_count = self.update_counts() | |
| 598 | GObject.idle_add(self.statusbar.update_ws_info, host_count, | |
| 599 | service_count, vuln_count) | |
| 600 | ||
| 601 | def delete_object(): | |
| 602 | if event.obj_id: | |
| 603 | GObject.idle_add(self.hosts_sidebar.remove_object, event.obj_id, event.obj_type) | |
| 604 | host_count, service_count, vuln_count = self.update_counts() | |
| 605 | GObject.idle_add(self.statusbar.update_ws_info, host_count, | |
| 606 | service_count, vuln_count) | |
| 607 | ||
| 608 | def update_object(): | |
| 609 | if event.obj: | |
| 610 | GObject.idle_add(self.hosts_sidebar.update_object, event.obj) | |
| 611 | host_count, service_count, vuln_count = self.update_counts() | |
| 612 | GObject.idle_add(self.statusbar.update_ws_info, host_count, | |
| 613 | service_count, vuln_count) | |
| 614 | ||
| 615 | dispatch = {3131: new_log_event, | |
| 616 | 3141: new_conflict_event, | |
| 617 | 5100: new_notification_event, | |
| 618 | 3140: workspace_changed_event, | |
| 619 | 3132: normal_error_event, | |
| 620 | 3134: important_error_event, | |
| 621 | 42424: lost_connection_to_server_event, | |
| 622 | 24242: workspace_not_accessible_event, | |
| 623 | 7777: add_object, | |
| 624 | 8888: delete_object, | |
| 625 | 9999: update_object} | |
| 626 | ||
| 627 | function = dispatch.get(event.type()) | |
| 628 | if function is not None: | |
| 629 | function() | |
| 630 | ||
| 631 | def show_normal_error(self, dialog_text): | |
| 632 | """Just a simple, normal, ignorable error""" | |
| 633 | dialog = Gtk.MessageDialog(self.window, 0, | |
| 634 | Gtk.MessageType.ERROR, | |
| 635 | Gtk.ButtonsType.OK, | |
| 636 | dialog_text) | |
| 637 | dialog.run() | |
| 638 | dialog.destroy() | |
| 639 | ||
| 640 | def show_important_error(self, event): | |
| 641 | """Creates an importan error dialog with a callback to send | |
| 642 | the developers the error traceback. | |
| 643 | """ | |
| 644 | dialog_text = event.text | |
| 645 | dialog = ImportantErrorDialog(self.window, dialog_text) | |
| 646 | response = dialog.run() | |
| 647 | if response == 42: | |
| 648 | error = event.error_name | |
| 649 | event.callback(error, *event.exception_objects) | |
| 650 | dialog.destroy() | |
| 651 | ||
| 652 | def do_startup(self): | |
| 653 | """ | |
| 654 | GTK calls this method after Gtk.Application.run() | |
| 655 | Creates instances of the sidebar, terminal, console log and | |
| 656 | statusbar to be added to the app window. | |
| 657 | Sets up necesary actions on menu and toolbar buttons | |
| 658 | Also reads the .xml file from menubar.xml | |
| 659 | """ | |
| 660 | Gtk.Application.do_startup(self) # deep GTK magic | |
| 661 | ||
| 662 | self.serverIO = ServerIO(CONF.getLastWorkspace()) | |
| 663 | self.serverIO.continously_check_server_connection() | |
| 664 | ||
| 665 | self.ws_sidebar = WorkspaceSidebar(self.serverIO, | |
| 666 | self.change_workspace, | |
| 667 | self.remove_workspace, | |
| 668 | self.on_new_button, | |
| 669 | CONF.getLastWorkspace()) | |
| 670 | ||
| 671 | # the dummy values here will be updated as soon as the ws is loaded. | |
| 672 | self.hosts_sidebar = HostsSidebar(self.show_host_info, self.serverIO.get_hosts, | |
| 673 | self.serverIO.get_host, self.icons) | |
| 674 | self.sidebar = Sidebar(self.ws_sidebar.get_box(), | |
| 675 | self.hosts_sidebar.get_box()) | |
| 676 | ||
| 677 | host_count, service_count, vuln_count = 0, 0, 0 # dummy values | |
| 678 | self.terminal = Terminal(CONF) | |
| 679 | self.console_log = ConsoleLog() | |
| 680 | self.statusbar = Statusbar(self.on_click_notifications, | |
| 681 | self.on_click_conflicts, | |
| 682 | host_count, service_count, vuln_count) | |
| 683 | ||
| 684 | self.notificationsModel = Gtk.ListStore(str) | |
| 685 | ||
| 686 | action_to_method = {"about": self.on_about, | |
| 687 | "quit": self.on_quit, | |
| 688 | "preferences": self.on_preferences, | |
| 689 | "pluginOptions": self.on_plugin_options, | |
| 690 | "faradayPlugin": self.on_faraday_plugin, | |
| 691 | "new": self.on_new_button, | |
| 692 | "new_terminal": self.on_new_terminal_button, | |
| 693 | "open_report": self.on_open_report_button, | |
| 694 | "go_to_web_ui": self.on_click_go_to_web_ui_button, | |
| 695 | "go_to_documentation": self.on_help_dispatch, | |
| 696 | "go_to_faq": self.on_help_dispatch, | |
| 697 | "go_to_troubleshooting": self.on_help_dispatch, | |
| 698 | "go_to_demos": self.on_help_dispatch, | |
| 699 | "go_to_issues": self.on_help_dispatch, | |
| 700 | "go_to_forum": self.on_help_dispatch, | |
| 701 | "go_to_irc": self.on_help_dispatch, | |
| 702 | "go_to_twitter": self.on_help_dispatch, | |
| 703 | "go_to_googlegroup": self.on_help_dispatch | |
| 704 | } | |
| 705 | ||
| 706 | for action, method in action_to_method.items(): | |
| 707 | gio_action = Gio.SimpleAction.new(action, None) | |
| 708 | gio_action.connect("activate", method) | |
| 709 | self.add_action(gio_action) | |
| 710 | ||
| 711 | dirname = os.path.dirname(os.path.abspath(__file__)) | |
| 712 | builder = Gtk.Builder.new_from_file(dirname + '/menubar.xml') | |
| 713 | builder.connect_signals(self) | |
| 714 | appmenu = builder.get_object('appmenu') | |
| 715 | self.set_app_menu(appmenu) | |
| 716 | ||
| 717 | topmenu = Gio.Menu() | |
| 718 | pluginmenu = Gio.Menu() | |
| 719 | ||
| 720 | topmenu.append('Faraday Plugin...', 'app.faradayPlugin') | |
| 721 | ||
| 722 | plugins = fplugin_utils.get_available_plugins() | |
| 723 | ||
| 724 | for plugin in sorted(plugins.keys()): | |
| 725 | gio_action = Gio.SimpleAction.new('fplugin_%s' % plugin, None) | |
| 726 | gio_action.connect("activate", self.type_faraday_plugin_command) | |
| 727 | self.add_action(gio_action) | |
| 728 | ||
| 729 | item = Gio.MenuItem.new(plugins[plugin]['prettyname'], 'app.fplugin_%s' % plugin) | |
| 730 | ||
| 731 | pluginmenu.append_item(item) | |
| 732 | ||
| 733 | fmenu = Gio.Menu() | |
| 734 | ||
| 735 | fmenu.append_section(None, topmenu) | |
| 736 | fmenu.append_section(None, pluginmenu) | |
| 737 | ||
| 738 | appmenu.insert_submenu(1, "Faraday Plugin", fmenu) | |
| 739 | ||
| 740 | helpMenu = builder.get_object('Help') | |
| 741 | self.set_menubar(helpMenu) | |
| 742 | ||
| 743 | def do_activate(self): | |
| 744 | """If there's no window, create one and present it (show it to user). | |
| 745 | If there's a window, just present it. Also add the log handler | |
| 746 | and the notifier to the application""" | |
| 747 | ||
| 748 | # We only allow a single window and raise any existing ones | |
| 749 | if not self.window: | |
| 750 | # Windows are associated with the application | |
| 751 | # when the last one is closed the application shuts down | |
| 752 | self.window = AppWindow(self.sidebar, | |
| 753 | self.ws_sidebar, | |
| 754 | self.hosts_sidebar, | |
| 755 | self.terminal, | |
| 756 | self.console_log, | |
| 757 | self.statusbar, | |
| 758 | application=self, | |
| 759 | title="Faraday " + str(CONF.getVersion())) | |
| 760 | ||
| 761 | self.window.set_icon(self.icon) | |
| 762 | self.window.present() | |
| 763 | ||
| 764 | self.loghandler = GUIHandler() | |
| 765 | if CONF.getDebugStatus(): | |
| 766 | self.loghandler.setLevel(logging.DEBUG) | |
| 767 | else: | |
| 768 | self.loghandler.setLevel(logging.INFO) | |
| 769 | faraday.client.model.guiapi.setMainApp(self) | |
| 770 | add_handler(self.loghandler) | |
| 771 | self.loghandler.registerGUIOutput(self.window) | |
| 772 | ||
| 773 | notifier = faraday.client.model.log.getNotifier() | |
| 774 | notifier.widget = self.window | |
| 775 | faraday.client.model.guiapi.notification_center.registerWidget(self.window) | |
| 776 | ||
| 777 | if self.serverIO.server_info() is None: | |
| 778 | ||
| 779 | should_login = self.lost_db_connection( | |
| 780 | handle_connection_lost=self.handle_connection_lost, | |
| 781 | connect_to_a_different_couch=self.force_change_couch_url) | |
| 782 | ||
| 783 | if not should_login: | |
| 784 | return | |
| 785 | ||
| 786 | if not is_authenticated(CONF.getServerURI(), CONF.getDBSessionCookies()): | |
| 787 | loginDialog = ForceLoginDialog(self.window, | |
| 788 | self.exit_faraday_without_confirm) | |
| 789 | loginDialog.run(3, CONF.getServerURI(), self.window) | |
| 790 | self.reload_workspaces() | |
| 791 | ||
| 792 | workspace_argument_set = self.open_workspace_from_args() | |
| 793 | if not workspace_argument_set: | |
| 794 | self.open_last_workspace() | |
| 795 | ||
| 796 | def on_quit(self, action=None, param=None): | |
| 797 | self.quit() | |
| 798 | ||
| 799 | def on_plugin_options(self, action, param): | |
| 800 | """Defines what happens when you press "Plugins" on the menu""" | |
| 801 | pluginsOption_window = PluginOptionsDialog(self.plugin_manager, | |
| 802 | self.window) | |
| 803 | pluginsOption_window.show_all() | |
| 804 | ||
| 805 | def on_faraday_plugin(self, action, param): | |
| 806 | """Defines what happens when you press "Faraday Plugin..." on the menu""" | |
| 807 | active_workspace = self.get_active_workspace() | |
| 808 | ||
| 809 | if active_workspace: | |
| 810 | name = active_workspace.getName() | |
| 811 | else: | |
| 812 | name = "" | |
| 813 | ||
| 814 | ||
| 815 | pluginsOption_window = FaradayPluginsDialog(self.window.get_current_focused_terminal(), | |
| 816 | name, | |
| 817 | self.window) | |
| 818 | pluginsOption_window.show_all() | |
| 819 | ||
| 820 | def on_new_button(self, action=None, params=None, title=None): | |
| 821 | """Defines what happens when you press the 'new' button on the toolbar | |
| 822 | """ | |
| 823 | new_workspace_dialog = NewWorkspaceDialog(self.createWorkspace, | |
| 824 | self.workspace_manager, | |
| 825 | self.ws_sidebar, self.window, | |
| 826 | title) | |
| 827 | new_workspace_dialog.show_all() | |
| 828 | ||
| 829 | def on_new_terminal_button(self, action, params): | |
| 830 | """When the user clicks on the new_terminal button, creates a new | |
| 831 | instance of the Terminal and tells the window to add it as a new tab | |
| 832 | for the notebook""" | |
| 833 | new_terminal = Terminal(CONF) | |
| 834 | terminal_scrolled = new_terminal.create_scrollable_terminal() | |
| 835 | self.window.new_tab(terminal_scrolled) | |
| 836 | ||
| 837 | def on_click_notifications(self, button): | |
| 838 | """Defines what happens when the user clicks on the notifications | |
| 839 | button: just show a silly window with a treeview containing | |
| 840 | all the notifications""" | |
| 841 | ||
| 842 | notifications_view = Gtk.TreeView(self.notificationsModel) | |
| 843 | renderer = Gtk.CellRendererText() | |
| 844 | column = Gtk.TreeViewColumn("Notifications", renderer, text=0) | |
| 845 | notifications_view.append_column(column) | |
| 846 | notifications_dialog = NotificationsDialog(notifications_view, | |
| 847 | self.delete_notifications, | |
| 848 | self.window) | |
| 849 | notifications_dialog.show_all() | |
| 850 | ||
| 851 | def on_click_conflicts(self, button=None): | |
| 852 | """Doesn't use the button at all, there cause GTK likes it. | |
| 853 | Shows the conflict dialog. | |
| 854 | """ | |
| 855 | conflicts = self.model_controller.getConflicts() | |
| 856 | if conflicts: | |
| 857 | dialog = ConflictsDialog(conflicts, | |
| 858 | self.window) | |
| 859 | dialog.show_all() | |
| 860 | ||
| 861 | else: | |
| 862 | dialog = Gtk.MessageDialog(self.window, 0, | |
| 863 | Gtk.MessageType.INFO, | |
| 864 | Gtk.ButtonsType.OK, | |
| 865 | "No conflicts to fix!") | |
| 866 | dialog.run() | |
| 867 | dialog.destroy() | |
| 868 | ||
| 869 | def on_open_report_button(self, action, param): | |
| 870 | """What happens when the user clicks the open report button. | |
| 871 | A dialog will present itself with a combobox to select a plugin. | |
| 872 | Then a file chooser to select a report. The report will be processed | |
| 873 | with the selected plugin. | |
| 874 | """ | |
| 875 | ||
| 876 | def select_plugin(): | |
| 877 | """Creates a simple dialog with a combo box to select a plugin""" | |
| 878 | plugins_id = list(self.plugin_manager.getPlugins()) | |
| 879 | plugins_id = sorted(plugins_id, key=lambda s: s.lower()) | |
| 880 | dialog = Gtk.Dialog("Select plugin", self.window, 0) | |
| 881 | ||
| 882 | combo_box = Gtk.ComboBoxText() | |
| 883 | combo_box.set_wrap_width(3) | |
| 884 | for plugin_id in plugins_id: | |
| 885 | combo_box.append_text(plugin_id) | |
| 886 | combo_box.show() | |
| 887 | ||
| 888 | dialog.vbox.pack_start(combo_box, False, True, 10) | |
| 889 | ||
| 890 | dialog.add_button("Cancel", Gtk.ResponseType.DELETE_EVENT) | |
| 891 | dialog.add_button("OK", Gtk.ResponseType.ACCEPT) | |
| 892 | ||
| 893 | response = dialog.run() | |
| 894 | selected = combo_box.get_active_text() | |
| 895 | ||
| 896 | dialog.destroy() | |
| 897 | return response, selected | |
| 898 | ||
| 899 | def on_file_selected(plugin_id, report): | |
| 900 | """Send the plugin_id and the report file to be processed""" | |
| 901 | try: | |
| 902 | self.report_manager.sendReportToPluginById(plugin_id, report) | |
| 903 | except Unauthorized: | |
| 904 | self.show_normal_error("You are not authorized to write data " | |
| 905 | "to this workspace.") | |
| 906 | ||
| 907 | plugin_response, plugin_id = select_plugin() | |
| 908 | ||
| 909 | while plugin_response == Gtk.ResponseType.ACCEPT and plugin_id is None: | |
| 910 | # force user to select a plugin if he did not do it | |
| 911 | errorDialog(self.window, | |
| 912 | "Please select a plugin to parse your report!") | |
| 913 | plugin_response, plugin_id = select_plugin() | |
| 914 | else: | |
| 915 | if plugin_response == Gtk.ResponseType.ACCEPT: | |
| 916 | dialog = Gtk.FileChooserDialog(title="Import a report", | |
| 917 | parent=self.window, | |
| 918 | action=Gtk.FileChooserAction.OPEN, | |
| 919 | buttons=("Open", Gtk.ResponseType.ACCEPT, | |
| 920 | "Cancel", Gtk.ResponseType.CANCEL) | |
| 921 | ) | |
| 922 | dialog.set_modal(True) | |
| 923 | ||
| 924 | res = dialog.run() | |
| 925 | if res == Gtk.ResponseType.ACCEPT: | |
| 926 | on_file_selected(plugin_id, dialog.get_filename()) | |
| 927 | dialog.destroy() | |
| 928 | ||
| 929 | def on_about(self, action, param): | |
| 930 | """ Defines what happens when you press 'about' on the menu""" | |
| 931 | about_dialog = aboutDialog(self.window) | |
| 932 | about_dialog.run() | |
| 933 | about_dialog.destroy() | |
| 934 | ||
| 935 | def on_preferences(self, action=None, param=None): | |
| 936 | """Defines what happens when you press 'preferences' on the menu. | |
| 937 | Sends as a callback reloadWsManager, so if the user actually | |
| 938 | changes her Couch URL, the sidebar will reload reflecting the | |
| 939 | new workspaces available""" | |
| 940 | ||
| 941 | preference_window = PreferenceWindowDialog(self.reload_workspaces, | |
| 942 | self.connect_to_couch, | |
| 943 | self.window) | |
| 944 | preference_window.show_all() | |
| 945 | ||
| 946 | def on_click_go_to_web_ui_button(self, action=None, param=None): | |
| 947 | """Opens the login on a new tab of the user's default browser""" | |
| 948 | ||
| 949 | ws_url = CONF.getServerURI() + "/_ui/#/login" | |
| 950 | webbrowser.open(ws_url, new=2) | |
| 951 | ||
| 952 | def on_help_dispatch(self, action, param=None): | |
| 953 | """Open the url contained in "action" in the user's browser.""" | |
| 954 | urls = {"go_to_documentation": "https://faradaysec.com/help/docs", | |
| 955 | "go_to_faq": "https://faradaysec.com/help/faq", | |
| 956 | "go_to_troubleshooting": "https://faradaysec.com/help/troubleshooting", | |
| 957 | "go_to_demos": "https://faradaysec.com/help/demos", | |
| 958 | "go_to_issues": "https://faradaysec.com/help/issues", | |
| 959 | "go_to_forum": "https://forum.faradaysec.com", | |
| 960 | "go_to_irc": "https://faradaysec.com/help/irc", | |
| 961 | "go_to_twitter": "https://faradaysec.com/help/twitter", | |
| 962 | "go_to_googlegroup": "https://faradaysec.com/help/googlegroup" | |
| 963 | } | |
| 964 | url = urls.get(action.get_name(), "https://faradaysec.com") | |
| 965 | webbrowser.open(url, new=2) | |
| 966 | ||
| 967 | def type_faraday_plugin_command(self, action, param=None): | |
| 968 | """ | |
| 969 | Types the faraday plugin command on the command line. | |
| 970 | """ | |
| 971 | ||
| 972 | plugin = "_".join(action.get_name().split('_')[1:]) | |
| 973 | terminal = self.window.get_current_focused_terminal() | |
| 974 | ||
| 975 | active_workspace = self.get_active_workspace() | |
| 976 | ||
| 977 | if active_workspace: | |
| 978 | command = fplugin_utils.build_faraday_plugin_command(plugin, active_workspace.getName()) | |
| 979 | fd = terminal.get_pty().get_fd() | |
| 980 | os.write(fd, command.encode()) | |
| 981 | ||
| 982 | ||
| 983 | # I'm Py3 |
| 0 | #!/usr/bin/python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | ||
| 7 | """ | |
| 8 | from __future__ import absolute_import | |
| 9 | ||
| 10 | import os | |
| 11 | import gi # pylint: disable=import-error | |
| 12 | ||
| 13 | from faraday.config.configuration import getInstanceConfiguration | |
| 14 | from faraday.client.start_client import FARADAY_CLIENT_BASE | |
| 15 | ||
| 16 | gi.require_version('Gtk', '3.0') | |
| 17 | ||
| 18 | from gi.repository import GLib, Gio, Gtk, GObject, Gdk # pylint: disable=import-error | |
| 19 | from faraday.client.gui.gtk.dialogs import ImportantErrorDialog | |
| 20 | ||
| 21 | CONF = getInstanceConfiguration() | |
| 22 | ||
| 23 | ||
| 24 | class AppWindow(Gtk.ApplicationWindow): | |
| 25 | """The main window of the GUI. Draws the toolbar. | |
| 26 | Positions the terminal, sidebar, consolelog and statusbar received from | |
| 27 | the app and defined in the mainwidgets module""" | |
| 28 | ||
| 29 | def __init__(self, sidebar, ws_sidebar, hosts_sidebar, terminal, | |
| 30 | console_log, statusbar, *args, **kwargs): | |
| 31 | super(Gtk.ApplicationWindow, self).__init__(*args, **kwargs) | |
| 32 | ||
| 33 | # This will be in the windows group and have the "win" prefix | |
| 34 | glib_variant = GLib.Variant.new_boolean(True) | |
| 35 | max_action = Gio.SimpleAction.new_stateful("maximize", None, | |
| 36 | glib_variant) | |
| 37 | max_action.connect("change-state", self.on_maximize_toggle) | |
| 38 | self.add_action(max_action) | |
| 39 | self.maximize() | |
| 40 | # Keep it in sync with the actual state. Deep dark GTK magic | |
| 41 | self.connect("notify::is-maximized", | |
| 42 | lambda obj, pspec: | |
| 43 | max_action.set_state( | |
| 44 | GLib.Variant.new_boolean(obj.props.is_maximized))) | |
| 45 | ||
| 46 | self.tab_number = 0 # 0 indexed, even when it shows 1 to the user | |
| 47 | self.sidebar = sidebar | |
| 48 | self.ws_sidebar = ws_sidebar | |
| 49 | self.hosts_sidebar = hosts_sidebar | |
| 50 | self.terminal = terminal | |
| 51 | self.log = console_log | |
| 52 | self.statusbar = statusbar | |
| 53 | self.user_confirmed_quit = False | |
| 54 | ||
| 55 | self.terminal.connect("child_exited", self.on_terminal_exit) | |
| 56 | self.icons = os.path.join(FARADAY_CLIENT_BASE, "data", "images", "icons") | |
| 57 | ||
| 58 | window = self.create_window_main_structure() | |
| 59 | self.add(window) | |
| 60 | ||
| 61 | self.append_remove_terminal_button_to_notebook() | |
| 62 | self.show_all() | |
| 63 | ||
| 64 | def create_window_main_structure(self): | |
| 65 | """Return a box with the main structure of the window. Looks like this: | |
| 66 | |-------------------------| | |
| 67 | | TOOLBAR | | |
| 68 | |-------------------------| | |
| 69 | | TERMINAL | SIDE | | |
| 70 | | | BAR | | |
| 71 | |-------------------------| | |
| 72 | | LOG BOX | | |
| 73 | | STATUSBAR | | |
| 74 | |-------------------------| | |
| 75 | """ | |
| 76 | scrollable_terminal = self.terminal.create_scrollable_terminal() | |
| 77 | terminal_event_box = self.create_event_box(scrollable_terminal) | |
| 78 | ||
| 79 | self.notebook = Gtk.Notebook() | |
| 80 | self.notebook.set_scrollable(True) | |
| 81 | self.notebook.append_page(terminal_event_box, Gtk.Label("1")) | |
| 82 | ||
| 83 | middle_pane = Gtk.Paned(orientation=Gtk.Orientation.HORIZONTAL) | |
| 84 | middle_pane.pack1(self.notebook, True, False) | |
| 85 | middle_pane.pack2(self.sidebar.box_it(), False, False) | |
| 86 | ||
| 87 | self.log_box = self.log.create_scrollable_logger() | |
| 88 | ||
| 89 | main_box = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 90 | main_box.pack_start(self.create_toolbar(), False, False, 0) | |
| 91 | main_box.pack_start(middle_pane, True, True, 0) | |
| 92 | main_box.pack_start(self.log_box, False, False, 0) | |
| 93 | main_box.pack_start(self.statusbar.mainBox, False, False, 0) | |
| 94 | return main_box | |
| 95 | ||
| 96 | def append_remove_terminal_button_to_notebook(self): | |
| 97 | """Apprends a remove_terminal_icon to the end of notebooks | |
| 98 | action area""" | |
| 99 | remove_terminal_icon = Gtk.Image.new_from_file(os.path.join(self.icons,"exit.png")) | |
| 100 | remove_terminal_button = Gtk.Button() | |
| 101 | remove_terminal_button.set_tooltip_text("Delete current tab") | |
| 102 | remove_terminal_button.connect("clicked", self.delete_tab) | |
| 103 | remove_terminal_button.set_image(remove_terminal_icon) | |
| 104 | remove_terminal_button.set_relief(Gtk.ReliefStyle.NONE) | |
| 105 | remove_terminal_button.show() | |
| 106 | self.notebook.set_action_widget(remove_terminal_button, Gtk.PackType.END) | |
| 107 | ||
| 108 | def receive_hosts(self, hosts): | |
| 109 | """Attaches the hosts to an object value, so it can be used by | |
| 110 | do_update_hosts_sidebar, a signal. GTK won't alow anything | |
| 111 | more than primitive names to be passed on by signals""" | |
| 112 | self.current_hosts = hosts | |
| 113 | ||
| 114 | def create_event_box(self, widget): | |
| 115 | """Given a terminal, creates an EventBox for the Box that has as a | |
| 116 | children said terminal""" | |
| 117 | event_box = Gtk.EventBox() | |
| 118 | event_box.connect("button_press_event", self.right_click) | |
| 119 | event_box.add(widget) | |
| 120 | return event_box | |
| 121 | ||
| 122 | def right_click(self, eventbox, event): | |
| 123 | """Defines the menu created when a user rightclicks on the | |
| 124 | terminal eventbox""" | |
| 125 | menu = Gtk.Menu() | |
| 126 | self.copy = Gtk.MenuItem("Copy") | |
| 127 | self.paste = Gtk.MenuItem("Paste") | |
| 128 | menu.append(self.paste) | |
| 129 | menu.append(self.copy) | |
| 130 | ||
| 131 | self.copy.connect("activate", self.copy_text) | |
| 132 | self.paste.connect("activate", self.paste_text) | |
| 133 | ||
| 134 | self.copy.show() | |
| 135 | self.paste.show() | |
| 136 | menu.popup(None, None, None, None, event.button, event.time) | |
| 137 | ||
| 138 | def copy_text(self, _): | |
| 139 | """When the user presses on the copy button on the menu...""" | |
| 140 | currentTerminal = self.get_current_focused_terminal() | |
| 141 | currentTerminal.copy_clipboard() | |
| 142 | ||
| 143 | def paste_text(self, _): | |
| 144 | """When the user presses on the paste button on the menu...""" | |
| 145 | currentTerminal = self.get_current_focused_terminal() | |
| 146 | currentTerminal.paste_clipboard() | |
| 147 | ||
| 148 | def get_current_focused_terminal(self): | |
| 149 | """Returns the current focused terminal""" | |
| 150 | ||
| 151 | # the focused terminal is the child of the event box which is | |
| 152 | # the top widget of the focused tab. that event box has as only child | |
| 153 | # only child a scrolled window, which has as only child the terminal. | |
| 154 | # Yeah. I know. | |
| 155 | ||
| 156 | current_tab = self.notebook.get_current_page() | |
| 157 | current_event_box = self.notebook.get_children()[current_tab] | |
| 158 | current_scrolled_window = current_event_box.get_children()[0] | |
| 159 | current_terminal = current_scrolled_window.get_child() | |
| 160 | return current_terminal | |
| 161 | ||
| 162 | def destroy_from_button(self, button=None): | |
| 163 | """Sometimes this stuff is needed, 'cause it needs to take a button | |
| 164 | as parameter. See do_delete_event() for explanation on why the | |
| 165 | _not_ is there. | |
| 166 | """ | |
| 167 | if not self.do_delete_event(): | |
| 168 | self.destroy() | |
| 169 | ||
| 170 | def on_maximize_toggle(self, action, value): | |
| 171 | """Defines what happens when the window gets the signal to maximize""" | |
| 172 | action.set_state(value) | |
| 173 | if value.get_boolean(): | |
| 174 | self.maximize() | |
| 175 | else: | |
| 176 | self.unmaximize() | |
| 177 | ||
| 178 | def create_toolbar(self): | |
| 179 | """Creates the toolbar for the window.""" | |
| 180 | ||
| 181 | toolbar = Gtk.Toolbar() | |
| 182 | toolbar.set_hexpand(True) | |
| 183 | icons = self.icons | |
| 184 | ||
| 185 | new_button_icon = Gtk.Image.new_from_file( | |
| 186 | os.path.join(icons, "Documentation.png")) | |
| 187 | new_terminal_icon = Gtk.Image.new_from_file( | |
| 188 | os.path.join(icons, "newshell.png")) | |
| 189 | preferences_icon = Gtk.Image.new_from_file( | |
| 190 | os.path.join(icons, "config.png")) | |
| 191 | toggle_log_icon = Gtk.Image.new_from_file( | |
| 192 | os.path.join(icons, "debug.png")) | |
| 193 | open_report_icon = Gtk.Image.new_from_file( | |
| 194 | os.path.join(icons, "FolderSteel-20.png")) | |
| 195 | go_to_web_ui_icon = Gtk.Image.new_from_file( | |
| 196 | os.path.join(icons, "visualize.png")) | |
| 197 | ||
| 198 | new_terminal_button = Gtk.ToolButton.new(new_terminal_icon, None) | |
| 199 | new_terminal_button.set_tooltip_text("Create a new tab") | |
| 200 | new_terminal_button.set_label("New tab") | |
| 201 | new_terminal_button.set_action_name('app.new_terminal') | |
| 202 | toolbar.insert(new_terminal_button, 0) | |
| 203 | ||
| 204 | new_button = Gtk.ToolButton.new(new_button_icon, None) | |
| 205 | new_button.set_tooltip_text("Create a new workspace") | |
| 206 | new_button.set_label("New Workspace") | |
| 207 | toolbar.insert(new_button, 1) | |
| 208 | new_button.set_action_name('app.new') | |
| 209 | ||
| 210 | preferences_button = Gtk.ToolButton.new(preferences_icon, None) | |
| 211 | preferences_button.set_tooltip_text("Preferences") | |
| 212 | preferences_button.set_label("Preferences") | |
| 213 | toolbar.insert(preferences_button, 2) | |
| 214 | preferences_button.set_action_name('app.preferences') | |
| 215 | ||
| 216 | toggle_log_button = Gtk.ToggleToolButton.new() | |
| 217 | toggle_log_button.set_icon_widget(toggle_log_icon) | |
| 218 | toggle_log_button.set_active(True) # log enabled by default | |
| 219 | toggle_log_button.set_tooltip_text("Toggle log console") | |
| 220 | toggle_log_button.set_label("Toggle log") | |
| 221 | toggle_log_button.connect("clicked", self.toggle_log) | |
| 222 | toolbar.insert(toggle_log_button, 3) | |
| 223 | ||
| 224 | go_to_web_ui_button = Gtk.ToolButton.new(go_to_web_ui_icon, None) | |
| 225 | go_to_web_ui_button.set_tooltip_text("Go to Faraday Web") | |
| 226 | go_to_web_ui_button.set_label("Faraday Web") | |
| 227 | go_to_web_ui_button.set_action_name("app.go_to_web_ui") | |
| 228 | toolbar.insert(go_to_web_ui_button, 4) | |
| 229 | ||
| 230 | space = Gtk.ToolItem() | |
| 231 | space.set_expand(True) | |
| 232 | toolbar.insert(space, 5) | |
| 233 | ||
| 234 | open_report_button = Gtk.ToolButton.new(open_report_icon, None) | |
| 235 | open_report_button.set_label("Import report") | |
| 236 | open_report_button.set_tooltip_text("Import report") | |
| 237 | open_report_button.set_action_name('app.open_report') | |
| 238 | toolbar.insert(open_report_button, 6) | |
| 239 | ||
| 240 | return toolbar | |
| 241 | ||
| 242 | def new_tab(self, scrolled_window): | |
| 243 | """The on_new_terminal_button redirects here from the application. | |
| 244 | The scrolled_window will be a scrolled window containing only a VTE | |
| 245 | terminal. | |
| 246 | """ | |
| 247 | ||
| 248 | terminal = scrolled_window.get_children()[0] | |
| 249 | terminal.connect("child_exited", self.on_terminal_exit) | |
| 250 | self.tab_number += 1 | |
| 251 | pageN = self.create_event_box(scrolled_window) | |
| 252 | self.notebook.append_page(pageN, Gtk.Label(str(self.tab_number+1))) | |
| 253 | self.notebook.show_all() | |
| 254 | ||
| 255 | def delete_tab(self, button=None, tab_number=None): | |
| 256 | """Deletes the tab number tab_number, by default the current, | |
| 257 | or closes the window if tab is only tab""" | |
| 258 | if self.tab_number == 0: | |
| 259 | # the following is confusing but its how gtks handles delete_event | |
| 260 | # if user said YES to confirmation, do_delete_event returns False | |
| 261 | if not self.do_delete_event(): | |
| 262 | self.destroy() | |
| 263 | ||
| 264 | else: | |
| 265 | if tab_number is None: | |
| 266 | page = self.notebook.get_current_page() | |
| 267 | else: | |
| 268 | page = self.notebook.get_nth_page(tab_number) | |
| 269 | ||
| 270 | self.notebook.remove_page(page) | |
| 271 | self.reorder_tab_names() | |
| 272 | ||
| 273 | def reorder_tab_names(self): | |
| 274 | """When a tab is deleted, all other tabs must be renamed to reacomodate | |
| 275 | the numbers""" | |
| 276 | ||
| 277 | # Tabs are zero indexed, but their labels start at one | |
| 278 | number_of_tabs = self.notebook.get_n_pages() | |
| 279 | for n in range(number_of_tabs): | |
| 280 | tab = self.notebook.get_nth_page(n) | |
| 281 | self.notebook.set_tab_label_text(tab, str(n+1)) | |
| 282 | self.tab_number = number_of_tabs-1 | |
| 283 | ||
| 284 | def toggle_log(self, button): | |
| 285 | """Reverses the visibility status of the log_box""" | |
| 286 | current_state = self.log_box.is_visible() | |
| 287 | self.log_box.set_visible(not current_state) | |
| 288 | ||
| 289 | def show_conflicts_warning(self): | |
| 290 | warning_string = ("There are conflicts that need manual " | |
| 291 | "handling. Closing Faraday or changing workspaces " | |
| 292 | "may result in the loss of relevant information. " | |
| 293 | "Are you sure you want to continue?") | |
| 294 | dialog = Gtk.MessageDialog(self, 0, | |
| 295 | Gtk.MessageType.QUESTION, | |
| 296 | Gtk.ButtonsType.YES_NO, | |
| 297 | warning_string) | |
| 298 | response = dialog.run() | |
| 299 | dialog.destroy() | |
| 300 | return response | |
| 301 | ||
| 302 | def do_delete_event(self, event=None, status=None, parent=None): | |
| 303 | """Override delete_event signal to show a confirmation dialog first. | |
| 304 | """ | |
| 305 | if self.user_confirmed_quit: | |
| 306 | return False # keep on going and destroy | |
| 307 | ||
| 308 | if parent is None: | |
| 309 | parent = self | |
| 310 | ||
| 311 | # NOTE: Return False for 'yes' is weird but that's how gtk likes it | |
| 312 | # Don't judge, man. Don't judge. | |
| 313 | if self.statusbar.conflict_button_label_int > 0: | |
| 314 | response = self.show_conflicts_warning() | |
| 315 | if response == Gtk.ResponseType.NO: | |
| 316 | return True | |
| 317 | else: | |
| 318 | return False | |
| 319 | ||
| 320 | dialog = Gtk.MessageDialog(transient_for=parent, | |
| 321 | modal=True, | |
| 322 | buttons=Gtk.ButtonsType.YES_NO) | |
| 323 | dialog.set_keep_above(True) | |
| 324 | dialog.set_modal(True) | |
| 325 | dialog.props.text = "Are you sure you want to quit Faraday?" | |
| 326 | response = dialog.run() | |
| 327 | dialog.destroy() | |
| 328 | ||
| 329 | if response == Gtk.ResponseType.YES: | |
| 330 | self.user_confirmed_quit = True | |
| 331 | return False # keep on going and destroy | |
| 332 | else: | |
| 333 | # user said "you know what i don't want to exit" | |
| 334 | return True | |
| 335 | ||
| 336 | def on_terminal_exit(self, terminal=None, status=None): | |
| 337 | """Really, it is *very* similar to delete_tab, but in this case | |
| 338 | we want to make sure that we restart Faraday if the user | |
| 339 | is not sure if he wants to exit""" | |
| 340 | self.delete_tab() | |
| 341 | terminal.start_faraday() | |
| 342 | ||
| 343 | ||
| 344 | # I'm Py3 |
| 0 | #!/usr/bin/python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | ||
| 7 | This module is intended to function as a compatibility layer to support both | |
| 8 | GObject Instrospection 3.12, 3.16 and 3.20 (Ubuntu 14.04, Brew on Mac OS and | |
| 9 | Arch, respectively) and VTE API 2.90 and 2.91 (Ubuntu 14.04 has 2.90, last one | |
| 10 | is 2.91) | |
| 11 | """ | |
| 12 | from __future__ import absolute_import | |
| 13 | ||
| 14 | import gi # pylint: disable=import-error | |
| 15 | gi_version = gi.__version__ | |
| 16 | ||
| 17 | gi.require_version('Gtk', '3.0') | |
| 18 | try: | |
| 19 | gi.require_version('Vte', '2.91') | |
| 20 | vte_version = '2.91' | |
| 21 | except ValueError: | |
| 22 | gi.require_version('Vte', '2.90') | |
| 23 | vte_version = '2.90' | |
| 24 | ||
| 25 | from gi.repository import Vte, Gtk # pylint: disable=import-error | |
| 26 | ||
| 27 | ||
| 28 | class CompatibleVteTerminal(Vte.Terminal): | |
| 29 | """A simple VTE terminal modified to be compatible with both 2.90 | |
| 30 | and 2.91 API""" | |
| 31 | def __init__(self): | |
| 32 | Vte.Terminal.__init__(self) | |
| 33 | ||
| 34 | def spawn_sync(self, pty_flags, working_directory, argument_vector, | |
| 35 | env_variables, glib_spawn_flags, child_setup, | |
| 36 | child_setup_data, cancellable=None): | |
| 37 | """Returns the corresponden version os 'spawn_sync' method | |
| 38 | according to the Vte version the user has""" | |
| 39 | if vte_version == '2.91': | |
| 40 | return Vte.Terminal.spawn_sync(self, pty_flags, working_directory, | |
| 41 | argument_vector, env_variables, | |
| 42 | glib_spawn_flags, child_setup, | |
| 43 | child_setup_data, cancellable) | |
| 44 | elif vte_version == '2.90': | |
| 45 | return Vte.Terminal.fork_command_full(self, pty_flags, | |
| 46 | working_directory, | |
| 47 | argument_vector, env_variables, | |
| 48 | glib_spawn_flags, child_setup, | |
| 49 | child_setup_data, cancellable) | |
| 50 | ||
| 51 | ||
| 52 | class CompatibleScrolledWindow(Gtk.ScrolledWindow): | |
| 53 | """A simple Gtk.ScrolledWindow, replacing set_overlay_scrolling for None | |
| 54 | if Gobject Instrospection is too old.""" | |
| 55 | def __init__(self, *args, **kwargs): | |
| 56 | Gtk.ScrolledWindow.__init__(self, *args, **kwargs) | |
| 57 | ||
| 58 | @staticmethod | |
| 59 | def new(hadjustment, vadjustment): | |
| 60 | return Gtk.ScrolledWindow.new(hadjustment, vadjustment) | |
| 61 | ||
| 62 | def set_overlay_scrolling(self, boolean): | |
| 63 | """Return the set_overlay_scrolling method, if it can.""" | |
| 64 | if gi_version in ['3.12.0', '3.14.0']: | |
| 65 | return None | |
| 66 | else: | |
| 67 | return Gtk.ScrolledWindow.set_overlay_scrolling(self, boolean) | |
| 68 | ||
| 69 | ||
| 70 | # I'm Py3 |
| 0 | # Faraday Penetration Test IDE | |
| 1 | # Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 2 | # See the file 'doc/LICENSE' for the license information | |
| 3 | from __future__ import absolute_import | |
| 4 | ||
| 5 | import requests | |
| 6 | from gi.repository import Gtk # pylint: disable=import-error | |
| 7 | from faraday.server.utils.logger import get_logger | |
| 8 | from functools import wraps | |
| 9 | from faraday.client.gui.gtk.compatibility import CompatibleScrolledWindow as GtkScrolledWindow | |
| 10 | from faraday.client.persistence.server.server_io_exceptions import ServerRequestException | |
| 11 | ||
| 12 | def safe_io_with_server(response_in_emergency): | |
| 13 | """A function that takes a response_in_emergency. It will return | |
| 14 | a safe_decorator, which will try to execture a funcion and in case | |
| 15 | anything happens, it will return the response in emergency. | |
| 16 | """ | |
| 17 | def safe_decorator(func): | |
| 18 | @wraps(func) | |
| 19 | def wrapper(*args, **kwargs): | |
| 20 | try: | |
| 21 | res = func(*args, **kwargs) | |
| 22 | except ServerRequestException as e: | |
| 23 | res = response_in_emergency | |
| 24 | get_logger("Server-GTK IO").warning(e) | |
| 25 | except (requests.exceptions.MissingSchema, requests.exceptions.InvalidSchema): | |
| 26 | res = response_in_emergency | |
| 27 | get_logger("Server-GTK IO").error("It looks like the Faraday Server " | |
| 28 | "URL is not correctly formated. Please change it and " | |
| 29 | "remember to set it with a valid protocol, like http.\n" | |
| 30 | "For example: http://faradayserver:port/") | |
| 31 | except Exception: | |
| 32 | res = response_in_emergency | |
| 33 | get_logger("Server-GTK IO").error("It looks like the Faraday Server is not running\n") | |
| 34 | ||
| 35 | return res | |
| 36 | return wrapper | |
| 37 | return safe_decorator | |
| 38 | ||
| 39 | def scrollable(width=-1, height=-1, overlay_scrolling=False): | |
| 40 | """A function that takes optinal width and height and returns | |
| 41 | the scrollable decorator. -1 is the default GTK option for both | |
| 42 | width and height.""" | |
| 43 | def scrollable_decorator(func): | |
| 44 | """Takes a function and returns the scroll_object_wrapper.""" | |
| 45 | @wraps(func) | |
| 46 | def scroll_object_wrapper(*args, **kwargs): | |
| 47 | """Takes arguments and obtains the original object from | |
| 48 | func(*args, **kwargs). Creates a box and puts the original | |
| 49 | inside that box. Creates a scrolled window and puts the | |
| 50 | box inside it. | |
| 51 | """ | |
| 52 | ||
| 53 | original = func(*args, **kwargs) | |
| 54 | scrolled_box = GtkScrolledWindow(None, None) | |
| 55 | scrolled_box.set_min_content_width(width) | |
| 56 | scrolled_box.set_min_content_height(height) | |
| 57 | scrolled_box.set_overlay_scrolling(overlay_scrolling) | |
| 58 | scrolled_box.add(original) | |
| 59 | return scrolled_box | |
| 60 | ||
| 61 | return scroll_object_wrapper | |
| 62 | ||
| 63 | return scrollable_decorator | |
| 64 | ||
| 65 | ||
| 66 | # I'm Py3 |
| 0 | #!/usr/bin/python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | ||
| 7 | """ | |
| 8 | from __future__ import absolute_import | |
| 9 | from past.builtins import basestring | |
| 10 | ||
| 11 | ||
| 12 | import webbrowser | |
| 13 | import gi # pylint: disable=import-error | |
| 14 | import os | |
| 15 | from faraday.client.start_client import FARADAY_CLIENT_BASE | |
| 16 | gi.require_version('Gtk', '3.0') | |
| 17 | ||
| 18 | from faraday.client.persistence.server.server import ResourceDoesNotExist | |
| 19 | from gi.repository import Gtk, GdkPixbuf, Gdk # pylint: disable=import-error | |
| 20 | from faraday.config.configuration import getInstanceConfiguration | |
| 21 | from faraday.client.persistence.server.server import is_authenticated, login_user, get_user_info, check_server_url | |
| 22 | from faraday.client.model import guiapi | |
| 23 | from faraday.client.gui.gtk.decorators import scrollable | |
| 24 | ||
| 25 | from faraday.client.gui.gtk.compatibility import CompatibleScrolledWindow as GtkScrolledWindow | |
| 26 | from faraday.client.plugins import fplugin_utils | |
| 27 | ||
| 28 | CONF = getInstanceConfiguration() | |
| 29 | ||
| 30 | ||
| 31 | class PreferenceWindowDialog(Gtk.Dialog): | |
| 32 | """Sets up a preference dialog with basically nothing more than a | |
| 33 | label, a text entry to input your Faraday server IP and a couple of buttons. | |
| 34 | Takes a callback function to the mainapp so that it can refresh the | |
| 35 | workspace list and information""" | |
| 36 | ||
| 37 | def __init__(self, reload_ws_callback, connect_to_couch, parent): | |
| 38 | """Initializes the simple preferences dialog. If force is set to | |
| 39 | True, user will NOT be able to cancel the dialog and app_exit_callback | |
| 40 | must NOT be None""" | |
| 41 | ||
| 42 | Gtk.Dialog.__init__(self, title="Preferences") | |
| 43 | self.parent = parent | |
| 44 | self.set_modal(True) | |
| 45 | self.set_size_request(400, 100) | |
| 46 | self.set_type_hint(Gdk.WindowTypeHint.DIALOG) | |
| 47 | self.set_transient_for(parent) | |
| 48 | self.reloadWorkspaces = reload_ws_callback | |
| 49 | self.connectCouchCallback = connect_to_couch | |
| 50 | ||
| 51 | main_box = self.get_content_area() | |
| 52 | ||
| 53 | ip_label = Gtk.Label() | |
| 54 | ip_label.set_text("Faraday Server IP or URL") | |
| 55 | main_box.pack_start(ip_label, True, False, 10) | |
| 56 | ||
| 57 | couch_uri = CONF.getServerURI() | |
| 58 | self.ip_entry = Gtk.Entry() | |
| 59 | text = couch_uri if couch_uri else "http://127.0.0.1:5050" | |
| 60 | self.ip_entry.set_text(text) | |
| 61 | main_box.pack_start(self.ip_entry, True, False, 10) | |
| 62 | ||
| 63 | button_box = Gtk.Box(spacing=6) | |
| 64 | main_box.pack_end(button_box, False, True, 10) | |
| 65 | ||
| 66 | OK_button = Gtk.Button.new_with_label("OK") | |
| 67 | OK_button.connect("clicked", self.on_click_ok) | |
| 68 | button_box.pack_start(OK_button, False, True, 10) | |
| 69 | cancel_button = Gtk.Button.new_with_label("Cancel") | |
| 70 | ||
| 71 | self.connect("key_press_event", key_reactions) | |
| 72 | cancel_button.connect("clicked", self.on_click_cancel) | |
| 73 | ||
| 74 | button_box.pack_end(cancel_button, False, True, 10) | |
| 75 | self.show_all() | |
| 76 | ||
| 77 | def on_click_ok(self, button=None): | |
| 78 | """Button is useless, only there because GTK likes it. Takes the | |
| 79 | repourl (Couch IP) from self.ip_entry and connect to it if possible. | |
| 80 | """ | |
| 81 | repourl = self.ip_entry.get_text() | |
| 82 | ||
| 83 | if not check_server_url(repourl): | |
| 84 | errorDialog(self, "Could not connect to Faraday Server.", | |
| 85 | ("Are you sure it is running and that the URL is correct?")) | |
| 86 | return False | |
| 87 | ||
| 88 | ||
| 89 | credentials_ok = self.credentialsOK(repourl) | |
| 90 | couch_connection_ok = self.connectCouchCallback(repourl, parent=self) | |
| 91 | if credentials_ok and couch_connection_ok: | |
| 92 | self.destroy() | |
| 93 | ||
| 94 | def credentialsOK(self, repourl): | |
| 95 | """Pops up a dialog (if necessary) to set up Faraday | |
| 96 | credentials. Dialog is a LoginDialog which emits a signal marked | |
| 97 | by 42 when the user clicks its button. The run method returns 42 | |
| 98 | on that click. Function will listen for that 42 at most three times. | |
| 99 | It's a boolean function, return True if auth ok, False if not. | |
| 100 | Number 42 was chosen for obvious reasons :) """ | |
| 101 | ||
| 102 | if is_authenticated(repourl, CONF.getDBSessionCookies()): | |
| 103 | return True | |
| 104 | ||
| 105 | # if that didn't work... | |
| 106 | loginDialog = LoginDialog(self) | |
| 107 | return loginDialog.run(3, repourl, self) | |
| 108 | ||
| 109 | ||
| 110 | def on_click_cancel(self, button=None): | |
| 111 | self.destroy() | |
| 112 | ||
| 113 | ||
| 114 | class ForcePreferenceWindowDialog(PreferenceWindowDialog): | |
| 115 | """A _forced_ version of the preference window, which means | |
| 116 | the user won't be able to exit it by any key combo or any cancel | |
| 117 | button. The cancel button now should redirect to a callback to | |
| 118 | exit the application. | |
| 119 | """ | |
| 120 | ||
| 121 | def __init__(self, reload_ws_callback, connect_to_couch, parent, | |
| 122 | exit_faraday_callback): | |
| 123 | """Inits just the same as preference window dialog, but | |
| 124 | disconnect from key_reactions and connect to strict_key_reaction. | |
| 125 | Also connect destroy with the OK function: if the user manages | |
| 126 | to close the dialog, that'd be just as pressing OK""" | |
| 127 | PreferenceWindowDialog.__init__(self, reload_ws_callback, | |
| 128 | connect_to_couch, | |
| 129 | parent) | |
| 130 | ||
| 131 | self.set_deletable(False) | |
| 132 | self.exit_faraday = exit_faraday_callback | |
| 133 | self.disconnect_by_func(key_reactions) | |
| 134 | self.connect("key_press_event", strict_key_reactions) | |
| 135 | self.connect("delete_event", lambda _, __: True) | |
| 136 | ||
| 137 | def on_click_cancel(self, button=None): | |
| 138 | """Override on_click_cancel to make it exit Faraday.""" | |
| 139 | self.exit_faraday(parent=self) | |
| 140 | ||
| 141 | ||
| 142 | class LoginDialog(Gtk.Dialog): | |
| 143 | """A simple login dialog with a user and password""" | |
| 144 | def __init__(self, parent): | |
| 145 | Gtk.Dialog.__init__(self, | |
| 146 | flags=Gtk.DialogFlags.MODAL, | |
| 147 | buttons=("OK", Gtk.ResponseType.OK, | |
| 148 | "Cancel", Gtk.ResponseType.CANCEL)) | |
| 149 | ||
| 150 | self.set_default_response(Gtk.ResponseType.OK) | |
| 151 | ||
| 152 | self.set_keep_above(True) | |
| 153 | ||
| 154 | self.set_transient_for(parent) | |
| 155 | content_area = self.get_content_area() | |
| 156 | ||
| 157 | instructions = Gtk.Label.new("Credentials needed to proceed." | |
| 158 | "You've got 3 tries.") | |
| 159 | instructions.set_line_wrap(True) | |
| 160 | instructions.set_max_width_chars(38) | |
| 161 | content_area.pack_start(instructions, True, True, 10) | |
| 162 | ||
| 163 | userBox = Gtk.Box() | |
| 164 | user_label = Gtk.Label() | |
| 165 | user_label.set_text("User:") | |
| 166 | self.user_entry = Gtk.Entry() | |
| 167 | self.user_entry.set_width_chars(24) | |
| 168 | self.user_entry.set_activates_default(True) | |
| 169 | userBox.pack_start(user_label, True, True, 3) | |
| 170 | userBox.pack_start(self.user_entry, False, False, 5) | |
| 171 | content_area.pack_start(userBox, True, True, 10) | |
| 172 | ||
| 173 | passwordBox = Gtk.Box() | |
| 174 | password_label = Gtk.Label() | |
| 175 | password_label.set_text("Password:") | |
| 176 | self.password_entry = Gtk.Entry() | |
| 177 | self.password_entry.set_visibility(False) | |
| 178 | self.password_entry.set_width_chars(24) | |
| 179 | self.password_entry.set_activates_default(True) | |
| 180 | passwordBox.pack_start(password_label, True, True, 3) | |
| 181 | passwordBox.pack_start(self.password_entry, False, False, 5) | |
| 182 | content_area.pack_start(passwordBox, True, True, 10) | |
| 183 | ||
| 184 | self.show_all() | |
| 185 | ||
| 186 | def getUser(self): | |
| 187 | if self.user_entry.get_text() is not None: | |
| 188 | res = self.user_entry.get_text() | |
| 189 | else: | |
| 190 | res = "" | |
| 191 | return res | |
| 192 | ||
| 193 | def getPassword(self): | |
| 194 | if self.password_entry.get_text() is not None: | |
| 195 | res = self.password_entry.get_text() | |
| 196 | else: | |
| 197 | res = "" | |
| 198 | return res | |
| 199 | ||
| 200 | def run(self, attempts, url, parent): | |
| 201 | for attempt in range(attempts): | |
| 202 | run = Gtk.Dialog.run(self) | |
| 203 | ||
| 204 | if run == Gtk.ResponseType.OK: | |
| 205 | newUser = self.getUser() | |
| 206 | newPass = self.getPassword() | |
| 207 | session_cookie = login_user(url, newUser, newPass) | |
| 208 | if not session_cookie: | |
| 209 | if attempt != attempts-1: | |
| 210 | errorDialog(self, ("Invalid credentials!. You " | |
| 211 | "have " + | |
| 212 | str(attempts-1-attempt) + | |
| 213 | " attempt(s) left.")) | |
| 214 | else: | |
| 215 | ||
| 216 | CONF.setDBUser(newUser) | |
| 217 | CONF.setDBSessionCookies(session_cookie) | |
| 218 | ||
| 219 | user_info = get_user_info() | |
| 220 | ||
| 221 | self.destroy() | |
| 222 | ||
| 223 | return True | |
| 224 | ||
| 225 | if run in [Gtk.ResponseType.CANCEL, -4]: | |
| 226 | # run returns -4 when escape key pressed | |
| 227 | self.exit() | |
| 228 | return False | |
| 229 | else: | |
| 230 | errorDialog(self, ("Invalid credentials after " + | |
| 231 | str(attempts) + " tries. " + | |
| 232 | "Check your credentials and try again.")) | |
| 233 | self.exit() | |
| 234 | return False | |
| 235 | ||
| 236 | def exit(self): | |
| 237 | self.destroy() | |
| 238 | ||
| 239 | ||
| 240 | class ForceLoginDialog(LoginDialog): | |
| 241 | """A simple login dialog with a user and password""" | |
| 242 | def __init__(self, parent, exit_faraday_callback): | |
| 243 | LoginDialog.__init__(self, parent) | |
| 244 | ||
| 245 | self.set_deletable(False) | |
| 246 | ||
| 247 | self.exit_faraday = exit_faraday_callback | |
| 248 | ||
| 249 | def exit(self, button=None): | |
| 250 | """Override destroy to make it exit Faraday.""" | |
| 251 | self.exit_faraday() | |
| 252 | ||
| 253 | ||
| 254 | class NewWorkspaceDialog(Gtk.Window): | |
| 255 | """Sets up the New Workspace Dialog, where the user can set a name, | |
| 256 | a description and a type for a new workspace. Also checks that the | |
| 257 | those attributes don't correspond to an existing workspace""" | |
| 258 | ||
| 259 | def __init__(self, create_ws_callback, workspace_manager, sidebar, parent, | |
| 260 | title=None): | |
| 261 | ||
| 262 | Gtk.Window.__init__(self, title="Create New Workspace") | |
| 263 | self.set_type_hint(Gdk.WindowTypeHint.DIALOG) | |
| 264 | self.set_transient_for(parent) | |
| 265 | self.set_modal(True) | |
| 266 | self.connect("key_press_event", key_reactions) | |
| 267 | self.set_size_request(200, 200) | |
| 268 | self.create_ws_callback = create_ws_callback | |
| 269 | self.sidebar = sidebar | |
| 270 | self.workspace_manager = workspace_manager | |
| 271 | self.title = title | |
| 272 | ||
| 273 | self.main_box = Gtk.Box(orientation=Gtk.Orientation.VERTICAL, spacing=6) | |
| 274 | ||
| 275 | name_box = self.create_name_box() | |
| 276 | description_box = self.create_description_box() | |
| 277 | button_box = self.create_button_box() | |
| 278 | ||
| 279 | self.main_box.pack_start(name_box, False, False, 10) | |
| 280 | self.main_box.pack_start(description_box, False, False, 10) | |
| 281 | self.main_box.pack_end(button_box, False, False, 10) | |
| 282 | ||
| 283 | self.add(self.main_box) | |
| 284 | ||
| 285 | def create_name_box(self): | |
| 286 | """Return a box with a Name label left of an entry.""" | |
| 287 | name_box = Gtk.Box(spacing=6) | |
| 288 | name_label = Gtk.Label() | |
| 289 | name_label.set_text("Name: ") | |
| 290 | self.name_entry = Gtk.Entry() | |
| 291 | if self.title is not None: | |
| 292 | self.name_entry.set_text(self.title) | |
| 293 | name_box.pack_start(name_label, False, False, 10) | |
| 294 | name_box.pack_end(self.name_entry, True, True, 10) | |
| 295 | return name_box | |
| 296 | ||
| 297 | def create_description_box(self): | |
| 298 | """Return a box with a Description label left of an entry.""" | |
| 299 | description_box = Gtk.Box(spacing=6) | |
| 300 | description_label = Gtk.Label() | |
| 301 | description_label.set_text("Description: ") | |
| 302 | self.description_entry = Gtk.Entry() | |
| 303 | description_box.pack_start(description_label, False, False, 10) | |
| 304 | description_box.pack_end(self.description_entry, True, True, 10) | |
| 305 | return description_box | |
| 306 | ||
| 307 | def create_button_box(self): | |
| 308 | """Return a box with OK and cancel buttons.""" | |
| 309 | button_box = Gtk.Box(spacing=6) | |
| 310 | OK_button = Gtk.Button.new_with_label("OK") | |
| 311 | OK_button.connect("clicked", self.on_click_ok) | |
| 312 | cancel_button = Gtk.Button.new_with_label("Cancel") | |
| 313 | cancel_button.connect("clicked", self.on_click_cancel) | |
| 314 | button_box.pack_start(OK_button, False, False, 10) | |
| 315 | button_box.pack_end(cancel_button, False, False, 10) | |
| 316 | return button_box | |
| 317 | ||
| 318 | def on_click_ok(self, button=None): | |
| 319 | """Check if the name provided for the WS is valid. If so, | |
| 320 | create it and add it to the sidebar. If not, show error. | |
| 321 | """ | |
| 322 | ws_name = self.name_entry.get_text() | |
| 323 | if self.workspace_manager.isWorkspaceNameValid(ws_name): | |
| 324 | ws_desc = self.description_entry.get_text() | |
| 325 | creation_ok = self.create_ws_callback(ws_name, ws_desc) | |
| 326 | if creation_ok: | |
| 327 | self.sidebar.add_workspace(ws_name) | |
| 328 | self.destroy() | |
| 329 | else: | |
| 330 | errorDialog(self, "Invalid workspace name", | |
| 331 | "A workspace must be named with " | |
| 332 | "all lowercase letters (a-z), digi" | |
| 333 | "ts(0-9) or any of the _$()+-/ " | |
| 334 | "characters. The name has to start" | |
| 335 | " with a lowercase letter") | |
| 336 | ||
| 337 | def on_click_cancel(self, button): | |
| 338 | self.destroy() | |
| 339 | ||
| 340 | ||
| 341 | class ForceNewWorkspaceDialog(NewWorkspaceDialog): | |
| 342 | """A very similar class to new workspace dialog, but this one forces | |
| 343 | the user to do so.""" | |
| 344 | ||
| 345 | def __init__(self, parent, create_ws_callback, workspace_manager, sidebar, | |
| 346 | exit_faraday_callback): | |
| 347 | """Init new workspace dialog, but make it so you can't press the | |
| 348 | cancel button or press scape.""" | |
| 349 | NewWorkspaceDialog.__init__(self, create_ws_callback, workspace_manager, | |
| 350 | sidebar, parent) | |
| 351 | self.set_deletable(False) | |
| 352 | self.set_keep_above(True) | |
| 353 | self.disconnect_by_func(key_reactions) | |
| 354 | self.connect("key_press_event", strict_key_reactions) | |
| 355 | self.connect("delete_event", lambda _, __: True) | |
| 356 | self.exit_faraday = exit_faraday_callback | |
| 357 | explanation_message = self.create_explanation_message() | |
| 358 | self.main_box.pack_start(explanation_message, True, True, 6) | |
| 359 | self.main_box.reorder_child(explanation_message, 0) | |
| 360 | ||
| 361 | def on_click_cancel(self, button): | |
| 362 | """Override parent's class cancel callback so it exits faraday.""" | |
| 363 | self.exit_faraday(parent=self) | |
| 364 | ||
| 365 | def create_explanation_message(self): | |
| 366 | """Returns a simple explanatory message inside a Label""" | |
| 367 | message = Gtk.Label() | |
| 368 | message.set_text("There are no workspaces available. You must " | |
| 369 | "create one to continue using Faraday.") | |
| 370 | return message | |
| 371 | ||
| 372 | ||
| 373 | class PluginOptionsDialog(Gtk.Window): | |
| 374 | """The dialog where the user can see details about installed plugins. | |
| 375 | It is not the prettiest thing in the world but it works. | |
| 376 | Creating and displaying the models of each plugin settings is specially | |
| 377 | messy , there's more info in the appropiate methods""" | |
| 378 | ||
| 379 | def __init__(self, plugin_manager, parent): | |
| 380 | ||
| 381 | Gtk.Window.__init__(self, title="Plugins Options") | |
| 382 | self.set_type_hint(Gdk.WindowTypeHint.DIALOG) | |
| 383 | self.set_transient_for(parent) | |
| 384 | self.set_modal(True) | |
| 385 | self.set_size_request(800, 300) | |
| 386 | self.plugin_manager = plugin_manager | |
| 387 | ||
| 388 | if plugin_manager is not None: | |
| 389 | self.plugin_settings = plugin_manager.getSettings() | |
| 390 | else: | |
| 391 | self.plugin_settings = {} | |
| 392 | ||
| 393 | plugin_info = self.createPluginInfo(plugin_manager) | |
| 394 | self.id_of_selected = plugin_info[0][1] # default selected is first item in list | |
| 395 | plugin_list = self.createPluginListView(plugin_info) | |
| 396 | left_side_box = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 397 | left_side_box.pack_start(plugin_list, True, True, 0) | |
| 398 | ||
| 399 | self.settings_view = None | |
| 400 | self.models = self.createPluginsSettingsModel() | |
| 401 | self.setSettingsView() | |
| 402 | ||
| 403 | buttonBox = Gtk.Box() | |
| 404 | OK_button = Gtk.Button.new_with_label("OK") | |
| 405 | cancel_button = Gtk.Button.new_with_label("Cancel") | |
| 406 | OK_button.connect("clicked", self.on_click_ok) | |
| 407 | cancel_button.connect("clicked", self.on_click_cancel) | |
| 408 | buttonBox.pack_start(OK_button, True, True, 10) | |
| 409 | buttonBox.pack_start(cancel_button, True, True, 10) | |
| 410 | ||
| 411 | left_side_box.pack_start(buttonBox, False, False, 10) | |
| 412 | ||
| 413 | infoBox = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 414 | nameBox, versionBox, pluginVersionBox = [Gtk.Box() for i in range(3)] | |
| 415 | ||
| 416 | nameLabel, versionLabel, pluginVersionLabel = [Gtk.Label() | |
| 417 | for i in range(3)] | |
| 418 | ||
| 419 | self.nameEntry, self.versionEntry, self.pluginVersionEntry = [ | |
| 420 | Gtk.Label() for i in range(3)] | |
| 421 | ||
| 422 | nameLabel.set_text("Name: ") | |
| 423 | versionLabel.set_text("Version: ") | |
| 424 | pluginVersionLabel.set_text("Plugin version: ") | |
| 425 | ||
| 426 | nameBox.pack_start(nameLabel, False, False, 5) | |
| 427 | nameBox.pack_start(self.nameEntry, False, True, 5) | |
| 428 | versionBox.pack_start(versionLabel, False, False, 5) | |
| 429 | versionBox.pack_start(self.versionEntry, False, True, 5) | |
| 430 | pluginVersionBox.pack_start(pluginVersionLabel, False, False, 5) | |
| 431 | pluginVersionBox.pack_start(self.pluginVersionEntry, False, True, 5) | |
| 432 | ||
| 433 | infoBox.pack_start(nameBox, False, False, 5) | |
| 434 | infoBox.pack_start(versionBox, False, False, 5) | |
| 435 | infoBox.pack_start(pluginVersionBox, False, False, 5) | |
| 436 | ||
| 437 | self.pluginSpecsBox = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 438 | self.pluginSpecsBox.pack_start(infoBox, False, False, 5) | |
| 439 | self.pluginSpecsBox.pack_start(self.settings_view, True, True, 0) | |
| 440 | ||
| 441 | self.mainBox = Gtk.Box(orientation=Gtk.Orientation.HORIZONTAL) | |
| 442 | self.mainBox.pack_start(left_side_box, False, True, 10) | |
| 443 | self.mainBox.pack_end(self.pluginSpecsBox, True, True, 10) | |
| 444 | ||
| 445 | self.add(self.mainBox) | |
| 446 | ||
| 447 | def on_click_ok(self, button=None): | |
| 448 | """On click OK button update the plugins settings and then destroy""" | |
| 449 | if self.plugin_manager is not None: | |
| 450 | self.plugin_manager.updateSettings(self.plugin_settings) | |
| 451 | self.destroy() | |
| 452 | ||
| 453 | def on_click_cancel(self, button): | |
| 454 | """On click cancel button, destroy brutally. No mercy""" | |
| 455 | self.destroy() | |
| 456 | ||
| 457 | def createPluginInfo(self, plugin_manager): | |
| 458 | """Creates and return a TreeStore where the basic information about | |
| 459 | the plugins: the plugin ID, name, intended version of the tool | |
| 460 | and plugin version""" | |
| 461 | plugin_info = Gtk.TreeStore(str, str, str, str) | |
| 462 | ||
| 463 | for plugin_id, params in self.plugin_settings.items(): | |
| 464 | plugin_info.append(None, [plugin_id, | |
| 465 | params["name"], | |
| 466 | params["version"], # tool version | |
| 467 | params["plugin_version"]]) | |
| 468 | ||
| 469 | # Sort it! | |
| 470 | sorted_plugin_info = Gtk.TreeModelSort(model=plugin_info) | |
| 471 | sorted_plugin_info.set_sort_column_id(1, Gtk.SortType.ASCENDING) | |
| 472 | return sorted_plugin_info | |
| 473 | ||
| 474 | @scrollable(width=300) | |
| 475 | def createPluginListView(self, plugin_info): | |
| 476 | """Creates the view for the left-hand side list of the dialog. | |
| 477 | It uses an instance of the plugin manager to get a list | |
| 478 | of all available plugins""" | |
| 479 | ||
| 480 | plugin_list_view = Gtk.TreeView(plugin_info) | |
| 481 | renderer = Gtk.CellRendererText() | |
| 482 | column = Gtk.TreeViewColumn("Title", renderer, text=1) | |
| 483 | column.set_sort_column_id(1) | |
| 484 | plugin_list_view.append_column(column) | |
| 485 | ||
| 486 | selection = plugin_list_view.get_selection() | |
| 487 | selection.connect("changed", self.on_plugin_selection) | |
| 488 | ||
| 489 | return plugin_list_view | |
| 490 | ||
| 491 | def createPluginsSettingsModel(self): | |
| 492 | """Creates a dictionary with | |
| 493 | {plugin-name : [(setting-name, setting-value)]} structure. This is used | |
| 494 | to hold all the plugins settings models""" | |
| 495 | ||
| 496 | models = {} | |
| 497 | ||
| 498 | for plugin_id in self.plugin_settings.items(): | |
| 499 | # iter through the plugins | |
| 500 | plugin_info = plugin_id[1] # get dictionary associated to plugin | |
| 501 | store = Gtk.ListStore(str, str) # create the store for that plugin | |
| 502 | ||
| 503 | # iter through settings dictionary | |
| 504 | for setting in plugin_info["settings"].items(): | |
| 505 | setting_name = setting[0] | |
| 506 | setting_value = setting[1] | |
| 507 | store.append([setting_name, setting_value]) | |
| 508 | ||
| 509 | models[plugin_id[1]["name"]] = store # populate dict with store | |
| 510 | return models | |
| 511 | ||
| 512 | def createAdecuatePluginSettingView(self, store): | |
| 513 | """Create the adecuate plugin settings view. The first time this is | |
| 514 | executed, it will be none and it will tell the view which columns | |
| 515 | to display. After that, it will just change the model displayed""" | |
| 516 | self.active_store = store | |
| 517 | ||
| 518 | if self.settings_view is None: | |
| 519 | self.settings_view = Gtk.TreeView(store) | |
| 520 | renderer_text = Gtk.CellRendererText() | |
| 521 | column_text = Gtk.TreeViewColumn("Settings", renderer_text, text=0) | |
| 522 | self.settings_view.append_column(column_text) | |
| 523 | ||
| 524 | renderer_editable_text = Gtk.CellRendererText() | |
| 525 | renderer_editable_text.set_property("editable", True) | |
| 526 | renderer_editable_text.connect("edited", self.value_changed) | |
| 527 | column_editabletext = Gtk.TreeViewColumn("Value", | |
| 528 | renderer_editable_text, | |
| 529 | text=1) | |
| 530 | ||
| 531 | self.settings_view.append_column(column_editabletext) | |
| 532 | ||
| 533 | else: | |
| 534 | self.settings_view.set_model(store) | |
| 535 | ||
| 536 | def value_changed(self, widget, path, text): | |
| 537 | """Save new settings""" | |
| 538 | self.active_store[path][1] = text | |
| 539 | setting = self.active_store[path][0] | |
| 540 | settings = self.plugin_settings[self.name_of_selected]["settings"] | |
| 541 | settings[setting.strip()] = text.strip() | |
| 542 | ||
| 543 | def on_plugin_selection(self, selection): | |
| 544 | """When the user selects a plugin, it will change the text | |
| 545 | displeyed on the entries to their corresponding values""" | |
| 546 | ||
| 547 | # if the user searches for something that doesn't exists, | |
| 548 | # for example, the plugin 'jsaljfdlajs', this avoids | |
| 549 | # the program trying to get settings for that non-existing plugin | |
| 550 | try: | |
| 551 | model, treeiter = selection.get_selected() | |
| 552 | self.name_of_selected = model[treeiter][0] | |
| 553 | self.id_of_selected = model[treeiter][1] | |
| 554 | tool_version = model[treeiter][2] | |
| 555 | plugin_version = model[treeiter][3] | |
| 556 | ||
| 557 | self.setSettingsView() | |
| 558 | ||
| 559 | self.nameEntry.set_label(self.name_of_selected) | |
| 560 | ||
| 561 | if tool_version: | |
| 562 | self.versionEntry.set_label(tool_version) | |
| 563 | else: | |
| 564 | self.versionEntry.set_label("") | |
| 565 | ||
| 566 | if plugin_version: | |
| 567 | self.pluginVersionEntry.set_label(plugin_version) | |
| 568 | else: | |
| 569 | self.pluginVersionEntry.set_label("") | |
| 570 | except TypeError: | |
| 571 | pass | |
| 572 | ||
| 573 | def setSettingsView(self): | |
| 574 | """Makes the window match the selected plugin with the settings | |
| 575 | displayed""" | |
| 576 | ||
| 577 | adecuateModel = self.models[self.id_of_selected] | |
| 578 | self.createAdecuatePluginSettingView(adecuateModel) | |
| 579 | ||
| 580 | ||
| 581 | class FaradayPluginsDialog(Gtk.Window): | |
| 582 | """The dialog where the user can see details about installed plugins. | |
| 583 | It is not the prettiest thing in the world but it works. | |
| 584 | Creating and displaying the models of each plugin settings is specially | |
| 585 | messy , there's more info in the appropiate methods""" | |
| 586 | ||
| 587 | def __init__(self, terminal, workspace_name, parent): | |
| 588 | ||
| 589 | Gtk.Window.__init__(self, title="Faraday Plugin") | |
| 590 | self.set_type_hint(Gdk.WindowTypeHint.DIALOG) | |
| 591 | self.set_transient_for(parent) | |
| 592 | self.set_modal(True) | |
| 593 | self.set_size_request(800, 300) | |
| 594 | self._terminal = terminal | |
| 595 | self._workspace_name = workspace_name | |
| 596 | ||
| 597 | plugin_info = self.createPluginInfo() | |
| 598 | ||
| 599 | # self.id_of_selected = plugin_info[0][0] # default selected is first item in list | |
| 600 | plugin_list = self.createPluginListView(plugin_info) | |
| 601 | left_side_box = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 602 | left_side_box.pack_start(plugin_list, True, True, 0) | |
| 603 | ||
| 604 | buttonBox = Gtk.Box() | |
| 605 | append_button = Gtk.Button.new_with_label("Append") | |
| 606 | cancel_button = Gtk.Button.new_with_label("Cancel") | |
| 607 | append_button.connect("clicked", self.on_click_append) | |
| 608 | cancel_button.connect("clicked", self.on_click_cancel) | |
| 609 | buttonBox.pack_start(append_button, True, True, 10) | |
| 610 | buttonBox.pack_start(cancel_button, True, True, 10) | |
| 611 | ||
| 612 | left_side_box.pack_start(buttonBox, False, False, 10) | |
| 613 | ||
| 614 | infoBox = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 615 | descriptionBox = Gtk.Box() | |
| 616 | ||
| 617 | descriptionLabel = Gtk.Label() | |
| 618 | ||
| 619 | self.descriptionEntry = Gtk.Label() | |
| 620 | ||
| 621 | descriptionLabel.set_text("Description: ") | |
| 622 | ||
| 623 | descriptionBox.pack_start(descriptionLabel, False, False, 5) | |
| 624 | descriptionBox.pack_start(self.descriptionEntry, False, True, 5) | |
| 625 | ||
| 626 | infoBox.pack_start(descriptionBox, False, False, 5) | |
| 627 | ||
| 628 | self.pluginSpecsBox = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 629 | self.pluginSpecsBox.pack_start(infoBox, False, False, 5) | |
| 630 | ||
| 631 | self.mainBox = Gtk.Box(orientation=Gtk.Orientation.HORIZONTAL) | |
| 632 | self.mainBox.pack_start(left_side_box, False, True, 10) | |
| 633 | self.mainBox.pack_end(self.pluginSpecsBox, True, True, 10) | |
| 634 | ||
| 635 | self.add(self.mainBox) | |
| 636 | ||
| 637 | def on_click_append(self, button=None): | |
| 638 | """On click OK button update the plugins settings and then destroy""" | |
| 639 | ||
| 640 | self.type_faraday_plugin_command(self.name_of_selected) | |
| 641 | ||
| 642 | self.destroy() | |
| 643 | ||
| 644 | def on_click_cancel(self, button): | |
| 645 | """On click cancel button, destroy brutally. No mercy""" | |
| 646 | self.destroy() | |
| 647 | ||
| 648 | def createPluginInfo(self): | |
| 649 | """Creates and return a TreeStore where the basic information about | |
| 650 | the plugins: the plugin ID, name, intended version of the tool | |
| 651 | and plugin version""" | |
| 652 | plugin_info = Gtk.TreeStore(str, str, str) | |
| 653 | ||
| 654 | for key, plugin_dic in fplugin_utils.get_available_plugins().items(): | |
| 655 | plugin_info.append(None, [key, | |
| 656 | plugin_dic["description"], | |
| 657 | plugin_dic["prettyname"] | |
| 658 | ] | |
| 659 | ) | |
| 660 | ||
| 661 | # Sort it! | |
| 662 | sorted_plugin_info = Gtk.TreeModelSort(model=plugin_info) | |
| 663 | sorted_plugin_info.set_sort_column_id(2, Gtk.SortType.ASCENDING) | |
| 664 | return sorted_plugin_info | |
| 665 | ||
| 666 | @scrollable(width=300) | |
| 667 | def createPluginListView(self, plugin_info): | |
| 668 | """Creates the view for the left-hand side list of the dialog. | |
| 669 | It uses an instance of the plugin manager to get a list | |
| 670 | of all available plugins""" | |
| 671 | ||
| 672 | plugin_list_view = Gtk.TreeView(plugin_info) | |
| 673 | renderer = Gtk.CellRendererText() | |
| 674 | column = Gtk.TreeViewColumn("Title", renderer, text=2) | |
| 675 | column.set_sort_column_id(1) | |
| 676 | plugin_list_view.append_column(column) | |
| 677 | ||
| 678 | selection = plugin_list_view.get_selection() | |
| 679 | selection.connect("changed", self.on_plugin_selection) | |
| 680 | ||
| 681 | return plugin_list_view | |
| 682 | ||
| 683 | def on_plugin_selection(self, selection): | |
| 684 | """When the user selects a plugin, it will change the text | |
| 685 | displeyed on the entries to their corresponding values""" | |
| 686 | ||
| 687 | # if the user searches for something that doesn't exists, | |
| 688 | # for example, the plugin 'jsaljfdlajs', this avoids | |
| 689 | # the program trying to get settings for that non-existing plugin | |
| 690 | try: | |
| 691 | model, treeiter = selection.get_selected() | |
| 692 | self.name_of_selected = model[treeiter][0] | |
| 693 | # self.id_of_selected = model[treeiter][1] | |
| 694 | description = model[treeiter][1] | |
| 695 | ||
| 696 | self.descriptionEntry.set_label(description) | |
| 697 | ||
| 698 | except TypeError: | |
| 699 | pass | |
| 700 | ||
| 701 | def type_faraday_plugin_command(self, plugin): | |
| 702 | ||
| 703 | command = fplugin_utils.build_faraday_plugin_command(plugin, self._workspace_name) | |
| 704 | fd = self._terminal.get_pty().get_fd() | |
| 705 | ||
| 706 | os.write(fd, command) | |
| 707 | ||
| 708 | ||
| 709 | class HostInfoDialog(Gtk.Window): | |
| 710 | """Sets the blueprints for a simple host info window. It will display | |
| 711 | basic information in labels as well as services in a treeview. | |
| 712 | ||
| 713 | While working in this class, keep in mind the distinction between | |
| 714 | selections (which are part of a model that holds data about an object as | |
| 715 | strings and ints) and the object per se, which are in the model folder and | |
| 716 | are totally alien to GTK. | |
| 717 | """ | |
| 718 | def __init__(self, parent, active_ws_name, host): | |
| 719 | """Creates a window with the information about a given hosts. | |
| 720 | The parent is needed so the window can set transient for | |
| 721 | """ | |
| 722 | window_title = "Host " + host.name + " information" | |
| 723 | Gtk.Window.__init__(self, title=window_title) | |
| 724 | ||
| 725 | self.set_transient_for(parent) | |
| 726 | self.set_size_request(1200, 500) | |
| 727 | self.set_modal(True) | |
| 728 | self.connect("key_press_event", key_reactions) | |
| 729 | ||
| 730 | self.host = host | |
| 731 | self.model = self.create_model(self.host) | |
| 732 | host_info = self.model[0] | |
| 733 | ||
| 734 | host_id = self.model[0][0] | |
| 735 | couch_url = CONF.getServerURI() | |
| 736 | base_url = couch_url + "/_ui/#/host/ws/" | |
| 737 | self.edit_url = base_url + active_ws_name + "/hid/" + host_id | |
| 738 | ||
| 739 | host_info_frame = self.create_host_info_frame(host_info) | |
| 740 | ||
| 741 | self.specific_info = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 742 | self.specific_info_frame = self.create_scroll_frame( | |
| 743 | self.specific_info, | |
| 744 | "Service Information") | |
| 745 | ||
| 746 | self.vuln_info = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 747 | self.vuln_info_frame = self.create_scroll_frame( | |
| 748 | self.vuln_info, | |
| 749 | "Vulnerability Information") | |
| 750 | ||
| 751 | main_tree = self.create_main_tree_view(self.model) | |
| 752 | vuln_list = self.create_vuln_list() | |
| 753 | ||
| 754 | button_box = self.create_button_box() | |
| 755 | ||
| 756 | main_box = Gtk.Box() | |
| 757 | ||
| 758 | info_box = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 759 | info_box.pack_start(host_info_frame, True, True, 10) | |
| 760 | info_box.pack_start(self.specific_info_frame, True, True, 10) | |
| 761 | info_box.pack_start(self.vuln_info_frame, True, True, 10) | |
| 762 | info_box.pack_start(button_box, False, False, 10) | |
| 763 | ||
| 764 | main_tree_box = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 765 | main_tree_box.pack_start(main_tree, True, True, 10) | |
| 766 | main_tree_box.pack_start(Gtk.Box(), False, False, 10) | |
| 767 | ||
| 768 | vuln_list_box = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 769 | vuln_list_box.pack_start(vuln_list, True, True, 10) | |
| 770 | vuln_list_box.pack_start(Gtk.Box(), False, False, 10) | |
| 771 | ||
| 772 | main_box.pack_start(main_tree_box, False, False, 5) | |
| 773 | main_box.pack_start(vuln_list_box, False, False, 0) | |
| 774 | main_box.pack_start(info_box, True, True, 5) | |
| 775 | ||
| 776 | self.add(main_box) | |
| 777 | ||
| 778 | def create_button_box(self): | |
| 779 | """Creates an horizontal box to hold the buttons.""" | |
| 780 | button_box = Gtk.Box() | |
| 781 | ||
| 782 | ok_button = Gtk.Button.new_with_label("OK") | |
| 783 | ok_button.connect("clicked", self.on_click_ok) | |
| 784 | ||
| 785 | html_edit_url = '<a href="' + self.edit_url + '"> Edit host </a>' | |
| 786 | edit_button = Gtk.Button() | |
| 787 | edit_label = Gtk.Label() | |
| 788 | edit_label.set_markup(html_edit_url) | |
| 789 | edit_button.add(edit_label) | |
| 790 | edit_button.connect("clicked", self.on_edit_host) | |
| 791 | ||
| 792 | button_box.pack_start(edit_button, True, True, 0) | |
| 793 | button_box.pack_start(ok_button, True, True, 0) | |
| 794 | return button_box | |
| 795 | ||
| 796 | def on_edit_host(self, button): | |
| 797 | """Tries to open self.edit_url (url which directs to the host in the | |
| 798 | web ui) in the default browser.""" | |
| 799 | webbrowser.open(self.edit_url, new=2) | |
| 800 | ||
| 801 | def create_scroll_frame(self, inner_box, label_str): | |
| 802 | """Create a scrollable frame containing inner_box and with label_str | |
| 803 | as its title. | |
| 804 | """ | |
| 805 | ||
| 806 | label = Gtk.Label() | |
| 807 | label.set_markup("<big>" + label_str + "</big>") | |
| 808 | ||
| 809 | scroll_box = GtkScrolledWindow(None, None) | |
| 810 | scroll_box.set_overlay_scrolling(False) | |
| 811 | scroll_box.set_policy(Gtk.PolicyType.AUTOMATIC, | |
| 812 | Gtk.PolicyType.ALWAYS) | |
| 813 | ||
| 814 | scroll_box.add(inner_box) | |
| 815 | ||
| 816 | frame = Gtk.Frame() | |
| 817 | frame.set_label_widget(label) | |
| 818 | frame.add(scroll_box) | |
| 819 | ||
| 820 | return frame | |
| 821 | ||
| 822 | def create_host_info_frame(self, host_info): | |
| 823 | """Return a box where the basic information about the host | |
| 824 | lives in labels. It include names, OS, Owned status and vulnerability | |
| 825 | count. | |
| 826 | """ | |
| 827 | box = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 828 | ||
| 829 | prop_names = self.get_properties_names("Host") | |
| 830 | self.show_info_in_box(host_info, prop_names, box) | |
| 831 | ||
| 832 | host_info_frame = self.create_scroll_frame(box, "Host Information") | |
| 833 | ||
| 834 | return host_info_frame | |
| 835 | ||
| 836 | @scrollable(width=250) | |
| 837 | def create_vuln_list(self): | |
| 838 | """Creates a simple view of vulnerabilities for the object | |
| 839 | and returns a box containing it. The vuln_list will be a value of the | |
| 840 | instance. | |
| 841 | """ | |
| 842 | ||
| 843 | self.vuln_list = Gtk.TreeView() | |
| 844 | self.vuln_list.set_activate_on_single_click(True) | |
| 845 | renderer = Gtk.CellRendererText() | |
| 846 | column = Gtk.TreeViewColumn("Vulnerabilities", renderer, text=1) | |
| 847 | column.set_sort_column_id(1) | |
| 848 | self.vuln_list.append_column(column) | |
| 849 | self.vuln_list.set_search_column(1) | |
| 850 | ||
| 851 | vuln_selection = self.vuln_list.get_selection() | |
| 852 | vuln_selection.connect("changed", self.on_vuln_selection) | |
| 853 | ||
| 854 | return self.vuln_list | |
| 855 | ||
| 856 | def create_model(self, host): | |
| 857 | """Return a model for the given host. It holds quite a bit of info. | |
| 858 | It has 15 columns holding the host ID and name as parent, | |
| 859 | all the information about the services. | |
| 860 | ||
| 861 | The model is difficult to draw because of its nested nature, but | |
| 862 | you can think of it like this, keeping in mind each node has | |
| 863 | several columns | |
| 864 | ||
| 865 | HOST | |
| 866 | ------------> SERVICE1 | |
| 867 | ------------> SERVICE2 | |
| 868 | ||
| 869 | And so on and so on, like Zizek says. | |
| 870 | """ | |
| 871 | ||
| 872 | # those are 13 strings | |
| 873 | model = Gtk.TreeStore(str, str, str, str, str, str, str, | |
| 874 | str, str, str, str, str, str) | |
| 875 | ||
| 876 | # GTK is very strict about how many columns the model has. | |
| 877 | # only the ID and the name are needed, but i still need to 'fill' | |
| 878 | # the other columns with dummy info | |
| 879 | ||
| 880 | display_str = host.getName() + " (" + str(host.getVulnsAmount()) + ")" | |
| 881 | owned_status = ("Yes" if host.isOwned() else "No") | |
| 882 | host_position = model.append(None, [str(host.getID()), host.getName(), | |
| 883 | host.getOS(), owned_status, | |
| 884 | str(host.getVulnsAmount()), "", | |
| 885 | "", "", "", "", "", "", | |
| 886 | display_str]) | |
| 887 | ||
| 888 | # some convenient functions just to separate and clarify what | |
| 889 | # the code does. they are used in the nested for loop directly | |
| 890 | # below them. | |
| 891 | ||
| 892 | def lst_to_str(lst): | |
| 893 | """Convenient function to avoid this long line everywhere""" | |
| 894 | return ', '.join([str(word) for word in lst if word]) | |
| 895 | ||
| 896 | def add_service_to_host_in_model(service, model): | |
| 897 | """Append a service to an host in the given | |
| 898 | model. Return None. Modifies the model""" | |
| 899 | display_str = service.getName() + " (" + str(service.getVulnsAmount()) + ")" | |
| 900 | model.append(host_position, [str(service.getID()), | |
| 901 | service.getName(), | |
| 902 | service.getDescription(), | |
| 903 | service.getProtocol(), | |
| 904 | service.getStatus(), | |
| 905 | lst_to_str(service.getPorts()), | |
| 906 | service.getVersion(), | |
| 907 | "Yes" if service.isOwned() else "No", | |
| 908 | "", "", "", "", display_str]) | |
| 909 | ||
| 910 | services = host.getServices() | |
| 911 | for service in services: | |
| 912 | add_service_to_host_in_model(service, model) | |
| 913 | ||
| 914 | return model | |
| 915 | ||
| 916 | @scrollable(width=250) | |
| 917 | def create_main_tree_view(self, model): | |
| 918 | """Return a box containing the main tree (the one showing | |
| 919 | Host/Services) as its content. | |
| 920 | """ | |
| 921 | view = Gtk.TreeView(model) | |
| 922 | view.set_activate_on_single_click(True) | |
| 923 | view.set_search_column(-1) | |
| 924 | view.set_enable_tree_lines(True) | |
| 925 | view.expand_all() | |
| 926 | ||
| 927 | renderer = Gtk.CellRendererText() | |
| 928 | column = Gtk.TreeViewColumn("Host/Services", | |
| 929 | renderer, text=12) | |
| 930 | ||
| 931 | view.append_column(column) | |
| 932 | view.set_expander_column(column) | |
| 933 | selection = view.get_selection() | |
| 934 | selection.connect("changed", self.on_main_tree_selection) | |
| 935 | ||
| 936 | return view | |
| 937 | ||
| 938 | def on_main_tree_selection(self, tree_selection): | |
| 939 | """Fire up neccesary actions when selection on the main tree changes""" | |
| 940 | model, tree_iter = tree_selection.get_selected() | |
| 941 | ||
| 942 | if tree_iter is None: | |
| 943 | # NOTE: GTK returns "None" on the tree_iter when | |
| 944 | # selection is changed with interactive search and everything | |
| 945 | # explodes. Just return False if that's the case. | |
| 946 | return False | |
| 947 | ||
| 948 | object_info = model[tree_iter] | |
| 949 | ||
| 950 | iter_depth = model.iter_depth(tree_iter) | |
| 951 | object_type = {0: 'Host', 1: 'Service'}[iter_depth] | |
| 952 | ||
| 953 | if object_type == 'Host': | |
| 954 | self.set_vuln_model(self.create_vuln_model(self.host)) | |
| 955 | self.clear(self.specific_info) | |
| 956 | self.clear(self.vuln_info) | |
| 957 | ||
| 958 | elif object_type == 'Service': | |
| 959 | self.clear(self.specific_info) | |
| 960 | self.clear(self.vuln_info) | |
| 961 | self.change_label_in_frame(self.specific_info_frame, object_type) | |
| 962 | prop_names = self.get_properties_names(object_type) | |
| 963 | self.show_info_in_box(object_info, prop_names, self.specific_info) | |
| 964 | actual_object = self.get_object(object_info, object_type) | |
| 965 | if not actual_object: | |
| 966 | return None | |
| 967 | vuln_model = self.create_vuln_model(actual_object) | |
| 968 | self.set_vuln_model(vuln_model) | |
| 969 | ||
| 970 | def on_vuln_selection(self, vuln_selection): | |
| 971 | """Fill the vuln_info box with the vulnerability selected. | |
| 972 | ||
| 973 | The try/except block is necesary 'cause GTK | |
| 974 | is silly (ie: doesn't behave like it would be best for me now) | |
| 975 | and will emit the selection changed signal if the model | |
| 976 | changes even if nothing is selected. | |
| 977 | """ | |
| 978 | model, vuln_iter = vuln_selection.get_selected() | |
| 979 | if vuln_iter is None: | |
| 980 | # NOTE: for some reason, GTK returns "None" on the tree_iter when | |
| 981 | # selection is changed with interactive search and everything | |
| 982 | # explodes. Just return False if that's the case. | |
| 983 | return False | |
| 984 | ||
| 985 | selected = model[vuln_iter] | |
| 986 | vuln_type = selected[0] | |
| 987 | self.clear(self.vuln_info) | |
| 988 | self.change_label_in_frame(self.vuln_info_frame, | |
| 989 | vuln_type) | |
| 990 | prop_names = self.get_properties_names(vuln_type) | |
| 991 | self.show_info_in_box(selected, prop_names, | |
| 992 | self.vuln_info) | |
| 993 | ||
| 994 | def set_vuln_model(self, model): | |
| 995 | """Sets the vulnerability view to show the given model""" | |
| 996 | self.vuln_list.set_model(model) | |
| 997 | ||
| 998 | def create_vuln_model(self, obj): | |
| 999 | """Return the model for the vulnerabilities of the obj object. | |
| 1000 | It will be sorted alphabetically. | |
| 1001 | """ | |
| 1002 | def params_to_string(params): # XXX | |
| 1003 | """Converts params to a string, in case it gets here as a list. | |
| 1004 | It's pretty anoyting, but needed for backwards compatibility. | |
| 1005 | """ | |
| 1006 | if isinstance(params, basestring): | |
| 1007 | params_string = params | |
| 1008 | elif isinstance(params, list): | |
| 1009 | params_string = " ".join(params) | |
| 1010 | elif params is None: | |
| 1011 | params_string = "" | |
| 1012 | else: # just make sure that if params is anything else just crash | |
| 1013 | raise TypeError | |
| 1014 | return params_string | |
| 1015 | ||
| 1016 | # those are 16 strings | |
| 1017 | model = Gtk.ListStore(str, str, str, str, str, str, str, str, | |
| 1018 | str, str, str, str, str, str, str, str) | |
| 1019 | ||
| 1020 | vulns = obj.getVulns() | |
| 1021 | for vuln in vulns: | |
| 1022 | _type = vuln.class_signature | |
| 1023 | if _type == "Vulnerability": | |
| 1024 | # again filling up the model with dumb strings | |
| 1025 | # because gtk | |
| 1026 | model.append([_type, vuln.getName(), | |
| 1027 | vuln.getDescription(), | |
| 1028 | vuln.getData(), | |
| 1029 | vuln.getSeverity(), | |
| 1030 | ', '.join([str(v) for v in vuln.getRefs() if v]), | |
| 1031 | vuln.getStatus(), | |
| 1032 | "", "", "", "", "", "", "", "", ""]) | |
| 1033 | ||
| 1034 | elif _type == "VulnerabilityWeb": | |
| 1035 | model.append([_type, vuln.getName(), | |
| 1036 | vuln.getDescription(), | |
| 1037 | vuln.getData(), | |
| 1038 | vuln.getSeverity(), | |
| 1039 | ", ".join([str(v) for v in vuln.getRefs() if v]), | |
| 1040 | vuln.getPath(), | |
| 1041 | vuln.getWebsite(), | |
| 1042 | vuln.getRequest(), | |
| 1043 | vuln.getResponse(), | |
| 1044 | vuln.getMethod(), | |
| 1045 | vuln.getPname(), | |
| 1046 | params_to_string(vuln.getParams()), | |
| 1047 | vuln.getQuery(), | |
| 1048 | vuln.getStatus(), | |
| 1049 | ""]) | |
| 1050 | # sort it! | |
| 1051 | sorted_model = Gtk.TreeModelSort(model=model) | |
| 1052 | sorted_model.set_sort_column_id(1, Gtk.SortType.ASCENDING) | |
| 1053 | ||
| 1054 | return sorted_model | |
| 1055 | ||
| 1056 | def change_label_in_frame(self, frame, string): | |
| 1057 | """Changes the label in the given frame to 'string Information'""" | |
| 1058 | label = frame.get_label_widget() | |
| 1059 | label.set_markup("<big>" + string + " " + "Information" + "</big>") | |
| 1060 | ||
| 1061 | def show_info_in_box(self, object_info, property_names, box): | |
| 1062 | """Appends several boxes vertically to the box. The appended boxes will | |
| 1063 | all contain two labels, together forming something like this: | |
| 1064 | '<b>property_name:</b> object_info'. It will also append a separator | |
| 1065 | on top of each one of these boxes. | |
| 1066 | ||
| 1067 | It is important to notice that the first element of object_info | |
| 1068 | is ignored. This is because of how the models in this class contain | |
| 1069 | information. Thus, there'll be as many of this small boxes as | |
| 1070 | len(property_names) minus one. | |
| 1071 | """ | |
| 1072 | ||
| 1073 | for index, prop_name in enumerate(property_names, start=1): | |
| 1074 | if index != 1: | |
| 1075 | # do not append to the first prop_name | |
| 1076 | separator = Gtk.Separator.new(orientation=Gtk.Orientation.HORIZONTAL) | |
| 1077 | box.pack_start(separator, False, True, 0) | |
| 1078 | ||
| 1079 | prop_box = Gtk.Box() | |
| 1080 | prop_value = object_info[index] | |
| 1081 | ||
| 1082 | prop_label = Gtk.Label() | |
| 1083 | prop_label.set_markup("<b> %s </b>" % (prop_name)) | |
| 1084 | prop_label.set_selectable(True) | |
| 1085 | ||
| 1086 | value_label = Gtk.Label(prop_value) | |
| 1087 | value_label.set_selectable(True) | |
| 1088 | prop_box.pack_start(prop_label, False, False, 0) | |
| 1089 | prop_box.pack_start(value_label, False, False, 0) | |
| 1090 | box.pack_start(prop_box, True, True, 0) | |
| 1091 | ||
| 1092 | box.show_all() | |
| 1093 | ||
| 1094 | def get_object(self, selected_object, object_type): | |
| 1095 | """Take a selection as selected_object and an object_type | |
| 1096 | and return the actual object, not the model's selection. | |
| 1097 | """ | |
| 1098 | def safely(func): | |
| 1099 | def safe_wrapper(*args, **kwargs): | |
| 1100 | try: | |
| 1101 | return func(*args, **kwargs) | |
| 1102 | except (IndexError, ValueError): | |
| 1103 | dialog = errorDialog(self, ("There has been a problem. " | |
| 1104 | "The object you clicked on " | |
| 1105 | "does not exist anymore.")) | |
| 1106 | self.destroy() # exit | |
| 1107 | return safe_wrapper | |
| 1108 | ||
| 1109 | object_id = selected_object[0] | |
| 1110 | object_ = None | |
| 1111 | if object_type == 'Service': | |
| 1112 | object_ = safely(self.host.getService)(object_id) | |
| 1113 | ||
| 1114 | return object_ | |
| 1115 | ||
| 1116 | def get_properties_names(self, object_type): | |
| 1117 | """Return a list with the property names for objects of type | |
| 1118 | Service, Vulnerability and VulnerabilityWeb (passed as a | |
| 1119 | string). | |
| 1120 | """ | |
| 1121 | if object_type == "Host": | |
| 1122 | property_names = ["Name: ", "OS: ", "Owned: ", | |
| 1123 | "Vulnerabilities: "] | |
| 1124 | ||
| 1125 | elif object_type == "Service": | |
| 1126 | property_names = ["Name: ", "Description: ", "Protocol: ", | |
| 1127 | "Status: ", "Port: ", "Version: ", "Is Owned?: "] | |
| 1128 | ||
| 1129 | elif object_type == "Vulnerability": | |
| 1130 | property_names = ["Name: ", "Description: ", "Data: ", | |
| 1131 | "Severity: ", "Refs: ", "Status: "] | |
| 1132 | ||
| 1133 | elif object_type == "VulnerabilityWeb": | |
| 1134 | property_names = ["Name: ", "Description: ", "Data: ", | |
| 1135 | "Severity: ", "Refs: ", "Path: ", | |
| 1136 | "Website: ", "Request: ", "Response: ", | |
| 1137 | "Method: ", "Pname: ", "Params: ", | |
| 1138 | "Query: ", "Status: "] | |
| 1139 | return property_names | |
| 1140 | ||
| 1141 | def clear(self, box): | |
| 1142 | """Remove all the widgets from box.""" | |
| 1143 | ||
| 1144 | def remove(widget, box): | |
| 1145 | """Removes widget from box""" | |
| 1146 | box.remove(widget) | |
| 1147 | ||
| 1148 | box.foreach(remove, box) | |
| 1149 | ||
| 1150 | def on_click_ok(self, button=None): | |
| 1151 | self.destroy() | |
| 1152 | ||
| 1153 | ||
| 1154 | class ConflictsDialog(Gtk.Window): | |
| 1155 | """Blueprints for a beautiful, colorful, gtk-esque conflicts | |
| 1156 | dialog. The user is confronted with two objects, one at the left, | |
| 1157 | one at the right, and is able to edit any of the object's properties, | |
| 1158 | choosing either one of them with a button""" | |
| 1159 | ||
| 1160 | def __init__(self, conflicts, parent): | |
| 1161 | """Inits the window with its title and size, presents the | |
| 1162 | user with the first conflict found. If there aren't conflict | |
| 1163 | an empty window will be presented""" | |
| 1164 | ||
| 1165 | Gtk.Window.__init__(self, title="Conflicts") | |
| 1166 | self.set_transient_for(parent) | |
| 1167 | self.set_size_request(600, 400) | |
| 1168 | self.set_modal(True) | |
| 1169 | self.conflicts = conflicts | |
| 1170 | self.conflict_n = 0 | |
| 1171 | self.current_conflict = self.conflicts[self.conflict_n] | |
| 1172 | self.view = None | |
| 1173 | ||
| 1174 | self.views_box = Gtk.Box() | |
| 1175 | ||
| 1176 | # TODO: FIX THIS | |
| 1177 | # this is the wrong way to do it, I'm creating a useless gtk.tree | |
| 1178 | # so I can know the user's default color background | |
| 1179 | # that not being bad enought, get_background_color is deprecated | |
| 1180 | dumpy_tree = Gtk.TreeView() | |
| 1181 | style = dumpy_tree.get_style_context() | |
| 1182 | self.bg_color = style.get_background_color(Gtk.StateFlags.NORMAL) | |
| 1183 | self.bg_color = self.bg_color.to_string() | |
| 1184 | ||
| 1185 | button_box = self.create_buttons() | |
| 1186 | ||
| 1187 | self.models = self.create_conflicts_models(conflicts) | |
| 1188 | self.set_conflict_view(self.conflict_n) | |
| 1189 | self.current_conflict_model = self.models[self.conflict_n] | |
| 1190 | ||
| 1191 | main_box = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 1192 | main_box.pack_start(self.views_box, True, True, 5) | |
| 1193 | main_box.pack_start(button_box, False, True, 5) | |
| 1194 | ||
| 1195 | self.add(main_box) | |
| 1196 | ||
| 1197 | def update_current_conflict_model(self): | |
| 1198 | self.current_conflict_model = self.models[self.conflict_n] | |
| 1199 | ||
| 1200 | def update_current_conflict(self): | |
| 1201 | self.current_conflict = self.conflicts[self.conflict_n] | |
| 1202 | ||
| 1203 | def create_buttons(self): | |
| 1204 | """Creates and connects the button for the window""" | |
| 1205 | button_box = Gtk.Box() | |
| 1206 | keep_right = Gtk.Button.new_with_label("Keep RIGHT") | |
| 1207 | keep_left = Gtk.Button.new_with_label("Keep LEFT") | |
| 1208 | quit = Gtk.Button.new_with_label("Quit") | |
| 1209 | ||
| 1210 | keep_right.connect("clicked", self.save, "right") | |
| 1211 | keep_left.connect("clicked", self.save, "left") | |
| 1212 | quit.connect("clicked", self.on_quit) | |
| 1213 | ||
| 1214 | space = Gtk.Box() | |
| 1215 | button_box.pack_start(quit, False, False, 5) | |
| 1216 | button_box.pack_start(space, True, True, 5) | |
| 1217 | button_box.pack_start(keep_left, False, False, 5) | |
| 1218 | button_box.pack_start(keep_right, False, False, 5) | |
| 1219 | return button_box | |
| 1220 | ||
| 1221 | def _next_conflict_or_close(self): | |
| 1222 | """Move to next conflict and update current conflict View and model.""" | |
| 1223 | if len(self.conflicts) - 1 > self.conflict_n: | |
| 1224 | self.conflict_n += 1 | |
| 1225 | self.update_current_conflict() | |
| 1226 | self.update_current_conflict_model() | |
| 1227 | self.set_conflict_view(self.conflict_n) | |
| 1228 | else: | |
| 1229 | self.destroy() | |
| 1230 | ||
| 1231 | def save(self, button, keeper): | |
| 1232 | """Saves information to Faraday. Keeper is needed to know if user | |
| 1233 | wanted to keep left or right view""" | |
| 1234 | current_conflict_type = self.current_conflict.getModelObjectType() | |
| 1235 | ||
| 1236 | # right is represented by column 2 of the model, left by column 1 | |
| 1237 | if keeper == "right": | |
| 1238 | n = 2 | |
| 1239 | elif keeper == "left": | |
| 1240 | n = 1 | |
| 1241 | ||
| 1242 | solution = {} | |
| 1243 | for row in self.current_conflict_model: | |
| 1244 | solution[row[0].lower()] = self.uncook(row[n], row[4]) | |
| 1245 | ||
| 1246 | try: | |
| 1247 | guiapi.resolveConflict(self.current_conflict, solution) | |
| 1248 | self._next_conflict_or_close() | |
| 1249 | # if this isn't the last conflict... | |
| 1250 | ||
| 1251 | except ValueError: | |
| 1252 | dialog = Gtk.MessageDialog(self, 0, | |
| 1253 | Gtk.MessageType.INFO, | |
| 1254 | Gtk.ButtonsType.OK, | |
| 1255 | ("You tried to set some invalid " | |
| 1256 | "information. Make sure all True/False" | |
| 1257 | " settings are either True or False, " | |
| 1258 | "all values that should be numbers are" | |
| 1259 | " numbers, and so on.")) | |
| 1260 | dialog.run() | |
| 1261 | dialog.destroy() | |
| 1262 | ||
| 1263 | except ResourceDoesNotExist: # TODO: revert this hack to prevent exception when | |
| 1264 | # fixing conflict of non existent object | |
| 1265 | dialog = Gtk.MessageDialog(self, 0, | |
| 1266 | Gtk.MessageType.INFO, | |
| 1267 | Gtk.ButtonsType.OK, | |
| 1268 | ("It seems like this conflict does not " | |
| 1269 | "exist anymore. Most probably someone " | |
| 1270 | "deleted the conflicting object from " | |
| 1271 | "the DB \n" | |
| 1272 | "Moving on to the next conflict.")) | |
| 1273 | ||
| 1274 | guiapi.conflictMissing(self.current_conflict) | |
| 1275 | dialog.run() | |
| 1276 | dialog.destroy() | |
| 1277 | self._next_conflict_or_close() | |
| 1278 | ||
| 1279 | def on_quit(self, button): | |
| 1280 | """Exits the window""" | |
| 1281 | self.destroy() | |
| 1282 | ||
| 1283 | def set_conflict_view(self, conflict_n): | |
| 1284 | """Creates two views for the model corresponding to the conflict number | |
| 1285 | n. If first conflict, self.view will be none. If user is past the first | |
| 1286 | conflict, self.view will not be none""" | |
| 1287 | ||
| 1288 | @scrollable() | |
| 1289 | def make_scrollable(view): | |
| 1290 | """Just a function to wrap around a target _view_ so as to use | |
| 1291 | the scrollable decorator. | |
| 1292 | """ | |
| 1293 | return view | |
| 1294 | ||
| 1295 | def on_selection(selection, target): | |
| 1296 | """Connected to the view of both the view and the secon view. | |
| 1297 | Target should be either 'first' or 'second' for clarity. | |
| 1298 | Whenever a view selection changes, change the selection | |
| 1299 | of target accordingly. | |
| 1300 | """ | |
| 1301 | target = self.view if target == 'first' else self.second_view | |
| 1302 | original_selection = selection.get_selected()[1] | |
| 1303 | target_selection = target.get_selection() | |
| 1304 | if original_selection is not None: | |
| 1305 | target_selection.select_iter(original_selection) | |
| 1306 | ||
| 1307 | if self.view is None: | |
| 1308 | ||
| 1309 | renderer = Gtk.CellRendererText() | |
| 1310 | ||
| 1311 | original_renderer = Gtk.CellRendererText() | |
| 1312 | original_renderer.set_property("editable", True) | |
| 1313 | original_renderer.connect("edited", self.value_changed, "original") | |
| 1314 | ||
| 1315 | conflict_renderer = Gtk.CellRendererText() | |
| 1316 | conflict_renderer.set_property("editable", True) | |
| 1317 | conflict_renderer.connect("edited", self.value_changed, "conflict") | |
| 1318 | ||
| 1319 | prop_column = Gtk.TreeViewColumn("", renderer, text=0, | |
| 1320 | background=3) | |
| 1321 | ||
| 1322 | obj_column = Gtk.TreeViewColumn("ORIGINAL", original_renderer, | |
| 1323 | text=1, background=3) | |
| 1324 | ||
| 1325 | prop2_column = Gtk.TreeViewColumn("", renderer, text=0, | |
| 1326 | background=3) | |
| 1327 | obj2_column = Gtk.TreeViewColumn("CONFLICTING", conflict_renderer, | |
| 1328 | text=2, background=3) | |
| 1329 | ||
| 1330 | self.view = Gtk.TreeView(self.models[conflict_n]) | |
| 1331 | self.view.append_column(prop_column) | |
| 1332 | self.view.append_column(obj_column) | |
| 1333 | self.second_view = Gtk.TreeView(self.models[conflict_n]) | |
| 1334 | ||
| 1335 | self.second_view.append_column(prop2_column) | |
| 1336 | self.second_view.append_column(obj2_column) | |
| 1337 | ||
| 1338 | view_selection = self.view.get_selection() | |
| 1339 | second_view_selection = self.second_view.get_selection() | |
| 1340 | view_selection.connect("changed", on_selection, 'second') | |
| 1341 | second_view_selection.connect("changed", on_selection, 'first') | |
| 1342 | ||
| 1343 | scrolled_view = make_scrollable(self.view) | |
| 1344 | second_scrolled_view = make_scrollable(self.second_view) | |
| 1345 | ||
| 1346 | self.views_box.pack_start(scrolled_view, True, True, 5) | |
| 1347 | self.views_box.pack_start(second_scrolled_view, True, True, 5) | |
| 1348 | ||
| 1349 | else: | |
| 1350 | self.view.set_model(self.models[conflict_n]) | |
| 1351 | self.second_view.set_model(self.models[conflict_n]) | |
| 1352 | ||
| 1353 | def value_changed(self, widget, path, text, which_changed): | |
| 1354 | """Sets the model to keep the information which the user gave on | |
| 1355 | Return Key""" | |
| 1356 | active_store = self.current_conflict_model | |
| 1357 | if which_changed == "original": | |
| 1358 | active_store[path][1] = text | |
| 1359 | elif which_changed == "conflict": | |
| 1360 | active_store[path][2] = text | |
| 1361 | ||
| 1362 | def create_conflicts_models(self, conflicts): | |
| 1363 | """ Creates a list of models, one for each conflict. Each model has | |
| 1364 | five columns, as shown in an example with only two rows below: | |
| 1365 | | PROPERTY | OBJECT 1 | OBJECT 2 | ROW COLOR | INPUT TYPE | | |
| 1366 | ----------------------------------------------------------- | |
| 1367 | | NAME | A | B | RED | STRING | | |
| 1368 | | PORTS | 5050, 20 | 5050, 20 | WHITE | LIST | | |
| 1369 | =========================================================== | |
| 1370 | ROW COLOR and INPUT TYPE are never shown to the user. | |
| 1371 | """ | |
| 1372 | ||
| 1373 | models = [] | |
| 1374 | for conflict in conflicts: | |
| 1375 | model = Gtk.ListStore(str, str, str, str, str) | |
| 1376 | obj1 = conflict.getFirstObject() | |
| 1377 | obj2 = conflict.getSecondObject() | |
| 1378 | conflict_type = conflict.getModelObjectType() | |
| 1379 | ||
| 1380 | if conflict_type == "Service": | |
| 1381 | self.fill_service_conflict_model(model, obj1, obj2) | |
| 1382 | elif conflict_type == "Host": | |
| 1383 | self.fill_host_conflict_model(model, obj1, obj2) | |
| 1384 | elif conflict_type == "Vulnerability": | |
| 1385 | self.fill_vuln_conflict_model(model, obj1, obj2) | |
| 1386 | elif conflict_type == "VulnerabilityWeb": | |
| 1387 | self.fill_webvuln_conflict_model(model, obj1, obj2) | |
| 1388 | ||
| 1389 | models.append(model) | |
| 1390 | ||
| 1391 | return models | |
| 1392 | ||
| 1393 | def fill_service_conflict_model(self, model, obj1, obj2): | |
| 1394 | """ | |
| 1395 | Precondition: the model has 5 string columns, obj1 && obj2 are services | |
| 1396 | Will get a model and two objects and return a | |
| 1397 | model with all the appropiate information""" | |
| 1398 | attr = [] | |
| 1399 | for obj in [obj1, obj2]: | |
| 1400 | attr.append((obj.getName(), | |
| 1401 | obj.getDescription(), | |
| 1402 | obj.getProtocol(), | |
| 1403 | obj.getStatus(), | |
| 1404 | obj.getPorts(), | |
| 1405 | obj.getVersion(), | |
| 1406 | obj.isOwned())) | |
| 1407 | ||
| 1408 | props = ["Name", "Description", "Protocol", "Status", "Ports", | |
| 1409 | "Version", "Owned"] | |
| 1410 | ||
| 1411 | model = self.fill_model_from_props_and_attr(model, attr, props) | |
| 1412 | return model | |
| 1413 | ||
| 1414 | def fill_host_conflict_model(self, model, obj1, obj2): | |
| 1415 | """ | |
| 1416 | Precondition: the model has 5 string columns, obj1 && obj2 are hosts | |
| 1417 | Will get a model and two objects and return a | |
| 1418 | model with all the appropiate information""" | |
| 1419 | attr = [] | |
| 1420 | for obj in [obj1, obj2]: | |
| 1421 | attr.append((obj.getName(), | |
| 1422 | obj.getDescription(), | |
| 1423 | obj.getOS(), | |
| 1424 | obj.isOwned())) | |
| 1425 | ||
| 1426 | props = ["Name", "Description", "OS", "Owned"] | |
| 1427 | model = self.fill_model_from_props_and_attr(model, attr, props) | |
| 1428 | return model | |
| 1429 | ||
| 1430 | def fill_vuln_conflict_model(self, model, obj1, obj2): | |
| 1431 | """ | |
| 1432 | Precondition: the model has 5 string columns, obj1 && obj2 are vulns | |
| 1433 | Will get a model and two objects and return a | |
| 1434 | model with all the appropiate information""" | |
| 1435 | attr = [] | |
| 1436 | for obj in [obj1, obj2]: | |
| 1437 | attr.append((obj.getName(), | |
| 1438 | obj.getDescription(), | |
| 1439 | obj.getData(), | |
| 1440 | obj.getSeverity(), | |
| 1441 | obj.getRefs(), | |
| 1442 | obj.getResolution(), | |
| 1443 | obj.getStatus())) | |
| 1444 | ||
| 1445 | props = ["Name", "Desc", "Data", "Severity", "Refs", "Resolution", "Status"] | |
| 1446 | model = self.fill_model_from_props_and_attr(model, attr, props) | |
| 1447 | return model | |
| 1448 | ||
| 1449 | def fill_webvuln_conflict_model(self, model, obj1, obj2): | |
| 1450 | """ | |
| 1451 | Precondition: the model has 5 string columns, obj1 && obj2 are web vuln | |
| 1452 | Will get a model and two objects and return a | |
| 1453 | model with all the appropiate information""" | |
| 1454 | attr = [] | |
| 1455 | for obj in [obj1, obj2]: | |
| 1456 | attr.append((obj.getName(), | |
| 1457 | obj.getDescription(), | |
| 1458 | obj.getData(), | |
| 1459 | obj.getSeverity(), | |
| 1460 | obj.getRefs(), | |
| 1461 | obj.getPath(), | |
| 1462 | obj.getWebsite(), | |
| 1463 | obj.getRequest(), | |
| 1464 | obj.getResponse(), | |
| 1465 | obj.getMethod(), | |
| 1466 | obj.getPname(), | |
| 1467 | obj.getParams(), | |
| 1468 | obj.getQuery(), | |
| 1469 | obj.getStatus())) | |
| 1470 | ||
| 1471 | props = ["Name", "Desc", "Data", "Severity", "Refs", "Path", | |
| 1472 | "Website", "Request", "Response", "Method", "Pname", | |
| 1473 | "Params", "Query", "Status"] | |
| 1474 | ||
| 1475 | model = self.fill_model_from_props_and_attr(model, attr, props) | |
| 1476 | return model | |
| 1477 | ||
| 1478 | def fill_model_from_props_and_attr(self, model, attr, props): | |
| 1479 | """Preconditions: the model has 5 string columns, | |
| 1480 | len(attr[0]) == len(attr[1]) == len(props), | |
| 1481 | type(attr[0][i]) == type(attr[1][i]) for every i | |
| 1482 | attr is a list with two tuples. the first tuple holds info about obj1, | |
| 1483 | the second about obj2, for example: | |
| 1484 | [(name_obj1, ports_obj1), (name_obj2, porst_obj2)] | |
| 1485 | props is the list with names of such attributes, for example: | |
| 1486 | ["Name: ", "Ports: "] | |
| 1487 | ||
| 1488 | Will return a model filled up with information as detailed in | |
| 1489 | self.create_conflicts_models. | |
| 1490 | """ | |
| 1491 | ||
| 1492 | def decide_type(raw_prop): | |
| 1493 | """Returns the name of a type of an object. | |
| 1494 | Keep in mind, type(type("a")) is Type, | |
| 1495 | type(type("a").__name__) is Str | |
| 1496 | """ | |
| 1497 | type_as_string = type(first_raw_prop).__name__ | |
| 1498 | return type_as_string | |
| 1499 | ||
| 1500 | def decide_bg(): | |
| 1501 | """Decides which background should the row have depending on | |
| 1502 | the users default theme (light, dark, or unknown abomination) | |
| 1503 | Pretty ugly, but it works""" | |
| 1504 | color = self.bg_color.split("(")[1] | |
| 1505 | color = color.split(",") | |
| 1506 | color1 = int(color[0]) | |
| 1507 | color2 = int(color[1]) | |
| 1508 | color3 = int(color[2][:-1:]) | |
| 1509 | ||
| 1510 | # that weird string formats from rgb to hexa | |
| 1511 | default_bg = '#%02x%02x%02x' % (color1, color2, color3) | |
| 1512 | ||
| 1513 | if color1 > 200 and color2 > 200 and color3 > 200: | |
| 1514 | return "pink" if first_prop != sec_prop else default_bg | |
| 1515 | elif color1 < 100 and color2 < 100 and color3 < 100: | |
| 1516 | return "darkred" if first_prop != sec_prop else default_bg | |
| 1517 | else: | |
| 1518 | # if your theme doesn't go for either dark or light | |
| 1519 | # just use that color, screw highlights | |
| 1520 | return '#%02x%02x%02x' % (color1, color2, color3) | |
| 1521 | ||
| 1522 | for index, prop in enumerate(props): | |
| 1523 | # remember props is a list like [(obj1_prop1, obj1_prop2...), | |
| 1524 | # (obj2_prop1, obj2, prop2...)] | |
| 1525 | first_raw_prop = attr[0][index] | |
| 1526 | sec_raw_prop = attr[1][index] | |
| 1527 | first_prop = self.cook(first_raw_prop) | |
| 1528 | sec_prop = self.cook(sec_raw_prop) | |
| 1529 | ||
| 1530 | model.append([prop, first_prop, sec_prop, | |
| 1531 | decide_bg(), | |
| 1532 | decide_type(first_raw_prop)]) | |
| 1533 | ||
| 1534 | return model | |
| 1535 | ||
| 1536 | def cook(self, raw_prop): | |
| 1537 | """We need to cook our properties: not all of them are strings by | |
| 1538 | default, and Gtk's models refuse to deal with lists or dictionaries. | |
| 1539 | Returns a string from a list, a bool, a float, or a string. | |
| 1540 | DO NOT use for dictionaries""" | |
| 1541 | ||
| 1542 | if type(raw_prop) is list: | |
| 1543 | cooked_prop = ",".join([str(p) for p in raw_prop]) | |
| 1544 | ||
| 1545 | elif type(raw_prop) is bool: | |
| 1546 | cooked_prop = str(raw_prop) | |
| 1547 | ||
| 1548 | elif type(raw_prop) is int or type(raw_prop) is float: | |
| 1549 | cooked_prop = str(raw_prop) | |
| 1550 | ||
| 1551 | else: | |
| 1552 | cooked_prop = raw_prop | |
| 1553 | ||
| 1554 | return cooked_prop | |
| 1555 | ||
| 1556 | def uncook(self, prop, original_type): | |
| 1557 | """We need to get our raw information again: Gtk may like strings, | |
| 1558 | but Faraday needs lists, booleans, floats, and such. | |
| 1559 | Do not try to use for dictionaries. | |
| 1560 | """ | |
| 1561 | ||
| 1562 | # XXX: params is a weird stupid thing that can come up as a string, | |
| 1563 | # a list, a nonetype, whatever. but we're making it _always_ be a string | |
| 1564 | # across faraday, so just force it to be so | |
| 1565 | if prop == "params": | |
| 1566 | original_type = "str" | |
| 1567 | ||
| 1568 | if original_type == "list": | |
| 1569 | if prop: | |
| 1570 | prop = prop.replace(" ", "") | |
| 1571 | raw_prop = prop.split(",") | |
| 1572 | else: | |
| 1573 | raw_prop = [] | |
| 1574 | ||
| 1575 | elif original_type == "bool": | |
| 1576 | prop = prop.replace(" ", "") | |
| 1577 | if prop.lower() == "true": | |
| 1578 | raw_prop = True | |
| 1579 | elif prop.lower() == "false": | |
| 1580 | raw_prop = False | |
| 1581 | ||
| 1582 | elif original_type == "int": | |
| 1583 | raw_prop = int(prop) | |
| 1584 | ||
| 1585 | elif original_type == "float": | |
| 1586 | raw_prop = float(prop) | |
| 1587 | ||
| 1588 | elif original_type in ["str", "unicode"]: | |
| 1589 | raw_prop = prop | |
| 1590 | else: | |
| 1591 | raw_prop = prop | |
| 1592 | return raw_prop | |
| 1593 | ||
| 1594 | ||
| 1595 | class ForceChooseWorkspaceDialog(Gtk.Window): | |
| 1596 | """A dialog to force the user to choose a workspace in case he suddenly | |
| 1597 | finds himself without an active workspace. | |
| 1598 | """ | |
| 1599 | ||
| 1600 | def __init__(self, parent_window, workspaces_model, change_ws_callback): | |
| 1601 | """Initializes a simple modal dialog which forces the user to choose | |
| 1602 | a workspace from a list.""" | |
| 1603 | Gtk.Window.__init__(self, title="Choose a Workspace") | |
| 1604 | self.set_type_hint(Gdk.WindowTypeHint.DIALOG) | |
| 1605 | self.set_deletable(False) | |
| 1606 | self.set_transient_for(parent_window) | |
| 1607 | self.set_modal(True) | |
| 1608 | self.connect("key_press_event", strict_key_reactions) | |
| 1609 | self.connect("delete_event", lambda _, __: True) | |
| 1610 | ||
| 1611 | self.change_ws_callback = change_ws_callback | |
| 1612 | ||
| 1613 | message = self.create_explanation_message() | |
| 1614 | scroll_view = self.create_view(workspaces_model) | |
| 1615 | button_box = self.create_button_box() | |
| 1616 | ||
| 1617 | content_box = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 1618 | content_box.pack_start(message, True, True, 6) | |
| 1619 | content_box.pack_start(scroll_view, True, True, 6) | |
| 1620 | content_box.pack_start(button_box, True, True, 6) | |
| 1621 | ||
| 1622 | self.add(content_box) | |
| 1623 | ||
| 1624 | def create_button_box(self): | |
| 1625 | button_box = Gtk.Box() | |
| 1626 | OK_button = Gtk.Button.new_with_label("OK") | |
| 1627 | OK_button.connect("clicked", self.on_click_ok) | |
| 1628 | button_box.pack_start(OK_button, False, False, 6) | |
| 1629 | button_box.pack_start(Gtk.Box(), True, True, 6) | |
| 1630 | return button_box | |
| 1631 | ||
| 1632 | def create_explanation_message(self): | |
| 1633 | """Returns a simple explanatory message inside a Label""" | |
| 1634 | message = Gtk.Label() | |
| 1635 | message.set_text("Your last workspace is not accessible. \n" | |
| 1636 | "You must select one of the below workspaces to " | |
| 1637 | "continue using Faraday. \n" | |
| 1638 | "If your problem persists, double check you are " | |
| 1639 | "logged in. You may want to start faraday with the " | |
| 1640 | "--login flag.") | |
| 1641 | return message | |
| 1642 | ||
| 1643 | @scrollable(height=200) | |
| 1644 | def create_view(self, workspace_model): | |
| 1645 | """Returns and assigns to the instance a view listing all the | |
| 1646 | workspaces names. | |
| 1647 | """ | |
| 1648 | self.ws_view = Gtk.TreeView(workspace_model) | |
| 1649 | renderer = Gtk.CellRendererText() | |
| 1650 | column = Gtk.TreeViewColumn("Workspaces", renderer, text=0) | |
| 1651 | self.ws_view.append_column(column) | |
| 1652 | return self.ws_view | |
| 1653 | ||
| 1654 | def on_click_ok(self, button=None): | |
| 1655 | """On click ok, change the workspace in the app with out selection | |
| 1656 | and destroy. | |
| 1657 | """ | |
| 1658 | selection = self.ws_view.get_selection() | |
| 1659 | model, iter_ = selection.get_selected() | |
| 1660 | if model and iter_: | |
| 1661 | ws_name = model[iter_][0] | |
| 1662 | self.change_ws_callback(ws_name) | |
| 1663 | self.destroy() | |
| 1664 | ||
| 1665 | ||
| 1666 | class NotificationsDialog(Gtk.Window): | |
| 1667 | """Defines a simple notification dialog. It isn't much, really""" | |
| 1668 | ||
| 1669 | def __init__(self, view, callback, parent): | |
| 1670 | Gtk.Window.__init__(self, title="Notifications") | |
| 1671 | self.set_type_hint(Gdk.WindowTypeHint.DIALOG) | |
| 1672 | self.set_transient_for(parent) | |
| 1673 | self.set_size_request(400, 200) | |
| 1674 | self.set_modal(True) | |
| 1675 | self.connect("key_press_event", key_reactions) | |
| 1676 | self.destroy_notifications = callback | |
| 1677 | ||
| 1678 | scrolled_list = self.create_view_box(view) | |
| 1679 | ||
| 1680 | self.button = Gtk.Button() | |
| 1681 | self.button.set_label("OK") | |
| 1682 | self.button.connect("clicked", self.on_click_ok) | |
| 1683 | ||
| 1684 | self.mainBox = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 1685 | self.mainBox.pack_start(scrolled_list, True, True, 0) | |
| 1686 | self.mainBox.pack_start(self.button, False, False, 0) | |
| 1687 | ||
| 1688 | self.add(self.mainBox) | |
| 1689 | ||
| 1690 | @scrollable(width=250, height=350) | |
| 1691 | def create_view_box(self, view): | |
| 1692 | return view | |
| 1693 | ||
| 1694 | def on_click_ok(self, button=None): | |
| 1695 | self.destroy_notifications() | |
| 1696 | self.destroy() | |
| 1697 | ||
| 1698 | ||
| 1699 | class aboutDialog(Gtk.AboutDialog): | |
| 1700 | """The simple about dialog displayed when the user clicks on "about" | |
| 1701 | ont the menu. Could be in application.py, but for consistency reasons | |
| 1702 | its here""" | |
| 1703 | def __init__(self, main_window): | |
| 1704 | ||
| 1705 | Gtk.AboutDialog.__init__(self, transient_for=main_window, modal=True) | |
| 1706 | icons = os.path.join(FARADAY_CLIENT_BASE, "data", "images", "icons") | |
| 1707 | faraday_icon = GdkPixbuf.Pixbuf.new_from_file( | |
| 1708 | os.path.join(icons, "about.png")) | |
| 1709 | self.set_logo(faraday_icon) | |
| 1710 | self.set_program_name("Faraday") | |
| 1711 | self.set_comments("Penetration Test IDE -" | |
| 1712 | " Infobyte LLC. - All rights reserved") | |
| 1713 | faraday_website = "http://www.infobytesec.com/faraday.html" | |
| 1714 | self.set_website(faraday_website) | |
| 1715 | self.set_website_label("Learn more about Faraday") | |
| 1716 | ||
| 1717 | class errorDialog(Gtk.MessageDialog): | |
| 1718 | """A simple error dialog to show the user where things went wrong. | |
| 1719 | Takes the parent window, (Gtk.Window or Gtk.Dialog, most probably) | |
| 1720 | the error and explanation (strings, nothing fancy) as arguments""" | |
| 1721 | ||
| 1722 | def __init__(self, parent_window, error, explanation=None): | |
| 1723 | Gtk.MessageDialog.__init__(self, parent_window, 0, | |
| 1724 | Gtk.MessageType.ERROR, | |
| 1725 | Gtk.ButtonsType.OK, | |
| 1726 | error) | |
| 1727 | if explanation is not None: | |
| 1728 | self.format_secondary_text(explanation) | |
| 1729 | self.run() | |
| 1730 | self.destroy() | |
| 1731 | ||
| 1732 | ||
| 1733 | class ImportantErrorDialog(Gtk.Dialog): | |
| 1734 | """Blueprints for an uncaught exception handler. Presents the | |
| 1735 | traceback and has option to send error report to developers. | |
| 1736 | """ | |
| 1737 | ||
| 1738 | def __init__(self, parent_window, error): | |
| 1739 | Gtk.Dialog.__init__(self, "Error!", parent_window, 0) | |
| 1740 | self.add_button("Send report to developers...", 42) | |
| 1741 | self.add_button("Ignore", 0) | |
| 1742 | self.set_size_request(200, 200) | |
| 1743 | ||
| 1744 | textBuffer = Gtk.TextBuffer() | |
| 1745 | textBuffer.set_text(error) | |
| 1746 | ||
| 1747 | text_view_box = self.create_text_view_box(textBuffer) | |
| 1748 | ||
| 1749 | content = self.get_content_area() | |
| 1750 | ||
| 1751 | content.pack_start(text_view_box, True, True, 0) | |
| 1752 | self.show_all() | |
| 1753 | ||
| 1754 | @scrollable(width=200, height=200) | |
| 1755 | def create_text_view_box(self, textBuffer): | |
| 1756 | textView = Gtk.TextView() | |
| 1757 | textView.set_editable(False) | |
| 1758 | textView.set_buffer(textBuffer) | |
| 1759 | return textView | |
| 1760 | ||
| 1761 | ||
| 1762 | def key_reactions(window, event): | |
| 1763 | """Silly function to destroy a window on escape key, to use | |
| 1764 | with all the dialogs that should be Gtk.Dialogs but are Gtk.Windows | |
| 1765 | or with windows that are too complex for gtk dialogs but should behave | |
| 1766 | as a dialog too""" | |
| 1767 | key = Gdk.keyval_name(event.get_keyval()[1]) | |
| 1768 | if key == 'Escape': | |
| 1769 | window.destroy() | |
| 1770 | return True | |
| 1771 | elif key == 'Return': | |
| 1772 | window.on_click_ok() | |
| 1773 | return True | |
| 1774 | ||
| 1775 | ||
| 1776 | def strict_key_reactions(window, event): | |
| 1777 | """Similar to key_reactions, but will not let the user do anything but | |
| 1778 | press return.""" | |
| 1779 | key = Gdk.keyval_name(event.get_keyval()[1]) | |
| 1780 | if key == 'Return': | |
| 1781 | window.on_click_ok() | |
| 1782 | return True | |
| 1783 | else: | |
| 1784 | return False | |
| 1785 | ||
| 1786 | ||
| 1787 | # I'm Py3 |
| 0 | #!/usr/bin/python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | ||
| 7 | """ | |
| 8 | from __future__ import absolute_import | |
| 9 | from __future__ import division | |
| 10 | ||
| 11 | import gi # pylint: disable=import-error | |
| 12 | import os | |
| 13 | import math | |
| 14 | import webbrowser | |
| 15 | ||
| 16 | gi.require_version('Gtk', '3.0') | |
| 17 | ||
| 18 | try: | |
| 19 | gi.require_version('Vte', '2.91') | |
| 20 | except ValueError: | |
| 21 | gi.require_version('Vte', '2.90') | |
| 22 | ||
| 23 | from gi.repository import Gtk, Gdk, GLib, Pango, GdkPixbuf, Vte # pylint: disable=import-error | |
| 24 | ||
| 25 | from faraday.client.gui.gtk.decorators import scrollable | |
| 26 | from faraday.client.gui.gtk.compatibility import CompatibleVteTerminal as VteTerminal | |
| 27 | from faraday.client.gui.gtk.compatibility import CompatibleScrolledWindow as GtkScrolledWindow | |
| 28 | ||
| 29 | ||
| 30 | class Terminal(VteTerminal): | |
| 31 | """Defines a simple terminal that will execute faraday-terminal with the | |
| 32 | corresponding host and port as specified by the CONF. | |
| 33 | Inherits from Compatibility.Vte, which is just Vte.Terminal with | |
| 34 | spawn_sync overrode to function with API 2.90 and 2.91""" | |
| 35 | ||
| 36 | def __init__(self, CONF): | |
| 37 | """Initialize terminal with infinite scrollback, no bell, connecting | |
| 38 | all keys presses to copy_or_past, and starting faraday-terminal | |
| 39 | """ | |
| 40 | from faraday.client.start_client import FARADAY_BASE, FARADAY_CLIENT_BASE # pylint:disable=import-outside-toplevel | |
| 41 | VteTerminal.__init__(self) | |
| 42 | self.set_scrollback_lines(-1) | |
| 43 | self.set_audible_bell(0) | |
| 44 | self.connect("key_press_event", self.copy_or_paste) | |
| 45 | self.host, self.port = CONF.getApiRestfulConInfo() | |
| 46 | ||
| 47 | self.faraday_directory = FARADAY_BASE | |
| 48 | self.faraday_exec = os.path.join(FARADAY_CLIENT_BASE, "zsh/faraday-terminal.zsh") | |
| 49 | ||
| 50 | self.start_faraday() | |
| 51 | ||
| 52 | @scrollable(overlay_scrolling=True) | |
| 53 | def create_scrollable_terminal(self): | |
| 54 | """Returns a scrolled_window with the terminal inside it thanks | |
| 55 | to the scrollable decorator.""" | |
| 56 | return self | |
| 57 | ||
| 58 | def start_faraday(self): | |
| 59 | """Starts a Faraday process with the appropiate host and port.""" | |
| 60 | ||
| 61 | home_dir = os.path.expanduser('~') | |
| 62 | self.spawn_sync(Vte.PtyFlags.DEFAULT, | |
| 63 | home_dir, | |
| 64 | [self.faraday_exec, str(self.host), str(self.port)], | |
| 65 | ['FARADAY_PATH=%s' % self.faraday_directory], | |
| 66 | GLib.SpawnFlags.DO_NOT_REAP_CHILD, | |
| 67 | None, | |
| 68 | None, | |
| 69 | None) | |
| 70 | ||
| 71 | def copy_or_paste(self, widget, event): | |
| 72 | """Decides if the Ctrl+Shift is pressed, in which case returns True. | |
| 73 | If Ctrl+Shift+C or Ctrl+Shift+V are pressed, copies or pastes, | |
| 74 | acordingly. Return necesary so it doesn't perform other action, | |
| 75 | like killing the process on Ctrl+C. | |
| 76 | ||
| 77 | Note that it won't care about order: Shift+Ctrl+V will work just as | |
| 78 | Ctrl+Shift+V. | |
| 79 | """ | |
| 80 | control_key = 'control-mask' | |
| 81 | shift_key = 'shift-mask' | |
| 82 | last_pressed_key = Gdk.keyval_name(event.get_keyval()[1]) | |
| 83 | set_pressed_special_keys = set(event.state.value_nicks) | |
| 84 | if event.type == Gdk.EventType.KEY_PRESS: | |
| 85 | if {control_key, shift_key} <= set_pressed_special_keys: | |
| 86 | # '<=' means 'is a subset of' in sets | |
| 87 | if last_pressed_key == 'C': | |
| 88 | self.copy_clipboard() | |
| 89 | elif last_pressed_key == 'V': | |
| 90 | self.paste_clipboard() | |
| 91 | return True | |
| 92 | ||
| 93 | ||
| 94 | class Sidebar(Gtk.Notebook): | |
| 95 | """Defines the bigger sidebar in a notebook. One of its tabs will contain | |
| 96 | the workspace view, listing all the workspaces (WorkspaceSidebar) and the | |
| 97 | other will contain the information about hosts, services, and vulns | |
| 98 | (HostsSidebar) | |
| 99 | """ | |
| 100 | ||
| 101 | def __init__(self, workspace_sidebar, hosts_sidebar): | |
| 102 | """Attach to the notebok the workspace sidebar and the host_sidebar""" | |
| 103 | super(Gtk.Notebook, self).__init__() | |
| 104 | self.workspace_sidebar = workspace_sidebar | |
| 105 | self.hosts_sidebar = hosts_sidebar | |
| 106 | self.set_tab_pos(Gtk.PositionType.BOTTOM) | |
| 107 | ||
| 108 | self.append_page(self.workspace_sidebar, Gtk.Label("Workspaces")) | |
| 109 | self.append_page(self.hosts_sidebar, Gtk.Label("Hosts")) | |
| 110 | ||
| 111 | def box_it(self): | |
| 112 | """Wraps the notebook inside a little box.""" | |
| 113 | box = Gtk.Box() | |
| 114 | box.pack_start(self, True, True, 0) | |
| 115 | return box | |
| 116 | ||
| 117 | ||
| 118 | class HostsSidebar(Gtk.Widget): | |
| 119 | """Defines the widget displayed when the user is in the "Hosts" tab of | |
| 120 | the Sidebar notebook. Will list all the host, and when clicking on one, | |
| 121 | will open a window with more information about it""" | |
| 122 | ||
| 123 | def __init__(self, open_dialog_callback, get_several_hosts_function, | |
| 124 | get_single_host_function, icons): | |
| 125 | """Initializes the HostsSidebar. Initialization by itself does | |
| 126 | almost nothing, the application will inmediatly call create_model | |
| 127 | with the last workspace and create_view with that model upon startup. | |
| 128 | ||
| 129 | The model looks like this: | |
| 130 | | HOST_ID | HOST_OS_PIXBUF | OS_STR | DISPLAY_STR | VULN_COUNT| | |
| 131 | ====================================================================== | |
| 132 | | a923fd | PixBufIcon(linux)| linux | 192.168.1.2 (5) | 5 | | |
| 133 | """ | |
| 134 | ||
| 135 | Gtk.Widget.__init__(self) | |
| 136 | self.open_dialog_callback = open_dialog_callback | |
| 137 | self.get_hosts_function = get_several_hosts_function | |
| 138 | self.get_single_host_function = get_single_host_function | |
| 139 | self.model = Gtk.ListStore(str, GdkPixbuf.Pixbuf(), str, str, int) | |
| 140 | self.create_view() | |
| 141 | self.progress_label = Gtk.Label("") | |
| 142 | self.host_amount_total = 0 | |
| 143 | self.host_amount_in_model = 0 | |
| 144 | self.page = 1 | |
| 145 | self.host_id_to_iter = {} | |
| 146 | self.linux_icon = os.path.join(icons, "tux.png") | |
| 147 | self.windows_icon = os.path.join(icons, "windows.png") | |
| 148 | self.mac_icon = os.path.join(icons, "Apple.png") | |
| 149 | self.no_os_icon = os.path.join(icons, "TreeHost.png") | |
| 150 | ||
| 151 | @property | |
| 152 | def number_of_pages(self): | |
| 153 | if self.host_amount_total == 0: | |
| 154 | return 1 | |
| 155 | return int(math.ceil(self.host_amount_total / 20.0)) | |
| 156 | ||
| 157 | @scrollable(width=160) | |
| 158 | def scrollable_view(self): | |
| 159 | return self.view | |
| 160 | ||
| 161 | def create_view(self): | |
| 162 | """Creates a view for the hosts model. | |
| 163 | It will contain two columns, the first with the OS icon given in | |
| 164 | the second column of the model. The second column of the view will | |
| 165 | be the string contained in the fourth column of the model. | |
| 166 | The first column of the view will be orderer according to the | |
| 167 | second column of the model, and the second column of the view will | |
| 168 | be ordered according to its fifth column. | |
| 169 | Will connect activation of a row with the on_click method | |
| 170 | """ | |
| 171 | self.view = Gtk.TreeView(self.model) | |
| 172 | self.view.set_activate_on_single_click(False) | |
| 173 | text_renderer = Gtk.CellRendererText() | |
| 174 | icon_renderer = Gtk.CellRendererPixbuf() | |
| 175 | column_hosts = Gtk.TreeViewColumn("Hosts", text_renderer, text=3) | |
| 176 | column_hosts.set_sort_column_id(4) | |
| 177 | column_hosts.set_sort_indicator(True) | |
| 178 | column_os = Gtk.TreeViewColumn("", icon_renderer, pixbuf=1) | |
| 179 | column_os.set_sort_column_id(2) | |
| 180 | column_os.set_sort_indicator(True) | |
| 181 | self.view.append_column(column_os) | |
| 182 | self.view.append_column(column_hosts) | |
| 183 | self.view.connect("row_activated", self.on_click) | |
| 184 | self.view.set_enable_search(True) | |
| 185 | self.view.set_search_column(2) | |
| 186 | return self.view | |
| 187 | ||
| 188 | def reset_model(self, hosts): | |
| 189 | """Resets the model to a new list of hosts. | |
| 190 | Use for changing of pages, _not_ for changing of workspaces, | |
| 191 | there's reset_model_after_workspace_changed for that. | |
| 192 | """ | |
| 193 | self.model.clear() | |
| 194 | self.host_amount_in_model = 0 | |
| 195 | self.host_id_to_iter = {} | |
| 196 | self.add_relevant_hosts_to_model(hosts) | |
| 197 | self.set_move_buttons_sensitivity() | |
| 198 | ||
| 199 | def reset_model_after_workspace_changed(self, hosts, total_host_amount): | |
| 200 | """Reset the model and also sets the page to 0 and the new total | |
| 201 | host amount will be the length of host.""" | |
| 202 | self.page = 1 | |
| 203 | self.host_amount_total = total_host_amount | |
| 204 | self.reset_model(hosts) | |
| 205 | self.update_progress_label() | |
| 206 | ||
| 207 | def __decide_icon(self, os): | |
| 208 | """Return the GdkPixbuf icon according to 'os' paramather string | |
| 209 | and a str_id to that GdkPixbuf for easy comparison and ordering | |
| 210 | of the view ('os' paramether string is complicated and has caps). | |
| 211 | """ | |
| 212 | os = os.lower() if os else "" | |
| 213 | if "linux" in os or "unix" in os: | |
| 214 | icon = GdkPixbuf.Pixbuf.new_from_file(self.linux_icon) | |
| 215 | str_id = "linux" | |
| 216 | elif "windows" in os: | |
| 217 | icon = GdkPixbuf.Pixbuf.new_from_file(self.windows_icon) | |
| 218 | str_id = "windows" | |
| 219 | elif "mac" in os: | |
| 220 | icon = GdkPixbuf.Pixbuf.new_from_file(self.mac_icon) | |
| 221 | str_id = "mac" | |
| 222 | else: | |
| 223 | icon = GdkPixbuf.Pixbuf.new_from_file(self.no_os_icon) | |
| 224 | str_id = "unknown" | |
| 225 | return icon, str_id | |
| 226 | ||
| 227 | def _find_host_id(self, object_): | |
| 228 | """Return the ID of the object's parent host.""" | |
| 229 | if object_.getParentType() == 'Host': | |
| 230 | return object_.getParent() | |
| 231 | ||
| 232 | def _is_host_in_model_by_host_id(self, host_id): | |
| 233 | """Return a boolean indicating if host_id is in the model""" | |
| 234 | return self.host_id_to_iter.get(host_id) is not None | |
| 235 | ||
| 236 | def _get_vuln_amount_from_model(self, host_iter): | |
| 237 | """Return the amount of vulns the model thinks host_iter has. | |
| 238 | ||
| 239 | @preconditions: host_iter in self.model | |
| 240 | """ | |
| 241 | return self.model[host_iter][4] | |
| 242 | ||
| 243 | def _vulns_ids_of_host(self, host): | |
| 244 | """Return a list of vulnerabilities IDs for the given host. | |
| 245 | It will return [] if host is None (or any other falsey value). | |
| 246 | """ | |
| 247 | return [v.getID() for v in host.getVulns()] if host else [] | |
| 248 | ||
| 249 | def _is_vuln_of_host(self, vuln_id, host_id): | |
| 250 | """Return a boolean indicating whether vuln_id is associated with the | |
| 251 | host of host_id. Potentially slow, as it makes a request to the server. | |
| 252 | """ | |
| 253 | host = self.get_single_host_function(host_id) | |
| 254 | return vuln_id in self._vulns_ids_of_host(host) | |
| 255 | ||
| 256 | def _add_single_host_to_model(self, host): | |
| 257 | """Add a single host to the model. Return None.""" | |
| 258 | vuln_count = host.getVulnsAmount() | |
| 259 | os_icon, os_str = self.__decide_icon(host.getOS()) | |
| 260 | display_str = str(host) | |
| 261 | if str(host.id) not in [host_data[0] for host_data in self.model]: | |
| 262 | host_iter = self.model.append([str(host.id), os_icon, os_str, display_str, vuln_count]) | |
| 263 | self.host_id_to_iter[host.id] = host_iter | |
| 264 | self.host_amount_in_model += 1 | |
| 265 | ||
| 266 | def add_relevant_hosts_to_model(self, hosts): | |
| 267 | """Takes a list of hosts. Add the hosts to the model without going | |
| 268 | over the maximun size of the model. Return None. | |
| 269 | """ | |
| 270 | space_left_in_sidebar = 20 - self.host_amount_in_model | |
| 271 | relevant_hosts = hosts[0:space_left_in_sidebar] # just ignore those coming after | |
| 272 | [self._add_single_host_to_model(h) for h in relevant_hosts] | |
| 273 | ||
| 274 | def _update_single_host_name_in_model(self, host_id, host_iter): | |
| 275 | """Take a host_id and a host_iter. Changes the string representation | |
| 276 | of the host in the model. Potentially slow, makes a request to the server. | |
| 277 | Return None. | |
| 278 | ||
| 279 | @precondtions: host_iter must be in self.model | |
| 280 | """ | |
| 281 | host = self.get_single_host_function(host_id) | |
| 282 | new_name = host.getName() | |
| 283 | vuln_amount = self._get_vuln_amount_from_model(host_iter) | |
| 284 | new_string = "{0} ({1})".format(new_name, vuln_amount) | |
| 285 | self.model.set_value(host_iter, 3, new_string) | |
| 286 | ||
| 287 | def update_relevant_host_names_in_model(self, hosts): | |
| 288 | """Takes a list of hosts and updates their string representation | |
| 289 | in the model. Potentially slow, makes len(hosts) requests to the server. | |
| 290 | Return None. | |
| 291 | """ | |
| 292 | hosts_ids = [h.id for h in hosts] | |
| 293 | relevant_hosts = list(filter(self._is_host_in_model_by_host_id, hosts_ids)) | |
| 294 | host_iters = [self.host_id_to_iter[h] for h in relevant_hosts] | |
| 295 | list(map(self._update_single_host_name_in_model, relevant_hosts, host_iters)) | |
| 296 | ||
| 297 | def _remove_single_host_from_model(self, host_id): | |
| 298 | """Remove the host of host_id from the model. Return None. | |
| 299 | ||
| 300 | @preconditions: host_id must be in self.host_id_to_iter, | |
| 301 | self.host_id_to_iter[host_id] must be in model | |
| 302 | """ | |
| 303 | host_iter = self.host_id_to_iter[host_id] | |
| 304 | del self.host_id_to_iter[host_id] | |
| 305 | self.model.remove(host_iter) | |
| 306 | self.host_amount_total -= 1 | |
| 307 | self.host_amount_in_model -= 1 | |
| 308 | ||
| 309 | def remove_relevant_hosts_from_model(self, host_ids): | |
| 310 | """Takes a list of host_ids and deletes the one found on the model | |
| 311 | from there. Return None.""" | |
| 312 | relevant_host_ids = list(filter(self._is_host_in_model_by_host_id, host_ids)) | |
| 313 | list(map(self._remove_single_host_from_model, relevant_host_ids)) | |
| 314 | ||
| 315 | def _modify_vuln_amount_of_single_host_in_model(self, host_id, new_vuln_amount): | |
| 316 | """Take a host_id and a new_vuln amount and modify the string representation | |
| 317 | and the vuln amount of the host of id host_id in the model according | |
| 318 | to the new_vuln_amount. Return None. | |
| 319 | ||
| 320 | @preconditions: host_id must be in self.host_id_to_iter, | |
| 321 | self.host_id_to_iter[host_id] must in the model. | |
| 322 | """ | |
| 323 | ||
| 324 | # Let's first check if the host_id is in the model to avoid an exception bellow. | |
| 325 | # Added because of a race condition (?) between the client and the server, where a deletion | |
| 326 | # in bulk by the fplugin would trigger a KeyError | |
| 327 | if not self._is_host_in_model_by_host_id(host_id): | |
| 328 | return | |
| 329 | ||
| 330 | host_iter = self.host_id_to_iter[host_id] | |
| 331 | current_host_name = self.model[host_iter][3].split(" ")[0] | |
| 332 | new_host_string = "{0} ({1})".format(current_host_name, new_vuln_amount) | |
| 333 | self.model.set_value(host_iter, 4, new_vuln_amount) | |
| 334 | self.model.set_value(host_iter, 3, new_host_string) | |
| 335 | ||
| 336 | def _modify_vuln_amounts_of_hosts_in_model(self, host_ids, plus_one_or_minus_one): | |
| 337 | """Takes host_ids (a list of host ids) and a function which should | |
| 338 | add or take one from an input. Modify the string representation | |
| 339 | and the vuln_amount of the host_ids found in the model by adding or taking | |
| 340 | one vulnerability from them, according to the plus_one_or_minus_one | |
| 341 | function. Return None. | |
| 342 | """ | |
| 343 | relevant_host_ids = list(filter(self._is_host_in_model_by_host_id, host_ids)) | |
| 344 | host_iters = [self.host_id_to_iter[h] for h in relevant_host_ids] | |
| 345 | vuln_amount_of_those_hosts = [self._get_vuln_amount_from_model(h) for h in host_iters] | |
| 346 | new_vuln_amounts = [plus_one_or_minus_one(h) for h in vuln_amount_of_those_hosts] | |
| 347 | list(map(self._modify_vuln_amount_of_single_host_in_model, relevant_host_ids, new_vuln_amounts)) | |
| 348 | ||
| 349 | def add_relevant_vulns_to_model(self, vulns): | |
| 350 | """Takes vulns, a list of vulnerability object, and adds them to the | |
| 351 | model by modifying their corresponding hosts in the model. Return None. | |
| 352 | """ | |
| 353 | host_ids = [host_id for host_id in [self._find_host_id(v) for v in vulns] if host_id is not None] | |
| 354 | self._modify_vuln_amounts_of_hosts_in_model(host_ids, lambda x: x + 1) | |
| 355 | ||
| 356 | def remove_relevant_vulns_from_model(self, vulns_ids): | |
| 357 | """Takes vulns_ids, a list of vuln ids, and removes them from | |
| 358 | the model by modifying their corresponding hosts in the model. | |
| 359 | Return None. | |
| 360 | """ | |
| 361 | host_ids = [v.getID().split(".")[0] for v in vulns_ids] | |
| 362 | self._modify_vuln_amounts_of_hosts_in_model(host_ids, lambda x: x - 1) | |
| 363 | ||
| 364 | def add_host(self, host): | |
| 365 | """Adds host to the model. Do not use for hosts added after | |
| 366 | the initial load of the workspace, use add_host_after_initial_load | |
| 367 | for that. | |
| 368 | """ | |
| 369 | self.add_relevant_hosts_to_model([host]) | |
| 370 | ||
| 371 | def remove_host(self, host_id): | |
| 372 | """Remove host of host_id from the model, if found in it.""" | |
| 373 | self.remove_relevant_hosts_from_model([host_id]) | |
| 374 | ||
| 375 | def update_host_name(self, host): | |
| 376 | """Update the host name of host in the model, if found in it.""" | |
| 377 | self.update_relevant_host_names_in_model([host]) | |
| 378 | ||
| 379 | def add_vuln(self, vuln): | |
| 380 | """Adds vuln to the corresponding host, if the host is found in the model.""" | |
| 381 | self.add_relevant_vulns_to_model([vuln]) | |
| 382 | ||
| 383 | def remove_vuln(self, vuln_id): | |
| 384 | """Removes a vuln from its host, if the host is found in the model.""" | |
| 385 | self.remove_relevant_vulns_from_model([vuln_id]) | |
| 386 | ||
| 387 | def add_host_after_initial_load(self, host): | |
| 388 | """Adds a host after the initial load of the sidebar. | |
| 389 | This implies modifiying the total host amount and potentially | |
| 390 | updating the progress buttons senstivity. | |
| 391 | """ | |
| 392 | self.host_amount_total += 1 | |
| 393 | self.add_host(host) | |
| 394 | self.set_move_buttons_sensitivity() | |
| 395 | ||
| 396 | def add_object(self, obj): | |
| 397 | """Add and object obj of unkwonw type to the model, if found there""" | |
| 398 | object_type = obj.class_signature | |
| 399 | if object_type == 'Host': | |
| 400 | self.add_host_after_initial_load(host=obj) | |
| 401 | if object_type in ["Vulnerability", "VulnerabilityWeb"]: | |
| 402 | self.add_vuln(vuln=obj) | |
| 403 | ||
| 404 | def remove_object(self, obj_id, obj_type): | |
| 405 | """Remove an obj of id obj_id from the model, if found there""" | |
| 406 | if obj_type == 'Host': | |
| 407 | self.remove_host(host_id=obj_id) | |
| 408 | elif obj_type == 'Service': | |
| 409 | # Yeah, we query to server about services | |
| 410 | # We are not using a cached version of model | |
| 411 | pass | |
| 412 | else: | |
| 413 | # Since we don't know the type of the delete object, | |
| 414 | # we have to assume it's a vulnerability so the host's | |
| 415 | # name is updated with the ammount of vulns | |
| 416 | host = self.get_single_host_function(obj_id) | |
| 417 | if host: | |
| 418 | self._modify_vuln_amount_of_single_host_in_model(host.getID(), host.getVulnsAmount()) | |
| 419 | ||
| 420 | def update_object(self, obj): | |
| 421 | """Update the obj in the model, if found there""" | |
| 422 | object_type = obj.class_signature | |
| 423 | if object_type == 'Host': | |
| 424 | self.update_host_name(obj) | |
| 425 | ||
| 426 | def on_click(self, tree_view, path, column): | |
| 427 | """Sends the host_id of the clicked host back to the application""" | |
| 428 | tree_iter = self.model.get_iter(path) | |
| 429 | host_id = self.model[tree_iter][0] | |
| 430 | self.open_dialog_callback(host_id) | |
| 431 | ||
| 432 | def set_move_buttons_sensitivity(self): | |
| 433 | """Update the sensitity of the prev and next buttons according to the | |
| 434 | page we're on and the total number of pages. | |
| 435 | """ | |
| 436 | self.prev_button.set_sensitive(self.page >= 2) # its a boolean! | |
| 437 | ||
| 438 | # we add one to self.page 'cause they start at zero, but number of pages is | |
| 439 | # always at least one :) | |
| 440 | self.next_button.set_sensitive(self.number_of_pages > self.page) | |
| 441 | ||
| 442 | def get_box(self): | |
| 443 | """Return the sidebar_box, which contains all the elements of the | |
| 444 | sidebar. | |
| 445 | """ | |
| 446 | search_entry = self.create_search_entry() | |
| 447 | scrollable_view = self.scrollable_view() | |
| 448 | button_box = self.button_box() | |
| 449 | sidebar_box = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 450 | sidebar_box.pack_start(search_entry, False, False, 0) | |
| 451 | sidebar_box.pack_start(scrollable_view, True, True, 0) | |
| 452 | sidebar_box.pack_start(button_box, False, True, 0) | |
| 453 | return sidebar_box | |
| 454 | ||
| 455 | def button_box(self): | |
| 456 | """Return the button_box, which contains the prev and next button | |
| 457 | as well the progress label. Creates the instance attributes | |
| 458 | self.prev_button and self.next_button. | |
| 459 | """ | |
| 460 | button_box = Gtk.Box() | |
| 461 | button_box.override_background_color(Gtk.StateType.NORMAL, Gdk.RGBA(.1, .1, .1, .1)) | |
| 462 | self.prev_button = Gtk.Button.new_with_label("<<") | |
| 463 | self.next_button = Gtk.Button.new_with_label(">>") | |
| 464 | self.prev_button.connect("clicked", self.on_click_move_page, lambda x: x - 1) | |
| 465 | self.next_button.connect("clicked", self.on_click_move_page, lambda x: x + 1) | |
| 466 | button_box.pack_start(self.prev_button, True, True, 0) | |
| 467 | button_box.pack_start(self.progress_label, True, True, 0) | |
| 468 | button_box.pack_start(self.next_button, True, True, 0) | |
| 469 | return button_box | |
| 470 | ||
| 471 | def on_click_move_page(self, button, change_page_number_func, *args, **kwargs): | |
| 472 | """What happens when the user clicks on either self.prev_button | |
| 473 | or self.next_button. Change self.page according to the change_page_number_func, | |
| 474 | and resets the model to a new list of hosts requested from the server. | |
| 475 | """ | |
| 476 | self.page = change_page_number_func(self.page) | |
| 477 | hosts = self.get_hosts_function(page=str(self.page), | |
| 478 | page_size=20, | |
| 479 | search=self.search_entry.get_text(), | |
| 480 | sort='vulns', | |
| 481 | sort_dir='desc') | |
| 482 | self.reset_model(hosts) | |
| 483 | self.update_progress_label() | |
| 484 | ||
| 485 | def update_progress_label(self): | |
| 486 | """Updates the progress label with values from self.page and self.number_of_pages.""" | |
| 487 | self.progress_label.set_label("{0} / {1}".format(self.page , self.number_of_pages)) | |
| 488 | ||
| 489 | def create_search_entry(self): | |
| 490 | """Returns a simple search entry""" | |
| 491 | self.search_entry = Gtk.Entry() | |
| 492 | self.search_entry.set_placeholder_text("Search a host by ip...") | |
| 493 | self.search_entry.connect("activate", self.on_search_enter_key) | |
| 494 | self.search_entry.show() | |
| 495 | return self.search_entry | |
| 496 | ||
| 497 | def on_search_enter_key(self, entry): | |
| 498 | """Rebuild the model with the search, but self.page stays the same. | |
| 499 | """ | |
| 500 | self.on_click_move_page(Gtk.Button(), lambda i: i) | |
| 501 | ||
| 502 | ||
| 503 | class WorkspaceSidebar(Gtk.Widget): | |
| 504 | """Defines the sidebar widget to be used by the AppWindow, passed as an | |
| 505 | instance to the application. It only handles the view and the model, | |
| 506 | all the backend word is handled by the application via the callback""" | |
| 507 | ||
| 508 | def __init__(self, server_io, callback_to_change_workspace, | |
| 509 | callback_to_remove_workspace, callback_to_create_workspace, | |
| 510 | last_workspace): | |
| 511 | ||
| 512 | Gtk.Widget.__init__(self) | |
| 513 | self.change_ws = callback_to_change_workspace | |
| 514 | self.remove_ws = callback_to_remove_workspace | |
| 515 | self.create_ws = callback_to_create_workspace | |
| 516 | self.last_workspace = last_workspace | |
| 517 | self.serverIO = server_io | |
| 518 | ||
| 519 | self.workspaces = self.serverIO.get_workspaces_names() | |
| 520 | self.search_entry = self.create_search_entry() | |
| 521 | ||
| 522 | self.workspace_model = self.create_ws_model() | |
| 523 | self.workspace_view = self.create_ws_view(self.workspace_model) | |
| 524 | ||
| 525 | self.sidebar_button = Gtk.Button.new_with_label("Refresh workspaces") | |
| 526 | self.sidebar_button.connect("clicked", self.refresh_sidebar) | |
| 527 | ||
| 528 | def get_box(self): | |
| 529 | """Creates a return a simple vertical box containing all the widgets | |
| 530 | that make the sidebar. | |
| 531 | """ | |
| 532 | box = Gtk.Box(orientation=Gtk.Orientation.VERTICAL) | |
| 533 | box.pack_start(self.search_entry, False, False, 0) | |
| 534 | box.pack_start(self.workspace_view, True, True, 0) | |
| 535 | box.pack_start(self.sidebar_button, False, False, 0) | |
| 536 | return box | |
| 537 | ||
| 538 | def create_search_entry(self): | |
| 539 | """Returns a simple search entry""" | |
| 540 | search_entry = Gtk.Entry() | |
| 541 | search_entry.set_placeholder_text("Search...") | |
| 542 | search_entry.connect("activate", self.on_search_enter_key) | |
| 543 | return search_entry | |
| 544 | ||
| 545 | def on_search_enter_key(self, entry): | |
| 546 | """When the users preses enter, if the workspace exists, | |
| 547 | select it. If not, present the window to create a workspace with | |
| 548 | that name""" | |
| 549 | selection = self.ws_view.get_selection() | |
| 550 | model, ws_iter = selection.get_selected() | |
| 551 | ||
| 552 | if ws_iter is None: | |
| 553 | self.create_ws(title=entry.get_text()) | |
| 554 | entry.set_text("") | |
| 555 | else: | |
| 556 | self.change_ws(self.get_selected_ws_name()) | |
| 557 | ws_iter = self.get_selected_ws_iter() | |
| 558 | entry.set_text("") | |
| 559 | self.select_ws_by_iter(ws_iter) | |
| 560 | ||
| 561 | def refresh_sidebar(self, button=None): | |
| 562 | """Function called when the user press the refresh button. | |
| 563 | Gets an updated copy of the workspaces and checks against | |
| 564 | the model to see which are already there and which arent""" | |
| 565 | ||
| 566 | self.workspaces = self.serverIO.get_workspaces_names() | |
| 567 | ||
| 568 | model = self.workspace_model | |
| 569 | added_workspaces = [added_ws[0] for added_ws in model] | |
| 570 | for ws in self.workspaces: | |
| 571 | if ws not in added_workspaces: | |
| 572 | ws_iter = self.workspace_model.append([ws]) | |
| 573 | self.valid_ws_iters.append(ws_iter) | |
| 574 | ||
| 575 | for ws in added_workspaces: | |
| 576 | if ws not in self.workspaces: | |
| 577 | iter = self.get_iter_by_name(ws) | |
| 578 | self.workspace_model.remove(iter) | |
| 579 | ||
| 580 | def clear_sidebar(self): | |
| 581 | """Brutaly clear all the information from the model. | |
| 582 | No one survives""" | |
| 583 | self.valid_ws_iters = [] | |
| 584 | self.workspace_model.clear() | |
| 585 | ||
| 586 | def create_ws_model(self): | |
| 587 | """Creates and the workspace model. Also tries to assign | |
| 588 | self.default_selection to the tree_iter which represents the | |
| 589 | last active workspace""" | |
| 590 | workspace_model = Gtk.ListStore(str) | |
| 591 | self.default_selection = None | |
| 592 | self.valid_ws_iters = [] | |
| 593 | ||
| 594 | for ws in self.workspaces: | |
| 595 | tree_iter = workspace_model.append([ws]) | |
| 596 | self.valid_ws_iters.append(tree_iter) | |
| 597 | if ws == self.last_workspace: | |
| 598 | self.default_selection = tree_iter | |
| 599 | ||
| 600 | return workspace_model | |
| 601 | ||
| 602 | @scrollable(width=160) | |
| 603 | def create_ws_view(self, model): | |
| 604 | """Populate the workspace view. Also select by default | |
| 605 | self.default_selection (see workspace_model method). Also connect | |
| 606 | a selection with the change workspace callback""" | |
| 607 | ||
| 608 | self.ws_view = Gtk.TreeView(model) | |
| 609 | self.ws_view.set_activate_on_single_click(False) | |
| 610 | renderer = Gtk.CellRendererText() | |
| 611 | column = Gtk.TreeViewColumn("Workspaces", renderer, text=0) | |
| 612 | self.ws_view.append_column(column) | |
| 613 | self.ws_view.set_search_entry(self.search_entry) | |
| 614 | ||
| 615 | # select by default the last active workspace | |
| 616 | if self.default_selection is not None: | |
| 617 | self.select_default = self.ws_view.get_selection() | |
| 618 | self.select_default.select_iter(self.default_selection) | |
| 619 | ||
| 620 | selection = self.ws_view.get_selection() | |
| 621 | selection.set_mode(Gtk.SelectionMode.BROWSE) | |
| 622 | ||
| 623 | self.ws_view.connect("button-press-event", self.on_right_click) | |
| 624 | self.ws_view.connect("row-activated", self.on_left_click) | |
| 625 | ||
| 626 | return self.ws_view | |
| 627 | ||
| 628 | def on_left_click(self, view, path, column): | |
| 629 | ||
| 630 | # force selection of newly selected | |
| 631 | # before actually changing workspace | |
| 632 | select = view.get_selection() | |
| 633 | select.select_path(path) | |
| 634 | ||
| 635 | # change the workspace to the newly selected | |
| 636 | self.change_ws(self.get_selected_ws_name()) | |
| 637 | return True # prevents the click from selecting a workspace | |
| 638 | # this is handled manually by us on self.change_ws | |
| 639 | ||
| 640 | def on_right_click(self, view, event): | |
| 641 | """On click, check if it was a right click. If it was, | |
| 642 | create a menu with the delete option. On click on that option, | |
| 643 | delete the workspace that occupied the position where the user | |
| 644 | clicked. Returns True if it was a right click""" | |
| 645 | ||
| 646 | # if it isnt right click just do nothing | |
| 647 | if event.button != 3: | |
| 648 | return False | |
| 649 | ||
| 650 | # we really do care about where the user clicked, that is our | |
| 651 | # connection to the soon to be selection. if this didn't exist, | |
| 652 | # we couldn't do much: the selection of the view is still | |
| 653 | # whatever the user had selected before clicking | |
| 654 | try: | |
| 655 | path = view.get_path_at_pos(int(event.x), int(event.y))[0] | |
| 656 | except TypeError: | |
| 657 | # if the user didn't click on a workspace there no path to work on | |
| 658 | return False | |
| 659 | ||
| 660 | menu = Gtk.Menu() | |
| 661 | delete_item = Gtk.MenuItem("Delete") | |
| 662 | menu.append(delete_item) | |
| 663 | ||
| 664 | # get tree_iter from path. then get its name. then delete | |
| 665 | # that workspace | |
| 666 | ||
| 667 | tree_iter = self.workspace_model.get_iter(path) | |
| 668 | ws_name = self.workspace_model[tree_iter][0] | |
| 669 | ||
| 670 | delete_item.connect("activate", self.remove_ws, ws_name) | |
| 671 | ||
| 672 | delete_item.show() | |
| 673 | menu.popup(None, None, None, None, event.button, event.time) | |
| 674 | return True # prevents the click from selecting a workspace | |
| 675 | ||
| 676 | def get_selected_ws_iter(self): | |
| 677 | """Returns the tree_iter of the current selected workspace""" | |
| 678 | selection = self.ws_view.get_selection() | |
| 679 | _iter = selection.get_selected()[1] | |
| 680 | return _iter | |
| 681 | ||
| 682 | def get_selected_ws_name(self): | |
| 683 | """Return the name of the selected workspace""" | |
| 684 | selection = self.ws_view.get_selection() | |
| 685 | model, ws_iter = selection.get_selected() | |
| 686 | workspace_name = model[ws_iter][0] | |
| 687 | return workspace_name | |
| 688 | ||
| 689 | def select_ws_by_iter(self, ws_iter): | |
| 690 | """Selects workspace of iter ws_iter in the list""" | |
| 691 | selection = self.ws_view.get_selection() | |
| 692 | selection.select_iter(ws_iter) | |
| 693 | ||
| 694 | def get_iter_by_name(self, ws_name): | |
| 695 | """Returns the iter associated to the workspace ws_name or None | |
| 696 | if not found. | |
| 697 | """ | |
| 698 | # NOTE. this function should really be replaced by a dictionary | |
| 699 | for ws_iter in self.valid_ws_iters: | |
| 700 | if self.workspace_model.iter_is_valid(ws_iter): | |
| 701 | if self.workspace_model[ws_iter][0] == ws_name: | |
| 702 | return ws_iter | |
| 703 | return None | |
| 704 | ||
| 705 | def select_ws_by_name(self, ws_name): | |
| 706 | """Selects the workspace by name ws_name""" | |
| 707 | ws_iter = self.get_iter_by_name(ws_name) | |
| 708 | if ws_iter is not None: | |
| 709 | self.select_ws_by_iter(ws_iter) | |
| 710 | ||
| 711 | def add_workspace(self, ws): | |
| 712 | """Adds a workspace to the model and to the list of valid iters.""" | |
| 713 | ws_iter = self.workspace_model.append([ws]) | |
| 714 | self.valid_ws_iters.append(ws_iter) | |
| 715 | ||
| 716 | ||
| 717 | class ConsoleLog(Gtk.Widget): | |
| 718 | """Defines a textView and a textBuffer to be used for displaying | |
| 719 | and updating logging information in the appwindow.""" | |
| 720 | ||
| 721 | def __init__(self): | |
| 722 | super(Gtk.Widget, self).__init__() | |
| 723 | ||
| 724 | self.textBuffer = Gtk.TextBuffer() | |
| 725 | self.textBuffer.new() | |
| 726 | ||
| 727 | self.red = self.textBuffer.create_tag("error", foreground='Red') | |
| 728 | self.green = self.textBuffer.create_tag("debug", foreground='Green') | |
| 729 | self.blue = self.textBuffer.create_tag("notif", foreground="Blue") | |
| 730 | self.orange = self.textBuffer.create_tag("warning", | |
| 731 | foreground="#F5760F") | |
| 732 | self.bold = self.textBuffer.create_tag("bold", | |
| 733 | weight=Pango.Weight.BOLD) | |
| 734 | ||
| 735 | self.textBuffer.set_text("Welcome to Faraday!\n\0", | |
| 736 | -1) | |
| 737 | ||
| 738 | self.textBuffer.apply_tag(self.bold, | |
| 739 | self.textBuffer.get_iter_at_line(0), | |
| 740 | self.textBuffer.get_end_iter()) | |
| 741 | ||
| 742 | self.textView = Gtk.TextView() | |
| 743 | self.textView.set_editable(False) | |
| 744 | # TODO: only execute monospace if Gi >= 3.16 | |
| 745 | # self.textView.set_monospace(True) | |
| 746 | self.textView.set_justification(Gtk.Justification.LEFT) | |
| 747 | ||
| 748 | self.textView.set_buffer(self.textBuffer) | |
| 749 | ||
| 750 | @scrollable(height=100, width=100) | |
| 751 | def create_scrollable_logger(self): | |
| 752 | """Returns the ScrolledWindow used to contain the view""" | |
| 753 | return self.textView | |
| 754 | ||
| 755 | def news_button(self, url, description): | |
| 756 | ||
| 757 | anchor = self.textBuffer.create_child_anchor( | |
| 758 | self.textBuffer.get_end_iter()) | |
| 759 | ||
| 760 | button = Gtk.Button() | |
| 761 | label = Gtk.Label() | |
| 762 | ||
| 763 | label.set_markup( | |
| 764 | 'Faraday News: <a href="' + url + '"> ' + | |
| 765 | description + "</a>") | |
| 766 | ||
| 767 | button.add(label) | |
| 768 | button.set_relief(Gtk.ReliefStyle.NONE) | |
| 769 | ||
| 770 | button.connect("clicked", lambda o: webbrowser.open(url)) | |
| 771 | ||
| 772 | label.show() | |
| 773 | button.show() | |
| 774 | self.update("\n") | |
| 775 | ||
| 776 | self.textView.add_child_at_anchor(button, anchor) | |
| 777 | ||
| 778 | def customEvent(self, text): | |
| 779 | """Filters event so that only those with type 3131 get to the log. | |
| 780 | Also split them, so we can add the correct formatting to the first | |
| 781 | part of the message""" | |
| 782 | ||
| 783 | text = text.split('-', 1) | |
| 784 | if text[0] == "INFO ": | |
| 785 | self.update("[ " + text[0] + "]", self.bold) | |
| 786 | elif text[0] == "DEBUG ": | |
| 787 | self.update("[ " + text[0] + "]", self.bold, self.green) | |
| 788 | elif text[0] == "ERROR " or text[0] == "CRITICAL: ": | |
| 789 | self.update("[ " + text[0] + "]", self.bold, self.red) | |
| 790 | elif text[0] == "WARNING ": | |
| 791 | self.update("[ " + text[0] + "]", self.bold, self.orange) | |
| 792 | elif text[0] == "NOTIFICATION ": | |
| 793 | self.update("[ " + text[0] + "]", self.bold, self.blue) | |
| 794 | elif text[0] == "NEWS ": | |
| 795 | # Format of data : 'NEWS - URL|DESC' | |
| 796 | data_url_desc = text[1].split('|') | |
| 797 | self.news_button(data_url_desc[0], data_url_desc[1]) | |
| 798 | return | |
| 799 | ||
| 800 | self.update("-" + '-'.join(text[1:]) + "\n") | |
| 801 | ||
| 802 | def update(self, text, *tags): | |
| 803 | """Updates the textBuffer with the event sent. Also scrolls to last | |
| 804 | posted automatically""" | |
| 805 | last_position = self.textBuffer.get_end_iter() | |
| 806 | self.textBuffer.insert(last_position, text, len(text)) | |
| 807 | ||
| 808 | # we need to take 1 from the lines to compensate for the default line | |
| 809 | lines = self.textBuffer.get_line_count() | |
| 810 | begin = self.textBuffer.get_iter_at_line(lines - 1) | |
| 811 | ||
| 812 | # update last position, it isn't the same as when the funcion started | |
| 813 | last_position = self.textBuffer.get_end_iter() | |
| 814 | ||
| 815 | for tag in tags: | |
| 816 | self.textBuffer.apply_tag(tag, begin, last_position) | |
| 817 | ||
| 818 | self.scroll_to_insert(self.textBuffer.get_insert()) | |
| 819 | ||
| 820 | def scroll_to_insert(self, insert): | |
| 821 | """Scrolls the view to a particular insert point""" | |
| 822 | self.textView.scroll_to_mark(insert, 0, False, 1, 1) | |
| 823 | ||
| 824 | ||
| 825 | class Statusbar(Gtk.Widget): | |
| 826 | """Defines a statusbar. Will have a notifications button, | |
| 827 | a string informing of how many hosts/services/vulns are in the | |
| 828 | current workspace nad the conflicts button.""" | |
| 829 | ||
| 830 | def __init__(self, notif_callback, conflict_callback, | |
| 831 | host_count, service_count, vuln_count): | |
| 832 | """Initializes the statusbar. Takes a notification_callback | |
| 833 | to open the notifiacion window, conflick_callback to open | |
| 834 | the conclifcts window, and a host, service and vuln counts | |
| 835 | to be displayed""" | |
| 836 | Gtk.Widget.__init__(self) | |
| 837 | initial_strings = self.create_strings(host_count, service_count, | |
| 838 | vuln_count) | |
| 839 | ||
| 840 | self.active_workspace_label = Gtk.Label() | |
| 841 | self.active_workspace_label.set_use_markup(True) | |
| 842 | self.notif_text = "Notifications: " | |
| 843 | self.conflict_text = "Conflicts: " | |
| 844 | ||
| 845 | self.host_count_str = initial_strings[0] | |
| 846 | self.service_count_str = initial_strings[1] | |
| 847 | self.vuln_count_str = initial_strings[2] | |
| 848 | ||
| 849 | self.ws_info = self.create_initial_ws_info() | |
| 850 | ||
| 851 | self.notif_button = Gtk.Button.new() | |
| 852 | self.set_default_notif_label() | |
| 853 | self.notif_button.connect("clicked", notif_callback) | |
| 854 | self.notif_button.connect("clicked", self.set_default_notif_label) | |
| 855 | ||
| 856 | self.conflict_button = Gtk.Button.new() | |
| 857 | self.set_default_conflict_label() | |
| 858 | self.conflict_button.connect("clicked", conflict_callback) | |
| 859 | ||
| 860 | self.mainBox = Gtk.Box() | |
| 861 | self.mainBox.pack_start(self.notif_button, False, False, 5) | |
| 862 | self.mainBox.pack_start(self.ws_info, False, True, 5) | |
| 863 | self.mainBox.pack_start(Gtk.Box(), True, True, 5) # blank space | |
| 864 | self.mainBox.pack_start(self.active_workspace_label, False, True, 5) | |
| 865 | self.mainBox.pack_end(self.conflict_button, False, True, 5) | |
| 866 | ||
| 867 | def set_workspace_label(self, new_label): | |
| 868 | self.active_workspace_label.set_label("Active workspace: <b>{0}</b>".format(new_label)) | |
| 869 | ||
| 870 | def inc_notif_button_label(self): | |
| 871 | """Increments the button label, sets bold so user knows there are | |
| 872 | unread notifications""" | |
| 873 | ||
| 874 | self.notif_button_label_int += 1 | |
| 875 | child = self.notif_button.get_child() | |
| 876 | self.notif_button.remove(child) | |
| 877 | label = Gtk.Label.new() | |
| 878 | label.set_markup("<b> %s %s </b>" | |
| 879 | % (self.notif_text, str(self.notif_button_label_int))) | |
| 880 | ||
| 881 | label.show() | |
| 882 | self.notif_button.add(label) | |
| 883 | ||
| 884 | def update_conflict_button_label(self, n): | |
| 885 | self.conflict_button_label_int += n | |
| 886 | child = self.conflict_button.get_child() | |
| 887 | self.conflict_button.remove(child) | |
| 888 | label = Gtk.Label.new(self.conflict_text + | |
| 889 | str(self.conflict_button_label_int)) | |
| 890 | label.show() | |
| 891 | self.conflict_button.add(label) | |
| 892 | ||
| 893 | def set_default_notif_label(self, button=None): | |
| 894 | """Creates the default label""" | |
| 895 | self.notif_button_label_int = 0 | |
| 896 | self.notif_button.set_label(self.notif_text + | |
| 897 | str(self.notif_button_label_int)) | |
| 898 | ||
| 899 | def set_default_conflict_label(self): | |
| 900 | self.conflict_button_label_int = 0 | |
| 901 | self.conflict_button.set_label(self.conflict_text + | |
| 902 | str(self.conflict_button_label_int)) | |
| 903 | ||
| 904 | def create_initial_ws_info(self): | |
| 905 | box = Gtk.Box() | |
| 906 | self.explain = Gtk.Label.new("Workspace status: ") | |
| 907 | self.host_label = Gtk.Label.new(self.host_count_str) | |
| 908 | self.service_label = Gtk.Label.new(self.service_count_str) | |
| 909 | self.vuln_label = Gtk.Label.new(self.vuln_count_str) | |
| 910 | ||
| 911 | box.pack_start(self.explain, True, True, 0) | |
| 912 | box.pack_start(self.host_label, True, True, 0) | |
| 913 | box.pack_start(self.service_label, True, True, 0) | |
| 914 | box.pack_start(self.vuln_label, True, True, 0) | |
| 915 | return box | |
| 916 | ||
| 917 | def update_ws_info(self, new_host_count, new_service_count, | |
| 918 | new_vuln_count): | |
| 919 | host, service, vuln = self.create_strings(new_host_count, | |
| 920 | new_service_count, | |
| 921 | new_vuln_count) | |
| 922 | self.host_label.set_text(host) | |
| 923 | self.service_label.set_text(service) | |
| 924 | self.vuln_label.set_text(vuln) | |
| 925 | ||
| 926 | def create_strings(self, host_count, service_count, vuln_count): | |
| 927 | host_string = str(host_count) + " hosts, " | |
| 928 | service_string = str(service_count) + " services, " | |
| 929 | vuln_string = str(vuln_count) + " vulnerabilities." | |
| 930 | ||
| 931 | return host_string, service_string, vuln_string | |
| 932 | ||
| 933 | ||
| 934 | # I'm Py3 |
| 0 | <!-- | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | --> | |
| 5 | ||
| 6 | <?xml version="1.0"?> | |
| 7 | <interface> | |
| 8 | <menu id="appmenu"> | |
| 9 | <section> | |
| 10 | <item> | |
| 11 | <attribute name="label" translatable="yes">Preferences</attribute> | |
| 12 | <attribute name="action">app.preferences</attribute> | |
| 13 | </item> | |
| 14 | <item> | |
| 15 | <attribute name="label" translatable="yes">Plugins</attribute> | |
| 16 | <attribute name="action">app.pluginOptions</attribute> | |
| 17 | </item> | |
| 18 | </section> | |
| 19 | <section> | |
| 20 | <item> | |
| 21 | <attribute name="label" translatable="yes">About</attribute> | |
| 22 | <attribute name="action">app.about</attribute> | |
| 23 | </item> | |
| 24 | <submenu> | |
| 25 | <attribute name="label">Help</attribute> | |
| 26 | <item> | |
| 27 | <attribute name="label" translatable="yes">Documentation</attribute> | |
| 28 | <attribute name="action">app.go_to_documentation</attribute> | |
| 29 | </item> | |
| 30 | <item> | |
| 31 | <attribute name="label" translatable="yes">FAQ</attribute> | |
| 32 | <attribute name="action">app.go_to_faq</attribute> | |
| 33 | </item> | |
| 34 | <item> | |
| 35 | <attribute name="label" translatable="yes">Troubleshooting</attribute> | |
| 36 | <attribute name="action">app.go_to_troubleshooting</attribute> | |
| 37 | </item> | |
| 38 | <item> | |
| 39 | <attribute name="label" translatable="yes">Demos</attribute> | |
| 40 | <attribute name="action">app.go_to_demos</attribute> | |
| 41 | </item> | |
| 42 | <item> | |
| 43 | <attribute name="label" translatable="yes">Issues</attribute> | |
| 44 | <attribute name="action">app.go_to_issues</attribute> | |
| 45 | </item> | |
| 46 | <item> | |
| 47 | <attribute name="label" translatable="yes">Forum</attribute> | |
| 48 | <attribute name="action">app.go_to_forum</attribute> | |
| 49 | </item> | |
| 50 | <item> | |
| 51 | <attribute name="label" translatable="yes">IRC</attribute> | |
| 52 | <attribute name="action">app.go_to_irc</attribute> | |
| 53 | </item> | |
| 54 | <item> | |
| 55 | <attribute name="label" translatable="yes">Twitter</attribute> | |
| 56 | <attribute name="action">app.go_to_twitter</attribute> | |
| 57 | </item> | |
| 58 | <item> | |
| 59 | <attribute name="label" translatable="yes">Google Group</attribute> | |
| 60 | <attribute name="action">app.go_to_googlegroup</attribute> | |
| 61 | </item> | |
| 62 | </submenu> | |
| 63 | <item> | |
| 64 | <attribute name="label" translatable="yes">Quit</attribute> | |
| 65 | <attribute name="action">app.quit</attribute> | |
| 66 | <attribute name="accel"><Primary>q</attribute> | |
| 67 | </item> | |
| 68 | </section> | |
| 69 | </menu> | |
| 70 | </interface> | |
| 71 |
| 0 | #!/usr/bin/python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | ||
| 7 | """ | |
| 8 | from __future__ import absolute_import | |
| 9 | ||
| 10 | import time | |
| 11 | import threading | |
| 12 | ||
| 13 | from faraday.client.model.guiapi import notification_center | |
| 14 | from faraday.client.gui.gtk.decorators import safe_io_with_server | |
| 15 | from faraday.client.persistence.server import models, server_io_exceptions | |
| 16 | ||
| 17 | ||
| 18 | class ServerIO: | |
| 19 | def __init__(self, active_workspace): | |
| 20 | self.__active_workspace = active_workspace | |
| 21 | self.stream = None # will be set when active workpsace is set | |
| 22 | self.changes_lock = models.get_changes_lock() | |
| 23 | ||
| 24 | @property | |
| 25 | def active_workspace(self): | |
| 26 | return self.__active_workspace | |
| 27 | ||
| 28 | @active_workspace.setter | |
| 29 | def active_workspace(self, new_workspace): | |
| 30 | self.__active_workspace = new_workspace | |
| 31 | if self.stream: | |
| 32 | self.stream.stop() | |
| 33 | self.stream = self.get_changes_stream() | |
| 34 | self.continously_get_changes() | |
| 35 | ||
| 36 | @safe_io_with_server([]) | |
| 37 | def get_hosts(self, **params): | |
| 38 | return models.get_hosts(self.active_workspace, **params) | |
| 39 | ||
| 40 | @safe_io_with_server(0) | |
| 41 | def get_hosts_number(self): | |
| 42 | return models.get_hosts_number(self.active_workspace) | |
| 43 | ||
| 44 | @safe_io_with_server([]) | |
| 45 | def get_interfaces(self, **params): | |
| 46 | return models.get_interfaces(self.active_workspace, **params) | |
| 47 | ||
| 48 | @safe_io_with_server(0) | |
| 49 | def get_interfaces_number(self): | |
| 50 | return models.get_interfaces_number(self.active_workspace) | |
| 51 | ||
| 52 | @safe_io_with_server([]) | |
| 53 | def get_services(self, **params): | |
| 54 | return models.get_services(self.active_workspace, **params) | |
| 55 | ||
| 56 | @safe_io_with_server(0) | |
| 57 | def get_services_number(self): | |
| 58 | return models.get_services_number(self.active_workspace) | |
| 59 | ||
| 60 | @safe_io_with_server([]) | |
| 61 | def get_all_vulns(self, **params): | |
| 62 | return models.get_all_vulns(self.active_workspace, **params) | |
| 63 | ||
| 64 | @safe_io_with_server(0) | |
| 65 | def get_vulns_number(self): | |
| 66 | return models.get_vulns_number(self.active_workspace) | |
| 67 | ||
| 68 | @safe_io_with_server([]) | |
| 69 | def get_workspaces_names(self): | |
| 70 | return models.get_workspaces_names() | |
| 71 | ||
| 72 | @safe_io_with_server(None) | |
| 73 | def get_object(self, object_signature, object_id): | |
| 74 | return models.get_object(self.active_workspace, object_signature, object_id) | |
| 75 | ||
| 76 | @safe_io_with_server(None) | |
| 77 | def get_host(self, host_id): | |
| 78 | return models.get_host(self.active_workspace, host_id) | |
| 79 | ||
| 80 | @safe_io_with_server((0, 0, 0)) | |
| 81 | def get_workspace_numbers(self): | |
| 82 | return models.get_workspace_numbers(self.active_workspace) | |
| 83 | ||
| 84 | @safe_io_with_server(False) | |
| 85 | def server_info(self): | |
| 86 | return models.server_info() | |
| 87 | ||
| 88 | @safe_io_with_server(False) | |
| 89 | def check_server_url(self, url): | |
| 90 | return models.check_server_url(url) | |
| 91 | ||
| 92 | @safe_io_with_server(None) | |
| 93 | def get_changes_stream(self): | |
| 94 | return models.get_changes_stream(self.active_workspace) | |
| 95 | ||
| 96 | @safe_io_with_server((None, None)) | |
| 97 | def get_deleted_object_name_and_type(self, obj_id): | |
| 98 | return models.get_deleted_object_name_and_type(self.active_workspace, obj_id) | |
| 99 | ||
| 100 | def continously_get_changes(self): | |
| 101 | """Creates a thread which will continuously check the changes | |
| 102 | coming from other instances of Faraday. Return the thread on any | |
| 103 | exception, of if self.stream is None. | |
| 104 | """ | |
| 105 | ||
| 106 | def get_changes(): | |
| 107 | if not self.stream: | |
| 108 | return False | |
| 109 | while True: | |
| 110 | try: | |
| 111 | for obj_information in self.stream: | |
| 112 | action = obj_information.get('action') | |
| 113 | obj_id = obj_information.get('id') | |
| 114 | obj_type = obj_information.get('type') | |
| 115 | obj_name = obj_information.get('name') | |
| 116 | if action == 'CREATE': | |
| 117 | obj = self.get_object(obj_type, obj_id) | |
| 118 | notification_center.addObject(obj) | |
| 119 | elif action == 'UPDATE': | |
| 120 | obj = self.get_object(obj_type, obj_id) | |
| 121 | notification_center.editObject(obj) | |
| 122 | elif action == 'DELETE': | |
| 123 | notification_center.deleteObject(obj_id, obj_type) | |
| 124 | else: | |
| 125 | raise Exception('Invalid action') | |
| 126 | notification_center.changeFromInstance( | |
| 127 | action, | |
| 128 | obj_id, | |
| 129 | obj_type, | |
| 130 | obj_name) | |
| 131 | except server_io_exceptions.ChangesStreamStoppedAbruptly: | |
| 132 | notification_center.WorkspaceProblem() | |
| 133 | return False | |
| 134 | time.sleep(0.5) | |
| 135 | ||
| 136 | get_changes_thread = threading.Thread(target=get_changes, name='get_changes') | |
| 137 | get_changes_thread.daemon = True | |
| 138 | get_changes_thread.start() | |
| 139 | ||
| 140 | def continously_check_server_connection(self): | |
| 141 | """Starts a thread which requests from the server every second, so | |
| 142 | we know if the connection is still alive. | |
| 143 | """ | |
| 144 | def test_server_connection(): | |
| 145 | tolerance = 0 | |
| 146 | while True: | |
| 147 | time.sleep(1) | |
| 148 | test_was_successful = self.server_info() is not None | |
| 149 | if test_was_successful: | |
| 150 | tolerance = 0 | |
| 151 | else: | |
| 152 | tolerance += 1 | |
| 153 | if tolerance == 3: | |
| 154 | notification_center.DBConnectionProblem() | |
| 155 | ||
| 156 | test_server_thread = threading.Thread(target=test_server_connection) | |
| 157 | test_server_thread.daemon = True | |
| 158 | test_server_thread.start() | |
| 159 | ||
| 160 | ||
| 161 | # I'm Py3 |
| 0 | #!/usr/bin/env python | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | ||
| 9 | from faraday.client.managers.reports_managers import ReportManager | |
| 10 | ||
| 11 | from faraday.config.configuration import getInstanceConfiguration | |
| 12 | CONF = getInstanceConfiguration() | |
| 13 | ||
| 14 | ||
| 15 | class UiFactory: | |
| 16 | @staticmethod | |
| 17 | def create(model_controller, plugin_manager, workspace_manager, plugin_controller, gui="gtk"): | |
| 18 | if gui == "gtk": | |
| 19 | from faraday.client.gui.gtk.application import GuiApp # pylint:disable=import-outside-toplevel | |
| 20 | else: | |
| 21 | from faraday.client.gui.nogui.application import GuiApp # pylint:disable=import-outside-toplevel | |
| 22 | ||
| 23 | return GuiApp(model_controller, plugin_manager, workspace_manager, plugin_controller) | |
| 24 | ||
| 25 | ||
| 26 | class FaradayUi: | |
| 27 | def __init__(self, model_controller, plugin_manager, | |
| 28 | workspace_manager, plugin_controller, gui="gtk"): | |
| 29 | self.model_controller = model_controller | |
| 30 | self.plugin_manager = plugin_manager | |
| 31 | self.workspace_manager = workspace_manager | |
| 32 | self.plugin_controller = plugin_controller | |
| 33 | self.report_manager = None | |
| 34 | ||
| 35 | def getModelController(self): | |
| 36 | return self.model_controller | |
| 37 | ||
| 38 | def getPluginManager(self): | |
| 39 | return self.plugin_manager | |
| 40 | ||
| 41 | def getWorkspaceManager(self): | |
| 42 | return self.workspace_manager | |
| 43 | ||
| 44 | def setSplashImage(self, ipath): | |
| 45 | pass | |
| 46 | ||
| 47 | def startSplashScreen(self): | |
| 48 | pass | |
| 49 | ||
| 50 | def stopSplashScreen(self): | |
| 51 | pass | |
| 52 | ||
| 53 | def splashMessage(self, message): | |
| 54 | pass | |
| 55 | ||
| 56 | def loadWorkspaces(self): | |
| 57 | pass | |
| 58 | ||
| 59 | def run(self, args): | |
| 60 | pass | |
| 61 | ||
| 62 | def quit(self): | |
| 63 | pass | |
| 64 | ||
| 65 | def postEvent(self, receiver, event): | |
| 66 | pass | |
| 67 | ||
| 68 | def createLoggerWidget(self): | |
| 69 | pass | |
| 70 | ||
| 71 | def openWorkspace(self, name): | |
| 72 | """Open a workspace by name. Returns the workspace of raises an | |
| 73 | exception if for some reason it couldn't. | |
| 74 | """ | |
| 75 | if self.report_manager: | |
| 76 | self.report_manager.stop() | |
| 77 | self.report_manager.join() | |
| 78 | try: | |
| 79 | ws = self.getWorkspaceManager().openWorkspace(name) | |
| 80 | self.report_manager = ReportManager( | |
| 81 | 10, | |
| 82 | name, | |
| 83 | self.plugin_controller | |
| 84 | ) | |
| 85 | self.report_manager.start() | |
| 86 | except Exception as e: | |
| 87 | raise e | |
| 88 | return ws | |
| 89 | ||
| 90 | ||
| 91 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | import logging | |
| 9 | import threading | |
| 10 | import faraday.client.model.guiapi | |
| 11 | from faraday.client.gui.customevents import LogCustomEvent | |
| 12 | ||
| 13 | class GUIHandler(logging.Handler): | |
| 14 | def __init__(self): | |
| 15 | logging.Handler.__init__(self) | |
| 16 | self._widgets = [] | |
| 17 | self._widgets_lock = threading.RLock() | |
| 18 | formatter = logging.Formatter( | |
| 19 | '%(levelname)s - %(asctime)s - %(name)s - %(message)s') | |
| 20 | self.setFormatter(formatter) | |
| 21 | ||
| 22 | def registerGUIOutput(self, widget): | |
| 23 | self._widgets_lock.acquire() | |
| 24 | self._widgets.append(widget) | |
| 25 | self._widgets_lock.release() | |
| 26 | ||
| 27 | def clearWidgets(self): | |
| 28 | self._widgets_lock.acquire() | |
| 29 | self._widgets = [] | |
| 30 | self._widgets_lock.release() | |
| 31 | ||
| 32 | def emit(self, record): | |
| 33 | try: | |
| 34 | msg = self.format(record) | |
| 35 | self._widgets_lock.acquire() | |
| 36 | for widget in self._widgets: | |
| 37 | event = LogCustomEvent(msg) | |
| 38 | faraday.client.model.guiapi.postCustomEvent(event, widget) | |
| 39 | self._widgets_lock.release() | |
| 40 | except: | |
| 41 | self.handleError(record) | |
| 42 | ||
| 43 | ||
| 44 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | ||
| 7 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | ||
| 9 | import time | |
| 10 | ||
| 11 | from faraday.client.gui.gui_app import FaradayUi | |
| 12 | from faraday.client.gui.nogui.eventwatcher import EventWatcher | |
| 13 | import faraday.client.model.guiapi | |
| 14 | from faraday.server.utils.logger import get_logger | |
| 15 | ||
| 16 | from faraday.config.configuration import getInstanceConfiguration | |
| 17 | CONF = getInstanceConfiguration() | |
| 18 | ||
| 19 | ||
| 20 | class GuiApp(FaradayUi): | |
| 21 | def __init__(self, model_controller, plugin_manager, workspace_manager, plugin_controller): | |
| 22 | FaradayUi.__init__(self, | |
| 23 | model_controller, | |
| 24 | plugin_manager, | |
| 25 | workspace_manager, | |
| 26 | plugin_controller) | |
| 27 | self._stop = False | |
| 28 | faraday.client.model.guiapi.setMainApp(self) | |
| 29 | self.event_watcher = EventWatcher() | |
| 30 | faraday.client.model.guiapi.notification_center.registerWidget(self.event_watcher) | |
| 31 | ||
| 32 | def run(self, args): | |
| 33 | workspace = args.workspace | |
| 34 | try: | |
| 35 | ws = super(GuiApp, self).openWorkspace(workspace) | |
| 36 | except Exception as e: | |
| 37 | get_logger(self).error( | |
| 38 | ("Your last workspace %s is not accessible, " | |
| 39 | "check configuration.") % workspace) | |
| 40 | get_logger(self).error( | |
| 41 | "You may try and go to ~/.faraday/config/user.xml " | |
| 42 | "to set a valid api_uri and last_workspace") | |
| 43 | get_logger(self).error(str(e)) | |
| 44 | valid = False | |
| 45 | for i in range(4): | |
| 46 | workspace = raw_input("Please write the correct, Workspace): ") | |
| 47 | try: | |
| 48 | ws = super(GuiApp, self).openWorkspace(workspace) | |
| 49 | valid = True | |
| 50 | break | |
| 51 | except Exception as err: | |
| 52 | get_logger(self).error( | |
| 53 | ("Your last workspace %s is not accessible, " | |
| 54 | "check configuration.") % workspace) | |
| 55 | get_logger(self).error( | |
| 56 | "You may try and go to ~/.faraday/config/user.xml " | |
| 57 | "to set a valid api_uri and last_workspace") | |
| 58 | get_logger(self).error(str(err)) | |
| 59 | if not valid: | |
| 60 | return -1 | |
| 61 | workspace = ws.name | |
| 62 | CONF.setLastWorkspace(workspace) | |
| 63 | CONF.saveConfig() | |
| 64 | get_logger(self).info("Workspace %s loaded" % workspace) | |
| 65 | while True: | |
| 66 | if self._stop: | |
| 67 | return | |
| 68 | time.sleep(0.01) | |
| 69 | ||
| 70 | def quit(self): | |
| 71 | self._stop = True | |
| 72 | ||
| 73 | def postEvent(self, receiver, event): | |
| 74 | receiver.update(event) | |
| 75 | ||
| 76 | ||
| 77 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | from faraday.server.utils.logger import get_logger | |
| 9 | from faraday.client.gui.customevents import CHANGEFROMINSTANCE | |
| 10 | ||
| 11 | ||
| 12 | class EventWatcher: | |
| 13 | def __init__(self): | |
| 14 | self.logger = get_logger(self) | |
| 15 | ||
| 16 | def update(self, event): | |
| 17 | if event.type() == CHANGEFROMINSTANCE: | |
| 18 | get_logger(self).info( | |
| 19 | "[Update Received] " + event.change.getMessage()) | |
| 20 | ||
| 21 | ||
| 22 | # I'm Py3 |
| 0 | #!/usr/bin/env python | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | ||
| 9 | import threading | |
| 10 | from faraday.client.gui.gui_app import FaradayUi | |
| 11 | import faraday.client.gui.customevents as events | |
| 12 | ||
| 13 | ||
| 14 | class NotificationCenter(): | |
| 15 | def __init__(self, uiapp=FaradayUi(None, None, None, None, None)): | |
| 16 | self.uiapp = uiapp | |
| 17 | self._consumers = [] | |
| 18 | self._consumers_lock = threading.RLock() | |
| 19 | self.last_events = {} | |
| 20 | ||
| 21 | def setUiApp(self, uiapp): | |
| 22 | self.uiapp = uiapp | |
| 23 | ||
| 24 | def registerWidget(self, consumer): | |
| 25 | self._consumers_lock.acquire() | |
| 26 | if consumer not in self._consumers: | |
| 27 | self._consumers.append(consumer) | |
| 28 | self._consumers_lock.release() | |
| 29 | ||
| 30 | def deregisterWidget(self, consumer): | |
| 31 | self._consumers_lock.acquire() | |
| 32 | if consumer in self._consumers: | |
| 33 | self._consumers.remove(consumer) | |
| 34 | self._consumers_lock.release() | |
| 35 | ||
| 36 | def postCustomEvent(self, event, receiver=None): | |
| 37 | if self.last_events.get(event.type(), None): | |
| 38 | if self.last_events[event.type()] > event.time(): | |
| 39 | return | |
| 40 | self.last_events[event.type()] = event.time() | |
| 41 | self.uiapp.postEvent(receiver, event) | |
| 42 | ||
| 43 | def _notifyWidgets(self, event): | |
| 44 | self._consumers_lock.acquire() | |
| 45 | for w in self._consumers: | |
| 46 | self.postCustomEvent(event, w) | |
| 47 | self._consumers_lock.release() | |
| 48 | ||
| 49 | def showPopup(self, msg): | |
| 50 | self._notifyWidgets(events.ShowPopupCustomEvent(msg)) | |
| 51 | ||
| 52 | def showDialog(self, msg, level="INFORMATION"): | |
| 53 | self._notifyWidgets(events.ShowDialogCustomEvent(msg, level)) | |
| 54 | ||
| 55 | def workspaceChanged(self, workspace): | |
| 56 | self._notifyWidgets(events.WorkspaceChangedCustomEvent(workspace)) | |
| 57 | ||
| 58 | def DBConnectionProblem(self, problem=None): | |
| 59 | self._notifyWidgets(events.ShowExceptionConnectionRefusedCustomEvent(problem)) | |
| 60 | ||
| 61 | def WorkspaceProblem(self, problem=None): | |
| 62 | self._notifyWidgets(events.WorkspaceProblemCustomEvent(problem)) | |
| 63 | ||
| 64 | def addHost(self, host): | |
| 65 | self._notifyWidgets(events.AddHostCustomEvent(host)) | |
| 66 | ||
| 67 | def delHost(self, host_id): | |
| 68 | self._notifyWidgets(events.DeleteHostCustomEvent(host_id)) | |
| 69 | ||
| 70 | def editHost(self, host): | |
| 71 | self._notifyWidgets(events.EditHostCustomEvent(host)) | |
| 72 | ||
| 73 | def conflictUpdate(self, vulns_changed): | |
| 74 | self._notifyWidgets(events.ConflictUpdatedCustomEvent(vulns_changed)) | |
| 75 | ||
| 76 | def conflictResolution(self, conflicts): | |
| 77 | self._notifyWidgets(events.ResolveConflictsCustomEvent(conflicts)) | |
| 78 | ||
| 79 | def changeFromInstance(self, action, obj_id, obj_type, obj_name): | |
| 80 | self._notifyWidgets(events.ChangeFromInstanceCustomEvent(action, | |
| 81 | obj_id, | |
| 82 | obj_type, | |
| 83 | obj_name)) | |
| 84 | ||
| 85 | def addHostFromChanges(self, obj): | |
| 86 | self._notifyWidgets(events.AddHostChangesEvent(obj)) | |
| 87 | ||
| 88 | def editObject(self, obj): | |
| 89 | self._notifyWidgets(events.UpdateObjectCustomEvent(obj)) | |
| 90 | ||
| 91 | def deleteObject(self, obj_id, obj_type): | |
| 92 | self._notifyWidgets(events.DeleteObjectCustomEvent(obj_id, obj_type)) | |
| 93 | ||
| 94 | def addObject(self, new_object): | |
| 95 | self._notifyWidgets(events.AddObjectCustomEvent(new_object)) | |
| 96 | ||
| 97 | def sendCustomLog(self, log_obj): | |
| 98 | self._notifyWidgets(events.LogCustomEvent(log_obj)) | |
| 99 | ||
| 100 | ||
| 101 | # I'm Py3 |
| 0 | #!/usr/bin/env python3 | |
| 1 | ||
| 2 | """ | |
| 3 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | Author: Ezequiel Tavella | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | ||
| 7 | This script generate a CSV file with information about the cfdb database. | |
| 8 | CSV Format: | |
| 9 | cwe,name,description,resolution,exploitation,references | |
| 10 | """ | |
| 11 | from __future__ import absolute_import | |
| 12 | from __future__ import print_function | |
| 13 | ||
| 14 | from subprocess import call | |
| 15 | from os import walk | |
| 16 | import csv | |
| 17 | ||
| 18 | URL_PROYECT = 'https://github.com/mubix/cfdb' | |
| 19 | DB_PATH = './cfdb/' | |
| 20 | ||
| 21 | class parseFile(): | |
| 22 | ||
| 23 | def __init__(self, file_md): | |
| 24 | ||
| 25 | self.cwe = '' | |
| 26 | self.name = None | |
| 27 | self.description = None | |
| 28 | self.resolution = None | |
| 29 | self.explotation = None | |
| 30 | self.references = None | |
| 31 | ||
| 32 | self.file = file_md | |
| 33 | self.parse() | |
| 34 | ||
| 35 | def getContent(self): | |
| 36 | ||
| 37 | result = [] | |
| 38 | while True: | |
| 39 | ||
| 40 | subLine = self.file.readline().strip('\n\r') | |
| 41 | if subLine != '\n': | |
| 42 | #If EOF -> break | |
| 43 | if subLine == '' : | |
| 44 | break | |
| 45 | ||
| 46 | if not subLine.startswith('##') : | |
| 47 | result.append(subLine) | |
| 48 | else: | |
| 49 | break | |
| 50 | ||
| 51 | return ''.join(result) | |
| 52 | ||
| 53 | def parse(self): | |
| 54 | ||
| 55 | line = self.file.readline() | |
| 56 | while line != '': | |
| 57 | ||
| 58 | title = line.startswith('Title: ') | |
| 59 | description = line.startswith('Description: ') | |
| 60 | resolution = line.startswith('## Remediation') | |
| 61 | references = line.startswith('## References') | |
| 62 | explotation = line.startswith('## Exploitation') | |
| 63 | ||
| 64 | #Slice title... read line and continue with other line | |
| 65 | if title: | |
| 66 | ||
| 67 | self.name = line[title + 6:].strip('\n\r') | |
| 68 | line = self.file.readline() | |
| 69 | continue | |
| 70 | ||
| 71 | #Read first line with \n and read the content | |
| 72 | elif description: | |
| 73 | line = self.file.readline() | |
| 74 | self.description = self.getContent() | |
| 75 | elif resolution: | |
| 76 | line = self.file.readline() | |
| 77 | self.resolution = self.getContent() | |
| 78 | elif references: | |
| 79 | line = self.file.readline() | |
| 80 | self.references = self.getContent() | |
| 81 | elif explotation: | |
| 82 | line = self.file.readline() | |
| 83 | self.explotation = self.getContent() | |
| 84 | #Nothing here...read line | |
| 85 | else: | |
| 86 | line = self.file.readline() | |
| 87 | ||
| 88 | ||
| 89 | def main(): | |
| 90 | ||
| 91 | #Get DB cfdb | |
| 92 | print('[*]Execute git clone...') | |
| 93 | return_code = call(['git', 'clone', URL_PROYECT]) | |
| 94 | ||
| 95 | if return_code != 0 and return_code != 128: | |
| 96 | print('[!]Error:\n Git return code: ' + str(return_code)) | |
| 97 | ||
| 98 | file_csv = open('cfdb.csv','w') | |
| 99 | ||
| 100 | file_csv.write( | |
| 101 | 'cwe,name,description,resolution,exploitation,references\n' | |
| 102 | ) | |
| 103 | ||
| 104 | #CSV Writer | |
| 105 | writer = csv.writer( | |
| 106 | file_csv, | |
| 107 | quotechar = '"', | |
| 108 | delimiter = ',', | |
| 109 | quoting = csv.QUOTE_ALL | |
| 110 | ) | |
| 111 | ||
| 112 | #Get DB names... | |
| 113 | print('[*]Looking for DBs...') | |
| 114 | for (root, dirs, files) in walk(DB_PATH): | |
| 115 | ||
| 116 | #Jump dirs without info | |
| 117 | if root.find('.git') < 0 and root.find('.gitignore') < 0: | |
| 118 | if root != './cfdb/': | |
| 119 | ||
| 120 | print('[*]Parsing folder: ' + root) | |
| 121 | for file_db in files: | |
| 122 | ||
| 123 | print('[_]File: ' + root + '/' + file_db) | |
| 124 | with open(root + '/' + file_db, 'r') as file_md: | |
| 125 | ||
| 126 | csv_content = parseFile(file_md) | |
| 127 | ||
| 128 | result = ( | |
| 129 | csv_content.cwe, | |
| 130 | csv_content.name, | |
| 131 | csv_content.description, | |
| 132 | csv_content.resolution, | |
| 133 | csv_content.explotation, | |
| 134 | csv_content.references | |
| 135 | ) | |
| 136 | ||
| 137 | writer.writerow(result) | |
| 138 | ||
| 139 | print('[*]Parse folder finished...\n') | |
| 140 | ||
| 141 | print('[*]All Finished... OK') | |
| 142 | ||
| 143 | file_csv.close() | |
| 144 | ||
| 145 | if __name__ == '__main__': | |
| 146 | main() | |
| 147 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python3 | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2014 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | This script fixes invalid XMLs. | |
| 7 | """ | |
| 8 | from __future__ import absolute_import | |
| 9 | ||
| 10 | import argparse | |
| 11 | from bs4 import BeautifulSoup | |
| 12 | ||
| 13 | def main(): | |
| 14 | parser = argparse.ArgumentParser(prog='cleanXML', epilog="Example: ./%(prog)s.py") | |
| 15 | ||
| 16 | parser.add_argument('-i', '--input', action='store', type=str, | |
| 17 | dest='infile', help='XML File to read from', | |
| 18 | required=True) | |
| 19 | parser.add_argument('-o', '--output', action='store', type=str, | |
| 20 | dest='outfile', help='Filename to write output', | |
| 21 | default="clean.xml") | |
| 22 | ||
| 23 | args = parser.parse_args() | |
| 24 | ||
| 25 | xml = open(args.infile, 'r') | |
| 26 | soup = BeautifulSoup(xml.read(), 'xml') | |
| 27 | ||
| 28 | out = open(args.outfile, 'w') | |
| 29 | out.write(soup.encode('utf-8')) | |
| 30 | out.flush() | |
| 31 | out.close() | |
| 32 | ||
| 33 | xml.close() | |
| 34 | ||
| 35 | if __name__ == "__main__": | |
| 36 | main() | |
| 37 | # I'm Py3⏎ |
| 0 | <?xml version="1.0" encoding="UTF-8"?> | |
| 1 | <glade-interface> | |
| 2 | <!-- interface-requires gtk+ 2.24 --> | |
| 3 | <!-- interface-naming-policy project-wide --> | |
| 4 | <widget class="GtkDialog" id="exploit_dialog"> | |
| 5 | <property name="can_focus">False</property> | |
| 6 | <property name="border_width">5</property> | |
| 7 | <property name="title" translatable="yes">Faraday Report</property> | |
| 8 | <property name="type_hint">dialog</property> | |
| 9 | <child internal-child="vbox"> | |
| 10 | <widget class="GtkVBox" id="dialog-vbox1"> | |
| 11 | <property name="visible">True</property> | |
| 12 | <property name="can_focus">False</property> | |
| 13 | <property name="spacing">2</property> | |
| 14 | <child internal-child="action_area"> | |
| 15 | <widget class="GtkHButtonBox" id="dialog-action_area1"> | |
| 16 | <property name="visible">True</property> | |
| 17 | <property name="can_focus">False</property> | |
| 18 | <property name="layout_style">end</property> | |
| 19 | <child> | |
| 20 | <widget class="GtkButton" id="button1"> | |
| 21 | <property name="label">gtk-cancel</property> | |
| 22 | <property name="response_id">-6</property> | |
| 23 | <property name="visible">True</property> | |
| 24 | <property name="can_focus">True</property> | |
| 25 | <property name="receives_default">True</property> | |
| 26 | <property name="use_stock">True</property> | |
| 27 | </widget> | |
| 28 | <packing> | |
| 29 | <property name="expand">False</property> | |
| 30 | <property name="fill">False</property> | |
| 31 | <property name="position">0</property> | |
| 32 | </packing> | |
| 33 | </child> | |
| 34 | <child> | |
| 35 | <widget class="GtkButton" id="button2"> | |
| 36 | <property name="label">gtk-ok</property> | |
| 37 | <property name="response_id">-5</property> | |
| 38 | <property name="visible">True</property> | |
| 39 | <property name="can_focus">True</property> | |
| 40 | <property name="receives_default">True</property> | |
| 41 | <property name="use_stock">True</property> | |
| 42 | </widget> | |
| 43 | <packing> | |
| 44 | <property name="expand">False</property> | |
| 45 | <property name="fill">False</property> | |
| 46 | <property name="position">1</property> | |
| 47 | </packing> | |
| 48 | </child> | |
| 49 | </widget> | |
| 50 | <packing> | |
| 51 | <property name="expand">True</property> | |
| 52 | <property name="fill">True</property> | |
| 53 | <property name="position">0</property> | |
| 54 | </packing> | |
| 55 | </child> | |
| 56 | <child> | |
| 57 | <widget class="GtkTable" id="table1"> | |
| 58 | <property name="visible">True</property> | |
| 59 | <property name="can_focus">False</property> | |
| 60 | <property name="n_rows">3</property> | |
| 61 | <property name="n_columns">3</property> | |
| 62 | <child> | |
| 63 | <placeholder/> | |
| 64 | </child> | |
| 65 | <child> | |
| 66 | <placeholder/> | |
| 67 | </child> | |
| 68 | <child> | |
| 69 | <widget class="GtkLabel" id="label1"> | |
| 70 | <property name="visible">True</property> | |
| 71 | <property name="can_focus">False</property> | |
| 72 | <property name="label" translatable="yes">Faraday RPC ( http//IP:PORT )</property> | |
| 73 | </widget> | |
| 74 | <packing> | |
| 75 | <property name="top_attach">2</property> | |
| 76 | <property name="bottom_attach">3</property> | |
| 77 | </packing> | |
| 78 | </child> | |
| 79 | <child> | |
| 80 | <widget class="GtkLabel" id="label2"> | |
| 81 | <property name="visible">True</property> | |
| 82 | <property name="can_focus">False</property> | |
| 83 | <property name="label" translatable="yes">Pickle file</property> | |
| 84 | </widget> | |
| 85 | </child> | |
| 86 | <child> | |
| 87 | <widget class="GtkEntry" id="faraday_rpc"> | |
| 88 | <property name="visible">True</property> | |
| 89 | <property name="can_focus">True</property> | |
| 90 | <property name="invisible_char">●</property> | |
| 91 | <property name="primary_icon_activatable">False</property> | |
| 92 | <property name="secondary_icon_activatable">False</property> | |
| 93 | <property name="primary_icon_sensitive">True</property> | |
| 94 | <property name="secondary_icon_sensitive">True</property> | |
| 95 | </widget> | |
| 96 | <packing> | |
| 97 | <property name="left_attach">1</property> | |
| 98 | <property name="right_attach">2</property> | |
| 99 | <property name="top_attach">2</property> | |
| 100 | <property name="bottom_attach">3</property> | |
| 101 | </packing> | |
| 102 | </child> | |
| 103 | <child> | |
| 104 | <widget class="GtkLabel" id="label3"> | |
| 105 | <property name="visible">True</property> | |
| 106 | <property name="can_focus">False</property> | |
| 107 | <property name="label" translatable="yes">Report Type</property> | |
| 108 | </widget> | |
| 109 | <packing> | |
| 110 | <property name="top_attach">1</property> | |
| 111 | <property name="bottom_attach">2</property> | |
| 112 | </packing> | |
| 113 | </child> | |
| 114 | <child> | |
| 115 | <widget class="GtkEntry" id="data_file"> | |
| 116 | <property name="visible">True</property> | |
| 117 | <property name="can_focus">True</property> | |
| 118 | <property name="invisible_char">●</property> | |
| 119 | <property name="primary_icon_activatable">False</property> | |
| 120 | <property name="secondary_icon_activatable">False</property> | |
| 121 | <property name="primary_icon_sensitive">True</property> | |
| 122 | <property name="secondary_icon_sensitive">True</property> | |
| 123 | </widget> | |
| 124 | <packing> | |
| 125 | <property name="left_attach">1</property> | |
| 126 | <property name="right_attach">2</property> | |
| 127 | </packing> | |
| 128 | </child> | |
| 129 | <child> | |
| 130 | <widget class="GtkComboBox" id="report_type"> | |
| 131 | <property name="visible">True</property> | |
| 132 | <property name="can_focus">False</property> | |
| 133 | <property name="items" translatable="yes">canvas | |
| 134 | clientd</property> | |
| 135 | </widget> | |
| 136 | <packing> | |
| 137 | <property name="left_attach">1</property> | |
| 138 | <property name="right_attach">2</property> | |
| 139 | <property name="top_attach">1</property> | |
| 140 | <property name="bottom_attach">2</property> | |
| 141 | </packing> | |
| 142 | </child> | |
| 143 | <child> | |
| 144 | <widget class="GtkButton" id="pickle_file_button"> | |
| 145 | <property name="visible">True</property> | |
| 146 | <property name="can_focus">True</property> | |
| 147 | <property name="receives_default">True</property> | |
| 148 | <property name="relief">none</property> | |
| 149 | <child> | |
| 150 | <widget class="GtkImage" id="image1"> | |
| 151 | <property name="visible">True</property> | |
| 152 | <property name="can_focus">False</property> | |
| 153 | <property name="stock">gtk-open</property> | |
| 154 | </widget> | |
| 155 | </child> | |
| 156 | </widget> | |
| 157 | <packing> | |
| 158 | <property name="left_attach">2</property> | |
| 159 | <property name="right_attach">3</property> | |
| 160 | </packing> | |
| 161 | </child> | |
| 162 | </widget> | |
| 163 | <packing> | |
| 164 | <property name="expand">True</property> | |
| 165 | <property name="fill">True</property> | |
| 166 | <property name="position">1</property> | |
| 167 | </packing> | |
| 168 | </child> | |
| 169 | </widget> | |
| 170 | </child> | |
| 171 | </widget> | |
| 172 | </glade-interface> |
| 0 | #!/usr/bin/env python | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | """ | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2015 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | """ | |
| 9 | ||
| 10 | """ | |
| 11 | Create a report using the libs.reports package. | |
| 12 | Send the information to Faraday, using RPC API. | |
| 13 | ||
| 14 | """ | |
| 15 | ||
| 16 | import xmlrpclib | |
| 17 | import pprint | |
| 18 | import sys | |
| 19 | import os | |
| 20 | ||
| 21 | if '.' not in sys.path: sys.path.append('.') | |
| 22 | if 'libs' not in sys.path: sys.path.append('libs') | |
| 23 | if 'exploits' not in sys.path: sys.path.append('./exploits/server/clientd') | |
| 24 | ||
| 25 | from exploitutils import * | |
| 26 | ||
| 27 | from libs.reports import utils | |
| 28 | from libs.reports import canvas_report | |
| 29 | import report as ClientdReport | |
| 30 | ||
| 31 | from ExploitTypes.utility import Utility | |
| 32 | ||
| 33 | NAME = 'faraday_report' | |
| 34 | VERSION = '0.1' | |
| 35 | DESCRIPTION = 'Creates a report from CANVAS event pickles and send the information to Faraday.' | |
| 36 | ||
| 37 | DOCUMENTATION = {} | |
| 38 | DOCUMENTATION['Repeatability'] = 'Infinite' | |
| 39 | DOCUMENTATION['Usage'] = """Select the type of report to generate and supply | |
| 40 | the path to a data pickle, in addition to the URL faraday RPC""" | |
| 41 | ||
| 42 | DOCUMENTATION['Notes'] = NOTES = """This module is not backwards compatible | |
| 43 | with reporting pickles created by previous versions of CANVAS. | |
| 44 | ||
| 45 | It should also be noted that the new reporting pickle is not compatible with | |
| 46 | with any of the previous CANVAS reporting modules, such as "report_timeline". | |
| 47 | """ | |
| 48 | ||
| 49 | PROPERTY = {} | |
| 50 | PROPERTY['TYPE'] = 'Reporting' | |
| 51 | PROPERTY['SITE'] = 'Local' | |
| 52 | ||
| 53 | DEFAULT_DATA_FILE = 'report.pkl' | |
| 54 | DEFAULT_FARADAY_RPC = 'http://127.0.0.1:9876/' | |
| 55 | DEFAULT_DATA_PATH = utils.get_reports_path(filename=DEFAULT_DATA_FILE) | |
| 56 | ||
| 57 | ||
| 58 | ||
| 59 | class Host(): | |
| 60 | def __init__(self, ip, host_id): | |
| 61 | ||
| 62 | self.ip = ip | |
| 63 | self.host_id = host_id | |
| 64 | #{IP:INTERFACE_ID} | |
| 65 | self.dict_interfaces = {} | |
| 66 | #{IP:{PORT:SERVICE_ID}} | |
| 67 | self.dict_services = {} | |
| 68 | ||
| 69 | def addInterface(self, ip_interface, interface_id): | |
| 70 | ||
| 71 | self.dict_interfaces.update({ip_interface: interface_id}) | |
| 72 | ||
| 73 | def getInterfaceId(self, ip_interface): | |
| 74 | ||
| 75 | try: | |
| 76 | return self.dict_interfaces[ip_interface] | |
| 77 | except: | |
| 78 | return None | |
| 79 | ||
| 80 | def addService(self, ip_interface, port, service_id): | |
| 81 | ||
| 82 | if ip_interface in self.dict_services: | |
| 83 | temp = self.dict_services[ip_interface] | |
| 84 | temp.update({port: service_id}) | |
| 85 | self.dict_services.update({ip_interface: temp}) | |
| 86 | else: | |
| 87 | self.dict_services.update({ ip_interface: {port:service_id} }) | |
| 88 | ||
| 89 | def getServiceId(self, ip_interface, port): | |
| 90 | ||
| 91 | try: | |
| 92 | return self.dict_services[ip_interface][port] | |
| 93 | except: | |
| 94 | return None | |
| 95 | ||
| 96 | ||
| 97 | ||
| 98 | class ParsingCanvas(): | |
| 99 | ||
| 100 | def __init__(self, faraday_api, data_file): | |
| 101 | ||
| 102 | self.faraday_api = faraday_api | |
| 103 | self.data_file = data_file | |
| 104 | self.data = canvas_report.Collector().collect(self.data_file) | |
| 105 | self.host_list = [] | |
| 106 | ||
| 107 | def getAndCreateNewHost(self, node): | |
| 108 | ||
| 109 | #Get OS | |
| 110 | try: | |
| 111 | for attack in node['attacks']: | |
| 112 | if attack['node_type'] != '': | |
| 113 | op_sy = attack['node_type'] | |
| 114 | break | |
| 115 | except: | |
| 116 | op_sy = 'Undefined' | |
| 117 | ||
| 118 | #Create Host | |
| 119 | host_id = self.faraday_api.createAndAddHost( | |
| 120 | node['resolved_from'], | |
| 121 | op_sy) | |
| 122 | ||
| 123 | host = Host(node['ip'], host_id) | |
| 124 | self.host_list.append(host) | |
| 125 | return host | |
| 126 | ||
| 127 | def getSeverity(self, cvss): | |
| 128 | ||
| 129 | #Get severity CVSS version 3 | |
| 130 | values_cvss = {3.9:'Low', 6.9:'Medium', 8.9:'High', 10.0:'Critical' } | |
| 131 | values = [3.9, 6.9, 8.9, 10.0] | |
| 132 | #Get the score more close... | |
| 133 | score = min(values, key=lambda x:abs(x-cvss)) | |
| 134 | return values_cvss[score] | |
| 135 | ||
| 136 | def getAndCreateVulnerabilities(self, node, host): | |
| 137 | ||
| 138 | #Get interface id | |
| 139 | for host in self.host_list: | |
| 140 | interface_id = host.getInterfaceId(node['ip']) | |
| 141 | if interface_id != None: | |
| 142 | break | |
| 143 | ||
| 144 | for attack in node['attacks']: | |
| 145 | ||
| 146 | #Create service | |
| 147 | for x, y, name_exploit in self.data['_exploits']: | |
| 148 | ||
| 149 | if name_exploit == attack['name']: | |
| 150 | ||
| 151 | port = self.data['_exploits'][(x, y, name_exploit)]['arguments']['port'] | |
| 152 | ip = self.data['_exploits'][(x, y, name_exploit)]['arguments']['host'] | |
| 153 | ||
| 154 | #Check service created | |
| 155 | service_id = host.getServiceId(ip, port) | |
| 156 | if service_id != None: | |
| 157 | break | |
| 158 | ||
| 159 | service_id = self.faraday_api.createAndAddServiceToInterface( | |
| 160 | host.host_id, | |
| 161 | interface_id, | |
| 162 | str(int(float(port))), | |
| 163 | 'tcp?', | |
| 164 | [int(float(port)]) | |
| 165 | ) | |
| 166 | ||
| 167 | host.addService(ip, port, service_id) | |
| 168 | break | |
| 169 | ||
| 170 | #Create vulnerability | |
| 171 | try: | |
| 172 | title = attack['title'] | |
| 173 | description = self.data['exploits'][attack['name']]['description'] | |
| 174 | cve = self.data['exploits'][attack['name']]['cve'] | |
| 175 | severity = self.data['exploits'][attack['name']]['properties']['CVSS'] | |
| 176 | severity = self.getSeverity(float(severity)) | |
| 177 | except: | |
| 178 | title = '' | |
| 179 | description = '' | |
| 180 | cve = [] | |
| 181 | severity = '' | |
| 182 | ||
| 183 | self.faraday_api.createAndAddVulnToService( | |
| 184 | host.host_id, | |
| 185 | service_id, | |
| 186 | title, | |
| 187 | description, | |
| 188 | [cve], | |
| 189 | severity, | |
| 190 | '' | |
| 191 | ) | |
| 192 | ||
| 193 | ||
| 194 | def getAndCreateInterfaces(self, node, host): | |
| 195 | #Get Interfaces Ipv6 or Ipv4 | |
| 196 | for element in self.data['_nodes']: | |
| 197 | ||
| 198 | if element['ip'] == node['ip']: | |
| 199 | ||
| 200 | for ip in element['ips']: | |
| 201 | #Ipv6 | |
| 202 | if ip.find(':') > -1 and ip != '127.0.0.1': | |
| 203 | ||
| 204 | interface_id = self.faraday_api.createAndAddInterface( | |
| 205 | host.host_id, | |
| 206 | ip, | |
| 207 | '00:00:00:00:00:00', | |
| 208 | '0.0.0.0', | |
| 209 | '0.0.0.0', | |
| 210 | '0.0.0.0', | |
| 211 | [], | |
| 212 | ip | |
| 213 | ) | |
| 214 | host.addInterface(ip, interface_id) | |
| 215 | #Ipv4 | |
| 216 | elif ip.find(':') <= -1 and ip != '127.0.0.1': | |
| 217 | ||
| 218 | interface_id = self.faraday_api.createAndAddInterface( | |
| 219 | host.host_id, | |
| 220 | ip, | |
| 221 | '00:00:00:00:00:00', | |
| 222 | ip | |
| 223 | ) | |
| 224 | host.addInterface(ip, interface_id) | |
| 225 | break | |
| 226 | ||
| 227 | def getAndCreateStatisticsLog(self, data_file, data_nodes): | |
| 228 | ||
| 229 | #Canvas Statistics | |
| 230 | ip_callback = data_nodes[0]['parent']['ip'] | |
| 231 | host_id = self.faraday_api.createAndAddHost(ip_callback) | |
| 232 | ||
| 233 | text = ( | |
| 234 | 'Exploits attempted: {0}\n' | |
| 235 | 'Exploits successful : {1}\n' | |
| 236 | 'Hosts attacked: {2}\n' | |
| 237 | 'Hosts compromised: {3}\n' | |
| 238 | 'Hosts discovered: {4}\n' | |
| 239 | 'Total exploits attempted: {5}\n' | |
| 240 | 'Total exploits successful: {6}\n' | |
| 241 | ).format( | |
| 242 | self.data['stats']['exploits_attempted'], | |
| 243 | self.data['stats']['exploits_successful'], | |
| 244 | self.data['stats']['hosts_attacked'], | |
| 245 | self.data['stats']['hosts_compromised'], | |
| 246 | self.data['stats']['hosts_discovered'], | |
| 247 | self.data['stats']['total_exploits_attempted'], | |
| 248 | self.data['stats']['total_exploits_successful'] | |
| 249 | ) | |
| 250 | ||
| 251 | self.faraday_api.createAndAddNoteToHost(host_id, 'Statistics canvas', text) | |
| 252 | ||
| 253 | #Canvas log | |
| 254 | log_path = os.path.dirname(data_file) | |
| 255 | with open( os.path.join( log_path, 'CANVAS.log'), 'r') as file_log: | |
| 256 | ||
| 257 | data_to_save = [] | |
| 258 | for line in file_log.readlines(): | |
| 259 | ||
| 260 | if line.find('canvasexploit.py') > -1 or line.find('.py] -') == -1 : | |
| 261 | data_to_save.append(line.strip('\r\n')) | |
| 262 | ||
| 263 | data_save = pprint.pformat(data_to_save) | |
| 264 | self.faraday_api.createAndAddNoteToHost(host_id, 'Canvas Log', data_save ) | |
| 265 | ||
| 266 | def parsingAndSendCanvas(self): | |
| 267 | ||
| 268 | #Iterate over hosts and create the entities. | |
| 269 | hosts = self.data['hosts'] | |
| 270 | ||
| 271 | for ip in hosts: | |
| 272 | ||
| 273 | for obj_host in self.host_list: | |
| 274 | ||
| 275 | #Ip is a interface , not is a new host. | |
| 276 | if obj_host.getInterfaceId(ip) != None: | |
| 277 | self.getAndCreateVulnerabilities( | |
| 278 | hosts[ip], | |
| 279 | obj_host | |
| 280 | ) | |
| 281 | break | |
| 282 | ||
| 283 | host = self.getAndCreateNewHost(hosts[ip]) | |
| 284 | self.getAndCreateInterfaces(hosts[ip], host) | |
| 285 | self.getAndCreateVulnerabilities(hosts[ip], host) | |
| 286 | ||
| 287 | self.getAndCreateStatisticsLog(self.data_file, self.data['_nodes']) | |
| 288 | ||
| 289 | ||
| 290 | ||
| 291 | class ParsingClientd(ParsingCanvas): | |
| 292 | ||
| 293 | def __init__(self, faraday_api, data_file): | |
| 294 | ||
| 295 | self.faraday_api = faraday_api | |
| 296 | self.data_file = data_file | |
| 297 | self.data = ClientdReport.Collector().collect(data_file) | |
| 298 | ||
| 299 | def parsingAndSendClientd(self): | |
| 300 | #Iterate over sessions and create the entities. | |
| 301 | hosts = self.data['sessions'] | |
| 302 | ||
| 303 | for session in hosts: | |
| 304 | ||
| 305 | #Get data | |
| 306 | ip = hosts[session]['ip'] | |
| 307 | agent = hosts[session]['agent'] | |
| 308 | os = self.data['clients'][ip]['agents'][agent]['os'] | |
| 309 | info_host = self.data['clients'][ip]['agents'][agent] | |
| 310 | ||
| 311 | #Create Host | |
| 312 | host_id = self.faraday_api.createAndAddHost(ip, os) | |
| 313 | ||
| 314 | #'IE Flash' is a keyword only for Internet Explorer??' | |
| 315 | try: | |
| 316 | flash_player = info_host['plugins']['IE Flash'] | |
| 317 | except: | |
| 318 | flash_player = "Unknown" | |
| 319 | ||
| 320 | #Get information about host | |
| 321 | text = ( | |
| 322 | 'Platform: {0}\n' | |
| 323 | 'Language: {1}\n' | |
| 324 | 'Browser: {2}\n' | |
| 325 | 'Plugins: Flash: {3}\n' | |
| 326 | 'Java : {4}\n' | |
| 327 | 'Office: {5}\n' | |
| 328 | 'Agent: {6}\n' | |
| 329 | 'Email: {7}\n' | |
| 330 | 'Country: {8}\n' | |
| 331 | 'Cpu: {9}\n' | |
| 332 | 'Os: {10}\n' | |
| 333 | ).format( | |
| 334 | info_host['platform'], | |
| 335 | info_host['language'], | |
| 336 | info_host['browser'], | |
| 337 | flash_player, | |
| 338 | info_host['plugins']['Java'], | |
| 339 | info_host['plugins']['Office'], | |
| 340 | agent, | |
| 341 | self.data['clients'][ip]['email'], | |
| 342 | self.data['clients'][ip]['ip_country'], | |
| 343 | info_host['cpu'], | |
| 344 | os | |
| 345 | ) | |
| 346 | ||
| 347 | #Create note with recon data. | |
| 348 | self.faraday_api.createAndAddNoteToHost(host_id, 'Recon Information', text) | |
| 349 | ||
| 350 | #If any exploit is successful | |
| 351 | if (self.data['clients'][ip]['session_count'] >= 1): | |
| 352 | ||
| 353 | for name, session_id in self.data['attacks']: | |
| 354 | ||
| 355 | #If session Ids equals and exploits is sucessful | |
| 356 | if session_id == hosts[session]['sid']: | |
| 357 | if self.data['attacks'][(name, session_id)]['successful'] == True: | |
| 358 | ||
| 359 | #Get info about vulnerability | |
| 360 | name = self.data['attacks'][(name, session_id)]['exploit']['name'] | |
| 361 | description= self.data['attacks'][(name, session_id)]['exploit']['description'] | |
| 362 | ref = [self.data['attacks'][(name, session_id)]['exploit']['cve']] | |
| 363 | ||
| 364 | #Create vulnerability | |
| 365 | self.faraday_api.createAndAddVulnToHost( | |
| 366 | host_id, | |
| 367 | name, | |
| 368 | description, | |
| 369 | ref, | |
| 370 | '', | |
| 371 | '' | |
| 372 | ) | |
| 373 | ||
| 374 | ||
| 375 | ||
| 376 | class theexploit(Utility): | |
| 377 | ||
| 378 | def __init__(self): | |
| 379 | ||
| 380 | Utility.__init__(self) | |
| 381 | self.name = NAME | |
| 382 | self.report_type = 'canvas' | |
| 383 | self.data_file = DEFAULT_DATA_PATH | |
| 384 | self.faraday_rpc = DEFAULT_FARADAY_RPC | |
| 385 | ||
| 386 | def getargs(self): | |
| 387 | ||
| 388 | self.getarg('report_type') | |
| 389 | self.getarg('data_file') | |
| 390 | self.getarg('faraday_rpc') | |
| 391 | ||
| 392 | def run(self): | |
| 393 | ||
| 394 | self.getargs() | |
| 395 | ||
| 396 | msg = 'Sending information to Faraday ...' | |
| 397 | self.log(msg) | |
| 398 | self.setInfo(msg) | |
| 399 | ||
| 400 | try: | |
| 401 | faraday_api = xmlrpclib.ServerProxy(self.faraday_rpc) | |
| 402 | except Exception as e: | |
| 403 | ||
| 404 | self.log('Faraday RPC API Exception: {0}'.format(e.message)) | |
| 405 | self.setInfo('Faraday RPC API Exception: {0}'.format(e.message)) | |
| 406 | ||
| 407 | if self.report_type == 'canvas': | |
| 408 | parser = ParsingCanvas(faraday_api, self.data_file) | |
| 409 | parser.parsingAndSendCanvas() | |
| 410 | else: | |
| 411 | parser = ParsingClientd(faraday_api, self.data_file) | |
| 412 | parser.parsingAndSendClientd() | |
| 413 | ||
| 414 | #Finished. | |
| 415 | msg = 'Done. Information sent to faraday.' | |
| 416 | self.log(msg) | |
| 417 | self.setInfo(msg) | |
| 418 | return 1 | |
| 419 | ||
| 420 | def select_path(b, gtk, dialog, action, widget): | |
| 421 | ||
| 422 | dialog = gtk.FileChooserDialog('Select filename...', dialog, action, | |
| 423 | (gtk.STOCK_CANCEL, gtk.RESPONSE_CANCEL, gtk.STOCK_OPEN, gtk.RESPONSE_OK)) | |
| 424 | try: | |
| 425 | dialog.set_filename(widget.get_text()) | |
| 426 | ||
| 427 | if dialog.run() == gtk.RESPONSE_OK: | |
| 428 | fname = dialog.get_filename() | |
| 429 | widget.set_text(fname) | |
| 430 | finally: | |
| 431 | dialog.destroy() | |
| 432 | ||
| 433 | def dialog_update(gtk, wtree): | |
| 434 | ||
| 435 | dialog = wtree.get_widget('exploit_dialog') | |
| 436 | signal_ids = [] | |
| 437 | ||
| 438 | widget = wtree.get_widget('report_type') | |
| 439 | widget.set_active(0) | |
| 440 | ||
| 441 | widget = wtree.get_widget('data_file') | |
| 442 | widget.set_text(DEFAULT_DATA_PATH) | |
| 443 | ||
| 444 | button = wtree.get_widget('pickle_file_button') | |
| 445 | sig = button.connect('clicked', select_path, gtk, dialog, | |
| 446 | gtk.FILE_CHOOSER_ACTION_OPEN, widget) | |
| 447 | signal_ids.append((button, sig)) | |
| 448 | ||
| 449 | widget = wtree.get_widget('faraday_rpc') | |
| 450 | widget.set_text(DEFAULT_FARADAY_RPC) | |
| 451 | ||
| 452 | def disconnect(w): | |
| 453 | ||
| 454 | for w, sig in signal_ids: | |
| 455 | w.disconnect(sig) | |
| 456 | sig = dialog.connect('hide', disconnect) | |
| 457 | signal_ids.append((dialog, sig)) | |
| 458 | ||
| 459 | if __name__ == '__main__': | |
| 460 | ||
| 461 | app = theexploit() | |
| 462 | ret = standard_callback_commandline(app) | |
| 463 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python3 | |
| 1 | ||
| 2 | """ | |
| 3 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | Author: Ezequiel Tavella | |
| 5 | ||
| 6 | This script generate a CSV file with information about the vulndb database. | |
| 7 | CSV Format: | |
| 8 | cwe,name,desc_summary,description,resolution,exploitation,references | |
| 9 | """ | |
| 10 | from __future__ import absolute_import | |
| 11 | from __future__ import print_function | |
| 12 | ||
| 13 | from subprocess import call | |
| 14 | from os import walk, path | |
| 15 | import json | |
| 16 | import csv | |
| 17 | import re | |
| 18 | ||
| 19 | URL_PROYECT = 'https://github.com/vulndb/data' | |
| 20 | DB_PATH = './data/db/' | |
| 21 | ||
| 22 | ||
| 23 | class JsonToCsv(): | |
| 24 | ||
| 25 | def __init__(self, file): | |
| 26 | ||
| 27 | self.cwe = None | |
| 28 | self.name = None | |
| 29 | self.description = None | |
| 30 | self.resolution = None | |
| 31 | self.references = None | |
| 32 | self.severity = None | |
| 33 | ||
| 34 | self.content = self.getContent(file) | |
| 35 | self.parse() | |
| 36 | ||
| 37 | def getContent(self, file): | |
| 38 | ||
| 39 | try: | |
| 40 | return json.load(file) | |
| 41 | except: | |
| 42 | return None | |
| 43 | ||
| 44 | def parse(self): | |
| 45 | ||
| 46 | """ | |
| 47 | Available information of vulndb: | |
| 48 | cwe,name,description,resolution,references | |
| 49 | """ | |
| 50 | ||
| 51 | if not self.content: | |
| 52 | return | |
| 53 | ||
| 54 | self.cwe = self.content.get('cwe') | |
| 55 | if self.cwe: | |
| 56 | self.cwe = self.cwe[0] | |
| 57 | ||
| 58 | self.name = self.content.get('title') | |
| 59 | self.severity = self.content.get('severity') | |
| 60 | # Reference to description file | |
| 61 | self.description = ''.join(self.content.get('description').get('$ref')) | |
| 62 | ||
| 63 | # Reference to fix file | |
| 64 | self.resolution = ''.join(self.content.get('fix').get('guidance').get('$ref')) | |
| 65 | ||
| 66 | try: | |
| 67 | self.references = [] | |
| 68 | for reference in self.content.get('references'): | |
| 69 | ||
| 70 | self.references.append( | |
| 71 | reference['title'] + ': ' + reference['url'] | |
| 72 | ) | |
| 73 | ||
| 74 | except: | |
| 75 | self.references = [] | |
| 76 | ||
| 77 | ||
| 78 | def main(): | |
| 79 | ||
| 80 | #Get DB of vulndb | |
| 81 | print('[*]Execute git clone...') | |
| 82 | return_code = call(['git', 'clone', URL_PROYECT]) | |
| 83 | ||
| 84 | if return_code != 0 and return_code != 128: | |
| 85 | print('[!]Error:\n Git return code: ' + str(return_code)) | |
| 86 | ||
| 87 | #Get DB names... | |
| 88 | print('[*]Looking for DBs...') | |
| 89 | ||
| 90 | with open('vulndb.csv', mode='w') as file_csv: | |
| 91 | file_csv.write( | |
| 92 | 'cwe,name,description,resolution,exploitation,references\n' | |
| 93 | ) | |
| 94 | for (root, dirs, files) in walk(DB_PATH): | |
| 95 | if root == './data/db/en': | |
| 96 | vulndb_path = root | |
| 97 | vulndb_files = files | |
| 98 | elif root == './data/db/en/fix': | |
| 99 | # Folder /fix/ contains files with the resolution of every vuln | |
| 100 | fix_files = { | |
| 101 | 'path': root, | |
| 102 | 'filenames': parse_filenames(files) | |
| 103 | } | |
| 104 | elif root == './data/db/en/description': | |
| 105 | # Folder /description/ contains files with the description of every vuln | |
| 106 | desc_files = { | |
| 107 | 'path': root, | |
| 108 | 'filenames': parse_filenames(files) | |
| 109 | } | |
| 110 | ||
| 111 | writer = csv.writer( | |
| 112 | file_csv, | |
| 113 | quotechar = '"', | |
| 114 | delimiter = ',', | |
| 115 | quoting = csv.QUOTE_ALL | |
| 116 | ) | |
| 117 | ||
| 118 | for file_db in vulndb_files: | |
| 119 | ||
| 120 | print('[*]Parsing ' + file_db) | |
| 121 | with open(path.join(vulndb_path, file_db), 'r') as file_object: | |
| 122 | csv_content = JsonToCsv(file_object) | |
| 123 | description = get_data_from_file(csv_content.description, desc_files) | |
| 124 | resolution = get_data_from_file(csv_content.resolution, fix_files) | |
| 125 | result = ( | |
| 126 | csv_content.cwe, | |
| 127 | csv_content.name, | |
| 128 | description, | |
| 129 | resolution, | |
| 130 | csv_content.severity, | |
| 131 | ' '.join(csv_content.references or []) | |
| 132 | ) | |
| 133 | ||
| 134 | writer.writerow(result) | |
| 135 | ||
| 136 | print('[*]Parse finished...') | |
| 137 | ||
| 138 | def parse_filenames(files): | |
| 139 | # Parse filenames from description or fix folders | |
| 140 | files_dict = {} | |
| 141 | for filename in files: | |
| 142 | file_number = re.search('\d+', filename) | |
| 143 | if file_number: | |
| 144 | files_dict[file_number.group()] = filename | |
| 145 | return files_dict | |
| 146 | ||
| 147 | def get_data_from_file(csv_content, files): | |
| 148 | # Get description or fix from the file reference parsed in JsonToCsv class | |
| 149 | data = '' | |
| 150 | number_from_file = re.search('\d+', csv_content) | |
| 151 | if not number_from_file: | |
| 152 | return data | |
| 153 | else: | |
| 154 | file_number = number_from_file.group() | |
| 155 | ||
| 156 | if file_number in files['filenames']: | |
| 157 | filename = files['filenames'][file_number] | |
| 158 | else: | |
| 159 | return data | |
| 160 | ||
| 161 | with open(path.join(files['path'], filename)) as file_object: | |
| 162 | data = file_object.read() | |
| 163 | ||
| 164 | return data | |
| 165 | ||
| 166 | if __name__ == '__main__': | |
| 167 | main() | |
| 168 | ||
| 169 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | ||
| 7 | ||
| 8 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | """ | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | """ | |
| 9 | from __future__ import absolute_import | |
| 10 | ||
| 11 | import os | |
| 12 | ||
| 13 | # TODO: remove this in next versions | |
| 14 | ||
| 15 | ||
| 16 | class ViewsManager: | |
| 17 | """docstring for ViewsWrapper""" | |
| 18 | def __init__(self): | |
| 19 | self.vw = ViewsListObject() | |
| 20 | ||
| 21 | def addView(self, design_doc, workspaceDB): | |
| 22 | designer.push(design_doc, workspaceDB, atomic = False) | |
| 23 | ||
| 24 | def addViewForFS(self, design_doc, workspaceDB): | |
| 25 | designer.fs.push(design_doc, workspaceDB, encode_attachments = False) | |
| 26 | ||
| 27 | def getAvailableViews(self): | |
| 28 | return self.vw.get_all_views() | |
| 29 | ||
| 30 | def getViews(self, workspaceDB): | |
| 31 | views = {} | |
| 32 | result = workspaceDB.all_docs(startkey='_design', endkey='_design0') | |
| 33 | if result: | |
| 34 | for doc in result.all(): | |
| 35 | designdoc = workspaceDB.get(doc['id']) | |
| 36 | views.update(designdoc.get("views", [])) | |
| 37 | return views | |
| 38 | ||
| 39 | def addViews(self, workspaceDB, force = False): | |
| 40 | installed_views = self.getViews(workspaceDB) | |
| 41 | for v in self.getAvailableViews(): | |
| 42 | if v not in installed_views or force: | |
| 43 | self.addView(v, workspaceDB) | |
| 44 | ||
| 45 | ||
| 46 | class ViewsListObject: | |
| 47 | """ Representation of the FS Views """ | |
| 48 | def __init__(self): | |
| 49 | self.views_path = os.path.join(os.getcwd(), "views") | |
| 50 | self.designs_path = os.path.join(self.views_path, "reports", "_attachments", "views") | |
| 51 | ||
| 52 | def _listPath(self, path): | |
| 53 | flist = list(filter(lambda x: not x.startswith('.'), os.listdir(path))) | |
| 54 | return [os.path.join(path, x) for x in flist] | |
| 55 | ||
| 56 | def get_fs_designs(self): | |
| 57 | return self._listPath(self.designs_path) | |
| 58 | ||
| 59 | def get_all_views(self): | |
| 60 | return self.get_fs_designs() | |
| 61 | ||
| 62 | ||
| 63 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | import logging | |
| 6 | from faraday.client.persistence.server.models import create_object, get_object, update_object, delete_object | |
| 7 | ||
| 8 | # NOTE: This class is intended to be instantiated by the | |
| 9 | # service or controller that needs it. | |
| 10 | # IMPORTANT: There should be only one instance of this | |
| 11 | # class, since it creates the datamappers and those should | |
| 12 | # be unique too (they have identity maps for every model object) | |
| 13 | logger = logging.getLogger(__name__) | |
| 14 | ||
| 15 | ||
| 16 | class MapperManager: | |
| 17 | def __init__(self): | |
| 18 | # create and store the datamappers | |
| 19 | self.workspace_name = None | |
| 20 | self.session = None | |
| 21 | ||
| 22 | def createMappers(self, workpace_name): | |
| 23 | self.workspace_name = workpace_name | |
| 24 | ||
| 25 | def save(self, obj, command_id=None): | |
| 26 | saved_raw_obj = create_object(self.workspace_name, obj.class_signature, obj, command_id) | |
| 27 | if '_id' in saved_raw_obj or 'id' in saved_raw_obj: | |
| 28 | return saved_raw_obj.get('_id', None) or saved_raw_obj['id'] | |
| 29 | raise RuntimeError('Could not retrieve id from server.') | |
| 30 | ||
| 31 | def update(self, obj, command_id=None): | |
| 32 | if update_object(self.workspace_name, obj.class_signature, obj, command_id): | |
| 33 | return True | |
| 34 | return False | |
| 35 | ||
| 36 | def find(self, class_signature, obj_id): | |
| 37 | if self.workspace_name is None: | |
| 38 | logger.warning('No workspace detected. please call createMappers first.') | |
| 39 | return get_object(self.workspace_name, class_signature, obj_id) | |
| 40 | ||
| 41 | def remove(self, obj_id, class_signature): | |
| 42 | return delete_object(self.workspace_name, class_signature, obj_id) | |
| 43 | ||
| 44 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2018 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | import json | |
| 6 | import os | |
| 7 | import re | |
| 8 | import time | |
| 9 | import traceback | |
| 10 | import logging | |
| 11 | ||
| 12 | from random import random | |
| 13 | from threading import Thread, Timer | |
| 14 | ||
| 15 | from faraday.config.configuration import getInstanceConfiguration | |
| 16 | CONF = getInstanceConfiguration() | |
| 17 | ||
| 18 | logger = logging.getLogger(__name__) | |
| 19 | ||
| 20 | try: | |
| 21 | import xml.etree.cElementTree as ET | |
| 22 | except ImportError: | |
| 23 | print("cElementTree could not be imported. Using ElementTree instead") | |
| 24 | import xml.etree.ElementTree as ET | |
| 25 | ||
| 26 | ||
| 27 | class OnlinePlugins(Thread): | |
| 28 | ||
| 29 | def __init__(self, plugin_controller): | |
| 30 | ||
| 31 | Thread.__init__(self, name="OnlinePluginsThread") | |
| 32 | self.setDaemon(True) | |
| 33 | self._must_stop = False | |
| 34 | ||
| 35 | self.online_plugins = { | |
| 36 | "MetasploitOn": { | |
| 37 | "time": 30, | |
| 38 | "command": "./metasploiton online"}, | |
| 39 | "Beef": { | |
| 40 | "time": 30, | |
| 41 | "command": "./beef online"}, | |
| 42 | "Sentinel": { | |
| 43 | "time": 60, | |
| 44 | "command": "sentinel"} | |
| 45 | } | |
| 46 | ||
| 47 | self.plugins_settings = CONF.getPluginSettings() | |
| 48 | self.plugin_controller = plugin_controller | |
| 49 | ||
| 50 | def runPluginThread(self, cmd): | |
| 51 | random_id = random() | |
| 52 | self.plugin_controller.processCommandInput(random_id, cmd, './') | |
| 53 | self.plugin_controller.onCommandFinished(random_id, 0, cmd) | |
| 54 | logger.debug("Running online plugin...") | |
| 55 | ||
| 56 | def stop(self): | |
| 57 | self._must_stop = True | |
| 58 | ||
| 59 | def run(self): | |
| 60 | ||
| 61 | while not self._must_stop: | |
| 62 | ||
| 63 | for name, config_dict in self.online_plugins.items(): | |
| 64 | if name in self.plugins_settings: | |
| 65 | if self.plugins_settings[name]['settings']['Enable'] == "1": | |
| 66 | ||
| 67 | t = Timer( | |
| 68 | config_dict["time"], | |
| 69 | self.runPluginThread, args=(config_dict["command"],)) | |
| 70 | ||
| 71 | logger.debug( | |
| 72 | "Starting Thread for online plugin: %s" % name) | |
| 73 | ||
| 74 | self.online_plugins[name]["thread_running"] = True | |
| 75 | t.start() | |
| 76 | ||
| 77 | time.sleep(60) | |
| 78 | ||
| 79 | ||
| 80 | class ReportProcessor: | |
| 81 | ||
| 82 | def __init__(self, plugin_controller, ws_name=None): | |
| 83 | self.plugin_controller = plugin_controller | |
| 84 | self.ws_name = ws_name | |
| 85 | ||
| 86 | def processReport(self, filename): | |
| 87 | """ Process one Report """ | |
| 88 | logger.debug("Report file is %s" % filename) | |
| 89 | report_analyzer = ReportAnalyzer(self.plugin_controller, filename) | |
| 90 | plugin_id = report_analyzer.get_plugin_id() | |
| 91 | if not plugin_id: | |
| 92 | logger.error('Plugin not found: automatic and manual try!') | |
| 93 | return None | |
| 94 | return self.sendReport(plugin_id, filename) | |
| 95 | ||
| 96 | def sendReport(self, plugin_id, filename): | |
| 97 | """Sends a report to the appropiate plugin specified by plugin_id""" | |
| 98 | logger.info('The file is %s, %s', filename, plugin_id) | |
| 99 | command_id = self.plugin_controller.processReport(plugin_id, filename, ws_name=self.ws_name) | |
| 100 | if not command_id: | |
| 101 | logger.error("Faraday doesn't have a plugin for this tool... Processing: ABORT") | |
| 102 | return None | |
| 103 | return command_id | |
| 104 | ||
| 105 | ||
| 106 | class ReportManager(Thread): | |
| 107 | ||
| 108 | def __init__(self, timer, ws_name, plugin_controller, polling=True): | |
| 109 | Thread.__init__(self) | |
| 110 | self.setDaemon(True) | |
| 111 | self.polling = polling | |
| 112 | self.ws_name = ws_name | |
| 113 | self.timer = timer | |
| 114 | self._must_stop = False | |
| 115 | self._report_path = os.path.join(CONF.getReportPath(), ws_name) | |
| 116 | self._report_ppath = os.path.join(self._report_path, "process") | |
| 117 | self._report_upath = os.path.join(self._report_path, "unprocessed") | |
| 118 | self.processor = ReportProcessor(plugin_controller, ws_name) | |
| 119 | self.online_plugins = OnlinePlugins(plugin_controller) | |
| 120 | if not os.path.exists(self._report_path): | |
| 121 | os.mkdir(self._report_path) | |
| 122 | if not os.path.exists(self._report_ppath): | |
| 123 | os.mkdir(self._report_ppath) | |
| 124 | if not os.path.exists(self._report_upath): | |
| 125 | os.mkdir(self._report_upath) | |
| 126 | ||
| 127 | def run(self): | |
| 128 | self.online_plugins.start() | |
| 129 | tmp_timer = .0 | |
| 130 | while not self._must_stop: | |
| 131 | time.sleep(.1) | |
| 132 | tmp_timer += .1 | |
| 133 | if tmp_timer >= self.timer: | |
| 134 | try: | |
| 135 | self.syncReports() | |
| 136 | if not self.polling: | |
| 137 | break | |
| 138 | except Exception: | |
| 139 | logger.error("An exception was captured while saving reports\n%s", traceback.format_exc()) | |
| 140 | finally: | |
| 141 | tmp_timer = 0 | |
| 142 | ||
| 143 | def stop(self): | |
| 144 | self._must_stop = True | |
| 145 | self.online_plugins.stop() | |
| 146 | ||
| 147 | def syncReports(self): | |
| 148 | """ | |
| 149 | Synchronize report directory using the DataManager and Plugins online | |
| 150 | We first make sure that all shared reports were added to the repo | |
| 151 | """ | |
| 152 | for root, dirs, files in os.walk(self._report_path, False): | |
| 153 | # skip processed and unprocessed directories | |
| 154 | if root == self._report_path: | |
| 155 | for name in files: | |
| 156 | filename = os.path.join(root, name) | |
| 157 | name = os.path.basename(filename) | |
| 158 | # If plugin not is detected... move to unprocessed | |
| 159 | # PluginCommiter will rename the file to processed or unprocessed | |
| 160 | # when the plugin finishes | |
| 161 | if self.processor.processReport(filename) is False: | |
| 162 | logger.info('Plugin not detected. Moving {0} to unprocessed'.format(filename)) | |
| 163 | os.rename(filename, os.path.join(self._report_upath, name)) | |
| 164 | else: | |
| 165 | logger.info("Detected valid report {%s}", filename) | |
| 166 | os.rename(filename, os.path.join(self._report_ppath, name)) | |
| 167 | ||
| 168 | def sendReportToPluginById(self, plugin_id, filename): | |
| 169 | """Sends a report to be processed by the specified plugin_id""" | |
| 170 | self.processor.sendReport(plugin_id, filename) | |
| 171 | ||
| 172 | ||
| 173 | class ReportAnalyzer: | |
| 174 | ||
| 175 | def __init__(self, plugin_controller, report_path): | |
| 176 | self.plugin_controller = plugin_controller | |
| 177 | self.report_path = report_path | |
| 178 | ||
| 179 | def get_plugin_id(self): | |
| 180 | if not os.path.isfile(self.report_path): | |
| 181 | logger.error("Report [%s] don't exists", self.report_path) | |
| 182 | return None | |
| 183 | else: | |
| 184 | file_name = os.path.basename(self.report_path) | |
| 185 | plugin_id = self._get_plugin_by_name(file_name) | |
| 186 | if not plugin_id: # Was unable to detect plugin from report file name | |
| 187 | logger.debug("Plugin by name not found") | |
| 188 | plugin_id = self._get_plugin_by_file_type(self.report_path) | |
| 189 | if not plugin_id: | |
| 190 | logger.debug("Plugin by file not found") | |
| 191 | return plugin_id | |
| 192 | ||
| 193 | def _get_plugin_by_file_type(self, report_path): | |
| 194 | plugin_id = None | |
| 195 | file_name = os.path.basename(self.report_path) | |
| 196 | file_name_base, file_extension = os.path.splitext(file_name) | |
| 197 | file_extension = file_extension.lower() | |
| 198 | main_tag = None | |
| 199 | logger.debug("Analyze report File") | |
| 200 | # Try to parse as xml | |
| 201 | try: | |
| 202 | report_file = open(report_path) | |
| 203 | except Exception as e: | |
| 204 | logger.error("Error reading report content [%s]", e) | |
| 205 | else: | |
| 206 | try: | |
| 207 | for event, elem in ET.iterparse(report_file, ('start',)): | |
| 208 | main_tag = elem.tag | |
| 209 | break | |
| 210 | logger.debug("Found XML content on file: %s - Main tag: %s", report_path, main_tag) | |
| 211 | except Exception as e: | |
| 212 | logger.info("Non XML content [%s] - %s", report_path, e) | |
| 213 | finally: | |
| 214 | report_file.close() | |
| 215 | for _plugin_id, _plugin in self.plugin_controller.getAvailablePlugins().items(): | |
| 216 | if _plugin.report_belongs_to(main_tag=main_tag, report_path=report_path, extension=file_extension): | |
| 217 | plugin_id = _plugin_id | |
| 218 | break | |
| 219 | return plugin_id | |
| 220 | ||
| 221 | def _get_plugin_by_name(self, file_name_base): | |
| 222 | plugin_id = None | |
| 223 | plugin_name_regex = r".*_faraday_(?P<plugin_name>.+)\..*$" | |
| 224 | match = re.match(plugin_name_regex, file_name_base) | |
| 225 | if match: | |
| 226 | plugin_id = match.groupdict()['plugin_name'].lower() | |
| 227 | logger.debug("Plugin name match: %s", plugin_id) | |
| 228 | if plugin_id in self.plugin_controller.getAvailablePlugins(): | |
| 229 | return plugin_id | |
| 230 | else: | |
| 231 | logger.info("Invalid plugin from file name: %s", plugin_id) | |
| 232 | return None | |
| 233 | else: | |
| 234 | logger.debug("Could not extract plugin_id from filename: %s", file_name_base) | |
| 235 | return plugin_id | |
| 236 | ||
| 237 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | import re | |
| 7 | import time | |
| 8 | ||
| 9 | from faraday.client.model.workspace import Workspace | |
| 10 | from faraday.client.persistence.server.models import create_workspace, get_workspaces_names, get_workspace, delete_workspace | |
| 11 | from faraday.client.persistence.server.server_io_exceptions import Unauthorized | |
| 12 | from faraday.client.model.guiapi import notification_center | |
| 13 | ||
| 14 | from faraday.config.configuration import getInstanceConfiguration | |
| 15 | from faraday.config.constant import CONST_BLACKDBS | |
| 16 | CONF = getInstanceConfiguration() | |
| 17 | ||
| 18 | ||
| 19 | class WorkspaceException(Exception): | |
| 20 | pass | |
| 21 | ||
| 22 | ||
| 23 | class WorkspaceManager: | |
| 24 | """ | |
| 25 | This class is in charge of creating, deleting and opening workspaces | |
| 26 | """ | |
| 27 | ||
| 28 | def __init__(self, mappersManager, *args, **kwargs): | |
| 29 | self.mappersManager = mappersManager | |
| 30 | self.active_workspace = None | |
| 31 | ||
| 32 | def getWorkspacesNames(self): | |
| 33 | """Returns the names of the workspaces as a list of strings""" | |
| 34 | return get_workspaces_names() | |
| 35 | ||
| 36 | def createWorkspace(self, name, desc, start_date=int(time.time() * 1000), | |
| 37 | finish_date=int(time.time() * 1000), customer=""): | |
| 38 | # XXX: DEPRECATE NEXT LINE | |
| 39 | workspace = Workspace(name, desc) | |
| 40 | try: | |
| 41 | create_workspace(name, description=desc, start_date=start_date, | |
| 42 | finish_date=finish_date, customer=customer) | |
| 43 | except Unauthorized: | |
| 44 | raise WorkspaceException( | |
| 45 | ("You're not authorized to create workspaces\n" | |
| 46 | "Make sure you're an admin and add your credentials" | |
| 47 | "to your user configuration " | |
| 48 | "file in $HOME/.faraday/config/user.xml\n" | |
| 49 | "For example: " | |
| 50 | "<couch_uri>http://john:[email protected]:5984</couch_uri>")) | |
| 51 | except Exception as e: | |
| 52 | raise WorkspaceException(str(e)) | |
| 53 | self.mappersManager.createMappers(name) | |
| 54 | self.setActiveWorkspace(workspace) | |
| 55 | notification_center.workspaceChanged(workspace) | |
| 56 | return name | |
| 57 | ||
| 58 | def openWorkspace(self, name): | |
| 59 | """Open a workspace by name. Returns the workspace. Raises an | |
| 60 | WorkspaceException if something went wrong along the way. | |
| 61 | """ | |
| 62 | if name not in get_workspaces_names(): | |
| 63 | raise WorkspaceException("Workspace %s wasn't found" % name) | |
| 64 | ||
| 65 | try: | |
| 66 | workspace = get_workspace(name) | |
| 67 | except Unauthorized: | |
| 68 | raise WorkspaceException( | |
| 69 | ("You're not authorized to access this workspace\n" | |
| 70 | "Add your credentials to your user configuration " | |
| 71 | "file in $HOME/.faraday/config/user.xml\n" | |
| 72 | "For example: " | |
| 73 | "<couch_uri>http://john:[email protected]:5984</couch_uri>")) | |
| 74 | except Exception as e: | |
| 75 | notification_center.DBConnectionProblem(e) | |
| 76 | raise WorkspaceException(str(e)) | |
| 77 | self.mappersManager.createMappers(name) | |
| 78 | self.setActiveWorkspace(workspace) | |
| 79 | notification_center.workspaceChanged(workspace) | |
| 80 | return workspace | |
| 81 | ||
| 82 | def removeWorkspace(self, name): | |
| 83 | if name in self.getWorkspacesNames(): | |
| 84 | try: | |
| 85 | return delete_workspace(name) | |
| 86 | except Unauthorized: | |
| 87 | notification_center.showDialog("You are not authorized to " | |
| 88 | "delete this workspace. \n") | |
| 89 | ||
| 90 | def setActiveWorkspace(self, workspace): | |
| 91 | self.active_workspace = workspace | |
| 92 | ||
| 93 | def getActiveWorkspace(self): | |
| 94 | return self.active_workspace | |
| 95 | ||
| 96 | def workspaceExists(self, name): | |
| 97 | return name in self.getWorkspacesNames() | |
| 98 | ||
| 99 | def isActive(self, name): | |
| 100 | return self.active_workspace.getName() == name | |
| 101 | ||
| 102 | def isWorkspaceNameValid(self, ws_name): | |
| 103 | """Returns True if the ws_name is valid, else if it's not""" | |
| 104 | letters_or_numbers = r"^[a-z0-9][a-z0-9\_\$()\+\-\/]*$" | |
| 105 | regex_name = re.match(letters_or_numbers, ws_name) | |
| 106 | if regex_name and regex_name.string not in CONST_BLACKDBS: | |
| 107 | return True | |
| 108 | else: | |
| 109 | return False | |
| 110 | ||
| 111 | ||
| 112 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | ||
| 7 | class Modelactions: | |
| 8 | ADDHOST = 2000 | |
| 9 | DELHOST = 2001 | |
| 10 | ADDSERVICEHOST = 2008 | |
| 11 | ADDSERVICEHOST = 20008 | |
| 12 | ADDCATEGORY = 2011 # TODO migration: check why isn't implemented | |
| 13 | ADDVULNHOST = 2017 | |
| 14 | DELVULNHOST = 2018 | |
| 15 | ADDVULNSRV = 2019 | |
| 16 | DELVULNSRV = 2020 | |
| 17 | ADDNOTEHOST = 2025 | |
| 18 | DELNOTEHOST = 2026 | |
| 19 | ADDNOTESRV = 2027 | |
| 20 | DELNOTESRV = 2028 | |
| 21 | RENAMEROOT = 2029 # TODO migration: check why isn't implemented | |
| 22 | ADDNOTEVULN = 2030 | |
| 23 | DELNOTEVULN = 2031 # TODO migration: check why isn't implemented | |
| 24 | EDITHOST = 2032 | |
| 25 | EDITSERVICE = 2035 | |
| 26 | ADDCREDSRV = 2036 | |
| 27 | DELCREDSRV = 2037 | |
| 28 | ADDVULNWEBSRV = 2038 | |
| 29 | DELVULNWEBSRV = 2039 # TODO migration: check why isn't implemented | |
| 30 | ADDNOTENOTE = 2040 | |
| 31 | DELNOTENOTE = 2041 # TODO migration: check why isn't implemented | |
| 32 | EDITNOTE = 2042 | |
| 33 | EDITVULN = 2043 | |
| 34 | ADDNOTE = 2044 | |
| 35 | DELNOTE = 2045 | |
| 36 | ADDVULN = 2046 | |
| 37 | DELVULN = 2047 | |
| 38 | EDITCRED = 2048 | |
| 39 | ADDCRED = 2049 | |
| 40 | DELCRED = 2050 | |
| 41 | PLUGINSTART = 3000 | |
| 42 | PLUGINEND = 3001 | |
| 43 | LOG = 3002 | |
| 44 | DEVLOG = 3003 | |
| 45 | ||
| 46 | __descriptions = { | |
| 47 | ADDHOST: "ADDHOST", | |
| 48 | DELHOST: "DELHOST", | |
| 49 | ADDCATEGORY: "ADDCATEGORY", | |
| 50 | ADDVULNHOST: "ADDVULNHOST", | |
| 51 | DELVULNHOST: "DELVULNHOST", | |
| 52 | ADDVULNSRV: "ADDVULNSRV", | |
| 53 | DELVULNSRV: "DELVULNSRV", | |
| 54 | ADDNOTEVULN: "ADDNOTEVULN", | |
| 55 | DELNOTEVULN: "DELNOTEVULN", | |
| 56 | ADDNOTENOTE: "ADDNOTENOTE", | |
| 57 | DELNOTENOTE: "DELNOTENOTE", | |
| 58 | EDITHOST: "EDITHOST", | |
| 59 | ADDCREDSRV: "ADDCREDSRV", | |
| 60 | DELCREDSRV: "DELCREDSRV", | |
| 61 | ADDVULNWEBSRV: "ADDVULNSWEBRV", | |
| 62 | DELVULNWEBSRV: "DELVULNWEBSRV", | |
| 63 | EDITNOTE: "EDITNOTE", | |
| 64 | EDITVULN: "EDITVULN", | |
| 65 | EDITCRED: "EDITCRED", | |
| 66 | ADDNOTE: "ADDNOTE", | |
| 67 | DELNOTE: "DELNOTE", | |
| 68 | ADDVULN: "ADDVULN", | |
| 69 | DELVULN: "DELVULN", | |
| 70 | ADDCRED: "ADDCRED", | |
| 71 | DELCRED: "DELCRED", | |
| 72 | PLUGINSTART: "PLUGINSTART", | |
| 73 | PLUGINEND: "PLUGINEND" | |
| 74 | } | |
| 75 | ||
| 76 | @staticmethod | |
| 77 | def getDescription(action): | |
| 78 | return modelactions.__descriptions.get(action, "")# I'm Py3⏎ |
| 0 | #!/usr/bin/env python | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | ||
| 9 | import os | |
| 10 | import shutil | |
| 11 | import logging | |
| 12 | ||
| 13 | import faraday.client.model.common | |
| 14 | from faraday.config.configuration import getInstanceConfiguration | |
| 15 | import faraday.client.model.log | |
| 16 | from faraday.client.model import Modelactions | |
| 17 | from faraday.utils.common import socket, gateway | |
| 18 | ||
| 19 | CONF = getInstanceConfiguration() | |
| 20 | ||
| 21 | # global reference only for this module to work with the model controller | |
| 22 | __model_controller = None | |
| 23 | ||
| 24 | __workspace_manager = None | |
| 25 | ||
| 26 | _xmlrpc_api_server = None | |
| 27 | _plugin_controller_api = None | |
| 28 | ||
| 29 | #XXX: temp way to replicate info | |
| 30 | _remote_servers_proxy = [] | |
| 31 | ||
| 32 | _remote_sync_server_proxy = None | |
| 33 | ||
| 34 | # name of the currently logged user | |
| 35 | __current_logged_user = "" | |
| 36 | ||
| 37 | logger = logging.getLogger(__name__) | |
| 38 | ||
| 39 | ||
| 40 | def setUpAPIs(controller, workspace_manager, hostname=None, port=None): | |
| 41 | global __model_controller | |
| 42 | __model_controller = controller | |
| 43 | global __workspace_manager | |
| 44 | __workspace_manager = workspace_manager | |
| 45 | _setUpAPIServer(hostname, port) | |
| 46 | ||
| 47 | ||
| 48 | def startAPIServer(): | |
| 49 | global _xmlrpc_api_server | |
| 50 | if _xmlrpc_api_server is not None: | |
| 51 | devlog("starting xmlrpc api server...") | |
| 52 | #_xmlrpc_api_server.serve_forever() | |
| 53 | _xmlrpc_api_server.start() | |
| 54 | ||
| 55 | ||
| 56 | def stopAPIServer(): | |
| 57 | global _xmlrpc_api_server | |
| 58 | if _xmlrpc_api_server is not None: | |
| 59 | _xmlrpc_api_server.stop_server() | |
| 60 | devlog("called stop on xmlrpc server") | |
| 61 | _xmlrpc_api_server.join() | |
| 62 | devlog("xmlrpc thread joined") | |
| 63 | ||
| 64 | ||
| 65 | def _setUpAPIServer(hostname=None, port=None): | |
| 66 | global _xmlrpc_api_server | |
| 67 | global api_conn_info | |
| 68 | if _xmlrpc_api_server is None: | |
| 69 | #TODO: some way to get defaults.. from config? | |
| 70 | if str(hostname) == "None": | |
| 71 | hostname = "127.0.0.1" | |
| 72 | if str(port) == "None": | |
| 73 | port = 9876 | |
| 74 | ||
| 75 | if CONF.getApiConInfo() is None: | |
| 76 | CONF.setApiConInfo(hostname, port) | |
| 77 | devlog("starting XMLRPCServer with api_conn_info = %s" % str(CONF.getApiConInfo())) | |
| 78 | ||
| 79 | hostnames = [hostname] | |
| 80 | if hostname == "localhost": | |
| 81 | hostnames.append("127.0.0.1") | |
| 82 | ||
| 83 | listening = False | |
| 84 | for hostname in hostnames: | |
| 85 | ||
| 86 | try: | |
| 87 | _xmlrpc_api_server = faraday.client.model.common.XMLRPCServer((hostname,CONF.getApiConInfoPort())) | |
| 88 | # Registers the XML-RPC introspection functions system.listMethods, system.methodHelp and system.methodSignature. | |
| 89 | _xmlrpc_api_server.register_introspection_functions() | |
| 90 | ||
| 91 | # register a function to nicely stop server | |
| 92 | _xmlrpc_api_server.register_function(_xmlrpc_api_server.stop_server) | |
| 93 | ||
| 94 | # register all the api functions to be exposed by the server | |
| 95 | _xmlrpc_api_server.register_function(createAndAddHost) | |
| 96 | _xmlrpc_api_server.register_function(createAndAddInterface) | |
| 97 | _xmlrpc_api_server.register_function(createAndAddServiceToInterface) | |
| 98 | _xmlrpc_api_server.register_function(createAndAddServiceToHost) | |
| 99 | _xmlrpc_api_server.register_function(createAndAddNoteToService) | |
| 100 | _xmlrpc_api_server.register_function(createAndAddNoteToHost) | |
| 101 | _xmlrpc_api_server.register_function(createAndAddNoteToNote) | |
| 102 | _xmlrpc_api_server.register_function(createAndAddVulnWebToService) | |
| 103 | _xmlrpc_api_server.register_function(createAndAddVulnToService) | |
| 104 | _xmlrpc_api_server.register_function(createAndAddVulnToHost) | |
| 105 | _xmlrpc_api_server.register_function(addHost) | |
| 106 | _xmlrpc_api_server.register_function(newHost) | |
| 107 | _xmlrpc_api_server.register_function(newService) | |
| 108 | _xmlrpc_api_server.register_function(devlog) | |
| 109 | ||
| 110 | #TODO: check if all necessary APIs are registered here!! | |
| 111 | listening = True | |
| 112 | CONF.setApiConInfo(hostname, port) | |
| 113 | CONF.saveConfig() | |
| 114 | ||
| 115 | logger.info( | |
| 116 | "XMLRPC API server configured on %s" % str( | |
| 117 | CONF.getApiConInfo())) | |
| 118 | break | |
| 119 | ||
| 120 | except socket.error as e: | |
| 121 | msg = "There was an error creating the XMLRPC API Server (Host:{}): {}".format(hostname,e) | |
| 122 | log(msg) | |
| 123 | devlog("[WARNING] - %s" % msg) | |
| 124 | ||
| 125 | if not listening: | |
| 126 | raise RuntimeError("Port already in use") | |
| 127 | ||
| 128 | #------------------------------------------------------------------------------- | |
| 129 | # APIs to create and add elements to model | |
| 130 | #------------------------------------------------------------------------------- | |
| 131 | ||
| 132 | #TODO: create a decorator to find the caller of an api to try to determine which | |
| 133 | # plugin created the object | |
| 134 | ||
| 135 | ||
| 136 | def createAndAddHost(ip, os="Unknown", hostnames=None): | |
| 137 | host = newHost(ip, os, hostnames=hostnames) | |
| 138 | if addHost(host): | |
| 139 | return host.getID() | |
| 140 | return None | |
| 141 | ||
| 142 | ||
| 143 | def createAndAddInterface(host_id, name="", mac="00:00:00:00:00:00", ipv4_address="0.0.0.0", ipv4_mask="0.0.0.0", | |
| 144 | ipv4_gateway="0.0.0.0", ipv4_dns=[], ipv6_address="0000:0000:0000:0000:0000:0000:0000:0000", | |
| 145 | ipv6_prefix="00", ipv6_gateway="0000:0000:0000:0000:0000:0000:0000:0000", ipv6_dns=[], | |
| 146 | network_segment="", hostname_resolution=[]): | |
| 147 | return host_id | |
| 148 | ||
| 149 | ||
| 150 | def createAndAddServiceToInterface(host_id, interface_id, name, protocol = "tcp?", | |
| 151 | ports = [], status = "running", version = "unknown", description = ""): | |
| 152 | ||
| 153 | # interface_id unused, now unique parent of service is host_id | |
| 154 | service = newService(name, protocol, ports, status, version, description, parent_id=host_id) | |
| 155 | if addServiceToHost(service): | |
| 156 | return service.getID() | |
| 157 | return None | |
| 158 | ||
| 159 | ||
| 160 | def createAndAddServiceToHost(host_id, name, | |
| 161 | protocol="tcp?", ports=[], | |
| 162 | status="open", version="unknown", | |
| 163 | description=""): | |
| 164 | service = newService(name, protocol, ports, status, version, description, host_id) | |
| 165 | ||
| 166 | if addServiceToHost(service): | |
| 167 | return service.getID() | |
| 168 | return None | |
| 169 | ||
| 170 | ||
| 171 | # Vulnerability | |
| 172 | def createAndAddVulnToHost(host_id, name, desc, ref, severity, resolution, external_id=None): | |
| 173 | vuln = newVuln(name, desc, ref, severity, resolution, parent_id=host_id, external_id=external_id) | |
| 174 | if addVulnToHost(host_id, vuln): | |
| 175 | return vuln.getID() | |
| 176 | return None | |
| 177 | ||
| 178 | ||
| 179 | def createAndAddVulnToService(host_id, service_id, name, desc, ref, severity, resolution, external_id=None): | |
| 180 | #we should give the application_id too? I think we should... | |
| 181 | vuln = newVuln(name, desc, ref, severity, resolution, parent_id=service_id, external_id=external_id) | |
| 182 | if addVulnToService(host_id, service_id, vuln): | |
| 183 | return vuln.getID() | |
| 184 | return None | |
| 185 | ||
| 186 | #WebVuln | |
| 187 | ||
| 188 | def createAndAddVulnWebToService(host_id, service_id, name, desc, ref, severity, resolution, website, path, request, response, | |
| 189 | method,pname, params,query,category,external_id=None): | |
| 190 | #we should give the application_id too? I think we should... | |
| 191 | vuln = newVulnWeb(name, desc, ref, severity, resolution, website, path, request, response, | |
| 192 | method,pname, params, query, category, parent_id=service_id, external_id=external_id) | |
| 193 | if addVulnWebToService(host_id, service_id, vuln): | |
| 194 | return vuln.getID() | |
| 195 | return None | |
| 196 | ||
| 197 | # Note | |
| 198 | ||
| 199 | def createAndAddNoteToHost(host_id, name, text): | |
| 200 | return None | |
| 201 | ||
| 202 | ||
| 203 | def createAndAddNoteToService(host_id, service_id, name, text): | |
| 204 | return None | |
| 205 | ||
| 206 | ||
| 207 | def createAndAddNoteToNote(host_id, service_id, note_id, name, text): | |
| 208 | return None | |
| 209 | ||
| 210 | ||
| 211 | def createAndAddCredToService(host_id, service_id, username, password): | |
| 212 | cred = newCred(username, password, parent_id=service_id) | |
| 213 | if addCredToService(host_id, service_id, cred): | |
| 214 | return cred.getID() | |
| 215 | return None | |
| 216 | ||
| 217 | #------------------------------------------------------------------------------- | |
| 218 | # APIs to add already created objets to the model | |
| 219 | #------------------------------------------------------------------------------- | |
| 220 | ||
| 221 | #TODO: add class check to object passed to be sure we are adding the right thing to the model | |
| 222 | def addHost(host): | |
| 223 | if host is not None: | |
| 224 | __model_controller.add_action((Modelactions.ADDHOST, host)) | |
| 225 | #addHostASYNC(host) | |
| 226 | return True | |
| 227 | return False | |
| 228 | ||
| 229 | ||
| 230 | def addServiceToHost(service): | |
| 231 | if service is not None: | |
| 232 | __model_controller.add_action((Modelactions.ADDSERVICEHOST, service)) | |
| 233 | return True | |
| 234 | return False | |
| 235 | ||
| 236 | # Vulnerability | |
| 237 | ||
| 238 | def addVulnToHost(host_id, vuln): | |
| 239 | if vuln is not None: | |
| 240 | __model_controller.add_action((Modelactions.ADDVULNHOST, vuln)) | |
| 241 | return True | |
| 242 | return False | |
| 243 | ||
| 244 | ||
| 245 | def addVulnToService(host_id, service_id, vuln): | |
| 246 | if vuln is not None: | |
| 247 | __model_controller.add_action((Modelactions.ADDVULNSRV, vuln)) | |
| 248 | return True | |
| 249 | return False | |
| 250 | ||
| 251 | #VulnWeb | |
| 252 | def addVulnWebToService(host_id, service_id, vuln): | |
| 253 | if vuln is not None: | |
| 254 | __model_controller.add_action((Modelactions.ADDVULNWEBSRV, vuln)) | |
| 255 | return True | |
| 256 | return False | |
| 257 | ||
| 258 | ||
| 259 | # Notes | |
| 260 | def addNoteToHost(host_id, note): | |
| 261 | if note is not None: | |
| 262 | __model_controller.add_action( | |
| 263 | (Modelactions.ADDNOTEHOST, note)) | |
| 264 | return True | |
| 265 | return False | |
| 266 | ||
| 267 | ||
| 268 | def addNoteToService(host_id, service_id, note): | |
| 269 | if note is not None: | |
| 270 | __model_controller.add_action( | |
| 271 | (Modelactions.ADDNOTESRV, note)) | |
| 272 | return True | |
| 273 | return False | |
| 274 | ||
| 275 | def addNoteToNote(host_id, service_id, note_id, note): | |
| 276 | if note is not None: | |
| 277 | __model_controller.add_action((Modelactions.ADDNOTENOTE, note)) | |
| 278 | return True | |
| 279 | return False | |
| 280 | ||
| 281 | def addCredToService(host_id, service_id, cred): | |
| 282 | if cred is not None: | |
| 283 | __model_controller.add_action((Modelactions.ADDCREDSRV, cred)) | |
| 284 | return True | |
| 285 | return False | |
| 286 | ||
| 287 | #------------------------------------------------------------------------------- | |
| 288 | # APIs to delete elements to model | |
| 289 | #------------------------------------------------------------------------------- | |
| 290 | #TODO: delete functions are still missing | |
| 291 | def delHost(hostname): | |
| 292 | __model_controller.delHostASYNC(hostname) | |
| 293 | return True | |
| 294 | ||
| 295 | ||
| 296 | def delServiceFromHost(hostname, service): | |
| 297 | __model_controller.delServiceFromHostASYNC(hostname, service) | |
| 298 | return True | |
| 299 | ||
| 300 | ||
| 301 | #------------------------------------------------------------------------------- | |
| 302 | def delVulnFromHost(vuln, hostname): | |
| 303 | __model_controller.delVulnFromHostASYNC(hostname,vuln) | |
| 304 | return True | |
| 305 | ||
| 306 | #------------------------------------------------------------------------------- | |
| 307 | def delVulnFromService(vuln, hostname, srvname): | |
| 308 | __model_controller.delVulnFromServiceASYNC(hostname,srvname, vuln) | |
| 309 | return True | |
| 310 | ||
| 311 | ||
| 312 | #------------------------------------------------------------------------------- | |
| 313 | def delNoteFromHost(note, hostname): | |
| 314 | __model_controller.delNoteFromHostASYNC(hostname, note) | |
| 315 | return True | |
| 316 | ||
| 317 | #------------------------------------------------------------------------------- | |
| 318 | def delNoteFromService(note, hostname, srvname): | |
| 319 | __model_controller.delNoteFromServiceASYNC(hostname,srvname, note) | |
| 320 | return True | |
| 321 | ||
| 322 | #------------------------------------------------------------------------------- | |
| 323 | def delCredFromService(cred, hostname, srvname): | |
| 324 | __model_controller.delCredFromServiceASYNC(hostname,srvname, cred) | |
| 325 | return True | |
| 326 | ||
| 327 | #------------------------------------------------------------------------------- | |
| 328 | # CREATION APIS | |
| 329 | #------------------------------------------------------------------------------- | |
| 330 | ||
| 331 | def newHost(ip, os = "Unknown", hostnames=None): | |
| 332 | """ | |
| 333 | It creates and returns a Host object. | |
| 334 | The object created is not added to the model. | |
| 335 | """ | |
| 336 | return __model_controller.newHost(ip, os, hostnames=hostnames) | |
| 337 | ||
| 338 | ||
| 339 | def newService(name, protocol = "tcp?", ports = [], status = "running", | |
| 340 | version = "unknown", description = "", parent_id=None): | |
| 341 | """ | |
| 342 | It creates and returns a Service object. | |
| 343 | The created object is not added to the model. | |
| 344 | """ | |
| 345 | return __model_controller.newService( | |
| 346 | name, protocol, ports, status, version, description, parent_id) | |
| 347 | ||
| 348 | ||
| 349 | def newVuln(name, desc="", ref=None, severity="", resolution="", | |
| 350 | confirmed=False, parent_id=None, external_id=None): | |
| 351 | """ | |
| 352 | It creates and returns a Vulnerability object. | |
| 353 | The created object is not added to the model. | |
| 354 | """ | |
| 355 | return __model_controller.newVuln( | |
| 356 | name, desc, ref, severity, resolution, confirmed, parent_id, external_id) | |
| 357 | ||
| 358 | ||
| 359 | def newVulnWeb(name, desc="", ref=None, severity="", resolution="", website="", | |
| 360 | path="", request="", response="", method="", pname="", | |
| 361 | params="", query="", category="", confirmed=False, | |
| 362 | parent_id=None, external_id=None): | |
| 363 | """ | |
| 364 | It creates and returns a Vulnerability object. | |
| 365 | The created object is not added to the model. | |
| 366 | """ | |
| 367 | return __model_controller.newVulnWeb( | |
| 368 | name, desc, ref, severity, resolution, website, path, request, | |
| 369 | response, method, pname, params, query, category, confirmed, | |
| 370 | parent_id, external_id) | |
| 371 | ||
| 372 | ||
| 373 | def newNote(name, text, parent_id=None, parent_type=None): | |
| 374 | """ | |
| 375 | It creates and returns a Note object. | |
| 376 | The created object is not added to the model. | |
| 377 | """ | |
| 378 | return __model_controller.newNote(name, text, parent_id, parent_type) | |
| 379 | ||
| 380 | ||
| 381 | def newCred(username, password, parent_id=None): | |
| 382 | """ | |
| 383 | It creates and returns a Cred object. | |
| 384 | The created object is not added to the model. | |
| 385 | """ | |
| 386 | return __model_controller.newCred(username, password, parent_id) | |
| 387 | ||
| 388 | #------------------------------------------------------------------------------- | |
| 389 | ||
| 390 | #getConflicts: get the current conflicts | |
| 391 | def getConflicts(): | |
| 392 | return __model_controller.getConflicts() | |
| 393 | ||
| 394 | #------------------------------------------------------------------------------- | |
| 395 | # EVIDENCE | |
| 396 | #------------------------------------------------------------------------------- | |
| 397 | #TODO: refactor!! acomodar estos metodos para que no accedan a cosas directas del model_controller | |
| 398 | def addEvidence(file_path): | |
| 399 | """ | |
| 400 | Copy evidence file to the repository | |
| 401 | """ | |
| 402 | filename=os.path.basename(file_path) | |
| 403 | ###: Ver de sacar ese nombre evidences del config | |
| 404 | ||
| 405 | dpath="%s/evidences/" % (__model_controller._persistence_dir) | |
| 406 | dpathfilename="%s%s" % (dpath,filename) | |
| 407 | ||
| 408 | #devlog("[addEvidence] File added ("+file_path+") destination path ("+dpathfilename+")") | |
| 409 | ||
| 410 | if os.path.isfile(dpathfilename): | |
| 411 | devlog("[addEvidence] - File evidence (" + dpathfilename +") exists abort adding") | |
| 412 | else: | |
| 413 | if not os.path.isdir(dpath): | |
| 414 | os.mkdir(dpath) | |
| 415 | ||
| 416 | shutil.copyfile(file_path,dpathfilename) | |
| 417 | if os.path.isfile(dpathfilename): | |
| 418 | #XXX: la idea es no acceder directamente a cosas privadas del model controller como esto de _check_evidences | |
| 419 | __model_controller._check_evidences.append(dpathfilename) | |
| 420 | return dpathfilename | |
| 421 | ||
| 422 | return False | |
| 423 | ||
| 424 | def checkEvidence(file_path): | |
| 425 | """ | |
| 426 | Copy evidence file to the repository | |
| 427 | """ | |
| 428 | if not os.path.isfile(file_path): | |
| 429 | devlog("[addEvidence] - File evidence (" + dpathfilename +") doesnt exists abort adding") | |
| 430 | else: | |
| 431 | __model_controller._check_evidences.append(file_path) | |
| 432 | return True | |
| 433 | ||
| 434 | return False | |
| 435 | ||
| 436 | def cleanEvidence(): | |
| 437 | """ | |
| 438 | Copy evidence file to the repository | |
| 439 | """ | |
| 440 | check_evidences=__model_controller._check_evidences | |
| 441 | #devlog("[cleanEvidence] check_evidence values=" + str(check_evidences)) | |
| 442 | ||
| 443 | evidence_path="%s/evidences/" % (__model_controller._persistence_dir) | |
| 444 | for root, dirs, files in os.walk(evidence_path): | |
| 445 | for filename in files: | |
| 446 | if os.path.splitext(filename)[1].lower() == ".png": | |
| 447 | f=os.path.join(root, filename) | |
| 448 | if f in check_evidences: | |
| 449 | devlog("[cleanEvidence] - The following file is in the evidence xml" + os.path.join(root, filename)) | |
| 450 | else: | |
| 451 | delEvidence(f) | |
| 452 | #__model_controller._check_evidences=[] | |
| 453 | return True | |
| 454 | ||
| 455 | return False | |
| 456 | ||
| 457 | def delEvidence(file_path): | |
| 458 | """ | |
| 459 | Add file_path to the queue to be delete from the svn and filesystem | |
| 460 | """ | |
| 461 | if os.path.isfile(file_path): | |
| 462 | devlog("[addEvidence] - Adding file (" + file_path +") to the delete queue") | |
| 463 | __model_controller._deleted_evidences.append(file_path) | |
| 464 | return True | |
| 465 | else: | |
| 466 | devlog("[addEvidence] - File evidence (" + file_path +") doesnt exist abort deleting") | |
| 467 | ||
| 468 | return False | |
| 469 | ||
| 470 | #------------------------------------------------------------------------------- | |
| 471 | # MISC APIS | |
| 472 | #------------------------------------------------------------------------------- | |
| 473 | ||
| 474 | def log(msg ,level = "INFO"): | |
| 475 | """ | |
| 476 | This api will log the text in the GUI console without the level | |
| 477 | it will also log to a file with the corresponding level | |
| 478 | if logger was configured that way | |
| 479 | """ | |
| 480 | levels = { | |
| 481 | "CRITICAL": logging.CRITICAL, | |
| 482 | "ERROR": logging.ERROR, | |
| 483 | "WARNING": logging.WARNING, | |
| 484 | "INFO": logging.INFO, | |
| 485 | "DEBUG": logging.DEBUG, | |
| 486 | "NOTSET": logging.NOTSET | |
| 487 | } | |
| 488 | level = levels.get(level, logging.NOTSET) | |
| 489 | logger.log(level, msg) | |
| 490 | ||
| 491 | def devlog(msg): | |
| 492 | """ | |
| 493 | If DEBUG is set it will print information directly to stdout | |
| 494 | """ | |
| 495 | logger.debug(msg) | |
| 496 | ||
| 497 | def showDialog(msg, level="Information"): | |
| 498 | return faraday.client.model.log.getNotifier().showDialog(msg, level) | |
| 499 | ||
| 500 | def showPopup(msg, level="Information"): | |
| 501 | return faraday.client.model.log.getNotifier().showPopup(msg, level) | |
| 502 | ||
| 503 | ||
| 504 | # Plugin status | |
| 505 | ||
| 506 | def pluginStart(name): | |
| 507 | __model_controller.addPluginStart(name) | |
| 508 | ||
| 509 | def pluginEnd(name): | |
| 510 | __model_controller.addPluginEnd(name) | |
| 511 | ||
| 512 | #------------------------------------------------------------------------------- | |
| 513 | def getLoggedUser(): | |
| 514 | """ | |
| 515 | Returns the currently logged username | |
| 516 | """ | |
| 517 | global __current_logged_user | |
| 518 | return __current_logged_user | |
| 519 | #------------------------------------------------------------------------------- | |
| 520 | ||
| 521 | #TODO: implement!!!!! | |
| 522 | def getLocalDefaultGateway(): | |
| 523 | return gateway() | |
| 524 | ||
| 525 | def getActiveWorkspace(): | |
| 526 | return __workspace_manager.getActiveWorkspace() | |
| 527 | ||
| 528 | ||
| 529 | # I'm Py3 |
| 0 | #!/usr/bin/env python | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | from __future__ import print_function | |
| 9 | ||
| 10 | import os | |
| 11 | import sys | |
| 12 | import signal | |
| 13 | import json | |
| 14 | ||
| 15 | from faraday.server import TimerClass | |
| 16 | ||
| 17 | try: | |
| 18 | from Queue import Queue | |
| 19 | except ImportError: | |
| 20 | from queue import Queue | |
| 21 | import logging | |
| 22 | ||
| 23 | from faraday.client.model.controller import ModelController | |
| 24 | from faraday.client.managers.workspace_manager import WorkspaceManager | |
| 25 | from faraday.client.plugins.controller import PluginController | |
| 26 | from faraday.client.persistence.server.server import login_user | |
| 27 | ||
| 28 | import faraday.client.model.api | |
| 29 | import faraday.client.model.guiapi | |
| 30 | import faraday.client.apis.rest.api as restapi | |
| 31 | import faraday.client.model.log | |
| 32 | from faraday.client.plugins.manager import PluginManager | |
| 33 | from faraday.client.managers.mapper_manager import MapperManager | |
| 34 | from faraday.utils.error_report import exception_handler | |
| 35 | from faraday.utils.error_report import installThreadExcepthook | |
| 36 | ||
| 37 | from faraday.client.gui.gui_app import UiFactory | |
| 38 | from faraday.client.model.cli_app import CliApp | |
| 39 | ||
| 40 | from faraday.config.configuration import getInstanceConfiguration | |
| 41 | CONF = getInstanceConfiguration() | |
| 42 | ||
| 43 | ||
| 44 | logger = logging.getLogger(__name__) | |
| 45 | ||
| 46 | ||
| 47 | class MainApplication: | |
| 48 | ||
| 49 | def __init__(self, args): | |
| 50 | self._original_excepthook = sys.excepthook | |
| 51 | ||
| 52 | self.args = args | |
| 53 | ||
| 54 | if args.creds_file: | |
| 55 | try: | |
| 56 | with open(args.creds_file, 'r') as fp: | |
| 57 | creds = json.loads(fp.read()) | |
| 58 | username = creds.get('username') | |
| 59 | password = creds.get('password') | |
| 60 | session_cookie = login_user(CONF.getServerURI(), | |
| 61 | username, password) | |
| 62 | if session_cookie: | |
| 63 | logger.info('Login successful') | |
| 64 | CONF.setDBUser(username) | |
| 65 | CONF.setDBSessionCookies(session_cookie) | |
| 66 | else: | |
| 67 | logger.error('Login failed') | |
| 68 | except (IOError, ValueError): | |
| 69 | logger.error("Credentials file couldn't be loaded") | |
| 70 | ||
| 71 | self._mappers_manager = MapperManager() | |
| 72 | pending_actions = Queue() | |
| 73 | self._model_controller = ModelController(self._mappers_manager, pending_actions) | |
| 74 | ||
| 75 | self._plugin_manager = PluginManager( | |
| 76 | os.path.join(CONF.getConfigPath(), "plugins"), | |
| 77 | pending_actions=pending_actions, | |
| 78 | ) | |
| 79 | ||
| 80 | self._workspace_manager = WorkspaceManager( | |
| 81 | self._mappers_manager) | |
| 82 | ||
| 83 | # Create a PluginController and send this to UI selected. | |
| 84 | self._plugin_controller = PluginController( | |
| 85 | 'PluginController', | |
| 86 | self._plugin_manager, | |
| 87 | self._mappers_manager, | |
| 88 | pending_actions | |
| 89 | ) | |
| 90 | ||
| 91 | if self.args.cli: | |
| 92 | ||
| 93 | self.app = CliApp(self._workspace_manager, self._plugin_controller) | |
| 94 | ||
| 95 | if self.args.keep_old: | |
| 96 | CONF.setMergeStrategy("old") | |
| 97 | else: | |
| 98 | CONF.setMergeStrategy("new") | |
| 99 | ||
| 100 | else: | |
| 101 | self.app = UiFactory.create(self._model_controller, | |
| 102 | self._plugin_manager, | |
| 103 | self._workspace_manager, | |
| 104 | self._plugin_controller, | |
| 105 | self.args.gui) | |
| 106 | ||
| 107 | self.timer = TimerClass() | |
| 108 | self.timer.start() | |
| 109 | ||
| 110 | def on_connection_lost(self): | |
| 111 | """All it does is send a notification to the notification center""" | |
| 112 | faraday.client.model.guiapi.notification_center.DBConnectionProblem() | |
| 113 | ||
| 114 | def enableExceptHook(self): | |
| 115 | sys.excepthook = exception_handler | |
| 116 | installThreadExcepthook() | |
| 117 | ||
| 118 | def start(self): | |
| 119 | try: | |
| 120 | signal.signal(signal.SIGINT, self.ctrlC) | |
| 121 | ||
| 122 | faraday.client.model.api.devlog("Starting application...") | |
| 123 | faraday.client.model.api.devlog("Setting up remote API's...") | |
| 124 | ||
| 125 | if not self.args.workspace: | |
| 126 | workspace = CONF.getLastWorkspace() | |
| 127 | self.args.workspace = workspace | |
| 128 | ||
| 129 | faraday.client.model.api.setUpAPIs( | |
| 130 | self._model_controller, | |
| 131 | self._workspace_manager, | |
| 132 | CONF.getApiConInfoHost(), | |
| 133 | CONF.getApiConInfoPort()) | |
| 134 | faraday.client.model.guiapi.setUpGUIAPIs(self._model_controller) | |
| 135 | ||
| 136 | faraday.client.model.api.devlog("Starting model controller daemon...") | |
| 137 | ||
| 138 | self._model_controller.start() | |
| 139 | faraday.client.model.api.startAPIServer() | |
| 140 | restapi.startAPIs( | |
| 141 | self._plugin_controller, | |
| 142 | self._model_controller, | |
| 143 | CONF.getApiConInfoHost(), | |
| 144 | CONF.getApiRestfulConInfoPort() | |
| 145 | ) | |
| 146 | ||
| 147 | faraday.client.model.api.devlog("Faraday ready...") | |
| 148 | ||
| 149 | exit_code = self.app.run(self.args) | |
| 150 | ||
| 151 | except Exception as exception: | |
| 152 | print("There was an error while starting Faraday:") | |
| 153 | print("*" * 3) | |
| 154 | print(exception) # instead of traceback.print_exc() | |
| 155 | print("*" * 3) | |
| 156 | exit_code = -1 | |
| 157 | ||
| 158 | finally: | |
| 159 | return self.__exit(exit_code) | |
| 160 | ||
| 161 | def __exit(self, exit_code=0): | |
| 162 | """ | |
| 163 | Exits the application with the provided code. | |
| 164 | It also waits until all app threads end. | |
| 165 | """ | |
| 166 | faraday.client.model.api.log("Closing Faraday...") | |
| 167 | faraday.client.model.api.devlog("stopping model controller thread...") | |
| 168 | faraday.client.model.api.stopAPIServer() | |
| 169 | restapi.stopServer() | |
| 170 | self._model_controller.stop() | |
| 171 | if self._model_controller.isAlive(): | |
| 172 | # runs only if thread has started, i.e. self._model_controller.start() is run first | |
| 173 | self._model_controller.join() | |
| 174 | self.timer.stop() | |
| 175 | faraday.client.model.api.devlog("Waiting for controller threads to end...") | |
| 176 | return exit_code | |
| 177 | ||
| 178 | def quit(self): | |
| 179 | """ | |
| 180 | Redefined quit handler to nicely end up things | |
| 181 | """ | |
| 182 | self.app.quit() | |
| 183 | ||
| 184 | def ctrlC(self, signal, frame): | |
| 185 | logger.info("Exiting...") | |
| 186 | self.app.quit() | |
| 187 | ||
| 188 | ||
| 189 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | import logging | |
| 9 | ||
| 10 | from faraday.client.managers.reports_managers import ReportProcessor | |
| 11 | ||
| 12 | logger = logging.getLogger(__name__) | |
| 13 | ||
| 14 | class CliApp(): | |
| 15 | def __init__(self, workspace_manager, plugin_controller): | |
| 16 | self.workspace_manager = workspace_manager | |
| 17 | self.plugin_controller = plugin_controller | |
| 18 | ||
| 19 | def run(self, args): | |
| 20 | workspace = args.workspace | |
| 21 | try: | |
| 22 | self.workspace_manager.openWorkspace(workspace) | |
| 23 | except Exception as e: | |
| 24 | logger.error( | |
| 25 | ("The workspace %s is not accessible, " | |
| 26 | "check configuration") % workspace) | |
| 27 | logger.error(str(e)) | |
| 28 | return -1 | |
| 29 | ||
| 30 | rp = ReportProcessor(self.plugin_controller) | |
| 31 | rp.processReport(args.filename) | |
| 32 | ||
| 33 | ||
| 34 | # I'm Py3 |
| 0 | #!/usr/bin/env python | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | """ | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | """ | |
| 9 | from __future__ import absolute_import | |
| 10 | ||
| 11 | import socket | |
| 12 | import subprocess | |
| 13 | import getpass | |
| 14 | ||
| 15 | from threading import Event | |
| 16 | from sys import platform as _platform | |
| 17 | ||
| 18 | ||
| 19 | def get_private_ip(): | |
| 20 | """ | |
| 21 | This method returns the first private ip address | |
| 22 | configured for this machine. | |
| 23 | TODO: The problem is what happens when the machine | |
| 24 | has more than one private ip | |
| 25 | """ | |
| 26 | try: | |
| 27 | ip = socket.gethostbyname(socket.gethostname()) | |
| 28 | except socket.gaierror: | |
| 29 | return '' | |
| 30 | if ip: | |
| 31 | if not ip.startswith('127'): | |
| 32 | return ip | |
| 33 | ip = socket.gethostbyname(socket.getfqdn()) | |
| 34 | if ip: | |
| 35 | if not ip.startswith('127'): | |
| 36 | return ip | |
| 37 | if _platform in ["linux", "linux2"]: # linux | |
| 38 | ip = subprocess.check_output(["ip addr | grep 'state UP' -A2 | tail -n1 | awk '{print $2}' | cut -f1 -d'/'"], shell=True) | |
| 39 | elif _platform == "darwin": # MAC OS X | |
| 40 | ip = subprocess.check_output(["ifconfig | grep 'inet ' | grep -Fv 127.0.0.1 | awk '{print $2}' "], shell=True) | |
| 41 | ip = ip.rstrip() # removes '\n' | |
| 42 | return ip | |
| 43 | ||
| 44 | ||
| 45 | def get_hostname(): | |
| 46 | return socket.gethostname() | |
| 47 | ||
| 48 | def get_user(): | |
| 49 | return getpass.getuser() | |
| 50 | ||
| 51 | ||
| 52 | class CommandRunInformation: | |
| 53 | """Command Run information object containing: | |
| 54 | command, parameters, time, workspace, etc.""" | |
| 55 | class_signature = "CommandRunInformation" | |
| 56 | ||
| 57 | def __init__(self, **kwargs): | |
| 58 | self.type = self.__class__.__name__ | |
| 59 | self.user = get_user() | |
| 60 | self.ip = get_private_ip() | |
| 61 | self.hostname = get_hostname() | |
| 62 | self.itime = None | |
| 63 | self.duration = None | |
| 64 | self.params = None | |
| 65 | self.workspace = None | |
| 66 | self.import_source = None | |
| 67 | self._id = None | |
| 68 | self.id_available = Event() | |
| 69 | ||
| 70 | for k, v in kwargs.items(): | |
| 71 | setattr(self, k, v) | |
| 72 | ||
| 73 | def getID(self): | |
| 74 | if self._id is None: | |
| 75 | self.id_available.wait(timeout=1) | |
| 76 | return self._id | |
| 77 | ||
| 78 | def setID(self, id): | |
| 79 | self._id = id | |
| 80 | self.id_available.set() | |
| 81 | ||
| 82 | def toDict(self): | |
| 83 | return self.__dict__ | |
| 84 | ||
| 85 | def fromDict(self, dictt): | |
| 86 | for k, v in dictt.items(): | |
| 87 | setattr(self, k, v) | |
| 88 | return self | |
| 89 | ||
| 90 | ||
| 91 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | import sys | |
| 9 | import traceback | |
| 10 | import threading | |
| 11 | import logging | |
| 12 | try: | |
| 13 | import xmlrpclib | |
| 14 | from SimpleXMLRPCServer import SimpleXMLRPCServer, SimpleXMLRPCRequestHandler | |
| 15 | except ImportError: | |
| 16 | from xmlrpc import client as xmlrpclib | |
| 17 | from xmlrpc.server import SimpleXMLRPCServer, SimpleXMLRPCRequestHandler | |
| 18 | ||
| 19 | try: | |
| 20 | from faraday.client.model import api | |
| 21 | except AttributeError as e: | |
| 22 | import api | |
| 23 | ||
| 24 | from faraday.config.configuration import getInstanceConfiguration | |
| 25 | CONF = getInstanceConfiguration() | |
| 26 | logger = logging.getLogger(__name__) | |
| 27 | ||
| 28 | ||
| 29 | # ------------------------------------------------------------------------------- | |
| 30 | # TODO: refactor this class to make it generic so this can be used also for plugins | |
| 31 | # then create a subclass and inherit the generic factory | |
| 32 | class ModelObjectFactory: | |
| 33 | """ | |
| 34 | Factory to creat any ModelObject type | |
| 35 | """ | |
| 36 | def __init__(self): | |
| 37 | self._registered_objects = dict() | |
| 38 | ||
| 39 | def register(self, model_object): | |
| 40 | """registers a class into the factory""" | |
| 41 | self._registered_objects[model_object.class_signature] = model_object | |
| 42 | ||
| 43 | def listModelObjectClasses(self): | |
| 44 | """returns a list of registered classes""" | |
| 45 | return list(self._registered_objects.values()) | |
| 46 | ||
| 47 | def getModelObjectClass(self, name): | |
| 48 | """get the class for a particular object typename""" | |
| 49 | return self._registered_objects[name] | |
| 50 | ||
| 51 | def listModelObjectTypes(self): | |
| 52 | """returns an array with object typenames the factory is able to create""" | |
| 53 | names = list(self._registered_objects.keys()) | |
| 54 | names.sort() | |
| 55 | return names | |
| 56 | ||
| 57 | def generateID(self, classname, parent_id='', **objargs): | |
| 58 | """Given a classname, parent_id and necessary objargs, return the ID | |
| 59 | of the object. | |
| 60 | ||
| 61 | Necesary objargs vary according to the object: | |
| 62 | Host --> name | |
| 63 | Cred --> Name, password | |
| 64 | Note --> Name, text | |
| 65 | Service --> Protocol, ports | |
| 66 | Interface --> Network segments, ipv4_address, ipv6_address | |
| 67 | Vuln --> name, desc | |
| 68 | VulnWeb --> name, website | |
| 69 | """ | |
| 70 | ||
| 71 | # see how nicely formated that dictionary is | |
| 72 | # it's a building about to go down on an eathquake! | |
| 73 | # let's try not to make that an analogy about my code, ok? thank you :) | |
| 74 | # appropiate_class = self._registered_objects[classname] | |
| 75 | # class_to_args = {'Host': (objargs.get('name'),), | |
| 76 | # 'Cred': (objargs.get('name'), objargs.get('password')), | |
| 77 | # 'Note': (objargs.get('name'), | |
| 78 | # objargs.get('text')), | |
| 79 | # 'Service': (objargs.get('protocol'), | |
| 80 | # objargs.get('ports')), | |
| 81 | # 'Interface': (objargs.get('network_segment'), | |
| 82 | # objargs.get('ipv4_address'), | |
| 83 | # objargs.get('ipv6_address')), | |
| 84 | # 'Vulnerability': (objargs.get('name'), | |
| 85 | # objargs.get('desc')), | |
| 86 | # 'VulnerabilityWeb': (objargs.get('name'), | |
| 87 | # objargs.get('website')) | |
| 88 | # } | |
| 89 | # try: | |
| 90 | # id = appropiate_class.generateID(parent_id, *class_to_args[classname]) | |
| 91 | # except KeyError: | |
| 92 | # raise Exception("You've provided an invalid classname") | |
| 93 | # return id | |
| 94 | ||
| 95 | def createModelObject(self, classname, object_name, workspace_name=None, parent_id=None, **objargs): | |
| 96 | """Given a registered classname, create an object of name object_name and | |
| 97 | with the properties found on objargs. ID will be generated for you. | |
| 98 | ||
| 99 | If workspace_name is None, it will be inferred from the CONF module. | |
| 100 | parent_id should only be None if classname is 'Host' or maybe 'Note' or 'Credential'. | |
| 101 | """ | |
| 102 | if not workspace_name: | |
| 103 | workspace_name = CONF.getLastWorkspace() | |
| 104 | logger.warn('No workspace selected. Using last workspace {0}'.format(workspace_name)) | |
| 105 | if classname in self._registered_objects: | |
| 106 | if object_name is not None: | |
| 107 | objargs['name'] = object_name | |
| 108 | if parent_id: | |
| 109 | objargs['parent'] = parent_id | |
| 110 | tmpObj = self._registered_objects[classname](objargs, workspace_name) | |
| 111 | return tmpObj | |
| 112 | else: | |
| 113 | raise Exception("Object name parameter missing. Cannot create object class: %s" % classname) | |
| 114 | else: | |
| 115 | raise Exception("Object class %s not registered in factory. Cannot create object." % classname) | |
| 116 | ||
| 117 | # ------------------------------------------------------------------------------- | |
| 118 | # global reference kind of a singleton | |
| 119 | factory = ModelObjectFactory() | |
| 120 | ||
| 121 | # ------------------------------------------------------------------------------- | |
| 122 | ||
| 123 | class CustomXMLRPCRequestHandler(SimpleXMLRPCRequestHandler): | |
| 124 | ||
| 125 | def __init__(self, *args, **kwargs): | |
| 126 | SimpleXMLRPCRequestHandler.__init__(self, *args, **kwargs) | |
| 127 | ||
| 128 | def handle(self): | |
| 129 | try: | |
| 130 | api.devlog("-" * 60) | |
| 131 | api.devlog("[XMLRPCHandler] - request = %s" % str(self.request)) | |
| 132 | api.devlog("[XMLRPCHandler] - client_address = %s" % str(self.client_address)) | |
| 133 | api.devlog("[XMLRPCHandler] - server = %s" % str(self.server)) | |
| 134 | api.devlog("-" * 60) | |
| 135 | SimpleXMLRPCRequestHandler.handle(self) | |
| 136 | except Exception: | |
| 137 | api.devlog("[XMLRPCHandler] - An error ocurred while handling a request\n%s" % traceback.format_exc()) | |
| 138 | ||
| 139 | def do_POST(self): | |
| 140 | """ | |
| 141 | Handles the HTTP POST request. | |
| 142 | Attempts to interpret all HTTP POST requests as XML-RPC calls, | |
| 143 | which are forwarded to the server's _dispatch method for handling. | |
| 144 | ||
| 145 | This is a copy of the original do_POST, but it sends information about | |
| 146 | the client calling the server to the marshaled dispatch. This info | |
| 147 | can be later passed to the server | |
| 148 | """ | |
| 149 | ||
| 150 | # Check that the path is legal | |
| 151 | if not self.is_rpc_path_valid(): | |
| 152 | self.report_404() | |
| 153 | return | |
| 154 | ||
| 155 | try: | |
| 156 | # Get arguments by reading body of request. | |
| 157 | # We read this in chunks to avoid straining | |
| 158 | # socket.read(); around the 10 or 15Mb mark, some platforms | |
| 159 | # begin to have problems (bug #792570). | |
| 160 | max_chunk_size = 10*1024*1024 | |
| 161 | size_remaining = int(self.headers["content-length"]) | |
| 162 | L = [] | |
| 163 | while size_remaining: | |
| 164 | chunk_size = min(size_remaining, max_chunk_size) | |
| 165 | L.append(self.rfile.read(chunk_size)) | |
| 166 | size_remaining -= len(L[-1]) | |
| 167 | data = ''.join(L) | |
| 168 | ||
| 169 | # In previous versions of SimpleXMLRPCServer, _dispatch | |
| 170 | # could be overridden in this class, instead of in | |
| 171 | # SimpleXMLRPCDispatcher. To maintain backwards compatibility, | |
| 172 | # check to see if a subclass implements _dispatch and dispatch | |
| 173 | # using that method if present. | |
| 174 | response = self.server._marshaled_dispatch( | |
| 175 | data, getattr(self, '_dispatch', None) | |
| 176 | ) | |
| 177 | except Exception as e: # This should only happen if the module is buggy | |
| 178 | # internal error, report as HTTP server error | |
| 179 | self.send_response(500) | |
| 180 | ||
| 181 | # Send information about the exception if requested | |
| 182 | if hasattr(self.server, '_send_traceback_header') and \ | |
| 183 | self.server._send_traceback_header: | |
| 184 | self.send_header("X-exception", str(e)) | |
| 185 | self.send_header("X-traceback", traceback.format_exc()) | |
| 186 | ||
| 187 | self.end_headers() | |
| 188 | else: | |
| 189 | # got a valid XML RPC response | |
| 190 | self.send_response(200) | |
| 191 | self.send_header("Content-type", "text/xml") | |
| 192 | self.send_header("Content-length", str(len(response))) | |
| 193 | self.end_headers() | |
| 194 | self.wfile.write(response) | |
| 195 | ||
| 196 | # shut down the connection | |
| 197 | self.wfile.flush() | |
| 198 | self.connection.shutdown(1) | |
| 199 | # ------------------------------------------------------------------------------- | |
| 200 | # custom XMLRPC server with stopping function | |
| 201 | # TODO: check http://epydoc.sourceforge.net/stdlib/SimpleXMLRPCServer.SimpleXMLRPCServer-class.html | |
| 202 | # see if there is a way to know the ip caller | |
| 203 | # looks like the request handler can give us that info | |
| 204 | # http://epydoc.sourceforge.net/stdlib/BaseHTTPServer.BaseHTTPRequestHandler-class.html#address_string | |
| 205 | # | |
| 206 | ||
| 207 | class XMLRPCServer(SimpleXMLRPCServer, threading.Thread): | |
| 208 | """ | |
| 209 | Stoppable XMLRPC Server with custom dispatch to send over complete traceback | |
| 210 | in case of exception. | |
| 211 | """ | |
| 212 | def __init__(self, *args, **kwargs): | |
| 213 | threading.Thread.__init__(self) | |
| 214 | SimpleXMLRPCServer.__init__(self, | |
| 215 | requestHandler=CustomXMLRPCRequestHandler, | |
| 216 | allow_none=True, *args, **kwargs) | |
| 217 | self._must_stop = False | |
| 218 | # set timeout for handle_request. If we don't the server will hang | |
| 219 | self.timeout = 2 | |
| 220 | ||
| 221 | def run(self): | |
| 222 | self.serve_forever() | |
| 223 | api.devlog("serve_forever ended") | |
| 224 | ||
| 225 | # overloaded method to be able to stop server | |
| 226 | def serve_forever(self): | |
| 227 | while not self._must_stop: | |
| 228 | self.handle_request() | |
| 229 | api.devlog("server forever stopped by flag") | |
| 230 | ||
| 231 | def stop_server(self): | |
| 232 | api.devlog("server stopping...") | |
| 233 | self._must_stop = True | |
| 234 | ||
| 235 | # The default dispatcher does not send across the whole stack trace. | |
| 236 | # Only type and value are passed back. The client has no way of knowing | |
| 237 | # the exact place where error occurred in the server (short of some | |
| 238 | # other means such as server logging). This dispatcher sends the whole | |
| 239 | # stack trace. | |
| 240 | def _dispatch(self, method, params): | |
| 241 | """Dispatches the XML-RPC method. | |
| 242 | ||
| 243 | XML-RPC calls are forwarded to a registered function that | |
| 244 | matches the called XML-RPC method name. If no such function | |
| 245 | exists then the call is forwarded to the registered instance, | |
| 246 | if available. | |
| 247 | ||
| 248 | If the registered instance has a _dispatch method then that | |
| 249 | method will be called with the name of the XML-RPC method and | |
| 250 | its parameters as a tuple | |
| 251 | e.g. instance._dispatch('add',(2,3)) | |
| 252 | ||
| 253 | If the registered instance does not have a _dispatch method | |
| 254 | then the instance will be searched to find a matching method | |
| 255 | and, if found, will be called. | |
| 256 | ||
| 257 | Methods beginning with an '_' are considered private and will | |
| 258 | not be called. | |
| 259 | """ | |
| 260 | ||
| 261 | func = None | |
| 262 | try: | |
| 263 | # check to see if a matching function has been registered | |
| 264 | func = self.funcs[method] | |
| 265 | except KeyError: | |
| 266 | if self.instance is not None: | |
| 267 | # check for a _dispatch method | |
| 268 | if hasattr(self.instance, '_dispatch'): | |
| 269 | return self.instance._dispatch(method, params) | |
| 270 | else: | |
| 271 | # call instance method directly | |
| 272 | try: | |
| 273 | func = SimpleXMLRPCServer.resolve_dotted_attribute( | |
| 274 | self.instance, | |
| 275 | method, | |
| 276 | self.allow_dotted_names | |
| 277 | ) | |
| 278 | except AttributeError: | |
| 279 | pass | |
| 280 | ||
| 281 | if func is not None: | |
| 282 | try: | |
| 283 | # since we are using a keyword xmlrpc proxy this is sending | |
| 284 | # the info comes in form of args and kwargs | |
| 285 | # so params has 2 items, the first being a list or tuple | |
| 286 | # and the second a dictionary | |
| 287 | if len(params) == 2 and isinstance(params[1], dict) and\ | |
| 288 | (isinstance(params[0], list) or isinstance(params[-1], tuple)): | |
| 289 | return func(*params[0], **params[1]) | |
| 290 | else: | |
| 291 | # this is the default way in case a normal xmlrpclib.ServerProxy is used | |
| 292 | return func(*params) | |
| 293 | except Exception: | |
| 294 | # extended functionality to let the client have the full traceback | |
| 295 | msg = traceback.format_exc() | |
| 296 | raise xmlrpclib.Fault(1, msg) | |
| 297 | else: | |
| 298 | raise Exception('method "%s" is not supported' % method) | |
| 299 | ||
| 300 | def _marshaled_dispatch(self, data, dispatch_method=None): | |
| 301 | """Dispatches an XML-RPC method from marshalled (XML) data. | |
| 302 | ||
| 303 | XML-RPC methods are dispatched from the marshalled (XML) data | |
| 304 | using the _dispatch method and the result is returned as | |
| 305 | marshalled data. For backwards compatibility, a dispatch | |
| 306 | function can be provided as an argument (see comment in | |
| 307 | SimpleXMLRPCRequestHandler.do_POST) but overriding the | |
| 308 | existing method through subclassing is the prefered means | |
| 309 | of changing method dispatch behavior. | |
| 310 | """ | |
| 311 | ||
| 312 | try: | |
| 313 | params, method = xmlrpclib.loads(data) | |
| 314 | ||
| 315 | # generate response | |
| 316 | if dispatch_method is not None: | |
| 317 | response = dispatch_method(method, params) | |
| 318 | else: | |
| 319 | response = self._dispatch(method, params) | |
| 320 | # wrap response in a singleton tuple | |
| 321 | response = (response,) | |
| 322 | response = xmlrpclib.dumps(response, methodresponse=1, | |
| 323 | allow_none=self.allow_none, encoding=self.encoding) | |
| 324 | except Exception: | |
| 325 | # report exception back to server | |
| 326 | exc_type, exc_value, exc_tb = sys.exc_info() | |
| 327 | response = xmlrpclib.dumps( | |
| 328 | xmlrpclib.Fault(1, "%s:%s" % (exc_type, exc_value)), | |
| 329 | encoding=self.encoding, allow_none=self.allow_none, | |
| 330 | ) | |
| 331 | ||
| 332 | return response | |
| 333 | ||
| 334 | class XMLRPCKeywordProxy: | |
| 335 | """ | |
| 336 | custom XMLRPC Server Proxy capable of receiving keyword arguments | |
| 337 | when calling remote methods | |
| 338 | """ | |
| 339 | def __init__(self, *args, **kwargs): | |
| 340 | self._xmlrpc_server_proxy = xmlrpclib.ServerProxy(*args, **kwargs) | |
| 341 | ||
| 342 | def __getattr__(self, name): | |
| 343 | call_proxy = getattr(self._xmlrpc_server_proxy, name) | |
| 344 | ||
| 345 | def _call(*args, **kwargs): | |
| 346 | return call_proxy(args, kwargs) | |
| 347 | return _call | |
| 348 | ||
| 349 | ||
| 350 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | ||
| 7 | ||
| 8 | class Conflict(): | |
| 9 | ||
| 10 | def __init__(self, old_object, new_object): | |
| 11 | self.type = None | |
| 12 | self.model_object_type = old_object.class_signature | |
| 13 | self.first_object = old_object | |
| 14 | self.second_object = new_object | |
| 15 | ||
| 16 | def getFirstObject(self): | |
| 17 | return self.first_object | |
| 18 | ||
| 19 | def getSecondObject(self): | |
| 20 | return self.second_object | |
| 21 | ||
| 22 | def getType(self): | |
| 23 | return self.type | |
| 24 | ||
| 25 | def getModelObjectType(self): | |
| 26 | return self.model_object_type | |
| 27 | ||
| 28 | def resolve(self, kwargs): | |
| 29 | return False | |
| 30 | ||
| 31 | ||
| 32 | class ConflictUpdate(Conflict): | |
| 33 | ||
| 34 | def __init__(self, first_object, second_object): | |
| 35 | Conflict.__init__(self, first_object, second_object) | |
| 36 | self.type = "Update" | |
| 37 | ||
| 38 | def resolve(self, kwargs): | |
| 39 | self.first_object.updateAttributes(**kwargs) | |
| 40 | self.first_object.updateResolved(self) | |
| 41 | return True | |
| 42 | # I'm Py3⏎ |
| 0 | #!/usr/bin/python | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | ||
| 9 | ||
| 10 | class ModelObjectContainer(dict): | |
| 11 | ||
| 12 | """Used to provide a consistent interface while adding model objects to the currently running environment""" | |
| 13 | def __init__(self, *args): | |
| 14 | self.container = {} | |
| 15 | ||
| 16 | def __setitem__(self, k, v): | |
| 17 | ||
| 18 | self.container.__setitem__(k, v) | |
| 19 | ||
| 20 | def __getitem__(self, k): | |
| 21 | return self.container.get(k) | |
| 22 | ||
| 23 | def __getattr__( self, name): | |
| 24 | return getattr(self.container, name) | |
| 25 | ||
| 26 | def values(self): | |
| 27 | return list(self.container.values()) | |
| 28 | ||
| 29 | def keys(self): | |
| 30 | return list(self.container.keys()) | |
| 31 | ||
| 32 | def __str__(self): | |
| 33 | return str(self.container) | |
| 34 | ||
| 35 | def clear(self): | |
| 36 | self.container.clear() | |
| 37 | ||
| 38 | def __contains__(self, elem): | |
| 39 | return self.container.__contains__(elem) | |
| 40 | ||
| 41 | def containsByAttr(self, attrName, attrValue): | |
| 42 | for k, elem in self.container: | |
| 43 | if elem.__getattribute__(attrName) == attrValue: | |
| 44 | return True | |
| 45 | return False | |
| 46 | ||
| 47 | def __len__(self): | |
| 48 | return len(self.container) | |
| 49 | ||
| 50 | def __delitem__(self, k): | |
| 51 | self.container.__delitem__(k) | |
| 52 | ||
| 53 | ||
| 54 | class CouchedModelObjectContainer(ModelObjectContainer): | |
| 55 | def __init__(self, workspaceName, couchManager): | |
| 56 | ModelObjectContainer.__init__(self) | |
| 57 | self.cdm = couchManager | |
| 58 | self.workspaceName = workspaceName | |
| 59 | ||
| 60 | def __setitem__(self, k, v): | |
| 61 | ModelObjectContainer.__setitem__(self, k, v) | |
| 62 | ||
| 63 | ||
| 64 | ||
| 65 | ||
| 66 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | import time | |
| 9 | import logging | |
| 10 | import traceback | |
| 11 | import faraday.client.model.common # this is to make sure the factory is created | |
| 12 | from multiprocessing import Lock | |
| 13 | from queue import Empty | |
| 14 | from threading import Thread | |
| 15 | ||
| 16 | from faraday.config.configuration import getInstanceConfiguration | |
| 17 | from faraday.client.model import Modelactions | |
| 18 | from faraday.client.persistence.server.server_io_exceptions import ConflictInDatabase | |
| 19 | import faraday.client.model.api as api | |
| 20 | from faraday.client.model.guiapi import notification_center as notifier | |
| 21 | from functools import wraps | |
| 22 | from faraday.client.persistence.server import models | |
| 23 | ||
| 24 | # XXX: consider re-writing this module! There's alot of repeated code | |
| 25 | # and things are really messy | |
| 26 | # XXX-2019: we should consider deleting this module! | |
| 27 | ||
| 28 | CONF = getInstanceConfiguration() | |
| 29 | logger = logging.getLogger(__name__) | |
| 30 | ||
| 31 | ||
| 32 | class ModelController(Thread): | |
| 33 | ||
| 34 | def __init__(self, mappers_manager, pending_actions): | |
| 35 | #Thread.__init__(self) | |
| 36 | super().__init__(name="ModelControllerThread") | |
| 37 | ||
| 38 | self.mappers_manager = mappers_manager | |
| 39 | ||
| 40 | # set as daemon | |
| 41 | # self.setDaemon(True) | |
| 42 | # sets the flag to stop the thread when it has finished processing | |
| 43 | self._must_stop = False | |
| 44 | ||
| 45 | # locks needed to make model thread-safe | |
| 46 | self._hosts_lock = Lock() | |
| 47 | ||
| 48 | # count of plugins sending actions | |
| 49 | self.active_plugins_count = 0 | |
| 50 | self.active_plugins_count_lock = Lock() | |
| 51 | ||
| 52 | # TODO: check if it is better using collections.deque | |
| 53 | # a performance analysis should be done | |
| 54 | # http://docs.python.org/library/collections.html#collections.deque | |
| 55 | ||
| 56 | # the actions queue | |
| 57 | self._pending_actions = pending_actions | |
| 58 | ||
| 59 | # a reference to the ModelObjectFactory | |
| 60 | self._object_factory = faraday.client.model.common.factory | |
| 61 | self._registerObjectTypes() | |
| 62 | ||
| 63 | # sync api request flag. This flag is used to let the model know | |
| 64 | # there's some other object trying to use a sync api, and it should | |
| 65 | # give priority to that and stop processing the queue | |
| 66 | self._sync_api_request = False | |
| 67 | ||
| 68 | # This flag & lock are used when the complete model is being persisted | |
| 69 | self._saving_model_flag = False | |
| 70 | self._saving_model_lock = Lock() | |
| 71 | ||
| 72 | self._actionDispatcher = None | |
| 73 | self._setupActionDispatcher() | |
| 74 | ||
| 75 | self.objects_with_updates = [] | |
| 76 | self.processing = False | |
| 77 | ||
| 78 | # Fix for using PyDev in DEBUG | |
| 79 | self.is_pydev_daemon_thread = "" | |
| 80 | self.__pydevd_id__ = "" | |
| 81 | self.pydev_do_not_trace = "" | |
| 82 | ||
| 83 | def __getattr__(self, name): | |
| 84 | logger.debug("ModelObject attribute to refactor: %s", name) | |
| 85 | ||
| 86 | def __acquire_host_lock(self): | |
| 87 | self._saving_model_lock.acquire() | |
| 88 | self._saving_model_lock.release() | |
| 89 | self._hosts_lock.acquire() | |
| 90 | ||
| 91 | def __release_host_lock(self): | |
| 92 | try: | |
| 93 | self._hosts_lock.release() | |
| 94 | except RuntimeError: | |
| 95 | pass | |
| 96 | ||
| 97 | def _registerObjectTypes(self): | |
| 98 | """ | |
| 99 | Registers in the factory all object types that can be created | |
| 100 | """ | |
| 101 | # This could be done in hosts module, but it seems easier to maintain | |
| 102 | # if we have all in one place inside the controller | |
| 103 | self._object_factory.register(models.Host) | |
| 104 | self._object_factory.register(models.Service) | |
| 105 | self._object_factory.register(models.Vuln) | |
| 106 | self._object_factory.register(models.VulnWeb) | |
| 107 | self._object_factory.register(models.Note) | |
| 108 | self._object_factory.register(models.Credential) | |
| 109 | ||
| 110 | def _checkParent(self, parent_type): | |
| 111 | """Takes a parent_type and returns the appropiate checkParentDecorator, | |
| 112 | a function that takes another function (most probably you are using | |
| 113 | it for the __add method) and checks if the object as a parent of | |
| 114 | parent_type before adding it. | |
| 115 | """ | |
| 116 | def checkParentDecorator(add_func): | |
| 117 | @wraps(add_func) | |
| 118 | def addWrapper(new_obj, parent_id=None, *args): | |
| 119 | parent = self.mappers_manager.find(parent_type, parent_id) | |
| 120 | if parent: | |
| 121 | add_func(new_obj, parent_id, *args) | |
| 122 | else: | |
| 123 | msg = "A parent is needed for %s objects" % new_obj.class_signature | |
| 124 | logger.error(msg) | |
| 125 | return False | |
| 126 | return addWrapper | |
| 127 | return checkParentDecorator | |
| 128 | ||
| 129 | def _setupActionDispatcher(self): | |
| 130 | ||
| 131 | self._actionDispatcher = { | |
| 132 | Modelactions.ADDHOST: self.__add, | |
| 133 | Modelactions.DELHOST: self.__del, | |
| 134 | Modelactions.EDITHOST: self.__edit, | |
| 135 | Modelactions.EDITSERVICE: self.__edit, | |
| 136 | # Vulnerability | |
| 137 | Modelactions.ADDVULNHOST: self.__add, | |
| 138 | Modelactions.DELVULNHOST: self.__del, | |
| 139 | Modelactions.ADDVULNSRV: self.__add, | |
| 140 | Modelactions.DELVULNSRV: self.__del, | |
| 141 | Modelactions.ADDVULN: self.__add, | |
| 142 | Modelactions.DELVULN: self.__del, | |
| 143 | Modelactions.ADDVULNWEBSRV: self.__add, | |
| 144 | Modelactions.EDITVULN: self.__edit, | |
| 145 | #Service | |
| 146 | Modelactions.ADDSERVICEHOST: self.__add, | |
| 147 | # Note | |
| 148 | Modelactions.ADDNOTEHOST: self.__add, | |
| 149 | Modelactions.DELNOTEHOST: self.__del, | |
| 150 | Modelactions.ADDNOTESRV: self.__add, | |
| 151 | Modelactions.DELNOTESRV: self.__del, | |
| 152 | Modelactions.ADDNOTEVULN: self.__add, | |
| 153 | Modelactions.ADDNOTE: self.__add, | |
| 154 | Modelactions.DELNOTE: self.__del, | |
| 155 | Modelactions.ADDCREDSRV: self.__add, | |
| 156 | Modelactions.DELCREDSRV: self.__del, | |
| 157 | Modelactions.ADDNOTENOTE: self.__add, | |
| 158 | Modelactions.EDITNOTE: self.__edit, | |
| 159 | Modelactions.EDITCRED: self.__edit, | |
| 160 | Modelactions.ADDCRED: self.__add, | |
| 161 | Modelactions.DELCRED: self.__del, | |
| 162 | # Plugin states | |
| 163 | Modelactions.PLUGINSTART: self._pluginStart, | |
| 164 | Modelactions.PLUGINEND: self._pluginEnd, | |
| 165 | Modelactions.DEVLOG: self._devlog, | |
| 166 | Modelactions.LOG: self._log, | |
| 167 | } | |
| 168 | ||
| 169 | def run(self): | |
| 170 | return self._main() | |
| 171 | ||
| 172 | def stop(self): | |
| 173 | """ | |
| 174 | Sets the flag to stop daemon | |
| 175 | """ | |
| 176 | self._must_stop = True | |
| 177 | ||
| 178 | def _dispatchActionWithLock(self, action_callback, *args): | |
| 179 | res = False | |
| 180 | self.__acquire_host_lock() | |
| 181 | try: | |
| 182 | res = action_callback(*args) | |
| 183 | except Exception: | |
| 184 | api.log("An exception occurred while dispatching an action (%r(%r)\n%s" % | |
| 185 | (action_callback, args, traceback.format_exc()), "ERROR") | |
| 186 | finally: | |
| 187 | self.__release_host_lock() | |
| 188 | return res | |
| 189 | ||
| 190 | def _processAction(self, action, parameters, sync=False): | |
| 191 | """ | |
| 192 | decodes and performs the action given | |
| 193 | It works kind of a dispatcher | |
| 194 | """ | |
| 195 | if sync: | |
| 196 | self._sync_api_request = True | |
| 197 | ||
| 198 | api.devlog("_processAction - %s - parameters = %s" % | |
| 199 | (action, str(parameters))) | |
| 200 | ||
| 201 | action_callback = self._actionDispatcher[action] | |
| 202 | res = self._dispatchActionWithLock(action_callback, *parameters) | |
| 203 | ||
| 204 | # finally we notify the widgets about this change | |
| 205 | # if res: # notify only if action was done successfuly | |
| 206 | # self._notifyModelUpdated(*parameters) | |
| 207 | # else: | |
| 208 | if not res: | |
| 209 | api.devlog("Action code %d failed. Parameters = %s" % | |
| 210 | (action, str(parameters))) | |
| 211 | if sync: | |
| 212 | self._sync_api_request = False | |
| 213 | ||
| 214 | def conflictMissing(self, conflict): | |
| 215 | """ | |
| 216 | Conflict missing (Resolved by another one) | |
| 217 | Remove conflict in original object and notify to clients | |
| 218 | """ | |
| 219 | conflict.getFirstObject().updateResolved(conflict) | |
| 220 | notifier.conflictUpdate(-1) | |
| 221 | ||
| 222 | def getConflicts(self): | |
| 223 | conflicts = [] | |
| 224 | for obj in self.objects_with_updates: | |
| 225 | conflicts += obj.getUpdates() | |
| 226 | return conflicts | |
| 227 | ||
| 228 | def resolveConflicts(self): | |
| 229 | notifier.conflictResolution(self.getConflicts()) | |
| 230 | ||
| 231 | def resolveConflict(self, conflict, kwargs): | |
| 232 | if self.__edit(conflict.getFirstObject(), **kwargs): | |
| 233 | conflict.getFirstObject().updateResolved(conflict) | |
| 234 | notifier.conflictUpdate(-1) | |
| 235 | # notifier.editHost(conflict.getFirstObject().getHost()) | |
| 236 | # self._notifyModelUpdated() | |
| 237 | ||
| 238 | def removeConflictsByObject(self, obj): | |
| 239 | if obj in self.objects_with_updates: | |
| 240 | self.objects_with_updates.remove(obj) | |
| 241 | notifier.conflictUpdate(-len(obj.getUpdates())) | |
| 242 | ||
| 243 | def setSavingModel(self, value): | |
| 244 | api.devlog("setSavingModel: %s" % value) | |
| 245 | self._saving_model_flag = value | |
| 246 | if value: | |
| 247 | self._saving_model_lock.acquire() | |
| 248 | else: | |
| 249 | try: | |
| 250 | self._saving_model_lock.release() | |
| 251 | except RuntimeError: | |
| 252 | pass | |
| 253 | ||
| 254 | def _main(self): | |
| 255 | """ | |
| 256 | The main method for the thread. | |
| 257 | The controller will be constantly checking a queue | |
| 258 | to see if new actions were added. | |
| 259 | This will make host addition and removal "thread-safe" and will | |
| 260 | avoid locking components that need to interact with the model | |
| 261 | """ | |
| 262 | while not self._must_stop or self.processing: | |
| 263 | # check if thread must finish | |
| 264 | # no plugin should be active to stop the controller | |
| 265 | if self._must_stop and self.active_plugins_count == 0: | |
| 266 | break | |
| 267 | # first we check if there is a sync api request | |
| 268 | # or if the model is being saved/sync'ed | |
| 269 | # or if we have pending duplicated hosts that need to be | |
| 270 | # merged by the userget | |
| 271 | if not self._sync_api_request and not self._saving_model_flag: | |
| 272 | self.processAction() | |
| 273 | else: | |
| 274 | # there is some object requesting for a sync api so we | |
| 275 | # sleep the thread execution for a moment to let others work | |
| 276 | # XXX: check if this time is not too much... | |
| 277 | time.sleep(0.01) | |
| 278 | ||
| 279 | def processAllPendingActions(self): | |
| 280 | for _ in range(self._pending_actions.qsize()): | |
| 281 | self.processAction() | |
| 282 | ||
| 283 | def processAction(self): | |
| 284 | # check the queue for new actions | |
| 285 | # if there is no new action it will block until timeout is reached | |
| 286 | try: | |
| 287 | # get new action or timeout (in secs) | |
| 288 | # TODO: timeout should be set through config | |
| 289 | current_action = self._pending_actions.get(timeout=2) | |
| 290 | action = current_action[0] | |
| 291 | parameters = current_action[1:] | |
| 292 | # dispatch the action | |
| 293 | self._processAction(action, list(parameters)) | |
| 294 | except Empty: | |
| 295 | # if timeout was reached, just let the daemon run again | |
| 296 | # this is done just to be able to test the stop flag | |
| 297 | # because if we don't do it, the daemon will be blocked forever | |
| 298 | pass | |
| 299 | except Exception as ex: | |
| 300 | logger.debug( | |
| 301 | "something strange happened... unhandled exception?") | |
| 302 | logger.debug(traceback.format_exc()) | |
| 303 | ||
| 304 | def sync_lock(self): | |
| 305 | self._sync_api_request = True | |
| 306 | self.__acquire_host_lock() | |
| 307 | ||
| 308 | def sync_unlock(self): | |
| 309 | self._sync_api_request = False | |
| 310 | self.__release_host_lock() | |
| 311 | ||
| 312 | # TODO: >>> APIs <<< we have to know which plugin called the apis to store | |
| 313 | # in the history | |
| 314 | ||
| 315 | def add_action(self, action): | |
| 316 | self._pending_actions.put(action) | |
| 317 | ||
| 318 | def __addPendingAction(self, *args): | |
| 319 | """ | |
| 320 | Adds a new pending action to the queue | |
| 321 | Action is build with generic args tuple. | |
| 322 | The caller of this function has to build the action in the right | |
| 323 | way since no checks are preformed over args | |
| 324 | """ | |
| 325 | new_action = args | |
| 326 | self._pending_actions.put(new_action) | |
| 327 | ||
| 328 | def addUpdate(self, old_object, new_object, command_id): | |
| 329 | # Returns True if the update was resolved without user interaction | |
| 330 | try: | |
| 331 | mergeAction = old_object.addUpdate(new_object, command_id) | |
| 332 | if mergeAction: | |
| 333 | if old_object not in self.objects_with_updates: | |
| 334 | self.objects_with_updates.append(old_object) | |
| 335 | notifier.conflictUpdate(1) | |
| 336 | return False | |
| 337 | except Exception as ex: | |
| 338 | api.devlog("(%s).addUpdate(%s, %s) - failed" % | |
| 339 | (self, old_object, new_object)) | |
| 340 | return False | |
| 341 | self.mappers_manager.update(old_object, command_id) | |
| 342 | notifier.editHost(old_object) | |
| 343 | return True | |
| 344 | ||
| 345 | def find(self, class_signature, obj_id): | |
| 346 | return self.mappers_manager.find(class_signature, obj_id) | |
| 347 | ||
| 348 | def _save_new_object(self, new_object, command_id): | |
| 349 | res = None | |
| 350 | try: | |
| 351 | res = self.mappers_manager.save(new_object, command_id) | |
| 352 | finally: | |
| 353 | new_object.setID(res) | |
| 354 | if res: | |
| 355 | notifier.addObject(new_object) | |
| 356 | return res | |
| 357 | ||
| 358 | def _handle_conflict(self, old_obj, new_obj, command_id): | |
| 359 | if not old_obj.needs_merge(new_obj): return True | |
| 360 | return self.addUpdate(old_obj, new_obj, command_id) | |
| 361 | ||
| 362 | def __add(self, new_obj, command_id=None, *args): | |
| 363 | """ | |
| 364 | This method sends requests to the faraday-server. | |
| 365 | ||
| 366 | :param new_obj: | |
| 367 | :param command_id: | |
| 368 | :param args: | |
| 369 | :return: | |
| 370 | """ | |
| 371 | try: | |
| 372 | self._save_new_object(new_obj, command_id) | |
| 373 | except ConflictInDatabase as conflict: | |
| 374 | old_obj = new_obj.__class__(conflict.answer.json()['object'], new_obj._workspace_name) | |
| 375 | new_obj.setID(old_obj.getID()) | |
| 376 | return self._handle_conflict(old_obj, new_obj, command_id) | |
| 377 | except Exception as ex: | |
| 378 | logger.exception(ex) | |
| 379 | new_obj.setID(None) | |
| 380 | raise | |
| 381 | ||
| 382 | def __edit(self, obj, command_id=None, *args, **kwargs): | |
| 383 | obj.updateAttributes(*args, **kwargs) | |
| 384 | self.mappers_manager.update(obj, command_id) | |
| 385 | notifier.editHost(obj) | |
| 386 | return True | |
| 387 | ||
| 388 | def __del(self, objId, *args): | |
| 389 | obj = self.mappers_manager.find(objId) | |
| 390 | if obj: | |
| 391 | obj_parent = obj.getParent() | |
| 392 | if obj_parent: | |
| 393 | obj_parent.deleteChild(objId) | |
| 394 | ||
| 395 | self.removeConflictsByObject(obj) | |
| 396 | ||
| 397 | self.mappers_manager.remove(objId, obj.class_signature) | |
| 398 | ||
| 399 | if obj.class_signature == models.Host.class_signature: | |
| 400 | notifier.delHost(objId) | |
| 401 | else: | |
| 402 | notifier.editHost(obj.getHost()) | |
| 403 | return True | |
| 404 | return False | |
| 405 | ||
| 406 | ||
| 407 | def __editService(self, service, name=None, description=None, | |
| 408 | protocol=None, ports=None, status=None, | |
| 409 | version=None, owned=None): | |
| 410 | res = False | |
| 411 | if service is not None: | |
| 412 | service.updateAttributes( | |
| 413 | name, description, protocol, ports, status, version, owned) | |
| 414 | notifier.editHost(service.getHost()) | |
| 415 | res = True | |
| 416 | return res | |
| 417 | ||
| 418 | def addPluginStart(self, name): | |
| 419 | self.__addPendingAction(Modelactions.PLUGINSTART, name) | |
| 420 | ||
| 421 | def addPluginEnd(self, name): | |
| 422 | self.__addPendingAction(Modelactions.PLUGINEND, name) | |
| 423 | ||
| 424 | def _pluginStart(self, name, command_id): | |
| 425 | self.active_plugins_count_lock.acquire() | |
| 426 | self.processing = True | |
| 427 | if name not in ["MetasploitOn", "Beef", "Sentinel"]: | |
| 428 | logger.info("Plugin Started: {0}. ".format(name, command_id)) | |
| 429 | self.active_plugins_count += 1 | |
| 430 | self.active_plugins_count_lock.release() | |
| 431 | return True | |
| 432 | ||
| 433 | def _pluginEnd(self, name, command_id): | |
| 434 | self.active_plugins_count_lock.acquire() | |
| 435 | if name not in ["MetasploitOn", "Beef", "Sentinel"]: | |
| 436 | logger.info("Plugin Ended: {0}".format(name)) | |
| 437 | if self.active_plugins_count == 0: | |
| 438 | self.active_plugins_count_lock.release() | |
| 439 | logger.warn("All plugins ended, but a plugin end action was received.") | |
| 440 | return True | |
| 441 | self.active_plugins_count -= 1 | |
| 442 | if self.active_plugins_count == 0: | |
| 443 | self.processing = False | |
| 444 | self.active_plugins_count_lock.release() | |
| 445 | return True | |
| 446 | ||
| 447 | def _devlog(self, msg, *args, **kwargs): | |
| 448 | # I have no idea what I am doing | |
| 449 | api.devlog(msg) | |
| 450 | return True | |
| 451 | ||
| 452 | def _log(self, msg, *args, **kwargs): | |
| 453 | # I have no idea what I am doing | |
| 454 | api.log(msg, *args[:-1]) | |
| 455 | return True | |
| 456 | ||
| 457 | def newHost(self, ip, os="Unknown", hostnames=None): | |
| 458 | return faraday.client.model.common.factory.createModelObject( | |
| 459 | models.Host.class_signature, ip, | |
| 460 | workspace_name=self.mappers_manager.workspace_name, os=os, parent_id=None, hostnames=hostnames) | |
| 461 | ||
| 462 | def newService(self, name, protocol="tcp?", ports=[], status="running", | |
| 463 | version="unknown", description="", parent_id=None): | |
| 464 | return faraday.client.model.common.factory.createModelObject( | |
| 465 | models.Service.class_signature, name, | |
| 466 | workspace_name=self.mappers_manager.workspace_name, protocol=protocol, ports=ports, status=status, | |
| 467 | version=version, description=description, parent_id=parent_id) | |
| 468 | ||
| 469 | def newVuln(self, name, desc="", ref=None, severity="", resolution="", | |
| 470 | confirmed=False, parent_id=None, external_id=None): | |
| 471 | return faraday.client.model.common.factory.createModelObject( | |
| 472 | models.Vuln.class_signature, name, | |
| 473 | workspace_name=self.mappers_manager.workspace_name, desc=desc, ref=ref, severity=severity, resolution=resolution, | |
| 474 | confirmed=confirmed, parent_id=parent_id, external_id=external_id) | |
| 475 | ||
| 476 | def newVulnWeb(self, name, desc="", ref=None, severity="", resolution="", | |
| 477 | website="", path="", request="", response="", method="", | |
| 478 | pname="", params="", query="", category="", confirmed=False, | |
| 479 | parent_id=None, external_id=None): | |
| 480 | return faraday.client.model.common.factory.createModelObject( | |
| 481 | models.VulnWeb.class_signature, name, | |
| 482 | workspace_name=self.mappers_manager.workspace_name, desc=desc, ref=ref, severity=severity, resolution=resolution, | |
| 483 | website=website, path=path, request=request, response=response, | |
| 484 | method=method, pname=pname, params=params, query=query, | |
| 485 | category=category, confirmed=confirmed, parent_id=parent_id, external_id=external_id) | |
| 486 | ||
| 487 | def newNote(self, name, text, parent_id=None, parent_type=None): | |
| 488 | return faraday.client.model.common.factory.createModelObject( | |
| 489 | models.Note.class_signature, name, | |
| 490 | workspace_name=self.mappers_manager.workspace_name, text=text, parent_id=parent_id, parent_type=parent_type) | |
| 491 | ||
| 492 | def newCred(self, username, password, parent_id=None): | |
| 493 | return faraday.client.model.common.factory.createModelObject( | |
| 494 | models.Credential.class_signature, name, | |
| 495 | username, workspace_name=self.mappers_manager.workspace_name, password=password, parent_id=parent_id) | |
| 496 | ||
| 497 | def getHost(self, name): | |
| 498 | hosts_mapper = self.mappers_manager.getMapper(models.Host.class_signature) | |
| 499 | return hosts_mapper.find(name) | |
| 500 | ||
| 501 | def getAllHosts(self): | |
| 502 | """Return a list with every host. If there's an exception, assume there | |
| 503 | are no hosts. | |
| 504 | """ | |
| 505 | try: | |
| 506 | hosts = self.mappers_manager.getMapper( | |
| 507 | models.Host.class_signature.getAll()) | |
| 508 | except: | |
| 509 | hosts = [] | |
| 510 | return hosts | |
| 511 | ||
| 512 | def getWebVulns(self): | |
| 513 | return self.mappers_manager.getMapper( | |
| 514 | models.Vuln.class_signature).getAll() | |
| 515 | ||
| 516 | def getHostsCount(self): | |
| 517 | """Get how many hosts are in the workspace. If it can't, it will | |
| 518 | return zero.""" | |
| 519 | try: | |
| 520 | hosts = models.Hosts.class_signature | |
| 521 | count = self.mappers_manager.getMapper(hosts).getCount() | |
| 522 | except: | |
| 523 | logger.debug( | |
| 524 | "Couldn't get host count: assuming it is zero.") | |
| 525 | count = 0 | |
| 526 | return count | |
| 527 | ||
| 528 | def getServicesCount(self): | |
| 529 | """Get how many services are in the workspace. If it can't, it will | |
| 530 | return zero.""" | |
| 531 | try: | |
| 532 | services = models.Service.class_signature | |
| 533 | count = self.mappers_manager.getMapper(services).getCount() | |
| 534 | except: | |
| 535 | logger.debug( | |
| 536 | "Couldn't get services count: assuming it is zero.") | |
| 537 | count = 0 | |
| 538 | return count | |
| 539 | ||
| 540 | def getVulnsCount(self): | |
| 541 | """Get how many vulns (web + normal) are in the workspace. | |
| 542 | If it can't, it will return zero.""" | |
| 543 | try: | |
| 544 | vulns = models.Vuln.class_signature | |
| 545 | web_vulns = models.WebVuln.class_signature | |
| 546 | count = (self.mappers_manager.getMapper(vulns).getCount() + | |
| 547 | self.mappers_manager.getMapper(web_vulns).getCount()) | |
| 548 | except: | |
| 549 | logger.debug( | |
| 550 | "Couldn't get vulnerabilities count: assuming it is zero.") | |
| 551 | count = 0 | |
| 552 | return count | |
| 553 | ||
| 554 | ||
| 555 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | ||
| 7 | ||
| 8 | class ModelObjectDiff: | |
| 9 | def __init__(self, objLeft, objRight): | |
| 10 | try: | |
| 11 | if not getattr(objLeft, 'class_signature') == getattr(objRight, 'class_signature'): | |
| 12 | raise Exception("Cannot compare objects of different signature. objLeft (%s) vs objRight (%s)" | |
| 13 | % (objLeft.class_signature, objRight.class_signature)) | |
| 14 | except: | |
| 15 | raise Exception("Cannot compare objects of different classes. objLeft (%s) vs objRight (%s)" | |
| 16 | % (objLeft.__class__.__name__, objRight.__class__.__name__)) | |
| 17 | ||
| 18 | self.obj1, self.obj2 = objLeft, objRight | |
| 19 | ||
| 20 | self.conflicting = [] | |
| 21 | self.conflicting.extend(self.getPropertiesDiff()) | |
| 22 | ||
| 23 | self.only_in_obj1 = {} | |
| 24 | self.only_in_obj2 = {} | |
| 25 | ||
| 26 | def existDiff(self): | |
| 27 | return bool(self.conflicting) or bool(self.only_in_obj1) or bool(self.only_in_obj2) | |
| 28 | ||
| 29 | def getPropertiesDiff(self): | |
| 30 | prop_diff = {} | |
| 31 | for attrname in self.obj1.publicattrsrefs().keys(): | |
| 32 | def info(attr_ref): return attr_ref() if callable(attr_ref) else attr_ref | |
| 33 | prop1 = info(self.obj1.__getattribute__(self.obj1.publicattrsrefs().get(attrname))) | |
| 34 | prop2 = info(self.obj2.__getattribute__(self.obj2.publicattrsrefs().get(attrname))) | |
| 35 | if prop1 != prop2: | |
| 36 | prop_diff[attrname] = (prop1, prop2) | |
| 37 | ||
| 38 | return prop_diff | |
| 39 | ||
| 40 | # def getDifferences(self, ObjDiff, getAllFunc, getById): | |
| 41 | # """ Polymorphic method to get the differences between the list of objects on a ModelObject. | |
| 42 | # Pass the ObjectDiff class, the unbound method to get all the objects and the one to get one by ID""" | |
| 43 | ||
| 44 | # only_in_obj1 = [i for i in getAllFunc(self.obj1) if not i in getAllFunc(self.obj2)] | |
| 45 | # only_in_obj2 = [i for i in getAllFunc(self.obj2) if not i in getAllFunc(self.obj1)] | |
| 46 | ||
| 47 | # return (only_in_obj1, only_in_obj2) | |
| 48 | ||
| 49 | # def getDifferencesIn(self, getAllFunc): | |
| 50 | # """ Polymorphic method to get the differences between the list of objects on a ModelObject. | |
| 51 | # Pass the ObjectDiff class, the unbound method to get all the objects and the one to get one by ID""" | |
| 52 | # only_in_obj1 = [i for i in getAllFunc(self.obj1) if not i in getAllFunc(self.obj2)] | |
| 53 | # only_in_obj2 = [i for i in getAllFunc(self.obj2) if not i in getAllFunc(self.obj1)] | |
| 54 | ||
| 55 | # return only_in_obj1, only_in_obj2 | |
| 56 | ||
| 57 | ||
| 58 | class MergeStrategy: | |
| 59 | @staticmethod | |
| 60 | def solve(old, new): | |
| 61 | raise NotImplementedError("This is an abstract class") | |
| 62 | ||
| 63 | ||
| 64 | class MergeKeepNew(MergeStrategy): | |
| 65 | @staticmethod | |
| 66 | def solve(old, new): | |
| 67 | return new | |
| 68 | ||
| 69 | ||
| 70 | class MergeKeepOld(MergeStrategy): | |
| 71 | @staticmethod | |
| 72 | def solve(old, new): | |
| 73 | return old | |
| 74 | ||
| 75 | ||
| 76 | class MergeSolver: | |
| 77 | def __init__(self, strategy): | |
| 78 | if strategy == "new": | |
| 79 | self.strategy = MergeKeepNew | |
| 80 | elif strategy == "old": | |
| 81 | self.strategy = MergeKeepOld | |
| 82 | else: | |
| 83 | raise Exception("Invalid strategy to resolve merges") | |
| 84 | ||
| 85 | def solve(self, old, new): | |
| 86 | return self.strategy.solve(old, new) | |
| 87 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | ||
| 9 | import faraday.client.model.common | |
| 10 | from faraday.client.gui.notifier import NotificationCenter | |
| 11 | from faraday.config.configuration import getInstanceConfiguration | |
| 12 | import faraday.client.model.api | |
| 13 | ||
| 14 | CONF = getInstanceConfiguration() | |
| 15 | ||
| 16 | ||
| 17 | notification_center = NotificationCenter() | |
| 18 | __the_mainapp = None | |
| 19 | __model_controller = None | |
| 20 | ||
| 21 | ||
| 22 | def setMainApp(ref): | |
| 23 | global __the_mainapp | |
| 24 | __the_mainapp = ref | |
| 25 | notification_center.setUiApp(__the_mainapp) | |
| 26 | ||
| 27 | ||
| 28 | def getMainApp(): | |
| 29 | global __the_mainapp | |
| 30 | return __the_mainapp | |
| 31 | ||
| 32 | ||
| 33 | def getMainWindow(): | |
| 34 | global __the_mainapp | |
| 35 | return __the_mainapp.getMainWindow() | |
| 36 | ||
| 37 | ||
| 38 | def postCustomEvent(event, receiver=None): | |
| 39 | if receiver is None: | |
| 40 | receiver = getMainWindow() | |
| 41 | __the_mainapp.postEvent(receiver, event) | |
| 42 | ||
| 43 | ||
| 44 | def sendCustomEvent(event, receiver=None): | |
| 45 | if receiver is None: | |
| 46 | receiver = getMainWindow() | |
| 47 | __the_mainapp.sendEvent(receiver, event) | |
| 48 | ||
| 49 | ||
| 50 | def setUpGUIAPIs(controller): | |
| 51 | global __model_controller | |
| 52 | __model_controller = controller | |
| 53 | ||
| 54 | ||
| 55 | def registerWidget(widget): | |
| 56 | if widget is not None: | |
| 57 | notification_center.registerWidget(widget) | |
| 58 | ||
| 59 | ||
| 60 | def deregisterWidget(widget): | |
| 61 | if widget is not None: | |
| 62 | notification_center.deregisterWidget(widget) | |
| 63 | ||
| 64 | ||
| 65 | def createAndAddHost(name, os="Unknown"): | |
| 66 | host = faraday.client.model.api.newHost(name, os) | |
| 67 | if addHost(host): | |
| 68 | return host.getID() | |
| 69 | return None | |
| 70 | ||
| 71 | ||
| 72 | def createAndAddInterface(host_id, name = "", mac = "00:00:00:00:00:00", | |
| 73 | ipv4_address = "0.0.0.0", ipv4_mask = "0.0.0.0", | |
| 74 | ipv4_gateway = "0.0.0.0", ipv4_dns = [], | |
| 75 | ipv6_address = "0000:0000:0000:0000:0000:0000:0000:0000", ipv6_prefix = "00", | |
| 76 | ipv6_gateway = "0000:0000:0000:0000:0000:0000:0000:0000", ipv6_dns = [], | |
| 77 | network_segment = "", hostname_resolution = []): | |
| 78 | """ | |
| 79 | Creates a new interface object with the parameters provided and adds it to | |
| 80 | the host selected. | |
| 81 | If interface is successfuly created and the host exists, it returns the inteface id | |
| 82 | It returns None otherwise | |
| 83 | """ | |
| 84 | interface = faraday.client.model.api.newInterface(name, mac, ipv4_address, ipv4_mask, ipv4_gateway, | |
| 85 | ipv4_dns, network_segment, hostname_resolution, parent_id=host_id) | |
| 86 | if addInterface(host_id, interface): | |
| 87 | return interface.getID() | |
| 88 | return None | |
| 89 | ||
| 90 | ||
| 91 | def createAndAddServiceToInterface(host_id, interface_id, name, protocol = "tcp?", | |
| 92 | ports = [], status = "running", version = "unknown", description = ""): | |
| 93 | service = faraday.client.model.api.newService(name, protocol, ports, status, version, description, parent_id=interface_id) | |
| 94 | if addServiceToInterface(host_id, interface_id, service): | |
| 95 | return service.getID() | |
| 96 | return None | |
| 97 | ||
| 98 | ||
| 99 | def createAndAddVulnToHost(host_id, name, desc, ref, severity="0", | |
| 100 | resolution="", confirmed=True): | |
| 101 | vuln = faraday.client.model.api.newVuln(name, desc, ref, severity, resolution, | |
| 102 | confirmed=confirmed, parent_id=host_id) | |
| 103 | if addVulnToHost(host_id, vuln): | |
| 104 | return vuln.getID() | |
| 105 | return None | |
| 106 | ||
| 107 | ||
| 108 | def createAndAddVulnToInterface(host_id, interface_id, name, desc, ref, | |
| 109 | severity="0", resolution="", confirmed=True): | |
| 110 | vuln = faraday.client.model.api.newVuln(name, desc, ref, severity, resolution, | |
| 111 | confirmed=confirmed, parent_id=interface_id) | |
| 112 | if addVulnToInterface(host_id, interface_id, vuln): | |
| 113 | return vuln.getID() | |
| 114 | return None | |
| 115 | ||
| 116 | ||
| 117 | def createAndAddVulnToService(host_id, service_id, name, desc, ref, | |
| 118 | severity="0", resolution="", confirmed=True): | |
| 119 | vuln = faraday.client.model.api.newVuln(name, desc, ref, severity, resolution, | |
| 120 | confirmed=confirmed, parent_id=service_id) | |
| 121 | if addVulnToService(host_id, service_id, vuln): | |
| 122 | return vuln.getID() | |
| 123 | return None | |
| 124 | ||
| 125 | ||
| 126 | def createAndAddVulnWebToService(host_id, service_id, name, desc, website, | |
| 127 | path, ref=None, severity="0", resolution="", | |
| 128 | request=None, response=None, method=None, | |
| 129 | pname=None, params=None, query=None, | |
| 130 | category=None, confirmed=True): | |
| 131 | vuln = faraday.client.model.api.newVulnWeb(name, desc, website, path, ref, severity, | |
| 132 | resolution, request, response, method, pname, | |
| 133 | params, query, category, confirmed=confirmed, | |
| 134 | parent_id=service_id) | |
| 135 | if addVulnToService(host_id, service_id, vuln): | |
| 136 | return vuln.getID() | |
| 137 | return None | |
| 138 | ||
| 139 | ||
| 140 | def createAndAddVuln(model_object, name, desc, ref=None, severity="0", | |
| 141 | resolution="", confirmed=True): | |
| 142 | vuln = faraday.client.model.api.newVuln(name, desc, ref, severity, resolution, | |
| 143 | confirmed=confirmed, | |
| 144 | parent_id=model_object.getID()) | |
| 145 | if addVuln(model_object.getID(), vuln): | |
| 146 | return vuln.getID() | |
| 147 | return None | |
| 148 | ||
| 149 | ||
| 150 | def createAndAddVulnWeb(model_object, name, desc, website, path, ref=None, | |
| 151 | severity="0", resolution="", request=None, | |
| 152 | response=None, method=None, pname=None, params=None, | |
| 153 | query=None, category=None, confirmed=True): | |
| 154 | vuln = faraday.client.model.api.newVulnWeb(name, desc, ref, severity, resolution, website, | |
| 155 | path, request, response, method, pname, params, | |
| 156 | query, category, confirmed=confirmed, | |
| 157 | parent_id=model_object.getID()) | |
| 158 | if addVuln(model_object.getID(), vuln): | |
| 159 | return vuln.getID() | |
| 160 | return None | |
| 161 | ||
| 162 | ||
| 163 | def createAndAddNoteToHost(host_id, name, text): | |
| 164 | ||
| 165 | return None | |
| 166 | ||
| 167 | ||
| 168 | def createAndAddNoteToInterface(host_id, interface_id, name, text): | |
| 169 | ||
| 170 | return None | |
| 171 | ||
| 172 | ||
| 173 | def createAndAddNoteToService(host_id, service_id, name, text): | |
| 174 | ||
| 175 | return None | |
| 176 | ||
| 177 | ||
| 178 | def createAndAddNote(model_object, name, text): | |
| 179 | return None | |
| 180 | def createAndAddCred(model_object, username, password): | |
| 181 | cred = faraday.client.model.api.newCred(username, password, parent_id=model_object.getID()) | |
| 182 | if addCred(model_object.getID(), cred): | |
| 183 | return cred.getID() | |
| 184 | return None | |
| 185 | ||
| 186 | ||
| 187 | def createAndAddCredToHost(host_id, username, password): | |
| 188 | cred = faraday.client.model.api.newCred(username, password, parent_id=host_id) | |
| 189 | if addCredToHost(host_id, cred): | |
| 190 | return cred.getID() | |
| 191 | return None | |
| 192 | ||
| 193 | ||
| 194 | def createAndAddCredToService(host_id, service_id, username, password): | |
| 195 | cred = faraday.client.model.api.newCred(username, password, parent_id=service_id) | |
| 196 | if addCredToService(host_id, service_id, cred): | |
| 197 | return cred.getID() | |
| 198 | return None | |
| 199 | ||
| 200 | ||
| 201 | def addHost(host): | |
| 202 | if host is not None: | |
| 203 | __model_controller.addHostSYNC(host) | |
| 204 | return True | |
| 205 | return False | |
| 206 | ||
| 207 | def addInterface(host_id, interface): | |
| 208 | if interface is not None: | |
| 209 | __model_controller.addInterfaceSYNC(host_id, interface) | |
| 210 | return True | |
| 211 | return False | |
| 212 | ||
| 213 | def addApplication(host_id, application): | |
| 214 | if application is not None: | |
| 215 | __model_controller.addApplicationSYNC(host_id, application) | |
| 216 | return True | |
| 217 | return False | |
| 218 | ||
| 219 | def addServiceToApplication(host_id, application_id, service): | |
| 220 | if service is not None: | |
| 221 | __model_controller.addServiceToApplicationSYNC(host_id, application_id, service) | |
| 222 | return True | |
| 223 | return False | |
| 224 | ||
| 225 | ||
| 226 | def addVulnToHost(host_id, vuln): | |
| 227 | if vuln is not None: | |
| 228 | __model_controller.addVulnToHostSYNC(host_id, vuln) | |
| 229 | return True | |
| 230 | return False | |
| 231 | ||
| 232 | ||
| 233 | def addVulnToApplication(host_id, application_id, vuln): | |
| 234 | if vuln is not None: | |
| 235 | __model_controller.addVulnToApplicationSYNC(host_id, application_id, vuln) | |
| 236 | return True | |
| 237 | return False | |
| 238 | ||
| 239 | def addVulnToService(host_id, service_id, vuln): | |
| 240 | if vuln is not None: | |
| 241 | __model_controller.addVulnToServiceSYNC(host_id, service_id, vuln) | |
| 242 | return True | |
| 243 | return False | |
| 244 | ||
| 245 | def addVuln(model_object_id, vuln): | |
| 246 | if vuln is not None: | |
| 247 | __model_controller.addVulnSYNC(model_object_id, vuln) | |
| 248 | return True | |
| 249 | return False | |
| 250 | ||
| 251 | ||
| 252 | ||
| 253 | def addNoteToHost(host_id, note): | |
| 254 | if note is not None: | |
| 255 | __model_controller.addNoteToHostSYNC(host_id, note) | |
| 256 | return True | |
| 257 | return False | |
| 258 | ||
| 259 | def addNoteToInterface(host_id, interface_id, note): | |
| 260 | if note is not None: | |
| 261 | __model_controller.addNoteToInterfaceSYNC(host_id, interface_id, note) | |
| 262 | return True | |
| 263 | return False | |
| 264 | ||
| 265 | def addNoteToApplication(host_id, application_id, note): | |
| 266 | if note is not None: | |
| 267 | __model_controller.addNoteToApplicationSYNC(host_id, application_id, note) | |
| 268 | return True | |
| 269 | return False | |
| 270 | ||
| 271 | def addNoteToService(host_id, service_id, note): | |
| 272 | if note is not None: | |
| 273 | __model_controller.addNoteToServiceSYNC(host_id, service_id, note) | |
| 274 | return True | |
| 275 | return False | |
| 276 | ||
| 277 | def addNote(model_object_id, note): | |
| 278 | if note is not None: | |
| 279 | __model_controller.addNoteSYNC(model_object_id, note) | |
| 280 | return True | |
| 281 | return False | |
| 282 | ||
| 283 | ||
| 284 | def addCred(model_object_id, cred): | |
| 285 | if cred is not None: | |
| 286 | __model_controller.addCredSYNC(model_object_id, cred) | |
| 287 | return True | |
| 288 | return False | |
| 289 | ||
| 290 | def addCredToService(host_id, service_id, cred): | |
| 291 | if cred is not None: | |
| 292 | __model_controller.addCredToServiceSYNC(host_id, service_id, cred) | |
| 293 | return True | |
| 294 | return False | |
| 295 | ||
| 296 | def addCredToHost(host_id, cred): | |
| 297 | if cred is not None: | |
| 298 | __model_controller.addCredToHostSYNC(host_id, cred) | |
| 299 | return True | |
| 300 | return False | |
| 301 | ||
| 302 | ||
| 303 | def delHost(host_id): | |
| 304 | __model_controller.delHostSYNC(host_id) | |
| 305 | return True | |
| 306 | ||
| 307 | def delApplication(host_id, application_id): | |
| 308 | __model_controller.delApplicationSYNC(host_id, application_id) | |
| 309 | return True | |
| 310 | ||
| 311 | def delInterface(host_id, interface_id): | |
| 312 | __model_controller.delInterfaceSYNC(host_id, interface_id) | |
| 313 | return True | |
| 314 | ||
| 315 | def delServiceFromHost(host_id, service_id): | |
| 316 | __model_controller.delServiceFromHostSYNC(host_id, service_id) | |
| 317 | return True | |
| 318 | ||
| 319 | def delServiceFromInterface(host_id, interface_id, service_id): | |
| 320 | __model_controller.delServiceFromInterfaceSYNC(host_id, interface_id, service_id) | |
| 321 | return True | |
| 322 | ||
| 323 | def delServiceFromApplication(host_id, application_id, service_id): | |
| 324 | __model_controller.delServiceFromApplicationSYNC(host_id, application_id, service_id) | |
| 325 | return True | |
| 326 | ||
| 327 | ||
| 328 | ||
| 329 | def delVulnFromApplication(vuln, hostname, appname): | |
| 330 | __model_controller.delVulnFromApplicationSYNC(hostname, appname, vuln) | |
| 331 | return True | |
| 332 | ||
| 333 | def delVulnFromInterface(vuln, hostname, intname): | |
| 334 | __model_controller.delVulnFromInterfaceSYNC(hostname,intname, vuln) | |
| 335 | return True | |
| 336 | ||
| 337 | def delVulnFromHost(vuln, hostname): | |
| 338 | __model_controller.delVulnFromHostSYNC(hostname,vuln) | |
| 339 | return True | |
| 340 | ||
| 341 | ||
| 342 | def delVulnFromService(vuln, hostname, srvname): | |
| 343 | __model_controller.delVulnFromServiceSYNC(hostname,srvname, vuln) | |
| 344 | return True | |
| 345 | ||
| 346 | def delVuln(model_object_id, vuln_id): | |
| 347 | __model_controller.delVulnSYNC(model_object_id, vuln_id) | |
| 348 | return True | |
| 349 | ||
| 350 | ||
| 351 | ||
| 352 | def delNoteFromApplication(note, hostname, appname): | |
| 353 | __model_controller.delNoteFromApplicationSYNC(hostname, appname, note) | |
| 354 | return True | |
| 355 | ||
| 356 | def delNoteFromInterface(note, hostname, intname): | |
| 357 | __model_controller.delNoteFromInterfaceSYNC(hostname,intname, note) | |
| 358 | return True | |
| 359 | ||
| 360 | def delNoteFromHost(note, hostname): | |
| 361 | __model_controller.delNoteFromHostSYNC(hostname, note) | |
| 362 | return True | |
| 363 | ||
| 364 | ||
| 365 | def delNoteFromService(note, hostname, srvname): | |
| 366 | __model_controller.delNoteFromServiceSYNC(hostname,srvname, note) | |
| 367 | return True | |
| 368 | ||
| 369 | def delNote(model_object_id, note_id): | |
| 370 | __model_controller.delNoteSYNC(model_object_id, note_id) | |
| 371 | return True | |
| 372 | ||
| 373 | ||
| 374 | def delCred(model_object_id, cred_id): | |
| 375 | __model_controller.delCredSYNC(model_object_id, cred_id) | |
| 376 | return True | |
| 377 | ||
| 378 | def delCredFromHost(cred, hostname): | |
| 379 | __model_controller.delCredFromHostSYNC(hostname, cred) | |
| 380 | return True | |
| 381 | ||
| 382 | ||
| 383 | def delCredFromService(cred, hostname, srvname): | |
| 384 | __model_controller.delCredFromServiceSYNC(hostname,srvname, cred) | |
| 385 | return True | |
| 386 | ||
| 387 | ||
| 388 | ||
| 389 | ||
| 390 | ||
| 391 | def editHost(host, name=None, description=None, os=None, owned=None): | |
| 392 | __model_controller.editHostSYNC(host, name, description, os, owned) | |
| 393 | return True | |
| 394 | ||
| 395 | def editService(service, name=None, description=None, protocol=None, ports=None, status=None, version=None, owned=None): | |
| 396 | __model_controller.editServiceSYNC(service, name, description, protocol, ports, status, version, owned) | |
| 397 | return True | |
| 398 | ||
| 399 | def editApplication(application, name, description, status, version, owned): | |
| 400 | __model_controller.editApplicationSYNC(application, name, description, status, version, owned) | |
| 401 | return True | |
| 402 | ||
| 403 | def editInterface(interface, name=None, description=None, hostnames=None, mac=None, ipv4=None, ipv6=None, network_segment=None, | |
| 404 | amount_ports_opened=None, amount_ports_closed=None, amount_ports_filtered=None, owned=None): | |
| 405 | __model_controller.editInterfaceSYNC(interface, name, description, hostnames, mac, ipv4, ipv6, network_segment, | |
| 406 | amount_ports_opened, amount_ports_closed, amount_ports_filtered, owned) | |
| 407 | return True | |
| 408 | ||
| 409 | def editNote(note, name=None, text=None): | |
| 410 | __model_controller.editNoteSYNC(note, name, text) | |
| 411 | return True | |
| 412 | ||
| 413 | def editVuln(vuln, name=None, desc=None, severity=None, resolution=None, refs=None): | |
| 414 | __model_controller.editVulnSYNC(vuln, name, desc, severity, resolution, refs) | |
| 415 | return True | |
| 416 | ||
| 417 | def editVulnWeb(vuln, name=None, desc=None, website=None, path=None, refs=None, severity=None, resolution=None, | |
| 418 | request=None, response=None, method=None, pname=None, params=None, query=None, category=None): | |
| 419 | __model_controller.editVulnWebSYNC(vuln, name, desc, website, path, refs, severity, resolution, | |
| 420 | request, response, method, pname, params, query, category) | |
| 421 | return True | |
| 422 | ||
| 423 | def editCred(cred, username=None, password=None): | |
| 424 | __model_controller.editCredSYNC(cred, username, password) | |
| 425 | return True | |
| 426 | ||
| 427 | ||
| 428 | def getParent(parent_id): | |
| 429 | return __model_controller.find(parent_id) | |
| 430 | ||
| 431 | ||
| 432 | def conflictMissing(conflict): | |
| 433 | __model_controller.conflictMissing(conflict) | |
| 434 | ||
| 435 | ||
| 436 | def resolveConflicts(): | |
| 437 | __model_controller.resolveConflicts() | |
| 438 | ||
| 439 | ||
| 440 | def resolveConflict(conflict, kwargs): | |
| 441 | __model_controller.resolveConflict(conflict, kwargs) | |
| 442 | ||
| 443 | ||
| 444 | def merge(host1, host2): | |
| 445 | return __model_controller.merge(host1, host2) | |
| 446 | ||
| 447 | ||
| 448 | def addHostFromChanges(obj): | |
| 449 | if obj is not None: | |
| 450 | notification_center.addHostFromChanges(obj) | |
| 451 | return True | |
| 452 | return False | |
| 453 | ||
| 454 | ||
| 455 | def deleteHostFromChanges(obj): | |
| 456 | if obj is not None: | |
| 457 | notification_center.deleteHostFromChanges(obj) | |
| 458 | return True | |
| 459 | return False | |
| 460 | ||
| 461 | ||
| 462 | def editHostFromChanges(obj): | |
| 463 | if obj is not None: | |
| 464 | notification_center.editHostFromChanges(obj) | |
| 465 | return True | |
| 466 | return False | |
| 467 | ||
| 468 | # I'm Py3 |
| 0 | #!/usr/bin/env python | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | ||
| 9 | import logging | |
| 10 | from faraday.client.gui.customevents import (ShowPopupCustomEvent, | |
| 11 | ShowDialogCustomEvent) | |
| 12 | import faraday.client.model.guiapi | |
| 13 | from faraday.config.configuration import getInstanceConfiguration | |
| 14 | ||
| 15 | CONF = getInstanceConfiguration() | |
| 16 | ||
| 17 | __notifier = None | |
| 18 | ||
| 19 | ||
| 20 | def getNotifier(singleton=True): | |
| 21 | global __notifier | |
| 22 | if singleton: | |
| 23 | if __notifier is None: | |
| 24 | __notifier = Notifier() | |
| 25 | return __notifier | |
| 26 | else: | |
| 27 | return Notifier() | |
| 28 | ||
| 29 | ||
| 30 | class Notifier: | |
| 31 | """ | |
| 32 | This class is used to show information to the user using dialog boxes or | |
| 33 | little pop ups (like tooltips). | |
| 34 | Also all notifications get logged using the Application Logger | |
| 35 | """ | |
| 36 | ||
| 37 | # TODO: change the implementation to send/post custom events to avoid | |
| 38 | # problems with threads like we had before | |
| 39 | def __init__(self): | |
| 40 | self.widget = None | |
| 41 | ||
| 42 | def _postCustomEvent(self, text, level, customEventClass): | |
| 43 | logging.getLogger(__name__).log(text, "INFO") | |
| 44 | if self.widget is not None: | |
| 45 | event = customEventClass(text, level) | |
| 46 | faraday.client.model.guiapi.postEvent(event, self.widget) | |
| 47 | ||
| 48 | def showDialog(self, text, level="Information"): | |
| 49 | self._postCustomEvent(text, level, ShowDialogCustomEvent) | |
| 50 | ||
| 51 | def showPopup(self, text, level="Information"): | |
| 52 | self._postCustomEvent(text, level, ShowPopupCustomEvent) | |
| 53 | ||
| 54 | ||
| 55 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | import datetime | |
| 9 | import hashlib | |
| 10 | ||
| 11 | ||
| 12 | class Session: | |
| 13 | """ | |
| 14 | It will handle a Faraday session, that contains: | |
| 15 | - current user logged in | |
| 16 | - session start time | |
| 17 | - duration | |
| 18 | - workspace history (?...here?) | |
| 19 | - current workspace (?...here?) | |
| 20 | """ | |
| 21 | ||
| 22 | def __init__(self, user): | |
| 23 | self.logged_user = user | |
| 24 | self.start_time = datetime.datetime.now() | |
| 25 | ||
| 26 | self.workspace_history = [] | |
| 27 | self.current_workspace = None | |
| 28 | ||
| 29 | self.__token = hashlib.sha224("%s_%s" % (self.logged_user, self.start_time)).hexdigest() | |
| 30 | ||
| 31 | def get_token(): | |
| 32 | return self.__token | |
| 33 | ||
| 34 | ||
| 35 | # I'm Py3 |
| 0 | #!/usr/bin/env python | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | """ | |
| 7 | ||
| 8 | class Branch: | |
| 9 | pass | |
| 10 | ||
| 11 | class BranchItem: | |
| 12 | pass | |
| 13 | ||
| 14 | ||
| 15 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | """ | |
| 7 | ||
| 8 | class View: | |
| 9 | """A view for the data in a CouchDB""" | |
| 10 | def __init__(self): | |
| 11 | pass | |
| 12 | ||
| 13 | ||
| 14 | class HostsServiceFrequencies(View): | |
| 15 | pass | |
| 16 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | """ | |
| 7 | Contains base classes used to represent the application model | |
| 8 | and some other common objects and functions used in the model | |
| 9 | """ | |
| 10 | ||
| 11 | ||
| 12 | class ModelObjectVisitor: | |
| 13 | def visit(self, modelObjectInstance): | |
| 14 | raise NotImplemented('Abstract method') | |
| 15 | ||
| 16 | ||
| 17 | class VulnsLookupVisitor(ModelObjectVisitor): | |
| 18 | def __init__(self, vulnId): | |
| 19 | self.vulnId = vulnId | |
| 20 | self.parents = [] | |
| 21 | self.vulns = [] | |
| 22 | ||
| 23 | def visit(self, modelObject): | |
| 24 | vuln = modelObject.getVuln(self.vulnId) | |
| 25 | parents = [] | |
| 26 | if vuln: | |
| 27 | self.vulns.append(vuln) | |
| 28 | parent = vuln.getParent() | |
| 29 | while parent: | |
| 30 | parents.append(parent) | |
| 31 | parent = parent.getParent() | |
| 32 | ||
| 33 | self.parents.append(parents) | |
| 34 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | ||
| 9 | import time | |
| 10 | ||
| 11 | from faraday.config.configuration import getInstanceConfiguration | |
| 12 | CONF = getInstanceConfiguration() | |
| 13 | ||
| 14 | ||
| 15 | class Workspace: | |
| 16 | """ | |
| 17 | Handles a complete workspace (or project) | |
| 18 | It contains a reference to the model and the command execution | |
| 19 | history for all users working on the same workspace. | |
| 20 | It has a list with all existing workspaces just in case user wants to | |
| 21 | open a new one. | |
| 22 | """ | |
| 23 | class_signature = "Workspace" | |
| 24 | ||
| 25 | def __init__(self, name, desc=None, manager=None, shared=None): | |
| 26 | if not shared: | |
| 27 | shared = CONF.getAutoShareWorkspace() | |
| 28 | self.name = name | |
| 29 | self.description = desc | |
| 30 | self.customer = "" | |
| 31 | self.start_date = int(time.time() * 1000) | |
| 32 | self.finish_date = int(time.time() * 1000) | |
| 33 | self._id = name | |
| 34 | self._command_history = None | |
| 35 | self.shared = shared | |
| 36 | self.hosts = {} | |
| 37 | ||
| 38 | def getID(self): | |
| 39 | return self._id | |
| 40 | ||
| 41 | def setID(self, id): | |
| 42 | self._id = id | |
| 43 | ||
| 44 | def getName(self): | |
| 45 | return self.name | |
| 46 | ||
| 47 | def setName(self, name): | |
| 48 | self.name = name | |
| 49 | ||
| 50 | def getDescription(self): | |
| 51 | return self.description | |
| 52 | ||
| 53 | def setDescription(self, desc): | |
| 54 | self.description = desc | |
| 55 | ||
| 56 | def getCustomer(self): | |
| 57 | return self.customer | |
| 58 | ||
| 59 | def setCustomer(self, customer): | |
| 60 | self.customer = customer | |
| 61 | ||
| 62 | def getStartDate(self): | |
| 63 | return self.start_date | |
| 64 | ||
| 65 | def setStartDate(self, start_date): | |
| 66 | self.start_date = start_date | |
| 67 | ||
| 68 | def getEndDate(self): | |
| 69 | return self.end_date | |
| 70 | ||
| 71 | def setEndDate(self, edate): | |
| 72 | self.end_date = edate | |
| 73 | ||
| 74 | def isActive(self): | |
| 75 | return self.name == self._workspace_manager.getActiveWorkspace().name | |
| 76 | ||
| 77 | def getHosts(self): | |
| 78 | return list(self.hosts.values()) | |
| 79 | ||
| 80 | def setHosts(self, hosts): | |
| 81 | self.hosts = hosts | |
| 82 | ||
| 83 | ||
| 84 | ||
| 85 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | __all__ = [] | |
| 7 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | ||
| 7 | # I'm Py3⏎ |
| 0 | #!/usr/bin/python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | ||
| 7 | """ | |
| 8 | from __future__ import absolute_import | |
| 9 | from __future__ import print_function | |
| 10 | from past.builtins import basestring | |
| 11 | ||
| 12 | import json | |
| 13 | import logging | |
| 14 | import threading | |
| 15 | from queue import Queue, Empty | |
| 16 | import requests | |
| 17 | import websocket | |
| 18 | ||
| 19 | from faraday.client.persistence.server.server_io_exceptions import ( | |
| 20 | ChangesStreamStoppedAbruptly | |
| 21 | ) | |
| 22 | logger = logging.getLogger(__name__) | |
| 23 | ||
| 24 | ||
| 25 | class ChangesStream: | |
| 26 | ||
| 27 | def __enter__(self): | |
| 28 | return self | |
| 29 | ||
| 30 | def __exit__(self, type, value, traceback): | |
| 31 | return False | |
| 32 | ||
| 33 | def __next__(self): | |
| 34 | return self | |
| 35 | ||
| 36 | def __iter__(self): | |
| 37 | raise NotImplementedError('Abstract class') | |
| 38 | ||
| 39 | def _get_object_type_and_name_from_change(self, change): | |
| 40 | try: | |
| 41 | id = change['id'] | |
| 42 | response = requests.get("{0}/{1}".format(self._base_url, id), **self._params) | |
| 43 | object_json = response.json() | |
| 44 | except Exception: | |
| 45 | return None, None | |
| 46 | return object_json.get('type'), object_json.get('name') | |
| 47 | ||
| 48 | def _sanitize(self, raw_line): | |
| 49 | if not isinstance(raw_line, basestring): | |
| 50 | return None | |
| 51 | line = raw_line.strip() | |
| 52 | if not line or line in ('{"results":', '],'): | |
| 53 | return None | |
| 54 | if line.startswith('"last_seq"'): | |
| 55 | line = '{' + line | |
| 56 | if line.endswith(","): | |
| 57 | line = line[:-1] | |
| 58 | return line | |
| 59 | ||
| 60 | def _parse_change(self, line): | |
| 61 | try: | |
| 62 | obj = json.loads(line) | |
| 63 | return obj | |
| 64 | except ValueError: | |
| 65 | return None | |
| 66 | ||
| 67 | def stop(self): | |
| 68 | if self._response is not None: | |
| 69 | self._response.close() | |
| 70 | self._response = None | |
| 71 | self._stop = True | |
| 72 | ||
| 73 | ||
| 74 | class WebsocketsChangesStream(ChangesStream): | |
| 75 | ||
| 76 | def __init__(self, workspace_name, server_url, **params): | |
| 77 | self._base_url = server_url | |
| 78 | self.changes_queue = Queue() | |
| 79 | self.workspace_name = workspace_name | |
| 80 | self._response = None | |
| 81 | self.ws = websocket.WebSocketApp( | |
| 82 | "ws://{0}:9000".format(self._base_url), | |
| 83 | on_message=self.on_message, | |
| 84 | on_error=self.on_error, | |
| 85 | on_open=self.on_open, | |
| 86 | on_close=self.on_close) | |
| 87 | # ws.run_forever will call on_message, on_error, on_close and on_open | |
| 88 | # see websocket client python docs on: | |
| 89 | # https://github.com/websocket-client/websocket-client | |
| 90 | thread = threading.Thread(target=self.ws.run_forever, args=(), | |
| 91 | name='WebsocketsChangesStream') | |
| 92 | thread.daemon = True | |
| 93 | thread.start() | |
| 94 | ||
| 95 | def stop(self): | |
| 96 | self.ws.close() | |
| 97 | super(WebsocketsChangesStream, self).stop() | |
| 98 | ||
| 99 | def on_open(self): | |
| 100 | from faraday.client.persistence.server.server import _create_server_api_url, _post # pylint:disable=import-outside-toplevel | |
| 101 | ||
| 102 | response = _post( | |
| 103 | _create_server_api_url() + | |
| 104 | '/ws/{}/websocket_token/'.format(self.workspace_name), | |
| 105 | expected_response=200) | |
| 106 | token = response['token'] | |
| 107 | self.ws.send(json.dumps({ | |
| 108 | 'action': 'JOIN_WORKSPACE', | |
| 109 | 'workspace': self.workspace_name, | |
| 110 | 'token': token, | |
| 111 | })) | |
| 112 | ||
| 113 | def on_message(self, message): | |
| 114 | logger.debug('New message {0}'.format(message)) | |
| 115 | self.changes_queue.put(message) | |
| 116 | ||
| 117 | def on_error(ws, error): | |
| 118 | pass | |
| 119 | print(error) | |
| 120 | ||
| 121 | def on_close(self): | |
| 122 | pass | |
| 123 | ||
| 124 | def __enter__(self): | |
| 125 | return self | |
| 126 | ||
| 127 | def __exit__(self, type, value, traceback): | |
| 128 | return False | |
| 129 | ||
| 130 | def __next__(self): | |
| 131 | return self | |
| 132 | ||
| 133 | def __iter__(self): | |
| 134 | try: | |
| 135 | data = json.loads(self.changes_queue.get_nowait()) | |
| 136 | except Empty: | |
| 137 | return | |
| 138 | yield data | |
| 139 | ||
| 140 | def _get_object_type_and_name_from_change(self, change): | |
| 141 | try: | |
| 142 | id = change['id'] | |
| 143 | response = requests.get("{0}/{1}".format(self._base_url, id), **self._params) | |
| 144 | object_json = response.json() | |
| 145 | except Exception: | |
| 146 | return None, None | |
| 147 | return object_json.get('type'), object_json.get('name') | |
| 148 | ||
| 149 | ||
| 150 | class CouchChangesStream(ChangesStream): | |
| 151 | ||
| 152 | def __init__(self, workspace_name, server_url, since=0, heartbeat='1000', feed='continuous', **params): | |
| 153 | self._base_url = server_url | |
| 154 | self._change_url = "{0}/_changes".format(server_url) | |
| 155 | self.since = since | |
| 156 | self.heartbeat = heartbeat | |
| 157 | self.feed = feed | |
| 158 | self._params = params | |
| 159 | self._response = None | |
| 160 | self._stop = False | |
| 161 | ||
| 162 | def __iter__(self): | |
| 163 | try: | |
| 164 | params = {'since' : self.since, 'heartbeat': self.heartbeat, 'feed': self.feed} | |
| 165 | self._response = requests.get(self._change_url, stream=True, params=params, **self._params) | |
| 166 | if self._response: | |
| 167 | for raw_line in self._response.iter_lines(): | |
| 168 | line = self._sanitize(raw_line) | |
| 169 | if not line: | |
| 170 | if not self._stop: | |
| 171 | continue | |
| 172 | change = self._parse_change(line) | |
| 173 | if not change: | |
| 174 | continue | |
| 175 | object_type, object_name = self._get_object_type_and_name_from_change(change) | |
| 176 | yield change, object_type, object_name | |
| 177 | if not self._stop: # why did we stop if no one asked me to stop? | |
| 178 | raise ChangesStreamStoppedAbruptly | |
| 179 | ||
| 180 | except (requests.exceptions.RequestException, ChangesStreamStoppedAbruptly): | |
| 181 | self.stop() | |
| 182 | raise ChangesStreamStoppedAbruptly | |
| 183 | except Exception as e: | |
| 184 | self.stop() | |
| 185 | ||
| 186 | ||
| 187 | # I'm Py3 |
| 0 | # Makefile for Sphinx documentation | |
| 1 | # | |
| 2 | ||
| 3 | # You can set these variables from the command line. | |
| 4 | SPHINXOPTS = | |
| 5 | SPHINXBUILD = sphinx-build | |
| 6 | PAPER = | |
| 7 | BUILDDIR = _build | |
| 8 | ||
| 9 | # Internal variables. | |
| 10 | PAPEROPT_a4 = -D latex_paper_size=a4 | |
| 11 | PAPEROPT_letter = -D latex_paper_size=letter | |
| 12 | ALLSPHINXOPTS = -d $(BUILDDIR)/doctrees $(PAPEROPT_$(PAPER)) $(SPHINXOPTS) . | |
| 13 | # the i18n builder cannot share the environment and doctrees with the others | |
| 14 | I18NSPHINXOPTS = $(PAPEROPT_$(PAPER)) $(SPHINXOPTS) . | |
| 15 | ||
| 16 | .PHONY: help | |
| 17 | help: | |
| 18 | @echo "Please use \`make <target>' where <target> is one of" | |
| 19 | @echo " html to make standalone HTML files" | |
| 20 | @echo " dirhtml to make HTML files named index.html in directories" | |
| 21 | @echo " singlehtml to make a single large HTML file" | |
| 22 | @echo " pickle to make pickle files" | |
| 23 | @echo " json to make JSON files" | |
| 24 | @echo " htmlhelp to make HTML files and a HTML help project" | |
| 25 | @echo " qthelp to make HTML files and a qthelp project" | |
| 26 | @echo " applehelp to make an Apple Help Book" | |
| 27 | @echo " devhelp to make HTML files and a Devhelp project" | |
| 28 | @echo " epub to make an epub" | |
| 29 | @echo " epub3 to make an epub3" | |
| 30 | @echo " latex to make LaTeX files, you can set PAPER=a4 or PAPER=letter" | |
| 31 | @echo " latexpdf to make LaTeX files and run them through pdflatex" | |
| 32 | @echo " latexpdfja to make LaTeX files and run them through platex/dvipdfmx" | |
| 33 | @echo " text to make text files" | |
| 34 | @echo " man to make manual pages" | |
| 35 | @echo " texinfo to make Texinfo files" | |
| 36 | @echo " info to make Texinfo files and run them through makeinfo" | |
| 37 | @echo " gettext to make PO message catalogs" | |
| 38 | @echo " changes to make an overview of all changed/added/deprecated items" | |
| 39 | @echo " xml to make Docutils-native XML files" | |
| 40 | @echo " pseudoxml to make pseudoxml-XML files for display purposes" | |
| 41 | @echo " linkcheck to check all external links for integrity" | |
| 42 | @echo " doctest to run all doctests embedded in the documentation (if enabled)" | |
| 43 | @echo " coverage to run coverage check of the documentation (if enabled)" | |
| 44 | @echo " dummy to check syntax errors of document sources" | |
| 45 | ||
| 46 | .PHONY: clean | |
| 47 | clean: | |
| 48 | rm -rf $(BUILDDIR)/* | |
| 49 | ||
| 50 | .PHONY: html | |
| 51 | html: | |
| 52 | $(SPHINXBUILD) -b html $(ALLSPHINXOPTS) $(BUILDDIR)/html | |
| 53 | @echo | |
| 54 | @echo "Build finished. The HTML pages are in $(BUILDDIR)/html." | |
| 55 | ||
| 56 | .PHONY: dirhtml | |
| 57 | dirhtml: | |
| 58 | $(SPHINXBUILD) -b dirhtml $(ALLSPHINXOPTS) $(BUILDDIR)/dirhtml | |
| 59 | @echo | |
| 60 | @echo "Build finished. The HTML pages are in $(BUILDDIR)/dirhtml." | |
| 61 | ||
| 62 | .PHONY: singlehtml | |
| 63 | singlehtml: | |
| 64 | $(SPHINXBUILD) -b singlehtml $(ALLSPHINXOPTS) $(BUILDDIR)/singlehtml | |
| 65 | @echo | |
| 66 | @echo "Build finished. The HTML page is in $(BUILDDIR)/singlehtml." | |
| 67 | ||
| 68 | .PHONY: pickle | |
| 69 | pickle: | |
| 70 | $(SPHINXBUILD) -b pickle $(ALLSPHINXOPTS) $(BUILDDIR)/pickle | |
| 71 | @echo | |
| 72 | @echo "Build finished; now you can process the pickle files." | |
| 73 | ||
| 74 | .PHONY: json | |
| 75 | json: | |
| 76 | $(SPHINXBUILD) -b json $(ALLSPHINXOPTS) $(BUILDDIR)/json | |
| 77 | @echo | |
| 78 | @echo "Build finished; now you can process the JSON files." | |
| 79 | ||
| 80 | .PHONY: htmlhelp | |
| 81 | htmlhelp: | |
| 82 | $(SPHINXBUILD) -b htmlhelp $(ALLSPHINXOPTS) $(BUILDDIR)/htmlhelp | |
| 83 | @echo | |
| 84 | @echo "Build finished; now you can run HTML Help Workshop with the" \ | |
| 85 | ".hhp project file in $(BUILDDIR)/htmlhelp." | |
| 86 | ||
| 87 | .PHONY: qthelp | |
| 88 | qthelp: | |
| 89 | $(SPHINXBUILD) -b qthelp $(ALLSPHINXOPTS) $(BUILDDIR)/qthelp | |
| 90 | @echo | |
| 91 | @echo "Build finished; now you can run "qcollectiongenerator" with the" \ | |
| 92 | ".qhcp project file in $(BUILDDIR)/qthelp, like this:" | |
| 93 | @echo "# qcollectiongenerator $(BUILDDIR)/qthelp/Faraday.qhcp" | |
| 94 | @echo "To view the help file:" | |
| 95 | @echo "# assistant -collectionFile $(BUILDDIR)/qthelp/Faraday.qhc" | |
| 96 | ||
| 97 | .PHONY: applehelp | |
| 98 | applehelp: | |
| 99 | $(SPHINXBUILD) -b applehelp $(ALLSPHINXOPTS) $(BUILDDIR)/applehelp | |
| 100 | @echo | |
| 101 | @echo "Build finished. The help book is in $(BUILDDIR)/applehelp." | |
| 102 | @echo "N.B. You won't be able to view it unless you put it in" \ | |
| 103 | "~/Library/Documentation/Help or install it in your application" \ | |
| 104 | "bundle." | |
| 105 | ||
| 106 | .PHONY: devhelp | |
| 107 | devhelp: | |
| 108 | $(SPHINXBUILD) -b devhelp $(ALLSPHINXOPTS) $(BUILDDIR)/devhelp | |
| 109 | @echo | |
| 110 | @echo "Build finished." | |
| 111 | @echo "To view the help file:" | |
| 112 | @echo "# mkdir -p $$HOME/.local/share/devhelp/Faraday" | |
| 113 | @echo "# ln -s $(BUILDDIR)/devhelp $$HOME/.local/share/devhelp/Faraday" | |
| 114 | @echo "# devhelp" | |
| 115 | ||
| 116 | .PHONY: epub | |
| 117 | epub: | |
| 118 | $(SPHINXBUILD) -b epub $(ALLSPHINXOPTS) $(BUILDDIR)/epub | |
| 119 | @echo | |
| 120 | @echo "Build finished. The epub file is in $(BUILDDIR)/epub." | |
| 121 | ||
| 122 | .PHONY: epub3 | |
| 123 | epub3: | |
| 124 | $(SPHINXBUILD) -b epub3 $(ALLSPHINXOPTS) $(BUILDDIR)/epub3 | |
| 125 | @echo | |
| 126 | @echo "Build finished. The epub3 file is in $(BUILDDIR)/epub3." | |
| 127 | ||
| 128 | .PHONY: latex | |
| 129 | latex: | |
| 130 | $(SPHINXBUILD) -b latex $(ALLSPHINXOPTS) $(BUILDDIR)/latex | |
| 131 | @echo | |
| 132 | @echo "Build finished; the LaTeX files are in $(BUILDDIR)/latex." | |
| 133 | @echo "Run \`make' in that directory to run these through (pdf)latex" \ | |
| 134 | "(use \`make latexpdf' here to do that automatically)." | |
| 135 | ||
| 136 | .PHONY: latexpdf | |
| 137 | latexpdf: | |
| 138 | $(SPHINXBUILD) -b latex $(ALLSPHINXOPTS) $(BUILDDIR)/latex | |
| 139 | @echo "Running LaTeX files through pdflatex..." | |
| 140 | $(MAKE) -C $(BUILDDIR)/latex all-pdf | |
| 141 | @echo "pdflatex finished; the PDF files are in $(BUILDDIR)/latex." | |
| 142 | ||
| 143 | .PHONY: latexpdfja | |
| 144 | latexpdfja: | |
| 145 | $(SPHINXBUILD) -b latex $(ALLSPHINXOPTS) $(BUILDDIR)/latex | |
| 146 | @echo "Running LaTeX files through platex and dvipdfmx..." | |
| 147 | $(MAKE) -C $(BUILDDIR)/latex all-pdf-ja | |
| 148 | @echo "pdflatex finished; the PDF files are in $(BUILDDIR)/latex." | |
| 149 | ||
| 150 | .PHONY: text | |
| 151 | text: | |
| 152 | $(SPHINXBUILD) -b text $(ALLSPHINXOPTS) $(BUILDDIR)/text | |
| 153 | @echo | |
| 154 | @echo "Build finished. The text files are in $(BUILDDIR)/text." | |
| 155 | ||
| 156 | .PHONY: man | |
| 157 | man: | |
| 158 | $(SPHINXBUILD) -b man $(ALLSPHINXOPTS) $(BUILDDIR)/man | |
| 159 | @echo | |
| 160 | @echo "Build finished. The manual pages are in $(BUILDDIR)/man." | |
| 161 | ||
| 162 | .PHONY: texinfo | |
| 163 | texinfo: | |
| 164 | $(SPHINXBUILD) -b texinfo $(ALLSPHINXOPTS) $(BUILDDIR)/texinfo | |
| 165 | @echo | |
| 166 | @echo "Build finished. The Texinfo files are in $(BUILDDIR)/texinfo." | |
| 167 | @echo "Run \`make' in that directory to run these through makeinfo" \ | |
| 168 | "(use \`make info' here to do that automatically)." | |
| 169 | ||
| 170 | .PHONY: info | |
| 171 | info: | |
| 172 | $(SPHINXBUILD) -b texinfo $(ALLSPHINXOPTS) $(BUILDDIR)/texinfo | |
| 173 | @echo "Running Texinfo files through makeinfo..." | |
| 174 | make -C $(BUILDDIR)/texinfo info | |
| 175 | @echo "makeinfo finished; the Info files are in $(BUILDDIR)/texinfo." | |
| 176 | ||
| 177 | .PHONY: gettext | |
| 178 | gettext: | |
| 179 | $(SPHINXBUILD) -b gettext $(I18NSPHINXOPTS) $(BUILDDIR)/locale | |
| 180 | @echo | |
| 181 | @echo "Build finished. The message catalogs are in $(BUILDDIR)/locale." | |
| 182 | ||
| 183 | .PHONY: changes | |
| 184 | changes: | |
| 185 | $(SPHINXBUILD) -b changes $(ALLSPHINXOPTS) $(BUILDDIR)/changes | |
| 186 | @echo | |
| 187 | @echo "The overview file is in $(BUILDDIR)/changes." | |
| 188 | ||
| 189 | .PHONY: linkcheck | |
| 190 | linkcheck: | |
| 191 | $(SPHINXBUILD) -b linkcheck $(ALLSPHINXOPTS) $(BUILDDIR)/linkcheck | |
| 192 | @echo | |
| 193 | @echo "Link check complete; look for any errors in the above output " \ | |
| 194 | "or in $(BUILDDIR)/linkcheck/output.txt." | |
| 195 | ||
| 196 | .PHONY: doctest | |
| 197 | doctest: | |
| 198 | $(SPHINXBUILD) -b doctest $(ALLSPHINXOPTS) $(BUILDDIR)/doctest | |
| 199 | @echo "Testing of doctests in the sources finished, look at the " \ | |
| 200 | "results in $(BUILDDIR)/doctest/output.txt." | |
| 201 | ||
| 202 | .PHONY: coverage | |
| 203 | coverage: | |
| 204 | $(SPHINXBUILD) -b coverage $(ALLSPHINXOPTS) $(BUILDDIR)/coverage | |
| 205 | @echo "Testing of coverage in the sources finished, look at the " \ | |
| 206 | "results in $(BUILDDIR)/coverage/python.txt." | |
| 207 | ||
| 208 | .PHONY: xml | |
| 209 | xml: | |
| 210 | $(SPHINXBUILD) -b xml $(ALLSPHINXOPTS) $(BUILDDIR)/xml | |
| 211 | @echo | |
| 212 | @echo "Build finished. The XML files are in $(BUILDDIR)/xml." | |
| 213 | ||
| 214 | .PHONY: pseudoxml | |
| 215 | pseudoxml: | |
| 216 | $(SPHINXBUILD) -b pseudoxml $(ALLSPHINXOPTS) $(BUILDDIR)/pseudoxml | |
| 217 | @echo | |
| 218 | @echo "Build finished. The pseudo-XML files are in $(BUILDDIR)/pseudoxml." | |
| 219 | ||
| 220 | .PHONY: dummy | |
| 221 | dummy: | |
| 222 | $(SPHINXBUILD) -b dummy $(ALLSPHINXOPTS) $(BUILDDIR)/dummy | |
| 223 | @echo | |
| 224 | @echo "Build finished. Dummy builder generates no files." |
Binary diff not shown
Binary diff not shown
Binary diff not shown
Binary diff not shown
| 0 | # Sphinx build info version 1 | |
| 1 | # This file hashes the configuration used when building these files. When it is not found, a full rebuild will be done. | |
| 2 | config: c6d263bc12eb4868c7d35c857befe3f4 | |
| 3 | tags: 645f666f9bcd5a90fca523b33c5a78b7 |
| 0 | ||
| 1 | ||
| 2 | <!DOCTYPE html> | |
| 3 | <!--[if IE 8]><html class="no-js lt-ie9" lang="en" > <![endif]--> | |
| 4 | <!--[if gt IE 8]><!--> <html class="no-js" lang="en" > <!--<![endif]--> | |
| 5 | <head> | |
| 6 | <meta charset="utf-8"> | |
| 7 | ||
| 8 | <meta name="viewport" content="width=device-width, initial-scale=1.0"> | |
| 9 | ||
| 10 | <title>Overview: module code — Faraday 0.1 documentation</title> | |
| 11 | ||
| 12 | ||
| 13 | ||
| 14 | ||
| 15 | ||
| 16 | ||
| 17 | ||
| 18 | ||
| 19 | ||
| 20 | ||
| 21 | ||
| 22 | ||
| 23 | ||
| 24 | ||
| 25 | ||
| 26 | <link rel="stylesheet" href="../_static/css/theme.css" type="text/css" /> | |
| 27 | ||
| 28 | ||
| 29 | ||
| 30 | ||
| 31 | ||
| 32 | <link rel="index" title="Index" | |
| 33 | href="../genindex.html"/> | |
| 34 | <link rel="search" title="Search" href="../search.html"/> | |
| 35 | <link rel="top" title="Faraday 0.1 documentation" href="../index.html"/> | |
| 36 | ||
| 37 | ||
| 38 | <script src="../_static/js/modernizr.min.js"></script> | |
| 39 | ||
| 40 | </head> | |
| 41 | ||
| 42 | <body class="wy-body-for-nav" role="document"> | |
| 43 | ||
| 44 | <div class="wy-grid-for-nav"> | |
| 45 | ||
| 46 | ||
| 47 | <nav data-toggle="wy-nav-shift" class="wy-nav-side"> | |
| 48 | <div class="wy-side-scroll"> | |
| 49 | <div class="wy-side-nav-search"> | |
| 50 | ||
| 51 | ||
| 52 | ||
| 53 | <a href="../index.html" class="icon icon-home"> Faraday | |
| 54 | ||
| 55 | ||
| 56 | ||
| 57 | </a> | |
| 58 | ||
| 59 | ||
| 60 | ||
| 61 | ||
| 62 | <div class="version"> | |
| 63 | 0.1 | |
| 64 | </div> | |
| 65 | ||
| 66 | ||
| 67 | ||
| 68 | ||
| 69 | <div role="search"> | |
| 70 | <form id="rtd-search-form" class="wy-form" action="../search.html" method="get"> | |
| 71 | <input type="text" name="q" placeholder="Search docs" /> | |
| 72 | <input type="hidden" name="check_keywords" value="yes" /> | |
| 73 | <input type="hidden" name="area" value="default" /> | |
| 74 | </form> | |
| 75 | </div> | |
| 76 | ||
| 77 | ||
| 78 | </div> | |
| 79 | ||
| 80 | <div class="wy-menu wy-menu-vertical" data-spy="affix" role="navigation" aria-label="main navigation"> | |
| 81 | ||
| 82 | ||
| 83 | ||
| 84 | <!-- Local TOC --> | |
| 85 | <div class="local-toc"></div> | |
| 86 | ||
| 87 | ||
| 88 | </div> | |
| 89 | </div> | |
| 90 | </nav> | |
| 91 | ||
| 92 | <section data-toggle="wy-nav-shift" class="wy-nav-content-wrap"> | |
| 93 | ||
| 94 | ||
| 95 | <nav class="wy-nav-top" role="navigation" aria-label="top navigation"> | |
| 96 | <i data-toggle="wy-nav-top" class="fa fa-bars"></i> | |
| 97 | <a href="../index.html">Faraday</a> | |
| 98 | </nav> | |
| 99 | ||
| 100 | ||
| 101 | ||
| 102 | <div class="wy-nav-content"> | |
| 103 | <div class="rst-content"> | |
| 104 | ||
| 105 | ||
| 106 | ||
| 107 | ||
| 108 | ||
| 109 | ||
| 110 | <div role="navigation" aria-label="breadcrumbs navigation"> | |
| 111 | <ul class="wy-breadcrumbs"> | |
| 112 | <li><a href="../index.html">Docs</a> »</li> | |
| 113 | ||
| 114 | <li>Overview: module code</li> | |
| 115 | <li class="wy-breadcrumbs-aside"> | |
| 116 | ||
| 117 | ||
| 118 | ||
| 119 | </li> | |
| 120 | </ul> | |
| 121 | <hr/> | |
| 122 | </div> | |
| 123 | <div role="main" class="document" itemscope="itemscope" itemtype="http://schema.org/Article"> | |
| 124 | <div itemprop="articleBody"> | |
| 125 | ||
| 126 | <h1>All modules for which code is available</h1> | |
| 127 | <ul><li><a href="persistence/server/server.html">persistence.server.server</a></li> | |
| 128 | </ul> | |
| 129 | ||
| 130 | </div> | |
| 131 | </div> | |
| 132 | <footer> | |
| 133 | ||
| 134 | ||
| 135 | <hr/> | |
| 136 | ||
| 137 | <div role="contentinfo"> | |
| 138 | <p> | |
| 139 | © Copyright 2016, Infobyte. | |
| 140 | ||
| 141 | </p> | |
| 142 | </div> | |
| 143 | Built with <a href="http://sphinx-doc.org/">Sphinx</a> using a <a href="https://github.com/snide/sphinx_rtd_theme">theme</a> provided by <a href="https://readthedocs.org">Read the Docs</a>. | |
| 144 | ||
| 145 | </footer> | |
| 146 | ||
| 147 | </div> | |
| 148 | </div> | |
| 149 | ||
| 150 | </section> | |
| 151 | ||
| 152 | </div> | |
| 153 | ||
| 154 | ||
| 155 | ||
| 156 | ||
| 157 | ||
| 158 | <script type="text/javascript"> | |
| 159 | var DOCUMENTATION_OPTIONS = { | |
| 160 | URL_ROOT:'../', | |
| 161 | VERSION:'0.1', | |
| 162 | COLLAPSE_INDEX:false, | |
| 163 | FILE_SUFFIX:'.html', | |
| 164 | HAS_SOURCE: true | |
| 165 | }; | |
| 166 | </script> | |
| 167 | <script type="text/javascript" src="../_static/jquery.js"></script> | |
| 168 | <script type="text/javascript" src="../_static/underscore.js"></script> | |
| 169 | <script type="text/javascript" src="../_static/doctools.js"></script> | |
| 170 | ||
| 171 | ||
| 172 | ||
| 173 | ||
| 174 | ||
| 175 | <script type="text/javascript" src="../_static/js/theme.js"></script> | |
| 176 | ||
| 177 | ||
| 178 | ||
| 179 | ||
| 180 | <script type="text/javascript"> | |
| 181 | jQuery(function () { | |
| 182 | SphinxRtdTheme.StickyNav.enable(); | |
| 183 | }); | |
| 184 | </script> | |
| 185 | ||
| 186 | ||
| 187 | </body> | |
| 188 | </html>⏎ |
+0
-1662
| 0 | ||
| 1 | ||
| 2 | <!DOCTYPE html> | |
| 3 | <!--[if IE 8]><html class="no-js lt-ie9" lang="en" > <![endif]--> | |
| 4 | <!--[if gt IE 8]><!--> <html class="no-js" lang="en" > <!--<![endif]--> | |
| 5 | <head> | |
| 6 | <meta charset="utf-8"> | |
| 7 | ||
| 8 | <meta name="viewport" content="width=device-width, initial-scale=1.0"> | |
| 9 | ||
| 10 | <title>persistence.server.server — Faraday 0.1 documentation</title> | |
| 11 | ||
| 12 | ||
| 13 | ||
| 14 | ||
| 15 | ||
| 16 | ||
| 17 | ||
| 18 | ||
| 19 | ||
| 20 | ||
| 21 | ||
| 22 | ||
| 23 | ||
| 24 | ||
| 25 | ||
| 26 | <link rel="stylesheet" href="../../../_static/css/theme.css" type="text/css" /> | |
| 27 | ||
| 28 | ||
| 29 | ||
| 30 | ||
| 31 | ||
| 32 | <link rel="index" title="Index" | |
| 33 | href="../../../genindex.html"/> | |
| 34 | <link rel="search" title="Search" href="../../../search.html"/> | |
| 35 | <link rel="top" title="Faraday 0.1 documentation" href="../../../index.html"/> | |
| 36 | <link rel="up" title="Module code" href="../../index.html"/> | |
| 37 | ||
| 38 | ||
| 39 | <script src="../../../_static/js/modernizr.min.js"></script> | |
| 40 | ||
| 41 | </head> | |
| 42 | ||
| 43 | <body class="wy-body-for-nav" role="document"> | |
| 44 | ||
| 45 | <div class="wy-grid-for-nav"> | |
| 46 | ||
| 47 | ||
| 48 | <nav data-toggle="wy-nav-shift" class="wy-nav-side"> | |
| 49 | <div class="wy-side-scroll"> | |
| 50 | <div class="wy-side-nav-search"> | |
| 51 | ||
| 52 | ||
| 53 | ||
| 54 | <a href="../../../index.html" class="icon icon-home"> Faraday | |
| 55 | ||
| 56 | ||
| 57 | ||
| 58 | </a> | |
| 59 | ||
| 60 | ||
| 61 | ||
| 62 | ||
| 63 | <div class="version"> | |
| 64 | 0.1 | |
| 65 | </div> | |
| 66 | ||
| 67 | ||
| 68 | ||
| 69 | ||
| 70 | <div role="search"> | |
| 71 | <form id="rtd-search-form" class="wy-form" action="../../../search.html" method="get"> | |
| 72 | <input type="text" name="q" placeholder="Search docs" /> | |
| 73 | <input type="hidden" name="check_keywords" value="yes" /> | |
| 74 | <input type="hidden" name="area" value="default" /> | |
| 75 | </form> | |
| 76 | </div> | |
| 77 | ||
| 78 | ||
| 79 | </div> | |
| 80 | ||
| 81 | <div class="wy-menu wy-menu-vertical" data-spy="affix" role="navigation" aria-label="main navigation"> | |
| 82 | ||
| 83 | ||
| 84 | ||
| 85 | <!-- Local TOC --> | |
| 86 | <div class="local-toc"></div> | |
| 87 | ||
| 88 | ||
| 89 | </div> | |
| 90 | </div> | |
| 91 | </nav> | |
| 92 | ||
| 93 | <section data-toggle="wy-nav-shift" class="wy-nav-content-wrap"> | |
| 94 | ||
| 95 | ||
| 96 | <nav class="wy-nav-top" role="navigation" aria-label="top navigation"> | |
| 97 | <i data-toggle="wy-nav-top" class="fa fa-bars"></i> | |
| 98 | <a href="../../../index.html">Faraday</a> | |
| 99 | </nav> | |
| 100 | ||
| 101 | ||
| 102 | ||
| 103 | <div class="wy-nav-content"> | |
| 104 | <div class="rst-content"> | |
| 105 | ||
| 106 | ||
| 107 | ||
| 108 | ||
| 109 | ||
| 110 | ||
| 111 | <div role="navigation" aria-label="breadcrumbs navigation"> | |
| 112 | <ul class="wy-breadcrumbs"> | |
| 113 | <li><a href="../../../index.html">Docs</a> »</li> | |
| 114 | ||
| 115 | <li><a href="../../index.html">Module code</a> »</li> | |
| 116 | ||
| 117 | <li>persistence.server.server</li> | |
| 118 | <li class="wy-breadcrumbs-aside"> | |
| 119 | ||
| 120 | ||
| 121 | ||
| 122 | </li> | |
| 123 | </ul> | |
| 124 | <hr/> | |
| 125 | </div> | |
| 126 | <div role="main" class="document" itemscope="itemscope" itemtype="http://schema.org/Article"> | |
| 127 | <div itemprop="articleBody"> | |
| 128 | ||
| 129 | <h1>Source code for persistence.server.server</h1><div class="highlight"><pre> | |
| 130 | <span></span><span class="ch">#!/usr/bin/python3</span> | |
| 131 | <span class="c1"># -*- coding: utf-8 -*-</span> | |
| 132 | ||
| 133 | <span class="c1"># Faraday Penetration Test IDE</span> | |
| 134 | <span class="c1"># Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/)</span> | |
| 135 | <span class="c1"># See the file 'doc/LICENSE' for the license information</span> | |
| 136 | ||
| 137 | ||
| 138 | <span class="sd">"""A module to handle request to the Faraday Server.</span> | |
| 139 | ||
| 140 | <span class="sd">Note:</span> | |
| 141 | <span class="sd"> Before using this as an API, you should copy this file and edit</span> | |
| 142 | <span class="sd"> the FARADAY_UP and the SERVER_URL variables found inmediatly</span> | |
| 143 | <span class="sd"> below the imports.</span> | |
| 144 | ||
| 145 | <span class="sd"> FARADAY_UP should be set to False in the copy of the file, and SERVER_URL</span> | |
| 146 | <span class="sd"> must be a valid server url.</span> | |
| 147 | ||
| 148 | <span class="sd">Warning:</span> | |
| 149 | <span class="sd"> This module was though of primarly as a way of querying and removing</span> | |
| 150 | <span class="sd"> information from the Faraday Server. Adding objects is supported, but should</span> | |
| 151 | <span class="sd"> be used with care, specially regarding the ID of objects, which must</span> | |
| 152 | <span class="sd"> be always unique.</span> | |
| 153 | <span class="sd">"""</span> | |
| 154 | ||
| 155 | <span class="kn">import</span> <span class="nn">requests</span> | |
| 156 | <span class="kn">import</span> <span class="nn">json</span> | |
| 157 | <span class="kn">from</span> <span class="nn">persistence.server.utils</span> <span class="k">import</span> <span class="n">force_unique</span> | |
| 158 | <span class="kn">from</span> <span class="nn">persistence.server.server_io_exceptions</span> <span class="k">import</span> <span class="p">(</span><span class="n">WrongObjectSignature</span><span class="p">,</span> | |
| 159 | <span class="n">CantCommunicateWithServerError</span><span class="p">,</span> | |
| 160 | <span class="n">ConflictInDatabase</span><span class="p">,</span> | |
| 161 | <span class="n">ResourceDoesNotExist</span><span class="p">,</span> | |
| 162 | <span class="n">Unauthorized</span><span class="p">,</span> | |
| 163 | <span class="n">MoreThanOneObjectFoundByID</span><span class="p">)</span> | |
| 164 | ||
| 165 | <span class="kn">from</span> <span class="nn">persistence.server.changes_stream</span> <span class="k">import</span> <span class="n">CouchChangesStream</span> | |
| 166 | ||
| 167 | <span class="c1"># NOTE: Change is you want to use this module by itself.</span> | |
| 168 | <span class="c1"># If FARADAY_UP is False, SERVER_URL must be a valid faraday server url</span> | |
| 169 | <span class="n">FARADAY_UP</span> <span class="o">=</span> <span class="kc">True</span> | |
| 170 | <span class="n">SERVER_URL</span> <span class="o">=</span> <span class="s2">"http://127.0.0.1:5984"</span> | |
| 171 | ||
| 172 | <span class="k">def</span> <span class="nf">_conf</span><span class="p">():</span> | |
| 173 | <span class="kn">from</span> <span class="nn">config.configuration</span> <span class="k">import</span> <span class="n">getInstanceConfiguration</span> | |
| 174 | <span class="n">CONF</span> <span class="o">=</span> <span class="n">getInstanceConfiguration</span><span class="p">()</span> | |
| 175 | <span class="k">return</span> <span class="n">CONF</span> | |
| 176 | ||
| 177 | <span class="k">def</span> <span class="nf">_get_base_server_url</span><span class="p">():</span> | |
| 178 | <span class="k">if</span> <span class="n">FARADAY_UP</span><span class="p">:</span> | |
| 179 | <span class="n">server_url</span> <span class="o">=</span> <span class="n">_conf</span><span class="p">()</span><span class="o">.</span><span class="n">getCouchURI</span><span class="p">()</span> | |
| 180 | <span class="k">else</span><span class="p">:</span> | |
| 181 | <span class="n">server_url</span> <span class="o">=</span> <span class="n">SERVER_URL</span> | |
| 182 | <span class="k">return</span> <span class="n">server_url</span> | |
| 183 | ||
| 184 | ||
| 185 | <span class="k">def</span> <span class="nf">_create_server_api_url</span><span class="p">():</span> | |
| 186 | <span class="sd">"""Return the server's api url."""</span> | |
| 187 | <span class="k">return</span> <span class="s2">"</span><span class="si">{0}</span><span class="s2">/_api"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">_get_base_server_url</span><span class="p">())</span> | |
| 188 | ||
| 189 | <span class="k">def</span> <span class="nf">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_name</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 190 | <span class="sd">"""Creates a url to get from the server. Takes the workspace name</span> | |
| 191 | <span class="sd"> as a string, an object_name paramter which is the object you want to</span> | |
| 192 | <span class="sd"> query as a string ('hosts', 'interfaces', etc) .</span> | |
| 193 | ||
| 194 | <span class="sd"> object_name may be None if you want to get the workspace itself.</span> | |
| 195 | ||
| 196 | <span class="sd"> Return the get_url as a string.</span> | |
| 197 | <span class="sd"> """</span> | |
| 198 | <span class="n">object_name</span> <span class="o">=</span> <span class="s2">"/</span><span class="si">{0}</span><span class="s2">"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">object_name</span><span class="p">)</span> <span class="k">if</span> <span class="n">object_name</span> <span class="k">else</span> <span class="s2">""</span> | |
| 199 | <span class="n">get_url</span> <span class="o">=</span> <span class="s1">'</span><span class="si">{0}</span><span class="s1">/ws/</span><span class="si">{1}{2}</span><span class="s1">'</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">_create_server_api_url</span><span class="p">(),</span> | |
| 200 | <span class="n">workspace_name</span><span class="p">,</span> | |
| 201 | <span class="n">object_name</span><span class="p">)</span> | |
| 202 | <span class="k">return</span> <span class="n">get_url</span> | |
| 203 | ||
| 204 | ||
| 205 | <span class="k">def</span> <span class="nf">_create_server_post_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">):</span> | |
| 206 | <span class="n">server_api_url</span> <span class="o">=</span> <span class="n">_create_server_api_url</span><span class="p">()</span> | |
| 207 | <span class="n">post_url</span> <span class="o">=</span> <span class="s1">'</span><span class="si">{0}</span><span class="s1">/ws/</span><span class="si">{1}</span><span class="s1">/doc/</span><span class="si">{2}</span><span class="s1">'</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">server_api_url</span><span class="p">,</span> <span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">)</span> | |
| 208 | <span class="k">return</span> <span class="n">post_url</span> | |
| 209 | ||
| 210 | ||
| 211 | <span class="k">def</span> <span class="nf">_create_server_delete_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">):</span> | |
| 212 | <span class="k">return</span> <span class="n">_create_server_post_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">)</span> | |
| 213 | ||
| 214 | <span class="c1"># XXX: COUCH IT!</span> | |
| 215 | <span class="k">def</span> <span class="nf">_create_couch_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">):</span> | |
| 216 | <span class="n">server_url</span> <span class="o">=</span> <span class="n">_get_base_server_url</span><span class="p">()</span> | |
| 217 | <span class="k">return</span> <span class="s2">"</span><span class="si">{0}</span><span class="s2">/</span><span class="si">{1}</span><span class="s2">/</span><span class="si">{2}</span><span class="s2">"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">server_url</span><span class="p">,</span> <span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">)</span> | |
| 218 | ||
| 219 | ||
| 220 | <span class="c1"># XXX: COUCH IT!</span> | |
| 221 | <span class="k">def</span> <span class="nf">_create_couch_post_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">):</span> | |
| 222 | <span class="k">return</span> <span class="n">_create_couch_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">)</span> | |
| 223 | ||
| 224 | ||
| 225 | <span class="c1"># XXX: COUCH IT!</span> | |
| 226 | <span class="k">def</span> <span class="nf">_create_couch_db_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">):</span> | |
| 227 | <span class="n">server_base_url</span> <span class="o">=</span> <span class="n">_get_base_server_url</span><span class="p">()</span> | |
| 228 | <span class="n">db_url</span> <span class="o">=</span> <span class="s1">'</span><span class="si">{0}</span><span class="s1">/</span><span class="si">{1}</span><span class="s1">'</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">server_base_url</span><span class="p">,</span> <span class="n">workspace_name</span><span class="p">)</span> | |
| 229 | <span class="k">return</span> <span class="n">db_url</span> | |
| 230 | ||
| 231 | <span class="k">def</span> <span class="nf">_create_server_db_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">):</span> | |
| 232 | <span class="n">server_api_url</span> <span class="o">=</span> <span class="n">_create_server_api_url</span><span class="p">()</span> | |
| 233 | <span class="n">db_url</span> <span class="o">=</span> <span class="s1">'</span><span class="si">{0}</span><span class="s1">/ws/</span><span class="si">{1}</span><span class="s1">'</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">server_api_url</span><span class="p">,</span> <span class="n">workspace_name</span><span class="p">)</span> | |
| 234 | <span class="k">return</span> <span class="n">db_url</span> | |
| 235 | ||
| 236 | <span class="k">def</span> <span class="nf">_unsafe_io_with_server</span><span class="p">(</span><span class="n">server_io_function</span><span class="p">,</span> <span class="n">server_expected_response</span><span class="p">,</span> | |
| 237 | <span class="n">server_url</span><span class="p">,</span> <span class="o">**</span><span class="n">payload</span><span class="p">):</span> | |
| 238 | <span class="sd">"""A wrapper for functions which deals with I/O to or from the server.</span> | |
| 239 | <span class="sd"> It calls the server_io_function with url server_url and the payload,</span> | |
| 240 | <span class="sd"> raising an CantCommunicateWithServerError if the response wasn't</span> | |
| 241 | <span class="sd"> server_expected_response or if there was a Connection Error.</span> | |
| 242 | ||
| 243 | <span class="sd"> Return the response from the server.</span> | |
| 244 | <span class="sd"> """</span> | |
| 245 | <span class="k">try</span><span class="p">:</span> | |
| 246 | <span class="n">answer</span> <span class="o">=</span> <span class="n">server_io_function</span><span class="p">(</span><span class="n">server_url</span><span class="p">,</span> <span class="o">**</span><span class="n">payload</span><span class="p">)</span> | |
| 247 | <span class="k">if</span> <span class="n">answer</span><span class="o">.</span><span class="n">status_code</span> <span class="o">==</span> <span class="mi">409</span> <span class="ow">and</span> <span class="n">answer</span><span class="o">.</span><span class="n">json</span><span class="p">()[</span><span class="s1">'error'</span><span class="p">]</span> <span class="o">==</span> <span class="s1">'conflict'</span><span class="p">:</span> | |
| 248 | <span class="k">raise</span> <span class="n">ConflictInDatabase</span><span class="p">(</span><span class="n">answer</span><span class="p">)</span> | |
| 249 | <span class="k">if</span> <span class="n">answer</span><span class="o">.</span><span class="n">status_code</span> <span class="o">==</span> <span class="mi">404</span><span class="p">:</span> | |
| 250 | <span class="k">raise</span> <span class="n">ResourceDoesNotExist</span><span class="p">(</span><span class="n">server_url</span><span class="p">)</span> | |
| 251 | <span class="k">if</span> <span class="n">answer</span><span class="o">.</span><span class="n">status_code</span> <span class="o">==</span> <span class="mi">403</span> <span class="ow">or</span> <span class="n">answer</span><span class="o">.</span><span class="n">status_code</span> <span class="o">==</span> <span class="mi">401</span><span class="p">:</span> | |
| 252 | <span class="k">raise</span> <span class="n">Unauthorized</span><span class="p">(</span><span class="n">answer</span><span class="p">)</span> | |
| 253 | <span class="k">if</span> <span class="n">answer</span><span class="o">.</span><span class="n">status_code</span> <span class="o">!=</span> <span class="n">server_expected_response</span><span class="p">:</span> | |
| 254 | <span class="k">raise</span> <span class="n">requests</span><span class="o">.</span><span class="n">exceptions</span><span class="o">.</span><span class="n">RequestException</span><span class="p">(</span><span class="n">response</span><span class="o">=</span><span class="n">answer</span><span class="p">)</span> | |
| 255 | <span class="k">except</span> <span class="n">requests</span><span class="o">.</span><span class="n">exceptions</span><span class="o">.</span><span class="n">RequestException</span><span class="p">:</span> | |
| 256 | <span class="k">raise</span> <span class="n">CantCommunicateWithServerError</span><span class="p">(</span><span class="n">server_io_function</span><span class="p">,</span> <span class="n">server_url</span><span class="p">,</span> <span class="n">payload</span><span class="p">)</span> | |
| 257 | <span class="k">return</span> <span class="n">answer</span> | |
| 258 | ||
| 259 | ||
| 260 | <span class="k">def</span> <span class="nf">_parse_json</span><span class="p">(</span><span class="n">response_object</span><span class="p">):</span> | |
| 261 | <span class="sd">"""Takes a response object and return its response as a dictionary."""</span> | |
| 262 | <span class="k">try</span><span class="p">:</span> | |
| 263 | <span class="k">return</span> <span class="n">response_object</span><span class="o">.</span><span class="n">json</span><span class="p">()</span> | |
| 264 | <span class="k">except</span> <span class="ne">ValueError</span><span class="p">:</span> | |
| 265 | <span class="k">return</span> <span class="p">{}</span> | |
| 266 | ||
| 267 | ||
| 268 | <span class="k">def</span> <span class="nf">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 269 | <span class="sd">"""Get from the request_url. Takes an arbitrary number of parameters</span> | |
| 270 | <span class="sd"> to customize the request_url if necessary.</span> | |
| 271 | ||
| 272 | <span class="sd"> Will raise a CantCommunicateWithServerError if requests cant stablish</span> | |
| 273 | <span class="sd"> connection to server or if response is not equal to 200.</span> | |
| 274 | ||
| 275 | <span class="sd"> Return a dictionary with the information in the json.</span> | |
| 276 | <span class="sd"> """</span> | |
| 277 | <span class="k">return</span> <span class="n">_parse_json</span><span class="p">(</span><span class="n">_unsafe_io_with_server</span><span class="p">(</span><span class="n">requests</span><span class="o">.</span><span class="n">get</span><span class="p">,</span> | |
| 278 | <span class="mi">200</span><span class="p">,</span> | |
| 279 | <span class="n">request_url</span><span class="p">,</span> | |
| 280 | <span class="n">params</span><span class="o">=</span><span class="n">params</span><span class="p">))</span> | |
| 281 | ||
| 282 | <span class="k">def</span> <span class="nf">_put</span><span class="p">(</span><span class="n">post_url</span><span class="p">,</span> <span class="n">update</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">expected_response</span><span class="o">=</span><span class="mi">201</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 283 | <span class="sd">"""Put to the post_url. If update is True, try to get the object</span> | |
| 284 | <span class="sd"> revision first so as to update the object in Couch. You can</span> | |
| 285 | <span class="sd"> customize the expected response (it should be 201, but Couchdbkit returns</span> | |
| 286 | <span class="sd"> 200, so...). Also take an arbitrary number of parameters to put into the</span> | |
| 287 | <span class="sd"> post_url.</span> | |
| 288 | ||
| 289 | <span class="sd"> Will raise a CantCommunicateWithServerError if requests cant stablish</span> | |
| 290 | <span class="sd"> connection to server or if response is not equal to 201.</span> | |
| 291 | ||
| 292 | <span class="sd"> Return a dictionary with the response from couchdb, which looks like this:</span> | |
| 293 | <span class="sd"> {u'id': u'61', u'ok': True, u'rev': u'1-967a00dff5e02add41819138abb3284d'}</span> | |
| 294 | <span class="sd"> """</span> | |
| 295 | <span class="k">if</span> <span class="n">update</span><span class="p">:</span> | |
| 296 | <span class="n">last_rev</span> <span class="o">=</span> <span class="n">_get</span><span class="p">(</span><span class="n">post_url</span><span class="p">)[</span><span class="s1">'_rev'</span><span class="p">]</span> | |
| 297 | <span class="n">params</span><span class="p">[</span><span class="s1">'_rev'</span><span class="p">]</span> <span class="o">=</span> <span class="n">last_rev</span> | |
| 298 | <span class="k">return</span> <span class="n">_parse_json</span><span class="p">(</span><span class="n">_unsafe_io_with_server</span><span class="p">(</span><span class="n">requests</span><span class="o">.</span><span class="n">put</span><span class="p">,</span> | |
| 299 | <span class="n">expected_response</span><span class="p">,</span> | |
| 300 | <span class="n">post_url</span><span class="p">,</span> | |
| 301 | <span class="n">json</span><span class="o">=</span><span class="n">params</span><span class="p">))</span> | |
| 302 | ||
| 303 | ||
| 304 | <span class="k">def</span> <span class="nf">_delete</span><span class="p">(</span><span class="n">delete_url</span><span class="p">,</span> <span class="n">database</span><span class="o">=</span><span class="kc">False</span><span class="p">):</span> | |
| 305 | <span class="sd">"""Deletes the object on delete_url. If you're deleting a database,</span> | |
| 306 | <span class="sd"> specify the database parameter to True"""</span> | |
| 307 | <span class="n">params</span> <span class="o">=</span> <span class="p">{}</span> | |
| 308 | <span class="k">if</span> <span class="ow">not</span> <span class="n">database</span><span class="p">:</span> | |
| 309 | <span class="n">last_rev</span> <span class="o">=</span> <span class="n">_get</span><span class="p">(</span><span class="n">delete_url</span><span class="p">)[</span><span class="s1">'_rev'</span><span class="p">]</span> | |
| 310 | <span class="n">params</span> <span class="o">=</span> <span class="p">{</span><span class="s1">'rev'</span><span class="p">:</span> <span class="n">last_rev</span><span class="p">}</span> | |
| 311 | <span class="k">return</span> <span class="n">_parse_json</span><span class="p">(</span><span class="n">_unsafe_io_with_server</span><span class="p">(</span><span class="n">requests</span><span class="o">.</span><span class="n">delete</span><span class="p">,</span> | |
| 312 | <span class="mi">200</span><span class="p">,</span> | |
| 313 | <span class="n">delete_url</span><span class="p">,</span> | |
| 314 | <span class="n">params</span><span class="o">=</span><span class="n">params</span><span class="p">))</span> | |
| 315 | ||
| 316 | ||
| 317 | <span class="k">def</span> <span class="nf">_get_raw_hosts</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 318 | <span class="sd">"""Take a workspace_name and an arbitrary number of params and return</span> | |
| 319 | <span class="sd"> a dictionary with the hosts table."""</span> | |
| 320 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'hosts'</span><span class="p">)</span> | |
| 321 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 322 | ||
| 323 | ||
| 324 | <span class="k">def</span> <span class="nf">_get_raw_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 325 | <span class="sd">"""Take a workspace_name and an arbitrary number of params and return</span> | |
| 326 | <span class="sd"> a dictionary with the vulns table."""</span> | |
| 327 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'vulns'</span><span class="p">)</span> | |
| 328 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 329 | ||
| 330 | ||
| 331 | <span class="k">def</span> <span class="nf">_get_raw_interfaces</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 332 | <span class="sd">"""Take a workspace_name and an arbitrary number of params and return</span> | |
| 333 | <span class="sd"> a dictionary with the interfaces table."""</span> | |
| 334 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'interfaces'</span><span class="p">)</span> | |
| 335 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 336 | ||
| 337 | ||
| 338 | <span class="k">def</span> <span class="nf">_get_raw_services</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 339 | <span class="sd">"""Take a workspace_name and an arbitrary number of params and return</span> | |
| 340 | <span class="sd"> a dictionary with the services table."""</span> | |
| 341 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'services'</span><span class="p">)</span> | |
| 342 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 343 | ||
| 344 | ||
| 345 | <span class="k">def</span> <span class="nf">_get_raw_notes</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 346 | <span class="sd">"""Take a workspace name and an arbitrary number of params and</span> | |
| 347 | <span class="sd"> return a dictionary with the notes table."""</span> | |
| 348 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'notes'</span><span class="p">)</span> | |
| 349 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 350 | ||
| 351 | ||
| 352 | <span class="k">def</span> <span class="nf">_get_raw_credentials</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 353 | <span class="sd">"""Take a workspace name and an arbitrary number of params and</span> | |
| 354 | <span class="sd"> return a dictionary with the credentials table."""</span> | |
| 355 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'credentials'</span><span class="p">)</span> | |
| 356 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 357 | ||
| 358 | ||
| 359 | <span class="k">def</span> <span class="nf">_get_raw_commands</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 360 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'commands'</span><span class="p">)</span> | |
| 361 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 362 | ||
| 363 | ||
| 364 | <span class="k">def</span> <span class="nf">_get_raw_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">):</span> | |
| 365 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'summary'</span><span class="p">)</span> | |
| 366 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">)</span> | |
| 367 | ||
| 368 | <span class="c1"># XXX: COUCH IT!</span> | |
| 369 | <span class="k">def</span> <span class="nf">_save_to_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 370 | <span class="n">post_url</span> <span class="o">=</span> <span class="n">_create_couch_post_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">)</span> | |
| 371 | <span class="k">return</span> <span class="n">_put</span><span class="p">(</span><span class="n">post_url</span><span class="p">,</span> <span class="n">update</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 372 | ||
| 373 | <span class="c1"># XXX: COUCH IT!</span> | |
| 374 | <span class="k">def</span> <span class="nf">_update_in_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 375 | <span class="n">post_url</span> <span class="o">=</span> <span class="n">_create_server_post_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">)</span> | |
| 376 | <span class="k">return</span> <span class="n">_put</span><span class="p">(</span><span class="n">post_url</span><span class="p">,</span> <span class="n">update</span><span class="o">=</span><span class="kc">True</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 377 | ||
| 378 | <span class="k">def</span> <span class="nf">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 379 | <span class="n">post_url</span> <span class="o">=</span> <span class="n">_create_server_post_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">)</span> | |
| 380 | <span class="k">return</span> <span class="n">_put</span><span class="p">(</span><span class="n">post_url</span><span class="p">,</span> <span class="n">update</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">expected_response</span><span class="o">=</span><span class="mi">200</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 381 | ||
| 382 | <span class="k">def</span> <span class="nf">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 383 | <span class="n">post_url</span> <span class="o">=</span> <span class="n">_create_server_post_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">)</span> | |
| 384 | <span class="k">return</span> <span class="n">_put</span><span class="p">(</span><span class="n">post_url</span><span class="p">,</span> <span class="n">update</span><span class="o">=</span><span class="kc">True</span><span class="p">,</span> <span class="n">expected_response</span><span class="o">=</span><span class="mi">200</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 385 | ||
| 386 | <span class="k">def</span> <span class="nf">_save_db_to_server</span><span class="p">(</span><span class="n">db_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 387 | <span class="n">post_url</span> <span class="o">=</span> <span class="n">_create_server_db_url</span><span class="p">(</span><span class="n">db_name</span><span class="p">)</span> | |
| 388 | <span class="k">return</span> <span class="n">_put</span><span class="p">(</span><span class="n">post_url</span><span class="p">,</span> <span class="n">expected_response</span><span class="o">=</span><span class="mi">200</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 389 | ||
| 390 | <span class="c1"># XXX: SEMI COUCH IT!</span> | |
| 391 | <span class="k">def</span> <span class="nf">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">):</span> | |
| 392 | <span class="n">delete_url</span> <span class="o">=</span> <span class="n">_create_server_delete_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">)</span> | |
| 393 | <span class="k">return</span> <span class="n">_delete</span><span class="p">(</span><span class="n">delete_url</span><span class="p">)</span> | |
| 394 | ||
| 395 | <span class="c1"># XXX: COUCH IT!</span> | |
| 396 | <span class="k">def</span> <span class="nf">_couch_changes</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 397 | <span class="k">return</span> <span class="n">CouchChangesStream</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 398 | <span class="n">_create_couch_db_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">),</span> | |
| 399 | <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 400 | ||
| 401 | ||
| 402 | <span class="k">def</span> <span class="nf">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_name</span><span class="p">,</span> | |
| 403 | <span class="n">faraday_object_row_name</span><span class="p">,</span> <span class="n">full_table</span><span class="o">=</span><span class="kc">True</span><span class="p">,</span> | |
| 404 | <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 405 | <span class="sd">"""Takes a workspace_name (str), a faraday_object_name (str),</span> | |
| 406 | <span class="sd"> a faraday_object_row_name (str) and an arbitrary number of params.</span> | |
| 407 | <span class="sd"> Return a list of dictionaries that hold the information for the objects</span> | |
| 408 | <span class="sd"> in table faraday_object_name.</span> | |
| 409 | ||
| 410 | <span class="sd"> The full_table paramether may be used to get the full dictionary instead</span> | |
| 411 | <span class="sd"> of just the one inside the 'value' key which holds information about the</span> | |
| 412 | <span class="sd"> object.</span> | |
| 413 | ||
| 414 | <span class="sd"> Preconditions:</span> | |
| 415 | <span class="sd"> faraday_object_name == 'host', 'vuln', 'interface', 'service', 'note'</span> | |
| 416 | <span class="sd"> or 'credential'</span> | |
| 417 | ||
| 418 | <span class="sd"> faraday_object_row_name must be the key to the dictionary which holds</span> | |
| 419 | <span class="sd"> the information of the object per se in the table. most times this is 'rows'</span> | |
| 420 | <span class="sd"> """</span> | |
| 421 | <span class="n">object_to_func</span> <span class="o">=</span> <span class="p">{</span><span class="s1">'hosts'</span><span class="p">:</span> <span class="n">_get_raw_hosts</span><span class="p">,</span> | |
| 422 | <span class="s1">'vulns'</span><span class="p">:</span> <span class="n">_get_raw_vulns</span><span class="p">,</span> | |
| 423 | <span class="s1">'interfaces'</span><span class="p">:</span> <span class="n">_get_raw_interfaces</span><span class="p">,</span> | |
| 424 | <span class="s1">'services'</span><span class="p">:</span> <span class="n">_get_raw_services</span><span class="p">,</span> | |
| 425 | <span class="s1">'notes'</span><span class="p">:</span> <span class="n">_get_raw_notes</span><span class="p">,</span> | |
| 426 | <span class="s1">'credentials'</span><span class="p">:</span> <span class="n">_get_raw_credentials</span><span class="p">,</span> | |
| 427 | <span class="s1">'commands'</span><span class="p">:</span> <span class="n">_get_raw_commands</span><span class="p">}</span> | |
| 428 | ||
| 429 | <span class="n">appropiate_function</span> <span class="o">=</span> <span class="n">object_to_func</span><span class="p">[</span><span class="n">faraday_object_name</span><span class="p">]</span> | |
| 430 | <span class="n">appropiate_dictionary</span> <span class="o">=</span> <span class="n">appropiate_function</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 431 | <span class="n">faraday_ready_dictionaries</span> <span class="o">=</span> <span class="p">[]</span> | |
| 432 | <span class="k">if</span> <span class="n">appropiate_dictionary</span><span class="p">:</span> | |
| 433 | <span class="k">for</span> <span class="n">raw_dictionary</span> <span class="ow">in</span> <span class="n">appropiate_dictionary</span><span class="p">[</span><span class="n">faraday_object_row_name</span><span class="p">]:</span> | |
| 434 | <span class="k">if</span> <span class="ow">not</span> <span class="n">full_table</span><span class="p">:</span> | |
| 435 | <span class="n">faraday_ready_dictionaries</span><span class="o">.</span><span class="n">append</span><span class="p">(</span><span class="n">raw_dictionary</span><span class="p">[</span><span class="s1">'value'</span><span class="p">])</span> | |
| 436 | <span class="k">else</span><span class="p">:</span> | |
| 437 | <span class="n">faraday_ready_dictionaries</span><span class="o">.</span><span class="n">append</span><span class="p">(</span><span class="n">raw_dictionary</span><span class="p">)</span> | |
| 438 | <span class="k">return</span> <span class="n">faraday_ready_dictionaries</span> | |
| 439 | ||
| 440 | ||
| 441 | <div class="viewcode-block" id="get_hosts"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_hosts">[docs]</a><span class="k">def</span> <span class="nf">get_hosts</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 442 | <span class="sd">"""Get hosts from the server.</span> | |
| 443 | ||
| 444 | <span class="sd"> Args:</span> | |
| 445 | <span class="sd"> workspace_name (str): the workspace from which to get the hosts.</span> | |
| 446 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 447 | ||
| 448 | <span class="sd"> Returns:</span> | |
| 449 | <span class="sd"> A dictionary containing the hosts matching the query.</span> | |
| 450 | <span class="sd"> """</span> | |
| 451 | <span class="k">return</span> <span class="n">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'hosts'</span><span class="p">,</span> | |
| 452 | <span class="s1">'rows'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 453 | ||
| 454 | ||
| 455 | <div class="viewcode-block" id="get_all_vulns"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_all_vulns">[docs]</a><span class="k">def</span> <span class="nf">get_all_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 456 | <span class="sd">"""Get vulns, both normal and web, from the server.</span> | |
| 457 | ||
| 458 | <span class="sd"> Args:</span> | |
| 459 | <span class="sd"> workspace_name (str): the workspace from which to get the vulns.</span> | |
| 460 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 461 | ||
| 462 | <span class="sd"> Returns:</span> | |
| 463 | <span class="sd"> A dictionary containing the vulns matching the query.</span> | |
| 464 | <span class="sd"> """</span> | |
| 465 | <span class="k">return</span> <span class="n">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'vulns'</span><span class="p">,</span> | |
| 466 | <span class="s1">'vulnerabilities'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 467 | ||
| 468 | ||
| 469 | <div class="viewcode-block" id="get_vulns"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_vulns">[docs]</a><span class="k">def</span> <span class="nf">get_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 470 | <span class="sd">"""Get only normal vulns from the server.</span> | |
| 471 | ||
| 472 | <span class="sd"> Args:</span> | |
| 473 | <span class="sd"> workspace_name (str): the workspace from which to get the vulns.</span> | |
| 474 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 475 | ||
| 476 | <span class="sd"> Returns:</span> | |
| 477 | <span class="sd"> A dictionary containing the vulns matching the query.</span> | |
| 478 | <span class="sd"> """</span> | |
| 479 | <span class="k">return</span> <span class="n">get_all_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">type</span><span class="o">=</span><span class="s1">'Vulnerability'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 480 | ||
| 481 | ||
| 482 | <div class="viewcode-block" id="get_web_vulns"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_web_vulns">[docs]</a><span class="k">def</span> <span class="nf">get_web_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 483 | <span class="sd">"""Get only web vulns from the server.</span> | |
| 484 | ||
| 485 | <span class="sd"> Args:</span> | |
| 486 | <span class="sd"> workspace_name (str): the workspace from which to get the vulns.</span> | |
| 487 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 488 | ||
| 489 | <span class="sd"> Returns:</span> | |
| 490 | <span class="sd"> A dictionary containing the vulns matching the query.</span> | |
| 491 | <span class="sd"> """</span> | |
| 492 | <span class="k">return</span> <span class="n">get_all_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">type</span><span class="o">=</span><span class="s2">"VulnerabilityWeb"</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 493 | ||
| 494 | <div class="viewcode-block" id="get_interfaces"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_interfaces">[docs]</a><span class="k">def</span> <span class="nf">get_interfaces</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 495 | <span class="sd">"""Get interfaces from the server.</span> | |
| 496 | ||
| 497 | <span class="sd"> Args:</span> | |
| 498 | <span class="sd"> workspace_name (str): the workspace from which to get the interfaces.</span> | |
| 499 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 500 | ||
| 501 | <span class="sd"> Returns:</span> | |
| 502 | <span class="sd"> A dictionary containing the interfaces matching the query.</span> | |
| 503 | <span class="sd"> """</span> | |
| 504 | <span class="k">return</span> <span class="n">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'interfaces'</span><span class="p">,</span> | |
| 505 | <span class="s1">'interfaces'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 506 | ||
| 507 | <div class="viewcode-block" id="get_services"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_services">[docs]</a><span class="k">def</span> <span class="nf">get_services</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 508 | <span class="sd">"""Get services from the server.</span> | |
| 509 | ||
| 510 | <span class="sd"> Args:</span> | |
| 511 | <span class="sd"> workspace_name (str): the workspace from which to get the services.</span> | |
| 512 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 513 | ||
| 514 | <span class="sd"> Returns:</span> | |
| 515 | <span class="sd"> A dictionary containing the services matching the query.</span> | |
| 516 | <span class="sd"> """</span> | |
| 517 | <span class="k">return</span> <span class="n">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'services'</span><span class="p">,</span> | |
| 518 | <span class="s1">'services'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 519 | ||
| 520 | <div class="viewcode-block" id="get_credentials"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_credentials">[docs]</a><span class="k">def</span> <span class="nf">get_credentials</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 521 | <span class="sd">"""Get credentials from the server.</span> | |
| 522 | ||
| 523 | <span class="sd"> Args:</span> | |
| 524 | <span class="sd"> workspace_name (str): the workspace from which to get the credentials.</span> | |
| 525 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 526 | ||
| 527 | <span class="sd"> Returns:</span> | |
| 528 | <span class="sd"> A dictionary containing the credentials matching the query.</span> | |
| 529 | <span class="sd"> """</span> | |
| 530 | <span class="k">return</span> <span class="n">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'credentials'</span><span class="p">,</span> | |
| 531 | <span class="s1">'rows'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 532 | ||
| 533 | <div class="viewcode-block" id="get_notes"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_notes">[docs]</a><span class="k">def</span> <span class="nf">get_notes</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 534 | <span class="sd">"""Get notes from the server.</span> | |
| 535 | ||
| 536 | <span class="sd"> Args:</span> | |
| 537 | <span class="sd"> workspace_name (str): the workspace from which to get the notes.</span> | |
| 538 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 539 | ||
| 540 | <span class="sd"> Returns:</span> | |
| 541 | <span class="sd"> A dictionary containing the notes matching the query.</span> | |
| 542 | <span class="sd"> """</span> | |
| 543 | <span class="k">return</span> <span class="n">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'notes'</span><span class="p">,</span> | |
| 544 | <span class="s1">'rows'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 545 | ||
| 546 | <div class="viewcode-block" id="get_commands"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_commands">[docs]</a><span class="k">def</span> <span class="nf">get_commands</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 547 | <span class="sd">"""Get commands from the server.</span> | |
| 548 | ||
| 549 | <span class="sd"> Args:</span> | |
| 550 | <span class="sd"> workspace_name (str): the workspace from which to get the commands.</span> | |
| 551 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 552 | ||
| 553 | <span class="sd"> Returns:</span> | |
| 554 | <span class="sd"> A dictionary containing the commands matching the query.</span> | |
| 555 | <span class="sd"> """</span> | |
| 556 | <span class="k">return</span> <span class="n">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'commands'</span><span class="p">,</span> | |
| 557 | <span class="s1">'commands'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 558 | ||
| 559 | <div class="viewcode-block" id="get_objects"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_objects">[docs]</a><span class="k">def</span> <span class="nf">get_objects</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_signature</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 560 | <span class="sd">"""Get any type of object from the server, be it hosts, vulns, interfaces,</span> | |
| 561 | <span class="sd"> services, credentials, commands or notes.</span> | |
| 562 | ||
| 563 | <span class="sd"> Args:</span> | |
| 564 | <span class="sd"> workspace_name (str): the workspace from which to get the commands.</span> | |
| 565 | <span class="sd"> object_signature (str): the type of object to get. Must equal 'hosts',</span> | |
| 566 | <span class="sd"> 'vulns', 'interfaces', 'services', 'credentials', 'notes' or 'commands'</span> | |
| 567 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 568 | ||
| 569 | <span class="sd"> Returns:</span> | |
| 570 | <span class="sd"> A dictionary containing the commands matching the query.</span> | |
| 571 | ||
| 572 | <span class="sd"> Raises:</span> | |
| 573 | <span class="sd"> WrongObjectSignature: if the object_signature string didn't match</span> | |
| 574 | <span class="sd"> a faraday object.</span> | |
| 575 | <span class="sd"> """</span> | |
| 576 | <span class="n">object_to_func</span> <span class="o">=</span> <span class="p">{</span><span class="s1">'hosts'</span><span class="p">:</span> <span class="n">get_hosts</span><span class="p">,</span> | |
| 577 | <span class="s1">'vulns'</span><span class="p">:</span> <span class="n">get_vulns</span><span class="p">,</span> | |
| 578 | <span class="s1">'interfaces'</span><span class="p">:</span> <span class="n">get_interfaces</span><span class="p">,</span> | |
| 579 | <span class="s1">'services'</span><span class="p">:</span> <span class="n">get_services</span><span class="p">,</span> | |
| 580 | <span class="s1">'credentials'</span><span class="p">:</span> <span class="n">get_credentials</span><span class="p">,</span> | |
| 581 | <span class="s1">'notes'</span><span class="p">:</span> <span class="n">get_notes</span><span class="p">,</span> | |
| 582 | <span class="s1">'commands'</span><span class="p">:</span> <span class="n">get_commands</span><span class="p">}</span> | |
| 583 | <span class="k">try</span><span class="p">:</span> | |
| 584 | <span class="n">appropiate_function</span> <span class="o">=</span> <span class="n">object_to_func</span><span class="p">[</span><span class="n">object_signature</span><span class="p">]</span> | |
| 585 | <span class="k">except</span> <span class="ne">KeyError</span><span class="p">:</span> | |
| 586 | <span class="k">raise</span> <span class="n">WrongObjectSignature</span><span class="p">(</span><span class="n">object_signature</span><span class="p">)</span> | |
| 587 | ||
| 588 | <span class="k">return</span> <span class="n">appropiate_function</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 589 | ||
| 590 | <span class="c1"># cha cha cha chaaaanges!</span> | |
| 591 | <div class="viewcode-block" id="get_changes_stream"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_changes_stream">[docs]</a><span class="k">def</span> <span class="nf">get_changes_stream</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">since</span><span class="o">=</span><span class="mi">0</span><span class="p">,</span> <span class="n">heartbeat</span><span class="o">=</span><span class="s1">'1000'</span><span class="p">,</span> <span class="o">**</span><span class="n">extra_params</span><span class="p">):</span> | |
| 592 | <span class="k">return</span> <span class="n">_couch_changes</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">since</span><span class="o">=</span><span class="n">since</span><span class="p">,</span> <span class="n">feed</span><span class="o">=</span><span class="s1">'continuous'</span><span class="p">,</span> | |
| 593 | <span class="n">heartbeat</span><span class="o">=</span><span class="n">heartbeat</span><span class="p">,</span> <span class="o">**</span><span class="n">extra_params</span><span class="p">)</span></div> | |
| 594 | ||
| 595 | <div class="viewcode-block" id="get_workspaces_names"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_workspaces_names">[docs]</a><span class="k">def</span> <span class="nf">get_workspaces_names</span><span class="p">():</span> | |
| 596 | <span class="sd">"""Returns:</span> | |
| 597 | <span class="sd"> A dictionary with a list with the workspaces names."""</span> | |
| 598 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="s2">"</span><span class="si">{0}</span><span class="s2">/ws"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">_create_server_api_url</span><span class="p">()))</span></div> | |
| 599 | ||
| 600 | <span class="c1"># XXX: COUCH IT!</span> | |
| 601 | <span class="k">def</span> <span class="nf">_clean_up_stupid_couch_response</span><span class="p">(</span><span class="n">response_string</span><span class="p">):</span> | |
| 602 | <span class="sd">"""Couch likes to give invalid jsons as a response :). So nice."""</span> | |
| 603 | <span class="n">interesting_part</span> <span class="o">=</span> <span class="s2">"{"</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">response_string</span><span class="o">.</span><span class="n">split</span><span class="p">(</span><span class="s2">"{"</span><span class="p">)[</span><span class="mi">1</span><span class="p">:])</span> | |
| 604 | <span class="n">almost_there</span> <span class="o">=</span> <span class="n">interesting_part</span><span class="o">.</span><span class="n">split</span><span class="p">(</span><span class="s2">"}"</span><span class="p">)[</span><span class="mi">0</span><span class="p">:</span><span class="o">-</span><span class="mi">1</span><span class="p">]</span> | |
| 605 | <span class="n">ok_yeah</span> <span class="o">=</span> <span class="s2">"}"</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">almost_there</span><span class="p">)</span> | |
| 606 | <span class="n">hopefully_valid_json</span> <span class="o">=</span> <span class="s2">"{{</span><span class="si">{0}</span><span class="s2">}}"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">ok_yeah</span><span class="p">)</span> | |
| 607 | <span class="k">return</span> <span class="n">json</span><span class="o">.</span><span class="n">loads</span><span class="p">(</span><span class="n">hopefully_valid_json</span><span class="p">)</span> | |
| 608 | ||
| 609 | <span class="c1"># XXX: COUCH IT!</span> | |
| 610 | <span class="c1"># COUCH IT LEVEL: REVOLUTIONS</span> | |
| 611 | <div class="viewcode-block" id="get_object_before_last_revision"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_object_before_last_revision">[docs]</a><span class="k">def</span> <span class="nf">get_object_before_last_revision</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">):</span> | |
| 612 | <span class="sd">"""Get an object before its last revision. Useful to get information about</span> | |
| 613 | <span class="sd"> recently deleted objects.</span> | |
| 614 | ||
| 615 | <span class="sd"> Warning:</span> | |
| 616 | <span class="sd"> Error-pronce process. You should check for 'None' after usage,</span> | |
| 617 | <span class="sd"> as that's the return value if any problem arose during execution.</span> | |
| 618 | ||
| 619 | <span class="sd"> Args:</span> | |
| 620 | <span class="sd"> workspace_name (str): the workspace where the object was</span> | |
| 621 | <span class="sd"> object_id (str): the id of the object</span> | |
| 622 | ||
| 623 | <span class="sd"> Returns:</span> | |
| 624 | <span class="sd"> A dictionary with the object's information.</span> | |
| 625 | <span class="sd"> """</span> | |
| 626 | <span class="n">get_url</span> <span class="o">=</span> <span class="n">_create_couch_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">)</span> | |
| 627 | <span class="n">response</span> <span class="o">=</span> <span class="n">_unsafe_io_with_server</span><span class="p">(</span><span class="n">requests</span><span class="o">.</span><span class="n">get</span><span class="p">,</span> <span class="mi">200</span><span class="p">,</span> <span class="n">get_url</span><span class="p">,</span> | |
| 628 | <span class="n">params</span><span class="o">=</span><span class="p">{</span><span class="s1">'revs'</span><span class="p">:</span> <span class="s1">'true'</span><span class="p">,</span> <span class="s1">'open_revs'</span><span class="p">:</span> <span class="s1">'all'</span><span class="p">})</span> | |
| 629 | <span class="k">try</span><span class="p">:</span> | |
| 630 | <span class="n">valid_json_response</span> <span class="o">=</span> <span class="n">_clean_up_stupid_couch_response</span><span class="p">(</span><span class="n">response</span><span class="o">.</span><span class="n">text</span><span class="p">)</span> | |
| 631 | <span class="k">except</span> <span class="ne">ValueError</span><span class="p">:</span> | |
| 632 | <span class="k">return</span> <span class="kc">None</span> | |
| 633 | <span class="k">try</span><span class="p">:</span> | |
| 634 | <span class="n">id_before_del</span> <span class="o">=</span> <span class="n">valid_json_response</span><span class="p">[</span><span class="s1">'_revisions'</span><span class="p">][</span><span class="s1">'ids'</span><span class="p">][</span><span class="mi">1</span><span class="p">]</span> | |
| 635 | <span class="n">new_number_for_rev</span> <span class="o">=</span> <span class="n">valid_json_response</span><span class="p">[</span><span class="s1">'_revisions'</span><span class="p">][</span><span class="s1">'start'</span><span class="p">]</span> <span class="o">-</span> <span class="mi">1</span> | |
| 636 | <span class="k">except</span> <span class="ne">KeyError</span><span class="p">:</span> <span class="c1"># one if never too safe when you call a function called "_clean_up_stupid_couch_response"</span> | |
| 637 | <span class="k">return</span> <span class="kc">None</span> | |
| 638 | ||
| 639 | <span class="n">rev_id_before_del</span> <span class="o">=</span> <span class="s2">"</span><span class="si">{0}</span><span class="s2">-</span><span class="si">{1}</span><span class="s2">"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">new_number_for_rev</span><span class="p">,</span> <span class="n">id_before_del</span><span class="p">)</span> | |
| 640 | <span class="n">object_dict</span> <span class="o">=</span> <span class="n">_get</span><span class="p">(</span><span class="n">get_url</span><span class="p">,</span> <span class="n">rev</span><span class="o">=</span><span class="n">rev_id_before_del</span><span class="p">)</span> | |
| 641 | <span class="k">return</span> <span class="n">object_dict</span></div> | |
| 642 | ||
| 643 | ||
| 644 | <div class="viewcode-block" id="get_object"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_object">[docs]</a><span class="k">def</span> <span class="nf">get_object</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_signature</span><span class="p">,</span> <span class="n">object_id</span><span class="p">):</span> | |
| 645 | <span class="sd">"""Get an unique object of arbitrary type.</span> | |
| 646 | ||
| 647 | <span class="sd"> Args:</span> | |
| 648 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 649 | <span class="sd"> object_signature (str): must be either 'hosts', 'vulns', 'interfaces'</span> | |
| 650 | <span class="sd"> 'services', 'credentials', 'notes' or 'commands'.</span> | |
| 651 | <span class="sd"> object_id (str): the id of the object</span> | |
| 652 | ||
| 653 | <span class="sd"> Returns:</span> | |
| 654 | <span class="sd"> A dictionary containing information about the object.</span> | |
| 655 | ||
| 656 | <span class="sd"> Raises:</span> | |
| 657 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the object_id is shared</span> | |
| 658 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 659 | <span class="sd"> contact Infobyte LCC.</span> | |
| 660 | <span class="sd"> """</span> | |
| 661 | <span class="n">objects</span> <span class="o">=</span> <span class="n">get_objects</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_signature</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">object_id</span><span class="p">)</span> | |
| 662 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">objects</span><span class="p">)</span></div> | |
| 663 | ||
| 664 | <div class="viewcode-block" id="get_host"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_host">[docs]</a><span class="k">def</span> <span class="nf">get_host</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">host_id</span><span class="p">):</span> | |
| 665 | <span class="sd">"""Get an unique host.</span> | |
| 666 | ||
| 667 | <span class="sd"> Args:</span> | |
| 668 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 669 | <span class="sd"> host_id (str): the id of the host</span> | |
| 670 | ||
| 671 | <span class="sd"> Returns:</span> | |
| 672 | <span class="sd"> A dictionary containing information about the host.</span> | |
| 673 | ||
| 674 | <span class="sd"> Raises:</span> | |
| 675 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the host id is shared</span> | |
| 676 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 677 | <span class="sd"> contact Infobyte LCC.</span> | |
| 678 | <span class="sd"> """</span> | |
| 679 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_hosts</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">host_id</span><span class="p">))</span></div> | |
| 680 | ||
| 681 | <div class="viewcode-block" id="get_vuln"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_vuln">[docs]</a><span class="k">def</span> <span class="nf">get_vuln</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">vuln_id</span><span class="p">):</span> | |
| 682 | <span class="sd">"""Get an unique vuln.</span> | |
| 683 | ||
| 684 | <span class="sd"> Args:</span> | |
| 685 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 686 | <span class="sd"> vuln_id (str): the id of the vuln</span> | |
| 687 | ||
| 688 | <span class="sd"> Returns:</span> | |
| 689 | <span class="sd"> A dictionary containing information about the vuln.</span> | |
| 690 | ||
| 691 | <span class="sd"> Raises:</span> | |
| 692 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the vuln id is shared</span> | |
| 693 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 694 | <span class="sd"> contact Infobyte LCC.</span> | |
| 695 | <span class="sd"> """</span> | |
| 696 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">vuln_id</span><span class="p">))</span></div> | |
| 697 | ||
| 698 | <div class="viewcode-block" id="get_web_vuln"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_web_vuln">[docs]</a><span class="k">def</span> <span class="nf">get_web_vuln</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">vuln_id</span><span class="p">):</span> | |
| 699 | <span class="sd">"""Get an unique web vuln.</span> | |
| 700 | ||
| 701 | <span class="sd"> Args:</span> | |
| 702 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 703 | <span class="sd"> web vuln_id (str): the id of the web vuln</span> | |
| 704 | ||
| 705 | <span class="sd"> Returns:</span> | |
| 706 | <span class="sd"> A dictionary containing information about the web vuln.</span> | |
| 707 | ||
| 708 | <span class="sd"> Raises:</span> | |
| 709 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the web vuln id is shared</span> | |
| 710 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 711 | <span class="sd"> contact Infobyte LCC.</span> | |
| 712 | <span class="sd"> """</span> | |
| 713 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_web_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">vuln_id</span><span class="p">))</span></div> | |
| 714 | ||
| 715 | <div class="viewcode-block" id="get_interface"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_interface">[docs]</a><span class="k">def</span> <span class="nf">get_interface</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">interface_id</span><span class="p">):</span> | |
| 716 | <span class="sd">"""Get an unique interface.</span> | |
| 717 | ||
| 718 | <span class="sd"> Args:</span> | |
| 719 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 720 | <span class="sd"> interface_id (str): the id of the interface</span> | |
| 721 | ||
| 722 | <span class="sd"> Returns:</span> | |
| 723 | <span class="sd"> A dictionary containing information about the interface.</span> | |
| 724 | ||
| 725 | <span class="sd"> Raises:</span> | |
| 726 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the interface id is shared</span> | |
| 727 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 728 | <span class="sd"> contact Infobyte LCC.</span> | |
| 729 | <span class="sd"> """</span> | |
| 730 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_interfaces</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">interface_id</span><span class="p">))</span></div> | |
| 731 | ||
| 732 | <div class="viewcode-block" id="get_service"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_service">[docs]</a><span class="k">def</span> <span class="nf">get_service</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">service_id</span><span class="p">):</span> | |
| 733 | <span class="sd">"""Get an unique service.</span> | |
| 734 | ||
| 735 | <span class="sd"> Args:</span> | |
| 736 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 737 | <span class="sd"> service_id (str): the id of the service</span> | |
| 738 | ||
| 739 | <span class="sd"> Returns:</span> | |
| 740 | <span class="sd"> A dictionary containing information about the service.</span> | |
| 741 | ||
| 742 | <span class="sd"> Raises:</span> | |
| 743 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the service id is shared</span> | |
| 744 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 745 | <span class="sd"> contact Infobyte LCC.</span> | |
| 746 | <span class="sd"> """</span> | |
| 747 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_services</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">service_id</span><span class="p">))</span></div> | |
| 748 | ||
| 749 | <div class="viewcode-block" id="get_note"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_note">[docs]</a><span class="k">def</span> <span class="nf">get_note</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">note_id</span><span class="p">):</span> | |
| 750 | <span class="sd">"""Get an unique note.</span> | |
| 751 | ||
| 752 | <span class="sd"> Args:</span> | |
| 753 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 754 | <span class="sd"> note_id (str): the id of the note</span> | |
| 755 | ||
| 756 | <span class="sd"> Returns:</span> | |
| 757 | <span class="sd"> A dictionary containing information about the note.</span> | |
| 758 | ||
| 759 | <span class="sd"> Raises:</span> | |
| 760 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the note id is shared</span> | |
| 761 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 762 | <span class="sd"> contact Infobyte LCC.</span> | |
| 763 | <span class="sd"> """</span> | |
| 764 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_notes</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">note_id</span><span class="p">))</span></div> | |
| 765 | ||
| 766 | <div class="viewcode-block" id="get_credential"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_credential">[docs]</a><span class="k">def</span> <span class="nf">get_credential</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">credential_id</span><span class="p">):</span> | |
| 767 | <span class="sd">"""Get an unique credential.</span> | |
| 768 | ||
| 769 | <span class="sd"> Args:</span> | |
| 770 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 771 | <span class="sd"> credential_id (str): the id of the credential</span> | |
| 772 | ||
| 773 | <span class="sd"> Returns:</span> | |
| 774 | <span class="sd"> A dictionary containing information about the credential.</span> | |
| 775 | ||
| 776 | <span class="sd"> Raises:</span> | |
| 777 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the credential id is shared</span> | |
| 778 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 779 | <span class="sd"> contact Infobyte LCC.</span> | |
| 780 | <span class="sd"> """</span> | |
| 781 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_services</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">credential_id</span><span class="p">))</span></div> | |
| 782 | ||
| 783 | <div class="viewcode-block" id="get_command"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_command">[docs]</a><span class="k">def</span> <span class="nf">get_command</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">command_id</span><span class="p">):</span> | |
| 784 | <span class="sd">"""Get an unique command.</span> | |
| 785 | ||
| 786 | <span class="sd"> Args:</span> | |
| 787 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 788 | <span class="sd"> command_id (str): the id of the command</span> | |
| 789 | ||
| 790 | <span class="sd"> Returns:</span> | |
| 791 | <span class="sd"> A dictionary containing information about the command.</span> | |
| 792 | ||
| 793 | <span class="sd"> Raises:</span> | |
| 794 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the command id is shared</span> | |
| 795 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 796 | <span class="sd"> contact Infobyte LCC.</span> | |
| 797 | <span class="sd"> """</span> | |
| 798 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_commands</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">command_id</span><span class="p">))</span></div> | |
| 799 | ||
| 800 | <div class="viewcode-block" id="get_workspace"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_workspace">[docs]</a><span class="k">def</span> <span class="nf">get_workspace</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 801 | <span class="sd">"""Get an unique command.</span> | |
| 802 | ||
| 803 | <span class="sd"> Args:</span> | |
| 804 | <span class="sd"> command_name (str): the command where the object should be found.</span> | |
| 805 | <span class="sd"> command_id (str): the id of the command</span> | |
| 806 | ||
| 807 | <span class="sd"> Returns:</span> | |
| 808 | <span class="sd"> A dictionary containing information about the command.</span> | |
| 809 | ||
| 810 | <span class="sd"> Raises:</span> | |
| 811 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the command id is shared</span> | |
| 812 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 813 | <span class="sd"> contact Infobyte LCC.</span> | |
| 814 | <span class="sd"> """</span> | |
| 815 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)</span> | |
| 816 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 817 | ||
| 818 | <div class="viewcode-block" id="get_workspace_summary"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_workspace_summary">[docs]</a><span class="k">def</span> <span class="nf">get_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">):</span> | |
| 819 | <span class="sd">"""Get a collection of data about the workspace.</span> | |
| 820 | ||
| 821 | <span class="sd"> Args:</span> | |
| 822 | <span class="sd"> workspace_name (str): the workspace to get the stats from.</span> | |
| 823 | ||
| 824 | <span class="sd"> Returns:</span> | |
| 825 | <span class="sd"> A dictionary with the workspace's information</span> | |
| 826 | <span class="sd"> """</span> | |
| 827 | <span class="k">return</span> <span class="n">_get_raw_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)[</span><span class="s1">'stats'</span><span class="p">]</span></div> | |
| 828 | ||
| 829 | <div class="viewcode-block" id="get_workspace_numbers"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_workspace_numbers">[docs]</a><span class="k">def</span> <span class="nf">get_workspace_numbers</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">):</span> | |
| 830 | <span class="sd">"""Get the number of hosts, interfaces, services and vulns in the workspace.</span> | |
| 831 | ||
| 832 | <span class="sd"> Args:</span> | |
| 833 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 834 | ||
| 835 | <span class="sd"> Return:</span> | |
| 836 | <span class="sd"> A tuple of 4 elements with the amounts of hosts, interfaces, services and vulns.</span> | |
| 837 | <span class="sd"> """</span> | |
| 838 | <span class="n">stats</span> <span class="o">=</span> <span class="n">_get_raw_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)[</span><span class="s1">'stats'</span><span class="p">]</span> | |
| 839 | <span class="k">return</span> <span class="n">stats</span><span class="p">[</span><span class="s1">'hosts'</span><span class="p">],</span> <span class="n">stats</span><span class="p">[</span><span class="s1">'interfaces'</span><span class="p">],</span> <span class="n">stats</span><span class="p">[</span><span class="s1">'services'</span><span class="p">],</span> <span class="n">stats</span><span class="p">[</span><span class="s1">'total_vulns'</span><span class="p">]</span></div> | |
| 840 | ||
| 841 | <div class="viewcode-block" id="get_hosts_number"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_hosts_number">[docs]</a><span class="k">def</span> <span class="nf">get_hosts_number</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 842 | <span class="sd">"""</span> | |
| 843 | <span class="sd"> Args:</span> | |
| 844 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 845 | <span class="sd"> **params: any of the Couchdb request parameters</span> | |
| 846 | ||
| 847 | <span class="sd"> Returns:</span> | |
| 848 | <span class="sd"> The amount of hosts in the workspace as an integer.</span> | |
| 849 | <span class="sd"> """</span> | |
| 850 | <span class="k">return</span> <span class="nb">int</span><span class="p">(</span><span class="n">get_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)[</span><span class="s1">'hosts'</span><span class="p">])</span></div> | |
| 851 | ||
| 852 | <div class="viewcode-block" id="get_services_number"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_services_number">[docs]</a><span class="k">def</span> <span class="nf">get_services_number</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 853 | <span class="sd">"""</span> | |
| 854 | <span class="sd"> Args:</span> | |
| 855 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 856 | <span class="sd"> **params: any of the Couchdb request parameters</span> | |
| 857 | ||
| 858 | <span class="sd"> Returns:</span> | |
| 859 | <span class="sd"> The amount of services in the workspace as an integer.</span> | |
| 860 | <span class="sd"> """</span> | |
| 861 | <span class="k">return</span> <span class="nb">int</span><span class="p">(</span><span class="n">get_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)[</span><span class="s1">'interfaces'</span><span class="p">])</span></div> | |
| 862 | ||
| 863 | <div class="viewcode-block" id="get_interfaces_number"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_interfaces_number">[docs]</a><span class="k">def</span> <span class="nf">get_interfaces_number</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 864 | <span class="sd">"""</span> | |
| 865 | <span class="sd"> Args:</span> | |
| 866 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 867 | <span class="sd"> **params: any of the Couchdb request parameters</span> | |
| 868 | ||
| 869 | <span class="sd"> Returns:</span> | |
| 870 | <span class="sd"> The amount of interfaces in the workspace as an integer.</span> | |
| 871 | <span class="sd"> """</span> | |
| 872 | <span class="k">return</span> <span class="nb">int</span><span class="p">(</span><span class="n">get_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)[</span><span class="s1">'interfaces'</span><span class="p">])</span></div> | |
| 873 | ||
| 874 | <div class="viewcode-block" id="get_vulns_number"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_vulns_number">[docs]</a><span class="k">def</span> <span class="nf">get_vulns_number</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 875 | <span class="sd">"""</span> | |
| 876 | <span class="sd"> Args:</span> | |
| 877 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 878 | <span class="sd"> **params: any of the Couchdb request parameters</span> | |
| 879 | ||
| 880 | <span class="sd"> Returns:</span> | |
| 881 | <span class="sd"> The amount of vulns in the workspace as an integer.</span> | |
| 882 | <span class="sd"> """</span> | |
| 883 | <span class="k">return</span> <span class="nb">int</span><span class="p">(</span><span class="n">get_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)[</span><span class="s1">'total_vulns'</span><span class="p">])</span></div> | |
| 884 | ||
| 885 | <div class="viewcode-block" id="get_notes_number"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_notes_number">[docs]</a><span class="k">def</span> <span class="nf">get_notes_number</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 886 | <span class="sd">"""</span> | |
| 887 | <span class="sd"> Args:</span> | |
| 888 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 889 | <span class="sd"> **params: any of the Couchdb request parameters</span> | |
| 890 | ||
| 891 | <span class="sd"> Returns:</span> | |
| 892 | <span class="sd"> The amount of notes in the workspace as an integer.</span> | |
| 893 | <span class="sd"> """</span> | |
| 894 | <span class="k">return</span> <span class="nb">int</span><span class="p">(</span><span class="n">get_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)[</span><span class="s1">'notes'</span><span class="p">])</span></div> | |
| 895 | ||
| 896 | <div class="viewcode-block" id="get_credentials_number"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_credentials_number">[docs]</a><span class="k">def</span> <span class="nf">get_credentials_number</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 897 | <span class="sd">"""</span> | |
| 898 | <span class="sd"> Args:</span> | |
| 899 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 900 | <span class="sd"> **params: any of the Couchdb request parameters</span> | |
| 901 | ||
| 902 | <span class="sd"> Returns:</span> | |
| 903 | <span class="sd"> The amount of credentials in the workspace as an integer.</span> | |
| 904 | <span class="sd"> """</span> | |
| 905 | <span class="k">return</span> <span class="nb">int</span><span class="p">(</span><span class="n">_get_raw_credentials</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">))</span></div> | |
| 906 | ||
| 907 | <div class="viewcode-block" id="get_commands_number"><a class="viewcode-back" href="../../../server.html#persistence.server.server.get_commands_number">[docs]</a><span class="k">def</span> <span class="nf">get_commands_number</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 908 | <span class="sd">"""</span> | |
| 909 | <span class="sd"> Args:</span> | |
| 910 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 911 | <span class="sd"> **params: any of the Couchdb request parameters</span> | |
| 912 | ||
| 913 | <span class="sd"> Returns:</span> | |
| 914 | <span class="sd"> The amount of commands in the workspace as an integer.</span> | |
| 915 | <span class="sd"> """</span> | |
| 916 | <span class="k">return</span> <span class="nb">int</span><span class="p">(</span><span class="n">_get_raw_commands</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">))</span></div> | |
| 917 | ||
| 918 | <div class="viewcode-block" id="create_host"><a class="viewcode-back" href="../../../server.html#persistence.server.server.create_host">[docs]</a><span class="k">def</span> <span class="nf">create_host</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">os</span><span class="p">,</span> <span class="n">default_gateway</span><span class="p">,</span> | |
| 919 | <span class="n">description</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 920 | <span class="n">parent</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 921 | <span class="sd">"""Create a host.</span> | |
| 922 | ||
| 923 | <span class="sd"> Args:</span> | |
| 924 | <span class="sd"> workspace_name (str): the name of the workspace where the host will be saved.</span> | |
| 925 | <span class="sd"> id (str): the id of the host. Must be unique.</span> | |
| 926 | <span class="sd"> name (str): the host's name</span> | |
| 927 | <span class="sd"> os (str): the operative system of the host</span> | |
| 928 | <span class="sd"> default_gateway (str): the host's default_gateway</span> | |
| 929 | <span class="sd"> description (str): a description.</span> | |
| 930 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 931 | <span class="sd"> on None.</span> | |
| 932 | <span class="sd"> owned (bool): is the host owned or not?</span> | |
| 933 | <span class="sd"> owner (str): an owner for the host</span> | |
| 934 | <span class="sd"> parent (Faraday Object): the host's parent. If you don't know this, leave</span> | |
| 935 | <span class="sd"> on None.</span> | |
| 936 | ||
| 937 | <span class="sd"> Returns:</span> | |
| 938 | <span class="sd"> A dictionary with the server's response.</span> | |
| 939 | <span class="sd"> """</span> | |
| 940 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 941 | <span class="nb">id</span><span class="p">,</span> | |
| 942 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> <span class="n">os</span><span class="o">=</span><span class="n">os</span><span class="p">,</span> | |
| 943 | <span class="n">default_gateway</span><span class="o">=</span><span class="n">default_gateway</span><span class="p">,</span> | |
| 944 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 945 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">,</span> | |
| 946 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 947 | <span class="n">parent</span><span class="o">=</span><span class="n">parent</span><span class="p">,</span> | |
| 948 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 949 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Host"</span><span class="p">)</span></div> | |
| 950 | ||
| 951 | <div class="viewcode-block" id="update_host"><a class="viewcode-back" href="../../../server.html#persistence.server.server.update_host">[docs]</a><span class="k">def</span> <span class="nf">update_host</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">os</span><span class="p">,</span> <span class="n">default_gateway</span><span class="p">,</span> | |
| 952 | <span class="n">description</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 953 | <span class="n">parent</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 954 | <span class="sd">"""Updates a host.</span> | |
| 955 | ||
| 956 | <span class="sd"> Args:</span> | |
| 957 | <span class="sd"> workspace_name (str): the name of the workspace where the host will be saved.</span> | |
| 958 | <span class="sd"> id (str): the id of the host. Must be unique.</span> | |
| 959 | <span class="sd"> name (str): the host's name</span> | |
| 960 | <span class="sd"> os (str): the operative system of the host</span> | |
| 961 | <span class="sd"> default_gateway (str): the host's default_gateway</span> | |
| 962 | <span class="sd"> description (str): a description.</span> | |
| 963 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 964 | <span class="sd"> on None, it will be created automatically.</span> | |
| 965 | <span class="sd"> owned (bool): is the host owned or not?</span> | |
| 966 | <span class="sd"> owner (str): an owner for the host</span> | |
| 967 | <span class="sd"> parent (Faraday Object): the host's parent. If you don't know this, leave</span> | |
| 968 | <span class="sd"> on None.</span> | |
| 969 | ||
| 970 | <span class="sd"> Returns:</span> | |
| 971 | <span class="sd"> A dictionary with the server's response.</span> | |
| 972 | <span class="sd"> """</span> | |
| 973 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 974 | <span class="nb">id</span><span class="p">,</span> | |
| 975 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> <span class="n">os</span><span class="o">=</span><span class="n">os</span><span class="p">,</span> | |
| 976 | <span class="n">default_gateway</span><span class="o">=</span><span class="n">default_gateway</span><span class="p">,</span> | |
| 977 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 978 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">,</span> | |
| 979 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 980 | <span class="n">parent</span><span class="o">=</span><span class="n">parent</span><span class="p">,</span> | |
| 981 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 982 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Host"</span><span class="p">)</span></div> | |
| 983 | ||
| 984 | ||
| 985 | <span class="c1"># TODO: FIX. If you actually pass ipv4 or ipv6 as None, which are the defaults</span> | |
| 986 | <span class="c1"># values here, the server will complain. Review if this should be fixed on</span> | |
| 987 | <span class="c1"># the client or on the server.</span> | |
| 988 | <div class="viewcode-block" id="create_interface"><a class="viewcode-back" href="../../../server.html#persistence.server.server.create_interface">[docs]</a><span class="k">def</span> <span class="nf">create_interface</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">mac</span><span class="p">,</span> | |
| 989 | <span class="n">owned</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">hostnames</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">network_segment</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 990 | <span class="n">ipv4</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">ipv6</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 991 | <span class="sd">"""Creates an interface.</span> | |
| 992 | ||
| 993 | <span class="sd"> Warning:</span> | |
| 994 | <span class="sd"> DO NOT leave ipv4 and ipv6 values on None, as the default indicated.</span> | |
| 995 | <span class="sd"> This is a known bug and we're working to fix it. ipv4 and ipv6 need to</span> | |
| 996 | <span class="sd"> be valid IP addresses, or, in case one of them is irrelevant, empty strings.</span> | |
| 997 | ||
| 998 | <span class="sd"> Args:</span> | |
| 999 | <span class="sd"> workspace_name (str): the name of the workspace where the interface will be saved.</span> | |
| 1000 | <span class="sd"> id (str): the id of the interface. Must be unique.</span> | |
| 1001 | <span class="sd"> name (str): the interface's name</span> | |
| 1002 | <span class="sd"> description (str): a description.</span> | |
| 1003 | <span class="sd"> mac (str) the mac address of the interface</span> | |
| 1004 | <span class="sd"> owned (bool): is the host owned or not?</span> | |
| 1005 | <span class="sd"> owner (str): an owner for the host</span> | |
| 1006 | <span class="sd"> hostnames ([str]): a list of hostnames</span> | |
| 1007 | <span class="sd"> network_segment (str): the network segment</span> | |
| 1008 | <span class="sd"> ipv4 (str): the ipv4 direction of the interface.</span> | |
| 1009 | <span class="sd"> ipv6 (str): the ipv6 direction of the interface.</span> | |
| 1010 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1011 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1012 | ||
| 1013 | <span class="sd"> Returns:</span> | |
| 1014 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1015 | <span class="sd"> """</span> | |
| 1016 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1017 | <span class="nb">id</span><span class="p">,</span> | |
| 1018 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1019 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1020 | <span class="n">mac</span><span class="o">=</span><span class="n">mac</span><span class="p">,</span> | |
| 1021 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1022 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1023 | <span class="n">hostnames</span><span class="o">=</span><span class="n">hostnames</span><span class="p">,</span> | |
| 1024 | <span class="n">network_segment</span><span class="o">=</span><span class="n">network_segment</span><span class="p">,</span> | |
| 1025 | <span class="n">ipv4</span><span class="o">=</span><span class="n">ipv4</span><span class="p">,</span> | |
| 1026 | <span class="n">ipv6</span><span class="o">=</span><span class="n">ipv6</span><span class="p">,</span> | |
| 1027 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Interface"</span><span class="p">,</span> | |
| 1028 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1029 | ||
| 1030 | <div class="viewcode-block" id="update_interface"><a class="viewcode-back" href="../../../server.html#persistence.server.server.update_interface">[docs]</a><span class="k">def</span> <span class="nf">update_interface</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">mac</span><span class="p">,</span> | |
| 1031 | <span class="n">owned</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">hostnames</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">network_segment</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1032 | <span class="n">ipv4</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">ipv6</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1033 | <span class="sd">"""Creates an interface.</span> | |
| 1034 | ||
| 1035 | <span class="sd"> Warning:</span> | |
| 1036 | <span class="sd"> DO NOT leave ipv4 and ipv6 values on None, as the default indicated.</span> | |
| 1037 | <span class="sd"> This is a known bug and we're working to fix it. ipv4 and ipv6 need to</span> | |
| 1038 | <span class="sd"> be valid IP addresses, or, in case one of them is irrelevant, empty strings.</span> | |
| 1039 | ||
| 1040 | <span class="sd"> Args:</span> | |
| 1041 | <span class="sd"> workspace_name (str): the name of the workspace where the interface will be saved.</span> | |
| 1042 | <span class="sd"> id (str): the id of the interface. Must be unique.</span> | |
| 1043 | <span class="sd"> name (str): the interface's name</span> | |
| 1044 | <span class="sd"> description (str): a description.</span> | |
| 1045 | <span class="sd"> mac (str) the mac address of the interface</span> | |
| 1046 | <span class="sd"> owned (bool): is the host owned or not?</span> | |
| 1047 | <span class="sd"> owner (str): an owner for the host</span> | |
| 1048 | <span class="sd"> hostnames ([str]): a list of hostnames</span> | |
| 1049 | <span class="sd"> network_segment (str): the network segment</span> | |
| 1050 | <span class="sd"> ipv4 (str): the ipv4 direction of the interface.</span> | |
| 1051 | <span class="sd"> ipv6 (str): the ipv6 direction of the interface.</span> | |
| 1052 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1053 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1054 | ||
| 1055 | <span class="sd"> Returns:</span> | |
| 1056 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1057 | <span class="sd"> """</span> | |
| 1058 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1059 | <span class="nb">id</span><span class="p">,</span> | |
| 1060 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1061 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1062 | <span class="n">mac</span><span class="o">=</span><span class="n">mac</span><span class="p">,</span> | |
| 1063 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1064 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1065 | <span class="n">hostnames</span><span class="o">=</span><span class="n">hostnames</span><span class="p">,</span> | |
| 1066 | <span class="n">network_segment</span><span class="o">=</span><span class="n">network_segment</span><span class="p">,</span> | |
| 1067 | <span class="n">ipv4</span><span class="o">=</span><span class="n">ipv4</span><span class="p">,</span> | |
| 1068 | <span class="n">ipv6</span><span class="o">=</span><span class="n">ipv6</span><span class="p">,</span> | |
| 1069 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Interface"</span><span class="p">,</span> | |
| 1070 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1071 | ||
| 1072 | <div class="viewcode-block" id="create_service"><a class="viewcode-back" href="../../../server.html#persistence.server.server.create_service">[docs]</a><span class="k">def</span> <span class="nf">create_service</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">ports</span><span class="p">,</span> | |
| 1073 | <span class="n">owned</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">protocol</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">status</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">version</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1074 | <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1075 | <span class="sd">"""Creates a service.</span> | |
| 1076 | ||
| 1077 | <span class="sd"> Args:</span> | |
| 1078 | <span class="sd"> workspace_name (str): the name of the workspace where the service will be saved.</span> | |
| 1079 | <span class="sd"> id (str): the id of the service. Must be unique.</span> | |
| 1080 | <span class="sd"> name (str): the host's name</span> | |
| 1081 | <span class="sd"> description (str): a description.</span> | |
| 1082 | <span class="sd"> ports ([str]): a list of ports for the service.</span> | |
| 1083 | <span class="sd"> owned (bool): is the service owned or not?</span> | |
| 1084 | <span class="sd"> owner (str): an owner for the service</span> | |
| 1085 | <span class="sd"> protocol (str): the service's protocol</span> | |
| 1086 | <span class="sd"> status (str): the service's status</span> | |
| 1087 | <span class="sd"> version (str): the service's version</span> | |
| 1088 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1089 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1090 | ||
| 1091 | <span class="sd"> Returns:</span> | |
| 1092 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1093 | <span class="sd"> """</span> | |
| 1094 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1095 | <span class="nb">id</span><span class="p">,</span> | |
| 1096 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1097 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1098 | <span class="n">ports</span><span class="o">=</span><span class="n">ports</span><span class="p">,</span> | |
| 1099 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1100 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1101 | <span class="n">protocol</span><span class="o">=</span><span class="n">protocol</span><span class="p">,</span> | |
| 1102 | <span class="n">status</span><span class="o">=</span><span class="n">status</span><span class="p">,</span> | |
| 1103 | <span class="n">version</span><span class="o">=</span><span class="n">version</span><span class="p">,</span> | |
| 1104 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Service"</span><span class="p">,</span> | |
| 1105 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1106 | ||
| 1107 | <div class="viewcode-block" id="update_service"><a class="viewcode-back" href="../../../server.html#persistence.server.server.update_service">[docs]</a><span class="k">def</span> <span class="nf">update_service</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">ports</span><span class="p">,</span> | |
| 1108 | <span class="n">owned</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">protocol</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">status</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">version</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1109 | <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1110 | <span class="sd">"""Creates a service.</span> | |
| 1111 | ||
| 1112 | <span class="sd"> Args:</span> | |
| 1113 | <span class="sd"> workspace_name (str): the name of the workspace where the service will be saved.</span> | |
| 1114 | <span class="sd"> id (str): the id of the service. Must be unique.</span> | |
| 1115 | <span class="sd"> name (str): the service's name</span> | |
| 1116 | <span class="sd"> description (str): a description.</span> | |
| 1117 | <span class="sd"> ports ([str]): a list of ports for the service.</span> | |
| 1118 | <span class="sd"> owned (bool): is the host owned or not?</span> | |
| 1119 | <span class="sd"> owner (str): an owner for the service</span> | |
| 1120 | <span class="sd"> protocol (str): the service's protocol</span> | |
| 1121 | <span class="sd"> status (str): the service's status</span> | |
| 1122 | <span class="sd"> version (str): the service's version</span> | |
| 1123 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1124 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1125 | ||
| 1126 | <span class="sd"> Returns:</span> | |
| 1127 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1128 | <span class="sd"> """</span> | |
| 1129 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1130 | <span class="nb">id</span><span class="p">,</span> | |
| 1131 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1132 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1133 | <span class="n">ports</span><span class="o">=</span><span class="n">ports</span><span class="p">,</span> | |
| 1134 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1135 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1136 | <span class="n">protocol</span><span class="o">=</span><span class="n">protocol</span><span class="p">,</span> | |
| 1137 | <span class="n">status</span><span class="o">=</span><span class="n">status</span><span class="p">,</span> | |
| 1138 | <span class="n">version</span><span class="o">=</span><span class="n">version</span><span class="p">,</span> | |
| 1139 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Service"</span><span class="p">,</span> | |
| 1140 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1141 | ||
| 1142 | ||
| 1143 | <div class="viewcode-block" id="create_vuln"><a class="viewcode-back" href="../../../server.html#persistence.server.server.create_vuln">[docs]</a><span class="k">def</span> <span class="nf">create_vuln</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1144 | <span class="n">confirmed</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">data</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">refs</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">severity</span><span class="o">=</span><span class="s2">"info"</span><span class="p">,</span> <span class="n">resolution</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1145 | <span class="n">desc</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">status</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1146 | <span class="sd">"""Creates a vuln.</span> | |
| 1147 | ||
| 1148 | <span class="sd"> Args:</span> | |
| 1149 | <span class="sd"> workspace_name (str): the name of the workspace where the vuln will be saved.</span> | |
| 1150 | <span class="sd"> id (str): the id of the vuln. Must be unique.</span> | |
| 1151 | <span class="sd"> name (str): the vuln's name</span> | |
| 1152 | <span class="sd"> description (str): a description.</span> | |
| 1153 | <span class="sd"> owned (bool): is the vuln owned or not?</span> | |
| 1154 | <span class="sd"> owner (str): an owner for the vuln</span> | |
| 1155 | <span class="sd"> confirmed (bool): is the vulnerability confirmed?</span> | |
| 1156 | <span class="sd"> data (str): any aditional data about the vuln</span> | |
| 1157 | <span class="sd"> refs ([str]): references for the vulnerability</span> | |
| 1158 | <span class="sd"> severity (str): a string indicating the vuln's severity. can be 'info',</span> | |
| 1159 | <span class="sd"> 'low', 'med', 'high', 'critical'</span> | |
| 1160 | <span class="sd"> resolution (str): the vuln's possible resolution</span> | |
| 1161 | <span class="sd"> desc (str): a vuln's description.</span> | |
| 1162 | <span class="sd"> status (str): the service's status</span> | |
| 1163 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1164 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1165 | ||
| 1166 | <span class="sd"> Returns:</span> | |
| 1167 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1168 | <span class="sd"> """</span> | |
| 1169 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1170 | <span class="nb">id</span><span class="p">,</span> | |
| 1171 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1172 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1173 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1174 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1175 | <span class="n">confirmed</span><span class="o">=</span><span class="n">confirmed</span><span class="p">,</span> | |
| 1176 | <span class="n">data</span><span class="o">=</span><span class="n">data</span><span class="p">,</span> | |
| 1177 | <span class="n">refs</span><span class="o">=</span><span class="n">refs</span><span class="p">,</span> | |
| 1178 | <span class="n">severity</span><span class="o">=</span><span class="n">severity</span><span class="p">,</span> | |
| 1179 | <span class="n">resolution</span><span class="o">=</span><span class="n">resolution</span><span class="p">,</span> | |
| 1180 | <span class="n">desc</span><span class="o">=</span><span class="n">desc</span><span class="p">,</span> | |
| 1181 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Vulnerability"</span><span class="p">,</span> | |
| 1182 | <span class="n">status</span><span class="o">=</span><span class="n">status</span><span class="p">,</span> | |
| 1183 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1184 | ||
| 1185 | <div class="viewcode-block" id="update_vuln"><a class="viewcode-back" href="../../../server.html#persistence.server.server.update_vuln">[docs]</a><span class="k">def</span> <span class="nf">update_vuln</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1186 | <span class="n">confirmed</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">data</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">refs</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">severity</span><span class="o">=</span><span class="s2">"info"</span><span class="p">,</span> <span class="n">resolution</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1187 | <span class="n">desc</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">status</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1188 | <span class="sd">"""Updates a vuln.</span> | |
| 1189 | ||
| 1190 | <span class="sd"> Args:</span> | |
| 1191 | <span class="sd"> workspace_name (str): the name of the workspace where the host will be saved.</span> | |
| 1192 | <span class="sd"> id (str): the id of the host. Must be unique.</span> | |
| 1193 | <span class="sd"> name (str): the host's name</span> | |
| 1194 | <span class="sd"> description (str): a description.</span> | |
| 1195 | <span class="sd"> owned (bool): is the vuln owned or not?</span> | |
| 1196 | <span class="sd"> owner (str): an owner for the vuln</span> | |
| 1197 | <span class="sd"> confirmed (bool): is the vulnerability confirmed?</span> | |
| 1198 | <span class="sd"> data (str): any aditional data about the vuln</span> | |
| 1199 | <span class="sd"> refs ([str]): references for the vulnerability</span> | |
| 1200 | <span class="sd"> severity (str): a string indicating the vuln's severity. can be 'info',</span> | |
| 1201 | <span class="sd"> 'low', 'med', 'high', 'critical'</span> | |
| 1202 | <span class="sd"> resolution (str): the vuln's possible resolution</span> | |
| 1203 | <span class="sd"> desc (str): a vuln's description.</span> | |
| 1204 | <span class="sd"> status (str): the service's status</span> | |
| 1205 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1206 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1207 | ||
| 1208 | <span class="sd"> Returns:</span> | |
| 1209 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1210 | <span class="sd"> """</span> | |
| 1211 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1212 | <span class="nb">id</span><span class="p">,</span> | |
| 1213 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1214 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1215 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1216 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1217 | <span class="n">confirmed</span><span class="o">=</span><span class="n">confirmed</span><span class="p">,</span> | |
| 1218 | <span class="n">data</span><span class="o">=</span><span class="n">data</span><span class="p">,</span> | |
| 1219 | <span class="n">refs</span><span class="o">=</span><span class="n">refs</span><span class="p">,</span> | |
| 1220 | <span class="n">severity</span><span class="o">=</span><span class="n">severity</span><span class="p">,</span> | |
| 1221 | <span class="n">resolution</span><span class="o">=</span><span class="n">resolution</span><span class="p">,</span> | |
| 1222 | <span class="n">desc</span><span class="o">=</span><span class="n">desc</span><span class="p">,</span> | |
| 1223 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Vulnerability"</span><span class="p">,</span> | |
| 1224 | <span class="n">status</span><span class="o">=</span><span class="n">status</span><span class="p">,</span> | |
| 1225 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1226 | ||
| 1227 | <div class="viewcode-block" id="create_vuln_web"><a class="viewcode-back" href="../../../server.html#persistence.server.server.create_vuln_web">[docs]</a><span class="k">def</span> <span class="nf">create_vuln_web</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1228 | <span class="n">confirmed</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">data</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">refs</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">severity</span><span class="o">=</span><span class="s2">"info"</span><span class="p">,</span> <span class="n">resolution</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1229 | <span class="n">desc</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">method</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">params</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">path</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">pname</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1230 | <span class="n">query</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">request</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">response</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">category</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">website</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1231 | <span class="n">status</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1232 | <span class="sd">"""Creates a vuln web.</span> | |
| 1233 | ||
| 1234 | <span class="sd"> Args:</span> | |
| 1235 | <span class="sd"> workspace_name (str): the name of the workspace where the vuln web will be saved.</span> | |
| 1236 | <span class="sd"> id (str): the id of the vuln web. Must be unique.</span> | |
| 1237 | <span class="sd"> name (str): the vuln web's name</span> | |
| 1238 | <span class="sd"> description (str): a description.</span> | |
| 1239 | <span class="sd"> owner (str): an owner for the host</span> | |
| 1240 | <span class="sd"> confirmed (bool): is the vulnerability confirmed?</span> | |
| 1241 | <span class="sd"> data (str): any aditional data about the vuln</span> | |
| 1242 | <span class="sd"> refs ([str]): references for the vulnerability</span> | |
| 1243 | <span class="sd"> severity (str): a string indicating the vuln's severity. can be 'info',</span> | |
| 1244 | <span class="sd"> 'low', 'med', 'high', 'critical'</span> | |
| 1245 | <span class="sd"> resolution (str): the vuln's possible resolution</span> | |
| 1246 | <span class="sd"> desc (str): a vuln's description.</span> | |
| 1247 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1248 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1249 | <span class="sd"> method (str): the web vuln method</span> | |
| 1250 | <span class="sd"> params (str): the parameters for the web vuln</span> | |
| 1251 | <span class="sd"> path (str): the web vuln's path</span> | |
| 1252 | <span class="sd"> query (str): the web vuln's query</span> | |
| 1253 | <span class="sd"> request (str): the web vuln's request</span> | |
| 1254 | <span class="sd"> response (str): the web vuln's response</span> | |
| 1255 | <span class="sd"> category (str): a category for the web vuln's</span> | |
| 1256 | <span class="sd"> website (str): the website where the vuln was found</span> | |
| 1257 | <span class="sd"> status (str): the web vulns's status</span> | |
| 1258 | ||
| 1259 | <span class="sd"> Returns:</span> | |
| 1260 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1261 | <span class="sd"> """</span> | |
| 1262 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1263 | <span class="nb">id</span><span class="p">,</span> | |
| 1264 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1265 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1266 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1267 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1268 | <span class="n">confirmed</span><span class="o">=</span><span class="n">confirmed</span><span class="p">,</span> | |
| 1269 | <span class="n">data</span><span class="o">=</span><span class="n">data</span><span class="p">,</span> | |
| 1270 | <span class="n">refs</span><span class="o">=</span><span class="n">refs</span><span class="p">,</span> | |
| 1271 | <span class="n">severity</span><span class="o">=</span><span class="n">severity</span><span class="p">,</span> | |
| 1272 | <span class="n">resolution</span><span class="o">=</span><span class="n">resolution</span><span class="p">,</span> | |
| 1273 | <span class="n">desc</span><span class="o">=</span><span class="n">desc</span><span class="p">,</span> | |
| 1274 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">,</span> | |
| 1275 | <span class="n">method</span><span class="o">=</span><span class="n">method</span><span class="p">,</span> | |
| 1276 | <span class="n">params</span><span class="o">=</span><span class="n">params</span><span class="p">,</span> | |
| 1277 | <span class="n">path</span><span class="o">=</span><span class="n">path</span><span class="p">,</span> | |
| 1278 | <span class="n">pname</span><span class="o">=</span><span class="n">pname</span><span class="p">,</span> | |
| 1279 | <span class="n">query</span><span class="o">=</span><span class="n">query</span><span class="p">,</span> | |
| 1280 | <span class="n">request</span><span class="o">=</span><span class="n">request</span><span class="p">,</span> | |
| 1281 | <span class="n">response</span><span class="o">=</span><span class="n">response</span><span class="p">,</span> | |
| 1282 | <span class="n">website</span><span class="o">=</span><span class="n">website</span><span class="p">,</span> | |
| 1283 | <span class="n">category</span><span class="o">=</span><span class="n">category</span><span class="p">,</span> | |
| 1284 | <span class="n">status</span><span class="o">=</span><span class="n">status</span><span class="p">,</span> | |
| 1285 | <span class="nb">type</span><span class="o">=</span><span class="s1">'VulnerabilityWeb'</span><span class="p">)</span></div> | |
| 1286 | ||
| 1287 | <div class="viewcode-block" id="update_vuln_web"><a class="viewcode-back" href="../../../server.html#persistence.server.server.update_vuln_web">[docs]</a><span class="k">def</span> <span class="nf">update_vuln_web</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1288 | <span class="n">confirmed</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">data</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">refs</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">severity</span><span class="o">=</span><span class="s2">"info"</span><span class="p">,</span> <span class="n">resolution</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1289 | <span class="n">desc</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">method</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">params</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">path</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">pname</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1290 | <span class="n">query</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">request</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">response</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">category</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">website</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1291 | <span class="n">status</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1292 | <span class="sd">"""Creates a vuln web.</span> | |
| 1293 | ||
| 1294 | <span class="sd"> Args:</span> | |
| 1295 | <span class="sd"> workspace_name (str): the name of the workspace where the vuln web will be saved.</span> | |
| 1296 | <span class="sd"> id (str): the id of the vuln web. Must be unique.</span> | |
| 1297 | <span class="sd"> name (str): the vuln web's name</span> | |
| 1298 | <span class="sd"> description (str): a description.</span> | |
| 1299 | <span class="sd"> owner (str): an owner for the host</span> | |
| 1300 | <span class="sd"> confirmed (bool): is the vulnerability confirmed?</span> | |
| 1301 | <span class="sd"> data (str): any aditional data about the vuln</span> | |
| 1302 | <span class="sd"> refs ([str]): references for the vulnerability</span> | |
| 1303 | <span class="sd"> severity (str): a string indicating the vuln's severity. can be 'info',</span> | |
| 1304 | <span class="sd"> 'low', 'med', 'high', 'critical'</span> | |
| 1305 | <span class="sd"> resolution (str): the vuln's possible resolution</span> | |
| 1306 | <span class="sd"> desc (str): a vuln's description.</span> | |
| 1307 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1308 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1309 | <span class="sd"> method (str): the web vuln method</span> | |
| 1310 | <span class="sd"> params (str): the parameters for the web vuln</span> | |
| 1311 | <span class="sd"> path (str): the web vuln's path</span> | |
| 1312 | <span class="sd"> query (str): the web vuln's query</span> | |
| 1313 | <span class="sd"> request (str): the web vuln's request</span> | |
| 1314 | <span class="sd"> response (str): the web vuln's response</span> | |
| 1315 | <span class="sd"> category (str): a category for the web vuln's</span> | |
| 1316 | <span class="sd"> website (str): the website where the vuln was found</span> | |
| 1317 | <span class="sd"> status (str): the web vulns's status</span> | |
| 1318 | ||
| 1319 | <span class="sd"> Returns:</span> | |
| 1320 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1321 | <span class="sd"> """</span> | |
| 1322 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1323 | <span class="nb">id</span><span class="p">,</span> | |
| 1324 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1325 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1326 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1327 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1328 | <span class="n">confirmed</span><span class="o">=</span><span class="n">confirmed</span><span class="p">,</span> | |
| 1329 | <span class="n">data</span><span class="o">=</span><span class="n">data</span><span class="p">,</span> | |
| 1330 | <span class="n">refs</span><span class="o">=</span><span class="n">refs</span><span class="p">,</span> | |
| 1331 | <span class="n">severity</span><span class="o">=</span><span class="n">severity</span><span class="p">,</span> | |
| 1332 | <span class="n">resolution</span><span class="o">=</span><span class="n">resolution</span><span class="p">,</span> | |
| 1333 | <span class="n">desc</span><span class="o">=</span><span class="n">desc</span><span class="p">,</span> | |
| 1334 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">,</span> | |
| 1335 | <span class="n">method</span><span class="o">=</span><span class="n">method</span><span class="p">,</span> | |
| 1336 | <span class="n">params</span><span class="o">=</span><span class="n">params</span><span class="p">,</span> | |
| 1337 | <span class="n">path</span><span class="o">=</span><span class="n">path</span><span class="p">,</span> | |
| 1338 | <span class="n">pname</span><span class="o">=</span><span class="n">pname</span><span class="p">,</span> | |
| 1339 | <span class="n">query</span><span class="o">=</span><span class="n">query</span><span class="p">,</span> | |
| 1340 | <span class="n">request</span><span class="o">=</span><span class="n">request</span><span class="p">,</span> | |
| 1341 | <span class="n">response</span><span class="o">=</span><span class="n">response</span><span class="p">,</span> | |
| 1342 | <span class="n">website</span><span class="o">=</span><span class="n">website</span><span class="p">,</span> | |
| 1343 | <span class="n">category</span><span class="o">=</span><span class="n">category</span><span class="p">,</span> | |
| 1344 | <span class="n">status</span><span class="o">=</span><span class="n">status</span><span class="p">,</span> | |
| 1345 | <span class="nb">type</span><span class="o">=</span><span class="s1">'VulnerabilityWeb'</span><span class="p">)</span></div> | |
| 1346 | ||
| 1347 | <div class="viewcode-block" id="create_note"><a class="viewcode-back" href="../../../server.html#persistence.server.server.create_note">[docs]</a><span class="k">def</span> <span class="nf">create_note</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">text</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1348 | <span class="n">description</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1349 | <span class="sd">"""Creates a note.</span> | |
| 1350 | ||
| 1351 | <span class="sd"> Args:</span> | |
| 1352 | <span class="sd"> workspace_name (str): the name of the workspace where the vuln web will be saved.</span> | |
| 1353 | <span class="sd"> id (str): the id of the vuln web. Must be unique.</span> | |
| 1354 | <span class="sd"> name (str): the vuln web's name</span> | |
| 1355 | <span class="sd"> text (str): the note's text</span> | |
| 1356 | <span class="sd"> owned (bool): is the note owned?</span> | |
| 1357 | <span class="sd"> owner (str): the note's owner</span> | |
| 1358 | <span class="sd"> description (str): a description</span> | |
| 1359 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1360 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1361 | ||
| 1362 | <span class="sd"> Returns:</span> | |
| 1363 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1364 | <span class="sd"> """</span> | |
| 1365 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1366 | <span class="nb">id</span><span class="p">,</span> | |
| 1367 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1368 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1369 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1370 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1371 | <span class="n">text</span><span class="o">=</span><span class="n">text</span><span class="p">,</span> | |
| 1372 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Note"</span><span class="p">,</span> | |
| 1373 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1374 | ||
| 1375 | <div class="viewcode-block" id="update_note"><a class="viewcode-back" href="../../../server.html#persistence.server.server.update_note">[docs]</a><span class="k">def</span> <span class="nf">update_note</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">text</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1376 | <span class="n">description</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1377 | <span class="sd">"""Updates a note.</span> | |
| 1378 | ||
| 1379 | <span class="sd"> Args:</span> | |
| 1380 | <span class="sd"> workspace_name (str): the name of the workspace where the vuln web will be saved.</span> | |
| 1381 | <span class="sd"> id (str): the id of the vuln web. Must be unique.</span> | |
| 1382 | <span class="sd"> name (str): the vuln web's name</span> | |
| 1383 | <span class="sd"> text (str): the note's text</span> | |
| 1384 | <span class="sd"> owned (bool): is the note owned?</span> | |
| 1385 | <span class="sd"> owner (str): the note's owner</span> | |
| 1386 | <span class="sd"> description (str): a description</span> | |
| 1387 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1388 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1389 | ||
| 1390 | <span class="sd"> Returns:</span> | |
| 1391 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1392 | <span class="sd"> """</span> | |
| 1393 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1394 | <span class="nb">id</span><span class="p">,</span> | |
| 1395 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1396 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1397 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1398 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1399 | <span class="n">text</span><span class="o">=</span><span class="n">text</span><span class="p">,</span> | |
| 1400 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Note"</span><span class="p">,</span> | |
| 1401 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1402 | ||
| 1403 | ||
| 1404 | <div class="viewcode-block" id="create_credential"><a class="viewcode-back" href="../../../server.html#persistence.server.server.create_credential">[docs]</a><span class="k">def</span> <span class="nf">create_credential</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">username</span><span class="p">,</span> <span class="n">password</span><span class="p">,</span> | |
| 1405 | <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">description</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1406 | <span class="sd">"""Creates a credential.</span> | |
| 1407 | ||
| 1408 | <span class="sd"> Args:</span> | |
| 1409 | <span class="sd"> workspace_name (str): the name of the workspace where the vuln web will be saved.</span> | |
| 1410 | <span class="sd"> id (str): the id of the vuln web. Must be unique.</span> | |
| 1411 | <span class="sd"> name (str): the vuln web's name</span> | |
| 1412 | <span class="sd"> username (str)</span> | |
| 1413 | <span class="sd"> password (str)</span> | |
| 1414 | <span class="sd"> owned (bool): is the note owned?</span> | |
| 1415 | <span class="sd"> owner (str): the note's owner</span> | |
| 1416 | <span class="sd"> description (str): a description</span> | |
| 1417 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1418 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1419 | ||
| 1420 | <span class="sd"> Returns:</span> | |
| 1421 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1422 | <span class="sd"> """</span> | |
| 1423 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1424 | <span class="nb">id</span><span class="p">,</span> | |
| 1425 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1426 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1427 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1428 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1429 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">,</span> | |
| 1430 | <span class="n">username</span><span class="o">=</span><span class="n">username</span><span class="p">,</span> | |
| 1431 | <span class="n">password</span><span class="o">=</span><span class="n">password</span><span class="p">,</span> | |
| 1432 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Credential"</span><span class="p">)</span></div> | |
| 1433 | ||
| 1434 | <div class="viewcode-block" id="update_credential"><a class="viewcode-back" href="../../../server.html#persistence.server.server.update_credential">[docs]</a><span class="k">def</span> <span class="nf">update_credential</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">username</span><span class="p">,</span> <span class="n">password</span><span class="p">,</span> | |
| 1435 | <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">description</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1436 | <span class="sd">"""Updates a credential.</span> | |
| 1437 | ||
| 1438 | <span class="sd"> Args:</span> | |
| 1439 | <span class="sd"> workspace_name (str): the name of the workspace where the vuln web will be saved.</span> | |
| 1440 | <span class="sd"> id (str): the id of the vuln web. Must be unique.</span> | |
| 1441 | <span class="sd"> name (str): the vuln web's name</span> | |
| 1442 | <span class="sd"> username (str)</span> | |
| 1443 | <span class="sd"> password (str)</span> | |
| 1444 | <span class="sd"> owned (bool): is the note owned?</span> | |
| 1445 | <span class="sd"> owner (str): the note's owner</span> | |
| 1446 | <span class="sd"> description (str): a description</span> | |
| 1447 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1448 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1449 | ||
| 1450 | <span class="sd"> Returns:</span> | |
| 1451 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1452 | <span class="sd"> """</span> | |
| 1453 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1454 | <span class="nb">id</span><span class="p">,</span> | |
| 1455 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1456 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1457 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1458 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1459 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">,</span> | |
| 1460 | <span class="n">username</span><span class="o">=</span><span class="n">username</span><span class="p">,</span> | |
| 1461 | <span class="n">password</span><span class="o">=</span><span class="n">password</span><span class="p">,</span> | |
| 1462 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Credential"</span><span class="p">)</span></div> | |
| 1463 | ||
| 1464 | <div class="viewcode-block" id="create_command"><a class="viewcode-back" href="../../../server.html#persistence.server.server.create_command">[docs]</a><span class="k">def</span> <span class="nf">create_command</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">command</span><span class="p">,</span> <span class="n">duration</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">hostname</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1465 | <span class="n">ip</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">itime</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">params</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">user</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1466 | <span class="sd">"""Creates a command.</span> | |
| 1467 | ||
| 1468 | <span class="sd"> Args:</span> | |
| 1469 | <span class="sd"> workspace_name (str): the name of the workspace where the vuln web will be saved.</span> | |
| 1470 | <span class="sd"> id (str): the id of the vuln web. Must be unique.</span> | |
| 1471 | <span class="sd"> command (str): the command to be created</span> | |
| 1472 | <span class="sd"> duration (str). the command's duration</span> | |
| 1473 | <span class="sd"> hostname (str): the hostname where the command was executed</span> | |
| 1474 | <span class="sd"> ip (str): the ip of the host where the command was executed</span> | |
| 1475 | <span class="sd"> itime (str): the time it took to run</span> | |
| 1476 | <span class="sd"> params (str): the parameters given</span> | |
| 1477 | <span class="sd"> user (str): the user that ran the command</span> | |
| 1478 | ||
| 1479 | <span class="sd"> Returns:</span> | |
| 1480 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1481 | <span class="sd"> """</span> | |
| 1482 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1483 | <span class="nb">id</span><span class="p">,</span> | |
| 1484 | <span class="n">command</span><span class="o">=</span><span class="n">command</span><span class="p">,</span> | |
| 1485 | <span class="n">duration</span><span class="o">=</span><span class="n">duration</span><span class="p">,</span> | |
| 1486 | <span class="n">hostname</span><span class="o">=</span><span class="n">hostname</span><span class="p">,</span> | |
| 1487 | <span class="n">ip</span><span class="o">=</span><span class="n">ip</span><span class="p">,</span> | |
| 1488 | <span class="n">itime</span><span class="o">=</span><span class="n">itime</span><span class="p">,</span> | |
| 1489 | <span class="n">params</span><span class="o">=</span><span class="n">params</span><span class="p">,</span> | |
| 1490 | <span class="n">user</span><span class="o">=</span><span class="n">user</span><span class="p">,</span> | |
| 1491 | <span class="n">workspace</span><span class="o">=</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1492 | <span class="nb">type</span><span class="o">=</span><span class="s2">"CommandRunInformation"</span><span class="p">)</span></div> | |
| 1493 | ||
| 1494 | <div class="viewcode-block" id="update_command"><a class="viewcode-back" href="../../../server.html#persistence.server.server.update_command">[docs]</a><span class="k">def</span> <span class="nf">update_command</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">command</span><span class="p">,</span> <span class="n">duration</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">hostname</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1495 | <span class="n">ip</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">itime</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">params</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">user</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1496 | <span class="sd">"""Updates a command.</span> | |
| 1497 | ||
| 1498 | <span class="sd"> Args:</span> | |
| 1499 | <span class="sd"> workspace_name (str): the name of the workspace where the vuln web will be saved.</span> | |
| 1500 | <span class="sd"> id (str): the id of the vuln web. Must be unique.</span> | |
| 1501 | <span class="sd"> command (str): the command to be created</span> | |
| 1502 | <span class="sd"> duration (str). the command's duration</span> | |
| 1503 | <span class="sd"> hostname (str): the hostname where the command was executed</span> | |
| 1504 | <span class="sd"> ip (str): the ip of the host where the command was executed</span> | |
| 1505 | <span class="sd"> itime (str): the time it took to run</span> | |
| 1506 | <span class="sd"> params (str): the parameters given</span> | |
| 1507 | <span class="sd"> user (str): the user that ran the command</span> | |
| 1508 | ||
| 1509 | <span class="sd"> Returns:</span> | |
| 1510 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1511 | <span class="sd"> """</span> | |
| 1512 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1513 | <span class="nb">id</span><span class="p">,</span> | |
| 1514 | <span class="n">command</span><span class="o">=</span><span class="n">command</span><span class="p">,</span> | |
| 1515 | <span class="n">duration</span><span class="o">=</span><span class="n">duration</span><span class="p">,</span> | |
| 1516 | <span class="n">hostname</span><span class="o">=</span><span class="n">hostname</span><span class="p">,</span> | |
| 1517 | <span class="n">ip</span><span class="o">=</span><span class="n">ip</span><span class="p">,</span> | |
| 1518 | <span class="n">itime</span><span class="o">=</span><span class="n">itime</span><span class="p">,</span> | |
| 1519 | <span class="n">params</span><span class="o">=</span><span class="n">params</span><span class="p">,</span> | |
| 1520 | <span class="n">user</span><span class="o">=</span><span class="n">user</span><span class="p">,</span> | |
| 1521 | <span class="n">workspace</span><span class="o">=</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1522 | <span class="nb">type</span><span class="o">=</span><span class="s2">"CommandRunInformation"</span><span class="p">)</span></div> | |
| 1523 | ||
| 1524 | ||
| 1525 | <div class="viewcode-block" id="create_workspace"><a class="viewcode-back" href="../../../server.html#persistence.server.server.create_workspace">[docs]</a><span class="k">def</span> <span class="nf">create_workspace</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">start_date</span><span class="p">,</span> <span class="n">finish_date</span><span class="p">,</span> | |
| 1526 | <span class="n">customer</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1527 | <span class="sd">"""Create a workspace.</span> | |
| 1528 | ||
| 1529 | <span class="sd"> Args:</span> | |
| 1530 | <span class="sd"> workspace_name (str): the workspace's name</span> | |
| 1531 | <span class="sd"> description (str): a description for the worksapce</span> | |
| 1532 | <span class="sd"> start_date (str): a date to represent when work began in the workspace</span> | |
| 1533 | <span class="sd"> finish_date (str): a date to represent when work will be finished on the workspace</span> | |
| 1534 | <span class="sd"> customer (str): the customer for which we are creating the workspace</span> | |
| 1535 | ||
| 1536 | <span class="sd"> Returns:</span> | |
| 1537 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1538 | <span class="sd"> """</span> | |
| 1539 | <span class="k">return</span> <span class="n">_save_db_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1540 | <span class="n">name</span><span class="o">=</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1541 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1542 | <span class="n">customer</span><span class="o">=</span><span class="n">customer</span><span class="p">,</span> | |
| 1543 | <span class="n">sdate</span><span class="o">=</span><span class="n">start_date</span><span class="p">,</span> | |
| 1544 | <span class="n">fdate</span><span class="o">=</span><span class="n">finish_date</span><span class="p">,</span> | |
| 1545 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Workspace"</span><span class="p">)</span></div> | |
| 1546 | ||
| 1547 | <div class="viewcode-block" id="delete_host"><a class="viewcode-back" href="../../../server.html#persistence.server.server.delete_host">[docs]</a><span class="k">def</span> <span class="nf">delete_host</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">host_id</span><span class="p">):</span> | |
| 1548 | <span class="sd">"""Delete host of id host_id from the database."""</span> | |
| 1549 | <span class="k">return</span> <span class="n">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">host_id</span><span class="p">)</span></div> | |
| 1550 | ||
| 1551 | <div class="viewcode-block" id="delete_interface"><a class="viewcode-back" href="../../../server.html#persistence.server.server.delete_interface">[docs]</a><span class="k">def</span> <span class="nf">delete_interface</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">interface_id</span><span class="p">):</span> | |
| 1552 | <span class="sd">"""Delete interface of id interface_id from the database."""</span> | |
| 1553 | <span class="k">return</span> <span class="n">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">interface_id</span><span class="p">)</span></div> | |
| 1554 | ||
| 1555 | <div class="viewcode-block" id="delete_service"><a class="viewcode-back" href="../../../server.html#persistence.server.server.delete_service">[docs]</a><span class="k">def</span> <span class="nf">delete_service</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">service_id</span><span class="p">):</span> | |
| 1556 | <span class="sd">"""Delete service of id service_id from the database."""</span> | |
| 1557 | <span class="k">return</span> <span class="n">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">service_id</span><span class="p">)</span></div> | |
| 1558 | ||
| 1559 | <div class="viewcode-block" id="delete_vuln"><a class="viewcode-back" href="../../../server.html#persistence.server.server.delete_vuln">[docs]</a><span class="k">def</span> <span class="nf">delete_vuln</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">vuln_id</span><span class="p">):</span> | |
| 1560 | <span class="sd">"""Delete vuln of id vuln_id from the database."""</span> | |
| 1561 | <span class="k">return</span> <span class="n">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">vuln_id</span><span class="p">)</span></div> | |
| 1562 | ||
| 1563 | <div class="viewcode-block" id="delete_note"><a class="viewcode-back" href="../../../server.html#persistence.server.server.delete_note">[docs]</a><span class="k">def</span> <span class="nf">delete_note</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">note_id</span><span class="p">):</span> | |
| 1564 | <span class="sd">"""Delete note of id note_id from the database."""</span> | |
| 1565 | <span class="k">return</span> <span class="n">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">note_id</span><span class="p">)</span></div> | |
| 1566 | ||
| 1567 | <div class="viewcode-block" id="delete_credential"><a class="viewcode-back" href="../../../server.html#persistence.server.server.delete_credential">[docs]</a><span class="k">def</span> <span class="nf">delete_credential</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">credential_id</span><span class="p">):</span> | |
| 1568 | <span class="sd">"""Delete credential of id credential_id from the database."""</span> | |
| 1569 | <span class="k">return</span> <span class="n">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">credential_id</span><span class="p">)</span></div> | |
| 1570 | ||
| 1571 | <div class="viewcode-block" id="delete_command"><a class="viewcode-back" href="../../../server.html#persistence.server.server.delete_command">[docs]</a><span class="k">def</span> <span class="nf">delete_command</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">command_id</span><span class="p">):</span> | |
| 1572 | <span class="sd">"""Delete command of id command_id from the database."""</span> | |
| 1573 | <span class="k">return</span> <span class="n">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">command_id</span><span class="p">)</span></div> | |
| 1574 | ||
| 1575 | <div class="viewcode-block" id="delete_workspace"><a class="viewcode-back" href="../../../server.html#persistence.server.server.delete_workspace">[docs]</a><span class="k">def</span> <span class="nf">delete_workspace</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">):</span> | |
| 1576 | <span class="sd">"""Delete the couch database of id workspace_name"""</span> | |
| 1577 | <span class="n">db_url</span> <span class="o">=</span> <span class="n">_create_server_db_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)</span> | |
| 1578 | <span class="k">return</span> <span class="n">_delete</span><span class="p">(</span><span class="n">db_url</span><span class="p">,</span> <span class="n">database</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span></div> | |
| 1579 | ||
| 1580 | <div class="viewcode-block" id="is_server_up"><a class="viewcode-back" href="../../../server.html#persistence.server.server.is_server_up">[docs]</a><span class="k">def</span> <span class="nf">is_server_up</span><span class="p">():</span> | |
| 1581 | <span class="sd">"""Return True if we can stablish a connection with the server,</span> | |
| 1582 | <span class="sd"> False otherwise.</span> | |
| 1583 | <span class="sd"> """</span> | |
| 1584 | <span class="k">try</span><span class="p">:</span> | |
| 1585 | <span class="n">_get</span><span class="p">(</span><span class="s2">"</span><span class="si">{0}</span><span class="s2">/info"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">_create_server_api_url</span><span class="p">()))</span> | |
| 1586 | <span class="n">is_server_up</span> <span class="o">=</span> <span class="kc">True</span> | |
| 1587 | <span class="k">except</span><span class="p">:</span> | |
| 1588 | <span class="n">is_server_up</span> <span class="o">=</span> <span class="kc">False</span> | |
| 1589 | <span class="k">return</span> <span class="n">is_server_up</span></div> | |
| 1590 | ||
| 1591 | <div class="viewcode-block" id="test_server_url"><a class="viewcode-back" href="../../../server.html#persistence.server.server.test_server_url">[docs]</a><span class="k">def</span> <span class="nf">check_server_url</span><span class="p">(</span><span class="n">url_to_test</span><span class="p">):</span> | |
| 1592 | <span class="sd">"""Return True if the url_to_test is indeed a valid Faraday Server URL.</span> | |
| 1593 | <span class="sd"> False otherwise.</span> | |
| 1594 | <span class="sd"> """</span> | |
| 1595 | <span class="k">try</span><span class="p">:</span> | |
| 1596 | <span class="n">_get</span><span class="p">(</span><span class="s2">"</span><span class="si">{0}</span><span class="s2">/_api/info"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">url_to_test</span><span class="p">))</span> | |
| 1597 | <span class="n">test_okey</span> <span class="o">=</span> <span class="kc">True</span> | |
| 1598 | <span class="k">except</span><span class="p">:</span> | |
| 1599 | <span class="n">test_okey</span> <span class="o">=</span> <span class="kc">False</span> | |
| 1600 | <span class="k">return</span> <span class="n">test_okey</span></div> | |
| 1601 | </pre></div> | |
| 1602 | ||
| 1603 | </div> | |
| 1604 | </div> | |
| 1605 | <footer> | |
| 1606 | ||
| 1607 | ||
| 1608 | <hr/> | |
| 1609 | ||
| 1610 | <div role="contentinfo"> | |
| 1611 | <p> | |
| 1612 | © Copyright 2016, Infobyte. | |
| 1613 | ||
| 1614 | </p> | |
| 1615 | </div> | |
| 1616 | Built with <a href="http://sphinx-doc.org/">Sphinx</a> using a <a href="https://github.com/snide/sphinx_rtd_theme">theme</a> provided by <a href="https://readthedocs.org">Read the Docs</a>. | |
| 1617 | ||
| 1618 | </footer> | |
| 1619 | ||
| 1620 | </div> | |
| 1621 | </div> | |
| 1622 | ||
| 1623 | </section> | |
| 1624 | ||
| 1625 | </div> | |
| 1626 | ||
| 1627 | ||
| 1628 | ||
| 1629 | ||
| 1630 | ||
| 1631 | <script type="text/javascript"> | |
| 1632 | var DOCUMENTATION_OPTIONS = { | |
| 1633 | URL_ROOT:'../../../', | |
| 1634 | VERSION:'0.1', | |
| 1635 | COLLAPSE_INDEX:false, | |
| 1636 | FILE_SUFFIX:'.html', | |
| 1637 | HAS_SOURCE: true | |
| 1638 | }; | |
| 1639 | </script> | |
| 1640 | <script type="text/javascript" src="../../../_static/jquery.js"></script> | |
| 1641 | <script type="text/javascript" src="../../../_static/underscore.js"></script> | |
| 1642 | <script type="text/javascript" src="../../../_static/doctools.js"></script> | |
| 1643 | ||
| 1644 | ||
| 1645 | ||
| 1646 | ||
| 1647 | ||
| 1648 | <script type="text/javascript" src="../../../_static/js/theme.js"></script> | |
| 1649 | ||
| 1650 | ||
| 1651 | ||
| 1652 | ||
| 1653 | <script type="text/javascript"> | |
| 1654 | jQuery(function () { | |
| 1655 | SphinxRtdTheme.StickyNav.enable(); | |
| 1656 | }); | |
| 1657 | </script> | |
| 1658 | ||
| 1659 | ||
| 1660 | </body> | |
| 1661 | </html>⏎ |
| 0 | ||
| 1 | ||
| 2 | <!DOCTYPE html> | |
| 3 | <!--[if IE 8]><html class="no-js lt-ie9" lang="en" > <![endif]--> | |
| 4 | <!--[if gt IE 8]><!--> <html class="no-js" lang="en" > <!--<![endif]--> | |
| 5 | <head> | |
| 6 | <meta charset="utf-8"> | |
| 7 | ||
| 8 | <meta name="viewport" content="width=device-width, initial-scale=1.0"> | |
| 9 | ||
| 10 | <title>server.models — Faraday 0.1 documentation</title> | |
| 11 | ||
| 12 | ||
| 13 | ||
| 14 | ||
| 15 | ||
| 16 | ||
| 17 | ||
| 18 | ||
| 19 | ||
| 20 | ||
| 21 | ||
| 22 | ||
| 23 | ||
| 24 | ||
| 25 | ||
| 26 | <link rel="stylesheet" href="../../_static/css/theme.css" type="text/css" /> | |
| 27 | ||
| 28 | ||
| 29 | ||
| 30 | ||
| 31 | ||
| 32 | <link rel="index" title="Index" | |
| 33 | href="../../genindex.html"/> | |
| 34 | <link rel="search" title="Search" href="../../search.html"/> | |
| 35 | <link rel="top" title="Faraday 0.1 documentation" href="../../index.html"/> | |
| 36 | <link rel="up" title="server" href="../server.html"/> | |
| 37 | ||
| 38 | ||
| 39 | <script src="../../_static/js/modernizr.min.js"></script> | |
| 40 | ||
| 41 | </head> | |
| 42 | ||
| 43 | <body class="wy-body-for-nav" role="document"> | |
| 44 | ||
| 45 | <div class="wy-grid-for-nav"> | |
| 46 | ||
| 47 | ||
| 48 | <nav data-toggle="wy-nav-shift" class="wy-nav-side"> | |
| 49 | <div class="wy-side-scroll"> | |
| 50 | <div class="wy-side-nav-search"> | |
| 51 | ||
| 52 | ||
| 53 | ||
| 54 | <a href="../../index.html" class="icon icon-home"> Faraday | |
| 55 | ||
| 56 | ||
| 57 | ||
| 58 | </a> | |
| 59 | ||
| 60 | ||
| 61 | ||
| 62 | ||
| 63 | <div class="version"> | |
| 64 | 0.1 | |
| 65 | </div> | |
| 66 | ||
| 67 | ||
| 68 | ||
| 69 | ||
| 70 | <div role="search"> | |
| 71 | <form id="rtd-search-form" class="wy-form" action="../../search.html" method="get"> | |
| 72 | <input type="text" name="q" placeholder="Search docs" /> | |
| 73 | <input type="hidden" name="check_keywords" value="yes" /> | |
| 74 | <input type="hidden" name="area" value="default" /> | |
| 75 | </form> | |
| 76 | </div> | |
| 77 | ||
| 78 | ||
| 79 | </div> | |
| 80 | ||
| 81 | <div class="wy-menu wy-menu-vertical" data-spy="affix" role="navigation" aria-label="main navigation"> | |
| 82 | ||
| 83 | ||
| 84 | ||
| 85 | <!-- Local TOC --> | |
| 86 | <div class="local-toc"></div> | |
| 87 | ||
| 88 | ||
| 89 | </div> | |
| 90 | </div> | |
| 91 | </nav> | |
| 92 | ||
| 93 | <section data-toggle="wy-nav-shift" class="wy-nav-content-wrap"> | |
| 94 | ||
| 95 | ||
| 96 | <nav class="wy-nav-top" role="navigation" aria-label="top navigation"> | |
| 97 | <i data-toggle="wy-nav-top" class="fa fa-bars"></i> | |
| 98 | <a href="../../index.html">Faraday</a> | |
| 99 | </nav> | |
| 100 | ||
| 101 | ||
| 102 | ||
| 103 | <div class="wy-nav-content"> | |
| 104 | <div class="rst-content"> | |
| 105 | ||
| 106 | ||
| 107 | ||
| 108 | ||
| 109 | ||
| 110 | ||
| 111 | <div role="navigation" aria-label="breadcrumbs navigation"> | |
| 112 | <ul class="wy-breadcrumbs"> | |
| 113 | <li><a href="../../index.html">Docs</a> »</li> | |
| 114 | ||
| 115 | <li><a href="../index.html">Module code</a> »</li> | |
| 116 | ||
| 117 | <li><a href="../server.html">server</a> »</li> | |
| 118 | ||
| 119 | <li>server.models</li> | |
| 120 | <li class="wy-breadcrumbs-aside"> | |
| 121 | ||
| 122 | ||
| 123 | ||
| 124 | </li> | |
| 125 | </ul> | |
| 126 | <hr/> | |
| 127 | </div> | |
| 128 | <div role="main" class="document" itemscope="itemscope" itemtype="http://schema.org/Article"> | |
| 129 | <div itemprop="articleBody"> | |
| 130 | ||
| 131 | <h1>Source code for server.models</h1><div class="highlight"><pre> | |
| 132 | <span></span><span class="c1"># Faraday Penetration Test IDE</span> | |
| 133 | <span class="c1"># Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/)</span> | |
| 134 | <span class="c1"># See the file 'doc/LICENSE' for the license information</span> | |
| 135 | ||
| 136 | <span class="kn">import</span> <span class="nn">json</span> | |
| 137 | ||
| 138 | <span class="kn">from</span> <span class="nn">sqlalchemy</span> <span class="k">import</span> <span class="n">Column</span><span class="p">,</span> <span class="n">Integer</span><span class="p">,</span> <span class="n">String</span><span class="p">,</span> <span class="n">Boolean</span><span class="p">,</span> <span class="n">ForeignKey</span><span class="p">,</span> <span class="n">Float</span><span class="p">,</span> <span class="n">Text</span><span class="p">,</span> <span class="n">UniqueConstraint</span> | |
| 139 | <span class="kn">from</span> <span class="nn">sqlalchemy.orm</span> <span class="k">import</span> <span class="n">relationship</span> | |
| 140 | <span class="kn">from</span> <span class="nn">sqlalchemy.ext.declarative</span> <span class="k">import</span> <span class="n">declarative_base</span> | |
| 141 | ||
| 142 | ||
| 143 | <span class="n">SCHEMA_VERSION</span> <span class="o">=</span> <span class="s1">'W.2.2.0'</span> | |
| 144 | ||
| 145 | <span class="n">Base</span> <span class="o">=</span> <span class="n">declarative_base</span><span class="p">()</span> | |
| 146 | ||
| 147 | <div class="viewcode-block" id="EntityNotFound"><a class="viewcode-back" href="../../server.html#server.models.EntityNotFound">[docs]</a><span class="k">class</span> <span class="nc">EntityNotFound</span><span class="p">(</span><span class="ne">Exception</span><span class="p">):</span> | |
| 148 | <span class="k">def</span> <span class="nf">__init__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">entity_id</span><span class="p">):</span> | |
| 149 | <span class="nb">super</span><span class="p">(</span><span class="n">EntityNotFound</span><span class="p">,</span> <span class="bp">self</span><span class="p">)</span><span class="o">.</span><span class="n">__init__</span><span class="p">(</span><span class="s2">"Entity (</span><span class="si">%s</span><span class="s2">) wasn't found"</span> <span class="o">%</span> <span class="n">entity_id</span><span class="p">)</span></div> | |
| 150 | ||
| 151 | <div class="viewcode-block" id="FaradayEntity"><a class="viewcode-back" href="../../server.html#server.models.FaradayEntity">[docs]</a><span class="k">class</span> <span class="nc">FaradayEntity</span><span class="p">(</span><span class="nb">object</span><span class="p">):</span> | |
| 152 | <span class="c1"># Document Types: [u'Service', u'Communication', u'Vulnerability', u'CommandRunInformation', u'Reports', u'Host', u'Workspace', u'Interface']</span> | |
| 153 | <span class="nd">@classmethod</span> | |
| 154 | <div class="viewcode-block" id="FaradayEntity.parse"><a class="viewcode-back" href="../../server.html#server.models.FaradayEntity.parse">[docs]</a> <span class="k">def</span> <span class="nf">parse</span><span class="p">(</span><span class="n">cls</span><span class="p">,</span> <span class="n">document</span><span class="p">):</span> | |
| 155 | <span class="sd">"""Get an instance of a DAO object given a document"""</span> | |
| 156 | <span class="n">entity_cls</span> <span class="o">=</span> <span class="n">cls</span><span class="o">.</span><span class="n">get_entity_class_from_doc</span><span class="p">(</span><span class="n">document</span><span class="p">)</span> | |
| 157 | <span class="k">if</span> <span class="n">entity_cls</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span><span class="p">:</span> | |
| 158 | <span class="n">entity</span> <span class="o">=</span> <span class="n">entity_cls</span><span class="p">(</span><span class="n">document</span><span class="p">)</span> | |
| 159 | <span class="n">metadata</span> <span class="o">=</span> <span class="n">EntityMetadata</span><span class="p">(</span><span class="n">document</span><span class="p">)</span> | |
| 160 | <span class="n">entity</span><span class="o">.</span><span class="n">entity_metadata</span> <span class="o">=</span> <span class="n">metadata</span> | |
| 161 | <span class="k">return</span> <span class="n">entity</span> | |
| 162 | <span class="k">return</span> <span class="kc">None</span></div> | |
| 163 | ||
| 164 | <span class="nd">@classmethod</span> | |
| 165 | <div class="viewcode-block" id="FaradayEntity.get_entity_class_from_doc"><a class="viewcode-back" href="../../server.html#server.models.FaradayEntity.get_entity_class_from_doc">[docs]</a> <span class="k">def</span> <span class="nf">get_entity_class_from_doc</span><span class="p">(</span><span class="n">cls</span><span class="p">,</span> <span class="n">document</span><span class="p">):</span> | |
| 166 | <span class="k">return</span> <span class="n">cls</span><span class="o">.</span><span class="n">get_entity_class_from_type</span><span class="p">(</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'type'</span><span class="p">,</span> <span class="kc">None</span><span class="p">))</span></div> | |
| 167 | ||
| 168 | <span class="nd">@classmethod</span> | |
| 169 | <div class="viewcode-block" id="FaradayEntity.get_entity_class_from_type"><a class="viewcode-back" href="../../server.html#server.models.FaradayEntity.get_entity_class_from_type">[docs]</a> <span class="k">def</span> <span class="nf">get_entity_class_from_type</span><span class="p">(</span><span class="n">cls</span><span class="p">,</span> <span class="n">doc_type</span><span class="p">):</span> | |
| 170 | <span class="k">for</span> <span class="n">entity_cls</span> <span class="ow">in</span> <span class="n">cls</span><span class="o">.</span><span class="n">__subclasses__</span><span class="p">():</span> | |
| 171 | <span class="k">if</span> <span class="nb">isinstance</span><span class="p">(</span><span class="n">entity_cls</span><span class="o">.</span><span class="n">DOC_TYPE</span><span class="p">,</span> <span class="n">basestring</span><span class="p">):</span> | |
| 172 | <span class="k">if</span> <span class="n">entity_cls</span><span class="o">.</span><span class="n">DOC_TYPE</span> <span class="o">==</span> <span class="n">doc_type</span><span class="p">:</span> | |
| 173 | <span class="k">return</span> <span class="n">entity_cls</span> | |
| 174 | <span class="k">else</span><span class="p">:</span> | |
| 175 | <span class="k">if</span> <span class="n">doc_type</span> <span class="ow">in</span> <span class="n">entity_cls</span><span class="o">.</span><span class="n">DOC_TYPE</span><span class="p">:</span> | |
| 176 | <span class="k">return</span> <span class="n">entity_cls</span> | |
| 177 | <span class="k">return</span> <span class="kc">None</span></div> | |
| 178 | ||
| 179 | <span class="k">def</span> <span class="nf">__init__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">document</span><span class="p">):</span> | |
| 180 | <span class="bp">self</span><span class="o">.</span><span class="n">update_from_document</span><span class="p">(</span><span class="n">document</span><span class="p">)</span> | |
| 181 | ||
| 182 | <div class="viewcode-block" id="FaradayEntity.update_from_document"><a class="viewcode-back" href="../../server.html#server.models.FaradayEntity.update_from_document">[docs]</a> <span class="k">def</span> <span class="nf">update_from_document</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">document</span><span class="p">):</span> | |
| 183 | <span class="k">raise</span> <span class="ne">Exception</span><span class="p">(</span><span class="s1">'MUST IMPLEMENT'</span><span class="p">)</span></div> | |
| 184 | ||
| 185 | <div class="viewcode-block" id="FaradayEntity.add_relationships_from_dict"><a class="viewcode-back" href="../../server.html#server.models.FaradayEntity.add_relationships_from_dict">[docs]</a> <span class="k">def</span> <span class="nf">add_relationships_from_dict</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">entities</span><span class="p">):</span> | |
| 186 | <span class="k">pass</span></div> | |
| 187 | ||
| 188 | <div class="viewcode-block" id="FaradayEntity.add_relationships_from_db"><a class="viewcode-back" href="../../server.html#server.models.FaradayEntity.add_relationships_from_db">[docs]</a> <span class="k">def</span> <span class="nf">add_relationships_from_db</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">session</span><span class="p">):</span> | |
| 189 | <span class="k">pass</span></div></div> | |
| 190 | ||
| 191 | ||
| 192 | <div class="viewcode-block" id="DatabaseMetadata"><a class="viewcode-back" href="../../server.html#server.models.DatabaseMetadata">[docs]</a><span class="k">class</span> <span class="nc">DatabaseMetadata</span><span class="p">(</span><span class="n">Base</span><span class="p">):</span> | |
| 193 | <span class="n">__tablename__</span> <span class="o">=</span> <span class="s1">'db_metadata'</span> | |
| 194 | <span class="nb">id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">primary_key</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 195 | <span class="n">option</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span> | |
| 196 | <span class="n">value</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span></div> | |
| 197 | ||
| 198 | ||
| 199 | <div class="viewcode-block" id="EntityMetadata"><a class="viewcode-back" href="../../server.html#server.models.EntityMetadata">[docs]</a><span class="k">class</span> <span class="nc">EntityMetadata</span><span class="p">(</span><span class="n">Base</span><span class="p">):</span> | |
| 200 | <span class="c1"># Table schema</span> | |
| 201 | <span class="n">__tablename__</span> <span class="o">=</span> <span class="s1">'metadata'</span> | |
| 202 | <span class="n">__table_args__</span> <span class="o">=</span> <span class="p">(</span> | |
| 203 | <span class="n">UniqueConstraint</span><span class="p">(</span><span class="s1">'couchdb_id'</span><span class="p">),</span> | |
| 204 | <span class="p">)</span> | |
| 205 | ||
| 206 | <span class="nb">id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">primary_key</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 207 | <span class="n">update_time</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Float</span><span class="p">,</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 208 | <span class="n">update_user</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 209 | <span class="n">update_action</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 210 | <span class="n">create_time</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Float</span><span class="p">,</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 211 | <span class="n">update_controller_action</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 212 | <span class="n">creator</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 213 | <span class="n">owner</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 214 | <span class="n">command_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 215 | ||
| 216 | <span class="n">couchdb_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 217 | <span class="n">revision</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 218 | <span class="n">document_type</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 219 | ||
| 220 | <span class="k">def</span> <span class="nf">__init__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">document</span><span class="p">):</span> | |
| 221 | <span class="bp">self</span><span class="o">.</span><span class="n">update_from_document</span><span class="p">(</span><span class="n">document</span><span class="p">)</span> | |
| 222 | ||
| 223 | <div class="viewcode-block" id="EntityMetadata.update_from_document"><a class="viewcode-back" href="../../server.html#server.models.EntityMetadata.update_from_document">[docs]</a> <span class="k">def</span> <span class="nf">update_from_document</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">document</span><span class="p">):</span> | |
| 224 | <span class="n">metadata</span> <span class="o">=</span> <span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'metadata'</span><span class="p">,</span> <span class="nb">dict</span><span class="p">())</span> | |
| 225 | <span class="bp">self</span><span class="o">.</span><span class="n">update_time</span><span class="o">=</span><span class="n">metadata</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'update_time'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 226 | <span class="bp">self</span><span class="o">.</span><span class="n">update_user</span><span class="o">=</span><span class="n">metadata</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'update_user'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 227 | <span class="bp">self</span><span class="o">.</span><span class="n">update_action</span><span class="o">=</span><span class="n">metadata</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'update_action'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 228 | <span class="bp">self</span><span class="o">.</span><span class="n">creator</span><span class="o">=</span><span class="n">metadata</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'creator'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 229 | <span class="bp">self</span><span class="o">.</span><span class="n">owner</span><span class="o">=</span><span class="n">metadata</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'owner'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 230 | <span class="bp">self</span><span class="o">.</span><span class="n">create_time</span><span class="o">=</span><span class="n">metadata</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'create_time'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 231 | <span class="bp">self</span><span class="o">.</span><span class="n">update_controller_action</span><span class="o">=</span><span class="n">metadata</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'update_controller_action'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 232 | <span class="bp">self</span><span class="o">.</span><span class="n">couchdb_id</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'_id'</span><span class="p">)</span> | |
| 233 | <span class="bp">self</span><span class="o">.</span><span class="n">revision</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'_rev'</span><span class="p">)</span> | |
| 234 | <span class="bp">self</span><span class="o">.</span><span class="n">document_type</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'type'</span><span class="p">)</span> | |
| 235 | <span class="bp">self</span><span class="o">.</span><span class="n">command_id</span> <span class="o">=</span> <span class="n">metadata</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'command_id'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 236 | ||
| 237 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">create_time</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span><span class="p">:</span> | |
| 238 | <span class="bp">self</span><span class="o">.</span><span class="n">create_time</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">__truncate_to_epoch_in_seconds</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">create_time</span><span class="p">)</span></div> | |
| 239 | ||
| 240 | <span class="k">def</span> <span class="nf">__truncate_to_epoch_in_seconds</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">timestamp</span><span class="p">):</span> | |
| 241 | <span class="sd">""" In a not so elegant fashion, identifies and truncate</span> | |
| 242 | <span class="sd"> epoch timestamps expressed in milliseconds to seconds"""</span> | |
| 243 | <span class="n">limit</span> <span class="o">=</span> <span class="mi">32503680000</span> <span class="c1"># 01 Jan 3000 00:00:00 GMT</span> | |
| 244 | <span class="k">if</span> <span class="n">timestamp</span> <span class="o">></span> <span class="n">limit</span><span class="p">:</span> | |
| 245 | <span class="k">return</span> <span class="n">timestamp</span> <span class="o">/</span> <span class="mi">1000</span> | |
| 246 | <span class="k">else</span><span class="p">:</span> | |
| 247 | <span class="k">return</span> <span class="n">timestamp</span></div> | |
| 248 | ||
| 249 | ||
| 250 | <div class="viewcode-block" id="Host"><a class="viewcode-back" href="../../server.html#server.models.Host">[docs]</a><span class="k">class</span> <span class="nc">Host</span><span class="p">(</span><span class="n">FaradayEntity</span><span class="p">,</span> <span class="n">Base</span><span class="p">):</span> | |
| 251 | <span class="n">DOC_TYPE</span> <span class="o">=</span> <span class="s1">'Host'</span> | |
| 252 | ||
| 253 | <span class="c1"># Table schema</span> | |
| 254 | <span class="n">__tablename__</span> <span class="o">=</span> <span class="s1">'host'</span> | |
| 255 | <span class="nb">id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">primary_key</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 256 | <span class="n">name</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span> | |
| 257 | <span class="n">description</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Text</span><span class="p">(),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span> | |
| 258 | <span class="n">os</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span> | |
| 259 | ||
| 260 | <span class="n">owned</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Boolean</span><span class="p">)</span> | |
| 261 | ||
| 262 | <span class="n">default_gateway_ip</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 263 | <span class="n">default_gateway_mac</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 264 | ||
| 265 | <span class="n">entity_metadata</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="p">,</span> <span class="n">uselist</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">cascade</span><span class="o">=</span><span class="s2">"all, delete-orphan"</span><span class="p">,</span> <span class="n">single_parent</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 266 | <span class="n">entity_metadata_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">ForeignKey</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="o">.</span><span class="n">id</span><span class="p">),</span> <span class="n">index</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 267 | ||
| 268 | <span class="n">interfaces</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="s1">'Interface'</span><span class="p">)</span> | |
| 269 | <span class="n">services</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="s1">'Service'</span><span class="p">)</span> | |
| 270 | <span class="n">vulnerabilities</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="s1">'Vulnerability'</span><span class="p">)</span> | |
| 271 | <span class="n">credentials</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="s1">'Credential'</span><span class="p">)</span> | |
| 272 | ||
| 273 | <div class="viewcode-block" id="Host.update_from_document"><a class="viewcode-back" href="../../server.html#server.models.Host.update_from_document">[docs]</a> <span class="k">def</span> <span class="nf">update_from_document</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">document</span><span class="p">):</span> | |
| 274 | <span class="c1"># Ticket #3387: if the 'os' field is None, we default to 'unknown'</span> | |
| 275 | <span class="k">if</span> <span class="ow">not</span> <span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'os'</span><span class="p">):</span> <span class="n">document</span><span class="p">[</span><span class="s1">'os'</span><span class="p">]</span><span class="o">=</span><span class="s1">'unknown'</span> | |
| 276 | ||
| 277 | <span class="n">default_gateway</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">__get_default_gateway</span><span class="p">(</span><span class="n">document</span><span class="p">)</span> | |
| 278 | ||
| 279 | <span class="bp">self</span><span class="o">.</span><span class="n">name</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'name'</span><span class="p">)</span> | |
| 280 | <span class="bp">self</span><span class="o">.</span><span class="n">description</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'description'</span><span class="p">)</span> | |
| 281 | <span class="bp">self</span><span class="o">.</span><span class="n">os</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'os'</span><span class="p">)</span> | |
| 282 | <span class="bp">self</span><span class="o">.</span><span class="n">default_gateway_ip</span><span class="o">=</span><span class="n">default_gateway</span><span class="p">[</span><span class="mi">0</span><span class="p">]</span> | |
| 283 | <span class="bp">self</span><span class="o">.</span><span class="n">default_gateway_mac</span><span class="o">=</span><span class="n">default_gateway</span><span class="p">[</span><span class="mi">1</span><span class="p">]</span> | |
| 284 | <span class="bp">self</span><span class="o">.</span><span class="n">owned</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'owned'</span><span class="p">,</span> <span class="kc">False</span><span class="p">)</span></div> | |
| 285 | ||
| 286 | <span class="k">def</span> <span class="nf">__get_default_gateway</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">document</span><span class="p">):</span> | |
| 287 | <span class="n">default_gateway</span> <span class="o">=</span> <span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'default_gateway'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 288 | <span class="k">if</span> <span class="n">default_gateway</span><span class="p">:</span> | |
| 289 | <span class="k">return</span> <span class="n">default_gateway</span> | |
| 290 | <span class="k">else</span><span class="p">:</span> | |
| 291 | <span class="k">return</span> <span class="s1">u''</span><span class="p">,</span> <span class="s1">u''</span></div> | |
| 292 | ||
| 293 | ||
| 294 | <div class="viewcode-block" id="Interface"><a class="viewcode-back" href="../../server.html#server.models.Interface">[docs]</a><span class="k">class</span> <span class="nc">Interface</span><span class="p">(</span><span class="n">FaradayEntity</span><span class="p">,</span> <span class="n">Base</span><span class="p">):</span> | |
| 295 | <span class="n">DOC_TYPE</span> <span class="o">=</span> <span class="s1">'Interface'</span> | |
| 296 | ||
| 297 | <span class="c1"># Table schema</span> | |
| 298 | <span class="n">__tablename__</span> <span class="o">=</span> <span class="s1">'interface'</span> | |
| 299 | <span class="nb">id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">primary_key</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 300 | <span class="n">name</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span> | |
| 301 | <span class="n">description</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span> | |
| 302 | <span class="n">mac</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span> | |
| 303 | <span class="n">owned</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Boolean</span><span class="p">)</span> | |
| 304 | ||
| 305 | <span class="n">hostnames</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 306 | <span class="n">network_segment</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 307 | ||
| 308 | <span class="n">ipv4_address</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 309 | <span class="n">ipv4_gateway</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 310 | <span class="n">ipv4_dns</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 311 | <span class="n">ipv4_mask</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 312 | ||
| 313 | <span class="n">ipv6_address</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 314 | <span class="n">ipv6_gateway</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 315 | <span class="n">ipv6_dns</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 316 | <span class="n">ipv6_prefix</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 317 | ||
| 318 | <span class="n">ports_filtered</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">)</span> | |
| 319 | <span class="n">ports_opened</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">)</span> | |
| 320 | <span class="n">ports_closed</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">)</span> | |
| 321 | ||
| 322 | <span class="n">entity_metadata</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="p">,</span> <span class="n">uselist</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">cascade</span><span class="o">=</span><span class="s2">"all, delete-orphan"</span><span class="p">,</span> <span class="n">single_parent</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 323 | <span class="n">entity_metadata_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">ForeignKey</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="o">.</span><span class="n">id</span><span class="p">),</span> <span class="n">index</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 324 | ||
| 325 | <span class="n">host_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">ForeignKey</span><span class="p">(</span><span class="n">Host</span><span class="o">.</span><span class="n">id</span><span class="p">),</span> <span class="n">index</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 326 | <span class="n">host</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="s1">'Host'</span><span class="p">,</span> <span class="n">back_populates</span><span class="o">=</span><span class="s1">'interfaces'</span><span class="p">)</span> | |
| 327 | ||
| 328 | <span class="n">services</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="s1">'Service'</span><span class="p">)</span> | |
| 329 | ||
| 330 | <div class="viewcode-block" id="Interface.update_from_document"><a class="viewcode-back" href="../../server.html#server.models.Interface.update_from_document">[docs]</a> <span class="k">def</span> <span class="nf">update_from_document</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">document</span><span class="p">):</span> | |
| 331 | <span class="bp">self</span><span class="o">.</span><span class="n">name</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'name'</span><span class="p">)</span> | |
| 332 | <span class="bp">self</span><span class="o">.</span><span class="n">description</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'description'</span><span class="p">)</span> | |
| 333 | <span class="bp">self</span><span class="o">.</span><span class="n">mac</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'mac'</span><span class="p">)</span> | |
| 334 | <span class="bp">self</span><span class="o">.</span><span class="n">owned</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'owned'</span><span class="p">,</span> <span class="kc">False</span><span class="p">)</span> | |
| 335 | <span class="bp">self</span><span class="o">.</span><span class="n">hostnames</span><span class="o">=</span><span class="s1">u','</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'hostnames'</span><span class="p">))</span> | |
| 336 | <span class="bp">self</span><span class="o">.</span><span class="n">network_segment</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'network_segment'</span><span class="p">)</span> | |
| 337 | <span class="bp">self</span><span class="o">.</span><span class="n">ipv4_address</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'ipv4'</span><span class="p">)</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'address'</span><span class="p">)</span> | |
| 338 | <span class="bp">self</span><span class="o">.</span><span class="n">ipv4_gateway</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'ipv4'</span><span class="p">)</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'gateway'</span><span class="p">)</span> | |
| 339 | <span class="bp">self</span><span class="o">.</span><span class="n">ipv4_dns</span><span class="o">=</span><span class="s1">u','</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'ipv4'</span><span class="p">)</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'DNS'</span><span class="p">))</span> | |
| 340 | <span class="bp">self</span><span class="o">.</span><span class="n">ipv4_mask</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'ipv4'</span><span class="p">)</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'mask'</span><span class="p">)</span> | |
| 341 | <span class="bp">self</span><span class="o">.</span><span class="n">ipv6_address</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'ipv6'</span><span class="p">)</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'address'</span><span class="p">)</span> | |
| 342 | <span class="bp">self</span><span class="o">.</span><span class="n">ipv6_gateway</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'ipv6'</span><span class="p">)</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'gateway'</span><span class="p">)</span> | |
| 343 | <span class="bp">self</span><span class="o">.</span><span class="n">ipv6_dns</span><span class="o">=</span><span class="s1">u','</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'ipv6'</span><span class="p">)</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'DNS'</span><span class="p">))</span> | |
| 344 | <span class="bp">self</span><span class="o">.</span><span class="n">ipv6_prefix</span><span class="o">=</span><span class="nb">str</span><span class="p">(</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'ipv6'</span><span class="p">)</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'prefix'</span><span class="p">))</span> | |
| 345 | <span class="bp">self</span><span class="o">.</span><span class="n">ports_filtered</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'ports'</span><span class="p">,{})</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'filtered'</span><span class="p">)</span> | |
| 346 | <span class="bp">self</span><span class="o">.</span><span class="n">ports_opened</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'ports'</span><span class="p">,{})</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'opened'</span><span class="p">)</span> | |
| 347 | <span class="bp">self</span><span class="o">.</span><span class="n">ports_closed</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'ports'</span><span class="p">,{})</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'closed'</span><span class="p">)</span></div> | |
| 348 | ||
| 349 | <div class="viewcode-block" id="Interface.add_relationships_from_dict"><a class="viewcode-back" href="../../server.html#server.models.Interface.add_relationships_from_dict">[docs]</a> <span class="k">def</span> <span class="nf">add_relationships_from_dict</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">entities</span><span class="p">):</span> | |
| 350 | <span class="n">host_id</span> <span class="o">=</span> <span class="s1">'.'</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">entity_metadata</span><span class="o">.</span><span class="n">couchdb_id</span><span class="o">.</span><span class="n">split</span><span class="p">(</span><span class="s1">'.'</span><span class="p">)[:</span><span class="o">-</span><span class="mi">1</span><span class="p">])</span> | |
| 351 | <span class="k">if</span> <span class="n">host_id</span> <span class="ow">not</span> <span class="ow">in</span> <span class="n">entities</span><span class="p">:</span> | |
| 352 | <span class="k">raise</span> <span class="n">EntityNotFound</span><span class="p">(</span><span class="n">host_id</span><span class="p">)</span> | |
| 353 | <span class="bp">self</span><span class="o">.</span><span class="n">host</span> <span class="o">=</span> <span class="n">entities</span><span class="p">[</span><span class="n">host_id</span><span class="p">]</span></div> | |
| 354 | ||
| 355 | <div class="viewcode-block" id="Interface.add_relationships_from_db"><a class="viewcode-back" href="../../server.html#server.models.Interface.add_relationships_from_db">[docs]</a> <span class="k">def</span> <span class="nf">add_relationships_from_db</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">session</span><span class="p">):</span> | |
| 356 | <span class="n">host_id</span> <span class="o">=</span> <span class="s1">'.'</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">entity_metadata</span><span class="o">.</span><span class="n">couchdb_id</span><span class="o">.</span><span class="n">split</span><span class="p">(</span><span class="s1">'.'</span><span class="p">)[:</span><span class="o">-</span><span class="mi">1</span><span class="p">])</span> | |
| 357 | <span class="n">query</span> <span class="o">=</span> <span class="n">session</span><span class="o">.</span><span class="n">query</span><span class="p">(</span><span class="n">Host</span><span class="p">)</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="p">)</span><span class="o">.</span><span class="n">filter</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="o">.</span><span class="n">couchdb_id</span> <span class="o">==</span> <span class="n">host_id</span><span class="p">)</span> | |
| 358 | <span class="bp">self</span><span class="o">.</span><span class="n">host</span> <span class="o">=</span> <span class="n">query</span><span class="o">.</span><span class="n">one</span><span class="p">()</span></div></div> | |
| 359 | ||
| 360 | <div class="viewcode-block" id="Service"><a class="viewcode-back" href="../../server.html#server.models.Service">[docs]</a><span class="k">class</span> <span class="nc">Service</span><span class="p">(</span><span class="n">FaradayEntity</span><span class="p">,</span> <span class="n">Base</span><span class="p">):</span> | |
| 361 | <span class="n">DOC_TYPE</span> <span class="o">=</span> <span class="s1">'Service'</span> | |
| 362 | ||
| 363 | <span class="c1"># Table schema</span> | |
| 364 | <span class="n">__tablename__</span> <span class="o">=</span> <span class="s1">'service'</span> | |
| 365 | <span class="nb">id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">primary_key</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 366 | <span class="n">name</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span> | |
| 367 | <span class="n">description</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span> | |
| 368 | <span class="n">ports</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span> | |
| 369 | <span class="n">owned</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Boolean</span><span class="p">)</span> | |
| 370 | ||
| 371 | <span class="n">protocol</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 372 | <span class="n">status</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 373 | <span class="n">version</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 374 | ||
| 375 | <span class="n">entity_metadata</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="p">,</span> <span class="n">uselist</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">cascade</span><span class="o">=</span><span class="s2">"all, delete-orphan"</span><span class="p">,</span> <span class="n">single_parent</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 376 | <span class="n">entity_metadata_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">ForeignKey</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="o">.</span><span class="n">id</span><span class="p">),</span> <span class="n">index</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 377 | ||
| 378 | <span class="n">host_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">ForeignKey</span><span class="p">(</span><span class="n">Host</span><span class="o">.</span><span class="n">id</span><span class="p">),</span> <span class="n">index</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 379 | <span class="n">host</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="s1">'Host'</span><span class="p">,</span> <span class="n">back_populates</span><span class="o">=</span><span class="s1">'services'</span><span class="p">)</span> | |
| 380 | ||
| 381 | <span class="n">interface_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">ForeignKey</span><span class="p">(</span><span class="n">Interface</span><span class="o">.</span><span class="n">id</span><span class="p">),</span> <span class="n">index</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 382 | <span class="n">interface</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="s1">'Interface'</span><span class="p">,</span> <span class="n">back_populates</span><span class="o">=</span><span class="s1">'services'</span><span class="p">)</span> | |
| 383 | ||
| 384 | <span class="n">vulnerabilities</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="s1">'Vulnerability'</span><span class="p">)</span> | |
| 385 | <span class="n">credentials</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="s1">'Credential'</span><span class="p">)</span> | |
| 386 | ||
| 387 | <div class="viewcode-block" id="Service.update_from_document"><a class="viewcode-back" href="../../server.html#server.models.Service.update_from_document">[docs]</a> <span class="k">def</span> <span class="nf">update_from_document</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">document</span><span class="p">):</span> | |
| 388 | <span class="bp">self</span><span class="o">.</span><span class="n">name</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'name'</span><span class="p">)</span> | |
| 389 | <span class="bp">self</span><span class="o">.</span><span class="n">description</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'description'</span><span class="p">)</span> | |
| 390 | <span class="bp">self</span><span class="o">.</span><span class="n">owned</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'owned'</span><span class="p">,</span> <span class="kc">False</span><span class="p">)</span> | |
| 391 | <span class="bp">self</span><span class="o">.</span><span class="n">protocol</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'protocol'</span><span class="p">)</span> | |
| 392 | <span class="bp">self</span><span class="o">.</span><span class="n">status</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'status'</span><span class="p">)</span> | |
| 393 | <span class="bp">self</span><span class="o">.</span><span class="n">version</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'version'</span><span class="p">)</span> | |
| 394 | ||
| 395 | <span class="c1"># We found workspaces where ports are defined as an integer</span> | |
| 396 | <span class="k">if</span> <span class="nb">isinstance</span><span class="p">(</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'ports'</span><span class="p">,</span> <span class="kc">None</span><span class="p">),</span> <span class="p">(</span><span class="nb">int</span><span class="p">,</span> <span class="n">long</span><span class="p">)):</span> | |
| 397 | <span class="bp">self</span><span class="o">.</span><span class="n">ports</span> <span class="o">=</span> <span class="nb">str</span><span class="p">(</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'ports'</span><span class="p">))</span> | |
| 398 | <span class="k">else</span><span class="p">:</span> | |
| 399 | <span class="bp">self</span><span class="o">.</span><span class="n">ports</span> <span class="o">=</span> <span class="s1">u','</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="nb">map</span><span class="p">(</span><span class="nb">str</span><span class="p">,</span> <span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'ports'</span><span class="p">)))</span></div> | |
| 400 | ||
| 401 | <div class="viewcode-block" id="Service.add_relationships_from_dict"><a class="viewcode-back" href="../../server.html#server.models.Service.add_relationships_from_dict">[docs]</a> <span class="k">def</span> <span class="nf">add_relationships_from_dict</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">entities</span><span class="p">):</span> | |
| 402 | <span class="n">couchdb_id</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">entity_metadata</span><span class="o">.</span><span class="n">couchdb_id</span> | |
| 403 | ||
| 404 | <span class="n">host_id</span> <span class="o">=</span> <span class="n">couchdb_id</span><span class="o">.</span><span class="n">split</span><span class="p">(</span><span class="s1">'.'</span><span class="p">)[</span><span class="mi">0</span><span class="p">]</span> | |
| 405 | <span class="k">if</span> <span class="n">host_id</span> <span class="ow">not</span> <span class="ow">in</span> <span class="n">entities</span><span class="p">:</span> | |
| 406 | <span class="k">raise</span> <span class="n">EntityNotFound</span><span class="p">(</span><span class="n">host_id</span><span class="p">)</span> | |
| 407 | <span class="bp">self</span><span class="o">.</span><span class="n">host</span> <span class="o">=</span> <span class="n">entities</span><span class="p">[</span><span class="n">host_id</span><span class="p">]</span> | |
| 408 | ||
| 409 | <span class="n">interface_id</span> <span class="o">=</span> <span class="s1">'.'</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">couchdb_id</span><span class="o">.</span><span class="n">split</span><span class="p">(</span><span class="s1">'.'</span><span class="p">)[:</span><span class="o">-</span><span class="mi">1</span><span class="p">])</span> | |
| 410 | <span class="k">if</span> <span class="n">interface_id</span> <span class="ow">not</span> <span class="ow">in</span> <span class="n">entities</span><span class="p">:</span> | |
| 411 | <span class="k">raise</span> <span class="n">EntityNotFound</span><span class="p">(</span><span class="n">interface_id</span><span class="p">)</span> | |
| 412 | <span class="bp">self</span><span class="o">.</span><span class="n">interface</span> <span class="o">=</span> <span class="n">entities</span><span class="p">[</span><span class="n">interface_id</span><span class="p">]</span></div> | |
| 413 | ||
| 414 | <div class="viewcode-block" id="Service.add_relationships_from_db"><a class="viewcode-back" href="../../server.html#server.models.Service.add_relationships_from_db">[docs]</a> <span class="k">def</span> <span class="nf">add_relationships_from_db</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">session</span><span class="p">):</span> | |
| 415 | <span class="n">couchdb_id</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">entity_metadata</span><span class="o">.</span><span class="n">couchdb_id</span> | |
| 416 | <span class="n">host_id</span> <span class="o">=</span> <span class="n">couchdb_id</span><span class="o">.</span><span class="n">split</span><span class="p">(</span><span class="s1">'.'</span><span class="p">)[</span><span class="mi">0</span><span class="p">]</span> | |
| 417 | <span class="n">query</span> <span class="o">=</span> <span class="n">session</span><span class="o">.</span><span class="n">query</span><span class="p">(</span><span class="n">Host</span><span class="p">)</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="p">)</span><span class="o">.</span><span class="n">filter</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="o">.</span><span class="n">couchdb_id</span> <span class="o">==</span> <span class="n">host_id</span><span class="p">)</span> | |
| 418 | <span class="bp">self</span><span class="o">.</span><span class="n">host</span> <span class="o">=</span> <span class="n">query</span><span class="o">.</span><span class="n">one</span><span class="p">()</span> | |
| 419 | ||
| 420 | <span class="n">interface_id</span> <span class="o">=</span> <span class="s1">'.'</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">couchdb_id</span><span class="o">.</span><span class="n">split</span><span class="p">(</span><span class="s1">'.'</span><span class="p">)[:</span><span class="o">-</span><span class="mi">1</span><span class="p">])</span> | |
| 421 | <span class="n">query</span> <span class="o">=</span> <span class="n">session</span><span class="o">.</span><span class="n">query</span><span class="p">(</span><span class="n">Interface</span><span class="p">)</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="p">)</span><span class="o">.</span><span class="n">filter</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="o">.</span><span class="n">couchdb_id</span> <span class="o">==</span> <span class="n">interface_id</span><span class="p">)</span> | |
| 422 | <span class="bp">self</span><span class="o">.</span><span class="n">interface</span> <span class="o">=</span> <span class="n">query</span><span class="o">.</span><span class="n">one</span><span class="p">()</span></div></div> | |
| 423 | ||
| 424 | ||
| 425 | <div class="viewcode-block" id="Vulnerability"><a class="viewcode-back" href="../../server.html#server.models.Vulnerability">[docs]</a><span class="k">class</span> <span class="nc">Vulnerability</span><span class="p">(</span><span class="n">FaradayEntity</span><span class="p">,</span> <span class="n">Base</span><span class="p">):</span> | |
| 426 | <span class="n">DOC_TYPE</span> <span class="o">=</span> <span class="p">[</span><span class="s1">'Vulnerability'</span><span class="p">,</span> <span class="s1">'VulnerabilityWeb'</span><span class="p">]</span> | |
| 427 | ||
| 428 | <span class="c1"># Table schema</span> | |
| 429 | <span class="n">__tablename__</span> <span class="o">=</span> <span class="s1">'vulnerability'</span> | |
| 430 | <span class="nb">id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">primary_key</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 431 | <span class="n">name</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span> | |
| 432 | <span class="n">description</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Text</span><span class="p">(),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span> | |
| 433 | ||
| 434 | <span class="n">confirmed</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Boolean</span><span class="p">)</span> | |
| 435 | <span class="n">vuln_type</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 436 | <span class="n">data</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Text</span><span class="p">())</span> | |
| 437 | <span class="n">easeofresolution</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">50</span><span class="p">))</span> | |
| 438 | <span class="n">refs</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Text</span><span class="p">())</span> | |
| 439 | <span class="n">resolution</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Text</span><span class="p">())</span> | |
| 440 | <span class="n">severity</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">50</span><span class="p">))</span> | |
| 441 | <span class="n">owned</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Boolean</span><span class="p">)</span> | |
| 442 | <span class="n">attachments</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Text</span><span class="p">(),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 443 | ||
| 444 | <span class="n">impact_accountability</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Boolean</span><span class="p">)</span> | |
| 445 | <span class="n">impact_availability</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Boolean</span><span class="p">)</span> | |
| 446 | <span class="n">impact_confidentiality</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Boolean</span><span class="p">)</span> | |
| 447 | <span class="n">impact_integrity</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Boolean</span><span class="p">)</span> | |
| 448 | ||
| 449 | <span class="n">method</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">50</span><span class="p">))</span> | |
| 450 | <span class="n">params</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">500</span><span class="p">))</span> | |
| 451 | <span class="n">path</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">500</span><span class="p">))</span> | |
| 452 | <span class="n">pname</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 453 | <span class="n">query</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Text</span><span class="p">())</span> | |
| 454 | <span class="n">request</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Text</span><span class="p">())</span> | |
| 455 | <span class="n">response</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Text</span><span class="p">())</span> | |
| 456 | <span class="n">website</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 457 | ||
| 458 | <span class="n">status</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">))</span> | |
| 459 | ||
| 460 | <span class="n">entity_metadata</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="p">,</span> <span class="n">uselist</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">cascade</span><span class="o">=</span><span class="s2">"all, delete-orphan"</span><span class="p">,</span> <span class="n">single_parent</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 461 | <span class="n">entity_metadata_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">ForeignKey</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="o">.</span><span class="n">id</span><span class="p">),</span> <span class="n">index</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 462 | ||
| 463 | <span class="n">host_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">ForeignKey</span><span class="p">(</span><span class="n">Host</span><span class="o">.</span><span class="n">id</span><span class="p">),</span> <span class="n">index</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 464 | <span class="n">host</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="s1">'Host'</span><span class="p">,</span> <span class="n">back_populates</span><span class="o">=</span><span class="s1">'vulnerabilities'</span><span class="p">)</span> | |
| 465 | ||
| 466 | <span class="n">service_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">ForeignKey</span><span class="p">(</span><span class="n">Service</span><span class="o">.</span><span class="n">id</span><span class="p">),</span> <span class="n">index</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 467 | <span class="n">service</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="s1">'Service'</span><span class="p">,</span> <span class="n">back_populates</span><span class="o">=</span><span class="s1">'vulnerabilities'</span><span class="p">)</span> | |
| 468 | ||
| 469 | <div class="viewcode-block" id="Vulnerability.update_from_document"><a class="viewcode-back" href="../../server.html#server.models.Vulnerability.update_from_document">[docs]</a> <span class="k">def</span> <span class="nf">update_from_document</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">document</span><span class="p">):</span> | |
| 470 | <span class="bp">self</span><span class="o">.</span><span class="n">name</span> <span class="o">=</span> <span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'name'</span><span class="p">)</span> | |
| 471 | <span class="bp">self</span><span class="o">.</span><span class="n">description</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'desc'</span><span class="p">)</span> | |
| 472 | <span class="bp">self</span><span class="o">.</span><span class="n">confirmed</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'confirmed'</span><span class="p">)</span> | |
| 473 | <span class="bp">self</span><span class="o">.</span><span class="n">vuln_type</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'type'</span><span class="p">)</span> | |
| 474 | <span class="bp">self</span><span class="o">.</span><span class="n">data</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'data'</span><span class="p">)</span> | |
| 475 | <span class="bp">self</span><span class="o">.</span><span class="n">easeofresolution</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'easeofresolution'</span><span class="p">)</span> | |
| 476 | <span class="bp">self</span><span class="o">.</span><span class="n">refs</span><span class="o">=</span><span class="n">json</span><span class="o">.</span><span class="n">dumps</span><span class="p">(</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'refs'</span><span class="p">,</span> <span class="p">[]))</span> | |
| 477 | <span class="bp">self</span><span class="o">.</span><span class="n">resolution</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'resolution'</span><span class="p">)</span> | |
| 478 | <span class="bp">self</span><span class="o">.</span><span class="n">severity</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'severity'</span><span class="p">)</span> | |
| 479 | <span class="bp">self</span><span class="o">.</span><span class="n">owned</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'owned'</span><span class="p">,</span> <span class="kc">False</span><span class="p">)</span> | |
| 480 | <span class="bp">self</span><span class="o">.</span><span class="n">attachments</span> <span class="o">=</span> <span class="n">json</span><span class="o">.</span><span class="n">dumps</span><span class="p">(</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'_attachments'</span><span class="p">,</span> <span class="p">{}))</span> | |
| 481 | <span class="bp">self</span><span class="o">.</span><span class="n">impact_accountability</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'impact'</span><span class="p">,</span> <span class="p">{})</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'accountability'</span><span class="p">)</span> | |
| 482 | <span class="bp">self</span><span class="o">.</span><span class="n">impact_availability</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'impact'</span><span class="p">,</span> <span class="p">{})</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'availability'</span><span class="p">)</span> | |
| 483 | <span class="bp">self</span><span class="o">.</span><span class="n">impact_confidentiality</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'impact'</span><span class="p">,</span> <span class="p">{})</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'confidentiality'</span><span class="p">)</span> | |
| 484 | <span class="bp">self</span><span class="o">.</span><span class="n">impact_integrity</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'impact'</span><span class="p">,</span> <span class="p">{})</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'integrity'</span><span class="p">)</span> | |
| 485 | <span class="bp">self</span><span class="o">.</span><span class="n">method</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'method'</span><span class="p">)</span> | |
| 486 | <span class="bp">self</span><span class="o">.</span><span class="n">path</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'path'</span><span class="p">)</span> | |
| 487 | <span class="bp">self</span><span class="o">.</span><span class="n">pname</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'pname'</span><span class="p">)</span> | |
| 488 | <span class="bp">self</span><span class="o">.</span><span class="n">query</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'query'</span><span class="p">)</span> | |
| 489 | <span class="bp">self</span><span class="o">.</span><span class="n">request</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'request'</span><span class="p">)</span> | |
| 490 | <span class="bp">self</span><span class="o">.</span><span class="n">response</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'response'</span><span class="p">)</span> | |
| 491 | <span class="bp">self</span><span class="o">.</span><span class="n">website</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'website'</span><span class="p">)</span> | |
| 492 | <span class="bp">self</span><span class="o">.</span><span class="n">status</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'status'</span><span class="p">,</span> <span class="s1">'opened'</span><span class="p">)</span> | |
| 493 | ||
| 494 | <span class="n">params</span> <span class="o">=</span> <span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'params'</span><span class="p">,</span> <span class="s1">u''</span><span class="p">)</span> | |
| 495 | <span class="k">if</span> <span class="nb">isinstance</span><span class="p">(</span><span class="n">params</span><span class="p">,</span> <span class="p">(</span><span class="nb">list</span><span class="p">,</span> <span class="nb">tuple</span><span class="p">)):</span> | |
| 496 | <span class="bp">self</span><span class="o">.</span><span class="n">params</span> <span class="o">=</span> <span class="p">(</span><span class="s1">u' '</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">params</span><span class="p">))</span><span class="o">.</span><span class="n">strip</span><span class="p">()</span> | |
| 497 | <span class="k">else</span><span class="p">:</span> | |
| 498 | <span class="bp">self</span><span class="o">.</span><span class="n">params</span> <span class="o">=</span> <span class="n">params</span> <span class="k">if</span> <span class="n">params</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span> <span class="k">else</span> <span class="s1">u''</span></div> | |
| 499 | ||
| 500 | <div class="viewcode-block" id="Vulnerability.add_relationships_from_dict"><a class="viewcode-back" href="../../server.html#server.models.Vulnerability.add_relationships_from_dict">[docs]</a> <span class="k">def</span> <span class="nf">add_relationships_from_dict</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">entities</span><span class="p">):</span> | |
| 501 | <span class="n">couchdb_id</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">entity_metadata</span><span class="o">.</span><span class="n">couchdb_id</span> | |
| 502 | <span class="n">host_id</span> <span class="o">=</span> <span class="n">couchdb_id</span><span class="o">.</span><span class="n">split</span><span class="p">(</span><span class="s1">'.'</span><span class="p">)[</span><span class="mi">0</span><span class="p">]</span> | |
| 503 | <span class="k">if</span> <span class="n">host_id</span> <span class="ow">not</span> <span class="ow">in</span> <span class="n">entities</span><span class="p">:</span> | |
| 504 | <span class="k">raise</span> <span class="n">EntityNotFound</span><span class="p">(</span><span class="n">host_id</span><span class="p">)</span> | |
| 505 | <span class="bp">self</span><span class="o">.</span><span class="n">host</span> <span class="o">=</span> <span class="n">entities</span><span class="p">[</span><span class="n">host_id</span><span class="p">]</span> | |
| 506 | ||
| 507 | <span class="n">parent_id</span> <span class="o">=</span> <span class="s1">'.'</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">couchdb_id</span><span class="o">.</span><span class="n">split</span><span class="p">(</span><span class="s1">'.'</span><span class="p">)[:</span><span class="o">-</span><span class="mi">1</span><span class="p">])</span> | |
| 508 | <span class="k">if</span> <span class="n">parent_id</span> <span class="o">!=</span> <span class="n">host_id</span><span class="p">:</span> | |
| 509 | <span class="k">if</span> <span class="n">parent_id</span> <span class="ow">not</span> <span class="ow">in</span> <span class="n">entities</span><span class="p">:</span> | |
| 510 | <span class="k">raise</span> <span class="n">EntityNotFound</span><span class="p">(</span><span class="n">parent_id</span><span class="p">)</span> | |
| 511 | <span class="bp">self</span><span class="o">.</span><span class="n">service</span> <span class="o">=</span> <span class="n">entities</span><span class="p">[</span><span class="n">parent_id</span><span class="p">]</span></div> | |
| 512 | ||
| 513 | <div class="viewcode-block" id="Vulnerability.add_relationships_from_db"><a class="viewcode-back" href="../../server.html#server.models.Vulnerability.add_relationships_from_db">[docs]</a> <span class="k">def</span> <span class="nf">add_relationships_from_db</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">session</span><span class="p">):</span> | |
| 514 | <span class="n">couchdb_id</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">entity_metadata</span><span class="o">.</span><span class="n">couchdb_id</span> | |
| 515 | <span class="n">host_id</span> <span class="o">=</span> <span class="n">couchdb_id</span><span class="o">.</span><span class="n">split</span><span class="p">(</span><span class="s1">'.'</span><span class="p">)[</span><span class="mi">0</span><span class="p">]</span> | |
| 516 | <span class="n">query</span> <span class="o">=</span> <span class="n">session</span><span class="o">.</span><span class="n">query</span><span class="p">(</span><span class="n">Host</span><span class="p">)</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="p">)</span><span class="o">.</span><span class="n">filter</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="o">.</span><span class="n">couchdb_id</span> <span class="o">==</span> <span class="n">host_id</span><span class="p">)</span> | |
| 517 | <span class="bp">self</span><span class="o">.</span><span class="n">host</span> <span class="o">=</span> <span class="n">query</span><span class="o">.</span><span class="n">one</span><span class="p">()</span> | |
| 518 | ||
| 519 | <span class="n">parent_id</span> <span class="o">=</span> <span class="s1">'.'</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">couchdb_id</span><span class="o">.</span><span class="n">split</span><span class="p">(</span><span class="s1">'.'</span><span class="p">)[:</span><span class="o">-</span><span class="mi">1</span><span class="p">])</span> | |
| 520 | <span class="k">if</span> <span class="n">parent_id</span> <span class="o">!=</span> <span class="n">host_id</span><span class="p">:</span> | |
| 521 | <span class="n">query</span> <span class="o">=</span> <span class="n">session</span><span class="o">.</span><span class="n">query</span><span class="p">(</span><span class="n">Service</span><span class="p">)</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="p">)</span><span class="o">.</span><span class="n">filter</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="o">.</span><span class="n">couchdb_id</span> <span class="o">==</span> <span class="n">parent_id</span><span class="p">)</span> | |
| 522 | <span class="bp">self</span><span class="o">.</span><span class="n">service</span> <span class="o">=</span> <span class="n">query</span><span class="o">.</span><span class="n">one</span><span class="p">()</span></div></div> | |
| 523 | ||
| 524 | <div class="viewcode-block" id="Note"><a class="viewcode-back" href="../../server.html#server.models.Note">[docs]</a><span class="k">class</span> <span class="nc">Note</span><span class="p">(</span><span class="n">FaradayEntity</span><span class="p">,</span> <span class="n">Base</span><span class="p">):</span> | |
| 525 | <span class="n">DOC_TYPE</span> <span class="o">=</span> <span class="s1">'Note'</span> | |
| 526 | ||
| 527 | <span class="c1"># Table schema</span> | |
| 528 | <span class="n">__tablename__</span> <span class="o">=</span> <span class="s1">'note'</span> | |
| 529 | <span class="nb">id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">primary_key</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 530 | <span class="n">name</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span> | |
| 531 | <span class="n">text</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Text</span><span class="p">(),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 532 | <span class="n">description</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Text</span><span class="p">(),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 533 | <span class="n">owned</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Boolean</span><span class="p">)</span> | |
| 534 | ||
| 535 | <span class="n">entity_metadata</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="p">,</span> <span class="n">uselist</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">cascade</span><span class="o">=</span><span class="s2">"all, delete-orphan"</span><span class="p">,</span> <span class="n">single_parent</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 536 | <span class="n">entity_metadata_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">ForeignKey</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="o">.</span><span class="n">id</span><span class="p">),</span> <span class="n">index</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 537 | ||
| 538 | <div class="viewcode-block" id="Note.update_from_document"><a class="viewcode-back" href="../../server.html#server.models.Note.update_from_document">[docs]</a> <span class="k">def</span> <span class="nf">update_from_document</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">document</span><span class="p">):</span> | |
| 539 | <span class="bp">self</span><span class="o">.</span><span class="n">name</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'name'</span><span class="p">)</span> | |
| 540 | <span class="bp">self</span><span class="o">.</span><span class="n">text</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'text'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 541 | <span class="bp">self</span><span class="o">.</span><span class="n">description</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'description'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 542 | <span class="bp">self</span><span class="o">.</span><span class="n">owned</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'owned'</span><span class="p">,</span> <span class="kc">False</span><span class="p">)</span></div></div> | |
| 543 | ||
| 544 | <div class="viewcode-block" id="Credential"><a class="viewcode-back" href="../../server.html#server.models.Credential">[docs]</a><span class="k">class</span> <span class="nc">Credential</span><span class="p">(</span><span class="n">FaradayEntity</span><span class="p">,</span> <span class="n">Base</span><span class="p">):</span> | |
| 545 | <span class="n">DOC_TYPE</span> <span class="o">=</span> <span class="s1">'Cred'</span> | |
| 546 | ||
| 547 | <span class="c1"># Table schema</span> | |
| 548 | <span class="n">__tablename__</span> <span class="o">=</span> <span class="s1">'credential'</span> | |
| 549 | <span class="nb">id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">primary_key</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 550 | <span class="n">username</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span> | |
| 551 | <span class="n">password</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Text</span><span class="p">(),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">False</span><span class="p">)</span> | |
| 552 | <span class="n">owned</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Boolean</span><span class="p">)</span> | |
| 553 | <span class="n">description</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Text</span><span class="p">(),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 554 | <span class="n">name</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 555 | ||
| 556 | <span class="n">entity_metadata</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="p">,</span> <span class="n">uselist</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">cascade</span><span class="o">=</span><span class="s2">"all, delete-orphan"</span><span class="p">,</span> <span class="n">single_parent</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 557 | <span class="n">entity_metadata_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">ForeignKey</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="o">.</span><span class="n">id</span><span class="p">),</span> <span class="n">index</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 558 | ||
| 559 | <span class="n">host_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">ForeignKey</span><span class="p">(</span><span class="n">Host</span><span class="o">.</span><span class="n">id</span><span class="p">),</span> <span class="n">index</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 560 | <span class="n">host</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="s1">'Host'</span><span class="p">,</span> <span class="n">back_populates</span><span class="o">=</span><span class="s1">'credentials'</span><span class="p">)</span> | |
| 561 | ||
| 562 | <span class="n">service_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">ForeignKey</span><span class="p">(</span><span class="n">Service</span><span class="o">.</span><span class="n">id</span><span class="p">),</span> <span class="n">index</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 563 | <span class="n">service</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="s1">'Service'</span><span class="p">,</span> <span class="n">back_populates</span><span class="o">=</span><span class="s1">'credentials'</span><span class="p">)</span> | |
| 564 | ||
| 565 | <div class="viewcode-block" id="Credential.update_from_document"><a class="viewcode-back" href="../../server.html#server.models.Credential.update_from_document">[docs]</a> <span class="k">def</span> <span class="nf">update_from_document</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">document</span><span class="p">):</span> | |
| 566 | <span class="bp">self</span><span class="o">.</span><span class="n">username</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'username'</span><span class="p">)</span> | |
| 567 | <span class="bp">self</span><span class="o">.</span><span class="n">password</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'password'</span><span class="p">,</span> <span class="s1">''</span><span class="p">)</span> | |
| 568 | <span class="bp">self</span><span class="o">.</span><span class="n">owned</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'owned'</span><span class="p">,</span> <span class="kc">False</span><span class="p">)</span> | |
| 569 | <span class="bp">self</span><span class="o">.</span><span class="n">description</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'description'</span><span class="p">,</span> <span class="s1">''</span><span class="p">)</span> | |
| 570 | <span class="bp">self</span><span class="o">.</span><span class="n">name</span><span class="o">=</span><span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'name'</span><span class="p">,</span><span class="s1">''</span><span class="p">)</span></div></div> | |
| 571 | ||
| 572 | <div class="viewcode-block" id="Command"><a class="viewcode-back" href="../../server.html#server.models.Command">[docs]</a><span class="k">class</span> <span class="nc">Command</span><span class="p">(</span><span class="n">FaradayEntity</span><span class="p">,</span> <span class="n">Base</span><span class="p">):</span> | |
| 573 | <span class="n">DOC_TYPE</span> <span class="o">=</span> <span class="s1">'CommandRunInformation'</span> | |
| 574 | ||
| 575 | <span class="c1"># Table schema</span> | |
| 576 | <span class="n">__tablename__</span> <span class="o">=</span> <span class="s1">'command'</span> | |
| 577 | <span class="nb">id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">primary_key</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 578 | <span class="n">command</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 579 | <span class="n">duration</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Float</span><span class="p">,</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 580 | <span class="n">itime</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Float</span><span class="p">,</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 581 | <span class="n">ip</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 582 | <span class="n">hostname</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 583 | <span class="n">params</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 584 | <span class="n">user</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 585 | <span class="n">workspace</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">String</span><span class="p">(</span><span class="mi">250</span><span class="p">),</span> <span class="n">nullable</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 586 | ||
| 587 | ||
| 588 | <span class="n">entity_metadata</span> <span class="o">=</span> <span class="n">relationship</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="p">,</span> <span class="n">uselist</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">cascade</span><span class="o">=</span><span class="s2">"all, delete-orphan"</span><span class="p">,</span> <span class="n">single_parent</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 589 | <span class="n">entity_metadata_id</span> <span class="o">=</span> <span class="n">Column</span><span class="p">(</span><span class="n">Integer</span><span class="p">,</span> <span class="n">ForeignKey</span><span class="p">(</span><span class="n">EntityMetadata</span><span class="o">.</span><span class="n">id</span><span class="p">),</span> <span class="n">index</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 590 | ||
| 591 | <div class="viewcode-block" id="Command.update_from_document"><a class="viewcode-back" href="../../server.html#server.models.Command.update_from_document">[docs]</a> <span class="k">def</span> <span class="nf">update_from_document</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">document</span><span class="p">):</span> | |
| 592 | <span class="bp">self</span><span class="o">.</span><span class="n">command</span> <span class="o">=</span> <span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'command'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 593 | <span class="bp">self</span><span class="o">.</span><span class="n">duration</span> <span class="o">=</span> <span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'duration'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 594 | <span class="bp">self</span><span class="o">.</span><span class="n">itime</span> <span class="o">=</span> <span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'itime'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 595 | <span class="bp">self</span><span class="o">.</span><span class="n">ip</span> <span class="o">=</span> <span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'ip'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 596 | <span class="bp">self</span><span class="o">.</span><span class="n">hostname</span> <span class="o">=</span> <span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'hostname'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 597 | <span class="bp">self</span><span class="o">.</span><span class="n">params</span> <span class="o">=</span> <span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'params'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 598 | <span class="bp">self</span><span class="o">.</span><span class="n">user</span> <span class="o">=</span> <span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'user'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 599 | <span class="bp">self</span><span class="o">.</span><span class="n">workspace</span> <span class="o">=</span> <span class="n">document</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s1">'workspace'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span></div></div> | |
| 600 | ||
| 601 | </pre></div> | |
| 602 | ||
| 603 | </div> | |
| 604 | </div> | |
| 605 | <footer> | |
| 606 | ||
| 607 | ||
| 608 | <hr/> | |
| 609 | ||
| 610 | <div role="contentinfo"> | |
| 611 | <p> | |
| 612 | © Copyright 2016, Infobyte. | |
| 613 | ||
| 614 | </p> | |
| 615 | </div> | |
| 616 | Built with <a href="http://sphinx-doc.org/">Sphinx</a> using a <a href="https://github.com/snide/sphinx_rtd_theme">theme</a> provided by <a href="https://readthedocs.org">Read the Docs</a>. | |
| 617 | ||
| 618 | </footer> | |
| 619 | ||
| 620 | </div> | |
| 621 | </div> | |
| 622 | ||
| 623 | </section> | |
| 624 | ||
| 625 | </div> | |
| 626 | ||
| 627 | ||
| 628 | ||
| 629 | ||
| 630 | ||
| 631 | <script type="text/javascript"> | |
| 632 | var DOCUMENTATION_OPTIONS = { | |
| 633 | URL_ROOT:'../../', | |
| 634 | VERSION:'0.1', | |
| 635 | COLLAPSE_INDEX:false, | |
| 636 | FILE_SUFFIX:'.html', | |
| 637 | HAS_SOURCE: true | |
| 638 | }; | |
| 639 | </script> | |
| 640 | <script type="text/javascript" src="../../_static/jquery.js"></script> | |
| 641 | <script type="text/javascript" src="../../_static/underscore.js"></script> | |
| 642 | <script type="text/javascript" src="../../_static/doctools.js"></script> | |
| 643 | ||
| 644 | ||
| 645 | ||
| 646 | ||
| 647 | ||
| 648 | <script type="text/javascript" src="../../_static/js/theme.js"></script> | |
| 649 | ||
| 650 | ||
| 651 | ||
| 652 | ||
| 653 | <script type="text/javascript"> | |
| 654 | jQuery(function () { | |
| 655 | SphinxRtdTheme.StickyNav.enable(); | |
| 656 | }); | |
| 657 | </script> | |
| 658 | ||
| 659 | ||
| 660 | </body> | |
| 661 | </html>⏎ |
| 0 | ||
| 1 | ||
| 2 | <!DOCTYPE html> | |
| 3 | <!--[if IE 8]><html class="no-js lt-ie9" lang="en" > <![endif]--> | |
| 4 | <!--[if gt IE 8]><!--> <html class="no-js" lang="en" > <!--<![endif]--> | |
| 5 | <head> | |
| 6 | <meta charset="utf-8"> | |
| 7 | ||
| 8 | <meta name="viewport" content="width=device-width, initial-scale=1.0"> | |
| 9 | ||
| 10 | <title>server — Faraday 0.1 documentation</title> | |
| 11 | ||
| 12 | ||
| 13 | ||
| 14 | ||
| 15 | ||
| 16 | ||
| 17 | ||
| 18 | ||
| 19 | ||
| 20 | ||
| 21 | ||
| 22 | ||
| 23 | ||
| 24 | ||
| 25 | ||
| 26 | <link rel="stylesheet" href="../_static/css/theme.css" type="text/css" /> | |
| 27 | ||
| 28 | ||
| 29 | ||
| 30 | ||
| 31 | ||
| 32 | <link rel="index" title="Index" | |
| 33 | href="../genindex.html"/> | |
| 34 | <link rel="search" title="Search" href="../search.html"/> | |
| 35 | <link rel="top" title="Faraday 0.1 documentation" href="../index.html"/> | |
| 36 | <link rel="up" title="Module code" href="index.html"/> | |
| 37 | ||
| 38 | ||
| 39 | <script src="../_static/js/modernizr.min.js"></script> | |
| 40 | ||
| 41 | </head> | |
| 42 | ||
| 43 | <body class="wy-body-for-nav" role="document"> | |
| 44 | ||
| 45 | <div class="wy-grid-for-nav"> | |
| 46 | ||
| 47 | ||
| 48 | <nav data-toggle="wy-nav-shift" class="wy-nav-side"> | |
| 49 | <div class="wy-side-scroll"> | |
| 50 | <div class="wy-side-nav-search"> | |
| 51 | ||
| 52 | ||
| 53 | ||
| 54 | <a href="../index.html" class="icon icon-home"> Faraday | |
| 55 | ||
| 56 | ||
| 57 | ||
| 58 | </a> | |
| 59 | ||
| 60 | ||
| 61 | ||
| 62 | ||
| 63 | <div class="version"> | |
| 64 | 0.1 | |
| 65 | </div> | |
| 66 | ||
| 67 | ||
| 68 | ||
| 69 | ||
| 70 | <div role="search"> | |
| 71 | <form id="rtd-search-form" class="wy-form" action="../search.html" method="get"> | |
| 72 | <input type="text" name="q" placeholder="Search docs" /> | |
| 73 | <input type="hidden" name="check_keywords" value="yes" /> | |
| 74 | <input type="hidden" name="area" value="default" /> | |
| 75 | </form> | |
| 76 | </div> | |
| 77 | ||
| 78 | ||
| 79 | </div> | |
| 80 | ||
| 81 | <div class="wy-menu wy-menu-vertical" data-spy="affix" role="navigation" aria-label="main navigation"> | |
| 82 | ||
| 83 | ||
| 84 | ||
| 85 | <!-- Local TOC --> | |
| 86 | <div class="local-toc"></div> | |
| 87 | ||
| 88 | ||
| 89 | </div> | |
| 90 | </div> | |
| 91 | </nav> | |
| 92 | ||
| 93 | <section data-toggle="wy-nav-shift" class="wy-nav-content-wrap"> | |
| 94 | ||
| 95 | ||
| 96 | <nav class="wy-nav-top" role="navigation" aria-label="top navigation"> | |
| 97 | <i data-toggle="wy-nav-top" class="fa fa-bars"></i> | |
| 98 | <a href="../index.html">Faraday</a> | |
| 99 | </nav> | |
| 100 | ||
| 101 | ||
| 102 | ||
| 103 | <div class="wy-nav-content"> | |
| 104 | <div class="rst-content"> | |
| 105 | ||
| 106 | ||
| 107 | ||
| 108 | ||
| 109 | ||
| 110 | ||
| 111 | <div role="navigation" aria-label="breadcrumbs navigation"> | |
| 112 | <ul class="wy-breadcrumbs"> | |
| 113 | <li><a href="../index.html">Docs</a> »</li> | |
| 114 | ||
| 115 | <li><a href="index.html">Module code</a> »</li> | |
| 116 | ||
| 117 | <li>server</li> | |
| 118 | <li class="wy-breadcrumbs-aside"> | |
| 119 | ||
| 120 | ||
| 121 | ||
| 122 | </li> | |
| 123 | </ul> | |
| 124 | <hr/> | |
| 125 | </div> | |
| 126 | <div role="main" class="document" itemscope="itemscope" itemtype="http://schema.org/Article"> | |
| 127 | <div itemprop="articleBody"> | |
| 128 | ||
| 129 | <h1>Source code for server</h1><div class="highlight"><pre> | |
| 130 | <span></span><span class="ch">#!/usr/bin/python3</span> | |
| 131 | <span class="c1"># -*- coding: utf-8 -*-</span> | |
| 132 | <span class="sd">'''</span> | |
| 133 | <span class="sd">Faraday Penetration Test IDE</span> | |
| 134 | <span class="sd">Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/)</span> | |
| 135 | <span class="sd">See the file 'doc/LICENSE' for the license information</span> | |
| 136 | ||
| 137 | <span class="sd">'''</span> | |
| 138 | <span class="kn">import</span> <span class="nn">requests</span> | |
| 139 | <span class="kn">import</span> <span class="nn">json</span> | |
| 140 | <span class="kn">from</span> <span class="nn">persistence.server.utils</span> <span class="k">import</span> <span class="n">force_unique</span> | |
| 141 | <span class="kn">from</span> <span class="nn">persistence.server.server_io_exceptions</span> <span class="k">import</span> <span class="p">(</span><span class="n">WrongObjectSignature</span><span class="p">,</span> | |
| 142 | <span class="n">CantCommunicateWithServerError</span><span class="p">,</span> | |
| 143 | <span class="n">ConflictInDatabase</span><span class="p">,</span> | |
| 144 | <span class="n">ResourceDoesNotExist</span><span class="p">,</span> | |
| 145 | <span class="n">Unauthorized</span><span class="p">,</span> | |
| 146 | <span class="n">MoreThanOneObjectFoundByID</span><span class="p">)</span> | |
| 147 | ||
| 148 | <span class="kn">from</span> <span class="nn">persistence.server.changes_stream</span> <span class="k">import</span> <span class="n">CouchChangesStream</span> | |
| 149 | ||
| 150 | <span class="c1"># NOTE: Change is you want to use this module by itself.</span> | |
| 151 | <span class="c1"># If FARADAY_UP is False, SERVER_URL must be a valid faraday server url</span> | |
| 152 | <span class="n">FARADAY_UP</span> <span class="o">=</span> <span class="kc">True</span> | |
| 153 | <span class="n">SERVER_URL</span> <span class="o">=</span> <span class="s2">"http://127.0.0.1:5984"</span> | |
| 154 | ||
| 155 | <span class="k">def</span> <span class="nf">_conf</span><span class="p">():</span> | |
| 156 | <span class="kn">from</span> <span class="nn">config.configuration</span> <span class="k">import</span> <span class="n">getInstanceConfiguration</span> | |
| 157 | <span class="n">CONF</span> <span class="o">=</span> <span class="n">getInstanceConfiguration</span><span class="p">()</span> | |
| 158 | <span class="k">return</span> <span class="n">CONF</span> | |
| 159 | ||
| 160 | <span class="k">def</span> <span class="nf">_get_base_server_url</span><span class="p">():</span> | |
| 161 | <span class="k">if</span> <span class="n">FARADAY_UP</span><span class="p">:</span> | |
| 162 | <span class="n">server_url</span> <span class="o">=</span> <span class="n">_conf</span><span class="p">()</span><span class="o">.</span><span class="n">getCouchURI</span><span class="p">()</span> | |
| 163 | <span class="k">else</span><span class="p">:</span> | |
| 164 | <span class="n">server_url</span> <span class="o">=</span> <span class="n">SERVER_URL</span> | |
| 165 | <span class="k">return</span> <span class="n">server_url</span> | |
| 166 | ||
| 167 | ||
| 168 | <span class="k">def</span> <span class="nf">_create_server_api_url</span><span class="p">():</span> | |
| 169 | <span class="sd">"""Return the server's api url."""</span> | |
| 170 | <span class="k">return</span> <span class="s2">"</span><span class="si">{0}</span><span class="s2">/_api"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">_get_base_server_url</span><span class="p">())</span> | |
| 171 | ||
| 172 | <span class="k">def</span> <span class="nf">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_name</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 173 | <span class="sd">"""Creates a url to get from the server. Takes the workspace name</span> | |
| 174 | <span class="sd"> as a string, an object_name paramter which is the object you want to</span> | |
| 175 | <span class="sd"> query as a string ('hosts', 'interfaces', etc) .</span> | |
| 176 | ||
| 177 | <span class="sd"> object_name may be None if you want to get the workspace itself.</span> | |
| 178 | ||
| 179 | <span class="sd"> Return the get_url as a string.</span> | |
| 180 | <span class="sd"> """</span> | |
| 181 | <span class="n">object_name</span> <span class="o">=</span> <span class="s2">"/</span><span class="si">{0}</span><span class="s2">"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">object_name</span><span class="p">)</span> <span class="k">if</span> <span class="n">object_name</span> <span class="k">else</span> <span class="s2">""</span> | |
| 182 | <span class="n">get_url</span> <span class="o">=</span> <span class="s1">'</span><span class="si">{0}</span><span class="s1">/ws/</span><span class="si">{1}{2}</span><span class="s1">'</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">_create_server_api_url</span><span class="p">(),</span> | |
| 183 | <span class="n">workspace_name</span><span class="p">,</span> | |
| 184 | <span class="n">object_name</span><span class="p">)</span> | |
| 185 | <span class="k">return</span> <span class="n">get_url</span> | |
| 186 | ||
| 187 | ||
| 188 | <span class="k">def</span> <span class="nf">_create_server_post_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">):</span> | |
| 189 | <span class="n">server_api_url</span> <span class="o">=</span> <span class="n">_create_server_api_url</span><span class="p">()</span> | |
| 190 | <span class="n">post_url</span> <span class="o">=</span> <span class="s1">'</span><span class="si">{0}</span><span class="s1">/ws/</span><span class="si">{1}</span><span class="s1">/doc/</span><span class="si">{2}</span><span class="s1">'</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">server_api_url</span><span class="p">,</span> <span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">)</span> | |
| 191 | <span class="k">return</span> <span class="n">post_url</span> | |
| 192 | ||
| 193 | ||
| 194 | <span class="k">def</span> <span class="nf">_create_server_delete_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">):</span> | |
| 195 | <span class="k">return</span> <span class="n">_create_server_post_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">)</span> | |
| 196 | ||
| 197 | <span class="c1"># XXX: COUCH IT!</span> | |
| 198 | <span class="k">def</span> <span class="nf">_create_couch_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">):</span> | |
| 199 | <span class="n">server_url</span> <span class="o">=</span> <span class="n">_get_base_server_url</span><span class="p">()</span> | |
| 200 | <span class="k">return</span> <span class="s2">"</span><span class="si">{0}</span><span class="s2">/</span><span class="si">{1}</span><span class="s2">/</span><span class="si">{2}</span><span class="s2">"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">server_url</span><span class="p">,</span> <span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">)</span> | |
| 201 | ||
| 202 | ||
| 203 | <span class="c1"># XXX: COUCH IT!</span> | |
| 204 | <span class="k">def</span> <span class="nf">_create_couch_post_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">):</span> | |
| 205 | <span class="k">return</span> <span class="n">_create_couch_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">)</span> | |
| 206 | ||
| 207 | ||
| 208 | <span class="c1"># XXX: COUCH IT!</span> | |
| 209 | <span class="k">def</span> <span class="nf">_create_couch_db_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">):</span> | |
| 210 | <span class="n">server_base_url</span> <span class="o">=</span> <span class="n">_get_base_server_url</span><span class="p">()</span> | |
| 211 | <span class="n">db_url</span> <span class="o">=</span> <span class="s1">'</span><span class="si">{0}</span><span class="s1">/</span><span class="si">{1}</span><span class="s1">'</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">server_base_url</span><span class="p">,</span> <span class="n">workspace_name</span><span class="p">)</span> | |
| 212 | <span class="k">return</span> <span class="n">db_url</span> | |
| 213 | ||
| 214 | <span class="k">def</span> <span class="nf">_create_server_db_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">):</span> | |
| 215 | <span class="n">server_api_url</span> <span class="o">=</span> <span class="n">_create_server_api_url</span><span class="p">()</span> | |
| 216 | <span class="n">db_url</span> <span class="o">=</span> <span class="s1">'</span><span class="si">{0}</span><span class="s1">/ws/</span><span class="si">{1}</span><span class="s1">'</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">server_api_url</span><span class="p">,</span> <span class="n">workspace_name</span><span class="p">)</span> | |
| 217 | <span class="k">return</span> <span class="n">db_url</span> | |
| 218 | ||
| 219 | <span class="k">def</span> <span class="nf">_unsafe_io_with_server</span><span class="p">(</span><span class="n">server_io_function</span><span class="p">,</span> <span class="n">server_expected_response</span><span class="p">,</span> | |
| 220 | <span class="n">server_url</span><span class="p">,</span> <span class="o">**</span><span class="n">payload</span><span class="p">):</span> | |
| 221 | <span class="sd">"""A wrapper for functions which deals with I/O to or from the server.</span> | |
| 222 | <span class="sd"> It calls the server_io_function with url server_url and the payload,</span> | |
| 223 | <span class="sd"> raising an CantCommunicateWithServerError if the response wasn't</span> | |
| 224 | <span class="sd"> server_expected_response or if there was a Connection Error.</span> | |
| 225 | ||
| 226 | <span class="sd"> Return the response from the server.</span> | |
| 227 | <span class="sd"> """</span> | |
| 228 | <span class="k">try</span><span class="p">:</span> | |
| 229 | <span class="n">answer</span> <span class="o">=</span> <span class="n">server_io_function</span><span class="p">(</span><span class="n">server_url</span><span class="p">,</span> <span class="o">**</span><span class="n">payload</span><span class="p">)</span> | |
| 230 | <span class="k">if</span> <span class="n">answer</span><span class="o">.</span><span class="n">status_code</span> <span class="o">==</span> <span class="mi">409</span> <span class="ow">and</span> <span class="n">answer</span><span class="o">.</span><span class="n">json</span><span class="p">()[</span><span class="s1">'error'</span><span class="p">]</span> <span class="o">==</span> <span class="s1">'conflict'</span><span class="p">:</span> | |
| 231 | <span class="k">raise</span> <span class="n">ConflictInDatabase</span><span class="p">(</span><span class="n">answer</span><span class="p">)</span> | |
| 232 | <span class="k">if</span> <span class="n">answer</span><span class="o">.</span><span class="n">status_code</span> <span class="o">==</span> <span class="mi">404</span><span class="p">:</span> | |
| 233 | <span class="k">raise</span> <span class="n">ResourceDoesNotExist</span><span class="p">(</span><span class="n">server_url</span><span class="p">)</span> | |
| 234 | <span class="k">if</span> <span class="n">answer</span><span class="o">.</span><span class="n">status_code</span> <span class="o">==</span> <span class="mi">403</span> <span class="ow">or</span> <span class="n">answer</span><span class="o">.</span><span class="n">status_code</span> <span class="o">==</span> <span class="mi">401</span><span class="p">:</span> | |
| 235 | <span class="k">raise</span> <span class="n">Unauthorized</span><span class="p">(</span><span class="n">answer</span><span class="p">)</span> | |
| 236 | <span class="k">if</span> <span class="n">answer</span><span class="o">.</span><span class="n">status_code</span> <span class="o">!=</span> <span class="n">server_expected_response</span><span class="p">:</span> | |
| 237 | <span class="k">raise</span> <span class="n">requests</span><span class="o">.</span><span class="n">exceptions</span><span class="o">.</span><span class="n">RequestException</span><span class="p">(</span><span class="n">response</span><span class="o">=</span><span class="n">answer</span><span class="p">)</span> | |
| 238 | <span class="k">except</span> <span class="n">requests</span><span class="o">.</span><span class="n">exceptions</span><span class="o">.</span><span class="n">RequestException</span><span class="p">:</span> | |
| 239 | <span class="k">raise</span> <span class="n">CantCommunicateWithServerError</span><span class="p">(</span><span class="n">server_io_function</span><span class="p">,</span> <span class="n">server_url</span><span class="p">,</span> <span class="n">payload</span><span class="p">)</span> | |
| 240 | <span class="k">return</span> <span class="n">answer</span> | |
| 241 | ||
| 242 | ||
| 243 | <span class="k">def</span> <span class="nf">_parse_json</span><span class="p">(</span><span class="n">response_object</span><span class="p">):</span> | |
| 244 | <span class="sd">"""Takes a response object and return its response as a dictionary."""</span> | |
| 245 | <span class="k">try</span><span class="p">:</span> | |
| 246 | <span class="k">return</span> <span class="n">response_object</span><span class="o">.</span><span class="n">json</span><span class="p">()</span> | |
| 247 | <span class="k">except</span> <span class="ne">ValueError</span><span class="p">:</span> | |
| 248 | <span class="k">return</span> <span class="p">{}</span> | |
| 249 | ||
| 250 | ||
| 251 | <span class="k">def</span> <span class="nf">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 252 | <span class="sd">"""Get from the request_url. Takes an arbitrary number of parameters</span> | |
| 253 | <span class="sd"> to customize the request_url if necessary.</span> | |
| 254 | ||
| 255 | <span class="sd"> Will raise a CantCommunicateWithServerError if requests cant stablish</span> | |
| 256 | <span class="sd"> connection to server or if response is not equal to 200.</span> | |
| 257 | ||
| 258 | <span class="sd"> Return a dictionary with the information in the json.</span> | |
| 259 | <span class="sd"> """</span> | |
| 260 | <span class="k">return</span> <span class="n">_parse_json</span><span class="p">(</span><span class="n">_unsafe_io_with_server</span><span class="p">(</span><span class="n">requests</span><span class="o">.</span><span class="n">get</span><span class="p">,</span> | |
| 261 | <span class="mi">200</span><span class="p">,</span> | |
| 262 | <span class="n">request_url</span><span class="p">,</span> | |
| 263 | <span class="n">params</span><span class="o">=</span><span class="n">params</span><span class="p">))</span> | |
| 264 | ||
| 265 | <span class="k">def</span> <span class="nf">_put</span><span class="p">(</span><span class="n">post_url</span><span class="p">,</span> <span class="n">update</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">expected_response</span><span class="o">=</span><span class="mi">201</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 266 | <span class="sd">"""Put to the post_url. If update is True, try to get the object</span> | |
| 267 | <span class="sd"> revision first so as to update the object in Couch. You can</span> | |
| 268 | <span class="sd"> customize the expected response (it should be 201, but Couchdbkit returns</span> | |
| 269 | <span class="sd"> 200, so...). Also take an arbitrary number of parameters to put into the</span> | |
| 270 | <span class="sd"> post_url.</span> | |
| 271 | ||
| 272 | <span class="sd"> Will raise a CantCommunicateWithServerError if requests cant stablish</span> | |
| 273 | <span class="sd"> connection to server or if response is not equal to 201.</span> | |
| 274 | ||
| 275 | <span class="sd"> Return a dictionary with the response from couchdb, which looks like this:</span> | |
| 276 | <span class="sd"> {u'id': u'61', u'ok': True, u'rev': u'1-967a00dff5e02add41819138abb3284d'}</span> | |
| 277 | <span class="sd"> """</span> | |
| 278 | <span class="k">if</span> <span class="n">update</span><span class="p">:</span> | |
| 279 | <span class="n">last_rev</span> <span class="o">=</span> <span class="n">_get</span><span class="p">(</span><span class="n">post_url</span><span class="p">)[</span><span class="s1">'_rev'</span><span class="p">]</span> | |
| 280 | <span class="n">params</span><span class="p">[</span><span class="s1">'_rev'</span><span class="p">]</span> <span class="o">=</span> <span class="n">last_rev</span> | |
| 281 | <span class="k">return</span> <span class="n">_parse_json</span><span class="p">(</span><span class="n">_unsafe_io_with_server</span><span class="p">(</span><span class="n">requests</span><span class="o">.</span><span class="n">put</span><span class="p">,</span> | |
| 282 | <span class="n">expected_response</span><span class="p">,</span> | |
| 283 | <span class="n">post_url</span><span class="p">,</span> | |
| 284 | <span class="n">json</span><span class="o">=</span><span class="n">params</span><span class="p">))</span> | |
| 285 | ||
| 286 | ||
| 287 | <span class="k">def</span> <span class="nf">_delete</span><span class="p">(</span><span class="n">delete_url</span><span class="p">,</span> <span class="n">database</span><span class="o">=</span><span class="kc">False</span><span class="p">):</span> | |
| 288 | <span class="sd">"""Deletes the object on delete_url. If you're deleting a database,</span> | |
| 289 | <span class="sd"> specify the database parameter to True"""</span> | |
| 290 | <span class="n">params</span> <span class="o">=</span> <span class="p">{}</span> | |
| 291 | <span class="k">if</span> <span class="ow">not</span> <span class="n">database</span><span class="p">:</span> | |
| 292 | <span class="n">last_rev</span> <span class="o">=</span> <span class="n">_get</span><span class="p">(</span><span class="n">delete_url</span><span class="p">)[</span><span class="s1">'_rev'</span><span class="p">]</span> | |
| 293 | <span class="n">params</span> <span class="o">=</span> <span class="p">{</span><span class="s1">'rev'</span><span class="p">:</span> <span class="n">last_rev</span><span class="p">}</span> | |
| 294 | <span class="k">return</span> <span class="n">_parse_json</span><span class="p">(</span><span class="n">_unsafe_io_with_server</span><span class="p">(</span><span class="n">requests</span><span class="o">.</span><span class="n">delete</span><span class="p">,</span> | |
| 295 | <span class="mi">200</span><span class="p">,</span> | |
| 296 | <span class="n">delete_url</span><span class="p">,</span> | |
| 297 | <span class="n">params</span><span class="o">=</span><span class="n">params</span><span class="p">))</span> | |
| 298 | ||
| 299 | ||
| 300 | <span class="k">def</span> <span class="nf">_get_raw_hosts</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 301 | <span class="sd">"""Take a workspace_name and an arbitrary number of params and return</span> | |
| 302 | <span class="sd"> a dictionary with the hosts table."""</span> | |
| 303 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'hosts'</span><span class="p">)</span> | |
| 304 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 305 | ||
| 306 | ||
| 307 | <span class="k">def</span> <span class="nf">_get_raw_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 308 | <span class="sd">"""Take a workspace_name and an arbitrary number of params and return</span> | |
| 309 | <span class="sd"> a dictionary with the vulns table."""</span> | |
| 310 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'vulns'</span><span class="p">)</span> | |
| 311 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 312 | ||
| 313 | ||
| 314 | <span class="k">def</span> <span class="nf">_get_raw_interfaces</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 315 | <span class="sd">"""Take a workspace_name and an arbitrary number of params and return</span> | |
| 316 | <span class="sd"> a dictionary with the interfaces table."""</span> | |
| 317 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'interfaces'</span><span class="p">)</span> | |
| 318 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 319 | ||
| 320 | ||
| 321 | <span class="k">def</span> <span class="nf">_get_raw_services</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 322 | <span class="sd">"""Take a workspace_name and an arbitrary number of params and return</span> | |
| 323 | <span class="sd"> a dictionary with the services table."""</span> | |
| 324 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'services'</span><span class="p">)</span> | |
| 325 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 326 | ||
| 327 | ||
| 328 | <span class="k">def</span> <span class="nf">_get_raw_notes</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 329 | <span class="sd">"""Take a workspace name and an arbitrary number of params and</span> | |
| 330 | <span class="sd"> return a dictionary with the notes table."""</span> | |
| 331 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'notes'</span><span class="p">)</span> | |
| 332 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 333 | ||
| 334 | ||
| 335 | <span class="k">def</span> <span class="nf">_get_raw_credentials</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 336 | <span class="sd">"""Take a workspace name and an arbitrary number of params and</span> | |
| 337 | <span class="sd"> return a dictionary with the credentials table."""</span> | |
| 338 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'credentials'</span><span class="p">)</span> | |
| 339 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 340 | ||
| 341 | ||
| 342 | <span class="k">def</span> <span class="nf">_get_raw_commands</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 343 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'commands'</span><span class="p">)</span> | |
| 344 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 345 | ||
| 346 | ||
| 347 | <span class="k">def</span> <span class="nf">_get_raw_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">):</span> | |
| 348 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'summary'</span><span class="p">)</span> | |
| 349 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">)</span> | |
| 350 | ||
| 351 | <span class="c1"># XXX: COUCH IT!</span> | |
| 352 | <span class="k">def</span> <span class="nf">_save_to_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 353 | <span class="n">post_url</span> <span class="o">=</span> <span class="n">_create_couch_post_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">)</span> | |
| 354 | <span class="k">return</span> <span class="n">_put</span><span class="p">(</span><span class="n">post_url</span><span class="p">,</span> <span class="n">update</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 355 | ||
| 356 | <span class="c1"># XXX: COUCH IT!</span> | |
| 357 | <span class="k">def</span> <span class="nf">_update_in_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 358 | <span class="n">post_url</span> <span class="o">=</span> <span class="n">_create_server_post_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">)</span> | |
| 359 | <span class="k">return</span> <span class="n">_put</span><span class="p">(</span><span class="n">post_url</span><span class="p">,</span> <span class="n">update</span><span class="o">=</span><span class="kc">True</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 360 | ||
| 361 | <span class="k">def</span> <span class="nf">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 362 | <span class="n">post_url</span> <span class="o">=</span> <span class="n">_create_server_post_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">)</span> | |
| 363 | <span class="k">return</span> <span class="n">_put</span><span class="p">(</span><span class="n">post_url</span><span class="p">,</span> <span class="n">update</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">expected_response</span><span class="o">=</span><span class="mi">200</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 364 | ||
| 365 | <span class="k">def</span> <span class="nf">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 366 | <span class="n">post_url</span> <span class="o">=</span> <span class="n">_create_server_post_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">)</span> | |
| 367 | <span class="k">return</span> <span class="n">_put</span><span class="p">(</span><span class="n">post_url</span><span class="p">,</span> <span class="n">update</span><span class="o">=</span><span class="kc">True</span><span class="p">,</span> <span class="n">expected_response</span><span class="o">=</span><span class="mi">200</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 368 | ||
| 369 | <span class="k">def</span> <span class="nf">_save_db_to_server</span><span class="p">(</span><span class="n">db_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 370 | <span class="n">post_url</span> <span class="o">=</span> <span class="n">_create_server_db_url</span><span class="p">(</span><span class="n">db_name</span><span class="p">)</span> | |
| 371 | <span class="k">return</span> <span class="n">_put</span><span class="p">(</span><span class="n">post_url</span><span class="p">,</span> <span class="n">expected_response</span><span class="o">=</span><span class="mi">200</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 372 | ||
| 373 | <span class="c1"># XXX: SEMI COUCH IT!</span> | |
| 374 | <span class="k">def</span> <span class="nf">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">):</span> | |
| 375 | <span class="n">delete_url</span> <span class="o">=</span> <span class="n">_create_server_delete_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_id</span><span class="p">)</span> | |
| 376 | <span class="k">return</span> <span class="n">_delete</span><span class="p">(</span><span class="n">delete_url</span><span class="p">)</span> | |
| 377 | ||
| 378 | <span class="c1"># XXX: COUCH IT!</span> | |
| 379 | <span class="k">def</span> <span class="nf">_couch_changes</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 380 | <span class="k">return</span> <span class="n">CouchChangesStream</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 381 | <span class="n">_create_couch_db_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">),</span> | |
| 382 | <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 383 | ||
| 384 | ||
| 385 | <span class="k">def</span> <span class="nf">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">faraday_object_name</span><span class="p">,</span> | |
| 386 | <span class="n">faraday_object_row_name</span><span class="p">,</span> <span class="n">full_table</span><span class="o">=</span><span class="kc">True</span><span class="p">,</span> | |
| 387 | <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 388 | <span class="sd">"""Takes a workspace_name (str), a faraday_object_name (str),</span> | |
| 389 | <span class="sd"> a faraday_object_row_name (str) and an arbitrary number of params.</span> | |
| 390 | <span class="sd"> Return a list of dictionaries that hold the information for the objects</span> | |
| 391 | <span class="sd"> in table faraday_object_name.</span> | |
| 392 | ||
| 393 | <span class="sd"> The full_table paramether may be used to get the full dictionary instead</span> | |
| 394 | <span class="sd"> of just the one inside the 'value' key which holds information about the</span> | |
| 395 | <span class="sd"> object.</span> | |
| 396 | ||
| 397 | <span class="sd"> Preconditions:</span> | |
| 398 | <span class="sd"> faraday_object_name == 'host', 'vuln', 'interface', 'service', 'note'</span> | |
| 399 | <span class="sd"> or 'credential'</span> | |
| 400 | ||
| 401 | <span class="sd"> faraday_object_row_name must be the key to the dictionary which holds</span> | |
| 402 | <span class="sd"> the information of the object per se in the table. most times this is 'rows'</span> | |
| 403 | <span class="sd"> """</span> | |
| 404 | <span class="n">object_to_func</span> <span class="o">=</span> <span class="p">{</span><span class="s1">'hosts'</span><span class="p">:</span> <span class="n">_get_raw_hosts</span><span class="p">,</span> | |
| 405 | <span class="s1">'vulns'</span><span class="p">:</span> <span class="n">_get_raw_vulns</span><span class="p">,</span> | |
| 406 | <span class="s1">'interfaces'</span><span class="p">:</span> <span class="n">_get_raw_interfaces</span><span class="p">,</span> | |
| 407 | <span class="s1">'services'</span><span class="p">:</span> <span class="n">_get_raw_services</span><span class="p">,</span> | |
| 408 | <span class="s1">'notes'</span><span class="p">:</span> <span class="n">_get_raw_notes</span><span class="p">,</span> | |
| 409 | <span class="s1">'credentials'</span><span class="p">:</span> <span class="n">_get_raw_credentials</span><span class="p">,</span> | |
| 410 | <span class="s1">'commands'</span><span class="p">:</span> <span class="n">_get_raw_commands</span><span class="p">}</span> | |
| 411 | ||
| 412 | <span class="n">appropiate_function</span> <span class="o">=</span> <span class="n">object_to_func</span><span class="p">[</span><span class="n">faraday_object_name</span><span class="p">]</span> | |
| 413 | <span class="n">appropiate_dictionary</span> <span class="o">=</span> <span class="n">appropiate_function</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span> | |
| 414 | <span class="n">faraday_ready_dictionaries</span> <span class="o">=</span> <span class="p">[]</span> | |
| 415 | <span class="k">if</span> <span class="n">appropiate_dictionary</span><span class="p">:</span> | |
| 416 | <span class="k">for</span> <span class="n">raw_dictionary</span> <span class="ow">in</span> <span class="n">appropiate_dictionary</span><span class="p">[</span><span class="n">faraday_object_row_name</span><span class="p">]:</span> | |
| 417 | <span class="k">if</span> <span class="ow">not</span> <span class="n">full_table</span><span class="p">:</span> | |
| 418 | <span class="n">faraday_ready_dictionaries</span><span class="o">.</span><span class="n">append</span><span class="p">(</span><span class="n">raw_dictionary</span><span class="p">[</span><span class="s1">'value'</span><span class="p">])</span> | |
| 419 | <span class="k">else</span><span class="p">:</span> | |
| 420 | <span class="n">faraday_ready_dictionaries</span><span class="o">.</span><span class="n">append</span><span class="p">(</span><span class="n">raw_dictionary</span><span class="p">)</span> | |
| 421 | <span class="k">return</span> <span class="n">faraday_ready_dictionaries</span> | |
| 422 | ||
| 423 | ||
| 424 | <div class="viewcode-block" id="get_hosts"><a class="viewcode-back" href="../server.html#server.get_hosts">[docs]</a><span class="k">def</span> <span class="nf">get_hosts</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 425 | <span class="sd">"""Get hosts from the server.</span> | |
| 426 | ||
| 427 | <span class="sd"> Args:</span> | |
| 428 | <span class="sd"> workspace_name (str): the workspace from which to get the hosts.</span> | |
| 429 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 430 | ||
| 431 | <span class="sd"> Returns:</span> | |
| 432 | <span class="sd"> A dictionary containing the hosts matching the query.</span> | |
| 433 | <span class="sd"> """</span> | |
| 434 | <span class="k">return</span> <span class="n">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'hosts'</span><span class="p">,</span> | |
| 435 | <span class="s1">'rows'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 436 | ||
| 437 | ||
| 438 | <div class="viewcode-block" id="get_all_vulns"><a class="viewcode-back" href="../server.html#server.get_all_vulns">[docs]</a><span class="k">def</span> <span class="nf">get_all_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 439 | <span class="sd">"""Get vulns, both normal and web, from the server.</span> | |
| 440 | ||
| 441 | <span class="sd"> Args:</span> | |
| 442 | <span class="sd"> workspace_name (str): the workspace from which to get the vulns.</span> | |
| 443 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 444 | ||
| 445 | <span class="sd"> Returns:</span> | |
| 446 | <span class="sd"> A dictionary containing the vulns matching the query.</span> | |
| 447 | <span class="sd"> """</span> | |
| 448 | <span class="k">return</span> <span class="n">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'vulns'</span><span class="p">,</span> | |
| 449 | <span class="s1">'vulnerabilities'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 450 | ||
| 451 | ||
| 452 | <div class="viewcode-block" id="get_vulns"><a class="viewcode-back" href="../server.html#server.get_vulns">[docs]</a><span class="k">def</span> <span class="nf">get_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 453 | <span class="sd">"""Get only normal vulns from the server.</span> | |
| 454 | ||
| 455 | <span class="sd"> Args:</span> | |
| 456 | <span class="sd"> workspace_name (str): the workspace from which to get the vulns.</span> | |
| 457 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 458 | ||
| 459 | <span class="sd"> Returns:</span> | |
| 460 | <span class="sd"> A dictionary containing the vulns matching the query.</span> | |
| 461 | <span class="sd"> """</span> | |
| 462 | <span class="k">return</span> <span class="n">get_all_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">type</span><span class="o">=</span><span class="s1">'Vulnerability'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 463 | ||
| 464 | ||
| 465 | <div class="viewcode-block" id="get_web_vulns"><a class="viewcode-back" href="../server.html#server.get_web_vulns">[docs]</a><span class="k">def</span> <span class="nf">get_web_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 466 | <span class="sd">"""Get only web vulns from the server.</span> | |
| 467 | ||
| 468 | <span class="sd"> Args:</span> | |
| 469 | <span class="sd"> workspace_name (str): the workspace from which to get the vulns.</span> | |
| 470 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 471 | ||
| 472 | <span class="sd"> Returns:</span> | |
| 473 | <span class="sd"> A dictionary containing the vulns matching the query.</span> | |
| 474 | <span class="sd"> """</span> | |
| 475 | <span class="k">return</span> <span class="n">get_all_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">type</span><span class="o">=</span><span class="s2">"VulnerabilityWeb"</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 476 | ||
| 477 | <div class="viewcode-block" id="get_interfaces"><a class="viewcode-back" href="../server.html#server.get_interfaces">[docs]</a><span class="k">def</span> <span class="nf">get_interfaces</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 478 | <span class="sd">"""Get interfaces from the server.</span> | |
| 479 | ||
| 480 | <span class="sd"> Args:</span> | |
| 481 | <span class="sd"> workspace_name (str): the workspace from which to get the interfaces.</span> | |
| 482 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 483 | ||
| 484 | <span class="sd"> Returns:</span> | |
| 485 | <span class="sd"> A dictionary containing the interfaces matching the query.</span> | |
| 486 | <span class="sd"> """</span> | |
| 487 | <span class="k">return</span> <span class="n">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'interfaces'</span><span class="p">,</span> | |
| 488 | <span class="s1">'interfaces'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 489 | ||
| 490 | <div class="viewcode-block" id="get_services"><a class="viewcode-back" href="../server.html#server.get_services">[docs]</a><span class="k">def</span> <span class="nf">get_services</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 491 | <span class="sd">"""Get services from the server.</span> | |
| 492 | ||
| 493 | <span class="sd"> Args:</span> | |
| 494 | <span class="sd"> workspace_name (str): the workspace from which to get the services.</span> | |
| 495 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 496 | ||
| 497 | <span class="sd"> Returns:</span> | |
| 498 | <span class="sd"> A dictionary containing the services matching the query.</span> | |
| 499 | <span class="sd"> """</span> | |
| 500 | <span class="k">return</span> <span class="n">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'services'</span><span class="p">,</span> | |
| 501 | <span class="s1">'services'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 502 | ||
| 503 | <div class="viewcode-block" id="get_credentials"><a class="viewcode-back" href="../server.html#server.get_credentials">[docs]</a><span class="k">def</span> <span class="nf">get_credentials</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 504 | <span class="sd">"""Get credentials from the server.</span> | |
| 505 | ||
| 506 | <span class="sd"> Args:</span> | |
| 507 | <span class="sd"> workspace_name (str): the workspace from which to get the credentials.</span> | |
| 508 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 509 | ||
| 510 | <span class="sd"> Returns:</span> | |
| 511 | <span class="sd"> A dictionary containing the credentials matching the query.</span> | |
| 512 | <span class="sd"> """</span> | |
| 513 | <span class="k">return</span> <span class="n">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'credentials'</span><span class="p">,</span> | |
| 514 | <span class="s1">'rows'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 515 | ||
| 516 | <div class="viewcode-block" id="get_notes"><a class="viewcode-back" href="../server.html#server.get_notes">[docs]</a><span class="k">def</span> <span class="nf">get_notes</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 517 | <span class="sd">"""Get notes from the server.</span> | |
| 518 | ||
| 519 | <span class="sd"> Args:</span> | |
| 520 | <span class="sd"> workspace_name (str): the workspace from which to get the notes.</span> | |
| 521 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 522 | ||
| 523 | <span class="sd"> Returns:</span> | |
| 524 | <span class="sd"> A dictionary containing the notes matching the query.</span> | |
| 525 | <span class="sd"> """</span> | |
| 526 | <span class="k">return</span> <span class="n">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'notes'</span><span class="p">,</span> | |
| 527 | <span class="s1">'rows'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 528 | ||
| 529 | <div class="viewcode-block" id="get_commands"><a class="viewcode-back" href="../server.html#server.get_commands">[docs]</a><span class="k">def</span> <span class="nf">get_commands</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 530 | <span class="sd">"""Get commands from the server.</span> | |
| 531 | ||
| 532 | <span class="sd"> Args:</span> | |
| 533 | <span class="sd"> workspace_name (str): the workspace from which to get the commands.</span> | |
| 534 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 535 | ||
| 536 | <span class="sd"> Returns:</span> | |
| 537 | <span class="sd"> A dictionary containing the commands matching the query.</span> | |
| 538 | <span class="sd"> """</span> | |
| 539 | <span class="k">return</span> <span class="n">_get_faraday_ready_dictionaries</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="s1">'commands'</span><span class="p">,</span> | |
| 540 | <span class="s1">'commands'</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 541 | ||
| 542 | <div class="viewcode-block" id="get_objects"><a class="viewcode-back" href="../server.html#server.get_objects">[docs]</a><span class="k">def</span> <span class="nf">get_objects</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_signature</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 543 | <span class="sd">"""Get any type of object from the server, be it hosts, vulns, interfaces,</span> | |
| 544 | <span class="sd"> services, credentials, commands or notes.</span> | |
| 545 | ||
| 546 | <span class="sd"> Args:</span> | |
| 547 | <span class="sd"> workspace_name (str): the workspace from which to get the commands.</span> | |
| 548 | <span class="sd"> object_signature (str): the type of object to get. Must equal 'hosts',</span> | |
| 549 | <span class="sd"> 'vulns', 'interfaces', 'services', 'credentials', 'notes' or 'commands'</span> | |
| 550 | <span class="sd"> **params: any of valid request parameters for CouchDB.</span> | |
| 551 | ||
| 552 | <span class="sd"> Returns:</span> | |
| 553 | <span class="sd"> A dictionary containing the commands matching the query.</span> | |
| 554 | ||
| 555 | <span class="sd"> Raises:</span> | |
| 556 | <span class="sd"> WrongObjectSignature: if the object_signature string didn't match</span> | |
| 557 | <span class="sd"> a faraday object.</span> | |
| 558 | <span class="sd"> """</span> | |
| 559 | <span class="n">object_to_func</span> <span class="o">=</span> <span class="p">{</span><span class="s1">'hosts'</span><span class="p">:</span> <span class="n">get_hosts</span><span class="p">,</span> | |
| 560 | <span class="s1">'vulns'</span><span class="p">:</span> <span class="n">get_vulns</span><span class="p">,</span> | |
| 561 | <span class="s1">'interfaces'</span><span class="p">:</span> <span class="n">get_interfaces</span><span class="p">,</span> | |
| 562 | <span class="s1">'services'</span><span class="p">:</span> <span class="n">get_services</span><span class="p">,</span> | |
| 563 | <span class="s1">'credentials'</span><span class="p">:</span> <span class="n">get_credentials</span><span class="p">,</span> | |
| 564 | <span class="s1">'notes'</span><span class="p">:</span> <span class="n">get_notes</span><span class="p">,</span> | |
| 565 | <span class="s1">'commands'</span><span class="p">:</span> <span class="n">get_commands</span><span class="p">}</span> | |
| 566 | <span class="k">try</span><span class="p">:</span> | |
| 567 | <span class="n">appropiate_function</span> <span class="o">=</span> <span class="n">object_to_func</span><span class="p">[</span><span class="n">object_signature</span><span class="p">]</span> | |
| 568 | <span class="k">except</span> <span class="ne">KeyError</span><span class="p">:</span> | |
| 569 | <span class="k">raise</span> <span class="n">WrongObjectSignature</span><span class="p">(</span><span class="n">object_signature</span><span class="p">)</span> | |
| 570 | ||
| 571 | <span class="k">return</span> <span class="n">appropiate_function</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 572 | ||
| 573 | <span class="c1"># cha cha cha chaaaanges!</span> | |
| 574 | <div class="viewcode-block" id="get_changes_stream"><a class="viewcode-back" href="../server.html#server.get_changes_stream">[docs]</a><span class="k">def</span> <span class="nf">get_changes_stream</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">since</span><span class="o">=</span><span class="mi">0</span><span class="p">,</span> <span class="n">heartbeat</span><span class="o">=</span><span class="s1">'1000'</span><span class="p">,</span> <span class="o">**</span><span class="n">extra_params</span><span class="p">):</span> | |
| 575 | <span class="k">return</span> <span class="n">_couch_changes</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">since</span><span class="o">=</span><span class="n">since</span><span class="p">,</span> <span class="n">feed</span><span class="o">=</span><span class="s1">'continuous'</span><span class="p">,</span> | |
| 576 | <span class="n">heartbeat</span><span class="o">=</span><span class="n">heartbeat</span><span class="p">,</span> <span class="o">**</span><span class="n">extra_params</span><span class="p">)</span></div> | |
| 577 | ||
| 578 | <div class="viewcode-block" id="get_workspaces_names"><a class="viewcode-back" href="../server.html#server.get_workspaces_names">[docs]</a><span class="k">def</span> <span class="nf">get_workspaces_names</span><span class="p">():</span> | |
| 579 | <span class="sd">"""Returns:</span> | |
| 580 | <span class="sd"> A dictionary with a list with the workspaces names."""</span> | |
| 581 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="s2">"</span><span class="si">{0}</span><span class="s2">/ws"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">_create_server_api_url</span><span class="p">()))</span></div> | |
| 582 | ||
| 583 | <span class="c1"># XXX: COUCH IT!</span> | |
| 584 | <span class="k">def</span> <span class="nf">_clean_up_stupid_couch_response</span><span class="p">(</span><span class="n">response_string</span><span class="p">):</span> | |
| 585 | <span class="sd">"""Couch likes to give invalid jsons as a response :). So nice."""</span> | |
| 586 | <span class="n">interesting_part</span> <span class="o">=</span> <span class="s2">"{"</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">response_string</span><span class="o">.</span><span class="n">split</span><span class="p">(</span><span class="s2">"{"</span><span class="p">)[</span><span class="mi">1</span><span class="p">:])</span> | |
| 587 | <span class="n">almost_there</span> <span class="o">=</span> <span class="n">interesting_part</span><span class="o">.</span><span class="n">split</span><span class="p">(</span><span class="s2">"}"</span><span class="p">)[</span><span class="mi">0</span><span class="p">:</span><span class="o">-</span><span class="mi">1</span><span class="p">]</span> | |
| 588 | <span class="n">ok_yeah</span> <span class="o">=</span> <span class="s2">"}"</span><span class="o">.</span><span class="n">join</span><span class="p">(</span><span class="n">almost_there</span><span class="p">)</span> | |
| 589 | <span class="n">hopefully_valid_json</span> <span class="o">=</span> <span class="s2">"{{</span><span class="si">{0}</span><span class="s2">}}"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">ok_yeah</span><span class="p">)</span> | |
| 590 | <span class="k">return</span> <span class="n">json</span><span class="o">.</span><span class="n">loads</span><span class="p">(</span><span class="n">hopefully_valid_json</span><span class="p">)</span> | |
| 591 | ||
| 592 | <span class="c1"># XXX: COUCH IT!</span> | |
| 593 | <span class="c1"># COUCH IT LEVEL: REVOLUTIONS</span> | |
| 594 | <div class="viewcode-block" id="get_object_before_last_revision"><a class="viewcode-back" href="../server.html#server.get_object_before_last_revision">[docs]</a><span class="k">def</span> <span class="nf">get_object_before_last_revision</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">):</span> | |
| 595 | <span class="sd">"""Get an object before its last revision. Useful to get information about</span> | |
| 596 | <span class="sd"> recently deleted objects.</span> | |
| 597 | ||
| 598 | <span class="sd"> Warning:</span> | |
| 599 | <span class="sd"> Error-pronce process. You should check for 'None' after usage,</span> | |
| 600 | <span class="sd"> as that's the return value if any problem arose during execution.</span> | |
| 601 | ||
| 602 | <span class="sd"> Args:</span> | |
| 603 | <span class="sd"> workspace_name (str): the workspace where the object was</span> | |
| 604 | <span class="sd"> object_id (str): the id of the object</span> | |
| 605 | ||
| 606 | <span class="sd"> Returns:</span> | |
| 607 | <span class="sd"> A dictionary with the object's information.</span> | |
| 608 | <span class="sd"> """</span> | |
| 609 | <span class="n">get_url</span> <span class="o">=</span> <span class="n">_create_couch_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_id</span><span class="p">)</span> | |
| 610 | <span class="n">response</span> <span class="o">=</span> <span class="n">_unsafe_io_with_server</span><span class="p">(</span><span class="n">requests</span><span class="o">.</span><span class="n">get</span><span class="p">,</span> <span class="mi">200</span><span class="p">,</span> <span class="n">get_url</span><span class="p">,</span> | |
| 611 | <span class="n">params</span><span class="o">=</span><span class="p">{</span><span class="s1">'revs'</span><span class="p">:</span> <span class="s1">'true'</span><span class="p">,</span> <span class="s1">'open_revs'</span><span class="p">:</span> <span class="s1">'all'</span><span class="p">})</span> | |
| 612 | <span class="k">try</span><span class="p">:</span> | |
| 613 | <span class="n">valid_json_response</span> <span class="o">=</span> <span class="n">_clean_up_stupid_couch_response</span><span class="p">(</span><span class="n">response</span><span class="o">.</span><span class="n">text</span><span class="p">)</span> | |
| 614 | <span class="k">except</span> <span class="ne">ValueError</span><span class="p">:</span> | |
| 615 | <span class="k">return</span> <span class="kc">None</span> | |
| 616 | <span class="k">try</span><span class="p">:</span> | |
| 617 | <span class="n">id_before_del</span> <span class="o">=</span> <span class="n">valid_json_response</span><span class="p">[</span><span class="s1">'_revisions'</span><span class="p">][</span><span class="s1">'ids'</span><span class="p">][</span><span class="mi">1</span><span class="p">]</span> | |
| 618 | <span class="n">new_number_for_rev</span> <span class="o">=</span> <span class="n">valid_json_response</span><span class="p">[</span><span class="s1">'_revisions'</span><span class="p">][</span><span class="s1">'start'</span><span class="p">]</span> <span class="o">-</span> <span class="mi">1</span> | |
| 619 | <span class="k">except</span> <span class="ne">KeyError</span><span class="p">:</span> <span class="c1"># one if never too safe when you call a function called "_clean_up_stupid_couch_response"</span> | |
| 620 | <span class="k">return</span> <span class="kc">None</span> | |
| 621 | ||
| 622 | <span class="n">rev_id_before_del</span> <span class="o">=</span> <span class="s2">"</span><span class="si">{0}</span><span class="s2">-</span><span class="si">{1}</span><span class="s2">"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">new_number_for_rev</span><span class="p">,</span> <span class="n">id_before_del</span><span class="p">)</span> | |
| 623 | <span class="n">object_dict</span> <span class="o">=</span> <span class="n">_get</span><span class="p">(</span><span class="n">get_url</span><span class="p">,</span> <span class="n">rev</span><span class="o">=</span><span class="n">rev_id_before_del</span><span class="p">)</span> | |
| 624 | <span class="k">return</span> <span class="n">object_dict</span></div> | |
| 625 | ||
| 626 | ||
| 627 | <div class="viewcode-block" id="get_object"><a class="viewcode-back" href="../server.html#server.get_object">[docs]</a><span class="k">def</span> <span class="nf">get_object</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_signature</span><span class="p">,</span> <span class="n">object_id</span><span class="p">):</span> | |
| 628 | <span class="sd">"""Get an unique object of arbitrary type.</span> | |
| 629 | ||
| 630 | <span class="sd"> Args:</span> | |
| 631 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 632 | <span class="sd"> object_signature (str): must be either 'hosts', 'vulns', 'interfaces'</span> | |
| 633 | <span class="sd"> 'services', 'credentials', 'notes' or 'commands'.</span> | |
| 634 | <span class="sd"> object_id (str): the id of the object</span> | |
| 635 | ||
| 636 | <span class="sd"> Returns:</span> | |
| 637 | <span class="sd"> A dictionary containing information about the object.</span> | |
| 638 | ||
| 639 | <span class="sd"> Raises:</span> | |
| 640 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the object_id is shared</span> | |
| 641 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 642 | <span class="sd"> contact Infobyte LCC.</span> | |
| 643 | <span class="sd"> """</span> | |
| 644 | <span class="n">objects</span> <span class="o">=</span> <span class="n">get_objects</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">object_signature</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">object_id</span><span class="p">)</span> | |
| 645 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">objects</span><span class="p">)</span></div> | |
| 646 | ||
| 647 | <div class="viewcode-block" id="get_host"><a class="viewcode-back" href="../server.html#server.get_host">[docs]</a><span class="k">def</span> <span class="nf">get_host</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">host_id</span><span class="p">):</span> | |
| 648 | <span class="sd">"""Get an unique host.</span> | |
| 649 | ||
| 650 | <span class="sd"> Args:</span> | |
| 651 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 652 | <span class="sd"> host_id (str): the id of the host</span> | |
| 653 | ||
| 654 | <span class="sd"> Returns:</span> | |
| 655 | <span class="sd"> A dictionary containing information about the host.</span> | |
| 656 | ||
| 657 | <span class="sd"> Raises:</span> | |
| 658 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the host id is shared</span> | |
| 659 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 660 | <span class="sd"> contact Infobyte LCC.</span> | |
| 661 | <span class="sd"> """</span> | |
| 662 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_hosts</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">host_id</span><span class="p">))</span></div> | |
| 663 | ||
| 664 | <div class="viewcode-block" id="get_vuln"><a class="viewcode-back" href="../server.html#server.get_vuln">[docs]</a><span class="k">def</span> <span class="nf">get_vuln</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">vuln_id</span><span class="p">):</span> | |
| 665 | <span class="sd">"""Get an unique vuln.</span> | |
| 666 | ||
| 667 | <span class="sd"> Args:</span> | |
| 668 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 669 | <span class="sd"> vuln_id (str): the id of the vuln</span> | |
| 670 | ||
| 671 | <span class="sd"> Returns:</span> | |
| 672 | <span class="sd"> A dictionary containing information about the vuln.</span> | |
| 673 | ||
| 674 | <span class="sd"> Raises:</span> | |
| 675 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the vuln id is shared</span> | |
| 676 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 677 | <span class="sd"> contact Infobyte LCC.</span> | |
| 678 | <span class="sd"> """</span> | |
| 679 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">vuln_id</span><span class="p">))</span></div> | |
| 680 | ||
| 681 | <div class="viewcode-block" id="get_web_vuln"><a class="viewcode-back" href="../server.html#server.get_web_vuln">[docs]</a><span class="k">def</span> <span class="nf">get_web_vuln</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">vuln_id</span><span class="p">):</span> | |
| 682 | <span class="sd">"""Get an unique web vuln.</span> | |
| 683 | ||
| 684 | <span class="sd"> Args:</span> | |
| 685 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 686 | <span class="sd"> web vuln_id (str): the id of the web vuln</span> | |
| 687 | ||
| 688 | <span class="sd"> Returns:</span> | |
| 689 | <span class="sd"> A dictionary containing information about the web vuln.</span> | |
| 690 | ||
| 691 | <span class="sd"> Raises:</span> | |
| 692 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the web vuln id is shared</span> | |
| 693 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 694 | <span class="sd"> contact Infobyte LCC.</span> | |
| 695 | <span class="sd"> """</span> | |
| 696 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_web_vulns</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">vuln_id</span><span class="p">))</span></div> | |
| 697 | ||
| 698 | <div class="viewcode-block" id="get_interface"><a class="viewcode-back" href="../server.html#server.get_interface">[docs]</a><span class="k">def</span> <span class="nf">get_interface</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">interface_id</span><span class="p">):</span> | |
| 699 | <span class="sd">"""Get an unique interface.</span> | |
| 700 | ||
| 701 | <span class="sd"> Args:</span> | |
| 702 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 703 | <span class="sd"> interface_id (str): the id of the interface</span> | |
| 704 | ||
| 705 | <span class="sd"> Returns:</span> | |
| 706 | <span class="sd"> A dictionary containing information about the interface.</span> | |
| 707 | ||
| 708 | <span class="sd"> Raises:</span> | |
| 709 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the interface id is shared</span> | |
| 710 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 711 | <span class="sd"> contact Infobyte LCC.</span> | |
| 712 | <span class="sd"> """</span> | |
| 713 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_interfaces</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">interface_id</span><span class="p">))</span></div> | |
| 714 | ||
| 715 | <div class="viewcode-block" id="get_service"><a class="viewcode-back" href="../server.html#server.get_service">[docs]</a><span class="k">def</span> <span class="nf">get_service</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">service_id</span><span class="p">):</span> | |
| 716 | <span class="sd">"""Get an unique service.</span> | |
| 717 | ||
| 718 | <span class="sd"> Args:</span> | |
| 719 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 720 | <span class="sd"> service_id (str): the id of the service</span> | |
| 721 | ||
| 722 | <span class="sd"> Returns:</span> | |
| 723 | <span class="sd"> A dictionary containing information about the service.</span> | |
| 724 | ||
| 725 | <span class="sd"> Raises:</span> | |
| 726 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the service id is shared</span> | |
| 727 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 728 | <span class="sd"> contact Infobyte LCC.</span> | |
| 729 | <span class="sd"> """</span> | |
| 730 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_services</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">service_id</span><span class="p">))</span></div> | |
| 731 | ||
| 732 | <div class="viewcode-block" id="get_note"><a class="viewcode-back" href="../server.html#server.get_note">[docs]</a><span class="k">def</span> <span class="nf">get_note</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">note_id</span><span class="p">):</span> | |
| 733 | <span class="sd">"""Get an unique note.</span> | |
| 734 | ||
| 735 | <span class="sd"> Args:</span> | |
| 736 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 737 | <span class="sd"> note_id (str): the id of the note</span> | |
| 738 | ||
| 739 | <span class="sd"> Returns:</span> | |
| 740 | <span class="sd"> A dictionary containing information about the note.</span> | |
| 741 | ||
| 742 | <span class="sd"> Raises:</span> | |
| 743 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the note id is shared</span> | |
| 744 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 745 | <span class="sd"> contact Infobyte LCC.</span> | |
| 746 | <span class="sd"> """</span> | |
| 747 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_notes</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">note_id</span><span class="p">))</span></div> | |
| 748 | ||
| 749 | <div class="viewcode-block" id="get_credential"><a class="viewcode-back" href="../server.html#server.get_credential">[docs]</a><span class="k">def</span> <span class="nf">get_credential</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">credential_id</span><span class="p">):</span> | |
| 750 | <span class="sd">"""Get an unique credential.</span> | |
| 751 | ||
| 752 | <span class="sd"> Args:</span> | |
| 753 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 754 | <span class="sd"> credential_id (str): the id of the credential</span> | |
| 755 | ||
| 756 | <span class="sd"> Returns:</span> | |
| 757 | <span class="sd"> A dictionary containing information about the credential.</span> | |
| 758 | ||
| 759 | <span class="sd"> Raises:</span> | |
| 760 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the credential id is shared</span> | |
| 761 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 762 | <span class="sd"> contact Infobyte LCC.</span> | |
| 763 | <span class="sd"> """</span> | |
| 764 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_services</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">credential_id</span><span class="p">))</span></div> | |
| 765 | ||
| 766 | <div class="viewcode-block" id="get_command"><a class="viewcode-back" href="../server.html#server.get_command">[docs]</a><span class="k">def</span> <span class="nf">get_command</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">command_id</span><span class="p">):</span> | |
| 767 | <span class="sd">"""Get an unique command.</span> | |
| 768 | ||
| 769 | <span class="sd"> Args:</span> | |
| 770 | <span class="sd"> workspace_name (str): the workspace where the object should be found.</span> | |
| 771 | <span class="sd"> command_id (str): the id of the command</span> | |
| 772 | ||
| 773 | <span class="sd"> Returns:</span> | |
| 774 | <span class="sd"> A dictionary containing information about the command.</span> | |
| 775 | ||
| 776 | <span class="sd"> Raises:</span> | |
| 777 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the command id is shared</span> | |
| 778 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 779 | <span class="sd"> contact Infobyte LCC.</span> | |
| 780 | <span class="sd"> """</span> | |
| 781 | <span class="k">return</span> <span class="n">force_unique</span><span class="p">(</span><span class="n">get_commands</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">couchid</span><span class="o">=</span><span class="n">command_id</span><span class="p">))</span></div> | |
| 782 | ||
| 783 | <div class="viewcode-block" id="get_workspace"><a class="viewcode-back" href="../server.html#server.get_workspace">[docs]</a><span class="k">def</span> <span class="nf">get_workspace</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 784 | <span class="sd">"""Get an unique command.</span> | |
| 785 | ||
| 786 | <span class="sd"> Args:</span> | |
| 787 | <span class="sd"> command_name (str): the command where the object should be found.</span> | |
| 788 | <span class="sd"> command_id (str): the id of the command</span> | |
| 789 | ||
| 790 | <span class="sd"> Returns:</span> | |
| 791 | <span class="sd"> A dictionary containing information about the command.</span> | |
| 792 | ||
| 793 | <span class="sd"> Raises:</span> | |
| 794 | <span class="sd"> MoreThanOneObjectFoundByID: if for some reason the command id is shared</span> | |
| 795 | <span class="sd"> by two or more objects. This should never happen. If it does,</span> | |
| 796 | <span class="sd"> contact Infobyte LCC.</span> | |
| 797 | <span class="sd"> """</span> | |
| 798 | <span class="n">request_url</span> <span class="o">=</span> <span class="n">_create_server_get_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)</span> | |
| 799 | <span class="k">return</span> <span class="n">_get</span><span class="p">(</span><span class="n">request_url</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">)</span></div> | |
| 800 | ||
| 801 | <div class="viewcode-block" id="get_workspace_summary"><a class="viewcode-back" href="../server.html#server.get_workspace_summary">[docs]</a><span class="k">def</span> <span class="nf">get_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">):</span> | |
| 802 | <span class="sd">"""Get a collection of data about the workspace.</span> | |
| 803 | ||
| 804 | <span class="sd"> Args:</span> | |
| 805 | <span class="sd"> workspace_name (str): the workspace to get the stats from.</span> | |
| 806 | ||
| 807 | <span class="sd"> Returns:</span> | |
| 808 | <span class="sd"> A dictionary with the workspace's information</span> | |
| 809 | <span class="sd"> """</span> | |
| 810 | <span class="k">return</span> <span class="n">_get_raw_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)[</span><span class="s1">'stats'</span><span class="p">]</span></div> | |
| 811 | ||
| 812 | <div class="viewcode-block" id="get_workspace_numbers"><a class="viewcode-back" href="../server.html#server.get_workspace_numbers">[docs]</a><span class="k">def</span> <span class="nf">get_workspace_numbers</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">):</span> | |
| 813 | <span class="sd">"""Get the number of hosts, interfaces, services and vulns in the workspace.</span> | |
| 814 | ||
| 815 | <span class="sd"> Args:</span> | |
| 816 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 817 | ||
| 818 | <span class="sd"> Return:</span> | |
| 819 | <span class="sd"> A tuple of 4 elements with the amounts of hosts, interfaces, services and vulns.</span> | |
| 820 | <span class="sd"> """</span> | |
| 821 | <span class="n">stats</span> <span class="o">=</span> <span class="n">_get_raw_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)[</span><span class="s1">'stats'</span><span class="p">]</span> | |
| 822 | <span class="k">return</span> <span class="n">stats</span><span class="p">[</span><span class="s1">'hosts'</span><span class="p">],</span> <span class="n">stats</span><span class="p">[</span><span class="s1">'interfaces'</span><span class="p">],</span> <span class="n">stats</span><span class="p">[</span><span class="s1">'services'</span><span class="p">],</span> <span class="n">stats</span><span class="p">[</span><span class="s1">'total_vulns'</span><span class="p">]</span></div> | |
| 823 | ||
| 824 | <div class="viewcode-block" id="get_hosts_number"><a class="viewcode-back" href="../server.html#server.get_hosts_number">[docs]</a><span class="k">def</span> <span class="nf">get_hosts_number</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 825 | <span class="sd">"""</span> | |
| 826 | <span class="sd"> Args:</span> | |
| 827 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 828 | <span class="sd"> **params: any of the Couchdb request parameters</span> | |
| 829 | ||
| 830 | <span class="sd"> Returns:</span> | |
| 831 | <span class="sd"> The amount of hosts in the workspace as an integer.</span> | |
| 832 | <span class="sd"> """</span> | |
| 833 | <span class="k">return</span> <span class="nb">int</span><span class="p">(</span><span class="n">get_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)[</span><span class="s1">'hosts'</span><span class="p">])</span></div> | |
| 834 | ||
| 835 | <div class="viewcode-block" id="get_services_number"><a class="viewcode-back" href="../server.html#server.get_services_number">[docs]</a><span class="k">def</span> <span class="nf">get_services_number</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 836 | <span class="sd">"""</span> | |
| 837 | <span class="sd"> Args:</span> | |
| 838 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 839 | <span class="sd"> **params: any of the Couchdb request parameters</span> | |
| 840 | ||
| 841 | <span class="sd"> Returns:</span> | |
| 842 | <span class="sd"> The amount of services in the workspace as an integer.</span> | |
| 843 | <span class="sd"> """</span> | |
| 844 | <span class="k">return</span> <span class="nb">int</span><span class="p">(</span><span class="n">get_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)[</span><span class="s1">'interfaces'</span><span class="p">])</span></div> | |
| 845 | ||
| 846 | <div class="viewcode-block" id="get_interfaces_number"><a class="viewcode-back" href="../server.html#server.get_interfaces_number">[docs]</a><span class="k">def</span> <span class="nf">get_interfaces_number</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 847 | <span class="sd">"""</span> | |
| 848 | <span class="sd"> Args:</span> | |
| 849 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 850 | <span class="sd"> **params: any of the Couchdb request parameters</span> | |
| 851 | ||
| 852 | <span class="sd"> Returns:</span> | |
| 853 | <span class="sd"> The amount of interfaces in the workspace as an integer.</span> | |
| 854 | <span class="sd"> """</span> | |
| 855 | <span class="k">return</span> <span class="nb">int</span><span class="p">(</span><span class="n">get_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)[</span><span class="s1">'interfaces'</span><span class="p">])</span></div> | |
| 856 | ||
| 857 | <div class="viewcode-block" id="get_vulns_number"><a class="viewcode-back" href="../server.html#server.get_vulns_number">[docs]</a><span class="k">def</span> <span class="nf">get_vulns_number</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 858 | <span class="sd">"""</span> | |
| 859 | <span class="sd"> Args:</span> | |
| 860 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 861 | <span class="sd"> **params: any of the Couchdb request parameters</span> | |
| 862 | ||
| 863 | <span class="sd"> Returns:</span> | |
| 864 | <span class="sd"> The amount of vulns in the workspace as an integer.</span> | |
| 865 | <span class="sd"> """</span> | |
| 866 | <span class="k">return</span> <span class="nb">int</span><span class="p">(</span><span class="n">get_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)[</span><span class="s1">'total_vulns'</span><span class="p">])</span></div> | |
| 867 | ||
| 868 | <div class="viewcode-block" id="get_notes_number"><a class="viewcode-back" href="../server.html#server.get_notes_number">[docs]</a><span class="k">def</span> <span class="nf">get_notes_number</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 869 | <span class="sd">"""</span> | |
| 870 | <span class="sd"> Args:</span> | |
| 871 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 872 | <span class="sd"> **params: any of the Couchdb request parameters</span> | |
| 873 | ||
| 874 | <span class="sd"> Returns:</span> | |
| 875 | <span class="sd"> The amount of notes in the workspace as an integer.</span> | |
| 876 | <span class="sd"> """</span> | |
| 877 | <span class="k">return</span> <span class="nb">int</span><span class="p">(</span><span class="n">get_workspace_summary</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)[</span><span class="s1">'notes'</span><span class="p">])</span></div> | |
| 878 | ||
| 879 | <div class="viewcode-block" id="get_credentials_number"><a class="viewcode-back" href="../server.html#server.get_credentials_number">[docs]</a><span class="k">def</span> <span class="nf">get_credentials_number</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 880 | <span class="sd">"""</span> | |
| 881 | <span class="sd"> Args:</span> | |
| 882 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 883 | <span class="sd"> **params: any of the Couchdb request parameters</span> | |
| 884 | ||
| 885 | <span class="sd"> Returns:</span> | |
| 886 | <span class="sd"> The amount of credentials in the workspace as an integer.</span> | |
| 887 | <span class="sd"> """</span> | |
| 888 | <span class="k">return</span> <span class="nb">int</span><span class="p">(</span><span class="n">_get_raw_credentials</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">))</span></div> | |
| 889 | ||
| 890 | <div class="viewcode-block" id="get_commands_number"><a class="viewcode-back" href="../server.html#server.get_commands_number">[docs]</a><span class="k">def</span> <span class="nf">get_commands_number</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">):</span> | |
| 891 | <span class="sd">"""</span> | |
| 892 | <span class="sd"> Args:</span> | |
| 893 | <span class="sd"> workspace_name (str): the name of the workspace to query</span> | |
| 894 | <span class="sd"> **params: any of the Couchdb request parameters</span> | |
| 895 | ||
| 896 | <span class="sd"> Returns:</span> | |
| 897 | <span class="sd"> The amount of commands in the workspace as an integer.</span> | |
| 898 | <span class="sd"> """</span> | |
| 899 | <span class="k">return</span> <span class="nb">int</span><span class="p">(</span><span class="n">_get_raw_commands</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="o">**</span><span class="n">params</span><span class="p">))</span></div> | |
| 900 | ||
| 901 | <div class="viewcode-block" id="create_host"><a class="viewcode-back" href="../server.html#server.create_host">[docs]</a><span class="k">def</span> <span class="nf">create_host</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">os</span><span class="p">,</span> <span class="n">default_gateway</span><span class="p">,</span> | |
| 902 | <span class="n">description</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 903 | <span class="n">parent</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 904 | <span class="sd">"""Create a host.</span> | |
| 905 | ||
| 906 | <span class="sd"> Args:</span> | |
| 907 | <span class="sd"> workspace_name (str): the name of the workspace where the host will be saved.</span> | |
| 908 | <span class="sd"> id (str): the id of the host. Must be unique.</span> | |
| 909 | <span class="sd"> name (str): the host's name</span> | |
| 910 | <span class="sd"> os (str): the operative system of the host</span> | |
| 911 | <span class="sd"> default_gateway (str): the host's default_gateway</span> | |
| 912 | <span class="sd"> description (str): a description.</span> | |
| 913 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 914 | <span class="sd"> on None.</span> | |
| 915 | <span class="sd"> owned (bool): is the host owned or not?</span> | |
| 916 | <span class="sd"> owner (str): an owner for the host</span> | |
| 917 | <span class="sd"> parent (Faraday Object): the host's parent. If you don't know this, leave</span> | |
| 918 | <span class="sd"> on None.</span> | |
| 919 | ||
| 920 | <span class="sd"> Returns:</span> | |
| 921 | <span class="sd"> A dictionary with the server's response.</span> | |
| 922 | <span class="sd"> """</span> | |
| 923 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 924 | <span class="nb">id</span><span class="p">,</span> | |
| 925 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> <span class="n">os</span><span class="o">=</span><span class="n">os</span><span class="p">,</span> | |
| 926 | <span class="n">default_gateway</span><span class="o">=</span><span class="n">default_gateway</span><span class="p">,</span> | |
| 927 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 928 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">,</span> | |
| 929 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 930 | <span class="n">parent</span><span class="o">=</span><span class="n">parent</span><span class="p">,</span> | |
| 931 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 932 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Host"</span><span class="p">)</span></div> | |
| 933 | ||
| 934 | <div class="viewcode-block" id="update_host"><a class="viewcode-back" href="../server.html#server.update_host">[docs]</a><span class="k">def</span> <span class="nf">update_host</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">os</span><span class="p">,</span> <span class="n">default_gateway</span><span class="p">,</span> | |
| 935 | <span class="n">description</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 936 | <span class="n">parent</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 937 | <span class="sd">"""Updates a host.</span> | |
| 938 | ||
| 939 | <span class="sd"> Args:</span> | |
| 940 | <span class="sd"> workspace_name (str): the name of the workspace where the host will be saved.</span> | |
| 941 | <span class="sd"> id (str): the id of the host. Must be unique.</span> | |
| 942 | <span class="sd"> name (str): the host's name</span> | |
| 943 | <span class="sd"> os (str): the operative system of the host</span> | |
| 944 | <span class="sd"> default_gateway (str): the host's default_gateway</span> | |
| 945 | <span class="sd"> description (str): a description.</span> | |
| 946 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 947 | <span class="sd"> on None, it will be created automatically.</span> | |
| 948 | <span class="sd"> owned (bool): is the host owned or not?</span> | |
| 949 | <span class="sd"> owner (str): an owner for the host</span> | |
| 950 | <span class="sd"> parent (Faraday Object): the host's parent. If you don't know this, leave</span> | |
| 951 | <span class="sd"> on None.</span> | |
| 952 | ||
| 953 | <span class="sd"> Returns:</span> | |
| 954 | <span class="sd"> A dictionary with the server's response.</span> | |
| 955 | <span class="sd"> """</span> | |
| 956 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 957 | <span class="nb">id</span><span class="p">,</span> | |
| 958 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> <span class="n">os</span><span class="o">=</span><span class="n">os</span><span class="p">,</span> | |
| 959 | <span class="n">default_gateway</span><span class="o">=</span><span class="n">default_gateway</span><span class="p">,</span> | |
| 960 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 961 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">,</span> | |
| 962 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 963 | <span class="n">parent</span><span class="o">=</span><span class="n">parent</span><span class="p">,</span> | |
| 964 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 965 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Host"</span><span class="p">)</span></div> | |
| 966 | ||
| 967 | ||
| 968 | <span class="c1"># TODO: FIX. If you actually pass ipv4 or ipv6 as None, which are the defaults</span> | |
| 969 | <span class="c1"># values here, the server will complain. Review if this should be fixed on</span> | |
| 970 | <span class="c1"># the client or on the server.</span> | |
| 971 | <div class="viewcode-block" id="create_interface"><a class="viewcode-back" href="../server.html#server.create_interface">[docs]</a><span class="k">def</span> <span class="nf">create_interface</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">mac</span><span class="p">,</span> | |
| 972 | <span class="n">owned</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">hostnames</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">network_segment</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 973 | <span class="n">ipv4</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">ipv6</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 974 | <span class="sd">"""Creates an interface.</span> | |
| 975 | ||
| 976 | <span class="sd"> Warning:</span> | |
| 977 | <span class="sd"> DO NOT leave ipv4 and ipv6 values on None, as the default indicated.</span> | |
| 978 | <span class="sd"> This is a known bug and we're working to fix it. ipv4 and ipv6 need to</span> | |
| 979 | <span class="sd"> be valid IP addresses, or, in case one of them is irrelevant, empty strings.</span> | |
| 980 | ||
| 981 | <span class="sd"> Args:</span> | |
| 982 | <span class="sd"> workspace_name (str): the name of the workspace where the interface will be saved.</span> | |
| 983 | <span class="sd"> id (str): the id of the interface. Must be unique.</span> | |
| 984 | <span class="sd"> name (str): the interface's name</span> | |
| 985 | <span class="sd"> description (str): a description.</span> | |
| 986 | <span class="sd"> mac (str) the mac address of the interface</span> | |
| 987 | <span class="sd"> owned (bool): is the host owned or not?</span> | |
| 988 | <span class="sd"> owner (str): an owner for the host</span> | |
| 989 | <span class="sd"> hostnames ([str]): a list of hostnames</span> | |
| 990 | <span class="sd"> network_segment (str): the network segment</span> | |
| 991 | <span class="sd"> ipv4 (str): the ipv4 direction of the interface.</span> | |
| 992 | <span class="sd"> ipv6 (str): the ipv6 direction of the interface.</span> | |
| 993 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 994 | <span class="sd"> on None, it will be created automatically.</span> | |
| 995 | ||
| 996 | <span class="sd"> Returns:</span> | |
| 997 | <span class="sd"> A dictionary with the server's response.</span> | |
| 998 | <span class="sd"> """</span> | |
| 999 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1000 | <span class="nb">id</span><span class="p">,</span> | |
| 1001 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1002 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1003 | <span class="n">mac</span><span class="o">=</span><span class="n">mac</span><span class="p">,</span> | |
| 1004 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1005 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1006 | <span class="n">hostnames</span><span class="o">=</span><span class="n">hostnames</span><span class="p">,</span> | |
| 1007 | <span class="n">network_segment</span><span class="o">=</span><span class="n">network_segment</span><span class="p">,</span> | |
| 1008 | <span class="n">ipv4</span><span class="o">=</span><span class="n">ipv4</span><span class="p">,</span> | |
| 1009 | <span class="n">ipv6</span><span class="o">=</span><span class="n">ipv6</span><span class="p">,</span> | |
| 1010 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Interface"</span><span class="p">,</span> | |
| 1011 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1012 | ||
| 1013 | <div class="viewcode-block" id="update_interface"><a class="viewcode-back" href="../server.html#server.update_interface">[docs]</a><span class="k">def</span> <span class="nf">update_interface</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">mac</span><span class="p">,</span> | |
| 1014 | <span class="n">owned</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">hostnames</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">network_segment</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1015 | <span class="n">ipv4</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">ipv6</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1016 | <span class="sd">"""Creates an interface.</span> | |
| 1017 | ||
| 1018 | <span class="sd"> Warning:</span> | |
| 1019 | <span class="sd"> DO NOT leave ipv4 and ipv6 values on None, as the default indicated.</span> | |
| 1020 | <span class="sd"> This is a known bug and we're working to fix it. ipv4 and ipv6 need to</span> | |
| 1021 | <span class="sd"> be valid IP addresses, or, in case one of them is irrelevant, empty strings.</span> | |
| 1022 | ||
| 1023 | <span class="sd"> Args:</span> | |
| 1024 | <span class="sd"> workspace_name (str): the name of the workspace where the interface will be saved.</span> | |
| 1025 | <span class="sd"> id (str): the id of the interface. Must be unique.</span> | |
| 1026 | <span class="sd"> name (str): the interface's name</span> | |
| 1027 | <span class="sd"> description (str): a description.</span> | |
| 1028 | <span class="sd"> mac (str) the mac address of the interface</span> | |
| 1029 | <span class="sd"> owned (bool): is the host owned or not?</span> | |
| 1030 | <span class="sd"> owner (str): an owner for the host</span> | |
| 1031 | <span class="sd"> hostnames ([str]): a list of hostnames</span> | |
| 1032 | <span class="sd"> network_segment (str): the network segment</span> | |
| 1033 | <span class="sd"> ipv4 (str): the ipv4 direction of the interface.</span> | |
| 1034 | <span class="sd"> ipv6 (str): the ipv6 direction of the interface.</span> | |
| 1035 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1036 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1037 | ||
| 1038 | <span class="sd"> Returns:</span> | |
| 1039 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1040 | <span class="sd"> """</span> | |
| 1041 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1042 | <span class="nb">id</span><span class="p">,</span> | |
| 1043 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1044 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1045 | <span class="n">mac</span><span class="o">=</span><span class="n">mac</span><span class="p">,</span> | |
| 1046 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1047 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1048 | <span class="n">hostnames</span><span class="o">=</span><span class="n">hostnames</span><span class="p">,</span> | |
| 1049 | <span class="n">network_segment</span><span class="o">=</span><span class="n">network_segment</span><span class="p">,</span> | |
| 1050 | <span class="n">ipv4</span><span class="o">=</span><span class="n">ipv4</span><span class="p">,</span> | |
| 1051 | <span class="n">ipv6</span><span class="o">=</span><span class="n">ipv6</span><span class="p">,</span> | |
| 1052 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Interface"</span><span class="p">,</span> | |
| 1053 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1054 | ||
| 1055 | <div class="viewcode-block" id="create_service"><a class="viewcode-back" href="../server.html#server.create_service">[docs]</a><span class="k">def</span> <span class="nf">create_service</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">ports</span><span class="p">,</span> | |
| 1056 | <span class="n">owned</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">protocol</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">status</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">version</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1057 | <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1058 | <span class="sd">"""Creates a service.</span> | |
| 1059 | ||
| 1060 | <span class="sd"> Args:</span> | |
| 1061 | <span class="sd"> workspace_name (str): the name of the workspace where the service will be saved.</span> | |
| 1062 | <span class="sd"> id (str): the id of the service. Must be unique.</span> | |
| 1063 | <span class="sd"> name (str): the host's name</span> | |
| 1064 | <span class="sd"> description (str): a description.</span> | |
| 1065 | <span class="sd"> ports ([str]): a list of ports for the service.</span> | |
| 1066 | <span class="sd"> owned (bool): is the service owned or not?</span> | |
| 1067 | <span class="sd"> owner (str): an owner for the service</span> | |
| 1068 | <span class="sd"> protocol (str): the service's protocol</span> | |
| 1069 | <span class="sd"> status (str): the service's status</span> | |
| 1070 | <span class="sd"> version (str): the service's version</span> | |
| 1071 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1072 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1073 | ||
| 1074 | <span class="sd"> Returns:</span> | |
| 1075 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1076 | <span class="sd"> """</span> | |
| 1077 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1078 | <span class="nb">id</span><span class="p">,</span> | |
| 1079 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1080 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1081 | <span class="n">ports</span><span class="o">=</span><span class="n">ports</span><span class="p">,</span> | |
| 1082 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1083 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1084 | <span class="n">protocol</span><span class="o">=</span><span class="n">protocol</span><span class="p">,</span> | |
| 1085 | <span class="n">status</span><span class="o">=</span><span class="n">status</span><span class="p">,</span> | |
| 1086 | <span class="n">version</span><span class="o">=</span><span class="n">version</span><span class="p">,</span> | |
| 1087 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Service"</span><span class="p">,</span> | |
| 1088 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1089 | ||
| 1090 | <div class="viewcode-block" id="update_service"><a class="viewcode-back" href="../server.html#server.update_service">[docs]</a><span class="k">def</span> <span class="nf">update_service</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">ports</span><span class="p">,</span> | |
| 1091 | <span class="n">owned</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">protocol</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">status</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">version</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1092 | <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1093 | <span class="sd">"""Creates a service.</span> | |
| 1094 | ||
| 1095 | <span class="sd"> Args:</span> | |
| 1096 | <span class="sd"> workspace_name (str): the name of the workspace where the service will be saved.</span> | |
| 1097 | <span class="sd"> id (str): the id of the service. Must be unique.</span> | |
| 1098 | <span class="sd"> name (str): the service's name</span> | |
| 1099 | <span class="sd"> description (str): a description.</span> | |
| 1100 | <span class="sd"> ports ([str]): a list of ports for the service.</span> | |
| 1101 | <span class="sd"> owned (bool): is the host owned or not?</span> | |
| 1102 | <span class="sd"> owner (str): an owner for the service</span> | |
| 1103 | <span class="sd"> protocol (str): the service's protocol</span> | |
| 1104 | <span class="sd"> status (str): the service's status</span> | |
| 1105 | <span class="sd"> version (str): the service's version</span> | |
| 1106 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1107 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1108 | ||
| 1109 | <span class="sd"> Returns:</span> | |
| 1110 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1111 | <span class="sd"> """</span> | |
| 1112 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1113 | <span class="nb">id</span><span class="p">,</span> | |
| 1114 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1115 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1116 | <span class="n">ports</span><span class="o">=</span><span class="n">ports</span><span class="p">,</span> | |
| 1117 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1118 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1119 | <span class="n">protocol</span><span class="o">=</span><span class="n">protocol</span><span class="p">,</span> | |
| 1120 | <span class="n">status</span><span class="o">=</span><span class="n">status</span><span class="p">,</span> | |
| 1121 | <span class="n">version</span><span class="o">=</span><span class="n">version</span><span class="p">,</span> | |
| 1122 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Service"</span><span class="p">,</span> | |
| 1123 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1124 | ||
| 1125 | ||
| 1126 | <div class="viewcode-block" id="create_vuln"><a class="viewcode-back" href="../server.html#server.create_vuln">[docs]</a><span class="k">def</span> <span class="nf">create_vuln</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1127 | <span class="n">confirmed</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">data</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">refs</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">severity</span><span class="o">=</span><span class="s2">"info"</span><span class="p">,</span> <span class="n">resolution</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1128 | <span class="n">desc</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">status</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1129 | <span class="sd">"""Creates a vuln.</span> | |
| 1130 | ||
| 1131 | <span class="sd"> Args:</span> | |
| 1132 | <span class="sd"> workspace_name (str): the name of the workspace where the vuln will be saved.</span> | |
| 1133 | <span class="sd"> id (str): the id of the vuln. Must be unique.</span> | |
| 1134 | <span class="sd"> name (str): the vuln's name</span> | |
| 1135 | <span class="sd"> description (str): a description.</span> | |
| 1136 | <span class="sd"> owned (bool): is the vuln owned or not?</span> | |
| 1137 | <span class="sd"> owner (str): an owner for the vuln</span> | |
| 1138 | <span class="sd"> confirmed (bool): is the vulnerability confirmed?</span> | |
| 1139 | <span class="sd"> data (str): any aditional data about the vuln</span> | |
| 1140 | <span class="sd"> refs ([str]): references for the vulnerability</span> | |
| 1141 | <span class="sd"> severity (str): a string indicating the vuln's severity. can be 'info',</span> | |
| 1142 | <span class="sd"> 'low', 'med', 'high', 'critical'</span> | |
| 1143 | <span class="sd"> resolution (str): the vuln's possible resolution</span> | |
| 1144 | <span class="sd"> desc (str): a vuln's description.</span> | |
| 1145 | <span class="sd"> status (str): the service's status</span> | |
| 1146 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1147 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1148 | ||
| 1149 | <span class="sd"> Returns:</span> | |
| 1150 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1151 | <span class="sd"> """</span> | |
| 1152 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1153 | <span class="nb">id</span><span class="p">,</span> | |
| 1154 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1155 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1156 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1157 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1158 | <span class="n">confirmed</span><span class="o">=</span><span class="n">confirmed</span><span class="p">,</span> | |
| 1159 | <span class="n">data</span><span class="o">=</span><span class="n">data</span><span class="p">,</span> | |
| 1160 | <span class="n">refs</span><span class="o">=</span><span class="n">refs</span><span class="p">,</span> | |
| 1161 | <span class="n">severity</span><span class="o">=</span><span class="n">severity</span><span class="p">,</span> | |
| 1162 | <span class="n">resolution</span><span class="o">=</span><span class="n">resolution</span><span class="p">,</span> | |
| 1163 | <span class="n">desc</span><span class="o">=</span><span class="n">desc</span><span class="p">,</span> | |
| 1164 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Vulnerability"</span><span class="p">,</span> | |
| 1165 | <span class="n">status</span><span class="o">=</span><span class="n">status</span><span class="p">,</span> | |
| 1166 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1167 | ||
| 1168 | <div class="viewcode-block" id="update_vuln"><a class="viewcode-back" href="../server.html#server.update_vuln">[docs]</a><span class="k">def</span> <span class="nf">update_vuln</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1169 | <span class="n">confirmed</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">data</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">refs</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">severity</span><span class="o">=</span><span class="s2">"info"</span><span class="p">,</span> <span class="n">resolution</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1170 | <span class="n">desc</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">status</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1171 | <span class="sd">"""Updates a vuln.</span> | |
| 1172 | ||
| 1173 | <span class="sd"> Args:</span> | |
| 1174 | <span class="sd"> workspace_name (str): the name of the workspace where the host will be saved.</span> | |
| 1175 | <span class="sd"> id (str): the id of the host. Must be unique.</span> | |
| 1176 | <span class="sd"> name (str): the host's name</span> | |
| 1177 | <span class="sd"> description (str): a description.</span> | |
| 1178 | <span class="sd"> owned (bool): is the vuln owned or not?</span> | |
| 1179 | <span class="sd"> owner (str): an owner for the vuln</span> | |
| 1180 | <span class="sd"> confirmed (bool): is the vulnerability confirmed?</span> | |
| 1181 | <span class="sd"> data (str): any aditional data about the vuln</span> | |
| 1182 | <span class="sd"> refs ([str]): references for the vulnerability</span> | |
| 1183 | <span class="sd"> severity (str): a string indicating the vuln's severity. can be 'info',</span> | |
| 1184 | <span class="sd"> 'low', 'med', 'high', 'critical'</span> | |
| 1185 | <span class="sd"> resolution (str): the vuln's possible resolution</span> | |
| 1186 | <span class="sd"> desc (str): a vuln's description.</span> | |
| 1187 | <span class="sd"> status (str): the service's status</span> | |
| 1188 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1189 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1190 | ||
| 1191 | <span class="sd"> Returns:</span> | |
| 1192 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1193 | <span class="sd"> """</span> | |
| 1194 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1195 | <span class="nb">id</span><span class="p">,</span> | |
| 1196 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1197 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1198 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1199 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1200 | <span class="n">confirmed</span><span class="o">=</span><span class="n">confirmed</span><span class="p">,</span> | |
| 1201 | <span class="n">data</span><span class="o">=</span><span class="n">data</span><span class="p">,</span> | |
| 1202 | <span class="n">refs</span><span class="o">=</span><span class="n">refs</span><span class="p">,</span> | |
| 1203 | <span class="n">severity</span><span class="o">=</span><span class="n">severity</span><span class="p">,</span> | |
| 1204 | <span class="n">resolution</span><span class="o">=</span><span class="n">resolution</span><span class="p">,</span> | |
| 1205 | <span class="n">desc</span><span class="o">=</span><span class="n">desc</span><span class="p">,</span> | |
| 1206 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Vulnerability"</span><span class="p">,</span> | |
| 1207 | <span class="n">status</span><span class="o">=</span><span class="n">status</span><span class="p">,</span> | |
| 1208 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1209 | ||
| 1210 | <div class="viewcode-block" id="create_vuln_web"><a class="viewcode-back" href="../server.html#server.create_vuln_web">[docs]</a><span class="k">def</span> <span class="nf">create_vuln_web</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1211 | <span class="n">confirmed</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">data</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">refs</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">severity</span><span class="o">=</span><span class="s2">"info"</span><span class="p">,</span> <span class="n">resolution</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1212 | <span class="n">desc</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">method</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">params</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">path</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">pname</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1213 | <span class="n">query</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">request</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">response</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">category</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">website</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1214 | <span class="n">status</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1215 | <span class="sd">"""Creates a vuln web.</span> | |
| 1216 | ||
| 1217 | <span class="sd"> Args:</span> | |
| 1218 | <span class="sd"> workspace_name (str): the name of the workspace where the vuln web will be saved.</span> | |
| 1219 | <span class="sd"> id (str): the id of the vuln web. Must be unique.</span> | |
| 1220 | <span class="sd"> name (str): the vuln web's name</span> | |
| 1221 | <span class="sd"> description (str): a description.</span> | |
| 1222 | <span class="sd"> owner (str): an owner for the host</span> | |
| 1223 | <span class="sd"> confirmed (bool): is the vulnerability confirmed?</span> | |
| 1224 | <span class="sd"> data (str): any aditional data about the vuln</span> | |
| 1225 | <span class="sd"> refs ([str]): references for the vulnerability</span> | |
| 1226 | <span class="sd"> severity (str): a string indicating the vuln's severity. can be 'info',</span> | |
| 1227 | <span class="sd"> 'low', 'med', 'high', 'critical'</span> | |
| 1228 | <span class="sd"> resolution (str): the vuln's possible resolution</span> | |
| 1229 | <span class="sd"> desc (str): a vuln's description.</span> | |
| 1230 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1231 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1232 | <span class="sd"> method (str): the web vuln method</span> | |
| 1233 | <span class="sd"> params (str): the parameters for the web vuln</span> | |
| 1234 | <span class="sd"> path (str): the web vuln's path</span> | |
| 1235 | <span class="sd"> query (str): the web vuln's query</span> | |
| 1236 | <span class="sd"> request (str): the web vuln's request</span> | |
| 1237 | <span class="sd"> response (str): the web vuln's response</span> | |
| 1238 | <span class="sd"> category (str): a category for the web vuln's</span> | |
| 1239 | <span class="sd"> website (str): the website where the vuln was found</span> | |
| 1240 | <span class="sd"> status (str): the web vulns's status</span> | |
| 1241 | ||
| 1242 | <span class="sd"> Returns:</span> | |
| 1243 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1244 | <span class="sd"> """</span> | |
| 1245 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1246 | <span class="nb">id</span><span class="p">,</span> | |
| 1247 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1248 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1249 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1250 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1251 | <span class="n">confirmed</span><span class="o">=</span><span class="n">confirmed</span><span class="p">,</span> | |
| 1252 | <span class="n">data</span><span class="o">=</span><span class="n">data</span><span class="p">,</span> | |
| 1253 | <span class="n">refs</span><span class="o">=</span><span class="n">refs</span><span class="p">,</span> | |
| 1254 | <span class="n">severity</span><span class="o">=</span><span class="n">severity</span><span class="p">,</span> | |
| 1255 | <span class="n">resolution</span><span class="o">=</span><span class="n">resolution</span><span class="p">,</span> | |
| 1256 | <span class="n">desc</span><span class="o">=</span><span class="n">desc</span><span class="p">,</span> | |
| 1257 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">,</span> | |
| 1258 | <span class="n">method</span><span class="o">=</span><span class="n">method</span><span class="p">,</span> | |
| 1259 | <span class="n">params</span><span class="o">=</span><span class="n">params</span><span class="p">,</span> | |
| 1260 | <span class="n">path</span><span class="o">=</span><span class="n">path</span><span class="p">,</span> | |
| 1261 | <span class="n">pname</span><span class="o">=</span><span class="n">pname</span><span class="p">,</span> | |
| 1262 | <span class="n">query</span><span class="o">=</span><span class="n">query</span><span class="p">,</span> | |
| 1263 | <span class="n">request</span><span class="o">=</span><span class="n">request</span><span class="p">,</span> | |
| 1264 | <span class="n">response</span><span class="o">=</span><span class="n">response</span><span class="p">,</span> | |
| 1265 | <span class="n">website</span><span class="o">=</span><span class="n">website</span><span class="p">,</span> | |
| 1266 | <span class="n">category</span><span class="o">=</span><span class="n">category</span><span class="p">,</span> | |
| 1267 | <span class="n">status</span><span class="o">=</span><span class="n">status</span><span class="p">,</span> | |
| 1268 | <span class="nb">type</span><span class="o">=</span><span class="s1">'VulnerabilityWeb'</span><span class="p">)</span></div> | |
| 1269 | ||
| 1270 | <div class="viewcode-block" id="update_vuln_web"><a class="viewcode-back" href="../server.html#server.update_vuln_web">[docs]</a><span class="k">def</span> <span class="nf">update_vuln_web</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1271 | <span class="n">confirmed</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">data</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">refs</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">severity</span><span class="o">=</span><span class="s2">"info"</span><span class="p">,</span> <span class="n">resolution</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1272 | <span class="n">desc</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">method</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">params</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">path</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">pname</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1273 | <span class="n">query</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">request</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">response</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">category</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">website</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1274 | <span class="n">status</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1275 | <span class="sd">"""Creates a vuln web.</span> | |
| 1276 | ||
| 1277 | <span class="sd"> Args:</span> | |
| 1278 | <span class="sd"> workspace_name (str): the name of the workspace where the vuln web will be saved.</span> | |
| 1279 | <span class="sd"> id (str): the id of the vuln web. Must be unique.</span> | |
| 1280 | <span class="sd"> name (str): the vuln web's name</span> | |
| 1281 | <span class="sd"> description (str): a description.</span> | |
| 1282 | <span class="sd"> owner (str): an owner for the host</span> | |
| 1283 | <span class="sd"> confirmed (bool): is the vulnerability confirmed?</span> | |
| 1284 | <span class="sd"> data (str): any aditional data about the vuln</span> | |
| 1285 | <span class="sd"> refs ([str]): references for the vulnerability</span> | |
| 1286 | <span class="sd"> severity (str): a string indicating the vuln's severity. can be 'info',</span> | |
| 1287 | <span class="sd"> 'low', 'med', 'high', 'critical'</span> | |
| 1288 | <span class="sd"> resolution (str): the vuln's possible resolution</span> | |
| 1289 | <span class="sd"> desc (str): a vuln's description.</span> | |
| 1290 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1291 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1292 | <span class="sd"> method (str): the web vuln method</span> | |
| 1293 | <span class="sd"> params (str): the parameters for the web vuln</span> | |
| 1294 | <span class="sd"> path (str): the web vuln's path</span> | |
| 1295 | <span class="sd"> query (str): the web vuln's query</span> | |
| 1296 | <span class="sd"> request (str): the web vuln's request</span> | |
| 1297 | <span class="sd"> response (str): the web vuln's response</span> | |
| 1298 | <span class="sd"> category (str): a category for the web vuln's</span> | |
| 1299 | <span class="sd"> website (str): the website where the vuln was found</span> | |
| 1300 | <span class="sd"> status (str): the web vulns's status</span> | |
| 1301 | ||
| 1302 | <span class="sd"> Returns:</span> | |
| 1303 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1304 | <span class="sd"> """</span> | |
| 1305 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1306 | <span class="nb">id</span><span class="p">,</span> | |
| 1307 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1308 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1309 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1310 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1311 | <span class="n">confirmed</span><span class="o">=</span><span class="n">confirmed</span><span class="p">,</span> | |
| 1312 | <span class="n">data</span><span class="o">=</span><span class="n">data</span><span class="p">,</span> | |
| 1313 | <span class="n">refs</span><span class="o">=</span><span class="n">refs</span><span class="p">,</span> | |
| 1314 | <span class="n">severity</span><span class="o">=</span><span class="n">severity</span><span class="p">,</span> | |
| 1315 | <span class="n">resolution</span><span class="o">=</span><span class="n">resolution</span><span class="p">,</span> | |
| 1316 | <span class="n">desc</span><span class="o">=</span><span class="n">desc</span><span class="p">,</span> | |
| 1317 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">,</span> | |
| 1318 | <span class="n">method</span><span class="o">=</span><span class="n">method</span><span class="p">,</span> | |
| 1319 | <span class="n">params</span><span class="o">=</span><span class="n">params</span><span class="p">,</span> | |
| 1320 | <span class="n">path</span><span class="o">=</span><span class="n">path</span><span class="p">,</span> | |
| 1321 | <span class="n">pname</span><span class="o">=</span><span class="n">pname</span><span class="p">,</span> | |
| 1322 | <span class="n">query</span><span class="o">=</span><span class="n">query</span><span class="p">,</span> | |
| 1323 | <span class="n">request</span><span class="o">=</span><span class="n">request</span><span class="p">,</span> | |
| 1324 | <span class="n">response</span><span class="o">=</span><span class="n">response</span><span class="p">,</span> | |
| 1325 | <span class="n">website</span><span class="o">=</span><span class="n">website</span><span class="p">,</span> | |
| 1326 | <span class="n">category</span><span class="o">=</span><span class="n">category</span><span class="p">,</span> | |
| 1327 | <span class="n">status</span><span class="o">=</span><span class="n">status</span><span class="p">,</span> | |
| 1328 | <span class="nb">type</span><span class="o">=</span><span class="s1">'VulnerabilityWeb'</span><span class="p">)</span></div> | |
| 1329 | ||
| 1330 | <div class="viewcode-block" id="create_note"><a class="viewcode-back" href="../server.html#server.create_note">[docs]</a><span class="k">def</span> <span class="nf">create_note</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">text</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1331 | <span class="n">description</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1332 | <span class="sd">"""Creates a note.</span> | |
| 1333 | ||
| 1334 | <span class="sd"> Args:</span> | |
| 1335 | <span class="sd"> workspace_name (str): the name of the workspace where the vuln web will be saved.</span> | |
| 1336 | <span class="sd"> id (str): the id of the vuln web. Must be unique.</span> | |
| 1337 | <span class="sd"> name (str): the vuln web's name</span> | |
| 1338 | <span class="sd"> text (str): the note's text</span> | |
| 1339 | <span class="sd"> owned (bool): is the note owned?</span> | |
| 1340 | <span class="sd"> owner (str): the note's owner</span> | |
| 1341 | <span class="sd"> description (str): a description</span> | |
| 1342 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1343 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1344 | ||
| 1345 | <span class="sd"> Returns:</span> | |
| 1346 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1347 | <span class="sd"> """</span> | |
| 1348 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1349 | <span class="nb">id</span><span class="p">,</span> | |
| 1350 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1351 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1352 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1353 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1354 | <span class="n">text</span><span class="o">=</span><span class="n">text</span><span class="p">,</span> | |
| 1355 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Note"</span><span class="p">,</span> | |
| 1356 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1357 | ||
| 1358 | <div class="viewcode-block" id="update_note"><a class="viewcode-back" href="../server.html#server.update_note">[docs]</a><span class="k">def</span> <span class="nf">update_note</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">text</span><span class="p">,</span> <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> | |
| 1359 | <span class="n">description</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1360 | <span class="sd">"""Updates a note.</span> | |
| 1361 | ||
| 1362 | <span class="sd"> Args:</span> | |
| 1363 | <span class="sd"> workspace_name (str): the name of the workspace where the vuln web will be saved.</span> | |
| 1364 | <span class="sd"> id (str): the id of the vuln web. Must be unique.</span> | |
| 1365 | <span class="sd"> name (str): the vuln web's name</span> | |
| 1366 | <span class="sd"> text (str): the note's text</span> | |
| 1367 | <span class="sd"> owned (bool): is the note owned?</span> | |
| 1368 | <span class="sd"> owner (str): the note's owner</span> | |
| 1369 | <span class="sd"> description (str): a description</span> | |
| 1370 | <span class="sd"> metadata: a collection of metadata. If you don't know the metada. leave</span> | |
| 1371 | <span class="sd"> on None, it will be created automatically.</span> | |
| 1372 | ||
| 1373 | <span class="sd"> Returns:</span> | |
| 1374 | <span class="sd"> A dictionary with the server's response.</span> | |
| 1375 | <span class="sd"> """</span> | |
| 1376 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1377 | <span class="nb">id</span><span class="p">,</span> | |
| 1378 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1379 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1380 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1381 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1382 | <span class="n">text</span><span class="o">=</span><span class="n">text</span><span class="p">,</span> | |
| 1383 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Note"</span><span class="p">,</span> | |
| 1384 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">)</span></div> | |
| 1385 | ||
| 1386 | ||
| 1387 | <div class="viewcode-block" id="create_credential"><a class="viewcode-back" href="../server.html#server.create_credential">[docs]</a><span class="k">def</span> <span class="nf">create_credential</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">username</span><span class="p">,</span> <span class="n">password</span><span class="p">,</span> | |
| 1388 | <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">description</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1389 | <span class="sd">"""Save a credential to the server. Return the json with the</span> | |
| 1390 | <span class="sd"> server's response.</span> | |
| 1391 | <span class="sd"> """</span> | |
| 1392 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1393 | <span class="nb">id</span><span class="p">,</span> | |
| 1394 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1395 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1396 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1397 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1398 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">,</span> | |
| 1399 | <span class="n">username</span><span class="o">=</span><span class="n">username</span><span class="p">,</span> | |
| 1400 | <span class="n">password</span><span class="o">=</span><span class="n">password</span><span class="p">,</span> | |
| 1401 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Credential"</span><span class="p">)</span></div> | |
| 1402 | ||
| 1403 | <div class="viewcode-block" id="update_credential"><a class="viewcode-back" href="../server.html#server.update_credential">[docs]</a><span class="k">def</span> <span class="nf">update_credential</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">name</span><span class="p">,</span> <span class="n">username</span><span class="p">,</span> <span class="n">password</span><span class="p">,</span> | |
| 1404 | <span class="n">owned</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">owner</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">description</span><span class="o">=</span><span class="s2">""</span><span class="p">,</span> <span class="n">metadata</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1405 | <span class="sd">"""Update a credential in the server. Return the json with the</span> | |
| 1406 | <span class="sd"> server's response.</span> | |
| 1407 | <span class="sd"> """</span> | |
| 1408 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1409 | <span class="nb">id</span><span class="p">,</span> | |
| 1410 | <span class="n">name</span><span class="o">=</span><span class="n">name</span><span class="p">,</span> | |
| 1411 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1412 | <span class="n">owned</span><span class="o">=</span><span class="n">owned</span><span class="p">,</span> | |
| 1413 | <span class="n">owner</span><span class="o">=</span><span class="n">owner</span><span class="p">,</span> | |
| 1414 | <span class="n">metadata</span><span class="o">=</span><span class="n">metadata</span><span class="p">,</span> | |
| 1415 | <span class="n">username</span><span class="o">=</span><span class="n">username</span><span class="p">,</span> | |
| 1416 | <span class="n">password</span><span class="o">=</span><span class="n">password</span><span class="p">,</span> | |
| 1417 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Credential"</span><span class="p">)</span></div> | |
| 1418 | ||
| 1419 | <div class="viewcode-block" id="create_command"><a class="viewcode-back" href="../server.html#server.create_command">[docs]</a><span class="k">def</span> <span class="nf">create_command</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">command</span><span class="p">,</span> <span class="n">duration</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">hostname</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1420 | <span class="n">ip</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">itime</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">params</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">user</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1421 | <span class="sd">"""Create a command in the server. Return the json with the</span> | |
| 1422 | <span class="sd"> server's response.</span> | |
| 1423 | <span class="sd"> """</span> | |
| 1424 | <span class="k">return</span> <span class="n">_save_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1425 | <span class="nb">id</span><span class="p">,</span> | |
| 1426 | <span class="n">command</span><span class="o">=</span><span class="n">command</span><span class="p">,</span> | |
| 1427 | <span class="n">duration</span><span class="o">=</span><span class="n">duration</span><span class="p">,</span> | |
| 1428 | <span class="n">hostname</span><span class="o">=</span><span class="n">hostname</span><span class="p">,</span> | |
| 1429 | <span class="n">ip</span><span class="o">=</span><span class="n">ip</span><span class="p">,</span> | |
| 1430 | <span class="n">itime</span><span class="o">=</span><span class="n">itime</span><span class="p">,</span> | |
| 1431 | <span class="n">params</span><span class="o">=</span><span class="n">params</span><span class="p">,</span> | |
| 1432 | <span class="n">user</span><span class="o">=</span><span class="n">user</span><span class="p">,</span> | |
| 1433 | <span class="n">workspace</span><span class="o">=</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1434 | <span class="nb">type</span><span class="o">=</span><span class="s2">"CommandRunInformation"</span><span class="p">)</span></div> | |
| 1435 | ||
| 1436 | <div class="viewcode-block" id="update_command"><a class="viewcode-back" href="../server.html#server.update_command">[docs]</a><span class="k">def</span> <span class="nf">update_command</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="nb">id</span><span class="p">,</span> <span class="n">command</span><span class="p">,</span> <span class="n">duration</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">hostname</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1437 | <span class="n">ip</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">itime</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">params</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">user</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1438 | <span class="sd">"""Update a command in the server. Return the json with the</span> | |
| 1439 | <span class="sd"> server's response.</span> | |
| 1440 | <span class="sd"> """</span> | |
| 1441 | <span class="k">return</span> <span class="n">_update_in_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1442 | <span class="nb">id</span><span class="p">,</span> | |
| 1443 | <span class="n">command</span><span class="o">=</span><span class="n">command</span><span class="p">,</span> | |
| 1444 | <span class="n">duration</span><span class="o">=</span><span class="n">duration</span><span class="p">,</span> | |
| 1445 | <span class="n">hostname</span><span class="o">=</span><span class="n">hostname</span><span class="p">,</span> | |
| 1446 | <span class="n">ip</span><span class="o">=</span><span class="n">ip</span><span class="p">,</span> | |
| 1447 | <span class="n">itime</span><span class="o">=</span><span class="n">itime</span><span class="p">,</span> | |
| 1448 | <span class="n">params</span><span class="o">=</span><span class="n">params</span><span class="p">,</span> | |
| 1449 | <span class="n">user</span><span class="o">=</span><span class="n">user</span><span class="p">,</span> | |
| 1450 | <span class="n">workspace</span><span class="o">=</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1451 | <span class="nb">type</span><span class="o">=</span><span class="s2">"CommandRunInformation"</span><span class="p">)</span></div> | |
| 1452 | ||
| 1453 | ||
| 1454 | <div class="viewcode-block" id="create_workspace"><a class="viewcode-back" href="../server.html#server.create_workspace">[docs]</a><span class="k">def</span> <span class="nf">create_workspace</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">description</span><span class="p">,</span> <span class="n">start_date</span><span class="p">,</span> <span class="n">finish_date</span><span class="p">,</span> | |
| 1455 | <span class="n">customer</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1456 | <span class="sd">"""Create a workspace in the server. Return the json with the</span> | |
| 1457 | <span class="sd"> server's response.</span> | |
| 1458 | <span class="sd"> """</span> | |
| 1459 | <span class="k">return</span> <span class="n">_save_db_to_server</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1460 | <span class="n">name</span><span class="o">=</span><span class="n">workspace_name</span><span class="p">,</span> | |
| 1461 | <span class="n">description</span><span class="o">=</span><span class="n">description</span><span class="p">,</span> | |
| 1462 | <span class="n">customer</span><span class="o">=</span><span class="n">customer</span><span class="p">,</span> | |
| 1463 | <span class="n">sdate</span><span class="o">=</span><span class="n">start_date</span><span class="p">,</span> | |
| 1464 | <span class="n">fdate</span><span class="o">=</span><span class="n">finish_date</span><span class="p">,</span> | |
| 1465 | <span class="nb">type</span><span class="o">=</span><span class="s2">"Workspace"</span><span class="p">)</span></div> | |
| 1466 | ||
| 1467 | <div class="viewcode-block" id="delete_host"><a class="viewcode-back" href="../server.html#server.delete_host">[docs]</a><span class="k">def</span> <span class="nf">delete_host</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">host_id</span><span class="p">):</span> | |
| 1468 | <span class="sd">"""Delete host of id host_id from the database."""</span> | |
| 1469 | <span class="k">return</span> <span class="n">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">host_id</span><span class="p">)</span></div> | |
| 1470 | ||
| 1471 | <div class="viewcode-block" id="delete_interface"><a class="viewcode-back" href="../server.html#server.delete_interface">[docs]</a><span class="k">def</span> <span class="nf">delete_interface</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">interface_id</span><span class="p">):</span> | |
| 1472 | <span class="sd">"""Delete interface of id interface_id from the database."""</span> | |
| 1473 | <span class="k">return</span> <span class="n">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">interface_id</span><span class="p">)</span></div> | |
| 1474 | ||
| 1475 | <div class="viewcode-block" id="delete_service"><a class="viewcode-back" href="../server.html#server.delete_service">[docs]</a><span class="k">def</span> <span class="nf">delete_service</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">service_id</span><span class="p">):</span> | |
| 1476 | <span class="sd">"""Delete service of id service_id from the database."""</span> | |
| 1477 | <span class="k">return</span> <span class="n">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">service_id</span><span class="p">)</span></div> | |
| 1478 | ||
| 1479 | <div class="viewcode-block" id="delete_vuln"><a class="viewcode-back" href="../server.html#server.delete_vuln">[docs]</a><span class="k">def</span> <span class="nf">delete_vuln</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">vuln_id</span><span class="p">):</span> | |
| 1480 | <span class="sd">"""Delete vuln of id vuln_id from the database."""</span> | |
| 1481 | <span class="k">return</span> <span class="n">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">vuln_id</span><span class="p">)</span></div> | |
| 1482 | ||
| 1483 | <div class="viewcode-block" id="delete_note"><a class="viewcode-back" href="../server.html#server.delete_note">[docs]</a><span class="k">def</span> <span class="nf">delete_note</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">note_id</span><span class="p">):</span> | |
| 1484 | <span class="sd">"""Delete note of id note_id from the database."""</span> | |
| 1485 | <span class="k">return</span> <span class="n">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">note_id</span><span class="p">)</span></div> | |
| 1486 | ||
| 1487 | <div class="viewcode-block" id="delete_credential"><a class="viewcode-back" href="../server.html#server.delete_credential">[docs]</a><span class="k">def</span> <span class="nf">delete_credential</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">credential_id</span><span class="p">):</span> | |
| 1488 | <span class="sd">"""Delete credential of id credential_id from the database."""</span> | |
| 1489 | <span class="k">return</span> <span class="n">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">credential_id</span><span class="p">)</span></div> | |
| 1490 | ||
| 1491 | <div class="viewcode-block" id="delete_command"><a class="viewcode-back" href="../server.html#server.delete_command">[docs]</a><span class="k">def</span> <span class="nf">delete_command</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">command_id</span><span class="p">):</span> | |
| 1492 | <span class="sd">"""Delete command of id command_id from the database."""</span> | |
| 1493 | <span class="k">return</span> <span class="n">_delete_from_couch</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">,</span> <span class="n">command_id</span><span class="p">)</span></div> | |
| 1494 | ||
| 1495 | <div class="viewcode-block" id="delete_workspace"><a class="viewcode-back" href="../server.html#server.delete_workspace">[docs]</a><span class="k">def</span> <span class="nf">delete_workspace</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">):</span> | |
| 1496 | <span class="sd">"""Delete the couch database of id workspace_name"""</span> | |
| 1497 | <span class="n">db_url</span> <span class="o">=</span> <span class="n">_create_server_db_url</span><span class="p">(</span><span class="n">workspace_name</span><span class="p">)</span> | |
| 1498 | <span class="k">return</span> <span class="n">_delete</span><span class="p">(</span><span class="n">db_url</span><span class="p">,</span> <span class="n">database</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span></div> | |
| 1499 | ||
| 1500 | <div class="viewcode-block" id="is_server_up"><a class="viewcode-back" href="../server.html#server.is_server_up">[docs]</a><span class="k">def</span> <span class="nf">is_server_up</span><span class="p">():</span> | |
| 1501 | <span class="sd">"""Return True if we can stablish a connection with the server,</span> | |
| 1502 | <span class="sd"> False otherwise.</span> | |
| 1503 | <span class="sd"> """</span> | |
| 1504 | <span class="k">try</span><span class="p">:</span> | |
| 1505 | <span class="n">_get</span><span class="p">(</span><span class="s2">"</span><span class="si">{0}</span><span class="s2">/info"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">_create_server_api_url</span><span class="p">()))</span> | |
| 1506 | <span class="n">is_server_up</span> <span class="o">=</span> <span class="kc">True</span> | |
| 1507 | <span class="k">except</span><span class="p">:</span> | |
| 1508 | <span class="n">is_server_up</span> <span class="o">=</span> <span class="kc">False</span> | |
| 1509 | <span class="k">return</span> <span class="n">is_server_up</span></div> | |
| 1510 | ||
| 1511 | <div class="viewcode-block" id="test_server_url"><a class="viewcode-back" href="../server.html#server.test_server_url">[docs]</a><span class="k">def</span> <span class="nf">check_server_url</span><span class="p">(</span><span class="n">url_to_test</span><span class="p">):</span> | |
| 1512 | <span class="sd">"""Return True if the url_to_test is indeed a valid Faraday Server URL.</span> | |
| 1513 | <span class="sd"> False otherwise.</span> | |
| 1514 | <span class="sd"> """</span> | |
| 1515 | <span class="k">try</span><span class="p">:</span> | |
| 1516 | <span class="n">_get</span><span class="p">(</span><span class="s2">"</span><span class="si">{0}</span><span class="s2">/_api/info"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">url_to_test</span><span class="p">))</span> | |
| 1517 | <span class="n">test_okey</span> <span class="o">=</span> <span class="kc">True</span> | |
| 1518 | <span class="k">except</span><span class="p">:</span> | |
| 1519 | <span class="n">test_okey</span> <span class="o">=</span> <span class="kc">False</span> | |
| 1520 | <span class="k">return</span> <span class="n">test_okey</span></div> | |
| 1521 | </pre></div> | |
| 1522 | ||
| 1523 | </div> | |
| 1524 | </div> | |
| 1525 | <footer> | |
| 1526 | ||
| 1527 | ||
| 1528 | <hr/> | |
| 1529 | ||
| 1530 | <div role="contentinfo"> | |
| 1531 | <p> | |
| 1532 | © Copyright 2016, Infobyte. | |
| 1533 | ||
| 1534 | </p> | |
| 1535 | </div> | |
| 1536 | Built with <a href="http://sphinx-doc.org/">Sphinx</a> using a <a href="https://github.com/snide/sphinx_rtd_theme">theme</a> provided by <a href="https://readthedocs.org">Read the Docs</a>. | |
| 1537 | ||
| 1538 | </footer> | |
| 1539 | ||
| 1540 | </div> | |
| 1541 | </div> | |
| 1542 | ||
| 1543 | </section> | |
| 1544 | ||
| 1545 | </div> | |
| 1546 | ||
| 1547 | ||
| 1548 | ||
| 1549 | ||
| 1550 | ||
| 1551 | <script type="text/javascript"> | |
| 1552 | var DOCUMENTATION_OPTIONS = { | |
| 1553 | URL_ROOT:'../', | |
| 1554 | VERSION:'0.1', | |
| 1555 | COLLAPSE_INDEX:false, | |
| 1556 | FILE_SUFFIX:'.html', | |
| 1557 | HAS_SOURCE: true | |
| 1558 | }; | |
| 1559 | </script> | |
| 1560 | <script type="text/javascript" src="../_static/jquery.js"></script> | |
| 1561 | <script type="text/javascript" src="../_static/underscore.js"></script> | |
| 1562 | <script type="text/javascript" src="../_static/doctools.js"></script> | |
| 1563 | ||
| 1564 | ||
| 1565 | ||
| 1566 | ||
| 1567 | ||
| 1568 | <script type="text/javascript" src="../_static/js/theme.js"></script> | |
| 1569 | ||
| 1570 | ||
| 1571 | ||
| 1572 | ||
| 1573 | <script type="text/javascript"> | |
| 1574 | jQuery(function () { | |
| 1575 | SphinxRtdTheme.StickyNav.enable(); | |
| 1576 | }); | |
| 1577 | </script> | |
| 1578 | ||
| 1579 | ||
| 1580 | </body> | |
| 1581 | </html>⏎ |
+0
-1789
| 0 | ||
| 1 | ||
| 2 | <!DOCTYPE html> | |
| 3 | <!--[if IE 8]><html class="no-js lt-ie9" lang="en" > <![endif]--> | |
| 4 | <!--[if gt IE 8]><!--> <html class="no-js" lang="en" > <!--<![endif]--> | |
| 5 | <head> | |
| 6 | <meta charset="utf-8"> | |
| 7 | ||
| 8 | <meta name="viewport" content="width=device-width, initial-scale=1.0"> | |
| 9 | ||
| 10 | <title>sqlalchemy.orm.attributes — Faraday 0.1 documentation</title> | |
| 11 | ||
| 12 | ||
| 13 | ||
| 14 | ||
| 15 | ||
| 16 | ||
| 17 | ||
| 18 | ||
| 19 | ||
| 20 | ||
| 21 | ||
| 22 | ||
| 23 | ||
| 24 | ||
| 25 | ||
| 26 | <link rel="stylesheet" href="../../../_static/css/theme.css" type="text/css" /> | |
| 27 | ||
| 28 | ||
| 29 | ||
| 30 | ||
| 31 | ||
| 32 | <link rel="index" title="Index" | |
| 33 | href="../../../genindex.html"/> | |
| 34 | <link rel="search" title="Search" href="../../../search.html"/> | |
| 35 | <link rel="top" title="Faraday 0.1 documentation" href="../../../index.html"/> | |
| 36 | <link rel="up" title="Module code" href="../../index.html"/> | |
| 37 | ||
| 38 | ||
| 39 | <script src="../../../_static/js/modernizr.min.js"></script> | |
| 40 | ||
| 41 | </head> | |
| 42 | ||
| 43 | <body class="wy-body-for-nav" role="document"> | |
| 44 | ||
| 45 | <div class="wy-grid-for-nav"> | |
| 46 | ||
| 47 | ||
| 48 | <nav data-toggle="wy-nav-shift" class="wy-nav-side"> | |
| 49 | <div class="wy-side-scroll"> | |
| 50 | <div class="wy-side-nav-search"> | |
| 51 | ||
| 52 | ||
| 53 | ||
| 54 | <a href="../../../index.html" class="icon icon-home"> Faraday | |
| 55 | ||
| 56 | ||
| 57 | ||
| 58 | </a> | |
| 59 | ||
| 60 | ||
| 61 | ||
| 62 | ||
| 63 | <div class="version"> | |
| 64 | 0.1 | |
| 65 | </div> | |
| 66 | ||
| 67 | ||
| 68 | ||
| 69 | ||
| 70 | <div role="search"> | |
| 71 | <form id="rtd-search-form" class="wy-form" action="../../../search.html" method="get"> | |
| 72 | <input type="text" name="q" placeholder="Search docs" /> | |
| 73 | <input type="hidden" name="check_keywords" value="yes" /> | |
| 74 | <input type="hidden" name="area" value="default" /> | |
| 75 | </form> | |
| 76 | </div> | |
| 77 | ||
| 78 | ||
| 79 | </div> | |
| 80 | ||
| 81 | <div class="wy-menu wy-menu-vertical" data-spy="affix" role="navigation" aria-label="main navigation"> | |
| 82 | ||
| 83 | ||
| 84 | ||
| 85 | <!-- Local TOC --> | |
| 86 | <div class="local-toc"></div> | |
| 87 | ||
| 88 | ||
| 89 | </div> | |
| 90 | </div> | |
| 91 | </nav> | |
| 92 | ||
| 93 | <section data-toggle="wy-nav-shift" class="wy-nav-content-wrap"> | |
| 94 | ||
| 95 | ||
| 96 | <nav class="wy-nav-top" role="navigation" aria-label="top navigation"> | |
| 97 | <i data-toggle="wy-nav-top" class="fa fa-bars"></i> | |
| 98 | <a href="../../../index.html">Faraday</a> | |
| 99 | </nav> | |
| 100 | ||
| 101 | ||
| 102 | ||
| 103 | <div class="wy-nav-content"> | |
| 104 | <div class="rst-content"> | |
| 105 | ||
| 106 | ||
| 107 | ||
| 108 | ||
| 109 | ||
| 110 | ||
| 111 | <div role="navigation" aria-label="breadcrumbs navigation"> | |
| 112 | <ul class="wy-breadcrumbs"> | |
| 113 | <li><a href="../../../index.html">Docs</a> »</li> | |
| 114 | ||
| 115 | <li><a href="../../index.html">Module code</a> »</li> | |
| 116 | ||
| 117 | <li>sqlalchemy.orm.attributes</li> | |
| 118 | <li class="wy-breadcrumbs-aside"> | |
| 119 | ||
| 120 | ||
| 121 | ||
| 122 | </li> | |
| 123 | </ul> | |
| 124 | <hr/> | |
| 125 | </div> | |
| 126 | <div role="main" class="document" itemscope="itemscope" itemtype="http://schema.org/Article"> | |
| 127 | <div itemprop="articleBody"> | |
| 128 | ||
| 129 | <h1>Source code for sqlalchemy.orm.attributes</h1><div class="highlight"><pre> | |
| 130 | <span></span><span class="c1"># orm/attributes.py</span> | |
| 131 | <span class="c1"># Copyright (C) 2005-2016 the SQLAlchemy authors and contributors</span> | |
| 132 | <span class="c1"># <see AUTHORS file></span> | |
| 133 | <span class="c1">#</span> | |
| 134 | <span class="c1"># This module is part of SQLAlchemy and is released under</span> | |
| 135 | <span class="c1"># the MIT License: http://www.opensource.org/licenses/mit-license.php</span> | |
| 136 | ||
| 137 | <span class="sd">"""Defines instrumentation for class attributes and their interaction</span> | |
| 138 | <span class="sd">with instances.</span> | |
| 139 | ||
| 140 | <span class="sd">This module is usually not directly visible to user applications, but</span> | |
| 141 | <span class="sd">defines a large part of the ORM's interactivity.</span> | |
| 142 | ||
| 143 | ||
| 144 | <span class="sd">"""</span> | |
| 145 | ||
| 146 | <span class="kn">import</span> <span class="nn">operator</span> | |
| 147 | <span class="kn">from</span> <span class="nn">..</span> <span class="k">import</span> <span class="n">util</span><span class="p">,</span> <span class="n">event</span><span class="p">,</span> <span class="n">inspection</span> | |
| 148 | <span class="kn">from</span> <span class="nn">.</span> <span class="k">import</span> <span class="n">interfaces</span><span class="p">,</span> <span class="n">collections</span><span class="p">,</span> <span class="n">exc</span> <span class="k">as</span> <span class="n">orm_exc</span> | |
| 149 | ||
| 150 | <span class="kn">from</span> <span class="nn">.base</span> <span class="k">import</span> <span class="n">instance_state</span><span class="p">,</span> <span class="n">instance_dict</span><span class="p">,</span> <span class="n">manager_of_class</span> | |
| 151 | ||
| 152 | <span class="kn">from</span> <span class="nn">.base</span> <span class="k">import</span> <span class="n">PASSIVE_NO_RESULT</span><span class="p">,</span> <span class="n">ATTR_WAS_SET</span><span class="p">,</span> <span class="n">ATTR_EMPTY</span><span class="p">,</span> <span class="n">NO_VALUE</span><span class="p">,</span>\ | |
| 153 | <span class="n">NEVER_SET</span><span class="p">,</span> <span class="n">NO_CHANGE</span><span class="p">,</span> <span class="n">CALLABLES_OK</span><span class="p">,</span> <span class="n">SQL_OK</span><span class="p">,</span> <span class="n">RELATED_OBJECT_OK</span><span class="p">,</span>\ | |
| 154 | <span class="n">INIT_OK</span><span class="p">,</span> <span class="n">NON_PERSISTENT_OK</span><span class="p">,</span> <span class="n">LOAD_AGAINST_COMMITTED</span><span class="p">,</span> <span class="n">PASSIVE_OFF</span><span class="p">,</span>\ | |
| 155 | <span class="n">PASSIVE_RETURN_NEVER_SET</span><span class="p">,</span> <span class="n">PASSIVE_NO_INITIALIZE</span><span class="p">,</span> <span class="n">PASSIVE_NO_FETCH</span><span class="p">,</span>\ | |
| 156 | <span class="n">PASSIVE_NO_FETCH_RELATED</span><span class="p">,</span> <span class="n">PASSIVE_ONLY_PERSISTENT</span><span class="p">,</span> <span class="n">NO_AUTOFLUSH</span> | |
| 157 | <span class="kn">from</span> <span class="nn">.base</span> <span class="k">import</span> <span class="n">state_str</span><span class="p">,</span> <span class="n">instance_str</span> | |
| 158 | ||
| 159 | ||
| 160 | <span class="nd">@inspection</span><span class="o">.</span><span class="n">_self_inspects</span> | |
| 161 | <span class="k">class</span> <span class="nc">QueryableAttribute</span><span class="p">(</span><span class="n">interfaces</span><span class="o">.</span><span class="n">_MappedAttribute</span><span class="p">,</span> | |
| 162 | <span class="n">interfaces</span><span class="o">.</span><span class="n">InspectionAttr</span><span class="p">,</span> | |
| 163 | <span class="n">interfaces</span><span class="o">.</span><span class="n">PropComparator</span><span class="p">):</span> | |
| 164 | <span class="sd">"""Base class for :term:`descriptor` objects that intercept</span> | |
| 165 | <span class="sd"> attribute events on behalf of a :class:`.MapperProperty`</span> | |
| 166 | <span class="sd"> object. The actual :class:`.MapperProperty` is accessible</span> | |
| 167 | <span class="sd"> via the :attr:`.QueryableAttribute.property`</span> | |
| 168 | <span class="sd"> attribute.</span> | |
| 169 | ||
| 170 | ||
| 171 | <span class="sd"> .. seealso::</span> | |
| 172 | ||
| 173 | <span class="sd"> :class:`.InstrumentedAttribute`</span> | |
| 174 | ||
| 175 | <span class="sd"> :class:`.MapperProperty`</span> | |
| 176 | ||
| 177 | <span class="sd"> :attr:`.Mapper.all_orm_descriptors`</span> | |
| 178 | ||
| 179 | <span class="sd"> :attr:`.Mapper.attrs`</span> | |
| 180 | <span class="sd"> """</span> | |
| 181 | ||
| 182 | <span class="n">is_attribute</span> <span class="o">=</span> <span class="kc">True</span> | |
| 183 | ||
| 184 | <span class="k">def</span> <span class="nf">__init__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">class_</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">impl</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 185 | <span class="n">comparator</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">parententity</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 186 | <span class="n">of_type</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 187 | <span class="bp">self</span><span class="o">.</span><span class="n">class_</span> <span class="o">=</span> <span class="n">class_</span> | |
| 188 | <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="o">=</span> <span class="n">key</span> | |
| 189 | <span class="bp">self</span><span class="o">.</span><span class="n">impl</span> <span class="o">=</span> <span class="n">impl</span> | |
| 190 | <span class="bp">self</span><span class="o">.</span><span class="n">comparator</span> <span class="o">=</span> <span class="n">comparator</span> | |
| 191 | <span class="bp">self</span><span class="o">.</span><span class="n">_parententity</span> <span class="o">=</span> <span class="n">parententity</span> | |
| 192 | <span class="bp">self</span><span class="o">.</span><span class="n">_of_type</span> <span class="o">=</span> <span class="n">of_type</span> | |
| 193 | ||
| 194 | <span class="n">manager</span> <span class="o">=</span> <span class="n">manager_of_class</span><span class="p">(</span><span class="n">class_</span><span class="p">)</span> | |
| 195 | <span class="c1"># manager is None in the case of AliasedClass</span> | |
| 196 | <span class="k">if</span> <span class="n">manager</span><span class="p">:</span> | |
| 197 | <span class="c1"># propagate existing event listeners from</span> | |
| 198 | <span class="c1"># immediate superclass</span> | |
| 199 | <span class="k">for</span> <span class="n">base</span> <span class="ow">in</span> <span class="n">manager</span><span class="o">.</span><span class="n">_bases</span><span class="p">:</span> | |
| 200 | <span class="k">if</span> <span class="n">key</span> <span class="ow">in</span> <span class="n">base</span><span class="p">:</span> | |
| 201 | <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">_update</span><span class="p">(</span><span class="n">base</span><span class="p">[</span><span class="n">key</span><span class="p">]</span><span class="o">.</span><span class="n">dispatch</span><span class="p">)</span> | |
| 202 | ||
| 203 | <span class="nd">@util</span><span class="o">.</span><span class="n">memoized_property</span> | |
| 204 | <span class="k">def</span> <span class="nf">_supports_population</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 205 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">impl</span><span class="o">.</span><span class="n">supports_population</span> | |
| 206 | ||
| 207 | <span class="k">def</span> <span class="nf">get_history</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">instance</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 208 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">impl</span><span class="o">.</span><span class="n">get_history</span><span class="p">(</span><span class="n">instance_state</span><span class="p">(</span><span class="n">instance</span><span class="p">),</span> | |
| 209 | <span class="n">instance_dict</span><span class="p">(</span><span class="n">instance</span><span class="p">),</span> <span class="n">passive</span><span class="p">)</span> | |
| 210 | ||
| 211 | <span class="k">def</span> <span class="nf">__selectable__</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 212 | <span class="c1"># TODO: conditionally attach this method based on clause_element ?</span> | |
| 213 | <span class="k">return</span> <span class="bp">self</span> | |
| 214 | ||
| 215 | <span class="nd">@util</span><span class="o">.</span><span class="n">memoized_property</span> | |
| 216 | <span class="k">def</span> <span class="nf">info</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 217 | <span class="sd">"""Return the 'info' dictionary for the underlying SQL element.</span> | |
| 218 | ||
| 219 | <span class="sd"> The behavior here is as follows:</span> | |
| 220 | ||
| 221 | <span class="sd"> * If the attribute is a column-mapped property, i.e.</span> | |
| 222 | <span class="sd"> :class:`.ColumnProperty`, which is mapped directly</span> | |
| 223 | <span class="sd"> to a schema-level :class:`.Column` object, this attribute</span> | |
| 224 | <span class="sd"> will return the :attr:`.SchemaItem.info` dictionary associated</span> | |
| 225 | <span class="sd"> with the core-level :class:`.Column` object.</span> | |
| 226 | ||
| 227 | <span class="sd"> * If the attribute is a :class:`.ColumnProperty` but is mapped to</span> | |
| 228 | <span class="sd"> any other kind of SQL expression other than a :class:`.Column`,</span> | |
| 229 | <span class="sd"> the attribute will refer to the :attr:`.MapperProperty.info`</span> | |
| 230 | <span class="sd"> dictionary associated directly with the :class:`.ColumnProperty`,</span> | |
| 231 | <span class="sd"> assuming the SQL expression itself does not have its own ``.info``</span> | |
| 232 | <span class="sd"> attribute (which should be the case, unless a user-defined SQL</span> | |
| 233 | <span class="sd"> construct has defined one).</span> | |
| 234 | ||
| 235 | <span class="sd"> * If the attribute refers to any other kind of</span> | |
| 236 | <span class="sd"> :class:`.MapperProperty`, including :class:`.RelationshipProperty`,</span> | |
| 237 | <span class="sd"> the attribute will refer to the :attr:`.MapperProperty.info`</span> | |
| 238 | <span class="sd"> dictionary associated with that :class:`.MapperProperty`.</span> | |
| 239 | ||
| 240 | <span class="sd"> * To access the :attr:`.MapperProperty.info` dictionary of the</span> | |
| 241 | <span class="sd"> :class:`.MapperProperty` unconditionally, including for a</span> | |
| 242 | <span class="sd"> :class:`.ColumnProperty` that's associated directly with a</span> | |
| 243 | <span class="sd"> :class:`.schema.Column`, the attribute can be referred to using</span> | |
| 244 | <span class="sd"> :attr:`.QueryableAttribute.property` attribute, as</span> | |
| 245 | <span class="sd"> ``MyClass.someattribute.property.info``.</span> | |
| 246 | ||
| 247 | <span class="sd"> .. versionadded:: 0.8.0</span> | |
| 248 | ||
| 249 | <span class="sd"> .. seealso::</span> | |
| 250 | ||
| 251 | <span class="sd"> :attr:`.SchemaItem.info`</span> | |
| 252 | ||
| 253 | <span class="sd"> :attr:`.MapperProperty.info`</span> | |
| 254 | ||
| 255 | <span class="sd"> """</span> | |
| 256 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">comparator</span><span class="o">.</span><span class="n">info</span> | |
| 257 | ||
| 258 | <span class="nd">@util</span><span class="o">.</span><span class="n">memoized_property</span> | |
| 259 | <span class="k">def</span> <span class="nf">parent</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 260 | <span class="sd">"""Return an inspection instance representing the parent.</span> | |
| 261 | ||
| 262 | <span class="sd"> This will be either an instance of :class:`.Mapper`</span> | |
| 263 | <span class="sd"> or :class:`.AliasedInsp`, depending upon the nature</span> | |
| 264 | <span class="sd"> of the parent entity which this attribute is associated</span> | |
| 265 | <span class="sd"> with.</span> | |
| 266 | ||
| 267 | <span class="sd"> """</span> | |
| 268 | <span class="k">return</span> <span class="n">inspection</span><span class="o">.</span><span class="n">inspect</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">_parententity</span><span class="p">)</span> | |
| 269 | ||
| 270 | <span class="nd">@property</span> | |
| 271 | <span class="k">def</span> <span class="nf">expression</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 272 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">comparator</span><span class="o">.</span><span class="n">__clause_element__</span><span class="p">()</span> | |
| 273 | ||
| 274 | <span class="k">def</span> <span class="nf">__clause_element__</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 275 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">comparator</span><span class="o">.</span><span class="n">__clause_element__</span><span class="p">()</span> | |
| 276 | ||
| 277 | <span class="k">def</span> <span class="nf">_query_clause_element</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 278 | <span class="sd">"""like __clause_element__(), but called specifically</span> | |
| 279 | <span class="sd"> by :class:`.Query` to allow special behavior."""</span> | |
| 280 | ||
| 281 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">comparator</span><span class="o">.</span><span class="n">_query_clause_element</span><span class="p">()</span> | |
| 282 | ||
| 283 | <span class="k">def</span> <span class="nf">adapt_to_entity</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">adapt_to_entity</span><span class="p">):</span> | |
| 284 | <span class="k">assert</span> <span class="ow">not</span> <span class="bp">self</span><span class="o">.</span><span class="n">_of_type</span> | |
| 285 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">__class__</span><span class="p">(</span><span class="n">adapt_to_entity</span><span class="o">.</span><span class="n">entity</span><span class="p">,</span> | |
| 286 | <span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">,</span> <span class="n">impl</span><span class="o">=</span><span class="bp">self</span><span class="o">.</span><span class="n">impl</span><span class="p">,</span> | |
| 287 | <span class="n">comparator</span><span class="o">=</span><span class="bp">self</span><span class="o">.</span><span class="n">comparator</span><span class="o">.</span><span class="n">adapt_to_entity</span><span class="p">(</span> | |
| 288 | <span class="n">adapt_to_entity</span><span class="p">),</span> | |
| 289 | <span class="n">parententity</span><span class="o">=</span><span class="n">adapt_to_entity</span><span class="p">)</span> | |
| 290 | ||
| 291 | <span class="k">def</span> <span class="nf">of_type</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">cls</span><span class="p">):</span> | |
| 292 | <span class="k">return</span> <span class="n">QueryableAttribute</span><span class="p">(</span> | |
| 293 | <span class="bp">self</span><span class="o">.</span><span class="n">class_</span><span class="p">,</span> | |
| 294 | <span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">,</span> | |
| 295 | <span class="bp">self</span><span class="o">.</span><span class="n">impl</span><span class="p">,</span> | |
| 296 | <span class="bp">self</span><span class="o">.</span><span class="n">comparator</span><span class="o">.</span><span class="n">of_type</span><span class="p">(</span><span class="n">cls</span><span class="p">),</span> | |
| 297 | <span class="bp">self</span><span class="o">.</span><span class="n">_parententity</span><span class="p">,</span> | |
| 298 | <span class="n">of_type</span><span class="o">=</span><span class="n">cls</span><span class="p">)</span> | |
| 299 | ||
| 300 | <span class="k">def</span> <span class="nf">label</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">name</span><span class="p">):</span> | |
| 301 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">_query_clause_element</span><span class="p">()</span><span class="o">.</span><span class="n">label</span><span class="p">(</span><span class="n">name</span><span class="p">)</span> | |
| 302 | ||
| 303 | <span class="k">def</span> <span class="nf">operate</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">op</span><span class="p">,</span> <span class="o">*</span><span class="n">other</span><span class="p">,</span> <span class="o">**</span><span class="n">kwargs</span><span class="p">):</span> | |
| 304 | <span class="k">return</span> <span class="n">op</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">comparator</span><span class="p">,</span> <span class="o">*</span><span class="n">other</span><span class="p">,</span> <span class="o">**</span><span class="n">kwargs</span><span class="p">)</span> | |
| 305 | ||
| 306 | <span class="k">def</span> <span class="nf">reverse_operate</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">op</span><span class="p">,</span> <span class="n">other</span><span class="p">,</span> <span class="o">**</span><span class="n">kwargs</span><span class="p">):</span> | |
| 307 | <span class="k">return</span> <span class="n">op</span><span class="p">(</span><span class="n">other</span><span class="p">,</span> <span class="bp">self</span><span class="o">.</span><span class="n">comparator</span><span class="p">,</span> <span class="o">**</span><span class="n">kwargs</span><span class="p">)</span> | |
| 308 | ||
| 309 | <span class="k">def</span> <span class="nf">hasparent</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">optimistic</span><span class="o">=</span><span class="kc">False</span><span class="p">):</span> | |
| 310 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">impl</span><span class="o">.</span><span class="n">hasparent</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">optimistic</span><span class="o">=</span><span class="n">optimistic</span><span class="p">)</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">False</span> | |
| 311 | ||
| 312 | <span class="k">def</span> <span class="nf">__getattr__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">key</span><span class="p">):</span> | |
| 313 | <span class="k">try</span><span class="p">:</span> | |
| 314 | <span class="k">return</span> <span class="nb">getattr</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">comparator</span><span class="p">,</span> <span class="n">key</span><span class="p">)</span> | |
| 315 | <span class="k">except</span> <span class="ne">AttributeError</span><span class="p">:</span> | |
| 316 | <span class="k">raise</span> <span class="ne">AttributeError</span><span class="p">(</span> | |
| 317 | <span class="s1">'Neither </span><span class="si">%r</span><span class="s1"> object nor </span><span class="si">%r</span><span class="s1"> object associated with </span><span class="si">%s</span><span class="s1"> '</span> | |
| 318 | <span class="s1">'has an attribute </span><span class="si">%r</span><span class="s1">'</span> <span class="o">%</span> <span class="p">(</span> | |
| 319 | <span class="nb">type</span><span class="p">(</span><span class="bp">self</span><span class="p">)</span><span class="o">.</span><span class="n">__name__</span><span class="p">,</span> | |
| 320 | <span class="nb">type</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">comparator</span><span class="p">)</span><span class="o">.</span><span class="n">__name__</span><span class="p">,</span> | |
| 321 | <span class="bp">self</span><span class="p">,</span> | |
| 322 | <span class="n">key</span><span class="p">)</span> | |
| 323 | <span class="p">)</span> | |
| 324 | ||
| 325 | <span class="k">def</span> <span class="nf">__str__</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 326 | <span class="k">return</span> <span class="s2">"</span><span class="si">%s</span><span class="s2">.</span><span class="si">%s</span><span class="s2">"</span> <span class="o">%</span> <span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">class_</span><span class="o">.</span><span class="n">__name__</span><span class="p">,</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">)</span> | |
| 327 | ||
| 328 | <span class="nd">@util</span><span class="o">.</span><span class="n">memoized_property</span> | |
| 329 | <span class="k">def</span> <span class="nf">property</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 330 | <span class="sd">"""Return the :class:`.MapperProperty` associated with this</span> | |
| 331 | <span class="sd"> :class:`.QueryableAttribute`.</span> | |
| 332 | ||
| 333 | ||
| 334 | <span class="sd"> Return values here will commonly be instances of</span> | |
| 335 | <span class="sd"> :class:`.ColumnProperty` or :class:`.RelationshipProperty`.</span> | |
| 336 | ||
| 337 | ||
| 338 | <span class="sd"> """</span> | |
| 339 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">comparator</span><span class="o">.</span><span class="n">property</span> | |
| 340 | ||
| 341 | ||
| 342 | <span class="k">class</span> <span class="nc">InstrumentedAttribute</span><span class="p">(</span><span class="n">QueryableAttribute</span><span class="p">):</span> | |
| 343 | <span class="sd">"""Class bound instrumented attribute which adds basic</span> | |
| 344 | <span class="sd"> :term:`descriptor` methods.</span> | |
| 345 | ||
| 346 | <span class="sd"> See :class:`.QueryableAttribute` for a description of most features.</span> | |
| 347 | ||
| 348 | ||
| 349 | <span class="sd"> """</span> | |
| 350 | ||
| 351 | <span class="k">def</span> <span class="nf">__set__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">instance</span><span class="p">,</span> <span class="n">value</span><span class="p">):</span> | |
| 352 | <span class="bp">self</span><span class="o">.</span><span class="n">impl</span><span class="o">.</span><span class="n">set</span><span class="p">(</span><span class="n">instance_state</span><span class="p">(</span><span class="n">instance</span><span class="p">),</span> | |
| 353 | <span class="n">instance_dict</span><span class="p">(</span><span class="n">instance</span><span class="p">),</span> <span class="n">value</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 354 | ||
| 355 | <span class="k">def</span> <span class="nf">__delete__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">instance</span><span class="p">):</span> | |
| 356 | <span class="bp">self</span><span class="o">.</span><span class="n">impl</span><span class="o">.</span><span class="n">delete</span><span class="p">(</span><span class="n">instance_state</span><span class="p">(</span><span class="n">instance</span><span class="p">),</span> <span class="n">instance_dict</span><span class="p">(</span><span class="n">instance</span><span class="p">))</span> | |
| 357 | ||
| 358 | <span class="k">def</span> <span class="nf">__get__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">instance</span><span class="p">,</span> <span class="n">owner</span><span class="p">):</span> | |
| 359 | <span class="k">if</span> <span class="n">instance</span> <span class="ow">is</span> <span class="kc">None</span><span class="p">:</span> | |
| 360 | <span class="k">return</span> <span class="bp">self</span> | |
| 361 | ||
| 362 | <span class="n">dict_</span> <span class="o">=</span> <span class="n">instance_dict</span><span class="p">(</span><span class="n">instance</span><span class="p">)</span> | |
| 363 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">_supports_population</span> <span class="ow">and</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="ow">in</span> <span class="n">dict_</span><span class="p">:</span> | |
| 364 | <span class="k">return</span> <span class="n">dict_</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> | |
| 365 | <span class="k">else</span><span class="p">:</span> | |
| 366 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">impl</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">instance_state</span><span class="p">(</span><span class="n">instance</span><span class="p">),</span> <span class="n">dict_</span><span class="p">)</span> | |
| 367 | ||
| 368 | ||
| 369 | <span class="k">def</span> <span class="nf">create_proxied_attribute</span><span class="p">(</span><span class="n">descriptor</span><span class="p">):</span> | |
| 370 | <span class="sd">"""Create an QueryableAttribute / user descriptor hybrid.</span> | |
| 371 | ||
| 372 | <span class="sd"> Returns a new QueryableAttribute type that delegates descriptor</span> | |
| 373 | <span class="sd"> behavior and getattr() to the given descriptor.</span> | |
| 374 | <span class="sd"> """</span> | |
| 375 | ||
| 376 | <span class="c1"># TODO: can move this to descriptor_props if the need for this</span> | |
| 377 | <span class="c1"># function is removed from ext/hybrid.py</span> | |
| 378 | ||
| 379 | <span class="k">class</span> <span class="nc">Proxy</span><span class="p">(</span><span class="n">QueryableAttribute</span><span class="p">):</span> | |
| 380 | <span class="sd">"""Presents the :class:`.QueryableAttribute` interface as a</span> | |
| 381 | <span class="sd"> proxy on top of a Python descriptor / :class:`.PropComparator`</span> | |
| 382 | <span class="sd"> combination.</span> | |
| 383 | ||
| 384 | <span class="sd"> """</span> | |
| 385 | ||
| 386 | <span class="k">def</span> <span class="nf">__init__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">class_</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">descriptor</span><span class="p">,</span> | |
| 387 | <span class="n">comparator</span><span class="p">,</span> | |
| 388 | <span class="n">adapt_to_entity</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">doc</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 389 | <span class="n">original_property</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 390 | <span class="bp">self</span><span class="o">.</span><span class="n">class_</span> <span class="o">=</span> <span class="n">class_</span> | |
| 391 | <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="o">=</span> <span class="n">key</span> | |
| 392 | <span class="bp">self</span><span class="o">.</span><span class="n">descriptor</span> <span class="o">=</span> <span class="n">descriptor</span> | |
| 393 | <span class="bp">self</span><span class="o">.</span><span class="n">original_property</span> <span class="o">=</span> <span class="n">original_property</span> | |
| 394 | <span class="bp">self</span><span class="o">.</span><span class="n">_comparator</span> <span class="o">=</span> <span class="n">comparator</span> | |
| 395 | <span class="bp">self</span><span class="o">.</span><span class="n">_adapt_to_entity</span> <span class="o">=</span> <span class="n">adapt_to_entity</span> | |
| 396 | <span class="bp">self</span><span class="o">.</span><span class="n">__doc__</span> <span class="o">=</span> <span class="n">doc</span> | |
| 397 | ||
| 398 | <span class="nd">@property</span> | |
| 399 | <span class="k">def</span> <span class="nf">property</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 400 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">comparator</span><span class="o">.</span><span class="n">property</span> | |
| 401 | ||
| 402 | <span class="nd">@util</span><span class="o">.</span><span class="n">memoized_property</span> | |
| 403 | <span class="k">def</span> <span class="nf">comparator</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 404 | <span class="k">if</span> <span class="n">util</span><span class="o">.</span><span class="n">callable</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">_comparator</span><span class="p">):</span> | |
| 405 | <span class="bp">self</span><span class="o">.</span><span class="n">_comparator</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">_comparator</span><span class="p">()</span> | |
| 406 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">_adapt_to_entity</span><span class="p">:</span> | |
| 407 | <span class="bp">self</span><span class="o">.</span><span class="n">_comparator</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">_comparator</span><span class="o">.</span><span class="n">adapt_to_entity</span><span class="p">(</span> | |
| 408 | <span class="bp">self</span><span class="o">.</span><span class="n">_adapt_to_entity</span><span class="p">)</span> | |
| 409 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">_comparator</span> | |
| 410 | ||
| 411 | <span class="k">def</span> <span class="nf">adapt_to_entity</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">adapt_to_entity</span><span class="p">):</span> | |
| 412 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">__class__</span><span class="p">(</span><span class="n">adapt_to_entity</span><span class="o">.</span><span class="n">entity</span><span class="p">,</span> | |
| 413 | <span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">,</span> | |
| 414 | <span class="bp">self</span><span class="o">.</span><span class="n">descriptor</span><span class="p">,</span> | |
| 415 | <span class="bp">self</span><span class="o">.</span><span class="n">_comparator</span><span class="p">,</span> | |
| 416 | <span class="n">adapt_to_entity</span><span class="p">)</span> | |
| 417 | ||
| 418 | <span class="k">def</span> <span class="nf">__get__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">instance</span><span class="p">,</span> <span class="n">owner</span><span class="p">):</span> | |
| 419 | <span class="k">if</span> <span class="n">instance</span> <span class="ow">is</span> <span class="kc">None</span><span class="p">:</span> | |
| 420 | <span class="k">return</span> <span class="bp">self</span> | |
| 421 | <span class="k">else</span><span class="p">:</span> | |
| 422 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">descriptor</span><span class="o">.</span><span class="n">__get__</span><span class="p">(</span><span class="n">instance</span><span class="p">,</span> <span class="n">owner</span><span class="p">)</span> | |
| 423 | ||
| 424 | <span class="k">def</span> <span class="nf">__str__</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 425 | <span class="k">return</span> <span class="s2">"</span><span class="si">%s</span><span class="s2">.</span><span class="si">%s</span><span class="s2">"</span> <span class="o">%</span> <span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">class_</span><span class="o">.</span><span class="n">__name__</span><span class="p">,</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">)</span> | |
| 426 | ||
| 427 | <span class="k">def</span> <span class="nf">__getattr__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">attribute</span><span class="p">):</span> | |
| 428 | <span class="sd">"""Delegate __getattr__ to the original descriptor and/or</span> | |
| 429 | <span class="sd"> comparator."""</span> | |
| 430 | ||
| 431 | <span class="k">try</span><span class="p">:</span> | |
| 432 | <span class="k">return</span> <span class="nb">getattr</span><span class="p">(</span><span class="n">descriptor</span><span class="p">,</span> <span class="n">attribute</span><span class="p">)</span> | |
| 433 | <span class="k">except</span> <span class="ne">AttributeError</span><span class="p">:</span> | |
| 434 | <span class="k">try</span><span class="p">:</span> | |
| 435 | <span class="k">return</span> <span class="nb">getattr</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">comparator</span><span class="p">,</span> <span class="n">attribute</span><span class="p">)</span> | |
| 436 | <span class="k">except</span> <span class="ne">AttributeError</span><span class="p">:</span> | |
| 437 | <span class="k">raise</span> <span class="ne">AttributeError</span><span class="p">(</span> | |
| 438 | <span class="s1">'Neither </span><span class="si">%r</span><span class="s1"> object nor </span><span class="si">%r</span><span class="s1"> object associated with </span><span class="si">%s</span><span class="s1"> '</span> | |
| 439 | <span class="s1">'has an attribute </span><span class="si">%r</span><span class="s1">'</span> <span class="o">%</span> <span class="p">(</span> | |
| 440 | <span class="nb">type</span><span class="p">(</span><span class="n">descriptor</span><span class="p">)</span><span class="o">.</span><span class="n">__name__</span><span class="p">,</span> | |
| 441 | <span class="nb">type</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">comparator</span><span class="p">)</span><span class="o">.</span><span class="n">__name__</span><span class="p">,</span> | |
| 442 | <span class="bp">self</span><span class="p">,</span> | |
| 443 | <span class="n">attribute</span><span class="p">)</span> | |
| 444 | <span class="p">)</span> | |
| 445 | ||
| 446 | <span class="n">Proxy</span><span class="o">.</span><span class="n">__name__</span> <span class="o">=</span> <span class="nb">type</span><span class="p">(</span><span class="n">descriptor</span><span class="p">)</span><span class="o">.</span><span class="n">__name__</span> <span class="o">+</span> <span class="s1">'Proxy'</span> | |
| 447 | ||
| 448 | <span class="n">util</span><span class="o">.</span><span class="n">monkeypatch_proxied_specials</span><span class="p">(</span><span class="n">Proxy</span><span class="p">,</span> <span class="nb">type</span><span class="p">(</span><span class="n">descriptor</span><span class="p">),</span> | |
| 449 | <span class="n">name</span><span class="o">=</span><span class="s1">'descriptor'</span><span class="p">,</span> | |
| 450 | <span class="n">from_instance</span><span class="o">=</span><span class="n">descriptor</span><span class="p">)</span> | |
| 451 | <span class="k">return</span> <span class="n">Proxy</span> | |
| 452 | ||
| 453 | <span class="n">OP_REMOVE</span> <span class="o">=</span> <span class="n">util</span><span class="o">.</span><span class="n">symbol</span><span class="p">(</span><span class="s2">"REMOVE"</span><span class="p">)</span> | |
| 454 | <span class="n">OP_APPEND</span> <span class="o">=</span> <span class="n">util</span><span class="o">.</span><span class="n">symbol</span><span class="p">(</span><span class="s2">"APPEND"</span><span class="p">)</span> | |
| 455 | <span class="n">OP_REPLACE</span> <span class="o">=</span> <span class="n">util</span><span class="o">.</span><span class="n">symbol</span><span class="p">(</span><span class="s2">"REPLACE"</span><span class="p">)</span> | |
| 456 | ||
| 457 | ||
| 458 | <span class="k">class</span> <span class="nc">Event</span><span class="p">(</span><span class="nb">object</span><span class="p">):</span> | |
| 459 | <span class="sd">"""A token propagated throughout the course of a chain of attribute</span> | |
| 460 | <span class="sd"> events.</span> | |
| 461 | ||
| 462 | <span class="sd"> Serves as an indicator of the source of the event and also provides</span> | |
| 463 | <span class="sd"> a means of controlling propagation across a chain of attribute</span> | |
| 464 | <span class="sd"> operations.</span> | |
| 465 | ||
| 466 | <span class="sd"> The :class:`.Event` object is sent as the ``initiator`` argument</span> | |
| 467 | <span class="sd"> when dealing with the :meth:`.AttributeEvents.append`,</span> | |
| 468 | <span class="sd"> :meth:`.AttributeEvents.set`,</span> | |
| 469 | <span class="sd"> and :meth:`.AttributeEvents.remove` events.</span> | |
| 470 | ||
| 471 | <span class="sd"> The :class:`.Event` object is currently interpreted by the backref</span> | |
| 472 | <span class="sd"> event handlers, and is used to control the propagation of operations</span> | |
| 473 | <span class="sd"> across two mutually-dependent attributes.</span> | |
| 474 | ||
| 475 | <span class="sd"> .. versionadded:: 0.9.0</span> | |
| 476 | ||
| 477 | <span class="sd"> :var impl: The :class:`.AttributeImpl` which is the current event</span> | |
| 478 | <span class="sd"> initiator.</span> | |
| 479 | ||
| 480 | <span class="sd"> :var op: The symbol :attr:`.OP_APPEND`, :attr:`.OP_REMOVE` or</span> | |
| 481 | <span class="sd"> :attr:`.OP_REPLACE`, indicating the source operation.</span> | |
| 482 | ||
| 483 | <span class="sd"> """</span> | |
| 484 | ||
| 485 | <span class="n">__slots__</span> <span class="o">=</span> <span class="s1">'impl'</span><span class="p">,</span> <span class="s1">'op'</span><span class="p">,</span> <span class="s1">'parent_token'</span> | |
| 486 | ||
| 487 | <span class="k">def</span> <span class="nf">__init__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">attribute_impl</span><span class="p">,</span> <span class="n">op</span><span class="p">):</span> | |
| 488 | <span class="bp">self</span><span class="o">.</span><span class="n">impl</span> <span class="o">=</span> <span class="n">attribute_impl</span> | |
| 489 | <span class="bp">self</span><span class="o">.</span><span class="n">op</span> <span class="o">=</span> <span class="n">op</span> | |
| 490 | <span class="bp">self</span><span class="o">.</span><span class="n">parent_token</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">impl</span><span class="o">.</span><span class="n">parent_token</span> | |
| 491 | ||
| 492 | <span class="k">def</span> <span class="nf">__eq__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">other</span><span class="p">):</span> | |
| 493 | <span class="k">return</span> <span class="nb">isinstance</span><span class="p">(</span><span class="n">other</span><span class="p">,</span> <span class="n">Event</span><span class="p">)</span> <span class="ow">and</span> \ | |
| 494 | <span class="n">other</span><span class="o">.</span><span class="n">impl</span> <span class="ow">is</span> <span class="bp">self</span><span class="o">.</span><span class="n">impl</span> <span class="ow">and</span> \ | |
| 495 | <span class="n">other</span><span class="o">.</span><span class="n">op</span> <span class="o">==</span> <span class="bp">self</span><span class="o">.</span><span class="n">op</span> | |
| 496 | ||
| 497 | <span class="nd">@property</span> | |
| 498 | <span class="k">def</span> <span class="nf">key</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 499 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">impl</span><span class="o">.</span><span class="n">key</span> | |
| 500 | ||
| 501 | <span class="k">def</span> <span class="nf">hasparent</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">):</span> | |
| 502 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">impl</span><span class="o">.</span><span class="n">hasparent</span><span class="p">(</span><span class="n">state</span><span class="p">)</span> | |
| 503 | ||
| 504 | ||
| 505 | <span class="k">class</span> <span class="nc">AttributeImpl</span><span class="p">(</span><span class="nb">object</span><span class="p">):</span> | |
| 506 | <span class="sd">"""internal implementation for instrumented attributes."""</span> | |
| 507 | ||
| 508 | <span class="k">def</span> <span class="nf">__init__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">class_</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> | |
| 509 | <span class="n">callable_</span><span class="p">,</span> <span class="n">dispatch</span><span class="p">,</span> <span class="n">trackparent</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">extension</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 510 | <span class="n">compare_function</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">active_history</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> | |
| 511 | <span class="n">parent_token</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">expire_missing</span><span class="o">=</span><span class="kc">True</span><span class="p">,</span> | |
| 512 | <span class="n">send_modified_events</span><span class="o">=</span><span class="kc">True</span><span class="p">,</span> | |
| 513 | <span class="o">**</span><span class="n">kwargs</span><span class="p">):</span> | |
| 514 | <span class="sd">"""Construct an AttributeImpl.</span> | |
| 515 | ||
| 516 | <span class="sd"> \class_</span> | |
| 517 | <span class="sd"> associated class</span> | |
| 518 | ||
| 519 | <span class="sd"> key</span> | |
| 520 | <span class="sd"> string name of the attribute</span> | |
| 521 | ||
| 522 | <span class="sd"> \callable_</span> | |
| 523 | <span class="sd"> optional function which generates a callable based on a parent</span> | |
| 524 | <span class="sd"> instance, which produces the "default" values for a scalar or</span> | |
| 525 | <span class="sd"> collection attribute when it's first accessed, if not present</span> | |
| 526 | <span class="sd"> already.</span> | |
| 527 | ||
| 528 | <span class="sd"> trackparent</span> | |
| 529 | <span class="sd"> if True, attempt to track if an instance has a parent attached</span> | |
| 530 | <span class="sd"> to it via this attribute.</span> | |
| 531 | ||
| 532 | <span class="sd"> extension</span> | |
| 533 | <span class="sd"> a single or list of AttributeExtension object(s) which will</span> | |
| 534 | <span class="sd"> receive set/delete/append/remove/etc. events. Deprecated.</span> | |
| 535 | <span class="sd"> The event package is now used.</span> | |
| 536 | ||
| 537 | <span class="sd"> compare_function</span> | |
| 538 | <span class="sd"> a function that compares two values which are normally</span> | |
| 539 | <span class="sd"> assignable to this attribute.</span> | |
| 540 | ||
| 541 | <span class="sd"> active_history</span> | |
| 542 | <span class="sd"> indicates that get_history() should always return the "old" value,</span> | |
| 543 | <span class="sd"> even if it means executing a lazy callable upon attribute change.</span> | |
| 544 | ||
| 545 | <span class="sd"> parent_token</span> | |
| 546 | <span class="sd"> Usually references the MapperProperty, used as a key for</span> | |
| 547 | <span class="sd"> the hasparent() function to identify an "owning" attribute.</span> | |
| 548 | <span class="sd"> Allows multiple AttributeImpls to all match a single</span> | |
| 549 | <span class="sd"> owner attribute.</span> | |
| 550 | ||
| 551 | <span class="sd"> expire_missing</span> | |
| 552 | <span class="sd"> if False, don't add an "expiry" callable to this attribute</span> | |
| 553 | <span class="sd"> during state.expire_attributes(None), if no value is present</span> | |
| 554 | <span class="sd"> for this key.</span> | |
| 555 | ||
| 556 | <span class="sd"> send_modified_events</span> | |
| 557 | <span class="sd"> if False, the InstanceState._modified_event method will have no</span> | |
| 558 | <span class="sd"> effect; this means the attribute will never show up as changed in a</span> | |
| 559 | <span class="sd"> history entry.</span> | |
| 560 | <span class="sd"> """</span> | |
| 561 | <span class="bp">self</span><span class="o">.</span><span class="n">class_</span> <span class="o">=</span> <span class="n">class_</span> | |
| 562 | <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="o">=</span> <span class="n">key</span> | |
| 563 | <span class="bp">self</span><span class="o">.</span><span class="n">callable_</span> <span class="o">=</span> <span class="n">callable_</span> | |
| 564 | <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span> <span class="o">=</span> <span class="n">dispatch</span> | |
| 565 | <span class="bp">self</span><span class="o">.</span><span class="n">trackparent</span> <span class="o">=</span> <span class="n">trackparent</span> | |
| 566 | <span class="bp">self</span><span class="o">.</span><span class="n">parent_token</span> <span class="o">=</span> <span class="n">parent_token</span> <span class="ow">or</span> <span class="bp">self</span> | |
| 567 | <span class="bp">self</span><span class="o">.</span><span class="n">send_modified_events</span> <span class="o">=</span> <span class="n">send_modified_events</span> | |
| 568 | <span class="k">if</span> <span class="n">compare_function</span> <span class="ow">is</span> <span class="kc">None</span><span class="p">:</span> | |
| 569 | <span class="bp">self</span><span class="o">.</span><span class="n">is_equal</span> <span class="o">=</span> <span class="n">operator</span><span class="o">.</span><span class="n">eq</span> | |
| 570 | <span class="k">else</span><span class="p">:</span> | |
| 571 | <span class="bp">self</span><span class="o">.</span><span class="n">is_equal</span> <span class="o">=</span> <span class="n">compare_function</span> | |
| 572 | ||
| 573 | <span class="c1"># TODO: pass in the manager here</span> | |
| 574 | <span class="c1"># instead of doing a lookup</span> | |
| 575 | <span class="n">attr</span> <span class="o">=</span> <span class="n">manager_of_class</span><span class="p">(</span><span class="n">class_</span><span class="p">)[</span><span class="n">key</span><span class="p">]</span> | |
| 576 | ||
| 577 | <span class="k">for</span> <span class="n">ext</span> <span class="ow">in</span> <span class="n">util</span><span class="o">.</span><span class="n">to_list</span><span class="p">(</span><span class="n">extension</span> <span class="ow">or</span> <span class="p">[]):</span> | |
| 578 | <span class="n">ext</span><span class="o">.</span><span class="n">_adapt_listener</span><span class="p">(</span><span class="n">attr</span><span class="p">,</span> <span class="n">ext</span><span class="p">)</span> | |
| 579 | ||
| 580 | <span class="k">if</span> <span class="n">active_history</span><span class="p">:</span> | |
| 581 | <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">_active_history</span> <span class="o">=</span> <span class="kc">True</span> | |
| 582 | ||
| 583 | <span class="bp">self</span><span class="o">.</span><span class="n">expire_missing</span> <span class="o">=</span> <span class="n">expire_missing</span> | |
| 584 | ||
| 585 | <span class="n">__slots__</span> <span class="o">=</span> <span class="p">(</span> | |
| 586 | <span class="s1">'class_'</span><span class="p">,</span> <span class="s1">'key'</span><span class="p">,</span> <span class="s1">'callable_'</span><span class="p">,</span> <span class="s1">'dispatch'</span><span class="p">,</span> <span class="s1">'trackparent'</span><span class="p">,</span> | |
| 587 | <span class="s1">'parent_token'</span><span class="p">,</span> <span class="s1">'send_modified_events'</span><span class="p">,</span> <span class="s1">'is_equal'</span><span class="p">,</span> <span class="s1">'expire_missing'</span> | |
| 588 | <span class="p">)</span> | |
| 589 | ||
| 590 | <span class="k">def</span> <span class="nf">__str__</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 591 | <span class="k">return</span> <span class="s2">"</span><span class="si">%s</span><span class="s2">.</span><span class="si">%s</span><span class="s2">"</span> <span class="o">%</span> <span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">class_</span><span class="o">.</span><span class="n">__name__</span><span class="p">,</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">)</span> | |
| 592 | ||
| 593 | <span class="k">def</span> <span class="nf">_get_active_history</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 594 | <span class="sd">"""Backwards compat for impl.active_history"""</span> | |
| 595 | ||
| 596 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">_active_history</span> | |
| 597 | ||
| 598 | <span class="k">def</span> <span class="nf">_set_active_history</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">value</span><span class="p">):</span> | |
| 599 | <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">_active_history</span> <span class="o">=</span> <span class="n">value</span> | |
| 600 | ||
| 601 | <span class="n">active_history</span> <span class="o">=</span> <span class="nb">property</span><span class="p">(</span><span class="n">_get_active_history</span><span class="p">,</span> <span class="n">_set_active_history</span><span class="p">)</span> | |
| 602 | ||
| 603 | <span class="k">def</span> <span class="nf">hasparent</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">optimistic</span><span class="o">=</span><span class="kc">False</span><span class="p">):</span> | |
| 604 | <span class="sd">"""Return the boolean value of a `hasparent` flag attached to</span> | |
| 605 | <span class="sd"> the given state.</span> | |
| 606 | ||
| 607 | <span class="sd"> The `optimistic` flag determines what the default return value</span> | |
| 608 | <span class="sd"> should be if no `hasparent` flag can be located.</span> | |
| 609 | ||
| 610 | <span class="sd"> As this function is used to determine if an instance is an</span> | |
| 611 | <span class="sd"> *orphan*, instances that were loaded from storage should be</span> | |
| 612 | <span class="sd"> assumed to not be orphans, until a True/False value for this</span> | |
| 613 | <span class="sd"> flag is set.</span> | |
| 614 | ||
| 615 | <span class="sd"> An instance attribute that is loaded by a callable function</span> | |
| 616 | <span class="sd"> will also not have a `hasparent` flag.</span> | |
| 617 | ||
| 618 | <span class="sd"> """</span> | |
| 619 | <span class="n">msg</span> <span class="o">=</span> <span class="s2">"This AttributeImpl is not configured to track parents."</span> | |
| 620 | <span class="k">assert</span> <span class="bp">self</span><span class="o">.</span><span class="n">trackparent</span><span class="p">,</span> <span class="n">msg</span> | |
| 621 | ||
| 622 | <span class="k">return</span> <span class="n">state</span><span class="o">.</span><span class="n">parents</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="nb">id</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">parent_token</span><span class="p">),</span> <span class="n">optimistic</span><span class="p">)</span> \ | |
| 623 | <span class="ow">is</span> <span class="ow">not</span> <span class="kc">False</span> | |
| 624 | ||
| 625 | <span class="k">def</span> <span class="nf">sethasparent</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">parent_state</span><span class="p">,</span> <span class="n">value</span><span class="p">):</span> | |
| 626 | <span class="sd">"""Set a boolean flag on the given item corresponding to</span> | |
| 627 | <span class="sd"> whether or not it is attached to a parent object via the</span> | |
| 628 | <span class="sd"> attribute represented by this ``InstrumentedAttribute``.</span> | |
| 629 | ||
| 630 | <span class="sd"> """</span> | |
| 631 | <span class="n">msg</span> <span class="o">=</span> <span class="s2">"This AttributeImpl is not configured to track parents."</span> | |
| 632 | <span class="k">assert</span> <span class="bp">self</span><span class="o">.</span><span class="n">trackparent</span><span class="p">,</span> <span class="n">msg</span> | |
| 633 | ||
| 634 | <span class="n">id_</span> <span class="o">=</span> <span class="nb">id</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">parent_token</span><span class="p">)</span> | |
| 635 | <span class="k">if</span> <span class="n">value</span><span class="p">:</span> | |
| 636 | <span class="n">state</span><span class="o">.</span><span class="n">parents</span><span class="p">[</span><span class="n">id_</span><span class="p">]</span> <span class="o">=</span> <span class="n">parent_state</span> | |
| 637 | <span class="k">else</span><span class="p">:</span> | |
| 638 | <span class="k">if</span> <span class="n">id_</span> <span class="ow">in</span> <span class="n">state</span><span class="o">.</span><span class="n">parents</span><span class="p">:</span> | |
| 639 | <span class="n">last_parent</span> <span class="o">=</span> <span class="n">state</span><span class="o">.</span><span class="n">parents</span><span class="p">[</span><span class="n">id_</span><span class="p">]</span> | |
| 640 | ||
| 641 | <span class="k">if</span> <span class="n">last_parent</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">False</span> <span class="ow">and</span> \ | |
| 642 | <span class="n">last_parent</span><span class="o">.</span><span class="n">key</span> <span class="o">!=</span> <span class="n">parent_state</span><span class="o">.</span><span class="n">key</span><span class="p">:</span> | |
| 643 | ||
| 644 | <span class="k">if</span> <span class="n">last_parent</span><span class="o">.</span><span class="n">obj</span><span class="p">()</span> <span class="ow">is</span> <span class="kc">None</span><span class="p">:</span> | |
| 645 | <span class="k">raise</span> <span class="n">orm_exc</span><span class="o">.</span><span class="n">StaleDataError</span><span class="p">(</span> | |
| 646 | <span class="s2">"Removing state </span><span class="si">%s</span><span class="s2"> from parent "</span> | |
| 647 | <span class="s2">"state </span><span class="si">%s</span><span class="s2"> along attribute '</span><span class="si">%s</span><span class="s2">', "</span> | |
| 648 | <span class="s2">"but the parent record "</span> | |
| 649 | <span class="s2">"has gone stale, can't be sure this "</span> | |
| 650 | <span class="s2">"is the most recent parent."</span> <span class="o">%</span> | |
| 651 | <span class="p">(</span><span class="n">state_str</span><span class="p">(</span><span class="n">state</span><span class="p">),</span> | |
| 652 | <span class="n">state_str</span><span class="p">(</span><span class="n">parent_state</span><span class="p">),</span> | |
| 653 | <span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">))</span> | |
| 654 | ||
| 655 | <span class="k">return</span> | |
| 656 | ||
| 657 | <span class="n">state</span><span class="o">.</span><span class="n">parents</span><span class="p">[</span><span class="n">id_</span><span class="p">]</span> <span class="o">=</span> <span class="kc">False</span> | |
| 658 | ||
| 659 | <span class="k">def</span> <span class="nf">get_history</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 660 | <span class="k">raise</span> <span class="ne">NotImplementedError</span><span class="p">()</span> | |
| 661 | ||
| 662 | <span class="k">def</span> <span class="nf">get_all_pending</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_NO_INITIALIZE</span><span class="p">):</span> | |
| 663 | <span class="sd">"""Return a list of tuples of (state, obj)</span> | |
| 664 | <span class="sd"> for all objects in this attribute's current state</span> | |
| 665 | <span class="sd"> + history.</span> | |
| 666 | ||
| 667 | <span class="sd"> Only applies to object-based attributes.</span> | |
| 668 | ||
| 669 | <span class="sd"> This is an inlining of existing functionality</span> | |
| 670 | <span class="sd"> which roughly corresponds to:</span> | |
| 671 | ||
| 672 | <span class="sd"> get_state_history(</span> | |
| 673 | <span class="sd"> state,</span> | |
| 674 | <span class="sd"> key,</span> | |
| 675 | <span class="sd"> passive=PASSIVE_NO_INITIALIZE).sum()</span> | |
| 676 | ||
| 677 | <span class="sd"> """</span> | |
| 678 | <span class="k">raise</span> <span class="ne">NotImplementedError</span><span class="p">()</span> | |
| 679 | ||
| 680 | <span class="k">def</span> <span class="nf">initialize</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">):</span> | |
| 681 | <span class="sd">"""Initialize the given state's attribute with an empty value."""</span> | |
| 682 | ||
| 683 | <span class="c1"># As of 1.0, we don't actually set a value in</span> | |
| 684 | <span class="c1"># dict_. This is so that the state of the object does not get</span> | |
| 685 | <span class="c1"># modified without emitting the appropriate events.</span> | |
| 686 | ||
| 687 | ||
| 688 | <span class="k">return</span> <span class="kc">None</span> | |
| 689 | ||
| 690 | <span class="k">def</span> <span class="nf">get</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 691 | <span class="sd">"""Retrieve a value from the given object.</span> | |
| 692 | <span class="sd"> If a callable is assembled on this object's attribute, and</span> | |
| 693 | <span class="sd"> passive is False, the callable will be executed and the</span> | |
| 694 | <span class="sd"> resulting value will be set as the new value for this attribute.</span> | |
| 695 | <span class="sd"> """</span> | |
| 696 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="ow">in</span> <span class="n">dict_</span><span class="p">:</span> | |
| 697 | <span class="k">return</span> <span class="n">dict_</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> | |
| 698 | <span class="k">else</span><span class="p">:</span> | |
| 699 | <span class="c1"># if history present, don't load</span> | |
| 700 | <span class="n">key</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span> | |
| 701 | <span class="k">if</span> <span class="n">key</span> <span class="ow">not</span> <span class="ow">in</span> <span class="n">state</span><span class="o">.</span><span class="n">committed_state</span> <span class="ow">or</span> \ | |
| 702 | <span class="n">state</span><span class="o">.</span><span class="n">committed_state</span><span class="p">[</span><span class="n">key</span><span class="p">]</span> <span class="ow">is</span> <span class="n">NEVER_SET</span><span class="p">:</span> | |
| 703 | <span class="k">if</span> <span class="ow">not</span> <span class="n">passive</span> <span class="o">&</span> <span class="n">CALLABLES_OK</span><span class="p">:</span> | |
| 704 | <span class="k">return</span> <span class="n">PASSIVE_NO_RESULT</span> | |
| 705 | ||
| 706 | <span class="k">if</span> <span class="n">key</span> <span class="ow">in</span> <span class="n">state</span><span class="o">.</span><span class="n">expired_attributes</span><span class="p">:</span> | |
| 707 | <span class="n">value</span> <span class="o">=</span> <span class="n">state</span><span class="o">.</span><span class="n">_load_expired</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">passive</span><span class="p">)</span> | |
| 708 | <span class="k">elif</span> <span class="n">key</span> <span class="ow">in</span> <span class="n">state</span><span class="o">.</span><span class="n">callables</span><span class="p">:</span> | |
| 709 | <span class="n">callable_</span> <span class="o">=</span> <span class="n">state</span><span class="o">.</span><span class="n">callables</span><span class="p">[</span><span class="n">key</span><span class="p">]</span> | |
| 710 | <span class="n">value</span> <span class="o">=</span> <span class="n">callable_</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">passive</span><span class="p">)</span> | |
| 711 | <span class="k">elif</span> <span class="bp">self</span><span class="o">.</span><span class="n">callable_</span><span class="p">:</span> | |
| 712 | <span class="n">value</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">callable_</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">passive</span><span class="p">)</span> | |
| 713 | <span class="k">else</span><span class="p">:</span> | |
| 714 | <span class="n">value</span> <span class="o">=</span> <span class="n">ATTR_EMPTY</span> | |
| 715 | ||
| 716 | <span class="k">if</span> <span class="n">value</span> <span class="ow">is</span> <span class="n">PASSIVE_NO_RESULT</span> <span class="ow">or</span> <span class="n">value</span> <span class="ow">is</span> <span class="n">NEVER_SET</span><span class="p">:</span> | |
| 717 | <span class="k">return</span> <span class="n">value</span> | |
| 718 | <span class="k">elif</span> <span class="n">value</span> <span class="ow">is</span> <span class="n">ATTR_WAS_SET</span><span class="p">:</span> | |
| 719 | <span class="k">try</span><span class="p">:</span> | |
| 720 | <span class="k">return</span> <span class="n">dict_</span><span class="p">[</span><span class="n">key</span><span class="p">]</span> | |
| 721 | <span class="k">except</span> <span class="ne">KeyError</span><span class="p">:</span> | |
| 722 | <span class="c1"># TODO: no test coverage here.</span> | |
| 723 | <span class="k">raise</span> <span class="ne">KeyError</span><span class="p">(</span> | |
| 724 | <span class="s2">"Deferred loader for attribute "</span> | |
| 725 | <span class="s2">"</span><span class="si">%r</span><span class="s2"> failed to populate "</span> | |
| 726 | <span class="s2">"correctly"</span> <span class="o">%</span> <span class="n">key</span><span class="p">)</span> | |
| 727 | <span class="k">elif</span> <span class="n">value</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">ATTR_EMPTY</span><span class="p">:</span> | |
| 728 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">set_committed_value</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">)</span> | |
| 729 | ||
| 730 | <span class="k">if</span> <span class="ow">not</span> <span class="n">passive</span> <span class="o">&</span> <span class="n">INIT_OK</span><span class="p">:</span> | |
| 731 | <span class="k">return</span> <span class="n">NEVER_SET</span> | |
| 732 | <span class="k">else</span><span class="p">:</span> | |
| 733 | <span class="c1"># Return a new, empty value</span> | |
| 734 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">initialize</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">)</span> | |
| 735 | ||
| 736 | <span class="k">def</span> <span class="nf">append</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 737 | <span class="bp">self</span><span class="o">.</span><span class="n">set</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">passive</span><span class="p">)</span> | |
| 738 | ||
| 739 | <span class="k">def</span> <span class="nf">remove</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 740 | <span class="bp">self</span><span class="o">.</span><span class="n">set</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="kc">None</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> | |
| 741 | <span class="n">passive</span><span class="o">=</span><span class="n">passive</span><span class="p">,</span> <span class="n">check_old</span><span class="o">=</span><span class="n">value</span><span class="p">)</span> | |
| 742 | ||
| 743 | <span class="k">def</span> <span class="nf">pop</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 744 | <span class="bp">self</span><span class="o">.</span><span class="n">set</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="kc">None</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> | |
| 745 | <span class="n">passive</span><span class="o">=</span><span class="n">passive</span><span class="p">,</span> <span class="n">check_old</span><span class="o">=</span><span class="n">value</span><span class="p">,</span> <span class="n">pop</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 746 | ||
| 747 | <span class="k">def</span> <span class="nf">set</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> | |
| 748 | <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">,</span> <span class="n">check_old</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">pop</span><span class="o">=</span><span class="kc">False</span><span class="p">):</span> | |
| 749 | <span class="k">raise</span> <span class="ne">NotImplementedError</span><span class="p">()</span> | |
| 750 | ||
| 751 | <span class="k">def</span> <span class="nf">get_committed_value</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 752 | <span class="sd">"""return the unchanged value of this attribute"""</span> | |
| 753 | ||
| 754 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="ow">in</span> <span class="n">state</span><span class="o">.</span><span class="n">committed_state</span><span class="p">:</span> | |
| 755 | <span class="n">value</span> <span class="o">=</span> <span class="n">state</span><span class="o">.</span><span class="n">committed_state</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> | |
| 756 | <span class="k">if</span> <span class="n">value</span> <span class="ow">in</span> <span class="p">(</span><span class="n">NO_VALUE</span><span class="p">,</span> <span class="n">NEVER_SET</span><span class="p">):</span> | |
| 757 | <span class="k">return</span> <span class="kc">None</span> | |
| 758 | <span class="k">else</span><span class="p">:</span> | |
| 759 | <span class="k">return</span> <span class="n">value</span> | |
| 760 | <span class="k">else</span><span class="p">:</span> | |
| 761 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">passive</span><span class="p">)</span> | |
| 762 | ||
| 763 | <span class="k">def</span> <span class="nf">set_committed_value</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">):</span> | |
| 764 | <span class="sd">"""set an attribute value on the given instance and 'commit' it."""</span> | |
| 765 | ||
| 766 | <span class="n">dict_</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> <span class="o">=</span> <span class="n">value</span> | |
| 767 | <span class="n">state</span><span class="o">.</span><span class="n">_commit</span><span class="p">(</span><span class="n">dict_</span><span class="p">,</span> <span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">])</span> | |
| 768 | <span class="k">return</span> <span class="n">value</span> | |
| 769 | ||
| 770 | ||
| 771 | <span class="k">class</span> <span class="nc">ScalarAttributeImpl</span><span class="p">(</span><span class="n">AttributeImpl</span><span class="p">):</span> | |
| 772 | <span class="sd">"""represents a scalar value-holding InstrumentedAttribute."""</span> | |
| 773 | ||
| 774 | <span class="n">accepts_scalar_loader</span> <span class="o">=</span> <span class="kc">True</span> | |
| 775 | <span class="n">uses_objects</span> <span class="o">=</span> <span class="kc">False</span> | |
| 776 | <span class="n">supports_population</span> <span class="o">=</span> <span class="kc">True</span> | |
| 777 | <span class="n">collection</span> <span class="o">=</span> <span class="kc">False</span> | |
| 778 | ||
| 779 | <span class="n">__slots__</span> <span class="o">=</span> <span class="s1">'_replace_token'</span><span class="p">,</span> <span class="s1">'_append_token'</span><span class="p">,</span> <span class="s1">'_remove_token'</span> | |
| 780 | ||
| 781 | <span class="k">def</span> <span class="nf">__init__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="o">*</span><span class="n">arg</span><span class="p">,</span> <span class="o">**</span><span class="n">kw</span><span class="p">):</span> | |
| 782 | <span class="nb">super</span><span class="p">(</span><span class="n">ScalarAttributeImpl</span><span class="p">,</span> <span class="bp">self</span><span class="p">)</span><span class="o">.</span><span class="n">__init__</span><span class="p">(</span><span class="o">*</span><span class="n">arg</span><span class="p">,</span> <span class="o">**</span><span class="n">kw</span><span class="p">)</span> | |
| 783 | <span class="bp">self</span><span class="o">.</span><span class="n">_replace_token</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">_append_token</span> <span class="o">=</span> <span class="kc">None</span> | |
| 784 | <span class="bp">self</span><span class="o">.</span><span class="n">_remove_token</span> <span class="o">=</span> <span class="kc">None</span> | |
| 785 | ||
| 786 | <span class="k">def</span> <span class="nf">_init_append_token</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 787 | <span class="bp">self</span><span class="o">.</span><span class="n">_replace_token</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">_append_token</span> <span class="o">=</span> <span class="n">Event</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">OP_REPLACE</span><span class="p">)</span> | |
| 788 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">_replace_token</span> | |
| 789 | ||
| 790 | <span class="n">_init_append_or_replace_token</span> <span class="o">=</span> <span class="n">_init_append_token</span> | |
| 791 | ||
| 792 | <span class="k">def</span> <span class="nf">_init_remove_token</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 793 | <span class="bp">self</span><span class="o">.</span><span class="n">_remove_token</span> <span class="o">=</span> <span class="n">Event</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">OP_REMOVE</span><span class="p">)</span> | |
| 794 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">_remove_token</span> | |
| 795 | ||
| 796 | <span class="k">def</span> <span class="nf">delete</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">):</span> | |
| 797 | ||
| 798 | <span class="c1"># TODO: catch key errors, convert to attributeerror?</span> | |
| 799 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">_active_history</span><span class="p">:</span> | |
| 800 | <span class="n">old</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">PASSIVE_RETURN_NEVER_SET</span><span class="p">)</span> | |
| 801 | <span class="k">else</span><span class="p">:</span> | |
| 802 | <span class="n">old</span> <span class="o">=</span> <span class="n">dict_</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">,</span> <span class="n">NO_VALUE</span><span class="p">)</span> | |
| 803 | ||
| 804 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">remove</span><span class="p">:</span> | |
| 805 | <span class="bp">self</span><span class="o">.</span><span class="n">fire_remove_event</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">old</span><span class="p">,</span> <span class="bp">self</span><span class="o">.</span><span class="n">_remove_token</span><span class="p">)</span> | |
| 806 | <span class="n">state</span><span class="o">.</span><span class="n">_modified_event</span><span class="p">(</span><span class="n">dict_</span><span class="p">,</span> <span class="bp">self</span><span class="p">,</span> <span class="n">old</span><span class="p">)</span> | |
| 807 | <span class="k">del</span> <span class="n">dict_</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> | |
| 808 | ||
| 809 | <span class="k">def</span> <span class="nf">get_history</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 810 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="ow">in</span> <span class="n">dict_</span><span class="p">:</span> | |
| 811 | <span class="k">return</span> <span class="n">History</span><span class="o">.</span><span class="n">from_scalar_attribute</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">])</span> | |
| 812 | <span class="k">else</span><span class="p">:</span> | |
| 813 | <span class="k">if</span> <span class="n">passive</span> <span class="o">&</span> <span class="n">INIT_OK</span><span class="p">:</span> | |
| 814 | <span class="n">passive</span> <span class="o">^=</span> <span class="n">INIT_OK</span> | |
| 815 | <span class="n">current</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">passive</span><span class="p">)</span> | |
| 816 | <span class="k">if</span> <span class="n">current</span> <span class="ow">is</span> <span class="n">PASSIVE_NO_RESULT</span><span class="p">:</span> | |
| 817 | <span class="k">return</span> <span class="n">HISTORY_BLANK</span> | |
| 818 | <span class="k">else</span><span class="p">:</span> | |
| 819 | <span class="k">return</span> <span class="n">History</span><span class="o">.</span><span class="n">from_scalar_attribute</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">current</span><span class="p">)</span> | |
| 820 | ||
| 821 | <span class="k">def</span> <span class="nf">set</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> | |
| 822 | <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">,</span> <span class="n">check_old</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">pop</span><span class="o">=</span><span class="kc">False</span><span class="p">):</span> | |
| 823 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">_active_history</span><span class="p">:</span> | |
| 824 | <span class="n">old</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">PASSIVE_RETURN_NEVER_SET</span><span class="p">)</span> | |
| 825 | <span class="k">else</span><span class="p">:</span> | |
| 826 | <span class="n">old</span> <span class="o">=</span> <span class="n">dict_</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">,</span> <span class="n">NO_VALUE</span><span class="p">)</span> | |
| 827 | ||
| 828 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">set</span><span class="p">:</span> | |
| 829 | <span class="n">value</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">fire_replace_event</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> | |
| 830 | <span class="n">value</span><span class="p">,</span> <span class="n">old</span><span class="p">,</span> <span class="n">initiator</span><span class="p">)</span> | |
| 831 | <span class="n">state</span><span class="o">.</span><span class="n">_modified_event</span><span class="p">(</span><span class="n">dict_</span><span class="p">,</span> <span class="bp">self</span><span class="p">,</span> <span class="n">old</span><span class="p">)</span> | |
| 832 | <span class="n">dict_</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> <span class="o">=</span> <span class="n">value</span> | |
| 833 | ||
| 834 | <span class="k">def</span> <span class="nf">fire_replace_event</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">previous</span><span class="p">,</span> <span class="n">initiator</span><span class="p">):</span> | |
| 835 | <span class="k">for</span> <span class="n">fn</span> <span class="ow">in</span> <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">set</span><span class="p">:</span> | |
| 836 | <span class="n">value</span> <span class="o">=</span> <span class="n">fn</span><span class="p">(</span> | |
| 837 | <span class="n">state</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">previous</span><span class="p">,</span> | |
| 838 | <span class="n">initiator</span> <span class="ow">or</span> <span class="bp">self</span><span class="o">.</span><span class="n">_replace_token</span> <span class="ow">or</span> | |
| 839 | <span class="bp">self</span><span class="o">.</span><span class="n">_init_append_or_replace_token</span><span class="p">())</span> | |
| 840 | <span class="k">return</span> <span class="n">value</span> | |
| 841 | ||
| 842 | <span class="k">def</span> <span class="nf">fire_remove_event</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">):</span> | |
| 843 | <span class="k">for</span> <span class="n">fn</span> <span class="ow">in</span> <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">remove</span><span class="p">:</span> | |
| 844 | <span class="n">fn</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> | |
| 845 | <span class="n">initiator</span> <span class="ow">or</span> <span class="bp">self</span><span class="o">.</span><span class="n">_remove_token</span> <span class="ow">or</span> <span class="bp">self</span><span class="o">.</span><span class="n">_init_remove_token</span><span class="p">())</span> | |
| 846 | ||
| 847 | <span class="nd">@property</span> | |
| 848 | <span class="k">def</span> <span class="nf">type</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 849 | <span class="bp">self</span><span class="o">.</span><span class="n">property</span><span class="o">.</span><span class="n">columns</span><span class="p">[</span><span class="mi">0</span><span class="p">]</span><span class="o">.</span><span class="n">type</span> | |
| 850 | ||
| 851 | ||
| 852 | <span class="k">class</span> <span class="nc">ScalarObjectAttributeImpl</span><span class="p">(</span><span class="n">ScalarAttributeImpl</span><span class="p">):</span> | |
| 853 | <span class="sd">"""represents a scalar-holding InstrumentedAttribute,</span> | |
| 854 | <span class="sd"> where the target object is also instrumented.</span> | |
| 855 | ||
| 856 | <span class="sd"> Adds events to delete/set operations.</span> | |
| 857 | ||
| 858 | <span class="sd"> """</span> | |
| 859 | ||
| 860 | <span class="n">accepts_scalar_loader</span> <span class="o">=</span> <span class="kc">False</span> | |
| 861 | <span class="n">uses_objects</span> <span class="o">=</span> <span class="kc">True</span> | |
| 862 | <span class="n">supports_population</span> <span class="o">=</span> <span class="kc">True</span> | |
| 863 | <span class="n">collection</span> <span class="o">=</span> <span class="kc">False</span> | |
| 864 | ||
| 865 | <span class="n">__slots__</span> <span class="o">=</span> <span class="p">()</span> | |
| 866 | ||
| 867 | <span class="k">def</span> <span class="nf">delete</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">):</span> | |
| 868 | <span class="n">old</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">)</span> | |
| 869 | <span class="bp">self</span><span class="o">.</span><span class="n">fire_remove_event</span><span class="p">(</span> | |
| 870 | <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">old</span><span class="p">,</span> | |
| 871 | <span class="bp">self</span><span class="o">.</span><span class="n">_remove_token</span> <span class="ow">or</span> <span class="bp">self</span><span class="o">.</span><span class="n">_init_remove_token</span><span class="p">())</span> | |
| 872 | <span class="k">del</span> <span class="n">dict_</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> | |
| 873 | ||
| 874 | <span class="k">def</span> <span class="nf">get_history</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 875 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="ow">in</span> <span class="n">dict_</span><span class="p">:</span> | |
| 876 | <span class="k">return</span> <span class="n">History</span><span class="o">.</span><span class="n">from_object_attribute</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">])</span> | |
| 877 | <span class="k">else</span><span class="p">:</span> | |
| 878 | <span class="k">if</span> <span class="n">passive</span> <span class="o">&</span> <span class="n">INIT_OK</span><span class="p">:</span> | |
| 879 | <span class="n">passive</span> <span class="o">^=</span> <span class="n">INIT_OK</span> | |
| 880 | <span class="n">current</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">passive</span><span class="p">)</span> | |
| 881 | <span class="k">if</span> <span class="n">current</span> <span class="ow">is</span> <span class="n">PASSIVE_NO_RESULT</span><span class="p">:</span> | |
| 882 | <span class="k">return</span> <span class="n">HISTORY_BLANK</span> | |
| 883 | <span class="k">else</span><span class="p">:</span> | |
| 884 | <span class="k">return</span> <span class="n">History</span><span class="o">.</span><span class="n">from_object_attribute</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">current</span><span class="p">)</span> | |
| 885 | ||
| 886 | <span class="k">def</span> <span class="nf">get_all_pending</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_NO_INITIALIZE</span><span class="p">):</span> | |
| 887 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="ow">in</span> <span class="n">dict_</span><span class="p">:</span> | |
| 888 | <span class="n">current</span> <span class="o">=</span> <span class="n">dict_</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> | |
| 889 | <span class="k">elif</span> <span class="n">passive</span> <span class="o">&</span> <span class="n">CALLABLES_OK</span><span class="p">:</span> | |
| 890 | <span class="n">current</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">passive</span><span class="p">)</span> | |
| 891 | <span class="k">else</span><span class="p">:</span> | |
| 892 | <span class="k">return</span> <span class="p">[]</span> | |
| 893 | ||
| 894 | <span class="c1"># can't use __hash__(), can't use __eq__() here</span> | |
| 895 | <span class="k">if</span> <span class="n">current</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span> <span class="ow">and</span> \ | |
| 896 | <span class="n">current</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">PASSIVE_NO_RESULT</span> <span class="ow">and</span> \ | |
| 897 | <span class="n">current</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">NEVER_SET</span><span class="p">:</span> | |
| 898 | <span class="n">ret</span> <span class="o">=</span> <span class="p">[(</span><span class="n">instance_state</span><span class="p">(</span><span class="n">current</span><span class="p">),</span> <span class="n">current</span><span class="p">)]</span> | |
| 899 | <span class="k">else</span><span class="p">:</span> | |
| 900 | <span class="n">ret</span> <span class="o">=</span> <span class="p">[(</span><span class="kc">None</span><span class="p">,</span> <span class="kc">None</span><span class="p">)]</span> | |
| 901 | ||
| 902 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="ow">in</span> <span class="n">state</span><span class="o">.</span><span class="n">committed_state</span><span class="p">:</span> | |
| 903 | <span class="n">original</span> <span class="o">=</span> <span class="n">state</span><span class="o">.</span><span class="n">committed_state</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> | |
| 904 | <span class="k">if</span> <span class="n">original</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span> <span class="ow">and</span> \ | |
| 905 | <span class="n">original</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">PASSIVE_NO_RESULT</span> <span class="ow">and</span> \ | |
| 906 | <span class="n">original</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">NEVER_SET</span> <span class="ow">and</span> \ | |
| 907 | <span class="n">original</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">current</span><span class="p">:</span> | |
| 908 | ||
| 909 | <span class="n">ret</span><span class="o">.</span><span class="n">append</span><span class="p">((</span><span class="n">instance_state</span><span class="p">(</span><span class="n">original</span><span class="p">),</span> <span class="n">original</span><span class="p">))</span> | |
| 910 | <span class="k">return</span> <span class="n">ret</span> | |
| 911 | ||
| 912 | <span class="k">def</span> <span class="nf">set</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> | |
| 913 | <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">,</span> <span class="n">check_old</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">pop</span><span class="o">=</span><span class="kc">False</span><span class="p">):</span> | |
| 914 | <span class="sd">"""Set a value on the given InstanceState.</span> | |
| 915 | ||
| 916 | <span class="sd"> """</span> | |
| 917 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">_active_history</span><span class="p">:</span> | |
| 918 | <span class="n">old</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">get</span><span class="p">(</span> | |
| 919 | <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_ONLY_PERSISTENT</span> <span class="o">|</span> <span class="n">NO_AUTOFLUSH</span><span class="p">)</span> | |
| 920 | <span class="k">else</span><span class="p">:</span> | |
| 921 | <span class="n">old</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_NO_FETCH</span> <span class="o">^</span> <span class="n">INIT_OK</span><span class="p">)</span> | |
| 922 | ||
| 923 | <span class="k">if</span> <span class="n">check_old</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span> <span class="ow">and</span> \ | |
| 924 | <span class="n">old</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">PASSIVE_NO_RESULT</span> <span class="ow">and</span> \ | |
| 925 | <span class="n">check_old</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">old</span><span class="p">:</span> | |
| 926 | <span class="k">if</span> <span class="n">pop</span><span class="p">:</span> | |
| 927 | <span class="k">return</span> | |
| 928 | <span class="k">else</span><span class="p">:</span> | |
| 929 | <span class="k">raise</span> <span class="ne">ValueError</span><span class="p">(</span> | |
| 930 | <span class="s2">"Object </span><span class="si">%s</span><span class="s2"> not associated with </span><span class="si">%s</span><span class="s2"> on attribute '</span><span class="si">%s</span><span class="s2">'"</span> <span class="o">%</span> <span class="p">(</span> | |
| 931 | <span class="n">instance_str</span><span class="p">(</span><span class="n">check_old</span><span class="p">),</span> | |
| 932 | <span class="n">state_str</span><span class="p">(</span><span class="n">state</span><span class="p">),</span> | |
| 933 | <span class="bp">self</span><span class="o">.</span><span class="n">key</span> | |
| 934 | <span class="p">))</span> | |
| 935 | ||
| 936 | <span class="n">value</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">fire_replace_event</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">old</span><span class="p">,</span> <span class="n">initiator</span><span class="p">)</span> | |
| 937 | <span class="n">dict_</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> <span class="o">=</span> <span class="n">value</span> | |
| 938 | ||
| 939 | <span class="k">def</span> <span class="nf">fire_remove_event</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">):</span> | |
| 940 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">trackparent</span> <span class="ow">and</span> <span class="n">value</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span><span class="p">:</span> | |
| 941 | <span class="bp">self</span><span class="o">.</span><span class="n">sethasparent</span><span class="p">(</span><span class="n">instance_state</span><span class="p">(</span><span class="n">value</span><span class="p">),</span> <span class="n">state</span><span class="p">,</span> <span class="kc">False</span><span class="p">)</span> | |
| 942 | ||
| 943 | <span class="k">for</span> <span class="n">fn</span> <span class="ow">in</span> <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">remove</span><span class="p">:</span> | |
| 944 | <span class="n">fn</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span> <span class="ow">or</span> | |
| 945 | <span class="bp">self</span><span class="o">.</span><span class="n">_remove_token</span> <span class="ow">or</span> <span class="bp">self</span><span class="o">.</span><span class="n">_init_remove_token</span><span class="p">())</span> | |
| 946 | ||
| 947 | <span class="n">state</span><span class="o">.</span><span class="n">_modified_event</span><span class="p">(</span><span class="n">dict_</span><span class="p">,</span> <span class="bp">self</span><span class="p">,</span> <span class="n">value</span><span class="p">)</span> | |
| 948 | ||
| 949 | <span class="k">def</span> <span class="nf">fire_replace_event</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">previous</span><span class="p">,</span> <span class="n">initiator</span><span class="p">):</span> | |
| 950 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">trackparent</span><span class="p">:</span> | |
| 951 | <span class="k">if</span> <span class="p">(</span><span class="n">previous</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">value</span> <span class="ow">and</span> | |
| 952 | <span class="n">previous</span> <span class="ow">not</span> <span class="ow">in</span> <span class="p">(</span><span class="kc">None</span><span class="p">,</span> <span class="n">PASSIVE_NO_RESULT</span><span class="p">,</span> <span class="n">NEVER_SET</span><span class="p">)):</span> | |
| 953 | <span class="bp">self</span><span class="o">.</span><span class="n">sethasparent</span><span class="p">(</span><span class="n">instance_state</span><span class="p">(</span><span class="n">previous</span><span class="p">),</span> <span class="n">state</span><span class="p">,</span> <span class="kc">False</span><span class="p">)</span> | |
| 954 | ||
| 955 | <span class="k">for</span> <span class="n">fn</span> <span class="ow">in</span> <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">set</span><span class="p">:</span> | |
| 956 | <span class="n">value</span> <span class="o">=</span> <span class="n">fn</span><span class="p">(</span> | |
| 957 | <span class="n">state</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">previous</span><span class="p">,</span> <span class="n">initiator</span> <span class="ow">or</span> | |
| 958 | <span class="bp">self</span><span class="o">.</span><span class="n">_replace_token</span> <span class="ow">or</span> <span class="bp">self</span><span class="o">.</span><span class="n">_init_append_or_replace_token</span><span class="p">())</span> | |
| 959 | ||
| 960 | <span class="n">state</span><span class="o">.</span><span class="n">_modified_event</span><span class="p">(</span><span class="n">dict_</span><span class="p">,</span> <span class="bp">self</span><span class="p">,</span> <span class="n">previous</span><span class="p">)</span> | |
| 961 | ||
| 962 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">trackparent</span><span class="p">:</span> | |
| 963 | <span class="k">if</span> <span class="n">value</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span><span class="p">:</span> | |
| 964 | <span class="bp">self</span><span class="o">.</span><span class="n">sethasparent</span><span class="p">(</span><span class="n">instance_state</span><span class="p">(</span><span class="n">value</span><span class="p">),</span> <span class="n">state</span><span class="p">,</span> <span class="kc">True</span><span class="p">)</span> | |
| 965 | ||
| 966 | <span class="k">return</span> <span class="n">value</span> | |
| 967 | ||
| 968 | ||
| 969 | <span class="k">class</span> <span class="nc">CollectionAttributeImpl</span><span class="p">(</span><span class="n">AttributeImpl</span><span class="p">):</span> | |
| 970 | <span class="sd">"""A collection-holding attribute that instruments changes in membership.</span> | |
| 971 | ||
| 972 | <span class="sd"> Only handles collections of instrumented objects.</span> | |
| 973 | ||
| 974 | <span class="sd"> InstrumentedCollectionAttribute holds an arbitrary, user-specified</span> | |
| 975 | <span class="sd"> container object (defaulting to a list) and brokers access to the</span> | |
| 976 | <span class="sd"> CollectionAdapter, a "view" onto that object that presents consistent bag</span> | |
| 977 | <span class="sd"> semantics to the orm layer independent of the user data implementation.</span> | |
| 978 | ||
| 979 | <span class="sd"> """</span> | |
| 980 | <span class="n">accepts_scalar_loader</span> <span class="o">=</span> <span class="kc">False</span> | |
| 981 | <span class="n">uses_objects</span> <span class="o">=</span> <span class="kc">True</span> | |
| 982 | <span class="n">supports_population</span> <span class="o">=</span> <span class="kc">True</span> | |
| 983 | <span class="n">collection</span> <span class="o">=</span> <span class="kc">True</span> | |
| 984 | ||
| 985 | <span class="n">__slots__</span> <span class="o">=</span> <span class="s1">'copy'</span><span class="p">,</span> <span class="s1">'collection_factory'</span><span class="p">,</span> <span class="s1">'_append_token'</span><span class="p">,</span> <span class="s1">'_remove_token'</span> | |
| 986 | ||
| 987 | <span class="k">def</span> <span class="nf">__init__</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">class_</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">callable_</span><span class="p">,</span> <span class="n">dispatch</span><span class="p">,</span> | |
| 988 | <span class="n">typecallable</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">trackparent</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">extension</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 989 | <span class="n">copy_function</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">compare_function</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="o">**</span><span class="n">kwargs</span><span class="p">):</span> | |
| 990 | <span class="nb">super</span><span class="p">(</span><span class="n">CollectionAttributeImpl</span><span class="p">,</span> <span class="bp">self</span><span class="p">)</span><span class="o">.</span><span class="n">__init__</span><span class="p">(</span> | |
| 991 | <span class="n">class_</span><span class="p">,</span> | |
| 992 | <span class="n">key</span><span class="p">,</span> | |
| 993 | <span class="n">callable_</span><span class="p">,</span> <span class="n">dispatch</span><span class="p">,</span> | |
| 994 | <span class="n">trackparent</span><span class="o">=</span><span class="n">trackparent</span><span class="p">,</span> | |
| 995 | <span class="n">extension</span><span class="o">=</span><span class="n">extension</span><span class="p">,</span> | |
| 996 | <span class="n">compare_function</span><span class="o">=</span><span class="n">compare_function</span><span class="p">,</span> | |
| 997 | <span class="o">**</span><span class="n">kwargs</span><span class="p">)</span> | |
| 998 | ||
| 999 | <span class="k">if</span> <span class="n">copy_function</span> <span class="ow">is</span> <span class="kc">None</span><span class="p">:</span> | |
| 1000 | <span class="n">copy_function</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">__copy</span> | |
| 1001 | <span class="bp">self</span><span class="o">.</span><span class="n">copy</span> <span class="o">=</span> <span class="n">copy_function</span> | |
| 1002 | <span class="bp">self</span><span class="o">.</span><span class="n">collection_factory</span> <span class="o">=</span> <span class="n">typecallable</span> | |
| 1003 | <span class="bp">self</span><span class="o">.</span><span class="n">_append_token</span> <span class="o">=</span> <span class="kc">None</span> | |
| 1004 | <span class="bp">self</span><span class="o">.</span><span class="n">_remove_token</span> <span class="o">=</span> <span class="kc">None</span> | |
| 1005 | ||
| 1006 | <span class="k">if</span> <span class="nb">getattr</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">collection_factory</span><span class="p">,</span> <span class="s2">"_sa_linker"</span><span class="p">,</span> <span class="kc">None</span><span class="p">):</span> | |
| 1007 | ||
| 1008 | <span class="nd">@event</span><span class="o">.</span><span class="n">listens_for</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="s2">"init_collection"</span><span class="p">)</span> | |
| 1009 | <span class="k">def</span> <span class="nf">link</span><span class="p">(</span><span class="n">target</span><span class="p">,</span> <span class="n">collection</span><span class="p">,</span> <span class="n">collection_adapter</span><span class="p">):</span> | |
| 1010 | <span class="n">collection</span><span class="o">.</span><span class="n">_sa_linker</span><span class="p">(</span><span class="n">collection_adapter</span><span class="p">)</span> | |
| 1011 | ||
| 1012 | <span class="nd">@event</span><span class="o">.</span><span class="n">listens_for</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="s2">"dispose_collection"</span><span class="p">)</span> | |
| 1013 | <span class="k">def</span> <span class="nf">unlink</span><span class="p">(</span><span class="n">target</span><span class="p">,</span> <span class="n">collection</span><span class="p">,</span> <span class="n">collection_adapter</span><span class="p">):</span> | |
| 1014 | <span class="n">collection</span><span class="o">.</span><span class="n">_sa_linker</span><span class="p">(</span><span class="kc">None</span><span class="p">)</span> | |
| 1015 | ||
| 1016 | <span class="k">def</span> <span class="nf">_init_append_token</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 1017 | <span class="bp">self</span><span class="o">.</span><span class="n">_append_token</span> <span class="o">=</span> <span class="n">Event</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">OP_APPEND</span><span class="p">)</span> | |
| 1018 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">_append_token</span> | |
| 1019 | ||
| 1020 | <span class="k">def</span> <span class="nf">_init_remove_token</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 1021 | <span class="bp">self</span><span class="o">.</span><span class="n">_remove_token</span> <span class="o">=</span> <span class="n">Event</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">OP_REMOVE</span><span class="p">)</span> | |
| 1022 | <span class="k">return</span> <span class="bp">self</span><span class="o">.</span><span class="n">_remove_token</span> | |
| 1023 | ||
| 1024 | <span class="k">def</span> <span class="nf">__copy</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">item</span><span class="p">):</span> | |
| 1025 | <span class="k">return</span> <span class="p">[</span><span class="n">y</span> <span class="k">for</span> <span class="n">y</span> <span class="ow">in</span> <span class="n">collections</span><span class="o">.</span><span class="n">collection_adapter</span><span class="p">(</span><span class="n">item</span><span class="p">)]</span> | |
| 1026 | ||
| 1027 | <span class="k">def</span> <span class="nf">get_history</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 1028 | <span class="n">current</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">passive</span><span class="p">)</span> | |
| 1029 | <span class="k">if</span> <span class="n">current</span> <span class="ow">is</span> <span class="n">PASSIVE_NO_RESULT</span><span class="p">:</span> | |
| 1030 | <span class="k">return</span> <span class="n">HISTORY_BLANK</span> | |
| 1031 | <span class="k">else</span><span class="p">:</span> | |
| 1032 | <span class="k">return</span> <span class="n">History</span><span class="o">.</span><span class="n">from_collection</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">current</span><span class="p">)</span> | |
| 1033 | ||
| 1034 | <span class="k">def</span> <span class="nf">get_all_pending</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_NO_INITIALIZE</span><span class="p">):</span> | |
| 1035 | <span class="c1"># NOTE: passive is ignored here at the moment</span> | |
| 1036 | ||
| 1037 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="ow">not</span> <span class="ow">in</span> <span class="n">dict_</span><span class="p">:</span> | |
| 1038 | <span class="k">return</span> <span class="p">[]</span> | |
| 1039 | ||
| 1040 | <span class="n">current</span> <span class="o">=</span> <span class="n">dict_</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> | |
| 1041 | <span class="n">current</span> <span class="o">=</span> <span class="nb">getattr</span><span class="p">(</span><span class="n">current</span><span class="p">,</span> <span class="s1">'_sa_adapter'</span><span class="p">)</span> | |
| 1042 | ||
| 1043 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="ow">in</span> <span class="n">state</span><span class="o">.</span><span class="n">committed_state</span><span class="p">:</span> | |
| 1044 | <span class="n">original</span> <span class="o">=</span> <span class="n">state</span><span class="o">.</span><span class="n">committed_state</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> | |
| 1045 | <span class="k">if</span> <span class="n">original</span> <span class="ow">not</span> <span class="ow">in</span> <span class="p">(</span><span class="n">NO_VALUE</span><span class="p">,</span> <span class="n">NEVER_SET</span><span class="p">):</span> | |
| 1046 | <span class="n">current_states</span> <span class="o">=</span> <span class="p">[((</span><span class="n">c</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span><span class="p">)</span> <span class="ow">and</span> | |
| 1047 | <span class="n">instance_state</span><span class="p">(</span><span class="n">c</span><span class="p">)</span> <span class="ow">or</span> <span class="kc">None</span><span class="p">,</span> <span class="n">c</span><span class="p">)</span> | |
| 1048 | <span class="k">for</span> <span class="n">c</span> <span class="ow">in</span> <span class="n">current</span><span class="p">]</span> | |
| 1049 | <span class="n">original_states</span> <span class="o">=</span> <span class="p">[((</span><span class="n">c</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span><span class="p">)</span> <span class="ow">and</span> | |
| 1050 | <span class="n">instance_state</span><span class="p">(</span><span class="n">c</span><span class="p">)</span> <span class="ow">or</span> <span class="kc">None</span><span class="p">,</span> <span class="n">c</span><span class="p">)</span> | |
| 1051 | <span class="k">for</span> <span class="n">c</span> <span class="ow">in</span> <span class="n">original</span><span class="p">]</span> | |
| 1052 | ||
| 1053 | <span class="n">current_set</span> <span class="o">=</span> <span class="nb">dict</span><span class="p">(</span><span class="n">current_states</span><span class="p">)</span> | |
| 1054 | <span class="n">original_set</span> <span class="o">=</span> <span class="nb">dict</span><span class="p">(</span><span class="n">original_states</span><span class="p">)</span> | |
| 1055 | ||
| 1056 | <span class="k">return</span> \ | |
| 1057 | <span class="p">[(</span><span class="n">s</span><span class="p">,</span> <span class="n">o</span><span class="p">)</span> <span class="k">for</span> <span class="n">s</span><span class="p">,</span> <span class="n">o</span> <span class="ow">in</span> <span class="n">current_states</span> | |
| 1058 | <span class="k">if</span> <span class="n">s</span> <span class="ow">not</span> <span class="ow">in</span> <span class="n">original_set</span><span class="p">]</span> <span class="o">+</span> \ | |
| 1059 | <span class="p">[(</span><span class="n">s</span><span class="p">,</span> <span class="n">o</span><span class="p">)</span> <span class="k">for</span> <span class="n">s</span><span class="p">,</span> <span class="n">o</span> <span class="ow">in</span> <span class="n">current_states</span> | |
| 1060 | <span class="k">if</span> <span class="n">s</span> <span class="ow">in</span> <span class="n">original_set</span><span class="p">]</span> <span class="o">+</span> \ | |
| 1061 | <span class="p">[(</span><span class="n">s</span><span class="p">,</span> <span class="n">o</span><span class="p">)</span> <span class="k">for</span> <span class="n">s</span><span class="p">,</span> <span class="n">o</span> <span class="ow">in</span> <span class="n">original_states</span> | |
| 1062 | <span class="k">if</span> <span class="n">s</span> <span class="ow">not</span> <span class="ow">in</span> <span class="n">current_set</span><span class="p">]</span> | |
| 1063 | ||
| 1064 | <span class="k">return</span> <span class="p">[(</span><span class="n">instance_state</span><span class="p">(</span><span class="n">o</span><span class="p">),</span> <span class="n">o</span><span class="p">)</span> <span class="k">for</span> <span class="n">o</span> <span class="ow">in</span> <span class="n">current</span><span class="p">]</span> | |
| 1065 | ||
| 1066 | <span class="k">def</span> <span class="nf">fire_append_event</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">):</span> | |
| 1067 | <span class="k">for</span> <span class="n">fn</span> <span class="ow">in</span> <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">append</span><span class="p">:</span> | |
| 1068 | <span class="n">value</span> <span class="o">=</span> <span class="n">fn</span><span class="p">(</span> | |
| 1069 | <span class="n">state</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> | |
| 1070 | <span class="n">initiator</span> <span class="ow">or</span> <span class="bp">self</span><span class="o">.</span><span class="n">_append_token</span> <span class="ow">or</span> <span class="bp">self</span><span class="o">.</span><span class="n">_init_append_token</span><span class="p">())</span> | |
| 1071 | ||
| 1072 | <span class="n">state</span><span class="o">.</span><span class="n">_modified_event</span><span class="p">(</span><span class="n">dict_</span><span class="p">,</span> <span class="bp">self</span><span class="p">,</span> <span class="n">NEVER_SET</span><span class="p">,</span> <span class="kc">True</span><span class="p">)</span> | |
| 1073 | ||
| 1074 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">trackparent</span> <span class="ow">and</span> <span class="n">value</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span><span class="p">:</span> | |
| 1075 | <span class="bp">self</span><span class="o">.</span><span class="n">sethasparent</span><span class="p">(</span><span class="n">instance_state</span><span class="p">(</span><span class="n">value</span><span class="p">),</span> <span class="n">state</span><span class="p">,</span> <span class="kc">True</span><span class="p">)</span> | |
| 1076 | ||
| 1077 | <span class="k">return</span> <span class="n">value</span> | |
| 1078 | ||
| 1079 | <span class="k">def</span> <span class="nf">fire_pre_remove_event</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">initiator</span><span class="p">):</span> | |
| 1080 | <span class="n">state</span><span class="o">.</span><span class="n">_modified_event</span><span class="p">(</span><span class="n">dict_</span><span class="p">,</span> <span class="bp">self</span><span class="p">,</span> <span class="n">NEVER_SET</span><span class="p">,</span> <span class="kc">True</span><span class="p">)</span> | |
| 1081 | ||
| 1082 | <span class="k">def</span> <span class="nf">fire_remove_event</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">):</span> | |
| 1083 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">trackparent</span> <span class="ow">and</span> <span class="n">value</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span><span class="p">:</span> | |
| 1084 | <span class="bp">self</span><span class="o">.</span><span class="n">sethasparent</span><span class="p">(</span><span class="n">instance_state</span><span class="p">(</span><span class="n">value</span><span class="p">),</span> <span class="n">state</span><span class="p">,</span> <span class="kc">False</span><span class="p">)</span> | |
| 1085 | ||
| 1086 | <span class="k">for</span> <span class="n">fn</span> <span class="ow">in</span> <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">remove</span><span class="p">:</span> | |
| 1087 | <span class="n">fn</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> | |
| 1088 | <span class="n">initiator</span> <span class="ow">or</span> <span class="bp">self</span><span class="o">.</span><span class="n">_remove_token</span> <span class="ow">or</span> <span class="bp">self</span><span class="o">.</span><span class="n">_init_remove_token</span><span class="p">())</span> | |
| 1089 | ||
| 1090 | <span class="n">state</span><span class="o">.</span><span class="n">_modified_event</span><span class="p">(</span><span class="n">dict_</span><span class="p">,</span> <span class="bp">self</span><span class="p">,</span> <span class="n">NEVER_SET</span><span class="p">,</span> <span class="kc">True</span><span class="p">)</span> | |
| 1091 | ||
| 1092 | <span class="k">def</span> <span class="nf">delete</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">):</span> | |
| 1093 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="ow">not</span> <span class="ow">in</span> <span class="n">dict_</span><span class="p">:</span> | |
| 1094 | <span class="k">return</span> | |
| 1095 | ||
| 1096 | <span class="n">state</span><span class="o">.</span><span class="n">_modified_event</span><span class="p">(</span><span class="n">dict_</span><span class="p">,</span> <span class="bp">self</span><span class="p">,</span> <span class="n">NEVER_SET</span><span class="p">,</span> <span class="kc">True</span><span class="p">)</span> | |
| 1097 | ||
| 1098 | <span class="n">collection</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">get_collection</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">state</span><span class="o">.</span><span class="n">dict</span><span class="p">)</span> | |
| 1099 | <span class="n">collection</span><span class="o">.</span><span class="n">clear_with_event</span><span class="p">()</span> | |
| 1100 | <span class="c1"># TODO: catch key errors, convert to attributeerror?</span> | |
| 1101 | <span class="k">del</span> <span class="n">dict_</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> | |
| 1102 | ||
| 1103 | <span class="k">def</span> <span class="nf">initialize</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">):</span> | |
| 1104 | <span class="sd">"""Initialize this attribute with an empty collection."""</span> | |
| 1105 | ||
| 1106 | <span class="n">_</span><span class="p">,</span> <span class="n">user_data</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">_initialize_collection</span><span class="p">(</span><span class="n">state</span><span class="p">)</span> | |
| 1107 | <span class="n">dict_</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> <span class="o">=</span> <span class="n">user_data</span> | |
| 1108 | <span class="k">return</span> <span class="n">user_data</span> | |
| 1109 | ||
| 1110 | <span class="k">def</span> <span class="nf">_initialize_collection</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">):</span> | |
| 1111 | ||
| 1112 | <span class="n">adapter</span><span class="p">,</span> <span class="n">collection</span> <span class="o">=</span> <span class="n">state</span><span class="o">.</span><span class="n">manager</span><span class="o">.</span><span class="n">initialize_collection</span><span class="p">(</span> | |
| 1113 | <span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="bp">self</span><span class="o">.</span><span class="n">collection_factory</span><span class="p">)</span> | |
| 1114 | ||
| 1115 | <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">init_collection</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">collection</span><span class="p">,</span> <span class="n">adapter</span><span class="p">)</span> | |
| 1116 | ||
| 1117 | <span class="k">return</span> <span class="n">adapter</span><span class="p">,</span> <span class="n">collection</span> | |
| 1118 | ||
| 1119 | <span class="k">def</span> <span class="nf">append</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 1120 | <span class="n">collection</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">get_collection</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">passive</span><span class="p">)</span> | |
| 1121 | <span class="k">if</span> <span class="n">collection</span> <span class="ow">is</span> <span class="n">PASSIVE_NO_RESULT</span><span class="p">:</span> | |
| 1122 | <span class="n">value</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">fire_append_event</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">)</span> | |
| 1123 | <span class="k">assert</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="ow">not</span> <span class="ow">in</span> <span class="n">dict_</span><span class="p">,</span> \ | |
| 1124 | <span class="s2">"Collection was loaded during event handling."</span> | |
| 1125 | <span class="n">state</span><span class="o">.</span><span class="n">_get_pending_mutation</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">)</span><span class="o">.</span><span class="n">append</span><span class="p">(</span><span class="n">value</span><span class="p">)</span> | |
| 1126 | <span class="k">else</span><span class="p">:</span> | |
| 1127 | <span class="n">collection</span><span class="o">.</span><span class="n">append_with_event</span><span class="p">(</span><span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">)</span> | |
| 1128 | ||
| 1129 | <span class="k">def</span> <span class="nf">remove</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 1130 | <span class="n">collection</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">get_collection</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">state</span><span class="o">.</span><span class="n">dict</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">passive</span><span class="p">)</span> | |
| 1131 | <span class="k">if</span> <span class="n">collection</span> <span class="ow">is</span> <span class="n">PASSIVE_NO_RESULT</span><span class="p">:</span> | |
| 1132 | <span class="bp">self</span><span class="o">.</span><span class="n">fire_remove_event</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">)</span> | |
| 1133 | <span class="k">assert</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="ow">not</span> <span class="ow">in</span> <span class="n">dict_</span><span class="p">,</span> \ | |
| 1134 | <span class="s2">"Collection was loaded during event handling."</span> | |
| 1135 | <span class="n">state</span><span class="o">.</span><span class="n">_get_pending_mutation</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">)</span><span class="o">.</span><span class="n">remove</span><span class="p">(</span><span class="n">value</span><span class="p">)</span> | |
| 1136 | <span class="k">else</span><span class="p">:</span> | |
| 1137 | <span class="n">collection</span><span class="o">.</span><span class="n">remove_with_event</span><span class="p">(</span><span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">)</span> | |
| 1138 | ||
| 1139 | <span class="k">def</span> <span class="nf">pop</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 1140 | <span class="k">try</span><span class="p">:</span> | |
| 1141 | <span class="c1"># TODO: better solution here would be to add</span> | |
| 1142 | <span class="c1"># a "popper" role to collections.py to complement</span> | |
| 1143 | <span class="c1"># "remover".</span> | |
| 1144 | <span class="bp">self</span><span class="o">.</span><span class="n">remove</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">passive</span><span class="p">)</span> | |
| 1145 | <span class="k">except</span> <span class="p">(</span><span class="ne">ValueError</span><span class="p">,</span> <span class="ne">KeyError</span><span class="p">,</span> <span class="ne">IndexError</span><span class="p">):</span> | |
| 1146 | <span class="k">pass</span> | |
| 1147 | ||
| 1148 | <span class="k">def</span> <span class="nf">set</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> | |
| 1149 | <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">,</span> <span class="n">pop</span><span class="o">=</span><span class="kc">False</span><span class="p">):</span> | |
| 1150 | <span class="sd">"""Set a value on the given object.</span> | |
| 1151 | ||
| 1152 | <span class="sd"> """</span> | |
| 1153 | ||
| 1154 | <span class="bp">self</span><span class="o">.</span><span class="n">_set_iterable</span><span class="p">(</span> | |
| 1155 | <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> | |
| 1156 | <span class="k">lambda</span> <span class="n">adapter</span><span class="p">,</span> <span class="n">i</span><span class="p">:</span> <span class="n">adapter</span><span class="o">.</span><span class="n">adapt_like_to_iterable</span><span class="p">(</span><span class="n">i</span><span class="p">))</span> | |
| 1157 | ||
| 1158 | <span class="k">def</span> <span class="nf">_set_iterable</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">iterable</span><span class="p">,</span> <span class="n">adapter</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1159 | <span class="sd">"""Set a collection value from an iterable of state-bearers.</span> | |
| 1160 | ||
| 1161 | <span class="sd"> ``adapter`` is an optional callable invoked with a CollectionAdapter</span> | |
| 1162 | <span class="sd"> and the iterable. Should return an iterable of state-bearing</span> | |
| 1163 | <span class="sd"> instances suitable for appending via a CollectionAdapter. Can be used</span> | |
| 1164 | <span class="sd"> for, e.g., adapting an incoming dictionary into an iterator of values</span> | |
| 1165 | <span class="sd"> rather than keys.</span> | |
| 1166 | ||
| 1167 | <span class="sd"> """</span> | |
| 1168 | <span class="c1"># pulling a new collection first so that an adaptation exception does</span> | |
| 1169 | <span class="c1"># not trigger a lazy load of the old collection.</span> | |
| 1170 | <span class="n">new_collection</span><span class="p">,</span> <span class="n">user_data</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">_initialize_collection</span><span class="p">(</span><span class="n">state</span><span class="p">)</span> | |
| 1171 | <span class="k">if</span> <span class="n">adapter</span><span class="p">:</span> | |
| 1172 | <span class="n">new_values</span> <span class="o">=</span> <span class="nb">list</span><span class="p">(</span><span class="n">adapter</span><span class="p">(</span><span class="n">new_collection</span><span class="p">,</span> <span class="n">iterable</span><span class="p">))</span> | |
| 1173 | <span class="k">else</span><span class="p">:</span> | |
| 1174 | <span class="n">new_values</span> <span class="o">=</span> <span class="nb">list</span><span class="p">(</span><span class="n">iterable</span><span class="p">)</span> | |
| 1175 | ||
| 1176 | <span class="n">old</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_ONLY_PERSISTENT</span><span class="p">)</span> | |
| 1177 | <span class="k">if</span> <span class="n">old</span> <span class="ow">is</span> <span class="n">PASSIVE_NO_RESULT</span><span class="p">:</span> | |
| 1178 | <span class="n">old</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">initialize</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">)</span> | |
| 1179 | <span class="k">elif</span> <span class="n">old</span> <span class="ow">is</span> <span class="n">iterable</span><span class="p">:</span> | |
| 1180 | <span class="c1"># ignore re-assignment of the current collection, as happens</span> | |
| 1181 | <span class="c1"># implicitly with in-place operators (foo.collection |= other)</span> | |
| 1182 | <span class="k">return</span> | |
| 1183 | ||
| 1184 | <span class="c1"># place a copy of "old" in state.committed_state</span> | |
| 1185 | <span class="n">state</span><span class="o">.</span><span class="n">_modified_event</span><span class="p">(</span><span class="n">dict_</span><span class="p">,</span> <span class="bp">self</span><span class="p">,</span> <span class="n">old</span><span class="p">,</span> <span class="kc">True</span><span class="p">)</span> | |
| 1186 | ||
| 1187 | <span class="n">old_collection</span> <span class="o">=</span> <span class="n">old</span><span class="o">.</span><span class="n">_sa_adapter</span> | |
| 1188 | ||
| 1189 | <span class="n">dict_</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> <span class="o">=</span> <span class="n">user_data</span> | |
| 1190 | ||
| 1191 | <span class="n">collections</span><span class="o">.</span><span class="n">bulk_replace</span><span class="p">(</span><span class="n">new_values</span><span class="p">,</span> <span class="n">old_collection</span><span class="p">,</span> <span class="n">new_collection</span><span class="p">)</span> | |
| 1192 | ||
| 1193 | <span class="k">del</span> <span class="n">old</span><span class="o">.</span><span class="n">_sa_adapter</span> | |
| 1194 | <span class="bp">self</span><span class="o">.</span><span class="n">dispatch</span><span class="o">.</span><span class="n">dispose_collection</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">old</span><span class="p">,</span> <span class="n">old_collection</span><span class="p">)</span> | |
| 1195 | ||
| 1196 | <span class="k">def</span> <span class="nf">_invalidate_collection</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">collection</span><span class="p">):</span> | |
| 1197 | <span class="n">adapter</span> <span class="o">=</span> <span class="nb">getattr</span><span class="p">(</span><span class="n">collection</span><span class="p">,</span> <span class="s1">'_sa_adapter'</span><span class="p">)</span> | |
| 1198 | <span class="n">adapter</span><span class="o">.</span><span class="n">invalidated</span> <span class="o">=</span> <span class="kc">True</span> | |
| 1199 | ||
| 1200 | <span class="k">def</span> <span class="nf">set_committed_value</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">):</span> | |
| 1201 | <span class="sd">"""Set an attribute value on the given instance and 'commit' it."""</span> | |
| 1202 | ||
| 1203 | <span class="n">collection</span><span class="p">,</span> <span class="n">user_data</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">_initialize_collection</span><span class="p">(</span><span class="n">state</span><span class="p">)</span> | |
| 1204 | ||
| 1205 | <span class="k">if</span> <span class="n">value</span><span class="p">:</span> | |
| 1206 | <span class="n">collection</span><span class="o">.</span><span class="n">append_multiple_without_event</span><span class="p">(</span><span class="n">value</span><span class="p">)</span> | |
| 1207 | ||
| 1208 | <span class="n">state</span><span class="o">.</span><span class="n">dict</span><span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">]</span> <span class="o">=</span> <span class="n">user_data</span> | |
| 1209 | ||
| 1210 | <span class="n">state</span><span class="o">.</span><span class="n">_commit</span><span class="p">(</span><span class="n">dict_</span><span class="p">,</span> <span class="p">[</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">])</span> | |
| 1211 | ||
| 1212 | <span class="k">if</span> <span class="bp">self</span><span class="o">.</span><span class="n">key</span> <span class="ow">in</span> <span class="n">state</span><span class="o">.</span><span class="n">_pending_mutations</span><span class="p">:</span> | |
| 1213 | <span class="c1"># pending items exist. issue a modified event,</span> | |
| 1214 | <span class="c1"># add/remove new items.</span> | |
| 1215 | <span class="n">state</span><span class="o">.</span><span class="n">_modified_event</span><span class="p">(</span><span class="n">dict_</span><span class="p">,</span> <span class="bp">self</span><span class="p">,</span> <span class="n">user_data</span><span class="p">,</span> <span class="kc">True</span><span class="p">)</span> | |
| 1216 | ||
| 1217 | <span class="n">pending</span> <span class="o">=</span> <span class="n">state</span><span class="o">.</span><span class="n">_pending_mutations</span><span class="o">.</span><span class="n">pop</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">key</span><span class="p">)</span> | |
| 1218 | <span class="n">added</span> <span class="o">=</span> <span class="n">pending</span><span class="o">.</span><span class="n">added_items</span> | |
| 1219 | <span class="n">removed</span> <span class="o">=</span> <span class="n">pending</span><span class="o">.</span><span class="n">deleted_items</span> | |
| 1220 | <span class="k">for</span> <span class="n">item</span> <span class="ow">in</span> <span class="n">added</span><span class="p">:</span> | |
| 1221 | <span class="n">collection</span><span class="o">.</span><span class="n">append_without_event</span><span class="p">(</span><span class="n">item</span><span class="p">)</span> | |
| 1222 | <span class="k">for</span> <span class="n">item</span> <span class="ow">in</span> <span class="n">removed</span><span class="p">:</span> | |
| 1223 | <span class="n">collection</span><span class="o">.</span><span class="n">remove_without_event</span><span class="p">(</span><span class="n">item</span><span class="p">)</span> | |
| 1224 | ||
| 1225 | <span class="k">return</span> <span class="n">user_data</span> | |
| 1226 | ||
| 1227 | <span class="k">def</span> <span class="nf">get_collection</span><span class="p">(</span><span class="bp">self</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> | |
| 1228 | <span class="n">user_data</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 1229 | <span class="sd">"""Retrieve the CollectionAdapter associated with the given state.</span> | |
| 1230 | ||
| 1231 | <span class="sd"> Creates a new CollectionAdapter if one does not exist.</span> | |
| 1232 | ||
| 1233 | <span class="sd"> """</span> | |
| 1234 | <span class="k">if</span> <span class="n">user_data</span> <span class="ow">is</span> <span class="kc">None</span><span class="p">:</span> | |
| 1235 | <span class="n">user_data</span> <span class="o">=</span> <span class="bp">self</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">passive</span><span class="p">)</span> | |
| 1236 | <span class="k">if</span> <span class="n">user_data</span> <span class="ow">is</span> <span class="n">PASSIVE_NO_RESULT</span><span class="p">:</span> | |
| 1237 | <span class="k">return</span> <span class="n">user_data</span> | |
| 1238 | ||
| 1239 | <span class="k">return</span> <span class="nb">getattr</span><span class="p">(</span><span class="n">user_data</span><span class="p">,</span> <span class="s1">'_sa_adapter'</span><span class="p">)</span> | |
| 1240 | ||
| 1241 | ||
| 1242 | <span class="k">def</span> <span class="nf">backref_listeners</span><span class="p">(</span><span class="n">attribute</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">uselist</span><span class="p">):</span> | |
| 1243 | <span class="sd">"""Apply listeners to synchronize a two-way relationship."""</span> | |
| 1244 | ||
| 1245 | <span class="c1"># use easily recognizable names for stack traces</span> | |
| 1246 | ||
| 1247 | <span class="n">parent_token</span> <span class="o">=</span> <span class="n">attribute</span><span class="o">.</span><span class="n">impl</span><span class="o">.</span><span class="n">parent_token</span> | |
| 1248 | <span class="n">parent_impl</span> <span class="o">=</span> <span class="n">attribute</span><span class="o">.</span><span class="n">impl</span> | |
| 1249 | ||
| 1250 | <span class="k">def</span> <span class="nf">_acceptable_key_err</span><span class="p">(</span><span class="n">child_state</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> <span class="n">child_impl</span><span class="p">):</span> | |
| 1251 | <span class="k">raise</span> <span class="ne">ValueError</span><span class="p">(</span> | |
| 1252 | <span class="s2">"Bidirectional attribute conflict detected: "</span> | |
| 1253 | <span class="s1">'Passing object </span><span class="si">%s</span><span class="s1"> to attribute "</span><span class="si">%s</span><span class="s1">" '</span> | |
| 1254 | <span class="s1">'triggers a modify event on attribute "</span><span class="si">%s</span><span class="s1">" '</span> | |
| 1255 | <span class="s1">'via the backref "</span><span class="si">%s</span><span class="s1">".'</span> <span class="o">%</span> <span class="p">(</span> | |
| 1256 | <span class="n">state_str</span><span class="p">(</span><span class="n">child_state</span><span class="p">),</span> | |
| 1257 | <span class="n">initiator</span><span class="o">.</span><span class="n">parent_token</span><span class="p">,</span> | |
| 1258 | <span class="n">child_impl</span><span class="o">.</span><span class="n">parent_token</span><span class="p">,</span> | |
| 1259 | <span class="n">attribute</span><span class="o">.</span><span class="n">impl</span><span class="o">.</span><span class="n">parent_token</span> | |
| 1260 | <span class="p">)</span> | |
| 1261 | <span class="p">)</span> | |
| 1262 | ||
| 1263 | <span class="k">def</span> <span class="nf">emit_backref_from_scalar_set_event</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">child</span><span class="p">,</span> <span class="n">oldchild</span><span class="p">,</span> <span class="n">initiator</span><span class="p">):</span> | |
| 1264 | <span class="k">if</span> <span class="n">oldchild</span> <span class="ow">is</span> <span class="n">child</span><span class="p">:</span> | |
| 1265 | <span class="k">return</span> <span class="n">child</span> | |
| 1266 | <span class="k">if</span> <span class="n">oldchild</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span> <span class="ow">and</span> \ | |
| 1267 | <span class="n">oldchild</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">PASSIVE_NO_RESULT</span> <span class="ow">and</span> \ | |
| 1268 | <span class="n">oldchild</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">NEVER_SET</span><span class="p">:</span> | |
| 1269 | <span class="c1"># With lazy=None, there's no guarantee that the full collection is</span> | |
| 1270 | <span class="c1"># present when updating via a backref.</span> | |
| 1271 | <span class="n">old_state</span><span class="p">,</span> <span class="n">old_dict</span> <span class="o">=</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">oldchild</span><span class="p">),</span>\ | |
| 1272 | <span class="n">instance_dict</span><span class="p">(</span><span class="n">oldchild</span><span class="p">)</span> | |
| 1273 | <span class="n">impl</span> <span class="o">=</span> <span class="n">old_state</span><span class="o">.</span><span class="n">manager</span><span class="p">[</span><span class="n">key</span><span class="p">]</span><span class="o">.</span><span class="n">impl</span> | |
| 1274 | ||
| 1275 | <span class="k">if</span> <span class="n">initiator</span><span class="o">.</span><span class="n">impl</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">impl</span> <span class="ow">or</span> \ | |
| 1276 | <span class="n">initiator</span><span class="o">.</span><span class="n">op</span> <span class="ow">not</span> <span class="ow">in</span> <span class="p">(</span><span class="n">OP_REPLACE</span><span class="p">,</span> <span class="n">OP_REMOVE</span><span class="p">):</span> | |
| 1277 | <span class="n">impl</span><span class="o">.</span><span class="n">pop</span><span class="p">(</span><span class="n">old_state</span><span class="p">,</span> | |
| 1278 | <span class="n">old_dict</span><span class="p">,</span> | |
| 1279 | <span class="n">state</span><span class="o">.</span><span class="n">obj</span><span class="p">(),</span> | |
| 1280 | <span class="n">parent_impl</span><span class="o">.</span><span class="n">_append_token</span> <span class="ow">or</span> | |
| 1281 | <span class="n">parent_impl</span><span class="o">.</span><span class="n">_init_append_token</span><span class="p">(),</span> | |
| 1282 | <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_NO_FETCH</span><span class="p">)</span> | |
| 1283 | ||
| 1284 | <span class="k">if</span> <span class="n">child</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span><span class="p">:</span> | |
| 1285 | <span class="n">child_state</span><span class="p">,</span> <span class="n">child_dict</span> <span class="o">=</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">child</span><span class="p">),</span>\ | |
| 1286 | <span class="n">instance_dict</span><span class="p">(</span><span class="n">child</span><span class="p">)</span> | |
| 1287 | <span class="n">child_impl</span> <span class="o">=</span> <span class="n">child_state</span><span class="o">.</span><span class="n">manager</span><span class="p">[</span><span class="n">key</span><span class="p">]</span><span class="o">.</span><span class="n">impl</span> | |
| 1288 | <span class="k">if</span> <span class="n">initiator</span><span class="o">.</span><span class="n">parent_token</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">parent_token</span> <span class="ow">and</span> \ | |
| 1289 | <span class="n">initiator</span><span class="o">.</span><span class="n">parent_token</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">child_impl</span><span class="o">.</span><span class="n">parent_token</span><span class="p">:</span> | |
| 1290 | <span class="n">_acceptable_key_err</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> <span class="n">child_impl</span><span class="p">)</span> | |
| 1291 | <span class="k">elif</span> <span class="n">initiator</span><span class="o">.</span><span class="n">impl</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">child_impl</span> <span class="ow">or</span> \ | |
| 1292 | <span class="n">initiator</span><span class="o">.</span><span class="n">op</span> <span class="ow">not</span> <span class="ow">in</span> <span class="p">(</span><span class="n">OP_APPEND</span><span class="p">,</span> <span class="n">OP_REPLACE</span><span class="p">):</span> | |
| 1293 | <span class="n">child_impl</span><span class="o">.</span><span class="n">append</span><span class="p">(</span> | |
| 1294 | <span class="n">child_state</span><span class="p">,</span> | |
| 1295 | <span class="n">child_dict</span><span class="p">,</span> | |
| 1296 | <span class="n">state</span><span class="o">.</span><span class="n">obj</span><span class="p">(),</span> | |
| 1297 | <span class="n">initiator</span><span class="p">,</span> | |
| 1298 | <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_NO_FETCH</span><span class="p">)</span> | |
| 1299 | <span class="k">return</span> <span class="n">child</span> | |
| 1300 | ||
| 1301 | <span class="k">def</span> <span class="nf">emit_backref_from_collection_append_event</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">child</span><span class="p">,</span> <span class="n">initiator</span><span class="p">):</span> | |
| 1302 | <span class="k">if</span> <span class="n">child</span> <span class="ow">is</span> <span class="kc">None</span><span class="p">:</span> | |
| 1303 | <span class="k">return</span> | |
| 1304 | ||
| 1305 | <span class="n">child_state</span><span class="p">,</span> <span class="n">child_dict</span> <span class="o">=</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">child</span><span class="p">),</span> \ | |
| 1306 | <span class="n">instance_dict</span><span class="p">(</span><span class="n">child</span><span class="p">)</span> | |
| 1307 | <span class="n">child_impl</span> <span class="o">=</span> <span class="n">child_state</span><span class="o">.</span><span class="n">manager</span><span class="p">[</span><span class="n">key</span><span class="p">]</span><span class="o">.</span><span class="n">impl</span> | |
| 1308 | ||
| 1309 | <span class="k">if</span> <span class="n">initiator</span><span class="o">.</span><span class="n">parent_token</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">parent_token</span> <span class="ow">and</span> \ | |
| 1310 | <span class="n">initiator</span><span class="o">.</span><span class="n">parent_token</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">child_impl</span><span class="o">.</span><span class="n">parent_token</span><span class="p">:</span> | |
| 1311 | <span class="n">_acceptable_key_err</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">initiator</span><span class="p">,</span> <span class="n">child_impl</span><span class="p">)</span> | |
| 1312 | <span class="k">elif</span> <span class="n">initiator</span><span class="o">.</span><span class="n">impl</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">child_impl</span> <span class="ow">or</span> \ | |
| 1313 | <span class="n">initiator</span><span class="o">.</span><span class="n">op</span> <span class="ow">not</span> <span class="ow">in</span> <span class="p">(</span><span class="n">OP_APPEND</span><span class="p">,</span> <span class="n">OP_REPLACE</span><span class="p">):</span> | |
| 1314 | <span class="n">child_impl</span><span class="o">.</span><span class="n">append</span><span class="p">(</span> | |
| 1315 | <span class="n">child_state</span><span class="p">,</span> | |
| 1316 | <span class="n">child_dict</span><span class="p">,</span> | |
| 1317 | <span class="n">state</span><span class="o">.</span><span class="n">obj</span><span class="p">(),</span> | |
| 1318 | <span class="n">initiator</span><span class="p">,</span> | |
| 1319 | <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_NO_FETCH</span><span class="p">)</span> | |
| 1320 | <span class="k">return</span> <span class="n">child</span> | |
| 1321 | ||
| 1322 | <span class="k">def</span> <span class="nf">emit_backref_from_collection_remove_event</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">child</span><span class="p">,</span> <span class="n">initiator</span><span class="p">):</span> | |
| 1323 | <span class="k">if</span> <span class="n">child</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span><span class="p">:</span> | |
| 1324 | <span class="n">child_state</span><span class="p">,</span> <span class="n">child_dict</span> <span class="o">=</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">child</span><span class="p">),</span>\ | |
| 1325 | <span class="n">instance_dict</span><span class="p">(</span><span class="n">child</span><span class="p">)</span> | |
| 1326 | <span class="n">child_impl</span> <span class="o">=</span> <span class="n">child_state</span><span class="o">.</span><span class="n">manager</span><span class="p">[</span><span class="n">key</span><span class="p">]</span><span class="o">.</span><span class="n">impl</span> | |
| 1327 | <span class="k">if</span> <span class="n">initiator</span><span class="o">.</span><span class="n">impl</span> <span class="ow">is</span> <span class="ow">not</span> <span class="n">child_impl</span> <span class="ow">or</span> \ | |
| 1328 | <span class="n">initiator</span><span class="o">.</span><span class="n">op</span> <span class="ow">not</span> <span class="ow">in</span> <span class="p">(</span><span class="n">OP_REMOVE</span><span class="p">,</span> <span class="n">OP_REPLACE</span><span class="p">):</span> | |
| 1329 | <span class="n">child_impl</span><span class="o">.</span><span class="n">pop</span><span class="p">(</span> | |
| 1330 | <span class="n">child_state</span><span class="p">,</span> | |
| 1331 | <span class="n">child_dict</span><span class="p">,</span> | |
| 1332 | <span class="n">state</span><span class="o">.</span><span class="n">obj</span><span class="p">(),</span> | |
| 1333 | <span class="n">initiator</span><span class="p">,</span> | |
| 1334 | <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_NO_FETCH</span><span class="p">)</span> | |
| 1335 | ||
| 1336 | <span class="k">if</span> <span class="n">uselist</span><span class="p">:</span> | |
| 1337 | <span class="n">event</span><span class="o">.</span><span class="n">listen</span><span class="p">(</span><span class="n">attribute</span><span class="p">,</span> <span class="s2">"append"</span><span class="p">,</span> | |
| 1338 | <span class="n">emit_backref_from_collection_append_event</span><span class="p">,</span> | |
| 1339 | <span class="n">retval</span><span class="o">=</span><span class="kc">True</span><span class="p">,</span> <span class="n">raw</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 1340 | <span class="k">else</span><span class="p">:</span> | |
| 1341 | <span class="n">event</span><span class="o">.</span><span class="n">listen</span><span class="p">(</span><span class="n">attribute</span><span class="p">,</span> <span class="s2">"set"</span><span class="p">,</span> | |
| 1342 | <span class="n">emit_backref_from_scalar_set_event</span><span class="p">,</span> | |
| 1343 | <span class="n">retval</span><span class="o">=</span><span class="kc">True</span><span class="p">,</span> <span class="n">raw</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 1344 | <span class="c1"># TODO: need coverage in test/orm/ of remove event</span> | |
| 1345 | <span class="n">event</span><span class="o">.</span><span class="n">listen</span><span class="p">(</span><span class="n">attribute</span><span class="p">,</span> <span class="s2">"remove"</span><span class="p">,</span> | |
| 1346 | <span class="n">emit_backref_from_collection_remove_event</span><span class="p">,</span> | |
| 1347 | <span class="n">retval</span><span class="o">=</span><span class="kc">True</span><span class="p">,</span> <span class="n">raw</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 1348 | ||
| 1349 | <span class="n">_NO_HISTORY</span> <span class="o">=</span> <span class="n">util</span><span class="o">.</span><span class="n">symbol</span><span class="p">(</span><span class="s1">'NO_HISTORY'</span><span class="p">)</span> | |
| 1350 | <span class="n">_NO_STATE_SYMBOLS</span> <span class="o">=</span> <span class="nb">frozenset</span><span class="p">([</span> | |
| 1351 | <span class="nb">id</span><span class="p">(</span><span class="n">PASSIVE_NO_RESULT</span><span class="p">),</span> | |
| 1352 | <span class="nb">id</span><span class="p">(</span><span class="n">NO_VALUE</span><span class="p">),</span> | |
| 1353 | <span class="nb">id</span><span class="p">(</span><span class="n">NEVER_SET</span><span class="p">)])</span> | |
| 1354 | ||
| 1355 | <span class="n">History</span> <span class="o">=</span> <span class="n">util</span><span class="o">.</span><span class="n">namedtuple</span><span class="p">(</span><span class="s2">"History"</span><span class="p">,</span> <span class="p">[</span> | |
| 1356 | <span class="s2">"added"</span><span class="p">,</span> <span class="s2">"unchanged"</span><span class="p">,</span> <span class="s2">"deleted"</span> | |
| 1357 | <span class="p">])</span> | |
| 1358 | ||
| 1359 | ||
| 1360 | <span class="k">class</span> <span class="nc">History</span><span class="p">(</span><span class="n">History</span><span class="p">):</span> | |
| 1361 | <span class="sd">"""A 3-tuple of added, unchanged and deleted values,</span> | |
| 1362 | <span class="sd"> representing the changes which have occurred on an instrumented</span> | |
| 1363 | <span class="sd"> attribute.</span> | |
| 1364 | ||
| 1365 | <span class="sd"> The easiest way to get a :class:`.History` object for a particular</span> | |
| 1366 | <span class="sd"> attribute on an object is to use the :func:`.inspect` function::</span> | |
| 1367 | ||
| 1368 | <span class="sd"> from sqlalchemy import inspect</span> | |
| 1369 | ||
| 1370 | <span class="sd"> hist = inspect(myobject).attrs.myattribute.history</span> | |
| 1371 | ||
| 1372 | <span class="sd"> Each tuple member is an iterable sequence:</span> | |
| 1373 | ||
| 1374 | <span class="sd"> * ``added`` - the collection of items added to the attribute (the first</span> | |
| 1375 | <span class="sd"> tuple element).</span> | |
| 1376 | ||
| 1377 | <span class="sd"> * ``unchanged`` - the collection of items that have not changed on the</span> | |
| 1378 | <span class="sd"> attribute (the second tuple element).</span> | |
| 1379 | ||
| 1380 | <span class="sd"> * ``deleted`` - the collection of items that have been removed from the</span> | |
| 1381 | <span class="sd"> attribute (the third tuple element).</span> | |
| 1382 | ||
| 1383 | <span class="sd"> """</span> | |
| 1384 | ||
| 1385 | <span class="k">def</span> <span class="nf">__bool__</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 1386 | <span class="k">return</span> <span class="bp">self</span> <span class="o">!=</span> <span class="n">HISTORY_BLANK</span> | |
| 1387 | <span class="n">__nonzero__</span> <span class="o">=</span> <span class="n">__bool__</span> | |
| 1388 | ||
| 1389 | <span class="k">def</span> <span class="nf">empty</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 1390 | <span class="sd">"""Return True if this :class:`.History` has no changes</span> | |
| 1391 | <span class="sd"> and no existing, unchanged state.</span> | |
| 1392 | ||
| 1393 | <span class="sd"> """</span> | |
| 1394 | ||
| 1395 | <span class="k">return</span> <span class="ow">not</span> <span class="nb">bool</span><span class="p">(</span> | |
| 1396 | <span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">added</span> <span class="ow">or</span> <span class="bp">self</span><span class="o">.</span><span class="n">deleted</span><span class="p">)</span> | |
| 1397 | <span class="ow">or</span> <span class="bp">self</span><span class="o">.</span><span class="n">unchanged</span> | |
| 1398 | <span class="p">)</span> | |
| 1399 | ||
| 1400 | <span class="k">def</span> <span class="nf">sum</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 1401 | <span class="sd">"""Return a collection of added + unchanged + deleted."""</span> | |
| 1402 | ||
| 1403 | <span class="k">return</span> <span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">added</span> <span class="ow">or</span> <span class="p">[])</span> <span class="o">+</span>\ | |
| 1404 | <span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">unchanged</span> <span class="ow">or</span> <span class="p">[])</span> <span class="o">+</span>\ | |
| 1405 | <span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">deleted</span> <span class="ow">or</span> <span class="p">[])</span> | |
| 1406 | ||
| 1407 | <span class="k">def</span> <span class="nf">non_deleted</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 1408 | <span class="sd">"""Return a collection of added + unchanged."""</span> | |
| 1409 | ||
| 1410 | <span class="k">return</span> <span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">added</span> <span class="ow">or</span> <span class="p">[])</span> <span class="o">+</span>\ | |
| 1411 | <span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">unchanged</span> <span class="ow">or</span> <span class="p">[])</span> | |
| 1412 | ||
| 1413 | <span class="k">def</span> <span class="nf">non_added</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 1414 | <span class="sd">"""Return a collection of unchanged + deleted."""</span> | |
| 1415 | ||
| 1416 | <span class="k">return</span> <span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">unchanged</span> <span class="ow">or</span> <span class="p">[])</span> <span class="o">+</span>\ | |
| 1417 | <span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">deleted</span> <span class="ow">or</span> <span class="p">[])</span> | |
| 1418 | ||
| 1419 | <span class="k">def</span> <span class="nf">has_changes</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 1420 | <span class="sd">"""Return True if this :class:`.History` has changes."""</span> | |
| 1421 | ||
| 1422 | <span class="k">return</span> <span class="nb">bool</span><span class="p">(</span><span class="bp">self</span><span class="o">.</span><span class="n">added</span> <span class="ow">or</span> <span class="bp">self</span><span class="o">.</span><span class="n">deleted</span><span class="p">)</span> | |
| 1423 | ||
| 1424 | <span class="k">def</span> <span class="nf">as_state</span><span class="p">(</span><span class="bp">self</span><span class="p">):</span> | |
| 1425 | <span class="k">return</span> <span class="n">History</span><span class="p">(</span> | |
| 1426 | <span class="p">[(</span><span class="n">c</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span><span class="p">)</span> | |
| 1427 | <span class="ow">and</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">c</span><span class="p">)</span> <span class="ow">or</span> <span class="kc">None</span> | |
| 1428 | <span class="k">for</span> <span class="n">c</span> <span class="ow">in</span> <span class="bp">self</span><span class="o">.</span><span class="n">added</span><span class="p">],</span> | |
| 1429 | <span class="p">[(</span><span class="n">c</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span><span class="p">)</span> | |
| 1430 | <span class="ow">and</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">c</span><span class="p">)</span> <span class="ow">or</span> <span class="kc">None</span> | |
| 1431 | <span class="k">for</span> <span class="n">c</span> <span class="ow">in</span> <span class="bp">self</span><span class="o">.</span><span class="n">unchanged</span><span class="p">],</span> | |
| 1432 | <span class="p">[(</span><span class="n">c</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span><span class="p">)</span> | |
| 1433 | <span class="ow">and</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">c</span><span class="p">)</span> <span class="ow">or</span> <span class="kc">None</span> | |
| 1434 | <span class="k">for</span> <span class="n">c</span> <span class="ow">in</span> <span class="bp">self</span><span class="o">.</span><span class="n">deleted</span><span class="p">],</span> | |
| 1435 | <span class="p">)</span> | |
| 1436 | ||
| 1437 | <span class="nd">@classmethod</span> | |
| 1438 | <span class="k">def</span> <span class="nf">from_scalar_attribute</span><span class="p">(</span><span class="n">cls</span><span class="p">,</span> <span class="n">attribute</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">current</span><span class="p">):</span> | |
| 1439 | <span class="n">original</span> <span class="o">=</span> <span class="n">state</span><span class="o">.</span><span class="n">committed_state</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">attribute</span><span class="o">.</span><span class="n">key</span><span class="p">,</span> <span class="n">_NO_HISTORY</span><span class="p">)</span> | |
| 1440 | ||
| 1441 | <span class="k">if</span> <span class="n">original</span> <span class="ow">is</span> <span class="n">_NO_HISTORY</span><span class="p">:</span> | |
| 1442 | <span class="k">if</span> <span class="n">current</span> <span class="ow">is</span> <span class="n">NEVER_SET</span><span class="p">:</span> | |
| 1443 | <span class="k">return</span> <span class="n">cls</span><span class="p">((),</span> <span class="p">(),</span> <span class="p">())</span> | |
| 1444 | <span class="k">else</span><span class="p">:</span> | |
| 1445 | <span class="k">return</span> <span class="n">cls</span><span class="p">((),</span> <span class="p">[</span><span class="n">current</span><span class="p">],</span> <span class="p">())</span> | |
| 1446 | <span class="c1"># don't let ClauseElement expressions here trip things up</span> | |
| 1447 | <span class="k">elif</span> <span class="n">attribute</span><span class="o">.</span><span class="n">is_equal</span><span class="p">(</span><span class="n">current</span><span class="p">,</span> <span class="n">original</span><span class="p">)</span> <span class="ow">is</span> <span class="kc">True</span><span class="p">:</span> | |
| 1448 | <span class="k">return</span> <span class="n">cls</span><span class="p">((),</span> <span class="p">[</span><span class="n">current</span><span class="p">],</span> <span class="p">())</span> | |
| 1449 | <span class="k">else</span><span class="p">:</span> | |
| 1450 | <span class="c1"># current convention on native scalars is to not</span> | |
| 1451 | <span class="c1"># include information</span> | |
| 1452 | <span class="c1"># about missing previous value in "deleted", but</span> | |
| 1453 | <span class="c1"># we do include None, which helps in some primary</span> | |
| 1454 | <span class="c1"># key situations</span> | |
| 1455 | <span class="k">if</span> <span class="nb">id</span><span class="p">(</span><span class="n">original</span><span class="p">)</span> <span class="ow">in</span> <span class="n">_NO_STATE_SYMBOLS</span><span class="p">:</span> | |
| 1456 | <span class="n">deleted</span> <span class="o">=</span> <span class="p">()</span> | |
| 1457 | <span class="k">else</span><span class="p">:</span> | |
| 1458 | <span class="n">deleted</span> <span class="o">=</span> <span class="p">[</span><span class="n">original</span><span class="p">]</span> | |
| 1459 | <span class="k">if</span> <span class="n">current</span> <span class="ow">is</span> <span class="n">NEVER_SET</span><span class="p">:</span> | |
| 1460 | <span class="k">return</span> <span class="n">cls</span><span class="p">((),</span> <span class="p">(),</span> <span class="n">deleted</span><span class="p">)</span> | |
| 1461 | <span class="k">else</span><span class="p">:</span> | |
| 1462 | <span class="k">return</span> <span class="n">cls</span><span class="p">([</span><span class="n">current</span><span class="p">],</span> <span class="p">(),</span> <span class="n">deleted</span><span class="p">)</span> | |
| 1463 | ||
| 1464 | <span class="nd">@classmethod</span> | |
| 1465 | <span class="k">def</span> <span class="nf">from_object_attribute</span><span class="p">(</span><span class="n">cls</span><span class="p">,</span> <span class="n">attribute</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">current</span><span class="p">):</span> | |
| 1466 | <span class="n">original</span> <span class="o">=</span> <span class="n">state</span><span class="o">.</span><span class="n">committed_state</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">attribute</span><span class="o">.</span><span class="n">key</span><span class="p">,</span> <span class="n">_NO_HISTORY</span><span class="p">)</span> | |
| 1467 | ||
| 1468 | <span class="k">if</span> <span class="n">original</span> <span class="ow">is</span> <span class="n">_NO_HISTORY</span><span class="p">:</span> | |
| 1469 | <span class="k">if</span> <span class="n">current</span> <span class="ow">is</span> <span class="n">NO_VALUE</span> <span class="ow">or</span> <span class="n">current</span> <span class="ow">is</span> <span class="n">NEVER_SET</span><span class="p">:</span> | |
| 1470 | <span class="k">return</span> <span class="n">cls</span><span class="p">((),</span> <span class="p">(),</span> <span class="p">())</span> | |
| 1471 | <span class="k">else</span><span class="p">:</span> | |
| 1472 | <span class="k">return</span> <span class="n">cls</span><span class="p">((),</span> <span class="p">[</span><span class="n">current</span><span class="p">],</span> <span class="p">())</span> | |
| 1473 | <span class="k">elif</span> <span class="n">current</span> <span class="ow">is</span> <span class="n">original</span><span class="p">:</span> | |
| 1474 | <span class="k">return</span> <span class="n">cls</span><span class="p">((),</span> <span class="p">[</span><span class="n">current</span><span class="p">],</span> <span class="p">())</span> | |
| 1475 | <span class="k">else</span><span class="p">:</span> | |
| 1476 | <span class="c1"># current convention on related objects is to not</span> | |
| 1477 | <span class="c1"># include information</span> | |
| 1478 | <span class="c1"># about missing previous value in "deleted", and</span> | |
| 1479 | <span class="c1"># to also not include None - the dependency.py rules</span> | |
| 1480 | <span class="c1"># ignore the None in any case.</span> | |
| 1481 | <span class="k">if</span> <span class="nb">id</span><span class="p">(</span><span class="n">original</span><span class="p">)</span> <span class="ow">in</span> <span class="n">_NO_STATE_SYMBOLS</span> <span class="ow">or</span> <span class="n">original</span> <span class="ow">is</span> <span class="kc">None</span><span class="p">:</span> | |
| 1482 | <span class="n">deleted</span> <span class="o">=</span> <span class="p">()</span> | |
| 1483 | <span class="k">else</span><span class="p">:</span> | |
| 1484 | <span class="n">deleted</span> <span class="o">=</span> <span class="p">[</span><span class="n">original</span><span class="p">]</span> | |
| 1485 | <span class="k">if</span> <span class="n">current</span> <span class="ow">is</span> <span class="n">NO_VALUE</span> <span class="ow">or</span> <span class="n">current</span> <span class="ow">is</span> <span class="n">NEVER_SET</span><span class="p">:</span> | |
| 1486 | <span class="k">return</span> <span class="n">cls</span><span class="p">((),</span> <span class="p">(),</span> <span class="n">deleted</span><span class="p">)</span> | |
| 1487 | <span class="k">else</span><span class="p">:</span> | |
| 1488 | <span class="k">return</span> <span class="n">cls</span><span class="p">([</span><span class="n">current</span><span class="p">],</span> <span class="p">(),</span> <span class="n">deleted</span><span class="p">)</span> | |
| 1489 | ||
| 1490 | <span class="nd">@classmethod</span> | |
| 1491 | <span class="k">def</span> <span class="nf">from_collection</span><span class="p">(</span><span class="n">cls</span><span class="p">,</span> <span class="n">attribute</span><span class="p">,</span> <span class="n">state</span><span class="p">,</span> <span class="n">current</span><span class="p">):</span> | |
| 1492 | <span class="n">original</span> <span class="o">=</span> <span class="n">state</span><span class="o">.</span><span class="n">committed_state</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">attribute</span><span class="o">.</span><span class="n">key</span><span class="p">,</span> <span class="n">_NO_HISTORY</span><span class="p">)</span> | |
| 1493 | ||
| 1494 | <span class="k">if</span> <span class="n">current</span> <span class="ow">is</span> <span class="n">NO_VALUE</span> <span class="ow">or</span> <span class="n">current</span> <span class="ow">is</span> <span class="n">NEVER_SET</span><span class="p">:</span> | |
| 1495 | <span class="k">return</span> <span class="n">cls</span><span class="p">((),</span> <span class="p">(),</span> <span class="p">())</span> | |
| 1496 | ||
| 1497 | <span class="n">current</span> <span class="o">=</span> <span class="nb">getattr</span><span class="p">(</span><span class="n">current</span><span class="p">,</span> <span class="s1">'_sa_adapter'</span><span class="p">)</span> | |
| 1498 | <span class="k">if</span> <span class="n">original</span> <span class="ow">in</span> <span class="p">(</span><span class="n">NO_VALUE</span><span class="p">,</span> <span class="n">NEVER_SET</span><span class="p">):</span> | |
| 1499 | <span class="k">return</span> <span class="n">cls</span><span class="p">(</span><span class="nb">list</span><span class="p">(</span><span class="n">current</span><span class="p">),</span> <span class="p">(),</span> <span class="p">())</span> | |
| 1500 | <span class="k">elif</span> <span class="n">original</span> <span class="ow">is</span> <span class="n">_NO_HISTORY</span><span class="p">:</span> | |
| 1501 | <span class="k">return</span> <span class="n">cls</span><span class="p">((),</span> <span class="nb">list</span><span class="p">(</span><span class="n">current</span><span class="p">),</span> <span class="p">())</span> | |
| 1502 | <span class="k">else</span><span class="p">:</span> | |
| 1503 | ||
| 1504 | <span class="n">current_states</span> <span class="o">=</span> <span class="p">[((</span><span class="n">c</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span><span class="p">)</span> <span class="ow">and</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">c</span><span class="p">)</span> | |
| 1505 | <span class="ow">or</span> <span class="kc">None</span><span class="p">,</span> <span class="n">c</span><span class="p">)</span> | |
| 1506 | <span class="k">for</span> <span class="n">c</span> <span class="ow">in</span> <span class="n">current</span> | |
| 1507 | <span class="p">]</span> | |
| 1508 | <span class="n">original_states</span> <span class="o">=</span> <span class="p">[((</span><span class="n">c</span> <span class="ow">is</span> <span class="ow">not</span> <span class="kc">None</span><span class="p">)</span> <span class="ow">and</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">c</span><span class="p">)</span> | |
| 1509 | <span class="ow">or</span> <span class="kc">None</span><span class="p">,</span> <span class="n">c</span><span class="p">)</span> | |
| 1510 | <span class="k">for</span> <span class="n">c</span> <span class="ow">in</span> <span class="n">original</span> | |
| 1511 | <span class="p">]</span> | |
| 1512 | ||
| 1513 | <span class="n">current_set</span> <span class="o">=</span> <span class="nb">dict</span><span class="p">(</span><span class="n">current_states</span><span class="p">)</span> | |
| 1514 | <span class="n">original_set</span> <span class="o">=</span> <span class="nb">dict</span><span class="p">(</span><span class="n">original_states</span><span class="p">)</span> | |
| 1515 | ||
| 1516 | <span class="k">return</span> <span class="n">cls</span><span class="p">(</span> | |
| 1517 | <span class="p">[</span><span class="n">o</span> <span class="k">for</span> <span class="n">s</span><span class="p">,</span> <span class="n">o</span> <span class="ow">in</span> <span class="n">current_states</span> <span class="k">if</span> <span class="n">s</span> <span class="ow">not</span> <span class="ow">in</span> <span class="n">original_set</span><span class="p">],</span> | |
| 1518 | <span class="p">[</span><span class="n">o</span> <span class="k">for</span> <span class="n">s</span><span class="p">,</span> <span class="n">o</span> <span class="ow">in</span> <span class="n">current_states</span> <span class="k">if</span> <span class="n">s</span> <span class="ow">in</span> <span class="n">original_set</span><span class="p">],</span> | |
| 1519 | <span class="p">[</span><span class="n">o</span> <span class="k">for</span> <span class="n">s</span><span class="p">,</span> <span class="n">o</span> <span class="ow">in</span> <span class="n">original_states</span> <span class="k">if</span> <span class="n">s</span> <span class="ow">not</span> <span class="ow">in</span> <span class="n">current_set</span><span class="p">]</span> | |
| 1520 | <span class="p">)</span> | |
| 1521 | ||
| 1522 | <span class="n">HISTORY_BLANK</span> <span class="o">=</span> <span class="n">History</span><span class="p">(</span><span class="kc">None</span><span class="p">,</span> <span class="kc">None</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 1523 | ||
| 1524 | ||
| 1525 | <span class="k">def</span> <span class="nf">get_history</span><span class="p">(</span><span class="n">obj</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 1526 | <span class="sd">"""Return a :class:`.History` record for the given object</span> | |
| 1527 | <span class="sd"> and attribute key.</span> | |
| 1528 | ||
| 1529 | <span class="sd"> :param obj: an object whose class is instrumented by the</span> | |
| 1530 | <span class="sd"> attributes package.</span> | |
| 1531 | ||
| 1532 | <span class="sd"> :param key: string attribute name.</span> | |
| 1533 | ||
| 1534 | <span class="sd"> :param passive: indicates loading behavior for the attribute</span> | |
| 1535 | <span class="sd"> if the value is not already present. This is a</span> | |
| 1536 | <span class="sd"> bitflag attribute, which defaults to the symbol</span> | |
| 1537 | <span class="sd"> :attr:`.PASSIVE_OFF` indicating all necessary SQL</span> | |
| 1538 | <span class="sd"> should be emitted.</span> | |
| 1539 | ||
| 1540 | <span class="sd"> """</span> | |
| 1541 | <span class="k">if</span> <span class="n">passive</span> <span class="ow">is</span> <span class="kc">True</span><span class="p">:</span> | |
| 1542 | <span class="n">util</span><span class="o">.</span><span class="n">warn_deprecated</span><span class="p">(</span><span class="s2">"Passing True for 'passive' is deprecated. "</span> | |
| 1543 | <span class="s2">"Use attributes.PASSIVE_NO_INITIALIZE"</span><span class="p">)</span> | |
| 1544 | <span class="n">passive</span> <span class="o">=</span> <span class="n">PASSIVE_NO_INITIALIZE</span> | |
| 1545 | <span class="k">elif</span> <span class="n">passive</span> <span class="ow">is</span> <span class="kc">False</span><span class="p">:</span> | |
| 1546 | <span class="n">util</span><span class="o">.</span><span class="n">warn_deprecated</span><span class="p">(</span><span class="s2">"Passing False for 'passive' is "</span> | |
| 1547 | <span class="s2">"deprecated. Use attributes.PASSIVE_OFF"</span><span class="p">)</span> | |
| 1548 | <span class="n">passive</span> <span class="o">=</span> <span class="n">PASSIVE_OFF</span> | |
| 1549 | ||
| 1550 | <span class="k">return</span> <span class="n">get_state_history</span><span class="p">(</span><span class="n">instance_state</span><span class="p">(</span><span class="n">obj</span><span class="p">),</span> <span class="n">key</span><span class="p">,</span> <span class="n">passive</span><span class="p">)</span> | |
| 1551 | ||
| 1552 | ||
| 1553 | <span class="k">def</span> <span class="nf">get_state_history</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">passive</span><span class="o">=</span><span class="n">PASSIVE_OFF</span><span class="p">):</span> | |
| 1554 | <span class="k">return</span> <span class="n">state</span><span class="o">.</span><span class="n">get_history</span><span class="p">(</span><span class="n">key</span><span class="p">,</span> <span class="n">passive</span><span class="p">)</span> | |
| 1555 | ||
| 1556 | ||
| 1557 | <span class="k">def</span> <span class="nf">has_parent</span><span class="p">(</span><span class="n">cls</span><span class="p">,</span> <span class="n">obj</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">optimistic</span><span class="o">=</span><span class="kc">False</span><span class="p">):</span> | |
| 1558 | <span class="sd">"""TODO"""</span> | |
| 1559 | <span class="n">manager</span> <span class="o">=</span> <span class="n">manager_of_class</span><span class="p">(</span><span class="n">cls</span><span class="p">)</span> | |
| 1560 | <span class="n">state</span> <span class="o">=</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">obj</span><span class="p">)</span> | |
| 1561 | <span class="k">return</span> <span class="n">manager</span><span class="o">.</span><span class="n">has_parent</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">optimistic</span><span class="p">)</span> | |
| 1562 | ||
| 1563 | ||
| 1564 | <span class="k">def</span> <span class="nf">register_attribute</span><span class="p">(</span><span class="n">class_</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="o">**</span><span class="n">kw</span><span class="p">):</span> | |
| 1565 | <span class="n">comparator</span> <span class="o">=</span> <span class="n">kw</span><span class="o">.</span><span class="n">pop</span><span class="p">(</span><span class="s1">'comparator'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 1566 | <span class="n">parententity</span> <span class="o">=</span> <span class="n">kw</span><span class="o">.</span><span class="n">pop</span><span class="p">(</span><span class="s1">'parententity'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 1567 | <span class="n">doc</span> <span class="o">=</span> <span class="n">kw</span><span class="o">.</span><span class="n">pop</span><span class="p">(</span><span class="s1">'doc'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 1568 | <span class="n">desc</span> <span class="o">=</span> <span class="n">register_descriptor</span><span class="p">(</span><span class="n">class_</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> | |
| 1569 | <span class="n">comparator</span><span class="p">,</span> <span class="n">parententity</span><span class="p">,</span> <span class="n">doc</span><span class="o">=</span><span class="n">doc</span><span class="p">)</span> | |
| 1570 | <span class="n">register_attribute_impl</span><span class="p">(</span><span class="n">class_</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="o">**</span><span class="n">kw</span><span class="p">)</span> | |
| 1571 | <span class="k">return</span> <span class="n">desc</span> | |
| 1572 | ||
| 1573 | ||
| 1574 | <span class="k">def</span> <span class="nf">register_attribute_impl</span><span class="p">(</span><span class="n">class_</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> | |
| 1575 | <span class="n">uselist</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> <span class="n">callable_</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1576 | <span class="n">useobject</span><span class="o">=</span><span class="kc">False</span><span class="p">,</span> | |
| 1577 | <span class="n">impl_class</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">backref</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="o">**</span><span class="n">kw</span><span class="p">):</span> | |
| 1578 | ||
| 1579 | <span class="n">manager</span> <span class="o">=</span> <span class="n">manager_of_class</span><span class="p">(</span><span class="n">class_</span><span class="p">)</span> | |
| 1580 | <span class="k">if</span> <span class="n">uselist</span><span class="p">:</span> | |
| 1581 | <span class="n">factory</span> <span class="o">=</span> <span class="n">kw</span><span class="o">.</span><span class="n">pop</span><span class="p">(</span><span class="s1">'typecallable'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 1582 | <span class="n">typecallable</span> <span class="o">=</span> <span class="n">manager</span><span class="o">.</span><span class="n">instrument_collection_class</span><span class="p">(</span> | |
| 1583 | <span class="n">key</span><span class="p">,</span> <span class="n">factory</span> <span class="ow">or</span> <span class="nb">list</span><span class="p">)</span> | |
| 1584 | <span class="k">else</span><span class="p">:</span> | |
| 1585 | <span class="n">typecallable</span> <span class="o">=</span> <span class="n">kw</span><span class="o">.</span><span class="n">pop</span><span class="p">(</span><span class="s1">'typecallable'</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 1586 | ||
| 1587 | <span class="n">dispatch</span> <span class="o">=</span> <span class="n">manager</span><span class="p">[</span><span class="n">key</span><span class="p">]</span><span class="o">.</span><span class="n">dispatch</span> | |
| 1588 | ||
| 1589 | <span class="k">if</span> <span class="n">impl_class</span><span class="p">:</span> | |
| 1590 | <span class="n">impl</span> <span class="o">=</span> <span class="n">impl_class</span><span class="p">(</span><span class="n">class_</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">typecallable</span><span class="p">,</span> <span class="n">dispatch</span><span class="p">,</span> <span class="o">**</span><span class="n">kw</span><span class="p">)</span> | |
| 1591 | <span class="k">elif</span> <span class="n">uselist</span><span class="p">:</span> | |
| 1592 | <span class="n">impl</span> <span class="o">=</span> <span class="n">CollectionAttributeImpl</span><span class="p">(</span><span class="n">class_</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">callable_</span><span class="p">,</span> <span class="n">dispatch</span><span class="p">,</span> | |
| 1593 | <span class="n">typecallable</span><span class="o">=</span><span class="n">typecallable</span><span class="p">,</span> <span class="o">**</span><span class="n">kw</span><span class="p">)</span> | |
| 1594 | <span class="k">elif</span> <span class="n">useobject</span><span class="p">:</span> | |
| 1595 | <span class="n">impl</span> <span class="o">=</span> <span class="n">ScalarObjectAttributeImpl</span><span class="p">(</span><span class="n">class_</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">callable_</span><span class="p">,</span> | |
| 1596 | <span class="n">dispatch</span><span class="p">,</span> <span class="o">**</span><span class="n">kw</span><span class="p">)</span> | |
| 1597 | <span class="k">else</span><span class="p">:</span> | |
| 1598 | <span class="n">impl</span> <span class="o">=</span> <span class="n">ScalarAttributeImpl</span><span class="p">(</span><span class="n">class_</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">callable_</span><span class="p">,</span> <span class="n">dispatch</span><span class="p">,</span> <span class="o">**</span><span class="n">kw</span><span class="p">)</span> | |
| 1599 | ||
| 1600 | <span class="n">manager</span><span class="p">[</span><span class="n">key</span><span class="p">]</span><span class="o">.</span><span class="n">impl</span> <span class="o">=</span> <span class="n">impl</span> | |
| 1601 | ||
| 1602 | <span class="k">if</span> <span class="n">backref</span><span class="p">:</span> | |
| 1603 | <span class="n">backref_listeners</span><span class="p">(</span><span class="n">manager</span><span class="p">[</span><span class="n">key</span><span class="p">],</span> <span class="n">backref</span><span class="p">,</span> <span class="n">uselist</span><span class="p">)</span> | |
| 1604 | ||
| 1605 | <span class="n">manager</span><span class="o">.</span><span class="n">post_configure_attribute</span><span class="p">(</span><span class="n">key</span><span class="p">)</span> | |
| 1606 | <span class="k">return</span> <span class="n">manager</span><span class="p">[</span><span class="n">key</span><span class="p">]</span> | |
| 1607 | ||
| 1608 | ||
| 1609 | <span class="k">def</span> <span class="nf">register_descriptor</span><span class="p">(</span><span class="n">class_</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">comparator</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> | |
| 1610 | <span class="n">parententity</span><span class="o">=</span><span class="kc">None</span><span class="p">,</span> <span class="n">doc</span><span class="o">=</span><span class="kc">None</span><span class="p">):</span> | |
| 1611 | <span class="n">manager</span> <span class="o">=</span> <span class="n">manager_of_class</span><span class="p">(</span><span class="n">class_</span><span class="p">)</span> | |
| 1612 | ||
| 1613 | <span class="n">descriptor</span> <span class="o">=</span> <span class="n">InstrumentedAttribute</span><span class="p">(</span><span class="n">class_</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">comparator</span><span class="o">=</span><span class="n">comparator</span><span class="p">,</span> | |
| 1614 | <span class="n">parententity</span><span class="o">=</span><span class="n">parententity</span><span class="p">)</span> | |
| 1615 | ||
| 1616 | <span class="n">descriptor</span><span class="o">.</span><span class="n">__doc__</span> <span class="o">=</span> <span class="n">doc</span> | |
| 1617 | ||
| 1618 | <span class="n">manager</span><span class="o">.</span><span class="n">instrument_attribute</span><span class="p">(</span><span class="n">key</span><span class="p">,</span> <span class="n">descriptor</span><span class="p">)</span> | |
| 1619 | <span class="k">return</span> <span class="n">descriptor</span> | |
| 1620 | ||
| 1621 | ||
| 1622 | <span class="k">def</span> <span class="nf">unregister_attribute</span><span class="p">(</span><span class="n">class_</span><span class="p">,</span> <span class="n">key</span><span class="p">):</span> | |
| 1623 | <span class="n">manager_of_class</span><span class="p">(</span><span class="n">class_</span><span class="p">)</span><span class="o">.</span><span class="n">uninstrument_attribute</span><span class="p">(</span><span class="n">key</span><span class="p">)</span> | |
| 1624 | ||
| 1625 | ||
| 1626 | <span class="k">def</span> <span class="nf">init_collection</span><span class="p">(</span><span class="n">obj</span><span class="p">,</span> <span class="n">key</span><span class="p">):</span> | |
| 1627 | <span class="sd">"""Initialize a collection attribute and return the collection adapter.</span> | |
| 1628 | ||
| 1629 | <span class="sd"> This function is used to provide direct access to collection internals</span> | |
| 1630 | <span class="sd"> for a previously unloaded attribute. e.g.::</span> | |
| 1631 | ||
| 1632 | <span class="sd"> collection_adapter = init_collection(someobject, 'elements')</span> | |
| 1633 | <span class="sd"> for elem in values:</span> | |
| 1634 | <span class="sd"> collection_adapter.append_without_event(elem)</span> | |
| 1635 | ||
| 1636 | <span class="sd"> For an easier way to do the above, see</span> | |
| 1637 | <span class="sd"> :func:`~sqlalchemy.orm.attributes.set_committed_value`.</span> | |
| 1638 | ||
| 1639 | <span class="sd"> obj is an instrumented object instance. An InstanceState</span> | |
| 1640 | <span class="sd"> is accepted directly for backwards compatibility but</span> | |
| 1641 | <span class="sd"> this usage is deprecated.</span> | |
| 1642 | ||
| 1643 | <span class="sd"> """</span> | |
| 1644 | <span class="n">state</span> <span class="o">=</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">obj</span><span class="p">)</span> | |
| 1645 | <span class="n">dict_</span> <span class="o">=</span> <span class="n">state</span><span class="o">.</span><span class="n">dict</span> | |
| 1646 | <span class="k">return</span> <span class="n">init_state_collection</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">key</span><span class="p">)</span> | |
| 1647 | ||
| 1648 | ||
| 1649 | <span class="k">def</span> <span class="nf">init_state_collection</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">key</span><span class="p">):</span> | |
| 1650 | <span class="sd">"""Initialize a collection attribute and return the collection adapter."""</span> | |
| 1651 | ||
| 1652 | <span class="n">attr</span> <span class="o">=</span> <span class="n">state</span><span class="o">.</span><span class="n">manager</span><span class="p">[</span><span class="n">key</span><span class="p">]</span><span class="o">.</span><span class="n">impl</span> | |
| 1653 | <span class="n">user_data</span> <span class="o">=</span> <span class="n">attr</span><span class="o">.</span><span class="n">initialize</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">)</span> | |
| 1654 | <span class="k">return</span> <span class="n">attr</span><span class="o">.</span><span class="n">get_collection</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">user_data</span><span class="p">)</span> | |
| 1655 | ||
| 1656 | ||
| 1657 | <span class="k">def</span> <span class="nf">set_committed_value</span><span class="p">(</span><span class="n">instance</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">value</span><span class="p">):</span> | |
| 1658 | <span class="sd">"""Set the value of an attribute with no history events.</span> | |
| 1659 | ||
| 1660 | <span class="sd"> Cancels any previous history present. The value should be</span> | |
| 1661 | <span class="sd"> a scalar value for scalar-holding attributes, or</span> | |
| 1662 | <span class="sd"> an iterable for any collection-holding attribute.</span> | |
| 1663 | ||
| 1664 | <span class="sd"> This is the same underlying method used when a lazy loader</span> | |
| 1665 | <span class="sd"> fires off and loads additional data from the database.</span> | |
| 1666 | <span class="sd"> In particular, this method can be used by application code</span> | |
| 1667 | <span class="sd"> which has loaded additional attributes or collections through</span> | |
| 1668 | <span class="sd"> separate queries, which can then be attached to an instance</span> | |
| 1669 | <span class="sd"> as though it were part of its original loaded state.</span> | |
| 1670 | ||
| 1671 | <span class="sd"> """</span> | |
| 1672 | <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span> <span class="o">=</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">instance</span><span class="p">),</span> <span class="n">instance_dict</span><span class="p">(</span><span class="n">instance</span><span class="p">)</span> | |
| 1673 | <span class="n">state</span><span class="o">.</span><span class="n">manager</span><span class="p">[</span><span class="n">key</span><span class="p">]</span><span class="o">.</span><span class="n">impl</span><span class="o">.</span><span class="n">set_committed_value</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">)</span> | |
| 1674 | ||
| 1675 | ||
| 1676 | <span class="k">def</span> <span class="nf">set_attribute</span><span class="p">(</span><span class="n">instance</span><span class="p">,</span> <span class="n">key</span><span class="p">,</span> <span class="n">value</span><span class="p">):</span> | |
| 1677 | <span class="sd">"""Set the value of an attribute, firing history events.</span> | |
| 1678 | ||
| 1679 | <span class="sd"> This function may be used regardless of instrumentation</span> | |
| 1680 | <span class="sd"> applied directly to the class, i.e. no descriptors are required.</span> | |
| 1681 | <span class="sd"> Custom attribute management schemes will need to make usage</span> | |
| 1682 | <span class="sd"> of this method to establish attribute state as understood</span> | |
| 1683 | <span class="sd"> by SQLAlchemy.</span> | |
| 1684 | ||
| 1685 | <span class="sd"> """</span> | |
| 1686 | <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span> <span class="o">=</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">instance</span><span class="p">),</span> <span class="n">instance_dict</span><span class="p">(</span><span class="n">instance</span><span class="p">)</span> | |
| 1687 | <span class="n">state</span><span class="o">.</span><span class="n">manager</span><span class="p">[</span><span class="n">key</span><span class="p">]</span><span class="o">.</span><span class="n">impl</span><span class="o">.</span><span class="n">set</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">,</span> <span class="n">value</span><span class="p">,</span> <span class="kc">None</span><span class="p">)</span> | |
| 1688 | ||
| 1689 | ||
| 1690 | <span class="k">def</span> <span class="nf">get_attribute</span><span class="p">(</span><span class="n">instance</span><span class="p">,</span> <span class="n">key</span><span class="p">):</span> | |
| 1691 | <span class="sd">"""Get the value of an attribute, firing any callables required.</span> | |
| 1692 | ||
| 1693 | <span class="sd"> This function may be used regardless of instrumentation</span> | |
| 1694 | <span class="sd"> applied directly to the class, i.e. no descriptors are required.</span> | |
| 1695 | <span class="sd"> Custom attribute management schemes will need to make usage</span> | |
| 1696 | <span class="sd"> of this method to make usage of attribute state as understood</span> | |
| 1697 | <span class="sd"> by SQLAlchemy.</span> | |
| 1698 | ||
| 1699 | <span class="sd"> """</span> | |
| 1700 | <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span> <span class="o">=</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">instance</span><span class="p">),</span> <span class="n">instance_dict</span><span class="p">(</span><span class="n">instance</span><span class="p">)</span> | |
| 1701 | <span class="k">return</span> <span class="n">state</span><span class="o">.</span><span class="n">manager</span><span class="p">[</span><span class="n">key</span><span class="p">]</span><span class="o">.</span><span class="n">impl</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">)</span> | |
| 1702 | ||
| 1703 | ||
| 1704 | <span class="k">def</span> <span class="nf">del_attribute</span><span class="p">(</span><span class="n">instance</span><span class="p">,</span> <span class="n">key</span><span class="p">):</span> | |
| 1705 | <span class="sd">"""Delete the value of an attribute, firing history events.</span> | |
| 1706 | ||
| 1707 | <span class="sd"> This function may be used regardless of instrumentation</span> | |
| 1708 | <span class="sd"> applied directly to the class, i.e. no descriptors are required.</span> | |
| 1709 | <span class="sd"> Custom attribute management schemes will need to make usage</span> | |
| 1710 | <span class="sd"> of this method to establish attribute state as understood</span> | |
| 1711 | <span class="sd"> by SQLAlchemy.</span> | |
| 1712 | ||
| 1713 | <span class="sd"> """</span> | |
| 1714 | <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span> <span class="o">=</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">instance</span><span class="p">),</span> <span class="n">instance_dict</span><span class="p">(</span><span class="n">instance</span><span class="p">)</span> | |
| 1715 | <span class="n">state</span><span class="o">.</span><span class="n">manager</span><span class="p">[</span><span class="n">key</span><span class="p">]</span><span class="o">.</span><span class="n">impl</span><span class="o">.</span><span class="n">delete</span><span class="p">(</span><span class="n">state</span><span class="p">,</span> <span class="n">dict_</span><span class="p">)</span> | |
| 1716 | ||
| 1717 | ||
| 1718 | <span class="k">def</span> <span class="nf">flag_modified</span><span class="p">(</span><span class="n">instance</span><span class="p">,</span> <span class="n">key</span><span class="p">):</span> | |
| 1719 | <span class="sd">"""Mark an attribute on an instance as 'modified'.</span> | |
| 1720 | ||
| 1721 | <span class="sd"> This sets the 'modified' flag on the instance and</span> | |
| 1722 | <span class="sd"> establishes an unconditional change event for the given attribute.</span> | |
| 1723 | ||
| 1724 | <span class="sd"> """</span> | |
| 1725 | <span class="n">state</span><span class="p">,</span> <span class="n">dict_</span> <span class="o">=</span> <span class="n">instance_state</span><span class="p">(</span><span class="n">instance</span><span class="p">),</span> <span class="n">instance_dict</span><span class="p">(</span><span class="n">instance</span><span class="p">)</span> | |
| 1726 | <span class="n">impl</span> <span class="o">=</span> <span class="n">state</span><span class="o">.</span><span class="n">manager</span><span class="p">[</span><span class="n">key</span><span class="p">]</span><span class="o">.</span><span class="n">impl</span> | |
| 1727 | <span class="n">state</span><span class="o">.</span><span class="n">_modified_event</span><span class="p">(</span><span class="n">dict_</span><span class="p">,</span> <span class="n">impl</span><span class="p">,</span> <span class="n">NO_VALUE</span><span class="p">,</span> <span class="n">force</span><span class="o">=</span><span class="kc">True</span><span class="p">)</span> | |
| 1728 | </pre></div> | |
| 1729 | ||
| 1730 | </div> | |
| 1731 | </div> | |
| 1732 | <footer> | |
| 1733 | ||
| 1734 | ||
| 1735 | <hr/> | |
| 1736 | ||
| 1737 | <div role="contentinfo"> | |
| 1738 | <p> | |
| 1739 | © Copyright 2016, Infobyte. | |
| 1740 | ||
| 1741 | </p> | |
| 1742 | </div> | |
| 1743 | Built with <a href="http://sphinx-doc.org/">Sphinx</a> using a <a href="https://github.com/snide/sphinx_rtd_theme">theme</a> provided by <a href="https://readthedocs.org">Read the Docs</a>. | |
| 1744 | ||
| 1745 | </footer> | |
| 1746 | ||
| 1747 | </div> | |
| 1748 | </div> | |
| 1749 | ||
| 1750 | </section> | |
| 1751 | ||
| 1752 | </div> | |
| 1753 | ||
| 1754 | ||
| 1755 | ||
| 1756 | ||
| 1757 | ||
| 1758 | <script type="text/javascript"> | |
| 1759 | var DOCUMENTATION_OPTIONS = { | |
| 1760 | URL_ROOT:'../../../', | |
| 1761 | VERSION:'0.1', | |
| 1762 | COLLAPSE_INDEX:false, | |
| 1763 | FILE_SUFFIX:'.html', | |
| 1764 | HAS_SOURCE: true | |
| 1765 | }; | |
| 1766 | </script> | |
| 1767 | <script type="text/javascript" src="../../../_static/jquery.js"></script> | |
| 1768 | <script type="text/javascript" src="../../../_static/underscore.js"></script> | |
| 1769 | <script type="text/javascript" src="../../../_static/doctools.js"></script> | |
| 1770 | ||
| 1771 | ||
| 1772 | ||
| 1773 | ||
| 1774 | ||
| 1775 | <script type="text/javascript" src="../../../_static/js/theme.js"></script> | |
| 1776 | ||
| 1777 | ||
| 1778 | ||
| 1779 | ||
| 1780 | <script type="text/javascript"> | |
| 1781 | jQuery(function () { | |
| 1782 | SphinxRtdTheme.StickyNav.enable(); | |
| 1783 | }); | |
| 1784 | </script> | |
| 1785 | ||
| 1786 | ||
| 1787 | </body> | |
| 1788 | </html>⏎ |
| 0 | .. Faraday documentation master file, created by | |
| 1 | sphinx-quickstart on Fri Dec 9 14:53:21 2016. | |
| 2 | You can adapt this file completely to your liking, but it should at least | |
| 3 | contain the root `toctree` directive. | |
| 4 | ||
| 5 | Welcome to Faraday's documentation! | |
| 6 | =================================== | |
| 7 | ||
| 8 | Contents: | |
| 9 | ||
| 10 | .. toctree:: | |
| 11 | :maxdepth: 2 | |
| 12 | ||
| 13 | ||
| 14 | ||
| 15 | Indices and tables | |
| 16 | ================== | |
| 17 | ||
| 18 | * :ref:`genindex` | |
| 19 | * :ref:`modindex` | |
| 20 | * :ref:`search` | |
| 21 |
| 0 | .. Faraday documentation master file, created by | |
| 1 | sphinx-quickstart on Fri Dec 9 14:53:21 2016. | |
| 2 | You can adapt this file completely to your liking, but it should at least | |
| 3 | contain the root `toctree` directive. | |
| 4 | ||
| 5 | Welcome to Faraday's documentation! | |
| 6 | =================================== | |
| 7 | ||
| 8 | Contents: | |
| 9 | ||
| 10 | .. toctree:: | |
| 11 | :maxdepth: 2 | |
| 12 | ||
| 13 | ||
| 14 | ||
| 15 | Indices and tables | |
| 16 | ================== | |
| 17 | ||
| 18 | * :ref:`genindex` | |
| 19 | * :ref:`modindex` | |
| 20 | * :ref:`search` | |
| 21 |
| 0 | server package | |
| 1 | ============== | |
| 2 | ||
| 3 | Submodules | |
| 4 | ---------- | |
| 5 | ||
| 6 | server.utils module | |
| 7 | ------------------- | |
| 8 | ||
| 9 | .. automodule:: persistence.server.server | |
| 10 | :members: | |
| 11 | :undoc-members: | |
| 12 | :show-inheritance: |
| 0 | server package | |
| 1 | ============== | |
| 2 | ||
| 3 | Submodules | |
| 4 | ---------- | |
| 5 | ||
| 6 | server.changes_stream module | |
| 7 | ---------------------------- | |
| 8 | ||
| 9 | .. automodule:: server.changes_stream | |
| 10 | :members: | |
| 11 | :undoc-members: | |
| 12 | :show-inheritance: | |
| 13 | ||
| 14 | server.conf module | |
| 15 | ------------------ | |
| 16 | ||
| 17 | .. automodule:: server.conf | |
| 18 | :members: | |
| 19 | :undoc-members: | |
| 20 | :show-inheritance: | |
| 21 | ||
| 22 | server.models module | |
| 23 | -------------------- | |
| 24 | ||
| 25 | .. automodule:: server.models | |
| 26 | :members: | |
| 27 | :undoc-members: | |
| 28 | :show-inheritance: | |
| 29 | ||
| 30 | server.server module | |
| 31 | -------------------- | |
| 32 | ||
| 33 | .. automodule:: server.server | |
| 34 | :members: | |
| 35 | :undoc-members: | |
| 36 | :show-inheritance: | |
| 37 | ||
| 38 | server.server_io_exceptions module | |
| 39 | ---------------------------------- | |
| 40 | ||
| 41 | .. automodule:: server.server_io_exceptions | |
| 42 | :members: | |
| 43 | :undoc-members: | |
| 44 | :show-inheritance: | |
| 45 | ||
| 46 | server.utils module | |
| 47 | ------------------- | |
| 48 | ||
| 49 | .. automodule:: server.utils | |
| 50 | :members: | |
| 51 | :undoc-members: | |
| 52 | :show-inheritance: | |
| 53 | ||
| 54 | ||
| 55 | Module contents | |
| 56 | --------------- | |
| 57 | ||
| 58 | .. automodule:: server | |
| 59 | :members: | |
| 60 | :undoc-members: | |
| 61 | :show-inheritance: |
Binary diff not shown
| 0 | ||
| 1 | ||
| 2 | ||
| 3 | ||
| 4 | ||
| 5 | ||
| 6 | ||
| 7 | ||
| 8 | ||
| 9 | ||
| 10 | ||
| 11 | ||
| 12 | ||
| 13 | ||
| 14 | ||
| 15 | ||
| 16 | ||
| 17 | ||
| 18 | ||
| 19 | ||
| 20 | ||
| 21 | ||
| 22 | ||
| 23 | ||
| 24 | ||
| 25 | ||
| 26 | ||
| 27 | ||
| 28 | ||
| 29 | ||
| 30 | ||
| 31 | ||
| 32 | ||
| 33 | ||
| 34 | ||
| 35 | ||
| 36 | ||
| 37 | ||
| 38 | ||
| 39 | ||
| 40 | ||
| 41 | ||
| 42 | ||
| 43 | ||
| 44 | ||
| 45 | ||
| 46 | ||
| 47 | ||
| 48 | ||
| 49 | ||
| 50 | ||
| 51 | ||
| 52 | @import url("basic.css"); | |
| 53 | ||
| 54 | /* -- page layout ----------------------------------------------------------- */ | |
| 55 | ||
| 56 | body { | |
| 57 | font-family: 'goudy old style', 'minion pro', 'bell mt', Georgia, 'Hiragino Mincho Pro', serif; | |
| 58 | font-size: 17px; | |
| 59 | background-color: #fff; | |
| 60 | color: #000; | |
| 61 | margin: 0; | |
| 62 | padding: 0; | |
| 63 | } | |
| 64 | ||
| 65 | ||
| 66 | div.document { | |
| 67 | width: 940px; | |
| 68 | margin: 30px auto 0 auto; | |
| 69 | } | |
| 70 | ||
| 71 | div.documentwrapper { | |
| 72 | float: left; | |
| 73 | width: 100%; | |
| 74 | } | |
| 75 | ||
| 76 | div.bodywrapper { | |
| 77 | margin: 0 0 0 220px; | |
| 78 | } | |
| 79 | ||
| 80 | div.sphinxsidebar { | |
| 81 | width: 220px; | |
| 82 | font-size: 14px; | |
| 83 | line-height: 1.5; | |
| 84 | } | |
| 85 | ||
| 86 | hr { | |
| 87 | border: 1px solid #B1B4B6; | |
| 88 | } | |
| 89 | ||
| 90 | div.body { | |
| 91 | background-color: #fff; | |
| 92 | color: #3E4349; | |
| 93 | padding: 0 30px 0 30px; | |
| 94 | } | |
| 95 | ||
| 96 | div.body > .section { | |
| 97 | text-align: left; | |
| 98 | } | |
| 99 | ||
| 100 | div.footer { | |
| 101 | width: 940px; | |
| 102 | margin: 20px auto 30px auto; | |
| 103 | font-size: 14px; | |
| 104 | color: #888; | |
| 105 | text-align: right; | |
| 106 | } | |
| 107 | ||
| 108 | div.footer a { | |
| 109 | color: #888; | |
| 110 | } | |
| 111 | ||
| 112 | p.caption { | |
| 113 | font-family: inherit; | |
| 114 | font-size: inherit; | |
| 115 | } | |
| 116 | ||
| 117 | ||
| 118 | div.relations { | |
| 119 | display: none; | |
| 120 | } | |
| 121 | ||
| 122 | ||
| 123 | div.sphinxsidebar a { | |
| 124 | color: #444; | |
| 125 | text-decoration: none; | |
| 126 | border-bottom: 1px dotted #999; | |
| 127 | } | |
| 128 | ||
| 129 | div.sphinxsidebar a:hover { | |
| 130 | border-bottom: 1px solid #999; | |
| 131 | } | |
| 132 | ||
| 133 | div.sphinxsidebarwrapper { | |
| 134 | padding: 18px 10px; | |
| 135 | } | |
| 136 | ||
| 137 | div.sphinxsidebarwrapper p.logo { | |
| 138 | padding: 0; | |
| 139 | margin: -10px 0 0 0px; | |
| 140 | text-align: center; | |
| 141 | } | |
| 142 | ||
| 143 | div.sphinxsidebarwrapper h1.logo { | |
| 144 | margin-top: -10px; | |
| 145 | text-align: center; | |
| 146 | margin-bottom: 5px; | |
| 147 | text-align: left; | |
| 148 | } | |
| 149 | ||
| 150 | div.sphinxsidebarwrapper h1.logo-name { | |
| 151 | margin-top: 0px; | |
| 152 | } | |
| 153 | ||
| 154 | div.sphinxsidebarwrapper p.blurb { | |
| 155 | margin-top: 0; | |
| 156 | font-style: normal; | |
| 157 | } | |
| 158 | ||
| 159 | div.sphinxsidebar h3, | |
| 160 | div.sphinxsidebar h4 { | |
| 161 | font-family: 'Garamond', 'Georgia', serif; | |
| 162 | color: #444; | |
| 163 | font-size: 24px; | |
| 164 | font-weight: normal; | |
| 165 | margin: 0 0 5px 0; | |
| 166 | padding: 0; | |
| 167 | } | |
| 168 | ||
| 169 | div.sphinxsidebar h4 { | |
| 170 | font-size: 20px; | |
| 171 | } | |
| 172 | ||
| 173 | div.sphinxsidebar h3 a { | |
| 174 | color: #444; | |
| 175 | } | |
| 176 | ||
| 177 | div.sphinxsidebar p.logo a, | |
| 178 | div.sphinxsidebar h3 a, | |
| 179 | div.sphinxsidebar p.logo a:hover, | |
| 180 | div.sphinxsidebar h3 a:hover { | |
| 181 | border: none; | |
| 182 | } | |
| 183 | ||
| 184 | div.sphinxsidebar p { | |
| 185 | color: #555; | |
| 186 | margin: 10px 0; | |
| 187 | } | |
| 188 | ||
| 189 | div.sphinxsidebar ul { | |
| 190 | margin: 10px 0; | |
| 191 | padding: 0; | |
| 192 | color: #000; | |
| 193 | } | |
| 194 | ||
| 195 | div.sphinxsidebar ul li.toctree-l1 > a { | |
| 196 | font-size: 120%; | |
| 197 | } | |
| 198 | ||
| 199 | div.sphinxsidebar ul li.toctree-l2 > a { | |
| 200 | font-size: 110%; | |
| 201 | } | |
| 202 | ||
| 203 | div.sphinxsidebar input { | |
| 204 | border: 1px solid #CCC; | |
| 205 | font-family: 'goudy old style', 'minion pro', 'bell mt', Georgia, 'Hiragino Mincho Pro', serif; | |
| 206 | font-size: 1em; | |
| 207 | } | |
| 208 | ||
| 209 | div.sphinxsidebar hr { | |
| 210 | border: none; | |
| 211 | height: 1px; | |
| 212 | color: #AAA; | |
| 213 | background: #AAA; | |
| 214 | ||
| 215 | text-align: left; | |
| 216 | margin-left: 0; | |
| 217 | width: 50%; | |
| 218 | } | |
| 219 | ||
| 220 | /* -- body styles ----------------------------------------------------------- */ | |
| 221 | ||
| 222 | a { | |
| 223 | color: #004B6B; | |
| 224 | text-decoration: underline; | |
| 225 | } | |
| 226 | ||
| 227 | a:hover { | |
| 228 | color: #6D4100; | |
| 229 | text-decoration: underline; | |
| 230 | } | |
| 231 | ||
| 232 | div.body h1, | |
| 233 | div.body h2, | |
| 234 | div.body h3, | |
| 235 | div.body h4, | |
| 236 | div.body h5, | |
| 237 | div.body h6 { | |
| 238 | font-family: 'Garamond', 'Georgia', serif; | |
| 239 | font-weight: normal; | |
| 240 | margin: 30px 0px 10px 0px; | |
| 241 | padding: 0; | |
| 242 | } | |
| 243 | ||
| 244 | div.body h1 { margin-top: 0; padding-top: 0; font-size: 240%; } | |
| 245 | div.body h2 { font-size: 180%; } | |
| 246 | div.body h3 { font-size: 150%; } | |
| 247 | div.body h4 { font-size: 130%; } | |
| 248 | div.body h5 { font-size: 100%; } | |
| 249 | div.body h6 { font-size: 100%; } | |
| 250 | ||
| 251 | a.headerlink { | |
| 252 | color: #DDD; | |
| 253 | padding: 0 4px; | |
| 254 | text-decoration: none; | |
| 255 | } | |
| 256 | ||
| 257 | a.headerlink:hover { | |
| 258 | color: #444; | |
| 259 | background: #EAEAEA; | |
| 260 | } | |
| 261 | ||
| 262 | div.body p, div.body dd, div.body li { | |
| 263 | line-height: 1.4em; | |
| 264 | } | |
| 265 | ||
| 266 | div.admonition { | |
| 267 | margin: 20px 0px; | |
| 268 | padding: 10px 30px; | |
| 269 | background-color: #EEE; | |
| 270 | border: 1px solid #CCC; | |
| 271 | } | |
| 272 | ||
| 273 | div.admonition tt.xref, div.admonition code.xref, div.admonition a tt { | |
| 274 | background-color: ; | |
| 275 | border-bottom: 1px solid #fafafa; | |
| 276 | } | |
| 277 | ||
| 278 | dd div.admonition { | |
| 279 | margin-left: -60px; | |
| 280 | padding-left: 60px; | |
| 281 | } | |
| 282 | ||
| 283 | div.admonition p.admonition-title { | |
| 284 | font-family: 'Garamond', 'Georgia', serif; | |
| 285 | font-weight: normal; | |
| 286 | font-size: 24px; | |
| 287 | margin: 0 0 10px 0; | |
| 288 | padding: 0; | |
| 289 | line-height: 1; | |
| 290 | } | |
| 291 | ||
| 292 | div.admonition p.last { | |
| 293 | margin-bottom: 0; | |
| 294 | } | |
| 295 | ||
| 296 | div.highlight { | |
| 297 | background-color: #fff; | |
| 298 | } | |
| 299 | ||
| 300 | dt:target, .highlight { | |
| 301 | background: #FAF3E8; | |
| 302 | } | |
| 303 | ||
| 304 | div.warning { | |
| 305 | background-color: #FCC; | |
| 306 | border: 1px solid #FAA; | |
| 307 | } | |
| 308 | ||
| 309 | div.danger { | |
| 310 | background-color: #FCC; | |
| 311 | border: 1px solid #FAA; | |
| 312 | -moz-box-shadow: 2px 2px 4px #D52C2C; | |
| 313 | -webkit-box-shadow: 2px 2px 4px #D52C2C; | |
| 314 | box-shadow: 2px 2px 4px #D52C2C; | |
| 315 | } | |
| 316 | ||
| 317 | div.error { | |
| 318 | background-color: #FCC; | |
| 319 | border: 1px solid #FAA; | |
| 320 | -moz-box-shadow: 2px 2px 4px #D52C2C; | |
| 321 | -webkit-box-shadow: 2px 2px 4px #D52C2C; | |
| 322 | box-shadow: 2px 2px 4px #D52C2C; | |
| 323 | } | |
| 324 | ||
| 325 | div.caution { | |
| 326 | background-color: #FCC; | |
| 327 | border: 1px solid #FAA; | |
| 328 | } | |
| 329 | ||
| 330 | div.attention { | |
| 331 | background-color: #FCC; | |
| 332 | border: 1px solid #FAA; | |
| 333 | } | |
| 334 | ||
| 335 | div.important { | |
| 336 | background-color: #EEE; | |
| 337 | border: 1px solid #CCC; | |
| 338 | } | |
| 339 | ||
| 340 | div.note { | |
| 341 | background-color: #EEE; | |
| 342 | border: 1px solid #CCC; | |
| 343 | } | |
| 344 | ||
| 345 | div.tip { | |
| 346 | background-color: #EEE; | |
| 347 | border: 1px solid #CCC; | |
| 348 | } | |
| 349 | ||
| 350 | div.hint { | |
| 351 | background-color: #EEE; | |
| 352 | border: 1px solid #CCC; | |
| 353 | } | |
| 354 | ||
| 355 | div.seealso { | |
| 356 | background-color: #EEE; | |
| 357 | border: 1px solid #CCC; | |
| 358 | } | |
| 359 | ||
| 360 | div.topic { | |
| 361 | background-color: #EEE; | |
| 362 | } | |
| 363 | ||
| 364 | p.admonition-title { | |
| 365 | display: inline; | |
| 366 | } | |
| 367 | ||
| 368 | p.admonition-title:after { | |
| 369 | content: ":"; | |
| 370 | } | |
| 371 | ||
| 372 | pre, tt, code { | |
| 373 | font-family: 'Consolas', 'Menlo', 'Deja Vu Sans Mono', 'Bitstream Vera Sans Mono', monospace; | |
| 374 | font-size: 0.9em; | |
| 375 | } | |
| 376 | ||
| 377 | .hll { | |
| 378 | background-color: #FFC; | |
| 379 | margin: 0 -12px; | |
| 380 | padding: 0 12px; | |
| 381 | display: block; | |
| 382 | } | |
| 383 | ||
| 384 | img.screenshot { | |
| 385 | } | |
| 386 | ||
| 387 | tt.descname, tt.descclassname, code.descname, code.descclassname { | |
| 388 | font-size: 0.95em; | |
| 389 | } | |
| 390 | ||
| 391 | tt.descname, code.descname { | |
| 392 | padding-right: 0.08em; | |
| 393 | } | |
| 394 | ||
| 395 | img.screenshot { | |
| 396 | -moz-box-shadow: 2px 2px 4px #EEE; | |
| 397 | -webkit-box-shadow: 2px 2px 4px #EEE; | |
| 398 | box-shadow: 2px 2px 4px #EEE; | |
| 399 | } | |
| 400 | ||
| 401 | table.docutils { | |
| 402 | border: 1px solid #888; | |
| 403 | -moz-box-shadow: 2px 2px 4px #EEE; | |
| 404 | -webkit-box-shadow: 2px 2px 4px #EEE; | |
| 405 | box-shadow: 2px 2px 4px #EEE; | |
| 406 | } | |
| 407 | ||
| 408 | table.docutils td, table.docutils th { | |
| 409 | border: 1px solid #888; | |
| 410 | padding: 0.25em 0.7em; | |
| 411 | } | |
| 412 | ||
| 413 | table.field-list, table.footnote { | |
| 414 | border: none; | |
| 415 | -moz-box-shadow: none; | |
| 416 | -webkit-box-shadow: none; | |
| 417 | box-shadow: none; | |
| 418 | } | |
| 419 | ||
| 420 | table.footnote { | |
| 421 | margin: 15px 0; | |
| 422 | width: 100%; | |
| 423 | border: 1px solid #EEE; | |
| 424 | background: #FDFDFD; | |
| 425 | font-size: 0.9em; | |
| 426 | } | |
| 427 | ||
| 428 | table.footnote + table.footnote { | |
| 429 | margin-top: -15px; | |
| 430 | border-top: none; | |
| 431 | } | |
| 432 | ||
| 433 | table.field-list th { | |
| 434 | padding: 0 0.8em 0 0; | |
| 435 | } | |
| 436 | ||
| 437 | table.field-list td { | |
| 438 | padding: 0; | |
| 439 | } | |
| 440 | ||
| 441 | table.field-list p { | |
| 442 | margin-bottom: 0.8em; | |
| 443 | } | |
| 444 | ||
| 445 | table.footnote td.label { | |
| 446 | width: .1px; | |
| 447 | padding: 0.3em 0 0.3em 0.5em; | |
| 448 | } | |
| 449 | ||
| 450 | table.footnote td { | |
| 451 | padding: 0.3em 0.5em; | |
| 452 | } | |
| 453 | ||
| 454 | dl { | |
| 455 | margin: 0; | |
| 456 | padding: 0; | |
| 457 | } | |
| 458 | ||
| 459 | dl dd { | |
| 460 | margin-left: 30px; | |
| 461 | } | |
| 462 | ||
| 463 | blockquote { | |
| 464 | margin: 0 0 0 30px; | |
| 465 | padding: 0; | |
| 466 | } | |
| 467 | ||
| 468 | ul, ol { | |
| 469 | /* Matches the 30px from the narrow-screen "li > ul" selector below */ | |
| 470 | margin: 10px 0 10px 30px; | |
| 471 | padding: 0; | |
| 472 | } | |
| 473 | ||
| 474 | pre { | |
| 475 | background: #EEE; | |
| 476 | padding: 7px 30px; | |
| 477 | margin: 15px 0px; | |
| 478 | line-height: 1.3em; | |
| 479 | } | |
| 480 | ||
| 481 | div.viewcode-block:target { | |
| 482 | background: #ffd; | |
| 483 | } | |
| 484 | ||
| 485 | dl pre, blockquote pre, li pre { | |
| 486 | margin-left: 0; | |
| 487 | padding-left: 30px; | |
| 488 | } | |
| 489 | ||
| 490 | dl dl pre { | |
| 491 | margin-left: -90px; | |
| 492 | padding-left: 90px; | |
| 493 | } | |
| 494 | ||
| 495 | tt, code { | |
| 496 | background-color: #ecf0f3; | |
| 497 | color: #222; | |
| 498 | /* padding: 1px 2px; */ | |
| 499 | } | |
| 500 | ||
| 501 | tt.xref, code.xref, a tt { | |
| 502 | background-color: #FBFBFB; | |
| 503 | border-bottom: 1px solid #fff; | |
| 504 | } | |
| 505 | ||
| 506 | a.reference { | |
| 507 | text-decoration: none; | |
| 508 | border-bottom: 1px dotted #004B6B; | |
| 509 | } | |
| 510 | ||
| 511 | /* Don't put an underline on images */ | |
| 512 | a.image-reference, a.image-reference:hover { | |
| 513 | border-bottom: none; | |
| 514 | } | |
| 515 | ||
| 516 | a.reference:hover { | |
| 517 | border-bottom: 1px solid #6D4100; | |
| 518 | } | |
| 519 | ||
| 520 | a.footnote-reference { | |
| 521 | text-decoration: none; | |
| 522 | font-size: 0.7em; | |
| 523 | vertical-align: top; | |
| 524 | border-bottom: 1px dotted #004B6B; | |
| 525 | } | |
| 526 | ||
| 527 | a.footnote-reference:hover { | |
| 528 | border-bottom: 1px solid #6D4100; | |
| 529 | } | |
| 530 | ||
| 531 | a:hover tt, a:hover code { | |
| 532 | background: #EEE; | |
| 533 | } | |
| 534 | ||
| 535 | ||
| 536 | @media screen and (max-width: 870px) { | |
| 537 | ||
| 538 | div.sphinxsidebar { | |
| 539 | display: none; | |
| 540 | } | |
| 541 | ||
| 542 | div.document { | |
| 543 | width: 100%; | |
| 544 | ||
| 545 | } | |
| 546 | ||
| 547 | div.documentwrapper { | |
| 548 | margin-left: 0; | |
| 549 | margin-top: 0; | |
| 550 | margin-right: 0; | |
| 551 | margin-bottom: 0; | |
| 552 | } | |
| 553 | ||
| 554 | div.bodywrapper { | |
| 555 | margin-top: 0; | |
| 556 | margin-right: 0; | |
| 557 | margin-bottom: 0; | |
| 558 | margin-left: 0; | |
| 559 | } | |
| 560 | ||
| 561 | ul { | |
| 562 | margin-left: 0; | |
| 563 | } | |
| 564 | ||
| 565 | li > ul { | |
| 566 | /* Matches the 30px from the "ul, ol" selector above */ | |
| 567 | margin-left: 30px; | |
| 568 | } | |
| 569 | ||
| 570 | .document { | |
| 571 | width: auto; | |
| 572 | } | |
| 573 | ||
| 574 | .footer { | |
| 575 | width: auto; | |
| 576 | } | |
| 577 | ||
| 578 | .bodywrapper { | |
| 579 | margin: 0; | |
| 580 | } | |
| 581 | ||
| 582 | .footer { | |
| 583 | width: auto; | |
| 584 | } | |
| 585 | ||
| 586 | .github { | |
| 587 | display: none; | |
| 588 | } | |
| 589 | ||
| 590 | ||
| 591 | ||
| 592 | } | |
| 593 | ||
| 594 | ||
| 595 | ||
| 596 | @media screen and (max-width: 875px) { | |
| 597 | ||
| 598 | body { | |
| 599 | margin: 0; | |
| 600 | padding: 20px 30px; | |
| 601 | } | |
| 602 | ||
| 603 | div.documentwrapper { | |
| 604 | float: none; | |
| 605 | background: #fff; | |
| 606 | } | |
| 607 | ||
| 608 | div.sphinxsidebar { | |
| 609 | display: block; | |
| 610 | float: none; | |
| 611 | width: 102.5%; | |
| 612 | margin: 50px -30px -20px -30px; | |
| 613 | padding: 10px 20px; | |
| 614 | background: #333; | |
| 615 | color: #FFF; | |
| 616 | } | |
| 617 | ||
| 618 | div.sphinxsidebar h3, div.sphinxsidebar h4, div.sphinxsidebar p, | |
| 619 | div.sphinxsidebar h3 a { | |
| 620 | color: #fff; | |
| 621 | } | |
| 622 | ||
| 623 | div.sphinxsidebar a { | |
| 624 | color: #AAA; | |
| 625 | } | |
| 626 | ||
| 627 | div.sphinxsidebar p.logo { | |
| 628 | display: none; | |
| 629 | } | |
| 630 | ||
| 631 | div.document { | |
| 632 | width: 100%; | |
| 633 | margin: 0; | |
| 634 | } | |
| 635 | ||
| 636 | div.footer { | |
| 637 | display: none; | |
| 638 | } | |
| 639 | ||
| 640 | div.bodywrapper { | |
| 641 | margin: 0; | |
| 642 | } | |
| 643 | ||
| 644 | div.body { | |
| 645 | min-height: 0; | |
| 646 | padding: 0; | |
| 647 | } | |
| 648 | ||
| 649 | .rtd_doc_footer { | |
| 650 | display: none; | |
| 651 | } | |
| 652 | ||
| 653 | .document { | |
| 654 | width: auto; | |
| 655 | } | |
| 656 | ||
| 657 | .footer { | |
| 658 | width: auto; | |
| 659 | } | |
| 660 | ||
| 661 | .footer { | |
| 662 | width: auto; | |
| 663 | } | |
| 664 | ||
| 665 | .github { | |
| 666 | display: none; | |
| 667 | } | |
| 668 | } | |
| 669 | ||
| 670 | ||
| 671 | /* misc. */ | |
| 672 | ||
| 673 | .revsys-inline { | |
| 674 | display: none!important; | |
| 675 | } | |
| 676 | ||
| 677 | /* Make nested-list/multi-paragraph items look better in Releases changelog | |
| 678 | * pages. Without this, docutils' magical list fuckery causes inconsistent | |
| 679 | * formatting between different release sub-lists. | |
| 680 | */ | |
| 681 | div#changelog > div.section > ul > li > p:only-child { | |
| 682 | margin-bottom: 0; | |
| 683 | } | |
| 684 | ||
| 685 | /* Hide fugly table cell borders in ..bibliography:: directive output */ | |
| 686 | table.docutils.citation, table.docutils.citation td, table.docutils.citation th { | |
| 687 | border: none; | |
| 688 | /* Below needed in some edge cases; if not applied, bottom shadows appear */ | |
| 689 | -moz-box-shadow: none; | |
| 690 | -webkit-box-shadow: none; | |
| 691 | box-shadow: none; | |
| 692 | }⏎ |
| 0 | /* | |
| 1 | * basic.css | |
| 2 | * ~~~~~~~~~ | |
| 3 | * | |
| 4 | * Sphinx stylesheet -- basic theme. | |
| 5 | * | |
| 6 | * :copyright: Copyright 2007-2016 by the Sphinx team, see AUTHORS. | |
| 7 | * :license: BSD, see LICENSE for details. | |
| 8 | * | |
| 9 | */ | |
| 10 | ||
| 11 | /* -- main layout ----------------------------------------------------------- */ | |
| 12 | ||
| 13 | div.clearer { | |
| 14 | clear: both; | |
| 15 | } | |
| 16 | ||
| 17 | /* -- relbar ---------------------------------------------------------------- */ | |
| 18 | ||
| 19 | div.related { | |
| 20 | width: 100%; | |
| 21 | font-size: 90%; | |
| 22 | } | |
| 23 | ||
| 24 | div.related h3 { | |
| 25 | display: none; | |
| 26 | } | |
| 27 | ||
| 28 | div.related ul { | |
| 29 | margin: 0; | |
| 30 | padding: 0 0 0 10px; | |
| 31 | list-style: none; | |
| 32 | } | |
| 33 | ||
| 34 | div.related li { | |
| 35 | display: inline; | |
| 36 | } | |
| 37 | ||
| 38 | div.related li.right { | |
| 39 | float: right; | |
| 40 | margin-right: 5px; | |
| 41 | } | |
| 42 | ||
| 43 | /* -- sidebar --------------------------------------------------------------- */ | |
| 44 | ||
| 45 | div.sphinxsidebarwrapper { | |
| 46 | padding: 10px 5px 0 10px; | |
| 47 | } | |
| 48 | ||
| 49 | div.sphinxsidebar { | |
| 50 | float: left; | |
| 51 | width: 230px; | |
| 52 | margin-left: -100%; | |
| 53 | font-size: 90%; | |
| 54 | word-wrap: break-word; | |
| 55 | overflow-wrap : break-word; | |
| 56 | } | |
| 57 | ||
| 58 | div.sphinxsidebar ul { | |
| 59 | list-style: none; | |
| 60 | } | |
| 61 | ||
| 62 | div.sphinxsidebar ul ul, | |
| 63 | div.sphinxsidebar ul.want-points { | |
| 64 | margin-left: 20px; | |
| 65 | list-style: square; | |
| 66 | } | |
| 67 | ||
| 68 | div.sphinxsidebar ul ul { | |
| 69 | margin-top: 0; | |
| 70 | margin-bottom: 0; | |
| 71 | } | |
| 72 | ||
| 73 | div.sphinxsidebar form { | |
| 74 | margin-top: 10px; | |
| 75 | } | |
| 76 | ||
| 77 | div.sphinxsidebar input { | |
| 78 | border: 1px solid #98dbcc; | |
| 79 | font-family: sans-serif; | |
| 80 | font-size: 1em; | |
| 81 | } | |
| 82 | ||
| 83 | div.sphinxsidebar #searchbox input[type="text"] { | |
| 84 | width: 170px; | |
| 85 | } | |
| 86 | ||
| 87 | img { | |
| 88 | border: 0; | |
| 89 | max-width: 100%; | |
| 90 | } | |
| 91 | ||
| 92 | /* -- search page ----------------------------------------------------------- */ | |
| 93 | ||
| 94 | ul.search { | |
| 95 | margin: 10px 0 0 20px; | |
| 96 | padding: 0; | |
| 97 | } | |
| 98 | ||
| 99 | ul.search li { | |
| 100 | padding: 5px 0 5px 20px; | |
| 101 | background-image: url(file.png); | |
| 102 | background-repeat: no-repeat; | |
| 103 | background-position: 0 7px; | |
| 104 | } | |
| 105 | ||
| 106 | ul.search li a { | |
| 107 | font-weight: bold; | |
| 108 | } | |
| 109 | ||
| 110 | ul.search li div.context { | |
| 111 | color: #888; | |
| 112 | margin: 2px 0 0 30px; | |
| 113 | text-align: left; | |
| 114 | } | |
| 115 | ||
| 116 | ul.keywordmatches li.goodmatch a { | |
| 117 | font-weight: bold; | |
| 118 | } | |
| 119 | ||
| 120 | /* -- index page ------------------------------------------------------------ */ | |
| 121 | ||
| 122 | table.contentstable { | |
| 123 | width: 90%; | |
| 124 | margin-left: auto; | |
| 125 | margin-right: auto; | |
| 126 | } | |
| 127 | ||
| 128 | table.contentstable p.biglink { | |
| 129 | line-height: 150%; | |
| 130 | } | |
| 131 | ||
| 132 | a.biglink { | |
| 133 | font-size: 1.3em; | |
| 134 | } | |
| 135 | ||
| 136 | span.linkdescr { | |
| 137 | font-style: italic; | |
| 138 | padding-top: 5px; | |
| 139 | font-size: 90%; | |
| 140 | } | |
| 141 | ||
| 142 | /* -- general index --------------------------------------------------------- */ | |
| 143 | ||
| 144 | table.indextable { | |
| 145 | width: 100%; | |
| 146 | } | |
| 147 | ||
| 148 | table.indextable td { | |
| 149 | text-align: left; | |
| 150 | vertical-align: top; | |
| 151 | } | |
| 152 | ||
| 153 | table.indextable ul { | |
| 154 | margin-top: 0; | |
| 155 | margin-bottom: 0; | |
| 156 | list-style-type: none; | |
| 157 | } | |
| 158 | ||
| 159 | table.indextable > tbody > tr > td > ul { | |
| 160 | padding-left: 0em; | |
| 161 | } | |
| 162 | ||
| 163 | table.indextable tr.pcap { | |
| 164 | height: 10px; | |
| 165 | } | |
| 166 | ||
| 167 | table.indextable tr.cap { | |
| 168 | margin-top: 10px; | |
| 169 | background-color: #f2f2f2; | |
| 170 | } | |
| 171 | ||
| 172 | img.toggler { | |
| 173 | margin-right: 3px; | |
| 174 | margin-top: 3px; | |
| 175 | cursor: pointer; | |
| 176 | } | |
| 177 | ||
| 178 | div.modindex-jumpbox { | |
| 179 | border-top: 1px solid #ddd; | |
| 180 | border-bottom: 1px solid #ddd; | |
| 181 | margin: 1em 0 1em 0; | |
| 182 | padding: 0.4em; | |
| 183 | } | |
| 184 | ||
| 185 | div.genindex-jumpbox { | |
| 186 | border-top: 1px solid #ddd; | |
| 187 | border-bottom: 1px solid #ddd; | |
| 188 | margin: 1em 0 1em 0; | |
| 189 | padding: 0.4em; | |
| 190 | } | |
| 191 | ||
| 192 | /* -- domain module index --------------------------------------------------- */ | |
| 193 | ||
| 194 | table.modindextable td { | |
| 195 | padding: 2px; | |
| 196 | border-collapse: collapse; | |
| 197 | } | |
| 198 | ||
| 199 | /* -- general body styles --------------------------------------------------- */ | |
| 200 | ||
| 201 | div.body p, div.body dd, div.body li, div.body blockquote { | |
| 202 | -moz-hyphens: auto; | |
| 203 | -ms-hyphens: auto; | |
| 204 | -webkit-hyphens: auto; | |
| 205 | hyphens: auto; | |
| 206 | } | |
| 207 | ||
| 208 | a.headerlink { | |
| 209 | visibility: hidden; | |
| 210 | } | |
| 211 | ||
| 212 | h1:hover > a.headerlink, | |
| 213 | h2:hover > a.headerlink, | |
| 214 | h3:hover > a.headerlink, | |
| 215 | h4:hover > a.headerlink, | |
| 216 | h5:hover > a.headerlink, | |
| 217 | h6:hover > a.headerlink, | |
| 218 | dt:hover > a.headerlink, | |
| 219 | caption:hover > a.headerlink, | |
| 220 | p.caption:hover > a.headerlink, | |
| 221 | div.code-block-caption:hover > a.headerlink { | |
| 222 | visibility: visible; | |
| 223 | } | |
| 224 | ||
| 225 | div.body p.caption { | |
| 226 | text-align: inherit; | |
| 227 | } | |
| 228 | ||
| 229 | div.body td { | |
| 230 | text-align: left; | |
| 231 | } | |
| 232 | ||
| 233 | .first { | |
| 234 | margin-top: 0 !important; | |
| 235 | } | |
| 236 | ||
| 237 | p.rubric { | |
| 238 | margin-top: 30px; | |
| 239 | font-weight: bold; | |
| 240 | } | |
| 241 | ||
| 242 | img.align-left, .figure.align-left, object.align-left { | |
| 243 | clear: left; | |
| 244 | float: left; | |
| 245 | margin-right: 1em; | |
| 246 | } | |
| 247 | ||
| 248 | img.align-right, .figure.align-right, object.align-right { | |
| 249 | clear: right; | |
| 250 | float: right; | |
| 251 | margin-left: 1em; | |
| 252 | } | |
| 253 | ||
| 254 | img.align-center, .figure.align-center, object.align-center { | |
| 255 | display: block; | |
| 256 | margin-left: auto; | |
| 257 | margin-right: auto; | |
| 258 | } | |
| 259 | ||
| 260 | .align-left { | |
| 261 | text-align: left; | |
| 262 | } | |
| 263 | ||
| 264 | .align-center { | |
| 265 | text-align: center; | |
| 266 | } | |
| 267 | ||
| 268 | .align-right { | |
| 269 | text-align: right; | |
| 270 | } | |
| 271 | ||
| 272 | /* -- sidebars -------------------------------------------------------------- */ | |
| 273 | ||
| 274 | div.sidebar { | |
| 275 | margin: 0 0 0.5em 1em; | |
| 276 | border: 1px solid #ddb; | |
| 277 | padding: 7px 7px 0 7px; | |
| 278 | background-color: #ffe; | |
| 279 | width: 40%; | |
| 280 | float: right; | |
| 281 | } | |
| 282 | ||
| 283 | p.sidebar-title { | |
| 284 | font-weight: bold; | |
| 285 | } | |
| 286 | ||
| 287 | /* -- topics ---------------------------------------------------------------- */ | |
| 288 | ||
| 289 | div.topic { | |
| 290 | border: 1px solid #ccc; | |
| 291 | padding: 7px 7px 0 7px; | |
| 292 | margin: 10px 0 10px 0; | |
| 293 | } | |
| 294 | ||
| 295 | p.topic-title { | |
| 296 | font-size: 1.1em; | |
| 297 | font-weight: bold; | |
| 298 | margin-top: 10px; | |
| 299 | } | |
| 300 | ||
| 301 | /* -- admonitions ----------------------------------------------------------- */ | |
| 302 | ||
| 303 | div.admonition { | |
| 304 | margin-top: 10px; | |
| 305 | margin-bottom: 10px; | |
| 306 | padding: 7px; | |
| 307 | } | |
| 308 | ||
| 309 | div.admonition dt { | |
| 310 | font-weight: bold; | |
| 311 | } | |
| 312 | ||
| 313 | div.admonition dl { | |
| 314 | margin-bottom: 0; | |
| 315 | } | |
| 316 | ||
| 317 | p.admonition-title { | |
| 318 | margin: 0px 10px 5px 0px; | |
| 319 | font-weight: bold; | |
| 320 | } | |
| 321 | ||
| 322 | div.body p.centered { | |
| 323 | text-align: center; | |
| 324 | margin-top: 25px; | |
| 325 | } | |
| 326 | ||
| 327 | /* -- tables ---------------------------------------------------------------- */ | |
| 328 | ||
| 329 | table.docutils { | |
| 330 | border: 0; | |
| 331 | border-collapse: collapse; | |
| 332 | } | |
| 333 | ||
| 334 | table caption span.caption-number { | |
| 335 | font-style: italic; | |
| 336 | } | |
| 337 | ||
| 338 | table caption span.caption-text { | |
| 339 | } | |
| 340 | ||
| 341 | table.docutils td, table.docutils th { | |
| 342 | padding: 1px 8px 1px 5px; | |
| 343 | border-top: 0; | |
| 344 | border-left: 0; | |
| 345 | border-right: 0; | |
| 346 | border-bottom: 1px solid #aaa; | |
| 347 | } | |
| 348 | ||
| 349 | table.footnote td, table.footnote th { | |
| 350 | border: 0 !important; | |
| 351 | } | |
| 352 | ||
| 353 | th { | |
| 354 | text-align: left; | |
| 355 | padding-right: 5px; | |
| 356 | } | |
| 357 | ||
| 358 | table.citation { | |
| 359 | border-left: solid 1px gray; | |
| 360 | margin-left: 1px; | |
| 361 | } | |
| 362 | ||
| 363 | table.citation td { | |
| 364 | border-bottom: none; | |
| 365 | } | |
| 366 | ||
| 367 | /* -- figures --------------------------------------------------------------- */ | |
| 368 | ||
| 369 | div.figure { | |
| 370 | margin: 0.5em; | |
| 371 | padding: 0.5em; | |
| 372 | } | |
| 373 | ||
| 374 | div.figure p.caption { | |
| 375 | padding: 0.3em; | |
| 376 | } | |
| 377 | ||
| 378 | div.figure p.caption span.caption-number { | |
| 379 | font-style: italic; | |
| 380 | } | |
| 381 | ||
| 382 | div.figure p.caption span.caption-text { | |
| 383 | } | |
| 384 | ||
| 385 | /* -- field list styles ----------------------------------------------------- */ | |
| 386 | ||
| 387 | table.field-list td, table.field-list th { | |
| 388 | border: 0 !important; | |
| 389 | } | |
| 390 | ||
| 391 | .field-list ul { | |
| 392 | margin: 0; | |
| 393 | padding-left: 1em; | |
| 394 | } | |
| 395 | ||
| 396 | .field-list p { | |
| 397 | margin: 0; | |
| 398 | } | |
| 399 | ||
| 400 | /* -- other body styles ----------------------------------------------------- */ | |
| 401 | ||
| 402 | ol.arabic { | |
| 403 | list-style: decimal; | |
| 404 | } | |
| 405 | ||
| 406 | ol.loweralpha { | |
| 407 | list-style: lower-alpha; | |
| 408 | } | |
| 409 | ||
| 410 | ol.upperalpha { | |
| 411 | list-style: upper-alpha; | |
| 412 | } | |
| 413 | ||
| 414 | ol.lowerroman { | |
| 415 | list-style: lower-roman; | |
| 416 | } | |
| 417 | ||
| 418 | ol.upperroman { | |
| 419 | list-style: upper-roman; | |
| 420 | } | |
| 421 | ||
| 422 | dl { | |
| 423 | margin-bottom: 15px; | |
| 424 | } | |
| 425 | ||
| 426 | dd p { | |
| 427 | margin-top: 0px; | |
| 428 | } | |
| 429 | ||
| 430 | dd ul, dd table { | |
| 431 | margin-bottom: 10px; | |
| 432 | } | |
| 433 | ||
| 434 | dd { | |
| 435 | margin-top: 3px; | |
| 436 | margin-bottom: 10px; | |
| 437 | margin-left: 30px; | |
| 438 | } | |
| 439 | ||
| 440 | dt:target, .highlighted { | |
| 441 | background-color: #fbe54e; | |
| 442 | } | |
| 443 | ||
| 444 | dl.glossary dt { | |
| 445 | font-weight: bold; | |
| 446 | font-size: 1.1em; | |
| 447 | } | |
| 448 | ||
| 449 | .optional { | |
| 450 | font-size: 1.3em; | |
| 451 | } | |
| 452 | ||
| 453 | .sig-paren { | |
| 454 | font-size: larger; | |
| 455 | } | |
| 456 | ||
| 457 | .versionmodified { | |
| 458 | font-style: italic; | |
| 459 | } | |
| 460 | ||
| 461 | .system-message { | |
| 462 | background-color: #fda; | |
| 463 | padding: 5px; | |
| 464 | border: 3px solid red; | |
| 465 | } | |
| 466 | ||
| 467 | .footnote:target { | |
| 468 | background-color: #ffa; | |
| 469 | } | |
| 470 | ||
| 471 | .line-block { | |
| 472 | display: block; | |
| 473 | margin-top: 1em; | |
| 474 | margin-bottom: 1em; | |
| 475 | } | |
| 476 | ||
| 477 | .line-block .line-block { | |
| 478 | margin-top: 0; | |
| 479 | margin-bottom: 0; | |
| 480 | margin-left: 1.5em; | |
| 481 | } | |
| 482 | ||
| 483 | .guilabel, .menuselection { | |
| 484 | font-family: sans-serif; | |
| 485 | } | |
| 486 | ||
| 487 | .accelerator { | |
| 488 | text-decoration: underline; | |
| 489 | } | |
| 490 | ||
| 491 | .classifier { | |
| 492 | font-style: oblique; | |
| 493 | } | |
| 494 | ||
| 495 | abbr, acronym { | |
| 496 | border-bottom: dotted 1px; | |
| 497 | cursor: help; | |
| 498 | } | |
| 499 | ||
| 500 | /* -- code displays --------------------------------------------------------- */ | |
| 501 | ||
| 502 | pre { | |
| 503 | overflow: auto; | |
| 504 | overflow-y: hidden; /* fixes display issues on Chrome browsers */ | |
| 505 | } | |
| 506 | ||
| 507 | span.pre { | |
| 508 | -moz-hyphens: none; | |
| 509 | -ms-hyphens: none; | |
| 510 | -webkit-hyphens: none; | |
| 511 | hyphens: none; | |
| 512 | } | |
| 513 | ||
| 514 | td.linenos pre { | |
| 515 | padding: 5px 0px; | |
| 516 | border: 0; | |
| 517 | background-color: transparent; | |
| 518 | color: #aaa; | |
| 519 | } | |
| 520 | ||
| 521 | table.highlighttable { | |
| 522 | margin-left: 0.5em; | |
| 523 | } | |
| 524 | ||
| 525 | table.highlighttable td { | |
| 526 | padding: 0 0.5em 0 0.5em; | |
| 527 | } | |
| 528 | ||
| 529 | div.code-block-caption { | |
| 530 | padding: 2px 5px; | |
| 531 | font-size: small; | |
| 532 | } | |
| 533 | ||
| 534 | div.code-block-caption code { | |
| 535 | background-color: transparent; | |
| 536 | } | |
| 537 | ||
| 538 | div.code-block-caption + div > div.highlight > pre { | |
| 539 | margin-top: 0; | |
| 540 | } | |
| 541 | ||
| 542 | div.code-block-caption span.caption-number { | |
| 543 | padding: 0.1em 0.3em; | |
| 544 | font-style: italic; | |
| 545 | } | |
| 546 | ||
| 547 | div.code-block-caption span.caption-text { | |
| 548 | } | |
| 549 | ||
| 550 | div.literal-block-wrapper { | |
| 551 | padding: 1em 1em 0; | |
| 552 | } | |
| 553 | ||
| 554 | div.literal-block-wrapper div.highlight { | |
| 555 | margin: 0; | |
| 556 | } | |
| 557 | ||
| 558 | code.descname { | |
| 559 | background-color: transparent; | |
| 560 | font-weight: bold; | |
| 561 | font-size: 1.2em; | |
| 562 | } | |
| 563 | ||
| 564 | code.descclassname { | |
| 565 | background-color: transparent; | |
| 566 | } | |
| 567 | ||
| 568 | code.xref, a code { | |
| 569 | background-color: transparent; | |
| 570 | font-weight: bold; | |
| 571 | } | |
| 572 | ||
| 573 | h1 code, h2 code, h3 code, h4 code, h5 code, h6 code { | |
| 574 | background-color: transparent; | |
| 575 | } | |
| 576 | ||
| 577 | .viewcode-link { | |
| 578 | float: right; | |
| 579 | } | |
| 580 | ||
| 581 | .viewcode-back { | |
| 582 | float: right; | |
| 583 | font-family: sans-serif; | |
| 584 | } | |
| 585 | ||
| 586 | div.viewcode-block:target { | |
| 587 | margin: -1px -10px; | |
| 588 | padding: 0 10px; | |
| 589 | } | |
| 590 | ||
| 591 | /* -- math display ---------------------------------------------------------- */ | |
| 592 | ||
| 593 | img.math { | |
| 594 | vertical-align: middle; | |
| 595 | } | |
| 596 | ||
| 597 | div.body div.math p { | |
| 598 | text-align: center; | |
| 599 | } | |
| 600 | ||
| 601 | span.eqno { | |
| 602 | float: right; | |
| 603 | } | |
| 604 | ||
| 605 | span.eqno a.headerlink { | |
| 606 | position: relative; | |
| 607 | left: 0px; | |
| 608 | z-index: 1; | |
| 609 | } | |
| 610 | ||
| 611 | div.math:hover a.headerlink { | |
| 612 | visibility: visible; | |
| 613 | } | |
| 614 | ||
| 615 | /* -- printout stylesheet --------------------------------------------------- */ | |
| 616 | ||
| 617 | @media print { | |
| 618 | div.document, | |
| 619 | div.documentwrapper, | |
| 620 | div.bodywrapper { | |
| 621 | margin: 0 !important; | |
| 622 | width: 100%; | |
| 623 | } | |
| 624 | ||
| 625 | div.sphinxsidebar, | |
| 626 | div.related, | |
| 627 | div.footer, | |
| 628 | #top-link { | |
| 629 | display: none; | |
| 630 | } | |
| 631 | }⏎ |
Binary diff not shown
Binary diff not shown
Binary diff not shown
| 0 | .fa:before{-webkit-font-smoothing:antialiased}.clearfix{*zoom:1}.clearfix:before,.clearfix:after{display:table;content:""}.clearfix:after{clear:both}@font-face{font-family:FontAwesome;font-weight:normal;font-style:normal;src:url("../font/fontawesome_webfont.eot");src:url("../font/fontawesome_webfont.eot?#iefix") format("embedded-opentype"),url("../font/fontawesome_webfont.woff") format("woff"),url("../font/fontawesome_webfont.ttf") format("truetype"),url("../font/fontawesome_webfont.svg#FontAwesome") format("svg")}.fa:before{display:inline-block;font-family:FontAwesome;font-style:normal;font-weight:normal;line-height:1;text-decoration:inherit}a .fa{display:inline-block;text-decoration:inherit}li .fa{display:inline-block}li .fa-large:before,li .fa-large:before{width:1.875em}ul.fas{list-style-type:none;margin-left:2em;text-indent:-0.8em}ul.fas li .fa{width:0.8em}ul.fas li .fa-large:before,ul.fas li .fa-large:before{vertical-align:baseline}.fa-book:before{content:""}.icon-book:before{content:""}.fa-caret-down:before{content:""}.icon-caret-down:before{content:""}.fa-caret-up:before{content:""}.icon-caret-up:before{content:""}.fa-caret-left:before{content:""}.icon-caret-left:before{content:""}.fa-caret-right:before{content:""}.icon-caret-right:before{content:""}.rst-versions{position:fixed;bottom:0;left:0;width:300px;color:#fcfcfc;background:#1f1d1d;border-top:solid 10px #343131;font-family:"Lato","proxima-nova","Helvetica Neue",Arial,sans-serif;z-index:400}.rst-versions a{color:#2980B9;text-decoration:none}.rst-versions .rst-badge-small{display:none}.rst-versions .rst-current-version{padding:12px;background-color:#272525;display:block;text-align:right;font-size:90%;cursor:pointer;color:#27AE60;*zoom:1}.rst-versions .rst-current-version:before,.rst-versions .rst-current-version:after{display:table;content:""}.rst-versions .rst-current-version:after{clear:both}.rst-versions .rst-current-version .fa{color:#fcfcfc}.rst-versions .rst-current-version .fa-book{float:left}.rst-versions .rst-current-version .icon-book{float:left}.rst-versions .rst-current-version.rst-out-of-date{background-color:#E74C3C;color:#fff}.rst-versions .rst-current-version.rst-active-old-version{background-color:#F1C40F;color:#000}.rst-versions.shift-up .rst-other-versions{display:block}.rst-versions .rst-other-versions{font-size:90%;padding:12px;color:gray;display:none}.rst-versions .rst-other-versions hr{display:block;height:1px;border:0;margin:20px 0;padding:0;border-top:solid 1px #413d3d}.rst-versions .rst-other-versions dd{display:inline-block;margin:0}.rst-versions .rst-other-versions dd a{display:inline-block;padding:6px;color:#fcfcfc}.rst-versions.rst-badge{width:auto;bottom:20px;right:20px;left:auto;border:none;max-width:300px}.rst-versions.rst-badge .icon-book{float:none}.rst-versions.rst-badge .fa-book{float:none}.rst-versions.rst-badge.shift-up .rst-current-version{text-align:right}.rst-versions.rst-badge.shift-up .rst-current-version .fa-book{float:left}.rst-versions.rst-badge.shift-up .rst-current-version .icon-book{float:left}.rst-versions.rst-badge .rst-current-version{width:auto;height:30px;line-height:30px;padding:0 6px;display:block;text-align:center}@media screen and (max-width: 768px){.rst-versions{width:85%;display:none}.rst-versions.shift{display:block}img{width:100%;height:auto}} | |
| 1 | /*# sourceMappingURL=badge_only.css.map */ |
| 0 | *{-webkit-box-sizing:border-box;-moz-box-sizing:border-box;box-sizing:border-box}article,aside,details,figcaption,figure,footer,header,hgroup,nav,section{display:block}audio,canvas,video{display:inline-block;*display:inline;*zoom:1}audio:not([controls]){display:none}[hidden]{display:none}*{-webkit-box-sizing:border-box;-moz-box-sizing:border-box;box-sizing:border-box}html{font-size:100%;-webkit-text-size-adjust:100%;-ms-text-size-adjust:100%}body{margin:0}a:hover,a:active{outline:0}abbr[title]{border-bottom:1px dotted}b,strong{font-weight:bold}blockquote{margin:0}dfn{font-style:italic}ins{background:#ff9;color:#000;text-decoration:none}mark{background:#ff0;color:#000;font-style:italic;font-weight:bold}pre,code,.rst-content tt,.rst-content code,kbd,samp{font-family:monospace,serif;_font-family:"courier new",monospace;font-size:1em}pre{white-space:pre}q{quotes:none}q:before,q:after{content:"";content:none}small{font-size:85%}sub,sup{font-size:75%;line-height:0;position:relative;vertical-align:baseline}sup{top:-0.5em}sub{bottom:-0.25em}ul,ol,dl{margin:0;padding:0;list-style:none;list-style-image:none}li{list-style:none}dd{margin:0}img{border:0;-ms-interpolation-mode:bicubic;vertical-align:middle;max-width:100%}svg:not(:root){overflow:hidden}figure{margin:0}form{margin:0}fieldset{border:0;margin:0;padding:0}label{cursor:pointer}legend{border:0;*margin-left:-7px;padding:0;white-space:normal}button,input,select,textarea{font-size:100%;margin:0;vertical-align:baseline;*vertical-align:middle}button,input{line-height:normal}button,input[type="button"],input[type="reset"],input[type="submit"]{cursor:pointer;-webkit-appearance:button;*overflow:visible}button[disabled],input[disabled]{cursor:default}input[type="checkbox"],input[type="radio"]{box-sizing:border-box;padding:0;*width:13px;*height:13px}input[type="search"]{-webkit-appearance:textfield;-moz-box-sizing:content-box;-webkit-box-sizing:content-box;box-sizing:content-box}input[type="search"]::-webkit-search-decoration,input[type="search"]::-webkit-search-cancel-button{-webkit-appearance:none}button::-moz-focus-inner,input::-moz-focus-inner{border:0;padding:0}textarea{overflow:auto;vertical-align:top;resize:vertical}table{border-collapse:collapse;border-spacing:0}td{vertical-align:top}.chromeframe{margin:0.2em 0;background:#ccc;color:#000;padding:0.2em 0}.ir{display:block;border:0;text-indent:-999em;overflow:hidden;background-color:transparent;background-repeat:no-repeat;text-align:left;direction:ltr;*line-height:0}.ir br{display:none}.hidden{display:none !important;visibility:hidden}.visuallyhidden{border:0;clip:rect(0 0 0 0);height:1px;margin:-1px;overflow:hidden;padding:0;position:absolute;width:1px}.visuallyhidden.focusable:active,.visuallyhidden.focusable:focus{clip:auto;height:auto;margin:0;overflow:visible;position:static;width:auto}.invisible{visibility:hidden}.relative{position:relative}big,small{font-size:100%}@media print{html,body,section{background:none !important}*{box-shadow:none !important;text-shadow:none !important;filter:none !important;-ms-filter:none !important}a,a:visited{text-decoration:underline}.ir a:after,a[href^="javascript:"]:after,a[href^="#"]:after{content:""}pre,blockquote{page-break-inside:avoid}thead{display:table-header-group}tr,img{page-break-inside:avoid}img{max-width:100% !important}@page{margin:0.5cm}p,h2,.rst-content .toctree-wrapper p.caption,h3{orphans:3;widows:3}h2,.rst-content .toctree-wrapper p.caption,h3{page-break-after:avoid}}.fa:before,.wy-menu-vertical li span.toctree-expand:before,.wy-menu-vertical li.on a span.toctree-expand:before,.wy-menu-vertical li.current>a span.toctree-expand:before,.rst-content .admonition-title:before,.rst-content h1 .headerlink:before,.rst-content h2 .headerlink:before,.rst-content h3 .headerlink:before,.rst-content h4 .headerlink:before,.rst-content h5 .headerlink:before,.rst-content h6 .headerlink:before,.rst-content dl dt .headerlink:before,.rst-content p.caption .headerlink:before,.rst-content tt.download span:first-child:before,.rst-content code.download span:first-child:before,.icon:before,.wy-dropdown .caret:before,.wy-inline-validate.wy-inline-validate-success .wy-input-context:before,.wy-inline-validate.wy-inline-validate-danger .wy-input-context:before,.wy-inline-validate.wy-inline-validate-warning .wy-input-context:before,.wy-inline-validate.wy-inline-validate-info .wy-input-context:before,.wy-alert,.rst-content .note,.rst-content .attention,.rst-content .caution,.rst-content .danger,.rst-content .error,.rst-content .hint,.rst-content .important,.rst-content .tip,.rst-content .warning,.rst-content .seealso,.rst-content .admonition-todo,.btn,input[type="text"],input[type="password"],input[type="email"],input[type="url"],input[type="date"],input[type="month"],input[type="time"],input[type="datetime"],input[type="datetime-local"],input[type="week"],input[type="number"],input[type="search"],input[type="tel"],input[type="color"],select,textarea,.wy-menu-vertical li.on a,.wy-menu-vertical li.current>a,.wy-side-nav-search>a,.wy-side-nav-search .wy-dropdown>a,.wy-nav-top a{-webkit-font-smoothing:antialiased}.clearfix{*zoom:1}.clearfix:before,.clearfix:after{display:table;content:""}.clearfix:after{clear:both}/*! | |
| 1 | * Font Awesome 4.2.0 by @davegandy - http://fontawesome.io - @fontawesome | |
| 2 | * License - http://fontawesome.io/license (Font: SIL OFL 1.1, CSS: MIT License) | |
| 3 | */@font-face{font-family:'FontAwesome';src:url("../fonts/fontawesome-webfont.eot?v=4.2.0");src:url("../fonts/fontawesome-webfont.eot?#iefix&v=4.2.0") format("embedded-opentype"),url("../fonts/fontawesome-webfont.woff?v=4.2.0") format("woff"),url("../fonts/fontawesome-webfont.ttf?v=4.2.0") format("truetype"),url("../fonts/fontawesome-webfont.svg?v=4.2.0#fontawesomeregular") format("svg");font-weight:normal;font-style:normal}.fa,.wy-menu-vertical li span.toctree-expand,.wy-menu-vertical li.on a span.toctree-expand,.wy-menu-vertical li.current>a span.toctree-expand,.rst-content .admonition-title,.rst-content h1 .headerlink,.rst-content h2 .headerlink,.rst-content h3 .headerlink,.rst-content h4 .headerlink,.rst-content h5 .headerlink,.rst-content h6 .headerlink,.rst-content dl dt .headerlink,.rst-content p.caption .headerlink,.rst-content tt.download span:first-child,.rst-content code.download span:first-child,.icon{display:inline-block;font:normal normal normal 14px/1 FontAwesome;font-size:inherit;text-rendering:auto;-webkit-font-smoothing:antialiased;-moz-osx-font-smoothing:grayscale}.fa-lg{font-size:1.33333em;line-height:0.75em;vertical-align:-15%}.fa-2x{font-size:2em}.fa-3x{font-size:3em}.fa-4x{font-size:4em}.fa-5x{font-size:5em}.fa-fw{width:1.28571em;text-align:center}.fa-ul{padding-left:0;margin-left:2.14286em;list-style-type:none}.fa-ul>li{position:relative}.fa-li{position:absolute;left:-2.14286em;width:2.14286em;top:0.14286em;text-align:center}.fa-li.fa-lg{left:-1.85714em}.fa-border{padding:.2em .25em .15em;border:solid 0.08em #eee;border-radius:.1em}.pull-right{float:right}.pull-left{float:left}.fa.pull-left,.wy-menu-vertical li span.pull-left.toctree-expand,.wy-menu-vertical li.on a span.pull-left.toctree-expand,.wy-menu-vertical li.current>a span.pull-left.toctree-expand,.rst-content .pull-left.admonition-title,.rst-content h1 .pull-left.headerlink,.rst-content h2 .pull-left.headerlink,.rst-content h3 .pull-left.headerlink,.rst-content h4 .pull-left.headerlink,.rst-content h5 .pull-left.headerlink,.rst-content h6 .pull-left.headerlink,.rst-content dl dt .pull-left.headerlink,.rst-content p.caption .pull-left.headerlink,.rst-content tt.download span.pull-left:first-child,.rst-content code.download span.pull-left:first-child,.pull-left.icon{margin-right:.3em}.fa.pull-right,.wy-menu-vertical li span.pull-right.toctree-expand,.wy-menu-vertical li.on a span.pull-right.toctree-expand,.wy-menu-vertical li.current>a span.pull-right.toctree-expand,.rst-content .pull-right.admonition-title,.rst-content h1 .pull-right.headerlink,.rst-content h2 .pull-right.headerlink,.rst-content h3 .pull-right.headerlink,.rst-content h4 .pull-right.headerlink,.rst-content h5 .pull-right.headerlink,.rst-content h6 .pull-right.headerlink,.rst-content dl dt .pull-right.headerlink,.rst-content p.caption .pull-right.headerlink,.rst-content tt.download span.pull-right:first-child,.rst-content code.download span.pull-right:first-child,.pull-right.icon{margin-left:.3em}.fa-spin{-webkit-animation:fa-spin 2s infinite linear;animation:fa-spin 2s infinite linear}@-webkit-keyframes fa-spin{0%{-webkit-transform:rotate(0deg);transform:rotate(0deg)}100%{-webkit-transform:rotate(359deg);transform:rotate(359deg)}}@keyframes fa-spin{0%{-webkit-transform:rotate(0deg);transform:rotate(0deg)}100%{-webkit-transform:rotate(359deg);transform:rotate(359deg)}}.fa-rotate-90{filter:progid:DXImageTransform.Microsoft.BasicImage(rotation=1);-webkit-transform:rotate(90deg);-ms-transform:rotate(90deg);transform:rotate(90deg)}.fa-rotate-180{filter:progid:DXImageTransform.Microsoft.BasicImage(rotation=2);-webkit-transform:rotate(180deg);-ms-transform:rotate(180deg);transform:rotate(180deg)}.fa-rotate-270{filter:progid:DXImageTransform.Microsoft.BasicImage(rotation=3);-webkit-transform:rotate(270deg);-ms-transform:rotate(270deg);transform:rotate(270deg)}.fa-flip-horizontal{filter:progid:DXImageTransform.Microsoft.BasicImage(rotation=0);-webkit-transform:scale(-1, 1);-ms-transform:scale(-1, 1);transform:scale(-1, 1)}.fa-flip-vertical{filter:progid:DXImageTransform.Microsoft.BasicImage(rotation=2);-webkit-transform:scale(1, -1);-ms-transform:scale(1, -1);transform:scale(1, -1)}:root .fa-rotate-90,:root .fa-rotate-180,:root .fa-rotate-270,:root .fa-flip-horizontal,:root .fa-flip-vertical{filter:none}.fa-stack{position:relative;display:inline-block;width:2em;height:2em;line-height:2em;vertical-align:middle}.fa-stack-1x,.fa-stack-2x{position:absolute;left:0;width:100%;text-align:center}.fa-stack-1x{line-height:inherit}.fa-stack-2x{font-size:2em}.fa-inverse{color:#fff}.fa-glass:before{content:""}.fa-music:before{content:""}.fa-search:before,.icon-search:before{content:""}.fa-envelope-o:before{content:""}.fa-heart:before{content:""}.fa-star:before{content:""}.fa-star-o:before{content:""}.fa-user:before{content:""}.fa-film:before{content:""}.fa-th-large:before{content:""}.fa-th:before{content:""}.fa-th-list:before{content:""}.fa-check:before{content:""}.fa-remove:before,.fa-close:before,.fa-times:before{content:""}.fa-search-plus:before{content:""}.fa-search-minus:before{content:""}.fa-power-off:before{content:""}.fa-signal:before{content:""}.fa-gear:before,.fa-cog:before{content:""}.fa-trash-o:before{content:""}.fa-home:before,.icon-home:before{content:""}.fa-file-o:before{content:""}.fa-clock-o:before{content:""}.fa-road:before{content:""}.fa-download:before,.rst-content tt.download span:first-child:before,.rst-content code.download span:first-child:before{content:""}.fa-arrow-circle-o-down:before{content:""}.fa-arrow-circle-o-up:before{content:""}.fa-inbox:before{content:""}.fa-play-circle-o:before{content:""}.fa-rotate-right:before,.fa-repeat:before{content:""}.fa-refresh:before{content:""}.fa-list-alt:before{content:""}.fa-lock:before{content:""}.fa-flag:before{content:""}.fa-headphones:before{content:""}.fa-volume-off:before{content:""}.fa-volume-down:before{content:""}.fa-volume-up:before{content:""}.fa-qrcode:before{content:""}.fa-barcode:before{content:""}.fa-tag:before{content:""}.fa-tags:before{content:""}.fa-book:before,.icon-book:before{content:""}.fa-bookmark:before{content:""}.fa-print:before{content:""}.fa-camera:before{content:""}.fa-font:before{content:""}.fa-bold:before{content:""}.fa-italic:before{content:""}.fa-text-height:before{content:""}.fa-text-width:before{content:""}.fa-align-left:before{content:""}.fa-align-center:before{content:""}.fa-align-right:before{content:""}.fa-align-justify:before{content:""}.fa-list:before{content:""}.fa-dedent:before,.fa-outdent:before{content:""}.fa-indent:before{content:""}.fa-video-camera:before{content:""}.fa-photo:before,.fa-image:before,.fa-picture-o:before{content:""}.fa-pencil:before{content:""}.fa-map-marker:before{content:""}.fa-adjust:before{content:""}.fa-tint:before{content:""}.fa-edit:before,.fa-pencil-square-o:before{content:""}.fa-share-square-o:before{content:""}.fa-check-square-o:before{content:""}.fa-arrows:before{content:""}.fa-step-backward:before{content:""}.fa-fast-backward:before{content:""}.fa-backward:before{content:""}.fa-play:before{content:""}.fa-pause:before{content:""}.fa-stop:before{content:""}.fa-forward:before{content:""}.fa-fast-forward:before{content:""}.fa-step-forward:before{content:""}.fa-eject:before{content:""}.fa-chevron-left:before{content:""}.fa-chevron-right:before{content:""}.fa-plus-circle:before{content:""}.fa-minus-circle:before{content:""}.fa-times-circle:before,.wy-inline-validate.wy-inline-validate-danger .wy-input-context:before{content:""}.fa-check-circle:before,.wy-inline-validate.wy-inline-validate-success .wy-input-context:before{content:""}.fa-question-circle:before{content:""}.fa-info-circle:before{content:""}.fa-crosshairs:before{content:""}.fa-times-circle-o:before{content:""}.fa-check-circle-o:before{content:""}.fa-ban:before{content:""}.fa-arrow-left:before{content:""}.fa-arrow-right:before{content:""}.fa-arrow-up:before{content:""}.fa-arrow-down:before{content:""}.fa-mail-forward:before,.fa-share:before{content:""}.fa-expand:before{content:""}.fa-compress:before{content:""}.fa-plus:before{content:""}.fa-minus:before{content:""}.fa-asterisk:before{content:""}.fa-exclamation-circle:before,.wy-inline-validate.wy-inline-validate-warning .wy-input-context:before,.wy-inline-validate.wy-inline-validate-info .wy-input-context:before,.rst-content .admonition-title:before{content:""}.fa-gift:before{content:""}.fa-leaf:before{content:""}.fa-fire:before,.icon-fire:before{content:""}.fa-eye:before{content:""}.fa-eye-slash:before{content:""}.fa-warning:before,.fa-exclamation-triangle:before{content:""}.fa-plane:before{content:""}.fa-calendar:before{content:""}.fa-random:before{content:""}.fa-comment:before{content:""}.fa-magnet:before{content:""}.fa-chevron-up:before{content:""}.fa-chevron-down:before{content:""}.fa-retweet:before{content:""}.fa-shopping-cart:before{content:""}.fa-folder:before{content:""}.fa-folder-open:before{content:""}.fa-arrows-v:before{content:""}.fa-arrows-h:before{content:""}.fa-bar-chart-o:before,.fa-bar-chart:before{content:""}.fa-twitter-square:before{content:""}.fa-facebook-square:before{content:""}.fa-camera-retro:before{content:""}.fa-key:before{content:""}.fa-gears:before,.fa-cogs:before{content:""}.fa-comments:before{content:""}.fa-thumbs-o-up:before{content:""}.fa-thumbs-o-down:before{content:""}.fa-star-half:before{content:""}.fa-heart-o:before{content:""}.fa-sign-out:before{content:""}.fa-linkedin-square:before{content:""}.fa-thumb-tack:before{content:""}.fa-external-link:before{content:""}.fa-sign-in:before{content:""}.fa-trophy:before{content:""}.fa-github-square:before{content:""}.fa-upload:before{content:""}.fa-lemon-o:before{content:""}.fa-phone:before{content:""}.fa-square-o:before{content:""}.fa-bookmark-o:before{content:""}.fa-phone-square:before{content:""}.fa-twitter:before{content:""}.fa-facebook:before{content:""}.fa-github:before,.icon-github:before{content:""}.fa-unlock:before{content:""}.fa-credit-card:before{content:""}.fa-rss:before{content:""}.fa-hdd-o:before{content:""}.fa-bullhorn:before{content:""}.fa-bell:before{content:""}.fa-certificate:before{content:""}.fa-hand-o-right:before{content:""}.fa-hand-o-left:before{content:""}.fa-hand-o-up:before{content:""}.fa-hand-o-down:before{content:""}.fa-arrow-circle-left:before,.icon-circle-arrow-left:before{content:""}.fa-arrow-circle-right:before,.icon-circle-arrow-right:before{content:""}.fa-arrow-circle-up:before{content:""}.fa-arrow-circle-down:before{content:""}.fa-globe:before{content:""}.fa-wrench:before{content:""}.fa-tasks:before{content:""}.fa-filter:before{content:""}.fa-briefcase:before{content:""}.fa-arrows-alt:before{content:""}.fa-group:before,.fa-users:before{content:""}.fa-chain:before,.fa-link:before,.icon-link:before{content:""}.fa-cloud:before{content:""}.fa-flask:before{content:""}.fa-cut:before,.fa-scissors:before{content:""}.fa-copy:before,.fa-files-o:before{content:""}.fa-paperclip:before{content:""}.fa-save:before,.fa-floppy-o:before{content:""}.fa-square:before{content:""}.fa-navicon:before,.fa-reorder:before,.fa-bars:before{content:""}.fa-list-ul:before{content:""}.fa-list-ol:before{content:""}.fa-strikethrough:before{content:""}.fa-underline:before{content:""}.fa-table:before{content:""}.fa-magic:before{content:""}.fa-truck:before{content:""}.fa-pinterest:before{content:""}.fa-pinterest-square:before{content:""}.fa-google-plus-square:before{content:""}.fa-google-plus:before{content:""}.fa-money:before{content:""}.fa-caret-down:before,.wy-dropdown .caret:before,.icon-caret-down:before{content:""}.fa-caret-up:before{content:""}.fa-caret-left:before{content:""}.fa-caret-right:before{content:""}.fa-columns:before{content:""}.fa-unsorted:before,.fa-sort:before{content:""}.fa-sort-down:before,.fa-sort-desc:before{content:""}.fa-sort-up:before,.fa-sort-asc:before{content:""}.fa-envelope:before{content:""}.fa-linkedin:before{content:""}.fa-rotate-left:before,.fa-undo:before{content:""}.fa-legal:before,.fa-gavel:before{content:""}.fa-dashboard:before,.fa-tachometer:before{content:""}.fa-comment-o:before{content:""}.fa-comments-o:before{content:""}.fa-flash:before,.fa-bolt:before{content:""}.fa-sitemap:before{content:""}.fa-umbrella:before{content:""}.fa-paste:before,.fa-clipboard:before{content:""}.fa-lightbulb-o:before{content:""}.fa-exchange:before{content:""}.fa-cloud-download:before{content:""}.fa-cloud-upload:before{content:""}.fa-user-md:before{content:""}.fa-stethoscope:before{content:""}.fa-suitcase:before{content:""}.fa-bell-o:before{content:""}.fa-coffee:before{content:""}.fa-cutlery:before{content:""}.fa-file-text-o:before{content:""}.fa-building-o:before{content:""}.fa-hospital-o:before{content:""}.fa-ambulance:before{content:""}.fa-medkit:before{content:""}.fa-fighter-jet:before{content:""}.fa-beer:before{content:""}.fa-h-square:before{content:""}.fa-plus-square:before{content:""}.fa-angle-double-left:before{content:""}.fa-angle-double-right:before{content:""}.fa-angle-double-up:before{content:""}.fa-angle-double-down:before{content:""}.fa-angle-left:before{content:""}.fa-angle-right:before{content:""}.fa-angle-up:before{content:""}.fa-angle-down:before{content:""}.fa-desktop:before{content:""}.fa-laptop:before{content:""}.fa-tablet:before{content:""}.fa-mobile-phone:before,.fa-mobile:before{content:""}.fa-circle-o:before{content:""}.fa-quote-left:before{content:""}.fa-quote-right:before{content:""}.fa-spinner:before{content:""}.fa-circle:before{content:""}.fa-mail-reply:before,.fa-reply:before{content:""}.fa-github-alt:before{content:""}.fa-folder-o:before{content:""}.fa-folder-open-o:before{content:""}.fa-smile-o:before{content:""}.fa-frown-o:before{content:""}.fa-meh-o:before{content:""}.fa-gamepad:before{content:""}.fa-keyboard-o:before{content:""}.fa-flag-o:before{content:""}.fa-flag-checkered:before{content:""}.fa-terminal:before{content:""}.fa-code:before{content:""}.fa-mail-reply-all:before,.fa-reply-all:before{content:""}.fa-star-half-empty:before,.fa-star-half-full:before,.fa-star-half-o:before{content:""}.fa-location-arrow:before{content:""}.fa-crop:before{content:""}.fa-code-fork:before{content:""}.fa-unlink:before,.fa-chain-broken:before{content:""}.fa-question:before{content:""}.fa-info:before{content:""}.fa-exclamation:before{content:""}.fa-superscript:before{content:""}.fa-subscript:before{content:""}.fa-eraser:before{content:""}.fa-puzzle-piece:before{content:""}.fa-microphone:before{content:""}.fa-microphone-slash:before{content:""}.fa-shield:before{content:""}.fa-calendar-o:before{content:""}.fa-fire-extinguisher:before{content:""}.fa-rocket:before{content:""}.fa-maxcdn:before{content:""}.fa-chevron-circle-left:before{content:""}.fa-chevron-circle-right:before{content:""}.fa-chevron-circle-up:before{content:""}.fa-chevron-circle-down:before{content:""}.fa-html5:before{content:""}.fa-css3:before{content:""}.fa-anchor:before{content:""}.fa-unlock-alt:before{content:""}.fa-bullseye:before{content:""}.fa-ellipsis-h:before{content:""}.fa-ellipsis-v:before{content:""}.fa-rss-square:before{content:""}.fa-play-circle:before{content:""}.fa-ticket:before{content:""}.fa-minus-square:before{content:""}.fa-minus-square-o:before,.wy-menu-vertical li.on a span.toctree-expand:before,.wy-menu-vertical li.current>a span.toctree-expand:before{content:""}.fa-level-up:before{content:""}.fa-level-down:before{content:""}.fa-check-square:before{content:""}.fa-pencil-square:before{content:""}.fa-external-link-square:before{content:""}.fa-share-square:before{content:""}.fa-compass:before{content:""}.fa-toggle-down:before,.fa-caret-square-o-down:before{content:""}.fa-toggle-up:before,.fa-caret-square-o-up:before{content:""}.fa-toggle-right:before,.fa-caret-square-o-right:before{content:""}.fa-euro:before,.fa-eur:before{content:""}.fa-gbp:before{content:""}.fa-dollar:before,.fa-usd:before{content:""}.fa-rupee:before,.fa-inr:before{content:""}.fa-cny:before,.fa-rmb:before,.fa-yen:before,.fa-jpy:before{content:""}.fa-ruble:before,.fa-rouble:before,.fa-rub:before{content:""}.fa-won:before,.fa-krw:before{content:""}.fa-bitcoin:before,.fa-btc:before{content:""}.fa-file:before{content:""}.fa-file-text:before{content:""}.fa-sort-alpha-asc:before{content:""}.fa-sort-alpha-desc:before{content:""}.fa-sort-amount-asc:before{content:""}.fa-sort-amount-desc:before{content:""}.fa-sort-numeric-asc:before{content:""}.fa-sort-numeric-desc:before{content:""}.fa-thumbs-up:before{content:""}.fa-thumbs-down:before{content:""}.fa-youtube-square:before{content:""}.fa-youtube:before{content:""}.fa-xing:before{content:""}.fa-xing-square:before{content:""}.fa-youtube-play:before{content:""}.fa-dropbox:before{content:""}.fa-stack-overflow:before{content:""}.fa-instagram:before{content:""}.fa-flickr:before{content:""}.fa-adn:before{content:""}.fa-bitbucket:before,.icon-bitbucket:before{content:""}.fa-bitbucket-square:before{content:""}.fa-tumblr:before{content:""}.fa-tumblr-square:before{content:""}.fa-long-arrow-down:before{content:""}.fa-long-arrow-up:before{content:""}.fa-long-arrow-left:before{content:""}.fa-long-arrow-right:before{content:""}.fa-apple:before{content:""}.fa-windows:before{content:""}.fa-android:before{content:""}.fa-linux:before{content:""}.fa-dribbble:before{content:""}.fa-skype:before{content:""}.fa-foursquare:before{content:""}.fa-trello:before{content:""}.fa-female:before{content:""}.fa-male:before{content:""}.fa-gittip:before{content:""}.fa-sun-o:before{content:""}.fa-moon-o:before{content:""}.fa-archive:before{content:""}.fa-bug:before{content:""}.fa-vk:before{content:""}.fa-weibo:before{content:""}.fa-renren:before{content:""}.fa-pagelines:before{content:""}.fa-stack-exchange:before{content:""}.fa-arrow-circle-o-right:before{content:""}.fa-arrow-circle-o-left:before{content:""}.fa-toggle-left:before,.fa-caret-square-o-left:before{content:""}.fa-dot-circle-o:before{content:""}.fa-wheelchair:before{content:""}.fa-vimeo-square:before{content:""}.fa-turkish-lira:before,.fa-try:before{content:""}.fa-plus-square-o:before,.wy-menu-vertical li span.toctree-expand:before{content:""}.fa-space-shuttle:before{content:""}.fa-slack:before{content:""}.fa-envelope-square:before{content:""}.fa-wordpress:before{content:""}.fa-openid:before{content:""}.fa-institution:before,.fa-bank:before,.fa-university:before{content:""}.fa-mortar-board:before,.fa-graduation-cap:before{content:""}.fa-yahoo:before{content:""}.fa-google:before{content:""}.fa-reddit:before{content:""}.fa-reddit-square:before{content:""}.fa-stumbleupon-circle:before{content:""}.fa-stumbleupon:before{content:""}.fa-delicious:before{content:""}.fa-digg:before{content:""}.fa-pied-piper:before{content:""}.fa-pied-piper-alt:before{content:""}.fa-drupal:before{content:""}.fa-joomla:before{content:""}.fa-language:before{content:""}.fa-fax:before{content:""}.fa-building:before{content:""}.fa-child:before{content:""}.fa-paw:before{content:""}.fa-spoon:before{content:""}.fa-cube:before{content:""}.fa-cubes:before{content:""}.fa-behance:before{content:""}.fa-behance-square:before{content:""}.fa-steam:before{content:""}.fa-steam-square:before{content:""}.fa-recycle:before{content:""}.fa-automobile:before,.fa-car:before{content:""}.fa-cab:before,.fa-taxi:before{content:""}.fa-tree:before{content:""}.fa-spotify:before{content:""}.fa-deviantart:before{content:""}.fa-soundcloud:before{content:""}.fa-database:before{content:""}.fa-file-pdf-o:before{content:""}.fa-file-word-o:before{content:""}.fa-file-excel-o:before{content:""}.fa-file-powerpoint-o:before{content:""}.fa-file-photo-o:before,.fa-file-picture-o:before,.fa-file-image-o:before{content:""}.fa-file-zip-o:before,.fa-file-archive-o:before{content:""}.fa-file-sound-o:before,.fa-file-audio-o:before{content:""}.fa-file-movie-o:before,.fa-file-video-o:before{content:""}.fa-file-code-o:before{content:""}.fa-vine:before{content:""}.fa-codepen:before{content:""}.fa-jsfiddle:before{content:""}.fa-life-bouy:before,.fa-life-buoy:before,.fa-life-saver:before,.fa-support:before,.fa-life-ring:before{content:""}.fa-circle-o-notch:before{content:""}.fa-ra:before,.fa-rebel:before{content:""}.fa-ge:before,.fa-empire:before{content:""}.fa-git-square:before{content:""}.fa-git:before{content:""}.fa-hacker-news:before{content:""}.fa-tencent-weibo:before{content:""}.fa-qq:before{content:""}.fa-wechat:before,.fa-weixin:before{content:""}.fa-send:before,.fa-paper-plane:before{content:""}.fa-send-o:before,.fa-paper-plane-o:before{content:""}.fa-history:before{content:""}.fa-circle-thin:before{content:""}.fa-header:before{content:""}.fa-paragraph:before{content:""}.fa-sliders:before{content:""}.fa-share-alt:before{content:""}.fa-share-alt-square:before{content:""}.fa-bomb:before{content:""}.fa-soccer-ball-o:before,.fa-futbol-o:before{content:""}.fa-tty:before{content:""}.fa-binoculars:before{content:""}.fa-plug:before{content:""}.fa-slideshare:before{content:""}.fa-twitch:before{content:""}.fa-yelp:before{content:""}.fa-newspaper-o:before{content:""}.fa-wifi:before{content:""}.fa-calculator:before{content:""}.fa-paypal:before{content:""}.fa-google-wallet:before{content:""}.fa-cc-visa:before{content:""}.fa-cc-mastercard:before{content:""}.fa-cc-discover:before{content:""}.fa-cc-amex:before{content:""}.fa-cc-paypal:before{content:""}.fa-cc-stripe:before{content:""}.fa-bell-slash:before{content:""}.fa-bell-slash-o:before{content:""}.fa-trash:before{content:""}.fa-copyright:before{content:""}.fa-at:before{content:""}.fa-eyedropper:before{content:""}.fa-paint-brush:before{content:""}.fa-birthday-cake:before{content:""}.fa-area-chart:before{content:""}.fa-pie-chart:before{content:""}.fa-line-chart:before{content:""}.fa-lastfm:before{content:""}.fa-lastfm-square:before{content:""}.fa-toggle-off:before{content:""}.fa-toggle-on:before{content:""}.fa-bicycle:before{content:""}.fa-bus:before{content:""}.fa-ioxhost:before{content:""}.fa-angellist:before{content:""}.fa-cc:before{content:""}.fa-shekel:before,.fa-sheqel:before,.fa-ils:before{content:""}.fa-meanpath:before{content:""}.fa,.wy-menu-vertical li span.toctree-expand,.wy-menu-vertical li.on a span.toctree-expand,.wy-menu-vertical li.current>a span.toctree-expand,.rst-content .admonition-title,.rst-content h1 .headerlink,.rst-content h2 .headerlink,.rst-content h3 .headerlink,.rst-content h4 .headerlink,.rst-content h5 .headerlink,.rst-content h6 .headerlink,.rst-content dl dt .headerlink,.rst-content p.caption .headerlink,.rst-content tt.download span:first-child,.rst-content code.download span:first-child,.icon,.wy-dropdown .caret,.wy-inline-validate.wy-inline-validate-success .wy-input-context,.wy-inline-validate.wy-inline-validate-danger .wy-input-context,.wy-inline-validate.wy-inline-validate-warning .wy-input-context,.wy-inline-validate.wy-inline-validate-info .wy-input-context{font-family:inherit}.fa:before,.wy-menu-vertical li span.toctree-expand:before,.wy-menu-vertical li.on a span.toctree-expand:before,.wy-menu-vertical li.current>a span.toctree-expand:before,.rst-content .admonition-title:before,.rst-content h1 .headerlink:before,.rst-content h2 .headerlink:before,.rst-content h3 .headerlink:before,.rst-content h4 .headerlink:before,.rst-content h5 .headerlink:before,.rst-content h6 .headerlink:before,.rst-content dl dt .headerlink:before,.rst-content p.caption .headerlink:before,.rst-content tt.download span:first-child:before,.rst-content code.download span:first-child:before,.icon:before,.wy-dropdown .caret:before,.wy-inline-validate.wy-inline-validate-success .wy-input-context:before,.wy-inline-validate.wy-inline-validate-danger .wy-input-context:before,.wy-inline-validate.wy-inline-validate-warning .wy-input-context:before,.wy-inline-validate.wy-inline-validate-info .wy-input-context:before{font-family:"FontAwesome";display:inline-block;font-style:normal;font-weight:normal;line-height:1;text-decoration:inherit}a .fa,a .wy-menu-vertical li span.toctree-expand,.wy-menu-vertical li a span.toctree-expand,.wy-menu-vertical li.on a span.toctree-expand,.wy-menu-vertical li.current>a span.toctree-expand,a .rst-content .admonition-title,.rst-content a .admonition-title,a .rst-content h1 .headerlink,.rst-content h1 a .headerlink,a .rst-content h2 .headerlink,.rst-content h2 a .headerlink,a .rst-content h3 .headerlink,.rst-content h3 a .headerlink,a .rst-content h4 .headerlink,.rst-content h4 a .headerlink,a .rst-content h5 .headerlink,.rst-content h5 a .headerlink,a .rst-content h6 .headerlink,.rst-content h6 a .headerlink,a .rst-content dl dt .headerlink,.rst-content dl dt a .headerlink,a .rst-content p.caption .headerlink,.rst-content p.caption a .headerlink,a .rst-content tt.download span:first-child,.rst-content tt.download a span:first-child,a .rst-content code.download span:first-child,.rst-content code.download a span:first-child,a .icon{display:inline-block;text-decoration:inherit}.btn .fa,.btn .wy-menu-vertical li span.toctree-expand,.wy-menu-vertical li .btn span.toctree-expand,.btn .wy-menu-vertical li.on a span.toctree-expand,.wy-menu-vertical li.on a .btn span.toctree-expand,.btn .wy-menu-vertical li.current>a span.toctree-expand,.wy-menu-vertical li.current>a .btn span.toctree-expand,.btn .rst-content .admonition-title,.rst-content .btn .admonition-title,.btn .rst-content h1 .headerlink,.rst-content h1 .btn .headerlink,.btn .rst-content h2 .headerlink,.rst-content h2 .btn .headerlink,.btn .rst-content h3 .headerlink,.rst-content h3 .btn .headerlink,.btn .rst-content h4 .headerlink,.rst-content h4 .btn .headerlink,.btn .rst-content h5 .headerlink,.rst-content h5 .btn .headerlink,.btn .rst-content h6 .headerlink,.rst-content h6 .btn .headerlink,.btn .rst-content dl dt .headerlink,.rst-content dl dt .btn .headerlink,.btn .rst-content p.caption .headerlink,.rst-content p.caption .btn .headerlink,.btn .rst-content tt.download span:first-child,.rst-content tt.download .btn span:first-child,.btn .rst-content code.download span:first-child,.rst-content code.download .btn span:first-child,.btn .icon,.nav .fa,.nav .wy-menu-vertical li span.toctree-expand,.wy-menu-vertical li .nav span.toctree-expand,.nav .wy-menu-vertical li.on a span.toctree-expand,.wy-menu-vertical li.on a .nav span.toctree-expand,.nav .wy-menu-vertical li.current>a span.toctree-expand,.wy-menu-vertical li.current>a .nav span.toctree-expand,.nav .rst-content .admonition-title,.rst-content .nav .admonition-title,.nav .rst-content h1 .headerlink,.rst-content h1 .nav .headerlink,.nav .rst-content h2 .headerlink,.rst-content h2 .nav .headerlink,.nav .rst-content h3 .headerlink,.rst-content h3 .nav .headerlink,.nav .rst-content h4 .headerlink,.rst-content h4 .nav .headerlink,.nav .rst-content h5 .headerlink,.rst-content h5 .nav .headerlink,.nav .rst-content h6 .headerlink,.rst-content h6 .nav .headerlink,.nav .rst-content dl dt .headerlink,.rst-content dl dt .nav .headerlink,.nav .rst-content p.caption .headerlink,.rst-content p.caption .nav .headerlink,.nav .rst-content tt.download span:first-child,.rst-content tt.download .nav span:first-child,.nav .rst-content code.download span:first-child,.rst-content code.download .nav span:first-child,.nav .icon{display:inline}.btn .fa.fa-large,.btn .wy-menu-vertical li span.fa-large.toctree-expand,.wy-menu-vertical li .btn span.fa-large.toctree-expand,.btn .rst-content .fa-large.admonition-title,.rst-content .btn .fa-large.admonition-title,.btn .rst-content h1 .fa-large.headerlink,.rst-content h1 .btn .fa-large.headerlink,.btn .rst-content h2 .fa-large.headerlink,.rst-content h2 .btn .fa-large.headerlink,.btn .rst-content h3 .fa-large.headerlink,.rst-content h3 .btn .fa-large.headerlink,.btn .rst-content h4 .fa-large.headerlink,.rst-content h4 .btn .fa-large.headerlink,.btn .rst-content h5 .fa-large.headerlink,.rst-content h5 .btn .fa-large.headerlink,.btn .rst-content h6 .fa-large.headerlink,.rst-content h6 .btn .fa-large.headerlink,.btn .rst-content dl dt .fa-large.headerlink,.rst-content dl dt .btn .fa-large.headerlink,.btn .rst-content p.caption .fa-large.headerlink,.rst-content p.caption .btn .fa-large.headerlink,.btn .rst-content tt.download span.fa-large:first-child,.rst-content tt.download .btn span.fa-large:first-child,.btn .rst-content code.download span.fa-large:first-child,.rst-content code.download .btn span.fa-large:first-child,.btn .fa-large.icon,.nav .fa.fa-large,.nav .wy-menu-vertical li span.fa-large.toctree-expand,.wy-menu-vertical li .nav span.fa-large.toctree-expand,.nav .rst-content .fa-large.admonition-title,.rst-content .nav .fa-large.admonition-title,.nav .rst-content h1 .fa-large.headerlink,.rst-content h1 .nav .fa-large.headerlink,.nav .rst-content h2 .fa-large.headerlink,.rst-content h2 .nav .fa-large.headerlink,.nav .rst-content h3 .fa-large.headerlink,.rst-content h3 .nav .fa-large.headerlink,.nav .rst-content h4 .fa-large.headerlink,.rst-content h4 .nav .fa-large.headerlink,.nav .rst-content h5 .fa-large.headerlink,.rst-content h5 .nav .fa-large.headerlink,.nav .rst-content h6 .fa-large.headerlink,.rst-content h6 .nav .fa-large.headerlink,.nav .rst-content dl dt .fa-large.headerlink,.rst-content dl dt .nav .fa-large.headerlink,.nav .rst-content p.caption .fa-large.headerlink,.rst-content p.caption .nav .fa-large.headerlink,.nav .rst-content tt.download span.fa-large:first-child,.rst-content tt.download .nav span.fa-large:first-child,.nav .rst-content code.download span.fa-large:first-child,.rst-content code.download .nav span.fa-large:first-child,.nav .fa-large.icon{line-height:0.9em}.btn .fa.fa-spin,.btn .wy-menu-vertical li span.fa-spin.toctree-expand,.wy-menu-vertical li .btn span.fa-spin.toctree-expand,.btn .rst-content .fa-spin.admonition-title,.rst-content .btn .fa-spin.admonition-title,.btn .rst-content h1 .fa-spin.headerlink,.rst-content h1 .btn .fa-spin.headerlink,.btn .rst-content h2 .fa-spin.headerlink,.rst-content h2 .btn .fa-spin.headerlink,.btn .rst-content h3 .fa-spin.headerlink,.rst-content h3 .btn .fa-spin.headerlink,.btn .rst-content h4 .fa-spin.headerlink,.rst-content h4 .btn .fa-spin.headerlink,.btn .rst-content h5 .fa-spin.headerlink,.rst-content h5 .btn .fa-spin.headerlink,.btn .rst-content h6 .fa-spin.headerlink,.rst-content h6 .btn .fa-spin.headerlink,.btn .rst-content dl dt .fa-spin.headerlink,.rst-content dl dt .btn .fa-spin.headerlink,.btn .rst-content p.caption .fa-spin.headerlink,.rst-content p.caption .btn .fa-spin.headerlink,.btn .rst-content tt.download span.fa-spin:first-child,.rst-content tt.download .btn span.fa-spin:first-child,.btn .rst-content code.download span.fa-spin:first-child,.rst-content code.download .btn span.fa-spin:first-child,.btn .fa-spin.icon,.nav .fa.fa-spin,.nav .wy-menu-vertical li span.fa-spin.toctree-expand,.wy-menu-vertical li .nav span.fa-spin.toctree-expand,.nav .rst-content .fa-spin.admonition-title,.rst-content .nav .fa-spin.admonition-title,.nav .rst-content h1 .fa-spin.headerlink,.rst-content h1 .nav .fa-spin.headerlink,.nav .rst-content h2 .fa-spin.headerlink,.rst-content h2 .nav .fa-spin.headerlink,.nav .rst-content h3 .fa-spin.headerlink,.rst-content h3 .nav .fa-spin.headerlink,.nav .rst-content h4 .fa-spin.headerlink,.rst-content h4 .nav .fa-spin.headerlink,.nav .rst-content h5 .fa-spin.headerlink,.rst-content h5 .nav .fa-spin.headerlink,.nav .rst-content h6 .fa-spin.headerlink,.rst-content h6 .nav .fa-spin.headerlink,.nav .rst-content dl dt .fa-spin.headerlink,.rst-content dl dt .nav .fa-spin.headerlink,.nav .rst-content p.caption .fa-spin.headerlink,.rst-content p.caption .nav .fa-spin.headerlink,.nav .rst-content tt.download span.fa-spin:first-child,.rst-content tt.download .nav span.fa-spin:first-child,.nav .rst-content code.download span.fa-spin:first-child,.rst-content code.download .nav span.fa-spin:first-child,.nav .fa-spin.icon{display:inline-block}.btn.fa:before,.wy-menu-vertical li span.btn.toctree-expand:before,.rst-content .btn.admonition-title:before,.rst-content h1 .btn.headerlink:before,.rst-content h2 .btn.headerlink:before,.rst-content h3 .btn.headerlink:before,.rst-content h4 .btn.headerlink:before,.rst-content h5 .btn.headerlink:before,.rst-content h6 .btn.headerlink:before,.rst-content dl dt .btn.headerlink:before,.rst-content p.caption .btn.headerlink:before,.rst-content tt.download span.btn:first-child:before,.rst-content code.download span.btn:first-child:before,.btn.icon:before{opacity:0.5;-webkit-transition:opacity 0.05s ease-in;-moz-transition:opacity 0.05s ease-in;transition:opacity 0.05s ease-in}.btn.fa:hover:before,.wy-menu-vertical li span.btn.toctree-expand:hover:before,.rst-content .btn.admonition-title:hover:before,.rst-content h1 .btn.headerlink:hover:before,.rst-content h2 .btn.headerlink:hover:before,.rst-content h3 .btn.headerlink:hover:before,.rst-content h4 .btn.headerlink:hover:before,.rst-content h5 .btn.headerlink:hover:before,.rst-content h6 .btn.headerlink:hover:before,.rst-content dl dt .btn.headerlink:hover:before,.rst-content p.caption .btn.headerlink:hover:before,.rst-content tt.download span.btn:first-child:hover:before,.rst-content code.download span.btn:first-child:hover:before,.btn.icon:hover:before{opacity:1}.btn-mini .fa:before,.btn-mini .wy-menu-vertical li span.toctree-expand:before,.wy-menu-vertical li .btn-mini span.toctree-expand:before,.btn-mini .rst-content .admonition-title:before,.rst-content .btn-mini .admonition-title:before,.btn-mini .rst-content h1 .headerlink:before,.rst-content h1 .btn-mini .headerlink:before,.btn-mini .rst-content h2 .headerlink:before,.rst-content h2 .btn-mini .headerlink:before,.btn-mini .rst-content h3 .headerlink:before,.rst-content h3 .btn-mini .headerlink:before,.btn-mini .rst-content h4 .headerlink:before,.rst-content h4 .btn-mini .headerlink:before,.btn-mini .rst-content h5 .headerlink:before,.rst-content h5 .btn-mini .headerlink:before,.btn-mini .rst-content h6 .headerlink:before,.rst-content h6 .btn-mini .headerlink:before,.btn-mini .rst-content dl dt .headerlink:before,.rst-content dl dt .btn-mini .headerlink:before,.btn-mini .rst-content p.caption .headerlink:before,.rst-content p.caption .btn-mini .headerlink:before,.btn-mini .rst-content tt.download span:first-child:before,.rst-content tt.download .btn-mini span:first-child:before,.btn-mini .rst-content code.download span:first-child:before,.rst-content code.download .btn-mini span:first-child:before,.btn-mini .icon:before{font-size:14px;vertical-align:-15%}.wy-alert,.rst-content .note,.rst-content .attention,.rst-content .caution,.rst-content .danger,.rst-content .error,.rst-content .hint,.rst-content .important,.rst-content .tip,.rst-content .warning,.rst-content .seealso,.rst-content .admonition-todo{padding:12px;line-height:24px;margin-bottom:24px;background:#e7f2fa}.wy-alert-title,.rst-content .admonition-title{color:#fff;font-weight:bold;display:block;color:#fff;background:#6ab0de;margin:-12px;padding:6px 12px;margin-bottom:12px}.wy-alert.wy-alert-danger,.rst-content .wy-alert-danger.note,.rst-content .wy-alert-danger.attention,.rst-content .wy-alert-danger.caution,.rst-content .danger,.rst-content .error,.rst-content .wy-alert-danger.hint,.rst-content .wy-alert-danger.important,.rst-content .wy-alert-danger.tip,.rst-content .wy-alert-danger.warning,.rst-content .wy-alert-danger.seealso,.rst-content .wy-alert-danger.admonition-todo{background:#fdf3f2}.wy-alert.wy-alert-danger .wy-alert-title,.rst-content .wy-alert-danger.note .wy-alert-title,.rst-content .wy-alert-danger.attention .wy-alert-title,.rst-content .wy-alert-danger.caution .wy-alert-title,.rst-content .danger .wy-alert-title,.rst-content .error .wy-alert-title,.rst-content .wy-alert-danger.hint .wy-alert-title,.rst-content .wy-alert-danger.important .wy-alert-title,.rst-content .wy-alert-danger.tip .wy-alert-title,.rst-content .wy-alert-danger.warning .wy-alert-title,.rst-content .wy-alert-danger.seealso .wy-alert-title,.rst-content .wy-alert-danger.admonition-todo .wy-alert-title,.wy-alert.wy-alert-danger .rst-content .admonition-title,.rst-content .wy-alert.wy-alert-danger .admonition-title,.rst-content .wy-alert-danger.note .admonition-title,.rst-content .wy-alert-danger.attention .admonition-title,.rst-content .wy-alert-danger.caution .admonition-title,.rst-content .danger .admonition-title,.rst-content .error .admonition-title,.rst-content .wy-alert-danger.hint .admonition-title,.rst-content .wy-alert-danger.important .admonition-title,.rst-content .wy-alert-danger.tip .admonition-title,.rst-content .wy-alert-danger.warning .admonition-title,.rst-content .wy-alert-danger.seealso .admonition-title,.rst-content .wy-alert-danger.admonition-todo .admonition-title{background:#f29f97}.wy-alert.wy-alert-warning,.rst-content .wy-alert-warning.note,.rst-content .attention,.rst-content .caution,.rst-content .wy-alert-warning.danger,.rst-content .wy-alert-warning.error,.rst-content .wy-alert-warning.hint,.rst-content .wy-alert-warning.important,.rst-content .wy-alert-warning.tip,.rst-content .warning,.rst-content .wy-alert-warning.seealso,.rst-content .admonition-todo{background:#ffedcc}.wy-alert.wy-alert-warning .wy-alert-title,.rst-content .wy-alert-warning.note .wy-alert-title,.rst-content .attention .wy-alert-title,.rst-content .caution .wy-alert-title,.rst-content .wy-alert-warning.danger .wy-alert-title,.rst-content .wy-alert-warning.error .wy-alert-title,.rst-content .wy-alert-warning.hint .wy-alert-title,.rst-content .wy-alert-warning.important .wy-alert-title,.rst-content .wy-alert-warning.tip .wy-alert-title,.rst-content .warning .wy-alert-title,.rst-content .wy-alert-warning.seealso .wy-alert-title,.rst-content .admonition-todo .wy-alert-title,.wy-alert.wy-alert-warning .rst-content .admonition-title,.rst-content .wy-alert.wy-alert-warning .admonition-title,.rst-content .wy-alert-warning.note .admonition-title,.rst-content .attention .admonition-title,.rst-content .caution .admonition-title,.rst-content .wy-alert-warning.danger .admonition-title,.rst-content .wy-alert-warning.error .admonition-title,.rst-content .wy-alert-warning.hint .admonition-title,.rst-content .wy-alert-warning.important .admonition-title,.rst-content .wy-alert-warning.tip .admonition-title,.rst-content .warning .admonition-title,.rst-content .wy-alert-warning.seealso .admonition-title,.rst-content .admonition-todo .admonition-title{background:#f0b37e}.wy-alert.wy-alert-info,.rst-content .note,.rst-content .wy-alert-info.attention,.rst-content .wy-alert-info.caution,.rst-content .wy-alert-info.danger,.rst-content .wy-alert-info.error,.rst-content .wy-alert-info.hint,.rst-content .wy-alert-info.important,.rst-content .wy-alert-info.tip,.rst-content .wy-alert-info.warning,.rst-content .seealso,.rst-content .wy-alert-info.admonition-todo{background:#e7f2fa}.wy-alert.wy-alert-info .wy-alert-title,.rst-content .note .wy-alert-title,.rst-content .wy-alert-info.attention .wy-alert-title,.rst-content .wy-alert-info.caution .wy-alert-title,.rst-content .wy-alert-info.danger .wy-alert-title,.rst-content .wy-alert-info.error .wy-alert-title,.rst-content .wy-alert-info.hint .wy-alert-title,.rst-content .wy-alert-info.important .wy-alert-title,.rst-content .wy-alert-info.tip .wy-alert-title,.rst-content .wy-alert-info.warning .wy-alert-title,.rst-content .seealso .wy-alert-title,.rst-content .wy-alert-info.admonition-todo .wy-alert-title,.wy-alert.wy-alert-info .rst-content .admonition-title,.rst-content .wy-alert.wy-alert-info .admonition-title,.rst-content .note .admonition-title,.rst-content .wy-alert-info.attention .admonition-title,.rst-content .wy-alert-info.caution .admonition-title,.rst-content .wy-alert-info.danger .admonition-title,.rst-content .wy-alert-info.error .admonition-title,.rst-content .wy-alert-info.hint .admonition-title,.rst-content .wy-alert-info.important .admonition-title,.rst-content .wy-alert-info.tip .admonition-title,.rst-content .wy-alert-info.warning .admonition-title,.rst-content .seealso .admonition-title,.rst-content .wy-alert-info.admonition-todo .admonition-title{background:#6ab0de}.wy-alert.wy-alert-success,.rst-content .wy-alert-success.note,.rst-content .wy-alert-success.attention,.rst-content .wy-alert-success.caution,.rst-content .wy-alert-success.danger,.rst-content .wy-alert-success.error,.rst-content .hint,.rst-content .important,.rst-content .tip,.rst-content .wy-alert-success.warning,.rst-content .wy-alert-success.seealso,.rst-content .wy-alert-success.admonition-todo{background:#dbfaf4}.wy-alert.wy-alert-success .wy-alert-title,.rst-content .wy-alert-success.note .wy-alert-title,.rst-content .wy-alert-success.attention .wy-alert-title,.rst-content .wy-alert-success.caution .wy-alert-title,.rst-content .wy-alert-success.danger .wy-alert-title,.rst-content .wy-alert-success.error .wy-alert-title,.rst-content .hint .wy-alert-title,.rst-content .important .wy-alert-title,.rst-content .tip .wy-alert-title,.rst-content .wy-alert-success.warning .wy-alert-title,.rst-content .wy-alert-success.seealso .wy-alert-title,.rst-content .wy-alert-success.admonition-todo .wy-alert-title,.wy-alert.wy-alert-success .rst-content .admonition-title,.rst-content .wy-alert.wy-alert-success .admonition-title,.rst-content .wy-alert-success.note .admonition-title,.rst-content .wy-alert-success.attention .admonition-title,.rst-content .wy-alert-success.caution .admonition-title,.rst-content .wy-alert-success.danger .admonition-title,.rst-content .wy-alert-success.error .admonition-title,.rst-content .hint .admonition-title,.rst-content .important .admonition-title,.rst-content .tip .admonition-title,.rst-content .wy-alert-success.warning .admonition-title,.rst-content .wy-alert-success.seealso .admonition-title,.rst-content .wy-alert-success.admonition-todo .admonition-title{background:#1abc9c}.wy-alert.wy-alert-neutral,.rst-content .wy-alert-neutral.note,.rst-content .wy-alert-neutral.attention,.rst-content .wy-alert-neutral.caution,.rst-content .wy-alert-neutral.danger,.rst-content .wy-alert-neutral.error,.rst-content .wy-alert-neutral.hint,.rst-content .wy-alert-neutral.important,.rst-content .wy-alert-neutral.tip,.rst-content .wy-alert-neutral.warning,.rst-content .wy-alert-neutral.seealso,.rst-content .wy-alert-neutral.admonition-todo{background:#f3f6f6}.wy-alert.wy-alert-neutral .wy-alert-title,.rst-content .wy-alert-neutral.note .wy-alert-title,.rst-content .wy-alert-neutral.attention .wy-alert-title,.rst-content .wy-alert-neutral.caution .wy-alert-title,.rst-content .wy-alert-neutral.danger .wy-alert-title,.rst-content .wy-alert-neutral.error .wy-alert-title,.rst-content .wy-alert-neutral.hint .wy-alert-title,.rst-content .wy-alert-neutral.important .wy-alert-title,.rst-content .wy-alert-neutral.tip .wy-alert-title,.rst-content .wy-alert-neutral.warning .wy-alert-title,.rst-content .wy-alert-neutral.seealso .wy-alert-title,.rst-content .wy-alert-neutral.admonition-todo .wy-alert-title,.wy-alert.wy-alert-neutral .rst-content .admonition-title,.rst-content .wy-alert.wy-alert-neutral .admonition-title,.rst-content .wy-alert-neutral.note .admonition-title,.rst-content .wy-alert-neutral.attention .admonition-title,.rst-content .wy-alert-neutral.caution .admonition-title,.rst-content .wy-alert-neutral.danger .admonition-title,.rst-content .wy-alert-neutral.error .admonition-title,.rst-content .wy-alert-neutral.hint .admonition-title,.rst-content .wy-alert-neutral.important .admonition-title,.rst-content .wy-alert-neutral.tip .admonition-title,.rst-content .wy-alert-neutral.warning .admonition-title,.rst-content .wy-alert-neutral.seealso .admonition-title,.rst-content .wy-alert-neutral.admonition-todo .admonition-title{color:#404040;background:#e1e4e5}.wy-alert.wy-alert-neutral a,.rst-content .wy-alert-neutral.note a,.rst-content .wy-alert-neutral.attention a,.rst-content .wy-alert-neutral.caution a,.rst-content .wy-alert-neutral.danger a,.rst-content .wy-alert-neutral.error a,.rst-content .wy-alert-neutral.hint a,.rst-content .wy-alert-neutral.important a,.rst-content .wy-alert-neutral.tip a,.rst-content .wy-alert-neutral.warning a,.rst-content .wy-alert-neutral.seealso a,.rst-content .wy-alert-neutral.admonition-todo a{color:#2980B9}.wy-alert p:last-child,.rst-content .note p:last-child,.rst-content .attention p:last-child,.rst-content .caution p:last-child,.rst-content .danger p:last-child,.rst-content .error p:last-child,.rst-content .hint p:last-child,.rst-content .important p:last-child,.rst-content .tip p:last-child,.rst-content .warning p:last-child,.rst-content .seealso p:last-child,.rst-content .admonition-todo p:last-child{margin-bottom:0}.wy-tray-container{position:fixed;bottom:0px;left:0;z-index:600}.wy-tray-container li{display:block;width:300px;background:transparent;color:#fff;text-align:center;box-shadow:0 5px 5px 0 rgba(0,0,0,0.1);padding:0 24px;min-width:20%;opacity:0;height:0;line-height:56px;overflow:hidden;-webkit-transition:all 0.3s ease-in;-moz-transition:all 0.3s ease-in;transition:all 0.3s ease-in}.wy-tray-container li.wy-tray-item-success{background:#27AE60}.wy-tray-container li.wy-tray-item-info{background:#2980B9}.wy-tray-container li.wy-tray-item-warning{background:#E67E22}.wy-tray-container li.wy-tray-item-danger{background:#E74C3C}.wy-tray-container li.on{opacity:1;height:56px}@media screen and (max-width: 768px){.wy-tray-container{bottom:auto;top:0;width:100%}.wy-tray-container li{width:100%}}button{font-size:100%;margin:0;vertical-align:baseline;*vertical-align:middle;cursor:pointer;line-height:normal;-webkit-appearance:button;*overflow:visible}button::-moz-focus-inner,input::-moz-focus-inner{border:0;padding:0}button[disabled]{cursor:default}.btn{display:inline-block;border-radius:2px;line-height:normal;white-space:nowrap;text-align:center;cursor:pointer;font-size:100%;padding:6px 12px 8px 12px;color:#fff;border:1px solid rgba(0,0,0,0.1);background-color:#27AE60;text-decoration:none;font-weight:normal;font-family:"Lato","proxima-nova","Helvetica Neue",Arial,sans-serif;box-shadow:0px 1px 2px -1px rgba(255,255,255,0.5) inset,0px -2px 0px 0px rgba(0,0,0,0.1) inset;outline-none:false;vertical-align:middle;*display:inline;zoom:1;-webkit-user-drag:none;-webkit-user-select:none;-moz-user-select:none;-ms-user-select:none;user-select:none;-webkit-transition:all 0.1s linear;-moz-transition:all 0.1s linear;transition:all 0.1s linear}.btn-hover{background:#2e8ece;color:#fff}.btn:hover{background:#2cc36b;color:#fff}.btn:focus{background:#2cc36b;outline:0}.btn:active{box-shadow:0px -1px 0px 0px rgba(0,0,0,0.05) inset,0px 2px 0px 0px rgba(0,0,0,0.1) inset;padding:8px 12px 6px 12px}.btn:visited{color:#fff}.btn:disabled{background-image:none;filter:progid:DXImageTransform.Microsoft.gradient(enabled = false);filter:alpha(opacity=40);opacity:0.4;cursor:not-allowed;box-shadow:none}.btn-disabled{background-image:none;filter:progid:DXImageTransform.Microsoft.gradient(enabled = false);filter:alpha(opacity=40);opacity:0.4;cursor:not-allowed;box-shadow:none}.btn-disabled:hover,.btn-disabled:focus,.btn-disabled:active{background-image:none;filter:progid:DXImageTransform.Microsoft.gradient(enabled = false);filter:alpha(opacity=40);opacity:0.4;cursor:not-allowed;box-shadow:none}.btn::-moz-focus-inner{padding:0;border:0}.btn-small{font-size:80%}.btn-info{background-color:#2980B9 !important}.btn-info:hover{background-color:#2e8ece !important}.btn-neutral{background-color:#f3f6f6 !important;color:#404040 !important}.btn-neutral:hover{background-color:#e5ebeb !important;color:#404040}.btn-neutral:visited{color:#404040 !important}.btn-success{background-color:#27AE60 !important}.btn-success:hover{background-color:#295 !important}.btn-danger{background-color:#E74C3C !important}.btn-danger:hover{background-color:#ea6153 !important}.btn-warning{background-color:#E67E22 !important}.btn-warning:hover{background-color:#e98b39 !important}.btn-invert{background-color:#222}.btn-invert:hover{background-color:#2f2f2f !important}.btn-link{background-color:transparent !important;color:#2980B9;box-shadow:none;border-color:transparent !important}.btn-link:hover{background-color:transparent !important;color:#409ad5 !important;box-shadow:none}.btn-link:active{background-color:transparent !important;color:#409ad5 !important;box-shadow:none}.btn-link:visited{color:#9B59B6}.wy-btn-group .btn,.wy-control .btn{vertical-align:middle}.wy-btn-group{margin-bottom:24px;*zoom:1}.wy-btn-group:before,.wy-btn-group:after{display:table;content:""}.wy-btn-group:after{clear:both}.wy-dropdown{position:relative;display:inline-block}.wy-dropdown-active .wy-dropdown-menu{display:block}.wy-dropdown-menu{position:absolute;left:0;display:none;float:left;top:100%;min-width:100%;background:#fcfcfc;z-index:100;border:solid 1px #cfd7dd;box-shadow:0 2px 2px 0 rgba(0,0,0,0.1);padding:12px}.wy-dropdown-menu>dd>a{display:block;clear:both;color:#404040;white-space:nowrap;font-size:90%;padding:0 12px;cursor:pointer}.wy-dropdown-menu>dd>a:hover{background:#2980B9;color:#fff}.wy-dropdown-menu>dd.divider{border-top:solid 1px #cfd7dd;margin:6px 0}.wy-dropdown-menu>dd.search{padding-bottom:12px}.wy-dropdown-menu>dd.search input[type="search"]{width:100%}.wy-dropdown-menu>dd.call-to-action{background:#e3e3e3;text-transform:uppercase;font-weight:500;font-size:80%}.wy-dropdown-menu>dd.call-to-action:hover{background:#e3e3e3}.wy-dropdown-menu>dd.call-to-action .btn{color:#fff}.wy-dropdown.wy-dropdown-up .wy-dropdown-menu{bottom:100%;top:auto;left:auto;right:0}.wy-dropdown.wy-dropdown-bubble .wy-dropdown-menu{background:#fcfcfc;margin-top:2px}.wy-dropdown.wy-dropdown-bubble .wy-dropdown-menu a{padding:6px 12px}.wy-dropdown.wy-dropdown-bubble .wy-dropdown-menu a:hover{background:#2980B9;color:#fff}.wy-dropdown.wy-dropdown-left .wy-dropdown-menu{right:0;left:auto;text-align:right}.wy-dropdown-arrow:before{content:" ";border-bottom:5px solid #f5f5f5;border-left:5px solid transparent;border-right:5px solid transparent;position:absolute;display:block;top:-4px;left:50%;margin-left:-3px}.wy-dropdown-arrow.wy-dropdown-arrow-left:before{left:11px}.wy-form-stacked select{display:block}.wy-form-aligned input,.wy-form-aligned textarea,.wy-form-aligned select,.wy-form-aligned .wy-help-inline,.wy-form-aligned label{display:inline-block;*display:inline;*zoom:1;vertical-align:middle}.wy-form-aligned .wy-control-group>label{display:inline-block;vertical-align:middle;width:10em;margin:6px 12px 0 0;float:left}.wy-form-aligned .wy-control{float:left}.wy-form-aligned .wy-control label{display:block}.wy-form-aligned .wy-control select{margin-top:6px}fieldset{border:0;margin:0;padding:0}legend{display:block;width:100%;border:0;padding:0;white-space:normal;margin-bottom:24px;font-size:150%;*margin-left:-7px}label{display:block;margin:0 0 0.3125em 0;color:#333;font-size:90%}input,select,textarea{font-size:100%;margin:0;vertical-align:baseline;*vertical-align:middle}.wy-control-group{margin-bottom:24px;*zoom:1;max-width:68em;margin-left:auto;margin-right:auto;*zoom:1}.wy-control-group:before,.wy-control-group:after{display:table;content:""}.wy-control-group:after{clear:both}.wy-control-group:before,.wy-control-group:after{display:table;content:""}.wy-control-group:after{clear:both}.wy-control-group.wy-control-group-required>label:after{content:" *";color:#E74C3C}.wy-control-group .wy-form-full,.wy-control-group .wy-form-halves,.wy-control-group .wy-form-thirds{padding-bottom:12px}.wy-control-group .wy-form-full select,.wy-control-group .wy-form-halves select,.wy-control-group .wy-form-thirds select{width:100%}.wy-control-group .wy-form-full input[type="text"],.wy-control-group .wy-form-full input[type="password"],.wy-control-group .wy-form-full input[type="email"],.wy-control-group .wy-form-full input[type="url"],.wy-control-group .wy-form-full input[type="date"],.wy-control-group .wy-form-full input[type="month"],.wy-control-group .wy-form-full input[type="time"],.wy-control-group .wy-form-full input[type="datetime"],.wy-control-group .wy-form-full input[type="datetime-local"],.wy-control-group .wy-form-full input[type="week"],.wy-control-group .wy-form-full input[type="number"],.wy-control-group .wy-form-full input[type="search"],.wy-control-group .wy-form-full input[type="tel"],.wy-control-group .wy-form-full input[type="color"],.wy-control-group .wy-form-halves input[type="text"],.wy-control-group .wy-form-halves input[type="password"],.wy-control-group .wy-form-halves input[type="email"],.wy-control-group .wy-form-halves input[type="url"],.wy-control-group .wy-form-halves input[type="date"],.wy-control-group .wy-form-halves input[type="month"],.wy-control-group .wy-form-halves input[type="time"],.wy-control-group .wy-form-halves input[type="datetime"],.wy-control-group .wy-form-halves input[type="datetime-local"],.wy-control-group .wy-form-halves input[type="week"],.wy-control-group .wy-form-halves input[type="number"],.wy-control-group .wy-form-halves input[type="search"],.wy-control-group .wy-form-halves input[type="tel"],.wy-control-group .wy-form-halves input[type="color"],.wy-control-group .wy-form-thirds input[type="text"],.wy-control-group .wy-form-thirds input[type="password"],.wy-control-group .wy-form-thirds input[type="email"],.wy-control-group .wy-form-thirds input[type="url"],.wy-control-group .wy-form-thirds input[type="date"],.wy-control-group .wy-form-thirds input[type="month"],.wy-control-group .wy-form-thirds input[type="time"],.wy-control-group .wy-form-thirds input[type="datetime"],.wy-control-group .wy-form-thirds input[type="datetime-local"],.wy-control-group .wy-form-thirds input[type="week"],.wy-control-group .wy-form-thirds input[type="number"],.wy-control-group .wy-form-thirds input[type="search"],.wy-control-group .wy-form-thirds input[type="tel"],.wy-control-group .wy-form-thirds input[type="color"]{width:100%}.wy-control-group .wy-form-full{float:left;display:block;margin-right:2.35765%;width:100%;margin-right:0}.wy-control-group .wy-form-full:last-child{margin-right:0}.wy-control-group .wy-form-halves{float:left;display:block;margin-right:2.35765%;width:48.82117%}.wy-control-group .wy-form-halves:last-child{margin-right:0}.wy-control-group .wy-form-halves:nth-of-type(2n){margin-right:0}.wy-control-group .wy-form-halves:nth-of-type(2n+1){clear:left}.wy-control-group .wy-form-thirds{float:left;display:block;margin-right:2.35765%;width:31.76157%}.wy-control-group .wy-form-thirds:last-child{margin-right:0}.wy-control-group .wy-form-thirds:nth-of-type(3n){margin-right:0}.wy-control-group .wy-form-thirds:nth-of-type(3n+1){clear:left}.wy-control-group.wy-control-group-no-input .wy-control{margin:6px 0 0 0;font-size:90%}.wy-control-no-input{display:inline-block;margin:6px 0 0 0;font-size:90%}.wy-control-group.fluid-input input[type="text"],.wy-control-group.fluid-input input[type="password"],.wy-control-group.fluid-input input[type="email"],.wy-control-group.fluid-input input[type="url"],.wy-control-group.fluid-input input[type="date"],.wy-control-group.fluid-input input[type="month"],.wy-control-group.fluid-input input[type="time"],.wy-control-group.fluid-input input[type="datetime"],.wy-control-group.fluid-input input[type="datetime-local"],.wy-control-group.fluid-input input[type="week"],.wy-control-group.fluid-input input[type="number"],.wy-control-group.fluid-input input[type="search"],.wy-control-group.fluid-input input[type="tel"],.wy-control-group.fluid-input input[type="color"]{width:100%}.wy-form-message-inline{display:inline-block;padding-left:0.3em;color:#666;vertical-align:middle;font-size:90%}.wy-form-message{display:block;color:#999;font-size:70%;margin-top:0.3125em;font-style:italic}.wy-form-message p{font-size:inherit;font-style:italic;margin-bottom:6px}.wy-form-message p:last-child{margin-bottom:0}input{line-height:normal}input[type="button"],input[type="reset"],input[type="submit"]{-webkit-appearance:button;cursor:pointer;font-family:"Lato","proxima-nova","Helvetica Neue",Arial,sans-serif;*overflow:visible}input[type="text"],input[type="password"],input[type="email"],input[type="url"],input[type="date"],input[type="month"],input[type="time"],input[type="datetime"],input[type="datetime-local"],input[type="week"],input[type="number"],input[type="search"],input[type="tel"],input[type="color"]{-webkit-appearance:none;padding:6px;display:inline-block;border:1px solid #ccc;font-size:80%;font-family:"Lato","proxima-nova","Helvetica Neue",Arial,sans-serif;box-shadow:inset 0 1px 3px #ddd;border-radius:0;-webkit-transition:border 0.3s linear;-moz-transition:border 0.3s linear;transition:border 0.3s linear}input[type="datetime-local"]{padding:0.34375em 0.625em}input[disabled]{cursor:default}input[type="checkbox"],input[type="radio"]{-webkit-box-sizing:border-box;-moz-box-sizing:border-box;box-sizing:border-box;padding:0;margin-right:0.3125em;*height:13px;*width:13px}input[type="search"]{-webkit-box-sizing:border-box;-moz-box-sizing:border-box;box-sizing:border-box}input[type="search"]::-webkit-search-cancel-button,input[type="search"]::-webkit-search-decoration{-webkit-appearance:none}input[type="text"]:focus,input[type="password"]:focus,input[type="email"]:focus,input[type="url"]:focus,input[type="date"]:focus,input[type="month"]:focus,input[type="time"]:focus,input[type="datetime"]:focus,input[type="datetime-local"]:focus,input[type="week"]:focus,input[type="number"]:focus,input[type="search"]:focus,input[type="tel"]:focus,input[type="color"]:focus{outline:0;outline:thin dotted \9;border-color:#333}input.no-focus:focus{border-color:#ccc !important}input[type="file"]:focus,input[type="radio"]:focus,input[type="checkbox"]:focus{outline:thin dotted #333;outline:1px auto #129FEA}input[type="text"][disabled],input[type="password"][disabled],input[type="email"][disabled],input[type="url"][disabled],input[type="date"][disabled],input[type="month"][disabled],input[type="time"][disabled],input[type="datetime"][disabled],input[type="datetime-local"][disabled],input[type="week"][disabled],input[type="number"][disabled],input[type="search"][disabled],input[type="tel"][disabled],input[type="color"][disabled]{cursor:not-allowed;background-color:#fafafa}input:focus:invalid,textarea:focus:invalid,select:focus:invalid{color:#E74C3C;border:1px solid #E74C3C}input:focus:invalid:focus,textarea:focus:invalid:focus,select:focus:invalid:focus{border-color:#E74C3C}input[type="file"]:focus:invalid:focus,input[type="radio"]:focus:invalid:focus,input[type="checkbox"]:focus:invalid:focus{outline-color:#E74C3C}input.wy-input-large{padding:12px;font-size:100%}textarea{overflow:auto;vertical-align:top;width:100%;font-family:"Lato","proxima-nova","Helvetica Neue",Arial,sans-serif}select,textarea{padding:0.5em 0.625em;display:inline-block;border:1px solid #ccc;font-size:80%;box-shadow:inset 0 1px 3px #ddd;-webkit-transition:border 0.3s linear;-moz-transition:border 0.3s linear;transition:border 0.3s linear}select{border:1px solid #ccc;background-color:#fff}select[multiple]{height:auto}select:focus,textarea:focus{outline:0}select[disabled],textarea[disabled],input[readonly],select[readonly],textarea[readonly]{cursor:not-allowed;background-color:#fafafa}input[type="radio"][disabled],input[type="checkbox"][disabled]{cursor:not-allowed}.wy-checkbox,.wy-radio{margin:6px 0;color:#404040;display:block}.wy-checkbox input,.wy-radio input{vertical-align:baseline}.wy-form-message-inline{display:inline-block;*display:inline;*zoom:1;vertical-align:middle}.wy-input-prefix,.wy-input-suffix{white-space:nowrap;padding:6px}.wy-input-prefix .wy-input-context,.wy-input-suffix .wy-input-context{line-height:27px;padding:0 8px;display:inline-block;font-size:80%;background-color:#f3f6f6;border:solid 1px #ccc;color:#999}.wy-input-suffix .wy-input-context{border-left:0}.wy-input-prefix .wy-input-context{border-right:0}.wy-switch{width:36px;height:12px;margin:12px 0;position:relative;border-radius:4px;background:#ccc;cursor:pointer;-webkit-transition:all 0.2s ease-in-out;-moz-transition:all 0.2s ease-in-out;transition:all 0.2s ease-in-out}.wy-switch:before{position:absolute;content:"";display:block;width:18px;height:18px;border-radius:4px;background:#999;left:-3px;top:-3px;-webkit-transition:all 0.2s ease-in-out;-moz-transition:all 0.2s ease-in-out;transition:all 0.2s ease-in-out}.wy-switch:after{content:"false";position:absolute;left:48px;display:block;font-size:12px;color:#ccc}.wy-switch.active{background:#1e8449}.wy-switch.active:before{left:24px;background:#27AE60}.wy-switch.active:after{content:"true"}.wy-switch.disabled,.wy-switch.active.disabled{cursor:not-allowed}.wy-control-group.wy-control-group-error .wy-form-message,.wy-control-group.wy-control-group-error>label{color:#E74C3C}.wy-control-group.wy-control-group-error input[type="text"],.wy-control-group.wy-control-group-error input[type="password"],.wy-control-group.wy-control-group-error input[type="email"],.wy-control-group.wy-control-group-error input[type="url"],.wy-control-group.wy-control-group-error input[type="date"],.wy-control-group.wy-control-group-error input[type="month"],.wy-control-group.wy-control-group-error input[type="time"],.wy-control-group.wy-control-group-error input[type="datetime"],.wy-control-group.wy-control-group-error input[type="datetime-local"],.wy-control-group.wy-control-group-error input[type="week"],.wy-control-group.wy-control-group-error input[type="number"],.wy-control-group.wy-control-group-error input[type="search"],.wy-control-group.wy-control-group-error input[type="tel"],.wy-control-group.wy-control-group-error input[type="color"]{border:solid 1px #E74C3C}.wy-control-group.wy-control-group-error textarea{border:solid 1px #E74C3C}.wy-inline-validate{white-space:nowrap}.wy-inline-validate .wy-input-context{padding:0.5em 0.625em;display:inline-block;font-size:80%}.wy-inline-validate.wy-inline-validate-success .wy-input-context{color:#27AE60}.wy-inline-validate.wy-inline-validate-danger .wy-input-context{color:#E74C3C}.wy-inline-validate.wy-inline-validate-warning .wy-input-context{color:#E67E22}.wy-inline-validate.wy-inline-validate-info .wy-input-context{color:#2980B9}.rotate-90{-webkit-transform:rotate(90deg);-moz-transform:rotate(90deg);-ms-transform:rotate(90deg);-o-transform:rotate(90deg);transform:rotate(90deg)}.rotate-180{-webkit-transform:rotate(180deg);-moz-transform:rotate(180deg);-ms-transform:rotate(180deg);-o-transform:rotate(180deg);transform:rotate(180deg)}.rotate-270{-webkit-transform:rotate(270deg);-moz-transform:rotate(270deg);-ms-transform:rotate(270deg);-o-transform:rotate(270deg);transform:rotate(270deg)}.mirror{-webkit-transform:scaleX(-1);-moz-transform:scaleX(-1);-ms-transform:scaleX(-1);-o-transform:scaleX(-1);transform:scaleX(-1)}.mirror.rotate-90{-webkit-transform:scaleX(-1) rotate(90deg);-moz-transform:scaleX(-1) rotate(90deg);-ms-transform:scaleX(-1) rotate(90deg);-o-transform:scaleX(-1) rotate(90deg);transform:scaleX(-1) rotate(90deg)}.mirror.rotate-180{-webkit-transform:scaleX(-1) rotate(180deg);-moz-transform:scaleX(-1) rotate(180deg);-ms-transform:scaleX(-1) rotate(180deg);-o-transform:scaleX(-1) rotate(180deg);transform:scaleX(-1) rotate(180deg)}.mirror.rotate-270{-webkit-transform:scaleX(-1) rotate(270deg);-moz-transform:scaleX(-1) rotate(270deg);-ms-transform:scaleX(-1) rotate(270deg);-o-transform:scaleX(-1) rotate(270deg);transform:scaleX(-1) rotate(270deg)}@media only screen and (max-width: 480px){.wy-form button[type="submit"]{margin:0.7em 0 0}.wy-form input[type="text"],.wy-form input[type="password"],.wy-form input[type="email"],.wy-form input[type="url"],.wy-form input[type="date"],.wy-form input[type="month"],.wy-form input[type="time"],.wy-form input[type="datetime"],.wy-form input[type="datetime-local"],.wy-form input[type="week"],.wy-form input[type="number"],.wy-form input[type="search"],.wy-form input[type="tel"],.wy-form input[type="color"]{margin-bottom:0.3em;display:block}.wy-form label{margin-bottom:0.3em;display:block}.wy-form input[type="password"],.wy-form input[type="email"],.wy-form input[type="url"],.wy-form input[type="date"],.wy-form input[type="month"],.wy-form input[type="time"],.wy-form input[type="datetime"],.wy-form input[type="datetime-local"],.wy-form input[type="week"],.wy-form input[type="number"],.wy-form input[type="search"],.wy-form input[type="tel"],.wy-form input[type="color"]{margin-bottom:0}.wy-form-aligned .wy-control-group label{margin-bottom:0.3em;text-align:left;display:block;width:100%}.wy-form-aligned .wy-control{margin:1.5em 0 0 0}.wy-form .wy-help-inline,.wy-form-message-inline,.wy-form-message{display:block;font-size:80%;padding:6px 0}}@media screen and (max-width: 768px){.tablet-hide{display:none}}@media screen and (max-width: 480px){.mobile-hide{display:none}}.float-left{float:left}.float-right{float:right}.full-width{width:100%}.wy-table,.rst-content table.docutils,.rst-content table.field-list{border-collapse:collapse;border-spacing:0;empty-cells:show;margin-bottom:24px}.wy-table caption,.rst-content table.docutils caption,.rst-content table.field-list caption{color:#000;font:italic 85%/1 arial,sans-serif;padding:1em 0;text-align:center}.wy-table td,.rst-content table.docutils td,.rst-content table.field-list td,.wy-table th,.rst-content table.docutils th,.rst-content table.field-list th{font-size:90%;margin:0;overflow:visible;padding:8px 16px}.wy-table td:first-child,.rst-content table.docutils td:first-child,.rst-content table.field-list td:first-child,.wy-table th:first-child,.rst-content table.docutils th:first-child,.rst-content table.field-list th:first-child{border-left-width:0}.wy-table thead,.rst-content table.docutils thead,.rst-content table.field-list thead{color:#000;text-align:left;vertical-align:bottom;white-space:nowrap}.wy-table thead th,.rst-content table.docutils thead th,.rst-content table.field-list thead th{font-weight:bold;border-bottom:solid 2px #e1e4e5}.wy-table td,.rst-content table.docutils td,.rst-content table.field-list td{background-color:transparent;vertical-align:middle}.wy-table td p,.rst-content table.docutils td p,.rst-content table.field-list td p{line-height:18px}.wy-table td p:last-child,.rst-content table.docutils td p:last-child,.rst-content table.field-list td p:last-child{margin-bottom:0}.wy-table .wy-table-cell-min,.rst-content table.docutils .wy-table-cell-min,.rst-content table.field-list .wy-table-cell-min{width:1%;padding-right:0}.wy-table .wy-table-cell-min input[type=checkbox],.rst-content table.docutils .wy-table-cell-min input[type=checkbox],.rst-content table.field-list .wy-table-cell-min input[type=checkbox],.wy-table .wy-table-cell-min input[type=checkbox],.rst-content table.docutils .wy-table-cell-min input[type=checkbox],.rst-content table.field-list .wy-table-cell-min input[type=checkbox]{margin:0}.wy-table-secondary{color:gray;font-size:90%}.wy-table-tertiary{color:gray;font-size:80%}.wy-table-odd td,.wy-table-striped tr:nth-child(2n-1) td,.rst-content table.docutils:not(.field-list) tr:nth-child(2n-1) td{background-color:#f3f6f6}.wy-table-backed{background-color:#f3f6f6}.wy-table-bordered-all,.rst-content table.docutils{border:1px solid #e1e4e5}.wy-table-bordered-all td,.rst-content table.docutils td{border-bottom:1px solid #e1e4e5;border-left:1px solid #e1e4e5}.wy-table-bordered-all tbody>tr:last-child td,.rst-content table.docutils tbody>tr:last-child td{border-bottom-width:0}.wy-table-bordered{border:1px solid #e1e4e5}.wy-table-bordered-rows td{border-bottom:1px solid #e1e4e5}.wy-table-bordered-rows tbody>tr:last-child td{border-bottom-width:0}.wy-table-horizontal tbody>tr:last-child td{border-bottom-width:0}.wy-table-horizontal td,.wy-table-horizontal th{border-width:0 0 1px 0;border-bottom:1px solid #e1e4e5}.wy-table-horizontal tbody>tr:last-child td{border-bottom-width:0}.wy-table-responsive{margin-bottom:24px;max-width:100%;overflow:auto}.wy-table-responsive table{margin-bottom:0 !important}.wy-table-responsive table td,.wy-table-responsive table th{white-space:nowrap}a{color:#2980B9;text-decoration:none;cursor:pointer}a:hover{color:#3091d1}a:visited{color:#9B59B6}html{height:100%;overflow-x:hidden}body{font-family:"Lato","proxima-nova","Helvetica Neue",Arial,sans-serif;font-weight:normal;color:#404040;min-height:100%;overflow-x:hidden;background:#edf0f2}.wy-text-left{text-align:left}.wy-text-center{text-align:center}.wy-text-right{text-align:right}.wy-text-large{font-size:120%}.wy-text-normal{font-size:100%}.wy-text-small,small{font-size:80%}.wy-text-strike{text-decoration:line-through}.wy-text-warning{color:#E67E22 !important}a.wy-text-warning:hover{color:#eb9950 !important}.wy-text-info{color:#2980B9 !important}a.wy-text-info:hover{color:#409ad5 !important}.wy-text-success{color:#27AE60 !important}a.wy-text-success:hover{color:#36d278 !important}.wy-text-danger{color:#E74C3C !important}a.wy-text-danger:hover{color:#ed7669 !important}.wy-text-neutral{color:#404040 !important}a.wy-text-neutral:hover{color:#595959 !important}h1,h2,.rst-content .toctree-wrapper p.caption,h3,h4,h5,h6,legend{margin-top:0;font-weight:700;font-family:"Roboto Slab","ff-tisa-web-pro","Georgia",Arial,sans-serif}p{line-height:24px;margin:0;font-size:16px;margin-bottom:24px}h1{font-size:175%}h2,.rst-content .toctree-wrapper p.caption{font-size:150%}h3{font-size:125%}h4{font-size:115%}h5{font-size:110%}h6{font-size:100%}hr{display:block;height:1px;border:0;border-top:1px solid #e1e4e5;margin:24px 0;padding:0}code,.rst-content tt,.rst-content code{white-space:nowrap;max-width:100%;background:#fff;border:solid 1px #e1e4e5;font-size:75%;padding:0 5px;font-family:Consolas,"Andale Mono WT","Andale Mono","Lucida Console","Lucida Sans Typewriter","DejaVu Sans Mono","Bitstream Vera Sans Mono","Liberation Mono","Nimbus Mono L",Monaco,"Courier New",Courier,monospace;color:#E74C3C;overflow-x:auto}code.code-large,.rst-content tt.code-large{font-size:90%}.wy-plain-list-disc,.rst-content .section ul,.rst-content .toctree-wrapper ul,article ul{list-style:disc;line-height:24px;margin-bottom:24px}.wy-plain-list-disc li,.rst-content .section ul li,.rst-content .toctree-wrapper ul li,article ul li{list-style:disc;margin-left:24px}.wy-plain-list-disc li p:last-child,.rst-content .section ul li p:last-child,.rst-content .toctree-wrapper ul li p:last-child,article ul li p:last-child{margin-bottom:0}.wy-plain-list-disc li ul,.rst-content .section ul li ul,.rst-content .toctree-wrapper ul li ul,article ul li ul{margin-bottom:0}.wy-plain-list-disc li li,.rst-content .section ul li li,.rst-content .toctree-wrapper ul li li,article ul li li{list-style:circle}.wy-plain-list-disc li li li,.rst-content .section ul li li li,.rst-content .toctree-wrapper ul li li li,article ul li li li{list-style:square}.wy-plain-list-disc li ol li,.rst-content .section ul li ol li,.rst-content .toctree-wrapper ul li ol li,article ul li ol li{list-style:decimal}.wy-plain-list-decimal,.rst-content .section ol,.rst-content ol.arabic,article ol{list-style:decimal;line-height:24px;margin-bottom:24px}.wy-plain-list-decimal li,.rst-content .section ol li,.rst-content ol.arabic li,article ol li{list-style:decimal;margin-left:24px}.wy-plain-list-decimal li p:last-child,.rst-content .section ol li p:last-child,.rst-content ol.arabic li p:last-child,article ol li p:last-child{margin-bottom:0}.wy-plain-list-decimal li ul,.rst-content .section ol li ul,.rst-content ol.arabic li ul,article ol li ul{margin-bottom:0}.wy-plain-list-decimal li ul li,.rst-content .section ol li ul li,.rst-content ol.arabic li ul li,article ol li ul li{list-style:disc}.codeblock-example{border:1px solid #e1e4e5;border-bottom:none;padding:24px;padding-top:48px;font-weight:500;background:#fff;position:relative}.codeblock-example:after{content:"Example";position:absolute;top:0px;left:0px;background:#9B59B6;color:#fff;padding:6px 12px}.codeblock-example.prettyprint-example-only{border:1px solid #e1e4e5;margin-bottom:24px}.codeblock,pre.literal-block,.rst-content .literal-block,.rst-content pre.literal-block,div[class^='highlight']{border:1px solid #e1e4e5;padding:0px;overflow-x:auto;background:#fff;margin:1px 0 24px 0}.codeblock div[class^='highlight'],pre.literal-block div[class^='highlight'],.rst-content .literal-block div[class^='highlight'],div[class^='highlight'] div[class^='highlight']{border:none;background:none;margin:0}div[class^='highlight'] td.code{width:100%}.linenodiv pre{border-right:solid 1px #e6e9ea;margin:0;padding:12px 12px;font-family:Consolas,"Andale Mono WT","Andale Mono","Lucida Console","Lucida Sans Typewriter","DejaVu Sans Mono","Bitstream Vera Sans Mono","Liberation Mono","Nimbus Mono L",Monaco,"Courier New",Courier,monospace;font-size:12px;line-height:1.5;color:#d9d9d9}div[class^='highlight'] pre{white-space:pre;margin:0;padding:12px 12px;font-family:Consolas,"Andale Mono WT","Andale Mono","Lucida Console","Lucida Sans Typewriter","DejaVu Sans Mono","Bitstream Vera Sans Mono","Liberation Mono","Nimbus Mono L",Monaco,"Courier New",Courier,monospace;font-size:12px;line-height:1.5;display:block;overflow:auto;color:#404040}@media print{.codeblock,pre.literal-block,.rst-content .literal-block,.rst-content pre.literal-block,div[class^='highlight'],div[class^='highlight'] pre{white-space:pre-wrap}}.hll{background-color:#ffc;margin:0 -12px;padding:0 12px;display:block}.c{color:#998;font-style:italic}.err{color:#a61717;background-color:#e3d2d2}.k{font-weight:bold}.o{font-weight:bold}.cm{color:#998;font-style:italic}.cp{color:#999;font-weight:bold}.c1{color:#998;font-style:italic}.cs{color:#999;font-weight:bold;font-style:italic}.gd{color:#000;background-color:#fdd}.gd .x{color:#000;background-color:#faa}.ge{font-style:italic}.gr{color:#a00}.gh{color:#999}.gi{color:#000;background-color:#dfd}.gi .x{color:#000;background-color:#afa}.go{color:#888}.gp{color:#555}.gs{font-weight:bold}.gu{color:purple;font-weight:bold}.gt{color:#a00}.kc{font-weight:bold}.kd{font-weight:bold}.kn{font-weight:bold}.kp{font-weight:bold}.kr{font-weight:bold}.kt{color:#458;font-weight:bold}.m{color:#099}.s{color:#d14}.n{color:#333}.na{color:teal}.nb{color:#0086b3}.nc{color:#458;font-weight:bold}.no{color:teal}.ni{color:purple}.ne{color:#900;font-weight:bold}.nf{color:#900;font-weight:bold}.nn{color:#555}.nt{color:navy}.nv{color:teal}.ow{font-weight:bold}.w{color:#bbb}.mf{color:#099}.mh{color:#099}.mi{color:#099}.mo{color:#099}.sb{color:#d14}.sc{color:#d14}.sd{color:#d14}.s2{color:#d14}.se{color:#d14}.sh{color:#d14}.si{color:#d14}.sx{color:#d14}.sr{color:#009926}.s1{color:#d14}.ss{color:#990073}.bp{color:#999}.vc{color:teal}.vg{color:teal}.vi{color:teal}.il{color:#099}.gc{color:#999;background-color:#EAF2F5}.wy-breadcrumbs li{display:inline-block}.wy-breadcrumbs li.wy-breadcrumbs-aside{float:right}.wy-breadcrumbs li a{display:inline-block;padding:5px}.wy-breadcrumbs li a:first-child{padding-left:0}.wy-breadcrumbs li code,.wy-breadcrumbs li .rst-content tt,.rst-content .wy-breadcrumbs li tt{padding:5px;border:none;background:none}.wy-breadcrumbs li code.literal,.wy-breadcrumbs li .rst-content tt.literal,.rst-content .wy-breadcrumbs li tt.literal{color:#404040}.wy-breadcrumbs-extra{margin-bottom:0;color:#b3b3b3;font-size:80%;display:inline-block}@media screen and (max-width: 480px){.wy-breadcrumbs-extra{display:none}.wy-breadcrumbs li.wy-breadcrumbs-aside{display:none}}@media print{.wy-breadcrumbs li.wy-breadcrumbs-aside{display:none}}.wy-affix{position:fixed;top:1.618em}.wy-menu a:hover{text-decoration:none}.wy-menu-horiz{*zoom:1}.wy-menu-horiz:before,.wy-menu-horiz:after{display:table;content:""}.wy-menu-horiz:after{clear:both}.wy-menu-horiz ul,.wy-menu-horiz li{display:inline-block}.wy-menu-horiz li:hover{background:rgba(255,255,255,0.1)}.wy-menu-horiz li.divide-left{border-left:solid 1px #404040}.wy-menu-horiz li.divide-right{border-right:solid 1px #404040}.wy-menu-horiz a{height:32px;display:inline-block;line-height:32px;padding:0 16px}.wy-menu-vertical{width:300px}.wy-menu-vertical header,.wy-menu-vertical p.caption{height:32px;display:inline-block;line-height:32px;padding:0 1.618em;margin-bottom:0;display:block;font-weight:bold;text-transform:uppercase;font-size:80%;color:#555;white-space:nowrap}.wy-menu-vertical ul{margin-bottom:0}.wy-menu-vertical li.divide-top{border-top:solid 1px #404040}.wy-menu-vertical li.divide-bottom{border-bottom:solid 1px #404040}.wy-menu-vertical li.current{background:#e3e3e3}.wy-menu-vertical li.current a{color:gray;border-right:solid 1px #c9c9c9;padding:0.4045em 2.427em}.wy-menu-vertical li.current a:hover{background:#d6d6d6}.wy-menu-vertical li code,.wy-menu-vertical li .rst-content tt,.rst-content .wy-menu-vertical li tt{border:none;background:inherit;color:inherit;padding-left:0;padding-right:0}.wy-menu-vertical li span.toctree-expand{display:block;float:left;margin-left:-1.2em;font-size:0.8em;line-height:1.6em;color:#4d4d4d}.wy-menu-vertical li.on a,.wy-menu-vertical li.current>a{color:#404040;padding:0.4045em 1.618em;font-weight:bold;position:relative;background:#fcfcfc;border:none;border-bottom:solid 1px #c9c9c9;border-top:solid 1px #c9c9c9;padding-left:1.618em -4px}.wy-menu-vertical li.on a:hover,.wy-menu-vertical li.current>a:hover{background:#fcfcfc}.wy-menu-vertical li.on a:hover span.toctree-expand,.wy-menu-vertical li.current>a:hover span.toctree-expand{color:gray}.wy-menu-vertical li.on a span.toctree-expand,.wy-menu-vertical li.current>a span.toctree-expand{display:block;font-size:0.8em;line-height:1.6em;color:#333}.wy-menu-vertical li.toctree-l1.current li.toctree-l2>ul,.wy-menu-vertical li.toctree-l2.current li.toctree-l3>ul{display:none}.wy-menu-vertical li.toctree-l1.current li.toctree-l2.current>ul,.wy-menu-vertical li.toctree-l2.current li.toctree-l3.current>ul{display:block}.wy-menu-vertical li.toctree-l2.current>a{background:#c9c9c9;padding:0.4045em 2.427em}.wy-menu-vertical li.toctree-l2.current li.toctree-l3>a{display:block;background:#c9c9c9;padding:0.4045em 4.045em}.wy-menu-vertical li.toctree-l2 a:hover span.toctree-expand{color:gray}.wy-menu-vertical li.toctree-l2 span.toctree-expand{color:#a3a3a3}.wy-menu-vertical li.toctree-l3{font-size:0.9em}.wy-menu-vertical li.toctree-l3.current>a{background:#bdbdbd;padding:0.4045em 4.045em}.wy-menu-vertical li.toctree-l3.current li.toctree-l4>a{display:block;background:#bdbdbd;padding:0.4045em 5.663em;border-top:none;border-bottom:none}.wy-menu-vertical li.toctree-l3 a:hover span.toctree-expand{color:gray}.wy-menu-vertical li.toctree-l3 span.toctree-expand{color:#969696}.wy-menu-vertical li.toctree-l4{font-size:0.9em}.wy-menu-vertical li.current ul{display:block}.wy-menu-vertical li ul{margin-bottom:0;display:none}.wy-menu-vertical .local-toc li ul{display:block}.wy-menu-vertical li ul li a{margin-bottom:0;color:#b3b3b3;font-weight:normal}.wy-menu-vertical a{display:inline-block;line-height:18px;padding:0.4045em 1.618em;display:block;position:relative;font-size:90%;color:#b3b3b3}.wy-menu-vertical a:hover{background-color:#4e4a4a;cursor:pointer}.wy-menu-vertical a:hover span.toctree-expand{color:#b3b3b3}.wy-menu-vertical a:active{background-color:#2980B9;cursor:pointer;color:#fff}.wy-menu-vertical a:active span.toctree-expand{color:#fff}.wy-side-nav-search{display:block;width:300px;padding:0.809em;margin-bottom:0.809em;z-index:200;background-color:#2980B9;text-align:center;padding:0.809em;display:block;color:#fcfcfc;margin-bottom:0.809em}.wy-side-nav-search input[type=text]{width:100%;border-radius:50px;padding:6px 12px;border-color:#2472a4}.wy-side-nav-search img{display:block;margin:auto auto 0.809em auto;height:45px;width:45px;background-color:#2980B9;padding:5px;border-radius:100%}.wy-side-nav-search>a,.wy-side-nav-search .wy-dropdown>a{color:#fcfcfc;font-size:100%;font-weight:bold;display:inline-block;padding:4px 6px;margin-bottom:0.809em}.wy-side-nav-search>a:hover,.wy-side-nav-search .wy-dropdown>a:hover{background:rgba(255,255,255,0.1)}.wy-side-nav-search>a img.logo,.wy-side-nav-search .wy-dropdown>a img.logo{display:block;margin:0 auto;height:auto;width:auto;border-radius:0;max-width:100%;background:transparent}.wy-side-nav-search>a.icon img.logo,.wy-side-nav-search .wy-dropdown>a.icon img.logo{margin-top:0.85em}.wy-side-nav-search>div.version{margin-top:-0.4045em;margin-bottom:0.809em;font-weight:normal;color:rgba(255,255,255,0.3)}.wy-nav .wy-menu-vertical header{color:#2980B9}.wy-nav .wy-menu-vertical a{color:#b3b3b3}.wy-nav .wy-menu-vertical a:hover{background-color:#2980B9;color:#fff}[data-menu-wrap]{-webkit-transition:all 0.2s ease-in;-moz-transition:all 0.2s ease-in;transition:all 0.2s ease-in;position:absolute;opacity:1;width:100%;opacity:0}[data-menu-wrap].move-center{left:0;right:auto;opacity:1}[data-menu-wrap].move-left{right:auto;left:-100%;opacity:0}[data-menu-wrap].move-right{right:-100%;left:auto;opacity:0}.wy-body-for-nav{background:left repeat-y #fcfcfc;background-image:url(data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAAEAAAABCAIAAACQd1PeAAAAGXRFWHRTb2Z0d2FyZQBBZG9iZSBJbWFnZVJlYWR5ccllPAAAAyRpVFh0WE1MOmNvbS5hZG9iZS54bXAAAAAAADw/eHBhY2tldCBiZWdpbj0i77u/IiBpZD0iVzVNME1wQ2VoaUh6cmVTek5UY3prYzlkIj8+IDx4OnhtcG1ldGEgeG1sbnM6eD0iYWRvYmU6bnM6bWV0YS8iIHg6eG1wdGs9IkFkb2JlIFhNUCBDb3JlIDUuMy1jMDExIDY2LjE0NTY2MSwgMjAxMi8wMi8wNi0xNDo1NjoyNyAgICAgICAgIj4gPHJkZjpSREYgeG1sbnM6cmRmPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5LzAyLzIyLXJkZi1zeW50YXgtbnMjIj4gPHJkZjpEZXNjcmlwdGlvbiByZGY6YWJvdXQ9IiIgeG1sbnM6eG1wPSJodHRwOi8vbnMuYWRvYmUuY29tL3hhcC8xLjAvIiB4bWxuczp4bXBNTT0iaHR0cDovL25zLmFkb2JlLmNvbS94YXAvMS4wL21tLyIgeG1sbnM6c3RSZWY9Imh0dHA6Ly9ucy5hZG9iZS5jb20veGFwLzEuMC9zVHlwZS9SZXNvdXJjZVJlZiMiIHhtcDpDcmVhdG9yVG9vbD0iQWRvYmUgUGhvdG9zaG9wIENTNiAoTWFjaW50b3NoKSIgeG1wTU06SW5zdGFuY2VJRD0ieG1wLmlpZDoxOERBMTRGRDBFMUUxMUUzODUwMkJCOThDMEVFNURFMCIgeG1wTU06RG9jdW1lbnRJRD0ieG1wLmRpZDoxOERBMTRGRTBFMUUxMUUzODUwMkJCOThDMEVFNURFMCI+IDx4bXBNTTpEZXJpdmVkRnJvbSBzdFJlZjppbnN0YW5jZUlEPSJ4bXAuaWlkOjE4REExNEZCMEUxRTExRTM4NTAyQkI5OEMwRUU1REUwIiBzdFJlZjpkb2N1bWVudElEPSJ4bXAuZGlkOjE4REExNEZDMEUxRTExRTM4NTAyQkI5OEMwRUU1REUwIi8+IDwvcmRmOkRlc2NyaXB0aW9uPiA8L3JkZjpSREY+IDwveDp4bXBtZXRhPiA8P3hwYWNrZXQgZW5kPSJyIj8+EwrlwAAAAA5JREFUeNpiMDU0BAgwAAE2AJgB9BnaAAAAAElFTkSuQmCC);background-size:300px 1px}.wy-grid-for-nav{position:absolute;width:100%;height:100%}.wy-nav-side{position:fixed;top:0;bottom:0;left:0;padding-bottom:2em;width:300px;overflow-x:hidden;overflow-y:hidden;min-height:100%;background:#343131;z-index:200}.wy-side-scroll{width:320px;position:relative;overflow-x:hidden;overflow-y:scroll;height:100%}.wy-nav-top{display:none;background:#2980B9;color:#fff;padding:0.4045em 0.809em;position:relative;line-height:50px;text-align:center;font-size:100%;*zoom:1}.wy-nav-top:before,.wy-nav-top:after{display:table;content:""}.wy-nav-top:after{clear:both}.wy-nav-top a{color:#fff;font-weight:bold}.wy-nav-top img{margin-right:12px;height:45px;width:45px;background-color:#2980B9;padding:5px;border-radius:100%}.wy-nav-top i{font-size:30px;float:left;cursor:pointer}.wy-nav-content-wrap{margin-left:300px;background:#fcfcfc;min-height:100%}.wy-nav-content{padding:1.618em 3.236em;height:100%;max-width:800px;margin:auto}.wy-body-mask{position:fixed;width:100%;height:100%;background:rgba(0,0,0,0.2);display:none;z-index:499}.wy-body-mask.on{display:block}footer{color:#999}footer p{margin-bottom:12px}footer span.commit code,footer span.commit .rst-content tt,.rst-content footer span.commit tt{padding:0px;font-family:Consolas,"Andale Mono WT","Andale Mono","Lucida Console","Lucida Sans Typewriter","DejaVu Sans Mono","Bitstream Vera Sans Mono","Liberation Mono","Nimbus Mono L",Monaco,"Courier New",Courier,monospace;font-size:1em;background:none;border:none;color:#999}.rst-footer-buttons{*zoom:1}.rst-footer-buttons:before,.rst-footer-buttons:after{display:table;content:""}.rst-footer-buttons:after{clear:both}#search-results .search li{margin-bottom:24px;border-bottom:solid 1px #e1e4e5;padding-bottom:24px}#search-results .search li:first-child{border-top:solid 1px #e1e4e5;padding-top:24px}#search-results .search li a{font-size:120%;margin-bottom:12px;display:inline-block}#search-results .context{color:gray;font-size:90%}@media screen and (max-width: 768px){.wy-body-for-nav{background:#fcfcfc}.wy-nav-top{display:block}.wy-nav-side{left:-300px}.wy-nav-side.shift{width:85%;left:0}.wy-side-scroll{width:auto}.wy-side-nav-search{width:auto}.wy-menu.wy-menu-vertical{width:auto}.wy-nav-content-wrap{margin-left:0}.wy-nav-content-wrap .wy-nav-content{padding:1.618em}.wy-nav-content-wrap.shift{position:fixed;min-width:100%;left:85%;top:0;height:100%;overflow:hidden}}@media screen and (min-width: 1400px){.wy-nav-content-wrap{background:rgba(0,0,0,0.05)}.wy-nav-content{margin:0;background:#fcfcfc}}@media print{.rst-versions,footer,.wy-nav-side{display:none}.wy-nav-content-wrap{margin-left:0}}.rst-versions{position:fixed;bottom:0;left:0;width:300px;color:#fcfcfc;background:#1f1d1d;border-top:solid 10px #343131;font-family:"Lato","proxima-nova","Helvetica Neue",Arial,sans-serif;z-index:400}.rst-versions a{color:#2980B9;text-decoration:none}.rst-versions .rst-badge-small{display:none}.rst-versions .rst-current-version{padding:12px;background-color:#272525;display:block;text-align:right;font-size:90%;cursor:pointer;color:#27AE60;*zoom:1}.rst-versions .rst-current-version:before,.rst-versions .rst-current-version:after{display:table;content:""}.rst-versions .rst-current-version:after{clear:both}.rst-versions .rst-current-version .fa,.rst-versions .rst-current-version .wy-menu-vertical li span.toctree-expand,.wy-menu-vertical li .rst-versions .rst-current-version span.toctree-expand,.rst-versions .rst-current-version .rst-content .admonition-title,.rst-content .rst-versions .rst-current-version .admonition-title,.rst-versions .rst-current-version .rst-content h1 .headerlink,.rst-content h1 .rst-versions .rst-current-version .headerlink,.rst-versions .rst-current-version .rst-content h2 .headerlink,.rst-content h2 .rst-versions .rst-current-version .headerlink,.rst-versions .rst-current-version .rst-content h3 .headerlink,.rst-content h3 .rst-versions .rst-current-version .headerlink,.rst-versions .rst-current-version .rst-content h4 .headerlink,.rst-content h4 .rst-versions .rst-current-version .headerlink,.rst-versions .rst-current-version .rst-content h5 .headerlink,.rst-content h5 .rst-versions .rst-current-version .headerlink,.rst-versions .rst-current-version .rst-content h6 .headerlink,.rst-content h6 .rst-versions .rst-current-version .headerlink,.rst-versions .rst-current-version .rst-content dl dt .headerlink,.rst-content dl dt .rst-versions .rst-current-version .headerlink,.rst-versions .rst-current-version .rst-content p.caption .headerlink,.rst-content p.caption .rst-versions .rst-current-version .headerlink,.rst-versions .rst-current-version .rst-content tt.download span:first-child,.rst-content tt.download .rst-versions .rst-current-version span:first-child,.rst-versions .rst-current-version .rst-content code.download span:first-child,.rst-content code.download .rst-versions .rst-current-version span:first-child,.rst-versions .rst-current-version .icon{color:#fcfcfc}.rst-versions .rst-current-version .fa-book,.rst-versions .rst-current-version .icon-book{float:left}.rst-versions .rst-current-version .icon-book{float:left}.rst-versions .rst-current-version.rst-out-of-date{background-color:#E74C3C;color:#fff}.rst-versions .rst-current-version.rst-active-old-version{background-color:#F1C40F;color:#000}.rst-versions.shift-up .rst-other-versions{display:block}.rst-versions .rst-other-versions{font-size:90%;padding:12px;color:gray;display:none}.rst-versions .rst-other-versions hr{display:block;height:1px;border:0;margin:20px 0;padding:0;border-top:solid 1px #413d3d}.rst-versions .rst-other-versions dd{display:inline-block;margin:0}.rst-versions .rst-other-versions dd a{display:inline-block;padding:6px;color:#fcfcfc}.rst-versions.rst-badge{width:auto;bottom:20px;right:20px;left:auto;border:none;max-width:300px}.rst-versions.rst-badge .icon-book{float:none}.rst-versions.rst-badge .fa-book,.rst-versions.rst-badge .icon-book{float:none}.rst-versions.rst-badge.shift-up .rst-current-version{text-align:right}.rst-versions.rst-badge.shift-up .rst-current-version .fa-book,.rst-versions.rst-badge.shift-up .rst-current-version .icon-book{float:left}.rst-versions.rst-badge.shift-up .rst-current-version .icon-book{float:left}.rst-versions.rst-badge .rst-current-version{width:auto;height:30px;line-height:30px;padding:0 6px;display:block;text-align:center}@media screen and (max-width: 768px){.rst-versions{width:85%;display:none}.rst-versions.shift{display:block}img{width:100%;height:auto}}.rst-content img{max-width:100%;height:auto !important}.rst-content div.figure{margin-bottom:24px}.rst-content div.figure p.caption{font-style:italic}.rst-content div.figure.align-center{text-align:center}.rst-content .section>img,.rst-content .section>a>img{margin-bottom:24px}.rst-content blockquote{margin-left:24px;line-height:24px;margin-bottom:24px}.rst-content .note .last,.rst-content .attention .last,.rst-content .caution .last,.rst-content .danger .last,.rst-content .error .last,.rst-content .hint .last,.rst-content .important .last,.rst-content .tip .last,.rst-content .warning .last,.rst-content .seealso .last,.rst-content .admonition-todo .last{margin-bottom:0}.rst-content .admonition-title:before{margin-right:4px}.rst-content .admonition table{border-color:rgba(0,0,0,0.1)}.rst-content .admonition table td,.rst-content .admonition table th{background:transparent !important;border-color:rgba(0,0,0,0.1) !important}.rst-content .section ol.loweralpha,.rst-content .section ol.loweralpha li{list-style:lower-alpha}.rst-content .section ol.upperalpha,.rst-content .section ol.upperalpha li{list-style:upper-alpha}.rst-content .section ol p,.rst-content .section ul p{margin-bottom:12px}.rst-content .line-block{margin-left:24px}.rst-content .topic-title{font-weight:bold;margin-bottom:12px}.rst-content .toc-backref{color:#404040}.rst-content .align-right{float:right;margin:0px 0px 24px 24px}.rst-content .align-left{float:left;margin:0px 24px 24px 0px}.rst-content .align-center{margin:auto;display:block}.rst-content h1 .headerlink,.rst-content h2 .headerlink,.rst-content .toctree-wrapper p.caption .headerlink,.rst-content h3 .headerlink,.rst-content h4 .headerlink,.rst-content h5 .headerlink,.rst-content h6 .headerlink,.rst-content dl dt .headerlink,.rst-content p.caption .headerlink{display:none;visibility:hidden;font-size:14px}.rst-content h1 .headerlink:after,.rst-content h2 .headerlink:after,.rst-content .toctree-wrapper p.caption .headerlink:after,.rst-content h3 .headerlink:after,.rst-content h4 .headerlink:after,.rst-content h5 .headerlink:after,.rst-content h6 .headerlink:after,.rst-content dl dt .headerlink:after,.rst-content p.caption .headerlink:after{visibility:visible;content:"";font-family:FontAwesome;display:inline-block}.rst-content h1:hover .headerlink,.rst-content h2:hover .headerlink,.rst-content .toctree-wrapper p.caption:hover .headerlink,.rst-content h3:hover .headerlink,.rst-content h4:hover .headerlink,.rst-content h5:hover .headerlink,.rst-content h6:hover .headerlink,.rst-content dl dt:hover .headerlink,.rst-content p.caption:hover .headerlink{display:inline-block}.rst-content .sidebar{float:right;width:40%;display:block;margin:0 0 24px 24px;padding:24px;background:#f3f6f6;border:solid 1px #e1e4e5}.rst-content .sidebar p,.rst-content .sidebar ul,.rst-content .sidebar dl{font-size:90%}.rst-content .sidebar .last{margin-bottom:0}.rst-content .sidebar .sidebar-title{display:block;font-family:"Roboto Slab","ff-tisa-web-pro","Georgia",Arial,sans-serif;font-weight:bold;background:#e1e4e5;padding:6px 12px;margin:-24px;margin-bottom:24px;font-size:100%}.rst-content .highlighted{background:#F1C40F;display:inline-block;font-weight:bold;padding:0 6px}.rst-content .footnote-reference,.rst-content .citation-reference{vertical-align:super;font-size:90%}.rst-content table.docutils.citation,.rst-content table.docutils.footnote{background:none;border:none;color:#999}.rst-content table.docutils.citation td,.rst-content table.docutils.citation tr,.rst-content table.docutils.footnote td,.rst-content table.docutils.footnote tr{border:none;background-color:transparent !important;white-space:normal}.rst-content table.docutils.citation td.label,.rst-content table.docutils.footnote td.label{padding-left:0;padding-right:0;vertical-align:top}.rst-content table.docutils.citation tt,.rst-content table.docutils.citation code,.rst-content table.docutils.footnote tt,.rst-content table.docutils.footnote code{color:#555}.rst-content table.field-list{border:none}.rst-content table.field-list td{border:none;padding-top:5px}.rst-content table.field-list td>strong{display:inline-block;margin-top:3px}.rst-content table.field-list .field-name{padding-right:10px;text-align:left;white-space:nowrap}.rst-content table.field-list .field-body{text-align:left;padding-left:0}.rst-content tt,.rst-content tt,.rst-content code{color:#000;padding:2px 5px}.rst-content tt big,.rst-content tt em,.rst-content tt big,.rst-content code big,.rst-content tt em,.rst-content code em{font-size:100% !important;line-height:normal}.rst-content tt.literal,.rst-content tt.literal,.rst-content code.literal{color:#E74C3C}.rst-content tt.xref,a .rst-content tt,.rst-content tt.xref,.rst-content code.xref,a .rst-content tt,a .rst-content code{font-weight:bold;color:#404040}.rst-content a tt,.rst-content a tt,.rst-content a code{color:#2980B9}.rst-content dl{margin-bottom:24px}.rst-content dl dt{font-weight:bold}.rst-content dl p,.rst-content dl table,.rst-content dl ul,.rst-content dl ol{margin-bottom:12px !important}.rst-content dl dd{margin:0 0 12px 24px}.rst-content dl:not(.docutils){margin-bottom:24px}.rst-content dl:not(.docutils) dt{display:inline-block;margin:6px 0;font-size:90%;line-height:normal;background:#e7f2fa;color:#2980B9;border-top:solid 3px #6ab0de;padding:6px;position:relative}.rst-content dl:not(.docutils) dt:before{color:#6ab0de}.rst-content dl:not(.docutils) dt .headerlink{color:#404040;font-size:100% !important}.rst-content dl:not(.docutils) dl dt{margin-bottom:6px;border:none;border-left:solid 3px #ccc;background:#f0f0f0;color:#555}.rst-content dl:not(.docutils) dl dt .headerlink{color:#404040;font-size:100% !important}.rst-content dl:not(.docutils) dt:first-child{margin-top:0}.rst-content dl:not(.docutils) tt,.rst-content dl:not(.docutils) tt,.rst-content dl:not(.docutils) code{font-weight:bold}.rst-content dl:not(.docutils) tt.descname,.rst-content dl:not(.docutils) tt.descclassname,.rst-content dl:not(.docutils) tt.descname,.rst-content dl:not(.docutils) code.descname,.rst-content dl:not(.docutils) tt.descclassname,.rst-content dl:not(.docutils) code.descclassname{background-color:transparent;border:none;padding:0;font-size:100% !important}.rst-content dl:not(.docutils) tt.descname,.rst-content dl:not(.docutils) tt.descname,.rst-content dl:not(.docutils) code.descname{font-weight:bold}.rst-content dl:not(.docutils) .optional{display:inline-block;padding:0 4px;color:#000;font-weight:bold}.rst-content dl:not(.docutils) .property{display:inline-block;padding-right:8px}.rst-content .viewcode-link,.rst-content .viewcode-back{display:inline-block;color:#27AE60;font-size:80%;padding-left:24px}.rst-content .viewcode-back{display:block;float:right}.rst-content p.rubric{margin-bottom:12px;font-weight:bold}.rst-content tt.download,.rst-content code.download{background:inherit;padding:inherit;font-family:inherit;font-size:inherit;color:inherit;border:inherit;white-space:inherit}.rst-content tt.download span:first-child:before,.rst-content code.download span:first-child:before{margin-right:4px}@media screen and (max-width: 480px){.rst-content .sidebar{width:100%}}span[id*='MathJax-Span']{color:#404040}.math{text-align:center}@font-face{font-family:"Inconsolata";font-style:normal;font-weight:400;src:local("Inconsolata"),local("Inconsolata-Regular"),url(../fonts/Inconsolata-Regular.ttf) format("truetype")}@font-face{font-family:"Inconsolata";font-style:normal;font-weight:700;src:local("Inconsolata Bold"),local("Inconsolata-Bold"),url(../fonts/Inconsolata-Bold.ttf) format("truetype")}@font-face{font-family:"Lato";font-style:normal;font-weight:400;src:local("Lato Regular"),local("Lato-Regular"),url(../fonts/Lato-Regular.ttf) format("truetype")}@font-face{font-family:"Lato";font-style:normal;font-weight:700;src:local("Lato Bold"),local("Lato-Bold"),url(../fonts/Lato-Bold.ttf) format("truetype")}@font-face{font-family:"Roboto Slab";font-style:normal;font-weight:400;src:local("Roboto Slab Regular"),local("RobotoSlab-Regular"),url(../fonts/RobotoSlab-Regular.ttf) format("truetype")}@font-face{font-family:"Roboto Slab";font-style:normal;font-weight:700;src:local("Roboto Slab Bold"),local("RobotoSlab-Bold"),url(../fonts/RobotoSlab-Bold.ttf) format("truetype")} | |
| 4 | /*# sourceMappingURL=theme.css.map */ |
| 0 | /* This file intentionally left blank. */ |
| 0 | /* | |
| 1 | * doctools.js | |
| 2 | * ~~~~~~~~~~~ | |
| 3 | * | |
| 4 | * Sphinx JavaScript utilities for all documentation. | |
| 5 | * | |
| 6 | * :copyright: Copyright 2007-2016 by the Sphinx team, see AUTHORS. | |
| 7 | * :license: BSD, see LICENSE for details. | |
| 8 | * | |
| 9 | */ | |
| 10 | ||
| 11 | /** | |
| 12 | * select a different prefix for underscore | |
| 13 | */ | |
| 14 | $u = _.noConflict(); | |
| 15 | ||
| 16 | /** | |
| 17 | * make the code below compatible with browsers without | |
| 18 | * an installed firebug like debugger | |
| 19 | if (!window.console || !console.firebug) { | |
| 20 | var names = ["log", "debug", "info", "warn", "error", "assert", "dir", | |
| 21 | "dirxml", "group", "groupEnd", "time", "timeEnd", "count", "trace", | |
| 22 | "profile", "profileEnd"]; | |
| 23 | window.console = {}; | |
| 24 | for (var i = 0; i < names.length; ++i) | |
| 25 | window.console[names[i]] = function() {}; | |
| 26 | } | |
| 27 | */ | |
| 28 | ||
| 29 | /** | |
| 30 | * small helper function to urldecode strings | |
| 31 | */ | |
| 32 | jQuery.urldecode = function(x) { | |
| 33 | return decodeURIComponent(x).replace(/\+/g, ' '); | |
| 34 | }; | |
| 35 | ||
| 36 | /** | |
| 37 | * small helper function to urlencode strings | |
| 38 | */ | |
| 39 | jQuery.urlencode = encodeURIComponent; | |
| 40 | ||
| 41 | /** | |
| 42 | * This function returns the parsed url parameters of the | |
| 43 | * current request. Multiple values per key are supported, | |
| 44 | * it will always return arrays of strings for the value parts. | |
| 45 | */ | |
| 46 | jQuery.getQueryParameters = function(s) { | |
| 47 | if (typeof s == 'undefined') | |
| 48 | s = document.location.search; | |
| 49 | var parts = s.substr(s.indexOf('?') + 1).split('&'); | |
| 50 | var result = {}; | |
| 51 | for (var i = 0; i < parts.length; i++) { | |
| 52 | var tmp = parts[i].split('=', 2); | |
| 53 | var key = jQuery.urldecode(tmp[0]); | |
| 54 | var value = jQuery.urldecode(tmp[1]); | |
| 55 | if (key in result) | |
| 56 | result[key].push(value); | |
| 57 | else | |
| 58 | result[key] = [value]; | |
| 59 | } | |
| 60 | return result; | |
| 61 | }; | |
| 62 | ||
| 63 | /** | |
| 64 | * highlight a given string on a jquery object by wrapping it in | |
| 65 | * span elements with the given class name. | |
| 66 | */ | |
| 67 | jQuery.fn.highlightText = function(text, className) { | |
| 68 | function highlight(node) { | |
| 69 | if (node.nodeType == 3) { | |
| 70 | var val = node.nodeValue; | |
| 71 | var pos = val.toLowerCase().indexOf(text); | |
| 72 | if (pos >= 0 && !jQuery(node.parentNode).hasClass(className)) { | |
| 73 | var span = document.createElement("span"); | |
| 74 | span.className = className; | |
| 75 | span.appendChild(document.createTextNode(val.substr(pos, text.length))); | |
| 76 | node.parentNode.insertBefore(span, node.parentNode.insertBefore( | |
| 77 | document.createTextNode(val.substr(pos + text.length)), | |
| 78 | node.nextSibling)); | |
| 79 | node.nodeValue = val.substr(0, pos); | |
| 80 | } | |
| 81 | } | |
| 82 | else if (!jQuery(node).is("button, select, textarea")) { | |
| 83 | jQuery.each(node.childNodes, function() { | |
| 84 | highlight(this); | |
| 85 | }); | |
| 86 | } | |
| 87 | } | |
| 88 | return this.each(function() { | |
| 89 | highlight(this); | |
| 90 | }); | |
| 91 | }; | |
| 92 | ||
| 93 | /* | |
| 94 | * backward compatibility for jQuery.browser | |
| 95 | * This will be supported until firefox bug is fixed. | |
| 96 | */ | |
| 97 | if (!jQuery.browser) { | |
| 98 | jQuery.uaMatch = function(ua) { | |
| 99 | ua = ua.toLowerCase(); | |
| 100 | ||
| 101 | var match = /(chrome)[ \/]([\w.]+)/.exec(ua) || | |
| 102 | /(webkit)[ \/]([\w.]+)/.exec(ua) || | |
| 103 | /(opera)(?:.*version|)[ \/]([\w.]+)/.exec(ua) || | |
| 104 | /(msie) ([\w.]+)/.exec(ua) || | |
| 105 | ua.indexOf("compatible") < 0 && /(mozilla)(?:.*? rv:([\w.]+)|)/.exec(ua) || | |
| 106 | []; | |
| 107 | ||
| 108 | return { | |
| 109 | browser: match[ 1 ] || "", | |
| 110 | version: match[ 2 ] || "0" | |
| 111 | }; | |
| 112 | }; | |
| 113 | jQuery.browser = {}; | |
| 114 | jQuery.browser[jQuery.uaMatch(navigator.userAgent).browser] = true; | |
| 115 | } | |
| 116 | ||
| 117 | /** | |
| 118 | * Small JavaScript module for the documentation. | |
| 119 | */ | |
| 120 | var Documentation = { | |
| 121 | ||
| 122 | init : function() { | |
| 123 | this.fixFirefoxAnchorBug(); | |
| 124 | this.highlightSearchWords(); | |
| 125 | this.initIndexTable(); | |
| 126 | ||
| 127 | }, | |
| 128 | ||
| 129 | /** | |
| 130 | * i18n support | |
| 131 | */ | |
| 132 | TRANSLATIONS : {}, | |
| 133 | PLURAL_EXPR : function(n) { return n == 1 ? 0 : 1; }, | |
| 134 | LOCALE : 'unknown', | |
| 135 | ||
| 136 | // gettext and ngettext don't access this so that the functions | |
| 137 | // can safely bound to a different name (_ = Documentation.gettext) | |
| 138 | gettext : function(string) { | |
| 139 | var translated = Documentation.TRANSLATIONS[string]; | |
| 140 | if (typeof translated == 'undefined') | |
| 141 | return string; | |
| 142 | return (typeof translated == 'string') ? translated : translated[0]; | |
| 143 | }, | |
| 144 | ||
| 145 | ngettext : function(singular, plural, n) { | |
| 146 | var translated = Documentation.TRANSLATIONS[singular]; | |
| 147 | if (typeof translated == 'undefined') | |
| 148 | return (n == 1) ? singular : plural; | |
| 149 | return translated[Documentation.PLURALEXPR(n)]; | |
| 150 | }, | |
| 151 | ||
| 152 | addTranslations : function(catalog) { | |
| 153 | for (var key in catalog.messages) | |
| 154 | this.TRANSLATIONS[key] = catalog.messages[key]; | |
| 155 | this.PLURAL_EXPR = new Function('n', 'return +(' + catalog.plural_expr + ')'); | |
| 156 | this.LOCALE = catalog.locale; | |
| 157 | }, | |
| 158 | ||
| 159 | /** | |
| 160 | * add context elements like header anchor links | |
| 161 | */ | |
| 162 | addContextElements : function() { | |
| 163 | $('div[id] > :header:first').each(function() { | |
| 164 | $('<a class="headerlink">\u00B6</a>'). | |
| 165 | attr('href', '#' + this.id). | |
| 166 | attr('title', _('Permalink to this headline')). | |
| 167 | appendTo(this); | |
| 168 | }); | |
| 169 | $('dt[id]').each(function() { | |
| 170 | $('<a class="headerlink">\u00B6</a>'). | |
| 171 | attr('href', '#' + this.id). | |
| 172 | attr('title', _('Permalink to this definition')). | |
| 173 | appendTo(this); | |
| 174 | }); | |
| 175 | }, | |
| 176 | ||
| 177 | /** | |
| 178 | * workaround a firefox stupidity | |
| 179 | * see: https://bugzilla.mozilla.org/show_bug.cgi?id=645075 | |
| 180 | */ | |
| 181 | fixFirefoxAnchorBug : function() { | |
| 182 | if (document.location.hash) | |
| 183 | window.setTimeout(function() { | |
| 184 | document.location.href += ''; | |
| 185 | }, 10); | |
| 186 | }, | |
| 187 | ||
| 188 | /** | |
| 189 | * highlight the search words provided in the url in the text | |
| 190 | */ | |
| 191 | highlightSearchWords : function() { | |
| 192 | var params = $.getQueryParameters(); | |
| 193 | var terms = (params.highlight) ? params.highlight[0].split(/\s+/) : []; | |
| 194 | if (terms.length) { | |
| 195 | var body = $('div.body'); | |
| 196 | if (!body.length) { | |
| 197 | body = $('body'); | |
| 198 | } | |
| 199 | window.setTimeout(function() { | |
| 200 | $.each(terms, function() { | |
| 201 | body.highlightText(this.toLowerCase(), 'highlighted'); | |
| 202 | }); | |
| 203 | }, 10); | |
| 204 | $('<p class="highlight-link"><a href="javascript:Documentation.' + | |
| 205 | 'hideSearchWords()">' + _('Hide Search Matches') + '</a></p>') | |
| 206 | .appendTo($('#searchbox')); | |
| 207 | } | |
| 208 | }, | |
| 209 | ||
| 210 | /** | |
| 211 | * init the domain index toggle buttons | |
| 212 | */ | |
| 213 | initIndexTable : function() { | |
| 214 | var togglers = $('img.toggler').click(function() { | |
| 215 | var src = $(this).attr('src'); | |
| 216 | var idnum = $(this).attr('id').substr(7); | |
| 217 | $('tr.cg-' + idnum).toggle(); | |
| 218 | if (src.substr(-9) == 'minus.png') | |
| 219 | $(this).attr('src', src.substr(0, src.length-9) + 'plus.png'); | |
| 220 | else | |
| 221 | $(this).attr('src', src.substr(0, src.length-8) + 'minus.png'); | |
| 222 | }).css('display', ''); | |
| 223 | if (DOCUMENTATION_OPTIONS.COLLAPSE_INDEX) { | |
| 224 | togglers.click(); | |
| 225 | } | |
| 226 | }, | |
| 227 | ||
| 228 | /** | |
| 229 | * helper function to hide the search marks again | |
| 230 | */ | |
| 231 | hideSearchWords : function() { | |
| 232 | $('#searchbox .highlight-link').fadeOut(300); | |
| 233 | $('span.highlighted').removeClass('highlighted'); | |
| 234 | }, | |
| 235 | ||
| 236 | /** | |
| 237 | * make the url absolute | |
| 238 | */ | |
| 239 | makeURL : function(relativeURL) { | |
| 240 | return DOCUMENTATION_OPTIONS.URL_ROOT + '/' + relativeURL; | |
| 241 | }, | |
| 242 | ||
| 243 | /** | |
| 244 | * get the current relative url | |
| 245 | */ | |
| 246 | getCurrentURL : function() { | |
| 247 | var path = document.location.pathname; | |
| 248 | var parts = path.split(/\//); | |
| 249 | $.each(DOCUMENTATION_OPTIONS.URL_ROOT.split(/\//), function() { | |
| 250 | if (this == '..') | |
| 251 | parts.pop(); | |
| 252 | }); | |
| 253 | var url = parts.join('/'); | |
| 254 | return path.substring(url.lastIndexOf('/') + 1, path.length - 1); | |
| 255 | }, | |
| 256 | ||
| 257 | initOnKeyListeners: function() { | |
| 258 | $(document).keyup(function(event) { | |
| 259 | var activeElementType = document.activeElement.tagName; | |
| 260 | // don't navigate when in search box or textarea | |
| 261 | if (activeElementType !== 'TEXTAREA' && activeElementType !== 'INPUT' && activeElementType !== 'SELECT') { | |
| 262 | switch (event.keyCode) { | |
| 263 | case 37: // left | |
| 264 | var prevHref = $('link[rel="prev"]').prop('href'); | |
| 265 | if (prevHref) { | |
| 266 | window.location.href = prevHref; | |
| 267 | return false; | |
| 268 | } | |
| 269 | case 39: // right | |
| 270 | var nextHref = $('link[rel="next"]').prop('href'); | |
| 271 | if (nextHref) { | |
| 272 | window.location.href = nextHref; | |
| 273 | return false; | |
| 274 | } | |
| 275 | } | |
| 276 | } | |
| 277 | }); | |
| 278 | } | |
| 279 | }; | |
| 280 | ||
| 281 | // quick alias for translations | |
| 282 | _ = Documentation.gettext; | |
| 283 | ||
| 284 | $(document).ready(function() { | |
| 285 | Documentation.init(); | |
| 286 | });⏎ |
Binary diff not shown
Binary diff not shown
Binary diff not shown
Binary diff not shown
Binary diff not shown
Binary diff not shown
Binary diff not shown
Binary diff not shown
+0
-520
| 0 | <?xml version="1.0" standalone="no"?> | |
| 1 | <!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd" > | |
| 2 | <svg xmlns="http://www.w3.org/2000/svg"> | |
| 3 | <metadata></metadata> | |
| 4 | <defs> | |
| 5 | <font id="fontawesomeregular" horiz-adv-x="1536" > | |
| 6 | <font-face units-per-em="1792" ascent="1536" descent="-256" /> | |
| 7 | <missing-glyph horiz-adv-x="448" /> | |
| 8 | <glyph unicode=" " horiz-adv-x="448" /> | |
| 9 | <glyph unicode="	" horiz-adv-x="448" /> | |
| 10 | <glyph unicode=" " horiz-adv-x="448" /> | |
| 11 | <glyph unicode="¨" horiz-adv-x="1792" /> | |
| 12 | <glyph unicode="©" horiz-adv-x="1792" /> | |
| 13 | <glyph unicode="®" horiz-adv-x="1792" /> | |
| 14 | <glyph unicode="´" horiz-adv-x="1792" /> | |
| 15 | <glyph unicode="Æ" horiz-adv-x="1792" /> | |
| 16 | <glyph unicode="Ø" horiz-adv-x="1792" /> | |
| 17 | <glyph unicode=" " horiz-adv-x="768" /> | |
| 18 | <glyph unicode=" " horiz-adv-x="1537" /> | |
| 19 | <glyph unicode=" " horiz-adv-x="768" /> | |
| 20 | <glyph unicode=" " horiz-adv-x="1537" /> | |
| 21 | <glyph unicode=" " horiz-adv-x="512" /> | |
| 22 | <glyph unicode=" " horiz-adv-x="384" /> | |
| 23 | <glyph unicode=" " horiz-adv-x="256" /> | |
| 24 | <glyph unicode=" " horiz-adv-x="256" /> | |
| 25 | <glyph unicode=" " horiz-adv-x="192" /> | |
| 26 | <glyph unicode=" " horiz-adv-x="307" /> | |
| 27 | <glyph unicode=" " horiz-adv-x="85" /> | |
| 28 | <glyph unicode=" " horiz-adv-x="307" /> | |
| 29 | <glyph unicode=" " horiz-adv-x="384" /> | |
| 30 | <glyph unicode="™" horiz-adv-x="1792" /> | |
| 31 | <glyph unicode="∞" horiz-adv-x="1792" /> | |
| 32 | <glyph unicode="≠" horiz-adv-x="1792" /> | |
| 33 | <glyph unicode="◼" horiz-adv-x="500" d="M0 0z" /> | |
| 34 | <glyph unicode="" horiz-adv-x="1792" d="M1699 1350q0 -35 -43 -78l-632 -632v-768h320q26 0 45 -19t19 -45t-19 -45t-45 -19h-896q-26 0 -45 19t-19 45t19 45t45 19h320v768l-632 632q-43 43 -43 78q0 23 18 36.5t38 17.5t43 4h1408q23 0 43 -4t38 -17.5t18 -36.5z" /> | |
| 35 | <glyph unicode="" d="M1536 1312v-1120q0 -50 -34 -89t-86 -60.5t-103.5 -32t-96.5 -10.5t-96.5 10.5t-103.5 32t-86 60.5t-34 89t34 89t86 60.5t103.5 32t96.5 10.5q105 0 192 -39v537l-768 -237v-709q0 -50 -34 -89t-86 -60.5t-103.5 -32t-96.5 -10.5t-96.5 10.5t-103.5 32t-86 60.5t-34 89 t34 89t86 60.5t103.5 32t96.5 10.5q105 0 192 -39v967q0 31 19 56.5t49 35.5l832 256q12 4 28 4q40 0 68 -28t28 -68z" /> | |
| 36 | <glyph unicode="" horiz-adv-x="1664" d="M1152 704q0 185 -131.5 316.5t-316.5 131.5t-316.5 -131.5t-131.5 -316.5t131.5 -316.5t316.5 -131.5t316.5 131.5t131.5 316.5zM1664 -128q0 -52 -38 -90t-90 -38q-54 0 -90 38l-343 342q-179 -124 -399 -124q-143 0 -273.5 55.5t-225 150t-150 225t-55.5 273.5 t55.5 273.5t150 225t225 150t273.5 55.5t273.5 -55.5t225 -150t150 -225t55.5 -273.5q0 -220 -124 -399l343 -343q37 -37 37 -90z" /> | |
| 37 | <glyph unicode="" horiz-adv-x="1792" d="M1664 32v768q-32 -36 -69 -66q-268 -206 -426 -338q-51 -43 -83 -67t-86.5 -48.5t-102.5 -24.5h-1h-1q-48 0 -102.5 24.5t-86.5 48.5t-83 67q-158 132 -426 338q-37 30 -69 66v-768q0 -13 9.5 -22.5t22.5 -9.5h1472q13 0 22.5 9.5t9.5 22.5zM1664 1083v11v13.5t-0.5 13 t-3 12.5t-5.5 9t-9 7.5t-14 2.5h-1472q-13 0 -22.5 -9.5t-9.5 -22.5q0 -168 147 -284q193 -152 401 -317q6 -5 35 -29.5t46 -37.5t44.5 -31.5t50.5 -27.5t43 -9h1h1q20 0 43 9t50.5 27.5t44.5 31.5t46 37.5t35 29.5q208 165 401 317q54 43 100.5 115.5t46.5 131.5z M1792 1120v-1088q0 -66 -47 -113t-113 -47h-1472q-66 0 -113 47t-47 113v1088q0 66 47 113t113 47h1472q66 0 113 -47t47 -113z" /> | |
| 38 | <glyph unicode="" horiz-adv-x="1792" d="M896 -128q-26 0 -44 18l-624 602q-10 8 -27.5 26t-55.5 65.5t-68 97.5t-53.5 121t-23.5 138q0 220 127 344t351 124q62 0 126.5 -21.5t120 -58t95.5 -68.5t76 -68q36 36 76 68t95.5 68.5t120 58t126.5 21.5q224 0 351 -124t127 -344q0 -221 -229 -450l-623 -600 q-18 -18 -44 -18z" /> | |
| 39 | <glyph unicode="" horiz-adv-x="1664" d="M1664 889q0 -22 -26 -48l-363 -354l86 -500q1 -7 1 -20q0 -21 -10.5 -35.5t-30.5 -14.5q-19 0 -40 12l-449 236l-449 -236q-22 -12 -40 -12q-21 0 -31.5 14.5t-10.5 35.5q0 6 2 20l86 500l-364 354q-25 27 -25 48q0 37 56 46l502 73l225 455q19 41 49 41t49 -41l225 -455 l502 -73q56 -9 56 -46z" /> | |
| 40 | <glyph unicode="" horiz-adv-x="1664" d="M1137 532l306 297l-422 62l-189 382l-189 -382l-422 -62l306 -297l-73 -421l378 199l377 -199zM1664 889q0 -22 -26 -48l-363 -354l86 -500q1 -7 1 -20q0 -50 -41 -50q-19 0 -40 12l-449 236l-449 -236q-22 -12 -40 -12q-21 0 -31.5 14.5t-10.5 35.5q0 6 2 20l86 500 l-364 354q-25 27 -25 48q0 37 56 46l502 73l225 455q19 41 49 41t49 -41l225 -455l502 -73q56 -9 56 -46z" /> | |
| 41 | <glyph unicode="" horiz-adv-x="1408" d="M1408 131q0 -120 -73 -189.5t-194 -69.5h-874q-121 0 -194 69.5t-73 189.5q0 53 3.5 103.5t14 109t26.5 108.5t43 97.5t62 81t85.5 53.5t111.5 20q9 0 42 -21.5t74.5 -48t108 -48t133.5 -21.5t133.5 21.5t108 48t74.5 48t42 21.5q61 0 111.5 -20t85.5 -53.5t62 -81 t43 -97.5t26.5 -108.5t14 -109t3.5 -103.5zM1088 1024q0 -159 -112.5 -271.5t-271.5 -112.5t-271.5 112.5t-112.5 271.5t112.5 271.5t271.5 112.5t271.5 -112.5t112.5 -271.5z" /> | |
| 42 | <glyph unicode="" horiz-adv-x="1920" d="M384 -64v128q0 26 -19 45t-45 19h-128q-26 0 -45 -19t-19 -45v-128q0 -26 19 -45t45 -19h128q26 0 45 19t19 45zM384 320v128q0 26 -19 45t-45 19h-128q-26 0 -45 -19t-19 -45v-128q0 -26 19 -45t45 -19h128q26 0 45 19t19 45zM384 704v128q0 26 -19 45t-45 19h-128 q-26 0 -45 -19t-19 -45v-128q0 -26 19 -45t45 -19h128q26 0 45 19t19 45zM1408 -64v512q0 26 -19 45t-45 19h-768q-26 0 -45 -19t-19 -45v-512q0 -26 19 -45t45 -19h768q26 0 45 19t19 45zM384 1088v128q0 26 -19 45t-45 19h-128q-26 0 -45 -19t-19 -45v-128q0 -26 19 -45 t45 -19h128q26 0 45 19t19 45zM1792 -64v128q0 26 -19 45t-45 19h-128q-26 0 -45 -19t-19 -45v-128q0 -26 19 -45t45 -19h128q26 0 45 19t19 45zM1408 704v512q0 26 -19 45t-45 19h-768q-26 0 -45 -19t-19 -45v-512q0 -26 19 -45t45 -19h768q26 0 45 19t19 45zM1792 320v128 q0 26 -19 45t-45 19h-128q-26 0 -45 -19t-19 -45v-128q0 -26 19 -45t45 -19h128q26 0 45 19t19 45zM1792 704v128q0 26 -19 45t-45 19h-128q-26 0 -45 -19t-19 -45v-128q0 -26 19 -45t45 -19h128q26 0 45 19t19 45zM1792 1088v128q0 26 -19 45t-45 19h-128q-26 0 -45 -19 t-19 -45v-128q0 -26 19 -45t45 -19h128q26 0 45 19t19 45zM1920 1248v-1344q0 -66 -47 -113t-113 -47h-1600q-66 0 -113 47t-47 113v1344q0 66 47 113t113 47h1600q66 0 113 -47t47 -113z" /> | |
| 43 | <glyph unicode="" horiz-adv-x="1664" d="M768 512v-384q0 -52 -38 -90t-90 -38h-512q-52 0 -90 38t-38 90v384q0 52 38 90t90 38h512q52 0 90 -38t38 -90zM768 1280v-384q0 -52 -38 -90t-90 -38h-512q-52 0 -90 38t-38 90v384q0 52 38 90t90 38h512q52 0 90 -38t38 -90zM1664 512v-384q0 -52 -38 -90t-90 -38 h-512q-52 0 -90 38t-38 90v384q0 52 38 90t90 38h512q52 0 90 -38t38 -90zM1664 1280v-384q0 -52 -38 -90t-90 -38h-512q-52 0 -90 38t-38 90v384q0 52 38 90t90 38h512q52 0 90 -38t38 -90z" /> | |
| 44 | <glyph unicode="" horiz-adv-x="1792" d="M512 288v-192q0 -40 -28 -68t-68 -28h-320q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h320q40 0 68 -28t28 -68zM512 800v-192q0 -40 -28 -68t-68 -28h-320q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h320q40 0 68 -28t28 -68zM1152 288v-192q0 -40 -28 -68t-68 -28h-320 q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h320q40 0 68 -28t28 -68zM512 1312v-192q0 -40 -28 -68t-68 -28h-320q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h320q40 0 68 -28t28 -68zM1152 800v-192q0 -40 -28 -68t-68 -28h-320q-40 0 -68 28t-28 68v192q0 40 28 68t68 28 h320q40 0 68 -28t28 -68zM1792 288v-192q0 -40 -28 -68t-68 -28h-320q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h320q40 0 68 -28t28 -68zM1152 1312v-192q0 -40 -28 -68t-68 -28h-320q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h320q40 0 68 -28t28 -68zM1792 800v-192 q0 -40 -28 -68t-68 -28h-320q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h320q40 0 68 -28t28 -68zM1792 1312v-192q0 -40 -28 -68t-68 -28h-320q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h320q40 0 68 -28t28 -68z" /> | |
| 45 | <glyph unicode="" horiz-adv-x="1792" d="M512 288v-192q0 -40 -28 -68t-68 -28h-320q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h320q40 0 68 -28t28 -68zM512 800v-192q0 -40 -28 -68t-68 -28h-320q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h320q40 0 68 -28t28 -68zM1792 288v-192q0 -40 -28 -68t-68 -28h-960 q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h960q40 0 68 -28t28 -68zM512 1312v-192q0 -40 -28 -68t-68 -28h-320q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h320q40 0 68 -28t28 -68zM1792 800v-192q0 -40 -28 -68t-68 -28h-960q-40 0 -68 28t-28 68v192q0 40 28 68t68 28 h960q40 0 68 -28t28 -68zM1792 1312v-192q0 -40 -28 -68t-68 -28h-960q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h960q40 0 68 -28t28 -68z" /> | |
| 46 | <glyph unicode="" horiz-adv-x="1792" d="M1671 970q0 -40 -28 -68l-724 -724l-136 -136q-28 -28 -68 -28t-68 28l-136 136l-362 362q-28 28 -28 68t28 68l136 136q28 28 68 28t68 -28l294 -295l656 657q28 28 68 28t68 -28l136 -136q28 -28 28 -68z" /> | |
| 47 | <glyph unicode="" horiz-adv-x="1408" d="M1298 214q0 -40 -28 -68l-136 -136q-28 -28 -68 -28t-68 28l-294 294l-294 -294q-28 -28 -68 -28t-68 28l-136 136q-28 28 -28 68t28 68l294 294l-294 294q-28 28 -28 68t28 68l136 136q28 28 68 28t68 -28l294 -294l294 294q28 28 68 28t68 -28l136 -136q28 -28 28 -68 t-28 -68l-294 -294l294 -294q28 -28 28 -68z" /> | |
| 48 | <glyph unicode="" horiz-adv-x="1664" d="M1024 736v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-224v-224q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v224h-224q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h224v224q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5v-224h224 q13 0 22.5 -9.5t9.5 -22.5zM1152 704q0 185 -131.5 316.5t-316.5 131.5t-316.5 -131.5t-131.5 -316.5t131.5 -316.5t316.5 -131.5t316.5 131.5t131.5 316.5zM1664 -128q0 -53 -37.5 -90.5t-90.5 -37.5q-54 0 -90 38l-343 342q-179 -124 -399 -124q-143 0 -273.5 55.5 t-225 150t-150 225t-55.5 273.5t55.5 273.5t150 225t225 150t273.5 55.5t273.5 -55.5t225 -150t150 -225t55.5 -273.5q0 -220 -124 -399l343 -343q37 -37 37 -90z" /> | |
| 49 | <glyph unicode="" horiz-adv-x="1664" d="M1024 736v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-576q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h576q13 0 22.5 -9.5t9.5 -22.5zM1152 704q0 185 -131.5 316.5t-316.5 131.5t-316.5 -131.5t-131.5 -316.5t131.5 -316.5t316.5 -131.5t316.5 131.5t131.5 316.5z M1664 -128q0 -53 -37.5 -90.5t-90.5 -37.5q-54 0 -90 38l-343 342q-179 -124 -399 -124q-143 0 -273.5 55.5t-225 150t-150 225t-55.5 273.5t55.5 273.5t150 225t225 150t273.5 55.5t273.5 -55.5t225 -150t150 -225t55.5 -273.5q0 -220 -124 -399l343 -343q37 -37 37 -90z " /> | |
| 50 | <glyph unicode="" d="M1536 640q0 -156 -61 -298t-164 -245t-245 -164t-298 -61t-298 61t-245 164t-164 245t-61 298q0 182 80.5 343t226.5 270q43 32 95.5 25t83.5 -50q32 -42 24.5 -94.5t-49.5 -84.5q-98 -74 -151.5 -181t-53.5 -228q0 -104 40.5 -198.5t109.5 -163.5t163.5 -109.5 t198.5 -40.5t198.5 40.5t163.5 109.5t109.5 163.5t40.5 198.5q0 121 -53.5 228t-151.5 181q-42 32 -49.5 84.5t24.5 94.5q31 43 84 50t95 -25q146 -109 226.5 -270t80.5 -343zM896 1408v-640q0 -52 -38 -90t-90 -38t-90 38t-38 90v640q0 52 38 90t90 38t90 -38t38 -90z" /> | |
| 51 | <glyph unicode="" horiz-adv-x="1792" d="M256 96v-192q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h192q14 0 23 -9t9 -23zM640 224v-320q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23v320q0 14 9 23t23 9h192q14 0 23 -9t9 -23zM1024 480v-576q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23 v576q0 14 9 23t23 9h192q14 0 23 -9t9 -23zM1408 864v-960q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23v960q0 14 9 23t23 9h192q14 0 23 -9t9 -23zM1792 1376v-1472q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23v1472q0 14 9 23t23 9h192q14 0 23 -9t9 -23z" /> | |
| 52 | <glyph unicode="" d="M1024 640q0 106 -75 181t-181 75t-181 -75t-75 -181t75 -181t181 -75t181 75t75 181zM1536 749v-222q0 -12 -8 -23t-20 -13l-185 -28q-19 -54 -39 -91q35 -50 107 -138q10 -12 10 -25t-9 -23q-27 -37 -99 -108t-94 -71q-12 0 -26 9l-138 108q-44 -23 -91 -38 q-16 -136 -29 -186q-7 -28 -36 -28h-222q-14 0 -24.5 8.5t-11.5 21.5l-28 184q-49 16 -90 37l-141 -107q-10 -9 -25 -9q-14 0 -25 11q-126 114 -165 168q-7 10 -7 23q0 12 8 23q15 21 51 66.5t54 70.5q-27 50 -41 99l-183 27q-13 2 -21 12.5t-8 23.5v222q0 12 8 23t19 13 l186 28q14 46 39 92q-40 57 -107 138q-10 12 -10 24q0 10 9 23q26 36 98.5 107.5t94.5 71.5q13 0 26 -10l138 -107q44 23 91 38q16 136 29 186q7 28 36 28h222q14 0 24.5 -8.5t11.5 -21.5l28 -184q49 -16 90 -37l142 107q9 9 24 9q13 0 25 -10q129 -119 165 -170q7 -8 7 -22 q0 -12 -8 -23q-15 -21 -51 -66.5t-54 -70.5q26 -50 41 -98l183 -28q13 -2 21 -12.5t8 -23.5z" /> | |
| 53 | <glyph unicode="" horiz-adv-x="1408" d="M512 800v-576q0 -14 -9 -23t-23 -9h-64q-14 0 -23 9t-9 23v576q0 14 9 23t23 9h64q14 0 23 -9t9 -23zM768 800v-576q0 -14 -9 -23t-23 -9h-64q-14 0 -23 9t-9 23v576q0 14 9 23t23 9h64q14 0 23 -9t9 -23zM1024 800v-576q0 -14 -9 -23t-23 -9h-64q-14 0 -23 9t-9 23v576 q0 14 9 23t23 9h64q14 0 23 -9t9 -23zM1152 76v948h-896v-948q0 -22 7 -40.5t14.5 -27t10.5 -8.5h832q3 0 10.5 8.5t14.5 27t7 40.5zM480 1152h448l-48 117q-7 9 -17 11h-317q-10 -2 -17 -11zM1408 1120v-64q0 -14 -9 -23t-23 -9h-96v-948q0 -83 -47 -143.5t-113 -60.5h-832 q-66 0 -113 58.5t-47 141.5v952h-96q-14 0 -23 9t-9 23v64q0 14 9 23t23 9h309l70 167q15 37 54 63t79 26h320q40 0 79 -26t54 -63l70 -167h309q14 0 23 -9t9 -23z" /> | |
| 54 | <glyph unicode="" horiz-adv-x="1664" d="M1408 544v-480q0 -26 -19 -45t-45 -19h-384v384h-256v-384h-384q-26 0 -45 19t-19 45v480q0 1 0.5 3t0.5 3l575 474l575 -474q1 -2 1 -6zM1631 613l-62 -74q-8 -9 -21 -11h-3q-13 0 -21 7l-692 577l-692 -577q-12 -8 -24 -7q-13 2 -21 11l-62 74q-8 10 -7 23.5t11 21.5 l719 599q32 26 76 26t76 -26l244 -204v195q0 14 9 23t23 9h192q14 0 23 -9t9 -23v-408l219 -182q10 -8 11 -21.5t-7 -23.5z" /> | |
| 55 | <glyph unicode="" d="M1468 1156q28 -28 48 -76t20 -88v-1152q0 -40 -28 -68t-68 -28h-1344q-40 0 -68 28t-28 68v1600q0 40 28 68t68 28h896q40 0 88 -20t76 -48zM1024 1400v-376h376q-10 29 -22 41l-313 313q-12 12 -41 22zM1408 -128v1024h-416q-40 0 -68 28t-28 68v416h-768v-1536h1280z " /> | |
| 56 | <glyph unicode="" d="M896 992v-448q0 -14 -9 -23t-23 -9h-320q-14 0 -23 9t-9 23v64q0 14 9 23t23 9h224v352q0 14 9 23t23 9h64q14 0 23 -9t9 -23zM1312 640q0 148 -73 273t-198 198t-273 73t-273 -73t-198 -198t-73 -273t73 -273t198 -198t273 -73t273 73t198 198t73 273zM1536 640 q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 57 | <glyph unicode="" horiz-adv-x="1920" d="M1111 540v4l-24 320q-1 13 -11 22.5t-23 9.5h-186q-13 0 -23 -9.5t-11 -22.5l-24 -320v-4q-1 -12 8 -20t21 -8h244q12 0 21 8t8 20zM1870 73q0 -73 -46 -73h-704q13 0 22 9.5t8 22.5l-20 256q-1 13 -11 22.5t-23 9.5h-272q-13 0 -23 -9.5t-11 -22.5l-20 -256 q-1 -13 8 -22.5t22 -9.5h-704q-46 0 -46 73q0 54 26 116l417 1044q8 19 26 33t38 14h339q-13 0 -23 -9.5t-11 -22.5l-15 -192q-1 -14 8 -23t22 -9h166q13 0 22 9t8 23l-15 192q-1 13 -11 22.5t-23 9.5h339q20 0 38 -14t26 -33l417 -1044q26 -62 26 -116z" /> | |
| 58 | <glyph unicode="" horiz-adv-x="1664" d="M1280 192q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45t45 -19t45 19t19 45zM1536 192q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45t45 -19t45 19t19 45zM1664 416v-320q0 -40 -28 -68t-68 -28h-1472q-40 0 -68 28t-28 68v320q0 40 28 68t68 28h465l135 -136 q58 -56 136 -56t136 56l136 136h464q40 0 68 -28t28 -68zM1339 985q17 -41 -14 -70l-448 -448q-18 -19 -45 -19t-45 19l-448 448q-31 29 -14 70q17 39 59 39h256v448q0 26 19 45t45 19h256q26 0 45 -19t19 -45v-448h256q42 0 59 -39z" /> | |
| 59 | <glyph unicode="" d="M1120 608q0 -12 -10 -24l-319 -319q-11 -9 -23 -9t-23 9l-320 320q-15 16 -7 35q8 20 30 20h192v352q0 14 9 23t23 9h192q14 0 23 -9t9 -23v-352h192q14 0 23 -9t9 -23zM768 1184q-148 0 -273 -73t-198 -198t-73 -273t73 -273t198 -198t273 -73t273 73t198 198t73 273 t-73 273t-198 198t-273 73zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 60 | <glyph unicode="" d="M1118 660q-8 -20 -30 -20h-192v-352q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23v352h-192q-14 0 -23 9t-9 23q0 12 10 24l319 319q11 9 23 9t23 -9l320 -320q15 -16 7 -35zM768 1184q-148 0 -273 -73t-198 -198t-73 -273t73 -273t198 -198t273 -73t273 73t198 198 t73 273t-73 273t-198 198t-273 73zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 61 | <glyph unicode="" d="M1023 576h316q-1 3 -2.5 8t-2.5 8l-212 496h-708l-212 -496q-1 -2 -2.5 -8t-2.5 -8h316l95 -192h320zM1536 546v-482q0 -26 -19 -45t-45 -19h-1408q-26 0 -45 19t-19 45v482q0 62 25 123l238 552q10 25 36.5 42t52.5 17h832q26 0 52.5 -17t36.5 -42l238 -552 q25 -61 25 -123z" /> | |
| 62 | <glyph unicode="" d="M1184 640q0 -37 -32 -55l-544 -320q-15 -9 -32 -9q-16 0 -32 8q-32 19 -32 56v640q0 37 32 56q33 18 64 -1l544 -320q32 -18 32 -55zM1312 640q0 148 -73 273t-198 198t-273 73t-273 -73t-198 -198t-73 -273t73 -273t198 -198t273 -73t273 73t198 198t73 273zM1536 640 q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 63 | <glyph unicode="" d="M1536 1280v-448q0 -26 -19 -45t-45 -19h-448q-42 0 -59 40q-17 39 14 69l138 138q-148 137 -349 137q-104 0 -198.5 -40.5t-163.5 -109.5t-109.5 -163.5t-40.5 -198.5t40.5 -198.5t109.5 -163.5t163.5 -109.5t198.5 -40.5q119 0 225 52t179 147q7 10 23 12q14 0 25 -9 l137 -138q9 -8 9.5 -20.5t-7.5 -22.5q-109 -132 -264 -204.5t-327 -72.5q-156 0 -298 61t-245 164t-164 245t-61 298t61 298t164 245t245 164t298 61q147 0 284.5 -55.5t244.5 -156.5l130 129q29 31 70 14q39 -17 39 -59z" /> | |
| 64 | <glyph unicode="" d="M1511 480q0 -5 -1 -7q-64 -268 -268 -434.5t-478 -166.5q-146 0 -282.5 55t-243.5 157l-129 -129q-19 -19 -45 -19t-45 19t-19 45v448q0 26 19 45t45 19h448q26 0 45 -19t19 -45t-19 -45l-137 -137q71 -66 161 -102t187 -36q134 0 250 65t186 179q11 17 53 117 q8 23 30 23h192q13 0 22.5 -9.5t9.5 -22.5zM1536 1280v-448q0 -26 -19 -45t-45 -19h-448q-26 0 -45 19t-19 45t19 45l138 138q-148 137 -349 137q-134 0 -250 -65t-186 -179q-11 -17 -53 -117q-8 -23 -30 -23h-199q-13 0 -22.5 9.5t-9.5 22.5v7q65 268 270 434.5t480 166.5 q146 0 284 -55.5t245 -156.5l130 129q19 19 45 19t45 -19t19 -45z" /> | |
| 65 | <glyph unicode="" horiz-adv-x="1792" d="M384 352v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM384 608v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5z M384 864v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM1536 352v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-960q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h960q13 0 22.5 -9.5t9.5 -22.5z M1536 608v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-960q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h960q13 0 22.5 -9.5t9.5 -22.5zM1536 864v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-960q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h960q13 0 22.5 -9.5 t9.5 -22.5zM1664 160v832q0 13 -9.5 22.5t-22.5 9.5h-1472q-13 0 -22.5 -9.5t-9.5 -22.5v-832q0 -13 9.5 -22.5t22.5 -9.5h1472q13 0 22.5 9.5t9.5 22.5zM1792 1248v-1088q0 -66 -47 -113t-113 -47h-1472q-66 0 -113 47t-47 113v1088q0 66 47 113t113 47h1472q66 0 113 -47 t47 -113z" /> | |
| 66 | <glyph unicode="" horiz-adv-x="1152" d="M320 768h512v192q0 106 -75 181t-181 75t-181 -75t-75 -181v-192zM1152 672v-576q0 -40 -28 -68t-68 -28h-960q-40 0 -68 28t-28 68v576q0 40 28 68t68 28h32v192q0 184 132 316t316 132t316 -132t132 -316v-192h32q40 0 68 -28t28 -68z" /> | |
| 67 | <glyph unicode="" horiz-adv-x="1792" d="M320 1280q0 -72 -64 -110v-1266q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v1266q-64 38 -64 110q0 53 37.5 90.5t90.5 37.5t90.5 -37.5t37.5 -90.5zM1792 1216v-763q0 -25 -12.5 -38.5t-39.5 -27.5q-215 -116 -369 -116q-61 0 -123.5 22t-108.5 48 t-115.5 48t-142.5 22q-192 0 -464 -146q-17 -9 -33 -9q-26 0 -45 19t-19 45v742q0 32 31 55q21 14 79 43q236 120 421 120q107 0 200 -29t219 -88q38 -19 88 -19q54 0 117.5 21t110 47t88 47t54.5 21q26 0 45 -19t19 -45z" /> | |
| 68 | <glyph unicode="" horiz-adv-x="1664" d="M1664 650q0 -166 -60 -314l-20 -49l-185 -33q-22 -83 -90.5 -136.5t-156.5 -53.5v-32q0 -14 -9 -23t-23 -9h-64q-14 0 -23 9t-9 23v576q0 14 9 23t23 9h64q14 0 23 -9t9 -23v-32q71 0 130 -35.5t93 -95.5l68 12q29 95 29 193q0 148 -88 279t-236.5 209t-315.5 78 t-315.5 -78t-236.5 -209t-88 -279q0 -98 29 -193l68 -12q34 60 93 95.5t130 35.5v32q0 14 9 23t23 9h64q14 0 23 -9t9 -23v-576q0 -14 -9 -23t-23 -9h-64q-14 0 -23 9t-9 23v32q-88 0 -156.5 53.5t-90.5 136.5l-185 33l-20 49q-60 148 -60 314q0 151 67 291t179 242.5 t266 163.5t320 61t320 -61t266 -163.5t179 -242.5t67 -291z" /> | |
| 69 | <glyph unicode="" horiz-adv-x="768" d="M768 1184v-1088q0 -26 -19 -45t-45 -19t-45 19l-333 333h-262q-26 0 -45 19t-19 45v384q0 26 19 45t45 19h262l333 333q19 19 45 19t45 -19t19 -45z" /> | |
| 70 | <glyph unicode="" horiz-adv-x="1152" d="M768 1184v-1088q0 -26 -19 -45t-45 -19t-45 19l-333 333h-262q-26 0 -45 19t-19 45v384q0 26 19 45t45 19h262l333 333q19 19 45 19t45 -19t19 -45zM1152 640q0 -76 -42.5 -141.5t-112.5 -93.5q-10 -5 -25 -5q-26 0 -45 18.5t-19 45.5q0 21 12 35.5t29 25t34 23t29 35.5 t12 57t-12 57t-29 35.5t-34 23t-29 25t-12 35.5q0 27 19 45.5t45 18.5q15 0 25 -5q70 -27 112.5 -93t42.5 -142z" /> | |
| 71 | <glyph unicode="" horiz-adv-x="1664" d="M768 1184v-1088q0 -26 -19 -45t-45 -19t-45 19l-333 333h-262q-26 0 -45 19t-19 45v384q0 26 19 45t45 19h262l333 333q19 19 45 19t45 -19t19 -45zM1152 640q0 -76 -42.5 -141.5t-112.5 -93.5q-10 -5 -25 -5q-26 0 -45 18.5t-19 45.5q0 21 12 35.5t29 25t34 23t29 35.5 t12 57t-12 57t-29 35.5t-34 23t-29 25t-12 35.5q0 27 19 45.5t45 18.5q15 0 25 -5q70 -27 112.5 -93t42.5 -142zM1408 640q0 -153 -85 -282.5t-225 -188.5q-13 -5 -25 -5q-27 0 -46 19t-19 45q0 39 39 59q56 29 76 44q74 54 115.5 135.5t41.5 173.5t-41.5 173.5 t-115.5 135.5q-20 15 -76 44q-39 20 -39 59q0 26 19 45t45 19q13 0 26 -5q140 -59 225 -188.5t85 -282.5zM1664 640q0 -230 -127 -422.5t-338 -283.5q-13 -5 -26 -5q-26 0 -45 19t-19 45q0 36 39 59q7 4 22.5 10.5t22.5 10.5q46 25 82 51q123 91 192 227t69 289t-69 289 t-192 227q-36 26 -82 51q-7 4 -22.5 10.5t-22.5 10.5q-39 23 -39 59q0 26 19 45t45 19q13 0 26 -5q211 -91 338 -283.5t127 -422.5z" /> | |
| 72 | <glyph unicode="" horiz-adv-x="1408" d="M384 384v-128h-128v128h128zM384 1152v-128h-128v128h128zM1152 1152v-128h-128v128h128zM128 129h384v383h-384v-383zM128 896h384v384h-384v-384zM896 896h384v384h-384v-384zM640 640v-640h-640v640h640zM1152 128v-128h-128v128h128zM1408 128v-128h-128v128h128z M1408 640v-384h-384v128h-128v-384h-128v640h384v-128h128v128h128zM640 1408v-640h-640v640h640zM1408 1408v-640h-640v640h640z" /> | |
| 73 | <glyph unicode="" horiz-adv-x="1792" d="M63 0h-63v1408h63v-1408zM126 1h-32v1407h32v-1407zM220 1h-31v1407h31v-1407zM377 1h-31v1407h31v-1407zM534 1h-62v1407h62v-1407zM660 1h-31v1407h31v-1407zM723 1h-31v1407h31v-1407zM786 1h-31v1407h31v-1407zM943 1h-63v1407h63v-1407zM1100 1h-63v1407h63v-1407z M1226 1h-63v1407h63v-1407zM1352 1h-63v1407h63v-1407zM1446 1h-63v1407h63v-1407zM1635 1h-94v1407h94v-1407zM1698 1h-32v1407h32v-1407zM1792 0h-63v1408h63v-1408z" /> | |
| 74 | <glyph unicode="" d="M448 1088q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1515 512q0 -53 -37 -90l-491 -492q-39 -37 -91 -37q-53 0 -90 37l-715 716q-38 37 -64.5 101t-26.5 117v416q0 52 38 90t90 38h416q53 0 117 -26.5t102 -64.5 l715 -714q37 -39 37 -91z" /> | |
| 75 | <glyph unicode="" horiz-adv-x="1920" d="M448 1088q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1515 512q0 -53 -37 -90l-491 -492q-39 -37 -91 -37q-53 0 -90 37l-715 716q-38 37 -64.5 101t-26.5 117v416q0 52 38 90t90 38h416q53 0 117 -26.5t102 -64.5 l715 -714q37 -39 37 -91zM1899 512q0 -53 -37 -90l-491 -492q-39 -37 -91 -37q-36 0 -59 14t-53 45l470 470q37 37 37 90q0 52 -37 91l-715 714q-38 38 -102 64.5t-117 26.5h224q53 0 117 -26.5t102 -64.5l715 -714q37 -39 37 -91z" /> | |
| 76 | <glyph unicode="" horiz-adv-x="1664" d="M1639 1058q40 -57 18 -129l-275 -906q-19 -64 -76.5 -107.5t-122.5 -43.5h-923q-77 0 -148.5 53.5t-99.5 131.5q-24 67 -2 127q0 4 3 27t4 37q1 8 -3 21.5t-3 19.5q2 11 8 21t16.5 23.5t16.5 23.5q23 38 45 91.5t30 91.5q3 10 0.5 30t-0.5 28q3 11 17 28t17 23 q21 36 42 92t25 90q1 9 -2.5 32t0.5 28q4 13 22 30.5t22 22.5q19 26 42.5 84.5t27.5 96.5q1 8 -3 25.5t-2 26.5q2 8 9 18t18 23t17 21q8 12 16.5 30.5t15 35t16 36t19.5 32t26.5 23.5t36 11.5t47.5 -5.5l-1 -3q38 9 51 9h761q74 0 114 -56t18 -130l-274 -906 q-36 -119 -71.5 -153.5t-128.5 -34.5h-869q-27 0 -38 -15q-11 -16 -1 -43q24 -70 144 -70h923q29 0 56 15.5t35 41.5l300 987q7 22 5 57q38 -15 59 -43zM575 1056q-4 -13 2 -22.5t20 -9.5h608q13 0 25.5 9.5t16.5 22.5l21 64q4 13 -2 22.5t-20 9.5h-608q-13 0 -25.5 -9.5 t-16.5 -22.5zM492 800q-4 -13 2 -22.5t20 -9.5h608q13 0 25.5 9.5t16.5 22.5l21 64q4 13 -2 22.5t-20 9.5h-608q-13 0 -25.5 -9.5t-16.5 -22.5z" /> | |
| 77 | <glyph unicode="" horiz-adv-x="1280" d="M1164 1408q23 0 44 -9q33 -13 52.5 -41t19.5 -62v-1289q0 -34 -19.5 -62t-52.5 -41q-19 -8 -44 -8q-48 0 -83 32l-441 424l-441 -424q-36 -33 -83 -33q-23 0 -44 9q-33 13 -52.5 41t-19.5 62v1289q0 34 19.5 62t52.5 41q21 9 44 9h1048z" /> | |
| 78 | <glyph unicode="" horiz-adv-x="1664" d="M384 0h896v256h-896v-256zM384 640h896v384h-160q-40 0 -68 28t-28 68v160h-640v-640zM1536 576q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45t45 -19t45 19t19 45zM1664 576v-416q0 -13 -9.5 -22.5t-22.5 -9.5h-224v-160q0 -40 -28 -68t-68 -28h-960q-40 0 -68 28t-28 68 v160h-224q-13 0 -22.5 9.5t-9.5 22.5v416q0 79 56.5 135.5t135.5 56.5h64v544q0 40 28 68t68 28h672q40 0 88 -20t76 -48l152 -152q28 -28 48 -76t20 -88v-256h64q79 0 135.5 -56.5t56.5 -135.5z" /> | |
| 79 | <glyph unicode="" horiz-adv-x="1920" d="M960 864q119 0 203.5 -84.5t84.5 -203.5t-84.5 -203.5t-203.5 -84.5t-203.5 84.5t-84.5 203.5t84.5 203.5t203.5 84.5zM1664 1280q106 0 181 -75t75 -181v-896q0 -106 -75 -181t-181 -75h-1408q-106 0 -181 75t-75 181v896q0 106 75 181t181 75h224l51 136 q19 49 69.5 84.5t103.5 35.5h512q53 0 103.5 -35.5t69.5 -84.5l51 -136h224zM960 128q185 0 316.5 131.5t131.5 316.5t-131.5 316.5t-316.5 131.5t-316.5 -131.5t-131.5 -316.5t131.5 -316.5t316.5 -131.5z" /> | |
| 80 | <glyph unicode="" horiz-adv-x="1664" d="M725 977l-170 -450q33 0 136.5 -2t160.5 -2q19 0 57 2q-87 253 -184 452zM0 -128l2 79q23 7 56 12.5t57 10.5t49.5 14.5t44.5 29t31 50.5l237 616l280 724h75h53q8 -14 11 -21l205 -480q33 -78 106 -257.5t114 -274.5q15 -34 58 -144.5t72 -168.5q20 -45 35 -57 q19 -15 88 -29.5t84 -20.5q6 -38 6 -57q0 -4 -0.5 -13t-0.5 -13q-63 0 -190 8t-191 8q-76 0 -215 -7t-178 -8q0 43 4 78l131 28q1 0 12.5 2.5t15.5 3.5t14.5 4.5t15 6.5t11 8t9 11t2.5 14q0 16 -31 96.5t-72 177.5t-42 100l-450 2q-26 -58 -76.5 -195.5t-50.5 -162.5 q0 -22 14 -37.5t43.5 -24.5t48.5 -13.5t57 -8.5t41 -4q1 -19 1 -58q0 -9 -2 -27q-58 0 -174.5 10t-174.5 10q-8 0 -26.5 -4t-21.5 -4q-80 -14 -188 -14z" /> | |
| 81 | <glyph unicode="" horiz-adv-x="1408" d="M555 15q74 -32 140 -32q376 0 376 335q0 114 -41 180q-27 44 -61.5 74t-67.5 46.5t-80.5 25t-84 10.5t-94.5 2q-73 0 -101 -10q0 -53 -0.5 -159t-0.5 -158q0 -8 -1 -67.5t-0.5 -96.5t4.5 -83.5t12 -66.5zM541 761q42 -7 109 -7q82 0 143 13t110 44.5t74.5 89.5t25.5 142 q0 70 -29 122.5t-79 82t-108 43.5t-124 14q-50 0 -130 -13q0 -50 4 -151t4 -152q0 -27 -0.5 -80t-0.5 -79q0 -46 1 -69zM0 -128l2 94q15 4 85 16t106 27q7 12 12.5 27t8.5 33.5t5.5 32.5t3 37.5t0.5 34v35.5v30q0 982 -22 1025q-4 8 -22 14.5t-44.5 11t-49.5 7t-48.5 4.5 t-30.5 3l-4 83q98 2 340 11.5t373 9.5q23 0 68.5 -0.5t67.5 -0.5q70 0 136.5 -13t128.5 -42t108 -71t74 -104.5t28 -137.5q0 -52 -16.5 -95.5t-39 -72t-64.5 -57.5t-73 -45t-84 -40q154 -35 256.5 -134t102.5 -248q0 -100 -35 -179.5t-93.5 -130.5t-138 -85.5t-163.5 -48.5 t-176 -14q-44 0 -132 3t-132 3q-106 0 -307 -11t-231 -12z" /> | |
| 82 | <glyph unicode="" horiz-adv-x="1024" d="M0 -126l17 85q6 2 81.5 21.5t111.5 37.5q28 35 41 101q1 7 62 289t114 543.5t52 296.5v25q-24 13 -54.5 18.5t-69.5 8t-58 5.5l19 103q33 -2 120 -6.5t149.5 -7t120.5 -2.5q48 0 98.5 2.5t121 7t98.5 6.5q-5 -39 -19 -89q-30 -10 -101.5 -28.5t-108.5 -33.5 q-8 -19 -14 -42.5t-9 -40t-7.5 -45.5t-6.5 -42q-27 -148 -87.5 -419.5t-77.5 -355.5q-2 -9 -13 -58t-20 -90t-16 -83.5t-6 -57.5l1 -18q17 -4 185 -31q-3 -44 -16 -99q-11 0 -32.5 -1.5t-32.5 -1.5q-29 0 -87 10t-86 10q-138 2 -206 2q-51 0 -143 -9t-121 -11z" /> | |
| 83 | <glyph unicode="" horiz-adv-x="1792" d="M1744 128q33 0 42 -18.5t-11 -44.5l-126 -162q-20 -26 -49 -26t-49 26l-126 162q-20 26 -11 44.5t42 18.5h80v1024h-80q-33 0 -42 18.5t11 44.5l126 162q20 26 49 26t49 -26l126 -162q20 -26 11 -44.5t-42 -18.5h-80v-1024h80zM81 1407l54 -27q12 -5 211 -5q44 0 132 2 t132 2q36 0 107.5 -0.5t107.5 -0.5h293q6 0 21 -0.5t20.5 0t16 3t17.5 9t15 17.5l42 1q4 0 14 -0.5t14 -0.5q2 -112 2 -336q0 -80 -5 -109q-39 -14 -68 -18q-25 44 -54 128q-3 9 -11 48t-14.5 73.5t-7.5 35.5q-6 8 -12 12.5t-15.5 6t-13 2.5t-18 0.5t-16.5 -0.5 q-17 0 -66.5 0.5t-74.5 0.5t-64 -2t-71 -6q-9 -81 -8 -136q0 -94 2 -388t2 -455q0 -16 -2.5 -71.5t0 -91.5t12.5 -69q40 -21 124 -42.5t120 -37.5q5 -40 5 -50q0 -14 -3 -29l-34 -1q-76 -2 -218 8t-207 10q-50 0 -151 -9t-152 -9q-3 51 -3 52v9q17 27 61.5 43t98.5 29t78 27 q19 42 19 383q0 101 -3 303t-3 303v117q0 2 0.5 15.5t0.5 25t-1 25.5t-3 24t-5 14q-11 12 -162 12q-33 0 -93 -12t-80 -26q-19 -13 -34 -72.5t-31.5 -111t-42.5 -53.5q-42 26 -56 44v383z" /> | |
| 84 | <glyph unicode="" d="M81 1407l54 -27q12 -5 211 -5q44 0 132 2t132 2q70 0 246.5 1t304.5 0.5t247 -4.5q33 -1 56 31l42 1q4 0 14 -0.5t14 -0.5q2 -112 2 -336q0 -80 -5 -109q-39 -14 -68 -18q-25 44 -54 128q-3 9 -11 47.5t-15 73.5t-7 36q-10 13 -27 19q-5 2 -66 2q-30 0 -93 1t-103 1 t-94 -2t-96 -7q-9 -81 -8 -136l1 -152v52q0 -55 1 -154t1.5 -180t0.5 -153q0 -16 -2.5 -71.5t0 -91.5t12.5 -69q40 -21 124 -42.5t120 -37.5q5 -40 5 -50q0 -14 -3 -29l-34 -1q-76 -2 -218 8t-207 10q-50 0 -151 -9t-152 -9q-3 51 -3 52v9q17 27 61.5 43t98.5 29t78 27 q7 16 11.5 74t6 145.5t1.5 155t-0.5 153.5t-0.5 89q0 7 -2.5 21.5t-2.5 22.5q0 7 0.5 44t1 73t0 76.5t-3 67.5t-6.5 32q-11 12 -162 12q-41 0 -163 -13.5t-138 -24.5q-19 -12 -34 -71.5t-31.5 -111.5t-42.5 -54q-42 26 -56 44v383zM1310 125q12 0 42 -19.5t57.5 -41.5 t59.5 -49t36 -30q26 -21 26 -49t-26 -49q-4 -3 -36 -30t-59.5 -49t-57.5 -41.5t-42 -19.5q-13 0 -20.5 10.5t-10 28.5t-2.5 33.5t1.5 33t1.5 19.5h-1024q0 -2 1.5 -19.5t1.5 -33t-2.5 -33.5t-10 -28.5t-20.5 -10.5q-12 0 -42 19.5t-57.5 41.5t-59.5 49t-36 30q-26 21 -26 49 t26 49q4 3 36 30t59.5 49t57.5 41.5t42 19.5q13 0 20.5 -10.5t10 -28.5t2.5 -33.5t-1.5 -33t-1.5 -19.5h1024q0 2 -1.5 19.5t-1.5 33t2.5 33.5t10 28.5t20.5 10.5z" /> | |
| 85 | <glyph unicode="" horiz-adv-x="1792" d="M1792 192v-128q0 -26 -19 -45t-45 -19h-1664q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1664q26 0 45 -19t19 -45zM1408 576v-128q0 -26 -19 -45t-45 -19h-1280q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1280q26 0 45 -19t19 -45zM1664 960v-128q0 -26 -19 -45 t-45 -19h-1536q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1536q26 0 45 -19t19 -45zM1280 1344v-128q0 -26 -19 -45t-45 -19h-1152q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1152q26 0 45 -19t19 -45z" /> | |
| 86 | <glyph unicode="" horiz-adv-x="1792" d="M1792 192v-128q0 -26 -19 -45t-45 -19h-1664q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1664q26 0 45 -19t19 -45zM1408 576v-128q0 -26 -19 -45t-45 -19h-896q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h896q26 0 45 -19t19 -45zM1664 960v-128q0 -26 -19 -45t-45 -19 h-1408q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1408q26 0 45 -19t19 -45zM1280 1344v-128q0 -26 -19 -45t-45 -19h-640q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h640q26 0 45 -19t19 -45z" /> | |
| 87 | <glyph unicode="" horiz-adv-x="1792" d="M1792 192v-128q0 -26 -19 -45t-45 -19h-1664q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1664q26 0 45 -19t19 -45zM1792 576v-128q0 -26 -19 -45t-45 -19h-1280q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1280q26 0 45 -19t19 -45zM1792 960v-128q0 -26 -19 -45 t-45 -19h-1536q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1536q26 0 45 -19t19 -45zM1792 1344v-128q0 -26 -19 -45t-45 -19h-1152q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1152q26 0 45 -19t19 -45z" /> | |
| 88 | <glyph unicode="" horiz-adv-x="1792" d="M1792 192v-128q0 -26 -19 -45t-45 -19h-1664q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1664q26 0 45 -19t19 -45zM1792 576v-128q0 -26 -19 -45t-45 -19h-1664q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1664q26 0 45 -19t19 -45zM1792 960v-128q0 -26 -19 -45 t-45 -19h-1664q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1664q26 0 45 -19t19 -45zM1792 1344v-128q0 -26 -19 -45t-45 -19h-1664q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1664q26 0 45 -19t19 -45z" /> | |
| 89 | <glyph unicode="" horiz-adv-x="1792" d="M256 224v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-192q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h192q13 0 22.5 -9.5t9.5 -22.5zM256 608v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-192q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h192q13 0 22.5 -9.5 t9.5 -22.5zM256 992v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-192q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h192q13 0 22.5 -9.5t9.5 -22.5zM1792 224v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1344q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h1344 q13 0 22.5 -9.5t9.5 -22.5zM256 1376v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-192q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h192q13 0 22.5 -9.5t9.5 -22.5zM1792 608v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1344q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5 t22.5 9.5h1344q13 0 22.5 -9.5t9.5 -22.5zM1792 992v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1344q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h1344q13 0 22.5 -9.5t9.5 -22.5zM1792 1376v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1344q-13 0 -22.5 9.5t-9.5 22.5v192 q0 13 9.5 22.5t22.5 9.5h1344q13 0 22.5 -9.5t9.5 -22.5z" /> | |
| 90 | <glyph unicode="" horiz-adv-x="1792" d="M384 992v-576q0 -13 -9.5 -22.5t-22.5 -9.5q-14 0 -23 9l-288 288q-9 9 -9 23t9 23l288 288q9 9 23 9q13 0 22.5 -9.5t9.5 -22.5zM1792 224v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1728q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h1728q13 0 22.5 -9.5 t9.5 -22.5zM1792 608v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1088q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h1088q13 0 22.5 -9.5t9.5 -22.5zM1792 992v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1088q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h1088 q13 0 22.5 -9.5t9.5 -22.5zM1792 1376v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1728q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h1728q13 0 22.5 -9.5t9.5 -22.5z" /> | |
| 91 | <glyph unicode="" horiz-adv-x="1792" d="M352 704q0 -14 -9 -23l-288 -288q-9 -9 -23 -9q-13 0 -22.5 9.5t-9.5 22.5v576q0 13 9.5 22.5t22.5 9.5q14 0 23 -9l288 -288q9 -9 9 -23zM1792 224v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1728q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h1728q13 0 22.5 -9.5 t9.5 -22.5zM1792 608v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1088q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h1088q13 0 22.5 -9.5t9.5 -22.5zM1792 992v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1088q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h1088 q13 0 22.5 -9.5t9.5 -22.5zM1792 1376v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1728q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h1728q13 0 22.5 -9.5t9.5 -22.5z" /> | |
| 92 | <glyph unicode="" horiz-adv-x="1792" d="M1792 1184v-1088q0 -42 -39 -59q-13 -5 -25 -5q-27 0 -45 19l-403 403v-166q0 -119 -84.5 -203.5t-203.5 -84.5h-704q-119 0 -203.5 84.5t-84.5 203.5v704q0 119 84.5 203.5t203.5 84.5h704q119 0 203.5 -84.5t84.5 -203.5v-165l403 402q18 19 45 19q12 0 25 -5 q39 -17 39 -59z" /> | |
| 93 | <glyph unicode="" horiz-adv-x="1920" d="M640 960q0 -80 -56 -136t-136 -56t-136 56t-56 136t56 136t136 56t136 -56t56 -136zM1664 576v-448h-1408v192l320 320l160 -160l512 512zM1760 1280h-1600q-13 0 -22.5 -9.5t-9.5 -22.5v-1216q0 -13 9.5 -22.5t22.5 -9.5h1600q13 0 22.5 9.5t9.5 22.5v1216 q0 13 -9.5 22.5t-22.5 9.5zM1920 1248v-1216q0 -66 -47 -113t-113 -47h-1600q-66 0 -113 47t-47 113v1216q0 66 47 113t113 47h1600q66 0 113 -47t47 -113z" /> | |
| 94 | <glyph unicode="" d="M363 0l91 91l-235 235l-91 -91v-107h128v-128h107zM886 928q0 22 -22 22q-10 0 -17 -7l-542 -542q-7 -7 -7 -17q0 -22 22 -22q10 0 17 7l542 542q7 7 7 17zM832 1120l416 -416l-832 -832h-416v416zM1515 1024q0 -53 -37 -90l-166 -166l-416 416l166 165q36 38 90 38 q53 0 91 -38l235 -234q37 -39 37 -91z" /> | |
| 95 | <glyph unicode="" horiz-adv-x="1024" d="M768 896q0 106 -75 181t-181 75t-181 -75t-75 -181t75 -181t181 -75t181 75t75 181zM1024 896q0 -109 -33 -179l-364 -774q-16 -33 -47.5 -52t-67.5 -19t-67.5 19t-46.5 52l-365 774q-33 70 -33 179q0 212 150 362t362 150t362 -150t150 -362z" /> | |
| 96 | <glyph unicode="" d="M768 96v1088q-148 0 -273 -73t-198 -198t-73 -273t73 -273t198 -198t273 -73zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 97 | <glyph unicode="" horiz-adv-x="1024" d="M512 384q0 36 -20 69q-1 1 -15.5 22.5t-25.5 38t-25 44t-21 50.5q-4 16 -21 16t-21 -16q-7 -23 -21 -50.5t-25 -44t-25.5 -38t-15.5 -22.5q-20 -33 -20 -69q0 -53 37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1024 512q0 -212 -150 -362t-362 -150t-362 150t-150 362 q0 145 81 275q6 9 62.5 90.5t101 151t99.5 178t83 201.5q9 30 34 47t51 17t51.5 -17t33.5 -47q28 -93 83 -201.5t99.5 -178t101 -151t62.5 -90.5q81 -127 81 -275z" /> | |
| 98 | <glyph unicode="" horiz-adv-x="1792" d="M888 352l116 116l-152 152l-116 -116v-56h96v-96h56zM1328 1072q-16 16 -33 -1l-350 -350q-17 -17 -1 -33t33 1l350 350q17 17 1 33zM1408 478v-190q0 -119 -84.5 -203.5t-203.5 -84.5h-832q-119 0 -203.5 84.5t-84.5 203.5v832q0 119 84.5 203.5t203.5 84.5h832 q63 0 117 -25q15 -7 18 -23q3 -17 -9 -29l-49 -49q-14 -14 -32 -8q-23 6 -45 6h-832q-66 0 -113 -47t-47 -113v-832q0 -66 47 -113t113 -47h832q66 0 113 47t47 113v126q0 13 9 22l64 64q15 15 35 7t20 -29zM1312 1216l288 -288l-672 -672h-288v288zM1756 1084l-92 -92 l-288 288l92 92q28 28 68 28t68 -28l152 -152q28 -28 28 -68t-28 -68z" /> | |
| 99 | <glyph unicode="" horiz-adv-x="1664" d="M1408 547v-259q0 -119 -84.5 -203.5t-203.5 -84.5h-832q-119 0 -203.5 84.5t-84.5 203.5v832q0 119 84.5 203.5t203.5 84.5h255v0q13 0 22.5 -9.5t9.5 -22.5q0 -27 -26 -32q-77 -26 -133 -60q-10 -4 -16 -4h-112q-66 0 -113 -47t-47 -113v-832q0 -66 47 -113t113 -47h832 q66 0 113 47t47 113v214q0 19 18 29q28 13 54 37q16 16 35 8q21 -9 21 -29zM1645 1043l-384 -384q-18 -19 -45 -19q-12 0 -25 5q-39 17 -39 59v192h-160q-323 0 -438 -131q-119 -137 -74 -473q3 -23 -20 -34q-8 -2 -12 -2q-16 0 -26 13q-10 14 -21 31t-39.5 68.5t-49.5 99.5 t-38.5 114t-17.5 122q0 49 3.5 91t14 90t28 88t47 81.5t68.5 74t94.5 61.5t124.5 48.5t159.5 30.5t196.5 11h160v192q0 42 39 59q13 5 25 5q26 0 45 -19l384 -384q19 -19 19 -45t-19 -45z" /> | |
| 100 | <glyph unicode="" horiz-adv-x="1664" d="M1408 606v-318q0 -119 -84.5 -203.5t-203.5 -84.5h-832q-119 0 -203.5 84.5t-84.5 203.5v832q0 119 84.5 203.5t203.5 84.5h832q63 0 117 -25q15 -7 18 -23q3 -17 -9 -29l-49 -49q-10 -10 -23 -10q-3 0 -9 2q-23 6 -45 6h-832q-66 0 -113 -47t-47 -113v-832 q0 -66 47 -113t113 -47h832q66 0 113 47t47 113v254q0 13 9 22l64 64q10 10 23 10q6 0 12 -3q20 -8 20 -29zM1639 1095l-814 -814q-24 -24 -57 -24t-57 24l-430 430q-24 24 -24 57t24 57l110 110q24 24 57 24t57 -24l263 -263l647 647q24 24 57 24t57 -24l110 -110 q24 -24 24 -57t-24 -57z" /> | |
| 101 | <glyph unicode="" horiz-adv-x="1792" d="M1792 640q0 -26 -19 -45l-256 -256q-19 -19 -45 -19t-45 19t-19 45v128h-384v-384h128q26 0 45 -19t19 -45t-19 -45l-256 -256q-19 -19 -45 -19t-45 19l-256 256q-19 19 -19 45t19 45t45 19h128v384h-384v-128q0 -26 -19 -45t-45 -19t-45 19l-256 256q-19 19 -19 45 t19 45l256 256q19 19 45 19t45 -19t19 -45v-128h384v384h-128q-26 0 -45 19t-19 45t19 45l256 256q19 19 45 19t45 -19l256 -256q19 -19 19 -45t-19 -45t-45 -19h-128v-384h384v128q0 26 19 45t45 19t45 -19l256 -256q19 -19 19 -45z" /> | |
| 102 | <glyph unicode="" horiz-adv-x="1024" d="M979 1395q19 19 32 13t13 -32v-1472q0 -26 -13 -32t-32 13l-710 710q-9 9 -13 19v-678q0 -26 -19 -45t-45 -19h-128q-26 0 -45 19t-19 45v1408q0 26 19 45t45 19h128q26 0 45 -19t19 -45v-678q4 11 13 19z" /> | |
| 103 | <glyph unicode="" horiz-adv-x="1792" d="M1747 1395q19 19 32 13t13 -32v-1472q0 -26 -13 -32t-32 13l-710 710q-9 9 -13 19v-710q0 -26 -13 -32t-32 13l-710 710q-9 9 -13 19v-678q0 -26 -19 -45t-45 -19h-128q-26 0 -45 19t-19 45v1408q0 26 19 45t45 19h128q26 0 45 -19t19 -45v-678q4 11 13 19l710 710 q19 19 32 13t13 -32v-710q4 11 13 19z" /> | |
| 104 | <glyph unicode="" horiz-adv-x="1664" d="M1619 1395q19 19 32 13t13 -32v-1472q0 -26 -13 -32t-32 13l-710 710q-8 9 -13 19v-710q0 -26 -13 -32t-32 13l-710 710q-19 19 -19 45t19 45l710 710q19 19 32 13t13 -32v-710q5 11 13 19z" /> | |
| 105 | <glyph unicode="" horiz-adv-x="1408" d="M1384 609l-1328 -738q-23 -13 -39.5 -3t-16.5 36v1472q0 26 16.5 36t39.5 -3l1328 -738q23 -13 23 -31t-23 -31z" /> | |
| 106 | <glyph unicode="" d="M1536 1344v-1408q0 -26 -19 -45t-45 -19h-512q-26 0 -45 19t-19 45v1408q0 26 19 45t45 19h512q26 0 45 -19t19 -45zM640 1344v-1408q0 -26 -19 -45t-45 -19h-512q-26 0 -45 19t-19 45v1408q0 26 19 45t45 19h512q26 0 45 -19t19 -45z" /> | |
| 107 | <glyph unicode="" d="M1536 1344v-1408q0 -26 -19 -45t-45 -19h-1408q-26 0 -45 19t-19 45v1408q0 26 19 45t45 19h1408q26 0 45 -19t19 -45z" /> | |
| 108 | <glyph unicode="" horiz-adv-x="1664" d="M45 -115q-19 -19 -32 -13t-13 32v1472q0 26 13 32t32 -13l710 -710q8 -8 13 -19v710q0 26 13 32t32 -13l710 -710q19 -19 19 -45t-19 -45l-710 -710q-19 -19 -32 -13t-13 32v710q-5 -10 -13 -19z" /> | |
| 109 | <glyph unicode="" horiz-adv-x="1792" d="M45 -115q-19 -19 -32 -13t-13 32v1472q0 26 13 32t32 -13l710 -710q8 -8 13 -19v710q0 26 13 32t32 -13l710 -710q8 -8 13 -19v678q0 26 19 45t45 19h128q26 0 45 -19t19 -45v-1408q0 -26 -19 -45t-45 -19h-128q-26 0 -45 19t-19 45v678q-5 -10 -13 -19l-710 -710 q-19 -19 -32 -13t-13 32v710q-5 -10 -13 -19z" /> | |
| 110 | <glyph unicode="" horiz-adv-x="1024" d="M45 -115q-19 -19 -32 -13t-13 32v1472q0 26 13 32t32 -13l710 -710q8 -8 13 -19v678q0 26 19 45t45 19h128q26 0 45 -19t19 -45v-1408q0 -26 -19 -45t-45 -19h-128q-26 0 -45 19t-19 45v678q-5 -10 -13 -19z" /> | |
| 111 | <glyph unicode="" horiz-adv-x="1538" d="M14 557l710 710q19 19 45 19t45 -19l710 -710q19 -19 13 -32t-32 -13h-1472q-26 0 -32 13t13 32zM1473 0h-1408q-26 0 -45 19t-19 45v256q0 26 19 45t45 19h1408q26 0 45 -19t19 -45v-256q0 -26 -19 -45t-45 -19z" /> | |
| 112 | <glyph unicode="" horiz-adv-x="1280" d="M1171 1235l-531 -531l531 -531q19 -19 19 -45t-19 -45l-166 -166q-19 -19 -45 -19t-45 19l-742 742q-19 19 -19 45t19 45l742 742q19 19 45 19t45 -19l166 -166q19 -19 19 -45t-19 -45z" /> | |
| 113 | <glyph unicode="" horiz-adv-x="1280" d="M1107 659l-742 -742q-19 -19 -45 -19t-45 19l-166 166q-19 19 -19 45t19 45l531 531l-531 531q-19 19 -19 45t19 45l166 166q19 19 45 19t45 -19l742 -742q19 -19 19 -45t-19 -45z" /> | |
| 114 | <glyph unicode="" d="M1216 576v128q0 26 -19 45t-45 19h-256v256q0 26 -19 45t-45 19h-128q-26 0 -45 -19t-19 -45v-256h-256q-26 0 -45 -19t-19 -45v-128q0 -26 19 -45t45 -19h256v-256q0 -26 19 -45t45 -19h128q26 0 45 19t19 45v256h256q26 0 45 19t19 45zM1536 640q0 -209 -103 -385.5 t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 115 | <glyph unicode="" d="M1216 576v128q0 26 -19 45t-45 19h-768q-26 0 -45 -19t-19 -45v-128q0 -26 19 -45t45 -19h768q26 0 45 19t19 45zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5 t103 -385.5z" /> | |
| 116 | <glyph unicode="" d="M1149 414q0 26 -19 45l-181 181l181 181q19 19 19 45q0 27 -19 46l-90 90q-19 19 -46 19q-26 0 -45 -19l-181 -181l-181 181q-19 19 -45 19q-27 0 -46 -19l-90 -90q-19 -19 -19 -46q0 -26 19 -45l181 -181l-181 -181q-19 -19 -19 -45q0 -27 19 -46l90 -90q19 -19 46 -19 q26 0 45 19l181 181l181 -181q19 -19 45 -19q27 0 46 19l90 90q19 19 19 46zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 117 | <glyph unicode="" d="M1284 802q0 28 -18 46l-91 90q-19 19 -45 19t-45 -19l-408 -407l-226 226q-19 19 -45 19t-45 -19l-91 -90q-18 -18 -18 -46q0 -27 18 -45l362 -362q19 -19 45 -19q27 0 46 19l543 543q18 18 18 45zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103 t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 118 | <glyph unicode="" d="M896 160v192q0 14 -9 23t-23 9h-192q-14 0 -23 -9t-9 -23v-192q0 -14 9 -23t23 -9h192q14 0 23 9t9 23zM1152 832q0 88 -55.5 163t-138.5 116t-170 41q-243 0 -371 -213q-15 -24 8 -42l132 -100q7 -6 19 -6q16 0 25 12q53 68 86 92q34 24 86 24q48 0 85.5 -26t37.5 -59 q0 -38 -20 -61t-68 -45q-63 -28 -115.5 -86.5t-52.5 -125.5v-36q0 -14 9 -23t23 -9h192q14 0 23 9t9 23q0 19 21.5 49.5t54.5 49.5q32 18 49 28.5t46 35t44.5 48t28 60.5t12.5 81zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5 t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 119 | <glyph unicode="" d="M1024 160v160q0 14 -9 23t-23 9h-96v512q0 14 -9 23t-23 9h-320q-14 0 -23 -9t-9 -23v-160q0 -14 9 -23t23 -9h96v-320h-96q-14 0 -23 -9t-9 -23v-160q0 -14 9 -23t23 -9h448q14 0 23 9t9 23zM896 1056v160q0 14 -9 23t-23 9h-192q-14 0 -23 -9t-9 -23v-160q0 -14 9 -23 t23 -9h192q14 0 23 9t9 23zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 120 | <glyph unicode="" d="M1197 512h-109q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h109q-32 108 -112.5 188.5t-188.5 112.5v-109q0 -26 -19 -45t-45 -19h-128q-26 0 -45 19t-19 45v109q-108 -32 -188.5 -112.5t-112.5 -188.5h109q26 0 45 -19t19 -45v-128q0 -26 -19 -45t-45 -19h-109 q32 -108 112.5 -188.5t188.5 -112.5v109q0 26 19 45t45 19h128q26 0 45 -19t19 -45v-109q108 32 188.5 112.5t112.5 188.5zM1536 704v-128q0 -26 -19 -45t-45 -19h-143q-37 -161 -154.5 -278.5t-278.5 -154.5v-143q0 -26 -19 -45t-45 -19h-128q-26 0 -45 19t-19 45v143 q-161 37 -278.5 154.5t-154.5 278.5h-143q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h143q37 161 154.5 278.5t278.5 154.5v143q0 26 19 45t45 19h128q26 0 45 -19t19 -45v-143q161 -37 278.5 -154.5t154.5 -278.5h143q26 0 45 -19t19 -45z" /> | |
| 121 | <glyph unicode="" d="M1097 457l-146 -146q-10 -10 -23 -10t-23 10l-137 137l-137 -137q-10 -10 -23 -10t-23 10l-146 146q-10 10 -10 23t10 23l137 137l-137 137q-10 10 -10 23t10 23l146 146q10 10 23 10t23 -10l137 -137l137 137q10 10 23 10t23 -10l146 -146q10 -10 10 -23t-10 -23 l-137 -137l137 -137q10 -10 10 -23t-10 -23zM1312 640q0 148 -73 273t-198 198t-273 73t-273 -73t-198 -198t-73 -273t73 -273t198 -198t273 -73t273 73t198 198t73 273zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5 t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 122 | <glyph unicode="" d="M1171 723l-422 -422q-19 -19 -45 -19t-45 19l-294 294q-19 19 -19 45t19 45l102 102q19 19 45 19t45 -19l147 -147l275 275q19 19 45 19t45 -19l102 -102q19 -19 19 -45t-19 -45zM1312 640q0 148 -73 273t-198 198t-273 73t-273 -73t-198 -198t-73 -273t73 -273t198 -198 t273 -73t273 73t198 198t73 273zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 123 | <glyph unicode="" d="M1312 643q0 161 -87 295l-754 -753q137 -89 297 -89q111 0 211.5 43.5t173.5 116.5t116 174.5t43 212.5zM313 344l755 754q-135 91 -300 91q-148 0 -273 -73t-198 -199t-73 -274q0 -162 89 -299zM1536 643q0 -157 -61 -300t-163.5 -246t-245 -164t-298.5 -61t-298.5 61 t-245 164t-163.5 246t-61 300t61 299.5t163.5 245.5t245 164t298.5 61t298.5 -61t245 -164t163.5 -245.5t61 -299.5z" /> | |
| 124 | <glyph unicode="" d="M1536 640v-128q0 -53 -32.5 -90.5t-84.5 -37.5h-704l293 -294q38 -36 38 -90t-38 -90l-75 -76q-37 -37 -90 -37q-52 0 -91 37l-651 652q-37 37 -37 90q0 52 37 91l651 650q38 38 91 38q52 0 90 -38l75 -74q38 -38 38 -91t-38 -91l-293 -293h704q52 0 84.5 -37.5 t32.5 -90.5z" /> | |
| 125 | <glyph unicode="" d="M1472 576q0 -54 -37 -91l-651 -651q-39 -37 -91 -37q-51 0 -90 37l-75 75q-38 38 -38 91t38 91l293 293h-704q-52 0 -84.5 37.5t-32.5 90.5v128q0 53 32.5 90.5t84.5 37.5h704l-293 294q-38 36 -38 90t38 90l75 75q38 38 90 38q53 0 91 -38l651 -651q37 -35 37 -90z" /> | |
| 126 | <glyph unicode="" horiz-adv-x="1664" d="M1611 565q0 -51 -37 -90l-75 -75q-38 -38 -91 -38q-54 0 -90 38l-294 293v-704q0 -52 -37.5 -84.5t-90.5 -32.5h-128q-53 0 -90.5 32.5t-37.5 84.5v704l-294 -293q-36 -38 -90 -38t-90 38l-75 75q-38 38 -38 90q0 53 38 91l651 651q35 37 90 37q54 0 91 -37l651 -651 q37 -39 37 -91z" /> | |
| 127 | <glyph unicode="" horiz-adv-x="1664" d="M1611 704q0 -53 -37 -90l-651 -652q-39 -37 -91 -37q-53 0 -90 37l-651 652q-38 36 -38 90q0 53 38 91l74 75q39 37 91 37q53 0 90 -37l294 -294v704q0 52 38 90t90 38h128q52 0 90 -38t38 -90v-704l294 294q37 37 90 37q52 0 91 -37l75 -75q37 -39 37 -91z" /> | |
| 128 | <glyph unicode="" horiz-adv-x="1792" d="M1792 896q0 -26 -19 -45l-512 -512q-19 -19 -45 -19t-45 19t-19 45v256h-224q-98 0 -175.5 -6t-154 -21.5t-133 -42.5t-105.5 -69.5t-80 -101t-48.5 -138.5t-17.5 -181q0 -55 5 -123q0 -6 2.5 -23.5t2.5 -26.5q0 -15 -8.5 -25t-23.5 -10q-16 0 -28 17q-7 9 -13 22 t-13.5 30t-10.5 24q-127 285 -127 451q0 199 53 333q162 403 875 403h224v256q0 26 19 45t45 19t45 -19l512 -512q19 -19 19 -45z" /> | |
| 129 | <glyph unicode="" d="M755 480q0 -13 -10 -23l-332 -332l144 -144q19 -19 19 -45t-19 -45t-45 -19h-448q-26 0 -45 19t-19 45v448q0 26 19 45t45 19t45 -19l144 -144l332 332q10 10 23 10t23 -10l114 -114q10 -10 10 -23zM1536 1344v-448q0 -26 -19 -45t-45 -19t-45 19l-144 144l-332 -332 q-10 -10 -23 -10t-23 10l-114 114q-10 10 -10 23t10 23l332 332l-144 144q-19 19 -19 45t19 45t45 19h448q26 0 45 -19t19 -45z" /> | |
| 130 | <glyph unicode="" d="M768 576v-448q0 -26 -19 -45t-45 -19t-45 19l-144 144l-332 -332q-10 -10 -23 -10t-23 10l-114 114q-10 10 -10 23t10 23l332 332l-144 144q-19 19 -19 45t19 45t45 19h448q26 0 45 -19t19 -45zM1523 1248q0 -13 -10 -23l-332 -332l144 -144q19 -19 19 -45t-19 -45 t-45 -19h-448q-26 0 -45 19t-19 45v448q0 26 19 45t45 19t45 -19l144 -144l332 332q10 10 23 10t23 -10l114 -114q10 -10 10 -23z" /> | |
| 131 | <glyph unicode="" horiz-adv-x="1408" d="M1408 800v-192q0 -40 -28 -68t-68 -28h-416v-416q0 -40 -28 -68t-68 -28h-192q-40 0 -68 28t-28 68v416h-416q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h416v416q0 40 28 68t68 28h192q40 0 68 -28t28 -68v-416h416q40 0 68 -28t28 -68z" /> | |
| 132 | <glyph unicode="" horiz-adv-x="1408" d="M1408 800v-192q0 -40 -28 -68t-68 -28h-1216q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h1216q40 0 68 -28t28 -68z" /> | |
| 133 | <glyph unicode="" horiz-adv-x="1664" d="M1482 486q46 -26 59.5 -77.5t-12.5 -97.5l-64 -110q-26 -46 -77.5 -59.5t-97.5 12.5l-266 153v-307q0 -52 -38 -90t-90 -38h-128q-52 0 -90 38t-38 90v307l-266 -153q-46 -26 -97.5 -12.5t-77.5 59.5l-64 110q-26 46 -12.5 97.5t59.5 77.5l266 154l-266 154 q-46 26 -59.5 77.5t12.5 97.5l64 110q26 46 77.5 59.5t97.5 -12.5l266 -153v307q0 52 38 90t90 38h128q52 0 90 -38t38 -90v-307l266 153q46 26 97.5 12.5t77.5 -59.5l64 -110q26 -46 12.5 -97.5t-59.5 -77.5l-266 -154z" /> | |
| 134 | <glyph unicode="" d="M768 1408q209 0 385.5 -103t279.5 -279.5t103 -385.5t-103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103zM896 161v190q0 14 -9 23.5t-22 9.5h-192q-13 0 -23 -10t-10 -23v-190q0 -13 10 -23t23 -10h192 q13 0 22 9.5t9 23.5zM894 505l18 621q0 12 -10 18q-10 8 -24 8h-220q-14 0 -24 -8q-10 -6 -10 -18l17 -621q0 -10 10 -17.5t24 -7.5h185q14 0 23.5 7.5t10.5 17.5z" /> | |
| 135 | <glyph unicode="" d="M928 180v56v468v192h-320v-192v-468v-56q0 -25 18 -38.5t46 -13.5h192q28 0 46 13.5t18 38.5zM472 1024h195l-126 161q-26 31 -69 31q-40 0 -68 -28t-28 -68t28 -68t68 -28zM1160 1120q0 40 -28 68t-68 28q-43 0 -69 -31l-125 -161h194q40 0 68 28t28 68zM1536 864v-320 q0 -14 -9 -23t-23 -9h-96v-416q0 -40 -28 -68t-68 -28h-1088q-40 0 -68 28t-28 68v416h-96q-14 0 -23 9t-9 23v320q0 14 9 23t23 9h440q-93 0 -158.5 65.5t-65.5 158.5t65.5 158.5t158.5 65.5q107 0 168 -77l128 -165l128 165q61 77 168 77q93 0 158.5 -65.5t65.5 -158.5 t-65.5 -158.5t-158.5 -65.5h440q14 0 23 -9t9 -23z" /> | |
| 136 | <glyph unicode="" horiz-adv-x="1792" d="M1280 832q0 26 -19 45t-45 19q-172 0 -318 -49.5t-259.5 -134t-235.5 -219.5q-19 -21 -19 -45q0 -26 19 -45t45 -19q24 0 45 19q27 24 74 71t67 66q137 124 268.5 176t313.5 52q26 0 45 19t19 45zM1792 1030q0 -95 -20 -193q-46 -224 -184.5 -383t-357.5 -268 q-214 -108 -438 -108q-148 0 -286 47q-15 5 -88 42t-96 37q-16 0 -39.5 -32t-45 -70t-52.5 -70t-60 -32q-30 0 -51 11t-31 24t-27 42q-2 4 -6 11t-5.5 10t-3 9.5t-1.5 13.5q0 35 31 73.5t68 65.5t68 56t31 48q0 4 -14 38t-16 44q-9 51 -9 104q0 115 43.5 220t119 184.5 t170.5 139t204 95.5q55 18 145 25.5t179.5 9t178.5 6t163.5 24t113.5 56.5l29.5 29.5t29.5 28t27 20t36.5 16t43.5 4.5q39 0 70.5 -46t47.5 -112t24 -124t8 -96z" /> | |
| 137 | <glyph unicode="" horiz-adv-x="1408" d="M1408 -160v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-1344q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h1344q13 0 22.5 -9.5t9.5 -22.5zM1152 896q0 -78 -24.5 -144t-64 -112.5t-87.5 -88t-96 -77.5t-87.5 -72t-64 -81.5t-24.5 -96.5q0 -96 67 -224l-4 1l1 -1 q-90 41 -160 83t-138.5 100t-113.5 122.5t-72.5 150.5t-27.5 184q0 78 24.5 144t64 112.5t87.5 88t96 77.5t87.5 72t64 81.5t24.5 96.5q0 94 -66 224l3 -1l-1 1q90 -41 160 -83t138.5 -100t113.5 -122.5t72.5 -150.5t27.5 -184z" /> | |
| 138 | <glyph unicode="" horiz-adv-x="1792" d="M1664 576q-152 236 -381 353q61 -104 61 -225q0 -185 -131.5 -316.5t-316.5 -131.5t-316.5 131.5t-131.5 316.5q0 121 61 225q-229 -117 -381 -353q133 -205 333.5 -326.5t434.5 -121.5t434.5 121.5t333.5 326.5zM944 960q0 20 -14 34t-34 14q-125 0 -214.5 -89.5 t-89.5 -214.5q0 -20 14 -34t34 -14t34 14t14 34q0 86 61 147t147 61q20 0 34 14t14 34zM1792 576q0 -34 -20 -69q-140 -230 -376.5 -368.5t-499.5 -138.5t-499.5 139t-376.5 368q-20 35 -20 69t20 69q140 229 376.5 368t499.5 139t499.5 -139t376.5 -368q20 -35 20 -69z" /> | |
| 139 | <glyph unicode="" horiz-adv-x="1792" d="M555 201l78 141q-87 63 -136 159t-49 203q0 121 61 225q-229 -117 -381 -353q167 -258 427 -375zM944 960q0 20 -14 34t-34 14q-125 0 -214.5 -89.5t-89.5 -214.5q0 -20 14 -34t34 -14t34 14t14 34q0 86 61 147t147 61q20 0 34 14t14 34zM1307 1151q0 -7 -1 -9 q-105 -188 -315 -566t-316 -567l-49 -89q-10 -16 -28 -16q-12 0 -134 70q-16 10 -16 28q0 12 44 87q-143 65 -263.5 173t-208.5 245q-20 31 -20 69t20 69q153 235 380 371t496 136q89 0 180 -17l54 97q10 16 28 16q5 0 18 -6t31 -15.5t33 -18.5t31.5 -18.5t19.5 -11.5 q16 -10 16 -27zM1344 704q0 -139 -79 -253.5t-209 -164.5l280 502q8 -45 8 -84zM1792 576q0 -35 -20 -69q-39 -64 -109 -145q-150 -172 -347.5 -267t-419.5 -95l74 132q212 18 392.5 137t301.5 307q-115 179 -282 294l63 112q95 -64 182.5 -153t144.5 -184q20 -34 20 -69z " /> | |
| 140 | <glyph unicode="" horiz-adv-x="1792" d="M1024 161v190q0 14 -9.5 23.5t-22.5 9.5h-192q-13 0 -22.5 -9.5t-9.5 -23.5v-190q0 -14 9.5 -23.5t22.5 -9.5h192q13 0 22.5 9.5t9.5 23.5zM1022 535l18 459q0 12 -10 19q-13 11 -24 11h-220q-11 0 -24 -11q-10 -7 -10 -21l17 -457q0 -10 10 -16.5t24 -6.5h185 q14 0 23.5 6.5t10.5 16.5zM1008 1469l768 -1408q35 -63 -2 -126q-17 -29 -46.5 -46t-63.5 -17h-1536q-34 0 -63.5 17t-46.5 46q-37 63 -2 126l768 1408q17 31 47 49t65 18t65 -18t47 -49z" /> | |
| 141 | <glyph unicode="" horiz-adv-x="1408" d="M1376 1376q44 -52 12 -148t-108 -172l-161 -161l160 -696q5 -19 -12 -33l-128 -96q-7 -6 -19 -6q-4 0 -7 1q-15 3 -21 16l-279 508l-259 -259l53 -194q5 -17 -8 -31l-96 -96q-9 -9 -23 -9h-2q-15 2 -24 13l-189 252l-252 189q-11 7 -13 23q-1 13 9 25l96 97q9 9 23 9 q6 0 8 -1l194 -53l259 259l-508 279q-14 8 -17 24q-2 16 9 27l128 128q14 13 30 8l665 -159l160 160q76 76 172 108t148 -12z" /> | |
| 142 | <glyph unicode="" horiz-adv-x="1664" d="M128 -128h288v288h-288v-288zM480 -128h320v288h-320v-288zM128 224h288v320h-288v-320zM480 224h320v320h-320v-320zM128 608h288v288h-288v-288zM864 -128h320v288h-320v-288zM480 608h320v288h-320v-288zM1248 -128h288v288h-288v-288zM864 224h320v320h-320v-320z M512 1088v288q0 13 -9.5 22.5t-22.5 9.5h-64q-13 0 -22.5 -9.5t-9.5 -22.5v-288q0 -13 9.5 -22.5t22.5 -9.5h64q13 0 22.5 9.5t9.5 22.5zM1248 224h288v320h-288v-320zM864 608h320v288h-320v-288zM1248 608h288v288h-288v-288zM1280 1088v288q0 13 -9.5 22.5t-22.5 9.5h-64 q-13 0 -22.5 -9.5t-9.5 -22.5v-288q0 -13 9.5 -22.5t22.5 -9.5h64q13 0 22.5 9.5t9.5 22.5zM1664 1152v-1280q0 -52 -38 -90t-90 -38h-1408q-52 0 -90 38t-38 90v1280q0 52 38 90t90 38h128v96q0 66 47 113t113 47h64q66 0 113 -47t47 -113v-96h384v96q0 66 47 113t113 47 h64q66 0 113 -47t47 -113v-96h128q52 0 90 -38t38 -90z" /> | |
| 143 | <glyph unicode="" horiz-adv-x="1792" d="M666 1055q-60 -92 -137 -273q-22 45 -37 72.5t-40.5 63.5t-51 56.5t-63 35t-81.5 14.5h-224q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h224q250 0 410 -225zM1792 256q0 -14 -9 -23l-320 -320q-9 -9 -23 -9q-13 0 -22.5 9.5t-9.5 22.5v192q-32 0 -85 -0.5t-81 -1t-73 1 t-71 5t-64 10.5t-63 18.5t-58 28.5t-59 40t-55 53.5t-56 69.5q59 93 136 273q22 -45 37 -72.5t40.5 -63.5t51 -56.5t63 -35t81.5 -14.5h256v192q0 14 9 23t23 9q12 0 24 -10l319 -319q9 -9 9 -23zM1792 1152q0 -14 -9 -23l-320 -320q-9 -9 -23 -9q-13 0 -22.5 9.5t-9.5 22.5 v192h-256q-48 0 -87 -15t-69 -45t-51 -61.5t-45 -77.5q-32 -62 -78 -171q-29 -66 -49.5 -111t-54 -105t-64 -100t-74 -83t-90 -68.5t-106.5 -42t-128 -16.5h-224q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h224q48 0 87 15t69 45t51 61.5t45 77.5q32 62 78 171q29 66 49.5 111 t54 105t64 100t74 83t90 68.5t106.5 42t128 16.5h256v192q0 14 9 23t23 9q12 0 24 -10l319 -319q9 -9 9 -23z" /> | |
| 144 | <glyph unicode="" horiz-adv-x="1792" d="M1792 640q0 -174 -120 -321.5t-326 -233t-450 -85.5q-70 0 -145 8q-198 -175 -460 -242q-49 -14 -114 -22q-17 -2 -30.5 9t-17.5 29v1q-3 4 -0.5 12t2 10t4.5 9.5l6 9t7 8.5t8 9q7 8 31 34.5t34.5 38t31 39.5t32.5 51t27 59t26 76q-157 89 -247.5 220t-90.5 281 q0 130 71 248.5t191 204.5t286 136.5t348 50.5q244 0 450 -85.5t326 -233t120 -321.5z" /> | |
| 145 | <glyph unicode="" d="M1536 704v-128q0 -201 -98.5 -362t-274 -251.5t-395.5 -90.5t-395.5 90.5t-274 251.5t-98.5 362v128q0 26 19 45t45 19h384q26 0 45 -19t19 -45v-128q0 -52 23.5 -90t53.5 -57t71 -30t64 -13t44 -2t44 2t64 13t71 30t53.5 57t23.5 90v128q0 26 19 45t45 19h384 q26 0 45 -19t19 -45zM512 1344v-384q0 -26 -19 -45t-45 -19h-384q-26 0 -45 19t-19 45v384q0 26 19 45t45 19h384q26 0 45 -19t19 -45zM1536 1344v-384q0 -26 -19 -45t-45 -19h-384q-26 0 -45 19t-19 45v384q0 26 19 45t45 19h384q26 0 45 -19t19 -45z" /> | |
| 146 | <glyph unicode="" horiz-adv-x="1792" d="M1683 205l-166 -165q-19 -19 -45 -19t-45 19l-531 531l-531 -531q-19 -19 -45 -19t-45 19l-166 165q-19 19 -19 45.5t19 45.5l742 741q19 19 45 19t45 -19l742 -741q19 -19 19 -45.5t-19 -45.5z" /> | |
| 147 | <glyph unicode="" horiz-adv-x="1792" d="M1683 728l-742 -741q-19 -19 -45 -19t-45 19l-742 741q-19 19 -19 45.5t19 45.5l166 165q19 19 45 19t45 -19l531 -531l531 531q19 19 45 19t45 -19l166 -165q19 -19 19 -45.5t-19 -45.5z" /> | |
| 148 | <glyph unicode="" horiz-adv-x="1920" d="M1280 32q0 -13 -9.5 -22.5t-22.5 -9.5h-960q-8 0 -13.5 2t-9 7t-5.5 8t-3 11.5t-1 11.5v13v11v160v416h-192q-26 0 -45 19t-19 45q0 24 15 41l320 384q19 22 49 22t49 -22l320 -384q15 -17 15 -41q0 -26 -19 -45t-45 -19h-192v-384h576q16 0 25 -11l160 -192q7 -11 7 -21 zM1920 448q0 -24 -15 -41l-320 -384q-20 -23 -49 -23t-49 23l-320 384q-15 17 -15 41q0 26 19 45t45 19h192v384h-576q-16 0 -25 12l-160 192q-7 9 -7 20q0 13 9.5 22.5t22.5 9.5h960q8 0 13.5 -2t9 -7t5.5 -8t3 -11.5t1 -11.5v-13v-11v-160v-416h192q26 0 45 -19t19 -45z " /> | |
| 149 | <glyph unicode="" horiz-adv-x="1664" d="M640 0q0 -53 -37.5 -90.5t-90.5 -37.5t-90.5 37.5t-37.5 90.5t37.5 90.5t90.5 37.5t90.5 -37.5t37.5 -90.5zM1536 0q0 -53 -37.5 -90.5t-90.5 -37.5t-90.5 37.5t-37.5 90.5t37.5 90.5t90.5 37.5t90.5 -37.5t37.5 -90.5zM1664 1088v-512q0 -24 -16 -42.5t-41 -21.5 l-1044 -122q1 -7 4.5 -21.5t6 -26.5t2.5 -22q0 -16 -24 -64h920q26 0 45 -19t19 -45t-19 -45t-45 -19h-1024q-26 0 -45 19t-19 45q0 14 11 39.5t29.5 59.5t20.5 38l-177 823h-204q-26 0 -45 19t-19 45t19 45t45 19h256q16 0 28.5 -6.5t20 -15.5t13 -24.5t7.5 -26.5 t5.5 -29.5t4.5 -25.5h1201q26 0 45 -19t19 -45z" /> | |
| 150 | <glyph unicode="" horiz-adv-x="1664" d="M1664 928v-704q0 -92 -66 -158t-158 -66h-1216q-92 0 -158 66t-66 158v960q0 92 66 158t158 66h320q92 0 158 -66t66 -158v-32h672q92 0 158 -66t66 -158z" /> | |
| 151 | <glyph unicode="" horiz-adv-x="1920" d="M1879 584q0 -31 -31 -66l-336 -396q-43 -51 -120.5 -86.5t-143.5 -35.5h-1088q-34 0 -60.5 13t-26.5 43q0 31 31 66l336 396q43 51 120.5 86.5t143.5 35.5h1088q34 0 60.5 -13t26.5 -43zM1536 928v-160h-832q-94 0 -197 -47.5t-164 -119.5l-337 -396l-5 -6q0 4 -0.5 12.5 t-0.5 12.5v960q0 92 66 158t158 66h320q92 0 158 -66t66 -158v-32h544q92 0 158 -66t66 -158z" /> | |
| 152 | <glyph unicode="" horiz-adv-x="768" d="M704 1216q0 -26 -19 -45t-45 -19h-128v-1024h128q26 0 45 -19t19 -45t-19 -45l-256 -256q-19 -19 -45 -19t-45 19l-256 256q-19 19 -19 45t19 45t45 19h128v1024h-128q-26 0 -45 19t-19 45t19 45l256 256q19 19 45 19t45 -19l256 -256q19 -19 19 -45z" /> | |
| 153 | <glyph unicode="" horiz-adv-x="1792" d="M1792 640q0 -26 -19 -45l-256 -256q-19 -19 -45 -19t-45 19t-19 45v128h-1024v-128q0 -26 -19 -45t-45 -19t-45 19l-256 256q-19 19 -19 45t19 45l256 256q19 19 45 19t45 -19t19 -45v-128h1024v128q0 26 19 45t45 19t45 -19l256 -256q19 -19 19 -45z" /> | |
| 154 | <glyph unicode="" horiz-adv-x="2048" d="M640 640v-512h-256v512h256zM1024 1152v-1024h-256v1024h256zM2048 0v-128h-2048v1536h128v-1408h1920zM1408 896v-768h-256v768h256zM1792 1280v-1152h-256v1152h256z" /> | |
| 155 | <glyph unicode="" d="M1280 926q-56 -25 -121 -34q68 40 93 117q-65 -38 -134 -51q-61 66 -153 66q-87 0 -148.5 -61.5t-61.5 -148.5q0 -29 5 -48q-129 7 -242 65t-192 155q-29 -50 -29 -106q0 -114 91 -175q-47 1 -100 26v-2q0 -75 50 -133.5t123 -72.5q-29 -8 -51 -8q-13 0 -39 4 q21 -63 74.5 -104t121.5 -42q-116 -90 -261 -90q-26 0 -50 3q148 -94 322 -94q112 0 210 35.5t168 95t120.5 137t75 162t24.5 168.5q0 18 -1 27q63 45 105 109zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5 t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 156 | <glyph unicode="" d="M1536 160q0 -119 -84.5 -203.5t-203.5 -84.5h-192v608h203l30 224h-233v143q0 54 28 83t96 29l132 1v207q-96 9 -180 9q-136 0 -218 -80.5t-82 -225.5v-166h-224v-224h224v-608h-544q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960 q119 0 203.5 -84.5t84.5 -203.5v-960z" /> | |
| 157 | <glyph unicode="" horiz-adv-x="1792" d="M928 704q0 14 -9 23t-23 9q-66 0 -113 -47t-47 -113q0 -14 9 -23t23 -9t23 9t9 23q0 40 28 68t68 28q14 0 23 9t9 23zM1152 574q0 -106 -75 -181t-181 -75t-181 75t-75 181t75 181t181 75t181 -75t75 -181zM128 0h1536v128h-1536v-128zM1280 574q0 159 -112.5 271.5 t-271.5 112.5t-271.5 -112.5t-112.5 -271.5t112.5 -271.5t271.5 -112.5t271.5 112.5t112.5 271.5zM256 1216h384v128h-384v-128zM128 1024h1536v118v138h-828l-64 -128h-644v-128zM1792 1280v-1280q0 -53 -37.5 -90.5t-90.5 -37.5h-1536q-53 0 -90.5 37.5t-37.5 90.5v1280 q0 53 37.5 90.5t90.5 37.5h1536q53 0 90.5 -37.5t37.5 -90.5z" /> | |
| 158 | <glyph unicode="" horiz-adv-x="1792" d="M832 1024q0 80 -56 136t-136 56t-136 -56t-56 -136q0 -42 19 -83q-41 19 -83 19q-80 0 -136 -56t-56 -136t56 -136t136 -56t136 56t56 136q0 42 -19 83q41 -19 83 -19q80 0 136 56t56 136zM1683 320q0 -17 -49 -66t-66 -49q-9 0 -28.5 16t-36.5 33t-38.5 40t-24.5 26 l-96 -96l220 -220q28 -28 28 -68q0 -42 -39 -81t-81 -39q-40 0 -68 28l-671 671q-176 -131 -365 -131q-163 0 -265.5 102.5t-102.5 265.5q0 160 95 313t248 248t313 95q163 0 265.5 -102.5t102.5 -265.5q0 -189 -131 -365l355 -355l96 96q-3 3 -26 24.5t-40 38.5t-33 36.5 t-16 28.5q0 17 49 66t66 49q13 0 23 -10q6 -6 46 -44.5t82 -79.5t86.5 -86t73 -78t28.5 -41z" /> | |
| 159 | <glyph unicode="" horiz-adv-x="1920" d="M896 640q0 106 -75 181t-181 75t-181 -75t-75 -181t75 -181t181 -75t181 75t75 181zM1664 128q0 52 -38 90t-90 38t-90 -38t-38 -90q0 -53 37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1664 1152q0 52 -38 90t-90 38t-90 -38t-38 -90q0 -53 37.5 -90.5t90.5 -37.5 t90.5 37.5t37.5 90.5zM1280 731v-185q0 -10 -7 -19.5t-16 -10.5l-155 -24q-11 -35 -32 -76q34 -48 90 -115q7 -10 7 -20q0 -12 -7 -19q-23 -30 -82.5 -89.5t-78.5 -59.5q-11 0 -21 7l-115 90q-37 -19 -77 -31q-11 -108 -23 -155q-7 -24 -30 -24h-186q-11 0 -20 7.5t-10 17.5 l-23 153q-34 10 -75 31l-118 -89q-7 -7 -20 -7q-11 0 -21 8q-144 133 -144 160q0 9 7 19q10 14 41 53t47 61q-23 44 -35 82l-152 24q-10 1 -17 9.5t-7 19.5v185q0 10 7 19.5t16 10.5l155 24q11 35 32 76q-34 48 -90 115q-7 11 -7 20q0 12 7 20q22 30 82 89t79 59q11 0 21 -7 l115 -90q34 18 77 32q11 108 23 154q7 24 30 24h186q11 0 20 -7.5t10 -17.5l23 -153q34 -10 75 -31l118 89q8 7 20 7q11 0 21 -8q144 -133 144 -160q0 -9 -7 -19q-12 -16 -42 -54t-45 -60q23 -48 34 -82l152 -23q10 -2 17 -10.5t7 -19.5zM1920 198v-140q0 -16 -149 -31 q-12 -27 -30 -52q51 -113 51 -138q0 -4 -4 -7q-122 -71 -124 -71q-8 0 -46 47t-52 68q-20 -2 -30 -2t-30 2q-14 -21 -52 -68t-46 -47q-2 0 -124 71q-4 3 -4 7q0 25 51 138q-18 25 -30 52q-149 15 -149 31v140q0 16 149 31q13 29 30 52q-51 113 -51 138q0 4 4 7q4 2 35 20 t59 34t30 16q8 0 46 -46.5t52 -67.5q20 2 30 2t30 -2q51 71 92 112l6 2q4 0 124 -70q4 -3 4 -7q0 -25 -51 -138q17 -23 30 -52q149 -15 149 -31zM1920 1222v-140q0 -16 -149 -31q-12 -27 -30 -52q51 -113 51 -138q0 -4 -4 -7q-122 -71 -124 -71q-8 0 -46 47t-52 68 q-20 -2 -30 -2t-30 2q-14 -21 -52 -68t-46 -47q-2 0 -124 71q-4 3 -4 7q0 25 51 138q-18 25 -30 52q-149 15 -149 31v140q0 16 149 31q13 29 30 52q-51 113 -51 138q0 4 4 7q4 2 35 20t59 34t30 16q8 0 46 -46.5t52 -67.5q20 2 30 2t30 -2q51 71 92 112l6 2q4 0 124 -70 q4 -3 4 -7q0 -25 -51 -138q17 -23 30 -52q149 -15 149 -31z" /> | |
| 160 | <glyph unicode="" horiz-adv-x="1792" d="M1408 768q0 -139 -94 -257t-256.5 -186.5t-353.5 -68.5q-86 0 -176 16q-124 -88 -278 -128q-36 -9 -86 -16h-3q-11 0 -20.5 8t-11.5 21q-1 3 -1 6.5t0.5 6.5t2 6l2.5 5t3.5 5.5t4 5t4.5 5t4 4.5q5 6 23 25t26 29.5t22.5 29t25 38.5t20.5 44q-124 72 -195 177t-71 224 q0 139 94 257t256.5 186.5t353.5 68.5t353.5 -68.5t256.5 -186.5t94 -257zM1792 512q0 -120 -71 -224.5t-195 -176.5q10 -24 20.5 -44t25 -38.5t22.5 -29t26 -29.5t23 -25q1 -1 4 -4.5t4.5 -5t4 -5t3.5 -5.5l2.5 -5t2 -6t0.5 -6.5t-1 -6.5q-3 -14 -13 -22t-22 -7 q-50 7 -86 16q-154 40 -278 128q-90 -16 -176 -16q-271 0 -472 132q58 -4 88 -4q161 0 309 45t264 129q125 92 192 212t67 254q0 77 -23 152q129 -71 204 -178t75 -230z" /> | |
| 161 | <glyph unicode="" d="M256 192q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45t45 -19t45 19t19 45zM1408 768q0 51 -39 89.5t-89 38.5h-352q0 58 48 159.5t48 160.5q0 98 -32 145t-128 47q-26 -26 -38 -85t-30.5 -125.5t-59.5 -109.5q-22 -23 -77 -91q-4 -5 -23 -30t-31.5 -41t-34.5 -42.5 t-40 -44t-38.5 -35.5t-40 -27t-35.5 -9h-32v-640h32q13 0 31.5 -3t33 -6.5t38 -11t35 -11.5t35.5 -12.5t29 -10.5q211 -73 342 -73h121q192 0 192 167q0 26 -5 56q30 16 47.5 52.5t17.5 73.5t-18 69q53 50 53 119q0 25 -10 55.5t-25 47.5q32 1 53.5 47t21.5 81zM1536 769 q0 -89 -49 -163q9 -33 9 -69q0 -77 -38 -144q3 -21 3 -43q0 -101 -60 -178q1 -139 -85 -219.5t-227 -80.5h-36h-93q-96 0 -189.5 22.5t-216.5 65.5q-116 40 -138 40h-288q-53 0 -90.5 37.5t-37.5 90.5v640q0 53 37.5 90.5t90.5 37.5h274q36 24 137 155q58 75 107 128 q24 25 35.5 85.5t30.5 126.5t62 108q39 37 90 37q84 0 151 -32.5t102 -101.5t35 -186q0 -93 -48 -192h176q104 0 180 -76t76 -179z" /> | |
| 162 | <glyph unicode="" d="M256 1088q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45t45 -19t45 19t19 45zM1408 512q0 35 -21.5 81t-53.5 47q15 17 25 47.5t10 55.5q0 69 -53 119q18 32 18 69t-17.5 73.5t-47.5 52.5q5 30 5 56q0 85 -49 126t-136 41h-128q-131 0 -342 -73q-5 -2 -29 -10.5 t-35.5 -12.5t-35 -11.5t-38 -11t-33 -6.5t-31.5 -3h-32v-640h32q16 0 35.5 -9t40 -27t38.5 -35.5t40 -44t34.5 -42.5t31.5 -41t23 -30q55 -68 77 -91q41 -43 59.5 -109.5t30.5 -125.5t38 -85q96 0 128 47t32 145q0 59 -48 160.5t-48 159.5h352q50 0 89 38.5t39 89.5z M1536 511q0 -103 -76 -179t-180 -76h-176q48 -99 48 -192q0 -118 -35 -186q-35 -69 -102 -101.5t-151 -32.5q-51 0 -90 37q-34 33 -54 82t-25.5 90.5t-17.5 84.5t-31 64q-48 50 -107 127q-101 131 -137 155h-274q-53 0 -90.5 37.5t-37.5 90.5v640q0 53 37.5 90.5t90.5 37.5 h288q22 0 138 40q128 44 223 66t200 22h112q140 0 226.5 -79t85.5 -216v-5q60 -77 60 -178q0 -22 -3 -43q38 -67 38 -144q0 -36 -9 -69q49 -74 49 -163z" /> | |
| 163 | <glyph unicode="" horiz-adv-x="896" d="M832 1504v-1339l-449 -236q-22 -12 -40 -12q-21 0 -31.5 14.5t-10.5 35.5q0 6 2 20l86 500l-364 354q-25 27 -25 48q0 37 56 46l502 73l225 455q19 41 49 41z" /> | |
| 164 | <glyph unicode="" horiz-adv-x="1792" d="M1664 940q0 81 -21.5 143t-55 98.5t-81.5 59.5t-94 31t-98 8t-112 -25.5t-110.5 -64t-86.5 -72t-60 -61.5q-18 -22 -49 -22t-49 22q-24 28 -60 61.5t-86.5 72t-110.5 64t-112 25.5t-98 -8t-94 -31t-81.5 -59.5t-55 -98.5t-21.5 -143q0 -168 187 -355l581 -560l580 559 q188 188 188 356zM1792 940q0 -221 -229 -450l-623 -600q-18 -18 -44 -18t-44 18l-624 602q-10 8 -27.5 26t-55.5 65.5t-68 97.5t-53.5 121t-23.5 138q0 220 127 344t351 124q62 0 126.5 -21.5t120 -58t95.5 -68.5t76 -68q36 36 76 68t95.5 68.5t120 58t126.5 21.5 q224 0 351 -124t127 -344z" /> | |
| 165 | <glyph unicode="" horiz-adv-x="1664" d="M640 96q0 -4 1 -20t0.5 -26.5t-3 -23.5t-10 -19.5t-20.5 -6.5h-320q-119 0 -203.5 84.5t-84.5 203.5v704q0 119 84.5 203.5t203.5 84.5h320q13 0 22.5 -9.5t9.5 -22.5q0 -4 1 -20t0.5 -26.5t-3 -23.5t-10 -19.5t-20.5 -6.5h-320q-66 0 -113 -47t-47 -113v-704 q0 -66 47 -113t113 -47h288h11h13t11.5 -1t11.5 -3t8 -5.5t7 -9t2 -13.5zM1568 640q0 -26 -19 -45l-544 -544q-19 -19 -45 -19t-45 19t-19 45v288h-448q-26 0 -45 19t-19 45v384q0 26 19 45t45 19h448v288q0 26 19 45t45 19t45 -19l544 -544q19 -19 19 -45z" /> | |
| 166 | <glyph unicode="" d="M237 122h231v694h-231v-694zM483 1030q-1 52 -36 86t-93 34t-94.5 -34t-36.5 -86q0 -51 35.5 -85.5t92.5 -34.5h1q59 0 95 34.5t36 85.5zM1068 122h231v398q0 154 -73 233t-193 79q-136 0 -209 -117h2v101h-231q3 -66 0 -694h231v388q0 38 7 56q15 35 45 59.5t74 24.5 q116 0 116 -157v-371zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 167 | <glyph unicode="" horiz-adv-x="1152" d="M480 672v448q0 14 -9 23t-23 9t-23 -9t-9 -23v-448q0 -14 9 -23t23 -9t23 9t9 23zM1152 320q0 -26 -19 -45t-45 -19h-429l-51 -483q-2 -12 -10.5 -20.5t-20.5 -8.5h-1q-27 0 -32 27l-76 485h-404q-26 0 -45 19t-19 45q0 123 78.5 221.5t177.5 98.5v512q-52 0 -90 38 t-38 90t38 90t90 38h640q52 0 90 -38t38 -90t-38 -90t-90 -38v-512q99 0 177.5 -98.5t78.5 -221.5z" /> | |
| 168 | <glyph unicode="" horiz-adv-x="1792" d="M1408 608v-320q0 -119 -84.5 -203.5t-203.5 -84.5h-832q-119 0 -203.5 84.5t-84.5 203.5v832q0 119 84.5 203.5t203.5 84.5h704q14 0 23 -9t9 -23v-64q0 -14 -9 -23t-23 -9h-704q-66 0 -113 -47t-47 -113v-832q0 -66 47 -113t113 -47h832q66 0 113 47t47 113v320 q0 14 9 23t23 9h64q14 0 23 -9t9 -23zM1792 1472v-512q0 -26 -19 -45t-45 -19t-45 19l-176 176l-652 -652q-10 -10 -23 -10t-23 10l-114 114q-10 10 -10 23t10 23l652 652l-176 176q-19 19 -19 45t19 45t45 19h512q26 0 45 -19t19 -45z" /> | |
| 169 | <glyph unicode="" d="M1184 640q0 -26 -19 -45l-544 -544q-19 -19 -45 -19t-45 19t-19 45v288h-448q-26 0 -45 19t-19 45v384q0 26 19 45t45 19h448v288q0 26 19 45t45 19t45 -19l544 -544q19 -19 19 -45zM1536 992v-704q0 -119 -84.5 -203.5t-203.5 -84.5h-320q-13 0 -22.5 9.5t-9.5 22.5 q0 4 -1 20t-0.5 26.5t3 23.5t10 19.5t20.5 6.5h320q66 0 113 47t47 113v704q0 66 -47 113t-113 47h-288h-11h-13t-11.5 1t-11.5 3t-8 5.5t-7 9t-2 13.5q0 4 -1 20t-0.5 26.5t3 23.5t10 19.5t20.5 6.5h320q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 170 | <glyph unicode="" horiz-adv-x="1664" d="M458 653q-74 162 -74 371h-256v-96q0 -78 94.5 -162t235.5 -113zM1536 928v96h-256q0 -209 -74 -371q141 29 235.5 113t94.5 162zM1664 1056v-128q0 -71 -41.5 -143t-112 -130t-173 -97.5t-215.5 -44.5q-42 -54 -95 -95q-38 -34 -52.5 -72.5t-14.5 -89.5q0 -54 30.5 -91 t97.5 -37q75 0 133.5 -45.5t58.5 -114.5v-64q0 -14 -9 -23t-23 -9h-832q-14 0 -23 9t-9 23v64q0 69 58.5 114.5t133.5 45.5q67 0 97.5 37t30.5 91q0 51 -14.5 89.5t-52.5 72.5q-53 41 -95 95q-113 5 -215.5 44.5t-173 97.5t-112 130t-41.5 143v128q0 40 28 68t68 28h288v96 q0 66 47 113t113 47h576q66 0 113 -47t47 -113v-96h288q40 0 68 -28t28 -68z" /> | |
| 171 | <glyph unicode="" d="M394 184q-8 -9 -20 3q-13 11 -4 19q8 9 20 -3q12 -11 4 -19zM352 245q9 -12 0 -19q-8 -6 -17 7t0 18q9 7 17 -6zM291 305q-5 -7 -13 -2q-10 5 -7 12q3 5 13 2q10 -5 7 -12zM322 271q-6 -7 -16 3q-9 11 -2 16q6 6 16 -3q9 -11 2 -16zM451 159q-4 -12 -19 -6q-17 4 -13 15 t19 7q16 -5 13 -16zM514 154q0 -11 -16 -11q-17 -2 -17 11q0 11 16 11q17 2 17 -11zM572 164q2 -10 -14 -14t-18 8t14 15q16 2 18 -9zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-224q-16 0 -24.5 1t-19.5 5t-16 14.5t-5 27.5v239q0 97 -52 142q57 6 102.5 18t94 39 t81 66.5t53 105t20.5 150.5q0 121 -79 206q37 91 -8 204q-28 9 -81 -11t-92 -44l-38 -24q-93 26 -192 26t-192 -26q-16 11 -42.5 27t-83.5 38.5t-86 13.5q-44 -113 -7 -204q-79 -85 -79 -206q0 -85 20.5 -150t52.5 -105t80.5 -67t94 -39t102.5 -18q-40 -36 -49 -103 q-21 -10 -45 -15t-57 -5t-65.5 21.5t-55.5 62.5q-19 32 -48.5 52t-49.5 24l-20 3q-21 0 -29 -4.5t-5 -11.5t9 -14t13 -12l7 -5q22 -10 43.5 -38t31.5 -51l10 -23q13 -38 44 -61.5t67 -30t69.5 -7t55.5 3.5l23 4q0 -38 0.5 -103t0.5 -68q0 -22 -11 -33.5t-22 -13t-33 -1.5 h-224q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 172 | <glyph unicode="" horiz-adv-x="1664" d="M1280 64q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45t45 -19t45 19t19 45zM1536 64q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45t45 -19t45 19t19 45zM1664 288v-320q0 -40 -28 -68t-68 -28h-1472q-40 0 -68 28t-28 68v320q0 40 28 68t68 28h427q21 -56 70.5 -92 t110.5 -36h256q61 0 110.5 36t70.5 92h427q40 0 68 -28t28 -68zM1339 936q-17 -40 -59 -40h-256v-448q0 -26 -19 -45t-45 -19h-256q-26 0 -45 19t-19 45v448h-256q-42 0 -59 40q-17 39 14 69l448 448q18 19 45 19t45 -19l448 -448q31 -30 14 -69z" /> | |
| 173 | <glyph unicode="" d="M1407 710q0 44 -7 113.5t-18 96.5q-12 30 -17 44t-9 36.5t-4 48.5q0 23 5 68.5t5 67.5q0 37 -10 55q-4 1 -13 1q-19 0 -58 -4.5t-59 -4.5q-60 0 -176 24t-175 24q-43 0 -94.5 -11.5t-85 -23.5t-89.5 -34q-137 -54 -202 -103q-96 -73 -159.5 -189.5t-88 -236t-24.5 -248.5 q0 -40 12.5 -120t12.5 -121q0 -23 -11 -66.5t-11 -65.5t12 -36.5t34 -14.5q24 0 72.5 11t73.5 11q57 0 169.5 -15.5t169.5 -15.5q181 0 284 36q129 45 235.5 152.5t166 245.5t59.5 275zM1535 712q0 -165 -70 -327.5t-196 -288t-281 -180.5q-124 -44 -326 -44 q-57 0 -170 14.5t-169 14.5q-24 0 -72.5 -14.5t-73.5 -14.5q-73 0 -123.5 55.5t-50.5 128.5q0 24 11 68t11 67q0 40 -12.5 120.5t-12.5 121.5q0 111 18 217.5t54.5 209.5t100.5 194t150 156q78 59 232 120q194 78 316 78q60 0 175.5 -24t173.5 -24q19 0 57 5t58 5 q81 0 118 -50.5t37 -134.5q0 -23 -5 -68t-5 -68q0 -10 1 -18.5t3 -17t4 -13.5t6.5 -16t6.5 -17q16 -40 25 -118.5t9 -136.5z" /> | |
| 174 | <glyph unicode="" horiz-adv-x="1408" d="M1408 296q0 -27 -10 -70.5t-21 -68.5q-21 -50 -122 -106q-94 -51 -186 -51q-27 0 -52.5 3.5t-57.5 12.5t-47.5 14.5t-55.5 20.5t-49 18q-98 35 -175 83q-128 79 -264.5 215.5t-215.5 264.5q-48 77 -83 175q-3 9 -18 49t-20.5 55.5t-14.5 47.5t-12.5 57.5t-3.5 52.5 q0 92 51 186q56 101 106 122q25 11 68.5 21t70.5 10q14 0 21 -3q18 -6 53 -76q11 -19 30 -54t35 -63.5t31 -53.5q3 -4 17.5 -25t21.5 -35.5t7 -28.5q0 -20 -28.5 -50t-62 -55t-62 -53t-28.5 -46q0 -9 5 -22.5t8.5 -20.5t14 -24t11.5 -19q76 -137 174 -235t235 -174 q2 -1 19 -11.5t24 -14t20.5 -8.5t22.5 -5q18 0 46 28.5t53 62t55 62t50 28.5q14 0 28.5 -7t35.5 -21.5t25 -17.5q25 -15 53.5 -31t63.5 -35t54 -30q70 -35 76 -53q3 -7 3 -21z" /> | |
| 175 | <glyph unicode="" horiz-adv-x="1408" d="M1120 1280h-832q-66 0 -113 -47t-47 -113v-832q0 -66 47 -113t113 -47h832q66 0 113 47t47 113v832q0 66 -47 113t-113 47zM1408 1120v-832q0 -119 -84.5 -203.5t-203.5 -84.5h-832q-119 0 -203.5 84.5t-84.5 203.5v832q0 119 84.5 203.5t203.5 84.5h832 q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 176 | <glyph unicode="" horiz-adv-x="1280" d="M1152 1280h-1024v-1242l423 406l89 85l89 -85l423 -406v1242zM1164 1408q23 0 44 -9q33 -13 52.5 -41t19.5 -62v-1289q0 -34 -19.5 -62t-52.5 -41q-19 -8 -44 -8q-48 0 -83 32l-441 424l-441 -424q-36 -33 -83 -33q-23 0 -44 9q-33 13 -52.5 41t-19.5 62v1289 q0 34 19.5 62t52.5 41q21 9 44 9h1048z" /> | |
| 177 | <glyph unicode="" d="M1280 343q0 11 -2 16q-3 8 -38.5 29.5t-88.5 49.5l-53 29q-5 3 -19 13t-25 15t-21 5q-18 0 -47 -32.5t-57 -65.5t-44 -33q-7 0 -16.5 3.5t-15.5 6.5t-17 9.5t-14 8.5q-99 55 -170.5 126.5t-126.5 170.5q-2 3 -8.5 14t-9.5 17t-6.5 15.5t-3.5 16.5q0 13 20.5 33.5t45 38.5 t45 39.5t20.5 36.5q0 10 -5 21t-15 25t-13 19q-3 6 -15 28.5t-25 45.5t-26.5 47.5t-25 40.5t-16.5 18t-16 2q-48 0 -101 -22q-46 -21 -80 -94.5t-34 -130.5q0 -16 2.5 -34t5 -30.5t9 -33t10 -29.5t12.5 -33t11 -30q60 -164 216.5 -320.5t320.5 -216.5q6 -2 30 -11t33 -12.5 t29.5 -10t33 -9t30.5 -5t34 -2.5q57 0 130.5 34t94.5 80q22 53 22 101zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 178 | <glyph unicode="" horiz-adv-x="1664" d="M1620 1128q-67 -98 -162 -167q1 -14 1 -42q0 -130 -38 -259.5t-115.5 -248.5t-184.5 -210.5t-258 -146t-323 -54.5q-271 0 -496 145q35 -4 78 -4q225 0 401 138q-105 2 -188 64.5t-114 159.5q33 -5 61 -5q43 0 85 11q-112 23 -185.5 111.5t-73.5 205.5v4q68 -38 146 -41 q-66 44 -105 115t-39 154q0 88 44 163q121 -149 294.5 -238.5t371.5 -99.5q-8 38 -8 74q0 134 94.5 228.5t228.5 94.5q140 0 236 -102q109 21 205 78q-37 -115 -142 -178q93 10 186 50z" /> | |
| 179 | <glyph unicode="" horiz-adv-x="1024" d="M959 1524v-264h-157q-86 0 -116 -36t-30 -108v-189h293l-39 -296h-254v-759h-306v759h-255v296h255v218q0 186 104 288.5t277 102.5q147 0 228 -12z" /> | |
| 180 | <glyph unicode="" d="M1536 640q0 -251 -146.5 -451.5t-378.5 -277.5q-27 -5 -39.5 7t-12.5 30v211q0 97 -52 142q57 6 102.5 18t94 39t81 66.5t53 105t20.5 150.5q0 121 -79 206q37 91 -8 204q-28 9 -81 -11t-92 -44l-38 -24q-93 26 -192 26t-192 -26q-16 11 -42.5 27t-83.5 38.5t-86 13.5 q-44 -113 -7 -204q-79 -85 -79 -206q0 -85 20.5 -150t52.5 -105t80.5 -67t94 -39t102.5 -18q-40 -36 -49 -103q-21 -10 -45 -15t-57 -5t-65.5 21.5t-55.5 62.5q-19 32 -48.5 52t-49.5 24l-20 3q-21 0 -29 -4.5t-5 -11.5t9 -14t13 -12l7 -5q22 -10 43.5 -38t31.5 -51l10 -23 q13 -38 44 -61.5t67 -30t69.5 -7t55.5 3.5l23 4q0 -38 0.5 -89t0.5 -54q0 -18 -13 -30t-40 -7q-232 77 -378.5 277.5t-146.5 451.5q0 209 103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 181 | <glyph unicode="" horiz-adv-x="1664" d="M1664 960v-256q0 -26 -19 -45t-45 -19h-64q-26 0 -45 19t-19 45v256q0 106 -75 181t-181 75t-181 -75t-75 -181v-192h96q40 0 68 -28t28 -68v-576q0 -40 -28 -68t-68 -28h-960q-40 0 -68 28t-28 68v576q0 40 28 68t68 28h672v192q0 185 131.5 316.5t316.5 131.5 t316.5 -131.5t131.5 -316.5z" /> | |
| 182 | <glyph unicode="" horiz-adv-x="1920" d="M1760 1408q66 0 113 -47t47 -113v-1216q0 -66 -47 -113t-113 -47h-1600q-66 0 -113 47t-47 113v1216q0 66 47 113t113 47h1600zM160 1280q-13 0 -22.5 -9.5t-9.5 -22.5v-224h1664v224q0 13 -9.5 22.5t-22.5 9.5h-1600zM1760 0q13 0 22.5 9.5t9.5 22.5v608h-1664v-608 q0 -13 9.5 -22.5t22.5 -9.5h1600zM256 128v128h256v-128h-256zM640 128v128h384v-128h-384z" /> | |
| 183 | <glyph unicode="" horiz-adv-x="1408" d="M384 192q0 -80 -56 -136t-136 -56t-136 56t-56 136t56 136t136 56t136 -56t56 -136zM896 69q2 -28 -17 -48q-18 -21 -47 -21h-135q-25 0 -43 16.5t-20 41.5q-22 229 -184.5 391.5t-391.5 184.5q-25 2 -41.5 20t-16.5 43v135q0 29 21 47q17 17 43 17h5q160 -13 306 -80.5 t259 -181.5q114 -113 181.5 -259t80.5 -306zM1408 67q2 -27 -18 -47q-18 -20 -46 -20h-143q-26 0 -44.5 17.5t-19.5 42.5q-12 215 -101 408.5t-231.5 336t-336 231.5t-408.5 102q-25 1 -42.5 19.5t-17.5 43.5v143q0 28 20 46q18 18 44 18h3q262 -13 501.5 -120t425.5 -294 q187 -186 294 -425.5t120 -501.5z" /> | |
| 184 | <glyph unicode="" d="M1040 320q0 -33 -23.5 -56.5t-56.5 -23.5t-56.5 23.5t-23.5 56.5t23.5 56.5t56.5 23.5t56.5 -23.5t23.5 -56.5zM1296 320q0 -33 -23.5 -56.5t-56.5 -23.5t-56.5 23.5t-23.5 56.5t23.5 56.5t56.5 23.5t56.5 -23.5t23.5 -56.5zM1408 160v320q0 13 -9.5 22.5t-22.5 9.5 h-1216q-13 0 -22.5 -9.5t-9.5 -22.5v-320q0 -13 9.5 -22.5t22.5 -9.5h1216q13 0 22.5 9.5t9.5 22.5zM178 640h1180l-157 482q-4 13 -16 21.5t-26 8.5h-782q-14 0 -26 -8.5t-16 -21.5zM1536 480v-320q0 -66 -47 -113t-113 -47h-1216q-66 0 -113 47t-47 113v320q0 25 16 75 l197 606q17 53 63 86t101 33h782q55 0 101 -33t63 -86l197 -606q16 -50 16 -75z" /> | |
| 185 | <glyph unicode="" horiz-adv-x="1792" d="M1664 896q53 0 90.5 -37.5t37.5 -90.5t-37.5 -90.5t-90.5 -37.5v-384q0 -52 -38 -90t-90 -38q-417 347 -812 380q-58 -19 -91 -66t-31 -100.5t40 -92.5q-20 -33 -23 -65.5t6 -58t33.5 -55t48 -50t61.5 -50.5q-29 -58 -111.5 -83t-168.5 -11.5t-132 55.5q-7 23 -29.5 87.5 t-32 94.5t-23 89t-15 101t3.5 98.5t22 110.5h-122q-66 0 -113 47t-47 113v192q0 66 47 113t113 47h480q435 0 896 384q52 0 90 -38t38 -90v-384zM1536 292v954q-394 -302 -768 -343v-270q377 -42 768 -341z" /> | |
| 186 | <glyph unicode="" horiz-adv-x="1792" d="M912 -160q0 16 -16 16q-59 0 -101.5 42.5t-42.5 101.5q0 16 -16 16t-16 -16q0 -73 51.5 -124.5t124.5 -51.5q16 0 16 16zM246 128h1300q-266 300 -266 832q0 51 -24 105t-69 103t-121.5 80.5t-169.5 31.5t-169.5 -31.5t-121.5 -80.5t-69 -103t-24 -105q0 -532 -266 -832z M1728 128q0 -52 -38 -90t-90 -38h-448q0 -106 -75 -181t-181 -75t-181 75t-75 181h-448q-52 0 -90 38t-38 90q50 42 91 88t85 119.5t74.5 158.5t50 206t19.5 260q0 152 117 282.5t307 158.5q-8 19 -8 39q0 40 28 68t68 28t68 -28t28 -68q0 -20 -8 -39q190 -28 307 -158.5 t117 -282.5q0 -139 19.5 -260t50 -206t74.5 -158.5t85 -119.5t91 -88z" /> | |
| 187 | <glyph unicode="" d="M1376 640l138 -135q30 -28 20 -70q-12 -41 -52 -51l-188 -48l53 -186q12 -41 -19 -70q-29 -31 -70 -19l-186 53l-48 -188q-10 -40 -51 -52q-12 -2 -19 -2q-31 0 -51 22l-135 138l-135 -138q-28 -30 -70 -20q-41 11 -51 52l-48 188l-186 -53q-41 -12 -70 19q-31 29 -19 70 l53 186l-188 48q-40 10 -52 51q-10 42 20 70l138 135l-138 135q-30 28 -20 70q12 41 52 51l188 48l-53 186q-12 41 19 70q29 31 70 19l186 -53l48 188q10 41 51 51q41 12 70 -19l135 -139l135 139q29 30 70 19q41 -10 51 -51l48 -188l186 53q41 12 70 -19q31 -29 19 -70 l-53 -186l188 -48q40 -10 52 -51q10 -42 -20 -70z" /> | |
| 188 | <glyph unicode="" horiz-adv-x="1792" d="M256 192q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45t45 -19t45 19t19 45zM1664 768q0 51 -39 89.5t-89 38.5h-576q0 20 15 48.5t33 55t33 68t15 84.5q0 67 -44.5 97.5t-115.5 30.5q-24 0 -90 -139q-24 -44 -37 -65q-40 -64 -112 -145q-71 -81 -101 -106 q-69 -57 -140 -57h-32v-640h32q72 0 167 -32t193.5 -64t179.5 -32q189 0 189 167q0 26 -5 56q30 16 47.5 52.5t17.5 73.5t-18 69q53 50 53 119q0 25 -10 55.5t-25 47.5h331q52 0 90 38t38 90zM1792 769q0 -105 -75.5 -181t-180.5 -76h-169q-4 -62 -37 -119q3 -21 3 -43 q0 -101 -60 -178q1 -139 -85 -219.5t-227 -80.5q-133 0 -322 69q-164 59 -223 59h-288q-53 0 -90.5 37.5t-37.5 90.5v640q0 53 37.5 90.5t90.5 37.5h288q10 0 21.5 4.5t23.5 14t22.5 18t24 22.5t20.5 21.5t19 21.5t14 17q65 74 100 129q13 21 33 62t37 72t40.5 63t55 49.5 t69.5 17.5q125 0 206.5 -67t81.5 -189q0 -68 -22 -128h374q104 0 180 -76t76 -179z" /> | |
| 189 | <glyph unicode="" horiz-adv-x="1792" d="M1376 128h32v640h-32q-35 0 -67.5 12t-62.5 37t-50 46t-49 54q-2 3 -3.5 4.5t-4 4.5t-4.5 5q-72 81 -112 145q-14 22 -38 68q-1 3 -10.5 22.5t-18.5 36t-20 35.5t-21.5 30.5t-18.5 11.5q-71 0 -115.5 -30.5t-44.5 -97.5q0 -43 15 -84.5t33 -68t33 -55t15 -48.5h-576 q-50 0 -89 -38.5t-39 -89.5q0 -52 38 -90t90 -38h331q-15 -17 -25 -47.5t-10 -55.5q0 -69 53 -119q-18 -32 -18 -69t17.5 -73.5t47.5 -52.5q-4 -24 -4 -56q0 -85 48.5 -126t135.5 -41q84 0 183 32t194 64t167 32zM1664 192q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45 t45 -19t45 19t19 45zM1792 768v-640q0 -53 -37.5 -90.5t-90.5 -37.5h-288q-59 0 -223 -59q-190 -69 -317 -69q-142 0 -230 77.5t-87 217.5l1 5q-61 76 -61 178q0 22 3 43q-33 57 -37 119h-169q-105 0 -180.5 76t-75.5 181q0 103 76 179t180 76h374q-22 60 -22 128 q0 122 81.5 189t206.5 67q38 0 69.5 -17.5t55 -49.5t40.5 -63t37 -72t33 -62q35 -55 100 -129q2 -3 14 -17t19 -21.5t20.5 -21.5t24 -22.5t22.5 -18t23.5 -14t21.5 -4.5h288q53 0 90.5 -37.5t37.5 -90.5z" /> | |
| 190 | <glyph unicode="" d="M1280 -64q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45t45 -19t45 19t19 45zM1408 700q0 189 -167 189q-26 0 -56 -5q-16 30 -52.5 47.5t-73.5 17.5t-69 -18q-50 53 -119 53q-25 0 -55.5 -10t-47.5 -25v331q0 52 -38 90t-90 38q-51 0 -89.5 -39t-38.5 -89v-576 q-20 0 -48.5 15t-55 33t-68 33t-84.5 15q-67 0 -97.5 -44.5t-30.5 -115.5q0 -24 139 -90q44 -24 65 -37q64 -40 145 -112q81 -71 106 -101q57 -69 57 -140v-32h640v32q0 72 32 167t64 193.5t32 179.5zM1536 705q0 -133 -69 -322q-59 -164 -59 -223v-288q0 -53 -37.5 -90.5 t-90.5 -37.5h-640q-53 0 -90.5 37.5t-37.5 90.5v288q0 10 -4.5 21.5t-14 23.5t-18 22.5t-22.5 24t-21.5 20.5t-21.5 19t-17 14q-74 65 -129 100q-21 13 -62 33t-72 37t-63 40.5t-49.5 55t-17.5 69.5q0 125 67 206.5t189 81.5q68 0 128 -22v374q0 104 76 180t179 76 q105 0 181 -75.5t76 -180.5v-169q62 -4 119 -37q21 3 43 3q101 0 178 -60q139 1 219.5 -85t80.5 -227z" /> | |
| 191 | <glyph unicode="" d="M1408 576q0 84 -32 183t-64 194t-32 167v32h-640v-32q0 -35 -12 -67.5t-37 -62.5t-46 -50t-54 -49q-9 -8 -14 -12q-81 -72 -145 -112q-22 -14 -68 -38q-3 -1 -22.5 -10.5t-36 -18.5t-35.5 -20t-30.5 -21.5t-11.5 -18.5q0 -71 30.5 -115.5t97.5 -44.5q43 0 84.5 15t68 33 t55 33t48.5 15v-576q0 -50 38.5 -89t89.5 -39q52 0 90 38t38 90v331q46 -35 103 -35q69 0 119 53q32 -18 69 -18t73.5 17.5t52.5 47.5q24 -4 56 -4q85 0 126 48.5t41 135.5zM1280 1344q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45t45 -19t45 19t19 45zM1536 580 q0 -142 -77.5 -230t-217.5 -87l-5 1q-76 -61 -178 -61q-22 0 -43 3q-54 -30 -119 -37v-169q0 -105 -76 -180.5t-181 -75.5q-103 0 -179 76t-76 180v374q-54 -22 -128 -22q-121 0 -188.5 81.5t-67.5 206.5q0 38 17.5 69.5t49.5 55t63 40.5t72 37t62 33q55 35 129 100 q3 2 17 14t21.5 19t21.5 20.5t22.5 24t18 22.5t14 23.5t4.5 21.5v288q0 53 37.5 90.5t90.5 37.5h640q53 0 90.5 -37.5t37.5 -90.5v-288q0 -59 59 -223q69 -190 69 -317z" /> | |
| 192 | <glyph unicode="" d="M1280 576v128q0 26 -19 45t-45 19h-502l189 189q19 19 19 45t-19 45l-91 91q-18 18 -45 18t-45 -18l-362 -362l-91 -91q-18 -18 -18 -45t18 -45l91 -91l362 -362q18 -18 45 -18t45 18l91 91q18 18 18 45t-18 45l-189 189h502q26 0 45 19t19 45zM1536 640 q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 193 | <glyph unicode="" d="M1285 640q0 27 -18 45l-91 91l-362 362q-18 18 -45 18t-45 -18l-91 -91q-18 -18 -18 -45t18 -45l189 -189h-502q-26 0 -45 -19t-19 -45v-128q0 -26 19 -45t45 -19h502l-189 -189q-19 -19 -19 -45t19 -45l91 -91q18 -18 45 -18t45 18l362 362l91 91q18 18 18 45zM1536 640 q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 194 | <glyph unicode="" d="M1284 641q0 27 -18 45l-362 362l-91 91q-18 18 -45 18t-45 -18l-91 -91l-362 -362q-18 -18 -18 -45t18 -45l91 -91q18 -18 45 -18t45 18l189 189v-502q0 -26 19 -45t45 -19h128q26 0 45 19t19 45v502l189 -189q19 -19 45 -19t45 19l91 91q18 18 18 45zM1536 640 q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 195 | <glyph unicode="" d="M1284 639q0 27 -18 45l-91 91q-18 18 -45 18t-45 -18l-189 -189v502q0 26 -19 45t-45 19h-128q-26 0 -45 -19t-19 -45v-502l-189 189q-19 19 -45 19t-45 -19l-91 -91q-18 -18 -18 -45t18 -45l362 -362l91 -91q18 -18 45 -18t45 18l91 91l362 362q18 18 18 45zM1536 640 q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 196 | <glyph unicode="" d="M768 1408q209 0 385.5 -103t279.5 -279.5t103 -385.5t-103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103zM1042 887q-2 -1 -9.5 -9.5t-13.5 -9.5q2 0 4.5 5t5 11t3.5 7q6 7 22 15q14 6 52 12q34 8 51 -11 q-2 2 9.5 13t14.5 12q3 2 15 4.5t15 7.5l2 22q-12 -1 -17.5 7t-6.5 21q0 -2 -6 -8q0 7 -4.5 8t-11.5 -1t-9 -1q-10 3 -15 7.5t-8 16.5t-4 15q-2 5 -9.5 10.5t-9.5 10.5q-1 2 -2.5 5.5t-3 6.5t-4 5.5t-5.5 2.5t-7 -5t-7.5 -10t-4.5 -5q-3 2 -6 1.5t-4.5 -1t-4.5 -3t-5 -3.5 q-3 -2 -8.5 -3t-8.5 -2q15 5 -1 11q-10 4 -16 3q9 4 7.5 12t-8.5 14h5q-1 4 -8.5 8.5t-17.5 8.5t-13 6q-8 5 -34 9.5t-33 0.5q-5 -6 -4.5 -10.5t4 -14t3.5 -12.5q1 -6 -5.5 -13t-6.5 -12q0 -7 14 -15.5t10 -21.5q-3 -8 -16 -16t-16 -12q-5 -8 -1.5 -18.5t10.5 -16.5 q2 -2 1.5 -4t-3.5 -4.5t-5.5 -4t-6.5 -3.5l-3 -2q-11 -5 -20.5 6t-13.5 26q-7 25 -16 30q-23 8 -29 -1q-5 13 -41 26q-25 9 -58 4q6 1 0 15q-7 15 -19 12q3 6 4 17.5t1 13.5q3 13 12 23q1 1 7 8.5t9.5 13.5t0.5 6q35 -4 50 11q5 5 11.5 17t10.5 17q9 6 14 5.5t14.5 -5.5 t14.5 -5q14 -1 15.5 11t-7.5 20q12 -1 3 17q-5 7 -8 9q-12 4 -27 -5q-8 -4 2 -8q-1 1 -9.5 -10.5t-16.5 -17.5t-16 5q-1 1 -5.5 13.5t-9.5 13.5q-8 0 -16 -15q3 8 -11 15t-24 8q19 12 -8 27q-7 4 -20.5 5t-19.5 -4q-5 -7 -5.5 -11.5t5 -8t10.5 -5.5t11.5 -4t8.5 -3 q14 -10 8 -14q-2 -1 -8.5 -3.5t-11.5 -4.5t-6 -4q-3 -4 0 -14t-2 -14q-5 5 -9 17.5t-7 16.5q7 -9 -25 -6l-10 1q-4 0 -16 -2t-20.5 -1t-13.5 8q-4 8 0 20q1 4 4 2q-4 3 -11 9.5t-10 8.5q-46 -15 -94 -41q6 -1 12 1q5 2 13 6.5t10 5.5q34 14 42 7l5 5q14 -16 20 -25 q-7 4 -30 1q-20 -6 -22 -12q7 -12 5 -18q-4 3 -11.5 10t-14.5 11t-15 5q-16 0 -22 -1q-146 -80 -235 -222q7 -7 12 -8q4 -1 5 -9t2.5 -11t11.5 3q9 -8 3 -19q1 1 44 -27q19 -17 21 -21q3 -11 -10 -18q-1 2 -9 9t-9 4q-3 -5 0.5 -18.5t10.5 -12.5q-7 0 -9.5 -16t-2.5 -35.5 t-1 -23.5l2 -1q-3 -12 5.5 -34.5t21.5 -19.5q-13 -3 20 -43q6 -8 8 -9q3 -2 12 -7.5t15 -10t10 -10.5q4 -5 10 -22.5t14 -23.5q-2 -6 9.5 -20t10.5 -23q-1 0 -2.5 -1t-2.5 -1q3 -7 15.5 -14t15.5 -13q1 -3 2 -10t3 -11t8 -2q2 20 -24 62q-15 25 -17 29q-3 5 -5.5 15.5 t-4.5 14.5q2 0 6 -1.5t8.5 -3.5t7.5 -4t2 -3q-3 -7 2 -17.5t12 -18.5t17 -19t12 -13q6 -6 14 -19.5t0 -13.5q9 0 20 -10t17 -20q5 -8 8 -26t5 -24q2 -7 8.5 -13.5t12.5 -9.5l16 -8t13 -7q5 -2 18.5 -10.5t21.5 -11.5q10 -4 16 -4t14.5 2.5t13.5 3.5q15 2 29 -15t21 -21 q36 -19 55 -11q-2 -1 0.5 -7.5t8 -15.5t9 -14.5t5.5 -8.5q5 -6 18 -15t18 -15q6 4 7 9q-3 -8 7 -20t18 -10q14 3 14 32q-31 -15 -49 18q0 1 -2.5 5.5t-4 8.5t-2.5 8.5t0 7.5t5 3q9 0 10 3.5t-2 12.5t-4 13q-1 8 -11 20t-12 15q-5 -9 -16 -8t-16 9q0 -1 -1.5 -5.5t-1.5 -6.5 q-13 0 -15 1q1 3 2.5 17.5t3.5 22.5q1 4 5.5 12t7.5 14.5t4 12.5t-4.5 9.5t-17.5 2.5q-19 -1 -26 -20q-1 -3 -3 -10.5t-5 -11.5t-9 -7q-7 -3 -24 -2t-24 5q-13 8 -22.5 29t-9.5 37q0 10 2.5 26.5t3 25t-5.5 24.5q3 2 9 9.5t10 10.5q2 1 4.5 1.5t4.5 0t4 1.5t3 6q-1 1 -4 3 q-3 3 -4 3q7 -3 28.5 1.5t27.5 -1.5q15 -11 22 2q0 1 -2.5 9.5t-0.5 13.5q5 -27 29 -9q3 -3 15.5 -5t17.5 -5q3 -2 7 -5.5t5.5 -4.5t5 0.5t8.5 6.5q10 -14 12 -24q11 -40 19 -44q7 -3 11 -2t4.5 9.5t0 14t-1.5 12.5l-1 8v18l-1 8q-15 3 -18.5 12t1.5 18.5t15 18.5q1 1 8 3.5 t15.5 6.5t12.5 8q21 19 15 35q7 0 11 9q-1 0 -5 3t-7.5 5t-4.5 2q9 5 2 16q5 3 7.5 11t7.5 10q9 -12 21 -2q7 8 1 16q5 7 20.5 10.5t18.5 9.5q7 -2 8 2t1 12t3 12q4 5 15 9t13 5l17 11q3 4 0 4q18 -2 31 11q10 11 -6 20q3 6 -3 9.5t-15 5.5q3 1 11.5 0.5t10.5 1.5 q15 10 -7 16q-17 5 -43 -12zM879 10q206 36 351 189q-3 3 -12.5 4.5t-12.5 3.5q-18 7 -24 8q1 7 -2.5 13t-8 9t-12.5 8t-11 7q-2 2 -7 6t-7 5.5t-7.5 4.5t-8.5 2t-10 -1l-3 -1q-3 -1 -5.5 -2.5t-5.5 -3t-4 -3t0 -2.5q-21 17 -36 22q-5 1 -11 5.5t-10.5 7t-10 1.5t-11.5 -7 q-5 -5 -6 -15t-2 -13q-7 5 0 17.5t2 18.5q-3 6 -10.5 4.5t-12 -4.5t-11.5 -8.5t-9 -6.5t-8.5 -5.5t-8.5 -7.5q-3 -4 -6 -12t-5 -11q-2 4 -11.5 6.5t-9.5 5.5q2 -10 4 -35t5 -38q7 -31 -12 -48q-27 -25 -29 -40q-4 -22 12 -26q0 -7 -8 -20.5t-7 -21.5q0 -6 2 -16z" /> | |
| 197 | <glyph unicode="" horiz-adv-x="1664" d="M384 64q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45t45 -19t45 19t19 45zM1028 484l-682 -682q-37 -37 -90 -37q-52 0 -91 37l-106 108q-38 36 -38 90q0 53 38 91l681 681q39 -98 114.5 -173.5t173.5 -114.5zM1662 919q0 -39 -23 -106q-47 -134 -164.5 -217.5 t-258.5 -83.5q-185 0 -316.5 131.5t-131.5 316.5t131.5 316.5t316.5 131.5q58 0 121.5 -16.5t107.5 -46.5q16 -11 16 -28t-16 -28l-293 -169v-224l193 -107q5 3 79 48.5t135.5 81t70.5 35.5q15 0 23.5 -10t8.5 -25z" /> | |
| 198 | <glyph unicode="" horiz-adv-x="1792" d="M1024 128h640v128h-640v-128zM640 640h1024v128h-1024v-128zM1280 1152h384v128h-384v-128zM1792 320v-256q0 -26 -19 -45t-45 -19h-1664q-26 0 -45 19t-19 45v256q0 26 19 45t45 19h1664q26 0 45 -19t19 -45zM1792 832v-256q0 -26 -19 -45t-45 -19h-1664q-26 0 -45 19 t-19 45v256q0 26 19 45t45 19h1664q26 0 45 -19t19 -45zM1792 1344v-256q0 -26 -19 -45t-45 -19h-1664q-26 0 -45 19t-19 45v256q0 26 19 45t45 19h1664q26 0 45 -19t19 -45z" /> | |
| 199 | <glyph unicode="" horiz-adv-x="1408" d="M1403 1241q17 -41 -14 -70l-493 -493v-742q0 -42 -39 -59q-13 -5 -25 -5q-27 0 -45 19l-256 256q-19 19 -19 45v486l-493 493q-31 29 -14 70q17 39 59 39h1280q42 0 59 -39z" /> | |
| 200 | <glyph unicode="" horiz-adv-x="1792" d="M640 1280h512v128h-512v-128zM1792 640v-480q0 -66 -47 -113t-113 -47h-1472q-66 0 -113 47t-47 113v480h672v-160q0 -26 19 -45t45 -19h320q26 0 45 19t19 45v160h672zM1024 640v-128h-256v128h256zM1792 1120v-384h-1792v384q0 66 47 113t113 47h352v160q0 40 28 68 t68 28h576q40 0 68 -28t28 -68v-160h352q66 0 113 -47t47 -113z" /> | |
| 201 | <glyph unicode="" d="M1283 995l-355 -355l355 -355l144 144q29 31 70 14q39 -17 39 -59v-448q0 -26 -19 -45t-45 -19h-448q-42 0 -59 40q-17 39 14 69l144 144l-355 355l-355 -355l144 -144q31 -30 14 -69q-17 -40 -59 -40h-448q-26 0 -45 19t-19 45v448q0 42 40 59q39 17 69 -14l144 -144 l355 355l-355 355l-144 -144q-19 -19 -45 -19q-12 0 -24 5q-40 17 -40 59v448q0 26 19 45t45 19h448q42 0 59 -40q17 -39 -14 -69l-144 -144l355 -355l355 355l-144 144q-31 30 -14 69q17 40 59 40h448q26 0 45 -19t19 -45v-448q0 -42 -39 -59q-13 -5 -25 -5q-26 0 -45 19z " /> | |
| 202 | <glyph unicode="" horiz-adv-x="1920" d="M593 640q-162 -5 -265 -128h-134q-82 0 -138 40.5t-56 118.5q0 353 124 353q6 0 43.5 -21t97.5 -42.5t119 -21.5q67 0 133 23q-5 -37 -5 -66q0 -139 81 -256zM1664 3q0 -120 -73 -189.5t-194 -69.5h-874q-121 0 -194 69.5t-73 189.5q0 53 3.5 103.5t14 109t26.5 108.5 t43 97.5t62 81t85.5 53.5t111.5 20q10 0 43 -21.5t73 -48t107 -48t135 -21.5t135 21.5t107 48t73 48t43 21.5q61 0 111.5 -20t85.5 -53.5t62 -81t43 -97.5t26.5 -108.5t14 -109t3.5 -103.5zM640 1280q0 -106 -75 -181t-181 -75t-181 75t-75 181t75 181t181 75t181 -75 t75 -181zM1344 896q0 -159 -112.5 -271.5t-271.5 -112.5t-271.5 112.5t-112.5 271.5t112.5 271.5t271.5 112.5t271.5 -112.5t112.5 -271.5zM1920 671q0 -78 -56 -118.5t-138 -40.5h-134q-103 123 -265 128q81 117 81 256q0 29 -5 66q66 -23 133 -23q59 0 119 21.5t97.5 42.5 t43.5 21q124 0 124 -353zM1792 1280q0 -106 -75 -181t-181 -75t-181 75t-75 181t75 181t181 75t181 -75t75 -181z" /> | |
| 203 | <glyph unicode="" horiz-adv-x="1664" d="M1456 320q0 40 -28 68l-208 208q-28 28 -68 28q-42 0 -72 -32q3 -3 19 -18.5t21.5 -21.5t15 -19t13 -25.5t3.5 -27.5q0 -40 -28 -68t-68 -28q-15 0 -27.5 3.5t-25.5 13t-19 15t-21.5 21.5t-18.5 19q-33 -31 -33 -73q0 -40 28 -68l206 -207q27 -27 68 -27q40 0 68 26 l147 146q28 28 28 67zM753 1025q0 40 -28 68l-206 207q-28 28 -68 28q-39 0 -68 -27l-147 -146q-28 -28 -28 -67q0 -40 28 -68l208 -208q27 -27 68 -27q42 0 72 31q-3 3 -19 18.5t-21.5 21.5t-15 19t-13 25.5t-3.5 27.5q0 40 28 68t68 28q15 0 27.5 -3.5t25.5 -13t19 -15 t21.5 -21.5t18.5 -19q33 31 33 73zM1648 320q0 -120 -85 -203l-147 -146q-83 -83 -203 -83q-121 0 -204 85l-206 207q-83 83 -83 203q0 123 88 209l-88 88q-86 -88 -208 -88q-120 0 -204 84l-208 208q-84 84 -84 204t85 203l147 146q83 83 203 83q121 0 204 -85l206 -207 q83 -83 83 -203q0 -123 -88 -209l88 -88q86 88 208 88q120 0 204 -84l208 -208q84 -84 84 -204z" /> | |
| 204 | <glyph unicode="" horiz-adv-x="1920" d="M1920 384q0 -159 -112.5 -271.5t-271.5 -112.5h-1088q-185 0 -316.5 131.5t-131.5 316.5q0 132 71 241.5t187 163.5q-2 28 -2 43q0 212 150 362t362 150q158 0 286.5 -88t187.5 -230q70 62 166 62q106 0 181 -75t75 -181q0 -75 -41 -138q129 -30 213 -134.5t84 -239.5z " /> | |
| 205 | <glyph unicode="" horiz-adv-x="1664" d="M1527 88q56 -89 21.5 -152.5t-140.5 -63.5h-1152q-106 0 -140.5 63.5t21.5 152.5l503 793v399h-64q-26 0 -45 19t-19 45t19 45t45 19h512q26 0 45 -19t19 -45t-19 -45t-45 -19h-64v-399zM748 813l-272 -429h712l-272 429l-20 31v37v399h-128v-399v-37z" /> | |
| 206 | <glyph unicode="" horiz-adv-x="1792" d="M960 640q26 0 45 -19t19 -45t-19 -45t-45 -19t-45 19t-19 45t19 45t45 19zM1260 576l507 -398q28 -20 25 -56q-5 -35 -35 -51l-128 -64q-13 -7 -29 -7q-17 0 -31 8l-690 387l-110 -66q-8 -4 -12 -5q14 -49 10 -97q-7 -77 -56 -147.5t-132 -123.5q-132 -84 -277 -84 q-136 0 -222 78q-90 84 -79 207q7 76 56 147t131 124q132 84 278 84q83 0 151 -31q9 13 22 22l122 73l-122 73q-13 9 -22 22q-68 -31 -151 -31q-146 0 -278 84q-82 53 -131 124t-56 147q-5 59 15.5 113t63.5 93q85 79 222 79q145 0 277 -84q83 -52 132 -123t56 -148 q4 -48 -10 -97q4 -1 12 -5l110 -66l690 387q14 8 31 8q16 0 29 -7l128 -64q30 -16 35 -51q3 -36 -25 -56zM579 836q46 42 21 108t-106 117q-92 59 -192 59q-74 0 -113 -36q-46 -42 -21 -108t106 -117q92 -59 192 -59q74 0 113 36zM494 91q81 51 106 117t-21 108 q-39 36 -113 36q-100 0 -192 -59q-81 -51 -106 -117t21 -108q39 -36 113 -36q100 0 192 59zM672 704l96 -58v11q0 36 33 56l14 8l-79 47l-26 -26q-3 -3 -10 -11t-12 -12q-2 -2 -4 -3.5t-3 -2.5zM896 480l96 -32l736 576l-128 64l-768 -431v-113l-160 -96l9 -8q2 -2 7 -6 q4 -4 11 -12t11 -12l26 -26zM1600 64l128 64l-520 408l-177 -138q-2 -3 -13 -7z" /> | |
| 207 | <glyph unicode="" horiz-adv-x="1792" d="M1696 1152q40 0 68 -28t28 -68v-1216q0 -40 -28 -68t-68 -28h-960q-40 0 -68 28t-28 68v288h-544q-40 0 -68 28t-28 68v672q0 40 20 88t48 76l408 408q28 28 76 48t88 20h416q40 0 68 -28t28 -68v-328q68 40 128 40h416zM1152 939l-299 -299h299v299zM512 1323l-299 -299 h299v299zM708 676l316 316v416h-384v-416q0 -40 -28 -68t-68 -28h-416v-640h512v256q0 40 20 88t48 76zM1664 -128v1152h-384v-416q0 -40 -28 -68t-68 -28h-416v-640h896z" /> | |
| 208 | <glyph unicode="" horiz-adv-x="1408" d="M1404 151q0 -117 -79 -196t-196 -79q-135 0 -235 100l-777 776q-113 115 -113 271q0 159 110 270t269 111q158 0 273 -113l605 -606q10 -10 10 -22q0 -16 -30.5 -46.5t-46.5 -30.5q-13 0 -23 10l-606 607q-79 77 -181 77q-106 0 -179 -75t-73 -181q0 -105 76 -181 l776 -777q63 -63 145 -63q64 0 106 42t42 106q0 82 -63 145l-581 581q-26 24 -60 24q-29 0 -48 -19t-19 -48q0 -32 25 -59l410 -410q10 -10 10 -22q0 -16 -31 -47t-47 -31q-12 0 -22 10l-410 410q-63 61 -63 149q0 82 57 139t139 57q88 0 149 -63l581 -581q100 -98 100 -235 z" /> | |
| 209 | <glyph unicode="" d="M384 0h768v384h-768v-384zM1280 0h128v896q0 14 -10 38.5t-20 34.5l-281 281q-10 10 -34 20t-39 10v-416q0 -40 -28 -68t-68 -28h-576q-40 0 -68 28t-28 68v416h-128v-1280h128v416q0 40 28 68t68 28h832q40 0 68 -28t28 -68v-416zM896 928v320q0 13 -9.5 22.5t-22.5 9.5 h-192q-13 0 -22.5 -9.5t-9.5 -22.5v-320q0 -13 9.5 -22.5t22.5 -9.5h192q13 0 22.5 9.5t9.5 22.5zM1536 896v-928q0 -40 -28 -68t-68 -28h-1344q-40 0 -68 28t-28 68v1344q0 40 28 68t68 28h928q40 0 88 -20t76 -48l280 -280q28 -28 48 -76t20 -88z" /> | |
| 210 | <glyph unicode="" d="M1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 211 | <glyph unicode="" d="M1536 192v-128q0 -26 -19 -45t-45 -19h-1408q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1408q26 0 45 -19t19 -45zM1536 704v-128q0 -26 -19 -45t-45 -19h-1408q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1408q26 0 45 -19t19 -45zM1536 1216v-128q0 -26 -19 -45 t-45 -19h-1408q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h1408q26 0 45 -19t19 -45z" /> | |
| 212 | <glyph unicode="" horiz-adv-x="1792" d="M384 128q0 -80 -56 -136t-136 -56t-136 56t-56 136t56 136t136 56t136 -56t56 -136zM384 640q0 -80 -56 -136t-136 -56t-136 56t-56 136t56 136t136 56t136 -56t56 -136zM1792 224v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1216q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5 t22.5 9.5h1216q13 0 22.5 -9.5t9.5 -22.5zM384 1152q0 -80 -56 -136t-136 -56t-136 56t-56 136t56 136t136 56t136 -56t56 -136zM1792 736v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1216q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h1216q13 0 22.5 -9.5t9.5 -22.5z M1792 1248v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1216q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h1216q13 0 22.5 -9.5t9.5 -22.5z" /> | |
| 213 | <glyph unicode="" horiz-adv-x="1792" d="M381 -84q0 -80 -54.5 -126t-135.5 -46q-106 0 -172 66l57 88q49 -45 106 -45q29 0 50.5 14.5t21.5 42.5q0 64 -105 56l-26 56q8 10 32.5 43.5t42.5 54t37 38.5v1q-16 0 -48.5 -1t-48.5 -1v-53h-106v152h333v-88l-95 -115q51 -12 81 -49t30 -88zM383 543v-159h-362 q-6 36 -6 54q0 51 23.5 93t56.5 68t66 47.5t56.5 43.5t23.5 45q0 25 -14.5 38.5t-39.5 13.5q-46 0 -81 -58l-85 59q24 51 71.5 79.5t105.5 28.5q73 0 123 -41.5t50 -112.5q0 -50 -34 -91.5t-75 -64.5t-75.5 -50.5t-35.5 -52.5h127v60h105zM1792 224v-192q0 -13 -9.5 -22.5 t-22.5 -9.5h-1216q-13 0 -22.5 9.5t-9.5 22.5v192q0 14 9 23t23 9h1216q13 0 22.5 -9.5t9.5 -22.5zM384 1123v-99h-335v99h107q0 41 0.5 122t0.5 121v12h-2q-8 -17 -50 -54l-71 76l136 127h106v-404h108zM1792 736v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1216q-13 0 -22.5 9.5 t-9.5 22.5v192q0 14 9 23t23 9h1216q13 0 22.5 -9.5t9.5 -22.5zM1792 1248v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1216q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h1216q13 0 22.5 -9.5t9.5 -22.5z" /> | |
| 214 | <glyph unicode="" horiz-adv-x="1792" d="M1760 640q14 0 23 -9t9 -23v-64q0 -14 -9 -23t-23 -9h-1728q-14 0 -23 9t-9 23v64q0 14 9 23t23 9h1728zM483 704q-28 35 -51 80q-48 97 -48 188q0 181 134 309q133 127 393 127q50 0 167 -19q66 -12 177 -48q10 -38 21 -118q14 -123 14 -183q0 -18 -5 -45l-12 -3l-84 6 l-14 2q-50 149 -103 205q-88 91 -210 91q-114 0 -182 -59q-67 -58 -67 -146q0 -73 66 -140t279 -129q69 -20 173 -66q58 -28 95 -52h-743zM990 448h411q7 -39 7 -92q0 -111 -41 -212q-23 -55 -71 -104q-37 -35 -109 -81q-80 -48 -153 -66q-80 -21 -203 -21q-114 0 -195 23 l-140 40q-57 16 -72 28q-8 8 -8 22v13q0 108 -2 156q-1 30 0 68l2 37v44l102 2q15 -34 30 -71t22.5 -56t12.5 -27q35 -57 80 -94q43 -36 105 -57q59 -22 132 -22q64 0 139 27q77 26 122 86q47 61 47 129q0 84 -81 157q-34 29 -137 71z" /> | |
| 215 | <glyph unicode="" d="M48 1313q-37 2 -45 4l-3 88q13 1 40 1q60 0 112 -4q132 -7 166 -7q86 0 168 3q116 4 146 5q56 0 86 2l-1 -14l2 -64v-9q-60 -9 -124 -9q-60 0 -79 -25q-13 -14 -13 -132q0 -13 0.5 -32.5t0.5 -25.5l1 -229l14 -280q6 -124 51 -202q35 -59 96 -92q88 -47 177 -47 q104 0 191 28q56 18 99 51q48 36 65 64q36 56 53 114q21 73 21 229q0 79 -3.5 128t-11 122.5t-13.5 159.5l-4 59q-5 67 -24 88q-34 35 -77 34l-100 -2l-14 3l2 86h84l205 -10q76 -3 196 10l18 -2q6 -38 6 -51q0 -7 -4 -31q-45 -12 -84 -13q-73 -11 -79 -17q-15 -15 -15 -41 q0 -7 1.5 -27t1.5 -31q8 -19 22 -396q6 -195 -15 -304q-15 -76 -41 -122q-38 -65 -112 -123q-75 -57 -182 -89q-109 -33 -255 -33q-167 0 -284 46q-119 47 -179 122q-61 76 -83 195q-16 80 -16 237v333q0 188 -17 213q-25 36 -147 39zM1536 -96v64q0 14 -9 23t-23 9h-1472 q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h1472q14 0 23 9t9 23z" /> | |
| 216 | <glyph unicode="" horiz-adv-x="1664" d="M512 160v192q0 14 -9 23t-23 9h-320q-14 0 -23 -9t-9 -23v-192q0 -14 9 -23t23 -9h320q14 0 23 9t9 23zM512 544v192q0 14 -9 23t-23 9h-320q-14 0 -23 -9t-9 -23v-192q0 -14 9 -23t23 -9h320q14 0 23 9t9 23zM1024 160v192q0 14 -9 23t-23 9h-320q-14 0 -23 -9t-9 -23 v-192q0 -14 9 -23t23 -9h320q14 0 23 9t9 23zM512 928v192q0 14 -9 23t-23 9h-320q-14 0 -23 -9t-9 -23v-192q0 -14 9 -23t23 -9h320q14 0 23 9t9 23zM1024 544v192q0 14 -9 23t-23 9h-320q-14 0 -23 -9t-9 -23v-192q0 -14 9 -23t23 -9h320q14 0 23 9t9 23zM1536 160v192 q0 14 -9 23t-23 9h-320q-14 0 -23 -9t-9 -23v-192q0 -14 9 -23t23 -9h320q14 0 23 9t9 23zM1024 928v192q0 14 -9 23t-23 9h-320q-14 0 -23 -9t-9 -23v-192q0 -14 9 -23t23 -9h320q14 0 23 9t9 23zM1536 544v192q0 14 -9 23t-23 9h-320q-14 0 -23 -9t-9 -23v-192 q0 -14 9 -23t23 -9h320q14 0 23 9t9 23zM1536 928v192q0 14 -9 23t-23 9h-320q-14 0 -23 -9t-9 -23v-192q0 -14 9 -23t23 -9h320q14 0 23 9t9 23zM1664 1248v-1088q0 -66 -47 -113t-113 -47h-1344q-66 0 -113 47t-47 113v1088q0 66 47 113t113 47h1344q66 0 113 -47t47 -113 z" /> | |
| 217 | <glyph unicode="" horiz-adv-x="1664" d="M1190 955l293 293l-107 107l-293 -293zM1637 1248q0 -27 -18 -45l-1286 -1286q-18 -18 -45 -18t-45 18l-198 198q-18 18 -18 45t18 45l1286 1286q18 18 45 18t45 -18l198 -198q18 -18 18 -45zM286 1438l98 -30l-98 -30l-30 -98l-30 98l-98 30l98 30l30 98zM636 1276 l196 -60l-196 -60l-60 -196l-60 196l-196 60l196 60l60 196zM1566 798l98 -30l-98 -30l-30 -98l-30 98l-98 30l98 30l30 98zM926 1438l98 -30l-98 -30l-30 -98l-30 98l-98 30l98 30l30 98z" /> | |
| 218 | <glyph unicode="" horiz-adv-x="1792" d="M640 128q0 52 -38 90t-90 38t-90 -38t-38 -90t38 -90t90 -38t90 38t38 90zM256 640h384v256h-158q-13 0 -22 -9l-195 -195q-9 -9 -9 -22v-30zM1536 128q0 52 -38 90t-90 38t-90 -38t-38 -90t38 -90t90 -38t90 38t38 90zM1792 1216v-1024q0 -15 -4 -26.5t-13.5 -18.5 t-16.5 -11.5t-23.5 -6t-22.5 -2t-25.5 0t-22.5 0.5q0 -106 -75 -181t-181 -75t-181 75t-75 181h-384q0 -106 -75 -181t-181 -75t-181 75t-75 181h-64q-3 0 -22.5 -0.5t-25.5 0t-22.5 2t-23.5 6t-16.5 11.5t-13.5 18.5t-4 26.5q0 26 19 45t45 19v320q0 8 -0.5 35t0 38 t2.5 34.5t6.5 37t14 30.5t22.5 30l198 198q19 19 50.5 32t58.5 13h160v192q0 26 19 45t45 19h1024q26 0 45 -19t19 -45z" /> | |
| 219 | <glyph unicode="" d="M1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103q-111 0 -218 32q59 93 78 164q9 34 54 211q20 -39 73 -67.5t114 -28.5q121 0 216 68.5t147 188.5t52 270q0 114 -59.5 214t-172.5 163t-255 63q-105 0 -196 -29t-154.5 -77t-109 -110.5t-67 -129.5t-21.5 -134 q0 -104 40 -183t117 -111q30 -12 38 20q2 7 8 31t8 30q6 23 -11 43q-51 61 -51 151q0 151 104.5 259.5t273.5 108.5q151 0 235.5 -82t84.5 -213q0 -170 -68.5 -289t-175.5 -119q-61 0 -98 43.5t-23 104.5q8 35 26.5 93.5t30 103t11.5 75.5q0 50 -27 83t-77 33 q-62 0 -105 -57t-43 -142q0 -73 25 -122l-99 -418q-17 -70 -13 -177q-206 91 -333 281t-127 423q0 209 103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 220 | <glyph unicode="" d="M1248 1408q119 0 203.5 -84.5t84.5 -203.5v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-725q85 122 108 210q9 34 53 209q21 -39 73.5 -67t112.5 -28q181 0 295.5 147.5t114.5 373.5q0 84 -35 162.5t-96.5 139t-152.5 97t-197 36.5q-104 0 -194.5 -28.5t-153 -76.5 t-107.5 -109.5t-66.5 -128t-21.5 -132.5q0 -102 39.5 -180t116.5 -110q13 -5 23.5 0t14.5 19q10 44 15 61q6 23 -11 42q-50 62 -50 150q0 150 103.5 256.5t270.5 106.5q149 0 232.5 -81t83.5 -210q0 -168 -67.5 -286t-173.5 -118q-60 0 -97 43.5t-23 103.5q8 34 26.5 92.5 t29.5 102t11 74.5q0 49 -26.5 81.5t-75.5 32.5q-61 0 -103.5 -56.5t-42.5 -139.5q0 -72 24 -121l-98 -414q-24 -100 -7 -254h-183q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960z" /> | |
| 221 | <glyph unicode="" d="M829 318q0 -76 -58.5 -112.5t-139.5 -36.5q-41 0 -80.5 9.5t-75.5 28.5t-58 53t-22 78q0 46 25 80t65.5 51.5t82 25t84.5 7.5q20 0 31 -2q2 -1 23 -16.5t26 -19t23 -18t24.5 -22t19 -22.5t17 -26t9 -26.5t4.5 -31.5zM755 863q0 -60 -33 -99.5t-92 -39.5q-53 0 -93 42.5 t-57.5 96.5t-17.5 106q0 61 32 104t92 43q53 0 93.5 -45t58 -101t17.5 -107zM861 1120l88 64h-265q-85 0 -161 -32t-127.5 -98t-51.5 -153q0 -93 64.5 -154.5t158.5 -61.5q22 0 43 3q-13 -29 -13 -54q0 -44 40 -94q-175 -12 -257 -63q-47 -29 -75.5 -73t-28.5 -95 q0 -43 18.5 -77.5t48.5 -56.5t69 -37t77.5 -21t76.5 -6q60 0 120.5 15.5t113.5 46t86 82.5t33 117q0 49 -20 89.5t-49 66.5t-58 47.5t-49 44t-20 44.5t15.5 42.5t37.5 39.5t44 42t37.5 59.5t15.5 82.5q0 60 -22.5 99.5t-72.5 90.5h83zM1152 672h128v64h-128v128h-64v-128 h-128v-64h128v-160h64v160zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 222 | <glyph unicode="" horiz-adv-x="1664" d="M735 740q0 -36 32 -70.5t77.5 -68t90.5 -73.5t77 -104t32 -142q0 -90 -48 -173q-72 -122 -211 -179.5t-298 -57.5q-132 0 -246.5 41.5t-171.5 137.5q-37 60 -37 131q0 81 44.5 150t118.5 115q131 82 404 100q-32 42 -47.5 74t-15.5 73q0 36 21 85q-46 -4 -68 -4 q-148 0 -249.5 96.5t-101.5 244.5q0 82 36 159t99 131q77 66 182.5 98t217.5 32h418l-138 -88h-131q74 -63 112 -133t38 -160q0 -72 -24.5 -129.5t-59 -93t-69.5 -65t-59.5 -61.5t-24.5 -66zM589 836q38 0 78 16.5t66 43.5q53 57 53 159q0 58 -17 125t-48.5 129.5 t-84.5 103.5t-117 41q-42 0 -82.5 -19.5t-65.5 -52.5q-47 -59 -47 -160q0 -46 10 -97.5t31.5 -103t52 -92.5t75 -67t96.5 -26zM591 -37q58 0 111.5 13t99 39t73 73t27.5 109q0 25 -7 49t-14.5 42t-27 41.5t-29.5 35t-38.5 34.5t-36.5 29t-41.5 30t-36.5 26q-16 2 -48 2 q-53 0 -105 -7t-107.5 -25t-97 -46t-68.5 -74.5t-27 -105.5q0 -70 35 -123.5t91.5 -83t119 -44t127.5 -14.5zM1401 839h213v-108h-213v-219h-105v219h-212v108h212v217h105v-217z" /> | |
| 223 | <glyph unicode="" horiz-adv-x="1920" d="M768 384h384v96h-128v448h-114l-148 -137l77 -80q42 37 55 57h2v-288h-128v-96zM1280 640q0 -70 -21 -142t-59.5 -134t-101.5 -101t-138 -39t-138 39t-101.5 101t-59.5 134t-21 142t21 142t59.5 134t101.5 101t138 39t138 -39t101.5 -101t59.5 -134t21 -142zM1792 384 v512q-106 0 -181 75t-75 181h-1152q0 -106 -75 -181t-181 -75v-512q106 0 181 -75t75 -181h1152q0 106 75 181t181 75zM1920 1216v-1152q0 -26 -19 -45t-45 -19h-1792q-26 0 -45 19t-19 45v1152q0 26 19 45t45 19h1792q26 0 45 -19t19 -45z" /> | |
| 224 | <glyph unicode="" horiz-adv-x="1024" d="M1024 832q0 -26 -19 -45l-448 -448q-19 -19 -45 -19t-45 19l-448 448q-19 19 -19 45t19 45t45 19h896q26 0 45 -19t19 -45z" /> | |
| 225 | <glyph unicode="" horiz-adv-x="1024" d="M1024 320q0 -26 -19 -45t-45 -19h-896q-26 0 -45 19t-19 45t19 45l448 448q19 19 45 19t45 -19l448 -448q19 -19 19 -45z" /> | |
| 226 | <glyph unicode="" horiz-adv-x="640" d="M640 1088v-896q0 -26 -19 -45t-45 -19t-45 19l-448 448q-19 19 -19 45t19 45l448 448q19 19 45 19t45 -19t19 -45z" /> | |
| 227 | <glyph unicode="" horiz-adv-x="640" d="M576 640q0 -26 -19 -45l-448 -448q-19 -19 -45 -19t-45 19t-19 45v896q0 26 19 45t45 19t45 -19l448 -448q19 -19 19 -45z" /> | |
| 228 | <glyph unicode="" horiz-adv-x="1664" d="M160 0h608v1152h-640v-1120q0 -13 9.5 -22.5t22.5 -9.5zM1536 32v1120h-640v-1152h608q13 0 22.5 9.5t9.5 22.5zM1664 1248v-1216q0 -66 -47 -113t-113 -47h-1344q-66 0 -113 47t-47 113v1216q0 66 47 113t113 47h1344q66 0 113 -47t47 -113z" /> | |
| 229 | <glyph unicode="" horiz-adv-x="1024" d="M1024 448q0 -26 -19 -45l-448 -448q-19 -19 -45 -19t-45 19l-448 448q-19 19 -19 45t19 45t45 19h896q26 0 45 -19t19 -45zM1024 832q0 -26 -19 -45t-45 -19h-896q-26 0 -45 19t-19 45t19 45l448 448q19 19 45 19t45 -19l448 -448q19 -19 19 -45z" /> | |
| 230 | <glyph unicode="" horiz-adv-x="1024" d="M1024 448q0 -26 -19 -45l-448 -448q-19 -19 -45 -19t-45 19l-448 448q-19 19 -19 45t19 45t45 19h896q26 0 45 -19t19 -45z" /> | |
| 231 | <glyph unicode="" horiz-adv-x="1024" d="M1024 832q0 -26 -19 -45t-45 -19h-896q-26 0 -45 19t-19 45t19 45l448 448q19 19 45 19t45 -19l448 -448q19 -19 19 -45z" /> | |
| 232 | <glyph unicode="" horiz-adv-x="1792" d="M1792 826v-794q0 -66 -47 -113t-113 -47h-1472q-66 0 -113 47t-47 113v794q44 -49 101 -87q362 -246 497 -345q57 -42 92.5 -65.5t94.5 -48t110 -24.5h1h1q51 0 110 24.5t94.5 48t92.5 65.5q170 123 498 345q57 39 100 87zM1792 1120q0 -79 -49 -151t-122 -123 q-376 -261 -468 -325q-10 -7 -42.5 -30.5t-54 -38t-52 -32.5t-57.5 -27t-50 -9h-1h-1q-23 0 -50 9t-57.5 27t-52 32.5t-54 38t-42.5 30.5q-91 64 -262 182.5t-205 142.5q-62 42 -117 115.5t-55 136.5q0 78 41.5 130t118.5 52h1472q65 0 112.5 -47t47.5 -113z" /> | |
| 233 | <glyph unicode="" d="M349 911v-991h-330v991h330zM370 1217q1 -73 -50.5 -122t-135.5 -49h-2q-82 0 -132 49t-50 122q0 74 51.5 122.5t134.5 48.5t133 -48.5t51 -122.5zM1536 488v-568h-329v530q0 105 -40.5 164.5t-126.5 59.5q-63 0 -105.5 -34.5t-63.5 -85.5q-11 -30 -11 -81v-553h-329 q2 399 2 647t-1 296l-1 48h329v-144h-2q20 32 41 56t56.5 52t87 43.5t114.5 15.5q171 0 275 -113.5t104 -332.5z" /> | |
| 234 | <glyph unicode="" d="M1536 640q0 -156 -61 -298t-164 -245t-245 -164t-298 -61q-172 0 -327 72.5t-264 204.5q-7 10 -6.5 22.5t8.5 20.5l137 138q10 9 25 9q16 -2 23 -12q73 -95 179 -147t225 -52q104 0 198.5 40.5t163.5 109.5t109.5 163.5t40.5 198.5t-40.5 198.5t-109.5 163.5 t-163.5 109.5t-198.5 40.5q-98 0 -188 -35.5t-160 -101.5l137 -138q31 -30 14 -69q-17 -40 -59 -40h-448q-26 0 -45 19t-19 45v448q0 42 40 59q39 17 69 -14l130 -129q107 101 244.5 156.5t284.5 55.5q156 0 298 -61t245 -164t164 -245t61 -298z" /> | |
| 235 | <glyph unicode="" horiz-adv-x="1792" d="M1771 0q0 -53 -37 -90l-107 -108q-39 -37 -91 -37q-53 0 -90 37l-363 364q-38 36 -38 90q0 53 43 96l-256 256l-126 -126q-14 -14 -34 -14t-34 14q2 -2 12.5 -12t12.5 -13t10 -11.5t10 -13.5t6 -13.5t5.5 -16.5t1.5 -18q0 -38 -28 -68q-3 -3 -16.5 -18t-19 -20.5 t-18.5 -16.5t-22 -15.5t-22 -9t-26 -4.5q-40 0 -68 28l-408 408q-28 28 -28 68q0 13 4.5 26t9 22t15.5 22t16.5 18.5t20.5 19t18 16.5q30 28 68 28q10 0 18 -1.5t16.5 -5.5t13.5 -6t13.5 -10t11.5 -10t13 -12.5t12 -12.5q-14 14 -14 34t14 34l348 348q14 14 34 14t34 -14 q-2 2 -12.5 12t-12.5 13t-10 11.5t-10 13.5t-6 13.5t-5.5 16.5t-1.5 18q0 38 28 68q3 3 16.5 18t19 20.5t18.5 16.5t22 15.5t22 9t26 4.5q40 0 68 -28l408 -408q28 -28 28 -68q0 -13 -4.5 -26t-9 -22t-15.5 -22t-16.5 -18.5t-20.5 -19t-18 -16.5q-30 -28 -68 -28 q-10 0 -18 1.5t-16.5 5.5t-13.5 6t-13.5 10t-11.5 10t-13 12.5t-12 12.5q14 -14 14 -34t-14 -34l-126 -126l256 -256q43 43 96 43q52 0 91 -37l363 -363q37 -39 37 -91z" /> | |
| 236 | <glyph unicode="" horiz-adv-x="1792" d="M384 384q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM576 832q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1004 351l101 382q6 26 -7.5 48.5t-38.5 29.5 t-48 -6.5t-30 -39.5l-101 -382q-60 -5 -107 -43.5t-63 -98.5q-20 -77 20 -146t117 -89t146 20t89 117q16 60 -6 117t-72 91zM1664 384q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1024 1024q0 53 -37.5 90.5 t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1472 832q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1792 384q0 -261 -141 -483q-19 -29 -54 -29h-1402q-35 0 -54 29 q-141 221 -141 483q0 182 71 348t191 286t286 191t348 71t348 -71t286 -191t191 -286t71 -348z" /> | |
| 237 | <glyph unicode="" horiz-adv-x="1792" d="M896 1152q-204 0 -381.5 -69.5t-282 -187.5t-104.5 -255q0 -112 71.5 -213.5t201.5 -175.5l87 -50l-27 -96q-24 -91 -70 -172q152 63 275 171l43 38l57 -6q69 -8 130 -8q204 0 381.5 69.5t282 187.5t104.5 255t-104.5 255t-282 187.5t-381.5 69.5zM1792 640 q0 -174 -120 -321.5t-326 -233t-450 -85.5q-70 0 -145 8q-198 -175 -460 -242q-49 -14 -114 -22h-5q-15 0 -27 10.5t-16 27.5v1q-3 4 -0.5 12t2 10t4.5 9.5l6 9t7 8.5t8 9q7 8 31 34.5t34.5 38t31 39.5t32.5 51t27 59t26 76q-157 89 -247.5 220t-90.5 281q0 174 120 321.5 t326 233t450 85.5t450 -85.5t326 -233t120 -321.5z" /> | |
| 238 | <glyph unicode="" horiz-adv-x="1792" d="M704 1152q-153 0 -286 -52t-211.5 -141t-78.5 -191q0 -82 53 -158t149 -132l97 -56l-35 -84q34 20 62 39l44 31l53 -10q78 -14 153 -14q153 0 286 52t211.5 141t78.5 191t-78.5 191t-211.5 141t-286 52zM704 1280q191 0 353.5 -68.5t256.5 -186.5t94 -257t-94 -257 t-256.5 -186.5t-353.5 -68.5q-86 0 -176 16q-124 -88 -278 -128q-36 -9 -86 -16h-3q-11 0 -20.5 8t-11.5 21q-1 3 -1 6.5t0.5 6.5t2 6l2.5 5t3.5 5.5t4 5t4.5 5t4 4.5q5 6 23 25t26 29.5t22.5 29t25 38.5t20.5 44q-124 72 -195 177t-71 224q0 139 94 257t256.5 186.5 t353.5 68.5zM1526 111q10 -24 20.5 -44t25 -38.5t22.5 -29t26 -29.5t23 -25q1 -1 4 -4.5t4.5 -5t4 -5t3.5 -5.5l2.5 -5t2 -6t0.5 -6.5t-1 -6.5q-3 -14 -13 -22t-22 -7q-50 7 -86 16q-154 40 -278 128q-90 -16 -176 -16q-271 0 -472 132q58 -4 88 -4q161 0 309 45t264 129 q125 92 192 212t67 254q0 77 -23 152q129 -71 204 -178t75 -230q0 -120 -71 -224.5t-195 -176.5z" /> | |
| 239 | <glyph unicode="" horiz-adv-x="896" d="M885 970q18 -20 7 -44l-540 -1157q-13 -25 -42 -25q-4 0 -14 2q-17 5 -25.5 19t-4.5 30l197 808l-406 -101q-4 -1 -12 -1q-18 0 -31 11q-18 15 -13 39l201 825q4 14 16 23t28 9h328q19 0 32 -12.5t13 -29.5q0 -8 -5 -18l-171 -463l396 98q8 2 12 2q19 0 34 -15z" /> | |
| 240 | <glyph unicode="" horiz-adv-x="1792" d="M1792 288v-320q0 -40 -28 -68t-68 -28h-320q-40 0 -68 28t-28 68v320q0 40 28 68t68 28h96v192h-512v-192h96q40 0 68 -28t28 -68v-320q0 -40 -28 -68t-68 -28h-320q-40 0 -68 28t-28 68v320q0 40 28 68t68 28h96v192h-512v-192h96q40 0 68 -28t28 -68v-320 q0 -40 -28 -68t-68 -28h-320q-40 0 -68 28t-28 68v320q0 40 28 68t68 28h96v192q0 52 38 90t90 38h512v192h-96q-40 0 -68 28t-28 68v320q0 40 28 68t68 28h320q40 0 68 -28t28 -68v-320q0 -40 -28 -68t-68 -28h-96v-192h512q52 0 90 -38t38 -90v-192h96q40 0 68 -28t28 -68 z" /> | |
| 241 | <glyph unicode="" horiz-adv-x="1664" d="M896 708v-580q0 -104 -76 -180t-180 -76t-180 76t-76 180q0 26 19 45t45 19t45 -19t19 -45q0 -50 39 -89t89 -39t89 39t39 89v580q33 11 64 11t64 -11zM1664 681q0 -13 -9.5 -22.5t-22.5 -9.5q-11 0 -23 10q-49 46 -93 69t-102 23q-68 0 -128 -37t-103 -97 q-7 -10 -17.5 -28t-14.5 -24q-11 -17 -28 -17q-18 0 -29 17q-4 6 -14.5 24t-17.5 28q-43 60 -102.5 97t-127.5 37t-127.5 -37t-102.5 -97q-7 -10 -17.5 -28t-14.5 -24q-11 -17 -29 -17q-17 0 -28 17q-4 6 -14.5 24t-17.5 28q-43 60 -103 97t-128 37q-58 0 -102 -23t-93 -69 q-12 -10 -23 -10q-13 0 -22.5 9.5t-9.5 22.5q0 5 1 7q45 183 172.5 319.5t298 204.5t360.5 68q140 0 274.5 -40t246.5 -113.5t194.5 -187t115.5 -251.5q1 -2 1 -7zM896 1408v-98q-42 2 -64 2t-64 -2v98q0 26 19 45t45 19t45 -19t19 -45z" /> | |
| 242 | <glyph unicode="" horiz-adv-x="1792" d="M768 -128h896v640h-416q-40 0 -68 28t-28 68v416h-384v-1152zM1024 1312v64q0 13 -9.5 22.5t-22.5 9.5h-704q-13 0 -22.5 -9.5t-9.5 -22.5v-64q0 -13 9.5 -22.5t22.5 -9.5h704q13 0 22.5 9.5t9.5 22.5zM1280 640h299l-299 299v-299zM1792 512v-672q0 -40 -28 -68t-68 -28 h-960q-40 0 -68 28t-28 68v160h-544q-40 0 -68 28t-28 68v1344q0 40 28 68t68 28h1088q40 0 68 -28t28 -68v-328q21 -13 36 -28l408 -408q28 -28 48 -76t20 -88z" /> | |
| 243 | <glyph unicode="" horiz-adv-x="1024" d="M736 960q0 -13 -9.5 -22.5t-22.5 -9.5t-22.5 9.5t-9.5 22.5q0 46 -54 71t-106 25q-13 0 -22.5 9.5t-9.5 22.5t9.5 22.5t22.5 9.5q50 0 99.5 -16t87 -54t37.5 -90zM896 960q0 72 -34.5 134t-90 101.5t-123 62t-136.5 22.5t-136.5 -22.5t-123 -62t-90 -101.5t-34.5 -134 q0 -101 68 -180q10 -11 30.5 -33t30.5 -33q128 -153 141 -298h228q13 145 141 298q10 11 30.5 33t30.5 33q68 79 68 180zM1024 960q0 -155 -103 -268q-45 -49 -74.5 -87t-59.5 -95.5t-34 -107.5q47 -28 47 -82q0 -37 -25 -64q25 -27 25 -64q0 -52 -45 -81q13 -23 13 -47 q0 -46 -31.5 -71t-77.5 -25q-20 -44 -60 -70t-87 -26t-87 26t-60 70q-46 0 -77.5 25t-31.5 71q0 24 13 47q-45 29 -45 81q0 37 25 64q-25 27 -25 64q0 54 47 82q-4 50 -34 107.5t-59.5 95.5t-74.5 87q-103 113 -103 268q0 99 44.5 184.5t117 142t164 89t186.5 32.5 t186.5 -32.5t164 -89t117 -142t44.5 -184.5z" /> | |
| 244 | <glyph unicode="" horiz-adv-x="1792" d="M1792 352v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-1376v-192q0 -13 -9.5 -22.5t-22.5 -9.5q-12 0 -24 10l-319 320q-9 9 -9 22q0 14 9 23l320 320q9 9 23 9q13 0 22.5 -9.5t9.5 -22.5v-192h1376q13 0 22.5 -9.5t9.5 -22.5zM1792 896q0 -14 -9 -23l-320 -320q-9 -9 -23 -9 q-13 0 -22.5 9.5t-9.5 22.5v192h-1376q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h1376v192q0 14 9 23t23 9q12 0 24 -10l319 -319q9 -9 9 -23z" /> | |
| 245 | <glyph unicode="" horiz-adv-x="1920" d="M1280 608q0 14 -9 23t-23 9h-224v352q0 13 -9.5 22.5t-22.5 9.5h-192q-13 0 -22.5 -9.5t-9.5 -22.5v-352h-224q-13 0 -22.5 -9.5t-9.5 -22.5q0 -14 9 -23l352 -352q9 -9 23 -9t23 9l351 351q10 12 10 24zM1920 384q0 -159 -112.5 -271.5t-271.5 -112.5h-1088 q-185 0 -316.5 131.5t-131.5 316.5q0 130 70 240t188 165q-2 30 -2 43q0 212 150 362t362 150q156 0 285.5 -87t188.5 -231q71 62 166 62q106 0 181 -75t75 -181q0 -76 -41 -138q130 -31 213.5 -135.5t83.5 -238.5z" /> | |
| 246 | <glyph unicode="" horiz-adv-x="1920" d="M1280 672q0 14 -9 23l-352 352q-9 9 -23 9t-23 -9l-351 -351q-10 -12 -10 -24q0 -14 9 -23t23 -9h224v-352q0 -13 9.5 -22.5t22.5 -9.5h192q13 0 22.5 9.5t9.5 22.5v352h224q13 0 22.5 9.5t9.5 22.5zM1920 384q0 -159 -112.5 -271.5t-271.5 -112.5h-1088 q-185 0 -316.5 131.5t-131.5 316.5q0 130 70 240t188 165q-2 30 -2 43q0 212 150 362t362 150q156 0 285.5 -87t188.5 -231q71 62 166 62q106 0 181 -75t75 -181q0 -76 -41 -138q130 -31 213.5 -135.5t83.5 -238.5z" /> | |
| 247 | <glyph unicode="" horiz-adv-x="1408" d="M384 192q0 -26 -19 -45t-45 -19t-45 19t-19 45t19 45t45 19t45 -19t19 -45zM1408 131q0 -121 -73 -190t-194 -69h-874q-121 0 -194 69t-73 190q0 68 5.5 131t24 138t47.5 132.5t81 103t120 60.5q-22 -52 -22 -120v-203q-58 -20 -93 -70t-35 -111q0 -80 56 -136t136 -56 t136 56t56 136q0 61 -35.5 111t-92.5 70v203q0 62 25 93q132 -104 295 -104t295 104q25 -31 25 -93v-64q-106 0 -181 -75t-75 -181v-89q-32 -29 -32 -71q0 -40 28 -68t68 -28t68 28t28 68q0 42 -32 71v89q0 52 38 90t90 38t90 -38t38 -90v-89q-32 -29 -32 -71q0 -40 28 -68 t68 -28t68 28t28 68q0 42 -32 71v89q0 68 -34.5 127.5t-93.5 93.5q0 10 0.5 42.5t0 48t-2.5 41.5t-7 47t-13 40q68 -15 120 -60.5t81 -103t47.5 -132.5t24 -138t5.5 -131zM1088 1024q0 -159 -112.5 -271.5t-271.5 -112.5t-271.5 112.5t-112.5 271.5t112.5 271.5t271.5 112.5 t271.5 -112.5t112.5 -271.5z" /> | |
| 248 | <glyph unicode="" horiz-adv-x="1408" d="M1280 832q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45t45 -19t45 19t19 45zM1408 832q0 -62 -35.5 -111t-92.5 -70v-395q0 -159 -131.5 -271.5t-316.5 -112.5t-316.5 112.5t-131.5 271.5v132q-164 20 -274 128t-110 252v512q0 26 19 45t45 19q6 0 16 -2q17 30 47 48 t65 18q53 0 90.5 -37.5t37.5 -90.5t-37.5 -90.5t-90.5 -37.5q-33 0 -64 18v-402q0 -106 94 -181t226 -75t226 75t94 181v402q-31 -18 -64 -18q-53 0 -90.5 37.5t-37.5 90.5t37.5 90.5t90.5 37.5q35 0 65 -18t47 -48q10 2 16 2q26 0 45 -19t19 -45v-512q0 -144 -110 -252 t-274 -128v-132q0 -106 94 -181t226 -75t226 75t94 181v395q-57 21 -92.5 70t-35.5 111q0 80 56 136t136 56t136 -56t56 -136z" /> | |
| 249 | <glyph unicode="" horiz-adv-x="1792" d="M640 1152h512v128h-512v-128zM288 1152v-1280h-64q-92 0 -158 66t-66 158v832q0 92 66 158t158 66h64zM1408 1152v-1280h-1024v1280h128v160q0 40 28 68t68 28h576q40 0 68 -28t28 -68v-160h128zM1792 928v-832q0 -92 -66 -158t-158 -66h-64v1280h64q92 0 158 -66 t66 -158z" /> | |
| 250 | <glyph unicode="" horiz-adv-x="1792" d="M912 -160q0 16 -16 16q-59 0 -101.5 42.5t-42.5 101.5q0 16 -16 16t-16 -16q0 -73 51.5 -124.5t124.5 -51.5q16 0 16 16zM1728 128q0 -52 -38 -90t-90 -38h-448q0 -106 -75 -181t-181 -75t-181 75t-75 181h-448q-52 0 -90 38t-38 90q50 42 91 88t85 119.5t74.5 158.5 t50 206t19.5 260q0 152 117 282.5t307 158.5q-8 19 -8 39q0 40 28 68t68 28t68 -28t28 -68q0 -20 -8 -39q190 -28 307 -158.5t117 -282.5q0 -139 19.5 -260t50 -206t74.5 -158.5t85 -119.5t91 -88z" /> | |
| 251 | <glyph unicode="" horiz-adv-x="1920" d="M1664 896q0 80 -56 136t-136 56h-64v-384h64q80 0 136 56t56 136zM0 128h1792q0 -106 -75 -181t-181 -75h-1280q-106 0 -181 75t-75 181zM1856 896q0 -159 -112.5 -271.5t-271.5 -112.5h-64v-32q0 -92 -66 -158t-158 -66h-704q-92 0 -158 66t-66 158v736q0 26 19 45 t45 19h1152q159 0 271.5 -112.5t112.5 -271.5z" /> | |
| 252 | <glyph unicode="" horiz-adv-x="1408" d="M640 1472v-640q0 -61 -35.5 -111t-92.5 -70v-779q0 -52 -38 -90t-90 -38h-128q-52 0 -90 38t-38 90v779q-57 20 -92.5 70t-35.5 111v640q0 26 19 45t45 19t45 -19t19 -45v-416q0 -26 19 -45t45 -19t45 19t19 45v416q0 26 19 45t45 19t45 -19t19 -45v-416q0 -26 19 -45 t45 -19t45 19t19 45v416q0 26 19 45t45 19t45 -19t19 -45zM1408 1472v-1600q0 -52 -38 -90t-90 -38h-128q-52 0 -90 38t-38 90v512h-224q-13 0 -22.5 9.5t-9.5 22.5v800q0 132 94 226t226 94h256q26 0 45 -19t19 -45z" /> | |
| 253 | <glyph unicode="" d="M1468 1156q28 -28 48 -76t20 -88v-1152q0 -40 -28 -68t-68 -28h-1344q-40 0 -68 28t-28 68v1600q0 40 28 68t68 28h896q40 0 88 -20t76 -48zM1024 1400v-376h376q-10 29 -22 41l-313 313q-12 12 -41 22zM1408 -128v1024h-416q-40 0 -68 28t-28 68v416h-768v-1536h1280z M384 736q0 14 9 23t23 9h704q14 0 23 -9t9 -23v-64q0 -14 -9 -23t-23 -9h-704q-14 0 -23 9t-9 23v64zM1120 512q14 0 23 -9t9 -23v-64q0 -14 -9 -23t-23 -9h-704q-14 0 -23 9t-9 23v64q0 14 9 23t23 9h704zM1120 256q14 0 23 -9t9 -23v-64q0 -14 -9 -23t-23 -9h-704 q-14 0 -23 9t-9 23v64q0 14 9 23t23 9h704z" /> | |
| 254 | <glyph unicode="" horiz-adv-x="1408" d="M384 224v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM384 480v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5z M640 480v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM384 736v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5z M1152 224v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM896 480v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5z M640 736v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM384 992v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5z M1152 480v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM896 736v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5z M640 992v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM384 1248v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5z M1152 736v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM896 992v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5z M640 1248v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM1152 992v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5z M896 1248v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM1152 1248v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5z M896 -128h384v1536h-1152v-1536h384v224q0 13 9.5 22.5t22.5 9.5h320q13 0 22.5 -9.5t9.5 -22.5v-224zM1408 1472v-1664q0 -26 -19 -45t-45 -19h-1280q-26 0 -45 19t-19 45v1664q0 26 19 45t45 19h1280q26 0 45 -19t19 -45z" /> | |
| 255 | <glyph unicode="" horiz-adv-x="1408" d="M384 224v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM384 480v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5z M640 480v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM384 736v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5z M1152 224v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM896 480v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5z M640 736v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM1152 480v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5z M896 736v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5zM1152 736v-64q0 -13 -9.5 -22.5t-22.5 -9.5h-64q-13 0 -22.5 9.5t-9.5 22.5v64q0 13 9.5 22.5t22.5 9.5h64q13 0 22.5 -9.5t9.5 -22.5z M896 -128h384v1152h-256v-32q0 -40 -28 -68t-68 -28h-448q-40 0 -68 28t-28 68v32h-256v-1152h384v224q0 13 9.5 22.5t22.5 9.5h320q13 0 22.5 -9.5t9.5 -22.5v-224zM896 1056v320q0 13 -9.5 22.5t-22.5 9.5h-64q-13 0 -22.5 -9.5t-9.5 -22.5v-96h-128v96q0 13 -9.5 22.5 t-22.5 9.5h-64q-13 0 -22.5 -9.5t-9.5 -22.5v-320q0 -13 9.5 -22.5t22.5 -9.5h64q13 0 22.5 9.5t9.5 22.5v96h128v-96q0 -13 9.5 -22.5t22.5 -9.5h64q13 0 22.5 9.5t9.5 22.5zM1408 1088v-1280q0 -26 -19 -45t-45 -19h-1280q-26 0 -45 19t-19 45v1280q0 26 19 45t45 19h320 v288q0 40 28 68t68 28h448q40 0 68 -28t28 -68v-288h320q26 0 45 -19t19 -45z" /> | |
| 256 | <glyph unicode="" horiz-adv-x="1920" d="M640 128q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM256 640h384v256h-158q-14 -2 -22 -9l-195 -195q-7 -12 -9 -22v-30zM1536 128q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5 t90.5 37.5t37.5 90.5zM1664 800v192q0 14 -9 23t-23 9h-224v224q0 14 -9 23t-23 9h-192q-14 0 -23 -9t-9 -23v-224h-224q-14 0 -23 -9t-9 -23v-192q0 -14 9 -23t23 -9h224v-224q0 -14 9 -23t23 -9h192q14 0 23 9t9 23v224h224q14 0 23 9t9 23zM1920 1344v-1152 q0 -26 -19 -45t-45 -19h-192q0 -106 -75 -181t-181 -75t-181 75t-75 181h-384q0 -106 -75 -181t-181 -75t-181 75t-75 181h-128q-26 0 -45 19t-19 45t19 45t45 19v416q0 26 13 58t32 51l198 198q19 19 51 32t58 13h160v320q0 26 19 45t45 19h1152q26 0 45 -19t19 -45z" /> | |
| 257 | <glyph unicode="" horiz-adv-x="1792" d="M1280 416v192q0 14 -9 23t-23 9h-224v224q0 14 -9 23t-23 9h-192q-14 0 -23 -9t-9 -23v-224h-224q-14 0 -23 -9t-9 -23v-192q0 -14 9 -23t23 -9h224v-224q0 -14 9 -23t23 -9h192q14 0 23 9t9 23v224h224q14 0 23 9t9 23zM640 1152h512v128h-512v-128zM256 1152v-1280h-32 q-92 0 -158 66t-66 158v832q0 92 66 158t158 66h32zM1440 1152v-1280h-1088v1280h160v160q0 40 28 68t68 28h576q40 0 68 -28t28 -68v-160h160zM1792 928v-832q0 -92 -66 -158t-158 -66h-32v1280h32q92 0 158 -66t66 -158z" /> | |
| 258 | <glyph unicode="" horiz-adv-x="1920" d="M1920 576q-1 -32 -288 -96l-352 -32l-224 -64h-64l-293 -352h69q26 0 45 -4.5t19 -11.5t-19 -11.5t-45 -4.5h-96h-160h-64v32h64v416h-160l-192 -224h-96l-32 32v192h32v32h128v8l-192 24v128l192 24v8h-128v32h-32v192l32 32h96l192 -224h160v416h-64v32h64h160h96 q26 0 45 -4.5t19 -11.5t-19 -11.5t-45 -4.5h-69l293 -352h64l224 -64l352 -32q261 -58 287 -93z" /> | |
| 259 | <glyph unicode="" horiz-adv-x="1664" d="M640 640v384h-256v-256q0 -53 37.5 -90.5t90.5 -37.5h128zM1664 192v-192h-1152v192l128 192h-128q-159 0 -271.5 112.5t-112.5 271.5v320l-64 64l32 128h480l32 128h960l32 -192l-64 -32v-800z" /> | |
| 260 | <glyph unicode="" d="M1280 192v896q0 26 -19 45t-45 19h-128q-26 0 -45 -19t-19 -45v-320h-512v320q0 26 -19 45t-45 19h-128q-26 0 -45 -19t-19 -45v-896q0 -26 19 -45t45 -19h128q26 0 45 19t19 45v320h512v-320q0 -26 19 -45t45 -19h128q26 0 45 19t19 45zM1536 1120v-960 q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 261 | <glyph unicode="" d="M1280 576v128q0 26 -19 45t-45 19h-320v320q0 26 -19 45t-45 19h-128q-26 0 -45 -19t-19 -45v-320h-320q-26 0 -45 -19t-19 -45v-128q0 -26 19 -45t45 -19h320v-320q0 -26 19 -45t45 -19h128q26 0 45 19t19 45v320h320q26 0 45 19t19 45zM1536 1120v-960 q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 262 | <glyph unicode="" horiz-adv-x="1024" d="M627 160q0 -13 -10 -23l-50 -50q-10 -10 -23 -10t-23 10l-466 466q-10 10 -10 23t10 23l466 466q10 10 23 10t23 -10l50 -50q10 -10 10 -23t-10 -23l-393 -393l393 -393q10 -10 10 -23zM1011 160q0 -13 -10 -23l-50 -50q-10 -10 -23 -10t-23 10l-466 466q-10 10 -10 23 t10 23l466 466q10 10 23 10t23 -10l50 -50q10 -10 10 -23t-10 -23l-393 -393l393 -393q10 -10 10 -23z" /> | |
| 263 | <glyph unicode="" horiz-adv-x="1024" d="M595 576q0 -13 -10 -23l-466 -466q-10 -10 -23 -10t-23 10l-50 50q-10 10 -10 23t10 23l393 393l-393 393q-10 10 -10 23t10 23l50 50q10 10 23 10t23 -10l466 -466q10 -10 10 -23zM979 576q0 -13 -10 -23l-466 -466q-10 -10 -23 -10t-23 10l-50 50q-10 10 -10 23t10 23 l393 393l-393 393q-10 10 -10 23t10 23l50 50q10 10 23 10t23 -10l466 -466q10 -10 10 -23z" /> | |
| 264 | <glyph unicode="" horiz-adv-x="1152" d="M1075 224q0 -13 -10 -23l-50 -50q-10 -10 -23 -10t-23 10l-393 393l-393 -393q-10 -10 -23 -10t-23 10l-50 50q-10 10 -10 23t10 23l466 466q10 10 23 10t23 -10l466 -466q10 -10 10 -23zM1075 608q0 -13 -10 -23l-50 -50q-10 -10 -23 -10t-23 10l-393 393l-393 -393 q-10 -10 -23 -10t-23 10l-50 50q-10 10 -10 23t10 23l466 466q10 10 23 10t23 -10l466 -466q10 -10 10 -23z" /> | |
| 265 | <glyph unicode="" horiz-adv-x="1152" d="M1075 672q0 -13 -10 -23l-466 -466q-10 -10 -23 -10t-23 10l-466 466q-10 10 -10 23t10 23l50 50q10 10 23 10t23 -10l393 -393l393 393q10 10 23 10t23 -10l50 -50q10 -10 10 -23zM1075 1056q0 -13 -10 -23l-466 -466q-10 -10 -23 -10t-23 10l-466 466q-10 10 -10 23 t10 23l50 50q10 10 23 10t23 -10l393 -393l393 393q10 10 23 10t23 -10l50 -50q10 -10 10 -23z" /> | |
| 266 | <glyph unicode="" horiz-adv-x="640" d="M627 992q0 -13 -10 -23l-393 -393l393 -393q10 -10 10 -23t-10 -23l-50 -50q-10 -10 -23 -10t-23 10l-466 466q-10 10 -10 23t10 23l466 466q10 10 23 10t23 -10l50 -50q10 -10 10 -23z" /> | |
| 267 | <glyph unicode="" horiz-adv-x="640" d="M595 576q0 -13 -10 -23l-466 -466q-10 -10 -23 -10t-23 10l-50 50q-10 10 -10 23t10 23l393 393l-393 393q-10 10 -10 23t10 23l50 50q10 10 23 10t23 -10l466 -466q10 -10 10 -23z" /> | |
| 268 | <glyph unicode="" horiz-adv-x="1152" d="M1075 352q0 -13 -10 -23l-50 -50q-10 -10 -23 -10t-23 10l-393 393l-393 -393q-10 -10 -23 -10t-23 10l-50 50q-10 10 -10 23t10 23l466 466q10 10 23 10t23 -10l466 -466q10 -10 10 -23z" /> | |
| 269 | <glyph unicode="" horiz-adv-x="1152" d="M1075 800q0 -13 -10 -23l-466 -466q-10 -10 -23 -10t-23 10l-466 466q-10 10 -10 23t10 23l50 50q10 10 23 10t23 -10l393 -393l393 393q10 10 23 10t23 -10l50 -50q10 -10 10 -23z" /> | |
| 270 | <glyph unicode="" horiz-adv-x="1920" d="M1792 544v832q0 13 -9.5 22.5t-22.5 9.5h-1600q-13 0 -22.5 -9.5t-9.5 -22.5v-832q0 -13 9.5 -22.5t22.5 -9.5h1600q13 0 22.5 9.5t9.5 22.5zM1920 1376v-1088q0 -66 -47 -113t-113 -47h-544q0 -37 16 -77.5t32 -71t16 -43.5q0 -26 -19 -45t-45 -19h-512q-26 0 -45 19 t-19 45q0 14 16 44t32 70t16 78h-544q-66 0 -113 47t-47 113v1088q0 66 47 113t113 47h1600q66 0 113 -47t47 -113z" /> | |
| 271 | <glyph unicode="" horiz-adv-x="1920" d="M416 256q-66 0 -113 47t-47 113v704q0 66 47 113t113 47h1088q66 0 113 -47t47 -113v-704q0 -66 -47 -113t-113 -47h-1088zM384 1120v-704q0 -13 9.5 -22.5t22.5 -9.5h1088q13 0 22.5 9.5t9.5 22.5v704q0 13 -9.5 22.5t-22.5 9.5h-1088q-13 0 -22.5 -9.5t-9.5 -22.5z M1760 192h160v-96q0 -40 -47 -68t-113 -28h-1600q-66 0 -113 28t-47 68v96h160h1600zM1040 96q16 0 16 16t-16 16h-160q-16 0 -16 -16t16 -16h160z" /> | |
| 272 | <glyph unicode="" horiz-adv-x="1152" d="M640 128q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45t45 -19t45 19t19 45zM1024 288v960q0 13 -9.5 22.5t-22.5 9.5h-832q-13 0 -22.5 -9.5t-9.5 -22.5v-960q0 -13 9.5 -22.5t22.5 -9.5h832q13 0 22.5 9.5t9.5 22.5zM1152 1248v-1088q0 -66 -47 -113t-113 -47h-832 q-66 0 -113 47t-47 113v1088q0 66 47 113t113 47h832q66 0 113 -47t47 -113z" /> | |
| 273 | <glyph unicode="" horiz-adv-x="768" d="M464 128q0 33 -23.5 56.5t-56.5 23.5t-56.5 -23.5t-23.5 -56.5t23.5 -56.5t56.5 -23.5t56.5 23.5t23.5 56.5zM672 288v704q0 13 -9.5 22.5t-22.5 9.5h-512q-13 0 -22.5 -9.5t-9.5 -22.5v-704q0 -13 9.5 -22.5t22.5 -9.5h512q13 0 22.5 9.5t9.5 22.5zM480 1136 q0 16 -16 16h-160q-16 0 -16 -16t16 -16h160q16 0 16 16zM768 1152v-1024q0 -52 -38 -90t-90 -38h-512q-52 0 -90 38t-38 90v1024q0 52 38 90t90 38h512q52 0 90 -38t38 -90z" /> | |
| 274 | <glyph unicode="" d="M768 1184q-148 0 -273 -73t-198 -198t-73 -273t73 -273t198 -198t273 -73t273 73t198 198t73 273t-73 273t-198 198t-273 73zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103 t279.5 -279.5t103 -385.5z" /> | |
| 275 | <glyph unicode="" horiz-adv-x="1664" d="M768 576v-384q0 -80 -56 -136t-136 -56h-384q-80 0 -136 56t-56 136v704q0 104 40.5 198.5t109.5 163.5t163.5 109.5t198.5 40.5h64q26 0 45 -19t19 -45v-128q0 -26 -19 -45t-45 -19h-64q-106 0 -181 -75t-75 -181v-32q0 -40 28 -68t68 -28h224q80 0 136 -56t56 -136z M1664 576v-384q0 -80 -56 -136t-136 -56h-384q-80 0 -136 56t-56 136v704q0 104 40.5 198.5t109.5 163.5t163.5 109.5t198.5 40.5h64q26 0 45 -19t19 -45v-128q0 -26 -19 -45t-45 -19h-64q-106 0 -181 -75t-75 -181v-32q0 -40 28 -68t68 -28h224q80 0 136 -56t56 -136z" /> | |
| 276 | <glyph unicode="" horiz-adv-x="1664" d="M768 1216v-704q0 -104 -40.5 -198.5t-109.5 -163.5t-163.5 -109.5t-198.5 -40.5h-64q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h64q106 0 181 75t75 181v32q0 40 -28 68t-68 28h-224q-80 0 -136 56t-56 136v384q0 80 56 136t136 56h384q80 0 136 -56t56 -136zM1664 1216 v-704q0 -104 -40.5 -198.5t-109.5 -163.5t-163.5 -109.5t-198.5 -40.5h-64q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h64q106 0 181 75t75 181v32q0 40 -28 68t-68 28h-224q-80 0 -136 56t-56 136v384q0 80 56 136t136 56h384q80 0 136 -56t56 -136z" /> | |
| 277 | <glyph unicode="" horiz-adv-x="1568" d="M496 192q0 -60 -42.5 -102t-101.5 -42q-60 0 -102 42t-42 102t42 102t102 42q59 0 101.5 -42t42.5 -102zM928 0q0 -53 -37.5 -90.5t-90.5 -37.5t-90.5 37.5t-37.5 90.5t37.5 90.5t90.5 37.5t90.5 -37.5t37.5 -90.5zM320 640q0 -66 -47 -113t-113 -47t-113 47t-47 113 t47 113t113 47t113 -47t47 -113zM1360 192q0 -46 -33 -79t-79 -33t-79 33t-33 79t33 79t79 33t79 -33t33 -79zM528 1088q0 -73 -51.5 -124.5t-124.5 -51.5t-124.5 51.5t-51.5 124.5t51.5 124.5t124.5 51.5t124.5 -51.5t51.5 -124.5zM992 1280q0 -80 -56 -136t-136 -56 t-136 56t-56 136t56 136t136 56t136 -56t56 -136zM1536 640q0 -40 -28 -68t-68 -28t-68 28t-28 68t28 68t68 28t68 -28t28 -68zM1328 1088q0 -33 -23.5 -56.5t-56.5 -23.5t-56.5 23.5t-23.5 56.5t23.5 56.5t56.5 23.5t56.5 -23.5t23.5 -56.5z" /> | |
| 278 | <glyph unicode="" d="M1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 279 | <glyph unicode="" horiz-adv-x="1792" d="M1792 416q0 -166 -127 -451q-3 -7 -10.5 -24t-13.5 -30t-13 -22q-12 -17 -28 -17q-15 0 -23.5 10t-8.5 25q0 9 2.5 26.5t2.5 23.5q5 68 5 123q0 101 -17.5 181t-48.5 138.5t-80 101t-105.5 69.5t-133 42.5t-154 21.5t-175.5 6h-224v-256q0 -26 -19 -45t-45 -19t-45 19 l-512 512q-19 19 -19 45t19 45l512 512q19 19 45 19t45 -19t19 -45v-256h224q713 0 875 -403q53 -134 53 -333z" /> | |
| 280 | <glyph unicode="" horiz-adv-x="1664" d="M640 320q0 -40 -12.5 -82t-43 -76t-72.5 -34t-72.5 34t-43 76t-12.5 82t12.5 82t43 76t72.5 34t72.5 -34t43 -76t12.5 -82zM1280 320q0 -40 -12.5 -82t-43 -76t-72.5 -34t-72.5 34t-43 76t-12.5 82t12.5 82t43 76t72.5 34t72.5 -34t43 -76t12.5 -82zM1440 320 q0 120 -69 204t-187 84q-41 0 -195 -21q-71 -11 -157 -11t-157 11q-152 21 -195 21q-118 0 -187 -84t-69 -204q0 -88 32 -153.5t81 -103t122 -60t140 -29.5t149 -7h168q82 0 149 7t140 29.5t122 60t81 103t32 153.5zM1664 496q0 -207 -61 -331q-38 -77 -105.5 -133t-141 -86 t-170 -47.5t-171.5 -22t-167 -4.5q-78 0 -142 3t-147.5 12.5t-152.5 30t-137 51.5t-121 81t-86 115q-62 123 -62 331q0 237 136 396q-27 82 -27 170q0 116 51 218q108 0 190 -39.5t189 -123.5q147 35 309 35q148 0 280 -32q105 82 187 121t189 39q51 -102 51 -218 q0 -87 -27 -168q136 -160 136 -398z" /> | |
| 281 | <glyph unicode="" horiz-adv-x="1664" d="M1536 224v704q0 40 -28 68t-68 28h-704q-40 0 -68 28t-28 68v64q0 40 -28 68t-68 28h-320q-40 0 -68 -28t-28 -68v-960q0 -40 28 -68t68 -28h1216q40 0 68 28t28 68zM1664 928v-704q0 -92 -66 -158t-158 -66h-1216q-92 0 -158 66t-66 158v960q0 92 66 158t158 66h320 q92 0 158 -66t66 -158v-32h672q92 0 158 -66t66 -158z" /> | |
| 282 | <glyph unicode="" horiz-adv-x="1920" d="M1781 605q0 35 -53 35h-1088q-40 0 -85.5 -21.5t-71.5 -52.5l-294 -363q-18 -24 -18 -40q0 -35 53 -35h1088q40 0 86 22t71 53l294 363q18 22 18 39zM640 768h768v160q0 40 -28 68t-68 28h-576q-40 0 -68 28t-28 68v64q0 40 -28 68t-68 28h-320q-40 0 -68 -28t-28 -68 v-853l256 315q44 53 116 87.5t140 34.5zM1909 605q0 -62 -46 -120l-295 -363q-43 -53 -116 -87.5t-140 -34.5h-1088q-92 0 -158 66t-66 158v960q0 92 66 158t158 66h320q92 0 158 -66t66 -158v-32h544q92 0 158 -66t66 -158v-160h192q54 0 99 -24.5t67 -70.5q15 -32 15 -68z " /> | |
| 283 | <glyph unicode="" horiz-adv-x="1792" /> | |
| 284 | <glyph unicode="" horiz-adv-x="1792" /> | |
| 285 | <glyph unicode="" d="M1134 461q-37 -121 -138 -195t-228 -74t-228 74t-138 195q-8 25 4 48.5t38 31.5q25 8 48.5 -4t31.5 -38q25 -80 92.5 -129.5t151.5 -49.5t151.5 49.5t92.5 129.5q8 26 32 38t49 4t37 -31.5t4 -48.5zM640 896q0 -53 -37.5 -90.5t-90.5 -37.5t-90.5 37.5t-37.5 90.5 t37.5 90.5t90.5 37.5t90.5 -37.5t37.5 -90.5zM1152 896q0 -53 -37.5 -90.5t-90.5 -37.5t-90.5 37.5t-37.5 90.5t37.5 90.5t90.5 37.5t90.5 -37.5t37.5 -90.5zM1408 640q0 130 -51 248.5t-136.5 204t-204 136.5t-248.5 51t-248.5 -51t-204 -136.5t-136.5 -204t-51 -248.5 t51 -248.5t136.5 -204t204 -136.5t248.5 -51t248.5 51t204 136.5t136.5 204t51 248.5zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 286 | <glyph unicode="" d="M1134 307q8 -25 -4 -48.5t-37 -31.5t-49 4t-32 38q-25 80 -92.5 129.5t-151.5 49.5t-151.5 -49.5t-92.5 -129.5q-8 -26 -31.5 -38t-48.5 -4q-26 8 -38 31.5t-4 48.5q37 121 138 195t228 74t228 -74t138 -195zM640 896q0 -53 -37.5 -90.5t-90.5 -37.5t-90.5 37.5 t-37.5 90.5t37.5 90.5t90.5 37.5t90.5 -37.5t37.5 -90.5zM1152 896q0 -53 -37.5 -90.5t-90.5 -37.5t-90.5 37.5t-37.5 90.5t37.5 90.5t90.5 37.5t90.5 -37.5t37.5 -90.5zM1408 640q0 130 -51 248.5t-136.5 204t-204 136.5t-248.5 51t-248.5 -51t-204 -136.5t-136.5 -204 t-51 -248.5t51 -248.5t136.5 -204t204 -136.5t248.5 -51t248.5 51t204 136.5t136.5 204t51 248.5zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 287 | <glyph unicode="" d="M1152 448q0 -26 -19 -45t-45 -19h-640q-26 0 -45 19t-19 45t19 45t45 19h640q26 0 45 -19t19 -45zM640 896q0 -53 -37.5 -90.5t-90.5 -37.5t-90.5 37.5t-37.5 90.5t37.5 90.5t90.5 37.5t90.5 -37.5t37.5 -90.5zM1152 896q0 -53 -37.5 -90.5t-90.5 -37.5t-90.5 37.5 t-37.5 90.5t37.5 90.5t90.5 37.5t90.5 -37.5t37.5 -90.5zM1408 640q0 130 -51 248.5t-136.5 204t-204 136.5t-248.5 51t-248.5 -51t-204 -136.5t-136.5 -204t-51 -248.5t51 -248.5t136.5 -204t204 -136.5t248.5 -51t248.5 51t204 136.5t136.5 204t51 248.5zM1536 640 q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 288 | <glyph unicode="" horiz-adv-x="1920" d="M832 448v128q0 14 -9 23t-23 9h-192v192q0 14 -9 23t-23 9h-128q-14 0 -23 -9t-9 -23v-192h-192q-14 0 -23 -9t-9 -23v-128q0 -14 9 -23t23 -9h192v-192q0 -14 9 -23t23 -9h128q14 0 23 9t9 23v192h192q14 0 23 9t9 23zM1408 384q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5 t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1664 640q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1920 512q0 -212 -150 -362t-362 -150q-192 0 -338 128h-220q-146 -128 -338 -128q-212 0 -362 150 t-150 362t150 362t362 150h896q212 0 362 -150t150 -362z" /> | |
| 289 | <glyph unicode="" horiz-adv-x="1920" d="M384 368v-96q0 -16 -16 -16h-96q-16 0 -16 16v96q0 16 16 16h96q16 0 16 -16zM512 624v-96q0 -16 -16 -16h-224q-16 0 -16 16v96q0 16 16 16h224q16 0 16 -16zM384 880v-96q0 -16 -16 -16h-96q-16 0 -16 16v96q0 16 16 16h96q16 0 16 -16zM1408 368v-96q0 -16 -16 -16 h-864q-16 0 -16 16v96q0 16 16 16h864q16 0 16 -16zM768 624v-96q0 -16 -16 -16h-96q-16 0 -16 16v96q0 16 16 16h96q16 0 16 -16zM640 880v-96q0 -16 -16 -16h-96q-16 0 -16 16v96q0 16 16 16h96q16 0 16 -16zM1024 624v-96q0 -16 -16 -16h-96q-16 0 -16 16v96q0 16 16 16 h96q16 0 16 -16zM896 880v-96q0 -16 -16 -16h-96q-16 0 -16 16v96q0 16 16 16h96q16 0 16 -16zM1280 624v-96q0 -16 -16 -16h-96q-16 0 -16 16v96q0 16 16 16h96q16 0 16 -16zM1664 368v-96q0 -16 -16 -16h-96q-16 0 -16 16v96q0 16 16 16h96q16 0 16 -16zM1152 880v-96 q0 -16 -16 -16h-96q-16 0 -16 16v96q0 16 16 16h96q16 0 16 -16zM1408 880v-96q0 -16 -16 -16h-96q-16 0 -16 16v96q0 16 16 16h96q16 0 16 -16zM1664 880v-352q0 -16 -16 -16h-224q-16 0 -16 16v96q0 16 16 16h112v240q0 16 16 16h96q16 0 16 -16zM1792 128v896h-1664v-896 h1664zM1920 1024v-896q0 -53 -37.5 -90.5t-90.5 -37.5h-1664q-53 0 -90.5 37.5t-37.5 90.5v896q0 53 37.5 90.5t90.5 37.5h1664q53 0 90.5 -37.5t37.5 -90.5z" /> | |
| 290 | <glyph unicode="" horiz-adv-x="1792" d="M1664 491v616q-169 -91 -306 -91q-82 0 -145 32q-100 49 -184 76.5t-178 27.5q-173 0 -403 -127v-599q245 113 433 113q55 0 103.5 -7.5t98 -26t77 -31t82.5 -39.5l28 -14q44 -22 101 -22q120 0 293 92zM320 1280q0 -35 -17.5 -64t-46.5 -46v-1266q0 -14 -9 -23t-23 -9 h-64q-14 0 -23 9t-9 23v1266q-29 17 -46.5 46t-17.5 64q0 53 37.5 90.5t90.5 37.5t90.5 -37.5t37.5 -90.5zM1792 1216v-763q0 -39 -35 -57q-10 -5 -17 -9q-218 -116 -369 -116q-88 0 -158 35l-28 14q-64 33 -99 48t-91 29t-114 14q-102 0 -235.5 -44t-228.5 -102 q-15 -9 -33 -9q-16 0 -32 8q-32 19 -32 56v742q0 35 31 55q35 21 78.5 42.5t114 52t152.5 49.5t155 19q112 0 209 -31t209 -86q38 -19 89 -19q122 0 310 112q22 12 31 17q31 16 62 -2q31 -20 31 -55z" /> | |
| 291 | <glyph unicode="" horiz-adv-x="1792" d="M832 536v192q-181 -16 -384 -117v-185q205 96 384 110zM832 954v197q-172 -8 -384 -126v-189q215 111 384 118zM1664 491v184q-235 -116 -384 -71v224q-20 6 -39 15q-5 3 -33 17t-34.5 17t-31.5 15t-34.5 15.5t-32.5 13t-36 12.5t-35 8.5t-39.5 7.5t-39.5 4t-44 2 q-23 0 -49 -3v-222h19q102 0 192.5 -29t197.5 -82q19 -9 39 -15v-188q42 -17 91 -17q120 0 293 92zM1664 918v189q-169 -91 -306 -91q-45 0 -78 8v-196q148 -42 384 90zM320 1280q0 -35 -17.5 -64t-46.5 -46v-1266q0 -14 -9 -23t-23 -9h-64q-14 0 -23 9t-9 23v1266 q-29 17 -46.5 46t-17.5 64q0 53 37.5 90.5t90.5 37.5t90.5 -37.5t37.5 -90.5zM1792 1216v-763q0 -39 -35 -57q-10 -5 -17 -9q-218 -116 -369 -116q-88 0 -158 35l-28 14q-64 33 -99 48t-91 29t-114 14q-102 0 -235.5 -44t-228.5 -102q-15 -9 -33 -9q-16 0 -32 8 q-32 19 -32 56v742q0 35 31 55q35 21 78.5 42.5t114 52t152.5 49.5t155 19q112 0 209 -31t209 -86q38 -19 89 -19q122 0 310 112q22 12 31 17q31 16 62 -2q31 -20 31 -55z" /> | |
| 292 | <glyph unicode="" horiz-adv-x="1664" d="M585 553l-466 -466q-10 -10 -23 -10t-23 10l-50 50q-10 10 -10 23t10 23l393 393l-393 393q-10 10 -10 23t10 23l50 50q10 10 23 10t23 -10l466 -466q10 -10 10 -23t-10 -23zM1664 96v-64q0 -14 -9 -23t-23 -9h-960q-14 0 -23 9t-9 23v64q0 14 9 23t23 9h960q14 0 23 -9 t9 -23z" /> | |
| 293 | <glyph unicode="" horiz-adv-x="1920" d="M617 137l-50 -50q-10 -10 -23 -10t-23 10l-466 466q-10 10 -10 23t10 23l466 466q10 10 23 10t23 -10l50 -50q10 -10 10 -23t-10 -23l-393 -393l393 -393q10 -10 10 -23t-10 -23zM1208 1204l-373 -1291q-4 -13 -15.5 -19.5t-23.5 -2.5l-62 17q-13 4 -19.5 15.5t-2.5 24.5 l373 1291q4 13 15.5 19.5t23.5 2.5l62 -17q13 -4 19.5 -15.5t2.5 -24.5zM1865 553l-466 -466q-10 -10 -23 -10t-23 10l-50 50q-10 10 -10 23t10 23l393 393l-393 393q-10 10 -10 23t10 23l50 50q10 10 23 10t23 -10l466 -466q10 -10 10 -23t-10 -23z" /> | |
| 294 | <glyph unicode="" horiz-adv-x="1792" d="M640 454v-70q0 -42 -39 -59q-13 -5 -25 -5q-27 0 -45 19l-512 512q-19 19 -19 45t19 45l512 512q29 31 70 14q39 -17 39 -59v-69l-397 -398q-19 -19 -19 -45t19 -45zM1792 416q0 -58 -17 -133.5t-38.5 -138t-48 -125t-40.5 -90.5l-20 -40q-8 -17 -28 -17q-6 0 -9 1 q-25 8 -23 34q43 400 -106 565q-64 71 -170.5 110.5t-267.5 52.5v-251q0 -42 -39 -59q-13 -5 -25 -5q-27 0 -45 19l-512 512q-19 19 -19 45t19 45l512 512q29 31 70 14q39 -17 39 -59v-262q411 -28 599 -221q169 -173 169 -509z" /> | |
| 295 | <glyph unicode="" horiz-adv-x="1664" d="M1186 579l257 250l-356 52l-66 10l-30 60l-159 322v-963l59 -31l318 -168l-60 355l-12 66zM1638 841l-363 -354l86 -500q5 -33 -6 -51.5t-34 -18.5q-17 0 -40 12l-449 236l-449 -236q-23 -12 -40 -12q-23 0 -34 18.5t-6 51.5l86 500l-364 354q-32 32 -23 59.5t54 34.5 l502 73l225 455q20 41 49 41q28 0 49 -41l225 -455l502 -73q45 -7 54 -34.5t-24 -59.5z" /> | |
| 296 | <glyph unicode="" horiz-adv-x="1408" d="M1401 1187l-640 -1280q-17 -35 -57 -35q-5 0 -15 2q-22 5 -35.5 22.5t-13.5 39.5v576h-576q-22 0 -39.5 13.5t-22.5 35.5t4 42t29 30l1280 640q13 7 29 7q27 0 45 -19q15 -14 18.5 -34.5t-6.5 -39.5z" /> | |
| 297 | <glyph unicode="" horiz-adv-x="1664" d="M557 256h595v595zM512 301l595 595h-595v-595zM1664 224v-192q0 -14 -9 -23t-23 -9h-224v-224q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23v224h-864q-14 0 -23 9t-9 23v864h-224q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h224v224q0 14 9 23t23 9h192q14 0 23 -9t9 -23 v-224h851l246 247q10 9 23 9t23 -9q9 -10 9 -23t-9 -23l-247 -246v-851h224q14 0 23 -9t9 -23z" /> | |
| 298 | <glyph unicode="" horiz-adv-x="1024" d="M288 64q0 40 -28 68t-68 28t-68 -28t-28 -68t28 -68t68 -28t68 28t28 68zM288 1216q0 40 -28 68t-68 28t-68 -28t-28 -68t28 -68t68 -28t68 28t28 68zM928 1088q0 40 -28 68t-68 28t-68 -28t-28 -68t28 -68t68 -28t68 28t28 68zM1024 1088q0 -52 -26 -96.5t-70 -69.5 q-2 -287 -226 -414q-68 -38 -203 -81q-128 -40 -169.5 -71t-41.5 -100v-26q44 -25 70 -69.5t26 -96.5q0 -80 -56 -136t-136 -56t-136 56t-56 136q0 52 26 96.5t70 69.5v820q-44 25 -70 69.5t-26 96.5q0 80 56 136t136 56t136 -56t56 -136q0 -52 -26 -96.5t-70 -69.5v-497 q54 26 154 57q55 17 87.5 29.5t70.5 31t59 39.5t40.5 51t28 69.5t8.5 91.5q-44 25 -70 69.5t-26 96.5q0 80 56 136t136 56t136 -56t56 -136z" /> | |
| 299 | <glyph unicode="" horiz-adv-x="1664" d="M439 265l-256 -256q-10 -9 -23 -9q-12 0 -23 9q-9 10 -9 23t9 23l256 256q10 9 23 9t23 -9q9 -10 9 -23t-9 -23zM608 224v-320q0 -14 -9 -23t-23 -9t-23 9t-9 23v320q0 14 9 23t23 9t23 -9t9 -23zM384 448q0 -14 -9 -23t-23 -9h-320q-14 0 -23 9t-9 23t9 23t23 9h320 q14 0 23 -9t9 -23zM1648 320q0 -120 -85 -203l-147 -146q-83 -83 -203 -83q-121 0 -204 85l-334 335q-21 21 -42 56l239 18l273 -274q27 -27 68 -27.5t68 26.5l147 146q28 28 28 67q0 40 -28 68l-274 275l18 239q35 -21 56 -42l336 -336q84 -86 84 -204zM1031 1044l-239 -18 l-273 274q-28 28 -68 28q-39 0 -68 -27l-147 -146q-28 -28 -28 -67q0 -40 28 -68l274 -274l-18 -240q-35 21 -56 42l-336 336q-84 86 -84 204q0 120 85 203l147 146q83 83 203 83q121 0 204 -85l334 -335q21 -21 42 -56zM1664 960q0 -14 -9 -23t-23 -9h-320q-14 0 -23 9 t-9 23t9 23t23 9h320q14 0 23 -9t9 -23zM1120 1504v-320q0 -14 -9 -23t-23 -9t-23 9t-9 23v320q0 14 9 23t23 9t23 -9t9 -23zM1527 1353l-256 -256q-11 -9 -23 -9t-23 9q-9 10 -9 23t9 23l256 256q10 9 23 9t23 -9q9 -10 9 -23t-9 -23z" /> | |
| 300 | <glyph unicode="" horiz-adv-x="1024" d="M704 280v-240q0 -16 -12 -28t-28 -12h-240q-16 0 -28 12t-12 28v240q0 16 12 28t28 12h240q16 0 28 -12t12 -28zM1020 880q0 -54 -15.5 -101t-35 -76.5t-55 -59.5t-57.5 -43.5t-61 -35.5q-41 -23 -68.5 -65t-27.5 -67q0 -17 -12 -32.5t-28 -15.5h-240q-15 0 -25.5 18.5 t-10.5 37.5v45q0 83 65 156.5t143 108.5q59 27 84 56t25 76q0 42 -46.5 74t-107.5 32q-65 0 -108 -29q-35 -25 -107 -115q-13 -16 -31 -16q-12 0 -25 8l-164 125q-13 10 -15.5 25t5.5 28q160 266 464 266q80 0 161 -31t146 -83t106 -127.5t41 -158.5z" /> | |
| 301 | <glyph unicode="" horiz-adv-x="640" d="M640 192v-128q0 -26 -19 -45t-45 -19h-512q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h64v384h-64q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h384q26 0 45 -19t19 -45v-576h64q26 0 45 -19t19 -45zM512 1344v-192q0 -26 -19 -45t-45 -19h-256q-26 0 -45 19t-19 45v192 q0 26 19 45t45 19h256q26 0 45 -19t19 -45z" /> | |
| 302 | <glyph unicode="" horiz-adv-x="640" d="M512 288v-224q0 -26 -19 -45t-45 -19h-256q-26 0 -45 19t-19 45v224q0 26 19 45t45 19h256q26 0 45 -19t19 -45zM542 1344l-28 -768q-1 -26 -20.5 -45t-45.5 -19h-256q-26 0 -45.5 19t-20.5 45l-28 768q-1 26 17.5 45t44.5 19h320q26 0 44.5 -19t17.5 -45z" /> | |
| 303 | <glyph unicode="" d="M897 167v-167h-248l-159 252l-24 42q-8 9 -11 21h-3l-9 -21q-10 -20 -25 -44l-155 -250h-258v167h128l197 291l-185 272h-137v168h276l139 -228q2 -4 23 -42q8 -9 11 -21h3q3 9 11 21l25 42l140 228h257v-168h-125l-184 -267l204 -296h109zM1534 846v-206h-514l-3 27 q-4 28 -4 46q0 64 26 117t65 86.5t84 65t84 54.5t65 54t26 64q0 38 -29.5 62.5t-70.5 24.5q-51 0 -97 -39q-14 -11 -36 -38l-105 92q26 37 63 66q83 65 188 65q110 0 178 -59.5t68 -158.5q0 -56 -24.5 -103t-62 -76.5t-81.5 -58.5t-82 -50.5t-65.5 -51.5t-30.5 -63h232v80 h126z" /> | |
| 304 | <glyph unicode="" d="M897 167v-167h-248l-159 252l-24 42q-8 9 -11 21h-3l-9 -21q-10 -20 -25 -44l-155 -250h-258v167h128l197 291l-185 272h-137v168h276l139 -228q2 -4 23 -42q8 -9 11 -21h3q3 9 11 21l25 42l140 228h257v-168h-125l-184 -267l204 -296h109zM1536 -50v-206h-514l-4 27 q-3 45 -3 46q0 64 26 117t65 86.5t84 65t84 54.5t65 54t26 64q0 38 -29.5 62.5t-70.5 24.5q-51 0 -97 -39q-14 -11 -36 -38l-105 92q26 37 63 66q80 65 188 65q110 0 178 -59.5t68 -158.5q0 -66 -34.5 -118.5t-84 -86t-99.5 -62.5t-87 -63t-41 -73h232v80h126z" /> | |
| 305 | <glyph unicode="" horiz-adv-x="1920" d="M896 128l336 384h-768l-336 -384h768zM1909 1205q15 -34 9.5 -71.5t-30.5 -65.5l-896 -1024q-38 -44 -96 -44h-768q-38 0 -69.5 20.5t-47.5 54.5q-15 34 -9.5 71.5t30.5 65.5l896 1024q38 44 96 44h768q38 0 69.5 -20.5t47.5 -54.5z" /> | |
| 306 | <glyph unicode="" horiz-adv-x="1664" d="M1664 438q0 -81 -44.5 -135t-123.5 -54q-41 0 -77.5 17.5t-59 38t-56.5 38t-71 17.5q-110 0 -110 -124q0 -39 16 -115t15 -115v-5q-22 0 -33 -1q-34 -3 -97.5 -11.5t-115.5 -13.5t-98 -5q-61 0 -103 26.5t-42 83.5q0 37 17.5 71t38 56.5t38 59t17.5 77.5q0 79 -54 123.5 t-135 44.5q-84 0 -143 -45.5t-59 -127.5q0 -43 15 -83t33.5 -64.5t33.5 -53t15 -50.5q0 -45 -46 -89q-37 -35 -117 -35q-95 0 -245 24q-9 2 -27.5 4t-27.5 4l-13 2q-1 0 -3 1q-2 0 -2 1v1024q2 -1 17.5 -3.5t34 -5t21.5 -3.5q150 -24 245 -24q80 0 117 35q46 44 46 89 q0 22 -15 50.5t-33.5 53t-33.5 64.5t-15 83q0 82 59 127.5t144 45.5q80 0 134 -44.5t54 -123.5q0 -41 -17.5 -77.5t-38 -59t-38 -56.5t-17.5 -71q0 -57 42 -83.5t103 -26.5q64 0 180 15t163 17v-2q-1 -2 -3.5 -17.5t-5 -34t-3.5 -21.5q-24 -150 -24 -245q0 -80 35 -117 q44 -46 89 -46q22 0 50.5 15t53 33.5t64.5 33.5t83 15q82 0 127.5 -59t45.5 -143z" /> | |
| 307 | <glyph unicode="" horiz-adv-x="1152" d="M1152 832v-128q0 -221 -147.5 -384.5t-364.5 -187.5v-132h256q26 0 45 -19t19 -45t-19 -45t-45 -19h-640q-26 0 -45 19t-19 45t19 45t45 19h256v132q-217 24 -364.5 187.5t-147.5 384.5v128q0 26 19 45t45 19t45 -19t19 -45v-128q0 -185 131.5 -316.5t316.5 -131.5 t316.5 131.5t131.5 316.5v128q0 26 19 45t45 19t45 -19t19 -45zM896 1216v-512q0 -132 -94 -226t-226 -94t-226 94t-94 226v512q0 132 94 226t226 94t226 -94t94 -226z" /> | |
| 308 | <glyph unicode="" horiz-adv-x="1408" d="M271 591l-101 -101q-42 103 -42 214v128q0 26 19 45t45 19t45 -19t19 -45v-128q0 -53 15 -113zM1385 1193l-361 -361v-128q0 -132 -94 -226t-226 -94q-55 0 -109 19l-96 -96q97 -51 205 -51q185 0 316.5 131.5t131.5 316.5v128q0 26 19 45t45 19t45 -19t19 -45v-128 q0 -221 -147.5 -384.5t-364.5 -187.5v-132h256q26 0 45 -19t19 -45t-19 -45t-45 -19h-640q-26 0 -45 19t-19 45t19 45t45 19h256v132q-125 13 -235 81l-254 -254q-10 -10 -23 -10t-23 10l-82 82q-10 10 -10 23t10 23l1234 1234q10 10 23 10t23 -10l82 -82q10 -10 10 -23 t-10 -23zM1005 1325l-621 -621v512q0 132 94 226t226 94q102 0 184.5 -59t116.5 -152z" /> | |
| 309 | <glyph unicode="" horiz-adv-x="1280" d="M1088 576v640h-448v-1137q119 63 213 137q235 184 235 360zM1280 1344v-768q0 -86 -33.5 -170.5t-83 -150t-118 -127.5t-126.5 -103t-121 -77.5t-89.5 -49.5t-42.5 -20q-12 -6 -26 -6t-26 6q-16 7 -42.5 20t-89.5 49.5t-121 77.5t-126.5 103t-118 127.5t-83 150 t-33.5 170.5v768q0 26 19 45t45 19h1152q26 0 45 -19t19 -45z" /> | |
| 310 | <glyph unicode="" horiz-adv-x="1664" d="M128 -128h1408v1024h-1408v-1024zM512 1088v288q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-288q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM1280 1088v288q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-288q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM1664 1152v-1280 q0 -52 -38 -90t-90 -38h-1408q-52 0 -90 38t-38 90v1280q0 52 38 90t90 38h128v96q0 66 47 113t113 47h64q66 0 113 -47t47 -113v-96h384v96q0 66 47 113t113 47h64q66 0 113 -47t47 -113v-96h128q52 0 90 -38t38 -90z" /> | |
| 311 | <glyph unicode="" horiz-adv-x="1408" d="M512 1344q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45t45 -19t45 19t19 45zM1408 1376v-320q0 -16 -12 -25q-8 -7 -20 -7q-4 0 -7 1l-448 96q-11 2 -18 11t-7 20h-256v-102q111 -23 183.5 -111t72.5 -203v-800q0 -26 -19 -45t-45 -19h-512q-26 0 -45 19t-19 45v800 q0 106 62.5 190.5t161.5 114.5v111h-32q-59 0 -115 -23.5t-91.5 -53t-66 -66.5t-40.5 -53.5t-14 -24.5q-17 -35 -57 -35q-16 0 -29 7q-23 12 -31.5 37t3.5 49q5 10 14.5 26t37.5 53.5t60.5 70t85 67t108.5 52.5q-25 42 -25 86q0 66 47 113t113 47t113 -47t47 -113 q0 -33 -14 -64h302q0 11 7 20t18 11l448 96q3 1 7 1q12 0 20 -7q12 -9 12 -25z" /> | |
| 312 | <glyph unicode="" horiz-adv-x="1664" d="M1440 1088q0 40 -28 68t-68 28t-68 -28t-28 -68t28 -68t68 -28t68 28t28 68zM1664 1376q0 -249 -75.5 -430.5t-253.5 -360.5q-81 -80 -195 -176l-20 -379q-2 -16 -16 -26l-384 -224q-7 -4 -16 -4q-12 0 -23 9l-64 64q-13 14 -8 32l85 276l-281 281l-276 -85q-3 -1 -9 -1 q-14 0 -23 9l-64 64q-17 19 -5 39l224 384q10 14 26 16l379 20q96 114 176 195q188 187 358 258t431 71q14 0 24 -9.5t10 -22.5z" /> | |
| 313 | <glyph unicode="" horiz-adv-x="1792" d="M1745 763l-164 -763h-334l178 832q13 56 -15 88q-27 33 -83 33h-169l-204 -953h-334l204 953h-286l-204 -953h-334l204 953l-153 327h1276q101 0 189.5 -40.5t147.5 -113.5q60 -73 81 -168.5t0 -194.5z" /> | |
| 314 | <glyph unicode="" d="M909 141l102 102q19 19 19 45t-19 45l-307 307l307 307q19 19 19 45t-19 45l-102 102q-19 19 -45 19t-45 -19l-454 -454q-19 -19 -19 -45t19 -45l454 -454q19 -19 45 -19t45 19zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5 t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 315 | <glyph unicode="" d="M717 141l454 454q19 19 19 45t-19 45l-454 454q-19 19 -45 19t-45 -19l-102 -102q-19 -19 -19 -45t19 -45l307 -307l-307 -307q-19 -19 -19 -45t19 -45l102 -102q19 -19 45 -19t45 19zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5 t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 316 | <glyph unicode="" d="M1165 397l102 102q19 19 19 45t-19 45l-454 454q-19 19 -45 19t-45 -19l-454 -454q-19 -19 -19 -45t19 -45l102 -102q19 -19 45 -19t45 19l307 307l307 -307q19 -19 45 -19t45 19zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5 t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 317 | <glyph unicode="" d="M813 237l454 454q19 19 19 45t-19 45l-102 102q-19 19 -45 19t-45 -19l-307 -307l-307 307q-19 19 -45 19t-45 -19l-102 -102q-19 -19 -19 -45t19 -45l454 -454q19 -19 45 -19t45 19zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5 t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 318 | <glyph unicode="" horiz-adv-x="1408" d="M1130 939l16 175h-884l47 -534h612l-22 -228l-197 -53l-196 53l-13 140h-175l22 -278l362 -100h4v1l359 99l50 544h-644l-15 181h674zM0 1408h1408l-128 -1438l-578 -162l-574 162z" /> | |
| 319 | <glyph unicode="" horiz-adv-x="1792" d="M275 1408h1505l-266 -1333l-804 -267l-698 267l71 356h297l-29 -147l422 -161l486 161l68 339h-1208l58 297h1209l38 191h-1208z" /> | |
| 320 | <glyph unicode="" horiz-adv-x="1792" d="M960 1280q0 26 -19 45t-45 19t-45 -19t-19 -45t19 -45t45 -19t45 19t19 45zM1792 352v-352q0 -22 -20 -30q-8 -2 -12 -2q-13 0 -23 9l-93 93q-119 -143 -318.5 -226.5t-429.5 -83.5t-429.5 83.5t-318.5 226.5l-93 -93q-9 -9 -23 -9q-4 0 -12 2q-20 8 -20 30v352 q0 14 9 23t23 9h352q22 0 30 -20q8 -19 -7 -35l-100 -100q67 -91 189.5 -153.5t271.5 -82.5v647h-192q-26 0 -45 19t-19 45v128q0 26 19 45t45 19h192v163q-58 34 -93 92.5t-35 128.5q0 106 75 181t181 75t181 -75t75 -181q0 -70 -35 -128.5t-93 -92.5v-163h192q26 0 45 -19 t19 -45v-128q0 -26 -19 -45t-45 -19h-192v-647q149 20 271.5 82.5t189.5 153.5l-100 100q-15 16 -7 35q8 20 30 20h352q14 0 23 -9t9 -23z" /> | |
| 321 | <glyph unicode="" horiz-adv-x="1152" d="M1056 768q40 0 68 -28t28 -68v-576q0 -40 -28 -68t-68 -28h-960q-40 0 -68 28t-28 68v576q0 40 28 68t68 28h32v320q0 185 131.5 316.5t316.5 131.5t316.5 -131.5t131.5 -316.5q0 -26 -19 -45t-45 -19h-64q-26 0 -45 19t-19 45q0 106 -75 181t-181 75t-181 -75t-75 -181 v-320h736z" /> | |
| 322 | <glyph unicode="" d="M1024 640q0 -106 -75 -181t-181 -75t-181 75t-75 181t75 181t181 75t181 -75t75 -181zM1152 640q0 159 -112.5 271.5t-271.5 112.5t-271.5 -112.5t-112.5 -271.5t112.5 -271.5t271.5 -112.5t271.5 112.5t112.5 271.5zM1280 640q0 -212 -150 -362t-362 -150t-362 150 t-150 362t150 362t362 150t362 -150t150 -362zM1408 640q0 130 -51 248.5t-136.5 204t-204 136.5t-248.5 51t-248.5 -51t-204 -136.5t-136.5 -204t-51 -248.5t51 -248.5t136.5 -204t204 -136.5t248.5 -51t248.5 51t204 136.5t136.5 204t51 248.5zM1536 640 q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 323 | <glyph unicode="" horiz-adv-x="1408" d="M384 800v-192q0 -40 -28 -68t-68 -28h-192q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h192q40 0 68 -28t28 -68zM896 800v-192q0 -40 -28 -68t-68 -28h-192q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h192q40 0 68 -28t28 -68zM1408 800v-192q0 -40 -28 -68t-68 -28h-192 q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h192q40 0 68 -28t28 -68z" /> | |
| 324 | <glyph unicode="" horiz-adv-x="384" d="M384 288v-192q0 -40 -28 -68t-68 -28h-192q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h192q40 0 68 -28t28 -68zM384 800v-192q0 -40 -28 -68t-68 -28h-192q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h192q40 0 68 -28t28 -68zM384 1312v-192q0 -40 -28 -68t-68 -28h-192 q-40 0 -68 28t-28 68v192q0 40 28 68t68 28h192q40 0 68 -28t28 -68z" /> | |
| 325 | <glyph unicode="" d="M512 256q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM863 162q-13 232 -177 396t-396 177q-14 1 -24 -9t-10 -23v-128q0 -13 8.5 -22t21.5 -10q154 -11 264 -121t121 -264q1 -13 10 -21.5t22 -8.5h128q13 0 23 10 t9 24zM1247 161q-5 154 -56 297.5t-139.5 260t-205 205t-260 139.5t-297.5 56q-14 1 -23 -9q-10 -10 -10 -23v-128q0 -13 9 -22t22 -10q204 -7 378 -111.5t278.5 -278.5t111.5 -378q1 -13 10 -22t22 -9h128q13 0 23 10q11 9 9 23zM1536 1120v-960q0 -119 -84.5 -203.5 t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 326 | <glyph unicode="" d="M768 1408q209 0 385.5 -103t279.5 -279.5t103 -385.5t-103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103zM1152 585q32 18 32 55t-32 55l-544 320q-31 19 -64 1q-32 -19 -32 -56v-640q0 -37 32 -56 q16 -8 32 -8q17 0 32 9z" /> | |
| 327 | <glyph unicode="" horiz-adv-x="1792" d="M1024 1084l316 -316l-572 -572l-316 316zM813 105l618 618q19 19 19 45t-19 45l-362 362q-18 18 -45 18t-45 -18l-618 -618q-19 -19 -19 -45t19 -45l362 -362q18 -18 45 -18t45 18zM1702 742l-907 -908q-37 -37 -90.5 -37t-90.5 37l-126 126q56 56 56 136t-56 136 t-136 56t-136 -56l-125 126q-37 37 -37 90.5t37 90.5l907 906q37 37 90.5 37t90.5 -37l125 -125q-56 -56 -56 -136t56 -136t136 -56t136 56l126 -125q37 -37 37 -90.5t-37 -90.5z" /> | |
| 328 | <glyph unicode="" d="M1280 576v128q0 26 -19 45t-45 19h-896q-26 0 -45 -19t-19 -45v-128q0 -26 19 -45t45 -19h896q26 0 45 19t19 45zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5 t84.5 -203.5z" /> | |
| 329 | <glyph unicode="" horiz-adv-x="1408" d="M1152 736v-64q0 -14 -9 -23t-23 -9h-832q-14 0 -23 9t-9 23v64q0 14 9 23t23 9h832q14 0 23 -9t9 -23zM1280 288v832q0 66 -47 113t-113 47h-832q-66 0 -113 -47t-47 -113v-832q0 -66 47 -113t113 -47h832q66 0 113 47t47 113zM1408 1120v-832q0 -119 -84.5 -203.5 t-203.5 -84.5h-832q-119 0 -203.5 84.5t-84.5 203.5v832q0 119 84.5 203.5t203.5 84.5h832q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 330 | <glyph unicode="" horiz-adv-x="1024" d="M1018 933q-18 -37 -58 -37h-192v-864q0 -14 -9 -23t-23 -9h-704q-21 0 -29 18q-8 20 4 35l160 192q9 11 25 11h320v640h-192q-40 0 -58 37q-17 37 9 68l320 384q18 22 49 22t49 -22l320 -384q27 -32 9 -68z" /> | |
| 331 | <glyph unicode="" horiz-adv-x="1024" d="M32 1280h704q13 0 22.5 -9.5t9.5 -23.5v-863h192q40 0 58 -37t-9 -69l-320 -384q-18 -22 -49 -22t-49 22l-320 384q-26 31 -9 69q18 37 58 37h192v640h-320q-14 0 -25 11l-160 192q-13 14 -4 34q9 19 29 19z" /> | |
| 332 | <glyph unicode="" d="M685 237l614 614q19 19 19 45t-19 45l-102 102q-19 19 -45 19t-45 -19l-467 -467l-211 211q-19 19 -45 19t-45 -19l-102 -102q-19 -19 -19 -45t19 -45l358 -358q19 -19 45 -19t45 19zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5 t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 333 | <glyph unicode="" d="M404 428l152 -152l-52 -52h-56v96h-96v56zM818 818q14 -13 -3 -30l-291 -291q-17 -17 -30 -3q-14 13 3 30l291 291q17 17 30 3zM544 128l544 544l-288 288l-544 -544v-288h288zM1152 736l92 92q28 28 28 68t-28 68l-152 152q-28 28 -68 28t-68 -28l-92 -92zM1536 1120 v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 334 | <glyph unicode="" d="M1280 608v480q0 26 -19 45t-45 19h-480q-42 0 -59 -39q-17 -41 14 -70l144 -144l-534 -534q-19 -19 -19 -45t19 -45l102 -102q19 -19 45 -19t45 19l534 534l144 -144q18 -19 45 -19q12 0 25 5q39 17 39 59zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960 q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 335 | <glyph unicode="" d="M1005 435l352 352q19 19 19 45t-19 45l-352 352q-30 31 -69 14q-40 -17 -40 -59v-160q-119 0 -216 -19.5t-162.5 -51t-114 -79t-76.5 -95.5t-44.5 -109t-21.5 -111.5t-5 -110.5q0 -181 167 -404q10 -12 25 -12q7 0 13 3q22 9 19 33q-44 354 62 473q46 52 130 75.5 t224 23.5v-160q0 -42 40 -59q12 -5 24 -5q26 0 45 19zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 336 | <glyph unicode="" d="M640 448l256 128l-256 128v-256zM1024 1039v-542l-512 -256v542zM1312 640q0 148 -73 273t-198 198t-273 73t-273 -73t-198 -198t-73 -273t73 -273t198 -198t273 -73t273 73t198 198t73 273zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103 t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 337 | <glyph unicode="" d="M1145 861q18 -35 -5 -66l-320 -448q-19 -27 -52 -27t-52 27l-320 448q-23 31 -5 66q17 35 57 35h640q40 0 57 -35zM1280 160v960q0 13 -9.5 22.5t-22.5 9.5h-960q-13 0 -22.5 -9.5t-9.5 -22.5v-960q0 -13 9.5 -22.5t22.5 -9.5h960q13 0 22.5 9.5t9.5 22.5zM1536 1120 v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 338 | <glyph unicode="" d="M1145 419q-17 -35 -57 -35h-640q-40 0 -57 35q-18 35 5 66l320 448q19 27 52 27t52 -27l320 -448q23 -31 5 -66zM1280 160v960q0 13 -9.5 22.5t-22.5 9.5h-960q-13 0 -22.5 -9.5t-9.5 -22.5v-960q0 -13 9.5 -22.5t22.5 -9.5h960q13 0 22.5 9.5t9.5 22.5zM1536 1120v-960 q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 339 | <glyph unicode="" d="M1088 640q0 -33 -27 -52l-448 -320q-31 -23 -66 -5q-35 17 -35 57v640q0 40 35 57q35 18 66 -5l448 -320q27 -19 27 -52zM1280 160v960q0 14 -9 23t-23 9h-960q-14 0 -23 -9t-9 -23v-960q0 -14 9 -23t23 -9h960q14 0 23 9t9 23zM1536 1120v-960q0 -119 -84.5 -203.5 t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 340 | <glyph unicode="" horiz-adv-x="1024" d="M976 229l35 -159q3 -12 -3 -22.5t-17 -14.5l-5 -1q-4 -2 -10.5 -3.5t-16 -4.5t-21.5 -5.5t-25.5 -5t-30 -5t-33.5 -4.5t-36.5 -3t-38.5 -1q-234 0 -409 130.5t-238 351.5h-95q-13 0 -22.5 9.5t-9.5 22.5v113q0 13 9.5 22.5t22.5 9.5h66q-2 57 1 105h-67q-14 0 -23 9 t-9 23v114q0 14 9 23t23 9h98q67 210 243.5 338t400.5 128q102 0 194 -23q11 -3 20 -15q6 -11 3 -24l-43 -159q-3 -13 -14 -19.5t-24 -2.5l-4 1q-4 1 -11.5 2.5l-17.5 3.5t-22.5 3.5t-26 3t-29 2.5t-29.5 1q-126 0 -226 -64t-150 -176h468q16 0 25 -12q10 -12 7 -26 l-24 -114q-5 -26 -32 -26h-488q-3 -37 0 -105h459q15 0 25 -12q9 -12 6 -27l-24 -112q-2 -11 -11 -18.5t-20 -7.5h-387q48 -117 149.5 -185.5t228.5 -68.5q18 0 36 1.5t33.5 3.5t29.5 4.5t24.5 5t18.5 4.5l12 3l5 2q13 5 26 -2q12 -7 15 -21z" /> | |
| 341 | <glyph unicode="" horiz-adv-x="1024" d="M1020 399v-367q0 -14 -9 -23t-23 -9h-956q-14 0 -23 9t-9 23v150q0 13 9.5 22.5t22.5 9.5h97v383h-95q-14 0 -23 9.5t-9 22.5v131q0 14 9 23t23 9h95v223q0 171 123.5 282t314.5 111q185 0 335 -125q9 -8 10 -20.5t-7 -22.5l-103 -127q-9 -11 -22 -12q-13 -2 -23 7 q-5 5 -26 19t-69 32t-93 18q-85 0 -137 -47t-52 -123v-215h305q13 0 22.5 -9t9.5 -23v-131q0 -13 -9.5 -22.5t-22.5 -9.5h-305v-379h414v181q0 13 9 22.5t23 9.5h162q14 0 23 -9.5t9 -22.5z" /> | |
| 342 | <glyph unicode="" horiz-adv-x="1024" d="M978 351q0 -153 -99.5 -263.5t-258.5 -136.5v-175q0 -14 -9 -23t-23 -9h-135q-13 0 -22.5 9.5t-9.5 22.5v175q-66 9 -127.5 31t-101.5 44.5t-74 48t-46.5 37.5t-17.5 18q-17 21 -2 41l103 135q7 10 23 12q15 2 24 -9l2 -2q113 -99 243 -125q37 -8 74 -8q81 0 142.5 43 t61.5 122q0 28 -15 53t-33.5 42t-58.5 37.5t-66 32t-80 32.5q-39 16 -61.5 25t-61.5 26.5t-62.5 31t-56.5 35.5t-53.5 42.5t-43.5 49t-35.5 58t-21 66.5t-8.5 78q0 138 98 242t255 134v180q0 13 9.5 22.5t22.5 9.5h135q14 0 23 -9t9 -23v-176q57 -6 110.5 -23t87 -33.5 t63.5 -37.5t39 -29t15 -14q17 -18 5 -38l-81 -146q-8 -15 -23 -16q-14 -3 -27 7q-3 3 -14.5 12t-39 26.5t-58.5 32t-74.5 26t-85.5 11.5q-95 0 -155 -43t-60 -111q0 -26 8.5 -48t29.5 -41.5t39.5 -33t56 -31t60.5 -27t70 -27.5q53 -20 81 -31.5t76 -35t75.5 -42.5t62 -50 t53 -63.5t31.5 -76.5t13 -94z" /> | |
| 343 | <glyph unicode="" horiz-adv-x="898" d="M898 1066v-102q0 -14 -9 -23t-23 -9h-168q-23 -144 -129 -234t-276 -110q167 -178 459 -536q14 -16 4 -34q-8 -18 -29 -18h-195q-16 0 -25 12q-306 367 -498 571q-9 9 -9 22v127q0 13 9.5 22.5t22.5 9.5h112q132 0 212.5 43t102.5 125h-427q-14 0 -23 9t-9 23v102 q0 14 9 23t23 9h413q-57 113 -268 113h-145q-13 0 -22.5 9.5t-9.5 22.5v133q0 14 9 23t23 9h832q14 0 23 -9t9 -23v-102q0 -14 -9 -23t-23 -9h-233q47 -61 64 -144h171q14 0 23 -9t9 -23z" /> | |
| 344 | <glyph unicode="" horiz-adv-x="1027" d="M603 0h-172q-13 0 -22.5 9t-9.5 23v330h-288q-13 0 -22.5 9t-9.5 23v103q0 13 9.5 22.5t22.5 9.5h288v85h-288q-13 0 -22.5 9t-9.5 23v104q0 13 9.5 22.5t22.5 9.5h214l-321 578q-8 16 0 32q10 16 28 16h194q19 0 29 -18l215 -425q19 -38 56 -125q10 24 30.5 68t27.5 61 l191 420q8 19 29 19h191q17 0 27 -16q9 -14 1 -31l-313 -579h215q13 0 22.5 -9.5t9.5 -22.5v-104q0 -14 -9.5 -23t-22.5 -9h-290v-85h290q13 0 22.5 -9.5t9.5 -22.5v-103q0 -14 -9.5 -23t-22.5 -9h-290v-330q0 -13 -9.5 -22.5t-22.5 -9.5z" /> | |
| 345 | <glyph unicode="" horiz-adv-x="1280" d="M1043 971q0 100 -65 162t-171 62h-320v-448h320q106 0 171 62t65 162zM1280 971q0 -193 -126.5 -315t-326.5 -122h-340v-118h505q14 0 23 -9t9 -23v-128q0 -14 -9 -23t-23 -9h-505v-192q0 -14 -9.5 -23t-22.5 -9h-167q-14 0 -23 9t-9 23v192h-224q-14 0 -23 9t-9 23v128 q0 14 9 23t23 9h224v118h-224q-14 0 -23 9t-9 23v149q0 13 9 22.5t23 9.5h224v629q0 14 9 23t23 9h539q200 0 326.5 -122t126.5 -315z" /> | |
| 346 | <glyph unicode="" horiz-adv-x="1792" d="M514 341l81 299h-159l75 -300q1 -1 1 -3t1 -3q0 1 0.5 3.5t0.5 3.5zM630 768l35 128h-292l32 -128h225zM822 768h139l-35 128h-70zM1271 340l78 300h-162l81 -299q0 -1 0.5 -3.5t1.5 -3.5q0 1 0.5 3t0.5 3zM1382 768l33 128h-297l34 -128h230zM1792 736v-64q0 -14 -9 -23 t-23 -9h-213l-164 -616q-7 -24 -31 -24h-159q-24 0 -31 24l-166 616h-209l-167 -616q-7 -24 -31 -24h-159q-11 0 -19.5 7t-10.5 17l-160 616h-208q-14 0 -23 9t-9 23v64q0 14 9 23t23 9h175l-33 128h-142q-14 0 -23 9t-9 23v64q0 14 9 23t23 9h109l-89 344q-5 15 5 28 q10 12 26 12h137q26 0 31 -24l90 -360h359l97 360q7 24 31 24h126q24 0 31 -24l98 -360h365l93 360q5 24 31 24h137q16 0 26 -12q10 -13 5 -28l-91 -344h111q14 0 23 -9t9 -23v-64q0 -14 -9 -23t-23 -9h-145l-34 -128h179q14 0 23 -9t9 -23z" /> | |
| 347 | <glyph unicode="" horiz-adv-x="1280" d="M1167 896q18 -182 -131 -258q117 -28 175 -103t45 -214q-7 -71 -32.5 -125t-64.5 -89t-97 -58.5t-121.5 -34.5t-145.5 -15v-255h-154v251q-80 0 -122 1v-252h-154v255q-18 0 -54 0.5t-55 0.5h-200l31 183h111q50 0 58 51v402h16q-6 1 -16 1v287q-13 68 -89 68h-111v164 l212 -1q64 0 97 1v252h154v-247q82 2 122 2v245h154v-252q79 -7 140 -22.5t113 -45t82.5 -78t36.5 -114.5zM952 351q0 36 -15 64t-37 46t-57.5 30.5t-65.5 18.5t-74 9t-69 3t-64.5 -1t-47.5 -1v-338q8 0 37 -0.5t48 -0.5t53 1.5t58.5 4t57 8.5t55.5 14t47.5 21t39.5 30 t24.5 40t9.5 51zM881 827q0 33 -12.5 58.5t-30.5 42t-48 28t-55 16.5t-61.5 8t-58 2.5t-54 -1t-39.5 -0.5v-307q5 0 34.5 -0.5t46.5 0t50 2t55 5.5t51.5 11t48.5 18.5t37 27t27 38.5t9 51z" /> | |
| 348 | <glyph unicode="" d="M1024 1024v472q22 -14 36 -28l408 -408q14 -14 28 -36h-472zM896 992q0 -40 28 -68t68 -28h544v-1056q0 -40 -28 -68t-68 -28h-1344q-40 0 -68 28t-28 68v1600q0 40 28 68t68 28h800v-544z" /> | |
| 349 | <glyph unicode="" d="M1468 1060q14 -14 28 -36h-472v472q22 -14 36 -28zM992 896h544v-1056q0 -40 -28 -68t-68 -28h-1344q-40 0 -68 28t-28 68v1600q0 40 28 68t68 28h800v-544q0 -40 28 -68t68 -28zM1152 160v64q0 14 -9 23t-23 9h-704q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h704 q14 0 23 9t9 23zM1152 416v64q0 14 -9 23t-23 9h-704q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h704q14 0 23 9t9 23zM1152 672v64q0 14 -9 23t-23 9h-704q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h704q14 0 23 9t9 23z" /> | |
| 350 | <glyph unicode="" horiz-adv-x="1664" d="M1191 1128h177l-72 218l-12 47q-2 16 -2 20h-4l-3 -20q0 -1 -3.5 -18t-7.5 -29zM736 96q0 -12 -10 -24l-319 -319q-10 -9 -23 -9q-12 0 -23 9l-320 320q-15 16 -7 35q8 20 30 20h192v1376q0 14 9 23t23 9h192q14 0 23 -9t9 -23v-1376h192q14 0 23 -9t9 -23zM1572 -23 v-233h-584v90l369 529q12 18 21 27l11 9v3q-2 0 -6.5 -0.5t-7.5 -0.5q-12 -3 -30 -3h-232v-115h-120v229h567v-89l-369 -530q-6 -8 -21 -26l-11 -11v-2l14 2q9 2 30 2h248v119h121zM1661 874v-106h-288v106h75l-47 144h-243l-47 -144h75v-106h-287v106h70l230 662h162 l230 -662h70z" /> | |
| 351 | <glyph unicode="" horiz-adv-x="1664" d="M1191 104h177l-72 218l-12 47q-2 16 -2 20h-4l-3 -20q0 -1 -3.5 -18t-7.5 -29zM736 96q0 -12 -10 -24l-319 -319q-10 -9 -23 -9q-12 0 -23 9l-320 320q-15 16 -7 35q8 20 30 20h192v1376q0 14 9 23t23 9h192q14 0 23 -9t9 -23v-1376h192q14 0 23 -9t9 -23zM1661 -150 v-106h-288v106h75l-47 144h-243l-47 -144h75v-106h-287v106h70l230 662h162l230 -662h70zM1572 1001v-233h-584v90l369 529q12 18 21 27l11 9v3q-2 0 -6.5 -0.5t-7.5 -0.5q-12 -3 -30 -3h-232v-115h-120v229h567v-89l-369 -530q-6 -8 -21 -26l-11 -10v-3l14 3q9 1 30 1h248 v119h121z" /> | |
| 352 | <glyph unicode="" horiz-adv-x="1792" d="M736 96q0 -12 -10 -24l-319 -319q-10 -9 -23 -9q-12 0 -23 9l-320 320q-15 16 -7 35q8 20 30 20h192v1376q0 14 9 23t23 9h192q14 0 23 -9t9 -23v-1376h192q14 0 23 -9t9 -23zM1792 -32v-192q0 -14 -9 -23t-23 -9h-832q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h832 q14 0 23 -9t9 -23zM1600 480v-192q0 -14 -9 -23t-23 -9h-640q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h640q14 0 23 -9t9 -23zM1408 992v-192q0 -14 -9 -23t-23 -9h-448q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h448q14 0 23 -9t9 -23zM1216 1504v-192q0 -14 -9 -23t-23 -9h-256 q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h256q14 0 23 -9t9 -23z" /> | |
| 353 | <glyph unicode="" horiz-adv-x="1792" d="M1216 -32v-192q0 -14 -9 -23t-23 -9h-256q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h256q14 0 23 -9t9 -23zM736 96q0 -12 -10 -24l-319 -319q-10 -9 -23 -9q-12 0 -23 9l-320 320q-15 16 -7 35q8 20 30 20h192v1376q0 14 9 23t23 9h192q14 0 23 -9t9 -23v-1376h192 q14 0 23 -9t9 -23zM1408 480v-192q0 -14 -9 -23t-23 -9h-448q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h448q14 0 23 -9t9 -23zM1600 992v-192q0 -14 -9 -23t-23 -9h-640q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h640q14 0 23 -9t9 -23zM1792 1504v-192q0 -14 -9 -23t-23 -9h-832 q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h832q14 0 23 -9t9 -23z" /> | |
| 354 | <glyph unicode="" d="M1346 223q0 63 -44 116t-103 53q-52 0 -83 -37t-31 -94t36.5 -95t104.5 -38q50 0 85 27t35 68zM736 96q0 -12 -10 -24l-319 -319q-10 -9 -23 -9q-12 0 -23 9l-320 320q-15 16 -7 35q8 20 30 20h192v1376q0 14 9 23t23 9h192q14 0 23 -9t9 -23v-1376h192q14 0 23 -9t9 -23 zM1486 165q0 -62 -13 -121.5t-41 -114t-68 -95.5t-98.5 -65.5t-127.5 -24.5q-62 0 -108 16q-24 8 -42 15l39 113q15 -7 31 -11q37 -13 75 -13q84 0 134.5 58.5t66.5 145.5h-2q-21 -23 -61.5 -37t-84.5 -14q-106 0 -173 71.5t-67 172.5q0 105 72 178t181 73q123 0 205 -94.5 t82 -252.5zM1456 882v-114h-469v114h167v432q0 7 0.5 19t0.5 17v16h-2l-7 -12q-8 -13 -26 -31l-62 -58l-82 86l192 185h123v-654h165z" /> | |
| 355 | <glyph unicode="" d="M1346 1247q0 63 -44 116t-103 53q-52 0 -83 -37t-31 -94t36.5 -95t104.5 -38q50 0 85 27t35 68zM736 96q0 -12 -10 -24l-319 -319q-10 -9 -23 -9q-12 0 -23 9l-320 320q-15 16 -7 35q8 20 30 20h192v1376q0 14 9 23t23 9h192q14 0 23 -9t9 -23v-1376h192q14 0 23 -9 t9 -23zM1456 -142v-114h-469v114h167v432q0 7 0.5 19t0.5 17v16h-2l-7 -12q-8 -13 -26 -31l-62 -58l-82 86l192 185h123v-654h165zM1486 1189q0 -62 -13 -121.5t-41 -114t-68 -95.5t-98.5 -65.5t-127.5 -24.5q-62 0 -108 16q-24 8 -42 15l39 113q15 -7 31 -11q37 -13 75 -13 q84 0 134.5 58.5t66.5 145.5h-2q-21 -23 -61.5 -37t-84.5 -14q-106 0 -173 71.5t-67 172.5q0 105 72 178t181 73q123 0 205 -94.5t82 -252.5z" /> | |
| 356 | <glyph unicode="" horiz-adv-x="1664" d="M256 192q0 26 -19 45t-45 19q-27 0 -45.5 -19t-18.5 -45q0 -27 18.5 -45.5t45.5 -18.5q26 0 45 18.5t19 45.5zM416 704v-640q0 -26 -19 -45t-45 -19h-288q-26 0 -45 19t-19 45v640q0 26 19 45t45 19h288q26 0 45 -19t19 -45zM1600 704q0 -86 -55 -149q15 -44 15 -76 q3 -76 -43 -137q17 -56 0 -117q-15 -57 -54 -94q9 -112 -49 -181q-64 -76 -197 -78h-36h-76h-17q-66 0 -144 15.5t-121.5 29t-120.5 39.5q-123 43 -158 44q-26 1 -45 19.5t-19 44.5v641q0 25 18 43.5t43 20.5q24 2 76 59t101 121q68 87 101 120q18 18 31 48t17.5 48.5 t13.5 60.5q7 39 12.5 61t19.5 52t34 50q19 19 45 19q46 0 82.5 -10.5t60 -26t40 -40.5t24 -45t12 -50t5 -45t0.5 -39q0 -38 -9.5 -76t-19 -60t-27.5 -56q-3 -6 -10 -18t-11 -22t-8 -24h277q78 0 135 -57t57 -135z" /> | |
| 357 | <glyph unicode="" horiz-adv-x="1664" d="M256 960q0 -26 -19 -45t-45 -19q-27 0 -45.5 19t-18.5 45q0 27 18.5 45.5t45.5 18.5q26 0 45 -18.5t19 -45.5zM416 448v640q0 26 -19 45t-45 19h-288q-26 0 -45 -19t-19 -45v-640q0 -26 19 -45t45 -19h288q26 0 45 19t19 45zM1545 597q55 -61 55 -149q-1 -78 -57.5 -135 t-134.5 -57h-277q4 -14 8 -24t11 -22t10 -18q18 -37 27 -57t19 -58.5t10 -76.5q0 -24 -0.5 -39t-5 -45t-12 -50t-24 -45t-40 -40.5t-60 -26t-82.5 -10.5q-26 0 -45 19q-20 20 -34 50t-19.5 52t-12.5 61q-9 42 -13.5 60.5t-17.5 48.5t-31 48q-33 33 -101 120q-49 64 -101 121 t-76 59q-25 2 -43 20.5t-18 43.5v641q0 26 19 44.5t45 19.5q35 1 158 44q77 26 120.5 39.5t121.5 29t144 15.5h17h76h36q133 -2 197 -78q58 -69 49 -181q39 -37 54 -94q17 -61 0 -117q46 -61 43 -137q0 -32 -15 -76z" /> | |
| 358 | <glyph unicode="" d="M919 233v157q0 50 -29 50q-17 0 -33 -16v-224q16 -16 33 -16q29 0 29 49zM1103 355h66v34q0 51 -33 51t-33 -51v-34zM532 621v-70h-80v-423h-74v423h-78v70h232zM733 495v-367h-67v40q-39 -45 -76 -45q-33 0 -42 28q-6 16 -6 54v290h66v-270q0 -24 1 -26q1 -15 15 -15 q20 0 42 31v280h67zM985 384v-146q0 -52 -7 -73q-12 -42 -53 -42q-35 0 -68 41v-36h-67v493h67v-161q32 40 68 40q41 0 53 -42q7 -21 7 -74zM1236 255v-9q0 -29 -2 -43q-3 -22 -15 -40q-27 -40 -80 -40q-52 0 -81 38q-21 27 -21 86v129q0 59 20 86q29 38 80 38t78 -38 q21 -28 21 -86v-76h-133v-65q0 -51 34 -51q24 0 30 26q0 1 0.5 7t0.5 16.5v21.5h68zM785 1079v-156q0 -51 -32 -51t-32 51v156q0 52 32 52t32 -52zM1318 366q0 177 -19 260q-10 44 -43 73.5t-76 34.5q-136 15 -412 15q-275 0 -411 -15q-44 -5 -76.5 -34.5t-42.5 -73.5 q-20 -87 -20 -260q0 -176 20 -260q10 -43 42.5 -73t75.5 -35q137 -15 412 -15t412 15q43 5 75.5 35t42.5 73q20 84 20 260zM563 1017l90 296h-75l-51 -195l-53 195h-78l24 -69t23 -69q35 -103 46 -158v-201h74v201zM852 936v130q0 58 -21 87q-29 38 -78 38q-51 0 -78 -38 q-21 -29 -21 -87v-130q0 -58 21 -87q27 -38 78 -38q49 0 78 38q21 27 21 87zM1033 816h67v370h-67v-283q-22 -31 -42 -31q-15 0 -16 16q-1 2 -1 26v272h-67v-293q0 -37 6 -55q11 -27 43 -27q36 0 77 45v-40zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960 q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 359 | <glyph unicode="" d="M971 292v-211q0 -67 -39 -67q-23 0 -45 22v301q22 22 45 22q39 0 39 -67zM1309 291v-46h-90v46q0 68 45 68t45 -68zM343 509h107v94h-312v-94h105v-569h100v569zM631 -60h89v494h-89v-378q-30 -42 -57 -42q-18 0 -21 21q-1 3 -1 35v364h-89v-391q0 -49 8 -73 q12 -37 58 -37q48 0 102 61v-54zM1060 88v197q0 73 -9 99q-17 56 -71 56q-50 0 -93 -54v217h-89v-663h89v48q45 -55 93 -55q54 0 71 55q9 27 9 100zM1398 98v13h-91q0 -51 -2 -61q-7 -36 -40 -36q-46 0 -46 69v87h179v103q0 79 -27 116q-39 51 -106 51q-68 0 -107 -51 q-28 -37 -28 -116v-173q0 -79 29 -116q39 -51 108 -51q72 0 108 53q18 27 21 54q2 9 2 58zM790 1011v210q0 69 -43 69t-43 -69v-210q0 -70 43 -70t43 70zM1509 260q0 -234 -26 -350q-14 -59 -58 -99t-102 -46q-184 -21 -555 -21t-555 21q-58 6 -102.5 46t-57.5 99 q-26 112 -26 350q0 234 26 350q14 59 58 99t103 47q183 20 554 20t555 -20q58 -7 102.5 -47t57.5 -99q26 -112 26 -350zM511 1536h102l-121 -399v-271h-100v271q-14 74 -61 212q-37 103 -65 187h106l71 -263zM881 1203v-175q0 -81 -28 -118q-37 -51 -106 -51q-67 0 -105 51 q-28 38 -28 118v175q0 80 28 117q38 51 105 51q69 0 106 -51q28 -37 28 -117zM1216 1365v-499h-91v55q-53 -62 -103 -62q-46 0 -59 37q-8 24 -8 75v394h91v-367q0 -33 1 -35q3 -22 21 -22q27 0 57 43v381h91z" /> | |
| 360 | <glyph unicode="" horiz-adv-x="1408" d="M597 869q-10 -18 -257 -456q-27 -46 -65 -46h-239q-21 0 -31 17t0 36l253 448q1 0 0 1l-161 279q-12 22 -1 37q9 15 32 15h239q40 0 66 -45zM1403 1511q11 -16 0 -37l-528 -934v-1l336 -615q11 -20 1 -37q-10 -15 -32 -15h-239q-42 0 -66 45l-339 622q18 32 531 942 q25 45 64 45h241q22 0 31 -15z" /> | |
| 361 | <glyph unicode="" d="M685 771q0 1 -126 222q-21 34 -52 34h-184q-18 0 -26 -11q-7 -12 1 -29l125 -216v-1l-196 -346q-9 -14 0 -28q8 -13 24 -13h185q31 0 50 36zM1309 1268q-7 12 -24 12h-187q-30 0 -49 -35l-411 -729q1 -2 262 -481q20 -35 52 -35h184q18 0 25 12q8 13 -1 28l-260 476v1 l409 723q8 16 0 28zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 362 | <glyph unicode="" horiz-adv-x="1792" d="M1280 640q0 37 -30 54l-512 320q-31 20 -65 2q-33 -18 -33 -56v-640q0 -38 33 -56q16 -8 31 -8q20 0 34 10l512 320q30 17 30 54zM1792 640q0 -96 -1 -150t-8.5 -136.5t-22.5 -147.5q-16 -73 -69 -123t-124 -58q-222 -25 -671 -25t-671 25q-71 8 -124.5 58t-69.5 123 q-14 65 -21.5 147.5t-8.5 136.5t-1 150t1 150t8.5 136.5t22.5 147.5q16 73 69 123t124 58q222 25 671 25t671 -25q71 -8 124.5 -58t69.5 -123q14 -65 21.5 -147.5t8.5 -136.5t1 -150z" /> | |
| 363 | <glyph unicode="" horiz-adv-x="1792" d="M402 829l494 -305l-342 -285l-490 319zM1388 274v-108l-490 -293v-1l-1 1l-1 -1v1l-489 293v108l147 -96l342 284v2l1 -1l1 1v-2l343 -284zM554 1418l342 -285l-494 -304l-338 270zM1390 829l338 -271l-489 -319l-343 285zM1239 1418l489 -319l-338 -270l-494 304z" /> | |
| 364 | <glyph unicode="" horiz-adv-x="1408" d="M928 135v-151l-707 -1v151zM1169 481v-701l-1 -35v-1h-1132l-35 1h-1v736h121v-618h928v618h120zM241 393l704 -65l-13 -150l-705 65zM309 709l683 -183l-39 -146l-683 183zM472 1058l609 -360l-77 -130l-609 360zM832 1389l398 -585l-124 -85l-399 584zM1285 1536 l121 -697l-149 -26l-121 697z" /> | |
| 365 | <glyph unicode="" d="M1362 110v648h-135q20 -63 20 -131q0 -126 -64 -232.5t-174 -168.5t-240 -62q-197 0 -337 135.5t-140 327.5q0 68 20 131h-141v-648q0 -26 17.5 -43.5t43.5 -17.5h1069q25 0 43 17.5t18 43.5zM1078 643q0 124 -90.5 211.5t-218.5 87.5q-127 0 -217.5 -87.5t-90.5 -211.5 t90.5 -211.5t217.5 -87.5q128 0 218.5 87.5t90.5 211.5zM1362 1003v165q0 28 -20 48.5t-49 20.5h-174q-29 0 -49 -20.5t-20 -48.5v-165q0 -29 20 -49t49 -20h174q29 0 49 20t20 49zM1536 1211v-1142q0 -81 -58 -139t-139 -58h-1142q-81 0 -139 58t-58 139v1142q0 81 58 139 t139 58h1142q81 0 139 -58t58 -139z" /> | |
| 366 | <glyph unicode="" d="M1248 1408q119 0 203.5 -84.5t84.5 -203.5v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960zM698 640q0 88 -62 150t-150 62t-150 -62t-62 -150t62 -150t150 -62t150 62t62 150zM1262 640q0 88 -62 150 t-150 62t-150 -62t-62 -150t62 -150t150 -62t150 62t62 150z" /> | |
| 367 | <glyph unicode="" d="M768 914l201 -306h-402zM1133 384h94l-459 691l-459 -691h94l104 160h522zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 368 | <glyph unicode="" horiz-adv-x="1408" d="M815 677q8 -63 -50.5 -101t-111.5 -6q-39 17 -53.5 58t-0.5 82t52 58q36 18 72.5 12t64 -35.5t27.5 -67.5zM926 698q-14 107 -113 164t-197 13q-63 -28 -100.5 -88.5t-34.5 -129.5q4 -91 77.5 -155t165.5 -56q91 8 152 84t50 168zM1165 1240q-20 27 -56 44.5t-58 22 t-71 12.5q-291 47 -566 -2q-43 -7 -66 -12t-55 -22t-50 -43q30 -28 76 -45.5t73.5 -22t87.5 -11.5q228 -29 448 -1q63 8 89.5 12t72.5 21.5t75 46.5zM1222 205q-8 -26 -15.5 -76.5t-14 -84t-28.5 -70t-58 -56.5q-86 -48 -189.5 -71.5t-202 -22t-201.5 18.5q-46 8 -81.5 18 t-76.5 27t-73 43.5t-52 61.5q-25 96 -57 292l6 16l18 9q223 -148 506.5 -148t507.5 148q21 -6 24 -23t-5 -45t-8 -37zM1403 1166q-26 -167 -111 -655q-5 -30 -27 -56t-43.5 -40t-54.5 -31q-252 -126 -610 -88q-248 27 -394 139q-15 12 -25.5 26.5t-17 35t-9 34t-6 39.5 t-5.5 35q-9 50 -26.5 150t-28 161.5t-23.5 147.5t-22 158q3 26 17.5 48.5t31.5 37.5t45 30t46 22.5t48 18.5q125 46 313 64q379 37 676 -50q155 -46 215 -122q16 -20 16.5 -51t-5.5 -54z" /> | |
| 369 | <glyph unicode="" d="M848 666q0 43 -41 66t-77 1q-43 -20 -42.5 -72.5t43.5 -70.5q39 -23 81 4t36 72zM928 682q8 -66 -36 -121t-110 -61t-119 40t-56 113q-2 49 25.5 93t72.5 64q70 31 141.5 -10t81.5 -118zM1100 1073q-20 -21 -53.5 -34t-53 -16t-63.5 -8q-155 -20 -324 0q-44 6 -63 9.5 t-52.5 16t-54.5 32.5q13 19 36 31t40 15.5t47 8.5q198 35 408 1q33 -5 51 -8.5t43 -16t39 -31.5zM1142 327q0 7 5.5 26.5t3 32t-17.5 16.5q-161 -106 -365 -106t-366 106l-12 -6l-5 -12q26 -154 41 -210q47 -81 204 -108q249 -46 428 53q34 19 49 51.5t22.5 85.5t12.5 71z M1272 1020q9 53 -8 75q-43 55 -155 88q-216 63 -487 36q-132 -12 -226 -46q-38 -15 -59.5 -25t-47 -34t-29.5 -54q8 -68 19 -138t29 -171t24 -137q1 -5 5 -31t7 -36t12 -27t22 -28q105 -80 284 -100q259 -28 440 63q24 13 39.5 23t31 29t19.5 40q48 267 80 473zM1536 1120 v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 370 | <glyph unicode="" horiz-adv-x="1024" d="M944 207l80 -237q-23 -35 -111 -66t-177 -32q-104 -2 -190.5 26t-142.5 74t-95 106t-55.5 120t-16.5 118v544h-168v215q72 26 129 69.5t91 90t58 102t34 99t15 88.5q1 5 4.5 8.5t7.5 3.5h244v-424h333v-252h-334v-518q0 -30 6.5 -56t22.5 -52.5t49.5 -41.5t81.5 -14 q78 2 134 29z" /> | |
| 371 | <glyph unicode="" d="M1136 75l-62 183q-44 -22 -103 -22q-36 -1 -62 10.5t-38.5 31.5t-17.5 40.5t-5 43.5v398h257v194h-256v326h-188q-8 0 -9 -10q-5 -44 -17.5 -87t-39 -95t-77 -95t-118.5 -68v-165h130v-418q0 -57 21.5 -115t65 -111t121 -85.5t176.5 -30.5q69 1 136.5 25t85.5 50z M1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 372 | <glyph unicode="" horiz-adv-x="768" d="M765 237q8 -19 -5 -35l-350 -384q-10 -10 -23 -10q-14 0 -24 10l-355 384q-13 16 -5 35q9 19 29 19h224v1248q0 14 9 23t23 9h192q14 0 23 -9t9 -23v-1248h224q21 0 29 -19z" /> | |
| 373 | <glyph unicode="" horiz-adv-x="768" d="M765 1043q-9 -19 -29 -19h-224v-1248q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23v1248h-224q-21 0 -29 19t5 35l350 384q10 10 23 10q14 0 24 -10l355 -384q13 -16 5 -35z" /> | |
| 374 | <glyph unicode="" horiz-adv-x="1792" d="M1792 736v-192q0 -14 -9 -23t-23 -9h-1248v-224q0 -21 -19 -29t-35 5l-384 350q-10 10 -10 23q0 14 10 24l384 354q16 14 35 6q19 -9 19 -29v-224h1248q14 0 23 -9t9 -23z" /> | |
| 375 | <glyph unicode="" horiz-adv-x="1792" d="M1728 643q0 -14 -10 -24l-384 -354q-16 -14 -35 -6q-19 9 -19 29v224h-1248q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h1248v224q0 21 19 29t35 -5l384 -350q10 -10 10 -23z" /> | |
| 376 | <glyph unicode="" horiz-adv-x="1408" d="M1393 321q-39 -125 -123 -250q-129 -196 -257 -196q-49 0 -140 32q-86 32 -151 32q-61 0 -142 -33q-81 -34 -132 -34q-152 0 -301 259q-147 261 -147 503q0 228 113 374q112 144 284 144q72 0 177 -30q104 -30 138 -30q45 0 143 34q102 34 173 34q119 0 213 -65 q52 -36 104 -100q-79 -67 -114 -118q-65 -94 -65 -207q0 -124 69 -223t158 -126zM1017 1494q0 -61 -29 -136q-30 -75 -93 -138q-54 -54 -108 -72q-37 -11 -104 -17q3 149 78 257q74 107 250 148q1 -3 2.5 -11t2.5 -11q0 -4 0.5 -10t0.5 -10z" /> | |
| 377 | <glyph unicode="" horiz-adv-x="1664" d="M682 530v-651l-682 94v557h682zM682 1273v-659h-682v565zM1664 530v-786l-907 125v661h907zM1664 1408v-794h-907v669z" /> | |
| 378 | <glyph unicode="" horiz-adv-x="1408" d="M493 1053q16 0 27.5 11.5t11.5 27.5t-11.5 27.5t-27.5 11.5t-27 -11.5t-11 -27.5t11 -27.5t27 -11.5zM915 1053q16 0 27 11.5t11 27.5t-11 27.5t-27 11.5t-27.5 -11.5t-11.5 -27.5t11.5 -27.5t27.5 -11.5zM103 869q42 0 72 -30t30 -72v-430q0 -43 -29.5 -73t-72.5 -30 t-73 30t-30 73v430q0 42 30 72t73 30zM1163 850v-666q0 -46 -32 -78t-77 -32h-75v-227q0 -43 -30 -73t-73 -30t-73 30t-30 73v227h-138v-227q0 -43 -30 -73t-73 -30q-42 0 -72 30t-30 73l-1 227h-74q-46 0 -78 32t-32 78v666h918zM931 1255q107 -55 171 -153.5t64 -215.5 h-925q0 117 64 215.5t172 153.5l-71 131q-7 13 5 20q13 6 20 -6l72 -132q95 42 201 42t201 -42l72 132q7 12 20 6q12 -7 5 -20zM1408 767v-430q0 -43 -30 -73t-73 -30q-42 0 -72 30t-30 73v430q0 43 30 72.5t72 29.5q43 0 73 -29.5t30 -72.5z" /> | |
| 379 | <glyph unicode="" d="M663 1125q-11 -1 -15.5 -10.5t-8.5 -9.5q-5 -1 -5 5q0 12 19 15h10zM750 1111q-4 -1 -11.5 6.5t-17.5 4.5q24 11 32 -2q3 -6 -3 -9zM399 684q-4 1 -6 -3t-4.5 -12.5t-5.5 -13.5t-10 -13q-7 -10 -1 -12q4 -1 12.5 7t12.5 18q1 3 2 7t2 6t1.5 4.5t0.5 4v3t-1 2.5t-3 2z M1254 325q0 18 -55 42q4 15 7.5 27.5t5 26t3 21.5t0.5 22.5t-1 19.5t-3.5 22t-4 20.5t-5 25t-5.5 26.5q-10 48 -47 103t-72 75q24 -20 57 -83q87 -162 54 -278q-11 -40 -50 -42q-31 -4 -38.5 18.5t-8 83.5t-11.5 107q-9 39 -19.5 69t-19.5 45.5t-15.5 24.5t-13 15t-7.5 7 q-14 62 -31 103t-29.5 56t-23.5 33t-15 40q-4 21 6 53.5t4.5 49.5t-44.5 25q-15 3 -44.5 18t-35.5 16q-8 1 -11 26t8 51t36 27q37 3 51 -30t4 -58q-11 -19 -2 -26.5t30 -0.5q13 4 13 36v37q-5 30 -13.5 50t-21 30.5t-23.5 15t-27 7.5q-107 -8 -89 -134q0 -15 -1 -15 q-9 9 -29.5 10.5t-33 -0.5t-15.5 5q1 57 -16 90t-45 34q-27 1 -41.5 -27.5t-16.5 -59.5q-1 -15 3.5 -37t13 -37.5t15.5 -13.5q10 3 16 14q4 9 -7 8q-7 0 -15.5 14.5t-9.5 33.5q-1 22 9 37t34 14q17 0 27 -21t9.5 -39t-1.5 -22q-22 -15 -31 -29q-8 -12 -27.5 -23.5 t-20.5 -12.5q-13 -14 -15.5 -27t7.5 -18q14 -8 25 -19.5t16 -19t18.5 -13t35.5 -6.5q47 -2 102 15q2 1 23 7t34.5 10.5t29.5 13t21 17.5q9 14 20 8q5 -3 6.5 -8.5t-3 -12t-16.5 -9.5q-20 -6 -56.5 -21.5t-45.5 -19.5q-44 -19 -70 -23q-25 -5 -79 2q-10 2 -9 -2t17 -19 q25 -23 67 -22q17 1 36 7t36 14t33.5 17.5t30 17t24.5 12t17.5 2.5t8.5 -11q0 -2 -1 -4.5t-4 -5t-6 -4.5t-8.5 -5t-9 -4.5t-10 -5t-9.5 -4.5q-28 -14 -67.5 -44t-66.5 -43t-49 -1q-21 11 -63 73q-22 31 -25 22q-1 -3 -1 -10q0 -25 -15 -56.5t-29.5 -55.5t-21 -58t11.5 -63 q-23 -6 -62.5 -90t-47.5 -141q-2 -18 -1.5 -69t-5.5 -59q-8 -24 -29 -3q-32 31 -36 94q-2 28 4 56q4 19 -1 18l-4 -5q-36 -65 10 -166q5 -12 25 -28t24 -20q20 -23 104 -90.5t93 -76.5q16 -15 17.5 -38t-14 -43t-45.5 -23q8 -15 29 -44.5t28 -54t7 -70.5q46 24 7 92 q-4 8 -10.5 16t-9.5 12t-2 6q3 5 13 9.5t20 -2.5q46 -52 166 -36q133 15 177 87q23 38 34 30q12 -6 10 -52q-1 -25 -23 -92q-9 -23 -6 -37.5t24 -15.5q3 19 14.5 77t13.5 90q2 21 -6.5 73.5t-7.5 97t23 70.5q15 18 51 18q1 37 34.5 53t72.5 10.5t60 -22.5zM626 1152 q3 17 -2.5 30t-11.5 15q-9 2 -9 -7q2 -5 5 -6q10 0 7 -15q-3 -20 8 -20q3 0 3 3zM1045 955q-2 8 -6.5 11.5t-13 5t-14.5 5.5q-5 3 -9.5 8t-7 8t-5.5 6.5t-4 4t-4 -1.5q-14 -16 7 -43.5t39 -31.5q9 -1 14.5 8t3.5 20zM867 1168q0 11 -5 19.5t-11 12.5t-9 3q-14 -1 -7 -7l4 -2 q14 -4 18 -31q0 -3 8 2zM921 1401q0 2 -2.5 5t-9 7t-9.5 6q-15 15 -24 15q-9 -1 -11.5 -7.5t-1 -13t-0.5 -12.5q-1 -4 -6 -10.5t-6 -9t3 -8.5q4 -3 8 0t11 9t15 9q1 1 9 1t15 2t9 7zM1486 60q20 -12 31 -24.5t12 -24t-2.5 -22.5t-15.5 -22t-23.5 -19.5t-30 -18.5 t-31.5 -16.5t-32 -15.5t-27 -13q-38 -19 -85.5 -56t-75.5 -64q-17 -16 -68 -19.5t-89 14.5q-18 9 -29.5 23.5t-16.5 25.5t-22 19.5t-47 9.5q-44 1 -130 1q-19 0 -57 -1.5t-58 -2.5q-44 -1 -79.5 -15t-53.5 -30t-43.5 -28.5t-53.5 -11.5q-29 1 -111 31t-146 43q-19 4 -51 9.5 t-50 9t-39.5 9.5t-33.5 14.5t-17 19.5q-10 23 7 66.5t18 54.5q1 16 -4 40t-10 42.5t-4.5 36.5t10.5 27q14 12 57 14t60 12q30 18 42 35t12 51q21 -73 -32 -106q-32 -20 -83 -15q-34 3 -43 -10q-13 -15 5 -57q2 -6 8 -18t8.5 -18t4.5 -17t1 -22q0 -15 -17 -49t-14 -48 q3 -17 37 -26q20 -6 84.5 -18.5t99.5 -20.5q24 -6 74 -22t82.5 -23t55.5 -4q43 6 64.5 28t23 48t-7.5 58.5t-19 52t-20 36.5q-121 190 -169 242q-68 74 -113 40q-11 -9 -15 15q-3 16 -2 38q1 29 10 52t24 47t22 42q8 21 26.5 72t29.5 78t30 61t39 54q110 143 124 195 q-12 112 -16 310q-2 90 24 151.5t106 104.5q39 21 104 21q53 1 106 -13.5t89 -41.5q57 -42 91.5 -121.5t29.5 -147.5q-5 -95 30 -214q34 -113 133 -218q55 -59 99.5 -163t59.5 -191q8 -49 5 -84.5t-12 -55.5t-20 -22q-10 -2 -23.5 -19t-27 -35.5t-40.5 -33.5t-61 -14 q-18 1 -31.5 5t-22.5 13.5t-13.5 15.5t-11.5 20.5t-9 19.5q-22 37 -41 30t-28 -49t7 -97q20 -70 1 -195q-10 -65 18 -100.5t73 -33t85 35.5q59 49 89.5 66.5t103.5 42.5q53 18 77 36.5t18.5 34.5t-25 28.5t-51.5 23.5q-33 11 -49.5 48t-15 72.5t15.5 47.5q1 -31 8 -56.5 t14.5 -40.5t20.5 -28.5t21 -19t21.5 -13t16.5 -9.5z" /> | |
| 380 | <glyph unicode="" d="M1024 36q-42 241 -140 498h-2l-2 -1q-16 -6 -43 -16.5t-101 -49t-137 -82t-131 -114.5t-103 -148l-15 11q184 -150 418 -150q132 0 256 52zM839 643q-21 49 -53 111q-311 -93 -673 -93q-1 -7 -1 -21q0 -124 44 -236.5t124 -201.5q50 89 123.5 166.5t142.5 124.5t130.5 81 t99.5 48l37 13q4 1 13 3.5t13 4.5zM732 855q-120 213 -244 378q-138 -65 -234 -186t-128 -272q302 0 606 80zM1416 536q-210 60 -409 29q87 -239 128 -469q111 75 185 189.5t96 250.5zM611 1277q-1 0 -2 -1q1 1 2 1zM1201 1132q-185 164 -433 164q-76 0 -155 -19 q131 -170 246 -382q69 26 130 60.5t96.5 61.5t65.5 57t37.5 40.5zM1424 647q-3 232 -149 410l-1 -1q-9 -12 -19 -24.5t-43.5 -44.5t-71 -60.5t-100 -65t-131.5 -64.5q25 -53 44 -95q2 -6 6.5 -17.5t7.5 -16.5q36 5 74.5 7t73.5 2t69 -1.5t64 -4t56.5 -5.5t48 -6.5t36.5 -6 t25 -4.5zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 381 | <glyph unicode="" d="M1173 473q0 50 -19.5 91.5t-48.5 68.5t-73 49t-82.5 34t-87.5 23l-104 24q-30 7 -44 10.5t-35 11.5t-30 16t-16.5 21t-7.5 30q0 77 144 77q43 0 77 -12t54 -28.5t38 -33.5t40 -29t48 -12q47 0 75.5 32t28.5 77q0 55 -56 99.5t-142 67.5t-182 23q-68 0 -132 -15.5 t-119.5 -47t-89 -87t-33.5 -128.5q0 -61 19 -106.5t56 -75.5t80 -48.5t103 -32.5l146 -36q90 -22 112 -36q32 -20 32 -60q0 -39 -40 -64.5t-105 -25.5q-51 0 -91.5 16t-65 38.5t-45.5 45t-46 38.5t-54 16q-50 0 -75.5 -30t-25.5 -75q0 -92 122 -157.5t291 -65.5 q73 0 140 18.5t122.5 53.5t88.5 93.5t33 131.5zM1536 256q0 -159 -112.5 -271.5t-271.5 -112.5q-130 0 -234 80q-77 -16 -150 -16q-143 0 -273.5 55.5t-225 150t-150 225t-55.5 273.5q0 73 16 150q-80 104 -80 234q0 159 112.5 271.5t271.5 112.5q130 0 234 -80 q77 16 150 16q143 0 273.5 -55.5t225 -150t150 -225t55.5 -273.5q0 -73 -16 -150q80 -104 80 -234z" /> | |
| 382 | <glyph unicode="" horiz-adv-x="1280" d="M1000 1102l37 194q5 23 -9 40t-35 17h-712q-23 0 -38.5 -17t-15.5 -37v-1101q0 -7 6 -1l291 352q23 26 38 33.5t48 7.5h239q22 0 37 14.5t18 29.5q24 130 37 191q4 21 -11.5 40t-36.5 19h-294q-29 0 -48 19t-19 48v42q0 29 19 47.5t48 18.5h346q18 0 35 13.5t20 29.5z M1227 1324q-15 -73 -53.5 -266.5t-69.5 -350t-35 -173.5q-6 -22 -9 -32.5t-14 -32.5t-24.5 -33t-38.5 -21t-58 -10h-271q-13 0 -22 -10q-8 -9 -426 -494q-22 -25 -58.5 -28.5t-48.5 5.5q-55 22 -55 98v1410q0 55 38 102.5t120 47.5h888q95 0 127 -53t10 -159zM1227 1324 l-158 -790q4 17 35 173.5t69.5 350t53.5 266.5z" /> | |
| 383 | <glyph unicode="" d="M704 192v1024q0 14 -9 23t-23 9h-480q-14 0 -23 -9t-9 -23v-1024q0 -14 9 -23t23 -9h480q14 0 23 9t9 23zM1376 576v640q0 14 -9 23t-23 9h-480q-14 0 -23 -9t-9 -23v-640q0 -14 9 -23t23 -9h480q14 0 23 9t9 23zM1536 1344v-1408q0 -26 -19 -45t-45 -19h-1408 q-26 0 -45 19t-19 45v1408q0 26 19 45t45 19h1408q26 0 45 -19t19 -45z" /> | |
| 384 | <glyph unicode="" horiz-adv-x="1280" d="M1280 480q0 -40 -28 -68t-68 -28q-51 0 -80 43l-227 341h-45v-132l247 -411q9 -15 9 -33q0 -26 -19 -45t-45 -19h-192v-272q0 -46 -33 -79t-79 -33h-160q-46 0 -79 33t-33 79v272h-192q-26 0 -45 19t-19 45q0 18 9 33l247 411v132h-45l-227 -341q-29 -43 -80 -43 q-40 0 -68 28t-28 68q0 29 16 53l256 384q73 107 176 107h384q103 0 176 -107l256 -384q16 -24 16 -53zM864 1280q0 -93 -65.5 -158.5t-158.5 -65.5t-158.5 65.5t-65.5 158.5t65.5 158.5t158.5 65.5t158.5 -65.5t65.5 -158.5z" /> | |
| 385 | <glyph unicode="" horiz-adv-x="1024" d="M1024 832v-416q0 -40 -28 -68t-68 -28t-68 28t-28 68v352h-64v-912q0 -46 -33 -79t-79 -33t-79 33t-33 79v464h-64v-464q0 -46 -33 -79t-79 -33t-79 33t-33 79v912h-64v-352q0 -40 -28 -68t-68 -28t-68 28t-28 68v416q0 80 56 136t136 56h640q80 0 136 -56t56 -136z M736 1280q0 -93 -65.5 -158.5t-158.5 -65.5t-158.5 65.5t-65.5 158.5t65.5 158.5t158.5 65.5t158.5 -65.5t65.5 -158.5z" /> | |
| 386 | <glyph unicode="" d="M773 234l350 473q16 22 24.5 59t-6 85t-61.5 79q-40 26 -83 25.5t-73.5 -17.5t-54.5 -45q-36 -40 -96 -40q-59 0 -95 40q-24 28 -54.5 45t-73.5 17.5t-84 -25.5q-46 -31 -60.5 -79t-6 -85t24.5 -59zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103 t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 387 | <glyph unicode="" horiz-adv-x="1792" d="M1472 640q0 117 -45.5 223.5t-123 184t-184 123t-223.5 45.5t-223.5 -45.5t-184 -123t-123 -184t-45.5 -223.5t45.5 -223.5t123 -184t184 -123t223.5 -45.5t223.5 45.5t184 123t123 184t45.5 223.5zM1748 363q-4 -15 -20 -20l-292 -96v-306q0 -16 -13 -26q-15 -10 -29 -4 l-292 94l-180 -248q-10 -13 -26 -13t-26 13l-180 248l-292 -94q-14 -6 -29 4q-13 10 -13 26v306l-292 96q-16 5 -20 20q-5 17 4 29l180 248l-180 248q-9 13 -4 29q4 15 20 20l292 96v306q0 16 13 26q15 10 29 4l292 -94l180 248q9 12 26 12t26 -12l180 -248l292 94 q14 6 29 -4q13 -10 13 -26v-306l292 -96q16 -5 20 -20q5 -16 -4 -29l-180 -248l180 -248q9 -12 4 -29z" /> | |
| 388 | <glyph unicode="" d="M1262 233q-54 -9 -110 -9q-182 0 -337 90t-245 245t-90 337q0 192 104 357q-201 -60 -328.5 -229t-127.5 -384q0 -130 51 -248.5t136.5 -204t204 -136.5t248.5 -51q144 0 273.5 61.5t220.5 171.5zM1465 318q-94 -203 -283.5 -324.5t-413.5 -121.5q-156 0 -298 61 t-245 164t-164 245t-61 298q0 153 57.5 292.5t156 241.5t235.5 164.5t290 68.5q44 2 61 -39q18 -41 -15 -72q-86 -78 -131.5 -181.5t-45.5 -218.5q0 -148 73 -273t198 -198t273 -73q118 0 228 51q41 18 72 -13q14 -14 17.5 -34t-4.5 -38z" /> | |
| 389 | <glyph unicode="" horiz-adv-x="1792" d="M1088 704q0 26 -19 45t-45 19h-256q-26 0 -45 -19t-19 -45t19 -45t45 -19h256q26 0 45 19t19 45zM1664 896v-960q0 -26 -19 -45t-45 -19h-1408q-26 0 -45 19t-19 45v960q0 26 19 45t45 19h1408q26 0 45 -19t19 -45zM1728 1344v-256q0 -26 -19 -45t-45 -19h-1536 q-26 0 -45 19t-19 45v256q0 26 19 45t45 19h1536q26 0 45 -19t19 -45z" /> | |
| 390 | <glyph unicode="" horiz-adv-x="1664" d="M1632 576q0 -26 -19 -45t-45 -19h-224q0 -171 -67 -290l208 -209q19 -19 19 -45t-19 -45q-18 -19 -45 -19t-45 19l-198 197q-5 -5 -15 -13t-42 -28.5t-65 -36.5t-82 -29t-97 -13v896h-128v-896q-51 0 -101.5 13.5t-87 33t-66 39t-43.5 32.5l-15 14l-183 -207 q-20 -21 -48 -21q-24 0 -43 16q-19 18 -20.5 44.5t15.5 46.5l202 227q-58 114 -58 274h-224q-26 0 -45 19t-19 45t19 45t45 19h224v294l-173 173q-19 19 -19 45t19 45t45 19t45 -19l173 -173h844l173 173q19 19 45 19t45 -19t19 -45t-19 -45l-173 -173v-294h224q26 0 45 -19 t19 -45zM1152 1152h-640q0 133 93.5 226.5t226.5 93.5t226.5 -93.5t93.5 -226.5z" /> | |
| 391 | <glyph unicode="" horiz-adv-x="1920" d="M1917 1016q23 -64 -150 -294q-24 -32 -65 -85q-78 -100 -90 -131q-17 -41 14 -81q17 -21 81 -82h1l1 -1l1 -1l2 -2q141 -131 191 -221q3 -5 6.5 -12.5t7 -26.5t-0.5 -34t-25 -27.5t-59 -12.5l-256 -4q-24 -5 -56 5t-52 22l-20 12q-30 21 -70 64t-68.5 77.5t-61 58 t-56.5 15.5q-3 -1 -8 -3.5t-17 -14.5t-21.5 -29.5t-17 -52t-6.5 -77.5q0 -15 -3.5 -27.5t-7.5 -18.5l-4 -5q-18 -19 -53 -22h-115q-71 -4 -146 16.5t-131.5 53t-103 66t-70.5 57.5l-25 24q-10 10 -27.5 30t-71.5 91t-106 151t-122.5 211t-130.5 272q-6 16 -6 27t3 16l4 6 q15 19 57 19l274 2q12 -2 23 -6.5t16 -8.5l5 -3q16 -11 24 -32q20 -50 46 -103.5t41 -81.5l16 -29q29 -60 56 -104t48.5 -68.5t41.5 -38.5t34 -14t27 5q2 1 5 5t12 22t13.5 47t9.5 81t0 125q-2 40 -9 73t-14 46l-6 12q-25 34 -85 43q-13 2 5 24q17 19 38 30q53 26 239 24 q82 -1 135 -13q20 -5 33.5 -13.5t20.5 -24t10.5 -32t3.5 -45.5t-1 -55t-2.5 -70.5t-1.5 -82.5q0 -11 -1 -42t-0.5 -48t3.5 -40.5t11.5 -39t22.5 -24.5q8 -2 17 -4t26 11t38 34.5t52 67t68 107.5q60 104 107 225q4 10 10 17.5t11 10.5l4 3l5 2.5t13 3t20 0.5l288 2 q39 5 64 -2.5t31 -16.5z" /> | |
| 392 | <glyph unicode="" horiz-adv-x="1792" d="M675 252q21 34 11 69t-45 50q-34 14 -73 1t-60 -46q-22 -34 -13 -68.5t43 -50.5t74.5 -2.5t62.5 47.5zM769 373q8 13 3.5 26.5t-17.5 18.5q-14 5 -28.5 -0.5t-21.5 -18.5q-17 -31 13 -45q14 -5 29 0.5t22 18.5zM943 266q-45 -102 -158 -150t-224 -12 q-107 34 -147.5 126.5t6.5 187.5q47 93 151.5 139t210.5 19q111 -29 158.5 -119.5t2.5 -190.5zM1255 426q-9 96 -89 170t-208.5 109t-274.5 21q-223 -23 -369.5 -141.5t-132.5 -264.5q9 -96 89 -170t208.5 -109t274.5 -21q223 23 369.5 141.5t132.5 264.5zM1563 422 q0 -68 -37 -139.5t-109 -137t-168.5 -117.5t-226 -83t-270.5 -31t-275 33.5t-240.5 93t-171.5 151t-65 199.5q0 115 69.5 245t197.5 258q169 169 341.5 236t246.5 -7q65 -64 20 -209q-4 -14 -1 -20t10 -7t14.5 0.5t13.5 3.5l6 2q139 59 246 59t153 -61q45 -63 0 -178 q-2 -13 -4.5 -20t4.5 -12.5t12 -7.5t17 -6q57 -18 103 -47t80 -81.5t34 -116.5zM1489 1046q42 -47 54.5 -108.5t-6.5 -117.5q-8 -23 -29.5 -34t-44.5 -4q-23 8 -34 29.5t-4 44.5q20 63 -24 111t-107 35q-24 -5 -45 8t-25 37q-5 24 8 44.5t37 25.5q60 13 119 -5.5t101 -65.5z M1670 1209q87 -96 112.5 -222.5t-13.5 -241.5q-9 -27 -34 -40t-52 -4t-40 34t-5 52q28 82 10 172t-80 158q-62 69 -148 95.5t-173 8.5q-28 -6 -52 9.5t-30 43.5t9.5 51.5t43.5 29.5q123 26 244 -11.5t208 -134.5z" /> | |
| 393 | <glyph unicode="" d="M1133 -34q-171 -94 -368 -94q-196 0 -367 94q138 87 235.5 211t131.5 268q35 -144 132.5 -268t235.5 -211zM638 1394v-485q0 -252 -126.5 -459.5t-330.5 -306.5q-181 215 -181 495q0 187 83.5 349.5t229.5 269.5t325 137zM1536 638q0 -280 -181 -495 q-204 99 -330.5 306.5t-126.5 459.5v485q179 -30 325 -137t229.5 -269.5t83.5 -349.5z" /> | |
| 394 | <glyph unicode="" horiz-adv-x="1408" d="M1402 433q-32 -80 -76 -138t-91 -88.5t-99 -46.5t-101.5 -14.5t-96.5 8.5t-86.5 22t-69.5 27.5t-46 22.5l-17 10q-113 -228 -289.5 -359.5t-384.5 -132.5q-19 0 -32 13t-13 32t13 31.5t32 12.5q173 1 322.5 107.5t251.5 294.5q-36 -14 -72 -23t-83 -13t-91 2.5t-93 28.5 t-92 59t-84.5 100t-74.5 146q114 47 214 57t167.5 -7.5t124.5 -56.5t88.5 -77t56.5 -82q53 131 79 291q-7 -1 -18 -2.5t-46.5 -2.5t-69.5 0.5t-81.5 10t-88.5 23t-84 42.5t-75 65t-54.5 94.5t-28.5 127.5q70 28 133.5 36.5t112.5 -1t92 -30t73.5 -50t56 -61t42 -63t27.5 -56 t16 -39.5l4 -16q12 122 12 195q-8 6 -21.5 16t-49 44.5t-63.5 71.5t-54 93t-33 112.5t12 127t70 138.5q73 -25 127.5 -61.5t84.5 -76.5t48 -85t20.5 -89t-0.5 -85.5t-13 -76.5t-19 -62t-17 -42l-7 -15q1 -5 1 -50.5t-1 -71.5q3 7 10 18.5t30.5 43t50.5 58t71 55.5t91.5 44.5 t112 14.5t132.5 -24q-2 -78 -21.5 -141.5t-50 -104.5t-69.5 -71.5t-81.5 -45.5t-84.5 -24t-80 -9.5t-67.5 1t-46.5 4.5l-17 3q-23 -147 -73 -283q6 7 18 18.5t49.5 41t77.5 52.5t99.5 42t117.5 20t129 -23.5t137 -77.5z" /> | |
| 395 | <glyph unicode="" horiz-adv-x="1280" d="M1259 283v-66q0 -85 -57.5 -144.5t-138.5 -59.5h-57l-260 -269v269h-529q-81 0 -138.5 59.5t-57.5 144.5v66h1238zM1259 609v-255h-1238v255h1238zM1259 937v-255h-1238v255h1238zM1259 1077v-67h-1238v67q0 84 57.5 143.5t138.5 59.5h846q81 0 138.5 -59.5t57.5 -143.5z " /> | |
| 396 | <glyph unicode="" d="M1152 640q0 -14 -9 -23l-320 -320q-9 -9 -23 -9q-13 0 -22.5 9.5t-9.5 22.5v192h-352q-13 0 -22.5 9.5t-9.5 22.5v192q0 13 9.5 22.5t22.5 9.5h352v192q0 14 9 23t23 9q12 0 24 -10l319 -319q9 -9 9 -23zM1312 640q0 148 -73 273t-198 198t-273 73t-273 -73t-198 -198 t-73 -273t73 -273t198 -198t273 -73t273 73t198 198t73 273zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 397 | <glyph unicode="" d="M1152 736v-192q0 -13 -9.5 -22.5t-22.5 -9.5h-352v-192q0 -14 -9 -23t-23 -9q-12 0 -24 10l-319 319q-9 9 -9 23t9 23l320 320q9 9 23 9q13 0 22.5 -9.5t9.5 -22.5v-192h352q13 0 22.5 -9.5t9.5 -22.5zM1312 640q0 148 -73 273t-198 198t-273 73t-273 -73t-198 -198 t-73 -273t73 -273t198 -198t273 -73t273 73t198 198t73 273zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 398 | <glyph unicode="" d="M1024 960v-640q0 -26 -19 -45t-45 -19q-20 0 -37 12l-448 320q-27 19 -27 52t27 52l448 320q17 12 37 12q26 0 45 -19t19 -45zM1280 160v960q0 13 -9.5 22.5t-22.5 9.5h-960q-13 0 -22.5 -9.5t-9.5 -22.5v-960q0 -13 9.5 -22.5t22.5 -9.5h960q13 0 22.5 9.5t9.5 22.5z M1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 399 | <glyph unicode="" d="M1024 640q0 -106 -75 -181t-181 -75t-181 75t-75 181t75 181t181 75t181 -75t75 -181zM768 1184q-148 0 -273 -73t-198 -198t-73 -273t73 -273t198 -198t273 -73t273 73t198 198t73 273t-73 273t-198 198t-273 73zM1536 640q0 -209 -103 -385.5t-279.5 -279.5 t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 400 | <glyph unicode="" horiz-adv-x="1664" d="M1023 349l102 -204q-58 -179 -210 -290t-339 -111q-156 0 -288.5 77.5t-210 210t-77.5 288.5q0 181 104.5 330t274.5 211l17 -131q-122 -54 -195 -165.5t-73 -244.5q0 -185 131.5 -316.5t316.5 -131.5q126 0 232.5 65t165 175.5t49.5 236.5zM1571 249l58 -114l-256 -128 q-13 -7 -29 -7q-40 0 -57 35l-239 477h-472q-24 0 -42.5 16.5t-21.5 40.5l-96 779q-2 16 6 42q14 51 57 82.5t97 31.5q66 0 113 -47t47 -113q0 -69 -52 -117.5t-120 -41.5l37 -289h423v-128h-407l16 -128h455q40 0 57 -35l228 -455z" /> | |
| 401 | <glyph unicode="" d="M1254 899q16 85 -21 132q-52 65 -187 45q-17 -3 -41 -12.5t-57.5 -30.5t-64.5 -48.5t-59.5 -70t-44.5 -91.5q80 7 113.5 -16t26.5 -99q-5 -52 -52 -143q-43 -78 -71 -99q-44 -32 -87 14q-23 24 -37.5 64.5t-19 73t-10 84t-8.5 71.5q-23 129 -34 164q-12 37 -35.5 69 t-50.5 40q-57 16 -127 -25q-54 -32 -136.5 -106t-122.5 -102v-7q16 -8 25.5 -26t21.5 -20q21 -3 54.5 8.5t58 10.5t41.5 -30q11 -18 18.5 -38.5t15 -48t12.5 -40.5q17 -46 53 -187q36 -146 57 -197q42 -99 103 -125q43 -12 85 -1.5t76 31.5q131 77 250 237 q104 139 172.5 292.5t82.5 226.5zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 402 | <glyph unicode="" horiz-adv-x="1152" d="M1152 704q0 -191 -94.5 -353t-256.5 -256.5t-353 -94.5h-160q-14 0 -23 9t-9 23v611l-215 -66q-3 -1 -9 -1q-10 0 -19 6q-13 10 -13 26v128q0 23 23 31l233 71v93l-215 -66q-3 -1 -9 -1q-10 0 -19 6q-13 10 -13 26v128q0 23 23 31l233 71v250q0 14 9 23t23 9h160 q14 0 23 -9t9 -23v-181l375 116q15 5 28 -5t13 -26v-128q0 -23 -23 -31l-393 -121v-93l375 116q15 5 28 -5t13 -26v-128q0 -23 -23 -31l-393 -121v-487q188 13 318 151t130 328q0 14 9 23t23 9h160q14 0 23 -9t9 -23z" /> | |
| 403 | <glyph unicode="" horiz-adv-x="1408" d="M1152 736v-64q0 -14 -9 -23t-23 -9h-352v-352q0 -14 -9 -23t-23 -9h-64q-14 0 -23 9t-9 23v352h-352q-14 0 -23 9t-9 23v64q0 14 9 23t23 9h352v352q0 14 9 23t23 9h64q14 0 23 -9t9 -23v-352h352q14 0 23 -9t9 -23zM1280 288v832q0 66 -47 113t-113 47h-832 q-66 0 -113 -47t-47 -113v-832q0 -66 47 -113t113 -47h832q66 0 113 47t47 113zM1408 1120v-832q0 -119 -84.5 -203.5t-203.5 -84.5h-832q-119 0 -203.5 84.5t-84.5 203.5v832q0 119 84.5 203.5t203.5 84.5h832q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 404 | <glyph unicode="" horiz-adv-x="2176" d="M620 416q-110 -64 -268 -64h-128v64h-64q-13 0 -22.5 23.5t-9.5 56.5q0 24 7 49q-58 2 -96.5 10.5t-38.5 20.5t38.5 20.5t96.5 10.5q-7 25 -7 49q0 33 9.5 56.5t22.5 23.5h64v64h128q158 0 268 -64h1113q42 -7 106.5 -18t80.5 -14q89 -15 150 -40.5t83.5 -47.5t22.5 -40 t-22.5 -40t-83.5 -47.5t-150 -40.5q-16 -3 -80.5 -14t-106.5 -18h-1113zM1739 668q53 -36 53 -92t-53 -92l81 -30q68 48 68 122t-68 122zM625 400h1015q-217 -38 -456 -80q-57 0 -113 -24t-83 -48l-28 -24l-288 -288q-26 -26 -70.5 -45t-89.5 -19h-96l-93 464h29 q157 0 273 64zM352 816h-29l93 464h96q46 0 90 -19t70 -45l288 -288q4 -4 11 -10.5t30.5 -23t48.5 -29t61.5 -23t72.5 -10.5l456 -80h-1015q-116 64 -273 64z" /> | |
| 405 | <glyph unicode="" horiz-adv-x="1664" d="M1519 760q62 0 103.5 -40.5t41.5 -101.5q0 -97 -93 -130l-172 -59l56 -167q7 -21 7 -47q0 -59 -42 -102t-101 -43q-47 0 -85.5 27t-53.5 72l-55 165l-310 -106l55 -164q8 -24 8 -47q0 -59 -42 -102t-102 -43q-47 0 -85 27t-53 72l-55 163l-153 -53q-29 -9 -50 -9 q-61 0 -101.5 40t-40.5 101q0 47 27.5 85t71.5 53l156 53l-105 313l-156 -54q-26 -8 -48 -8q-60 0 -101 40.5t-41 100.5q0 47 27.5 85t71.5 53l157 53l-53 159q-8 24 -8 47q0 60 42 102.5t102 42.5q47 0 85 -27t53 -72l54 -160l310 105l-54 160q-8 24 -8 47q0 59 42.5 102 t101.5 43q47 0 85.5 -27.5t53.5 -71.5l53 -161l162 55q21 6 43 6q60 0 102.5 -39.5t42.5 -98.5q0 -45 -30 -81.5t-74 -51.5l-157 -54l105 -316l164 56q24 8 46 8zM725 498l310 105l-105 315l-310 -107z" /> | |
| 406 | <glyph unicode="" d="M1248 1408q119 0 203.5 -84.5t84.5 -203.5v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960zM1280 352v436q-31 -35 -64 -55q-34 -22 -132.5 -85t-151.5 -99q-98 -69 -164 -69v0v0q-66 0 -164 69 q-46 32 -141.5 92.5t-142.5 92.5q-12 8 -33 27t-31 27v-436q0 -40 28 -68t68 -28h832q40 0 68 28t28 68zM1280 925q0 41 -27.5 70t-68.5 29h-832q-40 0 -68 -28t-28 -68q0 -37 30.5 -76.5t67.5 -64.5q47 -32 137.5 -89t129.5 -83q3 -2 17 -11.5t21 -14t21 -13t23.5 -13 t21.5 -9.5t22.5 -7.5t20.5 -2.5t20.5 2.5t22.5 7.5t21.5 9.5t23.5 13t21 13t21 14t17 11.5l267 174q35 23 66.5 62.5t31.5 73.5z" /> | |
| 407 | <glyph unicode="" horiz-adv-x="1792" d="M127 640q0 163 67 313l367 -1005q-196 95 -315 281t-119 411zM1415 679q0 -19 -2.5 -38.5t-10 -49.5t-11.5 -44t-17.5 -59t-17.5 -58l-76 -256l-278 826q46 3 88 8q19 2 26 18.5t-2.5 31t-28.5 13.5l-205 -10q-75 1 -202 10q-12 1 -20.5 -5t-11.5 -15t-1.5 -18.5t9 -16.5 t19.5 -8l80 -8l120 -328l-168 -504l-280 832q46 3 88 8q19 2 26 18.5t-2.5 31t-28.5 13.5l-205 -10q-7 0 -23 0.5t-26 0.5q105 160 274.5 253.5t367.5 93.5q147 0 280.5 -53t238.5 -149h-10q-55 0 -92 -40.5t-37 -95.5q0 -12 2 -24t4 -21.5t8 -23t9 -21t12 -22.5t12.5 -21 t14.5 -24t14 -23q63 -107 63 -212zM909 573l237 -647q1 -6 5 -11q-126 -44 -255 -44q-112 0 -217 32zM1570 1009q95 -174 95 -369q0 -209 -104 -385.5t-279 -278.5l235 678q59 169 59 276q0 42 -6 79zM896 1536q182 0 348 -71t286 -191t191 -286t71 -348t-71 -348t-191 -286 t-286 -191t-348 -71t-348 71t-286 191t-191 286t-71 348t71 348t191 286t286 191t348 71zM896 -215q173 0 331.5 68t273 182.5t182.5 273t68 331.5t-68 331.5t-182.5 273t-273 182.5t-331.5 68t-331.5 -68t-273 -182.5t-182.5 -273t-68 -331.5t68 -331.5t182.5 -273 t273 -182.5t331.5 -68z" /> | |
| 408 | <glyph unicode="" horiz-adv-x="1792" d="M1086 1536v-1536l-272 -128q-228 20 -414 102t-293 208.5t-107 272.5q0 140 100.5 263.5t275 205.5t391.5 108v-172q-217 -38 -356.5 -150t-139.5 -255q0 -152 154.5 -267t388.5 -145v1360zM1755 954l37 -390l-525 114l147 83q-119 70 -280 99v172q277 -33 481 -157z" /> | |
| 409 | <glyph unicode="" horiz-adv-x="2048" d="M960 1536l960 -384v-128h-128q0 -26 -20.5 -45t-48.5 -19h-1526q-28 0 -48.5 19t-20.5 45h-128v128zM256 896h256v-768h128v768h256v-768h128v768h256v-768h128v768h256v-768h59q28 0 48.5 -19t20.5 -45v-64h-1664v64q0 26 20.5 45t48.5 19h59v768zM1851 -64 q28 0 48.5 -19t20.5 -45v-128h-1920v128q0 26 20.5 45t48.5 19h1782z" /> | |
| 410 | <glyph unicode="" horiz-adv-x="2304" d="M1774 700l18 -316q4 -69 -82 -128t-235 -93.5t-323 -34.5t-323 34.5t-235 93.5t-82 128l18 316l574 -181q22 -7 48 -7t48 7zM2304 1024q0 -23 -22 -31l-1120 -352q-4 -1 -10 -1t-10 1l-652 206q-43 -34 -71 -111.5t-34 -178.5q63 -36 63 -109q0 -69 -58 -107l58 -433 q2 -14 -8 -25q-9 -11 -24 -11h-192q-15 0 -24 11q-10 11 -8 25l58 433q-58 38 -58 107q0 73 65 111q11 207 98 330l-333 104q-22 8 -22 31t22 31l1120 352q4 1 10 1t10 -1l1120 -352q22 -8 22 -31z" /> | |
| 411 | <glyph unicode="" d="M859 579l13 -707q-62 11 -105 11q-41 0 -105 -11l13 707q-40 69 -168.5 295.5t-216.5 374.5t-181 287q58 -15 108 -15q43 0 111 15q63 -111 133.5 -229.5t167 -276.5t138.5 -227q37 61 109.5 177.5t117.5 190t105 176t107 189.5q54 -14 107 -14q56 0 114 14v0 q-28 -39 -60 -88.5t-49.5 -78.5t-56.5 -96t-49 -84q-146 -248 -353 -610z" /> | |
| 412 | <glyph unicode="" horiz-adv-x="1280" d="M981 197q0 25 -7 49t-14.5 42t-27 41.5t-29.5 35t-38.5 34.5t-36.5 29t-41.5 30t-36.5 26q-16 2 -49 2q-53 0 -104.5 -7t-107 -25t-97 -46t-68.5 -74.5t-27 -105.5q0 -56 23.5 -102t61 -75.5t87 -50t100 -29t101.5 -8.5q58 0 111.5 13t99 39t73 73t27.5 109zM864 1055 q0 59 -17 125.5t-48 129t-84 103.5t-117 41q-42 0 -82.5 -19.5t-66.5 -52.5q-46 -59 -46 -160q0 -46 10 -97.5t31.5 -103t52 -92.5t75 -67t96.5 -26q37 0 77.5 16.5t65.5 43.5q53 56 53 159zM752 1536h417l-137 -88h-132q75 -63 113 -133t38 -160q0 -72 -24.5 -129.5 t-59.5 -93t-69.5 -65t-59 -61.5t-24.5 -66q0 -36 32 -70.5t77 -68t90.5 -73.5t77.5 -104t32 -142q0 -91 -49 -173q-71 -122 -209.5 -179.5t-298.5 -57.5q-132 0 -246.5 41.5t-172.5 137.5q-36 59 -36 131q0 81 44.5 150t118.5 115q131 82 404 100q-32 41 -47.5 73.5 t-15.5 73.5q0 40 21 85q-46 -4 -68 -4q-148 0 -249.5 96.5t-101.5 244.5q0 82 36 159t99 131q76 66 182 98t218 32z" /> | |
| 413 | <glyph unicode="" horiz-adv-x="1984" d="M831 572q0 -56 -40.5 -96t-96.5 -40q-57 0 -98 40t-41 96q0 57 41.5 98t97.5 41t96.5 -41t40.5 -98zM1292 711q56 0 96.5 -41t40.5 -98q0 -56 -40.5 -96t-96.5 -40q-57 0 -98 40t-41 96q0 57 41.5 98t97.5 41zM1984 722q0 -62 -31 -114t-83 -82q5 -33 5 -61 q0 -121 -68.5 -230.5t-197.5 -193.5q-125 -82 -285.5 -125.5t-335.5 -43.5q-176 0 -336.5 43.5t-284.5 125.5q-129 84 -197.5 193t-68.5 231q0 29 5 66q-48 31 -77 81.5t-29 109.5q0 94 66 160t160 66q83 0 148 -55q248 158 592 164l134 423q4 14 17.5 21.5t28.5 4.5 l347 -82q22 50 68.5 81t102.5 31q77 0 131.5 -54.5t54.5 -131.5t-54.5 -132t-131.5 -55q-76 0 -130.5 54t-55.5 131l-315 74l-116 -366q327 -14 560 -166q64 58 151 58q94 0 160 -66t66 -160zM1664 1459q-45 0 -77 -32t-32 -77t32 -77t77 -32t77 32t32 77t-32 77t-77 32z M77 722q0 -67 51 -111q49 131 180 235q-36 25 -82 25q-62 0 -105.5 -43.5t-43.5 -105.5zM1567 105q112 73 171.5 166t59.5 194t-59.5 193.5t-171.5 165.5q-116 75 -265.5 115.5t-313.5 40.5t-313.5 -40.5t-265.5 -115.5q-112 -73 -171.5 -165.5t-59.5 -193.5t59.5 -194 t171.5 -166q116 -75 265.5 -115.5t313.5 -40.5t313.5 40.5t265.5 115.5zM1850 605q57 46 57 117q0 62 -43.5 105.5t-105.5 43.5q-49 0 -86 -28q131 -105 178 -238zM1258 237q11 11 27 11t27 -11t11 -27.5t-11 -27.5q-99 -99 -319 -99h-2q-220 0 -319 99q-11 11 -11 27.5 t11 27.5t27 11t27 -11q77 -77 265 -77h2q188 0 265 77z" /> | |
| 414 | <glyph unicode="" d="M950 393q7 7 17.5 7t17.5 -7t7 -18t-7 -18q-65 -64 -208 -64h-1h-1q-143 0 -207 64q-8 7 -8 18t8 18q7 7 17.5 7t17.5 -7q49 -51 172 -51h1h1q122 0 173 51zM671 613q0 -37 -26 -64t-63 -27t-63 27t-26 64t26 63t63 26t63 -26t26 -63zM1214 1049q-29 0 -50 21t-21 50 q0 30 21 51t50 21q30 0 51 -21t21 -51q0 -29 -21 -50t-51 -21zM1216 1408q132 0 226 -94t94 -227v-894q0 -133 -94 -227t-226 -94h-896q-132 0 -226 94t-94 227v894q0 133 94 227t226 94h896zM1321 596q35 14 57 45.5t22 70.5q0 51 -36 87.5t-87 36.5q-60 0 -98 -48 q-151 107 -375 115l83 265l206 -49q1 -50 36.5 -85t84.5 -35q50 0 86 35.5t36 85.5t-36 86t-86 36q-36 0 -66 -20.5t-45 -53.5l-227 54q-9 2 -17.5 -2.5t-11.5 -14.5l-95 -302q-224 -4 -381 -113q-36 43 -93 43q-51 0 -87 -36.5t-36 -87.5q0 -37 19.5 -67.5t52.5 -45.5 q-7 -25 -7 -54q0 -98 74 -181.5t201.5 -132t278.5 -48.5q150 0 277.5 48.5t201.5 132t74 181.5q0 27 -6 54zM971 702q37 0 63 -26t26 -63t-26 -64t-63 -27t-63 27t-26 64t26 63t63 26z" /> | |
| 415 | <glyph unicode="" d="M866 697l90 27v62q0 79 -58 135t-138 56t-138 -55.5t-58 -134.5v-283q0 -20 -14 -33.5t-33 -13.5t-32.5 13.5t-13.5 33.5v120h-151v-122q0 -82 57.5 -139t139.5 -57q81 0 138.5 56.5t57.5 136.5v280q0 19 13.5 33t33.5 14q19 0 32.5 -14t13.5 -33v-54zM1199 502v122h-150 v-126q0 -20 -13.5 -33.5t-33.5 -13.5q-19 0 -32.5 14t-13.5 33v123l-90 -26l-60 28v-123q0 -80 58 -137t139 -57t138.5 57t57.5 139zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103 t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 416 | <glyph unicode="" horiz-adv-x="1920" d="M1062 824v118q0 42 -30 72t-72 30t-72 -30t-30 -72v-612q0 -175 -126 -299t-303 -124q-178 0 -303.5 125.5t-125.5 303.5v266h328v-262q0 -43 30 -72.5t72 -29.5t72 29.5t30 72.5v620q0 171 126.5 292t301.5 121q176 0 302 -122t126 -294v-136l-195 -58zM1592 602h328 v-266q0 -178 -125.5 -303.5t-303.5 -125.5q-177 0 -303 124.5t-126 300.5v268l131 -61l195 58v-270q0 -42 30 -71.5t72 -29.5t72 29.5t30 71.5v275z" /> | |
| 417 | <glyph unicode="" d="M1472 160v480h-704v704h-480q-93 0 -158.5 -65.5t-65.5 -158.5v-480h704v-704h480q93 0 158.5 65.5t65.5 158.5zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5 t84.5 -203.5z" /> | |
| 418 | <glyph unicode="" horiz-adv-x="2048" d="M328 1254h204v-983h-532v697h328v286zM328 435v369h-123v-369h123zM614 968v-697h205v697h-205zM614 1254v-204h205v204h-205zM901 968h533v-942h-533v163h328v82h-328v697zM1229 435v369h-123v-369h123zM1516 968h532v-942h-532v163h327v82h-327v697zM1843 435v369h-123 v-369h123z" /> | |
| 419 | <glyph unicode="" d="M1046 516q0 -64 -38 -109t-91 -45q-43 0 -70 15v277q28 17 70 17q53 0 91 -45.5t38 -109.5zM703 944q0 -64 -38 -109.5t-91 -45.5q-43 0 -70 15v277q28 17 70 17q53 0 91 -45t38 -109zM1265 513q0 134 -88 229t-213 95q-20 0 -39 -3q-23 -78 -78 -136q-87 -95 -211 -101 v-636l211 41v206q51 -19 117 -19q125 0 213 95t88 229zM922 940q0 134 -88.5 229t-213.5 95q-74 0 -141 -36h-186v-840l211 41v206q55 -19 116 -19q125 0 213.5 95t88.5 229zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960 q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 420 | <glyph unicode="" horiz-adv-x="2038" d="M1222 607q75 3 143.5 -20.5t118 -58.5t101 -94.5t84 -108t75.5 -120.5q33 -56 78.5 -109t75.5 -80.5t99 -88.5q-48 -30 -108.5 -57.5t-138.5 -59t-114 -47.5q-44 37 -74 115t-43.5 164.5t-33 180.5t-42.5 168.5t-72.5 123t-122.5 48.5l-10 -2l-6 -4q4 -5 13 -14 q6 -5 28 -23.5t25.5 -22t19 -18t18 -20.5t11.5 -21t10.5 -27.5t4.5 -31t4 -40.5l1 -33q1 -26 -2.5 -57.5t-7.5 -52t-12.5 -58.5t-11.5 -53q-35 1 -101 -9.5t-98 -10.5q-39 0 -72 10q-2 16 -2 47q0 74 3 96q2 13 31.5 41.5t57 59t26.5 51.5q-24 2 -43 -24 q-36 -53 -111.5 -99.5t-136.5 -46.5q-25 0 -75.5 63t-106.5 139.5t-84 96.5q-6 4 -27 30q-482 -112 -513 -112q-16 0 -28 11t-12 27q0 15 8.5 26.5t22.5 14.5l486 106q-8 14 -8 25t5.5 17.5t16 11.5t20 7t23 4.5t18.5 4.5q4 1 15.5 7.5t17.5 6.5q15 0 28 -16t20 -33 q163 37 172 37q17 0 29.5 -11t12.5 -28q0 -15 -8.5 -26t-23.5 -14l-182 -40l-1 -16q-1 -26 81.5 -117.5t104.5 -91.5q47 0 119 80t72 129q0 36 -23.5 53t-51 18.5t-51 11.5t-23.5 34q0 16 10 34l-68 19q43 44 43 117q0 26 -5 58q82 16 144 16q44 0 71.5 -1.5t48.5 -8.5 t31 -13.5t20.5 -24.5t15.5 -33.5t17 -47.5t24 -60l50 25q-3 -40 -23 -60t-42.5 -21t-40 -6.5t-16.5 -20.5zM1282 842q-5 5 -13.5 15.5t-12 14.5t-10.5 11.5t-10 10.5l-8 8t-8.5 7.5t-8 5t-8.5 4.5q-7 3 -14.5 5t-20.5 2.5t-22 0.5h-32.5h-37.5q-126 0 -217 -43 q16 30 36 46.5t54 29.5t65.5 36t46 36.5t50 55t43.5 50.5q12 -9 28 -31.5t32 -36.5t38 -13l12 1v-76l22 -1q247 95 371 190q28 21 50 39t42.5 37.5t33 31t29.5 34t24 31t24.5 37t23 38t27 47.5t29.5 53l7 9q-2 -53 -43 -139q-79 -165 -205 -264t-306 -142q-14 -3 -42 -7.5 t-50 -9.5t-39 -14q3 -19 24.5 -46t21.5 -34q0 -11 -26 -30zM1061 -79q39 26 131.5 47.5t146.5 21.5q9 0 22.5 -15.5t28 -42.5t26 -50t24 -51t14.5 -33q-121 -45 -244 -45q-61 0 -125 11zM822 568l48 12l109 -177l-73 -48zM1323 51q3 -15 3 -16q0 -7 -17.5 -14.5t-46 -13 t-54 -9.5t-53.5 -7.5t-32 -4.5l-7 43q21 2 60.5 8.5t72 10t60.5 3.5h14zM866 679l-96 -20l-6 17q10 1 32.5 7t34.5 6q19 0 35 -10zM1061 45h31l10 -83l-41 -12v95zM1950 1535v1v-1zM1950 1535l-1 -5l-2 -2l1 3zM1950 1535l1 1z" /> | |
| 421 | <glyph unicode="" d="M1167 -50q-5 19 -24 5q-30 -22 -87 -39t-131 -17q-129 0 -193 49q-5 4 -13 4q-11 0 -26 -12q-7 -6 -7.5 -16t7.5 -20q34 -32 87.5 -46t102.5 -12.5t99 4.5q41 4 84.5 20.5t65 30t28.5 20.5q12 12 7 29zM1128 65q-19 47 -39 61q-23 15 -76 15q-47 0 -71 -10 q-29 -12 -78 -56q-26 -24 -12 -44q9 -8 17.5 -4.5t31.5 23.5q3 2 10.5 8.5t10.5 8.5t10 7t11.5 7t12.5 5t15 4.5t16.5 2.5t20.5 1q27 0 44.5 -7.5t23 -14.5t13.5 -22q10 -17 12.5 -20t12.5 1q23 12 14 34zM1483 346q0 22 -5 44.5t-16.5 45t-34 36.5t-52.5 14 q-33 0 -97 -41.5t-129 -83.5t-101 -42q-27 -1 -63.5 19t-76 49t-83.5 58t-100 49t-111 19q-115 -1 -197 -78.5t-84 -178.5q-2 -112 74 -164q29 -20 62.5 -28.5t103.5 -8.5q57 0 132 32.5t134 71t120 70.5t93 31q26 -1 65 -31.5t71.5 -67t68 -67.5t55.5 -32q35 -3 58.5 14 t55.5 63q28 41 42.5 101t14.5 106zM1536 506q0 -164 -62 -304.5t-166 -236t-242.5 -149.5t-290.5 -54t-293 57.5t-247.5 157t-170.5 241.5t-64 302q0 89 19.5 172.5t49 145.5t70.5 118.5t78.5 94t78.5 69.5t64.5 46.5t42.5 24.5q14 8 51 26.5t54.5 28.5t48 30t60.5 44 q36 28 58 72.5t30 125.5q129 -155 186 -193q44 -29 130 -68t129 -66q21 -13 39 -25t60.5 -46.5t76 -70.5t75 -95t69 -122t47 -148.5t19.5 -177.5z" /> | |
| 422 | <glyph unicode="" d="M1070 463l-160 -160l-151 -152l-30 -30q-65 -64 -151.5 -87t-171.5 -2q-16 -70 -72 -115t-129 -45q-85 0 -145 60.5t-60 145.5q0 72 44.5 128t113.5 72q-22 86 1 173t88 152l12 12l151 -152l-11 -11q-37 -37 -37 -89t37 -90q37 -37 89 -37t89 37l30 30l151 152l161 160z M729 1145l12 -12l-152 -152l-12 12q-37 37 -89 37t-89 -37t-37 -89.5t37 -89.5l29 -29l152 -152l160 -160l-151 -152l-161 160l-151 152l-30 30q-68 67 -90 159.5t5 179.5q-70 15 -115 71t-45 129q0 85 60 145.5t145 60.5q76 0 133.5 -49t69.5 -123q84 20 169.5 -3.5 t149.5 -87.5zM1536 78q0 -85 -60 -145.5t-145 -60.5q-74 0 -131 47t-71 118q-86 -28 -179.5 -6t-161.5 90l-11 12l151 152l12 -12q37 -37 89 -37t89 37t37 89t-37 89l-30 30l-152 152l-160 160l152 152l160 -160l152 -152l29 -30q64 -64 87.5 -150.5t2.5 -171.5 q76 -11 126.5 -68.5t50.5 -134.5zM1534 1202q0 -77 -51 -135t-127 -69q26 -85 3 -176.5t-90 -158.5l-12 -12l-151 152l12 12q37 37 37 89t-37 89t-89 37t-89 -37l-30 -30l-152 -152l-160 -160l-152 152l161 160l152 152l29 30q67 67 159 89.5t178 -3.5q11 75 68.5 126 t135.5 51q85 0 145 -60.5t60 -145.5z" /> | |
| 423 | <glyph unicode="" d="M654 458q-1 -3 -12.5 0.5t-31.5 11.5l-20 9q-44 20 -87 49q-7 5 -41 31.5t-38 28.5q-67 -103 -134 -181q-81 -95 -105 -110q-4 -2 -19.5 -4t-18.5 0q6 4 82 92q21 24 85.5 115t78.5 118q17 30 51 98.5t36 77.5q-8 1 -110 -33q-8 -2 -27.5 -7.5t-34.5 -9.5t-17 -5 q-2 -2 -2 -10.5t-1 -9.5q-5 -10 -31 -15q-23 -7 -47 0q-18 4 -28 21q-4 6 -5 23q6 2 24.5 5t29.5 6q58 16 105 32q100 35 102 35q10 2 43 19.5t44 21.5q9 3 21.5 8t14.5 5.5t6 -0.5q2 -12 -1 -33q0 -2 -12.5 -27t-26.5 -53.5t-17 -33.5q-25 -50 -77 -131l64 -28 q12 -6 74.5 -32t67.5 -28q4 -1 10.5 -25.5t4.5 -30.5zM449 944q3 -15 -4 -28q-12 -23 -50 -38q-30 -12 -60 -12q-26 3 -49 26q-14 15 -18 41l1 3q3 -3 19.5 -5t26.5 0t58 16q36 12 55 14q17 0 21 -17zM1147 815l63 -227l-139 42zM39 15l694 232v1032l-694 -233v-1031z M1280 332l102 -31l-181 657l-100 31l-216 -536l102 -31l45 110l211 -65zM777 1294l573 -184v380zM1088 -29l158 -13l-54 -160l-40 66q-130 -83 -276 -108q-58 -12 -91 -12h-84q-79 0 -199.5 39t-183.5 85q-8 7 -8 16q0 8 5 13.5t13 5.5q4 0 18 -7.5t30.5 -16.5t20.5 -11 q73 -37 159.5 -61.5t157.5 -24.5q95 0 167 14.5t157 50.5q15 7 30.5 15.5t34 19t28.5 16.5zM1536 1050v-1079l-774 246q-14 -6 -375 -127.5t-368 -121.5q-13 0 -18 13q0 1 -1 3v1078q3 9 4 10q5 6 20 11q106 35 149 50v384l558 -198q2 0 160.5 55t316 108.5t161.5 53.5 q20 0 20 -21v-418z" /> | |
| 424 | <glyph unicode="" horiz-adv-x="1792" d="M288 1152q66 0 113 -47t47 -113v-1088q0 -66 -47 -113t-113 -47h-128q-66 0 -113 47t-47 113v1088q0 66 47 113t113 47h128zM1664 989q58 -34 93 -93t35 -128v-768q0 -106 -75 -181t-181 -75h-864q-66 0 -113 47t-47 113v1536q0 40 28 68t68 28h672q40 0 88 -20t76 -48 l152 -152q28 -28 48 -76t20 -88v-163zM928 0v128q0 14 -9 23t-23 9h-128q-14 0 -23 -9t-9 -23v-128q0 -14 9 -23t23 -9h128q14 0 23 9t9 23zM928 256v128q0 14 -9 23t-23 9h-128q-14 0 -23 -9t-9 -23v-128q0 -14 9 -23t23 -9h128q14 0 23 9t9 23zM928 512v128q0 14 -9 23 t-23 9h-128q-14 0 -23 -9t-9 -23v-128q0 -14 9 -23t23 -9h128q14 0 23 9t9 23zM1184 0v128q0 14 -9 23t-23 9h-128q-14 0 -23 -9t-9 -23v-128q0 -14 9 -23t23 -9h128q14 0 23 9t9 23zM1184 256v128q0 14 -9 23t-23 9h-128q-14 0 -23 -9t-9 -23v-128q0 -14 9 -23t23 -9h128 q14 0 23 9t9 23zM1184 512v128q0 14 -9 23t-23 9h-128q-14 0 -23 -9t-9 -23v-128q0 -14 9 -23t23 -9h128q14 0 23 9t9 23zM1440 0v128q0 14 -9 23t-23 9h-128q-14 0 -23 -9t-9 -23v-128q0 -14 9 -23t23 -9h128q14 0 23 9t9 23zM1440 256v128q0 14 -9 23t-23 9h-128 q-14 0 -23 -9t-9 -23v-128q0 -14 9 -23t23 -9h128q14 0 23 9t9 23zM1440 512v128q0 14 -9 23t-23 9h-128q-14 0 -23 -9t-9 -23v-128q0 -14 9 -23t23 -9h128q14 0 23 9t9 23zM1536 896v256h-160q-40 0 -68 28t-28 68v160h-640v-512h896z" /> | |
| 425 | <glyph unicode="" d="M1344 1536q26 0 45 -19t19 -45v-1664q0 -26 -19 -45t-45 -19h-1280q-26 0 -45 19t-19 45v1664q0 26 19 45t45 19h1280zM512 1248v-64q0 -14 9 -23t23 -9h64q14 0 23 9t9 23v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23zM512 992v-64q0 -14 9 -23t23 -9h64q14 0 23 9 t9 23v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23zM512 736v-64q0 -14 9 -23t23 -9h64q14 0 23 9t9 23v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23zM512 480v-64q0 -14 9 -23t23 -9h64q14 0 23 9t9 23v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23zM384 160v64 q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM384 416v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM384 672v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h64 q14 0 23 9t9 23zM384 928v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM384 1184v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM896 -96v192q0 14 -9 23t-23 9h-320q-14 0 -23 -9 t-9 -23v-192q0 -14 9 -23t23 -9h320q14 0 23 9t9 23zM896 416v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM896 672v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM896 928v64 q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM896 1184v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM1152 160v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h64 q14 0 23 9t9 23zM1152 416v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM1152 672v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM1152 928v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9 t-9 -23v-64q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM1152 1184v64q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-64q0 -14 9 -23t23 -9h64q14 0 23 9t9 23z" /> | |
| 426 | <glyph unicode="" horiz-adv-x="1280" d="M1188 988l-292 -292v-824q0 -46 -33 -79t-79 -33t-79 33t-33 79v384h-64v-384q0 -46 -33 -79t-79 -33t-79 33t-33 79v824l-292 292q-28 28 -28 68t28 68t68 28t68 -28l228 -228h368l228 228q28 28 68 28t68 -28t28 -68t-28 -68zM864 1152q0 -93 -65.5 -158.5 t-158.5 -65.5t-158.5 65.5t-65.5 158.5t65.5 158.5t158.5 65.5t158.5 -65.5t65.5 -158.5z" /> | |
| 427 | <glyph unicode="" horiz-adv-x="1664" d="M780 1064q0 -60 -19 -113.5t-63 -92.5t-105 -39q-76 0 -138 57.5t-92 135.5t-30 151q0 60 19 113.5t63 92.5t105 39q77 0 138.5 -57.5t91.5 -135t30 -151.5zM438 581q0 -80 -42 -139t-119 -59q-76 0 -141.5 55.5t-100.5 133.5t-35 152q0 80 42 139.5t119 59.5 q76 0 141.5 -55.5t100.5 -134t35 -152.5zM832 608q118 0 255 -97.5t229 -237t92 -254.5q0 -46 -17 -76.5t-48.5 -45t-64.5 -20t-76 -5.5q-68 0 -187.5 45t-182.5 45q-66 0 -192.5 -44.5t-200.5 -44.5q-183 0 -183 146q0 86 56 191.5t139.5 192.5t187.5 146t193 59zM1071 819 q-61 0 -105 39t-63 92.5t-19 113.5q0 74 30 151.5t91.5 135t138.5 57.5q61 0 105 -39t63 -92.5t19 -113.5q0 -73 -30 -151t-92 -135.5t-138 -57.5zM1503 923q77 0 119 -59.5t42 -139.5q0 -74 -35 -152t-100.5 -133.5t-141.5 -55.5q-77 0 -119 59t-42 139q0 74 35 152.5 t100.5 134t141.5 55.5z" /> | |
| 428 | <glyph unicode="" horiz-adv-x="768" d="M704 1008q0 -145 -57 -243.5t-152 -135.5l45 -821q2 -26 -16 -45t-44 -19h-192q-26 0 -44 19t-16 45l45 821q-95 37 -152 135.5t-57 243.5q0 128 42.5 249.5t117.5 200t160 78.5t160 -78.5t117.5 -200t42.5 -249.5z" /> | |
| 429 | <glyph unicode="" horiz-adv-x="1792" d="M896 -93l640 349v636l-640 -233v-752zM832 772l698 254l-698 254l-698 -254zM1664 1024v-768q0 -35 -18 -65t-49 -47l-704 -384q-28 -16 -61 -16t-61 16l-704 384q-31 17 -49 47t-18 65v768q0 40 23 73t61 47l704 256q22 8 44 8t44 -8l704 -256q38 -14 61 -47t23 -73z " /> | |
| 430 | <glyph unicode="" horiz-adv-x="2304" d="M640 -96l384 192v314l-384 -164v-342zM576 358l404 173l-404 173l-404 -173zM1664 -96l384 192v314l-384 -164v-342zM1600 358l404 173l-404 173l-404 -173zM1152 651l384 165v266l-384 -164v-267zM1088 1030l441 189l-441 189l-441 -189zM2176 512v-416q0 -36 -19 -67 t-52 -47l-448 -224q-25 -14 -57 -14t-57 14l-448 224q-5 2 -7 4q-2 -2 -7 -4l-448 -224q-25 -14 -57 -14t-57 14l-448 224q-33 16 -52 47t-19 67v416q0 38 21.5 70t56.5 48l434 186v400q0 38 21.5 70t56.5 48l448 192q23 10 50 10t50 -10l448 -192q35 -16 56.5 -48t21.5 -70 v-400l434 -186q36 -16 57 -48t21 -70z" /> | |
| 431 | <glyph unicode="" horiz-adv-x="2048" d="M1848 1197h-511v-124h511v124zM1596 771q-90 0 -146 -52.5t-62 -142.5h408q-18 195 -200 195zM1612 186q63 0 122 32t76 87h221q-100 -307 -427 -307q-214 0 -340.5 132t-126.5 347q0 208 130.5 345.5t336.5 137.5q138 0 240.5 -68t153 -179t50.5 -248q0 -17 -2 -47h-658 q0 -111 57.5 -171.5t166.5 -60.5zM277 236h296q205 0 205 167q0 180 -199 180h-302v-347zM277 773h281q78 0 123.5 36.5t45.5 113.5q0 144 -190 144h-260v-294zM0 1282h594q87 0 155 -14t126.5 -47.5t90 -96.5t31.5 -154q0 -181 -172 -263q114 -32 172 -115t58 -204 q0 -75 -24.5 -136.5t-66 -103.5t-98.5 -71t-121 -42t-134 -13h-611v1260z" /> | |
| 432 | <glyph unicode="" d="M1248 1408q119 0 203.5 -84.5t84.5 -203.5v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960zM499 1041h-371v-787h382q117 0 197 57.5t80 170.5q0 158 -143 200q107 52 107 164q0 57 -19.5 96.5 t-56.5 60.5t-79 29.5t-97 8.5zM477 723h-176v184h163q119 0 119 -90q0 -94 -106 -94zM486 388h-185v217h189q124 0 124 -113q0 -104 -128 -104zM1136 356q-68 0 -104 38t-36 107h411q1 10 1 30q0 132 -74.5 220.5t-203.5 88.5q-128 0 -210 -86t-82 -216q0 -135 79 -217 t213 -82q205 0 267 191h-138q-11 -34 -47.5 -54t-75.5 -20zM1126 722q113 0 124 -122h-254q4 56 39 89t91 33zM964 988h319v-77h-319v77z" /> | |
| 433 | <glyph unicode="" horiz-adv-x="1792" d="M1582 954q0 -101 -71.5 -172.5t-172.5 -71.5t-172.5 71.5t-71.5 172.5t71.5 172.5t172.5 71.5t172.5 -71.5t71.5 -172.5zM812 212q0 104 -73 177t-177 73q-27 0 -54 -6l104 -42q77 -31 109.5 -106.5t1.5 -151.5q-31 -77 -107 -109t-152 -1q-21 8 -62 24.5t-61 24.5 q32 -60 91 -96.5t130 -36.5q104 0 177 73t73 177zM1642 953q0 126 -89.5 215.5t-215.5 89.5q-127 0 -216.5 -89.5t-89.5 -215.5q0 -127 89.5 -216t216.5 -89q126 0 215.5 89t89.5 216zM1792 953q0 -189 -133.5 -322t-321.5 -133l-437 -319q-12 -129 -109 -218t-229 -89 q-121 0 -214 76t-118 192l-230 92v429l389 -157q79 48 173 48q13 0 35 -2l284 407q2 187 135.5 319t320.5 132q188 0 321.5 -133.5t133.5 -321.5z" /> | |
| 434 | <glyph unicode="" d="M1242 889q0 80 -57 136.5t-137 56.5t-136.5 -57t-56.5 -136q0 -80 56.5 -136.5t136.5 -56.5t137 56.5t57 136.5zM632 301q0 -83 -58 -140.5t-140 -57.5q-56 0 -103 29t-72 77q52 -20 98 -40q60 -24 120 1.5t85 86.5q24 60 -1.5 120t-86.5 84l-82 33q22 5 42 5 q82 0 140 -57.5t58 -140.5zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v153l172 -69q20 -92 93.5 -152t168.5 -60q104 0 181 70t87 173l345 252q150 0 255.5 105.5t105.5 254.5q0 150 -105.5 255.5t-255.5 105.5 q-148 0 -253 -104.5t-107 -252.5l-225 -322q-9 1 -28 1q-75 0 -137 -37l-297 119v468q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5zM1289 887q0 -100 -71 -170.5t-171 -70.5t-170.5 70.5t-70.5 170.5t70.5 171t170.5 71q101 0 171.5 -70.5t70.5 -171.5z " /> | |
| 435 | <glyph unicode="" horiz-adv-x="1792" d="M836 367l-15 -368l-2 -22l-420 29q-36 3 -67 31.5t-47 65.5q-11 27 -14.5 55t4 65t12 55t21.5 64t19 53q78 -12 509 -28zM449 953l180 -379l-147 92q-63 -72 -111.5 -144.5t-72.5 -125t-39.5 -94.5t-18.5 -63l-4 -21l-190 357q-17 26 -18 56t6 47l8 18q35 63 114 188 l-140 86zM1680 436l-188 -359q-12 -29 -36.5 -46.5t-43.5 -20.5l-18 -4q-71 -7 -219 -12l8 -164l-230 367l211 362l7 -173q170 -16 283 -5t170 33zM895 1360q-47 -63 -265 -435l-317 187l-19 12l225 356q20 31 60 45t80 10q24 -2 48.5 -12t42 -21t41.5 -33t36 -34.5 t36 -39.5t32 -35zM1550 1053l212 -363q18 -37 12.5 -76t-27.5 -74q-13 -20 -33 -37t-38 -28t-48.5 -22t-47 -16t-51.5 -14t-46 -12q-34 72 -265 436l313 195zM1407 1279l142 83l-220 -373l-419 20l151 86q-34 89 -75 166t-75.5 123.5t-64.5 80t-47 46.5l-17 13l405 -1 q31 3 58 -10.5t39 -28.5l11 -15q39 -61 112 -190z" /> | |
| 436 | <glyph unicode="" horiz-adv-x="2048" d="M480 448q0 66 -47 113t-113 47t-113 -47t-47 -113t47 -113t113 -47t113 47t47 113zM516 768h1016l-89 357q-2 8 -14 17.5t-21 9.5h-768q-9 0 -21 -9.5t-14 -17.5zM1888 448q0 66 -47 113t-113 47t-113 -47t-47 -113t47 -113t113 -47t113 47t47 113zM2048 544v-384 q0 -14 -9 -23t-23 -9h-96v-128q0 -80 -56 -136t-136 -56t-136 56t-56 136v128h-1024v-128q0 -80 -56 -136t-136 -56t-136 56t-56 136v128h-96q-14 0 -23 9t-9 23v384q0 93 65.5 158.5t158.5 65.5h28l105 419q23 94 104 157.5t179 63.5h768q98 0 179 -63.5t104 -157.5 l105 -419h28q93 0 158.5 -65.5t65.5 -158.5z" /> | |
| 437 | <glyph unicode="" horiz-adv-x="2048" d="M1824 640q93 0 158.5 -65.5t65.5 -158.5v-384q0 -14 -9 -23t-23 -9h-96v-64q0 -80 -56 -136t-136 -56t-136 56t-56 136v64h-1024v-64q0 -80 -56 -136t-136 -56t-136 56t-56 136v64h-96q-14 0 -23 9t-9 23v384q0 93 65.5 158.5t158.5 65.5h28l105 419q23 94 104 157.5 t179 63.5h128v224q0 14 9 23t23 9h448q14 0 23 -9t9 -23v-224h128q98 0 179 -63.5t104 -157.5l105 -419h28zM320 160q66 0 113 47t47 113t-47 113t-113 47t-113 -47t-47 -113t47 -113t113 -47zM516 640h1016l-89 357q-2 8 -14 17.5t-21 9.5h-768q-9 0 -21 -9.5t-14 -17.5z M1728 160q66 0 113 47t47 113t-47 113t-113 47t-113 -47t-47 -113t47 -113t113 -47z" /> | |
| 438 | <glyph unicode="" d="M1504 64q0 -26 -19 -45t-45 -19h-462q1 -17 6 -87.5t5 -108.5q0 -25 -18 -42.5t-43 -17.5h-320q-25 0 -43 17.5t-18 42.5q0 38 5 108.5t6 87.5h-462q-26 0 -45 19t-19 45t19 45l402 403h-229q-26 0 -45 19t-19 45t19 45l402 403h-197q-26 0 -45 19t-19 45t19 45l384 384 q19 19 45 19t45 -19l384 -384q19 -19 19 -45t-19 -45t-45 -19h-197l402 -403q19 -19 19 -45t-19 -45t-45 -19h-229l402 -403q19 -19 19 -45z" /> | |
| 439 | <glyph unicode="" d="M1127 326q0 32 -30 51q-193 115 -447 115q-133 0 -287 -34q-42 -9 -42 -52q0 -20 13.5 -34.5t35.5 -14.5q5 0 37 8q132 27 243 27q226 0 397 -103q19 -11 33 -11q19 0 33 13.5t14 34.5zM1223 541q0 40 -35 61q-237 141 -548 141q-153 0 -303 -42q-48 -13 -48 -64 q0 -25 17.5 -42.5t42.5 -17.5q7 0 37 8q122 33 251 33q279 0 488 -124q24 -13 38 -13q25 0 42.5 17.5t17.5 42.5zM1331 789q0 47 -40 70q-126 73 -293 110.5t-343 37.5q-204 0 -364 -47q-23 -7 -38.5 -25.5t-15.5 -48.5q0 -31 20.5 -52t51.5 -21q11 0 40 8q133 37 307 37 q159 0 309.5 -34t253.5 -95q21 -12 40 -12q29 0 50.5 20.5t21.5 51.5zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 440 | <glyph unicode="" d="M1397 1408q58 0 98.5 -40.5t40.5 -98.5v-1258q0 -58 -40.5 -98.5t-98.5 -40.5h-1258q-58 0 -98.5 40.5t-40.5 98.5v1258q0 58 40.5 98.5t98.5 40.5h1258zM1465 11v1258q0 28 -20 48t-48 20h-1258q-28 0 -48 -20t-20 -48v-1258q0 -28 20 -48t48 -20h1258q28 0 48 20t20 48 zM694 749l188 -387l533 145v-496q0 -7 -5.5 -12.5t-12.5 -5.5h-1258q-7 0 -12.5 5.5t-5.5 12.5v141l711 195l-212 439q4 1 12 2.5t12 1.5q170 32 303.5 21.5t221 -46t143.5 -94.5q27 -28 -25 -42q-64 -16 -256 -62l-97 198q-111 7 -240 -16zM1397 1287q7 0 12.5 -5.5 t5.5 -12.5v-428q-85 30 -188 52q-294 64 -645 12l-18 -3l-65 134h-233l85 -190q-132 -51 -230 -137v560q0 7 5.5 12.5t12.5 5.5h1258zM286 387q-14 -3 -26 4.5t-14 21.5q-24 203 166 305l129 -270z" /> | |
| 441 | <glyph unicode="" horiz-adv-x="2304" d="M784 164l16 241l-16 523q-1 10 -7.5 17t-16.5 7q-9 0 -16 -7t-7 -17l-14 -523l14 -241q1 -10 7.5 -16.5t15.5 -6.5q22 0 24 23zM1080 193l11 211l-12 586q0 16 -13 24q-8 5 -16 5t-16 -5q-13 -8 -13 -24l-1 -6l-10 -579q0 -1 11 -236v-1q0 -10 6 -17q9 -11 23 -11 q11 0 20 9q9 7 9 20zM35 533l20 -128l-20 -126q-2 -9 -9 -9t-9 9l-17 126l17 128q2 9 9 9t9 -9zM121 612l26 -207l-26 -203q-2 -9 -10 -9q-9 0 -9 10l-23 202l23 207q0 9 9 9q8 0 10 -9zM401 159zM213 650l25 -245l-25 -237q0 -11 -11 -11q-10 0 -12 11l-21 237l21 245 q2 12 12 12q11 0 11 -12zM307 657l23 -252l-23 -244q-2 -13 -14 -13q-13 0 -13 13l-21 244l21 252q0 13 13 13q12 0 14 -13zM401 639l21 -234l-21 -246q-2 -16 -16 -16q-6 0 -10.5 4.5t-4.5 11.5l-20 246l20 234q0 6 4.5 10.5t10.5 4.5q14 0 16 -15zM784 164zM495 785 l21 -380l-21 -246q0 -7 -5 -12.5t-12 -5.5q-16 0 -18 18l-18 246l18 380q2 18 18 18q7 0 12 -5.5t5 -12.5zM589 871l19 -468l-19 -244q0 -8 -5.5 -13.5t-13.5 -5.5q-18 0 -20 19l-16 244l16 468q2 19 20 19q8 0 13.5 -5.5t5.5 -13.5zM687 911l18 -506l-18 -242 q-2 -21 -22 -21q-19 0 -21 21l-16 242l16 506q0 9 6.5 15.5t14.5 6.5q9 0 15 -6.5t7 -15.5zM1079 169v0v0zM881 915l15 -510l-15 -239q0 -10 -7.5 -17.5t-17.5 -7.5t-17 7t-8 18l-14 239l14 510q0 11 7.5 18t17.5 7t17.5 -7t7.5 -18zM980 896l14 -492l-14 -236q0 -11 -8 -19 t-19 -8t-19 8t-9 19l-12 236l12 492q1 12 9 20t19 8t18.5 -8t8.5 -20zM1192 404l-14 -231v0q0 -13 -9 -22t-22 -9t-22 9t-10 22l-6 114l-6 117l12 636v3q2 15 12 24q9 7 20 7q8 0 15 -5q14 -8 16 -26zM2304 423q0 -117 -83 -199.5t-200 -82.5h-786q-13 2 -22 11t-9 22v899 q0 23 28 33q85 34 181 34q195 0 338 -131.5t160 -323.5q53 22 110 22q117 0 200 -83t83 -201z" /> | |
| 442 | <glyph unicode="" d="M768 768q237 0 443 43t325 127v-170q0 -69 -103 -128t-280 -93.5t-385 -34.5t-385 34.5t-280 93.5t-103 128v170q119 -84 325 -127t443 -43zM768 0q237 0 443 43t325 127v-170q0 -69 -103 -128t-280 -93.5t-385 -34.5t-385 34.5t-280 93.5t-103 128v170q119 -84 325 -127 t443 -43zM768 384q237 0 443 43t325 127v-170q0 -69 -103 -128t-280 -93.5t-385 -34.5t-385 34.5t-280 93.5t-103 128v170q119 -84 325 -127t443 -43zM768 1536q208 0 385 -34.5t280 -93.5t103 -128v-128q0 -69 -103 -128t-280 -93.5t-385 -34.5t-385 34.5t-280 93.5 t-103 128v128q0 69 103 128t280 93.5t385 34.5z" /> | |
| 443 | <glyph unicode="" d="M1468 1156q28 -28 48 -76t20 -88v-1152q0 -40 -28 -68t-68 -28h-1344q-40 0 -68 28t-28 68v1600q0 40 28 68t68 28h896q40 0 88 -20t76 -48zM1024 1400v-376h376q-10 29 -22 41l-313 313q-12 12 -41 22zM1408 -128v1024h-416q-40 0 -68 28t-28 68v416h-768v-1536h1280z M894 465q33 -26 84 -56q59 7 117 7q147 0 177 -49q16 -22 2 -52q0 -1 -1 -2l-2 -2v-1q-6 -38 -71 -38q-48 0 -115 20t-130 53q-221 -24 -392 -83q-153 -262 -242 -262q-15 0 -28 7l-24 12q-1 1 -6 5q-10 10 -6 36q9 40 56 91.5t132 96.5q14 9 23 -6q2 -2 2 -4q52 85 107 197 q68 136 104 262q-24 82 -30.5 159.5t6.5 127.5q11 40 42 40h21h1q23 0 35 -15q18 -21 9 -68q-2 -6 -4 -8q1 -3 1 -8v-30q-2 -123 -14 -192q55 -164 146 -238zM318 54q52 24 137 158q-51 -40 -87.5 -84t-49.5 -74zM716 974q-15 -42 -2 -132q1 7 7 44q0 3 7 43q1 4 4 8 q-1 1 -1 2t-0.5 1.5t-0.5 1.5q-1 22 -13 36q0 -1 -1 -2v-2zM592 313q135 54 284 81q-2 1 -13 9.5t-16 13.5q-76 67 -127 176q-27 -86 -83 -197q-30 -56 -45 -83zM1238 329q-24 24 -140 24q76 -28 124 -28q14 0 18 1q0 1 -2 3z" /> | |
| 444 | <glyph unicode="" d="M1468 1156q28 -28 48 -76t20 -88v-1152q0 -40 -28 -68t-68 -28h-1344q-40 0 -68 28t-28 68v1600q0 40 28 68t68 28h896q40 0 88 -20t76 -48zM1024 1400v-376h376q-10 29 -22 41l-313 313q-12 12 -41 22zM1408 -128v1024h-416q-40 0 -68 28t-28 68v416h-768v-1536h1280z M233 768v-107h70l164 -661h159l128 485q7 20 10 46q2 16 2 24h4l3 -24q1 -3 3.5 -20t5.5 -26l128 -485h159l164 661h70v107h-300v-107h90l-99 -438q-5 -20 -7 -46l-2 -21h-4l-3 21q-1 5 -4 21t-5 25l-144 545h-114l-144 -545q-2 -9 -4.5 -24.5t-3.5 -21.5l-4 -21h-4l-2 21 q-2 26 -7 46l-99 438h90v107h-300z" /> | |
| 445 | <glyph unicode="" d="M1468 1156q28 -28 48 -76t20 -88v-1152q0 -40 -28 -68t-68 -28h-1344q-40 0 -68 28t-28 68v1600q0 40 28 68t68 28h896q40 0 88 -20t76 -48zM1024 1400v-376h376q-10 29 -22 41l-313 313q-12 12 -41 22zM1408 -128v1024h-416q-40 0 -68 28t-28 68v416h-768v-1536h1280z M429 106v-106h281v106h-75l103 161q5 7 10 16.5t7.5 13.5t3.5 4h2q1 -4 5 -10q2 -4 4.5 -7.5t6 -8t6.5 -8.5l107 -161h-76v-106h291v106h-68l-192 273l195 282h67v107h-279v-107h74l-103 -159q-4 -7 -10 -16.5t-9 -13.5l-2 -3h-2q-1 4 -5 10q-6 11 -17 23l-106 159h76v107 h-290v-107h68l189 -272l-194 -283h-68z" /> | |
| 446 | <glyph unicode="" d="M1468 1156q28 -28 48 -76t20 -88v-1152q0 -40 -28 -68t-68 -28h-1344q-40 0 -68 28t-28 68v1600q0 40 28 68t68 28h896q40 0 88 -20t76 -48zM1024 1400v-376h376q-10 29 -22 41l-313 313q-12 12 -41 22zM1408 -128v1024h-416q-40 0 -68 28t-28 68v416h-768v-1536h1280z M416 106v-106h327v106h-93v167h137q76 0 118 15q67 23 106.5 87t39.5 146q0 81 -37 141t-100 87q-48 19 -130 19h-368v-107h92v-555h-92zM769 386h-119v268h120q52 0 83 -18q56 -33 56 -115q0 -89 -62 -120q-31 -15 -78 -15z" /> | |
| 447 | <glyph unicode="" d="M1468 1156q28 -28 48 -76t20 -88v-1152q0 -40 -28 -68t-68 -28h-1344q-40 0 -68 28t-28 68v1600q0 40 28 68t68 28h896q40 0 88 -20t76 -48zM1024 1400v-376h376q-10 29 -22 41l-313 313q-12 12 -41 22zM1408 -128v1024h-416q-40 0 -68 28t-28 68v416h-768v-1536h1280z M1280 320v-320h-1024v192l192 192l128 -128l384 384zM448 512q-80 0 -136 56t-56 136t56 136t136 56t136 -56t56 -136t-56 -136t-136 -56z" /> | |
| 448 | <glyph unicode="" d="M640 1152v128h-128v-128h128zM768 1024v128h-128v-128h128zM640 896v128h-128v-128h128zM768 768v128h-128v-128h128zM1468 1156q28 -28 48 -76t20 -88v-1152q0 -40 -28 -68t-68 -28h-1344q-40 0 -68 28t-28 68v1600q0 40 28 68t68 28h896q40 0 88 -20t76 -48zM1024 1400 v-376h376q-10 29 -22 41l-313 313q-12 12 -41 22zM1408 -128v1024h-416q-40 0 -68 28t-28 68v416h-128v-128h-128v128h-512v-1536h1280zM781 593l107 -349q8 -27 8 -52q0 -83 -72.5 -137.5t-183.5 -54.5t-183.5 54.5t-72.5 137.5q0 25 8 52q21 63 120 396v128h128v-128h79 q22 0 39 -13t23 -34zM640 128q53 0 90.5 19t37.5 45t-37.5 45t-90.5 19t-90.5 -19t-37.5 -45t37.5 -45t90.5 -19z" /> | |
| 449 | <glyph unicode="" d="M1468 1156q28 -28 48 -76t20 -88v-1152q0 -40 -28 -68t-68 -28h-1344q-40 0 -68 28t-28 68v1600q0 40 28 68t68 28h896q40 0 88 -20t76 -48zM1024 1400v-376h376q-10 29 -22 41l-313 313q-12 12 -41 22zM1408 -128v1024h-416q-40 0 -68 28t-28 68v416h-768v-1536h1280z M620 686q20 -8 20 -30v-544q0 -22 -20 -30q-8 -2 -12 -2q-12 0 -23 9l-166 167h-131q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h131l166 167q16 15 35 7zM1037 -3q31 0 50 24q129 159 129 363t-129 363q-16 21 -43 24t-47 -14q-21 -17 -23.5 -43.5t14.5 -47.5 q100 -123 100 -282t-100 -282q-17 -21 -14.5 -47.5t23.5 -42.5q18 -15 40 -15zM826 145q27 0 47 20q87 93 87 219t-87 219q-18 19 -45 20t-46 -17t-20 -44.5t18 -46.5q52 -57 52 -131t-52 -131q-19 -20 -18 -46.5t20 -44.5q20 -17 44 -17z" /> | |
| 450 | <glyph unicode="" d="M1468 1156q28 -28 48 -76t20 -88v-1152q0 -40 -28 -68t-68 -28h-1344q-40 0 -68 28t-28 68v1600q0 40 28 68t68 28h896q40 0 88 -20t76 -48zM1024 1400v-376h376q-10 29 -22 41l-313 313q-12 12 -41 22zM1408 -128v1024h-416q-40 0 -68 28t-28 68v416h-768v-1536h1280z M768 768q52 0 90 -38t38 -90v-384q0 -52 -38 -90t-90 -38h-384q-52 0 -90 38t-38 90v384q0 52 38 90t90 38h384zM1260 766q20 -8 20 -30v-576q0 -22 -20 -30q-8 -2 -12 -2q-14 0 -23 9l-265 266v90l265 266q9 9 23 9q4 0 12 -2z" /> | |
| 451 | <glyph unicode="" d="M1468 1156q28 -28 48 -76t20 -88v-1152q0 -40 -28 -68t-68 -28h-1344q-40 0 -68 28t-28 68v1600q0 40 28 68t68 28h896q40 0 88 -20t76 -48zM1024 1400v-376h376q-10 29 -22 41l-313 313q-12 12 -41 22zM1408 -128v1024h-416q-40 0 -68 28t-28 68v416h-768v-1536h1280z M480 768q8 11 21 12.5t24 -6.5l51 -38q11 -8 12.5 -21t-6.5 -24l-182 -243l182 -243q8 -11 6.5 -24t-12.5 -21l-51 -38q-11 -8 -24 -6.5t-21 12.5l-226 301q-14 19 0 38zM1282 467q14 -19 0 -38l-226 -301q-8 -11 -21 -12.5t-24 6.5l-51 38q-11 8 -12.5 21t6.5 24l182 243 l-182 243q-8 11 -6.5 24t12.5 21l51 38q11 8 24 6.5t21 -12.5zM662 6q-13 2 -20.5 13t-5.5 24l138 831q2 13 13 20.5t24 5.5l63 -10q13 -2 20.5 -13t5.5 -24l-138 -831q-2 -13 -13 -20.5t-24 -5.5z" /> | |
| 452 | <glyph unicode="" d="M1497 709v-198q-101 -23 -198 -23q-65 -136 -165.5 -271t-181.5 -215.5t-128 -106.5q-80 -45 -162 3q-28 17 -60.5 43.5t-85 83.5t-102.5 128.5t-107.5 184t-105.5 244t-91.5 314.5t-70.5 390h283q26 -218 70 -398.5t104.5 -317t121.5 -235.5t140 -195q169 169 287 406 q-142 72 -223 220t-81 333q0 192 104 314.5t284 122.5q178 0 273 -105.5t95 -297.5q0 -159 -58 -286q-7 -1 -19.5 -3t-46 -2t-63 6t-62 25.5t-50.5 51.5q31 103 31 184q0 87 -29 132t-79 45q-53 0 -85 -49.5t-32 -140.5q0 -186 105 -293.5t267 -107.5q62 0 121 14z" /> | |
| 453 | <glyph unicode="" horiz-adv-x="1792" d="M216 367l603 -402v359l-334 223zM154 511l193 129l-193 129v-258zM973 -35l603 402l-269 180l-334 -223v-359zM896 458l272 182l-272 182l-272 -182zM485 733l334 223v359l-603 -402zM1445 640l193 -129v258zM1307 733l269 180l-603 402v-359zM1792 913v-546 q0 -41 -34 -64l-819 -546q-21 -13 -43 -13t-43 13l-819 546q-34 23 -34 64v546q0 41 34 64l819 546q21 13 43 13t43 -13l819 -546q34 -23 34 -64z" /> | |
| 454 | <glyph unicode="" horiz-adv-x="2048" d="M1800 764q111 -46 179.5 -145.5t68.5 -221.5q0 -164 -118 -280.5t-285 -116.5q-4 0 -11.5 0.5t-10.5 0.5h-1209h-1h-2h-5q-170 10 -288 125.5t-118 280.5q0 110 55 203t147 147q-12 39 -12 82q0 115 82 196t199 81q95 0 172 -58q75 154 222.5 248t326.5 94 q166 0 306 -80.5t221.5 -218.5t81.5 -301q0 -6 -0.5 -18t-0.5 -18zM468 498q0 -122 84 -193t208 -71q137 0 240 99q-16 20 -47.5 56.5t-43.5 50.5q-67 -65 -144 -65q-55 0 -93.5 33.5t-38.5 87.5q0 53 38.5 87t91.5 34q44 0 84.5 -21t73 -55t65 -75t69 -82t77 -75t97 -55 t121.5 -21q121 0 204.5 71.5t83.5 190.5q0 121 -84 192t-207 71q-143 0 -241 -97q14 -16 29.5 -34t34.5 -40t29 -34q66 64 142 64q52 0 92 -33t40 -84q0 -57 -37 -91.5t-94 -34.5q-43 0 -82.5 21t-72 55t-65.5 75t-69.5 82t-77.5 75t-96.5 55t-118.5 21q-122 0 -207 -70.5 t-85 -189.5z" /> | |
| 455 | <glyph unicode="" horiz-adv-x="1792" d="M896 1536q182 0 348 -71t286 -191t191 -286t71 -348t-71 -348t-191 -286t-286 -191t-348 -71t-348 71t-286 191t-191 286t-71 348t71 348t191 286t286 191t348 71zM896 1408q-190 0 -361 -90l194 -194q82 28 167 28t167 -28l194 194q-171 90 -361 90zM218 279l194 194 q-28 82 -28 167t28 167l-194 194q-90 -171 -90 -361t90 -361zM896 -128q190 0 361 90l-194 194q-82 -28 -167 -28t-167 28l-194 -194q171 -90 361 -90zM896 256q159 0 271.5 112.5t112.5 271.5t-112.5 271.5t-271.5 112.5t-271.5 -112.5t-112.5 -271.5t112.5 -271.5 t271.5 -112.5zM1380 473l194 -194q90 171 90 361t-90 361l-194 -194q28 -82 28 -167t-28 -167z" /> | |
| 456 | <glyph unicode="" horiz-adv-x="1792" d="M1792 640q0 -182 -71 -348t-191 -286t-286 -191t-348 -71t-348 71t-286 191t-191 286t-71 348q0 222 101 414.5t276.5 317t390.5 155.5v-260q-221 -45 -366.5 -221t-145.5 -406q0 -130 51 -248.5t136.5 -204t204 -136.5t248.5 -51t248.5 51t204 136.5t136.5 204t51 248.5 q0 230 -145.5 406t-366.5 221v260q215 -31 390.5 -155.5t276.5 -317t101 -414.5z" /> | |
| 457 | <glyph unicode="" horiz-adv-x="1792" d="M19 662q8 217 116 406t305 318h5q0 -1 -1 -3q-8 -8 -28 -33.5t-52 -76.5t-60 -110.5t-44.5 -135.5t-14 -150.5t39 -157.5t108.5 -154q50 -50 102 -69.5t90.5 -11.5t69.5 23.5t47 32.5l16 16q39 51 53 116.5t6.5 122.5t-21 107t-26.5 80l-14 29q-10 25 -30.5 49.5t-43 41 t-43.5 29.5t-35 19l-13 6l104 115q39 -17 78 -52t59 -61l19 -27q1 48 -18.5 103.5t-40.5 87.5l-20 31l161 183l160 -181q-33 -46 -52.5 -102.5t-22.5 -90.5l-4 -33q22 37 61.5 72.5t67.5 52.5l28 17l103 -115q-44 -14 -85 -50t-60 -65l-19 -29q-31 -56 -48 -133.5t-7 -170 t57 -156.5q33 -45 77.5 -60.5t85 -5.5t76 26.5t57.5 33.5l21 16q60 53 96.5 115t48.5 121.5t10 121.5t-18 118t-37 107.5t-45.5 93t-45 72t-34.5 47.5l-13 17q-14 13 -7 13l10 -3q40 -29 62.5 -46t62 -50t64 -58t58.5 -65t55.5 -77t45.5 -88t38 -103t23.5 -117t10.5 -136 q3 -259 -108 -465t-312 -321t-456 -115q-185 0 -351 74t-283.5 198t-184 293t-60.5 353z" /> | |
| 458 | <glyph unicode="" horiz-adv-x="1792" d="M874 -102v-66q-208 6 -385 109.5t-283 275.5l58 34q29 -49 73 -99l65 57q148 -168 368 -212l-17 -86q65 -12 121 -13zM276 428l-83 -28q22 -60 49 -112l-57 -33q-98 180 -98 385t98 385l57 -33q-30 -56 -49 -112l82 -28q-35 -100 -35 -212q0 -109 36 -212zM1528 251 l58 -34q-106 -172 -283 -275.5t-385 -109.5v66q56 1 121 13l-17 86q220 44 368 212l65 -57q44 50 73 99zM1377 805l-233 -80q14 -42 14 -85t-14 -85l232 -80q-31 -92 -98 -169l-185 162q-57 -67 -147 -85l48 -241q-52 -10 -98 -10t-98 10l48 241q-90 18 -147 85l-185 -162 q-67 77 -98 169l232 80q-14 42 -14 85t14 85l-233 80q33 93 99 169l185 -162q59 68 147 86l-48 240q44 10 98 10t98 -10l-48 -240q88 -18 147 -86l185 162q66 -76 99 -169zM874 1448v-66q-65 -2 -121 -13l17 -86q-220 -42 -368 -211l-65 56q-38 -42 -73 -98l-57 33 q106 172 282 275.5t385 109.5zM1705 640q0 -205 -98 -385l-57 33q27 52 49 112l-83 28q36 103 36 212q0 112 -35 212l82 28q-19 56 -49 112l57 33q98 -180 98 -385zM1585 1063l-57 -33q-35 56 -73 98l-65 -56q-148 169 -368 211l17 86q-56 11 -121 13v66q209 -6 385 -109.5 t282 -275.5zM1748 640q0 173 -67.5 331t-181.5 272t-272 181.5t-331 67.5t-331 -67.5t-272 -181.5t-181.5 -272t-67.5 -331t67.5 -331t181.5 -272t272 -181.5t331 -67.5t331 67.5t272 181.5t181.5 272t67.5 331zM1792 640q0 -182 -71 -348t-191 -286t-286 -191t-348 -71 t-348 71t-286 191t-191 286t-71 348t71 348t191 286t286 191t348 71t348 -71t286 -191t191 -286t71 -348z" /> | |
| 459 | <glyph unicode="" d="M582 228q0 -66 -93 -66q-107 0 -107 63q0 64 98 64q102 0 102 -61zM546 694q0 -85 -74 -85q-77 0 -77 84q0 90 77 90q36 0 55 -25.5t19 -63.5zM712 769v125q-78 -29 -135 -29q-50 29 -110 29q-86 0 -145 -57t-59 -143q0 -50 29.5 -102t73.5 -67v-3q-38 -17 -38 -85 q0 -53 41 -77v-3q-113 -37 -113 -139q0 -45 20 -78.5t54 -51t72 -25.5t81 -8q224 0 224 188q0 67 -48 99t-126 46q-27 5 -51.5 20.5t-24.5 39.5q0 44 49 52q77 15 122 70t45 134q0 24 -10 52q37 9 49 13zM771 350h137q-2 27 -2 82v387q0 46 2 69h-137q3 -23 3 -71v-392 q0 -50 -3 -75zM1280 366v121q-30 -21 -68 -21q-53 0 -53 82v225h52q9 0 26.5 -1t26.5 -1v117h-105q0 82 3 102h-140q4 -24 4 -55v-47h-60v-117q36 3 37 3q3 0 11 -0.5t12 -0.5v-2h-2v-217q0 -37 2.5 -64t11.5 -56.5t24.5 -48.5t43.5 -31t66 -12q64 0 108 24zM924 1072 q0 36 -24 63.5t-60 27.5t-60.5 -27t-24.5 -64q0 -36 25 -62.5t60 -26.5t59.5 27t24.5 62zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 460 | <glyph unicode="" horiz-adv-x="1792" d="M595 22q0 100 -165 100q-158 0 -158 -104q0 -101 172 -101q151 0 151 105zM536 777q0 61 -30 102t-89 41q-124 0 -124 -145q0 -135 124 -135q119 0 119 137zM805 1101v-202q-36 -12 -79 -22q16 -43 16 -84q0 -127 -73 -216.5t-197 -112.5q-40 -8 -59.5 -27t-19.5 -58 q0 -31 22.5 -51.5t58 -32t78.5 -22t86 -25.5t78.5 -37.5t58 -64t22.5 -98.5q0 -304 -363 -304q-69 0 -130 12.5t-116 41t-87.5 82t-32.5 127.5q0 165 182 225v4q-67 41 -67 126q0 109 63 137v4q-72 24 -119.5 108.5t-47.5 165.5q0 139 95 231.5t235 92.5q96 0 178 -47 q98 0 218 47zM1123 220h-222q4 45 4 134v609q0 94 -4 128h222q-4 -33 -4 -124v-613q0 -89 4 -134zM1724 442v-196q-71 -39 -174 -39q-62 0 -107 20t-70 50t-39.5 78t-18.5 92t-4 103v351h2v4q-7 0 -19 1t-18 1q-21 0 -59 -6v190h96v76q0 54 -6 89h227q-6 -41 -6 -165h171 v-190q-15 0 -43.5 2t-42.5 2h-85v-365q0 -131 87 -131q61 0 109 33zM1148 1389q0 -58 -39 -101.5t-96 -43.5q-58 0 -98 43.5t-40 101.5q0 59 39.5 103t98.5 44q58 0 96.5 -44.5t38.5 -102.5z" /> | |
| 461 | <glyph unicode="" d="M825 547l343 588h-150q-21 -39 -63.5 -118.5t-68 -128.5t-59.5 -118.5t-60 -128.5h-3q-21 48 -44.5 97t-52 105.5t-46.5 92t-54 104.5t-49 95h-150l323 -589v-435h134v436zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960 q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 462 | <glyph unicode="" horiz-adv-x="1280" d="M842 964q0 -80 -57 -136.5t-136 -56.5q-60 0 -111 35q-62 -67 -115 -146q-247 -371 -202 -859q1 -22 -12.5 -38.5t-34.5 -18.5h-5q-20 0 -35 13.5t-17 33.5q-14 126 -3.5 247.5t29.5 217t54 186t69 155.5t74 125q61 90 132 165q-16 35 -16 77q0 80 56.5 136.5t136.5 56.5 t136.5 -56.5t56.5 -136.5zM1223 953q0 -158 -78 -292t-212.5 -212t-292.5 -78q-64 0 -131 14q-21 5 -32.5 23.5t-6.5 39.5q5 20 23 31.5t39 7.5q51 -13 108 -13q97 0 186 38t153 102t102 153t38 186t-38 186t-102 153t-153 102t-186 38t-186 -38t-153 -102t-102 -153 t-38 -186q0 -114 52 -218q10 -20 3.5 -40t-25.5 -30t-39.5 -3t-30.5 26q-64 123 -64 265q0 119 46.5 227t124.5 186t186 124t226 46q158 0 292.5 -78t212.5 -212.5t78 -292.5z" /> | |
| 463 | <glyph unicode="" horiz-adv-x="1792" d="M270 730q-8 19 -8 52q0 20 11 49t24 45q-1 22 7.5 53t22.5 43q0 139 92.5 288.5t217.5 209.5q139 66 324 66q133 0 266 -55q49 -21 90 -48t71 -56t55 -68t42 -74t32.5 -84.5t25.5 -89.5t22 -98l1 -5q55 -83 55 -150q0 -14 -9 -40t-9 -38q0 -1 1.5 -3.5t3.5 -5t2 -3.5 q77 -114 120.5 -214.5t43.5 -208.5q0 -43 -19.5 -100t-55.5 -57q-9 0 -19.5 7.5t-19 17.5t-19 26t-16 26.5t-13.5 26t-9 17.5q-1 1 -3 1l-5 -4q-59 -154 -132 -223q20 -20 61.5 -38.5t69 -41.5t35.5 -65q-2 -4 -4 -16t-7 -18q-64 -97 -302 -97q-53 0 -110.5 9t-98 20 t-104.5 30q-15 5 -23 7q-14 4 -46 4.5t-40 1.5q-41 -45 -127.5 -65t-168.5 -20q-35 0 -69 1.5t-93 9t-101 20.5t-74.5 40t-32.5 64q0 40 10 59.5t41 48.5q11 2 40.5 13t49.5 12q4 0 14 2q2 2 2 4l-2 3q-48 11 -108 105.5t-73 156.5l-5 3q-4 0 -12 -20q-18 -41 -54.5 -74.5 t-77.5 -37.5h-1q-4 0 -6 4.5t-5 5.5q-23 54 -23 100q0 275 252 466z" /> | |
| 464 | <glyph unicode="" horiz-adv-x="2048" d="M580 1075q0 41 -25 66t-66 25q-43 0 -76 -25.5t-33 -65.5q0 -39 33 -64.5t76 -25.5q41 0 66 24.5t25 65.5zM1323 568q0 28 -25.5 50t-65.5 22q-27 0 -49.5 -22.5t-22.5 -49.5q0 -28 22.5 -50.5t49.5 -22.5q40 0 65.5 22t25.5 51zM1087 1075q0 41 -24.5 66t-65.5 25 q-43 0 -76 -25.5t-33 -65.5q0 -39 33 -64.5t76 -25.5q41 0 65.5 24.5t24.5 65.5zM1722 568q0 28 -26 50t-65 22q-27 0 -49.5 -22.5t-22.5 -49.5q0 -28 22.5 -50.5t49.5 -22.5q39 0 65 22t26 51zM1456 965q-31 4 -70 4q-169 0 -311 -77t-223.5 -208.5t-81.5 -287.5 q0 -78 23 -152q-35 -3 -68 -3q-26 0 -50 1.5t-55 6.5t-44.5 7t-54.5 10.5t-50 10.5l-253 -127l72 218q-290 203 -290 490q0 169 97.5 311t264 223.5t363.5 81.5q176 0 332.5 -66t262 -182.5t136.5 -260.5zM2048 404q0 -117 -68.5 -223.5t-185.5 -193.5l55 -181l-199 109 q-150 -37 -218 -37q-169 0 -311 70.5t-223.5 191.5t-81.5 264t81.5 264t223.5 191.5t311 70.5q161 0 303 -70.5t227.5 -192t85.5 -263.5z" /> | |
| 465 | <glyph unicode="" horiz-adv-x="1792" d="M1764 1525q33 -24 27 -64l-256 -1536q-5 -29 -32 -45q-14 -8 -31 -8q-11 0 -24 5l-453 185l-242 -295q-18 -23 -49 -23q-13 0 -22 4q-19 7 -30.5 23.5t-11.5 36.5v349l864 1059l-1069 -925l-395 162q-37 14 -40 55q-2 40 32 59l1664 960q15 9 32 9q20 0 36 -11z" /> | |
| 466 | <glyph unicode="" horiz-adv-x="1792" d="M1764 1525q33 -24 27 -64l-256 -1536q-5 -29 -32 -45q-14 -8 -31 -8q-11 0 -24 5l-527 215l-298 -327q-18 -21 -47 -21q-14 0 -23 4q-19 7 -30 23.5t-11 36.5v452l-472 193q-37 14 -40 55q-3 39 32 59l1664 960q35 21 68 -2zM1422 26l221 1323l-1434 -827l336 -137 l863 639l-478 -797z" /> | |
| 467 | <glyph unicode="" d="M1536 640q0 -156 -61 -298t-164 -245t-245 -164t-298 -61q-172 0 -327 72.5t-264 204.5q-7 10 -6.5 22.5t8.5 20.5l137 138q10 9 25 9q16 -2 23 -12q73 -95 179 -147t225 -52q104 0 198.5 40.5t163.5 109.5t109.5 163.5t40.5 198.5t-40.5 198.5t-109.5 163.5 t-163.5 109.5t-198.5 40.5q-98 0 -188 -35.5t-160 -101.5l137 -138q31 -30 14 -69q-17 -40 -59 -40h-448q-26 0 -45 19t-19 45v448q0 42 40 59q39 17 69 -14l130 -129q107 101 244.5 156.5t284.5 55.5q156 0 298 -61t245 -164t164 -245t61 -298zM896 928v-448q0 -14 -9 -23 t-23 -9h-320q-14 0 -23 9t-9 23v64q0 14 9 23t23 9h224v352q0 14 9 23t23 9h64q14 0 23 -9t9 -23z" /> | |
| 468 | <glyph unicode="" d="M768 1280q-130 0 -248.5 -51t-204 -136.5t-136.5 -204t-51 -248.5t51 -248.5t136.5 -204t204 -136.5t248.5 -51t248.5 51t204 136.5t136.5 204t51 248.5t-51 248.5t-136.5 204t-204 136.5t-248.5 51zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103 t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 469 | <glyph unicode="" horiz-adv-x="1792" d="M1682 -128q-44 0 -132.5 3.5t-133.5 3.5q-44 0 -132 -3.5t-132 -3.5q-24 0 -37 20.5t-13 45.5q0 31 17 46t39 17t51 7t45 15q33 21 33 140l-1 391q0 21 -1 31q-13 4 -50 4h-675q-38 0 -51 -4q-1 -10 -1 -31l-1 -371q0 -142 37 -164q16 -10 48 -13t57 -3.5t45 -15 t20 -45.5q0 -26 -12.5 -48t-36.5 -22q-47 0 -139.5 3.5t-138.5 3.5q-43 0 -128 -3.5t-127 -3.5q-23 0 -35.5 21t-12.5 45q0 30 15.5 45t36 17.5t47.5 7.5t42 15q33 23 33 143l-1 57v813q0 3 0.5 26t0 36.5t-1.5 38.5t-3.5 42t-6.5 36.5t-11 31.5t-16 18q-15 10 -45 12t-53 2 t-41 14t-18 45q0 26 12 48t36 22q46 0 138.5 -3.5t138.5 -3.5q42 0 126.5 3.5t126.5 3.5q25 0 37.5 -22t12.5 -48q0 -30 -17 -43.5t-38.5 -14.5t-49.5 -4t-43 -13q-35 -21 -35 -160l1 -320q0 -21 1 -32q13 -3 39 -3h699q25 0 38 3q1 11 1 32l1 320q0 139 -35 160 q-18 11 -58.5 12.5t-66 13t-25.5 49.5q0 26 12.5 48t37.5 22q44 0 132 -3.5t132 -3.5q43 0 129 3.5t129 3.5q25 0 37.5 -22t12.5 -48q0 -30 -17.5 -44t-40 -14.5t-51.5 -3t-44 -12.5q-35 -23 -35 -161l1 -943q0 -119 34 -140q16 -10 46 -13.5t53.5 -4.5t41.5 -15.5t18 -44.5 q0 -26 -12 -48t-36 -22z" /> | |
| 470 | <glyph unicode="" horiz-adv-x="1280" d="M1278 1347v-73q0 -29 -18.5 -61t-42.5 -32q-50 0 -54 -1q-26 -6 -32 -31q-3 -11 -3 -64v-1152q0 -25 -18 -43t-43 -18h-108q-25 0 -43 18t-18 43v1218h-143v-1218q0 -25 -17.5 -43t-43.5 -18h-108q-26 0 -43.5 18t-17.5 43v496q-147 12 -245 59q-126 58 -192 179 q-64 117 -64 259q0 166 88 286q88 118 209 159q111 37 417 37h479q25 0 43 -18t18 -43z" /> | |
| 471 | <glyph unicode="" d="M352 128v-128h-352v128h352zM704 256q26 0 45 -19t19 -45v-256q0 -26 -19 -45t-45 -19h-256q-26 0 -45 19t-19 45v256q0 26 19 45t45 19h256zM864 640v-128h-864v128h864zM224 1152v-128h-224v128h224zM1536 128v-128h-736v128h736zM576 1280q26 0 45 -19t19 -45v-256 q0 -26 -19 -45t-45 -19h-256q-26 0 -45 19t-19 45v256q0 26 19 45t45 19h256zM1216 768q26 0 45 -19t19 -45v-256q0 -26 -19 -45t-45 -19h-256q-26 0 -45 19t-19 45v256q0 26 19 45t45 19h256zM1536 640v-128h-224v128h224zM1536 1152v-128h-864v128h864z" /> | |
| 472 | <glyph unicode="" d="M1216 512q133 0 226.5 -93.5t93.5 -226.5t-93.5 -226.5t-226.5 -93.5t-226.5 93.5t-93.5 226.5q0 12 2 34l-360 180q-92 -86 -218 -86q-133 0 -226.5 93.5t-93.5 226.5t93.5 226.5t226.5 93.5q126 0 218 -86l360 180q-2 22 -2 34q0 133 93.5 226.5t226.5 93.5 t226.5 -93.5t93.5 -226.5t-93.5 -226.5t-226.5 -93.5q-126 0 -218 86l-360 -180q2 -22 2 -34t-2 -34l360 -180q92 86 218 86z" /> | |
| 473 | <glyph unicode="" d="M1280 341q0 88 -62.5 151t-150.5 63q-84 0 -145 -58l-241 120q2 16 2 23t-2 23l241 120q61 -58 145 -58q88 0 150.5 63t62.5 151t-62.5 150.5t-150.5 62.5t-151 -62.5t-63 -150.5q0 -7 2 -23l-241 -120q-62 57 -145 57q-88 0 -150.5 -62.5t-62.5 -150.5t62.5 -150.5 t150.5 -62.5q83 0 145 57l241 -120q-2 -16 -2 -23q0 -88 63 -150.5t151 -62.5t150.5 62.5t62.5 150.5zM1536 1120v-960q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 474 | <glyph unicode="" horiz-adv-x="1792" d="M571 947q-10 25 -34 35t-49 0q-108 -44 -191 -127t-127 -191q-10 -25 0 -49t35 -34q13 -5 24 -5q42 0 60 40q34 84 98.5 148.5t148.5 98.5q25 11 35 35t0 49zM1513 1303l46 -46l-244 -243l68 -68q19 -19 19 -45.5t-19 -45.5l-64 -64q89 -161 89 -343q0 -143 -55.5 -273.5 t-150 -225t-225 -150t-273.5 -55.5t-273.5 55.5t-225 150t-150 225t-55.5 273.5t55.5 273.5t150 225t225 150t273.5 55.5q182 0 343 -89l64 64q19 19 45.5 19t45.5 -19l68 -68zM1521 1359q-10 -10 -22 -10q-13 0 -23 10l-91 90q-9 10 -9 23t9 23q10 9 23 9t23 -9l90 -91 q10 -9 10 -22.5t-10 -22.5zM1751 1129q-11 -9 -23 -9t-23 9l-90 91q-10 9 -10 22.5t10 22.5q9 10 22.5 10t22.5 -10l91 -90q9 -10 9 -23t-9 -23zM1792 1312q0 -14 -9 -23t-23 -9h-96q-14 0 -23 9t-9 23t9 23t23 9h96q14 0 23 -9t9 -23zM1600 1504v-96q0 -14 -9 -23t-23 -9 t-23 9t-9 23v96q0 14 9 23t23 9t23 -9t9 -23zM1751 1449l-91 -90q-10 -10 -22 -10q-13 0 -23 10q-10 9 -10 22.5t10 22.5l90 91q10 9 23 9t23 -9q9 -10 9 -23t-9 -23z" /> | |
| 475 | <glyph unicode="" horiz-adv-x="1792" d="M609 720l287 208l287 -208l-109 -336h-355zM896 1536q182 0 348 -71t286 -191t191 -286t71 -348t-71 -348t-191 -286t-286 -191t-348 -71t-348 71t-286 191t-191 286t-71 348t71 348t191 286t286 191t348 71zM1515 186q149 203 149 454v3l-102 -89l-240 224l63 323 l134 -12q-150 206 -389 282l53 -124l-287 -159l-287 159l53 124q-239 -76 -389 -282l135 12l62 -323l-240 -224l-102 89v-3q0 -251 149 -454l30 132l326 -40l139 -298l-116 -69q117 -39 240 -39t240 39l-116 69l139 298l326 40z" /> | |
| 476 | <glyph unicode="" horiz-adv-x="1792" d="M448 224v-192q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h192q14 0 23 -9t9 -23zM256 608v-192q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h192q14 0 23 -9t9 -23zM832 224v-192q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23 v192q0 14 9 23t23 9h192q14 0 23 -9t9 -23zM640 608v-192q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h192q14 0 23 -9t9 -23zM66 768q-28 0 -47 19t-19 46v129h514v-129q0 -27 -19 -46t-46 -19h-383zM1216 224v-192q0 -14 -9 -23t-23 -9h-192 q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h192q14 0 23 -9t9 -23zM1024 608v-192q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h192q14 0 23 -9t9 -23zM1600 224v-192q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h192q14 0 23 -9t9 -23 zM1408 608v-192q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h192q14 0 23 -9t9 -23zM1792 1016v-13h-514v10q0 104 -382 102q-382 -1 -382 -102v-10h-514v13q0 17 8.5 43t34 64t65.5 75.5t110.5 76t160 67.5t224 47.5t293.5 18.5t293 -18.5t224 -47.5 t160.5 -67.5t110.5 -76t65.5 -75.5t34 -64t8.5 -43zM1792 608v-192q0 -14 -9 -23t-23 -9h-192q-14 0 -23 9t-9 23v192q0 14 9 23t23 9h192q14 0 23 -9t9 -23zM1792 962v-129q0 -27 -19 -46t-46 -19h-384q-27 0 -46 19t-19 46v129h514z" /> | |
| 477 | <glyph unicode="" horiz-adv-x="1792" d="M704 1216v-768q0 -26 -19 -45t-45 -19v-576q0 -26 -19 -45t-45 -19h-512q-26 0 -45 19t-19 45v512l249 873q7 23 31 23h424zM1024 1216v-704h-256v704h256zM1792 320v-512q0 -26 -19 -45t-45 -19h-512q-26 0 -45 19t-19 45v576q-26 0 -45 19t-19 45v768h424q24 0 31 -23z M736 1504v-224h-352v224q0 14 9 23t23 9h288q14 0 23 -9t9 -23zM1408 1504v-224h-352v224q0 14 9 23t23 9h288q14 0 23 -9t9 -23z" /> | |
| 478 | <glyph unicode="" horiz-adv-x="1792" d="M1755 1083q37 -37 37 -90t-37 -91l-401 -400l150 -150l-160 -160q-163 -163 -389.5 -186.5t-411.5 100.5l-362 -362h-181v181l362 362q-124 185 -100.5 411.5t186.5 389.5l160 160l150 -150l400 401q38 37 91 37t90 -37t37 -90.5t-37 -90.5l-400 -401l234 -234l401 400 q38 37 91 37t90 -37z" /> | |
| 479 | <glyph unicode="" horiz-adv-x="1792" d="M873 796q0 -83 -63.5 -142.5t-152.5 -59.5t-152.5 59.5t-63.5 142.5q0 84 63.5 143t152.5 59t152.5 -59t63.5 -143zM1375 796q0 -83 -63 -142.5t-153 -59.5q-89 0 -152.5 59.5t-63.5 142.5q0 84 63.5 143t152.5 59q90 0 153 -59t63 -143zM1600 616v667q0 87 -32 123.5 t-111 36.5h-1112q-83 0 -112.5 -34t-29.5 -126v-673q43 -23 88.5 -40t81 -28t81 -18.5t71 -11t70 -4t58.5 -0.5t56.5 2t44.5 2q68 1 95 -27q6 -6 10 -9q26 -25 61 -51q7 91 118 87q5 0 36.5 -1.5t43 -2t45.5 -1t53 1t54.5 4.5t61 8.5t62 13.5t67 19.5t67.5 27t72 34.5z M1763 621q-121 -149 -372 -252q84 -285 -23 -465q-66 -113 -183 -148q-104 -32 -182 15q-86 51 -82 164l-1 326v1q-8 2 -24.5 6t-23.5 5l-1 -338q4 -114 -83 -164q-79 -47 -183 -15q-117 36 -182 150q-105 180 -22 463q-251 103 -372 252q-25 37 -4 63t60 -1q3 -2 11 -7 t11 -8v694q0 72 47 123t114 51h1257q67 0 114 -51t47 -123v-694l21 15q39 27 60 1t-4 -63z" /> | |
| 480 | <glyph unicode="" horiz-adv-x="1792" d="M896 1102v-434h-145v434h145zM1294 1102v-434h-145v434h145zM1294 342l253 254v795h-1194v-1049h326v-217l217 217h398zM1692 1536v-1013l-434 -434h-326l-217 -217h-217v217h-398v1158l109 289h1483z" /> | |
| 481 | <glyph unicode="" d="M773 217v-127q-1 -292 -6 -305q-12 -32 -51 -40q-54 -9 -181.5 38t-162.5 89q-13 15 -17 36q-1 12 4 26q4 10 34 47t181 216q1 0 60 70q15 19 39.5 24.5t49.5 -3.5q24 -10 37.5 -29t12.5 -42zM624 468q-3 -55 -52 -70l-120 -39q-275 -88 -292 -88q-35 2 -54 36 q-12 25 -17 75q-8 76 1 166.5t30 124.5t56 32q13 0 202 -77q70 -29 115 -47l84 -34q23 -9 35.5 -30.5t11.5 -48.5zM1450 171q-7 -54 -91.5 -161t-135.5 -127q-37 -14 -63 7q-14 10 -184 287l-47 77q-14 21 -11.5 46t19.5 46q35 43 83 26q1 -1 119 -40q203 -66 242 -79.5 t47 -20.5q28 -22 22 -61zM778 803q5 -102 -54 -122q-58 -17 -114 71l-378 598q-8 35 19 62q41 43 207.5 89.5t224.5 31.5q40 -10 49 -45q3 -18 22 -305.5t24 -379.5zM1440 695q3 -39 -26 -59q-15 -10 -329 -86q-67 -15 -91 -23l1 2q-23 -6 -46 4t-37 32q-30 47 0 87 q1 1 75 102q125 171 150 204t34 39q28 19 65 2q48 -23 123 -133.5t81 -167.5v-3z" /> | |
| 482 | <glyph unicode="" horiz-adv-x="2048" d="M1024 1024h-384v-384h384v384zM1152 384v-128h-640v128h640zM1152 1152v-640h-640v640h640zM1792 384v-128h-512v128h512zM1792 640v-128h-512v128h512zM1792 896v-128h-512v128h512zM1792 1152v-128h-512v128h512zM256 192v960h-128v-960q0 -26 19 -45t45 -19t45 19 t19 45zM1920 192v1088h-1536v-1088q0 -33 -11 -64h1483q26 0 45 19t19 45zM2048 1408v-1216q0 -80 -56 -136t-136 -56h-1664q-80 0 -136 56t-56 136v1088h256v128h1792z" /> | |
| 483 | <glyph unicode="" horiz-adv-x="2048" d="M1024 13q-20 0 -93 73.5t-73 93.5q0 32 62.5 54t103.5 22t103.5 -22t62.5 -54q0 -20 -73 -93.5t-93 -73.5zM1294 284q-2 0 -40 25t-101.5 50t-128.5 25t-128.5 -25t-101 -50t-40.5 -25q-18 0 -93.5 75t-75.5 93q0 13 10 23q78 77 196 121t233 44t233 -44t196 -121 q10 -10 10 -23q0 -18 -75.5 -93t-93.5 -75zM1567 556q-11 0 -23 8q-136 105 -252 154.5t-268 49.5q-85 0 -170.5 -22t-149 -53t-113.5 -62t-79 -53t-31 -22q-17 0 -92 75t-75 93q0 12 10 22q132 132 320 205t380 73t380 -73t320 -205q10 -10 10 -22q0 -18 -75 -93t-92 -75z M1838 827q-11 0 -22 9q-179 157 -371.5 236.5t-420.5 79.5t-420.5 -79.5t-371.5 -236.5q-11 -9 -22 -9q-17 0 -92.5 75t-75.5 93q0 13 10 23q187 186 445 288t527 102t527 -102t445 -288q10 -10 10 -23q0 -18 -75.5 -93t-92.5 -75z" /> | |
| 484 | <glyph unicode="" horiz-adv-x="1792" d="M384 0q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM768 0q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM384 384q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5 t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1152 0q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM768 384q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5 t37.5 90.5zM384 768q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1152 384q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM768 768q0 53 -37.5 90.5t-90.5 37.5 t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1536 0v384q0 52 -38 90t-90 38t-90 -38t-38 -90v-384q0 -52 38 -90t90 -38t90 38t38 90zM1152 768q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5z M1536 1088v256q0 26 -19 45t-45 19h-1280q-26 0 -45 -19t-19 -45v-256q0 -26 19 -45t45 -19h1280q26 0 45 19t19 45zM1536 768q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1664 1408v-1536q0 -52 -38 -90t-90 -38 h-1408q-52 0 -90 38t-38 90v1536q0 52 38 90t90 38h1408q52 0 90 -38t38 -90z" /> | |
| 485 | <glyph unicode="" horiz-adv-x="1792" d="M1112 1090q0 159 -237 159h-70q-32 0 -59.5 -21.5t-34.5 -52.5l-63 -276q-2 -5 -2 -16q0 -24 17 -39.5t41 -15.5h53q69 0 128.5 13t112.5 41t83.5 81.5t30.5 126.5zM1716 938q0 -265 -220 -428q-219 -161 -612 -161h-61q-32 0 -59 -21.5t-34 -52.5l-73 -316 q-8 -36 -40.5 -61.5t-69.5 -25.5h-213q-31 0 -53 20t-22 51q0 10 13 65h151q34 0 64 23.5t38 56.5l73 316q8 33 37.5 57t63.5 24h61q390 0 607 160t217 421q0 129 -51 207q183 -92 183 -335zM1533 1123q0 -264 -221 -428q-218 -161 -612 -161h-60q-32 0 -59.5 -22t-34.5 -53 l-73 -315q-8 -36 -40 -61.5t-69 -25.5h-214q-31 0 -52.5 19.5t-21.5 51.5q0 8 2 20l300 1301q8 36 40.5 61.5t69.5 25.5h444q68 0 125 -4t120.5 -15t113.5 -30t96.5 -50.5t77.5 -74t49.5 -103.5t18.5 -136z" /> | |
| 486 | <glyph unicode="" horiz-adv-x="1792" d="M602 949q19 -61 31 -123.5t17 -141.5t-14 -159t-62 -145q-21 81 -67 157t-95.5 127t-99 90.5t-78.5 57.5t-33 19q-62 34 -81.5 100t14.5 128t101 81.5t129 -14.5q138 -83 238 -177zM927 1236q11 -25 20.5 -46t36.5 -100.5t42.5 -150.5t25.5 -179.5t0 -205.5t-47.5 -209.5 t-105.5 -208.5q-51 -72 -138 -72q-54 0 -98 31q-57 40 -69 109t28 127q60 85 81 195t13 199.5t-32 180.5t-39 128t-22 52q-31 63 -8.5 129.5t85.5 97.5q34 17 75 17q47 0 88.5 -25t63.5 -69zM1248 567q-17 -160 -72 -311q-17 131 -63 246q25 174 -5 361q-27 178 -94 342 q114 -90 212 -211q9 -37 15 -80q26 -179 7 -347zM1520 1440q9 -17 23.5 -49.5t43.5 -117.5t50.5 -178t34 -227.5t5 -269t-47 -300t-112.5 -323.5q-22 -48 -66 -75.5t-95 -27.5q-39 0 -74 16q-67 31 -92.5 100t4.5 136q58 126 90 257.5t37.5 239.5t-3.5 213.5t-26.5 180.5 t-38.5 138.5t-32.5 90t-15.5 32.5q-34 65 -11.5 135.5t87.5 104.5q37 20 81 20q49 0 91.5 -25.5t66.5 -70.5z" /> | |
| 487 | <glyph unicode="" horiz-adv-x="2304" d="M1975 546h-138q14 37 66 179l3 9q4 10 10 26t9 26l12 -55zM531 611l-58 295q-11 54 -75 54h-268l-2 -13q311 -79 403 -336zM710 960l-162 -438l-17 89q-26 70 -85 129.5t-131 88.5l135 -510h175l261 641h-176zM849 318h166l104 642h-166zM1617 944q-69 27 -149 27 q-123 0 -201 -59t-79 -153q-1 -102 145 -174q48 -23 67 -41t19 -39q0 -30 -30 -46t-69 -16q-86 0 -156 33l-22 11l-23 -144q74 -34 185 -34q130 -1 208.5 59t80.5 160q0 106 -140 174q-49 25 -71 42t-22 38q0 22 24.5 38.5t70.5 16.5q70 1 124 -24l15 -8zM2042 960h-128 q-65 0 -87 -54l-246 -588h174l35 96h212q5 -22 20 -96h154zM2304 1280v-1280q0 -52 -38 -90t-90 -38h-2048q-52 0 -90 38t-38 90v1280q0 52 38 90t90 38h2048q52 0 90 -38t38 -90z" /> | |
| 488 | <glyph unicode="" horiz-adv-x="2304" d="M671 603h-13q-47 0 -47 -32q0 -22 20 -22q17 0 28 15t12 39zM1066 639h62v3q1 4 0.5 6.5t-1 7t-2 8t-4.5 6.5t-7.5 5t-11.5 2q-28 0 -36 -38zM1606 603h-12q-48 0 -48 -32q0 -22 20 -22q17 0 28 15t12 39zM1925 629q0 41 -30 41q-19 0 -31 -20t-12 -51q0 -42 28 -42 q20 0 32.5 20t12.5 52zM480 770h87l-44 -262h-56l32 201l-71 -201h-39l-4 200l-34 -200h-53l44 262h81l2 -163zM733 663q0 -6 -4 -42q-16 -101 -17 -113h-47l1 22q-20 -26 -58 -26q-23 0 -37.5 16t-14.5 42q0 39 26 60.5t73 21.5q14 0 23 -1q0 3 0.5 5.5t1 4.5t0.5 3 q0 20 -36 20q-29 0 -59 -10q0 4 7 48q38 11 67 11q74 0 74 -62zM889 721l-8 -49q-22 3 -41 3q-27 0 -27 -17q0 -8 4.5 -12t21.5 -11q40 -19 40 -60q0 -72 -87 -71q-34 0 -58 6q0 2 7 49q29 -8 51 -8q32 0 32 19q0 7 -4.5 11.5t-21.5 12.5q-43 20 -43 59q0 72 84 72 q30 0 50 -4zM977 721h28l-7 -52h-29q-2 -17 -6.5 -40.5t-7 -38.5t-2.5 -18q0 -16 19 -16q8 0 16 2l-8 -47q-21 -7 -40 -7q-43 0 -45 47q0 12 8 56q3 20 25 146h55zM1180 648q0 -23 -7 -52h-111q-3 -22 10 -33t38 -11q30 0 58 14l-9 -54q-30 -8 -57 -8q-95 0 -95 95 q0 55 27.5 90.5t69.5 35.5q35 0 55.5 -21t20.5 -56zM1319 722q-13 -23 -22 -62q-22 2 -31 -24t-25 -128h-56l3 14q22 130 29 199h51l-3 -33q14 21 25.5 29.5t28.5 4.5zM1506 763l-9 -57q-28 14 -50 14q-31 0 -51 -27.5t-20 -70.5q0 -30 13.5 -47t38.5 -17q21 0 48 13 l-10 -59q-28 -8 -50 -8q-45 0 -71.5 30.5t-26.5 82.5q0 70 35.5 114.5t91.5 44.5q26 0 61 -13zM1668 663q0 -18 -4 -42q-13 -79 -17 -113h-46l1 22q-20 -26 -59 -26q-23 0 -37 16t-14 42q0 39 25.5 60.5t72.5 21.5q15 0 23 -1q2 7 2 13q0 20 -36 20q-29 0 -59 -10q0 4 8 48 q38 11 67 11q73 0 73 -62zM1809 722q-14 -24 -21 -62q-23 2 -31.5 -23t-25.5 -129h-56l3 14q19 104 29 199h52q0 -11 -4 -33q15 21 26.5 29.5t27.5 4.5zM1950 770h56l-43 -262h-53l3 19q-23 -23 -52 -23q-31 0 -49.5 24t-18.5 64q0 53 27.5 92t64.5 39q31 0 53 -29z M2061 640q0 148 -72.5 273t-198 198t-273.5 73q-181 0 -328 -110q127 -116 171 -284h-50q-44 150 -158 253q-114 -103 -158 -253h-50q44 168 171 284q-147 110 -328 110q-148 0 -273.5 -73t-198 -198t-72.5 -273t72.5 -273t198 -198t273.5 -73q181 0 328 110 q-120 111 -165 264h50q46 -138 152 -233q106 95 152 233h50q-45 -153 -165 -264q147 -110 328 -110q148 0 273.5 73t198 198t72.5 273zM2304 1280v-1280q0 -52 -38 -90t-90 -38h-2048q-52 0 -90 38t-38 90v1280q0 52 38 90t90 38h2048q52 0 90 -38t38 -90z" /> | |
| 489 | <glyph unicode="" horiz-adv-x="2304" d="M313 759q0 -51 -36 -84q-29 -26 -89 -26h-17v220h17q61 0 89 -27q36 -31 36 -83zM2089 824q0 -52 -64 -52h-19v101h20q63 0 63 -49zM380 759q0 74 -50 120.5t-129 46.5h-95v-333h95q74 0 119 38q60 51 60 128zM410 593h65v333h-65v-333zM730 694q0 40 -20.5 62t-75.5 42 q-29 10 -39.5 19t-10.5 23q0 16 13.5 26.5t34.5 10.5q29 0 53 -27l34 44q-41 37 -98 37q-44 0 -74 -27.5t-30 -67.5q0 -35 18 -55.5t64 -36.5q37 -13 45 -19q19 -12 19 -34q0 -20 -14 -33.5t-36 -13.5q-48 0 -71 44l-42 -40q44 -64 115 -64q51 0 83 30.5t32 79.5zM1008 604 v77q-37 -37 -78 -37q-49 0 -80.5 32.5t-31.5 82.5q0 48 31.5 81.5t77.5 33.5q43 0 81 -38v77q-40 20 -80 20q-74 0 -125.5 -50.5t-51.5 -123.5t51 -123.5t125 -50.5q42 0 81 19zM2240 0v527q-65 -40 -144.5 -84t-237.5 -117t-329.5 -137.5t-417.5 -134.5t-504 -118h1569 q26 0 45 19t19 45zM1389 757q0 75 -53 128t-128 53t-128 -53t-53 -128t53 -128t128 -53t128 53t53 128zM1541 584l144 342h-71l-90 -224l-89 224h-71l142 -342h35zM1714 593h184v56h-119v90h115v56h-115v74h119v57h-184v-333zM2105 593h80l-105 140q76 16 76 94q0 47 -31 73 t-87 26h-97v-333h65v133h9zM2304 1274v-1268q0 -56 -38.5 -95t-93.5 -39h-2040q-55 0 -93.5 39t-38.5 95v1268q0 56 38.5 95t93.5 39h2040q55 0 93.5 -39t38.5 -95z" /> | |
| 490 | <glyph unicode="" horiz-adv-x="2304" d="M119 854h89l-45 108zM740 328l74 79l-70 79h-163v-49h142v-55h-142v-54h159zM898 406l99 -110v217zM1186 453q0 33 -40 33h-84v-69h83q41 0 41 36zM1475 457q0 29 -42 29h-82v-61h81q43 0 43 32zM1197 923q0 29 -42 29h-82v-60h81q43 0 43 31zM1656 854h89l-44 108z M699 1009v-271h-66v212l-94 -212h-57l-94 212v-212h-132l-25 60h-135l-25 -60h-70l116 271h96l110 -257v257h106l85 -184l77 184h108zM1255 453q0 -20 -5.5 -35t-14 -25t-22.5 -16.5t-26 -10t-31.5 -4.5t-31.5 -1t-32.5 0.5t-29.5 0.5v-91h-126l-80 90l-83 -90h-256v271h260 l80 -89l82 89h207q109 0 109 -89zM964 794v-56h-217v271h217v-57h-152v-49h148v-55h-148v-54h152zM2304 235v-229q0 -55 -38.5 -94.5t-93.5 -39.5h-2040q-55 0 -93.5 39.5t-38.5 94.5v678h111l25 61h55l25 -61h218v46l19 -46h113l20 47v-47h541v99l10 1q10 0 10 -14v-86h279 v23q23 -12 55 -18t52.5 -6.5t63 0.5t51.5 1l25 61h56l25 -61h227v58l34 -58h182v378h-180v-44l-25 44h-185v-44l-23 44h-249q-69 0 -109 -22v22h-172v-22q-24 22 -73 22h-628l-43 -97l-43 97h-198v-44l-22 44h-169l-78 -179v391q0 55 38.5 94.5t93.5 39.5h2040 q55 0 93.5 -39.5t38.5 -94.5v-678h-120q-51 0 -81 -22v22h-177q-55 0 -78 -22v22h-316v-22q-31 22 -87 22h-209v-22q-23 22 -91 22h-234l-54 -58l-50 58h-349v-378h343l55 59l52 -59h211v89h21q59 0 90 13v-102h174v99h8q8 0 10 -2t2 -10v-87h529q57 0 88 24v-24h168 q60 0 95 17zM1546 469q0 -23 -12 -43t-34 -29q25 -9 34 -26t9 -46v-54h-65v45q0 33 -12 43.5t-46 10.5h-69v-99h-65v271h154q48 0 77 -15t29 -58zM1269 936q0 -24 -12.5 -44t-33.5 -29q26 -9 34.5 -25.5t8.5 -46.5v-53h-65q0 9 0.5 26.5t0 25t-3 18.5t-8.5 16t-17.5 8.5 t-29.5 3.5h-70v-98h-64v271l153 -1q49 0 78 -14.5t29 -57.5zM1798 327v-56h-216v271h216v-56h-151v-49h148v-55h-148v-54zM1372 1009v-271h-66v271h66zM2065 357q0 -86 -102 -86h-126v58h126q34 0 34 25q0 16 -17 21t-41.5 5t-49.5 3.5t-42 22.5t-17 55q0 39 26 60t66 21 h130v-57h-119q-36 0 -36 -25q0 -16 17.5 -20.5t42 -4t49 -2.5t42 -21.5t17.5 -54.5zM2304 407v-101q-24 -35 -88 -35h-125v58h125q33 0 33 25q0 13 -12.5 19t-31 5.5t-40 2t-40 8t-31 24t-12.5 48.5q0 39 26.5 60t66.5 21h129v-57h-118q-36 0 -36 -25q0 -20 29 -22t68.5 -5 t56.5 -26zM2139 1008v-270h-92l-122 203v-203h-132l-26 60h-134l-25 -60h-75q-129 0 -129 133q0 138 133 138h63v-59q-7 0 -28 1t-28.5 0.5t-23 -2t-21.5 -6.5t-14.5 -13.5t-11.5 -23t-3 -33.5q0 -38 13.5 -58t49.5 -20h29l92 213h97l109 -256v256h99l114 -188v188h66z" /> | |
| 491 | <glyph unicode="" horiz-adv-x="2304" d="M322 689h-15q-19 0 -19 18q0 28 19 85q5 15 15 19.5t28 4.5q77 0 77 -49q0 -41 -30.5 -59.5t-74.5 -18.5zM664 528q-47 0 -47 29q0 62 123 62l3 -3q-5 -88 -79 -88zM1438 687h-15q-19 0 -19 19q0 28 19 85q5 15 14.5 19t28.5 4q77 0 77 -49q0 -41 -30.5 -59.5 t-74.5 -18.5zM1780 527q-47 0 -47 30q0 62 123 62l3 -3q-5 -89 -79 -89zM373 894h-128q-8 0 -14.5 -4t-8.5 -7.5t-7 -12.5q-3 -7 -45 -190t-42 -192q0 -7 5.5 -12.5t13.5 -5.5h62q25 0 32.5 34.5l15 69t32.5 34.5q47 0 87.5 7.5t80.5 24.5t63.5 52.5t23.5 84.5 q0 36 -14.5 61t-41 36.5t-53.5 15.5t-62 4zM719 798q-38 0 -74 -6q-2 0 -8.5 -1t-9 -1.5l-7.5 -1.5t-7.5 -2t-6.5 -3t-6.5 -4t-5 -5t-4.5 -7t-4 -9q-9 -29 -9 -39t9 -10q5 0 21.5 5t19.5 6q30 8 58 8q74 0 74 -36q0 -11 -10 -14q-8 -2 -18 -3t-21.5 -1.5t-17.5 -1.5 q-38 -4 -64.5 -10t-56.5 -19.5t-45.5 -39t-15.5 -62.5q0 -38 26 -59.5t64 -21.5q24 0 45.5 6.5t33 13t38.5 23.5q-3 -7 -3 -15t5.5 -13.5t12.5 -5.5h56q1 1 7 3.5t7.5 3.5t5 3.5t5 5.5t2.5 8l45 194q4 13 4 30q0 81 -145 81zM1247 793h-74q-22 0 -39 -23q-5 -7 -29.5 -51 t-46.5 -81.5t-26 -38.5l-5 4q0 77 -27 166q-1 5 -3.5 8.5t-6 6.5t-6.5 5t-8.5 3t-8.5 1.5t-9.5 1t-9 0.5h-10h-8.5q-38 0 -38 -21l1 -5q5 -53 25 -151t25 -143q2 -16 2 -24q0 -19 -30.5 -61.5t-30.5 -58.5q0 -13 40 -13q61 0 76 25l245 415q10 20 10 26q0 9 -8 9zM1489 892 h-129q-18 0 -29 -23q-6 -13 -46.5 -191.5t-40.5 -190.5q0 -20 43 -20h7.5h9h9t9.5 1t8.5 2t8.5 3t6.5 4.5t5.5 6t3 8.5l21 91q2 10 10.5 17t19.5 7q47 0 87.5 7t80.5 24.5t63.5 52.5t23.5 84q0 36 -14.5 61t-41 36.5t-53.5 15.5t-62 4zM1835 798q-26 0 -74 -6 q-38 -6 -48 -16q-7 -8 -11 -19q-8 -24 -8 -39q0 -10 8 -10q1 0 41 12q30 8 58 8q74 0 74 -36q0 -12 -10 -14q-4 -1 -57 -7q-38 -4 -64.5 -10t-56.5 -19.5t-45.5 -39t-15.5 -62.5t26 -58.5t64 -21.5q24 0 45 6t34 13t38 24q-3 -15 -3 -16q0 -5 2 -8.5t6.5 -5.5t8 -3.5 t10.5 -2t9.5 -0.5h9.5h8q42 0 48 25l45 194q3 15 3 31q0 81 -145 81zM2157 889h-55q-25 0 -33 -40q-10 -44 -36.5 -167t-42.5 -190v-5q0 -16 16 -18h1h57q10 0 18.5 6.5t10.5 16.5l83 374h-1l1 5q0 7 -5.5 12.5t-13.5 5.5zM2304 1280v-1280q0 -52 -38 -90t-90 -38h-2048 q-52 0 -90 38t-38 90v1280q0 52 38 90t90 38h2048q52 0 90 -38t38 -90z" /> | |
| 492 | <glyph unicode="" horiz-adv-x="2304" d="M1597 633q0 -69 -21 -106q-19 -35 -52 -35q-23 0 -41 9v224q29 30 57 30q57 0 57 -122zM2035 669h-110q6 98 56 98q51 0 54 -98zM476 534q0 59 -33 91.5t-101 57.5q-36 13 -52 24t-16 25q0 26 38 26q58 0 124 -33l18 112q-67 32 -149 32q-77 0 -123 -38q-48 -39 -48 -109 q0 -58 32.5 -90.5t99.5 -56.5q39 -14 54.5 -25.5t15.5 -27.5q0 -31 -48 -31q-29 0 -70 12.5t-72 30.5l-18 -113q72 -41 168 -41q81 0 129 37q51 41 51 117zM771 749l19 111h-96v135l-129 -21l-18 -114l-46 -8l-17 -103h62v-219q0 -84 44 -120q38 -30 111 -30q32 0 79 11v118 q-32 -7 -44 -7q-42 0 -42 50v197h77zM1087 724v139q-15 3 -28 3q-32 0 -55.5 -16t-33.5 -46l-10 56h-131v-471h150v306q26 31 82 31q16 0 26 -2zM1124 389h150v471h-150v-471zM1746 638q0 122 -45 179q-40 52 -111 52q-64 0 -117 -56l-8 47h-132v-645l150 25v151 q36 -11 68 -11q83 0 134 56q61 65 61 202zM1278 986q0 33 -23 56t-56 23t-56 -23t-23 -56t23 -56.5t56 -23.5t56 23.5t23 56.5zM2176 629q0 113 -48 176q-50 64 -144 64q-96 0 -151.5 -66t-55.5 -180q0 -128 63 -188q55 -55 161 -55q101 0 160 40l-16 103q-57 -31 -128 -31 q-43 0 -63 19q-23 19 -28 66h248q2 14 2 52zM2304 1280v-1280q0 -52 -38 -90t-90 -38h-2048q-52 0 -90 38t-38 90v1280q0 52 38 90t90 38h2048q52 0 90 -38t38 -90z" /> | |
| 493 | <glyph unicode="" horiz-adv-x="2048" d="M1558 684q61 -356 298 -556q0 -52 -38 -90t-90 -38h-448q0 -106 -75 -181t-181 -75t-180.5 74.5t-75.5 180.5zM1024 -176q16 0 16 16t-16 16q-59 0 -101.5 42.5t-42.5 101.5q0 16 -16 16t-16 -16q0 -73 51.5 -124.5t124.5 -51.5zM2026 1424q8 -10 7.5 -23.5t-10.5 -22.5 l-1872 -1622q-10 -8 -23.5 -7t-21.5 11l-84 96q-8 10 -7.5 23.5t10.5 21.5l186 161q-19 32 -19 66q50 42 91 88t85 119.5t74.5 158.5t50 206t19.5 260q0 152 117 282.5t307 158.5q-8 19 -8 39q0 40 28 68t68 28t68 -28t28 -68q0 -20 -8 -39q124 -18 219 -82.5t148 -157.5 l418 363q10 8 23.5 7t21.5 -11z" /> | |
| 494 | <glyph unicode="" horiz-adv-x="2048" d="M1040 -160q0 16 -16 16q-59 0 -101.5 42.5t-42.5 101.5q0 16 -16 16t-16 -16q0 -73 51.5 -124.5t124.5 -51.5q16 0 16 16zM503 315l877 760q-42 88 -132.5 146.5t-223.5 58.5q-93 0 -169.5 -31.5t-121.5 -80.5t-69 -103t-24 -105q0 -384 -137 -645zM1856 128 q0 -52 -38 -90t-90 -38h-448q0 -106 -75 -181t-181 -75t-180.5 74.5t-75.5 180.5l149 129h757q-166 187 -227 459l111 97q61 -356 298 -556zM1942 1520l84 -96q8 -10 7.5 -23.5t-10.5 -22.5l-1872 -1622q-10 -8 -23.5 -7t-21.5 11l-84 96q-8 10 -7.5 23.5t10.5 21.5l186 161 q-19 32 -19 66q50 42 91 88t85 119.5t74.5 158.5t50 206t19.5 260q0 152 117 282.5t307 158.5q-8 19 -8 39q0 40 28 68t68 28t68 -28t28 -68q0 -20 -8 -39q124 -18 219 -82.5t148 -157.5l418 363q10 8 23.5 7t21.5 -11z" /> | |
| 495 | <glyph unicode="" horiz-adv-x="1408" d="M512 160v704q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-704q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM768 160v704q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-704q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM1024 160v704q0 14 -9 23t-23 9h-64q-14 0 -23 -9t-9 -23v-704 q0 -14 9 -23t23 -9h64q14 0 23 9t9 23zM480 1152h448l-48 117q-7 9 -17 11h-317q-10 -2 -17 -11zM1408 1120v-64q0 -14 -9 -23t-23 -9h-96v-948q0 -83 -47 -143.5t-113 -60.5h-832q-66 0 -113 58.5t-47 141.5v952h-96q-14 0 -23 9t-9 23v64q0 14 9 23t23 9h309l70 167 q15 37 54 63t79 26h320q40 0 79 -26t54 -63l70 -167h309q14 0 23 -9t9 -23z" /> | |
| 496 | <glyph unicode="" d="M1150 462v-109q0 -50 -36.5 -89t-94 -60.5t-118 -32.5t-117.5 -11q-205 0 -342.5 139t-137.5 346q0 203 136 339t339 136q34 0 75.5 -4.5t93 -18t92.5 -34t69 -56.5t28 -81v-109q0 -16 -16 -16h-118q-16 0 -16 16v70q0 43 -65.5 67.5t-137.5 24.5q-140 0 -228.5 -91.5 t-88.5 -237.5q0 -151 91.5 -249.5t233.5 -98.5q68 0 138 24t70 66v70q0 7 4.5 11.5t10.5 4.5h119q6 0 11 -4.5t5 -11.5zM768 1280q-130 0 -248.5 -51t-204 -136.5t-136.5 -204t-51 -248.5t51 -248.5t136.5 -204t204 -136.5t248.5 -51t248.5 51t204 136.5t136.5 204t51 248.5 t-51 248.5t-136.5 204t-204 136.5t-248.5 51zM1536 640q0 -209 -103 -385.5t-279.5 -279.5t-385.5 -103t-385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103t385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 497 | <glyph unicode="" d="M972 761q0 108 -53.5 169t-147.5 61q-63 0 -124 -30.5t-110 -84.5t-79.5 -137t-30.5 -180q0 -112 53.5 -173t150.5 -61q96 0 176 66.5t122.5 166t42.5 203.5zM1536 640q0 -111 -37 -197t-98.5 -135t-131.5 -74.5t-145 -27.5q-6 0 -15.5 -0.5t-16.5 -0.5q-95 0 -142 53 q-28 33 -33 83q-52 -66 -131.5 -110t-173.5 -44q-161 0 -249.5 95.5t-88.5 269.5q0 157 66 290t179 210.5t246 77.5q87 0 155 -35.5t106 -99.5l2 19l11 56q1 6 5.5 12t9.5 6h118q5 0 13 -11q5 -5 3 -16l-120 -614q-5 -24 -5 -48q0 -39 12.5 -52t44.5 -13q28 1 57 5.5t73 24 t77 50t57 89.5t24 137q0 292 -174 466t-466 174q-130 0 -248.5 -51t-204 -136.5t-136.5 -204t-51 -248.5t51 -248.5t136.5 -204t204 -136.5t248.5 -51q228 0 405 144q11 9 24 8t21 -12l41 -49q8 -12 7 -24q-2 -13 -12 -22q-102 -83 -227.5 -128t-258.5 -45q-156 0 -298 61 t-245 164t-164 245t-61 298t61 298t164 245t245 164t298 61q344 0 556 -212t212 -556z" /> | |
| 498 | <glyph unicode="" horiz-adv-x="1792" d="M1698 1442q94 -94 94 -226.5t-94 -225.5l-225 -223l104 -104q10 -10 10 -23t-10 -23l-210 -210q-10 -10 -23 -10t-23 10l-105 105l-603 -603q-37 -37 -90 -37h-203l-256 -128l-64 64l128 256v203q0 53 37 90l603 603l-105 105q-10 10 -10 23t10 23l210 210q10 10 23 10 t23 -10l104 -104l223 225q93 94 225.5 94t226.5 -94zM512 64l576 576l-192 192l-576 -576v-192h192z" /> | |
| 499 | <glyph unicode="" horiz-adv-x="1792" d="M1615 1536q70 0 122.5 -46.5t52.5 -116.5q0 -63 -45 -151q-332 -629 -465 -752q-97 -91 -218 -91q-126 0 -216.5 92.5t-90.5 219.5q0 128 92 212l638 579q59 54 130 54zM706 502q39 -76 106.5 -130t150.5 -76l1 -71q4 -213 -129.5 -347t-348.5 -134q-123 0 -218 46.5 t-152.5 127.5t-86.5 183t-29 220q7 -5 41 -30t62 -44.5t59 -36.5t46 -17q41 0 55 37q25 66 57.5 112.5t69.5 76t88 47.5t103 25.5t125 10.5z" /> | |
| 500 | <glyph unicode="" horiz-adv-x="1792" d="M1792 128v-384h-1792v384q45 0 85 14t59 27.5t47 37.5q30 27 51.5 38t56.5 11t55.5 -11t52.5 -38q29 -25 47 -38t58 -27t86 -14q45 0 85 14.5t58 27t48 37.5q21 19 32.5 27t31 15t43.5 7q35 0 56.5 -11t51.5 -38q28 -24 47 -37.5t59 -27.5t85 -14t85 14t59 27.5t47 37.5 q30 27 51.5 38t56.5 11q34 0 55.5 -11t51.5 -38q28 -24 47 -37.5t59 -27.5t85 -14zM1792 448v-192q-35 0 -55.5 11t-52.5 38q-29 25 -47 38t-58 27t-85 14q-46 0 -86 -14t-58 -27t-47 -38q-22 -19 -33 -27t-31 -15t-44 -7q-35 0 -56.5 11t-51.5 38q-29 25 -47 38t-58 27 t-86 14q-45 0 -85 -14.5t-58 -27t-48 -37.5q-21 -19 -32.5 -27t-31 -15t-43.5 -7q-35 0 -56.5 11t-51.5 38q-28 24 -47 37.5t-59 27.5t-85 14q-46 0 -86 -14t-58 -27t-47 -38q-30 -27 -51.5 -38t-56.5 -11v192q0 80 56 136t136 56h64v448h256v-448h256v448h256v-448h256v448 h256v-448h64q80 0 136 -56t56 -136zM512 1312q0 -77 -36 -118.5t-92 -41.5q-53 0 -90.5 37.5t-37.5 90.5q0 29 9.5 51t23.5 34t31 28t31 31.5t23.5 44.5t9.5 67q38 0 83 -74t45 -150zM1024 1312q0 -77 -36 -118.5t-92 -41.5q-53 0 -90.5 37.5t-37.5 90.5q0 29 9.5 51 t23.5 34t31 28t31 31.5t23.5 44.5t9.5 67q38 0 83 -74t45 -150zM1536 1312q0 -77 -36 -118.5t-92 -41.5q-53 0 -90.5 37.5t-37.5 90.5q0 29 9.5 51t23.5 34t31 28t31 31.5t23.5 44.5t9.5 67q38 0 83 -74t45 -150z" /> | |
| 501 | <glyph unicode="" horiz-adv-x="2048" d="M2048 0v-128h-2048v1536h128v-1408h1920zM1664 1024l256 -896h-1664v576l448 576l576 -576z" /> | |
| 502 | <glyph unicode="" horiz-adv-x="1792" d="M768 646l546 -546q-106 -108 -247.5 -168t-298.5 -60q-209 0 -385.5 103t-279.5 279.5t-103 385.5t103 385.5t279.5 279.5t385.5 103v-762zM955 640h773q0 -157 -60 -298.5t-168 -247.5zM1664 768h-768v768q209 0 385.5 -103t279.5 -279.5t103 -385.5z" /> | |
| 503 | <glyph unicode="" horiz-adv-x="2048" d="M2048 0v-128h-2048v1536h128v-1408h1920zM1920 1248v-435q0 -21 -19.5 -29.5t-35.5 7.5l-121 121l-633 -633q-10 -10 -23 -10t-23 10l-233 233l-416 -416l-192 192l585 585q10 10 23 10t23 -10l233 -233l464 464l-121 121q-16 16 -7.5 35.5t29.5 19.5h435q14 0 23 -9 t9 -23z" /> | |
| 504 | <glyph unicode="" horiz-adv-x="1792" d="M1292 832q0 -6 10 -41q10 -29 25 -49.5t41 -34t44 -20t55 -16.5q325 -91 325 -332q0 -146 -105.5 -242.5t-254.5 -96.5q-59 0 -111.5 18.5t-91.5 45.5t-77 74.5t-63 87.5t-53.5 103.5t-43.5 103t-39.5 106.5t-35.5 95q-32 81 -61.5 133.5t-73.5 96.5t-104 64t-142 20 q-96 0 -183 -55.5t-138 -144.5t-51 -185q0 -160 106.5 -279.5t263.5 -119.5q177 0 258 95q56 63 83 116l84 -152q-15 -34 -44 -70l1 -1q-131 -152 -388 -152q-147 0 -269.5 79t-190.5 207.5t-68 274.5q0 105 43.5 206t116 176.5t172 121.5t204.5 46q87 0 159 -19t123.5 -50 t95 -80t72.5 -99t58.5 -117t50.5 -124.5t50 -130.5t55 -127q96 -200 233 -200q81 0 138.5 48.5t57.5 128.5q0 42 -19 72t-50.5 46t-72.5 31.5t-84.5 27t-87.5 34t-81 52t-65 82t-39 122.5q-3 16 -3 33q0 110 87.5 192t198.5 78q78 -3 120.5 -14.5t90.5 -53.5h-1 q12 -11 23 -24.5t26 -36t19 -27.5l-129 -99q-26 49 -54 70v1q-23 21 -97 21q-49 0 -84 -33t-35 -83z" /> | |
| 505 | <glyph unicode="" d="M1432 484q0 173 -234 239q-35 10 -53 16.5t-38 25t-29 46.5q0 2 -2 8.5t-3 12t-1 7.5q0 36 24.5 59.5t60.5 23.5q54 0 71 -15h-1q20 -15 39 -51l93 71q-39 54 -49 64q-33 29 -67.5 39t-85.5 10q-80 0 -142 -57.5t-62 -137.5q0 -7 2 -23q16 -96 64.5 -140t148.5 -73 q29 -8 49 -15.5t45 -21.5t38.5 -34.5t13.5 -46.5v-5q1 -58 -40.5 -93t-100.5 -35q-97 0 -167 144q-23 47 -51.5 121.5t-48 125.5t-54 110.5t-74 95.5t-103.5 60.5t-147 24.5q-101 0 -192 -56t-144 -148t-50 -192v-1q4 -108 50.5 -199t133.5 -147.5t196 -56.5q186 0 279 110 q20 27 31 51l-60 109q-42 -80 -99 -116t-146 -36q-115 0 -191 87t-76 204q0 105 82 189t186 84q112 0 170 -53.5t104 -172.5q8 -21 25.5 -68.5t28.5 -76.5t31.5 -74.5t38.5 -74t45.5 -62.5t55.5 -53.5t66 -33t80 -13.5q107 0 183 69.5t76 174.5zM1536 1120v-960 q0 -119 -84.5 -203.5t-203.5 -84.5h-960q-119 0 -203.5 84.5t-84.5 203.5v960q0 119 84.5 203.5t203.5 84.5h960q119 0 203.5 -84.5t84.5 -203.5z" /> | |
| 506 | <glyph unicode="" horiz-adv-x="2048" d="M1152 640q0 104 -40.5 198.5t-109.5 163.5t-163.5 109.5t-198.5 40.5t-198.5 -40.5t-163.5 -109.5t-109.5 -163.5t-40.5 -198.5t40.5 -198.5t109.5 -163.5t163.5 -109.5t198.5 -40.5t198.5 40.5t163.5 109.5t109.5 163.5t40.5 198.5zM1920 640q0 104 -40.5 198.5 t-109.5 163.5t-163.5 109.5t-198.5 40.5h-386q119 -90 188.5 -224t69.5 -288t-69.5 -288t-188.5 -224h386q104 0 198.5 40.5t163.5 109.5t109.5 163.5t40.5 198.5zM2048 640q0 -130 -51 -248.5t-136.5 -204t-204 -136.5t-248.5 -51h-768q-130 0 -248.5 51t-204 136.5 t-136.5 204t-51 248.5t51 248.5t136.5 204t204 136.5t248.5 51h768q130 0 248.5 -51t204 -136.5t136.5 -204t51 -248.5z" /> | |
| 507 | <glyph unicode="" horiz-adv-x="2048" d="M0 640q0 130 51 248.5t136.5 204t204 136.5t248.5 51h768q130 0 248.5 -51t204 -136.5t136.5 -204t51 -248.5t-51 -248.5t-136.5 -204t-204 -136.5t-248.5 -51h-768q-130 0 -248.5 51t-204 136.5t-136.5 204t-51 248.5zM1408 128q104 0 198.5 40.5t163.5 109.5 t109.5 163.5t40.5 198.5t-40.5 198.5t-109.5 163.5t-163.5 109.5t-198.5 40.5t-198.5 -40.5t-163.5 -109.5t-109.5 -163.5t-40.5 -198.5t40.5 -198.5t109.5 -163.5t163.5 -109.5t198.5 -40.5z" /> | |
| 508 | <glyph unicode="" horiz-adv-x="2304" d="M762 384h-314q-40 0 -57.5 35t6.5 67l188 251q-65 31 -137 31q-132 0 -226 -94t-94 -226t94 -226t226 -94q115 0 203 72.5t111 183.5zM576 512h186q-18 85 -75 148zM1056 512l288 384h-480l-99 -132q105 -103 126 -252h165zM2176 448q0 132 -94 226t-226 94 q-60 0 -121 -24l174 -260q15 -23 10 -49t-27 -40q-15 -11 -36 -11q-35 0 -53 29l-174 260q-93 -95 -93 -225q0 -132 94 -226t226 -94t226 94t94 226zM2304 448q0 -185 -131.5 -316.5t-316.5 -131.5t-316.5 131.5t-131.5 316.5q0 97 39.5 183.5t109.5 149.5l-65 98l-353 -469 q-18 -26 -51 -26h-197q-23 -164 -149 -274t-294 -110q-185 0 -316.5 131.5t-131.5 316.5t131.5 316.5t316.5 131.5q114 0 215 -55l137 183h-224q-26 0 -45 19t-19 45t19 45t45 19h384v-128h435l-85 128h-222q-26 0 -45 19t-19 45t19 45t45 19h256q33 0 53 -28l267 -400 q91 44 192 44q185 0 316.5 -131.5t131.5 -316.5z" /> | |
| 509 | <glyph unicode="" d="M384 320q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1408 320q0 53 -37.5 90.5t-90.5 37.5t-90.5 -37.5t-37.5 -90.5t37.5 -90.5t90.5 -37.5t90.5 37.5t37.5 90.5zM1362 716l-72 384q-5 23 -22.5 37.5t-40.5 14.5 h-918q-23 0 -40.5 -14.5t-22.5 -37.5l-72 -384q-5 -30 14 -53t49 -23h1062q30 0 49 23t14 53zM1136 1328q0 20 -14 34t-34 14h-640q-20 0 -34 -14t-14 -34t14 -34t34 -14h640q20 0 34 14t14 34zM1536 603v-603h-128v-128q0 -53 -37.5 -90.5t-90.5 -37.5t-90.5 37.5 t-37.5 90.5v128h-768v-128q0 -53 -37.5 -90.5t-90.5 -37.5t-90.5 37.5t-37.5 90.5v128h-128v603q0 112 25 223l103 454q9 78 97.5 137t230 89t312.5 30t312.5 -30t230 -89t97.5 -137l105 -454q23 -102 23 -223z" /> | |
| 510 | <glyph unicode="" horiz-adv-x="2048" d="M1463 704q0 -35 -25 -60.5t-61 -25.5h-702q-36 0 -61 25.5t-25 60.5t25 60.5t61 25.5h702q36 0 61 -25.5t25 -60.5zM1677 704q0 86 -23 170h-982q-36 0 -61 25t-25 60q0 36 25 61t61 25h908q-88 143 -235 227t-320 84q-177 0 -327.5 -87.5t-238 -237.5t-87.5 -327 q0 -86 23 -170h982q36 0 61 -25t25 -60q0 -36 -25 -61t-61 -25h-908q88 -143 235.5 -227t320.5 -84q132 0 253 51.5t208 139t139 208t52 253.5zM2048 959q0 -35 -25 -60t-61 -25h-131q17 -85 17 -170q0 -167 -65.5 -319.5t-175.5 -263t-262.5 -176t-319.5 -65.5 q-246 0 -448.5 133t-301.5 350h-189q-36 0 -61 25t-25 61q0 35 25 60t61 25h132q-17 85 -17 170q0 167 65.5 319.5t175.5 263t262.5 176t320.5 65.5q245 0 447.5 -133t301.5 -350h188q36 0 61 -25t25 -61z" /> | |
| 511 | <glyph unicode="" horiz-adv-x="1280" d="M953 1158l-114 -328l117 -21q165 451 165 518q0 56 -38 56q-57 0 -130 -225zM654 471l33 -88q37 42 71 67l-33 5.5t-38.5 7t-32.5 8.5zM362 1367q0 -98 159 -521q18 10 49 10q15 0 75 -5l-121 351q-75 220 -123 220q-19 0 -29 -17.5t-10 -37.5zM283 608q0 -36 51.5 -119 t117.5 -153t100 -70q14 0 25.5 13t11.5 27q0 24 -32 102q-13 32 -32 72t-47.5 89t-61.5 81t-62 32q-20 0 -45.5 -27t-25.5 -47zM125 273q0 -41 25 -104q59 -145 183.5 -227t281.5 -82q227 0 382 170q152 169 152 427q0 43 -1 67t-11.5 62t-30.5 56q-56 49 -211.5 75.5 t-270.5 26.5q-37 0 -49 -11q-12 -5 -12 -35q0 -34 21.5 -60t55.5 -40t77.5 -23.5t87.5 -11.5t85 -4t70 0h23q24 0 40 -19q15 -19 19 -55q-28 -28 -96 -54q-61 -22 -93 -46q-64 -46 -108.5 -114t-44.5 -137q0 -31 18.5 -88.5t18.5 -87.5l-3 -12q-4 -12 -4 -14 q-137 10 -146 216q-8 -2 -41 -2q2 -7 2 -21q0 -53 -40.5 -89.5t-94.5 -36.5q-82 0 -166.5 78t-84.5 159q0 34 33 67q52 -64 60 -76q77 -104 133 -104q12 0 26.5 8.5t14.5 20.5q0 34 -87.5 145t-116.5 111q-43 0 -70 -44.5t-27 -90.5zM11 264q0 101 42.5 163t136.5 88 q-28 74 -28 104q0 62 61 123t122 61q29 0 70 -15q-163 462 -163 567q0 80 41 130.5t119 50.5q131 0 325 -581q6 -17 8 -23q6 16 29 79.5t43.5 118.5t54 127.5t64.5 123t70.5 86.5t76.5 36q71 0 112 -49t41 -122q0 -108 -159 -550q61 -15 100.5 -46t58.5 -78t26 -93.5 t7 -110.5q0 -150 -47 -280t-132 -225t-211 -150t-278 -55q-111 0 -223 42q-149 57 -258 191.5t-109 286.5z" /> | |
| 512 | <glyph unicode="" horiz-adv-x="2048" d="M785 528h207q-14 -158 -98.5 -248.5t-214.5 -90.5q-162 0 -254.5 116t-92.5 316q0 194 93 311.5t233 117.5q148 0 232 -87t97 -247h-203q-5 64 -35.5 99t-81.5 35q-57 0 -88.5 -60.5t-31.5 -177.5q0 -48 5 -84t18 -69.5t40 -51.5t66 -18q95 0 109 139zM1497 528h206 q-14 -158 -98 -248.5t-214 -90.5q-162 0 -254.5 116t-92.5 316q0 194 93 311.5t233 117.5q148 0 232 -87t97 -247h-204q-4 64 -35 99t-81 35q-57 0 -88.5 -60.5t-31.5 -177.5q0 -48 5 -84t18 -69.5t39.5 -51.5t65.5 -18q49 0 76.5 38t33.5 101zM1856 647q0 207 -15.5 307 t-60.5 161q-6 8 -13.5 14t-21.5 15t-16 11q-86 63 -697 63q-625 0 -710 -63q-5 -4 -17.5 -11.5t-21 -14t-14.5 -14.5q-45 -60 -60 -159.5t-15 -308.5q0 -208 15 -307.5t60 -160.5q6 -8 15 -15t20.5 -14t17.5 -12q44 -33 239.5 -49t470.5 -16q610 0 697 65q5 4 17 11t20.5 14 t13.5 16q46 60 61 159t15 309zM2048 1408v-1536h-2048v1536h2048z" /> | |
| 513 | <glyph unicode="" d="M992 912v-496q0 -14 -9 -23t-23 -9h-160q-14 0 -23 9t-9 23v496q0 112 -80 192t-192 80h-272v-1152q0 -14 -9 -23t-23 -9h-160q-14 0 -23 9t-9 23v1344q0 14 9 23t23 9h464q135 0 249 -66.5t180.5 -180.5t66.5 -249zM1376 1376v-880q0 -135 -66.5 -249t-180.5 -180.5 t-249 -66.5h-464q-14 0 -23 9t-9 23v960q0 14 9 23t23 9h160q14 0 23 -9t9 -23v-768h272q112 0 192 80t80 192v880q0 14 9 23t23 9h160q14 0 23 -9t9 -23z" /> | |
| 514 | <glyph unicode="" d="M1311 694v-114q0 -24 -13.5 -38t-37.5 -14h-202q-24 0 -38 14t-14 38v114q0 24 14 38t38 14h202q24 0 37.5 -14t13.5 -38zM821 464v250q0 53 -32.5 85.5t-85.5 32.5h-133q-68 0 -96 -52q-28 52 -96 52h-130q-53 0 -85.5 -32.5t-32.5 -85.5v-250q0 -22 21 -22h55 q22 0 22 22v230q0 24 13.5 38t38.5 14h94q24 0 38 -14t14 -38v-230q0 -22 21 -22h54q22 0 22 22v230q0 24 14 38t38 14h97q24 0 37.5 -14t13.5 -38v-230q0 -22 22 -22h55q21 0 21 22zM1410 560v154q0 53 -33 85.5t-86 32.5h-264q-53 0 -86 -32.5t-33 -85.5v-410 q0 -21 22 -21h55q21 0 21 21v180q31 -42 94 -42h191q53 0 86 32.5t33 85.5zM1536 1176v-1072q0 -96 -68 -164t-164 -68h-1072q-96 0 -164 68t-68 164v1072q0 96 68 164t164 68h1072q96 0 164 -68t68 -164z" /> | |
| 515 | <glyph unicode="" horiz-adv-x="1792" /> | |
| 516 | <glyph unicode="" horiz-adv-x="1792" /> | |
| 517 | <glyph unicode="" horiz-adv-x="1792" /> | |
| 518 | </font> | |
| 519 | </defs></svg> ⏎ |
Binary diff not shown
Binary diff not shown
| 0 | /*! | |
| 1 | * jQuery JavaScript Library v1.11.1 | |
| 2 | * http://jquery.com/ | |
| 3 | * | |
| 4 | * Includes Sizzle.js | |
| 5 | * http://sizzlejs.com/ | |
| 6 | * | |
| 7 | * Copyright 2005, 2014 jQuery Foundation, Inc. and other contributors | |
| 8 | * Released under the MIT license | |
| 9 | * http://jquery.org/license | |
| 10 | * | |
| 11 | * Date: 2014-05-01T17:42Z | |
| 12 | */ | |
| 13 | ||
| 14 | (function( global, factory ) { | |
| 15 | ||
| 16 | if ( typeof module === "object" && typeof module.exports === "object" ) { | |
| 17 | // For CommonJS and CommonJS-like environments where a proper window is present, | |
| 18 | // execute the factory and get jQuery | |
| 19 | // For environments that do not inherently posses a window with a document | |
| 20 | // (such as Node.js), expose a jQuery-making factory as module.exports | |
| 21 | // This accentuates the need for the creation of a real window | |
| 22 | // e.g. var jQuery = require("jquery")(window); | |
| 23 | // See ticket #14549 for more info | |
| 24 | module.exports = global.document ? | |
| 25 | factory( global, true ) : | |
| 26 | function( w ) { | |
| 27 | if ( !w.document ) { | |
| 28 | throw new Error( "jQuery requires a window with a document" ); | |
| 29 | } | |
| 30 | return factory( w ); | |
| 31 | }; | |
| 32 | } else { | |
| 33 | factory( global ); | |
| 34 | } | |
| 35 | ||
| 36 | // Pass this if window is not defined yet | |
| 37 | }(typeof window !== "undefined" ? window : this, function( window, noGlobal ) { | |
| 38 | ||
| 39 | // Can't do this because several apps including ASP.NET trace | |
| 40 | // the stack via arguments.caller.callee and Firefox dies if | |
| 41 | // you try to trace through "use strict" call chains. (#13335) | |
| 42 | // Support: Firefox 18+ | |
| 43 | // | |
| 44 | ||
| 45 | var deletedIds = []; | |
| 46 | ||
| 47 | var slice = deletedIds.slice; | |
| 48 | ||
| 49 | var concat = deletedIds.concat; | |
| 50 | ||
| 51 | var push = deletedIds.push; | |
| 52 | ||
| 53 | var indexOf = deletedIds.indexOf; | |
| 54 | ||
| 55 | var class2type = {}; | |
| 56 | ||
| 57 | var toString = class2type.toString; | |
| 58 | ||
| 59 | var hasOwn = class2type.hasOwnProperty; | |
| 60 | ||
| 61 | var support = {}; | |
| 62 | ||
| 63 | ||
| 64 | ||
| 65 | var | |
| 66 | version = "1.11.1", | |
| 67 | ||
| 68 | // Define a local copy of jQuery | |
| 69 | jQuery = function( selector, context ) { | |
| 70 | // The jQuery object is actually just the init constructor 'enhanced' | |
| 71 | // Need init if jQuery is called (just allow error to be thrown if not included) | |
| 72 | return new jQuery.fn.init( selector, context ); | |
| 73 | }, | |
| 74 | ||
| 75 | // Support: Android<4.1, IE<9 | |
| 76 | // Make sure we trim BOM and NBSP | |
| 77 | rtrim = /^[\s\uFEFF\xA0]+|[\s\uFEFF\xA0]+$/g, | |
| 78 | ||
| 79 | // Matches dashed string for camelizing | |
| 80 | rmsPrefix = /^-ms-/, | |
| 81 | rdashAlpha = /-([\da-z])/gi, | |
| 82 | ||
| 83 | // Used by jQuery.camelCase as callback to replace() | |
| 84 | fcamelCase = function( all, letter ) { | |
| 85 | return letter.toUpperCase(); | |
| 86 | }; | |
| 87 | ||
| 88 | jQuery.fn = jQuery.prototype = { | |
| 89 | // The current version of jQuery being used | |
| 90 | jquery: version, | |
| 91 | ||
| 92 | constructor: jQuery, | |
| 93 | ||
| 94 | // Start with an empty selector | |
| 95 | selector: "", | |
| 96 | ||
| 97 | // The default length of a jQuery object is 0 | |
| 98 | length: 0, | |
| 99 | ||
| 100 | toArray: function() { | |
| 101 | return slice.call( this ); | |
| 102 | }, | |
| 103 | ||
| 104 | // Get the Nth element in the matched element set OR | |
| 105 | // Get the whole matched element set as a clean array | |
| 106 | get: function( num ) { | |
| 107 | return num != null ? | |
| 108 | ||
| 109 | // Return just the one element from the set | |
| 110 | ( num < 0 ? this[ num + this.length ] : this[ num ] ) : | |
| 111 | ||
| 112 | // Return all the elements in a clean array | |
| 113 | slice.call( this ); | |
| 114 | }, | |
| 115 | ||
| 116 | // Take an array of elements and push it onto the stack | |
| 117 | // (returning the new matched element set) | |
| 118 | pushStack: function( elems ) { | |
| 119 | ||
| 120 | // Build a new jQuery matched element set | |
| 121 | var ret = jQuery.merge( this.constructor(), elems ); | |
| 122 | ||
| 123 | // Add the old object onto the stack (as a reference) | |
| 124 | ret.prevObject = this; | |
| 125 | ret.context = this.context; | |
| 126 | ||
| 127 | // Return the newly-formed element set | |
| 128 | return ret; | |
| 129 | }, | |
| 130 | ||
| 131 | // Execute a callback for every element in the matched set. | |
| 132 | // (You can seed the arguments with an array of args, but this is | |
| 133 | // only used internally.) | |
| 134 | each: function( callback, args ) { | |
| 135 | return jQuery.each( this, callback, args ); | |
| 136 | }, | |
| 137 | ||
| 138 | map: function( callback ) { | |
| 139 | return this.pushStack( jQuery.map(this, function( elem, i ) { | |
| 140 | return callback.call( elem, i, elem ); | |
| 141 | })); | |
| 142 | }, | |
| 143 | ||
| 144 | slice: function() { | |
| 145 | return this.pushStack( slice.apply( this, arguments ) ); | |
| 146 | }, | |
| 147 | ||
| 148 | first: function() { | |
| 149 | return this.eq( 0 ); | |
| 150 | }, | |
| 151 | ||
| 152 | last: function() { | |
| 153 | return this.eq( -1 ); | |
| 154 | }, | |
| 155 | ||
| 156 | eq: function( i ) { | |
| 157 | var len = this.length, | |
| 158 | j = +i + ( i < 0 ? len : 0 ); | |
| 159 | return this.pushStack( j >= 0 && j < len ? [ this[j] ] : [] ); | |
| 160 | }, | |
| 161 | ||
| 162 | end: function() { | |
| 163 | return this.prevObject || this.constructor(null); | |
| 164 | }, | |
| 165 | ||
| 166 | // For internal use only. | |
| 167 | // Behaves like an Array's method, not like a jQuery method. | |
| 168 | push: push, | |
| 169 | sort: deletedIds.sort, | |
| 170 | splice: deletedIds.splice | |
| 171 | }; | |
| 172 | ||
| 173 | jQuery.extend = jQuery.fn.extend = function() { | |
| 174 | var src, copyIsArray, copy, name, options, clone, | |
| 175 | target = arguments[0] || {}, | |
| 176 | i = 1, | |
| 177 | length = arguments.length, | |
| 178 | deep = false; | |
| 179 | ||
| 180 | // Handle a deep copy situation | |
| 181 | if ( typeof target === "boolean" ) { | |
| 182 | deep = target; | |
| 183 | ||
| 184 | // skip the boolean and the target | |
| 185 | target = arguments[ i ] || {}; | |
| 186 | i++; | |
| 187 | } | |
| 188 | ||
| 189 | // Handle case when target is a string or something (possible in deep copy) | |
| 190 | if ( typeof target !== "object" && !jQuery.isFunction(target) ) { | |
| 191 | target = {}; | |
| 192 | } | |
| 193 | ||
| 194 | // extend jQuery itself if only one argument is passed | |
| 195 | if ( i === length ) { | |
| 196 | target = this; | |
| 197 | i--; | |
| 198 | } | |
| 199 | ||
| 200 | for ( ; i < length; i++ ) { | |
| 201 | // Only deal with non-null/undefined values | |
| 202 | if ( (options = arguments[ i ]) != null ) { | |
| 203 | // Extend the base object | |
| 204 | for ( name in options ) { | |
| 205 | src = target[ name ]; | |
| 206 | copy = options[ name ]; | |
| 207 | ||
| 208 | // Prevent never-ending loop | |
| 209 | if ( target === copy ) { | |
| 210 | continue; | |
| 211 | } | |
| 212 | ||
| 213 | // Recurse if we're merging plain objects or arrays | |
| 214 | if ( deep && copy && ( jQuery.isPlainObject(copy) || (copyIsArray = jQuery.isArray(copy)) ) ) { | |
| 215 | if ( copyIsArray ) { | |
| 216 | copyIsArray = false; | |
| 217 | clone = src && jQuery.isArray(src) ? src : []; | |
| 218 | ||
| 219 | } else { | |
| 220 | clone = src && jQuery.isPlainObject(src) ? src : {}; | |
| 221 | } | |
| 222 | ||
| 223 | // Never move original objects, clone them | |
| 224 | target[ name ] = jQuery.extend( deep, clone, copy ); | |
| 225 | ||
| 226 | // Don't bring in undefined values | |
| 227 | } else if ( copy !== undefined ) { | |
| 228 | target[ name ] = copy; | |
| 229 | } | |
| 230 | } | |
| 231 | } | |
| 232 | } | |
| 233 | ||
| 234 | // Return the modified object | |
| 235 | return target; | |
| 236 | }; | |
| 237 | ||
| 238 | jQuery.extend({ | |
| 239 | // Unique for each copy of jQuery on the page | |
| 240 | expando: "jQuery" + ( version + Math.random() ).replace( /\D/g, "" ), | |
| 241 | ||
| 242 | // Assume jQuery is ready without the ready module | |
| 243 | isReady: true, | |
| 244 | ||
| 245 | error: function( msg ) { | |
| 246 | throw new Error( msg ); | |
| 247 | }, | |
| 248 | ||
| 249 | noop: function() {}, | |
| 250 | ||
| 251 | // See test/unit/core.js for details concerning isFunction. | |
| 252 | // Since version 1.3, DOM methods and functions like alert | |
| 253 | // aren't supported. They return false on IE (#2968). | |
| 254 | isFunction: function( obj ) { | |
| 255 | return jQuery.type(obj) === "function"; | |
| 256 | }, | |
| 257 | ||
| 258 | isArray: Array.isArray || function( obj ) { | |
| 259 | return jQuery.type(obj) === "array"; | |
| 260 | }, | |
| 261 | ||
| 262 | isWindow: function( obj ) { | |
| 263 | /* jshint eqeqeq: false */ | |
| 264 | return obj != null && obj == obj.window; | |
| 265 | }, | |
| 266 | ||
| 267 | isNumeric: function( obj ) { | |
| 268 | // parseFloat NaNs numeric-cast false positives (null|true|false|"") | |
| 269 | // ...but misinterprets leading-number strings, particularly hex literals ("0x...") | |
| 270 | // subtraction forces infinities to NaN | |
| 271 | return !jQuery.isArray( obj ) && obj - parseFloat( obj ) >= 0; | |
| 272 | }, | |
| 273 | ||
| 274 | isEmptyObject: function( obj ) { | |
| 275 | var name; | |
| 276 | for ( name in obj ) { | |
| 277 | return false; | |
| 278 | } | |
| 279 | return true; | |
| 280 | }, | |
| 281 | ||
| 282 | isPlainObject: function( obj ) { | |
| 283 | var key; | |
| 284 | ||
| 285 | // Must be an Object. | |
| 286 | // Because of IE, we also have to check the presence of the constructor property. | |
| 287 | // Make sure that DOM nodes and window objects don't pass through, as well | |
| 288 | if ( !obj || jQuery.type(obj) !== "object" || obj.nodeType || jQuery.isWindow( obj ) ) { | |
| 289 | return false; | |
| 290 | } | |
| 291 | ||
| 292 | try { | |
| 293 | // Not own constructor property must be Object | |
| 294 | if ( obj.constructor && | |
| 295 | !hasOwn.call(obj, "constructor") && | |
| 296 | !hasOwn.call(obj.constructor.prototype, "isPrototypeOf") ) { | |
| 297 | return false; | |
| 298 | } | |
| 299 | } catch ( e ) { | |
| 300 | // IE8,9 Will throw exceptions on certain host objects #9897 | |
| 301 | return false; | |
| 302 | } | |
| 303 | ||
| 304 | // Support: IE<9 | |
| 305 | // Handle iteration over inherited properties before own properties. | |
| 306 | if ( support.ownLast ) { | |
| 307 | for ( key in obj ) { | |
| 308 | return hasOwn.call( obj, key ); | |
| 309 | } | |
| 310 | } | |
| 311 | ||
| 312 | // Own properties are enumerated firstly, so to speed up, | |
| 313 | // if last one is own, then all properties are own. | |
| 314 | for ( key in obj ) {} | |
| 315 | ||
| 316 | return key === undefined || hasOwn.call( obj, key ); | |
| 317 | }, | |
| 318 | ||
| 319 | type: function( obj ) { | |
| 320 | if ( obj == null ) { | |
| 321 | return obj + ""; | |
| 322 | } | |
| 323 | return typeof obj === "object" || typeof obj === "function" ? | |
| 324 | class2type[ toString.call(obj) ] || "object" : | |
| 325 | typeof obj; | |
| 326 | }, | |
| 327 | ||
| 328 | // Evaluates a script in a global context | |
| 329 | // Workarounds based on findings by Jim Driscoll | |
| 330 | // http://weblogs.java.net/blog/driscoll/archive/2009/09/08/eval-javascript-global-context | |
| 331 | globalEval: function( data ) { | |
| 332 | if ( data && jQuery.trim( data ) ) { | |
| 333 | // We use execScript on Internet Explorer | |
| 334 | // We use an anonymous function so that context is window | |
| 335 | // rather than jQuery in Firefox | |
| 336 | ( window.execScript || function( data ) { | |
| 337 | window[ "eval" ].call( window, data ); | |
| 338 | } )( data ); | |
| 339 | } | |
| 340 | }, | |
| 341 | ||
| 342 | // Convert dashed to camelCase; used by the css and data modules | |
| 343 | // Microsoft forgot to hump their vendor prefix (#9572) | |
| 344 | camelCase: function( string ) { | |
| 345 | return string.replace( rmsPrefix, "ms-" ).replace( rdashAlpha, fcamelCase ); | |
| 346 | }, | |
| 347 | ||
| 348 | nodeName: function( elem, name ) { | |
| 349 | return elem.nodeName && elem.nodeName.toLowerCase() === name.toLowerCase(); | |
| 350 | }, | |
| 351 | ||
| 352 | // args is for internal usage only | |
| 353 | each: function( obj, callback, args ) { | |
| 354 | var value, | |
| 355 | i = 0, | |
| 356 | length = obj.length, | |
| 357 | isArray = isArraylike( obj ); | |
| 358 | ||
| 359 | if ( args ) { | |
| 360 | if ( isArray ) { | |
| 361 | for ( ; i < length; i++ ) { | |
| 362 | value = callback.apply( obj[ i ], args ); | |
| 363 | ||
| 364 | if ( value === false ) { | |
| 365 | break; | |
| 366 | } | |
| 367 | } | |
| 368 | } else { | |
| 369 | for ( i in obj ) { | |
| 370 | value = callback.apply( obj[ i ], args ); | |
| 371 | ||
| 372 | if ( value === false ) { | |
| 373 | break; | |
| 374 | } | |
| 375 | } | |
| 376 | } | |
| 377 | ||
| 378 | // A special, fast, case for the most common use of each | |
| 379 | } else { | |
| 380 | if ( isArray ) { | |
| 381 | for ( ; i < length; i++ ) { | |
| 382 | value = callback.call( obj[ i ], i, obj[ i ] ); | |
| 383 | ||
| 384 | if ( value === false ) { | |
| 385 | break; | |
| 386 | } | |
| 387 | } | |
| 388 | } else { | |
| 389 | for ( i in obj ) { | |
| 390 | value = callback.call( obj[ i ], i, obj[ i ] ); | |
| 391 | ||
| 392 | if ( value === false ) { | |
| 393 | break; | |
| 394 | } | |
| 395 | } | |
| 396 | } | |
| 397 | } | |
| 398 | ||
| 399 | return obj; | |
| 400 | }, | |
| 401 | ||
| 402 | // Support: Android<4.1, IE<9 | |
| 403 | trim: function( text ) { | |
| 404 | return text == null ? | |
| 405 | "" : | |
| 406 | ( text + "" ).replace( rtrim, "" ); | |
| 407 | }, | |
| 408 | ||
| 409 | // results is for internal usage only | |
| 410 | makeArray: function( arr, results ) { | |
| 411 | var ret = results || []; | |
| 412 | ||
| 413 | if ( arr != null ) { | |
| 414 | if ( isArraylike( Object(arr) ) ) { | |
| 415 | jQuery.merge( ret, | |
| 416 | typeof arr === "string" ? | |
| 417 | [ arr ] : arr | |
| 418 | ); | |
| 419 | } else { | |
| 420 | push.call( ret, arr ); | |
| 421 | } | |
| 422 | } | |
| 423 | ||
| 424 | return ret; | |
| 425 | }, | |
| 426 | ||
| 427 | inArray: function( elem, arr, i ) { | |
| 428 | var len; | |
| 429 | ||
| 430 | if ( arr ) { | |
| 431 | if ( indexOf ) { | |
| 432 | return indexOf.call( arr, elem, i ); | |
| 433 | } | |
| 434 | ||
| 435 | len = arr.length; | |
| 436 | i = i ? i < 0 ? Math.max( 0, len + i ) : i : 0; | |
| 437 | ||
| 438 | for ( ; i < len; i++ ) { | |
| 439 | // Skip accessing in sparse arrays | |
| 440 | if ( i in arr && arr[ i ] === elem ) { | |
| 441 | return i; | |
| 442 | } | |
| 443 | } | |
| 444 | } | |
| 445 | ||
| 446 | return -1; | |
| 447 | }, | |
| 448 | ||
| 449 | merge: function( first, second ) { | |
| 450 | var len = +second.length, | |
| 451 | j = 0, | |
| 452 | i = first.length; | |
| 453 | ||
| 454 | while ( j < len ) { | |
| 455 | first[ i++ ] = second[ j++ ]; | |
| 456 | } | |
| 457 | ||
| 458 | // Support: IE<9 | |
| 459 | // Workaround casting of .length to NaN on otherwise arraylike objects (e.g., NodeLists) | |
| 460 | if ( len !== len ) { | |
| 461 | while ( second[j] !== undefined ) { | |
| 462 | first[ i++ ] = second[ j++ ]; | |
| 463 | } | |
| 464 | } | |
| 465 | ||
| 466 | first.length = i; | |
| 467 | ||
| 468 | return first; | |
| 469 | }, | |
| 470 | ||
| 471 | grep: function( elems, callback, invert ) { | |
| 472 | var callbackInverse, | |
| 473 | matches = [], | |
| 474 | i = 0, | |
| 475 | length = elems.length, | |
| 476 | callbackExpect = !invert; | |
| 477 | ||
| 478 | // Go through the array, only saving the items | |
| 479 | // that pass the validator function | |
| 480 | for ( ; i < length; i++ ) { | |
| 481 | callbackInverse = !callback( elems[ i ], i ); | |
| 482 | if ( callbackInverse !== callbackExpect ) { | |
| 483 | matches.push( elems[ i ] ); | |
| 484 | } | |
| 485 | } | |
| 486 | ||
| 487 | return matches; | |
| 488 | }, | |
| 489 | ||
| 490 | // arg is for internal usage only | |
| 491 | map: function( elems, callback, arg ) { | |
| 492 | var value, | |
| 493 | i = 0, | |
| 494 | length = elems.length, | |
| 495 | isArray = isArraylike( elems ), | |
| 496 | ret = []; | |
| 497 | ||
| 498 | // Go through the array, translating each of the items to their new values | |
| 499 | if ( isArray ) { | |
| 500 | for ( ; i < length; i++ ) { | |
| 501 | value = callback( elems[ i ], i, arg ); | |
| 502 | ||
| 503 | if ( value != null ) { | |
| 504 | ret.push( value ); | |
| 505 | } | |
| 506 | } | |
| 507 | ||
| 508 | // Go through every key on the object, | |
| 509 | } else { | |
| 510 | for ( i in elems ) { | |
| 511 | value = callback( elems[ i ], i, arg ); | |
| 512 | ||
| 513 | if ( value != null ) { | |
| 514 | ret.push( value ); | |
| 515 | } | |
| 516 | } | |
| 517 | } | |
| 518 | ||
| 519 | // Flatten any nested arrays | |
| 520 | return concat.apply( [], ret ); | |
| 521 | }, | |
| 522 | ||
| 523 | // A global GUID counter for objects | |
| 524 | guid: 1, | |
| 525 | ||
| 526 | // Bind a function to a context, optionally partially applying any | |
| 527 | // arguments. | |
| 528 | proxy: function( fn, context ) { | |
| 529 | var args, proxy, tmp; | |
| 530 | ||
| 531 | if ( typeof context === "string" ) { | |
| 532 | tmp = fn[ context ]; | |
| 533 | context = fn; | |
| 534 | fn = tmp; | |
| 535 | } | |
| 536 | ||
| 537 | // Quick check to determine if target is callable, in the spec | |
| 538 | // this throws a TypeError, but we will just return undefined. | |
| 539 | if ( !jQuery.isFunction( fn ) ) { | |
| 540 | return undefined; | |
| 541 | } | |
| 542 | ||
| 543 | // Simulated bind | |
| 544 | args = slice.call( arguments, 2 ); | |
| 545 | proxy = function() { | |
| 546 | return fn.apply( context || this, args.concat( slice.call( arguments ) ) ); | |
| 547 | }; | |
| 548 | ||
| 549 | // Set the guid of unique handler to the same of original handler, so it can be removed | |
| 550 | proxy.guid = fn.guid = fn.guid || jQuery.guid++; | |
| 551 | ||
| 552 | return proxy; | |
| 553 | }, | |
| 554 | ||
| 555 | now: function() { | |
| 556 | return +( new Date() ); | |
| 557 | }, | |
| 558 | ||
| 559 | // jQuery.support is not used in Core but other projects attach their | |
| 560 | // properties to it so it needs to exist. | |
| 561 | support: support | |
| 562 | }); | |
| 563 | ||
| 564 | // Populate the class2type map | |
| 565 | jQuery.each("Boolean Number String Function Array Date RegExp Object Error".split(" "), function(i, name) { | |
| 566 | class2type[ "[object " + name + "]" ] = name.toLowerCase(); | |
| 567 | }); | |
| 568 | ||
| 569 | function isArraylike( obj ) { | |
| 570 | var length = obj.length, | |
| 571 | type = jQuery.type( obj ); | |
| 572 | ||
| 573 | if ( type === "function" || jQuery.isWindow( obj ) ) { | |
| 574 | return false; | |
| 575 | } | |
| 576 | ||
| 577 | if ( obj.nodeType === 1 && length ) { | |
| 578 | return true; | |
| 579 | } | |
| 580 | ||
| 581 | return type === "array" || length === 0 || | |
| 582 | typeof length === "number" && length > 0 && ( length - 1 ) in obj; | |
| 583 | } | |
| 584 | var Sizzle = | |
| 585 | /*! | |
| 586 | * Sizzle CSS Selector Engine v1.10.19 | |
| 587 | * http://sizzlejs.com/ | |
| 588 | * | |
| 589 | * Copyright 2013 jQuery Foundation, Inc. and other contributors | |
| 590 | * Released under the MIT license | |
| 591 | * http://jquery.org/license | |
| 592 | * | |
| 593 | * Date: 2014-04-18 | |
| 594 | */ | |
| 595 | (function( window ) { | |
| 596 | ||
| 597 | var i, | |
| 598 | support, | |
| 599 | Expr, | |
| 600 | getText, | |
| 601 | isXML, | |
| 602 | tokenize, | |
| 603 | compile, | |
| 604 | select, | |
| 605 | outermostContext, | |
| 606 | sortInput, | |
| 607 | hasDuplicate, | |
| 608 | ||
| 609 | // Local document vars | |
| 610 | setDocument, | |
| 611 | document, | |
| 612 | docElem, | |
| 613 | documentIsHTML, | |
| 614 | rbuggyQSA, | |
| 615 | rbuggyMatches, | |
| 616 | matches, | |
| 617 | contains, | |
| 618 | ||
| 619 | // Instance-specific data | |
| 620 | expando = "sizzle" + -(new Date()), | |
| 621 | preferredDoc = window.document, | |
| 622 | dirruns = 0, | |
| 623 | done = 0, | |
| 624 | classCache = createCache(), | |
| 625 | tokenCache = createCache(), | |
| 626 | compilerCache = createCache(), | |
| 627 | sortOrder = function( a, b ) { | |
| 628 | if ( a === b ) { | |
| 629 | hasDuplicate = true; | |
| 630 | } | |
| 631 | return 0; | |
| 632 | }, | |
| 633 | ||
| 634 | // General-purpose constants | |
| 635 | strundefined = typeof undefined, | |
| 636 | MAX_NEGATIVE = 1 << 31, | |
| 637 | ||
| 638 | // Instance methods | |
| 639 | hasOwn = ({}).hasOwnProperty, | |
| 640 | arr = [], | |
| 641 | pop = arr.pop, | |
| 642 | push_native = arr.push, | |
| 643 | push = arr.push, | |
| 644 | slice = arr.slice, | |
| 645 | // Use a stripped-down indexOf if we can't use a native one | |
| 646 | indexOf = arr.indexOf || function( elem ) { | |
| 647 | var i = 0, | |
| 648 | len = this.length; | |
| 649 | for ( ; i < len; i++ ) { | |
| 650 | if ( this[i] === elem ) { | |
| 651 | return i; | |
| 652 | } | |
| 653 | } | |
| 654 | return -1; | |
| 655 | }, | |
| 656 | ||
| 657 | booleans = "checked|selected|async|autofocus|autoplay|controls|defer|disabled|hidden|ismap|loop|multiple|open|readonly|required|scoped", | |
| 658 | ||
| 659 | // Regular expressions | |
| 660 | ||
| 661 | // Whitespace characters http://www.w3.org/TR/css3-selectors/#whitespace | |
| 662 | whitespace = "[\\x20\\t\\r\\n\\f]", | |
| 663 | // http://www.w3.org/TR/css3-syntax/#characters | |
| 664 | characterEncoding = "(?:\\\\.|[\\w-]|[^\\x00-\\xa0])+", | |
| 665 | ||
| 666 | // Loosely modeled on CSS identifier characters | |
| 667 | // An unquoted value should be a CSS identifier http://www.w3.org/TR/css3-selectors/#attribute-selectors | |
| 668 | // Proper syntax: http://www.w3.org/TR/CSS21/syndata.html#value-def-identifier | |
| 669 | identifier = characterEncoding.replace( "w", "w#" ), | |
| 670 | ||
| 671 | // Attribute selectors: http://www.w3.org/TR/selectors/#attribute-selectors | |
| 672 | attributes = "\\[" + whitespace + "*(" + characterEncoding + ")(?:" + whitespace + | |
| 673 | // Operator (capture 2) | |
| 674 | "*([*^$|!~]?=)" + whitespace + | |
| 675 | // "Attribute values must be CSS identifiers [capture 5] or strings [capture 3 or capture 4]" | |
| 676 | "*(?:'((?:\\\\.|[^\\\\'])*)'|\"((?:\\\\.|[^\\\\\"])*)\"|(" + identifier + "))|)" + whitespace + | |
| 677 | "*\\]", | |
| 678 | ||
| 679 | pseudos = ":(" + characterEncoding + ")(?:\\((" + | |
| 680 | // To reduce the number of selectors needing tokenize in the preFilter, prefer arguments: | |
| 681 | // 1. quoted (capture 3; capture 4 or capture 5) | |
| 682 | "('((?:\\\\.|[^\\\\'])*)'|\"((?:\\\\.|[^\\\\\"])*)\")|" + | |
| 683 | // 2. simple (capture 6) | |
| 684 | "((?:\\\\.|[^\\\\()[\\]]|" + attributes + ")*)|" + | |
| 685 | // 3. anything else (capture 2) | |
| 686 | ".*" + | |
| 687 | ")\\)|)", | |
| 688 | ||
| 689 | // Leading and non-escaped trailing whitespace, capturing some non-whitespace characters preceding the latter | |
| 690 | rtrim = new RegExp( "^" + whitespace + "+|((?:^|[^\\\\])(?:\\\\.)*)" + whitespace + "+$", "g" ), | |
| 691 | ||
| 692 | rcomma = new RegExp( "^" + whitespace + "*," + whitespace + "*" ), | |
| 693 | rcombinators = new RegExp( "^" + whitespace + "*([>+~]|" + whitespace + ")" + whitespace + "*" ), | |
| 694 | ||
| 695 | rattributeQuotes = new RegExp( "=" + whitespace + "*([^\\]'\"]*?)" + whitespace + "*\\]", "g" ), | |
| 696 | ||
| 697 | rpseudo = new RegExp( pseudos ), | |
| 698 | ridentifier = new RegExp( "^" + identifier + "$" ), | |
| 699 | ||
| 700 | matchExpr = { | |
| 701 | "ID": new RegExp( "^#(" + characterEncoding + ")" ), | |
| 702 | "CLASS": new RegExp( "^\\.(" + characterEncoding + ")" ), | |
| 703 | "TAG": new RegExp( "^(" + characterEncoding.replace( "w", "w*" ) + ")" ), | |
| 704 | "ATTR": new RegExp( "^" + attributes ), | |
| 705 | "PSEUDO": new RegExp( "^" + pseudos ), | |
| 706 | "CHILD": new RegExp( "^:(only|first|last|nth|nth-last)-(child|of-type)(?:\\(" + whitespace + | |
| 707 | "*(even|odd|(([+-]|)(\\d*)n|)" + whitespace + "*(?:([+-]|)" + whitespace + | |
| 708 | "*(\\d+)|))" + whitespace + "*\\)|)", "i" ), | |
| 709 | "bool": new RegExp( "^(?:" + booleans + ")$", "i" ), | |
| 710 | // For use in libraries implementing .is() | |
| 711 | // We use this for POS matching in `select` | |
| 712 | "needsContext": new RegExp( "^" + whitespace + "*[>+~]|:(even|odd|eq|gt|lt|nth|first|last)(?:\\(" + | |
| 713 | whitespace + "*((?:-\\d)?\\d*)" + whitespace + "*\\)|)(?=[^-]|$)", "i" ) | |
| 714 | }, | |
| 715 | ||
| 716 | rinputs = /^(?:input|select|textarea|button)$/i, | |
| 717 | rheader = /^h\d$/i, | |
| 718 | ||
| 719 | rnative = /^[^{]+\{\s*\[native \w/, | |
| 720 | ||
| 721 | // Easily-parseable/retrievable ID or TAG or CLASS selectors | |
| 722 | rquickExpr = /^(?:#([\w-]+)|(\w+)|\.([\w-]+))$/, | |
| 723 | ||
| 724 | rsibling = /[+~]/, | |
| 725 | rescape = /'|\\/g, | |
| 726 | ||
| 727 | // CSS escapes http://www.w3.org/TR/CSS21/syndata.html#escaped-characters | |
| 728 | runescape = new RegExp( "\\\\([\\da-f]{1,6}" + whitespace + "?|(" + whitespace + ")|.)", "ig" ), | |
| 729 | funescape = function( _, escaped, escapedWhitespace ) { | |
| 730 | var high = "0x" + escaped - 0x10000; | |
| 731 | // NaN means non-codepoint | |
| 732 | // Support: Firefox<24 | |
| 733 | // Workaround erroneous numeric interpretation of +"0x" | |
| 734 | return high !== high || escapedWhitespace ? | |
| 735 | escaped : | |
| 736 | high < 0 ? | |
| 737 | // BMP codepoint | |
| 738 | String.fromCharCode( high + 0x10000 ) : | |
| 739 | // Supplemental Plane codepoint (surrogate pair) | |
| 740 | String.fromCharCode( high >> 10 | 0xD800, high & 0x3FF | 0xDC00 ); | |
| 741 | }; | |
| 742 | ||
| 743 | // Optimize for push.apply( _, NodeList ) | |
| 744 | try { | |
| 745 | push.apply( | |
| 746 | (arr = slice.call( preferredDoc.childNodes )), | |
| 747 | preferredDoc.childNodes | |
| 748 | ); | |
| 749 | // Support: Android<4.0 | |
| 750 | // Detect silently failing push.apply | |
| 751 | arr[ preferredDoc.childNodes.length ].nodeType; | |
| 752 | } catch ( e ) { | |
| 753 | push = { apply: arr.length ? | |
| 754 | ||
| 755 | // Leverage slice if possible | |
| 756 | function( target, els ) { | |
| 757 | push_native.apply( target, slice.call(els) ); | |
| 758 | } : | |
| 759 | ||
| 760 | // Support: IE<9 | |
| 761 | // Otherwise append directly | |
| 762 | function( target, els ) { | |
| 763 | var j = target.length, | |
| 764 | i = 0; | |
| 765 | // Can't trust NodeList.length | |
| 766 | while ( (target[j++] = els[i++]) ) {} | |
| 767 | target.length = j - 1; | |
| 768 | } | |
| 769 | }; | |
| 770 | } | |
| 771 | ||
| 772 | function Sizzle( selector, context, results, seed ) { | |
| 773 | var match, elem, m, nodeType, | |
| 774 | // QSA vars | |
| 775 | i, groups, old, nid, newContext, newSelector; | |
| 776 | ||
| 777 | if ( ( context ? context.ownerDocument || context : preferredDoc ) !== document ) { | |
| 778 | setDocument( context ); | |
| 779 | } | |
| 780 | ||
| 781 | context = context || document; | |
| 782 | results = results || []; | |
| 783 | ||
| 784 | if ( !selector || typeof selector !== "string" ) { | |
| 785 | return results; | |
| 786 | } | |
| 787 | ||
| 788 | if ( (nodeType = context.nodeType) !== 1 && nodeType !== 9 ) { | |
| 789 | return []; | |
| 790 | } | |
| 791 | ||
| 792 | if ( documentIsHTML && !seed ) { | |
| 793 | ||
| 794 | // Shortcuts | |
| 795 | if ( (match = rquickExpr.exec( selector )) ) { | |
| 796 | // Speed-up: Sizzle("#ID") | |
| 797 | if ( (m = match[1]) ) { | |
| 798 | if ( nodeType === 9 ) { | |
| 799 | elem = context.getElementById( m ); | |
| 800 | // Check parentNode to catch when Blackberry 4.6 returns | |
| 801 | // nodes that are no longer in the document (jQuery #6963) | |
| 802 | if ( elem && elem.parentNode ) { | |
| 803 | // Handle the case where IE, Opera, and Webkit return items | |
| 804 | // by name instead of ID | |
| 805 | if ( elem.id === m ) { | |
| 806 | results.push( elem ); | |
| 807 | return results; | |
| 808 | } | |
| 809 | } else { | |
| 810 | return results; | |
| 811 | } | |
| 812 | } else { | |
| 813 | // Context is not a document | |
| 814 | if ( context.ownerDocument && (elem = context.ownerDocument.getElementById( m )) && | |
| 815 | contains( context, elem ) && elem.id === m ) { | |
| 816 | results.push( elem ); | |
| 817 | return results; | |
| 818 | } | |
| 819 | } | |
| 820 | ||
| 821 | // Speed-up: Sizzle("TAG") | |
| 822 | } else if ( match[2] ) { | |
| 823 | push.apply( results, context.getElementsByTagName( selector ) ); | |
| 824 | return results; | |
| 825 | ||
| 826 | // Speed-up: Sizzle(".CLASS") | |
| 827 | } else if ( (m = match[3]) && support.getElementsByClassName && context.getElementsByClassName ) { | |
| 828 | push.apply( results, context.getElementsByClassName( m ) ); | |
| 829 | return results; | |
| 830 | } | |
| 831 | } | |
| 832 | ||
| 833 | // QSA path | |
| 834 | if ( support.qsa && (!rbuggyQSA || !rbuggyQSA.test( selector )) ) { | |
| 835 | nid = old = expando; | |
| 836 | newContext = context; | |
| 837 | newSelector = nodeType === 9 && selector; | |
| 838 | ||
| 839 | // qSA works strangely on Element-rooted queries | |
| 840 | // We can work around this by specifying an extra ID on the root | |
| 841 | // and working up from there (Thanks to Andrew Dupont for the technique) | |
| 842 | // IE 8 doesn't work on object elements | |
| 843 | if ( nodeType === 1 && context.nodeName.toLowerCase() !== "object" ) { | |
| 844 | groups = tokenize( selector ); | |
| 845 | ||
| 846 | if ( (old = context.getAttribute("id")) ) { | |
| 847 | nid = old.replace( rescape, "\\$&" ); | |
| 848 | } else { | |
| 849 | context.setAttribute( "id", nid ); | |
| 850 | } | |
| 851 | nid = "[id='" + nid + "'] "; | |
| 852 | ||
| 853 | i = groups.length; | |
| 854 | while ( i-- ) { | |
| 855 | groups[i] = nid + toSelector( groups[i] ); | |
| 856 | } | |
| 857 | newContext = rsibling.test( selector ) && testContext( context.parentNode ) || context; | |
| 858 | newSelector = groups.join(","); | |
| 859 | } | |
| 860 | ||
| 861 | if ( newSelector ) { | |
| 862 | try { | |
| 863 | push.apply( results, | |
| 864 | newContext.querySelectorAll( newSelector ) | |
| 865 | ); | |
| 866 | return results; | |
| 867 | } catch(qsaError) { | |
| 868 | } finally { | |
| 869 | if ( !old ) { | |
| 870 | context.removeAttribute("id"); | |
| 871 | } | |
| 872 | } | |
| 873 | } | |
| 874 | } | |
| 875 | } | |
| 876 | ||
| 877 | // All others | |
| 878 | return select( selector.replace( rtrim, "$1" ), context, results, seed ); | |
| 879 | } | |
| 880 | ||
| 881 | /** | |
| 882 | * Create key-value caches of limited size | |
| 883 | * @returns {Function(string, Object)} Returns the Object data after storing it on itself with | |
| 884 | * property name the (space-suffixed) string and (if the cache is larger than Expr.cacheLength) | |
| 885 | * deleting the oldest entry | |
| 886 | */ | |
| 887 | function createCache() { | |
| 888 | var keys = []; | |
| 889 | ||
| 890 | function cache( key, value ) { | |
| 891 | // Use (key + " ") to avoid collision with native prototype properties (see Issue #157) | |
| 892 | if ( keys.push( key + " " ) > Expr.cacheLength ) { | |
| 893 | // Only keep the most recent entries | |
| 894 | delete cache[ keys.shift() ]; | |
| 895 | } | |
| 896 | return (cache[ key + " " ] = value); | |
| 897 | } | |
| 898 | return cache; | |
| 899 | } | |
| 900 | ||
| 901 | /** | |
| 902 | * Mark a function for special use by Sizzle | |
| 903 | * @param {Function} fn The function to mark | |
| 904 | */ | |
| 905 | function markFunction( fn ) { | |
| 906 | fn[ expando ] = true; | |
| 907 | return fn; | |
| 908 | } | |
| 909 | ||
| 910 | /** | |
| 911 | * Support testing using an element | |
| 912 | * @param {Function} fn Passed the created div and expects a boolean result | |
| 913 | */ | |
| 914 | function assert( fn ) { | |
| 915 | var div = document.createElement("div"); | |
| 916 | ||
| 917 | try { | |
| 918 | return !!fn( div ); | |
| 919 | } catch (e) { | |
| 920 | return false; | |
| 921 | } finally { | |
| 922 | // Remove from its parent by default | |
| 923 | if ( div.parentNode ) { | |
| 924 | div.parentNode.removeChild( div ); | |
| 925 | } | |
| 926 | // release memory in IE | |
| 927 | div = null; | |
| 928 | } | |
| 929 | } | |
| 930 | ||
| 931 | /** | |
| 932 | * Adds the same handler for all of the specified attrs | |
| 933 | * @param {String} attrs Pipe-separated list of attributes | |
| 934 | * @param {Function} handler The method that will be applied | |
| 935 | */ | |
| 936 | function addHandle( attrs, handler ) { | |
| 937 | var arr = attrs.split("|"), | |
| 938 | i = attrs.length; | |
| 939 | ||
| 940 | while ( i-- ) { | |
| 941 | Expr.attrHandle[ arr[i] ] = handler; | |
| 942 | } | |
| 943 | } | |
| 944 | ||
| 945 | /** | |
| 946 | * Checks document order of two siblings | |
| 947 | * @param {Element} a | |
| 948 | * @param {Element} b | |
| 949 | * @returns {Number} Returns less than 0 if a precedes b, greater than 0 if a follows b | |
| 950 | */ | |
| 951 | function siblingCheck( a, b ) { | |
| 952 | var cur = b && a, | |
| 953 | diff = cur && a.nodeType === 1 && b.nodeType === 1 && | |
| 954 | ( ~b.sourceIndex || MAX_NEGATIVE ) - | |
| 955 | ( ~a.sourceIndex || MAX_NEGATIVE ); | |
| 956 | ||
| 957 | // Use IE sourceIndex if available on both nodes | |
| 958 | if ( diff ) { | |
| 959 | return diff; | |
| 960 | } | |
| 961 | ||
| 962 | // Check if b follows a | |
| 963 | if ( cur ) { | |
| 964 | while ( (cur = cur.nextSibling) ) { | |
| 965 | if ( cur === b ) { | |
| 966 | return -1; | |
| 967 | } | |
| 968 | } | |
| 969 | } | |
| 970 | ||
| 971 | return a ? 1 : -1; | |
| 972 | } | |
| 973 | ||
| 974 | /** | |
| 975 | * Returns a function to use in pseudos for input types | |
| 976 | * @param {String} type | |
| 977 | */ | |
| 978 | function createInputPseudo( type ) { | |
| 979 | return function( elem ) { | |
| 980 | var name = elem.nodeName.toLowerCase(); | |
| 981 | return name === "input" && elem.type === type; | |
| 982 | }; | |
| 983 | } | |
| 984 | ||
| 985 | /** | |
| 986 | * Returns a function to use in pseudos for buttons | |
| 987 | * @param {String} type | |
| 988 | */ | |
| 989 | function createButtonPseudo( type ) { | |
| 990 | return function( elem ) { | |
| 991 | var name = elem.nodeName.toLowerCase(); | |
| 992 | return (name === "input" || name === "button") && elem.type === type; | |
| 993 | }; | |
| 994 | } | |
| 995 | ||
| 996 | /** | |
| 997 | * Returns a function to use in pseudos for positionals | |
| 998 | * @param {Function} fn | |
| 999 | */ | |
| 1000 | function createPositionalPseudo( fn ) { | |
| 1001 | return markFunction(function( argument ) { | |
| 1002 | argument = +argument; | |
| 1003 | return markFunction(function( seed, matches ) { | |
| 1004 | var j, | |
| 1005 | matchIndexes = fn( [], seed.length, argument ), | |
| 1006 | i = matchIndexes.length; | |
| 1007 | ||
| 1008 | // Match elements found at the specified indexes | |
| 1009 | while ( i-- ) { | |
| 1010 | if ( seed[ (j = matchIndexes[i]) ] ) { | |
| 1011 | seed[j] = !(matches[j] = seed[j]); | |
| 1012 | } | |
| 1013 | } | |
| 1014 | }); | |
| 1015 | }); | |
| 1016 | } | |
| 1017 | ||
| 1018 | /** | |
| 1019 | * Checks a node for validity as a Sizzle context | |
| 1020 | * @param {Element|Object=} context | |
| 1021 | * @returns {Element|Object|Boolean} The input node if acceptable, otherwise a falsy value | |
| 1022 | */ | |
| 1023 | function testContext( context ) { | |
| 1024 | return context && typeof context.getElementsByTagName !== strundefined && context; | |
| 1025 | } | |
| 1026 | ||
| 1027 | // Expose support vars for convenience | |
| 1028 | support = Sizzle.support = {}; | |
| 1029 | ||
| 1030 | /** | |
| 1031 | * Detects XML nodes | |
| 1032 | * @param {Element|Object} elem An element or a document | |
| 1033 | * @returns {Boolean} True iff elem is a non-HTML XML node | |
| 1034 | */ | |
| 1035 | isXML = Sizzle.isXML = function( elem ) { | |
| 1036 | // documentElement is verified for cases where it doesn't yet exist | |
| 1037 | // (such as loading iframes in IE - #4833) | |
| 1038 | var documentElement = elem && (elem.ownerDocument || elem).documentElement; | |
| 1039 | return documentElement ? documentElement.nodeName !== "HTML" : false; | |
| 1040 | }; | |
| 1041 | ||
| 1042 | /** | |
| 1043 | * Sets document-related variables once based on the current document | |
| 1044 | * @param {Element|Object} [doc] An element or document object to use to set the document | |
| 1045 | * @returns {Object} Returns the current document | |
| 1046 | */ | |
| 1047 | setDocument = Sizzle.setDocument = function( node ) { | |
| 1048 | var hasCompare, | |
| 1049 | doc = node ? node.ownerDocument || node : preferredDoc, | |
| 1050 | parent = doc.defaultView; | |
| 1051 | ||
| 1052 | // If no document and documentElement is available, return | |
| 1053 | if ( doc === document || doc.nodeType !== 9 || !doc.documentElement ) { | |
| 1054 | return document; | |
| 1055 | } | |
| 1056 | ||
| 1057 | // Set our document | |
| 1058 | document = doc; | |
| 1059 | docElem = doc.documentElement; | |
| 1060 | ||
| 1061 | // Support tests | |
| 1062 | documentIsHTML = !isXML( doc ); | |
| 1063 | ||
| 1064 | // Support: IE>8 | |
| 1065 | // If iframe document is assigned to "document" variable and if iframe has been reloaded, | |
| 1066 | // IE will throw "permission denied" error when accessing "document" variable, see jQuery #13936 | |
| 1067 | // IE6-8 do not support the defaultView property so parent will be undefined | |
| 1068 | if ( parent && parent !== parent.top ) { | |
| 1069 | // IE11 does not have attachEvent, so all must suffer | |
| 1070 | if ( parent.addEventListener ) { | |
| 1071 | parent.addEventListener( "unload", function() { | |
| 1072 | setDocument(); | |
| 1073 | }, false ); | |
| 1074 | } else if ( parent.attachEvent ) { | |
| 1075 | parent.attachEvent( "onunload", function() { | |
| 1076 | setDocument(); | |
| 1077 | }); | |
| 1078 | } | |
| 1079 | } | |
| 1080 | ||
| 1081 | /* Attributes | |
| 1082 | ---------------------------------------------------------------------- */ | |
| 1083 | ||
| 1084 | // Support: IE<8 | |
| 1085 | // Verify that getAttribute really returns attributes and not properties (excepting IE8 booleans) | |
| 1086 | support.attributes = assert(function( div ) { | |
| 1087 | div.className = "i"; | |
| 1088 | return !div.getAttribute("className"); | |
| 1089 | }); | |
| 1090 | ||
| 1091 | /* getElement(s)By* | |
| 1092 | ---------------------------------------------------------------------- */ | |
| 1093 | ||
| 1094 | // Check if getElementsByTagName("*") returns only elements | |
| 1095 | support.getElementsByTagName = assert(function( div ) { | |
| 1096 | div.appendChild( doc.createComment("") ); | |
| 1097 | return !div.getElementsByTagName("*").length; | |
| 1098 | }); | |
| 1099 | ||
| 1100 | // Check if getElementsByClassName can be trusted | |
| 1101 | support.getElementsByClassName = rnative.test( doc.getElementsByClassName ) && assert(function( div ) { | |
| 1102 | div.innerHTML = "<div class='a'></div><div class='a i'></div>"; | |
| 1103 | ||
| 1104 | // Support: Safari<4 | |
| 1105 | // Catch class over-caching | |
| 1106 | div.firstChild.className = "i"; | |
| 1107 | // Support: Opera<10 | |
| 1108 | // Catch gEBCN failure to find non-leading classes | |
| 1109 | return div.getElementsByClassName("i").length === 2; | |
| 1110 | }); | |
| 1111 | ||
| 1112 | // Support: IE<10 | |
| 1113 | // Check if getElementById returns elements by name | |
| 1114 | // The broken getElementById methods don't pick up programatically-set names, | |
| 1115 | // so use a roundabout getElementsByName test | |
| 1116 | support.getById = assert(function( div ) { | |
| 1117 | docElem.appendChild( div ).id = expando; | |
| 1118 | return !doc.getElementsByName || !doc.getElementsByName( expando ).length; | |
| 1119 | }); | |
| 1120 | ||
| 1121 | // ID find and filter | |
| 1122 | if ( support.getById ) { | |
| 1123 | Expr.find["ID"] = function( id, context ) { | |
| 1124 | if ( typeof context.getElementById !== strundefined && documentIsHTML ) { | |
| 1125 | var m = context.getElementById( id ); | |
| 1126 | // Check parentNode to catch when Blackberry 4.6 returns | |
| 1127 | // nodes that are no longer in the document #6963 | |
| 1128 | return m && m.parentNode ? [ m ] : []; | |
| 1129 | } | |
| 1130 | }; | |
| 1131 | Expr.filter["ID"] = function( id ) { | |
| 1132 | var attrId = id.replace( runescape, funescape ); | |
| 1133 | return function( elem ) { | |
| 1134 | return elem.getAttribute("id") === attrId; | |
| 1135 | }; | |
| 1136 | }; | |
| 1137 | } else { | |
| 1138 | // Support: IE6/7 | |
| 1139 | // getElementById is not reliable as a find shortcut | |
| 1140 | delete Expr.find["ID"]; | |
| 1141 | ||
| 1142 | Expr.filter["ID"] = function( id ) { | |
| 1143 | var attrId = id.replace( runescape, funescape ); | |
| 1144 | return function( elem ) { | |
| 1145 | var node = typeof elem.getAttributeNode !== strundefined && elem.getAttributeNode("id"); | |
| 1146 | return node && node.value === attrId; | |
| 1147 | }; | |
| 1148 | }; | |
| 1149 | } | |
| 1150 | ||
| 1151 | // Tag | |
| 1152 | Expr.find["TAG"] = support.getElementsByTagName ? | |
| 1153 | function( tag, context ) { | |
| 1154 | if ( typeof context.getElementsByTagName !== strundefined ) { | |
| 1155 | return context.getElementsByTagName( tag ); | |
| 1156 | } | |
| 1157 | } : | |
| 1158 | function( tag, context ) { | |
| 1159 | var elem, | |
| 1160 | tmp = [], | |
| 1161 | i = 0, | |
| 1162 | results = context.getElementsByTagName( tag ); | |
| 1163 | ||
| 1164 | // Filter out possible comments | |
| 1165 | if ( tag === "*" ) { | |
| 1166 | while ( (elem = results[i++]) ) { | |
| 1167 | if ( elem.nodeType === 1 ) { | |
| 1168 | tmp.push( elem ); | |
| 1169 | } | |
| 1170 | } | |
| 1171 | ||
| 1172 | return tmp; | |
| 1173 | } | |
| 1174 | return results; | |
| 1175 | }; | |
| 1176 | ||
| 1177 | // Class | |
| 1178 | Expr.find["CLASS"] = support.getElementsByClassName && function( className, context ) { | |
| 1179 | if ( typeof context.getElementsByClassName !== strundefined && documentIsHTML ) { | |
| 1180 | return context.getElementsByClassName( className ); | |
| 1181 | } | |
| 1182 | }; | |
| 1183 | ||
| 1184 | /* QSA/matchesSelector | |
| 1185 | ---------------------------------------------------------------------- */ | |
| 1186 | ||
| 1187 | // QSA and matchesSelector support | |
| 1188 | ||
| 1189 | // matchesSelector(:active) reports false when true (IE9/Opera 11.5) | |
| 1190 | rbuggyMatches = []; | |
| 1191 | ||
| 1192 | // qSa(:focus) reports false when true (Chrome 21) | |
| 1193 | // We allow this because of a bug in IE8/9 that throws an error | |
| 1194 | // whenever `document.activeElement` is accessed on an iframe | |
| 1195 | // So, we allow :focus to pass through QSA all the time to avoid the IE error | |
| 1196 | // See http://bugs.jquery.com/ticket/13378 | |
| 1197 | rbuggyQSA = []; | |
| 1198 | ||
| 1199 | if ( (support.qsa = rnative.test( doc.querySelectorAll )) ) { | |
| 1200 | // Build QSA regex | |
| 1201 | // Regex strategy adopted from Diego Perini | |
| 1202 | assert(function( div ) { | |
| 1203 | // Select is set to empty string on purpose | |
| 1204 | // This is to test IE's treatment of not explicitly | |
| 1205 | // setting a boolean content attribute, | |
| 1206 | // since its presence should be enough | |
| 1207 | // http://bugs.jquery.com/ticket/12359 | |
| 1208 | div.innerHTML = "<select msallowclip=''><option selected=''></option></select>"; | |
| 1209 | ||
| 1210 | // Support: IE8, Opera 11-12.16 | |
| 1211 | // Nothing should be selected when empty strings follow ^= or $= or *= | |
| 1212 | // The test attribute must be unknown in Opera but "safe" for WinRT | |
| 1213 | // http://msdn.microsoft.com/en-us/library/ie/hh465388.aspx#attribute_section | |
| 1214 | if ( div.querySelectorAll("[msallowclip^='']").length ) { | |
| 1215 | rbuggyQSA.push( "[*^$]=" + whitespace + "*(?:''|\"\")" ); | |
| 1216 | } | |
| 1217 | ||
| 1218 | // Support: IE8 | |
| 1219 | // Boolean attributes and "value" are not treated correctly | |
| 1220 | if ( !div.querySelectorAll("[selected]").length ) { | |
| 1221 | rbuggyQSA.push( "\\[" + whitespace + "*(?:value|" + booleans + ")" ); | |
| 1222 | } | |
| 1223 | ||
| 1224 | // Webkit/Opera - :checked should return selected option elements | |
| 1225 | // http://www.w3.org/TR/2011/REC-css3-selectors-20110929/#checked | |
| 1226 | // IE8 throws error here and will not see later tests | |
| 1227 | if ( !div.querySelectorAll(":checked").length ) { | |
| 1228 | rbuggyQSA.push(":checked"); | |
| 1229 | } | |
| 1230 | }); | |
| 1231 | ||
| 1232 | assert(function( div ) { | |
| 1233 | // Support: Windows 8 Native Apps | |
| 1234 | // The type and name attributes are restricted during .innerHTML assignment | |
| 1235 | var input = doc.createElement("input"); | |
| 1236 | input.setAttribute( "type", "hidden" ); | |
| 1237 | div.appendChild( input ).setAttribute( "name", "D" ); | |
| 1238 | ||
| 1239 | // Support: IE8 | |
| 1240 | // Enforce case-sensitivity of name attribute | |
| 1241 | if ( div.querySelectorAll("[name=d]").length ) { | |
| 1242 | rbuggyQSA.push( "name" + whitespace + "*[*^$|!~]?=" ); | |
| 1243 | } | |
| 1244 | ||
| 1245 | // FF 3.5 - :enabled/:disabled and hidden elements (hidden elements are still enabled) | |
| 1246 | // IE8 throws error here and will not see later tests | |
| 1247 | if ( !div.querySelectorAll(":enabled").length ) { | |
| 1248 | rbuggyQSA.push( ":enabled", ":disabled" ); | |
| 1249 | } | |
| 1250 | ||
| 1251 | // Opera 10-11 does not throw on post-comma invalid pseudos | |
| 1252 | div.querySelectorAll("*,:x"); | |
| 1253 | rbuggyQSA.push(",.*:"); | |
| 1254 | }); | |
| 1255 | } | |
| 1256 | ||
| 1257 | if ( (support.matchesSelector = rnative.test( (matches = docElem.matches || | |
| 1258 | docElem.webkitMatchesSelector || | |
| 1259 | docElem.mozMatchesSelector || | |
| 1260 | docElem.oMatchesSelector || | |
| 1261 | docElem.msMatchesSelector) )) ) { | |
| 1262 | ||
| 1263 | assert(function( div ) { | |
| 1264 | // Check to see if it's possible to do matchesSelector | |
| 1265 | // on a disconnected node (IE 9) | |
| 1266 | support.disconnectedMatch = matches.call( div, "div" ); | |
| 1267 | ||
| 1268 | // This should fail with an exception | |
| 1269 | // Gecko does not error, returns false instead | |
| 1270 | matches.call( div, "[s!='']:x" ); | |
| 1271 | rbuggyMatches.push( "!=", pseudos ); | |
| 1272 | }); | |
| 1273 | } | |
| 1274 | ||
| 1275 | rbuggyQSA = rbuggyQSA.length && new RegExp( rbuggyQSA.join("|") ); | |
| 1276 | rbuggyMatches = rbuggyMatches.length && new RegExp( rbuggyMatches.join("|") ); | |
| 1277 | ||
| 1278 | /* Contains | |
| 1279 | ---------------------------------------------------------------------- */ | |
| 1280 | hasCompare = rnative.test( docElem.compareDocumentPosition ); | |
| 1281 | ||
| 1282 | // Element contains another | |
| 1283 | // Purposefully does not implement inclusive descendent | |
| 1284 | // As in, an element does not contain itself | |
| 1285 | contains = hasCompare || rnative.test( docElem.contains ) ? | |
| 1286 | function( a, b ) { | |
| 1287 | var adown = a.nodeType === 9 ? a.documentElement : a, | |
| 1288 | bup = b && b.parentNode; | |
| 1289 | return a === bup || !!( bup && bup.nodeType === 1 && ( | |
| 1290 | adown.contains ? | |
| 1291 | adown.contains( bup ) : | |
| 1292 | a.compareDocumentPosition && a.compareDocumentPosition( bup ) & 16 | |
| 1293 | )); | |
| 1294 | } : | |
| 1295 | function( a, b ) { | |
| 1296 | if ( b ) { | |
| 1297 | while ( (b = b.parentNode) ) { | |
| 1298 | if ( b === a ) { | |
| 1299 | return true; | |
| 1300 | } | |
| 1301 | } | |
| 1302 | } | |
| 1303 | return false; | |
| 1304 | }; | |
| 1305 | ||
| 1306 | /* Sorting | |
| 1307 | ---------------------------------------------------------------------- */ | |
| 1308 | ||
| 1309 | // Document order sorting | |
| 1310 | sortOrder = hasCompare ? | |
| 1311 | function( a, b ) { | |
| 1312 | ||
| 1313 | // Flag for duplicate removal | |
| 1314 | if ( a === b ) { | |
| 1315 | hasDuplicate = true; | |
| 1316 | return 0; | |
| 1317 | } | |
| 1318 | ||
| 1319 | // Sort on method existence if only one input has compareDocumentPosition | |
| 1320 | var compare = !a.compareDocumentPosition - !b.compareDocumentPosition; | |
| 1321 | if ( compare ) { | |
| 1322 | return compare; | |
| 1323 | } | |
| 1324 | ||
| 1325 | // Calculate position if both inputs belong to the same document | |
| 1326 | compare = ( a.ownerDocument || a ) === ( b.ownerDocument || b ) ? | |
| 1327 | a.compareDocumentPosition( b ) : | |
| 1328 | ||
| 1329 | // Otherwise we know they are disconnected | |
| 1330 | 1; | |
| 1331 | ||
| 1332 | // Disconnected nodes | |
| 1333 | if ( compare & 1 || | |
| 1334 | (!support.sortDetached && b.compareDocumentPosition( a ) === compare) ) { | |
| 1335 | ||
| 1336 | // Choose the first element that is related to our preferred document | |
| 1337 | if ( a === doc || a.ownerDocument === preferredDoc && contains(preferredDoc, a) ) { | |
| 1338 | return -1; | |
| 1339 | } | |
| 1340 | if ( b === doc || b.ownerDocument === preferredDoc && contains(preferredDoc, b) ) { | |
| 1341 | return 1; | |
| 1342 | } | |
| 1343 | ||
| 1344 | // Maintain original order | |
| 1345 | return sortInput ? | |
| 1346 | ( indexOf.call( sortInput, a ) - indexOf.call( sortInput, b ) ) : | |
| 1347 | 0; | |
| 1348 | } | |
| 1349 | ||
| 1350 | return compare & 4 ? -1 : 1; | |
| 1351 | } : | |
| 1352 | function( a, b ) { | |
| 1353 | // Exit early if the nodes are identical | |
| 1354 | if ( a === b ) { | |
| 1355 | hasDuplicate = true; | |
| 1356 | return 0; | |
| 1357 | } | |
| 1358 | ||
| 1359 | var cur, | |
| 1360 | i = 0, | |
| 1361 | aup = a.parentNode, | |
| 1362 | bup = b.parentNode, | |
| 1363 | ap = [ a ], | |
| 1364 | bp = [ b ]; | |
| 1365 | ||
| 1366 | // Parentless nodes are either documents or disconnected | |
| 1367 | if ( !aup || !bup ) { | |
| 1368 | return a === doc ? -1 : | |
| 1369 | b === doc ? 1 : | |
| 1370 | aup ? -1 : | |
| 1371 | bup ? 1 : | |
| 1372 | sortInput ? | |
| 1373 | ( indexOf.call( sortInput, a ) - indexOf.call( sortInput, b ) ) : | |
| 1374 | 0; | |
| 1375 | ||
| 1376 | // If the nodes are siblings, we can do a quick check | |
| 1377 | } else if ( aup === bup ) { | |
| 1378 | return siblingCheck( a, b ); | |
| 1379 | } | |
| 1380 | ||
| 1381 | // Otherwise we need full lists of their ancestors for comparison | |
| 1382 | cur = a; | |
| 1383 | while ( (cur = cur.parentNode) ) { | |
| 1384 | ap.unshift( cur ); | |
| 1385 | } | |
| 1386 | cur = b; | |
| 1387 | while ( (cur = cur.parentNode) ) { | |
| 1388 | bp.unshift( cur ); | |
| 1389 | } | |
| 1390 | ||
| 1391 | // Walk down the tree looking for a discrepancy | |
| 1392 | while ( ap[i] === bp[i] ) { | |
| 1393 | i++; | |
| 1394 | } | |
| 1395 | ||
| 1396 | return i ? | |
| 1397 | // Do a sibling check if the nodes have a common ancestor | |
| 1398 | siblingCheck( ap[i], bp[i] ) : | |
| 1399 | ||
| 1400 | // Otherwise nodes in our document sort first | |
| 1401 | ap[i] === preferredDoc ? -1 : | |
| 1402 | bp[i] === preferredDoc ? 1 : | |
| 1403 | 0; | |
| 1404 | }; | |
| 1405 | ||
| 1406 | return doc; | |
| 1407 | }; | |
| 1408 | ||
| 1409 | Sizzle.matches = function( expr, elements ) { | |
| 1410 | return Sizzle( expr, null, null, elements ); | |
| 1411 | }; | |
| 1412 | ||
| 1413 | Sizzle.matchesSelector = function( elem, expr ) { | |
| 1414 | // Set document vars if needed | |
| 1415 | if ( ( elem.ownerDocument || elem ) !== document ) { | |
| 1416 | setDocument( elem ); | |
| 1417 | } | |
| 1418 | ||
| 1419 | // Make sure that attribute selectors are quoted | |
| 1420 | expr = expr.replace( rattributeQuotes, "='$1']" ); | |
| 1421 | ||
| 1422 | if ( support.matchesSelector && documentIsHTML && | |
| 1423 | ( !rbuggyMatches || !rbuggyMatches.test( expr ) ) && | |
| 1424 | ( !rbuggyQSA || !rbuggyQSA.test( expr ) ) ) { | |
| 1425 | ||
| 1426 | try { | |
| 1427 | var ret = matches.call( elem, expr ); | |
| 1428 | ||
| 1429 | // IE 9's matchesSelector returns false on disconnected nodes | |
| 1430 | if ( ret || support.disconnectedMatch || | |
| 1431 | // As well, disconnected nodes are said to be in a document | |
| 1432 | // fragment in IE 9 | |
| 1433 | elem.document && elem.document.nodeType !== 11 ) { | |
| 1434 | return ret; | |
| 1435 | } | |
| 1436 | } catch(e) {} | |
| 1437 | } | |
| 1438 | ||
| 1439 | return Sizzle( expr, document, null, [ elem ] ).length > 0; | |
| 1440 | }; | |
| 1441 | ||
| 1442 | Sizzle.contains = function( context, elem ) { | |
| 1443 | // Set document vars if needed | |
| 1444 | if ( ( context.ownerDocument || context ) !== document ) { | |
| 1445 | setDocument( context ); | |
| 1446 | } | |
| 1447 | return contains( context, elem ); | |
| 1448 | }; | |
| 1449 | ||
| 1450 | Sizzle.attr = function( elem, name ) { | |
| 1451 | // Set document vars if needed | |
| 1452 | if ( ( elem.ownerDocument || elem ) !== document ) { | |
| 1453 | setDocument( elem ); | |
| 1454 | } | |
| 1455 | ||
| 1456 | var fn = Expr.attrHandle[ name.toLowerCase() ], | |
| 1457 | // Don't get fooled by Object.prototype properties (jQuery #13807) | |
| 1458 | val = fn && hasOwn.call( Expr.attrHandle, name.toLowerCase() ) ? | |
| 1459 | fn( elem, name, !documentIsHTML ) : | |
| 1460 | undefined; | |
| 1461 | ||
| 1462 | return val !== undefined ? | |
| 1463 | val : | |
| 1464 | support.attributes || !documentIsHTML ? | |
| 1465 | elem.getAttribute( name ) : | |
| 1466 | (val = elem.getAttributeNode(name)) && val.specified ? | |
| 1467 | val.value : | |
| 1468 | null; | |
| 1469 | }; | |
| 1470 | ||
| 1471 | Sizzle.error = function( msg ) { | |
| 1472 | throw new Error( "Syntax error, unrecognized expression: " + msg ); | |
| 1473 | }; | |
| 1474 | ||
| 1475 | /** | |
| 1476 | * Document sorting and removing duplicates | |
| 1477 | * @param {ArrayLike} results | |
| 1478 | */ | |
| 1479 | Sizzle.uniqueSort = function( results ) { | |
| 1480 | var elem, | |
| 1481 | duplicates = [], | |
| 1482 | j = 0, | |
| 1483 | i = 0; | |
| 1484 | ||
| 1485 | // Unless we *know* we can detect duplicates, assume their presence | |
| 1486 | hasDuplicate = !support.detectDuplicates; | |
| 1487 | sortInput = !support.sortStable && results.slice( 0 ); | |
| 1488 | results.sort( sortOrder ); | |
| 1489 | ||
| 1490 | if ( hasDuplicate ) { | |
| 1491 | while ( (elem = results[i++]) ) { | |
| 1492 | if ( elem === results[ i ] ) { | |
| 1493 | j = duplicates.push( i ); | |
| 1494 | } | |
| 1495 | } | |
| 1496 | while ( j-- ) { | |
| 1497 | results.splice( duplicates[ j ], 1 ); | |
| 1498 | } | |
| 1499 | } | |
| 1500 | ||
| 1501 | // Clear input after sorting to release objects | |
| 1502 | // See https://github.com/jquery/sizzle/pull/225 | |
| 1503 | sortInput = null; | |
| 1504 | ||
| 1505 | return results; | |
| 1506 | }; | |
| 1507 | ||
| 1508 | /** | |
| 1509 | * Utility function for retrieving the text value of an array of DOM nodes | |
| 1510 | * @param {Array|Element} elem | |
| 1511 | */ | |
| 1512 | getText = Sizzle.getText = function( elem ) { | |
| 1513 | var node, | |
| 1514 | ret = "", | |
| 1515 | i = 0, | |
| 1516 | nodeType = elem.nodeType; | |
| 1517 | ||
| 1518 | if ( !nodeType ) { | |
| 1519 | // If no nodeType, this is expected to be an array | |
| 1520 | while ( (node = elem[i++]) ) { | |
| 1521 | // Do not traverse comment nodes | |
| 1522 | ret += getText( node ); | |
| 1523 | } | |
| 1524 | } else if ( nodeType === 1 || nodeType === 9 || nodeType === 11 ) { | |
| 1525 | // Use textContent for elements | |
| 1526 | // innerText usage removed for consistency of new lines (jQuery #11153) | |
| 1527 | if ( typeof elem.textContent === "string" ) { | |
| 1528 | return elem.textContent; | |
| 1529 | } else { | |
| 1530 | // Traverse its children | |
| 1531 | for ( elem = elem.firstChild; elem; elem = elem.nextSibling ) { | |
| 1532 | ret += getText( elem ); | |
| 1533 | } | |
| 1534 | } | |
| 1535 | } else if ( nodeType === 3 || nodeType === 4 ) { | |
| 1536 | return elem.nodeValue; | |
| 1537 | } | |
| 1538 | // Do not include comment or processing instruction nodes | |
| 1539 | ||
| 1540 | return ret; | |
| 1541 | }; | |
| 1542 | ||
| 1543 | Expr = Sizzle.selectors = { | |
| 1544 | ||
| 1545 | // Can be adjusted by the user | |
| 1546 | cacheLength: 50, | |
| 1547 | ||
| 1548 | createPseudo: markFunction, | |
| 1549 | ||
| 1550 | match: matchExpr, | |
| 1551 | ||
| 1552 | attrHandle: {}, | |
| 1553 | ||
| 1554 | find: {}, | |
| 1555 | ||
| 1556 | relative: { | |
| 1557 | ">": { dir: "parentNode", first: true }, | |
| 1558 | " ": { dir: "parentNode" }, | |
| 1559 | "+": { dir: "previousSibling", first: true }, | |
| 1560 | "~": { dir: "previousSibling" } | |
| 1561 | }, | |
| 1562 | ||
| 1563 | preFilter: { | |
| 1564 | "ATTR": function( match ) { | |
| 1565 | match[1] = match[1].replace( runescape, funescape ); | |
| 1566 | ||
| 1567 | // Move the given value to match[3] whether quoted or unquoted | |
| 1568 | match[3] = ( match[3] || match[4] || match[5] || "" ).replace( runescape, funescape ); | |
| 1569 | ||
| 1570 | if ( match[2] === "~=" ) { | |
| 1571 | match[3] = " " + match[3] + " "; | |
| 1572 | } | |
| 1573 | ||
| 1574 | return match.slice( 0, 4 ); | |
| 1575 | }, | |
| 1576 | ||
| 1577 | "CHILD": function( match ) { | |
| 1578 | /* matches from matchExpr["CHILD"] | |
| 1579 | 1 type (only|nth|...) | |
| 1580 | 2 what (child|of-type) | |
| 1581 | 3 argument (even|odd|\d*|\d*n([+-]\d+)?|...) | |
| 1582 | 4 xn-component of xn+y argument ([+-]?\d*n|) | |
| 1583 | 5 sign of xn-component | |
| 1584 | 6 x of xn-component | |
| 1585 | 7 sign of y-component | |
| 1586 | 8 y of y-component | |
| 1587 | */ | |
| 1588 | match[1] = match[1].toLowerCase(); | |
| 1589 | ||
| 1590 | if ( match[1].slice( 0, 3 ) === "nth" ) { | |
| 1591 | // nth-* requires argument | |
| 1592 | if ( !match[3] ) { | |
| 1593 | Sizzle.error( match[0] ); | |
| 1594 | } | |
| 1595 | ||
| 1596 | // numeric x and y parameters for Expr.filter.CHILD | |
| 1597 | // remember that false/true cast respectively to 0/1 | |
| 1598 | match[4] = +( match[4] ? match[5] + (match[6] || 1) : 2 * ( match[3] === "even" || match[3] === "odd" ) ); | |
| 1599 | match[5] = +( ( match[7] + match[8] ) || match[3] === "odd" ); | |
| 1600 | ||
| 1601 | // other types prohibit arguments | |
| 1602 | } else if ( match[3] ) { | |
| 1603 | Sizzle.error( match[0] ); | |
| 1604 | } | |
| 1605 | ||
| 1606 | return match; | |
| 1607 | }, | |
| 1608 | ||
| 1609 | "PSEUDO": function( match ) { | |
| 1610 | var excess, | |
| 1611 | unquoted = !match[6] && match[2]; | |
| 1612 | ||
| 1613 | if ( matchExpr["CHILD"].test( match[0] ) ) { | |
| 1614 | return null; | |
| 1615 | } | |
| 1616 | ||
| 1617 | // Accept quoted arguments as-is | |
| 1618 | if ( match[3] ) { | |
| 1619 | match[2] = match[4] || match[5] || ""; | |
| 1620 | ||
| 1621 | // Strip excess characters from unquoted arguments | |
| 1622 | } else if ( unquoted && rpseudo.test( unquoted ) && | |
| 1623 | // Get excess from tokenize (recursively) | |
| 1624 | (excess = tokenize( unquoted, true )) && | |
| 1625 | // advance to the next closing parenthesis | |
| 1626 | (excess = unquoted.indexOf( ")", unquoted.length - excess ) - unquoted.length) ) { | |
| 1627 | ||
| 1628 | // excess is a negative index | |
| 1629 | match[0] = match[0].slice( 0, excess ); | |
| 1630 | match[2] = unquoted.slice( 0, excess ); | |
| 1631 | } | |
| 1632 | ||
| 1633 | // Return only captures needed by the pseudo filter method (type and argument) | |
| 1634 | return match.slice( 0, 3 ); | |
| 1635 | } | |
| 1636 | }, | |
| 1637 | ||
| 1638 | filter: { | |
| 1639 | ||
| 1640 | "TAG": function( nodeNameSelector ) { | |
| 1641 | var nodeName = nodeNameSelector.replace( runescape, funescape ).toLowerCase(); | |
| 1642 | return nodeNameSelector === "*" ? | |
| 1643 | function() { return true; } : | |
| 1644 | function( elem ) { | |
| 1645 | return elem.nodeName && elem.nodeName.toLowerCase() === nodeName; | |
| 1646 | }; | |
| 1647 | }, | |
| 1648 | ||
| 1649 | "CLASS": function( className ) { | |
| 1650 | var pattern = classCache[ className + " " ]; | |
| 1651 | ||
| 1652 | return pattern || | |
| 1653 | (pattern = new RegExp( "(^|" + whitespace + ")" + className + "(" + whitespace + "|$)" )) && | |
| 1654 | classCache( className, function( elem ) { | |
| 1655 | return pattern.test( typeof elem.className === "string" && elem.className || typeof elem.getAttribute !== strundefined && elem.getAttribute("class") || "" ); | |
| 1656 | }); | |
| 1657 | }, | |
| 1658 | ||
| 1659 | "ATTR": function( name, operator, check ) { | |
| 1660 | return function( elem ) { | |
| 1661 | var result = Sizzle.attr( elem, name ); | |
| 1662 | ||
| 1663 | if ( result == null ) { | |
| 1664 | return operator === "!="; | |
| 1665 | } | |
| 1666 | if ( !operator ) { | |
| 1667 | return true; | |
| 1668 | } | |
| 1669 | ||
| 1670 | result += ""; | |
| 1671 | ||
| 1672 | return operator === "=" ? result === check : | |
| 1673 | operator === "!=" ? result !== check : | |
| 1674 | operator === "^=" ? check && result.indexOf( check ) === 0 : | |
| 1675 | operator === "*=" ? check && result.indexOf( check ) > -1 : | |
| 1676 | operator === "$=" ? check && result.slice( -check.length ) === check : | |
| 1677 | operator === "~=" ? ( " " + result + " " ).indexOf( check ) > -1 : | |
| 1678 | operator === "|=" ? result === check || result.slice( 0, check.length + 1 ) === check + "-" : | |
| 1679 | false; | |
| 1680 | }; | |
| 1681 | }, | |
| 1682 | ||
| 1683 | "CHILD": function( type, what, argument, first, last ) { | |
| 1684 | var simple = type.slice( 0, 3 ) !== "nth", | |
| 1685 | forward = type.slice( -4 ) !== "last", | |
| 1686 | ofType = what === "of-type"; | |
| 1687 | ||
| 1688 | return first === 1 && last === 0 ? | |
| 1689 | ||
| 1690 | // Shortcut for :nth-*(n) | |
| 1691 | function( elem ) { | |
| 1692 | return !!elem.parentNode; | |
| 1693 | } : | |
| 1694 | ||
| 1695 | function( elem, context, xml ) { | |
| 1696 | var cache, outerCache, node, diff, nodeIndex, start, | |
| 1697 | dir = simple !== forward ? "nextSibling" : "previousSibling", | |
| 1698 | parent = elem.parentNode, | |
| 1699 | name = ofType && elem.nodeName.toLowerCase(), | |
| 1700 | useCache = !xml && !ofType; | |
| 1701 | ||
| 1702 | if ( parent ) { | |
| 1703 | ||
| 1704 | // :(first|last|only)-(child|of-type) | |
| 1705 | if ( simple ) { | |
| 1706 | while ( dir ) { | |
| 1707 | node = elem; | |
| 1708 | while ( (node = node[ dir ]) ) { | |
| 1709 | if ( ofType ? node.nodeName.toLowerCase() === name : node.nodeType === 1 ) { | |
| 1710 | return false; | |
| 1711 | } | |
| 1712 | } | |
| 1713 | // Reverse direction for :only-* (if we haven't yet done so) | |
| 1714 | start = dir = type === "only" && !start && "nextSibling"; | |
| 1715 | } | |
| 1716 | return true; | |
| 1717 | } | |
| 1718 | ||
| 1719 | start = [ forward ? parent.firstChild : parent.lastChild ]; | |
| 1720 | ||
| 1721 | // non-xml :nth-child(...) stores cache data on `parent` | |
| 1722 | if ( forward && useCache ) { | |
| 1723 | // Seek `elem` from a previously-cached index | |
| 1724 | outerCache = parent[ expando ] || (parent[ expando ] = {}); | |
| 1725 | cache = outerCache[ type ] || []; | |
| 1726 | nodeIndex = cache[0] === dirruns && cache[1]; | |
| 1727 | diff = cache[0] === dirruns && cache[2]; | |
| 1728 | node = nodeIndex && parent.childNodes[ nodeIndex ]; | |
| 1729 | ||
| 1730 | while ( (node = ++nodeIndex && node && node[ dir ] || | |
| 1731 | ||
| 1732 | // Fallback to seeking `elem` from the start | |
| 1733 | (diff = nodeIndex = 0) || start.pop()) ) { | |
| 1734 | ||
| 1735 | // When found, cache indexes on `parent` and break | |
| 1736 | if ( node.nodeType === 1 && ++diff && node === elem ) { | |
| 1737 | outerCache[ type ] = [ dirruns, nodeIndex, diff ]; | |
| 1738 | break; | |
| 1739 | } | |
| 1740 | } | |
| 1741 | ||
| 1742 | // Use previously-cached element index if available | |
| 1743 | } else if ( useCache && (cache = (elem[ expando ] || (elem[ expando ] = {}))[ type ]) && cache[0] === dirruns ) { | |
| 1744 | diff = cache[1]; | |
| 1745 | ||
| 1746 | // xml :nth-child(...) or :nth-last-child(...) or :nth(-last)?-of-type(...) | |
| 1747 | } else { | |
| 1748 | // Use the same loop as above to seek `elem` from the start | |
| 1749 | while ( (node = ++nodeIndex && node && node[ dir ] || | |
| 1750 | (diff = nodeIndex = 0) || start.pop()) ) { | |
| 1751 | ||
| 1752 | if ( ( ofType ? node.nodeName.toLowerCase() === name : node.nodeType === 1 ) && ++diff ) { | |
| 1753 | // Cache the index of each encountered element | |
| 1754 | if ( useCache ) { | |
| 1755 | (node[ expando ] || (node[ expando ] = {}))[ type ] = [ dirruns, diff ]; | |
| 1756 | } | |
| 1757 | ||
| 1758 | if ( node === elem ) { | |
| 1759 | break; | |
| 1760 | } | |
| 1761 | } | |
| 1762 | } | |
| 1763 | } | |
| 1764 | ||
| 1765 | // Incorporate the offset, then check against cycle size | |
| 1766 | diff -= last; | |
| 1767 | return diff === first || ( diff % first === 0 && diff / first >= 0 ); | |
| 1768 | } | |
| 1769 | }; | |
| 1770 | }, | |
| 1771 | ||
| 1772 | "PSEUDO": function( pseudo, argument ) { | |
| 1773 | // pseudo-class names are case-insensitive | |
| 1774 | // http://www.w3.org/TR/selectors/#pseudo-classes | |
| 1775 | // Prioritize by case sensitivity in case custom pseudos are added with uppercase letters | |
| 1776 | // Remember that setFilters inherits from pseudos | |
| 1777 | var args, | |
| 1778 | fn = Expr.pseudos[ pseudo ] || Expr.setFilters[ pseudo.toLowerCase() ] || | |
| 1779 | Sizzle.error( "unsupported pseudo: " + pseudo ); | |
| 1780 | ||
| 1781 | // The user may use createPseudo to indicate that | |
| 1782 | // arguments are needed to create the filter function | |
| 1783 | // just as Sizzle does | |
| 1784 | if ( fn[ expando ] ) { | |
| 1785 | return fn( argument ); | |
| 1786 | } | |
| 1787 | ||
| 1788 | // But maintain support for old signatures | |
| 1789 | if ( fn.length > 1 ) { | |
| 1790 | args = [ pseudo, pseudo, "", argument ]; | |
| 1791 | return Expr.setFilters.hasOwnProperty( pseudo.toLowerCase() ) ? | |
| 1792 | markFunction(function( seed, matches ) { | |
| 1793 | var idx, | |
| 1794 | matched = fn( seed, argument ), | |
| 1795 | i = matched.length; | |
| 1796 | while ( i-- ) { | |
| 1797 | idx = indexOf.call( seed, matched[i] ); | |
| 1798 | seed[ idx ] = !( matches[ idx ] = matched[i] ); | |
| 1799 | } | |
| 1800 | }) : | |
| 1801 | function( elem ) { | |
| 1802 | return fn( elem, 0, args ); | |
| 1803 | }; | |
| 1804 | } | |
| 1805 | ||
| 1806 | return fn; | |
| 1807 | } | |
| 1808 | }, | |
| 1809 | ||
| 1810 | pseudos: { | |
| 1811 | // Potentially complex pseudos | |
| 1812 | "not": markFunction(function( selector ) { | |
| 1813 | // Trim the selector passed to compile | |
| 1814 | // to avoid treating leading and trailing | |
| 1815 | // spaces as combinators | |
| 1816 | var input = [], | |
| 1817 | results = [], | |
| 1818 | matcher = compile( selector.replace( rtrim, "$1" ) ); | |
| 1819 | ||
| 1820 | return matcher[ expando ] ? | |
| 1821 | markFunction(function( seed, matches, context, xml ) { | |
| 1822 | var elem, | |
| 1823 | unmatched = matcher( seed, null, xml, [] ), | |
| 1824 | i = seed.length; | |
| 1825 | ||
| 1826 | // Match elements unmatched by `matcher` | |
| 1827 | while ( i-- ) { | |
| 1828 | if ( (elem = unmatched[i]) ) { | |
| 1829 | seed[i] = !(matches[i] = elem); | |
| 1830 | } | |
| 1831 | } | |
| 1832 | }) : | |
| 1833 | function( elem, context, xml ) { | |
| 1834 | input[0] = elem; | |
| 1835 | matcher( input, null, xml, results ); | |
| 1836 | return !results.pop(); | |
| 1837 | }; | |
| 1838 | }), | |
| 1839 | ||
| 1840 | "has": markFunction(function( selector ) { | |
| 1841 | return function( elem ) { | |
| 1842 | return Sizzle( selector, elem ).length > 0; | |
| 1843 | }; | |
| 1844 | }), | |
| 1845 | ||
| 1846 | "contains": markFunction(function( text ) { | |
| 1847 | return function( elem ) { | |
| 1848 | return ( elem.textContent || elem.innerText || getText( elem ) ).indexOf( text ) > -1; | |
| 1849 | }; | |
| 1850 | }), | |
| 1851 | ||
| 1852 | // "Whether an element is represented by a :lang() selector | |
| 1853 | // is based solely on the element's language value | |
| 1854 | // being equal to the identifier C, | |
| 1855 | // or beginning with the identifier C immediately followed by "-". | |
| 1856 | // The matching of C against the element's language value is performed case-insensitively. | |
| 1857 | // The identifier C does not have to be a valid language name." | |
| 1858 | // http://www.w3.org/TR/selectors/#lang-pseudo | |
| 1859 | "lang": markFunction( function( lang ) { | |
| 1860 | // lang value must be a valid identifier | |
| 1861 | if ( !ridentifier.test(lang || "") ) { | |
| 1862 | Sizzle.error( "unsupported lang: " + lang ); | |
| 1863 | } | |
| 1864 | lang = lang.replace( runescape, funescape ).toLowerCase(); | |
| 1865 | return function( elem ) { | |
| 1866 | var elemLang; | |
| 1867 | do { | |
| 1868 | if ( (elemLang = documentIsHTML ? | |
| 1869 | elem.lang : | |
| 1870 | elem.getAttribute("xml:lang") || elem.getAttribute("lang")) ) { | |
| 1871 | ||
| 1872 | elemLang = elemLang.toLowerCase(); | |
| 1873 | return elemLang === lang || elemLang.indexOf( lang + "-" ) === 0; | |
| 1874 | } | |
| 1875 | } while ( (elem = elem.parentNode) && elem.nodeType === 1 ); | |
| 1876 | return false; | |
| 1877 | }; | |
| 1878 | }), | |
| 1879 | ||
| 1880 | // Miscellaneous | |
| 1881 | "target": function( elem ) { | |
| 1882 | var hash = window.location && window.location.hash; | |
| 1883 | return hash && hash.slice( 1 ) === elem.id; | |
| 1884 | }, | |
| 1885 | ||
| 1886 | "root": function( elem ) { | |
| 1887 | return elem === docElem; | |
| 1888 | }, | |
| 1889 | ||
| 1890 | "focus": function( elem ) { | |
| 1891 | return elem === document.activeElement && (!document.hasFocus || document.hasFocus()) && !!(elem.type || elem.href || ~elem.tabIndex); | |
| 1892 | }, | |
| 1893 | ||
| 1894 | // Boolean properties | |
| 1895 | "enabled": function( elem ) { | |
| 1896 | return elem.disabled === false; | |
| 1897 | }, | |
| 1898 | ||
| 1899 | "disabled": function( elem ) { | |
| 1900 | return elem.disabled === true; | |
| 1901 | }, | |
| 1902 | ||
| 1903 | "checked": function( elem ) { | |
| 1904 | // In CSS3, :checked should return both checked and selected elements | |
| 1905 | // http://www.w3.org/TR/2011/REC-css3-selectors-20110929/#checked | |
| 1906 | var nodeName = elem.nodeName.toLowerCase(); | |
| 1907 | return (nodeName === "input" && !!elem.checked) || (nodeName === "option" && !!elem.selected); | |
| 1908 | }, | |
| 1909 | ||
| 1910 | "selected": function( elem ) { | |
| 1911 | // Accessing this property makes selected-by-default | |
| 1912 | // options in Safari work properly | |
| 1913 | if ( elem.parentNode ) { | |
| 1914 | elem.parentNode.selectedIndex; | |
| 1915 | } | |
| 1916 | ||
| 1917 | return elem.selected === true; | |
| 1918 | }, | |
| 1919 | ||
| 1920 | // Contents | |
| 1921 | "empty": function( elem ) { | |
| 1922 | // http://www.w3.org/TR/selectors/#empty-pseudo | |
| 1923 | // :empty is negated by element (1) or content nodes (text: 3; cdata: 4; entity ref: 5), | |
| 1924 | // but not by others (comment: 8; processing instruction: 7; etc.) | |
| 1925 | // nodeType < 6 works because attributes (2) do not appear as children | |
| 1926 | for ( elem = elem.firstChild; elem; elem = elem.nextSibling ) { | |
| 1927 | if ( elem.nodeType < 6 ) { | |
| 1928 | return false; | |
| 1929 | } | |
| 1930 | } | |
| 1931 | return true; | |
| 1932 | }, | |
| 1933 | ||
| 1934 | "parent": function( elem ) { | |
| 1935 | return !Expr.pseudos["empty"]( elem ); | |
| 1936 | }, | |
| 1937 | ||
| 1938 | // Element/input types | |
| 1939 | "header": function( elem ) { | |
| 1940 | return rheader.test( elem.nodeName ); | |
| 1941 | }, | |
| 1942 | ||
| 1943 | "input": function( elem ) { | |
| 1944 | return rinputs.test( elem.nodeName ); | |
| 1945 | }, | |
| 1946 | ||
| 1947 | "button": function( elem ) { | |
| 1948 | var name = elem.nodeName.toLowerCase(); | |
| 1949 | return name === "input" && elem.type === "button" || name === "button"; | |
| 1950 | }, | |
| 1951 | ||
| 1952 | "text": function( elem ) { | |
| 1953 | var attr; | |
| 1954 | return elem.nodeName.toLowerCase() === "input" && | |
| 1955 | elem.type === "text" && | |
| 1956 | ||
| 1957 | // Support: IE<8 | |
| 1958 | // New HTML5 attribute values (e.g., "search") appear with elem.type === "text" | |
| 1959 | ( (attr = elem.getAttribute("type")) == null || attr.toLowerCase() === "text" ); | |
| 1960 | }, | |
| 1961 | ||
| 1962 | // Position-in-collection | |
| 1963 | "first": createPositionalPseudo(function() { | |
| 1964 | return [ 0 ]; | |
| 1965 | }), | |
| 1966 | ||
| 1967 | "last": createPositionalPseudo(function( matchIndexes, length ) { | |
| 1968 | return [ length - 1 ]; | |
| 1969 | }), | |
| 1970 | ||
| 1971 | "eq": createPositionalPseudo(function( matchIndexes, length, argument ) { | |
| 1972 | return [ argument < 0 ? argument + length : argument ]; | |
| 1973 | }), | |
| 1974 | ||
| 1975 | "even": createPositionalPseudo(function( matchIndexes, length ) { | |
| 1976 | var i = 0; | |
| 1977 | for ( ; i < length; i += 2 ) { | |
| 1978 | matchIndexes.push( i ); | |
| 1979 | } | |
| 1980 | return matchIndexes; | |
| 1981 | }), | |
| 1982 | ||
| 1983 | "odd": createPositionalPseudo(function( matchIndexes, length ) { | |
| 1984 | var i = 1; | |
| 1985 | for ( ; i < length; i += 2 ) { | |
| 1986 | matchIndexes.push( i ); | |
| 1987 | } | |
| 1988 | return matchIndexes; | |
| 1989 | }), | |
| 1990 | ||
| 1991 | "lt": createPositionalPseudo(function( matchIndexes, length, argument ) { | |
| 1992 | var i = argument < 0 ? argument + length : argument; | |
| 1993 | for ( ; --i >= 0; ) { | |
| 1994 | matchIndexes.push( i ); | |
| 1995 | } | |
| 1996 | return matchIndexes; | |
| 1997 | }), | |
| 1998 | ||
| 1999 | "gt": createPositionalPseudo(function( matchIndexes, length, argument ) { | |
| 2000 | var i = argument < 0 ? argument + length : argument; | |
| 2001 | for ( ; ++i < length; ) { | |
| 2002 | matchIndexes.push( i ); | |
| 2003 | } | |
| 2004 | return matchIndexes; | |
| 2005 | }) | |
| 2006 | } | |
| 2007 | }; | |
| 2008 | ||
| 2009 | Expr.pseudos["nth"] = Expr.pseudos["eq"]; | |
| 2010 | ||
| 2011 | // Add button/input type pseudos | |
| 2012 | for ( i in { radio: true, checkbox: true, file: true, password: true, image: true } ) { | |
| 2013 | Expr.pseudos[ i ] = createInputPseudo( i ); | |
| 2014 | } | |
| 2015 | for ( i in { submit: true, reset: true } ) { | |
| 2016 | Expr.pseudos[ i ] = createButtonPseudo( i ); | |
| 2017 | } | |
| 2018 | ||
| 2019 | // Easy API for creating new setFilters | |
| 2020 | function setFilters() {} | |
| 2021 | setFilters.prototype = Expr.filters = Expr.pseudos; | |
| 2022 | Expr.setFilters = new setFilters(); | |
| 2023 | ||
| 2024 | tokenize = Sizzle.tokenize = function( selector, parseOnly ) { | |
| 2025 | var matched, match, tokens, type, | |
| 2026 | soFar, groups, preFilters, | |
| 2027 | cached = tokenCache[ selector + " " ]; | |
| 2028 | ||
| 2029 | if ( cached ) { | |
| 2030 | return parseOnly ? 0 : cached.slice( 0 ); | |
| 2031 | } | |
| 2032 | ||
| 2033 | soFar = selector; | |
| 2034 | groups = []; | |
| 2035 | preFilters = Expr.preFilter; | |
| 2036 | ||
| 2037 | while ( soFar ) { | |
| 2038 | ||
| 2039 | // Comma and first run | |
| 2040 | if ( !matched || (match = rcomma.exec( soFar )) ) { | |
| 2041 | if ( match ) { | |
| 2042 | // Don't consume trailing commas as valid | |
| 2043 | soFar = soFar.slice( match[0].length ) || soFar; | |
| 2044 | } | |
| 2045 | groups.push( (tokens = []) ); | |
| 2046 | } | |
| 2047 | ||
| 2048 | matched = false; | |
| 2049 | ||
| 2050 | // Combinators | |
| 2051 | if ( (match = rcombinators.exec( soFar )) ) { | |
| 2052 | matched = match.shift(); | |
| 2053 | tokens.push({ | |
| 2054 | value: matched, | |
| 2055 | // Cast descendant combinators to space | |
| 2056 | type: match[0].replace( rtrim, " " ) | |
| 2057 | }); | |
| 2058 | soFar = soFar.slice( matched.length ); | |
| 2059 | } | |
| 2060 | ||
| 2061 | // Filters | |
| 2062 | for ( type in Expr.filter ) { | |
| 2063 | if ( (match = matchExpr[ type ].exec( soFar )) && (!preFilters[ type ] || | |
| 2064 | (match = preFilters[ type ]( match ))) ) { | |
| 2065 | matched = match.shift(); | |
| 2066 | tokens.push({ | |
| 2067 | value: matched, | |
| 2068 | type: type, | |
| 2069 | matches: match | |
| 2070 | }); | |
| 2071 | soFar = soFar.slice( matched.length ); | |
| 2072 | } | |
| 2073 | } | |
| 2074 | ||
| 2075 | if ( !matched ) { | |
| 2076 | break; | |
| 2077 | } | |
| 2078 | } | |
| 2079 | ||
| 2080 | // Return the length of the invalid excess | |
| 2081 | // if we're just parsing | |
| 2082 | // Otherwise, throw an error or return tokens | |
| 2083 | return parseOnly ? | |
| 2084 | soFar.length : | |
| 2085 | soFar ? | |
| 2086 | Sizzle.error( selector ) : | |
| 2087 | // Cache the tokens | |
| 2088 | tokenCache( selector, groups ).slice( 0 ); | |
| 2089 | }; | |
| 2090 | ||
| 2091 | function toSelector( tokens ) { | |
| 2092 | var i = 0, | |
| 2093 | len = tokens.length, | |
| 2094 | selector = ""; | |
| 2095 | for ( ; i < len; i++ ) { | |
| 2096 | selector += tokens[i].value; | |
| 2097 | } | |
| 2098 | return selector; | |
| 2099 | } | |
| 2100 | ||
| 2101 | function addCombinator( matcher, combinator, base ) { | |
| 2102 | var dir = combinator.dir, | |
| 2103 | checkNonElements = base && dir === "parentNode", | |
| 2104 | doneName = done++; | |
| 2105 | ||
| 2106 | return combinator.first ? | |
| 2107 | // Check against closest ancestor/preceding element | |
| 2108 | function( elem, context, xml ) { | |
| 2109 | while ( (elem = elem[ dir ]) ) { | |
| 2110 | if ( elem.nodeType === 1 || checkNonElements ) { | |
| 2111 | return matcher( elem, context, xml ); | |
| 2112 | } | |
| 2113 | } | |
| 2114 | } : | |
| 2115 | ||
| 2116 | // Check against all ancestor/preceding elements | |
| 2117 | function( elem, context, xml ) { | |
| 2118 | var oldCache, outerCache, | |
| 2119 | newCache = [ dirruns, doneName ]; | |
| 2120 | ||
| 2121 | // We can't set arbitrary data on XML nodes, so they don't benefit from dir caching | |
| 2122 | if ( xml ) { | |
| 2123 | while ( (elem = elem[ dir ]) ) { | |
| 2124 | if ( elem.nodeType === 1 || checkNonElements ) { | |
| 2125 | if ( matcher( elem, context, xml ) ) { | |
| 2126 | return true; | |
| 2127 | } | |
| 2128 | } | |
| 2129 | } | |
| 2130 | } else { | |
| 2131 | while ( (elem = elem[ dir ]) ) { | |
| 2132 | if ( elem.nodeType === 1 || checkNonElements ) { | |
| 2133 | outerCache = elem[ expando ] || (elem[ expando ] = {}); | |
| 2134 | if ( (oldCache = outerCache[ dir ]) && | |
| 2135 | oldCache[ 0 ] === dirruns && oldCache[ 1 ] === doneName ) { | |
| 2136 | ||
| 2137 | // Assign to newCache so results back-propagate to previous elements | |
| 2138 | return (newCache[ 2 ] = oldCache[ 2 ]); | |
| 2139 | } else { | |
| 2140 | // Reuse newcache so results back-propagate to previous elements | |
| 2141 | outerCache[ dir ] = newCache; | |
| 2142 | ||
| 2143 | // A match means we're done; a fail means we have to keep checking | |
| 2144 | if ( (newCache[ 2 ] = matcher( elem, context, xml )) ) { | |
| 2145 | return true; | |
| 2146 | } | |
| 2147 | } | |
| 2148 | } | |
| 2149 | } | |
| 2150 | } | |
| 2151 | }; | |
| 2152 | } | |
| 2153 | ||
| 2154 | function elementMatcher( matchers ) { | |
| 2155 | return matchers.length > 1 ? | |
| 2156 | function( elem, context, xml ) { | |
| 2157 | var i = matchers.length; | |
| 2158 | while ( i-- ) { | |
| 2159 | if ( !matchers[i]( elem, context, xml ) ) { | |
| 2160 | return false; | |
| 2161 | } | |
| 2162 | } | |
| 2163 | return true; | |
| 2164 | } : | |
| 2165 | matchers[0]; | |
| 2166 | } | |
| 2167 | ||
| 2168 | function multipleContexts( selector, contexts, results ) { | |
| 2169 | var i = 0, | |
| 2170 | len = contexts.length; | |
| 2171 | for ( ; i < len; i++ ) { | |
| 2172 | Sizzle( selector, contexts[i], results ); | |
| 2173 | } | |
| 2174 | return results; | |
| 2175 | } | |
| 2176 | ||
| 2177 | function condense( unmatched, map, filter, context, xml ) { | |
| 2178 | var elem, | |
| 2179 | newUnmatched = [], | |
| 2180 | i = 0, | |
| 2181 | len = unmatched.length, | |
| 2182 | mapped = map != null; | |
| 2183 | ||
| 2184 | for ( ; i < len; i++ ) { | |
| 2185 | if ( (elem = unmatched[i]) ) { | |
| 2186 | if ( !filter || filter( elem, context, xml ) ) { | |
| 2187 | newUnmatched.push( elem ); | |
| 2188 | if ( mapped ) { | |
| 2189 | map.push( i ); | |
| 2190 | } | |
| 2191 | } | |
| 2192 | } | |
| 2193 | } | |
| 2194 | ||
| 2195 | return newUnmatched; | |
| 2196 | } | |
| 2197 | ||
| 2198 | function setMatcher( preFilter, selector, matcher, postFilter, postFinder, postSelector ) { | |
| 2199 | if ( postFilter && !postFilter[ expando ] ) { | |
| 2200 | postFilter = setMatcher( postFilter ); | |
| 2201 | } | |
| 2202 | if ( postFinder && !postFinder[ expando ] ) { | |
| 2203 | postFinder = setMatcher( postFinder, postSelector ); | |
| 2204 | } | |
| 2205 | return markFunction(function( seed, results, context, xml ) { | |
| 2206 | var temp, i, elem, | |
| 2207 | preMap = [], | |
| 2208 | postMap = [], | |
| 2209 | preexisting = results.length, | |
| 2210 | ||
| 2211 | // Get initial elements from seed or context | |
| 2212 | elems = seed || multipleContexts( selector || "*", context.nodeType ? [ context ] : context, [] ), | |
| 2213 | ||
| 2214 | // Prefilter to get matcher input, preserving a map for seed-results synchronization | |
| 2215 | matcherIn = preFilter && ( seed || !selector ) ? | |
| 2216 | condense( elems, preMap, preFilter, context, xml ) : | |
| 2217 | elems, | |
| 2218 | ||
| 2219 | matcherOut = matcher ? | |
| 2220 | // If we have a postFinder, or filtered seed, or non-seed postFilter or preexisting results, | |
| 2221 | postFinder || ( seed ? preFilter : preexisting || postFilter ) ? | |
| 2222 | ||
| 2223 | // ...intermediate processing is necessary | |
| 2224 | [] : | |
| 2225 | ||
| 2226 | // ...otherwise use results directly | |
| 2227 | results : | |
| 2228 | matcherIn; | |
| 2229 | ||
| 2230 | // Find primary matches | |
| 2231 | if ( matcher ) { | |
| 2232 | matcher( matcherIn, matcherOut, context, xml ); | |
| 2233 | } | |
| 2234 | ||
| 2235 | // Apply postFilter | |
| 2236 | if ( postFilter ) { | |
| 2237 | temp = condense( matcherOut, postMap ); | |
| 2238 | postFilter( temp, [], context, xml ); | |
| 2239 | ||
| 2240 | // Un-match failing elements by moving them back to matcherIn | |
| 2241 | i = temp.length; | |
| 2242 | while ( i-- ) { | |
| 2243 | if ( (elem = temp[i]) ) { | |
| 2244 | matcherOut[ postMap[i] ] = !(matcherIn[ postMap[i] ] = elem); | |
| 2245 | } | |
| 2246 | } | |
| 2247 | } | |
| 2248 | ||
| 2249 | if ( seed ) { | |
| 2250 | if ( postFinder || preFilter ) { | |
| 2251 | if ( postFinder ) { | |
| 2252 | // Get the final matcherOut by condensing this intermediate into postFinder contexts | |
| 2253 | temp = []; | |
| 2254 | i = matcherOut.length; | |
| 2255 | while ( i-- ) { | |
| 2256 | if ( (elem = matcherOut[i]) ) { | |
| 2257 | // Restore matcherIn since elem is not yet a final match | |
| 2258 | temp.push( (matcherIn[i] = elem) ); | |
| 2259 | } | |
| 2260 | } | |
| 2261 | postFinder( null, (matcherOut = []), temp, xml ); | |
| 2262 | } | |
| 2263 | ||
| 2264 | // Move matched elements from seed to results to keep them synchronized | |
| 2265 | i = matcherOut.length; | |
| 2266 | while ( i-- ) { | |
| 2267 | if ( (elem = matcherOut[i]) && | |
| 2268 | (temp = postFinder ? indexOf.call( seed, elem ) : preMap[i]) > -1 ) { | |
| 2269 | ||
| 2270 | seed[temp] = !(results[temp] = elem); | |
| 2271 | } | |
| 2272 | } | |
| 2273 | } | |
| 2274 | ||
| 2275 | // Add elements to results, through postFinder if defined | |
| 2276 | } else { | |
| 2277 | matcherOut = condense( | |
| 2278 | matcherOut === results ? | |
| 2279 | matcherOut.splice( preexisting, matcherOut.length ) : | |
| 2280 | matcherOut | |
| 2281 | ); | |
| 2282 | if ( postFinder ) { | |
| 2283 | postFinder( null, results, matcherOut, xml ); | |
| 2284 | } else { | |
| 2285 | push.apply( results, matcherOut ); | |
| 2286 | } | |
| 2287 | } | |
| 2288 | }); | |
| 2289 | } | |
| 2290 | ||
| 2291 | function matcherFromTokens( tokens ) { | |
| 2292 | var checkContext, matcher, j, | |
| 2293 | len = tokens.length, | |
| 2294 | leadingRelative = Expr.relative[ tokens[0].type ], | |
| 2295 | implicitRelative = leadingRelative || Expr.relative[" "], | |
| 2296 | i = leadingRelative ? 1 : 0, | |
| 2297 | ||
| 2298 | // The foundational matcher ensures that elements are reachable from top-level context(s) | |
| 2299 | matchContext = addCombinator( function( elem ) { | |
| 2300 | return elem === checkContext; | |
| 2301 | }, implicitRelative, true ), | |
| 2302 | matchAnyContext = addCombinator( function( elem ) { | |
| 2303 | return indexOf.call( checkContext, elem ) > -1; | |
| 2304 | }, implicitRelative, true ), | |
| 2305 | matchers = [ function( elem, context, xml ) { | |
| 2306 | return ( !leadingRelative && ( xml || context !== outermostContext ) ) || ( | |
| 2307 | (checkContext = context).nodeType ? | |
| 2308 | matchContext( elem, context, xml ) : | |
| 2309 | matchAnyContext( elem, context, xml ) ); | |
| 2310 | } ]; | |
| 2311 | ||
| 2312 | for ( ; i < len; i++ ) { | |
| 2313 | if ( (matcher = Expr.relative[ tokens[i].type ]) ) { | |
| 2314 | matchers = [ addCombinator(elementMatcher( matchers ), matcher) ]; | |
| 2315 | } else { | |
| 2316 | matcher = Expr.filter[ tokens[i].type ].apply( null, tokens[i].matches ); | |
| 2317 | ||
| 2318 | // Return special upon seeing a positional matcher | |
| 2319 | if ( matcher[ expando ] ) { | |
| 2320 | // Find the next relative operator (if any) for proper handling | |
| 2321 | j = ++i; | |
| 2322 | for ( ; j < len; j++ ) { | |
| 2323 | if ( Expr.relative[ tokens[j].type ] ) { | |
| 2324 | break; | |
| 2325 | } | |
| 2326 | } | |
| 2327 | return setMatcher( | |
| 2328 | i > 1 && elementMatcher( matchers ), | |
| 2329 | i > 1 && toSelector( | |
| 2330 | // If the preceding token was a descendant combinator, insert an implicit any-element `*` | |
| 2331 | tokens.slice( 0, i - 1 ).concat({ value: tokens[ i - 2 ].type === " " ? "*" : "" }) | |
| 2332 | ).replace( rtrim, "$1" ), | |
| 2333 | matcher, | |
| 2334 | i < j && matcherFromTokens( tokens.slice( i, j ) ), | |
| 2335 | j < len && matcherFromTokens( (tokens = tokens.slice( j )) ), | |
| 2336 | j < len && toSelector( tokens ) | |
| 2337 | ); | |
| 2338 | } | |
| 2339 | matchers.push( matcher ); | |
| 2340 | } | |
| 2341 | } | |
| 2342 | ||
| 2343 | return elementMatcher( matchers ); | |
| 2344 | } | |
| 2345 | ||
| 2346 | function matcherFromGroupMatchers( elementMatchers, setMatchers ) { | |
| 2347 | var bySet = setMatchers.length > 0, | |
| 2348 | byElement = elementMatchers.length > 0, | |
| 2349 | superMatcher = function( seed, context, xml, results, outermost ) { | |
| 2350 | var elem, j, matcher, | |
| 2351 | matchedCount = 0, | |
| 2352 | i = "0", | |
| 2353 | unmatched = seed && [], | |
| 2354 | setMatched = [], | |
| 2355 | contextBackup = outermostContext, | |
| 2356 | // We must always have either seed elements or outermost context | |
| 2357 | elems = seed || byElement && Expr.find["TAG"]( "*", outermost ), | |
| 2358 | // Use integer dirruns iff this is the outermost matcher | |
| 2359 | dirrunsUnique = (dirruns += contextBackup == null ? 1 : Math.random() || 0.1), | |
| 2360 | len = elems.length; | |
| 2361 | ||
| 2362 | if ( outermost ) { | |
| 2363 | outermostContext = context !== document && context; | |
| 2364 | } | |
| 2365 | ||
| 2366 | // Add elements passing elementMatchers directly to results | |
| 2367 | // Keep `i` a string if there are no elements so `matchedCount` will be "00" below | |
| 2368 | // Support: IE<9, Safari | |
| 2369 | // Tolerate NodeList properties (IE: "length"; Safari: <number>) matching elements by id | |
| 2370 | for ( ; i !== len && (elem = elems[i]) != null; i++ ) { | |
| 2371 | if ( byElement && elem ) { | |
| 2372 | j = 0; | |
| 2373 | while ( (matcher = elementMatchers[j++]) ) { | |
| 2374 | if ( matcher( elem, context, xml ) ) { | |
| 2375 | results.push( elem ); | |
| 2376 | break; | |
| 2377 | } | |
| 2378 | } | |
| 2379 | if ( outermost ) { | |
| 2380 | dirruns = dirrunsUnique; | |
| 2381 | } | |
| 2382 | } | |
| 2383 | ||
| 2384 | // Track unmatched elements for set filters | |
| 2385 | if ( bySet ) { | |
| 2386 | // They will have gone through all possible matchers | |
| 2387 | if ( (elem = !matcher && elem) ) { | |
| 2388 | matchedCount--; | |
| 2389 | } | |
| 2390 | ||
| 2391 | // Lengthen the array for every element, matched or not | |
| 2392 | if ( seed ) { | |
| 2393 | unmatched.push( elem ); | |
| 2394 | } | |
| 2395 | } | |
| 2396 | } | |
| 2397 | ||
| 2398 | // Apply set filters to unmatched elements | |
| 2399 | matchedCount += i; | |
| 2400 | if ( bySet && i !== matchedCount ) { | |
| 2401 | j = 0; | |
| 2402 | while ( (matcher = setMatchers[j++]) ) { | |
| 2403 | matcher( unmatched, setMatched, context, xml ); | |
| 2404 | } | |
| 2405 | ||
| 2406 | if ( seed ) { | |
| 2407 | // Reintegrate element matches to eliminate the need for sorting | |
| 2408 | if ( matchedCount > 0 ) { | |
| 2409 | while ( i-- ) { | |
| 2410 | if ( !(unmatched[i] || setMatched[i]) ) { | |
| 2411 | setMatched[i] = pop.call( results ); | |
| 2412 | } | |
| 2413 | } | |
| 2414 | } | |
| 2415 | ||
| 2416 | // Discard index placeholder values to get only actual matches | |
| 2417 | setMatched = condense( setMatched ); | |
| 2418 | } | |
| 2419 | ||
| 2420 | // Add matches to results | |
| 2421 | push.apply( results, setMatched ); | |
| 2422 | ||
| 2423 | // Seedless set matches succeeding multiple successful matchers stipulate sorting | |
| 2424 | if ( outermost && !seed && setMatched.length > 0 && | |
| 2425 | ( matchedCount + setMatchers.length ) > 1 ) { | |
| 2426 | ||
| 2427 | Sizzle.uniqueSort( results ); | |
| 2428 | } | |
| 2429 | } | |
| 2430 | ||
| 2431 | // Override manipulation of globals by nested matchers | |
| 2432 | if ( outermost ) { | |
| 2433 | dirruns = dirrunsUnique; | |
| 2434 | outermostContext = contextBackup; | |
| 2435 | } | |
| 2436 | ||
| 2437 | return unmatched; | |
| 2438 | }; | |
| 2439 | ||
| 2440 | return bySet ? | |
| 2441 | markFunction( superMatcher ) : | |
| 2442 | superMatcher; | |
| 2443 | } | |
| 2444 | ||
| 2445 | compile = Sizzle.compile = function( selector, match /* Internal Use Only */ ) { | |
| 2446 | var i, | |
| 2447 | setMatchers = [], | |
| 2448 | elementMatchers = [], | |
| 2449 | cached = compilerCache[ selector + " " ]; | |
| 2450 | ||
| 2451 | if ( !cached ) { | |
| 2452 | // Generate a function of recursive functions that can be used to check each element | |
| 2453 | if ( !match ) { | |
| 2454 | match = tokenize( selector ); | |
| 2455 | } | |
| 2456 | i = match.length; | |
| 2457 | while ( i-- ) { | |
| 2458 | cached = matcherFromTokens( match[i] ); | |
| 2459 | if ( cached[ expando ] ) { | |
| 2460 | setMatchers.push( cached ); | |
| 2461 | } else { | |
| 2462 | elementMatchers.push( cached ); | |
| 2463 | } | |
| 2464 | } | |
| 2465 | ||
| 2466 | // Cache the compiled function | |
| 2467 | cached = compilerCache( selector, matcherFromGroupMatchers( elementMatchers, setMatchers ) ); | |
| 2468 | ||
| 2469 | // Save selector and tokenization | |
| 2470 | cached.selector = selector; | |
| 2471 | } | |
| 2472 | return cached; | |
| 2473 | }; | |
| 2474 | ||
| 2475 | /** | |
| 2476 | * A low-level selection function that works with Sizzle's compiled | |
| 2477 | * selector functions | |
| 2478 | * @param {String|Function} selector A selector or a pre-compiled | |
| 2479 | * selector function built with Sizzle.compile | |
| 2480 | * @param {Element} context | |
| 2481 | * @param {Array} [results] | |
| 2482 | * @param {Array} [seed] A set of elements to match against | |
| 2483 | */ | |
| 2484 | select = Sizzle.select = function( selector, context, results, seed ) { | |
| 2485 | var i, tokens, token, type, find, | |
| 2486 | compiled = typeof selector === "function" && selector, | |
| 2487 | match = !seed && tokenize( (selector = compiled.selector || selector) ); | |
| 2488 | ||
| 2489 | results = results || []; | |
| 2490 | ||
| 2491 | // Try to minimize operations if there is no seed and only one group | |
| 2492 | if ( match.length === 1 ) { | |
| 2493 | ||
| 2494 | // Take a shortcut and set the context if the root selector is an ID | |
| 2495 | tokens = match[0] = match[0].slice( 0 ); | |
| 2496 | if ( tokens.length > 2 && (token = tokens[0]).type === "ID" && | |
| 2497 | support.getById && context.nodeType === 9 && documentIsHTML && | |
| 2498 | Expr.relative[ tokens[1].type ] ) { | |
| 2499 | ||
| 2500 | context = ( Expr.find["ID"]( token.matches[0].replace(runescape, funescape), context ) || [] )[0]; | |
| 2501 | if ( !context ) { | |
| 2502 | return results; | |
| 2503 | ||
| 2504 | // Precompiled matchers will still verify ancestry, so step up a level | |
| 2505 | } else if ( compiled ) { | |
| 2506 | context = context.parentNode; | |
| 2507 | } | |
| 2508 | ||
| 2509 | selector = selector.slice( tokens.shift().value.length ); | |
| 2510 | } | |
| 2511 | ||
| 2512 | // Fetch a seed set for right-to-left matching | |
| 2513 | i = matchExpr["needsContext"].test( selector ) ? 0 : tokens.length; | |
| 2514 | while ( i-- ) { | |
| 2515 | token = tokens[i]; | |
| 2516 | ||
| 2517 | // Abort if we hit a combinator | |
| 2518 | if ( Expr.relative[ (type = token.type) ] ) { | |
| 2519 | break; | |
| 2520 | } | |
| 2521 | if ( (find = Expr.find[ type ]) ) { | |
| 2522 | // Search, expanding context for leading sibling combinators | |
| 2523 | if ( (seed = find( | |
| 2524 | token.matches[0].replace( runescape, funescape ), | |
| 2525 | rsibling.test( tokens[0].type ) && testContext( context.parentNode ) || context | |
| 2526 | )) ) { | |
| 2527 | ||
| 2528 | // If seed is empty or no tokens remain, we can return early | |
| 2529 | tokens.splice( i, 1 ); | |
| 2530 | selector = seed.length && toSelector( tokens ); | |
| 2531 | if ( !selector ) { | |
| 2532 | push.apply( results, seed ); | |
| 2533 | return results; | |
| 2534 | } | |
| 2535 | ||
| 2536 | break; | |
| 2537 | } | |
| 2538 | } | |
| 2539 | } | |
| 2540 | } | |
| 2541 | ||
| 2542 | // Compile and execute a filtering function if one is not provided | |
| 2543 | // Provide `match` to avoid retokenization if we modified the selector above | |
| 2544 | ( compiled || compile( selector, match ) )( | |
| 2545 | seed, | |
| 2546 | context, | |
| 2547 | !documentIsHTML, | |
| 2548 | results, | |
| 2549 | rsibling.test( selector ) && testContext( context.parentNode ) || context | |
| 2550 | ); | |
| 2551 | return results; | |
| 2552 | }; | |
| 2553 | ||
| 2554 | // One-time assignments | |
| 2555 | ||
| 2556 | // Sort stability | |
| 2557 | support.sortStable = expando.split("").sort( sortOrder ).join("") === expando; | |
| 2558 | ||
| 2559 | // Support: Chrome<14 | |
| 2560 | // Always assume duplicates if they aren't passed to the comparison function | |
| 2561 | support.detectDuplicates = !!hasDuplicate; | |
| 2562 | ||
| 2563 | // Initialize against the default document | |
| 2564 | setDocument(); | |
| 2565 | ||
| 2566 | // Support: Webkit<537.32 - Safari 6.0.3/Chrome 25 (fixed in Chrome 27) | |
| 2567 | // Detached nodes confoundingly follow *each other* | |
| 2568 | support.sortDetached = assert(function( div1 ) { | |
| 2569 | // Should return 1, but returns 4 (following) | |
| 2570 | return div1.compareDocumentPosition( document.createElement("div") ) & 1; | |
| 2571 | }); | |
| 2572 | ||
| 2573 | // Support: IE<8 | |
| 2574 | // Prevent attribute/property "interpolation" | |
| 2575 | // http://msdn.microsoft.com/en-us/library/ms536429%28VS.85%29.aspx | |
| 2576 | if ( !assert(function( div ) { | |
| 2577 | div.innerHTML = "<a href='#'></a>"; | |
| 2578 | return div.firstChild.getAttribute("href") === "#" ; | |
| 2579 | }) ) { | |
| 2580 | addHandle( "type|href|height|width", function( elem, name, isXML ) { | |
| 2581 | if ( !isXML ) { | |
| 2582 | return elem.getAttribute( name, name.toLowerCase() === "type" ? 1 : 2 ); | |
| 2583 | } | |
| 2584 | }); | |
| 2585 | } | |
| 2586 | ||
| 2587 | // Support: IE<9 | |
| 2588 | // Use defaultValue in place of getAttribute("value") | |
| 2589 | if ( !support.attributes || !assert(function( div ) { | |
| 2590 | div.innerHTML = "<input/>"; | |
| 2591 | div.firstChild.setAttribute( "value", "" ); | |
| 2592 | return div.firstChild.getAttribute( "value" ) === ""; | |
| 2593 | }) ) { | |
| 2594 | addHandle( "value", function( elem, name, isXML ) { | |
| 2595 | if ( !isXML && elem.nodeName.toLowerCase() === "input" ) { | |
| 2596 | return elem.defaultValue; | |
| 2597 | } | |
| 2598 | }); | |
| 2599 | } | |
| 2600 | ||
| 2601 | // Support: IE<9 | |
| 2602 | // Use getAttributeNode to fetch booleans when getAttribute lies | |
| 2603 | if ( !assert(function( div ) { | |
| 2604 | return div.getAttribute("disabled") == null; | |
| 2605 | }) ) { | |
| 2606 | addHandle( booleans, function( elem, name, isXML ) { | |
| 2607 | var val; | |
| 2608 | if ( !isXML ) { | |
| 2609 | return elem[ name ] === true ? name.toLowerCase() : | |
| 2610 | (val = elem.getAttributeNode( name )) && val.specified ? | |
| 2611 | val.value : | |
| 2612 | null; | |
| 2613 | } | |
| 2614 | }); | |
| 2615 | } | |
| 2616 | ||
| 2617 | return Sizzle; | |
| 2618 | ||
| 2619 | })( window ); | |
| 2620 | ||
| 2621 | ||
| 2622 | ||
| 2623 | jQuery.find = Sizzle; | |
| 2624 | jQuery.expr = Sizzle.selectors; | |
| 2625 | jQuery.expr[":"] = jQuery.expr.pseudos; | |
| 2626 | jQuery.unique = Sizzle.uniqueSort; | |
| 2627 | jQuery.text = Sizzle.getText; | |
| 2628 | jQuery.isXMLDoc = Sizzle.isXML; | |
| 2629 | jQuery.contains = Sizzle.contains; | |
| 2630 | ||
| 2631 | ||
| 2632 | ||
| 2633 | var rneedsContext = jQuery.expr.match.needsContext; | |
| 2634 | ||
| 2635 | var rsingleTag = (/^<(\w+)\s*\/?>(?:<\/\1>|)$/); | |
| 2636 | ||
| 2637 | ||
| 2638 | ||
| 2639 | var risSimple = /^.[^:#\[\.,]*$/; | |
| 2640 | ||
| 2641 | // Implement the identical functionality for filter and not | |
| 2642 | function winnow( elements, qualifier, not ) { | |
| 2643 | if ( jQuery.isFunction( qualifier ) ) { | |
| 2644 | return jQuery.grep( elements, function( elem, i ) { | |
| 2645 | /* jshint -W018 */ | |
| 2646 | return !!qualifier.call( elem, i, elem ) !== not; | |
| 2647 | }); | |
| 2648 | ||
| 2649 | } | |
| 2650 | ||
| 2651 | if ( qualifier.nodeType ) { | |
| 2652 | return jQuery.grep( elements, function( elem ) { | |
| 2653 | return ( elem === qualifier ) !== not; | |
| 2654 | }); | |
| 2655 | ||
| 2656 | } | |
| 2657 | ||
| 2658 | if ( typeof qualifier === "string" ) { | |
| 2659 | if ( risSimple.test( qualifier ) ) { | |
| 2660 | return jQuery.filter( qualifier, elements, not ); | |
| 2661 | } | |
| 2662 | ||
| 2663 | qualifier = jQuery.filter( qualifier, elements ); | |
| 2664 | } | |
| 2665 | ||
| 2666 | return jQuery.grep( elements, function( elem ) { | |
| 2667 | return ( jQuery.inArray( elem, qualifier ) >= 0 ) !== not; | |
| 2668 | }); | |
| 2669 | } | |
| 2670 | ||
| 2671 | jQuery.filter = function( expr, elems, not ) { | |
| 2672 | var elem = elems[ 0 ]; | |
| 2673 | ||
| 2674 | if ( not ) { | |
| 2675 | expr = ":not(" + expr + ")"; | |
| 2676 | } | |
| 2677 | ||
| 2678 | return elems.length === 1 && elem.nodeType === 1 ? | |
| 2679 | jQuery.find.matchesSelector( elem, expr ) ? [ elem ] : [] : | |
| 2680 | jQuery.find.matches( expr, jQuery.grep( elems, function( elem ) { | |
| 2681 | return elem.nodeType === 1; | |
| 2682 | })); | |
| 2683 | }; | |
| 2684 | ||
| 2685 | jQuery.fn.extend({ | |
| 2686 | find: function( selector ) { | |
| 2687 | var i, | |
| 2688 | ret = [], | |
| 2689 | self = this, | |
| 2690 | len = self.length; | |
| 2691 | ||
| 2692 | if ( typeof selector !== "string" ) { | |
| 2693 | return this.pushStack( jQuery( selector ).filter(function() { | |
| 2694 | for ( i = 0; i < len; i++ ) { | |
| 2695 | if ( jQuery.contains( self[ i ], this ) ) { | |
| 2696 | return true; | |
| 2697 | } | |
| 2698 | } | |
| 2699 | }) ); | |
| 2700 | } | |
| 2701 | ||
| 2702 | for ( i = 0; i < len; i++ ) { | |
| 2703 | jQuery.find( selector, self[ i ], ret ); | |
| 2704 | } | |
| 2705 | ||
| 2706 | // Needed because $( selector, context ) becomes $( context ).find( selector ) | |
| 2707 | ret = this.pushStack( len > 1 ? jQuery.unique( ret ) : ret ); | |
| 2708 | ret.selector = this.selector ? this.selector + " " + selector : selector; | |
| 2709 | return ret; | |
| 2710 | }, | |
| 2711 | filter: function( selector ) { | |
| 2712 | return this.pushStack( winnow(this, selector || [], false) ); | |
| 2713 | }, | |
| 2714 | not: function( selector ) { | |
| 2715 | return this.pushStack( winnow(this, selector || [], true) ); | |
| 2716 | }, | |
| 2717 | is: function( selector ) { | |
| 2718 | return !!winnow( | |
| 2719 | this, | |
| 2720 | ||
| 2721 | // If this is a positional/relative selector, check membership in the returned set | |
| 2722 | // so $("p:first").is("p:last") won't return true for a doc with two "p". | |
| 2723 | typeof selector === "string" && rneedsContext.test( selector ) ? | |
| 2724 | jQuery( selector ) : | |
| 2725 | selector || [], | |
| 2726 | false | |
| 2727 | ).length; | |
| 2728 | } | |
| 2729 | }); | |
| 2730 | ||
| 2731 | ||
| 2732 | // Initialize a jQuery object | |
| 2733 | ||
| 2734 | ||
| 2735 | // A central reference to the root jQuery(document) | |
| 2736 | var rootjQuery, | |
| 2737 | ||
| 2738 | // Use the correct document accordingly with window argument (sandbox) | |
| 2739 | document = window.document, | |
| 2740 | ||
| 2741 | // A simple way to check for HTML strings | |
| 2742 | // Prioritize #id over <tag> to avoid XSS via location.hash (#9521) | |
| 2743 | // Strict HTML recognition (#11290: must start with <) | |
| 2744 | rquickExpr = /^(?:\s*(<[\w\W]+>)[^>]*|#([\w-]*))$/, | |
| 2745 | ||
| 2746 | init = jQuery.fn.init = function( selector, context ) { | |
| 2747 | var match, elem; | |
| 2748 | ||
| 2749 | // HANDLE: $(""), $(null), $(undefined), $(false) | |
| 2750 | if ( !selector ) { | |
| 2751 | return this; | |
| 2752 | } | |
| 2753 | ||
| 2754 | // Handle HTML strings | |
| 2755 | if ( typeof selector === "string" ) { | |
| 2756 | if ( selector.charAt(0) === "<" && selector.charAt( selector.length - 1 ) === ">" && selector.length >= 3 ) { | |
| 2757 | // Assume that strings that start and end with <> are HTML and skip the regex check | |
| 2758 | match = [ null, selector, null ]; | |
| 2759 | ||
| 2760 | } else { | |
| 2761 | match = rquickExpr.exec( selector ); | |
| 2762 | } | |
| 2763 | ||
| 2764 | // Match html or make sure no context is specified for #id | |
| 2765 | if ( match && (match[1] || !context) ) { | |
| 2766 | ||
| 2767 | // HANDLE: $(html) -> $(array) | |
| 2768 | if ( match[1] ) { | |
| 2769 | context = context instanceof jQuery ? context[0] : context; | |
| 2770 | ||
| 2771 | // scripts is true for back-compat | |
| 2772 | // Intentionally let the error be thrown if parseHTML is not present | |
| 2773 | jQuery.merge( this, jQuery.parseHTML( | |
| 2774 | match[1], | |
| 2775 | context && context.nodeType ? context.ownerDocument || context : document, | |
| 2776 | true | |
| 2777 | ) ); | |
| 2778 | ||
| 2779 | // HANDLE: $(html, props) | |
| 2780 | if ( rsingleTag.test( match[1] ) && jQuery.isPlainObject( context ) ) { | |
| 2781 | for ( match in context ) { | |
| 2782 | // Properties of context are called as methods if possible | |
| 2783 | if ( jQuery.isFunction( this[ match ] ) ) { | |
| 2784 | this[ match ]( context[ match ] ); | |
| 2785 | ||
| 2786 | // ...and otherwise set as attributes | |
| 2787 | } else { | |
| 2788 | this.attr( match, context[ match ] ); | |
| 2789 | } | |
| 2790 | } | |
| 2791 | } | |
| 2792 | ||
| 2793 | return this; | |
| 2794 | ||
| 2795 | // HANDLE: $(#id) | |
| 2796 | } else { | |
| 2797 | elem = document.getElementById( match[2] ); | |
| 2798 | ||
| 2799 | // Check parentNode to catch when Blackberry 4.6 returns | |
| 2800 | // nodes that are no longer in the document #6963 | |
| 2801 | if ( elem && elem.parentNode ) { | |
| 2802 | // Handle the case where IE and Opera return items | |
| 2803 | // by name instead of ID | |
| 2804 | if ( elem.id !== match[2] ) { | |
| 2805 | return rootjQuery.find( selector ); | |
| 2806 | } | |
| 2807 | ||
| 2808 | // Otherwise, we inject the element directly into the jQuery object | |
| 2809 | this.length = 1; | |
| 2810 | this[0] = elem; | |
| 2811 | } | |
| 2812 | ||
| 2813 | this.context = document; | |
| 2814 | this.selector = selector; | |
| 2815 | return this; | |
| 2816 | } | |
| 2817 | ||
| 2818 | // HANDLE: $(expr, $(...)) | |
| 2819 | } else if ( !context || context.jquery ) { | |
| 2820 | return ( context || rootjQuery ).find( selector ); | |
| 2821 | ||
| 2822 | // HANDLE: $(expr, context) | |
| 2823 | // (which is just equivalent to: $(context).find(expr) | |
| 2824 | } else { | |
| 2825 | return this.constructor( context ).find( selector ); | |
| 2826 | } | |
| 2827 | ||
| 2828 | // HANDLE: $(DOMElement) | |
| 2829 | } else if ( selector.nodeType ) { | |
| 2830 | this.context = this[0] = selector; | |
| 2831 | this.length = 1; | |
| 2832 | return this; | |
| 2833 | ||
| 2834 | // HANDLE: $(function) | |
| 2835 | // Shortcut for document ready | |
| 2836 | } else if ( jQuery.isFunction( selector ) ) { | |
| 2837 | return typeof rootjQuery.ready !== "undefined" ? | |
| 2838 | rootjQuery.ready( selector ) : | |
| 2839 | // Execute immediately if ready is not present | |
| 2840 | selector( jQuery ); | |
| 2841 | } | |
| 2842 | ||
| 2843 | if ( selector.selector !== undefined ) { | |
| 2844 | this.selector = selector.selector; | |
| 2845 | this.context = selector.context; | |
| 2846 | } | |
| 2847 | ||
| 2848 | return jQuery.makeArray( selector, this ); | |
| 2849 | }; | |
| 2850 | ||
| 2851 | // Give the init function the jQuery prototype for later instantiation | |
| 2852 | init.prototype = jQuery.fn; | |
| 2853 | ||
| 2854 | // Initialize central reference | |
| 2855 | rootjQuery = jQuery( document ); | |
| 2856 | ||
| 2857 | ||
| 2858 | var rparentsprev = /^(?:parents|prev(?:Until|All))/, | |
| 2859 | // methods guaranteed to produce a unique set when starting from a unique set | |
| 2860 | guaranteedUnique = { | |
| 2861 | children: true, | |
| 2862 | contents: true, | |
| 2863 | next: true, | |
| 2864 | prev: true | |
| 2865 | }; | |
| 2866 | ||
| 2867 | jQuery.extend({ | |
| 2868 | dir: function( elem, dir, until ) { | |
| 2869 | var matched = [], | |
| 2870 | cur = elem[ dir ]; | |
| 2871 | ||
| 2872 | while ( cur && cur.nodeType !== 9 && (until === undefined || cur.nodeType !== 1 || !jQuery( cur ).is( until )) ) { | |
| 2873 | if ( cur.nodeType === 1 ) { | |
| 2874 | matched.push( cur ); | |
| 2875 | } | |
| 2876 | cur = cur[dir]; | |
| 2877 | } | |
| 2878 | return matched; | |
| 2879 | }, | |
| 2880 | ||
| 2881 | sibling: function( n, elem ) { | |
| 2882 | var r = []; | |
| 2883 | ||
| 2884 | for ( ; n; n = n.nextSibling ) { | |
| 2885 | if ( n.nodeType === 1 && n !== elem ) { | |
| 2886 | r.push( n ); | |
| 2887 | } | |
| 2888 | } | |
| 2889 | ||
| 2890 | return r; | |
| 2891 | } | |
| 2892 | }); | |
| 2893 | ||
| 2894 | jQuery.fn.extend({ | |
| 2895 | has: function( target ) { | |
| 2896 | var i, | |
| 2897 | targets = jQuery( target, this ), | |
| 2898 | len = targets.length; | |
| 2899 | ||
| 2900 | return this.filter(function() { | |
| 2901 | for ( i = 0; i < len; i++ ) { | |
| 2902 | if ( jQuery.contains( this, targets[i] ) ) { | |
| 2903 | return true; | |
| 2904 | } | |
| 2905 | } | |
| 2906 | }); | |
| 2907 | }, | |
| 2908 | ||
| 2909 | closest: function( selectors, context ) { | |
| 2910 | var cur, | |
| 2911 | i = 0, | |
| 2912 | l = this.length, | |
| 2913 | matched = [], | |
| 2914 | pos = rneedsContext.test( selectors ) || typeof selectors !== "string" ? | |
| 2915 | jQuery( selectors, context || this.context ) : | |
| 2916 | 0; | |
| 2917 | ||
| 2918 | for ( ; i < l; i++ ) { | |
| 2919 | for ( cur = this[i]; cur && cur !== context; cur = cur.parentNode ) { | |
| 2920 | // Always skip document fragments | |
| 2921 | if ( cur.nodeType < 11 && (pos ? | |
| 2922 | pos.index(cur) > -1 : | |
| 2923 | ||
| 2924 | // Don't pass non-elements to Sizzle | |
| 2925 | cur.nodeType === 1 && | |
| 2926 | jQuery.find.matchesSelector(cur, selectors)) ) { | |
| 2927 | ||
| 2928 | matched.push( cur ); | |
| 2929 | break; | |
| 2930 | } | |
| 2931 | } | |
| 2932 | } | |
| 2933 | ||
| 2934 | return this.pushStack( matched.length > 1 ? jQuery.unique( matched ) : matched ); | |
| 2935 | }, | |
| 2936 | ||
| 2937 | // Determine the position of an element within | |
| 2938 | // the matched set of elements | |
| 2939 | index: function( elem ) { | |
| 2940 | ||
| 2941 | // No argument, return index in parent | |
| 2942 | if ( !elem ) { | |
| 2943 | return ( this[0] && this[0].parentNode ) ? this.first().prevAll().length : -1; | |
| 2944 | } | |
| 2945 | ||
| 2946 | // index in selector | |
| 2947 | if ( typeof elem === "string" ) { | |
| 2948 | return jQuery.inArray( this[0], jQuery( elem ) ); | |
| 2949 | } | |
| 2950 | ||
| 2951 | // Locate the position of the desired element | |
| 2952 | return jQuery.inArray( | |
| 2953 | // If it receives a jQuery object, the first element is used | |
| 2954 | elem.jquery ? elem[0] : elem, this ); | |
| 2955 | }, | |
| 2956 | ||
| 2957 | add: function( selector, context ) { | |
| 2958 | return this.pushStack( | |
| 2959 | jQuery.unique( | |
| 2960 | jQuery.merge( this.get(), jQuery( selector, context ) ) | |
| 2961 | ) | |
| 2962 | ); | |
| 2963 | }, | |
| 2964 | ||
| 2965 | addBack: function( selector ) { | |
| 2966 | return this.add( selector == null ? | |
| 2967 | this.prevObject : this.prevObject.filter(selector) | |
| 2968 | ); | |
| 2969 | } | |
| 2970 | }); | |
| 2971 | ||
| 2972 | function sibling( cur, dir ) { | |
| 2973 | do { | |
| 2974 | cur = cur[ dir ]; | |
| 2975 | } while ( cur && cur.nodeType !== 1 ); | |
| 2976 | ||
| 2977 | return cur; | |
| 2978 | } | |
| 2979 | ||
| 2980 | jQuery.each({ | |
| 2981 | parent: function( elem ) { | |
| 2982 | var parent = elem.parentNode; | |
| 2983 | return parent && parent.nodeType !== 11 ? parent : null; | |
| 2984 | }, | |
| 2985 | parents: function( elem ) { | |
| 2986 | return jQuery.dir( elem, "parentNode" ); | |
| 2987 | }, | |
| 2988 | parentsUntil: function( elem, i, until ) { | |
| 2989 | return jQuery.dir( elem, "parentNode", until ); | |
| 2990 | }, | |
| 2991 | next: function( elem ) { | |
| 2992 | return sibling( elem, "nextSibling" ); | |
| 2993 | }, | |
| 2994 | prev: function( elem ) { | |
| 2995 | return sibling( elem, "previousSibling" ); | |
| 2996 | }, | |
| 2997 | nextAll: function( elem ) { | |
| 2998 | return jQuery.dir( elem, "nextSibling" ); | |
| 2999 | }, | |
| 3000 | prevAll: function( elem ) { | |
| 3001 | return jQuery.dir( elem, "previousSibling" ); | |
| 3002 | }, | |
| 3003 | nextUntil: function( elem, i, until ) { | |
| 3004 | return jQuery.dir( elem, "nextSibling", until ); | |
| 3005 | }, | |
| 3006 | prevUntil: function( elem, i, until ) { | |
| 3007 | return jQuery.dir( elem, "previousSibling", until ); | |
| 3008 | }, | |
| 3009 | siblings: function( elem ) { | |
| 3010 | return jQuery.sibling( ( elem.parentNode || {} ).firstChild, elem ); | |
| 3011 | }, | |
| 3012 | children: function( elem ) { | |
| 3013 | return jQuery.sibling( elem.firstChild ); | |
| 3014 | }, | |
| 3015 | contents: function( elem ) { | |
| 3016 | return jQuery.nodeName( elem, "iframe" ) ? | |
| 3017 | elem.contentDocument || elem.contentWindow.document : | |
| 3018 | jQuery.merge( [], elem.childNodes ); | |
| 3019 | } | |
| 3020 | }, function( name, fn ) { | |
| 3021 | jQuery.fn[ name ] = function( until, selector ) { | |
| 3022 | var ret = jQuery.map( this, fn, until ); | |
| 3023 | ||
| 3024 | if ( name.slice( -5 ) !== "Until" ) { | |
| 3025 | selector = until; | |
| 3026 | } | |
| 3027 | ||
| 3028 | if ( selector && typeof selector === "string" ) { | |
| 3029 | ret = jQuery.filter( selector, ret ); | |
| 3030 | } | |
| 3031 | ||
| 3032 | if ( this.length > 1 ) { | |
| 3033 | // Remove duplicates | |
| 3034 | if ( !guaranteedUnique[ name ] ) { | |
| 3035 | ret = jQuery.unique( ret ); | |
| 3036 | } | |
| 3037 | ||
| 3038 | // Reverse order for parents* and prev-derivatives | |
| 3039 | if ( rparentsprev.test( name ) ) { | |
| 3040 | ret = ret.reverse(); | |
| 3041 | } | |
| 3042 | } | |
| 3043 | ||
| 3044 | return this.pushStack( ret ); | |
| 3045 | }; | |
| 3046 | }); | |
| 3047 | var rnotwhite = (/\S+/g); | |
| 3048 | ||
| 3049 | ||
| 3050 | ||
| 3051 | // String to Object options format cache | |
| 3052 | var optionsCache = {}; | |
| 3053 | ||
| 3054 | // Convert String-formatted options into Object-formatted ones and store in cache | |
| 3055 | function createOptions( options ) { | |
| 3056 | var object = optionsCache[ options ] = {}; | |
| 3057 | jQuery.each( options.match( rnotwhite ) || [], function( _, flag ) { | |
| 3058 | object[ flag ] = true; | |
| 3059 | }); | |
| 3060 | return object; | |
| 3061 | } | |
| 3062 | ||
| 3063 | /* | |
| 3064 | * Create a callback list using the following parameters: | |
| 3065 | * | |
| 3066 | * options: an optional list of space-separated options that will change how | |
| 3067 | * the callback list behaves or a more traditional option object | |
| 3068 | * | |
| 3069 | * By default a callback list will act like an event callback list and can be | |
| 3070 | * "fired" multiple times. | |
| 3071 | * | |
| 3072 | * Possible options: | |
| 3073 | * | |
| 3074 | * once: will ensure the callback list can only be fired once (like a Deferred) | |
| 3075 | * | |
| 3076 | * memory: will keep track of previous values and will call any callback added | |
| 3077 | * after the list has been fired right away with the latest "memorized" | |
| 3078 | * values (like a Deferred) | |
| 3079 | * | |
| 3080 | * unique: will ensure a callback can only be added once (no duplicate in the list) | |
| 3081 | * | |
| 3082 | * stopOnFalse: interrupt callings when a callback returns false | |
| 3083 | * | |
| 3084 | */ | |
| 3085 | jQuery.Callbacks = function( options ) { | |
| 3086 | ||
| 3087 | // Convert options from String-formatted to Object-formatted if needed | |
| 3088 | // (we check in cache first) | |
| 3089 | options = typeof options === "string" ? | |
| 3090 | ( optionsCache[ options ] || createOptions( options ) ) : | |
| 3091 | jQuery.extend( {}, options ); | |
| 3092 | ||
| 3093 | var // Flag to know if list is currently firing | |
| 3094 | firing, | |
| 3095 | // Last fire value (for non-forgettable lists) | |
| 3096 | memory, | |
| 3097 | // Flag to know if list was already fired | |
| 3098 | fired, | |
| 3099 | // End of the loop when firing | |
| 3100 | firingLength, | |
| 3101 | // Index of currently firing callback (modified by remove if needed) | |
| 3102 | firingIndex, | |
| 3103 | // First callback to fire (used internally by add and fireWith) | |
| 3104 | firingStart, | |
| 3105 | // Actual callback list | |
| 3106 | list = [], | |
| 3107 | // Stack of fire calls for repeatable lists | |
| 3108 | stack = !options.once && [], | |
| 3109 | // Fire callbacks | |
| 3110 | fire = function( data ) { | |
| 3111 | memory = options.memory && data; | |
| 3112 | fired = true; | |
| 3113 | firingIndex = firingStart || 0; | |
| 3114 | firingStart = 0; | |
| 3115 | firingLength = list.length; | |
| 3116 | firing = true; | |
| 3117 | for ( ; list && firingIndex < firingLength; firingIndex++ ) { | |
| 3118 | if ( list[ firingIndex ].apply( data[ 0 ], data[ 1 ] ) === false && options.stopOnFalse ) { | |
| 3119 | memory = false; // To prevent further calls using add | |
| 3120 | break; | |
| 3121 | } | |
| 3122 | } | |
| 3123 | firing = false; | |
| 3124 | if ( list ) { | |
| 3125 | if ( stack ) { | |
| 3126 | if ( stack.length ) { | |
| 3127 | fire( stack.shift() ); | |
| 3128 | } | |
| 3129 | } else if ( memory ) { | |
| 3130 | list = []; | |
| 3131 | } else { | |
| 3132 | self.disable(); | |
| 3133 | } | |
| 3134 | } | |
| 3135 | }, | |
| 3136 | // Actual Callbacks object | |
| 3137 | self = { | |
| 3138 | // Add a callback or a collection of callbacks to the list | |
| 3139 | add: function() { | |
| 3140 | if ( list ) { | |
| 3141 | // First, we save the current length | |
| 3142 | var start = list.length; | |
| 3143 | (function add( args ) { | |
| 3144 | jQuery.each( args, function( _, arg ) { | |
| 3145 | var type = jQuery.type( arg ); | |
| 3146 | if ( type === "function" ) { | |
| 3147 | if ( !options.unique || !self.has( arg ) ) { | |
| 3148 | list.push( arg ); | |
| 3149 | } | |
| 3150 | } else if ( arg && arg.length && type !== "string" ) { | |
| 3151 | // Inspect recursively | |
| 3152 | add( arg ); | |
| 3153 | } | |
| 3154 | }); | |
| 3155 | })( arguments ); | |
| 3156 | // Do we need to add the callbacks to the | |
| 3157 | // current firing batch? | |
| 3158 | if ( firing ) { | |
| 3159 | firingLength = list.length; | |
| 3160 | // With memory, if we're not firing then | |
| 3161 | // we should call right away | |
| 3162 | } else if ( memory ) { | |
| 3163 | firingStart = start; | |
| 3164 | fire( memory ); | |
| 3165 | } | |
| 3166 | } | |
| 3167 | return this; | |
| 3168 | }, | |
| 3169 | // Remove a callback from the list | |
| 3170 | remove: function() { | |
| 3171 | if ( list ) { | |
| 3172 | jQuery.each( arguments, function( _, arg ) { | |
| 3173 | var index; | |
| 3174 | while ( ( index = jQuery.inArray( arg, list, index ) ) > -1 ) { | |
| 3175 | list.splice( index, 1 ); | |
| 3176 | // Handle firing indexes | |
| 3177 | if ( firing ) { | |
| 3178 | if ( index <= firingLength ) { | |
| 3179 | firingLength--; | |
| 3180 | } | |
| 3181 | if ( index <= firingIndex ) { | |
| 3182 | firingIndex--; | |
| 3183 | } | |
| 3184 | } | |
| 3185 | } | |
| 3186 | }); | |
| 3187 | } | |
| 3188 | return this; | |
| 3189 | }, | |
| 3190 | // Check if a given callback is in the list. | |
| 3191 | // If no argument is given, return whether or not list has callbacks attached. | |
| 3192 | has: function( fn ) { | |
| 3193 | return fn ? jQuery.inArray( fn, list ) > -1 : !!( list && list.length ); | |
| 3194 | }, | |
| 3195 | // Remove all callbacks from the list | |
| 3196 | empty: function() { | |
| 3197 | list = []; | |
| 3198 | firingLength = 0; | |
| 3199 | return this; | |
| 3200 | }, | |
| 3201 | // Have the list do nothing anymore | |
| 3202 | disable: function() { | |
| 3203 | list = stack = memory = undefined; | |
| 3204 | return this; | |
| 3205 | }, | |
| 3206 | // Is it disabled? | |
| 3207 | disabled: function() { | |
| 3208 | return !list; | |
| 3209 | }, | |
| 3210 | // Lock the list in its current state | |
| 3211 | lock: function() { | |
| 3212 | stack = undefined; | |
| 3213 | if ( !memory ) { | |
| 3214 | self.disable(); | |
| 3215 | } | |
| 3216 | return this; | |
| 3217 | }, | |
| 3218 | // Is it locked? | |
| 3219 | locked: function() { | |
| 3220 | return !stack; | |
| 3221 | }, | |
| 3222 | // Call all callbacks with the given context and arguments | |
| 3223 | fireWith: function( context, args ) { | |
| 3224 | if ( list && ( !fired || stack ) ) { | |
| 3225 | args = args || []; | |
| 3226 | args = [ context, args.slice ? args.slice() : args ]; | |
| 3227 | if ( firing ) { | |
| 3228 | stack.push( args ); | |
| 3229 | } else { | |
| 3230 | fire( args ); | |
| 3231 | } | |
| 3232 | } | |
| 3233 | return this; | |
| 3234 | }, | |
| 3235 | // Call all the callbacks with the given arguments | |
| 3236 | fire: function() { | |
| 3237 | self.fireWith( this, arguments ); | |
| 3238 | return this; | |
| 3239 | }, | |
| 3240 | // To know if the callbacks have already been called at least once | |
| 3241 | fired: function() { | |
| 3242 | return !!fired; | |
| 3243 | } | |
| 3244 | }; | |
| 3245 | ||
| 3246 | return self; | |
| 3247 | }; | |
| 3248 | ||
| 3249 | ||
| 3250 | jQuery.extend({ | |
| 3251 | ||
| 3252 | Deferred: function( func ) { | |
| 3253 | var tuples = [ | |
| 3254 | // action, add listener, listener list, final state | |
| 3255 | [ "resolve", "done", jQuery.Callbacks("once memory"), "resolved" ], | |
| 3256 | [ "reject", "fail", jQuery.Callbacks("once memory"), "rejected" ], | |
| 3257 | [ "notify", "progress", jQuery.Callbacks("memory") ] | |
| 3258 | ], | |
| 3259 | state = "pending", | |
| 3260 | promise = { | |
| 3261 | state: function() { | |
| 3262 | return state; | |
| 3263 | }, | |
| 3264 | always: function() { | |
| 3265 | deferred.done( arguments ).fail( arguments ); | |
| 3266 | return this; | |
| 3267 | }, | |
| 3268 | then: function( /* fnDone, fnFail, fnProgress */ ) { | |
| 3269 | var fns = arguments; | |
| 3270 | return jQuery.Deferred(function( newDefer ) { | |
| 3271 | jQuery.each( tuples, function( i, tuple ) { | |
| 3272 | var fn = jQuery.isFunction( fns[ i ] ) && fns[ i ]; | |
| 3273 | // deferred[ done | fail | progress ] for forwarding actions to newDefer | |
| 3274 | deferred[ tuple[1] ](function() { | |
| 3275 | var returned = fn && fn.apply( this, arguments ); | |
| 3276 | if ( returned && jQuery.isFunction( returned.promise ) ) { | |
| 3277 | returned.promise() | |
| 3278 | .done( newDefer.resolve ) | |
| 3279 | .fail( newDefer.reject ) | |
| 3280 | .progress( newDefer.notify ); | |
| 3281 | } else { | |
| 3282 | newDefer[ tuple[ 0 ] + "With" ]( this === promise ? newDefer.promise() : this, fn ? [ returned ] : arguments ); | |
| 3283 | } | |
| 3284 | }); | |
| 3285 | }); | |
| 3286 | fns = null; | |
| 3287 | }).promise(); | |
| 3288 | }, | |
| 3289 | // Get a promise for this deferred | |
| 3290 | // If obj is provided, the promise aspect is added to the object | |
| 3291 | promise: function( obj ) { | |
| 3292 | return obj != null ? jQuery.extend( obj, promise ) : promise; | |
| 3293 | } | |
| 3294 | }, | |
| 3295 | deferred = {}; | |
| 3296 | ||
| 3297 | // Keep pipe for back-compat | |
| 3298 | promise.pipe = promise.then; | |
| 3299 | ||
| 3300 | // Add list-specific methods | |
| 3301 | jQuery.each( tuples, function( i, tuple ) { | |
| 3302 | var list = tuple[ 2 ], | |
| 3303 | stateString = tuple[ 3 ]; | |
| 3304 | ||
| 3305 | // promise[ done | fail | progress ] = list.add | |
| 3306 | promise[ tuple[1] ] = list.add; | |
| 3307 | ||
| 3308 | // Handle state | |
| 3309 | if ( stateString ) { | |
| 3310 | list.add(function() { | |
| 3311 | // state = [ resolved | rejected ] | |
| 3312 | state = stateString; | |
| 3313 | ||
| 3314 | // [ reject_list | resolve_list ].disable; progress_list.lock | |
| 3315 | }, tuples[ i ^ 1 ][ 2 ].disable, tuples[ 2 ][ 2 ].lock ); | |
| 3316 | } | |
| 3317 | ||
| 3318 | // deferred[ resolve | reject | notify ] | |
| 3319 | deferred[ tuple[0] ] = function() { | |
| 3320 | deferred[ tuple[0] + "With" ]( this === deferred ? promise : this, arguments ); | |
| 3321 | return this; | |
| 3322 | }; | |
| 3323 | deferred[ tuple[0] + "With" ] = list.fireWith; | |
| 3324 | }); | |
| 3325 | ||
| 3326 | // Make the deferred a promise | |
| 3327 | promise.promise( deferred ); | |
| 3328 | ||
| 3329 | // Call given func if any | |
| 3330 | if ( func ) { | |
| 3331 | func.call( deferred, deferred ); | |
| 3332 | } | |
| 3333 | ||
| 3334 | // All done! | |
| 3335 | return deferred; | |
| 3336 | }, | |
| 3337 | ||
| 3338 | // Deferred helper | |
| 3339 | when: function( subordinate /* , ..., subordinateN */ ) { | |
| 3340 | var i = 0, | |
| 3341 | resolveValues = slice.call( arguments ), | |
| 3342 | length = resolveValues.length, | |
| 3343 | ||
| 3344 | // the count of uncompleted subordinates | |
| 3345 | remaining = length !== 1 || ( subordinate && jQuery.isFunction( subordinate.promise ) ) ? length : 0, | |
| 3346 | ||
| 3347 | // the master Deferred. If resolveValues consist of only a single Deferred, just use that. | |
| 3348 | deferred = remaining === 1 ? subordinate : jQuery.Deferred(), | |
| 3349 | ||
| 3350 | // Update function for both resolve and progress values | |
| 3351 | updateFunc = function( i, contexts, values ) { | |
| 3352 | return function( value ) { | |
| 3353 | contexts[ i ] = this; | |
| 3354 | values[ i ] = arguments.length > 1 ? slice.call( arguments ) : value; | |
| 3355 | if ( values === progressValues ) { | |
| 3356 | deferred.notifyWith( contexts, values ); | |
| 3357 | ||
| 3358 | } else if ( !(--remaining) ) { | |
| 3359 | deferred.resolveWith( contexts, values ); | |
| 3360 | } | |
| 3361 | }; | |
| 3362 | }, | |
| 3363 | ||
| 3364 | progressValues, progressContexts, resolveContexts; | |
| 3365 | ||
| 3366 | // add listeners to Deferred subordinates; treat others as resolved | |
| 3367 | if ( length > 1 ) { | |
| 3368 | progressValues = new Array( length ); | |
| 3369 | progressContexts = new Array( length ); | |
| 3370 | resolveContexts = new Array( length ); | |
| 3371 | for ( ; i < length; i++ ) { | |
| 3372 | if ( resolveValues[ i ] && jQuery.isFunction( resolveValues[ i ].promise ) ) { | |
| 3373 | resolveValues[ i ].promise() | |
| 3374 | .done( updateFunc( i, resolveContexts, resolveValues ) ) | |
| 3375 | .fail( deferred.reject ) | |
| 3376 | .progress( updateFunc( i, progressContexts, progressValues ) ); | |
| 3377 | } else { | |
| 3378 | --remaining; | |
| 3379 | } | |
| 3380 | } | |
| 3381 | } | |
| 3382 | ||
| 3383 | // if we're not waiting on anything, resolve the master | |
| 3384 | if ( !remaining ) { | |
| 3385 | deferred.resolveWith( resolveContexts, resolveValues ); | |
| 3386 | } | |
| 3387 | ||
| 3388 | return deferred.promise(); | |
| 3389 | } | |
| 3390 | }); | |
| 3391 | ||
| 3392 | ||
| 3393 | // The deferred used on DOM ready | |
| 3394 | var readyList; | |
| 3395 | ||
| 3396 | jQuery.fn.ready = function( fn ) { | |
| 3397 | // Add the callback | |
| 3398 | jQuery.ready.promise().done( fn ); | |
| 3399 | ||
| 3400 | return this; | |
| 3401 | }; | |
| 3402 | ||
| 3403 | jQuery.extend({ | |
| 3404 | // Is the DOM ready to be used? Set to true once it occurs. | |
| 3405 | isReady: false, | |
| 3406 | ||
| 3407 | // A counter to track how many items to wait for before | |
| 3408 | // the ready event fires. See #6781 | |
| 3409 | readyWait: 1, | |
| 3410 | ||
| 3411 | // Hold (or release) the ready event | |
| 3412 | holdReady: function( hold ) { | |
| 3413 | if ( hold ) { | |
| 3414 | jQuery.readyWait++; | |
| 3415 | } else { | |
| 3416 | jQuery.ready( true ); | |
| 3417 | } | |
| 3418 | }, | |
| 3419 | ||
| 3420 | // Handle when the DOM is ready | |
| 3421 | ready: function( wait ) { | |
| 3422 | ||
| 3423 | // Abort if there are pending holds or we're already ready | |
| 3424 | if ( wait === true ? --jQuery.readyWait : jQuery.isReady ) { | |
| 3425 | return; | |
| 3426 | } | |
| 3427 | ||
| 3428 | // Make sure body exists, at least, in case IE gets a little overzealous (ticket #5443). | |
| 3429 | if ( !document.body ) { | |
| 3430 | return setTimeout( jQuery.ready ); | |
| 3431 | } | |
| 3432 | ||
| 3433 | // Remember that the DOM is ready | |
| 3434 | jQuery.isReady = true; | |
| 3435 | ||
| 3436 | // If a normal DOM Ready event fired, decrement, and wait if need be | |
| 3437 | if ( wait !== true && --jQuery.readyWait > 0 ) { | |
| 3438 | return; | |
| 3439 | } | |
| 3440 | ||
| 3441 | // If there are functions bound, to execute | |
| 3442 | readyList.resolveWith( document, [ jQuery ] ); | |
| 3443 | ||
| 3444 | // Trigger any bound ready events | |
| 3445 | if ( jQuery.fn.triggerHandler ) { | |
| 3446 | jQuery( document ).triggerHandler( "ready" ); | |
| 3447 | jQuery( document ).off( "ready" ); | |
| 3448 | } | |
| 3449 | } | |
| 3450 | }); | |
| 3451 | ||
| 3452 | /** | |
| 3453 | * Clean-up method for dom ready events | |
| 3454 | */ | |
| 3455 | function detach() { | |
| 3456 | if ( document.addEventListener ) { | |
| 3457 | document.removeEventListener( "DOMContentLoaded", completed, false ); | |
| 3458 | window.removeEventListener( "load", completed, false ); | |
| 3459 | ||
| 3460 | } else { | |
| 3461 | document.detachEvent( "onreadystatechange", completed ); | |
| 3462 | window.detachEvent( "onload", completed ); | |
| 3463 | } | |
| 3464 | } | |
| 3465 | ||
| 3466 | /** | |
| 3467 | * The ready event handler and self cleanup method | |
| 3468 | */ | |
| 3469 | function completed() { | |
| 3470 | // readyState === "complete" is good enough for us to call the dom ready in oldIE | |
| 3471 | if ( document.addEventListener || event.type === "load" || document.readyState === "complete" ) { | |
| 3472 | detach(); | |
| 3473 | jQuery.ready(); | |
| 3474 | } | |
| 3475 | } | |
| 3476 | ||
| 3477 | jQuery.ready.promise = function( obj ) { | |
| 3478 | if ( !readyList ) { | |
| 3479 | ||
| 3480 | readyList = jQuery.Deferred(); | |
| 3481 | ||
| 3482 | // Catch cases where $(document).ready() is called after the browser event has already occurred. | |
| 3483 | // we once tried to use readyState "interactive" here, but it caused issues like the one | |
| 3484 | // discovered by ChrisS here: http://bugs.jquery.com/ticket/12282#comment:15 | |
| 3485 | if ( document.readyState === "complete" ) { | |
| 3486 | // Handle it asynchronously to allow scripts the opportunity to delay ready | |
| 3487 | setTimeout( jQuery.ready ); | |
| 3488 | ||
| 3489 | // Standards-based browsers support DOMContentLoaded | |
| 3490 | } else if ( document.addEventListener ) { | |
| 3491 | // Use the handy event callback | |
| 3492 | document.addEventListener( "DOMContentLoaded", completed, false ); | |
| 3493 | ||
| 3494 | // A fallback to window.onload, that will always work | |
| 3495 | window.addEventListener( "load", completed, false ); | |
| 3496 | ||
| 3497 | // If IE event model is used | |
| 3498 | } else { | |
| 3499 | // Ensure firing before onload, maybe late but safe also for iframes | |
| 3500 | document.attachEvent( "onreadystatechange", completed ); | |
| 3501 | ||
| 3502 | // A fallback to window.onload, that will always work | |
| 3503 | window.attachEvent( "onload", completed ); | |
| 3504 | ||
| 3505 | // If IE and not a frame | |
| 3506 | // continually check to see if the document is ready | |
| 3507 | var top = false; | |
| 3508 | ||
| 3509 | try { | |
| 3510 | top = window.frameElement == null && document.documentElement; | |
| 3511 | } catch(e) {} | |
| 3512 | ||
| 3513 | if ( top && top.doScroll ) { | |
| 3514 | (function doScrollCheck() { | |
| 3515 | if ( !jQuery.isReady ) { | |
| 3516 | ||
| 3517 | try { | |
| 3518 | // Use the trick by Diego Perini | |
| 3519 | // http://javascript.nwbox.com/IEContentLoaded/ | |
| 3520 | top.doScroll("left"); | |
| 3521 | } catch(e) { | |
| 3522 | return setTimeout( doScrollCheck, 50 ); | |
| 3523 | } | |
| 3524 | ||
| 3525 | // detach all dom ready events | |
| 3526 | detach(); | |
| 3527 | ||
| 3528 | // and execute any waiting functions | |
| 3529 | jQuery.ready(); | |
| 3530 | } | |
| 3531 | })(); | |
| 3532 | } | |
| 3533 | } | |
| 3534 | } | |
| 3535 | return readyList.promise( obj ); | |
| 3536 | }; | |
| 3537 | ||
| 3538 | ||
| 3539 | var strundefined = typeof undefined; | |
| 3540 | ||
| 3541 | ||
| 3542 | ||
| 3543 | // Support: IE<9 | |
| 3544 | // Iteration over object's inherited properties before its own | |
| 3545 | var i; | |
| 3546 | for ( i in jQuery( support ) ) { | |
| 3547 | break; | |
| 3548 | } | |
| 3549 | support.ownLast = i !== "0"; | |
| 3550 | ||
| 3551 | // Note: most support tests are defined in their respective modules. | |
| 3552 | // false until the test is run | |
| 3553 | support.inlineBlockNeedsLayout = false; | |
| 3554 | ||
| 3555 | // Execute ASAP in case we need to set body.style.zoom | |
| 3556 | jQuery(function() { | |
| 3557 | // Minified: var a,b,c,d | |
| 3558 | var val, div, body, container; | |
| 3559 | ||
| 3560 | body = document.getElementsByTagName( "body" )[ 0 ]; | |
| 3561 | if ( !body || !body.style ) { | |
| 3562 | // Return for frameset docs that don't have a body | |
| 3563 | return; | |
| 3564 | } | |
| 3565 | ||
| 3566 | // Setup | |
| 3567 | div = document.createElement( "div" ); | |
| 3568 | container = document.createElement( "div" ); | |
| 3569 | container.style.cssText = "position:absolute;border:0;width:0;height:0;top:0;left:-9999px"; | |
| 3570 | body.appendChild( container ).appendChild( div ); | |
| 3571 | ||
| 3572 | if ( typeof div.style.zoom !== strundefined ) { | |
| 3573 | // Support: IE<8 | |
| 3574 | // Check if natively block-level elements act like inline-block | |
| 3575 | // elements when setting their display to 'inline' and giving | |
| 3576 | // them layout | |
| 3577 | div.style.cssText = "display:inline;margin:0;border:0;padding:1px;width:1px;zoom:1"; | |
| 3578 | ||
| 3579 | support.inlineBlockNeedsLayout = val = div.offsetWidth === 3; | |
| 3580 | if ( val ) { | |
| 3581 | // Prevent IE 6 from affecting layout for positioned elements #11048 | |
| 3582 | // Prevent IE from shrinking the body in IE 7 mode #12869 | |
| 3583 | // Support: IE<8 | |
| 3584 | body.style.zoom = 1; | |
| 3585 | } | |
| 3586 | } | |
| 3587 | ||
| 3588 | body.removeChild( container ); | |
| 3589 | }); | |
| 3590 | ||
| 3591 | ||
| 3592 | ||
| 3593 | ||
| 3594 | (function() { | |
| 3595 | var div = document.createElement( "div" ); | |
| 3596 | ||
| 3597 | // Execute the test only if not already executed in another module. | |
| 3598 | if (support.deleteExpando == null) { | |
| 3599 | // Support: IE<9 | |
| 3600 | support.deleteExpando = true; | |
| 3601 | try { | |
| 3602 | delete div.test; | |
| 3603 | } catch( e ) { | |
| 3604 | support.deleteExpando = false; | |
| 3605 | } | |
| 3606 | } | |
| 3607 | ||
| 3608 | // Null elements to avoid leaks in IE. | |
| 3609 | div = null; | |
| 3610 | })(); | |
| 3611 | ||
| 3612 | ||
| 3613 | /** | |
| 3614 | * Determines whether an object can have data | |
| 3615 | */ | |
| 3616 | jQuery.acceptData = function( elem ) { | |
| 3617 | var noData = jQuery.noData[ (elem.nodeName + " ").toLowerCase() ], | |
| 3618 | nodeType = +elem.nodeType || 1; | |
| 3619 | ||
| 3620 | // Do not set data on non-element DOM nodes because it will not be cleared (#8335). | |
| 3621 | return nodeType !== 1 && nodeType !== 9 ? | |
| 3622 | false : | |
| 3623 | ||
| 3624 | // Nodes accept data unless otherwise specified; rejection can be conditional | |
| 3625 | !noData || noData !== true && elem.getAttribute("classid") === noData; | |
| 3626 | }; | |
| 3627 | ||
| 3628 | ||
| 3629 | var rbrace = /^(?:\{[\w\W]*\}|\[[\w\W]*\])$/, | |
| 3630 | rmultiDash = /([A-Z])/g; | |
| 3631 | ||
| 3632 | function dataAttr( elem, key, data ) { | |
| 3633 | // If nothing was found internally, try to fetch any | |
| 3634 | // data from the HTML5 data-* attribute | |
| 3635 | if ( data === undefined && elem.nodeType === 1 ) { | |
| 3636 | ||
| 3637 | var name = "data-" + key.replace( rmultiDash, "-$1" ).toLowerCase(); | |
| 3638 | ||
| 3639 | data = elem.getAttribute( name ); | |
| 3640 | ||
| 3641 | if ( typeof data === "string" ) { | |
| 3642 | try { | |
| 3643 | data = data === "true" ? true : | |
| 3644 | data === "false" ? false : | |
| 3645 | data === "null" ? null : | |
| 3646 | // Only convert to a number if it doesn't change the string | |
| 3647 | +data + "" === data ? +data : | |
| 3648 | rbrace.test( data ) ? jQuery.parseJSON( data ) : | |
| 3649 | data; | |
| 3650 | } catch( e ) {} | |
| 3651 | ||
| 3652 | // Make sure we set the data so it isn't changed later | |
| 3653 | jQuery.data( elem, key, data ); | |
| 3654 | ||
| 3655 | } else { | |
| 3656 | data = undefined; | |
| 3657 | } | |
| 3658 | } | |
| 3659 | ||
| 3660 | return data; | |
| 3661 | } | |
| 3662 | ||
| 3663 | // checks a cache object for emptiness | |
| 3664 | function isEmptyDataObject( obj ) { | |
| 3665 | var name; | |
| 3666 | for ( name in obj ) { | |
| 3667 | ||
| 3668 | // if the public data object is empty, the private is still empty | |
| 3669 | if ( name === "data" && jQuery.isEmptyObject( obj[name] ) ) { | |
| 3670 | continue; | |
| 3671 | } | |
| 3672 | if ( name !== "toJSON" ) { | |
| 3673 | return false; | |
| 3674 | } | |
| 3675 | } | |
| 3676 | ||
| 3677 | return true; | |
| 3678 | } | |
| 3679 | ||
| 3680 | function internalData( elem, name, data, pvt /* Internal Use Only */ ) { | |
| 3681 | if ( !jQuery.acceptData( elem ) ) { | |
| 3682 | return; | |
| 3683 | } | |
| 3684 | ||
| 3685 | var ret, thisCache, | |
| 3686 | internalKey = jQuery.expando, | |
| 3687 | ||
| 3688 | // We have to handle DOM nodes and JS objects differently because IE6-7 | |
| 3689 | // can't GC object references properly across the DOM-JS boundary | |
| 3690 | isNode = elem.nodeType, | |
| 3691 | ||
| 3692 | // Only DOM nodes need the global jQuery cache; JS object data is | |
| 3693 | // attached directly to the object so GC can occur automatically | |
| 3694 | cache = isNode ? jQuery.cache : elem, | |
| 3695 | ||
| 3696 | // Only defining an ID for JS objects if its cache already exists allows | |
| 3697 | // the code to shortcut on the same path as a DOM node with no cache | |
| 3698 | id = isNode ? elem[ internalKey ] : elem[ internalKey ] && internalKey; | |
| 3699 | ||
| 3700 | // Avoid doing any more work than we need to when trying to get data on an | |
| 3701 | // object that has no data at all | |
| 3702 | if ( (!id || !cache[id] || (!pvt && !cache[id].data)) && data === undefined && typeof name === "string" ) { | |
| 3703 | return; | |
| 3704 | } | |
| 3705 | ||
| 3706 | if ( !id ) { | |
| 3707 | // Only DOM nodes need a new unique ID for each element since their data | |
| 3708 | // ends up in the global cache | |
| 3709 | if ( isNode ) { | |
| 3710 | id = elem[ internalKey ] = deletedIds.pop() || jQuery.guid++; | |
| 3711 | } else { | |
| 3712 | id = internalKey; | |
| 3713 | } | |
| 3714 | } | |
| 3715 | ||
| 3716 | if ( !cache[ id ] ) { | |
| 3717 | // Avoid exposing jQuery metadata on plain JS objects when the object | |
| 3718 | // is serialized using JSON.stringify | |
| 3719 | cache[ id ] = isNode ? {} : { toJSON: jQuery.noop }; | |
| 3720 | } | |
| 3721 | ||
| 3722 | // An object can be passed to jQuery.data instead of a key/value pair; this gets | |
| 3723 | // shallow copied over onto the existing cache | |
| 3724 | if ( typeof name === "object" || typeof name === "function" ) { | |
| 3725 | if ( pvt ) { | |
| 3726 | cache[ id ] = jQuery.extend( cache[ id ], name ); | |
| 3727 | } else { | |
| 3728 | cache[ id ].data = jQuery.extend( cache[ id ].data, name ); | |
| 3729 | } | |
| 3730 | } | |
| 3731 | ||
| 3732 | thisCache = cache[ id ]; | |
| 3733 | ||
| 3734 | // jQuery data() is stored in a separate object inside the object's internal data | |
| 3735 | // cache in order to avoid key collisions between internal data and user-defined | |
| 3736 | // data. | |
| 3737 | if ( !pvt ) { | |
| 3738 | if ( !thisCache.data ) { | |
| 3739 | thisCache.data = {}; | |
| 3740 | } | |
| 3741 | ||
| 3742 | thisCache = thisCache.data; | |
| 3743 | } | |
| 3744 | ||
| 3745 | if ( data !== undefined ) { | |
| 3746 | thisCache[ jQuery.camelCase( name ) ] = data; | |
| 3747 | } | |
| 3748 | ||
| 3749 | // Check for both converted-to-camel and non-converted data property names | |
| 3750 | // If a data property was specified | |
| 3751 | if ( typeof name === "string" ) { | |
| 3752 | ||
| 3753 | // First Try to find as-is property data | |
| 3754 | ret = thisCache[ name ]; | |
| 3755 | ||
| 3756 | // Test for null|undefined property data | |
| 3757 | if ( ret == null ) { | |
| 3758 | ||
| 3759 | // Try to find the camelCased property | |
| 3760 | ret = thisCache[ jQuery.camelCase( name ) ]; | |
| 3761 | } | |
| 3762 | } else { | |
| 3763 | ret = thisCache; | |
| 3764 | } | |
| 3765 | ||
| 3766 | return ret; | |
| 3767 | } | |
| 3768 | ||
| 3769 | function internalRemoveData( elem, name, pvt ) { | |
| 3770 | if ( !jQuery.acceptData( elem ) ) { | |
| 3771 | return; | |
| 3772 | } | |
| 3773 | ||
| 3774 | var thisCache, i, | |
| 3775 | isNode = elem.nodeType, | |
| 3776 | ||
| 3777 | // See jQuery.data for more information | |
| 3778 | cache = isNode ? jQuery.cache : elem, | |
| 3779 | id = isNode ? elem[ jQuery.expando ] : jQuery.expando; | |
| 3780 | ||
| 3781 | // If there is already no cache entry for this object, there is no | |
| 3782 | // purpose in continuing | |
| 3783 | if ( !cache[ id ] ) { | |
| 3784 | return; | |
| 3785 | } | |
| 3786 | ||
| 3787 | if ( name ) { | |
| 3788 | ||
| 3789 | thisCache = pvt ? cache[ id ] : cache[ id ].data; | |
| 3790 | ||
| 3791 | if ( thisCache ) { | |
| 3792 | ||
| 3793 | // Support array or space separated string names for data keys | |
| 3794 | if ( !jQuery.isArray( name ) ) { | |
| 3795 | ||
| 3796 | // try the string as a key before any manipulation | |
| 3797 | if ( name in thisCache ) { | |
| 3798 | name = [ name ]; | |
| 3799 | } else { | |
| 3800 | ||
| 3801 | // split the camel cased version by spaces unless a key with the spaces exists | |
| 3802 | name = jQuery.camelCase( name ); | |
| 3803 | if ( name in thisCache ) { | |
| 3804 | name = [ name ]; | |
| 3805 | } else { | |
| 3806 | name = name.split(" "); | |
| 3807 | } | |
| 3808 | } | |
| 3809 | } else { | |
| 3810 | // If "name" is an array of keys... | |
| 3811 | // When data is initially created, via ("key", "val") signature, | |
| 3812 | // keys will be converted to camelCase. | |
| 3813 | // Since there is no way to tell _how_ a key was added, remove | |
| 3814 | // both plain key and camelCase key. #12786 | |
| 3815 | // This will only penalize the array argument path. | |
| 3816 | name = name.concat( jQuery.map( name, jQuery.camelCase ) ); | |
| 3817 | } | |
| 3818 | ||
| 3819 | i = name.length; | |
| 3820 | while ( i-- ) { | |
| 3821 | delete thisCache[ name[i] ]; | |
| 3822 | } | |
| 3823 | ||
| 3824 | // If there is no data left in the cache, we want to continue | |
| 3825 | // and let the cache object itself get destroyed | |
| 3826 | if ( pvt ? !isEmptyDataObject(thisCache) : !jQuery.isEmptyObject(thisCache) ) { | |
| 3827 | return; | |
| 3828 | } | |
| 3829 | } | |
| 3830 | } | |
| 3831 | ||
| 3832 | // See jQuery.data for more information | |
| 3833 | if ( !pvt ) { | |
| 3834 | delete cache[ id ].data; | |
| 3835 | ||
| 3836 | // Don't destroy the parent cache unless the internal data object | |
| 3837 | // had been the only thing left in it | |
| 3838 | if ( !isEmptyDataObject( cache[ id ] ) ) { | |
| 3839 | return; | |
| 3840 | } | |
| 3841 | } | |
| 3842 | ||
| 3843 | // Destroy the cache | |
| 3844 | if ( isNode ) { | |
| 3845 | jQuery.cleanData( [ elem ], true ); | |
| 3846 | ||
| 3847 | // Use delete when supported for expandos or `cache` is not a window per isWindow (#10080) | |
| 3848 | /* jshint eqeqeq: false */ | |
| 3849 | } else if ( support.deleteExpando || cache != cache.window ) { | |
| 3850 | /* jshint eqeqeq: true */ | |
| 3851 | delete cache[ id ]; | |
| 3852 | ||
| 3853 | // When all else fails, null | |
| 3854 | } else { | |
| 3855 | cache[ id ] = null; | |
| 3856 | } | |
| 3857 | } | |
| 3858 | ||
| 3859 | jQuery.extend({ | |
| 3860 | cache: {}, | |
| 3861 | ||
| 3862 | // The following elements (space-suffixed to avoid Object.prototype collisions) | |
| 3863 | // throw uncatchable exceptions if you attempt to set expando properties | |
| 3864 | noData: { | |
| 3865 | "applet ": true, | |
| 3866 | "embed ": true, | |
| 3867 | // ...but Flash objects (which have this classid) *can* handle expandos | |
| 3868 | "object ": "clsid:D27CDB6E-AE6D-11cf-96B8-444553540000" | |
| 3869 | }, | |
| 3870 | ||
| 3871 | hasData: function( elem ) { | |
| 3872 | elem = elem.nodeType ? jQuery.cache[ elem[jQuery.expando] ] : elem[ jQuery.expando ]; | |
| 3873 | return !!elem && !isEmptyDataObject( elem ); | |
| 3874 | }, | |
| 3875 | ||
| 3876 | data: function( elem, name, data ) { | |
| 3877 | return internalData( elem, name, data ); | |
| 3878 | }, | |
| 3879 | ||
| 3880 | removeData: function( elem, name ) { | |
| 3881 | return internalRemoveData( elem, name ); | |
| 3882 | }, | |
| 3883 | ||
| 3884 | // For internal use only. | |
| 3885 | _data: function( elem, name, data ) { | |
| 3886 | return internalData( elem, name, data, true ); | |
| 3887 | }, | |
| 3888 | ||
| 3889 | _removeData: function( elem, name ) { | |
| 3890 | return internalRemoveData( elem, name, true ); | |
| 3891 | } | |
| 3892 | }); | |
| 3893 | ||
| 3894 | jQuery.fn.extend({ | |
| 3895 | data: function( key, value ) { | |
| 3896 | var i, name, data, | |
| 3897 | elem = this[0], | |
| 3898 | attrs = elem && elem.attributes; | |
| 3899 | ||
| 3900 | // Special expections of .data basically thwart jQuery.access, | |
| 3901 | // so implement the relevant behavior ourselves | |
| 3902 | ||
| 3903 | // Gets all values | |
| 3904 | if ( key === undefined ) { | |
| 3905 | if ( this.length ) { | |
| 3906 | data = jQuery.data( elem ); | |
| 3907 | ||
| 3908 | if ( elem.nodeType === 1 && !jQuery._data( elem, "parsedAttrs" ) ) { | |
| 3909 | i = attrs.length; | |
| 3910 | while ( i-- ) { | |
| 3911 | ||
| 3912 | // Support: IE11+ | |
| 3913 | // The attrs elements can be null (#14894) | |
| 3914 | if ( attrs[ i ] ) { | |
| 3915 | name = attrs[ i ].name; | |
| 3916 | if ( name.indexOf( "data-" ) === 0 ) { | |
| 3917 | name = jQuery.camelCase( name.slice(5) ); | |
| 3918 | dataAttr( elem, name, data[ name ] ); | |
| 3919 | } | |
| 3920 | } | |
| 3921 | } | |
| 3922 | jQuery._data( elem, "parsedAttrs", true ); | |
| 3923 | } | |
| 3924 | } | |
| 3925 | ||
| 3926 | return data; | |
| 3927 | } | |
| 3928 | ||
| 3929 | // Sets multiple values | |
| 3930 | if ( typeof key === "object" ) { | |
| 3931 | return this.each(function() { | |
| 3932 | jQuery.data( this, key ); | |
| 3933 | }); | |
| 3934 | } | |
| 3935 | ||
| 3936 | return arguments.length > 1 ? | |
| 3937 | ||
| 3938 | // Sets one value | |
| 3939 | this.each(function() { | |
| 3940 | jQuery.data( this, key, value ); | |
| 3941 | }) : | |
| 3942 | ||
| 3943 | // Gets one value | |
| 3944 | // Try to fetch any internally stored data first | |
| 3945 | elem ? dataAttr( elem, key, jQuery.data( elem, key ) ) : undefined; | |
| 3946 | }, | |
| 3947 | ||
| 3948 | removeData: function( key ) { | |
| 3949 | return this.each(function() { | |
| 3950 | jQuery.removeData( this, key ); | |
| 3951 | }); | |
| 3952 | } | |
| 3953 | }); | |
| 3954 | ||
| 3955 | ||
| 3956 | jQuery.extend({ | |
| 3957 | queue: function( elem, type, data ) { | |
| 3958 | var queue; | |
| 3959 | ||
| 3960 | if ( elem ) { | |
| 3961 | type = ( type || "fx" ) + "queue"; | |
| 3962 | queue = jQuery._data( elem, type ); | |
| 3963 | ||
| 3964 | // Speed up dequeue by getting out quickly if this is just a lookup | |
| 3965 | if ( data ) { | |
| 3966 | if ( !queue || jQuery.isArray(data) ) { | |
| 3967 | queue = jQuery._data( elem, type, jQuery.makeArray(data) ); | |
| 3968 | } else { | |
| 3969 | queue.push( data ); | |
| 3970 | } | |
| 3971 | } | |
| 3972 | return queue || []; | |
| 3973 | } | |
| 3974 | }, | |
| 3975 | ||
| 3976 | dequeue: function( elem, type ) { | |
| 3977 | type = type || "fx"; | |
| 3978 | ||
| 3979 | var queue = jQuery.queue( elem, type ), | |
| 3980 | startLength = queue.length, | |
| 3981 | fn = queue.shift(), | |
| 3982 | hooks = jQuery._queueHooks( elem, type ), | |
| 3983 | next = function() { | |
| 3984 | jQuery.dequeue( elem, type ); | |
| 3985 | }; | |
| 3986 | ||
| 3987 | // If the fx queue is dequeued, always remove the progress sentinel | |
| 3988 | if ( fn === "inprogress" ) { | |
| 3989 | fn = queue.shift(); | |
| 3990 | startLength--; | |
| 3991 | } | |
| 3992 | ||
| 3993 | if ( fn ) { | |
| 3994 | ||
| 3995 | // Add a progress sentinel to prevent the fx queue from being | |
| 3996 | // automatically dequeued | |
| 3997 | if ( type === "fx" ) { | |
| 3998 | queue.unshift( "inprogress" ); | |
| 3999 | } | |
| 4000 | ||
| 4001 | // clear up the last queue stop function | |
| 4002 | delete hooks.stop; | |
| 4003 | fn.call( elem, next, hooks ); | |
| 4004 | } | |
| 4005 | ||
| 4006 | if ( !startLength && hooks ) { | |
| 4007 | hooks.empty.fire(); | |
| 4008 | } | |
| 4009 | }, | |
| 4010 | ||
| 4011 | // not intended for public consumption - generates a queueHooks object, or returns the current one | |
| 4012 | _queueHooks: function( elem, type ) { | |
| 4013 | var key = type + "queueHooks"; | |
| 4014 | return jQuery._data( elem, key ) || jQuery._data( elem, key, { | |
| 4015 | empty: jQuery.Callbacks("once memory").add(function() { | |
| 4016 | jQuery._removeData( elem, type + "queue" ); | |
| 4017 | jQuery._removeData( elem, key ); | |
| 4018 | }) | |
| 4019 | }); | |
| 4020 | } | |
| 4021 | }); | |
| 4022 | ||
| 4023 | jQuery.fn.extend({ | |
| 4024 | queue: function( type, data ) { | |
| 4025 | var setter = 2; | |
| 4026 | ||
| 4027 | if ( typeof type !== "string" ) { | |
| 4028 | data = type; | |
| 4029 | type = "fx"; | |
| 4030 | setter--; | |
| 4031 | } | |
| 4032 | ||
| 4033 | if ( arguments.length < setter ) { | |
| 4034 | return jQuery.queue( this[0], type ); | |
| 4035 | } | |
| 4036 | ||
| 4037 | return data === undefined ? | |
| 4038 | this : | |
| 4039 | this.each(function() { | |
| 4040 | var queue = jQuery.queue( this, type, data ); | |
| 4041 | ||
| 4042 | // ensure a hooks for this queue | |
| 4043 | jQuery._queueHooks( this, type ); | |
| 4044 | ||
| 4045 | if ( type === "fx" && queue[0] !== "inprogress" ) { | |
| 4046 | jQuery.dequeue( this, type ); | |
| 4047 | } | |
| 4048 | }); | |
| 4049 | }, | |
| 4050 | dequeue: function( type ) { | |
| 4051 | return this.each(function() { | |
| 4052 | jQuery.dequeue( this, type ); | |
| 4053 | }); | |
| 4054 | }, | |
| 4055 | clearQueue: function( type ) { | |
| 4056 | return this.queue( type || "fx", [] ); | |
| 4057 | }, | |
| 4058 | // Get a promise resolved when queues of a certain type | |
| 4059 | // are emptied (fx is the type by default) | |
| 4060 | promise: function( type, obj ) { | |
| 4061 | var tmp, | |
| 4062 | count = 1, | |
| 4063 | defer = jQuery.Deferred(), | |
| 4064 | elements = this, | |
| 4065 | i = this.length, | |
| 4066 | resolve = function() { | |
| 4067 | if ( !( --count ) ) { | |
| 4068 | defer.resolveWith( elements, [ elements ] ); | |
| 4069 | } | |
| 4070 | }; | |
| 4071 | ||
| 4072 | if ( typeof type !== "string" ) { | |
| 4073 | obj = type; | |
| 4074 | type = undefined; | |
| 4075 | } | |
| 4076 | type = type || "fx"; | |
| 4077 | ||
| 4078 | while ( i-- ) { | |
| 4079 | tmp = jQuery._data( elements[ i ], type + "queueHooks" ); | |
| 4080 | if ( tmp && tmp.empty ) { | |
| 4081 | count++; | |
| 4082 | tmp.empty.add( resolve ); | |
| 4083 | } | |
| 4084 | } | |
| 4085 | resolve(); | |
| 4086 | return defer.promise( obj ); | |
| 4087 | } | |
| 4088 | }); | |
| 4089 | var pnum = (/[+-]?(?:\d*\.|)\d+(?:[eE][+-]?\d+|)/).source; | |
| 4090 | ||
| 4091 | var cssExpand = [ "Top", "Right", "Bottom", "Left" ]; | |
| 4092 | ||
| 4093 | var isHidden = function( elem, el ) { | |
| 4094 | // isHidden might be called from jQuery#filter function; | |
| 4095 | // in that case, element will be second argument | |
| 4096 | elem = el || elem; | |
| 4097 | return jQuery.css( elem, "display" ) === "none" || !jQuery.contains( elem.ownerDocument, elem ); | |
| 4098 | }; | |
| 4099 | ||
| 4100 | ||
| 4101 | ||
| 4102 | // Multifunctional method to get and set values of a collection | |
| 4103 | // The value/s can optionally be executed if it's a function | |
| 4104 | var access = jQuery.access = function( elems, fn, key, value, chainable, emptyGet, raw ) { | |
| 4105 | var i = 0, | |
| 4106 | length = elems.length, | |
| 4107 | bulk = key == null; | |
| 4108 | ||
| 4109 | // Sets many values | |
| 4110 | if ( jQuery.type( key ) === "object" ) { | |
| 4111 | chainable = true; | |
| 4112 | for ( i in key ) { | |
| 4113 | jQuery.access( elems, fn, i, key[i], true, emptyGet, raw ); | |
| 4114 | } | |
| 4115 | ||
| 4116 | // Sets one value | |
| 4117 | } else if ( value !== undefined ) { | |
| 4118 | chainable = true; | |
| 4119 | ||
| 4120 | if ( !jQuery.isFunction( value ) ) { | |
| 4121 | raw = true; | |
| 4122 | } | |
| 4123 | ||
| 4124 | if ( bulk ) { | |
| 4125 | // Bulk operations run against the entire set | |
| 4126 | if ( raw ) { | |
| 4127 | fn.call( elems, value ); | |
| 4128 | fn = null; | |
| 4129 | ||
| 4130 | // ...except when executing function values | |
| 4131 | } else { | |
| 4132 | bulk = fn; | |
| 4133 | fn = function( elem, key, value ) { | |
| 4134 | return bulk.call( jQuery( elem ), value ); | |
| 4135 | }; | |
| 4136 | } | |
| 4137 | } | |
| 4138 | ||
| 4139 | if ( fn ) { | |
| 4140 | for ( ; i < length; i++ ) { | |
| 4141 | fn( elems[i], key, raw ? value : value.call( elems[i], i, fn( elems[i], key ) ) ); | |
| 4142 | } | |
| 4143 | } | |
| 4144 | } | |
| 4145 | ||
| 4146 | return chainable ? | |
| 4147 | elems : | |
| 4148 | ||
| 4149 | // Gets | |
| 4150 | bulk ? | |
| 4151 | fn.call( elems ) : | |
| 4152 | length ? fn( elems[0], key ) : emptyGet; | |
| 4153 | }; | |
| 4154 | var rcheckableType = (/^(?:checkbox|radio)$/i); | |
| 4155 | ||
| 4156 | ||
| 4157 | ||
| 4158 | (function() { | |
| 4159 | // Minified: var a,b,c | |
| 4160 | var input = document.createElement( "input" ), | |
| 4161 | div = document.createElement( "div" ), | |
| 4162 | fragment = document.createDocumentFragment(); | |
| 4163 | ||
| 4164 | // Setup | |
| 4165 | div.innerHTML = " <link/><table></table><a href='/a'>a</a><input type='checkbox'/>"; | |
| 4166 | ||
| 4167 | // IE strips leading whitespace when .innerHTML is used | |
| 4168 | support.leadingWhitespace = div.firstChild.nodeType === 3; | |
| 4169 | ||
| 4170 | // Make sure that tbody elements aren't automatically inserted | |
| 4171 | // IE will insert them into empty tables | |
| 4172 | support.tbody = !div.getElementsByTagName( "tbody" ).length; | |
| 4173 | ||
| 4174 | // Make sure that link elements get serialized correctly by innerHTML | |
| 4175 | // This requires a wrapper element in IE | |
| 4176 | support.htmlSerialize = !!div.getElementsByTagName( "link" ).length; | |
| 4177 | ||
| 4178 | // Makes sure cloning an html5 element does not cause problems | |
| 4179 | // Where outerHTML is undefined, this still works | |
| 4180 | support.html5Clone = | |
| 4181 | document.createElement( "nav" ).cloneNode( true ).outerHTML !== "<:nav></:nav>"; | |
| 4182 | ||
| 4183 | // Check if a disconnected checkbox will retain its checked | |
| 4184 | // value of true after appended to the DOM (IE6/7) | |
| 4185 | input.type = "checkbox"; | |
| 4186 | input.checked = true; | |
| 4187 | fragment.appendChild( input ); | |
| 4188 | support.appendChecked = input.checked; | |
| 4189 | ||
| 4190 | // Make sure textarea (and checkbox) defaultValue is properly cloned | |
| 4191 | // Support: IE6-IE11+ | |
| 4192 | div.innerHTML = "<textarea>x</textarea>"; | |
| 4193 | support.noCloneChecked = !!div.cloneNode( true ).lastChild.defaultValue; | |
| 4194 | ||
| 4195 | // #11217 - WebKit loses check when the name is after the checked attribute | |
| 4196 | fragment.appendChild( div ); | |
| 4197 | div.innerHTML = "<input type='radio' checked='checked' name='t'/>"; | |
| 4198 | ||
| 4199 | // Support: Safari 5.1, iOS 5.1, Android 4.x, Android 2.3 | |
| 4200 | // old WebKit doesn't clone checked state correctly in fragments | |
| 4201 | support.checkClone = div.cloneNode( true ).cloneNode( true ).lastChild.checked; | |
| 4202 | ||
| 4203 | // Support: IE<9 | |
| 4204 | // Opera does not clone events (and typeof div.attachEvent === undefined). | |
| 4205 | // IE9-10 clones events bound via attachEvent, but they don't trigger with .click() | |
| 4206 | support.noCloneEvent = true; | |
| 4207 | if ( div.attachEvent ) { | |
| 4208 | div.attachEvent( "onclick", function() { | |
| 4209 | support.noCloneEvent = false; | |
| 4210 | }); | |
| 4211 | ||
| 4212 | div.cloneNode( true ).click(); | |
| 4213 | } | |
| 4214 | ||
| 4215 | // Execute the test only if not already executed in another module. | |
| 4216 | if (support.deleteExpando == null) { | |
| 4217 | // Support: IE<9 | |
| 4218 | support.deleteExpando = true; | |
| 4219 | try { | |
| 4220 | delete div.test; | |
| 4221 | } catch( e ) { | |
| 4222 | support.deleteExpando = false; | |
| 4223 | } | |
| 4224 | } | |
| 4225 | })(); | |
| 4226 | ||
| 4227 | ||
| 4228 | (function() { | |
| 4229 | var i, eventName, | |
| 4230 | div = document.createElement( "div" ); | |
| 4231 | ||
| 4232 | // Support: IE<9 (lack submit/change bubble), Firefox 23+ (lack focusin event) | |
| 4233 | for ( i in { submit: true, change: true, focusin: true }) { | |
| 4234 | eventName = "on" + i; | |
| 4235 | ||
| 4236 | if ( !(support[ i + "Bubbles" ] = eventName in window) ) { | |
| 4237 | // Beware of CSP restrictions (https://developer.mozilla.org/en/Security/CSP) | |
| 4238 | div.setAttribute( eventName, "t" ); | |
| 4239 | support[ i + "Bubbles" ] = div.attributes[ eventName ].expando === false; | |
| 4240 | } | |
| 4241 | } | |
| 4242 | ||
| 4243 | // Null elements to avoid leaks in IE. | |
| 4244 | div = null; | |
| 4245 | })(); | |
| 4246 | ||
| 4247 | ||
| 4248 | var rformElems = /^(?:input|select|textarea)$/i, | |
| 4249 | rkeyEvent = /^key/, | |
| 4250 | rmouseEvent = /^(?:mouse|pointer|contextmenu)|click/, | |
| 4251 | rfocusMorph = /^(?:focusinfocus|focusoutblur)$/, | |
| 4252 | rtypenamespace = /^([^.]*)(?:\.(.+)|)$/; | |
| 4253 | ||
| 4254 | function returnTrue() { | |
| 4255 | return true; | |
| 4256 | } | |
| 4257 | ||
| 4258 | function returnFalse() { | |
| 4259 | return false; | |
| 4260 | } | |
| 4261 | ||
| 4262 | function safeActiveElement() { | |
| 4263 | try { | |
| 4264 | return document.activeElement; | |
| 4265 | } catch ( err ) { } | |
| 4266 | } | |
| 4267 | ||
| 4268 | /* | |
| 4269 | * Helper functions for managing events -- not part of the public interface. | |
| 4270 | * Props to Dean Edwards' addEvent library for many of the ideas. | |
| 4271 | */ | |
| 4272 | jQuery.event = { | |
| 4273 | ||
| 4274 | global: {}, | |
| 4275 | ||
| 4276 | add: function( elem, types, handler, data, selector ) { | |
| 4277 | var tmp, events, t, handleObjIn, | |
| 4278 | special, eventHandle, handleObj, | |
| 4279 | handlers, type, namespaces, origType, | |
| 4280 | elemData = jQuery._data( elem ); | |
| 4281 | ||
| 4282 | // Don't attach events to noData or text/comment nodes (but allow plain objects) | |
| 4283 | if ( !elemData ) { | |
| 4284 | return; | |
| 4285 | } | |
| 4286 | ||
| 4287 | // Caller can pass in an object of custom data in lieu of the handler | |
| 4288 | if ( handler.handler ) { | |
| 4289 | handleObjIn = handler; | |
| 4290 | handler = handleObjIn.handler; | |
| 4291 | selector = handleObjIn.selector; | |
| 4292 | } | |
| 4293 | ||
| 4294 | // Make sure that the handler has a unique ID, used to find/remove it later | |
| 4295 | if ( !handler.guid ) { | |
| 4296 | handler.guid = jQuery.guid++; | |
| 4297 | } | |
| 4298 | ||
| 4299 | // Init the element's event structure and main handler, if this is the first | |
| 4300 | if ( !(events = elemData.events) ) { | |
| 4301 | events = elemData.events = {}; | |
| 4302 | } | |
| 4303 | if ( !(eventHandle = elemData.handle) ) { | |
| 4304 | eventHandle = elemData.handle = function( e ) { | |
| 4305 | // Discard the second event of a jQuery.event.trigger() and | |
| 4306 | // when an event is called after a page has unloaded | |
| 4307 | return typeof jQuery !== strundefined && (!e || jQuery.event.triggered !== e.type) ? | |
| 4308 | jQuery.event.dispatch.apply( eventHandle.elem, arguments ) : | |
| 4309 | undefined; | |
| 4310 | }; | |
| 4311 | // Add elem as a property of the handle fn to prevent a memory leak with IE non-native events | |
| 4312 | eventHandle.elem = elem; | |
| 4313 | } | |
| 4314 | ||
| 4315 | // Handle multiple events separated by a space | |
| 4316 | types = ( types || "" ).match( rnotwhite ) || [ "" ]; | |
| 4317 | t = types.length; | |
| 4318 | while ( t-- ) { | |
| 4319 | tmp = rtypenamespace.exec( types[t] ) || []; | |
| 4320 | type = origType = tmp[1]; | |
| 4321 | namespaces = ( tmp[2] || "" ).split( "." ).sort(); | |
| 4322 | ||
| 4323 | // There *must* be a type, no attaching namespace-only handlers | |
| 4324 | if ( !type ) { | |
| 4325 | continue; | |
| 4326 | } | |
| 4327 | ||
| 4328 | // If event changes its type, use the special event handlers for the changed type | |
| 4329 | special = jQuery.event.special[ type ] || {}; | |
| 4330 | ||
| 4331 | // If selector defined, determine special event api type, otherwise given type | |
| 4332 | type = ( selector ? special.delegateType : special.bindType ) || type; | |
| 4333 | ||
| 4334 | // Update special based on newly reset type | |
| 4335 | special = jQuery.event.special[ type ] || {}; | |
| 4336 | ||
| 4337 | // handleObj is passed to all event handlers | |
| 4338 | handleObj = jQuery.extend({ | |
| 4339 | type: type, | |
| 4340 | origType: origType, | |
| 4341 | data: data, | |
| 4342 | handler: handler, | |
| 4343 | guid: handler.guid, | |
| 4344 | selector: selector, | |
| 4345 | needsContext: selector && jQuery.expr.match.needsContext.test( selector ), | |
| 4346 | namespace: namespaces.join(".") | |
| 4347 | }, handleObjIn ); | |
| 4348 | ||
| 4349 | // Init the event handler queue if we're the first | |
| 4350 | if ( !(handlers = events[ type ]) ) { | |
| 4351 | handlers = events[ type ] = []; | |
| 4352 | handlers.delegateCount = 0; | |
| 4353 | ||
| 4354 | // Only use addEventListener/attachEvent if the special events handler returns false | |
| 4355 | if ( !special.setup || special.setup.call( elem, data, namespaces, eventHandle ) === false ) { | |
| 4356 | // Bind the global event handler to the element | |
| 4357 | if ( elem.addEventListener ) { | |
| 4358 | elem.addEventListener( type, eventHandle, false ); | |
| 4359 | ||
| 4360 | } else if ( elem.attachEvent ) { | |
| 4361 | elem.attachEvent( "on" + type, eventHandle ); | |
| 4362 | } | |
| 4363 | } | |
| 4364 | } | |
| 4365 | ||
| 4366 | if ( special.add ) { | |
| 4367 | special.add.call( elem, handleObj ); | |
| 4368 | ||
| 4369 | if ( !handleObj.handler.guid ) { | |
| 4370 | handleObj.handler.guid = handler.guid; | |
| 4371 | } | |
| 4372 | } | |
| 4373 | ||
| 4374 | // Add to the element's handler list, delegates in front | |
| 4375 | if ( selector ) { | |
| 4376 | handlers.splice( handlers.delegateCount++, 0, handleObj ); | |
| 4377 | } else { | |
| 4378 | handlers.push( handleObj ); | |
| 4379 | } | |
| 4380 | ||
| 4381 | // Keep track of which events have ever been used, for event optimization | |
| 4382 | jQuery.event.global[ type ] = true; | |
| 4383 | } | |
| 4384 | ||
| 4385 | // Nullify elem to prevent memory leaks in IE | |
| 4386 | elem = null; | |
| 4387 | }, | |
| 4388 | ||
| 4389 | // Detach an event or set of events from an element | |
| 4390 | remove: function( elem, types, handler, selector, mappedTypes ) { | |
| 4391 | var j, handleObj, tmp, | |
| 4392 | origCount, t, events, | |
| 4393 | special, handlers, type, | |
| 4394 | namespaces, origType, | |
| 4395 | elemData = jQuery.hasData( elem ) && jQuery._data( elem ); | |
| 4396 | ||
| 4397 | if ( !elemData || !(events = elemData.events) ) { | |
| 4398 | return; | |
| 4399 | } | |
| 4400 | ||
| 4401 | // Once for each type.namespace in types; type may be omitted | |
| 4402 | types = ( types || "" ).match( rnotwhite ) || [ "" ]; | |
| 4403 | t = types.length; | |
| 4404 | while ( t-- ) { | |
| 4405 | tmp = rtypenamespace.exec( types[t] ) || []; | |
| 4406 | type = origType = tmp[1]; | |
| 4407 | namespaces = ( tmp[2] || "" ).split( "." ).sort(); | |
| 4408 | ||
| 4409 | // Unbind all events (on this namespace, if provided) for the element | |
| 4410 | if ( !type ) { | |
| 4411 | for ( type in events ) { | |
| 4412 | jQuery.event.remove( elem, type + types[ t ], handler, selector, true ); | |
| 4413 | } | |
| 4414 | continue; | |
| 4415 | } | |
| 4416 | ||
| 4417 | special = jQuery.event.special[ type ] || {}; | |
| 4418 | type = ( selector ? special.delegateType : special.bindType ) || type; | |
| 4419 | handlers = events[ type ] || []; | |
| 4420 | tmp = tmp[2] && new RegExp( "(^|\\.)" + namespaces.join("\\.(?:.*\\.|)") + "(\\.|$)" ); | |
| 4421 | ||
| 4422 | // Remove matching events | |
| 4423 | origCount = j = handlers.length; | |
| 4424 | while ( j-- ) { | |
| 4425 | handleObj = handlers[ j ]; | |
| 4426 | ||
| 4427 | if ( ( mappedTypes || origType === handleObj.origType ) && | |
| 4428 | ( !handler || handler.guid === handleObj.guid ) && | |
| 4429 | ( !tmp || tmp.test( handleObj.namespace ) ) && | |
| 4430 | ( !selector || selector === handleObj.selector || selector === "**" && handleObj.selector ) ) { | |
| 4431 | handlers.splice( j, 1 ); | |
| 4432 | ||
| 4433 | if ( handleObj.selector ) { | |
| 4434 | handlers.delegateCount--; | |
| 4435 | } | |
| 4436 | if ( special.remove ) { | |
| 4437 | special.remove.call( elem, handleObj ); | |
| 4438 | } | |
| 4439 | } | |
| 4440 | } | |
| 4441 | ||
| 4442 | // Remove generic event handler if we removed something and no more handlers exist | |
| 4443 | // (avoids potential for endless recursion during removal of special event handlers) | |
| 4444 | if ( origCount && !handlers.length ) { | |
| 4445 | if ( !special.teardown || special.teardown.call( elem, namespaces, elemData.handle ) === false ) { | |
| 4446 | jQuery.removeEvent( elem, type, elemData.handle ); | |
| 4447 | } | |
| 4448 | ||
| 4449 | delete events[ type ]; | |
| 4450 | } | |
| 4451 | } | |
| 4452 | ||
| 4453 | // Remove the expando if it's no longer used | |
| 4454 | if ( jQuery.isEmptyObject( events ) ) { | |
| 4455 | delete elemData.handle; | |
| 4456 | ||
| 4457 | // removeData also checks for emptiness and clears the expando if empty | |
| 4458 | // so use it instead of delete | |
| 4459 | jQuery._removeData( elem, "events" ); | |
| 4460 | } | |
| 4461 | }, | |
| 4462 | ||
| 4463 | trigger: function( event, data, elem, onlyHandlers ) { | |
| 4464 | var handle, ontype, cur, | |
| 4465 | bubbleType, special, tmp, i, | |
| 4466 | eventPath = [ elem || document ], | |
| 4467 | type = hasOwn.call( event, "type" ) ? event.type : event, | |
| 4468 | namespaces = hasOwn.call( event, "namespace" ) ? event.namespace.split(".") : []; | |
| 4469 | ||
| 4470 | cur = tmp = elem = elem || document; | |
| 4471 | ||
| 4472 | // Don't do events on text and comment nodes | |
| 4473 | if ( elem.nodeType === 3 || elem.nodeType === 8 ) { | |
| 4474 | return; | |
| 4475 | } | |
| 4476 | ||
| 4477 | // focus/blur morphs to focusin/out; ensure we're not firing them right now | |
| 4478 | if ( rfocusMorph.test( type + jQuery.event.triggered ) ) { | |
| 4479 | return; | |
| 4480 | } | |
| 4481 | ||
| 4482 | if ( type.indexOf(".") >= 0 ) { | |
| 4483 | // Namespaced trigger; create a regexp to match event type in handle() | |
| 4484 | namespaces = type.split("."); | |
| 4485 | type = namespaces.shift(); | |
| 4486 | namespaces.sort(); | |
| 4487 | } | |
| 4488 | ontype = type.indexOf(":") < 0 && "on" + type; | |
| 4489 | ||
| 4490 | // Caller can pass in a jQuery.Event object, Object, or just an event type string | |
| 4491 | event = event[ jQuery.expando ] ? | |
| 4492 | event : | |
| 4493 | new jQuery.Event( type, typeof event === "object" && event ); | |
| 4494 | ||
| 4495 | // Trigger bitmask: & 1 for native handlers; & 2 for jQuery (always true) | |
| 4496 | event.isTrigger = onlyHandlers ? 2 : 3; | |
| 4497 | event.namespace = namespaces.join("."); | |
| 4498 | event.namespace_re = event.namespace ? | |
| 4499 | new RegExp( "(^|\\.)" + namespaces.join("\\.(?:.*\\.|)") + "(\\.|$)" ) : | |
| 4500 | null; | |
| 4501 | ||
| 4502 | // Clean up the event in case it is being reused | |
| 4503 | event.result = undefined; | |
| 4504 | if ( !event.target ) { | |
| 4505 | event.target = elem; | |
| 4506 | } | |
| 4507 | ||
| 4508 | // Clone any incoming data and prepend the event, creating the handler arg list | |
| 4509 | data = data == null ? | |
| 4510 | [ event ] : | |
| 4511 | jQuery.makeArray( data, [ event ] ); | |
| 4512 | ||
| 4513 | // Allow special events to draw outside the lines | |
| 4514 | special = jQuery.event.special[ type ] || {}; | |
| 4515 | if ( !onlyHandlers && special.trigger && special.trigger.apply( elem, data ) === false ) { | |
| 4516 | return; | |
| 4517 | } | |
| 4518 | ||
| 4519 | // Determine event propagation path in advance, per W3C events spec (#9951) | |
| 4520 | // Bubble up to document, then to window; watch for a global ownerDocument var (#9724) | |
| 4521 | if ( !onlyHandlers && !special.noBubble && !jQuery.isWindow( elem ) ) { | |
| 4522 | ||
| 4523 | bubbleType = special.delegateType || type; | |
| 4524 | if ( !rfocusMorph.test( bubbleType + type ) ) { | |
| 4525 | cur = cur.parentNode; | |
| 4526 | } | |
| 4527 | for ( ; cur; cur = cur.parentNode ) { | |
| 4528 | eventPath.push( cur ); | |
| 4529 | tmp = cur; | |
| 4530 | } | |
| 4531 | ||
| 4532 | // Only add window if we got to document (e.g., not plain obj or detached DOM) | |
| 4533 | if ( tmp === (elem.ownerDocument || document) ) { | |
| 4534 | eventPath.push( tmp.defaultView || tmp.parentWindow || window ); | |
| 4535 | } | |
| 4536 | } | |
| 4537 | ||
| 4538 | // Fire handlers on the event path | |
| 4539 | i = 0; | |
| 4540 | while ( (cur = eventPath[i++]) && !event.isPropagationStopped() ) { | |
| 4541 | ||
| 4542 | event.type = i > 1 ? | |
| 4543 | bubbleType : | |
| 4544 | special.bindType || type; | |
| 4545 | ||
| 4546 | // jQuery handler | |
| 4547 | handle = ( jQuery._data( cur, "events" ) || {} )[ event.type ] && jQuery._data( cur, "handle" ); | |
| 4548 | if ( handle ) { | |
| 4549 | handle.apply( cur, data ); | |
| 4550 | } | |
| 4551 | ||
| 4552 | // Native handler | |
| 4553 | handle = ontype && cur[ ontype ]; | |
| 4554 | if ( handle && handle.apply && jQuery.acceptData( cur ) ) { | |
| 4555 | event.result = handle.apply( cur, data ); | |
| 4556 | if ( event.result === false ) { | |
| 4557 | event.preventDefault(); | |
| 4558 | } | |
| 4559 | } | |
| 4560 | } | |
| 4561 | event.type = type; | |
| 4562 | ||
| 4563 | // If nobody prevented the default action, do it now | |
| 4564 | if ( !onlyHandlers && !event.isDefaultPrevented() ) { | |
| 4565 | ||
| 4566 | if ( (!special._default || special._default.apply( eventPath.pop(), data ) === false) && | |
| 4567 | jQuery.acceptData( elem ) ) { | |
| 4568 | ||
| 4569 | // Call a native DOM method on the target with the same name name as the event. | |
| 4570 | // Can't use an .isFunction() check here because IE6/7 fails that test. | |
| 4571 | // Don't do default actions on window, that's where global variables be (#6170) | |
| 4572 | if ( ontype && elem[ type ] && !jQuery.isWindow( elem ) ) { | |
| 4573 | ||
| 4574 | // Don't re-trigger an onFOO event when we call its FOO() method | |
| 4575 | tmp = elem[ ontype ]; | |
| 4576 | ||
| 4577 | if ( tmp ) { | |
| 4578 | elem[ ontype ] = null; | |
| 4579 | } | |
| 4580 | ||
| 4581 | // Prevent re-triggering of the same event, since we already bubbled it above | |
| 4582 | jQuery.event.triggered = type; | |
| 4583 | try { | |
| 4584 | elem[ type ](); | |
| 4585 | } catch ( e ) { | |
| 4586 | // IE<9 dies on focus/blur to hidden element (#1486,#12518) | |
| 4587 | // only reproducible on winXP IE8 native, not IE9 in IE8 mode | |
| 4588 | } | |
| 4589 | jQuery.event.triggered = undefined; | |
| 4590 | ||
| 4591 | if ( tmp ) { | |
| 4592 | elem[ ontype ] = tmp; | |
| 4593 | } | |
| 4594 | } | |
| 4595 | } | |
| 4596 | } | |
| 4597 | ||
| 4598 | return event.result; | |
| 4599 | }, | |
| 4600 | ||
| 4601 | dispatch: function( event ) { | |
| 4602 | ||
| 4603 | // Make a writable jQuery.Event from the native event object | |
| 4604 | event = jQuery.event.fix( event ); | |
| 4605 | ||
| 4606 | var i, ret, handleObj, matched, j, | |
| 4607 | handlerQueue = [], | |
| 4608 | args = slice.call( arguments ), | |
| 4609 | handlers = ( jQuery._data( this, "events" ) || {} )[ event.type ] || [], | |
| 4610 | special = jQuery.event.special[ event.type ] || {}; | |
| 4611 | ||
| 4612 | // Use the fix-ed jQuery.Event rather than the (read-only) native event | |
| 4613 | args[0] = event; | |
| 4614 | event.delegateTarget = this; | |
| 4615 | ||
| 4616 | // Call the preDispatch hook for the mapped type, and let it bail if desired | |
| 4617 | if ( special.preDispatch && special.preDispatch.call( this, event ) === false ) { | |
| 4618 | return; | |
| 4619 | } | |
| 4620 | ||
| 4621 | // Determine handlers | |
| 4622 | handlerQueue = jQuery.event.handlers.call( this, event, handlers ); | |
| 4623 | ||
| 4624 | // Run delegates first; they may want to stop propagation beneath us | |
| 4625 | i = 0; | |
| 4626 | while ( (matched = handlerQueue[ i++ ]) && !event.isPropagationStopped() ) { | |
| 4627 | event.currentTarget = matched.elem; | |
| 4628 | ||
| 4629 | j = 0; | |
| 4630 | while ( (handleObj = matched.handlers[ j++ ]) && !event.isImmediatePropagationStopped() ) { | |
| 4631 | ||
| 4632 | // Triggered event must either 1) have no namespace, or | |
| 4633 | // 2) have namespace(s) a subset or equal to those in the bound event (both can have no namespace). | |
| 4634 | if ( !event.namespace_re || event.namespace_re.test( handleObj.namespace ) ) { | |
| 4635 | ||
| 4636 | event.handleObj = handleObj; | |
| 4637 | event.data = handleObj.data; | |
| 4638 | ||
| 4639 | ret = ( (jQuery.event.special[ handleObj.origType ] || {}).handle || handleObj.handler ) | |
| 4640 | .apply( matched.elem, args ); | |
| 4641 | ||
| 4642 | if ( ret !== undefined ) { | |
| 4643 | if ( (event.result = ret) === false ) { | |
| 4644 | event.preventDefault(); | |
| 4645 | event.stopPropagation(); | |
| 4646 | } | |
| 4647 | } | |
| 4648 | } | |
| 4649 | } | |
| 4650 | } | |
| 4651 | ||
| 4652 | // Call the postDispatch hook for the mapped type | |
| 4653 | if ( special.postDispatch ) { | |
| 4654 | special.postDispatch.call( this, event ); | |
| 4655 | } | |
| 4656 | ||
| 4657 | return event.result; | |
| 4658 | }, | |
| 4659 | ||
| 4660 | handlers: function( event, handlers ) { | |
| 4661 | var sel, handleObj, matches, i, | |
| 4662 | handlerQueue = [], | |
| 4663 | delegateCount = handlers.delegateCount, | |
| 4664 | cur = event.target; | |
| 4665 | ||
| 4666 | // Find delegate handlers | |
| 4667 | // Black-hole SVG <use> instance trees (#13180) | |
| 4668 | // Avoid non-left-click bubbling in Firefox (#3861) | |
| 4669 | if ( delegateCount && cur.nodeType && (!event.button || event.type !== "click") ) { | |
| 4670 | ||
| 4671 | /* jshint eqeqeq: false */ | |
| 4672 | for ( ; cur != this; cur = cur.parentNode || this ) { | |
| 4673 | /* jshint eqeqeq: true */ | |
| 4674 | ||
| 4675 | // Don't check non-elements (#13208) | |
| 4676 | // Don't process clicks on disabled elements (#6911, #8165, #11382, #11764) | |
| 4677 | if ( cur.nodeType === 1 && (cur.disabled !== true || event.type !== "click") ) { | |
| 4678 | matches = []; | |
| 4679 | for ( i = 0; i < delegateCount; i++ ) { | |
| 4680 | handleObj = handlers[ i ]; | |
| 4681 | ||
| 4682 | // Don't conflict with Object.prototype properties (#13203) | |
| 4683 | sel = handleObj.selector + " "; | |
| 4684 | ||
| 4685 | if ( matches[ sel ] === undefined ) { | |
| 4686 | matches[ sel ] = handleObj.needsContext ? | |
| 4687 | jQuery( sel, this ).index( cur ) >= 0 : | |
| 4688 | jQuery.find( sel, this, null, [ cur ] ).length; | |
| 4689 | } | |
| 4690 | if ( matches[ sel ] ) { | |
| 4691 | matches.push( handleObj ); | |
| 4692 | } | |
| 4693 | } | |
| 4694 | if ( matches.length ) { | |
| 4695 | handlerQueue.push({ elem: cur, handlers: matches }); | |
| 4696 | } | |
| 4697 | } | |
| 4698 | } | |
| 4699 | } | |
| 4700 | ||
| 4701 | // Add the remaining (directly-bound) handlers | |
| 4702 | if ( delegateCount < handlers.length ) { | |
| 4703 | handlerQueue.push({ elem: this, handlers: handlers.slice( delegateCount ) }); | |
| 4704 | } | |
| 4705 | ||
| 4706 | return handlerQueue; | |
| 4707 | }, | |
| 4708 | ||
| 4709 | fix: function( event ) { | |
| 4710 | if ( event[ jQuery.expando ] ) { | |
| 4711 | return event; | |
| 4712 | } | |
| 4713 | ||
| 4714 | // Create a writable copy of the event object and normalize some properties | |
| 4715 | var i, prop, copy, | |
| 4716 | type = event.type, | |
| 4717 | originalEvent = event, | |
| 4718 | fixHook = this.fixHooks[ type ]; | |
| 4719 | ||
| 4720 | if ( !fixHook ) { | |
| 4721 | this.fixHooks[ type ] = fixHook = | |
| 4722 | rmouseEvent.test( type ) ? this.mouseHooks : | |
| 4723 | rkeyEvent.test( type ) ? this.keyHooks : | |
| 4724 | {}; | |
| 4725 | } | |
| 4726 | copy = fixHook.props ? this.props.concat( fixHook.props ) : this.props; | |
| 4727 | ||
| 4728 | event = new jQuery.Event( originalEvent ); | |
| 4729 | ||
| 4730 | i = copy.length; | |
| 4731 | while ( i-- ) { | |
| 4732 | prop = copy[ i ]; | |
| 4733 | event[ prop ] = originalEvent[ prop ]; | |
| 4734 | } | |
| 4735 | ||
| 4736 | // Support: IE<9 | |
| 4737 | // Fix target property (#1925) | |
| 4738 | if ( !event.target ) { | |
| 4739 | event.target = originalEvent.srcElement || document; | |
| 4740 | } | |
| 4741 | ||
| 4742 | // Support: Chrome 23+, Safari? | |
| 4743 | // Target should not be a text node (#504, #13143) | |
| 4744 | if ( event.target.nodeType === 3 ) { | |
| 4745 | event.target = event.target.parentNode; | |
| 4746 | } | |
| 4747 | ||
| 4748 | // Support: IE<9 | |
| 4749 | // For mouse/key events, metaKey==false if it's undefined (#3368, #11328) | |
| 4750 | event.metaKey = !!event.metaKey; | |
| 4751 | ||
| 4752 | return fixHook.filter ? fixHook.filter( event, originalEvent ) : event; | |
| 4753 | }, | |
| 4754 | ||
| 4755 | // Includes some event props shared by KeyEvent and MouseEvent | |
| 4756 | props: "altKey bubbles cancelable ctrlKey currentTarget eventPhase metaKey relatedTarget shiftKey target timeStamp view which".split(" "), | |
| 4757 | ||
| 4758 | fixHooks: {}, | |
| 4759 | ||
| 4760 | keyHooks: { | |
| 4761 | props: "char charCode key keyCode".split(" "), | |
| 4762 | filter: function( event, original ) { | |
| 4763 | ||
| 4764 | // Add which for key events | |
| 4765 | if ( event.which == null ) { | |
| 4766 | event.which = original.charCode != null ? original.charCode : original.keyCode; | |
| 4767 | } | |
| 4768 | ||
| 4769 | return event; | |
| 4770 | } | |
| 4771 | }, | |
| 4772 | ||
| 4773 | mouseHooks: { | |
| 4774 | props: "button buttons clientX clientY fromElement offsetX offsetY pageX pageY screenX screenY toElement".split(" "), | |
| 4775 | filter: function( event, original ) { | |
| 4776 | var body, eventDoc, doc, | |
| 4777 | button = original.button, | |
| 4778 | fromElement = original.fromElement; | |
| 4779 | ||
| 4780 | // Calculate pageX/Y if missing and clientX/Y available | |
| 4781 | if ( event.pageX == null && original.clientX != null ) { | |
| 4782 | eventDoc = event.target.ownerDocument || document; | |
| 4783 | doc = eventDoc.documentElement; | |
| 4784 | body = eventDoc.body; | |
| 4785 | ||
| 4786 | event.pageX = original.clientX + ( doc && doc.scrollLeft || body && body.scrollLeft || 0 ) - ( doc && doc.clientLeft || body && body.clientLeft || 0 ); | |
| 4787 | event.pageY = original.clientY + ( doc && doc.scrollTop || body && body.scrollTop || 0 ) - ( doc && doc.clientTop || body && body.clientTop || 0 ); | |
| 4788 | } | |
| 4789 | ||
| 4790 | // Add relatedTarget, if necessary | |
| 4791 | if ( !event.relatedTarget && fromElement ) { | |
| 4792 | event.relatedTarget = fromElement === event.target ? original.toElement : fromElement; | |
| 4793 | } | |
| 4794 | ||
| 4795 | // Add which for click: 1 === left; 2 === middle; 3 === right | |
| 4796 | // Note: button is not normalized, so don't use it | |
| 4797 | if ( !event.which && button !== undefined ) { | |
| 4798 | event.which = ( button & 1 ? 1 : ( button & 2 ? 3 : ( button & 4 ? 2 : 0 ) ) ); | |
| 4799 | } | |
| 4800 | ||
| 4801 | return event; | |
| 4802 | } | |
| 4803 | }, | |
| 4804 | ||
| 4805 | special: { | |
| 4806 | load: { | |
| 4807 | // Prevent triggered image.load events from bubbling to window.load | |
| 4808 | noBubble: true | |
| 4809 | }, | |
| 4810 | focus: { | |
| 4811 | // Fire native event if possible so blur/focus sequence is correct | |
| 4812 | trigger: function() { | |
| 4813 | if ( this !== safeActiveElement() && this.focus ) { | |
| 4814 | try { | |
| 4815 | this.focus(); | |
| 4816 | return false; | |
| 4817 | } catch ( e ) { | |
| 4818 | // Support: IE<9 | |
| 4819 | // If we error on focus to hidden element (#1486, #12518), | |
| 4820 | // let .trigger() run the handlers | |
| 4821 | } | |
| 4822 | } | |
| 4823 | }, | |
| 4824 | delegateType: "focusin" | |
| 4825 | }, | |
| 4826 | blur: { | |
| 4827 | trigger: function() { | |
| 4828 | if ( this === safeActiveElement() && this.blur ) { | |
| 4829 | this.blur(); | |
| 4830 | return false; | |
| 4831 | } | |
| 4832 | }, | |
| 4833 | delegateType: "focusout" | |
| 4834 | }, | |
| 4835 | click: { | |
| 4836 | // For checkbox, fire native event so checked state will be right | |
| 4837 | trigger: function() { | |
| 4838 | if ( jQuery.nodeName( this, "input" ) && this.type === "checkbox" && this.click ) { | |
| 4839 | this.click(); | |
| 4840 | return false; | |
| 4841 | } | |
| 4842 | }, | |
| 4843 | ||
| 4844 | // For cross-browser consistency, don't fire native .click() on links | |
| 4845 | _default: function( event ) { | |
| 4846 | return jQuery.nodeName( event.target, "a" ); | |
| 4847 | } | |
| 4848 | }, | |
| 4849 | ||
| 4850 | beforeunload: { | |
| 4851 | postDispatch: function( event ) { | |
| 4852 | ||
| 4853 | // Support: Firefox 20+ | |
| 4854 | // Firefox doesn't alert if the returnValue field is not set. | |
| 4855 | if ( event.result !== undefined && event.originalEvent ) { | |
| 4856 | event.originalEvent.returnValue = event.result; | |
| 4857 | } | |
| 4858 | } | |
| 4859 | } | |
| 4860 | }, | |
| 4861 | ||
| 4862 | simulate: function( type, elem, event, bubble ) { | |
| 4863 | // Piggyback on a donor event to simulate a different one. | |
| 4864 | // Fake originalEvent to avoid donor's stopPropagation, but if the | |
| 4865 | // simulated event prevents default then we do the same on the donor. | |
| 4866 | var e = jQuery.extend( | |
| 4867 | new jQuery.Event(), | |
| 4868 | event, | |
| 4869 | { | |
| 4870 | type: type, | |
| 4871 | isSimulated: true, | |
| 4872 | originalEvent: {} | |
| 4873 | } | |
| 4874 | ); | |
| 4875 | if ( bubble ) { | |
| 4876 | jQuery.event.trigger( e, null, elem ); | |
| 4877 | } else { | |
| 4878 | jQuery.event.dispatch.call( elem, e ); | |
| 4879 | } | |
| 4880 | if ( e.isDefaultPrevented() ) { | |
| 4881 | event.preventDefault(); | |
| 4882 | } | |
| 4883 | } | |
| 4884 | }; | |
| 4885 | ||
| 4886 | jQuery.removeEvent = document.removeEventListener ? | |
| 4887 | function( elem, type, handle ) { | |
| 4888 | if ( elem.removeEventListener ) { | |
| 4889 | elem.removeEventListener( type, handle, false ); | |
| 4890 | } | |
| 4891 | } : | |
| 4892 | function( elem, type, handle ) { | |
| 4893 | var name = "on" + type; | |
| 4894 | ||
| 4895 | if ( elem.detachEvent ) { | |
| 4896 | ||
| 4897 | // #8545, #7054, preventing memory leaks for custom events in IE6-8 | |
| 4898 | // detachEvent needed property on element, by name of that event, to properly expose it to GC | |
| 4899 | if ( typeof elem[ name ] === strundefined ) { | |
| 4900 | elem[ name ] = null; | |
| 4901 | } | |
| 4902 | ||
| 4903 | elem.detachEvent( name, handle ); | |
| 4904 | } | |
| 4905 | }; | |
| 4906 | ||
| 4907 | jQuery.Event = function( src, props ) { | |
| 4908 | // Allow instantiation without the 'new' keyword | |
| 4909 | if ( !(this instanceof jQuery.Event) ) { | |
| 4910 | return new jQuery.Event( src, props ); | |
| 4911 | } | |
| 4912 | ||
| 4913 | // Event object | |
| 4914 | if ( src && src.type ) { | |
| 4915 | this.originalEvent = src; | |
| 4916 | this.type = src.type; | |
| 4917 | ||
| 4918 | // Events bubbling up the document may have been marked as prevented | |
| 4919 | // by a handler lower down the tree; reflect the correct value. | |
| 4920 | this.isDefaultPrevented = src.defaultPrevented || | |
| 4921 | src.defaultPrevented === undefined && | |
| 4922 | // Support: IE < 9, Android < 4.0 | |
| 4923 | src.returnValue === false ? | |
| 4924 | returnTrue : | |
| 4925 | returnFalse; | |
| 4926 | ||
| 4927 | // Event type | |
| 4928 | } else { | |
| 4929 | this.type = src; | |
| 4930 | } | |
| 4931 | ||
| 4932 | // Put explicitly provided properties onto the event object | |
| 4933 | if ( props ) { | |
| 4934 | jQuery.extend( this, props ); | |
| 4935 | } | |
| 4936 | ||
| 4937 | // Create a timestamp if incoming event doesn't have one | |
| 4938 | this.timeStamp = src && src.timeStamp || jQuery.now(); | |
| 4939 | ||
| 4940 | // Mark it as fixed | |
| 4941 | this[ jQuery.expando ] = true; | |
| 4942 | }; | |
| 4943 | ||
| 4944 | // jQuery.Event is based on DOM3 Events as specified by the ECMAScript Language Binding | |
| 4945 | // http://www.w3.org/TR/2003/WD-DOM-Level-3-Events-20030331/ecma-script-binding.html | |
| 4946 | jQuery.Event.prototype = { | |
| 4947 | isDefaultPrevented: returnFalse, | |
| 4948 | isPropagationStopped: returnFalse, | |
| 4949 | isImmediatePropagationStopped: returnFalse, | |
| 4950 | ||
| 4951 | preventDefault: function() { | |
| 4952 | var e = this.originalEvent; | |
| 4953 | ||
| 4954 | this.isDefaultPrevented = returnTrue; | |
| 4955 | if ( !e ) { | |
| 4956 | return; | |
| 4957 | } | |
| 4958 | ||
| 4959 | // If preventDefault exists, run it on the original event | |
| 4960 | if ( e.preventDefault ) { | |
| 4961 | e.preventDefault(); | |
| 4962 | ||
| 4963 | // Support: IE | |
| 4964 | // Otherwise set the returnValue property of the original event to false | |
| 4965 | } else { | |
| 4966 | e.returnValue = false; | |
| 4967 | } | |
| 4968 | }, | |
| 4969 | stopPropagation: function() { | |
| 4970 | var e = this.originalEvent; | |
| 4971 | ||
| 4972 | this.isPropagationStopped = returnTrue; | |
| 4973 | if ( !e ) { | |
| 4974 | return; | |
| 4975 | } | |
| 4976 | // If stopPropagation exists, run it on the original event | |
| 4977 | if ( e.stopPropagation ) { | |
| 4978 | e.stopPropagation(); | |
| 4979 | } | |
| 4980 | ||
| 4981 | // Support: IE | |
| 4982 | // Set the cancelBubble property of the original event to true | |
| 4983 | e.cancelBubble = true; | |
| 4984 | }, | |
| 4985 | stopImmediatePropagation: function() { | |
| 4986 | var e = this.originalEvent; | |
| 4987 | ||
| 4988 | this.isImmediatePropagationStopped = returnTrue; | |
| 4989 | ||
| 4990 | if ( e && e.stopImmediatePropagation ) { | |
| 4991 | e.stopImmediatePropagation(); | |
| 4992 | } | |
| 4993 | ||
| 4994 | this.stopPropagation(); | |
| 4995 | } | |
| 4996 | }; | |
| 4997 | ||
| 4998 | // Create mouseenter/leave events using mouseover/out and event-time checks | |
| 4999 | jQuery.each({ | |
| 5000 | mouseenter: "mouseover", | |
| 5001 | mouseleave: "mouseout", | |
| 5002 | pointerenter: "pointerover", | |
| 5003 | pointerleave: "pointerout" | |
| 5004 | }, function( orig, fix ) { | |
| 5005 | jQuery.event.special[ orig ] = { | |
| 5006 | delegateType: fix, | |
| 5007 | bindType: fix, | |
| 5008 | ||
| 5009 | handle: function( event ) { | |
| 5010 | var ret, | |
| 5011 | target = this, | |
| 5012 | related = event.relatedTarget, | |
| 5013 | handleObj = event.handleObj; | |
| 5014 | ||
| 5015 | // For mousenter/leave call the handler if related is outside the target. | |
| 5016 | // NB: No relatedTarget if the mouse left/entered the browser window | |
| 5017 | if ( !related || (related !== target && !jQuery.contains( target, related )) ) { | |
| 5018 | event.type = handleObj.origType; | |
| 5019 | ret = handleObj.handler.apply( this, arguments ); | |
| 5020 | event.type = fix; | |
| 5021 | } | |
| 5022 | return ret; | |
| 5023 | } | |
| 5024 | }; | |
| 5025 | }); | |
| 5026 | ||
| 5027 | // IE submit delegation | |
| 5028 | if ( !support.submitBubbles ) { | |
| 5029 | ||
| 5030 | jQuery.event.special.submit = { | |
| 5031 | setup: function() { | |
| 5032 | // Only need this for delegated form submit events | |
| 5033 | if ( jQuery.nodeName( this, "form" ) ) { | |
| 5034 | return false; | |
| 5035 | } | |
| 5036 | ||
| 5037 | // Lazy-add a submit handler when a descendant form may potentially be submitted | |
| 5038 | jQuery.event.add( this, "click._submit keypress._submit", function( e ) { | |
| 5039 | // Node name check avoids a VML-related crash in IE (#9807) | |
| 5040 | var elem = e.target, | |
| 5041 | form = jQuery.nodeName( elem, "input" ) || jQuery.nodeName( elem, "button" ) ? elem.form : undefined; | |
| 5042 | if ( form && !jQuery._data( form, "submitBubbles" ) ) { | |
| 5043 | jQuery.event.add( form, "submit._submit", function( event ) { | |
| 5044 | event._submit_bubble = true; | |
| 5045 | }); | |
| 5046 | jQuery._data( form, "submitBubbles", true ); | |
| 5047 | } | |
| 5048 | }); | |
| 5049 | // return undefined since we don't need an event listener | |
| 5050 | }, | |
| 5051 | ||
| 5052 | postDispatch: function( event ) { | |
| 5053 | // If form was submitted by the user, bubble the event up the tree | |
| 5054 | if ( event._submit_bubble ) { | |
| 5055 | delete event._submit_bubble; | |
| 5056 | if ( this.parentNode && !event.isTrigger ) { | |
| 5057 | jQuery.event.simulate( "submit", this.parentNode, event, true ); | |
| 5058 | } | |
| 5059 | } | |
| 5060 | }, | |
| 5061 | ||
| 5062 | teardown: function() { | |
| 5063 | // Only need this for delegated form submit events | |
| 5064 | if ( jQuery.nodeName( this, "form" ) ) { | |
| 5065 | return false; | |
| 5066 | } | |
| 5067 | ||
| 5068 | // Remove delegated handlers; cleanData eventually reaps submit handlers attached above | |
| 5069 | jQuery.event.remove( this, "._submit" ); | |
| 5070 | } | |
| 5071 | }; | |
| 5072 | } | |
| 5073 | ||
| 5074 | // IE change delegation and checkbox/radio fix | |
| 5075 | if ( !support.changeBubbles ) { | |
| 5076 | ||
| 5077 | jQuery.event.special.change = { | |
| 5078 | ||
| 5079 | setup: function() { | |
| 5080 | ||
| 5081 | if ( rformElems.test( this.nodeName ) ) { | |
| 5082 | // IE doesn't fire change on a check/radio until blur; trigger it on click | |
| 5083 | // after a propertychange. Eat the blur-change in special.change.handle. | |
| 5084 | // This still fires onchange a second time for check/radio after blur. | |
| 5085 | if ( this.type === "checkbox" || this.type === "radio" ) { | |
| 5086 | jQuery.event.add( this, "propertychange._change", function( event ) { | |
| 5087 | if ( event.originalEvent.propertyName === "checked" ) { | |
| 5088 | this._just_changed = true; | |
| 5089 | } | |
| 5090 | }); | |
| 5091 | jQuery.event.add( this, "click._change", function( event ) { | |
| 5092 | if ( this._just_changed && !event.isTrigger ) { | |
| 5093 | this._just_changed = false; | |
| 5094 | } | |
| 5095 | // Allow triggered, simulated change events (#11500) | |
| 5096 | jQuery.event.simulate( "change", this, event, true ); | |
| 5097 | }); | |
| 5098 | } | |
| 5099 | return false; | |
| 5100 | } | |
| 5101 | // Delegated event; lazy-add a change handler on descendant inputs | |
| 5102 | jQuery.event.add( this, "beforeactivate._change", function( e ) { | |
| 5103 | var elem = e.target; | |
| 5104 | ||
| 5105 | if ( rformElems.test( elem.nodeName ) && !jQuery._data( elem, "changeBubbles" ) ) { | |
| 5106 | jQuery.event.add( elem, "change._change", function( event ) { | |
| 5107 | if ( this.parentNode && !event.isSimulated && !event.isTrigger ) { | |
| 5108 | jQuery.event.simulate( "change", this.parentNode, event, true ); | |
| 5109 | } | |
| 5110 | }); | |
| 5111 | jQuery._data( elem, "changeBubbles", true ); | |
| 5112 | } | |
| 5113 | }); | |
| 5114 | }, | |
| 5115 | ||
| 5116 | handle: function( event ) { | |
| 5117 | var elem = event.target; | |
| 5118 | ||
| 5119 | // Swallow native change events from checkbox/radio, we already triggered them above | |
| 5120 | if ( this !== elem || event.isSimulated || event.isTrigger || (elem.type !== "radio" && elem.type !== "checkbox") ) { | |
| 5121 | return event.handleObj.handler.apply( this, arguments ); | |
| 5122 | } | |
| 5123 | }, | |
| 5124 | ||
| 5125 | teardown: function() { | |
| 5126 | jQuery.event.remove( this, "._change" ); | |
| 5127 | ||
| 5128 | return !rformElems.test( this.nodeName ); | |
| 5129 | } | |
| 5130 | }; | |
| 5131 | } | |
| 5132 | ||
| 5133 | // Create "bubbling" focus and blur events | |
| 5134 | if ( !support.focusinBubbles ) { | |
| 5135 | jQuery.each({ focus: "focusin", blur: "focusout" }, function( orig, fix ) { | |
| 5136 | ||
| 5137 | // Attach a single capturing handler on the document while someone wants focusin/focusout | |
| 5138 | var handler = function( event ) { | |
| 5139 | jQuery.event.simulate( fix, event.target, jQuery.event.fix( event ), true ); | |
| 5140 | }; | |
| 5141 | ||
| 5142 | jQuery.event.special[ fix ] = { | |
| 5143 | setup: function() { | |
| 5144 | var doc = this.ownerDocument || this, | |
| 5145 | attaches = jQuery._data( doc, fix ); | |
| 5146 | ||
| 5147 | if ( !attaches ) { | |
| 5148 | doc.addEventListener( orig, handler, true ); | |
| 5149 | } | |
| 5150 | jQuery._data( doc, fix, ( attaches || 0 ) + 1 ); | |
| 5151 | }, | |
| 5152 | teardown: function() { | |
| 5153 | var doc = this.ownerDocument || this, | |
| 5154 | attaches = jQuery._data( doc, fix ) - 1; | |
| 5155 | ||
| 5156 | if ( !attaches ) { | |
| 5157 | doc.removeEventListener( orig, handler, true ); | |
| 5158 | jQuery._removeData( doc, fix ); | |
| 5159 | } else { | |
| 5160 | jQuery._data( doc, fix, attaches ); | |
| 5161 | } | |
| 5162 | } | |
| 5163 | }; | |
| 5164 | }); | |
| 5165 | } | |
| 5166 | ||
| 5167 | jQuery.fn.extend({ | |
| 5168 | ||
| 5169 | on: function( types, selector, data, fn, /*INTERNAL*/ one ) { | |
| 5170 | var type, origFn; | |
| 5171 | ||
| 5172 | // Types can be a map of types/handlers | |
| 5173 | if ( typeof types === "object" ) { | |
| 5174 | // ( types-Object, selector, data ) | |
| 5175 | if ( typeof selector !== "string" ) { | |
| 5176 | // ( types-Object, data ) | |
| 5177 | data = data || selector; | |
| 5178 | selector = undefined; | |
| 5179 | } | |
| 5180 | for ( type in types ) { | |
| 5181 | this.on( type, selector, data, types[ type ], one ); | |
| 5182 | } | |
| 5183 | return this; | |
| 5184 | } | |
| 5185 | ||
| 5186 | if ( data == null && fn == null ) { | |
| 5187 | // ( types, fn ) | |
| 5188 | fn = selector; | |
| 5189 | data = selector = undefined; | |
| 5190 | } else if ( fn == null ) { | |
| 5191 | if ( typeof selector === "string" ) { | |
| 5192 | // ( types, selector, fn ) | |
| 5193 | fn = data; | |
| 5194 | data = undefined; | |
| 5195 | } else { | |
| 5196 | // ( types, data, fn ) | |
| 5197 | fn = data; | |
| 5198 | data = selector; | |
| 5199 | selector = undefined; | |
| 5200 | } | |
| 5201 | } | |
| 5202 | if ( fn === false ) { | |
| 5203 | fn = returnFalse; | |
| 5204 | } else if ( !fn ) { | |
| 5205 | return this; | |
| 5206 | } | |
| 5207 | ||
| 5208 | if ( one === 1 ) { | |
| 5209 | origFn = fn; | |
| 5210 | fn = function( event ) { | |
| 5211 | // Can use an empty set, since event contains the info | |
| 5212 | jQuery().off( event ); | |
| 5213 | return origFn.apply( this, arguments ); | |
| 5214 | }; | |
| 5215 | // Use same guid so caller can remove using origFn | |
| 5216 | fn.guid = origFn.guid || ( origFn.guid = jQuery.guid++ ); | |
| 5217 | } | |
| 5218 | return this.each( function() { | |
| 5219 | jQuery.event.add( this, types, fn, data, selector ); | |
| 5220 | }); | |
| 5221 | }, | |
| 5222 | one: function( types, selector, data, fn ) { | |
| 5223 | return this.on( types, selector, data, fn, 1 ); | |
| 5224 | }, | |
| 5225 | off: function( types, selector, fn ) { | |
| 5226 | var handleObj, type; | |
| 5227 | if ( types && types.preventDefault && types.handleObj ) { | |
| 5228 | // ( event ) dispatched jQuery.Event | |
| 5229 | handleObj = types.handleObj; | |
| 5230 | jQuery( types.delegateTarget ).off( | |
| 5231 | handleObj.namespace ? handleObj.origType + "." + handleObj.namespace : handleObj.origType, | |
| 5232 | handleObj.selector, | |
| 5233 | handleObj.handler | |
| 5234 | ); | |
| 5235 | return this; | |
| 5236 | } | |
| 5237 | if ( typeof types === "object" ) { | |
| 5238 | // ( types-object [, selector] ) | |
| 5239 | for ( type in types ) { | |
| 5240 | this.off( type, selector, types[ type ] ); | |
| 5241 | } | |
| 5242 | return this; | |
| 5243 | } | |
| 5244 | if ( selector === false || typeof selector === "function" ) { | |
| 5245 | // ( types [, fn] ) | |
| 5246 | fn = selector; | |
| 5247 | selector = undefined; | |
| 5248 | } | |
| 5249 | if ( fn === false ) { | |
| 5250 | fn = returnFalse; | |
| 5251 | } | |
| 5252 | return this.each(function() { | |
| 5253 | jQuery.event.remove( this, types, fn, selector ); | |
| 5254 | }); | |
| 5255 | }, | |
| 5256 | ||
| 5257 | trigger: function( type, data ) { | |
| 5258 | return this.each(function() { | |
| 5259 | jQuery.event.trigger( type, data, this ); | |
| 5260 | }); | |
| 5261 | }, | |
| 5262 | triggerHandler: function( type, data ) { | |
| 5263 | var elem = this[0]; | |
| 5264 | if ( elem ) { | |
| 5265 | return jQuery.event.trigger( type, data, elem, true ); | |
| 5266 | } | |
| 5267 | } | |
| 5268 | }); | |
| 5269 | ||
| 5270 | ||
| 5271 | function createSafeFragment( document ) { | |
| 5272 | var list = nodeNames.split( "|" ), | |
| 5273 | safeFrag = document.createDocumentFragment(); | |
| 5274 | ||
| 5275 | if ( safeFrag.createElement ) { | |
| 5276 | while ( list.length ) { | |
| 5277 | safeFrag.createElement( | |
| 5278 | list.pop() | |
| 5279 | ); | |
| 5280 | } | |
| 5281 | } | |
| 5282 | return safeFrag; | |
| 5283 | } | |
| 5284 | ||
| 5285 | var nodeNames = "abbr|article|aside|audio|bdi|canvas|data|datalist|details|figcaption|figure|footer|" + | |
| 5286 | "header|hgroup|mark|meter|nav|output|progress|section|summary|time|video", | |
| 5287 | rinlinejQuery = / jQuery\d+="(?:null|\d+)"/g, | |
| 5288 | rnoshimcache = new RegExp("<(?:" + nodeNames + ")[\\s/>]", "i"), | |
| 5289 | rleadingWhitespace = /^\s+/, | |
| 5290 | rxhtmlTag = /<(?!area|br|col|embed|hr|img|input|link|meta|param)(([\w:]+)[^>]*)\/>/gi, | |
| 5291 | rtagName = /<([\w:]+)/, | |
| 5292 | rtbody = /<tbody/i, | |
| 5293 | rhtml = /<|&#?\w+;/, | |
| 5294 | rnoInnerhtml = /<(?:script|style|link)/i, | |
| 5295 | // checked="checked" or checked | |
| 5296 | rchecked = /checked\s*(?:[^=]|=\s*.checked.)/i, | |
| 5297 | rscriptType = /^$|\/(?:java|ecma)script/i, | |
| 5298 | rscriptTypeMasked = /^true\/(.*)/, | |
| 5299 | rcleanScript = /^\s*<!(?:\[CDATA\[|--)|(?:\]\]|--)>\s*$/g, | |
| 5300 | ||
| 5301 | // We have to close these tags to support XHTML (#13200) | |
| 5302 | wrapMap = { | |
| 5303 | option: [ 1, "<select multiple='multiple'>", "</select>" ], | |
| 5304 | legend: [ 1, "<fieldset>", "</fieldset>" ], | |
| 5305 | area: [ 1, "<map>", "</map>" ], | |
| 5306 | param: [ 1, "<object>", "</object>" ], | |
| 5307 | thead: [ 1, "<table>", "</table>" ], | |
| 5308 | tr: [ 2, "<table><tbody>", "</tbody></table>" ], | |
| 5309 | col: [ 2, "<table><tbody></tbody><colgroup>", "</colgroup></table>" ], | |
| 5310 | td: [ 3, "<table><tbody><tr>", "</tr></tbody></table>" ], | |
| 5311 | ||
| 5312 | // IE6-8 can't serialize link, script, style, or any html5 (NoScope) tags, | |
| 5313 | // unless wrapped in a div with non-breaking characters in front of it. | |
| 5314 | _default: support.htmlSerialize ? [ 0, "", "" ] : [ 1, "X<div>", "</div>" ] | |
| 5315 | }, | |
| 5316 | safeFragment = createSafeFragment( document ), | |
| 5317 | fragmentDiv = safeFragment.appendChild( document.createElement("div") ); | |
| 5318 | ||
| 5319 | wrapMap.optgroup = wrapMap.option; | |
| 5320 | wrapMap.tbody = wrapMap.tfoot = wrapMap.colgroup = wrapMap.caption = wrapMap.thead; | |
| 5321 | wrapMap.th = wrapMap.td; | |
| 5322 | ||
| 5323 | function getAll( context, tag ) { | |
| 5324 | var elems, elem, | |
| 5325 | i = 0, | |
| 5326 | found = typeof context.getElementsByTagName !== strundefined ? context.getElementsByTagName( tag || "*" ) : | |
| 5327 | typeof context.querySelectorAll !== strundefined ? context.querySelectorAll( tag || "*" ) : | |
| 5328 | undefined; | |
| 5329 | ||
| 5330 | if ( !found ) { | |
| 5331 | for ( found = [], elems = context.childNodes || context; (elem = elems[i]) != null; i++ ) { | |
| 5332 | if ( !tag || jQuery.nodeName( elem, tag ) ) { | |
| 5333 | found.push( elem ); | |
| 5334 | } else { | |
| 5335 | jQuery.merge( found, getAll( elem, tag ) ); | |
| 5336 | } | |
| 5337 | } | |
| 5338 | } | |
| 5339 | ||
| 5340 | return tag === undefined || tag && jQuery.nodeName( context, tag ) ? | |
| 5341 | jQuery.merge( [ context ], found ) : | |
| 5342 | found; | |
| 5343 | } | |
| 5344 | ||
| 5345 | // Used in buildFragment, fixes the defaultChecked property | |
| 5346 | function fixDefaultChecked( elem ) { | |
| 5347 | if ( rcheckableType.test( elem.type ) ) { | |
| 5348 | elem.defaultChecked = elem.checked; | |
| 5349 | } | |
| 5350 | } | |
| 5351 | ||
| 5352 | // Support: IE<8 | |
| 5353 | // Manipulating tables requires a tbody | |
| 5354 | function manipulationTarget( elem, content ) { | |
| 5355 | return jQuery.nodeName( elem, "table" ) && | |
| 5356 | jQuery.nodeName( content.nodeType !== 11 ? content : content.firstChild, "tr" ) ? | |
| 5357 | ||
| 5358 | elem.getElementsByTagName("tbody")[0] || | |
| 5359 | elem.appendChild( elem.ownerDocument.createElement("tbody") ) : | |
| 5360 | elem; | |
| 5361 | } | |
| 5362 | ||
| 5363 | // Replace/restore the type attribute of script elements for safe DOM manipulation | |
| 5364 | function disableScript( elem ) { | |
| 5365 | elem.type = (jQuery.find.attr( elem, "type" ) !== null) + "/" + elem.type; | |
| 5366 | return elem; | |
| 5367 | } | |
| 5368 | function restoreScript( elem ) { | |
| 5369 | var match = rscriptTypeMasked.exec( elem.type ); | |
| 5370 | if ( match ) { | |
| 5371 | elem.type = match[1]; | |
| 5372 | } else { | |
| 5373 | elem.removeAttribute("type"); | |
| 5374 | } | |
| 5375 | return elem; | |
| 5376 | } | |
| 5377 | ||
| 5378 | // Mark scripts as having already been evaluated | |
| 5379 | function setGlobalEval( elems, refElements ) { | |
| 5380 | var elem, | |
| 5381 | i = 0; | |
| 5382 | for ( ; (elem = elems[i]) != null; i++ ) { | |
| 5383 | jQuery._data( elem, "globalEval", !refElements || jQuery._data( refElements[i], "globalEval" ) ); | |
| 5384 | } | |
| 5385 | } | |
| 5386 | ||
| 5387 | function cloneCopyEvent( src, dest ) { | |
| 5388 | ||
| 5389 | if ( dest.nodeType !== 1 || !jQuery.hasData( src ) ) { | |
| 5390 | return; | |
| 5391 | } | |
| 5392 | ||
| 5393 | var type, i, l, | |
| 5394 | oldData = jQuery._data( src ), | |
| 5395 | curData = jQuery._data( dest, oldData ), | |
| 5396 | events = oldData.events; | |
| 5397 | ||
| 5398 | if ( events ) { | |
| 5399 | delete curData.handle; | |
| 5400 | curData.events = {}; | |
| 5401 | ||
| 5402 | for ( type in events ) { | |
| 5403 | for ( i = 0, l = events[ type ].length; i < l; i++ ) { | |
| 5404 | jQuery.event.add( dest, type, events[ type ][ i ] ); | |
| 5405 | } | |
| 5406 | } | |
| 5407 | } | |
| 5408 | ||
| 5409 | // make the cloned public data object a copy from the original | |
| 5410 | if ( curData.data ) { | |
| 5411 | curData.data = jQuery.extend( {}, curData.data ); | |
| 5412 | } | |
| 5413 | } | |
| 5414 | ||
| 5415 | function fixCloneNodeIssues( src, dest ) { | |
| 5416 | var nodeName, e, data; | |
| 5417 | ||
| 5418 | // We do not need to do anything for non-Elements | |
| 5419 | if ( dest.nodeType !== 1 ) { | |
| 5420 | return; | |
| 5421 | } | |
| 5422 | ||
| 5423 | nodeName = dest.nodeName.toLowerCase(); | |
| 5424 | ||
| 5425 | // IE6-8 copies events bound via attachEvent when using cloneNode. | |
| 5426 | if ( !support.noCloneEvent && dest[ jQuery.expando ] ) { | |
| 5427 | data = jQuery._data( dest ); | |
| 5428 | ||
| 5429 | for ( e in data.events ) { | |
| 5430 | jQuery.removeEvent( dest, e, data.handle ); | |
| 5431 | } | |
| 5432 | ||
| 5433 | // Event data gets referenced instead of copied if the expando gets copied too | |
| 5434 | dest.removeAttribute( jQuery.expando ); | |
| 5435 | } | |
| 5436 | ||
| 5437 | // IE blanks contents when cloning scripts, and tries to evaluate newly-set text | |
| 5438 | if ( nodeName === "script" && dest.text !== src.text ) { | |
| 5439 | disableScript( dest ).text = src.text; | |
| 5440 | restoreScript( dest ); | |
| 5441 | ||
| 5442 | // IE6-10 improperly clones children of object elements using classid. | |
| 5443 | // IE10 throws NoModificationAllowedError if parent is null, #12132. | |
| 5444 | } else if ( nodeName === "object" ) { | |
| 5445 | if ( dest.parentNode ) { | |
| 5446 | dest.outerHTML = src.outerHTML; | |
| 5447 | } | |
| 5448 | ||
| 5449 | // This path appears unavoidable for IE9. When cloning an object | |
| 5450 | // element in IE9, the outerHTML strategy above is not sufficient. | |
| 5451 | // If the src has innerHTML and the destination does not, | |
| 5452 | // copy the src.innerHTML into the dest.innerHTML. #10324 | |
| 5453 | if ( support.html5Clone && ( src.innerHTML && !jQuery.trim(dest.innerHTML) ) ) { | |
| 5454 | dest.innerHTML = src.innerHTML; | |
| 5455 | } | |
| 5456 | ||
| 5457 | } else if ( nodeName === "input" && rcheckableType.test( src.type ) ) { | |
| 5458 | // IE6-8 fails to persist the checked state of a cloned checkbox | |
| 5459 | // or radio button. Worse, IE6-7 fail to give the cloned element | |
| 5460 | // a checked appearance if the defaultChecked value isn't also set | |
| 5461 | ||
| 5462 | dest.defaultChecked = dest.checked = src.checked; | |
| 5463 | ||
| 5464 | // IE6-7 get confused and end up setting the value of a cloned | |
| 5465 | // checkbox/radio button to an empty string instead of "on" | |
| 5466 | if ( dest.value !== src.value ) { | |
| 5467 | dest.value = src.value; | |
| 5468 | } | |
| 5469 | ||
| 5470 | // IE6-8 fails to return the selected option to the default selected | |
| 5471 | // state when cloning options | |
| 5472 | } else if ( nodeName === "option" ) { | |
| 5473 | dest.defaultSelected = dest.selected = src.defaultSelected; | |
| 5474 | ||
| 5475 | // IE6-8 fails to set the defaultValue to the correct value when | |
| 5476 | // cloning other types of input fields | |
| 5477 | } else if ( nodeName === "input" || nodeName === "textarea" ) { | |
| 5478 | dest.defaultValue = src.defaultValue; | |
| 5479 | } | |
| 5480 | } | |
| 5481 | ||
| 5482 | jQuery.extend({ | |
| 5483 | clone: function( elem, dataAndEvents, deepDataAndEvents ) { | |
| 5484 | var destElements, node, clone, i, srcElements, | |
| 5485 | inPage = jQuery.contains( elem.ownerDocument, elem ); | |
| 5486 | ||
| 5487 | if ( support.html5Clone || jQuery.isXMLDoc(elem) || !rnoshimcache.test( "<" + elem.nodeName + ">" ) ) { | |
| 5488 | clone = elem.cloneNode( true ); | |
| 5489 | ||
| 5490 | // IE<=8 does not properly clone detached, unknown element nodes | |
| 5491 | } else { | |
| 5492 | fragmentDiv.innerHTML = elem.outerHTML; | |
| 5493 | fragmentDiv.removeChild( clone = fragmentDiv.firstChild ); | |
| 5494 | } | |
| 5495 | ||
| 5496 | if ( (!support.noCloneEvent || !support.noCloneChecked) && | |
| 5497 | (elem.nodeType === 1 || elem.nodeType === 11) && !jQuery.isXMLDoc(elem) ) { | |
| 5498 | ||
| 5499 | // We eschew Sizzle here for performance reasons: http://jsperf.com/getall-vs-sizzle/2 | |
| 5500 | destElements = getAll( clone ); | |
| 5501 | srcElements = getAll( elem ); | |
| 5502 | ||
| 5503 | // Fix all IE cloning issues | |
| 5504 | for ( i = 0; (node = srcElements[i]) != null; ++i ) { | |
| 5505 | // Ensure that the destination node is not null; Fixes #9587 | |
| 5506 | if ( destElements[i] ) { | |
| 5507 | fixCloneNodeIssues( node, destElements[i] ); | |
| 5508 | } | |
| 5509 | } | |
| 5510 | } | |
| 5511 | ||
| 5512 | // Copy the events from the original to the clone | |
| 5513 | if ( dataAndEvents ) { | |
| 5514 | if ( deepDataAndEvents ) { | |
| 5515 | srcElements = srcElements || getAll( elem ); | |
| 5516 | destElements = destElements || getAll( clone ); | |
| 5517 | ||
| 5518 | for ( i = 0; (node = srcElements[i]) != null; i++ ) { | |
| 5519 | cloneCopyEvent( node, destElements[i] ); | |
| 5520 | } | |
| 5521 | } else { | |
| 5522 | cloneCopyEvent( elem, clone ); | |
| 5523 | } | |
| 5524 | } | |
| 5525 | ||
| 5526 | // Preserve script evaluation history | |
| 5527 | destElements = getAll( clone, "script" ); | |
| 5528 | if ( destElements.length > 0 ) { | |
| 5529 | setGlobalEval( destElements, !inPage && getAll( elem, "script" ) ); | |
| 5530 | } | |
| 5531 | ||
| 5532 | destElements = srcElements = node = null; | |
| 5533 | ||
| 5534 | // Return the cloned set | |
| 5535 | return clone; | |
| 5536 | }, | |
| 5537 | ||
| 5538 | buildFragment: function( elems, context, scripts, selection ) { | |
| 5539 | var j, elem, contains, | |
| 5540 | tmp, tag, tbody, wrap, | |
| 5541 | l = elems.length, | |
| 5542 | ||
| 5543 | // Ensure a safe fragment | |
| 5544 | safe = createSafeFragment( context ), | |
| 5545 | ||
| 5546 | nodes = [], | |
| 5547 | i = 0; | |
| 5548 | ||
| 5549 | for ( ; i < l; i++ ) { | |
| 5550 | elem = elems[ i ]; | |
| 5551 | ||
| 5552 | if ( elem || elem === 0 ) { | |
| 5553 | ||
| 5554 | // Add nodes directly | |
| 5555 | if ( jQuery.type( elem ) === "object" ) { | |
| 5556 | jQuery.merge( nodes, elem.nodeType ? [ elem ] : elem ); | |
| 5557 | ||
| 5558 | // Convert non-html into a text node | |
| 5559 | } else if ( !rhtml.test( elem ) ) { | |
| 5560 | nodes.push( context.createTextNode( elem ) ); | |
| 5561 | ||
| 5562 | // Convert html into DOM nodes | |
| 5563 | } else { | |
| 5564 | tmp = tmp || safe.appendChild( context.createElement("div") ); | |
| 5565 | ||
| 5566 | // Deserialize a standard representation | |
| 5567 | tag = (rtagName.exec( elem ) || [ "", "" ])[ 1 ].toLowerCase(); | |
| 5568 | wrap = wrapMap[ tag ] || wrapMap._default; | |
| 5569 | ||
| 5570 | tmp.innerHTML = wrap[1] + elem.replace( rxhtmlTag, "<$1></$2>" ) + wrap[2]; | |
| 5571 | ||
| 5572 | // Descend through wrappers to the right content | |
| 5573 | j = wrap[0]; | |
| 5574 | while ( j-- ) { | |
| 5575 | tmp = tmp.lastChild; | |
| 5576 | } | |
| 5577 | ||
| 5578 | // Manually add leading whitespace removed by IE | |
| 5579 | if ( !support.leadingWhitespace && rleadingWhitespace.test( elem ) ) { | |
| 5580 | nodes.push( context.createTextNode( rleadingWhitespace.exec( elem )[0] ) ); | |
| 5581 | } | |
| 5582 | ||
| 5583 | // Remove IE's autoinserted <tbody> from table fragments | |
| 5584 | if ( !support.tbody ) { | |
| 5585 | ||
| 5586 | // String was a <table>, *may* have spurious <tbody> | |
| 5587 | elem = tag === "table" && !rtbody.test( elem ) ? | |
| 5588 | tmp.firstChild : | |
| 5589 | ||
| 5590 | // String was a bare <thead> or <tfoot> | |
| 5591 | wrap[1] === "<table>" && !rtbody.test( elem ) ? | |
| 5592 | tmp : | |
| 5593 | 0; | |
| 5594 | ||
| 5595 | j = elem && elem.childNodes.length; | |
| 5596 | while ( j-- ) { | |
| 5597 | if ( jQuery.nodeName( (tbody = elem.childNodes[j]), "tbody" ) && !tbody.childNodes.length ) { | |
| 5598 | elem.removeChild( tbody ); | |
| 5599 | } | |
| 5600 | } | |
| 5601 | } | |
| 5602 | ||
| 5603 | jQuery.merge( nodes, tmp.childNodes ); | |
| 5604 | ||
| 5605 | // Fix #12392 for WebKit and IE > 9 | |
| 5606 | tmp.textContent = ""; | |
| 5607 | ||
| 5608 | // Fix #12392 for oldIE | |
| 5609 | while ( tmp.firstChild ) { | |
| 5610 | tmp.removeChild( tmp.firstChild ); | |
| 5611 | } | |
| 5612 | ||
| 5613 | // Remember the top-level container for proper cleanup | |
| 5614 | tmp = safe.lastChild; | |
| 5615 | } | |
| 5616 | } | |
| 5617 | } | |
| 5618 | ||
| 5619 | // Fix #11356: Clear elements from fragment | |
| 5620 | if ( tmp ) { | |
| 5621 | safe.removeChild( tmp ); | |
| 5622 | } | |
| 5623 | ||
| 5624 | // Reset defaultChecked for any radios and checkboxes | |
| 5625 | // about to be appended to the DOM in IE 6/7 (#8060) | |
| 5626 | if ( !support.appendChecked ) { | |
| 5627 | jQuery.grep( getAll( nodes, "input" ), fixDefaultChecked ); | |
| 5628 | } | |
| 5629 | ||
| 5630 | i = 0; | |
| 5631 | while ( (elem = nodes[ i++ ]) ) { | |
| 5632 | ||
| 5633 | // #4087 - If origin and destination elements are the same, and this is | |
| 5634 | // that element, do not do anything | |
| 5635 | if ( selection && jQuery.inArray( elem, selection ) !== -1 ) { | |
| 5636 | continue; | |
| 5637 | } | |
| 5638 | ||
| 5639 | contains = jQuery.contains( elem.ownerDocument, elem ); | |
| 5640 | ||
| 5641 | // Append to fragment | |
| 5642 | tmp = getAll( safe.appendChild( elem ), "script" ); | |
| 5643 | ||
| 5644 | // Preserve script evaluation history | |
| 5645 | if ( contains ) { | |
| 5646 | setGlobalEval( tmp ); | |
| 5647 | } | |
| 5648 | ||
| 5649 | // Capture executables | |
| 5650 | if ( scripts ) { | |
| 5651 | j = 0; | |
| 5652 | while ( (elem = tmp[ j++ ]) ) { | |
| 5653 | if ( rscriptType.test( elem.type || "" ) ) { | |
| 5654 | scripts.push( elem ); | |
| 5655 | } | |
| 5656 | } | |
| 5657 | } | |
| 5658 | } | |
| 5659 | ||
| 5660 | tmp = null; | |
| 5661 | ||
| 5662 | return safe; | |
| 5663 | }, | |
| 5664 | ||
| 5665 | cleanData: function( elems, /* internal */ acceptData ) { | |
| 5666 | var elem, type, id, data, | |
| 5667 | i = 0, | |
| 5668 | internalKey = jQuery.expando, | |
| 5669 | cache = jQuery.cache, | |
| 5670 | deleteExpando = support.deleteExpando, | |
| 5671 | special = jQuery.event.special; | |
| 5672 | ||
| 5673 | for ( ; (elem = elems[i]) != null; i++ ) { | |
| 5674 | if ( acceptData || jQuery.acceptData( elem ) ) { | |
| 5675 | ||
| 5676 | id = elem[ internalKey ]; | |
| 5677 | data = id && cache[ id ]; | |
| 5678 | ||
| 5679 | if ( data ) { | |
| 5680 | if ( data.events ) { | |
| 5681 | for ( type in data.events ) { | |
| 5682 | if ( special[ type ] ) { | |
| 5683 | jQuery.event.remove( elem, type ); | |
| 5684 | ||
| 5685 | // This is a shortcut to avoid jQuery.event.remove's overhead | |
| 5686 | } else { | |
| 5687 | jQuery.removeEvent( elem, type, data.handle ); | |
| 5688 | } | |
| 5689 | } | |
| 5690 | } | |
| 5691 | ||
| 5692 | // Remove cache only if it was not already removed by jQuery.event.remove | |
| 5693 | if ( cache[ id ] ) { | |
| 5694 | ||
| 5695 | delete cache[ id ]; | |
| 5696 | ||
| 5697 | // IE does not allow us to delete expando properties from nodes, | |
| 5698 | // nor does it have a removeAttribute function on Document nodes; | |
| 5699 | // we must handle all of these cases | |
| 5700 | if ( deleteExpando ) { | |
| 5701 | delete elem[ internalKey ]; | |
| 5702 | ||
| 5703 | } else if ( typeof elem.removeAttribute !== strundefined ) { | |
| 5704 | elem.removeAttribute( internalKey ); | |
| 5705 | ||
| 5706 | } else { | |
| 5707 | elem[ internalKey ] = null; | |
| 5708 | } | |
| 5709 | ||
| 5710 | deletedIds.push( id ); | |
| 5711 | } | |
| 5712 | } | |
| 5713 | } | |
| 5714 | } | |
| 5715 | } | |
| 5716 | }); | |
| 5717 | ||
| 5718 | jQuery.fn.extend({ | |
| 5719 | text: function( value ) { | |
| 5720 | return access( this, function( value ) { | |
| 5721 | return value === undefined ? | |
| 5722 | jQuery.text( this ) : | |
| 5723 | this.empty().append( ( this[0] && this[0].ownerDocument || document ).createTextNode( value ) ); | |
| 5724 | }, null, value, arguments.length ); | |
| 5725 | }, | |
| 5726 | ||
| 5727 | append: function() { | |
| 5728 | return this.domManip( arguments, function( elem ) { | |
| 5729 | if ( this.nodeType === 1 || this.nodeType === 11 || this.nodeType === 9 ) { | |
| 5730 | var target = manipulationTarget( this, elem ); | |
| 5731 | target.appendChild( elem ); | |
| 5732 | } | |
| 5733 | }); | |
| 5734 | }, | |
| 5735 | ||
| 5736 | prepend: function() { | |
| 5737 | return this.domManip( arguments, function( elem ) { | |
| 5738 | if ( this.nodeType === 1 || this.nodeType === 11 || this.nodeType === 9 ) { | |
| 5739 | var target = manipulationTarget( this, elem ); | |
| 5740 | target.insertBefore( elem, target.firstChild ); | |
| 5741 | } | |
| 5742 | }); | |
| 5743 | }, | |
| 5744 | ||
| 5745 | before: function() { | |
| 5746 | return this.domManip( arguments, function( elem ) { | |
| 5747 | if ( this.parentNode ) { | |
| 5748 | this.parentNode.insertBefore( elem, this ); | |
| 5749 | } | |
| 5750 | }); | |
| 5751 | }, | |
| 5752 | ||
| 5753 | after: function() { | |
| 5754 | return this.domManip( arguments, function( elem ) { | |
| 5755 | if ( this.parentNode ) { | |
| 5756 | this.parentNode.insertBefore( elem, this.nextSibling ); | |
| 5757 | } | |
| 5758 | }); | |
| 5759 | }, | |
| 5760 | ||
| 5761 | remove: function( selector, keepData /* Internal Use Only */ ) { | |
| 5762 | var elem, | |
| 5763 | elems = selector ? jQuery.filter( selector, this ) : this, | |
| 5764 | i = 0; | |
| 5765 | ||
| 5766 | for ( ; (elem = elems[i]) != null; i++ ) { | |
| 5767 | ||
| 5768 | if ( !keepData && elem.nodeType === 1 ) { | |
| 5769 | jQuery.cleanData( getAll( elem ) ); | |
| 5770 | } | |
| 5771 | ||
| 5772 | if ( elem.parentNode ) { | |
| 5773 | if ( keepData && jQuery.contains( elem.ownerDocument, elem ) ) { | |
| 5774 | setGlobalEval( getAll( elem, "script" ) ); | |
| 5775 | } | |
| 5776 | elem.parentNode.removeChild( elem ); | |
| 5777 | } | |
| 5778 | } | |
| 5779 | ||
| 5780 | return this; | |
| 5781 | }, | |
| 5782 | ||
| 5783 | empty: function() { | |
| 5784 | var elem, | |
| 5785 | i = 0; | |
| 5786 | ||
| 5787 | for ( ; (elem = this[i]) != null; i++ ) { | |
| 5788 | // Remove element nodes and prevent memory leaks | |
| 5789 | if ( elem.nodeType === 1 ) { | |
| 5790 | jQuery.cleanData( getAll( elem, false ) ); | |
| 5791 | } | |
| 5792 | ||
| 5793 | // Remove any remaining nodes | |
| 5794 | while ( elem.firstChild ) { | |
| 5795 | elem.removeChild( elem.firstChild ); | |
| 5796 | } | |
| 5797 | ||
| 5798 | // If this is a select, ensure that it displays empty (#12336) | |
| 5799 | // Support: IE<9 | |
| 5800 | if ( elem.options && jQuery.nodeName( elem, "select" ) ) { | |
| 5801 | elem.options.length = 0; | |
| 5802 | } | |
| 5803 | } | |
| 5804 | ||
| 5805 | return this; | |
| 5806 | }, | |
| 5807 | ||
| 5808 | clone: function( dataAndEvents, deepDataAndEvents ) { | |
| 5809 | dataAndEvents = dataAndEvents == null ? false : dataAndEvents; | |
| 5810 | deepDataAndEvents = deepDataAndEvents == null ? dataAndEvents : deepDataAndEvents; | |
| 5811 | ||
| 5812 | return this.map(function() { | |
| 5813 | return jQuery.clone( this, dataAndEvents, deepDataAndEvents ); | |
| 5814 | }); | |
| 5815 | }, | |
| 5816 | ||
| 5817 | html: function( value ) { | |
| 5818 | return access( this, function( value ) { | |
| 5819 | var elem = this[ 0 ] || {}, | |
| 5820 | i = 0, | |
| 5821 | l = this.length; | |
| 5822 | ||
| 5823 | if ( value === undefined ) { | |
| 5824 | return elem.nodeType === 1 ? | |
| 5825 | elem.innerHTML.replace( rinlinejQuery, "" ) : | |
| 5826 | undefined; | |
| 5827 | } | |
| 5828 | ||
| 5829 | // See if we can take a shortcut and just use innerHTML | |
| 5830 | if ( typeof value === "string" && !rnoInnerhtml.test( value ) && | |
| 5831 | ( support.htmlSerialize || !rnoshimcache.test( value ) ) && | |
| 5832 | ( support.leadingWhitespace || !rleadingWhitespace.test( value ) ) && | |
| 5833 | !wrapMap[ (rtagName.exec( value ) || [ "", "" ])[ 1 ].toLowerCase() ] ) { | |
| 5834 | ||
| 5835 | value = value.replace( rxhtmlTag, "<$1></$2>" ); | |
| 5836 | ||
| 5837 | try { | |
| 5838 | for (; i < l; i++ ) { | |
| 5839 | // Remove element nodes and prevent memory leaks | |
| 5840 | elem = this[i] || {}; | |
| 5841 | if ( elem.nodeType === 1 ) { | |
| 5842 | jQuery.cleanData( getAll( elem, false ) ); | |
| 5843 | elem.innerHTML = value; | |
| 5844 | } | |
| 5845 | } | |
| 5846 | ||
| 5847 | elem = 0; | |
| 5848 | ||
| 5849 | // If using innerHTML throws an exception, use the fallback method | |
| 5850 | } catch(e) {} | |
| 5851 | } | |
| 5852 | ||
| 5853 | if ( elem ) { | |
| 5854 | this.empty().append( value ); | |
| 5855 | } | |
| 5856 | }, null, value, arguments.length ); | |
| 5857 | }, | |
| 5858 | ||
| 5859 | replaceWith: function() { | |
| 5860 | var arg = arguments[ 0 ]; | |
| 5861 | ||
| 5862 | // Make the changes, replacing each context element with the new content | |
| 5863 | this.domManip( arguments, function( elem ) { | |
| 5864 | arg = this.parentNode; | |
| 5865 | ||
| 5866 | jQuery.cleanData( getAll( this ) ); | |
| 5867 | ||
| 5868 | if ( arg ) { | |
| 5869 | arg.replaceChild( elem, this ); | |
| 5870 | } | |
| 5871 | }); | |
| 5872 | ||
| 5873 | // Force removal if there was no new content (e.g., from empty arguments) | |
| 5874 | return arg && (arg.length || arg.nodeType) ? this : this.remove(); | |
| 5875 | }, | |
| 5876 | ||
| 5877 | detach: function( selector ) { | |
| 5878 | return this.remove( selector, true ); | |
| 5879 | }, | |
| 5880 | ||
| 5881 | domManip: function( args, callback ) { | |
| 5882 | ||
| 5883 | // Flatten any nested arrays | |
| 5884 | args = concat.apply( [], args ); | |
| 5885 | ||
| 5886 | var first, node, hasScripts, | |
| 5887 | scripts, doc, fragment, | |
| 5888 | i = 0, | |
| 5889 | l = this.length, | |
| 5890 | set = this, | |
| 5891 | iNoClone = l - 1, | |
| 5892 | value = args[0], | |
| 5893 | isFunction = jQuery.isFunction( value ); | |
| 5894 | ||
| 5895 | // We can't cloneNode fragments that contain checked, in WebKit | |
| 5896 | if ( isFunction || | |
| 5897 | ( l > 1 && typeof value === "string" && | |
| 5898 | !support.checkClone && rchecked.test( value ) ) ) { | |
| 5899 | return this.each(function( index ) { | |
| 5900 | var self = set.eq( index ); | |
| 5901 | if ( isFunction ) { | |
| 5902 | args[0] = value.call( this, index, self.html() ); | |
| 5903 | } | |
| 5904 | self.domManip( args, callback ); | |
| 5905 | }); | |
| 5906 | } | |
| 5907 | ||
| 5908 | if ( l ) { | |
| 5909 | fragment = jQuery.buildFragment( args, this[ 0 ].ownerDocument, false, this ); | |
| 5910 | first = fragment.firstChild; | |
| 5911 | ||
| 5912 | if ( fragment.childNodes.length === 1 ) { | |
| 5913 | fragment = first; | |
| 5914 | } | |
| 5915 | ||
| 5916 | if ( first ) { | |
| 5917 | scripts = jQuery.map( getAll( fragment, "script" ), disableScript ); | |
| 5918 | hasScripts = scripts.length; | |
| 5919 | ||
| 5920 | // Use the original fragment for the last item instead of the first because it can end up | |
| 5921 | // being emptied incorrectly in certain situations (#8070). | |
| 5922 | for ( ; i < l; i++ ) { | |
| 5923 | node = fragment; | |
| 5924 | ||
| 5925 | if ( i !== iNoClone ) { | |
| 5926 | node = jQuery.clone( node, true, true ); | |
| 5927 | ||
| 5928 | // Keep references to cloned scripts for later restoration | |
| 5929 | if ( hasScripts ) { | |
| 5930 | jQuery.merge( scripts, getAll( node, "script" ) ); | |
| 5931 | } | |
| 5932 | } | |
| 5933 | ||
| 5934 | callback.call( this[i], node, i ); | |
| 5935 | } | |
| 5936 | ||
| 5937 | if ( hasScripts ) { | |
| 5938 | doc = scripts[ scripts.length - 1 ].ownerDocument; | |
| 5939 | ||
| 5940 | // Reenable scripts | |
| 5941 | jQuery.map( scripts, restoreScript ); | |
| 5942 | ||
| 5943 | // Evaluate executable scripts on first document insertion | |
| 5944 | for ( i = 0; i < hasScripts; i++ ) { | |
| 5945 | node = scripts[ i ]; | |
| 5946 | if ( rscriptType.test( node.type || "" ) && | |
| 5947 | !jQuery._data( node, "globalEval" ) && jQuery.contains( doc, node ) ) { | |
| 5948 | ||
| 5949 | if ( node.src ) { | |
| 5950 | // Optional AJAX dependency, but won't run scripts if not present | |
| 5951 | if ( jQuery._evalUrl ) { | |
| 5952 | jQuery._evalUrl( node.src ); | |
| 5953 | } | |
| 5954 | } else { | |
| 5955 | jQuery.globalEval( ( node.text || node.textContent || node.innerHTML || "" ).replace( rcleanScript, "" ) ); | |
| 5956 | } | |
| 5957 | } | |
| 5958 | } | |
| 5959 | } | |
| 5960 | ||
| 5961 | // Fix #11809: Avoid leaking memory | |
| 5962 | fragment = first = null; | |
| 5963 | } | |
| 5964 | } | |
| 5965 | ||
| 5966 | return this; | |
| 5967 | } | |
| 5968 | }); | |
| 5969 | ||
| 5970 | jQuery.each({ | |
| 5971 | appendTo: "append", | |
| 5972 | prependTo: "prepend", | |
| 5973 | insertBefore: "before", | |
| 5974 | insertAfter: "after", | |
| 5975 | replaceAll: "replaceWith" | |
| 5976 | }, function( name, original ) { | |
| 5977 | jQuery.fn[ name ] = function( selector ) { | |
| 5978 | var elems, | |
| 5979 | i = 0, | |
| 5980 | ret = [], | |
| 5981 | insert = jQuery( selector ), | |
| 5982 | last = insert.length - 1; | |
| 5983 | ||
| 5984 | for ( ; i <= last; i++ ) { | |
| 5985 | elems = i === last ? this : this.clone(true); | |
| 5986 | jQuery( insert[i] )[ original ]( elems ); | |
| 5987 | ||
| 5988 | // Modern browsers can apply jQuery collections as arrays, but oldIE needs a .get() | |
| 5989 | push.apply( ret, elems.get() ); | |
| 5990 | } | |
| 5991 | ||
| 5992 | return this.pushStack( ret ); | |
| 5993 | }; | |
| 5994 | }); | |
| 5995 | ||
| 5996 | ||
| 5997 | var iframe, | |
| 5998 | elemdisplay = {}; | |
| 5999 | ||
| 6000 | /** | |
| 6001 | * Retrieve the actual display of a element | |
| 6002 | * @param {String} name nodeName of the element | |
| 6003 | * @param {Object} doc Document object | |
| 6004 | */ | |
| 6005 | // Called only from within defaultDisplay | |
| 6006 | function actualDisplay( name, doc ) { | |
| 6007 | var style, | |
| 6008 | elem = jQuery( doc.createElement( name ) ).appendTo( doc.body ), | |
| 6009 | ||
| 6010 | // getDefaultComputedStyle might be reliably used only on attached element | |
| 6011 | display = window.getDefaultComputedStyle && ( style = window.getDefaultComputedStyle( elem[ 0 ] ) ) ? | |
| 6012 | ||
| 6013 | // Use of this method is a temporary fix (more like optmization) until something better comes along, | |
| 6014 | // since it was removed from specification and supported only in FF | |
| 6015 | style.display : jQuery.css( elem[ 0 ], "display" ); | |
| 6016 | ||
| 6017 | // We don't have any data stored on the element, | |
| 6018 | // so use "detach" method as fast way to get rid of the element | |
| 6019 | elem.detach(); | |
| 6020 | ||
| 6021 | return display; | |
| 6022 | } | |
| 6023 | ||
| 6024 | /** | |
| 6025 | * Try to determine the default display value of an element | |
| 6026 | * @param {String} nodeName | |
| 6027 | */ | |
| 6028 | function defaultDisplay( nodeName ) { | |
| 6029 | var doc = document, | |
| 6030 | display = elemdisplay[ nodeName ]; | |
| 6031 | ||
| 6032 | if ( !display ) { | |
| 6033 | display = actualDisplay( nodeName, doc ); | |
| 6034 | ||
| 6035 | // If the simple way fails, read from inside an iframe | |
| 6036 | if ( display === "none" || !display ) { | |
| 6037 | ||
| 6038 | // Use the already-created iframe if possible | |
| 6039 | iframe = (iframe || jQuery( "<iframe frameborder='0' width='0' height='0'/>" )).appendTo( doc.documentElement ); | |
| 6040 | ||
| 6041 | // Always write a new HTML skeleton so Webkit and Firefox don't choke on reuse | |
| 6042 | doc = ( iframe[ 0 ].contentWindow || iframe[ 0 ].contentDocument ).document; | |
| 6043 | ||
| 6044 | // Support: IE | |
| 6045 | doc.write(); | |
| 6046 | doc.close(); | |
| 6047 | ||
| 6048 | display = actualDisplay( nodeName, doc ); | |
| 6049 | iframe.detach(); | |
| 6050 | } | |
| 6051 | ||
| 6052 | // Store the correct default display | |
| 6053 | elemdisplay[ nodeName ] = display; | |
| 6054 | } | |
| 6055 | ||
| 6056 | return display; | |
| 6057 | } | |
| 6058 | ||
| 6059 | ||
| 6060 | (function() { | |
| 6061 | var shrinkWrapBlocksVal; | |
| 6062 | ||
| 6063 | support.shrinkWrapBlocks = function() { | |
| 6064 | if ( shrinkWrapBlocksVal != null ) { | |
| 6065 | return shrinkWrapBlocksVal; | |
| 6066 | } | |
| 6067 | ||
| 6068 | // Will be changed later if needed. | |
| 6069 | shrinkWrapBlocksVal = false; | |
| 6070 | ||
| 6071 | // Minified: var b,c,d | |
| 6072 | var div, body, container; | |
| 6073 | ||
| 6074 | body = document.getElementsByTagName( "body" )[ 0 ]; | |
| 6075 | if ( !body || !body.style ) { | |
| 6076 | // Test fired too early or in an unsupported environment, exit. | |
| 6077 | return; | |
| 6078 | } | |
| 6079 | ||
| 6080 | // Setup | |
| 6081 | div = document.createElement( "div" ); | |
| 6082 | container = document.createElement( "div" ); | |
| 6083 | container.style.cssText = "position:absolute;border:0;width:0;height:0;top:0;left:-9999px"; | |
| 6084 | body.appendChild( container ).appendChild( div ); | |
| 6085 | ||
| 6086 | // Support: IE6 | |
| 6087 | // Check if elements with layout shrink-wrap their children | |
| 6088 | if ( typeof div.style.zoom !== strundefined ) { | |
| 6089 | // Reset CSS: box-sizing; display; margin; border | |
| 6090 | div.style.cssText = | |
| 6091 | // Support: Firefox<29, Android 2.3 | |
| 6092 | // Vendor-prefix box-sizing | |
| 6093 | "-webkit-box-sizing:content-box;-moz-box-sizing:content-box;" + | |
| 6094 | "box-sizing:content-box;display:block;margin:0;border:0;" + | |
| 6095 | "padding:1px;width:1px;zoom:1"; | |
| 6096 | div.appendChild( document.createElement( "div" ) ).style.width = "5px"; | |
| 6097 | shrinkWrapBlocksVal = div.offsetWidth !== 3; | |
| 6098 | } | |
| 6099 | ||
| 6100 | body.removeChild( container ); | |
| 6101 | ||
| 6102 | return shrinkWrapBlocksVal; | |
| 6103 | }; | |
| 6104 | ||
| 6105 | })(); | |
| 6106 | var rmargin = (/^margin/); | |
| 6107 | ||
| 6108 | var rnumnonpx = new RegExp( "^(" + pnum + ")(?!px)[a-z%]+$", "i" ); | |
| 6109 | ||
| 6110 | ||
| 6111 | ||
| 6112 | var getStyles, curCSS, | |
| 6113 | rposition = /^(top|right|bottom|left)$/; | |
| 6114 | ||
| 6115 | if ( window.getComputedStyle ) { | |
| 6116 | getStyles = function( elem ) { | |
| 6117 | return elem.ownerDocument.defaultView.getComputedStyle( elem, null ); | |
| 6118 | }; | |
| 6119 | ||
| 6120 | curCSS = function( elem, name, computed ) { | |
| 6121 | var width, minWidth, maxWidth, ret, | |
| 6122 | style = elem.style; | |
| 6123 | ||
| 6124 | computed = computed || getStyles( elem ); | |
| 6125 | ||
| 6126 | // getPropertyValue is only needed for .css('filter') in IE9, see #12537 | |
| 6127 | ret = computed ? computed.getPropertyValue( name ) || computed[ name ] : undefined; | |
| 6128 | ||
| 6129 | if ( computed ) { | |
| 6130 | ||
| 6131 | if ( ret === "" && !jQuery.contains( elem.ownerDocument, elem ) ) { | |
| 6132 | ret = jQuery.style( elem, name ); | |
| 6133 | } | |
| 6134 | ||
| 6135 | // A tribute to the "awesome hack by Dean Edwards" | |
| 6136 | // Chrome < 17 and Safari 5.0 uses "computed value" instead of "used value" for margin-right | |
| 6137 | // Safari 5.1.7 (at least) returns percentage for a larger set of values, but width seems to be reliably pixels | |
| 6138 | // this is against the CSSOM draft spec: http://dev.w3.org/csswg/cssom/#resolved-values | |
| 6139 | if ( rnumnonpx.test( ret ) && rmargin.test( name ) ) { | |
| 6140 | ||
| 6141 | // Remember the original values | |
| 6142 | width = style.width; | |
| 6143 | minWidth = style.minWidth; | |
| 6144 | maxWidth = style.maxWidth; | |
| 6145 | ||
| 6146 | // Put in the new values to get a computed value out | |
| 6147 | style.minWidth = style.maxWidth = style.width = ret; | |
| 6148 | ret = computed.width; | |
| 6149 | ||
| 6150 | // Revert the changed values | |
| 6151 | style.width = width; | |
| 6152 | style.minWidth = minWidth; | |
| 6153 | style.maxWidth = maxWidth; | |
| 6154 | } | |
| 6155 | } | |
| 6156 | ||
| 6157 | // Support: IE | |
| 6158 | // IE returns zIndex value as an integer. | |
| 6159 | return ret === undefined ? | |
| 6160 | ret : | |
| 6161 | ret + ""; | |
| 6162 | }; | |
| 6163 | } else if ( document.documentElement.currentStyle ) { | |
| 6164 | getStyles = function( elem ) { | |
| 6165 | return elem.currentStyle; | |
| 6166 | }; | |
| 6167 | ||
| 6168 | curCSS = function( elem, name, computed ) { | |
| 6169 | var left, rs, rsLeft, ret, | |
| 6170 | style = elem.style; | |
| 6171 | ||
| 6172 | computed = computed || getStyles( elem ); | |
| 6173 | ret = computed ? computed[ name ] : undefined; | |
| 6174 | ||
| 6175 | // Avoid setting ret to empty string here | |
| 6176 | // so we don't default to auto | |
| 6177 | if ( ret == null && style && style[ name ] ) { | |
| 6178 | ret = style[ name ]; | |
| 6179 | } | |
| 6180 | ||
| 6181 | // From the awesome hack by Dean Edwards | |
| 6182 | // http://erik.eae.net/archives/2007/07/27/18.54.15/#comment-102291 | |
| 6183 | ||
| 6184 | // If we're not dealing with a regular pixel number | |
| 6185 | // but a number that has a weird ending, we need to convert it to pixels | |
| 6186 | // but not position css attributes, as those are proportional to the parent element instead | |
| 6187 | // and we can't measure the parent instead because it might trigger a "stacking dolls" problem | |
| 6188 | if ( rnumnonpx.test( ret ) && !rposition.test( name ) ) { | |
| 6189 | ||
| 6190 | // Remember the original values | |
| 6191 | left = style.left; | |
| 6192 | rs = elem.runtimeStyle; | |
| 6193 | rsLeft = rs && rs.left; | |
| 6194 | ||
| 6195 | // Put in the new values to get a computed value out | |
| 6196 | if ( rsLeft ) { | |
| 6197 | rs.left = elem.currentStyle.left; | |
| 6198 | } | |
| 6199 | style.left = name === "fontSize" ? "1em" : ret; | |
| 6200 | ret = style.pixelLeft + "px"; | |
| 6201 | ||
| 6202 | // Revert the changed values | |
| 6203 | style.left = left; | |
| 6204 | if ( rsLeft ) { | |
| 6205 | rs.left = rsLeft; | |
| 6206 | } | |
| 6207 | } | |
| 6208 | ||
| 6209 | // Support: IE | |
| 6210 | // IE returns zIndex value as an integer. | |
| 6211 | return ret === undefined ? | |
| 6212 | ret : | |
| 6213 | ret + "" || "auto"; | |
| 6214 | }; | |
| 6215 | } | |
| 6216 | ||
| 6217 | ||
| 6218 | ||
| 6219 | ||
| 6220 | function addGetHookIf( conditionFn, hookFn ) { | |
| 6221 | // Define the hook, we'll check on the first run if it's really needed. | |
| 6222 | return { | |
| 6223 | get: function() { | |
| 6224 | var condition = conditionFn(); | |
| 6225 | ||
| 6226 | if ( condition == null ) { | |
| 6227 | // The test was not ready at this point; screw the hook this time | |
| 6228 | // but check again when needed next time. | |
| 6229 | return; | |
| 6230 | } | |
| 6231 | ||
| 6232 | if ( condition ) { | |
| 6233 | // Hook not needed (or it's not possible to use it due to missing dependency), | |
| 6234 | // remove it. | |
| 6235 | // Since there are no other hooks for marginRight, remove the whole object. | |
| 6236 | delete this.get; | |
| 6237 | return; | |
| 6238 | } | |
| 6239 | ||
| 6240 | // Hook needed; redefine it so that the support test is not executed again. | |
| 6241 | ||
| 6242 | return (this.get = hookFn).apply( this, arguments ); | |
| 6243 | } | |
| 6244 | }; | |
| 6245 | } | |
| 6246 | ||
| 6247 | ||
| 6248 | (function() { | |
| 6249 | // Minified: var b,c,d,e,f,g, h,i | |
| 6250 | var div, style, a, pixelPositionVal, boxSizingReliableVal, | |
| 6251 | reliableHiddenOffsetsVal, reliableMarginRightVal; | |
| 6252 | ||
| 6253 | // Setup | |
| 6254 | div = document.createElement( "div" ); | |
| 6255 | div.innerHTML = " <link/><table></table><a href='/a'>a</a><input type='checkbox'/>"; | |
| 6256 | a = div.getElementsByTagName( "a" )[ 0 ]; | |
| 6257 | style = a && a.style; | |
| 6258 | ||
| 6259 | // Finish early in limited (non-browser) environments | |
| 6260 | if ( !style ) { | |
| 6261 | return; | |
| 6262 | } | |
| 6263 | ||
| 6264 | style.cssText = "float:left;opacity:.5"; | |
| 6265 | ||
| 6266 | // Support: IE<9 | |
| 6267 | // Make sure that element opacity exists (as opposed to filter) | |
| 6268 | support.opacity = style.opacity === "0.5"; | |
| 6269 | ||
| 6270 | // Verify style float existence | |
| 6271 | // (IE uses styleFloat instead of cssFloat) | |
| 6272 | support.cssFloat = !!style.cssFloat; | |
| 6273 | ||
| 6274 | div.style.backgroundClip = "content-box"; | |
| 6275 | div.cloneNode( true ).style.backgroundClip = ""; | |
| 6276 | support.clearCloneStyle = div.style.backgroundClip === "content-box"; | |
| 6277 | ||
| 6278 | // Support: Firefox<29, Android 2.3 | |
| 6279 | // Vendor-prefix box-sizing | |
| 6280 | support.boxSizing = style.boxSizing === "" || style.MozBoxSizing === "" || | |
| 6281 | style.WebkitBoxSizing === ""; | |
| 6282 | ||
| 6283 | jQuery.extend(support, { | |
| 6284 | reliableHiddenOffsets: function() { | |
| 6285 | if ( reliableHiddenOffsetsVal == null ) { | |
| 6286 | computeStyleTests(); | |
| 6287 | } | |
| 6288 | return reliableHiddenOffsetsVal; | |
| 6289 | }, | |
| 6290 | ||
| 6291 | boxSizingReliable: function() { | |
| 6292 | if ( boxSizingReliableVal == null ) { | |
| 6293 | computeStyleTests(); | |
| 6294 | } | |
| 6295 | return boxSizingReliableVal; | |
| 6296 | }, | |
| 6297 | ||
| 6298 | pixelPosition: function() { | |
| 6299 | if ( pixelPositionVal == null ) { | |
| 6300 | computeStyleTests(); | |
| 6301 | } | |
| 6302 | return pixelPositionVal; | |
| 6303 | }, | |
| 6304 | ||
| 6305 | // Support: Android 2.3 | |
| 6306 | reliableMarginRight: function() { | |
| 6307 | if ( reliableMarginRightVal == null ) { | |
| 6308 | computeStyleTests(); | |
| 6309 | } | |
| 6310 | return reliableMarginRightVal; | |
| 6311 | } | |
| 6312 | }); | |
| 6313 | ||
| 6314 | function computeStyleTests() { | |
| 6315 | // Minified: var b,c,d,j | |
| 6316 | var div, body, container, contents; | |
| 6317 | ||
| 6318 | body = document.getElementsByTagName( "body" )[ 0 ]; | |
| 6319 | if ( !body || !body.style ) { | |
| 6320 | // Test fired too early or in an unsupported environment, exit. | |
| 6321 | return; | |
| 6322 | } | |
| 6323 | ||
| 6324 | // Setup | |
| 6325 | div = document.createElement( "div" ); | |
| 6326 | container = document.createElement( "div" ); | |
| 6327 | container.style.cssText = "position:absolute;border:0;width:0;height:0;top:0;left:-9999px"; | |
| 6328 | body.appendChild( container ).appendChild( div ); | |
| 6329 | ||
| 6330 | div.style.cssText = | |
| 6331 | // Support: Firefox<29, Android 2.3 | |
| 6332 | // Vendor-prefix box-sizing | |
| 6333 | "-webkit-box-sizing:border-box;-moz-box-sizing:border-box;" + | |
| 6334 | "box-sizing:border-box;display:block;margin-top:1%;top:1%;" + | |
| 6335 | "border:1px;padding:1px;width:4px;position:absolute"; | |
| 6336 | ||
| 6337 | // Support: IE<9 | |
| 6338 | // Assume reasonable values in the absence of getComputedStyle | |
| 6339 | pixelPositionVal = boxSizingReliableVal = false; | |
| 6340 | reliableMarginRightVal = true; | |
| 6341 | ||
| 6342 | // Check for getComputedStyle so that this code is not run in IE<9. | |
| 6343 | if ( window.getComputedStyle ) { | |
| 6344 | pixelPositionVal = ( window.getComputedStyle( div, null ) || {} ).top !== "1%"; | |
| 6345 | boxSizingReliableVal = | |
| 6346 | ( window.getComputedStyle( div, null ) || { width: "4px" } ).width === "4px"; | |
| 6347 | ||
| 6348 | // Support: Android 2.3 | |
| 6349 | // Div with explicit width and no margin-right incorrectly | |
| 6350 | // gets computed margin-right based on width of container (#3333) | |
| 6351 | // WebKit Bug 13343 - getComputedStyle returns wrong value for margin-right | |
| 6352 | contents = div.appendChild( document.createElement( "div" ) ); | |
| 6353 | ||
| 6354 | // Reset CSS: box-sizing; display; margin; border; padding | |
| 6355 | contents.style.cssText = div.style.cssText = | |
| 6356 | // Support: Firefox<29, Android 2.3 | |
| 6357 | // Vendor-prefix box-sizing | |
| 6358 | "-webkit-box-sizing:content-box;-moz-box-sizing:content-box;" + | |
| 6359 | "box-sizing:content-box;display:block;margin:0;border:0;padding:0"; | |
| 6360 | contents.style.marginRight = contents.style.width = "0"; | |
| 6361 | div.style.width = "1px"; | |
| 6362 | ||
| 6363 | reliableMarginRightVal = | |
| 6364 | !parseFloat( ( window.getComputedStyle( contents, null ) || {} ).marginRight ); | |
| 6365 | } | |
| 6366 | ||
| 6367 | // Support: IE8 | |
| 6368 | // Check if table cells still have offsetWidth/Height when they are set | |
| 6369 | // to display:none and there are still other visible table cells in a | |
| 6370 | // table row; if so, offsetWidth/Height are not reliable for use when | |
| 6371 | // determining if an element has been hidden directly using | |
| 6372 | // display:none (it is still safe to use offsets if a parent element is | |
| 6373 | // hidden; don safety goggles and see bug #4512 for more information). | |
| 6374 | div.innerHTML = "<table><tr><td></td><td>t</td></tr></table>"; | |
| 6375 | contents = div.getElementsByTagName( "td" ); | |
| 6376 | contents[ 0 ].style.cssText = "margin:0;border:0;padding:0;display:none"; | |
| 6377 | reliableHiddenOffsetsVal = contents[ 0 ].offsetHeight === 0; | |
| 6378 | if ( reliableHiddenOffsetsVal ) { | |
| 6379 | contents[ 0 ].style.display = ""; | |
| 6380 | contents[ 1 ].style.display = "none"; | |
| 6381 | reliableHiddenOffsetsVal = contents[ 0 ].offsetHeight === 0; | |
| 6382 | } | |
| 6383 | ||
| 6384 | body.removeChild( container ); | |
| 6385 | } | |
| 6386 | ||
| 6387 | })(); | |
| 6388 | ||
| 6389 | ||
| 6390 | // A method for quickly swapping in/out CSS properties to get correct calculations. | |
| 6391 | jQuery.swap = function( elem, options, callback, args ) { | |
| 6392 | var ret, name, | |
| 6393 | old = {}; | |
| 6394 | ||
| 6395 | // Remember the old values, and insert the new ones | |
| 6396 | for ( name in options ) { | |
| 6397 | old[ name ] = elem.style[ name ]; | |
| 6398 | elem.style[ name ] = options[ name ]; | |
| 6399 | } | |
| 6400 | ||
| 6401 | ret = callback.apply( elem, args || [] ); | |
| 6402 | ||
| 6403 | // Revert the old values | |
| 6404 | for ( name in options ) { | |
| 6405 | elem.style[ name ] = old[ name ]; | |
| 6406 | } | |
| 6407 | ||
| 6408 | return ret; | |
| 6409 | }; | |
| 6410 | ||
| 6411 | ||
| 6412 | var | |
| 6413 | ralpha = /alpha\([^)]*\)/i, | |
| 6414 | ropacity = /opacity\s*=\s*([^)]*)/, | |
| 6415 | ||
| 6416 | // swappable if display is none or starts with table except "table", "table-cell", or "table-caption" | |
| 6417 | // see here for display values: https://developer.mozilla.org/en-US/docs/CSS/display | |
| 6418 | rdisplayswap = /^(none|table(?!-c[ea]).+)/, | |
| 6419 | rnumsplit = new RegExp( "^(" + pnum + ")(.*)$", "i" ), | |
| 6420 | rrelNum = new RegExp( "^([+-])=(" + pnum + ")", "i" ), | |
| 6421 | ||
| 6422 | cssShow = { position: "absolute", visibility: "hidden", display: "block" }, | |
| 6423 | cssNormalTransform = { | |
| 6424 | letterSpacing: "0", | |
| 6425 | fontWeight: "400" | |
| 6426 | }, | |
| 6427 | ||
| 6428 | cssPrefixes = [ "Webkit", "O", "Moz", "ms" ]; | |
| 6429 | ||
| 6430 | ||
| 6431 | // return a css property mapped to a potentially vendor prefixed property | |
| 6432 | function vendorPropName( style, name ) { | |
| 6433 | ||
| 6434 | // shortcut for names that are not vendor prefixed | |
| 6435 | if ( name in style ) { | |
| 6436 | return name; | |
| 6437 | } | |
| 6438 | ||
| 6439 | // check for vendor prefixed names | |
| 6440 | var capName = name.charAt(0).toUpperCase() + name.slice(1), | |
| 6441 | origName = name, | |
| 6442 | i = cssPrefixes.length; | |
| 6443 | ||
| 6444 | while ( i-- ) { | |
| 6445 | name = cssPrefixes[ i ] + capName; | |
| 6446 | if ( name in style ) { | |
| 6447 | return name; | |
| 6448 | } | |
| 6449 | } | |
| 6450 | ||
| 6451 | return origName; | |
| 6452 | } | |
| 6453 | ||
| 6454 | function showHide( elements, show ) { | |
| 6455 | var display, elem, hidden, | |
| 6456 | values = [], | |
| 6457 | index = 0, | |
| 6458 | length = elements.length; | |
| 6459 | ||
| 6460 | for ( ; index < length; index++ ) { | |
| 6461 | elem = elements[ index ]; | |
| 6462 | if ( !elem.style ) { | |
| 6463 | continue; | |
| 6464 | } | |
| 6465 | ||
| 6466 | values[ index ] = jQuery._data( elem, "olddisplay" ); | |
| 6467 | display = elem.style.display; | |
| 6468 | if ( show ) { | |
| 6469 | // Reset the inline display of this element to learn if it is | |
| 6470 | // being hidden by cascaded rules or not | |
| 6471 | if ( !values[ index ] && display === "none" ) { | |
| 6472 | elem.style.display = ""; | |
| 6473 | } | |
| 6474 | ||
| 6475 | // Set elements which have been overridden with display: none | |
| 6476 | // in a stylesheet to whatever the default browser style is | |
| 6477 | // for such an element | |
| 6478 | if ( elem.style.display === "" && isHidden( elem ) ) { | |
| 6479 | values[ index ] = jQuery._data( elem, "olddisplay", defaultDisplay(elem.nodeName) ); | |
| 6480 | } | |
| 6481 | } else { | |
| 6482 | hidden = isHidden( elem ); | |
| 6483 | ||
| 6484 | if ( display && display !== "none" || !hidden ) { | |
| 6485 | jQuery._data( elem, "olddisplay", hidden ? display : jQuery.css( elem, "display" ) ); | |
| 6486 | } | |
| 6487 | } | |
| 6488 | } | |
| 6489 | ||
| 6490 | // Set the display of most of the elements in a second loop | |
| 6491 | // to avoid the constant reflow | |
| 6492 | for ( index = 0; index < length; index++ ) { | |
| 6493 | elem = elements[ index ]; | |
| 6494 | if ( !elem.style ) { | |
| 6495 | continue; | |
| 6496 | } | |
| 6497 | if ( !show || elem.style.display === "none" || elem.style.display === "" ) { | |
| 6498 | elem.style.display = show ? values[ index ] || "" : "none"; | |
| 6499 | } | |
| 6500 | } | |
| 6501 | ||
| 6502 | return elements; | |
| 6503 | } | |
| 6504 | ||
| 6505 | function setPositiveNumber( elem, value, subtract ) { | |
| 6506 | var matches = rnumsplit.exec( value ); | |
| 6507 | return matches ? | |
| 6508 | // Guard against undefined "subtract", e.g., when used as in cssHooks | |
| 6509 | Math.max( 0, matches[ 1 ] - ( subtract || 0 ) ) + ( matches[ 2 ] || "px" ) : | |
| 6510 | value; | |
| 6511 | } | |
| 6512 | ||
| 6513 | function augmentWidthOrHeight( elem, name, extra, isBorderBox, styles ) { | |
| 6514 | var i = extra === ( isBorderBox ? "border" : "content" ) ? | |
| 6515 | // If we already have the right measurement, avoid augmentation | |
| 6516 | 4 : | |
| 6517 | // Otherwise initialize for horizontal or vertical properties | |
| 6518 | name === "width" ? 1 : 0, | |
| 6519 | ||
| 6520 | val = 0; | |
| 6521 | ||
| 6522 | for ( ; i < 4; i += 2 ) { | |
| 6523 | // both box models exclude margin, so add it if we want it | |
| 6524 | if ( extra === "margin" ) { | |
| 6525 | val += jQuery.css( elem, extra + cssExpand[ i ], true, styles ); | |
| 6526 | } | |
| 6527 | ||
| 6528 | if ( isBorderBox ) { | |
| 6529 | // border-box includes padding, so remove it if we want content | |
| 6530 | if ( extra === "content" ) { | |
| 6531 | val -= jQuery.css( elem, "padding" + cssExpand[ i ], true, styles ); | |
| 6532 | } | |
| 6533 | ||
| 6534 | // at this point, extra isn't border nor margin, so remove border | |
| 6535 | if ( extra !== "margin" ) { | |
| 6536 | val -= jQuery.css( elem, "border" + cssExpand[ i ] + "Width", true, styles ); | |
| 6537 | } | |
| 6538 | } else { | |
| 6539 | // at this point, extra isn't content, so add padding | |
| 6540 | val += jQuery.css( elem, "padding" + cssExpand[ i ], true, styles ); | |
| 6541 | ||
| 6542 | // at this point, extra isn't content nor padding, so add border | |
| 6543 | if ( extra !== "padding" ) { | |
| 6544 | val += jQuery.css( elem, "border" + cssExpand[ i ] + "Width", true, styles ); | |
| 6545 | } | |
| 6546 | } | |
| 6547 | } | |
| 6548 | ||
| 6549 | return val; | |
| 6550 | } | |
| 6551 | ||
| 6552 | function getWidthOrHeight( elem, name, extra ) { | |
| 6553 | ||
| 6554 | // Start with offset property, which is equivalent to the border-box value | |
| 6555 | var valueIsBorderBox = true, | |
| 6556 | val = name === "width" ? elem.offsetWidth : elem.offsetHeight, | |
| 6557 | styles = getStyles( elem ), | |
| 6558 | isBorderBox = support.boxSizing && jQuery.css( elem, "boxSizing", false, styles ) === "border-box"; | |
| 6559 | ||
| 6560 | // some non-html elements return undefined for offsetWidth, so check for null/undefined | |
| 6561 | // svg - https://bugzilla.mozilla.org/show_bug.cgi?id=649285 | |
| 6562 | // MathML - https://bugzilla.mozilla.org/show_bug.cgi?id=491668 | |
| 6563 | if ( val <= 0 || val == null ) { | |
| 6564 | // Fall back to computed then uncomputed css if necessary | |
| 6565 | val = curCSS( elem, name, styles ); | |
| 6566 | if ( val < 0 || val == null ) { | |
| 6567 | val = elem.style[ name ]; | |
| 6568 | } | |
| 6569 | ||
| 6570 | // Computed unit is not pixels. Stop here and return. | |
| 6571 | if ( rnumnonpx.test(val) ) { | |
| 6572 | return val; | |
| 6573 | } | |
| 6574 | ||
| 6575 | // we need the check for style in case a browser which returns unreliable values | |
| 6576 | // for getComputedStyle silently falls back to the reliable elem.style | |
| 6577 | valueIsBorderBox = isBorderBox && ( support.boxSizingReliable() || val === elem.style[ name ] ); | |
| 6578 | ||
| 6579 | // Normalize "", auto, and prepare for extra | |
| 6580 | val = parseFloat( val ) || 0; | |
| 6581 | } | |
| 6582 | ||
| 6583 | // use the active box-sizing model to add/subtract irrelevant styles | |
| 6584 | return ( val + | |
| 6585 | augmentWidthOrHeight( | |
| 6586 | elem, | |
| 6587 | name, | |
| 6588 | extra || ( isBorderBox ? "border" : "content" ), | |
| 6589 | valueIsBorderBox, | |
| 6590 | styles | |
| 6591 | ) | |
| 6592 | ) + "px"; | |
| 6593 | } | |
| 6594 | ||
| 6595 | jQuery.extend({ | |
| 6596 | // Add in style property hooks for overriding the default | |
| 6597 | // behavior of getting and setting a style property | |
| 6598 | cssHooks: { | |
| 6599 | opacity: { | |
| 6600 | get: function( elem, computed ) { | |
| 6601 | if ( computed ) { | |
| 6602 | // We should always get a number back from opacity | |
| 6603 | var ret = curCSS( elem, "opacity" ); | |
| 6604 | return ret === "" ? "1" : ret; | |
| 6605 | } | |
| 6606 | } | |
| 6607 | } | |
| 6608 | }, | |
| 6609 | ||
| 6610 | // Don't automatically add "px" to these possibly-unitless properties | |
| 6611 | cssNumber: { | |
| 6612 | "columnCount": true, | |
| 6613 | "fillOpacity": true, | |
| 6614 | "flexGrow": true, | |
| 6615 | "flexShrink": true, | |
| 6616 | "fontWeight": true, | |
| 6617 | "lineHeight": true, | |
| 6618 | "opacity": true, | |
| 6619 | "order": true, | |
| 6620 | "orphans": true, | |
| 6621 | "widows": true, | |
| 6622 | "zIndex": true, | |
| 6623 | "zoom": true | |
| 6624 | }, | |
| 6625 | ||
| 6626 | // Add in properties whose names you wish to fix before | |
| 6627 | // setting or getting the value | |
| 6628 | cssProps: { | |
| 6629 | // normalize float css property | |
| 6630 | "float": support.cssFloat ? "cssFloat" : "styleFloat" | |
| 6631 | }, | |
| 6632 | ||
| 6633 | // Get and set the style property on a DOM Node | |
| 6634 | style: function( elem, name, value, extra ) { | |
| 6635 | // Don't set styles on text and comment nodes | |
| 6636 | if ( !elem || elem.nodeType === 3 || elem.nodeType === 8 || !elem.style ) { | |
| 6637 | return; | |
| 6638 | } | |
| 6639 | ||
| 6640 | // Make sure that we're working with the right name | |
| 6641 | var ret, type, hooks, | |
| 6642 | origName = jQuery.camelCase( name ), | |
| 6643 | style = elem.style; | |
| 6644 | ||
| 6645 | name = jQuery.cssProps[ origName ] || ( jQuery.cssProps[ origName ] = vendorPropName( style, origName ) ); | |
| 6646 | ||
| 6647 | // gets hook for the prefixed version | |
| 6648 | // followed by the unprefixed version | |
| 6649 | hooks = jQuery.cssHooks[ name ] || jQuery.cssHooks[ origName ]; | |
| 6650 | ||
| 6651 | // Check if we're setting a value | |
| 6652 | if ( value !== undefined ) { | |
| 6653 | type = typeof value; | |
| 6654 | ||
| 6655 | // convert relative number strings (+= or -=) to relative numbers. #7345 | |
| 6656 | if ( type === "string" && (ret = rrelNum.exec( value )) ) { | |
| 6657 | value = ( ret[1] + 1 ) * ret[2] + parseFloat( jQuery.css( elem, name ) ); | |
| 6658 | // Fixes bug #9237 | |
| 6659 | type = "number"; | |
| 6660 | } | |
| 6661 | ||
| 6662 | // Make sure that null and NaN values aren't set. See: #7116 | |
| 6663 | if ( value == null || value !== value ) { | |
| 6664 | return; | |
| 6665 | } | |
| 6666 | ||
| 6667 | // If a number was passed in, add 'px' to the (except for certain CSS properties) | |
| 6668 | if ( type === "number" && !jQuery.cssNumber[ origName ] ) { | |
| 6669 | value += "px"; | |
| 6670 | } | |
| 6671 | ||
| 6672 | // Fixes #8908, it can be done more correctly by specifing setters in cssHooks, | |
| 6673 | // but it would mean to define eight (for every problematic property) identical functions | |
| 6674 | if ( !support.clearCloneStyle && value === "" && name.indexOf("background") === 0 ) { | |
| 6675 | style[ name ] = "inherit"; | |
| 6676 | } | |
| 6677 | ||
| 6678 | // If a hook was provided, use that value, otherwise just set the specified value | |
| 6679 | if ( !hooks || !("set" in hooks) || (value = hooks.set( elem, value, extra )) !== undefined ) { | |
| 6680 | ||
| 6681 | // Support: IE | |
| 6682 | // Swallow errors from 'invalid' CSS values (#5509) | |
| 6683 | try { | |
| 6684 | style[ name ] = value; | |
| 6685 | } catch(e) {} | |
| 6686 | } | |
| 6687 | ||
| 6688 | } else { | |
| 6689 | // If a hook was provided get the non-computed value from there | |
| 6690 | if ( hooks && "get" in hooks && (ret = hooks.get( elem, false, extra )) !== undefined ) { | |
| 6691 | return ret; | |
| 6692 | } | |
| 6693 | ||
| 6694 | // Otherwise just get the value from the style object | |
| 6695 | return style[ name ]; | |
| 6696 | } | |
| 6697 | }, | |
| 6698 | ||
| 6699 | css: function( elem, name, extra, styles ) { | |
| 6700 | var num, val, hooks, | |
| 6701 | origName = jQuery.camelCase( name ); | |
| 6702 | ||
| 6703 | // Make sure that we're working with the right name | |
| 6704 | name = jQuery.cssProps[ origName ] || ( jQuery.cssProps[ origName ] = vendorPropName( elem.style, origName ) ); | |
| 6705 | ||
| 6706 | // gets hook for the prefixed version | |
| 6707 | // followed by the unprefixed version | |
| 6708 | hooks = jQuery.cssHooks[ name ] || jQuery.cssHooks[ origName ]; | |
| 6709 | ||
| 6710 | // If a hook was provided get the computed value from there | |
| 6711 | if ( hooks && "get" in hooks ) { | |
| 6712 | val = hooks.get( elem, true, extra ); | |
| 6713 | } | |
| 6714 | ||
| 6715 | // Otherwise, if a way to get the computed value exists, use that | |
| 6716 | if ( val === undefined ) { | |
| 6717 | val = curCSS( elem, name, styles ); | |
| 6718 | } | |
| 6719 | ||
| 6720 | //convert "normal" to computed value | |
| 6721 | if ( val === "normal" && name in cssNormalTransform ) { | |
| 6722 | val = cssNormalTransform[ name ]; | |
| 6723 | } | |
| 6724 | ||
| 6725 | // Return, converting to number if forced or a qualifier was provided and val looks numeric | |
| 6726 | if ( extra === "" || extra ) { | |
| 6727 | num = parseFloat( val ); | |
| 6728 | return extra === true || jQuery.isNumeric( num ) ? num || 0 : val; | |
| 6729 | } | |
| 6730 | return val; | |
| 6731 | } | |
| 6732 | }); | |
| 6733 | ||
| 6734 | jQuery.each([ "height", "width" ], function( i, name ) { | |
| 6735 | jQuery.cssHooks[ name ] = { | |
| 6736 | get: function( elem, computed, extra ) { | |
| 6737 | if ( computed ) { | |
| 6738 | // certain elements can have dimension info if we invisibly show them | |
| 6739 | // however, it must have a current display style that would benefit from this | |
| 6740 | return rdisplayswap.test( jQuery.css( elem, "display" ) ) && elem.offsetWidth === 0 ? | |
| 6741 | jQuery.swap( elem, cssShow, function() { | |
| 6742 | return getWidthOrHeight( elem, name, extra ); | |
| 6743 | }) : | |
| 6744 | getWidthOrHeight( elem, name, extra ); | |
| 6745 | } | |
| 6746 | }, | |
| 6747 | ||
| 6748 | set: function( elem, value, extra ) { | |
| 6749 | var styles = extra && getStyles( elem ); | |
| 6750 | return setPositiveNumber( elem, value, extra ? | |
| 6751 | augmentWidthOrHeight( | |
| 6752 | elem, | |
| 6753 | name, | |
| 6754 | extra, | |
| 6755 | support.boxSizing && jQuery.css( elem, "boxSizing", false, styles ) === "border-box", | |
| 6756 | styles | |
| 6757 | ) : 0 | |
| 6758 | ); | |
| 6759 | } | |
| 6760 | }; | |
| 6761 | }); | |
| 6762 | ||
| 6763 | if ( !support.opacity ) { | |
| 6764 | jQuery.cssHooks.opacity = { | |
| 6765 | get: function( elem, computed ) { | |
| 6766 | // IE uses filters for opacity | |
| 6767 | return ropacity.test( (computed && elem.currentStyle ? elem.currentStyle.filter : elem.style.filter) || "" ) ? | |
| 6768 | ( 0.01 * parseFloat( RegExp.$1 ) ) + "" : | |
| 6769 | computed ? "1" : ""; | |
| 6770 | }, | |
| 6771 | ||
| 6772 | set: function( elem, value ) { | |
| 6773 | var style = elem.style, | |
| 6774 | currentStyle = elem.currentStyle, | |
| 6775 | opacity = jQuery.isNumeric( value ) ? "alpha(opacity=" + value * 100 + ")" : "", | |
| 6776 | filter = currentStyle && currentStyle.filter || style.filter || ""; | |
| 6777 | ||
| 6778 | // IE has trouble with opacity if it does not have layout | |
| 6779 | // Force it by setting the zoom level | |
| 6780 | style.zoom = 1; | |
| 6781 | ||
| 6782 | // if setting opacity to 1, and no other filters exist - attempt to remove filter attribute #6652 | |
| 6783 | // if value === "", then remove inline opacity #12685 | |
| 6784 | if ( ( value >= 1 || value === "" ) && | |
| 6785 | jQuery.trim( filter.replace( ralpha, "" ) ) === "" && | |
| 6786 | style.removeAttribute ) { | |
| 6787 | ||
| 6788 | // Setting style.filter to null, "" & " " still leave "filter:" in the cssText | |
| 6789 | // if "filter:" is present at all, clearType is disabled, we want to avoid this | |
| 6790 | // style.removeAttribute is IE Only, but so apparently is this code path... | |
| 6791 | style.removeAttribute( "filter" ); | |
| 6792 | ||
| 6793 | // if there is no filter style applied in a css rule or unset inline opacity, we are done | |
| 6794 | if ( value === "" || currentStyle && !currentStyle.filter ) { | |
| 6795 | return; | |
| 6796 | } | |
| 6797 | } | |
| 6798 | ||
| 6799 | // otherwise, set new filter values | |
| 6800 | style.filter = ralpha.test( filter ) ? | |
| 6801 | filter.replace( ralpha, opacity ) : | |
| 6802 | filter + " " + opacity; | |
| 6803 | } | |
| 6804 | }; | |
| 6805 | } | |
| 6806 | ||
| 6807 | jQuery.cssHooks.marginRight = addGetHookIf( support.reliableMarginRight, | |
| 6808 | function( elem, computed ) { | |
| 6809 | if ( computed ) { | |
| 6810 | // WebKit Bug 13343 - getComputedStyle returns wrong value for margin-right | |
| 6811 | // Work around by temporarily setting element display to inline-block | |
| 6812 | return jQuery.swap( elem, { "display": "inline-block" }, | |
| 6813 | curCSS, [ elem, "marginRight" ] ); | |
| 6814 | } | |
| 6815 | } | |
| 6816 | ); | |
| 6817 | ||
| 6818 | // These hooks are used by animate to expand properties | |
| 6819 | jQuery.each({ | |
| 6820 | margin: "", | |
| 6821 | padding: "", | |
| 6822 | border: "Width" | |
| 6823 | }, function( prefix, suffix ) { | |
| 6824 | jQuery.cssHooks[ prefix + suffix ] = { | |
| 6825 | expand: function( value ) { | |
| 6826 | var i = 0, | |
| 6827 | expanded = {}, | |
| 6828 | ||
| 6829 | // assumes a single number if not a string | |
| 6830 | parts = typeof value === "string" ? value.split(" ") : [ value ]; | |
| 6831 | ||
| 6832 | for ( ; i < 4; i++ ) { | |
| 6833 | expanded[ prefix + cssExpand[ i ] + suffix ] = | |
| 6834 | parts[ i ] || parts[ i - 2 ] || parts[ 0 ]; | |
| 6835 | } | |
| 6836 | ||
| 6837 | return expanded; | |
| 6838 | } | |
| 6839 | }; | |
| 6840 | ||
| 6841 | if ( !rmargin.test( prefix ) ) { | |
| 6842 | jQuery.cssHooks[ prefix + suffix ].set = setPositiveNumber; | |
| 6843 | } | |
| 6844 | }); | |
| 6845 | ||
| 6846 | jQuery.fn.extend({ | |
| 6847 | css: function( name, value ) { | |
| 6848 | return access( this, function( elem, name, value ) { | |
| 6849 | var styles, len, | |
| 6850 | map = {}, | |
| 6851 | i = 0; | |
| 6852 | ||
| 6853 | if ( jQuery.isArray( name ) ) { | |
| 6854 | styles = getStyles( elem ); | |
| 6855 | len = name.length; | |
| 6856 | ||
| 6857 | for ( ; i < len; i++ ) { | |
| 6858 | map[ name[ i ] ] = jQuery.css( elem, name[ i ], false, styles ); | |
| 6859 | } | |
| 6860 | ||
| 6861 | return map; | |
| 6862 | } | |
| 6863 | ||
| 6864 | return value !== undefined ? | |
| 6865 | jQuery.style( elem, name, value ) : | |
| 6866 | jQuery.css( elem, name ); | |
| 6867 | }, name, value, arguments.length > 1 ); | |
| 6868 | }, | |
| 6869 | show: function() { | |
| 6870 | return showHide( this, true ); | |
| 6871 | }, | |
| 6872 | hide: function() { | |
| 6873 | return showHide( this ); | |
| 6874 | }, | |
| 6875 | toggle: function( state ) { | |
| 6876 | if ( typeof state === "boolean" ) { | |
| 6877 | return state ? this.show() : this.hide(); | |
| 6878 | } | |
| 6879 | ||
| 6880 | return this.each(function() { | |
| 6881 | if ( isHidden( this ) ) { | |
| 6882 | jQuery( this ).show(); | |
| 6883 | } else { | |
| 6884 | jQuery( this ).hide(); | |
| 6885 | } | |
| 6886 | }); | |
| 6887 | } | |
| 6888 | }); | |
| 6889 | ||
| 6890 | ||
| 6891 | function Tween( elem, options, prop, end, easing ) { | |
| 6892 | return new Tween.prototype.init( elem, options, prop, end, easing ); | |
| 6893 | } | |
| 6894 | jQuery.Tween = Tween; | |
| 6895 | ||
| 6896 | Tween.prototype = { | |
| 6897 | constructor: Tween, | |
| 6898 | init: function( elem, options, prop, end, easing, unit ) { | |
| 6899 | this.elem = elem; | |
| 6900 | this.prop = prop; | |
| 6901 | this.easing = easing || "swing"; | |
| 6902 | this.options = options; | |
| 6903 | this.start = this.now = this.cur(); | |
| 6904 | this.end = end; | |
| 6905 | this.unit = unit || ( jQuery.cssNumber[ prop ] ? "" : "px" ); | |
| 6906 | }, | |
| 6907 | cur: function() { | |
| 6908 | var hooks = Tween.propHooks[ this.prop ]; | |
| 6909 | ||
| 6910 | return hooks && hooks.get ? | |
| 6911 | hooks.get( this ) : | |
| 6912 | Tween.propHooks._default.get( this ); | |
| 6913 | }, | |
| 6914 | run: function( percent ) { | |
| 6915 | var eased, | |
| 6916 | hooks = Tween.propHooks[ this.prop ]; | |
| 6917 | ||
| 6918 | if ( this.options.duration ) { | |
| 6919 | this.pos = eased = jQuery.easing[ this.easing ]( | |
| 6920 | percent, this.options.duration * percent, 0, 1, this.options.duration | |
| 6921 | ); | |
| 6922 | } else { | |
| 6923 | this.pos = eased = percent; | |
| 6924 | } | |
| 6925 | this.now = ( this.end - this.start ) * eased + this.start; | |
| 6926 | ||
| 6927 | if ( this.options.step ) { | |
| 6928 | this.options.step.call( this.elem, this.now, this ); | |
| 6929 | } | |
| 6930 | ||
| 6931 | if ( hooks && hooks.set ) { | |
| 6932 | hooks.set( this ); | |
| 6933 | } else { | |
| 6934 | Tween.propHooks._default.set( this ); | |
| 6935 | } | |
| 6936 | return this; | |
| 6937 | } | |
| 6938 | }; | |
| 6939 | ||
| 6940 | Tween.prototype.init.prototype = Tween.prototype; | |
| 6941 | ||
| 6942 | Tween.propHooks = { | |
| 6943 | _default: { | |
| 6944 | get: function( tween ) { | |
| 6945 | var result; | |
| 6946 | ||
| 6947 | if ( tween.elem[ tween.prop ] != null && | |
| 6948 | (!tween.elem.style || tween.elem.style[ tween.prop ] == null) ) { | |
| 6949 | return tween.elem[ tween.prop ]; | |
| 6950 | } | |
| 6951 | ||
| 6952 | // passing an empty string as a 3rd parameter to .css will automatically | |
| 6953 | // attempt a parseFloat and fallback to a string if the parse fails | |
| 6954 | // so, simple values such as "10px" are parsed to Float. | |
| 6955 | // complex values such as "rotate(1rad)" are returned as is. | |
| 6956 | result = jQuery.css( tween.elem, tween.prop, "" ); | |
| 6957 | // Empty strings, null, undefined and "auto" are converted to 0. | |
| 6958 | return !result || result === "auto" ? 0 : result; | |
| 6959 | }, | |
| 6960 | set: function( tween ) { | |
| 6961 | // use step hook for back compat - use cssHook if its there - use .style if its | |
| 6962 | // available and use plain properties where available | |
| 6963 | if ( jQuery.fx.step[ tween.prop ] ) { | |
| 6964 | jQuery.fx.step[ tween.prop ]( tween ); | |
| 6965 | } else if ( tween.elem.style && ( tween.elem.style[ jQuery.cssProps[ tween.prop ] ] != null || jQuery.cssHooks[ tween.prop ] ) ) { | |
| 6966 | jQuery.style( tween.elem, tween.prop, tween.now + tween.unit ); | |
| 6967 | } else { | |
| 6968 | tween.elem[ tween.prop ] = tween.now; | |
| 6969 | } | |
| 6970 | } | |
| 6971 | } | |
| 6972 | }; | |
| 6973 | ||
| 6974 | // Support: IE <=9 | |
| 6975 | // Panic based approach to setting things on disconnected nodes | |
| 6976 | ||
| 6977 | Tween.propHooks.scrollTop = Tween.propHooks.scrollLeft = { | |
| 6978 | set: function( tween ) { | |
| 6979 | if ( tween.elem.nodeType && tween.elem.parentNode ) { | |
| 6980 | tween.elem[ tween.prop ] = tween.now; | |
| 6981 | } | |
| 6982 | } | |
| 6983 | }; | |
| 6984 | ||
| 6985 | jQuery.easing = { | |
| 6986 | linear: function( p ) { | |
| 6987 | return p; | |
| 6988 | }, | |
| 6989 | swing: function( p ) { | |
| 6990 | return 0.5 - Math.cos( p * Math.PI ) / 2; | |
| 6991 | } | |
| 6992 | }; | |
| 6993 | ||
| 6994 | jQuery.fx = Tween.prototype.init; | |
| 6995 | ||
| 6996 | // Back Compat <1.8 extension point | |
| 6997 | jQuery.fx.step = {}; | |
| 6998 | ||
| 6999 | ||
| 7000 | ||
| 7001 | ||
| 7002 | var | |
| 7003 | fxNow, timerId, | |
| 7004 | rfxtypes = /^(?:toggle|show|hide)$/, | |
| 7005 | rfxnum = new RegExp( "^(?:([+-])=|)(" + pnum + ")([a-z%]*)$", "i" ), | |
| 7006 | rrun = /queueHooks$/, | |
| 7007 | animationPrefilters = [ defaultPrefilter ], | |
| 7008 | tweeners = { | |
| 7009 | "*": [ function( prop, value ) { | |
| 7010 | var tween = this.createTween( prop, value ), | |
| 7011 | target = tween.cur(), | |
| 7012 | parts = rfxnum.exec( value ), | |
| 7013 | unit = parts && parts[ 3 ] || ( jQuery.cssNumber[ prop ] ? "" : "px" ), | |
| 7014 | ||
| 7015 | // Starting value computation is required for potential unit mismatches | |
| 7016 | start = ( jQuery.cssNumber[ prop ] || unit !== "px" && +target ) && | |
| 7017 | rfxnum.exec( jQuery.css( tween.elem, prop ) ), | |
| 7018 | scale = 1, | |
| 7019 | maxIterations = 20; | |
| 7020 | ||
| 7021 | if ( start && start[ 3 ] !== unit ) { | |
| 7022 | // Trust units reported by jQuery.css | |
| 7023 | unit = unit || start[ 3 ]; | |
| 7024 | ||
| 7025 | // Make sure we update the tween properties later on | |
| 7026 | parts = parts || []; | |
| 7027 | ||
| 7028 | // Iteratively approximate from a nonzero starting point | |
| 7029 | start = +target || 1; | |
| 7030 | ||
| 7031 | do { | |
| 7032 | // If previous iteration zeroed out, double until we get *something* | |
| 7033 | // Use a string for doubling factor so we don't accidentally see scale as unchanged below | |
| 7034 | scale = scale || ".5"; | |
| 7035 | ||
| 7036 | // Adjust and apply | |
| 7037 | start = start / scale; | |
| 7038 | jQuery.style( tween.elem, prop, start + unit ); | |
| 7039 | ||
| 7040 | // Update scale, tolerating zero or NaN from tween.cur() | |
| 7041 | // And breaking the loop if scale is unchanged or perfect, or if we've just had enough | |
| 7042 | } while ( scale !== (scale = tween.cur() / target) && scale !== 1 && --maxIterations ); | |
| 7043 | } | |
| 7044 | ||
| 7045 | // Update tween properties | |
| 7046 | if ( parts ) { | |
| 7047 | start = tween.start = +start || +target || 0; | |
| 7048 | tween.unit = unit; | |
| 7049 | // If a +=/-= token was provided, we're doing a relative animation | |
| 7050 | tween.end = parts[ 1 ] ? | |
| 7051 | start + ( parts[ 1 ] + 1 ) * parts[ 2 ] : | |
| 7052 | +parts[ 2 ]; | |
| 7053 | } | |
| 7054 | ||
| 7055 | return tween; | |
| 7056 | } ] | |
| 7057 | }; | |
| 7058 | ||
| 7059 | // Animations created synchronously will run synchronously | |
| 7060 | function createFxNow() { | |
| 7061 | setTimeout(function() { | |
| 7062 | fxNow = undefined; | |
| 7063 | }); | |
| 7064 | return ( fxNow = jQuery.now() ); | |
| 7065 | } | |
| 7066 | ||
| 7067 | // Generate parameters to create a standard animation | |
| 7068 | function genFx( type, includeWidth ) { | |
| 7069 | var which, | |
| 7070 | attrs = { height: type }, | |
| 7071 | i = 0; | |
| 7072 | ||
| 7073 | // if we include width, step value is 1 to do all cssExpand values, | |
| 7074 | // if we don't include width, step value is 2 to skip over Left and Right | |
| 7075 | includeWidth = includeWidth ? 1 : 0; | |
| 7076 | for ( ; i < 4 ; i += 2 - includeWidth ) { | |
| 7077 | which = cssExpand[ i ]; | |
| 7078 | attrs[ "margin" + which ] = attrs[ "padding" + which ] = type; | |
| 7079 | } | |
| 7080 | ||
| 7081 | if ( includeWidth ) { | |
| 7082 | attrs.opacity = attrs.width = type; | |
| 7083 | } | |
| 7084 | ||
| 7085 | return attrs; | |
| 7086 | } | |
| 7087 | ||
| 7088 | function createTween( value, prop, animation ) { | |
| 7089 | var tween, | |
| 7090 | collection = ( tweeners[ prop ] || [] ).concat( tweeners[ "*" ] ), | |
| 7091 | index = 0, | |
| 7092 | length = collection.length; | |
| 7093 | for ( ; index < length; index++ ) { | |
| 7094 | if ( (tween = collection[ index ].call( animation, prop, value )) ) { | |
| 7095 | ||
| 7096 | // we're done with this property | |
| 7097 | return tween; | |
| 7098 | } | |
| 7099 | } | |
| 7100 | } | |
| 7101 | ||
| 7102 | function defaultPrefilter( elem, props, opts ) { | |
| 7103 | /* jshint validthis: true */ | |
| 7104 | var prop, value, toggle, tween, hooks, oldfire, display, checkDisplay, | |
| 7105 | anim = this, | |
| 7106 | orig = {}, | |
| 7107 | style = elem.style, | |
| 7108 | hidden = elem.nodeType && isHidden( elem ), | |
| 7109 | dataShow = jQuery._data( elem, "fxshow" ); | |
| 7110 | ||
| 7111 | // handle queue: false promises | |
| 7112 | if ( !opts.queue ) { | |
| 7113 | hooks = jQuery._queueHooks( elem, "fx" ); | |
| 7114 | if ( hooks.unqueued == null ) { | |
| 7115 | hooks.unqueued = 0; | |
| 7116 | oldfire = hooks.empty.fire; | |
| 7117 | hooks.empty.fire = function() { | |
| 7118 | if ( !hooks.unqueued ) { | |
| 7119 | oldfire(); | |
| 7120 | } | |
| 7121 | }; | |
| 7122 | } | |
| 7123 | hooks.unqueued++; | |
| 7124 | ||
| 7125 | anim.always(function() { | |
| 7126 | // doing this makes sure that the complete handler will be called | |
| 7127 | // before this completes | |
| 7128 | anim.always(function() { | |
| 7129 | hooks.unqueued--; | |
| 7130 | if ( !jQuery.queue( elem, "fx" ).length ) { | |
| 7131 | hooks.empty.fire(); | |
| 7132 | } | |
| 7133 | }); | |
| 7134 | }); | |
| 7135 | } | |
| 7136 | ||
| 7137 | // height/width overflow pass | |
| 7138 | if ( elem.nodeType === 1 && ( "height" in props || "width" in props ) ) { | |
| 7139 | // Make sure that nothing sneaks out | |
| 7140 | // Record all 3 overflow attributes because IE does not | |
| 7141 | // change the overflow attribute when overflowX and | |
| 7142 | // overflowY are set to the same value | |
| 7143 | opts.overflow = [ style.overflow, style.overflowX, style.overflowY ]; | |
| 7144 | ||
| 7145 | // Set display property to inline-block for height/width | |
| 7146 | // animations on inline elements that are having width/height animated | |
| 7147 | display = jQuery.css( elem, "display" ); | |
| 7148 | ||
| 7149 | // Test default display if display is currently "none" | |
| 7150 | checkDisplay = display === "none" ? | |
| 7151 | jQuery._data( elem, "olddisplay" ) || defaultDisplay( elem.nodeName ) : display; | |
| 7152 | ||
| 7153 | if ( checkDisplay === "inline" && jQuery.css( elem, "float" ) === "none" ) { | |
| 7154 | ||
| 7155 | // inline-level elements accept inline-block; | |
| 7156 | // block-level elements need to be inline with layout | |
| 7157 | if ( !support.inlineBlockNeedsLayout || defaultDisplay( elem.nodeName ) === "inline" ) { | |
| 7158 | style.display = "inline-block"; | |
| 7159 | } else { | |
| 7160 | style.zoom = 1; | |
| 7161 | } | |
| 7162 | } | |
| 7163 | } | |
| 7164 | ||
| 7165 | if ( opts.overflow ) { | |
| 7166 | style.overflow = "hidden"; | |
| 7167 | if ( !support.shrinkWrapBlocks() ) { | |
| 7168 | anim.always(function() { | |
| 7169 | style.overflow = opts.overflow[ 0 ]; | |
| 7170 | style.overflowX = opts.overflow[ 1 ]; | |
| 7171 | style.overflowY = opts.overflow[ 2 ]; | |
| 7172 | }); | |
| 7173 | } | |
| 7174 | } | |
| 7175 | ||
| 7176 | // show/hide pass | |
| 7177 | for ( prop in props ) { | |
| 7178 | value = props[ prop ]; | |
| 7179 | if ( rfxtypes.exec( value ) ) { | |
| 7180 | delete props[ prop ]; | |
| 7181 | toggle = toggle || value === "toggle"; | |
| 7182 | if ( value === ( hidden ? "hide" : "show" ) ) { | |
| 7183 | ||
| 7184 | // If there is dataShow left over from a stopped hide or show and we are going to proceed with show, we should pretend to be hidden | |
| 7185 | if ( value === "show" && dataShow && dataShow[ prop ] !== undefined ) { | |
| 7186 | hidden = true; | |
| 7187 | } else { | |
| 7188 | continue; | |
| 7189 | } | |
| 7190 | } | |
| 7191 | orig[ prop ] = dataShow && dataShow[ prop ] || jQuery.style( elem, prop ); | |
| 7192 | ||
| 7193 | // Any non-fx value stops us from restoring the original display value | |
| 7194 | } else { | |
| 7195 | display = undefined; | |
| 7196 | } | |
| 7197 | } | |
| 7198 | ||
| 7199 | if ( !jQuery.isEmptyObject( orig ) ) { | |
| 7200 | if ( dataShow ) { | |
| 7201 | if ( "hidden" in dataShow ) { | |
| 7202 | hidden = dataShow.hidden; | |
| 7203 | } | |
| 7204 | } else { | |
| 7205 | dataShow = jQuery._data( elem, "fxshow", {} ); | |
| 7206 | } | |
| 7207 | ||
| 7208 | // store state if its toggle - enables .stop().toggle() to "reverse" | |
| 7209 | if ( toggle ) { | |
| 7210 | dataShow.hidden = !hidden; | |
| 7211 | } | |
| 7212 | if ( hidden ) { | |
| 7213 | jQuery( elem ).show(); | |
| 7214 | } else { | |
| 7215 | anim.done(function() { | |
| 7216 | jQuery( elem ).hide(); | |
| 7217 | }); | |
| 7218 | } | |
| 7219 | anim.done(function() { | |
| 7220 | var prop; | |
| 7221 | jQuery._removeData( elem, "fxshow" ); | |
| 7222 | for ( prop in orig ) { | |
| 7223 | jQuery.style( elem, prop, orig[ prop ] ); | |
| 7224 | } | |
| 7225 | }); | |
| 7226 | for ( prop in orig ) { | |
| 7227 | tween = createTween( hidden ? dataShow[ prop ] : 0, prop, anim ); | |
| 7228 | ||
| 7229 | if ( !( prop in dataShow ) ) { | |
| 7230 | dataShow[ prop ] = tween.start; | |
| 7231 | if ( hidden ) { | |
| 7232 | tween.end = tween.start; | |
| 7233 | tween.start = prop === "width" || prop === "height" ? 1 : 0; | |
| 7234 | } | |
| 7235 | } | |
| 7236 | } | |
| 7237 | ||
| 7238 | // If this is a noop like .hide().hide(), restore an overwritten display value | |
| 7239 | } else if ( (display === "none" ? defaultDisplay( elem.nodeName ) : display) === "inline" ) { | |
| 7240 | style.display = display; | |
| 7241 | } | |
| 7242 | } | |
| 7243 | ||
| 7244 | function propFilter( props, specialEasing ) { | |
| 7245 | var index, name, easing, value, hooks; | |
| 7246 | ||
| 7247 | // camelCase, specialEasing and expand cssHook pass | |
| 7248 | for ( index in props ) { | |
| 7249 | name = jQuery.camelCase( index ); | |
| 7250 | easing = specialEasing[ name ]; | |
| 7251 | value = props[ index ]; | |
| 7252 | if ( jQuery.isArray( value ) ) { | |
| 7253 | easing = value[ 1 ]; | |
| 7254 | value = props[ index ] = value[ 0 ]; | |
| 7255 | } | |
| 7256 | ||
| 7257 | if ( index !== name ) { | |
| 7258 | props[ name ] = value; | |
| 7259 | delete props[ index ]; | |
| 7260 | } | |
| 7261 | ||
| 7262 | hooks = jQuery.cssHooks[ name ]; | |
| 7263 | if ( hooks && "expand" in hooks ) { | |
| 7264 | value = hooks.expand( value ); | |
| 7265 | delete props[ name ]; | |
| 7266 | ||
| 7267 | // not quite $.extend, this wont overwrite keys already present. | |
| 7268 | // also - reusing 'index' from above because we have the correct "name" | |
| 7269 | for ( index in value ) { | |
| 7270 | if ( !( index in props ) ) { | |
| 7271 | props[ index ] = value[ index ]; | |
| 7272 | specialEasing[ index ] = easing; | |
| 7273 | } | |
| 7274 | } | |
| 7275 | } else { | |
| 7276 | specialEasing[ name ] = easing; | |
| 7277 | } | |
| 7278 | } | |
| 7279 | } | |
| 7280 | ||
| 7281 | function Animation( elem, properties, options ) { | |
| 7282 | var result, | |
| 7283 | stopped, | |
| 7284 | index = 0, | |
| 7285 | length = animationPrefilters.length, | |
| 7286 | deferred = jQuery.Deferred().always( function() { | |
| 7287 | // don't match elem in the :animated selector | |
| 7288 | delete tick.elem; | |
| 7289 | }), | |
| 7290 | tick = function() { | |
| 7291 | if ( stopped ) { | |
| 7292 | return false; | |
| 7293 | } | |
| 7294 | var currentTime = fxNow || createFxNow(), | |
| 7295 | remaining = Math.max( 0, animation.startTime + animation.duration - currentTime ), | |
| 7296 | // archaic crash bug won't allow us to use 1 - ( 0.5 || 0 ) (#12497) | |
| 7297 | temp = remaining / animation.duration || 0, | |
| 7298 | percent = 1 - temp, | |
| 7299 | index = 0, | |
| 7300 | length = animation.tweens.length; | |
| 7301 | ||
| 7302 | for ( ; index < length ; index++ ) { | |
| 7303 | animation.tweens[ index ].run( percent ); | |
| 7304 | } | |
| 7305 | ||
| 7306 | deferred.notifyWith( elem, [ animation, percent, remaining ]); | |
| 7307 | ||
| 7308 | if ( percent < 1 && length ) { | |
| 7309 | return remaining; | |
| 7310 | } else { | |
| 7311 | deferred.resolveWith( elem, [ animation ] ); | |
| 7312 | return false; | |
| 7313 | } | |
| 7314 | }, | |
| 7315 | animation = deferred.promise({ | |
| 7316 | elem: elem, | |
| 7317 | props: jQuery.extend( {}, properties ), | |
| 7318 | opts: jQuery.extend( true, { specialEasing: {} }, options ), | |
| 7319 | originalProperties: properties, | |
| 7320 | originalOptions: options, | |
| 7321 | startTime: fxNow || createFxNow(), | |
| 7322 | duration: options.duration, | |
| 7323 | tweens: [], | |
| 7324 | createTween: function( prop, end ) { | |
| 7325 | var tween = jQuery.Tween( elem, animation.opts, prop, end, | |
| 7326 | animation.opts.specialEasing[ prop ] || animation.opts.easing ); | |
| 7327 | animation.tweens.push( tween ); | |
| 7328 | return tween; | |
| 7329 | }, | |
| 7330 | stop: function( gotoEnd ) { | |
| 7331 | var index = 0, | |
| 7332 | // if we are going to the end, we want to run all the tweens | |
| 7333 | // otherwise we skip this part | |
| 7334 | length = gotoEnd ? animation.tweens.length : 0; | |
| 7335 | if ( stopped ) { | |
| 7336 | return this; | |
| 7337 | } | |
| 7338 | stopped = true; | |
| 7339 | for ( ; index < length ; index++ ) { | |
| 7340 | animation.tweens[ index ].run( 1 ); | |
| 7341 | } | |
| 7342 | ||
| 7343 | // resolve when we played the last frame | |
| 7344 | // otherwise, reject | |
| 7345 | if ( gotoEnd ) { | |
| 7346 | deferred.resolveWith( elem, [ animation, gotoEnd ] ); | |
| 7347 | } else { | |
| 7348 | deferred.rejectWith( elem, [ animation, gotoEnd ] ); | |
| 7349 | } | |
| 7350 | return this; | |
| 7351 | } | |
| 7352 | }), | |
| 7353 | props = animation.props; | |
| 7354 | ||
| 7355 | propFilter( props, animation.opts.specialEasing ); | |
| 7356 | ||
| 7357 | for ( ; index < length ; index++ ) { | |
| 7358 | result = animationPrefilters[ index ].call( animation, elem, props, animation.opts ); | |
| 7359 | if ( result ) { | |
| 7360 | return result; | |
| 7361 | } | |
| 7362 | } | |
| 7363 | ||
| 7364 | jQuery.map( props, createTween, animation ); | |
| 7365 | ||
| 7366 | if ( jQuery.isFunction( animation.opts.start ) ) { | |
| 7367 | animation.opts.start.call( elem, animation ); | |
| 7368 | } | |
| 7369 | ||
| 7370 | jQuery.fx.timer( | |
| 7371 | jQuery.extend( tick, { | |
| 7372 | elem: elem, | |
| 7373 | anim: animation, | |
| 7374 | queue: animation.opts.queue | |
| 7375 | }) | |
| 7376 | ); | |
| 7377 | ||
| 7378 | // attach callbacks from options | |
| 7379 | return animation.progress( animation.opts.progress ) | |
| 7380 | .done( animation.opts.done, animation.opts.complete ) | |
| 7381 | .fail( animation.opts.fail ) | |
| 7382 | .always( animation.opts.always ); | |
| 7383 | } | |
| 7384 | ||
| 7385 | jQuery.Animation = jQuery.extend( Animation, { | |
| 7386 | tweener: function( props, callback ) { | |
| 7387 | if ( jQuery.isFunction( props ) ) { | |
| 7388 | callback = props; | |
| 7389 | props = [ "*" ]; | |
| 7390 | } else { | |
| 7391 | props = props.split(" "); | |
| 7392 | } | |
| 7393 | ||
| 7394 | var prop, | |
| 7395 | index = 0, | |
| 7396 | length = props.length; | |
| 7397 | ||
| 7398 | for ( ; index < length ; index++ ) { | |
| 7399 | prop = props[ index ]; | |
| 7400 | tweeners[ prop ] = tweeners[ prop ] || []; | |
| 7401 | tweeners[ prop ].unshift( callback ); | |
| 7402 | } | |
| 7403 | }, | |
| 7404 | ||
| 7405 | prefilter: function( callback, prepend ) { | |
| 7406 | if ( prepend ) { | |
| 7407 | animationPrefilters.unshift( callback ); | |
| 7408 | } else { | |
| 7409 | animationPrefilters.push( callback ); | |
| 7410 | } | |
| 7411 | } | |
| 7412 | }); | |
| 7413 | ||
| 7414 | jQuery.speed = function( speed, easing, fn ) { | |
| 7415 | var opt = speed && typeof speed === "object" ? jQuery.extend( {}, speed ) : { | |
| 7416 | complete: fn || !fn && easing || | |
| 7417 | jQuery.isFunction( speed ) && speed, | |
| 7418 | duration: speed, | |
| 7419 | easing: fn && easing || easing && !jQuery.isFunction( easing ) && easing | |
| 7420 | }; | |
| 7421 | ||
| 7422 | opt.duration = jQuery.fx.off ? 0 : typeof opt.duration === "number" ? opt.duration : | |
| 7423 | opt.duration in jQuery.fx.speeds ? jQuery.fx.speeds[ opt.duration ] : jQuery.fx.speeds._default; | |
| 7424 | ||
| 7425 | // normalize opt.queue - true/undefined/null -> "fx" | |
| 7426 | if ( opt.queue == null || opt.queue === true ) { | |
| 7427 | opt.queue = "fx"; | |
| 7428 | } | |
| 7429 | ||
| 7430 | // Queueing | |
| 7431 | opt.old = opt.complete; | |
| 7432 | ||
| 7433 | opt.complete = function() { | |
| 7434 | if ( jQuery.isFunction( opt.old ) ) { | |
| 7435 | opt.old.call( this ); | |
| 7436 | } | |
| 7437 | ||
| 7438 | if ( opt.queue ) { | |
| 7439 | jQuery.dequeue( this, opt.queue ); | |
| 7440 | } | |
| 7441 | }; | |
| 7442 | ||
| 7443 | return opt; | |
| 7444 | }; | |
| 7445 | ||
| 7446 | jQuery.fn.extend({ | |
| 7447 | fadeTo: function( speed, to, easing, callback ) { | |
| 7448 | ||
| 7449 | // show any hidden elements after setting opacity to 0 | |
| 7450 | return this.filter( isHidden ).css( "opacity", 0 ).show() | |
| 7451 | ||
| 7452 | // animate to the value specified | |
| 7453 | .end().animate({ opacity: to }, speed, easing, callback ); | |
| 7454 | }, | |
| 7455 | animate: function( prop, speed, easing, callback ) { | |
| 7456 | var empty = jQuery.isEmptyObject( prop ), | |
| 7457 | optall = jQuery.speed( speed, easing, callback ), | |
| 7458 | doAnimation = function() { | |
| 7459 | // Operate on a copy of prop so per-property easing won't be lost | |
| 7460 | var anim = Animation( this, jQuery.extend( {}, prop ), optall ); | |
| 7461 | ||
| 7462 | // Empty animations, or finishing resolves immediately | |
| 7463 | if ( empty || jQuery._data( this, "finish" ) ) { | |
| 7464 | anim.stop( true ); | |
| 7465 | } | |
| 7466 | }; | |
| 7467 | doAnimation.finish = doAnimation; | |
| 7468 | ||
| 7469 | return empty || optall.queue === false ? | |
| 7470 | this.each( doAnimation ) : | |
| 7471 | this.queue( optall.queue, doAnimation ); | |
| 7472 | }, | |
| 7473 | stop: function( type, clearQueue, gotoEnd ) { | |
| 7474 | var stopQueue = function( hooks ) { | |
| 7475 | var stop = hooks.stop; | |
| 7476 | delete hooks.stop; | |
| 7477 | stop( gotoEnd ); | |
| 7478 | }; | |
| 7479 | ||
| 7480 | if ( typeof type !== "string" ) { | |
| 7481 | gotoEnd = clearQueue; | |
| 7482 | clearQueue = type; | |
| 7483 | type = undefined; | |
| 7484 | } | |
| 7485 | if ( clearQueue && type !== false ) { | |
| 7486 | this.queue( type || "fx", [] ); | |
| 7487 | } | |
| 7488 | ||
| 7489 | return this.each(function() { | |
| 7490 | var dequeue = true, | |
| 7491 | index = type != null && type + "queueHooks", | |
| 7492 | timers = jQuery.timers, | |
| 7493 | data = jQuery._data( this ); | |
| 7494 | ||
| 7495 | if ( index ) { | |
| 7496 | if ( data[ index ] && data[ index ].stop ) { | |
| 7497 | stopQueue( data[ index ] ); | |
| 7498 | } | |
| 7499 | } else { | |
| 7500 | for ( index in data ) { | |
| 7501 | if ( data[ index ] && data[ index ].stop && rrun.test( index ) ) { | |
| 7502 | stopQueue( data[ index ] ); | |
| 7503 | } | |
| 7504 | } | |
| 7505 | } | |
| 7506 | ||
| 7507 | for ( index = timers.length; index--; ) { | |
| 7508 | if ( timers[ index ].elem === this && (type == null || timers[ index ].queue === type) ) { | |
| 7509 | timers[ index ].anim.stop( gotoEnd ); | |
| 7510 | dequeue = false; | |
| 7511 | timers.splice( index, 1 ); | |
| 7512 | } | |
| 7513 | } | |
| 7514 | ||
| 7515 | // start the next in the queue if the last step wasn't forced | |
| 7516 | // timers currently will call their complete callbacks, which will dequeue | |
| 7517 | // but only if they were gotoEnd | |
| 7518 | if ( dequeue || !gotoEnd ) { | |
| 7519 | jQuery.dequeue( this, type ); | |
| 7520 | } | |
| 7521 | }); | |
| 7522 | }, | |
| 7523 | finish: function( type ) { | |
| 7524 | if ( type !== false ) { | |
| 7525 | type = type || "fx"; | |
| 7526 | } | |
| 7527 | return this.each(function() { | |
| 7528 | var index, | |
| 7529 | data = jQuery._data( this ), | |
| 7530 | queue = data[ type + "queue" ], | |
| 7531 | hooks = data[ type + "queueHooks" ], | |
| 7532 | timers = jQuery.timers, | |
| 7533 | length = queue ? queue.length : 0; | |
| 7534 | ||
| 7535 | // enable finishing flag on private data | |
| 7536 | data.finish = true; | |
| 7537 | ||
| 7538 | // empty the queue first | |
| 7539 | jQuery.queue( this, type, [] ); | |
| 7540 | ||
| 7541 | if ( hooks && hooks.stop ) { | |
| 7542 | hooks.stop.call( this, true ); | |
| 7543 | } | |
| 7544 | ||
| 7545 | // look for any active animations, and finish them | |
| 7546 | for ( index = timers.length; index--; ) { | |
| 7547 | if ( timers[ index ].elem === this && timers[ index ].queue === type ) { | |
| 7548 | timers[ index ].anim.stop( true ); | |
| 7549 | timers.splice( index, 1 ); | |
| 7550 | } | |
| 7551 | } | |
| 7552 | ||
| 7553 | // look for any animations in the old queue and finish them | |
| 7554 | for ( index = 0; index < length; index++ ) { | |
| 7555 | if ( queue[ index ] && queue[ index ].finish ) { | |
| 7556 | queue[ index ].finish.call( this ); | |
| 7557 | } | |
| 7558 | } | |
| 7559 | ||
| 7560 | // turn off finishing flag | |
| 7561 | delete data.finish; | |
| 7562 | }); | |
| 7563 | } | |
| 7564 | }); | |
| 7565 | ||
| 7566 | jQuery.each([ "toggle", "show", "hide" ], function( i, name ) { | |
| 7567 | var cssFn = jQuery.fn[ name ]; | |
| 7568 | jQuery.fn[ name ] = function( speed, easing, callback ) { | |
| 7569 | return speed == null || typeof speed === "boolean" ? | |
| 7570 | cssFn.apply( this, arguments ) : | |
| 7571 | this.animate( genFx( name, true ), speed, easing, callback ); | |
| 7572 | }; | |
| 7573 | }); | |
| 7574 | ||
| 7575 | // Generate shortcuts for custom animations | |
| 7576 | jQuery.each({ | |
| 7577 | slideDown: genFx("show"), | |
| 7578 | slideUp: genFx("hide"), | |
| 7579 | slideToggle: genFx("toggle"), | |
| 7580 | fadeIn: { opacity: "show" }, | |
| 7581 | fadeOut: { opacity: "hide" }, | |
| 7582 | fadeToggle: { opacity: "toggle" } | |
| 7583 | }, function( name, props ) { | |
| 7584 | jQuery.fn[ name ] = function( speed, easing, callback ) { | |
| 7585 | return this.animate( props, speed, easing, callback ); | |
| 7586 | }; | |
| 7587 | }); | |
| 7588 | ||
| 7589 | jQuery.timers = []; | |
| 7590 | jQuery.fx.tick = function() { | |
| 7591 | var timer, | |
| 7592 | timers = jQuery.timers, | |
| 7593 | i = 0; | |
| 7594 | ||
| 7595 | fxNow = jQuery.now(); | |
| 7596 | ||
| 7597 | for ( ; i < timers.length; i++ ) { | |
| 7598 | timer = timers[ i ]; | |
| 7599 | // Checks the timer has not already been removed | |
| 7600 | if ( !timer() && timers[ i ] === timer ) { | |
| 7601 | timers.splice( i--, 1 ); | |
| 7602 | } | |
| 7603 | } | |
| 7604 | ||
| 7605 | if ( !timers.length ) { | |
| 7606 | jQuery.fx.stop(); | |
| 7607 | } | |
| 7608 | fxNow = undefined; | |
| 7609 | }; | |
| 7610 | ||
| 7611 | jQuery.fx.timer = function( timer ) { | |
| 7612 | jQuery.timers.push( timer ); | |
| 7613 | if ( timer() ) { | |
| 7614 | jQuery.fx.start(); | |
| 7615 | } else { | |
| 7616 | jQuery.timers.pop(); | |
| 7617 | } | |
| 7618 | }; | |
| 7619 | ||
| 7620 | jQuery.fx.interval = 13; | |
| 7621 | ||
| 7622 | jQuery.fx.start = function() { | |
| 7623 | if ( !timerId ) { | |
| 7624 | timerId = setInterval( jQuery.fx.tick, jQuery.fx.interval ); | |
| 7625 | } | |
| 7626 | }; | |
| 7627 | ||
| 7628 | jQuery.fx.stop = function() { | |
| 7629 | clearInterval( timerId ); | |
| 7630 | timerId = null; | |
| 7631 | }; | |
| 7632 | ||
| 7633 | jQuery.fx.speeds = { | |
| 7634 | slow: 600, | |
| 7635 | fast: 200, | |
| 7636 | // Default speed | |
| 7637 | _default: 400 | |
| 7638 | }; | |
| 7639 | ||
| 7640 | ||
| 7641 | // Based off of the plugin by Clint Helfers, with permission. | |
| 7642 | // http://blindsignals.com/index.php/2009/07/jquery-delay/ | |
| 7643 | jQuery.fn.delay = function( time, type ) { | |
| 7644 | time = jQuery.fx ? jQuery.fx.speeds[ time ] || time : time; | |
| 7645 | type = type || "fx"; | |
| 7646 | ||
| 7647 | return this.queue( type, function( next, hooks ) { | |
| 7648 | var timeout = setTimeout( next, time ); | |
| 7649 | hooks.stop = function() { | |
| 7650 | clearTimeout( timeout ); | |
| 7651 | }; | |
| 7652 | }); | |
| 7653 | }; | |
| 7654 | ||
| 7655 | ||
| 7656 | (function() { | |
| 7657 | // Minified: var a,b,c,d,e | |
| 7658 | var input, div, select, a, opt; | |
| 7659 | ||
| 7660 | // Setup | |
| 7661 | div = document.createElement( "div" ); | |
| 7662 | div.setAttribute( "className", "t" ); | |
| 7663 | div.innerHTML = " <link/><table></table><a href='/a'>a</a><input type='checkbox'/>"; | |
| 7664 | a = div.getElementsByTagName("a")[ 0 ]; | |
| 7665 | ||
| 7666 | // First batch of tests. | |
| 7667 | select = document.createElement("select"); | |
| 7668 | opt = select.appendChild( document.createElement("option") ); | |
| 7669 | input = div.getElementsByTagName("input")[ 0 ]; | |
| 7670 | ||
| 7671 | a.style.cssText = "top:1px"; | |
| 7672 | ||
| 7673 | // Test setAttribute on camelCase class. If it works, we need attrFixes when doing get/setAttribute (ie6/7) | |
| 7674 | support.getSetAttribute = div.className !== "t"; | |
| 7675 | ||
| 7676 | // Get the style information from getAttribute | |
| 7677 | // (IE uses .cssText instead) | |
| 7678 | support.style = /top/.test( a.getAttribute("style") ); | |
| 7679 | ||
| 7680 | // Make sure that URLs aren't manipulated | |
| 7681 | // (IE normalizes it by default) | |
| 7682 | support.hrefNormalized = a.getAttribute("href") === "/a"; | |
| 7683 | ||
| 7684 | // Check the default checkbox/radio value ("" on WebKit; "on" elsewhere) | |
| 7685 | support.checkOn = !!input.value; | |
| 7686 | ||
| 7687 | // Make sure that a selected-by-default option has a working selected property. | |
| 7688 | // (WebKit defaults to false instead of true, IE too, if it's in an optgroup) | |
| 7689 | support.optSelected = opt.selected; | |
| 7690 | ||
| 7691 | // Tests for enctype support on a form (#6743) | |
| 7692 | support.enctype = !!document.createElement("form").enctype; | |
| 7693 | ||
| 7694 | // Make sure that the options inside disabled selects aren't marked as disabled | |
| 7695 | // (WebKit marks them as disabled) | |
| 7696 | select.disabled = true; | |
| 7697 | support.optDisabled = !opt.disabled; | |
| 7698 | ||
| 7699 | // Support: IE8 only | |
| 7700 | // Check if we can trust getAttribute("value") | |
| 7701 | input = document.createElement( "input" ); | |
| 7702 | input.setAttribute( "value", "" ); | |
| 7703 | support.input = input.getAttribute( "value" ) === ""; | |
| 7704 | ||
| 7705 | // Check if an input maintains its value after becoming a radio | |
| 7706 | input.value = "t"; | |
| 7707 | input.setAttribute( "type", "radio" ); | |
| 7708 | support.radioValue = input.value === "t"; | |
| 7709 | })(); | |
| 7710 | ||
| 7711 | ||
| 7712 | var rreturn = /\r/g; | |
| 7713 | ||
| 7714 | jQuery.fn.extend({ | |
| 7715 | val: function( value ) { | |
| 7716 | var hooks, ret, isFunction, | |
| 7717 | elem = this[0]; | |
| 7718 | ||
| 7719 | if ( !arguments.length ) { | |
| 7720 | if ( elem ) { | |
| 7721 | hooks = jQuery.valHooks[ elem.type ] || jQuery.valHooks[ elem.nodeName.toLowerCase() ]; | |
| 7722 | ||
| 7723 | if ( hooks && "get" in hooks && (ret = hooks.get( elem, "value" )) !== undefined ) { | |
| 7724 | return ret; | |
| 7725 | } | |
| 7726 | ||
| 7727 | ret = elem.value; | |
| 7728 | ||
| 7729 | return typeof ret === "string" ? | |
| 7730 | // handle most common string cases | |
| 7731 | ret.replace(rreturn, "") : | |
| 7732 | // handle cases where value is null/undef or number | |
| 7733 | ret == null ? "" : ret; | |
| 7734 | } | |
| 7735 | ||
| 7736 | return; | |
| 7737 | } | |
| 7738 | ||
| 7739 | isFunction = jQuery.isFunction( value ); | |
| 7740 | ||
| 7741 | return this.each(function( i ) { | |
| 7742 | var val; | |
| 7743 | ||
| 7744 | if ( this.nodeType !== 1 ) { | |
| 7745 | return; | |
| 7746 | } | |
| 7747 | ||
| 7748 | if ( isFunction ) { | |
| 7749 | val = value.call( this, i, jQuery( this ).val() ); | |
| 7750 | } else { | |
| 7751 | val = value; | |
| 7752 | } | |
| 7753 | ||
| 7754 | // Treat null/undefined as ""; convert numbers to string | |
| 7755 | if ( val == null ) { | |
| 7756 | val = ""; | |
| 7757 | } else if ( typeof val === "number" ) { | |
| 7758 | val += ""; | |
| 7759 | } else if ( jQuery.isArray( val ) ) { | |
| 7760 | val = jQuery.map( val, function( value ) { | |
| 7761 | return value == null ? "" : value + ""; | |
| 7762 | }); | |
| 7763 | } | |
| 7764 | ||
| 7765 | hooks = jQuery.valHooks[ this.type ] || jQuery.valHooks[ this.nodeName.toLowerCase() ]; | |
| 7766 | ||
| 7767 | // If set returns undefined, fall back to normal setting | |
| 7768 | if ( !hooks || !("set" in hooks) || hooks.set( this, val, "value" ) === undefined ) { | |
| 7769 | this.value = val; | |
| 7770 | } | |
| 7771 | }); | |
| 7772 | } | |
| 7773 | }); | |
| 7774 | ||
| 7775 | jQuery.extend({ | |
| 7776 | valHooks: { | |
| 7777 | option: { | |
| 7778 | get: function( elem ) { | |
| 7779 | var val = jQuery.find.attr( elem, "value" ); | |
| 7780 | return val != null ? | |
| 7781 | val : | |
| 7782 | // Support: IE10-11+ | |
| 7783 | // option.text throws exceptions (#14686, #14858) | |
| 7784 | jQuery.trim( jQuery.text( elem ) ); | |
| 7785 | } | |
| 7786 | }, | |
| 7787 | select: { | |
| 7788 | get: function( elem ) { | |
| 7789 | var value, option, | |
| 7790 | options = elem.options, | |
| 7791 | index = elem.selectedIndex, | |
| 7792 | one = elem.type === "select-one" || index < 0, | |
| 7793 | values = one ? null : [], | |
| 7794 | max = one ? index + 1 : options.length, | |
| 7795 | i = index < 0 ? | |
| 7796 | max : | |
| 7797 | one ? index : 0; | |
| 7798 | ||
| 7799 | // Loop through all the selected options | |
| 7800 | for ( ; i < max; i++ ) { | |
| 7801 | option = options[ i ]; | |
| 7802 | ||
| 7803 | // oldIE doesn't update selected after form reset (#2551) | |
| 7804 | if ( ( option.selected || i === index ) && | |
| 7805 | // Don't return options that are disabled or in a disabled optgroup | |
| 7806 | ( support.optDisabled ? !option.disabled : option.getAttribute("disabled") === null ) && | |
| 7807 | ( !option.parentNode.disabled || !jQuery.nodeName( option.parentNode, "optgroup" ) ) ) { | |
| 7808 | ||
| 7809 | // Get the specific value for the option | |
| 7810 | value = jQuery( option ).val(); | |
| 7811 | ||
| 7812 | // We don't need an array for one selects | |
| 7813 | if ( one ) { | |
| 7814 | return value; | |
| 7815 | } | |
| 7816 | ||
| 7817 | // Multi-Selects return an array | |
| 7818 | values.push( value ); | |
| 7819 | } | |
| 7820 | } | |
| 7821 | ||
| 7822 | return values; | |
| 7823 | }, | |
| 7824 | ||
| 7825 | set: function( elem, value ) { | |
| 7826 | var optionSet, option, | |
| 7827 | options = elem.options, | |
| 7828 | values = jQuery.makeArray( value ), | |
| 7829 | i = options.length; | |
| 7830 | ||
| 7831 | while ( i-- ) { | |
| 7832 | option = options[ i ]; | |
| 7833 | ||
| 7834 | if ( jQuery.inArray( jQuery.valHooks.option.get( option ), values ) >= 0 ) { | |
| 7835 | ||
| 7836 | // Support: IE6 | |
| 7837 | // When new option element is added to select box we need to | |
| 7838 | // force reflow of newly added node in order to workaround delay | |
| 7839 | // of initialization properties | |
| 7840 | try { | |
| 7841 | option.selected = optionSet = true; | |
| 7842 | ||
| 7843 | } catch ( _ ) { | |
| 7844 | ||
| 7845 | // Will be executed only in IE6 | |
| 7846 | option.scrollHeight; | |
| 7847 | } | |
| 7848 | ||
| 7849 | } else { | |
| 7850 | option.selected = false; | |
| 7851 | } | |
| 7852 | } | |
| 7853 | ||
| 7854 | // Force browsers to behave consistently when non-matching value is set | |
| 7855 | if ( !optionSet ) { | |
| 7856 | elem.selectedIndex = -1; | |
| 7857 | } | |
| 7858 | ||
| 7859 | return options; | |
| 7860 | } | |
| 7861 | } | |
| 7862 | } | |
| 7863 | }); | |
| 7864 | ||
| 7865 | // Radios and checkboxes getter/setter | |
| 7866 | jQuery.each([ "radio", "checkbox" ], function() { | |
| 7867 | jQuery.valHooks[ this ] = { | |
| 7868 | set: function( elem, value ) { | |
| 7869 | if ( jQuery.isArray( value ) ) { | |
| 7870 | return ( elem.checked = jQuery.inArray( jQuery(elem).val(), value ) >= 0 ); | |
| 7871 | } | |
| 7872 | } | |
| 7873 | }; | |
| 7874 | if ( !support.checkOn ) { | |
| 7875 | jQuery.valHooks[ this ].get = function( elem ) { | |
| 7876 | // Support: Webkit | |
| 7877 | // "" is returned instead of "on" if a value isn't specified | |
| 7878 | return elem.getAttribute("value") === null ? "on" : elem.value; | |
| 7879 | }; | |
| 7880 | } | |
| 7881 | }); | |
| 7882 | ||
| 7883 | ||
| 7884 | ||
| 7885 | ||
| 7886 | var nodeHook, boolHook, | |
| 7887 | attrHandle = jQuery.expr.attrHandle, | |
| 7888 | ruseDefault = /^(?:checked|selected)$/i, | |
| 7889 | getSetAttribute = support.getSetAttribute, | |
| 7890 | getSetInput = support.input; | |
| 7891 | ||
| 7892 | jQuery.fn.extend({ | |
| 7893 | attr: function( name, value ) { | |
| 7894 | return access( this, jQuery.attr, name, value, arguments.length > 1 ); | |
| 7895 | }, | |
| 7896 | ||
| 7897 | removeAttr: function( name ) { | |
| 7898 | return this.each(function() { | |
| 7899 | jQuery.removeAttr( this, name ); | |
| 7900 | }); | |
| 7901 | } | |
| 7902 | }); | |
| 7903 | ||
| 7904 | jQuery.extend({ | |
| 7905 | attr: function( elem, name, value ) { | |
| 7906 | var hooks, ret, | |
| 7907 | nType = elem.nodeType; | |
| 7908 | ||
| 7909 | // don't get/set attributes on text, comment and attribute nodes | |
| 7910 | if ( !elem || nType === 3 || nType === 8 || nType === 2 ) { | |
| 7911 | return; | |
| 7912 | } | |
| 7913 | ||
| 7914 | // Fallback to prop when attributes are not supported | |
| 7915 | if ( typeof elem.getAttribute === strundefined ) { | |
| 7916 | return jQuery.prop( elem, name, value ); | |
| 7917 | } | |
| 7918 | ||
| 7919 | // All attributes are lowercase | |
| 7920 | // Grab necessary hook if one is defined | |
| 7921 | if ( nType !== 1 || !jQuery.isXMLDoc( elem ) ) { | |
| 7922 | name = name.toLowerCase(); | |
| 7923 | hooks = jQuery.attrHooks[ name ] || | |
| 7924 | ( jQuery.expr.match.bool.test( name ) ? boolHook : nodeHook ); | |
| 7925 | } | |
| 7926 | ||
| 7927 | if ( value !== undefined ) { | |
| 7928 | ||
| 7929 | if ( value === null ) { | |
| 7930 | jQuery.removeAttr( elem, name ); | |
| 7931 | ||
| 7932 | } else if ( hooks && "set" in hooks && (ret = hooks.set( elem, value, name )) !== undefined ) { | |
| 7933 | return ret; | |
| 7934 | ||
| 7935 | } else { | |
| 7936 | elem.setAttribute( name, value + "" ); | |
| 7937 | return value; | |
| 7938 | } | |
| 7939 | ||
| 7940 | } else if ( hooks && "get" in hooks && (ret = hooks.get( elem, name )) !== null ) { | |
| 7941 | return ret; | |
| 7942 | ||
| 7943 | } else { | |
| 7944 | ret = jQuery.find.attr( elem, name ); | |
| 7945 | ||
| 7946 | // Non-existent attributes return null, we normalize to undefined | |
| 7947 | return ret == null ? | |
| 7948 | undefined : | |
| 7949 | ret; | |
| 7950 | } | |
| 7951 | }, | |
| 7952 | ||
| 7953 | removeAttr: function( elem, value ) { | |
| 7954 | var name, propName, | |
| 7955 | i = 0, | |
| 7956 | attrNames = value && value.match( rnotwhite ); | |
| 7957 | ||
| 7958 | if ( attrNames && elem.nodeType === 1 ) { | |
| 7959 | while ( (name = attrNames[i++]) ) { | |
| 7960 | propName = jQuery.propFix[ name ] || name; | |
| 7961 | ||
| 7962 | // Boolean attributes get special treatment (#10870) | |
| 7963 | if ( jQuery.expr.match.bool.test( name ) ) { | |
| 7964 | // Set corresponding property to false | |
| 7965 | if ( getSetInput && getSetAttribute || !ruseDefault.test( name ) ) { | |
| 7966 | elem[ propName ] = false; | |
| 7967 | // Support: IE<9 | |
| 7968 | // Also clear defaultChecked/defaultSelected (if appropriate) | |
| 7969 | } else { | |
| 7970 | elem[ jQuery.camelCase( "default-" + name ) ] = | |
| 7971 | elem[ propName ] = false; | |
| 7972 | } | |
| 7973 | ||
| 7974 | // See #9699 for explanation of this approach (setting first, then removal) | |
| 7975 | } else { | |
| 7976 | jQuery.attr( elem, name, "" ); | |
| 7977 | } | |
| 7978 | ||
| 7979 | elem.removeAttribute( getSetAttribute ? name : propName ); | |
| 7980 | } | |
| 7981 | } | |
| 7982 | }, | |
| 7983 | ||
| 7984 | attrHooks: { | |
| 7985 | type: { | |
| 7986 | set: function( elem, value ) { | |
| 7987 | if ( !support.radioValue && value === "radio" && jQuery.nodeName(elem, "input") ) { | |
| 7988 | // Setting the type on a radio button after the value resets the value in IE6-9 | |
| 7989 | // Reset value to default in case type is set after value during creation | |
| 7990 | var val = elem.value; | |
| 7991 | elem.setAttribute( "type", value ); | |
| 7992 | if ( val ) { | |
| 7993 | elem.value = val; | |
| 7994 | } | |
| 7995 | return value; | |
| 7996 | } | |
| 7997 | } | |
| 7998 | } | |
| 7999 | } | |
| 8000 | }); | |
| 8001 | ||
| 8002 | // Hook for boolean attributes | |
| 8003 | boolHook = { | |
| 8004 | set: function( elem, value, name ) { | |
| 8005 | if ( value === false ) { | |
| 8006 | // Remove boolean attributes when set to false | |
| 8007 | jQuery.removeAttr( elem, name ); | |
| 8008 | } else if ( getSetInput && getSetAttribute || !ruseDefault.test( name ) ) { | |
| 8009 | // IE<8 needs the *property* name | |
| 8010 | elem.setAttribute( !getSetAttribute && jQuery.propFix[ name ] || name, name ); | |
| 8011 | ||
| 8012 | // Use defaultChecked and defaultSelected for oldIE | |
| 8013 | } else { | |
| 8014 | elem[ jQuery.camelCase( "default-" + name ) ] = elem[ name ] = true; | |
| 8015 | } | |
| 8016 | ||
| 8017 | return name; | |
| 8018 | } | |
| 8019 | }; | |
| 8020 | ||
| 8021 | // Retrieve booleans specially | |
| 8022 | jQuery.each( jQuery.expr.match.bool.source.match( /\w+/g ), function( i, name ) { | |
| 8023 | ||
| 8024 | var getter = attrHandle[ name ] || jQuery.find.attr; | |
| 8025 | ||
| 8026 | attrHandle[ name ] = getSetInput && getSetAttribute || !ruseDefault.test( name ) ? | |
| 8027 | function( elem, name, isXML ) { | |
| 8028 | var ret, handle; | |
| 8029 | if ( !isXML ) { | |
| 8030 | // Avoid an infinite loop by temporarily removing this function from the getter | |
| 8031 | handle = attrHandle[ name ]; | |
| 8032 | attrHandle[ name ] = ret; | |
| 8033 | ret = getter( elem, name, isXML ) != null ? | |
| 8034 | name.toLowerCase() : | |
| 8035 | null; | |
| 8036 | attrHandle[ name ] = handle; | |
| 8037 | } | |
| 8038 | return ret; | |
| 8039 | } : | |
| 8040 | function( elem, name, isXML ) { | |
| 8041 | if ( !isXML ) { | |
| 8042 | return elem[ jQuery.camelCase( "default-" + name ) ] ? | |
| 8043 | name.toLowerCase() : | |
| 8044 | null; | |
| 8045 | } | |
| 8046 | }; | |
| 8047 | }); | |
| 8048 | ||
| 8049 | // fix oldIE attroperties | |
| 8050 | if ( !getSetInput || !getSetAttribute ) { | |
| 8051 | jQuery.attrHooks.value = { | |
| 8052 | set: function( elem, value, name ) { | |
| 8053 | if ( jQuery.nodeName( elem, "input" ) ) { | |
| 8054 | // Does not return so that setAttribute is also used | |
| 8055 | elem.defaultValue = value; | |
| 8056 | } else { | |
| 8057 | // Use nodeHook if defined (#1954); otherwise setAttribute is fine | |
| 8058 | return nodeHook && nodeHook.set( elem, value, name ); | |
| 8059 | } | |
| 8060 | } | |
| 8061 | }; | |
| 8062 | } | |
| 8063 | ||
| 8064 | // IE6/7 do not support getting/setting some attributes with get/setAttribute | |
| 8065 | if ( !getSetAttribute ) { | |
| 8066 | ||
| 8067 | // Use this for any attribute in IE6/7 | |
| 8068 | // This fixes almost every IE6/7 issue | |
| 8069 | nodeHook = { | |
| 8070 | set: function( elem, value, name ) { | |
| 8071 | // Set the existing or create a new attribute node | |
| 8072 | var ret = elem.getAttributeNode( name ); | |
| 8073 | if ( !ret ) { | |
| 8074 | elem.setAttributeNode( | |
| 8075 | (ret = elem.ownerDocument.createAttribute( name )) | |
| 8076 | ); | |
| 8077 | } | |
| 8078 | ||
| 8079 | ret.value = value += ""; | |
| 8080 | ||
| 8081 | // Break association with cloned elements by also using setAttribute (#9646) | |
| 8082 | if ( name === "value" || value === elem.getAttribute( name ) ) { | |
| 8083 | return value; | |
| 8084 | } | |
| 8085 | } | |
| 8086 | }; | |
| 8087 | ||
| 8088 | // Some attributes are constructed with empty-string values when not defined | |
| 8089 | attrHandle.id = attrHandle.name = attrHandle.coords = | |
| 8090 | function( elem, name, isXML ) { | |
| 8091 | var ret; | |
| 8092 | if ( !isXML ) { | |
| 8093 | return (ret = elem.getAttributeNode( name )) && ret.value !== "" ? | |
| 8094 | ret.value : | |
| 8095 | null; | |
| 8096 | } | |
| 8097 | }; | |
| 8098 | ||
| 8099 | // Fixing value retrieval on a button requires this module | |
| 8100 | jQuery.valHooks.button = { | |
| 8101 | get: function( elem, name ) { | |
| 8102 | var ret = elem.getAttributeNode( name ); | |
| 8103 | if ( ret && ret.specified ) { | |
| 8104 | return ret.value; | |
| 8105 | } | |
| 8106 | }, | |
| 8107 | set: nodeHook.set | |
| 8108 | }; | |
| 8109 | ||
| 8110 | // Set contenteditable to false on removals(#10429) | |
| 8111 | // Setting to empty string throws an error as an invalid value | |
| 8112 | jQuery.attrHooks.contenteditable = { | |
| 8113 | set: function( elem, value, name ) { | |
| 8114 | nodeHook.set( elem, value === "" ? false : value, name ); | |
| 8115 | } | |
| 8116 | }; | |
| 8117 | ||
| 8118 | // Set width and height to auto instead of 0 on empty string( Bug #8150 ) | |
| 8119 | // This is for removals | |
| 8120 | jQuery.each([ "width", "height" ], function( i, name ) { | |
| 8121 | jQuery.attrHooks[ name ] = { | |
| 8122 | set: function( elem, value ) { | |
| 8123 | if ( value === "" ) { | |
| 8124 | elem.setAttribute( name, "auto" ); | |
| 8125 | return value; | |
| 8126 | } | |
| 8127 | } | |
| 8128 | }; | |
| 8129 | }); | |
| 8130 | } | |
| 8131 | ||
| 8132 | if ( !support.style ) { | |
| 8133 | jQuery.attrHooks.style = { | |
| 8134 | get: function( elem ) { | |
| 8135 | // Return undefined in the case of empty string | |
| 8136 | // Note: IE uppercases css property names, but if we were to .toLowerCase() | |
| 8137 | // .cssText, that would destroy case senstitivity in URL's, like in "background" | |
| 8138 | return elem.style.cssText || undefined; | |
| 8139 | }, | |
| 8140 | set: function( elem, value ) { | |
| 8141 | return ( elem.style.cssText = value + "" ); | |
| 8142 | } | |
| 8143 | }; | |
| 8144 | } | |
| 8145 | ||
| 8146 | ||
| 8147 | ||
| 8148 | ||
| 8149 | var rfocusable = /^(?:input|select|textarea|button|object)$/i, | |
| 8150 | rclickable = /^(?:a|area)$/i; | |
| 8151 | ||
| 8152 | jQuery.fn.extend({ | |
| 8153 | prop: function( name, value ) { | |
| 8154 | return access( this, jQuery.prop, name, value, arguments.length > 1 ); | |
| 8155 | }, | |
| 8156 | ||
| 8157 | removeProp: function( name ) { | |
| 8158 | name = jQuery.propFix[ name ] || name; | |
| 8159 | return this.each(function() { | |
| 8160 | // try/catch handles cases where IE balks (such as removing a property on window) | |
| 8161 | try { | |
| 8162 | this[ name ] = undefined; | |
| 8163 | delete this[ name ]; | |
| 8164 | } catch( e ) {} | |
| 8165 | }); | |
| 8166 | } | |
| 8167 | }); | |
| 8168 | ||
| 8169 | jQuery.extend({ | |
| 8170 | propFix: { | |
| 8171 | "for": "htmlFor", | |
| 8172 | "class": "className" | |
| 8173 | }, | |
| 8174 | ||
| 8175 | prop: function( elem, name, value ) { | |
| 8176 | var ret, hooks, notxml, | |
| 8177 | nType = elem.nodeType; | |
| 8178 | ||
| 8179 | // don't get/set properties on text, comment and attribute nodes | |
| 8180 | if ( !elem || nType === 3 || nType === 8 || nType === 2 ) { | |
| 8181 | return; | |
| 8182 | } | |
| 8183 | ||
| 8184 | notxml = nType !== 1 || !jQuery.isXMLDoc( elem ); | |
| 8185 | ||
| 8186 | if ( notxml ) { | |
| 8187 | // Fix name and attach hooks | |
| 8188 | name = jQuery.propFix[ name ] || name; | |
| 8189 | hooks = jQuery.propHooks[ name ]; | |
| 8190 | } | |
| 8191 | ||
| 8192 | if ( value !== undefined ) { | |
| 8193 | return hooks && "set" in hooks && (ret = hooks.set( elem, value, name )) !== undefined ? | |
| 8194 | ret : | |
| 8195 | ( elem[ name ] = value ); | |
| 8196 | ||
| 8197 | } else { | |
| 8198 | return hooks && "get" in hooks && (ret = hooks.get( elem, name )) !== null ? | |
| 8199 | ret : | |
| 8200 | elem[ name ]; | |
| 8201 | } | |
| 8202 | }, | |
| 8203 | ||
| 8204 | propHooks: { | |
| 8205 | tabIndex: { | |
| 8206 | get: function( elem ) { | |
| 8207 | // elem.tabIndex doesn't always return the correct value when it hasn't been explicitly set | |
| 8208 | // http://fluidproject.org/blog/2008/01/09/getting-setting-and-removing-tabindex-values-with-javascript/ | |
| 8209 | // Use proper attribute retrieval(#12072) | |
| 8210 | var tabindex = jQuery.find.attr( elem, "tabindex" ); | |
| 8211 | ||
| 8212 | return tabindex ? | |
| 8213 | parseInt( tabindex, 10 ) : | |
| 8214 | rfocusable.test( elem.nodeName ) || rclickable.test( elem.nodeName ) && elem.href ? | |
| 8215 | 0 : | |
| 8216 | -1; | |
| 8217 | } | |
| 8218 | } | |
| 8219 | } | |
| 8220 | }); | |
| 8221 | ||
| 8222 | // Some attributes require a special call on IE | |
| 8223 | // http://msdn.microsoft.com/en-us/library/ms536429%28VS.85%29.aspx | |
| 8224 | if ( !support.hrefNormalized ) { | |
| 8225 | // href/src property should get the full normalized URL (#10299/#12915) | |
| 8226 | jQuery.each([ "href", "src" ], function( i, name ) { | |
| 8227 | jQuery.propHooks[ name ] = { | |
| 8228 | get: function( elem ) { | |
| 8229 | return elem.getAttribute( name, 4 ); | |
| 8230 | } | |
| 8231 | }; | |
| 8232 | }); | |
| 8233 | } | |
| 8234 | ||
| 8235 | // Support: Safari, IE9+ | |
| 8236 | // mis-reports the default selected property of an option | |
| 8237 | // Accessing the parent's selectedIndex property fixes it | |
| 8238 | if ( !support.optSelected ) { | |
| 8239 | jQuery.propHooks.selected = { | |
| 8240 | get: function( elem ) { | |
| 8241 | var parent = elem.parentNode; | |
| 8242 | ||
| 8243 | if ( parent ) { | |
| 8244 | parent.selectedIndex; | |
| 8245 | ||
| 8246 | // Make sure that it also works with optgroups, see #5701 | |
| 8247 | if ( parent.parentNode ) { | |
| 8248 | parent.parentNode.selectedIndex; | |
| 8249 | } | |
| 8250 | } | |
| 8251 | return null; | |
| 8252 | } | |
| 8253 | }; | |
| 8254 | } | |
| 8255 | ||
| 8256 | jQuery.each([ | |
| 8257 | "tabIndex", | |
| 8258 | "readOnly", | |
| 8259 | "maxLength", | |
| 8260 | "cellSpacing", | |
| 8261 | "cellPadding", | |
| 8262 | "rowSpan", | |
| 8263 | "colSpan", | |
| 8264 | "useMap", | |
| 8265 | "frameBorder", | |
| 8266 | "contentEditable" | |
| 8267 | ], function() { | |
| 8268 | jQuery.propFix[ this.toLowerCase() ] = this; | |
| 8269 | }); | |
| 8270 | ||
| 8271 | // IE6/7 call enctype encoding | |
| 8272 | if ( !support.enctype ) { | |
| 8273 | jQuery.propFix.enctype = "encoding"; | |
| 8274 | } | |
| 8275 | ||
| 8276 | ||
| 8277 | ||
| 8278 | ||
| 8279 | var rclass = /[\t\r\n\f]/g; | |
| 8280 | ||
| 8281 | jQuery.fn.extend({ | |
| 8282 | addClass: function( value ) { | |
| 8283 | var classes, elem, cur, clazz, j, finalValue, | |
| 8284 | i = 0, | |
| 8285 | len = this.length, | |
| 8286 | proceed = typeof value === "string" && value; | |
| 8287 | ||
| 8288 | if ( jQuery.isFunction( value ) ) { | |
| 8289 | return this.each(function( j ) { | |
| 8290 | jQuery( this ).addClass( value.call( this, j, this.className ) ); | |
| 8291 | }); | |
| 8292 | } | |
| 8293 | ||
| 8294 | if ( proceed ) { | |
| 8295 | // The disjunction here is for better compressibility (see removeClass) | |
| 8296 | classes = ( value || "" ).match( rnotwhite ) || []; | |
| 8297 | ||
| 8298 | for ( ; i < len; i++ ) { | |
| 8299 | elem = this[ i ]; | |
| 8300 | cur = elem.nodeType === 1 && ( elem.className ? | |
| 8301 | ( " " + elem.className + " " ).replace( rclass, " " ) : | |
| 8302 | " " | |
| 8303 | ); | |
| 8304 | ||
| 8305 | if ( cur ) { | |
| 8306 | j = 0; | |
| 8307 | while ( (clazz = classes[j++]) ) { | |
| 8308 | if ( cur.indexOf( " " + clazz + " " ) < 0 ) { | |
| 8309 | cur += clazz + " "; | |
| 8310 | } | |
| 8311 | } | |
| 8312 | ||
| 8313 | // only assign if different to avoid unneeded rendering. | |
| 8314 | finalValue = jQuery.trim( cur ); | |
| 8315 | if ( elem.className !== finalValue ) { | |
| 8316 | elem.className = finalValue; | |
| 8317 | } | |
| 8318 | } | |
| 8319 | } | |
| 8320 | } | |
| 8321 | ||
| 8322 | return this; | |
| 8323 | }, | |
| 8324 | ||
| 8325 | removeClass: function( value ) { | |
| 8326 | var classes, elem, cur, clazz, j, finalValue, | |
| 8327 | i = 0, | |
| 8328 | len = this.length, | |
| 8329 | proceed = arguments.length === 0 || typeof value === "string" && value; | |
| 8330 | ||
| 8331 | if ( jQuery.isFunction( value ) ) { | |
| 8332 | return this.each(function( j ) { | |
| 8333 | jQuery( this ).removeClass( value.call( this, j, this.className ) ); | |
| 8334 | }); | |
| 8335 | } | |
| 8336 | if ( proceed ) { | |
| 8337 | classes = ( value || "" ).match( rnotwhite ) || []; | |
| 8338 | ||
| 8339 | for ( ; i < len; i++ ) { | |
| 8340 | elem = this[ i ]; | |
| 8341 | // This expression is here for better compressibility (see addClass) | |
| 8342 | cur = elem.nodeType === 1 && ( elem.className ? | |
| 8343 | ( " " + elem.className + " " ).replace( rclass, " " ) : | |
| 8344 | "" | |
| 8345 | ); | |
| 8346 | ||
| 8347 | if ( cur ) { | |
| 8348 | j = 0; | |
| 8349 | while ( (clazz = classes[j++]) ) { | |
| 8350 | // Remove *all* instances | |
| 8351 | while ( cur.indexOf( " " + clazz + " " ) >= 0 ) { | |
| 8352 | cur = cur.replace( " " + clazz + " ", " " ); | |
| 8353 | } | |
| 8354 | } | |
| 8355 | ||
| 8356 | // only assign if different to avoid unneeded rendering. | |
| 8357 | finalValue = value ? jQuery.trim( cur ) : ""; | |
| 8358 | if ( elem.className !== finalValue ) { | |
| 8359 | elem.className = finalValue; | |
| 8360 | } | |
| 8361 | } | |
| 8362 | } | |
| 8363 | } | |
| 8364 | ||
| 8365 | return this; | |
| 8366 | }, | |
| 8367 | ||
| 8368 | toggleClass: function( value, stateVal ) { | |
| 8369 | var type = typeof value; | |
| 8370 | ||
| 8371 | if ( typeof stateVal === "boolean" && type === "string" ) { | |
| 8372 | return stateVal ? this.addClass( value ) : this.removeClass( value ); | |
| 8373 | } | |
| 8374 | ||
| 8375 | if ( jQuery.isFunction( value ) ) { | |
| 8376 | return this.each(function( i ) { | |
| 8377 | jQuery( this ).toggleClass( value.call(this, i, this.className, stateVal), stateVal ); | |
| 8378 | }); | |
| 8379 | } | |
| 8380 | ||
| 8381 | return this.each(function() { | |
| 8382 | if ( type === "string" ) { | |
| 8383 | // toggle individual class names | |
| 8384 | var className, | |
| 8385 | i = 0, | |
| 8386 | self = jQuery( this ), | |
| 8387 | classNames = value.match( rnotwhite ) || []; | |
| 8388 | ||
| 8389 | while ( (className = classNames[ i++ ]) ) { | |
| 8390 | // check each className given, space separated list | |
| 8391 | if ( self.hasClass( className ) ) { | |
| 8392 | self.removeClass( className ); | |
| 8393 | } else { | |
| 8394 | self.addClass( className ); | |
| 8395 | } | |
| 8396 | } | |
| 8397 | ||
| 8398 | // Toggle whole class name | |
| 8399 | } else if ( type === strundefined || type === "boolean" ) { | |
| 8400 | if ( this.className ) { | |
| 8401 | // store className if set | |
| 8402 | jQuery._data( this, "__className__", this.className ); | |
| 8403 | } | |
| 8404 | ||
| 8405 | // If the element has a class name or if we're passed "false", | |
| 8406 | // then remove the whole classname (if there was one, the above saved it). | |
| 8407 | // Otherwise bring back whatever was previously saved (if anything), | |
| 8408 | // falling back to the empty string if nothing was stored. | |
| 8409 | this.className = this.className || value === false ? "" : jQuery._data( this, "__className__" ) || ""; | |
| 8410 | } | |
| 8411 | }); | |
| 8412 | }, | |
| 8413 | ||
| 8414 | hasClass: function( selector ) { | |
| 8415 | var className = " " + selector + " ", | |
| 8416 | i = 0, | |
| 8417 | l = this.length; | |
| 8418 | for ( ; i < l; i++ ) { | |
| 8419 | if ( this[i].nodeType === 1 && (" " + this[i].className + " ").replace(rclass, " ").indexOf( className ) >= 0 ) { | |
| 8420 | return true; | |
| 8421 | } | |
| 8422 | } | |
| 8423 | ||
| 8424 | return false; | |
| 8425 | } | |
| 8426 | }); | |
| 8427 | ||
| 8428 | ||
| 8429 | ||
| 8430 | ||
| 8431 | // Return jQuery for attributes-only inclusion | |
| 8432 | ||
| 8433 | ||
| 8434 | jQuery.each( ("blur focus focusin focusout load resize scroll unload click dblclick " + | |
| 8435 | "mousedown mouseup mousemove mouseover mouseout mouseenter mouseleave " + | |
| 8436 | "change select submit keydown keypress keyup error contextmenu").split(" "), function( i, name ) { | |
| 8437 | ||
| 8438 | // Handle event binding | |
| 8439 | jQuery.fn[ name ] = function( data, fn ) { | |
| 8440 | return arguments.length > 0 ? | |
| 8441 | this.on( name, null, data, fn ) : | |
| 8442 | this.trigger( name ); | |
| 8443 | }; | |
| 8444 | }); | |
| 8445 | ||
| 8446 | jQuery.fn.extend({ | |
| 8447 | hover: function( fnOver, fnOut ) { | |
| 8448 | return this.mouseenter( fnOver ).mouseleave( fnOut || fnOver ); | |
| 8449 | }, | |
| 8450 | ||
| 8451 | bind: function( types, data, fn ) { | |
| 8452 | return this.on( types, null, data, fn ); | |
| 8453 | }, | |
| 8454 | unbind: function( types, fn ) { | |
| 8455 | return this.off( types, null, fn ); | |
| 8456 | }, | |
| 8457 | ||
| 8458 | delegate: function( selector, types, data, fn ) { | |
| 8459 | return this.on( types, selector, data, fn ); | |
| 8460 | }, | |
| 8461 | undelegate: function( selector, types, fn ) { | |
| 8462 | // ( namespace ) or ( selector, types [, fn] ) | |
| 8463 | return arguments.length === 1 ? this.off( selector, "**" ) : this.off( types, selector || "**", fn ); | |
| 8464 | } | |
| 8465 | }); | |
| 8466 | ||
| 8467 | ||
| 8468 | var nonce = jQuery.now(); | |
| 8469 | ||
| 8470 | var rquery = (/\?/); | |
| 8471 | ||
| 8472 | ||
| 8473 | ||
| 8474 | var rvalidtokens = /(,)|(\[|{)|(}|])|"(?:[^"\\\r\n]|\\["\\\/bfnrt]|\\u[\da-fA-F]{4})*"\s*:?|true|false|null|-?(?!0\d)\d+(?:\.\d+|)(?:[eE][+-]?\d+|)/g; | |
| 8475 | ||
| 8476 | jQuery.parseJSON = function( data ) { | |
| 8477 | // Attempt to parse using the native JSON parser first | |
| 8478 | if ( window.JSON && window.JSON.parse ) { | |
| 8479 | // Support: Android 2.3 | |
| 8480 | // Workaround failure to string-cast null input | |
| 8481 | return window.JSON.parse( data + "" ); | |
| 8482 | } | |
| 8483 | ||
| 8484 | var requireNonComma, | |
| 8485 | depth = null, | |
| 8486 | str = jQuery.trim( data + "" ); | |
| 8487 | ||
| 8488 | // Guard against invalid (and possibly dangerous) input by ensuring that nothing remains | |
| 8489 | // after removing valid tokens | |
| 8490 | return str && !jQuery.trim( str.replace( rvalidtokens, function( token, comma, open, close ) { | |
| 8491 | ||
| 8492 | // Force termination if we see a misplaced comma | |
| 8493 | if ( requireNonComma && comma ) { | |
| 8494 | depth = 0; | |
| 8495 | } | |
| 8496 | ||
| 8497 | // Perform no more replacements after returning to outermost depth | |
| 8498 | if ( depth === 0 ) { | |
| 8499 | return token; | |
| 8500 | } | |
| 8501 | ||
| 8502 | // Commas must not follow "[", "{", or "," | |
| 8503 | requireNonComma = open || comma; | |
| 8504 | ||
| 8505 | // Determine new depth | |
| 8506 | // array/object open ("[" or "{"): depth += true - false (increment) | |
| 8507 | // array/object close ("]" or "}"): depth += false - true (decrement) | |
| 8508 | // other cases ("," or primitive): depth += true - true (numeric cast) | |
| 8509 | depth += !close - !open; | |
| 8510 | ||
| 8511 | // Remove this token | |
| 8512 | return ""; | |
| 8513 | }) ) ? | |
| 8514 | ( Function( "return " + str ) )() : | |
| 8515 | jQuery.error( "Invalid JSON: " + data ); | |
| 8516 | }; | |
| 8517 | ||
| 8518 | ||
| 8519 | // Cross-browser xml parsing | |
| 8520 | jQuery.parseXML = function( data ) { | |
| 8521 | var xml, tmp; | |
| 8522 | if ( !data || typeof data !== "string" ) { | |
| 8523 | return null; | |
| 8524 | } | |
| 8525 | try { | |
| 8526 | if ( window.DOMParser ) { // Standard | |
| 8527 | tmp = new DOMParser(); | |
| 8528 | xml = tmp.parseFromString( data, "text/xml" ); | |
| 8529 | } else { // IE | |
| 8530 | xml = new ActiveXObject( "Microsoft.XMLDOM" ); | |
| 8531 | xml.async = "false"; | |
| 8532 | xml.loadXML( data ); | |
| 8533 | } | |
| 8534 | } catch( e ) { | |
| 8535 | xml = undefined; | |
| 8536 | } | |
| 8537 | if ( !xml || !xml.documentElement || xml.getElementsByTagName( "parsererror" ).length ) { | |
| 8538 | jQuery.error( "Invalid XML: " + data ); | |
| 8539 | } | |
| 8540 | return xml; | |
| 8541 | }; | |
| 8542 | ||
| 8543 | ||
| 8544 | var | |
| 8545 | // Document location | |
| 8546 | ajaxLocParts, | |
| 8547 | ajaxLocation, | |
| 8548 | ||
| 8549 | rhash = /#.*$/, | |
| 8550 | rts = /([?&])_=[^&]*/, | |
| 8551 | rheaders = /^(.*?):[ \t]*([^\r\n]*)\r?$/mg, // IE leaves an \r character at EOL | |
| 8552 | // #7653, #8125, #8152: local protocol detection | |
| 8553 | rlocalProtocol = /^(?:about|app|app-storage|.+-extension|file|res|widget):$/, | |
| 8554 | rnoContent = /^(?:GET|HEAD)$/, | |
| 8555 | rprotocol = /^\/\//, | |
| 8556 | rurl = /^([\w.+-]+:)(?:\/\/(?:[^\/?#]*@|)([^\/?#:]*)(?::(\d+)|)|)/, | |
| 8557 | ||
| 8558 | /* Prefilters | |
| 8559 | * 1) They are useful to introduce custom dataTypes (see ajax/jsonp.js for an example) | |
| 8560 | * 2) These are called: | |
| 8561 | * - BEFORE asking for a transport | |
| 8562 | * - AFTER param serialization (s.data is a string if s.processData is true) | |
| 8563 | * 3) key is the dataType | |
| 8564 | * 4) the catchall symbol "*" can be used | |
| 8565 | * 5) execution will start with transport dataType and THEN continue down to "*" if needed | |
| 8566 | */ | |
| 8567 | prefilters = {}, | |
| 8568 | ||
| 8569 | /* Transports bindings | |
| 8570 | * 1) key is the dataType | |
| 8571 | * 2) the catchall symbol "*" can be used | |
| 8572 | * 3) selection will start with transport dataType and THEN go to "*" if needed | |
| 8573 | */ | |
| 8574 | transports = {}, | |
| 8575 | ||
| 8576 | // Avoid comment-prolog char sequence (#10098); must appease lint and evade compression | |
| 8577 | allTypes = "*/".concat("*"); | |
| 8578 | ||
| 8579 | // #8138, IE may throw an exception when accessing | |
| 8580 | // a field from window.location if document.domain has been set | |
| 8581 | try { | |
| 8582 | ajaxLocation = location.href; | |
| 8583 | } catch( e ) { | |
| 8584 | // Use the href attribute of an A element | |
| 8585 | // since IE will modify it given document.location | |
| 8586 | ajaxLocation = document.createElement( "a" ); | |
| 8587 | ajaxLocation.href = ""; | |
| 8588 | ajaxLocation = ajaxLocation.href; | |
| 8589 | } | |
| 8590 | ||
| 8591 | // Segment location into parts | |
| 8592 | ajaxLocParts = rurl.exec( ajaxLocation.toLowerCase() ) || []; | |
| 8593 | ||
| 8594 | // Base "constructor" for jQuery.ajaxPrefilter and jQuery.ajaxTransport | |
| 8595 | function addToPrefiltersOrTransports( structure ) { | |
| 8596 | ||
| 8597 | // dataTypeExpression is optional and defaults to "*" | |
| 8598 | return function( dataTypeExpression, func ) { | |
| 8599 | ||
| 8600 | if ( typeof dataTypeExpression !== "string" ) { | |
| 8601 | func = dataTypeExpression; | |
| 8602 | dataTypeExpression = "*"; | |
| 8603 | } | |
| 8604 | ||
| 8605 | var dataType, | |
| 8606 | i = 0, | |
| 8607 | dataTypes = dataTypeExpression.toLowerCase().match( rnotwhite ) || []; | |
| 8608 | ||
| 8609 | if ( jQuery.isFunction( func ) ) { | |
| 8610 | // For each dataType in the dataTypeExpression | |
| 8611 | while ( (dataType = dataTypes[i++]) ) { | |
| 8612 | // Prepend if requested | |
| 8613 | if ( dataType.charAt( 0 ) === "+" ) { | |
| 8614 | dataType = dataType.slice( 1 ) || "*"; | |
| 8615 | (structure[ dataType ] = structure[ dataType ] || []).unshift( func ); | |
| 8616 | ||
| 8617 | // Otherwise append | |
| 8618 | } else { | |
| 8619 | (structure[ dataType ] = structure[ dataType ] || []).push( func ); | |
| 8620 | } | |
| 8621 | } | |
| 8622 | } | |
| 8623 | }; | |
| 8624 | } | |
| 8625 | ||
| 8626 | // Base inspection function for prefilters and transports | |
| 8627 | function inspectPrefiltersOrTransports( structure, options, originalOptions, jqXHR ) { | |
| 8628 | ||
| 8629 | var inspected = {}, | |
| 8630 | seekingTransport = ( structure === transports ); | |
| 8631 | ||
| 8632 | function inspect( dataType ) { | |
| 8633 | var selected; | |
| 8634 | inspected[ dataType ] = true; | |
| 8635 | jQuery.each( structure[ dataType ] || [], function( _, prefilterOrFactory ) { | |
| 8636 | var dataTypeOrTransport = prefilterOrFactory( options, originalOptions, jqXHR ); | |
| 8637 | if ( typeof dataTypeOrTransport === "string" && !seekingTransport && !inspected[ dataTypeOrTransport ] ) { | |
| 8638 | options.dataTypes.unshift( dataTypeOrTransport ); | |
| 8639 | inspect( dataTypeOrTransport ); | |
| 8640 | return false; | |
| 8641 | } else if ( seekingTransport ) { | |
| 8642 | return !( selected = dataTypeOrTransport ); | |
| 8643 | } | |
| 8644 | }); | |
| 8645 | return selected; | |
| 8646 | } | |
| 8647 | ||
| 8648 | return inspect( options.dataTypes[ 0 ] ) || !inspected[ "*" ] && inspect( "*" ); | |
| 8649 | } | |
| 8650 | ||
| 8651 | // A special extend for ajax options | |
| 8652 | // that takes "flat" options (not to be deep extended) | |
| 8653 | // Fixes #9887 | |
| 8654 | function ajaxExtend( target, src ) { | |
| 8655 | var deep, key, | |
| 8656 | flatOptions = jQuery.ajaxSettings.flatOptions || {}; | |
| 8657 | ||
| 8658 | for ( key in src ) { | |
| 8659 | if ( src[ key ] !== undefined ) { | |
| 8660 | ( flatOptions[ key ] ? target : ( deep || (deep = {}) ) )[ key ] = src[ key ]; | |
| 8661 | } | |
| 8662 | } | |
| 8663 | if ( deep ) { | |
| 8664 | jQuery.extend( true, target, deep ); | |
| 8665 | } | |
| 8666 | ||
| 8667 | return target; | |
| 8668 | } | |
| 8669 | ||
| 8670 | /* Handles responses to an ajax request: | |
| 8671 | * - finds the right dataType (mediates between content-type and expected dataType) | |
| 8672 | * - returns the corresponding response | |
| 8673 | */ | |
| 8674 | function ajaxHandleResponses( s, jqXHR, responses ) { | |
| 8675 | var firstDataType, ct, finalDataType, type, | |
| 8676 | contents = s.contents, | |
| 8677 | dataTypes = s.dataTypes; | |
| 8678 | ||
| 8679 | // Remove auto dataType and get content-type in the process | |
| 8680 | while ( dataTypes[ 0 ] === "*" ) { | |
| 8681 | dataTypes.shift(); | |
| 8682 | if ( ct === undefined ) { | |
| 8683 | ct = s.mimeType || jqXHR.getResponseHeader("Content-Type"); | |
| 8684 | } | |
| 8685 | } | |
| 8686 | ||
| 8687 | // Check if we're dealing with a known content-type | |
| 8688 | if ( ct ) { | |
| 8689 | for ( type in contents ) { | |
| 8690 | if ( contents[ type ] && contents[ type ].test( ct ) ) { | |
| 8691 | dataTypes.unshift( type ); | |
| 8692 | break; | |
| 8693 | } | |
| 8694 | } | |
| 8695 | } | |
| 8696 | ||
| 8697 | // Check to see if we have a response for the expected dataType | |
| 8698 | if ( dataTypes[ 0 ] in responses ) { | |
| 8699 | finalDataType = dataTypes[ 0 ]; | |
| 8700 | } else { | |
| 8701 | // Try convertible dataTypes | |
| 8702 | for ( type in responses ) { | |
| 8703 | if ( !dataTypes[ 0 ] || s.converters[ type + " " + dataTypes[0] ] ) { | |
| 8704 | finalDataType = type; | |
| 8705 | break; | |
| 8706 | } | |
| 8707 | if ( !firstDataType ) { | |
| 8708 | firstDataType = type; | |
| 8709 | } | |
| 8710 | } | |
| 8711 | // Or just use first one | |
| 8712 | finalDataType = finalDataType || firstDataType; | |
| 8713 | } | |
| 8714 | ||
| 8715 | // If we found a dataType | |
| 8716 | // We add the dataType to the list if needed | |
| 8717 | // and return the corresponding response | |
| 8718 | if ( finalDataType ) { | |
| 8719 | if ( finalDataType !== dataTypes[ 0 ] ) { | |
| 8720 | dataTypes.unshift( finalDataType ); | |
| 8721 | } | |
| 8722 | return responses[ finalDataType ]; | |
| 8723 | } | |
| 8724 | } | |
| 8725 | ||
| 8726 | /* Chain conversions given the request and the original response | |
| 8727 | * Also sets the responseXXX fields on the jqXHR instance | |
| 8728 | */ | |
| 8729 | function ajaxConvert( s, response, jqXHR, isSuccess ) { | |
| 8730 | var conv2, current, conv, tmp, prev, | |
| 8731 | converters = {}, | |
| 8732 | // Work with a copy of dataTypes in case we need to modify it for conversion | |
| 8733 | dataTypes = s.dataTypes.slice(); | |
| 8734 | ||
| 8735 | // Create converters map with lowercased keys | |
| 8736 | if ( dataTypes[ 1 ] ) { | |
| 8737 | for ( conv in s.converters ) { | |
| 8738 | converters[ conv.toLowerCase() ] = s.converters[ conv ]; | |
| 8739 | } | |
| 8740 | } | |
| 8741 | ||
| 8742 | current = dataTypes.shift(); | |
| 8743 | ||
| 8744 | // Convert to each sequential dataType | |
| 8745 | while ( current ) { | |
| 8746 | ||
| 8747 | if ( s.responseFields[ current ] ) { | |
| 8748 | jqXHR[ s.responseFields[ current ] ] = response; | |
| 8749 | } | |
| 8750 | ||
| 8751 | // Apply the dataFilter if provided | |
| 8752 | if ( !prev && isSuccess && s.dataFilter ) { | |
| 8753 | response = s.dataFilter( response, s.dataType ); | |
| 8754 | } | |
| 8755 | ||
| 8756 | prev = current; | |
| 8757 | current = dataTypes.shift(); | |
| 8758 | ||
| 8759 | if ( current ) { | |
| 8760 | ||
| 8761 | // There's only work to do if current dataType is non-auto | |
| 8762 | if ( current === "*" ) { | |
| 8763 | ||
| 8764 | current = prev; | |
| 8765 | ||
| 8766 | // Convert response if prev dataType is non-auto and differs from current | |
| 8767 | } else if ( prev !== "*" && prev !== current ) { | |
| 8768 | ||
| 8769 | // Seek a direct converter | |
| 8770 | conv = converters[ prev + " " + current ] || converters[ "* " + current ]; | |
| 8771 | ||
| 8772 | // If none found, seek a pair | |
| 8773 | if ( !conv ) { | |
| 8774 | for ( conv2 in converters ) { | |
| 8775 | ||
| 8776 | // If conv2 outputs current | |
| 8777 | tmp = conv2.split( " " ); | |
| 8778 | if ( tmp[ 1 ] === current ) { | |
| 8779 | ||
| 8780 | // If prev can be converted to accepted input | |
| 8781 | conv = converters[ prev + " " + tmp[ 0 ] ] || | |
| 8782 | converters[ "* " + tmp[ 0 ] ]; | |
| 8783 | if ( conv ) { | |
| 8784 | // Condense equivalence converters | |
| 8785 | if ( conv === true ) { | |
| 8786 | conv = converters[ conv2 ]; | |
| 8787 | ||
| 8788 | // Otherwise, insert the intermediate dataType | |
| 8789 | } else if ( converters[ conv2 ] !== true ) { | |
| 8790 | current = tmp[ 0 ]; | |
| 8791 | dataTypes.unshift( tmp[ 1 ] ); | |
| 8792 | } | |
| 8793 | break; | |
| 8794 | } | |
| 8795 | } | |
| 8796 | } | |
| 8797 | } | |
| 8798 | ||
| 8799 | // Apply converter (if not an equivalence) | |
| 8800 | if ( conv !== true ) { | |
| 8801 | ||
| 8802 | // Unless errors are allowed to bubble, catch and return them | |
| 8803 | if ( conv && s[ "throws" ] ) { | |
| 8804 | response = conv( response ); | |
| 8805 | } else { | |
| 8806 | try { | |
| 8807 | response = conv( response ); | |
| 8808 | } catch ( e ) { | |
| 8809 | return { state: "parsererror", error: conv ? e : "No conversion from " + prev + " to " + current }; | |
| 8810 | } | |
| 8811 | } | |
| 8812 | } | |
| 8813 | } | |
| 8814 | } | |
| 8815 | } | |
| 8816 | ||
| 8817 | return { state: "success", data: response }; | |
| 8818 | } | |
| 8819 | ||
| 8820 | jQuery.extend({ | |
| 8821 | ||
| 8822 | // Counter for holding the number of active queries | |
| 8823 | active: 0, | |
| 8824 | ||
| 8825 | // Last-Modified header cache for next request | |
| 8826 | lastModified: {}, | |
| 8827 | etag: {}, | |
| 8828 | ||
| 8829 | ajaxSettings: { | |
| 8830 | url: ajaxLocation, | |
| 8831 | type: "GET", | |
| 8832 | isLocal: rlocalProtocol.test( ajaxLocParts[ 1 ] ), | |
| 8833 | global: true, | |
| 8834 | processData: true, | |
| 8835 | async: true, | |
| 8836 | contentType: "application/x-www-form-urlencoded; charset=UTF-8", | |
| 8837 | /* | |
| 8838 | timeout: 0, | |
| 8839 | data: null, | |
| 8840 | dataType: null, | |
| 8841 | username: null, | |
| 8842 | password: null, | |
| 8843 | cache: null, | |
| 8844 | throws: false, | |
| 8845 | traditional: false, | |
| 8846 | headers: {}, | |
| 8847 | */ | |
| 8848 | ||
| 8849 | accepts: { | |
| 8850 | "*": allTypes, | |
| 8851 | text: "text/plain", | |
| 8852 | html: "text/html", | |
| 8853 | xml: "application/xml, text/xml", | |
| 8854 | json: "application/json, text/javascript" | |
| 8855 | }, | |
| 8856 | ||
| 8857 | contents: { | |
| 8858 | xml: /xml/, | |
| 8859 | html: /html/, | |
| 8860 | json: /json/ | |
| 8861 | }, | |
| 8862 | ||
| 8863 | responseFields: { | |
| 8864 | xml: "responseXML", | |
| 8865 | text: "responseText", | |
| 8866 | json: "responseJSON" | |
| 8867 | }, | |
| 8868 | ||
| 8869 | // Data converters | |
| 8870 | // Keys separate source (or catchall "*") and destination types with a single space | |
| 8871 | converters: { | |
| 8872 | ||
| 8873 | // Convert anything to text | |
| 8874 | "* text": String, | |
| 8875 | ||
| 8876 | // Text to html (true = no transformation) | |
| 8877 | "text html": true, | |
| 8878 | ||
| 8879 | // Evaluate text as a json expression | |
| 8880 | "text json": jQuery.parseJSON, | |
| 8881 | ||
| 8882 | // Parse text as xml | |
| 8883 | "text xml": jQuery.parseXML | |
| 8884 | }, | |
| 8885 | ||
| 8886 | // For options that shouldn't be deep extended: | |
| 8887 | // you can add your own custom options here if | |
| 8888 | // and when you create one that shouldn't be | |
| 8889 | // deep extended (see ajaxExtend) | |
| 8890 | flatOptions: { | |
| 8891 | url: true, | |
| 8892 | context: true | |
| 8893 | } | |
| 8894 | }, | |
| 8895 | ||
| 8896 | // Creates a full fledged settings object into target | |
| 8897 | // with both ajaxSettings and settings fields. | |
| 8898 | // If target is omitted, writes into ajaxSettings. | |
| 8899 | ajaxSetup: function( target, settings ) { | |
| 8900 | return settings ? | |
| 8901 | ||
| 8902 | // Building a settings object | |
| 8903 | ajaxExtend( ajaxExtend( target, jQuery.ajaxSettings ), settings ) : | |
| 8904 | ||
| 8905 | // Extending ajaxSettings | |
| 8906 | ajaxExtend( jQuery.ajaxSettings, target ); | |
| 8907 | }, | |
| 8908 | ||
| 8909 | ajaxPrefilter: addToPrefiltersOrTransports( prefilters ), | |
| 8910 | ajaxTransport: addToPrefiltersOrTransports( transports ), | |
| 8911 | ||
| 8912 | // Main method | |
| 8913 | ajax: function( url, options ) { | |
| 8914 | ||
| 8915 | // If url is an object, simulate pre-1.5 signature | |
| 8916 | if ( typeof url === "object" ) { | |
| 8917 | options = url; | |
| 8918 | url = undefined; | |
| 8919 | } | |
| 8920 | ||
| 8921 | // Force options to be an object | |
| 8922 | options = options || {}; | |
| 8923 | ||
| 8924 | var // Cross-domain detection vars | |
| 8925 | parts, | |
| 8926 | // Loop variable | |
| 8927 | i, | |
| 8928 | // URL without anti-cache param | |
| 8929 | cacheURL, | |
| 8930 | // Response headers as string | |
| 8931 | responseHeadersString, | |
| 8932 | // timeout handle | |
| 8933 | timeoutTimer, | |
| 8934 | ||
| 8935 | // To know if global events are to be dispatched | |
| 8936 | fireGlobals, | |
| 8937 | ||
| 8938 | transport, | |
| 8939 | // Response headers | |
| 8940 | responseHeaders, | |
| 8941 | // Create the final options object | |
| 8942 | s = jQuery.ajaxSetup( {}, options ), | |
| 8943 | // Callbacks context | |
| 8944 | callbackContext = s.context || s, | |
| 8945 | // Context for global events is callbackContext if it is a DOM node or jQuery collection | |
| 8946 | globalEventContext = s.context && ( callbackContext.nodeType || callbackContext.jquery ) ? | |
| 8947 | jQuery( callbackContext ) : | |
| 8948 | jQuery.event, | |
| 8949 | // Deferreds | |
| 8950 | deferred = jQuery.Deferred(), | |
| 8951 | completeDeferred = jQuery.Callbacks("once memory"), | |
| 8952 | // Status-dependent callbacks | |
| 8953 | statusCode = s.statusCode || {}, | |
| 8954 | // Headers (they are sent all at once) | |
| 8955 | requestHeaders = {}, | |
| 8956 | requestHeadersNames = {}, | |
| 8957 | // The jqXHR state | |
| 8958 | state = 0, | |
| 8959 | // Default abort message | |
| 8960 | strAbort = "canceled", | |
| 8961 | // Fake xhr | |
| 8962 | jqXHR = { | |
| 8963 | readyState: 0, | |
| 8964 | ||
| 8965 | // Builds headers hashtable if needed | |
| 8966 | getResponseHeader: function( key ) { | |
| 8967 | var match; | |
| 8968 | if ( state === 2 ) { | |
| 8969 | if ( !responseHeaders ) { | |
| 8970 | responseHeaders = {}; | |
| 8971 | while ( (match = rheaders.exec( responseHeadersString )) ) { | |
| 8972 | responseHeaders[ match[1].toLowerCase() ] = match[ 2 ]; | |
| 8973 | } | |
| 8974 | } | |
| 8975 | match = responseHeaders[ key.toLowerCase() ]; | |
| 8976 | } | |
| 8977 | return match == null ? null : match; | |
| 8978 | }, | |
| 8979 | ||
| 8980 | // Raw string | |
| 8981 | getAllResponseHeaders: function() { | |
| 8982 | return state === 2 ? responseHeadersString : null; | |
| 8983 | }, | |
| 8984 | ||
| 8985 | // Caches the header | |
| 8986 | setRequestHeader: function( name, value ) { | |
| 8987 | var lname = name.toLowerCase(); | |
| 8988 | if ( !state ) { | |
| 8989 | name = requestHeadersNames[ lname ] = requestHeadersNames[ lname ] || name; | |
| 8990 | requestHeaders[ name ] = value; | |
| 8991 | } | |
| 8992 | return this; | |
| 8993 | }, | |
| 8994 | ||
| 8995 | // Overrides response content-type header | |
| 8996 | overrideMimeType: function( type ) { | |
| 8997 | if ( !state ) { | |
| 8998 | s.mimeType = type; | |
| 8999 | } | |
| 9000 | return this; | |
| 9001 | }, | |
| 9002 | ||
| 9003 | // Status-dependent callbacks | |
| 9004 | statusCode: function( map ) { | |
| 9005 | var code; | |
| 9006 | if ( map ) { | |
| 9007 | if ( state < 2 ) { | |
| 9008 | for ( code in map ) { | |
| 9009 | // Lazy-add the new callback in a way that preserves old ones | |
| 9010 | statusCode[ code ] = [ statusCode[ code ], map[ code ] ]; | |
| 9011 | } | |
| 9012 | } else { | |
| 9013 | // Execute the appropriate callbacks | |
| 9014 | jqXHR.always( map[ jqXHR.status ] ); | |
| 9015 | } | |
| 9016 | } | |
| 9017 | return this; | |
| 9018 | }, | |
| 9019 | ||
| 9020 | // Cancel the request | |
| 9021 | abort: function( statusText ) { | |
| 9022 | var finalText = statusText || strAbort; | |
| 9023 | if ( transport ) { | |
| 9024 | transport.abort( finalText ); | |
| 9025 | } | |
| 9026 | done( 0, finalText ); | |
| 9027 | return this; | |
| 9028 | } | |
| 9029 | }; | |
| 9030 | ||
| 9031 | // Attach deferreds | |
| 9032 | deferred.promise( jqXHR ).complete = completeDeferred.add; | |
| 9033 | jqXHR.success = jqXHR.done; | |
| 9034 | jqXHR.error = jqXHR.fail; | |
| 9035 | ||
| 9036 | // Remove hash character (#7531: and string promotion) | |
| 9037 | // Add protocol if not provided (#5866: IE7 issue with protocol-less urls) | |
| 9038 | // Handle falsy url in the settings object (#10093: consistency with old signature) | |
| 9039 | // We also use the url parameter if available | |
| 9040 | s.url = ( ( url || s.url || ajaxLocation ) + "" ).replace( rhash, "" ).replace( rprotocol, ajaxLocParts[ 1 ] + "//" ); | |
| 9041 | ||
| 9042 | // Alias method option to type as per ticket #12004 | |
| 9043 | s.type = options.method || options.type || s.method || s.type; | |
| 9044 | ||
| 9045 | // Extract dataTypes list | |
| 9046 | s.dataTypes = jQuery.trim( s.dataType || "*" ).toLowerCase().match( rnotwhite ) || [ "" ]; | |
| 9047 | ||
| 9048 | // A cross-domain request is in order when we have a protocol:host:port mismatch | |
| 9049 | if ( s.crossDomain == null ) { | |
| 9050 | parts = rurl.exec( s.url.toLowerCase() ); | |
| 9051 | s.crossDomain = !!( parts && | |
| 9052 | ( parts[ 1 ] !== ajaxLocParts[ 1 ] || parts[ 2 ] !== ajaxLocParts[ 2 ] || | |
| 9053 | ( parts[ 3 ] || ( parts[ 1 ] === "http:" ? "80" : "443" ) ) !== | |
| 9054 | ( ajaxLocParts[ 3 ] || ( ajaxLocParts[ 1 ] === "http:" ? "80" : "443" ) ) ) | |
| 9055 | ); | |
| 9056 | } | |
| 9057 | ||
| 9058 | // Convert data if not already a string | |
| 9059 | if ( s.data && s.processData && typeof s.data !== "string" ) { | |
| 9060 | s.data = jQuery.param( s.data, s.traditional ); | |
| 9061 | } | |
| 9062 | ||
| 9063 | // Apply prefilters | |
| 9064 | inspectPrefiltersOrTransports( prefilters, s, options, jqXHR ); | |
| 9065 | ||
| 9066 | // If request was aborted inside a prefilter, stop there | |
| 9067 | if ( state === 2 ) { | |
| 9068 | return jqXHR; | |
| 9069 | } | |
| 9070 | ||
| 9071 | // We can fire global events as of now if asked to | |
| 9072 | fireGlobals = s.global; | |
| 9073 | ||
| 9074 | // Watch for a new set of requests | |
| 9075 | if ( fireGlobals && jQuery.active++ === 0 ) { | |
| 9076 | jQuery.event.trigger("ajaxStart"); | |
| 9077 | } | |
| 9078 | ||
| 9079 | // Uppercase the type | |
| 9080 | s.type = s.type.toUpperCase(); | |
| 9081 | ||
| 9082 | // Determine if request has content | |
| 9083 | s.hasContent = !rnoContent.test( s.type ); | |
| 9084 | ||
| 9085 | // Save the URL in case we're toying with the If-Modified-Since | |
| 9086 | // and/or If-None-Match header later on | |
| 9087 | cacheURL = s.url; | |
| 9088 | ||
| 9089 | // More options handling for requests with no content | |
| 9090 | if ( !s.hasContent ) { | |
| 9091 | ||
| 9092 | // If data is available, append data to url | |
| 9093 | if ( s.data ) { | |
| 9094 | cacheURL = ( s.url += ( rquery.test( cacheURL ) ? "&" : "?" ) + s.data ); | |
| 9095 | // #9682: remove data so that it's not used in an eventual retry | |
| 9096 | delete s.data; | |
| 9097 | } | |
| 9098 | ||
| 9099 | // Add anti-cache in url if needed | |
| 9100 | if ( s.cache === false ) { | |
| 9101 | s.url = rts.test( cacheURL ) ? | |
| 9102 | ||
| 9103 | // If there is already a '_' parameter, set its value | |
| 9104 | cacheURL.replace( rts, "$1_=" + nonce++ ) : | |
| 9105 | ||
| 9106 | // Otherwise add one to the end | |
| 9107 | cacheURL + ( rquery.test( cacheURL ) ? "&" : "?" ) + "_=" + nonce++; | |
| 9108 | } | |
| 9109 | } | |
| 9110 | ||
| 9111 | // Set the If-Modified-Since and/or If-None-Match header, if in ifModified mode. | |
| 9112 | if ( s.ifModified ) { | |
| 9113 | if ( jQuery.lastModified[ cacheURL ] ) { | |
| 9114 | jqXHR.setRequestHeader( "If-Modified-Since", jQuery.lastModified[ cacheURL ] ); | |
| 9115 | } | |
| 9116 | if ( jQuery.etag[ cacheURL ] ) { | |
| 9117 | jqXHR.setRequestHeader( "If-None-Match", jQuery.etag[ cacheURL ] ); | |
| 9118 | } | |
| 9119 | } | |
| 9120 | ||
| 9121 | // Set the correct header, if data is being sent | |
| 9122 | if ( s.data && s.hasContent && s.contentType !== false || options.contentType ) { | |
| 9123 | jqXHR.setRequestHeader( "Content-Type", s.contentType ); | |
| 9124 | } | |
| 9125 | ||
| 9126 | // Set the Accepts header for the server, depending on the dataType | |
| 9127 | jqXHR.setRequestHeader( | |
| 9128 | "Accept", | |
| 9129 | s.dataTypes[ 0 ] && s.accepts[ s.dataTypes[0] ] ? | |
| 9130 | s.accepts[ s.dataTypes[0] ] + ( s.dataTypes[ 0 ] !== "*" ? ", " + allTypes + "; q=0.01" : "" ) : | |
| 9131 | s.accepts[ "*" ] | |
| 9132 | ); | |
| 9133 | ||
| 9134 | // Check for headers option | |
| 9135 | for ( i in s.headers ) { | |
| 9136 | jqXHR.setRequestHeader( i, s.headers[ i ] ); | |
| 9137 | } | |
| 9138 | ||
| 9139 | // Allow custom headers/mimetypes and early abort | |
| 9140 | if ( s.beforeSend && ( s.beforeSend.call( callbackContext, jqXHR, s ) === false || state === 2 ) ) { | |
| 9141 | // Abort if not done already and return | |
| 9142 | return jqXHR.abort(); | |
| 9143 | } | |
| 9144 | ||
| 9145 | // aborting is no longer a cancellation | |
| 9146 | strAbort = "abort"; | |
| 9147 | ||
| 9148 | // Install callbacks on deferreds | |
| 9149 | for ( i in { success: 1, error: 1, complete: 1 } ) { | |
| 9150 | jqXHR[ i ]( s[ i ] ); | |
| 9151 | } | |
| 9152 | ||
| 9153 | // Get transport | |
| 9154 | transport = inspectPrefiltersOrTransports( transports, s, options, jqXHR ); | |
| 9155 | ||
| 9156 | // If no transport, we auto-abort | |
| 9157 | if ( !transport ) { | |
| 9158 | done( -1, "No Transport" ); | |
| 9159 | } else { | |
| 9160 | jqXHR.readyState = 1; | |
| 9161 | ||
| 9162 | // Send global event | |
| 9163 | if ( fireGlobals ) { | |
| 9164 | globalEventContext.trigger( "ajaxSend", [ jqXHR, s ] ); | |
| 9165 | } | |
| 9166 | // Timeout | |
| 9167 | if ( s.async && s.timeout > 0 ) { | |
| 9168 | timeoutTimer = setTimeout(function() { | |
| 9169 | jqXHR.abort("timeout"); | |
| 9170 | }, s.timeout ); | |
| 9171 | } | |
| 9172 | ||
| 9173 | try { | |
| 9174 | state = 1; | |
| 9175 | transport.send( requestHeaders, done ); | |
| 9176 | } catch ( e ) { | |
| 9177 | // Propagate exception as error if not done | |
| 9178 | if ( state < 2 ) { | |
| 9179 | done( -1, e ); | |
| 9180 | // Simply rethrow otherwise | |
| 9181 | } else { | |
| 9182 | throw e; | |
| 9183 | } | |
| 9184 | } | |
| 9185 | } | |
| 9186 | ||
| 9187 | // Callback for when everything is done | |
| 9188 | function done( status, nativeStatusText, responses, headers ) { | |
| 9189 | var isSuccess, success, error, response, modified, | |
| 9190 | statusText = nativeStatusText; | |
| 9191 | ||
| 9192 | // Called once | |
| 9193 | if ( state === 2 ) { | |
| 9194 | return; | |
| 9195 | } | |
| 9196 | ||
| 9197 | // State is "done" now | |
| 9198 | state = 2; | |
| 9199 | ||
| 9200 | // Clear timeout if it exists | |
| 9201 | if ( timeoutTimer ) { | |
| 9202 | clearTimeout( timeoutTimer ); | |
| 9203 | } | |
| 9204 | ||
| 9205 | // Dereference transport for early garbage collection | |
| 9206 | // (no matter how long the jqXHR object will be used) | |
| 9207 | transport = undefined; | |
| 9208 | ||
| 9209 | // Cache response headers | |
| 9210 | responseHeadersString = headers || ""; | |
| 9211 | ||
| 9212 | // Set readyState | |
| 9213 | jqXHR.readyState = status > 0 ? 4 : 0; | |
| 9214 | ||
| 9215 | // Determine if successful | |
| 9216 | isSuccess = status >= 200 && status < 300 || status === 304; | |
| 9217 | ||
| 9218 | // Get response data | |
| 9219 | if ( responses ) { | |
| 9220 | response = ajaxHandleResponses( s, jqXHR, responses ); | |
| 9221 | } | |
| 9222 | ||
| 9223 | // Convert no matter what (that way responseXXX fields are always set) | |
| 9224 | response = ajaxConvert( s, response, jqXHR, isSuccess ); | |
| 9225 | ||
| 9226 | // If successful, handle type chaining | |
| 9227 | if ( isSuccess ) { | |
| 9228 | ||
| 9229 | // Set the If-Modified-Since and/or If-None-Match header, if in ifModified mode. | |
| 9230 | if ( s.ifModified ) { | |
| 9231 | modified = jqXHR.getResponseHeader("Last-Modified"); | |
| 9232 | if ( modified ) { | |
| 9233 | jQuery.lastModified[ cacheURL ] = modified; | |
| 9234 | } | |
| 9235 | modified = jqXHR.getResponseHeader("etag"); | |
| 9236 | if ( modified ) { | |
| 9237 | jQuery.etag[ cacheURL ] = modified; | |
| 9238 | } | |
| 9239 | } | |
| 9240 | ||
| 9241 | // if no content | |
| 9242 | if ( status === 204 || s.type === "HEAD" ) { | |
| 9243 | statusText = "nocontent"; | |
| 9244 | ||
| 9245 | // if not modified | |
| 9246 | } else if ( status === 304 ) { | |
| 9247 | statusText = "notmodified"; | |
| 9248 | ||
| 9249 | // If we have data, let's convert it | |
| 9250 | } else { | |
| 9251 | statusText = response.state; | |
| 9252 | success = response.data; | |
| 9253 | error = response.error; | |
| 9254 | isSuccess = !error; | |
| 9255 | } | |
| 9256 | } else { | |
| 9257 | // We extract error from statusText | |
| 9258 | // then normalize statusText and status for non-aborts | |
| 9259 | error = statusText; | |
| 9260 | if ( status || !statusText ) { | |
| 9261 | statusText = "error"; | |
| 9262 | if ( status < 0 ) { | |
| 9263 | status = 0; | |
| 9264 | } | |
| 9265 | } | |
| 9266 | } | |
| 9267 | ||
| 9268 | // Set data for the fake xhr object | |
| 9269 | jqXHR.status = status; | |
| 9270 | jqXHR.statusText = ( nativeStatusText || statusText ) + ""; | |
| 9271 | ||
| 9272 | // Success/Error | |
| 9273 | if ( isSuccess ) { | |
| 9274 | deferred.resolveWith( callbackContext, [ success, statusText, jqXHR ] ); | |
| 9275 | } else { | |
| 9276 | deferred.rejectWith( callbackContext, [ jqXHR, statusText, error ] ); | |
| 9277 | } | |
| 9278 | ||
| 9279 | // Status-dependent callbacks | |
| 9280 | jqXHR.statusCode( statusCode ); | |
| 9281 | statusCode = undefined; | |
| 9282 | ||
| 9283 | if ( fireGlobals ) { | |
| 9284 | globalEventContext.trigger( isSuccess ? "ajaxSuccess" : "ajaxError", | |
| 9285 | [ jqXHR, s, isSuccess ? success : error ] ); | |
| 9286 | } | |
| 9287 | ||
| 9288 | // Complete | |
| 9289 | completeDeferred.fireWith( callbackContext, [ jqXHR, statusText ] ); | |
| 9290 | ||
| 9291 | if ( fireGlobals ) { | |
| 9292 | globalEventContext.trigger( "ajaxComplete", [ jqXHR, s ] ); | |
| 9293 | // Handle the global AJAX counter | |
| 9294 | if ( !( --jQuery.active ) ) { | |
| 9295 | jQuery.event.trigger("ajaxStop"); | |
| 9296 | } | |
| 9297 | } | |
| 9298 | } | |
| 9299 | ||
| 9300 | return jqXHR; | |
| 9301 | }, | |
| 9302 | ||
| 9303 | getJSON: function( url, data, callback ) { | |
| 9304 | return jQuery.get( url, data, callback, "json" ); | |
| 9305 | }, | |
| 9306 | ||
| 9307 | getScript: function( url, callback ) { | |
| 9308 | return jQuery.get( url, undefined, callback, "script" ); | |
| 9309 | } | |
| 9310 | }); | |
| 9311 | ||
| 9312 | jQuery.each( [ "get", "post" ], function( i, method ) { | |
| 9313 | jQuery[ method ] = function( url, data, callback, type ) { | |
| 9314 | // shift arguments if data argument was omitted | |
| 9315 | if ( jQuery.isFunction( data ) ) { | |
| 9316 | type = type || callback; | |
| 9317 | callback = data; | |
| 9318 | data = undefined; | |
| 9319 | } | |
| 9320 | ||
| 9321 | return jQuery.ajax({ | |
| 9322 | url: url, | |
| 9323 | type: method, | |
| 9324 | dataType: type, | |
| 9325 | data: data, | |
| 9326 | success: callback | |
| 9327 | }); | |
| 9328 | }; | |
| 9329 | }); | |
| 9330 | ||
| 9331 | // Attach a bunch of functions for handling common AJAX events | |
| 9332 | jQuery.each( [ "ajaxStart", "ajaxStop", "ajaxComplete", "ajaxError", "ajaxSuccess", "ajaxSend" ], function( i, type ) { | |
| 9333 | jQuery.fn[ type ] = function( fn ) { | |
| 9334 | return this.on( type, fn ); | |
| 9335 | }; | |
| 9336 | }); | |
| 9337 | ||
| 9338 | ||
| 9339 | jQuery._evalUrl = function( url ) { | |
| 9340 | return jQuery.ajax({ | |
| 9341 | url: url, | |
| 9342 | type: "GET", | |
| 9343 | dataType: "script", | |
| 9344 | async: false, | |
| 9345 | global: false, | |
| 9346 | "throws": true | |
| 9347 | }); | |
| 9348 | }; | |
| 9349 | ||
| 9350 | ||
| 9351 | jQuery.fn.extend({ | |
| 9352 | wrapAll: function( html ) { | |
| 9353 | if ( jQuery.isFunction( html ) ) { | |
| 9354 | return this.each(function(i) { | |
| 9355 | jQuery(this).wrapAll( html.call(this, i) ); | |
| 9356 | }); | |
| 9357 | } | |
| 9358 | ||
| 9359 | if ( this[0] ) { | |
| 9360 | // The elements to wrap the target around | |
| 9361 | var wrap = jQuery( html, this[0].ownerDocument ).eq(0).clone(true); | |
| 9362 | ||
| 9363 | if ( this[0].parentNode ) { | |
| 9364 | wrap.insertBefore( this[0] ); | |
| 9365 | } | |
| 9366 | ||
| 9367 | wrap.map(function() { | |
| 9368 | var elem = this; | |
| 9369 | ||
| 9370 | while ( elem.firstChild && elem.firstChild.nodeType === 1 ) { | |
| 9371 | elem = elem.firstChild; | |
| 9372 | } | |
| 9373 | ||
| 9374 | return elem; | |
| 9375 | }).append( this ); | |
| 9376 | } | |
| 9377 | ||
| 9378 | return this; | |
| 9379 | }, | |
| 9380 | ||
| 9381 | wrapInner: function( html ) { | |
| 9382 | if ( jQuery.isFunction( html ) ) { | |
| 9383 | return this.each(function(i) { | |
| 9384 | jQuery(this).wrapInner( html.call(this, i) ); | |
| 9385 | }); | |
| 9386 | } | |
| 9387 | ||
| 9388 | return this.each(function() { | |
| 9389 | var self = jQuery( this ), | |
| 9390 | contents = self.contents(); | |
| 9391 | ||
| 9392 | if ( contents.length ) { | |
| 9393 | contents.wrapAll( html ); | |
| 9394 | ||
| 9395 | } else { | |
| 9396 | self.append( html ); | |
| 9397 | } | |
| 9398 | }); | |
| 9399 | }, | |
| 9400 | ||
| 9401 | wrap: function( html ) { | |
| 9402 | var isFunction = jQuery.isFunction( html ); | |
| 9403 | ||
| 9404 | return this.each(function(i) { | |
| 9405 | jQuery( this ).wrapAll( isFunction ? html.call(this, i) : html ); | |
| 9406 | }); | |
| 9407 | }, | |
| 9408 | ||
| 9409 | unwrap: function() { | |
| 9410 | return this.parent().each(function() { | |
| 9411 | if ( !jQuery.nodeName( this, "body" ) ) { | |
| 9412 | jQuery( this ).replaceWith( this.childNodes ); | |
| 9413 | } | |
| 9414 | }).end(); | |
| 9415 | } | |
| 9416 | }); | |
| 9417 | ||
| 9418 | ||
| 9419 | jQuery.expr.filters.hidden = function( elem ) { | |
| 9420 | // Support: Opera <= 12.12 | |
| 9421 | // Opera reports offsetWidths and offsetHeights less than zero on some elements | |
| 9422 | return elem.offsetWidth <= 0 && elem.offsetHeight <= 0 || | |
| 9423 | (!support.reliableHiddenOffsets() && | |
| 9424 | ((elem.style && elem.style.display) || jQuery.css( elem, "display" )) === "none"); | |
| 9425 | }; | |
| 9426 | ||
| 9427 | jQuery.expr.filters.visible = function( elem ) { | |
| 9428 | return !jQuery.expr.filters.hidden( elem ); | |
| 9429 | }; | |
| 9430 | ||
| 9431 | ||
| 9432 | ||
| 9433 | ||
| 9434 | var r20 = /%20/g, | |
| 9435 | rbracket = /\[\]$/, | |
| 9436 | rCRLF = /\r?\n/g, | |
| 9437 | rsubmitterTypes = /^(?:submit|button|image|reset|file)$/i, | |
| 9438 | rsubmittable = /^(?:input|select|textarea|keygen)/i; | |
| 9439 | ||
| 9440 | function buildParams( prefix, obj, traditional, add ) { | |
| 9441 | var name; | |
| 9442 | ||
| 9443 | if ( jQuery.isArray( obj ) ) { | |
| 9444 | // Serialize array item. | |
| 9445 | jQuery.each( obj, function( i, v ) { | |
| 9446 | if ( traditional || rbracket.test( prefix ) ) { | |
| 9447 | // Treat each array item as a scalar. | |
| 9448 | add( prefix, v ); | |
| 9449 | ||
| 9450 | } else { | |
| 9451 | // Item is non-scalar (array or object), encode its numeric index. | |
| 9452 | buildParams( prefix + "[" + ( typeof v === "object" ? i : "" ) + "]", v, traditional, add ); | |
| 9453 | } | |
| 9454 | }); | |
| 9455 | ||
| 9456 | } else if ( !traditional && jQuery.type( obj ) === "object" ) { | |
| 9457 | // Serialize object item. | |
| 9458 | for ( name in obj ) { | |
| 9459 | buildParams( prefix + "[" + name + "]", obj[ name ], traditional, add ); | |
| 9460 | } | |
| 9461 | ||
| 9462 | } else { | |
| 9463 | // Serialize scalar item. | |
| 9464 | add( prefix, obj ); | |
| 9465 | } | |
| 9466 | } | |
| 9467 | ||
| 9468 | // Serialize an array of form elements or a set of | |
| 9469 | // key/values into a query string | |
| 9470 | jQuery.param = function( a, traditional ) { | |
| 9471 | var prefix, | |
| 9472 | s = [], | |
| 9473 | add = function( key, value ) { | |
| 9474 | // If value is a function, invoke it and return its value | |
| 9475 | value = jQuery.isFunction( value ) ? value() : ( value == null ? "" : value ); | |
| 9476 | s[ s.length ] = encodeURIComponent( key ) + "=" + encodeURIComponent( value ); | |
| 9477 | }; | |
| 9478 | ||
| 9479 | // Set traditional to true for jQuery <= 1.3.2 behavior. | |
| 9480 | if ( traditional === undefined ) { | |
| 9481 | traditional = jQuery.ajaxSettings && jQuery.ajaxSettings.traditional; | |
| 9482 | } | |
| 9483 | ||
| 9484 | // If an array was passed in, assume that it is an array of form elements. | |
| 9485 | if ( jQuery.isArray( a ) || ( a.jquery && !jQuery.isPlainObject( a ) ) ) { | |
| 9486 | // Serialize the form elements | |
| 9487 | jQuery.each( a, function() { | |
| 9488 | add( this.name, this.value ); | |
| 9489 | }); | |
| 9490 | ||
| 9491 | } else { | |
| 9492 | // If traditional, encode the "old" way (the way 1.3.2 or older | |
| 9493 | // did it), otherwise encode params recursively. | |
| 9494 | for ( prefix in a ) { | |
| 9495 | buildParams( prefix, a[ prefix ], traditional, add ); | |
| 9496 | } | |
| 9497 | } | |
| 9498 | ||
| 9499 | // Return the resulting serialization | |
| 9500 | return s.join( "&" ).replace( r20, "+" ); | |
| 9501 | }; | |
| 9502 | ||
| 9503 | jQuery.fn.extend({ | |
| 9504 | serialize: function() { | |
| 9505 | return jQuery.param( this.serializeArray() ); | |
| 9506 | }, | |
| 9507 | serializeArray: function() { | |
| 9508 | return this.map(function() { | |
| 9509 | // Can add propHook for "elements" to filter or add form elements | |
| 9510 | var elements = jQuery.prop( this, "elements" ); | |
| 9511 | return elements ? jQuery.makeArray( elements ) : this; | |
| 9512 | }) | |
| 9513 | .filter(function() { | |
| 9514 | var type = this.type; | |
| 9515 | // Use .is(":disabled") so that fieldset[disabled] works | |
| 9516 | return this.name && !jQuery( this ).is( ":disabled" ) && | |
| 9517 | rsubmittable.test( this.nodeName ) && !rsubmitterTypes.test( type ) && | |
| 9518 | ( this.checked || !rcheckableType.test( type ) ); | |
| 9519 | }) | |
| 9520 | .map(function( i, elem ) { | |
| 9521 | var val = jQuery( this ).val(); | |
| 9522 | ||
| 9523 | return val == null ? | |
| 9524 | null : | |
| 9525 | jQuery.isArray( val ) ? | |
| 9526 | jQuery.map( val, function( val ) { | |
| 9527 | return { name: elem.name, value: val.replace( rCRLF, "\r\n" ) }; | |
| 9528 | }) : | |
| 9529 | { name: elem.name, value: val.replace( rCRLF, "\r\n" ) }; | |
| 9530 | }).get(); | |
| 9531 | } | |
| 9532 | }); | |
| 9533 | ||
| 9534 | ||
| 9535 | // Create the request object | |
| 9536 | // (This is still attached to ajaxSettings for backward compatibility) | |
| 9537 | jQuery.ajaxSettings.xhr = window.ActiveXObject !== undefined ? | |
| 9538 | // Support: IE6+ | |
| 9539 | function() { | |
| 9540 | ||
| 9541 | // XHR cannot access local files, always use ActiveX for that case | |
| 9542 | return !this.isLocal && | |
| 9543 | ||
| 9544 | // Support: IE7-8 | |
| 9545 | // oldIE XHR does not support non-RFC2616 methods (#13240) | |
| 9546 | // See http://msdn.microsoft.com/en-us/library/ie/ms536648(v=vs.85).aspx | |
| 9547 | // and http://www.w3.org/Protocols/rfc2616/rfc2616-sec9.html#sec9 | |
| 9548 | // Although this check for six methods instead of eight | |
| 9549 | // since IE also does not support "trace" and "connect" | |
| 9550 | /^(get|post|head|put|delete|options)$/i.test( this.type ) && | |
| 9551 | ||
| 9552 | createStandardXHR() || createActiveXHR(); | |
| 9553 | } : | |
| 9554 | // For all other browsers, use the standard XMLHttpRequest object | |
| 9555 | createStandardXHR; | |
| 9556 | ||
| 9557 | var xhrId = 0, | |
| 9558 | xhrCallbacks = {}, | |
| 9559 | xhrSupported = jQuery.ajaxSettings.xhr(); | |
| 9560 | ||
| 9561 | // Support: IE<10 | |
| 9562 | // Open requests must be manually aborted on unload (#5280) | |
| 9563 | if ( window.ActiveXObject ) { | |
| 9564 | jQuery( window ).on( "unload", function() { | |
| 9565 | for ( var key in xhrCallbacks ) { | |
| 9566 | xhrCallbacks[ key ]( undefined, true ); | |
| 9567 | } | |
| 9568 | }); | |
| 9569 | } | |
| 9570 | ||
| 9571 | // Determine support properties | |
| 9572 | support.cors = !!xhrSupported && ( "withCredentials" in xhrSupported ); | |
| 9573 | xhrSupported = support.ajax = !!xhrSupported; | |
| 9574 | ||
| 9575 | // Create transport if the browser can provide an xhr | |
| 9576 | if ( xhrSupported ) { | |
| 9577 | ||
| 9578 | jQuery.ajaxTransport(function( options ) { | |
| 9579 | // Cross domain only allowed if supported through XMLHttpRequest | |
| 9580 | if ( !options.crossDomain || support.cors ) { | |
| 9581 | ||
| 9582 | var callback; | |
| 9583 | ||
| 9584 | return { | |
| 9585 | send: function( headers, complete ) { | |
| 9586 | var i, | |
| 9587 | xhr = options.xhr(), | |
| 9588 | id = ++xhrId; | |
| 9589 | ||
| 9590 | // Open the socket | |
| 9591 | xhr.open( options.type, options.url, options.async, options.username, options.password ); | |
| 9592 | ||
| 9593 | // Apply custom fields if provided | |
| 9594 | if ( options.xhrFields ) { | |
| 9595 | for ( i in options.xhrFields ) { | |
| 9596 | xhr[ i ] = options.xhrFields[ i ]; | |
| 9597 | } | |
| 9598 | } | |
| 9599 | ||
| 9600 | // Override mime type if needed | |
| 9601 | if ( options.mimeType && xhr.overrideMimeType ) { | |
| 9602 | xhr.overrideMimeType( options.mimeType ); | |
| 9603 | } | |
| 9604 | ||
| 9605 | // X-Requested-With header | |
| 9606 | // For cross-domain requests, seeing as conditions for a preflight are | |
| 9607 | // akin to a jigsaw puzzle, we simply never set it to be sure. | |
| 9608 | // (it can always be set on a per-request basis or even using ajaxSetup) | |
| 9609 | // For same-domain requests, won't change header if already provided. | |
| 9610 | if ( !options.crossDomain && !headers["X-Requested-With"] ) { | |
| 9611 | headers["X-Requested-With"] = "XMLHttpRequest"; | |
| 9612 | } | |
| 9613 | ||
| 9614 | // Set headers | |
| 9615 | for ( i in headers ) { | |
| 9616 | // Support: IE<9 | |
| 9617 | // IE's ActiveXObject throws a 'Type Mismatch' exception when setting | |
| 9618 | // request header to a null-value. | |
| 9619 | // | |
| 9620 | // To keep consistent with other XHR implementations, cast the value | |
| 9621 | // to string and ignore `undefined`. | |
| 9622 | if ( headers[ i ] !== undefined ) { | |
| 9623 | xhr.setRequestHeader( i, headers[ i ] + "" ); | |
| 9624 | } | |
| 9625 | } | |
| 9626 | ||
| 9627 | // Do send the request | |
| 9628 | // This may raise an exception which is actually | |
| 9629 | // handled in jQuery.ajax (so no try/catch here) | |
| 9630 | xhr.send( ( options.hasContent && options.data ) || null ); | |
| 9631 | ||
| 9632 | // Listener | |
| 9633 | callback = function( _, isAbort ) { | |
| 9634 | var status, statusText, responses; | |
| 9635 | ||
| 9636 | // Was never called and is aborted or complete | |
| 9637 | if ( callback && ( isAbort || xhr.readyState === 4 ) ) { | |
| 9638 | // Clean up | |
| 9639 | delete xhrCallbacks[ id ]; | |
| 9640 | callback = undefined; | |
| 9641 | xhr.onreadystatechange = jQuery.noop; | |
| 9642 | ||
| 9643 | // Abort manually if needed | |
| 9644 | if ( isAbort ) { | |
| 9645 | if ( xhr.readyState !== 4 ) { | |
| 9646 | xhr.abort(); | |
| 9647 | } | |
| 9648 | } else { | |
| 9649 | responses = {}; | |
| 9650 | status = xhr.status; | |
| 9651 | ||
| 9652 | // Support: IE<10 | |
| 9653 | // Accessing binary-data responseText throws an exception | |
| 9654 | // (#11426) | |
| 9655 | if ( typeof xhr.responseText === "string" ) { | |
| 9656 | responses.text = xhr.responseText; | |
| 9657 | } | |
| 9658 | ||
| 9659 | // Firefox throws an exception when accessing | |
| 9660 | // statusText for faulty cross-domain requests | |
| 9661 | try { | |
| 9662 | statusText = xhr.statusText; | |
| 9663 | } catch( e ) { | |
| 9664 | // We normalize with Webkit giving an empty statusText | |
| 9665 | statusText = ""; | |
| 9666 | } | |
| 9667 | ||
| 9668 | // Filter status for non standard behaviors | |
| 9669 | ||
| 9670 | // If the request is local and we have data: assume a success | |
| 9671 | // (success with no data won't get notified, that's the best we | |
| 9672 | // can do given current implementations) | |
| 9673 | if ( !status && options.isLocal && !options.crossDomain ) { | |
| 9674 | status = responses.text ? 200 : 404; | |
| 9675 | // IE - #1450: sometimes returns 1223 when it should be 204 | |
| 9676 | } else if ( status === 1223 ) { | |
| 9677 | status = 204; | |
| 9678 | } | |
| 9679 | } | |
| 9680 | } | |
| 9681 | ||
| 9682 | // Call complete if needed | |
| 9683 | if ( responses ) { | |
| 9684 | complete( status, statusText, responses, xhr.getAllResponseHeaders() ); | |
| 9685 | } | |
| 9686 | }; | |
| 9687 | ||
| 9688 | if ( !options.async ) { | |
| 9689 | // if we're in sync mode we fire the callback | |
| 9690 | callback(); | |
| 9691 | } else if ( xhr.readyState === 4 ) { | |
| 9692 | // (IE6 & IE7) if it's in cache and has been | |
| 9693 | // retrieved directly we need to fire the callback | |
| 9694 | setTimeout( callback ); | |
| 9695 | } else { | |
| 9696 | // Add to the list of active xhr callbacks | |
| 9697 | xhr.onreadystatechange = xhrCallbacks[ id ] = callback; | |
| 9698 | } | |
| 9699 | }, | |
| 9700 | ||
| 9701 | abort: function() { | |
| 9702 | if ( callback ) { | |
| 9703 | callback( undefined, true ); | |
| 9704 | } | |
| 9705 | } | |
| 9706 | }; | |
| 9707 | } | |
| 9708 | }); | |
| 9709 | } | |
| 9710 | ||
| 9711 | // Functions to create xhrs | |
| 9712 | function createStandardXHR() { | |
| 9713 | try { | |
| 9714 | return new window.XMLHttpRequest(); | |
| 9715 | } catch( e ) {} | |
| 9716 | } | |
| 9717 | ||
| 9718 | function createActiveXHR() { | |
| 9719 | try { | |
| 9720 | return new window.ActiveXObject( "Microsoft.XMLHTTP" ); | |
| 9721 | } catch( e ) {} | |
| 9722 | } | |
| 9723 | ||
| 9724 | ||
| 9725 | ||
| 9726 | ||
| 9727 | // Install script dataType | |
| 9728 | jQuery.ajaxSetup({ | |
| 9729 | accepts: { | |
| 9730 | script: "text/javascript, application/javascript, application/ecmascript, application/x-ecmascript" | |
| 9731 | }, | |
| 9732 | contents: { | |
| 9733 | script: /(?:java|ecma)script/ | |
| 9734 | }, | |
| 9735 | converters: { | |
| 9736 | "text script": function( text ) { | |
| 9737 | jQuery.globalEval( text ); | |
| 9738 | return text; | |
| 9739 | } | |
| 9740 | } | |
| 9741 | }); | |
| 9742 | ||
| 9743 | // Handle cache's special case and global | |
| 9744 | jQuery.ajaxPrefilter( "script", function( s ) { | |
| 9745 | if ( s.cache === undefined ) { | |
| 9746 | s.cache = false; | |
| 9747 | } | |
| 9748 | if ( s.crossDomain ) { | |
| 9749 | s.type = "GET"; | |
| 9750 | s.global = false; | |
| 9751 | } | |
| 9752 | }); | |
| 9753 | ||
| 9754 | // Bind script tag hack transport | |
| 9755 | jQuery.ajaxTransport( "script", function(s) { | |
| 9756 | ||
| 9757 | // This transport only deals with cross domain requests | |
| 9758 | if ( s.crossDomain ) { | |
| 9759 | ||
| 9760 | var script, | |
| 9761 | head = document.head || jQuery("head")[0] || document.documentElement; | |
| 9762 | ||
| 9763 | return { | |
| 9764 | ||
| 9765 | send: function( _, callback ) { | |
| 9766 | ||
| 9767 | script = document.createElement("script"); | |
| 9768 | ||
| 9769 | script.async = true; | |
| 9770 | ||
| 9771 | if ( s.scriptCharset ) { | |
| 9772 | script.charset = s.scriptCharset; | |
| 9773 | } | |
| 9774 | ||
| 9775 | script.src = s.url; | |
| 9776 | ||
| 9777 | // Attach handlers for all browsers | |
| 9778 | script.onload = script.onreadystatechange = function( _, isAbort ) { | |
| 9779 | ||
| 9780 | if ( isAbort || !script.readyState || /loaded|complete/.test( script.readyState ) ) { | |
| 9781 | ||
| 9782 | // Handle memory leak in IE | |
| 9783 | script.onload = script.onreadystatechange = null; | |
| 9784 | ||
| 9785 | // Remove the script | |
| 9786 | if ( script.parentNode ) { | |
| 9787 | script.parentNode.removeChild( script ); | |
| 9788 | } | |
| 9789 | ||
| 9790 | // Dereference the script | |
| 9791 | script = null; | |
| 9792 | ||
| 9793 | // Callback if not abort | |
| 9794 | if ( !isAbort ) { | |
| 9795 | callback( 200, "success" ); | |
| 9796 | } | |
| 9797 | } | |
| 9798 | }; | |
| 9799 | ||
| 9800 | // Circumvent IE6 bugs with base elements (#2709 and #4378) by prepending | |
| 9801 | // Use native DOM manipulation to avoid our domManip AJAX trickery | |
| 9802 | head.insertBefore( script, head.firstChild ); | |
| 9803 | }, | |
| 9804 | ||
| 9805 | abort: function() { | |
| 9806 | if ( script ) { | |
| 9807 | script.onload( undefined, true ); | |
| 9808 | } | |
| 9809 | } | |
| 9810 | }; | |
| 9811 | } | |
| 9812 | }); | |
| 9813 | ||
| 9814 | ||
| 9815 | ||
| 9816 | ||
| 9817 | var oldCallbacks = [], | |
| 9818 | rjsonp = /(=)\?(?=&|$)|\?\?/; | |
| 9819 | ||
| 9820 | // Default jsonp settings | |
| 9821 | jQuery.ajaxSetup({ | |
| 9822 | jsonp: "callback", | |
| 9823 | jsonpCallback: function() { | |
| 9824 | var callback = oldCallbacks.pop() || ( jQuery.expando + "_" + ( nonce++ ) ); | |
| 9825 | this[ callback ] = true; | |
| 9826 | return callback; | |
| 9827 | } | |
| 9828 | }); | |
| 9829 | ||
| 9830 | // Detect, normalize options and install callbacks for jsonp requests | |
| 9831 | jQuery.ajaxPrefilter( "json jsonp", function( s, originalSettings, jqXHR ) { | |
| 9832 | ||
| 9833 | var callbackName, overwritten, responseContainer, | |
| 9834 | jsonProp = s.jsonp !== false && ( rjsonp.test( s.url ) ? | |
| 9835 | "url" : | |
| 9836 | typeof s.data === "string" && !( s.contentType || "" ).indexOf("application/x-www-form-urlencoded") && rjsonp.test( s.data ) && "data" | |
| 9837 | ); | |
| 9838 | ||
| 9839 | // Handle iff the expected data type is "jsonp" or we have a parameter to set | |
| 9840 | if ( jsonProp || s.dataTypes[ 0 ] === "jsonp" ) { | |
| 9841 | ||
| 9842 | // Get callback name, remembering preexisting value associated with it | |
| 9843 | callbackName = s.jsonpCallback = jQuery.isFunction( s.jsonpCallback ) ? | |
| 9844 | s.jsonpCallback() : | |
| 9845 | s.jsonpCallback; | |
| 9846 | ||
| 9847 | // Insert callback into url or form data | |
| 9848 | if ( jsonProp ) { | |
| 9849 | s[ jsonProp ] = s[ jsonProp ].replace( rjsonp, "$1" + callbackName ); | |
| 9850 | } else if ( s.jsonp !== false ) { | |
| 9851 | s.url += ( rquery.test( s.url ) ? "&" : "?" ) + s.jsonp + "=" + callbackName; | |
| 9852 | } | |
| 9853 | ||
| 9854 | // Use data converter to retrieve json after script execution | |
| 9855 | s.converters["script json"] = function() { | |
| 9856 | if ( !responseContainer ) { | |
| 9857 | jQuery.error( callbackName + " was not called" ); | |
| 9858 | } | |
| 9859 | return responseContainer[ 0 ]; | |
| 9860 | }; | |
| 9861 | ||
| 9862 | // force json dataType | |
| 9863 | s.dataTypes[ 0 ] = "json"; | |
| 9864 | ||
| 9865 | // Install callback | |
| 9866 | overwritten = window[ callbackName ]; | |
| 9867 | window[ callbackName ] = function() { | |
| 9868 | responseContainer = arguments; | |
| 9869 | }; | |
| 9870 | ||
| 9871 | // Clean-up function (fires after converters) | |
| 9872 | jqXHR.always(function() { | |
| 9873 | // Restore preexisting value | |
| 9874 | window[ callbackName ] = overwritten; | |
| 9875 | ||
| 9876 | // Save back as free | |
| 9877 | if ( s[ callbackName ] ) { | |
| 9878 | // make sure that re-using the options doesn't screw things around | |
| 9879 | s.jsonpCallback = originalSettings.jsonpCallback; | |
| 9880 | ||
| 9881 | // save the callback name for future use | |
| 9882 | oldCallbacks.push( callbackName ); | |
| 9883 | } | |
| 9884 | ||
| 9885 | // Call if it was a function and we have a response | |
| 9886 | if ( responseContainer && jQuery.isFunction( overwritten ) ) { | |
| 9887 | overwritten( responseContainer[ 0 ] ); | |
| 9888 | } | |
| 9889 | ||
| 9890 | responseContainer = overwritten = undefined; | |
| 9891 | }); | |
| 9892 | ||
| 9893 | // Delegate to script | |
| 9894 | return "script"; | |
| 9895 | } | |
| 9896 | }); | |
| 9897 | ||
| 9898 | ||
| 9899 | ||
| 9900 | ||
| 9901 | // data: string of html | |
| 9902 | // context (optional): If specified, the fragment will be created in this context, defaults to document | |
| 9903 | // keepScripts (optional): If true, will include scripts passed in the html string | |
| 9904 | jQuery.parseHTML = function( data, context, keepScripts ) { | |
| 9905 | if ( !data || typeof data !== "string" ) { | |
| 9906 | return null; | |
| 9907 | } | |
| 9908 | if ( typeof context === "boolean" ) { | |
| 9909 | keepScripts = context; | |
| 9910 | context = false; | |
| 9911 | } | |
| 9912 | context = context || document; | |
| 9913 | ||
| 9914 | var parsed = rsingleTag.exec( data ), | |
| 9915 | scripts = !keepScripts && []; | |
| 9916 | ||
| 9917 | // Single tag | |
| 9918 | if ( parsed ) { | |
| 9919 | return [ context.createElement( parsed[1] ) ]; | |
| 9920 | } | |
| 9921 | ||
| 9922 | parsed = jQuery.buildFragment( [ data ], context, scripts ); | |
| 9923 | ||
| 9924 | if ( scripts && scripts.length ) { | |
| 9925 | jQuery( scripts ).remove(); | |
| 9926 | } | |
| 9927 | ||
| 9928 | return jQuery.merge( [], parsed.childNodes ); | |
| 9929 | }; | |
| 9930 | ||
| 9931 | ||
| 9932 | // Keep a copy of the old load method | |
| 9933 | var _load = jQuery.fn.load; | |
| 9934 | ||
| 9935 | /** | |
| 9936 | * Load a url into a page | |
| 9937 | */ | |
| 9938 | jQuery.fn.load = function( url, params, callback ) { | |
| 9939 | if ( typeof url !== "string" && _load ) { | |
| 9940 | return _load.apply( this, arguments ); | |
| 9941 | } | |
| 9942 | ||
| 9943 | var selector, response, type, | |
| 9944 | self = this, | |
| 9945 | off = url.indexOf(" "); | |
| 9946 | ||
| 9947 | if ( off >= 0 ) { | |
| 9948 | selector = jQuery.trim( url.slice( off, url.length ) ); | |
| 9949 | url = url.slice( 0, off ); | |
| 9950 | } | |
| 9951 | ||
| 9952 | // If it's a function | |
| 9953 | if ( jQuery.isFunction( params ) ) { | |
| 9954 | ||
| 9955 | // We assume that it's the callback | |
| 9956 | callback = params; | |
| 9957 | params = undefined; | |
| 9958 | ||
| 9959 | // Otherwise, build a param string | |
| 9960 | } else if ( params && typeof params === "object" ) { | |
| 9961 | type = "POST"; | |
| 9962 | } | |
| 9963 | ||
| 9964 | // If we have elements to modify, make the request | |
| 9965 | if ( self.length > 0 ) { | |
| 9966 | jQuery.ajax({ | |
| 9967 | url: url, | |
| 9968 | ||
| 9969 | // if "type" variable is undefined, then "GET" method will be used | |
| 9970 | type: type, | |
| 9971 | dataType: "html", | |
| 9972 | data: params | |
| 9973 | }).done(function( responseText ) { | |
| 9974 | ||
| 9975 | // Save response for use in complete callback | |
| 9976 | response = arguments; | |
| 9977 | ||
| 9978 | self.html( selector ? | |
| 9979 | ||
| 9980 | // If a selector was specified, locate the right elements in a dummy div | |
| 9981 | // Exclude scripts to avoid IE 'Permission Denied' errors | |
| 9982 | jQuery("<div>").append( jQuery.parseHTML( responseText ) ).find( selector ) : | |
| 9983 | ||
| 9984 | // Otherwise use the full result | |
| 9985 | responseText ); | |
| 9986 | ||
| 9987 | }).complete( callback && function( jqXHR, status ) { | |
| 9988 | self.each( callback, response || [ jqXHR.responseText, status, jqXHR ] ); | |
| 9989 | }); | |
| 9990 | } | |
| 9991 | ||
| 9992 | return this; | |
| 9993 | }; | |
| 9994 | ||
| 9995 | ||
| 9996 | ||
| 9997 | ||
| 9998 | jQuery.expr.filters.animated = function( elem ) { | |
| 9999 | return jQuery.grep(jQuery.timers, function( fn ) { | |
| 10000 | return elem === fn.elem; | |
| 10001 | }).length; | |
| 10002 | }; | |
| 10003 | ||
| 10004 | ||
| 10005 | ||
| 10006 | ||
| 10007 | ||
| 10008 | var docElem = window.document.documentElement; | |
| 10009 | ||
| 10010 | /** | |
| 10011 | * Gets a window from an element | |
| 10012 | */ | |
| 10013 | function getWindow( elem ) { | |
| 10014 | return jQuery.isWindow( elem ) ? | |
| 10015 | elem : | |
| 10016 | elem.nodeType === 9 ? | |
| 10017 | elem.defaultView || elem.parentWindow : | |
| 10018 | false; | |
| 10019 | } | |
| 10020 | ||
| 10021 | jQuery.offset = { | |
| 10022 | setOffset: function( elem, options, i ) { | |
| 10023 | var curPosition, curLeft, curCSSTop, curTop, curOffset, curCSSLeft, calculatePosition, | |
| 10024 | position = jQuery.css( elem, "position" ), | |
| 10025 | curElem = jQuery( elem ), | |
| 10026 | props = {}; | |
| 10027 | ||
| 10028 | // set position first, in-case top/left are set even on static elem | |
| 10029 | if ( position === "static" ) { | |
| 10030 | elem.style.position = "relative"; | |
| 10031 | } | |
| 10032 | ||
| 10033 | curOffset = curElem.offset(); | |
| 10034 | curCSSTop = jQuery.css( elem, "top" ); | |
| 10035 | curCSSLeft = jQuery.css( elem, "left" ); | |
| 10036 | calculatePosition = ( position === "absolute" || position === "fixed" ) && | |
| 10037 | jQuery.inArray("auto", [ curCSSTop, curCSSLeft ] ) > -1; | |
| 10038 | ||
| 10039 | // need to be able to calculate position if either top or left is auto and position is either absolute or fixed | |
| 10040 | if ( calculatePosition ) { | |
| 10041 | curPosition = curElem.position(); | |
| 10042 | curTop = curPosition.top; | |
| 10043 | curLeft = curPosition.left; | |
| 10044 | } else { | |
| 10045 | curTop = parseFloat( curCSSTop ) || 0; | |
| 10046 | curLeft = parseFloat( curCSSLeft ) || 0; | |
| 10047 | } | |
| 10048 | ||
| 10049 | if ( jQuery.isFunction( options ) ) { | |
| 10050 | options = options.call( elem, i, curOffset ); | |
| 10051 | } | |
| 10052 | ||
| 10053 | if ( options.top != null ) { | |
| 10054 | props.top = ( options.top - curOffset.top ) + curTop; | |
| 10055 | } | |
| 10056 | if ( options.left != null ) { | |
| 10057 | props.left = ( options.left - curOffset.left ) + curLeft; | |
| 10058 | } | |
| 10059 | ||
| 10060 | if ( "using" in options ) { | |
| 10061 | options.using.call( elem, props ); | |
| 10062 | } else { | |
| 10063 | curElem.css( props ); | |
| 10064 | } | |
| 10065 | } | |
| 10066 | }; | |
| 10067 | ||
| 10068 | jQuery.fn.extend({ | |
| 10069 | offset: function( options ) { | |
| 10070 | if ( arguments.length ) { | |
| 10071 | return options === undefined ? | |
| 10072 | this : | |
| 10073 | this.each(function( i ) { | |
| 10074 | jQuery.offset.setOffset( this, options, i ); | |
| 10075 | }); | |
| 10076 | } | |
| 10077 | ||
| 10078 | var docElem, win, | |
| 10079 | box = { top: 0, left: 0 }, | |
| 10080 | elem = this[ 0 ], | |
| 10081 | doc = elem && elem.ownerDocument; | |
| 10082 | ||
| 10083 | if ( !doc ) { | |
| 10084 | return; | |
| 10085 | } | |
| 10086 | ||
| 10087 | docElem = doc.documentElement; | |
| 10088 | ||
| 10089 | // Make sure it's not a disconnected DOM node | |
| 10090 | if ( !jQuery.contains( docElem, elem ) ) { | |
| 10091 | return box; | |
| 10092 | } | |
| 10093 | ||
| 10094 | // If we don't have gBCR, just use 0,0 rather than error | |
| 10095 | // BlackBerry 5, iOS 3 (original iPhone) | |
| 10096 | if ( typeof elem.getBoundingClientRect !== strundefined ) { | |
| 10097 | box = elem.getBoundingClientRect(); | |
| 10098 | } | |
| 10099 | win = getWindow( doc ); | |
| 10100 | return { | |
| 10101 | top: box.top + ( win.pageYOffset || docElem.scrollTop ) - ( docElem.clientTop || 0 ), | |
| 10102 | left: box.left + ( win.pageXOffset || docElem.scrollLeft ) - ( docElem.clientLeft || 0 ) | |
| 10103 | }; | |
| 10104 | }, | |
| 10105 | ||
| 10106 | position: function() { | |
| 10107 | if ( !this[ 0 ] ) { | |
| 10108 | return; | |
| 10109 | } | |
| 10110 | ||
| 10111 | var offsetParent, offset, | |
| 10112 | parentOffset = { top: 0, left: 0 }, | |
| 10113 | elem = this[ 0 ]; | |
| 10114 | ||
| 10115 | // fixed elements are offset from window (parentOffset = {top:0, left: 0}, because it is its only offset parent | |
| 10116 | if ( jQuery.css( elem, "position" ) === "fixed" ) { | |
| 10117 | // we assume that getBoundingClientRect is available when computed position is fixed | |
| 10118 | offset = elem.getBoundingClientRect(); | |
| 10119 | } else { | |
| 10120 | // Get *real* offsetParent | |
| 10121 | offsetParent = this.offsetParent(); | |
| 10122 | ||
| 10123 | // Get correct offsets | |
| 10124 | offset = this.offset(); | |
| 10125 | if ( !jQuery.nodeName( offsetParent[ 0 ], "html" ) ) { | |
| 10126 | parentOffset = offsetParent.offset(); | |
| 10127 | } | |
| 10128 | ||
| 10129 | // Add offsetParent borders | |
| 10130 | parentOffset.top += jQuery.css( offsetParent[ 0 ], "borderTopWidth", true ); | |
| 10131 | parentOffset.left += jQuery.css( offsetParent[ 0 ], "borderLeftWidth", true ); | |
| 10132 | } | |
| 10133 | ||
| 10134 | // Subtract parent offsets and element margins | |
| 10135 | // note: when an element has margin: auto the offsetLeft and marginLeft | |
| 10136 | // are the same in Safari causing offset.left to incorrectly be 0 | |
| 10137 | return { | |
| 10138 | top: offset.top - parentOffset.top - jQuery.css( elem, "marginTop", true ), | |
| 10139 | left: offset.left - parentOffset.left - jQuery.css( elem, "marginLeft", true) | |
| 10140 | }; | |
| 10141 | }, | |
| 10142 | ||
| 10143 | offsetParent: function() { | |
| 10144 | return this.map(function() { | |
| 10145 | var offsetParent = this.offsetParent || docElem; | |
| 10146 | ||
| 10147 | while ( offsetParent && ( !jQuery.nodeName( offsetParent, "html" ) && jQuery.css( offsetParent, "position" ) === "static" ) ) { | |
| 10148 | offsetParent = offsetParent.offsetParent; | |
| 10149 | } | |
| 10150 | return offsetParent || docElem; | |
| 10151 | }); | |
| 10152 | } | |
| 10153 | }); | |
| 10154 | ||
| 10155 | // Create scrollLeft and scrollTop methods | |
| 10156 | jQuery.each( { scrollLeft: "pageXOffset", scrollTop: "pageYOffset" }, function( method, prop ) { | |
| 10157 | var top = /Y/.test( prop ); | |
| 10158 | ||
| 10159 | jQuery.fn[ method ] = function( val ) { | |
| 10160 | return access( this, function( elem, method, val ) { | |
| 10161 | var win = getWindow( elem ); | |
| 10162 | ||
| 10163 | if ( val === undefined ) { | |
| 10164 | return win ? (prop in win) ? win[ prop ] : | |
| 10165 | win.document.documentElement[ method ] : | |
| 10166 | elem[ method ]; | |
| 10167 | } | |
| 10168 | ||
| 10169 | if ( win ) { | |
| 10170 | win.scrollTo( | |
| 10171 | !top ? val : jQuery( win ).scrollLeft(), | |
| 10172 | top ? val : jQuery( win ).scrollTop() | |
| 10173 | ); | |
| 10174 | ||
| 10175 | } else { | |
| 10176 | elem[ method ] = val; | |
| 10177 | } | |
| 10178 | }, method, val, arguments.length, null ); | |
| 10179 | }; | |
| 10180 | }); | |
| 10181 | ||
| 10182 | // Add the top/left cssHooks using jQuery.fn.position | |
| 10183 | // Webkit bug: https://bugs.webkit.org/show_bug.cgi?id=29084 | |
| 10184 | // getComputedStyle returns percent when specified for top/left/bottom/right | |
| 10185 | // rather than make the css module depend on the offset module, we just check for it here | |
| 10186 | jQuery.each( [ "top", "left" ], function( i, prop ) { | |
| 10187 | jQuery.cssHooks[ prop ] = addGetHookIf( support.pixelPosition, | |
| 10188 | function( elem, computed ) { | |
| 10189 | if ( computed ) { | |
| 10190 | computed = curCSS( elem, prop ); | |
| 10191 | // if curCSS returns percentage, fallback to offset | |
| 10192 | return rnumnonpx.test( computed ) ? | |
| 10193 | jQuery( elem ).position()[ prop ] + "px" : | |
| 10194 | computed; | |
| 10195 | } | |
| 10196 | } | |
| 10197 | ); | |
| 10198 | }); | |
| 10199 | ||
| 10200 | ||
| 10201 | // Create innerHeight, innerWidth, height, width, outerHeight and outerWidth methods | |
| 10202 | jQuery.each( { Height: "height", Width: "width" }, function( name, type ) { | |
| 10203 | jQuery.each( { padding: "inner" + name, content: type, "": "outer" + name }, function( defaultExtra, funcName ) { | |
| 10204 | // margin is only for outerHeight, outerWidth | |
| 10205 | jQuery.fn[ funcName ] = function( margin, value ) { | |
| 10206 | var chainable = arguments.length && ( defaultExtra || typeof margin !== "boolean" ), | |
| 10207 | extra = defaultExtra || ( margin === true || value === true ? "margin" : "border" ); | |
| 10208 | ||
| 10209 | return access( this, function( elem, type, value ) { | |
| 10210 | var doc; | |
| 10211 | ||
| 10212 | if ( jQuery.isWindow( elem ) ) { | |
| 10213 | // As of 5/8/2012 this will yield incorrect results for Mobile Safari, but there | |
| 10214 | // isn't a whole lot we can do. See pull request at this URL for discussion: | |
| 10215 | // https://github.com/jquery/jquery/pull/764 | |
| 10216 | return elem.document.documentElement[ "client" + name ]; | |
| 10217 | } | |
| 10218 | ||
| 10219 | // Get document width or height | |
| 10220 | if ( elem.nodeType === 9 ) { | |
| 10221 | doc = elem.documentElement; | |
| 10222 | ||
| 10223 | // Either scroll[Width/Height] or offset[Width/Height] or client[Width/Height], whichever is greatest | |
| 10224 | // unfortunately, this causes bug #3838 in IE6/8 only, but there is currently no good, small way to fix it. | |
| 10225 | return Math.max( | |
| 10226 | elem.body[ "scroll" + name ], doc[ "scroll" + name ], | |
| 10227 | elem.body[ "offset" + name ], doc[ "offset" + name ], | |
| 10228 | doc[ "client" + name ] | |
| 10229 | ); | |
| 10230 | } | |
| 10231 | ||
| 10232 | return value === undefined ? | |
| 10233 | // Get width or height on the element, requesting but not forcing parseFloat | |
| 10234 | jQuery.css( elem, type, extra ) : | |
| 10235 | ||
| 10236 | // Set width or height on the element | |
| 10237 | jQuery.style( elem, type, value, extra ); | |
| 10238 | }, type, chainable ? margin : undefined, chainable, null ); | |
| 10239 | }; | |
| 10240 | }); | |
| 10241 | }); | |
| 10242 | ||
| 10243 | ||
| 10244 | // The number of elements contained in the matched element set | |
| 10245 | jQuery.fn.size = function() { | |
| 10246 | return this.length; | |
| 10247 | }; | |
| 10248 | ||
| 10249 | jQuery.fn.andSelf = jQuery.fn.addBack; | |
| 10250 | ||
| 10251 | ||
| 10252 | ||
| 10253 | ||
| 10254 | // Register as a named AMD module, since jQuery can be concatenated with other | |
| 10255 | // files that may use define, but not via a proper concatenation script that | |
| 10256 | // understands anonymous AMD modules. A named AMD is safest and most robust | |
| 10257 | // way to register. Lowercase jquery is used because AMD module names are | |
| 10258 | // derived from file names, and jQuery is normally delivered in a lowercase | |
| 10259 | // file name. Do this after creating the global so that if an AMD module wants | |
| 10260 | // to call noConflict to hide this version of jQuery, it will work. | |
| 10261 | ||
| 10262 | // Note that for maximum portability, libraries that are not jQuery should | |
| 10263 | // declare themselves as anonymous modules, and avoid setting a global if an | |
| 10264 | // AMD loader is present. jQuery is a special case. For more information, see | |
| 10265 | // https://github.com/jrburke/requirejs/wiki/Updating-existing-libraries#wiki-anon | |
| 10266 | ||
| 10267 | if ( typeof define === "function" && define.amd ) { | |
| 10268 | define( "jquery", [], function() { | |
| 10269 | return jQuery; | |
| 10270 | }); | |
| 10271 | } | |
| 10272 | ||
| 10273 | ||
| 10274 | ||
| 10275 | ||
| 10276 | var | |
| 10277 | // Map over jQuery in case of overwrite | |
| 10278 | _jQuery = window.jQuery, | |
| 10279 | ||
| 10280 | // Map over the $ in case of overwrite | |
| 10281 | _$ = window.$; | |
| 10282 | ||
| 10283 | jQuery.noConflict = function( deep ) { | |
| 10284 | if ( window.$ === jQuery ) { | |
| 10285 | window.$ = _$; | |
| 10286 | } | |
| 10287 | ||
| 10288 | if ( deep && window.jQuery === jQuery ) { | |
| 10289 | window.jQuery = _jQuery; | |
| 10290 | } | |
| 10291 | ||
| 10292 | return jQuery; | |
| 10293 | }; | |
| 10294 | ||
| 10295 | // Expose jQuery and $ identifiers, even in | |
| 10296 | // AMD (#7102#comment:10, https://github.com/jquery/jquery/pull/557) | |
| 10297 | // and CommonJS for browser emulators (#13566) | |
| 10298 | if ( typeof noGlobal === strundefined ) { | |
| 10299 | window.jQuery = window.$ = jQuery; | |
| 10300 | } | |
| 10301 | ||
| 10302 | ||
| 10303 | ||
| 10304 | ||
| 10305 | return jQuery; | |
| 10306 | ||
| 10307 | })); |
| 0 | /*eslint-disable no-unused-vars*/ | |
| 1 | /*! | |
| 2 | * jQuery JavaScript Library v3.1.0 | |
| 3 | * https://jquery.com/ | |
| 4 | * | |
| 5 | * Includes Sizzle.js | |
| 6 | * https://sizzlejs.com/ | |
| 7 | * | |
| 8 | * Copyright jQuery Foundation and other contributors | |
| 9 | * Released under the MIT license | |
| 10 | * https://jquery.org/license | |
| 11 | * | |
| 12 | * Date: 2016-07-07T21:44Z | |
| 13 | */ | |
| 14 | ( function( global, factory ) { | |
| 15 | ||
| 16 | "use strict"; | |
| 17 | ||
| 18 | if ( typeof module === "object" && typeof module.exports === "object" ) { | |
| 19 | ||
| 20 | // For CommonJS and CommonJS-like environments where a proper `window` | |
| 21 | // is present, execute the factory and get jQuery. | |
| 22 | // For environments that do not have a `window` with a `document` | |
| 23 | // (such as Node.js), expose a factory as module.exports. | |
| 24 | // This accentuates the need for the creation of a real `window`. | |
| 25 | // e.g. var jQuery = require("jquery")(window); | |
| 26 | // See ticket #14549 for more info. | |
| 27 | module.exports = global.document ? | |
| 28 | factory( global, true ) : | |
| 29 | function( w ) { | |
| 30 | if ( !w.document ) { | |
| 31 | throw new Error( "jQuery requires a window with a document" ); | |
| 32 | } | |
| 33 | return factory( w ); | |
| 34 | }; | |
| 35 | } else { | |
| 36 | factory( global ); | |
| 37 | } | |
| 38 | ||
| 39 | // Pass this if window is not defined yet | |
| 40 | } )( typeof window !== "undefined" ? window : this, function( window, noGlobal ) { | |
| 41 | ||
| 42 | // Edge <= 12 - 13+, Firefox <=18 - 45+, IE 10 - 11, Safari 5.1 - 9+, iOS 6 - 9.1 | |
| 43 | // throw exceptions when non-strict code (e.g., ASP.NET 4.5) accesses strict mode | |
| 44 | // arguments.callee.caller (trac-13335). But as of jQuery 3.0 (2016), strict mode should be common | |
| 45 | // enough that all such attempts are guarded in a try block. | |
| 46 | "use strict"; | |
| 47 | ||
| 48 | var arr = []; | |
| 49 | ||
| 50 | var document = window.document; | |
| 51 | ||
| 52 | var getProto = Object.getPrototypeOf; | |
| 53 | ||
| 54 | var slice = arr.slice; | |
| 55 | ||
| 56 | var concat = arr.concat; | |
| 57 | ||
| 58 | var push = arr.push; | |
| 59 | ||
| 60 | var indexOf = arr.indexOf; | |
| 61 | ||
| 62 | var class2type = {}; | |
| 63 | ||
| 64 | var toString = class2type.toString; | |
| 65 | ||
| 66 | var hasOwn = class2type.hasOwnProperty; | |
| 67 | ||
| 68 | var fnToString = hasOwn.toString; | |
| 69 | ||
| 70 | var ObjectFunctionString = fnToString.call( Object ); | |
| 71 | ||
| 72 | var support = {}; | |
| 73 | ||
| 74 | ||
| 75 | ||
| 76 | function DOMEval( code, doc ) { | |
| 77 | doc = doc || document; | |
| 78 | ||
| 79 | var script = doc.createElement( "script" ); | |
| 80 | ||
| 81 | script.text = code; | |
| 82 | doc.head.appendChild( script ).parentNode.removeChild( script ); | |
| 83 | } | |
| 84 | /* global Symbol */ | |
| 85 | // Defining this global in .eslintrc would create a danger of using the global | |
| 86 | // unguarded in another place, it seems safer to define global only for this module | |
| 87 | ||
| 88 | ||
| 89 | ||
| 90 | var | |
| 91 | version = "3.1.0", | |
| 92 | ||
| 93 | // Define a local copy of jQuery | |
| 94 | jQuery = function( selector, context ) { | |
| 95 | ||
| 96 | // The jQuery object is actually just the init constructor 'enhanced' | |
| 97 | // Need init if jQuery is called (just allow error to be thrown if not included) | |
| 98 | return new jQuery.fn.init( selector, context ); | |
| 99 | }, | |
| 100 | ||
| 101 | // Support: Android <=4.0 only | |
| 102 | // Make sure we trim BOM and NBSP | |
| 103 | rtrim = /^[\s\uFEFF\xA0]+|[\s\uFEFF\xA0]+$/g, | |
| 104 | ||
| 105 | // Matches dashed string for camelizing | |
| 106 | rmsPrefix = /^-ms-/, | |
| 107 | rdashAlpha = /-([a-z])/g, | |
| 108 | ||
| 109 | // Used by jQuery.camelCase as callback to replace() | |
| 110 | fcamelCase = function( all, letter ) { | |
| 111 | return letter.toUpperCase(); | |
| 112 | }; | |
| 113 | ||
| 114 | jQuery.fn = jQuery.prototype = { | |
| 115 | ||
| 116 | // The current version of jQuery being used | |
| 117 | jquery: version, | |
| 118 | ||
| 119 | constructor: jQuery, | |
| 120 | ||
| 121 | // The default length of a jQuery object is 0 | |
| 122 | length: 0, | |
| 123 | ||
| 124 | toArray: function() { | |
| 125 | return slice.call( this ); | |
| 126 | }, | |
| 127 | ||
| 128 | // Get the Nth element in the matched element set OR | |
| 129 | // Get the whole matched element set as a clean array | |
| 130 | get: function( num ) { | |
| 131 | return num != null ? | |
| 132 | ||
| 133 | // Return just the one element from the set | |
| 134 | ( num < 0 ? this[ num + this.length ] : this[ num ] ) : | |
| 135 | ||
| 136 | // Return all the elements in a clean array | |
| 137 | slice.call( this ); | |
| 138 | }, | |
| 139 | ||
| 140 | // Take an array of elements and push it onto the stack | |
| 141 | // (returning the new matched element set) | |
| 142 | pushStack: function( elems ) { | |
| 143 | ||
| 144 | // Build a new jQuery matched element set | |
| 145 | var ret = jQuery.merge( this.constructor(), elems ); | |
| 146 | ||
| 147 | // Add the old object onto the stack (as a reference) | |
| 148 | ret.prevObject = this; | |
| 149 | ||
| 150 | // Return the newly-formed element set | |
| 151 | return ret; | |
| 152 | }, | |
| 153 | ||
| 154 | // Execute a callback for every element in the matched set. | |
| 155 | each: function( callback ) { | |
| 156 | return jQuery.each( this, callback ); | |
| 157 | }, | |
| 158 | ||
| 159 | map: function( callback ) { | |
| 160 | return this.pushStack( jQuery.map( this, function( elem, i ) { | |
| 161 | return callback.call( elem, i, elem ); | |
| 162 | } ) ); | |
| 163 | }, | |
| 164 | ||
| 165 | slice: function() { | |
| 166 | return this.pushStack( slice.apply( this, arguments ) ); | |
| 167 | }, | |
| 168 | ||
| 169 | first: function() { | |
| 170 | return this.eq( 0 ); | |
| 171 | }, | |
| 172 | ||
| 173 | last: function() { | |
| 174 | return this.eq( -1 ); | |
| 175 | }, | |
| 176 | ||
| 177 | eq: function( i ) { | |
| 178 | var len = this.length, | |
| 179 | j = +i + ( i < 0 ? len : 0 ); | |
| 180 | return this.pushStack( j >= 0 && j < len ? [ this[ j ] ] : [] ); | |
| 181 | }, | |
| 182 | ||
| 183 | end: function() { | |
| 184 | return this.prevObject || this.constructor(); | |
| 185 | }, | |
| 186 | ||
| 187 | // For internal use only. | |
| 188 | // Behaves like an Array's method, not like a jQuery method. | |
| 189 | push: push, | |
| 190 | sort: arr.sort, | |
| 191 | splice: arr.splice | |
| 192 | }; | |
| 193 | ||
| 194 | jQuery.extend = jQuery.fn.extend = function() { | |
| 195 | var options, name, src, copy, copyIsArray, clone, | |
| 196 | target = arguments[ 0 ] || {}, | |
| 197 | i = 1, | |
| 198 | length = arguments.length, | |
| 199 | deep = false; | |
| 200 | ||
| 201 | // Handle a deep copy situation | |
| 202 | if ( typeof target === "boolean" ) { | |
| 203 | deep = target; | |
| 204 | ||
| 205 | // Skip the boolean and the target | |
| 206 | target = arguments[ i ] || {}; | |
| 207 | i++; | |
| 208 | } | |
| 209 | ||
| 210 | // Handle case when target is a string or something (possible in deep copy) | |
| 211 | if ( typeof target !== "object" && !jQuery.isFunction( target ) ) { | |
| 212 | target = {}; | |
| 213 | } | |
| 214 | ||
| 215 | // Extend jQuery itself if only one argument is passed | |
| 216 | if ( i === length ) { | |
| 217 | target = this; | |
| 218 | i--; | |
| 219 | } | |
| 220 | ||
| 221 | for ( ; i < length; i++ ) { | |
| 222 | ||
| 223 | // Only deal with non-null/undefined values | |
| 224 | if ( ( options = arguments[ i ] ) != null ) { | |
| 225 | ||
| 226 | // Extend the base object | |
| 227 | for ( name in options ) { | |
| 228 | src = target[ name ]; | |
| 229 | copy = options[ name ]; | |
| 230 | ||
| 231 | // Prevent never-ending loop | |
| 232 | if ( target === copy ) { | |
| 233 | continue; | |
| 234 | } | |
| 235 | ||
| 236 | // Recurse if we're merging plain objects or arrays | |
| 237 | if ( deep && copy && ( jQuery.isPlainObject( copy ) || | |
| 238 | ( copyIsArray = jQuery.isArray( copy ) ) ) ) { | |
| 239 | ||
| 240 | if ( copyIsArray ) { | |
| 241 | copyIsArray = false; | |
| 242 | clone = src && jQuery.isArray( src ) ? src : []; | |
| 243 | ||
| 244 | } else { | |
| 245 | clone = src && jQuery.isPlainObject( src ) ? src : {}; | |
| 246 | } | |
| 247 | ||
| 248 | // Never move original objects, clone them | |
| 249 | target[ name ] = jQuery.extend( deep, clone, copy ); | |
| 250 | ||
| 251 | // Don't bring in undefined values | |
| 252 | } else if ( copy !== undefined ) { | |
| 253 | target[ name ] = copy; | |
| 254 | } | |
| 255 | } | |
| 256 | } | |
| 257 | } | |
| 258 | ||
| 259 | // Return the modified object | |
| 260 | return target; | |
| 261 | }; | |
| 262 | ||
| 263 | jQuery.extend( { | |
| 264 | ||
| 265 | // Unique for each copy of jQuery on the page | |
| 266 | expando: "jQuery" + ( version + Math.random() ).replace( /\D/g, "" ), | |
| 267 | ||
| 268 | // Assume jQuery is ready without the ready module | |
| 269 | isReady: true, | |
| 270 | ||
| 271 | error: function( msg ) { | |
| 272 | throw new Error( msg ); | |
| 273 | }, | |
| 274 | ||
| 275 | noop: function() {}, | |
| 276 | ||
| 277 | isFunction: function( obj ) { | |
| 278 | return jQuery.type( obj ) === "function"; | |
| 279 | }, | |
| 280 | ||
| 281 | isArray: Array.isArray, | |
| 282 | ||
| 283 | isWindow: function( obj ) { | |
| 284 | return obj != null && obj === obj.window; | |
| 285 | }, | |
| 286 | ||
| 287 | isNumeric: function( obj ) { | |
| 288 | ||
| 289 | // As of jQuery 3.0, isNumeric is limited to | |
| 290 | // strings and numbers (primitives or objects) | |
| 291 | // that can be coerced to finite numbers (gh-2662) | |
| 292 | var type = jQuery.type( obj ); | |
| 293 | return ( type === "number" || type === "string" ) && | |
| 294 | ||
| 295 | // parseFloat NaNs numeric-cast false positives ("") | |
| 296 | // ...but misinterprets leading-number strings, particularly hex literals ("0x...") | |
| 297 | // subtraction forces infinities to NaN | |
| 298 | !isNaN( obj - parseFloat( obj ) ); | |
| 299 | }, | |
| 300 | ||
| 301 | isPlainObject: function( obj ) { | |
| 302 | var proto, Ctor; | |
| 303 | ||
| 304 | // Detect obvious negatives | |
| 305 | // Use toString instead of jQuery.type to catch host objects | |
| 306 | if ( !obj || toString.call( obj ) !== "[object Object]" ) { | |
| 307 | return false; | |
| 308 | } | |
| 309 | ||
| 310 | proto = getProto( obj ); | |
| 311 | ||
| 312 | // Objects with no prototype (e.g., `Object.create( null )`) are plain | |
| 313 | if ( !proto ) { | |
| 314 | return true; | |
| 315 | } | |
| 316 | ||
| 317 | // Objects with prototype are plain iff they were constructed by a global Object function | |
| 318 | Ctor = hasOwn.call( proto, "constructor" ) && proto.constructor; | |
| 319 | return typeof Ctor === "function" && fnToString.call( Ctor ) === ObjectFunctionString; | |
| 320 | }, | |
| 321 | ||
| 322 | isEmptyObject: function( obj ) { | |
| 323 | ||
| 324 | /* eslint-disable no-unused-vars */ | |
| 325 | // See https://github.com/eslint/eslint/issues/6125 | |
| 326 | var name; | |
| 327 | ||
| 328 | for ( name in obj ) { | |
| 329 | return false; | |
| 330 | } | |
| 331 | return true; | |
| 332 | }, | |
| 333 | ||
| 334 | type: function( obj ) { | |
| 335 | if ( obj == null ) { | |
| 336 | return obj + ""; | |
| 337 | } | |
| 338 | ||
| 339 | // Support: Android <=2.3 only (functionish RegExp) | |
| 340 | return typeof obj === "object" || typeof obj === "function" ? | |
| 341 | class2type[ toString.call( obj ) ] || "object" : | |
| 342 | typeof obj; | |
| 343 | }, | |
| 344 | ||
| 345 | // Evaluates a script in a global context | |
| 346 | globalEval: function( code ) { | |
| 347 | DOMEval( code ); | |
| 348 | }, | |
| 349 | ||
| 350 | // Convert dashed to camelCase; used by the css and data modules | |
| 351 | // Support: IE <=9 - 11, Edge 12 - 13 | |
| 352 | // Microsoft forgot to hump their vendor prefix (#9572) | |
| 353 | camelCase: function( string ) { | |
| 354 | return string.replace( rmsPrefix, "ms-" ).replace( rdashAlpha, fcamelCase ); | |
| 355 | }, | |
| 356 | ||
| 357 | nodeName: function( elem, name ) { | |
| 358 | return elem.nodeName && elem.nodeName.toLowerCase() === name.toLowerCase(); | |
| 359 | }, | |
| 360 | ||
| 361 | each: function( obj, callback ) { | |
| 362 | var length, i = 0; | |
| 363 | ||
| 364 | if ( isArrayLike( obj ) ) { | |
| 365 | length = obj.length; | |
| 366 | for ( ; i < length; i++ ) { | |
| 367 | if ( callback.call( obj[ i ], i, obj[ i ] ) === false ) { | |
| 368 | break; | |
| 369 | } | |
| 370 | } | |
| 371 | } else { | |
| 372 | for ( i in obj ) { | |
| 373 | if ( callback.call( obj[ i ], i, obj[ i ] ) === false ) { | |
| 374 | break; | |
| 375 | } | |
| 376 | } | |
| 377 | } | |
| 378 | ||
| 379 | return obj; | |
| 380 | }, | |
| 381 | ||
| 382 | // Support: Android <=4.0 only | |
| 383 | trim: function( text ) { | |
| 384 | return text == null ? | |
| 385 | "" : | |
| 386 | ( text + "" ).replace( rtrim, "" ); | |
| 387 | }, | |
| 388 | ||
| 389 | // results is for internal usage only | |
| 390 | makeArray: function( arr, results ) { | |
| 391 | var ret = results || []; | |
| 392 | ||
| 393 | if ( arr != null ) { | |
| 394 | if ( isArrayLike( Object( arr ) ) ) { | |
| 395 | jQuery.merge( ret, | |
| 396 | typeof arr === "string" ? | |
| 397 | [ arr ] : arr | |
| 398 | ); | |
| 399 | } else { | |
| 400 | push.call( ret, arr ); | |
| 401 | } | |
| 402 | } | |
| 403 | ||
| 404 | return ret; | |
| 405 | }, | |
| 406 | ||
| 407 | inArray: function( elem, arr, i ) { | |
| 408 | return arr == null ? -1 : indexOf.call( arr, elem, i ); | |
| 409 | }, | |
| 410 | ||
| 411 | // Support: Android <=4.0 only, PhantomJS 1 only | |
| 412 | // push.apply(_, arraylike) throws on ancient WebKit | |
| 413 | merge: function( first, second ) { | |
| 414 | var len = +second.length, | |
| 415 | j = 0, | |
| 416 | i = first.length; | |
| 417 | ||
| 418 | for ( ; j < len; j++ ) { | |
| 419 | first[ i++ ] = second[ j ]; | |
| 420 | } | |
| 421 | ||
| 422 | first.length = i; | |
| 423 | ||
| 424 | return first; | |
| 425 | }, | |
| 426 | ||
| 427 | grep: function( elems, callback, invert ) { | |
| 428 | var callbackInverse, | |
| 429 | matches = [], | |
| 430 | i = 0, | |
| 431 | length = elems.length, | |
| 432 | callbackExpect = !invert; | |
| 433 | ||
| 434 | // Go through the array, only saving the items | |
| 435 | // that pass the validator function | |
| 436 | for ( ; i < length; i++ ) { | |
| 437 | callbackInverse = !callback( elems[ i ], i ); | |
| 438 | if ( callbackInverse !== callbackExpect ) { | |
| 439 | matches.push( elems[ i ] ); | |
| 440 | } | |
| 441 | } | |
| 442 | ||
| 443 | return matches; | |
| 444 | }, | |
| 445 | ||
| 446 | // arg is for internal usage only | |
| 447 | map: function( elems, callback, arg ) { | |
| 448 | var length, value, | |
| 449 | i = 0, | |
| 450 | ret = []; | |
| 451 | ||
| 452 | // Go through the array, translating each of the items to their new values | |
| 453 | if ( isArrayLike( elems ) ) { | |
| 454 | length = elems.length; | |
| 455 | for ( ; i < length; i++ ) { | |
| 456 | value = callback( elems[ i ], i, arg ); | |
| 457 | ||
| 458 | if ( value != null ) { | |
| 459 | ret.push( value ); | |
| 460 | } | |
| 461 | } | |
| 462 | ||
| 463 | // Go through every key on the object, | |
| 464 | } else { | |
| 465 | for ( i in elems ) { | |
| 466 | value = callback( elems[ i ], i, arg ); | |
| 467 | ||
| 468 | if ( value != null ) { | |
| 469 | ret.push( value ); | |
| 470 | } | |
| 471 | } | |
| 472 | } | |
| 473 | ||
| 474 | // Flatten any nested arrays | |
| 475 | return concat.apply( [], ret ); | |
| 476 | }, | |
| 477 | ||
| 478 | // A global GUID counter for objects | |
| 479 | guid: 1, | |
| 480 | ||
| 481 | // Bind a function to a context, optionally partially applying any | |
| 482 | // arguments. | |
| 483 | proxy: function( fn, context ) { | |
| 484 | var tmp, args, proxy; | |
| 485 | ||
| 486 | if ( typeof context === "string" ) { | |
| 487 | tmp = fn[ context ]; | |
| 488 | context = fn; | |
| 489 | fn = tmp; | |
| 490 | } | |
| 491 | ||
| 492 | // Quick check to determine if target is callable, in the spec | |
| 493 | // this throws a TypeError, but we will just return undefined. | |
| 494 | if ( !jQuery.isFunction( fn ) ) { | |
| 495 | return undefined; | |
| 496 | } | |
| 497 | ||
| 498 | // Simulated bind | |
| 499 | args = slice.call( arguments, 2 ); | |
| 500 | proxy = function() { | |
| 501 | return fn.apply( context || this, args.concat( slice.call( arguments ) ) ); | |
| 502 | }; | |
| 503 | ||
| 504 | // Set the guid of unique handler to the same of original handler, so it can be removed | |
| 505 | proxy.guid = fn.guid = fn.guid || jQuery.guid++; | |
| 506 | ||
| 507 | return proxy; | |
| 508 | }, | |
| 509 | ||
| 510 | now: Date.now, | |
| 511 | ||
| 512 | // jQuery.support is not used in Core but other projects attach their | |
| 513 | // properties to it so it needs to exist. | |
| 514 | support: support | |
| 515 | } ); | |
| 516 | ||
| 517 | if ( typeof Symbol === "function" ) { | |
| 518 | jQuery.fn[ Symbol.iterator ] = arr[ Symbol.iterator ]; | |
| 519 | } | |
| 520 | ||
| 521 | // Populate the class2type map | |
| 522 | jQuery.each( "Boolean Number String Function Array Date RegExp Object Error Symbol".split( " " ), | |
| 523 | function( i, name ) { | |
| 524 | class2type[ "[object " + name + "]" ] = name.toLowerCase(); | |
| 525 | } ); | |
| 526 | ||
| 527 | function isArrayLike( obj ) { | |
| 528 | ||
| 529 | // Support: real iOS 8.2 only (not reproducible in simulator) | |
| 530 | // `in` check used to prevent JIT error (gh-2145) | |
| 531 | // hasOwn isn't used here due to false negatives | |
| 532 | // regarding Nodelist length in IE | |
| 533 | var length = !!obj && "length" in obj && obj.length, | |
| 534 | type = jQuery.type( obj ); | |
| 535 | ||
| 536 | if ( type === "function" || jQuery.isWindow( obj ) ) { | |
| 537 | return false; | |
| 538 | } | |
| 539 | ||
| 540 | return type === "array" || length === 0 || | |
| 541 | typeof length === "number" && length > 0 && ( length - 1 ) in obj; | |
| 542 | } | |
| 543 | var Sizzle = | |
| 544 | /*! | |
| 545 | * Sizzle CSS Selector Engine v2.3.0 | |
| 546 | * https://sizzlejs.com/ | |
| 547 | * | |
| 548 | * Copyright jQuery Foundation and other contributors | |
| 549 | * Released under the MIT license | |
| 550 | * http://jquery.org/license | |
| 551 | * | |
| 552 | * Date: 2016-01-04 | |
| 553 | */ | |
| 554 | (function( window ) { | |
| 555 | ||
| 556 | var i, | |
| 557 | support, | |
| 558 | Expr, | |
| 559 | getText, | |
| 560 | isXML, | |
| 561 | tokenize, | |
| 562 | compile, | |
| 563 | select, | |
| 564 | outermostContext, | |
| 565 | sortInput, | |
| 566 | hasDuplicate, | |
| 567 | ||
| 568 | // Local document vars | |
| 569 | setDocument, | |
| 570 | document, | |
| 571 | docElem, | |
| 572 | documentIsHTML, | |
| 573 | rbuggyQSA, | |
| 574 | rbuggyMatches, | |
| 575 | matches, | |
| 576 | contains, | |
| 577 | ||
| 578 | // Instance-specific data | |
| 579 | expando = "sizzle" + 1 * new Date(), | |
| 580 | preferredDoc = window.document, | |
| 581 | dirruns = 0, | |
| 582 | done = 0, | |
| 583 | classCache = createCache(), | |
| 584 | tokenCache = createCache(), | |
| 585 | compilerCache = createCache(), | |
| 586 | sortOrder = function( a, b ) { | |
| 587 | if ( a === b ) { | |
| 588 | hasDuplicate = true; | |
| 589 | } | |
| 590 | return 0; | |
| 591 | }, | |
| 592 | ||
| 593 | // Instance methods | |
| 594 | hasOwn = ({}).hasOwnProperty, | |
| 595 | arr = [], | |
| 596 | pop = arr.pop, | |
| 597 | push_native = arr.push, | |
| 598 | push = arr.push, | |
| 599 | slice = arr.slice, | |
| 600 | // Use a stripped-down indexOf as it's faster than native | |
| 601 | // https://jsperf.com/thor-indexof-vs-for/5 | |
| 602 | indexOf = function( list, elem ) { | |
| 603 | var i = 0, | |
| 604 | len = list.length; | |
| 605 | for ( ; i < len; i++ ) { | |
| 606 | if ( list[i] === elem ) { | |
| 607 | return i; | |
| 608 | } | |
| 609 | } | |
| 610 | return -1; | |
| 611 | }, | |
| 612 | ||
| 613 | booleans = "checked|selected|async|autofocus|autoplay|controls|defer|disabled|hidden|ismap|loop|multiple|open|readonly|required|scoped", | |
| 614 | ||
| 615 | // Regular expressions | |
| 616 | ||
| 617 | // http://www.w3.org/TR/css3-selectors/#whitespace | |
| 618 | whitespace = "[\\x20\\t\\r\\n\\f]", | |
| 619 | ||
| 620 | // http://www.w3.org/TR/CSS21/syndata.html#value-def-identifier | |
| 621 | identifier = "(?:\\\\.|[\\w-]|[^\0-\\xa0])+", | |
| 622 | ||
| 623 | // Attribute selectors: http://www.w3.org/TR/selectors/#attribute-selectors | |
| 624 | attributes = "\\[" + whitespace + "*(" + identifier + ")(?:" + whitespace + | |
| 625 | // Operator (capture 2) | |
| 626 | "*([*^$|!~]?=)" + whitespace + | |
| 627 | // "Attribute values must be CSS identifiers [capture 5] or strings [capture 3 or capture 4]" | |
| 628 | "*(?:'((?:\\\\.|[^\\\\'])*)'|\"((?:\\\\.|[^\\\\\"])*)\"|(" + identifier + "))|)" + whitespace + | |
| 629 | "*\\]", | |
| 630 | ||
| 631 | pseudos = ":(" + identifier + ")(?:\\((" + | |
| 632 | // To reduce the number of selectors needing tokenize in the preFilter, prefer arguments: | |
| 633 | // 1. quoted (capture 3; capture 4 or capture 5) | |
| 634 | "('((?:\\\\.|[^\\\\'])*)'|\"((?:\\\\.|[^\\\\\"])*)\")|" + | |
| 635 | // 2. simple (capture 6) | |
| 636 | "((?:\\\\.|[^\\\\()[\\]]|" + attributes + ")*)|" + | |
| 637 | // 3. anything else (capture 2) | |
| 638 | ".*" + | |
| 639 | ")\\)|)", | |
| 640 | ||
| 641 | // Leading and non-escaped trailing whitespace, capturing some non-whitespace characters preceding the latter | |
| 642 | rwhitespace = new RegExp( whitespace + "+", "g" ), | |
| 643 | rtrim = new RegExp( "^" + whitespace + "+|((?:^|[^\\\\])(?:\\\\.)*)" + whitespace + "+$", "g" ), | |
| 644 | ||
| 645 | rcomma = new RegExp( "^" + whitespace + "*," + whitespace + "*" ), | |
| 646 | rcombinators = new RegExp( "^" + whitespace + "*([>+~]|" + whitespace + ")" + whitespace + "*" ), | |
| 647 | ||
| 648 | rattributeQuotes = new RegExp( "=" + whitespace + "*([^\\]'\"]*?)" + whitespace + "*\\]", "g" ), | |
| 649 | ||
| 650 | rpseudo = new RegExp( pseudos ), | |
| 651 | ridentifier = new RegExp( "^" + identifier + "$" ), | |
| 652 | ||
| 653 | matchExpr = { | |
| 654 | "ID": new RegExp( "^#(" + identifier + ")" ), | |
| 655 | "CLASS": new RegExp( "^\\.(" + identifier + ")" ), | |
| 656 | "TAG": new RegExp( "^(" + identifier + "|[*])" ), | |
| 657 | "ATTR": new RegExp( "^" + attributes ), | |
| 658 | "PSEUDO": new RegExp( "^" + pseudos ), | |
| 659 | "CHILD": new RegExp( "^:(only|first|last|nth|nth-last)-(child|of-type)(?:\\(" + whitespace + | |
| 660 | "*(even|odd|(([+-]|)(\\d*)n|)" + whitespace + "*(?:([+-]|)" + whitespace + | |
| 661 | "*(\\d+)|))" + whitespace + "*\\)|)", "i" ), | |
| 662 | "bool": new RegExp( "^(?:" + booleans + ")$", "i" ), | |
| 663 | // For use in libraries implementing .is() | |
| 664 | // We use this for POS matching in `select` | |
| 665 | "needsContext": new RegExp( "^" + whitespace + "*[>+~]|:(even|odd|eq|gt|lt|nth|first|last)(?:\\(" + | |
| 666 | whitespace + "*((?:-\\d)?\\d*)" + whitespace + "*\\)|)(?=[^-]|$)", "i" ) | |
| 667 | }, | |
| 668 | ||
| 669 | rinputs = /^(?:input|select|textarea|button)$/i, | |
| 670 | rheader = /^h\d$/i, | |
| 671 | ||
| 672 | rnative = /^[^{]+\{\s*\[native \w/, | |
| 673 | ||
| 674 | // Easily-parseable/retrievable ID or TAG or CLASS selectors | |
| 675 | rquickExpr = /^(?:#([\w-]+)|(\w+)|\.([\w-]+))$/, | |
| 676 | ||
| 677 | rsibling = /[+~]/, | |
| 678 | ||
| 679 | // CSS escapes | |
| 680 | // http://www.w3.org/TR/CSS21/syndata.html#escaped-characters | |
| 681 | runescape = new RegExp( "\\\\([\\da-f]{1,6}" + whitespace + "?|(" + whitespace + ")|.)", "ig" ), | |
| 682 | funescape = function( _, escaped, escapedWhitespace ) { | |
| 683 | var high = "0x" + escaped - 0x10000; | |
| 684 | // NaN means non-codepoint | |
| 685 | // Support: Firefox<24 | |
| 686 | // Workaround erroneous numeric interpretation of +"0x" | |
| 687 | return high !== high || escapedWhitespace ? | |
| 688 | escaped : | |
| 689 | high < 0 ? | |
| 690 | // BMP codepoint | |
| 691 | String.fromCharCode( high + 0x10000 ) : | |
| 692 | // Supplemental Plane codepoint (surrogate pair) | |
| 693 | String.fromCharCode( high >> 10 | 0xD800, high & 0x3FF | 0xDC00 ); | |
| 694 | }, | |
| 695 | ||
| 696 | // CSS string/identifier serialization | |
| 697 | // https://drafts.csswg.org/cssom/#common-serializing-idioms | |
| 698 | rcssescape = /([\0-\x1f\x7f]|^-?\d)|^-$|[^\x80-\uFFFF\w-]/g, | |
| 699 | fcssescape = function( ch, asCodePoint ) { | |
| 700 | if ( asCodePoint ) { | |
| 701 | ||
| 702 | // U+0000 NULL becomes U+FFFD REPLACEMENT CHARACTER | |
| 703 | if ( ch === "\0" ) { | |
| 704 | return "\uFFFD"; | |
| 705 | } | |
| 706 | ||
| 707 | // Control characters and (dependent upon position) numbers get escaped as code points | |
| 708 | return ch.slice( 0, -1 ) + "\\" + ch.charCodeAt( ch.length - 1 ).toString( 16 ) + " "; | |
| 709 | } | |
| 710 | ||
| 711 | // Other potentially-special ASCII characters get backslash-escaped | |
| 712 | return "\\" + ch; | |
| 713 | }, | |
| 714 | ||
| 715 | // Used for iframes | |
| 716 | // See setDocument() | |
| 717 | // Removing the function wrapper causes a "Permission Denied" | |
| 718 | // error in IE | |
| 719 | unloadHandler = function() { | |
| 720 | setDocument(); | |
| 721 | }, | |
| 722 | ||
| 723 | disabledAncestor = addCombinator( | |
| 724 | function( elem ) { | |
| 725 | return elem.disabled === true; | |
| 726 | }, | |
| 727 | { dir: "parentNode", next: "legend" } | |
| 728 | ); | |
| 729 | ||
| 730 | // Optimize for push.apply( _, NodeList ) | |
| 731 | try { | |
| 732 | push.apply( | |
| 733 | (arr = slice.call( preferredDoc.childNodes )), | |
| 734 | preferredDoc.childNodes | |
| 735 | ); | |
| 736 | // Support: Android<4.0 | |
| 737 | // Detect silently failing push.apply | |
| 738 | arr[ preferredDoc.childNodes.length ].nodeType; | |
| 739 | } catch ( e ) { | |
| 740 | push = { apply: arr.length ? | |
| 741 | ||
| 742 | // Leverage slice if possible | |
| 743 | function( target, els ) { | |
| 744 | push_native.apply( target, slice.call(els) ); | |
| 745 | } : | |
| 746 | ||
| 747 | // Support: IE<9 | |
| 748 | // Otherwise append directly | |
| 749 | function( target, els ) { | |
| 750 | var j = target.length, | |
| 751 | i = 0; | |
| 752 | // Can't trust NodeList.length | |
| 753 | while ( (target[j++] = els[i++]) ) {} | |
| 754 | target.length = j - 1; | |
| 755 | } | |
| 756 | }; | |
| 757 | } | |
| 758 | ||
| 759 | function Sizzle( selector, context, results, seed ) { | |
| 760 | var m, i, elem, nid, match, groups, newSelector, | |
| 761 | newContext = context && context.ownerDocument, | |
| 762 | ||
| 763 | // nodeType defaults to 9, since context defaults to document | |
| 764 | nodeType = context ? context.nodeType : 9; | |
| 765 | ||
| 766 | results = results || []; | |
| 767 | ||
| 768 | // Return early from calls with invalid selector or context | |
| 769 | if ( typeof selector !== "string" || !selector || | |
| 770 | nodeType !== 1 && nodeType !== 9 && nodeType !== 11 ) { | |
| 771 | ||
| 772 | return results; | |
| 773 | } | |
| 774 | ||
| 775 | // Try to shortcut find operations (as opposed to filters) in HTML documents | |
| 776 | if ( !seed ) { | |
| 777 | ||
| 778 | if ( ( context ? context.ownerDocument || context : preferredDoc ) !== document ) { | |
| 779 | setDocument( context ); | |
| 780 | } | |
| 781 | context = context || document; | |
| 782 | ||
| 783 | if ( documentIsHTML ) { | |
| 784 | ||
| 785 | // If the selector is sufficiently simple, try using a "get*By*" DOM method | |
| 786 | // (excepting DocumentFragment context, where the methods don't exist) | |
| 787 | if ( nodeType !== 11 && (match = rquickExpr.exec( selector )) ) { | |
| 788 | ||
| 789 | // ID selector | |
| 790 | if ( (m = match[1]) ) { | |
| 791 | ||
| 792 | // Document context | |
| 793 | if ( nodeType === 9 ) { | |
| 794 | if ( (elem = context.getElementById( m )) ) { | |
| 795 | ||
| 796 | // Support: IE, Opera, Webkit | |
| 797 | // TODO: identify versions | |
| 798 | // getElementById can match elements by name instead of ID | |
| 799 | if ( elem.id === m ) { | |
| 800 | results.push( elem ); | |
| 801 | return results; | |
| 802 | } | |
| 803 | } else { | |
| 804 | return results; | |
| 805 | } | |
| 806 | ||
| 807 | // Element context | |
| 808 | } else { | |
| 809 | ||
| 810 | // Support: IE, Opera, Webkit | |
| 811 | // TODO: identify versions | |
| 812 | // getElementById can match elements by name instead of ID | |
| 813 | if ( newContext && (elem = newContext.getElementById( m )) && | |
| 814 | contains( context, elem ) && | |
| 815 | elem.id === m ) { | |
| 816 | ||
| 817 | results.push( elem ); | |
| 818 | return results; | |
| 819 | } | |
| 820 | } | |
| 821 | ||
| 822 | // Type selector | |
| 823 | } else if ( match[2] ) { | |
| 824 | push.apply( results, context.getElementsByTagName( selector ) ); | |
| 825 | return results; | |
| 826 | ||
| 827 | // Class selector | |
| 828 | } else if ( (m = match[3]) && support.getElementsByClassName && | |
| 829 | context.getElementsByClassName ) { | |
| 830 | ||
| 831 | push.apply( results, context.getElementsByClassName( m ) ); | |
| 832 | return results; | |
| 833 | } | |
| 834 | } | |
| 835 | ||
| 836 | // Take advantage of querySelectorAll | |
| 837 | if ( support.qsa && | |
| 838 | !compilerCache[ selector + " " ] && | |
| 839 | (!rbuggyQSA || !rbuggyQSA.test( selector )) ) { | |
| 840 | ||
| 841 | if ( nodeType !== 1 ) { | |
| 842 | newContext = context; | |
| 843 | newSelector = selector; | |
| 844 | ||
| 845 | // qSA looks outside Element context, which is not what we want | |
| 846 | // Thanks to Andrew Dupont for this workaround technique | |
| 847 | // Support: IE <=8 | |
| 848 | // Exclude object elements | |
| 849 | } else if ( context.nodeName.toLowerCase() !== "object" ) { | |
| 850 | ||
| 851 | // Capture the context ID, setting it first if necessary | |
| 852 | if ( (nid = context.getAttribute( "id" )) ) { | |
| 853 | nid = nid.replace( rcssescape, fcssescape ); | |
| 854 | } else { | |
| 855 | context.setAttribute( "id", (nid = expando) ); | |
| 856 | } | |
| 857 | ||
| 858 | // Prefix every selector in the list | |
| 859 | groups = tokenize( selector ); | |
| 860 | i = groups.length; | |
| 861 | while ( i-- ) { | |
| 862 | groups[i] = "#" + nid + " " + toSelector( groups[i] ); | |
| 863 | } | |
| 864 | newSelector = groups.join( "," ); | |
| 865 | ||
| 866 | // Expand context for sibling selectors | |
| 867 | newContext = rsibling.test( selector ) && testContext( context.parentNode ) || | |
| 868 | context; | |
| 869 | } | |
| 870 | ||
| 871 | if ( newSelector ) { | |
| 872 | try { | |
| 873 | push.apply( results, | |
| 874 | newContext.querySelectorAll( newSelector ) | |
| 875 | ); | |
| 876 | return results; | |
| 877 | } catch ( qsaError ) { | |
| 878 | } finally { | |
| 879 | if ( nid === expando ) { | |
| 880 | context.removeAttribute( "id" ); | |
| 881 | } | |
| 882 | } | |
| 883 | } | |
| 884 | } | |
| 885 | } | |
| 886 | } | |
| 887 | ||
| 888 | // All others | |
| 889 | return select( selector.replace( rtrim, "$1" ), context, results, seed ); | |
| 890 | } | |
| 891 | ||
| 892 | /** | |
| 893 | * Create key-value caches of limited size | |
| 894 | * @returns {function(string, object)} Returns the Object data after storing it on itself with | |
| 895 | * property name the (space-suffixed) string and (if the cache is larger than Expr.cacheLength) | |
| 896 | * deleting the oldest entry | |
| 897 | */ | |
| 898 | function createCache() { | |
| 899 | var keys = []; | |
| 900 | ||
| 901 | function cache( key, value ) { | |
| 902 | // Use (key + " ") to avoid collision with native prototype properties (see Issue #157) | |
| 903 | if ( keys.push( key + " " ) > Expr.cacheLength ) { | |
| 904 | // Only keep the most recent entries | |
| 905 | delete cache[ keys.shift() ]; | |
| 906 | } | |
| 907 | return (cache[ key + " " ] = value); | |
| 908 | } | |
| 909 | return cache; | |
| 910 | } | |
| 911 | ||
| 912 | /** | |
| 913 | * Mark a function for special use by Sizzle | |
| 914 | * @param {Function} fn The function to mark | |
| 915 | */ | |
| 916 | function markFunction( fn ) { | |
| 917 | fn[ expando ] = true; | |
| 918 | return fn; | |
| 919 | } | |
| 920 | ||
| 921 | /** | |
| 922 | * Support testing using an element | |
| 923 | * @param {Function} fn Passed the created element and returns a boolean result | |
| 924 | */ | |
| 925 | function assert( fn ) { | |
| 926 | var el = document.createElement("fieldset"); | |
| 927 | ||
| 928 | try { | |
| 929 | return !!fn( el ); | |
| 930 | } catch (e) { | |
| 931 | return false; | |
| 932 | } finally { | |
| 933 | // Remove from its parent by default | |
| 934 | if ( el.parentNode ) { | |
| 935 | el.parentNode.removeChild( el ); | |
| 936 | } | |
| 937 | // release memory in IE | |
| 938 | el = null; | |
| 939 | } | |
| 940 | } | |
| 941 | ||
| 942 | /** | |
| 943 | * Adds the same handler for all of the specified attrs | |
| 944 | * @param {String} attrs Pipe-separated list of attributes | |
| 945 | * @param {Function} handler The method that will be applied | |
| 946 | */ | |
| 947 | function addHandle( attrs, handler ) { | |
| 948 | var arr = attrs.split("|"), | |
| 949 | i = arr.length; | |
| 950 | ||
| 951 | while ( i-- ) { | |
| 952 | Expr.attrHandle[ arr[i] ] = handler; | |
| 953 | } | |
| 954 | } | |
| 955 | ||
| 956 | /** | |
| 957 | * Checks document order of two siblings | |
| 958 | * @param {Element} a | |
| 959 | * @param {Element} b | |
| 960 | * @returns {Number} Returns less than 0 if a precedes b, greater than 0 if a follows b | |
| 961 | */ | |
| 962 | function siblingCheck( a, b ) { | |
| 963 | var cur = b && a, | |
| 964 | diff = cur && a.nodeType === 1 && b.nodeType === 1 && | |
| 965 | a.sourceIndex - b.sourceIndex; | |
| 966 | ||
| 967 | // Use IE sourceIndex if available on both nodes | |
| 968 | if ( diff ) { | |
| 969 | return diff; | |
| 970 | } | |
| 971 | ||
| 972 | // Check if b follows a | |
| 973 | if ( cur ) { | |
| 974 | while ( (cur = cur.nextSibling) ) { | |
| 975 | if ( cur === b ) { | |
| 976 | return -1; | |
| 977 | } | |
| 978 | } | |
| 979 | } | |
| 980 | ||
| 981 | return a ? 1 : -1; | |
| 982 | } | |
| 983 | ||
| 984 | /** | |
| 985 | * Returns a function to use in pseudos for input types | |
| 986 | * @param {String} type | |
| 987 | */ | |
| 988 | function createInputPseudo( type ) { | |
| 989 | return function( elem ) { | |
| 990 | var name = elem.nodeName.toLowerCase(); | |
| 991 | return name === "input" && elem.type === type; | |
| 992 | }; | |
| 993 | } | |
| 994 | ||
| 995 | /** | |
| 996 | * Returns a function to use in pseudos for buttons | |
| 997 | * @param {String} type | |
| 998 | */ | |
| 999 | function createButtonPseudo( type ) { | |
| 1000 | return function( elem ) { | |
| 1001 | var name = elem.nodeName.toLowerCase(); | |
| 1002 | return (name === "input" || name === "button") && elem.type === type; | |
| 1003 | }; | |
| 1004 | } | |
| 1005 | ||
| 1006 | /** | |
| 1007 | * Returns a function to use in pseudos for :enabled/:disabled | |
| 1008 | * @param {Boolean} disabled true for :disabled; false for :enabled | |
| 1009 | */ | |
| 1010 | function createDisabledPseudo( disabled ) { | |
| 1011 | // Known :disabled false positives: | |
| 1012 | // IE: *[disabled]:not(button, input, select, textarea, optgroup, option, menuitem, fieldset) | |
| 1013 | // not IE: fieldset[disabled] > legend:nth-of-type(n+2) :can-disable | |
| 1014 | return function( elem ) { | |
| 1015 | ||
| 1016 | // Check form elements and option elements for explicit disabling | |
| 1017 | return "label" in elem && elem.disabled === disabled || | |
| 1018 | "form" in elem && elem.disabled === disabled || | |
| 1019 | ||
| 1020 | // Check non-disabled form elements for fieldset[disabled] ancestors | |
| 1021 | "form" in elem && elem.disabled === false && ( | |
| 1022 | // Support: IE6-11+ | |
| 1023 | // Ancestry is covered for us | |
| 1024 | elem.isDisabled === disabled || | |
| 1025 | ||
| 1026 | // Otherwise, assume any non-<option> under fieldset[disabled] is disabled | |
| 1027 | /* jshint -W018 */ | |
| 1028 | elem.isDisabled !== !disabled && | |
| 1029 | ("label" in elem || !disabledAncestor( elem )) !== disabled | |
| 1030 | ); | |
| 1031 | }; | |
| 1032 | } | |
| 1033 | ||
| 1034 | /** | |
| 1035 | * Returns a function to use in pseudos for positionals | |
| 1036 | * @param {Function} fn | |
| 1037 | */ | |
| 1038 | function createPositionalPseudo( fn ) { | |
| 1039 | return markFunction(function( argument ) { | |
| 1040 | argument = +argument; | |
| 1041 | return markFunction(function( seed, matches ) { | |
| 1042 | var j, | |
| 1043 | matchIndexes = fn( [], seed.length, argument ), | |
| 1044 | i = matchIndexes.length; | |
| 1045 | ||
| 1046 | // Match elements found at the specified indexes | |
| 1047 | while ( i-- ) { | |
| 1048 | if ( seed[ (j = matchIndexes[i]) ] ) { | |
| 1049 | seed[j] = !(matches[j] = seed[j]); | |
| 1050 | } | |
| 1051 | } | |
| 1052 | }); | |
| 1053 | }); | |
| 1054 | } | |
| 1055 | ||
| 1056 | /** | |
| 1057 | * Checks a node for validity as a Sizzle context | |
| 1058 | * @param {Element|Object=} context | |
| 1059 | * @returns {Element|Object|Boolean} The input node if acceptable, otherwise a falsy value | |
| 1060 | */ | |
| 1061 | function testContext( context ) { | |
| 1062 | return context && typeof context.getElementsByTagName !== "undefined" && context; | |
| 1063 | } | |
| 1064 | ||
| 1065 | // Expose support vars for convenience | |
| 1066 | support = Sizzle.support = {}; | |
| 1067 | ||
| 1068 | /** | |
| 1069 | * Detects XML nodes | |
| 1070 | * @param {Element|Object} elem An element or a document | |
| 1071 | * @returns {Boolean} True iff elem is a non-HTML XML node | |
| 1072 | */ | |
| 1073 | isXML = Sizzle.isXML = function( elem ) { | |
| 1074 | // documentElement is verified for cases where it doesn't yet exist | |
| 1075 | // (such as loading iframes in IE - #4833) | |
| 1076 | var documentElement = elem && (elem.ownerDocument || elem).documentElement; | |
| 1077 | return documentElement ? documentElement.nodeName !== "HTML" : false; | |
| 1078 | }; | |
| 1079 | ||
| 1080 | /** | |
| 1081 | * Sets document-related variables once based on the current document | |
| 1082 | * @param {Element|Object} [doc] An element or document object to use to set the document | |
| 1083 | * @returns {Object} Returns the current document | |
| 1084 | */ | |
| 1085 | setDocument = Sizzle.setDocument = function( node ) { | |
| 1086 | var hasCompare, subWindow, | |
| 1087 | doc = node ? node.ownerDocument || node : preferredDoc; | |
| 1088 | ||
| 1089 | // Return early if doc is invalid or already selected | |
| 1090 | if ( doc === document || doc.nodeType !== 9 || !doc.documentElement ) { | |
| 1091 | return document; | |
| 1092 | } | |
| 1093 | ||
| 1094 | // Update global variables | |
| 1095 | document = doc; | |
| 1096 | docElem = document.documentElement; | |
| 1097 | documentIsHTML = !isXML( document ); | |
| 1098 | ||
| 1099 | // Support: IE 9-11, Edge | |
| 1100 | // Accessing iframe documents after unload throws "permission denied" errors (jQuery #13936) | |
| 1101 | if ( preferredDoc !== document && | |
| 1102 | (subWindow = document.defaultView) && subWindow.top !== subWindow ) { | |
| 1103 | ||
| 1104 | // Support: IE 11, Edge | |
| 1105 | if ( subWindow.addEventListener ) { | |
| 1106 | subWindow.addEventListener( "unload", unloadHandler, false ); | |
| 1107 | ||
| 1108 | // Support: IE 9 - 10 only | |
| 1109 | } else if ( subWindow.attachEvent ) { | |
| 1110 | subWindow.attachEvent( "onunload", unloadHandler ); | |
| 1111 | } | |
| 1112 | } | |
| 1113 | ||
| 1114 | /* Attributes | |
| 1115 | ---------------------------------------------------------------------- */ | |
| 1116 | ||
| 1117 | // Support: IE<8 | |
| 1118 | // Verify that getAttribute really returns attributes and not properties | |
| 1119 | // (excepting IE8 booleans) | |
| 1120 | support.attributes = assert(function( el ) { | |
| 1121 | el.className = "i"; | |
| 1122 | return !el.getAttribute("className"); | |
| 1123 | }); | |
| 1124 | ||
| 1125 | /* getElement(s)By* | |
| 1126 | ---------------------------------------------------------------------- */ | |
| 1127 | ||
| 1128 | // Check if getElementsByTagName("*") returns only elements | |
| 1129 | support.getElementsByTagName = assert(function( el ) { | |
| 1130 | el.appendChild( document.createComment("") ); | |
| 1131 | return !el.getElementsByTagName("*").length; | |
| 1132 | }); | |
| 1133 | ||
| 1134 | // Support: IE<9 | |
| 1135 | support.getElementsByClassName = rnative.test( document.getElementsByClassName ); | |
| 1136 | ||
| 1137 | // Support: IE<10 | |
| 1138 | // Check if getElementById returns elements by name | |
| 1139 | // The broken getElementById methods don't pick up programmatically-set names, | |
| 1140 | // so use a roundabout getElementsByName test | |
| 1141 | support.getById = assert(function( el ) { | |
| 1142 | docElem.appendChild( el ).id = expando; | |
| 1143 | return !document.getElementsByName || !document.getElementsByName( expando ).length; | |
| 1144 | }); | |
| 1145 | ||
| 1146 | // ID find and filter | |
| 1147 | if ( support.getById ) { | |
| 1148 | Expr.find["ID"] = function( id, context ) { | |
| 1149 | if ( typeof context.getElementById !== "undefined" && documentIsHTML ) { | |
| 1150 | var m = context.getElementById( id ); | |
| 1151 | return m ? [ m ] : []; | |
| 1152 | } | |
| 1153 | }; | |
| 1154 | Expr.filter["ID"] = function( id ) { | |
| 1155 | var attrId = id.replace( runescape, funescape ); | |
| 1156 | return function( elem ) { | |
| 1157 | return elem.getAttribute("id") === attrId; | |
| 1158 | }; | |
| 1159 | }; | |
| 1160 | } else { | |
| 1161 | // Support: IE6/7 | |
| 1162 | // getElementById is not reliable as a find shortcut | |
| 1163 | delete Expr.find["ID"]; | |
| 1164 | ||
| 1165 | Expr.filter["ID"] = function( id ) { | |
| 1166 | var attrId = id.replace( runescape, funescape ); | |
| 1167 | return function( elem ) { | |
| 1168 | var node = typeof elem.getAttributeNode !== "undefined" && | |
| 1169 | elem.getAttributeNode("id"); | |
| 1170 | return node && node.value === attrId; | |
| 1171 | }; | |
| 1172 | }; | |
| 1173 | } | |
| 1174 | ||
| 1175 | // Tag | |
| 1176 | Expr.find["TAG"] = support.getElementsByTagName ? | |
| 1177 | function( tag, context ) { | |
| 1178 | if ( typeof context.getElementsByTagName !== "undefined" ) { | |
| 1179 | return context.getElementsByTagName( tag ); | |
| 1180 | ||
| 1181 | // DocumentFragment nodes don't have gEBTN | |
| 1182 | } else if ( support.qsa ) { | |
| 1183 | return context.querySelectorAll( tag ); | |
| 1184 | } | |
| 1185 | } : | |
| 1186 | ||
| 1187 | function( tag, context ) { | |
| 1188 | var elem, | |
| 1189 | tmp = [], | |
| 1190 | i = 0, | |
| 1191 | // By happy coincidence, a (broken) gEBTN appears on DocumentFragment nodes too | |
| 1192 | results = context.getElementsByTagName( tag ); | |
| 1193 | ||
| 1194 | // Filter out possible comments | |
| 1195 | if ( tag === "*" ) { | |
| 1196 | while ( (elem = results[i++]) ) { | |
| 1197 | if ( elem.nodeType === 1 ) { | |
| 1198 | tmp.push( elem ); | |
| 1199 | } | |
| 1200 | } | |
| 1201 | ||
| 1202 | return tmp; | |
| 1203 | } | |
| 1204 | return results; | |
| 1205 | }; | |
| 1206 | ||
| 1207 | // Class | |
| 1208 | Expr.find["CLASS"] = support.getElementsByClassName && function( className, context ) { | |
| 1209 | if ( typeof context.getElementsByClassName !== "undefined" && documentIsHTML ) { | |
| 1210 | return context.getElementsByClassName( className ); | |
| 1211 | } | |
| 1212 | }; | |
| 1213 | ||
| 1214 | /* QSA/matchesSelector | |
| 1215 | ---------------------------------------------------------------------- */ | |
| 1216 | ||
| 1217 | // QSA and matchesSelector support | |
| 1218 | ||
| 1219 | // matchesSelector(:active) reports false when true (IE9/Opera 11.5) | |
| 1220 | rbuggyMatches = []; | |
| 1221 | ||
| 1222 | // qSa(:focus) reports false when true (Chrome 21) | |
| 1223 | // We allow this because of a bug in IE8/9 that throws an error | |
| 1224 | // whenever `document.activeElement` is accessed on an iframe | |
| 1225 | // So, we allow :focus to pass through QSA all the time to avoid the IE error | |
| 1226 | // See https://bugs.jquery.com/ticket/13378 | |
| 1227 | rbuggyQSA = []; | |
| 1228 | ||
| 1229 | if ( (support.qsa = rnative.test( document.querySelectorAll )) ) { | |
| 1230 | // Build QSA regex | |
| 1231 | // Regex strategy adopted from Diego Perini | |
| 1232 | assert(function( el ) { | |
| 1233 | // Select is set to empty string on purpose | |
| 1234 | // This is to test IE's treatment of not explicitly | |
| 1235 | // setting a boolean content attribute, | |
| 1236 | // since its presence should be enough | |
| 1237 | // https://bugs.jquery.com/ticket/12359 | |
| 1238 | docElem.appendChild( el ).innerHTML = "<a id='" + expando + "'></a>" + | |
| 1239 | "<select id='" + expando + "-\r\\' msallowcapture=''>" + | |
| 1240 | "<option selected=''></option></select>"; | |
| 1241 | ||
| 1242 | // Support: IE8, Opera 11-12.16 | |
| 1243 | // Nothing should be selected when empty strings follow ^= or $= or *= | |
| 1244 | // The test attribute must be unknown in Opera but "safe" for WinRT | |
| 1245 | // https://msdn.microsoft.com/en-us/library/ie/hh465388.aspx#attribute_section | |
| 1246 | if ( el.querySelectorAll("[msallowcapture^='']").length ) { | |
| 1247 | rbuggyQSA.push( "[*^$]=" + whitespace + "*(?:''|\"\")" ); | |
| 1248 | } | |
| 1249 | ||
| 1250 | // Support: IE8 | |
| 1251 | // Boolean attributes and "value" are not treated correctly | |
| 1252 | if ( !el.querySelectorAll("[selected]").length ) { | |
| 1253 | rbuggyQSA.push( "\\[" + whitespace + "*(?:value|" + booleans + ")" ); | |
| 1254 | } | |
| 1255 | ||
| 1256 | // Support: Chrome<29, Android<4.4, Safari<7.0+, iOS<7.0+, PhantomJS<1.9.8+ | |
| 1257 | if ( !el.querySelectorAll( "[id~=" + expando + "-]" ).length ) { | |
| 1258 | rbuggyQSA.push("~="); | |
| 1259 | } | |
| 1260 | ||
| 1261 | // Webkit/Opera - :checked should return selected option elements | |
| 1262 | // http://www.w3.org/TR/2011/REC-css3-selectors-20110929/#checked | |
| 1263 | // IE8 throws error here and will not see later tests | |
| 1264 | if ( !el.querySelectorAll(":checked").length ) { | |
| 1265 | rbuggyQSA.push(":checked"); | |
| 1266 | } | |
| 1267 | ||
| 1268 | // Support: Safari 8+, iOS 8+ | |
| 1269 | // https://bugs.webkit.org/show_bug.cgi?id=136851 | |
| 1270 | // In-page `selector#id sibling-combinator selector` fails | |
| 1271 | if ( !el.querySelectorAll( "a#" + expando + "+*" ).length ) { | |
| 1272 | rbuggyQSA.push(".#.+[+~]"); | |
| 1273 | } | |
| 1274 | }); | |
| 1275 | ||
| 1276 | assert(function( el ) { | |
| 1277 | el.innerHTML = "<a href='' disabled='disabled'></a>" + | |
| 1278 | "<select disabled='disabled'><option/></select>"; | |
| 1279 | ||
| 1280 | // Support: Windows 8 Native Apps | |
| 1281 | // The type and name attributes are restricted during .innerHTML assignment | |
| 1282 | var input = document.createElement("input"); | |
| 1283 | input.setAttribute( "type", "hidden" ); | |
| 1284 | el.appendChild( input ).setAttribute( "name", "D" ); | |
| 1285 | ||
| 1286 | // Support: IE8 | |
| 1287 | // Enforce case-sensitivity of name attribute | |
| 1288 | if ( el.querySelectorAll("[name=d]").length ) { | |
| 1289 | rbuggyQSA.push( "name" + whitespace + "*[*^$|!~]?=" ); | |
| 1290 | } | |
| 1291 | ||
| 1292 | // FF 3.5 - :enabled/:disabled and hidden elements (hidden elements are still enabled) | |
| 1293 | // IE8 throws error here and will not see later tests | |
| 1294 | if ( el.querySelectorAll(":enabled").length !== 2 ) { | |
| 1295 | rbuggyQSA.push( ":enabled", ":disabled" ); | |
| 1296 | } | |
| 1297 | ||
| 1298 | // Support: IE9-11+ | |
| 1299 | // IE's :disabled selector does not pick up the children of disabled fieldsets | |
| 1300 | docElem.appendChild( el ).disabled = true; | |
| 1301 | if ( el.querySelectorAll(":disabled").length !== 2 ) { | |
| 1302 | rbuggyQSA.push( ":enabled", ":disabled" ); | |
| 1303 | } | |
| 1304 | ||
| 1305 | // Opera 10-11 does not throw on post-comma invalid pseudos | |
| 1306 | el.querySelectorAll("*,:x"); | |
| 1307 | rbuggyQSA.push(",.*:"); | |
| 1308 | }); | |
| 1309 | } | |
| 1310 | ||
| 1311 | if ( (support.matchesSelector = rnative.test( (matches = docElem.matches || | |
| 1312 | docElem.webkitMatchesSelector || | |
| 1313 | docElem.mozMatchesSelector || | |
| 1314 | docElem.oMatchesSelector || | |
| 1315 | docElem.msMatchesSelector) )) ) { | |
| 1316 | ||
| 1317 | assert(function( el ) { | |
| 1318 | // Check to see if it's possible to do matchesSelector | |
| 1319 | // on a disconnected node (IE 9) | |
| 1320 | support.disconnectedMatch = matches.call( el, "*" ); | |
| 1321 | ||
| 1322 | // This should fail with an exception | |
| 1323 | // Gecko does not error, returns false instead | |
| 1324 | matches.call( el, "[s!='']:x" ); | |
| 1325 | rbuggyMatches.push( "!=", pseudos ); | |
| 1326 | }); | |
| 1327 | } | |
| 1328 | ||
| 1329 | rbuggyQSA = rbuggyQSA.length && new RegExp( rbuggyQSA.join("|") ); | |
| 1330 | rbuggyMatches = rbuggyMatches.length && new RegExp( rbuggyMatches.join("|") ); | |
| 1331 | ||
| 1332 | /* Contains | |
| 1333 | ---------------------------------------------------------------------- */ | |
| 1334 | hasCompare = rnative.test( docElem.compareDocumentPosition ); | |
| 1335 | ||
| 1336 | // Element contains another | |
| 1337 | // Purposefully self-exclusive | |
| 1338 | // As in, an element does not contain itself | |
| 1339 | contains = hasCompare || rnative.test( docElem.contains ) ? | |
| 1340 | function( a, b ) { | |
| 1341 | var adown = a.nodeType === 9 ? a.documentElement : a, | |
| 1342 | bup = b && b.parentNode; | |
| 1343 | return a === bup || !!( bup && bup.nodeType === 1 && ( | |
| 1344 | adown.contains ? | |
| 1345 | adown.contains( bup ) : | |
| 1346 | a.compareDocumentPosition && a.compareDocumentPosition( bup ) & 16 | |
| 1347 | )); | |
| 1348 | } : | |
| 1349 | function( a, b ) { | |
| 1350 | if ( b ) { | |
| 1351 | while ( (b = b.parentNode) ) { | |
| 1352 | if ( b === a ) { | |
| 1353 | return true; | |
| 1354 | } | |
| 1355 | } | |
| 1356 | } | |
| 1357 | return false; | |
| 1358 | }; | |
| 1359 | ||
| 1360 | /* Sorting | |
| 1361 | ---------------------------------------------------------------------- */ | |
| 1362 | ||
| 1363 | // Document order sorting | |
| 1364 | sortOrder = hasCompare ? | |
| 1365 | function( a, b ) { | |
| 1366 | ||
| 1367 | // Flag for duplicate removal | |
| 1368 | if ( a === b ) { | |
| 1369 | hasDuplicate = true; | |
| 1370 | return 0; | |
| 1371 | } | |
| 1372 | ||
| 1373 | // Sort on method existence if only one input has compareDocumentPosition | |
| 1374 | var compare = !a.compareDocumentPosition - !b.compareDocumentPosition; | |
| 1375 | if ( compare ) { | |
| 1376 | return compare; | |
| 1377 | } | |
| 1378 | ||
| 1379 | // Calculate position if both inputs belong to the same document | |
| 1380 | compare = ( a.ownerDocument || a ) === ( b.ownerDocument || b ) ? | |
| 1381 | a.compareDocumentPosition( b ) : | |
| 1382 | ||
| 1383 | // Otherwise we know they are disconnected | |
| 1384 | 1; | |
| 1385 | ||
| 1386 | // Disconnected nodes | |
| 1387 | if ( compare & 1 || | |
| 1388 | (!support.sortDetached && b.compareDocumentPosition( a ) === compare) ) { | |
| 1389 | ||
| 1390 | // Choose the first element that is related to our preferred document | |
| 1391 | if ( a === document || a.ownerDocument === preferredDoc && contains(preferredDoc, a) ) { | |
| 1392 | return -1; | |
| 1393 | } | |
| 1394 | if ( b === document || b.ownerDocument === preferredDoc && contains(preferredDoc, b) ) { | |
| 1395 | return 1; | |
| 1396 | } | |
| 1397 | ||
| 1398 | // Maintain original order | |
| 1399 | return sortInput ? | |
| 1400 | ( indexOf( sortInput, a ) - indexOf( sortInput, b ) ) : | |
| 1401 | 0; | |
| 1402 | } | |
| 1403 | ||
| 1404 | return compare & 4 ? -1 : 1; | |
| 1405 | } : | |
| 1406 | function( a, b ) { | |
| 1407 | // Exit early if the nodes are identical | |
| 1408 | if ( a === b ) { | |
| 1409 | hasDuplicate = true; | |
| 1410 | return 0; | |
| 1411 | } | |
| 1412 | ||
| 1413 | var cur, | |
| 1414 | i = 0, | |
| 1415 | aup = a.parentNode, | |
| 1416 | bup = b.parentNode, | |
| 1417 | ap = [ a ], | |
| 1418 | bp = [ b ]; | |
| 1419 | ||
| 1420 | // Parentless nodes are either documents or disconnected | |
| 1421 | if ( !aup || !bup ) { | |
| 1422 | return a === document ? -1 : | |
| 1423 | b === document ? 1 : | |
| 1424 | aup ? -1 : | |
| 1425 | bup ? 1 : | |
| 1426 | sortInput ? | |
| 1427 | ( indexOf( sortInput, a ) - indexOf( sortInput, b ) ) : | |
| 1428 | 0; | |
| 1429 | ||
| 1430 | // If the nodes are siblings, we can do a quick check | |
| 1431 | } else if ( aup === bup ) { | |
| 1432 | return siblingCheck( a, b ); | |
| 1433 | } | |
| 1434 | ||
| 1435 | // Otherwise we need full lists of their ancestors for comparison | |
| 1436 | cur = a; | |
| 1437 | while ( (cur = cur.parentNode) ) { | |
| 1438 | ap.unshift( cur ); | |
| 1439 | } | |
| 1440 | cur = b; | |
| 1441 | while ( (cur = cur.parentNode) ) { | |
| 1442 | bp.unshift( cur ); | |
| 1443 | } | |
| 1444 | ||
| 1445 | // Walk down the tree looking for a discrepancy | |
| 1446 | while ( ap[i] === bp[i] ) { | |
| 1447 | i++; | |
| 1448 | } | |
| 1449 | ||
| 1450 | return i ? | |
| 1451 | // Do a sibling check if the nodes have a common ancestor | |
| 1452 | siblingCheck( ap[i], bp[i] ) : | |
| 1453 | ||
| 1454 | // Otherwise nodes in our document sort first | |
| 1455 | ap[i] === preferredDoc ? -1 : | |
| 1456 | bp[i] === preferredDoc ? 1 : | |
| 1457 | 0; | |
| 1458 | }; | |
| 1459 | ||
| 1460 | return document; | |
| 1461 | }; | |
| 1462 | ||
| 1463 | Sizzle.matches = function( expr, elements ) { | |
| 1464 | return Sizzle( expr, null, null, elements ); | |
| 1465 | }; | |
| 1466 | ||
| 1467 | Sizzle.matchesSelector = function( elem, expr ) { | |
| 1468 | // Set document vars if needed | |
| 1469 | if ( ( elem.ownerDocument || elem ) !== document ) { | |
| 1470 | setDocument( elem ); | |
| 1471 | } | |
| 1472 | ||
| 1473 | // Make sure that attribute selectors are quoted | |
| 1474 | expr = expr.replace( rattributeQuotes, "='$1']" ); | |
| 1475 | ||
| 1476 | if ( support.matchesSelector && documentIsHTML && | |
| 1477 | !compilerCache[ expr + " " ] && | |
| 1478 | ( !rbuggyMatches || !rbuggyMatches.test( expr ) ) && | |
| 1479 | ( !rbuggyQSA || !rbuggyQSA.test( expr ) ) ) { | |
| 1480 | ||
| 1481 | try { | |
| 1482 | var ret = matches.call( elem, expr ); | |
| 1483 | ||
| 1484 | // IE 9's matchesSelector returns false on disconnected nodes | |
| 1485 | if ( ret || support.disconnectedMatch || | |
| 1486 | // As well, disconnected nodes are said to be in a document | |
| 1487 | // fragment in IE 9 | |
| 1488 | elem.document && elem.document.nodeType !== 11 ) { | |
| 1489 | return ret; | |
| 1490 | } | |
| 1491 | } catch (e) {} | |
| 1492 | } | |
| 1493 | ||
| 1494 | return Sizzle( expr, document, null, [ elem ] ).length > 0; | |
| 1495 | }; | |
| 1496 | ||
| 1497 | Sizzle.contains = function( context, elem ) { | |
| 1498 | // Set document vars if needed | |
| 1499 | if ( ( context.ownerDocument || context ) !== document ) { | |
| 1500 | setDocument( context ); | |
| 1501 | } | |
| 1502 | return contains( context, elem ); | |
| 1503 | }; | |
| 1504 | ||
| 1505 | Sizzle.attr = function( elem, name ) { | |
| 1506 | // Set document vars if needed | |
| 1507 | if ( ( elem.ownerDocument || elem ) !== document ) { | |
| 1508 | setDocument( elem ); | |
| 1509 | } | |
| 1510 | ||
| 1511 | var fn = Expr.attrHandle[ name.toLowerCase() ], | |
| 1512 | // Don't get fooled by Object.prototype properties (jQuery #13807) | |
| 1513 | val = fn && hasOwn.call( Expr.attrHandle, name.toLowerCase() ) ? | |
| 1514 | fn( elem, name, !documentIsHTML ) : | |
| 1515 | undefined; | |
| 1516 | ||
| 1517 | return val !== undefined ? | |
| 1518 | val : | |
| 1519 | support.attributes || !documentIsHTML ? | |
| 1520 | elem.getAttribute( name ) : | |
| 1521 | (val = elem.getAttributeNode(name)) && val.specified ? | |
| 1522 | val.value : | |
| 1523 | null; | |
| 1524 | }; | |
| 1525 | ||
| 1526 | Sizzle.escape = function( sel ) { | |
| 1527 | return (sel + "").replace( rcssescape, fcssescape ); | |
| 1528 | }; | |
| 1529 | ||
| 1530 | Sizzle.error = function( msg ) { | |
| 1531 | throw new Error( "Syntax error, unrecognized expression: " + msg ); | |
| 1532 | }; | |
| 1533 | ||
| 1534 | /** | |
| 1535 | * Document sorting and removing duplicates | |
| 1536 | * @param {ArrayLike} results | |
| 1537 | */ | |
| 1538 | Sizzle.uniqueSort = function( results ) { | |
| 1539 | var elem, | |
| 1540 | duplicates = [], | |
| 1541 | j = 0, | |
| 1542 | i = 0; | |
| 1543 | ||
| 1544 | // Unless we *know* we can detect duplicates, assume their presence | |
| 1545 | hasDuplicate = !support.detectDuplicates; | |
| 1546 | sortInput = !support.sortStable && results.slice( 0 ); | |
| 1547 | results.sort( sortOrder ); | |
| 1548 | ||
| 1549 | if ( hasDuplicate ) { | |
| 1550 | while ( (elem = results[i++]) ) { | |
| 1551 | if ( elem === results[ i ] ) { | |
| 1552 | j = duplicates.push( i ); | |
| 1553 | } | |
| 1554 | } | |
| 1555 | while ( j-- ) { | |
| 1556 | results.splice( duplicates[ j ], 1 ); | |
| 1557 | } | |
| 1558 | } | |
| 1559 | ||
| 1560 | // Clear input after sorting to release objects | |
| 1561 | // See https://github.com/jquery/sizzle/pull/225 | |
| 1562 | sortInput = null; | |
| 1563 | ||
| 1564 | return results; | |
| 1565 | }; | |
| 1566 | ||
| 1567 | /** | |
| 1568 | * Utility function for retrieving the text value of an array of DOM nodes | |
| 1569 | * @param {Array|Element} elem | |
| 1570 | */ | |
| 1571 | getText = Sizzle.getText = function( elem ) { | |
| 1572 | var node, | |
| 1573 | ret = "", | |
| 1574 | i = 0, | |
| 1575 | nodeType = elem.nodeType; | |
| 1576 | ||
| 1577 | if ( !nodeType ) { | |
| 1578 | // If no nodeType, this is expected to be an array | |
| 1579 | while ( (node = elem[i++]) ) { | |
| 1580 | // Do not traverse comment nodes | |
| 1581 | ret += getText( node ); | |
| 1582 | } | |
| 1583 | } else if ( nodeType === 1 || nodeType === 9 || nodeType === 11 ) { | |
| 1584 | // Use textContent for elements | |
| 1585 | // innerText usage removed for consistency of new lines (jQuery #11153) | |
| 1586 | if ( typeof elem.textContent === "string" ) { | |
| 1587 | return elem.textContent; | |
| 1588 | } else { | |
| 1589 | // Traverse its children | |
| 1590 | for ( elem = elem.firstChild; elem; elem = elem.nextSibling ) { | |
| 1591 | ret += getText( elem ); | |
| 1592 | } | |
| 1593 | } | |
| 1594 | } else if ( nodeType === 3 || nodeType === 4 ) { | |
| 1595 | return elem.nodeValue; | |
| 1596 | } | |
| 1597 | // Do not include comment or processing instruction nodes | |
| 1598 | ||
| 1599 | return ret; | |
| 1600 | }; | |
| 1601 | ||
| 1602 | Expr = Sizzle.selectors = { | |
| 1603 | ||
| 1604 | // Can be adjusted by the user | |
| 1605 | cacheLength: 50, | |
| 1606 | ||
| 1607 | createPseudo: markFunction, | |
| 1608 | ||
| 1609 | match: matchExpr, | |
| 1610 | ||
| 1611 | attrHandle: {}, | |
| 1612 | ||
| 1613 | find: {}, | |
| 1614 | ||
| 1615 | relative: { | |
| 1616 | ">": { dir: "parentNode", first: true }, | |
| 1617 | " ": { dir: "parentNode" }, | |
| 1618 | "+": { dir: "previousSibling", first: true }, | |
| 1619 | "~": { dir: "previousSibling" } | |
| 1620 | }, | |
| 1621 | ||
| 1622 | preFilter: { | |
| 1623 | "ATTR": function( match ) { | |
| 1624 | match[1] = match[1].replace( runescape, funescape ); | |
| 1625 | ||
| 1626 | // Move the given value to match[3] whether quoted or unquoted | |
| 1627 | match[3] = ( match[3] || match[4] || match[5] || "" ).replace( runescape, funescape ); | |
| 1628 | ||
| 1629 | if ( match[2] === "~=" ) { | |
| 1630 | match[3] = " " + match[3] + " "; | |
| 1631 | } | |
| 1632 | ||
| 1633 | return match.slice( 0, 4 ); | |
| 1634 | }, | |
| 1635 | ||
| 1636 | "CHILD": function( match ) { | |
| 1637 | /* matches from matchExpr["CHILD"] | |
| 1638 | 1 type (only|nth|...) | |
| 1639 | 2 what (child|of-type) | |
| 1640 | 3 argument (even|odd|\d*|\d*n([+-]\d+)?|...) | |
| 1641 | 4 xn-component of xn+y argument ([+-]?\d*n|) | |
| 1642 | 5 sign of xn-component | |
| 1643 | 6 x of xn-component | |
| 1644 | 7 sign of y-component | |
| 1645 | 8 y of y-component | |
| 1646 | */ | |
| 1647 | match[1] = match[1].toLowerCase(); | |
| 1648 | ||
| 1649 | if ( match[1].slice( 0, 3 ) === "nth" ) { | |
| 1650 | // nth-* requires argument | |
| 1651 | if ( !match[3] ) { | |
| 1652 | Sizzle.error( match[0] ); | |
| 1653 | } | |
| 1654 | ||
| 1655 | // numeric x and y parameters for Expr.filter.CHILD | |
| 1656 | // remember that false/true cast respectively to 0/1 | |
| 1657 | match[4] = +( match[4] ? match[5] + (match[6] || 1) : 2 * ( match[3] === "even" || match[3] === "odd" ) ); | |
| 1658 | match[5] = +( ( match[7] + match[8] ) || match[3] === "odd" ); | |
| 1659 | ||
| 1660 | // other types prohibit arguments | |
| 1661 | } else if ( match[3] ) { | |
| 1662 | Sizzle.error( match[0] ); | |
| 1663 | } | |
| 1664 | ||
| 1665 | return match; | |
| 1666 | }, | |
| 1667 | ||
| 1668 | "PSEUDO": function( match ) { | |
| 1669 | var excess, | |
| 1670 | unquoted = !match[6] && match[2]; | |
| 1671 | ||
| 1672 | if ( matchExpr["CHILD"].test( match[0] ) ) { | |
| 1673 | return null; | |
| 1674 | } | |
| 1675 | ||
| 1676 | // Accept quoted arguments as-is | |
| 1677 | if ( match[3] ) { | |
| 1678 | match[2] = match[4] || match[5] || ""; | |
| 1679 | ||
| 1680 | // Strip excess characters from unquoted arguments | |
| 1681 | } else if ( unquoted && rpseudo.test( unquoted ) && | |
| 1682 | // Get excess from tokenize (recursively) | |
| 1683 | (excess = tokenize( unquoted, true )) && | |
| 1684 | // advance to the next closing parenthesis | |
| 1685 | (excess = unquoted.indexOf( ")", unquoted.length - excess ) - unquoted.length) ) { | |
| 1686 | ||
| 1687 | // excess is a negative index | |
| 1688 | match[0] = match[0].slice( 0, excess ); | |
| 1689 | match[2] = unquoted.slice( 0, excess ); | |
| 1690 | } | |
| 1691 | ||
| 1692 | // Return only captures needed by the pseudo filter method (type and argument) | |
| 1693 | return match.slice( 0, 3 ); | |
| 1694 | } | |
| 1695 | }, | |
| 1696 | ||
| 1697 | filter: { | |
| 1698 | ||
| 1699 | "TAG": function( nodeNameSelector ) { | |
| 1700 | var nodeName = nodeNameSelector.replace( runescape, funescape ).toLowerCase(); | |
| 1701 | return nodeNameSelector === "*" ? | |
| 1702 | function() { return true; } : | |
| 1703 | function( elem ) { | |
| 1704 | return elem.nodeName && elem.nodeName.toLowerCase() === nodeName; | |
| 1705 | }; | |
| 1706 | }, | |
| 1707 | ||
| 1708 | "CLASS": function( className ) { | |
| 1709 | var pattern = classCache[ className + " " ]; | |
| 1710 | ||
| 1711 | return pattern || | |
| 1712 | (pattern = new RegExp( "(^|" + whitespace + ")" + className + "(" + whitespace + "|$)" )) && | |
| 1713 | classCache( className, function( elem ) { | |
| 1714 | return pattern.test( typeof elem.className === "string" && elem.className || typeof elem.getAttribute !== "undefined" && elem.getAttribute("class") || "" ); | |
| 1715 | }); | |
| 1716 | }, | |
| 1717 | ||
| 1718 | "ATTR": function( name, operator, check ) { | |
| 1719 | return function( elem ) { | |
| 1720 | var result = Sizzle.attr( elem, name ); | |
| 1721 | ||
| 1722 | if ( result == null ) { | |
| 1723 | return operator === "!="; | |
| 1724 | } | |
| 1725 | if ( !operator ) { | |
| 1726 | return true; | |
| 1727 | } | |
| 1728 | ||
| 1729 | result += ""; | |
| 1730 | ||
| 1731 | return operator === "=" ? result === check : | |
| 1732 | operator === "!=" ? result !== check : | |
| 1733 | operator === "^=" ? check && result.indexOf( check ) === 0 : | |
| 1734 | operator === "*=" ? check && result.indexOf( check ) > -1 : | |
| 1735 | operator === "$=" ? check && result.slice( -check.length ) === check : | |
| 1736 | operator === "~=" ? ( " " + result.replace( rwhitespace, " " ) + " " ).indexOf( check ) > -1 : | |
| 1737 | operator === "|=" ? result === check || result.slice( 0, check.length + 1 ) === check + "-" : | |
| 1738 | false; | |
| 1739 | }; | |
| 1740 | }, | |
| 1741 | ||
| 1742 | "CHILD": function( type, what, argument, first, last ) { | |
| 1743 | var simple = type.slice( 0, 3 ) !== "nth", | |
| 1744 | forward = type.slice( -4 ) !== "last", | |
| 1745 | ofType = what === "of-type"; | |
| 1746 | ||
| 1747 | return first === 1 && last === 0 ? | |
| 1748 | ||
| 1749 | // Shortcut for :nth-*(n) | |
| 1750 | function( elem ) { | |
| 1751 | return !!elem.parentNode; | |
| 1752 | } : | |
| 1753 | ||
| 1754 | function( elem, context, xml ) { | |
| 1755 | var cache, uniqueCache, outerCache, node, nodeIndex, start, | |
| 1756 | dir = simple !== forward ? "nextSibling" : "previousSibling", | |
| 1757 | parent = elem.parentNode, | |
| 1758 | name = ofType && elem.nodeName.toLowerCase(), | |
| 1759 | useCache = !xml && !ofType, | |
| 1760 | diff = false; | |
| 1761 | ||
| 1762 | if ( parent ) { | |
| 1763 | ||
| 1764 | // :(first|last|only)-(child|of-type) | |
| 1765 | if ( simple ) { | |
| 1766 | while ( dir ) { | |
| 1767 | node = elem; | |
| 1768 | while ( (node = node[ dir ]) ) { | |
| 1769 | if ( ofType ? | |
| 1770 | node.nodeName.toLowerCase() === name : | |
| 1771 | node.nodeType === 1 ) { | |
| 1772 | ||
| 1773 | return false; | |
| 1774 | } | |
| 1775 | } | |
| 1776 | // Reverse direction for :only-* (if we haven't yet done so) | |
| 1777 | start = dir = type === "only" && !start && "nextSibling"; | |
| 1778 | } | |
| 1779 | return true; | |
| 1780 | } | |
| 1781 | ||
| 1782 | start = [ forward ? parent.firstChild : parent.lastChild ]; | |
| 1783 | ||
| 1784 | // non-xml :nth-child(...) stores cache data on `parent` | |
| 1785 | if ( forward && useCache ) { | |
| 1786 | ||
| 1787 | // Seek `elem` from a previously-cached index | |
| 1788 | ||
| 1789 | // ...in a gzip-friendly way | |
| 1790 | node = parent; | |
| 1791 | outerCache = node[ expando ] || (node[ expando ] = {}); | |
| 1792 | ||
| 1793 | // Support: IE <9 only | |
| 1794 | // Defend against cloned attroperties (jQuery gh-1709) | |
| 1795 | uniqueCache = outerCache[ node.uniqueID ] || | |
| 1796 | (outerCache[ node.uniqueID ] = {}); | |
| 1797 | ||
| 1798 | cache = uniqueCache[ type ] || []; | |
| 1799 | nodeIndex = cache[ 0 ] === dirruns && cache[ 1 ]; | |
| 1800 | diff = nodeIndex && cache[ 2 ]; | |
| 1801 | node = nodeIndex && parent.childNodes[ nodeIndex ]; | |
| 1802 | ||
| 1803 | while ( (node = ++nodeIndex && node && node[ dir ] || | |
| 1804 | ||
| 1805 | // Fallback to seeking `elem` from the start | |
| 1806 | (diff = nodeIndex = 0) || start.pop()) ) { | |
| 1807 | ||
| 1808 | // When found, cache indexes on `parent` and break | |
| 1809 | if ( node.nodeType === 1 && ++diff && node === elem ) { | |
| 1810 | uniqueCache[ type ] = [ dirruns, nodeIndex, diff ]; | |
| 1811 | break; | |
| 1812 | } | |
| 1813 | } | |
| 1814 | ||
| 1815 | } else { | |
| 1816 | // Use previously-cached element index if available | |
| 1817 | if ( useCache ) { | |
| 1818 | // ...in a gzip-friendly way | |
| 1819 | node = elem; | |
| 1820 | outerCache = node[ expando ] || (node[ expando ] = {}); | |
| 1821 | ||
| 1822 | // Support: IE <9 only | |
| 1823 | // Defend against cloned attroperties (jQuery gh-1709) | |
| 1824 | uniqueCache = outerCache[ node.uniqueID ] || | |
| 1825 | (outerCache[ node.uniqueID ] = {}); | |
| 1826 | ||
| 1827 | cache = uniqueCache[ type ] || []; | |
| 1828 | nodeIndex = cache[ 0 ] === dirruns && cache[ 1 ]; | |
| 1829 | diff = nodeIndex; | |
| 1830 | } | |
| 1831 | ||
| 1832 | // xml :nth-child(...) | |
| 1833 | // or :nth-last-child(...) or :nth(-last)?-of-type(...) | |
| 1834 | if ( diff === false ) { | |
| 1835 | // Use the same loop as above to seek `elem` from the start | |
| 1836 | while ( (node = ++nodeIndex && node && node[ dir ] || | |
| 1837 | (diff = nodeIndex = 0) || start.pop()) ) { | |
| 1838 | ||
| 1839 | if ( ( ofType ? | |
| 1840 | node.nodeName.toLowerCase() === name : | |
| 1841 | node.nodeType === 1 ) && | |
| 1842 | ++diff ) { | |
| 1843 | ||
| 1844 | // Cache the index of each encountered element | |
| 1845 | if ( useCache ) { | |
| 1846 | outerCache = node[ expando ] || (node[ expando ] = {}); | |
| 1847 | ||
| 1848 | // Support: IE <9 only | |
| 1849 | // Defend against cloned attroperties (jQuery gh-1709) | |
| 1850 | uniqueCache = outerCache[ node.uniqueID ] || | |
| 1851 | (outerCache[ node.uniqueID ] = {}); | |
| 1852 | ||
| 1853 | uniqueCache[ type ] = [ dirruns, diff ]; | |
| 1854 | } | |
| 1855 | ||
| 1856 | if ( node === elem ) { | |
| 1857 | break; | |
| 1858 | } | |
| 1859 | } | |
| 1860 | } | |
| 1861 | } | |
| 1862 | } | |
| 1863 | ||
| 1864 | // Incorporate the offset, then check against cycle size | |
| 1865 | diff -= last; | |
| 1866 | return diff === first || ( diff % first === 0 && diff / first >= 0 ); | |
| 1867 | } | |
| 1868 | }; | |
| 1869 | }, | |
| 1870 | ||
| 1871 | "PSEUDO": function( pseudo, argument ) { | |
| 1872 | // pseudo-class names are case-insensitive | |
| 1873 | // http://www.w3.org/TR/selectors/#pseudo-classes | |
| 1874 | // Prioritize by case sensitivity in case custom pseudos are added with uppercase letters | |
| 1875 | // Remember that setFilters inherits from pseudos | |
| 1876 | var args, | |
| 1877 | fn = Expr.pseudos[ pseudo ] || Expr.setFilters[ pseudo.toLowerCase() ] || | |
| 1878 | Sizzle.error( "unsupported pseudo: " + pseudo ); | |
| 1879 | ||
| 1880 | // The user may use createPseudo to indicate that | |
| 1881 | // arguments are needed to create the filter function | |
| 1882 | // just as Sizzle does | |
| 1883 | if ( fn[ expando ] ) { | |
| 1884 | return fn( argument ); | |
| 1885 | } | |
| 1886 | ||
| 1887 | // But maintain support for old signatures | |
| 1888 | if ( fn.length > 1 ) { | |
| 1889 | args = [ pseudo, pseudo, "", argument ]; | |
| 1890 | return Expr.setFilters.hasOwnProperty( pseudo.toLowerCase() ) ? | |
| 1891 | markFunction(function( seed, matches ) { | |
| 1892 | var idx, | |
| 1893 | matched = fn( seed, argument ), | |
| 1894 | i = matched.length; | |
| 1895 | while ( i-- ) { | |
| 1896 | idx = indexOf( seed, matched[i] ); | |
| 1897 | seed[ idx ] = !( matches[ idx ] = matched[i] ); | |
| 1898 | } | |
| 1899 | }) : | |
| 1900 | function( elem ) { | |
| 1901 | return fn( elem, 0, args ); | |
| 1902 | }; | |
| 1903 | } | |
| 1904 | ||
| 1905 | return fn; | |
| 1906 | } | |
| 1907 | }, | |
| 1908 | ||
| 1909 | pseudos: { | |
| 1910 | // Potentially complex pseudos | |
| 1911 | "not": markFunction(function( selector ) { | |
| 1912 | // Trim the selector passed to compile | |
| 1913 | // to avoid treating leading and trailing | |
| 1914 | // spaces as combinators | |
| 1915 | var input = [], | |
| 1916 | results = [], | |
| 1917 | matcher = compile( selector.replace( rtrim, "$1" ) ); | |
| 1918 | ||
| 1919 | return matcher[ expando ] ? | |
| 1920 | markFunction(function( seed, matches, context, xml ) { | |
| 1921 | var elem, | |
| 1922 | unmatched = matcher( seed, null, xml, [] ), | |
| 1923 | i = seed.length; | |
| 1924 | ||
| 1925 | // Match elements unmatched by `matcher` | |
| 1926 | while ( i-- ) { | |
| 1927 | if ( (elem = unmatched[i]) ) { | |
| 1928 | seed[i] = !(matches[i] = elem); | |
| 1929 | } | |
| 1930 | } | |
| 1931 | }) : | |
| 1932 | function( elem, context, xml ) { | |
| 1933 | input[0] = elem; | |
| 1934 | matcher( input, null, xml, results ); | |
| 1935 | // Don't keep the element (issue #299) | |
| 1936 | input[0] = null; | |
| 1937 | return !results.pop(); | |
| 1938 | }; | |
| 1939 | }), | |
| 1940 | ||
| 1941 | "has": markFunction(function( selector ) { | |
| 1942 | return function( elem ) { | |
| 1943 | return Sizzle( selector, elem ).length > 0; | |
| 1944 | }; | |
| 1945 | }), | |
| 1946 | ||
| 1947 | "contains": markFunction(function( text ) { | |
| 1948 | text = text.replace( runescape, funescape ); | |
| 1949 | return function( elem ) { | |
| 1950 | return ( elem.textContent || elem.innerText || getText( elem ) ).indexOf( text ) > -1; | |
| 1951 | }; | |
| 1952 | }), | |
| 1953 | ||
| 1954 | // "Whether an element is represented by a :lang() selector | |
| 1955 | // is based solely on the element's language value | |
| 1956 | // being equal to the identifier C, | |
| 1957 | // or beginning with the identifier C immediately followed by "-". | |
| 1958 | // The matching of C against the element's language value is performed case-insensitively. | |
| 1959 | // The identifier C does not have to be a valid language name." | |
| 1960 | // http://www.w3.org/TR/selectors/#lang-pseudo | |
| 1961 | "lang": markFunction( function( lang ) { | |
| 1962 | // lang value must be a valid identifier | |
| 1963 | if ( !ridentifier.test(lang || "") ) { | |
| 1964 | Sizzle.error( "unsupported lang: " + lang ); | |
| 1965 | } | |
| 1966 | lang = lang.replace( runescape, funescape ).toLowerCase(); | |
| 1967 | return function( elem ) { | |
| 1968 | var elemLang; | |
| 1969 | do { | |
| 1970 | if ( (elemLang = documentIsHTML ? | |
| 1971 | elem.lang : | |
| 1972 | elem.getAttribute("xml:lang") || elem.getAttribute("lang")) ) { | |
| 1973 | ||
| 1974 | elemLang = elemLang.toLowerCase(); | |
| 1975 | return elemLang === lang || elemLang.indexOf( lang + "-" ) === 0; | |
| 1976 | } | |
| 1977 | } while ( (elem = elem.parentNode) && elem.nodeType === 1 ); | |
| 1978 | return false; | |
| 1979 | }; | |
| 1980 | }), | |
| 1981 | ||
| 1982 | // Miscellaneous | |
| 1983 | "target": function( elem ) { | |
| 1984 | var hash = window.location && window.location.hash; | |
| 1985 | return hash && hash.slice( 1 ) === elem.id; | |
| 1986 | }, | |
| 1987 | ||
| 1988 | "root": function( elem ) { | |
| 1989 | return elem === docElem; | |
| 1990 | }, | |
| 1991 | ||
| 1992 | "focus": function( elem ) { | |
| 1993 | return elem === document.activeElement && (!document.hasFocus || document.hasFocus()) && !!(elem.type || elem.href || ~elem.tabIndex); | |
| 1994 | }, | |
| 1995 | ||
| 1996 | // Boolean properties | |
| 1997 | "enabled": createDisabledPseudo( false ), | |
| 1998 | "disabled": createDisabledPseudo( true ), | |
| 1999 | ||
| 2000 | "checked": function( elem ) { | |
| 2001 | // In CSS3, :checked should return both checked and selected elements | |
| 2002 | // http://www.w3.org/TR/2011/REC-css3-selectors-20110929/#checked | |
| 2003 | var nodeName = elem.nodeName.toLowerCase(); | |
| 2004 | return (nodeName === "input" && !!elem.checked) || (nodeName === "option" && !!elem.selected); | |
| 2005 | }, | |
| 2006 | ||
| 2007 | "selected": function( elem ) { | |
| 2008 | // Accessing this property makes selected-by-default | |
| 2009 | // options in Safari work properly | |
| 2010 | if ( elem.parentNode ) { | |
| 2011 | elem.parentNode.selectedIndex; | |
| 2012 | } | |
| 2013 | ||
| 2014 | return elem.selected === true; | |
| 2015 | }, | |
| 2016 | ||
| 2017 | // Contents | |
| 2018 | "empty": function( elem ) { | |
| 2019 | // http://www.w3.org/TR/selectors/#empty-pseudo | |
| 2020 | // :empty is negated by element (1) or content nodes (text: 3; cdata: 4; entity ref: 5), | |
| 2021 | // but not by others (comment: 8; processing instruction: 7; etc.) | |
| 2022 | // nodeType < 6 works because attributes (2) do not appear as children | |
| 2023 | for ( elem = elem.firstChild; elem; elem = elem.nextSibling ) { | |
| 2024 | if ( elem.nodeType < 6 ) { | |
| 2025 | return false; | |
| 2026 | } | |
| 2027 | } | |
| 2028 | return true; | |
| 2029 | }, | |
| 2030 | ||
| 2031 | "parent": function( elem ) { | |
| 2032 | return !Expr.pseudos["empty"]( elem ); | |
| 2033 | }, | |
| 2034 | ||
| 2035 | // Element/input types | |
| 2036 | "header": function( elem ) { | |
| 2037 | return rheader.test( elem.nodeName ); | |
| 2038 | }, | |
| 2039 | ||
| 2040 | "input": function( elem ) { | |
| 2041 | return rinputs.test( elem.nodeName ); | |
| 2042 | }, | |
| 2043 | ||
| 2044 | "button": function( elem ) { | |
| 2045 | var name = elem.nodeName.toLowerCase(); | |
| 2046 | return name === "input" && elem.type === "button" || name === "button"; | |
| 2047 | }, | |
| 2048 | ||
| 2049 | "text": function( elem ) { | |
| 2050 | var attr; | |
| 2051 | return elem.nodeName.toLowerCase() === "input" && | |
| 2052 | elem.type === "text" && | |
| 2053 | ||
| 2054 | // Support: IE<8 | |
| 2055 | // New HTML5 attribute values (e.g., "search") appear with elem.type === "text" | |
| 2056 | ( (attr = elem.getAttribute("type")) == null || attr.toLowerCase() === "text" ); | |
| 2057 | }, | |
| 2058 | ||
| 2059 | // Position-in-collection | |
| 2060 | "first": createPositionalPseudo(function() { | |
| 2061 | return [ 0 ]; | |
| 2062 | }), | |
| 2063 | ||
| 2064 | "last": createPositionalPseudo(function( matchIndexes, length ) { | |
| 2065 | return [ length - 1 ]; | |
| 2066 | }), | |
| 2067 | ||
| 2068 | "eq": createPositionalPseudo(function( matchIndexes, length, argument ) { | |
| 2069 | return [ argument < 0 ? argument + length : argument ]; | |
| 2070 | }), | |
| 2071 | ||
| 2072 | "even": createPositionalPseudo(function( matchIndexes, length ) { | |
| 2073 | var i = 0; | |
| 2074 | for ( ; i < length; i += 2 ) { | |
| 2075 | matchIndexes.push( i ); | |
| 2076 | } | |
| 2077 | return matchIndexes; | |
| 2078 | }), | |
| 2079 | ||
| 2080 | "odd": createPositionalPseudo(function( matchIndexes, length ) { | |
| 2081 | var i = 1; | |
| 2082 | for ( ; i < length; i += 2 ) { | |
| 2083 | matchIndexes.push( i ); | |
| 2084 | } | |
| 2085 | return matchIndexes; | |
| 2086 | }), | |
| 2087 | ||
| 2088 | "lt": createPositionalPseudo(function( matchIndexes, length, argument ) { | |
| 2089 | var i = argument < 0 ? argument + length : argument; | |
| 2090 | for ( ; --i >= 0; ) { | |
| 2091 | matchIndexes.push( i ); | |
| 2092 | } | |
| 2093 | return matchIndexes; | |
| 2094 | }), | |
| 2095 | ||
| 2096 | "gt": createPositionalPseudo(function( matchIndexes, length, argument ) { | |
| 2097 | var i = argument < 0 ? argument + length : argument; | |
| 2098 | for ( ; ++i < length; ) { | |
| 2099 | matchIndexes.push( i ); | |
| 2100 | } | |
| 2101 | return matchIndexes; | |
| 2102 | }) | |
| 2103 | } | |
| 2104 | }; | |
| 2105 | ||
| 2106 | Expr.pseudos["nth"] = Expr.pseudos["eq"]; | |
| 2107 | ||
| 2108 | // Add button/input type pseudos | |
| 2109 | for ( i in { radio: true, checkbox: true, file: true, password: true, image: true } ) { | |
| 2110 | Expr.pseudos[ i ] = createInputPseudo( i ); | |
| 2111 | } | |
| 2112 | for ( i in { submit: true, reset: true } ) { | |
| 2113 | Expr.pseudos[ i ] = createButtonPseudo( i ); | |
| 2114 | } | |
| 2115 | ||
| 2116 | // Easy API for creating new setFilters | |
| 2117 | function setFilters() {} | |
| 2118 | setFilters.prototype = Expr.filters = Expr.pseudos; | |
| 2119 | Expr.setFilters = new setFilters(); | |
| 2120 | ||
| 2121 | tokenize = Sizzle.tokenize = function( selector, parseOnly ) { | |
| 2122 | var matched, match, tokens, type, | |
| 2123 | soFar, groups, preFilters, | |
| 2124 | cached = tokenCache[ selector + " " ]; | |
| 2125 | ||
| 2126 | if ( cached ) { | |
| 2127 | return parseOnly ? 0 : cached.slice( 0 ); | |
| 2128 | } | |
| 2129 | ||
| 2130 | soFar = selector; | |
| 2131 | groups = []; | |
| 2132 | preFilters = Expr.preFilter; | |
| 2133 | ||
| 2134 | while ( soFar ) { | |
| 2135 | ||
| 2136 | // Comma and first run | |
| 2137 | if ( !matched || (match = rcomma.exec( soFar )) ) { | |
| 2138 | if ( match ) { | |
| 2139 | // Don't consume trailing commas as valid | |
| 2140 | soFar = soFar.slice( match[0].length ) || soFar; | |
| 2141 | } | |
| 2142 | groups.push( (tokens = []) ); | |
| 2143 | } | |
| 2144 | ||
| 2145 | matched = false; | |
| 2146 | ||
| 2147 | // Combinators | |
| 2148 | if ( (match = rcombinators.exec( soFar )) ) { | |
| 2149 | matched = match.shift(); | |
| 2150 | tokens.push({ | |
| 2151 | value: matched, | |
| 2152 | // Cast descendant combinators to space | |
| 2153 | type: match[0].replace( rtrim, " " ) | |
| 2154 | }); | |
| 2155 | soFar = soFar.slice( matched.length ); | |
| 2156 | } | |
| 2157 | ||
| 2158 | // Filters | |
| 2159 | for ( type in Expr.filter ) { | |
| 2160 | if ( (match = matchExpr[ type ].exec( soFar )) && (!preFilters[ type ] || | |
| 2161 | (match = preFilters[ type ]( match ))) ) { | |
| 2162 | matched = match.shift(); | |
| 2163 | tokens.push({ | |
| 2164 | value: matched, | |
| 2165 | type: type, | |
| 2166 | matches: match | |
| 2167 | }); | |
| 2168 | soFar = soFar.slice( matched.length ); | |
| 2169 | } | |
| 2170 | } | |
| 2171 | ||
| 2172 | if ( !matched ) { | |
| 2173 | break; | |
| 2174 | } | |
| 2175 | } | |
| 2176 | ||
| 2177 | // Return the length of the invalid excess | |
| 2178 | // if we're just parsing | |
| 2179 | // Otherwise, throw an error or return tokens | |
| 2180 | return parseOnly ? | |
| 2181 | soFar.length : | |
| 2182 | soFar ? | |
| 2183 | Sizzle.error( selector ) : | |
| 2184 | // Cache the tokens | |
| 2185 | tokenCache( selector, groups ).slice( 0 ); | |
| 2186 | }; | |
| 2187 | ||
| 2188 | function toSelector( tokens ) { | |
| 2189 | var i = 0, | |
| 2190 | len = tokens.length, | |
| 2191 | selector = ""; | |
| 2192 | for ( ; i < len; i++ ) { | |
| 2193 | selector += tokens[i].value; | |
| 2194 | } | |
| 2195 | return selector; | |
| 2196 | } | |
| 2197 | ||
| 2198 | function addCombinator( matcher, combinator, base ) { | |
| 2199 | var dir = combinator.dir, | |
| 2200 | skip = combinator.next, | |
| 2201 | key = skip || dir, | |
| 2202 | checkNonElements = base && key === "parentNode", | |
| 2203 | doneName = done++; | |
| 2204 | ||
| 2205 | return combinator.first ? | |
| 2206 | // Check against closest ancestor/preceding element | |
| 2207 | function( elem, context, xml ) { | |
| 2208 | while ( (elem = elem[ dir ]) ) { | |
| 2209 | if ( elem.nodeType === 1 || checkNonElements ) { | |
| 2210 | return matcher( elem, context, xml ); | |
| 2211 | } | |
| 2212 | } | |
| 2213 | } : | |
| 2214 | ||
| 2215 | // Check against all ancestor/preceding elements | |
| 2216 | function( elem, context, xml ) { | |
| 2217 | var oldCache, uniqueCache, outerCache, | |
| 2218 | newCache = [ dirruns, doneName ]; | |
| 2219 | ||
| 2220 | // We can't set arbitrary data on XML nodes, so they don't benefit from combinator caching | |
| 2221 | if ( xml ) { | |
| 2222 | while ( (elem = elem[ dir ]) ) { | |
| 2223 | if ( elem.nodeType === 1 || checkNonElements ) { | |
| 2224 | if ( matcher( elem, context, xml ) ) { | |
| 2225 | return true; | |
| 2226 | } | |
| 2227 | } | |
| 2228 | } | |
| 2229 | } else { | |
| 2230 | while ( (elem = elem[ dir ]) ) { | |
| 2231 | if ( elem.nodeType === 1 || checkNonElements ) { | |
| 2232 | outerCache = elem[ expando ] || (elem[ expando ] = {}); | |
| 2233 | ||
| 2234 | // Support: IE <9 only | |
| 2235 | // Defend against cloned attroperties (jQuery gh-1709) | |
| 2236 | uniqueCache = outerCache[ elem.uniqueID ] || (outerCache[ elem.uniqueID ] = {}); | |
| 2237 | ||
| 2238 | if ( skip && skip === elem.nodeName.toLowerCase() ) { | |
| 2239 | elem = elem[ dir ] || elem; | |
| 2240 | } else if ( (oldCache = uniqueCache[ key ]) && | |
| 2241 | oldCache[ 0 ] === dirruns && oldCache[ 1 ] === doneName ) { | |
| 2242 | ||
| 2243 | // Assign to newCache so results back-propagate to previous elements | |
| 2244 | return (newCache[ 2 ] = oldCache[ 2 ]); | |
| 2245 | } else { | |
| 2246 | // Reuse newcache so results back-propagate to previous elements | |
| 2247 | uniqueCache[ key ] = newCache; | |
| 2248 | ||
| 2249 | // A match means we're done; a fail means we have to keep checking | |
| 2250 | if ( (newCache[ 2 ] = matcher( elem, context, xml )) ) { | |
| 2251 | return true; | |
| 2252 | } | |
| 2253 | } | |
| 2254 | } | |
| 2255 | } | |
| 2256 | } | |
| 2257 | }; | |
| 2258 | } | |
| 2259 | ||
| 2260 | function elementMatcher( matchers ) { | |
| 2261 | return matchers.length > 1 ? | |
| 2262 | function( elem, context, xml ) { | |
| 2263 | var i = matchers.length; | |
| 2264 | while ( i-- ) { | |
| 2265 | if ( !matchers[i]( elem, context, xml ) ) { | |
| 2266 | return false; | |
| 2267 | } | |
| 2268 | } | |
| 2269 | return true; | |
| 2270 | } : | |
| 2271 | matchers[0]; | |
| 2272 | } | |
| 2273 | ||
| 2274 | function multipleContexts( selector, contexts, results ) { | |
| 2275 | var i = 0, | |
| 2276 | len = contexts.length; | |
| 2277 | for ( ; i < len; i++ ) { | |
| 2278 | Sizzle( selector, contexts[i], results ); | |
| 2279 | } | |
| 2280 | return results; | |
| 2281 | } | |
| 2282 | ||
| 2283 | function condense( unmatched, map, filter, context, xml ) { | |
| 2284 | var elem, | |
| 2285 | newUnmatched = [], | |
| 2286 | i = 0, | |
| 2287 | len = unmatched.length, | |
| 2288 | mapped = map != null; | |
| 2289 | ||
| 2290 | for ( ; i < len; i++ ) { | |
| 2291 | if ( (elem = unmatched[i]) ) { | |
| 2292 | if ( !filter || filter( elem, context, xml ) ) { | |
| 2293 | newUnmatched.push( elem ); | |
| 2294 | if ( mapped ) { | |
| 2295 | map.push( i ); | |
| 2296 | } | |
| 2297 | } | |
| 2298 | } | |
| 2299 | } | |
| 2300 | ||
| 2301 | return newUnmatched; | |
| 2302 | } | |
| 2303 | ||
| 2304 | function setMatcher( preFilter, selector, matcher, postFilter, postFinder, postSelector ) { | |
| 2305 | if ( postFilter && !postFilter[ expando ] ) { | |
| 2306 | postFilter = setMatcher( postFilter ); | |
| 2307 | } | |
| 2308 | if ( postFinder && !postFinder[ expando ] ) { | |
| 2309 | postFinder = setMatcher( postFinder, postSelector ); | |
| 2310 | } | |
| 2311 | return markFunction(function( seed, results, context, xml ) { | |
| 2312 | var temp, i, elem, | |
| 2313 | preMap = [], | |
| 2314 | postMap = [], | |
| 2315 | preexisting = results.length, | |
| 2316 | ||
| 2317 | // Get initial elements from seed or context | |
| 2318 | elems = seed || multipleContexts( selector || "*", context.nodeType ? [ context ] : context, [] ), | |
| 2319 | ||
| 2320 | // Prefilter to get matcher input, preserving a map for seed-results synchronization | |
| 2321 | matcherIn = preFilter && ( seed || !selector ) ? | |
| 2322 | condense( elems, preMap, preFilter, context, xml ) : | |
| 2323 | elems, | |
| 2324 | ||
| 2325 | matcherOut = matcher ? | |
| 2326 | // If we have a postFinder, or filtered seed, or non-seed postFilter or preexisting results, | |
| 2327 | postFinder || ( seed ? preFilter : preexisting || postFilter ) ? | |
| 2328 | ||
| 2329 | // ...intermediate processing is necessary | |
| 2330 | [] : | |
| 2331 | ||
| 2332 | // ...otherwise use results directly | |
| 2333 | results : | |
| 2334 | matcherIn; | |
| 2335 | ||
| 2336 | // Find primary matches | |
| 2337 | if ( matcher ) { | |
| 2338 | matcher( matcherIn, matcherOut, context, xml ); | |
| 2339 | } | |
| 2340 | ||
| 2341 | // Apply postFilter | |
| 2342 | if ( postFilter ) { | |
| 2343 | temp = condense( matcherOut, postMap ); | |
| 2344 | postFilter( temp, [], context, xml ); | |
| 2345 | ||
| 2346 | // Un-match failing elements by moving them back to matcherIn | |
| 2347 | i = temp.length; | |
| 2348 | while ( i-- ) { | |
| 2349 | if ( (elem = temp[i]) ) { | |
| 2350 | matcherOut[ postMap[i] ] = !(matcherIn[ postMap[i] ] = elem); | |
| 2351 | } | |
| 2352 | } | |
| 2353 | } | |
| 2354 | ||
| 2355 | if ( seed ) { | |
| 2356 | if ( postFinder || preFilter ) { | |
| 2357 | if ( postFinder ) { | |
| 2358 | // Get the final matcherOut by condensing this intermediate into postFinder contexts | |
| 2359 | temp = []; | |
| 2360 | i = matcherOut.length; | |
| 2361 | while ( i-- ) { | |
| 2362 | if ( (elem = matcherOut[i]) ) { | |
| 2363 | // Restore matcherIn since elem is not yet a final match | |
| 2364 | temp.push( (matcherIn[i] = elem) ); | |
| 2365 | } | |
| 2366 | } | |
| 2367 | postFinder( null, (matcherOut = []), temp, xml ); | |
| 2368 | } | |
| 2369 | ||
| 2370 | // Move matched elements from seed to results to keep them synchronized | |
| 2371 | i = matcherOut.length; | |
| 2372 | while ( i-- ) { | |
| 2373 | if ( (elem = matcherOut[i]) && | |
| 2374 | (temp = postFinder ? indexOf( seed, elem ) : preMap[i]) > -1 ) { | |
| 2375 | ||
| 2376 | seed[temp] = !(results[temp] = elem); | |
| 2377 | } | |
| 2378 | } | |
| 2379 | } | |
| 2380 | ||
| 2381 | // Add elements to results, through postFinder if defined | |
| 2382 | } else { | |
| 2383 | matcherOut = condense( | |
| 2384 | matcherOut === results ? | |
| 2385 | matcherOut.splice( preexisting, matcherOut.length ) : | |
| 2386 | matcherOut | |
| 2387 | ); | |
| 2388 | if ( postFinder ) { | |
| 2389 | postFinder( null, results, matcherOut, xml ); | |
| 2390 | } else { | |
| 2391 | push.apply( results, matcherOut ); | |
| 2392 | } | |
| 2393 | } | |
| 2394 | }); | |
| 2395 | } | |
| 2396 | ||
| 2397 | function matcherFromTokens( tokens ) { | |
| 2398 | var checkContext, matcher, j, | |
| 2399 | len = tokens.length, | |
| 2400 | leadingRelative = Expr.relative[ tokens[0].type ], | |
| 2401 | implicitRelative = leadingRelative || Expr.relative[" "], | |
| 2402 | i = leadingRelative ? 1 : 0, | |
| 2403 | ||
| 2404 | // The foundational matcher ensures that elements are reachable from top-level context(s) | |
| 2405 | matchContext = addCombinator( function( elem ) { | |
| 2406 | return elem === checkContext; | |
| 2407 | }, implicitRelative, true ), | |
| 2408 | matchAnyContext = addCombinator( function( elem ) { | |
| 2409 | return indexOf( checkContext, elem ) > -1; | |
| 2410 | }, implicitRelative, true ), | |
| 2411 | matchers = [ function( elem, context, xml ) { | |
| 2412 | var ret = ( !leadingRelative && ( xml || context !== outermostContext ) ) || ( | |
| 2413 | (checkContext = context).nodeType ? | |
| 2414 | matchContext( elem, context, xml ) : | |
| 2415 | matchAnyContext( elem, context, xml ) ); | |
| 2416 | // Avoid hanging onto element (issue #299) | |
| 2417 | checkContext = null; | |
| 2418 | return ret; | |
| 2419 | } ]; | |
| 2420 | ||
| 2421 | for ( ; i < len; i++ ) { | |
| 2422 | if ( (matcher = Expr.relative[ tokens[i].type ]) ) { | |
| 2423 | matchers = [ addCombinator(elementMatcher( matchers ), matcher) ]; | |
| 2424 | } else { | |
| 2425 | matcher = Expr.filter[ tokens[i].type ].apply( null, tokens[i].matches ); | |
| 2426 | ||
| 2427 | // Return special upon seeing a positional matcher | |
| 2428 | if ( matcher[ expando ] ) { | |
| 2429 | // Find the next relative operator (if any) for proper handling | |
| 2430 | j = ++i; | |
| 2431 | for ( ; j < len; j++ ) { | |
| 2432 | if ( Expr.relative[ tokens[j].type ] ) { | |
| 2433 | break; | |
| 2434 | } | |
| 2435 | } | |
| 2436 | return setMatcher( | |
| 2437 | i > 1 && elementMatcher( matchers ), | |
| 2438 | i > 1 && toSelector( | |
| 2439 | // If the preceding token was a descendant combinator, insert an implicit any-element `*` | |
| 2440 | tokens.slice( 0, i - 1 ).concat({ value: tokens[ i - 2 ].type === " " ? "*" : "" }) | |
| 2441 | ).replace( rtrim, "$1" ), | |
| 2442 | matcher, | |
| 2443 | i < j && matcherFromTokens( tokens.slice( i, j ) ), | |
| 2444 | j < len && matcherFromTokens( (tokens = tokens.slice( j )) ), | |
| 2445 | j < len && toSelector( tokens ) | |
| 2446 | ); | |
| 2447 | } | |
| 2448 | matchers.push( matcher ); | |
| 2449 | } | |
| 2450 | } | |
| 2451 | ||
| 2452 | return elementMatcher( matchers ); | |
| 2453 | } | |
| 2454 | ||
| 2455 | function matcherFromGroupMatchers( elementMatchers, setMatchers ) { | |
| 2456 | var bySet = setMatchers.length > 0, | |
| 2457 | byElement = elementMatchers.length > 0, | |
| 2458 | superMatcher = function( seed, context, xml, results, outermost ) { | |
| 2459 | var elem, j, matcher, | |
| 2460 | matchedCount = 0, | |
| 2461 | i = "0", | |
| 2462 | unmatched = seed && [], | |
| 2463 | setMatched = [], | |
| 2464 | contextBackup = outermostContext, | |
| 2465 | // We must always have either seed elements or outermost context | |
| 2466 | elems = seed || byElement && Expr.find["TAG"]( "*", outermost ), | |
| 2467 | // Use integer dirruns iff this is the outermost matcher | |
| 2468 | dirrunsUnique = (dirruns += contextBackup == null ? 1 : Math.random() || 0.1), | |
| 2469 | len = elems.length; | |
| 2470 | ||
| 2471 | if ( outermost ) { | |
| 2472 | outermostContext = context === document || context || outermost; | |
| 2473 | } | |
| 2474 | ||
| 2475 | // Add elements passing elementMatchers directly to results | |
| 2476 | // Support: IE<9, Safari | |
| 2477 | // Tolerate NodeList properties (IE: "length"; Safari: <number>) matching elements by id | |
| 2478 | for ( ; i !== len && (elem = elems[i]) != null; i++ ) { | |
| 2479 | if ( byElement && elem ) { | |
| 2480 | j = 0; | |
| 2481 | if ( !context && elem.ownerDocument !== document ) { | |
| 2482 | setDocument( elem ); | |
| 2483 | xml = !documentIsHTML; | |
| 2484 | } | |
| 2485 | while ( (matcher = elementMatchers[j++]) ) { | |
| 2486 | if ( matcher( elem, context || document, xml) ) { | |
| 2487 | results.push( elem ); | |
| 2488 | break; | |
| 2489 | } | |
| 2490 | } | |
| 2491 | if ( outermost ) { | |
| 2492 | dirruns = dirrunsUnique; | |
| 2493 | } | |
| 2494 | } | |
| 2495 | ||
| 2496 | // Track unmatched elements for set filters | |
| 2497 | if ( bySet ) { | |
| 2498 | // They will have gone through all possible matchers | |
| 2499 | if ( (elem = !matcher && elem) ) { | |
| 2500 | matchedCount--; | |
| 2501 | } | |
| 2502 | ||
| 2503 | // Lengthen the array for every element, matched or not | |
| 2504 | if ( seed ) { | |
| 2505 | unmatched.push( elem ); | |
| 2506 | } | |
| 2507 | } | |
| 2508 | } | |
| 2509 | ||
| 2510 | // `i` is now the count of elements visited above, and adding it to `matchedCount` | |
| 2511 | // makes the latter nonnegative. | |
| 2512 | matchedCount += i; | |
| 2513 | ||
| 2514 | // Apply set filters to unmatched elements | |
| 2515 | // NOTE: This can be skipped if there are no unmatched elements (i.e., `matchedCount` | |
| 2516 | // equals `i`), unless we didn't visit _any_ elements in the above loop because we have | |
| 2517 | // no element matchers and no seed. | |
| 2518 | // Incrementing an initially-string "0" `i` allows `i` to remain a string only in that | |
| 2519 | // case, which will result in a "00" `matchedCount` that differs from `i` but is also | |
| 2520 | // numerically zero. | |
| 2521 | if ( bySet && i !== matchedCount ) { | |
| 2522 | j = 0; | |
| 2523 | while ( (matcher = setMatchers[j++]) ) { | |
| 2524 | matcher( unmatched, setMatched, context, xml ); | |
| 2525 | } | |
| 2526 | ||
| 2527 | if ( seed ) { | |
| 2528 | // Reintegrate element matches to eliminate the need for sorting | |
| 2529 | if ( matchedCount > 0 ) { | |
| 2530 | while ( i-- ) { | |
| 2531 | if ( !(unmatched[i] || setMatched[i]) ) { | |
| 2532 | setMatched[i] = pop.call( results ); | |
| 2533 | } | |
| 2534 | } | |
| 2535 | } | |
| 2536 | ||
| 2537 | // Discard index placeholder values to get only actual matches | |
| 2538 | setMatched = condense( setMatched ); | |
| 2539 | } | |
| 2540 | ||
| 2541 | // Add matches to results | |
| 2542 | push.apply( results, setMatched ); | |
| 2543 | ||
| 2544 | // Seedless set matches succeeding multiple successful matchers stipulate sorting | |
| 2545 | if ( outermost && !seed && setMatched.length > 0 && | |
| 2546 | ( matchedCount + setMatchers.length ) > 1 ) { | |
| 2547 | ||
| 2548 | Sizzle.uniqueSort( results ); | |
| 2549 | } | |
| 2550 | } | |
| 2551 | ||
| 2552 | // Override manipulation of globals by nested matchers | |
| 2553 | if ( outermost ) { | |
| 2554 | dirruns = dirrunsUnique; | |
| 2555 | outermostContext = contextBackup; | |
| 2556 | } | |
| 2557 | ||
| 2558 | return unmatched; | |
| 2559 | }; | |
| 2560 | ||
| 2561 | return bySet ? | |
| 2562 | markFunction( superMatcher ) : | |
| 2563 | superMatcher; | |
| 2564 | } | |
| 2565 | ||
| 2566 | compile = Sizzle.compile = function( selector, match /* Internal Use Only */ ) { | |
| 2567 | var i, | |
| 2568 | setMatchers = [], | |
| 2569 | elementMatchers = [], | |
| 2570 | cached = compilerCache[ selector + " " ]; | |
| 2571 | ||
| 2572 | if ( !cached ) { | |
| 2573 | // Generate a function of recursive functions that can be used to check each element | |
| 2574 | if ( !match ) { | |
| 2575 | match = tokenize( selector ); | |
| 2576 | } | |
| 2577 | i = match.length; | |
| 2578 | while ( i-- ) { | |
| 2579 | cached = matcherFromTokens( match[i] ); | |
| 2580 | if ( cached[ expando ] ) { | |
| 2581 | setMatchers.push( cached ); | |
| 2582 | } else { | |
| 2583 | elementMatchers.push( cached ); | |
| 2584 | } | |
| 2585 | } | |
| 2586 | ||
| 2587 | // Cache the compiled function | |
| 2588 | cached = compilerCache( selector, matcherFromGroupMatchers( elementMatchers, setMatchers ) ); | |
| 2589 | ||
| 2590 | // Save selector and tokenization | |
| 2591 | cached.selector = selector; | |
| 2592 | } | |
| 2593 | return cached; | |
| 2594 | }; | |
| 2595 | ||
| 2596 | /** | |
| 2597 | * A low-level selection function that works with Sizzle's compiled | |
| 2598 | * selector functions | |
| 2599 | * @param {String|Function} selector A selector or a pre-compiled | |
| 2600 | * selector function built with Sizzle.compile | |
| 2601 | * @param {Element} context | |
| 2602 | * @param {Array} [results] | |
| 2603 | * @param {Array} [seed] A set of elements to match against | |
| 2604 | */ | |
| 2605 | select = Sizzle.select = function( selector, context, results, seed ) { | |
| 2606 | var i, tokens, token, type, find, | |
| 2607 | compiled = typeof selector === "function" && selector, | |
| 2608 | match = !seed && tokenize( (selector = compiled.selector || selector) ); | |
| 2609 | ||
| 2610 | results = results || []; | |
| 2611 | ||
| 2612 | // Try to minimize operations if there is only one selector in the list and no seed | |
| 2613 | // (the latter of which guarantees us context) | |
| 2614 | if ( match.length === 1 ) { | |
| 2615 | ||
| 2616 | // Reduce context if the leading compound selector is an ID | |
| 2617 | tokens = match[0] = match[0].slice( 0 ); | |
| 2618 | if ( tokens.length > 2 && (token = tokens[0]).type === "ID" && | |
| 2619 | support.getById && context.nodeType === 9 && documentIsHTML && | |
| 2620 | Expr.relative[ tokens[1].type ] ) { | |
| 2621 | ||
| 2622 | context = ( Expr.find["ID"]( token.matches[0].replace(runescape, funescape), context ) || [] )[0]; | |
| 2623 | if ( !context ) { | |
| 2624 | return results; | |
| 2625 | ||
| 2626 | // Precompiled matchers will still verify ancestry, so step up a level | |
| 2627 | } else if ( compiled ) { | |
| 2628 | context = context.parentNode; | |
| 2629 | } | |
| 2630 | ||
| 2631 | selector = selector.slice( tokens.shift().value.length ); | |
| 2632 | } | |
| 2633 | ||
| 2634 | // Fetch a seed set for right-to-left matching | |
| 2635 | i = matchExpr["needsContext"].test( selector ) ? 0 : tokens.length; | |
| 2636 | while ( i-- ) { | |
| 2637 | token = tokens[i]; | |
| 2638 | ||
| 2639 | // Abort if we hit a combinator | |
| 2640 | if ( Expr.relative[ (type = token.type) ] ) { | |
| 2641 | break; | |
| 2642 | } | |
| 2643 | if ( (find = Expr.find[ type ]) ) { | |
| 2644 | // Search, expanding context for leading sibling combinators | |
| 2645 | if ( (seed = find( | |
| 2646 | token.matches[0].replace( runescape, funescape ), | |
| 2647 | rsibling.test( tokens[0].type ) && testContext( context.parentNode ) || context | |
| 2648 | )) ) { | |
| 2649 | ||
| 2650 | // If seed is empty or no tokens remain, we can return early | |
| 2651 | tokens.splice( i, 1 ); | |
| 2652 | selector = seed.length && toSelector( tokens ); | |
| 2653 | if ( !selector ) { | |
| 2654 | push.apply( results, seed ); | |
| 2655 | return results; | |
| 2656 | } | |
| 2657 | ||
| 2658 | break; | |
| 2659 | } | |
| 2660 | } | |
| 2661 | } | |
| 2662 | } | |
| 2663 | ||
| 2664 | // Compile and execute a filtering function if one is not provided | |
| 2665 | // Provide `match` to avoid retokenization if we modified the selector above | |
| 2666 | ( compiled || compile( selector, match ) )( | |
| 2667 | seed, | |
| 2668 | context, | |
| 2669 | !documentIsHTML, | |
| 2670 | results, | |
| 2671 | !context || rsibling.test( selector ) && testContext( context.parentNode ) || context | |
| 2672 | ); | |
| 2673 | return results; | |
| 2674 | }; | |
| 2675 | ||
| 2676 | // One-time assignments | |
| 2677 | ||
| 2678 | // Sort stability | |
| 2679 | support.sortStable = expando.split("").sort( sortOrder ).join("") === expando; | |
| 2680 | ||
| 2681 | // Support: Chrome 14-35+ | |
| 2682 | // Always assume duplicates if they aren't passed to the comparison function | |
| 2683 | support.detectDuplicates = !!hasDuplicate; | |
| 2684 | ||
| 2685 | // Initialize against the default document | |
| 2686 | setDocument(); | |
| 2687 | ||
| 2688 | // Support: Webkit<537.32 - Safari 6.0.3/Chrome 25 (fixed in Chrome 27) | |
| 2689 | // Detached nodes confoundingly follow *each other* | |
| 2690 | support.sortDetached = assert(function( el ) { | |
| 2691 | // Should return 1, but returns 4 (following) | |
| 2692 | return el.compareDocumentPosition( document.createElement("fieldset") ) & 1; | |
| 2693 | }); | |
| 2694 | ||
| 2695 | // Support: IE<8 | |
| 2696 | // Prevent attribute/property "interpolation" | |
| 2697 | // https://msdn.microsoft.com/en-us/library/ms536429%28VS.85%29.aspx | |
| 2698 | if ( !assert(function( el ) { | |
| 2699 | el.innerHTML = "<a href='#'></a>"; | |
| 2700 | return el.firstChild.getAttribute("href") === "#" ; | |
| 2701 | }) ) { | |
| 2702 | addHandle( "type|href|height|width", function( elem, name, isXML ) { | |
| 2703 | if ( !isXML ) { | |
| 2704 | return elem.getAttribute( name, name.toLowerCase() === "type" ? 1 : 2 ); | |
| 2705 | } | |
| 2706 | }); | |
| 2707 | } | |
| 2708 | ||
| 2709 | // Support: IE<9 | |
| 2710 | // Use defaultValue in place of getAttribute("value") | |
| 2711 | if ( !support.attributes || !assert(function( el ) { | |
| 2712 | el.innerHTML = "<input/>"; | |
| 2713 | el.firstChild.setAttribute( "value", "" ); | |
| 2714 | return el.firstChild.getAttribute( "value" ) === ""; | |
| 2715 | }) ) { | |
| 2716 | addHandle( "value", function( elem, name, isXML ) { | |
| 2717 | if ( !isXML && elem.nodeName.toLowerCase() === "input" ) { | |
| 2718 | return elem.defaultValue; | |
| 2719 | } | |
| 2720 | }); | |
| 2721 | } | |
| 2722 | ||
| 2723 | // Support: IE<9 | |
| 2724 | // Use getAttributeNode to fetch booleans when getAttribute lies | |
| 2725 | if ( !assert(function( el ) { | |
| 2726 | return el.getAttribute("disabled") == null; | |
| 2727 | }) ) { | |
| 2728 | addHandle( booleans, function( elem, name, isXML ) { | |
| 2729 | var val; | |
| 2730 | if ( !isXML ) { | |
| 2731 | return elem[ name ] === true ? name.toLowerCase() : | |
| 2732 | (val = elem.getAttributeNode( name )) && val.specified ? | |
| 2733 | val.value : | |
| 2734 | null; | |
| 2735 | } | |
| 2736 | }); | |
| 2737 | } | |
| 2738 | ||
| 2739 | return Sizzle; | |
| 2740 | ||
| 2741 | })( window ); | |
| 2742 | ||
| 2743 | ||
| 2744 | ||
| 2745 | jQuery.find = Sizzle; | |
| 2746 | jQuery.expr = Sizzle.selectors; | |
| 2747 | ||
| 2748 | // Deprecated | |
| 2749 | jQuery.expr[ ":" ] = jQuery.expr.pseudos; | |
| 2750 | jQuery.uniqueSort = jQuery.unique = Sizzle.uniqueSort; | |
| 2751 | jQuery.text = Sizzle.getText; | |
| 2752 | jQuery.isXMLDoc = Sizzle.isXML; | |
| 2753 | jQuery.contains = Sizzle.contains; | |
| 2754 | jQuery.escapeSelector = Sizzle.escape; | |
| 2755 | ||
| 2756 | ||
| 2757 | ||
| 2758 | ||
| 2759 | var dir = function( elem, dir, until ) { | |
| 2760 | var matched = [], | |
| 2761 | truncate = until !== undefined; | |
| 2762 | ||
| 2763 | while ( ( elem = elem[ dir ] ) && elem.nodeType !== 9 ) { | |
| 2764 | if ( elem.nodeType === 1 ) { | |
| 2765 | if ( truncate && jQuery( elem ).is( until ) ) { | |
| 2766 | break; | |
| 2767 | } | |
| 2768 | matched.push( elem ); | |
| 2769 | } | |
| 2770 | } | |
| 2771 | return matched; | |
| 2772 | }; | |
| 2773 | ||
| 2774 | ||
| 2775 | var siblings = function( n, elem ) { | |
| 2776 | var matched = []; | |
| 2777 | ||
| 2778 | for ( ; n; n = n.nextSibling ) { | |
| 2779 | if ( n.nodeType === 1 && n !== elem ) { | |
| 2780 | matched.push( n ); | |
| 2781 | } | |
| 2782 | } | |
| 2783 | ||
| 2784 | return matched; | |
| 2785 | }; | |
| 2786 | ||
| 2787 | ||
| 2788 | var rneedsContext = jQuery.expr.match.needsContext; | |
| 2789 | ||
| 2790 | var rsingleTag = ( /^<([a-z][^\/\0>:\x20\t\r\n\f]*)[\x20\t\r\n\f]*\/?>(?:<\/\1>|)$/i ); | |
| 2791 | ||
| 2792 | ||
| 2793 | ||
| 2794 | var risSimple = /^.[^:#\[\.,]*$/; | |
| 2795 | ||
| 2796 | // Implement the identical functionality for filter and not | |
| 2797 | function winnow( elements, qualifier, not ) { | |
| 2798 | if ( jQuery.isFunction( qualifier ) ) { | |
| 2799 | return jQuery.grep( elements, function( elem, i ) { | |
| 2800 | return !!qualifier.call( elem, i, elem ) !== not; | |
| 2801 | } ); | |
| 2802 | ||
| 2803 | } | |
| 2804 | ||
| 2805 | if ( qualifier.nodeType ) { | |
| 2806 | return jQuery.grep( elements, function( elem ) { | |
| 2807 | return ( elem === qualifier ) !== not; | |
| 2808 | } ); | |
| 2809 | ||
| 2810 | } | |
| 2811 | ||
| 2812 | if ( typeof qualifier === "string" ) { | |
| 2813 | if ( risSimple.test( qualifier ) ) { | |
| 2814 | return jQuery.filter( qualifier, elements, not ); | |
| 2815 | } | |
| 2816 | ||
| 2817 | qualifier = jQuery.filter( qualifier, elements ); | |
| 2818 | } | |
| 2819 | ||
| 2820 | return jQuery.grep( elements, function( elem ) { | |
| 2821 | return ( indexOf.call( qualifier, elem ) > -1 ) !== not && elem.nodeType === 1; | |
| 2822 | } ); | |
| 2823 | } | |
| 2824 | ||
| 2825 | jQuery.filter = function( expr, elems, not ) { | |
| 2826 | var elem = elems[ 0 ]; | |
| 2827 | ||
| 2828 | if ( not ) { | |
| 2829 | expr = ":not(" + expr + ")"; | |
| 2830 | } | |
| 2831 | ||
| 2832 | return elems.length === 1 && elem.nodeType === 1 ? | |
| 2833 | jQuery.find.matchesSelector( elem, expr ) ? [ elem ] : [] : | |
| 2834 | jQuery.find.matches( expr, jQuery.grep( elems, function( elem ) { | |
| 2835 | return elem.nodeType === 1; | |
| 2836 | } ) ); | |
| 2837 | }; | |
| 2838 | ||
| 2839 | jQuery.fn.extend( { | |
| 2840 | find: function( selector ) { | |
| 2841 | var i, ret, | |
| 2842 | len = this.length, | |
| 2843 | self = this; | |
| 2844 | ||
| 2845 | if ( typeof selector !== "string" ) { | |
| 2846 | return this.pushStack( jQuery( selector ).filter( function() { | |
| 2847 | for ( i = 0; i < len; i++ ) { | |
| 2848 | if ( jQuery.contains( self[ i ], this ) ) { | |
| 2849 | return true; | |
| 2850 | } | |
| 2851 | } | |
| 2852 | } ) ); | |
| 2853 | } | |
| 2854 | ||
| 2855 | ret = this.pushStack( [] ); | |
| 2856 | ||
| 2857 | for ( i = 0; i < len; i++ ) { | |
| 2858 | jQuery.find( selector, self[ i ], ret ); | |
| 2859 | } | |
| 2860 | ||
| 2861 | return len > 1 ? jQuery.uniqueSort( ret ) : ret; | |
| 2862 | }, | |
| 2863 | filter: function( selector ) { | |
| 2864 | return this.pushStack( winnow( this, selector || [], false ) ); | |
| 2865 | }, | |
| 2866 | not: function( selector ) { | |
| 2867 | return this.pushStack( winnow( this, selector || [], true ) ); | |
| 2868 | }, | |
| 2869 | is: function( selector ) { | |
| 2870 | return !!winnow( | |
| 2871 | this, | |
| 2872 | ||
| 2873 | // If this is a positional/relative selector, check membership in the returned set | |
| 2874 | // so $("p:first").is("p:last") won't return true for a doc with two "p". | |
| 2875 | typeof selector === "string" && rneedsContext.test( selector ) ? | |
| 2876 | jQuery( selector ) : | |
| 2877 | selector || [], | |
| 2878 | false | |
| 2879 | ).length; | |
| 2880 | } | |
| 2881 | } ); | |
| 2882 | ||
| 2883 | ||
| 2884 | // Initialize a jQuery object | |
| 2885 | ||
| 2886 | ||
| 2887 | // A central reference to the root jQuery(document) | |
| 2888 | var rootjQuery, | |
| 2889 | ||
| 2890 | // A simple way to check for HTML strings | |
| 2891 | // Prioritize #id over <tag> to avoid XSS via location.hash (#9521) | |
| 2892 | // Strict HTML recognition (#11290: must start with <) | |
| 2893 | // Shortcut simple #id case for speed | |
| 2894 | rquickExpr = /^(?:\s*(<[\w\W]+>)[^>]*|#([\w-]+))$/, | |
| 2895 | ||
| 2896 | init = jQuery.fn.init = function( selector, context, root ) { | |
| 2897 | var match, elem; | |
| 2898 | ||
| 2899 | // HANDLE: $(""), $(null), $(undefined), $(false) | |
| 2900 | if ( !selector ) { | |
| 2901 | return this; | |
| 2902 | } | |
| 2903 | ||
| 2904 | // Method init() accepts an alternate rootjQuery | |
| 2905 | // so migrate can support jQuery.sub (gh-2101) | |
| 2906 | root = root || rootjQuery; | |
| 2907 | ||
| 2908 | // Handle HTML strings | |
| 2909 | if ( typeof selector === "string" ) { | |
| 2910 | if ( selector[ 0 ] === "<" && | |
| 2911 | selector[ selector.length - 1 ] === ">" && | |
| 2912 | selector.length >= 3 ) { | |
| 2913 | ||
| 2914 | // Assume that strings that start and end with <> are HTML and skip the regex check | |
| 2915 | match = [ null, selector, null ]; | |
| 2916 | ||
| 2917 | } else { | |
| 2918 | match = rquickExpr.exec( selector ); | |
| 2919 | } | |
| 2920 | ||
| 2921 | // Match html or make sure no context is specified for #id | |
| 2922 | if ( match && ( match[ 1 ] || !context ) ) { | |
| 2923 | ||
| 2924 | // HANDLE: $(html) -> $(array) | |
| 2925 | if ( match[ 1 ] ) { | |
| 2926 | context = context instanceof jQuery ? context[ 0 ] : context; | |
| 2927 | ||
| 2928 | // Option to run scripts is true for back-compat | |
| 2929 | // Intentionally let the error be thrown if parseHTML is not present | |
| 2930 | jQuery.merge( this, jQuery.parseHTML( | |
| 2931 | match[ 1 ], | |
| 2932 | context && context.nodeType ? context.ownerDocument || context : document, | |
| 2933 | true | |
| 2934 | ) ); | |
| 2935 | ||
| 2936 | // HANDLE: $(html, props) | |
| 2937 | if ( rsingleTag.test( match[ 1 ] ) && jQuery.isPlainObject( context ) ) { | |
| 2938 | for ( match in context ) { | |
| 2939 | ||
| 2940 | // Properties of context are called as methods if possible | |
| 2941 | if ( jQuery.isFunction( this[ match ] ) ) { | |
| 2942 | this[ match ]( context[ match ] ); | |
| 2943 | ||
| 2944 | // ...and otherwise set as attributes | |
| 2945 | } else { | |
| 2946 | this.attr( match, context[ match ] ); | |
| 2947 | } | |
| 2948 | } | |
| 2949 | } | |
| 2950 | ||
| 2951 | return this; | |
| 2952 | ||
| 2953 | // HANDLE: $(#id) | |
| 2954 | } else { | |
| 2955 | elem = document.getElementById( match[ 2 ] ); | |
| 2956 | ||
| 2957 | if ( elem ) { | |
| 2958 | ||
| 2959 | // Inject the element directly into the jQuery object | |
| 2960 | this[ 0 ] = elem; | |
| 2961 | this.length = 1; | |
| 2962 | } | |
| 2963 | return this; | |
| 2964 | } | |
| 2965 | ||
| 2966 | // HANDLE: $(expr, $(...)) | |
| 2967 | } else if ( !context || context.jquery ) { | |
| 2968 | return ( context || root ).find( selector ); | |
| 2969 | ||
| 2970 | // HANDLE: $(expr, context) | |
| 2971 | // (which is just equivalent to: $(context).find(expr) | |
| 2972 | } else { | |
| 2973 | return this.constructor( context ).find( selector ); | |
| 2974 | } | |
| 2975 | ||
| 2976 | // HANDLE: $(DOMElement) | |
| 2977 | } else if ( selector.nodeType ) { | |
| 2978 | this[ 0 ] = selector; | |
| 2979 | this.length = 1; | |
| 2980 | return this; | |
| 2981 | ||
| 2982 | // HANDLE: $(function) | |
| 2983 | // Shortcut for document ready | |
| 2984 | } else if ( jQuery.isFunction( selector ) ) { | |
| 2985 | return root.ready !== undefined ? | |
| 2986 | root.ready( selector ) : | |
| 2987 | ||
| 2988 | // Execute immediately if ready is not present | |
| 2989 | selector( jQuery ); | |
| 2990 | } | |
| 2991 | ||
| 2992 | return jQuery.makeArray( selector, this ); | |
| 2993 | }; | |
| 2994 | ||
| 2995 | // Give the init function the jQuery prototype for later instantiation | |
| 2996 | init.prototype = jQuery.fn; | |
| 2997 | ||
| 2998 | // Initialize central reference | |
| 2999 | rootjQuery = jQuery( document ); | |
| 3000 | ||
| 3001 | ||
| 3002 | var rparentsprev = /^(?:parents|prev(?:Until|All))/, | |
| 3003 | ||
| 3004 | // Methods guaranteed to produce a unique set when starting from a unique set | |
| 3005 | guaranteedUnique = { | |
| 3006 | children: true, | |
| 3007 | contents: true, | |
| 3008 | next: true, | |
| 3009 | prev: true | |
| 3010 | }; | |
| 3011 | ||
| 3012 | jQuery.fn.extend( { | |
| 3013 | has: function( target ) { | |
| 3014 | var targets = jQuery( target, this ), | |
| 3015 | l = targets.length; | |
| 3016 | ||
| 3017 | return this.filter( function() { | |
| 3018 | var i = 0; | |
| 3019 | for ( ; i < l; i++ ) { | |
| 3020 | if ( jQuery.contains( this, targets[ i ] ) ) { | |
| 3021 | return true; | |
| 3022 | } | |
| 3023 | } | |
| 3024 | } ); | |
| 3025 | }, | |
| 3026 | ||
| 3027 | closest: function( selectors, context ) { | |
| 3028 | var cur, | |
| 3029 | i = 0, | |
| 3030 | l = this.length, | |
| 3031 | matched = [], | |
| 3032 | targets = typeof selectors !== "string" && jQuery( selectors ); | |
| 3033 | ||
| 3034 | // Positional selectors never match, since there's no _selection_ context | |
| 3035 | if ( !rneedsContext.test( selectors ) ) { | |
| 3036 | for ( ; i < l; i++ ) { | |
| 3037 | for ( cur = this[ i ]; cur && cur !== context; cur = cur.parentNode ) { | |
| 3038 | ||
| 3039 | // Always skip document fragments | |
| 3040 | if ( cur.nodeType < 11 && ( targets ? | |
| 3041 | targets.index( cur ) > -1 : | |
| 3042 | ||
| 3043 | // Don't pass non-elements to Sizzle | |
| 3044 | cur.nodeType === 1 && | |
| 3045 | jQuery.find.matchesSelector( cur, selectors ) ) ) { | |
| 3046 | ||
| 3047 | matched.push( cur ); | |
| 3048 | break; | |
| 3049 | } | |
| 3050 | } | |
| 3051 | } | |
| 3052 | } | |
| 3053 | ||
| 3054 | return this.pushStack( matched.length > 1 ? jQuery.uniqueSort( matched ) : matched ); | |
| 3055 | }, | |
| 3056 | ||
| 3057 | // Determine the position of an element within the set | |
| 3058 | index: function( elem ) { | |
| 3059 | ||
| 3060 | // No argument, return index in parent | |
| 3061 | if ( !elem ) { | |
| 3062 | return ( this[ 0 ] && this[ 0 ].parentNode ) ? this.first().prevAll().length : -1; | |
| 3063 | } | |
| 3064 | ||
| 3065 | // Index in selector | |
| 3066 | if ( typeof elem === "string" ) { | |
| 3067 | return indexOf.call( jQuery( elem ), this[ 0 ] ); | |
| 3068 | } | |
| 3069 | ||
| 3070 | // Locate the position of the desired element | |
| 3071 | return indexOf.call( this, | |
| 3072 | ||
| 3073 | // If it receives a jQuery object, the first element is used | |
| 3074 | elem.jquery ? elem[ 0 ] : elem | |
| 3075 | ); | |
| 3076 | }, | |
| 3077 | ||
| 3078 | add: function( selector, context ) { | |
| 3079 | return this.pushStack( | |
| 3080 | jQuery.uniqueSort( | |
| 3081 | jQuery.merge( this.get(), jQuery( selector, context ) ) | |
| 3082 | ) | |
| 3083 | ); | |
| 3084 | }, | |
| 3085 | ||
| 3086 | addBack: function( selector ) { | |
| 3087 | return this.add( selector == null ? | |
| 3088 | this.prevObject : this.prevObject.filter( selector ) | |
| 3089 | ); | |
| 3090 | } | |
| 3091 | } ); | |
| 3092 | ||
| 3093 | function sibling( cur, dir ) { | |
| 3094 | while ( ( cur = cur[ dir ] ) && cur.nodeType !== 1 ) {} | |
| 3095 | return cur; | |
| 3096 | } | |
| 3097 | ||
| 3098 | jQuery.each( { | |
| 3099 | parent: function( elem ) { | |
| 3100 | var parent = elem.parentNode; | |
| 3101 | return parent && parent.nodeType !== 11 ? parent : null; | |
| 3102 | }, | |
| 3103 | parents: function( elem ) { | |
| 3104 | return dir( elem, "parentNode" ); | |
| 3105 | }, | |
| 3106 | parentsUntil: function( elem, i, until ) { | |
| 3107 | return dir( elem, "parentNode", until ); | |
| 3108 | }, | |
| 3109 | next: function( elem ) { | |
| 3110 | return sibling( elem, "nextSibling" ); | |
| 3111 | }, | |
| 3112 | prev: function( elem ) { | |
| 3113 | return sibling( elem, "previousSibling" ); | |
| 3114 | }, | |
| 3115 | nextAll: function( elem ) { | |
| 3116 | return dir( elem, "nextSibling" ); | |
| 3117 | }, | |
| 3118 | prevAll: function( elem ) { | |
| 3119 | return dir( elem, "previousSibling" ); | |
| 3120 | }, | |
| 3121 | nextUntil: function( elem, i, until ) { | |
| 3122 | return dir( elem, "nextSibling", until ); | |
| 3123 | }, | |
| 3124 | prevUntil: function( elem, i, until ) { | |
| 3125 | return dir( elem, "previousSibling", until ); | |
| 3126 | }, | |
| 3127 | siblings: function( elem ) { | |
| 3128 | return siblings( ( elem.parentNode || {} ).firstChild, elem ); | |
| 3129 | }, | |
| 3130 | children: function( elem ) { | |
| 3131 | return siblings( elem.firstChild ); | |
| 3132 | }, | |
| 3133 | contents: function( elem ) { | |
| 3134 | return elem.contentDocument || jQuery.merge( [], elem.childNodes ); | |
| 3135 | } | |
| 3136 | }, function( name, fn ) { | |
| 3137 | jQuery.fn[ name ] = function( until, selector ) { | |
| 3138 | var matched = jQuery.map( this, fn, until ); | |
| 3139 | ||
| 3140 | if ( name.slice( -5 ) !== "Until" ) { | |
| 3141 | selector = until; | |
| 3142 | } | |
| 3143 | ||
| 3144 | if ( selector && typeof selector === "string" ) { | |
| 3145 | matched = jQuery.filter( selector, matched ); | |
| 3146 | } | |
| 3147 | ||
| 3148 | if ( this.length > 1 ) { | |
| 3149 | ||
| 3150 | // Remove duplicates | |
| 3151 | if ( !guaranteedUnique[ name ] ) { | |
| 3152 | jQuery.uniqueSort( matched ); | |
| 3153 | } | |
| 3154 | ||
| 3155 | // Reverse order for parents* and prev-derivatives | |
| 3156 | if ( rparentsprev.test( name ) ) { | |
| 3157 | matched.reverse(); | |
| 3158 | } | |
| 3159 | } | |
| 3160 | ||
| 3161 | return this.pushStack( matched ); | |
| 3162 | }; | |
| 3163 | } ); | |
| 3164 | var rnotwhite = ( /\S+/g ); | |
| 3165 | ||
| 3166 | ||
| 3167 | ||
| 3168 | // Convert String-formatted options into Object-formatted ones | |
| 3169 | function createOptions( options ) { | |
| 3170 | var object = {}; | |
| 3171 | jQuery.each( options.match( rnotwhite ) || [], function( _, flag ) { | |
| 3172 | object[ flag ] = true; | |
| 3173 | } ); | |
| 3174 | return object; | |
| 3175 | } | |
| 3176 | ||
| 3177 | /* | |
| 3178 | * Create a callback list using the following parameters: | |
| 3179 | * | |
| 3180 | * options: an optional list of space-separated options that will change how | |
| 3181 | * the callback list behaves or a more traditional option object | |
| 3182 | * | |
| 3183 | * By default a callback list will act like an event callback list and can be | |
| 3184 | * "fired" multiple times. | |
| 3185 | * | |
| 3186 | * Possible options: | |
| 3187 | * | |
| 3188 | * once: will ensure the callback list can only be fired once (like a Deferred) | |
| 3189 | * | |
| 3190 | * memory: will keep track of previous values and will call any callback added | |
| 3191 | * after the list has been fired right away with the latest "memorized" | |
| 3192 | * values (like a Deferred) | |
| 3193 | * | |
| 3194 | * unique: will ensure a callback can only be added once (no duplicate in the list) | |
| 3195 | * | |
| 3196 | * stopOnFalse: interrupt callings when a callback returns false | |
| 3197 | * | |
| 3198 | */ | |
| 3199 | jQuery.Callbacks = function( options ) { | |
| 3200 | ||
| 3201 | // Convert options from String-formatted to Object-formatted if needed | |
| 3202 | // (we check in cache first) | |
| 3203 | options = typeof options === "string" ? | |
| 3204 | createOptions( options ) : | |
| 3205 | jQuery.extend( {}, options ); | |
| 3206 | ||
| 3207 | var // Flag to know if list is currently firing | |
| 3208 | firing, | |
| 3209 | ||
| 3210 | // Last fire value for non-forgettable lists | |
| 3211 | memory, | |
| 3212 | ||
| 3213 | // Flag to know if list was already fired | |
| 3214 | fired, | |
| 3215 | ||
| 3216 | // Flag to prevent firing | |
| 3217 | locked, | |
| 3218 | ||
| 3219 | // Actual callback list | |
| 3220 | list = [], | |
| 3221 | ||
| 3222 | // Queue of execution data for repeatable lists | |
| 3223 | queue = [], | |
| 3224 | ||
| 3225 | // Index of currently firing callback (modified by add/remove as needed) | |
| 3226 | firingIndex = -1, | |
| 3227 | ||
| 3228 | // Fire callbacks | |
| 3229 | fire = function() { | |
| 3230 | ||
| 3231 | // Enforce single-firing | |
| 3232 | locked = options.once; | |
| 3233 | ||
| 3234 | // Execute callbacks for all pending executions, | |
| 3235 | // respecting firingIndex overrides and runtime changes | |
| 3236 | fired = firing = true; | |
| 3237 | for ( ; queue.length; firingIndex = -1 ) { | |
| 3238 | memory = queue.shift(); | |
| 3239 | while ( ++firingIndex < list.length ) { | |
| 3240 | ||
| 3241 | // Run callback and check for early termination | |
| 3242 | if ( list[ firingIndex ].apply( memory[ 0 ], memory[ 1 ] ) === false && | |
| 3243 | options.stopOnFalse ) { | |
| 3244 | ||
| 3245 | // Jump to end and forget the data so .add doesn't re-fire | |
| 3246 | firingIndex = list.length; | |
| 3247 | memory = false; | |
| 3248 | } | |
| 3249 | } | |
| 3250 | } | |
| 3251 | ||
| 3252 | // Forget the data if we're done with it | |
| 3253 | if ( !options.memory ) { | |
| 3254 | memory = false; | |
| 3255 | } | |
| 3256 | ||
| 3257 | firing = false; | |
| 3258 | ||
| 3259 | // Clean up if we're done firing for good | |
| 3260 | if ( locked ) { | |
| 3261 | ||
| 3262 | // Keep an empty list if we have data for future add calls | |
| 3263 | if ( memory ) { | |
| 3264 | list = []; | |
| 3265 | ||
| 3266 | // Otherwise, this object is spent | |
| 3267 | } else { | |
| 3268 | list = ""; | |
| 3269 | } | |
| 3270 | } | |
| 3271 | }, | |
| 3272 | ||
| 3273 | // Actual Callbacks object | |
| 3274 | self = { | |
| 3275 | ||
| 3276 | // Add a callback or a collection of callbacks to the list | |
| 3277 | add: function() { | |
| 3278 | if ( list ) { | |
| 3279 | ||
| 3280 | // If we have memory from a past run, we should fire after adding | |
| 3281 | if ( memory && !firing ) { | |
| 3282 | firingIndex = list.length - 1; | |
| 3283 | queue.push( memory ); | |
| 3284 | } | |
| 3285 | ||
| 3286 | ( function add( args ) { | |
| 3287 | jQuery.each( args, function( _, arg ) { | |
| 3288 | if ( jQuery.isFunction( arg ) ) { | |
| 3289 | if ( !options.unique || !self.has( arg ) ) { | |
| 3290 | list.push( arg ); | |
| 3291 | } | |
| 3292 | } else if ( arg && arg.length && jQuery.type( arg ) !== "string" ) { | |
| 3293 | ||
| 3294 | // Inspect recursively | |
| 3295 | add( arg ); | |
| 3296 | } | |
| 3297 | } ); | |
| 3298 | } )( arguments ); | |
| 3299 | ||
| 3300 | if ( memory && !firing ) { | |
| 3301 | fire(); | |
| 3302 | } | |
| 3303 | } | |
| 3304 | return this; | |
| 3305 | }, | |
| 3306 | ||
| 3307 | // Remove a callback from the list | |
| 3308 | remove: function() { | |
| 3309 | jQuery.each( arguments, function( _, arg ) { | |
| 3310 | var index; | |
| 3311 | while ( ( index = jQuery.inArray( arg, list, index ) ) > -1 ) { | |
| 3312 | list.splice( index, 1 ); | |
| 3313 | ||
| 3314 | // Handle firing indexes | |
| 3315 | if ( index <= firingIndex ) { | |
| 3316 | firingIndex--; | |
| 3317 | } | |
| 3318 | } | |
| 3319 | } ); | |
| 3320 | return this; | |
| 3321 | }, | |
| 3322 | ||
| 3323 | // Check if a given callback is in the list. | |
| 3324 | // If no argument is given, return whether or not list has callbacks attached. | |
| 3325 | has: function( fn ) { | |
| 3326 | return fn ? | |
| 3327 | jQuery.inArray( fn, list ) > -1 : | |
| 3328 | list.length > 0; | |
| 3329 | }, | |
| 3330 | ||
| 3331 | // Remove all callbacks from the list | |
| 3332 | empty: function() { | |
| 3333 | if ( list ) { | |
| 3334 | list = []; | |
| 3335 | } | |
| 3336 | return this; | |
| 3337 | }, | |
| 3338 | ||
| 3339 | // Disable .fire and .add | |
| 3340 | // Abort any current/pending executions | |
| 3341 | // Clear all callbacks and values | |
| 3342 | disable: function() { | |
| 3343 | locked = queue = []; | |
| 3344 | list = memory = ""; | |
| 3345 | return this; | |
| 3346 | }, | |
| 3347 | disabled: function() { | |
| 3348 | return !list; | |
| 3349 | }, | |
| 3350 | ||
| 3351 | // Disable .fire | |
| 3352 | // Also disable .add unless we have memory (since it would have no effect) | |
| 3353 | // Abort any pending executions | |
| 3354 | lock: function() { | |
| 3355 | locked = queue = []; | |
| 3356 | if ( !memory && !firing ) { | |
| 3357 | list = memory = ""; | |
| 3358 | } | |
| 3359 | return this; | |
| 3360 | }, | |
| 3361 | locked: function() { | |
| 3362 | return !!locked; | |
| 3363 | }, | |
| 3364 | ||
| 3365 | // Call all callbacks with the given context and arguments | |
| 3366 | fireWith: function( context, args ) { | |
| 3367 | if ( !locked ) { | |
| 3368 | args = args || []; | |
| 3369 | args = [ context, args.slice ? args.slice() : args ]; | |
| 3370 | queue.push( args ); | |
| 3371 | if ( !firing ) { | |
| 3372 | fire(); | |
| 3373 | } | |
| 3374 | } | |
| 3375 | return this; | |
| 3376 | }, | |
| 3377 | ||
| 3378 | // Call all the callbacks with the given arguments | |
| 3379 | fire: function() { | |
| 3380 | self.fireWith( this, arguments ); | |
| 3381 | return this; | |
| 3382 | }, | |
| 3383 | ||
| 3384 | // To know if the callbacks have already been called at least once | |
| 3385 | fired: function() { | |
| 3386 | return !!fired; | |
| 3387 | } | |
| 3388 | }; | |
| 3389 | ||
| 3390 | return self; | |
| 3391 | }; | |
| 3392 | ||
| 3393 | ||
| 3394 | function Identity( v ) { | |
| 3395 | return v; | |
| 3396 | } | |
| 3397 | function Thrower( ex ) { | |
| 3398 | throw ex; | |
| 3399 | } | |
| 3400 | ||
| 3401 | function adoptValue( value, resolve, reject ) { | |
| 3402 | var method; | |
| 3403 | ||
| 3404 | try { | |
| 3405 | ||
| 3406 | // Check for promise aspect first to privilege synchronous behavior | |
| 3407 | if ( value && jQuery.isFunction( ( method = value.promise ) ) ) { | |
| 3408 | method.call( value ).done( resolve ).fail( reject ); | |
| 3409 | ||
| 3410 | // Other thenables | |
| 3411 | } else if ( value && jQuery.isFunction( ( method = value.then ) ) ) { | |
| 3412 | method.call( value, resolve, reject ); | |
| 3413 | ||
| 3414 | // Other non-thenables | |
| 3415 | } else { | |
| 3416 | ||
| 3417 | // Support: Android 4.0 only | |
| 3418 | // Strict mode functions invoked without .call/.apply get global-object context | |
| 3419 | resolve.call( undefined, value ); | |
| 3420 | } | |
| 3421 | ||
| 3422 | // For Promises/A+, convert exceptions into rejections | |
| 3423 | // Since jQuery.when doesn't unwrap thenables, we can skip the extra checks appearing in | |
| 3424 | // Deferred#then to conditionally suppress rejection. | |
| 3425 | } catch ( value ) { | |
| 3426 | ||
| 3427 | // Support: Android 4.0 only | |
| 3428 | // Strict mode functions invoked without .call/.apply get global-object context | |
| 3429 | reject.call( undefined, value ); | |
| 3430 | } | |
| 3431 | } | |
| 3432 | ||
| 3433 | jQuery.extend( { | |
| 3434 | ||
| 3435 | Deferred: function( func ) { | |
| 3436 | var tuples = [ | |
| 3437 | ||
| 3438 | // action, add listener, callbacks, | |
| 3439 | // ... .then handlers, argument index, [final state] | |
| 3440 | [ "notify", "progress", jQuery.Callbacks( "memory" ), | |
| 3441 | jQuery.Callbacks( "memory" ), 2 ], | |
| 3442 | [ "resolve", "done", jQuery.Callbacks( "once memory" ), | |
| 3443 | jQuery.Callbacks( "once memory" ), 0, "resolved" ], | |
| 3444 | [ "reject", "fail", jQuery.Callbacks( "once memory" ), | |
| 3445 | jQuery.Callbacks( "once memory" ), 1, "rejected" ] | |
| 3446 | ], | |
| 3447 | state = "pending", | |
| 3448 | promise = { | |
| 3449 | state: function() { | |
| 3450 | return state; | |
| 3451 | }, | |
| 3452 | always: function() { | |
| 3453 | deferred.done( arguments ).fail( arguments ); | |
| 3454 | return this; | |
| 3455 | }, | |
| 3456 | "catch": function( fn ) { | |
| 3457 | return promise.then( null, fn ); | |
| 3458 | }, | |
| 3459 | ||
| 3460 | // Keep pipe for back-compat | |
| 3461 | pipe: function( /* fnDone, fnFail, fnProgress */ ) { | |
| 3462 | var fns = arguments; | |
| 3463 | ||
| 3464 | return jQuery.Deferred( function( newDefer ) { | |
| 3465 | jQuery.each( tuples, function( i, tuple ) { | |
| 3466 | ||
| 3467 | // Map tuples (progress, done, fail) to arguments (done, fail, progress) | |
| 3468 | var fn = jQuery.isFunction( fns[ tuple[ 4 ] ] ) && fns[ tuple[ 4 ] ]; | |
| 3469 | ||
| 3470 | // deferred.progress(function() { bind to newDefer or newDefer.notify }) | |
| 3471 | // deferred.done(function() { bind to newDefer or newDefer.resolve }) | |
| 3472 | // deferred.fail(function() { bind to newDefer or newDefer.reject }) | |
| 3473 | deferred[ tuple[ 1 ] ]( function() { | |
| 3474 | var returned = fn && fn.apply( this, arguments ); | |
| 3475 | if ( returned && jQuery.isFunction( returned.promise ) ) { | |
| 3476 | returned.promise() | |
| 3477 | .progress( newDefer.notify ) | |
| 3478 | .done( newDefer.resolve ) | |
| 3479 | .fail( newDefer.reject ); | |
| 3480 | } else { | |
| 3481 | newDefer[ tuple[ 0 ] + "With" ]( | |
| 3482 | this, | |
| 3483 | fn ? [ returned ] : arguments | |
| 3484 | ); | |
| 3485 | } | |
| 3486 | } ); | |
| 3487 | } ); | |
| 3488 | fns = null; | |
| 3489 | } ).promise(); | |
| 3490 | }, | |
| 3491 | then: function( onFulfilled, onRejected, onProgress ) { | |
| 3492 | var maxDepth = 0; | |
| 3493 | function resolve( depth, deferred, handler, special ) { | |
| 3494 | return function() { | |
| 3495 | var that = this, | |
| 3496 | args = arguments, | |
| 3497 | mightThrow = function() { | |
| 3498 | var returned, then; | |
| 3499 | ||
| 3500 | // Support: Promises/A+ section 2.3.3.3.3 | |
| 3501 | // https://promisesaplus.com/#point-59 | |
| 3502 | // Ignore double-resolution attempts | |
| 3503 | if ( depth < maxDepth ) { | |
| 3504 | return; | |
| 3505 | } | |
| 3506 | ||
| 3507 | returned = handler.apply( that, args ); | |
| 3508 | ||
| 3509 | // Support: Promises/A+ section 2.3.1 | |
| 3510 | // https://promisesaplus.com/#point-48 | |
| 3511 | if ( returned === deferred.promise() ) { | |
| 3512 | throw new TypeError( "Thenable self-resolution" ); | |
| 3513 | } | |
| 3514 | ||
| 3515 | // Support: Promises/A+ sections 2.3.3.1, 3.5 | |
| 3516 | // https://promisesaplus.com/#point-54 | |
| 3517 | // https://promisesaplus.com/#point-75 | |
| 3518 | // Retrieve `then` only once | |
| 3519 | then = returned && | |
| 3520 | ||
| 3521 | // Support: Promises/A+ section 2.3.4 | |
| 3522 | // https://promisesaplus.com/#point-64 | |
| 3523 | // Only check objects and functions for thenability | |
| 3524 | ( typeof returned === "object" || | |
| 3525 | typeof returned === "function" ) && | |
| 3526 | returned.then; | |
| 3527 | ||
| 3528 | // Handle a returned thenable | |
| 3529 | if ( jQuery.isFunction( then ) ) { | |
| 3530 | ||
| 3531 | // Special processors (notify) just wait for resolution | |
| 3532 | if ( special ) { | |
| 3533 | then.call( | |
| 3534 | returned, | |
| 3535 | resolve( maxDepth, deferred, Identity, special ), | |
| 3536 | resolve( maxDepth, deferred, Thrower, special ) | |
| 3537 | ); | |
| 3538 | ||
| 3539 | // Normal processors (resolve) also hook into progress | |
| 3540 | } else { | |
| 3541 | ||
| 3542 | // ...and disregard older resolution values | |
| 3543 | maxDepth++; | |
| 3544 | ||
| 3545 | then.call( | |
| 3546 | returned, | |
| 3547 | resolve( maxDepth, deferred, Identity, special ), | |
| 3548 | resolve( maxDepth, deferred, Thrower, special ), | |
| 3549 | resolve( maxDepth, deferred, Identity, | |
| 3550 | deferred.notifyWith ) | |
| 3551 | ); | |
| 3552 | } | |
| 3553 | ||
| 3554 | // Handle all other returned values | |
| 3555 | } else { | |
| 3556 | ||
| 3557 | // Only substitute handlers pass on context | |
| 3558 | // and multiple values (non-spec behavior) | |
| 3559 | if ( handler !== Identity ) { | |
| 3560 | that = undefined; | |
| 3561 | args = [ returned ]; | |
| 3562 | } | |
| 3563 | ||
| 3564 | // Process the value(s) | |
| 3565 | // Default process is resolve | |
| 3566 | ( special || deferred.resolveWith )( that, args ); | |
| 3567 | } | |
| 3568 | }, | |
| 3569 | ||
| 3570 | // Only normal processors (resolve) catch and reject exceptions | |
| 3571 | process = special ? | |
| 3572 | mightThrow : | |
| 3573 | function() { | |
| 3574 | try { | |
| 3575 | mightThrow(); | |
| 3576 | } catch ( e ) { | |
| 3577 | ||
| 3578 | if ( jQuery.Deferred.exceptionHook ) { | |
| 3579 | jQuery.Deferred.exceptionHook( e, | |
| 3580 | process.stackTrace ); | |
| 3581 | } | |
| 3582 | ||
| 3583 | // Support: Promises/A+ section 2.3.3.3.4.1 | |
| 3584 | // https://promisesaplus.com/#point-61 | |
| 3585 | // Ignore post-resolution exceptions | |
| 3586 | if ( depth + 1 >= maxDepth ) { | |
| 3587 | ||
| 3588 | // Only substitute handlers pass on context | |
| 3589 | // and multiple values (non-spec behavior) | |
| 3590 | if ( handler !== Thrower ) { | |
| 3591 | that = undefined; | |
| 3592 | args = [ e ]; | |
| 3593 | } | |
| 3594 | ||
| 3595 | deferred.rejectWith( that, args ); | |
| 3596 | } | |
| 3597 | } | |
| 3598 | }; | |
| 3599 | ||
| 3600 | // Support: Promises/A+ section 2.3.3.3.1 | |
| 3601 | // https://promisesaplus.com/#point-57 | |
| 3602 | // Re-resolve promises immediately to dodge false rejection from | |
| 3603 | // subsequent errors | |
| 3604 | if ( depth ) { | |
| 3605 | process(); | |
| 3606 | } else { | |
| 3607 | ||
| 3608 | // Call an optional hook to record the stack, in case of exception | |
| 3609 | // since it's otherwise lost when execution goes async | |
| 3610 | if ( jQuery.Deferred.getStackHook ) { | |
| 3611 | process.stackTrace = jQuery.Deferred.getStackHook(); | |
| 3612 | } | |
| 3613 | window.setTimeout( process ); | |
| 3614 | } | |
| 3615 | }; | |
| 3616 | } | |
| 3617 | ||
| 3618 | return jQuery.Deferred( function( newDefer ) { | |
| 3619 | ||
| 3620 | // progress_handlers.add( ... ) | |
| 3621 | tuples[ 0 ][ 3 ].add( | |
| 3622 | resolve( | |
| 3623 | 0, | |
| 3624 | newDefer, | |
| 3625 | jQuery.isFunction( onProgress ) ? | |
| 3626 | onProgress : | |
| 3627 | Identity, | |
| 3628 | newDefer.notifyWith | |
| 3629 | ) | |
| 3630 | ); | |
| 3631 | ||
| 3632 | // fulfilled_handlers.add( ... ) | |
| 3633 | tuples[ 1 ][ 3 ].add( | |
| 3634 | resolve( | |
| 3635 | 0, | |
| 3636 | newDefer, | |
| 3637 | jQuery.isFunction( onFulfilled ) ? | |
| 3638 | onFulfilled : | |
| 3639 | Identity | |
| 3640 | ) | |
| 3641 | ); | |
| 3642 | ||
| 3643 | // rejected_handlers.add( ... ) | |
| 3644 | tuples[ 2 ][ 3 ].add( | |
| 3645 | resolve( | |
| 3646 | 0, | |
| 3647 | newDefer, | |
| 3648 | jQuery.isFunction( onRejected ) ? | |
| 3649 | onRejected : | |
| 3650 | Thrower | |
| 3651 | ) | |
| 3652 | ); | |
| 3653 | } ).promise(); | |
| 3654 | }, | |
| 3655 | ||
| 3656 | // Get a promise for this deferred | |
| 3657 | // If obj is provided, the promise aspect is added to the object | |
| 3658 | promise: function( obj ) { | |
| 3659 | return obj != null ? jQuery.extend( obj, promise ) : promise; | |
| 3660 | } | |
| 3661 | }, | |
| 3662 | deferred = {}; | |
| 3663 | ||
| 3664 | // Add list-specific methods | |
| 3665 | jQuery.each( tuples, function( i, tuple ) { | |
| 3666 | var list = tuple[ 2 ], | |
| 3667 | stateString = tuple[ 5 ]; | |
| 3668 | ||
| 3669 | // promise.progress = list.add | |
| 3670 | // promise.done = list.add | |
| 3671 | // promise.fail = list.add | |
| 3672 | promise[ tuple[ 1 ] ] = list.add; | |
| 3673 | ||
| 3674 | // Handle state | |
| 3675 | if ( stateString ) { | |
| 3676 | list.add( | |
| 3677 | function() { | |
| 3678 | ||
| 3679 | // state = "resolved" (i.e., fulfilled) | |
| 3680 | // state = "rejected" | |
| 3681 | state = stateString; | |
| 3682 | }, | |
| 3683 | ||
| 3684 | // rejected_callbacks.disable | |
| 3685 | // fulfilled_callbacks.disable | |
| 3686 | tuples[ 3 - i ][ 2 ].disable, | |
| 3687 | ||
| 3688 | // progress_callbacks.lock | |
| 3689 | tuples[ 0 ][ 2 ].lock | |
| 3690 | ); | |
| 3691 | } | |
| 3692 | ||
| 3693 | // progress_handlers.fire | |
| 3694 | // fulfilled_handlers.fire | |
| 3695 | // rejected_handlers.fire | |
| 3696 | list.add( tuple[ 3 ].fire ); | |
| 3697 | ||
| 3698 | // deferred.notify = function() { deferred.notifyWith(...) } | |
| 3699 | // deferred.resolve = function() { deferred.resolveWith(...) } | |
| 3700 | // deferred.reject = function() { deferred.rejectWith(...) } | |
| 3701 | deferred[ tuple[ 0 ] ] = function() { | |
| 3702 | deferred[ tuple[ 0 ] + "With" ]( this === deferred ? undefined : this, arguments ); | |
| 3703 | return this; | |
| 3704 | }; | |
| 3705 | ||
| 3706 | // deferred.notifyWith = list.fireWith | |
| 3707 | // deferred.resolveWith = list.fireWith | |
| 3708 | // deferred.rejectWith = list.fireWith | |
| 3709 | deferred[ tuple[ 0 ] + "With" ] = list.fireWith; | |
| 3710 | } ); | |
| 3711 | ||
| 3712 | // Make the deferred a promise | |
| 3713 | promise.promise( deferred ); | |
| 3714 | ||
| 3715 | // Call given func if any | |
| 3716 | if ( func ) { | |
| 3717 | func.call( deferred, deferred ); | |
| 3718 | } | |
| 3719 | ||
| 3720 | // All done! | |
| 3721 | return deferred; | |
| 3722 | }, | |
| 3723 | ||
| 3724 | // Deferred helper | |
| 3725 | when: function( singleValue ) { | |
| 3726 | var | |
| 3727 | ||
| 3728 | // count of uncompleted subordinates | |
| 3729 | remaining = arguments.length, | |
| 3730 | ||
| 3731 | // count of unprocessed arguments | |
| 3732 | i = remaining, | |
| 3733 | ||
| 3734 | // subordinate fulfillment data | |
| 3735 | resolveContexts = Array( i ), | |
| 3736 | resolveValues = slice.call( arguments ), | |
| 3737 | ||
| 3738 | // the master Deferred | |
| 3739 | master = jQuery.Deferred(), | |
| 3740 | ||
| 3741 | // subordinate callback factory | |
| 3742 | updateFunc = function( i ) { | |
| 3743 | return function( value ) { | |
| 3744 | resolveContexts[ i ] = this; | |
| 3745 | resolveValues[ i ] = arguments.length > 1 ? slice.call( arguments ) : value; | |
| 3746 | if ( !( --remaining ) ) { | |
| 3747 | master.resolveWith( resolveContexts, resolveValues ); | |
| 3748 | } | |
| 3749 | }; | |
| 3750 | }; | |
| 3751 | ||
| 3752 | // Single- and empty arguments are adopted like Promise.resolve | |
| 3753 | if ( remaining <= 1 ) { | |
| 3754 | adoptValue( singleValue, master.done( updateFunc( i ) ).resolve, master.reject ); | |
| 3755 | ||
| 3756 | // Use .then() to unwrap secondary thenables (cf. gh-3000) | |
| 3757 | if ( master.state() === "pending" || | |
| 3758 | jQuery.isFunction( resolveValues[ i ] && resolveValues[ i ].then ) ) { | |
| 3759 | ||
| 3760 | return master.then(); | |
| 3761 | } | |
| 3762 | } | |
| 3763 | ||
| 3764 | // Multiple arguments are aggregated like Promise.all array elements | |
| 3765 | while ( i-- ) { | |
| 3766 | adoptValue( resolveValues[ i ], updateFunc( i ), master.reject ); | |
| 3767 | } | |
| 3768 | ||
| 3769 | return master.promise(); | |
| 3770 | } | |
| 3771 | } ); | |
| 3772 | ||
| 3773 | ||
| 3774 | // These usually indicate a programmer mistake during development, | |
| 3775 | // warn about them ASAP rather than swallowing them by default. | |
| 3776 | var rerrorNames = /^(Eval|Internal|Range|Reference|Syntax|Type|URI)Error$/; | |
| 3777 | ||
| 3778 | jQuery.Deferred.exceptionHook = function( error, stack ) { | |
| 3779 | ||
| 3780 | // Support: IE 8 - 9 only | |
| 3781 | // Console exists when dev tools are open, which can happen at any time | |
| 3782 | if ( window.console && window.console.warn && error && rerrorNames.test( error.name ) ) { | |
| 3783 | window.console.warn( "jQuery.Deferred exception: " + error.message, error.stack, stack ); | |
| 3784 | } | |
| 3785 | }; | |
| 3786 | ||
| 3787 | ||
| 3788 | ||
| 3789 | ||
| 3790 | jQuery.readyException = function( error ) { | |
| 3791 | window.setTimeout( function() { | |
| 3792 | throw error; | |
| 3793 | } ); | |
| 3794 | }; | |
| 3795 | ||
| 3796 | ||
| 3797 | ||
| 3798 | ||
| 3799 | // The deferred used on DOM ready | |
| 3800 | var readyList = jQuery.Deferred(); | |
| 3801 | ||
| 3802 | jQuery.fn.ready = function( fn ) { | |
| 3803 | ||
| 3804 | readyList | |
| 3805 | .then( fn ) | |
| 3806 | ||
| 3807 | // Wrap jQuery.readyException in a function so that the lookup | |
| 3808 | // happens at the time of error handling instead of callback | |
| 3809 | // registration. | |
| 3810 | .catch( function( error ) { | |
| 3811 | jQuery.readyException( error ); | |
| 3812 | } ); | |
| 3813 | ||
| 3814 | return this; | |
| 3815 | }; | |
| 3816 | ||
| 3817 | jQuery.extend( { | |
| 3818 | ||
| 3819 | // Is the DOM ready to be used? Set to true once it occurs. | |
| 3820 | isReady: false, | |
| 3821 | ||
| 3822 | // A counter to track how many items to wait for before | |
| 3823 | // the ready event fires. See #6781 | |
| 3824 | readyWait: 1, | |
| 3825 | ||
| 3826 | // Hold (or release) the ready event | |
| 3827 | holdReady: function( hold ) { | |
| 3828 | if ( hold ) { | |
| 3829 | jQuery.readyWait++; | |
| 3830 | } else { | |
| 3831 | jQuery.ready( true ); | |
| 3832 | } | |
| 3833 | }, | |
| 3834 | ||
| 3835 | // Handle when the DOM is ready | |
| 3836 | ready: function( wait ) { | |
| 3837 | ||
| 3838 | // Abort if there are pending holds or we're already ready | |
| 3839 | if ( wait === true ? --jQuery.readyWait : jQuery.isReady ) { | |
| 3840 | return; | |
| 3841 | } | |
| 3842 | ||
| 3843 | // Remember that the DOM is ready | |
| 3844 | jQuery.isReady = true; | |
| 3845 | ||
| 3846 | // If a normal DOM Ready event fired, decrement, and wait if need be | |
| 3847 | if ( wait !== true && --jQuery.readyWait > 0 ) { | |
| 3848 | return; | |
| 3849 | } | |
| 3850 | ||
| 3851 | // If there are functions bound, to execute | |
| 3852 | readyList.resolveWith( document, [ jQuery ] ); | |
| 3853 | } | |
| 3854 | } ); | |
| 3855 | ||
| 3856 | jQuery.ready.then = readyList.then; | |
| 3857 | ||
| 3858 | // The ready event handler and self cleanup method | |
| 3859 | function completed() { | |
| 3860 | document.removeEventListener( "DOMContentLoaded", completed ); | |
| 3861 | window.removeEventListener( "load", completed ); | |
| 3862 | jQuery.ready(); | |
| 3863 | } | |
| 3864 | ||
| 3865 | // Catch cases where $(document).ready() is called | |
| 3866 | // after the browser event has already occurred. | |
| 3867 | // Support: IE <=9 - 10 only | |
| 3868 | // Older IE sometimes signals "interactive" too soon | |
| 3869 | if ( document.readyState === "complete" || | |
| 3870 | ( document.readyState !== "loading" && !document.documentElement.doScroll ) ) { | |
| 3871 | ||
| 3872 | // Handle it asynchronously to allow scripts the opportunity to delay ready | |
| 3873 | window.setTimeout( jQuery.ready ); | |
| 3874 | ||
| 3875 | } else { | |
| 3876 | ||
| 3877 | // Use the handy event callback | |
| 3878 | document.addEventListener( "DOMContentLoaded", completed ); | |
| 3879 | ||
| 3880 | // A fallback to window.onload, that will always work | |
| 3881 | window.addEventListener( "load", completed ); | |
| 3882 | } | |
| 3883 | ||
| 3884 | ||
| 3885 | ||
| 3886 | ||
| 3887 | // Multifunctional method to get and set values of a collection | |
| 3888 | // The value/s can optionally be executed if it's a function | |
| 3889 | var access = function( elems, fn, key, value, chainable, emptyGet, raw ) { | |
| 3890 | var i = 0, | |
| 3891 | len = elems.length, | |
| 3892 | bulk = key == null; | |
| 3893 | ||
| 3894 | // Sets many values | |
| 3895 | if ( jQuery.type( key ) === "object" ) { | |
| 3896 | chainable = true; | |
| 3897 | for ( i in key ) { | |
| 3898 | access( elems, fn, i, key[ i ], true, emptyGet, raw ); | |
| 3899 | } | |
| 3900 | ||
| 3901 | // Sets one value | |
| 3902 | } else if ( value !== undefined ) { | |
| 3903 | chainable = true; | |
| 3904 | ||
| 3905 | if ( !jQuery.isFunction( value ) ) { | |
| 3906 | raw = true; | |
| 3907 | } | |
| 3908 | ||
| 3909 | if ( bulk ) { | |
| 3910 | ||
| 3911 | // Bulk operations run against the entire set | |
| 3912 | if ( raw ) { | |
| 3913 | fn.call( elems, value ); | |
| 3914 | fn = null; | |
| 3915 | ||
| 3916 | // ...except when executing function values | |
| 3917 | } else { | |
| 3918 | bulk = fn; | |
| 3919 | fn = function( elem, key, value ) { | |
| 3920 | return bulk.call( jQuery( elem ), value ); | |
| 3921 | }; | |
| 3922 | } | |
| 3923 | } | |
| 3924 | ||
| 3925 | if ( fn ) { | |
| 3926 | for ( ; i < len; i++ ) { | |
| 3927 | fn( | |
| 3928 | elems[ i ], key, raw ? | |
| 3929 | value : | |
| 3930 | value.call( elems[ i ], i, fn( elems[ i ], key ) ) | |
| 3931 | ); | |
| 3932 | } | |
| 3933 | } | |
| 3934 | } | |
| 3935 | ||
| 3936 | return chainable ? | |
| 3937 | elems : | |
| 3938 | ||
| 3939 | // Gets | |
| 3940 | bulk ? | |
| 3941 | fn.call( elems ) : | |
| 3942 | len ? fn( elems[ 0 ], key ) : emptyGet; | |
| 3943 | }; | |
| 3944 | var acceptData = function( owner ) { | |
| 3945 | ||
| 3946 | // Accepts only: | |
| 3947 | // - Node | |
| 3948 | // - Node.ELEMENT_NODE | |
| 3949 | // - Node.DOCUMENT_NODE | |
| 3950 | // - Object | |
| 3951 | // - Any | |
| 3952 | return owner.nodeType === 1 || owner.nodeType === 9 || !( +owner.nodeType ); | |
| 3953 | }; | |
| 3954 | ||
| 3955 | ||
| 3956 | ||
| 3957 | ||
| 3958 | function Data() { | |
| 3959 | this.expando = jQuery.expando + Data.uid++; | |
| 3960 | } | |
| 3961 | ||
| 3962 | Data.uid = 1; | |
| 3963 | ||
| 3964 | Data.prototype = { | |
| 3965 | ||
| 3966 | cache: function( owner ) { | |
| 3967 | ||
| 3968 | // Check if the owner object already has a cache | |
| 3969 | var value = owner[ this.expando ]; | |
| 3970 | ||
| 3971 | // If not, create one | |
| 3972 | if ( !value ) { | |
| 3973 | value = {}; | |
| 3974 | ||
| 3975 | // We can accept data for non-element nodes in modern browsers, | |
| 3976 | // but we should not, see #8335. | |
| 3977 | // Always return an empty object. | |
| 3978 | if ( acceptData( owner ) ) { | |
| 3979 | ||
| 3980 | // If it is a node unlikely to be stringify-ed or looped over | |
| 3981 | // use plain assignment | |
| 3982 | if ( owner.nodeType ) { | |
| 3983 | owner[ this.expando ] = value; | |
| 3984 | ||
| 3985 | // Otherwise secure it in a non-enumerable property | |
| 3986 | // configurable must be true to allow the property to be | |
| 3987 | // deleted when data is removed | |
| 3988 | } else { | |
| 3989 | Object.defineProperty( owner, this.expando, { | |
| 3990 | value: value, | |
| 3991 | configurable: true | |
| 3992 | } ); | |
| 3993 | } | |
| 3994 | } | |
| 3995 | } | |
| 3996 | ||
| 3997 | return value; | |
| 3998 | }, | |
| 3999 | set: function( owner, data, value ) { | |
| 4000 | var prop, | |
| 4001 | cache = this.cache( owner ); | |
| 4002 | ||
| 4003 | // Handle: [ owner, key, value ] args | |
| 4004 | // Always use camelCase key (gh-2257) | |
| 4005 | if ( typeof data === "string" ) { | |
| 4006 | cache[ jQuery.camelCase( data ) ] = value; | |
| 4007 | ||
| 4008 | // Handle: [ owner, { properties } ] args | |
| 4009 | } else { | |
| 4010 | ||
| 4011 | // Copy the properties one-by-one to the cache object | |
| 4012 | for ( prop in data ) { | |
| 4013 | cache[ jQuery.camelCase( prop ) ] = data[ prop ]; | |
| 4014 | } | |
| 4015 | } | |
| 4016 | return cache; | |
| 4017 | }, | |
| 4018 | get: function( owner, key ) { | |
| 4019 | return key === undefined ? | |
| 4020 | this.cache( owner ) : | |
| 4021 | ||
| 4022 | // Always use camelCase key (gh-2257) | |
| 4023 | owner[ this.expando ] && owner[ this.expando ][ jQuery.camelCase( key ) ]; | |
| 4024 | }, | |
| 4025 | access: function( owner, key, value ) { | |
| 4026 | ||
| 4027 | // In cases where either: | |
| 4028 | // | |
| 4029 | // 1. No key was specified | |
| 4030 | // 2. A string key was specified, but no value provided | |
| 4031 | // | |
| 4032 | // Take the "read" path and allow the get method to determine | |
| 4033 | // which value to return, respectively either: | |
| 4034 | // | |
| 4035 | // 1. The entire cache object | |
| 4036 | // 2. The data stored at the key | |
| 4037 | // | |
| 4038 | if ( key === undefined || | |
| 4039 | ( ( key && typeof key === "string" ) && value === undefined ) ) { | |
| 4040 | ||
| 4041 | return this.get( owner, key ); | |
| 4042 | } | |
| 4043 | ||
| 4044 | // When the key is not a string, or both a key and value | |
| 4045 | // are specified, set or extend (existing objects) with either: | |
| 4046 | // | |
| 4047 | // 1. An object of properties | |
| 4048 | // 2. A key and value | |
| 4049 | // | |
| 4050 | this.set( owner, key, value ); | |
| 4051 | ||
| 4052 | // Since the "set" path can have two possible entry points | |
| 4053 | // return the expected data based on which path was taken[*] | |
| 4054 | return value !== undefined ? value : key; | |
| 4055 | }, | |
| 4056 | remove: function( owner, key ) { | |
| 4057 | var i, | |
| 4058 | cache = owner[ this.expando ]; | |
| 4059 | ||
| 4060 | if ( cache === undefined ) { | |
| 4061 | return; | |
| 4062 | } | |
| 4063 | ||
| 4064 | if ( key !== undefined ) { | |
| 4065 | ||
| 4066 | // Support array or space separated string of keys | |
| 4067 | if ( jQuery.isArray( key ) ) { | |
| 4068 | ||
| 4069 | // If key is an array of keys... | |
| 4070 | // We always set camelCase keys, so remove that. | |
| 4071 | key = key.map( jQuery.camelCase ); | |
| 4072 | } else { | |
| 4073 | key = jQuery.camelCase( key ); | |
| 4074 | ||
| 4075 | // If a key with the spaces exists, use it. | |
| 4076 | // Otherwise, create an array by matching non-whitespace | |
| 4077 | key = key in cache ? | |
| 4078 | [ key ] : | |
| 4079 | ( key.match( rnotwhite ) || [] ); | |
| 4080 | } | |
| 4081 | ||
| 4082 | i = key.length; | |
| 4083 | ||
| 4084 | while ( i-- ) { | |
| 4085 | delete cache[ key[ i ] ]; | |
| 4086 | } | |
| 4087 | } | |
| 4088 | ||
| 4089 | // Remove the expando if there's no more data | |
| 4090 | if ( key === undefined || jQuery.isEmptyObject( cache ) ) { | |
| 4091 | ||
| 4092 | // Support: Chrome <=35 - 45 | |
| 4093 | // Webkit & Blink performance suffers when deleting properties | |
| 4094 | // from DOM nodes, so set to undefined instead | |
| 4095 | // https://bugs.chromium.org/p/chromium/issues/detail?id=378607 (bug restricted) | |
| 4096 | if ( owner.nodeType ) { | |
| 4097 | owner[ this.expando ] = undefined; | |
| 4098 | } else { | |
| 4099 | delete owner[ this.expando ]; | |
| 4100 | } | |
| 4101 | } | |
| 4102 | }, | |
| 4103 | hasData: function( owner ) { | |
| 4104 | var cache = owner[ this.expando ]; | |
| 4105 | return cache !== undefined && !jQuery.isEmptyObject( cache ); | |
| 4106 | } | |
| 4107 | }; | |
| 4108 | var dataPriv = new Data(); | |
| 4109 | ||
| 4110 | var dataUser = new Data(); | |
| 4111 | ||
| 4112 | ||
| 4113 | ||
| 4114 | // Implementation Summary | |
| 4115 | // | |
| 4116 | // 1. Enforce API surface and semantic compatibility with 1.9.x branch | |
| 4117 | // 2. Improve the module's maintainability by reducing the storage | |
| 4118 | // paths to a single mechanism. | |
| 4119 | // 3. Use the same single mechanism to support "private" and "user" data. | |
| 4120 | // 4. _Never_ expose "private" data to user code (TODO: Drop _data, _removeData) | |
| 4121 | // 5. Avoid exposing implementation details on user objects (eg. expando properties) | |
| 4122 | // 6. Provide a clear path for implementation upgrade to WeakMap in 2014 | |
| 4123 | ||
| 4124 | var rbrace = /^(?:\{[\w\W]*\}|\[[\w\W]*\])$/, | |
| 4125 | rmultiDash = /[A-Z]/g; | |
| 4126 | ||
| 4127 | function dataAttr( elem, key, data ) { | |
| 4128 | var name; | |
| 4129 | ||
| 4130 | // If nothing was found internally, try to fetch any | |
| 4131 | // data from the HTML5 data-* attribute | |
| 4132 | if ( data === undefined && elem.nodeType === 1 ) { | |
| 4133 | name = "data-" + key.replace( rmultiDash, "-$&" ).toLowerCase(); | |
| 4134 | data = elem.getAttribute( name ); | |
| 4135 | ||
| 4136 | if ( typeof data === "string" ) { | |
| 4137 | try { | |
| 4138 | data = data === "true" ? true : | |
| 4139 | data === "false" ? false : | |
| 4140 | data === "null" ? null : | |
| 4141 | ||
| 4142 | // Only convert to a number if it doesn't change the string | |
| 4143 | +data + "" === data ? +data : | |
| 4144 | rbrace.test( data ) ? JSON.parse( data ) : | |
| 4145 | data; | |
| 4146 | } catch ( e ) {} | |
| 4147 | ||
| 4148 | // Make sure we set the data so it isn't changed later | |
| 4149 | dataUser.set( elem, key, data ); | |
| 4150 | } else { | |
| 4151 | data = undefined; | |
| 4152 | } | |
| 4153 | } | |
| 4154 | return data; | |
| 4155 | } | |
| 4156 | ||
| 4157 | jQuery.extend( { | |
| 4158 | hasData: function( elem ) { | |
| 4159 | return dataUser.hasData( elem ) || dataPriv.hasData( elem ); | |
| 4160 | }, | |
| 4161 | ||
| 4162 | data: function( elem, name, data ) { | |
| 4163 | return dataUser.access( elem, name, data ); | |
| 4164 | }, | |
| 4165 | ||
| 4166 | removeData: function( elem, name ) { | |
| 4167 | dataUser.remove( elem, name ); | |
| 4168 | }, | |
| 4169 | ||
| 4170 | // TODO: Now that all calls to _data and _removeData have been replaced | |
| 4171 | // with direct calls to dataPriv methods, these can be deprecated. | |
| 4172 | _data: function( elem, name, data ) { | |
| 4173 | return dataPriv.access( elem, name, data ); | |
| 4174 | }, | |
| 4175 | ||
| 4176 | _removeData: function( elem, name ) { | |
| 4177 | dataPriv.remove( elem, name ); | |
| 4178 | } | |
| 4179 | } ); | |
| 4180 | ||
| 4181 | jQuery.fn.extend( { | |
| 4182 | data: function( key, value ) { | |
| 4183 | var i, name, data, | |
| 4184 | elem = this[ 0 ], | |
| 4185 | attrs = elem && elem.attributes; | |
| 4186 | ||
| 4187 | // Gets all values | |
| 4188 | if ( key === undefined ) { | |
| 4189 | if ( this.length ) { | |
| 4190 | data = dataUser.get( elem ); | |
| 4191 | ||
| 4192 | if ( elem.nodeType === 1 && !dataPriv.get( elem, "hasDataAttrs" ) ) { | |
| 4193 | i = attrs.length; | |
| 4194 | while ( i-- ) { | |
| 4195 | ||
| 4196 | // Support: IE 11 only | |
| 4197 | // The attrs elements can be null (#14894) | |
| 4198 | if ( attrs[ i ] ) { | |
| 4199 | name = attrs[ i ].name; | |
| 4200 | if ( name.indexOf( "data-" ) === 0 ) { | |
| 4201 | name = jQuery.camelCase( name.slice( 5 ) ); | |
| 4202 | dataAttr( elem, name, data[ name ] ); | |
| 4203 | } | |
| 4204 | } | |
| 4205 | } | |
| 4206 | dataPriv.set( elem, "hasDataAttrs", true ); | |
| 4207 | } | |
| 4208 | } | |
| 4209 | ||
| 4210 | return data; | |
| 4211 | } | |
| 4212 | ||
| 4213 | // Sets multiple values | |
| 4214 | if ( typeof key === "object" ) { | |
| 4215 | return this.each( function() { | |
| 4216 | dataUser.set( this, key ); | |
| 4217 | } ); | |
| 4218 | } | |
| 4219 | ||
| 4220 | return access( this, function( value ) { | |
| 4221 | var data; | |
| 4222 | ||
| 4223 | // The calling jQuery object (element matches) is not empty | |
| 4224 | // (and therefore has an element appears at this[ 0 ]) and the | |
| 4225 | // `value` parameter was not undefined. An empty jQuery object | |
| 4226 | // will result in `undefined` for elem = this[ 0 ] which will | |
| 4227 | // throw an exception if an attempt to read a data cache is made. | |
| 4228 | if ( elem && value === undefined ) { | |
| 4229 | ||
| 4230 | // Attempt to get data from the cache | |
| 4231 | // The key will always be camelCased in Data | |
| 4232 | data = dataUser.get( elem, key ); | |
| 4233 | if ( data !== undefined ) { | |
| 4234 | return data; | |
| 4235 | } | |
| 4236 | ||
| 4237 | // Attempt to "discover" the data in | |
| 4238 | // HTML5 custom data-* attrs | |
| 4239 | data = dataAttr( elem, key ); | |
| 4240 | if ( data !== undefined ) { | |
| 4241 | return data; | |
| 4242 | } | |
| 4243 | ||
| 4244 | // We tried really hard, but the data doesn't exist. | |
| 4245 | return; | |
| 4246 | } | |
| 4247 | ||
| 4248 | // Set the data... | |
| 4249 | this.each( function() { | |
| 4250 | ||
| 4251 | // We always store the camelCased key | |
| 4252 | dataUser.set( this, key, value ); | |
| 4253 | } ); | |
| 4254 | }, null, value, arguments.length > 1, null, true ); | |
| 4255 | }, | |
| 4256 | ||
| 4257 | removeData: function( key ) { | |
| 4258 | return this.each( function() { | |
| 4259 | dataUser.remove( this, key ); | |
| 4260 | } ); | |
| 4261 | } | |
| 4262 | } ); | |
| 4263 | ||
| 4264 | ||
| 4265 | jQuery.extend( { | |
| 4266 | queue: function( elem, type, data ) { | |
| 4267 | var queue; | |
| 4268 | ||
| 4269 | if ( elem ) { | |
| 4270 | type = ( type || "fx" ) + "queue"; | |
| 4271 | queue = dataPriv.get( elem, type ); | |
| 4272 | ||
| 4273 | // Speed up dequeue by getting out quickly if this is just a lookup | |
| 4274 | if ( data ) { | |
| 4275 | if ( !queue || jQuery.isArray( data ) ) { | |
| 4276 | queue = dataPriv.access( elem, type, jQuery.makeArray( data ) ); | |
| 4277 | } else { | |
| 4278 | queue.push( data ); | |
| 4279 | } | |
| 4280 | } | |
| 4281 | return queue || []; | |
| 4282 | } | |
| 4283 | }, | |
| 4284 | ||
| 4285 | dequeue: function( elem, type ) { | |
| 4286 | type = type || "fx"; | |
| 4287 | ||
| 4288 | var queue = jQuery.queue( elem, type ), | |
| 4289 | startLength = queue.length, | |
| 4290 | fn = queue.shift(), | |
| 4291 | hooks = jQuery._queueHooks( elem, type ), | |
| 4292 | next = function() { | |
| 4293 | jQuery.dequeue( elem, type ); | |
| 4294 | }; | |
| 4295 | ||
| 4296 | // If the fx queue is dequeued, always remove the progress sentinel | |
| 4297 | if ( fn === "inprogress" ) { | |
| 4298 | fn = queue.shift(); | |
| 4299 | startLength--; | |
| 4300 | } | |
| 4301 | ||
| 4302 | if ( fn ) { | |
| 4303 | ||
| 4304 | // Add a progress sentinel to prevent the fx queue from being | |
| 4305 | // automatically dequeued | |
| 4306 | if ( type === "fx" ) { | |
| 4307 | queue.unshift( "inprogress" ); | |
| 4308 | } | |
| 4309 | ||
| 4310 | // Clear up the last queue stop function | |
| 4311 | delete hooks.stop; | |
| 4312 | fn.call( elem, next, hooks ); | |
| 4313 | } | |
| 4314 | ||
| 4315 | if ( !startLength && hooks ) { | |
| 4316 | hooks.empty.fire(); | |
| 4317 | } | |
| 4318 | }, | |
| 4319 | ||
| 4320 | // Not public - generate a queueHooks object, or return the current one | |
| 4321 | _queueHooks: function( elem, type ) { | |
| 4322 | var key = type + "queueHooks"; | |
| 4323 | return dataPriv.get( elem, key ) || dataPriv.access( elem, key, { | |
| 4324 | empty: jQuery.Callbacks( "once memory" ).add( function() { | |
| 4325 | dataPriv.remove( elem, [ type + "queue", key ] ); | |
| 4326 | } ) | |
| 4327 | } ); | |
| 4328 | } | |
| 4329 | } ); | |
| 4330 | ||
| 4331 | jQuery.fn.extend( { | |
| 4332 | queue: function( type, data ) { | |
| 4333 | var setter = 2; | |
| 4334 | ||
| 4335 | if ( typeof type !== "string" ) { | |
| 4336 | data = type; | |
| 4337 | type = "fx"; | |
| 4338 | setter--; | |
| 4339 | } | |
| 4340 | ||
| 4341 | if ( arguments.length < setter ) { | |
| 4342 | return jQuery.queue( this[ 0 ], type ); | |
| 4343 | } | |
| 4344 | ||
| 4345 | return data === undefined ? | |
| 4346 | this : | |
| 4347 | this.each( function() { | |
| 4348 | var queue = jQuery.queue( this, type, data ); | |
| 4349 | ||
| 4350 | // Ensure a hooks for this queue | |
| 4351 | jQuery._queueHooks( this, type ); | |
| 4352 | ||
| 4353 | if ( type === "fx" && queue[ 0 ] !== "inprogress" ) { | |
| 4354 | jQuery.dequeue( this, type ); | |
| 4355 | } | |
| 4356 | } ); | |
| 4357 | }, | |
| 4358 | dequeue: function( type ) { | |
| 4359 | return this.each( function() { | |
| 4360 | jQuery.dequeue( this, type ); | |
| 4361 | } ); | |
| 4362 | }, | |
| 4363 | clearQueue: function( type ) { | |
| 4364 | return this.queue( type || "fx", [] ); | |
| 4365 | }, | |
| 4366 | ||
| 4367 | // Get a promise resolved when queues of a certain type | |
| 4368 | // are emptied (fx is the type by default) | |
| 4369 | promise: function( type, obj ) { | |
| 4370 | var tmp, | |
| 4371 | count = 1, | |
| 4372 | defer = jQuery.Deferred(), | |
| 4373 | elements = this, | |
| 4374 | i = this.length, | |
| 4375 | resolve = function() { | |
| 4376 | if ( !( --count ) ) { | |
| 4377 | defer.resolveWith( elements, [ elements ] ); | |
| 4378 | } | |
| 4379 | }; | |
| 4380 | ||
| 4381 | if ( typeof type !== "string" ) { | |
| 4382 | obj = type; | |
| 4383 | type = undefined; | |
| 4384 | } | |
| 4385 | type = type || "fx"; | |
| 4386 | ||
| 4387 | while ( i-- ) { | |
| 4388 | tmp = dataPriv.get( elements[ i ], type + "queueHooks" ); | |
| 4389 | if ( tmp && tmp.empty ) { | |
| 4390 | count++; | |
| 4391 | tmp.empty.add( resolve ); | |
| 4392 | } | |
| 4393 | } | |
| 4394 | resolve(); | |
| 4395 | return defer.promise( obj ); | |
| 4396 | } | |
| 4397 | } ); | |
| 4398 | var pnum = ( /[+-]?(?:\d*\.|)\d+(?:[eE][+-]?\d+|)/ ).source; | |
| 4399 | ||
| 4400 | var rcssNum = new RegExp( "^(?:([+-])=|)(" + pnum + ")([a-z%]*)$", "i" ); | |
| 4401 | ||
| 4402 | ||
| 4403 | var cssExpand = [ "Top", "Right", "Bottom", "Left" ]; | |
| 4404 | ||
| 4405 | var isHiddenWithinTree = function( elem, el ) { | |
| 4406 | ||
| 4407 | // isHiddenWithinTree might be called from jQuery#filter function; | |
| 4408 | // in that case, element will be second argument | |
| 4409 | elem = el || elem; | |
| 4410 | ||
| 4411 | // Inline style trumps all | |
| 4412 | return elem.style.display === "none" || | |
| 4413 | elem.style.display === "" && | |
| 4414 | ||
| 4415 | // Otherwise, check computed style | |
| 4416 | // Support: Firefox <=43 - 45 | |
| 4417 | // Disconnected elements can have computed display: none, so first confirm that elem is | |
| 4418 | // in the document. | |
| 4419 | jQuery.contains( elem.ownerDocument, elem ) && | |
| 4420 | ||
| 4421 | jQuery.css( elem, "display" ) === "none"; | |
| 4422 | }; | |
| 4423 | ||
| 4424 | var swap = function( elem, options, callback, args ) { | |
| 4425 | var ret, name, | |
| 4426 | old = {}; | |
| 4427 | ||
| 4428 | // Remember the old values, and insert the new ones | |
| 4429 | for ( name in options ) { | |
| 4430 | old[ name ] = elem.style[ name ]; | |
| 4431 | elem.style[ name ] = options[ name ]; | |
| 4432 | } | |
| 4433 | ||
| 4434 | ret = callback.apply( elem, args || [] ); | |
| 4435 | ||
| 4436 | // Revert the old values | |
| 4437 | for ( name in options ) { | |
| 4438 | elem.style[ name ] = old[ name ]; | |
| 4439 | } | |
| 4440 | ||
| 4441 | return ret; | |
| 4442 | }; | |
| 4443 | ||
| 4444 | ||
| 4445 | ||
| 4446 | ||
| 4447 | function adjustCSS( elem, prop, valueParts, tween ) { | |
| 4448 | var adjusted, | |
| 4449 | scale = 1, | |
| 4450 | maxIterations = 20, | |
| 4451 | currentValue = tween ? | |
| 4452 | function() { | |
| 4453 | return tween.cur(); | |
| 4454 | } : | |
| 4455 | function() { | |
| 4456 | return jQuery.css( elem, prop, "" ); | |
| 4457 | }, | |
| 4458 | initial = currentValue(), | |
| 4459 | unit = valueParts && valueParts[ 3 ] || ( jQuery.cssNumber[ prop ] ? "" : "px" ), | |
| 4460 | ||
| 4461 | // Starting value computation is required for potential unit mismatches | |
| 4462 | initialInUnit = ( jQuery.cssNumber[ prop ] || unit !== "px" && +initial ) && | |
| 4463 | rcssNum.exec( jQuery.css( elem, prop ) ); | |
| 4464 | ||
| 4465 | if ( initialInUnit && initialInUnit[ 3 ] !== unit ) { | |
| 4466 | ||
| 4467 | // Trust units reported by jQuery.css | |
| 4468 | unit = unit || initialInUnit[ 3 ]; | |
| 4469 | ||
| 4470 | // Make sure we update the tween properties later on | |
| 4471 | valueParts = valueParts || []; | |
| 4472 | ||
| 4473 | // Iteratively approximate from a nonzero starting point | |
| 4474 | initialInUnit = +initial || 1; | |
| 4475 | ||
| 4476 | do { | |
| 4477 | ||
| 4478 | // If previous iteration zeroed out, double until we get *something*. | |
| 4479 | // Use string for doubling so we don't accidentally see scale as unchanged below | |
| 4480 | scale = scale || ".5"; | |
| 4481 | ||
| 4482 | // Adjust and apply | |
| 4483 | initialInUnit = initialInUnit / scale; | |
| 4484 | jQuery.style( elem, prop, initialInUnit + unit ); | |
| 4485 | ||
| 4486 | // Update scale, tolerating zero or NaN from tween.cur() | |
| 4487 | // Break the loop if scale is unchanged or perfect, or if we've just had enough. | |
| 4488 | } while ( | |
| 4489 | scale !== ( scale = currentValue() / initial ) && scale !== 1 && --maxIterations | |
| 4490 | ); | |
| 4491 | } | |
| 4492 | ||
| 4493 | if ( valueParts ) { | |
| 4494 | initialInUnit = +initialInUnit || +initial || 0; | |
| 4495 | ||
| 4496 | // Apply relative offset (+=/-=) if specified | |
| 4497 | adjusted = valueParts[ 1 ] ? | |
| 4498 | initialInUnit + ( valueParts[ 1 ] + 1 ) * valueParts[ 2 ] : | |
| 4499 | +valueParts[ 2 ]; | |
| 4500 | if ( tween ) { | |
| 4501 | tween.unit = unit; | |
| 4502 | tween.start = initialInUnit; | |
| 4503 | tween.end = adjusted; | |
| 4504 | } | |
| 4505 | } | |
| 4506 | return adjusted; | |
| 4507 | } | |
| 4508 | ||
| 4509 | ||
| 4510 | var defaultDisplayMap = {}; | |
| 4511 | ||
| 4512 | function getDefaultDisplay( elem ) { | |
| 4513 | var temp, | |
| 4514 | doc = elem.ownerDocument, | |
| 4515 | nodeName = elem.nodeName, | |
| 4516 | display = defaultDisplayMap[ nodeName ]; | |
| 4517 | ||
| 4518 | if ( display ) { | |
| 4519 | return display; | |
| 4520 | } | |
| 4521 | ||
| 4522 | temp = doc.body.appendChild( doc.createElement( nodeName ) ), | |
| 4523 | display = jQuery.css( temp, "display" ); | |
| 4524 | ||
| 4525 | temp.parentNode.removeChild( temp ); | |
| 4526 | ||
| 4527 | if ( display === "none" ) { | |
| 4528 | display = "block"; | |
| 4529 | } | |
| 4530 | defaultDisplayMap[ nodeName ] = display; | |
| 4531 | ||
| 4532 | return display; | |
| 4533 | } | |
| 4534 | ||
| 4535 | function showHide( elements, show ) { | |
| 4536 | var display, elem, | |
| 4537 | values = [], | |
| 4538 | index = 0, | |
| 4539 | length = elements.length; | |
| 4540 | ||
| 4541 | // Determine new display value for elements that need to change | |
| 4542 | for ( ; index < length; index++ ) { | |
| 4543 | elem = elements[ index ]; | |
| 4544 | if ( !elem.style ) { | |
| 4545 | continue; | |
| 4546 | } | |
| 4547 | ||
| 4548 | display = elem.style.display; | |
| 4549 | if ( show ) { | |
| 4550 | ||
| 4551 | // Since we force visibility upon cascade-hidden elements, an immediate (and slow) | |
| 4552 | // check is required in this first loop unless we have a nonempty display value (either | |
| 4553 | // inline or about-to-be-restored) | |
| 4554 | if ( display === "none" ) { | |
| 4555 | values[ index ] = dataPriv.get( elem, "display" ) || null; | |
| 4556 | if ( !values[ index ] ) { | |
| 4557 | elem.style.display = ""; | |
| 4558 | } | |
| 4559 | } | |
| 4560 | if ( elem.style.display === "" && isHiddenWithinTree( elem ) ) { | |
| 4561 | values[ index ] = getDefaultDisplay( elem ); | |
| 4562 | } | |
| 4563 | } else { | |
| 4564 | if ( display !== "none" ) { | |
| 4565 | values[ index ] = "none"; | |
| 4566 | ||
| 4567 | // Remember what we're overwriting | |
| 4568 | dataPriv.set( elem, "display", display ); | |
| 4569 | } | |
| 4570 | } | |
| 4571 | } | |
| 4572 | ||
| 4573 | // Set the display of the elements in a second loop to avoid constant reflow | |
| 4574 | for ( index = 0; index < length; index++ ) { | |
| 4575 | if ( values[ index ] != null ) { | |
| 4576 | elements[ index ].style.display = values[ index ]; | |
| 4577 | } | |
| 4578 | } | |
| 4579 | ||
| 4580 | return elements; | |
| 4581 | } | |
| 4582 | ||
| 4583 | jQuery.fn.extend( { | |
| 4584 | show: function() { | |
| 4585 | return showHide( this, true ); | |
| 4586 | }, | |
| 4587 | hide: function() { | |
| 4588 | return showHide( this ); | |
| 4589 | }, | |
| 4590 | toggle: function( state ) { | |
| 4591 | if ( typeof state === "boolean" ) { | |
| 4592 | return state ? this.show() : this.hide(); | |
| 4593 | } | |
| 4594 | ||
| 4595 | return this.each( function() { | |
| 4596 | if ( isHiddenWithinTree( this ) ) { | |
| 4597 | jQuery( this ).show(); | |
| 4598 | } else { | |
| 4599 | jQuery( this ).hide(); | |
| 4600 | } | |
| 4601 | } ); | |
| 4602 | } | |
| 4603 | } ); | |
| 4604 | var rcheckableType = ( /^(?:checkbox|radio)$/i ); | |
| 4605 | ||
| 4606 | var rtagName = ( /<([a-z][^\/\0>\x20\t\r\n\f]+)/i ); | |
| 4607 | ||
| 4608 | var rscriptType = ( /^$|\/(?:java|ecma)script/i ); | |
| 4609 | ||
| 4610 | ||
| 4611 | ||
| 4612 | // We have to close these tags to support XHTML (#13200) | |
| 4613 | var wrapMap = { | |
| 4614 | ||
| 4615 | // Support: IE <=9 only | |
| 4616 | option: [ 1, "<select multiple='multiple'>", "</select>" ], | |
| 4617 | ||
| 4618 | // XHTML parsers do not magically insert elements in the | |
| 4619 | // same way that tag soup parsers do. So we cannot shorten | |
| 4620 | // this by omitting <tbody> or other required elements. | |
| 4621 | thead: [ 1, "<table>", "</table>" ], | |
| 4622 | col: [ 2, "<table><colgroup>", "</colgroup></table>" ], | |
| 4623 | tr: [ 2, "<table><tbody>", "</tbody></table>" ], | |
| 4624 | td: [ 3, "<table><tbody><tr>", "</tr></tbody></table>" ], | |
| 4625 | ||
| 4626 | _default: [ 0, "", "" ] | |
| 4627 | }; | |
| 4628 | ||
| 4629 | // Support: IE <=9 only | |
| 4630 | wrapMap.optgroup = wrapMap.option; | |
| 4631 | ||
| 4632 | wrapMap.tbody = wrapMap.tfoot = wrapMap.colgroup = wrapMap.caption = wrapMap.thead; | |
| 4633 | wrapMap.th = wrapMap.td; | |
| 4634 | ||
| 4635 | ||
| 4636 | function getAll( context, tag ) { | |
| 4637 | ||
| 4638 | // Support: IE <=9 - 11 only | |
| 4639 | // Use typeof to avoid zero-argument method invocation on host objects (#15151) | |
| 4640 | var ret = typeof context.getElementsByTagName !== "undefined" ? | |
| 4641 | context.getElementsByTagName( tag || "*" ) : | |
| 4642 | typeof context.querySelectorAll !== "undefined" ? | |
| 4643 | context.querySelectorAll( tag || "*" ) : | |
| 4644 | []; | |
| 4645 | ||
| 4646 | return tag === undefined || tag && jQuery.nodeName( context, tag ) ? | |
| 4647 | jQuery.merge( [ context ], ret ) : | |
| 4648 | ret; | |
| 4649 | } | |
| 4650 | ||
| 4651 | ||
| 4652 | // Mark scripts as having already been evaluated | |
| 4653 | function setGlobalEval( elems, refElements ) { | |
| 4654 | var i = 0, | |
| 4655 | l = elems.length; | |
| 4656 | ||
| 4657 | for ( ; i < l; i++ ) { | |
| 4658 | dataPriv.set( | |
| 4659 | elems[ i ], | |
| 4660 | "globalEval", | |
| 4661 | !refElements || dataPriv.get( refElements[ i ], "globalEval" ) | |
| 4662 | ); | |
| 4663 | } | |
| 4664 | } | |
| 4665 | ||
| 4666 | ||
| 4667 | var rhtml = /<|&#?\w+;/; | |
| 4668 | ||
| 4669 | function buildFragment( elems, context, scripts, selection, ignored ) { | |
| 4670 | var elem, tmp, tag, wrap, contains, j, | |
| 4671 | fragment = context.createDocumentFragment(), | |
| 4672 | nodes = [], | |
| 4673 | i = 0, | |
| 4674 | l = elems.length; | |
| 4675 | ||
| 4676 | for ( ; i < l; i++ ) { | |
| 4677 | elem = elems[ i ]; | |
| 4678 | ||
| 4679 | if ( elem || elem === 0 ) { | |
| 4680 | ||
| 4681 | // Add nodes directly | |
| 4682 | if ( jQuery.type( elem ) === "object" ) { | |
| 4683 | ||
| 4684 | // Support: Android <=4.0 only, PhantomJS 1 only | |
| 4685 | // push.apply(_, arraylike) throws on ancient WebKit | |
| 4686 | jQuery.merge( nodes, elem.nodeType ? [ elem ] : elem ); | |
| 4687 | ||
| 4688 | // Convert non-html into a text node | |
| 4689 | } else if ( !rhtml.test( elem ) ) { | |
| 4690 | nodes.push( context.createTextNode( elem ) ); | |
| 4691 | ||
| 4692 | // Convert html into DOM nodes | |
| 4693 | } else { | |
| 4694 | tmp = tmp || fragment.appendChild( context.createElement( "div" ) ); | |
| 4695 | ||
| 4696 | // Deserialize a standard representation | |
| 4697 | tag = ( rtagName.exec( elem ) || [ "", "" ] )[ 1 ].toLowerCase(); | |
| 4698 | wrap = wrapMap[ tag ] || wrapMap._default; | |
| 4699 | tmp.innerHTML = wrap[ 1 ] + jQuery.htmlPrefilter( elem ) + wrap[ 2 ]; | |
| 4700 | ||
| 4701 | // Descend through wrappers to the right content | |
| 4702 | j = wrap[ 0 ]; | |
| 4703 | while ( j-- ) { | |
| 4704 | tmp = tmp.lastChild; | |
| 4705 | } | |
| 4706 | ||
| 4707 | // Support: Android <=4.0 only, PhantomJS 1 only | |
| 4708 | // push.apply(_, arraylike) throws on ancient WebKit | |
| 4709 | jQuery.merge( nodes, tmp.childNodes ); | |
| 4710 | ||
| 4711 | // Remember the top-level container | |
| 4712 | tmp = fragment.firstChild; | |
| 4713 | ||
| 4714 | // Ensure the created nodes are orphaned (#12392) | |
| 4715 | tmp.textContent = ""; | |
| 4716 | } | |
| 4717 | } | |
| 4718 | } | |
| 4719 | ||
| 4720 | // Remove wrapper from fragment | |
| 4721 | fragment.textContent = ""; | |
| 4722 | ||
| 4723 | i = 0; | |
| 4724 | while ( ( elem = nodes[ i++ ] ) ) { | |
| 4725 | ||
| 4726 | // Skip elements already in the context collection (trac-4087) | |
| 4727 | if ( selection && jQuery.inArray( elem, selection ) > -1 ) { | |
| 4728 | if ( ignored ) { | |
| 4729 | ignored.push( elem ); | |
| 4730 | } | |
| 4731 | continue; | |
| 4732 | } | |
| 4733 | ||
| 4734 | contains = jQuery.contains( elem.ownerDocument, elem ); | |
| 4735 | ||
| 4736 | // Append to fragment | |
| 4737 | tmp = getAll( fragment.appendChild( elem ), "script" ); | |
| 4738 | ||
| 4739 | // Preserve script evaluation history | |
| 4740 | if ( contains ) { | |
| 4741 | setGlobalEval( tmp ); | |
| 4742 | } | |
| 4743 | ||
| 4744 | // Capture executables | |
| 4745 | if ( scripts ) { | |
| 4746 | j = 0; | |
| 4747 | while ( ( elem = tmp[ j++ ] ) ) { | |
| 4748 | if ( rscriptType.test( elem.type || "" ) ) { | |
| 4749 | scripts.push( elem ); | |
| 4750 | } | |
| 4751 | } | |
| 4752 | } | |
| 4753 | } | |
| 4754 | ||
| 4755 | return fragment; | |
| 4756 | } | |
| 4757 | ||
| 4758 | ||
| 4759 | ( function() { | |
| 4760 | var fragment = document.createDocumentFragment(), | |
| 4761 | div = fragment.appendChild( document.createElement( "div" ) ), | |
| 4762 | input = document.createElement( "input" ); | |
| 4763 | ||
| 4764 | // Support: Android 4.0 - 4.3 only | |
| 4765 | // Check state lost if the name is set (#11217) | |
| 4766 | // Support: Windows Web Apps (WWA) | |
| 4767 | // `name` and `type` must use .setAttribute for WWA (#14901) | |
| 4768 | input.setAttribute( "type", "radio" ); | |
| 4769 | input.setAttribute( "checked", "checked" ); | |
| 4770 | input.setAttribute( "name", "t" ); | |
| 4771 | ||
| 4772 | div.appendChild( input ); | |
| 4773 | ||
| 4774 | // Support: Android <=4.1 only | |
| 4775 | // Older WebKit doesn't clone checked state correctly in fragments | |
| 4776 | support.checkClone = div.cloneNode( true ).cloneNode( true ).lastChild.checked; | |
| 4777 | ||
| 4778 | // Support: IE <=11 only | |
| 4779 | // Make sure textarea (and checkbox) defaultValue is properly cloned | |
| 4780 | div.innerHTML = "<textarea>x</textarea>"; | |
| 4781 | support.noCloneChecked = !!div.cloneNode( true ).lastChild.defaultValue; | |
| 4782 | } )(); | |
| 4783 | var documentElement = document.documentElement; | |
| 4784 | ||
| 4785 | ||
| 4786 | ||
| 4787 | var | |
| 4788 | rkeyEvent = /^key/, | |
| 4789 | rmouseEvent = /^(?:mouse|pointer|contextmenu|drag|drop)|click/, | |
| 4790 | rtypenamespace = /^([^.]*)(?:\.(.+)|)/; | |
| 4791 | ||
| 4792 | function returnTrue() { | |
| 4793 | return true; | |
| 4794 | } | |
| 4795 | ||
| 4796 | function returnFalse() { | |
| 4797 | return false; | |
| 4798 | } | |
| 4799 | ||
| 4800 | // Support: IE <=9 only | |
| 4801 | // See #13393 for more info | |
| 4802 | function safeActiveElement() { | |
| 4803 | try { | |
| 4804 | return document.activeElement; | |
| 4805 | } catch ( err ) { } | |
| 4806 | } | |
| 4807 | ||
| 4808 | function on( elem, types, selector, data, fn, one ) { | |
| 4809 | var origFn, type; | |
| 4810 | ||
| 4811 | // Types can be a map of types/handlers | |
| 4812 | if ( typeof types === "object" ) { | |
| 4813 | ||
| 4814 | // ( types-Object, selector, data ) | |
| 4815 | if ( typeof selector !== "string" ) { | |
| 4816 | ||
| 4817 | // ( types-Object, data ) | |
| 4818 | data = data || selector; | |
| 4819 | selector = undefined; | |
| 4820 | } | |
| 4821 | for ( type in types ) { | |
| 4822 | on( elem, type, selector, data, types[ type ], one ); | |
| 4823 | } | |
| 4824 | return elem; | |
| 4825 | } | |
| 4826 | ||
| 4827 | if ( data == null && fn == null ) { | |
| 4828 | ||
| 4829 | // ( types, fn ) | |
| 4830 | fn = selector; | |
| 4831 | data = selector = undefined; | |
| 4832 | } else if ( fn == null ) { | |
| 4833 | if ( typeof selector === "string" ) { | |
| 4834 | ||
| 4835 | // ( types, selector, fn ) | |
| 4836 | fn = data; | |
| 4837 | data = undefined; | |
| 4838 | } else { | |
| 4839 | ||
| 4840 | // ( types, data, fn ) | |
| 4841 | fn = data; | |
| 4842 | data = selector; | |
| 4843 | selector = undefined; | |
| 4844 | } | |
| 4845 | } | |
| 4846 | if ( fn === false ) { | |
| 4847 | fn = returnFalse; | |
| 4848 | } else if ( !fn ) { | |
| 4849 | return elem; | |
| 4850 | } | |
| 4851 | ||
| 4852 | if ( one === 1 ) { | |
| 4853 | origFn = fn; | |
| 4854 | fn = function( event ) { | |
| 4855 | ||
| 4856 | // Can use an empty set, since event contains the info | |
| 4857 | jQuery().off( event ); | |
| 4858 | return origFn.apply( this, arguments ); | |
| 4859 | }; | |
| 4860 | ||
| 4861 | // Use same guid so caller can remove using origFn | |
| 4862 | fn.guid = origFn.guid || ( origFn.guid = jQuery.guid++ ); | |
| 4863 | } | |
| 4864 | return elem.each( function() { | |
| 4865 | jQuery.event.add( this, types, fn, data, selector ); | |
| 4866 | } ); | |
| 4867 | } | |
| 4868 | ||
| 4869 | /* | |
| 4870 | * Helper functions for managing events -- not part of the public interface. | |
| 4871 | * Props to Dean Edwards' addEvent library for many of the ideas. | |
| 4872 | */ | |
| 4873 | jQuery.event = { | |
| 4874 | ||
| 4875 | global: {}, | |
| 4876 | ||
| 4877 | add: function( elem, types, handler, data, selector ) { | |
| 4878 | ||
| 4879 | var handleObjIn, eventHandle, tmp, | |
| 4880 | events, t, handleObj, | |
| 4881 | special, handlers, type, namespaces, origType, | |
| 4882 | elemData = dataPriv.get( elem ); | |
| 4883 | ||
| 4884 | // Don't attach events to noData or text/comment nodes (but allow plain objects) | |
| 4885 | if ( !elemData ) { | |
| 4886 | return; | |
| 4887 | } | |
| 4888 | ||
| 4889 | // Caller can pass in an object of custom data in lieu of the handler | |
| 4890 | if ( handler.handler ) { | |
| 4891 | handleObjIn = handler; | |
| 4892 | handler = handleObjIn.handler; | |
| 4893 | selector = handleObjIn.selector; | |
| 4894 | } | |
| 4895 | ||
| 4896 | // Ensure that invalid selectors throw exceptions at attach time | |
| 4897 | // Evaluate against documentElement in case elem is a non-element node (e.g., document) | |
| 4898 | if ( selector ) { | |
| 4899 | jQuery.find.matchesSelector( documentElement, selector ); | |
| 4900 | } | |
| 4901 | ||
| 4902 | // Make sure that the handler has a unique ID, used to find/remove it later | |
| 4903 | if ( !handler.guid ) { | |
| 4904 | handler.guid = jQuery.guid++; | |
| 4905 | } | |
| 4906 | ||
| 4907 | // Init the element's event structure and main handler, if this is the first | |
| 4908 | if ( !( events = elemData.events ) ) { | |
| 4909 | events = elemData.events = {}; | |
| 4910 | } | |
| 4911 | if ( !( eventHandle = elemData.handle ) ) { | |
| 4912 | eventHandle = elemData.handle = function( e ) { | |
| 4913 | ||
| 4914 | // Discard the second event of a jQuery.event.trigger() and | |
| 4915 | // when an event is called after a page has unloaded | |
| 4916 | return typeof jQuery !== "undefined" && jQuery.event.triggered !== e.type ? | |
| 4917 | jQuery.event.dispatch.apply( elem, arguments ) : undefined; | |
| 4918 | }; | |
| 4919 | } | |
| 4920 | ||
| 4921 | // Handle multiple events separated by a space | |
| 4922 | types = ( types || "" ).match( rnotwhite ) || [ "" ]; | |
| 4923 | t = types.length; | |
| 4924 | while ( t-- ) { | |
| 4925 | tmp = rtypenamespace.exec( types[ t ] ) || []; | |
| 4926 | type = origType = tmp[ 1 ]; | |
| 4927 | namespaces = ( tmp[ 2 ] || "" ).split( "." ).sort(); | |
| 4928 | ||
| 4929 | // There *must* be a type, no attaching namespace-only handlers | |
| 4930 | if ( !type ) { | |
| 4931 | continue; | |
| 4932 | } | |
| 4933 | ||
| 4934 | // If event changes its type, use the special event handlers for the changed type | |
| 4935 | special = jQuery.event.special[ type ] || {}; | |
| 4936 | ||
| 4937 | // If selector defined, determine special event api type, otherwise given type | |
| 4938 | type = ( selector ? special.delegateType : special.bindType ) || type; | |
| 4939 | ||
| 4940 | // Update special based on newly reset type | |
| 4941 | special = jQuery.event.special[ type ] || {}; | |
| 4942 | ||
| 4943 | // handleObj is passed to all event handlers | |
| 4944 | handleObj = jQuery.extend( { | |
| 4945 | type: type, | |
| 4946 | origType: origType, | |
| 4947 | data: data, | |
| 4948 | handler: handler, | |
| 4949 | guid: handler.guid, | |
| 4950 | selector: selector, | |
| 4951 | needsContext: selector && jQuery.expr.match.needsContext.test( selector ), | |
| 4952 | namespace: namespaces.join( "." ) | |
| 4953 | }, handleObjIn ); | |
| 4954 | ||
| 4955 | // Init the event handler queue if we're the first | |
| 4956 | if ( !( handlers = events[ type ] ) ) { | |
| 4957 | handlers = events[ type ] = []; | |
| 4958 | handlers.delegateCount = 0; | |
| 4959 | ||
| 4960 | // Only use addEventListener if the special events handler returns false | |
| 4961 | if ( !special.setup || | |
| 4962 | special.setup.call( elem, data, namespaces, eventHandle ) === false ) { | |
| 4963 | ||
| 4964 | if ( elem.addEventListener ) { | |
| 4965 | elem.addEventListener( type, eventHandle ); | |
| 4966 | } | |
| 4967 | } | |
| 4968 | } | |
| 4969 | ||
| 4970 | if ( special.add ) { | |
| 4971 | special.add.call( elem, handleObj ); | |
| 4972 | ||
| 4973 | if ( !handleObj.handler.guid ) { | |
| 4974 | handleObj.handler.guid = handler.guid; | |
| 4975 | } | |
| 4976 | } | |
| 4977 | ||
| 4978 | // Add to the element's handler list, delegates in front | |
| 4979 | if ( selector ) { | |
| 4980 | handlers.splice( handlers.delegateCount++, 0, handleObj ); | |
| 4981 | } else { | |
| 4982 | handlers.push( handleObj ); | |
| 4983 | } | |
| 4984 | ||
| 4985 | // Keep track of which events have ever been used, for event optimization | |
| 4986 | jQuery.event.global[ type ] = true; | |
| 4987 | } | |
| 4988 | ||
| 4989 | }, | |
| 4990 | ||
| 4991 | // Detach an event or set of events from an element | |
| 4992 | remove: function( elem, types, handler, selector, mappedTypes ) { | |
| 4993 | ||
| 4994 | var j, origCount, tmp, | |
| 4995 | events, t, handleObj, | |
| 4996 | special, handlers, type, namespaces, origType, | |
| 4997 | elemData = dataPriv.hasData( elem ) && dataPriv.get( elem ); | |
| 4998 | ||
| 4999 | if ( !elemData || !( events = elemData.events ) ) { | |
| 5000 | return; | |
| 5001 | } | |
| 5002 | ||
| 5003 | // Once for each type.namespace in types; type may be omitted | |
| 5004 | types = ( types || "" ).match( rnotwhite ) || [ "" ]; | |
| 5005 | t = types.length; | |
| 5006 | while ( t-- ) { | |
| 5007 | tmp = rtypenamespace.exec( types[ t ] ) || []; | |
| 5008 | type = origType = tmp[ 1 ]; | |
| 5009 | namespaces = ( tmp[ 2 ] || "" ).split( "." ).sort(); | |
| 5010 | ||
| 5011 | // Unbind all events (on this namespace, if provided) for the element | |
| 5012 | if ( !type ) { | |
| 5013 | for ( type in events ) { | |
| 5014 | jQuery.event.remove( elem, type + types[ t ], handler, selector, true ); | |
| 5015 | } | |
| 5016 | continue; | |
| 5017 | } | |
| 5018 | ||
| 5019 | special = jQuery.event.special[ type ] || {}; | |
| 5020 | type = ( selector ? special.delegateType : special.bindType ) || type; | |
| 5021 | handlers = events[ type ] || []; | |
| 5022 | tmp = tmp[ 2 ] && | |
| 5023 | new RegExp( "(^|\\.)" + namespaces.join( "\\.(?:.*\\.|)" ) + "(\\.|$)" ); | |
| 5024 | ||
| 5025 | // Remove matching events | |
| 5026 | origCount = j = handlers.length; | |
| 5027 | while ( j-- ) { | |
| 5028 | handleObj = handlers[ j ]; | |
| 5029 | ||
| 5030 | if ( ( mappedTypes || origType === handleObj.origType ) && | |
| 5031 | ( !handler || handler.guid === handleObj.guid ) && | |
| 5032 | ( !tmp || tmp.test( handleObj.namespace ) ) && | |
| 5033 | ( !selector || selector === handleObj.selector || | |
| 5034 | selector === "**" && handleObj.selector ) ) { | |
| 5035 | handlers.splice( j, 1 ); | |
| 5036 | ||
| 5037 | if ( handleObj.selector ) { | |
| 5038 | handlers.delegateCount--; | |
| 5039 | } | |
| 5040 | if ( special.remove ) { | |
| 5041 | special.remove.call( elem, handleObj ); | |
| 5042 | } | |
| 5043 | } | |
| 5044 | } | |
| 5045 | ||
| 5046 | // Remove generic event handler if we removed something and no more handlers exist | |
| 5047 | // (avoids potential for endless recursion during removal of special event handlers) | |
| 5048 | if ( origCount && !handlers.length ) { | |
| 5049 | if ( !special.teardown || | |
| 5050 | special.teardown.call( elem, namespaces, elemData.handle ) === false ) { | |
| 5051 | ||
| 5052 | jQuery.removeEvent( elem, type, elemData.handle ); | |
| 5053 | } | |
| 5054 | ||
| 5055 | delete events[ type ]; | |
| 5056 | } | |
| 5057 | } | |
| 5058 | ||
| 5059 | // Remove data and the expando if it's no longer used | |
| 5060 | if ( jQuery.isEmptyObject( events ) ) { | |
| 5061 | dataPriv.remove( elem, "handle events" ); | |
| 5062 | } | |
| 5063 | }, | |
| 5064 | ||
| 5065 | dispatch: function( nativeEvent ) { | |
| 5066 | ||
| 5067 | // Make a writable jQuery.Event from the native event object | |
| 5068 | var event = jQuery.event.fix( nativeEvent ); | |
| 5069 | ||
| 5070 | var i, j, ret, matched, handleObj, handlerQueue, | |
| 5071 | args = new Array( arguments.length ), | |
| 5072 | handlers = ( dataPriv.get( this, "events" ) || {} )[ event.type ] || [], | |
| 5073 | special = jQuery.event.special[ event.type ] || {}; | |
| 5074 | ||
| 5075 | // Use the fix-ed jQuery.Event rather than the (read-only) native event | |
| 5076 | args[ 0 ] = event; | |
| 5077 | ||
| 5078 | for ( i = 1; i < arguments.length; i++ ) { | |
| 5079 | args[ i ] = arguments[ i ]; | |
| 5080 | } | |
| 5081 | ||
| 5082 | event.delegateTarget = this; | |
| 5083 | ||
| 5084 | // Call the preDispatch hook for the mapped type, and let it bail if desired | |
| 5085 | if ( special.preDispatch && special.preDispatch.call( this, event ) === false ) { | |
| 5086 | return; | |
| 5087 | } | |
| 5088 | ||
| 5089 | // Determine handlers | |
| 5090 | handlerQueue = jQuery.event.handlers.call( this, event, handlers ); | |
| 5091 | ||
| 5092 | // Run delegates first; they may want to stop propagation beneath us | |
| 5093 | i = 0; | |
| 5094 | while ( ( matched = handlerQueue[ i++ ] ) && !event.isPropagationStopped() ) { | |
| 5095 | event.currentTarget = matched.elem; | |
| 5096 | ||
| 5097 | j = 0; | |
| 5098 | while ( ( handleObj = matched.handlers[ j++ ] ) && | |
| 5099 | !event.isImmediatePropagationStopped() ) { | |
| 5100 | ||
| 5101 | // Triggered event must either 1) have no namespace, or 2) have namespace(s) | |
| 5102 | // a subset or equal to those in the bound event (both can have no namespace). | |
| 5103 | if ( !event.rnamespace || event.rnamespace.test( handleObj.namespace ) ) { | |
| 5104 | ||
| 5105 | event.handleObj = handleObj; | |
| 5106 | event.data = handleObj.data; | |
| 5107 | ||
| 5108 | ret = ( ( jQuery.event.special[ handleObj.origType ] || {} ).handle || | |
| 5109 | handleObj.handler ).apply( matched.elem, args ); | |
| 5110 | ||
| 5111 | if ( ret !== undefined ) { | |
| 5112 | if ( ( event.result = ret ) === false ) { | |
| 5113 | event.preventDefault(); | |
| 5114 | event.stopPropagation(); | |
| 5115 | } | |
| 5116 | } | |
| 5117 | } | |
| 5118 | } | |
| 5119 | } | |
| 5120 | ||
| 5121 | // Call the postDispatch hook for the mapped type | |
| 5122 | if ( special.postDispatch ) { | |
| 5123 | special.postDispatch.call( this, event ); | |
| 5124 | } | |
| 5125 | ||
| 5126 | return event.result; | |
| 5127 | }, | |
| 5128 | ||
| 5129 | handlers: function( event, handlers ) { | |
| 5130 | var i, matches, sel, handleObj, | |
| 5131 | handlerQueue = [], | |
| 5132 | delegateCount = handlers.delegateCount, | |
| 5133 | cur = event.target; | |
| 5134 | ||
| 5135 | // Support: IE <=9 | |
| 5136 | // Find delegate handlers | |
| 5137 | // Black-hole SVG <use> instance trees (#13180) | |
| 5138 | // | |
| 5139 | // Support: Firefox <=42 | |
| 5140 | // Avoid non-left-click in FF but don't block IE radio events (#3861, gh-2343) | |
| 5141 | if ( delegateCount && cur.nodeType && | |
| 5142 | ( event.type !== "click" || isNaN( event.button ) || event.button < 1 ) ) { | |
| 5143 | ||
| 5144 | for ( ; cur !== this; cur = cur.parentNode || this ) { | |
| 5145 | ||
| 5146 | // Don't check non-elements (#13208) | |
| 5147 | // Don't process clicks on disabled elements (#6911, #8165, #11382, #11764) | |
| 5148 | if ( cur.nodeType === 1 && ( cur.disabled !== true || event.type !== "click" ) ) { | |
| 5149 | matches = []; | |
| 5150 | for ( i = 0; i < delegateCount; i++ ) { | |
| 5151 | handleObj = handlers[ i ]; | |
| 5152 | ||
| 5153 | // Don't conflict with Object.prototype properties (#13203) | |
| 5154 | sel = handleObj.selector + " "; | |
| 5155 | ||
| 5156 | if ( matches[ sel ] === undefined ) { | |
| 5157 | matches[ sel ] = handleObj.needsContext ? | |
| 5158 | jQuery( sel, this ).index( cur ) > -1 : | |
| 5159 | jQuery.find( sel, this, null, [ cur ] ).length; | |
| 5160 | } | |
| 5161 | if ( matches[ sel ] ) { | |
| 5162 | matches.push( handleObj ); | |
| 5163 | } | |
| 5164 | } | |
| 5165 | if ( matches.length ) { | |
| 5166 | handlerQueue.push( { elem: cur, handlers: matches } ); | |
| 5167 | } | |
| 5168 | } | |
| 5169 | } | |
| 5170 | } | |
| 5171 | ||
| 5172 | // Add the remaining (directly-bound) handlers | |
| 5173 | if ( delegateCount < handlers.length ) { | |
| 5174 | handlerQueue.push( { elem: this, handlers: handlers.slice( delegateCount ) } ); | |
| 5175 | } | |
| 5176 | ||
| 5177 | return handlerQueue; | |
| 5178 | }, | |
| 5179 | ||
| 5180 | addProp: function( name, hook ) { | |
| 5181 | Object.defineProperty( jQuery.Event.prototype, name, { | |
| 5182 | enumerable: true, | |
| 5183 | configurable: true, | |
| 5184 | ||
| 5185 | get: jQuery.isFunction( hook ) ? | |
| 5186 | function() { | |
| 5187 | if ( this.originalEvent ) { | |
| 5188 | return hook( this.originalEvent ); | |
| 5189 | } | |
| 5190 | } : | |
| 5191 | function() { | |
| 5192 | if ( this.originalEvent ) { | |
| 5193 | return this.originalEvent[ name ]; | |
| 5194 | } | |
| 5195 | }, | |
| 5196 | ||
| 5197 | set: function( value ) { | |
| 5198 | Object.defineProperty( this, name, { | |
| 5199 | enumerable: true, | |
| 5200 | configurable: true, | |
| 5201 | writable: true, | |
| 5202 | value: value | |
| 5203 | } ); | |
| 5204 | } | |
| 5205 | } ); | |
| 5206 | }, | |
| 5207 | ||
| 5208 | fix: function( originalEvent ) { | |
| 5209 | return originalEvent[ jQuery.expando ] ? | |
| 5210 | originalEvent : | |
| 5211 | new jQuery.Event( originalEvent ); | |
| 5212 | }, | |
| 5213 | ||
| 5214 | special: { | |
| 5215 | load: { | |
| 5216 | ||
| 5217 | // Prevent triggered image.load events from bubbling to window.load | |
| 5218 | noBubble: true | |
| 5219 | }, | |
| 5220 | focus: { | |
| 5221 | ||
| 5222 | // Fire native event if possible so blur/focus sequence is correct | |
| 5223 | trigger: function() { | |
| 5224 | if ( this !== safeActiveElement() && this.focus ) { | |
| 5225 | this.focus(); | |
| 5226 | return false; | |
| 5227 | } | |
| 5228 | }, | |
| 5229 | delegateType: "focusin" | |
| 5230 | }, | |
| 5231 | blur: { | |
| 5232 | trigger: function() { | |
| 5233 | if ( this === safeActiveElement() && this.blur ) { | |
| 5234 | this.blur(); | |
| 5235 | return false; | |
| 5236 | } | |
| 5237 | }, | |
| 5238 | delegateType: "focusout" | |
| 5239 | }, | |
| 5240 | click: { | |
| 5241 | ||
| 5242 | // For checkbox, fire native event so checked state will be right | |
| 5243 | trigger: function() { | |
| 5244 | if ( this.type === "checkbox" && this.click && jQuery.nodeName( this, "input" ) ) { | |
| 5245 | this.click(); | |
| 5246 | return false; | |
| 5247 | } | |
| 5248 | }, | |
| 5249 | ||
| 5250 | // For cross-browser consistency, don't fire native .click() on links | |
| 5251 | _default: function( event ) { | |
| 5252 | return jQuery.nodeName( event.target, "a" ); | |
| 5253 | } | |
| 5254 | }, | |
| 5255 | ||
| 5256 | beforeunload: { | |
| 5257 | postDispatch: function( event ) { | |
| 5258 | ||
| 5259 | // Support: Firefox 20+ | |
| 5260 | // Firefox doesn't alert if the returnValue field is not set. | |
| 5261 | if ( event.result !== undefined && event.originalEvent ) { | |
| 5262 | event.originalEvent.returnValue = event.result; | |
| 5263 | } | |
| 5264 | } | |
| 5265 | } | |
| 5266 | } | |
| 5267 | }; | |
| 5268 | ||
| 5269 | jQuery.removeEvent = function( elem, type, handle ) { | |
| 5270 | ||
| 5271 | // This "if" is needed for plain objects | |
| 5272 | if ( elem.removeEventListener ) { | |
| 5273 | elem.removeEventListener( type, handle ); | |
| 5274 | } | |
| 5275 | }; | |
| 5276 | ||
| 5277 | jQuery.Event = function( src, props ) { | |
| 5278 | ||
| 5279 | // Allow instantiation without the 'new' keyword | |
| 5280 | if ( !( this instanceof jQuery.Event ) ) { | |
| 5281 | return new jQuery.Event( src, props ); | |
| 5282 | } | |
| 5283 | ||
| 5284 | // Event object | |
| 5285 | if ( src && src.type ) { | |
| 5286 | this.originalEvent = src; | |
| 5287 | this.type = src.type; | |
| 5288 | ||
| 5289 | // Events bubbling up the document may have been marked as prevented | |
| 5290 | // by a handler lower down the tree; reflect the correct value. | |
| 5291 | this.isDefaultPrevented = src.defaultPrevented || | |
| 5292 | src.defaultPrevented === undefined && | |
| 5293 | ||
| 5294 | // Support: Android <=2.3 only | |
| 5295 | src.returnValue === false ? | |
| 5296 | returnTrue : | |
| 5297 | returnFalse; | |
| 5298 | ||
| 5299 | // Create target properties | |
| 5300 | // Support: Safari <=6 - 7 only | |
| 5301 | // Target should not be a text node (#504, #13143) | |
| 5302 | this.target = ( src.target && src.target.nodeType === 3 ) ? | |
| 5303 | src.target.parentNode : | |
| 5304 | src.target; | |
| 5305 | ||
| 5306 | this.currentTarget = src.currentTarget; | |
| 5307 | this.relatedTarget = src.relatedTarget; | |
| 5308 | ||
| 5309 | // Event type | |
| 5310 | } else { | |
| 5311 | this.type = src; | |
| 5312 | } | |
| 5313 | ||
| 5314 | // Put explicitly provided properties onto the event object | |
| 5315 | if ( props ) { | |
| 5316 | jQuery.extend( this, props ); | |
| 5317 | } | |
| 5318 | ||
| 5319 | // Create a timestamp if incoming event doesn't have one | |
| 5320 | this.timeStamp = src && src.timeStamp || jQuery.now(); | |
| 5321 | ||
| 5322 | // Mark it as fixed | |
| 5323 | this[ jQuery.expando ] = true; | |
| 5324 | }; | |
| 5325 | ||
| 5326 | // jQuery.Event is based on DOM3 Events as specified by the ECMAScript Language Binding | |
| 5327 | // https://www.w3.org/TR/2003/WD-DOM-Level-3-Events-20030331/ecma-script-binding.html | |
| 5328 | jQuery.Event.prototype = { | |
| 5329 | constructor: jQuery.Event, | |
| 5330 | isDefaultPrevented: returnFalse, | |
| 5331 | isPropagationStopped: returnFalse, | |
| 5332 | isImmediatePropagationStopped: returnFalse, | |
| 5333 | isSimulated: false, | |
| 5334 | ||
| 5335 | preventDefault: function() { | |
| 5336 | var e = this.originalEvent; | |
| 5337 | ||
| 5338 | this.isDefaultPrevented = returnTrue; | |
| 5339 | ||
| 5340 | if ( e && !this.isSimulated ) { | |
| 5341 | e.preventDefault(); | |
| 5342 | } | |
| 5343 | }, | |
| 5344 | stopPropagation: function() { | |
| 5345 | var e = this.originalEvent; | |
| 5346 | ||
| 5347 | this.isPropagationStopped = returnTrue; | |
| 5348 | ||
| 5349 | if ( e && !this.isSimulated ) { | |
| 5350 | e.stopPropagation(); | |
| 5351 | } | |
| 5352 | }, | |
| 5353 | stopImmediatePropagation: function() { | |
| 5354 | var e = this.originalEvent; | |
| 5355 | ||
| 5356 | this.isImmediatePropagationStopped = returnTrue; | |
| 5357 | ||
| 5358 | if ( e && !this.isSimulated ) { | |
| 5359 | e.stopImmediatePropagation(); | |
| 5360 | } | |
| 5361 | ||
| 5362 | this.stopPropagation(); | |
| 5363 | } | |
| 5364 | }; | |
| 5365 | ||
| 5366 | // Includes all common event props including KeyEvent and MouseEvent specific props | |
| 5367 | jQuery.each( { | |
| 5368 | altKey: true, | |
| 5369 | bubbles: true, | |
| 5370 | cancelable: true, | |
| 5371 | changedTouches: true, | |
| 5372 | ctrlKey: true, | |
| 5373 | detail: true, | |
| 5374 | eventPhase: true, | |
| 5375 | metaKey: true, | |
| 5376 | pageX: true, | |
| 5377 | pageY: true, | |
| 5378 | shiftKey: true, | |
| 5379 | view: true, | |
| 5380 | "char": true, | |
| 5381 | charCode: true, | |
| 5382 | key: true, | |
| 5383 | keyCode: true, | |
| 5384 | button: true, | |
| 5385 | buttons: true, | |
| 5386 | clientX: true, | |
| 5387 | clientY: true, | |
| 5388 | offsetX: true, | |
| 5389 | offsetY: true, | |
| 5390 | pointerId: true, | |
| 5391 | pointerType: true, | |
| 5392 | screenX: true, | |
| 5393 | screenY: true, | |
| 5394 | targetTouches: true, | |
| 5395 | toElement: true, | |
| 5396 | touches: true, | |
| 5397 | ||
| 5398 | which: function( event ) { | |
| 5399 | var button = event.button; | |
| 5400 | ||
| 5401 | // Add which for key events | |
| 5402 | if ( event.which == null && rkeyEvent.test( event.type ) ) { | |
| 5403 | return event.charCode != null ? event.charCode : event.keyCode; | |
| 5404 | } | |
| 5405 | ||
| 5406 | // Add which for click: 1 === left; 2 === middle; 3 === right | |
| 5407 | if ( !event.which && button !== undefined && rmouseEvent.test( event.type ) ) { | |
| 5408 | return ( button & 1 ? 1 : ( button & 2 ? 3 : ( button & 4 ? 2 : 0 ) ) ); | |
| 5409 | } | |
| 5410 | ||
| 5411 | return event.which; | |
| 5412 | } | |
| 5413 | }, jQuery.event.addProp ); | |
| 5414 | ||
| 5415 | // Create mouseenter/leave events using mouseover/out and event-time checks | |
| 5416 | // so that event delegation works in jQuery. | |
| 5417 | // Do the same for pointerenter/pointerleave and pointerover/pointerout | |
| 5418 | // | |
| 5419 | // Support: Safari 7 only | |
| 5420 | // Safari sends mouseenter too often; see: | |
| 5421 | // https://bugs.chromium.org/p/chromium/issues/detail?id=470258 | |
| 5422 | // for the description of the bug (it existed in older Chrome versions as well). | |
| 5423 | jQuery.each( { | |
| 5424 | mouseenter: "mouseover", | |
| 5425 | mouseleave: "mouseout", | |
| 5426 | pointerenter: "pointerover", | |
| 5427 | pointerleave: "pointerout" | |
| 5428 | }, function( orig, fix ) { | |
| 5429 | jQuery.event.special[ orig ] = { | |
| 5430 | delegateType: fix, | |
| 5431 | bindType: fix, | |
| 5432 | ||
| 5433 | handle: function( event ) { | |
| 5434 | var ret, | |
| 5435 | target = this, | |
| 5436 | related = event.relatedTarget, | |
| 5437 | handleObj = event.handleObj; | |
| 5438 | ||
| 5439 | // For mouseenter/leave call the handler if related is outside the target. | |
| 5440 | // NB: No relatedTarget if the mouse left/entered the browser window | |
| 5441 | if ( !related || ( related !== target && !jQuery.contains( target, related ) ) ) { | |
| 5442 | event.type = handleObj.origType; | |
| 5443 | ret = handleObj.handler.apply( this, arguments ); | |
| 5444 | event.type = fix; | |
| 5445 | } | |
| 5446 | return ret; | |
| 5447 | } | |
| 5448 | }; | |
| 5449 | } ); | |
| 5450 | ||
| 5451 | jQuery.fn.extend( { | |
| 5452 | ||
| 5453 | on: function( types, selector, data, fn ) { | |
| 5454 | return on( this, types, selector, data, fn ); | |
| 5455 | }, | |
| 5456 | one: function( types, selector, data, fn ) { | |
| 5457 | return on( this, types, selector, data, fn, 1 ); | |
| 5458 | }, | |
| 5459 | off: function( types, selector, fn ) { | |
| 5460 | var handleObj, type; | |
| 5461 | if ( types && types.preventDefault && types.handleObj ) { | |
| 5462 | ||
| 5463 | // ( event ) dispatched jQuery.Event | |
| 5464 | handleObj = types.handleObj; | |
| 5465 | jQuery( types.delegateTarget ).off( | |
| 5466 | handleObj.namespace ? | |
| 5467 | handleObj.origType + "." + handleObj.namespace : | |
| 5468 | handleObj.origType, | |
| 5469 | handleObj.selector, | |
| 5470 | handleObj.handler | |
| 5471 | ); | |
| 5472 | return this; | |
| 5473 | } | |
| 5474 | if ( typeof types === "object" ) { | |
| 5475 | ||
| 5476 | // ( types-object [, selector] ) | |
| 5477 | for ( type in types ) { | |
| 5478 | this.off( type, selector, types[ type ] ); | |
| 5479 | } | |
| 5480 | return this; | |
| 5481 | } | |
| 5482 | if ( selector === false || typeof selector === "function" ) { | |
| 5483 | ||
| 5484 | // ( types [, fn] ) | |
| 5485 | fn = selector; | |
| 5486 | selector = undefined; | |
| 5487 | } | |
| 5488 | if ( fn === false ) { | |
| 5489 | fn = returnFalse; | |
| 5490 | } | |
| 5491 | return this.each( function() { | |
| 5492 | jQuery.event.remove( this, types, fn, selector ); | |
| 5493 | } ); | |
| 5494 | } | |
| 5495 | } ); | |
| 5496 | ||
| 5497 | ||
| 5498 | var | |
| 5499 | ||
| 5500 | /* eslint-disable max-len */ | |
| 5501 | ||
| 5502 | // See https://github.com/eslint/eslint/issues/3229 | |
| 5503 | rxhtmlTag = /<(?!area|br|col|embed|hr|img|input|link|meta|param)(([a-z][^\/\0>\x20\t\r\n\f]*)[^>]*)\/>/gi, | |
| 5504 | ||
| 5505 | /* eslint-enable */ | |
| 5506 | ||
| 5507 | // Support: IE <=10 - 11, Edge 12 - 13 | |
| 5508 | // In IE/Edge using regex groups here causes severe slowdowns. | |
| 5509 | // See https://connect.microsoft.com/IE/feedback/details/1736512/ | |
| 5510 | rnoInnerhtml = /<script|<style|<link/i, | |
| 5511 | ||
| 5512 | // checked="checked" or checked | |
| 5513 | rchecked = /checked\s*(?:[^=]|=\s*.checked.)/i, | |
| 5514 | rscriptTypeMasked = /^true\/(.*)/, | |
| 5515 | rcleanScript = /^\s*<!(?:\[CDATA\[|--)|(?:\]\]|--)>\s*$/g; | |
| 5516 | ||
| 5517 | function manipulationTarget( elem, content ) { | |
| 5518 | if ( jQuery.nodeName( elem, "table" ) && | |
| 5519 | jQuery.nodeName( content.nodeType !== 11 ? content : content.firstChild, "tr" ) ) { | |
| 5520 | ||
| 5521 | return elem.getElementsByTagName( "tbody" )[ 0 ] || elem; | |
| 5522 | } | |
| 5523 | ||
| 5524 | return elem; | |
| 5525 | } | |
| 5526 | ||
| 5527 | // Replace/restore the type attribute of script elements for safe DOM manipulation | |
| 5528 | function disableScript( elem ) { | |
| 5529 | elem.type = ( elem.getAttribute( "type" ) !== null ) + "/" + elem.type; | |
| 5530 | return elem; | |
| 5531 | } | |
| 5532 | function restoreScript( elem ) { | |
| 5533 | var match = rscriptTypeMasked.exec( elem.type ); | |
| 5534 | ||
| 5535 | if ( match ) { | |
| 5536 | elem.type = match[ 1 ]; | |
| 5537 | } else { | |
| 5538 | elem.removeAttribute( "type" ); | |
| 5539 | } | |
| 5540 | ||
| 5541 | return elem; | |
| 5542 | } | |
| 5543 | ||
| 5544 | function cloneCopyEvent( src, dest ) { | |
| 5545 | var i, l, type, pdataOld, pdataCur, udataOld, udataCur, events; | |
| 5546 | ||
| 5547 | if ( dest.nodeType !== 1 ) { | |
| 5548 | return; | |
| 5549 | } | |
| 5550 | ||
| 5551 | // 1. Copy private data: events, handlers, etc. | |
| 5552 | if ( dataPriv.hasData( src ) ) { | |
| 5553 | pdataOld = dataPriv.access( src ); | |
| 5554 | pdataCur = dataPriv.set( dest, pdataOld ); | |
| 5555 | events = pdataOld.events; | |
| 5556 | ||
| 5557 | if ( events ) { | |
| 5558 | delete pdataCur.handle; | |
| 5559 | pdataCur.events = {}; | |
| 5560 | ||
| 5561 | for ( type in events ) { | |
| 5562 | for ( i = 0, l = events[ type ].length; i < l; i++ ) { | |
| 5563 | jQuery.event.add( dest, type, events[ type ][ i ] ); | |
| 5564 | } | |
| 5565 | } | |
| 5566 | } | |
| 5567 | } | |
| 5568 | ||
| 5569 | // 2. Copy user data | |
| 5570 | if ( dataUser.hasData( src ) ) { | |
| 5571 | udataOld = dataUser.access( src ); | |
| 5572 | udataCur = jQuery.extend( {}, udataOld ); | |
| 5573 | ||
| 5574 | dataUser.set( dest, udataCur ); | |
| 5575 | } | |
| 5576 | } | |
| 5577 | ||
| 5578 | // Fix IE bugs, see support tests | |
| 5579 | function fixInput( src, dest ) { | |
| 5580 | var nodeName = dest.nodeName.toLowerCase(); | |
| 5581 | ||
| 5582 | // Fails to persist the checked state of a cloned checkbox or radio button. | |
| 5583 | if ( nodeName === "input" && rcheckableType.test( src.type ) ) { | |
| 5584 | dest.checked = src.checked; | |
| 5585 | ||
| 5586 | // Fails to return the selected option to the default selected state when cloning options | |
| 5587 | } else if ( nodeName === "input" || nodeName === "textarea" ) { | |
| 5588 | dest.defaultValue = src.defaultValue; | |
| 5589 | } | |
| 5590 | } | |
| 5591 | ||
| 5592 | function domManip( collection, args, callback, ignored ) { | |
| 5593 | ||
| 5594 | // Flatten any nested arrays | |
| 5595 | args = concat.apply( [], args ); | |
| 5596 | ||
| 5597 | var fragment, first, scripts, hasScripts, node, doc, | |
| 5598 | i = 0, | |
| 5599 | l = collection.length, | |
| 5600 | iNoClone = l - 1, | |
| 5601 | value = args[ 0 ], | |
| 5602 | isFunction = jQuery.isFunction( value ); | |
| 5603 | ||
| 5604 | // We can't cloneNode fragments that contain checked, in WebKit | |
| 5605 | if ( isFunction || | |
| 5606 | ( l > 1 && typeof value === "string" && | |
| 5607 | !support.checkClone && rchecked.test( value ) ) ) { | |
| 5608 | return collection.each( function( index ) { | |
| 5609 | var self = collection.eq( index ); | |
| 5610 | if ( isFunction ) { | |
| 5611 | args[ 0 ] = value.call( this, index, self.html() ); | |
| 5612 | } | |
| 5613 | domManip( self, args, callback, ignored ); | |
| 5614 | } ); | |
| 5615 | } | |
| 5616 | ||
| 5617 | if ( l ) { | |
| 5618 | fragment = buildFragment( args, collection[ 0 ].ownerDocument, false, collection, ignored ); | |
| 5619 | first = fragment.firstChild; | |
| 5620 | ||
| 5621 | if ( fragment.childNodes.length === 1 ) { | |
| 5622 | fragment = first; | |
| 5623 | } | |
| 5624 | ||
| 5625 | // Require either new content or an interest in ignored elements to invoke the callback | |
| 5626 | if ( first || ignored ) { | |
| 5627 | scripts = jQuery.map( getAll( fragment, "script" ), disableScript ); | |
| 5628 | hasScripts = scripts.length; | |
| 5629 | ||
| 5630 | // Use the original fragment for the last item | |
| 5631 | // instead of the first because it can end up | |
| 5632 | // being emptied incorrectly in certain situations (#8070). | |
| 5633 | for ( ; i < l; i++ ) { | |
| 5634 | node = fragment; | |
| 5635 | ||
| 5636 | if ( i !== iNoClone ) { | |
| 5637 | node = jQuery.clone( node, true, true ); | |
| 5638 | ||
| 5639 | // Keep references to cloned scripts for later restoration | |
| 5640 | if ( hasScripts ) { | |
| 5641 | ||
| 5642 | // Support: Android <=4.0 only, PhantomJS 1 only | |
| 5643 | // push.apply(_, arraylike) throws on ancient WebKit | |
| 5644 | jQuery.merge( scripts, getAll( node, "script" ) ); | |
| 5645 | } | |
| 5646 | } | |
| 5647 | ||
| 5648 | callback.call( collection[ i ], node, i ); | |
| 5649 | } | |
| 5650 | ||
| 5651 | if ( hasScripts ) { | |
| 5652 | doc = scripts[ scripts.length - 1 ].ownerDocument; | |
| 5653 | ||
| 5654 | // Reenable scripts | |
| 5655 | jQuery.map( scripts, restoreScript ); | |
| 5656 | ||
| 5657 | // Evaluate executable scripts on first document insertion | |
| 5658 | for ( i = 0; i < hasScripts; i++ ) { | |
| 5659 | node = scripts[ i ]; | |
| 5660 | if ( rscriptType.test( node.type || "" ) && | |
| 5661 | !dataPriv.access( node, "globalEval" ) && | |
| 5662 | jQuery.contains( doc, node ) ) { | |
| 5663 | ||
| 5664 | if ( node.src ) { | |
| 5665 | ||
| 5666 | // Optional AJAX dependency, but won't run scripts if not present | |
| 5667 | if ( jQuery._evalUrl ) { | |
| 5668 | jQuery._evalUrl( node.src ); | |
| 5669 | } | |
| 5670 | } else { | |
| 5671 | DOMEval( node.textContent.replace( rcleanScript, "" ), doc ); | |
| 5672 | } | |
| 5673 | } | |
| 5674 | } | |
| 5675 | } | |
| 5676 | } | |
| 5677 | } | |
| 5678 | ||
| 5679 | return collection; | |
| 5680 | } | |
| 5681 | ||
| 5682 | function remove( elem, selector, keepData ) { | |
| 5683 | var node, | |
| 5684 | nodes = selector ? jQuery.filter( selector, elem ) : elem, | |
| 5685 | i = 0; | |
| 5686 | ||
| 5687 | for ( ; ( node = nodes[ i ] ) != null; i++ ) { | |
| 5688 | if ( !keepData && node.nodeType === 1 ) { | |
| 5689 | jQuery.cleanData( getAll( node ) ); | |
| 5690 | } | |
| 5691 | ||
| 5692 | if ( node.parentNode ) { | |
| 5693 | if ( keepData && jQuery.contains( node.ownerDocument, node ) ) { | |
| 5694 | setGlobalEval( getAll( node, "script" ) ); | |
| 5695 | } | |
| 5696 | node.parentNode.removeChild( node ); | |
| 5697 | } | |
| 5698 | } | |
| 5699 | ||
| 5700 | return elem; | |
| 5701 | } | |
| 5702 | ||
| 5703 | jQuery.extend( { | |
| 5704 | htmlPrefilter: function( html ) { | |
| 5705 | return html.replace( rxhtmlTag, "<$1></$2>" ); | |
| 5706 | }, | |
| 5707 | ||
| 5708 | clone: function( elem, dataAndEvents, deepDataAndEvents ) { | |
| 5709 | var i, l, srcElements, destElements, | |
| 5710 | clone = elem.cloneNode( true ), | |
| 5711 | inPage = jQuery.contains( elem.ownerDocument, elem ); | |
| 5712 | ||
| 5713 | // Fix IE cloning issues | |
| 5714 | if ( !support.noCloneChecked && ( elem.nodeType === 1 || elem.nodeType === 11 ) && | |
| 5715 | !jQuery.isXMLDoc( elem ) ) { | |
| 5716 | ||
| 5717 | // We eschew Sizzle here for performance reasons: https://jsperf.com/getall-vs-sizzle/2 | |
| 5718 | destElements = getAll( clone ); | |
| 5719 | srcElements = getAll( elem ); | |
| 5720 | ||
| 5721 | for ( i = 0, l = srcElements.length; i < l; i++ ) { | |
| 5722 | fixInput( srcElements[ i ], destElements[ i ] ); | |
| 5723 | } | |
| 5724 | } | |
| 5725 | ||
| 5726 | // Copy the events from the original to the clone | |
| 5727 | if ( dataAndEvents ) { | |
| 5728 | if ( deepDataAndEvents ) { | |
| 5729 | srcElements = srcElements || getAll( elem ); | |
| 5730 | destElements = destElements || getAll( clone ); | |
| 5731 | ||
| 5732 | for ( i = 0, l = srcElements.length; i < l; i++ ) { | |
| 5733 | cloneCopyEvent( srcElements[ i ], destElements[ i ] ); | |
| 5734 | } | |
| 5735 | } else { | |
| 5736 | cloneCopyEvent( elem, clone ); | |
| 5737 | } | |
| 5738 | } | |
| 5739 | ||
| 5740 | // Preserve script evaluation history | |
| 5741 | destElements = getAll( clone, "script" ); | |
| 5742 | if ( destElements.length > 0 ) { | |
| 5743 | setGlobalEval( destElements, !inPage && getAll( elem, "script" ) ); | |
| 5744 | } | |
| 5745 | ||
| 5746 | // Return the cloned set | |
| 5747 | return clone; | |
| 5748 | }, | |
| 5749 | ||
| 5750 | cleanData: function( elems ) { | |
| 5751 | var data, elem, type, | |
| 5752 | special = jQuery.event.special, | |
| 5753 | i = 0; | |
| 5754 | ||
| 5755 | for ( ; ( elem = elems[ i ] ) !== undefined; i++ ) { | |
| 5756 | if ( acceptData( elem ) ) { | |
| 5757 | if ( ( data = elem[ dataPriv.expando ] ) ) { | |
| 5758 | if ( data.events ) { | |
| 5759 | for ( type in data.events ) { | |
| 5760 | if ( special[ type ] ) { | |
| 5761 | jQuery.event.remove( elem, type ); | |
| 5762 | ||
| 5763 | // This is a shortcut to avoid jQuery.event.remove's overhead | |
| 5764 | } else { | |
| 5765 | jQuery.removeEvent( elem, type, data.handle ); | |
| 5766 | } | |
| 5767 | } | |
| 5768 | } | |
| 5769 | ||
| 5770 | // Support: Chrome <=35 - 45+ | |
| 5771 | // Assign undefined instead of using delete, see Data#remove | |
| 5772 | elem[ dataPriv.expando ] = undefined; | |
| 5773 | } | |
| 5774 | if ( elem[ dataUser.expando ] ) { | |
| 5775 | ||
| 5776 | // Support: Chrome <=35 - 45+ | |
| 5777 | // Assign undefined instead of using delete, see Data#remove | |
| 5778 | elem[ dataUser.expando ] = undefined; | |
| 5779 | } | |
| 5780 | } | |
| 5781 | } | |
| 5782 | } | |
| 5783 | } ); | |
| 5784 | ||
| 5785 | jQuery.fn.extend( { | |
| 5786 | detach: function( selector ) { | |
| 5787 | return remove( this, selector, true ); | |
| 5788 | }, | |
| 5789 | ||
| 5790 | remove: function( selector ) { | |
| 5791 | return remove( this, selector ); | |
| 5792 | }, | |
| 5793 | ||
| 5794 | text: function( value ) { | |
| 5795 | return access( this, function( value ) { | |
| 5796 | return value === undefined ? | |
| 5797 | jQuery.text( this ) : | |
| 5798 | this.empty().each( function() { | |
| 5799 | if ( this.nodeType === 1 || this.nodeType === 11 || this.nodeType === 9 ) { | |
| 5800 | this.textContent = value; | |
| 5801 | } | |
| 5802 | } ); | |
| 5803 | }, null, value, arguments.length ); | |
| 5804 | }, | |
| 5805 | ||
| 5806 | append: function() { | |
| 5807 | return domManip( this, arguments, function( elem ) { | |
| 5808 | if ( this.nodeType === 1 || this.nodeType === 11 || this.nodeType === 9 ) { | |
| 5809 | var target = manipulationTarget( this, elem ); | |
| 5810 | target.appendChild( elem ); | |
| 5811 | } | |
| 5812 | } ); | |
| 5813 | }, | |
| 5814 | ||
| 5815 | prepend: function() { | |
| 5816 | return domManip( this, arguments, function( elem ) { | |
| 5817 | if ( this.nodeType === 1 || this.nodeType === 11 || this.nodeType === 9 ) { | |
| 5818 | var target = manipulationTarget( this, elem ); | |
| 5819 | target.insertBefore( elem, target.firstChild ); | |
| 5820 | } | |
| 5821 | } ); | |
| 5822 | }, | |
| 5823 | ||
| 5824 | before: function() { | |
| 5825 | return domManip( this, arguments, function( elem ) { | |
| 5826 | if ( this.parentNode ) { | |
| 5827 | this.parentNode.insertBefore( elem, this ); | |
| 5828 | } | |
| 5829 | } ); | |
| 5830 | }, | |
| 5831 | ||
| 5832 | after: function() { | |
| 5833 | return domManip( this, arguments, function( elem ) { | |
| 5834 | if ( this.parentNode ) { | |
| 5835 | this.parentNode.insertBefore( elem, this.nextSibling ); | |
| 5836 | } | |
| 5837 | } ); | |
| 5838 | }, | |
| 5839 | ||
| 5840 | empty: function() { | |
| 5841 | var elem, | |
| 5842 | i = 0; | |
| 5843 | ||
| 5844 | for ( ; ( elem = this[ i ] ) != null; i++ ) { | |
| 5845 | if ( elem.nodeType === 1 ) { | |
| 5846 | ||
| 5847 | // Prevent memory leaks | |
| 5848 | jQuery.cleanData( getAll( elem, false ) ); | |
| 5849 | ||
| 5850 | // Remove any remaining nodes | |
| 5851 | elem.textContent = ""; | |
| 5852 | } | |
| 5853 | } | |
| 5854 | ||
| 5855 | return this; | |
| 5856 | }, | |
| 5857 | ||
| 5858 | clone: function( dataAndEvents, deepDataAndEvents ) { | |
| 5859 | dataAndEvents = dataAndEvents == null ? false : dataAndEvents; | |
| 5860 | deepDataAndEvents = deepDataAndEvents == null ? dataAndEvents : deepDataAndEvents; | |
| 5861 | ||
| 5862 | return this.map( function() { | |
| 5863 | return jQuery.clone( this, dataAndEvents, deepDataAndEvents ); | |
| 5864 | } ); | |
| 5865 | }, | |
| 5866 | ||
| 5867 | html: function( value ) { | |
| 5868 | return access( this, function( value ) { | |
| 5869 | var elem = this[ 0 ] || {}, | |
| 5870 | i = 0, | |
| 5871 | l = this.length; | |
| 5872 | ||
| 5873 | if ( value === undefined && elem.nodeType === 1 ) { | |
| 5874 | return elem.innerHTML; | |
| 5875 | } | |
| 5876 | ||
| 5877 | // See if we can take a shortcut and just use innerHTML | |
| 5878 | if ( typeof value === "string" && !rnoInnerhtml.test( value ) && | |
| 5879 | !wrapMap[ ( rtagName.exec( value ) || [ "", "" ] )[ 1 ].toLowerCase() ] ) { | |
| 5880 | ||
| 5881 | value = jQuery.htmlPrefilter( value ); | |
| 5882 | ||
| 5883 | try { | |
| 5884 | for ( ; i < l; i++ ) { | |
| 5885 | elem = this[ i ] || {}; | |
| 5886 | ||
| 5887 | // Remove element nodes and prevent memory leaks | |
| 5888 | if ( elem.nodeType === 1 ) { | |
| 5889 | jQuery.cleanData( getAll( elem, false ) ); | |
| 5890 | elem.innerHTML = value; | |
| 5891 | } | |
| 5892 | } | |
| 5893 | ||
| 5894 | elem = 0; | |
| 5895 | ||
| 5896 | // If using innerHTML throws an exception, use the fallback method | |
| 5897 | } catch ( e ) {} | |
| 5898 | } | |
| 5899 | ||
| 5900 | if ( elem ) { | |
| 5901 | this.empty().append( value ); | |
| 5902 | } | |
| 5903 | }, null, value, arguments.length ); | |
| 5904 | }, | |
| 5905 | ||
| 5906 | replaceWith: function() { | |
| 5907 | var ignored = []; | |
| 5908 | ||
| 5909 | // Make the changes, replacing each non-ignored context element with the new content | |
| 5910 | return domManip( this, arguments, function( elem ) { | |
| 5911 | var parent = this.parentNode; | |
| 5912 | ||
| 5913 | if ( jQuery.inArray( this, ignored ) < 0 ) { | |
| 5914 | jQuery.cleanData( getAll( this ) ); | |
| 5915 | if ( parent ) { | |
| 5916 | parent.replaceChild( elem, this ); | |
| 5917 | } | |
| 5918 | } | |
| 5919 | ||
| 5920 | // Force callback invocation | |
| 5921 | }, ignored ); | |
| 5922 | } | |
| 5923 | } ); | |
| 5924 | ||
| 5925 | jQuery.each( { | |
| 5926 | appendTo: "append", | |
| 5927 | prependTo: "prepend", | |
| 5928 | insertBefore: "before", | |
| 5929 | insertAfter: "after", | |
| 5930 | replaceAll: "replaceWith" | |
| 5931 | }, function( name, original ) { | |
| 5932 | jQuery.fn[ name ] = function( selector ) { | |
| 5933 | var elems, | |
| 5934 | ret = [], | |
| 5935 | insert = jQuery( selector ), | |
| 5936 | last = insert.length - 1, | |
| 5937 | i = 0; | |
| 5938 | ||
| 5939 | for ( ; i <= last; i++ ) { | |
| 5940 | elems = i === last ? this : this.clone( true ); | |
| 5941 | jQuery( insert[ i ] )[ original ]( elems ); | |
| 5942 | ||
| 5943 | // Support: Android <=4.0 only, PhantomJS 1 only | |
| 5944 | // .get() because push.apply(_, arraylike) throws on ancient WebKit | |
| 5945 | push.apply( ret, elems.get() ); | |
| 5946 | } | |
| 5947 | ||
| 5948 | return this.pushStack( ret ); | |
| 5949 | }; | |
| 5950 | } ); | |
| 5951 | var rmargin = ( /^margin/ ); | |
| 5952 | ||
| 5953 | var rnumnonpx = new RegExp( "^(" + pnum + ")(?!px)[a-z%]+$", "i" ); | |
| 5954 | ||
| 5955 | var getStyles = function( elem ) { | |
| 5956 | ||
| 5957 | // Support: IE <=11 only, Firefox <=30 (#15098, #14150) | |
| 5958 | // IE throws on elements created in popups | |
| 5959 | // FF meanwhile throws on frame elements through "defaultView.getComputedStyle" | |
| 5960 | var view = elem.ownerDocument.defaultView; | |
| 5961 | ||
| 5962 | if ( !view || !view.opener ) { | |
| 5963 | view = window; | |
| 5964 | } | |
| 5965 | ||
| 5966 | return view.getComputedStyle( elem ); | |
| 5967 | }; | |
| 5968 | ||
| 5969 | ||
| 5970 | ||
| 5971 | ( function() { | |
| 5972 | ||
| 5973 | // Executing both pixelPosition & boxSizingReliable tests require only one layout | |
| 5974 | // so they're executed at the same time to save the second computation. | |
| 5975 | function computeStyleTests() { | |
| 5976 | ||
| 5977 | // This is a singleton, we need to execute it only once | |
| 5978 | if ( !div ) { | |
| 5979 | return; | |
| 5980 | } | |
| 5981 | ||
| 5982 | div.style.cssText = | |
| 5983 | "box-sizing:border-box;" + | |
| 5984 | "position:relative;display:block;" + | |
| 5985 | "margin:auto;border:1px;padding:1px;" + | |
| 5986 | "top:1%;width:50%"; | |
| 5987 | div.innerHTML = ""; | |
| 5988 | documentElement.appendChild( container ); | |
| 5989 | ||
| 5990 | var divStyle = window.getComputedStyle( div ); | |
| 5991 | pixelPositionVal = divStyle.top !== "1%"; | |
| 5992 | ||
| 5993 | // Support: Android 4.0 - 4.3 only, Firefox <=3 - 44 | |
| 5994 | reliableMarginLeftVal = divStyle.marginLeft === "2px"; | |
| 5995 | boxSizingReliableVal = divStyle.width === "4px"; | |
| 5996 | ||
| 5997 | // Support: Android 4.0 - 4.3 only | |
| 5998 | // Some styles come back with percentage values, even though they shouldn't | |
| 5999 | div.style.marginRight = "50%"; | |
| 6000 | pixelMarginRightVal = divStyle.marginRight === "4px"; | |
| 6001 | ||
| 6002 | documentElement.removeChild( container ); | |
| 6003 | ||
| 6004 | // Nullify the div so it wouldn't be stored in the memory and | |
| 6005 | // it will also be a sign that checks already performed | |
| 6006 | div = null; | |
| 6007 | } | |
| 6008 | ||
| 6009 | var pixelPositionVal, boxSizingReliableVal, pixelMarginRightVal, reliableMarginLeftVal, | |
| 6010 | container = document.createElement( "div" ), | |
| 6011 | div = document.createElement( "div" ); | |
| 6012 | ||
| 6013 | // Finish early in limited (non-browser) environments | |
| 6014 | if ( !div.style ) { | |
| 6015 | return; | |
| 6016 | } | |
| 6017 | ||
| 6018 | // Support: IE <=9 - 11 only | |
| 6019 | // Style of cloned element affects source element cloned (#8908) | |
| 6020 | div.style.backgroundClip = "content-box"; | |
| 6021 | div.cloneNode( true ).style.backgroundClip = ""; | |
| 6022 | support.clearCloneStyle = div.style.backgroundClip === "content-box"; | |
| 6023 | ||
| 6024 | container.style.cssText = "border:0;width:8px;height:0;top:0;left:-9999px;" + | |
| 6025 | "padding:0;margin-top:1px;position:absolute"; | |
| 6026 | container.appendChild( div ); | |
| 6027 | ||
| 6028 | jQuery.extend( support, { | |
| 6029 | pixelPosition: function() { | |
| 6030 | computeStyleTests(); | |
| 6031 | return pixelPositionVal; | |
| 6032 | }, | |
| 6033 | boxSizingReliable: function() { | |
| 6034 | computeStyleTests(); | |
| 6035 | return boxSizingReliableVal; | |
| 6036 | }, | |
| 6037 | pixelMarginRight: function() { | |
| 6038 | computeStyleTests(); | |
| 6039 | return pixelMarginRightVal; | |
| 6040 | }, | |
| 6041 | reliableMarginLeft: function() { | |
| 6042 | computeStyleTests(); | |
| 6043 | return reliableMarginLeftVal; | |
| 6044 | } | |
| 6045 | } ); | |
| 6046 | } )(); | |
| 6047 | ||
| 6048 | ||
| 6049 | function curCSS( elem, name, computed ) { | |
| 6050 | var width, minWidth, maxWidth, ret, | |
| 6051 | style = elem.style; | |
| 6052 | ||
| 6053 | computed = computed || getStyles( elem ); | |
| 6054 | ||
| 6055 | // Support: IE <=9 only | |
| 6056 | // getPropertyValue is only needed for .css('filter') (#12537) | |
| 6057 | if ( computed ) { | |
| 6058 | ret = computed.getPropertyValue( name ) || computed[ name ]; | |
| 6059 | ||
| 6060 | if ( ret === "" && !jQuery.contains( elem.ownerDocument, elem ) ) { | |
| 6061 | ret = jQuery.style( elem, name ); | |
| 6062 | } | |
| 6063 | ||
| 6064 | // A tribute to the "awesome hack by Dean Edwards" | |
| 6065 | // Android Browser returns percentage for some values, | |
| 6066 | // but width seems to be reliably pixels. | |
| 6067 | // This is against the CSSOM draft spec: | |
| 6068 | // https://drafts.csswg.org/cssom/#resolved-values | |
| 6069 | if ( !support.pixelMarginRight() && rnumnonpx.test( ret ) && rmargin.test( name ) ) { | |
| 6070 | ||
| 6071 | // Remember the original values | |
| 6072 | width = style.width; | |
| 6073 | minWidth = style.minWidth; | |
| 6074 | maxWidth = style.maxWidth; | |
| 6075 | ||
| 6076 | // Put in the new values to get a computed value out | |
| 6077 | style.minWidth = style.maxWidth = style.width = ret; | |
| 6078 | ret = computed.width; | |
| 6079 | ||
| 6080 | // Revert the changed values | |
| 6081 | style.width = width; | |
| 6082 | style.minWidth = minWidth; | |
| 6083 | style.maxWidth = maxWidth; | |
| 6084 | } | |
| 6085 | } | |
| 6086 | ||
| 6087 | return ret !== undefined ? | |
| 6088 | ||
| 6089 | // Support: IE <=9 - 11 only | |
| 6090 | // IE returns zIndex value as an integer. | |
| 6091 | ret + "" : | |
| 6092 | ret; | |
| 6093 | } | |
| 6094 | ||
| 6095 | ||
| 6096 | function addGetHookIf( conditionFn, hookFn ) { | |
| 6097 | ||
| 6098 | // Define the hook, we'll check on the first run if it's really needed. | |
| 6099 | return { | |
| 6100 | get: function() { | |
| 6101 | if ( conditionFn() ) { | |
| 6102 | ||
| 6103 | // Hook not needed (or it's not possible to use it due | |
| 6104 | // to missing dependency), remove it. | |
| 6105 | delete this.get; | |
| 6106 | return; | |
| 6107 | } | |
| 6108 | ||
| 6109 | // Hook needed; redefine it so that the support test is not executed again. | |
| 6110 | return ( this.get = hookFn ).apply( this, arguments ); | |
| 6111 | } | |
| 6112 | }; | |
| 6113 | } | |
| 6114 | ||
| 6115 | ||
| 6116 | var | |
| 6117 | ||
| 6118 | // Swappable if display is none or starts with table | |
| 6119 | // except "table", "table-cell", or "table-caption" | |
| 6120 | // See here for display values: https://developer.mozilla.org/en-US/docs/CSS/display | |
| 6121 | rdisplayswap = /^(none|table(?!-c[ea]).+)/, | |
| 6122 | cssShow = { position: "absolute", visibility: "hidden", display: "block" }, | |
| 6123 | cssNormalTransform = { | |
| 6124 | letterSpacing: "0", | |
| 6125 | fontWeight: "400" | |
| 6126 | }, | |
| 6127 | ||
| 6128 | cssPrefixes = [ "Webkit", "Moz", "ms" ], | |
| 6129 | emptyStyle = document.createElement( "div" ).style; | |
| 6130 | ||
| 6131 | // Return a css property mapped to a potentially vendor prefixed property | |
| 6132 | function vendorPropName( name ) { | |
| 6133 | ||
| 6134 | // Shortcut for names that are not vendor prefixed | |
| 6135 | if ( name in emptyStyle ) { | |
| 6136 | return name; | |
| 6137 | } | |
| 6138 | ||
| 6139 | // Check for vendor prefixed names | |
| 6140 | var capName = name[ 0 ].toUpperCase() + name.slice( 1 ), | |
| 6141 | i = cssPrefixes.length; | |
| 6142 | ||
| 6143 | while ( i-- ) { | |
| 6144 | name = cssPrefixes[ i ] + capName; | |
| 6145 | if ( name in emptyStyle ) { | |
| 6146 | return name; | |
| 6147 | } | |
| 6148 | } | |
| 6149 | } | |
| 6150 | ||
| 6151 | function setPositiveNumber( elem, value, subtract ) { | |
| 6152 | ||
| 6153 | // Any relative (+/-) values have already been | |
| 6154 | // normalized at this point | |
| 6155 | var matches = rcssNum.exec( value ); | |
| 6156 | return matches ? | |
| 6157 | ||
| 6158 | // Guard against undefined "subtract", e.g., when used as in cssHooks | |
| 6159 | Math.max( 0, matches[ 2 ] - ( subtract || 0 ) ) + ( matches[ 3 ] || "px" ) : | |
| 6160 | value; | |
| 6161 | } | |
| 6162 | ||
| 6163 | function augmentWidthOrHeight( elem, name, extra, isBorderBox, styles ) { | |
| 6164 | var i = extra === ( isBorderBox ? "border" : "content" ) ? | |
| 6165 | ||
| 6166 | // If we already have the right measurement, avoid augmentation | |
| 6167 | 4 : | |
| 6168 | ||
| 6169 | // Otherwise initialize for horizontal or vertical properties | |
| 6170 | name === "width" ? 1 : 0, | |
| 6171 | ||
| 6172 | val = 0; | |
| 6173 | ||
| 6174 | for ( ; i < 4; i += 2 ) { | |
| 6175 | ||
| 6176 | // Both box models exclude margin, so add it if we want it | |
| 6177 | if ( extra === "margin" ) { | |
| 6178 | val += jQuery.css( elem, extra + cssExpand[ i ], true, styles ); | |
| 6179 | } | |
| 6180 | ||
| 6181 | if ( isBorderBox ) { | |
| 6182 | ||
| 6183 | // border-box includes padding, so remove it if we want content | |
| 6184 | if ( extra === "content" ) { | |
| 6185 | val -= jQuery.css( elem, "padding" + cssExpand[ i ], true, styles ); | |
| 6186 | } | |
| 6187 | ||
| 6188 | // At this point, extra isn't border nor margin, so remove border | |
| 6189 | if ( extra !== "margin" ) { | |
| 6190 | val -= jQuery.css( elem, "border" + cssExpand[ i ] + "Width", true, styles ); | |
| 6191 | } | |
| 6192 | } else { | |
| 6193 | ||
| 6194 | // At this point, extra isn't content, so add padding | |
| 6195 | val += jQuery.css( elem, "padding" + cssExpand[ i ], true, styles ); | |
| 6196 | ||
| 6197 | // At this point, extra isn't content nor padding, so add border | |
| 6198 | if ( extra !== "padding" ) { | |
| 6199 | val += jQuery.css( elem, "border" + cssExpand[ i ] + "Width", true, styles ); | |
| 6200 | } | |
| 6201 | } | |
| 6202 | } | |
| 6203 | ||
| 6204 | return val; | |
| 6205 | } | |
| 6206 | ||
| 6207 | function getWidthOrHeight( elem, name, extra ) { | |
| 6208 | ||
| 6209 | // Start with offset property, which is equivalent to the border-box value | |
| 6210 | var val, | |
| 6211 | valueIsBorderBox = true, | |
| 6212 | styles = getStyles( elem ), | |
| 6213 | isBorderBox = jQuery.css( elem, "boxSizing", false, styles ) === "border-box"; | |
| 6214 | ||
| 6215 | // Support: IE <=11 only | |
| 6216 | // Running getBoundingClientRect on a disconnected node | |
| 6217 | // in IE throws an error. | |
| 6218 | if ( elem.getClientRects().length ) { | |
| 6219 | val = elem.getBoundingClientRect()[ name ]; | |
| 6220 | } | |
| 6221 | ||
| 6222 | // Some non-html elements return undefined for offsetWidth, so check for null/undefined | |
| 6223 | // svg - https://bugzilla.mozilla.org/show_bug.cgi?id=649285 | |
| 6224 | // MathML - https://bugzilla.mozilla.org/show_bug.cgi?id=491668 | |
| 6225 | if ( val <= 0 || val == null ) { | |
| 6226 | ||
| 6227 | // Fall back to computed then uncomputed css if necessary | |
| 6228 | val = curCSS( elem, name, styles ); | |
| 6229 | if ( val < 0 || val == null ) { | |
| 6230 | val = elem.style[ name ]; | |
| 6231 | } | |
| 6232 | ||
| 6233 | // Computed unit is not pixels. Stop here and return. | |
| 6234 | if ( rnumnonpx.test( val ) ) { | |
| 6235 | return val; | |
| 6236 | } | |
| 6237 | ||
| 6238 | // Check for style in case a browser which returns unreliable values | |
| 6239 | // for getComputedStyle silently falls back to the reliable elem.style | |
| 6240 | valueIsBorderBox = isBorderBox && | |
| 6241 | ( support.boxSizingReliable() || val === elem.style[ name ] ); | |
| 6242 | ||
| 6243 | // Normalize "", auto, and prepare for extra | |
| 6244 | val = parseFloat( val ) || 0; | |
| 6245 | } | |
| 6246 | ||
| 6247 | // Use the active box-sizing model to add/subtract irrelevant styles | |
| 6248 | return ( val + | |
| 6249 | augmentWidthOrHeight( | |
| 6250 | elem, | |
| 6251 | name, | |
| 6252 | extra || ( isBorderBox ? "border" : "content" ), | |
| 6253 | valueIsBorderBox, | |
| 6254 | styles | |
| 6255 | ) | |
| 6256 | ) + "px"; | |
| 6257 | } | |
| 6258 | ||
| 6259 | jQuery.extend( { | |
| 6260 | ||
| 6261 | // Add in style property hooks for overriding the default | |
| 6262 | // behavior of getting and setting a style property | |
| 6263 | cssHooks: { | |
| 6264 | opacity: { | |
| 6265 | get: function( elem, computed ) { | |
| 6266 | if ( computed ) { | |
| 6267 | ||
| 6268 | // We should always get a number back from opacity | |
| 6269 | var ret = curCSS( elem, "opacity" ); | |
| 6270 | return ret === "" ? "1" : ret; | |
| 6271 | } | |
| 6272 | } | |
| 6273 | } | |
| 6274 | }, | |
| 6275 | ||
| 6276 | // Don't automatically add "px" to these possibly-unitless properties | |
| 6277 | cssNumber: { | |
| 6278 | "animationIterationCount": true, | |
| 6279 | "columnCount": true, | |
| 6280 | "fillOpacity": true, | |
| 6281 | "flexGrow": true, | |
| 6282 | "flexShrink": true, | |
| 6283 | "fontWeight": true, | |
| 6284 | "lineHeight": true, | |
| 6285 | "opacity": true, | |
| 6286 | "order": true, | |
| 6287 | "orphans": true, | |
| 6288 | "widows": true, | |
| 6289 | "zIndex": true, | |
| 6290 | "zoom": true | |
| 6291 | }, | |
| 6292 | ||
| 6293 | // Add in properties whose names you wish to fix before | |
| 6294 | // setting or getting the value | |
| 6295 | cssProps: { | |
| 6296 | "float": "cssFloat" | |
| 6297 | }, | |
| 6298 | ||
| 6299 | // Get and set the style property on a DOM Node | |
| 6300 | style: function( elem, name, value, extra ) { | |
| 6301 | ||
| 6302 | // Don't set styles on text and comment nodes | |
| 6303 | if ( !elem || elem.nodeType === 3 || elem.nodeType === 8 || !elem.style ) { | |
| 6304 | return; | |
| 6305 | } | |
| 6306 | ||
| 6307 | // Make sure that we're working with the right name | |
| 6308 | var ret, type, hooks, | |
| 6309 | origName = jQuery.camelCase( name ), | |
| 6310 | style = elem.style; | |
| 6311 | ||
| 6312 | name = jQuery.cssProps[ origName ] || | |
| 6313 | ( jQuery.cssProps[ origName ] = vendorPropName( origName ) || origName ); | |
| 6314 | ||
| 6315 | // Gets hook for the prefixed version, then unprefixed version | |
| 6316 | hooks = jQuery.cssHooks[ name ] || jQuery.cssHooks[ origName ]; | |
| 6317 | ||
| 6318 | // Check if we're setting a value | |
| 6319 | if ( value !== undefined ) { | |
| 6320 | type = typeof value; | |
| 6321 | ||
| 6322 | // Convert "+=" or "-=" to relative numbers (#7345) | |
| 6323 | if ( type === "string" && ( ret = rcssNum.exec( value ) ) && ret[ 1 ] ) { | |
| 6324 | value = adjustCSS( elem, name, ret ); | |
| 6325 | ||
| 6326 | // Fixes bug #9237 | |
| 6327 | type = "number"; | |
| 6328 | } | |
| 6329 | ||
| 6330 | // Make sure that null and NaN values aren't set (#7116) | |
| 6331 | if ( value == null || value !== value ) { | |
| 6332 | return; | |
| 6333 | } | |
| 6334 | ||
| 6335 | // If a number was passed in, add the unit (except for certain CSS properties) | |
| 6336 | if ( type === "number" ) { | |
| 6337 | value += ret && ret[ 3 ] || ( jQuery.cssNumber[ origName ] ? "" : "px" ); | |
| 6338 | } | |
| 6339 | ||
| 6340 | // background-* props affect original clone's values | |
| 6341 | if ( !support.clearCloneStyle && value === "" && name.indexOf( "background" ) === 0 ) { | |
| 6342 | style[ name ] = "inherit"; | |
| 6343 | } | |
| 6344 | ||
| 6345 | // If a hook was provided, use that value, otherwise just set the specified value | |
| 6346 | if ( !hooks || !( "set" in hooks ) || | |
| 6347 | ( value = hooks.set( elem, value, extra ) ) !== undefined ) { | |
| 6348 | ||
| 6349 | style[ name ] = value; | |
| 6350 | } | |
| 6351 | ||
| 6352 | } else { | |
| 6353 | ||
| 6354 | // If a hook was provided get the non-computed value from there | |
| 6355 | if ( hooks && "get" in hooks && | |
| 6356 | ( ret = hooks.get( elem, false, extra ) ) !== undefined ) { | |
| 6357 | ||
| 6358 | return ret; | |
| 6359 | } | |
| 6360 | ||
| 6361 | // Otherwise just get the value from the style object | |
| 6362 | return style[ name ]; | |
| 6363 | } | |
| 6364 | }, | |
| 6365 | ||
| 6366 | css: function( elem, name, extra, styles ) { | |
| 6367 | var val, num, hooks, | |
| 6368 | origName = jQuery.camelCase( name ); | |
| 6369 | ||
| 6370 | // Make sure that we're working with the right name | |
| 6371 | name = jQuery.cssProps[ origName ] || | |
| 6372 | ( jQuery.cssProps[ origName ] = vendorPropName( origName ) || origName ); | |
| 6373 | ||
| 6374 | // Try prefixed name followed by the unprefixed name | |
| 6375 | hooks = jQuery.cssHooks[ name ] || jQuery.cssHooks[ origName ]; | |
| 6376 | ||
| 6377 | // If a hook was provided get the computed value from there | |
| 6378 | if ( hooks && "get" in hooks ) { | |
| 6379 | val = hooks.get( elem, true, extra ); | |
| 6380 | } | |
| 6381 | ||
| 6382 | // Otherwise, if a way to get the computed value exists, use that | |
| 6383 | if ( val === undefined ) { | |
| 6384 | val = curCSS( elem, name, styles ); | |
| 6385 | } | |
| 6386 | ||
| 6387 | // Convert "normal" to computed value | |
| 6388 | if ( val === "normal" && name in cssNormalTransform ) { | |
| 6389 | val = cssNormalTransform[ name ]; | |
| 6390 | } | |
| 6391 | ||
| 6392 | // Make numeric if forced or a qualifier was provided and val looks numeric | |
| 6393 | if ( extra === "" || extra ) { | |
| 6394 | num = parseFloat( val ); | |
| 6395 | return extra === true || isFinite( num ) ? num || 0 : val; | |
| 6396 | } | |
| 6397 | return val; | |
| 6398 | } | |
| 6399 | } ); | |
| 6400 | ||
| 6401 | jQuery.each( [ "height", "width" ], function( i, name ) { | |
| 6402 | jQuery.cssHooks[ name ] = { | |
| 6403 | get: function( elem, computed, extra ) { | |
| 6404 | if ( computed ) { | |
| 6405 | ||
| 6406 | // Certain elements can have dimension info if we invisibly show them | |
| 6407 | // but it must have a current display style that would benefit | |
| 6408 | return rdisplayswap.test( jQuery.css( elem, "display" ) ) && | |
| 6409 | ||
| 6410 | // Support: Safari 8+ | |
| 6411 | // Table columns in Safari have non-zero offsetWidth & zero | |
| 6412 | // getBoundingClientRect().width unless display is changed. | |
| 6413 | // Support: IE <=11 only | |
| 6414 | // Running getBoundingClientRect on a disconnected node | |
| 6415 | // in IE throws an error. | |
| 6416 | ( !elem.getClientRects().length || !elem.getBoundingClientRect().width ) ? | |
| 6417 | swap( elem, cssShow, function() { | |
| 6418 | return getWidthOrHeight( elem, name, extra ); | |
| 6419 | } ) : | |
| 6420 | getWidthOrHeight( elem, name, extra ); | |
| 6421 | } | |
| 6422 | }, | |
| 6423 | ||
| 6424 | set: function( elem, value, extra ) { | |
| 6425 | var matches, | |
| 6426 | styles = extra && getStyles( elem ), | |
| 6427 | subtract = extra && augmentWidthOrHeight( | |
| 6428 | elem, | |
| 6429 | name, | |
| 6430 | extra, | |
| 6431 | jQuery.css( elem, "boxSizing", false, styles ) === "border-box", | |
| 6432 | styles | |
| 6433 | ); | |
| 6434 | ||
| 6435 | // Convert to pixels if value adjustment is needed | |
| 6436 | if ( subtract && ( matches = rcssNum.exec( value ) ) && | |
| 6437 | ( matches[ 3 ] || "px" ) !== "px" ) { | |
| 6438 | ||
| 6439 | elem.style[ name ] = value; | |
| 6440 | value = jQuery.css( elem, name ); | |
| 6441 | } | |
| 6442 | ||
| 6443 | return setPositiveNumber( elem, value, subtract ); | |
| 6444 | } | |
| 6445 | }; | |
| 6446 | } ); | |
| 6447 | ||
| 6448 | jQuery.cssHooks.marginLeft = addGetHookIf( support.reliableMarginLeft, | |
| 6449 | function( elem, computed ) { | |
| 6450 | if ( computed ) { | |
| 6451 | return ( parseFloat( curCSS( elem, "marginLeft" ) ) || | |
| 6452 | elem.getBoundingClientRect().left - | |
| 6453 | swap( elem, { marginLeft: 0 }, function() { | |
| 6454 | return elem.getBoundingClientRect().left; | |
| 6455 | } ) | |
| 6456 | ) + "px"; | |
| 6457 | } | |
| 6458 | } | |
| 6459 | ); | |
| 6460 | ||
| 6461 | // These hooks are used by animate to expand properties | |
| 6462 | jQuery.each( { | |
| 6463 | margin: "", | |
| 6464 | padding: "", | |
| 6465 | border: "Width" | |
| 6466 | }, function( prefix, suffix ) { | |
| 6467 | jQuery.cssHooks[ prefix + suffix ] = { | |
| 6468 | expand: function( value ) { | |
| 6469 | var i = 0, | |
| 6470 | expanded = {}, | |
| 6471 | ||
| 6472 | // Assumes a single number if not a string | |
| 6473 | parts = typeof value === "string" ? value.split( " " ) : [ value ]; | |
| 6474 | ||
| 6475 | for ( ; i < 4; i++ ) { | |
| 6476 | expanded[ prefix + cssExpand[ i ] + suffix ] = | |
| 6477 | parts[ i ] || parts[ i - 2 ] || parts[ 0 ]; | |
| 6478 | } | |
| 6479 | ||
| 6480 | return expanded; | |
| 6481 | } | |
| 6482 | }; | |
| 6483 | ||
| 6484 | if ( !rmargin.test( prefix ) ) { | |
| 6485 | jQuery.cssHooks[ prefix + suffix ].set = setPositiveNumber; | |
| 6486 | } | |
| 6487 | } ); | |
| 6488 | ||
| 6489 | jQuery.fn.extend( { | |
| 6490 | css: function( name, value ) { | |
| 6491 | return access( this, function( elem, name, value ) { | |
| 6492 | var styles, len, | |
| 6493 | map = {}, | |
| 6494 | i = 0; | |
| 6495 | ||
| 6496 | if ( jQuery.isArray( name ) ) { | |
| 6497 | styles = getStyles( elem ); | |
| 6498 | len = name.length; | |
| 6499 | ||
| 6500 | for ( ; i < len; i++ ) { | |
| 6501 | map[ name[ i ] ] = jQuery.css( elem, name[ i ], false, styles ); | |
| 6502 | } | |
| 6503 | ||
| 6504 | return map; | |
| 6505 | } | |
| 6506 | ||
| 6507 | return value !== undefined ? | |
| 6508 | jQuery.style( elem, name, value ) : | |
| 6509 | jQuery.css( elem, name ); | |
| 6510 | }, name, value, arguments.length > 1 ); | |
| 6511 | } | |
| 6512 | } ); | |
| 6513 | ||
| 6514 | ||
| 6515 | function Tween( elem, options, prop, end, easing ) { | |
| 6516 | return new Tween.prototype.init( elem, options, prop, end, easing ); | |
| 6517 | } | |
| 6518 | jQuery.Tween = Tween; | |
| 6519 | ||
| 6520 | Tween.prototype = { | |
| 6521 | constructor: Tween, | |
| 6522 | init: function( elem, options, prop, end, easing, unit ) { | |
| 6523 | this.elem = elem; | |
| 6524 | this.prop = prop; | |
| 6525 | this.easing = easing || jQuery.easing._default; | |
| 6526 | this.options = options; | |
| 6527 | this.start = this.now = this.cur(); | |
| 6528 | this.end = end; | |
| 6529 | this.unit = unit || ( jQuery.cssNumber[ prop ] ? "" : "px" ); | |
| 6530 | }, | |
| 6531 | cur: function() { | |
| 6532 | var hooks = Tween.propHooks[ this.prop ]; | |
| 6533 | ||
| 6534 | return hooks && hooks.get ? | |
| 6535 | hooks.get( this ) : | |
| 6536 | Tween.propHooks._default.get( this ); | |
| 6537 | }, | |
| 6538 | run: function( percent ) { | |
| 6539 | var eased, | |
| 6540 | hooks = Tween.propHooks[ this.prop ]; | |
| 6541 | ||
| 6542 | if ( this.options.duration ) { | |
| 6543 | this.pos = eased = jQuery.easing[ this.easing ]( | |
| 6544 | percent, this.options.duration * percent, 0, 1, this.options.duration | |
| 6545 | ); | |
| 6546 | } else { | |
| 6547 | this.pos = eased = percent; | |
| 6548 | } | |
| 6549 | this.now = ( this.end - this.start ) * eased + this.start; | |
| 6550 | ||
| 6551 | if ( this.options.step ) { | |
| 6552 | this.options.step.call( this.elem, this.now, this ); | |
| 6553 | } | |
| 6554 | ||
| 6555 | if ( hooks && hooks.set ) { | |
| 6556 | hooks.set( this ); | |
| 6557 | } else { | |
| 6558 | Tween.propHooks._default.set( this ); | |
| 6559 | } | |
| 6560 | return this; | |
| 6561 | } | |
| 6562 | }; | |
| 6563 | ||
| 6564 | Tween.prototype.init.prototype = Tween.prototype; | |
| 6565 | ||
| 6566 | Tween.propHooks = { | |
| 6567 | _default: { | |
| 6568 | get: function( tween ) { | |
| 6569 | var result; | |
| 6570 | ||
| 6571 | // Use a property on the element directly when it is not a DOM element, | |
| 6572 | // or when there is no matching style property that exists. | |
| 6573 | if ( tween.elem.nodeType !== 1 || | |
| 6574 | tween.elem[ tween.prop ] != null && tween.elem.style[ tween.prop ] == null ) { | |
| 6575 | return tween.elem[ tween.prop ]; | |
| 6576 | } | |
| 6577 | ||
| 6578 | // Passing an empty string as a 3rd parameter to .css will automatically | |
| 6579 | // attempt a parseFloat and fallback to a string if the parse fails. | |
| 6580 | // Simple values such as "10px" are parsed to Float; | |
| 6581 | // complex values such as "rotate(1rad)" are returned as-is. | |
| 6582 | result = jQuery.css( tween.elem, tween.prop, "" ); | |
| 6583 | ||
| 6584 | // Empty strings, null, undefined and "auto" are converted to 0. | |
| 6585 | return !result || result === "auto" ? 0 : result; | |
| 6586 | }, | |
| 6587 | set: function( tween ) { | |
| 6588 | ||
| 6589 | // Use step hook for back compat. | |
| 6590 | // Use cssHook if its there. | |
| 6591 | // Use .style if available and use plain properties where available. | |
| 6592 | if ( jQuery.fx.step[ tween.prop ] ) { | |
| 6593 | jQuery.fx.step[ tween.prop ]( tween ); | |
| 6594 | } else if ( tween.elem.nodeType === 1 && | |
| 6595 | ( tween.elem.style[ jQuery.cssProps[ tween.prop ] ] != null || | |
| 6596 | jQuery.cssHooks[ tween.prop ] ) ) { | |
| 6597 | jQuery.style( tween.elem, tween.prop, tween.now + tween.unit ); | |
| 6598 | } else { | |
| 6599 | tween.elem[ tween.prop ] = tween.now; | |
| 6600 | } | |
| 6601 | } | |
| 6602 | } | |
| 6603 | }; | |
| 6604 | ||
| 6605 | // Support: IE <=9 only | |
| 6606 | // Panic based approach to setting things on disconnected nodes | |
| 6607 | Tween.propHooks.scrollTop = Tween.propHooks.scrollLeft = { | |
| 6608 | set: function( tween ) { | |
| 6609 | if ( tween.elem.nodeType && tween.elem.parentNode ) { | |
| 6610 | tween.elem[ tween.prop ] = tween.now; | |
| 6611 | } | |
| 6612 | } | |
| 6613 | }; | |
| 6614 | ||
| 6615 | jQuery.easing = { | |
| 6616 | linear: function( p ) { | |
| 6617 | return p; | |
| 6618 | }, | |
| 6619 | swing: function( p ) { | |
| 6620 | return 0.5 - Math.cos( p * Math.PI ) / 2; | |
| 6621 | }, | |
| 6622 | _default: "swing" | |
| 6623 | }; | |
| 6624 | ||
| 6625 | jQuery.fx = Tween.prototype.init; | |
| 6626 | ||
| 6627 | // Back compat <1.8 extension point | |
| 6628 | jQuery.fx.step = {}; | |
| 6629 | ||
| 6630 | ||
| 6631 | ||
| 6632 | ||
| 6633 | var | |
| 6634 | fxNow, timerId, | |
| 6635 | rfxtypes = /^(?:toggle|show|hide)$/, | |
| 6636 | rrun = /queueHooks$/; | |
| 6637 | ||
| 6638 | function raf() { | |
| 6639 | if ( timerId ) { | |
| 6640 | window.requestAnimationFrame( raf ); | |
| 6641 | jQuery.fx.tick(); | |
| 6642 | } | |
| 6643 | } | |
| 6644 | ||
| 6645 | // Animations created synchronously will run synchronously | |
| 6646 | function createFxNow() { | |
| 6647 | window.setTimeout( function() { | |
| 6648 | fxNow = undefined; | |
| 6649 | } ); | |
| 6650 | return ( fxNow = jQuery.now() ); | |
| 6651 | } | |
| 6652 | ||
| 6653 | // Generate parameters to create a standard animation | |
| 6654 | function genFx( type, includeWidth ) { | |
| 6655 | var which, | |
| 6656 | i = 0, | |
| 6657 | attrs = { height: type }; | |
| 6658 | ||
| 6659 | // If we include width, step value is 1 to do all cssExpand values, | |
| 6660 | // otherwise step value is 2 to skip over Left and Right | |
| 6661 | includeWidth = includeWidth ? 1 : 0; | |
| 6662 | for ( ; i < 4; i += 2 - includeWidth ) { | |
| 6663 | which = cssExpand[ i ]; | |
| 6664 | attrs[ "margin" + which ] = attrs[ "padding" + which ] = type; | |
| 6665 | } | |
| 6666 | ||
| 6667 | if ( includeWidth ) { | |
| 6668 | attrs.opacity = attrs.width = type; | |
| 6669 | } | |
| 6670 | ||
| 6671 | return attrs; | |
| 6672 | } | |
| 6673 | ||
| 6674 | function createTween( value, prop, animation ) { | |
| 6675 | var tween, | |
| 6676 | collection = ( Animation.tweeners[ prop ] || [] ).concat( Animation.tweeners[ "*" ] ), | |
| 6677 | index = 0, | |
| 6678 | length = collection.length; | |
| 6679 | for ( ; index < length; index++ ) { | |
| 6680 | if ( ( tween = collection[ index ].call( animation, prop, value ) ) ) { | |
| 6681 | ||
| 6682 | // We're done with this property | |
| 6683 | return tween; | |
| 6684 | } | |
| 6685 | } | |
| 6686 | } | |
| 6687 | ||
| 6688 | function defaultPrefilter( elem, props, opts ) { | |
| 6689 | var prop, value, toggle, hooks, oldfire, propTween, restoreDisplay, display, | |
| 6690 | isBox = "width" in props || "height" in props, | |
| 6691 | anim = this, | |
| 6692 | orig = {}, | |
| 6693 | style = elem.style, | |
| 6694 | hidden = elem.nodeType && isHiddenWithinTree( elem ), | |
| 6695 | dataShow = dataPriv.get( elem, "fxshow" ); | |
| 6696 | ||
| 6697 | // Queue-skipping animations hijack the fx hooks | |
| 6698 | if ( !opts.queue ) { | |
| 6699 | hooks = jQuery._queueHooks( elem, "fx" ); | |
| 6700 | if ( hooks.unqueued == null ) { | |
| 6701 | hooks.unqueued = 0; | |
| 6702 | oldfire = hooks.empty.fire; | |
| 6703 | hooks.empty.fire = function() { | |
| 6704 | if ( !hooks.unqueued ) { | |
| 6705 | oldfire(); | |
| 6706 | } | |
| 6707 | }; | |
| 6708 | } | |
| 6709 | hooks.unqueued++; | |
| 6710 | ||
| 6711 | anim.always( function() { | |
| 6712 | ||
| 6713 | // Ensure the complete handler is called before this completes | |
| 6714 | anim.always( function() { | |
| 6715 | hooks.unqueued--; | |
| 6716 | if ( !jQuery.queue( elem, "fx" ).length ) { | |
| 6717 | hooks.empty.fire(); | |
| 6718 | } | |
| 6719 | } ); | |
| 6720 | } ); | |
| 6721 | } | |
| 6722 | ||
| 6723 | // Detect show/hide animations | |
| 6724 | for ( prop in props ) { | |
| 6725 | value = props[ prop ]; | |
| 6726 | if ( rfxtypes.test( value ) ) { | |
| 6727 | delete props[ prop ]; | |
| 6728 | toggle = toggle || value === "toggle"; | |
| 6729 | if ( value === ( hidden ? "hide" : "show" ) ) { | |
| 6730 | ||
| 6731 | // Pretend to be hidden if this is a "show" and | |
| 6732 | // there is still data from a stopped show/hide | |
| 6733 | if ( value === "show" && dataShow && dataShow[ prop ] !== undefined ) { | |
| 6734 | hidden = true; | |
| 6735 | ||
| 6736 | // Ignore all other no-op show/hide data | |
| 6737 | } else { | |
| 6738 | continue; | |
| 6739 | } | |
| 6740 | } | |
| 6741 | orig[ prop ] = dataShow && dataShow[ prop ] || jQuery.style( elem, prop ); | |
| 6742 | } | |
| 6743 | } | |
| 6744 | ||
| 6745 | // Bail out if this is a no-op like .hide().hide() | |
| 6746 | propTween = !jQuery.isEmptyObject( props ); | |
| 6747 | if ( !propTween && jQuery.isEmptyObject( orig ) ) { | |
| 6748 | return; | |
| 6749 | } | |
| 6750 | ||
| 6751 | // Restrict "overflow" and "display" styles during box animations | |
| 6752 | if ( isBox && elem.nodeType === 1 ) { | |
| 6753 | ||
| 6754 | // Support: IE <=9 - 11, Edge 12 - 13 | |
| 6755 | // Record all 3 overflow attributes because IE does not infer the shorthand | |
| 6756 | // from identically-valued overflowX and overflowY | |
| 6757 | opts.overflow = [ style.overflow, style.overflowX, style.overflowY ]; | |
| 6758 | ||
| 6759 | // Identify a display type, preferring old show/hide data over the CSS cascade | |
| 6760 | restoreDisplay = dataShow && dataShow.display; | |
| 6761 | if ( restoreDisplay == null ) { | |
| 6762 | restoreDisplay = dataPriv.get( elem, "display" ); | |
| 6763 | } | |
| 6764 | display = jQuery.css( elem, "display" ); | |
| 6765 | if ( display === "none" ) { | |
| 6766 | if ( restoreDisplay ) { | |
| 6767 | display = restoreDisplay; | |
| 6768 | } else { | |
| 6769 | ||
| 6770 | // Get nonempty value(s) by temporarily forcing visibility | |
| 6771 | showHide( [ elem ], true ); | |
| 6772 | restoreDisplay = elem.style.display || restoreDisplay; | |
| 6773 | display = jQuery.css( elem, "display" ); | |
| 6774 | showHide( [ elem ] ); | |
| 6775 | } | |
| 6776 | } | |
| 6777 | ||
| 6778 | // Animate inline elements as inline-block | |
| 6779 | if ( display === "inline" || display === "inline-block" && restoreDisplay != null ) { | |
| 6780 | if ( jQuery.css( elem, "float" ) === "none" ) { | |
| 6781 | ||
| 6782 | // Restore the original display value at the end of pure show/hide animations | |
| 6783 | if ( !propTween ) { | |
| 6784 | anim.done( function() { | |
| 6785 | style.display = restoreDisplay; | |
| 6786 | } ); | |
| 6787 | if ( restoreDisplay == null ) { | |
| 6788 | display = style.display; | |
| 6789 | restoreDisplay = display === "none" ? "" : display; | |
| 6790 | } | |
| 6791 | } | |
| 6792 | style.display = "inline-block"; | |
| 6793 | } | |
| 6794 | } | |
| 6795 | } | |
| 6796 | ||
| 6797 | if ( opts.overflow ) { | |
| 6798 | style.overflow = "hidden"; | |
| 6799 | anim.always( function() { | |
| 6800 | style.overflow = opts.overflow[ 0 ]; | |
| 6801 | style.overflowX = opts.overflow[ 1 ]; | |
| 6802 | style.overflowY = opts.overflow[ 2 ]; | |
| 6803 | } ); | |
| 6804 | } | |
| 6805 | ||
| 6806 | // Implement show/hide animations | |
| 6807 | propTween = false; | |
| 6808 | for ( prop in orig ) { | |
| 6809 | ||
| 6810 | // General show/hide setup for this element animation | |
| 6811 | if ( !propTween ) { | |
| 6812 | if ( dataShow ) { | |
| 6813 | if ( "hidden" in dataShow ) { | |
| 6814 | hidden = dataShow.hidden; | |
| 6815 | } | |
| 6816 | } else { | |
| 6817 | dataShow = dataPriv.access( elem, "fxshow", { display: restoreDisplay } ); | |
| 6818 | } | |
| 6819 | ||
| 6820 | // Store hidden/visible for toggle so `.stop().toggle()` "reverses" | |
| 6821 | if ( toggle ) { | |
| 6822 | dataShow.hidden = !hidden; | |
| 6823 | } | |
| 6824 | ||
| 6825 | // Show elements before animating them | |
| 6826 | if ( hidden ) { | |
| 6827 | showHide( [ elem ], true ); | |
| 6828 | } | |
| 6829 | ||
| 6830 | /* eslint-disable no-loop-func */ | |
| 6831 | ||
| 6832 | anim.done( function() { | |
| 6833 | ||
| 6834 | /* eslint-enable no-loop-func */ | |
| 6835 | ||
| 6836 | // The final step of a "hide" animation is actually hiding the element | |
| 6837 | if ( !hidden ) { | |
| 6838 | showHide( [ elem ] ); | |
| 6839 | } | |
| 6840 | dataPriv.remove( elem, "fxshow" ); | |
| 6841 | for ( prop in orig ) { | |
| 6842 | jQuery.style( elem, prop, orig[ prop ] ); | |
| 6843 | } | |
| 6844 | } ); | |
| 6845 | } | |
| 6846 | ||
| 6847 | // Per-property setup | |
| 6848 | propTween = createTween( hidden ? dataShow[ prop ] : 0, prop, anim ); | |
| 6849 | if ( !( prop in dataShow ) ) { | |
| 6850 | dataShow[ prop ] = propTween.start; | |
| 6851 | if ( hidden ) { | |
| 6852 | propTween.end = propTween.start; | |
| 6853 | propTween.start = 0; | |
| 6854 | } | |
| 6855 | } | |
| 6856 | } | |
| 6857 | } | |
| 6858 | ||
| 6859 | function propFilter( props, specialEasing ) { | |
| 6860 | var index, name, easing, value, hooks; | |
| 6861 | ||
| 6862 | // camelCase, specialEasing and expand cssHook pass | |
| 6863 | for ( index in props ) { | |
| 6864 | name = jQuery.camelCase( index ); | |
| 6865 | easing = specialEasing[ name ]; | |
| 6866 | value = props[ index ]; | |
| 6867 | if ( jQuery.isArray( value ) ) { | |
| 6868 | easing = value[ 1 ]; | |
| 6869 | value = props[ index ] = value[ 0 ]; | |
| 6870 | } | |
| 6871 | ||
| 6872 | if ( index !== name ) { | |
| 6873 | props[ name ] = value; | |
| 6874 | delete props[ index ]; | |
| 6875 | } | |
| 6876 | ||
| 6877 | hooks = jQuery.cssHooks[ name ]; | |
| 6878 | if ( hooks && "expand" in hooks ) { | |
| 6879 | value = hooks.expand( value ); | |
| 6880 | delete props[ name ]; | |
| 6881 | ||
| 6882 | // Not quite $.extend, this won't overwrite existing keys. | |
| 6883 | // Reusing 'index' because we have the correct "name" | |
| 6884 | for ( index in value ) { | |
| 6885 | if ( !( index in props ) ) { | |
| 6886 | props[ index ] = value[ index ]; | |
| 6887 | specialEasing[ index ] = easing; | |
| 6888 | } | |
| 6889 | } | |
| 6890 | } else { | |
| 6891 | specialEasing[ name ] = easing; | |
| 6892 | } | |
| 6893 | } | |
| 6894 | } | |
| 6895 | ||
| 6896 | function Animation( elem, properties, options ) { | |
| 6897 | var result, | |
| 6898 | stopped, | |
| 6899 | index = 0, | |
| 6900 | length = Animation.prefilters.length, | |
| 6901 | deferred = jQuery.Deferred().always( function() { | |
| 6902 | ||
| 6903 | // Don't match elem in the :animated selector | |
| 6904 | delete tick.elem; | |
| 6905 | } ), | |
| 6906 | tick = function() { | |
| 6907 | if ( stopped ) { | |
| 6908 | return false; | |
| 6909 | } | |
| 6910 | var currentTime = fxNow || createFxNow(), | |
| 6911 | remaining = Math.max( 0, animation.startTime + animation.duration - currentTime ), | |
| 6912 | ||
| 6913 | // Support: Android 2.3 only | |
| 6914 | // Archaic crash bug won't allow us to use `1 - ( 0.5 || 0 )` (#12497) | |
| 6915 | temp = remaining / animation.duration || 0, | |
| 6916 | percent = 1 - temp, | |
| 6917 | index = 0, | |
| 6918 | length = animation.tweens.length; | |
| 6919 | ||
| 6920 | for ( ; index < length; index++ ) { | |
| 6921 | animation.tweens[ index ].run( percent ); | |
| 6922 | } | |
| 6923 | ||
| 6924 | deferred.notifyWith( elem, [ animation, percent, remaining ] ); | |
| 6925 | ||
| 6926 | if ( percent < 1 && length ) { | |
| 6927 | return remaining; | |
| 6928 | } else { | |
| 6929 | deferred.resolveWith( elem, [ animation ] ); | |
| 6930 | return false; | |
| 6931 | } | |
| 6932 | }, | |
| 6933 | animation = deferred.promise( { | |
| 6934 | elem: elem, | |
| 6935 | props: jQuery.extend( {}, properties ), | |
| 6936 | opts: jQuery.extend( true, { | |
| 6937 | specialEasing: {}, | |
| 6938 | easing: jQuery.easing._default | |
| 6939 | }, options ), | |
| 6940 | originalProperties: properties, | |
| 6941 | originalOptions: options, | |
| 6942 | startTime: fxNow || createFxNow(), | |
| 6943 | duration: options.duration, | |
| 6944 | tweens: [], | |
| 6945 | createTween: function( prop, end ) { | |
| 6946 | var tween = jQuery.Tween( elem, animation.opts, prop, end, | |
| 6947 | animation.opts.specialEasing[ prop ] || animation.opts.easing ); | |
| 6948 | animation.tweens.push( tween ); | |
| 6949 | return tween; | |
| 6950 | }, | |
| 6951 | stop: function( gotoEnd ) { | |
| 6952 | var index = 0, | |
| 6953 | ||
| 6954 | // If we are going to the end, we want to run all the tweens | |
| 6955 | // otherwise we skip this part | |
| 6956 | length = gotoEnd ? animation.tweens.length : 0; | |
| 6957 | if ( stopped ) { | |
| 6958 | return this; | |
| 6959 | } | |
| 6960 | stopped = true; | |
| 6961 | for ( ; index < length; index++ ) { | |
| 6962 | animation.tweens[ index ].run( 1 ); | |
| 6963 | } | |
| 6964 | ||
| 6965 | // Resolve when we played the last frame; otherwise, reject | |
| 6966 | if ( gotoEnd ) { | |
| 6967 | deferred.notifyWith( elem, [ animation, 1, 0 ] ); | |
| 6968 | deferred.resolveWith( elem, [ animation, gotoEnd ] ); | |
| 6969 | } else { | |
| 6970 | deferred.rejectWith( elem, [ animation, gotoEnd ] ); | |
| 6971 | } | |
| 6972 | return this; | |
| 6973 | } | |
| 6974 | } ), | |
| 6975 | props = animation.props; | |
| 6976 | ||
| 6977 | propFilter( props, animation.opts.specialEasing ); | |
| 6978 | ||
| 6979 | for ( ; index < length; index++ ) { | |
| 6980 | result = Animation.prefilters[ index ].call( animation, elem, props, animation.opts ); | |
| 6981 | if ( result ) { | |
| 6982 | if ( jQuery.isFunction( result.stop ) ) { | |
| 6983 | jQuery._queueHooks( animation.elem, animation.opts.queue ).stop = | |
| 6984 | jQuery.proxy( result.stop, result ); | |
| 6985 | } | |
| 6986 | return result; | |
| 6987 | } | |
| 6988 | } | |
| 6989 | ||
| 6990 | jQuery.map( props, createTween, animation ); | |
| 6991 | ||
| 6992 | if ( jQuery.isFunction( animation.opts.start ) ) { | |
| 6993 | animation.opts.start.call( elem, animation ); | |
| 6994 | } | |
| 6995 | ||
| 6996 | jQuery.fx.timer( | |
| 6997 | jQuery.extend( tick, { | |
| 6998 | elem: elem, | |
| 6999 | anim: animation, | |
| 7000 | queue: animation.opts.queue | |
| 7001 | } ) | |
| 7002 | ); | |
| 7003 | ||
| 7004 | // attach callbacks from options | |
| 7005 | return animation.progress( animation.opts.progress ) | |
| 7006 | .done( animation.opts.done, animation.opts.complete ) | |
| 7007 | .fail( animation.opts.fail ) | |
| 7008 | .always( animation.opts.always ); | |
| 7009 | } | |
| 7010 | ||
| 7011 | jQuery.Animation = jQuery.extend( Animation, { | |
| 7012 | ||
| 7013 | tweeners: { | |
| 7014 | "*": [ function( prop, value ) { | |
| 7015 | var tween = this.createTween( prop, value ); | |
| 7016 | adjustCSS( tween.elem, prop, rcssNum.exec( value ), tween ); | |
| 7017 | return tween; | |
| 7018 | } ] | |
| 7019 | }, | |
| 7020 | ||
| 7021 | tweener: function( props, callback ) { | |
| 7022 | if ( jQuery.isFunction( props ) ) { | |
| 7023 | callback = props; | |
| 7024 | props = [ "*" ]; | |
| 7025 | } else { | |
| 7026 | props = props.match( rnotwhite ); | |
| 7027 | } | |
| 7028 | ||
| 7029 | var prop, | |
| 7030 | index = 0, | |
| 7031 | length = props.length; | |
| 7032 | ||
| 7033 | for ( ; index < length; index++ ) { | |
| 7034 | prop = props[ index ]; | |
| 7035 | Animation.tweeners[ prop ] = Animation.tweeners[ prop ] || []; | |
| 7036 | Animation.tweeners[ prop ].unshift( callback ); | |
| 7037 | } | |
| 7038 | }, | |
| 7039 | ||
| 7040 | prefilters: [ defaultPrefilter ], | |
| 7041 | ||
| 7042 | prefilter: function( callback, prepend ) { | |
| 7043 | if ( prepend ) { | |
| 7044 | Animation.prefilters.unshift( callback ); | |
| 7045 | } else { | |
| 7046 | Animation.prefilters.push( callback ); | |
| 7047 | } | |
| 7048 | } | |
| 7049 | } ); | |
| 7050 | ||
| 7051 | jQuery.speed = function( speed, easing, fn ) { | |
| 7052 | var opt = speed && typeof speed === "object" ? jQuery.extend( {}, speed ) : { | |
| 7053 | complete: fn || !fn && easing || | |
| 7054 | jQuery.isFunction( speed ) && speed, | |
| 7055 | duration: speed, | |
| 7056 | easing: fn && easing || easing && !jQuery.isFunction( easing ) && easing | |
| 7057 | }; | |
| 7058 | ||
| 7059 | // Go to the end state if fx are off or if document is hidden | |
| 7060 | if ( jQuery.fx.off || document.hidden ) { | |
| 7061 | opt.duration = 0; | |
| 7062 | ||
| 7063 | } else { | |
| 7064 | opt.duration = typeof opt.duration === "number" ? | |
| 7065 | opt.duration : opt.duration in jQuery.fx.speeds ? | |
| 7066 | jQuery.fx.speeds[ opt.duration ] : jQuery.fx.speeds._default; | |
| 7067 | } | |
| 7068 | ||
| 7069 | // Normalize opt.queue - true/undefined/null -> "fx" | |
| 7070 | if ( opt.queue == null || opt.queue === true ) { | |
| 7071 | opt.queue = "fx"; | |
| 7072 | } | |
| 7073 | ||
| 7074 | // Queueing | |
| 7075 | opt.old = opt.complete; | |
| 7076 | ||
| 7077 | opt.complete = function() { | |
| 7078 | if ( jQuery.isFunction( opt.old ) ) { | |
| 7079 | opt.old.call( this ); | |
| 7080 | } | |
| 7081 | ||
| 7082 | if ( opt.queue ) { | |
| 7083 | jQuery.dequeue( this, opt.queue ); | |
| 7084 | } | |
| 7085 | }; | |
| 7086 | ||
| 7087 | return opt; | |
| 7088 | }; | |
| 7089 | ||
| 7090 | jQuery.fn.extend( { | |
| 7091 | fadeTo: function( speed, to, easing, callback ) { | |
| 7092 | ||
| 7093 | // Show any hidden elements after setting opacity to 0 | |
| 7094 | return this.filter( isHiddenWithinTree ).css( "opacity", 0 ).show() | |
| 7095 | ||
| 7096 | // Animate to the value specified | |
| 7097 | .end().animate( { opacity: to }, speed, easing, callback ); | |
| 7098 | }, | |
| 7099 | animate: function( prop, speed, easing, callback ) { | |
| 7100 | var empty = jQuery.isEmptyObject( prop ), | |
| 7101 | optall = jQuery.speed( speed, easing, callback ), | |
| 7102 | doAnimation = function() { | |
| 7103 | ||
| 7104 | // Operate on a copy of prop so per-property easing won't be lost | |
| 7105 | var anim = Animation( this, jQuery.extend( {}, prop ), optall ); | |
| 7106 | ||
| 7107 | // Empty animations, or finishing resolves immediately | |
| 7108 | if ( empty || dataPriv.get( this, "finish" ) ) { | |
| 7109 | anim.stop( true ); | |
| 7110 | } | |
| 7111 | }; | |
| 7112 | doAnimation.finish = doAnimation; | |
| 7113 | ||
| 7114 | return empty || optall.queue === false ? | |
| 7115 | this.each( doAnimation ) : | |
| 7116 | this.queue( optall.queue, doAnimation ); | |
| 7117 | }, | |
| 7118 | stop: function( type, clearQueue, gotoEnd ) { | |
| 7119 | var stopQueue = function( hooks ) { | |
| 7120 | var stop = hooks.stop; | |
| 7121 | delete hooks.stop; | |
| 7122 | stop( gotoEnd ); | |
| 7123 | }; | |
| 7124 | ||
| 7125 | if ( typeof type !== "string" ) { | |
| 7126 | gotoEnd = clearQueue; | |
| 7127 | clearQueue = type; | |
| 7128 | type = undefined; | |
| 7129 | } | |
| 7130 | if ( clearQueue && type !== false ) { | |
| 7131 | this.queue( type || "fx", [] ); | |
| 7132 | } | |
| 7133 | ||
| 7134 | return this.each( function() { | |
| 7135 | var dequeue = true, | |
| 7136 | index = type != null && type + "queueHooks", | |
| 7137 | timers = jQuery.timers, | |
| 7138 | data = dataPriv.get( this ); | |
| 7139 | ||
| 7140 | if ( index ) { | |
| 7141 | if ( data[ index ] && data[ index ].stop ) { | |
| 7142 | stopQueue( data[ index ] ); | |
| 7143 | } | |
| 7144 | } else { | |
| 7145 | for ( index in data ) { | |
| 7146 | if ( data[ index ] && data[ index ].stop && rrun.test( index ) ) { | |
| 7147 | stopQueue( data[ index ] ); | |
| 7148 | } | |
| 7149 | } | |
| 7150 | } | |
| 7151 | ||
| 7152 | for ( index = timers.length; index--; ) { | |
| 7153 | if ( timers[ index ].elem === this && | |
| 7154 | ( type == null || timers[ index ].queue === type ) ) { | |
| 7155 | ||
| 7156 | timers[ index ].anim.stop( gotoEnd ); | |
| 7157 | dequeue = false; | |
| 7158 | timers.splice( index, 1 ); | |
| 7159 | } | |
| 7160 | } | |
| 7161 | ||
| 7162 | // Start the next in the queue if the last step wasn't forced. | |
| 7163 | // Timers currently will call their complete callbacks, which | |
| 7164 | // will dequeue but only if they were gotoEnd. | |
| 7165 | if ( dequeue || !gotoEnd ) { | |
| 7166 | jQuery.dequeue( this, type ); | |
| 7167 | } | |
| 7168 | } ); | |
| 7169 | }, | |
| 7170 | finish: function( type ) { | |
| 7171 | if ( type !== false ) { | |
| 7172 | type = type || "fx"; | |
| 7173 | } | |
| 7174 | return this.each( function() { | |
| 7175 | var index, | |
| 7176 | data = dataPriv.get( this ), | |
| 7177 | queue = data[ type + "queue" ], | |
| 7178 | hooks = data[ type + "queueHooks" ], | |
| 7179 | timers = jQuery.timers, | |
| 7180 | length = queue ? queue.length : 0; | |
| 7181 | ||
| 7182 | // Enable finishing flag on private data | |
| 7183 | data.finish = true; | |
| 7184 | ||
| 7185 | // Empty the queue first | |
| 7186 | jQuery.queue( this, type, [] ); | |
| 7187 | ||
| 7188 | if ( hooks && hooks.stop ) { | |
| 7189 | hooks.stop.call( this, true ); | |
| 7190 | } | |
| 7191 | ||
| 7192 | // Look for any active animations, and finish them | |
| 7193 | for ( index = timers.length; index--; ) { | |
| 7194 | if ( timers[ index ].elem === this && timers[ index ].queue === type ) { | |
| 7195 | timers[ index ].anim.stop( true ); | |
| 7196 | timers.splice( index, 1 ); | |
| 7197 | } | |
| 7198 | } | |
| 7199 | ||
| 7200 | // Look for any animations in the old queue and finish them | |
| 7201 | for ( index = 0; index < length; index++ ) { | |
| 7202 | if ( queue[ index ] && queue[ index ].finish ) { | |
| 7203 | queue[ index ].finish.call( this ); | |
| 7204 | } | |
| 7205 | } | |
| 7206 | ||
| 7207 | // Turn off finishing flag | |
| 7208 | delete data.finish; | |
| 7209 | } ); | |
| 7210 | } | |
| 7211 | } ); | |
| 7212 | ||
| 7213 | jQuery.each( [ "toggle", "show", "hide" ], function( i, name ) { | |
| 7214 | var cssFn = jQuery.fn[ name ]; | |
| 7215 | jQuery.fn[ name ] = function( speed, easing, callback ) { | |
| 7216 | return speed == null || typeof speed === "boolean" ? | |
| 7217 | cssFn.apply( this, arguments ) : | |
| 7218 | this.animate( genFx( name, true ), speed, easing, callback ); | |
| 7219 | }; | |
| 7220 | } ); | |
| 7221 | ||
| 7222 | // Generate shortcuts for custom animations | |
| 7223 | jQuery.each( { | |
| 7224 | slideDown: genFx( "show" ), | |
| 7225 | slideUp: genFx( "hide" ), | |
| 7226 | slideToggle: genFx( "toggle" ), | |
| 7227 | fadeIn: { opacity: "show" }, | |
| 7228 | fadeOut: { opacity: "hide" }, | |
| 7229 | fadeToggle: { opacity: "toggle" } | |
| 7230 | }, function( name, props ) { | |
| 7231 | jQuery.fn[ name ] = function( speed, easing, callback ) { | |
| 7232 | return this.animate( props, speed, easing, callback ); | |
| 7233 | }; | |
| 7234 | } ); | |
| 7235 | ||
| 7236 | jQuery.timers = []; | |
| 7237 | jQuery.fx.tick = function() { | |
| 7238 | var timer, | |
| 7239 | i = 0, | |
| 7240 | timers = jQuery.timers; | |
| 7241 | ||
| 7242 | fxNow = jQuery.now(); | |
| 7243 | ||
| 7244 | for ( ; i < timers.length; i++ ) { | |
| 7245 | timer = timers[ i ]; | |
| 7246 | ||
| 7247 | // Checks the timer has not already been removed | |
| 7248 | if ( !timer() && timers[ i ] === timer ) { | |
| 7249 | timers.splice( i--, 1 ); | |
| 7250 | } | |
| 7251 | } | |
| 7252 | ||
| 7253 | if ( !timers.length ) { | |
| 7254 | jQuery.fx.stop(); | |
| 7255 | } | |
| 7256 | fxNow = undefined; | |
| 7257 | }; | |
| 7258 | ||
| 7259 | jQuery.fx.timer = function( timer ) { | |
| 7260 | jQuery.timers.push( timer ); | |
| 7261 | if ( timer() ) { | |
| 7262 | jQuery.fx.start(); | |
| 7263 | } else { | |
| 7264 | jQuery.timers.pop(); | |
| 7265 | } | |
| 7266 | }; | |
| 7267 | ||
| 7268 | jQuery.fx.interval = 13; | |
| 7269 | jQuery.fx.start = function() { | |
| 7270 | if ( !timerId ) { | |
| 7271 | timerId = window.requestAnimationFrame ? | |
| 7272 | window.requestAnimationFrame( raf ) : | |
| 7273 | window.setInterval( jQuery.fx.tick, jQuery.fx.interval ); | |
| 7274 | } | |
| 7275 | }; | |
| 7276 | ||
| 7277 | jQuery.fx.stop = function() { | |
| 7278 | if ( window.cancelAnimationFrame ) { | |
| 7279 | window.cancelAnimationFrame( timerId ); | |
| 7280 | } else { | |
| 7281 | window.clearInterval( timerId ); | |
| 7282 | } | |
| 7283 | ||
| 7284 | timerId = null; | |
| 7285 | }; | |
| 7286 | ||
| 7287 | jQuery.fx.speeds = { | |
| 7288 | slow: 600, | |
| 7289 | fast: 200, | |
| 7290 | ||
| 7291 | // Default speed | |
| 7292 | _default: 400 | |
| 7293 | }; | |
| 7294 | ||
| 7295 | ||
| 7296 | // Based off of the plugin by Clint Helfers, with permission. | |
| 7297 | // https://web.archive.org/web/20100324014747/http://blindsignals.com/index.php/2009/07/jquery-delay/ | |
| 7298 | jQuery.fn.delay = function( time, type ) { | |
| 7299 | time = jQuery.fx ? jQuery.fx.speeds[ time ] || time : time; | |
| 7300 | type = type || "fx"; | |
| 7301 | ||
| 7302 | return this.queue( type, function( next, hooks ) { | |
| 7303 | var timeout = window.setTimeout( next, time ); | |
| 7304 | hooks.stop = function() { | |
| 7305 | window.clearTimeout( timeout ); | |
| 7306 | }; | |
| 7307 | } ); | |
| 7308 | }; | |
| 7309 | ||
| 7310 | ||
| 7311 | ( function() { | |
| 7312 | var input = document.createElement( "input" ), | |
| 7313 | select = document.createElement( "select" ), | |
| 7314 | opt = select.appendChild( document.createElement( "option" ) ); | |
| 7315 | ||
| 7316 | input.type = "checkbox"; | |
| 7317 | ||
| 7318 | // Support: Android <=4.3 only | |
| 7319 | // Default value for a checkbox should be "on" | |
| 7320 | support.checkOn = input.value !== ""; | |
| 7321 | ||
| 7322 | // Support: IE <=11 only | |
| 7323 | // Must access selectedIndex to make default options select | |
| 7324 | support.optSelected = opt.selected; | |
| 7325 | ||
| 7326 | // Support: IE <=11 only | |
| 7327 | // An input loses its value after becoming a radio | |
| 7328 | input = document.createElement( "input" ); | |
| 7329 | input.value = "t"; | |
| 7330 | input.type = "radio"; | |
| 7331 | support.radioValue = input.value === "t"; | |
| 7332 | } )(); | |
| 7333 | ||
| 7334 | ||
| 7335 | var boolHook, | |
| 7336 | attrHandle = jQuery.expr.attrHandle; | |
| 7337 | ||
| 7338 | jQuery.fn.extend( { | |
| 7339 | attr: function( name, value ) { | |
| 7340 | return access( this, jQuery.attr, name, value, arguments.length > 1 ); | |
| 7341 | }, | |
| 7342 | ||
| 7343 | removeAttr: function( name ) { | |
| 7344 | return this.each( function() { | |
| 7345 | jQuery.removeAttr( this, name ); | |
| 7346 | } ); | |
| 7347 | } | |
| 7348 | } ); | |
| 7349 | ||
| 7350 | jQuery.extend( { | |
| 7351 | attr: function( elem, name, value ) { | |
| 7352 | var ret, hooks, | |
| 7353 | nType = elem.nodeType; | |
| 7354 | ||
| 7355 | // Don't get/set attributes on text, comment and attribute nodes | |
| 7356 | if ( nType === 3 || nType === 8 || nType === 2 ) { | |
| 7357 | return; | |
| 7358 | } | |
| 7359 | ||
| 7360 | // Fallback to prop when attributes are not supported | |
| 7361 | if ( typeof elem.getAttribute === "undefined" ) { | |
| 7362 | return jQuery.prop( elem, name, value ); | |
| 7363 | } | |
| 7364 | ||
| 7365 | // Attribute hooks are determined by the lowercase version | |
| 7366 | // Grab necessary hook if one is defined | |
| 7367 | if ( nType !== 1 || !jQuery.isXMLDoc( elem ) ) { | |
| 7368 | hooks = jQuery.attrHooks[ name.toLowerCase() ] || | |
| 7369 | ( jQuery.expr.match.bool.test( name ) ? boolHook : undefined ); | |
| 7370 | } | |
| 7371 | ||
| 7372 | if ( value !== undefined ) { | |
| 7373 | if ( value === null ) { | |
| 7374 | jQuery.removeAttr( elem, name ); | |
| 7375 | return; | |
| 7376 | } | |
| 7377 | ||
| 7378 | if ( hooks && "set" in hooks && | |
| 7379 | ( ret = hooks.set( elem, value, name ) ) !== undefined ) { | |
| 7380 | return ret; | |
| 7381 | } | |
| 7382 | ||
| 7383 | elem.setAttribute( name, value + "" ); | |
| 7384 | return value; | |
| 7385 | } | |
| 7386 | ||
| 7387 | if ( hooks && "get" in hooks && ( ret = hooks.get( elem, name ) ) !== null ) { | |
| 7388 | return ret; | |
| 7389 | } | |
| 7390 | ||
| 7391 | ret = jQuery.find.attr( elem, name ); | |
| 7392 | ||
| 7393 | // Non-existent attributes return null, we normalize to undefined | |
| 7394 | return ret == null ? undefined : ret; | |
| 7395 | }, | |
| 7396 | ||
| 7397 | attrHooks: { | |
| 7398 | type: { | |
| 7399 | set: function( elem, value ) { | |
| 7400 | if ( !support.radioValue && value === "radio" && | |
| 7401 | jQuery.nodeName( elem, "input" ) ) { | |
| 7402 | var val = elem.value; | |
| 7403 | elem.setAttribute( "type", value ); | |
| 7404 | if ( val ) { | |
| 7405 | elem.value = val; | |
| 7406 | } | |
| 7407 | return value; | |
| 7408 | } | |
| 7409 | } | |
| 7410 | } | |
| 7411 | }, | |
| 7412 | ||
| 7413 | removeAttr: function( elem, value ) { | |
| 7414 | var name, | |
| 7415 | i = 0, | |
| 7416 | attrNames = value && value.match( rnotwhite ); | |
| 7417 | ||
| 7418 | if ( attrNames && elem.nodeType === 1 ) { | |
| 7419 | while ( ( name = attrNames[ i++ ] ) ) { | |
| 7420 | elem.removeAttribute( name ); | |
| 7421 | } | |
| 7422 | } | |
| 7423 | } | |
| 7424 | } ); | |
| 7425 | ||
| 7426 | // Hooks for boolean attributes | |
| 7427 | boolHook = { | |
| 7428 | set: function( elem, value, name ) { | |
| 7429 | if ( value === false ) { | |
| 7430 | ||
| 7431 | // Remove boolean attributes when set to false | |
| 7432 | jQuery.removeAttr( elem, name ); | |
| 7433 | } else { | |
| 7434 | elem.setAttribute( name, name ); | |
| 7435 | } | |
| 7436 | return name; | |
| 7437 | } | |
| 7438 | }; | |
| 7439 | ||
| 7440 | jQuery.each( jQuery.expr.match.bool.source.match( /\w+/g ), function( i, name ) { | |
| 7441 | var getter = attrHandle[ name ] || jQuery.find.attr; | |
| 7442 | ||
| 7443 | attrHandle[ name ] = function( elem, name, isXML ) { | |
| 7444 | var ret, handle, | |
| 7445 | lowercaseName = name.toLowerCase(); | |
| 7446 | ||
| 7447 | if ( !isXML ) { | |
| 7448 | ||
| 7449 | // Avoid an infinite loop by temporarily removing this function from the getter | |
| 7450 | handle = attrHandle[ lowercaseName ]; | |
| 7451 | attrHandle[ lowercaseName ] = ret; | |
| 7452 | ret = getter( elem, name, isXML ) != null ? | |
| 7453 | lowercaseName : | |
| 7454 | null; | |
| 7455 | attrHandle[ lowercaseName ] = handle; | |
| 7456 | } | |
| 7457 | return ret; | |
| 7458 | }; | |
| 7459 | } ); | |
| 7460 | ||
| 7461 | ||
| 7462 | ||
| 7463 | ||
| 7464 | var rfocusable = /^(?:input|select|textarea|button)$/i, | |
| 7465 | rclickable = /^(?:a|area)$/i; | |
| 7466 | ||
| 7467 | jQuery.fn.extend( { | |
| 7468 | prop: function( name, value ) { | |
| 7469 | return access( this, jQuery.prop, name, value, arguments.length > 1 ); | |
| 7470 | }, | |
| 7471 | ||
| 7472 | removeProp: function( name ) { | |
| 7473 | return this.each( function() { | |
| 7474 | delete this[ jQuery.propFix[ name ] || name ]; | |
| 7475 | } ); | |
| 7476 | } | |
| 7477 | } ); | |
| 7478 | ||
| 7479 | jQuery.extend( { | |
| 7480 | prop: function( elem, name, value ) { | |
| 7481 | var ret, hooks, | |
| 7482 | nType = elem.nodeType; | |
| 7483 | ||
| 7484 | // Don't get/set properties on text, comment and attribute nodes | |
| 7485 | if ( nType === 3 || nType === 8 || nType === 2 ) { | |
| 7486 | return; | |
| 7487 | } | |
| 7488 | ||
| 7489 | if ( nType !== 1 || !jQuery.isXMLDoc( elem ) ) { | |
| 7490 | ||
| 7491 | // Fix name and attach hooks | |
| 7492 | name = jQuery.propFix[ name ] || name; | |
| 7493 | hooks = jQuery.propHooks[ name ]; | |
| 7494 | } | |
| 7495 | ||
| 7496 | if ( value !== undefined ) { | |
| 7497 | if ( hooks && "set" in hooks && | |
| 7498 | ( ret = hooks.set( elem, value, name ) ) !== undefined ) { | |
| 7499 | return ret; | |
| 7500 | } | |
| 7501 | ||
| 7502 | return ( elem[ name ] = value ); | |
| 7503 | } | |
| 7504 | ||
| 7505 | if ( hooks && "get" in hooks && ( ret = hooks.get( elem, name ) ) !== null ) { | |
| 7506 | return ret; | |
| 7507 | } | |
| 7508 | ||
| 7509 | return elem[ name ]; | |
| 7510 | }, | |
| 7511 | ||
| 7512 | propHooks: { | |
| 7513 | tabIndex: { | |
| 7514 | get: function( elem ) { | |
| 7515 | ||
| 7516 | // Support: IE <=9 - 11 only | |
| 7517 | // elem.tabIndex doesn't always return the | |
| 7518 | // correct value when it hasn't been explicitly set | |
| 7519 | // https://web.archive.org/web/20141116233347/http://fluidproject.org/blog/2008/01/09/getting-setting-and-removing-tabindex-values-with-javascript/ | |
| 7520 | // Use proper attribute retrieval(#12072) | |
| 7521 | var tabindex = jQuery.find.attr( elem, "tabindex" ); | |
| 7522 | ||
| 7523 | return tabindex ? | |
| 7524 | parseInt( tabindex, 10 ) : | |
| 7525 | rfocusable.test( elem.nodeName ) || | |
| 7526 | rclickable.test( elem.nodeName ) && elem.href ? | |
| 7527 | 0 : | |
| 7528 | -1; | |
| 7529 | } | |
| 7530 | } | |
| 7531 | }, | |
| 7532 | ||
| 7533 | propFix: { | |
| 7534 | "for": "htmlFor", | |
| 7535 | "class": "className" | |
| 7536 | } | |
| 7537 | } ); | |
| 7538 | ||
| 7539 | // Support: IE <=11 only | |
| 7540 | // Accessing the selectedIndex property | |
| 7541 | // forces the browser to respect setting selected | |
| 7542 | // on the option | |
| 7543 | // The getter ensures a default option is selected | |
| 7544 | // when in an optgroup | |
| 7545 | if ( !support.optSelected ) { | |
| 7546 | jQuery.propHooks.selected = { | |
| 7547 | get: function( elem ) { | |
| 7548 | var parent = elem.parentNode; | |
| 7549 | if ( parent && parent.parentNode ) { | |
| 7550 | parent.parentNode.selectedIndex; | |
| 7551 | } | |
| 7552 | return null; | |
| 7553 | }, | |
| 7554 | set: function( elem ) { | |
| 7555 | var parent = elem.parentNode; | |
| 7556 | if ( parent ) { | |
| 7557 | parent.selectedIndex; | |
| 7558 | ||
| 7559 | if ( parent.parentNode ) { | |
| 7560 | parent.parentNode.selectedIndex; | |
| 7561 | } | |
| 7562 | } | |
| 7563 | } | |
| 7564 | }; | |
| 7565 | } | |
| 7566 | ||
| 7567 | jQuery.each( [ | |
| 7568 | "tabIndex", | |
| 7569 | "readOnly", | |
| 7570 | "maxLength", | |
| 7571 | "cellSpacing", | |
| 7572 | "cellPadding", | |
| 7573 | "rowSpan", | |
| 7574 | "colSpan", | |
| 7575 | "useMap", | |
| 7576 | "frameBorder", | |
| 7577 | "contentEditable" | |
| 7578 | ], function() { | |
| 7579 | jQuery.propFix[ this.toLowerCase() ] = this; | |
| 7580 | } ); | |
| 7581 | ||
| 7582 | ||
| 7583 | ||
| 7584 | ||
| 7585 | var rclass = /[\t\r\n\f]/g; | |
| 7586 | ||
| 7587 | function getClass( elem ) { | |
| 7588 | return elem.getAttribute && elem.getAttribute( "class" ) || ""; | |
| 7589 | } | |
| 7590 | ||
| 7591 | jQuery.fn.extend( { | |
| 7592 | addClass: function( value ) { | |
| 7593 | var classes, elem, cur, curValue, clazz, j, finalValue, | |
| 7594 | i = 0; | |
| 7595 | ||
| 7596 | if ( jQuery.isFunction( value ) ) { | |
| 7597 | return this.each( function( j ) { | |
| 7598 | jQuery( this ).addClass( value.call( this, j, getClass( this ) ) ); | |
| 7599 | } ); | |
| 7600 | } | |
| 7601 | ||
| 7602 | if ( typeof value === "string" && value ) { | |
| 7603 | classes = value.match( rnotwhite ) || []; | |
| 7604 | ||
| 7605 | while ( ( elem = this[ i++ ] ) ) { | |
| 7606 | curValue = getClass( elem ); | |
| 7607 | cur = elem.nodeType === 1 && | |
| 7608 | ( " " + curValue + " " ).replace( rclass, " " ); | |
| 7609 | ||
| 7610 | if ( cur ) { | |
| 7611 | j = 0; | |
| 7612 | while ( ( clazz = classes[ j++ ] ) ) { | |
| 7613 | if ( cur.indexOf( " " + clazz + " " ) < 0 ) { | |
| 7614 | cur += clazz + " "; | |
| 7615 | } | |
| 7616 | } | |
| 7617 | ||
| 7618 | // Only assign if different to avoid unneeded rendering. | |
| 7619 | finalValue = jQuery.trim( cur ); | |
| 7620 | if ( curValue !== finalValue ) { | |
| 7621 | elem.setAttribute( "class", finalValue ); | |
| 7622 | } | |
| 7623 | } | |
| 7624 | } | |
| 7625 | } | |
| 7626 | ||
| 7627 | return this; | |
| 7628 | }, | |
| 7629 | ||
| 7630 | removeClass: function( value ) { | |
| 7631 | var classes, elem, cur, curValue, clazz, j, finalValue, | |
| 7632 | i = 0; | |
| 7633 | ||
| 7634 | if ( jQuery.isFunction( value ) ) { | |
| 7635 | return this.each( function( j ) { | |
| 7636 | jQuery( this ).removeClass( value.call( this, j, getClass( this ) ) ); | |
| 7637 | } ); | |
| 7638 | } | |
| 7639 | ||
| 7640 | if ( !arguments.length ) { | |
| 7641 | return this.attr( "class", "" ); | |
| 7642 | } | |
| 7643 | ||
| 7644 | if ( typeof value === "string" && value ) { | |
| 7645 | classes = value.match( rnotwhite ) || []; | |
| 7646 | ||
| 7647 | while ( ( elem = this[ i++ ] ) ) { | |
| 7648 | curValue = getClass( elem ); | |
| 7649 | ||
| 7650 | // This expression is here for better compressibility (see addClass) | |
| 7651 | cur = elem.nodeType === 1 && | |
| 7652 | ( " " + curValue + " " ).replace( rclass, " " ); | |
| 7653 | ||
| 7654 | if ( cur ) { | |
| 7655 | j = 0; | |
| 7656 | while ( ( clazz = classes[ j++ ] ) ) { | |
| 7657 | ||
| 7658 | // Remove *all* instances | |
| 7659 | while ( cur.indexOf( " " + clazz + " " ) > -1 ) { | |
| 7660 | cur = cur.replace( " " + clazz + " ", " " ); | |
| 7661 | } | |
| 7662 | } | |
| 7663 | ||
| 7664 | // Only assign if different to avoid unneeded rendering. | |
| 7665 | finalValue = jQuery.trim( cur ); | |
| 7666 | if ( curValue !== finalValue ) { | |
| 7667 | elem.setAttribute( "class", finalValue ); | |
| 7668 | } | |
| 7669 | } | |
| 7670 | } | |
| 7671 | } | |
| 7672 | ||
| 7673 | return this; | |
| 7674 | }, | |
| 7675 | ||
| 7676 | toggleClass: function( value, stateVal ) { | |
| 7677 | var type = typeof value; | |
| 7678 | ||
| 7679 | if ( typeof stateVal === "boolean" && type === "string" ) { | |
| 7680 | return stateVal ? this.addClass( value ) : this.removeClass( value ); | |
| 7681 | } | |
| 7682 | ||
| 7683 | if ( jQuery.isFunction( value ) ) { | |
| 7684 | return this.each( function( i ) { | |
| 7685 | jQuery( this ).toggleClass( | |
| 7686 | value.call( this, i, getClass( this ), stateVal ), | |
| 7687 | stateVal | |
| 7688 | ); | |
| 7689 | } ); | |
| 7690 | } | |
| 7691 | ||
| 7692 | return this.each( function() { | |
| 7693 | var className, i, self, classNames; | |
| 7694 | ||
| 7695 | if ( type === "string" ) { | |
| 7696 | ||
| 7697 | // Toggle individual class names | |
| 7698 | i = 0; | |
| 7699 | self = jQuery( this ); | |
| 7700 | classNames = value.match( rnotwhite ) || []; | |
| 7701 | ||
| 7702 | while ( ( className = classNames[ i++ ] ) ) { | |
| 7703 | ||
| 7704 | // Check each className given, space separated list | |
| 7705 | if ( self.hasClass( className ) ) { | |
| 7706 | self.removeClass( className ); | |
| 7707 | } else { | |
| 7708 | self.addClass( className ); | |
| 7709 | } | |
| 7710 | } | |
| 7711 | ||
| 7712 | // Toggle whole class name | |
| 7713 | } else if ( value === undefined || type === "boolean" ) { | |
| 7714 | className = getClass( this ); | |
| 7715 | if ( className ) { | |
| 7716 | ||
| 7717 | // Store className if set | |
| 7718 | dataPriv.set( this, "__className__", className ); | |
| 7719 | } | |
| 7720 | ||
| 7721 | // If the element has a class name or if we're passed `false`, | |
| 7722 | // then remove the whole classname (if there was one, the above saved it). | |
| 7723 | // Otherwise bring back whatever was previously saved (if anything), | |
| 7724 | // falling back to the empty string if nothing was stored. | |
| 7725 | if ( this.setAttribute ) { | |
| 7726 | this.setAttribute( "class", | |
| 7727 | className || value === false ? | |
| 7728 | "" : | |
| 7729 | dataPriv.get( this, "__className__" ) || "" | |
| 7730 | ); | |
| 7731 | } | |
| 7732 | } | |
| 7733 | } ); | |
| 7734 | }, | |
| 7735 | ||
| 7736 | hasClass: function( selector ) { | |
| 7737 | var className, elem, | |
| 7738 | i = 0; | |
| 7739 | ||
| 7740 | className = " " + selector + " "; | |
| 7741 | while ( ( elem = this[ i++ ] ) ) { | |
| 7742 | if ( elem.nodeType === 1 && | |
| 7743 | ( " " + getClass( elem ) + " " ).replace( rclass, " " ) | |
| 7744 | .indexOf( className ) > -1 | |
| 7745 | ) { | |
| 7746 | return true; | |
| 7747 | } | |
| 7748 | } | |
| 7749 | ||
| 7750 | return false; | |
| 7751 | } | |
| 7752 | } ); | |
| 7753 | ||
| 7754 | ||
| 7755 | ||
| 7756 | ||
| 7757 | var rreturn = /\r/g, | |
| 7758 | rspaces = /[\x20\t\r\n\f]+/g; | |
| 7759 | ||
| 7760 | jQuery.fn.extend( { | |
| 7761 | val: function( value ) { | |
| 7762 | var hooks, ret, isFunction, | |
| 7763 | elem = this[ 0 ]; | |
| 7764 | ||
| 7765 | if ( !arguments.length ) { | |
| 7766 | if ( elem ) { | |
| 7767 | hooks = jQuery.valHooks[ elem.type ] || | |
| 7768 | jQuery.valHooks[ elem.nodeName.toLowerCase() ]; | |
| 7769 | ||
| 7770 | if ( hooks && | |
| 7771 | "get" in hooks && | |
| 7772 | ( ret = hooks.get( elem, "value" ) ) !== undefined | |
| 7773 | ) { | |
| 7774 | return ret; | |
| 7775 | } | |
| 7776 | ||
| 7777 | ret = elem.value; | |
| 7778 | ||
| 7779 | return typeof ret === "string" ? | |
| 7780 | ||
| 7781 | // Handle most common string cases | |
| 7782 | ret.replace( rreturn, "" ) : | |
| 7783 | ||
| 7784 | // Handle cases where value is null/undef or number | |
| 7785 | ret == null ? "" : ret; | |
| 7786 | } | |
| 7787 | ||
| 7788 | return; | |
| 7789 | } | |
| 7790 | ||
| 7791 | isFunction = jQuery.isFunction( value ); | |
| 7792 | ||
| 7793 | return this.each( function( i ) { | |
| 7794 | var val; | |
| 7795 | ||
| 7796 | if ( this.nodeType !== 1 ) { | |
| 7797 | return; | |
| 7798 | } | |
| 7799 | ||
| 7800 | if ( isFunction ) { | |
| 7801 | val = value.call( this, i, jQuery( this ).val() ); | |
| 7802 | } else { | |
| 7803 | val = value; | |
| 7804 | } | |
| 7805 | ||
| 7806 | // Treat null/undefined as ""; convert numbers to string | |
| 7807 | if ( val == null ) { | |
| 7808 | val = ""; | |
| 7809 | ||
| 7810 | } else if ( typeof val === "number" ) { | |
| 7811 | val += ""; | |
| 7812 | ||
| 7813 | } else if ( jQuery.isArray( val ) ) { | |
| 7814 | val = jQuery.map( val, function( value ) { | |
| 7815 | return value == null ? "" : value + ""; | |
| 7816 | } ); | |
| 7817 | } | |
| 7818 | ||
| 7819 | hooks = jQuery.valHooks[ this.type ] || jQuery.valHooks[ this.nodeName.toLowerCase() ]; | |
| 7820 | ||
| 7821 | // If set returns undefined, fall back to normal setting | |
| 7822 | if ( !hooks || !( "set" in hooks ) || hooks.set( this, val, "value" ) === undefined ) { | |
| 7823 | this.value = val; | |
| 7824 | } | |
| 7825 | } ); | |
| 7826 | } | |
| 7827 | } ); | |
| 7828 | ||
| 7829 | jQuery.extend( { | |
| 7830 | valHooks: { | |
| 7831 | option: { | |
| 7832 | get: function( elem ) { | |
| 7833 | ||
| 7834 | var val = jQuery.find.attr( elem, "value" ); | |
| 7835 | return val != null ? | |
| 7836 | val : | |
| 7837 | ||
| 7838 | // Support: IE <=10 - 11 only | |
| 7839 | // option.text throws exceptions (#14686, #14858) | |
| 7840 | // Strip and collapse whitespace | |
| 7841 | // https://html.spec.whatwg.org/#strip-and-collapse-whitespace | |
| 7842 | jQuery.trim( jQuery.text( elem ) ).replace( rspaces, " " ); | |
| 7843 | } | |
| 7844 | }, | |
| 7845 | select: { | |
| 7846 | get: function( elem ) { | |
| 7847 | var value, option, | |
| 7848 | options = elem.options, | |
| 7849 | index = elem.selectedIndex, | |
| 7850 | one = elem.type === "select-one", | |
| 7851 | values = one ? null : [], | |
| 7852 | max = one ? index + 1 : options.length, | |
| 7853 | i = index < 0 ? | |
| 7854 | max : | |
| 7855 | one ? index : 0; | |
| 7856 | ||
| 7857 | // Loop through all the selected options | |
| 7858 | for ( ; i < max; i++ ) { | |
| 7859 | option = options[ i ]; | |
| 7860 | ||
| 7861 | // Support: IE <=9 only | |
| 7862 | // IE8-9 doesn't update selected after form reset (#2551) | |
| 7863 | if ( ( option.selected || i === index ) && | |
| 7864 | ||
| 7865 | // Don't return options that are disabled or in a disabled optgroup | |
| 7866 | !option.disabled && | |
| 7867 | ( !option.parentNode.disabled || | |
| 7868 | !jQuery.nodeName( option.parentNode, "optgroup" ) ) ) { | |
| 7869 | ||
| 7870 | // Get the specific value for the option | |
| 7871 | value = jQuery( option ).val(); | |
| 7872 | ||
| 7873 | // We don't need an array for one selects | |
| 7874 | if ( one ) { | |
| 7875 | return value; | |
| 7876 | } | |
| 7877 | ||
| 7878 | // Multi-Selects return an array | |
| 7879 | values.push( value ); | |
| 7880 | } | |
| 7881 | } | |
| 7882 | ||
| 7883 | return values; | |
| 7884 | }, | |
| 7885 | ||
| 7886 | set: function( elem, value ) { | |
| 7887 | var optionSet, option, | |
| 7888 | options = elem.options, | |
| 7889 | values = jQuery.makeArray( value ), | |
| 7890 | i = options.length; | |
| 7891 | ||
| 7892 | while ( i-- ) { | |
| 7893 | option = options[ i ]; | |
| 7894 | ||
| 7895 | /* eslint-disable no-cond-assign */ | |
| 7896 | ||
| 7897 | if ( option.selected = | |
| 7898 | jQuery.inArray( jQuery.valHooks.option.get( option ), values ) > -1 | |
| 7899 | ) { | |
| 7900 | optionSet = true; | |
| 7901 | } | |
| 7902 | ||
| 7903 | /* eslint-enable no-cond-assign */ | |
| 7904 | } | |
| 7905 | ||
| 7906 | // Force browsers to behave consistently when non-matching value is set | |
| 7907 | if ( !optionSet ) { | |
| 7908 | elem.selectedIndex = -1; | |
| 7909 | } | |
| 7910 | return values; | |
| 7911 | } | |
| 7912 | } | |
| 7913 | } | |
| 7914 | } ); | |
| 7915 | ||
| 7916 | // Radios and checkboxes getter/setter | |
| 7917 | jQuery.each( [ "radio", "checkbox" ], function() { | |
| 7918 | jQuery.valHooks[ this ] = { | |
| 7919 | set: function( elem, value ) { | |
| 7920 | if ( jQuery.isArray( value ) ) { | |
| 7921 | return ( elem.checked = jQuery.inArray( jQuery( elem ).val(), value ) > -1 ); | |
| 7922 | } | |
| 7923 | } | |
| 7924 | }; | |
| 7925 | if ( !support.checkOn ) { | |
| 7926 | jQuery.valHooks[ this ].get = function( elem ) { | |
| 7927 | return elem.getAttribute( "value" ) === null ? "on" : elem.value; | |
| 7928 | }; | |
| 7929 | } | |
| 7930 | } ); | |
| 7931 | ||
| 7932 | ||
| 7933 | ||
| 7934 | ||
| 7935 | // Return jQuery for attributes-only inclusion | |
| 7936 | ||
| 7937 | ||
| 7938 | var rfocusMorph = /^(?:focusinfocus|focusoutblur)$/; | |
| 7939 | ||
| 7940 | jQuery.extend( jQuery.event, { | |
| 7941 | ||
| 7942 | trigger: function( event, data, elem, onlyHandlers ) { | |
| 7943 | ||
| 7944 | var i, cur, tmp, bubbleType, ontype, handle, special, | |
| 7945 | eventPath = [ elem || document ], | |
| 7946 | type = hasOwn.call( event, "type" ) ? event.type : event, | |
| 7947 | namespaces = hasOwn.call( event, "namespace" ) ? event.namespace.split( "." ) : []; | |
| 7948 | ||
| 7949 | cur = tmp = elem = elem || document; | |
| 7950 | ||
| 7951 | // Don't do events on text and comment nodes | |
| 7952 | if ( elem.nodeType === 3 || elem.nodeType === 8 ) { | |
| 7953 | return; | |
| 7954 | } | |
| 7955 | ||
| 7956 | // focus/blur morphs to focusin/out; ensure we're not firing them right now | |
| 7957 | if ( rfocusMorph.test( type + jQuery.event.triggered ) ) { | |
| 7958 | return; | |
| 7959 | } | |
| 7960 | ||
| 7961 | if ( type.indexOf( "." ) > -1 ) { | |
| 7962 | ||
| 7963 | // Namespaced trigger; create a regexp to match event type in handle() | |
| 7964 | namespaces = type.split( "." ); | |
| 7965 | type = namespaces.shift(); | |
| 7966 | namespaces.sort(); | |
| 7967 | } | |
| 7968 | ontype = type.indexOf( ":" ) < 0 && "on" + type; | |
| 7969 | ||
| 7970 | // Caller can pass in a jQuery.Event object, Object, or just an event type string | |
| 7971 | event = event[ jQuery.expando ] ? | |
| 7972 | event : | |
| 7973 | new jQuery.Event( type, typeof event === "object" && event ); | |
| 7974 | ||
| 7975 | // Trigger bitmask: & 1 for native handlers; & 2 for jQuery (always true) | |
| 7976 | event.isTrigger = onlyHandlers ? 2 : 3; | |
| 7977 | event.namespace = namespaces.join( "." ); | |
| 7978 | event.rnamespace = event.namespace ? | |
| 7979 | new RegExp( "(^|\\.)" + namespaces.join( "\\.(?:.*\\.|)" ) + "(\\.|$)" ) : | |
| 7980 | null; | |
| 7981 | ||
| 7982 | // Clean up the event in case it is being reused | |
| 7983 | event.result = undefined; | |
| 7984 | if ( !event.target ) { | |
| 7985 | event.target = elem; | |
| 7986 | } | |
| 7987 | ||
| 7988 | // Clone any incoming data and prepend the event, creating the handler arg list | |
| 7989 | data = data == null ? | |
| 7990 | [ event ] : | |
| 7991 | jQuery.makeArray( data, [ event ] ); | |
| 7992 | ||
| 7993 | // Allow special events to draw outside the lines | |
| 7994 | special = jQuery.event.special[ type ] || {}; | |
| 7995 | if ( !onlyHandlers && special.trigger && special.trigger.apply( elem, data ) === false ) { | |
| 7996 | return; | |
| 7997 | } | |
| 7998 | ||
| 7999 | // Determine event propagation path in advance, per W3C events spec (#9951) | |
| 8000 | // Bubble up to document, then to window; watch for a global ownerDocument var (#9724) | |
| 8001 | if ( !onlyHandlers && !special.noBubble && !jQuery.isWindow( elem ) ) { | |
| 8002 | ||
| 8003 | bubbleType = special.delegateType || type; | |
| 8004 | if ( !rfocusMorph.test( bubbleType + type ) ) { | |
| 8005 | cur = cur.parentNode; | |
| 8006 | } | |
| 8007 | for ( ; cur; cur = cur.parentNode ) { | |
| 8008 | eventPath.push( cur ); | |
| 8009 | tmp = cur; | |
| 8010 | } | |
| 8011 | ||
| 8012 | // Only add window if we got to document (e.g., not plain obj or detached DOM) | |
| 8013 | if ( tmp === ( elem.ownerDocument || document ) ) { | |
| 8014 | eventPath.push( tmp.defaultView || tmp.parentWindow || window ); | |
| 8015 | } | |
| 8016 | } | |
| 8017 | ||
| 8018 | // Fire handlers on the event path | |
| 8019 | i = 0; | |
| 8020 | while ( ( cur = eventPath[ i++ ] ) && !event.isPropagationStopped() ) { | |
| 8021 | ||
| 8022 | event.type = i > 1 ? | |
| 8023 | bubbleType : | |
| 8024 | special.bindType || type; | |
| 8025 | ||
| 8026 | // jQuery handler | |
| 8027 | handle = ( dataPriv.get( cur, "events" ) || {} )[ event.type ] && | |
| 8028 | dataPriv.get( cur, "handle" ); | |
| 8029 | if ( handle ) { | |
| 8030 | handle.apply( cur, data ); | |
| 8031 | } | |
| 8032 | ||
| 8033 | // Native handler | |
| 8034 | handle = ontype && cur[ ontype ]; | |
| 8035 | if ( handle && handle.apply && acceptData( cur ) ) { | |
| 8036 | event.result = handle.apply( cur, data ); | |
| 8037 | if ( event.result === false ) { | |
| 8038 | event.preventDefault(); | |
| 8039 | } | |
| 8040 | } | |
| 8041 | } | |
| 8042 | event.type = type; | |
| 8043 | ||
| 8044 | // If nobody prevented the default action, do it now | |
| 8045 | if ( !onlyHandlers && !event.isDefaultPrevented() ) { | |
| 8046 | ||
| 8047 | if ( ( !special._default || | |
| 8048 | special._default.apply( eventPath.pop(), data ) === false ) && | |
| 8049 | acceptData( elem ) ) { | |
| 8050 | ||
| 8051 | // Call a native DOM method on the target with the same name as the event. | |
| 8052 | // Don't do default actions on window, that's where global variables be (#6170) | |
| 8053 | if ( ontype && jQuery.isFunction( elem[ type ] ) && !jQuery.isWindow( elem ) ) { | |
| 8054 | ||
| 8055 | // Don't re-trigger an onFOO event when we call its FOO() method | |
| 8056 | tmp = elem[ ontype ]; | |
| 8057 | ||
| 8058 | if ( tmp ) { | |
| 8059 | elem[ ontype ] = null; | |
| 8060 | } | |
| 8061 | ||
| 8062 | // Prevent re-triggering of the same event, since we already bubbled it above | |
| 8063 | jQuery.event.triggered = type; | |
| 8064 | elem[ type ](); | |
| 8065 | jQuery.event.triggered = undefined; | |
| 8066 | ||
| 8067 | if ( tmp ) { | |
| 8068 | elem[ ontype ] = tmp; | |
| 8069 | } | |
| 8070 | } | |
| 8071 | } | |
| 8072 | } | |
| 8073 | ||
| 8074 | return event.result; | |
| 8075 | }, | |
| 8076 | ||
| 8077 | // Piggyback on a donor event to simulate a different one | |
| 8078 | // Used only for `focus(in | out)` events | |
| 8079 | simulate: function( type, elem, event ) { | |
| 8080 | var e = jQuery.extend( | |
| 8081 | new jQuery.Event(), | |
| 8082 | event, | |
| 8083 | { | |
| 8084 | type: type, | |
| 8085 | isSimulated: true | |
| 8086 | } | |
| 8087 | ); | |
| 8088 | ||
| 8089 | jQuery.event.trigger( e, null, elem ); | |
| 8090 | } | |
| 8091 | ||
| 8092 | } ); | |
| 8093 | ||
| 8094 | jQuery.fn.extend( { | |
| 8095 | ||
| 8096 | trigger: function( type, data ) { | |
| 8097 | return this.each( function() { | |
| 8098 | jQuery.event.trigger( type, data, this ); | |
| 8099 | } ); | |
| 8100 | }, | |
| 8101 | triggerHandler: function( type, data ) { | |
| 8102 | var elem = this[ 0 ]; | |
| 8103 | if ( elem ) { | |
| 8104 | return jQuery.event.trigger( type, data, elem, true ); | |
| 8105 | } | |
| 8106 | } | |
| 8107 | } ); | |
| 8108 | ||
| 8109 | ||
| 8110 | jQuery.each( ( "blur focus focusin focusout resize scroll click dblclick " + | |
| 8111 | "mousedown mouseup mousemove mouseover mouseout mouseenter mouseleave " + | |
| 8112 | "change select submit keydown keypress keyup contextmenu" ).split( " " ), | |
| 8113 | function( i, name ) { | |
| 8114 | ||
| 8115 | // Handle event binding | |
| 8116 | jQuery.fn[ name ] = function( data, fn ) { | |
| 8117 | return arguments.length > 0 ? | |
| 8118 | this.on( name, null, data, fn ) : | |
| 8119 | this.trigger( name ); | |
| 8120 | }; | |
| 8121 | } ); | |
| 8122 | ||
| 8123 | jQuery.fn.extend( { | |
| 8124 | hover: function( fnOver, fnOut ) { | |
| 8125 | return this.mouseenter( fnOver ).mouseleave( fnOut || fnOver ); | |
| 8126 | } | |
| 8127 | } ); | |
| 8128 | ||
| 8129 | ||
| 8130 | ||
| 8131 | ||
| 8132 | support.focusin = "onfocusin" in window; | |
| 8133 | ||
| 8134 | ||
| 8135 | // Support: Firefox <=44 | |
| 8136 | // Firefox doesn't have focus(in | out) events | |
| 8137 | // Related ticket - https://bugzilla.mozilla.org/show_bug.cgi?id=687787 | |
| 8138 | // | |
| 8139 | // Support: Chrome <=48 - 49, Safari <=9.0 - 9.1 | |
| 8140 | // focus(in | out) events fire after focus & blur events, | |
| 8141 | // which is spec violation - http://www.w3.org/TR/DOM-Level-3-Events/#events-focusevent-event-order | |
| 8142 | // Related ticket - https://bugs.chromium.org/p/chromium/issues/detail?id=449857 | |
| 8143 | if ( !support.focusin ) { | |
| 8144 | jQuery.each( { focus: "focusin", blur: "focusout" }, function( orig, fix ) { | |
| 8145 | ||
| 8146 | // Attach a single capturing handler on the document while someone wants focusin/focusout | |
| 8147 | var handler = function( event ) { | |
| 8148 | jQuery.event.simulate( fix, event.target, jQuery.event.fix( event ) ); | |
| 8149 | }; | |
| 8150 | ||
| 8151 | jQuery.event.special[ fix ] = { | |
| 8152 | setup: function() { | |
| 8153 | var doc = this.ownerDocument || this, | |
| 8154 | attaches = dataPriv.access( doc, fix ); | |
| 8155 | ||
| 8156 | if ( !attaches ) { | |
| 8157 | doc.addEventListener( orig, handler, true ); | |
| 8158 | } | |
| 8159 | dataPriv.access( doc, fix, ( attaches || 0 ) + 1 ); | |
| 8160 | }, | |
| 8161 | teardown: function() { | |
| 8162 | var doc = this.ownerDocument || this, | |
| 8163 | attaches = dataPriv.access( doc, fix ) - 1; | |
| 8164 | ||
| 8165 | if ( !attaches ) { | |
| 8166 | doc.removeEventListener( orig, handler, true ); | |
| 8167 | dataPriv.remove( doc, fix ); | |
| 8168 | ||
| 8169 | } else { | |
| 8170 | dataPriv.access( doc, fix, attaches ); | |
| 8171 | } | |
| 8172 | } | |
| 8173 | }; | |
| 8174 | } ); | |
| 8175 | } | |
| 8176 | var location = window.location; | |
| 8177 | ||
| 8178 | var nonce = jQuery.now(); | |
| 8179 | ||
| 8180 | var rquery = ( /\?/ ); | |
| 8181 | ||
| 8182 | ||
| 8183 | ||
| 8184 | // Cross-browser xml parsing | |
| 8185 | jQuery.parseXML = function( data ) { | |
| 8186 | var xml; | |
| 8187 | if ( !data || typeof data !== "string" ) { | |
| 8188 | return null; | |
| 8189 | } | |
| 8190 | ||
| 8191 | // Support: IE 9 - 11 only | |
| 8192 | // IE throws on parseFromString with invalid input. | |
| 8193 | try { | |
| 8194 | xml = ( new window.DOMParser() ).parseFromString( data, "text/xml" ); | |
| 8195 | } catch ( e ) { | |
| 8196 | xml = undefined; | |
| 8197 | } | |
| 8198 | ||
| 8199 | if ( !xml || xml.getElementsByTagName( "parsererror" ).length ) { | |
| 8200 | jQuery.error( "Invalid XML: " + data ); | |
| 8201 | } | |
| 8202 | return xml; | |
| 8203 | }; | |
| 8204 | ||
| 8205 | ||
| 8206 | var | |
| 8207 | rbracket = /\[\]$/, | |
| 8208 | rCRLF = /\r?\n/g, | |
| 8209 | rsubmitterTypes = /^(?:submit|button|image|reset|file)$/i, | |
| 8210 | rsubmittable = /^(?:input|select|textarea|keygen)/i; | |
| 8211 | ||
| 8212 | function buildParams( prefix, obj, traditional, add ) { | |
| 8213 | var name; | |
| 8214 | ||
| 8215 | if ( jQuery.isArray( obj ) ) { | |
| 8216 | ||
| 8217 | // Serialize array item. | |
| 8218 | jQuery.each( obj, function( i, v ) { | |
| 8219 | if ( traditional || rbracket.test( prefix ) ) { | |
| 8220 | ||
| 8221 | // Treat each array item as a scalar. | |
| 8222 | add( prefix, v ); | |
| 8223 | ||
| 8224 | } else { | |
| 8225 | ||
| 8226 | // Item is non-scalar (array or object), encode its numeric index. | |
| 8227 | buildParams( | |
| 8228 | prefix + "[" + ( typeof v === "object" && v != null ? i : "" ) + "]", | |
| 8229 | v, | |
| 8230 | traditional, | |
| 8231 | add | |
| 8232 | ); | |
| 8233 | } | |
| 8234 | } ); | |
| 8235 | ||
| 8236 | } else if ( !traditional && jQuery.type( obj ) === "object" ) { | |
| 8237 | ||
| 8238 | // Serialize object item. | |
| 8239 | for ( name in obj ) { | |
| 8240 | buildParams( prefix + "[" + name + "]", obj[ name ], traditional, add ); | |
| 8241 | } | |
| 8242 | ||
| 8243 | } else { | |
| 8244 | ||
| 8245 | // Serialize scalar item. | |
| 8246 | add( prefix, obj ); | |
| 8247 | } | |
| 8248 | } | |
| 8249 | ||
| 8250 | // Serialize an array of form elements or a set of | |
| 8251 | // key/values into a query string | |
| 8252 | jQuery.param = function( a, traditional ) { | |
| 8253 | var prefix, | |
| 8254 | s = [], | |
| 8255 | add = function( key, valueOrFunction ) { | |
| 8256 | ||
| 8257 | // If value is a function, invoke it and use its return value | |
| 8258 | var value = jQuery.isFunction( valueOrFunction ) ? | |
| 8259 | valueOrFunction() : | |
| 8260 | valueOrFunction; | |
| 8261 | ||
| 8262 | s[ s.length ] = encodeURIComponent( key ) + "=" + | |
| 8263 | encodeURIComponent( value == null ? "" : value ); | |
| 8264 | }; | |
| 8265 | ||
| 8266 | // If an array was passed in, assume that it is an array of form elements. | |
| 8267 | if ( jQuery.isArray( a ) || ( a.jquery && !jQuery.isPlainObject( a ) ) ) { | |
| 8268 | ||
| 8269 | // Serialize the form elements | |
| 8270 | jQuery.each( a, function() { | |
| 8271 | add( this.name, this.value ); | |
| 8272 | } ); | |
| 8273 | ||
| 8274 | } else { | |
| 8275 | ||
| 8276 | // If traditional, encode the "old" way (the way 1.3.2 or older | |
| 8277 | // did it), otherwise encode params recursively. | |
| 8278 | for ( prefix in a ) { | |
| 8279 | buildParams( prefix, a[ prefix ], traditional, add ); | |
| 8280 | } | |
| 8281 | } | |
| 8282 | ||
| 8283 | // Return the resulting serialization | |
| 8284 | return s.join( "&" ); | |
| 8285 | }; | |
| 8286 | ||
| 8287 | jQuery.fn.extend( { | |
| 8288 | serialize: function() { | |
| 8289 | return jQuery.param( this.serializeArray() ); | |
| 8290 | }, | |
| 8291 | serializeArray: function() { | |
| 8292 | return this.map( function() { | |
| 8293 | ||
| 8294 | // Can add propHook for "elements" to filter or add form elements | |
| 8295 | var elements = jQuery.prop( this, "elements" ); | |
| 8296 | return elements ? jQuery.makeArray( elements ) : this; | |
| 8297 | } ) | |
| 8298 | .filter( function() { | |
| 8299 | var type = this.type; | |
| 8300 | ||
| 8301 | // Use .is( ":disabled" ) so that fieldset[disabled] works | |
| 8302 | return this.name && !jQuery( this ).is( ":disabled" ) && | |
| 8303 | rsubmittable.test( this.nodeName ) && !rsubmitterTypes.test( type ) && | |
| 8304 | ( this.checked || !rcheckableType.test( type ) ); | |
| 8305 | } ) | |
| 8306 | .map( function( i, elem ) { | |
| 8307 | var val = jQuery( this ).val(); | |
| 8308 | ||
| 8309 | return val == null ? | |
| 8310 | null : | |
| 8311 | jQuery.isArray( val ) ? | |
| 8312 | jQuery.map( val, function( val ) { | |
| 8313 | return { name: elem.name, value: val.replace( rCRLF, "\r\n" ) }; | |
| 8314 | } ) : | |
| 8315 | { name: elem.name, value: val.replace( rCRLF, "\r\n" ) }; | |
| 8316 | } ).get(); | |
| 8317 | } | |
| 8318 | } ); | |
| 8319 | ||
| 8320 | ||
| 8321 | var | |
| 8322 | r20 = /%20/g, | |
| 8323 | rhash = /#.*$/, | |
| 8324 | rts = /([?&])_=[^&]*/, | |
| 8325 | rheaders = /^(.*?):[ \t]*([^\r\n]*)$/mg, | |
| 8326 | ||
| 8327 | // #7653, #8125, #8152: local protocol detection | |
| 8328 | rlocalProtocol = /^(?:about|app|app-storage|.+-extension|file|res|widget):$/, | |
| 8329 | rnoContent = /^(?:GET|HEAD)$/, | |
| 8330 | rprotocol = /^\/\//, | |
| 8331 | ||
| 8332 | /* Prefilters | |
| 8333 | * 1) They are useful to introduce custom dataTypes (see ajax/jsonp.js for an example) | |
| 8334 | * 2) These are called: | |
| 8335 | * - BEFORE asking for a transport | |
| 8336 | * - AFTER param serialization (s.data is a string if s.processData is true) | |
| 8337 | * 3) key is the dataType | |
| 8338 | * 4) the catchall symbol "*" can be used | |
| 8339 | * 5) execution will start with transport dataType and THEN continue down to "*" if needed | |
| 8340 | */ | |
| 8341 | prefilters = {}, | |
| 8342 | ||
| 8343 | /* Transports bindings | |
| 8344 | * 1) key is the dataType | |
| 8345 | * 2) the catchall symbol "*" can be used | |
| 8346 | * 3) selection will start with transport dataType and THEN go to "*" if needed | |
| 8347 | */ | |
| 8348 | transports = {}, | |
| 8349 | ||
| 8350 | // Avoid comment-prolog char sequence (#10098); must appease lint and evade compression | |
| 8351 | allTypes = "*/".concat( "*" ), | |
| 8352 | ||
| 8353 | // Anchor tag for parsing the document origin | |
| 8354 | originAnchor = document.createElement( "a" ); | |
| 8355 | originAnchor.href = location.href; | |
| 8356 | ||
| 8357 | // Base "constructor" for jQuery.ajaxPrefilter and jQuery.ajaxTransport | |
| 8358 | function addToPrefiltersOrTransports( structure ) { | |
| 8359 | ||
| 8360 | // dataTypeExpression is optional and defaults to "*" | |
| 8361 | return function( dataTypeExpression, func ) { | |
| 8362 | ||
| 8363 | if ( typeof dataTypeExpression !== "string" ) { | |
| 8364 | func = dataTypeExpression; | |
| 8365 | dataTypeExpression = "*"; | |
| 8366 | } | |
| 8367 | ||
| 8368 | var dataType, | |
| 8369 | i = 0, | |
| 8370 | dataTypes = dataTypeExpression.toLowerCase().match( rnotwhite ) || []; | |
| 8371 | ||
| 8372 | if ( jQuery.isFunction( func ) ) { | |
| 8373 | ||
| 8374 | // For each dataType in the dataTypeExpression | |
| 8375 | while ( ( dataType = dataTypes[ i++ ] ) ) { | |
| 8376 | ||
| 8377 | // Prepend if requested | |
| 8378 | if ( dataType[ 0 ] === "+" ) { | |
| 8379 | dataType = dataType.slice( 1 ) || "*"; | |
| 8380 | ( structure[ dataType ] = structure[ dataType ] || [] ).unshift( func ); | |
| 8381 | ||
| 8382 | // Otherwise append | |
| 8383 | } else { | |
| 8384 | ( structure[ dataType ] = structure[ dataType ] || [] ).push( func ); | |
| 8385 | } | |
| 8386 | } | |
| 8387 | } | |
| 8388 | }; | |
| 8389 | } | |
| 8390 | ||
| 8391 | // Base inspection function for prefilters and transports | |
| 8392 | function inspectPrefiltersOrTransports( structure, options, originalOptions, jqXHR ) { | |
| 8393 | ||
| 8394 | var inspected = {}, | |
| 8395 | seekingTransport = ( structure === transports ); | |
| 8396 | ||
| 8397 | function inspect( dataType ) { | |
| 8398 | var selected; | |
| 8399 | inspected[ dataType ] = true; | |
| 8400 | jQuery.each( structure[ dataType ] || [], function( _, prefilterOrFactory ) { | |
| 8401 | var dataTypeOrTransport = prefilterOrFactory( options, originalOptions, jqXHR ); | |
| 8402 | if ( typeof dataTypeOrTransport === "string" && | |
| 8403 | !seekingTransport && !inspected[ dataTypeOrTransport ] ) { | |
| 8404 | ||
| 8405 | options.dataTypes.unshift( dataTypeOrTransport ); | |
| 8406 | inspect( dataTypeOrTransport ); | |
| 8407 | return false; | |
| 8408 | } else if ( seekingTransport ) { | |
| 8409 | return !( selected = dataTypeOrTransport ); | |
| 8410 | } | |
| 8411 | } ); | |
| 8412 | return selected; | |
| 8413 | } | |
| 8414 | ||
| 8415 | return inspect( options.dataTypes[ 0 ] ) || !inspected[ "*" ] && inspect( "*" ); | |
| 8416 | } | |
| 8417 | ||
| 8418 | // A special extend for ajax options | |
| 8419 | // that takes "flat" options (not to be deep extended) | |
| 8420 | // Fixes #9887 | |
| 8421 | function ajaxExtend( target, src ) { | |
| 8422 | var key, deep, | |
| 8423 | flatOptions = jQuery.ajaxSettings.flatOptions || {}; | |
| 8424 | ||
| 8425 | for ( key in src ) { | |
| 8426 | if ( src[ key ] !== undefined ) { | |
| 8427 | ( flatOptions[ key ] ? target : ( deep || ( deep = {} ) ) )[ key ] = src[ key ]; | |
| 8428 | } | |
| 8429 | } | |
| 8430 | if ( deep ) { | |
| 8431 | jQuery.extend( true, target, deep ); | |
| 8432 | } | |
| 8433 | ||
| 8434 | return target; | |
| 8435 | } | |
| 8436 | ||
| 8437 | /* Handles responses to an ajax request: | |
| 8438 | * - finds the right dataType (mediates between content-type and expected dataType) | |
| 8439 | * - returns the corresponding response | |
| 8440 | */ | |
| 8441 | function ajaxHandleResponses( s, jqXHR, responses ) { | |
| 8442 | ||
| 8443 | var ct, type, finalDataType, firstDataType, | |
| 8444 | contents = s.contents, | |
| 8445 | dataTypes = s.dataTypes; | |
| 8446 | ||
| 8447 | // Remove auto dataType and get content-type in the process | |
| 8448 | while ( dataTypes[ 0 ] === "*" ) { | |
| 8449 | dataTypes.shift(); | |
| 8450 | if ( ct === undefined ) { | |
| 8451 | ct = s.mimeType || jqXHR.getResponseHeader( "Content-Type" ); | |
| 8452 | } | |
| 8453 | } | |
| 8454 | ||
| 8455 | // Check if we're dealing with a known content-type | |
| 8456 | if ( ct ) { | |
| 8457 | for ( type in contents ) { | |
| 8458 | if ( contents[ type ] && contents[ type ].test( ct ) ) { | |
| 8459 | dataTypes.unshift( type ); | |
| 8460 | break; | |
| 8461 | } | |
| 8462 | } | |
| 8463 | } | |
| 8464 | ||
| 8465 | // Check to see if we have a response for the expected dataType | |
| 8466 | if ( dataTypes[ 0 ] in responses ) { | |
| 8467 | finalDataType = dataTypes[ 0 ]; | |
| 8468 | } else { | |
| 8469 | ||
| 8470 | // Try convertible dataTypes | |
| 8471 | for ( type in responses ) { | |
| 8472 | if ( !dataTypes[ 0 ] || s.converters[ type + " " + dataTypes[ 0 ] ] ) { | |
| 8473 | finalDataType = type; | |
| 8474 | break; | |
| 8475 | } | |
| 8476 | if ( !firstDataType ) { | |
| 8477 | firstDataType = type; | |
| 8478 | } | |
| 8479 | } | |
| 8480 | ||
| 8481 | // Or just use first one | |
| 8482 | finalDataType = finalDataType || firstDataType; | |
| 8483 | } | |
| 8484 | ||
| 8485 | // If we found a dataType | |
| 8486 | // We add the dataType to the list if needed | |
| 8487 | // and return the corresponding response | |
| 8488 | if ( finalDataType ) { | |
| 8489 | if ( finalDataType !== dataTypes[ 0 ] ) { | |
| 8490 | dataTypes.unshift( finalDataType ); | |
| 8491 | } | |
| 8492 | return responses[ finalDataType ]; | |
| 8493 | } | |
| 8494 | } | |
| 8495 | ||
| 8496 | /* Chain conversions given the request and the original response | |
| 8497 | * Also sets the responseXXX fields on the jqXHR instance | |
| 8498 | */ | |
| 8499 | function ajaxConvert( s, response, jqXHR, isSuccess ) { | |
| 8500 | var conv2, current, conv, tmp, prev, | |
| 8501 | converters = {}, | |
| 8502 | ||
| 8503 | // Work with a copy of dataTypes in case we need to modify it for conversion | |
| 8504 | dataTypes = s.dataTypes.slice(); | |
| 8505 | ||
| 8506 | // Create converters map with lowercased keys | |
| 8507 | if ( dataTypes[ 1 ] ) { | |
| 8508 | for ( conv in s.converters ) { | |
| 8509 | converters[ conv.toLowerCase() ] = s.converters[ conv ]; | |
| 8510 | } | |
| 8511 | } | |
| 8512 | ||
| 8513 | current = dataTypes.shift(); | |
| 8514 | ||
| 8515 | // Convert to each sequential dataType | |
| 8516 | while ( current ) { | |
| 8517 | ||
| 8518 | if ( s.responseFields[ current ] ) { | |
| 8519 | jqXHR[ s.responseFields[ current ] ] = response; | |
| 8520 | } | |
| 8521 | ||
| 8522 | // Apply the dataFilter if provided | |
| 8523 | if ( !prev && isSuccess && s.dataFilter ) { | |
| 8524 | response = s.dataFilter( response, s.dataType ); | |
| 8525 | } | |
| 8526 | ||
| 8527 | prev = current; | |
| 8528 | current = dataTypes.shift(); | |
| 8529 | ||
| 8530 | if ( current ) { | |
| 8531 | ||
| 8532 | // There's only work to do if current dataType is non-auto | |
| 8533 | if ( current === "*" ) { | |
| 8534 | ||
| 8535 | current = prev; | |
| 8536 | ||
| 8537 | // Convert response if prev dataType is non-auto and differs from current | |
| 8538 | } else if ( prev !== "*" && prev !== current ) { | |
| 8539 | ||
| 8540 | // Seek a direct converter | |
| 8541 | conv = converters[ prev + " " + current ] || converters[ "* " + current ]; | |
| 8542 | ||
| 8543 | // If none found, seek a pair | |
| 8544 | if ( !conv ) { | |
| 8545 | for ( conv2 in converters ) { | |
| 8546 | ||
| 8547 | // If conv2 outputs current | |
| 8548 | tmp = conv2.split( " " ); | |
| 8549 | if ( tmp[ 1 ] === current ) { | |
| 8550 | ||
| 8551 | // If prev can be converted to accepted input | |
| 8552 | conv = converters[ prev + " " + tmp[ 0 ] ] || | |
| 8553 | converters[ "* " + tmp[ 0 ] ]; | |
| 8554 | if ( conv ) { | |
| 8555 | ||
| 8556 | // Condense equivalence converters | |
| 8557 | if ( conv === true ) { | |
| 8558 | conv = converters[ conv2 ]; | |
| 8559 | ||
| 8560 | // Otherwise, insert the intermediate dataType | |
| 8561 | } else if ( converters[ conv2 ] !== true ) { | |
| 8562 | current = tmp[ 0 ]; | |
| 8563 | dataTypes.unshift( tmp[ 1 ] ); | |
| 8564 | } | |
| 8565 | break; | |
| 8566 | } | |
| 8567 | } | |
| 8568 | } | |
| 8569 | } | |
| 8570 | ||
| 8571 | // Apply converter (if not an equivalence) | |
| 8572 | if ( conv !== true ) { | |
| 8573 | ||
| 8574 | // Unless errors are allowed to bubble, catch and return them | |
| 8575 | if ( conv && s.throws ) { | |
| 8576 | response = conv( response ); | |
| 8577 | } else { | |
| 8578 | try { | |
| 8579 | response = conv( response ); | |
| 8580 | } catch ( e ) { | |
| 8581 | return { | |
| 8582 | state: "parsererror", | |
| 8583 | error: conv ? e : "No conversion from " + prev + " to " + current | |
| 8584 | }; | |
| 8585 | } | |
| 8586 | } | |
| 8587 | } | |
| 8588 | } | |
| 8589 | } | |
| 8590 | } | |
| 8591 | ||
| 8592 | return { state: "success", data: response }; | |
| 8593 | } | |
| 8594 | ||
| 8595 | jQuery.extend( { | |
| 8596 | ||
| 8597 | // Counter for holding the number of active queries | |
| 8598 | active: 0, | |
| 8599 | ||
| 8600 | // Last-Modified header cache for next request | |
| 8601 | lastModified: {}, | |
| 8602 | etag: {}, | |
| 8603 | ||
| 8604 | ajaxSettings: { | |
| 8605 | url: location.href, | |
| 8606 | type: "GET", | |
| 8607 | isLocal: rlocalProtocol.test( location.protocol ), | |
| 8608 | global: true, | |
| 8609 | processData: true, | |
| 8610 | async: true, | |
| 8611 | contentType: "application/x-www-form-urlencoded; charset=UTF-8", | |
| 8612 | ||
| 8613 | /* | |
| 8614 | timeout: 0, | |
| 8615 | data: null, | |
| 8616 | dataType: null, | |
| 8617 | username: null, | |
| 8618 | password: null, | |
| 8619 | cache: null, | |
| 8620 | throws: false, | |
| 8621 | traditional: false, | |
| 8622 | headers: {}, | |
| 8623 | */ | |
| 8624 | ||
| 8625 | accepts: { | |
| 8626 | "*": allTypes, | |
| 8627 | text: "text/plain", | |
| 8628 | html: "text/html", | |
| 8629 | xml: "application/xml, text/xml", | |
| 8630 | json: "application/json, text/javascript" | |
| 8631 | }, | |
| 8632 | ||
| 8633 | contents: { | |
| 8634 | xml: /\bxml\b/, | |
| 8635 | html: /\bhtml/, | |
| 8636 | json: /\bjson\b/ | |
| 8637 | }, | |
| 8638 | ||
| 8639 | responseFields: { | |
| 8640 | xml: "responseXML", | |
| 8641 | text: "responseText", | |
| 8642 | json: "responseJSON" | |
| 8643 | }, | |
| 8644 | ||
| 8645 | // Data converters | |
| 8646 | // Keys separate source (or catchall "*") and destination types with a single space | |
| 8647 | converters: { | |
| 8648 | ||
| 8649 | // Convert anything to text | |
| 8650 | "* text": String, | |
| 8651 | ||
| 8652 | // Text to html (true = no transformation) | |
| 8653 | "text html": true, | |
| 8654 | ||
| 8655 | // Evaluate text as a json expression | |
| 8656 | "text json": JSON.parse, | |
| 8657 | ||
| 8658 | // Parse text as xml | |
| 8659 | "text xml": jQuery.parseXML | |
| 8660 | }, | |
| 8661 | ||
| 8662 | // For options that shouldn't be deep extended: | |
| 8663 | // you can add your own custom options here if | |
| 8664 | // and when you create one that shouldn't be | |
| 8665 | // deep extended (see ajaxExtend) | |
| 8666 | flatOptions: { | |
| 8667 | url: true, | |
| 8668 | context: true | |
| 8669 | } | |
| 8670 | }, | |
| 8671 | ||
| 8672 | // Creates a full fledged settings object into target | |
| 8673 | // with both ajaxSettings and settings fields. | |
| 8674 | // If target is omitted, writes into ajaxSettings. | |
| 8675 | ajaxSetup: function( target, settings ) { | |
| 8676 | return settings ? | |
| 8677 | ||
| 8678 | // Building a settings object | |
| 8679 | ajaxExtend( ajaxExtend( target, jQuery.ajaxSettings ), settings ) : | |
| 8680 | ||
| 8681 | // Extending ajaxSettings | |
| 8682 | ajaxExtend( jQuery.ajaxSettings, target ); | |
| 8683 | }, | |
| 8684 | ||
| 8685 | ajaxPrefilter: addToPrefiltersOrTransports( prefilters ), | |
| 8686 | ajaxTransport: addToPrefiltersOrTransports( transports ), | |
| 8687 | ||
| 8688 | // Main method | |
| 8689 | ajax: function( url, options ) { | |
| 8690 | ||
| 8691 | // If url is an object, simulate pre-1.5 signature | |
| 8692 | if ( typeof url === "object" ) { | |
| 8693 | options = url; | |
| 8694 | url = undefined; | |
| 8695 | } | |
| 8696 | ||
| 8697 | // Force options to be an object | |
| 8698 | options = options || {}; | |
| 8699 | ||
| 8700 | var transport, | |
| 8701 | ||
| 8702 | // URL without anti-cache param | |
| 8703 | cacheURL, | |
| 8704 | ||
| 8705 | // Response headers | |
| 8706 | responseHeadersString, | |
| 8707 | responseHeaders, | |
| 8708 | ||
| 8709 | // timeout handle | |
| 8710 | timeoutTimer, | |
| 8711 | ||
| 8712 | // Url cleanup var | |
| 8713 | urlAnchor, | |
| 8714 | ||
| 8715 | // Request state (becomes false upon send and true upon completion) | |
| 8716 | completed, | |
| 8717 | ||
| 8718 | // To know if global events are to be dispatched | |
| 8719 | fireGlobals, | |
| 8720 | ||
| 8721 | // Loop variable | |
| 8722 | i, | |
| 8723 | ||
| 8724 | // uncached part of the url | |
| 8725 | uncached, | |
| 8726 | ||
| 8727 | // Create the final options object | |
| 8728 | s = jQuery.ajaxSetup( {}, options ), | |
| 8729 | ||
| 8730 | // Callbacks context | |
| 8731 | callbackContext = s.context || s, | |
| 8732 | ||
| 8733 | // Context for global events is callbackContext if it is a DOM node or jQuery collection | |
| 8734 | globalEventContext = s.context && | |
| 8735 | ( callbackContext.nodeType || callbackContext.jquery ) ? | |
| 8736 | jQuery( callbackContext ) : | |
| 8737 | jQuery.event, | |
| 8738 | ||
| 8739 | // Deferreds | |
| 8740 | deferred = jQuery.Deferred(), | |
| 8741 | completeDeferred = jQuery.Callbacks( "once memory" ), | |
| 8742 | ||
| 8743 | // Status-dependent callbacks | |
| 8744 | statusCode = s.statusCode || {}, | |
| 8745 | ||
| 8746 | // Headers (they are sent all at once) | |
| 8747 | requestHeaders = {}, | |
| 8748 | requestHeadersNames = {}, | |
| 8749 | ||
| 8750 | // Default abort message | |
| 8751 | strAbort = "canceled", | |
| 8752 | ||
| 8753 | // Fake xhr | |
| 8754 | jqXHR = { | |
| 8755 | readyState: 0, | |
| 8756 | ||
| 8757 | // Builds headers hashtable if needed | |
| 8758 | getResponseHeader: function( key ) { | |
| 8759 | var match; | |
| 8760 | if ( completed ) { | |
| 8761 | if ( !responseHeaders ) { | |
| 8762 | responseHeaders = {}; | |
| 8763 | while ( ( match = rheaders.exec( responseHeadersString ) ) ) { | |
| 8764 | responseHeaders[ match[ 1 ].toLowerCase() ] = match[ 2 ]; | |
| 8765 | } | |
| 8766 | } | |
| 8767 | match = responseHeaders[ key.toLowerCase() ]; | |
| 8768 | } | |
| 8769 | return match == null ? null : match; | |
| 8770 | }, | |
| 8771 | ||
| 8772 | // Raw string | |
| 8773 | getAllResponseHeaders: function() { | |
| 8774 | return completed ? responseHeadersString : null; | |
| 8775 | }, | |
| 8776 | ||
| 8777 | // Caches the header | |
| 8778 | setRequestHeader: function( name, value ) { | |
| 8779 | if ( completed == null ) { | |
| 8780 | name = requestHeadersNames[ name.toLowerCase() ] = | |
| 8781 | requestHeadersNames[ name.toLowerCase() ] || name; | |
| 8782 | requestHeaders[ name ] = value; | |
| 8783 | } | |
| 8784 | return this; | |
| 8785 | }, | |
| 8786 | ||
| 8787 | // Overrides response content-type header | |
| 8788 | overrideMimeType: function( type ) { | |
| 8789 | if ( completed == null ) { | |
| 8790 | s.mimeType = type; | |
| 8791 | } | |
| 8792 | return this; | |
| 8793 | }, | |
| 8794 | ||
| 8795 | // Status-dependent callbacks | |
| 8796 | statusCode: function( map ) { | |
| 8797 | var code; | |
| 8798 | if ( map ) { | |
| 8799 | if ( completed ) { | |
| 8800 | ||
| 8801 | // Execute the appropriate callbacks | |
| 8802 | jqXHR.always( map[ jqXHR.status ] ); | |
| 8803 | } else { | |
| 8804 | ||
| 8805 | // Lazy-add the new callbacks in a way that preserves old ones | |
| 8806 | for ( code in map ) { | |
| 8807 | statusCode[ code ] = [ statusCode[ code ], map[ code ] ]; | |
| 8808 | } | |
| 8809 | } | |
| 8810 | } | |
| 8811 | return this; | |
| 8812 | }, | |
| 8813 | ||
| 8814 | // Cancel the request | |
| 8815 | abort: function( statusText ) { | |
| 8816 | var finalText = statusText || strAbort; | |
| 8817 | if ( transport ) { | |
| 8818 | transport.abort( finalText ); | |
| 8819 | } | |
| 8820 | done( 0, finalText ); | |
| 8821 | return this; | |
| 8822 | } | |
| 8823 | }; | |
| 8824 | ||
| 8825 | // Attach deferreds | |
| 8826 | deferred.promise( jqXHR ); | |
| 8827 | ||
| 8828 | // Add protocol if not provided (prefilters might expect it) | |
| 8829 | // Handle falsy url in the settings object (#10093: consistency with old signature) | |
| 8830 | // We also use the url parameter if available | |
| 8831 | s.url = ( ( url || s.url || location.href ) + "" ) | |
| 8832 | .replace( rprotocol, location.protocol + "//" ); | |
| 8833 | ||
| 8834 | // Alias method option to type as per ticket #12004 | |
| 8835 | s.type = options.method || options.type || s.method || s.type; | |
| 8836 | ||
| 8837 | // Extract dataTypes list | |
| 8838 | s.dataTypes = ( s.dataType || "*" ).toLowerCase().match( rnotwhite ) || [ "" ]; | |
| 8839 | ||
| 8840 | // A cross-domain request is in order when the origin doesn't match the current origin. | |
| 8841 | if ( s.crossDomain == null ) { | |
| 8842 | urlAnchor = document.createElement( "a" ); | |
| 8843 | ||
| 8844 | // Support: IE <=8 - 11, Edge 12 - 13 | |
| 8845 | // IE throws exception on accessing the href property if url is malformed, | |
| 8846 | // e.g. http://example.com:80x/ | |
| 8847 | try { | |
| 8848 | urlAnchor.href = s.url; | |
| 8849 | ||
| 8850 | // Support: IE <=8 - 11 only | |
| 8851 | // Anchor's host property isn't correctly set when s.url is relative | |
| 8852 | urlAnchor.href = urlAnchor.href; | |
| 8853 | s.crossDomain = originAnchor.protocol + "//" + originAnchor.host !== | |
| 8854 | urlAnchor.protocol + "//" + urlAnchor.host; | |
| 8855 | } catch ( e ) { | |
| 8856 | ||
| 8857 | // If there is an error parsing the URL, assume it is crossDomain, | |
| 8858 | // it can be rejected by the transport if it is invalid | |
| 8859 | s.crossDomain = true; | |
| 8860 | } | |
| 8861 | } | |
| 8862 | ||
| 8863 | // Convert data if not already a string | |
| 8864 | if ( s.data && s.processData && typeof s.data !== "string" ) { | |
| 8865 | s.data = jQuery.param( s.data, s.traditional ); | |
| 8866 | } | |
| 8867 | ||
| 8868 | // Apply prefilters | |
| 8869 | inspectPrefiltersOrTransports( prefilters, s, options, jqXHR ); | |
| 8870 | ||
| 8871 | // If request was aborted inside a prefilter, stop there | |
| 8872 | if ( completed ) { | |
| 8873 | return jqXHR; | |
| 8874 | } | |
| 8875 | ||
| 8876 | // We can fire global events as of now if asked to | |
| 8877 | // Don't fire events if jQuery.event is undefined in an AMD-usage scenario (#15118) | |
| 8878 | fireGlobals = jQuery.event && s.global; | |
| 8879 | ||
| 8880 | // Watch for a new set of requests | |
| 8881 | if ( fireGlobals && jQuery.active++ === 0 ) { | |
| 8882 | jQuery.event.trigger( "ajaxStart" ); | |
| 8883 | } | |
| 8884 | ||
| 8885 | // Uppercase the type | |
| 8886 | s.type = s.type.toUpperCase(); | |
| 8887 | ||
| 8888 | // Determine if request has content | |
| 8889 | s.hasContent = !rnoContent.test( s.type ); | |
| 8890 | ||
| 8891 | // Save the URL in case we're toying with the If-Modified-Since | |
| 8892 | // and/or If-None-Match header later on | |
| 8893 | // Remove hash to simplify url manipulation | |
| 8894 | cacheURL = s.url.replace( rhash, "" ); | |
| 8895 | ||
| 8896 | // More options handling for requests with no content | |
| 8897 | if ( !s.hasContent ) { | |
| 8898 | ||
| 8899 | // Remember the hash so we can put it back | |
| 8900 | uncached = s.url.slice( cacheURL.length ); | |
| 8901 | ||
| 8902 | // If data is available, append data to url | |
| 8903 | if ( s.data ) { | |
| 8904 | cacheURL += ( rquery.test( cacheURL ) ? "&" : "?" ) + s.data; | |
| 8905 | ||
| 8906 | // #9682: remove data so that it's not used in an eventual retry | |
| 8907 | delete s.data; | |
| 8908 | } | |
| 8909 | ||
| 8910 | // Add anti-cache in uncached url if needed | |
| 8911 | if ( s.cache === false ) { | |
| 8912 | cacheURL = cacheURL.replace( rts, "" ); | |
| 8913 | uncached = ( rquery.test( cacheURL ) ? "&" : "?" ) + "_=" + ( nonce++ ) + uncached; | |
| 8914 | } | |
| 8915 | ||
| 8916 | // Put hash and anti-cache on the URL that will be requested (gh-1732) | |
| 8917 | s.url = cacheURL + uncached; | |
| 8918 | ||
| 8919 | // Change '%20' to '+' if this is encoded form body content (gh-2658) | |
| 8920 | } else if ( s.data && s.processData && | |
| 8921 | ( s.contentType || "" ).indexOf( "application/x-www-form-urlencoded" ) === 0 ) { | |
| 8922 | s.data = s.data.replace( r20, "+" ); | |
| 8923 | } | |
| 8924 | ||
| 8925 | // Set the If-Modified-Since and/or If-None-Match header, if in ifModified mode. | |
| 8926 | if ( s.ifModified ) { | |
| 8927 | if ( jQuery.lastModified[ cacheURL ] ) { | |
| 8928 | jqXHR.setRequestHeader( "If-Modified-Since", jQuery.lastModified[ cacheURL ] ); | |
| 8929 | } | |
| 8930 | if ( jQuery.etag[ cacheURL ] ) { | |
| 8931 | jqXHR.setRequestHeader( "If-None-Match", jQuery.etag[ cacheURL ] ); | |
| 8932 | } | |
| 8933 | } | |
| 8934 | ||
| 8935 | // Set the correct header, if data is being sent | |
| 8936 | if ( s.data && s.hasContent && s.contentType !== false || options.contentType ) { | |
| 8937 | jqXHR.setRequestHeader( "Content-Type", s.contentType ); | |
| 8938 | } | |
| 8939 | ||
| 8940 | // Set the Accepts header for the server, depending on the dataType | |
| 8941 | jqXHR.setRequestHeader( | |
| 8942 | "Accept", | |
| 8943 | s.dataTypes[ 0 ] && s.accepts[ s.dataTypes[ 0 ] ] ? | |
| 8944 | s.accepts[ s.dataTypes[ 0 ] ] + | |
| 8945 | ( s.dataTypes[ 0 ] !== "*" ? ", " + allTypes + "; q=0.01" : "" ) : | |
| 8946 | s.accepts[ "*" ] | |
| 8947 | ); | |
| 8948 | ||
| 8949 | // Check for headers option | |
| 8950 | for ( i in s.headers ) { | |
| 8951 | jqXHR.setRequestHeader( i, s.headers[ i ] ); | |
| 8952 | } | |
| 8953 | ||
| 8954 | // Allow custom headers/mimetypes and early abort | |
| 8955 | if ( s.beforeSend && | |
| 8956 | ( s.beforeSend.call( callbackContext, jqXHR, s ) === false || completed ) ) { | |
| 8957 | ||
| 8958 | // Abort if not done already and return | |
| 8959 | return jqXHR.abort(); | |
| 8960 | } | |
| 8961 | ||
| 8962 | // Aborting is no longer a cancellation | |
| 8963 | strAbort = "abort"; | |
| 8964 | ||
| 8965 | // Install callbacks on deferreds | |
| 8966 | completeDeferred.add( s.complete ); | |
| 8967 | jqXHR.done( s.success ); | |
| 8968 | jqXHR.fail( s.error ); | |
| 8969 | ||
| 8970 | // Get transport | |
| 8971 | transport = inspectPrefiltersOrTransports( transports, s, options, jqXHR ); | |
| 8972 | ||
| 8973 | // If no transport, we auto-abort | |
| 8974 | if ( !transport ) { | |
| 8975 | done( -1, "No Transport" ); | |
| 8976 | } else { | |
| 8977 | jqXHR.readyState = 1; | |
| 8978 | ||
| 8979 | // Send global event | |
| 8980 | if ( fireGlobals ) { | |
| 8981 | globalEventContext.trigger( "ajaxSend", [ jqXHR, s ] ); | |
| 8982 | } | |
| 8983 | ||
| 8984 | // If request was aborted inside ajaxSend, stop there | |
| 8985 | if ( completed ) { | |
| 8986 | return jqXHR; | |
| 8987 | } | |
| 8988 | ||
| 8989 | // Timeout | |
| 8990 | if ( s.async && s.timeout > 0 ) { | |
| 8991 | timeoutTimer = window.setTimeout( function() { | |
| 8992 | jqXHR.abort( "timeout" ); | |
| 8993 | }, s.timeout ); | |
| 8994 | } | |
| 8995 | ||
| 8996 | try { | |
| 8997 | completed = false; | |
| 8998 | transport.send( requestHeaders, done ); | |
| 8999 | } catch ( e ) { | |
| 9000 | ||
| 9001 | // Rethrow post-completion exceptions | |
| 9002 | if ( completed ) { | |
| 9003 | throw e; | |
| 9004 | } | |
| 9005 | ||
| 9006 | // Propagate others as results | |
| 9007 | done( -1, e ); | |
| 9008 | } | |
| 9009 | } | |
| 9010 | ||
| 9011 | // Callback for when everything is done | |
| 9012 | function done( status, nativeStatusText, responses, headers ) { | |
| 9013 | var isSuccess, success, error, response, modified, | |
| 9014 | statusText = nativeStatusText; | |
| 9015 | ||
| 9016 | // Ignore repeat invocations | |
| 9017 | if ( completed ) { | |
| 9018 | return; | |
| 9019 | } | |
| 9020 | ||
| 9021 | completed = true; | |
| 9022 | ||
| 9023 | // Clear timeout if it exists | |
| 9024 | if ( timeoutTimer ) { | |
| 9025 | window.clearTimeout( timeoutTimer ); | |
| 9026 | } | |
| 9027 | ||
| 9028 | // Dereference transport for early garbage collection | |
| 9029 | // (no matter how long the jqXHR object will be used) | |
| 9030 | transport = undefined; | |
| 9031 | ||
| 9032 | // Cache response headers | |
| 9033 | responseHeadersString = headers || ""; | |
| 9034 | ||
| 9035 | // Set readyState | |
| 9036 | jqXHR.readyState = status > 0 ? 4 : 0; | |
| 9037 | ||
| 9038 | // Determine if successful | |
| 9039 | isSuccess = status >= 200 && status < 300 || status === 304; | |
| 9040 | ||
| 9041 | // Get response data | |
| 9042 | if ( responses ) { | |
| 9043 | response = ajaxHandleResponses( s, jqXHR, responses ); | |
| 9044 | } | |
| 9045 | ||
| 9046 | // Convert no matter what (that way responseXXX fields are always set) | |
| 9047 | response = ajaxConvert( s, response, jqXHR, isSuccess ); | |
| 9048 | ||
| 9049 | // If successful, handle type chaining | |
| 9050 | if ( isSuccess ) { | |
| 9051 | ||
| 9052 | // Set the If-Modified-Since and/or If-None-Match header, if in ifModified mode. | |
| 9053 | if ( s.ifModified ) { | |
| 9054 | modified = jqXHR.getResponseHeader( "Last-Modified" ); | |
| 9055 | if ( modified ) { | |
| 9056 | jQuery.lastModified[ cacheURL ] = modified; | |
| 9057 | } | |
| 9058 | modified = jqXHR.getResponseHeader( "etag" ); | |
| 9059 | if ( modified ) { | |
| 9060 | jQuery.etag[ cacheURL ] = modified; | |
| 9061 | } | |
| 9062 | } | |
| 9063 | ||
| 9064 | // if no content | |
| 9065 | if ( status === 204 || s.type === "HEAD" ) { | |
| 9066 | statusText = "nocontent"; | |
| 9067 | ||
| 9068 | // if not modified | |
| 9069 | } else if ( status === 304 ) { | |
| 9070 | statusText = "notmodified"; | |
| 9071 | ||
| 9072 | // If we have data, let's convert it | |
| 9073 | } else { | |
| 9074 | statusText = response.state; | |
| 9075 | success = response.data; | |
| 9076 | error = response.error; | |
| 9077 | isSuccess = !error; | |
| 9078 | } | |
| 9079 | } else { | |
| 9080 | ||
| 9081 | // Extract error from statusText and normalize for non-aborts | |
| 9082 | error = statusText; | |
| 9083 | if ( status || !statusText ) { | |
| 9084 | statusText = "error"; | |
| 9085 | if ( status < 0 ) { | |
| 9086 | status = 0; | |
| 9087 | } | |
| 9088 | } | |
| 9089 | } | |
| 9090 | ||
| 9091 | // Set data for the fake xhr object | |
| 9092 | jqXHR.status = status; | |
| 9093 | jqXHR.statusText = ( nativeStatusText || statusText ) + ""; | |
| 9094 | ||
| 9095 | // Success/Error | |
| 9096 | if ( isSuccess ) { | |
| 9097 | deferred.resolveWith( callbackContext, [ success, statusText, jqXHR ] ); | |
| 9098 | } else { | |
| 9099 | deferred.rejectWith( callbackContext, [ jqXHR, statusText, error ] ); | |
| 9100 | } | |
| 9101 | ||
| 9102 | // Status-dependent callbacks | |
| 9103 | jqXHR.statusCode( statusCode ); | |
| 9104 | statusCode = undefined; | |
| 9105 | ||
| 9106 | if ( fireGlobals ) { | |
| 9107 | globalEventContext.trigger( isSuccess ? "ajaxSuccess" : "ajaxError", | |
| 9108 | [ jqXHR, s, isSuccess ? success : error ] ); | |
| 9109 | } | |
| 9110 | ||
| 9111 | // Complete | |
| 9112 | completeDeferred.fireWith( callbackContext, [ jqXHR, statusText ] ); | |
| 9113 | ||
| 9114 | if ( fireGlobals ) { | |
| 9115 | globalEventContext.trigger( "ajaxComplete", [ jqXHR, s ] ); | |
| 9116 | ||
| 9117 | // Handle the global AJAX counter | |
| 9118 | if ( !( --jQuery.active ) ) { | |
| 9119 | jQuery.event.trigger( "ajaxStop" ); | |
| 9120 | } | |
| 9121 | } | |
| 9122 | } | |
| 9123 | ||
| 9124 | return jqXHR; | |
| 9125 | }, | |
| 9126 | ||
| 9127 | getJSON: function( url, data, callback ) { | |
| 9128 | return jQuery.get( url, data, callback, "json" ); | |
| 9129 | }, | |
| 9130 | ||
| 9131 | getScript: function( url, callback ) { | |
| 9132 | return jQuery.get( url, undefined, callback, "script" ); | |
| 9133 | } | |
| 9134 | } ); | |
| 9135 | ||
| 9136 | jQuery.each( [ "get", "post" ], function( i, method ) { | |
| 9137 | jQuery[ method ] = function( url, data, callback, type ) { | |
| 9138 | ||
| 9139 | // Shift arguments if data argument was omitted | |
| 9140 | if ( jQuery.isFunction( data ) ) { | |
| 9141 | type = type || callback; | |
| 9142 | callback = data; | |
| 9143 | data = undefined; | |
| 9144 | } | |
| 9145 | ||
| 9146 | // The url can be an options object (which then must have .url) | |
| 9147 | return jQuery.ajax( jQuery.extend( { | |
| 9148 | url: url, | |
| 9149 | type: method, | |
| 9150 | dataType: type, | |
| 9151 | data: data, | |
| 9152 | success: callback | |
| 9153 | }, jQuery.isPlainObject( url ) && url ) ); | |
| 9154 | }; | |
| 9155 | } ); | |
| 9156 | ||
| 9157 | ||
| 9158 | jQuery._evalUrl = function( url ) { | |
| 9159 | return jQuery.ajax( { | |
| 9160 | url: url, | |
| 9161 | ||
| 9162 | // Make this explicit, since user can override this through ajaxSetup (#11264) | |
| 9163 | type: "GET", | |
| 9164 | dataType: "script", | |
| 9165 | cache: true, | |
| 9166 | async: false, | |
| 9167 | global: false, | |
| 9168 | "throws": true | |
| 9169 | } ); | |
| 9170 | }; | |
| 9171 | ||
| 9172 | ||
| 9173 | jQuery.fn.extend( { | |
| 9174 | wrapAll: function( html ) { | |
| 9175 | var wrap; | |
| 9176 | ||
| 9177 | if ( this[ 0 ] ) { | |
| 9178 | if ( jQuery.isFunction( html ) ) { | |
| 9179 | html = html.call( this[ 0 ] ); | |
| 9180 | } | |
| 9181 | ||
| 9182 | // The elements to wrap the target around | |
| 9183 | wrap = jQuery( html, this[ 0 ].ownerDocument ).eq( 0 ).clone( true ); | |
| 9184 | ||
| 9185 | if ( this[ 0 ].parentNode ) { | |
| 9186 | wrap.insertBefore( this[ 0 ] ); | |
| 9187 | } | |
| 9188 | ||
| 9189 | wrap.map( function() { | |
| 9190 | var elem = this; | |
| 9191 | ||
| 9192 | while ( elem.firstElementChild ) { | |
| 9193 | elem = elem.firstElementChild; | |
| 9194 | } | |
| 9195 | ||
| 9196 | return elem; | |
| 9197 | } ).append( this ); | |
| 9198 | } | |
| 9199 | ||
| 9200 | return this; | |
| 9201 | }, | |
| 9202 | ||
| 9203 | wrapInner: function( html ) { | |
| 9204 | if ( jQuery.isFunction( html ) ) { | |
| 9205 | return this.each( function( i ) { | |
| 9206 | jQuery( this ).wrapInner( html.call( this, i ) ); | |
| 9207 | } ); | |
| 9208 | } | |
| 9209 | ||
| 9210 | return this.each( function() { | |
| 9211 | var self = jQuery( this ), | |
| 9212 | contents = self.contents(); | |
| 9213 | ||
| 9214 | if ( contents.length ) { | |
| 9215 | contents.wrapAll( html ); | |
| 9216 | ||
| 9217 | } else { | |
| 9218 | self.append( html ); | |
| 9219 | } | |
| 9220 | } ); | |
| 9221 | }, | |
| 9222 | ||
| 9223 | wrap: function( html ) { | |
| 9224 | var isFunction = jQuery.isFunction( html ); | |
| 9225 | ||
| 9226 | return this.each( function( i ) { | |
| 9227 | jQuery( this ).wrapAll( isFunction ? html.call( this, i ) : html ); | |
| 9228 | } ); | |
| 9229 | }, | |
| 9230 | ||
| 9231 | unwrap: function( selector ) { | |
| 9232 | this.parent( selector ).not( "body" ).each( function() { | |
| 9233 | jQuery( this ).replaceWith( this.childNodes ); | |
| 9234 | } ); | |
| 9235 | return this; | |
| 9236 | } | |
| 9237 | } ); | |
| 9238 | ||
| 9239 | ||
| 9240 | jQuery.expr.pseudos.hidden = function( elem ) { | |
| 9241 | return !jQuery.expr.pseudos.visible( elem ); | |
| 9242 | }; | |
| 9243 | jQuery.expr.pseudos.visible = function( elem ) { | |
| 9244 | return !!( elem.offsetWidth || elem.offsetHeight || elem.getClientRects().length ); | |
| 9245 | }; | |
| 9246 | ||
| 9247 | ||
| 9248 | ||
| 9249 | ||
| 9250 | jQuery.ajaxSettings.xhr = function() { | |
| 9251 | try { | |
| 9252 | return new window.XMLHttpRequest(); | |
| 9253 | } catch ( e ) {} | |
| 9254 | }; | |
| 9255 | ||
| 9256 | var xhrSuccessStatus = { | |
| 9257 | ||
| 9258 | // File protocol always yields status code 0, assume 200 | |
| 9259 | 0: 200, | |
| 9260 | ||
| 9261 | // Support: IE <=9 only | |
| 9262 | // #1450: sometimes IE returns 1223 when it should be 204 | |
| 9263 | 1223: 204 | |
| 9264 | }, | |
| 9265 | xhrSupported = jQuery.ajaxSettings.xhr(); | |
| 9266 | ||
| 9267 | support.cors = !!xhrSupported && ( "withCredentials" in xhrSupported ); | |
| 9268 | support.ajax = xhrSupported = !!xhrSupported; | |
| 9269 | ||
| 9270 | jQuery.ajaxTransport( function( options ) { | |
| 9271 | var callback, errorCallback; | |
| 9272 | ||
| 9273 | // Cross domain only allowed if supported through XMLHttpRequest | |
| 9274 | if ( support.cors || xhrSupported && !options.crossDomain ) { | |
| 9275 | return { | |
| 9276 | send: function( headers, complete ) { | |
| 9277 | var i, | |
| 9278 | xhr = options.xhr(); | |
| 9279 | ||
| 9280 | xhr.open( | |
| 9281 | options.type, | |
| 9282 | options.url, | |
| 9283 | options.async, | |
| 9284 | options.username, | |
| 9285 | options.password | |
| 9286 | ); | |
| 9287 | ||
| 9288 | // Apply custom fields if provided | |
| 9289 | if ( options.xhrFields ) { | |
| 9290 | for ( i in options.xhrFields ) { | |
| 9291 | xhr[ i ] = options.xhrFields[ i ]; | |
| 9292 | } | |
| 9293 | } | |
| 9294 | ||
| 9295 | // Override mime type if needed | |
| 9296 | if ( options.mimeType && xhr.overrideMimeType ) { | |
| 9297 | xhr.overrideMimeType( options.mimeType ); | |
| 9298 | } | |
| 9299 | ||
| 9300 | // X-Requested-With header | |
| 9301 | // For cross-domain requests, seeing as conditions for a preflight are | |
| 9302 | // akin to a jigsaw puzzle, we simply never set it to be sure. | |
| 9303 | // (it can always be set on a per-request basis or even using ajaxSetup) | |
| 9304 | // For same-domain requests, won't change header if already provided. | |
| 9305 | if ( !options.crossDomain && !headers[ "X-Requested-With" ] ) { | |
| 9306 | headers[ "X-Requested-With" ] = "XMLHttpRequest"; | |
| 9307 | } | |
| 9308 | ||
| 9309 | // Set headers | |
| 9310 | for ( i in headers ) { | |
| 9311 | xhr.setRequestHeader( i, headers[ i ] ); | |
| 9312 | } | |
| 9313 | ||
| 9314 | // Callback | |
| 9315 | callback = function( type ) { | |
| 9316 | return function() { | |
| 9317 | if ( callback ) { | |
| 9318 | callback = errorCallback = xhr.onload = | |
| 9319 | xhr.onerror = xhr.onabort = xhr.onreadystatechange = null; | |
| 9320 | ||
| 9321 | if ( type === "abort" ) { | |
| 9322 | xhr.abort(); | |
| 9323 | } else if ( type === "error" ) { | |
| 9324 | ||
| 9325 | // Support: IE <=9 only | |
| 9326 | // On a manual native abort, IE9 throws | |
| 9327 | // errors on any property access that is not readyState | |
| 9328 | if ( typeof xhr.status !== "number" ) { | |
| 9329 | complete( 0, "error" ); | |
| 9330 | } else { | |
| 9331 | complete( | |
| 9332 | ||
| 9333 | // File: protocol always yields status 0; see #8605, #14207 | |
| 9334 | xhr.status, | |
| 9335 | xhr.statusText | |
| 9336 | ); | |
| 9337 | } | |
| 9338 | } else { | |
| 9339 | complete( | |
| 9340 | xhrSuccessStatus[ xhr.status ] || xhr.status, | |
| 9341 | xhr.statusText, | |
| 9342 | ||
| 9343 | // Support: IE <=9 only | |
| 9344 | // IE9 has no XHR2 but throws on binary (trac-11426) | |
| 9345 | // For XHR2 non-text, let the caller handle it (gh-2498) | |
| 9346 | ( xhr.responseType || "text" ) !== "text" || | |
| 9347 | typeof xhr.responseText !== "string" ? | |
| 9348 | { binary: xhr.response } : | |
| 9349 | { text: xhr.responseText }, | |
| 9350 | xhr.getAllResponseHeaders() | |
| 9351 | ); | |
| 9352 | } | |
| 9353 | } | |
| 9354 | }; | |
| 9355 | }; | |
| 9356 | ||
| 9357 | // Listen to events | |
| 9358 | xhr.onload = callback(); | |
| 9359 | errorCallback = xhr.onerror = callback( "error" ); | |
| 9360 | ||
| 9361 | // Support: IE 9 only | |
| 9362 | // Use onreadystatechange to replace onabort | |
| 9363 | // to handle uncaught aborts | |
| 9364 | if ( xhr.onabort !== undefined ) { | |
| 9365 | xhr.onabort = errorCallback; | |
| 9366 | } else { | |
| 9367 | xhr.onreadystatechange = function() { | |
| 9368 | ||
| 9369 | // Check readyState before timeout as it changes | |
| 9370 | if ( xhr.readyState === 4 ) { | |
| 9371 | ||
| 9372 | // Allow onerror to be called first, | |
| 9373 | // but that will not handle a native abort | |
| 9374 | // Also, save errorCallback to a variable | |
| 9375 | // as xhr.onerror cannot be accessed | |
| 9376 | window.setTimeout( function() { | |
| 9377 | if ( callback ) { | |
| 9378 | errorCallback(); | |
| 9379 | } | |
| 9380 | } ); | |
| 9381 | } | |
| 9382 | }; | |
| 9383 | } | |
| 9384 | ||
| 9385 | // Create the abort callback | |
| 9386 | callback = callback( "abort" ); | |
| 9387 | ||
| 9388 | try { | |
| 9389 | ||
| 9390 | // Do send the request (this may raise an exception) | |
| 9391 | xhr.send( options.hasContent && options.data || null ); | |
| 9392 | } catch ( e ) { | |
| 9393 | ||
| 9394 | // #14683: Only rethrow if this hasn't been notified as an error yet | |
| 9395 | if ( callback ) { | |
| 9396 | throw e; | |
| 9397 | } | |
| 9398 | } | |
| 9399 | }, | |
| 9400 | ||
| 9401 | abort: function() { | |
| 9402 | if ( callback ) { | |
| 9403 | callback(); | |
| 9404 | } | |
| 9405 | } | |
| 9406 | }; | |
| 9407 | } | |
| 9408 | } ); | |
| 9409 | ||
| 9410 | ||
| 9411 | ||
| 9412 | ||
| 9413 | // Prevent auto-execution of scripts when no explicit dataType was provided (See gh-2432) | |
| 9414 | jQuery.ajaxPrefilter( function( s ) { | |
| 9415 | if ( s.crossDomain ) { | |
| 9416 | s.contents.script = false; | |
| 9417 | } | |
| 9418 | } ); | |
| 9419 | ||
| 9420 | // Install script dataType | |
| 9421 | jQuery.ajaxSetup( { | |
| 9422 | accepts: { | |
| 9423 | script: "text/javascript, application/javascript, " + | |
| 9424 | "application/ecmascript, application/x-ecmascript" | |
| 9425 | }, | |
| 9426 | contents: { | |
| 9427 | script: /\b(?:java|ecma)script\b/ | |
| 9428 | }, | |
| 9429 | converters: { | |
| 9430 | "text script": function( text ) { | |
| 9431 | jQuery.globalEval( text ); | |
| 9432 | return text; | |
| 9433 | } | |
| 9434 | } | |
| 9435 | } ); | |
| 9436 | ||
| 9437 | // Handle cache's special case and crossDomain | |
| 9438 | jQuery.ajaxPrefilter( "script", function( s ) { | |
| 9439 | if ( s.cache === undefined ) { | |
| 9440 | s.cache = false; | |
| 9441 | } | |
| 9442 | if ( s.crossDomain ) { | |
| 9443 | s.type = "GET"; | |
| 9444 | } | |
| 9445 | } ); | |
| 9446 | ||
| 9447 | // Bind script tag hack transport | |
| 9448 | jQuery.ajaxTransport( "script", function( s ) { | |
| 9449 | ||
| 9450 | // This transport only deals with cross domain requests | |
| 9451 | if ( s.crossDomain ) { | |
| 9452 | var script, callback; | |
| 9453 | return { | |
| 9454 | send: function( _, complete ) { | |
| 9455 | script = jQuery( "<script>" ).prop( { | |
| 9456 | charset: s.scriptCharset, | |
| 9457 | src: s.url | |
| 9458 | } ).on( | |
| 9459 | "load error", | |
| 9460 | callback = function( evt ) { | |
| 9461 | script.remove(); | |
| 9462 | callback = null; | |
| 9463 | if ( evt ) { | |
| 9464 | complete( evt.type === "error" ? 404 : 200, evt.type ); | |
| 9465 | } | |
| 9466 | } | |
| 9467 | ); | |
| 9468 | ||
| 9469 | // Use native DOM manipulation to avoid our domManip AJAX trickery | |
| 9470 | document.head.appendChild( script[ 0 ] ); | |
| 9471 | }, | |
| 9472 | abort: function() { | |
| 9473 | if ( callback ) { | |
| 9474 | callback(); | |
| 9475 | } | |
| 9476 | } | |
| 9477 | }; | |
| 9478 | } | |
| 9479 | } ); | |
| 9480 | ||
| 9481 | ||
| 9482 | ||
| 9483 | ||
| 9484 | var oldCallbacks = [], | |
| 9485 | rjsonp = /(=)\?(?=&|$)|\?\?/; | |
| 9486 | ||
| 9487 | // Default jsonp settings | |
| 9488 | jQuery.ajaxSetup( { | |
| 9489 | jsonp: "callback", | |
| 9490 | jsonpCallback: function() { | |
| 9491 | var callback = oldCallbacks.pop() || ( jQuery.expando + "_" + ( nonce++ ) ); | |
| 9492 | this[ callback ] = true; | |
| 9493 | return callback; | |
| 9494 | } | |
| 9495 | } ); | |
| 9496 | ||
| 9497 | // Detect, normalize options and install callbacks for jsonp requests | |
| 9498 | jQuery.ajaxPrefilter( "json jsonp", function( s, originalSettings, jqXHR ) { | |
| 9499 | ||
| 9500 | var callbackName, overwritten, responseContainer, | |
| 9501 | jsonProp = s.jsonp !== false && ( rjsonp.test( s.url ) ? | |
| 9502 | "url" : | |
| 9503 | typeof s.data === "string" && | |
| 9504 | ( s.contentType || "" ) | |
| 9505 | .indexOf( "application/x-www-form-urlencoded" ) === 0 && | |
| 9506 | rjsonp.test( s.data ) && "data" | |
| 9507 | ); | |
| 9508 | ||
| 9509 | // Handle iff the expected data type is "jsonp" or we have a parameter to set | |
| 9510 | if ( jsonProp || s.dataTypes[ 0 ] === "jsonp" ) { | |
| 9511 | ||
| 9512 | // Get callback name, remembering preexisting value associated with it | |
| 9513 | callbackName = s.jsonpCallback = jQuery.isFunction( s.jsonpCallback ) ? | |
| 9514 | s.jsonpCallback() : | |
| 9515 | s.jsonpCallback; | |
| 9516 | ||
| 9517 | // Insert callback into url or form data | |
| 9518 | if ( jsonProp ) { | |
| 9519 | s[ jsonProp ] = s[ jsonProp ].replace( rjsonp, "$1" + callbackName ); | |
| 9520 | } else if ( s.jsonp !== false ) { | |
| 9521 | s.url += ( rquery.test( s.url ) ? "&" : "?" ) + s.jsonp + "=" + callbackName; | |
| 9522 | } | |
| 9523 | ||
| 9524 | // Use data converter to retrieve json after script execution | |
| 9525 | s.converters[ "script json" ] = function() { | |
| 9526 | if ( !responseContainer ) { | |
| 9527 | jQuery.error( callbackName + " was not called" ); | |
| 9528 | } | |
| 9529 | return responseContainer[ 0 ]; | |
| 9530 | }; | |
| 9531 | ||
| 9532 | // Force json dataType | |
| 9533 | s.dataTypes[ 0 ] = "json"; | |
| 9534 | ||
| 9535 | // Install callback | |
| 9536 | overwritten = window[ callbackName ]; | |
| 9537 | window[ callbackName ] = function() { | |
| 9538 | responseContainer = arguments; | |
| 9539 | }; | |
| 9540 | ||
| 9541 | // Clean-up function (fires after converters) | |
| 9542 | jqXHR.always( function() { | |
| 9543 | ||
| 9544 | // If previous value didn't exist - remove it | |
| 9545 | if ( overwritten === undefined ) { | |
| 9546 | jQuery( window ).removeProp( callbackName ); | |
| 9547 | ||
| 9548 | // Otherwise restore preexisting value | |
| 9549 | } else { | |
| 9550 | window[ callbackName ] = overwritten; | |
| 9551 | } | |
| 9552 | ||
| 9553 | // Save back as free | |
| 9554 | if ( s[ callbackName ] ) { | |
| 9555 | ||
| 9556 | // Make sure that re-using the options doesn't screw things around | |
| 9557 | s.jsonpCallback = originalSettings.jsonpCallback; | |
| 9558 | ||
| 9559 | // Save the callback name for future use | |
| 9560 | oldCallbacks.push( callbackName ); | |
| 9561 | } | |
| 9562 | ||
| 9563 | // Call if it was a function and we have a response | |
| 9564 | if ( responseContainer && jQuery.isFunction( overwritten ) ) { | |
| 9565 | overwritten( responseContainer[ 0 ] ); | |
| 9566 | } | |
| 9567 | ||
| 9568 | responseContainer = overwritten = undefined; | |
| 9569 | } ); | |
| 9570 | ||
| 9571 | // Delegate to script | |
| 9572 | return "script"; | |
| 9573 | } | |
| 9574 | } ); | |
| 9575 | ||
| 9576 | ||
| 9577 | ||
| 9578 | ||
| 9579 | // Support: Safari 8 only | |
| 9580 | // In Safari 8 documents created via document.implementation.createHTMLDocument | |
| 9581 | // collapse sibling forms: the second one becomes a child of the first one. | |
| 9582 | // Because of that, this security measure has to be disabled in Safari 8. | |
| 9583 | // https://bugs.webkit.org/show_bug.cgi?id=137337 | |
| 9584 | support.createHTMLDocument = ( function() { | |
| 9585 | var body = document.implementation.createHTMLDocument( "" ).body; | |
| 9586 | body.innerHTML = "<form></form><form></form>"; | |
| 9587 | return body.childNodes.length === 2; | |
| 9588 | } )(); | |
| 9589 | ||
| 9590 | ||
| 9591 | // Argument "data" should be string of html | |
| 9592 | // context (optional): If specified, the fragment will be created in this context, | |
| 9593 | // defaults to document | |
| 9594 | // keepScripts (optional): If true, will include scripts passed in the html string | |
| 9595 | jQuery.parseHTML = function( data, context, keepScripts ) { | |
| 9596 | if ( typeof data !== "string" ) { | |
| 9597 | return []; | |
| 9598 | } | |
| 9599 | if ( typeof context === "boolean" ) { | |
| 9600 | keepScripts = context; | |
| 9601 | context = false; | |
| 9602 | } | |
| 9603 | ||
| 9604 | var base, parsed, scripts; | |
| 9605 | ||
| 9606 | if ( !context ) { | |
| 9607 | ||
| 9608 | // Stop scripts or inline event handlers from being executed immediately | |
| 9609 | // by using document.implementation | |
| 9610 | if ( support.createHTMLDocument ) { | |
| 9611 | context = document.implementation.createHTMLDocument( "" ); | |
| 9612 | ||
| 9613 | // Set the base href for the created document | |
| 9614 | // so any parsed elements with URLs | |
| 9615 | // are based on the document's URL (gh-2965) | |
| 9616 | base = context.createElement( "base" ); | |
| 9617 | base.href = document.location.href; | |
| 9618 | context.head.appendChild( base ); | |
| 9619 | } else { | |
| 9620 | context = document; | |
| 9621 | } | |
| 9622 | } | |
| 9623 | ||
| 9624 | parsed = rsingleTag.exec( data ); | |
| 9625 | scripts = !keepScripts && []; | |
| 9626 | ||
| 9627 | // Single tag | |
| 9628 | if ( parsed ) { | |
| 9629 | return [ context.createElement( parsed[ 1 ] ) ]; | |
| 9630 | } | |
| 9631 | ||
| 9632 | parsed = buildFragment( [ data ], context, scripts ); | |
| 9633 | ||
| 9634 | if ( scripts && scripts.length ) { | |
| 9635 | jQuery( scripts ).remove(); | |
| 9636 | } | |
| 9637 | ||
| 9638 | return jQuery.merge( [], parsed.childNodes ); | |
| 9639 | }; | |
| 9640 | ||
| 9641 | ||
| 9642 | /** | |
| 9643 | * Load a url into a page | |
| 9644 | */ | |
| 9645 | jQuery.fn.load = function( url, params, callback ) { | |
| 9646 | var selector, type, response, | |
| 9647 | self = this, | |
| 9648 | off = url.indexOf( " " ); | |
| 9649 | ||
| 9650 | if ( off > -1 ) { | |
| 9651 | selector = jQuery.trim( url.slice( off ) ); | |
| 9652 | url = url.slice( 0, off ); | |
| 9653 | } | |
| 9654 | ||
| 9655 | // If it's a function | |
| 9656 | if ( jQuery.isFunction( params ) ) { | |
| 9657 | ||
| 9658 | // We assume that it's the callback | |
| 9659 | callback = params; | |
| 9660 | params = undefined; | |
| 9661 | ||
| 9662 | // Otherwise, build a param string | |
| 9663 | } else if ( params && typeof params === "object" ) { | |
| 9664 | type = "POST"; | |
| 9665 | } | |
| 9666 | ||
| 9667 | // If we have elements to modify, make the request | |
| 9668 | if ( self.length > 0 ) { | |
| 9669 | jQuery.ajax( { | |
| 9670 | url: url, | |
| 9671 | ||
| 9672 | // If "type" variable is undefined, then "GET" method will be used. | |
| 9673 | // Make value of this field explicit since | |
| 9674 | // user can override it through ajaxSetup method | |
| 9675 | type: type || "GET", | |
| 9676 | dataType: "html", | |
| 9677 | data: params | |
| 9678 | } ).done( function( responseText ) { | |
| 9679 | ||
| 9680 | // Save response for use in complete callback | |
| 9681 | response = arguments; | |
| 9682 | ||
| 9683 | self.html( selector ? | |
| 9684 | ||
| 9685 | // If a selector was specified, locate the right elements in a dummy div | |
| 9686 | // Exclude scripts to avoid IE 'Permission Denied' errors | |
| 9687 | jQuery( "<div>" ).append( jQuery.parseHTML( responseText ) ).find( selector ) : | |
| 9688 | ||
| 9689 | // Otherwise use the full result | |
| 9690 | responseText ); | |
| 9691 | ||
| 9692 | // If the request succeeds, this function gets "data", "status", "jqXHR" | |
| 9693 | // but they are ignored because response was set above. | |
| 9694 | // If it fails, this function gets "jqXHR", "status", "error" | |
| 9695 | } ).always( callback && function( jqXHR, status ) { | |
| 9696 | self.each( function() { | |
| 9697 | callback.apply( this, response || [ jqXHR.responseText, status, jqXHR ] ); | |
| 9698 | } ); | |
| 9699 | } ); | |
| 9700 | } | |
| 9701 | ||
| 9702 | return this; | |
| 9703 | }; | |
| 9704 | ||
| 9705 | ||
| 9706 | ||
| 9707 | ||
| 9708 | // Attach a bunch of functions for handling common AJAX events | |
| 9709 | jQuery.each( [ | |
| 9710 | "ajaxStart", | |
| 9711 | "ajaxStop", | |
| 9712 | "ajaxComplete", | |
| 9713 | "ajaxError", | |
| 9714 | "ajaxSuccess", | |
| 9715 | "ajaxSend" | |
| 9716 | ], function( i, type ) { | |
| 9717 | jQuery.fn[ type ] = function( fn ) { | |
| 9718 | return this.on( type, fn ); | |
| 9719 | }; | |
| 9720 | } ); | |
| 9721 | ||
| 9722 | ||
| 9723 | ||
| 9724 | ||
| 9725 | jQuery.expr.pseudos.animated = function( elem ) { | |
| 9726 | return jQuery.grep( jQuery.timers, function( fn ) { | |
| 9727 | return elem === fn.elem; | |
| 9728 | } ).length; | |
| 9729 | }; | |
| 9730 | ||
| 9731 | ||
| 9732 | ||
| 9733 | ||
| 9734 | /** | |
| 9735 | * Gets a window from an element | |
| 9736 | */ | |
| 9737 | function getWindow( elem ) { | |
| 9738 | return jQuery.isWindow( elem ) ? elem : elem.nodeType === 9 && elem.defaultView; | |
| 9739 | } | |
| 9740 | ||
| 9741 | jQuery.offset = { | |
| 9742 | setOffset: function( elem, options, i ) { | |
| 9743 | var curPosition, curLeft, curCSSTop, curTop, curOffset, curCSSLeft, calculatePosition, | |
| 9744 | position = jQuery.css( elem, "position" ), | |
| 9745 | curElem = jQuery( elem ), | |
| 9746 | props = {}; | |
| 9747 | ||
| 9748 | // Set position first, in-case top/left are set even on static elem | |
| 9749 | if ( position === "static" ) { | |
| 9750 | elem.style.position = "relative"; | |
| 9751 | } | |
| 9752 | ||
| 9753 | curOffset = curElem.offset(); | |
| 9754 | curCSSTop = jQuery.css( elem, "top" ); | |
| 9755 | curCSSLeft = jQuery.css( elem, "left" ); | |
| 9756 | calculatePosition = ( position === "absolute" || position === "fixed" ) && | |
| 9757 | ( curCSSTop + curCSSLeft ).indexOf( "auto" ) > -1; | |
| 9758 | ||
| 9759 | // Need to be able to calculate position if either | |
| 9760 | // top or left is auto and position is either absolute or fixed | |
| 9761 | if ( calculatePosition ) { | |
| 9762 | curPosition = curElem.position(); | |
| 9763 | curTop = curPosition.top; | |
| 9764 | curLeft = curPosition.left; | |
| 9765 | ||
| 9766 | } else { | |
| 9767 | curTop = parseFloat( curCSSTop ) || 0; | |
| 9768 | curLeft = parseFloat( curCSSLeft ) || 0; | |
| 9769 | } | |
| 9770 | ||
| 9771 | if ( jQuery.isFunction( options ) ) { | |
| 9772 | ||
| 9773 | // Use jQuery.extend here to allow modification of coordinates argument (gh-1848) | |
| 9774 | options = options.call( elem, i, jQuery.extend( {}, curOffset ) ); | |
| 9775 | } | |
| 9776 | ||
| 9777 | if ( options.top != null ) { | |
| 9778 | props.top = ( options.top - curOffset.top ) + curTop; | |
| 9779 | } | |
| 9780 | if ( options.left != null ) { | |
| 9781 | props.left = ( options.left - curOffset.left ) + curLeft; | |
| 9782 | } | |
| 9783 | ||
| 9784 | if ( "using" in options ) { | |
| 9785 | options.using.call( elem, props ); | |
| 9786 | ||
| 9787 | } else { | |
| 9788 | curElem.css( props ); | |
| 9789 | } | |
| 9790 | } | |
| 9791 | }; | |
| 9792 | ||
| 9793 | jQuery.fn.extend( { | |
| 9794 | offset: function( options ) { | |
| 9795 | ||
| 9796 | // Preserve chaining for setter | |
| 9797 | if ( arguments.length ) { | |
| 9798 | return options === undefined ? | |
| 9799 | this : | |
| 9800 | this.each( function( i ) { | |
| 9801 | jQuery.offset.setOffset( this, options, i ); | |
| 9802 | } ); | |
| 9803 | } | |
| 9804 | ||
| 9805 | var docElem, win, rect, doc, | |
| 9806 | elem = this[ 0 ]; | |
| 9807 | ||
| 9808 | if ( !elem ) { | |
| 9809 | return; | |
| 9810 | } | |
| 9811 | ||
| 9812 | // Support: IE <=11 only | |
| 9813 | // Running getBoundingClientRect on a | |
| 9814 | // disconnected node in IE throws an error | |
| 9815 | if ( !elem.getClientRects().length ) { | |
| 9816 | return { top: 0, left: 0 }; | |
| 9817 | } | |
| 9818 | ||
| 9819 | rect = elem.getBoundingClientRect(); | |
| 9820 | ||
| 9821 | // Make sure element is not hidden (display: none) | |
| 9822 | if ( rect.width || rect.height ) { | |
| 9823 | doc = elem.ownerDocument; | |
| 9824 | win = getWindow( doc ); | |
| 9825 | docElem = doc.documentElement; | |
| 9826 | ||
| 9827 | return { | |
| 9828 | top: rect.top + win.pageYOffset - docElem.clientTop, | |
| 9829 | left: rect.left + win.pageXOffset - docElem.clientLeft | |
| 9830 | }; | |
| 9831 | } | |
| 9832 | ||
| 9833 | // Return zeros for disconnected and hidden elements (gh-2310) | |
| 9834 | return rect; | |
| 9835 | }, | |
| 9836 | ||
| 9837 | position: function() { | |
| 9838 | if ( !this[ 0 ] ) { | |
| 9839 | return; | |
| 9840 | } | |
| 9841 | ||
| 9842 | var offsetParent, offset, | |
| 9843 | elem = this[ 0 ], | |
| 9844 | parentOffset = { top: 0, left: 0 }; | |
| 9845 | ||
| 9846 | // Fixed elements are offset from window (parentOffset = {top:0, left: 0}, | |
| 9847 | // because it is its only offset parent | |
| 9848 | if ( jQuery.css( elem, "position" ) === "fixed" ) { | |
| 9849 | ||
| 9850 | // Assume getBoundingClientRect is there when computed position is fixed | |
| 9851 | offset = elem.getBoundingClientRect(); | |
| 9852 | ||
| 9853 | } else { | |
| 9854 | ||
| 9855 | // Get *real* offsetParent | |
| 9856 | offsetParent = this.offsetParent(); | |
| 9857 | ||
| 9858 | // Get correct offsets | |
| 9859 | offset = this.offset(); | |
| 9860 | if ( !jQuery.nodeName( offsetParent[ 0 ], "html" ) ) { | |
| 9861 | parentOffset = offsetParent.offset(); | |
| 9862 | } | |
| 9863 | ||
| 9864 | // Add offsetParent borders | |
| 9865 | parentOffset = { | |
| 9866 | top: parentOffset.top + jQuery.css( offsetParent[ 0 ], "borderTopWidth", true ), | |
| 9867 | left: parentOffset.left + jQuery.css( offsetParent[ 0 ], "borderLeftWidth", true ) | |
| 9868 | }; | |
| 9869 | } | |
| 9870 | ||
| 9871 | // Subtract parent offsets and element margins | |
| 9872 | return { | |
| 9873 | top: offset.top - parentOffset.top - jQuery.css( elem, "marginTop", true ), | |
| 9874 | left: offset.left - parentOffset.left - jQuery.css( elem, "marginLeft", true ) | |
| 9875 | }; | |
| 9876 | }, | |
| 9877 | ||
| 9878 | // This method will return documentElement in the following cases: | |
| 9879 | // 1) For the element inside the iframe without offsetParent, this method will return | |
| 9880 | // documentElement of the parent window | |
| 9881 | // 2) For the hidden or detached element | |
| 9882 | // 3) For body or html element, i.e. in case of the html node - it will return itself | |
| 9883 | // | |
| 9884 | // but those exceptions were never presented as a real life use-cases | |
| 9885 | // and might be considered as more preferable results. | |
| 9886 | // | |
| 9887 | // This logic, however, is not guaranteed and can change at any point in the future | |
| 9888 | offsetParent: function() { | |
| 9889 | return this.map( function() { | |
| 9890 | var offsetParent = this.offsetParent; | |
| 9891 | ||
| 9892 | while ( offsetParent && jQuery.css( offsetParent, "position" ) === "static" ) { | |
| 9893 | offsetParent = offsetParent.offsetParent; | |
| 9894 | } | |
| 9895 | ||
| 9896 | return offsetParent || documentElement; | |
| 9897 | } ); | |
| 9898 | } | |
| 9899 | } ); | |
| 9900 | ||
| 9901 | // Create scrollLeft and scrollTop methods | |
| 9902 | jQuery.each( { scrollLeft: "pageXOffset", scrollTop: "pageYOffset" }, function( method, prop ) { | |
| 9903 | var top = "pageYOffset" === prop; | |
| 9904 | ||
| 9905 | jQuery.fn[ method ] = function( val ) { | |
| 9906 | return access( this, function( elem, method, val ) { | |
| 9907 | var win = getWindow( elem ); | |
| 9908 | ||
| 9909 | if ( val === undefined ) { | |
| 9910 | return win ? win[ prop ] : elem[ method ]; | |
| 9911 | } | |
| 9912 | ||
| 9913 | if ( win ) { | |
| 9914 | win.scrollTo( | |
| 9915 | !top ? val : win.pageXOffset, | |
| 9916 | top ? val : win.pageYOffset | |
| 9917 | ); | |
| 9918 | ||
| 9919 | } else { | |
| 9920 | elem[ method ] = val; | |
| 9921 | } | |
| 9922 | }, method, val, arguments.length ); | |
| 9923 | }; | |
| 9924 | } ); | |
| 9925 | ||
| 9926 | // Support: Safari <=7 - 9.1, Chrome <=37 - 49 | |
| 9927 | // Add the top/left cssHooks using jQuery.fn.position | |
| 9928 | // Webkit bug: https://bugs.webkit.org/show_bug.cgi?id=29084 | |
| 9929 | // Blink bug: https://bugs.chromium.org/p/chromium/issues/detail?id=589347 | |
| 9930 | // getComputedStyle returns percent when specified for top/left/bottom/right; | |
| 9931 | // rather than make the css module depend on the offset module, just check for it here | |
| 9932 | jQuery.each( [ "top", "left" ], function( i, prop ) { | |
| 9933 | jQuery.cssHooks[ prop ] = addGetHookIf( support.pixelPosition, | |
| 9934 | function( elem, computed ) { | |
| 9935 | if ( computed ) { | |
| 9936 | computed = curCSS( elem, prop ); | |
| 9937 | ||
| 9938 | // If curCSS returns percentage, fallback to offset | |
| 9939 | return rnumnonpx.test( computed ) ? | |
| 9940 | jQuery( elem ).position()[ prop ] + "px" : | |
| 9941 | computed; | |
| 9942 | } | |
| 9943 | } | |
| 9944 | ); | |
| 9945 | } ); | |
| 9946 | ||
| 9947 | ||
| 9948 | // Create innerHeight, innerWidth, height, width, outerHeight and outerWidth methods | |
| 9949 | jQuery.each( { Height: "height", Width: "width" }, function( name, type ) { | |
| 9950 | jQuery.each( { padding: "inner" + name, content: type, "": "outer" + name }, | |
| 9951 | function( defaultExtra, funcName ) { | |
| 9952 | ||
| 9953 | // Margin is only for outerHeight, outerWidth | |
| 9954 | jQuery.fn[ funcName ] = function( margin, value ) { | |
| 9955 | var chainable = arguments.length && ( defaultExtra || typeof margin !== "boolean" ), | |
| 9956 | extra = defaultExtra || ( margin === true || value === true ? "margin" : "border" ); | |
| 9957 | ||
| 9958 | return access( this, function( elem, type, value ) { | |
| 9959 | var doc; | |
| 9960 | ||
| 9961 | if ( jQuery.isWindow( elem ) ) { | |
| 9962 | ||
| 9963 | // $( window ).outerWidth/Height return w/h including scrollbars (gh-1729) | |
| 9964 | return funcName.indexOf( "outer" ) === 0 ? | |
| 9965 | elem[ "inner" + name ] : | |
| 9966 | elem.document.documentElement[ "client" + name ]; | |
| 9967 | } | |
| 9968 | ||
| 9969 | // Get document width or height | |
| 9970 | if ( elem.nodeType === 9 ) { | |
| 9971 | doc = elem.documentElement; | |
| 9972 | ||
| 9973 | // Either scroll[Width/Height] or offset[Width/Height] or client[Width/Height], | |
| 9974 | // whichever is greatest | |
| 9975 | return Math.max( | |
| 9976 | elem.body[ "scroll" + name ], doc[ "scroll" + name ], | |
| 9977 | elem.body[ "offset" + name ], doc[ "offset" + name ], | |
| 9978 | doc[ "client" + name ] | |
| 9979 | ); | |
| 9980 | } | |
| 9981 | ||
| 9982 | return value === undefined ? | |
| 9983 | ||
| 9984 | // Get width or height on the element, requesting but not forcing parseFloat | |
| 9985 | jQuery.css( elem, type, extra ) : | |
| 9986 | ||
| 9987 | // Set width or height on the element | |
| 9988 | jQuery.style( elem, type, value, extra ); | |
| 9989 | }, type, chainable ? margin : undefined, chainable ); | |
| 9990 | }; | |
| 9991 | } ); | |
| 9992 | } ); | |
| 9993 | ||
| 9994 | ||
| 9995 | jQuery.fn.extend( { | |
| 9996 | ||
| 9997 | bind: function( types, data, fn ) { | |
| 9998 | return this.on( types, null, data, fn ); | |
| 9999 | }, | |
| 10000 | unbind: function( types, fn ) { | |
| 10001 | return this.off( types, null, fn ); | |
| 10002 | }, | |
| 10003 | ||
| 10004 | delegate: function( selector, types, data, fn ) { | |
| 10005 | return this.on( types, selector, data, fn ); | |
| 10006 | }, | |
| 10007 | undelegate: function( selector, types, fn ) { | |
| 10008 | ||
| 10009 | // ( namespace ) or ( selector, types [, fn] ) | |
| 10010 | return arguments.length === 1 ? | |
| 10011 | this.off( selector, "**" ) : | |
| 10012 | this.off( types, selector || "**", fn ); | |
| 10013 | } | |
| 10014 | } ); | |
| 10015 | ||
| 10016 | jQuery.parseJSON = JSON.parse; | |
| 10017 | ||
| 10018 | ||
| 10019 | ||
| 10020 | ||
| 10021 | // Register as a named AMD module, since jQuery can be concatenated with other | |
| 10022 | // files that may use define, but not via a proper concatenation script that | |
| 10023 | // understands anonymous AMD modules. A named AMD is safest and most robust | |
| 10024 | // way to register. Lowercase jquery is used because AMD module names are | |
| 10025 | // derived from file names, and jQuery is normally delivered in a lowercase | |
| 10026 | // file name. Do this after creating the global so that if an AMD module wants | |
| 10027 | // to call noConflict to hide this version of jQuery, it will work. | |
| 10028 | ||
| 10029 | // Note that for maximum portability, libraries that are not jQuery should | |
| 10030 | // declare themselves as anonymous modules, and avoid setting a global if an | |
| 10031 | // AMD loader is present. jQuery is a special case. For more information, see | |
| 10032 | // https://github.com/jrburke/requirejs/wiki/Updating-existing-libraries#wiki-anon | |
| 10033 | ||
| 10034 | if ( typeof define === "function" && define.amd ) { | |
| 10035 | define( "jquery", [], function() { | |
| 10036 | return jQuery; | |
| 10037 | } ); | |
| 10038 | } | |
| 10039 | ||
| 10040 | ||
| 10041 | ||
| 10042 | ||
| 10043 | ||
| 10044 | var | |
| 10045 | ||
| 10046 | // Map over jQuery in case of overwrite | |
| 10047 | _jQuery = window.jQuery, | |
| 10048 | ||
| 10049 | // Map over the $ in case of overwrite | |
| 10050 | _$ = window.$; | |
| 10051 | ||
| 10052 | jQuery.noConflict = function( deep ) { | |
| 10053 | if ( window.$ === jQuery ) { | |
| 10054 | window.$ = _$; | |
| 10055 | } | |
| 10056 | ||
| 10057 | if ( deep && window.jQuery === jQuery ) { | |
| 10058 | window.jQuery = _jQuery; | |
| 10059 | } | |
| 10060 | ||
| 10061 | return jQuery; | |
| 10062 | }; | |
| 10063 | ||
| 10064 | // Expose jQuery and $ identifiers, even in AMD | |
| 10065 | // (#7102#comment:10, https://github.com/jquery/jquery/pull/557) | |
| 10066 | // and CommonJS for browser emulators (#13566) | |
| 10067 | if ( !noGlobal ) { | |
| 10068 | window.jQuery = window.$ = jQuery; | |
| 10069 | } | |
| 10070 | ||
| 10071 | ||
| 10072 | return jQuery; | |
| 10073 | } ); |
| 0 | /*! jQuery v3.1.0 | (c) jQuery Foundation | jquery.org/license */ | |
| 1 | !function(a,b){"use strict";"object"==typeof module&&"object"==typeof module.exports?module.exports=a.document?b(a,!0):function(a){if(!a.document)throw new Error("jQuery requires a window with a document");return b(a)}:b(a)}("undefined"!=typeof window?window:this,function(a,b){"use strict";var c=[],d=a.document,e=Object.getPrototypeOf,f=c.slice,g=c.concat,h=c.push,i=c.indexOf,j={},k=j.toString,l=j.hasOwnProperty,m=l.toString,n=m.call(Object),o={};function p(a,b){b=b||d;var c=b.createElement("script");c.text=a,b.head.appendChild(c).parentNode.removeChild(c)}var q="3.1.0",r=function(a,b){return new r.fn.init(a,b)},s=/^[\s\uFEFF\xA0]+|[\s\uFEFF\xA0]+$/g,t=/^-ms-/,u=/-([a-z])/g,v=function(a,b){return b.toUpperCase()};r.fn=r.prototype={jquery:q,constructor:r,length:0,toArray:function(){return f.call(this)},get:function(a){return null!=a?a<0?this[a+this.length]:this[a]:f.call(this)},pushStack:function(a){var b=r.merge(this.constructor(),a);return b.prevObject=this,b},each:function(a){return r.each(this,a)},map:function(a){return this.pushStack(r.map(this,function(b,c){return a.call(b,c,b)}))},slice:function(){return this.pushStack(f.apply(this,arguments))},first:function(){return this.eq(0)},last:function(){return this.eq(-1)},eq:function(a){var b=this.length,c=+a+(a<0?b:0);return this.pushStack(c>=0&&c<b?[this[c]]:[])},end:function(){return this.prevObject||this.constructor()},push:h,sort:c.sort,splice:c.splice},r.extend=r.fn.extend=function(){var a,b,c,d,e,f,g=arguments[0]||{},h=1,i=arguments.length,j=!1;for("boolean"==typeof g&&(j=g,g=arguments[h]||{},h++),"object"==typeof g||r.isFunction(g)||(g={}),h===i&&(g=this,h--);h<i;h++)if(null!=(a=arguments[h]))for(b in a)c=g[b],d=a[b],g!==d&&(j&&d&&(r.isPlainObject(d)||(e=r.isArray(d)))?(e?(e=!1,f=c&&r.isArray(c)?c:[]):f=c&&r.isPlainObject(c)?c:{},g[b]=r.extend(j,f,d)):void 0!==d&&(g[b]=d));return g},r.extend({expando:"jQuery"+(q+Math.random()).replace(/\D/g,""),isReady:!0,error:function(a){throw new Error(a)},noop:function(){},isFunction:function(a){return"function"===r.type(a)},isArray:Array.isArray,isWindow:function(a){return null!=a&&a===a.window},isNumeric:function(a){var b=r.type(a);return("number"===b||"string"===b)&&!isNaN(a-parseFloat(a))},isPlainObject:function(a){var b,c;return!(!a||"[object Object]"!==k.call(a))&&(!(b=e(a))||(c=l.call(b,"constructor")&&b.constructor,"function"==typeof c&&m.call(c)===n))},isEmptyObject:function(a){var b;for(b in a)return!1;return!0},type:function(a){return null==a?a+"":"object"==typeof a||"function"==typeof a?j[k.call(a)]||"object":typeof a},globalEval:function(a){p(a)},camelCase:function(a){return a.replace(t,"ms-").replace(u,v)},nodeName:function(a,b){return a.nodeName&&a.nodeName.toLowerCase()===b.toLowerCase()},each:function(a,b){var c,d=0;if(w(a)){for(c=a.length;d<c;d++)if(b.call(a[d],d,a[d])===!1)break}else for(d in a)if(b.call(a[d],d,a[d])===!1)break;return a},trim:function(a){return null==a?"":(a+"").replace(s,"")},makeArray:function(a,b){var c=b||[];return null!=a&&(w(Object(a))?r.merge(c,"string"==typeof a?[a]:a):h.call(c,a)),c},inArray:function(a,b,c){return null==b?-1:i.call(b,a,c)},merge:function(a,b){for(var c=+b.length,d=0,e=a.length;d<c;d++)a[e++]=b[d];return a.length=e,a},grep:function(a,b,c){for(var d,e=[],f=0,g=a.length,h=!c;f<g;f++)d=!b(a[f],f),d!==h&&e.push(a[f]);return e},map:function(a,b,c){var d,e,f=0,h=[];if(w(a))for(d=a.length;f<d;f++)e=b(a[f],f,c),null!=e&&h.push(e);else for(f in a)e=b(a[f],f,c),null!=e&&h.push(e);return g.apply([],h)},guid:1,proxy:function(a,b){var c,d,e;if("string"==typeof b&&(c=a[b],b=a,a=c),r.isFunction(a))return d=f.call(arguments,2),e=function(){return a.apply(b||this,d.concat(f.call(arguments)))},e.guid=a.guid=a.guid||r.guid++,e},now:Date.now,support:o}),"function"==typeof Symbol&&(r.fn[Symbol.iterator]=c[Symbol.iterator]),r.each("Boolean Number String Function Array Date RegExp Object Error Symbol".split(" "),function(a,b){j["[object "+b+"]"]=b.toLowerCase()});function w(a){var b=!!a&&"length"in a&&a.length,c=r.type(a);return"function"!==c&&!r.isWindow(a)&&("array"===c||0===b||"number"==typeof b&&b>0&&b-1 in a)}var x=function(a){var b,c,d,e,f,g,h,i,j,k,l,m,n,o,p,q,r,s,t,u="sizzle"+1*new Date,v=a.document,w=0,x=0,y=ha(),z=ha(),A=ha(),B=function(a,b){return a===b&&(l=!0),0},C={}.hasOwnProperty,D=[],E=D.pop,F=D.push,G=D.push,H=D.slice,I=function(a,b){for(var c=0,d=a.length;c<d;c++)if(a[c]===b)return c;return-1},J="checked|selected|async|autofocus|autoplay|controls|defer|disabled|hidden|ismap|loop|multiple|open|readonly|required|scoped",K="[\\x20\\t\\r\\n\\f]",L="(?:\\\\.|[\\w-]|[^\0-\\xa0])+",M="\\["+K+"*("+L+")(?:"+K+"*([*^$|!~]?=)"+K+"*(?:'((?:\\\\.|[^\\\\'])*)'|\"((?:\\\\.|[^\\\\\"])*)\"|("+L+"))|)"+K+"*\\]",N=":("+L+")(?:\\((('((?:\\\\.|[^\\\\'])*)'|\"((?:\\\\.|[^\\\\\"])*)\")|((?:\\\\.|[^\\\\()[\\]]|"+M+")*)|.*)\\)|)",O=new RegExp(K+"+","g"),P=new RegExp("^"+K+"+|((?:^|[^\\\\])(?:\\\\.)*)"+K+"+$","g"),Q=new RegExp("^"+K+"*,"+K+"*"),R=new RegExp("^"+K+"*([>+~]|"+K+")"+K+"*"),S=new RegExp("="+K+"*([^\\]'\"]*?)"+K+"*\\]","g"),T=new RegExp(N),U=new RegExp("^"+L+"$"),V={ID:new RegExp("^#("+L+")"),CLASS:new RegExp("^\\.("+L+")"),TAG:new RegExp("^("+L+"|[*])"),ATTR:new RegExp("^"+M),PSEUDO:new RegExp("^"+N),CHILD:new RegExp("^:(only|first|last|nth|nth-last)-(child|of-type)(?:\\("+K+"*(even|odd|(([+-]|)(\\d*)n|)"+K+"*(?:([+-]|)"+K+"*(\\d+)|))"+K+"*\\)|)","i"),bool:new RegExp("^(?:"+J+")$","i"),needsContext:new RegExp("^"+K+"*[>+~]|:(even|odd|eq|gt|lt|nth|first|last)(?:\\("+K+"*((?:-\\d)?\\d*)"+K+"*\\)|)(?=[^-]|$)","i")},W=/^(?:input|select|textarea|button)$/i,X=/^h\d$/i,Y=/^[^{]+\{\s*\[native \w/,Z=/^(?:#([\w-]+)|(\w+)|\.([\w-]+))$/,$=/[+~]/,_=new RegExp("\\\\([\\da-f]{1,6}"+K+"?|("+K+")|.)","ig"),aa=function(a,b,c){var d="0x"+b-65536;return d!==d||c?b:d<0?String.fromCharCode(d+65536):String.fromCharCode(d>>10|55296,1023&d|56320)},ba=/([\0-\x1f\x7f]|^-?\d)|^-$|[^\x80-\uFFFF\w-]/g,ca=function(a,b){return b?"\0"===a?"\ufffd":a.slice(0,-1)+"\\"+a.charCodeAt(a.length-1).toString(16)+" ":"\\"+a},da=function(){m()},ea=ta(function(a){return a.disabled===!0},{dir:"parentNode",next:"legend"});try{G.apply(D=H.call(v.childNodes),v.childNodes),D[v.childNodes.length].nodeType}catch(fa){G={apply:D.length?function(a,b){F.apply(a,H.call(b))}:function(a,b){var c=a.length,d=0;while(a[c++]=b[d++]);a.length=c-1}}}function ga(a,b,d,e){var f,h,j,k,l,o,r,s=b&&b.ownerDocument,w=b?b.nodeType:9;if(d=d||[],"string"!=typeof a||!a||1!==w&&9!==w&&11!==w)return d;if(!e&&((b?b.ownerDocument||b:v)!==n&&m(b),b=b||n,p)){if(11!==w&&(l=Z.exec(a)))if(f=l[1]){if(9===w){if(!(j=b.getElementById(f)))return d;if(j.id===f)return d.push(j),d}else if(s&&(j=s.getElementById(f))&&t(b,j)&&j.id===f)return d.push(j),d}else{if(l[2])return G.apply(d,b.getElementsByTagName(a)),d;if((f=l[3])&&c.getElementsByClassName&&b.getElementsByClassName)return G.apply(d,b.getElementsByClassName(f)),d}if(c.qsa&&!A[a+" "]&&(!q||!q.test(a))){if(1!==w)s=b,r=a;else if("object"!==b.nodeName.toLowerCase()){(k=b.getAttribute("id"))?k=k.replace(ba,ca):b.setAttribute("id",k=u),o=g(a),h=o.length;while(h--)o[h]="#"+k+" "+sa(o[h]);r=o.join(","),s=$.test(a)&&qa(b.parentNode)||b}if(r)try{return G.apply(d,s.querySelectorAll(r)),d}catch(x){}finally{k===u&&b.removeAttribute("id")}}}return i(a.replace(P,"$1"),b,d,e)}function ha(){var a=[];function b(c,e){return a.push(c+" ")>d.cacheLength&&delete b[a.shift()],b[c+" "]=e}return b}function ia(a){return a[u]=!0,a}function ja(a){var b=n.createElement("fieldset");try{return!!a(b)}catch(c){return!1}finally{b.parentNode&&b.parentNode.removeChild(b),b=null}}function ka(a,b){var c=a.split("|"),e=c.length;while(e--)d.attrHandle[c[e]]=b}function la(a,b){var c=b&&a,d=c&&1===a.nodeType&&1===b.nodeType&&a.sourceIndex-b.sourceIndex;if(d)return d;if(c)while(c=c.nextSibling)if(c===b)return-1;return a?1:-1}function ma(a){return function(b){var c=b.nodeName.toLowerCase();return"input"===c&&b.type===a}}function na(a){return function(b){var c=b.nodeName.toLowerCase();return("input"===c||"button"===c)&&b.type===a}}function oa(a){return function(b){return"label"in b&&b.disabled===a||"form"in b&&b.disabled===a||"form"in b&&b.disabled===!1&&(b.isDisabled===a||b.isDisabled!==!a&&("label"in b||!ea(b))!==a)}}function pa(a){return ia(function(b){return b=+b,ia(function(c,d){var e,f=a([],c.length,b),g=f.length;while(g--)c[e=f[g]]&&(c[e]=!(d[e]=c[e]))})})}function qa(a){return a&&"undefined"!=typeof a.getElementsByTagName&&a}c=ga.support={},f=ga.isXML=function(a){var b=a&&(a.ownerDocument||a).documentElement;return!!b&&"HTML"!==b.nodeName},m=ga.setDocument=function(a){var b,e,g=a?a.ownerDocument||a:v;return g!==n&&9===g.nodeType&&g.documentElement?(n=g,o=n.documentElement,p=!f(n),v!==n&&(e=n.defaultView)&&e.top!==e&&(e.addEventListener?e.addEventListener("unload",da,!1):e.attachEvent&&e.attachEvent("onunload",da)),c.attributes=ja(function(a){return a.className="i",!a.getAttribute("className")}),c.getElementsByTagName=ja(function(a){return a.appendChild(n.createComment("")),!a.getElementsByTagName("*").length}),c.getElementsByClassName=Y.test(n.getElementsByClassName),c.getById=ja(function(a){return o.appendChild(a).id=u,!n.getElementsByName||!n.getElementsByName(u).length}),c.getById?(d.find.ID=function(a,b){if("undefined"!=typeof b.getElementById&&p){var c=b.getElementById(a);return c?[c]:[]}},d.filter.ID=function(a){var b=a.replace(_,aa);return function(a){return a.getAttribute("id")===b}}):(delete d.find.ID,d.filter.ID=function(a){var b=a.replace(_,aa);return function(a){var c="undefined"!=typeof a.getAttributeNode&&a.getAttributeNode("id");return c&&c.value===b}}),d.find.TAG=c.getElementsByTagName?function(a,b){return"undefined"!=typeof b.getElementsByTagName?b.getElementsByTagName(a):c.qsa?b.querySelectorAll(a):void 0}:function(a,b){var c,d=[],e=0,f=b.getElementsByTagName(a);if("*"===a){while(c=f[e++])1===c.nodeType&&d.push(c);return d}return f},d.find.CLASS=c.getElementsByClassName&&function(a,b){if("undefined"!=typeof b.getElementsByClassName&&p)return b.getElementsByClassName(a)},r=[],q=[],(c.qsa=Y.test(n.querySelectorAll))&&(ja(function(a){o.appendChild(a).innerHTML="<a id='"+u+"'></a><select id='"+u+"-\r\\' msallowcapture=''><option selected=''></option></select>",a.querySelectorAll("[msallowcapture^='']").length&&q.push("[*^$]="+K+"*(?:''|\"\")"),a.querySelectorAll("[selected]").length||q.push("\\["+K+"*(?:value|"+J+")"),a.querySelectorAll("[id~="+u+"-]").length||q.push("~="),a.querySelectorAll(":checked").length||q.push(":checked"),a.querySelectorAll("a#"+u+"+*").length||q.push(".#.+[+~]")}),ja(function(a){a.innerHTML="<a href='' disabled='disabled'></a><select disabled='disabled'><option/></select>";var b=n.createElement("input");b.setAttribute("type","hidden"),a.appendChild(b).setAttribute("name","D"),a.querySelectorAll("[name=d]").length&&q.push("name"+K+"*[*^$|!~]?="),2!==a.querySelectorAll(":enabled").length&&q.push(":enabled",":disabled"),o.appendChild(a).disabled=!0,2!==a.querySelectorAll(":disabled").length&&q.push(":enabled",":disabled"),a.querySelectorAll("*,:x"),q.push(",.*:")})),(c.matchesSelector=Y.test(s=o.matches||o.webkitMatchesSelector||o.mozMatchesSelector||o.oMatchesSelector||o.msMatchesSelector))&&ja(function(a){c.disconnectedMatch=s.call(a,"*"),s.call(a,"[s!='']:x"),r.push("!=",N)}),q=q.length&&new RegExp(q.join("|")),r=r.length&&new RegExp(r.join("|")),b=Y.test(o.compareDocumentPosition),t=b||Y.test(o.contains)?function(a,b){var c=9===a.nodeType?a.documentElement:a,d=b&&b.parentNode;return a===d||!(!d||1!==d.nodeType||!(c.contains?c.contains(d):a.compareDocumentPosition&&16&a.compareDocumentPosition(d)))}:function(a,b){if(b)while(b=b.parentNode)if(b===a)return!0;return!1},B=b?function(a,b){if(a===b)return l=!0,0;var d=!a.compareDocumentPosition-!b.compareDocumentPosition;return d?d:(d=(a.ownerDocument||a)===(b.ownerDocument||b)?a.compareDocumentPosition(b):1,1&d||!c.sortDetached&&b.compareDocumentPosition(a)===d?a===n||a.ownerDocument===v&&t(v,a)?-1:b===n||b.ownerDocument===v&&t(v,b)?1:k?I(k,a)-I(k,b):0:4&d?-1:1)}:function(a,b){if(a===b)return l=!0,0;var c,d=0,e=a.parentNode,f=b.parentNode,g=[a],h=[b];if(!e||!f)return a===n?-1:b===n?1:e?-1:f?1:k?I(k,a)-I(k,b):0;if(e===f)return la(a,b);c=a;while(c=c.parentNode)g.unshift(c);c=b;while(c=c.parentNode)h.unshift(c);while(g[d]===h[d])d++;return d?la(g[d],h[d]):g[d]===v?-1:h[d]===v?1:0},n):n},ga.matches=function(a,b){return ga(a,null,null,b)},ga.matchesSelector=function(a,b){if((a.ownerDocument||a)!==n&&m(a),b=b.replace(S,"='$1']"),c.matchesSelector&&p&&!A[b+" "]&&(!r||!r.test(b))&&(!q||!q.test(b)))try{var d=s.call(a,b);if(d||c.disconnectedMatch||a.document&&11!==a.document.nodeType)return d}catch(e){}return ga(b,n,null,[a]).length>0},ga.contains=function(a,b){return(a.ownerDocument||a)!==n&&m(a),t(a,b)},ga.attr=function(a,b){(a.ownerDocument||a)!==n&&m(a);var e=d.attrHandle[b.toLowerCase()],f=e&&C.call(d.attrHandle,b.toLowerCase())?e(a,b,!p):void 0;return void 0!==f?f:c.attributes||!p?a.getAttribute(b):(f=a.getAttributeNode(b))&&f.specified?f.value:null},ga.escape=function(a){return(a+"").replace(ba,ca)},ga.error=function(a){throw new Error("Syntax error, unrecognized expression: "+a)},ga.uniqueSort=function(a){var b,d=[],e=0,f=0;if(l=!c.detectDuplicates,k=!c.sortStable&&a.slice(0),a.sort(B),l){while(b=a[f++])b===a[f]&&(e=d.push(f));while(e--)a.splice(d[e],1)}return k=null,a},e=ga.getText=function(a){var b,c="",d=0,f=a.nodeType;if(f){if(1===f||9===f||11===f){if("string"==typeof a.textContent)return a.textContent;for(a=a.firstChild;a;a=a.nextSibling)c+=e(a)}else if(3===f||4===f)return a.nodeValue}else while(b=a[d++])c+=e(b);return c},d=ga.selectors={cacheLength:50,createPseudo:ia,match:V,attrHandle:{},find:{},relative:{">":{dir:"parentNode",first:!0}," ":{dir:"parentNode"},"+":{dir:"previousSibling",first:!0},"~":{dir:"previousSibling"}},preFilter:{ATTR:function(a){return a[1]=a[1].replace(_,aa),a[3]=(a[3]||a[4]||a[5]||"").replace(_,aa),"~="===a[2]&&(a[3]=" "+a[3]+" "),a.slice(0,4)},CHILD:function(a){return a[1]=a[1].toLowerCase(),"nth"===a[1].slice(0,3)?(a[3]||ga.error(a[0]),a[4]=+(a[4]?a[5]+(a[6]||1):2*("even"===a[3]||"odd"===a[3])),a[5]=+(a[7]+a[8]||"odd"===a[3])):a[3]&&ga.error(a[0]),a},PSEUDO:function(a){var b,c=!a[6]&&a[2];return V.CHILD.test(a[0])?null:(a[3]?a[2]=a[4]||a[5]||"":c&&T.test(c)&&(b=g(c,!0))&&(b=c.indexOf(")",c.length-b)-c.length)&&(a[0]=a[0].slice(0,b),a[2]=c.slice(0,b)),a.slice(0,3))}},filter:{TAG:function(a){var b=a.replace(_,aa).toLowerCase();return"*"===a?function(){return!0}:function(a){return a.nodeName&&a.nodeName.toLowerCase()===b}},CLASS:function(a){var b=y[a+" "];return b||(b=new RegExp("(^|"+K+")"+a+"("+K+"|$)"))&&y(a,function(a){return b.test("string"==typeof a.className&&a.className||"undefined"!=typeof a.getAttribute&&a.getAttribute("class")||"")})},ATTR:function(a,b,c){return function(d){var e=ga.attr(d,a);return null==e?"!="===b:!b||(e+="","="===b?e===c:"!="===b?e!==c:"^="===b?c&&0===e.indexOf(c):"*="===b?c&&e.indexOf(c)>-1:"$="===b?c&&e.slice(-c.length)===c:"~="===b?(" "+e.replace(O," ")+" ").indexOf(c)>-1:"|="===b&&(e===c||e.slice(0,c.length+1)===c+"-"))}},CHILD:function(a,b,c,d,e){var f="nth"!==a.slice(0,3),g="last"!==a.slice(-4),h="of-type"===b;return 1===d&&0===e?function(a){return!!a.parentNode}:function(b,c,i){var j,k,l,m,n,o,p=f!==g?"nextSibling":"previousSibling",q=b.parentNode,r=h&&b.nodeName.toLowerCase(),s=!i&&!h,t=!1;if(q){if(f){while(p){m=b;while(m=m[p])if(h?m.nodeName.toLowerCase()===r:1===m.nodeType)return!1;o=p="only"===a&&!o&&"nextSibling"}return!0}if(o=[g?q.firstChild:q.lastChild],g&&s){m=q,l=m[u]||(m[u]={}),k=l[m.uniqueID]||(l[m.uniqueID]={}),j=k[a]||[],n=j[0]===w&&j[1],t=n&&j[2],m=n&&q.childNodes[n];while(m=++n&&m&&m[p]||(t=n=0)||o.pop())if(1===m.nodeType&&++t&&m===b){k[a]=[w,n,t];break}}else if(s&&(m=b,l=m[u]||(m[u]={}),k=l[m.uniqueID]||(l[m.uniqueID]={}),j=k[a]||[],n=j[0]===w&&j[1],t=n),t===!1)while(m=++n&&m&&m[p]||(t=n=0)||o.pop())if((h?m.nodeName.toLowerCase()===r:1===m.nodeType)&&++t&&(s&&(l=m[u]||(m[u]={}),k=l[m.uniqueID]||(l[m.uniqueID]={}),k[a]=[w,t]),m===b))break;return t-=e,t===d||t%d===0&&t/d>=0}}},PSEUDO:function(a,b){var c,e=d.pseudos[a]||d.setFilters[a.toLowerCase()]||ga.error("unsupported pseudo: "+a);return e[u]?e(b):e.length>1?(c=[a,a,"",b],d.setFilters.hasOwnProperty(a.toLowerCase())?ia(function(a,c){var d,f=e(a,b),g=f.length;while(g--)d=I(a,f[g]),a[d]=!(c[d]=f[g])}):function(a){return e(a,0,c)}):e}},pseudos:{not:ia(function(a){var b=[],c=[],d=h(a.replace(P,"$1"));return d[u]?ia(function(a,b,c,e){var f,g=d(a,null,e,[]),h=a.length;while(h--)(f=g[h])&&(a[h]=!(b[h]=f))}):function(a,e,f){return b[0]=a,d(b,null,f,c),b[0]=null,!c.pop()}}),has:ia(function(a){return function(b){return ga(a,b).length>0}}),contains:ia(function(a){return a=a.replace(_,aa),function(b){return(b.textContent||b.innerText||e(b)).indexOf(a)>-1}}),lang:ia(function(a){return U.test(a||"")||ga.error("unsupported lang: "+a),a=a.replace(_,aa).toLowerCase(),function(b){var c;do if(c=p?b.lang:b.getAttribute("xml:lang")||b.getAttribute("lang"))return c=c.toLowerCase(),c===a||0===c.indexOf(a+"-");while((b=b.parentNode)&&1===b.nodeType);return!1}}),target:function(b){var c=a.location&&a.location.hash;return c&&c.slice(1)===b.id},root:function(a){return a===o},focus:function(a){return a===n.activeElement&&(!n.hasFocus||n.hasFocus())&&!!(a.type||a.href||~a.tabIndex)},enabled:oa(!1),disabled:oa(!0),checked:function(a){var b=a.nodeName.toLowerCase();return"input"===b&&!!a.checked||"option"===b&&!!a.selected},selected:function(a){return a.parentNode&&a.parentNode.selectedIndex,a.selected===!0},empty:function(a){for(a=a.firstChild;a;a=a.nextSibling)if(a.nodeType<6)return!1;return!0},parent:function(a){return!d.pseudos.empty(a)},header:function(a){return X.test(a.nodeName)},input:function(a){return W.test(a.nodeName)},button:function(a){var b=a.nodeName.toLowerCase();return"input"===b&&"button"===a.type||"button"===b},text:function(a){var b;return"input"===a.nodeName.toLowerCase()&&"text"===a.type&&(null==(b=a.getAttribute("type"))||"text"===b.toLowerCase())},first:pa(function(){return[0]}),last:pa(function(a,b){return[b-1]}),eq:pa(function(a,b,c){return[c<0?c+b:c]}),even:pa(function(a,b){for(var c=0;c<b;c+=2)a.push(c);return a}),odd:pa(function(a,b){for(var c=1;c<b;c+=2)a.push(c);return a}),lt:pa(function(a,b,c){for(var d=c<0?c+b:c;--d>=0;)a.push(d);return a}),gt:pa(function(a,b,c){for(var d=c<0?c+b:c;++d<b;)a.push(d);return a})}},d.pseudos.nth=d.pseudos.eq;for(b in{radio:!0,checkbox:!0,file:!0,password:!0,image:!0})d.pseudos[b]=ma(b);for(b in{submit:!0,reset:!0})d.pseudos[b]=na(b);function ra(){}ra.prototype=d.filters=d.pseudos,d.setFilters=new ra,g=ga.tokenize=function(a,b){var c,e,f,g,h,i,j,k=z[a+" "];if(k)return b?0:k.slice(0);h=a,i=[],j=d.preFilter;while(h){c&&!(e=Q.exec(h))||(e&&(h=h.slice(e[0].length)||h),i.push(f=[])),c=!1,(e=R.exec(h))&&(c=e.shift(),f.push({value:c,type:e[0].replace(P," ")}),h=h.slice(c.length));for(g in d.filter)!(e=V[g].exec(h))||j[g]&&!(e=j[g](e))||(c=e.shift(),f.push({value:c,type:g,matches:e}),h=h.slice(c.length));if(!c)break}return b?h.length:h?ga.error(a):z(a,i).slice(0)};function sa(a){for(var b=0,c=a.length,d="";b<c;b++)d+=a[b].value;return d}function ta(a,b,c){var d=b.dir,e=b.next,f=e||d,g=c&&"parentNode"===f,h=x++;return b.first?function(b,c,e){while(b=b[d])if(1===b.nodeType||g)return a(b,c,e)}:function(b,c,i){var j,k,l,m=[w,h];if(i){while(b=b[d])if((1===b.nodeType||g)&&a(b,c,i))return!0}else while(b=b[d])if(1===b.nodeType||g)if(l=b[u]||(b[u]={}),k=l[b.uniqueID]||(l[b.uniqueID]={}),e&&e===b.nodeName.toLowerCase())b=b[d]||b;else{if((j=k[f])&&j[0]===w&&j[1]===h)return m[2]=j[2];if(k[f]=m,m[2]=a(b,c,i))return!0}}}function ua(a){return a.length>1?function(b,c,d){var e=a.length;while(e--)if(!a[e](b,c,d))return!1;return!0}:a[0]}function va(a,b,c){for(var d=0,e=b.length;d<e;d++)ga(a,b[d],c);return c}function wa(a,b,c,d,e){for(var f,g=[],h=0,i=a.length,j=null!=b;h<i;h++)(f=a[h])&&(c&&!c(f,d,e)||(g.push(f),j&&b.push(h)));return g}function xa(a,b,c,d,e,f){return d&&!d[u]&&(d=xa(d)),e&&!e[u]&&(e=xa(e,f)),ia(function(f,g,h,i){var j,k,l,m=[],n=[],o=g.length,p=f||va(b||"*",h.nodeType?[h]:h,[]),q=!a||!f&&b?p:wa(p,m,a,h,i),r=c?e||(f?a:o||d)?[]:g:q;if(c&&c(q,r,h,i),d){j=wa(r,n),d(j,[],h,i),k=j.length;while(k--)(l=j[k])&&(r[n[k]]=!(q[n[k]]=l))}if(f){if(e||a){if(e){j=[],k=r.length;while(k--)(l=r[k])&&j.push(q[k]=l);e(null,r=[],j,i)}k=r.length;while(k--)(l=r[k])&&(j=e?I(f,l):m[k])>-1&&(f[j]=!(g[j]=l))}}else r=wa(r===g?r.splice(o,r.length):r),e?e(null,g,r,i):G.apply(g,r)})}function ya(a){for(var b,c,e,f=a.length,g=d.relative[a[0].type],h=g||d.relative[" "],i=g?1:0,k=ta(function(a){return a===b},h,!0),l=ta(function(a){return I(b,a)>-1},h,!0),m=[function(a,c,d){var e=!g&&(d||c!==j)||((b=c).nodeType?k(a,c,d):l(a,c,d));return b=null,e}];i<f;i++)if(c=d.relative[a[i].type])m=[ta(ua(m),c)];else{if(c=d.filter[a[i].type].apply(null,a[i].matches),c[u]){for(e=++i;e<f;e++)if(d.relative[a[e].type])break;return xa(i>1&&ua(m),i>1&&sa(a.slice(0,i-1).concat({value:" "===a[i-2].type?"*":""})).replace(P,"$1"),c,i<e&&ya(a.slice(i,e)),e<f&&ya(a=a.slice(e)),e<f&&sa(a))}m.push(c)}return ua(m)}function za(a,b){var c=b.length>0,e=a.length>0,f=function(f,g,h,i,k){var l,o,q,r=0,s="0",t=f&&[],u=[],v=j,x=f||e&&d.find.TAG("*",k),y=w+=null==v?1:Math.random()||.1,z=x.length;for(k&&(j=g===n||g||k);s!==z&&null!=(l=x[s]);s++){if(e&&l){o=0,g||l.ownerDocument===n||(m(l),h=!p);while(q=a[o++])if(q(l,g||n,h)){i.push(l);break}k&&(w=y)}c&&((l=!q&&l)&&r--,f&&t.push(l))}if(r+=s,c&&s!==r){o=0;while(q=b[o++])q(t,u,g,h);if(f){if(r>0)while(s--)t[s]||u[s]||(u[s]=E.call(i));u=wa(u)}G.apply(i,u),k&&!f&&u.length>0&&r+b.length>1&&ga.uniqueSort(i)}return k&&(w=y,j=v),t};return c?ia(f):f}return h=ga.compile=function(a,b){var c,d=[],e=[],f=A[a+" "];if(!f){b||(b=g(a)),c=b.length;while(c--)f=ya(b[c]),f[u]?d.push(f):e.push(f);f=A(a,za(e,d)),f.selector=a}return f},i=ga.select=function(a,b,e,f){var i,j,k,l,m,n="function"==typeof a&&a,o=!f&&g(a=n.selector||a);if(e=e||[],1===o.length){if(j=o[0]=o[0].slice(0),j.length>2&&"ID"===(k=j[0]).type&&c.getById&&9===b.nodeType&&p&&d.relative[j[1].type]){if(b=(d.find.ID(k.matches[0].replace(_,aa),b)||[])[0],!b)return e;n&&(b=b.parentNode),a=a.slice(j.shift().value.length)}i=V.needsContext.test(a)?0:j.length;while(i--){if(k=j[i],d.relative[l=k.type])break;if((m=d.find[l])&&(f=m(k.matches[0].replace(_,aa),$.test(j[0].type)&&qa(b.parentNode)||b))){if(j.splice(i,1),a=f.length&&sa(j),!a)return G.apply(e,f),e;break}}}return(n||h(a,o))(f,b,!p,e,!b||$.test(a)&&qa(b.parentNode)||b),e},c.sortStable=u.split("").sort(B).join("")===u,c.detectDuplicates=!!l,m(),c.sortDetached=ja(function(a){return 1&a.compareDocumentPosition(n.createElement("fieldset"))}),ja(function(a){return a.innerHTML="<a href='#'></a>","#"===a.firstChild.getAttribute("href")})||ka("type|href|height|width",function(a,b,c){if(!c)return a.getAttribute(b,"type"===b.toLowerCase()?1:2)}),c.attributes&&ja(function(a){return a.innerHTML="<input/>",a.firstChild.setAttribute("value",""),""===a.firstChild.getAttribute("value")})||ka("value",function(a,b,c){if(!c&&"input"===a.nodeName.toLowerCase())return a.defaultValue}),ja(function(a){return null==a.getAttribute("disabled")})||ka(J,function(a,b,c){var d;if(!c)return a[b]===!0?b.toLowerCase():(d=a.getAttributeNode(b))&&d.specified?d.value:null}),ga}(a);r.find=x,r.expr=x.selectors,r.expr[":"]=r.expr.pseudos,r.uniqueSort=r.unique=x.uniqueSort,r.text=x.getText,r.isXMLDoc=x.isXML,r.contains=x.contains,r.escapeSelector=x.escape;var y=function(a,b,c){var d=[],e=void 0!==c;while((a=a[b])&&9!==a.nodeType)if(1===a.nodeType){if(e&&r(a).is(c))break;d.push(a)}return d},z=function(a,b){for(var c=[];a;a=a.nextSibling)1===a.nodeType&&a!==b&&c.push(a);return c},A=r.expr.match.needsContext,B=/^<([a-z][^\/\0>:\x20\t\r\n\f]*)[\x20\t\r\n\f]*\/?>(?:<\/\1>|)$/i,C=/^.[^:#\[\.,]*$/;function D(a,b,c){if(r.isFunction(b))return r.grep(a,function(a,d){return!!b.call(a,d,a)!==c});if(b.nodeType)return r.grep(a,function(a){return a===b!==c});if("string"==typeof b){if(C.test(b))return r.filter(b,a,c);b=r.filter(b,a)}return r.grep(a,function(a){return i.call(b,a)>-1!==c&&1===a.nodeType})}r.filter=function(a,b,c){var d=b[0];return c&&(a=":not("+a+")"),1===b.length&&1===d.nodeType?r.find.matchesSelector(d,a)?[d]:[]:r.find.matches(a,r.grep(b,function(a){return 1===a.nodeType}))},r.fn.extend({find:function(a){var b,c,d=this.length,e=this;if("string"!=typeof a)return this.pushStack(r(a).filter(function(){for(b=0;b<d;b++)if(r.contains(e[b],this))return!0}));for(c=this.pushStack([]),b=0;b<d;b++)r.find(a,e[b],c);return d>1?r.uniqueSort(c):c},filter:function(a){return this.pushStack(D(this,a||[],!1))},not:function(a){return this.pushStack(D(this,a||[],!0))},is:function(a){return!!D(this,"string"==typeof a&&A.test(a)?r(a):a||[],!1).length}});var E,F=/^(?:\s*(<[\w\W]+>)[^>]*|#([\w-]+))$/,G=r.fn.init=function(a,b,c){var e,f;if(!a)return this;if(c=c||E,"string"==typeof a){if(e="<"===a[0]&&">"===a[a.length-1]&&a.length>=3?[null,a,null]:F.exec(a),!e||!e[1]&&b)return!b||b.jquery?(b||c).find(a):this.constructor(b).find(a);if(e[1]){if(b=b instanceof r?b[0]:b,r.merge(this,r.parseHTML(e[1],b&&b.nodeType?b.ownerDocument||b:d,!0)),B.test(e[1])&&r.isPlainObject(b))for(e in b)r.isFunction(this[e])?this[e](b[e]):this.attr(e,b[e]);return this}return f=d.getElementById(e[2]),f&&(this[0]=f,this.length=1),this}return a.nodeType?(this[0]=a,this.length=1,this):r.isFunction(a)?void 0!==c.ready?c.ready(a):a(r):r.makeArray(a,this)};G.prototype=r.fn,E=r(d);var H=/^(?:parents|prev(?:Until|All))/,I={children:!0,contents:!0,next:!0,prev:!0};r.fn.extend({has:function(a){var b=r(a,this),c=b.length;return this.filter(function(){for(var a=0;a<c;a++)if(r.contains(this,b[a]))return!0})},closest:function(a,b){var c,d=0,e=this.length,f=[],g="string"!=typeof a&&r(a);if(!A.test(a))for(;d<e;d++)for(c=this[d];c&&c!==b;c=c.parentNode)if(c.nodeType<11&&(g?g.index(c)>-1:1===c.nodeType&&r.find.matchesSelector(c,a))){f.push(c);break}return this.pushStack(f.length>1?r.uniqueSort(f):f)},index:function(a){return a?"string"==typeof a?i.call(r(a),this[0]):i.call(this,a.jquery?a[0]:a):this[0]&&this[0].parentNode?this.first().prevAll().length:-1},add:function(a,b){return this.pushStack(r.uniqueSort(r.merge(this.get(),r(a,b))))},addBack:function(a){return this.add(null==a?this.prevObject:this.prevObject.filter(a))}});function J(a,b){while((a=a[b])&&1!==a.nodeType);return a}r.each({parent:function(a){var b=a.parentNode;return b&&11!==b.nodeType?b:null},parents:function(a){return y(a,"parentNode")},parentsUntil:function(a,b,c){return y(a,"parentNode",c)},next:function(a){return J(a,"nextSibling")},prev:function(a){return J(a,"previousSibling")},nextAll:function(a){return y(a,"nextSibling")},prevAll:function(a){return y(a,"previousSibling")},nextUntil:function(a,b,c){return y(a,"nextSibling",c)},prevUntil:function(a,b,c){return y(a,"previousSibling",c)},siblings:function(a){return z((a.parentNode||{}).firstChild,a)},children:function(a){return z(a.firstChild)},contents:function(a){return a.contentDocument||r.merge([],a.childNodes)}},function(a,b){r.fn[a]=function(c,d){var e=r.map(this,b,c);return"Until"!==a.slice(-5)&&(d=c),d&&"string"==typeof d&&(e=r.filter(d,e)),this.length>1&&(I[a]||r.uniqueSort(e),H.test(a)&&e.reverse()),this.pushStack(e)}});var K=/\S+/g;function L(a){var b={};return r.each(a.match(K)||[],function(a,c){b[c]=!0}),b}r.Callbacks=function(a){a="string"==typeof a?L(a):r.extend({},a);var b,c,d,e,f=[],g=[],h=-1,i=function(){for(e=a.once,d=b=!0;g.length;h=-1){c=g.shift();while(++h<f.length)f[h].apply(c[0],c[1])===!1&&a.stopOnFalse&&(h=f.length,c=!1)}a.memory||(c=!1),b=!1,e&&(f=c?[]:"")},j={add:function(){return f&&(c&&!b&&(h=f.length-1,g.push(c)),function d(b){r.each(b,function(b,c){r.isFunction(c)?a.unique&&j.has(c)||f.push(c):c&&c.length&&"string"!==r.type(c)&&d(c)})}(arguments),c&&!b&&i()),this},remove:function(){return r.each(arguments,function(a,b){var c;while((c=r.inArray(b,f,c))>-1)f.splice(c,1),c<=h&&h--}),this},has:function(a){return a?r.inArray(a,f)>-1:f.length>0},empty:function(){return f&&(f=[]),this},disable:function(){return e=g=[],f=c="",this},disabled:function(){return!f},lock:function(){return e=g=[],c||b||(f=c=""),this},locked:function(){return!!e},fireWith:function(a,c){return e||(c=c||[],c=[a,c.slice?c.slice():c],g.push(c),b||i()),this},fire:function(){return j.fireWith(this,arguments),this},fired:function(){return!!d}};return j};function M(a){return a}function N(a){throw a}function O(a,b,c){var d;try{a&&r.isFunction(d=a.promise)?d.call(a).done(b).fail(c):a&&r.isFunction(d=a.then)?d.call(a,b,c):b.call(void 0,a)}catch(a){c.call(void 0,a)}}r.extend({Deferred:function(b){var c=[["notify","progress",r.Callbacks("memory"),r.Callbacks("memory"),2],["resolve","done",r.Callbacks("once memory"),r.Callbacks("once memory"),0,"resolved"],["reject","fail",r.Callbacks("once memory"),r.Callbacks("once memory"),1,"rejected"]],d="pending",e={state:function(){return d},always:function(){return f.done(arguments).fail(arguments),this},"catch":function(a){return e.then(null,a)},pipe:function(){var a=arguments;return r.Deferred(function(b){r.each(c,function(c,d){var e=r.isFunction(a[d[4]])&&a[d[4]];f[d[1]](function(){var a=e&&e.apply(this,arguments);a&&r.isFunction(a.promise)?a.promise().progress(b.notify).done(b.resolve).fail(b.reject):b[d[0]+"With"](this,e?[a]:arguments)})}),a=null}).promise()},then:function(b,d,e){var f=0;function g(b,c,d,e){return function(){var h=this,i=arguments,j=function(){var a,j;if(!(b<f)){if(a=d.apply(h,i),a===c.promise())throw new TypeError("Thenable self-resolution");j=a&&("object"==typeof a||"function"==typeof a)&&a.then,r.isFunction(j)?e?j.call(a,g(f,c,M,e),g(f,c,N,e)):(f++,j.call(a,g(f,c,M,e),g(f,c,N,e),g(f,c,M,c.notifyWith))):(d!==M&&(h=void 0,i=[a]),(e||c.resolveWith)(h,i))}},k=e?j:function(){try{j()}catch(a){r.Deferred.exceptionHook&&r.Deferred.exceptionHook(a,k.stackTrace),b+1>=f&&(d!==N&&(h=void 0,i=[a]),c.rejectWith(h,i))}};b?k():(r.Deferred.getStackHook&&(k.stackTrace=r.Deferred.getStackHook()),a.setTimeout(k))}}return r.Deferred(function(a){c[0][3].add(g(0,a,r.isFunction(e)?e:M,a.notifyWith)),c[1][3].add(g(0,a,r.isFunction(b)?b:M)),c[2][3].add(g(0,a,r.isFunction(d)?d:N))}).promise()},promise:function(a){return null!=a?r.extend(a,e):e}},f={};return r.each(c,function(a,b){var g=b[2],h=b[5];e[b[1]]=g.add,h&&g.add(function(){d=h},c[3-a][2].disable,c[0][2].lock),g.add(b[3].fire),f[b[0]]=function(){return f[b[0]+"With"](this===f?void 0:this,arguments),this},f[b[0]+"With"]=g.fireWith}),e.promise(f),b&&b.call(f,f),f},when:function(a){var b=arguments.length,c=b,d=Array(c),e=f.call(arguments),g=r.Deferred(),h=function(a){return function(c){d[a]=this,e[a]=arguments.length>1?f.call(arguments):c,--b||g.resolveWith(d,e)}};if(b<=1&&(O(a,g.done(h(c)).resolve,g.reject),"pending"===g.state()||r.isFunction(e[c]&&e[c].then)))return g.then();while(c--)O(e[c],h(c),g.reject);return g.promise()}});var P=/^(Eval|Internal|Range|Reference|Syntax|Type|URI)Error$/;r.Deferred.exceptionHook=function(b,c){a.console&&a.console.warn&&b&&P.test(b.name)&&a.console.warn("jQuery.Deferred exception: "+b.message,b.stack,c)},r.readyException=function(b){a.setTimeout(function(){throw b})};var Q=r.Deferred();r.fn.ready=function(a){return Q.then(a)["catch"](function(a){r.readyException(a)}),this},r.extend({isReady:!1,readyWait:1,holdReady:function(a){a?r.readyWait++:r.ready(!0)},ready:function(a){(a===!0?--r.readyWait:r.isReady)||(r.isReady=!0,a!==!0&&--r.readyWait>0||Q.resolveWith(d,[r]))}}),r.ready.then=Q.then;function R(){d.removeEventListener("DOMContentLoaded",R),a.removeEventListener("load",R),r.ready()}"complete"===d.readyState||"loading"!==d.readyState&&!d.documentElement.doScroll?a.setTimeout(r.ready):(d.addEventListener("DOMContentLoaded",R),a.addEventListener("load",R));var S=function(a,b,c,d,e,f,g){var h=0,i=a.length,j=null==c;if("object"===r.type(c)){e=!0;for(h in c)S(a,b,h,c[h],!0,f,g)}else if(void 0!==d&&(e=!0, | |
| 2 | r.isFunction(d)||(g=!0),j&&(g?(b.call(a,d),b=null):(j=b,b=function(a,b,c){return j.call(r(a),c)})),b))for(;h<i;h++)b(a[h],c,g?d:d.call(a[h],h,b(a[h],c)));return e?a:j?b.call(a):i?b(a[0],c):f},T=function(a){return 1===a.nodeType||9===a.nodeType||!+a.nodeType};function U(){this.expando=r.expando+U.uid++}U.uid=1,U.prototype={cache:function(a){var b=a[this.expando];return b||(b={},T(a)&&(a.nodeType?a[this.expando]=b:Object.defineProperty(a,this.expando,{value:b,configurable:!0}))),b},set:function(a,b,c){var d,e=this.cache(a);if("string"==typeof b)e[r.camelCase(b)]=c;else for(d in b)e[r.camelCase(d)]=b[d];return e},get:function(a,b){return void 0===b?this.cache(a):a[this.expando]&&a[this.expando][r.camelCase(b)]},access:function(a,b,c){return void 0===b||b&&"string"==typeof b&&void 0===c?this.get(a,b):(this.set(a,b,c),void 0!==c?c:b)},remove:function(a,b){var c,d=a[this.expando];if(void 0!==d){if(void 0!==b){r.isArray(b)?b=b.map(r.camelCase):(b=r.camelCase(b),b=b in d?[b]:b.match(K)||[]),c=b.length;while(c--)delete d[b[c]]}(void 0===b||r.isEmptyObject(d))&&(a.nodeType?a[this.expando]=void 0:delete a[this.expando])}},hasData:function(a){var b=a[this.expando];return void 0!==b&&!r.isEmptyObject(b)}};var V=new U,W=new U,X=/^(?:\{[\w\W]*\}|\[[\w\W]*\])$/,Y=/[A-Z]/g;function Z(a,b,c){var d;if(void 0===c&&1===a.nodeType)if(d="data-"+b.replace(Y,"-$&").toLowerCase(),c=a.getAttribute(d),"string"==typeof c){try{c="true"===c||"false"!==c&&("null"===c?null:+c+""===c?+c:X.test(c)?JSON.parse(c):c)}catch(e){}W.set(a,b,c)}else c=void 0;return c}r.extend({hasData:function(a){return W.hasData(a)||V.hasData(a)},data:function(a,b,c){return W.access(a,b,c)},removeData:function(a,b){W.remove(a,b)},_data:function(a,b,c){return V.access(a,b,c)},_removeData:function(a,b){V.remove(a,b)}}),r.fn.extend({data:function(a,b){var c,d,e,f=this[0],g=f&&f.attributes;if(void 0===a){if(this.length&&(e=W.get(f),1===f.nodeType&&!V.get(f,"hasDataAttrs"))){c=g.length;while(c--)g[c]&&(d=g[c].name,0===d.indexOf("data-")&&(d=r.camelCase(d.slice(5)),Z(f,d,e[d])));V.set(f,"hasDataAttrs",!0)}return e}return"object"==typeof a?this.each(function(){W.set(this,a)}):S(this,function(b){var c;if(f&&void 0===b){if(c=W.get(f,a),void 0!==c)return c;if(c=Z(f,a),void 0!==c)return c}else this.each(function(){W.set(this,a,b)})},null,b,arguments.length>1,null,!0)},removeData:function(a){return this.each(function(){W.remove(this,a)})}}),r.extend({queue:function(a,b,c){var d;if(a)return b=(b||"fx")+"queue",d=V.get(a,b),c&&(!d||r.isArray(c)?d=V.access(a,b,r.makeArray(c)):d.push(c)),d||[]},dequeue:function(a,b){b=b||"fx";var c=r.queue(a,b),d=c.length,e=c.shift(),f=r._queueHooks(a,b),g=function(){r.dequeue(a,b)};"inprogress"===e&&(e=c.shift(),d--),e&&("fx"===b&&c.unshift("inprogress"),delete f.stop,e.call(a,g,f)),!d&&f&&f.empty.fire()},_queueHooks:function(a,b){var c=b+"queueHooks";return V.get(a,c)||V.access(a,c,{empty:r.Callbacks("once memory").add(function(){V.remove(a,[b+"queue",c])})})}}),r.fn.extend({queue:function(a,b){var c=2;return"string"!=typeof a&&(b=a,a="fx",c--),arguments.length<c?r.queue(this[0],a):void 0===b?this:this.each(function(){var c=r.queue(this,a,b);r._queueHooks(this,a),"fx"===a&&"inprogress"!==c[0]&&r.dequeue(this,a)})},dequeue:function(a){return this.each(function(){r.dequeue(this,a)})},clearQueue:function(a){return this.queue(a||"fx",[])},promise:function(a,b){var c,d=1,e=r.Deferred(),f=this,g=this.length,h=function(){--d||e.resolveWith(f,[f])};"string"!=typeof a&&(b=a,a=void 0),a=a||"fx";while(g--)c=V.get(f[g],a+"queueHooks"),c&&c.empty&&(d++,c.empty.add(h));return h(),e.promise(b)}});var $=/[+-]?(?:\d*\.|)\d+(?:[eE][+-]?\d+|)/.source,_=new RegExp("^(?:([+-])=|)("+$+")([a-z%]*)$","i"),aa=["Top","Right","Bottom","Left"],ba=function(a,b){return a=b||a,"none"===a.style.display||""===a.style.display&&r.contains(a.ownerDocument,a)&&"none"===r.css(a,"display")},ca=function(a,b,c,d){var e,f,g={};for(f in b)g[f]=a.style[f],a.style[f]=b[f];e=c.apply(a,d||[]);for(f in b)a.style[f]=g[f];return e};function da(a,b,c,d){var e,f=1,g=20,h=d?function(){return d.cur()}:function(){return r.css(a,b,"")},i=h(),j=c&&c[3]||(r.cssNumber[b]?"":"px"),k=(r.cssNumber[b]||"px"!==j&&+i)&&_.exec(r.css(a,b));if(k&&k[3]!==j){j=j||k[3],c=c||[],k=+i||1;do f=f||".5",k/=f,r.style(a,b,k+j);while(f!==(f=h()/i)&&1!==f&&--g)}return c&&(k=+k||+i||0,e=c[1]?k+(c[1]+1)*c[2]:+c[2],d&&(d.unit=j,d.start=k,d.end=e)),e}var ea={};function fa(a){var b,c=a.ownerDocument,d=a.nodeName,e=ea[d];return e?e:(b=c.body.appendChild(c.createElement(d)),e=r.css(b,"display"),b.parentNode.removeChild(b),"none"===e&&(e="block"),ea[d]=e,e)}function ga(a,b){for(var c,d,e=[],f=0,g=a.length;f<g;f++)d=a[f],d.style&&(c=d.style.display,b?("none"===c&&(e[f]=V.get(d,"display")||null,e[f]||(d.style.display="")),""===d.style.display&&ba(d)&&(e[f]=fa(d))):"none"!==c&&(e[f]="none",V.set(d,"display",c)));for(f=0;f<g;f++)null!=e[f]&&(a[f].style.display=e[f]);return a}r.fn.extend({show:function(){return ga(this,!0)},hide:function(){return ga(this)},toggle:function(a){return"boolean"==typeof a?a?this.show():this.hide():this.each(function(){ba(this)?r(this).show():r(this).hide()})}});var ha=/^(?:checkbox|radio)$/i,ia=/<([a-z][^\/\0>\x20\t\r\n\f]+)/i,ja=/^$|\/(?:java|ecma)script/i,ka={option:[1,"<select multiple='multiple'>","</select>"],thead:[1,"<table>","</table>"],col:[2,"<table><colgroup>","</colgroup></table>"],tr:[2,"<table><tbody>","</tbody></table>"],td:[3,"<table><tbody><tr>","</tr></tbody></table>"],_default:[0,"",""]};ka.optgroup=ka.option,ka.tbody=ka.tfoot=ka.colgroup=ka.caption=ka.thead,ka.th=ka.td;function la(a,b){var c="undefined"!=typeof a.getElementsByTagName?a.getElementsByTagName(b||"*"):"undefined"!=typeof a.querySelectorAll?a.querySelectorAll(b||"*"):[];return void 0===b||b&&r.nodeName(a,b)?r.merge([a],c):c}function ma(a,b){for(var c=0,d=a.length;c<d;c++)V.set(a[c],"globalEval",!b||V.get(b[c],"globalEval"))}var na=/<|&#?\w+;/;function oa(a,b,c,d,e){for(var f,g,h,i,j,k,l=b.createDocumentFragment(),m=[],n=0,o=a.length;n<o;n++)if(f=a[n],f||0===f)if("object"===r.type(f))r.merge(m,f.nodeType?[f]:f);else if(na.test(f)){g=g||l.appendChild(b.createElement("div")),h=(ia.exec(f)||["",""])[1].toLowerCase(),i=ka[h]||ka._default,g.innerHTML=i[1]+r.htmlPrefilter(f)+i[2],k=i[0];while(k--)g=g.lastChild;r.merge(m,g.childNodes),g=l.firstChild,g.textContent=""}else m.push(b.createTextNode(f));l.textContent="",n=0;while(f=m[n++])if(d&&r.inArray(f,d)>-1)e&&e.push(f);else if(j=r.contains(f.ownerDocument,f),g=la(l.appendChild(f),"script"),j&&ma(g),c){k=0;while(f=g[k++])ja.test(f.type||"")&&c.push(f)}return l}!function(){var a=d.createDocumentFragment(),b=a.appendChild(d.createElement("div")),c=d.createElement("input");c.setAttribute("type","radio"),c.setAttribute("checked","checked"),c.setAttribute("name","t"),b.appendChild(c),o.checkClone=b.cloneNode(!0).cloneNode(!0).lastChild.checked,b.innerHTML="<textarea>x</textarea>",o.noCloneChecked=!!b.cloneNode(!0).lastChild.defaultValue}();var pa=d.documentElement,qa=/^key/,ra=/^(?:mouse|pointer|contextmenu|drag|drop)|click/,sa=/^([^.]*)(?:\.(.+)|)/;function ta(){return!0}function ua(){return!1}function va(){try{return d.activeElement}catch(a){}}function wa(a,b,c,d,e,f){var g,h;if("object"==typeof b){"string"!=typeof c&&(d=d||c,c=void 0);for(h in b)wa(a,h,c,d,b[h],f);return a}if(null==d&&null==e?(e=c,d=c=void 0):null==e&&("string"==typeof c?(e=d,d=void 0):(e=d,d=c,c=void 0)),e===!1)e=ua;else if(!e)return a;return 1===f&&(g=e,e=function(a){return r().off(a),g.apply(this,arguments)},e.guid=g.guid||(g.guid=r.guid++)),a.each(function(){r.event.add(this,b,e,d,c)})}r.event={global:{},add:function(a,b,c,d,e){var f,g,h,i,j,k,l,m,n,o,p,q=V.get(a);if(q){c.handler&&(f=c,c=f.handler,e=f.selector),e&&r.find.matchesSelector(pa,e),c.guid||(c.guid=r.guid++),(i=q.events)||(i=q.events={}),(g=q.handle)||(g=q.handle=function(b){return"undefined"!=typeof r&&r.event.triggered!==b.type?r.event.dispatch.apply(a,arguments):void 0}),b=(b||"").match(K)||[""],j=b.length;while(j--)h=sa.exec(b[j])||[],n=p=h[1],o=(h[2]||"").split(".").sort(),n&&(l=r.event.special[n]||{},n=(e?l.delegateType:l.bindType)||n,l=r.event.special[n]||{},k=r.extend({type:n,origType:p,data:d,handler:c,guid:c.guid,selector:e,needsContext:e&&r.expr.match.needsContext.test(e),namespace:o.join(".")},f),(m=i[n])||(m=i[n]=[],m.delegateCount=0,l.setup&&l.setup.call(a,d,o,g)!==!1||a.addEventListener&&a.addEventListener(n,g)),l.add&&(l.add.call(a,k),k.handler.guid||(k.handler.guid=c.guid)),e?m.splice(m.delegateCount++,0,k):m.push(k),r.event.global[n]=!0)}},remove:function(a,b,c,d,e){var f,g,h,i,j,k,l,m,n,o,p,q=V.hasData(a)&&V.get(a);if(q&&(i=q.events)){b=(b||"").match(K)||[""],j=b.length;while(j--)if(h=sa.exec(b[j])||[],n=p=h[1],o=(h[2]||"").split(".").sort(),n){l=r.event.special[n]||{},n=(d?l.delegateType:l.bindType)||n,m=i[n]||[],h=h[2]&&new RegExp("(^|\\.)"+o.join("\\.(?:.*\\.|)")+"(\\.|$)"),g=f=m.length;while(f--)k=m[f],!e&&p!==k.origType||c&&c.guid!==k.guid||h&&!h.test(k.namespace)||d&&d!==k.selector&&("**"!==d||!k.selector)||(m.splice(f,1),k.selector&&m.delegateCount--,l.remove&&l.remove.call(a,k));g&&!m.length&&(l.teardown&&l.teardown.call(a,o,q.handle)!==!1||r.removeEvent(a,n,q.handle),delete i[n])}else for(n in i)r.event.remove(a,n+b[j],c,d,!0);r.isEmptyObject(i)&&V.remove(a,"handle events")}},dispatch:function(a){var b=r.event.fix(a),c,d,e,f,g,h,i=new Array(arguments.length),j=(V.get(this,"events")||{})[b.type]||[],k=r.event.special[b.type]||{};for(i[0]=b,c=1;c<arguments.length;c++)i[c]=arguments[c];if(b.delegateTarget=this,!k.preDispatch||k.preDispatch.call(this,b)!==!1){h=r.event.handlers.call(this,b,j),c=0;while((f=h[c++])&&!b.isPropagationStopped()){b.currentTarget=f.elem,d=0;while((g=f.handlers[d++])&&!b.isImmediatePropagationStopped())b.rnamespace&&!b.rnamespace.test(g.namespace)||(b.handleObj=g,b.data=g.data,e=((r.event.special[g.origType]||{}).handle||g.handler).apply(f.elem,i),void 0!==e&&(b.result=e)===!1&&(b.preventDefault(),b.stopPropagation()))}return k.postDispatch&&k.postDispatch.call(this,b),b.result}},handlers:function(a,b){var c,d,e,f,g=[],h=b.delegateCount,i=a.target;if(h&&i.nodeType&&("click"!==a.type||isNaN(a.button)||a.button<1))for(;i!==this;i=i.parentNode||this)if(1===i.nodeType&&(i.disabled!==!0||"click"!==a.type)){for(d=[],c=0;c<h;c++)f=b[c],e=f.selector+" ",void 0===d[e]&&(d[e]=f.needsContext?r(e,this).index(i)>-1:r.find(e,this,null,[i]).length),d[e]&&d.push(f);d.length&&g.push({elem:i,handlers:d})}return h<b.length&&g.push({elem:this,handlers:b.slice(h)}),g},addProp:function(a,b){Object.defineProperty(r.Event.prototype,a,{enumerable:!0,configurable:!0,get:r.isFunction(b)?function(){if(this.originalEvent)return b(this.originalEvent)}:function(){if(this.originalEvent)return this.originalEvent[a]},set:function(b){Object.defineProperty(this,a,{enumerable:!0,configurable:!0,writable:!0,value:b})}})},fix:function(a){return a[r.expando]?a:new r.Event(a)},special:{load:{noBubble:!0},focus:{trigger:function(){if(this!==va()&&this.focus)return this.focus(),!1},delegateType:"focusin"},blur:{trigger:function(){if(this===va()&&this.blur)return this.blur(),!1},delegateType:"focusout"},click:{trigger:function(){if("checkbox"===this.type&&this.click&&r.nodeName(this,"input"))return this.click(),!1},_default:function(a){return r.nodeName(a.target,"a")}},beforeunload:{postDispatch:function(a){void 0!==a.result&&a.originalEvent&&(a.originalEvent.returnValue=a.result)}}}},r.removeEvent=function(a,b,c){a.removeEventListener&&a.removeEventListener(b,c)},r.Event=function(a,b){return this instanceof r.Event?(a&&a.type?(this.originalEvent=a,this.type=a.type,this.isDefaultPrevented=a.defaultPrevented||void 0===a.defaultPrevented&&a.returnValue===!1?ta:ua,this.target=a.target&&3===a.target.nodeType?a.target.parentNode:a.target,this.currentTarget=a.currentTarget,this.relatedTarget=a.relatedTarget):this.type=a,b&&r.extend(this,b),this.timeStamp=a&&a.timeStamp||r.now(),void(this[r.expando]=!0)):new r.Event(a,b)},r.Event.prototype={constructor:r.Event,isDefaultPrevented:ua,isPropagationStopped:ua,isImmediatePropagationStopped:ua,isSimulated:!1,preventDefault:function(){var a=this.originalEvent;this.isDefaultPrevented=ta,a&&!this.isSimulated&&a.preventDefault()},stopPropagation:function(){var a=this.originalEvent;this.isPropagationStopped=ta,a&&!this.isSimulated&&a.stopPropagation()},stopImmediatePropagation:function(){var a=this.originalEvent;this.isImmediatePropagationStopped=ta,a&&!this.isSimulated&&a.stopImmediatePropagation(),this.stopPropagation()}},r.each({altKey:!0,bubbles:!0,cancelable:!0,changedTouches:!0,ctrlKey:!0,detail:!0,eventPhase:!0,metaKey:!0,pageX:!0,pageY:!0,shiftKey:!0,view:!0,"char":!0,charCode:!0,key:!0,keyCode:!0,button:!0,buttons:!0,clientX:!0,clientY:!0,offsetX:!0,offsetY:!0,pointerId:!0,pointerType:!0,screenX:!0,screenY:!0,targetTouches:!0,toElement:!0,touches:!0,which:function(a){var b=a.button;return null==a.which&&qa.test(a.type)?null!=a.charCode?a.charCode:a.keyCode:!a.which&&void 0!==b&&ra.test(a.type)?1&b?1:2&b?3:4&b?2:0:a.which}},r.event.addProp),r.each({mouseenter:"mouseover",mouseleave:"mouseout",pointerenter:"pointerover",pointerleave:"pointerout"},function(a,b){r.event.special[a]={delegateType:b,bindType:b,handle:function(a){var c,d=this,e=a.relatedTarget,f=a.handleObj;return e&&(e===d||r.contains(d,e))||(a.type=f.origType,c=f.handler.apply(this,arguments),a.type=b),c}}}),r.fn.extend({on:function(a,b,c,d){return wa(this,a,b,c,d)},one:function(a,b,c,d){return wa(this,a,b,c,d,1)},off:function(a,b,c){var d,e;if(a&&a.preventDefault&&a.handleObj)return d=a.handleObj,r(a.delegateTarget).off(d.namespace?d.origType+"."+d.namespace:d.origType,d.selector,d.handler),this;if("object"==typeof a){for(e in a)this.off(e,b,a[e]);return this}return b!==!1&&"function"!=typeof b||(c=b,b=void 0),c===!1&&(c=ua),this.each(function(){r.event.remove(this,a,c,b)})}});var xa=/<(?!area|br|col|embed|hr|img|input|link|meta|param)(([a-z][^\/\0>\x20\t\r\n\f]*)[^>]*)\/>/gi,ya=/<script|<style|<link/i,za=/checked\s*(?:[^=]|=\s*.checked.)/i,Aa=/^true\/(.*)/,Ba=/^\s*<!(?:\[CDATA\[|--)|(?:\]\]|--)>\s*$/g;function Ca(a,b){return r.nodeName(a,"table")&&r.nodeName(11!==b.nodeType?b:b.firstChild,"tr")?a.getElementsByTagName("tbody")[0]||a:a}function Da(a){return a.type=(null!==a.getAttribute("type"))+"/"+a.type,a}function Ea(a){var b=Aa.exec(a.type);return b?a.type=b[1]:a.removeAttribute("type"),a}function Fa(a,b){var c,d,e,f,g,h,i,j;if(1===b.nodeType){if(V.hasData(a)&&(f=V.access(a),g=V.set(b,f),j=f.events)){delete g.handle,g.events={};for(e in j)for(c=0,d=j[e].length;c<d;c++)r.event.add(b,e,j[e][c])}W.hasData(a)&&(h=W.access(a),i=r.extend({},h),W.set(b,i))}}function Ga(a,b){var c=b.nodeName.toLowerCase();"input"===c&&ha.test(a.type)?b.checked=a.checked:"input"!==c&&"textarea"!==c||(b.defaultValue=a.defaultValue)}function Ha(a,b,c,d){b=g.apply([],b);var e,f,h,i,j,k,l=0,m=a.length,n=m-1,q=b[0],s=r.isFunction(q);if(s||m>1&&"string"==typeof q&&!o.checkClone&&za.test(q))return a.each(function(e){var f=a.eq(e);s&&(b[0]=q.call(this,e,f.html())),Ha(f,b,c,d)});if(m&&(e=oa(b,a[0].ownerDocument,!1,a,d),f=e.firstChild,1===e.childNodes.length&&(e=f),f||d)){for(h=r.map(la(e,"script"),Da),i=h.length;l<m;l++)j=e,l!==n&&(j=r.clone(j,!0,!0),i&&r.merge(h,la(j,"script"))),c.call(a[l],j,l);if(i)for(k=h[h.length-1].ownerDocument,r.map(h,Ea),l=0;l<i;l++)j=h[l],ja.test(j.type||"")&&!V.access(j,"globalEval")&&r.contains(k,j)&&(j.src?r._evalUrl&&r._evalUrl(j.src):p(j.textContent.replace(Ba,""),k))}return a}function Ia(a,b,c){for(var d,e=b?r.filter(b,a):a,f=0;null!=(d=e[f]);f++)c||1!==d.nodeType||r.cleanData(la(d)),d.parentNode&&(c&&r.contains(d.ownerDocument,d)&&ma(la(d,"script")),d.parentNode.removeChild(d));return a}r.extend({htmlPrefilter:function(a){return a.replace(xa,"<$1></$2>")},clone:function(a,b,c){var d,e,f,g,h=a.cloneNode(!0),i=r.contains(a.ownerDocument,a);if(!(o.noCloneChecked||1!==a.nodeType&&11!==a.nodeType||r.isXMLDoc(a)))for(g=la(h),f=la(a),d=0,e=f.length;d<e;d++)Ga(f[d],g[d]);if(b)if(c)for(f=f||la(a),g=g||la(h),d=0,e=f.length;d<e;d++)Fa(f[d],g[d]);else Fa(a,h);return g=la(h,"script"),g.length>0&&ma(g,!i&&la(a,"script")),h},cleanData:function(a){for(var b,c,d,e=r.event.special,f=0;void 0!==(c=a[f]);f++)if(T(c)){if(b=c[V.expando]){if(b.events)for(d in b.events)e[d]?r.event.remove(c,d):r.removeEvent(c,d,b.handle);c[V.expando]=void 0}c[W.expando]&&(c[W.expando]=void 0)}}}),r.fn.extend({detach:function(a){return Ia(this,a,!0)},remove:function(a){return Ia(this,a)},text:function(a){return S(this,function(a){return void 0===a?r.text(this):this.empty().each(function(){1!==this.nodeType&&11!==this.nodeType&&9!==this.nodeType||(this.textContent=a)})},null,a,arguments.length)},append:function(){return Ha(this,arguments,function(a){if(1===this.nodeType||11===this.nodeType||9===this.nodeType){var b=Ca(this,a);b.appendChild(a)}})},prepend:function(){return Ha(this,arguments,function(a){if(1===this.nodeType||11===this.nodeType||9===this.nodeType){var b=Ca(this,a);b.insertBefore(a,b.firstChild)}})},before:function(){return Ha(this,arguments,function(a){this.parentNode&&this.parentNode.insertBefore(a,this)})},after:function(){return Ha(this,arguments,function(a){this.parentNode&&this.parentNode.insertBefore(a,this.nextSibling)})},empty:function(){for(var a,b=0;null!=(a=this[b]);b++)1===a.nodeType&&(r.cleanData(la(a,!1)),a.textContent="");return this},clone:function(a,b){return a=null!=a&&a,b=null==b?a:b,this.map(function(){return r.clone(this,a,b)})},html:function(a){return S(this,function(a){var b=this[0]||{},c=0,d=this.length;if(void 0===a&&1===b.nodeType)return b.innerHTML;if("string"==typeof a&&!ya.test(a)&&!ka[(ia.exec(a)||["",""])[1].toLowerCase()]){a=r.htmlPrefilter(a);try{for(;c<d;c++)b=this[c]||{},1===b.nodeType&&(r.cleanData(la(b,!1)),b.innerHTML=a);b=0}catch(e){}}b&&this.empty().append(a)},null,a,arguments.length)},replaceWith:function(){var a=[];return Ha(this,arguments,function(b){var c=this.parentNode;r.inArray(this,a)<0&&(r.cleanData(la(this)),c&&c.replaceChild(b,this))},a)}}),r.each({appendTo:"append",prependTo:"prepend",insertBefore:"before",insertAfter:"after",replaceAll:"replaceWith"},function(a,b){r.fn[a]=function(a){for(var c,d=[],e=r(a),f=e.length-1,g=0;g<=f;g++)c=g===f?this:this.clone(!0),r(e[g])[b](c),h.apply(d,c.get());return this.pushStack(d)}});var Ja=/^margin/,Ka=new RegExp("^("+$+")(?!px)[a-z%]+$","i"),La=function(b){var c=b.ownerDocument.defaultView;return c&&c.opener||(c=a),c.getComputedStyle(b)};!function(){function b(){if(i){i.style.cssText="box-sizing:border-box;position:relative;display:block;margin:auto;border:1px;padding:1px;top:1%;width:50%",i.innerHTML="",pa.appendChild(h);var b=a.getComputedStyle(i);c="1%"!==b.top,g="2px"===b.marginLeft,e="4px"===b.width,i.style.marginRight="50%",f="4px"===b.marginRight,pa.removeChild(h),i=null}}var c,e,f,g,h=d.createElement("div"),i=d.createElement("div");i.style&&(i.style.backgroundClip="content-box",i.cloneNode(!0).style.backgroundClip="",o.clearCloneStyle="content-box"===i.style.backgroundClip,h.style.cssText="border:0;width:8px;height:0;top:0;left:-9999px;padding:0;margin-top:1px;position:absolute",h.appendChild(i),r.extend(o,{pixelPosition:function(){return b(),c},boxSizingReliable:function(){return b(),e},pixelMarginRight:function(){return b(),f},reliableMarginLeft:function(){return b(),g}}))}();function Ma(a,b,c){var d,e,f,g,h=a.style;return c=c||La(a),c&&(g=c.getPropertyValue(b)||c[b],""!==g||r.contains(a.ownerDocument,a)||(g=r.style(a,b)),!o.pixelMarginRight()&&Ka.test(g)&&Ja.test(b)&&(d=h.width,e=h.minWidth,f=h.maxWidth,h.minWidth=h.maxWidth=h.width=g,g=c.width,h.width=d,h.minWidth=e,h.maxWidth=f)),void 0!==g?g+"":g}function Na(a,b){return{get:function(){return a()?void delete this.get:(this.get=b).apply(this,arguments)}}}var Oa=/^(none|table(?!-c[ea]).+)/,Pa={position:"absolute",visibility:"hidden",display:"block"},Qa={letterSpacing:"0",fontWeight:"400"},Ra=["Webkit","Moz","ms"],Sa=d.createElement("div").style;function Ta(a){if(a in Sa)return a;var b=a[0].toUpperCase()+a.slice(1),c=Ra.length;while(c--)if(a=Ra[c]+b,a in Sa)return a}function Ua(a,b,c){var d=_.exec(b);return d?Math.max(0,d[2]-(c||0))+(d[3]||"px"):b}function Va(a,b,c,d,e){for(var f=c===(d?"border":"content")?4:"width"===b?1:0,g=0;f<4;f+=2)"margin"===c&&(g+=r.css(a,c+aa[f],!0,e)),d?("content"===c&&(g-=r.css(a,"padding"+aa[f],!0,e)),"margin"!==c&&(g-=r.css(a,"border"+aa[f]+"Width",!0,e))):(g+=r.css(a,"padding"+aa[f],!0,e),"padding"!==c&&(g+=r.css(a,"border"+aa[f]+"Width",!0,e)));return g}function Wa(a,b,c){var d,e=!0,f=La(a),g="border-box"===r.css(a,"boxSizing",!1,f);if(a.getClientRects().length&&(d=a.getBoundingClientRect()[b]),d<=0||null==d){if(d=Ma(a,b,f),(d<0||null==d)&&(d=a.style[b]),Ka.test(d))return d;e=g&&(o.boxSizingReliable()||d===a.style[b]),d=parseFloat(d)||0}return d+Va(a,b,c||(g?"border":"content"),e,f)+"px"}r.extend({cssHooks:{opacity:{get:function(a,b){if(b){var c=Ma(a,"opacity");return""===c?"1":c}}}},cssNumber:{animationIterationCount:!0,columnCount:!0,fillOpacity:!0,flexGrow:!0,flexShrink:!0,fontWeight:!0,lineHeight:!0,opacity:!0,order:!0,orphans:!0,widows:!0,zIndex:!0,zoom:!0},cssProps:{"float":"cssFloat"},style:function(a,b,c,d){if(a&&3!==a.nodeType&&8!==a.nodeType&&a.style){var e,f,g,h=r.camelCase(b),i=a.style;return b=r.cssProps[h]||(r.cssProps[h]=Ta(h)||h),g=r.cssHooks[b]||r.cssHooks[h],void 0===c?g&&"get"in g&&void 0!==(e=g.get(a,!1,d))?e:i[b]:(f=typeof c,"string"===f&&(e=_.exec(c))&&e[1]&&(c=da(a,b,e),f="number"),null!=c&&c===c&&("number"===f&&(c+=e&&e[3]||(r.cssNumber[h]?"":"px")),o.clearCloneStyle||""!==c||0!==b.indexOf("background")||(i[b]="inherit"),g&&"set"in g&&void 0===(c=g.set(a,c,d))||(i[b]=c)),void 0)}},css:function(a,b,c,d){var e,f,g,h=r.camelCase(b);return b=r.cssProps[h]||(r.cssProps[h]=Ta(h)||h),g=r.cssHooks[b]||r.cssHooks[h],g&&"get"in g&&(e=g.get(a,!0,c)),void 0===e&&(e=Ma(a,b,d)),"normal"===e&&b in Qa&&(e=Qa[b]),""===c||c?(f=parseFloat(e),c===!0||isFinite(f)?f||0:e):e}}),r.each(["height","width"],function(a,b){r.cssHooks[b]={get:function(a,c,d){if(c)return!Oa.test(r.css(a,"display"))||a.getClientRects().length&&a.getBoundingClientRect().width?Wa(a,b,d):ca(a,Pa,function(){return Wa(a,b,d)})},set:function(a,c,d){var e,f=d&&La(a),g=d&&Va(a,b,d,"border-box"===r.css(a,"boxSizing",!1,f),f);return g&&(e=_.exec(c))&&"px"!==(e[3]||"px")&&(a.style[b]=c,c=r.css(a,b)),Ua(a,c,g)}}}),r.cssHooks.marginLeft=Na(o.reliableMarginLeft,function(a,b){if(b)return(parseFloat(Ma(a,"marginLeft"))||a.getBoundingClientRect().left-ca(a,{marginLeft:0},function(){return a.getBoundingClientRect().left}))+"px"}),r.each({margin:"",padding:"",border:"Width"},function(a,b){r.cssHooks[a+b]={expand:function(c){for(var d=0,e={},f="string"==typeof c?c.split(" "):[c];d<4;d++)e[a+aa[d]+b]=f[d]||f[d-2]||f[0];return e}},Ja.test(a)||(r.cssHooks[a+b].set=Ua)}),r.fn.extend({css:function(a,b){return S(this,function(a,b,c){var d,e,f={},g=0;if(r.isArray(b)){for(d=La(a),e=b.length;g<e;g++)f[b[g]]=r.css(a,b[g],!1,d);return f}return void 0!==c?r.style(a,b,c):r.css(a,b)},a,b,arguments.length>1)}});function Xa(a,b,c,d,e){return new Xa.prototype.init(a,b,c,d,e)}r.Tween=Xa,Xa.prototype={constructor:Xa,init:function(a,b,c,d,e,f){this.elem=a,this.prop=c,this.easing=e||r.easing._default,this.options=b,this.start=this.now=this.cur(),this.end=d,this.unit=f||(r.cssNumber[c]?"":"px")},cur:function(){var a=Xa.propHooks[this.prop];return a&&a.get?a.get(this):Xa.propHooks._default.get(this)},run:function(a){var b,c=Xa.propHooks[this.prop];return this.options.duration?this.pos=b=r.easing[this.easing](a,this.options.duration*a,0,1,this.options.duration):this.pos=b=a,this.now=(this.end-this.start)*b+this.start,this.options.step&&this.options.step.call(this.elem,this.now,this),c&&c.set?c.set(this):Xa.propHooks._default.set(this),this}},Xa.prototype.init.prototype=Xa.prototype,Xa.propHooks={_default:{get:function(a){var b;return 1!==a.elem.nodeType||null!=a.elem[a.prop]&&null==a.elem.style[a.prop]?a.elem[a.prop]:(b=r.css(a.elem,a.prop,""),b&&"auto"!==b?b:0)},set:function(a){r.fx.step[a.prop]?r.fx.step[a.prop](a):1!==a.elem.nodeType||null==a.elem.style[r.cssProps[a.prop]]&&!r.cssHooks[a.prop]?a.elem[a.prop]=a.now:r.style(a.elem,a.prop,a.now+a.unit)}}},Xa.propHooks.scrollTop=Xa.propHooks.scrollLeft={set:function(a){a.elem.nodeType&&a.elem.parentNode&&(a.elem[a.prop]=a.now)}},r.easing={linear:function(a){return a},swing:function(a){return.5-Math.cos(a*Math.PI)/2},_default:"swing"},r.fx=Xa.prototype.init,r.fx.step={};var Ya,Za,$a=/^(?:toggle|show|hide)$/,_a=/queueHooks$/;function ab(){Za&&(a.requestAnimationFrame(ab),r.fx.tick())}function bb(){return a.setTimeout(function(){Ya=void 0}),Ya=r.now()}function cb(a,b){var c,d=0,e={height:a};for(b=b?1:0;d<4;d+=2-b)c=aa[d],e["margin"+c]=e["padding"+c]=a;return b&&(e.opacity=e.width=a),e}function db(a,b,c){for(var d,e=(gb.tweeners[b]||[]).concat(gb.tweeners["*"]),f=0,g=e.length;f<g;f++)if(d=e[f].call(c,b,a))return d}function eb(a,b,c){var d,e,f,g,h,i,j,k,l="width"in b||"height"in b,m=this,n={},o=a.style,p=a.nodeType&&ba(a),q=V.get(a,"fxshow");c.queue||(g=r._queueHooks(a,"fx"),null==g.unqueued&&(g.unqueued=0,h=g.empty.fire,g.empty.fire=function(){g.unqueued||h()}),g.unqueued++,m.always(function(){m.always(function(){g.unqueued--,r.queue(a,"fx").length||g.empty.fire()})}));for(d in b)if(e=b[d],$a.test(e)){if(delete b[d],f=f||"toggle"===e,e===(p?"hide":"show")){if("show"!==e||!q||void 0===q[d])continue;p=!0}n[d]=q&&q[d]||r.style(a,d)}if(i=!r.isEmptyObject(b),i||!r.isEmptyObject(n)){l&&1===a.nodeType&&(c.overflow=[o.overflow,o.overflowX,o.overflowY],j=q&&q.display,null==j&&(j=V.get(a,"display")),k=r.css(a,"display"),"none"===k&&(j?k=j:(ga([a],!0),j=a.style.display||j,k=r.css(a,"display"),ga([a]))),("inline"===k||"inline-block"===k&&null!=j)&&"none"===r.css(a,"float")&&(i||(m.done(function(){o.display=j}),null==j&&(k=o.display,j="none"===k?"":k)),o.display="inline-block")),c.overflow&&(o.overflow="hidden",m.always(function(){o.overflow=c.overflow[0],o.overflowX=c.overflow[1],o.overflowY=c.overflow[2]})),i=!1;for(d in n)i||(q?"hidden"in q&&(p=q.hidden):q=V.access(a,"fxshow",{display:j}),f&&(q.hidden=!p),p&&ga([a],!0),m.done(function(){p||ga([a]),V.remove(a,"fxshow");for(d in n)r.style(a,d,n[d])})),i=db(p?q[d]:0,d,m),d in q||(q[d]=i.start,p&&(i.end=i.start,i.start=0))}}function fb(a,b){var c,d,e,f,g;for(c in a)if(d=r.camelCase(c),e=b[d],f=a[c],r.isArray(f)&&(e=f[1],f=a[c]=f[0]),c!==d&&(a[d]=f,delete a[c]),g=r.cssHooks[d],g&&"expand"in g){f=g.expand(f),delete a[d];for(c in f)c in a||(a[c]=f[c],b[c]=e)}else b[d]=e}function gb(a,b,c){var d,e,f=0,g=gb.prefilters.length,h=r.Deferred().always(function(){delete i.elem}),i=function(){if(e)return!1;for(var b=Ya||bb(),c=Math.max(0,j.startTime+j.duration-b),d=c/j.duration||0,f=1-d,g=0,i=j.tweens.length;g<i;g++)j.tweens[g].run(f);return h.notifyWith(a,[j,f,c]),f<1&&i?c:(h.resolveWith(a,[j]),!1)},j=h.promise({elem:a,props:r.extend({},b),opts:r.extend(!0,{specialEasing:{},easing:r.easing._default},c),originalProperties:b,originalOptions:c,startTime:Ya||bb(),duration:c.duration,tweens:[],createTween:function(b,c){var d=r.Tween(a,j.opts,b,c,j.opts.specialEasing[b]||j.opts.easing);return j.tweens.push(d),d},stop:function(b){var c=0,d=b?j.tweens.length:0;if(e)return this;for(e=!0;c<d;c++)j.tweens[c].run(1);return b?(h.notifyWith(a,[j,1,0]),h.resolveWith(a,[j,b])):h.rejectWith(a,[j,b]),this}}),k=j.props;for(fb(k,j.opts.specialEasing);f<g;f++)if(d=gb.prefilters[f].call(j,a,k,j.opts))return r.isFunction(d.stop)&&(r._queueHooks(j.elem,j.opts.queue).stop=r.proxy(d.stop,d)),d;return r.map(k,db,j),r.isFunction(j.opts.start)&&j.opts.start.call(a,j),r.fx.timer(r.extend(i,{elem:a,anim:j,queue:j.opts.queue})),j.progress(j.opts.progress).done(j.opts.done,j.opts.complete).fail(j.opts.fail).always(j.opts.always)}r.Animation=r.extend(gb,{tweeners:{"*":[function(a,b){var c=this.createTween(a,b);return da(c.elem,a,_.exec(b),c),c}]},tweener:function(a,b){r.isFunction(a)?(b=a,a=["*"]):a=a.match(K);for(var c,d=0,e=a.length;d<e;d++)c=a[d],gb.tweeners[c]=gb.tweeners[c]||[],gb.tweeners[c].unshift(b)},prefilters:[eb],prefilter:function(a,b){b?gb.prefilters.unshift(a):gb.prefilters.push(a)}}),r.speed=function(a,b,c){var e=a&&"object"==typeof a?r.extend({},a):{complete:c||!c&&b||r.isFunction(a)&&a,duration:a,easing:c&&b||b&&!r.isFunction(b)&&b};return r.fx.off||d.hidden?e.duration=0:e.duration="number"==typeof e.duration?e.duration:e.duration in r.fx.speeds?r.fx.speeds[e.duration]:r.fx.speeds._default,null!=e.queue&&e.queue!==!0||(e.queue="fx"),e.old=e.complete,e.complete=function(){r.isFunction(e.old)&&e.old.call(this),e.queue&&r.dequeue(this,e.queue)},e},r.fn.extend({fadeTo:function(a,b,c,d){return this.filter(ba).css("opacity",0).show().end().animate({opacity:b},a,c,d)},animate:function(a,b,c,d){var e=r.isEmptyObject(a),f=r.speed(b,c,d),g=function(){var b=gb(this,r.extend({},a),f);(e||V.get(this,"finish"))&&b.stop(!0)};return g.finish=g,e||f.queue===!1?this.each(g):this.queue(f.queue,g)},stop:function(a,b,c){var d=function(a){var b=a.stop;delete a.stop,b(c)};return"string"!=typeof a&&(c=b,b=a,a=void 0),b&&a!==!1&&this.queue(a||"fx",[]),this.each(function(){var b=!0,e=null!=a&&a+"queueHooks",f=r.timers,g=V.get(this);if(e)g[e]&&g[e].stop&&d(g[e]);else for(e in g)g[e]&&g[e].stop&&_a.test(e)&&d(g[e]);for(e=f.length;e--;)f[e].elem!==this||null!=a&&f[e].queue!==a||(f[e].anim.stop(c),b=!1,f.splice(e,1));!b&&c||r.dequeue(this,a)})},finish:function(a){return a!==!1&&(a=a||"fx"),this.each(function(){var b,c=V.get(this),d=c[a+"queue"],e=c[a+"queueHooks"],f=r.timers,g=d?d.length:0;for(c.finish=!0,r.queue(this,a,[]),e&&e.stop&&e.stop.call(this,!0),b=f.length;b--;)f[b].elem===this&&f[b].queue===a&&(f[b].anim.stop(!0),f.splice(b,1));for(b=0;b<g;b++)d[b]&&d[b].finish&&d[b].finish.call(this);delete c.finish})}}),r.each(["toggle","show","hide"],function(a,b){var c=r.fn[b];r.fn[b]=function(a,d,e){return null==a||"boolean"==typeof a?c.apply(this,arguments):this.animate(cb(b,!0),a,d,e)}}),r.each({slideDown:cb("show"),slideUp:cb("hide"),slideToggle:cb("toggle"),fadeIn:{opacity:"show"},fadeOut:{opacity:"hide"},fadeToggle:{opacity:"toggle"}},function(a,b){r.fn[a]=function(a,c,d){return this.animate(b,a,c,d)}}),r.timers=[],r.fx.tick=function(){var a,b=0,c=r.timers;for(Ya=r.now();b<c.length;b++)a=c[b],a()||c[b]!==a||c.splice(b--,1);c.length||r.fx.stop(),Ya=void 0},r.fx.timer=function(a){r.timers.push(a),a()?r.fx.start():r.timers.pop()},r.fx.interval=13,r.fx.start=function(){Za||(Za=a.requestAnimationFrame?a.requestAnimationFrame(ab):a.setInterval(r.fx.tick,r.fx.interval))},r.fx.stop=function(){a.cancelAnimationFrame?a.cancelAnimationFrame(Za):a.clearInterval(Za),Za=null},r.fx.speeds={slow:600,fast:200,_default:400},r.fn.delay=function(b,c){return b=r.fx?r.fx.speeds[b]||b:b,c=c||"fx",this.queue(c,function(c,d){var e=a.setTimeout(c,b);d.stop=function(){a.clearTimeout(e)}})},function(){var a=d.createElement("input"),b=d.createElement("select"),c=b.appendChild(d.createElement("option"));a.type="checkbox",o.checkOn=""!==a.value,o.optSelected=c.selected,a=d.createElement("input"),a.value="t",a.type="radio",o.radioValue="t"===a.value}();var hb,ib=r.expr.attrHandle;r.fn.extend({attr:function(a,b){return S(this,r.attr,a,b,arguments.length>1)},removeAttr:function(a){return this.each(function(){r.removeAttr(this,a)})}}),r.extend({attr:function(a,b,c){var d,e,f=a.nodeType;if(3!==f&&8!==f&&2!==f)return"undefined"==typeof a.getAttribute?r.prop(a,b,c):(1===f&&r.isXMLDoc(a)||(e=r.attrHooks[b.toLowerCase()]||(r.expr.match.bool.test(b)?hb:void 0)),void 0!==c?null===c?void r.removeAttr(a,b):e&&"set"in e&&void 0!==(d=e.set(a,c,b))?d:(a.setAttribute(b,c+""),c):e&&"get"in e&&null!==(d=e.get(a,b))?d:(d=r.find.attr(a,b),null==d?void 0:d))},attrHooks:{type:{set:function(a,b){if(!o.radioValue&&"radio"===b&&r.nodeName(a,"input")){var c=a.value;return a.setAttribute("type",b),c&&(a.value=c),b}}}},removeAttr:function(a,b){var c,d=0,e=b&&b.match(K); | |
| 3 | if(e&&1===a.nodeType)while(c=e[d++])a.removeAttribute(c)}}),hb={set:function(a,b,c){return b===!1?r.removeAttr(a,c):a.setAttribute(c,c),c}},r.each(r.expr.match.bool.source.match(/\w+/g),function(a,b){var c=ib[b]||r.find.attr;ib[b]=function(a,b,d){var e,f,g=b.toLowerCase();return d||(f=ib[g],ib[g]=e,e=null!=c(a,b,d)?g:null,ib[g]=f),e}});var jb=/^(?:input|select|textarea|button)$/i,kb=/^(?:a|area)$/i;r.fn.extend({prop:function(a,b){return S(this,r.prop,a,b,arguments.length>1)},removeProp:function(a){return this.each(function(){delete this[r.propFix[a]||a]})}}),r.extend({prop:function(a,b,c){var d,e,f=a.nodeType;if(3!==f&&8!==f&&2!==f)return 1===f&&r.isXMLDoc(a)||(b=r.propFix[b]||b,e=r.propHooks[b]),void 0!==c?e&&"set"in e&&void 0!==(d=e.set(a,c,b))?d:a[b]=c:e&&"get"in e&&null!==(d=e.get(a,b))?d:a[b]},propHooks:{tabIndex:{get:function(a){var b=r.find.attr(a,"tabindex");return b?parseInt(b,10):jb.test(a.nodeName)||kb.test(a.nodeName)&&a.href?0:-1}}},propFix:{"for":"htmlFor","class":"className"}}),o.optSelected||(r.propHooks.selected={get:function(a){var b=a.parentNode;return b&&b.parentNode&&b.parentNode.selectedIndex,null},set:function(a){var b=a.parentNode;b&&(b.selectedIndex,b.parentNode&&b.parentNode.selectedIndex)}}),r.each(["tabIndex","readOnly","maxLength","cellSpacing","cellPadding","rowSpan","colSpan","useMap","frameBorder","contentEditable"],function(){r.propFix[this.toLowerCase()]=this});var lb=/[\t\r\n\f]/g;function mb(a){return a.getAttribute&&a.getAttribute("class")||""}r.fn.extend({addClass:function(a){var b,c,d,e,f,g,h,i=0;if(r.isFunction(a))return this.each(function(b){r(this).addClass(a.call(this,b,mb(this)))});if("string"==typeof a&&a){b=a.match(K)||[];while(c=this[i++])if(e=mb(c),d=1===c.nodeType&&(" "+e+" ").replace(lb," ")){g=0;while(f=b[g++])d.indexOf(" "+f+" ")<0&&(d+=f+" ");h=r.trim(d),e!==h&&c.setAttribute("class",h)}}return this},removeClass:function(a){var b,c,d,e,f,g,h,i=0;if(r.isFunction(a))return this.each(function(b){r(this).removeClass(a.call(this,b,mb(this)))});if(!arguments.length)return this.attr("class","");if("string"==typeof a&&a){b=a.match(K)||[];while(c=this[i++])if(e=mb(c),d=1===c.nodeType&&(" "+e+" ").replace(lb," ")){g=0;while(f=b[g++])while(d.indexOf(" "+f+" ")>-1)d=d.replace(" "+f+" "," ");h=r.trim(d),e!==h&&c.setAttribute("class",h)}}return this},toggleClass:function(a,b){var c=typeof a;return"boolean"==typeof b&&"string"===c?b?this.addClass(a):this.removeClass(a):r.isFunction(a)?this.each(function(c){r(this).toggleClass(a.call(this,c,mb(this),b),b)}):this.each(function(){var b,d,e,f;if("string"===c){d=0,e=r(this),f=a.match(K)||[];while(b=f[d++])e.hasClass(b)?e.removeClass(b):e.addClass(b)}else void 0!==a&&"boolean"!==c||(b=mb(this),b&&V.set(this,"__className__",b),this.setAttribute&&this.setAttribute("class",b||a===!1?"":V.get(this,"__className__")||""))})},hasClass:function(a){var b,c,d=0;b=" "+a+" ";while(c=this[d++])if(1===c.nodeType&&(" "+mb(c)+" ").replace(lb," ").indexOf(b)>-1)return!0;return!1}});var nb=/\r/g,ob=/[\x20\t\r\n\f]+/g;r.fn.extend({val:function(a){var b,c,d,e=this[0];{if(arguments.length)return d=r.isFunction(a),this.each(function(c){var e;1===this.nodeType&&(e=d?a.call(this,c,r(this).val()):a,null==e?e="":"number"==typeof e?e+="":r.isArray(e)&&(e=r.map(e,function(a){return null==a?"":a+""})),b=r.valHooks[this.type]||r.valHooks[this.nodeName.toLowerCase()],b&&"set"in b&&void 0!==b.set(this,e,"value")||(this.value=e))});if(e)return b=r.valHooks[e.type]||r.valHooks[e.nodeName.toLowerCase()],b&&"get"in b&&void 0!==(c=b.get(e,"value"))?c:(c=e.value,"string"==typeof c?c.replace(nb,""):null==c?"":c)}}}),r.extend({valHooks:{option:{get:function(a){var b=r.find.attr(a,"value");return null!=b?b:r.trim(r.text(a)).replace(ob," ")}},select:{get:function(a){for(var b,c,d=a.options,e=a.selectedIndex,f="select-one"===a.type,g=f?null:[],h=f?e+1:d.length,i=e<0?h:f?e:0;i<h;i++)if(c=d[i],(c.selected||i===e)&&!c.disabled&&(!c.parentNode.disabled||!r.nodeName(c.parentNode,"optgroup"))){if(b=r(c).val(),f)return b;g.push(b)}return g},set:function(a,b){var c,d,e=a.options,f=r.makeArray(b),g=e.length;while(g--)d=e[g],(d.selected=r.inArray(r.valHooks.option.get(d),f)>-1)&&(c=!0);return c||(a.selectedIndex=-1),f}}}}),r.each(["radio","checkbox"],function(){r.valHooks[this]={set:function(a,b){if(r.isArray(b))return a.checked=r.inArray(r(a).val(),b)>-1}},o.checkOn||(r.valHooks[this].get=function(a){return null===a.getAttribute("value")?"on":a.value})});var pb=/^(?:focusinfocus|focusoutblur)$/;r.extend(r.event,{trigger:function(b,c,e,f){var g,h,i,j,k,m,n,o=[e||d],p=l.call(b,"type")?b.type:b,q=l.call(b,"namespace")?b.namespace.split("."):[];if(h=i=e=e||d,3!==e.nodeType&&8!==e.nodeType&&!pb.test(p+r.event.triggered)&&(p.indexOf(".")>-1&&(q=p.split("."),p=q.shift(),q.sort()),k=p.indexOf(":")<0&&"on"+p,b=b[r.expando]?b:new r.Event(p,"object"==typeof b&&b),b.isTrigger=f?2:3,b.namespace=q.join("."),b.rnamespace=b.namespace?new RegExp("(^|\\.)"+q.join("\\.(?:.*\\.|)")+"(\\.|$)"):null,b.result=void 0,b.target||(b.target=e),c=null==c?[b]:r.makeArray(c,[b]),n=r.event.special[p]||{},f||!n.trigger||n.trigger.apply(e,c)!==!1)){if(!f&&!n.noBubble&&!r.isWindow(e)){for(j=n.delegateType||p,pb.test(j+p)||(h=h.parentNode);h;h=h.parentNode)o.push(h),i=h;i===(e.ownerDocument||d)&&o.push(i.defaultView||i.parentWindow||a)}g=0;while((h=o[g++])&&!b.isPropagationStopped())b.type=g>1?j:n.bindType||p,m=(V.get(h,"events")||{})[b.type]&&V.get(h,"handle"),m&&m.apply(h,c),m=k&&h[k],m&&m.apply&&T(h)&&(b.result=m.apply(h,c),b.result===!1&&b.preventDefault());return b.type=p,f||b.isDefaultPrevented()||n._default&&n._default.apply(o.pop(),c)!==!1||!T(e)||k&&r.isFunction(e[p])&&!r.isWindow(e)&&(i=e[k],i&&(e[k]=null),r.event.triggered=p,e[p](),r.event.triggered=void 0,i&&(e[k]=i)),b.result}},simulate:function(a,b,c){var d=r.extend(new r.Event,c,{type:a,isSimulated:!0});r.event.trigger(d,null,b)}}),r.fn.extend({trigger:function(a,b){return this.each(function(){r.event.trigger(a,b,this)})},triggerHandler:function(a,b){var c=this[0];if(c)return r.event.trigger(a,b,c,!0)}}),r.each("blur focus focusin focusout resize scroll click dblclick mousedown mouseup mousemove mouseover mouseout mouseenter mouseleave change select submit keydown keypress keyup contextmenu".split(" "),function(a,b){r.fn[b]=function(a,c){return arguments.length>0?this.on(b,null,a,c):this.trigger(b)}}),r.fn.extend({hover:function(a,b){return this.mouseenter(a).mouseleave(b||a)}}),o.focusin="onfocusin"in a,o.focusin||r.each({focus:"focusin",blur:"focusout"},function(a,b){var c=function(a){r.event.simulate(b,a.target,r.event.fix(a))};r.event.special[b]={setup:function(){var d=this.ownerDocument||this,e=V.access(d,b);e||d.addEventListener(a,c,!0),V.access(d,b,(e||0)+1)},teardown:function(){var d=this.ownerDocument||this,e=V.access(d,b)-1;e?V.access(d,b,e):(d.removeEventListener(a,c,!0),V.remove(d,b))}}});var qb=a.location,rb=r.now(),sb=/\?/;r.parseXML=function(b){var c;if(!b||"string"!=typeof b)return null;try{c=(new a.DOMParser).parseFromString(b,"text/xml")}catch(d){c=void 0}return c&&!c.getElementsByTagName("parsererror").length||r.error("Invalid XML: "+b),c};var tb=/\[\]$/,ub=/\r?\n/g,vb=/^(?:submit|button|image|reset|file)$/i,wb=/^(?:input|select|textarea|keygen)/i;function xb(a,b,c,d){var e;if(r.isArray(b))r.each(b,function(b,e){c||tb.test(a)?d(a,e):xb(a+"["+("object"==typeof e&&null!=e?b:"")+"]",e,c,d)});else if(c||"object"!==r.type(b))d(a,b);else for(e in b)xb(a+"["+e+"]",b[e],c,d)}r.param=function(a,b){var c,d=[],e=function(a,b){var c=r.isFunction(b)?b():b;d[d.length]=encodeURIComponent(a)+"="+encodeURIComponent(null==c?"":c)};if(r.isArray(a)||a.jquery&&!r.isPlainObject(a))r.each(a,function(){e(this.name,this.value)});else for(c in a)xb(c,a[c],b,e);return d.join("&")},r.fn.extend({serialize:function(){return r.param(this.serializeArray())},serializeArray:function(){return this.map(function(){var a=r.prop(this,"elements");return a?r.makeArray(a):this}).filter(function(){var a=this.type;return this.name&&!r(this).is(":disabled")&&wb.test(this.nodeName)&&!vb.test(a)&&(this.checked||!ha.test(a))}).map(function(a,b){var c=r(this).val();return null==c?null:r.isArray(c)?r.map(c,function(a){return{name:b.name,value:a.replace(ub,"\r\n")}}):{name:b.name,value:c.replace(ub,"\r\n")}}).get()}});var yb=/%20/g,zb=/#.*$/,Ab=/([?&])_=[^&]*/,Bb=/^(.*?):[ \t]*([^\r\n]*)$/gm,Cb=/^(?:about|app|app-storage|.+-extension|file|res|widget):$/,Db=/^(?:GET|HEAD)$/,Eb=/^\/\//,Fb={},Gb={},Hb="*/".concat("*"),Ib=d.createElement("a");Ib.href=qb.href;function Jb(a){return function(b,c){"string"!=typeof b&&(c=b,b="*");var d,e=0,f=b.toLowerCase().match(K)||[];if(r.isFunction(c))while(d=f[e++])"+"===d[0]?(d=d.slice(1)||"*",(a[d]=a[d]||[]).unshift(c)):(a[d]=a[d]||[]).push(c)}}function Kb(a,b,c,d){var e={},f=a===Gb;function g(h){var i;return e[h]=!0,r.each(a[h]||[],function(a,h){var j=h(b,c,d);return"string"!=typeof j||f||e[j]?f?!(i=j):void 0:(b.dataTypes.unshift(j),g(j),!1)}),i}return g(b.dataTypes[0])||!e["*"]&&g("*")}function Lb(a,b){var c,d,e=r.ajaxSettings.flatOptions||{};for(c in b)void 0!==b[c]&&((e[c]?a:d||(d={}))[c]=b[c]);return d&&r.extend(!0,a,d),a}function Mb(a,b,c){var d,e,f,g,h=a.contents,i=a.dataTypes;while("*"===i[0])i.shift(),void 0===d&&(d=a.mimeType||b.getResponseHeader("Content-Type"));if(d)for(e in h)if(h[e]&&h[e].test(d)){i.unshift(e);break}if(i[0]in c)f=i[0];else{for(e in c){if(!i[0]||a.converters[e+" "+i[0]]){f=e;break}g||(g=e)}f=f||g}if(f)return f!==i[0]&&i.unshift(f),c[f]}function Nb(a,b,c,d){var e,f,g,h,i,j={},k=a.dataTypes.slice();if(k[1])for(g in a.converters)j[g.toLowerCase()]=a.converters[g];f=k.shift();while(f)if(a.responseFields[f]&&(c[a.responseFields[f]]=b),!i&&d&&a.dataFilter&&(b=a.dataFilter(b,a.dataType)),i=f,f=k.shift())if("*"===f)f=i;else if("*"!==i&&i!==f){if(g=j[i+" "+f]||j["* "+f],!g)for(e in j)if(h=e.split(" "),h[1]===f&&(g=j[i+" "+h[0]]||j["* "+h[0]])){g===!0?g=j[e]:j[e]!==!0&&(f=h[0],k.unshift(h[1]));break}if(g!==!0)if(g&&a["throws"])b=g(b);else try{b=g(b)}catch(l){return{state:"parsererror",error:g?l:"No conversion from "+i+" to "+f}}}return{state:"success",data:b}}r.extend({active:0,lastModified:{},etag:{},ajaxSettings:{url:qb.href,type:"GET",isLocal:Cb.test(qb.protocol),global:!0,processData:!0,async:!0,contentType:"application/x-www-form-urlencoded; charset=UTF-8",accepts:{"*":Hb,text:"text/plain",html:"text/html",xml:"application/xml, text/xml",json:"application/json, text/javascript"},contents:{xml:/\bxml\b/,html:/\bhtml/,json:/\bjson\b/},responseFields:{xml:"responseXML",text:"responseText",json:"responseJSON"},converters:{"* text":String,"text html":!0,"text json":JSON.parse,"text xml":r.parseXML},flatOptions:{url:!0,context:!0}},ajaxSetup:function(a,b){return b?Lb(Lb(a,r.ajaxSettings),b):Lb(r.ajaxSettings,a)},ajaxPrefilter:Jb(Fb),ajaxTransport:Jb(Gb),ajax:function(b,c){"object"==typeof b&&(c=b,b=void 0),c=c||{};var e,f,g,h,i,j,k,l,m,n,o=r.ajaxSetup({},c),p=o.context||o,q=o.context&&(p.nodeType||p.jquery)?r(p):r.event,s=r.Deferred(),t=r.Callbacks("once memory"),u=o.statusCode||{},v={},w={},x="canceled",y={readyState:0,getResponseHeader:function(a){var b;if(k){if(!h){h={};while(b=Bb.exec(g))h[b[1].toLowerCase()]=b[2]}b=h[a.toLowerCase()]}return null==b?null:b},getAllResponseHeaders:function(){return k?g:null},setRequestHeader:function(a,b){return null==k&&(a=w[a.toLowerCase()]=w[a.toLowerCase()]||a,v[a]=b),this},overrideMimeType:function(a){return null==k&&(o.mimeType=a),this},statusCode:function(a){var b;if(a)if(k)y.always(a[y.status]);else for(b in a)u[b]=[u[b],a[b]];return this},abort:function(a){var b=a||x;return e&&e.abort(b),A(0,b),this}};if(s.promise(y),o.url=((b||o.url||qb.href)+"").replace(Eb,qb.protocol+"//"),o.type=c.method||c.type||o.method||o.type,o.dataTypes=(o.dataType||"*").toLowerCase().match(K)||[""],null==o.crossDomain){j=d.createElement("a");try{j.href=o.url,j.href=j.href,o.crossDomain=Ib.protocol+"//"+Ib.host!=j.protocol+"//"+j.host}catch(z){o.crossDomain=!0}}if(o.data&&o.processData&&"string"!=typeof o.data&&(o.data=r.param(o.data,o.traditional)),Kb(Fb,o,c,y),k)return y;l=r.event&&o.global,l&&0===r.active++&&r.event.trigger("ajaxStart"),o.type=o.type.toUpperCase(),o.hasContent=!Db.test(o.type),f=o.url.replace(zb,""),o.hasContent?o.data&&o.processData&&0===(o.contentType||"").indexOf("application/x-www-form-urlencoded")&&(o.data=o.data.replace(yb,"+")):(n=o.url.slice(f.length),o.data&&(f+=(sb.test(f)?"&":"?")+o.data,delete o.data),o.cache===!1&&(f=f.replace(Ab,""),n=(sb.test(f)?"&":"?")+"_="+rb++ +n),o.url=f+n),o.ifModified&&(r.lastModified[f]&&y.setRequestHeader("If-Modified-Since",r.lastModified[f]),r.etag[f]&&y.setRequestHeader("If-None-Match",r.etag[f])),(o.data&&o.hasContent&&o.contentType!==!1||c.contentType)&&y.setRequestHeader("Content-Type",o.contentType),y.setRequestHeader("Accept",o.dataTypes[0]&&o.accepts[o.dataTypes[0]]?o.accepts[o.dataTypes[0]]+("*"!==o.dataTypes[0]?", "+Hb+"; q=0.01":""):o.accepts["*"]);for(m in o.headers)y.setRequestHeader(m,o.headers[m]);if(o.beforeSend&&(o.beforeSend.call(p,y,o)===!1||k))return y.abort();if(x="abort",t.add(o.complete),y.done(o.success),y.fail(o.error),e=Kb(Gb,o,c,y)){if(y.readyState=1,l&&q.trigger("ajaxSend",[y,o]),k)return y;o.async&&o.timeout>0&&(i=a.setTimeout(function(){y.abort("timeout")},o.timeout));try{k=!1,e.send(v,A)}catch(z){if(k)throw z;A(-1,z)}}else A(-1,"No Transport");function A(b,c,d,h){var j,m,n,v,w,x=c;k||(k=!0,i&&a.clearTimeout(i),e=void 0,g=h||"",y.readyState=b>0?4:0,j=b>=200&&b<300||304===b,d&&(v=Mb(o,y,d)),v=Nb(o,v,y,j),j?(o.ifModified&&(w=y.getResponseHeader("Last-Modified"),w&&(r.lastModified[f]=w),w=y.getResponseHeader("etag"),w&&(r.etag[f]=w)),204===b||"HEAD"===o.type?x="nocontent":304===b?x="notmodified":(x=v.state,m=v.data,n=v.error,j=!n)):(n=x,!b&&x||(x="error",b<0&&(b=0))),y.status=b,y.statusText=(c||x)+"",j?s.resolveWith(p,[m,x,y]):s.rejectWith(p,[y,x,n]),y.statusCode(u),u=void 0,l&&q.trigger(j?"ajaxSuccess":"ajaxError",[y,o,j?m:n]),t.fireWith(p,[y,x]),l&&(q.trigger("ajaxComplete",[y,o]),--r.active||r.event.trigger("ajaxStop")))}return y},getJSON:function(a,b,c){return r.get(a,b,c,"json")},getScript:function(a,b){return r.get(a,void 0,b,"script")}}),r.each(["get","post"],function(a,b){r[b]=function(a,c,d,e){return r.isFunction(c)&&(e=e||d,d=c,c=void 0),r.ajax(r.extend({url:a,type:b,dataType:e,data:c,success:d},r.isPlainObject(a)&&a))}}),r._evalUrl=function(a){return r.ajax({url:a,type:"GET",dataType:"script",cache:!0,async:!1,global:!1,"throws":!0})},r.fn.extend({wrapAll:function(a){var b;return this[0]&&(r.isFunction(a)&&(a=a.call(this[0])),b=r(a,this[0].ownerDocument).eq(0).clone(!0),this[0].parentNode&&b.insertBefore(this[0]),b.map(function(){var a=this;while(a.firstElementChild)a=a.firstElementChild;return a}).append(this)),this},wrapInner:function(a){return r.isFunction(a)?this.each(function(b){r(this).wrapInner(a.call(this,b))}):this.each(function(){var b=r(this),c=b.contents();c.length?c.wrapAll(a):b.append(a)})},wrap:function(a){var b=r.isFunction(a);return this.each(function(c){r(this).wrapAll(b?a.call(this,c):a)})},unwrap:function(a){return this.parent(a).not("body").each(function(){r(this).replaceWith(this.childNodes)}),this}}),r.expr.pseudos.hidden=function(a){return!r.expr.pseudos.visible(a)},r.expr.pseudos.visible=function(a){return!!(a.offsetWidth||a.offsetHeight||a.getClientRects().length)},r.ajaxSettings.xhr=function(){try{return new a.XMLHttpRequest}catch(b){}};var Ob={0:200,1223:204},Pb=r.ajaxSettings.xhr();o.cors=!!Pb&&"withCredentials"in Pb,o.ajax=Pb=!!Pb,r.ajaxTransport(function(b){var c,d;if(o.cors||Pb&&!b.crossDomain)return{send:function(e,f){var g,h=b.xhr();if(h.open(b.type,b.url,b.async,b.username,b.password),b.xhrFields)for(g in b.xhrFields)h[g]=b.xhrFields[g];b.mimeType&&h.overrideMimeType&&h.overrideMimeType(b.mimeType),b.crossDomain||e["X-Requested-With"]||(e["X-Requested-With"]="XMLHttpRequest");for(g in e)h.setRequestHeader(g,e[g]);c=function(a){return function(){c&&(c=d=h.onload=h.onerror=h.onabort=h.onreadystatechange=null,"abort"===a?h.abort():"error"===a?"number"!=typeof h.status?f(0,"error"):f(h.status,h.statusText):f(Ob[h.status]||h.status,h.statusText,"text"!==(h.responseType||"text")||"string"!=typeof h.responseText?{binary:h.response}:{text:h.responseText},h.getAllResponseHeaders()))}},h.onload=c(),d=h.onerror=c("error"),void 0!==h.onabort?h.onabort=d:h.onreadystatechange=function(){4===h.readyState&&a.setTimeout(function(){c&&d()})},c=c("abort");try{h.send(b.hasContent&&b.data||null)}catch(i){if(c)throw i}},abort:function(){c&&c()}}}),r.ajaxPrefilter(function(a){a.crossDomain&&(a.contents.script=!1)}),r.ajaxSetup({accepts:{script:"text/javascript, application/javascript, application/ecmascript, application/x-ecmascript"},contents:{script:/\b(?:java|ecma)script\b/},converters:{"text script":function(a){return r.globalEval(a),a}}}),r.ajaxPrefilter("script",function(a){void 0===a.cache&&(a.cache=!1),a.crossDomain&&(a.type="GET")}),r.ajaxTransport("script",function(a){if(a.crossDomain){var b,c;return{send:function(e,f){b=r("<script>").prop({charset:a.scriptCharset,src:a.url}).on("load error",c=function(a){b.remove(),c=null,a&&f("error"===a.type?404:200,a.type)}),d.head.appendChild(b[0])},abort:function(){c&&c()}}}});var Qb=[],Rb=/(=)\?(?=&|$)|\?\?/;r.ajaxSetup({jsonp:"callback",jsonpCallback:function(){var a=Qb.pop()||r.expando+"_"+rb++;return this[a]=!0,a}}),r.ajaxPrefilter("json jsonp",function(b,c,d){var e,f,g,h=b.jsonp!==!1&&(Rb.test(b.url)?"url":"string"==typeof b.data&&0===(b.contentType||"").indexOf("application/x-www-form-urlencoded")&&Rb.test(b.data)&&"data");if(h||"jsonp"===b.dataTypes[0])return e=b.jsonpCallback=r.isFunction(b.jsonpCallback)?b.jsonpCallback():b.jsonpCallback,h?b[h]=b[h].replace(Rb,"$1"+e):b.jsonp!==!1&&(b.url+=(sb.test(b.url)?"&":"?")+b.jsonp+"="+e),b.converters["script json"]=function(){return g||r.error(e+" was not called"),g[0]},b.dataTypes[0]="json",f=a[e],a[e]=function(){g=arguments},d.always(function(){void 0===f?r(a).removeProp(e):a[e]=f,b[e]&&(b.jsonpCallback=c.jsonpCallback,Qb.push(e)),g&&r.isFunction(f)&&f(g[0]),g=f=void 0}),"script"}),o.createHTMLDocument=function(){var a=d.implementation.createHTMLDocument("").body;return a.innerHTML="<form></form><form></form>",2===a.childNodes.length}(),r.parseHTML=function(a,b,c){if("string"!=typeof a)return[];"boolean"==typeof b&&(c=b,b=!1);var e,f,g;return b||(o.createHTMLDocument?(b=d.implementation.createHTMLDocument(""),e=b.createElement("base"),e.href=d.location.href,b.head.appendChild(e)):b=d),f=B.exec(a),g=!c&&[],f?[b.createElement(f[1])]:(f=oa([a],b,g),g&&g.length&&r(g).remove(),r.merge([],f.childNodes))},r.fn.load=function(a,b,c){var d,e,f,g=this,h=a.indexOf(" ");return h>-1&&(d=r.trim(a.slice(h)),a=a.slice(0,h)),r.isFunction(b)?(c=b,b=void 0):b&&"object"==typeof b&&(e="POST"),g.length>0&&r.ajax({url:a,type:e||"GET",dataType:"html",data:b}).done(function(a){f=arguments,g.html(d?r("<div>").append(r.parseHTML(a)).find(d):a)}).always(c&&function(a,b){g.each(function(){c.apply(this,f||[a.responseText,b,a])})}),this},r.each(["ajaxStart","ajaxStop","ajaxComplete","ajaxError","ajaxSuccess","ajaxSend"],function(a,b){r.fn[b]=function(a){return this.on(b,a)}}),r.expr.pseudos.animated=function(a){return r.grep(r.timers,function(b){return a===b.elem}).length};function Sb(a){return r.isWindow(a)?a:9===a.nodeType&&a.defaultView}r.offset={setOffset:function(a,b,c){var d,e,f,g,h,i,j,k=r.css(a,"position"),l=r(a),m={};"static"===k&&(a.style.position="relative"),h=l.offset(),f=r.css(a,"top"),i=r.css(a,"left"),j=("absolute"===k||"fixed"===k)&&(f+i).indexOf("auto")>-1,j?(d=l.position(),g=d.top,e=d.left):(g=parseFloat(f)||0,e=parseFloat(i)||0),r.isFunction(b)&&(b=b.call(a,c,r.extend({},h))),null!=b.top&&(m.top=b.top-h.top+g),null!=b.left&&(m.left=b.left-h.left+e),"using"in b?b.using.call(a,m):l.css(m)}},r.fn.extend({offset:function(a){if(arguments.length)return void 0===a?this:this.each(function(b){r.offset.setOffset(this,a,b)});var b,c,d,e,f=this[0];if(f)return f.getClientRects().length?(d=f.getBoundingClientRect(),d.width||d.height?(e=f.ownerDocument,c=Sb(e),b=e.documentElement,{top:d.top+c.pageYOffset-b.clientTop,left:d.left+c.pageXOffset-b.clientLeft}):d):{top:0,left:0}},position:function(){if(this[0]){var a,b,c=this[0],d={top:0,left:0};return"fixed"===r.css(c,"position")?b=c.getBoundingClientRect():(a=this.offsetParent(),b=this.offset(),r.nodeName(a[0],"html")||(d=a.offset()),d={top:d.top+r.css(a[0],"borderTopWidth",!0),left:d.left+r.css(a[0],"borderLeftWidth",!0)}),{top:b.top-d.top-r.css(c,"marginTop",!0),left:b.left-d.left-r.css(c,"marginLeft",!0)}}},offsetParent:function(){return this.map(function(){var a=this.offsetParent;while(a&&"static"===r.css(a,"position"))a=a.offsetParent;return a||pa})}}),r.each({scrollLeft:"pageXOffset",scrollTop:"pageYOffset"},function(a,b){var c="pageYOffset"===b;r.fn[a]=function(d){return S(this,function(a,d,e){var f=Sb(a);return void 0===e?f?f[b]:a[d]:void(f?f.scrollTo(c?f.pageXOffset:e,c?e:f.pageYOffset):a[d]=e)},a,d,arguments.length)}}),r.each(["top","left"],function(a,b){r.cssHooks[b]=Na(o.pixelPosition,function(a,c){if(c)return c=Ma(a,b),Ka.test(c)?r(a).position()[b]+"px":c})}),r.each({Height:"height",Width:"width"},function(a,b){r.each({padding:"inner"+a,content:b,"":"outer"+a},function(c,d){r.fn[d]=function(e,f){var g=arguments.length&&(c||"boolean"!=typeof e),h=c||(e===!0||f===!0?"margin":"border");return S(this,function(b,c,e){var f;return r.isWindow(b)?0===d.indexOf("outer")?b["inner"+a]:b.document.documentElement["client"+a]:9===b.nodeType?(f=b.documentElement,Math.max(b.body["scroll"+a],f["scroll"+a],b.body["offset"+a],f["offset"+a],f["client"+a])):void 0===e?r.css(b,c,h):r.style(b,c,e,h)},b,g?e:void 0,g)}})}),r.fn.extend({bind:function(a,b,c){return this.on(a,null,b,c)},unbind:function(a,b){return this.off(a,null,b)},delegate:function(a,b,c,d){return this.on(b,a,c,d)},undelegate:function(a,b,c){return 1===arguments.length?this.off(a,"**"):this.off(b,a||"**",c)}}),r.parseJSON=JSON.parse,"function"==typeof define&&define.amd&&define("jquery",[],function(){return r});var Tb=a.jQuery,Ub=a.$;return r.noConflict=function(b){return a.$===r&&(a.$=Ub),b&&a.jQuery===r&&(a.jQuery=Tb),r},b||(a.jQuery=a.$=r),r}); |
| 0 | /* Modernizr 2.6.2 (Custom Build) | MIT & BSD | |
| 1 | * Build: http://modernizr.com/download/#-fontface-backgroundsize-borderimage-borderradius-boxshadow-flexbox-hsla-multiplebgs-opacity-rgba-textshadow-cssanimations-csscolumns-generatedcontent-cssgradients-cssreflections-csstransforms-csstransforms3d-csstransitions-applicationcache-canvas-canvastext-draganddrop-hashchange-history-audio-video-indexeddb-input-inputtypes-localstorage-postmessage-sessionstorage-websockets-websqldatabase-webworkers-geolocation-inlinesvg-smil-svg-svgclippaths-touch-webgl-shiv-mq-cssclasses-addtest-prefixed-teststyles-testprop-testallprops-hasevent-prefixes-domprefixes-load | |
| 2 | */ | |
| 3 | ;window.Modernizr=function(a,b,c){function D(a){j.cssText=a}function E(a,b){return D(n.join(a+";")+(b||""))}function F(a,b){return typeof a===b}function G(a,b){return!!~(""+a).indexOf(b)}function H(a,b){for(var d in a){var e=a[d];if(!G(e,"-")&&j[e]!==c)return b=="pfx"?e:!0}return!1}function I(a,b,d){for(var e in a){var f=b[a[e]];if(f!==c)return d===!1?a[e]:F(f,"function")?f.bind(d||b):f}return!1}function J(a,b,c){var d=a.charAt(0).toUpperCase()+a.slice(1),e=(a+" "+p.join(d+" ")+d).split(" ");return F(b,"string")||F(b,"undefined")?H(e,b):(e=(a+" "+q.join(d+" ")+d).split(" "),I(e,b,c))}function K(){e.input=function(c){for(var d=0,e=c.length;d<e;d++)u[c[d]]=c[d]in k;return u.list&&(u.list=!!b.createElement("datalist")&&!!a.HTMLDataListElement),u}("autocomplete autofocus list placeholder max min multiple pattern required step".split(" ")),e.inputtypes=function(a){for(var d=0,e,f,h,i=a.length;d<i;d++)k.setAttribute("type",f=a[d]),e=k.type!=="text",e&&(k.value=l,k.style.cssText="position:absolute;visibility:hidden;",/^range$/.test(f)&&k.style.WebkitAppearance!==c?(g.appendChild(k),h=b.defaultView,e=h.getComputedStyle&&h.getComputedStyle(k,null).WebkitAppearance!=="textfield"&&k.offsetHeight!==0,g.removeChild(k)):/^(search|tel)$/.test(f)||(/^(url|email)$/.test(f)?e=k.checkValidity&&k.checkValidity()===!1:e=k.value!=l)),t[a[d]]=!!e;return t}("search tel url email datetime date month week time datetime-local number range color".split(" "))}var d="2.6.2",e={},f=!0,g=b.documentElement,h="modernizr",i=b.createElement(h),j=i.style,k=b.createElement("input"),l=":)",m={}.toString,n=" -webkit- -moz- -o- -ms- ".split(" "),o="Webkit Moz O ms",p=o.split(" "),q=o.toLowerCase().split(" "),r={svg:"http://www.w3.org/2000/svg"},s={},t={},u={},v=[],w=v.slice,x,y=function(a,c,d,e){var f,i,j,k,l=b.createElement("div"),m=b.body,n=m||b.createElement("body");if(parseInt(d,10))while(d--)j=b.createElement("div"),j.id=e?e[d]:h+(d+1),l.appendChild(j);return f=["­",'<style id="s',h,'">',a,"</style>"].join(""),l.id=h,(m?l:n).innerHTML+=f,n.appendChild(l),m||(n.style.background="",n.style.overflow="hidden",k=g.style.overflow,g.style.overflow="hidden",g.appendChild(n)),i=c(l,a),m?l.parentNode.removeChild(l):(n.parentNode.removeChild(n),g.style.overflow=k),!!i},z=function(b){var c=a.matchMedia||a.msMatchMedia;if(c)return c(b).matches;var d;return y("@media "+b+" { #"+h+" { position: absolute; } }",function(b){d=(a.getComputedStyle?getComputedStyle(b,null):b.currentStyle)["position"]=="absolute"}),d},A=function(){function d(d,e){e=e||b.createElement(a[d]||"div"),d="on"+d;var f=d in e;return f||(e.setAttribute||(e=b.createElement("div")),e.setAttribute&&e.removeAttribute&&(e.setAttribute(d,""),f=F(e[d],"function"),F(e[d],"undefined")||(e[d]=c),e.removeAttribute(d))),e=null,f}var a={select:"input",change:"input",submit:"form",reset:"form",error:"img",load:"img",abort:"img"};return d}(),B={}.hasOwnProperty,C;!F(B,"undefined")&&!F(B.call,"undefined")?C=function(a,b){return B.call(a,b)}:C=function(a,b){return b in a&&F(a.constructor.prototype[b],"undefined")},Function.prototype.bind||(Function.prototype.bind=function(b){var c=this;if(typeof c!="function")throw new TypeError;var d=w.call(arguments,1),e=function(){if(this instanceof e){var a=function(){};a.prototype=c.prototype;var f=new a,g=c.apply(f,d.concat(w.call(arguments)));return Object(g)===g?g:f}return c.apply(b,d.concat(w.call(arguments)))};return e}),s.flexbox=function(){return J("flexWrap")},s.canvas=function(){var a=b.createElement("canvas");return!!a.getContext&&!!a.getContext("2d")},s.canvastext=function(){return!!e.canvas&&!!F(b.createElement("canvas").getContext("2d").fillText,"function")},s.webgl=function(){return!!a.WebGLRenderingContext},s.touch=function(){var c;return"ontouchstart"in a||a.DocumentTouch&&b instanceof DocumentTouch?c=!0:y(["@media (",n.join("touch-enabled),("),h,")","{#modernizr{top:9px;position:absolute}}"].join(""),function(a){c=a.offsetTop===9}),c},s.geolocation=function(){return"geolocation"in navigator},s.postmessage=function(){return!!a.postMessage},s.websqldatabase=function(){return!!a.openDatabase},s.indexedDB=function(){return!!J("indexedDB",a)},s.hashchange=function(){return A("hashchange",a)&&(b.documentMode===c||b.documentMode>7)},s.history=function(){return!!a.history&&!!history.pushState},s.draganddrop=function(){var a=b.createElement("div");return"draggable"in a||"ondragstart"in a&&"ondrop"in a},s.websockets=function(){return"WebSocket"in a||"MozWebSocket"in a},s.rgba=function(){return D("background-color:rgba(150,255,150,.5)"),G(j.backgroundColor,"rgba")},s.hsla=function(){return D("background-color:hsla(120,40%,100%,.5)"),G(j.backgroundColor,"rgba")||G(j.backgroundColor,"hsla")},s.multiplebgs=function(){return D("background:url(https://),url(https://),red url(https://)"),/(url\s*\(.*?){3}/.test(j.background)},s.backgroundsize=function(){return J("backgroundSize")},s.borderimage=function(){return J("borderImage")},s.borderradius=function(){return J("borderRadius")},s.boxshadow=function(){return J("boxShadow")},s.textshadow=function(){return b.createElement("div").style.textShadow===""},s.opacity=function(){return E("opacity:.55"),/^0.55$/.test(j.opacity)},s.cssanimations=function(){return J("animationName")},s.csscolumns=function(){return J("columnCount")},s.cssgradients=function(){var a="background-image:",b="gradient(linear,left top,right bottom,from(#9f9),to(white));",c="linear-gradient(left top,#9f9, white);";return D((a+"-webkit- ".split(" ").join(b+a)+n.join(c+a)).slice(0,-a.length)),G(j.backgroundImage,"gradient")},s.cssreflections=function(){return J("boxReflect")},s.csstransforms=function(){return!!J("transform")},s.csstransforms3d=function(){var a=!!J("perspective");return a&&"webkitPerspective"in g.style&&y("@media (transform-3d),(-webkit-transform-3d){#modernizr{left:9px;position:absolute;height:3px;}}",function(b,c){a=b.offsetLeft===9&&b.offsetHeight===3}),a},s.csstransitions=function(){return J("transition")},s.fontface=function(){var a;return y('@font-face {font-family:"font";src:url("https://")}',function(c,d){var e=b.getElementById("smodernizr"),f=e.sheet||e.styleSheet,g=f?f.cssRules&&f.cssRules[0]?f.cssRules[0].cssText:f.cssText||"":"";a=/src/i.test(g)&&g.indexOf(d.split(" ")[0])===0}),a},s.generatedcontent=function(){var a;return y(["#",h,"{font:0/0 a}#",h,':after{content:"',l,'";visibility:hidden;font:3px/1 a}'].join(""),function(b){a=b.offsetHeight>=3}),a},s.video=function(){var a=b.createElement("video"),c=!1;try{if(c=!!a.canPlayType)c=new Boolean(c),c.ogg=a.canPlayType('video/ogg; codecs="theora"').replace(/^no$/,""),c.h264=a.canPlayType('video/mp4; codecs="avc1.42E01E"').replace(/^no$/,""),c.webm=a.canPlayType('video/webm; codecs="vp8, vorbis"').replace(/^no$/,"")}catch(d){}return c},s.audio=function(){var a=b.createElement("audio"),c=!1;try{if(c=!!a.canPlayType)c=new Boolean(c),c.ogg=a.canPlayType('audio/ogg; codecs="vorbis"').replace(/^no$/,""),c.mp3=a.canPlayType("audio/mpeg;").replace(/^no$/,""),c.wav=a.canPlayType('audio/wav; codecs="1"').replace(/^no$/,""),c.m4a=(a.canPlayType("audio/x-m4a;")||a.canPlayType("audio/aac;")).replace(/^no$/,"")}catch(d){}return c},s.localstorage=function(){try{return localStorage.setItem(h,h),localStorage.removeItem(h),!0}catch(a){return!1}},s.sessionstorage=function(){try{return sessionStorage.setItem(h,h),sessionStorage.removeItem(h),!0}catch(a){return!1}},s.webworkers=function(){return!!a.Worker},s.applicationcache=function(){return!!a.applicationCache},s.svg=function(){return!!b.createElementNS&&!!b.createElementNS(r.svg,"svg").createSVGRect},s.inlinesvg=function(){var a=b.createElement("div");return a.innerHTML="<svg/>",(a.firstChild&&a.firstChild.namespaceURI)==r.svg},s.smil=function(){return!!b.createElementNS&&/SVGAnimate/.test(m.call(b.createElementNS(r.svg,"animate")))},s.svgclippaths=function(){return!!b.createElementNS&&/SVGClipPath/.test(m.call(b.createElementNS(r.svg,"clipPath")))};for(var L in s)C(s,L)&&(x=L.toLowerCase(),e[x]=s[L](),v.push((e[x]?"":"no-")+x));return e.input||K(),e.addTest=function(a,b){if(typeof a=="object")for(var d in a)C(a,d)&&e.addTest(d,a[d]);else{a=a.toLowerCase();if(e[a]!==c)return e;b=typeof b=="function"?b():b,typeof f!="undefined"&&f&&(g.className+=" "+(b?"":"no-")+a),e[a]=b}return e},D(""),i=k=null,function(a,b){function k(a,b){var c=a.createElement("p"),d=a.getElementsByTagName("head")[0]||a.documentElement;return c.innerHTML="x<style>"+b+"</style>",d.insertBefore(c.lastChild,d.firstChild)}function l(){var a=r.elements;return typeof a=="string"?a.split(" "):a}function m(a){var b=i[a[g]];return b||(b={},h++,a[g]=h,i[h]=b),b}function n(a,c,f){c||(c=b);if(j)return c.createElement(a);f||(f=m(c));var g;return f.cache[a]?g=f.cache[a].cloneNode():e.test(a)?g=(f.cache[a]=f.createElem(a)).cloneNode():g=f.createElem(a),g.canHaveChildren&&!d.test(a)?f.frag.appendChild(g):g}function o(a,c){a||(a=b);if(j)return a.createDocumentFragment();c=c||m(a);var d=c.frag.cloneNode(),e=0,f=l(),g=f.length;for(;e<g;e++)d.createElement(f[e]);return d}function p(a,b){b.cache||(b.cache={},b.createElem=a.createElement,b.createFrag=a.createDocumentFragment,b.frag=b.createFrag()),a.createElement=function(c){return r.shivMethods?n(c,a,b):b.createElem(c)},a.createDocumentFragment=Function("h,f","return function(){var n=f.cloneNode(),c=n.createElement;h.shivMethods&&("+l().join().replace(/\w+/g,function(a){return b.createElem(a),b.frag.createElement(a),'c("'+a+'")'})+");return n}")(r,b.frag)}function q(a){a||(a=b);var c=m(a);return r.shivCSS&&!f&&!c.hasCSS&&(c.hasCSS=!!k(a,"article,aside,figcaption,figure,footer,header,hgroup,nav,section{display:block}mark{background:#FF0;color:#000}")),j||p(a,c),a}var c=a.html5||{},d=/^<|^(?:button|map|select|textarea|object|iframe|option|optgroup)$/i,e=/^(?:a|b|code|div|fieldset|h1|h2|h3|h4|h5|h6|i|label|li|ol|p|q|span|strong|style|table|tbody|td|th|tr|ul)$/i,f,g="_html5shiv",h=0,i={},j;(function(){try{var a=b.createElement("a");a.innerHTML="<xyz></xyz>",f="hidden"in a,j=a.childNodes.length==1||function(){b.createElement("a");var a=b.createDocumentFragment();return typeof a.cloneNode=="undefined"||typeof a.createDocumentFragment=="undefined"||typeof a.createElement=="undefined"}()}catch(c){f=!0,j=!0}})();var r={elements:c.elements||"abbr article aside audio bdi canvas data datalist details figcaption figure footer header hgroup mark meter nav output progress section summary time video",shivCSS:c.shivCSS!==!1,supportsUnknownElements:j,shivMethods:c.shivMethods!==!1,type:"default",shivDocument:q,createElement:n,createDocumentFragment:o};a.html5=r,q(b)}(this,b),e._version=d,e._prefixes=n,e._domPrefixes=q,e._cssomPrefixes=p,e.mq=z,e.hasEvent=A,e.testProp=function(a){return H([a])},e.testAllProps=J,e.testStyles=y,e.prefixed=function(a,b,c){return b?J(a,b,c):J(a,"pfx")},g.className=g.className.replace(/(^|\s)no-js(\s|$)/,"$1$2")+(f?" js "+v.join(" "):""),e}(this,this.document),function(a,b,c){function d(a){return"[object Function]"==o.call(a)}function e(a){return"string"==typeof a}function f(){}function g(a){return!a||"loaded"==a||"complete"==a||"uninitialized"==a}function h(){var a=p.shift();q=1,a?a.t?m(function(){("c"==a.t?B.injectCss:B.injectJs)(a.s,0,a.a,a.x,a.e,1)},0):(a(),h()):q=0}function i(a,c,d,e,f,i,j){function k(b){if(!o&&g(l.readyState)&&(u.r=o=1,!q&&h(),l.onload=l.onreadystatechange=null,b)){"img"!=a&&m(function(){t.removeChild(l)},50);for(var d in y[c])y[c].hasOwnProperty(d)&&y[c][d].onload()}}var j=j||B.errorTimeout,l=b.createElement(a),o=0,r=0,u={t:d,s:c,e:f,a:i,x:j};1===y[c]&&(r=1,y[c]=[]),"object"==a?l.data=c:(l.src=c,l.type=a),l.width=l.height="0",l.onerror=l.onload=l.onreadystatechange=function(){k.call(this,r)},p.splice(e,0,u),"img"!=a&&(r||2===y[c]?(t.insertBefore(l,s?null:n),m(k,j)):y[c].push(l))}function j(a,b,c,d,f){return q=0,b=b||"j",e(a)?i("c"==b?v:u,a,b,this.i++,c,d,f):(p.splice(this.i++,0,a),1==p.length&&h()),this}function k(){var a=B;return a.loader={load:j,i:0},a}var l=b.documentElement,m=a.setTimeout,n=b.getElementsByTagName("script")[0],o={}.toString,p=[],q=0,r="MozAppearance"in l.style,s=r&&!!b.createRange().compareNode,t=s?l:n.parentNode,l=a.opera&&"[object Opera]"==o.call(a.opera),l=!!b.attachEvent&&!l,u=r?"object":l?"script":"img",v=l?"script":u,w=Array.isArray||function(a){return"[object Array]"==o.call(a)},x=[],y={},z={timeout:function(a,b){return b.length&&(a.timeout=b[0]),a}},A,B;B=function(a){function b(a){var a=a.split("!"),b=x.length,c=a.pop(),d=a.length,c={url:c,origUrl:c,prefixes:a},e,f,g;for(f=0;f<d;f++)g=a[f].split("="),(e=z[g.shift()])&&(c=e(c,g));for(f=0;f<b;f++)c=x[f](c);return c}function g(a,e,f,g,h){var i=b(a),j=i.autoCallback;i.url.split(".").pop().split("?").shift(),i.bypass||(e&&(e=d(e)?e:e[a]||e[g]||e[a.split("/").pop().split("?")[0]]),i.instead?i.instead(a,e,f,g,h):(y[i.url]?i.noexec=!0:y[i.url]=1,f.load(i.url,i.forceCSS||!i.forceJS&&"css"==i.url.split(".").pop().split("?").shift()?"c":c,i.noexec,i.attrs,i.timeout),(d(e)||d(j))&&f.load(function(){k(),e&&e(i.origUrl,h,g),j&&j(i.origUrl,h,g),y[i.url]=2})))}function h(a,b){function c(a,c){if(a){if(e(a))c||(j=function(){var a=[].slice.call(arguments);k.apply(this,a),l()}),g(a,j,b,0,h);else if(Object(a)===a)for(n in m=function(){var b=0,c;for(c in a)a.hasOwnProperty(c)&&b++;return b}(),a)a.hasOwnProperty(n)&&(!c&&!--m&&(d(j)?j=function(){var a=[].slice.call(arguments);k.apply(this,a),l()}:j[n]=function(a){return function(){var b=[].slice.call(arguments);a&&a.apply(this,b),l()}}(k[n])),g(a[n],j,b,n,h))}else!c&&l()}var h=!!a.test,i=a.load||a.both,j=a.callback||f,k=j,l=a.complete||f,m,n;c(h?a.yep:a.nope,!!i),i&&c(i)}var i,j,l=this.yepnope.loader;if(e(a))g(a,0,l,0);else if(w(a))for(i=0;i<a.length;i++)j=a[i],e(j)?g(j,0,l,0):w(j)?B(j):Object(j)===j&&h(j,l);else Object(a)===a&&h(a,l)},B.addPrefix=function(a,b){z[a]=b},B.addFilter=function(a){x.push(a)},B.errorTimeout=1e4,null==b.readyState&&b.addEventListener&&(b.readyState="loading",b.addEventListener("DOMContentLoaded",A=function(){b.removeEventListener("DOMContentLoaded",A,0),b.readyState="complete"},0)),a.yepnope=k(),a.yepnope.executeStack=h,a.yepnope.injectJs=function(a,c,d,e,i,j){var k=b.createElement("script"),l,o,e=e||B.errorTimeout;k.src=a;for(o in d)k.setAttribute(o,d[o]);c=j?h:c||f,k.onreadystatechange=k.onload=function(){!l&&g(k.readyState)&&(l=1,c(),k.onload=k.onreadystatechange=null)},m(function(){l||(l=1,c(1))},e),i?k.onload():n.parentNode.insertBefore(k,n)},a.yepnope.injectCss=function(a,c,d,e,g,i){var e=b.createElement("link"),j,c=i?h:c||f;e.href=a,e.rel="stylesheet",e.type="text/css";for(j in d)e.setAttribute(j,d[j]);g||(n.parentNode.insertBefore(e,n),m(c,0))}}(this,document),Modernizr.load=function(){yepnope.apply(window,[].slice.call(arguments,0))}; |
| 0 | require=(function e(t,n,r){function s(o,u){if(!n[o]){if(!t[o]){var a=typeof require=="function"&&require;if(!u&&a)return a(o,!0);if(i)return i(o,!0);var f=new Error("Cannot find module '"+o+"'");throw f.code="MODULE_NOT_FOUND",f}var l=n[o]={exports:{}};t[o][0].call(l.exports,function(e){var n=t[o][1][e];return s(n?n:e)},l,l.exports,e,t,n,r)}return n[o].exports}var i=typeof require=="function"&&require;for(var o=0;o<r.length;o++)s(r[o]);return s})({"sphinx-rtd-theme":[function(require,module,exports){ | |
| 1 | var jQuery = (typeof(window) != 'undefined') ? window.jQuery : require('jquery'); | |
| 2 | ||
| 3 | // Sphinx theme nav state | |
| 4 | function ThemeNav () { | |
| 5 | ||
| 6 | var nav = { | |
| 7 | navBar: null, | |
| 8 | win: null, | |
| 9 | winScroll: false, | |
| 10 | winResize: false, | |
| 11 | linkScroll: false, | |
| 12 | winPosition: 0, | |
| 13 | winHeight: null, | |
| 14 | docHeight: null, | |
| 15 | isRunning: null | |
| 16 | }; | |
| 17 | ||
| 18 | nav.enable = function () { | |
| 19 | var self = this; | |
| 20 | ||
| 21 | jQuery(function ($) { | |
| 22 | self.init($); | |
| 23 | ||
| 24 | self.reset(); | |
| 25 | self.win.on('hashchange', self.reset); | |
| 26 | ||
| 27 | // Set scroll monitor | |
| 28 | self.win.on('scroll', function () { | |
| 29 | if (!self.linkScroll) { | |
| 30 | self.winScroll = true; | |
| 31 | } | |
| 32 | }); | |
| 33 | setInterval(function () { if (self.winScroll) self.onScroll(); }, 25); | |
| 34 | ||
| 35 | // Set resize monitor | |
| 36 | self.win.on('resize', function () { | |
| 37 | self.winResize = true; | |
| 38 | }); | |
| 39 | setInterval(function () { if (self.winResize) self.onResize(); }, 25); | |
| 40 | self.onResize(); | |
| 41 | }); | |
| 42 | }; | |
| 43 | ||
| 44 | nav.init = function ($) { | |
| 45 | var doc = $(document), | |
| 46 | self = this; | |
| 47 | ||
| 48 | this.navBar = $('div.wy-side-scroll:first'); | |
| 49 | this.win = $(window); | |
| 50 | ||
| 51 | // Set up javascript UX bits | |
| 52 | $(document) | |
| 53 | // Shift nav in mobile when clicking the menu. | |
| 54 | .on('click', "[data-toggle='wy-nav-top']", function() { | |
| 55 | $("[data-toggle='wy-nav-shift']").toggleClass("shift"); | |
| 56 | $("[data-toggle='rst-versions']").toggleClass("shift"); | |
| 57 | }) | |
| 58 | ||
| 59 | // Nav menu link click operations | |
| 60 | .on('click', ".wy-menu-vertical .current ul li a", function() { | |
| 61 | var target = $(this); | |
| 62 | // Close menu when you click a link. | |
| 63 | $("[data-toggle='wy-nav-shift']").removeClass("shift"); | |
| 64 | $("[data-toggle='rst-versions']").toggleClass("shift"); | |
| 65 | // Handle dynamic display of l3 and l4 nav lists | |
| 66 | self.toggleCurrent(target); | |
| 67 | self.hashChange(); | |
| 68 | }) | |
| 69 | .on('click', "[data-toggle='rst-current-version']", function() { | |
| 70 | $("[data-toggle='rst-versions']").toggleClass("shift-up"); | |
| 71 | }) | |
| 72 | ||
| 73 | // Make tables responsive | |
| 74 | $("table.docutils:not(.field-list)") | |
| 75 | .wrap("<div class='wy-table-responsive'></div>"); | |
| 76 | ||
| 77 | // Add expand links to all parents of nested ul | |
| 78 | $('.wy-menu-vertical ul').not('.simple').siblings('a').each(function () { | |
| 79 | var link = $(this); | |
| 80 | expand = $('<span class="toctree-expand"></span>'); | |
| 81 | expand.on('click', function (ev) { | |
| 82 | self.toggleCurrent(link); | |
| 83 | ev.stopPropagation(); | |
| 84 | return false; | |
| 85 | }); | |
| 86 | link.prepend(expand); | |
| 87 | }); | |
| 88 | }; | |
| 89 | ||
| 90 | nav.reset = function () { | |
| 91 | // Get anchor from URL and open up nested nav | |
| 92 | var anchor = encodeURI(window.location.hash); | |
| 93 | if (anchor) { | |
| 94 | try { | |
| 95 | var link = $('.wy-menu-vertical') | |
| 96 | .find('[href="' + anchor + '"]'); | |
| 97 | $('.wy-menu-vertical li.toctree-l1 li.current') | |
| 98 | .removeClass('current'); | |
| 99 | link.closest('li.toctree-l2').addClass('current'); | |
| 100 | link.closest('li.toctree-l3').addClass('current'); | |
| 101 | link.closest('li.toctree-l4').addClass('current'); | |
| 102 | } | |
| 103 | catch (err) { | |
| 104 | console.log("Error expanding nav for anchor", err); | |
| 105 | } | |
| 106 | } | |
| 107 | }; | |
| 108 | ||
| 109 | nav.onScroll = function () { | |
| 110 | this.winScroll = false; | |
| 111 | var newWinPosition = this.win.scrollTop(), | |
| 112 | winBottom = newWinPosition + this.winHeight, | |
| 113 | navPosition = this.navBar.scrollTop(), | |
| 114 | newNavPosition = navPosition + (newWinPosition - this.winPosition); | |
| 115 | if (newWinPosition < 0 || winBottom > this.docHeight) { | |
| 116 | return; | |
| 117 | } | |
| 118 | this.navBar.scrollTop(newNavPosition); | |
| 119 | this.winPosition = newWinPosition; | |
| 120 | }; | |
| 121 | ||
| 122 | nav.onResize = function () { | |
| 123 | this.winResize = false; | |
| 124 | this.winHeight = this.win.height(); | |
| 125 | this.docHeight = $(document).height(); | |
| 126 | }; | |
| 127 | ||
| 128 | nav.hashChange = function () { | |
| 129 | this.linkScroll = true; | |
| 130 | this.win.one('hashchange', function () { | |
| 131 | this.linkScroll = false; | |
| 132 | }); | |
| 133 | }; | |
| 134 | ||
| 135 | nav.toggleCurrent = function (elem) { | |
| 136 | var parent_li = elem.closest('li'); | |
| 137 | parent_li.siblings('li.current').removeClass('current'); | |
| 138 | parent_li.siblings().find('li.current').removeClass('current'); | |
| 139 | parent_li.find('> ul li.current').removeClass('current'); | |
| 140 | parent_li.toggleClass('current'); | |
| 141 | } | |
| 142 | ||
| 143 | return nav; | |
| 144 | }; | |
| 145 | ||
| 146 | module.exports.ThemeNav = ThemeNav(); | |
| 147 | ||
| 148 | if (typeof(window) != 'undefined') { | |
| 149 | window.SphinxRtdTheme = { StickyNav: module.exports.ThemeNav }; | |
| 150 | } | |
| 151 | ||
| 152 | },{"jquery":"jquery"}]},{},["sphinx-rtd-theme"]); |
Binary diff not shown
| 0 | .highlight .hll { background-color: #ffffcc } | |
| 1 | .highlight { background: #eeffcc; } | |
| 2 | .highlight .c { color: #408090; font-style: italic } /* Comment */ | |
| 3 | .highlight .err { border: 1px solid #FF0000 } /* Error */ | |
| 4 | .highlight .k { color: #007020; font-weight: bold } /* Keyword */ | |
| 5 | .highlight .o { color: #666666 } /* Operator */ | |
| 6 | .highlight .ch { color: #408090; font-style: italic } /* Comment.Hashbang */ | |
| 7 | .highlight .cm { color: #408090; font-style: italic } /* Comment.Multiline */ | |
| 8 | .highlight .cp { color: #007020 } /* Comment.Preproc */ | |
| 9 | .highlight .cpf { color: #408090; font-style: italic } /* Comment.PreprocFile */ | |
| 10 | .highlight .c1 { color: #408090; font-style: italic } /* Comment.Single */ | |
| 11 | .highlight .cs { color: #408090; background-color: #fff0f0 } /* Comment.Special */ | |
| 12 | .highlight .gd { color: #A00000 } /* Generic.Deleted */ | |
| 13 | .highlight .ge { font-style: italic } /* Generic.Emph */ | |
| 14 | .highlight .gr { color: #FF0000 } /* Generic.Error */ | |
| 15 | .highlight .gh { color: #000080; font-weight: bold } /* Generic.Heading */ | |
| 16 | .highlight .gi { color: #00A000 } /* Generic.Inserted */ | |
| 17 | .highlight .go { color: #333333 } /* Generic.Output */ | |
| 18 | .highlight .gp { color: #c65d09; font-weight: bold } /* Generic.Prompt */ | |
| 19 | .highlight .gs { font-weight: bold } /* Generic.Strong */ | |
| 20 | .highlight .gu { color: #800080; font-weight: bold } /* Generic.Subheading */ | |
| 21 | .highlight .gt { color: #0044DD } /* Generic.Traceback */ | |
| 22 | .highlight .kc { color: #007020; font-weight: bold } /* Keyword.Constant */ | |
| 23 | .highlight .kd { color: #007020; font-weight: bold } /* Keyword.Declaration */ | |
| 24 | .highlight .kn { color: #007020; font-weight: bold } /* Keyword.Namespace */ | |
| 25 | .highlight .kp { color: #007020 } /* Keyword.Pseudo */ | |
| 26 | .highlight .kr { color: #007020; font-weight: bold } /* Keyword.Reserved */ | |
| 27 | .highlight .kt { color: #902000 } /* Keyword.Type */ | |
| 28 | .highlight .m { color: #208050 } /* Literal.Number */ | |
| 29 | .highlight .s { color: #4070a0 } /* Literal.String */ | |
| 30 | .highlight .na { color: #4070a0 } /* Name.Attribute */ | |
| 31 | .highlight .nb { color: #007020 } /* Name.Builtin */ | |
| 32 | .highlight .nc { color: #0e84b5; font-weight: bold } /* Name.Class */ | |
| 33 | .highlight .no { color: #60add5 } /* Name.Constant */ | |
| 34 | .highlight .nd { color: #555555; font-weight: bold } /* Name.Decorator */ | |
| 35 | .highlight .ni { color: #d55537; font-weight: bold } /* Name.Entity */ | |
| 36 | .highlight .ne { color: #007020 } /* Name.Exception */ | |
| 37 | .highlight .nf { color: #06287e } /* Name.Function */ | |
| 38 | .highlight .nl { color: #002070; font-weight: bold } /* Name.Label */ | |
| 39 | .highlight .nn { color: #0e84b5; font-weight: bold } /* Name.Namespace */ | |
| 40 | .highlight .nt { color: #062873; font-weight: bold } /* Name.Tag */ | |
| 41 | .highlight .nv { color: #bb60d5 } /* Name.Variable */ | |
| 42 | .highlight .ow { color: #007020; font-weight: bold } /* Operator.Word */ | |
| 43 | .highlight .w { color: #bbbbbb } /* Text.Whitespace */ | |
| 44 | .highlight .mb { color: #208050 } /* Literal.Number.Bin */ | |
| 45 | .highlight .mf { color: #208050 } /* Literal.Number.Float */ | |
| 46 | .highlight .mh { color: #208050 } /* Literal.Number.Hex */ | |
| 47 | .highlight .mi { color: #208050 } /* Literal.Number.Integer */ | |
| 48 | .highlight .mo { color: #208050 } /* Literal.Number.Oct */ | |
| 49 | .highlight .sb { color: #4070a0 } /* Literal.String.Backtick */ | |
| 50 | .highlight .sc { color: #4070a0 } /* Literal.String.Char */ | |
| 51 | .highlight .sd { color: #4070a0; font-style: italic } /* Literal.String.Doc */ | |
| 52 | .highlight .s2 { color: #4070a0 } /* Literal.String.Double */ | |
| 53 | .highlight .se { color: #4070a0; font-weight: bold } /* Literal.String.Escape */ | |
| 54 | .highlight .sh { color: #4070a0 } /* Literal.String.Heredoc */ | |
| 55 | .highlight .si { color: #70a0d0; font-style: italic } /* Literal.String.Interpol */ | |
| 56 | .highlight .sx { color: #c65d09 } /* Literal.String.Other */ | |
| 57 | .highlight .sr { color: #235388 } /* Literal.String.Regex */ | |
| 58 | .highlight .s1 { color: #4070a0 } /* Literal.String.Single */ | |
| 59 | .highlight .ss { color: #517918 } /* Literal.String.Symbol */ | |
| 60 | .highlight .bp { color: #007020 } /* Name.Builtin.Pseudo */ | |
| 61 | .highlight .vc { color: #bb60d5 } /* Name.Variable.Class */ | |
| 62 | .highlight .vg { color: #bb60d5 } /* Name.Variable.Global */ | |
| 63 | .highlight .vi { color: #bb60d5 } /* Name.Variable.Instance */ | |
| 64 | .highlight .il { color: #208050 } /* Literal.Number.Integer.Long */⏎ |
| 0 | /* | |
| 1 | * searchtools.js_t | |
| 2 | * ~~~~~~~~~~~~~~~~ | |
| 3 | * | |
| 4 | * Sphinx JavaScript utilities for the full-text search. | |
| 5 | * | |
| 6 | * :copyright: Copyright 2007-2016 by the Sphinx team, see AUTHORS. | |
| 7 | * :license: BSD, see LICENSE for details. | |
| 8 | * | |
| 9 | */ | |
| 10 | ||
| 11 | ||
| 12 | /* Non-minified version JS is _stemmer.js if file is provided */ | |
| 13 | /** | |
| 14 | * Porter Stemmer | |
| 15 | */ | |
| 16 | var Stemmer = function() { | |
| 17 | ||
| 18 | var step2list = { | |
| 19 | ational: 'ate', | |
| 20 | tional: 'tion', | |
| 21 | enci: 'ence', | |
| 22 | anci: 'ance', | |
| 23 | izer: 'ize', | |
| 24 | bli: 'ble', | |
| 25 | alli: 'al', | |
| 26 | entli: 'ent', | |
| 27 | eli: 'e', | |
| 28 | ousli: 'ous', | |
| 29 | ization: 'ize', | |
| 30 | ation: 'ate', | |
| 31 | ator: 'ate', | |
| 32 | alism: 'al', | |
| 33 | iveness: 'ive', | |
| 34 | fulness: 'ful', | |
| 35 | ousness: 'ous', | |
| 36 | aliti: 'al', | |
| 37 | iviti: 'ive', | |
| 38 | biliti: 'ble', | |
| 39 | logi: 'log' | |
| 40 | }; | |
| 41 | ||
| 42 | var step3list = { | |
| 43 | icate: 'ic', | |
| 44 | ative: '', | |
| 45 | alize: 'al', | |
| 46 | iciti: 'ic', | |
| 47 | ical: 'ic', | |
| 48 | ful: '', | |
| 49 | ness: '' | |
| 50 | }; | |
| 51 | ||
| 52 | var c = "[^aeiou]"; // consonant | |
| 53 | var v = "[aeiouy]"; // vowel | |
| 54 | var C = c + "[^aeiouy]*"; // consonant sequence | |
| 55 | var V = v + "[aeiou]*"; // vowel sequence | |
| 56 | ||
| 57 | var mgr0 = "^(" + C + ")?" + V + C; // [C]VC... is m>0 | |
| 58 | var meq1 = "^(" + C + ")?" + V + C + "(" + V + ")?$"; // [C]VC[V] is m=1 | |
| 59 | var mgr1 = "^(" + C + ")?" + V + C + V + C; // [C]VCVC... is m>1 | |
| 60 | var s_v = "^(" + C + ")?" + v; // vowel in stem | |
| 61 | ||
| 62 | this.stemWord = function (w) { | |
| 63 | var stem; | |
| 64 | var suffix; | |
| 65 | var firstch; | |
| 66 | var origword = w; | |
| 67 | ||
| 68 | if (w.length < 3) | |
| 69 | return w; | |
| 70 | ||
| 71 | var re; | |
| 72 | var re2; | |
| 73 | var re3; | |
| 74 | var re4; | |
| 75 | ||
| 76 | firstch = w.substr(0,1); | |
| 77 | if (firstch == "y") | |
| 78 | w = firstch.toUpperCase() + w.substr(1); | |
| 79 | ||
| 80 | // Step 1a | |
| 81 | re = /^(.+?)(ss|i)es$/; | |
| 82 | re2 = /^(.+?)([^s])s$/; | |
| 83 | ||
| 84 | if (re.test(w)) | |
| 85 | w = w.replace(re,"$1$2"); | |
| 86 | else if (re2.test(w)) | |
| 87 | w = w.replace(re2,"$1$2"); | |
| 88 | ||
| 89 | // Step 1b | |
| 90 | re = /^(.+?)eed$/; | |
| 91 | re2 = /^(.+?)(ed|ing)$/; | |
| 92 | if (re.test(w)) { | |
| 93 | var fp = re.exec(w); | |
| 94 | re = new RegExp(mgr0); | |
| 95 | if (re.test(fp[1])) { | |
| 96 | re = /.$/; | |
| 97 | w = w.replace(re,""); | |
| 98 | } | |
| 99 | } | |
| 100 | else if (re2.test(w)) { | |
| 101 | var fp = re2.exec(w); | |
| 102 | stem = fp[1]; | |
| 103 | re2 = new RegExp(s_v); | |
| 104 | if (re2.test(stem)) { | |
| 105 | w = stem; | |
| 106 | re2 = /(at|bl|iz)$/; | |
| 107 | re3 = new RegExp("([^aeiouylsz])\\1$"); | |
| 108 | re4 = new RegExp("^" + C + v + "[^aeiouwxy]$"); | |
| 109 | if (re2.test(w)) | |
| 110 | w = w + "e"; | |
| 111 | else if (re3.test(w)) { | |
| 112 | re = /.$/; | |
| 113 | w = w.replace(re,""); | |
| 114 | } | |
| 115 | else if (re4.test(w)) | |
| 116 | w = w + "e"; | |
| 117 | } | |
| 118 | } | |
| 119 | ||
| 120 | // Step 1c | |
| 121 | re = /^(.+?)y$/; | |
| 122 | if (re.test(w)) { | |
| 123 | var fp = re.exec(w); | |
| 124 | stem = fp[1]; | |
| 125 | re = new RegExp(s_v); | |
| 126 | if (re.test(stem)) | |
| 127 | w = stem + "i"; | |
| 128 | } | |
| 129 | ||
| 130 | // Step 2 | |
| 131 | re = /^(.+?)(ational|tional|enci|anci|izer|bli|alli|entli|eli|ousli|ization|ation|ator|alism|iveness|fulness|ousness|aliti|iviti|biliti|logi)$/; | |
| 132 | if (re.test(w)) { | |
| 133 | var fp = re.exec(w); | |
| 134 | stem = fp[1]; | |
| 135 | suffix = fp[2]; | |
| 136 | re = new RegExp(mgr0); | |
| 137 | if (re.test(stem)) | |
| 138 | w = stem + step2list[suffix]; | |
| 139 | } | |
| 140 | ||
| 141 | // Step 3 | |
| 142 | re = /^(.+?)(icate|ative|alize|iciti|ical|ful|ness)$/; | |
| 143 | if (re.test(w)) { | |
| 144 | var fp = re.exec(w); | |
| 145 | stem = fp[1]; | |
| 146 | suffix = fp[2]; | |
| 147 | re = new RegExp(mgr0); | |
| 148 | if (re.test(stem)) | |
| 149 | w = stem + step3list[suffix]; | |
| 150 | } | |
| 151 | ||
| 152 | // Step 4 | |
| 153 | re = /^(.+?)(al|ance|ence|er|ic|able|ible|ant|ement|ment|ent|ou|ism|ate|iti|ous|ive|ize)$/; | |
| 154 | re2 = /^(.+?)(s|t)(ion)$/; | |
| 155 | if (re.test(w)) { | |
| 156 | var fp = re.exec(w); | |
| 157 | stem = fp[1]; | |
| 158 | re = new RegExp(mgr1); | |
| 159 | if (re.test(stem)) | |
| 160 | w = stem; | |
| 161 | } | |
| 162 | else if (re2.test(w)) { | |
| 163 | var fp = re2.exec(w); | |
| 164 | stem = fp[1] + fp[2]; | |
| 165 | re2 = new RegExp(mgr1); | |
| 166 | if (re2.test(stem)) | |
| 167 | w = stem; | |
| 168 | } | |
| 169 | ||
| 170 | // Step 5 | |
| 171 | re = /^(.+?)e$/; | |
| 172 | if (re.test(w)) { | |
| 173 | var fp = re.exec(w); | |
| 174 | stem = fp[1]; | |
| 175 | re = new RegExp(mgr1); | |
| 176 | re2 = new RegExp(meq1); | |
| 177 | re3 = new RegExp("^" + C + v + "[^aeiouwxy]$"); | |
| 178 | if (re.test(stem) || (re2.test(stem) && !(re3.test(stem)))) | |
| 179 | w = stem; | |
| 180 | } | |
| 181 | re = /ll$/; | |
| 182 | re2 = new RegExp(mgr1); | |
| 183 | if (re.test(w) && re2.test(w)) { | |
| 184 | re = /.$/; | |
| 185 | w = w.replace(re,""); | |
| 186 | } | |
| 187 | ||
| 188 | // and turn initial Y back to y | |
| 189 | if (firstch == "y") | |
| 190 | w = firstch.toLowerCase() + w.substr(1); | |
| 191 | return w; | |
| 192 | } | |
| 193 | } | |
| 194 | ||
| 195 | ||
| 196 | ||
| 197 | /** | |
| 198 | * Simple result scoring code. | |
| 199 | */ | |
| 200 | var Scorer = { | |
| 201 | // Implement the following function to further tweak the score for each result | |
| 202 | // The function takes a result array [filename, title, anchor, descr, score] | |
| 203 | // and returns the new score. | |
| 204 | /* | |
| 205 | score: function(result) { | |
| 206 | return result[4]; | |
| 207 | }, | |
| 208 | */ | |
| 209 | ||
| 210 | // query matches the full name of an object | |
| 211 | objNameMatch: 11, | |
| 212 | // or matches in the last dotted part of the object name | |
| 213 | objPartialMatch: 6, | |
| 214 | // Additive scores depending on the priority of the object | |
| 215 | objPrio: {0: 15, // used to be importantResults | |
| 216 | 1: 5, // used to be objectResults | |
| 217 | 2: -5}, // used to be unimportantResults | |
| 218 | // Used when the priority is not in the mapping. | |
| 219 | objPrioDefault: 0, | |
| 220 | ||
| 221 | // query found in title | |
| 222 | title: 15, | |
| 223 | // query found in terms | |
| 224 | term: 5 | |
| 225 | }; | |
| 226 | ||
| 227 | ||
| 228 | ||
| 229 | ||
| 230 | ||
| 231 | var splitChars = (function() { | |
| 232 | var result = {}; | |
| 233 | var singles = [96, 180, 187, 191, 215, 247, 749, 885, 903, 907, 909, 930, 1014, 1648, | |
| 234 | 1748, 1809, 2416, 2473, 2481, 2526, 2601, 2609, 2612, 2615, 2653, 2702, | |
| 235 | 2706, 2729, 2737, 2740, 2857, 2865, 2868, 2910, 2928, 2948, 2961, 2971, | |
| 236 | 2973, 3085, 3089, 3113, 3124, 3213, 3217, 3241, 3252, 3295, 3341, 3345, | |
| 237 | 3369, 3506, 3516, 3633, 3715, 3721, 3736, 3744, 3748, 3750, 3756, 3761, | |
| 238 | 3781, 3912, 4239, 4347, 4681, 4695, 4697, 4745, 4785, 4799, 4801, 4823, | |
| 239 | 4881, 5760, 5901, 5997, 6313, 7405, 8024, 8026, 8028, 8030, 8117, 8125, | |
| 240 | 8133, 8181, 8468, 8485, 8487, 8489, 8494, 8527, 11311, 11359, 11687, 11695, | |
| 241 | 11703, 11711, 11719, 11727, 11735, 12448, 12539, 43010, 43014, 43019, 43587, | |
| 242 | 43696, 43713, 64286, 64297, 64311, 64317, 64319, 64322, 64325, 65141]; | |
| 243 | var i, j, start, end; | |
| 244 | for (i = 0; i < singles.length; i++) { | |
| 245 | result[singles[i]] = true; | |
| 246 | } | |
| 247 | var ranges = [[0, 47], [58, 64], [91, 94], [123, 169], [171, 177], [182, 184], [706, 709], | |
| 248 | [722, 735], [741, 747], [751, 879], [888, 889], [894, 901], [1154, 1161], | |
| 249 | [1318, 1328], [1367, 1368], [1370, 1376], [1416, 1487], [1515, 1519], [1523, 1568], | |
| 250 | [1611, 1631], [1642, 1645], [1750, 1764], [1767, 1773], [1789, 1790], [1792, 1807], | |
| 251 | [1840, 1868], [1958, 1968], [1970, 1983], [2027, 2035], [2038, 2041], [2043, 2047], | |
| 252 | [2070, 2073], [2075, 2083], [2085, 2087], [2089, 2307], [2362, 2364], [2366, 2383], | |
| 253 | [2385, 2391], [2402, 2405], [2419, 2424], [2432, 2436], [2445, 2446], [2449, 2450], | |
| 254 | [2483, 2485], [2490, 2492], [2494, 2509], [2511, 2523], [2530, 2533], [2546, 2547], | |
| 255 | [2554, 2564], [2571, 2574], [2577, 2578], [2618, 2648], [2655, 2661], [2672, 2673], | |
| 256 | [2677, 2692], [2746, 2748], [2750, 2767], [2769, 2783], [2786, 2789], [2800, 2820], | |
| 257 | [2829, 2830], [2833, 2834], [2874, 2876], [2878, 2907], [2914, 2917], [2930, 2946], | |
| 258 | [2955, 2957], [2966, 2968], [2976, 2978], [2981, 2983], [2987, 2989], [3002, 3023], | |
| 259 | [3025, 3045], [3059, 3076], [3130, 3132], [3134, 3159], [3162, 3167], [3170, 3173], | |
| 260 | [3184, 3191], [3199, 3204], [3258, 3260], [3262, 3293], [3298, 3301], [3312, 3332], | |
| 261 | [3386, 3388], [3390, 3423], [3426, 3429], [3446, 3449], [3456, 3460], [3479, 3481], | |
| 262 | [3518, 3519], [3527, 3584], [3636, 3647], [3655, 3663], [3674, 3712], [3717, 3718], | |
| 263 | [3723, 3724], [3726, 3731], [3752, 3753], [3764, 3772], [3774, 3775], [3783, 3791], | |
| 264 | [3802, 3803], [3806, 3839], [3841, 3871], [3892, 3903], [3949, 3975], [3980, 4095], | |
| 265 | [4139, 4158], [4170, 4175], [4182, 4185], [4190, 4192], [4194, 4196], [4199, 4205], | |
| 266 | [4209, 4212], [4226, 4237], [4250, 4255], [4294, 4303], [4349, 4351], [4686, 4687], | |
| 267 | [4702, 4703], [4750, 4751], [4790, 4791], [4806, 4807], [4886, 4887], [4955, 4968], | |
| 268 | [4989, 4991], [5008, 5023], [5109, 5120], [5741, 5742], [5787, 5791], [5867, 5869], | |
| 269 | [5873, 5887], [5906, 5919], [5938, 5951], [5970, 5983], [6001, 6015], [6068, 6102], | |
| 270 | [6104, 6107], [6109, 6111], [6122, 6127], [6138, 6159], [6170, 6175], [6264, 6271], | |
| 271 | [6315, 6319], [6390, 6399], [6429, 6469], [6510, 6511], [6517, 6527], [6572, 6592], | |
| 272 | [6600, 6607], [6619, 6655], [6679, 6687], [6741, 6783], [6794, 6799], [6810, 6822], | |
| 273 | [6824, 6916], [6964, 6980], [6988, 6991], [7002, 7042], [7073, 7085], [7098, 7167], | |
| 274 | [7204, 7231], [7242, 7244], [7294, 7400], [7410, 7423], [7616, 7679], [7958, 7959], | |
| 275 | [7966, 7967], [8006, 8007], [8014, 8015], [8062, 8063], [8127, 8129], [8141, 8143], | |
| 276 | [8148, 8149], [8156, 8159], [8173, 8177], [8189, 8303], [8306, 8307], [8314, 8318], | |
| 277 | [8330, 8335], [8341, 8449], [8451, 8454], [8456, 8457], [8470, 8472], [8478, 8483], | |
| 278 | [8506, 8507], [8512, 8516], [8522, 8525], [8586, 9311], [9372, 9449], [9472, 10101], | |
| 279 | [10132, 11263], [11493, 11498], [11503, 11516], [11518, 11519], [11558, 11567], | |
| 280 | [11622, 11630], [11632, 11647], [11671, 11679], [11743, 11822], [11824, 12292], | |
| 281 | [12296, 12320], [12330, 12336], [12342, 12343], [12349, 12352], [12439, 12444], | |
| 282 | [12544, 12548], [12590, 12592], [12687, 12689], [12694, 12703], [12728, 12783], | |
| 283 | [12800, 12831], [12842, 12880], [12896, 12927], [12938, 12976], [12992, 13311], | |
| 284 | [19894, 19967], [40908, 40959], [42125, 42191], [42238, 42239], [42509, 42511], | |
| 285 | [42540, 42559], [42592, 42593], [42607, 42622], [42648, 42655], [42736, 42774], | |
| 286 | [42784, 42785], [42889, 42890], [42893, 43002], [43043, 43055], [43062, 43071], | |
| 287 | [43124, 43137], [43188, 43215], [43226, 43249], [43256, 43258], [43260, 43263], | |
| 288 | [43302, 43311], [43335, 43359], [43389, 43395], [43443, 43470], [43482, 43519], | |
| 289 | [43561, 43583], [43596, 43599], [43610, 43615], [43639, 43641], [43643, 43647], | |
| 290 | [43698, 43700], [43703, 43704], [43710, 43711], [43715, 43738], [43742, 43967], | |
| 291 | [44003, 44015], [44026, 44031], [55204, 55215], [55239, 55242], [55292, 55295], | |
| 292 | [57344, 63743], [64046, 64047], [64110, 64111], [64218, 64255], [64263, 64274], | |
| 293 | [64280, 64284], [64434, 64466], [64830, 64847], [64912, 64913], [64968, 65007], | |
| 294 | [65020, 65135], [65277, 65295], [65306, 65312], [65339, 65344], [65371, 65381], | |
| 295 | [65471, 65473], [65480, 65481], [65488, 65489], [65496, 65497]]; | |
| 296 | for (i = 0; i < ranges.length; i++) { | |
| 297 | start = ranges[i][0]; | |
| 298 | end = ranges[i][1]; | |
| 299 | for (j = start; j <= end; j++) { | |
| 300 | result[j] = true; | |
| 301 | } | |
| 302 | } | |
| 303 | return result; | |
| 304 | })(); | |
| 305 | ||
| 306 | function splitQuery(query) { | |
| 307 | var result = []; | |
| 308 | var start = -1; | |
| 309 | for (var i = 0; i < query.length; i++) { | |
| 310 | if (splitChars[query.charCodeAt(i)]) { | |
| 311 | if (start !== -1) { | |
| 312 | result.push(query.slice(start, i)); | |
| 313 | start = -1; | |
| 314 | } | |
| 315 | } else if (start === -1) { | |
| 316 | start = i; | |
| 317 | } | |
| 318 | } | |
| 319 | if (start !== -1) { | |
| 320 | result.push(query.slice(start)); | |
| 321 | } | |
| 322 | return result; | |
| 323 | } | |
| 324 | ||
| 325 | ||
| 326 | ||
| 327 | ||
| 328 | /** | |
| 329 | * Search Module | |
| 330 | */ | |
| 331 | var Search = { | |
| 332 | ||
| 333 | _index : null, | |
| 334 | _queued_query : null, | |
| 335 | _pulse_status : -1, | |
| 336 | ||
| 337 | init : function() { | |
| 338 | var params = $.getQueryParameters(); | |
| 339 | if (params.q) { | |
| 340 | var query = params.q[0]; | |
| 341 | $('input[name="q"]')[0].value = query; | |
| 342 | this.performSearch(query); | |
| 343 | } | |
| 344 | }, | |
| 345 | ||
| 346 | loadIndex : function(url) { | |
| 347 | $.ajax({type: "GET", url: url, data: null, | |
| 348 | dataType: "script", cache: true, | |
| 349 | complete: function(jqxhr, textstatus) { | |
| 350 | if (textstatus != "success") { | |
| 351 | document.getElementById("searchindexloader").src = url; | |
| 352 | } | |
| 353 | }}); | |
| 354 | }, | |
| 355 | ||
| 356 | setIndex : function(index) { | |
| 357 | var q; | |
| 358 | this._index = index; | |
| 359 | if ((q = this._queued_query) !== null) { | |
| 360 | this._queued_query = null; | |
| 361 | Search.query(q); | |
| 362 | } | |
| 363 | }, | |
| 364 | ||
| 365 | hasIndex : function() { | |
| 366 | return this._index !== null; | |
| 367 | }, | |
| 368 | ||
| 369 | deferQuery : function(query) { | |
| 370 | this._queued_query = query; | |
| 371 | }, | |
| 372 | ||
| 373 | stopPulse : function() { | |
| 374 | this._pulse_status = 0; | |
| 375 | }, | |
| 376 | ||
| 377 | startPulse : function() { | |
| 378 | if (this._pulse_status >= 0) | |
| 379 | return; | |
| 380 | function pulse() { | |
| 381 | var i; | |
| 382 | Search._pulse_status = (Search._pulse_status + 1) % 4; | |
| 383 | var dotString = ''; | |
| 384 | for (i = 0; i < Search._pulse_status; i++) | |
| 385 | dotString += '.'; | |
| 386 | Search.dots.text(dotString); | |
| 387 | if (Search._pulse_status > -1) | |
| 388 | window.setTimeout(pulse, 500); | |
| 389 | } | |
| 390 | pulse(); | |
| 391 | }, | |
| 392 | ||
| 393 | /** | |
| 394 | * perform a search for something (or wait until index is loaded) | |
| 395 | */ | |
| 396 | performSearch : function(query) { | |
| 397 | // create the required interface elements | |
| 398 | this.out = $('#search-results'); | |
| 399 | this.title = $('<h2>' + _('Searching') + '</h2>').appendTo(this.out); | |
| 400 | this.dots = $('<span></span>').appendTo(this.title); | |
| 401 | this.status = $('<p style="display: none"></p>').appendTo(this.out); | |
| 402 | this.output = $('<ul class="search"/>').appendTo(this.out); | |
| 403 | ||
| 404 | $('#search-progress').text(_('Preparing search...')); | |
| 405 | this.startPulse(); | |
| 406 | ||
| 407 | // index already loaded, the browser was quick! | |
| 408 | if (this.hasIndex()) | |
| 409 | this.query(query); | |
| 410 | else | |
| 411 | this.deferQuery(query); | |
| 412 | }, | |
| 413 | ||
| 414 | /** | |
| 415 | * execute search (requires search index to be loaded) | |
| 416 | */ | |
| 417 | query : function(query) { | |
| 418 | var i; | |
| 419 | var stopwords = ["a","and","are","as","at","be","but","by","for","if","in","into","is","it","near","no","not","of","on","or","such","that","the","their","then","there","these","they","this","to","was","will","with"]; | |
| 420 | ||
| 421 | // stem the searchterms and add them to the correct list | |
| 422 | var stemmer = new Stemmer(); | |
| 423 | var searchterms = []; | |
| 424 | var excluded = []; | |
| 425 | var hlterms = []; | |
| 426 | var tmp = splitQuery(query); | |
| 427 | var objectterms = []; | |
| 428 | for (i = 0; i < tmp.length; i++) { | |
| 429 | if (tmp[i] !== "") { | |
| 430 | objectterms.push(tmp[i].toLowerCase()); | |
| 431 | } | |
| 432 | ||
| 433 | if ($u.indexOf(stopwords, tmp[i].toLowerCase()) != -1 || tmp[i].match(/^\d+$/) || | |
| 434 | tmp[i] === "") { | |
| 435 | // skip this "word" | |
| 436 | continue; | |
| 437 | } | |
| 438 | // stem the word | |
| 439 | var word = stemmer.stemWord(tmp[i].toLowerCase()); | |
| 440 | // prevent stemmer from cutting word smaller than two chars | |
| 441 | if(word.length < 3 && tmp[i].length >= 3) { | |
| 442 | word = tmp[i]; | |
| 443 | } | |
| 444 | var toAppend; | |
| 445 | // select the correct list | |
| 446 | if (word[0] == '-') { | |
| 447 | toAppend = excluded; | |
| 448 | word = word.substr(1); | |
| 449 | } | |
| 450 | else { | |
| 451 | toAppend = searchterms; | |
| 452 | hlterms.push(tmp[i].toLowerCase()); | |
| 453 | } | |
| 454 | // only add if not already in the list | |
| 455 | if (!$u.contains(toAppend, word)) | |
| 456 | toAppend.push(word); | |
| 457 | } | |
| 458 | var highlightstring = '?highlight=' + $.urlencode(hlterms.join(" ")); | |
| 459 | ||
| 460 | // console.debug('SEARCH: searching for:'); | |
| 461 | // console.info('required: ', searchterms); | |
| 462 | // console.info('excluded: ', excluded); | |
| 463 | ||
| 464 | // prepare search | |
| 465 | var terms = this._index.terms; | |
| 466 | var titleterms = this._index.titleterms; | |
| 467 | ||
| 468 | // array of [filename, title, anchor, descr, score] | |
| 469 | var results = []; | |
| 470 | $('#search-progress').empty(); | |
| 471 | ||
| 472 | // lookup as object | |
| 473 | for (i = 0; i < objectterms.length; i++) { | |
| 474 | var others = [].concat(objectterms.slice(0, i), | |
| 475 | objectterms.slice(i+1, objectterms.length)); | |
| 476 | results = results.concat(this.performObjectSearch(objectterms[i], others)); | |
| 477 | } | |
| 478 | ||
| 479 | // lookup as search terms in fulltext | |
| 480 | results = results.concat(this.performTermsSearch(searchterms, excluded, terms, titleterms)); | |
| 481 | ||
| 482 | // let the scorer override scores with a custom scoring function | |
| 483 | if (Scorer.score) { | |
| 484 | for (i = 0; i < results.length; i++) | |
| 485 | results[i][4] = Scorer.score(results[i]); | |
| 486 | } | |
| 487 | ||
| 488 | // now sort the results by score (in opposite order of appearance, since the | |
| 489 | // display function below uses pop() to retrieve items) and then | |
| 490 | // alphabetically | |
| 491 | results.sort(function(a, b) { | |
| 492 | var left = a[4]; | |
| 493 | var right = b[4]; | |
| 494 | if (left > right) { | |
| 495 | return 1; | |
| 496 | } else if (left < right) { | |
| 497 | return -1; | |
| 498 | } else { | |
| 499 | // same score: sort alphabetically | |
| 500 | left = a[1].toLowerCase(); | |
| 501 | right = b[1].toLowerCase(); | |
| 502 | return (left > right) ? -1 : ((left < right) ? 1 : 0); | |
| 503 | } | |
| 504 | }); | |
| 505 | ||
| 506 | // for debugging | |
| 507 | //Search.lastresults = results.slice(); // a copy | |
| 508 | //console.info('search results:', Search.lastresults); | |
| 509 | ||
| 510 | // print the results | |
| 511 | var resultCount = results.length; | |
| 512 | function displayNextItem() { | |
| 513 | // results left, load the summary and display it | |
| 514 | if (results.length) { | |
| 515 | var item = results.pop(); | |
| 516 | var listItem = $('<li style="display:none"></li>'); | |
| 517 | if (DOCUMENTATION_OPTIONS.FILE_SUFFIX === '') { | |
| 518 | // dirhtml builder | |
| 519 | var dirname = item[0] + '/'; | |
| 520 | if (dirname.match(/\/index\/$/)) { | |
| 521 | dirname = dirname.substring(0, dirname.length-6); | |
| 522 | } else if (dirname == 'index/') { | |
| 523 | dirname = ''; | |
| 524 | } | |
| 525 | listItem.append($('<a/>').attr('href', | |
| 526 | DOCUMENTATION_OPTIONS.URL_ROOT + dirname + | |
| 527 | highlightstring + item[2]).html(item[1])); | |
| 528 | } else { | |
| 529 | // normal html builders | |
| 530 | listItem.append($('<a/>').attr('href', | |
| 531 | item[0] + DOCUMENTATION_OPTIONS.FILE_SUFFIX + | |
| 532 | highlightstring + item[2]).html(item[1])); | |
| 533 | } | |
| 534 | if (item[3]) { | |
| 535 | listItem.append($('<span> (' + item[3] + ')</span>')); | |
| 536 | Search.output.append(listItem); | |
| 537 | listItem.slideDown(5, function() { | |
| 538 | displayNextItem(); | |
| 539 | }); | |
| 540 | } else if (DOCUMENTATION_OPTIONS.HAS_SOURCE) { | |
| 541 | var suffix = DOCUMENTATION_OPTIONS.SOURCELINK_SUFFIX; | |
| 542 | $.ajax({url: DOCUMENTATION_OPTIONS.URL_ROOT + '_sources/' + item[5] + (item[5].slice(-suffix.length) === suffix ? '' : suffix), | |
| 543 | dataType: "text", | |
| 544 | complete: function(jqxhr, textstatus) { | |
| 545 | var data = jqxhr.responseText; | |
| 546 | if (data !== '' && data !== undefined) { | |
| 547 | listItem.append(Search.makeSearchSummary(data, searchterms, hlterms)); | |
| 548 | } | |
| 549 | Search.output.append(listItem); | |
| 550 | listItem.slideDown(5, function() { | |
| 551 | displayNextItem(); | |
| 552 | }); | |
| 553 | }}); | |
| 554 | } else { | |
| 555 | // no source available, just display title | |
| 556 | Search.output.append(listItem); | |
| 557 | listItem.slideDown(5, function() { | |
| 558 | displayNextItem(); | |
| 559 | }); | |
| 560 | } | |
| 561 | } | |
| 562 | // search finished, update title and status message | |
| 563 | else { | |
| 564 | Search.stopPulse(); | |
| 565 | Search.title.text(_('Search Results')); | |
| 566 | if (!resultCount) | |
| 567 | Search.status.text(_('Your search did not match any documents. Please make sure that all words are spelled correctly and that you\'ve selected enough categories.')); | |
| 568 | else | |
| 569 | Search.status.text(_('Search finished, found %s page(s) matching the search query.').replace('%s', resultCount)); | |
| 570 | Search.status.fadeIn(500); | |
| 571 | } | |
| 572 | } | |
| 573 | displayNextItem(); | |
| 574 | }, | |
| 575 | ||
| 576 | /** | |
| 577 | * search for object names | |
| 578 | */ | |
| 579 | performObjectSearch : function(object, otherterms) { | |
| 580 | var filenames = this._index.filenames; | |
| 581 | var docnames = this._index.docnames; | |
| 582 | var objects = this._index.objects; | |
| 583 | var objnames = this._index.objnames; | |
| 584 | var titles = this._index.titles; | |
| 585 | ||
| 586 | var i; | |
| 587 | var results = []; | |
| 588 | ||
| 589 | for (var prefix in objects) { | |
| 590 | for (var name in objects[prefix]) { | |
| 591 | var fullname = (prefix ? prefix + '.' : '') + name; | |
| 592 | if (fullname.toLowerCase().indexOf(object) > -1) { | |
| 593 | var score = 0; | |
| 594 | var parts = fullname.split('.'); | |
| 595 | // check for different match types: exact matches of full name or | |
| 596 | // "last name" (i.e. last dotted part) | |
| 597 | if (fullname == object || parts[parts.length - 1] == object) { | |
| 598 | score += Scorer.objNameMatch; | |
| 599 | // matches in last name | |
| 600 | } else if (parts[parts.length - 1].indexOf(object) > -1) { | |
| 601 | score += Scorer.objPartialMatch; | |
| 602 | } | |
| 603 | var match = objects[prefix][name]; | |
| 604 | var objname = objnames[match[1]][2]; | |
| 605 | var title = titles[match[0]]; | |
| 606 | // If more than one term searched for, we require other words to be | |
| 607 | // found in the name/title/description | |
| 608 | if (otherterms.length > 0) { | |
| 609 | var haystack = (prefix + ' ' + name + ' ' + | |
| 610 | objname + ' ' + title).toLowerCase(); | |
| 611 | var allfound = true; | |
| 612 | for (i = 0; i < otherterms.length; i++) { | |
| 613 | if (haystack.indexOf(otherterms[i]) == -1) { | |
| 614 | allfound = false; | |
| 615 | break; | |
| 616 | } | |
| 617 | } | |
| 618 | if (!allfound) { | |
| 619 | continue; | |
| 620 | } | |
| 621 | } | |
| 622 | var descr = objname + _(', in ') + title; | |
| 623 | ||
| 624 | var anchor = match[3]; | |
| 625 | if (anchor === '') | |
| 626 | anchor = fullname; | |
| 627 | else if (anchor == '-') | |
| 628 | anchor = objnames[match[1]][1] + '-' + fullname; | |
| 629 | // add custom score for some objects according to scorer | |
| 630 | if (Scorer.objPrio.hasOwnProperty(match[2])) { | |
| 631 | score += Scorer.objPrio[match[2]]; | |
| 632 | } else { | |
| 633 | score += Scorer.objPrioDefault; | |
| 634 | } | |
| 635 | results.push([docnames[match[0]], fullname, '#'+anchor, descr, score, filenames[match[0]]]); | |
| 636 | } | |
| 637 | } | |
| 638 | } | |
| 639 | ||
| 640 | return results; | |
| 641 | }, | |
| 642 | ||
| 643 | /** | |
| 644 | * search for full-text terms in the index | |
| 645 | */ | |
| 646 | performTermsSearch : function(searchterms, excluded, terms, titleterms) { | |
| 647 | var docnames = this._index.docnames; | |
| 648 | var filenames = this._index.filenames; | |
| 649 | var titles = this._index.titles; | |
| 650 | ||
| 651 | var i, j, file; | |
| 652 | var fileMap = {}; | |
| 653 | var scoreMap = {}; | |
| 654 | var results = []; | |
| 655 | ||
| 656 | // perform the search on the required terms | |
| 657 | for (i = 0; i < searchterms.length; i++) { | |
| 658 | var word = searchterms[i]; | |
| 659 | var files = []; | |
| 660 | var _o = [ | |
| 661 | {files: terms[word], score: Scorer.term}, | |
| 662 | {files: titleterms[word], score: Scorer.title} | |
| 663 | ]; | |
| 664 | ||
| 665 | // no match but word was a required one | |
| 666 | if ($u.every(_o, function(o){return o.files === undefined;})) { | |
| 667 | break; | |
| 668 | } | |
| 669 | // found search word in contents | |
| 670 | $u.each(_o, function(o) { | |
| 671 | var _files = o.files; | |
| 672 | if (_files === undefined) | |
| 673 | return | |
| 674 | ||
| 675 | if (_files.length === undefined) | |
| 676 | _files = [_files]; | |
| 677 | files = files.concat(_files); | |
| 678 | ||
| 679 | // set score for the word in each file to Scorer.term | |
| 680 | for (j = 0; j < _files.length; j++) { | |
| 681 | file = _files[j]; | |
| 682 | if (!(file in scoreMap)) | |
| 683 | scoreMap[file] = {} | |
| 684 | scoreMap[file][word] = o.score; | |
| 685 | } | |
| 686 | }); | |
| 687 | ||
| 688 | // create the mapping | |
| 689 | for (j = 0; j < files.length; j++) { | |
| 690 | file = files[j]; | |
| 691 | if (file in fileMap) | |
| 692 | fileMap[file].push(word); | |
| 693 | else | |
| 694 | fileMap[file] = [word]; | |
| 695 | } | |
| 696 | } | |
| 697 | ||
| 698 | // now check if the files don't contain excluded terms | |
| 699 | for (file in fileMap) { | |
| 700 | var valid = true; | |
| 701 | ||
| 702 | // check if all requirements are matched | |
| 703 | if (fileMap[file].length != searchterms.length) | |
| 704 | continue; | |
| 705 | ||
| 706 | // ensure that none of the excluded terms is in the search result | |
| 707 | for (i = 0; i < excluded.length; i++) { | |
| 708 | if (terms[excluded[i]] == file || | |
| 709 | titleterms[excluded[i]] == file || | |
| 710 | $u.contains(terms[excluded[i]] || [], file) || | |
| 711 | $u.contains(titleterms[excluded[i]] || [], file)) { | |
| 712 | valid = false; | |
| 713 | break; | |
| 714 | } | |
| 715 | } | |
| 716 | ||
| 717 | // if we have still a valid result we can add it to the result list | |
| 718 | if (valid) { | |
| 719 | // select one (max) score for the file. | |
| 720 | // for better ranking, we should calculate ranking by using words statistics like basic tf-idf... | |
| 721 | var score = $u.max($u.map(fileMap[file], function(w){return scoreMap[file][w]})); | |
| 722 | results.push([docnames[file], titles[file], '', null, score, filenames[file]]); | |
| 723 | } | |
| 724 | } | |
| 725 | return results; | |
| 726 | }, | |
| 727 | ||
| 728 | /** | |
| 729 | * helper function to return a node containing the | |
| 730 | * search summary for a given text. keywords is a list | |
| 731 | * of stemmed words, hlwords is the list of normal, unstemmed | |
| 732 | * words. the first one is used to find the occurrence, the | |
| 733 | * latter for highlighting it. | |
| 734 | */ | |
| 735 | makeSearchSummary : function(text, keywords, hlwords) { | |
| 736 | var textLower = text.toLowerCase(); | |
| 737 | var start = 0; | |
| 738 | $.each(keywords, function() { | |
| 739 | var i = textLower.indexOf(this.toLowerCase()); | |
| 740 | if (i > -1) | |
| 741 | start = i; | |
| 742 | }); | |
| 743 | start = Math.max(start - 120, 0); | |
| 744 | var excerpt = ((start > 0) ? '...' : '') + | |
| 745 | $.trim(text.substr(start, 240)) + | |
| 746 | ((start + 240 - text.length) ? '...' : ''); | |
| 747 | var rv = $('<div class="context"></div>').text(excerpt); | |
| 748 | $.each(hlwords, function() { | |
| 749 | rv = rv.highlightText(this, 'highlighted'); | |
| 750 | }); | |
| 751 | return rv; | |
| 752 | } | |
| 753 | }; | |
| 754 | ||
| 755 | $(document).ready(function() { | |
| 756 | Search.init(); | |
| 757 | });⏎ |
| 0 | // Underscore.js 1.3.1 | |
| 1 | // (c) 2009-2012 Jeremy Ashkenas, DocumentCloud Inc. | |
| 2 | // Underscore is freely distributable under the MIT license. | |
| 3 | // Portions of Underscore are inspired or borrowed from Prototype, | |
| 4 | // Oliver Steele's Functional, and John Resig's Micro-Templating. | |
| 5 | // For all details and documentation: | |
| 6 | // http://documentcloud.github.com/underscore | |
| 7 | ||
| 8 | (function() { | |
| 9 | ||
| 10 | // Baseline setup | |
| 11 | // -------------- | |
| 12 | ||
| 13 | // Establish the root object, `window` in the browser, or `global` on the server. | |
| 14 | var root = this; | |
| 15 | ||
| 16 | // Save the previous value of the `_` variable. | |
| 17 | var previousUnderscore = root._; | |
| 18 | ||
| 19 | // Establish the object that gets returned to break out of a loop iteration. | |
| 20 | var breaker = {}; | |
| 21 | ||
| 22 | // Save bytes in the minified (but not gzipped) version: | |
| 23 | var ArrayProto = Array.prototype, ObjProto = Object.prototype, FuncProto = Function.prototype; | |
| 24 | ||
| 25 | // Create quick reference variables for speed access to core prototypes. | |
| 26 | var slice = ArrayProto.slice, | |
| 27 | unshift = ArrayProto.unshift, | |
| 28 | toString = ObjProto.toString, | |
| 29 | hasOwnProperty = ObjProto.hasOwnProperty; | |
| 30 | ||
| 31 | // All **ECMAScript 5** native function implementations that we hope to use | |
| 32 | // are declared here. | |
| 33 | var | |
| 34 | nativeForEach = ArrayProto.forEach, | |
| 35 | nativeMap = ArrayProto.map, | |
| 36 | nativeReduce = ArrayProto.reduce, | |
| 37 | nativeReduceRight = ArrayProto.reduceRight, | |
| 38 | nativeFilter = ArrayProto.filter, | |
| 39 | nativeEvery = ArrayProto.every, | |
| 40 | nativeSome = ArrayProto.some, | |
| 41 | nativeIndexOf = ArrayProto.indexOf, | |
| 42 | nativeLastIndexOf = ArrayProto.lastIndexOf, | |
| 43 | nativeIsArray = Array.isArray, | |
| 44 | nativeKeys = Object.keys, | |
| 45 | nativeBind = FuncProto.bind; | |
| 46 | ||
| 47 | // Create a safe reference to the Underscore object for use below. | |
| 48 | var _ = function(obj) { return new wrapper(obj); }; | |
| 49 | ||
| 50 | // Export the Underscore object for **Node.js**, with | |
| 51 | // backwards-compatibility for the old `require()` API. If we're in | |
| 52 | // the browser, add `_` as a global object via a string identifier, | |
| 53 | // for Closure Compiler "advanced" mode. | |
| 54 | if (typeof exports !== 'undefined') { | |
| 55 | if (typeof module !== 'undefined' && module.exports) { | |
| 56 | exports = module.exports = _; | |
| 57 | } | |
| 58 | exports._ = _; | |
| 59 | } else { | |
| 60 | root['_'] = _; | |
| 61 | } | |
| 62 | ||
| 63 | // Current version. | |
| 64 | _.VERSION = '1.3.1'; | |
| 65 | ||
| 66 | // Collection Functions | |
| 67 | // -------------------- | |
| 68 | ||
| 69 | // The cornerstone, an `each` implementation, aka `forEach`. | |
| 70 | // Handles objects with the built-in `forEach`, arrays, and raw objects. | |
| 71 | // Delegates to **ECMAScript 5**'s native `forEach` if available. | |
| 72 | var each = _.each = _.forEach = function(obj, iterator, context) { | |
| 73 | if (obj == null) return; | |
| 74 | if (nativeForEach && obj.forEach === nativeForEach) { | |
| 75 | obj.forEach(iterator, context); | |
| 76 | } else if (obj.length === +obj.length) { | |
| 77 | for (var i = 0, l = obj.length; i < l; i++) { | |
| 78 | if (i in obj && iterator.call(context, obj[i], i, obj) === breaker) return; | |
| 79 | } | |
| 80 | } else { | |
| 81 | for (var key in obj) { | |
| 82 | if (_.has(obj, key)) { | |
| 83 | if (iterator.call(context, obj[key], key, obj) === breaker) return; | |
| 84 | } | |
| 85 | } | |
| 86 | } | |
| 87 | }; | |
| 88 | ||
| 89 | // Return the results of applying the iterator to each element. | |
| 90 | // Delegates to **ECMAScript 5**'s native `map` if available. | |
| 91 | _.map = _.collect = function(obj, iterator, context) { | |
| 92 | var results = []; | |
| 93 | if (obj == null) return results; | |
| 94 | if (nativeMap && obj.map === nativeMap) return obj.map(iterator, context); | |
| 95 | each(obj, function(value, index, list) { | |
| 96 | results[results.length] = iterator.call(context, value, index, list); | |
| 97 | }); | |
| 98 | if (obj.length === +obj.length) results.length = obj.length; | |
| 99 | return results; | |
| 100 | }; | |
| 101 | ||
| 102 | // **Reduce** builds up a single result from a list of values, aka `inject`, | |
| 103 | // or `foldl`. Delegates to **ECMAScript 5**'s native `reduce` if available. | |
| 104 | _.reduce = _.foldl = _.inject = function(obj, iterator, memo, context) { | |
| 105 | var initial = arguments.length > 2; | |
| 106 | if (obj == null) obj = []; | |
| 107 | if (nativeReduce && obj.reduce === nativeReduce) { | |
| 108 | if (context) iterator = _.bind(iterator, context); | |
| 109 | return initial ? obj.reduce(iterator, memo) : obj.reduce(iterator); | |
| 110 | } | |
| 111 | each(obj, function(value, index, list) { | |
| 112 | if (!initial) { | |
| 113 | memo = value; | |
| 114 | initial = true; | |
| 115 | } else { | |
| 116 | memo = iterator.call(context, memo, value, index, list); | |
| 117 | } | |
| 118 | }); | |
| 119 | if (!initial) throw new TypeError('Reduce of empty array with no initial value'); | |
| 120 | return memo; | |
| 121 | }; | |
| 122 | ||
| 123 | // The right-associative version of reduce, also known as `foldr`. | |
| 124 | // Delegates to **ECMAScript 5**'s native `reduceRight` if available. | |
| 125 | _.reduceRight = _.foldr = function(obj, iterator, memo, context) { | |
| 126 | var initial = arguments.length > 2; | |
| 127 | if (obj == null) obj = []; | |
| 128 | if (nativeReduceRight && obj.reduceRight === nativeReduceRight) { | |
| 129 | if (context) iterator = _.bind(iterator, context); | |
| 130 | return initial ? obj.reduceRight(iterator, memo) : obj.reduceRight(iterator); | |
| 131 | } | |
| 132 | var reversed = _.toArray(obj).reverse(); | |
| 133 | if (context && !initial) iterator = _.bind(iterator, context); | |
| 134 | return initial ? _.reduce(reversed, iterator, memo, context) : _.reduce(reversed, iterator); | |
| 135 | }; | |
| 136 | ||
| 137 | // Return the first value which passes a truth test. Aliased as `detect`. | |
| 138 | _.find = _.detect = function(obj, iterator, context) { | |
| 139 | var result; | |
| 140 | any(obj, function(value, index, list) { | |
| 141 | if (iterator.call(context, value, index, list)) { | |
| 142 | result = value; | |
| 143 | return true; | |
| 144 | } | |
| 145 | }); | |
| 146 | return result; | |
| 147 | }; | |
| 148 | ||
| 149 | // Return all the elements that pass a truth test. | |
| 150 | // Delegates to **ECMAScript 5**'s native `filter` if available. | |
| 151 | // Aliased as `select`. | |
| 152 | _.filter = _.select = function(obj, iterator, context) { | |
| 153 | var results = []; | |
| 154 | if (obj == null) return results; | |
| 155 | if (nativeFilter && obj.filter === nativeFilter) return obj.filter(iterator, context); | |
| 156 | each(obj, function(value, index, list) { | |
| 157 | if (iterator.call(context, value, index, list)) results[results.length] = value; | |
| 158 | }); | |
| 159 | return results; | |
| 160 | }; | |
| 161 | ||
| 162 | // Return all the elements for which a truth test fails. | |
| 163 | _.reject = function(obj, iterator, context) { | |
| 164 | var results = []; | |
| 165 | if (obj == null) return results; | |
| 166 | each(obj, function(value, index, list) { | |
| 167 | if (!iterator.call(context, value, index, list)) results[results.length] = value; | |
| 168 | }); | |
| 169 | return results; | |
| 170 | }; | |
| 171 | ||
| 172 | // Determine whether all of the elements match a truth test. | |
| 173 | // Delegates to **ECMAScript 5**'s native `every` if available. | |
| 174 | // Aliased as `all`. | |
| 175 | _.every = _.all = function(obj, iterator, context) { | |
| 176 | var result = true; | |
| 177 | if (obj == null) return result; | |
| 178 | if (nativeEvery && obj.every === nativeEvery) return obj.every(iterator, context); | |
| 179 | each(obj, function(value, index, list) { | |
| 180 | if (!(result = result && iterator.call(context, value, index, list))) return breaker; | |
| 181 | }); | |
| 182 | return result; | |
| 183 | }; | |
| 184 | ||
| 185 | // Determine if at least one element in the object matches a truth test. | |
| 186 | // Delegates to **ECMAScript 5**'s native `some` if available. | |
| 187 | // Aliased as `any`. | |
| 188 | var any = _.some = _.any = function(obj, iterator, context) { | |
| 189 | iterator || (iterator = _.identity); | |
| 190 | var result = false; | |
| 191 | if (obj == null) return result; | |
| 192 | if (nativeSome && obj.some === nativeSome) return obj.some(iterator, context); | |
| 193 | each(obj, function(value, index, list) { | |
| 194 | if (result || (result = iterator.call(context, value, index, list))) return breaker; | |
| 195 | }); | |
| 196 | return !!result; | |
| 197 | }; | |
| 198 | ||
| 199 | // Determine if a given value is included in the array or object using `===`. | |
| 200 | // Aliased as `contains`. | |
| 201 | _.include = _.contains = function(obj, target) { | |
| 202 | var found = false; | |
| 203 | if (obj == null) return found; | |
| 204 | if (nativeIndexOf && obj.indexOf === nativeIndexOf) return obj.indexOf(target) != -1; | |
| 205 | found = any(obj, function(value) { | |
| 206 | return value === target; | |
| 207 | }); | |
| 208 | return found; | |
| 209 | }; | |
| 210 | ||
| 211 | // Invoke a method (with arguments) on every item in a collection. | |
| 212 | _.invoke = function(obj, method) { | |
| 213 | var args = slice.call(arguments, 2); | |
| 214 | return _.map(obj, function(value) { | |
| 215 | return (_.isFunction(method) ? method || value : value[method]).apply(value, args); | |
| 216 | }); | |
| 217 | }; | |
| 218 | ||
| 219 | // Convenience version of a common use case of `map`: fetching a property. | |
| 220 | _.pluck = function(obj, key) { | |
| 221 | return _.map(obj, function(value){ return value[key]; }); | |
| 222 | }; | |
| 223 | ||
| 224 | // Return the maximum element or (element-based computation). | |
| 225 | _.max = function(obj, iterator, context) { | |
| 226 | if (!iterator && _.isArray(obj)) return Math.max.apply(Math, obj); | |
| 227 | if (!iterator && _.isEmpty(obj)) return -Infinity; | |
| 228 | var result = {computed : -Infinity}; | |
| 229 | each(obj, function(value, index, list) { | |
| 230 | var computed = iterator ? iterator.call(context, value, index, list) : value; | |
| 231 | computed >= result.computed && (result = {value : value, computed : computed}); | |
| 232 | }); | |
| 233 | return result.value; | |
| 234 | }; | |
| 235 | ||
| 236 | // Return the minimum element (or element-based computation). | |
| 237 | _.min = function(obj, iterator, context) { | |
| 238 | if (!iterator && _.isArray(obj)) return Math.min.apply(Math, obj); | |
| 239 | if (!iterator && _.isEmpty(obj)) return Infinity; | |
| 240 | var result = {computed : Infinity}; | |
| 241 | each(obj, function(value, index, list) { | |
| 242 | var computed = iterator ? iterator.call(context, value, index, list) : value; | |
| 243 | computed < result.computed && (result = {value : value, computed : computed}); | |
| 244 | }); | |
| 245 | return result.value; | |
| 246 | }; | |
| 247 | ||
| 248 | // Shuffle an array. | |
| 249 | _.shuffle = function(obj) { | |
| 250 | var shuffled = [], rand; | |
| 251 | each(obj, function(value, index, list) { | |
| 252 | if (index == 0) { | |
| 253 | shuffled[0] = value; | |
| 254 | } else { | |
| 255 | rand = Math.floor(Math.random() * (index + 1)); | |
| 256 | shuffled[index] = shuffled[rand]; | |
| 257 | shuffled[rand] = value; | |
| 258 | } | |
| 259 | }); | |
| 260 | return shuffled; | |
| 261 | }; | |
| 262 | ||
| 263 | // Sort the object's values by a criterion produced by an iterator. | |
| 264 | _.sortBy = function(obj, iterator, context) { | |
| 265 | return _.pluck(_.map(obj, function(value, index, list) { | |
| 266 | return { | |
| 267 | value : value, | |
| 268 | criteria : iterator.call(context, value, index, list) | |
| 269 | }; | |
| 270 | }).sort(function(left, right) { | |
| 271 | var a = left.criteria, b = right.criteria; | |
| 272 | return a < b ? -1 : a > b ? 1 : 0; | |
| 273 | }), 'value'); | |
| 274 | }; | |
| 275 | ||
| 276 | // Groups the object's values by a criterion. Pass either a string attribute | |
| 277 | // to group by, or a function that returns the criterion. | |
| 278 | _.groupBy = function(obj, val) { | |
| 279 | var result = {}; | |
| 280 | var iterator = _.isFunction(val) ? val : function(obj) { return obj[val]; }; | |
| 281 | each(obj, function(value, index) { | |
| 282 | var key = iterator(value, index); | |
| 283 | (result[key] || (result[key] = [])).push(value); | |
| 284 | }); | |
| 285 | return result; | |
| 286 | }; | |
| 287 | ||
| 288 | // Use a comparator function to figure out at what index an object should | |
| 289 | // be inserted so as to maintain order. Uses binary search. | |
| 290 | _.sortedIndex = function(array, obj, iterator) { | |
| 291 | iterator || (iterator = _.identity); | |
| 292 | var low = 0, high = array.length; | |
| 293 | while (low < high) { | |
| 294 | var mid = (low + high) >> 1; | |
| 295 | iterator(array[mid]) < iterator(obj) ? low = mid + 1 : high = mid; | |
| 296 | } | |
| 297 | return low; | |
| 298 | }; | |
| 299 | ||
| 300 | // Safely convert anything iterable into a real, live array. | |
| 301 | _.toArray = function(iterable) { | |
| 302 | if (!iterable) return []; | |
| 303 | if (iterable.toArray) return iterable.toArray(); | |
| 304 | if (_.isArray(iterable)) return slice.call(iterable); | |
| 305 | if (_.isArguments(iterable)) return slice.call(iterable); | |
| 306 | return _.values(iterable); | |
| 307 | }; | |
| 308 | ||
| 309 | // Return the number of elements in an object. | |
| 310 | _.size = function(obj) { | |
| 311 | return _.toArray(obj).length; | |
| 312 | }; | |
| 313 | ||
| 314 | // Array Functions | |
| 315 | // --------------- | |
| 316 | ||
| 317 | // Get the first element of an array. Passing **n** will return the first N | |
| 318 | // values in the array. Aliased as `head`. The **guard** check allows it to work | |
| 319 | // with `_.map`. | |
| 320 | _.first = _.head = function(array, n, guard) { | |
| 321 | return (n != null) && !guard ? slice.call(array, 0, n) : array[0]; | |
| 322 | }; | |
| 323 | ||
| 324 | // Returns everything but the last entry of the array. Especcialy useful on | |
| 325 | // the arguments object. Passing **n** will return all the values in | |
| 326 | // the array, excluding the last N. The **guard** check allows it to work with | |
| 327 | // `_.map`. | |
| 328 | _.initial = function(array, n, guard) { | |
| 329 | return slice.call(array, 0, array.length - ((n == null) || guard ? 1 : n)); | |
| 330 | }; | |
| 331 | ||
| 332 | // Get the last element of an array. Passing **n** will return the last N | |
| 333 | // values in the array. The **guard** check allows it to work with `_.map`. | |
| 334 | _.last = function(array, n, guard) { | |
| 335 | if ((n != null) && !guard) { | |
| 336 | return slice.call(array, Math.max(array.length - n, 0)); | |
| 337 | } else { | |
| 338 | return array[array.length - 1]; | |
| 339 | } | |
| 340 | }; | |
| 341 | ||
| 342 | // Returns everything but the first entry of the array. Aliased as `tail`. | |
| 343 | // Especially useful on the arguments object. Passing an **index** will return | |
| 344 | // the rest of the values in the array from that index onward. The **guard** | |
| 345 | // check allows it to work with `_.map`. | |
| 346 | _.rest = _.tail = function(array, index, guard) { | |
| 347 | return slice.call(array, (index == null) || guard ? 1 : index); | |
| 348 | }; | |
| 349 | ||
| 350 | // Trim out all falsy values from an array. | |
| 351 | _.compact = function(array) { | |
| 352 | return _.filter(array, function(value){ return !!value; }); | |
| 353 | }; | |
| 354 | ||
| 355 | // Return a completely flattened version of an array. | |
| 356 | _.flatten = function(array, shallow) { | |
| 357 | return _.reduce(array, function(memo, value) { | |
| 358 | if (_.isArray(value)) return memo.concat(shallow ? value : _.flatten(value)); | |
| 359 | memo[memo.length] = value; | |
| 360 | return memo; | |
| 361 | }, []); | |
| 362 | }; | |
| 363 | ||
| 364 | // Return a version of the array that does not contain the specified value(s). | |
| 365 | _.without = function(array) { | |
| 366 | return _.difference(array, slice.call(arguments, 1)); | |
| 367 | }; | |
| 368 | ||
| 369 | // Produce a duplicate-free version of the array. If the array has already | |
| 370 | // been sorted, you have the option of using a faster algorithm. | |
| 371 | // Aliased as `unique`. | |
| 372 | _.uniq = _.unique = function(array, isSorted, iterator) { | |
| 373 | var initial = iterator ? _.map(array, iterator) : array; | |
| 374 | var result = []; | |
| 375 | _.reduce(initial, function(memo, el, i) { | |
| 376 | if (0 == i || (isSorted === true ? _.last(memo) != el : !_.include(memo, el))) { | |
| 377 | memo[memo.length] = el; | |
| 378 | result[result.length] = array[i]; | |
| 379 | } | |
| 380 | return memo; | |
| 381 | }, []); | |
| 382 | return result; | |
| 383 | }; | |
| 384 | ||
| 385 | // Produce an array that contains the union: each distinct element from all of | |
| 386 | // the passed-in arrays. | |
| 387 | _.union = function() { | |
| 388 | return _.uniq(_.flatten(arguments, true)); | |
| 389 | }; | |
| 390 | ||
| 391 | // Produce an array that contains every item shared between all the | |
| 392 | // passed-in arrays. (Aliased as "intersect" for back-compat.) | |
| 393 | _.intersection = _.intersect = function(array) { | |
| 394 | var rest = slice.call(arguments, 1); | |
| 395 | return _.filter(_.uniq(array), function(item) { | |
| 396 | return _.every(rest, function(other) { | |
| 397 | return _.indexOf(other, item) >= 0; | |
| 398 | }); | |
| 399 | }); | |
| 400 | }; | |
| 401 | ||
| 402 | // Take the difference between one array and a number of other arrays. | |
| 403 | // Only the elements present in just the first array will remain. | |
| 404 | _.difference = function(array) { | |
| 405 | var rest = _.flatten(slice.call(arguments, 1)); | |
| 406 | return _.filter(array, function(value){ return !_.include(rest, value); }); | |
| 407 | }; | |
| 408 | ||
| 409 | // Zip together multiple lists into a single array -- elements that share | |
| 410 | // an index go together. | |
| 411 | _.zip = function() { | |
| 412 | var args = slice.call(arguments); | |
| 413 | var length = _.max(_.pluck(args, 'length')); | |
| 414 | var results = new Array(length); | |
| 415 | for (var i = 0; i < length; i++) results[i] = _.pluck(args, "" + i); | |
| 416 | return results; | |
| 417 | }; | |
| 418 | ||
| 419 | // If the browser doesn't supply us with indexOf (I'm looking at you, **MSIE**), | |
| 420 | // we need this function. Return the position of the first occurrence of an | |
| 421 | // item in an array, or -1 if the item is not included in the array. | |
| 422 | // Delegates to **ECMAScript 5**'s native `indexOf` if available. | |
| 423 | // If the array is large and already in sort order, pass `true` | |
| 424 | // for **isSorted** to use binary search. | |
| 425 | _.indexOf = function(array, item, isSorted) { | |
| 426 | if (array == null) return -1; | |
| 427 | var i, l; | |
| 428 | if (isSorted) { | |
| 429 | i = _.sortedIndex(array, item); | |
| 430 | return array[i] === item ? i : -1; | |
| 431 | } | |
| 432 | if (nativeIndexOf && array.indexOf === nativeIndexOf) return array.indexOf(item); | |
| 433 | for (i = 0, l = array.length; i < l; i++) if (i in array && array[i] === item) return i; | |
| 434 | return -1; | |
| 435 | }; | |
| 436 | ||
| 437 | // Delegates to **ECMAScript 5**'s native `lastIndexOf` if available. | |
| 438 | _.lastIndexOf = function(array, item) { | |
| 439 | if (array == null) return -1; | |
| 440 | if (nativeLastIndexOf && array.lastIndexOf === nativeLastIndexOf) return array.lastIndexOf(item); | |
| 441 | var i = array.length; | |
| 442 | while (i--) if (i in array && array[i] === item) return i; | |
| 443 | return -1; | |
| 444 | }; | |
| 445 | ||
| 446 | // Generate an integer Array containing an arithmetic progression. A port of | |
| 447 | // the native Python `range()` function. See | |
| 448 | // [the Python documentation](http://docs.python.org/library/functions.html#range). | |
| 449 | _.range = function(start, stop, step) { | |
| 450 | if (arguments.length <= 1) { | |
| 451 | stop = start || 0; | |
| 452 | start = 0; | |
| 453 | } | |
| 454 | step = arguments[2] || 1; | |
| 455 | ||
| 456 | var len = Math.max(Math.ceil((stop - start) / step), 0); | |
| 457 | var idx = 0; | |
| 458 | var range = new Array(len); | |
| 459 | ||
| 460 | while(idx < len) { | |
| 461 | range[idx++] = start; | |
| 462 | start += step; | |
| 463 | } | |
| 464 | ||
| 465 | return range; | |
| 466 | }; | |
| 467 | ||
| 468 | // Function (ahem) Functions | |
| 469 | // ------------------ | |
| 470 | ||
| 471 | // Reusable constructor function for prototype setting. | |
| 472 | var ctor = function(){}; | |
| 473 | ||
| 474 | // Create a function bound to a given object (assigning `this`, and arguments, | |
| 475 | // optionally). Binding with arguments is also known as `curry`. | |
| 476 | // Delegates to **ECMAScript 5**'s native `Function.bind` if available. | |
| 477 | // We check for `func.bind` first, to fail fast when `func` is undefined. | |
| 478 | _.bind = function bind(func, context) { | |
| 479 | var bound, args; | |
| 480 | if (func.bind === nativeBind && nativeBind) return nativeBind.apply(func, slice.call(arguments, 1)); | |
| 481 | if (!_.isFunction(func)) throw new TypeError; | |
| 482 | args = slice.call(arguments, 2); | |
| 483 | return bound = function() { | |
| 484 | if (!(this instanceof bound)) return func.apply(context, args.concat(slice.call(arguments))); | |
| 485 | ctor.prototype = func.prototype; | |
| 486 | var self = new ctor; | |
| 487 | var result = func.apply(self, args.concat(slice.call(arguments))); | |
| 488 | if (Object(result) === result) return result; | |
| 489 | return self; | |
| 490 | }; | |
| 491 | }; | |
| 492 | ||
| 493 | // Bind all of an object's methods to that object. Useful for ensuring that | |
| 494 | // all callbacks defined on an object belong to it. | |
| 495 | _.bindAll = function(obj) { | |
| 496 | var funcs = slice.call(arguments, 1); | |
| 497 | if (funcs.length == 0) funcs = _.functions(obj); | |
| 498 | each(funcs, function(f) { obj[f] = _.bind(obj[f], obj); }); | |
| 499 | return obj; | |
| 500 | }; | |
| 501 | ||
| 502 | // Memoize an expensive function by storing its results. | |
| 503 | _.memoize = function(func, hasher) { | |
| 504 | var memo = {}; | |
| 505 | hasher || (hasher = _.identity); | |
| 506 | return function() { | |
| 507 | var key = hasher.apply(this, arguments); | |
| 508 | return _.has(memo, key) ? memo[key] : (memo[key] = func.apply(this, arguments)); | |
| 509 | }; | |
| 510 | }; | |
| 511 | ||
| 512 | // Delays a function for the given number of milliseconds, and then calls | |
| 513 | // it with the arguments supplied. | |
| 514 | _.delay = function(func, wait) { | |
| 515 | var args = slice.call(arguments, 2); | |
| 516 | return setTimeout(function(){ return func.apply(func, args); }, wait); | |
| 517 | }; | |
| 518 | ||
| 519 | // Defers a function, scheduling it to run after the current call stack has | |
| 520 | // cleared. | |
| 521 | _.defer = function(func) { | |
| 522 | return _.delay.apply(_, [func, 1].concat(slice.call(arguments, 1))); | |
| 523 | }; | |
| 524 | ||
| 525 | // Returns a function, that, when invoked, will only be triggered at most once | |
| 526 | // during a given window of time. | |
| 527 | _.throttle = function(func, wait) { | |
| 528 | var context, args, timeout, throttling, more; | |
| 529 | var whenDone = _.debounce(function(){ more = throttling = false; }, wait); | |
| 530 | return function() { | |
| 531 | context = this; args = arguments; | |
| 532 | var later = function() { | |
| 533 | timeout = null; | |
| 534 | if (more) func.apply(context, args); | |
| 535 | whenDone(); | |
| 536 | }; | |
| 537 | if (!timeout) timeout = setTimeout(later, wait); | |
| 538 | if (throttling) { | |
| 539 | more = true; | |
| 540 | } else { | |
| 541 | func.apply(context, args); | |
| 542 | } | |
| 543 | whenDone(); | |
| 544 | throttling = true; | |
| 545 | }; | |
| 546 | }; | |
| 547 | ||
| 548 | // Returns a function, that, as long as it continues to be invoked, will not | |
| 549 | // be triggered. The function will be called after it stops being called for | |
| 550 | // N milliseconds. | |
| 551 | _.debounce = function(func, wait) { | |
| 552 | var timeout; | |
| 553 | return function() { | |
| 554 | var context = this, args = arguments; | |
| 555 | var later = function() { | |
| 556 | timeout = null; | |
| 557 | func.apply(context, args); | |
| 558 | }; | |
| 559 | clearTimeout(timeout); | |
| 560 | timeout = setTimeout(later, wait); | |
| 561 | }; | |
| 562 | }; | |
| 563 | ||
| 564 | // Returns a function that will be executed at most one time, no matter how | |
| 565 | // often you call it. Useful for lazy initialization. | |
| 566 | _.once = function(func) { | |
| 567 | var ran = false, memo; | |
| 568 | return function() { | |
| 569 | if (ran) return memo; | |
| 570 | ran = true; | |
| 571 | return memo = func.apply(this, arguments); | |
| 572 | }; | |
| 573 | }; | |
| 574 | ||
| 575 | // Returns the first function passed as an argument to the second, | |
| 576 | // allowing you to adjust arguments, run code before and after, and | |
| 577 | // conditionally execute the original function. | |
| 578 | _.wrap = function(func, wrapper) { | |
| 579 | return function() { | |
| 580 | var args = [func].concat(slice.call(arguments, 0)); | |
| 581 | return wrapper.apply(this, args); | |
| 582 | }; | |
| 583 | }; | |
| 584 | ||
| 585 | // Returns a function that is the composition of a list of functions, each | |
| 586 | // consuming the return value of the function that follows. | |
| 587 | _.compose = function() { | |
| 588 | var funcs = arguments; | |
| 589 | return function() { | |
| 590 | var args = arguments; | |
| 591 | for (var i = funcs.length - 1; i >= 0; i--) { | |
| 592 | args = [funcs[i].apply(this, args)]; | |
| 593 | } | |
| 594 | return args[0]; | |
| 595 | }; | |
| 596 | }; | |
| 597 | ||
| 598 | // Returns a function that will only be executed after being called N times. | |
| 599 | _.after = function(times, func) { | |
| 600 | if (times <= 0) return func(); | |
| 601 | return function() { | |
| 602 | if (--times < 1) { return func.apply(this, arguments); } | |
| 603 | }; | |
| 604 | }; | |
| 605 | ||
| 606 | // Object Functions | |
| 607 | // ---------------- | |
| 608 | ||
| 609 | // Retrieve the names of an object's properties. | |
| 610 | // Delegates to **ECMAScript 5**'s native `Object.keys` | |
| 611 | _.keys = nativeKeys || function(obj) { | |
| 612 | if (obj !== Object(obj)) throw new TypeError('Invalid object'); | |
| 613 | var keys = []; | |
| 614 | for (var key in obj) if (_.has(obj, key)) keys[keys.length] = key; | |
| 615 | return keys; | |
| 616 | }; | |
| 617 | ||
| 618 | // Retrieve the values of an object's properties. | |
| 619 | _.values = function(obj) { | |
| 620 | return _.map(obj, _.identity); | |
| 621 | }; | |
| 622 | ||
| 623 | // Return a sorted list of the function names available on the object. | |
| 624 | // Aliased as `methods` | |
| 625 | _.functions = _.methods = function(obj) { | |
| 626 | var names = []; | |
| 627 | for (var key in obj) { | |
| 628 | if (_.isFunction(obj[key])) names.push(key); | |
| 629 | } | |
| 630 | return names.sort(); | |
| 631 | }; | |
| 632 | ||
| 633 | // Extend a given object with all the properties in passed-in object(s). | |
| 634 | _.extend = function(obj) { | |
| 635 | each(slice.call(arguments, 1), function(source) { | |
| 636 | for (var prop in source) { | |
| 637 | obj[prop] = source[prop]; | |
| 638 | } | |
| 639 | }); | |
| 640 | return obj; | |
| 641 | }; | |
| 642 | ||
| 643 | // Fill in a given object with default properties. | |
| 644 | _.defaults = function(obj) { | |
| 645 | each(slice.call(arguments, 1), function(source) { | |
| 646 | for (var prop in source) { | |
| 647 | if (obj[prop] == null) obj[prop] = source[prop]; | |
| 648 | } | |
| 649 | }); | |
| 650 | return obj; | |
| 651 | }; | |
| 652 | ||
| 653 | // Create a (shallow-cloned) duplicate of an object. | |
| 654 | _.clone = function(obj) { | |
| 655 | if (!_.isObject(obj)) return obj; | |
| 656 | return _.isArray(obj) ? obj.slice() : _.extend({}, obj); | |
| 657 | }; | |
| 658 | ||
| 659 | // Invokes interceptor with the obj, and then returns obj. | |
| 660 | // The primary purpose of this method is to "tap into" a method chain, in | |
| 661 | // order to perform operations on intermediate results within the chain. | |
| 662 | _.tap = function(obj, interceptor) { | |
| 663 | interceptor(obj); | |
| 664 | return obj; | |
| 665 | }; | |
| 666 | ||
| 667 | // Internal recursive comparison function. | |
| 668 | function eq(a, b, stack) { | |
| 669 | // Identical objects are equal. `0 === -0`, but they aren't identical. | |
| 670 | // See the Harmony `egal` proposal: http://wiki.ecmascript.org/doku.php?id=harmony:egal. | |
| 671 | if (a === b) return a !== 0 || 1 / a == 1 / b; | |
| 672 | // A strict comparison is necessary because `null == undefined`. | |
| 673 | if (a == null || b == null) return a === b; | |
| 674 | // Unwrap any wrapped objects. | |
| 675 | if (a._chain) a = a._wrapped; | |
| 676 | if (b._chain) b = b._wrapped; | |
| 677 | // Invoke a custom `isEqual` method if one is provided. | |
| 678 | if (a.isEqual && _.isFunction(a.isEqual)) return a.isEqual(b); | |
| 679 | if (b.isEqual && _.isFunction(b.isEqual)) return b.isEqual(a); | |
| 680 | // Compare `[[Class]]` names. | |
| 681 | var className = toString.call(a); | |
| 682 | if (className != toString.call(b)) return false; | |
| 683 | switch (className) { | |
| 684 | // Strings, numbers, dates, and booleans are compared by value. | |
| 685 | case '[object String]': | |
| 686 | // Primitives and their corresponding object wrappers are equivalent; thus, `"5"` is | |
| 687 | // equivalent to `new String("5")`. | |
| 688 | return a == String(b); | |
| 689 | case '[object Number]': | |
| 690 | // `NaN`s are equivalent, but non-reflexive. An `egal` comparison is performed for | |
| 691 | // other numeric values. | |
| 692 | return a != +a ? b != +b : (a == 0 ? 1 / a == 1 / b : a == +b); | |
| 693 | case '[object Date]': | |
| 694 | case '[object Boolean]': | |
| 695 | // Coerce dates and booleans to numeric primitive values. Dates are compared by their | |
| 696 | // millisecond representations. Note that invalid dates with millisecond representations | |
| 697 | // of `NaN` are not equivalent. | |
| 698 | return +a == +b; | |
| 699 | // RegExps are compared by their source patterns and flags. | |
| 700 | case '[object RegExp]': | |
| 701 | return a.source == b.source && | |
| 702 | a.global == b.global && | |
| 703 | a.multiline == b.multiline && | |
| 704 | a.ignoreCase == b.ignoreCase; | |
| 705 | } | |
| 706 | if (typeof a != 'object' || typeof b != 'object') return false; | |
| 707 | // Assume equality for cyclic structures. The algorithm for detecting cyclic | |
| 708 | // structures is adapted from ES 5.1 section 15.12.3, abstract operation `JO`. | |
| 709 | var length = stack.length; | |
| 710 | while (length--) { | |
| 711 | // Linear search. Performance is inversely proportional to the number of | |
| 712 | // unique nested structures. | |
| 713 | if (stack[length] == a) return true; | |
| 714 | } | |
| 715 | // Add the first object to the stack of traversed objects. | |
| 716 | stack.push(a); | |
| 717 | var size = 0, result = true; | |
| 718 | // Recursively compare objects and arrays. | |
| 719 | if (className == '[object Array]') { | |
| 720 | // Compare array lengths to determine if a deep comparison is necessary. | |
| 721 | size = a.length; | |
| 722 | result = size == b.length; | |
| 723 | if (result) { | |
| 724 | // Deep compare the contents, ignoring non-numeric properties. | |
| 725 | while (size--) { | |
| 726 | // Ensure commutative equality for sparse arrays. | |
| 727 | if (!(result = size in a == size in b && eq(a[size], b[size], stack))) break; | |
| 728 | } | |
| 729 | } | |
| 730 | } else { | |
| 731 | // Objects with different constructors are not equivalent. | |
| 732 | if ('constructor' in a != 'constructor' in b || a.constructor != b.constructor) return false; | |
| 733 | // Deep compare objects. | |
| 734 | for (var key in a) { | |
| 735 | if (_.has(a, key)) { | |
| 736 | // Count the expected number of properties. | |
| 737 | size++; | |
| 738 | // Deep compare each member. | |
| 739 | if (!(result = _.has(b, key) && eq(a[key], b[key], stack))) break; | |
| 740 | } | |
| 741 | } | |
| 742 | // Ensure that both objects contain the same number of properties. | |
| 743 | if (result) { | |
| 744 | for (key in b) { | |
| 745 | if (_.has(b, key) && !(size--)) break; | |
| 746 | } | |
| 747 | result = !size; | |
| 748 | } | |
| 749 | } | |
| 750 | // Remove the first object from the stack of traversed objects. | |
| 751 | stack.pop(); | |
| 752 | return result; | |
| 753 | } | |
| 754 | ||
| 755 | // Perform a deep comparison to check if two objects are equal. | |
| 756 | _.isEqual = function(a, b) { | |
| 757 | return eq(a, b, []); | |
| 758 | }; | |
| 759 | ||
| 760 | // Is a given array, string, or object empty? | |
| 761 | // An "empty" object has no enumerable own-properties. | |
| 762 | _.isEmpty = function(obj) { | |
| 763 | if (_.isArray(obj) || _.isString(obj)) return obj.length === 0; | |
| 764 | for (var key in obj) if (_.has(obj, key)) return false; | |
| 765 | return true; | |
| 766 | }; | |
| 767 | ||
| 768 | // Is a given value a DOM element? | |
| 769 | _.isElement = function(obj) { | |
| 770 | return !!(obj && obj.nodeType == 1); | |
| 771 | }; | |
| 772 | ||
| 773 | // Is a given value an array? | |
| 774 | // Delegates to ECMA5's native Array.isArray | |
| 775 | _.isArray = nativeIsArray || function(obj) { | |
| 776 | return toString.call(obj) == '[object Array]'; | |
| 777 | }; | |
| 778 | ||
| 779 | // Is a given variable an object? | |
| 780 | _.isObject = function(obj) { | |
| 781 | return obj === Object(obj); | |
| 782 | }; | |
| 783 | ||
| 784 | // Is a given variable an arguments object? | |
| 785 | _.isArguments = function(obj) { | |
| 786 | return toString.call(obj) == '[object Arguments]'; | |
| 787 | }; | |
| 788 | if (!_.isArguments(arguments)) { | |
| 789 | _.isArguments = function(obj) { | |
| 790 | return !!(obj && _.has(obj, 'callee')); | |
| 791 | }; | |
| 792 | } | |
| 793 | ||
| 794 | // Is a given value a function? | |
| 795 | _.isFunction = function(obj) { | |
| 796 | return toString.call(obj) == '[object Function]'; | |
| 797 | }; | |
| 798 | ||
| 799 | // Is a given value a string? | |
| 800 | _.isString = function(obj) { | |
| 801 | return toString.call(obj) == '[object String]'; | |
| 802 | }; | |
| 803 | ||
| 804 | // Is a given value a number? | |
| 805 | _.isNumber = function(obj) { | |
| 806 | return toString.call(obj) == '[object Number]'; | |
| 807 | }; | |
| 808 | ||
| 809 | // Is the given value `NaN`? | |
| 810 | _.isNaN = function(obj) { | |
| 811 | // `NaN` is the only value for which `===` is not reflexive. | |
| 812 | return obj !== obj; | |
| 813 | }; | |
| 814 | ||
| 815 | // Is a given value a boolean? | |
| 816 | _.isBoolean = function(obj) { | |
| 817 | return obj === true || obj === false || toString.call(obj) == '[object Boolean]'; | |
| 818 | }; | |
| 819 | ||
| 820 | // Is a given value a date? | |
| 821 | _.isDate = function(obj) { | |
| 822 | return toString.call(obj) == '[object Date]'; | |
| 823 | }; | |
| 824 | ||
| 825 | // Is the given value a regular expression? | |
| 826 | _.isRegExp = function(obj) { | |
| 827 | return toString.call(obj) == '[object RegExp]'; | |
| 828 | }; | |
| 829 | ||
| 830 | // Is a given value equal to null? | |
| 831 | _.isNull = function(obj) { | |
| 832 | return obj === null; | |
| 833 | }; | |
| 834 | ||
| 835 | // Is a given variable undefined? | |
| 836 | _.isUndefined = function(obj) { | |
| 837 | return obj === void 0; | |
| 838 | }; | |
| 839 | ||
| 840 | // Has own property? | |
| 841 | _.has = function(obj, key) { | |
| 842 | return hasOwnProperty.call(obj, key); | |
| 843 | }; | |
| 844 | ||
| 845 | // Utility Functions | |
| 846 | // ----------------- | |
| 847 | ||
| 848 | // Run Underscore.js in *noConflict* mode, returning the `_` variable to its | |
| 849 | // previous owner. Returns a reference to the Underscore object. | |
| 850 | _.noConflict = function() { | |
| 851 | root._ = previousUnderscore; | |
| 852 | return this; | |
| 853 | }; | |
| 854 | ||
| 855 | // Keep the identity function around for default iterators. | |
| 856 | _.identity = function(value) { | |
| 857 | return value; | |
| 858 | }; | |
| 859 | ||
| 860 | // Run a function **n** times. | |
| 861 | _.times = function (n, iterator, context) { | |
| 862 | for (var i = 0; i < n; i++) iterator.call(context, i); | |
| 863 | }; | |
| 864 | ||
| 865 | // Escape a string for HTML interpolation. | |
| 866 | _.escape = function(string) { | |
| 867 | return (''+string).replace(/&/g, '&').replace(/</g, '<').replace(/>/g, '>').replace(/"/g, '"').replace(/'/g, ''').replace(/\//g,'/'); | |
| 868 | }; | |
| 869 | ||
| 870 | // Add your own custom functions to the Underscore object, ensuring that | |
| 871 | // they're correctly added to the OOP wrapper as well. | |
| 872 | _.mixin = function(obj) { | |
| 873 | each(_.functions(obj), function(name){ | |
| 874 | addToWrapper(name, _[name] = obj[name]); | |
| 875 | }); | |
| 876 | }; | |
| 877 | ||
| 878 | // Generate a unique integer id (unique within the entire client session). | |
| 879 | // Useful for temporary DOM ids. | |
| 880 | var idCounter = 0; | |
| 881 | _.uniqueId = function(prefix) { | |
| 882 | var id = idCounter++; | |
| 883 | return prefix ? prefix + id : id; | |
| 884 | }; | |
| 885 | ||
| 886 | // By default, Underscore uses ERB-style template delimiters, change the | |
| 887 | // following template settings to use alternative delimiters. | |
| 888 | _.templateSettings = { | |
| 889 | evaluate : /<%([\s\S]+?)%>/g, | |
| 890 | interpolate : /<%=([\s\S]+?)%>/g, | |
| 891 | escape : /<%-([\s\S]+?)%>/g | |
| 892 | }; | |
| 893 | ||
| 894 | // When customizing `templateSettings`, if you don't want to define an | |
| 895 | // interpolation, evaluation or escaping regex, we need one that is | |
| 896 | // guaranteed not to match. | |
| 897 | var noMatch = /.^/; | |
| 898 | ||
| 899 | // Within an interpolation, evaluation, or escaping, remove HTML escaping | |
| 900 | // that had been previously added. | |
| 901 | var unescape = function(code) { | |
| 902 | return code.replace(/\\\\/g, '\\').replace(/\\'/g, "'"); | |
| 903 | }; | |
| 904 | ||
| 905 | // JavaScript micro-templating, similar to John Resig's implementation. | |
| 906 | // Underscore templating handles arbitrary delimiters, preserves whitespace, | |
| 907 | // and correctly escapes quotes within interpolated code. | |
| 908 | _.template = function(str, data) { | |
| 909 | var c = _.templateSettings; | |
| 910 | var tmpl = 'var __p=[],print=function(){__p.push.apply(__p,arguments);};' + | |
| 911 | 'with(obj||{}){__p.push(\'' + | |
| 912 | str.replace(/\\/g, '\\\\') | |
| 913 | .replace(/'/g, "\\'") | |
| 914 | .replace(c.escape || noMatch, function(match, code) { | |
| 915 | return "',_.escape(" + unescape(code) + "),'"; | |
| 916 | }) | |
| 917 | .replace(c.interpolate || noMatch, function(match, code) { | |
| 918 | return "'," + unescape(code) + ",'"; | |
| 919 | }) | |
| 920 | .replace(c.evaluate || noMatch, function(match, code) { | |
| 921 | return "');" + unescape(code).replace(/[\r\n\t]/g, ' ') + ";__p.push('"; | |
| 922 | }) | |
| 923 | .replace(/\r/g, '\\r') | |
| 924 | .replace(/\n/g, '\\n') | |
| 925 | .replace(/\t/g, '\\t') | |
| 926 | + "');}return __p.join('');"; | |
| 927 | var func = new Function('obj', '_', tmpl); | |
| 928 | if (data) return func(data, _); | |
| 929 | return function(data) { | |
| 930 | return func.call(this, data, _); | |
| 931 | }; | |
| 932 | }; | |
| 933 | ||
| 934 | // Add a "chain" function, which will delegate to the wrapper. | |
| 935 | _.chain = function(obj) { | |
| 936 | return _(obj).chain(); | |
| 937 | }; | |
| 938 | ||
| 939 | // The OOP Wrapper | |
| 940 | // --------------- | |
| 941 | ||
| 942 | // If Underscore is called as a function, it returns a wrapped object that | |
| 943 | // can be used OO-style. This wrapper holds altered versions of all the | |
| 944 | // underscore functions. Wrapped objects may be chained. | |
| 945 | var wrapper = function(obj) { this._wrapped = obj; }; | |
| 946 | ||
| 947 | // Expose `wrapper.prototype` as `_.prototype` | |
| 948 | _.prototype = wrapper.prototype; | |
| 949 | ||
| 950 | // Helper function to continue chaining intermediate results. | |
| 951 | var result = function(obj, chain) { | |
| 952 | return chain ? _(obj).chain() : obj; | |
| 953 | }; | |
| 954 | ||
| 955 | // A method to easily add functions to the OOP wrapper. | |
| 956 | var addToWrapper = function(name, func) { | |
| 957 | wrapper.prototype[name] = function() { | |
| 958 | var args = slice.call(arguments); | |
| 959 | unshift.call(args, this._wrapped); | |
| 960 | return result(func.apply(_, args), this._chain); | |
| 961 | }; | |
| 962 | }; | |
| 963 | ||
| 964 | // Add all of the Underscore functions to the wrapper object. | |
| 965 | _.mixin(_); | |
| 966 | ||
| 967 | // Add all mutator Array functions to the wrapper. | |
| 968 | each(['pop', 'push', 'reverse', 'shift', 'sort', 'splice', 'unshift'], function(name) { | |
| 969 | var method = ArrayProto[name]; | |
| 970 | wrapper.prototype[name] = function() { | |
| 971 | var wrapped = this._wrapped; | |
| 972 | method.apply(wrapped, arguments); | |
| 973 | var length = wrapped.length; | |
| 974 | if ((name == 'shift' || name == 'splice') && length === 0) delete wrapped[0]; | |
| 975 | return result(wrapped, this._chain); | |
| 976 | }; | |
| 977 | }); | |
| 978 | ||
| 979 | // Add all accessor Array functions to the wrapper. | |
| 980 | each(['concat', 'join', 'slice'], function(name) { | |
| 981 | var method = ArrayProto[name]; | |
| 982 | wrapper.prototype[name] = function() { | |
| 983 | return result(method.apply(this._wrapped, arguments), this._chain); | |
| 984 | }; | |
| 985 | }); | |
| 986 | ||
| 987 | // Start chaining a wrapped Underscore object. | |
| 988 | wrapper.prototype.chain = function() { | |
| 989 | this._chain = true; | |
| 990 | return this; | |
| 991 | }; | |
| 992 | ||
| 993 | // Extracts the result from a wrapped and chained object. | |
| 994 | wrapper.prototype.value = function() { | |
| 995 | return this._wrapped; | |
| 996 | }; | |
| 997 | ||
| 998 | }).call(this); |
| 0 | // Underscore.js 1.3.1 | |
| 1 | // (c) 2009-2012 Jeremy Ashkenas, DocumentCloud Inc. | |
| 2 | // Underscore is freely distributable under the MIT license. | |
| 3 | // Portions of Underscore are inspired or borrowed from Prototype, | |
| 4 | // Oliver Steele's Functional, and John Resig's Micro-Templating. | |
| 5 | // For all details and documentation: | |
| 6 | // http://documentcloud.github.com/underscore | |
| 7 | (function(){function q(a,c,d){if(a===c)return a!==0||1/a==1/c;if(a==null||c==null)return a===c;if(a._chain)a=a._wrapped;if(c._chain)c=c._wrapped;if(a.isEqual&&b.isFunction(a.isEqual))return a.isEqual(c);if(c.isEqual&&b.isFunction(c.isEqual))return c.isEqual(a);var e=l.call(a);if(e!=l.call(c))return false;switch(e){case "[object String]":return a==String(c);case "[object Number]":return a!=+a?c!=+c:a==0?1/a==1/c:a==+c;case "[object Date]":case "[object Boolean]":return+a==+c;case "[object RegExp]":return a.source== | |
| 8 | c.source&&a.global==c.global&&a.multiline==c.multiline&&a.ignoreCase==c.ignoreCase}if(typeof a!="object"||typeof c!="object")return false;for(var f=d.length;f--;)if(d[f]==a)return true;d.push(a);var f=0,g=true;if(e=="[object Array]"){if(f=a.length,g=f==c.length)for(;f--;)if(!(g=f in a==f in c&&q(a[f],c[f],d)))break}else{if("constructor"in a!="constructor"in c||a.constructor!=c.constructor)return false;for(var h in a)if(b.has(a,h)&&(f++,!(g=b.has(c,h)&&q(a[h],c[h],d))))break;if(g){for(h in c)if(b.has(c, | |
| 9 | h)&&!f--)break;g=!f}}d.pop();return g}var r=this,G=r._,n={},k=Array.prototype,o=Object.prototype,i=k.slice,H=k.unshift,l=o.toString,I=o.hasOwnProperty,w=k.forEach,x=k.map,y=k.reduce,z=k.reduceRight,A=k.filter,B=k.every,C=k.some,p=k.indexOf,D=k.lastIndexOf,o=Array.isArray,J=Object.keys,s=Function.prototype.bind,b=function(a){return new m(a)};if(typeof exports!=="undefined"){if(typeof module!=="undefined"&&module.exports)exports=module.exports=b;exports._=b}else r._=b;b.VERSION="1.3.1";var j=b.each= | |
| 10 | b.forEach=function(a,c,d){if(a!=null)if(w&&a.forEach===w)a.forEach(c,d);else if(a.length===+a.length)for(var e=0,f=a.length;e<f;e++){if(e in a&&c.call(d,a[e],e,a)===n)break}else for(e in a)if(b.has(a,e)&&c.call(d,a[e],e,a)===n)break};b.map=b.collect=function(a,c,b){var e=[];if(a==null)return e;if(x&&a.map===x)return a.map(c,b);j(a,function(a,g,h){e[e.length]=c.call(b,a,g,h)});if(a.length===+a.length)e.length=a.length;return e};b.reduce=b.foldl=b.inject=function(a,c,d,e){var f=arguments.length>2;a== | |
| 11 | null&&(a=[]);if(y&&a.reduce===y)return e&&(c=b.bind(c,e)),f?a.reduce(c,d):a.reduce(c);j(a,function(a,b,i){f?d=c.call(e,d,a,b,i):(d=a,f=true)});if(!f)throw new TypeError("Reduce of empty array with no initial value");return d};b.reduceRight=b.foldr=function(a,c,d,e){var f=arguments.length>2;a==null&&(a=[]);if(z&&a.reduceRight===z)return e&&(c=b.bind(c,e)),f?a.reduceRight(c,d):a.reduceRight(c);var g=b.toArray(a).reverse();e&&!f&&(c=b.bind(c,e));return f?b.reduce(g,c,d,e):b.reduce(g,c)};b.find=b.detect= | |
| 12 | function(a,c,b){var e;E(a,function(a,g,h){if(c.call(b,a,g,h))return e=a,true});return e};b.filter=b.select=function(a,c,b){var e=[];if(a==null)return e;if(A&&a.filter===A)return a.filter(c,b);j(a,function(a,g,h){c.call(b,a,g,h)&&(e[e.length]=a)});return e};b.reject=function(a,c,b){var e=[];if(a==null)return e;j(a,function(a,g,h){c.call(b,a,g,h)||(e[e.length]=a)});return e};b.every=b.all=function(a,c,b){var e=true;if(a==null)return e;if(B&&a.every===B)return a.every(c,b);j(a,function(a,g,h){if(!(e= | |
| 13 | e&&c.call(b,a,g,h)))return n});return e};var E=b.some=b.any=function(a,c,d){c||(c=b.identity);var e=false;if(a==null)return e;if(C&&a.some===C)return a.some(c,d);j(a,function(a,b,h){if(e||(e=c.call(d,a,b,h)))return n});return!!e};b.include=b.contains=function(a,c){var b=false;if(a==null)return b;return p&&a.indexOf===p?a.indexOf(c)!=-1:b=E(a,function(a){return a===c})};b.invoke=function(a,c){var d=i.call(arguments,2);return b.map(a,function(a){return(b.isFunction(c)?c||a:a[c]).apply(a,d)})};b.pluck= | |
| 14 | function(a,c){return b.map(a,function(a){return a[c]})};b.max=function(a,c,d){if(!c&&b.isArray(a))return Math.max.apply(Math,a);if(!c&&b.isEmpty(a))return-Infinity;var e={computed:-Infinity};j(a,function(a,b,h){b=c?c.call(d,a,b,h):a;b>=e.computed&&(e={value:a,computed:b})});return e.value};b.min=function(a,c,d){if(!c&&b.isArray(a))return Math.min.apply(Math,a);if(!c&&b.isEmpty(a))return Infinity;var e={computed:Infinity};j(a,function(a,b,h){b=c?c.call(d,a,b,h):a;b<e.computed&&(e={value:a,computed:b})}); | |
| 15 | return e.value};b.shuffle=function(a){var b=[],d;j(a,function(a,f){f==0?b[0]=a:(d=Math.floor(Math.random()*(f+1)),b[f]=b[d],b[d]=a)});return b};b.sortBy=function(a,c,d){return b.pluck(b.map(a,function(a,b,g){return{value:a,criteria:c.call(d,a,b,g)}}).sort(function(a,b){var c=a.criteria,d=b.criteria;return c<d?-1:c>d?1:0}),"value")};b.groupBy=function(a,c){var d={},e=b.isFunction(c)?c:function(a){return a[c]};j(a,function(a,b){var c=e(a,b);(d[c]||(d[c]=[])).push(a)});return d};b.sortedIndex=function(a, | |
| 16 | c,d){d||(d=b.identity);for(var e=0,f=a.length;e<f;){var g=e+f>>1;d(a[g])<d(c)?e=g+1:f=g}return e};b.toArray=function(a){return!a?[]:a.toArray?a.toArray():b.isArray(a)?i.call(a):b.isArguments(a)?i.call(a):b.values(a)};b.size=function(a){return b.toArray(a).length};b.first=b.head=function(a,b,d){return b!=null&&!d?i.call(a,0,b):a[0]};b.initial=function(a,b,d){return i.call(a,0,a.length-(b==null||d?1:b))};b.last=function(a,b,d){return b!=null&&!d?i.call(a,Math.max(a.length-b,0)):a[a.length-1]};b.rest= | |
| 17 | b.tail=function(a,b,d){return i.call(a,b==null||d?1:b)};b.compact=function(a){return b.filter(a,function(a){return!!a})};b.flatten=function(a,c){return b.reduce(a,function(a,e){if(b.isArray(e))return a.concat(c?e:b.flatten(e));a[a.length]=e;return a},[])};b.without=function(a){return b.difference(a,i.call(arguments,1))};b.uniq=b.unique=function(a,c,d){var d=d?b.map(a,d):a,e=[];b.reduce(d,function(d,g,h){if(0==h||(c===true?b.last(d)!=g:!b.include(d,g)))d[d.length]=g,e[e.length]=a[h];return d},[]); | |
| 18 | return e};b.union=function(){return b.uniq(b.flatten(arguments,true))};b.intersection=b.intersect=function(a){var c=i.call(arguments,1);return b.filter(b.uniq(a),function(a){return b.every(c,function(c){return b.indexOf(c,a)>=0})})};b.difference=function(a){var c=b.flatten(i.call(arguments,1));return b.filter(a,function(a){return!b.include(c,a)})};b.zip=function(){for(var a=i.call(arguments),c=b.max(b.pluck(a,"length")),d=Array(c),e=0;e<c;e++)d[e]=b.pluck(a,""+e);return d};b.indexOf=function(a,c, | |
| 19 | d){if(a==null)return-1;var e;if(d)return d=b.sortedIndex(a,c),a[d]===c?d:-1;if(p&&a.indexOf===p)return a.indexOf(c);for(d=0,e=a.length;d<e;d++)if(d in a&&a[d]===c)return d;return-1};b.lastIndexOf=function(a,b){if(a==null)return-1;if(D&&a.lastIndexOf===D)return a.lastIndexOf(b);for(var d=a.length;d--;)if(d in a&&a[d]===b)return d;return-1};b.range=function(a,b,d){arguments.length<=1&&(b=a||0,a=0);for(var d=arguments[2]||1,e=Math.max(Math.ceil((b-a)/d),0),f=0,g=Array(e);f<e;)g[f++]=a,a+=d;return g}; | |
| 20 | var F=function(){};b.bind=function(a,c){var d,e;if(a.bind===s&&s)return s.apply(a,i.call(arguments,1));if(!b.isFunction(a))throw new TypeError;e=i.call(arguments,2);return d=function(){if(!(this instanceof d))return a.apply(c,e.concat(i.call(arguments)));F.prototype=a.prototype;var b=new F,g=a.apply(b,e.concat(i.call(arguments)));return Object(g)===g?g:b}};b.bindAll=function(a){var c=i.call(arguments,1);c.length==0&&(c=b.functions(a));j(c,function(c){a[c]=b.bind(a[c],a)});return a};b.memoize=function(a, | |
| 21 | c){var d={};c||(c=b.identity);return function(){var e=c.apply(this,arguments);return b.has(d,e)?d[e]:d[e]=a.apply(this,arguments)}};b.delay=function(a,b){var d=i.call(arguments,2);return setTimeout(function(){return a.apply(a,d)},b)};b.defer=function(a){return b.delay.apply(b,[a,1].concat(i.call(arguments,1)))};b.throttle=function(a,c){var d,e,f,g,h,i=b.debounce(function(){h=g=false},c);return function(){d=this;e=arguments;var b;f||(f=setTimeout(function(){f=null;h&&a.apply(d,e);i()},c));g?h=true: | |
| 22 | a.apply(d,e);i();g=true}};b.debounce=function(a,b){var d;return function(){var e=this,f=arguments;clearTimeout(d);d=setTimeout(function(){d=null;a.apply(e,f)},b)}};b.once=function(a){var b=false,d;return function(){if(b)return d;b=true;return d=a.apply(this,arguments)}};b.wrap=function(a,b){return function(){var d=[a].concat(i.call(arguments,0));return b.apply(this,d)}};b.compose=function(){var a=arguments;return function(){for(var b=arguments,d=a.length-1;d>=0;d--)b=[a[d].apply(this,b)];return b[0]}}; | |
| 23 | b.after=function(a,b){return a<=0?b():function(){if(--a<1)return b.apply(this,arguments)}};b.keys=J||function(a){if(a!==Object(a))throw new TypeError("Invalid object");var c=[],d;for(d in a)b.has(a,d)&&(c[c.length]=d);return c};b.values=function(a){return b.map(a,b.identity)};b.functions=b.methods=function(a){var c=[],d;for(d in a)b.isFunction(a[d])&&c.push(d);return c.sort()};b.extend=function(a){j(i.call(arguments,1),function(b){for(var d in b)a[d]=b[d]});return a};b.defaults=function(a){j(i.call(arguments, | |
| 24 | 1),function(b){for(var d in b)a[d]==null&&(a[d]=b[d])});return a};b.clone=function(a){return!b.isObject(a)?a:b.isArray(a)?a.slice():b.extend({},a)};b.tap=function(a,b){b(a);return a};b.isEqual=function(a,b){return q(a,b,[])};b.isEmpty=function(a){if(b.isArray(a)||b.isString(a))return a.length===0;for(var c in a)if(b.has(a,c))return false;return true};b.isElement=function(a){return!!(a&&a.nodeType==1)};b.isArray=o||function(a){return l.call(a)=="[object Array]"};b.isObject=function(a){return a===Object(a)}; | |
| 25 | b.isArguments=function(a){return l.call(a)=="[object Arguments]"};if(!b.isArguments(arguments))b.isArguments=function(a){return!(!a||!b.has(a,"callee"))};b.isFunction=function(a){return l.call(a)=="[object Function]"};b.isString=function(a){return l.call(a)=="[object String]"};b.isNumber=function(a){return l.call(a)=="[object Number]"};b.isNaN=function(a){return a!==a};b.isBoolean=function(a){return a===true||a===false||l.call(a)=="[object Boolean]"};b.isDate=function(a){return l.call(a)=="[object Date]"}; | |
| 26 | b.isRegExp=function(a){return l.call(a)=="[object RegExp]"};b.isNull=function(a){return a===null};b.isUndefined=function(a){return a===void 0};b.has=function(a,b){return I.call(a,b)};b.noConflict=function(){r._=G;return this};b.identity=function(a){return a};b.times=function(a,b,d){for(var e=0;e<a;e++)b.call(d,e)};b.escape=function(a){return(""+a).replace(/&/g,"&").replace(/</g,"<").replace(/>/g,">").replace(/"/g,""").replace(/'/g,"'").replace(/\//g,"/")};b.mixin=function(a){j(b.functions(a), | |
| 27 | function(c){K(c,b[c]=a[c])})};var L=0;b.uniqueId=function(a){var b=L++;return a?a+b:b};b.templateSettings={evaluate:/<%([\s\S]+?)%>/g,interpolate:/<%=([\s\S]+?)%>/g,escape:/<%-([\s\S]+?)%>/g};var t=/.^/,u=function(a){return a.replace(/\\\\/g,"\\").replace(/\\'/g,"'")};b.template=function(a,c){var d=b.templateSettings,d="var __p=[],print=function(){__p.push.apply(__p,arguments);};with(obj||{}){__p.push('"+a.replace(/\\/g,"\\\\").replace(/'/g,"\\'").replace(d.escape||t,function(a,b){return"',_.escape("+ | |
| 28 | u(b)+"),'"}).replace(d.interpolate||t,function(a,b){return"',"+u(b)+",'"}).replace(d.evaluate||t,function(a,b){return"');"+u(b).replace(/[\r\n\t]/g," ")+";__p.push('"}).replace(/\r/g,"\\r").replace(/\n/g,"\\n").replace(/\t/g,"\\t")+"');}return __p.join('');",e=new Function("obj","_",d);return c?e(c,b):function(a){return e.call(this,a,b)}};b.chain=function(a){return b(a).chain()};var m=function(a){this._wrapped=a};b.prototype=m.prototype;var v=function(a,c){return c?b(a).chain():a},K=function(a,c){m.prototype[a]= | |
| 29 | function(){var a=i.call(arguments);H.call(a,this._wrapped);return v(c.apply(b,a),this._chain)}};b.mixin(b);j("pop,push,reverse,shift,sort,splice,unshift".split(","),function(a){var b=k[a];m.prototype[a]=function(){var d=this._wrapped;b.apply(d,arguments);var e=d.length;(a=="shift"||a=="splice")&&e===0&&delete d[0];return v(d,this._chain)}});j(["concat","join","slice"],function(a){var b=k[a];m.prototype[a]=function(){return v(b.apply(this._wrapped,arguments),this._chain)}});m.prototype.chain=function(){this._chain= | |
| 30 | true;return this};m.prototype.value=function(){return this._wrapped}}).call(this); |
Binary diff not shown
| 0 | /* | |
| 1 | * websupport.js | |
| 2 | * ~~~~~~~~~~~~~ | |
| 3 | * | |
| 4 | * sphinx.websupport utilities for all documentation. | |
| 5 | * | |
| 6 | * :copyright: Copyright 2007-2016 by the Sphinx team, see AUTHORS. | |
| 7 | * :license: BSD, see LICENSE for details. | |
| 8 | * | |
| 9 | */ | |
| 10 | ||
| 11 | (function($) { | |
| 12 | $.fn.autogrow = function() { | |
| 13 | return this.each(function() { | |
| 14 | var textarea = this; | |
| 15 | ||
| 16 | $.fn.autogrow.resize(textarea); | |
| 17 | ||
| 18 | $(textarea) | |
| 19 | .focus(function() { | |
| 20 | textarea.interval = setInterval(function() { | |
| 21 | $.fn.autogrow.resize(textarea); | |
| 22 | }, 500); | |
| 23 | }) | |
| 24 | .blur(function() { | |
| 25 | clearInterval(textarea.interval); | |
| 26 | }); | |
| 27 | }); | |
| 28 | }; | |
| 29 | ||
| 30 | $.fn.autogrow.resize = function(textarea) { | |
| 31 | var lineHeight = parseInt($(textarea).css('line-height'), 10); | |
| 32 | var lines = textarea.value.split('\n'); | |
| 33 | var columns = textarea.cols; | |
| 34 | var lineCount = 0; | |
| 35 | $.each(lines, function() { | |
| 36 | lineCount += Math.ceil(this.length / columns) || 1; | |
| 37 | }); | |
| 38 | var height = lineHeight * (lineCount + 1); | |
| 39 | $(textarea).css('height', height); | |
| 40 | }; | |
| 41 | })(jQuery); | |
| 42 | ||
| 43 | (function($) { | |
| 44 | var comp, by; | |
| 45 | ||
| 46 | function init() { | |
| 47 | initEvents(); | |
| 48 | initComparator(); | |
| 49 | } | |
| 50 | ||
| 51 | function initEvents() { | |
| 52 | $(document).on("click", 'a.comment-close', function(event) { | |
| 53 | event.preventDefault(); | |
| 54 | hide($(this).attr('id').substring(2)); | |
| 55 | }); | |
| 56 | $(document).on("click", 'a.vote', function(event) { | |
| 57 | event.preventDefault(); | |
| 58 | handleVote($(this)); | |
| 59 | }); | |
| 60 | $(document).on("click", 'a.reply', function(event) { | |
| 61 | event.preventDefault(); | |
| 62 | openReply($(this).attr('id').substring(2)); | |
| 63 | }); | |
| 64 | $(document).on("click", 'a.close-reply', function(event) { | |
| 65 | event.preventDefault(); | |
| 66 | closeReply($(this).attr('id').substring(2)); | |
| 67 | }); | |
| 68 | $(document).on("click", 'a.sort-option', function(event) { | |
| 69 | event.preventDefault(); | |
| 70 | handleReSort($(this)); | |
| 71 | }); | |
| 72 | $(document).on("click", 'a.show-proposal', function(event) { | |
| 73 | event.preventDefault(); | |
| 74 | showProposal($(this).attr('id').substring(2)); | |
| 75 | }); | |
| 76 | $(document).on("click", 'a.hide-proposal', function(event) { | |
| 77 | event.preventDefault(); | |
| 78 | hideProposal($(this).attr('id').substring(2)); | |
| 79 | }); | |
| 80 | $(document).on("click", 'a.show-propose-change', function(event) { | |
| 81 | event.preventDefault(); | |
| 82 | showProposeChange($(this).attr('id').substring(2)); | |
| 83 | }); | |
| 84 | $(document).on("click", 'a.hide-propose-change', function(event) { | |
| 85 | event.preventDefault(); | |
| 86 | hideProposeChange($(this).attr('id').substring(2)); | |
| 87 | }); | |
| 88 | $(document).on("click", 'a.accept-comment', function(event) { | |
| 89 | event.preventDefault(); | |
| 90 | acceptComment($(this).attr('id').substring(2)); | |
| 91 | }); | |
| 92 | $(document).on("click", 'a.delete-comment', function(event) { | |
| 93 | event.preventDefault(); | |
| 94 | deleteComment($(this).attr('id').substring(2)); | |
| 95 | }); | |
| 96 | $(document).on("click", 'a.comment-markup', function(event) { | |
| 97 | event.preventDefault(); | |
| 98 | toggleCommentMarkupBox($(this).attr('id').substring(2)); | |
| 99 | }); | |
| 100 | } | |
| 101 | ||
| 102 | /** | |
| 103 | * Set comp, which is a comparator function used for sorting and | |
| 104 | * inserting comments into the list. | |
| 105 | */ | |
| 106 | function setComparator() { | |
| 107 | // If the first three letters are "asc", sort in ascending order | |
| 108 | // and remove the prefix. | |
| 109 | if (by.substring(0,3) == 'asc') { | |
| 110 | var i = by.substring(3); | |
| 111 | comp = function(a, b) { return a[i] - b[i]; }; | |
| 112 | } else { | |
| 113 | // Otherwise sort in descending order. | |
| 114 | comp = function(a, b) { return b[by] - a[by]; }; | |
| 115 | } | |
| 116 | ||
| 117 | // Reset link styles and format the selected sort option. | |
| 118 | $('a.sel').attr('href', '#').removeClass('sel'); | |
| 119 | $('a.by' + by).removeAttr('href').addClass('sel'); | |
| 120 | } | |
| 121 | ||
| 122 | /** | |
| 123 | * Create a comp function. If the user has preferences stored in | |
| 124 | * the sortBy cookie, use those, otherwise use the default. | |
| 125 | */ | |
| 126 | function initComparator() { | |
| 127 | by = 'rating'; // Default to sort by rating. | |
| 128 | // If the sortBy cookie is set, use that instead. | |
| 129 | if (document.cookie.length > 0) { | |
| 130 | var start = document.cookie.indexOf('sortBy='); | |
| 131 | if (start != -1) { | |
| 132 | start = start + 7; | |
| 133 | var end = document.cookie.indexOf(";", start); | |
| 134 | if (end == -1) { | |
| 135 | end = document.cookie.length; | |
| 136 | by = unescape(document.cookie.substring(start, end)); | |
| 137 | } | |
| 138 | } | |
| 139 | } | |
| 140 | setComparator(); | |
| 141 | } | |
| 142 | ||
| 143 | /** | |
| 144 | * Show a comment div. | |
| 145 | */ | |
| 146 | function show(id) { | |
| 147 | $('#ao' + id).hide(); | |
| 148 | $('#ah' + id).show(); | |
| 149 | var context = $.extend({id: id}, opts); | |
| 150 | var popup = $(renderTemplate(popupTemplate, context)).hide(); | |
| 151 | popup.find('textarea[name="proposal"]').hide(); | |
| 152 | popup.find('a.by' + by).addClass('sel'); | |
| 153 | var form = popup.find('#cf' + id); | |
| 154 | form.submit(function(event) { | |
| 155 | event.preventDefault(); | |
| 156 | addComment(form); | |
| 157 | }); | |
| 158 | $('#s' + id).after(popup); | |
| 159 | popup.slideDown('fast', function() { | |
| 160 | getComments(id); | |
| 161 | }); | |
| 162 | } | |
| 163 | ||
| 164 | /** | |
| 165 | * Hide a comment div. | |
| 166 | */ | |
| 167 | function hide(id) { | |
| 168 | $('#ah' + id).hide(); | |
| 169 | $('#ao' + id).show(); | |
| 170 | var div = $('#sc' + id); | |
| 171 | div.slideUp('fast', function() { | |
| 172 | div.remove(); | |
| 173 | }); | |
| 174 | } | |
| 175 | ||
| 176 | /** | |
| 177 | * Perform an ajax request to get comments for a node | |
| 178 | * and insert the comments into the comments tree. | |
| 179 | */ | |
| 180 | function getComments(id) { | |
| 181 | $.ajax({ | |
| 182 | type: 'GET', | |
| 183 | url: opts.getCommentsURL, | |
| 184 | data: {node: id}, | |
| 185 | success: function(data, textStatus, request) { | |
| 186 | var ul = $('#cl' + id); | |
| 187 | var speed = 100; | |
| 188 | $('#cf' + id) | |
| 189 | .find('textarea[name="proposal"]') | |
| 190 | .data('source', data.source); | |
| 191 | ||
| 192 | if (data.comments.length === 0) { | |
| 193 | ul.html('<li>No comments yet.</li>'); | |
| 194 | ul.data('empty', true); | |
| 195 | } else { | |
| 196 | // If there are comments, sort them and put them in the list. | |
| 197 | var comments = sortComments(data.comments); | |
| 198 | speed = data.comments.length * 100; | |
| 199 | appendComments(comments, ul); | |
| 200 | ul.data('empty', false); | |
| 201 | } | |
| 202 | $('#cn' + id).slideUp(speed + 200); | |
| 203 | ul.slideDown(speed); | |
| 204 | }, | |
| 205 | error: function(request, textStatus, error) { | |
| 206 | showError('Oops, there was a problem retrieving the comments.'); | |
| 207 | }, | |
| 208 | dataType: 'json' | |
| 209 | }); | |
| 210 | } | |
| 211 | ||
| 212 | /** | |
| 213 | * Add a comment via ajax and insert the comment into the comment tree. | |
| 214 | */ | |
| 215 | function addComment(form) { | |
| 216 | var node_id = form.find('input[name="node"]').val(); | |
| 217 | var parent_id = form.find('input[name="parent"]').val(); | |
| 218 | var text = form.find('textarea[name="comment"]').val(); | |
| 219 | var proposal = form.find('textarea[name="proposal"]').val(); | |
| 220 | ||
| 221 | if (text == '') { | |
| 222 | showError('Please enter a comment.'); | |
| 223 | return; | |
| 224 | } | |
| 225 | ||
| 226 | // Disable the form that is being submitted. | |
| 227 | form.find('textarea,input').attr('disabled', 'disabled'); | |
| 228 | ||
| 229 | // Send the comment to the server. | |
| 230 | $.ajax({ | |
| 231 | type: "POST", | |
| 232 | url: opts.addCommentURL, | |
| 233 | dataType: 'json', | |
| 234 | data: { | |
| 235 | node: node_id, | |
| 236 | parent: parent_id, | |
| 237 | text: text, | |
| 238 | proposal: proposal | |
| 239 | }, | |
| 240 | success: function(data, textStatus, error) { | |
| 241 | // Reset the form. | |
| 242 | if (node_id) { | |
| 243 | hideProposeChange(node_id); | |
| 244 | } | |
| 245 | form.find('textarea') | |
| 246 | .val('') | |
| 247 | .add(form.find('input')) | |
| 248 | .removeAttr('disabled'); | |
| 249 | var ul = $('#cl' + (node_id || parent_id)); | |
| 250 | if (ul.data('empty')) { | |
| 251 | $(ul).empty(); | |
| 252 | ul.data('empty', false); | |
| 253 | } | |
| 254 | insertComment(data.comment); | |
| 255 | var ao = $('#ao' + node_id); | |
| 256 | ao.find('img').attr({'src': opts.commentBrightImage}); | |
| 257 | if (node_id) { | |
| 258 | // if this was a "root" comment, remove the commenting box | |
| 259 | // (the user can get it back by reopening the comment popup) | |
| 260 | $('#ca' + node_id).slideUp(); | |
| 261 | } | |
| 262 | }, | |
| 263 | error: function(request, textStatus, error) { | |
| 264 | form.find('textarea,input').removeAttr('disabled'); | |
| 265 | showError('Oops, there was a problem adding the comment.'); | |
| 266 | } | |
| 267 | }); | |
| 268 | } | |
| 269 | ||
| 270 | /** | |
| 271 | * Recursively append comments to the main comment list and children | |
| 272 | * lists, creating the comment tree. | |
| 273 | */ | |
| 274 | function appendComments(comments, ul) { | |
| 275 | $.each(comments, function() { | |
| 276 | var div = createCommentDiv(this); | |
| 277 | ul.append($(document.createElement('li')).html(div)); | |
| 278 | appendComments(this.children, div.find('ul.comment-children')); | |
| 279 | // To avoid stagnating data, don't store the comments children in data. | |
| 280 | this.children = null; | |
| 281 | div.data('comment', this); | |
| 282 | }); | |
| 283 | } | |
| 284 | ||
| 285 | /** | |
| 286 | * After adding a new comment, it must be inserted in the correct | |
| 287 | * location in the comment tree. | |
| 288 | */ | |
| 289 | function insertComment(comment) { | |
| 290 | var div = createCommentDiv(comment); | |
| 291 | ||
| 292 | // To avoid stagnating data, don't store the comments children in data. | |
| 293 | comment.children = null; | |
| 294 | div.data('comment', comment); | |
| 295 | ||
| 296 | var ul = $('#cl' + (comment.node || comment.parent)); | |
| 297 | var siblings = getChildren(ul); | |
| 298 | ||
| 299 | var li = $(document.createElement('li')); | |
| 300 | li.hide(); | |
| 301 | ||
| 302 | // Determine where in the parents children list to insert this comment. | |
| 303 | for(i=0; i < siblings.length; i++) { | |
| 304 | if (comp(comment, siblings[i]) <= 0) { | |
| 305 | $('#cd' + siblings[i].id) | |
| 306 | .parent() | |
| 307 | .before(li.html(div)); | |
| 308 | li.slideDown('fast'); | |
| 309 | return; | |
| 310 | } | |
| 311 | } | |
| 312 | ||
| 313 | // If we get here, this comment rates lower than all the others, | |
| 314 | // or it is the only comment in the list. | |
| 315 | ul.append(li.html(div)); | |
| 316 | li.slideDown('fast'); | |
| 317 | } | |
| 318 | ||
| 319 | function acceptComment(id) { | |
| 320 | $.ajax({ | |
| 321 | type: 'POST', | |
| 322 | url: opts.acceptCommentURL, | |
| 323 | data: {id: id}, | |
| 324 | success: function(data, textStatus, request) { | |
| 325 | $('#cm' + id).fadeOut('fast'); | |
| 326 | $('#cd' + id).removeClass('moderate'); | |
| 327 | }, | |
| 328 | error: function(request, textStatus, error) { | |
| 329 | showError('Oops, there was a problem accepting the comment.'); | |
| 330 | } | |
| 331 | }); | |
| 332 | } | |
| 333 | ||
| 334 | function deleteComment(id) { | |
| 335 | $.ajax({ | |
| 336 | type: 'POST', | |
| 337 | url: opts.deleteCommentURL, | |
| 338 | data: {id: id}, | |
| 339 | success: function(data, textStatus, request) { | |
| 340 | var div = $('#cd' + id); | |
| 341 | if (data == 'delete') { | |
| 342 | // Moderator mode: remove the comment and all children immediately | |
| 343 | div.slideUp('fast', function() { | |
| 344 | div.remove(); | |
| 345 | }); | |
| 346 | return; | |
| 347 | } | |
| 348 | // User mode: only mark the comment as deleted | |
| 349 | div | |
| 350 | .find('span.user-id:first') | |
| 351 | .text('[deleted]').end() | |
| 352 | .find('div.comment-text:first') | |
| 353 | .text('[deleted]').end() | |
| 354 | .find('#cm' + id + ', #dc' + id + ', #ac' + id + ', #rc' + id + | |
| 355 | ', #sp' + id + ', #hp' + id + ', #cr' + id + ', #rl' + id) | |
| 356 | .remove(); | |
| 357 | var comment = div.data('comment'); | |
| 358 | comment.username = '[deleted]'; | |
| 359 | comment.text = '[deleted]'; | |
| 360 | div.data('comment', comment); | |
| 361 | }, | |
| 362 | error: function(request, textStatus, error) { | |
| 363 | showError('Oops, there was a problem deleting the comment.'); | |
| 364 | } | |
| 365 | }); | |
| 366 | } | |
| 367 | ||
| 368 | function showProposal(id) { | |
| 369 | $('#sp' + id).hide(); | |
| 370 | $('#hp' + id).show(); | |
| 371 | $('#pr' + id).slideDown('fast'); | |
| 372 | } | |
| 373 | ||
| 374 | function hideProposal(id) { | |
| 375 | $('#hp' + id).hide(); | |
| 376 | $('#sp' + id).show(); | |
| 377 | $('#pr' + id).slideUp('fast'); | |
| 378 | } | |
| 379 | ||
| 380 | function showProposeChange(id) { | |
| 381 | $('#pc' + id).hide(); | |
| 382 | $('#hc' + id).show(); | |
| 383 | var textarea = $('#pt' + id); | |
| 384 | textarea.val(textarea.data('source')); | |
| 385 | $.fn.autogrow.resize(textarea[0]); | |
| 386 | textarea.slideDown('fast'); | |
| 387 | } | |
| 388 | ||
| 389 | function hideProposeChange(id) { | |
| 390 | $('#hc' + id).hide(); | |
| 391 | $('#pc' + id).show(); | |
| 392 | var textarea = $('#pt' + id); | |
| 393 | textarea.val('').removeAttr('disabled'); | |
| 394 | textarea.slideUp('fast'); | |
| 395 | } | |
| 396 | ||
| 397 | function toggleCommentMarkupBox(id) { | |
| 398 | $('#mb' + id).toggle(); | |
| 399 | } | |
| 400 | ||
| 401 | /** Handle when the user clicks on a sort by link. */ | |
| 402 | function handleReSort(link) { | |
| 403 | var classes = link.attr('class').split(/\s+/); | |
| 404 | for (var i=0; i<classes.length; i++) { | |
| 405 | if (classes[i] != 'sort-option') { | |
| 406 | by = classes[i].substring(2); | |
| 407 | } | |
| 408 | } | |
| 409 | setComparator(); | |
| 410 | // Save/update the sortBy cookie. | |
| 411 | var expiration = new Date(); | |
| 412 | expiration.setDate(expiration.getDate() + 365); | |
| 413 | document.cookie= 'sortBy=' + escape(by) + | |
| 414 | ';expires=' + expiration.toUTCString(); | |
| 415 | $('ul.comment-ul').each(function(index, ul) { | |
| 416 | var comments = getChildren($(ul), true); | |
| 417 | comments = sortComments(comments); | |
| 418 | appendComments(comments, $(ul).empty()); | |
| 419 | }); | |
| 420 | } | |
| 421 | ||
| 422 | /** | |
| 423 | * Function to process a vote when a user clicks an arrow. | |
| 424 | */ | |
| 425 | function handleVote(link) { | |
| 426 | if (!opts.voting) { | |
| 427 | showError("You'll need to login to vote."); | |
| 428 | return; | |
| 429 | } | |
| 430 | ||
| 431 | var id = link.attr('id'); | |
| 432 | if (!id) { | |
| 433 | // Didn't click on one of the voting arrows. | |
| 434 | return; | |
| 435 | } | |
| 436 | // If it is an unvote, the new vote value is 0, | |
| 437 | // Otherwise it's 1 for an upvote, or -1 for a downvote. | |
| 438 | var value = 0; | |
| 439 | if (id.charAt(1) != 'u') { | |
| 440 | value = id.charAt(0) == 'u' ? 1 : -1; | |
| 441 | } | |
| 442 | // The data to be sent to the server. | |
| 443 | var d = { | |
| 444 | comment_id: id.substring(2), | |
| 445 | value: value | |
| 446 | }; | |
| 447 | ||
| 448 | // Swap the vote and unvote links. | |
| 449 | link.hide(); | |
| 450 | $('#' + id.charAt(0) + (id.charAt(1) == 'u' ? 'v' : 'u') + d.comment_id) | |
| 451 | .show(); | |
| 452 | ||
| 453 | // The div the comment is displayed in. | |
| 454 | var div = $('div#cd' + d.comment_id); | |
| 455 | var data = div.data('comment'); | |
| 456 | ||
| 457 | // If this is not an unvote, and the other vote arrow has | |
| 458 | // already been pressed, unpress it. | |
| 459 | if ((d.value !== 0) && (data.vote === d.value * -1)) { | |
| 460 | $('#' + (d.value == 1 ? 'd' : 'u') + 'u' + d.comment_id).hide(); | |
| 461 | $('#' + (d.value == 1 ? 'd' : 'u') + 'v' + d.comment_id).show(); | |
| 462 | } | |
| 463 | ||
| 464 | // Update the comments rating in the local data. | |
| 465 | data.rating += (data.vote === 0) ? d.value : (d.value - data.vote); | |
| 466 | data.vote = d.value; | |
| 467 | div.data('comment', data); | |
| 468 | ||
| 469 | // Change the rating text. | |
| 470 | div.find('.rating:first') | |
| 471 | .text(data.rating + ' point' + (data.rating == 1 ? '' : 's')); | |
| 472 | ||
| 473 | // Send the vote information to the server. | |
| 474 | $.ajax({ | |
| 475 | type: "POST", | |
| 476 | url: opts.processVoteURL, | |
| 477 | data: d, | |
| 478 | error: function(request, textStatus, error) { | |
| 479 | showError('Oops, there was a problem casting that vote.'); | |
| 480 | } | |
| 481 | }); | |
| 482 | } | |
| 483 | ||
| 484 | /** | |
| 485 | * Open a reply form used to reply to an existing comment. | |
| 486 | */ | |
| 487 | function openReply(id) { | |
| 488 | // Swap out the reply link for the hide link | |
| 489 | $('#rl' + id).hide(); | |
| 490 | $('#cr' + id).show(); | |
| 491 | ||
| 492 | // Add the reply li to the children ul. | |
| 493 | var div = $(renderTemplate(replyTemplate, {id: id})).hide(); | |
| 494 | $('#cl' + id) | |
| 495 | .prepend(div) | |
| 496 | // Setup the submit handler for the reply form. | |
| 497 | .find('#rf' + id) | |
| 498 | .submit(function(event) { | |
| 499 | event.preventDefault(); | |
| 500 | addComment($('#rf' + id)); | |
| 501 | closeReply(id); | |
| 502 | }) | |
| 503 | .find('input[type=button]') | |
| 504 | .click(function() { | |
| 505 | closeReply(id); | |
| 506 | }); | |
| 507 | div.slideDown('fast', function() { | |
| 508 | $('#rf' + id).find('textarea').focus(); | |
| 509 | }); | |
| 510 | } | |
| 511 | ||
| 512 | /** | |
| 513 | * Close the reply form opened with openReply. | |
| 514 | */ | |
| 515 | function closeReply(id) { | |
| 516 | // Remove the reply div from the DOM. | |
| 517 | $('#rd' + id).slideUp('fast', function() { | |
| 518 | $(this).remove(); | |
| 519 | }); | |
| 520 | ||
| 521 | // Swap out the hide link for the reply link | |
| 522 | $('#cr' + id).hide(); | |
| 523 | $('#rl' + id).show(); | |
| 524 | } | |
| 525 | ||
| 526 | /** | |
| 527 | * Recursively sort a tree of comments using the comp comparator. | |
| 528 | */ | |
| 529 | function sortComments(comments) { | |
| 530 | comments.sort(comp); | |
| 531 | $.each(comments, function() { | |
| 532 | this.children = sortComments(this.children); | |
| 533 | }); | |
| 534 | return comments; | |
| 535 | } | |
| 536 | ||
| 537 | /** | |
| 538 | * Get the children comments from a ul. If recursive is true, | |
| 539 | * recursively include childrens' children. | |
| 540 | */ | |
| 541 | function getChildren(ul, recursive) { | |
| 542 | var children = []; | |
| 543 | ul.children().children("[id^='cd']") | |
| 544 | .each(function() { | |
| 545 | var comment = $(this).data('comment'); | |
| 546 | if (recursive) | |
| 547 | comment.children = getChildren($(this).find('#cl' + comment.id), true); | |
| 548 | children.push(comment); | |
| 549 | }); | |
| 550 | return children; | |
| 551 | } | |
| 552 | ||
| 553 | /** Create a div to display a comment in. */ | |
| 554 | function createCommentDiv(comment) { | |
| 555 | if (!comment.displayed && !opts.moderator) { | |
| 556 | return $('<div class="moderate">Thank you! Your comment will show up ' | |
| 557 | + 'once it is has been approved by a moderator.</div>'); | |
| 558 | } | |
| 559 | // Prettify the comment rating. | |
| 560 | comment.pretty_rating = comment.rating + ' point' + | |
| 561 | (comment.rating == 1 ? '' : 's'); | |
| 562 | // Make a class (for displaying not yet moderated comments differently) | |
| 563 | comment.css_class = comment.displayed ? '' : ' moderate'; | |
| 564 | // Create a div for this comment. | |
| 565 | var context = $.extend({}, opts, comment); | |
| 566 | var div = $(renderTemplate(commentTemplate, context)); | |
| 567 | ||
| 568 | // If the user has voted on this comment, highlight the correct arrow. | |
| 569 | if (comment.vote) { | |
| 570 | var direction = (comment.vote == 1) ? 'u' : 'd'; | |
| 571 | div.find('#' + direction + 'v' + comment.id).hide(); | |
| 572 | div.find('#' + direction + 'u' + comment.id).show(); | |
| 573 | } | |
| 574 | ||
| 575 | if (opts.moderator || comment.text != '[deleted]') { | |
| 576 | div.find('a.reply').show(); | |
| 577 | if (comment.proposal_diff) | |
| 578 | div.find('#sp' + comment.id).show(); | |
| 579 | if (opts.moderator && !comment.displayed) | |
| 580 | div.find('#cm' + comment.id).show(); | |
| 581 | if (opts.moderator || (opts.username == comment.username)) | |
| 582 | div.find('#dc' + comment.id).show(); | |
| 583 | } | |
| 584 | return div; | |
| 585 | } | |
| 586 | ||
| 587 | /** | |
| 588 | * A simple template renderer. Placeholders such as <%id%> are replaced | |
| 589 | * by context['id'] with items being escaped. Placeholders such as <#id#> | |
| 590 | * are not escaped. | |
| 591 | */ | |
| 592 | function renderTemplate(template, context) { | |
| 593 | var esc = $(document.createElement('div')); | |
| 594 | ||
| 595 | function handle(ph, escape) { | |
| 596 | var cur = context; | |
| 597 | $.each(ph.split('.'), function() { | |
| 598 | cur = cur[this]; | |
| 599 | }); | |
| 600 | return escape ? esc.text(cur || "").html() : cur; | |
| 601 | } | |
| 602 | ||
| 603 | return template.replace(/<([%#])([\w\.]*)\1>/g, function() { | |
| 604 | return handle(arguments[2], arguments[1] == '%' ? true : false); | |
| 605 | }); | |
| 606 | } | |
| 607 | ||
| 608 | /** Flash an error message briefly. */ | |
| 609 | function showError(message) { | |
| 610 | $(document.createElement('div')).attr({'class': 'popup-error'}) | |
| 611 | .append($(document.createElement('div')) | |
| 612 | .attr({'class': 'error-message'}).text(message)) | |
| 613 | .appendTo('body') | |
| 614 | .fadeIn("slow") | |
| 615 | .delay(2000) | |
| 616 | .fadeOut("slow"); | |
| 617 | } | |
| 618 | ||
| 619 | /** Add a link the user uses to open the comments popup. */ | |
| 620 | $.fn.comment = function() { | |
| 621 | return this.each(function() { | |
| 622 | var id = $(this).attr('id').substring(1); | |
| 623 | var count = COMMENT_METADATA[id]; | |
| 624 | var title = count + ' comment' + (count == 1 ? '' : 's'); | |
| 625 | var image = count > 0 ? opts.commentBrightImage : opts.commentImage; | |
| 626 | var addcls = count == 0 ? ' nocomment' : ''; | |
| 627 | $(this) | |
| 628 | .append( | |
| 629 | $(document.createElement('a')).attr({ | |
| 630 | href: '#', | |
| 631 | 'class': 'sphinx-comment-open' + addcls, | |
| 632 | id: 'ao' + id | |
| 633 | }) | |
| 634 | .append($(document.createElement('img')).attr({ | |
| 635 | src: image, | |
| 636 | alt: 'comment', | |
| 637 | title: title | |
| 638 | })) | |
| 639 | .click(function(event) { | |
| 640 | event.preventDefault(); | |
| 641 | show($(this).attr('id').substring(2)); | |
| 642 | }) | |
| 643 | ) | |
| 644 | .append( | |
| 645 | $(document.createElement('a')).attr({ | |
| 646 | href: '#', | |
| 647 | 'class': 'sphinx-comment-close hidden', | |
| 648 | id: 'ah' + id | |
| 649 | }) | |
| 650 | .append($(document.createElement('img')).attr({ | |
| 651 | src: opts.closeCommentImage, | |
| 652 | alt: 'close', | |
| 653 | title: 'close' | |
| 654 | })) | |
| 655 | .click(function(event) { | |
| 656 | event.preventDefault(); | |
| 657 | hide($(this).attr('id').substring(2)); | |
| 658 | }) | |
| 659 | ); | |
| 660 | }); | |
| 661 | }; | |
| 662 | ||
| 663 | var opts = { | |
| 664 | processVoteURL: '/_process_vote', | |
| 665 | addCommentURL: '/_add_comment', | |
| 666 | getCommentsURL: '/_get_comments', | |
| 667 | acceptCommentURL: '/_accept_comment', | |
| 668 | deleteCommentURL: '/_delete_comment', | |
| 669 | commentImage: '/static/_static/comment.png', | |
| 670 | closeCommentImage: '/static/_static/comment-close.png', | |
| 671 | loadingImage: '/static/_static/ajax-loader.gif', | |
| 672 | commentBrightImage: '/static/_static/comment-bright.png', | |
| 673 | upArrow: '/static/_static/up.png', | |
| 674 | downArrow: '/static/_static/down.png', | |
| 675 | upArrowPressed: '/static/_static/up-pressed.png', | |
| 676 | downArrowPressed: '/static/_static/down-pressed.png', | |
| 677 | voting: false, | |
| 678 | moderator: false | |
| 679 | }; | |
| 680 | ||
| 681 | if (typeof COMMENT_OPTIONS != "undefined") { | |
| 682 | opts = jQuery.extend(opts, COMMENT_OPTIONS); | |
| 683 | } | |
| 684 | ||
| 685 | var popupTemplate = '\ | |
| 686 | <div class="sphinx-comments" id="sc<%id%>">\ | |
| 687 | <p class="sort-options">\ | |
| 688 | Sort by:\ | |
| 689 | <a href="#" class="sort-option byrating">best rated</a>\ | |
| 690 | <a href="#" class="sort-option byascage">newest</a>\ | |
| 691 | <a href="#" class="sort-option byage">oldest</a>\ | |
| 692 | </p>\ | |
| 693 | <div class="comment-header">Comments</div>\ | |
| 694 | <div class="comment-loading" id="cn<%id%>">\ | |
| 695 | loading comments... <img src="<%loadingImage%>" alt="" /></div>\ | |
| 696 | <ul id="cl<%id%>" class="comment-ul"></ul>\ | |
| 697 | <div id="ca<%id%>">\ | |
| 698 | <p class="add-a-comment">Add a comment\ | |
| 699 | (<a href="#" class="comment-markup" id="ab<%id%>">markup</a>):</p>\ | |
| 700 | <div class="comment-markup-box" id="mb<%id%>">\ | |
| 701 | reStructured text markup: <i>*emph*</i>, <b>**strong**</b>, \ | |
| 702 | <code>``code``</code>, \ | |
| 703 | code blocks: <code>::</code> and an indented block after blank line</div>\ | |
| 704 | <form method="post" id="cf<%id%>" class="comment-form" action="">\ | |
| 705 | <textarea name="comment" cols="80"></textarea>\ | |
| 706 | <p class="propose-button">\ | |
| 707 | <a href="#" id="pc<%id%>" class="show-propose-change">\ | |
| 708 | Propose a change ▹\ | |
| 709 | </a>\ | |
| 710 | <a href="#" id="hc<%id%>" class="hide-propose-change">\ | |
| 711 | Propose a change ▿\ | |
| 712 | </a>\ | |
| 713 | </p>\ | |
| 714 | <textarea name="proposal" id="pt<%id%>" cols="80"\ | |
| 715 | spellcheck="false"></textarea>\ | |
| 716 | <input type="submit" value="Add comment" />\ | |
| 717 | <input type="hidden" name="node" value="<%id%>" />\ | |
| 718 | <input type="hidden" name="parent" value="" />\ | |
| 719 | </form>\ | |
| 720 | </div>\ | |
| 721 | </div>'; | |
| 722 | ||
| 723 | var commentTemplate = '\ | |
| 724 | <div id="cd<%id%>" class="sphinx-comment<%css_class%>">\ | |
| 725 | <div class="vote">\ | |
| 726 | <div class="arrow">\ | |
| 727 | <a href="#" id="uv<%id%>" class="vote" title="vote up">\ | |
| 728 | <img src="<%upArrow%>" />\ | |
| 729 | </a>\ | |
| 730 | <a href="#" id="uu<%id%>" class="un vote" title="vote up">\ | |
| 731 | <img src="<%upArrowPressed%>" />\ | |
| 732 | </a>\ | |
| 733 | </div>\ | |
| 734 | <div class="arrow">\ | |
| 735 | <a href="#" id="dv<%id%>" class="vote" title="vote down">\ | |
| 736 | <img src="<%downArrow%>" id="da<%id%>" />\ | |
| 737 | </a>\ | |
| 738 | <a href="#" id="du<%id%>" class="un vote" title="vote down">\ | |
| 739 | <img src="<%downArrowPressed%>" />\ | |
| 740 | </a>\ | |
| 741 | </div>\ | |
| 742 | </div>\ | |
| 743 | <div class="comment-content">\ | |
| 744 | <p class="tagline comment">\ | |
| 745 | <span class="user-id"><%username%></span>\ | |
| 746 | <span class="rating"><%pretty_rating%></span>\ | |
| 747 | <span class="delta"><%time.delta%></span>\ | |
| 748 | </p>\ | |
| 749 | <div class="comment-text comment"><#text#></div>\ | |
| 750 | <p class="comment-opts comment">\ | |
| 751 | <a href="#" class="reply hidden" id="rl<%id%>">reply ▹</a>\ | |
| 752 | <a href="#" class="close-reply" id="cr<%id%>">reply ▿</a>\ | |
| 753 | <a href="#" id="sp<%id%>" class="show-proposal">proposal ▹</a>\ | |
| 754 | <a href="#" id="hp<%id%>" class="hide-proposal">proposal ▿</a>\ | |
| 755 | <a href="#" id="dc<%id%>" class="delete-comment hidden">delete</a>\ | |
| 756 | <span id="cm<%id%>" class="moderation hidden">\ | |
| 757 | <a href="#" id="ac<%id%>" class="accept-comment">accept</a>\ | |
| 758 | </span>\ | |
| 759 | </p>\ | |
| 760 | <pre class="proposal" id="pr<%id%>">\ | |
| 761 | <#proposal_diff#>\ | |
| 762 | </pre>\ | |
| 763 | <ul class="comment-children" id="cl<%id%>"></ul>\ | |
| 764 | </div>\ | |
| 765 | <div class="clearleft"></div>\ | |
| 766 | </div>\ | |
| 767 | </div>'; | |
| 768 | ||
| 769 | var replyTemplate = '\ | |
| 770 | <li>\ | |
| 771 | <div class="reply-div" id="rd<%id%>">\ | |
| 772 | <form id="rf<%id%>">\ | |
| 773 | <textarea name="comment" cols="80"></textarea>\ | |
| 774 | <input type="submit" value="Add reply" />\ | |
| 775 | <input type="button" value="Cancel" />\ | |
| 776 | <input type="hidden" name="parent" value="<%id%>" />\ | |
| 777 | <input type="hidden" name="node" value="" />\ | |
| 778 | </form>\ | |
| 779 | </div>\ | |
| 780 | </li>'; | |
| 781 | ||
| 782 | $(document).ready(function() { | |
| 783 | init(); | |
| 784 | }); | |
| 785 | })(jQuery); | |
| 786 | ||
| 787 | $(document).ready(function() { | |
| 788 | // add comment anchors for all paragraphs that are commentable | |
| 789 | $('.sphinx-has-comment').comment(); | |
| 790 | ||
| 791 | // highlight search words in search results | |
| 792 | $("div.context").each(function() { | |
| 793 | var params = $.getQueryParameters(); | |
| 794 | var terms = (params.q) ? params.q[0].split(/\s+/) : []; | |
| 795 | var result = $(this); | |
| 796 | $.each(terms, function() { | |
| 797 | result.highlightText(this.toLowerCase(), 'highlighted'); | |
| 798 | }); | |
| 799 | }); | |
| 800 | ||
| 801 | // directly open comment window if requested | |
| 802 | var anchor = document.location.hash; | |
| 803 | if (anchor.substring(0, 9) == '#comment-') { | |
| 804 | $('#ao' + anchor.substring(9)).click(); | |
| 805 | document.location.hash = '#s' + anchor.substring(9); | |
| 806 | } | |
| 807 | }); |
| 0 | ||
| 1 | ||
| 2 | ||
| 3 | <!DOCTYPE html> | |
| 4 | <!--[if IE 8]><html class="no-js lt-ie9" lang="en" > <![endif]--> | |
| 5 | <!--[if gt IE 8]><!--> <html class="no-js" lang="en" > <!--<![endif]--> | |
| 6 | <head> | |
| 7 | <meta charset="utf-8"> | |
| 8 | ||
| 9 | <meta name="viewport" content="width=device-width, initial-scale=1.0"> | |
| 10 | ||
| 11 | <title>Index — Faraday 0.1 documentation</title> | |
| 12 | ||
| 13 | ||
| 14 | ||
| 15 | ||
| 16 | ||
| 17 | ||
| 18 | ||
| 19 | ||
| 20 | ||
| 21 | ||
| 22 | ||
| 23 | ||
| 24 | ||
| 25 | ||
| 26 | ||
| 27 | <link rel="stylesheet" href="_static/css/theme.css" type="text/css" /> | |
| 28 | ||
| 29 | ||
| 30 | ||
| 31 | ||
| 32 | ||
| 33 | <link rel="index" title="Index" | |
| 34 | href="#"/> | |
| 35 | <link rel="search" title="Search" href="search.html"/> | |
| 36 | <link rel="top" title="Faraday 0.1 documentation" href="index.html"/> | |
| 37 | ||
| 38 | ||
| 39 | <script src="_static/js/modernizr.min.js"></script> | |
| 40 | ||
| 41 | </head> | |
| 42 | ||
| 43 | <body class="wy-body-for-nav" role="document"> | |
| 44 | ||
| 45 | <div class="wy-grid-for-nav"> | |
| 46 | ||
| 47 | ||
| 48 | <nav data-toggle="wy-nav-shift" class="wy-nav-side"> | |
| 49 | <div class="wy-side-scroll"> | |
| 50 | <div class="wy-side-nav-search"> | |
| 51 | ||
| 52 | ||
| 53 | ||
| 54 | <a href="index.html" class="icon icon-home"> Faraday | |
| 55 | ||
| 56 | ||
| 57 | ||
| 58 | </a> | |
| 59 | ||
| 60 | ||
| 61 | ||
| 62 | ||
| 63 | <div class="version"> | |
| 64 | 0.1 | |
| 65 | </div> | |
| 66 | ||
| 67 | ||
| 68 | ||
| 69 | ||
| 70 | <div role="search"> | |
| 71 | <form id="rtd-search-form" class="wy-form" action="search.html" method="get"> | |
| 72 | <input type="text" name="q" placeholder="Search docs" /> | |
| 73 | <input type="hidden" name="check_keywords" value="yes" /> | |
| 74 | <input type="hidden" name="area" value="default" /> | |
| 75 | </form> | |
| 76 | </div> | |
| 77 | ||
| 78 | ||
| 79 | </div> | |
| 80 | ||
| 81 | <div class="wy-menu wy-menu-vertical" data-spy="affix" role="navigation" aria-label="main navigation"> | |
| 82 | ||
| 83 | ||
| 84 | ||
| 85 | <!-- Local TOC --> | |
| 86 | <div class="local-toc"></div> | |
| 87 | ||
| 88 | ||
| 89 | </div> | |
| 90 | </div> | |
| 91 | </nav> | |
| 92 | ||
| 93 | <section data-toggle="wy-nav-shift" class="wy-nav-content-wrap"> | |
| 94 | ||
| 95 | ||
| 96 | <nav class="wy-nav-top" role="navigation" aria-label="top navigation"> | |
| 97 | <i data-toggle="wy-nav-top" class="fa fa-bars"></i> | |
| 98 | <a href="index.html">Faraday</a> | |
| 99 | </nav> | |
| 100 | ||
| 101 | ||
| 102 | ||
| 103 | <div class="wy-nav-content"> | |
| 104 | <div class="rst-content"> | |
| 105 | ||
| 106 | ||
| 107 | ||
| 108 | ||
| 109 | ||
| 110 | ||
| 111 | <div role="navigation" aria-label="breadcrumbs navigation"> | |
| 112 | <ul class="wy-breadcrumbs"> | |
| 113 | <li><a href="index.html">Docs</a> »</li> | |
| 114 | ||
| 115 | <li></li> | |
| 116 | <li class="wy-breadcrumbs-aside"> | |
| 117 | ||
| 118 | ||
| 119 | ||
| 120 | </li> | |
| 121 | </ul> | |
| 122 | <hr/> | |
| 123 | </div> | |
| 124 | <div role="main" class="document" itemscope="itemscope" itemtype="http://schema.org/Article"> | |
| 125 | <div itemprop="articleBody"> | |
| 126 | ||
| 127 | ||
| 128 | <h1 id="index">Index</h1> | |
| 129 | ||
| 130 | <div class="genindex-jumpbox"> | |
| 131 | <a href="#C"><strong>C</strong></a> | |
| 132 | | <a href="#D"><strong>D</strong></a> | |
| 133 | | <a href="#G"><strong>G</strong></a> | |
| 134 | | <a href="#I"><strong>I</strong></a> | |
| 135 | | <a href="#P"><strong>P</strong></a> | |
| 136 | | <a href="#T"><strong>T</strong></a> | |
| 137 | | <a href="#U"><strong>U</strong></a> | |
| 138 | ||
| 139 | </div> | |
| 140 | <h2 id="C">C</h2> | |
| 141 | <table style="width: 100%" class="indextable genindextable"><tr> | |
| 142 | <td style="width: 33%; vertical-align: top;"><ul> | |
| 143 | <li><a href="server.html#persistence.server.server.create_command">create_command() (in module persistence.server.server)</a> | |
| 144 | </li> | |
| 145 | <li><a href="server.html#persistence.server.server.create_credential">create_credential() (in module persistence.server.server)</a> | |
| 146 | </li> | |
| 147 | <li><a href="server.html#persistence.server.server.create_host">create_host() (in module persistence.server.server)</a> | |
| 148 | </li> | |
| 149 | <li><a href="server.html#persistence.server.server.create_interface">create_interface() (in module persistence.server.server)</a> | |
| 150 | </li> | |
| 151 | </ul></td> | |
| 152 | <td style="width: 33%; vertical-align: top;"><ul> | |
| 153 | <li><a href="server.html#persistence.server.server.create_note">create_note() (in module persistence.server.server)</a> | |
| 154 | </li> | |
| 155 | <li><a href="server.html#persistence.server.server.create_service">create_service() (in module persistence.server.server)</a> | |
| 156 | </li> | |
| 157 | <li><a href="server.html#persistence.server.server.create_vuln">create_vuln() (in module persistence.server.server)</a> | |
| 158 | </li> | |
| 159 | <li><a href="server.html#persistence.server.server.create_vuln_web">create_vuln_web() (in module persistence.server.server)</a> | |
| 160 | </li> | |
| 161 | <li><a href="server.html#persistence.server.server.create_workspace">create_workspace() (in module persistence.server.server)</a> | |
| 162 | </li> | |
| 163 | </ul></td> | |
| 164 | </tr></table> | |
| 165 | ||
| 166 | <h2 id="D">D</h2> | |
| 167 | <table style="width: 100%" class="indextable genindextable"><tr> | |
| 168 | <td style="width: 33%; vertical-align: top;"><ul> | |
| 169 | <li><a href="server.html#persistence.server.server.delete_command">delete_command() (in module persistence.server.server)</a> | |
| 170 | </li> | |
| 171 | <li><a href="server.html#persistence.server.server.delete_credential">delete_credential() (in module persistence.server.server)</a> | |
| 172 | </li> | |
| 173 | <li><a href="server.html#persistence.server.server.delete_host">delete_host() (in module persistence.server.server)</a> | |
| 174 | </li> | |
| 175 | <li><a href="server.html#persistence.server.server.delete_interface">delete_interface() (in module persistence.server.server)</a> | |
| 176 | </li> | |
| 177 | </ul></td> | |
| 178 | <td style="width: 33%; vertical-align: top;"><ul> | |
| 179 | <li><a href="server.html#persistence.server.server.delete_note">delete_note() (in module persistence.server.server)</a> | |
| 180 | </li> | |
| 181 | <li><a href="server.html#persistence.server.server.delete_service">delete_service() (in module persistence.server.server)</a> | |
| 182 | </li> | |
| 183 | <li><a href="server.html#persistence.server.server.delete_vuln">delete_vuln() (in module persistence.server.server)</a> | |
| 184 | </li> | |
| 185 | <li><a href="server.html#persistence.server.server.delete_workspace">delete_workspace() (in module persistence.server.server)</a> | |
| 186 | </li> | |
| 187 | </ul></td> | |
| 188 | </tr></table> | |
| 189 | ||
| 190 | <h2 id="G">G</h2> | |
| 191 | <table style="width: 100%" class="indextable genindextable"><tr> | |
| 192 | <td style="width: 33%; vertical-align: top;"><ul> | |
| 193 | <li><a href="server.html#persistence.server.server.get_all_vulns">get_all_vulns() (in module persistence.server.server)</a> | |
| 194 | </li> | |
| 195 | <li><a href="server.html#persistence.server.server.get_changes_stream">get_changes_stream() (in module persistence.server.server)</a> | |
| 196 | </li> | |
| 197 | <li><a href="server.html#persistence.server.server.get_command">get_command() (in module persistence.server.server)</a> | |
| 198 | </li> | |
| 199 | <li><a href="server.html#persistence.server.server.get_commands">get_commands() (in module persistence.server.server)</a> | |
| 200 | </li> | |
| 201 | <li><a href="server.html#persistence.server.server.get_commands_number">get_commands_number() (in module persistence.server.server)</a> | |
| 202 | </li> | |
| 203 | <li><a href="server.html#persistence.server.server.get_credential">get_credential() (in module persistence.server.server)</a> | |
| 204 | </li> | |
| 205 | <li><a href="server.html#persistence.server.server.get_credentials">get_credentials() (in module persistence.server.server)</a> | |
| 206 | </li> | |
| 207 | <li><a href="server.html#persistence.server.server.get_credentials_number">get_credentials_number() (in module persistence.server.server)</a> | |
| 208 | </li> | |
| 209 | <li><a href="server.html#persistence.server.server.get_host">get_host() (in module persistence.server.server)</a> | |
| 210 | </li> | |
| 211 | <li><a href="server.html#persistence.server.server.get_hosts">get_hosts() (in module persistence.server.server)</a> | |
| 212 | </li> | |
| 213 | <li><a href="server.html#persistence.server.server.get_hosts_number">get_hosts_number() (in module persistence.server.server)</a> | |
| 214 | </li> | |
| 215 | <li><a href="server.html#persistence.server.server.get_interface">get_interface() (in module persistence.server.server)</a> | |
| 216 | </li> | |
| 217 | <li><a href="server.html#persistence.server.server.get_interfaces">get_interfaces() (in module persistence.server.server)</a> | |
| 218 | </li> | |
| 219 | <li><a href="server.html#persistence.server.server.get_interfaces_number">get_interfaces_number() (in module persistence.server.server)</a> | |
| 220 | </li> | |
| 221 | <li><a href="server.html#persistence.server.server.get_note">get_note() (in module persistence.server.server)</a> | |
| 222 | </li> | |
| 223 | <li><a href="server.html#persistence.server.server.get_notes">get_notes() (in module persistence.server.server)</a> | |
| 224 | </li> | |
| 225 | </ul></td> | |
| 226 | <td style="width: 33%; vertical-align: top;"><ul> | |
| 227 | <li><a href="server.html#persistence.server.server.get_notes_number">get_notes_number() (in module persistence.server.server)</a> | |
| 228 | </li> | |
| 229 | <li><a href="server.html#persistence.server.server.get_object">get_object() (in module persistence.server.server)</a> | |
| 230 | </li> | |
| 231 | <li><a href="server.html#persistence.server.server.get_object_before_last_revision">get_object_before_last_revision() (in module persistence.server.server)</a> | |
| 232 | </li> | |
| 233 | <li><a href="server.html#persistence.server.server.get_objects">get_objects() (in module persistence.server.server)</a> | |
| 234 | </li> | |
| 235 | <li><a href="server.html#persistence.server.server.get_service">get_service() (in module persistence.server.server)</a> | |
| 236 | </li> | |
| 237 | <li><a href="server.html#persistence.server.server.get_services">get_services() (in module persistence.server.server)</a> | |
| 238 | </li> | |
| 239 | <li><a href="server.html#persistence.server.server.get_services_number">get_services_number() (in module persistence.server.server)</a> | |
| 240 | </li> | |
| 241 | <li><a href="server.html#persistence.server.server.get_vuln">get_vuln() (in module persistence.server.server)</a> | |
| 242 | </li> | |
| 243 | <li><a href="server.html#persistence.server.server.get_vulns">get_vulns() (in module persistence.server.server)</a> | |
| 244 | </li> | |
| 245 | <li><a href="server.html#persistence.server.server.get_vulns_number">get_vulns_number() (in module persistence.server.server)</a> | |
| 246 | </li> | |
| 247 | <li><a href="server.html#persistence.server.server.get_web_vuln">get_web_vuln() (in module persistence.server.server)</a> | |
| 248 | </li> | |
| 249 | <li><a href="server.html#persistence.server.server.get_web_vulns">get_web_vulns() (in module persistence.server.server)</a> | |
| 250 | </li> | |
| 251 | <li><a href="server.html#persistence.server.server.get_workspace">get_workspace() (in module persistence.server.server)</a> | |
| 252 | </li> | |
| 253 | <li><a href="server.html#persistence.server.server.get_workspace_numbers">get_workspace_numbers() (in module persistence.server.server)</a> | |
| 254 | </li> | |
| 255 | <li><a href="server.html#persistence.server.server.get_workspace_summary">get_workspace_summary() (in module persistence.server.server)</a> | |
| 256 | </li> | |
| 257 | <li><a href="server.html#persistence.server.server.get_workspaces_names">get_workspaces_names() (in module persistence.server.server)</a> | |
| 258 | </li> | |
| 259 | </ul></td> | |
| 260 | </tr></table> | |
| 261 | ||
| 262 | <h2 id="I">I</h2> | |
| 263 | <table style="width: 100%" class="indextable genindextable"><tr> | |
| 264 | <td style="width: 33%; vertical-align: top;"><ul> | |
| 265 | <li><a href="server.html#persistence.server.server.is_server_up">is_server_up() (in module persistence.server.server)</a> | |
| 266 | </li> | |
| 267 | </ul></td> | |
| 268 | </tr></table> | |
| 269 | ||
| 270 | <h2 id="P">P</h2> | |
| 271 | <table style="width: 100%" class="indextable genindextable"><tr> | |
| 272 | <td style="width: 33%; vertical-align: top;"><ul> | |
| 273 | <li><a href="server.html#module-persistence.server.server">persistence.server.server (module)</a> | |
| 274 | </li> | |
| 275 | </ul></td> | |
| 276 | </tr></table> | |
| 277 | ||
| 278 | <h2 id="T">T</h2> | |
| 279 | <table style="width: 100%" class="indextable genindextable"><tr> | |
| 280 | <td style="width: 33%; vertical-align: top;"><ul> | |
| 281 | <li><a href="server.html#persistence.server.server.test_server_url">check_server_url() (in module persistence.server.server)</a> | |
| 282 | </li> | |
| 283 | </ul></td> | |
| 284 | </tr></table> | |
| 285 | ||
| 286 | <h2 id="U">U</h2> | |
| 287 | <table style="width: 100%" class="indextable genindextable"><tr> | |
| 288 | <td style="width: 33%; vertical-align: top;"><ul> | |
| 289 | <li><a href="server.html#persistence.server.server.update_command">update_command() (in module persistence.server.server)</a> | |
| 290 | </li> | |
| 291 | <li><a href="server.html#persistence.server.server.update_credential">update_credential() (in module persistence.server.server)</a> | |
| 292 | </li> | |
| 293 | <li><a href="server.html#persistence.server.server.update_host">update_host() (in module persistence.server.server)</a> | |
| 294 | </li> | |
| 295 | <li><a href="server.html#persistence.server.server.update_interface">update_interface() (in module persistence.server.server)</a> | |
| 296 | </li> | |
| 297 | </ul></td> | |
| 298 | <td style="width: 33%; vertical-align: top;"><ul> | |
| 299 | <li><a href="server.html#persistence.server.server.update_note">update_note() (in module persistence.server.server)</a> | |
| 300 | </li> | |
| 301 | <li><a href="server.html#persistence.server.server.update_service">update_service() (in module persistence.server.server)</a> | |
| 302 | </li> | |
| 303 | <li><a href="server.html#persistence.server.server.update_vuln">update_vuln() (in module persistence.server.server)</a> | |
| 304 | </li> | |
| 305 | <li><a href="server.html#persistence.server.server.update_vuln_web">update_vuln_web() (in module persistence.server.server)</a> | |
| 306 | </li> | |
| 307 | </ul></td> | |
| 308 | </tr></table> | |
| 309 | ||
| 310 | ||
| 311 | ||
| 312 | </div> | |
| 313 | </div> | |
| 314 | <footer> | |
| 315 | ||
| 316 | ||
| 317 | <hr/> | |
| 318 | ||
| 319 | <div role="contentinfo"> | |
| 320 | <p> | |
| 321 | © Copyright 2016, Infobyte. | |
| 322 | ||
| 323 | </p> | |
| 324 | </div> | |
| 325 | Built with <a href="http://sphinx-doc.org/">Sphinx</a> using a <a href="https://github.com/snide/sphinx_rtd_theme">theme</a> provided by <a href="https://readthedocs.org">Read the Docs</a>. | |
| 326 | ||
| 327 | </footer> | |
| 328 | ||
| 329 | </div> | |
| 330 | </div> | |
| 331 | ||
| 332 | </section> | |
| 333 | ||
| 334 | </div> | |
| 335 | ||
| 336 | ||
| 337 | ||
| 338 | ||
| 339 | ||
| 340 | <script type="text/javascript"> | |
| 341 | var DOCUMENTATION_OPTIONS = { | |
| 342 | URL_ROOT:'./', | |
| 343 | VERSION:'0.1', | |
| 344 | COLLAPSE_INDEX:false, | |
| 345 | FILE_SUFFIX:'.html', | |
| 346 | HAS_SOURCE: true | |
| 347 | }; | |
| 348 | </script> | |
| 349 | <script type="text/javascript" src="_static/jquery.js"></script> | |
| 350 | <script type="text/javascript" src="_static/underscore.js"></script> | |
| 351 | <script type="text/javascript" src="_static/doctools.js"></script> | |
| 352 | ||
| 353 | ||
| 354 | ||
| 355 | ||
| 356 | ||
| 357 | <script type="text/javascript" src="_static/js/theme.js"></script> | |
| 358 | ||
| 359 | ||
| 360 | ||
| 361 | ||
| 362 | <script type="text/javascript"> | |
| 363 | jQuery(function () { | |
| 364 | SphinxRtdTheme.StickyNav.enable(); | |
| 365 | }); | |
| 366 | </script> | |
| 367 | ||
| 368 | ||
| 369 | </body> | |
| 370 | </html>⏎ |
| 0 | ||
| 1 | ||
| 2 | <!DOCTYPE html> | |
| 3 | <!--[if IE 8]><html class="no-js lt-ie9" lang="en" > <![endif]--> | |
| 4 | <!--[if gt IE 8]><!--> <html class="no-js" lang="en" > <!--<![endif]--> | |
| 5 | <head> | |
| 6 | <meta charset="utf-8"> | |
| 7 | ||
| 8 | <meta name="viewport" content="width=device-width, initial-scale=1.0"> | |
| 9 | ||
| 10 | <title>Welcome to Faraday’s documentation! — Faraday 0.1 documentation</title> | |
| 11 | ||
| 12 | ||
| 13 | ||
| 14 | ||
| 15 | ||
| 16 | ||
| 17 | ||
| 18 | ||
| 19 | ||
| 20 | ||
| 21 | ||
| 22 | ||
| 23 | ||
| 24 | ||
| 25 | ||
| 26 | <link rel="stylesheet" href="_static/css/theme.css" type="text/css" /> | |
| 27 | ||
| 28 | ||
| 29 | ||
| 30 | ||
| 31 | ||
| 32 | <link rel="index" title="Index" | |
| 33 | href="genindex.html"/> | |
| 34 | <link rel="search" title="Search" href="search.html"/> | |
| 35 | <link rel="top" title="Faraday 0.1 documentation" href="#"/> | |
| 36 | ||
| 37 | ||
| 38 | <script src="_static/js/modernizr.min.js"></script> | |
| 39 | ||
| 40 | </head> | |
| 41 | ||
| 42 | <body class="wy-body-for-nav" role="document"> | |
| 43 | ||
| 44 | <div class="wy-grid-for-nav"> | |
| 45 | ||
| 46 | ||
| 47 | <nav data-toggle="wy-nav-shift" class="wy-nav-side"> | |
| 48 | <div class="wy-side-scroll"> | |
| 49 | <div class="wy-side-nav-search"> | |
| 50 | ||
| 51 | ||
| 52 | ||
| 53 | <a href="#" class="icon icon-home"> Faraday | |
| 54 | ||
| 55 | ||
| 56 | ||
| 57 | </a> | |
| 58 | ||
| 59 | ||
| 60 | ||
| 61 | ||
| 62 | <div class="version"> | |
| 63 | 0.1 | |
| 64 | </div> | |
| 65 | ||
| 66 | ||
| 67 | ||
| 68 | ||
| 69 | <div role="search"> | |
| 70 | <form id="rtd-search-form" class="wy-form" action="search.html" method="get"> | |
| 71 | <input type="text" name="q" placeholder="Search docs" /> | |
| 72 | <input type="hidden" name="check_keywords" value="yes" /> | |
| 73 | <input type="hidden" name="area" value="default" /> | |
| 74 | </form> | |
| 75 | </div> | |
| 76 | ||
| 77 | ||
| 78 | </div> | |
| 79 | ||
| 80 | <div class="wy-menu wy-menu-vertical" data-spy="affix" role="navigation" aria-label="main navigation"> | |
| 81 | ||
| 82 | ||
| 83 | ||
| 84 | <!-- Local TOC --> | |
| 85 | <div class="local-toc"><ul> | |
| 86 | <li><a class="reference internal" href="#">Welcome to Faraday’s documentation!</a></li> | |
| 87 | <li><a class="reference internal" href="#indices-and-tables">Indices and tables</a></li> | |
| 88 | </ul> | |
| 89 | </div> | |
| 90 | ||
| 91 | ||
| 92 | </div> | |
| 93 | </div> | |
| 94 | </nav> | |
| 95 | ||
| 96 | <section data-toggle="wy-nav-shift" class="wy-nav-content-wrap"> | |
| 97 | ||
| 98 | ||
| 99 | <nav class="wy-nav-top" role="navigation" aria-label="top navigation"> | |
| 100 | <i data-toggle="wy-nav-top" class="fa fa-bars"></i> | |
| 101 | <a href="#">Faraday</a> | |
| 102 | </nav> | |
| 103 | ||
| 104 | ||
| 105 | ||
| 106 | <div class="wy-nav-content"> | |
| 107 | <div class="rst-content"> | |
| 108 | ||
| 109 | ||
| 110 | ||
| 111 | ||
| 112 | ||
| 113 | ||
| 114 | <div role="navigation" aria-label="breadcrumbs navigation"> | |
| 115 | <ul class="wy-breadcrumbs"> | |
| 116 | <li><a href="#">Docs</a> »</li> | |
| 117 | ||
| 118 | <li>Welcome to Faraday’s documentation!</li> | |
| 119 | <li class="wy-breadcrumbs-aside"> | |
| 120 | ||
| 121 | ||
| 122 | <a href="_sources/index.rst.txt" rel="nofollow"> View page source</a> | |
| 123 | ||
| 124 | ||
| 125 | </li> | |
| 126 | </ul> | |
| 127 | <hr/> | |
| 128 | </div> | |
| 129 | <div role="main" class="document" itemscope="itemscope" itemtype="http://schema.org/Article"> | |
| 130 | <div itemprop="articleBody"> | |
| 131 | ||
| 132 | <div class="section" id="welcome-to-faraday-s-documentation"> | |
| 133 | <h1>Welcome to Faraday’s documentation!<a class="headerlink" href="#welcome-to-faraday-s-documentation" title="Permalink to this headline">¶</a></h1> | |
| 134 | <p>Contents:</p> | |
| 135 | <div class="toctree-wrapper compound"> | |
| 136 | </div> | |
| 137 | </div> | |
| 138 | <div class="section" id="indices-and-tables"> | |
| 139 | <h1>Indices and tables<a class="headerlink" href="#indices-and-tables" title="Permalink to this headline">¶</a></h1> | |
| 140 | <ul class="simple"> | |
| 141 | <li><a class="reference internal" href="genindex.html"><span class="std std-ref">Index</span></a></li> | |
| 142 | <li><a class="reference internal" href="py-modindex.html"><span class="std std-ref">Module Index</span></a></li> | |
| 143 | <li><a class="reference internal" href="search.html"><span class="std std-ref">Search Page</span></a></li> | |
| 144 | </ul> | |
| 145 | </div> | |
| 146 | ||
| 147 | ||
| 148 | </div> | |
| 149 | </div> | |
| 150 | <footer> | |
| 151 | ||
| 152 | ||
| 153 | <hr/> | |
| 154 | ||
| 155 | <div role="contentinfo"> | |
| 156 | <p> | |
| 157 | © Copyright 2016, Infobyte. | |
| 158 | ||
| 159 | </p> | |
| 160 | </div> | |
| 161 | Built with <a href="http://sphinx-doc.org/">Sphinx</a> using a <a href="https://github.com/snide/sphinx_rtd_theme">theme</a> provided by <a href="https://readthedocs.org">Read the Docs</a>. | |
| 162 | ||
| 163 | </footer> | |
| 164 | ||
| 165 | </div> | |
| 166 | </div> | |
| 167 | ||
| 168 | </section> | |
| 169 | ||
| 170 | </div> | |
| 171 | ||
| 172 | ||
| 173 | ||
| 174 | ||
| 175 | ||
| 176 | <script type="text/javascript"> | |
| 177 | var DOCUMENTATION_OPTIONS = { | |
| 178 | URL_ROOT:'./', | |
| 179 | VERSION:'0.1', | |
| 180 | COLLAPSE_INDEX:false, | |
| 181 | FILE_SUFFIX:'.html', | |
| 182 | HAS_SOURCE: true | |
| 183 | }; | |
| 184 | </script> | |
| 185 | <script type="text/javascript" src="_static/jquery.js"></script> | |
| 186 | <script type="text/javascript" src="_static/underscore.js"></script> | |
| 187 | <script type="text/javascript" src="_static/doctools.js"></script> | |
| 188 | ||
| 189 | ||
| 190 | ||
| 191 | ||
| 192 | ||
| 193 | <script type="text/javascript" src="_static/js/theme.js"></script> | |
| 194 | ||
| 195 | ||
| 196 | ||
| 197 | ||
| 198 | <script type="text/javascript"> | |
| 199 | jQuery(function () { | |
| 200 | SphinxRtdTheme.StickyNav.enable(); | |
| 201 | }); | |
| 202 | </script> | |
| 203 | ||
| 204 | ||
| 205 | </body> | |
| 206 | </html>⏎ |
| 0 | ||
| 1 | ||
| 2 | <!DOCTYPE html> | |
| 3 | <!--[if IE 8]><html class="no-js lt-ie9" lang="en" > <![endif]--> | |
| 4 | <!--[if gt IE 8]><!--> <html class="no-js" lang="en" > <!--<![endif]--> | |
| 5 | <head> | |
| 6 | <meta charset="utf-8"> | |
| 7 | ||
| 8 | <meta name="viewport" content="width=device-width, initial-scale=1.0"> | |
| 9 | ||
| 10 | <title>server — Faraday 0.1 documentation</title> | |
| 11 | ||
| 12 | ||
| 13 | ||
| 14 | ||
| 15 | ||
| 16 | ||
| 17 | ||
| 18 | ||
| 19 | ||
| 20 | ||
| 21 | ||
| 22 | ||
| 23 | ||
| 24 | ||
| 25 | ||
| 26 | <link rel="stylesheet" href="_static/css/theme.css" type="text/css" /> | |
| 27 | ||
| 28 | ||
| 29 | ||
| 30 | ||
| 31 | ||
| 32 | <link rel="index" title="Index" | |
| 33 | href="genindex.html"/> | |
| 34 | <link rel="search" title="Search" href="search.html"/> | |
| 35 | <link rel="top" title="Faraday 0.1 documentation" href="index.html"/> | |
| 36 | ||
| 37 | ||
| 38 | <script src="_static/js/modernizr.min.js"></script> | |
| 39 | ||
| 40 | </head> | |
| 41 | ||
| 42 | <body class="wy-body-for-nav" role="document"> | |
| 43 | ||
| 44 | <div class="wy-grid-for-nav"> | |
| 45 | ||
| 46 | ||
| 47 | <nav data-toggle="wy-nav-shift" class="wy-nav-side"> | |
| 48 | <div class="wy-side-scroll"> | |
| 49 | <div class="wy-side-nav-search"> | |
| 50 | ||
| 51 | ||
| 52 | ||
| 53 | <a href="index.html" class="icon icon-home"> Faraday | |
| 54 | ||
| 55 | ||
| 56 | ||
| 57 | </a> | |
| 58 | ||
| 59 | ||
| 60 | ||
| 61 | ||
| 62 | <div class="version"> | |
| 63 | 0.1 | |
| 64 | </div> | |
| 65 | ||
| 66 | ||
| 67 | ||
| 68 | ||
| 69 | <div role="search"> | |
| 70 | <form id="rtd-search-form" class="wy-form" action="search.html" method="get"> | |
| 71 | <input type="text" name="q" placeholder="Search docs" /> | |
| 72 | <input type="hidden" name="check_keywords" value="yes" /> | |
| 73 | <input type="hidden" name="area" value="default" /> | |
| 74 | </form> | |
| 75 | </div> | |
| 76 | ||
| 77 | ||
| 78 | </div> | |
| 79 | ||
| 80 | <div class="wy-menu wy-menu-vertical" data-spy="affix" role="navigation" aria-label="main navigation"> | |
| 81 | ||
| 82 | ||
| 83 | ||
| 84 | <!-- Local TOC --> | |
| 85 | <div class="local-toc"><ul> | |
| 86 | <li><a class="reference internal" href="#">server</a></li> | |
| 87 | </ul> | |
| 88 | </div> | |
| 89 | ||
| 90 | ||
| 91 | </div> | |
| 92 | </div> | |
| 93 | </nav> | |
| 94 | ||
| 95 | <section data-toggle="wy-nav-shift" class="wy-nav-content-wrap"> | |
| 96 | ||
| 97 | ||
| 98 | <nav class="wy-nav-top" role="navigation" aria-label="top navigation"> | |
| 99 | <i data-toggle="wy-nav-top" class="fa fa-bars"></i> | |
| 100 | <a href="index.html">Faraday</a> | |
| 101 | </nav> | |
| 102 | ||
| 103 | ||
| 104 | ||
| 105 | <div class="wy-nav-content"> | |
| 106 | <div class="rst-content"> | |
| 107 | ||
| 108 | ||
| 109 | ||
| 110 | ||
| 111 | ||
| 112 | ||
| 113 | <div role="navigation" aria-label="breadcrumbs navigation"> | |
| 114 | <ul class="wy-breadcrumbs"> | |
| 115 | <li><a href="index.html">Docs</a> »</li> | |
| 116 | ||
| 117 | <li>server</li> | |
| 118 | <li class="wy-breadcrumbs-aside"> | |
| 119 | ||
| 120 | ||
| 121 | <a href="_sources/modules.rst.txt" rel="nofollow"> View page source</a> | |
| 122 | ||
| 123 | ||
| 124 | </li> | |
| 125 | </ul> | |
| 126 | <hr/> | |
| 127 | </div> | |
| 128 | <div role="main" class="document" itemscope="itemscope" itemtype="http://schema.org/Article"> | |
| 129 | <div itemprop="articleBody"> | |
| 130 | ||
| 131 | <div class="section" id="server"> | |
| 132 | <h1>server<a class="headerlink" href="#server" title="Permalink to this headline">¶</a></h1> | |
| 133 | <div class="toctree-wrapper compound"> | |
| 134 | <ul> | |
| 135 | <li class="toctree-l1"><a class="reference internal" href="server.html">server package</a><ul> | |
| 136 | <li class="toctree-l2"><a class="reference internal" href="server.html#submodules">Submodules</a></li> | |
| 137 | <li class="toctree-l2"><a class="reference internal" href="server.html#module-persistence.server.server">server.utils module</a></li> | |
| 138 | </ul> | |
| 139 | </li> | |
| 140 | </ul> | |
| 141 | </div> | |
| 142 | </div> | |
| 143 | ||
| 144 | ||
| 145 | </div> | |
| 146 | </div> | |
| 147 | <footer> | |
| 148 | ||
| 149 | ||
| 150 | <hr/> | |
| 151 | ||
| 152 | <div role="contentinfo"> | |
| 153 | <p> | |
| 154 | © Copyright 2016, Infobyte. | |
| 155 | ||
| 156 | </p> | |
| 157 | </div> | |
| 158 | Built with <a href="http://sphinx-doc.org/">Sphinx</a> using a <a href="https://github.com/snide/sphinx_rtd_theme">theme</a> provided by <a href="https://readthedocs.org">Read the Docs</a>. | |
| 159 | ||
| 160 | </footer> | |
| 161 | ||
| 162 | </div> | |
| 163 | </div> | |
| 164 | ||
| 165 | </section> | |
| 166 | ||
| 167 | </div> | |
| 168 | ||
| 169 | ||
| 170 | ||
| 171 | ||
| 172 | ||
| 173 | <script type="text/javascript"> | |
| 174 | var DOCUMENTATION_OPTIONS = { | |
| 175 | URL_ROOT:'./', | |
| 176 | VERSION:'0.1', | |
| 177 | COLLAPSE_INDEX:false, | |
| 178 | FILE_SUFFIX:'.html', | |
| 179 | HAS_SOURCE: true | |
| 180 | }; | |
| 181 | </script> | |
| 182 | <script type="text/javascript" src="_static/jquery.js"></script> | |
| 183 | <script type="text/javascript" src="_static/underscore.js"></script> | |
| 184 | <script type="text/javascript" src="_static/doctools.js"></script> | |
| 185 | ||
| 186 | ||
| 187 | ||
| 188 | ||
| 189 | ||
| 190 | <script type="text/javascript" src="_static/js/theme.js"></script> | |
| 191 | ||
| 192 | ||
| 193 | ||
| 194 | ||
| 195 | <script type="text/javascript"> | |
| 196 | jQuery(function () { | |
| 197 | SphinxRtdTheme.StickyNav.enable(); | |
| 198 | }); | |
| 199 | </script> | |
| 200 | ||
| 201 | ||
| 202 | </body> | |
| 203 | </html>⏎ |
| 0 | ||
| 1 | ||
| 2 | <!DOCTYPE html> | |
| 3 | <!--[if IE 8]><html class="no-js lt-ie9" lang="en" > <![endif]--> | |
| 4 | <!--[if gt IE 8]><!--> <html class="no-js" lang="en" > <!--<![endif]--> | |
| 5 | <head> | |
| 6 | <meta charset="utf-8"> | |
| 7 | ||
| 8 | <meta name="viewport" content="width=device-width, initial-scale=1.0"> | |
| 9 | ||
| 10 | <title>Python Module Index — Faraday 0.1 documentation</title> | |
| 11 | ||
| 12 | ||
| 13 | ||
| 14 | ||
| 15 | ||
| 16 | ||
| 17 | ||
| 18 | ||
| 19 | ||
| 20 | ||
| 21 | ||
| 22 | ||
| 23 | ||
| 24 | ||
| 25 | ||
| 26 | <link rel="stylesheet" href="_static/css/theme.css" type="text/css" /> | |
| 27 | ||
| 28 | ||
| 29 | ||
| 30 | ||
| 31 | ||
| 32 | <link rel="index" title="Index" | |
| 33 | href="genindex.html"/> | |
| 34 | <link rel="search" title="Search" href="search.html"/> | |
| 35 | <link rel="top" title="Faraday 0.1 documentation" href="index.html"/> | |
| 36 | ||
| 37 | ||
| 38 | ||
| 39 | ||
| 40 | ||
| 41 | <script src="_static/js/modernizr.min.js"></script> | |
| 42 | ||
| 43 | </head> | |
| 44 | ||
| 45 | <body class="wy-body-for-nav" role="document"> | |
| 46 | ||
| 47 | <div class="wy-grid-for-nav"> | |
| 48 | ||
| 49 | ||
| 50 | <nav data-toggle="wy-nav-shift" class="wy-nav-side"> | |
| 51 | <div class="wy-side-scroll"> | |
| 52 | <div class="wy-side-nav-search"> | |
| 53 | ||
| 54 | ||
| 55 | ||
| 56 | <a href="index.html" class="icon icon-home"> Faraday | |
| 57 | ||
| 58 | ||
| 59 | ||
| 60 | </a> | |
| 61 | ||
| 62 | ||
| 63 | ||
| 64 | ||
| 65 | <div class="version"> | |
| 66 | 0.1 | |
| 67 | </div> | |
| 68 | ||
| 69 | ||
| 70 | ||
| 71 | ||
| 72 | <div role="search"> | |
| 73 | <form id="rtd-search-form" class="wy-form" action="search.html" method="get"> | |
| 74 | <input type="text" name="q" placeholder="Search docs" /> | |
| 75 | <input type="hidden" name="check_keywords" value="yes" /> | |
| 76 | <input type="hidden" name="area" value="default" /> | |
| 77 | </form> | |
| 78 | </div> | |
| 79 | ||
| 80 | ||
| 81 | </div> | |
| 82 | ||
| 83 | <div class="wy-menu wy-menu-vertical" data-spy="affix" role="navigation" aria-label="main navigation"> | |
| 84 | ||
| 85 | ||
| 86 | ||
| 87 | <!-- Local TOC --> | |
| 88 | <div class="local-toc"></div> | |
| 89 | ||
| 90 | ||
| 91 | </div> | |
| 92 | </div> | |
| 93 | </nav> | |
| 94 | ||
| 95 | <section data-toggle="wy-nav-shift" class="wy-nav-content-wrap"> | |
| 96 | ||
| 97 | ||
| 98 | <nav class="wy-nav-top" role="navigation" aria-label="top navigation"> | |
| 99 | <i data-toggle="wy-nav-top" class="fa fa-bars"></i> | |
| 100 | <a href="index.html">Faraday</a> | |
| 101 | </nav> | |
| 102 | ||
| 103 | ||
| 104 | ||
| 105 | <div class="wy-nav-content"> | |
| 106 | <div class="rst-content"> | |
| 107 | ||
| 108 | ||
| 109 | ||
| 110 | ||
| 111 | ||
| 112 | ||
| 113 | <div role="navigation" aria-label="breadcrumbs navigation"> | |
| 114 | <ul class="wy-breadcrumbs"> | |
| 115 | <li><a href="index.html">Docs</a> »</li> | |
| 116 | ||
| 117 | <li></li> | |
| 118 | <li class="wy-breadcrumbs-aside"> | |
| 119 | ||
| 120 | ||
| 121 | ||
| 122 | </li> | |
| 123 | </ul> | |
| 124 | <hr/> | |
| 125 | </div> | |
| 126 | <div role="main" class="document" itemscope="itemscope" itemtype="http://schema.org/Article"> | |
| 127 | <div itemprop="articleBody"> | |
| 128 | ||
| 129 | ||
| 130 | <h1>Python Module Index</h1> | |
| 131 | ||
| 132 | <div class="modindex-jumpbox"> | |
| 133 | <a href="#cap-p"><strong>p</strong></a> | |
| 134 | </div> | |
| 135 | ||
| 136 | <table class="indextable modindextable"> | |
| 137 | <tr class="pcap"><td></td><td> </td><td></td></tr> | |
| 138 | <tr class="cap" id="cap-p"><td></td><td> | |
| 139 | <strong>p</strong></td><td></td></tr> | |
| 140 | <tr> | |
| 141 | <td><img src="_static/minus.png" class="toggler" | |
| 142 | id="toggle-1" style="display: none" alt="-" /></td> | |
| 143 | <td> | |
| 144 | <code class="xref">persistence</code></td><td> | |
| 145 | <em></em></td></tr> | |
| 146 | <tr class="cg-1"> | |
| 147 | <td></td> | |
| 148 | <td>    | |
| 149 | <a href="server.html#module-persistence.server.server"><code class="xref">persistence.server.server</code></a></td><td> | |
| 150 | <em></em></td></tr> | |
| 151 | </table> | |
| 152 | ||
| 153 | ||
| 154 | </div> | |
| 155 | </div> | |
| 156 | <footer> | |
| 157 | ||
| 158 | ||
| 159 | <hr/> | |
| 160 | ||
| 161 | <div role="contentinfo"> | |
| 162 | <p> | |
| 163 | © Copyright 2016, Infobyte. | |
| 164 | ||
| 165 | </p> | |
| 166 | </div> | |
| 167 | Built with <a href="http://sphinx-doc.org/">Sphinx</a> using a <a href="https://github.com/snide/sphinx_rtd_theme">theme</a> provided by <a href="https://readthedocs.org">Read the Docs</a>. | |
| 168 | ||
| 169 | </footer> | |
| 170 | ||
| 171 | </div> | |
| 172 | </div> | |
| 173 | ||
| 174 | </section> | |
| 175 | ||
| 176 | </div> | |
| 177 | ||
| 178 | ||
| 179 | ||
| 180 | ||
| 181 | ||
| 182 | <script type="text/javascript"> | |
| 183 | var DOCUMENTATION_OPTIONS = { | |
| 184 | URL_ROOT:'./', | |
| 185 | VERSION:'0.1', | |
| 186 | COLLAPSE_INDEX:false, | |
| 187 | FILE_SUFFIX:'.html', | |
| 188 | HAS_SOURCE: true | |
| 189 | }; | |
| 190 | </script> | |
| 191 | <script type="text/javascript" src="_static/jquery.js"></script> | |
| 192 | <script type="text/javascript" src="_static/underscore.js"></script> | |
| 193 | <script type="text/javascript" src="_static/doctools.js"></script> | |
| 194 | ||
| 195 | ||
| 196 | ||
| 197 | ||
| 198 | ||
| 199 | <script type="text/javascript" src="_static/js/theme.js"></script> | |
| 200 | ||
| 201 | ||
| 202 | ||
| 203 | ||
| 204 | <script type="text/javascript"> | |
| 205 | jQuery(function () { | |
| 206 | SphinxRtdTheme.StickyNav.enable(); | |
| 207 | }); | |
| 208 | </script> | |
| 209 | ||
| 210 | ||
| 211 | </body> | |
| 212 | </html>⏎ |
| 0 | ||
| 1 | ||
| 2 | <!DOCTYPE html> | |
| 3 | <!--[if IE 8]><html class="no-js lt-ie9" lang="en" > <![endif]--> | |
| 4 | <!--[if gt IE 8]><!--> <html class="no-js" lang="en" > <!--<![endif]--> | |
| 5 | <head> | |
| 6 | <meta charset="utf-8"> | |
| 7 | ||
| 8 | <meta name="viewport" content="width=device-width, initial-scale=1.0"> | |
| 9 | ||
| 10 | <title>Search — Faraday 0.1 documentation</title> | |
| 11 | ||
| 12 | ||
| 13 | ||
| 14 | ||
| 15 | ||
| 16 | ||
| 17 | ||
| 18 | ||
| 19 | ||
| 20 | ||
| 21 | ||
| 22 | ||
| 23 | ||
| 24 | ||
| 25 | ||
| 26 | <link rel="stylesheet" href="_static/css/theme.css" type="text/css" /> | |
| 27 | ||
| 28 | ||
| 29 | ||
| 30 | ||
| 31 | ||
| 32 | <link rel="index" title="Index" | |
| 33 | href="genindex.html"/> | |
| 34 | <link rel="search" title="Search" href="#"/> | |
| 35 | <link rel="top" title="Faraday 0.1 documentation" href="index.html"/> | |
| 36 | ||
| 37 | ||
| 38 | <script src="_static/js/modernizr.min.js"></script> | |
| 39 | ||
| 40 | </head> | |
| 41 | ||
| 42 | <body class="wy-body-for-nav" role="document"> | |
| 43 | ||
| 44 | <div class="wy-grid-for-nav"> | |
| 45 | ||
| 46 | ||
| 47 | <nav data-toggle="wy-nav-shift" class="wy-nav-side"> | |
| 48 | <div class="wy-side-scroll"> | |
| 49 | <div class="wy-side-nav-search"> | |
| 50 | ||
| 51 | ||
| 52 | ||
| 53 | <a href="index.html" class="icon icon-home"> Faraday | |
| 54 | ||
| 55 | ||
| 56 | ||
| 57 | </a> | |
| 58 | ||
| 59 | ||
| 60 | ||
| 61 | ||
| 62 | <div class="version"> | |
| 63 | 0.1 | |
| 64 | </div> | |
| 65 | ||
| 66 | ||
| 67 | ||
| 68 | ||
| 69 | <div role="search"> | |
| 70 | <form id="rtd-search-form" class="wy-form" action="#" method="get"> | |
| 71 | <input type="text" name="q" placeholder="Search docs" /> | |
| 72 | <input type="hidden" name="check_keywords" value="yes" /> | |
| 73 | <input type="hidden" name="area" value="default" /> | |
| 74 | </form> | |
| 75 | </div> | |
| 76 | ||
| 77 | ||
| 78 | </div> | |
| 79 | ||
| 80 | <div class="wy-menu wy-menu-vertical" data-spy="affix" role="navigation" aria-label="main navigation"> | |
| 81 | ||
| 82 | ||
| 83 | ||
| 84 | <!-- Local TOC --> | |
| 85 | <div class="local-toc"></div> | |
| 86 | ||
| 87 | ||
| 88 | </div> | |
| 89 | </div> | |
| 90 | </nav> | |
| 91 | ||
| 92 | <section data-toggle="wy-nav-shift" class="wy-nav-content-wrap"> | |
| 93 | ||
| 94 | ||
| 95 | <nav class="wy-nav-top" role="navigation" aria-label="top navigation"> | |
| 96 | <i data-toggle="wy-nav-top" class="fa fa-bars"></i> | |
| 97 | <a href="index.html">Faraday</a> | |
| 98 | </nav> | |
| 99 | ||
| 100 | ||
| 101 | ||
| 102 | <div class="wy-nav-content"> | |
| 103 | <div class="rst-content"> | |
| 104 | ||
| 105 | ||
| 106 | ||
| 107 | ||
| 108 | ||
| 109 | ||
| 110 | <div role="navigation" aria-label="breadcrumbs navigation"> | |
| 111 | <ul class="wy-breadcrumbs"> | |
| 112 | <li><a href="index.html">Docs</a> »</li> | |
| 113 | ||
| 114 | <li></li> | |
| 115 | <li class="wy-breadcrumbs-aside"> | |
| 116 | ||
| 117 | </li> | |
| 118 | </ul> | |
| 119 | <hr/> | |
| 120 | </div> | |
| 121 | <div role="main" class="document" itemscope="itemscope" itemtype="http://schema.org/Article"> | |
| 122 | <div itemprop="articleBody"> | |
| 123 | ||
| 124 | <noscript> | |
| 125 | <div id="fallback" class="admonition warning"> | |
| 126 | <p class="last"> | |
| 127 | Please activate JavaScript to enable the search | |
| 128 | functionality. | |
| 129 | </p> | |
| 130 | </div> | |
| 131 | </noscript> | |
| 132 | ||
| 133 | ||
| 134 | <div id="search-results"> | |
| 135 | ||
| 136 | </div> | |
| 137 | ||
| 138 | </div> | |
| 139 | </div> | |
| 140 | <footer> | |
| 141 | ||
| 142 | ||
| 143 | <hr/> | |
| 144 | ||
| 145 | <div role="contentinfo"> | |
| 146 | <p> | |
| 147 | © Copyright 2016, Infobyte. | |
| 148 | ||
| 149 | </p> | |
| 150 | </div> | |
| 151 | Built with <a href="http://sphinx-doc.org/">Sphinx</a> using a <a href="https://github.com/snide/sphinx_rtd_theme">theme</a> provided by <a href="https://readthedocs.org">Read the Docs</a>. | |
| 152 | ||
| 153 | </footer> | |
| 154 | ||
| 155 | </div> | |
| 156 | </div> | |
| 157 | ||
| 158 | </section> | |
| 159 | ||
| 160 | </div> | |
| 161 | ||
| 162 | ||
| 163 | ||
| 164 | ||
| 165 | ||
| 166 | <script type="text/javascript"> | |
| 167 | var DOCUMENTATION_OPTIONS = { | |
| 168 | URL_ROOT:'./', | |
| 169 | VERSION:'0.1', | |
| 170 | COLLAPSE_INDEX:false, | |
| 171 | FILE_SUFFIX:'.html', | |
| 172 | HAS_SOURCE: true | |
| 173 | }; | |
| 174 | </script> | |
| 175 | <script type="text/javascript" src="_static/jquery.js"></script> | |
| 176 | <script type="text/javascript" src="_static/underscore.js"></script> | |
| 177 | <script type="text/javascript" src="_static/doctools.js"></script> | |
| 178 | <script type="text/javascript" src="_static/searchtools.js"></script> | |
| 179 | ||
| 180 | ||
| 181 | ||
| 182 | ||
| 183 | ||
| 184 | <script type="text/javascript" src="_static/js/theme.js"></script> | |
| 185 | ||
| 186 | ||
| 187 | ||
| 188 | ||
| 189 | <script type="text/javascript"> | |
| 190 | jQuery(function () { | |
| 191 | SphinxRtdTheme.StickyNav.enable(); | |
| 192 | }); | |
| 193 | </script> | |
| 194 | ||
| 195 | <script type="text/javascript"> | |
| 196 | jQuery(function() { Search.loadIndex("searchindex.js"); }); | |
| 197 | </script> | |
| 198 | ||
| 199 | <script type="text/javascript" id="searchindexloader"></script> | |
| 200 | ||
| 201 | ||
| 202 | ||
| 203 | </body> | |
| 204 | </html>⏎ |
| 0 | Search.setIndex({docnames:["index","server"],envversion:50,filenames:["index.rst","server.rst"],objects:{"persistence.server":{server:[1,0,0,"-"]},"persistence.server.server":{create_command:[1,1,1,""],create_credential:[1,1,1,""],create_host:[1,1,1,""],create_interface:[1,1,1,""],create_note:[1,1,1,""],create_service:[1,1,1,""],create_vuln:[1,1,1,""],create_vuln_web:[1,1,1,""],create_workspace:[1,1,1,""],delete_command:[1,1,1,""],delete_credential:[1,1,1,""],delete_host:[1,1,1,""],delete_interface:[1,1,1,""],delete_note:[1,1,1,""],delete_service:[1,1,1,""],delete_vuln:[1,1,1,""],delete_workspace:[1,1,1,""],get_all_vulns:[1,1,1,""],get_changes_stream:[1,1,1,""],get_command:[1,1,1,""],get_commands:[1,1,1,""],get_commands_number:[1,1,1,""],get_credential:[1,1,1,""],get_credentials:[1,1,1,""],get_credentials_number:[1,1,1,""],get_host:[1,1,1,""],get_hosts:[1,1,1,""],get_hosts_number:[1,1,1,""],get_interface:[1,1,1,""],get_interfaces:[1,1,1,""],get_interfaces_number:[1,1,1,""],get_note:[1,1,1,""],get_notes:[1,1,1,""],get_notes_number:[1,1,1,""],get_object:[1,1,1,""],get_object_before_last_revision:[1,1,1,""],get_objects:[1,1,1,""],get_service:[1,1,1,""],get_services:[1,1,1,""],get_services_number:[1,1,1,""],get_vuln:[1,1,1,""],get_vulns:[1,1,1,""],get_vulns_number:[1,1,1,""],get_web_vuln:[1,1,1,""],get_web_vulns:[1,1,1,""],get_workspace:[1,1,1,""],get_workspace_numbers:[1,1,1,""],get_workspace_summary:[1,1,1,""],get_workspaces_names:[1,1,1,""],is_server_up:[1,1,1,""],test_server_url:[1,1,1,""],update_command:[1,1,1,""],update_credential:[1,1,1,""],update_host:[1,1,1,""],update_interface:[1,1,1,""],update_note:[1,1,1,""],update_service:[1,1,1,""],update_vuln:[1,1,1,""],update_vuln_web:[1,1,1,""]}},objnames:{"0":["py","module","Python module"],"1":["py","function","Python function"]},objtypes:{"0":"py:module","1":"py:function"},terms:{"case":1,"class":[],"default":1,"import":1,"return":1,"true":1,Adding:1,IDE:[],NOT:1,The:1,These:[],Useful:1,about:1,add_relationships_from_db:[],add_relationships_from_dict:[],address:1,adit:1,after:1,allow:[],alwai:1,amount:1,ani:1,api:1,arbitrari:1,aros:1,attach:[],attribut:[],automat:1,base:[],befor:1,began:1,below:1,bool:1,both:1,bug:1,can:1,care:1,categori:1,changes_stream:[],check:1,classmethod:[],collect:1,column:[],com:[],command:1,command_id:1,command_nam:1,commandruninform:[],conf:[],confirm:1,connect:1,construct:[],constructor:[],contact:1,contain:1,content:0,copi:1,copyright:[],couch:1,couchdb:1,couchdb_id:[],could:[],creat:1,create_command:1,create_credenti:1,create_host:1,create_interfac:1,create_not:1,create_servic:1,create_tim:[],create_vuln:1,create_vuln_web:1,create_workspac:1,creator:[],cred:[],credenti:1,credential_id:1,critic:1,custom:1,dao:[],data:1,databas:1,databasemetadata:[],date:1,declar:[],default_gatewai:1,default_gateway_ip:[],default_gateway_mac:[],delet:1,delete_command:1,delete_credenti:1,delete_host:1,delete_interfac:1,delete_not:1,delete_servic:1,delete_vuln:1,delete_workspac:1,desc:1,descript:1,dictionari:1,didn:1,direct:1,doc:[],doc_typ:[],document:[],document_typ:[],doe:1,don:1,durat:1,dure:1,easeofresolut:[],edit:1,either:1,element:1,empti:1,entiti:[],entity_id:[],entity_metadata:[],entity_metadata_id:[],entitymetadata:[],entitynotfound:[],equal:1,error:1,exampl:[],except:[],execut:1,ext:[],extra_param:1,fals:1,faradai:1,faraday_up:1,faradayent:[],file:1,finish:1,finish_d:1,fix:1,found:1,from:1,get:1,get_all_vuln:1,get_changes_stream:1,get_command:1,get_commands_numb:1,get_credenti:1,get_credentials_numb:1,get_entity_class_from_doc:[],get_entity_class_from_typ:[],get_host:1,get_hosts_numb:1,get_interfac:1,get_interfaces_numb:1,get_not:1,get_notes_numb:1,get_object:1,get_object_before_last_revis:1,get_servic:1,get_services_numb:1,get_vuln:1,get_vulns_numb:1,get_web_vuln:1,get_workspac:1,get_workspace_numb:1,get_workspace_summari:1,get_workspaces_nam:1,given:1,handl:1,happen:1,heartbeat:1,high:1,host:1,host_id:1,hostnam:1,http:[],impact_account:[],impact_avail:[],impact_confidenti:[],impact_integr:[],inde:1,index:0,indic:1,info:1,infobyt:1,infobytesec:[],inform:1,initi:[],inmediatli:1,instanc:[],integ:1,interfac:1,interface_id:1,ipv4:1,ipv4_address:[],ipv4_dn:[],ipv4_gatewai:[],ipv4_mask:[],ipv6:1,ipv6_address:[],ipv6_dn:[],ipv6_gatewai:[],ipv6_prefix:[],irrelev:1,is_server_up:1,itim:1,its:1,json:[],kei:[],know:1,known:1,kwarg:[],last:1,lcc:1,leav:1,licens:[],list:1,llc:[],low:1,mac:1,map:[],match:1,med:1,metada:1,metadata:1,method:1,model:[],modul:0,more:1,morethanoneobjectfoundbyid:1,must:1,name:1,need:1,network:1,network_seg:1,never:1,none:1,normal:1,note:1,note_id:1,number:1,object:1,object_id:1,object_signatur:1,one:1,onli:1,oper:1,option:[],otherwis:1,own:1,owner:1,packag:[],page:0,param:1,paramet:1,parent:1,pars:[],password:1,path:1,penetr:[],persist:1,pname:1,port:1,ports_clos:[],ports_filt:[],ports_open:[],possibl:1,present:[],primarli:1,problem:1,process:1,pronc:1,protocol:1,queri:1,rais:1,ran:1,reason:1,recent:1,ref:1,refer:1,regard:1,relationship:[],remov:1,repres:1,request:1,resolut:1,respons:1,revis:1,run:1,save:1,search:0,see:[],segment:1,server_io_except:[],server_url:1,servic:1,service_id:1,session:[],set:1,sever:1,share:1,should:1,simpl:[],sinc:1,some:1,sourc:1,special:1,sqlalchemi:[],stablish:1,start_dat:1,stat:1,statu:1,str:1,string:1,submodul:[],support:1,system:1,test:[],test_server_url:1,text:1,them:1,thi:1,though:1,time:1,took:1,tupl:1,two:1,type:1,uniqu:1,updat:1,update_act:[],update_command:1,update_controller_act:[],update_credenti:1,update_from_docu:[],update_host:1,update_interfac:1,update_not:1,update_servic:1,update_tim:[],update_us:[],update_vuln:1,update_vuln_web:1,url:1,url_to_test:1,usag:1,used:1,user:1,usernam:1,using:1,util:[],valid:1,valu:1,variabl:1,version:1,vuln:1,vuln_id:1,vuln_typ:[],vulner:1,vulnerabilityweb:[],wai:1,web:1,websit:1,when:1,where:1,which:1,work:1,worksapc:1,workspac:1,workspace_nam:1,wrongobjectsignatur:1,www:[],you:1},titles:["Welcome to Faraday’s documentation!","server package"],titleterms:{changes_stream:[],conf:[],content:[],document:0,faradai:0,indic:0,indice:[],model:[],modul:1,packag:1,server:1,server_io_except:[],submodul:1,tabl:0,util:1,welcom:0}})⏎ |
| 0 | ||
| 1 | ||
| 2 | <!DOCTYPE html> | |
| 3 | <!--[if IE 8]><html class="no-js lt-ie9" lang="en" > <![endif]--> | |
| 4 | <!--[if gt IE 8]><!--> <html class="no-js" lang="en" > <!--<![endif]--> | |
| 5 | <head> | |
| 6 | <meta charset="utf-8"> | |
| 7 | ||
| 8 | <meta name="viewport" content="width=device-width, initial-scale=1.0"> | |
| 9 | ||
| 10 | <title>server package — Faraday 0.1 documentation</title> | |
| 11 | ||
| 12 | ||
| 13 | ||
| 14 | ||
| 15 | ||
| 16 | ||
| 17 | ||
| 18 | ||
| 19 | ||
| 20 | ||
| 21 | ||
| 22 | ||
| 23 | ||
| 24 | ||
| 25 | ||
| 26 | <link rel="stylesheet" href="_static/css/theme.css" type="text/css" /> | |
| 27 | ||
| 28 | ||
| 29 | ||
| 30 | ||
| 31 | ||
| 32 | <link rel="index" title="Index" | |
| 33 | href="genindex.html"/> | |
| 34 | <link rel="search" title="Search" href="search.html"/> | |
| 35 | <link rel="top" title="Faraday 0.1 documentation" href="index.html"/> | |
| 36 | ||
| 37 | ||
| 38 | <script src="_static/js/modernizr.min.js"></script> | |
| 39 | ||
| 40 | </head> | |
| 41 | ||
| 42 | <body class="wy-body-for-nav" role="document"> | |
| 43 | ||
| 44 | <div class="wy-grid-for-nav"> | |
| 45 | ||
| 46 | ||
| 47 | <nav data-toggle="wy-nav-shift" class="wy-nav-side"> | |
| 48 | <div class="wy-side-scroll"> | |
| 49 | <div class="wy-side-nav-search"> | |
| 50 | ||
| 51 | ||
| 52 | ||
| 53 | <a href="index.html" class="icon icon-home"> Faraday | |
| 54 | ||
| 55 | ||
| 56 | ||
| 57 | </a> | |
| 58 | ||
| 59 | ||
| 60 | ||
| 61 | ||
| 62 | <div class="version"> | |
| 63 | 0.1 | |
| 64 | </div> | |
| 65 | ||
| 66 | ||
| 67 | ||
| 68 | ||
| 69 | <div role="search"> | |
| 70 | <form id="rtd-search-form" class="wy-form" action="search.html" method="get"> | |
| 71 | <input type="text" name="q" placeholder="Search docs" /> | |
| 72 | <input type="hidden" name="check_keywords" value="yes" /> | |
| 73 | <input type="hidden" name="area" value="default" /> | |
| 74 | </form> | |
| 75 | </div> | |
| 76 | ||
| 77 | ||
| 78 | </div> | |
| 79 | ||
| 80 | <div class="wy-menu wy-menu-vertical" data-spy="affix" role="navigation" aria-label="main navigation"> | |
| 81 | ||
| 82 | ||
| 83 | ||
| 84 | <!-- Local TOC --> | |
| 85 | <div class="local-toc"><ul> | |
| 86 | <li><a class="reference internal" href="#">server package</a><ul> | |
| 87 | <li><a class="reference internal" href="#submodules">Submodules</a></li> | |
| 88 | <li><a class="reference internal" href="#module-persistence.server.server">server.utils module</a></li> | |
| 89 | </ul> | |
| 90 | </li> | |
| 91 | </ul> | |
| 92 | </div> | |
| 93 | ||
| 94 | ||
| 95 | </div> | |
| 96 | </div> | |
| 97 | </nav> | |
| 98 | ||
| 99 | <section data-toggle="wy-nav-shift" class="wy-nav-content-wrap"> | |
| 100 | ||
| 101 | ||
| 102 | <nav class="wy-nav-top" role="navigation" aria-label="top navigation"> | |
| 103 | <i data-toggle="wy-nav-top" class="fa fa-bars"></i> | |
| 104 | <a href="index.html">Faraday</a> | |
| 105 | </nav> | |
| 106 | ||
| 107 | ||
| 108 | ||
| 109 | <div class="wy-nav-content"> | |
| 110 | <div class="rst-content"> | |
| 111 | ||
| 112 | ||
| 113 | ||
| 114 | ||
| 115 | ||
| 116 | ||
| 117 | <div role="navigation" aria-label="breadcrumbs navigation"> | |
| 118 | <ul class="wy-breadcrumbs"> | |
| 119 | <li><a href="index.html">Docs</a> »</li> | |
| 120 | ||
| 121 | <li>server package</li> | |
| 122 | <li class="wy-breadcrumbs-aside"> | |
| 123 | ||
| 124 | ||
| 125 | <a href="_sources/server.rst.txt" rel="nofollow"> View page source</a> | |
| 126 | ||
| 127 | ||
| 128 | </li> | |
| 129 | </ul> | |
| 130 | <hr/> | |
| 131 | </div> | |
| 132 | <div role="main" class="document" itemscope="itemscope" itemtype="http://schema.org/Article"> | |
| 133 | <div itemprop="articleBody"> | |
| 134 | ||
| 135 | <div class="section" id="server-package"> | |
| 136 | <h1>server package<a class="headerlink" href="#server-package" title="Permalink to this headline">¶</a></h1> | |
| 137 | <div class="section" id="submodules"> | |
| 138 | <h2>Submodules<a class="headerlink" href="#submodules" title="Permalink to this headline">¶</a></h2> | |
| 139 | </div> | |
| 140 | <div class="section" id="module-persistence.server.server"> | |
| 141 | <span id="server-utils-module"></span><h2>server.utils module<a class="headerlink" href="#module-persistence.server.server" title="Permalink to this headline">¶</a></h2> | |
| 142 | <p>A module to handle request to the Faraday Server.</p> | |
| 143 | <div class="admonition note"> | |
| 144 | <p class="first admonition-title">Note</p> | |
| 145 | <p>Before using this as an API, you should copy this file and edit | |
| 146 | the FARADAY_UP and the SERVER_URL variables found inmediatly | |
| 147 | below the imports.</p> | |
| 148 | <p class="last">FARADAY_UP should be set to False in the copy of the file, and SERVER_URL | |
| 149 | must be a valid server url.</p> | |
| 150 | </div> | |
| 151 | <div class="admonition warning"> | |
| 152 | <p class="first admonition-title">Warning</p> | |
| 153 | <p class="last">This module was though of primarly as a way of querying and removing | |
| 154 | information from the Faraday Server. Adding objects is supported, but should | |
| 155 | be used with care, specially regarding the ID of objects, which must | |
| 156 | be always unique.</p> | |
| 157 | </div> | |
| 158 | <dl class="function"> | |
| 159 | <dt id="persistence.server.server.get_hosts"> | |
| 160 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_hosts</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_hosts"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_hosts" title="Permalink to this definition">¶</a></dt> | |
| 161 | <dd><p>Get hosts from the server.</p> | |
| 162 | <table class="docutils field-list" frame="void" rules="none"> | |
| 163 | <col class="field-name" /> | |
| 164 | <col class="field-body" /> | |
| 165 | <tbody valign="top"> | |
| 166 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 167 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace from which to get the hosts.</li> | |
| 168 | <li><strong>**params</strong> – any of valid request parameters for CouchDB.</li> | |
| 169 | </ul> | |
| 170 | </td> | |
| 171 | </tr> | |
| 172 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary containing the hosts matching the query.</p> | |
| 173 | </td> | |
| 174 | </tr> | |
| 175 | </tbody> | |
| 176 | </table> | |
| 177 | </dd></dl> | |
| 178 | ||
| 179 | <dl class="function"> | |
| 180 | <dt id="persistence.server.server.get_all_vulns"> | |
| 181 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_all_vulns</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_all_vulns"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_all_vulns" title="Permalink to this definition">¶</a></dt> | |
| 182 | <dd><p>Get vulns, both normal and web, from the server.</p> | |
| 183 | <table class="docutils field-list" frame="void" rules="none"> | |
| 184 | <col class="field-name" /> | |
| 185 | <col class="field-body" /> | |
| 186 | <tbody valign="top"> | |
| 187 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 188 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace from which to get the vulns.</li> | |
| 189 | <li><strong>**params</strong> – any of valid request parameters for CouchDB.</li> | |
| 190 | </ul> | |
| 191 | </td> | |
| 192 | </tr> | |
| 193 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary containing the vulns matching the query.</p> | |
| 194 | </td> | |
| 195 | </tr> | |
| 196 | </tbody> | |
| 197 | </table> | |
| 198 | </dd></dl> | |
| 199 | ||
| 200 | <dl class="function"> | |
| 201 | <dt id="persistence.server.server.get_vulns"> | |
| 202 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_vulns</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_vulns"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_vulns" title="Permalink to this definition">¶</a></dt> | |
| 203 | <dd><p>Get only normal vulns from the server.</p> | |
| 204 | <table class="docutils field-list" frame="void" rules="none"> | |
| 205 | <col class="field-name" /> | |
| 206 | <col class="field-body" /> | |
| 207 | <tbody valign="top"> | |
| 208 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 209 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace from which to get the vulns.</li> | |
| 210 | <li><strong>**params</strong> – any of valid request parameters for CouchDB.</li> | |
| 211 | </ul> | |
| 212 | </td> | |
| 213 | </tr> | |
| 214 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary containing the vulns matching the query.</p> | |
| 215 | </td> | |
| 216 | </tr> | |
| 217 | </tbody> | |
| 218 | </table> | |
| 219 | </dd></dl> | |
| 220 | ||
| 221 | <dl class="function"> | |
| 222 | <dt id="persistence.server.server.get_web_vulns"> | |
| 223 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_web_vulns</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_web_vulns"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_web_vulns" title="Permalink to this definition">¶</a></dt> | |
| 224 | <dd><p>Get only web vulns from the server.</p> | |
| 225 | <table class="docutils field-list" frame="void" rules="none"> | |
| 226 | <col class="field-name" /> | |
| 227 | <col class="field-body" /> | |
| 228 | <tbody valign="top"> | |
| 229 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 230 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace from which to get the vulns.</li> | |
| 231 | <li><strong>**params</strong> – any of valid request parameters for CouchDB.</li> | |
| 232 | </ul> | |
| 233 | </td> | |
| 234 | </tr> | |
| 235 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary containing the vulns matching the query.</p> | |
| 236 | </td> | |
| 237 | </tr> | |
| 238 | </tbody> | |
| 239 | </table> | |
| 240 | </dd></dl> | |
| 241 | ||
| 242 | <dl class="function"> | |
| 243 | <dt id="persistence.server.server.get_interfaces"> | |
| 244 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_interfaces</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_interfaces"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_interfaces" title="Permalink to this definition">¶</a></dt> | |
| 245 | <dd><p>Get interfaces from the server.</p> | |
| 246 | <table class="docutils field-list" frame="void" rules="none"> | |
| 247 | <col class="field-name" /> | |
| 248 | <col class="field-body" /> | |
| 249 | <tbody valign="top"> | |
| 250 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 251 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace from which to get the interfaces.</li> | |
| 252 | <li><strong>**params</strong> – any of valid request parameters for CouchDB.</li> | |
| 253 | </ul> | |
| 254 | </td> | |
| 255 | </tr> | |
| 256 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary containing the interfaces matching the query.</p> | |
| 257 | </td> | |
| 258 | </tr> | |
| 259 | </tbody> | |
| 260 | </table> | |
| 261 | </dd></dl> | |
| 262 | ||
| 263 | <dl class="function"> | |
| 264 | <dt id="persistence.server.server.get_services"> | |
| 265 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_services</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_services"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_services" title="Permalink to this definition">¶</a></dt> | |
| 266 | <dd><p>Get services from the server.</p> | |
| 267 | <table class="docutils field-list" frame="void" rules="none"> | |
| 268 | <col class="field-name" /> | |
| 269 | <col class="field-body" /> | |
| 270 | <tbody valign="top"> | |
| 271 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 272 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace from which to get the services.</li> | |
| 273 | <li><strong>**params</strong> – any of valid request parameters for CouchDB.</li> | |
| 274 | </ul> | |
| 275 | </td> | |
| 276 | </tr> | |
| 277 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary containing the services matching the query.</p> | |
| 278 | </td> | |
| 279 | </tr> | |
| 280 | </tbody> | |
| 281 | </table> | |
| 282 | </dd></dl> | |
| 283 | ||
| 284 | <dl class="function"> | |
| 285 | <dt id="persistence.server.server.get_credentials"> | |
| 286 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_credentials</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_credentials"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_credentials" title="Permalink to this definition">¶</a></dt> | |
| 287 | <dd><p>Get credentials from the server.</p> | |
| 288 | <table class="docutils field-list" frame="void" rules="none"> | |
| 289 | <col class="field-name" /> | |
| 290 | <col class="field-body" /> | |
| 291 | <tbody valign="top"> | |
| 292 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 293 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace from which to get the credentials.</li> | |
| 294 | <li><strong>**params</strong> – any of valid request parameters for CouchDB.</li> | |
| 295 | </ul> | |
| 296 | </td> | |
| 297 | </tr> | |
| 298 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary containing the credentials matching the query.</p> | |
| 299 | </td> | |
| 300 | </tr> | |
| 301 | </tbody> | |
| 302 | </table> | |
| 303 | </dd></dl> | |
| 304 | ||
| 305 | <dl class="function"> | |
| 306 | <dt id="persistence.server.server.get_notes"> | |
| 307 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_notes</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_notes"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_notes" title="Permalink to this definition">¶</a></dt> | |
| 308 | <dd><p>Get notes from the server.</p> | |
| 309 | <table class="docutils field-list" frame="void" rules="none"> | |
| 310 | <col class="field-name" /> | |
| 311 | <col class="field-body" /> | |
| 312 | <tbody valign="top"> | |
| 313 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 314 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace from which to get the notes.</li> | |
| 315 | <li><strong>**params</strong> – any of valid request parameters for CouchDB.</li> | |
| 316 | </ul> | |
| 317 | </td> | |
| 318 | </tr> | |
| 319 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary containing the notes matching the query.</p> | |
| 320 | </td> | |
| 321 | </tr> | |
| 322 | </tbody> | |
| 323 | </table> | |
| 324 | </dd></dl> | |
| 325 | ||
| 326 | <dl class="function"> | |
| 327 | <dt id="persistence.server.server.get_commands"> | |
| 328 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_commands</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_commands"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_commands" title="Permalink to this definition">¶</a></dt> | |
| 329 | <dd><p>Get commands from the server.</p> | |
| 330 | <table class="docutils field-list" frame="void" rules="none"> | |
| 331 | <col class="field-name" /> | |
| 332 | <col class="field-body" /> | |
| 333 | <tbody valign="top"> | |
| 334 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 335 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace from which to get the commands.</li> | |
| 336 | <li><strong>**params</strong> – any of valid request parameters for CouchDB.</li> | |
| 337 | </ul> | |
| 338 | </td> | |
| 339 | </tr> | |
| 340 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary containing the commands matching the query.</p> | |
| 341 | </td> | |
| 342 | </tr> | |
| 343 | </tbody> | |
| 344 | </table> | |
| 345 | </dd></dl> | |
| 346 | ||
| 347 | <dl class="function"> | |
| 348 | <dt id="persistence.server.server.get_objects"> | |
| 349 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_objects</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>object_signature</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_objects"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_objects" title="Permalink to this definition">¶</a></dt> | |
| 350 | <dd><p>Get any type of object from the server, be it hosts, vulns, interfaces, | |
| 351 | services, credentials, commands or notes.</p> | |
| 352 | <table class="docutils field-list" frame="void" rules="none"> | |
| 353 | <col class="field-name" /> | |
| 354 | <col class="field-body" /> | |
| 355 | <tbody valign="top"> | |
| 356 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 357 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace from which to get the commands.</li> | |
| 358 | <li><strong>object_signature</strong> (<em>str</em>) – the type of object to get. Must equal ‘hosts’, | |
| 359 | ‘vulns’, ‘interfaces’, ‘services’, ‘credentials’, ‘notes’ or ‘commands’</li> | |
| 360 | <li><strong>**params</strong> – any of valid request parameters for CouchDB.</li> | |
| 361 | </ul> | |
| 362 | </td> | |
| 363 | </tr> | |
| 364 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first">A dictionary containing the commands matching the query.</p> | |
| 365 | </td> | |
| 366 | </tr> | |
| 367 | <tr class="field-odd field"><th class="field-name">Raises:</th><td class="field-body"><ul class="first last simple"> | |
| 368 | <li><code class="xref py py-exc docutils literal"><span class="pre">WrongObjectSignature</span></code> – if the object_signature string didn’t match</li> | |
| 369 | <li>a faraday object.</li> | |
| 370 | </ul> | |
| 371 | </td> | |
| 372 | </tr> | |
| 373 | </tbody> | |
| 374 | </table> | |
| 375 | </dd></dl> | |
| 376 | ||
| 377 | <dl class="function"> | |
| 378 | <dt id="persistence.server.server.get_changes_stream"> | |
| 379 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_changes_stream</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>since=0</em>, <em>heartbeat='1000'</em>, <em>**extra_params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_changes_stream"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_changes_stream" title="Permalink to this definition">¶</a></dt> | |
| 380 | <dd></dd></dl> | |
| 381 | ||
| 382 | <dl class="function"> | |
| 383 | <dt id="persistence.server.server.get_workspaces_names"> | |
| 384 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_workspaces_names</code><span class="sig-paren">(</span><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_workspaces_names"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_workspaces_names" title="Permalink to this definition">¶</a></dt> | |
| 385 | <dd><p>Returns: | |
| 386 | A dictionary with a list with the workspaces names.</p> | |
| 387 | </dd></dl> | |
| 388 | ||
| 389 | <dl class="function"> | |
| 390 | <dt id="persistence.server.server.get_object_before_last_revision"> | |
| 391 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_object_before_last_revision</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>object_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_object_before_last_revision"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_object_before_last_revision" title="Permalink to this definition">¶</a></dt> | |
| 392 | <dd><p>Get an object before its last revision. Useful to get information about | |
| 393 | recently deleted objects.</p> | |
| 394 | <div class="admonition warning"> | |
| 395 | <p class="first admonition-title">Warning</p> | |
| 396 | <p class="last">Error-pronce process. You should check for ‘None’ after usage, | |
| 397 | as that’s the return value if any problem arose during execution.</p> | |
| 398 | </div> | |
| 399 | <table class="docutils field-list" frame="void" rules="none"> | |
| 400 | <col class="field-name" /> | |
| 401 | <col class="field-body" /> | |
| 402 | <tbody valign="top"> | |
| 403 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 404 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace where the object was</li> | |
| 405 | <li><strong>object_id</strong> (<em>str</em>) – the id of the object</li> | |
| 406 | </ul> | |
| 407 | </td> | |
| 408 | </tr> | |
| 409 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the object’s information.</p> | |
| 410 | </td> | |
| 411 | </tr> | |
| 412 | </tbody> | |
| 413 | </table> | |
| 414 | </dd></dl> | |
| 415 | ||
| 416 | <dl class="function"> | |
| 417 | <dt id="persistence.server.server.get_object"> | |
| 418 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_object</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>object_signature</em>, <em>object_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_object"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_object" title="Permalink to this definition">¶</a></dt> | |
| 419 | <dd><p>Get an unique object of arbitrary type.</p> | |
| 420 | <table class="docutils field-list" frame="void" rules="none"> | |
| 421 | <col class="field-name" /> | |
| 422 | <col class="field-body" /> | |
| 423 | <tbody valign="top"> | |
| 424 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 425 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace where the object should be found.</li> | |
| 426 | <li><strong>object_signature</strong> (<em>str</em>) – must be either ‘hosts’, ‘vulns’, ‘interfaces’ | |
| 427 | ‘services’, ‘credentials’, ‘notes’ or ‘commands’.</li> | |
| 428 | <li><strong>object_id</strong> (<em>str</em>) – the id of the object</li> | |
| 429 | </ul> | |
| 430 | </td> | |
| 431 | </tr> | |
| 432 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first">A dictionary containing information about the object.</p> | |
| 433 | </td> | |
| 434 | </tr> | |
| 435 | <tr class="field-odd field"><th class="field-name">Raises:</th><td class="field-body"><ul class="first last simple"> | |
| 436 | <li><code class="xref py py-exc docutils literal"><span class="pre">MoreThanOneObjectFoundByID</span></code> – if for some reason the object_id is shared</li> | |
| 437 | <li>by two or more objects. This should never happen. If it does,</li> | |
| 438 | <li>contact Infobyte LCC.</li> | |
| 439 | </ul> | |
| 440 | </td> | |
| 441 | </tr> | |
| 442 | </tbody> | |
| 443 | </table> | |
| 444 | </dd></dl> | |
| 445 | ||
| 446 | <dl class="function"> | |
| 447 | <dt id="persistence.server.server.get_host"> | |
| 448 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_host</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>host_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_host"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_host" title="Permalink to this definition">¶</a></dt> | |
| 449 | <dd><p>Get an unique host.</p> | |
| 450 | <table class="docutils field-list" frame="void" rules="none"> | |
| 451 | <col class="field-name" /> | |
| 452 | <col class="field-body" /> | |
| 453 | <tbody valign="top"> | |
| 454 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 455 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace where the object should be found.</li> | |
| 456 | <li><strong>host_id</strong> (<em>str</em>) – the id of the host</li> | |
| 457 | </ul> | |
| 458 | </td> | |
| 459 | </tr> | |
| 460 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first">A dictionary containing information about the host.</p> | |
| 461 | </td> | |
| 462 | </tr> | |
| 463 | <tr class="field-odd field"><th class="field-name">Raises:</th><td class="field-body"><ul class="first last simple"> | |
| 464 | <li><code class="xref py py-exc docutils literal"><span class="pre">MoreThanOneObjectFoundByID</span></code> – if for some reason the host id is shared</li> | |
| 465 | <li>by two or more objects. This should never happen. If it does,</li> | |
| 466 | <li>contact Infobyte LCC.</li> | |
| 467 | </ul> | |
| 468 | </td> | |
| 469 | </tr> | |
| 470 | </tbody> | |
| 471 | </table> | |
| 472 | </dd></dl> | |
| 473 | ||
| 474 | <dl class="function"> | |
| 475 | <dt id="persistence.server.server.get_vuln"> | |
| 476 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_vuln</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>vuln_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_vuln"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_vuln" title="Permalink to this definition">¶</a></dt> | |
| 477 | <dd><p>Get an unique vuln.</p> | |
| 478 | <table class="docutils field-list" frame="void" rules="none"> | |
| 479 | <col class="field-name" /> | |
| 480 | <col class="field-body" /> | |
| 481 | <tbody valign="top"> | |
| 482 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 483 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace where the object should be found.</li> | |
| 484 | <li><strong>vuln_id</strong> (<em>str</em>) – the id of the vuln</li> | |
| 485 | </ul> | |
| 486 | </td> | |
| 487 | </tr> | |
| 488 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first">A dictionary containing information about the vuln.</p> | |
| 489 | </td> | |
| 490 | </tr> | |
| 491 | <tr class="field-odd field"><th class="field-name">Raises:</th><td class="field-body"><ul class="first last simple"> | |
| 492 | <li><code class="xref py py-exc docutils literal"><span class="pre">MoreThanOneObjectFoundByID</span></code> – if for some reason the vuln id is shared</li> | |
| 493 | <li>by two or more objects. This should never happen. If it does,</li> | |
| 494 | <li>contact Infobyte LCC.</li> | |
| 495 | </ul> | |
| 496 | </td> | |
| 497 | </tr> | |
| 498 | </tbody> | |
| 499 | </table> | |
| 500 | </dd></dl> | |
| 501 | ||
| 502 | <dl class="function"> | |
| 503 | <dt id="persistence.server.server.get_web_vuln"> | |
| 504 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_web_vuln</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>vuln_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_web_vuln"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_web_vuln" title="Permalink to this definition">¶</a></dt> | |
| 505 | <dd><p>Get an unique web vuln.</p> | |
| 506 | <table class="docutils field-list" frame="void" rules="none"> | |
| 507 | <col class="field-name" /> | |
| 508 | <col class="field-body" /> | |
| 509 | <tbody valign="top"> | |
| 510 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 511 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace where the object should be found.</li> | |
| 512 | <li><strong>vuln_id</strong> (<em>web</em>) – the id of the web vuln</li> | |
| 513 | </ul> | |
| 514 | </td> | |
| 515 | </tr> | |
| 516 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first">A dictionary containing information about the web vuln.</p> | |
| 517 | </td> | |
| 518 | </tr> | |
| 519 | <tr class="field-odd field"><th class="field-name">Raises:</th><td class="field-body"><ul class="first last simple"> | |
| 520 | <li><code class="xref py py-exc docutils literal"><span class="pre">MoreThanOneObjectFoundByID</span></code> – if for some reason the web vuln id is shared</li> | |
| 521 | <li>by two or more objects. This should never happen. If it does,</li> | |
| 522 | <li>contact Infobyte LCC.</li> | |
| 523 | </ul> | |
| 524 | </td> | |
| 525 | </tr> | |
| 526 | </tbody> | |
| 527 | </table> | |
| 528 | </dd></dl> | |
| 529 | ||
| 530 | <dl class="function"> | |
| 531 | <dt id="persistence.server.server.get_interface"> | |
| 532 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_interface</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>interface_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_interface"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_interface" title="Permalink to this definition">¶</a></dt> | |
| 533 | <dd><p>Get an unique interface.</p> | |
| 534 | <table class="docutils field-list" frame="void" rules="none"> | |
| 535 | <col class="field-name" /> | |
| 536 | <col class="field-body" /> | |
| 537 | <tbody valign="top"> | |
| 538 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 539 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace where the object should be found.</li> | |
| 540 | <li><strong>interface_id</strong> (<em>str</em>) – the id of the interface</li> | |
| 541 | </ul> | |
| 542 | </td> | |
| 543 | </tr> | |
| 544 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first">A dictionary containing information about the interface.</p> | |
| 545 | </td> | |
| 546 | </tr> | |
| 547 | <tr class="field-odd field"><th class="field-name">Raises:</th><td class="field-body"><ul class="first last simple"> | |
| 548 | <li><code class="xref py py-exc docutils literal"><span class="pre">MoreThanOneObjectFoundByID</span></code> – if for some reason the interface id is shared</li> | |
| 549 | <li>by two or more objects. This should never happen. If it does,</li> | |
| 550 | <li>contact Infobyte LCC.</li> | |
| 551 | </ul> | |
| 552 | </td> | |
| 553 | </tr> | |
| 554 | </tbody> | |
| 555 | </table> | |
| 556 | </dd></dl> | |
| 557 | ||
| 558 | <dl class="function"> | |
| 559 | <dt id="persistence.server.server.get_service"> | |
| 560 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_service</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>service_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_service"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_service" title="Permalink to this definition">¶</a></dt> | |
| 561 | <dd><p>Get an unique service.</p> | |
| 562 | <table class="docutils field-list" frame="void" rules="none"> | |
| 563 | <col class="field-name" /> | |
| 564 | <col class="field-body" /> | |
| 565 | <tbody valign="top"> | |
| 566 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 567 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace where the object should be found.</li> | |
| 568 | <li><strong>service_id</strong> (<em>str</em>) – the id of the service</li> | |
| 569 | </ul> | |
| 570 | </td> | |
| 571 | </tr> | |
| 572 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first">A dictionary containing information about the service.</p> | |
| 573 | </td> | |
| 574 | </tr> | |
| 575 | <tr class="field-odd field"><th class="field-name">Raises:</th><td class="field-body"><ul class="first last simple"> | |
| 576 | <li><code class="xref py py-exc docutils literal"><span class="pre">MoreThanOneObjectFoundByID</span></code> – if for some reason the service id is shared</li> | |
| 577 | <li>by two or more objects. This should never happen. If it does,</li> | |
| 578 | <li>contact Infobyte LCC.</li> | |
| 579 | </ul> | |
| 580 | </td> | |
| 581 | </tr> | |
| 582 | </tbody> | |
| 583 | </table> | |
| 584 | </dd></dl> | |
| 585 | ||
| 586 | <dl class="function"> | |
| 587 | <dt id="persistence.server.server.get_note"> | |
| 588 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_note</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>note_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_note"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_note" title="Permalink to this definition">¶</a></dt> | |
| 589 | <dd><p>Get an unique note.</p> | |
| 590 | <table class="docutils field-list" frame="void" rules="none"> | |
| 591 | <col class="field-name" /> | |
| 592 | <col class="field-body" /> | |
| 593 | <tbody valign="top"> | |
| 594 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 595 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace where the object should be found.</li> | |
| 596 | <li><strong>note_id</strong> (<em>str</em>) – the id of the note</li> | |
| 597 | </ul> | |
| 598 | </td> | |
| 599 | </tr> | |
| 600 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first">A dictionary containing information about the note.</p> | |
| 601 | </td> | |
| 602 | </tr> | |
| 603 | <tr class="field-odd field"><th class="field-name">Raises:</th><td class="field-body"><ul class="first last simple"> | |
| 604 | <li><code class="xref py py-exc docutils literal"><span class="pre">MoreThanOneObjectFoundByID</span></code> – if for some reason the note id is shared</li> | |
| 605 | <li>by two or more objects. This should never happen. If it does,</li> | |
| 606 | <li>contact Infobyte LCC.</li> | |
| 607 | </ul> | |
| 608 | </td> | |
| 609 | </tr> | |
| 610 | </tbody> | |
| 611 | </table> | |
| 612 | </dd></dl> | |
| 613 | ||
| 614 | <dl class="function"> | |
| 615 | <dt id="persistence.server.server.get_credential"> | |
| 616 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_credential</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>credential_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_credential"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_credential" title="Permalink to this definition">¶</a></dt> | |
| 617 | <dd><p>Get an unique credential.</p> | |
| 618 | <table class="docutils field-list" frame="void" rules="none"> | |
| 619 | <col class="field-name" /> | |
| 620 | <col class="field-body" /> | |
| 621 | <tbody valign="top"> | |
| 622 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 623 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace where the object should be found.</li> | |
| 624 | <li><strong>credential_id</strong> (<em>str</em>) – the id of the credential</li> | |
| 625 | </ul> | |
| 626 | </td> | |
| 627 | </tr> | |
| 628 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first">A dictionary containing information about the credential.</p> | |
| 629 | </td> | |
| 630 | </tr> | |
| 631 | <tr class="field-odd field"><th class="field-name">Raises:</th><td class="field-body"><ul class="first last simple"> | |
| 632 | <li><code class="xref py py-exc docutils literal"><span class="pre">MoreThanOneObjectFoundByID</span></code> – if for some reason the credential id is shared</li> | |
| 633 | <li>by two or more objects. This should never happen. If it does,</li> | |
| 634 | <li>contact Infobyte LCC.</li> | |
| 635 | </ul> | |
| 636 | </td> | |
| 637 | </tr> | |
| 638 | </tbody> | |
| 639 | </table> | |
| 640 | </dd></dl> | |
| 641 | ||
| 642 | <dl class="function"> | |
| 643 | <dt id="persistence.server.server.get_command"> | |
| 644 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_command</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>command_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_command"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_command" title="Permalink to this definition">¶</a></dt> | |
| 645 | <dd><p>Get an unique command.</p> | |
| 646 | <table class="docutils field-list" frame="void" rules="none"> | |
| 647 | <col class="field-name" /> | |
| 648 | <col class="field-body" /> | |
| 649 | <tbody valign="top"> | |
| 650 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 651 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace where the object should be found.</li> | |
| 652 | <li><strong>command_id</strong> (<em>str</em>) – the id of the command</li> | |
| 653 | </ul> | |
| 654 | </td> | |
| 655 | </tr> | |
| 656 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first">A dictionary containing information about the command.</p> | |
| 657 | </td> | |
| 658 | </tr> | |
| 659 | <tr class="field-odd field"><th class="field-name">Raises:</th><td class="field-body"><ul class="first last simple"> | |
| 660 | <li><code class="xref py py-exc docutils literal"><span class="pre">MoreThanOneObjectFoundByID</span></code> – if for some reason the command id is shared</li> | |
| 661 | <li>by two or more objects. This should never happen. If it does,</li> | |
| 662 | <li>contact Infobyte LCC.</li> | |
| 663 | </ul> | |
| 664 | </td> | |
| 665 | </tr> | |
| 666 | </tbody> | |
| 667 | </table> | |
| 668 | </dd></dl> | |
| 669 | ||
| 670 | <dl class="function"> | |
| 671 | <dt id="persistence.server.server.get_workspace"> | |
| 672 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_workspace</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_workspace"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_workspace" title="Permalink to this definition">¶</a></dt> | |
| 673 | <dd><p>Get an unique command.</p> | |
| 674 | <table class="docutils field-list" frame="void" rules="none"> | |
| 675 | <col class="field-name" /> | |
| 676 | <col class="field-body" /> | |
| 677 | <tbody valign="top"> | |
| 678 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 679 | <li><strong>command_name</strong> (<em>str</em>) – the command where the object should be found.</li> | |
| 680 | <li><strong>command_id</strong> (<em>str</em>) – the id of the command</li> | |
| 681 | </ul> | |
| 682 | </td> | |
| 683 | </tr> | |
| 684 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first">A dictionary containing information about the command.</p> | |
| 685 | </td> | |
| 686 | </tr> | |
| 687 | <tr class="field-odd field"><th class="field-name">Raises:</th><td class="field-body"><ul class="first last simple"> | |
| 688 | <li><code class="xref py py-exc docutils literal"><span class="pre">MoreThanOneObjectFoundByID</span></code> – if for some reason the command id is shared</li> | |
| 689 | <li>by two or more objects. This should never happen. If it does,</li> | |
| 690 | <li>contact Infobyte LCC.</li> | |
| 691 | </ul> | |
| 692 | </td> | |
| 693 | </tr> | |
| 694 | </tbody> | |
| 695 | </table> | |
| 696 | </dd></dl> | |
| 697 | ||
| 698 | <dl class="function"> | |
| 699 | <dt id="persistence.server.server.get_workspace_summary"> | |
| 700 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_workspace_summary</code><span class="sig-paren">(</span><em>workspace_name</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_workspace_summary"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_workspace_summary" title="Permalink to this definition">¶</a></dt> | |
| 701 | <dd><p>Get a collection of data about the workspace.</p> | |
| 702 | <table class="docutils field-list" frame="void" rules="none"> | |
| 703 | <col class="field-name" /> | |
| 704 | <col class="field-body" /> | |
| 705 | <tbody valign="top"> | |
| 706 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><strong>workspace_name</strong> (<em>str</em>) – the workspace to get the stats from.</td> | |
| 707 | </tr> | |
| 708 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body">A dictionary with the workspace’s information</td> | |
| 709 | </tr> | |
| 710 | </tbody> | |
| 711 | </table> | |
| 712 | </dd></dl> | |
| 713 | ||
| 714 | <dl class="function"> | |
| 715 | <dt id="persistence.server.server.get_workspace_numbers"> | |
| 716 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_workspace_numbers</code><span class="sig-paren">(</span><em>workspace_name</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_workspace_numbers"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_workspace_numbers" title="Permalink to this definition">¶</a></dt> | |
| 717 | <dd><p>Get the number of hosts, interfaces, services and vulns in the workspace.</p> | |
| 718 | <table class="docutils field-list" frame="void" rules="none"> | |
| 719 | <col class="field-name" /> | |
| 720 | <col class="field-body" /> | |
| 721 | <tbody valign="top"> | |
| 722 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace to query</td> | |
| 723 | </tr> | |
| 724 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body">A tuple of 4 elements with the amounts of hosts, interfaces, services and vulns.</td> | |
| 725 | </tr> | |
| 726 | </tbody> | |
| 727 | </table> | |
| 728 | </dd></dl> | |
| 729 | ||
| 730 | <dl class="function"> | |
| 731 | <dt id="persistence.server.server.get_hosts_number"> | |
| 732 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_hosts_number</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_hosts_number"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_hosts_number" title="Permalink to this definition">¶</a></dt> | |
| 733 | <dd><table class="docutils field-list" frame="void" rules="none"> | |
| 734 | <col class="field-name" /> | |
| 735 | <col class="field-body" /> | |
| 736 | <tbody valign="top"> | |
| 737 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 738 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace to query</li> | |
| 739 | <li><strong>**params</strong> – any of the Couchdb request parameters</li> | |
| 740 | </ul> | |
| 741 | </td> | |
| 742 | </tr> | |
| 743 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">The amount of hosts in the workspace as an integer.</p> | |
| 744 | </td> | |
| 745 | </tr> | |
| 746 | </tbody> | |
| 747 | </table> | |
| 748 | </dd></dl> | |
| 749 | ||
| 750 | <dl class="function"> | |
| 751 | <dt id="persistence.server.server.get_services_number"> | |
| 752 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_services_number</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_services_number"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_services_number" title="Permalink to this definition">¶</a></dt> | |
| 753 | <dd><table class="docutils field-list" frame="void" rules="none"> | |
| 754 | <col class="field-name" /> | |
| 755 | <col class="field-body" /> | |
| 756 | <tbody valign="top"> | |
| 757 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 758 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace to query</li> | |
| 759 | <li><strong>**params</strong> – any of the Couchdb request parameters</li> | |
| 760 | </ul> | |
| 761 | </td> | |
| 762 | </tr> | |
| 763 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">The amount of services in the workspace as an integer.</p> | |
| 764 | </td> | |
| 765 | </tr> | |
| 766 | </tbody> | |
| 767 | </table> | |
| 768 | </dd></dl> | |
| 769 | ||
| 770 | <dl class="function"> | |
| 771 | <dt id="persistence.server.server.get_interfaces_number"> | |
| 772 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_interfaces_number</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_interfaces_number"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_interfaces_number" title="Permalink to this definition">¶</a></dt> | |
| 773 | <dd><table class="docutils field-list" frame="void" rules="none"> | |
| 774 | <col class="field-name" /> | |
| 775 | <col class="field-body" /> | |
| 776 | <tbody valign="top"> | |
| 777 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 778 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace to query</li> | |
| 779 | <li><strong>**params</strong> – any of the Couchdb request parameters</li> | |
| 780 | </ul> | |
| 781 | </td> | |
| 782 | </tr> | |
| 783 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">The amount of interfaces in the workspace as an integer.</p> | |
| 784 | </td> | |
| 785 | </tr> | |
| 786 | </tbody> | |
| 787 | </table> | |
| 788 | </dd></dl> | |
| 789 | ||
| 790 | <dl class="function"> | |
| 791 | <dt id="persistence.server.server.get_vulns_number"> | |
| 792 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_vulns_number</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_vulns_number"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_vulns_number" title="Permalink to this definition">¶</a></dt> | |
| 793 | <dd><table class="docutils field-list" frame="void" rules="none"> | |
| 794 | <col class="field-name" /> | |
| 795 | <col class="field-body" /> | |
| 796 | <tbody valign="top"> | |
| 797 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 798 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace to query</li> | |
| 799 | <li><strong>**params</strong> – any of the Couchdb request parameters</li> | |
| 800 | </ul> | |
| 801 | </td> | |
| 802 | </tr> | |
| 803 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">The amount of vulns in the workspace as an integer.</p> | |
| 804 | </td> | |
| 805 | </tr> | |
| 806 | </tbody> | |
| 807 | </table> | |
| 808 | </dd></dl> | |
| 809 | ||
| 810 | <dl class="function"> | |
| 811 | <dt id="persistence.server.server.get_notes_number"> | |
| 812 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_notes_number</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_notes_number"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_notes_number" title="Permalink to this definition">¶</a></dt> | |
| 813 | <dd><table class="docutils field-list" frame="void" rules="none"> | |
| 814 | <col class="field-name" /> | |
| 815 | <col class="field-body" /> | |
| 816 | <tbody valign="top"> | |
| 817 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 818 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace to query</li> | |
| 819 | <li><strong>**params</strong> – any of the Couchdb request parameters</li> | |
| 820 | </ul> | |
| 821 | </td> | |
| 822 | </tr> | |
| 823 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">The amount of notes in the workspace as an integer.</p> | |
| 824 | </td> | |
| 825 | </tr> | |
| 826 | </tbody> | |
| 827 | </table> | |
| 828 | </dd></dl> | |
| 829 | ||
| 830 | <dl class="function"> | |
| 831 | <dt id="persistence.server.server.get_credentials_number"> | |
| 832 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_credentials_number</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_credentials_number"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_credentials_number" title="Permalink to this definition">¶</a></dt> | |
| 833 | <dd><table class="docutils field-list" frame="void" rules="none"> | |
| 834 | <col class="field-name" /> | |
| 835 | <col class="field-body" /> | |
| 836 | <tbody valign="top"> | |
| 837 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 838 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace to query</li> | |
| 839 | <li><strong>**params</strong> – any of the Couchdb request parameters</li> | |
| 840 | </ul> | |
| 841 | </td> | |
| 842 | </tr> | |
| 843 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">The amount of credentials in the workspace as an integer.</p> | |
| 844 | </td> | |
| 845 | </tr> | |
| 846 | </tbody> | |
| 847 | </table> | |
| 848 | </dd></dl> | |
| 849 | ||
| 850 | <dl class="function"> | |
| 851 | <dt id="persistence.server.server.get_commands_number"> | |
| 852 | <code class="descclassname">persistence.server.server.</code><code class="descname">get_commands_number</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>**params</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#get_commands_number"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.get_commands_number" title="Permalink to this definition">¶</a></dt> | |
| 853 | <dd><table class="docutils field-list" frame="void" rules="none"> | |
| 854 | <col class="field-name" /> | |
| 855 | <col class="field-body" /> | |
| 856 | <tbody valign="top"> | |
| 857 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 858 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace to query</li> | |
| 859 | <li><strong>**params</strong> – any of the Couchdb request parameters</li> | |
| 860 | </ul> | |
| 861 | </td> | |
| 862 | </tr> | |
| 863 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">The amount of commands in the workspace as an integer.</p> | |
| 864 | </td> | |
| 865 | </tr> | |
| 866 | </tbody> | |
| 867 | </table> | |
| 868 | </dd></dl> | |
| 869 | ||
| 870 | <dl class="function"> | |
| 871 | <dt id="persistence.server.server.create_host"> | |
| 872 | <code class="descclassname">persistence.server.server.</code><code class="descname">create_host</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>name</em>, <em>os</em>, <em>default_gateway</em>, <em>description=''</em>, <em>metadata=None</em>, <em>owned=False</em>, <em>owner=''</em>, <em>parent=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#create_host"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.create_host" title="Permalink to this definition">¶</a></dt> | |
| 873 | <dd><p>Create a host.</p> | |
| 874 | <table class="docutils field-list" frame="void" rules="none"> | |
| 875 | <col class="field-name" /> | |
| 876 | <col class="field-body" /> | |
| 877 | <tbody valign="top"> | |
| 878 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 879 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the host will be saved.</li> | |
| 880 | <li><strong>id</strong> (<em>str</em>) – the id of the host. Must be unique.</li> | |
| 881 | <li><strong>name</strong> (<em>str</em>) – the host’s name</li> | |
| 882 | <li><strong>os</strong> (<em>str</em>) – the operative system of the host</li> | |
| 883 | <li><strong>default_gateway</strong> (<em>str</em>) – the host’s default_gateway</li> | |
| 884 | <li><strong>description</strong> (<em>str</em>) – a description.</li> | |
| 885 | <li><strong>metadata</strong> – a collection of metadata. If you don’t know the metada. leave | |
| 886 | on None.</li> | |
| 887 | <li><strong>owned</strong> (<em>bool</em>) – is the host owned or not?</li> | |
| 888 | <li><strong>owner</strong> (<em>str</em>) – an owner for the host</li> | |
| 889 | <li><strong>parent</strong> (<em>Faraday Object</em>) – the host’s parent. If you don’t know this, leave | |
| 890 | on None.</li> | |
| 891 | </ul> | |
| 892 | </td> | |
| 893 | </tr> | |
| 894 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 895 | </td> | |
| 896 | </tr> | |
| 897 | </tbody> | |
| 898 | </table> | |
| 899 | </dd></dl> | |
| 900 | ||
| 901 | <dl class="function"> | |
| 902 | <dt id="persistence.server.server.update_host"> | |
| 903 | <code class="descclassname">persistence.server.server.</code><code class="descname">update_host</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>name</em>, <em>os</em>, <em>default_gateway</em>, <em>description=''</em>, <em>metadata=None</em>, <em>owned=False</em>, <em>owner=''</em>, <em>parent=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#update_host"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.update_host" title="Permalink to this definition">¶</a></dt> | |
| 904 | <dd><p>Updates a host.</p> | |
| 905 | <table class="docutils field-list" frame="void" rules="none"> | |
| 906 | <col class="field-name" /> | |
| 907 | <col class="field-body" /> | |
| 908 | <tbody valign="top"> | |
| 909 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 910 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the host will be saved.</li> | |
| 911 | <li><strong>id</strong> (<em>str</em>) – the id of the host. Must be unique.</li> | |
| 912 | <li><strong>name</strong> (<em>str</em>) – the host’s name</li> | |
| 913 | <li><strong>os</strong> (<em>str</em>) – the operative system of the host</li> | |
| 914 | <li><strong>default_gateway</strong> (<em>str</em>) – the host’s default_gateway</li> | |
| 915 | <li><strong>description</strong> (<em>str</em>) – a description.</li> | |
| 916 | <li><strong>metadata</strong> – a collection of metadata. If you don’t know the metada. leave | |
| 917 | on None, it will be created automatically.</li> | |
| 918 | <li><strong>owned</strong> (<em>bool</em>) – is the host owned or not?</li> | |
| 919 | <li><strong>owner</strong> (<em>str</em>) – an owner for the host</li> | |
| 920 | <li><strong>parent</strong> (<em>Faraday Object</em>) – the host’s parent. If you don’t know this, leave | |
| 921 | on None.</li> | |
| 922 | </ul> | |
| 923 | </td> | |
| 924 | </tr> | |
| 925 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 926 | </td> | |
| 927 | </tr> | |
| 928 | </tbody> | |
| 929 | </table> | |
| 930 | </dd></dl> | |
| 931 | ||
| 932 | <dl class="function"> | |
| 933 | <dt id="persistence.server.server.create_interface"> | |
| 934 | <code class="descclassname">persistence.server.server.</code><code class="descname">create_interface</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>name</em>, <em>description</em>, <em>mac</em>, <em>owned=False</em>, <em>owner=''</em>, <em>hostnames=None</em>, <em>network_segment=None</em>, <em>ipv4=None</em>, <em>ipv6=None</em>, <em>metadata=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#create_interface"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.create_interface" title="Permalink to this definition">¶</a></dt> | |
| 935 | <dd><p>Creates an interface.</p> | |
| 936 | <div class="admonition warning"> | |
| 937 | <p class="first admonition-title">Warning</p> | |
| 938 | <p class="last">DO NOT leave ipv4 and ipv6 values on None, as the default indicated. | |
| 939 | This is a known bug and we’re working to fix it. ipv4 and ipv6 need to | |
| 940 | be valid IP addresses, or, in case one of them is irrelevant, empty strings.</p> | |
| 941 | </div> | |
| 942 | <table class="docutils field-list" frame="void" rules="none"> | |
| 943 | <col class="field-name" /> | |
| 944 | <col class="field-body" /> | |
| 945 | <tbody valign="top"> | |
| 946 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 947 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the interface will be saved.</li> | |
| 948 | <li><strong>id</strong> (<em>str</em>) – the id of the interface. Must be unique.</li> | |
| 949 | <li><strong>name</strong> (<em>str</em>) – the interface’s name</li> | |
| 950 | <li><strong>description</strong> (<em>str</em>) – a description.</li> | |
| 951 | <li><strong>mac</strong> (<em>str</em>) – </li> | |
| 952 | <li><strong>owned</strong> (<em>bool</em>) – is the host owned or not?</li> | |
| 953 | <li><strong>owner</strong> (<em>str</em>) – an owner for the host</li> | |
| 954 | <li><strong>hostnames</strong> (<em></em><em>[</em><em>str</em><em>]</em><em></em>) – a list of hostnames</li> | |
| 955 | <li><strong>network_segment</strong> (<em>str</em>) – the network segment</li> | |
| 956 | <li><strong>ipv4</strong> (<em>str</em>) – the ipv4 direction of the interface.</li> | |
| 957 | <li><strong>ipv6</strong> (<em>str</em>) – the ipv6 direction of the interface.</li> | |
| 958 | <li><strong>metadata</strong> – a collection of metadata. If you don’t know the metada. leave | |
| 959 | on None, it will be created automatically.</li> | |
| 960 | </ul> | |
| 961 | </td> | |
| 962 | </tr> | |
| 963 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 964 | </td> | |
| 965 | </tr> | |
| 966 | </tbody> | |
| 967 | </table> | |
| 968 | </dd></dl> | |
| 969 | ||
| 970 | <dl class="function"> | |
| 971 | <dt id="persistence.server.server.update_interface"> | |
| 972 | <code class="descclassname">persistence.server.server.</code><code class="descname">update_interface</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>name</em>, <em>description</em>, <em>mac</em>, <em>owned=False</em>, <em>owner=''</em>, <em>hostnames=None</em>, <em>network_segment=None</em>, <em>ipv4=None</em>, <em>ipv6=None</em>, <em>metadata=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#update_interface"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.update_interface" title="Permalink to this definition">¶</a></dt> | |
| 973 | <dd><p>Creates an interface.</p> | |
| 974 | <div class="admonition warning"> | |
| 975 | <p class="first admonition-title">Warning</p> | |
| 976 | <p class="last">DO NOT leave ipv4 and ipv6 values on None, as the default indicated. | |
| 977 | This is a known bug and we’re working to fix it. ipv4 and ipv6 need to | |
| 978 | be valid IP addresses, or, in case one of them is irrelevant, empty strings.</p> | |
| 979 | </div> | |
| 980 | <table class="docutils field-list" frame="void" rules="none"> | |
| 981 | <col class="field-name" /> | |
| 982 | <col class="field-body" /> | |
| 983 | <tbody valign="top"> | |
| 984 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 985 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the interface will be saved.</li> | |
| 986 | <li><strong>id</strong> (<em>str</em>) – the id of the interface. Must be unique.</li> | |
| 987 | <li><strong>name</strong> (<em>str</em>) – the interface’s name</li> | |
| 988 | <li><strong>description</strong> (<em>str</em>) – a description.</li> | |
| 989 | <li><strong>mac</strong> (<em>str</em>) – </li> | |
| 990 | <li><strong>owned</strong> (<em>bool</em>) – is the host owned or not?</li> | |
| 991 | <li><strong>owner</strong> (<em>str</em>) – an owner for the host</li> | |
| 992 | <li><strong>hostnames</strong> (<em></em><em>[</em><em>str</em><em>]</em><em></em>) – a list of hostnames</li> | |
| 993 | <li><strong>network_segment</strong> (<em>str</em>) – the network segment</li> | |
| 994 | <li><strong>ipv4</strong> (<em>str</em>) – the ipv4 direction of the interface.</li> | |
| 995 | <li><strong>ipv6</strong> (<em>str</em>) – the ipv6 direction of the interface.</li> | |
| 996 | <li><strong>metadata</strong> – a collection of metadata. If you don’t know the metada. leave | |
| 997 | on None, it will be created automatically.</li> | |
| 998 | </ul> | |
| 999 | </td> | |
| 1000 | </tr> | |
| 1001 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 1002 | </td> | |
| 1003 | </tr> | |
| 1004 | </tbody> | |
| 1005 | </table> | |
| 1006 | </dd></dl> | |
| 1007 | ||
| 1008 | <dl class="function"> | |
| 1009 | <dt id="persistence.server.server.create_service"> | |
| 1010 | <code class="descclassname">persistence.server.server.</code><code class="descname">create_service</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>name</em>, <em>description</em>, <em>ports</em>, <em>owned=False</em>, <em>owner=''</em>, <em>protocol=''</em>, <em>status=''</em>, <em>version=''</em>, <em>metadata=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#create_service"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.create_service" title="Permalink to this definition">¶</a></dt> | |
| 1011 | <dd><p>Creates a service.</p> | |
| 1012 | <table class="docutils field-list" frame="void" rules="none"> | |
| 1013 | <col class="field-name" /> | |
| 1014 | <col class="field-body" /> | |
| 1015 | <tbody valign="top"> | |
| 1016 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 1017 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the service will be saved.</li> | |
| 1018 | <li><strong>id</strong> (<em>str</em>) – the id of the service. Must be unique.</li> | |
| 1019 | <li><strong>name</strong> (<em>str</em>) – the host’s name</li> | |
| 1020 | <li><strong>description</strong> (<em>str</em>) – a description.</li> | |
| 1021 | <li><strong>ports</strong> (<em></em><em>[</em><em>str</em><em>]</em><em></em>) – a list of ports for the service.</li> | |
| 1022 | <li><strong>owned</strong> (<em>bool</em>) – is the service owned or not?</li> | |
| 1023 | <li><strong>owner</strong> (<em>str</em>) – an owner for the service</li> | |
| 1024 | <li><strong>protocol</strong> (<em>str</em>) – the service’s protocol</li> | |
| 1025 | <li><strong>status</strong> (<em>str</em>) – the service’s status</li> | |
| 1026 | <li><strong>version</strong> (<em>str</em>) – the service’s version</li> | |
| 1027 | <li><strong>metadata</strong> – a collection of metadata. If you don’t know the metada. leave | |
| 1028 | on None, it will be created automatically.</li> | |
| 1029 | </ul> | |
| 1030 | </td> | |
| 1031 | </tr> | |
| 1032 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 1033 | </td> | |
| 1034 | </tr> | |
| 1035 | </tbody> | |
| 1036 | </table> | |
| 1037 | </dd></dl> | |
| 1038 | ||
| 1039 | <dl class="function"> | |
| 1040 | <dt id="persistence.server.server.update_service"> | |
| 1041 | <code class="descclassname">persistence.server.server.</code><code class="descname">update_service</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>name</em>, <em>description</em>, <em>ports</em>, <em>owned=False</em>, <em>owner=''</em>, <em>protocol=''</em>, <em>status=''</em>, <em>version=''</em>, <em>metadata=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#update_service"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.update_service" title="Permalink to this definition">¶</a></dt> | |
| 1042 | <dd><p>Creates a service.</p> | |
| 1043 | <table class="docutils field-list" frame="void" rules="none"> | |
| 1044 | <col class="field-name" /> | |
| 1045 | <col class="field-body" /> | |
| 1046 | <tbody valign="top"> | |
| 1047 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 1048 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the service will be saved.</li> | |
| 1049 | <li><strong>id</strong> (<em>str</em>) – the id of the service. Must be unique.</li> | |
| 1050 | <li><strong>name</strong> (<em>str</em>) – the service’s name</li> | |
| 1051 | <li><strong>description</strong> (<em>str</em>) – a description.</li> | |
| 1052 | <li><strong>ports</strong> (<em></em><em>[</em><em>str</em><em>]</em><em></em>) – a list of ports for the service.</li> | |
| 1053 | <li><strong>owned</strong> (<em>bool</em>) – is the host owned or not?</li> | |
| 1054 | <li><strong>owner</strong> (<em>str</em>) – an owner for the service</li> | |
| 1055 | <li><strong>protocol</strong> (<em>str</em>) – the service’s protocol</li> | |
| 1056 | <li><strong>status</strong> (<em>str</em>) – the service’s status</li> | |
| 1057 | <li><strong>version</strong> (<em>str</em>) – the service’s version</li> | |
| 1058 | <li><strong>metadata</strong> – a collection of metadata. If you don’t know the metada. leave | |
| 1059 | on None, it will be created automatically.</li> | |
| 1060 | </ul> | |
| 1061 | </td> | |
| 1062 | </tr> | |
| 1063 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 1064 | </td> | |
| 1065 | </tr> | |
| 1066 | </tbody> | |
| 1067 | </table> | |
| 1068 | </dd></dl> | |
| 1069 | ||
| 1070 | <dl class="function"> | |
| 1071 | <dt id="persistence.server.server.create_vuln"> | |
| 1072 | <code class="descclassname">persistence.server.server.</code><code class="descname">create_vuln</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>name</em>, <em>description</em>, <em>owned=None</em>, <em>owner=''</em>, <em>confirmed=False</em>, <em>data=''</em>, <em>refs=None</em>, <em>severity='info'</em>, <em>resolution=''</em>, <em>desc=''</em>, <em>metadata=None</em>, <em>status=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#create_vuln"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.create_vuln" title="Permalink to this definition">¶</a></dt> | |
| 1073 | <dd><p>Creates a vuln.</p> | |
| 1074 | <table class="docutils field-list" frame="void" rules="none"> | |
| 1075 | <col class="field-name" /> | |
| 1076 | <col class="field-body" /> | |
| 1077 | <tbody valign="top"> | |
| 1078 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 1079 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the vuln will be saved.</li> | |
| 1080 | <li><strong>id</strong> (<em>str</em>) – the id of the vuln. Must be unique.</li> | |
| 1081 | <li><strong>name</strong> (<em>str</em>) – the vuln’s name</li> | |
| 1082 | <li><strong>description</strong> (<em>str</em>) – a description.</li> | |
| 1083 | <li><strong>owned</strong> (<em>bool</em>) – is the vuln owned or not?</li> | |
| 1084 | <li><strong>owner</strong> (<em>str</em>) – an owner for the vuln</li> | |
| 1085 | <li><strong>confirmed</strong> (<em>bool</em>) – is the vulnerability confirmed?</li> | |
| 1086 | <li><strong>data</strong> (<em>str</em>) – any aditional data about the vuln</li> | |
| 1087 | <li><strong>refs</strong> (<em></em><em>[</em><em>str</em><em>]</em><em></em>) – references for the vulnerability</li> | |
| 1088 | <li><strong>severity</strong> (<em>str</em>) – a string indicating the vuln’s severity. can be ‘info’, | |
| 1089 | ‘low’, ‘med’, ‘high’, ‘critical’</li> | |
| 1090 | <li><strong>resolution</strong> (<em>str</em>) – the vuln’s possible resolution</li> | |
| 1091 | <li><strong>desc</strong> (<em>str</em>) – a vuln’s description.</li> | |
| 1092 | <li><strong>status</strong> (<em>str</em>) – the service’s status</li> | |
| 1093 | <li><strong>metadata</strong> – a collection of metadata. If you don’t know the metada. leave | |
| 1094 | on None, it will be created automatically.</li> | |
| 1095 | </ul> | |
| 1096 | </td> | |
| 1097 | </tr> | |
| 1098 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 1099 | </td> | |
| 1100 | </tr> | |
| 1101 | </tbody> | |
| 1102 | </table> | |
| 1103 | </dd></dl> | |
| 1104 | ||
| 1105 | <dl class="function"> | |
| 1106 | <dt id="persistence.server.server.update_vuln"> | |
| 1107 | <code class="descclassname">persistence.server.server.</code><code class="descname">update_vuln</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>name</em>, <em>description</em>, <em>owned=None</em>, <em>owner=''</em>, <em>confirmed=False</em>, <em>data=''</em>, <em>refs=None</em>, <em>severity='info'</em>, <em>resolution=''</em>, <em>desc=''</em>, <em>metadata=None</em>, <em>status=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#update_vuln"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.update_vuln" title="Permalink to this definition">¶</a></dt> | |
| 1108 | <dd><p>Updates a vuln.</p> | |
| 1109 | <table class="docutils field-list" frame="void" rules="none"> | |
| 1110 | <col class="field-name" /> | |
| 1111 | <col class="field-body" /> | |
| 1112 | <tbody valign="top"> | |
| 1113 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 1114 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the host will be saved.</li> | |
| 1115 | <li><strong>id</strong> (<em>str</em>) – the id of the host. Must be unique.</li> | |
| 1116 | <li><strong>name</strong> (<em>str</em>) – the host’s name</li> | |
| 1117 | <li><strong>description</strong> (<em>str</em>) – a description.</li> | |
| 1118 | <li><strong>owned</strong> (<em>bool</em>) – is the vuln owned or not?</li> | |
| 1119 | <li><strong>owner</strong> (<em>str</em>) – an owner for the vuln</li> | |
| 1120 | <li><strong>confirmed</strong> (<em>bool</em>) – is the vulnerability confirmed?</li> | |
| 1121 | <li><strong>data</strong> (<em>str</em>) – any aditional data about the vuln</li> | |
| 1122 | <li><strong>refs</strong> (<em></em><em>[</em><em>str</em><em>]</em><em></em>) – references for the vulnerability</li> | |
| 1123 | <li><strong>severity</strong> (<em>str</em>) – a string indicating the vuln’s severity. can be ‘info’, | |
| 1124 | ‘low’, ‘med’, ‘high’, ‘critical’</li> | |
| 1125 | <li><strong>resolution</strong> (<em>str</em>) – the vuln’s possible resolution</li> | |
| 1126 | <li><strong>desc</strong> (<em>str</em>) – a vuln’s description.</li> | |
| 1127 | <li><strong>status</strong> (<em>str</em>) – the service’s status</li> | |
| 1128 | <li><strong>metadata</strong> – a collection of metadata. If you don’t know the metada. leave | |
| 1129 | on None, it will be created automatically.</li> | |
| 1130 | </ul> | |
| 1131 | </td> | |
| 1132 | </tr> | |
| 1133 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 1134 | </td> | |
| 1135 | </tr> | |
| 1136 | </tbody> | |
| 1137 | </table> | |
| 1138 | </dd></dl> | |
| 1139 | ||
| 1140 | <dl class="function"> | |
| 1141 | <dt id="persistence.server.server.create_vuln_web"> | |
| 1142 | <code class="descclassname">persistence.server.server.</code><code class="descname">create_vuln_web</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>name</em>, <em>description</em>, <em>owned=None</em>, <em>owner=''</em>, <em>confirmed=False</em>, <em>data=''</em>, <em>refs=None</em>, <em>severity='info'</em>, <em>resolution=''</em>, <em>desc=''</em>, <em>metadata=None</em>, <em>method=None</em>, <em>params=''</em>, <em>path=None</em>, <em>pname=None</em>, <em>query=None</em>, <em>request=None</em>, <em>response=None</em>, <em>category=''</em>, <em>website=None</em>, <em>status=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#create_vuln_web"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.create_vuln_web" title="Permalink to this definition">¶</a></dt> | |
| 1143 | <dd><p>Creates a vuln web.</p> | |
| 1144 | <table class="docutils field-list" frame="void" rules="none"> | |
| 1145 | <col class="field-name" /> | |
| 1146 | <col class="field-body" /> | |
| 1147 | <tbody valign="top"> | |
| 1148 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 1149 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the vuln web will be saved.</li> | |
| 1150 | <li><strong>id</strong> (<em>str</em>) – the id of the vuln web. Must be unique.</li> | |
| 1151 | <li><strong>name</strong> (<em>str</em>) – the vuln web’s name</li> | |
| 1152 | <li><strong>description</strong> (<em>str</em>) – a description.</li> | |
| 1153 | <li><strong>owner</strong> (<em>str</em>) – an owner for the host</li> | |
| 1154 | <li><strong>confirmed</strong> (<em>bool</em>) – is the vulnerability confirmed?</li> | |
| 1155 | <li><strong>data</strong> (<em>str</em>) – any aditional data about the vuln</li> | |
| 1156 | <li><strong>refs</strong> (<em></em><em>[</em><em>str</em><em>]</em><em></em>) – references for the vulnerability</li> | |
| 1157 | <li><strong>severity</strong> (<em>str</em>) – a string indicating the vuln’s severity. can be ‘info’, | |
| 1158 | ‘low’, ‘med’, ‘high’, ‘critical’</li> | |
| 1159 | <li><strong>resolution</strong> (<em>str</em>) – the vuln’s possible resolution</li> | |
| 1160 | <li><strong>desc</strong> (<em>str</em>) – a vuln’s description.</li> | |
| 1161 | <li><strong>metadata</strong> – a collection of metadata. If you don’t know the metada. leave | |
| 1162 | on None, it will be created automatically.</li> | |
| 1163 | <li><strong>method</strong> (<em>str</em>) – the web vuln method</li> | |
| 1164 | <li><strong>params</strong> (<em>str</em>) – the parameters for the web vuln</li> | |
| 1165 | <li><strong>path</strong> (<em>str</em>) – the web vuln’s path</li> | |
| 1166 | <li><strong>query</strong> (<em>str</em>) – the web vuln’s query</li> | |
| 1167 | <li><strong>request</strong> (<em>str</em>) – the web vuln’s request</li> | |
| 1168 | <li><strong>response</strong> (<em>str</em>) – the web vuln’s response</li> | |
| 1169 | <li><strong>category</strong> (<em>str</em>) – a category for the web vuln’s</li> | |
| 1170 | <li><strong>website</strong> (<em>str</em>) – the website where the vuln was found</li> | |
| 1171 | <li><strong>status</strong> (<em>str</em>) – the web vulns’s status</li> | |
| 1172 | </ul> | |
| 1173 | </td> | |
| 1174 | </tr> | |
| 1175 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 1176 | </td> | |
| 1177 | </tr> | |
| 1178 | </tbody> | |
| 1179 | </table> | |
| 1180 | </dd></dl> | |
| 1181 | ||
| 1182 | <dl class="function"> | |
| 1183 | <dt id="persistence.server.server.update_vuln_web"> | |
| 1184 | <code class="descclassname">persistence.server.server.</code><code class="descname">update_vuln_web</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>name</em>, <em>description</em>, <em>owned=None</em>, <em>owner=''</em>, <em>confirmed=False</em>, <em>data=''</em>, <em>refs=None</em>, <em>severity='info'</em>, <em>resolution=''</em>, <em>desc=''</em>, <em>metadata=None</em>, <em>method=None</em>, <em>params=''</em>, <em>path=None</em>, <em>pname=None</em>, <em>query=None</em>, <em>request=None</em>, <em>response=None</em>, <em>category=''</em>, <em>website=None</em>, <em>status=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#update_vuln_web"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.update_vuln_web" title="Permalink to this definition">¶</a></dt> | |
| 1185 | <dd><p>Creates a vuln web.</p> | |
| 1186 | <table class="docutils field-list" frame="void" rules="none"> | |
| 1187 | <col class="field-name" /> | |
| 1188 | <col class="field-body" /> | |
| 1189 | <tbody valign="top"> | |
| 1190 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 1191 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the vuln web will be saved.</li> | |
| 1192 | <li><strong>id</strong> (<em>str</em>) – the id of the vuln web. Must be unique.</li> | |
| 1193 | <li><strong>name</strong> (<em>str</em>) – the vuln web’s name</li> | |
| 1194 | <li><strong>description</strong> (<em>str</em>) – a description.</li> | |
| 1195 | <li><strong>owner</strong> (<em>str</em>) – an owner for the host</li> | |
| 1196 | <li><strong>confirmed</strong> (<em>bool</em>) – is the vulnerability confirmed?</li> | |
| 1197 | <li><strong>data</strong> (<em>str</em>) – any aditional data about the vuln</li> | |
| 1198 | <li><strong>refs</strong> (<em></em><em>[</em><em>str</em><em>]</em><em></em>) – references for the vulnerability</li> | |
| 1199 | <li><strong>severity</strong> (<em>str</em>) – a string indicating the vuln’s severity. can be ‘info’, | |
| 1200 | ‘low’, ‘med’, ‘high’, ‘critical’</li> | |
| 1201 | <li><strong>resolution</strong> (<em>str</em>) – the vuln’s possible resolution</li> | |
| 1202 | <li><strong>desc</strong> (<em>str</em>) – a vuln’s description.</li> | |
| 1203 | <li><strong>metadata</strong> – a collection of metadata. If you don’t know the metada. leave | |
| 1204 | on None, it will be created automatically.</li> | |
| 1205 | <li><strong>method</strong> (<em>str</em>) – the web vuln method</li> | |
| 1206 | <li><strong>params</strong> (<em>str</em>) – the parameters for the web vuln</li> | |
| 1207 | <li><strong>path</strong> (<em>str</em>) – the web vuln’s path</li> | |
| 1208 | <li><strong>query</strong> (<em>str</em>) – the web vuln’s query</li> | |
| 1209 | <li><strong>request</strong> (<em>str</em>) – the web vuln’s request</li> | |
| 1210 | <li><strong>response</strong> (<em>str</em>) – the web vuln’s response</li> | |
| 1211 | <li><strong>category</strong> (<em>str</em>) – a category for the web vuln’s</li> | |
| 1212 | <li><strong>website</strong> (<em>str</em>) – the website where the vuln was found</li> | |
| 1213 | <li><strong>status</strong> (<em>str</em>) – the web vulns’s status</li> | |
| 1214 | </ul> | |
| 1215 | </td> | |
| 1216 | </tr> | |
| 1217 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 1218 | </td> | |
| 1219 | </tr> | |
| 1220 | </tbody> | |
| 1221 | </table> | |
| 1222 | </dd></dl> | |
| 1223 | ||
| 1224 | <dl class="function"> | |
| 1225 | <dt id="persistence.server.server.create_note"> | |
| 1226 | <code class="descclassname">persistence.server.server.</code><code class="descname">create_note</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>name</em>, <em>text</em>, <em>owned=None</em>, <em>owner=''</em>, <em>description=''</em>, <em>metadata=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#create_note"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.create_note" title="Permalink to this definition">¶</a></dt> | |
| 1227 | <dd><p>Creates a note.</p> | |
| 1228 | <table class="docutils field-list" frame="void" rules="none"> | |
| 1229 | <col class="field-name" /> | |
| 1230 | <col class="field-body" /> | |
| 1231 | <tbody valign="top"> | |
| 1232 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 1233 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the vuln web will be saved.</li> | |
| 1234 | <li><strong>id</strong> (<em>str</em>) – the id of the vuln web. Must be unique.</li> | |
| 1235 | <li><strong>name</strong> (<em>str</em>) – the vuln web’s name</li> | |
| 1236 | <li><strong>text</strong> (<em>str</em>) – the note’s text</li> | |
| 1237 | <li><strong>owned</strong> (<em>bool</em>) – is the note owned?</li> | |
| 1238 | <li><strong>owner</strong> (<em>str</em>) – the note’s owner</li> | |
| 1239 | <li><strong>description</strong> (<em>str</em>) – a description</li> | |
| 1240 | <li><strong>metadata</strong> – a collection of metadata. If you don’t know the metada. leave | |
| 1241 | on None, it will be created automatically.</li> | |
| 1242 | </ul> | |
| 1243 | </td> | |
| 1244 | </tr> | |
| 1245 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 1246 | </td> | |
| 1247 | </tr> | |
| 1248 | </tbody> | |
| 1249 | </table> | |
| 1250 | </dd></dl> | |
| 1251 | ||
| 1252 | <dl class="function"> | |
| 1253 | <dt id="persistence.server.server.update_note"> | |
| 1254 | <code class="descclassname">persistence.server.server.</code><code class="descname">update_note</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>name</em>, <em>text</em>, <em>owned=None</em>, <em>owner=''</em>, <em>description=''</em>, <em>metadata=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#update_note"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.update_note" title="Permalink to this definition">¶</a></dt> | |
| 1255 | <dd><p>Updates a note.</p> | |
| 1256 | <table class="docutils field-list" frame="void" rules="none"> | |
| 1257 | <col class="field-name" /> | |
| 1258 | <col class="field-body" /> | |
| 1259 | <tbody valign="top"> | |
| 1260 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 1261 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the vuln web will be saved.</li> | |
| 1262 | <li><strong>id</strong> (<em>str</em>) – the id of the vuln web. Must be unique.</li> | |
| 1263 | <li><strong>name</strong> (<em>str</em>) – the vuln web’s name</li> | |
| 1264 | <li><strong>text</strong> (<em>str</em>) – the note’s text</li> | |
| 1265 | <li><strong>owned</strong> (<em>bool</em>) – is the note owned?</li> | |
| 1266 | <li><strong>owner</strong> (<em>str</em>) – the note’s owner</li> | |
| 1267 | <li><strong>description</strong> (<em>str</em>) – a description</li> | |
| 1268 | <li><strong>metadata</strong> – a collection of metadata. If you don’t know the metada. leave | |
| 1269 | on None, it will be created automatically.</li> | |
| 1270 | </ul> | |
| 1271 | </td> | |
| 1272 | </tr> | |
| 1273 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 1274 | </td> | |
| 1275 | </tr> | |
| 1276 | </tbody> | |
| 1277 | </table> | |
| 1278 | </dd></dl> | |
| 1279 | ||
| 1280 | <dl class="function"> | |
| 1281 | <dt id="persistence.server.server.create_credential"> | |
| 1282 | <code class="descclassname">persistence.server.server.</code><code class="descname">create_credential</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>name</em>, <em>username</em>, <em>password</em>, <em>owned=None</em>, <em>owner=''</em>, <em>description=''</em>, <em>metadata=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#create_credential"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.create_credential" title="Permalink to this definition">¶</a></dt> | |
| 1283 | <dd><p>Creates a credential.</p> | |
| 1284 | <table class="docutils field-list" frame="void" rules="none"> | |
| 1285 | <col class="field-name" /> | |
| 1286 | <col class="field-body" /> | |
| 1287 | <tbody valign="top"> | |
| 1288 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 1289 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the vuln web will be saved.</li> | |
| 1290 | <li><strong>id</strong> (<em>str</em>) – the id of the vuln web. Must be unique.</li> | |
| 1291 | <li><strong>name</strong> (<em>str</em>) – the vuln web’s name</li> | |
| 1292 | <li><strong>username</strong> (<em>str</em>) – </li> | |
| 1293 | <li><strong>password</strong> (<em>str</em>) – </li> | |
| 1294 | <li><strong>owned</strong> (<em>bool</em>) – is the note owned?</li> | |
| 1295 | <li><strong>owner</strong> (<em>str</em>) – the note’s owner</li> | |
| 1296 | <li><strong>description</strong> (<em>str</em>) – a description</li> | |
| 1297 | <li><strong>metadata</strong> – a collection of metadata. If you don’t know the metada. leave | |
| 1298 | on None, it will be created automatically.</li> | |
| 1299 | </ul> | |
| 1300 | </td> | |
| 1301 | </tr> | |
| 1302 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 1303 | </td> | |
| 1304 | </tr> | |
| 1305 | </tbody> | |
| 1306 | </table> | |
| 1307 | </dd></dl> | |
| 1308 | ||
| 1309 | <dl class="function"> | |
| 1310 | <dt id="persistence.server.server.update_credential"> | |
| 1311 | <code class="descclassname">persistence.server.server.</code><code class="descname">update_credential</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>name</em>, <em>username</em>, <em>password</em>, <em>owned=None</em>, <em>owner=''</em>, <em>description=''</em>, <em>metadata=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#update_credential"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.update_credential" title="Permalink to this definition">¶</a></dt> | |
| 1312 | <dd><p>Updates a credential.</p> | |
| 1313 | <table class="docutils field-list" frame="void" rules="none"> | |
| 1314 | <col class="field-name" /> | |
| 1315 | <col class="field-body" /> | |
| 1316 | <tbody valign="top"> | |
| 1317 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 1318 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the vuln web will be saved.</li> | |
| 1319 | <li><strong>id</strong> (<em>str</em>) – the id of the vuln web. Must be unique.</li> | |
| 1320 | <li><strong>name</strong> (<em>str</em>) – the vuln web’s name</li> | |
| 1321 | <li><strong>username</strong> (<em>str</em>) – </li> | |
| 1322 | <li><strong>password</strong> (<em>str</em>) – </li> | |
| 1323 | <li><strong>owned</strong> (<em>bool</em>) – is the note owned?</li> | |
| 1324 | <li><strong>owner</strong> (<em>str</em>) – the note’s owner</li> | |
| 1325 | <li><strong>description</strong> (<em>str</em>) – a description</li> | |
| 1326 | <li><strong>metadata</strong> – a collection of metadata. If you don’t know the metada. leave | |
| 1327 | on None, it will be created automatically.</li> | |
| 1328 | </ul> | |
| 1329 | </td> | |
| 1330 | </tr> | |
| 1331 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 1332 | </td> | |
| 1333 | </tr> | |
| 1334 | </tbody> | |
| 1335 | </table> | |
| 1336 | </dd></dl> | |
| 1337 | ||
| 1338 | <dl class="function"> | |
| 1339 | <dt id="persistence.server.server.create_command"> | |
| 1340 | <code class="descclassname">persistence.server.server.</code><code class="descname">create_command</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>command</em>, <em>duration=None</em>, <em>hostname=None</em>, <em>ip=None</em>, <em>itime=None</em>, <em>params=None</em>, <em>user=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#create_command"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.create_command" title="Permalink to this definition">¶</a></dt> | |
| 1341 | <dd><p>Creates a command.</p> | |
| 1342 | <table class="docutils field-list" frame="void" rules="none"> | |
| 1343 | <col class="field-name" /> | |
| 1344 | <col class="field-body" /> | |
| 1345 | <tbody valign="top"> | |
| 1346 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 1347 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the vuln web will be saved.</li> | |
| 1348 | <li><strong>id</strong> (<em>str</em>) – the id of the vuln web. Must be unique.</li> | |
| 1349 | <li><strong>command</strong> (<em>str</em>) – the command to be created</li> | |
| 1350 | <li><strong>duration</strong> (<em>str</em>) – </li> | |
| 1351 | <li><strong>hostname</strong> (<em>str</em>) – the hostname where the command was executed</li> | |
| 1352 | <li><strong>ip</strong> (<em>str</em>) – the ip of the host where the command was executed</li> | |
| 1353 | <li><strong>itime</strong> (<em>str</em>) – the time it took to run</li> | |
| 1354 | <li><strong>params</strong> (<em>str</em>) – the parameters given</li> | |
| 1355 | <li><strong>user</strong> (<em>str</em>) – the user that ran the command</li> | |
| 1356 | </ul> | |
| 1357 | </td> | |
| 1358 | </tr> | |
| 1359 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 1360 | </td> | |
| 1361 | </tr> | |
| 1362 | </tbody> | |
| 1363 | </table> | |
| 1364 | </dd></dl> | |
| 1365 | ||
| 1366 | <dl class="function"> | |
| 1367 | <dt id="persistence.server.server.update_command"> | |
| 1368 | <code class="descclassname">persistence.server.server.</code><code class="descname">update_command</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>id</em>, <em>command</em>, <em>duration=None</em>, <em>hostname=None</em>, <em>ip=None</em>, <em>itime=None</em>, <em>params=None</em>, <em>user=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#update_command"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.update_command" title="Permalink to this definition">¶</a></dt> | |
| 1369 | <dd><p>Updates a command.</p> | |
| 1370 | <table class="docutils field-list" frame="void" rules="none"> | |
| 1371 | <col class="field-name" /> | |
| 1372 | <col class="field-body" /> | |
| 1373 | <tbody valign="top"> | |
| 1374 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 1375 | <li><strong>workspace_name</strong> (<em>str</em>) – the name of the workspace where the vuln web will be saved.</li> | |
| 1376 | <li><strong>id</strong> (<em>str</em>) – the id of the vuln web. Must be unique.</li> | |
| 1377 | <li><strong>command</strong> (<em>str</em>) – the command to be created</li> | |
| 1378 | <li><strong>duration</strong> (<em>str</em>) – </li> | |
| 1379 | <li><strong>hostname</strong> (<em>str</em>) – the hostname where the command was executed</li> | |
| 1380 | <li><strong>ip</strong> (<em>str</em>) – the ip of the host where the command was executed</li> | |
| 1381 | <li><strong>itime</strong> (<em>str</em>) – the time it took to run</li> | |
| 1382 | <li><strong>params</strong> (<em>str</em>) – the parameters given</li> | |
| 1383 | <li><strong>user</strong> (<em>str</em>) – the user that ran the command</li> | |
| 1384 | </ul> | |
| 1385 | </td> | |
| 1386 | </tr> | |
| 1387 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 1388 | </td> | |
| 1389 | </tr> | |
| 1390 | </tbody> | |
| 1391 | </table> | |
| 1392 | </dd></dl> | |
| 1393 | ||
| 1394 | <dl class="function"> | |
| 1395 | <dt id="persistence.server.server.create_workspace"> | |
| 1396 | <code class="descclassname">persistence.server.server.</code><code class="descname">create_workspace</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>description</em>, <em>start_date</em>, <em>finish_date</em>, <em>customer=None</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#create_workspace"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.create_workspace" title="Permalink to this definition">¶</a></dt> | |
| 1397 | <dd><p>Create a workspace.</p> | |
| 1398 | <table class="docutils field-list" frame="void" rules="none"> | |
| 1399 | <col class="field-name" /> | |
| 1400 | <col class="field-body" /> | |
| 1401 | <tbody valign="top"> | |
| 1402 | <tr class="field-odd field"><th class="field-name">Parameters:</th><td class="field-body"><ul class="first simple"> | |
| 1403 | <li><strong>workspace_name</strong> (<em>str</em>) – the workspace’s name</li> | |
| 1404 | <li><strong>description</strong> (<em>str</em>) – a description for the worksapce</li> | |
| 1405 | <li><strong>start_date</strong> (<em>str</em>) – a date to represent when work began in the workspace</li> | |
| 1406 | <li><strong>finish_date</strong> (<em>str</em>) – a date to represent when work will be finished on the workspace</li> | |
| 1407 | <li><strong>customer</strong> (<em>str</em>) – the customer for which we are creating the workspace</li> | |
| 1408 | </ul> | |
| 1409 | </td> | |
| 1410 | </tr> | |
| 1411 | <tr class="field-even field"><th class="field-name">Returns:</th><td class="field-body"><p class="first last">A dictionary with the server’s response.</p> | |
| 1412 | </td> | |
| 1413 | </tr> | |
| 1414 | </tbody> | |
| 1415 | </table> | |
| 1416 | </dd></dl> | |
| 1417 | ||
| 1418 | <dl class="function"> | |
| 1419 | <dt id="persistence.server.server.delete_host"> | |
| 1420 | <code class="descclassname">persistence.server.server.</code><code class="descname">delete_host</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>host_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#delete_host"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.delete_host" title="Permalink to this definition">¶</a></dt> | |
| 1421 | <dd><p>Delete host of id host_id from the database.</p> | |
| 1422 | </dd></dl> | |
| 1423 | ||
| 1424 | <dl class="function"> | |
| 1425 | <dt id="persistence.server.server.delete_interface"> | |
| 1426 | <code class="descclassname">persistence.server.server.</code><code class="descname">delete_interface</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>interface_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#delete_interface"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.delete_interface" title="Permalink to this definition">¶</a></dt> | |
| 1427 | <dd><p>Delete interface of id interface_id from the database.</p> | |
| 1428 | </dd></dl> | |
| 1429 | ||
| 1430 | <dl class="function"> | |
| 1431 | <dt id="persistence.server.server.delete_service"> | |
| 1432 | <code class="descclassname">persistence.server.server.</code><code class="descname">delete_service</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>service_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#delete_service"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.delete_service" title="Permalink to this definition">¶</a></dt> | |
| 1433 | <dd><p>Delete service of id service_id from the database.</p> | |
| 1434 | </dd></dl> | |
| 1435 | ||
| 1436 | <dl class="function"> | |
| 1437 | <dt id="persistence.server.server.delete_vuln"> | |
| 1438 | <code class="descclassname">persistence.server.server.</code><code class="descname">delete_vuln</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>vuln_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#delete_vuln"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.delete_vuln" title="Permalink to this definition">¶</a></dt> | |
| 1439 | <dd><p>Delete vuln of id vuln_id from the database.</p> | |
| 1440 | </dd></dl> | |
| 1441 | ||
| 1442 | <dl class="function"> | |
| 1443 | <dt id="persistence.server.server.delete_note"> | |
| 1444 | <code class="descclassname">persistence.server.server.</code><code class="descname">delete_note</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>note_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#delete_note"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.delete_note" title="Permalink to this definition">¶</a></dt> | |
| 1445 | <dd><p>Delete note of id note_id from the database.</p> | |
| 1446 | </dd></dl> | |
| 1447 | ||
| 1448 | <dl class="function"> | |
| 1449 | <dt id="persistence.server.server.delete_credential"> | |
| 1450 | <code class="descclassname">persistence.server.server.</code><code class="descname">delete_credential</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>credential_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#delete_credential"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.delete_credential" title="Permalink to this definition">¶</a></dt> | |
| 1451 | <dd><p>Delete credential of id credential_id from the database.</p> | |
| 1452 | </dd></dl> | |
| 1453 | ||
| 1454 | <dl class="function"> | |
| 1455 | <dt id="persistence.server.server.delete_command"> | |
| 1456 | <code class="descclassname">persistence.server.server.</code><code class="descname">delete_command</code><span class="sig-paren">(</span><em>workspace_name</em>, <em>command_id</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#delete_command"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.delete_command" title="Permalink to this definition">¶</a></dt> | |
| 1457 | <dd><p>Delete command of id command_id from the database.</p> | |
| 1458 | </dd></dl> | |
| 1459 | ||
| 1460 | <dl class="function"> | |
| 1461 | <dt id="persistence.server.server.delete_workspace"> | |
| 1462 | <code class="descclassname">persistence.server.server.</code><code class="descname">delete_workspace</code><span class="sig-paren">(</span><em>workspace_name</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#delete_workspace"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.delete_workspace" title="Permalink to this definition">¶</a></dt> | |
| 1463 | <dd><p>Delete the couch database of id workspace_name</p> | |
| 1464 | </dd></dl> | |
| 1465 | ||
| 1466 | <dl class="function"> | |
| 1467 | <dt id="persistence.server.server.is_server_up"> | |
| 1468 | <code class="descclassname">persistence.server.server.</code><code class="descname">is_server_up</code><span class="sig-paren">(</span><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#is_server_up"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.is_server_up" title="Permalink to this definition">¶</a></dt> | |
| 1469 | <dd><p>Return True if we can stablish a connection with the server, | |
| 1470 | False otherwise.</p> | |
| 1471 | </dd></dl> | |
| 1472 | ||
| 1473 | <dl class="function"> | |
| 1474 | <dt id="persistence.server.server.test_server_url"> | |
| 1475 | <code class="descclassname">persistence.server.server.</code><code class="descname">check_server_url</code><span class="sig-paren">(</span><em>url_to_test</em><span class="sig-paren">)</span><a class="reference internal" href="_modules/persistence/server/server.html#test_server_url"><span class="viewcode-link">[source]</span></a><a class="headerlink" href="#persistence.server.server.test_server_url" title="Permalink to this definition">¶</a></dt> | |
| 1476 | <dd><p>Return True if the url_to_test is indeed a valid Faraday Server URL. | |
| 1477 | False otherwise.</p> | |
| 1478 | </dd></dl> | |
| 1479 | ||
| 1480 | </div> | |
| 1481 | </div> | |
| 1482 | ||
| 1483 | ||
| 1484 | </div> | |
| 1485 | </div> | |
| 1486 | <footer> | |
| 1487 | ||
| 1488 | ||
| 1489 | <hr/> | |
| 1490 | ||
| 1491 | <div role="contentinfo"> | |
| 1492 | <p> | |
| 1493 | © Copyright 2016, Infobyte. | |
| 1494 | ||
| 1495 | </p> | |
| 1496 | </div> | |
| 1497 | Built with <a href="http://sphinx-doc.org/">Sphinx</a> using a <a href="https://github.com/snide/sphinx_rtd_theme">theme</a> provided by <a href="https://readthedocs.org">Read the Docs</a>. | |
| 1498 | ||
| 1499 | </footer> | |
| 1500 | ||
| 1501 | </div> | |
| 1502 | </div> | |
| 1503 | ||
| 1504 | </section> | |
| 1505 | ||
| 1506 | </div> | |
| 1507 | ||
| 1508 | ||
| 1509 | ||
| 1510 | ||
| 1511 | ||
| 1512 | <script type="text/javascript"> | |
| 1513 | var DOCUMENTATION_OPTIONS = { | |
| 1514 | URL_ROOT:'./', | |
| 1515 | VERSION:'0.1', | |
| 1516 | COLLAPSE_INDEX:false, | |
| 1517 | FILE_SUFFIX:'.html', | |
| 1518 | HAS_SOURCE: true | |
| 1519 | }; | |
| 1520 | </script> | |
| 1521 | <script type="text/javascript" src="_static/jquery.js"></script> | |
| 1522 | <script type="text/javascript" src="_static/underscore.js"></script> | |
| 1523 | <script type="text/javascript" src="_static/doctools.js"></script> | |
| 1524 | ||
| 1525 | ||
| 1526 | ||
| 1527 | ||
| 1528 | ||
| 1529 | <script type="text/javascript" src="_static/js/theme.js"></script> | |
| 1530 | ||
| 1531 | ||
| 1532 | ||
| 1533 | ||
| 1534 | <script type="text/javascript"> | |
| 1535 | jQuery(function () { | |
| 1536 | SphinxRtdTheme.StickyNav.enable(); | |
| 1537 | }); | |
| 1538 | </script> | |
| 1539 | ||
| 1540 | ||
| 1541 | </body> | |
| 1542 | </html>⏎ |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | # | |
| 3 | # Faraday documentation build configuration file, created by | |
| 4 | # sphinx-quickstart on Fri Dec 9 14:53:21 2016. | |
| 5 | # | |
| 6 | # This file is execfile()d with the current directory set to its | |
| 7 | # containing dir. | |
| 8 | # | |
| 9 | # Note that not all possible configuration values are present in this | |
| 10 | # autogenerated file. | |
| 11 | # | |
| 12 | # All configuration values have a default; values that are commented out | |
| 13 | # serve to show the default. | |
| 14 | ||
| 15 | # If extensions (or modules to document with autodoc) are in another directory, | |
| 16 | # add these directories to sys.path here. If the directory is relative to the | |
| 17 | # documentation root, use os.path.abspath to make it absolute, like shown here. | |
| 18 | # | |
| 19 | from __future__ import absolute_import | |
| 20 | from __future__ import print_function | |
| 21 | import os | |
| 22 | import sys | |
| 23 | ||
| 24 | print(os.path.abspath('..')) | |
| 25 | sys.path.insert(0, os.path.abspath('..')) | |
| 26 | sys.path.insert(0, os.path.abspath('../../..')) | |
| 27 | ||
| 28 | # -- General configuration ------------------------------------------------ | |
| 29 | autoclass_content = 'both' | |
| 30 | autodoc_member_order = 'bysource' | |
| 31 | ||
| 32 | # If your documentation needs a minimal Sphinx version, state it here. | |
| 33 | # | |
| 34 | # needs_sphinx = '1.0' | |
| 35 | ||
| 36 | # Add any Sphinx extension module names here, as strings. They can be | |
| 37 | # extensions coming with Sphinx (named 'sphinx.ext.*') or your custom | |
| 38 | # ones. | |
| 39 | extensions = [ | |
| 40 | 'sphinx.ext.autodoc', | |
| 41 | 'sphinx.ext.viewcode', | |
| 42 | 'sphinx.ext.napoleon' | |
| 43 | ] | |
| 44 | ||
| 45 | # Add any paths that contain templates here, relative to this directory. | |
| 46 | templates_path = ['_templates'] | |
| 47 | ||
| 48 | # The suffix(es) of source filenames. | |
| 49 | # You can specify multiple suffix as a list of string: | |
| 50 | # | |
| 51 | # source_suffix = ['.rst', '.md'] | |
| 52 | source_suffix = '.rst' | |
| 53 | ||
| 54 | # The encoding of source files. | |
| 55 | # | |
| 56 | # source_encoding = 'utf-8-sig' | |
| 57 | ||
| 58 | # The master toctree document. | |
| 59 | master_doc = 'index' | |
| 60 | ||
| 61 | # General information about the project. | |
| 62 | project = 'Faraday' | |
| 63 | copyright = '2016, Infobyte' | |
| 64 | author = 'Infobyte' | |
| 65 | ||
| 66 | # The version info for the project you're documenting, acts as replacement for | |
| 67 | # |version| and |release|, also used in various other places throughout the | |
| 68 | # built documents. | |
| 69 | # | |
| 70 | # The short X.Y version. | |
| 71 | version = '0.1' | |
| 72 | # The full version, including alpha/beta/rc tags. | |
| 73 | release = '0.1' | |
| 74 | ||
| 75 | # The language for content autogenerated by Sphinx. Refer to documentation | |
| 76 | # for a list of supported languages. | |
| 77 | # | |
| 78 | # This is also used if you do content translation via gettext catalogs. | |
| 79 | # Usually you set "language" from the command line for these cases. | |
| 80 | language = None | |
| 81 | ||
| 82 | # There are two options for replacing |today|: either, you set today to some | |
| 83 | # non-false value, then it is used: | |
| 84 | # | |
| 85 | # today = '' | |
| 86 | # | |
| 87 | # Else, today_fmt is used as the format for a strftime call. | |
| 88 | # | |
| 89 | # today_fmt = '%B %d, %Y' | |
| 90 | ||
| 91 | # List of patterns, relative to source directory, that match files and | |
| 92 | # directories to ignore when looking for source files. | |
| 93 | # This patterns also effect to html_static_path and html_extra_path | |
| 94 | exclude_patterns = ['_build', 'Thumbs.db', '.DS_Store'] | |
| 95 | ||
| 96 | # The reST default role (used for this markup: `text`) to use for all | |
| 97 | # documents. | |
| 98 | # | |
| 99 | # default_role = None | |
| 100 | ||
| 101 | # If true, '()' will be appended to :func: etc. cross-reference text. | |
| 102 | # | |
| 103 | # add_function_parentheses = True | |
| 104 | ||
| 105 | # If true, the current module name will be prepended to all description | |
| 106 | # unit titles (such as .. function::). | |
| 107 | # | |
| 108 | # add_module_names = True | |
| 109 | ||
| 110 | # If true, sectionauthor and moduleauthor directives will be shown in the | |
| 111 | # output. They are ignored by default. | |
| 112 | # | |
| 113 | # show_authors = False | |
| 114 | ||
| 115 | # The name of the Pygments (syntax highlighting) style to use. | |
| 116 | pygments_style = 'sphinx' | |
| 117 | ||
| 118 | # A list of ignored prefixes for module index sorting. | |
| 119 | # modindex_common_prefix = [] | |
| 120 | ||
| 121 | # If true, keep warnings as "system message" paragraphs in the built documents. | |
| 122 | # keep_warnings = False | |
| 123 | ||
| 124 | # If true, `todo` and `todoList` produce output, else they produce nothing. | |
| 125 | todo_include_todos = False | |
| 126 | ||
| 127 | ||
| 128 | # -- Options for HTML output ---------------------------------------------- | |
| 129 | ||
| 130 | # The theme to use for HTML and HTML Help pages. See the documentation for | |
| 131 | # a list of builtin themes. | |
| 132 | # | |
| 133 | # html_theme = 'alabaster' | |
| 134 | import sphinx_rtd_theme | |
| 135 | html_theme = "sphinx_rtd_theme" | |
| 136 | html_theme_path = [sphinx_rtd_theme.get_html_theme_path()] | |
| 137 | ||
| 138 | ||
| 139 | # Theme options are theme-specific and customize the look and feel of a theme | |
| 140 | # further. For a list of options available for each theme, see the | |
| 141 | # documentation. | |
| 142 | # | |
| 143 | # html_theme_options = {} | |
| 144 | ||
| 145 | # Add any paths that contain custom themes here, relative to this directory. | |
| 146 | # html_theme_path = [] | |
| 147 | ||
| 148 | # The name for this set of Sphinx documents. | |
| 149 | # "<project> v<release> documentation" by default. | |
| 150 | # | |
| 151 | # html_title = 'Faraday v0.1' | |
| 152 | ||
| 153 | # A shorter title for the navigation bar. Default is the same as html_title. | |
| 154 | # | |
| 155 | # html_short_title = None | |
| 156 | ||
| 157 | # The name of an image file (relative to this directory) to place at the top | |
| 158 | # of the sidebar. | |
| 159 | # | |
| 160 | # html_logo = None | |
| 161 | ||
| 162 | # The name of an image file (relative to this directory) to use as a favicon of | |
| 163 | # the docs. This file should be a Windows icon file (.ico) being 16x16 or 32x32 | |
| 164 | # pixels large. | |
| 165 | # | |
| 166 | # html_favicon = None | |
| 167 | ||
| 168 | # Add any paths that contain custom static files (such as style sheets) here, | |
| 169 | # relative to this directory. They are copied after the builtin static files, | |
| 170 | # so a file named "default.css" will overwrite the builtin "default.css". | |
| 171 | html_static_path = ['_static'] | |
| 172 | ||
| 173 | # Add any extra paths that contain custom files (such as robots.txt or | |
| 174 | # .htaccess) here, relative to this directory. These files are copied | |
| 175 | # directly to the root of the documentation. | |
| 176 | # | |
| 177 | # html_extra_path = [] | |
| 178 | ||
| 179 | # If not None, a 'Last updated on:' timestamp is inserted at every page | |
| 180 | # bottom, using the given strftime format. | |
| 181 | # The empty string is equivalent to '%b %d, %Y'. | |
| 182 | # | |
| 183 | # html_last_updated_fmt = None | |
| 184 | ||
| 185 | # If true, SmartyPants will be used to convert quotes and dashes to | |
| 186 | # typographically correct entities. | |
| 187 | # | |
| 188 | # html_use_smartypants = True | |
| 189 | ||
| 190 | # Custom sidebar templates, maps document names to template names. | |
| 191 | # | |
| 192 | # html_sidebars = {} | |
| 193 | ||
| 194 | # Additional templates that should be rendered to pages, maps page names to | |
| 195 | # template names. | |
| 196 | # | |
| 197 | # html_additional_pages = {} | |
| 198 | ||
| 199 | # If false, no module index is generated. | |
| 200 | # | |
| 201 | # html_domain_indices = True | |
| 202 | ||
| 203 | # If false, no index is generated. | |
| 204 | # | |
| 205 | # html_use_index = True | |
| 206 | ||
| 207 | # If true, the index is split into individual pages for each letter. | |
| 208 | # | |
| 209 | # html_split_index = False | |
| 210 | ||
| 211 | # If true, links to the reST sources are added to the pages. | |
| 212 | # | |
| 213 | # html_show_sourcelink = True | |
| 214 | ||
| 215 | # If true, "Created using Sphinx" is shown in the HTML footer. Default is True. | |
| 216 | # | |
| 217 | # html_show_sphinx = True | |
| 218 | ||
| 219 | # If true, "(C) Copyright ..." is shown in the HTML footer. Default is True. | |
| 220 | # | |
| 221 | # html_show_copyright = True | |
| 222 | ||
| 223 | # If true, an OpenSearch description file will be output, and all pages will | |
| 224 | # contain a <link> tag referring to it. The value of this option must be the | |
| 225 | # base URL from which the finished HTML is served. | |
| 226 | # | |
| 227 | # html_use_opensearch = '' | |
| 228 | ||
| 229 | # This is the file name suffix for HTML files (e.g. ".xhtml"). | |
| 230 | # html_file_suffix = None | |
| 231 | ||
| 232 | # Language to be used for generating the HTML full-text search index. | |
| 233 | # Sphinx supports the following languages: | |
| 234 | # 'da', 'de', 'en', 'es', 'fi', 'fr', 'h', 'it', 'ja' | |
| 235 | # 'nl', 'no', 'pt', 'ro', 'r', 'sv', 'tr', 'zh' | |
| 236 | # | |
| 237 | # html_search_language = 'en' | |
| 238 | ||
| 239 | # A dictionary with options for the search language support, empty by default. | |
| 240 | # 'ja' uses this config value. | |
| 241 | # 'zh' user can custom change `jieba` dictionary path. | |
| 242 | # | |
| 243 | # html_search_options = {'type': 'default'} | |
| 244 | ||
| 245 | # The name of a javascript file (relative to the configuration directory) that | |
| 246 | # implements a search results scorer. If empty, the default will be used. | |
| 247 | # | |
| 248 | # html_search_scorer = 'scorer.js' | |
| 249 | ||
| 250 | # Output file base name for HTML help builder. | |
| 251 | htmlhelp_basename = 'Faradaydoc' | |
| 252 | ||
| 253 | # -- Options for LaTeX output --------------------------------------------- | |
| 254 | ||
| 255 | latex_elements = { | |
| 256 | # The paper size ('letterpaper' or 'a4paper'). | |
| 257 | # | |
| 258 | # 'papersize': 'letterpaper', | |
| 259 | ||
| 260 | # The font size ('10pt', '11pt' or '12pt'). | |
| 261 | # | |
| 262 | # 'pointsize': '10pt', | |
| 263 | ||
| 264 | # Additional stuff for the LaTeX preamble. | |
| 265 | # | |
| 266 | # 'preamble': '', | |
| 267 | ||
| 268 | # Latex figure (float) alignment | |
| 269 | # | |
| 270 | # 'figure_align': 'htbp', | |
| 271 | } | |
| 272 | ||
| 273 | # Grouping the document tree into LaTeX files. List of tuples | |
| 274 | # (source start file, target name, title, | |
| 275 | # author, documentclass [howto, manual, or own class]). | |
| 276 | latex_documents = [ | |
| 277 | (master_doc, 'Faraday.tex', 'Faraday Documentation', | |
| 278 | 'Infobyte', 'manual'), | |
| 279 | ] | |
| 280 | ||
| 281 | # The name of an image file (relative to this directory) to place at the top of | |
| 282 | # the title page. | |
| 283 | # | |
| 284 | # latex_logo = None | |
| 285 | ||
| 286 | # For "manual" documents, if this is true, then toplevel headings are parts, | |
| 287 | # not chapters. | |
| 288 | # | |
| 289 | # latex_use_parts = False | |
| 290 | ||
| 291 | # If true, show page references after internal links. | |
| 292 | # | |
| 293 | # latex_show_pagerefs = False | |
| 294 | ||
| 295 | # If true, show URL addresses after external links. | |
| 296 | # | |
| 297 | # latex_show_urls = False | |
| 298 | ||
| 299 | # Documents to append as an appendix to all manuals. | |
| 300 | # | |
| 301 | # latex_appendices = [] | |
| 302 | ||
| 303 | # It false, will not define \strong, \code, itleref, \crossref ... but only | |
| 304 | # \sphinxstrong, ..., \sphinxtitleref, ... To help avoid clash with user added | |
| 305 | # packages. | |
| 306 | # | |
| 307 | # latex_keep_old_macro_names = True | |
| 308 | ||
| 309 | # If false, no module index is generated. | |
| 310 | # | |
| 311 | # latex_domain_indices = True | |
| 312 | ||
| 313 | ||
| 314 | # -- Options for manual page output --------------------------------------- | |
| 315 | ||
| 316 | # One entry per manual page. List of tuples | |
| 317 | # (source start file, name, description, authors, manual section). | |
| 318 | man_pages = [ | |
| 319 | (master_doc, 'faraday', 'Faraday Documentation', | |
| 320 | [author], 1) | |
| 321 | ] | |
| 322 | ||
| 323 | # If true, show URL addresses after external links. | |
| 324 | # | |
| 325 | # man_show_urls = False | |
| 326 | ||
| 327 | ||
| 328 | # -- Options for Texinfo output ------------------------------------------- | |
| 329 | ||
| 330 | # Grouping the document tree into Texinfo files. List of tuples | |
| 331 | # (source start file, target name, title, author, | |
| 332 | # dir menu entry, description, category) | |
| 333 | texinfo_documents = [ | |
| 334 | (master_doc, 'Faraday', 'Faraday Documentation', | |
| 335 | author, 'Faraday', 'One line description of project.', | |
| 336 | 'Miscellaneous'), | |
| 337 | ] | |
| 338 | ||
| 339 | # Documents to append as an appendix to all manuals. | |
| 340 | # | |
| 341 | # texinfo_appendices = [] | |
| 342 | ||
| 343 | # If false, no module index is generated. | |
| 344 | # | |
| 345 | # texinfo_domain_indices = True | |
| 346 | ||
| 347 | # How to display URL addresses: 'footnote', 'no', or 'inline'. | |
| 348 | # | |
| 349 | # texinfo_show_urls = 'footnote' | |
| 350 | ||
| 351 | # If true, do not generate a @detailmenu in the "Top" node's menu. | |
| 352 | # | |
| 353 | # texinfo_no_detailmenu = False | |
| 354 | # I'm Py3⏎ |
| 0 | .. Faraday documentation master file, created by | |
| 1 | sphinx-quickstart on Fri Dec 9 14:53:21 2016. | |
| 2 | You can adapt this file completely to your liking, but it should at least | |
| 3 | contain the root `toctree` directive. | |
| 4 | ||
| 5 | Welcome to Faraday's documentation! | |
| 6 | =================================== | |
| 7 | ||
| 8 | Contents: | |
| 9 | ||
| 10 | .. toctree:: | |
| 11 | :maxdepth: 2 | |
| 12 | ||
| 13 | ||
| 14 | ||
| 15 | Indices and tables | |
| 16 | ================== | |
| 17 | ||
| 18 | * :ref:`genindex` | |
| 19 | * :ref:`modindex` | |
| 20 | * :ref:`search` | |
| 21 |
| 0 | @ECHO OFF | |
| 1 | ||
| 2 | REM Command file for Sphinx documentation | |
| 3 | ||
| 4 | if "%SPHINXBUILD%" == "" ( | |
| 5 | set SPHINXBUILD=sphinx-build | |
| 6 | ) | |
| 7 | set BUILDDIR=_build | |
| 8 | set ALLSPHINXOPTS=-d %BUILDDIR%/doctrees %SPHINXOPTS% . | |
| 9 | set I18NSPHINXOPTS=%SPHINXOPTS% . | |
| 10 | if NOT "%PAPER%" == "" ( | |
| 11 | set ALLSPHINXOPTS=-D latex_paper_size=%PAPER% %ALLSPHINXOPTS% | |
| 12 | set I18NSPHINXOPTS=-D latex_paper_size=%PAPER% %I18NSPHINXOPTS% | |
| 13 | ) | |
| 14 | ||
| 15 | if "%1" == "" goto help | |
| 16 | ||
| 17 | if "%1" == "help" ( | |
| 18 | :help | |
| 19 | echo.Please use `make ^<target^>` where ^<target^> is one of | |
| 20 | echo. html to make standalone HTML files | |
| 21 | echo. dirhtml to make HTML files named index.html in directories | |
| 22 | echo. singlehtml to make a single large HTML file | |
| 23 | echo. pickle to make pickle files | |
| 24 | echo. json to make JSON files | |
| 25 | echo. htmlhelp to make HTML files and a HTML help project | |
| 26 | echo. qthelp to make HTML files and a qthelp project | |
| 27 | echo. devhelp to make HTML files and a Devhelp project | |
| 28 | echo. epub to make an epub | |
| 29 | echo. epub3 to make an epub3 | |
| 30 | echo. latex to make LaTeX files, you can set PAPER=a4 or PAPER=letter | |
| 31 | echo. text to make text files | |
| 32 | echo. man to make manual pages | |
| 33 | echo. texinfo to make Texinfo files | |
| 34 | echo. gettext to make PO message catalogs | |
| 35 | echo. changes to make an overview over all changed/added/deprecated items | |
| 36 | echo. xml to make Docutils-native XML files | |
| 37 | echo. pseudoxml to make pseudoxml-XML files for display purposes | |
| 38 | echo. linkcheck to check all external links for integrity | |
| 39 | echo. doctest to run all doctests embedded in the documentation if enabled | |
| 40 | echo. coverage to run coverage check of the documentation if enabled | |
| 41 | echo. dummy to check syntax errors of document sources | |
| 42 | goto end | |
| 43 | ) | |
| 44 | ||
| 45 | if "%1" == "clean" ( | |
| 46 | for /d %%i in (%BUILDDIR%\*) do rmdir /q /s %%i | |
| 47 | del /q /s %BUILDDIR%\* | |
| 48 | goto end | |
| 49 | ) | |
| 50 | ||
| 51 | ||
| 52 | REM Check if sphinx-build is available and fallback to Python version if any | |
| 53 | %SPHINXBUILD% 1>NUL 2>NUL | |
| 54 | if errorlevel 9009 goto sphinx_python | |
| 55 | goto sphinx_ok | |
| 56 | ||
| 57 | :sphinx_python | |
| 58 | ||
| 59 | set SPHINXBUILD=python -m sphinx.__init__ | |
| 60 | %SPHINXBUILD% 2> nul | |
| 61 | if errorlevel 9009 ( | |
| 62 | echo. | |
| 63 | echo.The 'sphinx-build' command was not found. Make sure you have Sphinx | |
| 64 | echo.installed, then set the SPHINXBUILD environment variable to point | |
| 65 | echo.to the full path of the 'sphinx-build' executable. Alternatively you | |
| 66 | echo.may add the Sphinx directory to PATH. | |
| 67 | echo. | |
| 68 | echo.If you don't have Sphinx installed, grab it from | |
| 69 | echo.http://sphinx-doc.org/ | |
| 70 | exit /b 1 | |
| 71 | ) | |
| 72 | ||
| 73 | :sphinx_ok | |
| 74 | ||
| 75 | ||
| 76 | if "%1" == "html" ( | |
| 77 | %SPHINXBUILD% -b html %ALLSPHINXOPTS% %BUILDDIR%/html | |
| 78 | if errorlevel 1 exit /b 1 | |
| 79 | echo. | |
| 80 | echo.Build finished. The HTML pages are in %BUILDDIR%/html. | |
| 81 | goto end | |
| 82 | ) | |
| 83 | ||
| 84 | if "%1" == "dirhtml" ( | |
| 85 | %SPHINXBUILD% -b dirhtml %ALLSPHINXOPTS% %BUILDDIR%/dirhtml | |
| 86 | if errorlevel 1 exit /b 1 | |
| 87 | echo. | |
| 88 | echo.Build finished. The HTML pages are in %BUILDDIR%/dirhtml. | |
| 89 | goto end | |
| 90 | ) | |
| 91 | ||
| 92 | if "%1" == "singlehtml" ( | |
| 93 | %SPHINXBUILD% -b singlehtml %ALLSPHINXOPTS% %BUILDDIR%/singlehtml | |
| 94 | if errorlevel 1 exit /b 1 | |
| 95 | echo. | |
| 96 | echo.Build finished. The HTML pages are in %BUILDDIR%/singlehtml. | |
| 97 | goto end | |
| 98 | ) | |
| 99 | ||
| 100 | if "%1" == "pickle" ( | |
| 101 | %SPHINXBUILD% -b pickle %ALLSPHINXOPTS% %BUILDDIR%/pickle | |
| 102 | if errorlevel 1 exit /b 1 | |
| 103 | echo. | |
| 104 | echo.Build finished; now you can process the pickle files. | |
| 105 | goto end | |
| 106 | ) | |
| 107 | ||
| 108 | if "%1" == "json" ( | |
| 109 | %SPHINXBUILD% -b json %ALLSPHINXOPTS% %BUILDDIR%/json | |
| 110 | if errorlevel 1 exit /b 1 | |
| 111 | echo. | |
| 112 | echo.Build finished; now you can process the JSON files. | |
| 113 | goto end | |
| 114 | ) | |
| 115 | ||
| 116 | if "%1" == "htmlhelp" ( | |
| 117 | %SPHINXBUILD% -b htmlhelp %ALLSPHINXOPTS% %BUILDDIR%/htmlhelp | |
| 118 | if errorlevel 1 exit /b 1 | |
| 119 | echo. | |
| 120 | echo.Build finished; now you can run HTML Help Workshop with the ^ | |
| 121 | .hhp project file in %BUILDDIR%/htmlhelp. | |
| 122 | goto end | |
| 123 | ) | |
| 124 | ||
| 125 | if "%1" == "qthelp" ( | |
| 126 | %SPHINXBUILD% -b qthelp %ALLSPHINXOPTS% %BUILDDIR%/qthelp | |
| 127 | if errorlevel 1 exit /b 1 | |
| 128 | echo. | |
| 129 | echo.Build finished; now you can run "qcollectiongenerator" with the ^ | |
| 130 | .qhcp project file in %BUILDDIR%/qthelp, like this: | |
| 131 | echo.^> qcollectiongenerator %BUILDDIR%\qthelp\Faraday.qhcp | |
| 132 | echo.To view the help file: | |
| 133 | echo.^> assistant -collectionFile %BUILDDIR%\qthelp\Faraday.ghc | |
| 134 | goto end | |
| 135 | ) | |
| 136 | ||
| 137 | if "%1" == "devhelp" ( | |
| 138 | %SPHINXBUILD% -b devhelp %ALLSPHINXOPTS% %BUILDDIR%/devhelp | |
| 139 | if errorlevel 1 exit /b 1 | |
| 140 | echo. | |
| 141 | echo.Build finished. | |
| 142 | goto end | |
| 143 | ) | |
| 144 | ||
| 145 | if "%1" == "epub" ( | |
| 146 | %SPHINXBUILD% -b epub %ALLSPHINXOPTS% %BUILDDIR%/epub | |
| 147 | if errorlevel 1 exit /b 1 | |
| 148 | echo. | |
| 149 | echo.Build finished. The epub file is in %BUILDDIR%/epub. | |
| 150 | goto end | |
| 151 | ) | |
| 152 | ||
| 153 | if "%1" == "epub3" ( | |
| 154 | %SPHINXBUILD% -b epub3 %ALLSPHINXOPTS% %BUILDDIR%/epub3 | |
| 155 | if errorlevel 1 exit /b 1 | |
| 156 | echo. | |
| 157 | echo.Build finished. The epub3 file is in %BUILDDIR%/epub3. | |
| 158 | goto end | |
| 159 | ) | |
| 160 | ||
| 161 | if "%1" == "latex" ( | |
| 162 | %SPHINXBUILD% -b latex %ALLSPHINXOPTS% %BUILDDIR%/latex | |
| 163 | if errorlevel 1 exit /b 1 | |
| 164 | echo. | |
| 165 | echo.Build finished; the LaTeX files are in %BUILDDIR%/latex. | |
| 166 | goto end | |
| 167 | ) | |
| 168 | ||
| 169 | if "%1" == "latexpdf" ( | |
| 170 | %SPHINXBUILD% -b latex %ALLSPHINXOPTS% %BUILDDIR%/latex | |
| 171 | cd %BUILDDIR%/latex | |
| 172 | make all-pdf | |
| 173 | cd %~dp0 | |
| 174 | echo. | |
| 175 | echo.Build finished; the PDF files are in %BUILDDIR%/latex. | |
| 176 | goto end | |
| 177 | ) | |
| 178 | ||
| 179 | if "%1" == "latexpdfja" ( | |
| 180 | %SPHINXBUILD% -b latex %ALLSPHINXOPTS% %BUILDDIR%/latex | |
| 181 | cd %BUILDDIR%/latex | |
| 182 | make all-pdf-ja | |
| 183 | cd %~dp0 | |
| 184 | echo. | |
| 185 | echo.Build finished; the PDF files are in %BUILDDIR%/latex. | |
| 186 | goto end | |
| 187 | ) | |
| 188 | ||
| 189 | if "%1" == "text" ( | |
| 190 | %SPHINXBUILD% -b text %ALLSPHINXOPTS% %BUILDDIR%/text | |
| 191 | if errorlevel 1 exit /b 1 | |
| 192 | echo. | |
| 193 | echo.Build finished. The text files are in %BUILDDIR%/text. | |
| 194 | goto end | |
| 195 | ) | |
| 196 | ||
| 197 | if "%1" == "man" ( | |
| 198 | %SPHINXBUILD% -b man %ALLSPHINXOPTS% %BUILDDIR%/man | |
| 199 | if errorlevel 1 exit /b 1 | |
| 200 | echo. | |
| 201 | echo.Build finished. The manual pages are in %BUILDDIR%/man. | |
| 202 | goto end | |
| 203 | ) | |
| 204 | ||
| 205 | if "%1" == "texinfo" ( | |
| 206 | %SPHINXBUILD% -b texinfo %ALLSPHINXOPTS% %BUILDDIR%/texinfo | |
| 207 | if errorlevel 1 exit /b 1 | |
| 208 | echo. | |
| 209 | echo.Build finished. The Texinfo files are in %BUILDDIR%/texinfo. | |
| 210 | goto end | |
| 211 | ) | |
| 212 | ||
| 213 | if "%1" == "gettext" ( | |
| 214 | %SPHINXBUILD% -b gettext %I18NSPHINXOPTS% %BUILDDIR%/locale | |
| 215 | if errorlevel 1 exit /b 1 | |
| 216 | echo. | |
| 217 | echo.Build finished. The message catalogs are in %BUILDDIR%/locale. | |
| 218 | goto end | |
| 219 | ) | |
| 220 | ||
| 221 | if "%1" == "changes" ( | |
| 222 | %SPHINXBUILD% -b changes %ALLSPHINXOPTS% %BUILDDIR%/changes | |
| 223 | if errorlevel 1 exit /b 1 | |
| 224 | echo. | |
| 225 | echo.The overview file is in %BUILDDIR%/changes. | |
| 226 | goto end | |
| 227 | ) | |
| 228 | ||
| 229 | if "%1" == "linkcheck" ( | |
| 230 | %SPHINXBUILD% -b linkcheck %ALLSPHINXOPTS% %BUILDDIR%/linkcheck | |
| 231 | if errorlevel 1 exit /b 1 | |
| 232 | echo. | |
| 233 | echo.Link check complete; look for any errors in the above output ^ | |
| 234 | or in %BUILDDIR%/linkcheck/output.txt. | |
| 235 | goto end | |
| 236 | ) | |
| 237 | ||
| 238 | if "%1" == "doctest" ( | |
| 239 | %SPHINXBUILD% -b doctest %ALLSPHINXOPTS% %BUILDDIR%/doctest | |
| 240 | if errorlevel 1 exit /b 1 | |
| 241 | echo. | |
| 242 | echo.Testing of doctests in the sources finished, look at the ^ | |
| 243 | results in %BUILDDIR%/doctest/output.txt. | |
| 244 | goto end | |
| 245 | ) | |
| 246 | ||
| 247 | if "%1" == "coverage" ( | |
| 248 | %SPHINXBUILD% -b coverage %ALLSPHINXOPTS% %BUILDDIR%/coverage | |
| 249 | if errorlevel 1 exit /b 1 | |
| 250 | echo. | |
| 251 | echo.Testing of coverage in the sources finished, look at the ^ | |
| 252 | results in %BUILDDIR%/coverage/python.txt. | |
| 253 | goto end | |
| 254 | ) | |
| 255 | ||
| 256 | if "%1" == "xml" ( | |
| 257 | %SPHINXBUILD% -b xml %ALLSPHINXOPTS% %BUILDDIR%/xml | |
| 258 | if errorlevel 1 exit /b 1 | |
| 259 | echo. | |
| 260 | echo.Build finished. The XML files are in %BUILDDIR%/xml. | |
| 261 | goto end | |
| 262 | ) | |
| 263 | ||
| 264 | if "%1" == "pseudoxml" ( | |
| 265 | %SPHINXBUILD% -b pseudoxml %ALLSPHINXOPTS% %BUILDDIR%/pseudoxml | |
| 266 | if errorlevel 1 exit /b 1 | |
| 267 | echo. | |
| 268 | echo.Build finished. The pseudo-XML files are in %BUILDDIR%/pseudoxml. | |
| 269 | goto end | |
| 270 | ) | |
| 271 | ||
| 272 | if "%1" == "dummy" ( | |
| 273 | %SPHINXBUILD% -b dummy %ALLSPHINXOPTS% %BUILDDIR%/dummy | |
| 274 | if errorlevel 1 exit /b 1 | |
| 275 | echo. | |
| 276 | echo.Build finished. Dummy builder generates no files. | |
| 277 | goto end | |
| 278 | ) | |
| 279 | ||
| 280 | :end |
| 0 | server package | |
| 1 | ============== | |
| 2 | ||
| 3 | Submodules | |
| 4 | ---------- | |
| 5 | ||
| 6 | server.utils module | |
| 7 | ------------------- | |
| 8 | ||
| 9 | .. automodule:: persistence.server.server | |
| 10 | :members: | |
| 11 | :undoc-members: | |
| 12 | :show-inheritance: |
| 0 | #!/usr/bin/python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | ||
| 7 | """ | |
| 8 | from __future__ import absolute_import | |
| 9 | ||
| 10 | import logging | |
| 11 | from time import time | |
| 12 | import traceback | |
| 13 | from threading import Lock, Condition, RLock, Event | |
| 14 | from faraday.client.persistence.server import server | |
| 15 | from faraday.client.persistence.server.server_io_exceptions import (WrongObjectSignature, | |
| 16 | CantAccessConfigurationWithoutTheClient) | |
| 17 | ||
| 18 | from faraday.client.persistence.server.utils import (force_unique, | |
| 19 | get_host_properties, | |
| 20 | get_service_properties, | |
| 21 | get_vuln_properties, | |
| 22 | get_vuln_web_properties, | |
| 23 | get_note_properties, | |
| 24 | get_credential_properties, | |
| 25 | get_command_properties) | |
| 26 | ||
| 27 | from faraday.client.model.diff import ModelObjectDiff, MergeSolver | |
| 28 | from faraday.client.model.conflict import ConflictUpdate | |
| 29 | from functools import wraps | |
| 30 | from difflib import Differ | |
| 31 | ||
| 32 | ||
| 33 | FARADAY_UP = True | |
| 34 | MERGE_STRATEGY = None # you may change it the string 'NEW' to prefer new objects | |
| 35 | # you may ask why this can be None type or 'New' as a string | |
| 36 | # the answer is: Faraday. | |
| 37 | logger = logging.getLogger(__name__) | |
| 38 | ||
| 39 | ||
| 40 | def _conf(): | |
| 41 | if FARADAY_UP: | |
| 42 | from faraday.config.configuration import getInstanceConfiguration # pylint:disable=import-outside-toplevel | |
| 43 | return getInstanceConfiguration() | |
| 44 | else: | |
| 45 | raise CantAccessConfigurationWithoutTheClient | |
| 46 | ||
| 47 | ||
| 48 | def _get_merge_strategy(): | |
| 49 | try: | |
| 50 | merge_strategy = _conf().getMergeStrategy() | |
| 51 | except CantAccessConfigurationWithoutTheClient: | |
| 52 | merge_strategy = MERGE_STRATEGY | |
| 53 | return merge_strategy | |
| 54 | ||
| 55 | _CHANGES_LOCK = Lock() | |
| 56 | ||
| 57 | ||
| 58 | def get_changes_lock(): | |
| 59 | return _CHANGES_LOCK | |
| 60 | ||
| 61 | _LOCAL_CHANGES_ID_TO_REV = {} | |
| 62 | ||
| 63 | ||
| 64 | def local_changes(): | |
| 65 | return _LOCAL_CHANGES_ID_TO_REV | |
| 66 | ||
| 67 | ||
| 68 | def _ignore_in_changes(func): | |
| 69 | @wraps(func) | |
| 70 | def func_wrapper(*args, **kwargs): | |
| 71 | with get_changes_lock(): | |
| 72 | json = func(*args, **kwargs) | |
| 73 | if json.get('ok'): | |
| 74 | _LOCAL_CHANGES_ID_TO_REV[json['id']] = json['rev'] | |
| 75 | return json | |
| 76 | return func_wrapper | |
| 77 | ||
| 78 | ||
| 79 | def _flatten_dictionary(dictionary): | |
| 80 | """Given a dictionary with dictionaries inside, create a new flattened | |
| 81 | dictionary from that one and return it. | |
| 82 | ||
| 83 | It's not as general as it sounds. Do not use without looking at the | |
| 84 | implementation. | |
| 85 | """ | |
| 86 | flattened_dict = {} | |
| 87 | if dictionary.get('_id'): | |
| 88 | flattened_dict[u'_id'] = dictionary['_id'] | |
| 89 | if dictionary.get('id'): | |
| 90 | flattened_dict[u'id'] = dictionary['id'] | |
| 91 | for k, v in dictionary.get('value', dictionary).items(): | |
| 92 | if k != '_id': | |
| 93 | flattened_dict[k] = v | |
| 94 | return flattened_dict | |
| 95 | ||
| 96 | # NOTE: what is a faraday_ready object? | |
| 97 | # it's an instance of the classes defined on this module | |
| 98 | # created from a dictionary of faraday_ready_dictionaries | |
| 99 | # faraday_ready_dictionaries are the dictionaries gotten from | |
| 100 | # the server's json response with adecuate transformations applied to them | |
| 101 | # so as to be able to create the needed objects | |
| 102 | ||
| 103 | # i called them 'faraday ready' because they are _ready_ for the faraday | |
| 104 | # client, even if they come from the server: they should have the same | |
| 105 | # interface as the old style objects, from when we kept them on memory | |
| 106 | ||
| 107 | ||
| 108 | def _get_faraday_ready_objects(workspace_name, faraday_ready_object_dictionaries, | |
| 109 | faraday_object_name): | |
| 110 | """Takes a workspace name, a faraday object ('hosts', 'vulns', | |
| 111 | or 'services') a row_name (the name of the row where | |
| 112 | the information about the objects live) and an arbitray number | |
| 113 | of params to customize to request. | |
| 114 | ||
| 115 | Return a list of faraday objects: either | |
| 116 | Host, Service, Vuln, VulnWeb, Credential or Command. | |
| 117 | """ | |
| 118 | object_to_class = {'hosts': Host, | |
| 119 | 'vulns': Vuln, | |
| 120 | 'vulns_web': VulnWeb, | |
| 121 | 'services': Service, | |
| 122 | 'notes': Note, | |
| 123 | 'credentials': Credential, | |
| 124 | 'commands': Command} | |
| 125 | ||
| 126 | appropiate_class = object_to_class[faraday_object_name] | |
| 127 | faraday_objects = [] | |
| 128 | if faraday_ready_object_dictionaries: | |
| 129 | for object_dictionary in faraday_ready_object_dictionaries: | |
| 130 | flattened_object_dictionary = _flatten_dictionary(object_dictionary) | |
| 131 | faraday_objects.append(appropiate_class(flattened_object_dictionary, workspace_name)) | |
| 132 | return faraday_objects | |
| 133 | ||
| 134 | ||
| 135 | def _get_faraday_ready_hosts(workspace_name, hosts_dictionaries): | |
| 136 | """Return a list of Hosts created with the information found on hosts_dictionaries""" | |
| 137 | return _get_faraday_ready_objects(workspace_name, hosts_dictionaries, 'hosts') | |
| 138 | ||
| 139 | ||
| 140 | def _get_faraday_ready_vulns(workspace_name, vulns_dictionaries, vulns_type=None): | |
| 141 | """Return a list of Vuln or VulnWeb objects created with the information found on | |
| 142 | vulns_dictionaries. | |
| 143 | ||
| 144 | If vulns_type is specified, the returned list will only contain vuln_type objects. | |
| 145 | Otherwise, vuln_type will be inferred for every vuln_dictionary. | |
| 146 | """ | |
| 147 | if vulns_type: | |
| 148 | return _get_faraday_ready_objects(workspace_name, vulns_dictionaries, vulns_type) | |
| 149 | ||
| 150 | vulns = [vuln for vuln in vulns_dictionaries if vuln['value']['type'] == 'Vulnerability'] | |
| 151 | web_vulns = [w_vuln for w_vuln in vulns_dictionaries if w_vuln['value']['type'] == 'VulnerabilityWeb'] | |
| 152 | faraday_ready_vulns = _get_faraday_ready_objects(workspace_name, vulns, 'vulns') | |
| 153 | faraday_ready_web_vulns = _get_faraday_ready_objects(workspace_name, web_vulns, 'vulns_web') | |
| 154 | return faraday_ready_vulns + faraday_ready_web_vulns | |
| 155 | ||
| 156 | ||
| 157 | def _get_faraday_ready_services(workspace_name, services_dictionaries): | |
| 158 | """Return a list of Services created with the information found on services_dictionaries""" | |
| 159 | return _get_faraday_ready_objects(workspace_name, services_dictionaries, 'services') | |
| 160 | ||
| 161 | ||
| 162 | def _get_faraday_ready_credentials(workspace_name, credentials_dictionaries): | |
| 163 | """Return a list of Credentials created with the information found on credentials_dictionaries""" | |
| 164 | return _get_faraday_ready_objects(workspace_name, credentials_dictionaries, 'credentials') | |
| 165 | ||
| 166 | ||
| 167 | def _get_faraday_ready_notes(workspace_name, notes_dictionaries): | |
| 168 | """Return a list of Notes created with the information found on notes_dictionaries""" | |
| 169 | return _get_faraday_ready_objects(workspace_name, notes_dictionaries, 'notes') | |
| 170 | ||
| 171 | ||
| 172 | def _get_faraday_ready_commands(workspace_name, commands_dictionaries): | |
| 173 | """Return a list of Commands created with the information found on commands_dictionaries""" | |
| 174 | return _get_faraday_ready_objects(workspace_name, commands_dictionaries, 'commands') | |
| 175 | ||
| 176 | ||
| 177 | def get_changes_stream(workspace_name): | |
| 178 | """Take a workspace_name as a string. | |
| 179 | Return a couchDB change_stream with the changes relevant to the workspace | |
| 180 | of name workspace_name. | |
| 181 | The change stream will have heartbeet set to 1000. | |
| 182 | """ | |
| 183 | return server.get_changes_stream(workspace_name, | |
| 184 | heartbeat='1000') | |
| 185 | ||
| 186 | ||
| 187 | def get_hosts(workspace_name, **params): | |
| 188 | """Take a workspace name and a arbitrary number of params to customize the | |
| 189 | request. | |
| 190 | ||
| 191 | Return a list of Host objects. | |
| 192 | """ | |
| 193 | host_dictionaries = server.get_hosts(workspace_name, **params) | |
| 194 | return _get_faraday_ready_hosts(workspace_name, host_dictionaries) | |
| 195 | ||
| 196 | ||
| 197 | def get_host(workspace_name, host_id=None, **params): | |
| 198 | """Return the host by host_id. None if it can't be found.""" | |
| 199 | hosts = get_hosts(workspace_name, object_id=host_id, **params) | |
| 200 | if len(hosts) == 0: | |
| 201 | return | |
| 202 | else: | |
| 203 | if len(hosts) > 1: | |
| 204 | logger.warn('More than one hosts found. returning only one of them.') | |
| 205 | return hosts.pop() | |
| 206 | ||
| 207 | ||
| 208 | def get_all_vulns(workspace_name, **params): | |
| 209 | """Take a workspace name and a arbitrary number of params to customize the | |
| 210 | request. | |
| 211 | ||
| 212 | Return a list with Vuln and VulnWeb objects. | |
| 213 | """ | |
| 214 | vulns_dictionaries = server.get_all_vulns(workspace_name, **params) | |
| 215 | return _get_faraday_ready_vulns(workspace_name, vulns_dictionaries) | |
| 216 | ||
| 217 | ||
| 218 | def get_vulns(workspace_name, **params): | |
| 219 | """Take a workspace name and a arbitrary number of params to customize the | |
| 220 | request. | |
| 221 | ||
| 222 | Return a list of Vuln objects. | |
| 223 | """ | |
| 224 | vulns_dictionaries = server.get_vulns(workspace_name, **params) | |
| 225 | return _get_faraday_ready_vulns(workspace_name, vulns_dictionaries, vulns_type='vulns') | |
| 226 | ||
| 227 | ||
| 228 | def get_vuln(workspace_name, vuln_id=None, **params): | |
| 229 | """Return the Vuln of id vuln_id. None if not found.""" | |
| 230 | return force_unique(get_vulns(workspace_name, object_id=vuln_id, **params)) | |
| 231 | ||
| 232 | ||
| 233 | def get_web_vulns(workspace_name, **params): | |
| 234 | """Take a workspace name and a arbitrary number of params to customize the | |
| 235 | request. | |
| 236 | ||
| 237 | Return a list of VulnWeb objects. | |
| 238 | """ | |
| 239 | vulns_web_dictionaries = server.get_web_vulns(workspace_name, **params) | |
| 240 | return _get_faraday_ready_vulns(workspace_name, vulns_web_dictionaries, vulns_type='vulns_web') | |
| 241 | ||
| 242 | ||
| 243 | def get_web_vuln(workspace_name, vuln_id=None, **params): | |
| 244 | """Return the WebVuln of id vuln_id. None if not found.""" | |
| 245 | return force_unique(get_web_vulns(workspace_name, object_id=vuln_id, **params)) | |
| 246 | ||
| 247 | ||
| 248 | def get_services(workspace_name, **params): | |
| 249 | """Take a workspace name and a arbitrary number of params to customize the | |
| 250 | request. | |
| 251 | ||
| 252 | Return a list of Services objects | |
| 253 | """ | |
| 254 | services_dictionary = server.get_services(workspace_name, **params) | |
| 255 | # List inside of list, use the inside list... | |
| 256 | if len(services_dictionary) > 0 and type(services_dictionary[0]) == list: | |
| 257 | services_dictionary = services_dictionary[0] | |
| 258 | return _get_faraday_ready_services(workspace_name, services_dictionary) | |
| 259 | ||
| 260 | ||
| 261 | def get_service(workspace_name, service_id=None, **params): | |
| 262 | """Return the Service of id service_id. None if not found.""" | |
| 263 | return force_unique(get_services(workspace_name, object_id=service_id, **params)) | |
| 264 | ||
| 265 | ||
| 266 | def get_credentials(workspace_name, **params): | |
| 267 | """Take a workspace name and a arbitrary number of params to customize the | |
| 268 | request. | |
| 269 | ||
| 270 | Return a list of Credential objects | |
| 271 | """ | |
| 272 | credentials_dictionary = server.get_credentials(workspace_name, **params) | |
| 273 | return _get_faraday_ready_credentials(workspace_name, credentials_dictionary) | |
| 274 | ||
| 275 | ||
| 276 | def get_credential(workspace_name, credential_id=None, **params): | |
| 277 | """Return the Credential of id credential_id. None if not found.""" | |
| 278 | return force_unique(get_credentials(workspace_name, id=credential_id, **params)) | |
| 279 | ||
| 280 | ||
| 281 | def get_notes(workspace_name, **params): | |
| 282 | """Take a workspace name and a arbitrary number of params to customize the | |
| 283 | request. | |
| 284 | ||
| 285 | Return a list of Note objects | |
| 286 | """ | |
| 287 | notes_dictionary = server.get_notes(workspace_name, **params) | |
| 288 | return _get_faraday_ready_notes(workspace_name, notes_dictionary) | |
| 289 | ||
| 290 | ||
| 291 | def get_note(workspace_name, note_id): | |
| 292 | """Return the Note of id note_id. None if not found.""" | |
| 293 | return force_unique(get_notes(workspace_name, id=note_id)) | |
| 294 | ||
| 295 | ||
| 296 | def get_workspace(workspace_name): | |
| 297 | """Return the Workspace of id workspace_name. None if not found.""" | |
| 298 | workspace = server.get_workspace(workspace_name) | |
| 299 | return _Workspace(workspace, workspace_name) if workspace else None | |
| 300 | ||
| 301 | ||
| 302 | def get_commands(workspace_name, **params): | |
| 303 | """Take a workspace name and a arbitrary number of params to customize the | |
| 304 | request. | |
| 305 | ||
| 306 | Return a list of Command objects | |
| 307 | """ | |
| 308 | commands_dictionary = server.get_commands(workspace_name, **params) | |
| 309 | return _get_faraday_ready_commands(workspace_name, commands_dictionary) | |
| 310 | ||
| 311 | ||
| 312 | def get_command(workspace_name, command_id): | |
| 313 | """Return the Command of id command_id. None if not found.""" | |
| 314 | return force_unique(get_commands(workspace_name, id=command_id)) | |
| 315 | ||
| 316 | ||
| 317 | def get_object(workspace_name, object_signature, object_id): | |
| 318 | """Given a workspace name, an object_signature as string and an arbitrary | |
| 319 | number of query params, return a list a dictionaries containg information | |
| 320 | about 'object_signature' objects matching the query. | |
| 321 | ||
| 322 | object_signature must be either 'Host', 'Vulnerability', 'VulnerabilityWeb', | |
| 323 | 'Service', 'Cred', 'Note' or 'CommandRunInformation'. | |
| 324 | Will raise an WrongObjectSignature error if this condition is not met. | |
| 325 | """ | |
| 326 | object_to_func = {Host.class_signature: get_host, | |
| 327 | Vuln.class_signature: get_vuln, | |
| 328 | VulnWeb.class_signature: get_web_vuln, | |
| 329 | Service.class_signature: get_service, | |
| 330 | Credential.class_signature: get_credential, | |
| 331 | Note.class_signature: get_note, | |
| 332 | Command.class_signature: get_command} | |
| 333 | try: | |
| 334 | appropiate_function = object_to_func[object_signature] | |
| 335 | except KeyError: | |
| 336 | raise WrongObjectSignature(object_signature) | |
| 337 | ||
| 338 | return appropiate_function(workspace_name, object_id) | |
| 339 | ||
| 340 | ||
| 341 | def get_deleted_object_name_and_type(workspace_name, object_id): | |
| 342 | """Return a tupe of (name, type) for the deleted object of object_id, | |
| 343 | if it can get around CouchDB to do it. Else None""" | |
| 344 | obj_dict = server.get_object_before_last_revision(workspace_name, object_id) | |
| 345 | return (obj_dict['name'], obj_dict['type']) if obj_dict else (None, None) | |
| 346 | ||
| 347 | ||
| 348 | @_ignore_in_changes | |
| 349 | def create_host(workspace_name, host, command_id=None): | |
| 350 | """Take a workspace_name and a host object and save it to the sever. | |
| 351 | ||
| 352 | Return the server's json response as a dictionary. | |
| 353 | """ | |
| 354 | host_properties = get_host_properties(host) | |
| 355 | ip = host_properties.pop('ip', None) | |
| 356 | if not ip: | |
| 357 | logger.error('Trying to create host without ip') | |
| 358 | return server.create_host(workspace_name, command_id, ip, **host_properties) | |
| 359 | ||
| 360 | ||
| 361 | @_ignore_in_changes | |
| 362 | def update_host(workspace_name, host, command_id): | |
| 363 | """Take a workspace_name and a host object and update it in the sever. | |
| 364 | ||
| 365 | Return the server's json response as a dictionary. | |
| 366 | """ | |
| 367 | host_properties = get_host_properties(host) | |
| 368 | return server.update_host(workspace_name, command_id, host.getID(), **host_properties) | |
| 369 | ||
| 370 | ||
| 371 | @_ignore_in_changes | |
| 372 | def create_service(workspace_name, service, command_id=None): | |
| 373 | """Take a workspace_name and a service object and save it to the sever. | |
| 374 | Return the server's json response as a dictionary. | |
| 375 | """ | |
| 376 | service_properties = get_service_properties(service) | |
| 377 | return server.create_service(workspace_name, command_id, **service_properties) | |
| 378 | ||
| 379 | ||
| 380 | @_ignore_in_changes | |
| 381 | def update_service(workspace_name, service, command_id): | |
| 382 | """Take a workspace_name and an service object and update it in the sever. | |
| 383 | ||
| 384 | Return the server's json response as a dictionary. | |
| 385 | """ | |
| 386 | service_properties = get_service_properties(service) | |
| 387 | return server.update_service(workspace_name, command_id, service.getID(), **service_properties) | |
| 388 | ||
| 389 | ||
| 390 | @_ignore_in_changes | |
| 391 | def create_vuln(workspace_name, vuln, command_id=None): | |
| 392 | """Take a workspace_name and an vulnerability object and save it to the | |
| 393 | sever. The rev parameter must be provided if you are updating the object. | |
| 394 | Return the server's json response as a dictionary. | |
| 395 | """ | |
| 396 | vuln_properties = get_vuln_properties(vuln) | |
| 397 | return server.create_vuln(workspace_name, command_id, **vuln_properties) | |
| 398 | ||
| 399 | ||
| 400 | @_ignore_in_changes | |
| 401 | def update_vuln(workspace_name, vuln, command_id=None): | |
| 402 | """Take a workspace_name and a Vuln object and update it in the sever. | |
| 403 | ||
| 404 | Return the server's json response as a dictionary. | |
| 405 | """ | |
| 406 | vuln_properties = get_vuln_properties(vuln) | |
| 407 | return server.update_vuln(workspace_name, command_id, vuln.getID(), **vuln_properties) | |
| 408 | ||
| 409 | ||
| 410 | @_ignore_in_changes | |
| 411 | def create_vuln_web(workspace_name, vuln_web, command_id=None): | |
| 412 | """Take a workspace_name and an vulnerabilityWeb object and save it to the | |
| 413 | sever. | |
| 414 | Return the server's json response as a dictionary. | |
| 415 | """ | |
| 416 | vuln_web_properties = get_vuln_web_properties(vuln_web) | |
| 417 | return server.create_vuln_web(workspace_name, command_id, **vuln_web_properties) | |
| 418 | ||
| 419 | ||
| 420 | @_ignore_in_changes | |
| 421 | def update_vuln_web(workspace_name, vuln_web, command_id=None): | |
| 422 | """Take a workspace_name and a VulnWeb object and update it in the sever. | |
| 423 | ||
| 424 | Return the server's json response as a dictionary. | |
| 425 | """ | |
| 426 | vuln_web_properties = get_vuln_web_properties(vuln_web) | |
| 427 | return server.update_vuln_web(workspace_name, command_id, vuln_web.getID(), **vuln_web_properties) | |
| 428 | ||
| 429 | ||
| 430 | @_ignore_in_changes | |
| 431 | def create_note(workspace_name, note, command_id=None): | |
| 432 | """Take a workspace_name and an note object and save it to the sever. | |
| 433 | Return the server's json response as a dictionary. | |
| 434 | """ | |
| 435 | note_properties = get_note_properties(note) | |
| 436 | return server.create_note(workspace_name, command_id, **note_properties) | |
| 437 | ||
| 438 | ||
| 439 | @_ignore_in_changes | |
| 440 | def update_note(workspace_name, note, command_id): | |
| 441 | """Take a workspace_name and a Note object and update it in the sever. | |
| 442 | Return the server's json response as a dictionary. | |
| 443 | """ | |
| 444 | note_properties = get_note_properties(note) | |
| 445 | return server.update_note(workspace_name, command_id, note.getID(), **note_properties) | |
| 446 | ||
| 447 | ||
| 448 | @_ignore_in_changes | |
| 449 | def create_credential(workspace_name, credential, command_id=None): | |
| 450 | """Take a workspace_name and an credential object and save it to the sever. | |
| 451 | Return the server's json response as a dictionary. | |
| 452 | """ | |
| 453 | credential_properties = get_credential_properties(credential) | |
| 454 | return server.create_credential(workspace_name, command_id, **credential_properties) | |
| 455 | ||
| 456 | ||
| 457 | @_ignore_in_changes | |
| 458 | def update_credential(workspace_name, credential, command_id): | |
| 459 | """Take a workspace_name and a Credential object and update it in the sever. | |
| 460 | Return the server's json response as a dictionary. | |
| 461 | """ | |
| 462 | credential_properties = get_credential_properties(credential) | |
| 463 | return server.update_credential(workspace_name, command_id, credential.getID(), **credential_properties) | |
| 464 | ||
| 465 | ||
| 466 | @_ignore_in_changes | |
| 467 | def create_command(workspace_name, command, command_id): | |
| 468 | """ | |
| 469 | This function uses command_id for compatibility (a ~duck typing idea). | |
| 470 | command_id will be always None here since we want to create the command. | |
| 471 | ||
| 472 | :param workspace_name: workspace to save the command | |
| 473 | :param command_id: Not used! | |
| 474 | :param command: dict with command date | |
| 475 | :return: | |
| 476 | """ | |
| 477 | command_properties = get_command_properties(command) | |
| 478 | return server.create_command(workspace_name, **command_properties) | |
| 479 | ||
| 480 | ||
| 481 | @_ignore_in_changes | |
| 482 | def update_command(workspace_name, command, command_id): | |
| 483 | """Take a workspace_name and a Command object and update it in the sever. | |
| 484 | Return the server's json response as a dictionary. | |
| 485 | """ | |
| 486 | command_properties = get_command_properties(command) | |
| 487 | return server.update_command(workspace_name, command.getID(), **command_properties) | |
| 488 | ||
| 489 | ||
| 490 | def create_object(workspace_name, object_signature, obj, command_id): | |
| 491 | """Given a workspace name, an object_signature as string and obj, a Faraday | |
| 492 | object, save that object on the server. | |
| 493 | ||
| 494 | object_signature must match the type of the object. | |
| 495 | ||
| 496 | object_signature must be either 'Host', 'Vulnerability', 'VulnerabilityWeb', | |
| 497 | 'Service', 'Cred', 'Note' or 'CommandRunInformation'. | |
| 498 | Will raise an WrongObjectSignature error if this condition is not met. | |
| 499 | """ | |
| 500 | object_to_func = {Host.class_signature: create_host, | |
| 501 | Vuln.class_signature: create_vuln, | |
| 502 | VulnWeb.class_signature: create_vuln_web, | |
| 503 | Service.class_signature: create_service, | |
| 504 | Credential.class_signature: create_credential, | |
| 505 | Note.class_signature: create_note, | |
| 506 | Command.class_signature: create_command} | |
| 507 | try: | |
| 508 | appropiate_function = object_to_func[object_signature] | |
| 509 | except KeyError: | |
| 510 | raise WrongObjectSignature(object_signature) | |
| 511 | ||
| 512 | return appropiate_function(workspace_name, obj, command_id) | |
| 513 | ||
| 514 | ||
| 515 | def update_object(workspace_name, object_signature, obj, command_id): | |
| 516 | """Given a workspace name, an object_signature as string and obj, a Faraday | |
| 517 | object, update that object on the server. | |
| 518 | ||
| 519 | object_signature must match the type of the object. | |
| 520 | ||
| 521 | object_signature must be either 'Host', 'Vulnerability', 'VulnerabilityWeb', | |
| 522 | 'Service', 'Cred', 'Note' or 'CommandRunInformation'. | |
| 523 | Will raise an WrongObjectSignature error if this condition is not met. | |
| 524 | ||
| 525 | """ | |
| 526 | object_to_func = {Host.class_signature: update_host, | |
| 527 | Vuln.class_signature: update_vuln, | |
| 528 | VulnWeb.class_signature: update_vuln_web, | |
| 529 | Service.class_signature: update_service, | |
| 530 | Credential.class_signature: update_credential, | |
| 531 | Note.class_signature: update_note, | |
| 532 | Command.class_signature: update_command} | |
| 533 | try: | |
| 534 | appropiate_function = object_to_func[object_signature] | |
| 535 | except KeyError: | |
| 536 | raise WrongObjectSignature(object_signature) | |
| 537 | ||
| 538 | return appropiate_function(workspace_name, obj, command_id) | |
| 539 | ||
| 540 | ||
| 541 | def create_workspace(workspace_name, description, start_date, finish_date, | |
| 542 | customer=None): | |
| 543 | """Take the workspace_name and create the database first, | |
| 544 | then the workspace's document. | |
| 545 | Return the server's json response as a dictionary, if it can. If the | |
| 546 | DB couldn't be created, it will return None. If the DB could be created | |
| 547 | but there was a problem creating its basic documents, it will delete | |
| 548 | the document an raise the corresponding error. | |
| 549 | """ | |
| 550 | return server.create_workspace(workspace_name, description, | |
| 551 | start_date, finish_date, customer) | |
| 552 | ||
| 553 | ||
| 554 | def get_workspace_summary(workspace_name): | |
| 555 | """Return the workspace summary as a dictionary | |
| 556 | """ | |
| 557 | return server.get_workspace_summary(workspace_name) | |
| 558 | ||
| 559 | ||
| 560 | def get_workspace_numbers(workspace_name): | |
| 561 | """Return a tuple with the number of hosts, services and vulns | |
| 562 | on the workspace of name workspace_name. | |
| 563 | """ | |
| 564 | return server.get_workspace_numbers(workspace_name) | |
| 565 | ||
| 566 | ||
| 567 | def get_hosts_number(workspace_name, **params): | |
| 568 | """Return the number of hosts found on the workspace of name workspace_name | |
| 569 | """ | |
| 570 | return server.get_hosts_number(workspace_name, **params) | |
| 571 | ||
| 572 | ||
| 573 | def get_services_number(workspace_name, **params): | |
| 574 | """Return the number of services found on the workspace of name workspace_name | |
| 575 | """ | |
| 576 | return server.get_services_number(workspace_name, **params) | |
| 577 | ||
| 578 | ||
| 579 | def get_vulns_number(workspace_name, **params): | |
| 580 | """Return the number of vulns found on the workspace of name workspace_name | |
| 581 | """ | |
| 582 | return server.get_vulns_number(workspace_name, **params) | |
| 583 | ||
| 584 | # NOTE: the delete functions are actually the same. | |
| 585 | # there's no difference between delete_host and | |
| 586 | # except for their names. | |
| 587 | # maybe implement some kind of validation in the future? | |
| 588 | ||
| 589 | ||
| 590 | @_ignore_in_changes | |
| 591 | def delete_host(workspace_name, host_id): | |
| 592 | """Delete the host of id host_id on workspace workspace_name. | |
| 593 | Return the json response from the server. | |
| 594 | """ | |
| 595 | return server.delete_host(workspace_name, host_id) | |
| 596 | ||
| 597 | ||
| 598 | @_ignore_in_changes | |
| 599 | def delete_service(workspace_name, service_id): | |
| 600 | """Delete the service of id service_id on workspace workspace_name. | |
| 601 | Return the json response from the server. | |
| 602 | """ | |
| 603 | return server.delete_service(workspace_name, service_id) | |
| 604 | ||
| 605 | ||
| 606 | @_ignore_in_changes | |
| 607 | def delete_vuln(workspace_name, vuln_id): | |
| 608 | """Delete the vuln of id vuln_id on workspace workspace_name. | |
| 609 | Return the json response from the server. | |
| 610 | """ | |
| 611 | return server.delete_vuln(workspace_name, vuln_id) | |
| 612 | ||
| 613 | ||
| 614 | @_ignore_in_changes | |
| 615 | def delete_note(workspace_name, note_id): | |
| 616 | """Delete the note of id note_id on workspace workspace_name. | |
| 617 | Return the json response from the server. | |
| 618 | """ | |
| 619 | return server.delete_note(workspace_name, note_id) | |
| 620 | ||
| 621 | ||
| 622 | @_ignore_in_changes | |
| 623 | def delete_credential(workspace_name, credential_id): | |
| 624 | """Delete the credential of id credential_id on workspace workspace_name. | |
| 625 | Return the json response from the server. | |
| 626 | """ | |
| 627 | return server.delete_credential(workspace_name, credential_id) | |
| 628 | ||
| 629 | ||
| 630 | @_ignore_in_changes | |
| 631 | def delete_vuln_web(workspace_name, vuln_id): | |
| 632 | """Delete the vulnweb of id vulnweb_id on workspace workspace_name. | |
| 633 | Return the json response from the server. | |
| 634 | """ | |
| 635 | return server.delete_vuln(workspace_name, vuln_id) | |
| 636 | ||
| 637 | ||
| 638 | @_ignore_in_changes | |
| 639 | def delete_command(workspace_name, command_id): | |
| 640 | """Delete the command of id command_id on workspace workspace_name. | |
| 641 | Return the json response from the server. | |
| 642 | """ | |
| 643 | return server.delete_command(workspace_name, command_id) | |
| 644 | ||
| 645 | ||
| 646 | def delete_object(workspace_name, object_signature, obj_id): | |
| 647 | """Given a workspace name, an object_signature as string and an object id. | |
| 648 | ||
| 649 | object_signature must be either 'Host', 'Vulnerability', 'VulnerabilityWeb', | |
| 650 | 'Service', 'Cred', 'Note' or 'CommandRunInformation'. | |
| 651 | Will raise an WrongObjectSignature error if this condition is not met. | |
| 652 | """ | |
| 653 | object_to_func = {Host.class_signature: delete_host, | |
| 654 | Vuln.class_signature: delete_vuln, | |
| 655 | VulnWeb.class_signature: delete_vuln_web, | |
| 656 | Service.class_signature: delete_service, | |
| 657 | Credential.class_signature: delete_credential, | |
| 658 | Note.class_signature: delete_note, | |
| 659 | Command.class_signature: delete_command} | |
| 660 | try: | |
| 661 | appropiate_function = object_to_func[object_signature] | |
| 662 | except KeyError: | |
| 663 | raise WrongObjectSignature(object_signature) | |
| 664 | ||
| 665 | return appropiate_function(workspace_name, obj_id) | |
| 666 | ||
| 667 | ||
| 668 | def delete_workspace(workspace_name): | |
| 669 | """Tries to delete the worskpace workspace_name and returns the json | |
| 670 | response. You should always try/except this function, at least catching | |
| 671 | server.Unathorized exception. | |
| 672 | """ | |
| 673 | return server.delete_workspace(workspace_name) | |
| 674 | ||
| 675 | ||
| 676 | def get_workspaces_names(): | |
| 677 | """Return a list with all the workspace names available.""" | |
| 678 | active_workspaces = list(filter(lambda ws: ws['active'], server.get_workspaces_names())) | |
| 679 | return [ws['name'] for ws in active_workspaces] | |
| 680 | ||
| 681 | ||
| 682 | def server_info(): | |
| 683 | """True if server is up, False otherwise.""" | |
| 684 | return server.server_info() | |
| 685 | ||
| 686 | ||
| 687 | def check_server_url(url_to_test): | |
| 688 | """Return True if url_to_test/_api/info is accessible, False otherwise""" | |
| 689 | return server.check_server_url(url_to_test) | |
| 690 | ||
| 691 | ||
| 692 | # NOTE: the whole 'which arguments are mandatory and which type should they be" | |
| 693 | # should probably be reviewed in a nice developmet meeting where | |
| 694 | # I think there are several # discrepancies between the models here, | |
| 695 | # those on the server and the parameters the apis specify, | |
| 696 | # and this leads to potential dissaster. Remember params? | |
| 697 | class ModelBase: | |
| 698 | """A model for all the Faraday Objects. | |
| 699 | There should be a one to one correspondance with the jsons the faraday | |
| 700 | server gives through apis and the classes inheriting from this one. | |
| 701 | That is: you can view this classes as an python-object representation | |
| 702 | of the server's json or viceversa. | |
| 703 | ||
| 704 | As all the classes take the obj dictionary as an mandatory parameter. | |
| 705 | The obj dictionary contains the information of the object we need to create | |
| 706 | an instance of. To specify a default argument for the objects attributes, | |
| 707 | use the .get method for dictionaries. Try to specifiy a default value that | |
| 708 | matches the type of the value you expect. | |
| 709 | ||
| 710 | All of the values used from the obj dictionary that are set to be | |
| 711 | non-nullable on the server's models (server/models.py) should be given a | |
| 712 | sane default argument, EXCEPT for those where we can't provide a one. | |
| 713 | For example, we can't provide a sane default argument for ID, that should be | |
| 714 | given to us and indeed raise an exception if it wasn't. We can provide | |
| 715 | a default argument for 'description': if nothing came, assume empty string, | |
| 716 | """ | |
| 717 | def __init__(self, obj, workspace_name): | |
| 718 | self._workspace_name = workspace_name | |
| 719 | self._server_id = obj.get('_id', None) | |
| 720 | self.id = obj.get('id', self._server_id) | |
| 721 | self.name = obj.get('name') | |
| 722 | self.description = obj.get('description', "") | |
| 723 | self.owned = obj.get('owned', False) | |
| 724 | self.owner = obj.get('owner', '') | |
| 725 | self._metadata = obj.get('metadata', Metadata(self.owner)) | |
| 726 | self.parent_id = obj.get('parent') | |
| 727 | self.updates = [] | |
| 728 | self.id_available = Event() | |
| 729 | if self.id is not None: | |
| 730 | self.id_available.set() | |
| 731 | self.parent_type = obj.get('parent_type', None) | |
| 732 | ||
| 733 | def getParentType(self): | |
| 734 | return self.parent_type | |
| 735 | ||
| 736 | def getParent(self): | |
| 737 | return self.parent_id | |
| 738 | ||
| 739 | def setParent(self, parent_id): | |
| 740 | self.parent_id = parent_id | |
| 741 | ||
| 742 | def setParentType(self, parent_type): | |
| 743 | self.parent_type = parent_type | |
| 744 | ||
| 745 | def setID(self, id): | |
| 746 | if id: | |
| 747 | self.id = id | |
| 748 | self.id_available.set() | |
| 749 | ||
| 750 | def getID(self): | |
| 751 | # getId will wait until the id is not None | |
| 752 | timeout = 1 | |
| 753 | retries = 1 | |
| 754 | max_retries = 4 | |
| 755 | while retries <= max_retries and self.id is None: | |
| 756 | if timeout >= 8: | |
| 757 | logger.info('Retrying getID timeout {0}'.format(timeout)) | |
| 758 | self.id_available.wait(timeout=timeout) | |
| 759 | timeout = timeout << retries - 1 | |
| 760 | retries += 1 | |
| 761 | return self.id | |
| 762 | ||
| 763 | @staticmethod | |
| 764 | def publicattrsrefs(): | |
| 765 | return {'Description': 'description', | |
| 766 | 'Name': 'name', | |
| 767 | 'Owned': 'owned'} | |
| 768 | ||
| 769 | def defaultValues(self): | |
| 770 | return [-1, 0, '', 'None', 'none', 'unknown', None, [], {}] | |
| 771 | ||
| 772 | def propertyTieBreaker(self, key, prop1, prop2): | |
| 773 | """ Breakes the conflict between two properties. If either of them | |
| 774 | is a default value returns the good one. | |
| 775 | If neither returns the default value. | |
| 776 | If conflicting returns a tuple with the values """ | |
| 777 | if prop1 in self.defaultValues(): | |
| 778 | return prop2 | |
| 779 | elif prop2 in self.defaultValues(): | |
| 780 | return prop1 | |
| 781 | elif self.tieBreakable(key): | |
| 782 | return self.tieBreak(key, prop1, prop2) | |
| 783 | else: | |
| 784 | return (prop1, prop2) | |
| 785 | ||
| 786 | def tieBreakable(self, key): | |
| 787 | """ | |
| 788 | Return true if we can auto resolve this conflict. | |
| 789 | """ | |
| 790 | return False | |
| 791 | ||
| 792 | def tieBreak(self, key, prop1, prop2): | |
| 793 | """ | |
| 794 | Return the 'choosen one' | |
| 795 | Return a tuple with prop1, prop2 if we cant resolve conflict. | |
| 796 | """ | |
| 797 | return None | |
| 798 | ||
| 799 | def addUpdate(self, newModelObject, command_id): | |
| 800 | conflict = False | |
| 801 | diff = ModelObjectDiff(self, newModelObject) | |
| 802 | ||
| 803 | for k, v in diff.getPropertiesDiff().items(): | |
| 804 | attribute = self.publicattrsrefs().get(k) | |
| 805 | prop_update = self.propertyTieBreaker(attribute, *v) | |
| 806 | option_choosen = prop_update | |
| 807 | ||
| 808 | # if there's a strategy set by the user, apply it | |
| 809 | if not isinstance(prop_update, tuple) or _get_merge_strategy(): | |
| 810 | ||
| 811 | if isinstance(prop_update, tuple): | |
| 812 | #Choose the new attribute based in merge strategy: old or new | |
| 813 | merge_solver = MergeSolver(_get_merge_strategy()) | |
| 814 | option_choosen = merge_solver.solve(prop_update[0], prop_update[1]) | |
| 815 | ||
| 816 | #Faraday have duplicated description field, so if we change | |
| 817 | #description, we need change also, the desc field used in WEBUI | |
| 818 | if attribute == "description" and (self.class_signature == "Vulnerability" or self.class_signature == "VulnerabilityWeb"): | |
| 819 | setattr(self, "desc", option_choosen) | |
| 820 | ||
| 821 | #Set the new choosen attribute | |
| 822 | setattr(self, attribute, option_choosen) | |
| 823 | else: | |
| 824 | conflict = True | |
| 825 | ||
| 826 | if conflict: | |
| 827 | self.updates.append(ConflictUpdate(self, newModelObject)) | |
| 828 | return conflict | |
| 829 | ||
| 830 | def getUpdates(self): | |
| 831 | return self.updates | |
| 832 | ||
| 833 | def updateResolved(self, update): | |
| 834 | self.updates.remove(update) | |
| 835 | ||
| 836 | def needs_merge(self, new_obj): | |
| 837 | return ModelObjectDiff(self, new_obj).existDiff() | |
| 838 | ||
| 839 | def getOwner(self): | |
| 840 | return self.owner | |
| 841 | def isOwned(self): | |
| 842 | return self.owned | |
| 843 | def getName(self): | |
| 844 | return self.name | |
| 845 | def getMetadata(self): | |
| 846 | return self._metadata | |
| 847 | def getDescription(self): | |
| 848 | return self.description | |
| 849 | ||
| 850 | ||
| 851 | class Host(ModelBase): | |
| 852 | """A simple Host class. Should implement all the methods of the | |
| 853 | Host object in Model.Host | |
| 854 | Any method here more than a couple of lines long probably represent | |
| 855 | a search the server is missing. | |
| 856 | """ | |
| 857 | class_signature = 'Host' | |
| 858 | ||
| 859 | def __init__(self, host, workspace_name): | |
| 860 | ModelBase.__init__(self, host, workspace_name) | |
| 861 | self.default_gateway = host.get('default_gateway') | |
| 862 | self.os = host.get('os') if host.get('os') else 'unknown' | |
| 863 | self.vuln_amount = int(host.get('vulns', 0)) | |
| 864 | self.ip = host.get('ip', self.name) | |
| 865 | self.hostnames = host.get('hostnames', []) if host.get('hostnames') else [] | |
| 866 | self.mac = host.get('mac', '') if host.get('mac') else '' | |
| 867 | ||
| 868 | def getName(self): | |
| 869 | return self.ip | |
| 870 | ||
| 871 | @staticmethod | |
| 872 | def publicattrsrefs(): | |
| 873 | publicattrs = dict(ModelBase.publicattrsrefs(), **{ | |
| 874 | 'Operating System' : 'os' | |
| 875 | }) | |
| 876 | return publicattrs | |
| 877 | ||
| 878 | def updateAttributes(self, name=None, description=None, os=None, owned=None): | |
| 879 | if name is not None: | |
| 880 | self.name = name | |
| 881 | if description is not None: | |
| 882 | self.description = description | |
| 883 | if os is not None: | |
| 884 | self.os = os | |
| 885 | if owned is not None: | |
| 886 | self.owned = owned | |
| 887 | ||
| 888 | def __str__(self): | |
| 889 | return "{0} ({1})".format(self.name, self.vuln_amount) | |
| 890 | ||
| 891 | def getOS(self): | |
| 892 | return self.os | |
| 893 | ||
| 894 | def getVulnsAmount(self): | |
| 895 | return self.vuln_amount | |
| 896 | ||
| 897 | def getDefaultGateway(self): | |
| 898 | return self.default_gateway | |
| 899 | ||
| 900 | def getHostnames(self): | |
| 901 | return self.hostnames | |
| 902 | ||
| 903 | def getMac(self): | |
| 904 | return self.mac | |
| 905 | ||
| 906 | def setHostnames(self, hostnames): | |
| 907 | self.hostnames = hostnames | |
| 908 | ||
| 909 | def setMac(self, mac): | |
| 910 | self.mac = mac | |
| 911 | ||
| 912 | def getVulns(self): | |
| 913 | """ | |
| 914 | Get all vulns of this host. | |
| 915 | """ | |
| 916 | return get_all_vulns(self._workspace_name, target=self.ip) | |
| 917 | ||
| 918 | def getServices(self): | |
| 919 | """ | |
| 920 | Get all services of this host. | |
| 921 | """ | |
| 922 | return get_services(self._workspace_name, host_id=self._server_id) | |
| 923 | ||
| 924 | def getService(self, service_id): | |
| 925 | """ | |
| 926 | Get a specific service id of this host. | |
| 927 | """ | |
| 928 | return get_service(self._workspace_name, hostid=self._server_id, service_id=service_id) | |
| 929 | ||
| 930 | class Service(ModelBase): | |
| 931 | """A simple Service class. Should implement all the methods of the | |
| 932 | Service object in Model.Host | |
| 933 | Any method here more than a couple of lines long probably represent | |
| 934 | a search the server is missing. | |
| 935 | """ | |
| 936 | class_signature = 'Service' | |
| 937 | ||
| 938 | def __init__(self, service, workspace_name): | |
| 939 | ModelBase.__init__(self, service, workspace_name) | |
| 940 | self.protocol = service['protocol'] | |
| 941 | self.parent_id = service.get('parent') or service.get('host_id') or service.get('service_id') | |
| 942 | if type(service['ports']) == int: | |
| 943 | # the new api returns an integer in ports | |
| 944 | self.ports = [service['ports']] | |
| 945 | else: | |
| 946 | # plugin creates a list of strings with the ports | |
| 947 | self.ports = list(map(int, service['ports'])) | |
| 948 | self.version = service['version'] | |
| 949 | self.status = service['status'] | |
| 950 | self.vuln_amount = int(service.get('vulns', 0)) | |
| 951 | ||
| 952 | @staticmethod | |
| 953 | def publicattrsrefs(): | |
| 954 | publicattrs = dict(ModelBase.publicattrsrefs(), **{ | |
| 955 | 'Ports': 'ports', | |
| 956 | 'Protocol': 'protocol', | |
| 957 | 'Status': 'status', | |
| 958 | 'Version': 'version' | |
| 959 | }) | |
| 960 | return publicattrs | |
| 961 | ||
| 962 | def updateAttributes(self, name=None, description=None, protocol=None, ports=None, | |
| 963 | status=None, version=None, owned=None): | |
| 964 | if name is not None: | |
| 965 | self.name = name | |
| 966 | if description is not None: | |
| 967 | self.description = description | |
| 968 | if protocol is not None: | |
| 969 | self.protocol = protocol | |
| 970 | if ports is not None: | |
| 971 | self.ports = ports | |
| 972 | if status is not None: | |
| 973 | self.status = status | |
| 974 | if version is not None: | |
| 975 | self.version = version | |
| 976 | if owned is not None: | |
| 977 | self.owned = owned | |
| 978 | ||
| 979 | def __str__(self): | |
| 980 | return "{0} ({1})".format(self.name, self.vuln_amount) | |
| 981 | ||
| 982 | def getParent(self): | |
| 983 | return self.parent_id | |
| 984 | ||
| 985 | def getStatus(self): | |
| 986 | return self.status | |
| 987 | ||
| 988 | def getPorts(self): | |
| 989 | return self.ports # this is a list of one element in faraday | |
| 990 | ||
| 991 | def getVersion(self): | |
| 992 | return self.version | |
| 993 | ||
| 994 | def getProtocol(self): | |
| 995 | return self.protocol | |
| 996 | ||
| 997 | def isOwned(self): | |
| 998 | return self.owned | |
| 999 | ||
| 1000 | def getVulnsAmount(self): | |
| 1001 | return self.vuln_amount | |
| 1002 | ||
| 1003 | def getVulns(self): | |
| 1004 | """ | |
| 1005 | Get all vulns of this service. | |
| 1006 | """ | |
| 1007 | return get_all_vulns(self._workspace_name, service_id=self._server_id) | |
| 1008 | ||
| 1009 | ||
| 1010 | class Vuln(ModelBase): | |
| 1011 | """A simple Vuln class. Should implement all the methods of the | |
| 1012 | Vuln object in Model.Common | |
| 1013 | Any method here more than a couple of lines long probably represent | |
| 1014 | a search the server is missing. | |
| 1015 | """ | |
| 1016 | class_signature = 'Vulnerability' | |
| 1017 | ||
| 1018 | def __init__(self, vuln, workspace_name): | |
| 1019 | ModelBase.__init__(self, vuln, workspace_name) | |
| 1020 | # this next two lines are stupid but so is life so you should get used to it :) | |
| 1021 | self.description = vuln['desc'] | |
| 1022 | self.desc = vuln['desc'] | |
| 1023 | self.data = vuln.get('data') | |
| 1024 | self.severity = self.standarize(vuln['severity']) | |
| 1025 | self.refs = vuln.get('refs') or [] | |
| 1026 | self.confirmed = vuln.get('confirmed', False) | |
| 1027 | self.resolution = vuln.get('resolution') | |
| 1028 | self.status = vuln.get('status', "opened") | |
| 1029 | self.policyviolations = vuln.get('policyviolations', list()) | |
| 1030 | self.external_id = vuln.get('external_id') | |
| 1031 | ||
| 1032 | @staticmethod | |
| 1033 | def publicattrsrefs(): | |
| 1034 | publicattrs = dict(ModelBase.publicattrsrefs(), **{ | |
| 1035 | 'Data': 'data', | |
| 1036 | 'Severity': 'severity', | |
| 1037 | 'Refs': 'refs', | |
| 1038 | 'Resolution': 'resolution', | |
| 1039 | 'Status': 'status' | |
| 1040 | }) | |
| 1041 | return publicattrs | |
| 1042 | ||
| 1043 | def tieBreakable(self, key): | |
| 1044 | """ | |
| 1045 | Return true if we can auto resolve this conflict. | |
| 1046 | """ | |
| 1047 | if key == "confirmed": | |
| 1048 | return True | |
| 1049 | if key == "status": | |
| 1050 | return True | |
| 1051 | if key == "refs": | |
| 1052 | return True | |
| 1053 | return False | |
| 1054 | ||
| 1055 | def tieBreak(self, key, prop1, prop2): | |
| 1056 | """ | |
| 1057 | Return the 'choosen one' | |
| 1058 | Return a tuple with prop1, prop2 if we cant resolve conflict. | |
| 1059 | """ | |
| 1060 | ||
| 1061 | if key == "refs": | |
| 1062 | prop1.extend([x for x in prop2 if x not in prop1]) | |
| 1063 | return prop1 | |
| 1064 | ||
| 1065 | if key == "confirmed": | |
| 1066 | return True | |
| 1067 | ||
| 1068 | if key == "status": | |
| 1069 | if prop1 in ["closed", "re-opened"]: | |
| 1070 | return "re-opened" | |
| 1071 | if prop1 == "risk-accepted": | |
| 1072 | return 'risk-accepted' | |
| 1073 | ||
| 1074 | return (prop1, prop2) | |
| 1075 | ||
| 1076 | def standarize(self, severity): | |
| 1077 | # Transform all severities into lower strings | |
| 1078 | severity = str(severity).lower() | |
| 1079 | # If it has info, med, high, critical in it, standarized to it: | |
| 1080 | ||
| 1081 | ||
| 1082 | def align_string_based_vulns(severity): | |
| 1083 | severities = ['info','low', 'med', 'high', 'critical'] | |
| 1084 | for sev in severities: | |
| 1085 | if severity[0:3] in sev: | |
| 1086 | return sev | |
| 1087 | return severity | |
| 1088 | ||
| 1089 | severity = align_string_based_vulns(severity) | |
| 1090 | ||
| 1091 | # Transform numeric severity into desc severity | |
| 1092 | numeric_severities = { '0' : 'info', | |
| 1093 | '1' : 'low', | |
| 1094 | '2' : 'med', | |
| 1095 | '3' : 'high', | |
| 1096 | "4" : 'critical' } | |
| 1097 | ||
| 1098 | ||
| 1099 | if not severity in numeric_severities.values(): | |
| 1100 | severity = numeric_severities.get(severity, 'unclassified') | |
| 1101 | ||
| 1102 | return severity | |
| 1103 | ||
| 1104 | def updateAttributes(self, name=None, desc=None, data=None, | |
| 1105 | severity=None, resolution=None, refs=None, status=None, policyviolations=None, external_id=None): | |
| 1106 | if name is not None: | |
| 1107 | self.name = name | |
| 1108 | if desc is not None: | |
| 1109 | self.desc = desc | |
| 1110 | if data is not None: | |
| 1111 | self.data = data | |
| 1112 | if resolution is not None: | |
| 1113 | self.resolution = resolution | |
| 1114 | if severity is not None: | |
| 1115 | self.severity = self.standarize(severity) | |
| 1116 | if refs is not None: | |
| 1117 | self.refs = refs | |
| 1118 | if status is not None: | |
| 1119 | self.setStatus(status) | |
| 1120 | if policyviolations is not None: | |
| 1121 | self.policyviolations = policyviolations | |
| 1122 | if external_id is not None: | |
| 1123 | self.external_id = external_id | |
| 1124 | ||
| 1125 | def getDesc(self): | |
| 1126 | return self.desc | |
| 1127 | ||
| 1128 | def getData(self): | |
| 1129 | return self.data | |
| 1130 | ||
| 1131 | def getSeverity(self): | |
| 1132 | return self.severity | |
| 1133 | ||
| 1134 | def getRefs(self): | |
| 1135 | return self.refs | |
| 1136 | ||
| 1137 | def getConfirmed(self): | |
| 1138 | return self.confirmed | |
| 1139 | ||
| 1140 | def getResolution(self): | |
| 1141 | return self.resolution | |
| 1142 | ||
| 1143 | def getStatus(self): | |
| 1144 | return self.status | |
| 1145 | ||
| 1146 | def getPolicyViolations(self): | |
| 1147 | return self.policyviolations | |
| 1148 | ||
| 1149 | def setStatus(self, status): | |
| 1150 | self.status = status | |
| 1151 | ||
| 1152 | def getExternalID(self): | |
| 1153 | return self.external_id | |
| 1154 | ||
| 1155 | ||
| 1156 | class VulnWeb(Vuln): | |
| 1157 | """A simple VulnWeb class. Should implement all the methods of the | |
| 1158 | VulnWeb object in Model.Common | |
| 1159 | Any method here more than a couple of lines long probably represent | |
| 1160 | a search the server is missing. | |
| 1161 | """ | |
| 1162 | class_signature = 'VulnerabilityWeb' | |
| 1163 | ||
| 1164 | def __init__(self, vuln_web, workspace_name): | |
| 1165 | Vuln.__init__(self, vuln_web, workspace_name) | |
| 1166 | self.path = vuln_web.get('path') | |
| 1167 | self.website = vuln_web.get('website') | |
| 1168 | self.request = vuln_web.get('request') | |
| 1169 | self.response = vuln_web.get('response') | |
| 1170 | self.method = vuln_web.get('method') or '' | |
| 1171 | self.pname = vuln_web.get('pname') | |
| 1172 | self.params = vuln_web.get('params') or '' | |
| 1173 | self.query = vuln_web.get('query') | |
| 1174 | self.resolution = vuln_web.get('resolution') | |
| 1175 | self.attachments = vuln_web.get('_attachments') | |
| 1176 | self.hostnames = vuln_web.get('hostnames') | |
| 1177 | self.impact = vuln_web.get('impact') | |
| 1178 | self.service = vuln_web.get('service') | |
| 1179 | self.tags = vuln_web.get('tags', list()) | |
| 1180 | self.target = vuln_web.get('target') | |
| 1181 | self.policyviolations = vuln_web.get('policyviolations', list()) | |
| 1182 | self.parent_type = 'Service' | |
| 1183 | self.external_id = vuln_web.get('external_id') | |
| 1184 | ||
| 1185 | @staticmethod | |
| 1186 | def publicattrsrefs(): | |
| 1187 | publicattrs = dict(ModelBase.publicattrsrefs(), **{ | |
| 1188 | 'Data': 'data', | |
| 1189 | 'Severity': 'severity', | |
| 1190 | 'Refs': 'refs', | |
| 1191 | 'Path': 'path', | |
| 1192 | 'Website': 'website', | |
| 1193 | 'Request': 'request', | |
| 1194 | 'Response': 'response', | |
| 1195 | 'Method': 'method', | |
| 1196 | 'Pname': 'pname', | |
| 1197 | 'Params': 'params', | |
| 1198 | 'Query': 'query', | |
| 1199 | 'Status': 'status'}) | |
| 1200 | return publicattrs | |
| 1201 | ||
| 1202 | def updateAttributes(self, name=None, desc=None, data=None, website=None, path=None, refs=None, | |
| 1203 | severity=None, resolution=None, request=None,response=None, method=None, | |
| 1204 | pname=None, params=None, query=None, category=None, status=None, policyviolations=None, external_id=None): | |
| 1205 | ||
| 1206 | super(self.__class__, self).updateAttributes(name, desc, data, severity, resolution, refs, status) | |
| 1207 | ||
| 1208 | if website is not None: | |
| 1209 | self.website = website | |
| 1210 | if path is not None: | |
| 1211 | self.path = path | |
| 1212 | if request is not None: | |
| 1213 | self.request = request | |
| 1214 | if response is not None: | |
| 1215 | self.response = response | |
| 1216 | if method is not None: | |
| 1217 | self.method = method | |
| 1218 | if pname is not None: | |
| 1219 | self.pname = pname | |
| 1220 | if params is not None: | |
| 1221 | self.params = params | |
| 1222 | if query is not None: | |
| 1223 | self.query = query | |
| 1224 | if category is not None: | |
| 1225 | self.category = category | |
| 1226 | if policyviolations is not None: | |
| 1227 | self.policyviolations = policyviolations | |
| 1228 | if external_id is not None: | |
| 1229 | self.external_id = external_id | |
| 1230 | ||
| 1231 | def getDescription(self): | |
| 1232 | return self.description | |
| 1233 | ||
| 1234 | def getPath(self): | |
| 1235 | return self.path | |
| 1236 | ||
| 1237 | def getWebsite(self): | |
| 1238 | return self.website | |
| 1239 | ||
| 1240 | def getRequest(self): | |
| 1241 | return self.request | |
| 1242 | ||
| 1243 | def getResponse(self): | |
| 1244 | return self.response | |
| 1245 | ||
| 1246 | def getMethod(self): | |
| 1247 | return self.method | |
| 1248 | ||
| 1249 | def getPname(self): | |
| 1250 | return self.pname | |
| 1251 | ||
| 1252 | def getParams(self): | |
| 1253 | return self.params | |
| 1254 | ||
| 1255 | def getQuery(self): | |
| 1256 | return self.query | |
| 1257 | ||
| 1258 | def getResolution(self): | |
| 1259 | return self.resolution | |
| 1260 | ||
| 1261 | def getAttachments(self): | |
| 1262 | return self.attachments | |
| 1263 | ||
| 1264 | def getEaseOfResolution(self): | |
| 1265 | return self.easeofresolution | |
| 1266 | ||
| 1267 | def getHostnames(self): | |
| 1268 | return self.hostnames | |
| 1269 | ||
| 1270 | def getImpact(self): | |
| 1271 | return self.impact | |
| 1272 | ||
| 1273 | def getService(self): | |
| 1274 | return self.service | |
| 1275 | ||
| 1276 | def getStatus(self): | |
| 1277 | return self.status | |
| 1278 | ||
| 1279 | def getTags(self): | |
| 1280 | return self.tags | |
| 1281 | ||
| 1282 | def getTarget(self): | |
| 1283 | return self.target | |
| 1284 | ||
| 1285 | def getPolicyViolations(self): | |
| 1286 | return self.policyviolations | |
| 1287 | ||
| 1288 | def getExternalID(self): | |
| 1289 | return self.external_id | |
| 1290 | ||
| 1291 | def tieBreakable(self, key): | |
| 1292 | """ | |
| 1293 | Return true if we can auto resolve this conflict. | |
| 1294 | """ | |
| 1295 | if key == "response": | |
| 1296 | return True | |
| 1297 | if key == "confirmed": | |
| 1298 | return True | |
| 1299 | if key == "status": | |
| 1300 | return True | |
| 1301 | if key == "refs": | |
| 1302 | return True | |
| 1303 | ||
| 1304 | return False | |
| 1305 | ||
| 1306 | def tieBreak(self, key, prop1, prop2): | |
| 1307 | """ | |
| 1308 | Return the 'choosen one' | |
| 1309 | Return a tuple with prop1, prop2 if we cant resolve conflict. | |
| 1310 | """ | |
| 1311 | ||
| 1312 | if key == "refs": | |
| 1313 | prop1.extend([x for x in prop2 if x not in prop1]) | |
| 1314 | return prop1 | |
| 1315 | ||
| 1316 | if key == "response": | |
| 1317 | return self._resolve_response(prop1, prop2) | |
| 1318 | ||
| 1319 | if key == "status": | |
| 1320 | if prop1 in ["closed", "re-opened"]: | |
| 1321 | return "re-opened" | |
| 1322 | if prop1 == "risk-accepted": | |
| 1323 | return 'risk-accepted' | |
| 1324 | ||
| 1325 | if key == "confirmed": | |
| 1326 | return True | |
| 1327 | ||
| 1328 | return (prop1, prop2) | |
| 1329 | ||
| 1330 | def _resolve_response(self ,res1, res2): | |
| 1331 | ||
| 1332 | differ = Differ() | |
| 1333 | result = list(differ.compare(res1.splitlines(), res2.splitlines())) | |
| 1334 | ||
| 1335 | counterNegative = 0 | |
| 1336 | counterPositive = 0 | |
| 1337 | ||
| 1338 | for i in result: | |
| 1339 | if i.startswith('-') and i.find('date:') != -1: | |
| 1340 | counterNegative += 1 | |
| 1341 | if i.startswith('+') and i.find('date:') != -1: | |
| 1342 | counterPositive += 1 | |
| 1343 | ||
| 1344 | if counterNegative == 1 and counterPositive == 1 and counterNegative == counterPositive: | |
| 1345 | return res2 | |
| 1346 | else: | |
| 1347 | return None | |
| 1348 | ||
| 1349 | class Note(ModelBase): | |
| 1350 | class_signature = 'Note' | |
| 1351 | ||
| 1352 | def __init__(self, note, workspace_name): | |
| 1353 | ModelBase.__init__(self, note, workspace_name) | |
| 1354 | self.text = note['text'] | |
| 1355 | self.object_id = note.get('object_id') or note.get('parent') | |
| 1356 | self.object_type = note.get('object_type') or note.get('parent_type') | |
| 1357 | ||
| 1358 | def updateAttributes(self, name=None, text=None): | |
| 1359 | if name is not None: | |
| 1360 | self.name = name | |
| 1361 | if text is not None: | |
| 1362 | self.text = text | |
| 1363 | ||
| 1364 | def getDescription(self): | |
| 1365 | return self.description | |
| 1366 | ||
| 1367 | def getText(self): | |
| 1368 | return self.text | |
| 1369 | ||
| 1370 | def getObjectID(self): | |
| 1371 | # sorry for adding camel case method. | |
| 1372 | return self.object_id | |
| 1373 | ||
| 1374 | def getObjectType(self): | |
| 1375 | # sorry for adding camel case method. | |
| 1376 | return self.object_type | |
| 1377 | ||
| 1378 | ||
| 1379 | class Credential(ModelBase): | |
| 1380 | class_signature = "Cred" | |
| 1381 | ||
| 1382 | def __init__(self, credential, workspace_name): | |
| 1383 | ModelBase.__init__(self, credential, workspace_name) | |
| 1384 | try: | |
| 1385 | self.username = credential['username'] | |
| 1386 | except KeyError: | |
| 1387 | self.username = credential['name'] | |
| 1388 | ||
| 1389 | self.password = credential['password'] | |
| 1390 | ||
| 1391 | def updateAttributes(self, username=None, password=None): | |
| 1392 | if username is not None: | |
| 1393 | self.username = username | |
| 1394 | if password is not None: | |
| 1395 | self.password = password | |
| 1396 | ||
| 1397 | def getUsername(self): | |
| 1398 | return self.username | |
| 1399 | ||
| 1400 | def getPassword(self): | |
| 1401 | return self.password | |
| 1402 | ||
| 1403 | ||
| 1404 | class Command: | |
| 1405 | class_signature = 'CommandRunInformation' | |
| 1406 | def __init__(self, command, workspace_name): | |
| 1407 | self._workspace_name = workspace_name | |
| 1408 | self.id = command.get('id', None) or command.get('_id', None) | |
| 1409 | self.command = command['command'] | |
| 1410 | self.duration = command['duration'] | |
| 1411 | self.hostname = command['hostname'] | |
| 1412 | self.ip = command['ip'] | |
| 1413 | self.itime = command['itime'] | |
| 1414 | self.params = command['params'] | |
| 1415 | self.user = command['user'] | |
| 1416 | self.workspace = command['workspace'] | |
| 1417 | self.import_source = command['import_source'] | |
| 1418 | ||
| 1419 | def getID(self): | |
| 1420 | return self.id | |
| 1421 | ||
| 1422 | def getCommand(self): | |
| 1423 | return self.command | |
| 1424 | ||
| 1425 | def getDuration(self): | |
| 1426 | return self.duration | |
| 1427 | ||
| 1428 | def getHostname(self): | |
| 1429 | return self.hostname | |
| 1430 | ||
| 1431 | def getIP(self): | |
| 1432 | return self.ip | |
| 1433 | ||
| 1434 | def getItime(self): | |
| 1435 | return self.itime | |
| 1436 | ||
| 1437 | def getParams(self): | |
| 1438 | return self.params | |
| 1439 | ||
| 1440 | def getUser(self): | |
| 1441 | return self.user | |
| 1442 | ||
| 1443 | def getWorkspace(self): | |
| 1444 | return self.workspace | |
| 1445 | ||
| 1446 | ||
| 1447 | class _Workspace: | |
| 1448 | class_signature = 'Workspace' | |
| 1449 | ||
| 1450 | def __init__(self, workspace, workspace_name): | |
| 1451 | self._id = workspace_name | |
| 1452 | self.name = workspace['name'] | |
| 1453 | self.description = workspace['description'] | |
| 1454 | self.customer = workspace['customer'] | |
| 1455 | if 'duration' in workspace: | |
| 1456 | self.start_date = workspace['duration']['start_date'] | |
| 1457 | self.end_date = workspace['duration']['end_date'] | |
| 1458 | ||
| 1459 | def getID(self): | |
| 1460 | return self._id | |
| 1461 | ||
| 1462 | def getName(self): | |
| 1463 | return self.name | |
| 1464 | ||
| 1465 | def getDescription(self): | |
| 1466 | return self.description | |
| 1467 | ||
| 1468 | def getCustomer(self): | |
| 1469 | return self.customer | |
| 1470 | ||
| 1471 | def getStartDate(self): | |
| 1472 | return self.start_date | |
| 1473 | ||
| 1474 | def getFinishDate(self): | |
| 1475 | return self.end_date | |
| 1476 | ||
| 1477 | ||
| 1478 | class MetadataUpdateActions: | |
| 1479 | """Constants for the actions made on the update""" | |
| 1480 | UNDEFINED = -1 | |
| 1481 | CREATE = 0 | |
| 1482 | UPDATE = 1 | |
| 1483 | ||
| 1484 | ||
| 1485 | class Metadata: | |
| 1486 | """To save information about the modification of ModelObjects. | |
| 1487 | All members declared public as this is only a wrapper""" | |
| 1488 | ||
| 1489 | class_signature = "Metadata" | |
| 1490 | ||
| 1491 | def __init__(self, user): | |
| 1492 | self.creator = user | |
| 1493 | self.owner = user | |
| 1494 | self.create_time = time() | |
| 1495 | self.update_time = time() | |
| 1496 | self.update_user = user | |
| 1497 | self.update_action = MetadataUpdateActions.CREATE | |
| 1498 | self.update_controller_action = self.__getUpdateAction() | |
| 1499 | self.command_id = '' | |
| 1500 | ||
| 1501 | def toDict(self): | |
| 1502 | return self.__dict__ | |
| 1503 | ||
| 1504 | def fromDict(self, dictt): | |
| 1505 | for k, v in dictt.items(): | |
| 1506 | setattr(self, k, v) | |
| 1507 | return self | |
| 1508 | ||
| 1509 | def update(self, user, action = MetadataUpdateActions.UPDATE): | |
| 1510 | """Update the local metadata giving a user and an action. | |
| 1511 | Update time gets modified to the current system time""" | |
| 1512 | self.update_user = user | |
| 1513 | self.update_time = time() | |
| 1514 | self.update_action = action | |
| 1515 | ||
| 1516 | self.update_controller_action = self.__getUpdateAction() | |
| 1517 | ||
| 1518 | def __getUpdateAction(self): | |
| 1519 | """This private method grabs the stackframes in look for the controller | |
| 1520 | call that generated the update""" | |
| 1521 | ||
| 1522 | l_strace = traceback.extract_stack(limit=10) | |
| 1523 | controller_funcallnames = [x[2] for x in l_strace if "controller" in x[0]] | |
| 1524 | ||
| 1525 | if controller_funcallnames: | |
| 1526 | return "ModelControler." + " ModelControler.".join(controller_funcallnames) | |
| 1527 | return "No model controller call" | |
| 1528 | ||
| 1529 | ||
| 1530 | # I'm Py3 |
| 0 | #!/usr/bin/python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | # Faraday Penetration Test IDE | |
| 4 | # Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | # See the file 'doc/LICENSE' for the license information | |
| 6 | ||
| 7 | ||
| 8 | """A module to handle request to the Faraday Server. | |
| 9 | ||
| 10 | Note: | |
| 11 | Before using this as an API, you should copy this file and edit | |
| 12 | the FARADAY_UP and the SERVER_URL variables found inmediatly | |
| 13 | below the imports. | |
| 14 | ||
| 15 | FARADAY_UP should be set to False in the copy of the file, and SERVER_URL | |
| 16 | must be a valid server url. | |
| 17 | ||
| 18 | Warning: | |
| 19 | This module was though of primarly as a way of querying and removing | |
| 20 | information from the Faraday Server. Adding objects is supported, but should | |
| 21 | be used with care, specially regarding the ID of objects, which must | |
| 22 | be always unique. | |
| 23 | """ | |
| 24 | from __future__ import absolute_import | |
| 25 | ||
| 26 | import urllib | |
| 27 | ||
| 28 | import os | |
| 29 | import json | |
| 30 | import logging | |
| 31 | ||
| 32 | try: | |
| 33 | import urlparse | |
| 34 | from urllib import urlencode | |
| 35 | except: # For Python 3 | |
| 36 | import urllib.parse as urlparse | |
| 37 | from urllib.parse import urlencode | |
| 38 | ||
| 39 | ||
| 40 | import requests | |
| 41 | ||
| 42 | from faraday import __version__ as f_version | |
| 43 | from faraday.client.persistence.server.utils import force_unique | |
| 44 | from faraday.client.persistence.server.server_io_exceptions import (WrongObjectSignature, | |
| 45 | CantCommunicateWithServerError, | |
| 46 | ConflictInDatabase, | |
| 47 | ResourceDoesNotExist, | |
| 48 | Unauthorized) | |
| 49 | ||
| 50 | from faraday.client.persistence.server.changes_stream import ( | |
| 51 | CouchChangesStream, | |
| 52 | WebsocketsChangesStream | |
| 53 | ) | |
| 54 | ||
| 55 | # NOTE: Change is you want to use this module by itself. | |
| 56 | # If FARADAY_UP is False, SERVER_URL must be a valid faraday server url | |
| 57 | logger = logging.getLogger(__name__) | |
| 58 | ||
| 59 | FARADAY_UP = True | |
| 60 | FARADAY_UPLOAD_REPORTS_WEB_COOKIE = None | |
| 61 | FARADAY_UPLOAD_REPORTS_OVERWRITE_SERVER_URL = None | |
| 62 | ||
| 63 | SERVER_URL = "http://127.0.0.1:5985" | |
| 64 | AUTH_USER = "" | |
| 65 | AUTH_PASS = "" | |
| 66 | OBJECT_TYPE_END_POINT_MAPPER = { | |
| 67 | 'CommandRunInformation': 'commands', | |
| 68 | 'Host': 'hosts', | |
| 69 | 'Vulnerability': 'vulns', | |
| 70 | 'VulnerabilityWeb': 'vulns', | |
| 71 | 'Service': 'services', | |
| 72 | 'Note': 'comment', | |
| 73 | 'Cred': 'credential', | |
| 74 | } | |
| 75 | ||
| 76 | ||
| 77 | ||
| 78 | def _conf(): | |
| 79 | from faraday.config.configuration import getInstanceConfiguration # pylint:disable=import-outside-toplevel | |
| 80 | CONF = getInstanceConfiguration() | |
| 81 | ||
| 82 | # If you are running this libs outside of Faraday, cookies are not setted. | |
| 83 | # you need get a valid cookie auth and set that. | |
| 84 | # Fplugin run in other instance, so this dont generate any trouble. | |
| 85 | if not CONF.getDBSessionCookies() and not FARADAY_UPLOAD_REPORTS_WEB_COOKIE: | |
| 86 | server_url = CONF.getServerURI() if FARADAY_UP else SERVER_URL | |
| 87 | cookie = login_user(server_url, CONF.getAPIUsername(), CONF.getAPIPassword()) | |
| 88 | CONF.setDBSessionCookies(cookie) | |
| 89 | ||
| 90 | return CONF | |
| 91 | ||
| 92 | ||
| 93 | def _get_base_server_url(): | |
| 94 | ||
| 95 | # Faraday server is running, and this module is used by upload_reports... | |
| 96 | if FARADAY_UPLOAD_REPORTS_OVERWRITE_SERVER_URL: | |
| 97 | server_url = FARADAY_UPLOAD_REPORTS_OVERWRITE_SERVER_URL | |
| 98 | elif FARADAY_UP: | |
| 99 | server_url = _conf().getAPIUrl() | |
| 100 | else: | |
| 101 | server_url = SERVER_URL | |
| 102 | return server_url.rstrip('/') | |
| 103 | ||
| 104 | ||
| 105 | def _create_server_api_url(): | |
| 106 | """Return the server's api url.""" | |
| 107 | return "{0}/_api/v2".format(_get_base_server_url()) | |
| 108 | ||
| 109 | def _create_server_get_url(workspace_name, object_name=None, object_id=None, **params): | |
| 110 | """Creates a url to get from the server. Takes the workspace name | |
| 111 | as a string, an object_name paramter which is the object you want to | |
| 112 | query as a string ('hosts', 'interfaces', etc) . | |
| 113 | ||
| 114 | object_name may be None if you want to get the workspace itself. | |
| 115 | ||
| 116 | Return the get_url as a string. | |
| 117 | """ | |
| 118 | get_url = "/{0}".format(object_name) if object_name else "" | |
| 119 | get_url += "/{0}/".format(object_id) if object_id else "" | |
| 120 | get_url = '{0}/ws/{1}{2}'.format(_create_server_api_url(), | |
| 121 | workspace_name, | |
| 122 | get_url) | |
| 123 | ||
| 124 | return get_url | |
| 125 | ||
| 126 | ||
| 127 | def _create_server_post_url(workspace_name, obj_type, command_id): | |
| 128 | server_api_url = _create_server_api_url() | |
| 129 | object_end_point_name = OBJECT_TYPE_END_POINT_MAPPER[obj_type] | |
| 130 | if obj_type == 'comment': | |
| 131 | object_end_point_name = object_end_point_name.strip('/') + '_unique/' | |
| 132 | post_url = '{0}/ws/{1}/{2}/'.format(server_api_url, workspace_name, object_end_point_name) | |
| 133 | if command_id: | |
| 134 | get_params = {'command_id': command_id} | |
| 135 | post_url += '?' + urlencode(get_params) | |
| 136 | return post_url | |
| 137 | ||
| 138 | ||
| 139 | def _create_server_put_url(workspace_name, obj_type, obj_id, command_id): | |
| 140 | server_api_url = _create_server_api_url() | |
| 141 | object_end_point_name = OBJECT_TYPE_END_POINT_MAPPER[obj_type] | |
| 142 | put_url = '{0}/ws/{1}/{2}/{3}/'.format(server_api_url, workspace_name, object_end_point_name, obj_id) | |
| 143 | if command_id: | |
| 144 | get_params = {'command_id': command_id} | |
| 145 | put_url += '?' + urlencode(get_params) | |
| 146 | return put_url | |
| 147 | ||
| 148 | ||
| 149 | def _create_server_delete_url(workspace_name, obj_type, object_id, command_id=None): | |
| 150 | return _create_server_put_url(workspace_name, obj_type, object_id, command_id) | |
| 151 | ||
| 152 | # XXX: COUCH IT! | |
| 153 | def _create_couch_get_url(workspace_name, object_id): | |
| 154 | server_url = _get_base_server_url() | |
| 155 | return "{0}/{1}/{2}".format(server_url, workspace_name, object_id) | |
| 156 | ||
| 157 | ||
| 158 | # XXX: COUCH IT! | |
| 159 | def _create_couch_post_url(workspace_name, object_id): | |
| 160 | return _create_couch_get_url(workspace_name, object_id) | |
| 161 | ||
| 162 | ||
| 163 | # XXX: COUCH IT! | |
| 164 | def _create_couch_db_url(workspace_name): | |
| 165 | server_base_url = _get_base_server_url() | |
| 166 | db_url = '{0}/{1}'.format(server_base_url, workspace_name) | |
| 167 | return db_url | |
| 168 | ||
| 169 | def _create_server_db_url(workspace_name): | |
| 170 | server_api_url = _create_server_api_url() | |
| 171 | db_url = '{0}/ws/'.format(server_api_url) | |
| 172 | return db_url | |
| 173 | ||
| 174 | def _add_session_cookies(func): | |
| 175 | """A decorator which wrapps a function dealing with I/O with the server and | |
| 176 | adds authentication to the parameters. | |
| 177 | """ | |
| 178 | def wrapper(*args, **kwargs): | |
| 179 | if FARADAY_UPLOAD_REPORTS_WEB_COOKIE: | |
| 180 | kwargs['cookies'] = FARADAY_UPLOAD_REPORTS_WEB_COOKIE | |
| 181 | else: | |
| 182 | kwargs['cookies'] = _conf().getDBSessionCookies() | |
| 183 | response = func(*args, **kwargs) | |
| 184 | return response | |
| 185 | return wrapper if FARADAY_UP else func | |
| 186 | ||
| 187 | ||
| 188 | @_add_session_cookies | |
| 189 | def _unsafe_io_with_server(server_io_function, server_expected_responses, | |
| 190 | server_url, **payload): | |
| 191 | """A wrapper for functions which deals with I/O to or from the server. | |
| 192 | It calls the server_io_function with url server_url and the payload, | |
| 193 | raising an CantCommunicateWithServerError if the response wasn't | |
| 194 | server_expected_response or if there was a Connection Error. | |
| 195 | ||
| 196 | Return the response from the server. | |
| 197 | """ | |
| 198 | answer = None | |
| 199 | try: | |
| 200 | answer = server_io_function(server_url, **payload) | |
| 201 | if answer.status_code == 409: | |
| 202 | raise ConflictInDatabase(answer) | |
| 203 | if answer.status_code == 404: | |
| 204 | raise ResourceDoesNotExist(server_url) | |
| 205 | if answer.status_code == 403 or answer.status_code == 401: | |
| 206 | raise Unauthorized(answer) | |
| 207 | if answer.status_code not in server_expected_responses: | |
| 208 | raise requests.exceptions.RequestException(response=answer) | |
| 209 | except requests.exceptions.RequestException as ex: | |
| 210 | logger.debug(ex) | |
| 211 | try: | |
| 212 | if answer and 'messages' in answer.json(): | |
| 213 | logger.info('Faraday server error message: {0}'.format(answer.json()['messages'])) | |
| 214 | except ValueError: | |
| 215 | logger.debug('Could not decode json from server') | |
| 216 | raise CantCommunicateWithServerError(server_io_function, server_url, payload, answer) | |
| 217 | return answer | |
| 218 | ||
| 219 | def _parse_json(response_object): | |
| 220 | """Takes a response object and return its response as a dictionary.""" | |
| 221 | try: | |
| 222 | return response_object.json() | |
| 223 | except ValueError: | |
| 224 | return {} | |
| 225 | ||
| 226 | ||
| 227 | def _get(request_url, **params): | |
| 228 | """Get from the request_url. Takes an arbitrary number of parameters | |
| 229 | to customize the request_url if necessary. | |
| 230 | ||
| 231 | Will raise a CantCommunicateWithServerError if requests cant stablish | |
| 232 | connection to server or if response is not equal to 200. | |
| 233 | ||
| 234 | Return a dictionary with the information in the json. | |
| 235 | """ | |
| 236 | return _parse_json(_unsafe_io_with_server(requests.get, | |
| 237 | [200], | |
| 238 | request_url, | |
| 239 | params=params)) | |
| 240 | ||
| 241 | def _put(post_url, expected_response=201, **params): | |
| 242 | """Put to the post_url. If update is True, try to get the object | |
| 243 | revision first so as to update the object in Couch. You can | |
| 244 | customize the expected response (it should be 201, but Couchdbkit returns | |
| 245 | 200, so...). Also take an arbitrary number of parameters to put into the | |
| 246 | post_url. | |
| 247 | ||
| 248 | Will raise a CantCommunicateWithServerError if requests cant stablish | |
| 249 | connection to server or if response is not equal to 201. | |
| 250 | ||
| 251 | Return a dictionary with the response from couchdb, which looks like this: | |
| 252 | {u'id': u'61', u'ok': True, u'rev': u'1-967a00dff5e02add41819138abb3284d'} | |
| 253 | """ | |
| 254 | return _parse_json(_unsafe_io_with_server(requests.put, | |
| 255 | [expected_response], | |
| 256 | post_url, | |
| 257 | json=params)) | |
| 258 | ||
| 259 | ||
| 260 | def _post(post_url, update=False, expected_response=201, **params): | |
| 261 | return _parse_json(_unsafe_io_with_server(requests.post, | |
| 262 | [expected_response], | |
| 263 | post_url, | |
| 264 | json=params)) | |
| 265 | ||
| 266 | ||
| 267 | def _delete(delete_url, database=False): | |
| 268 | """Deletes the object on delete_url. If you're deleting a database, | |
| 269 | specify the database parameter to True""" | |
| 270 | params = {} | |
| 271 | if not database: | |
| 272 | last_rev = _get(delete_url)['_rev'] | |
| 273 | params = {'rev': last_rev} | |
| 274 | return _parse_json(_unsafe_io_with_server(requests.delete, | |
| 275 | [200,204], | |
| 276 | delete_url, | |
| 277 | params=params)) | |
| 278 | ||
| 279 | ||
| 280 | def _get_raw_hosts(workspace_name, **params): | |
| 281 | """Take a workspace_name and an arbitrary number of params and return | |
| 282 | a dictionary with the hosts table.""" | |
| 283 | request_url = _create_server_get_url(workspace_name, 'hosts', **params) | |
| 284 | return _get(request_url, **params) | |
| 285 | ||
| 286 | ||
| 287 | def _get_raw_vulns(workspace_name, **params): | |
| 288 | """Take a workspace_name and an arbitrary number of params and return | |
| 289 | a dictionary with the vulns table.""" | |
| 290 | params = {key: value for key, value in params.items() if value} | |
| 291 | request_url = _create_server_get_url(workspace_name, 'vulns', **params) | |
| 292 | return _get(request_url, **params) | |
| 293 | ||
| 294 | ||
| 295 | def _get_raw_services(workspace_name, **params): | |
| 296 | """Take a workspace_name and an arbitrary number of params and return | |
| 297 | a dictionary with the services table. | |
| 298 | If you provide a host_id and services_of_host=True, it returns all services of that specified host""" | |
| 299 | ||
| 300 | request_url = _create_server_get_url(workspace_name, 'services', **params) | |
| 301 | return _get(request_url, **params) | |
| 302 | ||
| 303 | ||
| 304 | def _get_raw_notes(workspace_name, **params): | |
| 305 | """Take a workspace name and an arbitrary number of params and | |
| 306 | return a dictionary with the notes table.""" | |
| 307 | request_url = _create_server_get_url(workspace_name, 'comment', params.get('id', None)) | |
| 308 | return _get(request_url, **params) | |
| 309 | ||
| 310 | ||
| 311 | def _get_raw_credentials(workspace_name, **params): | |
| 312 | """Take a workspace name and an arbitrary number of params and | |
| 313 | return a dictionary with the credentials table.""" | |
| 314 | request_url = _create_server_get_url(workspace_name, 'credential', params.pop('id', None), **params) | |
| 315 | return _get(request_url, **params) | |
| 316 | ||
| 317 | ||
| 318 | def _get_raw_commands(workspace_name, **params): | |
| 319 | request_url = _create_server_get_url(workspace_name, 'commands', params.get('id', None)) | |
| 320 | return _get(request_url, **params) | |
| 321 | ||
| 322 | ||
| 323 | def _get_raw_workspace_summary(workspace_name): | |
| 324 | request_url = _create_server_get_url(workspace_name) | |
| 325 | return _get(request_url) | |
| 326 | ||
| 327 | def _save_to_server(workspace_name, **params): | |
| 328 | """ | |
| 329 | ||
| 330 | :param workspace_name: | |
| 331 | :param params: | |
| 332 | :return: | |
| 333 | """ | |
| 334 | post_url = _create_server_post_url(workspace_name, params['type'], params.get('command_id', None)) | |
| 335 | return _post(post_url, update=False, expected_response=201, **params) | |
| 336 | ||
| 337 | def _update_in_server(workspace_name, faraday_object_id, **params): | |
| 338 | put_url = _create_server_put_url(workspace_name, params['type'], faraday_object_id, params.get('command_id', None)) | |
| 339 | return _put(put_url, expected_response=200, **params) | |
| 340 | ||
| 341 | def _save_db_to_server(db_name, **params): | |
| 342 | post_url = _create_server_db_url(db_name) | |
| 343 | return _post(post_url, expected_response=201, **params) | |
| 344 | ||
| 345 | ||
| 346 | def _delete_from_server(workspace_name, faraday_object_type, faraday_object_id): | |
| 347 | delete_url = _create_server_delete_url(workspace_name, faraday_object_type, faraday_object_id) | |
| 348 | return _delete(delete_url) | |
| 349 | ||
| 350 | ||
| 351 | @_add_session_cookies | |
| 352 | def _couch_changes(workspace_name, **params): | |
| 353 | return CouchChangesStream(workspace_name, | |
| 354 | _create_couch_db_url(workspace_name), | |
| 355 | **params) | |
| 356 | ||
| 357 | ||
| 358 | def _get_faraday_ready_dictionaries(workspace_name, faraday_object_name, | |
| 359 | faraday_object_row_name, full_table=True, | |
| 360 | **params): | |
| 361 | """Takes a workspace_name (str), a faraday_object_name (str), | |
| 362 | a faraday_object_row_name (str) and an arbitrary number of params. | |
| 363 | Return a list of dictionaries that hold the information for the objects | |
| 364 | in table faraday_object_name. | |
| 365 | ||
| 366 | The full_table paramether may be used to get the full dictionary instead | |
| 367 | of just the one inside the 'value' key which holds information about the | |
| 368 | object. | |
| 369 | ||
| 370 | Preconditions: | |
| 371 | faraday_object_name == 'host', 'vuln', 'interface', 'service', 'note' | |
| 372 | or 'credential' | |
| 373 | ||
| 374 | faraday_object_row_name must be the key to the dictionary which holds | |
| 375 | the information of the object per se in the table. most times this is 'rows' | |
| 376 | """ | |
| 377 | object_to_func = {'hosts': _get_raw_hosts, | |
| 378 | 'vulns': _get_raw_vulns, | |
| 379 | 'services': _get_raw_services, | |
| 380 | 'notes': _get_raw_notes, | |
| 381 | 'credentials': _get_raw_credentials, | |
| 382 | 'commands': _get_raw_commands} | |
| 383 | ||
| 384 | appropiate_function = object_to_func[faraday_object_name] | |
| 385 | appropiate_dictionary = appropiate_function(workspace_name, **params) | |
| 386 | faraday_ready_dictionaries = [appropiate_dictionary] | |
| 387 | if faraday_object_row_name in appropiate_dictionary: | |
| 388 | faraday_ready_dictionaries = [] | |
| 389 | for raw_dictionary in appropiate_dictionary[faraday_object_row_name]: | |
| 390 | if not full_table: | |
| 391 | faraday_ready_dictionaries.append(raw_dictionary['value']) | |
| 392 | else: | |
| 393 | faraday_ready_dictionaries.append(raw_dictionary) | |
| 394 | return faraday_ready_dictionaries | |
| 395 | ||
| 396 | ||
| 397 | def get_hosts(workspace_name, **params): | |
| 398 | """Get hosts from the server. | |
| 399 | ||
| 400 | Args: | |
| 401 | workspace_name (str): the workspace from which to get the hosts. | |
| 402 | **params: any of valid request parameters for CouchDB. | |
| 403 | ||
| 404 | Returns: | |
| 405 | A dictionary containing the hosts matching the query. | |
| 406 | """ | |
| 407 | return _get_faraday_ready_dictionaries(workspace_name, 'hosts', | |
| 408 | 'rows', **params) | |
| 409 | ||
| 410 | ||
| 411 | def get_all_vulns(workspace_name, **params): | |
| 412 | """Get vulns, both normal and web, from the server. | |
| 413 | ||
| 414 | Args: | |
| 415 | workspace_name (str): the workspace from which to get the vulns. | |
| 416 | **params: any of valid request parameters for CouchDB. | |
| 417 | ||
| 418 | Returns: | |
| 419 | A dictionary containing the vulns matching the query. | |
| 420 | """ | |
| 421 | return _get_faraday_ready_dictionaries(workspace_name, 'vulns', | |
| 422 | 'vulnerabilities', **params) | |
| 423 | ||
| 424 | ||
| 425 | def get_vulns(workspace_name, **params): | |
| 426 | """Get only normal vulns from the server. | |
| 427 | ||
| 428 | Args: | |
| 429 | workspace_name (str): the workspace from which to get the vulns. | |
| 430 | **params: any of valid request parameters for CouchDB. | |
| 431 | ||
| 432 | Returns: | |
| 433 | A dictionary containing the vulns matching the query. | |
| 434 | """ | |
| 435 | return get_all_vulns(workspace_name, type='Vulnerability', **params) | |
| 436 | ||
| 437 | ||
| 438 | def get_web_vulns(workspace_name, **params): | |
| 439 | """Get only web vulns from the server. | |
| 440 | ||
| 441 | Args: | |
| 442 | workspace_name (str): the workspace from which to get the vulns. | |
| 443 | **params: any of valid request parameters for CouchDB. | |
| 444 | ||
| 445 | Returns: | |
| 446 | A dictionary containing the vulns matching the query. | |
| 447 | """ | |
| 448 | return get_all_vulns(workspace_name, type="VulnerabilityWeb", **params) | |
| 449 | ||
| 450 | def get_interfaces(workspace_name, **params): | |
| 451 | """Get interfaces from the server. | |
| 452 | ||
| 453 | Args: | |
| 454 | workspace_name (str): the workspace from which to get the interfaces. | |
| 455 | **params: any of valid request parameters for CouchDB. | |
| 456 | ||
| 457 | Returns: | |
| 458 | A dictionary containing the interfaces matching the query. | |
| 459 | """ | |
| 460 | return _get_faraday_ready_dictionaries(workspace_name, 'interfaces', | |
| 461 | 'interfaces', **params) | |
| 462 | ||
| 463 | def get_services(workspace_name, **params): | |
| 464 | """Get services from the server. | |
| 465 | ||
| 466 | Args: | |
| 467 | workspace_name (str): the workspace from which to get the services. | |
| 468 | **params: any of valid request parameters for CouchDB. | |
| 469 | ||
| 470 | Returns: | |
| 471 | A dictionary containing the services matching the query. | |
| 472 | """ | |
| 473 | return _get_faraday_ready_dictionaries(workspace_name, 'services', | |
| 474 | 'services', **params) | |
| 475 | ||
| 476 | def get_credentials(workspace_name, **params): | |
| 477 | """Get credentials from the server. | |
| 478 | ||
| 479 | Args: | |
| 480 | workspace_name (str): the workspace from which to get the credentials. | |
| 481 | **params: any of valid request parameters for CouchDB. | |
| 482 | ||
| 483 | Returns: | |
| 484 | A dictionary containing the credentials matching the query. | |
| 485 | """ | |
| 486 | return _get_faraday_ready_dictionaries(workspace_name, 'credentials', | |
| 487 | 'rows', **params) | |
| 488 | ||
| 489 | def get_notes(workspace_name, **params): | |
| 490 | """Get notes from the server. | |
| 491 | ||
| 492 | Args: | |
| 493 | workspace_name (str): the workspace from which to get the notes. | |
| 494 | **params: any of valid request parameters for CouchDB. | |
| 495 | ||
| 496 | Returns: | |
| 497 | A dictionary containing the notes matching the query. | |
| 498 | """ | |
| 499 | return _get_faraday_ready_dictionaries(workspace_name, 'notes', | |
| 500 | 'rows', **params) | |
| 501 | ||
| 502 | def get_commands(workspace_name, **params): | |
| 503 | """Get commands from the server. | |
| 504 | ||
| 505 | Args: | |
| 506 | workspace_name (str): the workspace from which to get the commands. | |
| 507 | **params: any of valid request parameters for CouchDB. | |
| 508 | ||
| 509 | Returns: | |
| 510 | A dictionary containing the commands matching the query. | |
| 511 | """ | |
| 512 | return _get_faraday_ready_dictionaries(workspace_name, 'commands', | |
| 513 | 'commands', **params) | |
| 514 | ||
| 515 | def get_objects(workspace_name, object_signature, **params): | |
| 516 | """Get any type of object from the server, be it hosts, vulns, interfaces, | |
| 517 | services, credentials, commands or notes. | |
| 518 | ||
| 519 | Args: | |
| 520 | workspace_name (str): the workspace from which to get the commands. | |
| 521 | object_signature (str): the type of object to get. Must equal 'hosts', | |
| 522 | 'vulns', 'interfaces', 'services', 'credentials', 'notes' or 'commands' | |
| 523 | **params: any of valid request parameters for CouchDB. | |
| 524 | ||
| 525 | Returns: | |
| 526 | A dictionary containing the commands matching the query. | |
| 527 | ||
| 528 | Raises: | |
| 529 | WrongObjectSignature: if the object_signature string didn't match | |
| 530 | a faraday object. | |
| 531 | """ | |
| 532 | object_to_func = {'hosts': get_hosts, | |
| 533 | 'vulns': get_vulns, | |
| 534 | 'interfaces': get_interfaces, | |
| 535 | 'services': get_services, | |
| 536 | 'credentials': get_credentials, | |
| 537 | 'notes': get_notes, | |
| 538 | 'commands': get_commands} | |
| 539 | try: | |
| 540 | appropiate_function = object_to_func[object_signature] | |
| 541 | except KeyError: | |
| 542 | raise WrongObjectSignature(object_signature) | |
| 543 | ||
| 544 | return appropiate_function(workspace_name, **params) | |
| 545 | ||
| 546 | ||
| 547 | def _websockets_changes(workspace_name, **extra_params): | |
| 548 | return WebsocketsChangesStream(workspace_name, 'localhost', **extra_params) | |
| 549 | ||
| 550 | ||
| 551 | # cha cha cha chaaaanges! | |
| 552 | def get_changes_stream(workspace_name, heartbeat='1000', stream_provider=_websockets_changes, **extra_params): | |
| 553 | """ | |
| 554 | stream_provider: A function that returns an instance of a Stream provider | |
| 555 | """ | |
| 556 | return stream_provider(workspace_name, feed='continuous', | |
| 557 | heartbeat=heartbeat, **extra_params) | |
| 558 | ||
| 559 | def get_workspaces_names(): | |
| 560 | """Returns: | |
| 561 | A dictionary with a list with the workspaces names.""" | |
| 562 | return _get("{0}/ws".format(_create_server_api_url())) | |
| 563 | ||
| 564 | # XXX: COUCH IT! | |
| 565 | def _clean_up_stupid_couch_response(response_string): | |
| 566 | """Couch likes to give invalid jsons as a response :). So nice.""" | |
| 567 | interesting_part = "{".join(response_string.split("{")[1:]) | |
| 568 | almost_there = interesting_part.split("}")[0:-1] | |
| 569 | ok_yeah = "}".join(almost_there) | |
| 570 | hopefully_valid_json = "{{{0}}}".format(ok_yeah) | |
| 571 | return json.loads(hopefully_valid_json) | |
| 572 | ||
| 573 | # XXX: COUCH IT! | |
| 574 | # COUCH IT LEVEL: REVOLUTIONS | |
| 575 | def get_object_before_last_revision(workspace_name, object_id): | |
| 576 | """Get an object before its last revision. Useful to get information about | |
| 577 | recently deleted objects. | |
| 578 | ||
| 579 | Warning: | |
| 580 | Error-pronce process. You should check for 'None' after usage, | |
| 581 | as that's the return value if any problem arose during execution. | |
| 582 | ||
| 583 | Args: | |
| 584 | workspace_name (str): the workspace where the object was | |
| 585 | object_id (str): the id of the object | |
| 586 | ||
| 587 | Returns: | |
| 588 | A dictionary with the object's information. | |
| 589 | """ | |
| 590 | get_url = _create_couch_get_url(workspace_name, object_id) | |
| 591 | ||
| 592 | response = _unsafe_io_with_server(requests.get, [200], get_url, | |
| 593 | params={'revs': 'true', 'open_revs': 'all'}) | |
| 594 | try: | |
| 595 | valid_json_response = _clean_up_stupid_couch_response(response.text) | |
| 596 | except ValueError: | |
| 597 | return None | |
| 598 | try: | |
| 599 | id_before_del = valid_json_response['_revisions']['ids'][1] | |
| 600 | new_number_for_rev = valid_json_response['_revisions']['start'] - 1 | |
| 601 | except KeyError: # one if never too safe when you call a function called "_clean_up_stupid_couch_response" | |
| 602 | return None | |
| 603 | ||
| 604 | rev_id_before_del = "{0}-{1}".format(new_number_for_rev, id_before_del) | |
| 605 | object_dict = _get(get_url, rev=rev_id_before_del) | |
| 606 | return object_dict | |
| 607 | ||
| 608 | ||
| 609 | def get_object(workspace_name, object_signature, object_id): | |
| 610 | """Get an unique object of arbitrary type. | |
| 611 | ||
| 612 | Args: | |
| 613 | workspace_name (str): the workspace where the object should be found. | |
| 614 | object_signature (str): must be either 'hosts', 'vulns', 'interfaces' | |
| 615 | 'services', 'credentials', 'notes' or 'commands'. | |
| 616 | object_id (str): the id of the object | |
| 617 | ||
| 618 | Returns: | |
| 619 | A dictionary containing information about the object. | |
| 620 | ||
| 621 | Raises: | |
| 622 | MoreThanOneObjectFoundByID: if for some reason the object_id is shared | |
| 623 | by two or more objects. This should never happen. If it does, | |
| 624 | contact Infobyte LCC. | |
| 625 | """ | |
| 626 | objects = get_objects(workspace_name, object_signature, couchid=object_id) | |
| 627 | return force_unique(objects) | |
| 628 | ||
| 629 | def get_host(workspace_name, host_id): | |
| 630 | """Get an unique host. | |
| 631 | ||
| 632 | Args: | |
| 633 | workspace_name (str): the workspace where the object should be found. | |
| 634 | host_id (str): the id of the host | |
| 635 | ||
| 636 | Returns: | |
| 637 | A dictionary containing information about the host. | |
| 638 | ||
| 639 | Raises: | |
| 640 | MoreThanOneObjectFoundByID: if for some reason the host id is shared | |
| 641 | by two or more objects. This should never happen. If it does, | |
| 642 | contact Infobyte LCC. | |
| 643 | """ | |
| 644 | return force_unique(get_hosts(workspace_name, couchid=host_id)) | |
| 645 | ||
| 646 | def get_vuln(workspace_name, vuln_id): | |
| 647 | """Get an unique vuln. | |
| 648 | ||
| 649 | Args: | |
| 650 | workspace_name (str): the workspace where the object should be found. | |
| 651 | vuln_id (str): the id of the vuln | |
| 652 | ||
| 653 | Returns: | |
| 654 | A dictionary containing information about the vuln. | |
| 655 | ||
| 656 | Raises: | |
| 657 | MoreThanOneObjectFoundByID: if for some reason the vuln id is shared | |
| 658 | by two or more objects. This should never happen. If it does, | |
| 659 | contact Infobyte LCC. | |
| 660 | """ | |
| 661 | return force_unique(get_vulns(workspace_name, couchid=vuln_id)) | |
| 662 | ||
| 663 | def get_web_vuln(workspace_name, vuln_id): | |
| 664 | """Get an unique web vuln. | |
| 665 | ||
| 666 | Args: | |
| 667 | workspace_name (str): the workspace where the object should be found. | |
| 668 | web vuln_id (str): the id of the web vuln | |
| 669 | ||
| 670 | Returns: | |
| 671 | A dictionary containing information about the web vuln. | |
| 672 | ||
| 673 | Raises: | |
| 674 | MoreThanOneObjectFoundByID: if for some reason the web vuln id is shared | |
| 675 | by two or more objects. This should never happen. If it does, | |
| 676 | contact Infobyte LCC. | |
| 677 | """ | |
| 678 | return force_unique(get_web_vulns(workspace_name, couchid=vuln_id)) | |
| 679 | ||
| 680 | def get_interface(workspace_name, interface_id): | |
| 681 | """Get an unique interface. | |
| 682 | ||
| 683 | Args: | |
| 684 | workspace_name (str): the workspace where the object should be found. | |
| 685 | interface_id (str): the id of the interface | |
| 686 | ||
| 687 | Returns: | |
| 688 | A dictionary containing information about the interface. | |
| 689 | ||
| 690 | Raises: | |
| 691 | MoreThanOneObjectFoundByID: if for some reason the interface id is shared | |
| 692 | by two or more objects. This should never happen. If it does, | |
| 693 | contact Infobyte LCC. | |
| 694 | """ | |
| 695 | return force_unique(get_interfaces(workspace_name, couchid=interface_id)) | |
| 696 | ||
| 697 | def get_service(workspace_name, service_id): | |
| 698 | """Get an unique service. | |
| 699 | ||
| 700 | Args: | |
| 701 | workspace_name (str): the workspace where the object should be found. | |
| 702 | service_id (str): the id of the service | |
| 703 | ||
| 704 | Returns: | |
| 705 | A dictionary containing information about the service. | |
| 706 | ||
| 707 | Raises: | |
| 708 | MoreThanOneObjectFoundByID: if for some reason the service id is shared | |
| 709 | by two or more objects. This should never happen. If it does, | |
| 710 | contact Infobyte LCC. | |
| 711 | """ | |
| 712 | return force_unique(get_services(workspace_name, couchid=service_id)) | |
| 713 | ||
| 714 | def get_note(workspace_name, note_id): | |
| 715 | """Get an unique note. | |
| 716 | ||
| 717 | Args: | |
| 718 | workspace_name (str): the workspace where the object should be found. | |
| 719 | note_id (str): the id of the note | |
| 720 | ||
| 721 | Returns: | |
| 722 | A dictionary containing information about the note. | |
| 723 | ||
| 724 | Raises: | |
| 725 | MoreThanOneObjectFoundByID: if for some reason the note id is shared | |
| 726 | by two or more objects. This should never happen. If it does, | |
| 727 | contact Infobyte LCC. | |
| 728 | """ | |
| 729 | return force_unique(get_notes(workspace_name, couchid=note_id)) | |
| 730 | ||
| 731 | def get_credential(workspace_name, credential_id): | |
| 732 | """Get an unique credential. | |
| 733 | ||
| 734 | Args: | |
| 735 | workspace_name (str): the workspace where the object should be found. | |
| 736 | credential_id (str): the id of the credential | |
| 737 | ||
| 738 | Returns: | |
| 739 | A dictionary containing information about the credential. | |
| 740 | ||
| 741 | Raises: | |
| 742 | MoreThanOneObjectFoundByID: if for some reason the credential id is shared | |
| 743 | by two or more objects. This should never happen. If it does, | |
| 744 | contact Infobyte LCC. | |
| 745 | """ | |
| 746 | return force_unique(get_services(workspace_name, couchid=credential_id)) | |
| 747 | ||
| 748 | def get_command(workspace_name, command_id): | |
| 749 | """Get an unique command. | |
| 750 | ||
| 751 | Args: | |
| 752 | workspace_name (str): the workspace where the object should be found. | |
| 753 | command_id (str): the id of the command | |
| 754 | ||
| 755 | Returns: | |
| 756 | A dictionary containing information about the command. | |
| 757 | ||
| 758 | Raises: | |
| 759 | MoreThanOneObjectFoundByID: if for some reason the command id is shared | |
| 760 | by two or more objects. This should never happen. If it does, | |
| 761 | contact Infobyte LCC. | |
| 762 | """ | |
| 763 | return force_unique(get_commands(workspace_name, couchid=command_id)) | |
| 764 | ||
| 765 | def get_workspace(workspace_name, **params): | |
| 766 | """Get an unique command. | |
| 767 | ||
| 768 | Args: | |
| 769 | command_name (str): the command where the object should be found. | |
| 770 | command_id (str): the id of the command | |
| 771 | ||
| 772 | Returns: | |
| 773 | A dictionary containing information about the command. | |
| 774 | ||
| 775 | Raises: | |
| 776 | MoreThanOneObjectFoundByID: if for some reason the command id is shared | |
| 777 | by two or more objects. This should never happen. If it does, | |
| 778 | contact Infobyte LCC. | |
| 779 | """ | |
| 780 | request_url = _create_server_get_url(workspace_name) | |
| 781 | return _get(request_url, **params) | |
| 782 | ||
| 783 | def get_workspace_summary(workspace_name): | |
| 784 | """Get a collection of data about the workspace. | |
| 785 | ||
| 786 | Args: | |
| 787 | workspace_name (str): the workspace to get the stats from. | |
| 788 | ||
| 789 | Returns: | |
| 790 | A dictionary with the workspace's information | |
| 791 | """ | |
| 792 | return _get_raw_workspace_summary(workspace_name)['stats'] | |
| 793 | ||
| 794 | def get_workspace_numbers(workspace_name): | |
| 795 | """Get the number of hosts, interfaces, services and vulns in the workspace. | |
| 796 | ||
| 797 | Args: | |
| 798 | workspace_name (str): the name of the workspace to query | |
| 799 | ||
| 800 | Return: | |
| 801 | A tuple of 4 elements with the amounts of hosts, interfaces, services and vulns. | |
| 802 | """ | |
| 803 | stats = _get_raw_workspace_summary(workspace_name)['stats'] | |
| 804 | return stats['hosts'], stats['services'], stats['total_vulns'] | |
| 805 | ||
| 806 | def get_hosts_number(workspace_name, **params): | |
| 807 | """ | |
| 808 | Args: | |
| 809 | workspace_name (str): the name of the workspace to query | |
| 810 | **params: any of the Couchdb request parameters | |
| 811 | ||
| 812 | Returns: | |
| 813 | The amount of hosts in the workspace as an integer. | |
| 814 | """ | |
| 815 | return int(get_workspace_summary(workspace_name)['hosts']) | |
| 816 | ||
| 817 | def get_services_number(workspace_name, **params): | |
| 818 | """ | |
| 819 | Args: | |
| 820 | workspace_name (str): the name of the workspace to query | |
| 821 | **params: any of the Couchdb request parameters | |
| 822 | ||
| 823 | Returns: | |
| 824 | The amount of services in the workspace as an integer. | |
| 825 | """ | |
| 826 | return int(get_workspace_summary(workspace_name)['services']) | |
| 827 | ||
| 828 | def get_interfaces_number(workspace_name, **params): | |
| 829 | """ | |
| 830 | Args: | |
| 831 | workspace_name (str): the name of the workspace to query | |
| 832 | **params: any of the Couchdb request parameters | |
| 833 | ||
| 834 | Returns: | |
| 835 | The amount of interfaces in the workspace as an integer. | |
| 836 | """ | |
| 837 | return int(get_workspace_summary(workspace_name)['interfaces']) | |
| 838 | ||
| 839 | def get_vulns_number(workspace_name, **params): | |
| 840 | """ | |
| 841 | Args: | |
| 842 | workspace_name (str): the name of the workspace to query | |
| 843 | **params: any of the Couchdb request parameters | |
| 844 | ||
| 845 | Returns: | |
| 846 | The amount of vulns in the workspace as an integer. | |
| 847 | """ | |
| 848 | return int(get_workspace_summary(workspace_name)['total_vulns']) | |
| 849 | ||
| 850 | def get_notes_number(workspace_name, **params): | |
| 851 | """ | |
| 852 | Args: | |
| 853 | workspace_name (str): the name of the workspace to query | |
| 854 | **params: any of the Couchdb request parameters | |
| 855 | ||
| 856 | Returns: | |
| 857 | The amount of notes in the workspace as an integer. | |
| 858 | """ | |
| 859 | return int(get_workspace_summary(workspace_name)['notes']) | |
| 860 | ||
| 861 | def get_credentials_number(workspace_name, **params): | |
| 862 | """ | |
| 863 | Args: | |
| 864 | workspace_name (str): the name of the workspace to query | |
| 865 | **params: any of the Couchdb request parameters | |
| 866 | ||
| 867 | Returns: | |
| 868 | The amount of credentials in the workspace as an integer. | |
| 869 | """ | |
| 870 | return int(_get_raw_credentials(workspace_name, **params)) | |
| 871 | ||
| 872 | def get_commands_number(workspace_name, **params): | |
| 873 | """ | |
| 874 | Args: | |
| 875 | workspace_name (str): the name of the workspace to query | |
| 876 | **params: any of the Couchdb request parameters | |
| 877 | ||
| 878 | Returns: | |
| 879 | The amount of commands in the workspace as an integer. | |
| 880 | """ | |
| 881 | return int(_get_raw_commands(workspace_name, **params)) | |
| 882 | ||
| 883 | def create_host(workspace_name, command_id, ip, os, default_gateway=None, | |
| 884 | description="", metadata=None, owned=False, owner="", | |
| 885 | parent=None, hostnames=None, mac=None): | |
| 886 | """Create a host. | |
| 887 | ||
| 888 | Args: | |
| 889 | workspace_name (str): the name of the workspace where the host will be saved. | |
| 890 | id (str): the id of the host. Must be unique. | |
| 891 | name (str): the host's name | |
| 892 | os (str): the operative system of the host | |
| 893 | default_gateway (str): the host's default_gateway | |
| 894 | description (str): a description. | |
| 895 | metadata: a collection of metadata. If you don't know the metada. leave | |
| 896 | on None. | |
| 897 | owned (bool): is the host owned or not? | |
| 898 | owner (str): an owner for the host | |
| 899 | parent (Faraday Object): the host's parent. If you don't know this, leave | |
| 900 | on None. | |
| 901 | ||
| 902 | Returns: | |
| 903 | A dictionary with the server's response. | |
| 904 | """ | |
| 905 | return _save_to_server(workspace_name, | |
| 906 | command_id=command_id, | |
| 907 | ip=ip, os=os, | |
| 908 | default_gateway=default_gateway, | |
| 909 | owned=owned, | |
| 910 | metadata=metadata, | |
| 911 | owner=owner, | |
| 912 | parent=parent, | |
| 913 | description=description, | |
| 914 | hostnames=hostnames, | |
| 915 | mac=mac, | |
| 916 | type="Host") | |
| 917 | ||
| 918 | def update_host(workspace_name, command_id, id, ip, os, default_gateway="", | |
| 919 | description="", metadata=None, owned=False, owner="", | |
| 920 | parent=None, hostnames=None, mac=None): | |
| 921 | """Updates a host. | |
| 922 | ||
| 923 | Args: | |
| 924 | workspace_name (str): the name of the workspace where the host will be saved. | |
| 925 | id (str): the id of the host. Must be unique. | |
| 926 | name (str): the host's name | |
| 927 | os (str): the operative system of the host | |
| 928 | default_gateway (str): the host's default_gateway | |
| 929 | description (str): a description. | |
| 930 | metadata: a collection of metadata. If you don't know the metada. leave | |
| 931 | on None, it will be created automatically. | |
| 932 | owned (bool): is the host owned or not? | |
| 933 | owner (str): an owner for the host | |
| 934 | parent (Faraday Object): the host's parent. If you don't know this, leave | |
| 935 | on None. | |
| 936 | ||
| 937 | Returns: | |
| 938 | A dictionary with the server's response. | |
| 939 | """ | |
| 940 | return _update_in_server(workspace_name, | |
| 941 | id, | |
| 942 | command_id=command_id, | |
| 943 | ip=ip, os=os, | |
| 944 | default_gateway=default_gateway, | |
| 945 | owned=owned, | |
| 946 | metadata=metadata, | |
| 947 | owner=owner, | |
| 948 | parent=parent, | |
| 949 | description=description, | |
| 950 | hostnames=hostnames, | |
| 951 | mac=mac, | |
| 952 | type="Host") | |
| 953 | ||
| 954 | ||
| 955 | def create_service(workspace_name, command_id, name, description, ports, parent, | |
| 956 | owned=False, owner="", protocol="", status="", version="", | |
| 957 | metadata=None): | |
| 958 | """Creates a service. | |
| 959 | ||
| 960 | Args: | |
| 961 | workspace_name (str): the name of the workspace where the service will be saved. | |
| 962 | id (str): the id of the service. Must be unique. | |
| 963 | name (str): the host's name | |
| 964 | description (str): a description. | |
| 965 | ports ([str]): a list of ports for the service. | |
| 966 | owned (bool): is the service owned or not? | |
| 967 | owner (str): an owner for the service | |
| 968 | protocol (str): the service's protocol | |
| 969 | status (str): the service's status | |
| 970 | version (str): the service's version | |
| 971 | metadata: a collection of metadata. If you don't know the metada. leave | |
| 972 | on None, it will be created automatically. | |
| 973 | ||
| 974 | Returns: | |
| 975 | A dictionary with the server's response. | |
| 976 | """ | |
| 977 | return _save_to_server(workspace_name, | |
| 978 | command_id=command_id, | |
| 979 | name=name, | |
| 980 | parent=parent, | |
| 981 | description=description, | |
| 982 | ports=ports, | |
| 983 | owned=owned, | |
| 984 | owner=owner, | |
| 985 | protocol=protocol, | |
| 986 | status=status, | |
| 987 | version=version, | |
| 988 | type="Service", | |
| 989 | metadata=metadata) | |
| 990 | ||
| 991 | def update_service(workspace_name, command_id, id, name, description, ports, | |
| 992 | parent, owned=False, owner="", protocol="", status="", | |
| 993 | version="", metadata=None): | |
| 994 | """Creates a service. | |
| 995 | ||
| 996 | Args: | |
| 997 | workspace_name (str): the name of the workspace where the service will be saved. | |
| 998 | id (str): the id of the service. Must be unique. | |
| 999 | name (str): the service's name | |
| 1000 | description (str): a description. | |
| 1001 | ports ([str]): a list of ports for the service. | |
| 1002 | owned (bool): is the host owned or not? | |
| 1003 | owner (str): an owner for the service | |
| 1004 | protocol (str): the service's protocol | |
| 1005 | status (str): the service's status | |
| 1006 | version (str): the service's version | |
| 1007 | metadata: a collection of metadata. If you don't know the metada. leave | |
| 1008 | on None, it will be created automatically. | |
| 1009 | ||
| 1010 | Returns: | |
| 1011 | A dictionary with the server's response. | |
| 1012 | """ | |
| 1013 | return _update_in_server(workspace_name, | |
| 1014 | id, | |
| 1015 | parent=parent, | |
| 1016 | command_id=command_id, | |
| 1017 | name=name, | |
| 1018 | description=description, | |
| 1019 | ports=ports, | |
| 1020 | owned=owned, | |
| 1021 | owner=owner, | |
| 1022 | protocol=protocol, | |
| 1023 | status=status, | |
| 1024 | version=version, | |
| 1025 | type="Service", | |
| 1026 | metadata=metadata) | |
| 1027 | ||
| 1028 | ||
| 1029 | def create_vuln(workspace_name, command_id, name, description, parent, parent_type, | |
| 1030 | owned=None, owner="", confirmed=False, | |
| 1031 | resolution="", data="", refs=None, severity="info", | |
| 1032 | desc="", metadata=None, status=None, policyviolations=[], external_id=None): | |
| 1033 | """Creates a vuln. | |
| 1034 | ||
| 1035 | Args: | |
| 1036 | workspace_name (str): the name of the workspace where the vuln will be saved. | |
| 1037 | id (str): the id of the vuln. Must be unique. | |
| 1038 | name (str): the vuln's name | |
| 1039 | description (str): a description. | |
| 1040 | owned (bool): is the vuln owned or not? | |
| 1041 | owner (str): an owner for the vuln | |
| 1042 | confirmed (bool): is the vulnerability confirmed? | |
| 1043 | data (str): any aditional data about the vuln | |
| 1044 | refs ([str]): references for the vulnerability | |
| 1045 | severity (str): a string indicating the vuln's severity. can be 'info', | |
| 1046 | 'low', 'med', 'high', 'critical' | |
| 1047 | resolution (str): the vuln's possible resolution | |
| 1048 | desc (str): a vuln's description. | |
| 1049 | status (str): the service's status | |
| 1050 | metadata: a collection of metadata. If you don't know the metada. leave | |
| 1051 | on None, it will be created automatically. | |
| 1052 | policyviolations (lst) : the policy violations | |
| 1053 | external_id (str) : plugin external id | |
| 1054 | ||
| 1055 | Returns: | |
| 1056 | A dictionary with the server's response. | |
| 1057 | """ | |
| 1058 | return _save_to_server(workspace_name, | |
| 1059 | command_id=command_id, | |
| 1060 | name=name, | |
| 1061 | description=description, | |
| 1062 | parent=parent, | |
| 1063 | parent_type=parent_type, | |
| 1064 | owned=owned, | |
| 1065 | owner=owner, | |
| 1066 | confirmed=confirmed, | |
| 1067 | data=data, | |
| 1068 | refs=refs, | |
| 1069 | severity=severity, | |
| 1070 | resolution=resolution, | |
| 1071 | desc=desc, | |
| 1072 | type="Vulnerability", | |
| 1073 | status=status, | |
| 1074 | metadata=metadata, | |
| 1075 | policyviolations=policyviolations, | |
| 1076 | external_id=external_id) | |
| 1077 | ||
| 1078 | def update_vuln(workspace_name, command_id, id, name, description, parent, | |
| 1079 | parent_type, owned=None, owner="", confirmed=False, data="", | |
| 1080 | refs=None, severity="info", resolution="", desc="", | |
| 1081 | metadata=None, status=None, policyviolations=[], external_id=None): | |
| 1082 | """Updates a vuln. | |
| 1083 | ||
| 1084 | Args: | |
| 1085 | workspace_name (str): the name of the workspace where the host will be saved. | |
| 1086 | id (str): the id of the host. Must be unique. | |
| 1087 | name (str): the host's name | |
| 1088 | description (str): a description. | |
| 1089 | owned (bool): is the vuln owned or not? | |
| 1090 | owner (str): an owner for the vuln | |
| 1091 | confirmed (bool): is the vulnerability confirmed? | |
| 1092 | data (str): any aditional data about the vuln | |
| 1093 | refs ([str]): references for the vulnerability | |
| 1094 | severity (str): a string indicating the vuln's severity. can be 'info', | |
| 1095 | 'low', 'med', 'high', 'critical' | |
| 1096 | resolution (str): the vuln's possible resolution | |
| 1097 | desc (str): a vuln's description. | |
| 1098 | status (str): the service's status | |
| 1099 | metadata: a collection of metadata. If you don't know the metada. leave | |
| 1100 | on None, it will be created automatically. | |
| 1101 | policyviolations (lst) : the policy violations | |
| 1102 | external_id (str) : plugin external id | |
| 1103 | ||
| 1104 | Returns: | |
| 1105 | A dictionary with the server's response. | |
| 1106 | """ | |
| 1107 | return _update_in_server(workspace_name, | |
| 1108 | id, | |
| 1109 | parent=parent, | |
| 1110 | parent_type=parent_type, | |
| 1111 | command_id=command_id, | |
| 1112 | name=name, | |
| 1113 | description=description, | |
| 1114 | owned=owned, | |
| 1115 | owner=owner, | |
| 1116 | confirmed=confirmed, | |
| 1117 | data=data, | |
| 1118 | refs=refs, | |
| 1119 | severity=severity, | |
| 1120 | resolution=resolution, | |
| 1121 | desc=desc, | |
| 1122 | type="Vulnerability", | |
| 1123 | status=status, | |
| 1124 | metadata=metadata, | |
| 1125 | policyviolations=policyviolations, | |
| 1126 | external_id=external_id) | |
| 1127 | ||
| 1128 | def create_vuln_web(workspace_name, command_id, name, description, parent, | |
| 1129 | parent_type, owned=None, owner="", confirmed=False, | |
| 1130 | data="", refs=None, severity="info", resolution="", | |
| 1131 | desc="", metadata=None, method=None, params="", | |
| 1132 | path=None, pname=None, query=None, request=None, | |
| 1133 | response=None, category="", website=None, | |
| 1134 | status=None, policyviolations=[], external_id=None): | |
| 1135 | """Creates a vuln web. | |
| 1136 | ||
| 1137 | Args: | |
| 1138 | workspace_name (str): the name of the workspace where the vuln web will be saved. | |
| 1139 | id (str): the id of the vuln web. Must be unique. | |
| 1140 | name (str): the vuln web's name | |
| 1141 | description (str): a description. | |
| 1142 | owner (str): an owner for the host | |
| 1143 | confirmed (bool): is the vulnerability confirmed? | |
| 1144 | data (str): any aditional data about the vuln | |
| 1145 | refs ([str]): references for the vulnerability | |
| 1146 | severity (str): a string indicating the vuln's severity. can be 'info', | |
| 1147 | 'low', 'med', 'high', 'critical' | |
| 1148 | resolution (str): the vuln's possible resolution | |
| 1149 | desc (str): a vuln's description. | |
| 1150 | metadata: a collection of metadata. If you don't know the metada. leave | |
| 1151 | on None, it will be created automatically. | |
| 1152 | method (str): the web vuln method | |
| 1153 | params (str): the parameters for the web vuln | |
| 1154 | path (str): the web vuln's path | |
| 1155 | query (str): the web vuln's query | |
| 1156 | request (str): the web vuln's request | |
| 1157 | response (str): the web vuln's response | |
| 1158 | category (str): a category for the web vuln's | |
| 1159 | website (str): the website where the vuln was found | |
| 1160 | status (str): the web vulns's status | |
| 1161 | policyviolations (lst) : the policy violations | |
| 1162 | external_id (str) : plugin external id | |
| 1163 | ||
| 1164 | Returns: | |
| 1165 | A dictionary with the server's response. | |
| 1166 | """ | |
| 1167 | return _save_to_server(workspace_name, | |
| 1168 | parent=parent, | |
| 1169 | parent_type=parent_type, | |
| 1170 | command_id=command_id, | |
| 1171 | name=name, | |
| 1172 | description=description, | |
| 1173 | owned=owned, | |
| 1174 | owner=owner, | |
| 1175 | confirmed=confirmed, | |
| 1176 | data=data, | |
| 1177 | refs=refs, | |
| 1178 | severity=severity, | |
| 1179 | resolution=resolution, | |
| 1180 | desc=desc, | |
| 1181 | metadata=metadata, | |
| 1182 | method=method, | |
| 1183 | params=params, | |
| 1184 | path=path, | |
| 1185 | pname=pname, | |
| 1186 | query=query, | |
| 1187 | request=request, | |
| 1188 | response=response, | |
| 1189 | website=website, | |
| 1190 | category=category, | |
| 1191 | status=status, | |
| 1192 | type='VulnerabilityWeb', | |
| 1193 | policyviolations=policyviolations, | |
| 1194 | external_id=external_id) | |
| 1195 | ||
| 1196 | def update_vuln_web(workspace_name, command_id, id, name, description, | |
| 1197 | parent, parent_type, owned=None, owner="", | |
| 1198 | confirmed=False, data="", refs=None, severity="info", resolution="", | |
| 1199 | desc="", metadata=None, method=None, params="", path=None, pname=None, | |
| 1200 | query=None, request=None, response=None, category="", website=None, | |
| 1201 | status=None, policyviolations=[], external_id=None): | |
| 1202 | """Creates a vuln web. | |
| 1203 | ||
| 1204 | Args: | |
| 1205 | workspace_name (str): the name of the workspace where the vuln web will be saved. | |
| 1206 | id (str): the id of the vuln web. Must be unique. | |
| 1207 | name (str): the vuln web's name | |
| 1208 | description (str): a description. | |
| 1209 | owner (str): an owner for the host | |
| 1210 | confirmed (bool): is the vulnerability confirmed? | |
| 1211 | data (str): any aditional data about the vuln | |
| 1212 | refs ([str]): references for the vulnerability | |
| 1213 | severity (str): a string indicating the vuln's severity. can be 'info', | |
| 1214 | 'low', 'med', 'high', 'critical' | |
| 1215 | resolution (str): the vuln's possible resolution | |
| 1216 | desc (str): a vuln's description. | |
| 1217 | metadata: a collection of metadata. If you don't know the metada. leave | |
| 1218 | on None, it will be created automatically. | |
| 1219 | method (str): the web vuln method | |
| 1220 | params (str): the parameters for the web vuln | |
| 1221 | path (str): the web vuln's path | |
| 1222 | query (str): the web vuln's query | |
| 1223 | request (str): the web vuln's request | |
| 1224 | response (str): the web vuln's response | |
| 1225 | category (str): a category for the web vuln's | |
| 1226 | website (str): the website where the vuln was found | |
| 1227 | status (str): the web vulns's status | |
| 1228 | policyviolations (lst) : the policy violations | |
| 1229 | external_id (str) : plugin external id | |
| 1230 | ||
| 1231 | Returns: | |
| 1232 | A dictionary with the server's response. | |
| 1233 | """ | |
| 1234 | ||
| 1235 | return _update_in_server(workspace_name, | |
| 1236 | id, | |
| 1237 | parent=parent, | |
| 1238 | parent_type=parent_type, | |
| 1239 | command_id=command_id, | |
| 1240 | name=name, | |
| 1241 | description=description, | |
| 1242 | owned=owned, | |
| 1243 | owner=owner, | |
| 1244 | confirmed=confirmed, | |
| 1245 | data=data, | |
| 1246 | refs=refs, | |
| 1247 | severity=severity, | |
| 1248 | resolution=resolution, | |
| 1249 | desc=desc, | |
| 1250 | metadata=metadata, | |
| 1251 | method=method, | |
| 1252 | params=params, | |
| 1253 | path=path, | |
| 1254 | pname=pname, | |
| 1255 | query=query, | |
| 1256 | request=request, | |
| 1257 | response=response, | |
| 1258 | website=website, | |
| 1259 | category=category, | |
| 1260 | status=status, | |
| 1261 | type='VulnerabilityWeb', | |
| 1262 | policyviolations=policyviolations, external_id=external_id) | |
| 1263 | ||
| 1264 | def create_note(workspace_name, command_id, object_type, object_id, name, text, owned=None, owner="", | |
| 1265 | description="", metadata=None): | |
| 1266 | """Creates a note. | |
| 1267 | ||
| 1268 | Args: | |
| 1269 | workspace_name (str): the name of the workspace where the vuln web will be saved. | |
| 1270 | id (str): the id of the vuln web. Must be unique. | |
| 1271 | name (str): the vuln web's name | |
| 1272 | text (str): the note's text | |
| 1273 | owned (bool): is the note owned? | |
| 1274 | owner (str): the note's owner | |
| 1275 | description (str): a description | |
| 1276 | metadata: a collection of metadata. If you don't know the metada. leave | |
| 1277 | on None, it will be created automatically. | |
| 1278 | ||
| 1279 | Returns: | |
| 1280 | A dictionary with the server's response. | |
| 1281 | """ | |
| 1282 | return _save_to_server(workspace_name, | |
| 1283 | command_id=command_id, | |
| 1284 | object_id=object_id, | |
| 1285 | object_type=object_type, | |
| 1286 | name=name, | |
| 1287 | description=description, | |
| 1288 | owned=owned, | |
| 1289 | owner=owner, | |
| 1290 | text=text, | |
| 1291 | type="Note", | |
| 1292 | metadata=metadata) | |
| 1293 | ||
| 1294 | def update_note(workspace_name, command_id, id, name, text, | |
| 1295 | object_type, object_id, owned=None, | |
| 1296 | owner="", description="", metadata=None): | |
| 1297 | """Updates a note. | |
| 1298 | ||
| 1299 | Args: | |
| 1300 | workspace_name (str): the name of the workspace where the vuln web will be saved. | |
| 1301 | id (str): the id of the vuln web. Must be unique. | |
| 1302 | name (str): the vuln web's name | |
| 1303 | text (str): the note's text | |
| 1304 | owned (bool): is the note owned? | |
| 1305 | owner (str): the note's owner | |
| 1306 | description (str): a description | |
| 1307 | metadata: a collection of metadata. If you don't know the metada. leave | |
| 1308 | on None, it will be created automatically. | |
| 1309 | ||
| 1310 | Returns: | |
| 1311 | A dictionary with the server's response. | |
| 1312 | """ | |
| 1313 | return _update_in_server(workspace_name, | |
| 1314 | id, | |
| 1315 | object_id=object_id, | |
| 1316 | object_type=object_type, | |
| 1317 | command_id=command_id, | |
| 1318 | name=name, | |
| 1319 | description=description, | |
| 1320 | owned=owned, | |
| 1321 | owner=owner, | |
| 1322 | text=text, | |
| 1323 | type="Note", | |
| 1324 | metadata=metadata) | |
| 1325 | ||
| 1326 | ||
| 1327 | def create_credential(workspace_name, command_id, name, username, password, | |
| 1328 | parent, parent_type, owned=None, owner="", | |
| 1329 | description="", metadata=None): | |
| 1330 | """Creates a credential. | |
| 1331 | ||
| 1332 | Args: | |
| 1333 | workspace_name (str): the name of the workspace where the vuln web will be saved. | |
| 1334 | id (str): the id of the vuln web. Must be unique. | |
| 1335 | name (str): the vuln web's name | |
| 1336 | username (str) | |
| 1337 | password (str) | |
| 1338 | owned (bool): is the note owned? | |
| 1339 | owner (str): the note's owner | |
| 1340 | description (str): a description | |
| 1341 | metadata: a collection of metadata. If you don't know the metada. leave | |
| 1342 | on None, it will be created automatically. | |
| 1343 | ||
| 1344 | Returns: | |
| 1345 | A dictionary with the server's response. | |
| 1346 | """ | |
| 1347 | return _save_to_server(workspace_name, | |
| 1348 | command_id=command_id, | |
| 1349 | parent=parent, | |
| 1350 | parent_type=parent_type, | |
| 1351 | name=name, | |
| 1352 | description=description, | |
| 1353 | owned=owned, | |
| 1354 | owner=owner, | |
| 1355 | metadata=metadata, | |
| 1356 | username=username, | |
| 1357 | password=password, | |
| 1358 | type="Cred") | |
| 1359 | ||
| 1360 | def update_credential(workspace_name, command_id, id, name, username, password, | |
| 1361 | parent, parent_type, owned=None, owner="", | |
| 1362 | description="", metadata=None): | |
| 1363 | """Updates a credential. | |
| 1364 | ||
| 1365 | Args: | |
| 1366 | workspace_name (str): the name of the workspace where the vuln web will be saved. | |
| 1367 | id (str): the id of the vuln web. Must be unique. | |
| 1368 | name (str): the vuln web's name | |
| 1369 | username (str) | |
| 1370 | password (str) | |
| 1371 | owned (bool): is the note owned? | |
| 1372 | owner (str): the note's owner | |
| 1373 | description (str): a description | |
| 1374 | metadata: a collection of metadata. If you don't know the metada. leave | |
| 1375 | on None, it will be created automatically. | |
| 1376 | ||
| 1377 | Returns: | |
| 1378 | A dictionary with the server's response. | |
| 1379 | """ | |
| 1380 | return _update_in_server(workspace_name, | |
| 1381 | id, | |
| 1382 | parent=parent, | |
| 1383 | parent_type=parent_type, | |
| 1384 | command_id=command_id, | |
| 1385 | name=name, | |
| 1386 | description=description, | |
| 1387 | owned=owned, | |
| 1388 | owner=owner, | |
| 1389 | metadata=metadata, | |
| 1390 | username=username, | |
| 1391 | password=password, | |
| 1392 | type="Cred") | |
| 1393 | ||
| 1394 | def create_command(workspace_name, command, tool, import_source, duration=None, hostname=None, | |
| 1395 | ip=None, itime=None, params=None, user=None): | |
| 1396 | """Creates a command. | |
| 1397 | ||
| 1398 | Args: | |
| 1399 | workspace_name (str): the name of the workspace where the vuln web will be saved. | |
| 1400 | command (str): the command to be created | |
| 1401 | duration (str). the command's duration | |
| 1402 | hostname (str): the hostname where the command was executed | |
| 1403 | ip (str): the ip of the host where the command was executed | |
| 1404 | itime (str): the time it took to run | |
| 1405 | params (str): the parameters given | |
| 1406 | user (str): the user that ran the command | |
| 1407 | ||
| 1408 | Returns: | |
| 1409 | A dictionary with the server's response. | |
| 1410 | """ | |
| 1411 | return _save_to_server(workspace_name, | |
| 1412 | command=command, | |
| 1413 | tool=tool, | |
| 1414 | import_source=import_source, | |
| 1415 | duration=duration, | |
| 1416 | hostname=hostname, | |
| 1417 | ip=ip, | |
| 1418 | itime=itime, | |
| 1419 | params=params, | |
| 1420 | user=user, | |
| 1421 | workspace=workspace_name, | |
| 1422 | type="CommandRunInformation") | |
| 1423 | ||
| 1424 | def update_command(workspace_name, command_id, command, tool, import_source | |
| 1425 | ,duration=None, hostname=None, | |
| 1426 | ip=None, itime=None, params=None, user=None): | |
| 1427 | """Updates a command. | |
| 1428 | ||
| 1429 | Args: | |
| 1430 | workspace_name (str): the name of the workspace where the vuln web will be saved. | |
| 1431 | id (str): the id of the vuln web. Must be unique. | |
| 1432 | command (str): the command to be created | |
| 1433 | duration (str). the command's duration | |
| 1434 | hostname (str): the hostname where the command was executed | |
| 1435 | ip (str): the ip of the host where the command was executed | |
| 1436 | itime (str): the time it took to run | |
| 1437 | params (str): the parameters given | |
| 1438 | user (str): the user that ran the command | |
| 1439 | ||
| 1440 | Returns: | |
| 1441 | A dictionary with the server's response. | |
| 1442 | """ | |
| 1443 | return _update_in_server(workspace_name, | |
| 1444 | command_id, | |
| 1445 | command=command, | |
| 1446 | tool=tool, | |
| 1447 | import_source=import_source, | |
| 1448 | duration=duration, | |
| 1449 | hostname=hostname, | |
| 1450 | ip=ip, | |
| 1451 | itime=itime, | |
| 1452 | params=params, | |
| 1453 | user=user, | |
| 1454 | workspace=workspace_name, | |
| 1455 | type="CommandRunInformation") | |
| 1456 | ||
| 1457 | ||
| 1458 | def create_workspace(workspace_name, description, start_date, finish_date, | |
| 1459 | customer=None, duration=None): | |
| 1460 | """Create a workspace. | |
| 1461 | ||
| 1462 | Args: | |
| 1463 | workspace_name (str): the workspace's name | |
| 1464 | description (str): a description for the worksapce | |
| 1465 | start_date (str): a date to represent when work began in the workspace | |
| 1466 | finish_date (str): a date to represent when work will be finished on the workspace | |
| 1467 | customer (str): the customer for which we are creating the workspace | |
| 1468 | ||
| 1469 | Returns: | |
| 1470 | A dictionary with the server's response. | |
| 1471 | """ | |
| 1472 | if duration is None: | |
| 1473 | duration = {"start": start_date, "end": finish_date} | |
| 1474 | return _save_db_to_server(workspace_name, | |
| 1475 | name=workspace_name, | |
| 1476 | description=description, | |
| 1477 | customer=customer, | |
| 1478 | duration=duration, | |
| 1479 | type="Workspace") | |
| 1480 | ||
| 1481 | ||
| 1482 | def delete_host(workspace_name, host_id): | |
| 1483 | """Delete host of id host_id from the database.""" | |
| 1484 | return _delete_from_server(workspace_name, 'Host', host_id) | |
| 1485 | ||
| 1486 | ||
| 1487 | def delete_service(workspace_name, service_id): | |
| 1488 | """Delete service of id service_id from the database.""" | |
| 1489 | return _delete_from_server(workspace_name, 'Service', service_id) | |
| 1490 | ||
| 1491 | ||
| 1492 | def delete_vuln(workspace_name, vuln_id): | |
| 1493 | """Delete vuln of id vuln_id from the database.""" | |
| 1494 | return _delete_from_server(workspace_name, 'Vulnerability', vuln_id) | |
| 1495 | ||
| 1496 | ||
| 1497 | def delete_note(workspace_name, note_id): | |
| 1498 | """Delete note of id note_id from the database.""" | |
| 1499 | return _delete_from_server(workspace_name, note_id) | |
| 1500 | ||
| 1501 | ||
| 1502 | def delete_credential(workspace_name, credential_id): | |
| 1503 | """Delete credential of id credential_id from the database.""" | |
| 1504 | return _delete_from_server(workspace_name, 'Credential', credential_id) | |
| 1505 | ||
| 1506 | ||
| 1507 | def delete_command(workspace_name, command_id): | |
| 1508 | """Delete command of id command_id from the database.""" | |
| 1509 | return _delete_from_server(workspace_name, 'Command', command_id) | |
| 1510 | ||
| 1511 | ||
| 1512 | def delete_workspace(workspace_name): | |
| 1513 | """Delete the couch database of id workspace_name""" | |
| 1514 | db_url = _create_server_db_url(workspace_name) | |
| 1515 | return _delete(db_url, database=True) | |
| 1516 | ||
| 1517 | def server_info(): | |
| 1518 | """Return server info if we can stablish a connection with the server, | |
| 1519 | None otherwise. | |
| 1520 | """ | |
| 1521 | try: | |
| 1522 | return _get("{0}/info".format(_create_server_api_url())) | |
| 1523 | except: | |
| 1524 | return None | |
| 1525 | ||
| 1526 | def login_user(uri, uname, upass): | |
| 1527 | auth = {"email": uname, "password": upass} | |
| 1528 | try: | |
| 1529 | resp = requests.post(urlparse.urljoin(uri, "/_api/login"), json=auth) | |
| 1530 | if resp.status_code == 401: | |
| 1531 | return None | |
| 1532 | else: | |
| 1533 | return resp.cookies | |
| 1534 | except requests.adapters.ConnectionError: | |
| 1535 | return None | |
| 1536 | except requests.adapters.ReadTimeout: | |
| 1537 | return None | |
| 1538 | ||
| 1539 | ||
| 1540 | def is_authenticated(uri, cookies): | |
| 1541 | try: | |
| 1542 | resp = requests.get(urlparse.urljoin(uri, "/_api/session"), cookies=cookies, timeout=1) | |
| 1543 | if resp.status_code != 403: | |
| 1544 | user_info = resp.json() | |
| 1545 | return bool(user_info.get('username', {})) | |
| 1546 | else: | |
| 1547 | return False | |
| 1548 | except requests.adapters.ConnectionError: | |
| 1549 | return False | |
| 1550 | except requests.adapters.ReadTimeout: | |
| 1551 | return False | |
| 1552 | ||
| 1553 | def check_faraday_version(): | |
| 1554 | """Raise RuntimeError if client and server aren't running the same version""" | |
| 1555 | info = server_info() | |
| 1556 | ||
| 1557 | faraday_directory = os.path.dirname(os.path.realpath('faraday.py')) | |
| 1558 | ||
| 1559 | if info is not None and f_version != info['Version']: | |
| 1560 | raise RuntimeError('Client and server versions do not match') | |
| 1561 | ||
| 1562 | def check_server_url(url_to_test): | |
| 1563 | """Return True if the url_to_test is indeed a valid Faraday Server URL. | |
| 1564 | False otherwise. | |
| 1565 | """ | |
| 1566 | try: | |
| 1567 | resp = _get("{0}/_api/v2/info".format(url_to_test)) | |
| 1568 | return 'Faraday Server' in resp | |
| 1569 | except Exception as ex: | |
| 1570 | logger.exception(ex) | |
| 1571 | test_okey = False | |
| 1572 | return test_okey | |
| 1573 | ||
| 1574 | def get_user_info(): | |
| 1575 | try: | |
| 1576 | resp = requests.get(urlparse.urljoin(_get_base_server_url(), "/_api/session"), cookies=_conf().getDBSessionCookies(), timeout=1) | |
| 1577 | if (resp.status_code != 401) and (resp.status_code != 403): | |
| 1578 | return resp.json() | |
| 1579 | else: | |
| 1580 | return False | |
| 1581 | except requests.adapters.ConnectionError: | |
| 1582 | return False | |
| 1583 | except requests.adapters.ReadTimeout: | |
| 1584 | return False | |
| 1585 | ||
| 1586 | ||
| 1587 | # I'm Py3 |
| 0 | #!/usr/bin/python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | ||
| 7 | """ | |
| 8 | class ServerRequestException(Exception): | |
| 9 | def __init__(self): | |
| 10 | pass | |
| 11 | ||
| 12 | class MoreThanOneObjectFoundByID(ServerRequestException): | |
| 13 | def __init__(self, faulty_list): | |
| 14 | self.faulty_list = faulty_list | |
| 15 | ||
| 16 | def __str__(self): | |
| 17 | return ("More than one object has been found." | |
| 18 | "These are all the objects found with the same ID: {0}" | |
| 19 | .format(self.faulty_list)) | |
| 20 | ||
| 21 | ||
| 22 | class CantCommunicateWithServerError(ServerRequestException): | |
| 23 | def __init__(self, function, server_url, payload, response=None): | |
| 24 | self.function = function | |
| 25 | self.server_url = server_url | |
| 26 | self.payload = payload | |
| 27 | self.response = response | |
| 28 | ||
| 29 | def __str__(self): | |
| 30 | if self.response is None: | |
| 31 | response_text = '' | |
| 32 | else: | |
| 33 | response_text = self.response.text | |
| 34 | return ("Couldn't get a valid response from the server when requesting " | |
| 35 | "to URL {0} and function {1}. Response was {2}".format(self.server_url, | |
| 36 | self.function, response_text)) | |
| 37 | ||
| 38 | class ConflictInDatabase(ServerRequestException): | |
| 39 | def __init__(self, answer): | |
| 40 | self.answer = answer | |
| 41 | ||
| 42 | def __str__(self): | |
| 43 | return ("There was a conflict trying to save your document. " | |
| 44 | "Most probably the document already existed and you " | |
| 45 | "did not provided a _rev argument to your payload. " | |
| 46 | "The answer from the server was {0}".format(self.answer)) | |
| 47 | ||
| 48 | class ResourceDoesNotExist(ServerRequestException): | |
| 49 | def __init__(self, url): | |
| 50 | self.url = url | |
| 51 | ||
| 52 | def __str__(self): | |
| 53 | return ("Can't find anything on URL {0}".format(self.url)) | |
| 54 | ||
| 55 | class Unauthorized(ServerRequestException): | |
| 56 | def __init__(self, answer): | |
| 57 | self.answer = answer | |
| 58 | ||
| 59 | def __str__(self): | |
| 60 | return ("You're not authorized to make this request. " | |
| 61 | "The answer from the server was {0}. Please check that your domain is the correct one and run Faraday GTK with option --login".format(self.answer)) | |
| 62 | ||
| 63 | class CouchDBException(Exception): | |
| 64 | def __init__(self): | |
| 65 | pass | |
| 66 | ||
| 67 | class ChangesStreamStoppedAbruptly(CouchDBException): | |
| 68 | def __str__(self): | |
| 69 | return ("The changes stream from CouchDB ended abruptly for some " | |
| 70 | "unkown reason.") | |
| 71 | ||
| 72 | ||
| 73 | class WrongObjectSignature(Exception): | |
| 74 | def __init__(self, param): | |
| 75 | self.param = param | |
| 76 | ||
| 77 | def __str__(self): | |
| 78 | return ("object_signature must be either 'host', 'vuln', 'vuln_web'," | |
| 79 | "'interface' 'service', 'credential' or 'note' and it was {0}" | |
| 80 | .format(self.param)) | |
| 81 | ||
| 82 | class CantAccessConfigurationWithoutTheClient(Exception): | |
| 83 | def __init__(self): | |
| 84 | pass | |
| 85 | ||
| 86 | def __str__(self): | |
| 87 | return ("You're tring to access to the Faraday Configuration without " | |
| 88 | "having the client up. This is not possible at the moment.") | |
| 89 | # I'm Py3⏎ |
| 0 | #!/usr/bin/python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | """ | |
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | ||
| 7 | """ | |
| 8 | from __future__ import absolute_import | |
| 9 | ||
| 10 | import re | |
| 11 | import logging | |
| 12 | import socket | |
| 13 | ||
| 14 | logger = logging.getLogger(__name__) | |
| 15 | ||
| 16 | ||
| 17 | from faraday.client.persistence.server.server_io_exceptions import MoreThanOneObjectFoundByID | |
| 18 | ||
| 19 | ||
| 20 | def force_unique(lst): | |
| 21 | """Takes a list and return its only member if the list len is 1, | |
| 22 | None if list is empty or raises an MoreThanOneObjectFoundByID error | |
| 23 | if list has more than one element. | |
| 24 | """ | |
| 25 | if len(lst) == 1: | |
| 26 | return lst[0] | |
| 27 | elif len(lst) == 0: | |
| 28 | return None | |
| 29 | else: | |
| 30 | raise MoreThanOneObjectFoundByID(lst) | |
| 31 | ||
| 32 | ||
| 33 | def get_object_properties(obj): | |
| 34 | # this sometimes is the metadata object and sometimes its a dictionary | |
| 35 | # a better fix awaits in a brighter future | |
| 36 | metadata = obj.getMetadata() | |
| 37 | if not isinstance(obj.getMetadata(), dict): | |
| 38 | metadata = metadata.toDict() | |
| 39 | ||
| 40 | return { | |
| 41 | 'name': obj.getName(), | |
| 42 | 'description': obj.getDescription(), | |
| 43 | 'metadata': metadata, | |
| 44 | 'owned': obj.isOwned(), | |
| 45 | 'owner': obj.getOwner() | |
| 46 | } | |
| 47 | ||
| 48 | ||
| 49 | def get_host_properties(host): | |
| 50 | host_dict = { | |
| 51 | 'os': host.getOS(), | |
| 52 | 'hostnames': host.getHostnames(), | |
| 53 | 'mac': host.getMac() | |
| 54 | } | |
| 55 | if host.getDefaultGateway(): | |
| 56 | host_dict['default_gateway'] = host.getDefaultGateway() | |
| 57 | host_dict.update(get_object_properties(host)) | |
| 58 | # name was removed from host and changed to ip | |
| 59 | ip = host_dict.pop('name') | |
| 60 | if 'ip' not in host_dict and ip: | |
| 61 | #TODO: check ip v6 | |
| 62 | if re.match(r"^\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}$", ip) is None: | |
| 63 | logger.warn('Host with invalid IP address detected.') | |
| 64 | logger.warn('Let\'s try to resolve %s', ip) | |
| 65 | try: | |
| 66 | #This is not perfect. Could resolve to different ip addr depending on the dns registry. | |
| 67 | hostname = ip | |
| 68 | ip = socket.gethostbyname(ip) | |
| 69 | logger.warn('Resolved to %s', ip) | |
| 70 | #Adding to hostnames list | |
| 71 | logger.debug('Adding host %s to hostnames list', ip) | |
| 72 | host_dict['hostnames'].append(hostname) | |
| 73 | #In case of dup hostnames | |
| 74 | host_dict['hostnames'] = list(set(host_dict['hostnames'])) | |
| 75 | except socket.gaierror as e: | |
| 76 | logger.warning('Couldn\'t resolve hostname %s', ip) | |
| 77 | host_dict['ip'] = ip | |
| 78 | return host_dict | |
| 79 | ||
| 80 | ||
| 81 | def get_service_properties(service): | |
| 82 | service_dict = { | |
| 83 | 'ports': service.getPorts(), | |
| 84 | 'protocol': service.getProtocol(), | |
| 85 | 'status': service.getStatus(), | |
| 86 | 'version': service.getVersion(), | |
| 87 | 'parent': service.getParent() | |
| 88 | } | |
| 89 | service_dict.update(get_object_properties(service)) | |
| 90 | return service_dict | |
| 91 | ||
| 92 | ||
| 93 | def get_vuln_properties(vuln): | |
| 94 | vuln_dict = { | |
| 95 | 'confirmed': vuln.getConfirmed(), | |
| 96 | 'data': vuln.getData(), | |
| 97 | 'refs': vuln.getRefs(), | |
| 98 | 'severity': vuln.getSeverity(), | |
| 99 | 'resolution': vuln.getResolution(), | |
| 100 | 'desc': vuln.getDesc(), | |
| 101 | 'status': vuln.getStatus(), | |
| 102 | 'policyviolations': vuln.getPolicyViolations(), | |
| 103 | 'parent': vuln.getParent(), | |
| 104 | 'parent_type': vuln.getParentType(), | |
| 105 | 'external_id': vuln.getExternalID() | |
| 106 | } | |
| 107 | vuln_dict.update(get_object_properties(vuln)) | |
| 108 | return vuln_dict | |
| 109 | ||
| 110 | ||
| 111 | def get_vuln_web_properties(vuln_web): | |
| 112 | vuln_web_dict = { | |
| 113 | 'method': vuln_web.getMethod(), | |
| 114 | 'params': vuln_web.getParams(), | |
| 115 | 'request': vuln_web.getRequest() or '', | |
| 116 | 'response': vuln_web.getResponse() or '', | |
| 117 | 'website': vuln_web.getWebsite(), | |
| 118 | 'path': vuln_web.getPath(), | |
| 119 | 'pname': vuln_web.getPname() or '', | |
| 120 | 'query': vuln_web.getQuery(), | |
| 121 | 'status': vuln_web.getStatus(), | |
| 122 | 'parent': vuln_web.getParent(), | |
| 123 | 'parent_type': vuln_web.getParentType(), | |
| 124 | 'external_id': vuln_web.getExternalID() | |
| 125 | } | |
| 126 | vuln_web_dict.update(get_object_properties(vuln_web)) | |
| 127 | vuln_web_dict.update(get_vuln_properties(vuln_web)) | |
| 128 | return vuln_web_dict | |
| 129 | ||
| 130 | ||
| 131 | def get_note_properties(note): | |
| 132 | text = note.getText() | |
| 133 | if note.getName(): | |
| 134 | text = '{0}\n{1}'.format(note.getName(), note.getText()) | |
| 135 | note_dict = { | |
| 136 | 'text': text, | |
| 137 | 'object_id': note.getObjectID(), | |
| 138 | 'object_type': note.getObjectType() | |
| 139 | } | |
| 140 | note_dict.update(get_object_properties(note)) | |
| 141 | return note_dict | |
| 142 | ||
| 143 | ||
| 144 | def get_credential_properties(credential): | |
| 145 | cred_dict = { | |
| 146 | 'username': credential.getUsername(), | |
| 147 | 'password': credential.getPassword(), | |
| 148 | 'parent': credential.getParent(), | |
| 149 | 'parent_type': credential.getParentType(), | |
| 150 | } | |
| 151 | cred_dict.update(get_object_properties(credential)) | |
| 152 | return cred_dict | |
| 153 | ||
| 154 | ||
| 155 | def get_command_properties(command): | |
| 156 | return { | |
| 157 | 'command': command.command, | |
| 158 | 'tool': command.command, | |
| 159 | 'user': command.user, | |
| 160 | 'ip': command.ip, | |
| 161 | 'hostname': command.hostname, | |
| 162 | 'itime': command.itime, | |
| 163 | 'duration': command.duration, | |
| 164 | 'params': command.params, | |
| 165 | 'import_source': command.import_source, | |
| 166 | } | |
| 167 | ||
| 168 | ||
| 169 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | """ | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | """ | |
| 9 | from past.builtins import basestring | |
| 10 | from builtins import range | |
| 11 | ||
| 12 | import os | |
| 13 | import time | |
| 14 | import shlex | |
| 15 | import logging | |
| 16 | from threading import Thread | |
| 17 | from multiprocessing import JoinableQueue, Process | |
| 18 | ||
| 19 | from faraday.config.configuration import getInstanceConfiguration | |
| 20 | from faraday.client.plugins.plugin import PluginProcess | |
| 21 | import faraday.client.model.api | |
| 22 | from faraday.client.model.commands_history import CommandRunInformation | |
| 23 | from faraday.client.model import Modelactions | |
| 24 | ||
| 25 | from faraday.config.constant import ( | |
| 26 | CONST_FARADAY_ZSH_OUTPUT_PATH, | |
| 27 | ) | |
| 28 | ||
| 29 | from faraday.client.start_client import ( | |
| 30 | CONST_FARADAY_HOME_PATH, | |
| 31 | ) | |
| 32 | CONF = getInstanceConfiguration() | |
| 33 | ||
| 34 | logger = logging.getLogger(__name__) | |
| 35 | ||
| 36 | ||
| 37 | class PluginCommiter(Thread): | |
| 38 | ||
| 39 | def __init__(self, output_queue, output, pending_actions, plugin, command, mapper_manager, end_event=None): | |
| 40 | super(PluginCommiter, self).__init__(name="PluginCommiterThread") | |
| 41 | self.output_queue = output_queue | |
| 42 | self.pending_actions = pending_actions | |
| 43 | self.stop = False | |
| 44 | self.plugin = plugin | |
| 45 | self.command = command | |
| 46 | self.mapper_manager = mapper_manager | |
| 47 | self.output = output | |
| 48 | self._report_path = os.path.join(CONF.getReportPath(), command.workspace) | |
| 49 | self._report_ppath = os.path.join(self._report_path, "process") | |
| 50 | self._report_upath = os.path.join(self._report_path, "unprocessed") | |
| 51 | self.end_event = end_event | |
| 52 | ||
| 53 | def stop(self): | |
| 54 | self.stop = True | |
| 55 | ||
| 56 | def commit(self): | |
| 57 | logger.info('Plugin end. Commiting to faraday server.') | |
| 58 | self.pending_actions.put( | |
| 59 | (Modelactions.PLUGINEND, self.plugin.id, self.command.getID())) | |
| 60 | self.command.duration = time.time() - self.command.itime | |
| 61 | self.mapper_manager.update(self.command) | |
| 62 | if self.end_event: | |
| 63 | self.end_event.set() | |
| 64 | ||
| 65 | def run(self): | |
| 66 | name = '' | |
| 67 | try: | |
| 68 | self.output_queue.join() | |
| 69 | self.commit() | |
| 70 | if b'\0' not in self.output and os.path.isfile(self.output): | |
| 71 | # sometimes output is a filepath | |
| 72 | name = os.path.basename(self.output) | |
| 73 | os.rename(self.output, | |
| 74 | os.path.join(self._report_ppath, name)) | |
| 75 | except Exception as ex: | |
| 76 | logger.exception(ex) | |
| 77 | logger.warning('Something failed, moving file to unprocessed') | |
| 78 | os.rename(self.output, os.path.join(self._report_upath, name)) | |
| 79 | ||
| 80 | ||
| 81 | ||
| 82 | class PluginController(Thread): | |
| 83 | """ | |
| 84 | TODO: Doc string. | |
| 85 | """ | |
| 86 | def __init__(self, id, plugin_manager, mapper_manager, pending_actions, end_event=None): | |
| 87 | super(PluginController, self).__init__(name="PluginControllerThread") | |
| 88 | self.plugin_manager = plugin_manager | |
| 89 | self._plugins = plugin_manager.getPlugins() | |
| 90 | self.id = id | |
| 91 | self._actionDispatcher = None | |
| 92 | self._setupActionDispatcher() | |
| 93 | self._mapper_manager = mapper_manager | |
| 94 | self.output_path = os.path.join( | |
| 95 | os.path.expanduser(CONST_FARADAY_HOME_PATH), | |
| 96 | CONST_FARADAY_ZSH_OUTPUT_PATH) | |
| 97 | self._active_plugins = {} | |
| 98 | self.plugin_sets = {} | |
| 99 | self.plugin_manager.addController(self, self.id) | |
| 100 | self.stop = False | |
| 101 | self.pending_actions = pending_actions | |
| 102 | self.end_event = end_event | |
| 103 | ||
| 104 | def _find_plugin(self, plugin_id): | |
| 105 | return self._plugins.get(plugin_id, None) | |
| 106 | ||
| 107 | def _is_command_malformed(self, original_command, modified_command): | |
| 108 | """ | |
| 109 | Checks if the command to be executed is safe and it's not in the | |
| 110 | block list defined by the user. Returns False if the modified | |
| 111 | command is ok, True if otherwise. | |
| 112 | """ | |
| 113 | block_chars = {"|", "$", "#"} | |
| 114 | ||
| 115 | if original_command == modified_command: | |
| 116 | return False | |
| 117 | ||
| 118 | orig_cmd_args = shlex.split(original_command) | |
| 119 | ||
| 120 | if not isinstance(modified_command, basestring): | |
| 121 | modified_command = "" | |
| 122 | mod_cmd_args = shlex.split(modified_command) | |
| 123 | ||
| 124 | block_flag = False | |
| 125 | orig_args_len = len(orig_cmd_args) | |
| 126 | for index in range(0, len(mod_cmd_args)): | |
| 127 | if (index < orig_args_len and | |
| 128 | orig_cmd_args[index] == mod_cmd_args[index]): | |
| 129 | continue | |
| 130 | ||
| 131 | for char in block_chars: | |
| 132 | if char in mod_cmd_args[index]: | |
| 133 | block_flag = True | |
| 134 | break | |
| 135 | ||
| 136 | return block_flag | |
| 137 | ||
| 138 | def _get_plugins_by_input(self, cmd, plugin_set): | |
| 139 | for plugin in plugin_set.values(): | |
| 140 | if isinstance(cmd, bytes): | |
| 141 | cmd = cmd.decode() | |
| 142 | if plugin.canParseCommandString(cmd): | |
| 143 | return plugin | |
| 144 | return None | |
| 145 | ||
| 146 | def getAvailablePlugins(self): | |
| 147 | """ | |
| 148 | Return a dictionary with the available plugins. | |
| 149 | Plugin ID's as keys and plugin instences as values | |
| 150 | """ | |
| 151 | return self._plugins | |
| 152 | ||
| 153 | def stop(self): | |
| 154 | self.plugin_process.stop() | |
| 155 | self.stop = True | |
| 156 | ||
| 157 | def processOutput(self, plugin, output, command, isReport=False): | |
| 158 | """ | |
| 159 | Process the output of the plugin. This will start the PluginProcess | |
| 160 | and also PluginCommiter (thread) that will informa to faraday server | |
| 161 | when the command finished. | |
| 162 | ||
| 163 | :param plugin: Plugin to execute | |
| 164 | :param output: read output from plugin or term | |
| 165 | :param command_id: command id that started the plugin | |
| 166 | :param isReport: Report or output from shell | |
| 167 | :return: None | |
| 168 | """ | |
| 169 | output_queue = JoinableQueue() | |
| 170 | plugin.set_actions_queue(self.pending_actions) | |
| 171 | self.plugin_process = PluginProcess(plugin, output_queue, isReport) | |
| 172 | logger.info("Created plugin_process (%d) for plugin instance (%d)", id(self.plugin_process), id(plugin)) | |
| 173 | self.pending_actions.put((Modelactions.PLUGINSTART, plugin.id, command.getID())) | |
| 174 | output_queue.put((output, command.getID())) | |
| 175 | plugin_commiter = PluginCommiter( | |
| 176 | output_queue, | |
| 177 | output, | |
| 178 | self.pending_actions, | |
| 179 | plugin, | |
| 180 | command, | |
| 181 | self._mapper_manager, | |
| 182 | self.end_event, | |
| 183 | ) | |
| 184 | plugin_commiter.start() | |
| 185 | # This process is stopped when plugin commiter joins output queue | |
| 186 | self.plugin_process.start() | |
| 187 | ||
| 188 | def _processAction(self, action, parameters): | |
| 189 | """ | |
| 190 | decodes and performs the action given | |
| 191 | It works kind of a dispatcher | |
| 192 | """ | |
| 193 | logger.debug("_processAction - %s - parameters = %s", action, parameters) | |
| 194 | self._actionDispatcher[action](*parameters) | |
| 195 | ||
| 196 | def _setupActionDispatcher(self): | |
| 197 | self._actionDispatcher = { | |
| 198 | Modelactions.ADDHOST: faraday.client.model.api.addHost, | |
| 199 | Modelactions.ADDSERVICEHOST: faraday.client.model.api.addServiceToHost, | |
| 200 | #Vulnerability | |
| 201 | Modelactions.ADDVULNHOST: faraday.client.model.api.addVulnToHost, | |
| 202 | Modelactions.ADDVULNSRV: faraday.client.model.api.addVulnToService, | |
| 203 | #VulnWeb | |
| 204 | Modelactions.ADDVULNWEBSRV: faraday.client.model.api.addVulnWebToService, | |
| 205 | #Note | |
| 206 | Modelactions.ADDNOTEHOST: faraday.client.model.api.addNoteToHost, | |
| 207 | Modelactions.ADDNOTESRV: faraday.client.model.api.addNoteToService, | |
| 208 | Modelactions.ADDNOTENOTE: faraday.client.model.api.addNoteToNote, | |
| 209 | #Creds | |
| 210 | Modelactions.ADDCREDSRV: faraday.client.model.api.addCredToService, | |
| 211 | #LOG | |
| 212 | Modelactions.LOG: faraday.client.model.api.log, | |
| 213 | Modelactions.DEVLOG: faraday.client.model.api.devlog, | |
| 214 | # Plugin state | |
| 215 | Modelactions.PLUGINSTART: faraday.client.model.api.pluginStart, | |
| 216 | Modelactions.PLUGINEND: faraday.client.model.api.pluginEnd | |
| 217 | } | |
| 218 | ||
| 219 | def updatePluginSettings(self, plugin_id, new_settings): | |
| 220 | for plugin_set in self.plugin_sets.values(): | |
| 221 | if plugin_id in plugin_set: | |
| 222 | plugin_set[plugin_id].updateSettings(new_settings) | |
| 223 | if plugin_id in self._plugins: | |
| 224 | self._plugins[plugin_id].updateSettings(new_settings) | |
| 225 | ||
| 226 | def createPluginSet(self, pid): | |
| 227 | self.plugin_sets[pid] = self.plugin_manager.getPlugins() | |
| 228 | ||
| 229 | def processCommandInput(self, pid, cmd, pwd): | |
| 230 | """ | |
| 231 | This method tries to find a plugin to parse the command sent | |
| 232 | by the terminal (identiefied by the process id). | |
| 233 | """ | |
| 234 | if pid not in self.plugin_sets: | |
| 235 | self.createPluginSet(pid) | |
| 236 | ||
| 237 | plugin = self._get_plugins_by_input(cmd, self.plugin_sets[pid]) | |
| 238 | ||
| 239 | if plugin: | |
| 240 | modified_cmd_string = plugin.processCommandString("", pwd, cmd) | |
| 241 | if not self._is_command_malformed(cmd, modified_cmd_string): | |
| 242 | ||
| 243 | cmd_info = CommandRunInformation( | |
| 244 | **{'workspace': faraday.client.model.api.getActiveWorkspace().name, | |
| 245 | 'itime': time.time(), | |
| 246 | 'import_source': 'shell', | |
| 247 | 'command': cmd.split()[0], | |
| 248 | 'params': ' '.join(cmd.split()[1:])}) | |
| 249 | cmd_info.setID(self._mapper_manager.save(cmd_info)) | |
| 250 | ||
| 251 | self._active_plugins[pid] = plugin, cmd_info | |
| 252 | ||
| 253 | return plugin.id, modified_cmd_string | |
| 254 | ||
| 255 | return None, None | |
| 256 | ||
| 257 | def onCommandFinished(self, pid, exit_code, term_output): | |
| 258 | if pid not in list(self._active_plugins.keys()): | |
| 259 | return False | |
| 260 | if exit_code != 0: | |
| 261 | del self._active_plugins[pid] | |
| 262 | return False | |
| 263 | ||
| 264 | plugin, cmd_info = self._active_plugins.get(pid) | |
| 265 | ||
| 266 | cmd_info.duration = time.time() - cmd_info.itime | |
| 267 | self._mapper_manager.update(cmd_info) | |
| 268 | ||
| 269 | self.processOutput(plugin, term_output, cmd_info) | |
| 270 | del self._active_plugins[pid] | |
| 271 | return True | |
| 272 | ||
| 273 | def processReport(self, plugin_id, filepath, ws_name=None): | |
| 274 | if plugin_id not in self._plugins: | |
| 275 | logger.warning("Unknown Plugin ID: %s", plugin_id) | |
| 276 | return False | |
| 277 | if not ws_name: | |
| 278 | ws_name = faraday.client.model.api.getActiveWorkspace().name | |
| 279 | ||
| 280 | cmd_info = CommandRunInformation( | |
| 281 | **{'workspace': ws_name, | |
| 282 | 'itime': time.time(), | |
| 283 | 'import_source': 'report', | |
| 284 | 'command': plugin_id, | |
| 285 | 'params': filepath, | |
| 286 | }) | |
| 287 | ||
| 288 | self._mapper_manager.createMappers(ws_name) | |
| 289 | command_id = self._mapper_manager.save(cmd_info) | |
| 290 | cmd_info.setID(command_id) | |
| 291 | ||
| 292 | if plugin_id in self._plugins: | |
| 293 | logger.info('Processing report with plugin {0}'.format(plugin_id)) | |
| 294 | self._plugins[plugin_id].workspace = ws_name | |
| 295 | with open(filepath, 'rb') as output: | |
| 296 | self.processOutput(self._plugins[plugin_id], output.read(), cmd_info, True) | |
| 297 | return command_id | |
| 298 | ||
| 299 | # Plugin to process this report not found, update duration of plugin process | |
| 300 | cmd_info.duration = time.time() - cmd_info.itime | |
| 301 | self._mapper_manager.update(cmd_info) | |
| 302 | return False | |
| 303 | ||
| 304 | def clearActivePlugins(self): | |
| 305 | self._active_plugins = {} | |
| 306 | ||
| 307 | ||
| 308 | # I'm Py3 |
| 0 | #!/usr/bin/env python | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | """ | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | """ | |
| 9 | from __future__ import absolute_import | |
| 10 | ||
| 11 | from faraday.client.plugins.plugin import PluginBase as PluginBaseExt | |
| 12 | ||
| 13 | # This class was moved to plugins.plugin so we need a way to | |
| 14 | # support plugins that are still inheriting from core | |
| 15 | PluginBase = PluginBaseExt | |
| 16 | ||
| 17 | ||
| 18 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | import imp | |
| 9 | import os | |
| 10 | import sys | |
| 11 | import logging | |
| 12 | ||
| 13 | from colorama import Fore | |
| 14 | ||
| 15 | from faraday.config.configuration import getInstanceConfiguration | |
| 16 | ||
| 17 | CONF = getInstanceConfiguration() | |
| 18 | logger = logging.getLogger(__name__) | |
| 19 | ||
| 20 | ||
| 21 | def get_available_plugins(): | |
| 22 | from faraday import client # pylint:disable=import-outside-toplevel | |
| 23 | client_base_path = os.path.dirname(os.path.abspath(client.__file__)) | |
| 24 | ||
| 25 | scan_path = os.path.join(client_base_path, "bin") | |
| 26 | plugin_list = os.listdir(scan_path) | |
| 27 | ||
| 28 | plugin_list = [ | |
| 29 | p for p in plugin_list | |
| 30 | if p.endswith('.py') | |
| 31 | ] | |
| 32 | plugin_list.remove('fplugin.py') | |
| 33 | plugin_list.remove('__init__.py') | |
| 34 | ||
| 35 | plugins_dic = {} | |
| 36 | ||
| 37 | for plugin in plugin_list: | |
| 38 | plugin_path = os.path.join(scan_path, plugin) | |
| 39 | ||
| 40 | try: | |
| 41 | ||
| 42 | plugin_name = os.path.splitext(plugin)[0] | |
| 43 | ||
| 44 | module = imp.load_source('module_fplugin_%s' % plugin_name, plugin_path) | |
| 45 | ||
| 46 | try: | |
| 47 | description = getattr(module, '__description__') | |
| 48 | except AttributeError: | |
| 49 | description = 'Empty' | |
| 50 | sys.stderr.write(Fore.YELLOW + | |
| 51 | "WARNING: Plugin missing a description. Please update it! [%s]\n" % plugin + | |
| 52 | Fore.RESET) | |
| 53 | ||
| 54 | try: | |
| 55 | prettyname = getattr(module, '__prettyname__') | |
| 56 | except AttributeError: | |
| 57 | prettyname = plugin_name | |
| 58 | sys.stderr.write(Fore.YELLOW + | |
| 59 | "WARNING: Plugin missing a pretty name. Please update it! [%s]\n" % plugin + | |
| 60 | Fore.RESET) | |
| 61 | ||
| 62 | try: | |
| 63 | main = getattr(module, 'main') | |
| 64 | except AttributeError: | |
| 65 | main = None | |
| 66 | sys.stderr.write(Fore.YELLOW + | |
| 67 | "WARNING: Plugin missing a main function. Please fix it! [%s]\n" % plugin + | |
| 68 | Fore.RESET) | |
| 69 | ||
| 70 | plugins_dic[plugin[:-3]] = { | |
| 71 | 'description': description, | |
| 72 | 'prettyname': prettyname, | |
| 73 | 'main': main | |
| 74 | } | |
| 75 | ||
| 76 | except Exception: | |
| 77 | logger.exception("Unable to import module %s\n" % plugin_path) | |
| 78 | ||
| 79 | return plugins_dic | |
| 80 | ||
| 81 | ||
| 82 | def build_faraday_plugin_command(plugin, workspace_name, absolute_path=False): | |
| 83 | faraday_directory = os.path.dirname(os.path.realpath(os.path.join(__file__, "../"))) | |
| 84 | path = os.path.join(faraday_directory, "bin/") | |
| 85 | ||
| 86 | return '{path}fplugin {command} -u {url} -w {workspace} '.format( | |
| 87 | path='"%s"' % path if absolute_path else '', | |
| 88 | command=plugin, | |
| 89 | url=CONF.getServerURI(), | |
| 90 | workspace=workspace_name | |
| 91 | ) | |
| 92 | ||
| 93 | ||
| 94 | # I'm Py3 |
| 0 | #!/usr/bin/env python | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | """ | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | """ | |
| 9 | from __future__ import absolute_import | |
| 10 | ||
| 11 | import os | |
| 12 | import re | |
| 13 | import sys | |
| 14 | import traceback | |
| 15 | import logging | |
| 16 | ||
| 17 | from importlib.machinery import SourceFileLoader | |
| 18 | ||
| 19 | from faraday.config.configuration import getInstanceConfiguration | |
| 20 | ||
| 21 | CONF = getInstanceConfiguration() | |
| 22 | ||
| 23 | logger = logging.getLogger(__name__) | |
| 24 | ||
| 25 | class PluginManager: | |
| 26 | ||
| 27 | def __init__(self, plugin_repo_path, pending_actions=None): | |
| 28 | self._controllers = {} | |
| 29 | self._plugin_modules = {} | |
| 30 | self._plugin_instances = {} | |
| 31 | self._loadPlugins(plugin_repo_path) | |
| 32 | self._plugin_settings = {} | |
| 33 | self.pending_actions = pending_actions | |
| 34 | self._loadSettings() | |
| 35 | ||
| 36 | def addController(self, controller, id): | |
| 37 | self._controllers[id] = controller | |
| 38 | ||
| 39 | def _loadSettings(self): | |
| 40 | _plugin_settings = CONF.getPluginSettings() | |
| 41 | if _plugin_settings: | |
| 42 | self._plugin_settings = _plugin_settings | |
| 43 | ||
| 44 | activep = self._instancePlugins() | |
| 45 | for plugin_id, plugin in activep.items(): | |
| 46 | if plugin_id in _plugin_settings: | |
| 47 | plugin.updateSettings(_plugin_settings[plugin_id]["settings"]) | |
| 48 | self._plugin_settings[plugin_id] = { | |
| 49 | "name": plugin.name, | |
| 50 | "description": plugin.description, | |
| 51 | "version": plugin.version, | |
| 52 | "plugin_version": plugin.plugin_version, | |
| 53 | "settings": dict(plugin.getSettings()) | |
| 54 | } | |
| 55 | ||
| 56 | dplugins = [] | |
| 57 | for k, v in self._plugin_settings.items(): | |
| 58 | if k not in activep: | |
| 59 | dplugins.append(k) | |
| 60 | ||
| 61 | for d in dplugins: | |
| 62 | del self._plugin_settings[d] | |
| 63 | ||
| 64 | CONF.setPluginSettings(self._plugin_settings) | |
| 65 | CONF.saveConfig() | |
| 66 | ||
| 67 | def getSettings(self): | |
| 68 | return self._plugin_settings | |
| 69 | ||
| 70 | def updateSettings(self, settings): | |
| 71 | self._plugin_settings = settings | |
| 72 | CONF.setPluginSettings(settings) | |
| 73 | CONF.saveConfig() | |
| 74 | for plugin_id, params in settings.items(): | |
| 75 | new_settings = params["settings"] | |
| 76 | for c_id, c_instance in self._controllers.items(): | |
| 77 | c_instance.updatePluginSettings(plugin_id, new_settings) | |
| 78 | ||
| 79 | def _instancePlugins(self): | |
| 80 | if not self._plugin_instances: | |
| 81 | for module in self._plugin_modules.values(): | |
| 82 | new_plugin = module.createPlugin() | |
| 83 | new_plugin.set_actions_queue(self.pending_actions) | |
| 84 | self._verifyPlugin(new_plugin) | |
| 85 | if new_plugin.id.lower() not in self._plugin_instances: | |
| 86 | self._plugin_instances[new_plugin.id.lower()] = new_plugin | |
| 87 | else: | |
| 88 | logger.warning("Duplicated Plugin ID (%s)", new_plugin.id.lower()) | |
| 89 | return self._plugin_instances | |
| 90 | ||
| 91 | def _loadPlugins(self, plugin_repo_path): | |
| 92 | """ | |
| 93 | Finds and load all the plugins that are | |
| 94 | available in the plugin_repo_path. | |
| 95 | """ | |
| 96 | try: | |
| 97 | os.stat(plugin_repo_path) | |
| 98 | except OSError: | |
| 99 | pass | |
| 100 | sys.path.append(plugin_repo_path) | |
| 101 | dir_name_regexp = re.compile(r"^[\d\w\-\_]+$") | |
| 102 | if not os.path.exists(plugin_repo_path): | |
| 103 | logger.error('Plugins path could not be opened, no pluging will be available!') | |
| 104 | return | |
| 105 | for name in os.listdir(plugin_repo_path): | |
| 106 | if dir_name_regexp.match(name) and name != "__pycache__": | |
| 107 | try: | |
| 108 | module_path = os.path.join(plugin_repo_path, name) | |
| 109 | sys.path.append(module_path) | |
| 110 | module_filename = os.path.join(module_path, "plugin.py") | |
| 111 | file_ext = os.path.splitext(module_filename)[1] | |
| 112 | if file_ext.lower() == '.py': | |
| 113 | loader = SourceFileLoader(name, module_filename) | |
| 114 | self._plugin_modules[name] = loader.load_module() | |
| 115 | logger.debug('Loading plugin {0}'.format(name)) | |
| 116 | except Exception as e: | |
| 117 | logger.debug("An error ocurred while loading plugin %s.\n%s", module_filename, traceback.format_exc()) | |
| 118 | logger.warning(e) | |
| 119 | ||
| 120 | def getPlugins(self): | |
| 121 | plugins = self._instancePlugins() | |
| 122 | for _id, plugin in plugins.items(): | |
| 123 | if _id in self._plugin_settings: | |
| 124 | plugin.updateSettings(self._plugin_settings[_id]["settings"]) | |
| 125 | return plugins | |
| 126 | ||
| 127 | def _verifyPlugin(self, new_plugin): | |
| 128 | """ | |
| 129 | Generic method that decides is a plugin is valid | |
| 130 | based on a predefined set of checks. | |
| 131 | """ | |
| 132 | try: | |
| 133 | assert(new_plugin.id is not None) | |
| 134 | assert(new_plugin.version is not None) | |
| 135 | assert(new_plugin.name is not None) | |
| 136 | assert(new_plugin.framework_version is not None) | |
| 137 | except (AssertionError, KeyError): | |
| 138 | return False | |
| 139 | return True | |
| 140 | ||
| 141 | ||
| 142 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | import os | |
| 7 | import re | |
| 8 | import time | |
| 9 | import logging | |
| 10 | import traceback | |
| 11 | import deprecation | |
| 12 | from threading import Thread | |
| 13 | ||
| 14 | import faraday.server.config | |
| 15 | import faraday.client.model.api | |
| 16 | import faraday.client.model.common | |
| 17 | from faraday import __license_version__ as license_version | |
| 18 | from faraday.client.model.common import factory | |
| 19 | from faraday.client.persistence.server.models import get_host, update_host | |
| 20 | from faraday.client.persistence.server.models import ( | |
| 21 | Host, | |
| 22 | Service, | |
| 23 | Vuln, | |
| 24 | VulnWeb, | |
| 25 | Credential, | |
| 26 | Note | |
| 27 | ) | |
| 28 | from faraday.client.model import Modelactions | |
| 29 | ||
| 30 | from faraday.config.configuration import getInstanceConfiguration | |
| 31 | CONF = getInstanceConfiguration() | |
| 32 | VERSION = license_version.split('-')[0].split('rc')[0] | |
| 33 | logger = logging.getLogger(__name__) | |
| 34 | ||
| 35 | ||
| 36 | class PluginBase: | |
| 37 | # TODO: Add class generic identifier | |
| 38 | class_signature = "PluginBase" | |
| 39 | ||
| 40 | def __init__(self): | |
| 41 | self.data_path = CONF.getDataPath() | |
| 42 | self.persistence_path = CONF.getPersistencePath() | |
| 43 | self.workspace = CONF.getLastWorkspace() | |
| 44 | # Must be unique. Check that there is not | |
| 45 | # an existant plugin with the same id. | |
| 46 | # TODO: Make script that list current ids. | |
| 47 | self.id = None | |
| 48 | self._rid = id(self) | |
| 49 | self.version = None | |
| 50 | self.name = None | |
| 51 | self.description = "" | |
| 52 | self._command_regex = None | |
| 53 | self._output_file_path = None | |
| 54 | self.framework_version = None | |
| 55 | self._completition = {} | |
| 56 | self._new_elems = [] | |
| 57 | self._settings = {} | |
| 58 | self.command_id = None | |
| 59 | self.logger = logger.getChild(self.__class__.__name__) | |
| 60 | ||
| 61 | def report_belongs_to(self, **kwargs): | |
| 62 | return False | |
| 63 | ||
| 64 | def has_custom_output(self): | |
| 65 | return bool(self._output_file_path) | |
| 66 | ||
| 67 | def get_custom_file_path(self): | |
| 68 | return self._output_file_path | |
| 69 | ||
| 70 | def set_actions_queue(self, _pending_actions): | |
| 71 | """ | |
| 72 | We use plugin controller queue to add actions created by plugins. | |
| 73 | Plugin controller will consume this actions. | |
| 74 | ||
| 75 | :param controller: plugin controller | |
| 76 | :return: None | |
| 77 | """ | |
| 78 | self._pending_actions = _pending_actions | |
| 79 | ||
| 80 | def setCommandID(self, command_id): | |
| 81 | self.command_id = command_id | |
| 82 | ||
| 83 | def getSettings(self): | |
| 84 | for param, (param_type, value) in self._settings.items(): | |
| 85 | yield param, value | |
| 86 | ||
| 87 | def get_ws(self): | |
| 88 | return CONF.getLastWorkspace() | |
| 89 | ||
| 90 | def getSetting(self, name): | |
| 91 | setting_type, value = self._settings[name] | |
| 92 | return value | |
| 93 | ||
| 94 | def addSetting(self, param, param_type, value): | |
| 95 | self._settings[param] = param_type, value | |
| 96 | ||
| 97 | def updateSettings(self, new_settings): | |
| 98 | for name, value in new_settings.items(): | |
| 99 | if name in self._settings: | |
| 100 | setting_type, curr_value = self._settings[name] | |
| 101 | self._settings[name] = setting_type, setting_type(value) | |
| 102 | ||
| 103 | def canParseCommandString(self, current_input): | |
| 104 | """ | |
| 105 | This method can be overriden in the plugin implementation | |
| 106 | if a different kind of check is needed | |
| 107 | """ | |
| 108 | return (self._command_regex is not None and | |
| 109 | self._command_regex.match(current_input.strip()) is not None) | |
| 110 | ||
| 111 | def getCompletitionSuggestionsList(self, current_input): | |
| 112 | """ | |
| 113 | This method can be overriden in the plugin implementation | |
| 114 | if a different kind of check is needed | |
| 115 | """ | |
| 116 | words = current_input.split(" ") | |
| 117 | cword = words[len(words) - 1] | |
| 118 | options = {} | |
| 119 | for k, v in self._completition.items(): | |
| 120 | if re.search(str("^" + cword), k, flags=re.IGNORECASE): | |
| 121 | options[k] = v | |
| 122 | return options | |
| 123 | ||
| 124 | def processOutput(self, term_output): | |
| 125 | output = term_output | |
| 126 | if self.has_custom_output() and os.path.isfile(self.get_custom_file_path()): | |
| 127 | self._parse_filename(self.get_custom_file_path()) | |
| 128 | else: | |
| 129 | self.parseOutputString(output) | |
| 130 | ||
| 131 | def _parse_filename(self, filename): | |
| 132 | with open(filename, 'rb') as output: | |
| 133 | self.parseOutputString(output.read()) | |
| 134 | ||
| 135 | def processReport(self, filepath): | |
| 136 | if os.path.isfile(filepath): | |
| 137 | self._parse_filename(filepath) | |
| 138 | ||
| 139 | def parseOutputString(self, output): | |
| 140 | """ | |
| 141 | This method must be implemented. | |
| 142 | This method will be called when the command finished executing and | |
| 143 | the complete output will be received to work with it | |
| 144 | Using the output the plugin can create and add hosts, interfaces, | |
| 145 | services, etc. | |
| 146 | """ | |
| 147 | raise NotImplementedError('This method must be implemented.') | |
| 148 | ||
| 149 | def processCommandString(self, username, current_path, command_string): | |
| 150 | """ | |
| 151 | With this method a plugin can add aditional arguments to the | |
| 152 | command that it's going to be executed. | |
| 153 | """ | |
| 154 | return None | |
| 155 | ||
| 156 | def __addPendingAction(self, *args): | |
| 157 | """ | |
| 158 | Adds a new pending action to the queue | |
| 159 | Action is build with generic args tuple. | |
| 160 | The caller of this function has to build the action in the right | |
| 161 | way since no checks are preformed over args | |
| 162 | """ | |
| 163 | if self.command_id: | |
| 164 | args = args + (self.command_id, ) | |
| 165 | else: | |
| 166 | logger.warning('Warning command id not set for action {%s}', args) | |
| 167 | logger.debug('AddPendingAction %s', args) | |
| 168 | self._pending_actions.put(args) | |
| 169 | ||
| 170 | def createAndAddHost(self, name, os="unknown", hostnames=None, mac=None): | |
| 171 | host_obj = factory.createModelObject( | |
| 172 | Host.class_signature, | |
| 173 | name, | |
| 174 | os=os, | |
| 175 | parent_id=None, | |
| 176 | workspace_name=self.workspace, | |
| 177 | hostnames=hostnames, | |
| 178 | mac=mac) | |
| 179 | host_obj._metadata.creatoserverr = self.id | |
| 180 | self.__addPendingAction(Modelactions.ADDHOST, host_obj) | |
| 181 | return host_obj.getID() | |
| 182 | ||
| 183 | @deprecation.deprecated(deprecated_in="3.0", removed_in="3.5", | |
| 184 | current_version=VERSION, | |
| 185 | details="Interface object removed. Use host or service instead") | |
| 186 | def createAndAddInterface( | |
| 187 | self, host_id, name="", mac="00:00:00:00:00:00", | |
| 188 | ipv4_address="0.0.0.0", ipv4_mask="0.0.0.0", ipv4_gateway="0.0.0.0", | |
| 189 | ipv4_dns=None, ipv6_address="0000:0000:0000:0000:0000:0000:0000:0000", | |
| 190 | ipv6_prefix="00", | |
| 191 | ipv6_gateway="0000:0000:0000:0000:0000:0000:0000:0000", ipv6_dns=None, | |
| 192 | network_segment="", hostname_resolution=None): | |
| 193 | if ipv4_dns is None: | |
| 194 | ipv4_dns = [] | |
| 195 | if ipv6_dns is None: | |
| 196 | ipv6_dns = [] | |
| 197 | if hostname_resolution is None: | |
| 198 | hostname_resolution = [] | |
| 199 | if not isinstance(hostname_resolution, list): | |
| 200 | logger.warning("hostname_resolution parameter must be a list and is (%s)", type(hostname_resolution)) | |
| 201 | hostname_resolution = [hostname_resolution] | |
| 202 | # We don't use interface anymore, so return a host id to maintain | |
| 203 | # backwards compatibility | |
| 204 | # Little hack because we dont want change all the plugins for add hostnames in Host object. | |
| 205 | # SHRUG | |
| 206 | try: | |
| 207 | host = get_host(self.workspace, host_id=host_id) | |
| 208 | host.hostnames += hostname_resolution | |
| 209 | host.mac = mac | |
| 210 | update_host(self.workspace, host, command_id=self.command_id) | |
| 211 | except: | |
| 212 | logger.info("Error updating Host with right hostname resolution...") | |
| 213 | return host_id | |
| 214 | ||
| 215 | @deprecation.deprecated(deprecated_in="3.0", removed_in="3.5", | |
| 216 | current_version=VERSION, | |
| 217 | details="Interface object removed. Use host or service instead. Service will be attached to Host!") | |
| 218 | def createAndAddServiceToInterface(self, host_id, interface_id, name, | |
| 219 | protocol="tcp?", ports=None, | |
| 220 | status="open", version="unknown", | |
| 221 | description=""): | |
| 222 | if not ports: | |
| 223 | ports = [] | |
| 224 | if status not in ("open", "closed", "filtered"): | |
| 225 | self.log( | |
| 226 | 'Unknown service status %s. Using "open" instead' % status, | |
| 227 | 'WARNING' | |
| 228 | ) | |
| 229 | status = 'open' | |
| 230 | ||
| 231 | serv_obj = faraday.client.model.common.factory.createModelObject( | |
| 232 | Service.class_signature, | |
| 233 | name, protocol=protocol, ports=ports, status=status, | |
| 234 | version=version, description=description, | |
| 235 | parent_type='Host', parent_id=host_id, | |
| 236 | workspace_name=self.workspace) | |
| 237 | ||
| 238 | serv_obj._metadata.creator = self.id | |
| 239 | self.__addPendingAction(Modelactions.ADDSERVICEHOST, serv_obj) | |
| 240 | return serv_obj.getID() | |
| 241 | ||
| 242 | def createAndAddServiceToHost(self, host_id, name, | |
| 243 | protocol="tcp?", ports=None, | |
| 244 | status="open", version="unknown", | |
| 245 | description=""): | |
| 246 | if not ports: | |
| 247 | ports = [] | |
| 248 | if status not in ("open", "closed", "filtered"): | |
| 249 | self.log( | |
| 250 | 'Unknown service status %s. Using "open" instead' % status, | |
| 251 | 'WARNING' | |
| 252 | ) | |
| 253 | status = 'open' | |
| 254 | ||
| 255 | serv_obj = faraday.client.model.common.factory.createModelObject( | |
| 256 | Service.class_signature, | |
| 257 | name, protocol=protocol, ports=ports, status=status, | |
| 258 | version=version, description=description, | |
| 259 | parent_type='Host', parent_id=host_id, | |
| 260 | workspace_name=self.workspace) | |
| 261 | ||
| 262 | serv_obj._metadata.creator = self.id | |
| 263 | self.__addPendingAction(Modelactions.ADDSERVICEHOST, serv_obj) | |
| 264 | return serv_obj.getID() | |
| 265 | ||
| 266 | def createAndAddVulnToHost(self, host_id, name, desc="", ref=None, | |
| 267 | severity="", resolution="", data="", external_id=None): | |
| 268 | if not ref: | |
| 269 | ref = [] | |
| 270 | vuln_obj = faraday.client.model.common.factory.createModelObject( | |
| 271 | Vuln.class_signature, | |
| 272 | name, data=data, desc=desc, refs=ref, severity=severity, | |
| 273 | resolution=resolution, confirmed=False, | |
| 274 | parent_id=host_id, parent_type='Host', | |
| 275 | workspace_name=self.workspace,external_id=external_id) | |
| 276 | ||
| 277 | vuln_obj._metadata.creator = self.id | |
| 278 | self.__addPendingAction(Modelactions.ADDVULNHOST, vuln_obj) | |
| 279 | return vuln_obj.getID() | |
| 280 | ||
| 281 | @deprecation.deprecated(deprecated_in="3.0", removed_in="3.5", | |
| 282 | current_version=VERSION, | |
| 283 | details="Interface object removed. Use host or service instead. Vuln will be added to Host") | |
| 284 | def createAndAddVulnToInterface(self, host_id, interface_id, name, | |
| 285 | desc="", ref=None, severity="", | |
| 286 | resolution="", data=""): | |
| 287 | if not ref: | |
| 288 | ref = [] | |
| 289 | vuln_obj = faraday.client.model.common.factory.createModelObject( | |
| 290 | Vuln.class_signature, | |
| 291 | name, data=data, desc=desc, refs=ref, severity=severity, | |
| 292 | resolution=resolution, confirmed=False, | |
| 293 | parent_type='Host', parent_id=host_id, | |
| 294 | workspace_name=self.workspace) | |
| 295 | ||
| 296 | vuln_obj._metadata.creator = self.id | |
| 297 | self.__addPendingAction(Modelactions.ADDVULNHOST, vuln_obj) | |
| 298 | return vuln_obj.getID() | |
| 299 | ||
| 300 | def createAndAddVulnToService(self, host_id, service_id, name, desc="", | |
| 301 | ref=None, severity="", resolution="", data="", external_id=None): | |
| 302 | if not ref: | |
| 303 | ref = [] | |
| 304 | vuln_obj = faraday.client.model.common.factory.createModelObject( | |
| 305 | Vuln.class_signature, | |
| 306 | name, data=data, desc=desc, refs=ref, severity=severity, | |
| 307 | resolution=resolution, confirmed=False, | |
| 308 | parent_type='Service', parent_id=service_id, | |
| 309 | workspace_name=self.workspace, external_id=external_id) | |
| 310 | ||
| 311 | vuln_obj._metadata.creator = self.id | |
| 312 | ||
| 313 | self.__addPendingAction(Modelactions.ADDVULNSRV, vuln_obj) | |
| 314 | return vuln_obj.getID() | |
| 315 | ||
| 316 | def createAndAddVulnWebToService(self, host_id, service_id, name, desc="", | |
| 317 | ref=None, severity="", resolution="", | |
| 318 | website="", path="", request="", | |
| 319 | response="", method="", pname="", | |
| 320 | params="", query="", category="", data="", external_id=None): | |
| 321 | if not ref: | |
| 322 | ref = [] | |
| 323 | vulnweb_obj = faraday.client.model.common.factory.createModelObject( | |
| 324 | VulnWeb.class_signature, | |
| 325 | name, data=data, desc=desc, refs=ref, severity=severity, | |
| 326 | resolution=resolution, website=website, path=path, | |
| 327 | request=request, response=response, method=method, | |
| 328 | pname=pname, params=params, query=query, | |
| 329 | category=category, confirmed=False, parent_id=service_id, | |
| 330 | parent_type='Service', | |
| 331 | workspace_name=self.workspace, external_id=external_id) | |
| 332 | ||
| 333 | vulnweb_obj._metadata.creator = self.id | |
| 334 | self.__addPendingAction(Modelactions.ADDVULNWEBSRV, vulnweb_obj) | |
| 335 | return vulnweb_obj.getID() | |
| 336 | ||
| 337 | def createAndAddNoteToHost(self, host_id, name, text): | |
| 338 | return None | |
| 339 | ||
| 340 | def createAndAddNoteToInterface(self, host_id, interface_id, name, text): | |
| 341 | return None | |
| 342 | ||
| 343 | def createAndAddNoteToService(self, host_id, service_id, name, text): | |
| 344 | return None | |
| 345 | ||
| 346 | def createAndAddNoteToNote(self, host_id, service_id, note_id, name, text): | |
| 347 | return None | |
| 348 | ||
| 349 | def createAndAddCredToService(self, host_id, service_id, username, | |
| 350 | password): | |
| 351 | ||
| 352 | cred_obj = faraday.client.model.common.factory.createModelObject( | |
| 353 | Credential.class_signature, | |
| 354 | username, password=password, parent_id=service_id, parent_type='Service', | |
| 355 | workspace_name=self.workspace) | |
| 356 | ||
| 357 | cred_obj._metadata.creator = self.id | |
| 358 | self.__addPendingAction(Modelactions.ADDCREDSRV, cred_obj) | |
| 359 | return cred_obj.getID() | |
| 360 | ||
| 361 | def log(self, msg, level='INFO'): | |
| 362 | self.__addPendingAction(Modelactions.LOG, msg, level) | |
| 363 | ||
| 364 | def devlog(self, msg): | |
| 365 | self.__addPendingAction(Modelactions.DEVLOG, msg) | |
| 366 | ||
| 367 | ||
| 368 | class PluginTerminalOutput(PluginBase): | |
| 369 | def __init__(self): | |
| 370 | super().__init__() | |
| 371 | ||
| 372 | def processOutput(self, term_output): | |
| 373 | try: | |
| 374 | self.parseOutputString(term_output) | |
| 375 | except Exception as e: | |
| 376 | self.logger.exception(e) | |
| 377 | ||
| 378 | ||
| 379 | class PluginCustomOutput(PluginBase): | |
| 380 | def __init__(self): | |
| 381 | super().__init__() | |
| 382 | ||
| 383 | def processOutput(self, term_output): | |
| 384 | # we discard the term_output since it's not necessary | |
| 385 | # for this type of plugins | |
| 386 | self.processReport(self._output_file_path) | |
| 387 | ||
| 388 | ||
| 389 | class PluginByExtension(PluginBase): | |
| 390 | def __init__(self): | |
| 391 | super().__init__() | |
| 392 | self.extension = [] | |
| 393 | ||
| 394 | def report_belongs_to(self, extension="", **kwargs): | |
| 395 | match = False | |
| 396 | if type(self.extension) == str: | |
| 397 | match = (self.extension == extension) | |
| 398 | elif type(self.extension) == list: | |
| 399 | match = (extension in self.extension) | |
| 400 | self.logger.debug("Extension Match: [%s =/in %s] -> %s", extension, self.extension, match) | |
| 401 | return match | |
| 402 | ||
| 403 | ||
| 404 | class PluginXMLFormat(PluginByExtension): | |
| 405 | ||
| 406 | def __init__(self): | |
| 407 | super().__init__() | |
| 408 | self.identifier_tag = [] | |
| 409 | self.extension = ".xml" | |
| 410 | ||
| 411 | def report_belongs_to(self, main_tag="", **kwargs): | |
| 412 | match = False | |
| 413 | if super().report_belongs_to(**kwargs): | |
| 414 | if type(self.identifier_tag) == str: | |
| 415 | match = (main_tag == self.identifier_tag) | |
| 416 | elif type(self.identifier_tag) == list: | |
| 417 | match = (main_tag in self.identifier_tag) | |
| 418 | self.logger.debug("Tag Match: [%s =/in %s] -> %s", main_tag, self.identifier_tag, match) | |
| 419 | return match | |
| 420 | ||
| 421 | ||
| 422 | class PluginJsonFormat(PluginByExtension): | |
| 423 | ||
| 424 | def __init__(self): | |
| 425 | super().__init__() | |
| 426 | self.json_keys = set() | |
| 427 | self.extension = ".json" | |
| 428 | ||
| 429 | def report_belongs_to(self, **kwargs): | |
| 430 | match = False | |
| 431 | if super().report_belongs_to(**kwargs): | |
| 432 | pass | |
| 433 | return match | |
| 434 | ||
| 435 | ||
| 436 | class PluginProcess(Thread): | |
| 437 | def __init__(self, plugin_instance, output_queue, isReport=False): | |
| 438 | """ | |
| 439 | Executes one plugin. | |
| 440 | ||
| 441 | :param plugin_instance: current plugin in execution. | |
| 442 | :param output_queue: queue with raw ouput of that the plugin needs. | |
| 443 | :param isReport: output data was read from file. | |
| 444 | """ | |
| 445 | super(PluginProcess, self).__init__(name="PluginProcessThread") | |
| 446 | self.output_queue = output_queue | |
| 447 | self.plugin = plugin_instance | |
| 448 | self.isReport = isReport | |
| 449 | self.setDaemon(True) | |
| 450 | self._must_stop = False | |
| 451 | ||
| 452 | def run(self): | |
| 453 | proc_name = self.name | |
| 454 | faraday.client.model.api.devlog("-" * 40) | |
| 455 | faraday.client.model.api.devlog(f"proc_name = {proc_name}") | |
| 456 | faraday.client.model.api.devlog(f"Starting run method on PluginProcess") | |
| 457 | faraday.client.model.api.devlog(f"parent process: {os.getppid()}") | |
| 458 | faraday.client.model.api.devlog(f"process id: {os.getpid()}") | |
| 459 | faraday.client.model.api.devlog("-" * 40) | |
| 460 | done = False | |
| 461 | while not done and not self._must_stop: | |
| 462 | output, command_id = self.output_queue.get() | |
| 463 | self.plugin.setCommandID(command_id) | |
| 464 | if output is not None: | |
| 465 | faraday.client.model.api.devlog(f"{proc_name}: New Output") | |
| 466 | try: | |
| 467 | if isinstance(output, bytes): | |
| 468 | output = output.decode() | |
| 469 | self.plugin.processOutput(output) | |
| 470 | except Exception as ex: | |
| 471 | faraday.client.model.api.devlog("Plugin raised an exception:") | |
| 472 | faraday.client.model.api.devlog(traceback.format_exc()) | |
| 473 | else: | |
| 474 | done = True | |
| 475 | faraday.client.model.api.devlog(f"{proc_name}: Exiting") | |
| 476 | self.output_queue.task_done() | |
| 477 | time.sleep(0.1) | |
| 478 | ||
| 479 | def stop(self): | |
| 480 | self._must_stop = True | |
| 481 | ||
| 482 | # I'm Py3 |
| 0 | #!/usr/bin/env python | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | """ | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | """ | |
| 9 | from __future__ import absolute_import | |
| 10 | ||
| 11 | try: | |
| 12 | from urlparse import urlsplit | |
| 13 | except ImportError: | |
| 14 | from urllib.parse import urlsplit | |
| 15 | ||
| 16 | def get_vulnweb_url_fields(url): | |
| 17 | """Given a URL, return kwargs to pass to createAndAddVulnWebToService.""" | |
| 18 | parse = urlsplit(url) | |
| 19 | return { | |
| 20 | "website": "{}://{}".format(parse.scheme, parse.netloc), | |
| 21 | "path": parse.path, | |
| 22 | "query": parse.query | |
| 23 | } | |
| 24 | ||
| 25 | ||
| 26 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | import os | |
| 9 | import logging | |
| 10 | ||
| 11 | from faraday.client.start_client import FARADAY_CLIENT_BASE | |
| 12 | ||
| 13 | SERVICE_MAPPER = None | |
| 14 | ||
| 15 | logger = logging.getLogger(__name__) | |
| 16 | ||
| 17 | ||
| 18 | def filter_services(): | |
| 19 | global SERVICE_MAPPER | |
| 20 | if not SERVICE_MAPPER: | |
| 21 | logger.debug("Load service mappers") | |
| 22 | filename = os.path.join(FARADAY_CLIENT_BASE, 'plugins/port_mapper.txt') | |
| 23 | with open(filename, encoding='utf-8') as fp: | |
| 24 | SERVICE_MAPPER = list(map(lambda x: x.strip().split('\t'), list(filter(len, fp.readlines())))) | |
| 25 | return SERVICE_MAPPER | |
| 26 | ||
| 27 | ||
| 28 | def get_all_protocols(): | |
| 29 | protocols = [ | |
| 30 | 'ip', | |
| 31 | 'tcp', | |
| 32 | 'udp', | |
| 33 | 'icmp', | |
| 34 | 'sctp', | |
| 35 | 'hopopt', | |
| 36 | 'igmp', | |
| 37 | 'ggp', | |
| 38 | 'ip-encap', | |
| 39 | 'st', | |
| 40 | 'egp', | |
| 41 | 'igp', | |
| 42 | 'pup', | |
| 43 | 'hmp', | |
| 44 | 'xns-idp', | |
| 45 | 'rdp', | |
| 46 | 'iso-tp4', | |
| 47 | 'dccp', | |
| 48 | 'xtp', | |
| 49 | 'ddp', | |
| 50 | 'idpr-cmtp', | |
| 51 | 'ipv6', | |
| 52 | 'ipv6-route', | |
| 53 | 'ipv6-frag', | |
| 54 | 'idrp', | |
| 55 | 'rsvp', | |
| 56 | 'gre', | |
| 57 | 'ipsec-esp', | |
| 58 | 'ipsec-ah', | |
| 59 | 'skip', | |
| 60 | 'ipv6-icmp', | |
| 61 | 'ipv6-nonxt', | |
| 62 | 'ipv6-opts', | |
| 63 | 'rspf cphb', | |
| 64 | 'vmtp', | |
| 65 | 'eigrp', | |
| 66 | 'ospfigp', | |
| 67 | 'ax.25', | |
| 68 | 'ipip', | |
| 69 | 'etherip', | |
| 70 | 'encap', | |
| 71 | 'pim', | |
| 72 | 'ipcomp', | |
| 73 | 'vrrp', | |
| 74 | 'l2tp', | |
| 75 | 'isis', | |
| 76 | 'fc', | |
| 77 | 'udplite', | |
| 78 | 'mpls-in-ip', | |
| 79 | 'hip', | |
| 80 | 'shim6', | |
| 81 | 'wesp', | |
| 82 | 'rohc', | |
| 83 | 'mobility-header' | |
| 84 | ] | |
| 85 | ||
| 86 | for item in protocols: | |
| 87 | yield item | |
| 88 | ||
| 89 | ||
| 90 | # I'm Py3 |
| 0 | 1/tcp tcpmux | |
| 1 | 7/tcp echo | |
| 2 | 7/udp echo | |
| 3 | 9/tcp discard | |
| 4 | 9/udp discard | |
| 5 | 11/tcp systat | |
| 6 | 13/tcp daytime | |
| 7 | 13/udp daytime | |
| 8 | 15/tcp netstat | |
| 9 | 17/tcp qotd | |
| 10 | 18/tcp msp | |
| 11 | 18/udp msp | |
| 12 | 19/tcp chargen | |
| 13 | 19/udp chargen | |
| 14 | 20/tcp ftp-data | |
| 15 | 21/tcp ftp | |
| 16 | 21/udp fsp | |
| 17 | 22/tcp ssh | |
| 18 | 22/udp ssh | |
| 19 | 23/tcp telnet | |
| 20 | 25/tcp smtp | |
| 21 | 37/tcp time | |
| 22 | 37/udp time | |
| 23 | 39/udp rlp | |
| 24 | 42/tcp nameserver | |
| 25 | 43/tcp whois | |
| 26 | 49/tcp tacacs | |
| 27 | 49/udp tacacs | |
| 28 | 50/tcp re-mail-ck | |
| 29 | 50/udp re-mail-ck | |
| 30 | 53/tcp domain | |
| 31 | 53/udp domain | |
| 32 | 57/tcp mtp | |
| 33 | 65/tcp tacacs-ds | |
| 34 | 65/udp tacacs-ds | |
| 35 | 67/tcp bootps | |
| 36 | 67/udp bootps | |
| 37 | 68/tcp bootpc | |
| 38 | 68/udp bootpc | |
| 39 | 69/udp tftp | |
| 40 | 70/tcp gopher | |
| 41 | 70/udp gopher | |
| 42 | 77/tcp rje | |
| 43 | 79/tcp finger | |
| 44 | 80/tcp http | |
| 45 | 80/udp http | |
| 46 | 87/tcp link | |
| 47 | 88/tcp kerberos | |
| 48 | 88/udp kerberos | |
| 49 | 95/tcp supdup | |
| 50 | 101/tcp hostnames | |
| 51 | 102/tcp iso-tsap | |
| 52 | 104/tcp acr-nema | |
| 53 | 104/udp acr-nema | |
| 54 | 105/tcp csnet-ns | |
| 55 | 105/udp csnet-ns | |
| 56 | 107/tcp rtelnet | |
| 57 | 107/udp rtelnet | |
| 58 | 109/tcp pop2 | |
| 59 | 109/udp pop2 | |
| 60 | 110/tcp pop3 | |
| 61 | 110/udp pop3 | |
| 62 | 111/tcp sunrpc | |
| 63 | 111/udp sunrpc | |
| 64 | 113/tcp auth | |
| 65 | 115/tcp sftp | |
| 66 | 117/tcp uucp-path | |
| 67 | 119/tcp nntp | |
| 68 | 123/tcp ntp | |
| 69 | 123/udp ntp | |
| 70 | 129/tcp pwdgen | |
| 71 | 129/udp pwdgen | |
| 72 | 135/tcp loc-srv | |
| 73 | 135/udp loc-srv | |
| 74 | 137/tcp netbios-ns | |
| 75 | 137/udp netbios-ns | |
| 76 | 138/tcp netbios-dgm | |
| 77 | 138/udp netbios-dgm | |
| 78 | 139/tcp netbios-ssn | |
| 79 | 139/udp netbios-ssn | |
| 80 | 143/tcp imap2 | |
| 81 | 143/udp imap2 | |
| 82 | 161/tcp snmp | |
| 83 | 161/udp snmp | |
| 84 | 162/tcp snmp-trap | |
| 85 | 162/udp snmp-trap | |
| 86 | 163/tcp cmip-man | |
| 87 | 163/udp cmip-man | |
| 88 | 164/tcp cmip-agent | |
| 89 | 164/udp cmip-agent | |
| 90 | 174/tcp mailq | |
| 91 | 174/udp mailq | |
| 92 | 177/tcp xdmcp | |
| 93 | 177/udp xdmcp | |
| 94 | 178/tcp nextstep | |
| 95 | 178/udp nextstep | |
| 96 | 179/tcp bgp | |
| 97 | 179/udp bgp | |
| 98 | 191/tcp prospero | |
| 99 | 191/udp prospero | |
| 100 | 194/tcp irc | |
| 101 | 194/udp irc | |
| 102 | 199/tcp smux | |
| 103 | 199/udp smux | |
| 104 | 201/tcp at-rtmp | |
| 105 | 201/udp at-rtmp | |
| 106 | 202/tcp at-nbp | |
| 107 | 202/udp at-nbp | |
| 108 | 204/tcp at-echo | |
| 109 | 204/udp at-echo | |
| 110 | 206/tcp at-zis | |
| 111 | 206/udp at-zis | |
| 112 | 209/tcp qmtp | |
| 113 | 209/udp qmtp | |
| 114 | 210/tcp z3950 | |
| 115 | 210/udp z3950 | |
| 116 | 213/tcp ipx | |
| 117 | 213/udp ipx | |
| 118 | 220/tcp imap3 | |
| 119 | 220/udp imap3 | |
| 120 | 345/tcp pawserv | |
| 121 | 345/udp pawserv | |
| 122 | 346/tcp zserv | |
| 123 | 346/udp zserv | |
| 124 | 347/tcp fatserv | |
| 125 | 347/udp fatserv | |
| 126 | 369/tcp rpc2portmap | |
| 127 | 369/udp rpc2portmap | |
| 128 | 370/tcp codaauth2 | |
| 129 | 370/udp codaauth2 | |
| 130 | 371/tcp clearcase | |
| 131 | 371/udp clearcase | |
| 132 | 372/tcp ulistserv | |
| 133 | 372/udp ulistserv | |
| 134 | 389/tcp ldap | |
| 135 | 389/udp ldap | |
| 136 | 406/tcp imsp | |
| 137 | 406/udp imsp | |
| 138 | 427/tcp svrloc | |
| 139 | 427/udp svrloc | |
| 140 | 443/tcp https | |
| 141 | 443/udp https | |
| 142 | 444/tcp snpp | |
| 143 | 444/udp snpp | |
| 144 | 445/tcp microsoft-ds | |
| 145 | 445/udp microsoft-ds | |
| 146 | 464/tcp kpasswd | |
| 147 | 464/udp kpasswd | |
| 148 | 465/tcp urd | |
| 149 | 487/tcp saft | |
| 150 | 487/udp saft | |
| 151 | 500/tcp isakmp | |
| 152 | 500/udp isakmp | |
| 153 | 554/tcp rtsp | |
| 154 | 554/udp rtsp | |
| 155 | 607/tcp nqs | |
| 156 | 607/udp nqs | |
| 157 | 610/tcp npmp-local | |
| 158 | 610/udp npmp-local | |
| 159 | 611/tcp npmp-gui | |
| 160 | 611/udp npmp-gui | |
| 161 | 612/tcp hmmp-ind | |
| 162 | 612/udp hmmp-ind | |
| 163 | 623/udp asf-rmcp | |
| 164 | 628/tcp qmqp | |
| 165 | 628/udp qmqp | |
| 166 | 631/tcp ipp | |
| 167 | 631/udp ipp | |
| 168 | 512/tcp exec | |
| 169 | 512/udp biff | |
| 170 | 513/tcp login | |
| 171 | 513/udp who | |
| 172 | 514/tcp shell | |
| 173 | 514/udp syslog | |
| 174 | 515/tcp printer | |
| 175 | 517/udp talk | |
| 176 | 518/udp ntalk | |
| 177 | 520/udp route | |
| 178 | 525/udp timed | |
| 179 | 526/tcp tempo | |
| 180 | 530/tcp courier | |
| 181 | 531/tcp conference | |
| 182 | 532/tcp netnews | |
| 183 | 533/udp netwall | |
| 184 | 538/tcp gdomap | |
| 185 | 538/udp gdomap | |
| 186 | 540/tcp uucp | |
| 187 | 543/tcp klogin | |
| 188 | 544/tcp kshell | |
| 189 | 546/tcp dhcpv6-client | |
| 190 | 546/udp dhcpv6-client | |
| 191 | 547/tcp dhcpv6-server | |
| 192 | 547/udp dhcpv6-server | |
| 193 | 548/tcp afpovertcp | |
| 194 | 548/udp afpovertcp | |
| 195 | 549/tcp idfp | |
| 196 | 549/udp idfp | |
| 197 | 556/tcp remotefs | |
| 198 | 563/tcp nntps | |
| 199 | 563/udp nntps | |
| 200 | 587/tcp submission | |
| 201 | 587/udp submission | |
| 202 | 636/tcp ldaps | |
| 203 | 636/udp ldaps | |
| 204 | 655/tcp tinc | |
| 205 | 655/udp tinc | |
| 206 | 706/tcp silc | |
| 207 | 706/udp silc | |
| 208 | 749/tcp kerberos-adm | |
| 209 | 765/tcp webster | |
| 210 | 765/udp webster | |
| 211 | 873/tcp rsync | |
| 212 | 873/udp rsync | |
| 213 | 989/tcp ftps-data | |
| 214 | 990/tcp ftps | |
| 215 | 992/tcp telnets | |
| 216 | 992/udp telnets | |
| 217 | 993/tcp imaps | |
| 218 | 993/udp imaps | |
| 219 | 994/tcp ircs | |
| 220 | 994/udp ircs | |
| 221 | 995/tcp pop3s | |
| 222 | 995/udp pop3s | |
| 223 | 1080/tcp socks | |
| 224 | 1080/udp socks | |
| 225 | 1093/tcp proofd | |
| 226 | 1093/udp proofd | |
| 227 | 1094/tcp rootd | |
| 228 | 1094/udp rootd | |
| 229 | 1194/tcp openvpn | |
| 230 | 1194/udp openvpn | |
| 231 | 1099/tcp rmiregistry | |
| 232 | 1099/udp rmiregistry | |
| 233 | 1214/tcp kazaa | |
| 234 | 1214/udp kazaa | |
| 235 | 1241/tcp nessus | |
| 236 | 1241/udp nessus | |
| 237 | 1352/tcp lotusnote | |
| 238 | 1352/udp lotusnote | |
| 239 | 1433/tcp ms-sql-s | |
| 240 | 1433/udp ms-sql-s | |
| 241 | 1434/tcp ms-sql-m | |
| 242 | 1434/udp ms-sql-m | |
| 243 | 1524/tcp ingreslock | |
| 244 | 1524/udp ingreslock | |
| 245 | 1525/tcp prospero-np | |
| 246 | 1525/udp prospero-np | |
| 247 | 1645/tcp datametrics | |
| 248 | 1645/udp datametrics | |
| 249 | 1646/tcp sa-msg-port | |
| 250 | 1646/udp sa-msg-port | |
| 251 | 1649/tcp kermit | |
| 252 | 1649/udp kermit | |
| 253 | 1677/tcp groupwise | |
| 254 | 1677/udp groupwise | |
| 255 | 1701/tcp l2f | |
| 256 | 1701/udp l2f | |
| 257 | 1812/tcp radius | |
| 258 | 1812/udp radius | |
| 259 | 1813/tcp radius-acct | |
| 260 | 1813/udp radius-acct | |
| 261 | 1863/tcp msnp | |
| 262 | 1863/udp msnp | |
| 263 | 1957/tcp unix-status | |
| 264 | 1958/tcp log-server | |
| 265 | 1959/tcp remoteping | |
| 266 | 2000/tcp cisco-sccp | |
| 267 | 2000/udp cisco-sccp | |
| 268 | 2010/tcp search | |
| 269 | 2010/tcp pipe-server | |
| 270 | 2049/tcp nfs | |
| 271 | 2049/udp nfs | |
| 272 | 2086/tcp gnunet | |
| 273 | 2086/udp gnunet | |
| 274 | 2101/tcp rtcm-sc104 | |
| 275 | 2101/udp rtcm-sc104 | |
| 276 | 2119/tcp gsigatekeeper | |
| 277 | 2119/udp gsigatekeeper | |
| 278 | 2135/tcp gris | |
| 279 | 2135/udp gris | |
| 280 | 2401/tcp cvspserver | |
| 281 | 2401/udp cvspserver | |
| 282 | 2430/tcp venus | |
| 283 | 2430/udp venus | |
| 284 | 2431/tcp venus-se | |
| 285 | 2431/udp venus-se | |
| 286 | 2432/tcp codasrv | |
| 287 | 2432/udp codasrv | |
| 288 | 2433/tcp codasrv-se | |
| 289 | 2433/udp codasrv-se | |
| 290 | 2583/tcp mon | |
| 291 | 2583/udp mon | |
| 292 | 2628/tcp dict | |
| 293 | 2628/udp dict | |
| 294 | 2792/tcp f5-globalsite | |
| 295 | 2792/udp f5-globalsite | |
| 296 | 2811/tcp gsiftp | |
| 297 | 2811/udp gsiftp | |
| 298 | 2947/tcp gpsd | |
| 299 | 2947/udp gpsd | |
| 300 | 3050/tcp gds-db | |
| 301 | 3050/udp gds-db | |
| 302 | 3130/tcp icpv2 | |
| 303 | 3130/udp icpv2 | |
| 304 | 3260/tcp iscsi-target | |
| 305 | 3306/tcp mysql | |
| 306 | 3306/udp mysql | |
| 307 | 3493/tcp nut | |
| 308 | 3493/udp nut | |
| 309 | 3632/tcp distcc | |
| 310 | 3632/udp distcc | |
| 311 | 3689/tcp daap | |
| 312 | 3689/udp daap | |
| 313 | 3690/tcp svn | |
| 314 | 3690/udp svn | |
| 315 | 4031/tcp suucp | |
| 316 | 4031/udp suucp | |
| 317 | 4094/tcp sysrqd | |
| 318 | 4094/udp sysrqd | |
| 319 | 4190/tcp sieve | |
| 320 | 4369/tcp epmd | |
| 321 | 4369/udp epmd | |
| 322 | 4373/tcp remctl | |
| 323 | 4373/udp remctl | |
| 324 | 4353/tcp f5-iquery | |
| 325 | 4353/udp f5-iquery | |
| 326 | 4500/udp ipsec-nat-t | |
| 327 | 4569/tcp iax | |
| 328 | 4569/udp iax | |
| 329 | 4691/tcp mtn | |
| 330 | 4691/udp mtn | |
| 331 | 4899/tcp radmin-port | |
| 332 | 4899/udp radmin-port | |
| 333 | 5002/udp rfe | |
| 334 | 5002/tcp rfe | |
| 335 | 5050/tcp mmcc | |
| 336 | 5050/udp mmcc | |
| 337 | 5060/tcp sip | |
| 338 | 5060/udp sip | |
| 339 | 5061/tcp sip-tls | |
| 340 | 5061/udp sip-tls | |
| 341 | 5190/tcp aol | |
| 342 | 5190/udp aol | |
| 343 | 5222/tcp xmpp-client | |
| 344 | 5222/udp xmpp-client | |
| 345 | 5269/tcp xmpp-server | |
| 346 | 5269/udp xmpp-server | |
| 347 | 5308/tcp cfengine | |
| 348 | 5308/udp cfengine | |
| 349 | 5353/tcp mdns | |
| 350 | 5353/udp mdns | |
| 351 | 5432/tcp postgresql | |
| 352 | 5432/udp postgresql | |
| 353 | 5556/tcp freeciv | |
| 354 | 5556/udp freeciv | |
| 355 | 5671/tcp amqps | |
| 356 | 5672/tcp amqp | |
| 357 | 5672/udp amqp | |
| 358 | 5672/sctp amqp | |
| 359 | 5688/tcp ggz | |
| 360 | 5688/udp ggz | |
| 361 | 6000/tcp x11 | |
| 362 | 6000/udp x11 | |
| 363 | 6001/tcp x11-1 | |
| 364 | 6001/udp x11-1 | |
| 365 | 6002/tcp x11-2 | |
| 366 | 6002/udp x11-2 | |
| 367 | 6003/tcp x11-3 | |
| 368 | 6003/udp x11-3 | |
| 369 | 6004/tcp x11-4 | |
| 370 | 6004/udp x11-4 | |
| 371 | 6005/tcp x11-5 | |
| 372 | 6005/udp x11-5 | |
| 373 | 6006/tcp x11-6 | |
| 374 | 6006/udp x11-6 | |
| 375 | 6007/tcp x11-7 | |
| 376 | 6007/udp x11-7 | |
| 377 | 6346/tcp gnutella-svc | |
| 378 | 6346/udp gnutella-svc | |
| 379 | 6347/tcp gnutella-rtr | |
| 380 | 6347/udp gnutella-rtr | |
| 381 | 6444/tcp sge-qmaster | |
| 382 | 6444/udp sge-qmaster | |
| 383 | 6445/tcp sge-execd | |
| 384 | 6445/udp sge-execd | |
| 385 | 6446/tcp mysql-proxy | |
| 386 | 6446/udp mysql-proxy | |
| 387 | 7000/tcp afs3-fileserver | |
| 388 | 7000/udp afs3-fileserver | |
| 389 | 7001/tcp afs3-callback | |
| 390 | 7001/udp afs3-callback | |
| 391 | 7002/tcp afs3-prserver | |
| 392 | 7002/udp afs3-prserver | |
| 393 | 7003/tcp afs3-vlserver | |
| 394 | 7003/udp afs3-vlserver | |
| 395 | 7004/tcp afs3-kaserver | |
| 396 | 7004/udp afs3-kaserver | |
| 397 | 7005/tcp afs3-volser | |
| 398 | 7005/udp afs3-volser | |
| 399 | 7006/tcp afs3-errors | |
| 400 | 7006/udp afs3-errors | |
| 401 | 7007/tcp afs3-bos | |
| 402 | 7007/udp afs3-bos | |
| 403 | 7008/tcp afs3-update | |
| 404 | 7008/udp afs3-update | |
| 405 | 7009/tcp afs3-rmtsys | |
| 406 | 7009/udp afs3-rmtsys | |
| 407 | 7100/tcp font-service | |
| 408 | 7100/udp font-service | |
| 409 | 8080/tcp http-alt | |
| 410 | 8080/udp http-alt | |
| 411 | 9101/tcp bacula-dir | |
| 412 | 9101/udp bacula-dir | |
| 413 | 9102/tcp bacula-fd | |
| 414 | 9102/udp bacula-fd | |
| 415 | 9103/tcp bacula-sd | |
| 416 | 9103/udp bacula-sd | |
| 417 | 9667/tcp xmms2 | |
| 418 | 9667/udp xmms2 | |
| 419 | 10809/tcp nbd | |
| 420 | 10050/tcp zabbix-agent | |
| 421 | 10050/udp zabbix-agent | |
| 422 | 10051/tcp zabbix-trapper | |
| 423 | 10051/udp zabbix-trapper | |
| 424 | 10080/tcp amanda | |
| 425 | 10080/udp amanda | |
| 426 | 11112/tcp dicom | |
| 427 | 11371/tcp hkp | |
| 428 | 11371/udp hkp | |
| 429 | 13720/tcp bprd | |
| 430 | 13720/udp bprd | |
| 431 | 13721/tcp bpdbm | |
| 432 | 13721/udp bpdbm | |
| 433 | 13722/tcp bpjava-msvc | |
| 434 | 13722/udp bpjava-msvc | |
| 435 | 13724/tcp vnetd | |
| 436 | 13724/udp vnetd | |
| 437 | 13782/tcp bpcd | |
| 438 | 13782/udp bpcd | |
| 439 | 13783/tcp vopied | |
| 440 | 13783/udp vopied | |
| 441 | 17500/tcp db-lsp | |
| 442 | 22125/tcp dcap | |
| 443 | 22128/tcp gsidcap | |
| 444 | 22273/tcp wnn6 | |
| 445 | 22273/udp wnn6 | |
| 446 | 1/ddp rtmp | |
| 447 | 2/ddp nbp | |
| 448 | 4/ddp echo | |
| 449 | 6/ddp zip | |
| 450 | 750/udp kerberos4 | |
| 451 | 750/tcp kerberos4 | |
| 452 | 751/udp kerberos-master | |
| 453 | 751/tcp kerberos-master | |
| 454 | 752/udp passwd-server | |
| 455 | 754/tcp krb-prop | |
| 456 | 760/tcp krbupdate | |
| 457 | 901/tcp swat | |
| 458 | 1109/tcp kpop | |
| 459 | 2053/tcp knetd | |
| 460 | 2102/udp zephyr-srv | |
| 461 | 2103/udp zephyr-clt | |
| 462 | 2104/udp zephyr-hm | |
| 463 | 2105/tcp eklogin | |
| 464 | 2111/tcp kx | |
| 465 | 2121/tcp iprop | |
| 466 | 871/tcp supfilesrv | |
| 467 | 1127/tcp supfiledbg | |
| 468 | 98/tcp linuxconf | |
| 469 | 106/tcp poppassd | |
| 470 | 106/udp poppassd | |
| 471 | 775/tcp moira-db | |
| 472 | 777/tcp moira-update | |
| 473 | 779/udp moira-ureg | |
| 474 | 783/tcp spamd | |
| 475 | 808/tcp omirr | |
| 476 | 808/udp omirr | |
| 477 | 1001/tcp customs | |
| 478 | 1001/udp customs | |
| 479 | 1178/tcp skkserv | |
| 480 | 1210/udp predict | |
| 481 | 1236/tcp rmtcfg | |
| 482 | 1300/tcp wipld | |
| 483 | 1313/tcp xtel | |
| 484 | 1314/tcp xtelw | |
| 485 | 1529/tcp support | |
| 486 | 2003/tcp cfinger | |
| 487 | 2121/tcp frox | |
| 488 | 2150/tcp ninstall | |
| 489 | 2150/udp ninstall | |
| 490 | 2600/tcp zebrasrv | |
| 491 | 2601/tcp zebra | |
| 492 | 2602/tcp ripd | |
| 493 | 2603/tcp ripngd | |
| 494 | 2604/tcp ospfd | |
| 495 | 2605/tcp bgpd | |
| 496 | 2606/tcp ospf6d | |
| 497 | 2607/tcp ospfapi | |
| 498 | 2608/tcp isisd | |
| 499 | 2988/tcp afbackup | |
| 500 | 2988/udp afbackup | |
| 501 | 2989/tcp afmbackup | |
| 502 | 2989/udp afmbackup | |
| 503 | 4224/tcp xtell | |
| 504 | 4557/tcp fax | |
| 505 | 4559/tcp hylafax | |
| 506 | 4600/tcp distmp3 | |
| 507 | 4949/tcp munin | |
| 508 | 5051/tcp enbd-cstatd | |
| 509 | 5052/tcp enbd-sstatd | |
| 510 | 5151/tcp pcrd | |
| 511 | 5354/tcp noclog | |
| 512 | 5354/udp noclog | |
| 513 | 5355/tcp hostmon | |
| 514 | 5355/udp hostmon | |
| 515 | 5555/udp rplay | |
| 516 | 5666/tcp nrpe | |
| 517 | 5667/tcp nsca | |
| 518 | 5674/tcp mrtd | |
| 519 | 5675/tcp bgpsim | |
| 520 | 5680/tcp canna | |
| 521 | 6514/tcp syslog-tls | |
| 522 | 6566/tcp sane-port | |
| 523 | 6667/tcp ircd | |
| 524 | 8021/tcp zope-ftp | |
| 525 | 8081/tcp tproxy | |
| 526 | 8088/tcp omniorb | |
| 527 | 8088/udp omniorb | |
| 528 | 8990/tcp clc-build-daemon | |
| 529 | 9098/tcp xinetd | |
| 530 | 9359/udp mandelspawn | |
| 531 | 9418/tcp git | |
| 532 | 9673/tcp zope | |
| 533 | 10000/tcp webmin | |
| 534 | 10081/tcp kamanda | |
| 535 | 10081/udp kamanda | |
| 536 | 10082/tcp amandaidx | |
| 537 | 10083/tcp amidxtape | |
| 538 | 11201/tcp smsqp | |
| 539 | 11201/udp smsqp | |
| 540 | 15345/tcp xpilot | |
| 541 | 15345/udp xpilot | |
| 542 | 17001/udp sgi-cmsd | |
| 543 | 17002/udp sgi-crsd | |
| 544 | 17003/udp sgi-gcd | |
| 545 | 17004/tcp sgi-cad | |
| 546 | 20011/tcp isdnlog | |
| 547 | 20011/udp isdnlog | |
| 548 | 20012/tcp vboxd | |
| 549 | 20012/udp vboxd | |
| 550 | 24554/tcp binkp | |
| 551 | 27374/tcp asp | |
| 552 | 27374/udp asp | |
| 553 | 30865/tcp csync2 | |
| 554 | 57000/tcp dircproxy | |
| 555 | 60177/tcp tfido | |
| 556 | 60179/tcp fido | |
| 557 | 1027/udp Native IPv6 behind IPv4-to-IPv4 NAT Customer Premises Equipment (6a44) | |
| 558 | 1058/tcp nim, IBM AIX Network Installation Manager (NIM) | |
| 559 | 1058/udp nim, IBM AIX Network Installation Manager (NIM) | |
| 560 | 1059/tcp nimreg, IBM AIX Network Installation Manager (NIM) | |
| 561 | 1059/udp nimreg, IBM AIX Network Installation Manager (NIM) | |
| 562 | 1080/tcp SOCKS proxy | |
| 563 | 1080/udp SOCKS proxy | |
| 564 | 1085/tcp WebObjects | |
| 565 | 1085/udp WebObjects | |
| 566 | 1098/tcp rmiactivation, Java remote method invocation (RMI) activation | |
| 567 | 1098/udp rmiactivation, Java remote method invocation (RMI) activation | |
| 568 | 1099/tcp rmiregistry, Java remote method invocation (RMI) registry | |
| 569 | 1099/assigned rmiregistry, Java remote method invocation (RMI) registry | |
| 570 | 1119/tcp Battle.net chat/game protocol, used by Blizzard's games | |
| 571 | 1119/udp Battle.net chat/game protocol, used by Blizzard's games | |
| 572 | 1167/udp Cisco IP SLA (Service Assurance Agent) | |
| 573 | 1167/tcp Cisco IP SLA (Service Assurance Agent) | |
| 574 | 1194/udp OpenVPN | |
| 575 | 1194/tcp OpenVPN | |
| 576 | 1198/udp The cajo project Free dynamic transparent distributed computing in Java | |
| 577 | 1198/tcp The cajo project Free dynamic transparent distributed computing in Java | |
| 578 | 1214/udp Kazaa | |
| 579 | 1214/tcp Kazaa | |
| 580 | 1234/udp Infoseek search agent | |
| 581 | 1234/tcp Infoseek search agent | |
| 582 | 1241/udp Nessus Security Scanner | |
| 583 | 1241/tcp Nessus Security Scanner | |
| 584 | 1270/udp Microsoft System Center Operations Manager (SCOM) (formerly Microsoft Operations Manager (MOM)) agent | |
| 585 | 1270/tcp Microsoft System Center Operations Manager (SCOM) (formerly Microsoft Operations Manager (MOM)) agent | |
| 586 | 1293/udp Internet Protocol Security (IPSec) | |
| 587 | 1293/tcp Internet Protocol Security (IPSec) | |
| 588 | 1311/udp Windows RxMon.exe | |
| 589 | 1311/tcp Windows RxMon.exe | |
| 590 | 1341/udp Qubes (Manufacturing Execution System) | |
| 591 | 1341/tcp Qubes (Manufacturing Execution System) | |
| 592 | 1344/udp Internet Content Adaptation Protocol | |
| 593 | 1344/tcp Internet Content Adaptation Protocol | |
| 594 | 1352/udp IBM Lotus Notes/Domino (RPC) protocol | |
| 595 | 1352/tcp IBM Lotus Notes/Domino (RPC) protocol | |
| 596 | 1360/udp Mimer SQL | |
| 597 | 1360/tcp Mimer SQL | |
| 598 | 1414/udp IBM WebSphere MQ (formerly known as MQSeries) | |
| 599 | 1414/tcp IBM WebSphere MQ (formerly known as MQSeries) | |
| 600 | 1417/udp Timbuktu Service 1 Port | |
| 601 | 1417/tcp Timbuktu Service 1 Port | |
| 602 | 1418/udp Timbuktu Service 2 Port | |
| 603 | 1418/tcp Timbuktu Service 2 Port | |
| 604 | 1419/udp Timbuktu Service 3 Port | |
| 605 | 1419/tcp Timbuktu Service 3 Port | |
| 606 | 1420/udp Timbuktu Service 4 Port | |
| 607 | 1420/tcp Timbuktu Service 4 Port | |
| 608 | 1433/udp Microsoft SQL Server database management system (MSSQL) server | |
| 609 | 1433/tcp Microsoft SQL Server database management system (MSSQL) server | |
| 610 | 1434/udp Microsoft SQL Server database management system (MSSQL) monitor | |
| 611 | 1434/tcp Microsoft SQL Server database management system (MSSQL) monitor | |
| 612 | 1512/udp Microsoft's Windows Internet Name Service (WINS) | |
| 613 | 1512/tcp Microsoft's Windows Internet Name Service (WINS) | |
| 614 | 1521/udp nCUBE License Manager | |
| 615 | 1521/tcp nCUBE License Manager | |
| 616 | 1524/udp ingreslock, ingres | |
| 617 | 1524/tcp ingreslock, ingres | |
| 618 | 1527/udp Oracle Net Services, formerly known as SQL*Net | |
| 619 | 1527/tcp Oracle Net Services, formerly known as SQL*Net | |
| 620 | 1533/udp IBM Sametime Virtual Places Chat | |
| 621 | 1533/tcp IBM Sametime Virtual Places Chat | |
| 622 | 1547/udp Laplink | |
| 623 | 1547/tcp Laplink | |
| 624 | 1581/udp MIL STD 2045-47001 VMF | |
| 625 | 1581/tcp MIL STD 2045-47001 VMF | |
| 626 | 1589/udp Cisco VLAN Query Protocol (VQP) | |
| 627 | 1589/tcp Cisco VLAN Query Protocol (VQP) | |
| 628 | 1628/udp LonTalk normal | |
| 629 | 1628/tcp LonTalk normal | |
| 630 | 1629/udp LonTalk urgent | |
| 631 | 1629/tcp LonTalk urgent | |
| 632 | 1677/udp Novell GroupWise clients in client/server access mode | |
| 633 | 1677/tcp Novell GroupWise clients in client/server access mode | |
| 634 | 1701/udp Layer 2 Forwarding Protocol (L2F) | |
| 635 | 1701/tcp Layer 2 Forwarding Protocol (L2F) | |
| 636 | 1701/udp Layer 2 Tunneling Protocol (L2TP) | |
| 637 | 1701/assigned Layer 2 Tunneling Protocol (L2TP) | |
| 638 | 1707/udp Windward Studios games (vdmplay) | |
| 639 | 1707/tcp Windward Studios games (vdmplay) | |
| 640 | 1719/udp H.323 registration and alternate communication | |
| 641 | 1719/tcp H.323 registration and alternate communication | |
| 642 | 1720/udp H.323 call signaling | |
| 643 | 1720/tcp H.323 call signaling | |
| 644 | 1755/udp Microsoft Media Services (MMS, ms-streaming) | |
| 645 | 1755/tcp Microsoft Media Services (MMS, ms-streaming) | |
| 646 | 1801/udp Microsoft Message Queuing | |
| 647 | 1801/tcp Microsoft Message Queuing | |
| 648 | 1812/udp RADIUS authentication protocol, radius | |
| 649 | 1812/tcp RADIUS authentication protocol, radius | |
| 650 | 1813/udp RADIUS accounting protocol, radius-acct | |
| 651 | 1813/tcp RADIUS accounting protocol, radius-acct | |
| 652 | 1863/udp Microsoft Notification Protocol (MSNP), used by the Microsoft Messenger service and a number of instant messaging Messenger clients | |
| 653 | 1863/tcp Microsoft Notification Protocol (MSNP), used by the Microsoft Messenger service and a number of instant messaging Messenger clients | |
| 654 | 1883/udp MQTT (formerly MQ Telemetry Transport) | |
| 655 | 1883/tcp MQTT (formerly MQ Telemetry Transport) | |
| 656 | 1900/udp Simple Service Discovery Protocol (SSDP), discovery of UPnP devices | |
| 657 | 1900/assigned Simple Service Discovery Protocol (SSDP), discovery of UPnP devices | |
| 658 | 1935/udp Macromedia Flash Communications Server MX, the precursor to Adobe Flash Media Server before Macromedia's acquisition by Adobe on December 3, 2005 | |
| 659 | 1935/tcp Macromedia Flash Communications Server MX, the precursor to Adobe Flash Media Server before Macromedia's acquisition by Adobe on December 3, 2005 | |
| 660 | 1970/udp Netop Remote Control | |
| 661 | 1970/tcp Netop Remote Control | |
| 662 | 1972/udp InterSystems Cache | |
| 663 | 1972/tcp InterSystems Cache | |
| 664 | 1984/udp Big Brother | |
| 665 | 1984/tcp Big Brother | |
| 666 | 1985/udp Cisco Hot Standby Router Protocol (HSRP) | |
| 667 | 1985/assigned Cisco Hot Standby Router Protocol (HSRP) | |
| 668 | 1998/udp Cisco X.25 over TCP (XOT) service | |
| 669 | 1998/tcp Cisco X.25 over TCP (XOT) service | |
| 670 | 2000/udp Cisco Skinny Client Control Protocol (SCCP) | |
| 671 | 2000/tcp Cisco Skinny Client Control Protocol (SCCP) | |
| 672 | 2080/udp Autodesk NLM (FLEXlm) | |
| 673 | 2080/tcp Autodesk NLM (FLEXlm) | |
| 674 | 2083/udp Secure RADIUS Service (radsec) | |
| 675 | 2083/tcp Secure RADIUS Service (radsec) | |
| 676 | 2086/udp GNUnet | |
| 677 | 2086/tcp GNUnet | |
| 678 | 2102/udp Zephyr Notification Service server | |
| 679 | 2102/tcp Zephyr Notification Service server | |
| 680 | 2103/udp Zephyr Notification Service serv-hm connection | |
| 681 | 2103/tcp Zephyr Notification Service serv-hm connection | |
| 682 | 2104/udp Zephyr Notification Service hostmanager | |
| 683 | 2104/tcp Zephyr Notification Service hostmanager | |
| 684 | 2123/udp GTP control messages (GTP-C) | |
| 685 | 2123/tcp GTP control messages (GTP-C) | |
| 686 | 2142/udp TDMoIP (TDM over IP) | |
| 687 | 2142/tcp TDMoIP (TDM over IP) | |
| 688 | 2152/udp GTP user data messages (GTP-U) | |
| 689 | 2152/tcp GTP user data messages (GTP-U) | |
| 690 | 2159/udp GDB remote debug port | |
| 691 | 2159/tcp GDB remote debug port | |
| 692 | 2181/udp EForward-document transport system | |
| 693 | 2181/tcp EForward-document transport system | |
| 694 | 2210/udp NOAAPORT Broadcast Network | |
| 695 | 2210/tcp NOAAPORT Broadcast Network | |
| 696 | 2211/udp EMWIN | |
| 697 | 2211/tcp EMWIN | |
| 698 | 2222/udp EtherNet/IP implicit messaging for IO data | |
| 699 | 2222/tcp EtherNet/IP implicit messaging for IO data | |
| 700 | 2261/udp CoMotion master | |
| 701 | 2261/tcp CoMotion master | |
| 702 | 2262/udp CoMotion backup | |
| 703 | 2262/tcp CoMotion backup | |
| 704 | 2266/udp M-Files | |
| 705 | 2266/tcp M-Files | |
| 706 | 2399/udp FileMaker Data Access Layer (ODBC/JDBC) | |
| 707 | 2399/tcp FileMaker Data Access Layer (ODBC/JDBC) | |
| 708 | 2401/udp CVS version control system password-based server | |
| 709 | 2401/tcp CVS version control system password-based server | |
| 710 | 2404/udp IEC 60870-5-104, used to send electric power telecontrol messages between two systems via directly connected data circuits | |
| 711 | 2404/tcp IEC 60870-5-104, used to send electric power telecontrol messages between two systems via directly connected data circuits | |
| 712 | 2427/udp Media Gateway Control Protocol (MGCP) media gateway | |
| 713 | 2427/tcp Media Gateway Control Protocol (MGCP) media gateway | |
| 714 | 2447/udp ovwdb OpenView Network Node Manager (NNM) daemon | |
| 715 | 2447/tcp ovwdb OpenView Network Node Manager (NNM) daemon | |
| 716 | 2483/udp Oracle database listening for insecure client connections to the listener, replaces port 1521 | |
| 717 | 2483/tcp Oracle database listening for insecure client connections to the listener, replaces port 1521 | |
| 718 | 2484/udp Oracle database listening for SSL client connections to the listener | |
| 719 | 2484/tcp Oracle database listening for SSL client connections to the listener | |
| 720 | 2535/udp Multicast Address Dynamic Client Allocation Protocol (MADCAP). All standard messages are UDP datagrams. | |
| 721 | 2535/tcp Multicast Address Dynamic Client Allocation Protocol (MADCAP). All standard messages are UDP datagrams. | |
| 722 | 2541/udp LonTalk/IP | |
| 723 | 2541/tcp LonTalk/IP | |
| 724 | 2546/udp EVault data protection services | |
| 725 | 2546/tcp EVault data protection services | |
| 726 | 2547/udp EVault data protection services | |
| 727 | 2547/tcp EVault data protection services | |
| 728 | 2548/udp EVault data protection services | |
| 729 | 2548/tcp EVault data protection services | |
| 730 | 2638/udp SQL Anywhere database server | |
| 731 | 2638/tcp SQL Anywhere database server | |
| 732 | 2727/udp Media Gateway Control Protocol (MGCP) media gateway controller (call agent) | |
| 733 | 2727/tcp Media Gateway Control Protocol (MGCP) media gateway controller (call agent) | |
| 734 | 2809/udp corbaloc:iiop URL, per the CORBA 3.0.3 specification | |
| 735 | 2809/tcp corbaloc:iiop URL, per the CORBA 3.0.3 specification | |
| 736 | 2811/udp gsi ftp, per the GridFTP specification | |
| 737 | 2811/tcp gsi ftp, per the GridFTP specification | |
| 738 | 2944/udp Megaco text H.248 | |
| 739 | 2944/tcp Megaco text H.248 | |
| 740 | 2945/udp Megaco binary (ASN.1) H.248 | |
| 741 | 2945/tcp Megaco binary (ASN.1) H.248 | |
| 742 | 2947/udp gpsd, GPS daemon | |
| 743 | 2947/tcp gpsd, GPS daemon | |
| 744 | 2948/udp WAP push Multimedia Messaging Service (MMS) | |
| 745 | 2948/tcp WAP push Multimedia Messaging Service (MMS) | |
| 746 | 2949/udp WAP push secure (MMS) | |
| 747 | 2949/tcp WAP push secure (MMS) | |
| 748 | 2967/udp Symantec System Center agent (SSC-AGENT) | |
| 749 | 2967/tcp Symantec System Center agent (SSC-AGENT) | |
| 750 | 3020/udp Common Internet File System (CIFS). See also port 445 for Server Message Block (SMB), a dialect of CIFS. | |
| 751 | 3020/tcp Common Internet File System (CIFS). See also port 445 for Server Message Block (SMB), a dialect of CIFS. | |
| 752 | 3050/udp gds-db (Interbase/Firebird databases) | |
| 753 | 3050/tcp gds-db (Interbase/Firebird databases) | |
| 754 | 3052/udp APC PowerChute Network | |
| 755 | 3052/tcp APC PowerChute Network | |
| 756 | 3074/udp Xbox LIVE and Games for Windows Live | |
| 757 | 3074/tcp Xbox LIVE and Games for Windows Live | |
| 758 | 3225/udp Fibre Channel over IP (FCIP) | |
| 759 | 3225/tcp Fibre Channel over IP (FCIP) | |
| 760 | 3233/udp WhiskerControl research control protocol | |
| 761 | 3233/tcp WhiskerControl research control protocol | |
| 762 | 3260/udp iSCSI | |
| 763 | 3260/tcp iSCSI | |
| 764 | 3268/udp msft-gc, Microsoft Global Catalog (LDAP service which contains data from Active Directory forests) | |
| 765 | 3268/tcp msft-gc, Microsoft Global Catalog (LDAP service which contains data from Active Directory forests) | |
| 766 | 3269/udp msft-gc-ssl, Microsoft Global Catalog over SSL (similar to port 3268, LDAP over SSL) | |
| 767 | 3269/tcp msft-gc-ssl, Microsoft Global Catalog over SSL (similar to port 3268, LDAP over SSL) | |
| 768 | 3283/udp Net Assistant, a predecessor to Apple Remote Desktop | |
| 769 | 3283/tcp Net Assistant, a predecessor to Apple Remote Desktop | |
| 770 | 3305/udp Odette File Transfer Protocol (OFTP) | |
| 771 | 3305/tcp Odette File Transfer Protocol (OFTP) | |
| 772 | 3386/udp GTP' 3GPP GSM/UMTS CDR logging protocol | |
| 773 | 3386/tcp GTP' 3GPP GSM/UMTS CDR logging protocol | |
| 774 | 3389/udp Microsoft Terminal Server (RDP) officially registered as Windows Based Terminal (WBT) | |
| 775 | 3389/tcp Microsoft Terminal Server (RDP) officially registered as Windows Based Terminal (WBT) | |
| 776 | 3396/udp Novell NDPS Printer Agent | |
| 777 | 3396/tcp Novell NDPS Printer Agent | |
| 778 | 3412/udp xmlBlaster | |
| 779 | 3412/tcp xmlBlaster | |
| 780 | 3455/udp Resource Reservation Protocol (RSVP) | |
| 781 | 3455/tcp Resource Reservation Protocol (RSVP) | |
| 782 | 3478/udp STUN, a protocol for NAT traversal | |
| 783 | 3478/tcp STUN, a protocol for NAT traversal | |
| 784 | 3478/udp TURN, a protocol for NAT traversal (extension to STUN) | |
| 785 | 3478/tcp TURN, a protocol for NAT traversal (extension to STUN) | |
| 786 | 3478/udp STUN Behavior Discovery. See also port 5349. | |
| 787 | 3478/tcp STUN Behavior Discovery. See also port 5349. | |
| 788 | 3493/udp Network UPS Tools (NUT) | |
| 789 | 3493/tcp Network UPS Tools (NUT) | |
| 790 | 3516/udp Smartcard Port | |
| 791 | 3516/tcp Smartcard Port | |
| 792 | 3645/udp Cyc | |
| 793 | 3645/tcp Cyc | |
| 794 | 3659/udp Apple SASL, used by Mac OS X Server Password Server | |
| 795 | 3659/tcp Apple SASL, used by Mac OS X Server Password Server | |
| 796 | 3667/udp Information Exchange | |
| 797 | 3667/tcp Information Exchange | |
| 798 | 3690/udp Subversion (SVN) version control system | |
| 799 | 3690/tcp Subversion (SVN) version control system | |
| 800 | 3702/udp Web Services Dynamic Discovery (WS-Discovery), used by various components of Windows Vista and later | |
| 801 | 3702/tcp Web Services Dynamic Discovery (WS-Discovery), used by various components of Windows Vista and later | |
| 802 | 3724/udp Some Blizzard games | |
| 803 | 3724/tcp Some Blizzard games | |
| 804 | 3725/udp Netia NA-ER Port | |
| 805 | 3725/tcp Netia NA-ER Port | |
| 806 | 3768/udp RBLcheckd server daemon | |
| 807 | 3768/tcp RBLcheckd server daemon | |
| 808 | 3804/udp Harman Professional HiQnet protocol | |
| 809 | 3804/tcp Harman Professional HiQnet protocol | |
| 810 | 3826/udp WarMUX game server | |
| 811 | 3826/tcp WarMUX game server | |
| 812 | 3830/udp System Management Agent, developed and used by Cerner to monitor and manage solutions | |
| 813 | 3830/tcp System Management Agent, developed and used by Cerner to monitor and manage solutions | |
| 814 | 3880/udp IGRS | |
| 815 | 3880/tcp IGRS | |
| 816 | 3999/udp Norman distributed scanning service | |
| 817 | 3999/tcp Norman distributed scanning service | |
| 818 | 4018/udp Protocol information and warnings | |
| 819 | 4018/tcp Protocol information and warnings | |
| 820 | 4089/udp OpenCORE Remote Control Service | |
| 821 | 4089/tcp OpenCORE Remote Control Service | |
| 822 | 4090/udp Kerio | |
| 823 | 4090/tcp Kerio | |
| 824 | 4093/udp PxPlus Client server interface ProvideX | |
| 825 | 4093/tcp PxPlus Client server interface ProvideX | |
| 826 | 4096/udp Ascom Timeplex Bridge Relay Element (BRE) | |
| 827 | 4096/tcp Ascom Timeplex Bridge Relay Element (BRE) | |
| 828 | 4105/udp Shofar (ShofarNexus) | |
| 829 | 4105/tcp Shofar (ShofarNexus) | |
| 830 | 4116/udp Smartcard-TLS | |
| 831 | 4116/tcp Smartcard-TLS | |
| 832 | 4172/udp Teradici PCoIP | |
| 833 | 4172/tcp Teradici PCoIP | |
| 834 | 4303/udp Simple Railroad Command Protocol (SRCP) | |
| 835 | 4303/tcp Simple Railroad Command Protocol (SRCP) | |
| 836 | 4486/udp Integrated Client Message Service (ICMS) | |
| 837 | 4486/tcp Integrated Client Message Service (ICMS) | |
| 838 | 4500/udp IPSec NAT Traversal (RFC 3947, RFC 4306) | |
| 839 | 4500/assigned IPSec NAT Traversal (RFC 3947, RFC 4306) | |
| 840 | 4662/udp OrbitNet Message Service | |
| 841 | 4662/tcp OrbitNet Message Service | |
| 842 | 4730/udp Gearman's job server | |
| 843 | 4730/tcp Gearman's job server | |
| 844 | 4739/udp IP Flow Information Export | |
| 845 | 4739/tcp IP Flow Information Export | |
| 846 | 4753/udp SIMON (service and discovery) | |
| 847 | 4753/tcp SIMON (service and discovery) | |
| 848 | 4840/udp OPC UA Connection Protocol (TCP) and OPC UA Multicast Datagram Protocol (UDP) for OPC Unified Architecture from OPC Foundation | |
| 849 | 4840/tcp OPC UA Connection Protocol (TCP) and OPC UA Multicast Datagram Protocol (UDP) for OPC Unified Architecture from OPC Foundation | |
| 850 | 4843/udp OPC UA TCP Protocol over TLS/SSL for OPC Unified Architecture from OPC Foundation | |
| 851 | 4843/tcp OPC UA TCP Protocol over TLS/SSL for OPC Unified Architecture from OPC Foundation | |
| 852 | 4847/udp Web Fresh Communication, Quadrion Software & Odorless Entertainment | |
| 853 | 4847/tcp Web Fresh Communication, Quadrion Software & Odorless Entertainment | |
| 854 | 4894/udp LysKOM Protocol A | |
| 855 | 4894/tcp LysKOM Protocol A | |
| 856 | 4950/udp Cylon Controls UC32 Communications Port | |
| 857 | 4950/tcp Cylon Controls UC32 Communications Port | |
| 858 | 5010/udp Registered to: TelePath (the IBM FlowMark workflow-management system messaging platform). The TCP port is now used for: IBM WebSphere MQ Workflow | |
| 859 | 5010/tcp Registered to: TelePath (the IBM FlowMark workflow-management system messaging platform). The TCP port is now used for: IBM WebSphere MQ Workflow | |
| 860 | 5011/udp TelePath (the IBM FlowMark workflow-management system messaging platform) | |
| 861 | 5011/tcp TelePath (the IBM FlowMark workflow-management system messaging platform) | |
| 862 | 5025/udp scpi-raw Standard Commands for Programmable Instruments | |
| 863 | 5025/tcp scpi-raw Standard Commands for Programmable Instruments | |
| 864 | 5060/udp Session Initiation Protocol (SIP) | |
| 865 | 5060/tcp Session Initiation Protocol (SIP) | |
| 866 | 5062/udp Localisation access | |
| 867 | 5062/tcp Localisation access | |
| 868 | 5064/udp EPICS Channel Access server | |
| 869 | 5064/tcp EPICS Channel Access server | |
| 870 | 5065/udp EPICS Channel Access repeater beacon | |
| 871 | 5065/tcp EPICS Channel Access repeater beacon | |
| 872 | 5084/udp EPCglobal Low Level Reader Protocol (LLRP) | |
| 873 | 5084/tcp EPCglobal Low Level Reader Protocol (LLRP) | |
| 874 | 5085/udp EPCglobal Low Level Reader Protocol (LLRP) over TLS | |
| 875 | 5085/tcp EPCglobal Low Level Reader Protocol (LLRP) over TLS | |
| 876 | 5099/udp SafeNet, Inc Sentinel LM, Sentinel RMS, License Manager, server-to-server | |
| 877 | 5099/tcp SafeNet, Inc Sentinel LM, Sentinel RMS, License Manager, server-to-server | |
| 878 | 5150/udp ATMP Ascend Tunnel Management Protocol | |
| 879 | 5150/tcp ATMP Ascend Tunnel Management Protocol | |
| 880 | 5154/udp BZFlag | |
| 881 | 5154/tcp BZFlag | |
| 882 | 5190/udp AOL Instant Messenger protocol. The chat app is defunct as of 15 December 2017. | |
| 883 | 5190/tcp AOL Instant Messenger protocol. The chat app is defunct as of 15 December 2017. | |
| 884 | 5298/udp Extensible Messaging and Presence Protocol (XMPP) | |
| 885 | 5298/tcp Extensible Messaging and Presence Protocol (XMPP) | |
| 886 | 5310/udp Outlaws (1997 video game). Both UDP and TCP are reserved, but only UDP is used | |
| 887 | 5310/tcp Outlaws (1997 video game). Both UDP and TCP are reserved, but only UDP is used | |
| 888 | 5353/udp Multicast DNS (mDNS) | |
| 889 | 5353/assigned Multicast DNS (mDNS) | |
| 890 | 5355/udp Link-Local Multicast Name Resolution (LLMNR), allows hosts to perform name resolution for hosts on the same local link (only provided by Windows Vista and Server 2008) | |
| 891 | 5355/tcp Link-Local Multicast Name Resolution (LLMNR), allows hosts to perform name resolution for hosts on the same local link (only provided by Windows Vista and Server 2008) | |
| 892 | 5402/udp Multicast File Transfer Protocol (MFTP) | |
| 893 | 5402/tcp Multicast File Transfer Protocol (MFTP) | |
| 894 | 5405/udp NetSupport Manager | |
| 895 | 5405/tcp NetSupport Manager | |
| 896 | 5412/udp IBM Rational Synergy (Telelogic Synergy) (Continuus CM) Message Router | |
| 897 | 5412/tcp IBM Rational Synergy (Telelogic Synergy) (Continuus CM) Message Router | |
| 898 | 5413/udp Wonderware SuiteLink service | |
| 899 | 5413/tcp Wonderware SuiteLink service | |
| 900 | 5417/udp SNS Agent | |
| 901 | 5417/tcp SNS Agent | |
| 902 | 5421/udp NetSupport Manager | |
| 903 | 5421/tcp NetSupport Manager | |
| 904 | 5556/udp Freeciv, Oracle WebLogic Server Node Manager | |
| 905 | 5556/tcp Freeciv, Oracle WebLogic Server Node Manager | |
| 906 | 5568/udp Session Data Transport (SDT), a part of Architecture for Control Networks (ACN) | |
| 907 | 5568/tcp Session Data Transport (SDT), a part of Architecture for Control Networks (ACN) | |
| 908 | 5722/udp Microsoft RPC, DFSR (SYSVOL) Replication Service | |
| 909 | 5722/tcp Microsoft RPC, DFSR (SYSVOL) Replication Service | |
| 910 | 5741/udp IDA Discover Port 1 | |
| 911 | 5741/tcp IDA Discover Port 1 | |
| 912 | 5742/udp IDA Discover Port 2 | |
| 913 | 5742/tcp IDA Discover Port 2 | |
| 914 | 5900/udp Remote Frame Buffer protocol (RFB) | |
| 915 | 5900/tcp Remote Frame Buffer protocol (RFB) | |
| 916 | 5931/udp AMMYY admin Remote Control | |
| 917 | 5931/tcp AMMYY admin Remote Control | |
| 918 | 5984/udp CouchDB database server | |
| 919 | 5984/tcp CouchDB database server | |
| 920 | 6000/udp X11-used between an X client and server over the network | |
| 921 | 6000/tcp X11-used between an X client and server over the network | |
| 922 | 6001/udp X11-used between an X client and server over the network | |
| 923 | 6001/tcp X11-used between an X client and server over the network | |
| 924 | 6002/udp X11-used between an X client and server over the network | |
| 925 | 6002/tcp X11-used between an X client and server over the network | |
| 926 | 6003/udp X11-used between an X client and server over the network | |
| 927 | 6003/tcp X11-used between an X client and server over the network | |
| 928 | 6004/udp X11-used between an X client and server over the network | |
| 929 | 6004/tcp X11-used between an X client and server over the network | |
| 930 | 6005/udp X11-used between an X client and server over the network | |
| 931 | 6005/tcp X11-used between an X client and server over the network | |
| 932 | 6006/udp X11-used between an X client and server over the network | |
| 933 | 6006/tcp X11-used between an X client and server over the network | |
| 934 | 6007/udp X11-used between an X client and server over the network | |
| 935 | 6007/tcp X11-used between an X client and server over the network | |
| 936 | 6008/udp X11-used between an X client and server over the network | |
| 937 | 6008/tcp X11-used between an X client and server over the network | |
| 938 | 6009/udp X11-used between an X client and server over the network | |
| 939 | 6009/tcp X11-used between an X client and server over the network | |
| 940 | 6010/udp X11-used between an X client and server over the network | |
| 941 | 6010/tcp X11-used between an X client and server over the network | |
| 942 | 6011/udp X11-used between an X client and server over the network | |
| 943 | 6011/tcp X11-used between an X client and server over the network | |
| 944 | 6012/udp X11-used between an X client and server over the network | |
| 945 | 6012/tcp X11-used between an X client and server over the network | |
| 946 | 6013/udp X11-used between an X client and server over the network | |
| 947 | 6013/tcp X11-used between an X client and server over the network | |
| 948 | 6014/udp X11-used between an X client and server over the network | |
| 949 | 6014/tcp X11-used between an X client and server over the network | |
| 950 | 6015/udp X11-used between an X client and server over the network | |
| 951 | 6015/tcp X11-used between an X client and server over the network | |
| 952 | 6016/udp X11-used between an X client and server over the network | |
| 953 | 6016/tcp X11-used between an X client and server over the network | |
| 954 | 6017/udp X11-used between an X client and server over the network | |
| 955 | 6017/tcp X11-used between an X client and server over the network | |
| 956 | 6018/udp X11-used between an X client and server over the network | |
| 957 | 6018/tcp X11-used between an X client and server over the network | |
| 958 | 6019/udp X11-used between an X client and server over the network | |
| 959 | 6019/tcp X11-used between an X client and server over the network | |
| 960 | 6020/udp X11-used between an X client and server over the network | |
| 961 | 6020/tcp X11-used between an X client and server over the network | |
| 962 | 6021/udp X11-used between an X client and server over the network | |
| 963 | 6021/tcp X11-used between an X client and server over the network | |
| 964 | 6022/udp X11-used between an X client and server over the network | |
| 965 | 6022/tcp X11-used between an X client and server over the network | |
| 966 | 6023/udp X11-used between an X client and server over the network | |
| 967 | 6023/tcp X11-used between an X client and server over the network | |
| 968 | 6024/udp X11-used between an X client and server over the network | |
| 969 | 6024/tcp X11-used between an X client and server over the network | |
| 970 | 6025/udp X11-used between an X client and server over the network | |
| 971 | 6025/tcp X11-used between an X client and server over the network | |
| 972 | 6026/udp X11-used between an X client and server over the network | |
| 973 | 6026/tcp X11-used between an X client and server over the network | |
| 974 | 6027/udp X11-used between an X client and server over the network | |
| 975 | 6027/tcp X11-used between an X client and server over the network | |
| 976 | 6028/udp X11-used between an X client and server over the network | |
| 977 | 6028/tcp X11-used between an X client and server over the network | |
| 978 | 6029/udp X11-used between an X client and server over the network | |
| 979 | 6029/tcp X11-used between an X client and server over the network | |
| 980 | 6030/udp X11-used between an X client and server over the network | |
| 981 | 6030/tcp X11-used between an X client and server over the network | |
| 982 | 6031/udp X11-used between an X client and server over the network | |
| 983 | 6031/tcp X11-used between an X client and server over the network | |
| 984 | 6032/udp X11-used between an X client and server over the network | |
| 985 | 6032/tcp X11-used between an X client and server over the network | |
| 986 | 6033/udp X11-used between an X client and server over the network | |
| 987 | 6033/tcp X11-used between an X client and server over the network | |
| 988 | 6034/udp X11-used between an X client and server over the network | |
| 989 | 6034/tcp X11-used between an X client and server over the network | |
| 990 | 6035/udp X11-used between an X client and server over the network | |
| 991 | 6035/tcp X11-used between an X client and server over the network | |
| 992 | 6036/udp X11-used between an X client and server over the network | |
| 993 | 6036/tcp X11-used between an X client and server over the network | |
| 994 | 6037/udp X11-used between an X client and server over the network | |
| 995 | 6037/tcp X11-used between an X client and server over the network | |
| 996 | 6038/udp X11-used between an X client and server over the network | |
| 997 | 6038/tcp X11-used between an X client and server over the network | |
| 998 | 6039/udp X11-used between an X client and server over the network | |
| 999 | 6039/tcp X11-used between an X client and server over the network | |
| 1000 | 6040/udp X11-used between an X client and server over the network | |
| 1001 | 6040/tcp X11-used between an X client and server over the network | |
| 1002 | 6041/udp X11-used between an X client and server over the network | |
| 1003 | 6041/tcp X11-used between an X client and server over the network | |
| 1004 | 6042/udp X11-used between an X client and server over the network | |
| 1005 | 6042/tcp X11-used between an X client and server over the network | |
| 1006 | 6043/udp X11-used between an X client and server over the network | |
| 1007 | 6043/tcp X11-used between an X client and server over the network | |
| 1008 | 6044/udp X11-used between an X client and server over the network | |
| 1009 | 6044/tcp X11-used between an X client and server over the network | |
| 1010 | 6045/udp X11-used between an X client and server over the network | |
| 1011 | 6045/tcp X11-used between an X client and server over the network | |
| 1012 | 6046/udp X11-used between an X client and server over the network | |
| 1013 | 6046/tcp X11-used between an X client and server over the network | |
| 1014 | 6047/udp X11-used between an X client and server over the network | |
| 1015 | 6047/tcp X11-used between an X client and server over the network | |
| 1016 | 6048/udp X11-used between an X client and server over the network | |
| 1017 | 6048/tcp X11-used between an X client and server over the network | |
| 1018 | 6049/udp X11-used between an X client and server over the network | |
| 1019 | 6049/tcp X11-used between an X client and server over the network | |
| 1020 | 6050/udp X11-used between an X client and server over the network | |
| 1021 | 6050/tcp X11-used between an X client and server over the network | |
| 1022 | 6051/udp X11-used between an X client and server over the network | |
| 1023 | 6051/tcp X11-used between an X client and server over the network | |
| 1024 | 6052/udp X11-used between an X client and server over the network | |
| 1025 | 6052/tcp X11-used between an X client and server over the network | |
| 1026 | 6053/udp X11-used between an X client and server over the network | |
| 1027 | 6053/tcp X11-used between an X client and server over the network | |
| 1028 | 6054/udp X11-used between an X client and server over the network | |
| 1029 | 6054/tcp X11-used between an X client and server over the network | |
| 1030 | 6055/udp X11-used between an X client and server over the network | |
| 1031 | 6055/tcp X11-used between an X client and server over the network | |
| 1032 | 6056/udp X11-used between an X client and server over the network | |
| 1033 | 6056/tcp X11-used between an X client and server over the network | |
| 1034 | 6057/udp X11-used between an X client and server over the network | |
| 1035 | 6057/tcp X11-used between an X client and server over the network | |
| 1036 | 6058/udp X11-used between an X client and server over the network | |
| 1037 | 6058/tcp X11-used between an X client and server over the network | |
| 1038 | 6059/udp X11-used between an X client and server over the network | |
| 1039 | 6059/tcp X11-used between an X client and server over the network | |
| 1040 | 6060/udp X11-used between an X client and server over the network | |
| 1041 | 6060/tcp X11-used between an X client and server over the network | |
| 1042 | 6061/udp X11-used between an X client and server over the network | |
| 1043 | 6061/tcp X11-used between an X client and server over the network | |
| 1044 | 6062/udp X11-used between an X client and server over the network | |
| 1045 | 6062/tcp X11-used between an X client and server over the network | |
| 1046 | 6063/udp X11-used between an X client and server over the network | |
| 1047 | 6063/tcp X11-used between an X client and server over the network | |
| 1048 | 6110/udp softcm, HP Softbench CM | |
| 1049 | 6110/tcp softcm, HP Softbench CM | |
| 1050 | 6111/udp spc, HP Softbench Sub-Process Control | |
| 1051 | 6111/tcp spc, HP Softbench Sub-Process Control | |
| 1052 | 6112/udp dtspcd, execute commands and launch applications remotely | |
| 1053 | 6112/tcp dtspcd, execute commands and launch applications remotely | |
| 1054 | 6346/udp gnutella-svc, gnutella (FrostWire, Limewire, Shareaza, etc.) | |
| 1055 | 6346/tcp gnutella-svc, gnutella (FrostWire, Limewire, Shareaza, etc.) | |
| 1056 | 6347/udp gnutella-rtr, Gnutella alternate | |
| 1057 | 6347/tcp gnutella-rtr, Gnutella alternate | |
| 1058 | 6350/udp App Discovery and Access Protocol | |
| 1059 | 6350/tcp App Discovery and Access Protocol | |
| 1060 | 6444/udp Sun Grid Engine Qmaster Service | |
| 1061 | 6444/tcp Sun Grid Engine Qmaster Service | |
| 1062 | 6445/udp Sun Grid Engine Execution Service | |
| 1063 | 6445/tcp Sun Grid Engine Execution Service | |
| 1064 | 6464/udp Port assignment for medical device communication in accordance to IEEE 11073-20701 | |
| 1065 | 6464/tcp Port assignment for medical device communication in accordance to IEEE 11073-20701 | |
| 1066 | 6515/udp Elipse RPC Protocol (REC) | |
| 1067 | 6515/tcp Elipse RPC Protocol (REC) | |
| 1068 | 6619/udp odette-ftps, Odette File Transfer Protocol (OFTP) over TLS/SSL | |
| 1069 | 6619/tcp odette-ftps, Odette File Transfer Protocol (OFTP) over TLS/SSL | |
| 1070 | 6622/udp Multicast FTP | |
| 1071 | 6622/tcp Multicast FTP | |
| 1072 | 6679/udp Osorno Automation Protocol (OSAUT) | |
| 1073 | 6679/tcp Osorno Automation Protocol (OSAUT) | |
| 1074 | 6888/udp MUSE | |
| 1075 | 6888/tcp MUSE | |
| 1076 | 6969/udp acmsoda | |
| 1077 | 6969/tcp acmsoda | |
| 1078 | 7262/udp CNAP (Calypso Network Access Protocol) | |
| 1079 | 7262/tcp CNAP (Calypso Network Access Protocol) | |
| 1080 | 7272/udp WatchMe - WatchMe Monitoring | |
| 1081 | 7272/tcp WatchMe - WatchMe Monitoring | |
| 1082 | 7400/udp RTPS (Real Time Publish Subscribe) DDS Discovery | |
| 1083 | 7400/tcp RTPS (Real Time Publish Subscribe) DDS Discovery | |
| 1084 | 7401/udp RTPS (Real Time Publish Subscribe) DDS User-Traffic | |
| 1085 | 7401/tcp RTPS (Real Time Publish Subscribe) DDS User-Traffic | |
| 1086 | 7402/udp RTPS (Real Time Publish Subscribe) DDS Meta-Traffic | |
| 1087 | 7402/tcp RTPS (Real Time Publish Subscribe) DDS Meta-Traffic | |
| 1088 | 7542/udp Saratoga file transfer protocol | |
| 1089 | 7542/tcp Saratoga file transfer protocol | |
| 1090 | 7547/udp CPE WAN Management Protocol (CWMP) Technical Report 069 | |
| 1091 | 7547/tcp CPE WAN Management Protocol (CWMP) Technical Report 069 | |
| 1092 | 7624/udp Instrument Neutral Distributed Interface | |
| 1093 | 7624/tcp Instrument Neutral Distributed Interface | |
| 1094 | 8008/udp Alternative port for HTTP. See also ports 80 and 8080. | |
| 1095 | 8008/tcp Alternative port for HTTP. See also ports 80 and 8080. | |
| 1096 | 8074/udp Gadu-Gadu | |
| 1097 | 8074/tcp Gadu-Gadu | |
| 1098 | 8080/udp Alternative port for HTTP. See also ports 80 and 8008. | |
| 1099 | 8080/tcp Alternative port for HTTP. See also ports 80 and 8008. | |
| 1100 | 8243/udp HTTPS listener for Apache Synapse | |
| 1101 | 8243/tcp HTTPS listener for Apache Synapse | |
| 1102 | 8280/udp HTTP listener for Apache Synapse | |
| 1103 | 8280/tcp HTTP listener for Apache Synapse | |
| 1104 | 8883/udp Secure MQTT (MQTT over TLS) | |
| 1105 | 8883/tcp Secure MQTT (MQTT over TLS) | |
| 1106 | 9001/udp ETL Service Manager | |
| 1107 | 9001/tcp ETL Service Manager | |
| 1108 | 9080/udp glrpc, Groove Collaboration software GLRPC | |
| 1109 | 9080/tcp glrpc, Groove Collaboration software GLRPC | |
| 1110 | 9101/udp Bacula Director | |
| 1111 | 9101/tcp Bacula Director | |
| 1112 | 9102/udp Bacula File Daemon | |
| 1113 | 9102/tcp Bacula File Daemon | |
| 1114 | 9103/udp Bacula Storage Daemon | |
| 1115 | 9103/tcp Bacula Storage Daemon | |
| 1116 | 9119/udp MXit Instant Messenger | |
| 1117 | 9119/tcp MXit Instant Messenger | |
| 1118 | 9389/udp adws, Microsoft AD DS Web Services, Powershell uses this port | |
| 1119 | 9389/tcp adws, Microsoft AD DS Web Services, Powershell uses this port | |
| 1120 | 9418/udp git, Git pack transfer service | |
| 1121 | 9418/tcp git, Git pack transfer service | |
| 1122 | 9535/udp mngsuite, LANDesk Management Suite Remote Control | |
| 1123 | 9535/tcp mngsuite, LANDesk Management Suite Remote Control | |
| 1124 | 9536/udp laes-bf, IP Fabrics Surveillance buffering function | |
| 1125 | 9536/tcp laes-bf, IP Fabrics Surveillance buffering function | |
| 1126 | 9800/udp WebDAV Source | |
| 1127 | 9800/tcp WebDAV Source | |
| 1128 | 10000/udp Network Data Management Protocol | |
| 1129 | 10000/tcp Network Data Management Protocol | |
| 1130 | 10050/udp Zabbix agent | |
| 1131 | 10050/tcp Zabbix agent | |
| 1132 | 10051/udp Zabbix trapper | |
| 1133 | 10051/tcp Zabbix trapper | |
| 1134 | 10110/udp NMEA 0183 Navigational Data. Transport of NMEA 0183 sentences over TCP or UDP | |
| 1135 | 10110/tcp NMEA 0183 Navigational Data. Transport of NMEA 0183 sentences over TCP or UDP | |
| 1136 | 11001/udp metasys ( Johnson Controls Metasys java AC control environment ) | |
| 1137 | 11001/tcp metasys ( Johnson Controls Metasys java AC control environment ) | |
| 1138 | 11112/udp ACR/NEMA Digital Imaging and Communications in Medicine (DICOM) | |
| 1139 | 11112/tcp ACR/NEMA Digital Imaging and Communications in Medicine (DICOM) | |
| 1140 | 11371/udp OpenPGP HTTP key server | |
| 1141 | 11371/tcp OpenPGP HTTP key server | |
| 1142 | 13720/udp Symantec NetBackup-bprd (formerly VERITAS) | |
| 1143 | 13720/tcp Symantec NetBackup-bprd (formerly VERITAS) | |
| 1144 | 13721/udp Symantec NetBackup-bpdbm (formerly VERITAS) | |
| 1145 | 13721/tcp Symantec NetBackup-bpdbm (formerly VERITAS) | |
| 1146 | 13724/udp Symantec Network Utility-vnetd (formerly VERITAS) | |
| 1147 | 13724/tcp Symantec Network Utility-vnetd (formerly VERITAS) | |
| 1148 | 13782/udp Symantec NetBackup-bpcd (formerly VERITAS) | |
| 1149 | 13782/tcp Symantec NetBackup-bpcd (formerly VERITAS) | |
| 1150 | 13783/udp Symantec VOPIED protocol (formerly VERITAS) | |
| 1151 | 13783/tcp Symantec VOPIED protocol (formerly VERITAS) | |
| 1152 | 13785/udp Symantec NetBackup Database-nbdb (formerly VERITAS) | |
| 1153 | 13785/tcp Symantec NetBackup Database-nbdb (formerly VERITAS) | |
| 1154 | 13786/udp Symantec nomdb (formerly VERITAS) | |
| 1155 | 13786/tcp Symantec nomdb (formerly VERITAS) | |
| 1156 | 15345/udp XPilot Contact | |
| 1157 | 15345/tcp XPilot Contact | |
| 1158 | 17500/udp Dropbox LanSync Protocol (db-lsp); used to synchronize file catalogs between Dropbox clients on a local network. | |
| 1159 | 17500/tcp Dropbox LanSync Protocol (db-lsp); used to synchronize file catalogs between Dropbox clients on a local network. | |
| 1160 | 19813/udp 4D database Client Server Communication | |
| 1161 | 19813/tcp 4D database Client Server Communication | |
| 1162 | 24465/udp Tonido Directory Server for Tonido which is a Personal Web App and P2P platform | |
| 1163 | 24465/tcp Tonido Directory Server for Tonido which is a Personal Web App and P2P platform | |
| 1164 | 24554/udp BINKP, Fidonet mail transfers over TCP/IP | |
| 1165 | 24554/tcp BINKP, Fidonet mail transfers over TCP/IP | |
| 1166 | 26000/udp id Software's Quake server | |
| 1167 | 26000/tcp id Software's Quake server | |
| 1168 | 27000/udp FlexNet Publisher's License server (from the range of default ports) | |
| 1169 | 27000/tcp FlexNet Publisher's License server (from the range of default ports) | |
| 1170 | 27001/udp FlexNet Publisher's License server (from the range of default ports) | |
| 1171 | 27001/tcp FlexNet Publisher's License server (from the range of default ports) | |
| 1172 | 27002/udp FlexNet Publisher's License server (from the range of default ports) | |
| 1173 | 27002/tcp FlexNet Publisher's License server (from the range of default ports) | |
| 1174 | 27003/udp FlexNet Publisher's License server (from the range of default ports) | |
| 1175 | 27003/tcp FlexNet Publisher's License server (from the range of default ports) | |
| 1176 | 27004/udp FlexNet Publisher's License server (from the range of default ports) | |
| 1177 | 27004/tcp FlexNet Publisher's License server (from the range of default ports) | |
| 1178 | 27005/udp FlexNet Publisher's License server (from the range of default ports) | |
| 1179 | 27005/tcp FlexNet Publisher's License server (from the range of default ports) | |
| 1180 | 27006/udp FlexNet Publisher's License server (from the range of default ports) | |
| 1181 | 27006/tcp FlexNet Publisher's License server (from the range of default ports) | |
| 1182 | 27007/udp FlexNet Publisher's License server (from the range of default ports) | |
| 1183 | 27007/tcp FlexNet Publisher's License server (from the range of default ports) | |
| 1184 | 27008/udp FlexNet Publisher's License server (from the range of default ports) | |
| 1185 | 27008/tcp FlexNet Publisher's License server (from the range of default ports) | |
| 1186 | 27009/udp FlexNet Publisher's License server (from the range of default ports) | |
| 1187 | 27009/tcp FlexNet Publisher's License server (from the range of default ports) | |
| 1188 | 33434/udp traceroute | |
| 1189 | 33434/tcp traceroute | |
| 1190 | 40000/udp SafetyNET p a real-time Industrial Ethernet protocol | |
| 1191 | 40000/tcp SafetyNET p a real-time Industrial Ethernet protocol | |
| 1192 | 44818/udp EtherNet/IP explicit messaging | |
| 1193 | 44818/tcp EtherNet/IP explicit messaging | |
| 1194 | 47808/udp BACnet Building Automation and Control Networks (4780810 = BAC016) | |
| 1195 | 47808/tcp BACnet Building Automation and Control Networks (4780810 = BAC016) | |
| 1196 | 49151/udp Reserved | |
| 1197 | 49151/tcp Reserved |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from urllib.parse import urlsplit | |
| 7 | import socket | |
| 8 | import re | |
| 9 | import os | |
| 10 | ||
| 11 | try: | |
| 12 | import xml.etree.cElementTree as ET | |
| 13 | import xml.etree.ElementTree as ET_ORIG | |
| 14 | ETREE_VERSION = ET_ORIG.VERSION | |
| 15 | except ImportError: | |
| 16 | import xml.etree.ElementTree as ET | |
| 17 | ETREE_VERSION = ET.VERSION | |
| 18 | ||
| 19 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 20 | from faraday.client.model import api | |
| 21 | ||
| 22 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 23 | ||
| 24 | current_path = os.path.abspath(os.getcwd()) | |
| 25 | ||
| 26 | __author__ = "Francisco Amato" | |
| 27 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 28 | __credits__ = ["Francisco Amato"] | |
| 29 | __version__ = "1.0.0" | |
| 30 | __maintainer__ = "Francisco Amato" | |
| 31 | __email__ = "[email protected]" | |
| 32 | __status__ = "Development" | |
| 33 | ||
| 34 | ||
| 35 | class AcunetixXmlParser: | |
| 36 | """ | |
| 37 | The objective of this class is to parse an xml file generated by | |
| 38 | the acunetix tool. | |
| 39 | ||
| 40 | TODO: Handle errors. | |
| 41 | TODO: Test acunetix output version. Handle what happens if | |
| 42 | the parser doesn't support it. | |
| 43 | TODO: Test cases. | |
| 44 | ||
| 45 | @param acunetix_xml_filepath A proper xml generated by acunetix | |
| 46 | """ | |
| 47 | ||
| 48 | def __init__(self, xml_output): | |
| 49 | tree = self.parse_xml(xml_output) | |
| 50 | if tree: | |
| 51 | self.sites = list(self.get_items(tree)) | |
| 52 | else: | |
| 53 | self.sites = [] | |
| 54 | ||
| 55 | def parse_xml(self, xml_output): | |
| 56 | """ | |
| 57 | Open and parse an xml file. | |
| 58 | ||
| 59 | TODO: Write custom parser to just read the nodes that we need instead | |
| 60 | of reading the whole file. | |
| 61 | ||
| 62 | @return xml_tree An xml tree instance. None if error. | |
| 63 | """ | |
| 64 | try: | |
| 65 | tree = ET.fromstring(xml_output) | |
| 66 | except SyntaxError as err: | |
| 67 | print("SyntaxError: %s. %s", err, xml_output) | |
| 68 | return None | |
| 69 | ||
| 70 | return tree | |
| 71 | ||
| 72 | def get_items(self, tree): | |
| 73 | """ | |
| 74 | @return items A list of Host instances | |
| 75 | """ | |
| 76 | ||
| 77 | for node in tree.findall('Scan'): | |
| 78 | yield Site(node) | |
| 79 | ||
| 80 | ||
| 81 | def get_attrib_from_subnode(xml_node, subnode_xpath_expr, attrib_name): | |
| 82 | """ | |
| 83 | Finds a subnode in the item node and the retrieves a value from it | |
| 84 | ||
| 85 | @return An attribute value | |
| 86 | """ | |
| 87 | global ETREE_VERSION | |
| 88 | node = None | |
| 89 | ||
| 90 | if ETREE_VERSION[0] <= 1 and ETREE_VERSION[1] < 3: | |
| 91 | ||
| 92 | match_obj = re.search( | |
| 93 | "([^\@]+?)\[\@([^=]*?)=\'([^\']*?)\'", | |
| 94 | subnode_xpath_expr) | |
| 95 | ||
| 96 | if match_obj is not None: | |
| 97 | node_to_find = match_obj.group(1) | |
| 98 | xpath_attrib = match_obj.group(2) | |
| 99 | xpath_value = match_obj.group(3) | |
| 100 | for node_found in xml_node.findall(node_to_find): | |
| 101 | if node_found.attrib[xpath_attrib] == xpath_value: | |
| 102 | node = node_found | |
| 103 | break | |
| 104 | else: | |
| 105 | node = xml_node.find(subnode_xpath_expr) | |
| 106 | ||
| 107 | else: | |
| 108 | node = xml_node.find(subnode_xpath_expr) | |
| 109 | ||
| 110 | if node is not None: | |
| 111 | return node.get(attrib_name) | |
| 112 | ||
| 113 | return None | |
| 114 | ||
| 115 | ||
| 116 | class Site: | |
| 117 | ||
| 118 | def __init__(self, item_node): | |
| 119 | self.node = item_node | |
| 120 | url_data = self.get_url(self.node) | |
| 121 | ||
| 122 | self.protocol = url_data.scheme | |
| 123 | self.host = url_data.hostname | |
| 124 | ||
| 125 | # Use the port in the URL if it is defined, or 80 or 443 by default | |
| 126 | self.port = url_data.port or (443 if url_data.scheme == "https" | |
| 127 | else 80) | |
| 128 | ||
| 129 | self.ip = self.resolve(self.host) | |
| 130 | self.os = self.get_text_from_subnode('Os') | |
| 131 | self.banner = self.get_text_from_subnode('Banner') | |
| 132 | self.items = [] | |
| 133 | for alert in self.node.findall('ReportItems/ReportItem'): | |
| 134 | self.items.append(Item(alert)) | |
| 135 | ||
| 136 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 137 | """ | |
| 138 | Finds a subnode in the host node and the retrieves a value from it. | |
| 139 | ||
| 140 | @return An attribute value | |
| 141 | """ | |
| 142 | sub_node = self.node.find(subnode_xpath_expr) | |
| 143 | if sub_node is not None: | |
| 144 | return sub_node.text | |
| 145 | ||
| 146 | return None | |
| 147 | ||
| 148 | def resolve(self, host): | |
| 149 | try: | |
| 150 | return socket.gethostbyname(host) | |
| 151 | except: | |
| 152 | api.log( | |
| 153 | '[ERROR] Acunetix XML Plugin: Ip of host unknown ' + host, | |
| 154 | level='ERROR') | |
| 155 | return None | |
| 156 | return host | |
| 157 | ||
| 158 | def get_url(self, node): | |
| 159 | url = self.get_text_from_subnode('StartURL') | |
| 160 | url_data = urlsplit(url) | |
| 161 | if not url_data.scheme: | |
| 162 | # Getting url from subnode 'Crawler' | |
| 163 | url_aux = get_attrib_from_subnode(node, 'Crawler', 'StartUrl') | |
| 164 | url_data = urlsplit(url_aux) | |
| 165 | ||
| 166 | return url_data | |
| 167 | ||
| 168 | ||
| 169 | class Item: | |
| 170 | """ | |
| 171 | An abstract representation of a Item | |
| 172 | ||
| 173 | ||
| 174 | @param item_node A item_node taken from an acunetix xml tree | |
| 175 | """ | |
| 176 | ||
| 177 | def __init__(self, item_node): | |
| 178 | self.node = item_node | |
| 179 | self.name = self.get_text_from_subnode('Name') | |
| 180 | self.severity = self.get_text_from_subnode('Severity') | |
| 181 | self.request = self.get_text_from_subnode('TechnicalDetails/Request') | |
| 182 | self.response = self.get_text_from_subnode('TechnicalDetails/Response') | |
| 183 | self.parameter = self.get_text_from_subnode('Parameter') | |
| 184 | self.uri = self.get_text_from_subnode('Affects') | |
| 185 | self.desc = self.get_text_from_subnode('Description') | |
| 186 | ||
| 187 | if self.get_text_from_subnode('Recommendation'): | |
| 188 | self.resolution = self.get_text_from_subnode('Recommendation') | |
| 189 | else: | |
| 190 | self.resolution = "" | |
| 191 | ||
| 192 | if self.get_text_from_subnode('reference'): | |
| 193 | self.desc += "\nDetails: " + self.get_text_from_subnode('Details') | |
| 194 | else: | |
| 195 | self.desc += "" | |
| 196 | ||
| 197 | # Add path and params to the description to create different IDs if at | |
| 198 | # least one of this fields is different | |
| 199 | if self.uri: | |
| 200 | self.desc += '\nPath: ' + self.uri | |
| 201 | if self.parameter: | |
| 202 | self.desc += '\nParameter: ' + self.parameter | |
| 203 | ||
| 204 | self.ref = [] | |
| 205 | for n in item_node.findall('References/Reference'): | |
| 206 | n2 = n.find('URL') | |
| 207 | self.ref.append(n2.text) | |
| 208 | ||
| 209 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 210 | """ | |
| 211 | Finds a subnode in the host node and the retrieves a value from it. | |
| 212 | ||
| 213 | @return An attribute value | |
| 214 | """ | |
| 215 | sub_node = self.node.find(subnode_xpath_expr) | |
| 216 | if sub_node is not None: | |
| 217 | return sub_node.text | |
| 218 | ||
| 219 | return None | |
| 220 | ||
| 221 | ||
| 222 | class AcunetixPlugin(PluginXMLFormat): | |
| 223 | """ | |
| 224 | Example plugin to parse acunetix output. | |
| 225 | """ | |
| 226 | ||
| 227 | def __init__(self): | |
| 228 | super().__init__() | |
| 229 | self.identifier_tag = "ScanGroup" | |
| 230 | self.id = "Acunetix" | |
| 231 | self.name = "Acunetix XML Output Plugin" | |
| 232 | self.plugin_version = "0.0.1" | |
| 233 | self.version = "9" | |
| 234 | self.framework_version = "1.0.0" | |
| 235 | self.options = None | |
| 236 | self._current_output = None | |
| 237 | self.target = None | |
| 238 | self._command_regex = re.compile(r'^(acunetix|sudo acunetix|\.\/acunetix).*?') | |
| 239 | ||
| 240 | global current_path | |
| 241 | self._output_file_path = os.path.join( | |
| 242 | self.data_path, | |
| 243 | "acunetix_output-%s.xml" % self._rid) | |
| 244 | ||
| 245 | def parseOutputString(self, output, debug=False): | |
| 246 | """ | |
| 247 | This method will discard the output the shell sends, it will read it | |
| 248 | from the xml where it expects it to be present. | |
| 249 | ||
| 250 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 251 | output being sent is valid. | |
| 252 | """ | |
| 253 | ||
| 254 | parser = AcunetixXmlParser(output) | |
| 255 | ||
| 256 | for site in parser.sites: | |
| 257 | if site.ip is None: | |
| 258 | continue | |
| 259 | host = [] | |
| 260 | if site.host != site.ip: | |
| 261 | host = [site.host] | |
| 262 | h_id = self.createAndAddHost(site.ip, site.os) | |
| 263 | i_id = self.createAndAddInterface( | |
| 264 | h_id, | |
| 265 | site.ip, | |
| 266 | ipv4_address=site.ip, | |
| 267 | hostname_resolution=host) | |
| 268 | s_id = self.createAndAddServiceToInterface( | |
| 269 | h_id, | |
| 270 | i_id, | |
| 271 | "http", | |
| 272 | "tcp", | |
| 273 | ports=[site.port], | |
| 274 | version=site.banner, | |
| 275 | status='open') | |
| 276 | for item in site.items: | |
| 277 | self.createAndAddVulnWebToService( | |
| 278 | h_id, | |
| 279 | s_id, | |
| 280 | item.name, | |
| 281 | item.desc, | |
| 282 | website=site.host, | |
| 283 | severity=item.severity, | |
| 284 | resolution=item.resolution, | |
| 285 | path=item.uri, | |
| 286 | params=item.parameter, | |
| 287 | request=item.request, | |
| 288 | response=item.response, | |
| 289 | ref=item.ref) | |
| 290 | del parser | |
| 291 | ||
| 292 | def processCommandString(self, username, current_path, command_string): | |
| 293 | return None | |
| 294 | ||
| 295 | def setHost(self): | |
| 296 | pass | |
| 297 | ||
| 298 | ||
| 299 | def createPlugin(): | |
| 300 | return AcunetixPlugin() |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import core | |
| 6 | import argparse | |
| 7 | import shlex | |
| 8 | import socket | |
| 9 | import random | |
| 10 | import re | |
| 11 | import os | |
| 12 | ||
| 13 | current_path = os.path.abspath(os.getcwd()) | |
| 14 | ||
| 15 | ||
| 16 | class AmapPlugin(core.PluginBase): | |
| 17 | """ Example plugin to parse amap output.""" | |
| 18 | ||
| 19 | def __init__(self): | |
| 20 | super().__init__() | |
| 21 | self.id = "Amap" | |
| 22 | self.name = "Amap Output Plugin" | |
| 23 | self.plugin_version = "0.0.3" | |
| 24 | self.version = "5.4" | |
| 25 | self.options = None | |
| 26 | self._current_output = None | |
| 27 | self._command_regex = re.compile(r'^(amap|sudo amap).*?') | |
| 28 | self._hosts = [] | |
| 29 | ||
| 30 | global current_path | |
| 31 | self._file_output_path = os.path.join( | |
| 32 | self.data_path, | |
| 33 | "amap_output-%s.txt" % random.uniform(1, 10)) | |
| 34 | ||
| 35 | def parseOutputString(self, output, debug=False): | |
| 36 | if not os.path.exists(self._file_output_path): | |
| 37 | return False | |
| 38 | ||
| 39 | if not debug: | |
| 40 | with open(self._file_output_path) as f: | |
| 41 | output = f.read() | |
| 42 | ||
| 43 | services = {} | |
| 44 | for line in output.split('\n'): | |
| 45 | if line.startswith('#'): | |
| 46 | continue | |
| 47 | ||
| 48 | fields = self.get_info(line) | |
| 49 | ||
| 50 | if len(fields) < 6: | |
| 51 | continue | |
| 52 | ||
| 53 | address = fields[0] | |
| 54 | h_id = self.createAndAddHost(address) | |
| 55 | ||
| 56 | port = fields[1] | |
| 57 | protocol = fields[2] | |
| 58 | port_status = fields[3] | |
| 59 | ||
| 60 | identification = fields[5] | |
| 61 | printable_banner = fields[6] | |
| 62 | ||
| 63 | if port in services.keys(): | |
| 64 | if identification != 'unidentified': | |
| 65 | services[port][5] += ', ' + identification | |
| 66 | else: | |
| 67 | services[port] = [ | |
| 68 | address, | |
| 69 | port, | |
| 70 | protocol, | |
| 71 | port_status, | |
| 72 | None, | |
| 73 | identification, | |
| 74 | printable_banner, | |
| 75 | None] | |
| 76 | ||
| 77 | args = {} | |
| 78 | ||
| 79 | if self.args.__getattribute__("6"): | |
| 80 | self.ip = self.get_ip_6(self.args.m) | |
| 81 | args['ipv6_address'] = address | |
| 82 | else: | |
| 83 | self.ip = self.getAddress(self.args.m) | |
| 84 | args['ipv4_address'] = address | |
| 85 | ||
| 86 | if address != self.args.m: | |
| 87 | args['hostname_resolution'] = [self.args.m] | |
| 88 | ||
| 89 | i_id = self.createAndAddInterface(h_id, name=address, **args) | |
| 90 | ||
| 91 | for key in services: | |
| 92 | service = services.get(key) | |
| 93 | self.createAndAddServiceToInterface( | |
| 94 | h_id, | |
| 95 | i_id, | |
| 96 | service[5], | |
| 97 | service[2], | |
| 98 | ports=[service[1]], | |
| 99 | status=service[3], | |
| 100 | description=service[6]) | |
| 101 | ||
| 102 | return True | |
| 103 | ||
| 104 | file_arg_re = re.compile(r"^.*(-o \s*[^\s]+\s+(?:-m|)).*$") | |
| 105 | ||
| 106 | def get_info(self, data): | |
| 107 | if self.args.__getattribute__("6"): | |
| 108 | f = re.search( | |
| 109 | r"^\[(.*)\]:(.*):(.*):(.*):(.*):(.*):(.*):(.*)", | |
| 110 | data) | |
| 111 | ||
| 112 | return [ | |
| 113 | f.group(1), | |
| 114 | f.group(2), | |
| 115 | f.group(3), | |
| 116 | f.group(4), | |
| 117 | f.group(5), | |
| 118 | f.group(6), | |
| 119 | f.group(7), | |
| 120 | f.group(8)] if f else [] | |
| 121 | ||
| 122 | else: | |
| 123 | return data.split(':') | |
| 124 | ||
| 125 | def get_ip_6(self, host, port=0): | |
| 126 | alladdr = socket.getaddrinfo(host, port) | |
| 127 | ip6 = list(filter( | |
| 128 | lambda x: x[0] == socket.AF_INET6, | |
| 129 | alladdr)) | |
| 130 | ||
| 131 | return ip6[0][4][0] | |
| 132 | ||
| 133 | def getAddress(self, hostname): | |
| 134 | """ | |
| 135 | Returns remote IP address from hostname. | |
| 136 | """ | |
| 137 | try: | |
| 138 | return socket.gethostbyname(hostname) | |
| 139 | except socket.error as msg: | |
| 140 | return hostname | |
| 141 | ||
| 142 | def processCommandString(self, username, current_path, command_string): | |
| 143 | """ | |
| 144 | Adds the -m parameter to get machine readable output. | |
| 145 | """ | |
| 146 | arg_match = self.file_arg_re.match(command_string) | |
| 147 | ||
| 148 | parser = argparse.ArgumentParser() | |
| 149 | ||
| 150 | parser.add_argument('-6', action='store_true') | |
| 151 | parser.add_argument('-o') | |
| 152 | parser.add_argument('-m') | |
| 153 | ||
| 154 | self._output_file_path = os.path.join( | |
| 155 | self.data_path, "%s_%s_output-%s.xml" % ( | |
| 156 | self.get_ws(), | |
| 157 | self.id, | |
| 158 | random.uniform(1, 10))) | |
| 159 | ||
| 160 | if arg_match is None: | |
| 161 | final = re.sub( | |
| 162 | r"(^.*?amap)", | |
| 163 | r"\1 -o %s -m " % self._file_output_path, | |
| 164 | command_string) | |
| 165 | else: | |
| 166 | final = re.sub( | |
| 167 | arg_match.group(1), | |
| 168 | r"-o %s -m " % self._file_output_path, | |
| 169 | command_string) | |
| 170 | ||
| 171 | cmd = shlex.split(re.sub(r'\-h|\-\-help', r'', final)) | |
| 172 | if "-6" in cmd: | |
| 173 | cmd.remove("-6") | |
| 174 | cmd.insert(1, "-6") | |
| 175 | ||
| 176 | args = None | |
| 177 | if len(cmd) > 4: | |
| 178 | try: | |
| 179 | args, unknown = parser.parse_known_args(cmd) | |
| 180 | except SystemExit: | |
| 181 | pass | |
| 182 | ||
| 183 | self.args = args | |
| 184 | return final | |
| 185 | ||
| 186 | def setHost(self): | |
| 187 | pass | |
| 188 | ||
| 189 | ||
| 190 | def createPlugin(): | |
| 191 | return AmapPlugin() | |
| 192 | ||
| 193 | ||
| 194 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2017 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | """ | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2017 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | """ | |
| 8 | ||
| 9 | import socket | |
| 10 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 11 | from lxml import objectify | |
| 12 | try: | |
| 13 | from urlparse import urlparse | |
| 14 | except ImportError: | |
| 15 | from urllib.parse import urlparse | |
| 16 | ||
| 17 | __author__ = "Alejando Parodi, Ezequiel Tavella" | |
| 18 | __copyright__ = "Copyright (c) 2015, Infobyte LLC" | |
| 19 | __credits__ = ["Alejando Parodi", "Ezequiel Tavella"] | |
| 20 | __license__ = "" | |
| 21 | __version__ = "1.0" | |
| 22 | __maintainer__ = "Ezequiel Tavella" | |
| 23 | __status__ = "Development" | |
| 24 | ||
| 25 | ||
| 26 | ||
| 27 | def cleaner_unicode(string): | |
| 28 | if string is not None: | |
| 29 | return string.encode('ascii', errors='backslashreplace') | |
| 30 | else: | |
| 31 | return string | |
| 32 | ||
| 33 | ||
| 34 | class AppscanParser(): | |
| 35 | ||
| 36 | def __init__(self, output, logger): | |
| 37 | self.issue_list = [] | |
| 38 | self.logger = logger | |
| 39 | self.obj_xml = objectify.fromstring(output.encode('utf-8')) | |
| 40 | ||
| 41 | def parse_issues(self): | |
| 42 | issue_type = self.parse_issue_type() | |
| 43 | for issue in self.obj_xml["issue-group"]["item"]: | |
| 44 | issue_data = issue_type[issue['issue-type']['ref']] | |
| 45 | obj_issue = {} | |
| 46 | obj_issue["name"] = issue_data["name"] | |
| 47 | obj_issue['advisory'] = issue_data["advisory"] | |
| 48 | if "cve" in issue_data: | |
| 49 | obj_issue['cve'] = issue_data["cve"].text | |
| 50 | obj_issue['url'] = self.get_url(issue['url']['ref'].text) | |
| 51 | obj_issue['cvss_score'] = issue["cvss-score"].text | |
| 52 | obj_issue['response'] = self.get_response(issue) | |
| 53 | obj_issue['request'] = issue['variant-group']['item']["test-http-traffic"].text | |
| 54 | obj_issue['method'] = self.get_method(issue['variant-group']['item']["test-http-traffic"].text) | |
| 55 | obj_issue['severity'] = issue['severity'].text | |
| 56 | obj_issue['issue-description'] = self.parse_advisory_group(issue_data['advisory']) | |
| 57 | for recommendation in self.obj_xml["fix-recommendation-group"]["item"]: | |
| 58 | full_data = "" | |
| 59 | if recommendation.attrib['id'] == issue_data["fix-recommendation"]: | |
| 60 | for data in recommendation['general']['fixRecommendation']["text"]: | |
| 61 | full_data += '' + data | |
| 62 | obj_issue["recomendation"] = full_data | |
| 63 | if hasattr(recommendation['general']['fixRecommendation'], 'link'): | |
| 64 | obj_issue["ref_link"] = recommendation['general']['fixRecommendation']['link'].text | |
| 65 | self.issue_list.append(obj_issue) | |
| 66 | return self.issue_list | |
| 67 | ||
| 68 | def parse_hosts(self): | |
| 69 | hosts_list = [] | |
| 70 | for host in self.obj_xml['scan-configuration']['scanned-hosts']['item']: | |
| 71 | hosts_dict = {} | |
| 72 | hosts_dict['ip'] = socket.gethostbyname(host['host'].text) | |
| 73 | hosts_dict['hostname'] = host['host'].text | |
| 74 | hosts_dict['os'] = host['operating-system'].text | |
| 75 | hosts_dict['port'] = host['port'].text | |
| 76 | if host['port'].text == '443': | |
| 77 | hosts_dict['scheme'] = 'https' | |
| 78 | else: | |
| 79 | hosts_dict['scheme'] = 'http' | |
| 80 | hosts_list.append(hosts_dict) | |
| 81 | return hosts_list | |
| 82 | ||
| 83 | def parse_issue_type(self): | |
| 84 | res = {} | |
| 85 | for issue_type in self.obj_xml["issue-type-group"]["item"]: | |
| 86 | res[issue_type.attrib['id']] = { | |
| 87 | 'name': issue_type.name.text, | |
| 88 | 'advisory': issue_type["advisory"]["ref"].text, | |
| 89 | 'fix-recommendation': issue_type["fix-recommendation"]["ref"].text | |
| 90 | } | |
| 91 | if "cve" in issue_type: | |
| 92 | res[issue_type.attrib['id']] = {'cve': issue_type["cve"].text} | |
| 93 | return res | |
| 94 | ||
| 95 | def parse_advisory_group(self, advisory): | |
| 96 | """ | |
| 97 | Function that parse advisory-group in order to get the item's description | |
| 98 | """ | |
| 99 | for item in self.obj_xml["advisory-group"]["item"]: | |
| 100 | if item.attrib['id'] == advisory: | |
| 101 | return item['advisory']['testTechnicalDescription']['text'].text | |
| 102 | ||
| 103 | def get_url(self, ref): | |
| 104 | for item in self.obj_xml['url-group']['item']: | |
| 105 | if item.attrib['id'] == ref: | |
| 106 | return item['name'].text | |
| 107 | ||
| 108 | def get_method(self, http_traffic): | |
| 109 | methods_list = ['GET', 'POST', 'PUT', 'DELETE', 'CONNECT', 'PATCH', 'HEAD', 'OPTIONS'] | |
| 110 | try: | |
| 111 | if http_traffic: | |
| 112 | for item in methods_list: | |
| 113 | if http_traffic.startswith(item): | |
| 114 | return item | |
| 115 | except TypeError: | |
| 116 | return None | |
| 117 | return None | |
| 118 | ||
| 119 | def get_response(self, node): | |
| 120 | try: | |
| 121 | response = node['variant-group']['item']['issue-information']["testResponseChunk"].text | |
| 122 | return response | |
| 123 | except AttributeError: | |
| 124 | return None | |
| 125 | ||
| 126 | def get_scan_information(self): | |
| 127 | ||
| 128 | scan_information = "File: " + self.obj_xml["scan-information"]["scan-file-name"]\ | |
| 129 | + "\nStart: " + self.obj_xml["scan-information"]["scan-date-and-time"]\ | |
| 130 | + "\nSoftware: " + self.obj_xml["scan-information"]["product-name"]\ | |
| 131 | + "\nVersion: " + self.obj_xml["scan-information"]["product-version"]\ | |
| 132 | + "\nScanner Elapsed time: " + self.obj_xml["scan-summary"]["scan-Duration"] | |
| 133 | ||
| 134 | return scan_information | |
| 135 | ||
| 136 | ||
| 137 | class AppscanPlugin(PluginXMLFormat): | |
| 138 | """ Example plugin to parse Appscan XML report""" | |
| 139 | ||
| 140 | def __init__(self): | |
| 141 | super().__init__() | |
| 142 | self.identifier_tag = "xml-report" | |
| 143 | self.id = "Appscan" | |
| 144 | self.name = "Appscan XML Plugin" | |
| 145 | self.plugin_version = "0.0.1" | |
| 146 | self.options = None | |
| 147 | ||
| 148 | def parseOutputString(self, output, debug=False): | |
| 149 | try: | |
| 150 | parser = AppscanParser(output, self.logger) | |
| 151 | issues = parser.parse_issues() | |
| 152 | scanned_hosts = parser.parse_hosts() | |
| 153 | hosts_dict = {} | |
| 154 | for host in scanned_hosts: | |
| 155 | host_id = self.createAndAddHost(host['ip'], os=host['os'], hostnames=[host['hostname']]) | |
| 156 | service_id = self.createAndAddServiceToHost( | |
| 157 | host_id, | |
| 158 | host['scheme'], | |
| 159 | ports=[host['port']], | |
| 160 | protocol="tcp?HTTP") | |
| 161 | if host['port']: | |
| 162 | key_url = f"{host['scheme']}://{host['hostname']}:{host['port']}" | |
| 163 | else: | |
| 164 | key_url = f"{host['scheme']}://{host['hostname']}" | |
| 165 | hosts_dict[key_url] = {'host_id': host_id, 'service_id': service_id} | |
| 166 | for issue in issues: | |
| 167 | url_parsed = urlparse(str(issue['url'])) | |
| 168 | url_string = '://'.join([url_parsed.scheme, url_parsed.netloc]) | |
| 169 | for key in hosts_dict: | |
| 170 | if url_string == key: | |
| 171 | h_id = hosts_dict[key]['host_id'] | |
| 172 | s_id = hosts_dict[key]['service_id'] | |
| 173 | refs = [] | |
| 174 | if "ref_link" in issue: | |
| 175 | refs.append(f"Fix link: {issue['ref_link']}" ) | |
| 176 | if "cvss_score" in issue: | |
| 177 | refs.append(f"CVSS Score: {issue['cvss_score']}") | |
| 178 | if "cve" in issue: | |
| 179 | refs.append(f"CVE: {issue['cve']}") | |
| 180 | if "advisory" in issue: | |
| 181 | refs.append(f"Advisory: {issue['advisory']}") | |
| 182 | self.createAndAddVulnWebToService( | |
| 183 | h_id, | |
| 184 | s_id, | |
| 185 | cleaner_unicode(issue["name"]), | |
| 186 | desc=cleaner_unicode(issue["issue_description"]) if "issue_description" in issue else "", | |
| 187 | ref=refs, | |
| 188 | severity=issue["severity"], | |
| 189 | resolution=cleaner_unicode(issue["recomendation"]), | |
| 190 | website=url_parsed.netloc, | |
| 191 | path=url_parsed.path, | |
| 192 | request=cleaner_unicode(issue["request"]) if "request" in issue else "", | |
| 193 | response=cleaner_unicode(issue["response"]) if issue["response"] else "", | |
| 194 | method=issue["method"] if issue["method"] else "") | |
| 195 | except Exception as e: | |
| 196 | self.logger.error("Parsing Output Error: %s", e) | |
| 197 | ||
| 198 | def processCommandString(self, username, current_path, command_string): | |
| 199 | return | |
| 200 | ||
| 201 | ||
| 202 | def createPlugin(): | |
| 203 | return AppscanPlugin() | |
| 204 | ||
| 205 | ||
| 206 | if __name__ == '__main__': | |
| 207 | parser = AppscanPlugin() | |
| 208 | with open('/home/javier/Reports_Testing/appscan-demo_testfire.xml', 'r') as report: | |
| 209 | parser.parseOutputString(report.read()) | |
| 210 | for item in parser.items: | |
| 211 | if item.status == 'up': | |
| 212 | print(item) | |
| 213 | ||
| 214 | ||
| 215 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | """ | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | """ | |
| 8 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 9 | from faraday.client.model import api | |
| 10 | import socket | |
| 11 | import os | |
| 12 | import random | |
| 13 | import re | |
| 14 | ||
| 15 | try: | |
| 16 | import xml.etree.cElementTree as ET | |
| 17 | except ImportError: | |
| 18 | import xml.etree.ElementTree as ET | |
| 19 | ||
| 20 | __author__ = 'Ezequiel Tavella' | |
| 21 | __copyright__ = 'Copyright 2016, Faraday Project' | |
| 22 | __credits__ = ['Ezequiel Tavella', 'Matías Ariel Ré Medina', 'Conrad Stein K'] | |
| 23 | __license__ = '' | |
| 24 | __version__ = '1.0.2' | |
| 25 | __status__ = 'Development' | |
| 26 | ||
| 27 | ||
| 28 | class ArachniXmlParser(): | |
| 29 | ||
| 30 | def __init__(self, xml_output): | |
| 31 | self.tree = self.parse_xml(xml_output) | |
| 32 | if self.tree: | |
| 33 | self.issues = self.getIssues(self.tree) | |
| 34 | self.plugins = self.getPlugins(self.tree) | |
| 35 | self.system = self.getSystem(self.tree) | |
| 36 | else: | |
| 37 | self.system = None | |
| 38 | self.issues = None | |
| 39 | self.plugins = None | |
| 40 | ||
| 41 | def parse_xml(self, xml_output): | |
| 42 | try: | |
| 43 | tree = ET.fromstring(xml_output) | |
| 44 | except SyntaxError as err: | |
| 45 | print('SyntaxError In xml: %s. %s' % (err, xml_output)) | |
| 46 | return None | |
| 47 | ||
| 48 | return tree | |
| 49 | ||
| 50 | def getIssues(self, tree): | |
| 51 | ||
| 52 | # Get vulnerabilities. | |
| 53 | issues_tree = tree.find('issues') | |
| 54 | for self.issue_node in issues_tree: | |
| 55 | yield Issue(self.issue_node) | |
| 56 | ||
| 57 | def getPlugins(self, tree): | |
| 58 | ||
| 59 | # Get info about plugins executed in scan. | |
| 60 | plugins_tree = tree.find('plugins') | |
| 61 | return Plugins(plugins_tree) | |
| 62 | ||
| 63 | def getSystem(self, tree): | |
| 64 | ||
| 65 | # Get options of scan. | |
| 66 | return System(tree) | |
| 67 | ||
| 68 | ||
| 69 | class Issue(): | |
| 70 | ||
| 71 | def __init__(self, issue_node): | |
| 72 | ||
| 73 | self.node = issue_node | |
| 74 | ||
| 75 | self.name = self.getDesc('name') | |
| 76 | self.severity = self.getDesc('severity') | |
| 77 | self.cwe = self.getDesc('cwe') | |
| 78 | ||
| 79 | self.remedy_guidance = self.getDesc('remedy_guidance') | |
| 80 | self.description = self.getDesc('description') | |
| 81 | ||
| 82 | self.var = self.getChildTag('vector', 'affected_input_name') | |
| 83 | self.url = self.getChildTag('vector', 'url') | |
| 84 | self.method = self.getChildTag('vector', 'method') | |
| 85 | ||
| 86 | self.references = self.getReferences() | |
| 87 | self.parameters = self.getParameters() | |
| 88 | ||
| 89 | self.request = self.getRequest() | |
| 90 | self.response = self.getResponse() | |
| 91 | ||
| 92 | def getDesc(self, tag): | |
| 93 | ||
| 94 | # Get value of tag xml | |
| 95 | description = self.node.find(tag) | |
| 96 | ||
| 97 | if description != None and description.text != None: | |
| 98 | return description.text.encode('ascii', 'ignore') | |
| 99 | else: | |
| 100 | return 'None' | |
| 101 | ||
| 102 | def getChildTag(self, main_tag, child_tag): | |
| 103 | ||
| 104 | # Get value of tag child xml | |
| 105 | main_entity = self.node.find(main_tag) | |
| 106 | ||
| 107 | if not main_entity: | |
| 108 | return 'None' | |
| 109 | ||
| 110 | result = main_entity.find(child_tag) | |
| 111 | ||
| 112 | if result != None and result.text != None: | |
| 113 | return result.text.encode('ascii', 'ignore') | |
| 114 | else: | |
| 115 | return 'None' | |
| 116 | ||
| 117 | def getReferences(self): | |
| 118 | """ | |
| 119 | Returns current issue references on this format | |
| 120 | {'url': 'http://www.site.com', 'name': 'WebSite'}. | |
| 121 | """ | |
| 122 | ||
| 123 | result = [] | |
| 124 | ||
| 125 | references = self.node.find('references') | |
| 126 | ||
| 127 | if not references: | |
| 128 | return result | |
| 129 | ||
| 130 | for tag in references.findall('reference'): | |
| 131 | url = tag.get('url') | |
| 132 | result.append(url) | |
| 133 | ||
| 134 | return result | |
| 135 | ||
| 136 | def getParameters(self): | |
| 137 | ||
| 138 | # Get parameters of query | |
| 139 | result = [] | |
| 140 | ||
| 141 | parameters = self.node.find('vector').find('inputs') | |
| 142 | ||
| 143 | if not parameters: | |
| 144 | return '' | |
| 145 | ||
| 146 | for param in parameters.findall('input'): | |
| 147 | name = param.get('name') | |
| 148 | result.append(name) | |
| 149 | ||
| 150 | return ' - '.join(result) | |
| 151 | ||
| 152 | def getRequest(self): | |
| 153 | ||
| 154 | # Get data about request. | |
| 155 | try: | |
| 156 | ||
| 157 | raw_data = self.node.find('page').find('request').find('raw') | |
| 158 | data = raw_data.text.encode('ascii', 'ignore') | |
| 159 | return data | |
| 160 | ||
| 161 | except: | |
| 162 | return 'None' | |
| 163 | ||
| 164 | def getResponse(self): | |
| 165 | ||
| 166 | # Get data about response. | |
| 167 | try: | |
| 168 | ||
| 169 | raw_data = self.node.find('page').find( | |
| 170 | 'response').find('raw_headers') | |
| 171 | data = raw_data.text.encode('ascii', 'ignore') | |
| 172 | return data | |
| 173 | ||
| 174 | except: | |
| 175 | return 'None' | |
| 176 | ||
| 177 | ||
| 178 | class System(): | |
| 179 | ||
| 180 | def __init__(self, node): | |
| 181 | ||
| 182 | self.node = node | |
| 183 | ||
| 184 | self.user_agent = 'None' | |
| 185 | self.url = 'None' | |
| 186 | self.audited_elements = 'None' | |
| 187 | self.modules = 'None' | |
| 188 | self.cookies = 'None' | |
| 189 | ||
| 190 | self.getOptions() | |
| 191 | ||
| 192 | self.version = self.getDesc('version') | |
| 193 | self.start_time = self.getDesc('start_datetime') | |
| 194 | self.finish_time = self.getDesc('finish_datetime') | |
| 195 | ||
| 196 | self.note = self.getNote() | |
| 197 | ||
| 198 | def getOptions(self): | |
| 199 | ||
| 200 | # Get values of options scan | |
| 201 | options_string = self.node.find('options').text | |
| 202 | ||
| 203 | if not options_string: | |
| 204 | return | |
| 205 | ||
| 206 | regex_modules = re.compile('checks:\n([\w\d\s\W\D\S]{0,})(platforms:)') | |
| 207 | regex_user_agent = re.compile('user_agent:(.+)') | |
| 208 | regex_cookies = re.compile('cookies: {()}') | |
| 209 | regex_url = re.compile('url:(.+)') | |
| 210 | ||
| 211 | regex_audited_elements = re.compile( | |
| 212 | 'audit:\n([\w\d\s\W\D\S]{0,})input:|session:' | |
| 213 | ) | |
| 214 | ||
| 215 | result = re.search(regex_modules, options_string) | |
| 216 | if result.group(1): | |
| 217 | self.modules = result.group(1) | |
| 218 | ||
| 219 | result = re.search(regex_user_agent, options_string) | |
| 220 | if result.group(1): | |
| 221 | self.user_agent = result.group(1) | |
| 222 | ||
| 223 | result = re.search(regex_cookies, options_string) | |
| 224 | if result.group(1): | |
| 225 | self.cookies = result.group(1) | |
| 226 | ||
| 227 | result = re.search(regex_url, options_string) | |
| 228 | if result.group(1): | |
| 229 | self.url = result.group(1) | |
| 230 | ||
| 231 | result = re.search(regex_audited_elements, options_string) | |
| 232 | if result.group(1): | |
| 233 | self.audited_elements = result.group(1) | |
| 234 | ||
| 235 | def getDesc(self, tag): | |
| 236 | ||
| 237 | # Return value of tag | |
| 238 | description = self.node.find(tag) | |
| 239 | ||
| 240 | if description != None and description.text != None: | |
| 241 | return description.text | |
| 242 | else: | |
| 243 | return 'None' | |
| 244 | ||
| 245 | def getNote(self): | |
| 246 | ||
| 247 | # Create string with scan information. | |
| 248 | result = ( | |
| 249 | 'Scan url:\n' + | |
| 250 | self.url + | |
| 251 | '\nUser Agent:\n' + | |
| 252 | self.user_agent + | |
| 253 | '\nVersion Arachni:\n' + | |
| 254 | self.version + | |
| 255 | '\nStart time:\n' + | |
| 256 | self.start_time + | |
| 257 | '\nFinish time:\n' + | |
| 258 | self.finish_time + | |
| 259 | '\nAudited Elements:\n' + | |
| 260 | self.audited_elements + | |
| 261 | '\nModules:\n' + | |
| 262 | self.modules + | |
| 263 | '\nCookies:\n' + | |
| 264 | self.cookies) | |
| 265 | ||
| 266 | return result | |
| 267 | ||
| 268 | ||
| 269 | class Plugins(): | |
| 270 | ||
| 271 | """ | |
| 272 | Support: | |
| 273 | WAF (Web Application Firewall) Detector (waf_detector) | |
| 274 | Healthmap (healthmap) | |
| 275 | """ | |
| 276 | ||
| 277 | def __init__(self, plugins_node): | |
| 278 | ||
| 279 | self.plugins_node = plugins_node | |
| 280 | ||
| 281 | self.healthmap = self.getHealthmap() | |
| 282 | self.waf = self.getWaf() | |
| 283 | ||
| 284 | def getHealthmap(self): | |
| 285 | ||
| 286 | # Get info about healthmap | |
| 287 | healthmap_tree = self.plugins_node.find('healthmap') | |
| 288 | if not healthmap_tree: | |
| 289 | return 'None' | |
| 290 | ||
| 291 | # Create urls list. | |
| 292 | list_urls = [] | |
| 293 | map_results = healthmap_tree.find('results').find('map') | |
| 294 | ||
| 295 | for url in map_results: | |
| 296 | ||
| 297 | if url.tag == 'with_issues': | |
| 298 | list_urls.append('With Issues: ' + url.text) | |
| 299 | else: | |
| 300 | list_urls.append('Without Issues: ' + url.text) | |
| 301 | ||
| 302 | try: | |
| 303 | ||
| 304 | result = ( | |
| 305 | 'Plugin Name: ' + | |
| 306 | healthmap_tree.find('name').text + | |
| 307 | '\nDescription: ' + | |
| 308 | healthmap_tree.find('description').text + | |
| 309 | '\nStatistics:' + | |
| 310 | '\nTotal: ' + | |
| 311 | healthmap_tree.find('results').find('total').text + | |
| 312 | '\nWith Issues: ' + | |
| 313 | healthmap_tree.find('results').find('with_issues').text + | |
| 314 | '\nWithout Issues: ' + | |
| 315 | healthmap_tree.find('results').find('without_issues').text + | |
| 316 | '\nIssues percentage: ' + | |
| 317 | healthmap_tree.find('results').find('issue_percentage').text + | |
| 318 | '\nResults Map:\n' + | |
| 319 | '\n'.join(list_urls)) | |
| 320 | return result | |
| 321 | ||
| 322 | except: | |
| 323 | return 'None' | |
| 324 | ||
| 325 | def getWaf(self): | |
| 326 | ||
| 327 | # Get info about waf plugin. | |
| 328 | waf_tree = self.plugins_node.find('waf_detector') | |
| 329 | ||
| 330 | try: | |
| 331 | ||
| 332 | result = ( | |
| 333 | 'Plugin Name: ' + | |
| 334 | waf_tree.find('name').text + | |
| 335 | '\nDescription: ' + | |
| 336 | waf_tree.find('description').text + | |
| 337 | '\nResults:' + | |
| 338 | '\nMessage: ' + | |
| 339 | waf_tree.find('results').find('message').text + | |
| 340 | '\nStatus: ' + | |
| 341 | waf_tree.find('results').find('status').text) | |
| 342 | ||
| 343 | return result | |
| 344 | ||
| 345 | except: | |
| 346 | return 'None' | |
| 347 | ||
| 348 | ||
| 349 | class ArachniPlugin(PluginXMLFormat): | |
| 350 | ||
| 351 | # Plugin that parses Arachni's XML report files. | |
| 352 | ||
| 353 | def __init__(self): | |
| 354 | super().__init__() | |
| 355 | self.identifier_tag = "report" | |
| 356 | self.id = 'Arachni' | |
| 357 | self.name = 'Arachni XML Output Plugin' | |
| 358 | self.plugin_version = '1.0.1' | |
| 359 | self.version = '1.3.2' | |
| 360 | self.framework_version = '1.0.0' | |
| 361 | self.options = None | |
| 362 | self._command_regex = re.compile(r'^(arachni |\.\/arachni).*?') | |
| 363 | self.protocol = None | |
| 364 | self.hostname = None | |
| 365 | self.port = '80' | |
| 366 | self.address = None | |
| 367 | ||
| 368 | def report_belongs_to(self, **kwargs): | |
| 369 | if super().report_belongs_to(**kwargs): | |
| 370 | report_path = kwargs.get("report_path", "") | |
| 371 | with open(report_path) as f: | |
| 372 | output = f.read() | |
| 373 | return re.search("https://raw.githubusercontent.com/Arachni/arachni/", output) is not None | |
| 374 | return False | |
| 375 | ||
| 376 | def parseOutputString(self, output, debug=False): | |
| 377 | """ | |
| 378 | This method will discard the output the shell sends, it will read it | |
| 379 | from the xml where it expects it to be present. | |
| 380 | """ | |
| 381 | ||
| 382 | parser = ArachniXmlParser(output) | |
| 383 | ||
| 384 | # Check xml parsed ok... | |
| 385 | if not parser.system: | |
| 386 | print('Error in xml report... Exiting...') | |
| 387 | return | |
| 388 | ||
| 389 | self.hostname = self.getHostname(parser.system.url) | |
| 390 | self.address = self.getAddress(self.hostname) | |
| 391 | ||
| 392 | # Create host and interface | |
| 393 | host_id = self.createAndAddHost(self.address) | |
| 394 | ||
| 395 | interface_id = self.createAndAddInterface( | |
| 396 | host_id, | |
| 397 | self.address, | |
| 398 | ipv4_address=self.address, | |
| 399 | hostname_resolution=[self.hostname]) | |
| 400 | ||
| 401 | # Create service | |
| 402 | service_id = self.createAndAddServiceToInterface( | |
| 403 | host_id, | |
| 404 | interface_id, | |
| 405 | self.protocol, | |
| 406 | 'tcp', | |
| 407 | ports=[self.port], | |
| 408 | status='Open', | |
| 409 | version='', | |
| 410 | description='') | |
| 411 | ||
| 412 | ||
| 413 | # Create issues. | |
| 414 | for issue in parser.issues: | |
| 415 | ||
| 416 | description = issue.description.replace(' ', ' ').replace('\n', ' ').replace('. ', '.\n\n') | |
| 417 | resol = issue.remedy_guidance.replace(' ', ' ').replace('\n', ' ').replace('. ', '.\n\n') | |
| 418 | ||
| 419 | references = issue.references | |
| 420 | if issue.cwe != 'None': | |
| 421 | references.append('CWE-' + issue.cwe) | |
| 422 | ||
| 423 | if resol == 'None': | |
| 424 | resol = '' | |
| 425 | ||
| 426 | self.createAndAddVulnWebToService( | |
| 427 | host_id, | |
| 428 | service_id, | |
| 429 | name=issue.name, | |
| 430 | desc=description, | |
| 431 | resolution=resol, | |
| 432 | ref=references, | |
| 433 | severity=issue.severity, | |
| 434 | website=self.hostname, | |
| 435 | path=issue.url, | |
| 436 | method=issue.method, | |
| 437 | pname=issue.var, | |
| 438 | params=issue.parameters, | |
| 439 | request=issue.request, | |
| 440 | response=issue.response) | |
| 441 | ||
| 442 | return | |
| 443 | ||
| 444 | def processCommandString(self, username, current_path, command_string): | |
| 445 | """ | |
| 446 | Use bash to run sequentialy arachni and arachni_reporter | |
| 447 | """ | |
| 448 | ||
| 449 | afr_output_file_path = os.path.join( | |
| 450 | self.data_path, | |
| 451 | "%s_%s_output-%s.afr" % ( | |
| 452 | self.get_ws(), | |
| 453 | self.id, | |
| 454 | random.uniform(1, 10)) | |
| 455 | ) | |
| 456 | ||
| 457 | report_arg_re = r"^.*(--report-save-path[=\s][^\s]+).*$" | |
| 458 | arg_match = re.match(report_arg_re,command_string) | |
| 459 | if arg_match is None: | |
| 460 | main_cmd = re.sub(r"(^.*?arachni)", | |
| 461 | r"\1 --report-save-path=%s" % afr_output_file_path, | |
| 462 | command_string) | |
| 463 | else: | |
| 464 | main_cmd = re.sub(arg_match.group(1), | |
| 465 | r"--report-save-path=%s" % afr_output_file_path, | |
| 466 | command_string) | |
| 467 | ||
| 468 | # add reporter | |
| 469 | self._output_file_path = re.sub('.afr', '.xml', afr_output_file_path) | |
| 470 | cmd_prefix_match = re.match(r"(^.*?)arachni ", command_string) | |
| 471 | cmd_prefix = cmd_prefix_match.group(1) | |
| 472 | reporter_cmd = "%s%s --reporter=\"xml:outfile=%s\" \"%s\"" % ( | |
| 473 | cmd_prefix, | |
| 474 | "arachni_reporter", | |
| 475 | self._output_file_path, | |
| 476 | afr_output_file_path) | |
| 477 | return "/usr/bin/env -- bash -c '%s 2>&1 && if [ -e \"%s\" ];then %s 2>&1;fi'" % (main_cmd, afr_output_file_path, reporter_cmd) | |
| 478 | ||
| 479 | ||
| 480 | def getHostname(self, url): | |
| 481 | ||
| 482 | # Strips protocol and gets hostname from URL. | |
| 483 | reg = re.search( | |
| 484 | '(http|https|ftp)\://([a-zA-Z0-9\.\-]+(\:[a-zA-Z0-9\.&%\$\-]+)*@)*(' | |
| 485 | '(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9])\.(25[0-5' | |
| 486 | ']|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9]|0)\.(25[0-5]|2[0' | |
| 487 | '-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9]|0)\.(25[0-5]|2[0-4][0' | |
| 488 | '-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[0-9])|localhost|([a-zA-Z0-9\-]+' | |
| 489 | '\.)*[a-zA-Z0-9\-]+\.(com|edu|gov|int|mil|net|org|biz|arpa|info|name|pr' | |
| 490 | 'o|aero|coop|museum|[a-zA-Z]{2}))[\:]*([0-9]+)*([/]*($|[a-zA-Z0-9\.\,\?' | |
| 491 | '\'\\\+&%\$#\=~_\-]+)).*?$', | |
| 492 | url | |
| 493 | ) | |
| 494 | ||
| 495 | self.protocol = reg.group(1) | |
| 496 | self.hostname = reg.group(4) | |
| 497 | ||
| 498 | if self.protocol == 'https': | |
| 499 | self.port = 443 | |
| 500 | if reg.group(11) is not None: | |
| 501 | self.port = reg.group(11) | |
| 502 | ||
| 503 | return self.hostname | |
| 504 | ||
| 505 | def getAddress(self, hostname): | |
| 506 | ||
| 507 | # Returns remote IP address from hostname. | |
| 508 | try: | |
| 509 | return socket.gethostbyname(hostname) | |
| 510 | except socket.error as msg: | |
| 511 | return self.hostname | |
| 512 | ||
| 513 | ||
| 514 | def createPlugin(): | |
| 515 | return ArachniPlugin() | |
| 516 | ||
| 517 | ||
| 518 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import core | |
| 6 | from faraday.client.model import api | |
| 7 | import re | |
| 8 | ||
| 9 | __author__ = "Federico Kirschbaum" | |
| 10 | __copyright__ = "Copyright 2013, Faraday Project" | |
| 11 | __credits__ = ["Federico Kirschbaum"] | |
| 12 | __license__ = "" | |
| 13 | __version__ = "1.0.0" | |
| 14 | __maintainer__ = "Federico Kirschbaum" | |
| 15 | __email__ = "[email protected]" | |
| 16 | __status__ = "Development" | |
| 17 | ||
| 18 | ||
| 19 | class CmdArpScanPlugin(core.PluginBase): | |
| 20 | """ | |
| 21 | This plugin handles arp-scan command. | |
| 22 | Basically inserts into the tree the ouput of this tool | |
| 23 | """ | |
| 24 | ||
| 25 | def __init__(self): | |
| 26 | super().__init__() | |
| 27 | self.id = "arp-scan" | |
| 28 | self.name = "arp-scan network scanner" | |
| 29 | self.plugin_version = "0.0.2" | |
| 30 | self.version = "1.8.1" | |
| 31 | self.framework_version = "1.0.0" | |
| 32 | self.options = None | |
| 33 | self._current_output = None | |
| 34 | self._command_regex = re.compile( | |
| 35 | r'^(sudo arp-scan|\.\/arp-scan|arp-scan).*?') | |
| 36 | self._host_ip = None | |
| 37 | ||
| 38 | def parseOutputString(self, output, debug=False): | |
| 39 | ||
| 40 | host_info = re.search( | |
| 41 | r"(\b(?:(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.){3}(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\b)", | |
| 42 | output) | |
| 43 | ||
| 44 | host_mac_addr = re.search(r"([\dA-F]{2}(?:[-:][\dA-F]{2}){5})", output, re.IGNORECASE) | |
| 45 | ||
| 46 | if host_info is None: | |
| 47 | api.devlog("No hosts detected") | |
| 48 | else: | |
| 49 | ||
| 50 | for line in output.split('\n'): | |
| 51 | vals = line.split("\t") | |
| 52 | ||
| 53 | if len(vals) == 3: | |
| 54 | ||
| 55 | if len(vals[0].split(".")) == 4: | |
| 56 | ||
| 57 | host = vals[0] | |
| 58 | h_id = self.createAndAddHost(host) | |
| 59 | i_id = self.createAndAddInterface(h_id, host, ipv4_address=host, mac=vals[1]) | |
| 60 | ||
| 61 | return True | |
| 62 | ||
| 63 | def processCommandString(self, username, current_path, command_string): | |
| 64 | return | |
| 65 | ||
| 66 | ||
| 67 | def createPlugin(): | |
| 68 | return CmdArpScanPlugin() | |
| 69 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import core | |
| 6 | from faraday.client.model import api | |
| 7 | import re | |
| 8 | import sys | |
| 9 | from urllib.request import urlopen | |
| 10 | import json | |
| 11 | ||
| 12 | __author__ = "Francisco Amato" | |
| 13 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 14 | __credits__ = ["Francisco Amato"] | |
| 15 | __license__ = "" | |
| 16 | __version__ = "1.0.0" | |
| 17 | __maintainer__ = "Francisco Amato" | |
| 18 | __email__ = "[email protected]" | |
| 19 | __status__ = "Development" | |
| 20 | ||
| 21 | ||
| 22 | class BeefPlugin(core.PluginBase): | |
| 23 | """ | |
| 24 | Example plugin to parse beef output. | |
| 25 | """ | |
| 26 | ||
| 27 | def __init__(self): | |
| 28 | super().__init__() | |
| 29 | self.id = "Beef" | |
| 30 | self.name = "BeEF Online Service Plugin" | |
| 31 | self.plugin_version = "0.0.1" | |
| 32 | self.version = "0.4.4.9-alpha" | |
| 33 | self.framework_version = "1.0.0" | |
| 34 | self.options = None | |
| 35 | self._current_output = None | |
| 36 | self.target = None | |
| 37 | self._command_regex = re.compile(r'^(beef|sudo beef|\.\/beef).*?') | |
| 38 | ||
| 39 | self.addSetting("Host", str, "http://127.0.0.1:3000/") | |
| 40 | self.addSetting( | |
| 41 | "Authkey", str, "c818c7798ae1da38b45a6406c8dd0d6d4d007098") | |
| 42 | self.addSetting("Enable", str, "0") | |
| 43 | ||
| 44 | def parseOutputString(self, output, debug=False): | |
| 45 | """ | |
| 46 | This method will discard the output the shell sends, it will read it from | |
| 47 | the xml where it expects it to be present. | |
| 48 | ||
| 49 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 50 | output being sent is valid. | |
| 51 | """ | |
| 52 | try: | |
| 53 | f = urlopen(self.getSetting( | |
| 54 | "Host") + "/api/hooks?token=" + self.getSetting("Authkey")) | |
| 55 | data = json.loads(f.read()) | |
| 56 | except: | |
| 57 | api.devlog("[BeEF] - Connection with api") | |
| 58 | return | |
| 59 | ||
| 60 | if "hooked-browsers" in data: | |
| 61 | ||
| 62 | for t in ["online", "offlne"]: | |
| 63 | for h in data["hooked-browsers"][t]: | |
| 64 | ||
| 65 | name = str(data["hooked-browsers"][t][h]['name']) | |
| 66 | version = str(data["hooked-browsers"][t][h]['version']) | |
| 67 | os = str(data["hooked-browsers"][t][h]['os']) | |
| 68 | platform = str(data["hooked-browsers"][t][h]['platform']) | |
| 69 | session = str(data["hooked-browsers"][t][h]['session']) | |
| 70 | ip = str(data["hooked-browsers"][t][h]['ip']) | |
| 71 | domain = str(data["hooked-browsers"][t][h]['domain']) | |
| 72 | port = str(data["hooked-browsers"][t][h]['port']) | |
| 73 | page_uri = str(data["hooked-browsers"][t][h]['page_uri']) | |
| 74 | ||
| 75 | desc = "Client ip:" + ip + \ | |
| 76 | " has been injected with BeEF using the url:" + page_uri + "\n" | |
| 77 | ||
| 78 | desc += "More information:" | |
| 79 | desc += "\ntype:" + t | |
| 80 | desc += "\nname:" + name | |
| 81 | desc += "\nversion:" + version | |
| 82 | desc += "\nos:" + os | |
| 83 | desc += "\nplatform:" + platform | |
| 84 | desc += "\nsession:" + session | |
| 85 | desc += "\nip:" + ip | |
| 86 | desc += "\ndomain:" + domain | |
| 87 | desc += "\nport:" + port | |
| 88 | desc += "\npage_uri:" + page_uri | |
| 89 | ||
| 90 | h_id = self.createAndAddHost(ip) | |
| 91 | v_id = self.createAndAddVulnToHost( | |
| 92 | h_id, | |
| 93 | "BeEF injected " + t + " session:" + session, | |
| 94 | desc=desc, | |
| 95 | ref=["http://http://beefproject.com/"], | |
| 96 | severity=3) | |
| 97 | ||
| 98 | def processCommandString(self, username, current_path, command_string): | |
| 99 | return None | |
| 100 | ||
| 101 | def setHost(self): | |
| 102 | pass | |
| 103 | ||
| 104 | ||
| 105 | def createPlugin(): | |
| 106 | return BeefPlugin() | |
| 107 | ||
| 108 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2018 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2018 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | import re | |
| 6 | import socket | |
| 7 | from urllib.parse import urlparse | |
| 8 | ||
| 9 | from faraday.client.plugins import core | |
| 10 | ||
| 11 | __author__ = "Roberto Focke" | |
| 12 | __copyright__ = "Copyright (c) 2017, Infobyte LLC" | |
| 13 | __license__ = "" | |
| 14 | __version__ = "1.0.0" | |
| 15 | ||
| 16 | ||
| 17 | class brutexss (core.PluginBase): | |
| 18 | ||
| 19 | def __init__(self): | |
| 20 | super().__init__() | |
| 21 | self.id = "brutexss" | |
| 22 | self.name = "brutexss" | |
| 23 | self.plugin_version = "0.0.2" | |
| 24 | self.version = "1.0.0" | |
| 25 | self.protocol='tcp' | |
| 26 | ||
| 27 | self._command_regex = re.compile(r'^(sudo brutexss|brutexss|sudo brutexss\.py|brutexss\.py|python brutexss\.py|\.\/brutexss\.py).*?') | |
| 28 | ||
| 29 | def parseOutputString(self, output, debug=False): | |
| 30 | lineas = output.split("\n") | |
| 31 | parametro = [] | |
| 32 | found_vuln = False | |
| 33 | for linea in lineas: | |
| 34 | if linea.find("is available! Good!") > 0: | |
| 35 | print(linea) | |
| 36 | url = re.findall('(?:[-\w.]|(?:%[\da-fA-F]{2}))+', linea)[0] | |
| 37 | port = 80 | |
| 38 | if urlparse(url).scheme == 'https': | |
| 39 | port = 443 | |
| 40 | netloc_splitted = urlparse(url).netloc.split(':') | |
| 41 | if len(netloc_splitted) > 1: | |
| 42 | port = netloc_splitted[1] | |
| 43 | if linea.find("Vulnerable") > 0 and "No" not in linea: | |
| 44 | vuln_list = re.findall("\w+", linea) | |
| 45 | if vuln_list[2] == "Vulnerable": | |
| 46 | parametro.append(vuln_list[1]) | |
| 47 | found_vuln=len(parametro) > 0 | |
| 48 | host_id = self.createAndAddHost(url) | |
| 49 | address=socket.gethostbyname(url) | |
| 50 | interface_id = self.createAndAddInterface(host_id,address,ipv4_address=address,hostname_resolution=[url]) | |
| 51 | service_id = self.createAndAddServiceToInterface(host_id, interface_id, self.protocol, 'tcp', | |
| 52 | ports=[port], status='Open', version="", description="") | |
| 53 | if found_vuln: | |
| 54 | self.createAndAddVulnWebToService(host_id,service_id, name="xss", desc="XSS", ref='', severity='med', | |
| 55 | website=url, path='', method='', pname='', params=''.join(parametro), | |
| 56 | request='', response='') | |
| 57 | ||
| 58 | def processCommandString(self, username, current_path, command_string): | |
| 59 | return None | |
| 60 | ||
| 61 | ||
| 62 | def createPlugin(): | |
| 63 | return brutexss() | |
| 64 | ||
| 65 | ||
| 66 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | """ | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | """ | |
| 9 | import re | |
| 10 | import os | |
| 11 | import sys | |
| 12 | import base64 | |
| 13 | from bs4 import BeautifulSoup, Comment | |
| 14 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 15 | try: | |
| 16 | from urlparse import urlsplit | |
| 17 | except ImportError: | |
| 18 | from urllib.parse import urlsplit | |
| 19 | import distutils.util #pylint: disable=import-error | |
| 20 | ||
| 21 | ||
| 22 | try: | |
| 23 | import xml.etree.cElementTree as ET | |
| 24 | import xml.etree.ElementTree as ET_ORIG | |
| 25 | ETREE_VERSION = ET_ORIG.VERSION | |
| 26 | except ImportError: | |
| 27 | import xml.etree.ElementTree as ET | |
| 28 | ETREE_VERSION = ET.VERSION | |
| 29 | ||
| 30 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 31 | ||
| 32 | current_path = os.path.abspath(os.getcwd()) | |
| 33 | ||
| 34 | __author__ = "Francisco Amato" | |
| 35 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 36 | __credits__ = ["Francisco Amato", "Micaela Ranea Sanchez"] | |
| 37 | __license__ = "" | |
| 38 | __version__ = "1.1.0" | |
| 39 | __maintainer__ = "Francisco Amato" | |
| 40 | __email__ = "[email protected]" | |
| 41 | __status__ = "Development" | |
| 42 | ||
| 43 | ||
| 44 | class BurpXmlParser: | |
| 45 | """ | |
| 46 | The objective of this class is to parse an xml file generated by the burp tool. | |
| 47 | ||
| 48 | TODO: Handle errors. | |
| 49 | TODO: Test burp output version. Handle what happens if the parser doesn't support it. | |
| 50 | TODO: Test cases. | |
| 51 | ||
| 52 | @param burp_xml_filepath A proper xml generated by burp | |
| 53 | """ | |
| 54 | ||
| 55 | def __init__(self, xml_output): | |
| 56 | ||
| 57 | self.target = None | |
| 58 | self.port = "80" | |
| 59 | self.host = None | |
| 60 | ||
| 61 | tree = self.parse_xml(xml_output) | |
| 62 | if tree: | |
| 63 | self.items = list(self.get_items(tree)) | |
| 64 | else: | |
| 65 | self.items = [] | |
| 66 | ||
| 67 | def parse_xml(self, xml_output): | |
| 68 | """ | |
| 69 | Open and parse an xml file. | |
| 70 | ||
| 71 | TODO: Write custom parser to just read the nodes that we need instead of | |
| 72 | reading the whole file. | |
| 73 | ||
| 74 | @return xml_tree An xml tree instance. None if error. | |
| 75 | """ | |
| 76 | try: | |
| 77 | tree = ET.fromstring(xml_output) | |
| 78 | except SyntaxError as err: | |
| 79 | print("SyntaxError: %s. %s" % (err, xml_output)) | |
| 80 | return None | |
| 81 | ||
| 82 | return tree | |
| 83 | ||
| 84 | def get_items(self, tree): | |
| 85 | """ | |
| 86 | @return items A list of Host instances | |
| 87 | """ | |
| 88 | bugtype = '' | |
| 89 | ||
| 90 | for node in tree.findall('issue'): | |
| 91 | yield Item(node) | |
| 92 | ||
| 93 | ||
| 94 | def get_attrib_from_subnode(xml_node, subnode_xpath_expr, attrib_name): | |
| 95 | """ | |
| 96 | Finds a subnode in the item node and the retrieves a value from it | |
| 97 | ||
| 98 | @return An attribute value | |
| 99 | """ | |
| 100 | global ETREE_VERSION | |
| 101 | node = None | |
| 102 | ||
| 103 | if ETREE_VERSION[0] <= 1 and ETREE_VERSION[1] < 3: | |
| 104 | ||
| 105 | match_obj = re.search( | |
| 106 | "([^\@]+?)\[\@([^=]*?)=\'([^\']*?)\'", subnode_xpath_expr) | |
| 107 | if match_obj is not None: | |
| 108 | ||
| 109 | node_to_find = match_obj.group(1) | |
| 110 | xpath_attrib = match_obj.group(2) | |
| 111 | xpath_value = match_obj.group(3) | |
| 112 | for node_found in xml_node.findall(node_to_find): | |
| 113 | if node_found.attrib[xpath_attrib] == xpath_value: | |
| 114 | node = node_found | |
| 115 | break | |
| 116 | else: | |
| 117 | node = xml_node.find(subnode_xpath_expr) | |
| 118 | ||
| 119 | else: | |
| 120 | node = xml_node.find(subnode_xpath_expr) | |
| 121 | ||
| 122 | if node is not None: | |
| 123 | return node.get(attrib_name) | |
| 124 | ||
| 125 | return None | |
| 126 | ||
| 127 | ||
| 128 | class Item: | |
| 129 | """ | |
| 130 | An abstract representation of a Item | |
| 131 | @param item_node A item_node taken from an burp xml tree | |
| 132 | """ | |
| 133 | ||
| 134 | def __init__(self, item_node): | |
| 135 | self.node = item_node | |
| 136 | ||
| 137 | name = item_node.findall('name')[0] | |
| 138 | host_node = item_node.findall('host')[0] | |
| 139 | path = item_node.findall('path')[0] | |
| 140 | location = item_node.findall('location')[0] | |
| 141 | severity = item_node.findall('severity')[0] | |
| 142 | external_id = item_node.findall('type')[0] | |
| 143 | request = self.decode_binary_node('./requestresponse/request') | |
| 144 | response = self.decode_binary_node('./requestresponse/response') | |
| 145 | ||
| 146 | detail = self.do_clean(item_node.findall('issueDetail')) | |
| 147 | remediation = self.do_clean(item_node.findall('remediationBackground')) | |
| 148 | background = self.do_clean(item_node.findall('issueBackground')) | |
| 149 | ||
| 150 | self.url = host_node.text | |
| 151 | ||
| 152 | url_data = urlsplit(self.url) | |
| 153 | ||
| 154 | self.protocol = url_data.scheme | |
| 155 | self.host = url_data.hostname | |
| 156 | ||
| 157 | # Use the port in the URL if it is defined, or 80 or 443 by default | |
| 158 | self.port = url_data.port or (443 if url_data.scheme == "https" | |
| 159 | else 80) | |
| 160 | ||
| 161 | self.name = name.text | |
| 162 | self.location = location.text | |
| 163 | self.path = path.text | |
| 164 | ||
| 165 | self.ip = host_node.get('ip') | |
| 166 | self.url = self.node.get('url') | |
| 167 | self.severity = severity.text | |
| 168 | self.request = request | |
| 169 | self.response = response | |
| 170 | self.detail = detail | |
| 171 | self.remediation = remediation | |
| 172 | self.background = background | |
| 173 | self.external_id = external_id.text | |
| 174 | ||
| 175 | ||
| 176 | def do_clean(self, value): | |
| 177 | ||
| 178 | myreturn = "" | |
| 179 | if value is not None: | |
| 180 | if len(value) > 0: | |
| 181 | myreturn = value[0].text | |
| 182 | return myreturn | |
| 183 | ||
| 184 | def decode_binary_node(self, path): | |
| 185 | """ | |
| 186 | Finds a subnode matching `path` and returns its inner text if | |
| 187 | it has no base64 attribute or its base64 decoded inner text if | |
| 188 | it has it. | |
| 189 | """ | |
| 190 | nodes = self.node.findall(path) | |
| 191 | try: | |
| 192 | subnode = nodes[0] | |
| 193 | except IndexError: | |
| 194 | return "" | |
| 195 | encoded = distutils.util.strtobool(subnode.get('base64', 'false')) | |
| 196 | if encoded: | |
| 197 | res = base64.b64decode(subnode.text).decode('utf-8', errors="backslashreplace") | |
| 198 | else: | |
| 199 | res = subnode.text | |
| 200 | return "".join([ch for ch in res if ord(ch) <= 128]) | |
| 201 | ||
| 202 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 203 | """ | |
| 204 | Finds a subnode in the host node and the retrieves a value from it. | |
| 205 | @return An attribute value | |
| 206 | """ | |
| 207 | ||
| 208 | sub_node = self.node.find(subnode_xpath_expr) | |
| 209 | if sub_node is not None: | |
| 210 | return sub_node.text | |
| 211 | ||
| 212 | return None | |
| 213 | ||
| 214 | ||
| 215 | class BurpPlugin(PluginXMLFormat): | |
| 216 | """ | |
| 217 | Example plugin to parse burp output. | |
| 218 | """ | |
| 219 | ||
| 220 | def __init__(self): | |
| 221 | super().__init__() | |
| 222 | self.identifier_tag = "issues" | |
| 223 | self.id = "Burp" | |
| 224 | self.name = "Burp XML Output Plugin" | |
| 225 | self.plugin_version = "0.0.2" | |
| 226 | self.version = "1.6.05 BurpPro" | |
| 227 | self.framework_version = "1.0.0" | |
| 228 | self.options = None | |
| 229 | self._current_output = None | |
| 230 | self.target = None | |
| 231 | self._command_regex = re.compile(r'^(sudo burp|\.\/burp).*?') | |
| 232 | ||
| 233 | global current_path | |
| 234 | self._output_file_path = os.path.join( | |
| 235 | self.data_path, | |
| 236 | "burp_output-%s.xml" % self._rid) | |
| 237 | ||
| 238 | def parseOutputString(self, output, debug=False): | |
| 239 | ||
| 240 | parser = BurpXmlParser(output) | |
| 241 | for item in parser.items: | |
| 242 | ||
| 243 | h_id = self.createAndAddHost(item.ip) | |
| 244 | ||
| 245 | i_id = self.createAndAddInterface( | |
| 246 | h_id, | |
| 247 | item.ip, | |
| 248 | ipv4_address=item.ip, | |
| 249 | hostname_resolution=[item.host]) | |
| 250 | ||
| 251 | s_id = self.createAndAddServiceToInterface( | |
| 252 | h_id, | |
| 253 | i_id, | |
| 254 | item.protocol, | |
| 255 | "tcp", | |
| 256 | ports=[str(item.port)], | |
| 257 | status="open") | |
| 258 | ||
| 259 | desc = "Detail\n" + item.detail | |
| 260 | if item.background: | |
| 261 | desc += "\nBackground\n" + item.background | |
| 262 | desc = self.removeHtml(desc) | |
| 263 | resolution = self.removeHtml(item.remediation) if item.remediation else "" | |
| 264 | ||
| 265 | v_id = self.createAndAddVulnWebToService( | |
| 266 | h_id, | |
| 267 | s_id, | |
| 268 | item.name, | |
| 269 | desc=desc, | |
| 270 | severity=item.severity, | |
| 271 | website=item.host, | |
| 272 | path=item.path, | |
| 273 | request=item.request, | |
| 274 | response=item.response, | |
| 275 | resolution=resolution, | |
| 276 | external_id=item.external_id) | |
| 277 | ||
| 278 | del parser | |
| 279 | ||
| 280 | def processCommandString(self, username, current_path, command_string): | |
| 281 | return None | |
| 282 | ||
| 283 | def removeHtml(self, markup): | |
| 284 | soup = BeautifulSoup(markup, "html.parser") | |
| 285 | ||
| 286 | # Replace line breaks and paragraphs for new lines | |
| 287 | for tag in soup.find_all(["br", "p"]): | |
| 288 | tag.append("\n") | |
| 289 | tag.unwrap() | |
| 290 | ||
| 291 | # Replace lists for * and new lines | |
| 292 | for tag in soup.find_all(["ul", "ol"]): | |
| 293 | for item in tag.find_all("li"): | |
| 294 | item.insert_before("* ") | |
| 295 | item.append("\n") | |
| 296 | item.unwrap() | |
| 297 | tag.unwrap() | |
| 298 | ||
| 299 | # Remove all other HTML tags | |
| 300 | for tag in soup.find_all(): | |
| 301 | tag.unwrap() | |
| 302 | ||
| 303 | # Remove all comments | |
| 304 | for child in soup.children: | |
| 305 | if isinstance(child, Comment): | |
| 306 | child.extract() | |
| 307 | ||
| 308 | return str(soup) | |
| 309 | ||
| 310 | def setHost(self): | |
| 311 | pass | |
| 312 | ||
| 313 | ||
| 314 | def createPlugin(): | |
| 315 | return BurpPlugin() | |
| 316 | ||
| 317 | if __name__ == '__main__': | |
| 318 | parser = BurpXmlParser(sys.argv[1]) | |
| 319 | for item in parser.items: | |
| 320 | if item.status == 'up': | |
| 321 | print(item) | |
| 322 | ||
| 323 | ||
| 324 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Updated by Mike Zhong, 25 Oct 2017. | |
| 2 | ||
| 3 | Faraday Penetration Test IDE | |
| 4 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | See the file 'doc/LICENSE' for the license information | |
| 6 | """ | |
| 7 | import re | |
| 8 | import socket | |
| 9 | ||
| 10 | from faraday.client.plugins import core | |
| 11 | ||
| 12 | __author__ = u"Andres Tarantini" | |
| 13 | __copyright__ = u"Copyright (c) 2015 Andres Tarantini" | |
| 14 | __credits__ = [u"Andres Tarantini"] | |
| 15 | __license__ = u"MIT" | |
| 16 | __version__ = u"0.0.1" | |
| 17 | __maintainer__ = u"Andres Tarantini" | |
| 18 | __email__ = u"[email protected]" | |
| 19 | __status__ = u"Development" | |
| 20 | ||
| 21 | ||
| 22 | class DigPlugin(core.PluginBase): | |
| 23 | """ | |
| 24 | Handle DiG (http://linux.die.net/man/1/dig) output | |
| 25 | """ | |
| 26 | ||
| 27 | def __init__(self): | |
| 28 | super().__init__() | |
| 29 | self.id = u"dig" | |
| 30 | self.name = u"DiG" | |
| 31 | self.plugin_version = u"0.0.1" | |
| 32 | self.version = u"9.9.5-3" | |
| 33 | self._command_regex = re.compile(r'^(dig).*?') | |
| 34 | ||
| 35 | def parseOutputString(self, output): | |
| 36 | # Ignore all lines that start with ";" | |
| 37 | parsed_output = [line for line in output.splitlines() if line and line[ | |
| 38 | 0] != u";"] | |
| 39 | if not parsed_output: | |
| 40 | return True | |
| 41 | ||
| 42 | # Parse results | |
| 43 | results = [] | |
| 44 | answer_section_columns = [u"domain", | |
| 45 | u"ttl", u"class", u"type", u"data"] | |
| 46 | for line in parsed_output: | |
| 47 | line_split = line.split() # the first 4 elements are domain, ttl, class, type; everything else data | |
| 48 | results.append(dict(zip(answer_section_columns, line_split[:4] + [line_split[4:]] ))) | |
| 49 | ||
| 50 | # Create hosts is results information is relevant | |
| 51 | try: | |
| 52 | for result in results: | |
| 53 | relevant_types = [u"A", u"AAAA", u"MX", u"NS", u"SOA", u"TXT"] | |
| 54 | # TODO implement more types from https://en.wikipedia.org/wiki/List_of_DNS_record_types | |
| 55 | ||
| 56 | if result.get(u"type") in relevant_types: | |
| 57 | ||
| 58 | # get domain | |
| 59 | domain = result.get(u"domain") | |
| 60 | ||
| 61 | ||
| 62 | # get IP address (special if type "A") | |
| 63 | if result.get(u"type") == u"A": # A = IPv4 address from dig | |
| 64 | ip_address = result.get(u"data")[0] | |
| 65 | else: # if not, from socket | |
| 66 | ip_address = socket.gethostbyname(domain) | |
| 67 | ||
| 68 | # Create host | |
| 69 | host_id = self.createAndAddHost(ip_address) | |
| 70 | ||
| 71 | # create interface (special if type "AAAA") | |
| 72 | if result.get(u"type") == u"AAAA": # AAAA = IPv6 address | |
| 73 | # TODO is there a function to dynamically update the paramter ipv6_address of an already-created interface? | |
| 74 | ipv6_address = result.get(u"data")[0] | |
| 75 | interface_id = self.createAndAddInterface( | |
| 76 | host_id, | |
| 77 | ip_address, | |
| 78 | ipv4_address=ip_address, | |
| 79 | ipv6_address=ipv6_address, | |
| 80 | hostname_resolution=[domain]) | |
| 81 | else: | |
| 82 | interface_id = self.createAndAddInterface( | |
| 83 | host_id, | |
| 84 | ip_address, | |
| 85 | ipv4_address=ip_address, | |
| 86 | hostname_resolution=[domain]) | |
| 87 | ||
| 88 | ||
| 89 | # all other TYPES that aren't 'A' and 'AAAA' are dealt here: | |
| 90 | if result.get(u"type") == u"MX": # Mail exchange record | |
| 91 | mx_priority = result.get(u"data")[0] | |
| 92 | mx_record = result.get(u"data")[1] | |
| 93 | ||
| 94 | service_id = self.createAndAddServiceToInterface( | |
| 95 | host_id=host_id, | |
| 96 | interface_id=interface_id, | |
| 97 | name=mx_record, | |
| 98 | protocol="SMTP", | |
| 99 | ports=[25], | |
| 100 | description="E-mail Server") | |
| 101 | ||
| 102 | text = "Priority: " + mx_priority | |
| 103 | self.createAndAddNoteToService( | |
| 104 | host_id=host_id, | |
| 105 | service_id=service_id, | |
| 106 | name="priority", | |
| 107 | text=text.encode('ascii', 'ignore')) | |
| 108 | ||
| 109 | elif result.get(u"type") == u"NS": # Name server record | |
| 110 | ns_record = result.get(u"data")[0] | |
| 111 | self.createAndAddServiceToInterface( | |
| 112 | host_id=host_id, | |
| 113 | interface_id=interface_id, | |
| 114 | name=ns_record, | |
| 115 | protocol="DNS", | |
| 116 | ports=[53], | |
| 117 | description="DNS Server") | |
| 118 | ||
| 119 | elif result.get(u"type") == u"SOA": # Start of Authority Record | |
| 120 | ns_record = result.get(u"data")[0] # primary namer server | |
| 121 | responsible_party = result.get(u"data")[1] # responsible party of domain | |
| 122 | timestamp = result.get(u"data")[2] | |
| 123 | refresh_zone_time = result.get(u"data")[3] | |
| 124 | retry_refresh_time = result.get(u"data")[4] | |
| 125 | upper_limit_time = result.get(u"data")[5] | |
| 126 | negative_result_ttl = result.get(u"data")[6] | |
| 127 | ||
| 128 | service_id = self.createAndAddServiceToInterface( | |
| 129 | host_id=host_id, | |
| 130 | interface_id=interface_id, | |
| 131 | name=ns_record, | |
| 132 | protocol="DNS", | |
| 133 | ports=[53], | |
| 134 | description="Authority Record") | |
| 135 | ||
| 136 | text = ( | |
| 137 | "Responsible Party: " + responsible_party + | |
| 138 | "\nTimestep: " + timestamp + | |
| 139 | "\nTime before zone refresh (sec): " + refresh_zone_time + | |
| 140 | "\nTime before retry refresh (sec): " + retry_refresh_time + | |
| 141 | "\nUpper Limit before Zone is no longer authoritive (sec): " + upper_limit_time + | |
| 142 | "\nNegative Result TTL: " + negative_result_ttl) | |
| 143 | ||
| 144 | self.createAndAddNoteToService( | |
| 145 | host_id=host_id, | |
| 146 | service_id=service_id, | |
| 147 | name="priority", | |
| 148 | text=text.encode('ascii', 'ignore')) | |
| 149 | ||
| 150 | elif result.get(u"type") == u"TXT": # TXT record | |
| 151 | text = " ".join(result.get(u"data")[:]) | |
| 152 | self.createAndAddNoteToHost( | |
| 153 | host_id=host_id, | |
| 154 | name="TXT Information", | |
| 155 | text=text.encode('ascii', 'ignore')) | |
| 156 | ||
| 157 | except Exception as ex: | |
| 158 | print("some part of the dig plug-in caused an error! Please check repo/dig/plugin.py") | |
| 159 | return False | |
| 160 | ||
| 161 | ||
| 162 | return True | |
| 163 | ||
| 164 | ||
| 165 | def createPlugin(): | |
| 166 | return DigPlugin() | |
| 167 | ||
| 168 | ||
| 169 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import core | |
| 6 | import re | |
| 7 | import socket | |
| 8 | ||
| 9 | __author__ = "Federico Fernandez - @q3rv0" | |
| 10 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 11 | __license__ = "" | |
| 12 | __version__ = "1.0.0" | |
| 13 | __maintainer__ = "Federico Fernandez" | |
| 14 | __email__ = "[email protected]" | |
| 15 | __status__ = "Development" | |
| 16 | ||
| 17 | ||
| 18 | class dirbPlugin(core.PluginBase): | |
| 19 | ||
| 20 | def __init__(self): | |
| 21 | super().__init__() | |
| 22 | self.id = "dirb" | |
| 23 | self.name = "Dirb" | |
| 24 | self.plugin_version = "0.0.1" | |
| 25 | self.version = "2.22" | |
| 26 | self.regexpUrl = r'((http[s]?)\:\/\/([\w\.]+)[.\S]+)' | |
| 27 | self._command_regex = re.compile(r'^(?:sudo dirb|dirb|\.\/dirb|sudo \.\/dirb)\s+(?:(http[s]?)\:\/\/([\w\.]+)[.\S]+)') | |
| 28 | self.text = [] | |
| 29 | ||
| 30 | def getPort(self, host, proto): | |
| 31 | p = re.search(r"\:([0-9]+)\/", host) | |
| 32 | if p is not None: | |
| 33 | return p.group(1) | |
| 34 | elif proto == 'https': | |
| 35 | return 443 | |
| 36 | else: | |
| 37 | return 80 | |
| 38 | ||
| 39 | def getIP(self, host): | |
| 40 | try: | |
| 41 | ip = socket.gethostbyname(host) | |
| 42 | except Exception: | |
| 43 | pass | |
| 44 | ||
| 45 | return ip | |
| 46 | ||
| 47 | def state(self, output): | |
| 48 | if output.find('COULDNT CONNECT') != -1: | |
| 49 | return "close" | |
| 50 | else: | |
| 51 | return "open" | |
| 52 | ||
| 53 | def pathsDirListing(self, output): | |
| 54 | data = [] | |
| 55 | r = re.findall(self.regexpUrl + r"[\-\._\w\*\s]+\s+\(!\) WARNING: Directory IS LISTABLE", | |
| 56 | output) | |
| 57 | for u in r: | |
| 58 | data.append(u[0]) | |
| 59 | ||
| 60 | paths = "\n".join(data) | |
| 61 | return paths | |
| 62 | ||
| 63 | def note(self, output): | |
| 64 | dirs = re.findall(r"==> DIRECTORY: "+self.regexpUrl, output) | |
| 65 | files = re.findall(r"\+ " + self.regexpUrl + r" \(.+\)", output) | |
| 66 | for d in dirs: | |
| 67 | self.text.append("DIRECTORY: " + d[0]) | |
| 68 | ||
| 69 | for f in files: | |
| 70 | self.text.append("FILE: " + f[0]) | |
| 71 | ||
| 72 | self.text = '\n'.join(self.text) | |
| 73 | ||
| 74 | def parseOutputString(self, output, debug=False): | |
| 75 | ||
| 76 | url = re.search(r"URL_BASE: " + self.regexpUrl, output) | |
| 77 | paths = self.pathsDirListing(output) | |
| 78 | status = self.state(output) | |
| 79 | self.note(output) | |
| 80 | ||
| 81 | if output.find('END_TIME') != -1 and url is not None: | |
| 82 | proto = url.group(2) | |
| 83 | domain = url.group(3) | |
| 84 | ip = self.getIP(domain) | |
| 85 | puerto = self.getPort(url.group(1), proto) | |
| 86 | ||
| 87 | host_id = self.createAndAddHost(ip) | |
| 88 | iface_id = self.createAndAddInterface(host_id, ip, ipv4_address = ip) | |
| 89 | ||
| 90 | serv_id = self.createAndAddServiceToInterface(host_id, iface_id, proto, protocol = proto, ports =[puerto], status = status) | |
| 91 | ||
| 92 | if len(self.text) > 0: | |
| 93 | self.createAndAddVulnWebToService(host_id, serv_id, 'Url Fuzzing', severity=0, desc=self.text, website=domain) | |
| 94 | ||
| 95 | if len(paths) > 0: | |
| 96 | self.createAndAddVulnWebToService(host_id, serv_id, "Directory Listing", severity = "med", website = domain, request = paths, method = "GET") | |
| 97 | ||
| 98 | return True | |
| 99 | ||
| 100 | def processCommandString(self, username, current_path, command_string): | |
| 101 | """ | |
| 102 | Adds the -oX parameter to get xml output to the command string that the | |
| 103 | user has set. | |
| 104 | """ | |
| 105 | ||
| 106 | no_stop_on_warn_msg_re = r"\s+-w" | |
| 107 | arg_search = re.search(no_stop_on_warn_msg_re,command_string) | |
| 108 | extra_arg = "" | |
| 109 | if arg_search is None: | |
| 110 | extra_arg +=" -w" | |
| 111 | ||
| 112 | silent_mode_re = r"\s+-S" | |
| 113 | arg_search = re.search(silent_mode_re,command_string) | |
| 114 | if arg_search is None: | |
| 115 | extra_arg +=" -S" | |
| 116 | return "%s%s" % (command_string, extra_arg) | |
| 117 | ||
| 118 | def createPlugin(): | |
| 119 | return dirbPlugin() | |
| 120 | ||
| 121 | ||
| 122 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | import re | |
| 6 | import os | |
| 7 | import json | |
| 8 | import shlex | |
| 9 | import socket | |
| 10 | import argparse | |
| 11 | import tempfile | |
| 12 | import urllib.parse as urlparse | |
| 13 | ||
| 14 | ||
| 15 | from faraday.client.plugins.plugin import PluginTerminalOutput | |
| 16 | from faraday.client.plugins.plugin_utils import get_vulnweb_url_fields | |
| 17 | ||
| 18 | ||
| 19 | __author__ = "Matías Lang" | |
| 20 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 21 | __credits__ = ["Matías Lang"] | |
| 22 | __license__ = "" | |
| 23 | __version__ = "0.0.1" | |
| 24 | __maintainer__ = "Matías Lang" | |
| 25 | __email__ = "[email protected]" | |
| 26 | __status__ = "Development" | |
| 27 | ||
| 28 | ||
| 29 | status_codes = { | |
| 30 | 200: "OK", 201: "Created", 202: "Accepted", | |
| 31 | 203: "Non-Authoritative Information", 204: "No Content", | |
| 32 | 205: "Reset Content", 206: "Partial Content", 207: "Multi-Status", | |
| 33 | 208: "Already Reported", 226: "IM Used", 300: "Multiple Choices", | |
| 34 | 301: "Moved Permanently", 302: "Found", 303: "See Other", | |
| 35 | 304: "Not Modified", 305: "Use Proxy", 306: "Switch Proxy", | |
| 36 | 307: "Temporary Redirect", 308: "Permanent Redirect", | |
| 37 | 400: "Bad Request", 401: "Unauthorized", 402: "Payment Required", | |
| 38 | 403: "Forbidden", 404: "Not Found", 405: "Method Not Allowed", | |
| 39 | 406: "Not Acceptable", 407: "Proxy Authentication Required", | |
| 40 | 408: "Request Timeout", 409: "Conflict", 410: "Gone", | |
| 41 | 411: "Length Required", 412: "Precondition Failed", | |
| 42 | 413: "Payload Too Large", 414: "URI Too Long", | |
| 43 | 415: "Unsupported Media Type", 416: "Range Not Satisfiable", | |
| 44 | 417: "Expectation Failed", 418: "I'm a teapot", | |
| 45 | 421: "Misdirected Request", 422: "Unprocessable Entity", 423: "Locked", | |
| 46 | 424: "Failed Dependency", 426: "Upgrade Required", | |
| 47 | 428: "Precondition Required", 429: "Too Many Requests", | |
| 48 | 431: "Request Header Fields Too Large", | |
| 49 | 451: "Unavailable For Legal Reasons", 500: "Internal Server Error", | |
| 50 | 501: "Not Implemented", 502: "Bad Gateway", 503: "Service Unavailable", | |
| 51 | 504: "Gateway Timeout", 505: "HTTP Version Not Supported", | |
| 52 | 506: "Variant Also Negotiates", 507: "Insufficient Storage", | |
| 53 | 508: "Loop Detected", 510: "Not Extended", | |
| 54 | 511: "Network Authentication Required", | |
| 55 | } | |
| 56 | ||
| 57 | ||
| 58 | class DirsearchPlugin(PluginTerminalOutput): | |
| 59 | def __init__(self): | |
| 60 | super().__init__() | |
| 61 | self.id = "dirsearch" | |
| 62 | self.name = "dirsearch" | |
| 63 | self.plugin_version = "0.0.1" | |
| 64 | self.version = "0.0.1" | |
| 65 | self._command_regex = re.compile( | |
| 66 | r'^(sudo )?(python[0-9\.]? )?dirsearch(\.py)?') | |
| 67 | self.ignore_parsing = False | |
| 68 | self.json_report_file = None | |
| 69 | self.addSetting("Ignore 403", str, "1") | |
| 70 | ||
| 71 | def parseOutputString(self, output, debug=False): | |
| 72 | if self.ignore_parsing: | |
| 73 | return | |
| 74 | if self.json_report_file: | |
| 75 | # We ran the plugin via command line | |
| 76 | try: | |
| 77 | fp = open(self.json_report_file) | |
| 78 | except IOError: | |
| 79 | self.log('Error opening JSON in the file {}'.format( | |
| 80 | self.json_report_file | |
| 81 | ), 'ERROR') | |
| 82 | else: | |
| 83 | self.parse_json(fp.read()) | |
| 84 | if self.remove_report: | |
| 85 | os.unlink(self.json_report_file) | |
| 86 | else: | |
| 87 | # We are importing a report | |
| 88 | self.parse_json(output) | |
| 89 | ||
| 90 | def resolve(self, domain): | |
| 91 | return socket.gethostbyname(domain) | |
| 92 | ||
| 93 | @property | |
| 94 | def should_ignore_403(self): | |
| 95 | val = self.getSetting('Ignore 403') | |
| 96 | if not val or not int(val): | |
| 97 | return False | |
| 98 | return True | |
| 99 | ||
| 100 | def parse_json(self, contents): | |
| 101 | try: | |
| 102 | data = json.loads(contents) | |
| 103 | except ValueError: | |
| 104 | self.log('Error parsing report. Make sure the file has valid ' | |
| 105 | 'JSON', 'ERROR') | |
| 106 | return | |
| 107 | for (base_url, items) in data.items(): | |
| 108 | base_split = urlparse.urlsplit(base_url) | |
| 109 | ip = self.resolve(base_split.hostname) | |
| 110 | h_id = self.createAndAddHost(ip) | |
| 111 | ||
| 112 | i_id = self.createAndAddInterface( | |
| 113 | h_id, | |
| 114 | name=ip, | |
| 115 | ipv4_address=ip, | |
| 116 | hostname_resolution=[base_split.hostname]) | |
| 117 | ||
| 118 | s_id = self.createAndAddServiceToInterface( | |
| 119 | h_id, | |
| 120 | i_id, | |
| 121 | base_split.scheme, | |
| 122 | 'tcp', | |
| 123 | [base_split.port], | |
| 124 | status="open") | |
| 125 | ||
| 126 | for item in items: | |
| 127 | self.parse_found_url(base_url, h_id, s_id, item) | |
| 128 | ||
| 129 | def parse_found_url(self, base_url, h_id, s_id, item): | |
| 130 | if self.should_ignore_403 and item['status'] == 403: | |
| 131 | return | |
| 132 | url = urlparse.urlsplit(urlparse.urljoin(base_url, item['path'])) | |
| 133 | response = "HTTP/1.1 {} {}\nContent-Length: {}".format( | |
| 134 | item['status'], status_codes.get(item['status'], 'unknown'), | |
| 135 | item['content-length']) | |
| 136 | redirect = item.get('redirect') | |
| 137 | if redirect is not None: | |
| 138 | response += '\nLocation: {}'.format(redirect) | |
| 139 | self.createAndAddVulnWebToService( | |
| 140 | h_id, | |
| 141 | s_id, | |
| 142 | name='Path found: {} ({})'.format(item['path'], item['status']), | |
| 143 | desc="Dirsearch tool found the following URL: {}".format( | |
| 144 | url.geturl()), | |
| 145 | severity="info", | |
| 146 | method='GET', | |
| 147 | response=response, | |
| 148 | **get_vulnweb_url_fields(url.geturl())) | |
| 149 | ||
| 150 | def processCommandString(self, username, current_path, command_string): | |
| 151 | parser = argparse.ArgumentParser(conflict_handler='resolve') | |
| 152 | parser.add_argument('-h', '--help', action='store_true') | |
| 153 | parser.add_argument('--json-report') | |
| 154 | args, unknown = parser.parse_known_args(shlex.split(command_string)) | |
| 155 | ||
| 156 | if args.help: | |
| 157 | self.devlog('help detected, ignoring parsing') | |
| 158 | return command_string | |
| 159 | if args.json_report: | |
| 160 | # The user already defined a path to the JSON report | |
| 161 | self.json_report_file = args.json_report | |
| 162 | self.remove_report = False | |
| 163 | return command_string | |
| 164 | else: | |
| 165 | # Use temporal file to save the report data | |
| 166 | self.json_report_file = tempfile.mktemp( | |
| 167 | prefix="dirsearch_report_", suffix=".json") | |
| 168 | self.devlog('Setting report file to {}'.format( | |
| 169 | self.json_report_file)) | |
| 170 | self.remove_report = True | |
| 171 | return '{} --json-report {}'.format(command_string, | |
| 172 | self.json_report_file) | |
| 173 | ||
| 174 | ||
| 175 | def createPlugin(): | |
| 176 | return DirsearchPlugin() | |
| 177 | ||
| 178 | ||
| 179 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | from faraday.client.model import api | |
| 8 | import re | |
| 9 | import os | |
| 10 | ||
| 11 | try: | |
| 12 | import xml.etree.cElementTree as ET | |
| 13 | import xml.etree.ElementTree as ET_ORIG | |
| 14 | ETREE_VERSION = ET_ORIG.VERSION | |
| 15 | except ImportError: | |
| 16 | import xml.etree.ElementTree as ET | |
| 17 | ETREE_VERSION = ET.VERSION | |
| 18 | ||
| 19 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 20 | ||
| 21 | current_path = os.path.abspath(os.getcwd()) | |
| 22 | ||
| 23 | __author__ = "Francisco Amato" | |
| 24 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 25 | __credits__ = ["Francisco Amato"] | |
| 26 | __license__ = "" | |
| 27 | __version__ = "1.0.0" | |
| 28 | __maintainer__ = "Francisco Amato" | |
| 29 | __email__ = "[email protected]" | |
| 30 | __status__ = "Development" | |
| 31 | ||
| 32 | ||
| 33 | class DnsenumXmlParser: | |
| 34 | """ | |
| 35 | The objective of this class is to parse an xml file generated by the dnsenum tool. | |
| 36 | ||
| 37 | TODO: Handle errors. | |
| 38 | TODO: Test dnsenum output version. Handle what happens if the parser doesn't support it. | |
| 39 | TODO: Test cases. | |
| 40 | ||
| 41 | @param dnsenum_xml_filepath A proper xml generated by dnsenum | |
| 42 | """ | |
| 43 | ||
| 44 | def __init__(self, xml_output): | |
| 45 | tree = self.parse_xml(xml_output) | |
| 46 | ||
| 47 | if tree: | |
| 48 | self.items = list(self.get_items(tree)) | |
| 49 | else: | |
| 50 | self.items = [] | |
| 51 | ||
| 52 | def parse_xml(self, xml_output): | |
| 53 | """ | |
| 54 | Open and parse an xml file. | |
| 55 | ||
| 56 | TODO: Write custom parser to just read the nodes that we need instead of | |
| 57 | reading the whole file. | |
| 58 | ||
| 59 | @return xml_tree An xml tree instance. None if error. | |
| 60 | """ | |
| 61 | try: | |
| 62 | tree = ET.fromstring(xml_output) | |
| 63 | except SyntaxError as err: | |
| 64 | print("SyntaxError: %s. %s" % (err, xml_output)) | |
| 65 | return None | |
| 66 | ||
| 67 | return tree | |
| 68 | ||
| 69 | def get_items(self, tree): | |
| 70 | """ | |
| 71 | @return items A list of Host instances | |
| 72 | """ | |
| 73 | bugtype = '' | |
| 74 | ||
| 75 | node = tree.findall('testdata')[0] | |
| 76 | for hostnode in node.findall('host'): | |
| 77 | yield Item(hostnode) | |
| 78 | ||
| 79 | ||
| 80 | def get_attrib_from_subnode(xml_node, subnode_xpath_expr, attrib_name): | |
| 81 | """ | |
| 82 | Finds a subnode in the item node and the retrieves a value from it | |
| 83 | ||
| 84 | @return An attribute value | |
| 85 | """ | |
| 86 | global ETREE_VERSION | |
| 87 | node = None | |
| 88 | ||
| 89 | if ETREE_VERSION[0] <= 1 and ETREE_VERSION[1] < 3: | |
| 90 | ||
| 91 | match_obj = re.search( | |
| 92 | "([^\@]+?)\[\@([^=]*?)=\'([^\']*?)\'", subnode_xpath_expr) | |
| 93 | if match_obj is not None: | |
| 94 | node_to_find = match_obj.group(1) | |
| 95 | xpath_attrib = match_obj.group(2) | |
| 96 | xpath_value = match_obj.group(3) | |
| 97 | for node_found in xml_node.findall(node_to_find): | |
| 98 | if node_found.attrib[xpath_attrib] == xpath_value: | |
| 99 | node = node_found | |
| 100 | break | |
| 101 | else: | |
| 102 | node = xml_node.find(subnode_xpath_expr) | |
| 103 | ||
| 104 | else: | |
| 105 | node = xml_node.find(subnode_xpath_expr) | |
| 106 | ||
| 107 | if node is not None: | |
| 108 | return node.get(attrib_name) | |
| 109 | ||
| 110 | return None | |
| 111 | ||
| 112 | ||
| 113 | class Item: | |
| 114 | """ | |
| 115 | An abstract representation of a Item | |
| 116 | ||
| 117 | TODO: Consider evaluating the attributes lazily | |
| 118 | TODO: Write what's expected to be present in the nodes | |
| 119 | TODO: Refactor both Host and the Port clases? | |
| 120 | ||
| 121 | @param item_node A item_node taken from an dnsenum xml tree | |
| 122 | """ | |
| 123 | ||
| 124 | def __init__(self, item_node): | |
| 125 | self.node = item_node | |
| 126 | ||
| 127 | self.hostname = self.get_text_from_subnode('hostname') | |
| 128 | self.ip = self.node.text | |
| 129 | ||
| 130 | def do_clean(self, value): | |
| 131 | myreturn = "" | |
| 132 | if value is not None: | |
| 133 | myreturn = re.sub("\n", "", value) | |
| 134 | return myreturn | |
| 135 | ||
| 136 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 137 | """ | |
| 138 | Finds a subnode in the host node and the retrieves a value from it. | |
| 139 | ||
| 140 | @return An attribute value | |
| 141 | """ | |
| 142 | sub_node = self.node.find(subnode_xpath_expr) | |
| 143 | if sub_node is not None: | |
| 144 | return sub_node.text | |
| 145 | ||
| 146 | return None | |
| 147 | ||
| 148 | ||
| 149 | class DnsenumPlugin(core.PluginBase): | |
| 150 | """ | |
| 151 | Example plugin to parse dnsenum output. | |
| 152 | """ | |
| 153 | ||
| 154 | def __init__(self): | |
| 155 | super().__init__() | |
| 156 | self.id = "Dnsenum" | |
| 157 | self.name = "Dnsenum XML Output Plugin" | |
| 158 | self.plugin_version = "0.0.1" | |
| 159 | self.version = "1.2.2" | |
| 160 | self.options = None | |
| 161 | self._current_output = None | |
| 162 | self._command_regex = re.compile( | |
| 163 | r'^(sudo dnsenum|dnsenum|sudo dnsenum\.pl|dnsenum\.pl|perl dnsenum\.pl|\.\/dnsenum\.pl).*?') | |
| 164 | ||
| 165 | global current_path | |
| 166 | ||
| 167 | self._output_file_path = os.path.join( | |
| 168 | self.data_path, | |
| 169 | "dnsenum_output-%s.xml" % self._rid) | |
| 170 | ||
| 171 | def parseOutputString(self, output, debug=False): | |
| 172 | """ | |
| 173 | This method will discard the output the shell sends, it will read it from | |
| 174 | the xml where it expects it to be present. | |
| 175 | ||
| 176 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 177 | output being sent is valid. | |
| 178 | """ | |
| 179 | ||
| 180 | parser = DnsenumXmlParser(output) | |
| 181 | ||
| 182 | for item in parser.items: | |
| 183 | h_id = self.createAndAddHost(item.ip) | |
| 184 | i_id = self.createAndAddInterface( | |
| 185 | h_id, | |
| 186 | item.ip, | |
| 187 | ipv4_address=item.ip, | |
| 188 | hostname_resolution=[item.hostname]) | |
| 189 | ||
| 190 | del parser | |
| 191 | ||
| 192 | xml_arg_re = re.compile(r"^.*(-o\s*[^\s]+).*$") | |
| 193 | ||
| 194 | def processCommandString(self, username, current_path, command_string): | |
| 195 | """ | |
| 196 | Adds the -oX parameter to get xml output to the command string that the | |
| 197 | user has set. | |
| 198 | """ | |
| 199 | ||
| 200 | arg_match = self.xml_arg_re.match(command_string) | |
| 201 | ||
| 202 | if arg_match is None: | |
| 203 | return re.sub( | |
| 204 | r"(^.*?dnsenum(\.pl)?)", | |
| 205 | r"\1 -o %s" % self._output_file_path, | |
| 206 | command_string) | |
| 207 | else: | |
| 208 | return re.sub(arg_match.group(1), | |
| 209 | r"-o %s" % self._output_file_path, | |
| 210 | command_string) | |
| 211 | ||
| 212 | def setHost(self): | |
| 213 | pass | |
| 214 | ||
| 215 | ||
| 216 | def createPlugin(): | |
| 217 | return DnsenumPlugin() | |
| 218 | ||
| 219 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """from __future__ import print_function | |
| 1 | ||
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | import re | |
| 8 | import os | |
| 9 | import sys | |
| 10 | import random | |
| 11 | from collections import defaultdict | |
| 12 | ||
| 13 | current_path = os.path.abspath(os.getcwd()) | |
| 14 | ||
| 15 | __author__ = "Francisco Amato" | |
| 16 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 17 | __credits__ = ["Francisco Amato"] | |
| 18 | __license__ = "" | |
| 19 | __version__ = "1.0.0" | |
| 20 | __maintainer__ = "Francisco Amato" | |
| 21 | __email__ = "[email protected]" | |
| 22 | __status__ = "Development" | |
| 23 | ||
| 24 | ||
| 25 | class DnsmapParser: | |
| 26 | """ | |
| 27 | The objective of this class is to parse an xml file generated by the | |
| 28 | dnsmap tool. | |
| 29 | ||
| 30 | TODO: Handle errors. | |
| 31 | TODO: Test dnsmap output version. Handle what happens if the parser | |
| 32 | doesn't support it. | |
| 33 | TODO: Test cases. | |
| 34 | ||
| 35 | @param dnsmap_filepath A proper simple report generated by dnsmap | |
| 36 | """ | |
| 37 | ||
| 38 | def __init__(self, output): | |
| 39 | self.items = defaultdict(list) | |
| 40 | if "\n\n" in output: | |
| 41 | self.parse_txt(output) | |
| 42 | else: | |
| 43 | self.parse_csv(output) | |
| 44 | ||
| 45 | def parse_txt(self, output): | |
| 46 | hosts = self.split_output_lines(output) | |
| 47 | ||
| 48 | for host_data in hosts: | |
| 49 | if len(host_data) == 2: | |
| 50 | ip = self.clean_ip(host_data[1]) | |
| 51 | hostname = host_data[0] | |
| 52 | self.add_host_info_to_items(ip, hostname) | |
| 53 | elif len(host_data) > 2: | |
| 54 | hostname = host_data.pop(0) | |
| 55 | for ip_address in host_data: | |
| 56 | ip = self.clean_ip(ip_address) | |
| 57 | self.add_host_info_to_items(ip, hostname) | |
| 58 | ||
| 59 | def parse_csv(self, output): | |
| 60 | hosts = list(filter(None, output.splitlines())) | |
| 61 | ||
| 62 | for host in hosts: | |
| 63 | host_data = host.split(",", 1) | |
| 64 | if host_data[1].count(',') == 0: | |
| 65 | ip = host_data[1] | |
| 66 | hostname = host_data[0] | |
| 67 | self.add_host_info_to_items(ip, hostname) | |
| 68 | else: | |
| 69 | hostname = host_data.pop(0) | |
| 70 | ips = host_data[0].split(",") | |
| 71 | for ip_address in ips: | |
| 72 | self.add_host_info_to_items(ip_address, hostname) | |
| 73 | ||
| 74 | def split_output_lines(self, output): | |
| 75 | splitted = output.splitlines() | |
| 76 | hosts_list = [] | |
| 77 | aux_list = [] | |
| 78 | for i in range(0, len(splitted)): | |
| 79 | if not splitted[i]: | |
| 80 | hosts_list.append(aux_list) | |
| 81 | aux_list = [] | |
| 82 | else: | |
| 83 | aux_list.append(splitted[i]) | |
| 84 | return hosts_list | |
| 85 | ||
| 86 | def clean_ip(self, item): | |
| 87 | ip = item.split(':', 1) | |
| 88 | return ip[1].strip() | |
| 89 | ||
| 90 | def add_host_info_to_items(self, ip_address, hostname): | |
| 91 | self.items[ip_address].append(hostname) | |
| 92 | ||
| 93 | ||
| 94 | class DnsmapPlugin(core.PluginBase): | |
| 95 | """Example plugin to parse dnsmap output.""" | |
| 96 | ||
| 97 | def __init__(self): | |
| 98 | super().__init__() | |
| 99 | self.id = "Dnsmap" | |
| 100 | self.name = "Dnsmap Output Plugin" | |
| 101 | self.plugin_version = "0.3" | |
| 102 | self.version = "0.30" | |
| 103 | self.options = None | |
| 104 | self._current_output = None | |
| 105 | self.current_path = None | |
| 106 | self._command_regex = re.compile(r'^(sudo dnsmap|dnsmap|\.\/dnsmap).*?') | |
| 107 | self.xml_arg_re = re.compile(r"^.*(-r\s*[^\s]+).*$") | |
| 108 | ||
| 109 | global current_path | |
| 110 | ||
| 111 | self._output_file_path = os.path.join( | |
| 112 | self.data_path, | |
| 113 | "%s_%s_output-%s.txt" % ( | |
| 114 | self.get_ws(), | |
| 115 | self.id, | |
| 116 | random.uniform(1, 10) | |
| 117 | ) | |
| 118 | ) | |
| 119 | ||
| 120 | def canParseCommandString(self, current_input): | |
| 121 | if self._command_regex.match(current_input.strip()): | |
| 122 | return True | |
| 123 | else: | |
| 124 | return False | |
| 125 | ||
| 126 | def parseOutputString(self, output, debug=False): | |
| 127 | """ | |
| 128 | This method will discard the output the shell sends, it will read it | |
| 129 | from the xml where it expects it to be present. | |
| 130 | """ | |
| 131 | parser = DnsmapParser(output) | |
| 132 | for ip_address, hostnames in parser.items.items(): | |
| 133 | h_id = self.createAndAddHost(ip_address, hostnames=hostnames) | |
| 134 | return True | |
| 135 | ||
| 136 | def processCommandString(self, username, current_path, command_string): | |
| 137 | """ | |
| 138 | Adds the parameter to get output to the command string that the | |
| 139 | user has set. | |
| 140 | """ | |
| 141 | arg_match = self.xml_arg_re.match(command_string) | |
| 142 | ||
| 143 | if arg_match is None: | |
| 144 | return "%s -r %s \\n" % (command_string, self._output_file_path) | |
| 145 | else: | |
| 146 | return re.sub(arg_match.group(1), | |
| 147 | r"-r %s" % self._output_file_path, | |
| 148 | command_string) | |
| 149 | ||
| 150 | ||
| 151 | def createPlugin(): | |
| 152 | return DnsmapPlugin() | |
| 153 | ||
| 154 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | """ | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | """ | |
| 8 | from faraday.client.plugins import core | |
| 9 | from faraday.client.model import api | |
| 10 | import re | |
| 11 | import os | |
| 12 | import sys | |
| 13 | ||
| 14 | try: | |
| 15 | import xml.etree.cElementTree as ET | |
| 16 | import xml.etree.ElementTree as ET_ORIG | |
| 17 | ETREE_VERSION = ET_ORIG.VERSION | |
| 18 | except ImportError: | |
| 19 | import xml.etree.ElementTree as ET | |
| 20 | ETREE_VERSION = ET.VERSION | |
| 21 | ||
| 22 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 23 | ||
| 24 | current_path = os.path.abspath(os.getcwd()) | |
| 25 | ||
| 26 | __author__ = "Francisco Amato" | |
| 27 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 28 | __credits__ = ["Francisco Amato"] | |
| 29 | __license__ = "" | |
| 30 | __version__ = "1.0.0" | |
| 31 | __maintainer__ = "Francisco Amato" | |
| 32 | __email__ = "[email protected]" | |
| 33 | __status__ = "Development" | |
| 34 | ||
| 35 | ||
| 36 | class DnsreconXmlParser: | |
| 37 | """ | |
| 38 | The objective of this class is to parse an xml file generated by the dnsrecon tool. | |
| 39 | ||
| 40 | TODO: Handle errors. | |
| 41 | TODO: Test dnsrecon output version. Handle what happens if the parser doesn't support it. | |
| 42 | TODO: Test cases. | |
| 43 | ||
| 44 | @param dnsrecon_xml_filepath A proper xml generated by dnsrecon | |
| 45 | """ | |
| 46 | ||
| 47 | def __init__(self, xml_output): | |
| 48 | ||
| 49 | tree = self.parse_xml(xml_output) | |
| 50 | ||
| 51 | if tree: | |
| 52 | self.hosts = list(self.get_hosts(tree)) | |
| 53 | else: | |
| 54 | self.hosts = [] | |
| 55 | ||
| 56 | def parse_xml(self, xml_output): | |
| 57 | """ | |
| 58 | Open and parse an xml file. | |
| 59 | ||
| 60 | TODO: Write custom parser to just read the nodes that we need instead of | |
| 61 | reading the whole file. | |
| 62 | ||
| 63 | @return xml_tree An xml tree instance. None if error. | |
| 64 | """ | |
| 65 | try: | |
| 66 | tree = ET.fromstring(xml_output) | |
| 67 | except SyntaxError as err: | |
| 68 | print("SyntaxError: %s. %s" % (err, xml_output)) | |
| 69 | return None | |
| 70 | ||
| 71 | return tree | |
| 72 | ||
| 73 | def get_hosts(self, tree): | |
| 74 | """ | |
| 75 | @return items A list of Host instances | |
| 76 | """ | |
| 77 | for item_node in tree.findall('record'): | |
| 78 | yield Item(item_node) | |
| 79 | ||
| 80 | ||
| 81 | def get_attrib_from_subnode(xml_node, subnode_xpath_expr, attrib_name): | |
| 82 | """ | |
| 83 | Finds a subnode in the item node and the retrieves a value from it | |
| 84 | ||
| 85 | @return An attribute value | |
| 86 | """ | |
| 87 | global ETREE_VERSION | |
| 88 | node = None | |
| 89 | ||
| 90 | if ETREE_VERSION[0] <= 1 and ETREE_VERSION[1] < 3: | |
| 91 | ||
| 92 | match_obj = re.search( | |
| 93 | "([^\@]+?)\[\@([^=]*?)=\'([^\']*?)\'", subnode_xpath_expr) | |
| 94 | if match_obj is not None: | |
| 95 | ||
| 96 | node_to_find = match_obj.group(1) | |
| 97 | xpath_attrib = match_obj.group(2) | |
| 98 | xpath_value = match_obj.group(3) | |
| 99 | for node_found in xml_node.findall(node_to_find): | |
| 100 | if node_found.attrib[xpath_attrib] == xpath_value: | |
| 101 | node = node_found | |
| 102 | break | |
| 103 | else: | |
| 104 | node = xml_node.find(subnode_xpath_expr) | |
| 105 | ||
| 106 | else: | |
| 107 | node = xml_node.find(subnode_xpath_expr) | |
| 108 | ||
| 109 | if node is not None: | |
| 110 | return node.get(attrib_name) | |
| 111 | ||
| 112 | return None | |
| 113 | ||
| 114 | ||
| 115 | class Item: | |
| 116 | """ | |
| 117 | An abstract representation of a Item | |
| 118 | ||
| 119 | TODO: Consider evaluating the attributes lazily | |
| 120 | TODO: Write what's expected to be present in the nodes | |
| 121 | TODO: Refactor both Host and the Port clases? | |
| 122 | ||
| 123 | @param item_node A item_node taken from an dnsrecon xml tree | |
| 124 | """ | |
| 125 | ||
| 126 | def __init__(self, item_node): | |
| 127 | self.node = item_node | |
| 128 | ||
| 129 | self.type = self.do_clean(self.node.get('type')) | |
| 130 | self.zonetransfer = self.do_clean(self.node.get('zone_transfer')) | |
| 131 | self.ns_server = self.do_clean(self.node.get('ns_server')) | |
| 132 | self.address = self.do_clean(self.node.get( | |
| 133 | 'address')) if not self.type == "info" else self.ns_server | |
| 134 | ||
| 135 | self.target = self.do_clean(self.node.get('target')) | |
| 136 | self.name = self.do_clean(self.node.get('name')) | |
| 137 | self.exchange = self.do_clean(self.node.get('exchange')) | |
| 138 | ||
| 139 | print("GENERATION:" + self.type, self.address, self.zonetransfer) | |
| 140 | ||
| 141 | def do_clean(self, value): | |
| 142 | myreturn = '' | |
| 143 | if value is not None: | |
| 144 | myreturn = re.sub(" |\n", "", value) | |
| 145 | return myreturn | |
| 146 | ||
| 147 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 148 | """ | |
| 149 | Finds a subnode in the host node and the retrieves a value from it. | |
| 150 | ||
| 151 | @return An attribute value | |
| 152 | """ | |
| 153 | sub_node = self.node.find(subnode_xpath_expr) | |
| 154 | if sub_node is not None: | |
| 155 | return sub_node.text | |
| 156 | ||
| 157 | return None | |
| 158 | ||
| 159 | ||
| 160 | class DnsreconPlugin(core.PluginBase): | |
| 161 | """ | |
| 162 | Example plugin to parse dnsrecon output. | |
| 163 | """ | |
| 164 | ||
| 165 | def __init__(self): | |
| 166 | super().__init__() | |
| 167 | self.id = "Dnsrecon" | |
| 168 | self.name = "Dnsrecon XML Output Plugin" | |
| 169 | self.plugin_version = "0.0.2" | |
| 170 | self.version = "0.8.7" | |
| 171 | self.framework_version = "1.0.0" | |
| 172 | self.options = None | |
| 173 | self._current_output = None | |
| 174 | self._command_regex = re.compile( | |
| 175 | r'^(sudo dnsrecon|dnsrecon|sudo dnsrecon\.py|dnsrecon\.py|python dnsrecon\.py|\.\/dnsrecon\.py).*?') | |
| 176 | ||
| 177 | global current_path | |
| 178 | self._output_file_path = os.path.join( | |
| 179 | self.data_path, | |
| 180 | "dnsrecon_output-%s.xml" % self._rid) | |
| 181 | ||
| 182 | def validHosts(self, hosts): | |
| 183 | valid_records = ["NS", "CNAME", "A", "MX", "info"] | |
| 184 | hosts = list(filter(lambda h: h.type in valid_records, hosts)) | |
| 185 | return hosts | |
| 186 | ||
| 187 | def parseOutputString(self, output, debug=False): | |
| 188 | """ | |
| 189 | This method will discard the output the shell sends, it will read it from | |
| 190 | the xml where it expects it to be present. | |
| 191 | ||
| 192 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 193 | output being sent is valid. | |
| 194 | """ | |
| 195 | ||
| 196 | parser = DnsreconXmlParser(output) | |
| 197 | ||
| 198 | for host in self.validHosts(parser.hosts): | |
| 199 | ||
| 200 | print(host.type, host.name, host.zonetransfer) | |
| 201 | hostname = host.target | |
| 202 | if host.type == "MX": | |
| 203 | hostname = host.exchange | |
| 204 | elif host.type == "A": | |
| 205 | hostname = host.name | |
| 206 | ||
| 207 | h_id = self.createAndAddHost(host.address) | |
| 208 | ||
| 209 | if self._isIPV4(str(host.address)): | |
| 210 | i_id = self.createAndAddInterface( | |
| 211 | h_id, | |
| 212 | name=host.address, | |
| 213 | ipv4_address=host.address, | |
| 214 | hostname_resolution=[hostname]) | |
| 215 | else: | |
| 216 | i_id = self.createAndAddInterface( | |
| 217 | h_id, | |
| 218 | name=host.address, | |
| 219 | ipv6_address=host.address, | |
| 220 | hostname_resolution=[hostname]) | |
| 221 | ||
| 222 | if host.type == "info": | |
| 223 | ||
| 224 | s_id = self.createAndAddServiceToInterface( | |
| 225 | h_id, | |
| 226 | i_id, | |
| 227 | "domain", | |
| 228 | protocol="tcp", | |
| 229 | ports=["53"], | |
| 230 | status="open") | |
| 231 | ||
| 232 | if host.zonetransfer == "success": | |
| 233 | v_id = self.createAndAddVulnToService( | |
| 234 | h_id, | |
| 235 | s_id, | |
| 236 | name="Zone transfer", | |
| 237 | desc="A Dns server allows unrestricted zone transfers", | |
| 238 | ref=["CVE-1999-0532"]) | |
| 239 | ||
| 240 | del parser | |
| 241 | ||
| 242 | def _isIPV4(self, ip): | |
| 243 | if len(ip.split(".")) == 4: | |
| 244 | return True | |
| 245 | else: | |
| 246 | return False | |
| 247 | ||
| 248 | xml_arg_re = re.compile(r"^.*(--xml\s*[^\s]+).*$") | |
| 249 | ||
| 250 | def processCommandString(self, username, current_path, command_string): | |
| 251 | """ | |
| 252 | Adds the -oX parameter to get xml output to the command string that the | |
| 253 | user has set. | |
| 254 | """ | |
| 255 | arg_match = self.xml_arg_re.match(command_string) | |
| 256 | ||
| 257 | if arg_match is None: | |
| 258 | return re.sub(r"(^.*?dnsrecon(\.py)?)", | |
| 259 | r"\1 --xml %s" % self._output_file_path, | |
| 260 | command_string) | |
| 261 | else: | |
| 262 | return re.sub(arg_match.group(1), | |
| 263 | r"--xml %s" % self._output_file_path, | |
| 264 | command_string) | |
| 265 | ||
| 266 | def setHost(self): | |
| 267 | pass | |
| 268 | ||
| 269 | ||
| 270 | def createPlugin(): | |
| 271 | return DnsreconPlugin() | |
| 272 | ||
| 273 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | ||
| 7 | from faraday.client.plugins import core | |
| 8 | import re | |
| 9 | import os | |
| 10 | import socket | |
| 11 | ||
| 12 | current_path = os.path.abspath(os.getcwd()) | |
| 13 | ||
| 14 | __author__ = "Francisco Amato" | |
| 15 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 16 | __credits__ = ["Francisco Amato"] | |
| 17 | __license__ = "" | |
| 18 | __version__ = "1.0.0" | |
| 19 | __maintainer__ = "Francisco Amato" | |
| 20 | __email__ = "[email protected]" | |
| 21 | __status__ = "Development" | |
| 22 | ||
| 23 | ||
| 24 | class DnswalkParser: | |
| 25 | """ | |
| 26 | The objective of this class is to parse an xml file generated | |
| 27 | by the dnswalk tool. | |
| 28 | ||
| 29 | TODO: Handle errors. | |
| 30 | TODO: Test dnswalk output version. Handle what happens if the parser | |
| 31 | doesn't support it. | |
| 32 | TODO: Test cases. | |
| 33 | ||
| 34 | @param dnswalk_filepath A proper simple report generated by dnswalk | |
| 35 | """ | |
| 36 | ||
| 37 | def __init__(self, output): | |
| 38 | ||
| 39 | lists = output.split("\n") | |
| 40 | self.items = [] | |
| 41 | ||
| 42 | for line in lists: | |
| 43 | mregex = re.search("WARN: ([\w\.]+) ([\w]+) ([\w\.]+):", line) | |
| 44 | if mregex is not None: | |
| 45 | ||
| 46 | item = { | |
| 47 | 'host': mregex.group(1), | |
| 48 | 'ip': mregex.group(3), | |
| 49 | 'type': mregex.group(2)} | |
| 50 | ||
| 51 | self.items.append(item) | |
| 52 | ||
| 53 | mregex = re.search( | |
| 54 | "Getting zone transfer of ([\w\.]+) from ([\w\.]+)\.\.\.done\.", | |
| 55 | line) | |
| 56 | ||
| 57 | if mregex is not None: | |
| 58 | ip = self.getAddress(mregex.group(2)) | |
| 59 | item = { | |
| 60 | 'host': mregex.group(1), | |
| 61 | 'ip': ip, | |
| 62 | 'type': 'info'} | |
| 63 | self.items.append(item) | |
| 64 | ||
| 65 | def getAddress(self, hostname): | |
| 66 | """Returns remote IP address from hostname.""" | |
| 67 | try: | |
| 68 | return socket.gethostbyname(hostname) | |
| 69 | except socket.error: | |
| 70 | return hostname | |
| 71 | ||
| 72 | ||
| 73 | class DnswalkPlugin(core.PluginBase): | |
| 74 | """ | |
| 75 | Example plugin to parse dnswalk output. | |
| 76 | """ | |
| 77 | ||
| 78 | def __init__(self): | |
| 79 | super().__init__() | |
| 80 | self.id = "Dnswalk" | |
| 81 | self.name = "Dnswalk XML Output Plugin" | |
| 82 | self.plugin_version = "0.0.1" | |
| 83 | self.version = "2.0.2" | |
| 84 | self.options = None | |
| 85 | self._current_output = None | |
| 86 | self._current_path = None | |
| 87 | self._command_regex = re.compile( | |
| 88 | r'^(sudo dnswalk|dnswalk|\.\/dnswalk).*?') | |
| 89 | ||
| 90 | global current_path | |
| 91 | ||
| 92 | def canParseCommandString(self, current_input): | |
| 93 | if self._command_regex.match(current_input.strip()): | |
| 94 | return True | |
| 95 | else: | |
| 96 | return False | |
| 97 | ||
| 98 | def parseOutputString(self, output, debug=False): | |
| 99 | """ | |
| 100 | output is the shell output of command Dnswalk. | |
| 101 | """ | |
| 102 | parser = DnswalkParser(output) | |
| 103 | ||
| 104 | for item in parser.items: | |
| 105 | ||
| 106 | if item['type'] == "A": | |
| 107 | ||
| 108 | h_id = self.createAndAddHost(item['ip']) | |
| 109 | i_id = self.createAndAddInterface( | |
| 110 | h_id, | |
| 111 | item['ip'], | |
| 112 | ipv4_address=item['ip'], | |
| 113 | hostname_resolution=[item['host']]) | |
| 114 | ||
| 115 | elif item['type'] == "info": | |
| 116 | ||
| 117 | h_id = self.createAndAddHost(item['ip']) | |
| 118 | ||
| 119 | i_id = self.createAndAddInterface( | |
| 120 | h_id, | |
| 121 | item['ip'], | |
| 122 | ipv4_address=item['ip'], | |
| 123 | hostname_resolution=[item['host']]) | |
| 124 | ||
| 125 | s_id = self.createAndAddServiceToInterface( | |
| 126 | h_id, | |
| 127 | i_id, | |
| 128 | "domain", | |
| 129 | "tcp", | |
| 130 | ports=['53']) | |
| 131 | ||
| 132 | self.createAndAddVulnToService( | |
| 133 | h_id, | |
| 134 | s_id, | |
| 135 | "Zone transfer", | |
| 136 | desc="A Dns server allows unrestricted zone transfers", | |
| 137 | ref=["CVE-1999-0532"]) | |
| 138 | ||
| 139 | return True | |
| 140 | ||
| 141 | def processCommandString(self, username, current_path, command_string): | |
| 142 | return None | |
| 143 | ||
| 144 | ||
| 145 | def createPlugin(): | |
| 146 | return DnswalkPlugin() | |
| 147 | ||
| 148 | ||
| 149 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | import socket | |
| 8 | import re | |
| 9 | import os | |
| 10 | import sys | |
| 11 | import random | |
| 12 | ||
| 13 | current_path = os.path.abspath(os.getcwd()) | |
| 14 | ||
| 15 | __author__ = "Francisco Amato" | |
| 16 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 17 | __credits__ = ["Francisco Amato"] | |
| 18 | __license__ = "" | |
| 19 | __version__ = "1.0.0" | |
| 20 | __maintainer__ = "Francisco Amato" | |
| 21 | __email__ = "[email protected]" | |
| 22 | __status__ = "Development" | |
| 23 | ||
| 24 | valid_records = ["NS", "CNAME", "A"] | |
| 25 | ||
| 26 | ||
| 27 | class FierceParser: | |
| 28 | """ | |
| 29 | The objective of this class is to parse an shell output generated by | |
| 30 | the fierce tool. | |
| 31 | ||
| 32 | TODO: Handle errors. | |
| 33 | TODO: Test fierce output version. Handle what happens if the parser | |
| 34 | doesn't support it. | |
| 35 | TODO: Test cases. | |
| 36 | ||
| 37 | @param fierce_filepath A proper simple report generated by fierce | |
| 38 | """ | |
| 39 | ||
| 40 | def __init__(self, output): | |
| 41 | self.target = None | |
| 42 | self.items = [] | |
| 43 | ||
| 44 | regex = re.search( | |
| 45 | "DNS Servers for ([\w\.-]+):\n([^$]+)Trying zone transfer first...", | |
| 46 | output) | |
| 47 | ||
| 48 | if regex is not None: | |
| 49 | self.target = regex.group(1) | |
| 50 | mstr = re.sub("\t", "", regex.group(2)) | |
| 51 | self.dns = list(filter(None, mstr.splitlines())) | |
| 52 | ||
| 53 | regex = re.search( | |
| 54 | "Now performing [\d]+ test\(s\)...\n([^$]+)\nSubnets found ", | |
| 55 | output) | |
| 56 | if regex is not None: | |
| 57 | hosts_list = regex.group(1).splitlines() | |
| 58 | for i in hosts_list: | |
| 59 | if i != "": | |
| 60 | mstr = i.split("\t") | |
| 61 | host = mstr[1] | |
| 62 | record = "A" | |
| 63 | ip = mstr[0] | |
| 64 | self.add_host_info_to_items(ip, host, record) | |
| 65 | ||
| 66 | self.isZoneVuln = False | |
| 67 | output = output.replace('\\$', '') | |
| 68 | regex = re.search( | |
| 69 | "Whoah, it worked - misconfigured DNS server found:([^$]+)\nThere isn't much point continuing, you have everything.", output) | |
| 70 | ||
| 71 | if regex is not None: | |
| 72 | self.isZoneVuln = True | |
| 73 | dns_list = regex.group(1).splitlines() | |
| 74 | for i in dns_list: | |
| 75 | if i != "": | |
| 76 | mstr = i.split() | |
| 77 | if (mstr and mstr[0] != "" and len(mstr) > 3 and mstr[3] in valid_records): | |
| 78 | host = mstr[0] | |
| 79 | record = mstr[3] | |
| 80 | ip = mstr[4] | |
| 81 | self.add_host_info_to_items(ip, host, record) | |
| 82 | ||
| 83 | def add_host_info_to_items(self, ip_address, hostname, record): | |
| 84 | data = {} | |
| 85 | exists = False | |
| 86 | for item in self.items: | |
| 87 | if ip_address in item['ip']: | |
| 88 | item['hosts'].append(hostname) | |
| 89 | exists = True | |
| 90 | ||
| 91 | if not exists: | |
| 92 | data['ip'] = ip_address | |
| 93 | data['hosts'] = [hostname] | |
| 94 | data['record'] = record | |
| 95 | self.items.append(data) | |
| 96 | ||
| 97 | ||
| 98 | class FiercePlugin(core.PluginBase): | |
| 99 | """ | |
| 100 | Example plugin to parse fierce output. | |
| 101 | """ | |
| 102 | ||
| 103 | def __init__(self): | |
| 104 | super().__init__() | |
| 105 | self.id = "Fierce" | |
| 106 | self.name = "Fierce Output Plugin" | |
| 107 | self.plugin_version = "0.0.1" | |
| 108 | self.version = "0.9.9" | |
| 109 | self.options = None | |
| 110 | self._current_output = None | |
| 111 | self._current_path = None | |
| 112 | self._command_regex = re.compile( | |
| 113 | r'^(sudo fierce|fierce|sudo fierce\.pl|fierce\.pl|perl fierce\.pl|\.\/fierce\.pl).*?') | |
| 114 | global current_path | |
| 115 | ||
| 116 | self.xml_arg_re = re.compile(r"^.*(>\s*[^\s]+).*$") | |
| 117 | ||
| 118 | def canParseCommandString(self, current_input): | |
| 119 | if self._command_regex.match(current_input.strip()): | |
| 120 | return True | |
| 121 | else: | |
| 122 | return False | |
| 123 | ||
| 124 | def resolveCNAME(self, item, items): | |
| 125 | for i in items: | |
| 126 | if (item['ip'] in i['hosts']): | |
| 127 | item['ip'] = i['ip'] | |
| 128 | return item | |
| 129 | try: | |
| 130 | item['ip'] = socket.gethostbyname(item['ip']) | |
| 131 | except: | |
| 132 | pass | |
| 133 | return item | |
| 134 | ||
| 135 | def resolveNS(self, item, items): | |
| 136 | try: | |
| 137 | item['hosts'][0] = item['ip'] | |
| 138 | item['ip'] = socket.gethostbyname(item['ip']) | |
| 139 | except: | |
| 140 | pass | |
| 141 | return item | |
| 142 | ||
| 143 | def parseOutputString(self, output, debug=False): | |
| 144 | ||
| 145 | parser = FierceParser(output) | |
| 146 | for item in parser.items: | |
| 147 | ||
| 148 | item['isResolver'] = False | |
| 149 | item['isZoneVuln'] = False | |
| 150 | if (item['record'] == "CNAME"): | |
| 151 | self.resolveCNAME(item, parser.items) | |
| 152 | if (item['record'] == "NS"): | |
| 153 | self.resolveNS(item, parser.items) | |
| 154 | item['isResolver'] = True | |
| 155 | item['isZoneVuln'] = parser.isZoneVuln | |
| 156 | for item2 in parser.items: | |
| 157 | ||
| 158 | if item['ip'] == item2['ip'] and item != item2: | |
| 159 | item2['isResolver'] = item['isResolver'] | |
| 160 | item2['isZoneVuln'] = item['isZoneVuln'] | |
| 161 | item['ip'] = '' | |
| 162 | ||
| 163 | for item in parser.items: | |
| 164 | if item['ip'] == "127.0.0.1" or item['ip'] == '': | |
| 165 | continue | |
| 166 | h_id = self.createAndAddHost( | |
| 167 | item['ip'], | |
| 168 | hostnames=item['hosts']) | |
| 169 | ||
| 170 | if item['isResolver']: | |
| 171 | s_id = self.createAndAddServiceToHost( | |
| 172 | h_id, | |
| 173 | "domain", | |
| 174 | "tcp", | |
| 175 | ports=['53']) | |
| 176 | ||
| 177 | if item['isZoneVuln']: | |
| 178 | self.createAndAddVulnToService( | |
| 179 | h_id, | |
| 180 | s_id, | |
| 181 | "Zone transfer", | |
| 182 | desc="A Dns server allows unrestricted zone transfers", | |
| 183 | ref=["CVE-1999-0532"]) | |
| 184 | ||
| 185 | def processCommandString(self, username, current_path, command_string): | |
| 186 | self._output_file_path = os.path.join( | |
| 187 | self.data_path, | |
| 188 | "%s_%s_output-%s.txt" % ( | |
| 189 | self.get_ws(), | |
| 190 | self.id, | |
| 191 | random.uniform(1, 10)) | |
| 192 | ) | |
| 193 | ||
| 194 | arg_match = self.xml_arg_re.match(command_string) | |
| 195 | ||
| 196 | if arg_match is None: | |
| 197 | return "%s > %s" % (command_string, self._output_file_path) | |
| 198 | else: | |
| 199 | return re.sub(arg_match.group(1), | |
| 200 | r"> %s" % self._output_file_path, | |
| 201 | command_string) | |
| 202 | ||
| 203 | ||
| 204 | def createPlugin(): | |
| 205 | return FiercePlugin() | |
| 206 | ||
| 207 | ||
| 208 | # I'm Py3 |
| 0 | import base64 | |
| 1 | import io | |
| 2 | import re | |
| 3 | from html.parser import HTMLParser | |
| 4 | from zipfile import ZipFile | |
| 5 | ||
| 6 | import html2text | |
| 7 | from lxml import objectify | |
| 8 | from faraday.client.plugins import core | |
| 9 | ||
| 10 | ||
| 11 | class FortifyPlugin(core.PluginBase): | |
| 12 | """ | |
| 13 | Example plugin to parse nmap output. | |
| 14 | """ | |
| 15 | ||
| 16 | def __init__(self): | |
| 17 | core.PluginBase.__init__(self) | |
| 18 | self.id = "Fortify" | |
| 19 | self.name = "Fortify XML Output Plugin" | |
| 20 | self.plugin_version = "0.0.1" | |
| 21 | ||
| 22 | def _process_fvdl_vulns(self, fp): | |
| 23 | ||
| 24 | for host in fp.hosts.keys(): | |
| 25 | fp.hosts[host] = self.createAndAddHost(host) | |
| 26 | ||
| 27 | for vuln in fp.vulns.keys(): | |
| 28 | self.createAndAddVulnToHost( | |
| 29 | host_id=fp.hosts[fp.vulns[vuln]['host']], | |
| 30 | name=fp.vulns[vuln]['name'], | |
| 31 | desc=fp.format_description(vuln), | |
| 32 | ref=fp.descriptions[fp.vulns[vuln]['class']]['references'], | |
| 33 | severity=fp.vulns[vuln]['severity'], | |
| 34 | resolution="", | |
| 35 | data="", | |
| 36 | external_id=vuln.text | |
| 37 | ) | |
| 38 | ||
| 39 | def _process_webinspect_vulns(self, fp): | |
| 40 | for vuln_data in fp.sast_vulns: | |
| 41 | host_id = self.createAndAddHost( | |
| 42 | vuln_data['host'] or vuln_data['website']) | |
| 43 | ||
| 44 | service_name = vuln_data['service'].get('name', 'unknown') | |
| 45 | protocol_name = 'line number' | |
| 46 | if vuln_data['service']['port'] == '443': | |
| 47 | service_name = 'https' | |
| 48 | protocol_name = 'tcp' | |
| 49 | if vuln_data['service']['port'] == '80': | |
| 50 | service_name = 'http' | |
| 51 | protocol_name = 'tcp' | |
| 52 | ||
| 53 | service_id = self.createAndAddServiceToHost( | |
| 54 | host_id, | |
| 55 | service_name, | |
| 56 | protocol=protocol_name, | |
| 57 | ports=[vuln_data['service']['port']]) | |
| 58 | ||
| 59 | self.createAndAddVulnWebToService( | |
| 60 | host_id, service_id, | |
| 61 | vuln_data['name'], | |
| 62 | website=vuln_data['website'] or '', | |
| 63 | path=vuln_data['path'] or '', | |
| 64 | query=vuln_data['query'] or '', | |
| 65 | method=vuln_data['method'] or '', | |
| 66 | request=vuln_data['request'] or '', | |
| 67 | ref=vuln_data['references'], | |
| 68 | response=vuln_data['response'] or '', | |
| 69 | desc=vuln_data['description'], | |
| 70 | #resolution=vuln_data[''], | |
| 71 | severity=vuln_data['severity'] | |
| 72 | ) | |
| 73 | ||
| 74 | def parseOutputString(self, output, debug=False): | |
| 75 | fp = FortifyParser(output) | |
| 76 | if fp.fvdl is not None: | |
| 77 | self._process_fvdl_vulns(fp) | |
| 78 | if fp.webinspect is not None: | |
| 79 | self._process_webinspect_vulns(fp) | |
| 80 | ||
| 81 | return True | |
| 82 | ||
| 83 | ||
| 84 | class FortifyParser: | |
| 85 | """ | |
| 86 | Parser for fortify on demand | |
| 87 | """ | |
| 88 | ||
| 89 | def __init__(self, output): | |
| 90 | self.vulns = {} | |
| 91 | self.sast_vulns = [] | |
| 92 | self.hosts = {} | |
| 93 | self.fvdl = None | |
| 94 | self.webinspect = None | |
| 95 | self.audit = None | |
| 96 | self.suppressed = [] | |
| 97 | self.vuln_classes = [] | |
| 98 | self.descriptions = {} | |
| 99 | ||
| 100 | self._uncompress_fpr(output) | |
| 101 | self._extract_vulns() | |
| 102 | self._prepare_description_templates() | |
| 103 | ||
| 104 | # regexes used in format_description | |
| 105 | self.remove_extra_chars = re.compile(r'&(\w*);') | |
| 106 | self.replacements_idx = re.compile(r'<Replace key="(.*?)"[\s\/].*?>') | |
| 107 | self.replacements_holders = re.compile(r'<Replace key=".*?"[\s\/].*?>') | |
| 108 | self.replacements_idx2 = re.compile(r'<Replace key="(.*?)"(\slink="(.*?)")?[\s\/].*?>') | |
| 109 | ||
| 110 | def _uncompress_fpr(self, output): | |
| 111 | with ZipFile(io.BytesIO(output)) as fprcontent: | |
| 112 | try: | |
| 113 | self.fvdl = objectify.fromstring(fprcontent.read('audit.fvdl')) | |
| 114 | except KeyError: | |
| 115 | pass | |
| 116 | try: | |
| 117 | self.webinspect = objectify.fromstring(fprcontent.read('webinspect.xml')) | |
| 118 | except KeyError: | |
| 119 | pass | |
| 120 | try: | |
| 121 | self.audit = objectify.fromstring(fprcontent.read('audit.xml')) | |
| 122 | except KeyError: | |
| 123 | pass | |
| 124 | ||
| 125 | def _process_fvdl(self): | |
| 126 | for vuln in self.fvdl.Vulnerabilities.iterchildren(): | |
| 127 | ||
| 128 | vulnID = vuln.InstanceInfo.InstanceID | |
| 129 | ||
| 130 | if vulnID in self.suppressed: | |
| 131 | continue | |
| 132 | ||
| 133 | self.vulns[vulnID] = {} | |
| 134 | ||
| 135 | # the last children of Primary (Entry tags) always contains vuln filename ,path and line | |
| 136 | _last_entry = None | |
| 137 | for _last_entry in vuln.AnalysisInfo.Unified.Trace.Primary.iterchildren(): | |
| 138 | pass | |
| 139 | ||
| 140 | path = _last_entry.Node.SourceLocation.get('path') | |
| 141 | ||
| 142 | self.vulns[vulnID]['host'] = path | |
| 143 | self.vulns[vulnID]['name'] = "{} {}".format(vuln.ClassInfo.Type, | |
| 144 | getattr(vuln.ClassInfo, "Subtype", "")) | |
| 145 | self.vulns[vulnID]['class'] = vuln.ClassInfo.ClassID | |
| 146 | self.vulns[vulnID]['replacements'] = {} | |
| 147 | ||
| 148 | self.vulns[vulnID]['severity'] = self.calculate_severity(vuln) | |
| 149 | ||
| 150 | # placeholder for storing hosts ids when created in main plugin method | |
| 151 | if path not in self.hosts: | |
| 152 | self.hosts[path] = None | |
| 153 | ||
| 154 | if vuln.ClassInfo.ClassID not in self.vuln_classes: | |
| 155 | self.vuln_classes.append(vuln.ClassInfo.ClassID) | |
| 156 | ||
| 157 | # fortify bug that when it has no replacements, shows blank in fortify dashboard | |
| 158 | if not hasattr(vuln.AnalysisInfo.Unified, "ReplacementDefinitions"): | |
| 159 | self.vulns[vulnID]['replacements'] = None | |
| 160 | continue | |
| 161 | ||
| 162 | try: | |
| 163 | getattr(vuln.AnalysisInfo.Unified, "ReplacementDefinitions") | |
| 164 | ||
| 165 | for repl in vuln.AnalysisInfo.Unified.ReplacementDefinitions.iterchildren( | |
| 166 | tag="{xmlns://www.fortifysoftware.com/schema/fvdl}Def"): | |
| 167 | ||
| 168 | repl_val = repl.get('key') | |
| 169 | if repl.get('link'): | |
| 170 | repl_val = repl.get('link') | |
| 171 | ||
| 172 | self.vulns[vulnID]['replacements'][repl_val] = repl.get('value') | |
| 173 | except AttributeError: | |
| 174 | self.vulns[vulnID]['replacements'] = None | |
| 175 | ||
| 176 | def _process_webinspect(self): | |
| 177 | for session in self.webinspect.getchildren(): | |
| 178 | hostname = session.Host.text | |
| 179 | port = session.Port.text | |
| 180 | service_data = {} | |
| 181 | if port: | |
| 182 | service_data['port'] = port | |
| 183 | ||
| 184 | path = session.Request.Path.text | |
| 185 | query = session.Request.FullQuery.text | |
| 186 | method = session.Request.Method.text | |
| 187 | request = '' | |
| 188 | if session.RawRequest.text: | |
| 189 | request = base64.b64decode(session.RawRequest.text) | |
| 190 | response = '' | |
| 191 | if session.RawResponse.text: | |
| 192 | response = base64.b64decode(session.RawResponse.text) | |
| 193 | status_code = session.Response.StatusCode.text | |
| 194 | ||
| 195 | for issues in session.Issues: | |
| 196 | for issue_data in issues.getchildren(): | |
| 197 | params = '' | |
| 198 | check_type = issue_data.CheckTypeID | |
| 199 | if check_type.text.lower() != 'vulnerability': | |
| 200 | # TODO: when plugins accept tags, we shoudl this as a tag. | |
| 201 | pass | |
| 202 | name = issue_data.Name.text | |
| 203 | external_id = issue_data.VulnerabilityID.text | |
| 204 | faraday_severities = { | |
| 205 | 0: 'info', | |
| 206 | 1: 'low', | |
| 207 | 2: 'med', | |
| 208 | 3: 'high', | |
| 209 | 4: 'critical' | |
| 210 | } | |
| 211 | severity = faraday_severities[issue_data.Severity] | |
| 212 | references = [] | |
| 213 | try: | |
| 214 | classifications = issue_data.Classifications.getchildren() | |
| 215 | except AttributeError: | |
| 216 | classifications = [] | |
| 217 | ||
| 218 | for classification in classifications: | |
| 219 | references.append(classification.text) | |
| 220 | ||
| 221 | # Build description | |
| 222 | description = u'' | |
| 223 | for report_section in issue_data.findall('./ReportSection'): | |
| 224 | description += u'{} \n'.format(report_section.Name.text) | |
| 225 | description += u'{} \n'.format(report_section.SectionText.text) | |
| 226 | description += u'{} \n'.format(issue_data.get('id')) | |
| 227 | ||
| 228 | h = html2text.HTML2Text() | |
| 229 | description = h.handle(description) | |
| 230 | ||
| 231 | for repro_step in issue_data.findall('./ReproSteps'): | |
| 232 | step = repro_step.ReproStep | |
| 233 | if step is not None: | |
| 234 | try: | |
| 235 | params = step.PostParams.text | |
| 236 | except AttributeError: | |
| 237 | pass | |
| 238 | ||
| 239 | if not hostname: | |
| 240 | # This seems to be a mobile app | |
| 241 | hostname = session.URL.text | |
| 242 | ||
| 243 | if not port: | |
| 244 | service_data['name'] = step.Url.text | |
| 245 | service_data['port'] = step.sourceline | |
| 246 | ||
| 247 | self.sast_vulns.append({ | |
| 248 | "host": hostname, | |
| 249 | "severity": severity, | |
| 250 | "service": service_data, | |
| 251 | "name": name, | |
| 252 | "description": description, | |
| 253 | "external_id": external_id, | |
| 254 | "references": references, | |
| 255 | "method": method, | |
| 256 | "query": query, | |
| 257 | "response": response, | |
| 258 | "request": request, | |
| 259 | "path": path, | |
| 260 | "params": params, | |
| 261 | "status_code": status_code, | |
| 262 | "website": session.URL.text | |
| 263 | }) | |
| 264 | ||
| 265 | def _extract_vulns(self): | |
| 266 | # make list of false positives | |
| 267 | try: | |
| 268 | issue_list = self.audit.IssueList.iterchildren() | |
| 269 | except AttributeError: | |
| 270 | issue_list = [] | |
| 271 | ||
| 272 | for issue in issue_list: | |
| 273 | if issue.get('suppressed', 'false').lower() == 'true': | |
| 274 | self.suppressed.append(issue.get('instanceId')) | |
| 275 | ||
| 276 | if self.fvdl: | |
| 277 | self._process_fvdl() | |
| 278 | ||
| 279 | if self.webinspect is not None: | |
| 280 | self._process_webinspect() | |
| 281 | ||
| 282 | def calculate_severity(self, vuln): | |
| 283 | ||
| 284 | severity = None # ["critical", "high", "medium", "low", "informational", "unclassified"] | |
| 285 | rulepath = objectify.ObjectPath("FVDL.EngineData.RuleInfo.Rule") | |
| 286 | impact = None | |
| 287 | probability = None | |
| 288 | accuracy = None | |
| 289 | ||
| 290 | # XML path /FVDL/EngineData/RuleInfo/Rule (many)/MetaInfo/Group (many) the attribute "name" | |
| 291 | # are keys for vuln properties | |
| 292 | ||
| 293 | for rule in rulepath(self.fvdl): | |
| 294 | if rule.get('id') == vuln.ClassInfo.ClassID: | |
| 295 | for group in rule.MetaInfo.iterchildren(): | |
| 296 | if group.get('name') == "Probability": | |
| 297 | probability = group | |
| 298 | if group.get('name') == "Impact": | |
| 299 | impact = group | |
| 300 | if group.get('name') == "Accuracy": | |
| 301 | accuracy = group | |
| 302 | ||
| 303 | likelihood = (accuracy * vuln.InstanceInfo.Confidence * probability) / 25.0 | |
| 304 | ||
| 305 | if impact and probability: | |
| 306 | ||
| 307 | if impact >= 2.5 and likelihood >= 2.5: | |
| 308 | severity = 'critical' | |
| 309 | elif impact >= 2.5 > likelihood: | |
| 310 | severity = 'high' | |
| 311 | elif impact < 2.5 <= likelihood: | |
| 312 | severity = 'medium' | |
| 313 | elif impact < 2.5 and likelihood < 2.5: | |
| 314 | severity = 'low' | |
| 315 | else: | |
| 316 | print("missing severity") | |
| 317 | ||
| 318 | # print("{}:{}:{}".format(vuln.InstanceInfo.InstanceID, vuln.InstanceInfo.InstanceSeverity, severity)) | |
| 319 | return severity | |
| 320 | ||
| 321 | def concat_vuln_name(self, vuln): | |
| 322 | return "{} {} {}:{}".format(vuln.ClassInfo.Type, vuln.ClassInfo.Subtype, | |
| 323 | self.vulns[vuln.InstanceInfo.InstanceID]['filename'], | |
| 324 | self.vulns[vuln.InstanceInfo.InstanceID]['line']) | |
| 325 | ||
| 326 | def _prepare_description_templates(self): | |
| 327 | if not self.fvdl: | |
| 328 | return | |
| 329 | for description in self.fvdl.Description: | |
| 330 | ||
| 331 | self.descriptions[description.get("classID")] = {} | |
| 332 | ||
| 333 | if description.get('classID') not in self.vuln_classes: | |
| 334 | continue | |
| 335 | ||
| 336 | tips = "" | |
| 337 | if hasattr(description, 'Tips'): | |
| 338 | for tip in description.Tips.getchildren(): | |
| 339 | tips += "\n" + tip.text | |
| 340 | ||
| 341 | htmlparser = HTMLParser() | |
| 342 | self.descriptions[description.get("classID")]['text'] = htmlparser.unescape( | |
| 343 | "Summary:\n{}\n\nExplanation:\n{}\n\nRecommendations:\n{}\n\nTips:{}".format( | |
| 344 | description.Abstract, description.Explanation, description.Recommendations, tips)) | |
| 345 | ||
| 346 | # group vuln references | |
| 347 | references = [] | |
| 348 | try: | |
| 349 | children = description.References.getchildren() | |
| 350 | except AttributeError: | |
| 351 | children = [] | |
| 352 | ||
| 353 | for reference in children: | |
| 354 | ||
| 355 | for attr in dir(reference): | |
| 356 | if attr == '__class__': | |
| 357 | break | |
| 358 | ||
| 359 | references.append("{}: {}\n".format(attr, getattr(reference, attr))) | |
| 360 | ||
| 361 | self.descriptions[description.get("classID")]['references'] = references | |
| 362 | ||
| 363 | def format_description(self, vulnID): | |
| 364 | ||
| 365 | text = self.descriptions[self.vulns[vulnID]['class']]['text'] | |
| 366 | replacements = self.vulns[vulnID]['replacements'] | |
| 367 | if not replacements: | |
| 368 | return text | |
| 369 | ||
| 370 | # special chars that must shown as-is, have the hmtlentity value duplicated | |
| 371 | text = self.remove_extra_chars.sub(r"&\1;", text) | |
| 372 | ||
| 373 | for placeholder in self.replacements_holders.findall(text, re.MULTILINE): | |
| 374 | ||
| 375 | torepl = '<Replace key="{}"/>' | |
| 376 | match = self.replacements_idx2.search(placeholder) | |
| 377 | ||
| 378 | replace_with = "" | |
| 379 | if match: | |
| 380 | idx = match.group(1) | |
| 381 | if match.group(3): | |
| 382 | idx = match.group(3) | |
| 383 | _filekey = "{}.file".format(idx) | |
| 384 | _linekey = "{}.line".format(idx) | |
| 385 | text = text.replace(placeholder, "").replace( | |
| 386 | torepl.format(_filekey), replacements[_filekey]).replace( | |
| 387 | torepl.format(_linekey), replacements[_linekey]) | |
| 388 | continue | |
| 389 | ||
| 390 | try: | |
| 391 | replace_with = replacements[idx] | |
| 392 | except KeyError: | |
| 393 | # Nothing to replace, use empty string | |
| 394 | text = text.replace(placeholder, "") | |
| 395 | ||
| 396 | text = text.replace(placeholder, replace_with) | |
| 397 | ||
| 398 | text += '{}\n Instance ID: {} \n'.format(text, vulnID) | |
| 399 | h = html2text.HTML2Text() | |
| 400 | description = h.handle(text) | |
| 401 | return text | |
| 402 | ||
| 403 | ||
| 404 | def createPlugin(): | |
| 405 | return FortifyPlugin() | |
| 406 | ||
| 407 | ||
| 408 | if __name__ == '__main__': | |
| 409 | ||
| 410 | with open('/Users/lcubo/workspace/faraday/tests/data/fortify/webgoatnetSAST.fpr', 'r') as f: | |
| 411 | fp = FortifyParser(f.read()) | |
| 412 | for vulnID in fp.vulns.keys(): | |
| 413 | print("{}{}{}".format("="*50, vulnID, "="*50)) | |
| 414 | print(fp.vulns[vulnID]['replacements']) | |
| 415 | print("{}{}{}".format("="*50, vulnID, "="*50)) | |
| 416 | print(fp.format_description(vulnID)) | |
| 417 | print("{}|{}|{}".format(vulnID, fp.vulns[vulnID].get('name'), fp.vulns[vulnID].get('severity'))) |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | #!/usr/bin/python | |
| 1 | """ | |
| 2 | Copyright (C) 2016 xtr4nge [_AT_] gmail.com | |
| 3 | ||
| 4 | This program is free software: you can redistribute it and/or modify | |
| 5 | it under the terms of the GNU General Public License as published by | |
| 6 | the Free Software Foundation, either version 3 of the License, or | |
| 7 | (at your option) any later version. | |
| 8 | ||
| 9 | This program is distributed in the hope that it will be useful, | |
| 10 | but WITHOUT ANY WARRANTY; without even the implied warranty of | |
| 11 | MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the | |
| 12 | GNU General Public License for more details. | |
| 13 | ||
| 14 | You should have received a copy of the GNU General Public License | |
| 15 | along with this program. If not, see <http://www.gnu.org/licenses/>. | |
| 16 | """ | |
| 17 | from __future__ import absolute_import | |
| 18 | from __future__ import print_function | |
| 19 | ||
| 20 | import sys, getopt | |
| 21 | import json | |
| 22 | import requests | |
| 23 | ||
| 24 | requests.packages.urllib3.disable_warnings() # DISABLE SSL CHECK WARNINGS | |
| 25 | ||
| 26 | gVersion = "1.0" | |
| 27 | server = "http://127.0.0.1:8000"; | |
| 28 | token = "e5dab9a69988dd65e578041416773149ea57a054" | |
| 29 | ||
| 30 | ||
| 31 | def usage(): | |
| 32 | print("\nFruityWiFi API " + gVersion + " by @xtr4nge") | |
| 33 | ||
| 34 | print("Usage: ./client <options>\n") | |
| 35 | print("Options:") | |
| 36 | print("-x <command>, --execute=<commnd> exec the command passed as parameter.") | |
| 37 | print("-t <token>, --token=<token> authentication token.") | |
| 38 | print("-s <server>, --server=<server> FruityWiFi server [http{s}://ip:port].") | |
| 39 | print("-h Print this help message.") | |
| 40 | print("") | |
| 41 | print("FruityWiFi: http://www.fruitywifi.com") | |
| 42 | print("") | |
| 43 | ||
| 44 | ||
| 45 | def parseOptions(argv): | |
| 46 | ||
| 47 | v_execute = "/log/dhcp" | |
| 48 | v_token = token | |
| 49 | v_server = server | |
| 50 | ||
| 51 | try: | |
| 52 | opts, args = getopt.getopt(argv, "hx:t:s:", | |
| 53 | ["help","execute=","token=","server="]) | |
| 54 | ||
| 55 | for opt, arg in opts: | |
| 56 | if opt in ("-h", "--help"): | |
| 57 | usage() | |
| 58 | sys.exit() | |
| 59 | elif opt in ("-x", "--execute"): | |
| 60 | v_execute = arg | |
| 61 | elif opt in ("-t", "--token"): | |
| 62 | v_token = arg | |
| 63 | elif opt in ("-s", "--server"): | |
| 64 | v_server = arg | |
| 65 | ||
| 66 | return (v_execute, v_token, v_server) | |
| 67 | ||
| 68 | except getopt.GetoptError: | |
| 69 | usage() | |
| 70 | sys.exit(2) | |
| 71 | ||
| 72 | (execute, token, server) = parseOptions(sys.argv[1:]) | |
| 73 | ||
| 74 | ||
| 75 | class webclient: | |
| 76 | ||
| 77 | def __init__(self, server, token): | |
| 78 | ||
| 79 | self.global_webserver = server | |
| 80 | self.path = "/modules/api/includes/ws_action.php" | |
| 81 | self.s = requests.session() | |
| 82 | self.token = token | |
| 83 | ||
| 84 | def login(self): | |
| 85 | ||
| 86 | payload = { | |
| 87 | 'action': 'login', | |
| 88 | 'token': self.token | |
| 89 | } | |
| 90 | ||
| 91 | self.s = requests.session() | |
| 92 | self.s.get(self.global_webserver, verify=False) # DISABLE SSL CHECK | |
| 93 | self.s.post(self.global_webserver + '/login.php', data=payload) | |
| 94 | ||
| 95 | def loginCheck(self): | |
| 96 | ||
| 97 | response = self.s.get(self.global_webserver + '/login_check.php') | |
| 98 | ||
| 99 | if response.text != "": | |
| 100 | self.login() | |
| 101 | ||
| 102 | if response.text != "": | |
| 103 | print(json.dumps("[FruityWiFi]: Ah, Ah, Ah! You didn't say the magic word! (check API token and server)")) | |
| 104 | sys.exit() | |
| 105 | ||
| 106 | return True | |
| 107 | ||
| 108 | def submitPost(self, data): | |
| 109 | response = self.s.post(self.global_webserver + data) | |
| 110 | return response.json | |
| 111 | ||
| 112 | def submitGet(self, data): | |
| 113 | response = self.s.get(self.global_webserver + self.path + "?" + data) | |
| 114 | ||
| 115 | return response | |
| 116 | ||
| 117 | try: | |
| 118 | w = webclient(server, token) | |
| 119 | w.login() | |
| 120 | w.loginCheck() | |
| 121 | except Exception as e: | |
| 122 | print(json.dumps("[FruityWiFi]: There is something wrong (%s)" % e)) | |
| 123 | sys.exit(1) | |
| 124 | ||
| 125 | _exec = "/log/dhcp" | |
| 126 | _exec = execute | |
| 127 | if _exec != "": | |
| 128 | try: | |
| 129 | out = w.submitGet("api=" + str(_exec)) | |
| 130 | json_output = out.json() | |
| 131 | except Exception as e: | |
| 132 | print(json.dumps("[FruityWiFi]: There is something wrong (%s)" % e)) | |
| 133 | sys.exit(1) | |
| 134 | ||
| 135 | output = [] | |
| 136 | if _exec == "/log/dhcp": | |
| 137 | for item in json_output: | |
| 138 | if item.strip() != "": | |
| 139 | output = [item.split(" ")] | |
| 140 | else: | |
| 141 | output = json_output | |
| 142 | ||
| 143 | if len(output) > 0: | |
| 144 | print(json.dumps(output)) | |
| 145 | else: | |
| 146 | print(json.dumps("No clients connected")) | |
| 147 | ||
| 148 | ||
| 149 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | import re | |
| 8 | import os, json | |
| 9 | import traceback | |
| 10 | ||
| 11 | __author__ = "xtr4nge" | |
| 12 | __copyright__ = "Copyright (c) 2016, FruityWiFi" | |
| 13 | __credits__ = ["xtr4nge"] | |
| 14 | __license__ = "" | |
| 15 | __version__ = "1.0.0" | |
| 16 | __maintainer__ = "xtr4nge" | |
| 17 | __email__ = "@xtr4nge" | |
| 18 | __status__ = "Development" | |
| 19 | ||
| 20 | class FruityWiFiPlugin(core.PluginBase): | |
| 21 | """ | |
| 22 | This plugin handles FruityWiFi clients. | |
| 23 | """ | |
| 24 | ||
| 25 | def __init__(self): | |
| 26 | super().__init__() | |
| 27 | self.id = "fruitywifi" | |
| 28 | self.name = "FruityWiFi" | |
| 29 | self.plugin_version = "0.0.1" | |
| 30 | self.version = "2.4" | |
| 31 | self.description = "http://www.fruitywifi.com" | |
| 32 | self.options = None | |
| 33 | self._current_output = None | |
| 34 | self.target = None | |
| 35 | ||
| 36 | self._command_regex = re.compile( | |
| 37 | r'^(fruitywifi).*?') | |
| 38 | ||
| 39 | self.addSetting("Token", str, "e5dab9a69988dd65e578041416773149ea57a054") | |
| 40 | self.addSetting("Server", str, "http://127.0.0.1:8000") | |
| 41 | self.addSetting("Severity", str, "high") | |
| 42 | ||
| 43 | def getSeverity(self, severity): | |
| 44 | if severity.lower() == "critical" or severity == "4": | |
| 45 | return 4 | |
| 46 | elif severity.lower() == "high" or severity == "3": | |
| 47 | return 3 | |
| 48 | elif severity.lower() == "med" or severity == "2": | |
| 49 | return 2 | |
| 50 | elif severity.lower() == "low" or severity == "1": | |
| 51 | return 1 | |
| 52 | elif severity.lower() == "info" or severity == "0": | |
| 53 | return 0 | |
| 54 | else: | |
| 55 | return 5 | |
| 56 | ||
| 57 | def createHostInterfaceVuln(self, ip_address, macaddress, hostname, desc, vuln_name, severity): | |
| 58 | h_id = self.createAndAddHost(ip_address) | |
| 59 | if self._isIPV4(ip_address): | |
| 60 | i_id = self.createAndAddInterface( | |
| 61 | h_id, | |
| 62 | ip_address, | |
| 63 | macaddress, | |
| 64 | ipv4_address=ip_address, | |
| 65 | hostname_resolution=[hostname] | |
| 66 | ) | |
| 67 | else: | |
| 68 | self.createAndAddInterface( | |
| 69 | h_id, ip_address, ipv6_address=ip_address, hostname_resolution=[hostname]) | |
| 70 | ||
| 71 | v_id = self.createAndAddVulnToHost( | |
| 72 | h_id, | |
| 73 | vuln_name, | |
| 74 | desc=desc, | |
| 75 | ref=["http://www.fruitywifi.com/"], | |
| 76 | severity=severity | |
| 77 | ) | |
| 78 | ||
| 79 | def parseOutputString(self, output, debug=False): | |
| 80 | ||
| 81 | try: | |
| 82 | output = json.loads(output) | |
| 83 | ||
| 84 | if len(output) > 0: | |
| 85 | ||
| 86 | if len(output[0]) == 3: | |
| 87 | ||
| 88 | severity = self.getSeverity(self.getSetting("Severity")) | |
| 89 | ||
| 90 | for item in output: | |
| 91 | ip_address = item[0] | |
| 92 | macaddress = item[1] | |
| 93 | hostname = item[2] | |
| 94 | vuln_name = "FruityWiFi" | |
| 95 | ||
| 96 | desc = "Client ip: " + ip_address + \ | |
| 97 | " has been connected to FruityWiFi\n" | |
| 98 | desc += "More information:" | |
| 99 | desc += "\nname: " + hostname | |
| 100 | ||
| 101 | self.createHostInterfaceVuln(ip_address, macaddress, hostname, desc, vuln_name, severity) | |
| 102 | ||
| 103 | elif len(output[0]) == 5: | |
| 104 | for item in output: | |
| 105 | ip_address = item[0] | |
| 106 | macaddress = item[1] | |
| 107 | hostname = item[2] | |
| 108 | vuln_name = item[3] | |
| 109 | severity = item[4] | |
| 110 | ||
| 111 | desc = "Client ip: " + ip_address + \ | |
| 112 | " has been connected to FruityWiFi\n" | |
| 113 | desc += "More information:" | |
| 114 | desc += "\nname: " + hostname | |
| 115 | ||
| 116 | self.createHostInterfaceVuln(ip_address, macaddress, hostname, desc, vuln_name, severity) | |
| 117 | ||
| 118 | except: | |
| 119 | traceback.print_exc() | |
| 120 | ||
| 121 | return True | |
| 122 | ||
| 123 | def _isIPV4(self, ip): | |
| 124 | if len(ip.split(".")) == 4: | |
| 125 | return True | |
| 126 | else: | |
| 127 | return False | |
| 128 | ||
| 129 | def processCommandString(self, username, current_path, command_string, debug=False): | |
| 130 | """ | |
| 131 | """ | |
| 132 | #params = command_string.replace("fruitywifi","") | |
| 133 | params = "-t %s -s %s" % (self.getSetting("Token"), self.getSetting("Server")) | |
| 134 | ||
| 135 | return "python " + os.path.dirname(__file__) + "/fruitywifi.py " + params | |
| 136 | #return None | |
| 137 | ||
| 138 | def createPlugin(): | |
| 139 | return FruityWiFiPlugin() | |
| 140 | ||
| 141 | ||
| 142 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | from faraday.client.model import api | |
| 8 | import re | |
| 9 | import os | |
| 10 | import socket | |
| 11 | ||
| 12 | current_path = os.path.abspath(os.getcwd()) | |
| 13 | ||
| 14 | __author__ = "Javier Victor Mariano Bruno" | |
| 15 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 16 | __credits__ = ["Javier Victor Mariano Bruno"] | |
| 17 | __license__ = "" | |
| 18 | __version__ = "1.0.0" | |
| 19 | __maintainer__ = "Javier Victor Mariano Bruno" | |
| 20 | __email__ = "[email protected]" | |
| 21 | __status__ = "Development" | |
| 22 | ||
| 23 | ||
| 24 | class CmdFtpPlugin(core.PluginBase): | |
| 25 | """ | |
| 26 | This plugin handles ftp command. | |
| 27 | Basically detects if user was able to connect to a device | |
| 28 | """ | |
| 29 | ||
| 30 | def __init__(self): | |
| 31 | super().__init__() | |
| 32 | self.id = "ftp" | |
| 33 | self.name = "Ftp" | |
| 34 | self.plugin_version = "0.0.1" | |
| 35 | self.version = "0.17" | |
| 36 | self.framework_version = "1.0.0" | |
| 37 | self.options = None | |
| 38 | self._current_output = None | |
| 39 | self._command_regex = re.compile(r'^ftp.*?') | |
| 40 | self._host_ip = None | |
| 41 | self._port = "21" | |
| 42 | self._info = 0 | |
| 43 | self._version = None | |
| 44 | ||
| 45 | global current_path | |
| 46 | ||
| 47 | def resolve(self, host): | |
| 48 | try: | |
| 49 | return socket.gethostbyname(host) | |
| 50 | except: | |
| 51 | pass | |
| 52 | return host | |
| 53 | ||
| 54 | def parseOutputString(self, output, debug=False): | |
| 55 | ||
| 56 | host_info = re.search(r"Connected to (.+)\.", output) | |
| 57 | banner = re.search("220?([\w\W]+)$", output) | |
| 58 | if re.search("Connection timed out", output) is None and host_info is not None: | |
| 59 | hostname = host_info.group(1) | |
| 60 | ip_address = self.resolve(hostname) | |
| 61 | self._version = banner.groups(0) if banner else "" | |
| 62 | if debug: | |
| 63 | print(ip_address) | |
| 64 | ||
| 65 | h_id = self.createAndAddHost(ip_address) | |
| 66 | ||
| 67 | i_id = self.createAndAddInterface( | |
| 68 | h_id, | |
| 69 | ip_address, | |
| 70 | ipv4_address=ip_address, | |
| 71 | hostname_resolution=[hostname]) | |
| 72 | ||
| 73 | s_id = self.createAndAddServiceToInterface( | |
| 74 | h_id, | |
| 75 | i_id, | |
| 76 | "ftp", | |
| 77 | "tcp", | |
| 78 | ports=[self._port], | |
| 79 | status="open") | |
| 80 | ||
| 81 | if debug is True: | |
| 82 | api.devlog("Debug is active") | |
| 83 | ||
| 84 | return True | |
| 85 | ||
| 86 | def processCommandString(self, username, current_path, command_string): | |
| 87 | """ | |
| 88 | """ | |
| 89 | count_args = command_string.split() | |
| 90 | ||
| 91 | c = count_args.__len__() | |
| 92 | self._port = "21" | |
| 93 | if re.search("[\d]+", count_args[c - 1]): | |
| 94 | self._port = count_args[c - 1] | |
| 95 | ||
| 96 | ||
| 97 | def createPlugin(): | |
| 98 | return CmdFtpPlugin() | |
| 99 | ||
| 100 | ||
| 101 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import core | |
| 6 | import socket | |
| 7 | import re | |
| 8 | import os | |
| 9 | ||
| 10 | current_path = os.path.abspath(os.getcwd()) | |
| 11 | ||
| 12 | __author__ = "Francisco Amato" | |
| 13 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 14 | __credits__ = ["Francisco Amato"] | |
| 15 | __license__ = "" | |
| 16 | __version__ = "1.0.0" | |
| 17 | __maintainer__ = "Francisco Amato" | |
| 18 | __email__ = "[email protected]" | |
| 19 | __status__ = "Development" | |
| 20 | ||
| 21 | ||
| 22 | class GoohostParser: | |
| 23 | """ | |
| 24 | The objective of this class is to parse an xml file generated by the goohost tool. | |
| 25 | ||
| 26 | TODO: Handle errors. | |
| 27 | TODO: Test goohost output version. Handle what happens if the parser doesn't support it. | |
| 28 | TODO: Test cases. | |
| 29 | ||
| 30 | @param goohost_scantype You could select scan type ip, mail or host | |
| 31 | """ | |
| 32 | ||
| 33 | def __init__(self, output, goohost_scantype): | |
| 34 | ||
| 35 | self.items = [] | |
| 36 | lines = list(filter(None, output.split('\n'))) | |
| 37 | for line in lines: | |
| 38 | if goohost_scantype == 'ip': | |
| 39 | data = line.split() | |
| 40 | item = {'host': data[0], 'ip': data[1]} | |
| 41 | self.add_host_info_to_items(item['ip'], item['host']) | |
| 42 | elif goohost_scantype == 'host': | |
| 43 | data = line.strip() | |
| 44 | item = {'host': data, 'ip': self.resolve(data)} | |
| 45 | self.add_host_info_to_items(item['ip'], item['host']) | |
| 46 | else: | |
| 47 | item = {'data': line} | |
| 48 | ||
| 49 | def resolve(self, host): | |
| 50 | try: | |
| 51 | return socket.gethostbyname(host) | |
| 52 | except: | |
| 53 | pass | |
| 54 | return host | |
| 55 | ||
| 56 | def add_host_info_to_items(self, ip_address, hostname): | |
| 57 | data = {} | |
| 58 | exists = False | |
| 59 | for item in self.items: | |
| 60 | if ip_address in item['ip']: | |
| 61 | item['hosts'].append(hostname) | |
| 62 | exists = True | |
| 63 | ||
| 64 | if not exists: | |
| 65 | data['ip'] = ip_address | |
| 66 | data['hosts'] = [hostname] | |
| 67 | self.items.append(data) | |
| 68 | ||
| 69 | ||
| 70 | class GoohostPlugin(core.PluginBase): | |
| 71 | """ | |
| 72 | Example plugin to parse goohost output. | |
| 73 | """ | |
| 74 | ||
| 75 | def __init__(self): | |
| 76 | super().__init__() | |
| 77 | self.id = "Goohost" | |
| 78 | self.name = "Goohost XML Output Plugin" | |
| 79 | self.plugin_version = "0.0.1" | |
| 80 | self.version = "v.0.0.1" | |
| 81 | self.options = None | |
| 82 | self._current_output = None | |
| 83 | self._current_path = None | |
| 84 | self._command_regex = re.compile( | |
| 85 | r'^(sudo goohost\.sh|goohost\.sh|sh goohost\.sh|\.\/goohost\.sh).*?') | |
| 86 | self.host = None | |
| 87 | ||
| 88 | global current_path | |
| 89 | self.output_path = None | |
| 90 | self._command_string = None | |
| 91 | ||
| 92 | def parseOutputString(self, output, debug=False): | |
| 93 | """ | |
| 94 | This method will check if the import was made through the console or by importing a Goohost report. | |
| 95 | ||
| 96 | Import from Console:The method will take the path of the report generated by Goohost from the output the shell sends and will read | |
| 97 | the information from the txt where it expects it to be present. | |
| 98 | ||
| 99 | Import from Report: The method receives the output of the txt report as parameter. | |
| 100 | ||
| 101 | self.scantype defines the method used to generate the Goohost report | |
| 102 | ||
| 103 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 104 | output being sent is valid. | |
| 105 | """ | |
| 106 | ||
| 107 | if self._command_string: | |
| 108 | # Import from console | |
| 109 | self.scantype = self.define_scantype_by_command(self._command_string) | |
| 110 | report_output = output | |
| 111 | output = self.read_output_file(report_output) | |
| 112 | else: | |
| 113 | # Import from report | |
| 114 | self.scantype = self.define_scantype_by_output(output) | |
| 115 | ||
| 116 | if debug: | |
| 117 | parser = GoohostParser(output, self.scantype) | |
| 118 | else: | |
| 119 | parser = GoohostParser(output, self.scantype) | |
| 120 | if self.scantype == 'host' or self.scantype == 'ip': | |
| 121 | for item in parser.items: | |
| 122 | h_id = self.createAndAddHost( | |
| 123 | item['ip'], | |
| 124 | hostnames=item['hosts']) | |
| 125 | ||
| 126 | del parser | |
| 127 | ||
| 128 | def processCommandString(self, username, current_path, command_string): | |
| 129 | """ | |
| 130 | Set output path for parser... | |
| 131 | """ | |
| 132 | self._current_path = current_path | |
| 133 | self._command_string = command_string | |
| 134 | ||
| 135 | def define_scantype_by_command(self, command): | |
| 136 | method_regex = re.compile(r'-m (mail|host|ip)') | |
| 137 | method = method_regex.search(command) | |
| 138 | if method: | |
| 139 | return method.group(1) | |
| 140 | ||
| 141 | return 'host' | |
| 142 | ||
| 143 | def define_scantype_by_output(self, output): | |
| 144 | lines = output.split('\n') | |
| 145 | line = lines[0].split(' ') | |
| 146 | ||
| 147 | if len(line) == 1: | |
| 148 | return 'host' | |
| 149 | elif len(line) == 2: | |
| 150 | return 'ip' | |
| 151 | ||
| 152 | def read_output_file(self, report_path): | |
| 153 | mypath = re.search("Results saved in file (\S+)", report_path) | |
| 154 | if not mypath: | |
| 155 | return False | |
| 156 | else: | |
| 157 | self.output_path = self._current_path + "/" + mypath.group(1) | |
| 158 | if not os.path.exists(self.output_path): | |
| 159 | return False | |
| 160 | with open(self.output_path, 'r') as report: | |
| 161 | output = report.read() | |
| 162 | ||
| 163 | return output | |
| 164 | ||
| 165 | ||
| 166 | def createPlugin(): | |
| 167 | return GoohostPlugin() | |
| 168 | ||
| 169 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2017 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import core | |
| 6 | import re | |
| 7 | ||
| 8 | __author__ = "Roberto Focke" | |
| 9 | __copyright__ = "Copyright (c) 2017, Infobyte LLC" | |
| 10 | __license__ = "" | |
| 11 | __version__ = "1.0.0" | |
| 12 | ||
| 13 | ||
| 14 | class hping3 (core.PluginBase): | |
| 15 | ||
| 16 | def __init__(self): | |
| 17 | super().__init__() | |
| 18 | self.id = "Hping3" | |
| 19 | self.name = "hping3" | |
| 20 | self.plugin_version = "0.0.1" | |
| 21 | self.version = "1.0.0" | |
| 22 | self.srv = {'21': ' ftp', '80': 'http', '143': 'imap', '1433': 'mssql', | |
| 23 | '3306': 'mysql', '524': 'ncp', '119': 'nntp', | |
| 24 | '5631': 'pcanywhere', '110': 'pop3', '5432': 'postgres', | |
| 25 | '512': 'rexec', '513': 'rlogin', '514': 'rsh', | |
| 26 | '25': 'smtp', '161': 'snmp', '22': 'ssh', '3690': 'svn', | |
| 27 | '23': 'telnet', '5900': 'vnc'} | |
| 28 | ||
| 29 | self._command_regex = re.compile(r'^(sudo hping3|hping3)\s+.*$') | |
| 30 | ||
| 31 | def parseOutputString(self, output, debug=False): | |
| 32 | ||
| 33 | regex_ipv4 = re.search(r"(([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\.){3}([0-9]|[1-9][0-9]|1[0-9]{2}|2[0-4][0-9]|25[0-5])\)\:", output) | |
| 34 | if regex_ipv4: | |
| 35 | ip_address = regex_ipv4.group(0).rstrip("):") # Regex pls | |
| 36 | else: | |
| 37 | # Exit plugin, ip address not found. bad output | |
| 38 | self.log("Abort plugin: Ip address not found", "INFO") | |
| 39 | return | |
| 40 | ||
| 41 | hostname = output.split(" ")[1] | |
| 42 | host_id = self.createAndAddHost(hostname) | |
| 43 | ||
| 44 | i_id = self.createAndAddInterface( | |
| 45 | host_id, ip_address, ipv4_address=ip_address, hostname_resolution=[hostname]) | |
| 46 | ||
| 47 | if re.match("HPING", output): | |
| 48 | ||
| 49 | sport = re.search(r"sport=(\d{1,6})", output) | |
| 50 | ssport = [sport.group(1)] | |
| 51 | reci = re.search(r"flags=(\w{2,3})", output) | |
| 52 | service = self.srv[sport.group(1)] | |
| 53 | ||
| 54 | if reci.group(1) == "SA": | |
| 55 | s_id = self.createAndAddServiceToInterface( | |
| 56 | host_id, i_id, service, protocol="tcp", ports=ssport, status="open") | |
| 57 | ||
| 58 | lineas = output.split("\n") | |
| 59 | ||
| 60 | for linea in lineas: | |
| 61 | if (re.match(" ", linea)): | |
| 62 | ||
| 63 | list = re.findall("\w+", linea) | |
| 64 | service = list[1] | |
| 65 | port = [list[0]] | |
| 66 | ||
| 67 | if list[2] == "S" and list[3] == "A": | |
| 68 | s_id = self.createAndAddServiceToInterface( | |
| 69 | host_id, i_id, service, protocol="tcp", ports=port, status="open") | |
| 70 | ||
| 71 | def processCommandString(self, username, current_path, command_string): | |
| 72 | return None | |
| 73 | ||
| 74 | ||
| 75 | def createPlugin(): | |
| 76 | return hping3() | |
| 77 | ||
| 78 | ||
| 79 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import core | |
| 6 | from faraday.client.model import api | |
| 7 | import re | |
| 8 | import os | |
| 9 | import sys | |
| 10 | import random | |
| 11 | ||
| 12 | current_path = os.path.abspath(os.getcwd()) | |
| 13 | ||
| 14 | __author__ = "Francisco Amato" | |
| 15 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 16 | __credits__ = ["Francisco Amato"] | |
| 17 | __license__ = "" | |
| 18 | __version__ = "1.0.0" | |
| 19 | __maintainer__ = "Francisco Amato" | |
| 20 | __email__ = "[email protected]" | |
| 21 | __status__ = "Development" | |
| 22 | ||
| 23 | ||
| 24 | class HydraParser: | |
| 25 | """ | |
| 26 | The objective of this class is to parse an xml file generated by the hydra tool. | |
| 27 | ||
| 28 | @param hydra_filepath A proper simple report generated by hydra | |
| 29 | """ | |
| 30 | ||
| 31 | def __init__(self, xml_output): | |
| 32 | lines = xml_output.splitlines() | |
| 33 | self.items = [] | |
| 34 | for l in lines: | |
| 35 | ||
| 36 | reg = re.search( | |
| 37 | "\[([^$]+)\]\[([^$]+)\] host: ([^$]+) login: ([^$]+) password: ([^$]+)", | |
| 38 | l) | |
| 39 | ||
| 40 | if reg: | |
| 41 | ||
| 42 | item = { | |
| 43 | 'port': reg.group(1), | |
| 44 | 'plugin': reg.group(2), | |
| 45 | 'ip': reg.group(3), | |
| 46 | 'login': reg.group(4), | |
| 47 | 'password': reg.group(5)} | |
| 48 | ||
| 49 | self.items.append(item) | |
| 50 | ||
| 51 | ||
| 52 | class HydraPlugin(core.PluginBase): | |
| 53 | """ | |
| 54 | Example plugin to parse hydra output. | |
| 55 | """ | |
| 56 | ||
| 57 | def __init__(self): | |
| 58 | super().__init__() | |
| 59 | self.id = "Hydra" | |
| 60 | self.name = "Hydra XML Output Plugin" | |
| 61 | self.plugin_version = "0.0.1" | |
| 62 | self.version = "7.5" | |
| 63 | self.options = None | |
| 64 | self._current_output = None | |
| 65 | self._current_path = None | |
| 66 | self._command_regex = re.compile( | |
| 67 | r'^(sudo hydra|sudo \.\/hydra|hydra|\.\/hydra).*?') | |
| 68 | self.host = None | |
| 69 | ||
| 70 | global current_path | |
| 71 | self._output_file_path = os.path.join( | |
| 72 | self.data_path, | |
| 73 | "hydra_output-%s.txt" % self._rid) | |
| 74 | ||
| 75 | def parseOutputString(self, output, debug=False): | |
| 76 | """ | |
| 77 | This method will discard the output the shell sends, it will read it from | |
| 78 | the xml where it expects it to be present. | |
| 79 | ||
| 80 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 81 | output being sent is valid. | |
| 82 | """ | |
| 83 | ||
| 84 | parser = HydraParser(output) | |
| 85 | ||
| 86 | i = 0 | |
| 87 | hosts = {} | |
| 88 | service = '' | |
| 89 | port = '' | |
| 90 | ||
| 91 | for item in parser.items: | |
| 92 | ||
| 93 | service = item['plugin'] | |
| 94 | port = item['port'] | |
| 95 | ||
| 96 | if item['ip'] not in hosts == False: | |
| 97 | hosts[item['ip']] = [] | |
| 98 | ||
| 99 | hosts[item['ip']].append([item['login'], item['password']]) | |
| 100 | ||
| 101 | for k, v in hosts.items(): | |
| 102 | ||
| 103 | h_id = self.createAndAddHost(k) | |
| 104 | ||
| 105 | if self._isIPV4(k): | |
| 106 | ||
| 107 | i_id = self.createAndAddInterface( | |
| 108 | h_id, | |
| 109 | k, | |
| 110 | ipv4_address=k) | |
| 111 | ||
| 112 | else: | |
| 113 | i_id = self.createAndAddInterface( | |
| 114 | h_id, | |
| 115 | k, | |
| 116 | ipv6_address=k) | |
| 117 | ||
| 118 | s_id = self.createAndAddServiceToInterface( | |
| 119 | h_id, | |
| 120 | i_id, | |
| 121 | service, | |
| 122 | ports=[port], | |
| 123 | protocol="tcp", | |
| 124 | status="open") | |
| 125 | ||
| 126 | for cred in v: | |
| 127 | self.createAndAddCredToService( | |
| 128 | h_id, | |
| 129 | s_id, | |
| 130 | cred[0], | |
| 131 | cred[1]) | |
| 132 | ||
| 133 | self.createAndAddVulnToService( | |
| 134 | h_id, | |
| 135 | s_id, | |
| 136 | "Weak Credentials", | |
| 137 | "[hydra found the following credentials]\nuser:%s\npass:%s" % (cred[0], cred[1]), | |
| 138 | severity="high") | |
| 139 | ||
| 140 | del parser | |
| 141 | ||
| 142 | xml_arg_re = re.compile(r"^.*(-o\s*[^\s]+).*$") | |
| 143 | ||
| 144 | def processCommandString(self, username, current_path, command_string): | |
| 145 | ||
| 146 | self._output_file_path = os.path.join( | |
| 147 | self.data_path, | |
| 148 | "hydra_output-%s.txt" % random.uniform(1, 10)) | |
| 149 | ||
| 150 | arg_match = self.xml_arg_re.match(command_string) | |
| 151 | ||
| 152 | if arg_match is None: | |
| 153 | return re.sub(r"(^.*?hydra?)", r"\1 -o %s" % self._output_file_path, command_string) | |
| 154 | else: | |
| 155 | return re.sub( | |
| 156 | arg_match.group(1), | |
| 157 | r"-o %s" % self._output_file_path, | |
| 158 | command_string) | |
| 159 | ||
| 160 | def _isIPV4(self, ip): | |
| 161 | if len(ip.split(".")) == 4: | |
| 162 | return True | |
| 163 | else: | |
| 164 | return False | |
| 165 | ||
| 166 | def setHost(self): | |
| 167 | pass | |
| 168 | ||
| 169 | ||
| 170 | def createPlugin(): | |
| 171 | return HydraPlugin() | |
| 172 | ||
| 173 | ||
| 174 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | import re | |
| 7 | import os | |
| 8 | import sys | |
| 9 | ||
| 10 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 11 | ||
| 12 | ||
| 13 | try: | |
| 14 | import xml.etree.cElementTree as ET | |
| 15 | import xml.etree.ElementTree as ET_ORIG | |
| 16 | ETREE_VERSION = ET_ORIG.VERSION | |
| 17 | except ImportError: | |
| 18 | import xml.etree.ElementTree as ET | |
| 19 | ETREE_VERSION = ET.VERSION | |
| 20 | ||
| 21 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 22 | ||
| 23 | current_path = os.path.abspath(os.getcwd()) | |
| 24 | ||
| 25 | __author__ = "Francisco Amato" | |
| 26 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 27 | __credits__ = ["Francisco Amato"] | |
| 28 | __license__ = "" | |
| 29 | __version__ = "1.0.0" | |
| 30 | __maintainer__ = "Francisco Amato" | |
| 31 | __email__ = "[email protected]" | |
| 32 | __status__ = "Development" | |
| 33 | ||
| 34 | ||
| 35 | class ImpactXmlParser: | |
| 36 | """ | |
| 37 | The objective of this class is to parse an xml file generated by the impact tool. | |
| 38 | ||
| 39 | TODO: Handle errors. | |
| 40 | TODO: Test impact output version. Handle what happens if the parser doesn't support it. | |
| 41 | TODO: Test cases. | |
| 42 | ||
| 43 | @param impact_xml_filepath A proper xml generated by impact | |
| 44 | """ | |
| 45 | ||
| 46 | def __init__(self, xml_output): | |
| 47 | tree = self.parse_xml(xml_output) | |
| 48 | if tree: | |
| 49 | self.items = list(self.get_items(tree)) | |
| 50 | else: | |
| 51 | self.items = [] | |
| 52 | ||
| 53 | def parse_xml(self, xml_output): | |
| 54 | """ | |
| 55 | Open and parse an xml file. | |
| 56 | ||
| 57 | TODO: Write custom parser to just read the nodes that we need instead of | |
| 58 | reading the whole file. | |
| 59 | ||
| 60 | @return xml_tree An xml tree instance. None if error. | |
| 61 | """ | |
| 62 | try: | |
| 63 | tree = ET.fromstring(xml_output) | |
| 64 | except SyntaxError as err: | |
| 65 | #logger.error("SyntaxError: %s. %s" % (err, xml_output)) | |
| 66 | return None | |
| 67 | ||
| 68 | return tree | |
| 69 | ||
| 70 | def get_items(self, tree): | |
| 71 | """ | |
| 72 | @return items A list of Host instances | |
| 73 | """ | |
| 74 | for node in tree.findall("entity/[@class='host']"): | |
| 75 | yield Item(node, tree) | |
| 76 | ||
| 77 | ||
| 78 | class Item: | |
| 79 | """ | |
| 80 | An abstract representation of a Item | |
| 81 | ||
| 82 | ||
| 83 | @param item_node A item_node taken from an impact xml tree | |
| 84 | """ | |
| 85 | ||
| 86 | def __init__(self, item_node, parent=None): | |
| 87 | self.node = item_node | |
| 88 | ||
| 89 | self.arch = self.get_text_from_subnode("property/[@key='arch']") | |
| 90 | ||
| 91 | self.host = self.get_text_from_subnode( | |
| 92 | "property/[@key='display_name']") | |
| 93 | ||
| 94 | self.ip = self.get_text_from_subnode("property/[@key='ip']") | |
| 95 | ||
| 96 | self.os = self.get_text_from_subnode( | |
| 97 | "property/[@key='os']/property/[@key='entity name']") | |
| 98 | ||
| 99 | self.ports = [] | |
| 100 | self.services = [] | |
| 101 | self.process_ports(item_node) | |
| 102 | self.process_services(item_node) | |
| 103 | ||
| 104 | self.agent = False | |
| 105 | ||
| 106 | for node in parent.findall("entity/[@class='agent']"): | |
| 107 | ||
| 108 | self.node = node | |
| 109 | agentip = node.get('name').split("/")[1] | |
| 110 | ||
| 111 | if self.ip == agentip: | |
| 112 | ||
| 113 | self.agentip = agentip | |
| 114 | ||
| 115 | self.ipfrom = self.get_text_from_subnode( | |
| 116 | "property/[@key='Connection Properties']/property/[@key='ip']") or agentip | |
| 117 | ||
| 118 | self.agentype = node.get("type") | |
| 119 | ||
| 120 | self.agentport = self.get_text_from_subnode( | |
| 121 | "property/[@key='Connection Properties']//property/[@key='port']") or "" | |
| 122 | ||
| 123 | self.agentsubtype = self.get_text_from_subnode( | |
| 124 | "property/[@key='Connection Properties']//property/[@key='subtype']") or "" | |
| 125 | ||
| 126 | self.agentcon = self.get_text_from_subnode( | |
| 127 | "property/[@key='Connection Properties']//property/[@key='type']") or "" | |
| 128 | ||
| 129 | self.agent = True | |
| 130 | break | |
| 131 | ||
| 132 | self.results = self.getResults(item_node) | |
| 133 | ||
| 134 | def process_ports(self, item_node): | |
| 135 | for p in item_node.findall("property/[@key='tcp_ports']/property/[@type='port']"): | |
| 136 | self.ports.append({'port': p.get('key'), | |
| 137 | 'protocol': "tcp", | |
| 138 | 'status': "open" if p.text == "listen" else p.text}) | |
| 139 | ||
| 140 | for p in item_node.findall("property/[@key='udp_ports']/property/[@type='port']"): | |
| 141 | self.ports.append({'port': p.get('key'), | |
| 142 | 'protocol': "udp", | |
| 143 | 'status': "open" if p.text == "listen" else p.text}) | |
| 144 | ||
| 145 | def process_services(self, item_node): | |
| 146 | for service in item_node.findall("property/[@key='services']/property"): | |
| 147 | service_name = service.get("key") | |
| 148 | port, protocol = service.findall('property')[0].get('key').split('-') | |
| 149 | self.services.append({ | |
| 150 | "name": service_name, | |
| 151 | "protocol": protocol, | |
| 152 | "port": port | |
| 153 | }) | |
| 154 | ||
| 155 | def getResults(self, tree): | |
| 156 | """ | |
| 157 | :param tree: | |
| 158 | """ | |
| 159 | for self.issues in tree.findall("property/[@key='Vulnerabilities']/property/[@type='container']"): | |
| 160 | yield Results(self.issues) | |
| 161 | # 2017R1 compatibility | |
| 162 | for self.issues in tree.findall("property/[@key='exposures']/property/[@type='container']"): | |
| 163 | yield Results(self.issues) | |
| 164 | ||
| 165 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 166 | """ | |
| 167 | Finds a subnode in the host node and the retrieves a value from it. | |
| 168 | ||
| 169 | @return An attribute value | |
| 170 | """ | |
| 171 | sub_node = self.node.find(subnode_xpath_expr) | |
| 172 | if sub_node is not None: | |
| 173 | return sub_node.text | |
| 174 | ||
| 175 | return None | |
| 176 | ||
| 177 | ||
| 178 | class Results(): | |
| 179 | ||
| 180 | def __init__(self, issue_node): | |
| 181 | self.node = issue_node | |
| 182 | self.ref = [issue_node.get("key")] | |
| 183 | self.severity = "" | |
| 184 | self.port = "Unknown" | |
| 185 | self.service_name = "n/a" | |
| 186 | self.protocol = "tcp?" | |
| 187 | vuln = issue_node.find("property/property") | |
| 188 | if not vuln: | |
| 189 | # 2017R1 compatibility | |
| 190 | self.ref = [] | |
| 191 | vuln = issue_node.find("property") | |
| 192 | self.name = self.get_text_from_subnode("property/[@key='title']") | |
| 193 | self.desc = self.get_text_from_subnode("property/[@key='description']") | |
| 194 | self.severity = self.get_text_from_subnode("property/[@key='severity']") | |
| 195 | self.service_name = self.get_text_from_subnode("property/[@key='service']") | |
| 196 | else: | |
| 197 | # 2013R3 xml version | |
| 198 | self.name = vuln.get("key") | |
| 199 | self.node = vuln | |
| 200 | self.desc = self.get_text_from_subnode("property/[@key='description']") | |
| 201 | self.port = self.get_text_from_subnode("property/[@key='port']") | |
| 202 | ||
| 203 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 204 | """ | |
| 205 | Finds a subnode in the host node and the retrieves a value from it. | |
| 206 | ||
| 207 | @return An attribute value | |
| 208 | """ | |
| 209 | sub_node = self.node.find(subnode_xpath_expr) | |
| 210 | if sub_node is not None: | |
| 211 | return sub_node.text | |
| 212 | ||
| 213 | return None | |
| 214 | ||
| 215 | ||
| 216 | class ImpactPlugin(PluginXMLFormat): | |
| 217 | """ | |
| 218 | Example plugin to parse impact output. | |
| 219 | """ | |
| 220 | ||
| 221 | def __init__(self): | |
| 222 | super().__init__() | |
| 223 | self.identifier_tag = "entities" | |
| 224 | self.id = "CoreImpact" | |
| 225 | self.name = "Core Impact XML Output Plugin" | |
| 226 | self.plugin_version = "0.0.2" | |
| 227 | self.version = "Core Impact 2013R1/2017R2" | |
| 228 | self.framework_version = "1.0.0" | |
| 229 | self.options = None | |
| 230 | self._current_output = None | |
| 231 | self._command_regex = re.compile(r'^(sudo impact|\.\/impact).*?') | |
| 232 | ||
| 233 | global current_path | |
| 234 | self._output_file_path = os.path.join(self.data_path, | |
| 235 | "impact_output-%s.xml" % self._rid) | |
| 236 | ||
| 237 | def parseOutputString(self, output, debug=False): | |
| 238 | parser = ImpactXmlParser(output) | |
| 239 | mapped_services = {} | |
| 240 | mapped_ports = {} | |
| 241 | for item in parser.items: | |
| 242 | ||
| 243 | h_id = self.createAndAddHost( | |
| 244 | item.ip, | |
| 245 | item.os + " " + item.arch) | |
| 246 | ||
| 247 | i_id = self.createAndAddInterface( | |
| 248 | h_id, | |
| 249 | item.ip, | |
| 250 | ipv4_address=item.ip, | |
| 251 | hostname_resolution=[item.host]) | |
| 252 | ||
| 253 | for service in item.services: | |
| 254 | s_id = self.createAndAddServiceToInterface( | |
| 255 | h_id, | |
| 256 | i_id, | |
| 257 | service['name'], | |
| 258 | service['protocol'], | |
| 259 | ports=[service['port']], | |
| 260 | status='open') | |
| 261 | mapped_services[service['name']] = s_id | |
| 262 | mapped_ports[service['port']] = s_id | |
| 263 | ||
| 264 | if item.agent: | |
| 265 | desc = "Agent Type: " + item.agentype | |
| 266 | desc += "\nConn from:" + item.ipfrom | |
| 267 | desc += "\nPort:" + item.agentport | |
| 268 | desc += "\nProtocol:" + item.agentsubtype | |
| 269 | desc += "\nConn:" + item.agentcon | |
| 270 | ||
| 271 | self.createAndAddVulnToHost( | |
| 272 | h_id, | |
| 273 | "Core Impact Agent", | |
| 274 | desc=desc, | |
| 275 | severity="HIGH") | |
| 276 | ||
| 277 | for v in item.results: | |
| 278 | if v.service_name == "n/a" and v.port == "Unknown": | |
| 279 | self.createAndAddVulnToHost( | |
| 280 | h_id, | |
| 281 | v.name, | |
| 282 | desc=v.desc, | |
| 283 | severity=v.severity, | |
| 284 | ref=v.ref) | |
| 285 | else: | |
| 286 | s_id = mapped_services.get(v.service_name) or mapped_ports.get(v.port) | |
| 287 | print(v.service_name) | |
| 288 | print(s_id) | |
| 289 | self.createAndAddVulnToService( | |
| 290 | h_id, | |
| 291 | s_id, | |
| 292 | v.name, | |
| 293 | desc=v.desc, | |
| 294 | severity=v.severity, | |
| 295 | ref=v.ref) | |
| 296 | ||
| 297 | for p in item.ports: | |
| 298 | s_id = self.createAndAddServiceToInterface( | |
| 299 | h_id, | |
| 300 | i_id, | |
| 301 | p['port'], | |
| 302 | p['protocol'], | |
| 303 | ports=[p['port']], | |
| 304 | status=p['status']) | |
| 305 | del parser | |
| 306 | ||
| 307 | def processCommandString(self, username, current_path, command_string): | |
| 308 | return None | |
| 309 | ||
| 310 | def setHost(self): | |
| 311 | pass | |
| 312 | ||
| 313 | ||
| 314 | def createPlugin(): | |
| 315 | return ImpactPlugin() | |
| 316 | ||
| 317 | ||
| 318 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2018 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2018 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | import csv | |
| 6 | from io import StringIO | |
| 7 | from faraday.client.plugins import core | |
| 8 | ||
| 9 | ||
| 10 | def calculate_severity(number): | |
| 11 | if number is None: | |
| 12 | return "info" | |
| 13 | number = float(number) | |
| 14 | # Based in CVSS V2 | |
| 15 | if 0 <= number < 4.0: | |
| 16 | return "low" | |
| 17 | elif 4.0 <= number < 7.0: | |
| 18 | return "med" | |
| 19 | elif 7.0 <= number <= 10: | |
| 20 | return "high" | |
| 21 | ||
| 22 | ||
| 23 | class Ip360Parser: | |
| 24 | ||
| 25 | def __init__(self, csv_content): | |
| 26 | self.csv_content = StringIO(csv_content.decode('ascii', 'ignore')) | |
| 27 | self.csv_reader = csv.DictReader(self.csv_content, delimiter=',', quotechar='"') | |
| 28 | ||
| 29 | def parse(self): | |
| 30 | ||
| 31 | result = [] | |
| 32 | for row in self.csv_reader: | |
| 33 | ||
| 34 | host = { | |
| 35 | "name": row.get("IP"), | |
| 36 | "os": row.get("OS") | |
| 37 | } | |
| 38 | ||
| 39 | interface = { | |
| 40 | "name": row.get("IP"), | |
| 41 | "hostname_resolution": [row.get("NetBIOS Name")], | |
| 42 | "network_segment": row.get("NetBIOS Domain"), | |
| 43 | } | |
| 44 | ||
| 45 | service = {"port": row.get("Port")} | |
| 46 | ||
| 47 | vulnerability = { | |
| 48 | "name": row.get("Vulnerability"), | |
| 49 | "description": row.get("Description"), | |
| 50 | "resolution": row.get("Remediation"), | |
| 51 | "ref": [ | |
| 52 | row.get("CVE"), | |
| 53 | "Vuln ID: " + row.get("Vulnerability ID"), | |
| 54 | "Risk: " + row.get("Risk"), | |
| 55 | "Skill: " + row.get("Skill"), | |
| 56 | "CVSS V2: " + row.get("CVSS V2"), | |
| 57 | "CVSS V3: " + row.get("CVSS V3")], | |
| 58 | "severity": row.get("CVSS V2") | |
| 59 | } | |
| 60 | ||
| 61 | result.append((host, interface, service, vulnerability)) | |
| 62 | ||
| 63 | return result | |
| 64 | ||
| 65 | class Ip360Plugin(core.PluginBase): | |
| 66 | """ | |
| 67 | Example plugin to parse Ip360 output. | |
| 68 | """ | |
| 69 | ||
| 70 | def __init__(self): | |
| 71 | super().__init__() | |
| 72 | self.id = "Ip360" | |
| 73 | self.name = "Ip360 CSV Output Plugin" | |
| 74 | self.plugin_version = "0.0.1" | |
| 75 | self.options = None | |
| 76 | ||
| 77 | def parseOutputString(self, output, debug=False): | |
| 78 | ||
| 79 | parser = Ip360Parser(output) | |
| 80 | for host, interface, service, vulnerability in parser.parse(): | |
| 81 | ||
| 82 | h_id = self.createAndAddHost(host.get("name"), host.get("os")) | |
| 83 | ||
| 84 | i_id = self.createAndAddInterface( | |
| 85 | h_id, | |
| 86 | interface.get("name"), | |
| 87 | ipv4_address=interface.get("name"), | |
| 88 | hostname_resolution=interface.get("hostname_resolution"), | |
| 89 | network_segment=interface.get("network_segment")) | |
| 90 | ||
| 91 | ||
| 92 | if service.get("port") == "-": | |
| 93 | port = "0" | |
| 94 | protocol = "unknown" | |
| 95 | else: | |
| 96 | port = service.get("port").split("/")[0] | |
| 97 | protocol = service.get("port").split("/")[1] | |
| 98 | ||
| 99 | s_id = self.createAndAddServiceToInterface( | |
| 100 | h_id, | |
| 101 | i_id, | |
| 102 | service.get("port"), | |
| 103 | protocol=protocol, | |
| 104 | ports=[port]) | |
| 105 | ||
| 106 | self.createAndAddVulnToService( | |
| 107 | h_id, | |
| 108 | s_id, | |
| 109 | vulnerability.get("name"), | |
| 110 | desc=vulnerability.get("description"), | |
| 111 | resolution=vulnerability.get("resolution"), | |
| 112 | severity=calculate_severity(vulnerability.get("severity")), | |
| 113 | ref=vulnerability.get("ref")) | |
| 114 | ||
| 115 | def createPlugin(): | |
| 116 | return Ip360Plugin() | |
| 117 | ||
| 118 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | from faraday.client.model import api | |
| 8 | import os | |
| 9 | from lxml import etree | |
| 10 | ||
| 11 | try: | |
| 12 | import xml.etree.cElementTree as ET | |
| 13 | import xml.etree.ElementTree as ET_ORIG | |
| 14 | ETREE_VERSION = ET_ORIG.VERSION | |
| 15 | except ImportError: | |
| 16 | import xml.etree.ElementTree as ET | |
| 17 | ETREE_VERSION = ET.VERSION | |
| 18 | ||
| 19 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 20 | ||
| 21 | current_path = os.path.abspath(os.getcwd()) | |
| 22 | ||
| 23 | __author__ = "Thierry Beauquier" | |
| 24 | __license__ = "" | |
| 25 | __version__ = "1.0.0" | |
| 26 | __maintainer__ = "Thierry Beauquier" | |
| 27 | __email__ = "[email protected]" | |
| 28 | __status__ = "Development" | |
| 29 | ||
| 30 | """ | |
| 31 | This plugin has been designed to be used with python-unittest2/paramiko script to perform security compliancy verification. It enables to have displayed both security scans results (nmap, | |
| 32 | nessus, ..) and security verification compliancy (CIS-CAT, compagny's product security requirement) by Faraday-IPE | |
| 33 | ||
| 34 | This plugin requires that a element "host" is added to <testcase/> (sed -i 's/<testcase/<testcase host=\"192.168.1.1\"/' junit.xml) | |
| 35 | ||
| 36 | <testsuite errors="0" failures="1" name="AccountsWithSuperuserPrivilegesShallBeDisabledByDefault-20170118090010" skipped="0" tests="1" time="0.144"> | |
| 37 | <testcase host="192.168.1.1" classname="AccountsWithSuperuserPrivilegesShallBeDisabledByDefault" name="test_sshdRootLogin" time="0.144"> | |
| 38 | <failure message="SSH for root account is not disabled: '' matches '' in ''" type="AssertionError"> | |
| 39 | <![CDATA[Traceback (most recent call last): | |
| 40 | File "bsr-ci.py", line 514, in test_sshdRootLogin | |
| 41 | self.assertNotRegexpMatches(_ssh('cat /etc/ssh/sshd_config | egrep "^PermitRootLogin" | awk \'{print $2}\' | egrep "no|No|NO"',host),'', 'SSH for root account is not disabled') | |
| 42 | AssertionError: SSH for root account is not disabled: '' matches '' in '' | |
| 43 | ]]> </failure> | |
| 44 | </testcase> | |
| 45 | <system-out> | |
| 46 | <![CDATA[]]> </system-out> | |
| 47 | <system-err> | |
| 48 | <![CDATA[]]> </system-err> | |
| 49 | </testsuite> | |
| 50 | ||
| 51 | ||
| 52 | """ | |
| 53 | ||
| 54 | ||
| 55 | class JunitXmlParser: | |
| 56 | """ | |
| 57 | The objective of this class is to parse an xml file generated by the junit. | |
| 58 | ||
| 59 | @param junit_xml_filepath A proper xml generated by junit | |
| 60 | """ | |
| 61 | ||
| 62 | def __init__(self, xml_output): | |
| 63 | ||
| 64 | tree = self.parse_xml(xml_output) | |
| 65 | if tree: | |
| 66 | self.items = list(self.get_items(tree)) | |
| 67 | else: | |
| 68 | self.items = [] | |
| 69 | ||
| 70 | def parse_xml(self, xml_output): | |
| 71 | """ | |
| 72 | Open and parse an xml file. | |
| 73 | ||
| 74 | @return xml_tree An xml tree instance. None if error. | |
| 75 | """ | |
| 76 | try: | |
| 77 | # return ET.fromstring(xml_output) | |
| 78 | tree = etree.fromstring(xml_output) | |
| 79 | except SyntaxError as err: | |
| 80 | print("SyntaxError: %s. %s" % (err, xml_output)) | |
| 81 | return None | |
| 82 | return tree | |
| 83 | ||
| 84 | def get_items(self, tree): | |
| 85 | """ | |
| 86 | @return items A list of Failure instances | |
| 87 | """ | |
| 88 | ||
| 89 | for node in tree.findall('testsuite/testcase/failure'): | |
| 90 | yield Testsuite(node) | |
| 91 | ||
| 92 | ||
| 93 | class Testsuite: | |
| 94 | ||
| 95 | def __init__(self, testsuite_node): | |
| 96 | self.node = testsuite_node | |
| 97 | ||
| 98 | self.parent = self.node.getparent() | |
| 99 | self.name = self.parent.get('name') | |
| 100 | self.host = self.parent.get('host') | |
| 101 | if self.host is None: | |
| 102 | print('host element is missing') | |
| 103 | self.host = '' | |
| 104 | ||
| 105 | self.message = self.get_text_from_subnode('message') | |
| 106 | ||
| 107 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 108 | """ | |
| 109 | Finds a subnode in the host node and the retrieves a value from it. | |
| 110 | ||
| 111 | @return An attribute value | |
| 112 | """ | |
| 113 | sub_node = self.node.get(subnode_xpath_expr) | |
| 114 | if sub_node is not None: | |
| 115 | return sub_node | |
| 116 | ||
| 117 | return None | |
| 118 | ||
| 119 | ||
| 120 | class JunitPlugin(core.PluginBase): | |
| 121 | """ | |
| 122 | Example plugin to parse junit output. | |
| 123 | """ | |
| 124 | ||
| 125 | def __init__(self): | |
| 126 | super().__init__() | |
| 127 | self.id = "Junit" | |
| 128 | self.name = "Junit XML Output Plugin" | |
| 129 | self.plugin_version = "0.0.1" | |
| 130 | self.version = "" | |
| 131 | self.framework_version = "1.0.0" | |
| 132 | self.options = None | |
| 133 | self._current_output = None | |
| 134 | self._command_regex = None | |
| 135 | ||
| 136 | def parseOutputString(self, output, debug=False): | |
| 137 | ||
| 138 | parser = JunitXmlParser(output) | |
| 139 | for item in parser.items: | |
| 140 | h_id = self.createAndAddHost(item.host, os="Linux") | |
| 141 | i_id = self.createAndAddInterface(h_id, item.host, ipv4_address=item.host) | |
| 142 | self.createAndAddVulnToHost(h_id, name=item.name, desc=item.message, ref=[], severity="High") | |
| 143 | del parser | |
| 144 | ||
| 145 | def createPlugin(): | |
| 146 | return JunitPlugin() | |
| 147 | ||
| 148 | ||
| 149 | ||
| 150 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import core | |
| 6 | from faraday.client.model import api | |
| 7 | import re | |
| 8 | import os | |
| 9 | ||
| 10 | current_path = os.path.abspath(os.getcwd()) | |
| 11 | ||
| 12 | __author__ = "Francisco Amato" | |
| 13 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 14 | __credits__ = ["Francisco Amato"] | |
| 15 | __version__ = "1.0.0" | |
| 16 | __maintainer__ = "Francisco Amato" | |
| 17 | __email__ = "[email protected]" | |
| 18 | __status__ = "Development" | |
| 19 | ||
| 20 | ||
| 21 | class ListurlsParser: | |
| 22 | """ | |
| 23 | The objective of this class is to parse an xml file generated by the listurls tool. | |
| 24 | ||
| 25 | TODO: Handle errors. | |
| 26 | TODO: Test listurls output version. Handle what happens if the parser doesn't support it. | |
| 27 | TODO: Test cases. | |
| 28 | ||
| 29 | @param listurls_filepath A proper simple report generated by listurls | |
| 30 | """ | |
| 31 | ||
| 32 | def __init__(self, output): | |
| 33 | ||
| 34 | lists = output.split("\r\n") | |
| 35 | i = 0 | |
| 36 | self.items = [] | |
| 37 | ||
| 38 | if re.search("Could not reach", output) is not None: | |
| 39 | self.fail = True | |
| 40 | return | |
| 41 | ||
| 42 | for line in lists: | |
| 43 | if i > 8: | |
| 44 | print(line) | |
| 45 | item = {'link': line} | |
| 46 | self.items.append(item) | |
| 47 | i = i + 1 | |
| 48 | ||
| 49 | ||
| 50 | class ListurlsPlugin(core.PluginBase): | |
| 51 | """ | |
| 52 | Example plugin to parse listurls output. | |
| 53 | """ | |
| 54 | ||
| 55 | def __init__(self): | |
| 56 | super().__init__() | |
| 57 | self.id = "Listurls" | |
| 58 | self.name = "Listurls XML Output Plugin" | |
| 59 | self.plugin_version = "0.0.1" | |
| 60 | self.version = "6.3" | |
| 61 | self.options = None | |
| 62 | self._current_output = None | |
| 63 | self._current_path = None | |
| 64 | self._command_regex = re.compile( | |
| 65 | r'^(sudo list-urls\.py|list-urls\.py|perl list-urls\.py|\.\/list-urls\.py).*?') | |
| 66 | self.host = None | |
| 67 | self.port = None | |
| 68 | self.protocol = None | |
| 69 | self.fail = None | |
| 70 | self._completition = { | |
| 71 | "": "./list-urls.py <web-page>"} | |
| 72 | ||
| 73 | global current_path | |
| 74 | self.output_file_path = os.path.join(self.data_path, | |
| 75 | "listurls_output-%s.txt" % self._rid) | |
| 76 | ||
| 77 | def canParseCommandString(self, current_input): | |
| 78 | if self._command_regex.match(current_input.strip()): | |
| 79 | return True | |
| 80 | else: | |
| 81 | return False | |
| 82 | ||
| 83 | def parseOutputString(self, output, debug=False): | |
| 84 | return | |
| 85 | ||
| 86 | def processCommandString(self, username, current_path, command_string): | |
| 87 | ||
| 88 | host = re.search( | |
| 89 | "(http|https|ftp)\://([a-zA-Z0-9\.\-]+(\:[a-zA-Z0-9\.&%\$\-]+)*@)*((25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9])\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9]|0)\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9]|0)\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[0-9])|localhost|([a-zA-Z0-9\-]+\.)*[a-zA-Z0-9\-]+\.(com|edu|gov|int|mil|net|org|biz|arpa|info|name|pro|aero|coop|museum|[a-zA-Z]{2}))[\:]*([0-9]+)*([/]*($|[a-zA-Z0-9\.\,\?\'\\\+&%\$#\=~_\-]+)).*?$", | |
| 90 | command_string) | |
| 91 | ||
| 92 | self.protocol = host.group(1) | |
| 93 | self.host = host.group(4) | |
| 94 | if self.protocol == 'https': | |
| 95 | self.port = 443 | |
| 96 | if host.group(11) is not None: | |
| 97 | self.port = host.group(11) | |
| 98 | ||
| 99 | def setHost(self): | |
| 100 | pass | |
| 101 | ||
| 102 | ||
| 103 | def createPlugin(): | |
| 104 | return ListurlsPlugin() | |
| 105 | ||
| 106 | ||
| 107 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2017 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2017 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | import re | |
| 6 | import os | |
| 7 | from collections import defaultdict | |
| 8 | ||
| 9 | from faraday.client.plugins.plugin import PluginByExtension | |
| 10 | from faraday.client.plugins.plugins_utils import filter_services, get_all_protocols | |
| 11 | ||
| 12 | ||
| 13 | current_path = os.path.abspath(os.getcwd()) | |
| 14 | ||
| 15 | ||
| 16 | class LynisLogDataExtracter(): | |
| 17 | def __init__(self, datfile=None, output=None): | |
| 18 | self.services = defaultdict(list) | |
| 19 | if datfile and os.path.exists(datfile): | |
| 20 | with open(datfile) as f: | |
| 21 | self.rawcontents = f.read() | |
| 22 | ||
| 23 | if output: | |
| 24 | self.rawcontents = output | |
| 25 | ||
| 26 | def _svcHelper(self, ip, port, protocol, name): | |
| 27 | self.services[ip].append({'port': port, 'protocol': protocol, 'name': name}) | |
| 28 | ||
| 29 | def hostname(self): | |
| 30 | hostname_match = re.search('^hostname=(.+)$', self.rawcontents, re.MULTILINE) | |
| 31 | hostname = hostname_match.group(1).strip() | |
| 32 | domain_match = re.search('^domainname=(.+)$', self.rawcontents, re.MULTILINE) | |
| 33 | if domain_match: | |
| 34 | domain = domain_match.group(1).strip() | |
| 35 | return ".".join([hostname,domain]) | |
| 36 | else: | |
| 37 | return hostname | |
| 38 | ||
| 39 | def osfullname(self): | |
| 40 | name_match = re.search('^os_name=(.+)$', self.rawcontents, re.MULTILINE) | |
| 41 | name = name_match.group(1).strip() | |
| 42 | version_match = re.search('^os_version=(.+)$', self.rawcontents, re.MULTILINE) | |
| 43 | version = version_match.group(1).strip() | |
| 44 | return " ".join([name, version]) | |
| 45 | ||
| 46 | def ipv4(self): | |
| 47 | ipv4addrs = [] | |
| 48 | ipv4s = re.findall('^network_ipv4_address\[\]=(.+)$', | |
| 49 | self.rawcontents, re.MULTILINE) | |
| 50 | ipv4addrs = self.ipv4_filter(ipv4s) | |
| 51 | return(ipv4addrs) | |
| 52 | ||
| 53 | def ipv6(self): | |
| 54 | ipv6addrs = [] | |
| 55 | ipv6s = re.findall('^network_ipv6_address\[\]=(.+)$', | |
| 56 | self.rawcontents, re.MULTILINE) | |
| 57 | ipv6addrs = self.ipv6_filter(ipv6s) | |
| 58 | return(ipv6addrs) | |
| 59 | ||
| 60 | def ipv4_filter(self, ips): | |
| 61 | ip_list = [] | |
| 62 | for ip in ips: | |
| 63 | if not ip == "127.0.0.1": | |
| 64 | ip_list.append(ip) | |
| 65 | ||
| 66 | return ip_list | |
| 67 | ||
| 68 | def ipv6_filter(self, ips): | |
| 69 | ip_list = [] | |
| 70 | for ip in ips: | |
| 71 | if not ip.startswith('fe80') and not ip.startswith('::1'): | |
| 72 | ip_list.append(ip) | |
| 73 | ||
| 74 | return ip_list | |
| 75 | ||
| 76 | def kernelVersion(self): | |
| 77 | versions_dict = {} | |
| 78 | ||
| 79 | version = re.search('^os_kernel_version=(.+)$', | |
| 80 | self.rawcontents, re.MULTILINE) | |
| 81 | if version: | |
| 82 | versions_dict['Kernel Version'] = version.group(1).strip() | |
| 83 | ||
| 84 | version_full = re.search('^os_kernel_version_full=(.+)$', | |
| 85 | self.rawcontents, re.MULTILINE) | |
| 86 | if version_full: | |
| 87 | versions_dict['Kernel Version Full'] = version_full.group(1).strip() | |
| 88 | ||
| 89 | return versions_dict | |
| 90 | ||
| 91 | def listeningservices(self): | |
| 92 | line = re.findall('^network_listen_port\[\]=(.+)$', | |
| 93 | self.rawcontents, re.MULTILINE) | |
| 94 | # To avoid local services, we will create the following list | |
| 95 | local_services = ['*', 'localhost'] | |
| 96 | ||
| 97 | for combo in line: | |
| 98 | elements = self.clean_services(combo, local_services) | |
| 99 | if elements is not None: | |
| 100 | self._svcHelper(elements['ip'], | |
| 101 | elements['port'], | |
| 102 | elements['protocol'], | |
| 103 | elements['name']) | |
| 104 | return self.services | |
| 105 | ||
| 106 | def clean_services(self, combo, local_services): | |
| 107 | add = False | |
| 108 | #if "localhost" in combo: | |
| 109 | if combo.count("|") > 1: | |
| 110 | # Service with url, protocol and perhaps name | |
| 111 | items_service = combo.split('|') | |
| 112 | if not self.local_service(items_service, local_services): | |
| 113 | # self.aux_items will be an auxiliar list. We will use it... | |
| 114 | # ...for poping the url and the protocol so that the last element... | |
| 115 | # ... of the list, will be the name of the service | |
| 116 | self.aux_items = list(filter(None, items_service)) | |
| 117 | elements_ip_port, count = self.get_ip_and_port(self.aux_items, remove_from_list=True) | |
| 118 | protocol = self.get_protocol() | |
| 119 | name = self.aux_items[0] | |
| 120 | add = True | |
| 121 | ||
| 122 | if name == '-': | |
| 123 | details = self.search_service(elements_ip_port[1]) | |
| 124 | name = details['name'] | |
| 125 | elif combo.count('|') == 1: | |
| 126 | # Service only with url | |
| 127 | items_service = combo.split('|') | |
| 128 | if not self.local_service(items_service, local_services): | |
| 129 | elements_ip_port, count = self.get_ip_and_port(items_service) | |
| 130 | details = self.search_service(elements_ip_port[1]) | |
| 131 | protocol = details['protocol'] | |
| 132 | name = details['name'] | |
| 133 | add = True | |
| 134 | else: | |
| 135 | items_service = combo | |
| 136 | count = items_service.count(':') | |
| 137 | elements_ip_port = items_service.split(':') | |
| 138 | details = self.search_service(elements_ip_port[1]) | |
| 139 | protocol = details['protocol'] | |
| 140 | name = details['name'] | |
| 141 | add = True | |
| 142 | ||
| 143 | if add: | |
| 144 | ip, port = self.colon_count(count, elements_ip_port, items_service) | |
| 145 | elements_dict = { | |
| 146 | "ip":ip, | |
| 147 | "port": port, | |
| 148 | "protocol": protocol, | |
| 149 | "name": name | |
| 150 | } | |
| 151 | return elements_dict | |
| 152 | else: | |
| 153 | return None | |
| 154 | ||
| 155 | def local_service(self, service_data, local_services): | |
| 156 | ip = self.get_ip_and_port(service_data)[0][0] | |
| 157 | local = True | |
| 158 | if not ip in local_services and not ip.startswith(':'): | |
| 159 | local = False | |
| 160 | ||
| 161 | return local | |
| 162 | ||
| 163 | def get_ip_and_port(self, service_data, remove_from_list=False): | |
| 164 | url_data = [url for url in service_data if ':' in url][0] | |
| 165 | count = url_data.count(':') | |
| 166 | ip_port = url_data.split(':') | |
| 167 | ||
| 168 | if remove_from_list: | |
| 169 | self.aux_items.remove(url_data) | |
| 170 | ||
| 171 | return ip_port, count | |
| 172 | ||
| 173 | def get_protocol(self): | |
| 174 | # network_listen_port variables are different in .log and .dat reports | |
| 175 | # .log: tcp4|127.0.0.1:5985|zabbix_age| | |
| 176 | # .dat: 127.0.0.1:5985|tcp4|zabbix_age| | |
| 177 | # This method will check if the protocol (from the function get_all_protocols()) | |
| 178 | # matches with the protocol that network_listen_port contains | |
| 179 | protocols = get_all_protocols() | |
| 180 | for item in protocols: | |
| 181 | protocol = [p for p in self.aux_items if item in p.lower()] | |
| 182 | if protocol: | |
| 183 | self.aux_items.remove(protocol[0]) | |
| 184 | return protocol[0] | |
| 185 | ||
| 186 | def search_service(self, port): | |
| 187 | srv = filter_services() | |
| 188 | details_dict = { | |
| 189 | 'name' : 'Unknown', | |
| 190 | 'protocol' : 'Unknown' | |
| 191 | } | |
| 192 | for item in srv: | |
| 193 | service_tuple = item[0].split('/') | |
| 194 | parsed_port = service_tuple[0] | |
| 195 | if parsed_port == port: | |
| 196 | details_dict['name'] = item[1] | |
| 197 | details_dict['protocol'] = service_tuple[1] | |
| 198 | return details_dict | |
| 199 | return details_dict | |
| 200 | ||
| 201 | def colon_count(self, count, elements_ip_port, items_service): | |
| 202 | #Ipv4 | |
| 203 | if count == 1: | |
| 204 | ip, port = elements_ip_port | |
| 205 | ||
| 206 | #Ipv6 | |
| 207 | elif count == 3: | |
| 208 | port = elements_ip_port[3] | |
| 209 | ip = '::' | |
| 210 | ||
| 211 | #Ipv6 | |
| 212 | elif count == 5: | |
| 213 | port = elements_ip_port[5] | |
| 214 | ip = items_service[0].replace(':{}'.format(port), '') | |
| 215 | ||
| 216 | return ip, port | |
| 217 | ||
| 218 | def parse_suggestions(self): | |
| 219 | sugs = {} | |
| 220 | m = re.findall('^suggestion\[\]=(.+)$', self.rawcontents, re.MULTILINE) | |
| 221 | for combo in m: | |
| 222 | x = combo.split('|') | |
| 223 | sugs[x[0]] = x[1] | |
| 224 | return(sugs) | |
| 225 | ||
| 226 | def parse_warnings(self): | |
| 227 | warns = {} | |
| 228 | m = re.findall('^warning\[\]=(.+)$', self.rawcontents, re.MULTILINE) | |
| 229 | for combo in m: | |
| 230 | x = combo.split('|') | |
| 231 | warns[x[0]] = x[1] | |
| 232 | return(warns) | |
| 233 | ||
| 234 | ||
| 235 | class LynisPlugin(PluginByExtension): | |
| 236 | """ Simple example plugin to parse lynis' lynis-report.dat file.""" | |
| 237 | ||
| 238 | def __init__(self): | |
| 239 | super().__init__() | |
| 240 | self.extension = [".dat", ".log"] | |
| 241 | self.id = "Lynis" | |
| 242 | self.name = "Lynis DAT Output Plugin" | |
| 243 | self.plugin_version = "0.4" | |
| 244 | self.version = "2.7.1" | |
| 245 | self.options = None | |
| 246 | self._current_output = None | |
| 247 | rr = r'^(lynis|sudo lynis|\.\/lynis|sudo \.\/lynis).*?' | |
| 248 | self._command_regex = re.compile(rr) | |
| 249 | self._hosts = [] | |
| 250 | ||
| 251 | global current_path | |
| 252 | ||
| 253 | def report_belongs_to(self, **kwargs): | |
| 254 | if super().report_belongs_to(**kwargs): | |
| 255 | report_path = kwargs.get("report_path", "") | |
| 256 | with open(report_path) as f: | |
| 257 | output = f.read() | |
| 258 | return output.startswith("# Lynis Report") | |
| 259 | return False | |
| 260 | ||
| 261 | def parseOutputString(self, output, debug=False): | |
| 262 | datpath = self.getDatPath(output) | |
| 263 | ||
| 264 | if datpath: | |
| 265 | lde = LynisLogDataExtracter(datfile=datpath) | |
| 266 | elif '# Lynis Report' in output: | |
| 267 | lde = LynisLogDataExtracter(output=output) | |
| 268 | hostname = lde.hostname() | |
| 269 | ipv4s = lde.ipv4() | |
| 270 | ipv6s = lde.ipv6() | |
| 271 | kernel_versions = lde.kernelVersion() | |
| 272 | services = lde.listeningservices() | |
| 273 | suggestions = lde.parse_suggestions() | |
| 274 | warnings = lde.parse_warnings() | |
| 275 | ||
| 276 | for ipv4 in ipv4s: | |
| 277 | h_id = self.createAndAddHost(name=ipv4, | |
| 278 | os=lde.osfullname(), | |
| 279 | hostnames=[hostname]) | |
| 280 | ||
| 281 | self.create_services(h_id, services, ipv4) | |
| 282 | self.create_vulns_with_kernel(h_id, kernel_versions) | |
| 283 | self.create_vulns_with_suggestions(h_id, suggestions) | |
| 284 | self.create_vulns_with_warns(h_id, warnings) | |
| 285 | ||
| 286 | for ipv6 in ipv6s: | |
| 287 | h_id = self.createAndAddHost(name=ipv6, | |
| 288 | os=lde.osfullname(), | |
| 289 | hostnames=[hostname]) | |
| 290 | ||
| 291 | self.create_services(h_id, services, ipv6) | |
| 292 | self.create_vulns_with_kernel(h_id, kernel_versions) | |
| 293 | self.create_vulns_with_suggestions(h_id, suggestions) | |
| 294 | self.create_vulns_with_warns(h_id, warnings) | |
| 295 | ||
| 296 | def create_services(self, host_id, parsed_services, ip_version): | |
| 297 | for service_data in parsed_services[ip_version]: | |
| 298 | self.createAndAddServiceToHost(host_id=host_id, | |
| 299 | name=service_data['name'], | |
| 300 | protocol=service_data['protocol'], | |
| 301 | ports=[service_data['port']]) | |
| 302 | ||
| 303 | if '0.0.0.0' in parsed_services: | |
| 304 | for service_data in parsed_services['0.0.0.0']: | |
| 305 | self.createAndAddServiceToHost(host_id=host_id, | |
| 306 | name=service_data['name'], | |
| 307 | protocol=service_data['protocol'], | |
| 308 | ports=[service_data['port']]) | |
| 309 | ||
| 310 | def create_vulns_with_kernel(self, host_id, kernel_versions): | |
| 311 | for kernel, version in kernel_versions.items(): | |
| 312 | self.createAndAddVulnToHost( | |
| 313 | host_id=host_id, | |
| 314 | name=kernel, | |
| 315 | severity='info', | |
| 316 | desc=version | |
| 317 | ) | |
| 318 | ||
| 319 | def create_vulns_with_suggestions(self, host_id, sugs): | |
| 320 | for sug in sugs: | |
| 321 | self.createAndAddVulnToHost( | |
| 322 | host_id=host_id, | |
| 323 | name=sug, | |
| 324 | severity='med', | |
| 325 | desc=sugs[sug] | |
| 326 | ) | |
| 327 | ||
| 328 | def create_vulns_with_warns(self, host_id, warns): | |
| 329 | for warn in warns: | |
| 330 | self.createAndAddVulnToHost( | |
| 331 | host_id=host_id, | |
| 332 | name=warn, | |
| 333 | severity='high', | |
| 334 | desc=warns[warn] | |
| 335 | ) | |
| 336 | ||
| 337 | def processCommandString(self, username, current_path, command_string): | |
| 338 | """ | |
| 339 | Lynis does not have a means to specify the location for the | |
| 340 | DAT file, which by default goes to /var/log/lynis-report.dat | |
| 341 | or /tmp/lynis-report.dat, depending on privileges. | |
| 342 | Because of that, we will extract the DAT location off | |
| 343 | lynis' output via parseOutputString(). | |
| 344 | """ | |
| 345 | return | |
| 346 | ||
| 347 | def getDatPath(self, output): | |
| 348 | m = re.search('(\/.+\.dat)$', output, re.MULTILINE) | |
| 349 | if m: | |
| 350 | return(m.group(0).strip()) | |
| 351 | ||
| 352 | ||
| 353 | def createPlugin(): | |
| 354 | return LynisPlugin() | |
| 355 | ||
| 356 | ||
| 357 | # I'm Py3 |
| 0 | <?xml version="1.0" encoding="UTF-8" standalone="no"?> | |
| 1 | <graphml xmlns="http://graphml.graphdrawing.org/xmlns" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:y="http://www.yworks.com/xml/graphml" xsi:schemaLocation="http://graphml.graphdrawing.org/xmlns http://www.yworks.com/xml/schema/graphml/1.1/ygraphml.xsd"> | |
| 2 | <!--Created by yFiles for Java 2.7.0.2--> | |
| 3 | <key for="graphml" id="d0" yfiles.type="resources"/> | |
| 4 | <key attr.name="MaltegoEntity" for="node" id="d1"/> | |
| 5 | <key for="node" id="d2" yfiles.type="nodegraphics"/> | |
| 6 | <key attr.name="MaltegoLink" for="edge" id="d3"/> | |
| 7 | <key for="edge" id="d4" yfiles.type="edgegraphics"/> | |
| 8 | <graph edgedefault="directed" id="G"> | |
| 9 | <node id="n0"> | |
| 10 | <data key="d1"> | |
| 11 | <mtg:MaltegoEntity xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.Domain"> | |
| 12 | <mtg:Properties displayValue="fqdn" value="fqdn"> | |
| 13 | <mtg:Property displayName="Domain Name" hidden="false" name="fqdn" nullable="true" readonly="false" type="string"> | |
| 14 | <mtg:Value>ekoparty.org</mtg:Value> | |
| 15 | </mtg:Property> | |
| 16 | <mtg:Property displayName="WHOIS Info" hidden="false" name="whois-info" nullable="true" readonly="false" type="string"> | |
| 17 | <mtg:Value/> | |
| 18 | </mtg:Property> | |
| 19 | </mtg:Properties> | |
| 20 | <mtg:DisplayInformation/> | |
| 21 | <mtg:Weight>0</mtg:Weight> | |
| 22 | </mtg:MaltegoEntity> | |
| 23 | </data> | |
| 24 | <data key="d2"> | |
| 25 | <mtg:EntityRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"> | |
| 26 | <mtg:Position x="412.79999999999995" y="46.46875"/> | |
| 27 | </mtg:EntityRenderer> | |
| 28 | </data> | |
| 29 | </node> | |
| 30 | <node id="n1"> | |
| 31 | <data key="d1"> | |
| 32 | <mtg:MaltegoEntity xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.MXRecord"> | |
| 33 | <mtg:Properties displayValue="fqdn" value="fqdn"> | |
| 34 | <mtg:Property displayName="Priority" hidden="false" name="mxrecord.priority" nullable="true" readonly="false" type="int"> | |
| 35 | <mtg:Value>0</mtg:Value> | |
| 36 | </mtg:Property> | |
| 37 | <mtg:Property displayName="MX Record" hidden="false" name="fqdn" nullable="true" readonly="false" type="string"> | |
| 38 | <mtg:Value>mail.ekoparty.org</mtg:Value> | |
| 39 | </mtg:Property> | |
| 40 | </mtg:Properties> | |
| 41 | <mtg:DisplayInformation> | |
| 42 | <mtg:DisplayElement name="Generator detail"><![CDATA[<table><tr><td class=three>Source</td><td class=two>ekoparty.org</td><td class=three>(Domain)</td></tr><tr><td class=three>Transform</td><td class=two colspan=2>To DNS Name - MX (mail server)</td></tr><tr><td class=three>Result</td><td class=two>mail.ekoparty.org</td><td class=three>(MXrecord)</td></tr><tr><td class=three>Gen. date</td><td class=two colspan=2>2011-6-27 23:46</td></tr></table></font>]]></mtg:DisplayElement> | |
| 43 | </mtg:DisplayInformation> | |
| 44 | <mtg:Weight>100</mtg:Weight> | |
| 45 | </mtg:MaltegoEntity> | |
| 46 | </data> | |
| 47 | <data key="d2"> | |
| 48 | <mtg:EntityRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"> | |
| 49 | <mtg:Position x="546.375" y="445.28125"/> | |
| 50 | </mtg:EntityRenderer> | |
| 51 | </data> | |
| 52 | </node> | |
| 53 | <node id="n2"> | |
| 54 | <data key="d1"> | |
| 55 | <mtg:MaltegoEntity xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.EmailAddress"> | |
| 56 | <mtg:Properties displayValue="email" value="email"> | |
| 57 | <mtg:Property displayName="URLs" hidden="false" name="URLS" nullable="true" readonly="false" type="string"> | |
| 58 | <mtg:Value>http://www.diariodecuyo.com.ar/home/new_noticia.php?noticia_id=420508 Diario de Cuyo - Conferencias internacionales de seguridad | |
| 59 | http://www.diariodecuyo.com.ar/imagenes/2010/09/EDICION/7menu24.pdf Pagina24y25_Maquetaci��n 1 | |
| 60 | </mtg:Value> | |
| 61 | </mtg:Property> | |
| 62 | <mtg:Property displayName="Email Address" hidden="false" name="email" nullable="true" readonly="false" type="string"> | |
| 63 | <mtg:Value>[email protected]</mtg:Value> | |
| 64 | </mtg:Property> | |
| 65 | </mtg:Properties> | |
| 66 | <mtg:DisplayInformation> | |
| 67 | <mtg:DisplayElement name="Generator detail"><![CDATA[<table><tr><td class=three>Source</td><td class=two>ekoparty.org</td><td class=three>(Domain)</td></tr><tr><td class=three>Transform</td><td class=two colspan=2>To Emails @domain [using Search Engine]</td></tr><tr><td class=three>Result</td><td class=two>[email protected]</td><td class=three>(EmailAddress)</td></tr><tr><td class=three>Gen. date</td><td class=two colspan=2>2011-6-27 23:49</td></tr></table></font>]]></mtg:DisplayElement> | |
| 68 | <mtg:DisplayElement name="Snippet(s):"><![CDATA[<table><tr><td class=one>Diario de Cuyo - Conferencias internacionales de seguridad</td><td class=three>Indexed on:2011/1/21</td></tr><tr><td class=one colspan=2><a href="http://www.diariodecuyo.com.ar/home/new_noticia.php?noticia_id=420508">[www.diariodecuyo.com.ar]</a></td></tr><tr><td class=two colspan=2>Son 23 las conferencias confirmadas para los d��as 16 y 17 de ' Sitio oficial: www.ekoparty.org. Contacto: [email protected] - (11) 6841 1010. Otras '</td></tr></table><br><table><tr><td class=one>Pagina24y25_Maquetaci��n 1</td><td class=three>Indexed on:2010/9/7</td></tr><tr><td class=one colspan=2><a href="http://www.diariodecuyo.com.ar/imagenes/2010/09/EDICION/7menu24.pdf">[www.diariodecuyo.com.ar]</a></td></tr><tr><td class=two colspan=2>M��s que la p��rdida material, lo. duro para cualquier usuario es el ' www.ekoparty.org - Contacto: [email protected] (11) 6841 1010. net. Una vez que el '</td></tr></table><br>]]></mtg:DisplayElement> | |
| 69 | </mtg:DisplayInformation> | |
| 70 | <mtg:Weight>200</mtg:Weight> | |
| 71 | </mtg:MaltegoEntity> | |
| 72 | </data> | |
| 73 | <data key="d2"> | |
| 74 | <mtg:EntityRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"> | |
| 75 | <mtg:Position x="250.0" y="194.40625"/> | |
| 76 | </mtg:EntityRenderer> | |
| 77 | </data> | |
| 78 | </node> | |
| 79 | <node id="n3"> | |
| 80 | <data key="d1"> | |
| 81 | <mtg:MaltegoEntity xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.EmailAddress"> | |
| 82 | <mtg:Properties displayValue="email" value="email"> | |
| 83 | <mtg:Property displayName="URLs" hidden="false" name="URLS" nullable="true" readonly="false" type="string"> | |
| 84 | <mtg:Value>http://zh-hk.facebook.com/pages/ekoparty-security-conference/16162244291 ekoparty security conference | Facebook | |
| 85 | http://www.tecnozona.com/zona_del_que_diran/ekoparty-ya-esta-en-marcha/ Ekoparty ya est�� en marcha | |
| 86 | </mtg:Value> | |
| 87 | </mtg:Property> | |
| 88 | <mtg:Property displayName="Email Address" hidden="false" name="email" nullable="true" readonly="false" type="string"> | |
| 89 | <mtg:Value>[email protected]</mtg:Value> | |
| 90 | </mtg:Property> | |
| 91 | </mtg:Properties> | |
| 92 | <mtg:DisplayInformation> | |
| 93 | <mtg:DisplayElement name="Generator detail"><![CDATA[<table><tr><td class=three>Source</td><td class=two>ekoparty.org</td><td class=three>(Domain)</td></tr><tr><td class=three>Transform</td><td class=two colspan=2>To Emails @domain [using Search Engine]</td></tr><tr><td class=three>Result</td><td class=two>[email protected]</td><td class=three>(EmailAddress)</td></tr><tr><td class=three>Gen. date</td><td class=two colspan=2>2011-6-27 23:49</td></tr></table></font>]]></mtg:DisplayElement> | |
| 94 | <mtg:DisplayElement name="Snippet(s):"><![CDATA[<table><tr><td class=one>ekoparty security conference | Facebook</td><td class=three>Indexed on:2010/7/15</td></tr><tr><td class=one colspan=2><a href="http://zh-hk.facebook.com/pages/ekoparty-security-conference/16162244291">[zh-hk.facebook.com]</a></td></tr><tr><td class=two colspan=2>������������Facebook������ ekoparty security conference ���������������������������Facebook��� ekoparty security conference ��������� ' Env��a tu slogans a [email protected]. Una vez recibidos y ordenados '</td></tr></table><br><table><tr><td class=one>Ekoparty ya est�� en marcha</td><td class=three>Indexed on:2011/6/9</td></tr><tr><td class=one colspan=2><a href="http://www.tecnozona.com/zona_del_que_diran/ekoparty-ya-esta-en-marcha/">[www.tecnozona.com]</a></td></tr><tr><td class=two colspan=2>Ten��s hasta el 26 de mayo para enviar tus slogans (hasta 3) a [email protected]. Una vez recibidos y ordenados, se va a hacer online una votaci��n '</td></tr></table><br>]]></mtg:DisplayElement> | |
| 95 | </mtg:DisplayInformation> | |
| 96 | <mtg:Weight>200</mtg:Weight> | |
| 97 | </mtg:MaltegoEntity> | |
| 98 | </data> | |
| 99 | <data key="d2"> | |
| 100 | <mtg:EntityRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"> | |
| 101 | <mtg:Position x="86.5" y="194.40625"/> | |
| 102 | </mtg:EntityRenderer> | |
| 103 | </data> | |
| 104 | </node> | |
| 105 | <node id="n4"> | |
| 106 | <data key="d1"> | |
| 107 | <mtg:MaltegoEntity xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.EmailAddress"> | |
| 108 | <mtg:Properties displayValue="email" value="email"> | |
| 109 | <mtg:Property displayName="URLs" hidden="false" name="URLS" nullable="true" readonly="false" type="string"> | |
| 110 | <mtg:Value>http://twitter.com/ekoparty/status/23111351685 Twitter / ekoparty: Just for fun! Resolve this ' | |
| 111 | http://zh-tw.facebook.com/pages/ekoparty-security-conference/16162244291?_fb_noscript=1 ekoparty security conference | Facebook | |
| 112 | http://www.madrimasd.org/iberoamerica/actividades/mostrar_info.asp?id=45272 Actividades | |
| 113 | http://www.canal-ar.com.ar/Sosnoticia/sosnoticiamuestra.asp?Id=1955 CanalAR - Core Security renueva su presencia en ekoparty ' | |
| 114 | </mtg:Value> | |
| 115 | </mtg:Property> | |
| 116 | <mtg:Property displayName="Email Address" hidden="false" name="email" nullable="true" readonly="false" type="string"> | |
| 117 | <mtg:Value>[email protected]</mtg:Value> | |
| 118 | </mtg:Property> | |
| 119 | </mtg:Properties> | |
| 120 | <mtg:DisplayInformation> | |
| 121 | <mtg:DisplayElement name="Generator detail"><![CDATA[<table><tr><td class=three>Source</td><td class=two>ekoparty.org</td><td class=three>(Domain)</td></tr><tr><td class=three>Transform</td><td class=two colspan=2>To Emails @domain [using Search Engine]</td></tr><tr><td class=three>Result</td><td class=two>[email protected]</td><td class=three>(EmailAddress)</td></tr><tr><td class=three>Gen. date</td><td class=two colspan=2>2011-6-27 23:49</td></tr></table></font>]]></mtg:DisplayElement> | |
| 122 | <mtg:DisplayElement name="Snippet(s):"><![CDATA[<table><tr><td class=one>Twitter / ekoparty: Just for fun! Resolve this '</td><td class=three>Indexed on:2010/9/6</td></tr><tr><td class=one colspan=2><a href="http://twitter.com/ekoparty/status/23111351685">[twitter.com]</a></td></tr><tr><td class=two colspan=2>Just for fun! Resolve this challenge and get a 15% off Send the token to organizacion @ ekoparty.org | DM http://bit.ly/avQpcx</td></tr></table><br><table><tr><td class=one>CanalAR - Core Security renueva su presencia en ekoparty '</td><td class=three>Indexed on:2011/6/3</td></tr><tr><td class=one colspan=2><a href="http://www.canal-ar.com.ar/Sosnoticia/sosnoticiamuestra.asp?Id=1955">[www.canal-ar.com.ar]</a></td></tr><tr><td class=two colspan=2>Periodismo y An��lisis en el mundo argentino de las tecnolog��as de la informaci��n ' en http://www.ekoparty.org/, escribir a [email protected] o comunicarse al (+54 '</td></tr></table><br><table><tr><td class=one>Actividades</td><td class=three>Indexed on:2011/6/10</td></tr><tr><td class=one colspan=2><a href="http://www.madrimasd.org/iberoamerica/actividades/mostrar_info.asp?id=45272">[www.madrimasd.org]</a></td></tr><tr><td class=two colspan=2>E-mail: [email protected]. Resumen: Asistentes, invitados, especialistas y referentes de todo el mundo tienen la oportunidad de involucrarse '</td></tr></table><br><table><tr><td class=one>ekoparty security conference | Facebook</td><td class=three>Indexed on:2011/5/26</td></tr><tr><td class=one colspan=2><a href="http://zh-tw.facebook.com/pages/ekoparty-security-conference/16162244291?_fb_noscript=1">[zh-tw.facebook.com]</a></td></tr><tr><td class=two colspan=2>ekoparty security conference - A security conference hosted yearly in Buenos Aires | Facebook ' un email a organizacion @ ekoparty.org te enviaremos una carpeta con '</td></tr></table><br>]]></mtg:DisplayElement> | |
| 123 | </mtg:DisplayInformation> | |
| 124 | <mtg:Weight>28</mtg:Weight> | |
| 125 | </mtg:MaltegoEntity> | |
| 126 | </data> | |
| 127 | <data key="d2"> | |
| 128 | <mtg:EntityRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"> | |
| 129 | <mtg:Position x="714.875" y="445.28125"/> | |
| 130 | </mtg:EntityRenderer> | |
| 131 | </data> | |
| 132 | </node> | |
| 133 | <node id="n5"> | |
| 134 | <data key="d1"> | |
| 135 | <mtg:MaltegoEntity xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.EmailAddress"> | |
| 136 | <mtg:Properties displayValue="email" value="email"> | |
| 137 | <mtg:Property displayName="URLs" hidden="false" name="URLS" nullable="true" readonly="false" type="string"> | |
| 138 | <mtg:Value>http://cfp.ekoparty.org/ ekoparty - CALL FOR PAPERS | |
| 139 | </mtg:Value> | |
| 140 | </mtg:Property> | |
| 141 | <mtg:Property displayName="Email Address" hidden="false" name="email" nullable="true" readonly="false" type="string"> | |
| 142 | <mtg:Value>[email protected]</mtg:Value> | |
| 143 | </mtg:Property> | |
| 144 | </mtg:Properties> | |
| 145 | <mtg:DisplayInformation> | |
| 146 | <mtg:DisplayElement name="Generator detail"><![CDATA[<table><tr><td class=three>Source</td><td class=two>ekoparty.org</td><td class=three>(Domain)</td></tr><tr><td class=three>Transform</td><td class=two colspan=2>To Emails @domain [using Search Engine]</td></tr><tr><td class=three>Result</td><td class=two>[email protected]</td><td class=three>(EmailAddress)</td></tr><tr><td class=three>Gen. date</td><td class=two colspan=2>2011-6-27 23:49</td></tr></table></font>]]></mtg:DisplayElement> | |
| 147 | <mtg:DisplayElement name="Snippet(s):"><![CDATA[<table><tr><td class=one>ekoparty - CALL FOR PAPERS</td><td class=three>Indexed on:2011/5/30</td></tr><tr><td class=one colspan=2><a href="http://cfp.ekoparty.org/">[cfp.ekoparty.org]</a></td></tr><tr><td class=two colspan=2>If you don't have an account, please Signup to get started. For training submissions, or questions about our CFP process, contact us directly at [email protected] '</td></tr></table><br>]]></mtg:DisplayElement> | |
| 148 | </mtg:DisplayInformation> | |
| 149 | <mtg:Weight>0</mtg:Weight> | |
| 150 | </mtg:MaltegoEntity> | |
| 151 | </data> | |
| 152 | <data key="d2"> | |
| 153 | <mtg:EntityRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"> | |
| 154 | <mtg:Position x="86.5" y="297.34375"/> | |
| 155 | </mtg:EntityRenderer> | |
| 156 | </data> | |
| 157 | </node> | |
| 158 | <node id="n6"> | |
| 159 | <data key="d1"> | |
| 160 | <mtg:MaltegoEntity xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.EmailAddress"> | |
| 161 | <mtg:Properties displayValue="email" value="email"> | |
| 162 | <mtg:Property displayName="URLs" hidden="false" name="URLS" nullable="true" readonly="false" type="string"> | |
| 163 | <mtg:Value>http://www.pay2pay.com.ar/clientes/ekoparty-security-conference/register-eng.php ekoparty Security Conference | |
| 164 | </mtg:Value> | |
| 165 | </mtg:Property> | |
| 166 | <mtg:Property displayName="Email Address" hidden="false" name="email" nullable="true" readonly="false" type="string"> | |
| 167 | <mtg:Value>[email protected]</mtg:Value> | |
| 168 | </mtg:Property> | |
| 169 | </mtg:Properties> | |
| 170 | <mtg:DisplayInformation> | |
| 171 | <mtg:DisplayElement name="Generator detail"><![CDATA[<table><tr><td class=three>Source</td><td class=two>ekoparty.org</td><td class=three>(Domain)</td></tr><tr><td class=three>Transform</td><td class=two colspan=2>To Emails @domain [using Search Engine]</td></tr><tr><td class=three>Result</td><td class=two>[email protected]</td><td class=three>(EmailAddress)</td></tr><tr><td class=three>Gen. date</td><td class=two colspan=2>2011-6-27 23:49</td></tr></table></font>]]></mtg:DisplayElement> | |
| 172 | <mtg:DisplayElement name="Snippet(s):"><![CDATA[<table><tr><td class=one>ekoparty Security Conference</td><td class=three>Indexed on:2011/6/17</td></tr><tr><td class=one colspan=2><a href="http://www.pay2pay.com.ar/clientes/ekoparty-security-conference/register-eng.php">[www.pay2pay.com.ar]</a></td></tr><tr><td class=two colspan=2>For press or coporate groups acreditations please send a mail to: organizacion ' sponsor at the seventh edition of ekoparty contact us at: [email protected] '</td></tr></table><br>]]></mtg:DisplayElement> | |
| 173 | </mtg:DisplayInformation> | |
| 174 | <mtg:Weight>0</mtg:Weight> | |
| 175 | </mtg:MaltegoEntity> | |
| 176 | </data> | |
| 177 | <data key="d2"> | |
| 178 | <mtg:EntityRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"> | |
| 179 | <mtg:Position x="425.25" y="179.40625"/> | |
| 180 | </mtg:EntityRenderer> | |
| 181 | </data> | |
| 182 | </node> | |
| 183 | <node id="n7"> | |
| 184 | <data key="d1"> | |
| 185 | <mtg:MaltegoEntity xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.DNSName"> | |
| 186 | <mtg:Properties displayValue="fqdn" value="fqdn"> | |
| 187 | <mtg:Property displayName="DNS Name" hidden="false" name="fqdn" nullable="true" readonly="false" type="string"> | |
| 188 | <mtg:Value>mail.ekoparty.org</mtg:Value> | |
| 189 | </mtg:Property> | |
| 190 | </mtg:Properties> | |
| 191 | <mtg:DisplayInformation> | |
| 192 | <mtg:DisplayElement name="Generator detail"><![CDATA[<table><tr><td class=three>Source</td><td class=two>ekoparty.org</td><td class=three>(Domain)</td></tr><tr><td class=three>Transform</td><td class=two colspan=2>To DNS Name [Find common DNS names]</td></tr><tr><td class=three>Result</td><td class=two>mail.ekoparty.org</td><td class=three>(DNSName)</td></tr><tr><td class=three>Gen. date</td><td class=two colspan=2>2011-6-27 23:50</td></tr></table></font>]]></mtg:DisplayElement> | |
| 193 | </mtg:DisplayInformation> | |
| 194 | <mtg:Weight>100</mtg:Weight> | |
| 195 | </mtg:MaltegoEntity> | |
| 196 | </data> | |
| 197 | <data key="d2"> | |
| 198 | <mtg:EntityRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"> | |
| 199 | <mtg:Position x="622.75" y="245.875"/> | |
| 200 | </mtg:EntityRenderer> | |
| 201 | </data> | |
| 202 | </node> | |
| 203 | <node id="n8"> | |
| 204 | <data key="d1"> | |
| 205 | <mtg:MaltegoEntity xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.DNSName"> | |
| 206 | <mtg:Properties displayValue="fqdn" value="fqdn"> | |
| 207 | <mtg:Property displayName="DNS Name" hidden="false" name="fqdn" nullable="true" readonly="false" type="string"> | |
| 208 | <mtg:Value>blog.ekoparty.org</mtg:Value> | |
| 209 | </mtg:Property> | |
| 210 | </mtg:Properties> | |
| 211 | <mtg:DisplayInformation> | |
| 212 | <mtg:DisplayElement name="Generator detail"><![CDATA[<table><tr><td class=three>Source</td><td class=two>ekoparty.org</td><td class=three>(Domain)</td></tr><tr><td class=three>Transform</td><td class=two colspan=2>To DNS Name [Find common DNS names]</td></tr><tr><td class=three>Result</td><td class=two>blog.ekoparty.org</td><td class=three>(DNSName)</td></tr><tr><td class=three>Gen. date</td><td class=two colspan=2>2011-6-27 23:50</td></tr></table></font>]]></mtg:DisplayElement> | |
| 213 | </mtg:DisplayInformation> | |
| 214 | <mtg:Weight>100</mtg:Weight> | |
| 215 | </mtg:MaltegoEntity> | |
| 216 | </data> | |
| 217 | <data key="d2"> | |
| 218 | <mtg:EntityRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"> | |
| 219 | <mtg:Position x="250.0" y="297.34375"/> | |
| 220 | </mtg:EntityRenderer> | |
| 221 | </data> | |
| 222 | </node> | |
| 223 | <edge id="e0" source="n0" target="n1"> | |
| 224 | <data key="d3"> | |
| 225 | <mtg:MaltegoLink xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.link.transform-link"> | |
| 226 | <mtg:Properties> | |
| 227 | <mtg:Property displayName="Weight" hidden="false" name="maltego.link.weight" nullable="true" readonly="false" type="int"> | |
| 228 | <mtg:Value>0</mtg:Value> | |
| 229 | </mtg:Property> | |
| 230 | <mtg:Property displayName="Show Label" hidden="false" name="maltego.link.show-label" nullable="true" readonly="false" type="int"> | |
| 231 | <mtg:Value>0</mtg:Value> | |
| 232 | </mtg:Property> | |
| 233 | <mtg:Property displayName="Thickness" hidden="false" name="maltego.link.thickness" nullable="true" readonly="false" type="int"> | |
| 234 | <mtg:Value>1</mtg:Value> | |
| 235 | </mtg:Property> | |
| 236 | <mtg:Property displayName="Date run" hidden="false" name="maltego.link.transform.run-date" nullable="true" readonly="true" type="date"> | |
| 237 | <mtg:Value>2011-06-27 19:46:28.176 EDT</mtg:Value> | |
| 238 | </mtg:Property> | |
| 239 | <mtg:Property displayName="Transform name" hidden="false" name="maltego.link.transform.display-name" nullable="true" readonly="true" type="string"> | |
| 240 | <mtg:Value>To DNS Name - MX (mail server)</mtg:Value> | |
| 241 | </mtg:Property> | |
| 242 | <mtg:Property displayName="Style" hidden="false" name="maltego.link.style" nullable="true" readonly="false" type="int"> | |
| 243 | <mtg:Value>0</mtg:Value> | |
| 244 | </mtg:Property> | |
| 245 | <mtg:Property displayName="Transform" hidden="true" name="maltego.link.transform.name" nullable="true" readonly="true" type="string"> | |
| 246 | <mtg:Value>paterva.v2.DomainToMXrecord_DNS</mtg:Value> | |
| 247 | </mtg:Property> | |
| 248 | <mtg:Property displayName="Color" hidden="false" name="maltego.link.color" nullable="true" readonly="false" type="color"> | |
| 249 | <mtg:Value>-4144960</mtg:Value> | |
| 250 | </mtg:Property> | |
| 251 | <mtg:Property displayName="Transform version" hidden="false" name="maltego.link.transform.version" nullable="true" readonly="true" type="string"> | |
| 252 | <mtg:Value>1.0.0</mtg:Value> | |
| 253 | </mtg:Property> | |
| 254 | </mtg:Properties> | |
| 255 | </mtg:MaltegoLink> | |
| 256 | </data> | |
| 257 | <data key="d4"> | |
| 258 | <mtg:LinkRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"/> | |
| 259 | </data> | |
| 260 | </edge> | |
| 261 | <edge id="e1" source="n0" target="n2"> | |
| 262 | <data key="d3"> | |
| 263 | <mtg:MaltegoLink xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.link.transform-link"> | |
| 264 | <mtg:Properties> | |
| 265 | <mtg:Property displayName="Weight" hidden="false" name="maltego.link.weight" nullable="true" readonly="false" type="int"> | |
| 266 | <mtg:Value>0</mtg:Value> | |
| 267 | </mtg:Property> | |
| 268 | <mtg:Property displayName="Show Label" hidden="false" name="maltego.link.show-label" nullable="true" readonly="false" type="int"> | |
| 269 | <mtg:Value>0</mtg:Value> | |
| 270 | </mtg:Property> | |
| 271 | <mtg:Property displayName="Thickness" hidden="false" name="maltego.link.thickness" nullable="true" readonly="false" type="int"> | |
| 272 | <mtg:Value>1</mtg:Value> | |
| 273 | </mtg:Property> | |
| 274 | <mtg:Property displayName="Date run" hidden="false" name="maltego.link.transform.run-date" nullable="true" readonly="true" type="date"> | |
| 275 | <mtg:Value>2011-06-27 19:49:20.365 EDT</mtg:Value> | |
| 276 | </mtg:Property> | |
| 277 | <mtg:Property displayName="Transform name" hidden="false" name="maltego.link.transform.display-name" nullable="true" readonly="true" type="string"> | |
| 278 | <mtg:Value>To Emails @domain [using Search Engine]</mtg:Value> | |
| 279 | </mtg:Property> | |
| 280 | <mtg:Property displayName="Style" hidden="false" name="maltego.link.style" nullable="true" readonly="false" type="int"> | |
| 281 | <mtg:Value>0</mtg:Value> | |
| 282 | </mtg:Property> | |
| 283 | <mtg:Property displayName="Transform" hidden="true" name="maltego.link.transform.name" nullable="true" readonly="true" type="string"> | |
| 284 | <mtg:Value>paterva.v2.DomainToEmailAddress_AtDomain_SE</mtg:Value> | |
| 285 | </mtg:Property> | |
| 286 | <mtg:Property displayName="Color" hidden="false" name="maltego.link.color" nullable="true" readonly="false" type="color"> | |
| 287 | <mtg:Value>-4144960</mtg:Value> | |
| 288 | </mtg:Property> | |
| 289 | <mtg:Property displayName="Transform version" hidden="false" name="maltego.link.transform.version" nullable="true" readonly="true" type="string"> | |
| 290 | <mtg:Value>1.0.0</mtg:Value> | |
| 291 | </mtg:Property> | |
| 292 | </mtg:Properties> | |
| 293 | </mtg:MaltegoLink> | |
| 294 | </data> | |
| 295 | <data key="d4"> | |
| 296 | <mtg:LinkRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"/> | |
| 297 | </data> | |
| 298 | </edge> | |
| 299 | <edge id="e2" source="n0" target="n3"> | |
| 300 | <data key="d3"> | |
| 301 | <mtg:MaltegoLink xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.link.transform-link"> | |
| 302 | <mtg:Properties> | |
| 303 | <mtg:Property displayName="Weight" hidden="false" name="maltego.link.weight" nullable="true" readonly="false" type="int"> | |
| 304 | <mtg:Value>0</mtg:Value> | |
| 305 | </mtg:Property> | |
| 306 | <mtg:Property displayName="Show Label" hidden="false" name="maltego.link.show-label" nullable="true" readonly="false" type="int"> | |
| 307 | <mtg:Value>0</mtg:Value> | |
| 308 | </mtg:Property> | |
| 309 | <mtg:Property displayName="Thickness" hidden="false" name="maltego.link.thickness" nullable="true" readonly="false" type="int"> | |
| 310 | <mtg:Value>1</mtg:Value> | |
| 311 | </mtg:Property> | |
| 312 | <mtg:Property displayName="Date run" hidden="false" name="maltego.link.transform.run-date" nullable="true" readonly="true" type="date"> | |
| 313 | <mtg:Value>2011-06-27 19:49:20.365 EDT</mtg:Value> | |
| 314 | </mtg:Property> | |
| 315 | <mtg:Property displayName="Transform name" hidden="false" name="maltego.link.transform.display-name" nullable="true" readonly="true" type="string"> | |
| 316 | <mtg:Value>To Emails @domain [using Search Engine]</mtg:Value> | |
| 317 | </mtg:Property> | |
| 318 | <mtg:Property displayName="Style" hidden="false" name="maltego.link.style" nullable="true" readonly="false" type="int"> | |
| 319 | <mtg:Value>0</mtg:Value> | |
| 320 | </mtg:Property> | |
| 321 | <mtg:Property displayName="Transform" hidden="true" name="maltego.link.transform.name" nullable="true" readonly="true" type="string"> | |
| 322 | <mtg:Value>paterva.v2.DomainToEmailAddress_AtDomain_SE</mtg:Value> | |
| 323 | </mtg:Property> | |
| 324 | <mtg:Property displayName="Color" hidden="false" name="maltego.link.color" nullable="true" readonly="false" type="color"> | |
| 325 | <mtg:Value>-4144960</mtg:Value> | |
| 326 | </mtg:Property> | |
| 327 | <mtg:Property displayName="Transform version" hidden="false" name="maltego.link.transform.version" nullable="true" readonly="true" type="string"> | |
| 328 | <mtg:Value>1.0.0</mtg:Value> | |
| 329 | </mtg:Property> | |
| 330 | </mtg:Properties> | |
| 331 | </mtg:MaltegoLink> | |
| 332 | </data> | |
| 333 | <data key="d4"> | |
| 334 | <mtg:LinkRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"/> | |
| 335 | </data> | |
| 336 | </edge> | |
| 337 | <edge id="e3" source="n0" target="n4"> | |
| 338 | <data key="d3"> | |
| 339 | <mtg:MaltegoLink xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.link.transform-link"> | |
| 340 | <mtg:Properties> | |
| 341 | <mtg:Property displayName="Weight" hidden="false" name="maltego.link.weight" nullable="true" readonly="false" type="int"> | |
| 342 | <mtg:Value>0</mtg:Value> | |
| 343 | </mtg:Property> | |
| 344 | <mtg:Property displayName="Show Label" hidden="false" name="maltego.link.show-label" nullable="true" readonly="false" type="int"> | |
| 345 | <mtg:Value>0</mtg:Value> | |
| 346 | </mtg:Property> | |
| 347 | <mtg:Property displayName="Thickness" hidden="false" name="maltego.link.thickness" nullable="true" readonly="false" type="int"> | |
| 348 | <mtg:Value>1</mtg:Value> | |
| 349 | </mtg:Property> | |
| 350 | <mtg:Property displayName="Date run" hidden="false" name="maltego.link.transform.run-date" nullable="true" readonly="true" type="date"> | |
| 351 | <mtg:Value>2011-06-27 19:49:20.365 EDT</mtg:Value> | |
| 352 | </mtg:Property> | |
| 353 | <mtg:Property displayName="Transform name" hidden="false" name="maltego.link.transform.display-name" nullable="true" readonly="true" type="string"> | |
| 354 | <mtg:Value>To Emails @domain [using Search Engine]</mtg:Value> | |
| 355 | </mtg:Property> | |
| 356 | <mtg:Property displayName="Style" hidden="false" name="maltego.link.style" nullable="true" readonly="false" type="int"> | |
| 357 | <mtg:Value>0</mtg:Value> | |
| 358 | </mtg:Property> | |
| 359 | <mtg:Property displayName="Transform" hidden="true" name="maltego.link.transform.name" nullable="true" readonly="true" type="string"> | |
| 360 | <mtg:Value>paterva.v2.DomainToEmailAddress_AtDomain_SE</mtg:Value> | |
| 361 | </mtg:Property> | |
| 362 | <mtg:Property displayName="Color" hidden="false" name="maltego.link.color" nullable="true" readonly="false" type="color"> | |
| 363 | <mtg:Value>-4144960</mtg:Value> | |
| 364 | </mtg:Property> | |
| 365 | <mtg:Property displayName="Transform version" hidden="false" name="maltego.link.transform.version" nullable="true" readonly="true" type="string"> | |
| 366 | <mtg:Value>1.0.0</mtg:Value> | |
| 367 | </mtg:Property> | |
| 368 | </mtg:Properties> | |
| 369 | </mtg:MaltegoLink> | |
| 370 | </data> | |
| 371 | <data key="d4"> | |
| 372 | <mtg:LinkRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"/> | |
| 373 | </data> | |
| 374 | </edge> | |
| 375 | <edge id="e4" source="n0" target="n5"> | |
| 376 | <data key="d3"> | |
| 377 | <mtg:MaltegoLink xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.link.transform-link"> | |
| 378 | <mtg:Properties> | |
| 379 | <mtg:Property displayName="Weight" hidden="false" name="maltego.link.weight" nullable="true" readonly="false" type="int"> | |
| 380 | <mtg:Value>0</mtg:Value> | |
| 381 | </mtg:Property> | |
| 382 | <mtg:Property displayName="Show Label" hidden="false" name="maltego.link.show-label" nullable="true" readonly="false" type="int"> | |
| 383 | <mtg:Value>0</mtg:Value> | |
| 384 | </mtg:Property> | |
| 385 | <mtg:Property displayName="Thickness" hidden="false" name="maltego.link.thickness" nullable="true" readonly="false" type="int"> | |
| 386 | <mtg:Value>1</mtg:Value> | |
| 387 | </mtg:Property> | |
| 388 | <mtg:Property displayName="Date run" hidden="false" name="maltego.link.transform.run-date" nullable="true" readonly="true" type="date"> | |
| 389 | <mtg:Value>2011-06-27 19:49:20.365 EDT</mtg:Value> | |
| 390 | </mtg:Property> | |
| 391 | <mtg:Property displayName="Transform name" hidden="false" name="maltego.link.transform.display-name" nullable="true" readonly="true" type="string"> | |
| 392 | <mtg:Value>To Emails @domain [using Search Engine]</mtg:Value> | |
| 393 | </mtg:Property> | |
| 394 | <mtg:Property displayName="Style" hidden="false" name="maltego.link.style" nullable="true" readonly="false" type="int"> | |
| 395 | <mtg:Value>0</mtg:Value> | |
| 396 | </mtg:Property> | |
| 397 | <mtg:Property displayName="Transform" hidden="true" name="maltego.link.transform.name" nullable="true" readonly="true" type="string"> | |
| 398 | <mtg:Value>paterva.v2.DomainToEmailAddress_AtDomain_SE</mtg:Value> | |
| 399 | </mtg:Property> | |
| 400 | <mtg:Property displayName="Color" hidden="false" name="maltego.link.color" nullable="true" readonly="false" type="color"> | |
| 401 | <mtg:Value>-4144960</mtg:Value> | |
| 402 | </mtg:Property> | |
| 403 | <mtg:Property displayName="Transform version" hidden="false" name="maltego.link.transform.version" nullable="true" readonly="true" type="string"> | |
| 404 | <mtg:Value>1.0.0</mtg:Value> | |
| 405 | </mtg:Property> | |
| 406 | </mtg:Properties> | |
| 407 | </mtg:MaltegoLink> | |
| 408 | </data> | |
| 409 | <data key="d4"> | |
| 410 | <mtg:LinkRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"/> | |
| 411 | </data> | |
| 412 | </edge> | |
| 413 | <edge id="e5" source="n0" target="n6"> | |
| 414 | <data key="d3"> | |
| 415 | <mtg:MaltegoLink xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.link.transform-link"> | |
| 416 | <mtg:Properties> | |
| 417 | <mtg:Property displayName="Weight" hidden="false" name="maltego.link.weight" nullable="true" readonly="false" type="int"> | |
| 418 | <mtg:Value>0</mtg:Value> | |
| 419 | </mtg:Property> | |
| 420 | <mtg:Property displayName="Show Label" hidden="false" name="maltego.link.show-label" nullable="true" readonly="false" type="int"> | |
| 421 | <mtg:Value>0</mtg:Value> | |
| 422 | </mtg:Property> | |
| 423 | <mtg:Property displayName="Thickness" hidden="false" name="maltego.link.thickness" nullable="true" readonly="false" type="int"> | |
| 424 | <mtg:Value>1</mtg:Value> | |
| 425 | </mtg:Property> | |
| 426 | <mtg:Property displayName="Date run" hidden="false" name="maltego.link.transform.run-date" nullable="true" readonly="true" type="date"> | |
| 427 | <mtg:Value>2011-06-27 19:49:20.365 EDT</mtg:Value> | |
| 428 | </mtg:Property> | |
| 429 | <mtg:Property displayName="Transform name" hidden="false" name="maltego.link.transform.display-name" nullable="true" readonly="true" type="string"> | |
| 430 | <mtg:Value>To Emails @domain [using Search Engine]</mtg:Value> | |
| 431 | </mtg:Property> | |
| 432 | <mtg:Property displayName="Style" hidden="false" name="maltego.link.style" nullable="true" readonly="false" type="int"> | |
| 433 | <mtg:Value>0</mtg:Value> | |
| 434 | </mtg:Property> | |
| 435 | <mtg:Property displayName="Transform" hidden="true" name="maltego.link.transform.name" nullable="true" readonly="true" type="string"> | |
| 436 | <mtg:Value>paterva.v2.DomainToEmailAddress_AtDomain_SE</mtg:Value> | |
| 437 | </mtg:Property> | |
| 438 | <mtg:Property displayName="Color" hidden="false" name="maltego.link.color" nullable="true" readonly="false" type="color"> | |
| 439 | <mtg:Value>-4144960</mtg:Value> | |
| 440 | </mtg:Property> | |
| 441 | <mtg:Property displayName="Transform version" hidden="false" name="maltego.link.transform.version" nullable="true" readonly="true" type="string"> | |
| 442 | <mtg:Value>1.0.0</mtg:Value> | |
| 443 | </mtg:Property> | |
| 444 | </mtg:Properties> | |
| 445 | </mtg:MaltegoLink> | |
| 446 | </data> | |
| 447 | <data key="d4"> | |
| 448 | <mtg:LinkRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"/> | |
| 449 | </data> | |
| 450 | </edge> | |
| 451 | <edge id="e6" source="n0" target="n8"> | |
| 452 | <data key="d3"> | |
| 453 | <mtg:MaltegoLink xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.link.transform-link"> | |
| 454 | <mtg:Properties> | |
| 455 | <mtg:Property displayName="Weight" hidden="false" name="maltego.link.weight" nullable="true" readonly="false" type="int"> | |
| 456 | <mtg:Value>0</mtg:Value> | |
| 457 | </mtg:Property> | |
| 458 | <mtg:Property displayName="Show Label" hidden="false" name="maltego.link.show-label" nullable="true" readonly="false" type="int"> | |
| 459 | <mtg:Value>0</mtg:Value> | |
| 460 | </mtg:Property> | |
| 461 | <mtg:Property displayName="Thickness" hidden="false" name="maltego.link.thickness" nullable="true" readonly="false" type="int"> | |
| 462 | <mtg:Value>1</mtg:Value> | |
| 463 | </mtg:Property> | |
| 464 | <mtg:Property displayName="Date run" hidden="false" name="maltego.link.transform.run-date" nullable="true" readonly="true" type="date"> | |
| 465 | <mtg:Value>2011-06-27 19:50:35.637 EDT</mtg:Value> | |
| 466 | </mtg:Property> | |
| 467 | <mtg:Property displayName="Transform name" hidden="false" name="maltego.link.transform.display-name" nullable="true" readonly="true" type="string"> | |
| 468 | <mtg:Value>To DNS Name [Find common DNS names]</mtg:Value> | |
| 469 | </mtg:Property> | |
| 470 | <mtg:Property displayName="Style" hidden="false" name="maltego.link.style" nullable="true" readonly="false" type="int"> | |
| 471 | <mtg:Value>0</mtg:Value> | |
| 472 | </mtg:Property> | |
| 473 | <mtg:Property displayName="Transform" hidden="true" name="maltego.link.transform.name" nullable="true" readonly="true" type="string"> | |
| 474 | <mtg:Value>paterva.v2.DomainToDNSName_DNSBrute</mtg:Value> | |
| 475 | </mtg:Property> | |
| 476 | <mtg:Property displayName="Color" hidden="false" name="maltego.link.color" nullable="true" readonly="false" type="color"> | |
| 477 | <mtg:Value>-4144960</mtg:Value> | |
| 478 | </mtg:Property> | |
| 479 | <mtg:Property displayName="Transform version" hidden="false" name="maltego.link.transform.version" nullable="true" readonly="true" type="string"> | |
| 480 | <mtg:Value>1.0.0</mtg:Value> | |
| 481 | </mtg:Property> | |
| 482 | </mtg:Properties> | |
| 483 | </mtg:MaltegoLink> | |
| 484 | </data> | |
| 485 | <data key="d4"> | |
| 486 | <mtg:LinkRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"/> | |
| 487 | </data> | |
| 488 | </edge> | |
| 489 | <edge id="e7" source="n0" target="n7"> | |
| 490 | <data key="d3"> | |
| 491 | <mtg:MaltegoLink xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.link.transform-link"> | |
| 492 | <mtg:Properties> | |
| 493 | <mtg:Property displayName="Weight" hidden="false" name="maltego.link.weight" nullable="true" readonly="false" type="int"> | |
| 494 | <mtg:Value>0</mtg:Value> | |
| 495 | </mtg:Property> | |
| 496 | <mtg:Property displayName="Show Label" hidden="false" name="maltego.link.show-label" nullable="true" readonly="false" type="int"> | |
| 497 | <mtg:Value>0</mtg:Value> | |
| 498 | </mtg:Property> | |
| 499 | <mtg:Property displayName="Thickness" hidden="false" name="maltego.link.thickness" nullable="true" readonly="false" type="int"> | |
| 500 | <mtg:Value>1</mtg:Value> | |
| 501 | </mtg:Property> | |
| 502 | <mtg:Property displayName="Date run" hidden="false" name="maltego.link.transform.run-date" nullable="true" readonly="true" type="date"> | |
| 503 | <mtg:Value>2011-06-27 19:50:35.636 EDT</mtg:Value> | |
| 504 | </mtg:Property> | |
| 505 | <mtg:Property displayName="Transform name" hidden="false" name="maltego.link.transform.display-name" nullable="true" readonly="true" type="string"> | |
| 506 | <mtg:Value>To DNS Name [Find common DNS names]</mtg:Value> | |
| 507 | </mtg:Property> | |
| 508 | <mtg:Property displayName="Style" hidden="false" name="maltego.link.style" nullable="true" readonly="false" type="int"> | |
| 509 | <mtg:Value>0</mtg:Value> | |
| 510 | </mtg:Property> | |
| 511 | <mtg:Property displayName="Transform" hidden="true" name="maltego.link.transform.name" nullable="true" readonly="true" type="string"> | |
| 512 | <mtg:Value>paterva.v2.DomainToDNSName_DNSBrute</mtg:Value> | |
| 513 | </mtg:Property> | |
| 514 | <mtg:Property displayName="Color" hidden="false" name="maltego.link.color" nullable="true" readonly="false" type="color"> | |
| 515 | <mtg:Value>-4144960</mtg:Value> | |
| 516 | </mtg:Property> | |
| 517 | <mtg:Property displayName="Transform version" hidden="false" name="maltego.link.transform.version" nullable="true" readonly="true" type="string"> | |
| 518 | <mtg:Value>1.0.0</mtg:Value> | |
| 519 | </mtg:Property> | |
| 520 | </mtg:Properties> | |
| 521 | </mtg:MaltegoLink> | |
| 522 | </data> | |
| 523 | <data key="d4"> | |
| 524 | <mtg:LinkRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"/> | |
| 525 | </data> | |
| 526 | </edge> | |
| 527 | <edge id="e8" source="n7" target="n1"> | |
| 528 | <data key="d3"> | |
| 529 | <mtg:MaltegoLink xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.link.manual-link"> | |
| 530 | <mtg:Properties> | |
| 531 | <mtg:Property displayName="Weight" hidden="false" name="maltego.link.weight" nullable="true" readonly="false" type="int"> | |
| 532 | <mtg:Value>0</mtg:Value> | |
| 533 | </mtg:Property> | |
| 534 | <mtg:Property displayName="Show Label" hidden="false" name="maltego.link.show-label" nullable="true" readonly="false" type="int"> | |
| 535 | <mtg:Value>0</mtg:Value> | |
| 536 | </mtg:Property> | |
| 537 | <mtg:Property displayName="Reference" hidden="false" name="maltego.link.manual.reference" nullable="true" readonly="false" type="string"> | |
| 538 | <mtg:Value/> | |
| 539 | </mtg:Property> | |
| 540 | <mtg:Property displayName="Thickness" hidden="false" name="maltego.link.thickness" nullable="true" readonly="false" type="int"> | |
| 541 | <mtg:Value>1</mtg:Value> | |
| 542 | </mtg:Property> | |
| 543 | <mtg:Property displayName="Label" hidden="false" name="maltego.link.manual.type" nullable="true" readonly="false" type="string"> | |
| 544 | <mtg:Value/> | |
| 545 | </mtg:Property> | |
| 546 | <mtg:Property displayName="Style" hidden="false" name="maltego.link.style" nullable="true" readonly="false" type="int"> | |
| 547 | <mtg:Value>0</mtg:Value> | |
| 548 | </mtg:Property> | |
| 549 | <mtg:Property displayName="Description" hidden="false" name="maltego.link.manual.description" nullable="true" readonly="false" type="string"> | |
| 550 | <mtg:Value/> | |
| 551 | </mtg:Property> | |
| 552 | <mtg:Property displayName="Color" hidden="false" name="maltego.link.color" nullable="true" readonly="false" type="color"> | |
| 553 | <mtg:Value>-6895466</mtg:Value> | |
| 554 | </mtg:Property> | |
| 555 | </mtg:Properties> | |
| 556 | </mtg:MaltegoLink> | |
| 557 | </data> | |
| 558 | <data key="d4"> | |
| 559 | <mtg:LinkRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"/> | |
| 560 | </data> | |
| 561 | </edge> | |
| 562 | <edge id="e9" source="n7" target="n4"> | |
| 563 | <data key="d3"> | |
| 564 | <mtg:MaltegoLink xmlns:mtg="http://maltego.paterva.com/xml/mtgx" type="maltego.link.manual-link"> | |
| 565 | <mtg:Properties> | |
| 566 | <mtg:Property displayName="Weight" hidden="false" name="maltego.link.weight" nullable="true" readonly="false" type="int"> | |
| 567 | <mtg:Value>0</mtg:Value> | |
| 568 | </mtg:Property> | |
| 569 | <mtg:Property displayName="Show Label" hidden="false" name="maltego.link.show-label" nullable="true" readonly="false" type="int"> | |
| 570 | <mtg:Value>0</mtg:Value> | |
| 571 | </mtg:Property> | |
| 572 | <mtg:Property displayName="Reference" hidden="false" name="maltego.link.manual.reference" nullable="true" readonly="false" type="string"> | |
| 573 | <mtg:Value/> | |
| 574 | </mtg:Property> | |
| 575 | <mtg:Property displayName="Thickness" hidden="false" name="maltego.link.thickness" nullable="true" readonly="false" type="int"> | |
| 576 | <mtg:Value>1</mtg:Value> | |
| 577 | </mtg:Property> | |
| 578 | <mtg:Property displayName="Label" hidden="false" name="maltego.link.manual.type" nullable="true" readonly="false" type="string"> | |
| 579 | <mtg:Value/> | |
| 580 | </mtg:Property> | |
| 581 | <mtg:Property displayName="Style" hidden="false" name="maltego.link.style" nullable="true" readonly="false" type="int"> | |
| 582 | <mtg:Value>0</mtg:Value> | |
| 583 | </mtg:Property> | |
| 584 | <mtg:Property displayName="Description" hidden="false" name="maltego.link.manual.description" nullable="true" readonly="false" type="string"> | |
| 585 | <mtg:Value/> | |
| 586 | </mtg:Property> | |
| 587 | <mtg:Property displayName="Color" hidden="false" name="maltego.link.color" nullable="true" readonly="false" type="color"> | |
| 588 | <mtg:Value>-6895466</mtg:Value> | |
| 589 | </mtg:Property> | |
| 590 | </mtg:Properties> | |
| 591 | </mtg:MaltegoLink> | |
| 592 | </data> | |
| 593 | <data key="d4"> | |
| 594 | <mtg:LinkRenderer xmlns:mtg="http://maltego.paterva.com/xml/mtgx"/> | |
| 595 | </data> | |
| 596 | </edge> | |
| 597 | </graph> | |
| 598 | <data key="d0"> | |
| 599 | <y:Resources/> | |
| 600 | </data> | |
| 601 | </graphml> |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2015 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 6 | ||
| 7 | import zipfile | |
| 8 | import re | |
| 9 | import os | |
| 10 | ||
| 11 | try: | |
| 12 | import xml.etree.cElementTree as ET | |
| 13 | import xml.etree.ElementTree as ET_ORIG | |
| 14 | ETREE_VERSION = ET_ORIG.VERSION | |
| 15 | except ImportError: | |
| 16 | import xml.etree.ElementTree as ET | |
| 17 | ETREE_VERSION = ET.VERSION | |
| 18 | ||
| 19 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 20 | ||
| 21 | current_path = os.path.abspath(os.getcwd()) | |
| 22 | ||
| 23 | __author__ = "Ezequiel Tavella" | |
| 24 | __copyright__ = "Copyright (c) 2015, Infobyte LLC" | |
| 25 | __credits__ = ["Ezequiel Tavella"] | |
| 26 | __license__ = "" | |
| 27 | __version__ = "1.0.1" | |
| 28 | __maintainer__ = "Ezequiel Tavella" | |
| 29 | __status__ = "Development" | |
| 30 | ||
| 31 | ||
| 32 | def openMtgx(mtgx_file): | |
| 33 | ||
| 34 | try: | |
| 35 | file = zipfile.ZipFile(mtgx_file, "r") | |
| 36 | xml = ET.parse(file.open('Graphs/Graph1.graphml')) | |
| 37 | ||
| 38 | except: | |
| 39 | print("Bad report format") | |
| 40 | return None | |
| 41 | ||
| 42 | file.close() | |
| 43 | return xml | |
| 44 | ||
| 45 | ||
| 46 | class Host(): | |
| 47 | ||
| 48 | def __init__(self): | |
| 49 | self.ip = "" | |
| 50 | self.node_id = "" | |
| 51 | self.dns_name = "" | |
| 52 | self.website = "" | |
| 53 | self.netblock = "" | |
| 54 | self.location = "" | |
| 55 | self.mx_record = "" | |
| 56 | self.ns_record = "" | |
| 57 | ||
| 58 | ||
| 59 | class MaltegoMtgxParser(): | |
| 60 | ||
| 61 | def __init__(self, xml_file): | |
| 62 | ||
| 63 | self.xml = openMtgx(xml_file) | |
| 64 | ||
| 65 | self.nodes = self.xml.findall( | |
| 66 | "{http://graphml.graphdrawing.org/xmlns}graph/" | |
| 67 | "{http://graphml.graphdrawing.org/xmlns}node") | |
| 68 | ||
| 69 | self.edges = self.xml.findall( | |
| 70 | "{http://graphml.graphdrawing.org/xmlns}graph/" | |
| 71 | "{http://graphml.graphdrawing.org/xmlns}edge") | |
| 72 | ||
| 73 | self.list_hosts = [] | |
| 74 | self.relations = {} | |
| 75 | ||
| 76 | def getRelations(self): | |
| 77 | """ | |
| 78 | Get relations between nodes. | |
| 79 | Two ways: Source-> Target | |
| 80 | Source <- Target | |
| 81 | """ | |
| 82 | for edge in self.edges: | |
| 83 | ||
| 84 | source = edge.get("source") | |
| 85 | target = edge.get("target") | |
| 86 | ||
| 87 | if source not in self.relations: | |
| 88 | self.relations.update({source: [target]}) | |
| 89 | ||
| 90 | if target not in self.relations: | |
| 91 | self.relations.update({target: [source]}) | |
| 92 | ||
| 93 | values = self.relations[source] | |
| 94 | values.append(target) | |
| 95 | self.relations.update({source: values}) | |
| 96 | ||
| 97 | values = self.relations[target] | |
| 98 | values.append(source) | |
| 99 | self.relations.update({target: values}) | |
| 100 | ||
| 101 | def getIpAndId(self, node): | |
| 102 | ||
| 103 | # Find node ID and maltego entity | |
| 104 | node_id = node.get("id") | |
| 105 | entity = node.find( | |
| 106 | "{http://graphml.graphdrawing.org/xmlns}data/" | |
| 107 | "{http://maltego.paterva.com/xml/mtgx}MaltegoEntity") | |
| 108 | ||
| 109 | # Check if is IPv4Address | |
| 110 | if entity.get("type") != "maltego.IPv4Address": | |
| 111 | return None | |
| 112 | ||
| 113 | # Get IP value | |
| 114 | value = entity.find( | |
| 115 | "{http://maltego.paterva.com/xml/mtgx}Properties/" | |
| 116 | "{http://maltego.paterva.com/xml/mtgx}Property/" | |
| 117 | "{http://maltego.paterva.com/xml/mtgx}Value") | |
| 118 | ||
| 119 | return {"node_id": node_id, "ip": value.text} | |
| 120 | ||
| 121 | def getNode(self, node_id): | |
| 122 | ||
| 123 | # Get node, filter by id | |
| 124 | for node in self.nodes: | |
| 125 | ||
| 126 | if node.get("id") == node_id: | |
| 127 | return node | |
| 128 | ||
| 129 | def getType(self, node): | |
| 130 | ||
| 131 | # Get type of this node | |
| 132 | entity = node.find( | |
| 133 | "{http://graphml.graphdrawing.org/xmlns}data/" | |
| 134 | "{http://maltego.paterva.com/xml/mtgx}MaltegoEntity") | |
| 135 | ||
| 136 | return entity.get("type") | |
| 137 | ||
| 138 | def getWebsite(self, target_node): | |
| 139 | ||
| 140 | # Parse Website Entity | |
| 141 | result = {"name": "", "ssl_enabled": "", "urls": ""} | |
| 142 | ||
| 143 | props = target_node.find( | |
| 144 | "{http://graphml.graphdrawing.org/xmlns}data/" | |
| 145 | "{http://maltego.paterva.com/xml/mtgx}MaltegoEntity/" | |
| 146 | "{http://maltego.paterva.com/xml/mtgx}Properties") | |
| 147 | ||
| 148 | for prop in props: | |
| 149 | ||
| 150 | name_property = prop.get("name") | |
| 151 | value = prop.find( | |
| 152 | "{http://maltego.paterva.com/xml/mtgx}Value").text | |
| 153 | ||
| 154 | if name_property == "fqdn": | |
| 155 | result["name"] = value | |
| 156 | elif name_property == "website.ssl-enabled": | |
| 157 | result["ssl_enabled"] = value | |
| 158 | elif name_property == "URLS": | |
| 159 | result["urls"] = value | |
| 160 | ||
| 161 | return result | |
| 162 | ||
| 163 | def getNetBlock(self, target_node): | |
| 164 | ||
| 165 | # Parse Netblock Entity | |
| 166 | result = {"ipv4_range": "", "network_owner": "", "country": ""} | |
| 167 | ||
| 168 | props = target_node.find( | |
| 169 | "{http://graphml.graphdrawing.org/xmlns}data/" | |
| 170 | "{http://maltego.paterva.com/xml/mtgx}MaltegoEntity/" | |
| 171 | "{http://maltego.paterva.com/xml/mtgx}Properties") | |
| 172 | ||
| 173 | for prop in props: | |
| 174 | ||
| 175 | name_property = prop.get("name") | |
| 176 | value = prop.find( | |
| 177 | "{http://maltego.paterva.com/xml/mtgx}Value").text | |
| 178 | ||
| 179 | if name_property == "ipv4-range": | |
| 180 | result["ipv4_range"] = value | |
| 181 | elif name_property == "description": | |
| 182 | result["network_owner"] = value | |
| 183 | elif name_property == "country": | |
| 184 | result["country"] = value | |
| 185 | ||
| 186 | return result | |
| 187 | ||
| 188 | def getLocation(self, target_node): | |
| 189 | ||
| 190 | # Parse Location Entity | |
| 191 | result = { | |
| 192 | "name": "", | |
| 193 | "area": "", | |
| 194 | "country_code": "", | |
| 195 | "longitude": "", | |
| 196 | "latitude": "", | |
| 197 | "area_2": ""} | |
| 198 | ||
| 199 | # Get relations with other nodes | |
| 200 | node_relations = self.relations[target_node.get("id")] | |
| 201 | ||
| 202 | # Find location node based in relation with netblock node. | |
| 203 | located = False | |
| 204 | for node_id in node_relations: | |
| 205 | ||
| 206 | target_node = self.getNode(node_id) | |
| 207 | if self.getType(target_node) == "maltego.Location": | |
| 208 | located = True | |
| 209 | break | |
| 210 | ||
| 211 | if not located: | |
| 212 | return None | |
| 213 | ||
| 214 | # Get properties and update data | |
| 215 | props = target_node.find( | |
| 216 | "{http://graphml.graphdrawing.org/xmlns}data/" | |
| 217 | "{http://maltego.paterva.com/xml/mtgx}MaltegoEntity/" | |
| 218 | "{http://maltego.paterva.com/xml/mtgx}Properties") | |
| 219 | ||
| 220 | for prop in props: | |
| 221 | ||
| 222 | name_property = prop.get("name") | |
| 223 | value = prop.find( | |
| 224 | "{http://maltego.paterva.com/xml/mtgx}Value").text | |
| 225 | ||
| 226 | if name_property == "location.name": | |
| 227 | result["name"] = value | |
| 228 | elif name_property == "location.area": | |
| 229 | result["area"] = value | |
| 230 | elif name_property == "countrycode": | |
| 231 | result["country_code"] = value | |
| 232 | elif name_property == "longitude": | |
| 233 | result["longitude"] = value | |
| 234 | elif name_property == "latitude": | |
| 235 | result["latitude"] = value | |
| 236 | elif name_property == "area": | |
| 237 | result["area_2"] = value | |
| 238 | ||
| 239 | return result | |
| 240 | ||
| 241 | def getValue(self, target_node): | |
| 242 | ||
| 243 | # Parse Entity | |
| 244 | result = {"value": ""} | |
| 245 | ||
| 246 | value = target_node.find( | |
| 247 | "{http://graphml.graphdrawing.org/xmlns}data/" | |
| 248 | "{http://maltego.paterva.com/xml/mtgx}MaltegoEntity/" | |
| 249 | "{http://maltego.paterva.com/xml/mtgx}Properties/" | |
| 250 | "{http://maltego.paterva.com/xml/mtgx}Property/" | |
| 251 | "{http://maltego.paterva.com/xml/mtgx}Value") | |
| 252 | ||
| 253 | result["value"] = value.text | |
| 254 | return result | |
| 255 | ||
| 256 | def parse(self): | |
| 257 | ||
| 258 | self.getRelations() | |
| 259 | ||
| 260 | for node in self.nodes: | |
| 261 | ||
| 262 | # Get IP Address if not continue with other node... | |
| 263 | result = self.getIpAndId(node) | |
| 264 | if not result: | |
| 265 | continue | |
| 266 | ||
| 267 | # Create host with values by default | |
| 268 | host = Host() | |
| 269 | host.ip = result["ip"] | |
| 270 | host.node_id = result["node_id"] | |
| 271 | ||
| 272 | # Get relations with other nodes | |
| 273 | node_relations = self.relations[host.node_id] | |
| 274 | ||
| 275 | for node_id in node_relations: | |
| 276 | ||
| 277 | # Get target node and type of node. | |
| 278 | target_node = self.getNode(node_id) | |
| 279 | target_type = self.getType(target_node) | |
| 280 | ||
| 281 | # Check type of node y add data to host... | |
| 282 | if target_type == "maltego.DNSName": | |
| 283 | host.dns_name = self.getValue(target_node) | |
| 284 | elif target_type == "maltego.Website": | |
| 285 | host.website = self.getWebsite(target_node) | |
| 286 | elif target_type == "maltego.Netblock": | |
| 287 | host.netblock = self.getNetBlock(target_node) | |
| 288 | # Get location based in relation: netblock -> location | |
| 289 | host.location = self.getLocation(target_node) | |
| 290 | elif target_type == "maltego.MXRecord": | |
| 291 | host.mx_record = self.getValue(target_node) | |
| 292 | elif target_type == "maltego.NSRecord": | |
| 293 | host.ns_record = self.getValue(target_node) | |
| 294 | ||
| 295 | self.list_hosts.append(host) | |
| 296 | ||
| 297 | return self.list_hosts | |
| 298 | ||
| 299 | ||
| 300 | class MaltegoPlugin(PluginXMLFormat): | |
| 301 | ||
| 302 | def __init__(self): | |
| 303 | super().__init__() | |
| 304 | self.identifier_tag = "maltego" | |
| 305 | self.id = "Maltego" | |
| 306 | self.name = "Maltego MTGX Output Plugin" | |
| 307 | self.plugin_version = "1.0.1" | |
| 308 | self.version = "Maltego 3.6" | |
| 309 | self.framework_version = "1.0.0" | |
| 310 | self.current_path = None | |
| 311 | self.options = None | |
| 312 | self._current_output = None | |
| 313 | ||
| 314 | self._command_regex = re.compile( | |
| 315 | r'^(sudo maltego|maltego|\.\/maltego).*?') | |
| 316 | ||
| 317 | global current_path | |
| 318 | ||
| 319 | def parseOutputString(self, filename, debug=False): | |
| 320 | ||
| 321 | maltego_parser = MaltegoMtgxParser(filename) | |
| 322 | for host in maltego_parser.parse(): | |
| 323 | # Create host | |
| 324 | try: | |
| 325 | old_hostname = host.dns_name["value"] | |
| 326 | except: | |
| 327 | old_hostname = "unknown" | |
| 328 | ||
| 329 | host_id = self.createAndAddHost( | |
| 330 | name=host.ip) | |
| 331 | ||
| 332 | # Create interface | |
| 333 | try: | |
| 334 | network_segment = host.netblock["ipv4_range"] | |
| 335 | hostname_resolution = [host.dns_name["value"]] | |
| 336 | except: | |
| 337 | network_segment = "unknown" | |
| 338 | hostname_resolution = "unknown" | |
| 339 | ||
| 340 | interface_id = self.createAndAddInterface( | |
| 341 | host_id=host_id, | |
| 342 | name=host.ip, | |
| 343 | ipv4_address=host.ip, | |
| 344 | network_segment=network_segment, | |
| 345 | hostname_resolution=hostname_resolution) | |
| 346 | ||
| 347 | # Create note with NetBlock information | |
| 348 | if host.netblock: | |
| 349 | try: | |
| 350 | text = ( | |
| 351 | "Network owner:\n" + | |
| 352 | host.netblock["network_owner"] or "unknown" + | |
| 353 | "Country:\n" + host.netblock["country"] or "unknown") | |
| 354 | except: | |
| 355 | text = "unknown" | |
| 356 | ||
| 357 | self.createAndAddNoteToHost( | |
| 358 | host_id=host_id, | |
| 359 | name="Netblock Information", | |
| 360 | text=text.encode('ascii', 'ignore') | |
| 361 | ) | |
| 362 | ||
| 363 | # Create note with host location | |
| 364 | if host.location: | |
| 365 | try: | |
| 366 | text = ( | |
| 367 | "Location:\n" + | |
| 368 | host.location["name"] + | |
| 369 | "\nArea:\n" + | |
| 370 | host.location["area"] + | |
| 371 | "\nArea 2:\n" + | |
| 372 | host.location["area_2"] + | |
| 373 | "\nCountry_code:\n" + | |
| 374 | host.location["country_code"] + | |
| 375 | "\nLatitude:\n" + | |
| 376 | host.location["latitude"] + | |
| 377 | "\nLongitude:\n" + | |
| 378 | host.location["longitude"]) | |
| 379 | except: | |
| 380 | text = "unknown" | |
| 381 | ||
| 382 | self.createAndAddNoteToHost( | |
| 383 | host_id=host_id, | |
| 384 | name="Location Information", | |
| 385 | text=text.encode('ascii', 'ignore')) | |
| 386 | ||
| 387 | # Create service web server | |
| 388 | if host.website: | |
| 389 | try: | |
| 390 | description = "SSL Enabled: " + host.website["ssl_enabled"] | |
| 391 | except: | |
| 392 | description = "unknown" | |
| 393 | ||
| 394 | service_id = self.createAndAddServiceToInterface( | |
| 395 | host_id=host_id, | |
| 396 | interface_id=interface_id, | |
| 397 | name=host.website["name"], | |
| 398 | protocol="TCP:HTTP", | |
| 399 | ports=[80], | |
| 400 | description=description) | |
| 401 | ||
| 402 | try: | |
| 403 | text = "Urls:\n" + host.website["urls"] | |
| 404 | ||
| 405 | self.createAndAddNoteToService( | |
| 406 | host_id=host_id, | |
| 407 | service_id=service_id, | |
| 408 | name="URLs", | |
| 409 | text=text.encode('ascii', 'ignore')) | |
| 410 | except: | |
| 411 | pass | |
| 412 | ||
| 413 | if host.mx_record: | |
| 414 | ||
| 415 | self.createAndAddServiceToInterface( | |
| 416 | host_id=host_id, | |
| 417 | interface_id=interface_id, | |
| 418 | name=host.mx_record["value"], | |
| 419 | protocol="SMTP", | |
| 420 | ports=[25], | |
| 421 | description="E-mail Server") | |
| 422 | ||
| 423 | if host.ns_record: | |
| 424 | ||
| 425 | self.createAndAddServiceToInterface( | |
| 426 | host_id=host_id, | |
| 427 | interface_id=interface_id, | |
| 428 | name=host.ns_record["value"], | |
| 429 | protocol="DNS", | |
| 430 | ports=[53], | |
| 431 | description="DNS Server") | |
| 432 | ||
| 433 | def processReport(self, filepath): | |
| 434 | self.parseOutputString(filepath) | |
| 435 | ||
| 436 | def processCommandString(self, username, current_path, command_string): | |
| 437 | pass | |
| 438 | ||
| 439 | ||
| 440 | def createPlugin(): | |
| 441 | return MaltegoPlugin() | |
| 442 | ||
| 443 | ||
| 444 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2015 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins.repo.nmap.plugin import NmapPlugin | |
| 6 | import os | |
| 7 | import re | |
| 8 | import random | |
| 9 | ||
| 10 | current_path = os.path.abspath(os.getcwd()) | |
| 11 | ||
| 12 | ||
| 13 | class CmdMasscanPlugin(NmapPlugin): | |
| 14 | """ | |
| 15 | Example plugin to parse amap output. | |
| 16 | """ | |
| 17 | ||
| 18 | def __init__(self): | |
| 19 | ||
| 20 | NmapPlugin.__init__(self) | |
| 21 | self.id = "Masscan" | |
| 22 | self.name = "Masscan Output Plugin" | |
| 23 | self.plugin_version = "0.0.1" | |
| 24 | self.version = "1.0.3" | |
| 25 | self.options = None | |
| 26 | ||
| 27 | self._command_regex = re.compile( | |
| 28 | r'^(masscan|sudo masscan|\.\/masscan|sudo \.\/masscan).*?') | |
| 29 | ||
| 30 | self._output_file_path = os.path.join( | |
| 31 | self.data_path, | |
| 32 | "masscan_output-%s.xml" % self._rid) | |
| 33 | ||
| 34 | def processCommandString(self, username, current_path, command_string): | |
| 35 | """ | |
| 36 | Adds the -oX parameter to get xml output to the command string that the | |
| 37 | user has set. | |
| 38 | """ | |
| 39 | self._output_file_path = os.path.join( | |
| 40 | self.data_path, | |
| 41 | "masscan_output-%s.xml" % random.uniform(1, 10)) | |
| 42 | ||
| 43 | arg_match = self.xml_arg_re.match(command_string) | |
| 44 | ||
| 45 | if arg_match is None: | |
| 46 | return re.sub( | |
| 47 | r"(^.*?masscan)", | |
| 48 | r"\1 -oX %s" % self._output_file_path, | |
| 49 | command_string) | |
| 50 | else: | |
| 51 | return re.sub( | |
| 52 | arg_match.group(1), | |
| 53 | r"-oX %s" % self._output_file_path, | |
| 54 | command_string) | |
| 55 | ||
| 56 | ||
| 57 | def createPlugin(): | |
| 58 | return CmdMasscanPlugin() | |
| 59 | ||
| 60 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import core | |
| 6 | from faraday.client.model import api | |
| 7 | import re | |
| 8 | import os | |
| 9 | import sys | |
| 10 | import random | |
| 11 | import socket | |
| 12 | ||
| 13 | current_path = os.path.abspath(os.getcwd()) | |
| 14 | ||
| 15 | __author__ = "Francisco Amato" | |
| 16 | __copyright__ = "Copyright 2013, Faraday Project" | |
| 17 | __credits__ = ["Francisco Amato"] | |
| 18 | __license__ = "" | |
| 19 | __version__ = "1.0.0" | |
| 20 | __maintainer__ = "Francisco Amato" | |
| 21 | __email__ = "[email protected]" | |
| 22 | __status__ = "Development" | |
| 23 | ||
| 24 | ||
| 25 | class MedusaParser: | |
| 26 | """ | |
| 27 | The objective of this class is to parse an xml file generated by the medusa tool. | |
| 28 | ||
| 29 | @param medusa_filepath A proper simple report generated by medusa | |
| 30 | """ | |
| 31 | ||
| 32 | def __init__(self, xml_output): | |
| 33 | self.srv = {'ftp': '21', 'http': '80', 'imap': '143', 'mssql': '1433', 'mysql': '3306', 'ncp': '524', 'nntp': '119', | |
| 34 | 'pcanywhere': '5631', 'pop3': '110', 'postgres': '5432', 'rexec': '512', 'rlogin': '513', 'rsh': '514', | |
| 35 | 'smbnt': 'smbnt', 'smtp': '25', 'smtp-vrfy': 'smtp-vrfy', 'snmp': '161', 'ssh': '22', 'svn': '3690', | |
| 36 | 'telnet': '23', 'vmauthd': 'vmauthd', 'vnc': '5900', 'web-form': 'web-form', 'wrapper': 'wrapper'} | |
| 37 | ||
| 38 | lines = xml_output.splitlines() | |
| 39 | self.items = [] | |
| 40 | ||
| 41 | for l in lines: | |
| 42 | ||
| 43 | reg = re.search( | |
| 44 | "ACCOUNT FOUND: \[([^$]+)\] Host: ([^$]+) User: ([^$]+) Password: ([^$]+) \[SUCCESS\]", | |
| 45 | l) | |
| 46 | ||
| 47 | print("REG" + str(reg)) | |
| 48 | ||
| 49 | if reg: | |
| 50 | ||
| 51 | item = { | |
| 52 | 'service': reg.group(1), | |
| 53 | 'host': reg.group(2), | |
| 54 | 'user': reg.group(3), | |
| 55 | 'pass': reg.group(4)} | |
| 56 | ||
| 57 | print("ITEM" + str(item)) | |
| 58 | item['ip'] = self.getAddress(item['host']) | |
| 59 | item['port'] = self.srv[item['service']] | |
| 60 | print("ITEM" + str(item)) | |
| 61 | self.items.append(item) | |
| 62 | ||
| 63 | def getAddress(self, hostname): | |
| 64 | """ | |
| 65 | Returns remote IP address from hostname. | |
| 66 | """ | |
| 67 | try: | |
| 68 | return socket.gethostbyname(hostname) | |
| 69 | except socket.error as msg: | |
| 70 | return hostname | |
| 71 | ||
| 72 | ||
| 73 | class MedusaPlugin(core.PluginBase): | |
| 74 | """ | |
| 75 | Example plugin to parse medusa output. | |
| 76 | """ | |
| 77 | ||
| 78 | def __init__(self): | |
| 79 | super().__init__() | |
| 80 | self.id = "Medusa" | |
| 81 | self.name = "Medusa Output Plugin" | |
| 82 | self.plugin_version = "0.0.1" | |
| 83 | self.version = "2.1.1" | |
| 84 | self.options = None | |
| 85 | self._current_output = None | |
| 86 | self._current_path = None | |
| 87 | self._command_regex = re.compile( | |
| 88 | r'^(sudo medusa|sudo \.\/medusa|medusa|\.\/medusa).*?') | |
| 89 | ||
| 90 | self.host = None | |
| 91 | self.port = "" | |
| 92 | ||
| 93 | global current_path | |
| 94 | ||
| 95 | self._output_file_path = os.path.join( | |
| 96 | self.data_path, | |
| 97 | "medusa_output-%s.txt" % self._rid) | |
| 98 | ||
| 99 | def parseOutputString(self, output, debug=False): | |
| 100 | """ | |
| 101 | This method will discard the output the shell sends, it will read it from | |
| 102 | the xml where it expects it to be present. | |
| 103 | ||
| 104 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 105 | output being sent is valid. | |
| 106 | """ | |
| 107 | parser = MedusaParser(output) | |
| 108 | ||
| 109 | for item in parser.items: | |
| 110 | ||
| 111 | h_id = self.createAndAddHost(item['ip']) | |
| 112 | if self._isIPV4(item['ip']): | |
| 113 | i_id = self.createAndAddInterface( | |
| 114 | h_id, | |
| 115 | item['ip'], | |
| 116 | ipv4_address=item['ip'], | |
| 117 | hostname_resolution=item['host']) | |
| 118 | else: | |
| 119 | i_id = self.createAndAddInterface( | |
| 120 | h_id, | |
| 121 | item['ip'], | |
| 122 | ipv6_address=item['ip'], | |
| 123 | hostname_resolution=item['host']) | |
| 124 | ||
| 125 | port = self.port if self.port else item['port'] | |
| 126 | ||
| 127 | s_id = self.createAndAddServiceToInterface( | |
| 128 | h_id, | |
| 129 | i_id, | |
| 130 | item['service'], | |
| 131 | ports=[port], | |
| 132 | protocol="tcp", | |
| 133 | status="open") | |
| 134 | ||
| 135 | self.createAndAddCredToService( | |
| 136 | h_id, | |
| 137 | s_id, | |
| 138 | item['user'], | |
| 139 | item['pass']) | |
| 140 | ||
| 141 | self.createAndAddVulnToService(h_id, | |
| 142 | s_id, | |
| 143 | "Weak Credentials", | |
| 144 | "[medusa found the following credentials]\nuser:%s\npass:%s" % ( item['user'], item['pass']), | |
| 145 | severity="high") | |
| 146 | ||
| 147 | del parser | |
| 148 | ||
| 149 | xml_arg_re = re.compile(r"^.*(-O\s*[^\s]+).*$") | |
| 150 | ||
| 151 | def processCommandString(self, username, current_path, command_string): | |
| 152 | ||
| 153 | self.port = "" | |
| 154 | self._output_file_path = os.path.join( | |
| 155 | self.data_path, "medusa_output-%s.txt" % random.uniform(1, 10)) | |
| 156 | arg_match = self.xml_arg_re.match(command_string) | |
| 157 | ||
| 158 | mreg = re.search(r"\-n( |)([\d]+)", command_string) | |
| 159 | if mreg: | |
| 160 | self.port = mreg.group(2) | |
| 161 | ||
| 162 | if arg_match is None: | |
| 163 | return re.sub( | |
| 164 | r"(^.*?medusa?)", r"\1 -O %s" % self._output_file_path, | |
| 165 | command_string) | |
| 166 | else: | |
| 167 | return re.sub( | |
| 168 | arg_match.group(1), | |
| 169 | r"-O %s" % self._output_file_path, | |
| 170 | command_string) | |
| 171 | ||
| 172 | def _isIPV4(self, ip): | |
| 173 | if len(ip.split(".")) == 4: | |
| 174 | return True | |
| 175 | else: | |
| 176 | return False | |
| 177 | ||
| 178 | def setHost(self): | |
| 179 | pass | |
| 180 | ||
| 181 | ||
| 182 | def createPlugin(): | |
| 183 | return MedusaPlugin() | |
| 184 | ||
| 185 | ||
| 186 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | from faraday.client.model import api | |
| 8 | import re | |
| 9 | import os | |
| 10 | import socket | |
| 11 | import sys | |
| 12 | ||
| 13 | ||
| 14 | current_path = os.path.abspath(os.getcwd()) | |
| 15 | ||
| 16 | __author__ = "Francisco Amato" | |
| 17 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 18 | __credits__ = ["Francisco Amato"] | |
| 19 | __license__ = "" | |
| 20 | __version__ = "1.0.0" | |
| 21 | __maintainer__ = "Francisco Amato" | |
| 22 | __email__ = "[email protected]" | |
| 23 | __status__ = "Development" | |
| 24 | ||
| 25 | ||
| 26 | class MetagoofilParser: | |
| 27 | """ | |
| 28 | The objective of this class is to parse an xml file generated by the metagoofil tool. | |
| 29 | ||
| 30 | TODO: Handle errors. | |
| 31 | TODO: Test metagoofil output version. Handle what happens if the parser doesn't support it. | |
| 32 | TODO: Test cases. | |
| 33 | ||
| 34 | @param metagoofil_filepath A proper simple report generated by metagoofil | |
| 35 | """ | |
| 36 | ||
| 37 | def __init__(self, output): | |
| 38 | ||
| 39 | self.items = [] | |
| 40 | ||
| 41 | mfile = open("/root/dev/faraday/trunk/src/del", "r") | |
| 42 | output = mfile.read() | |
| 43 | mfile.close() | |
| 44 | ||
| 45 | mregex = re.search( | |
| 46 | "\[\+\] List of paths and servers found:[-\s]+([^$]+)\[\+\] List of e-mails found:", output, re.M) | |
| 47 | if mregex is None: | |
| 48 | return | |
| 49 | ||
| 50 | self.users = mregex.group(1).split("\n") | |
| 51 | self.software = mregex.group(2).split("\n") | |
| 52 | self.servers = mregex.group(1).strip().split("\n") | |
| 53 | ||
| 54 | for line in self.servers: | |
| 55 | line = line.strip() | |
| 56 | item = {'host': line, 'ip': self.resolve(line)} | |
| 57 | self.items.append(item) | |
| 58 | ||
| 59 | def resolve(self, host): | |
| 60 | try: | |
| 61 | return socket.gethostbyname(host) | |
| 62 | except: | |
| 63 | pass | |
| 64 | return host | |
| 65 | ||
| 66 | ||
| 67 | class MetagoofilPlugin(core.PluginBase): | |
| 68 | """ | |
| 69 | Example plugin to parse metagoofil output. | |
| 70 | """ | |
| 71 | ||
| 72 | def __init__(self): | |
| 73 | super().__init__() | |
| 74 | self.id = "Metagoofil" | |
| 75 | self.name = "Metagoofil XML Output Plugin" | |
| 76 | self.plugin_version = "0.0.1" | |
| 77 | self.version = "2.2" | |
| 78 | self.options = None | |
| 79 | self._current_output = None | |
| 80 | self._current_path = None | |
| 81 | self._command_regex = re.compile( | |
| 82 | r'^(sudo metagoofil|metagoofil|sudo metagoofil\.py|metagoofil\.py|python metagoofil\.py|\.\/metagoofil\.py).*?') | |
| 83 | self._completition = { | |
| 84 | "": "metagoofil.py -d microsoft.com -t doc,pdf -l 200 -n 50 -o microsoftfiles -f results.html", | |
| 85 | "-d": "domain to search", | |
| 86 | "-t": "filetype to download (pdf,doc,xls,ppt,odp,ods,docx,xlsx,pptx)", | |
| 87 | "-l": "limit of results to search (default 200)", | |
| 88 | "-h": "work with documents in directory (use \"yes\" for local analysis)", | |
| 89 | "-n": "limit of files to download", | |
| 90 | "-o": "working directory", | |
| 91 | "-f": "output file", | |
| 92 | } | |
| 93 | ||
| 94 | global current_path | |
| 95 | ||
| 96 | def canParseCommandString(self, current_input): | |
| 97 | if self._command_regex.match(current_input.strip()): | |
| 98 | return True | |
| 99 | else: | |
| 100 | return False | |
| 101 | ||
| 102 | def parseOutputString(self, output, debug=False): | |
| 103 | """ | |
| 104 | This method will discard the output the shell sends, it will read it from | |
| 105 | the xml where it expects it to be present. | |
| 106 | ||
| 107 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 108 | output being sent is valid. | |
| 109 | """ | |
| 110 | ||
| 111 | def processCommandString(self, username, current_path, command_string): | |
| 112 | """ | |
| 113 | """ | |
| 114 | return None | |
| 115 | ||
| 116 | ||
| 117 | def createPlugin(): | |
| 118 | return MetagoofilPlugin() | |
| 119 | ||
| 120 | ||
| 121 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 6 | from faraday.client.model import api | |
| 7 | import re | |
| 8 | import os | |
| 9 | import sys | |
| 10 | ||
| 11 | try: | |
| 12 | import xml.etree.cElementTree as ET | |
| 13 | import xml.etree.ElementTree as ET_ORIG | |
| 14 | ETREE_VERSION = ET_ORIG.VERSION | |
| 15 | except ImportError: | |
| 16 | import xml.etree.ElementTree as ET | |
| 17 | ETREE_VERSION = ET.VERSION | |
| 18 | ||
| 19 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 20 | ||
| 21 | current_path = os.path.abspath(os.getcwd()) | |
| 22 | ||
| 23 | __author__ = "Francisco Amato" | |
| 24 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 25 | __credits__ = ["Francisco Amato"] | |
| 26 | __license__ = "" | |
| 27 | __version__ = "1.0.0" | |
| 28 | __maintainer__ = "Francisco Amato" | |
| 29 | __email__ = "[email protected]" | |
| 30 | __status__ = "Development" | |
| 31 | ||
| 32 | ||
| 33 | class MetasploitXmlParser: | |
| 34 | """ | |
| 35 | The objective of this class is to parse an xml file generated by the metasploit tool. | |
| 36 | ||
| 37 | TODO: Handle errors. | |
| 38 | TODO: Test metasploit output version. Handle what happens if the parser doesn't support it. | |
| 39 | TODO: Test cases. | |
| 40 | ||
| 41 | @param metasploit_xml_filepath A proper xml generated by metasploit | |
| 42 | """ | |
| 43 | ||
| 44 | def __init__(self, xml_output): | |
| 45 | tree = self.parse_xml(xml_output) | |
| 46 | if tree: | |
| 47 | servicesByWebsite = {} | |
| 48 | for site in tree.findall('web_sites/web_site'): | |
| 49 | servicesByWebsite[site.find('id').text] = site.find('service-id').text | |
| 50 | webVulnsByService = {} | |
| 51 | for v in self.get_vulns(tree, servicesByWebsite): | |
| 52 | if v.service_id not in webVulnsByService: | |
| 53 | webVulnsByService[v.service_id] = [] | |
| 54 | webVulnsByService[v.service_id].append(v) | |
| 55 | ||
| 56 | self.hosts = list(self.get_items( | |
| 57 | tree, | |
| 58 | webVulnsByService)) | |
| 59 | else: | |
| 60 | self.hosts = [] | |
| 61 | ||
| 62 | def parse_xml(self, xml_output): | |
| 63 | """ | |
| 64 | Open and parse an xml file. | |
| 65 | ||
| 66 | TODO: Write custom parser to just read the nodes that we need instead of | |
| 67 | reading the whole file. | |
| 68 | ||
| 69 | @return xml_tree An xml tree instance. None if error. | |
| 70 | """ | |
| 71 | try: | |
| 72 | tree = ET.fromstring(xml_output) | |
| 73 | except SyntaxError as err: | |
| 74 | print("SyntaxError: %s. %s" % (err, xml_output)) | |
| 75 | return None | |
| 76 | ||
| 77 | return tree | |
| 78 | ||
| 79 | def get_items(self, tree, webVulns): | |
| 80 | """ | |
| 81 | @return items A list of Host instances | |
| 82 | """ | |
| 83 | bugtype = "" | |
| 84 | ||
| 85 | for node in tree.findall('hosts/host'): | |
| 86 | yield Host(node, webVulns) | |
| 87 | ||
| 88 | def get_vulns(self, tree, services): | |
| 89 | """ | |
| 90 | @return items A list of WebVuln instances | |
| 91 | """ | |
| 92 | bugtype = "" | |
| 93 | for node in tree.findall('web_vulns/web_vuln'): | |
| 94 | yield WebVuln(node, services) | |
| 95 | ||
| 96 | ||
| 97 | def get_attrib_from_subnode(xml_node, subnode_xpath_expr, attrib_name): | |
| 98 | """ | |
| 99 | Finds a subnode in the item node and the retrieves a value from it | |
| 100 | ||
| 101 | @return An attribute value | |
| 102 | """ | |
| 103 | global ETREE_VERSION | |
| 104 | node = None | |
| 105 | ||
| 106 | if ETREE_VERSION[0] <= 1 and ETREE_VERSION[1] < 3: | |
| 107 | ||
| 108 | match_obj = re.search( | |
| 109 | "([^\@]+?)\[\@([^=]*?)=\'([^\']*?)\'", subnode_xpath_expr) | |
| 110 | if match_obj is not None: | |
| 111 | node_to_find = match_obj.group(1) | |
| 112 | xpath_attrib = match_obj.group(2) | |
| 113 | xpath_value = match_obj.group(3) | |
| 114 | for node_found in xml_node.findall(node_to_find): | |
| 115 | if node_found.attrib[xpath_attrib] == xpath_value: | |
| 116 | node = node_found | |
| 117 | break | |
| 118 | else: | |
| 119 | node = xml_node.find(subnode_xpath_expr) | |
| 120 | ||
| 121 | else: | |
| 122 | node = xml_node.find(subnode_xpath_expr) | |
| 123 | ||
| 124 | if node is not None: | |
| 125 | return node.get(attrib_name) | |
| 126 | ||
| 127 | return None | |
| 128 | ||
| 129 | ||
| 130 | class Host: | |
| 131 | ||
| 132 | def __init__(self, item_node, webVulnsByService): | |
| 133 | self.node = item_node | |
| 134 | self.id = self.get_text_from_subnode('id') | |
| 135 | self.host = self.get_text_from_subnode('name') | |
| 136 | self.ip = self.get_text_from_subnode('address') | |
| 137 | self.os = self.get_text_from_subnode('os-name') | |
| 138 | ||
| 139 | self.services = [] | |
| 140 | self.vulnsByService = {} | |
| 141 | self.vulnsByHost = [] | |
| 142 | self.notesByService = {} | |
| 143 | self.credsByService = {} | |
| 144 | for s in self.node.findall('services/service'): | |
| 145 | service = {'id': None, 'port': None, 'proto': None, | |
| 146 | 'state': None, 'name': None, 'info': None} | |
| 147 | for attr in service: | |
| 148 | service[attr] = s.find(attr).text | |
| 149 | if not service['name']: | |
| 150 | service['name'] = 'unknown' | |
| 151 | if not service['state']: | |
| 152 | service['state'] = 'unknown' | |
| 153 | if not service['info']: | |
| 154 | service['info'] = 'unknown' | |
| 155 | ||
| 156 | self.services.append(service) | |
| 157 | self.vulnsByService[service['id']] = [] | |
| 158 | self.notesByService[service['id']] = [] | |
| 159 | if service['id'] in webVulnsByService: | |
| 160 | self.vulnsByService[service['id']] += webVulnsByService[service['id']] | |
| 161 | ||
| 162 | for v in self.node.findall('vulns/vuln'): | |
| 163 | vuln = HostVuln(v) | |
| 164 | if vuln.service_id: | |
| 165 | self.vulnsByService[vuln.service_id].append(vuln) | |
| 166 | else: | |
| 167 | self.vulnsByHost.append(vuln) | |
| 168 | ||
| 169 | for n in self.node.findall('notes/note'): | |
| 170 | note = HostNote(n) | |
| 171 | key = self.id + "_" + note.service_id | |
| 172 | if not key in self.notesByService: | |
| 173 | self.notesByService[key] = [] | |
| 174 | ||
| 175 | self.notesByService[key].append(note) | |
| 176 | ||
| 177 | for c in self.node.findall('creds/cred'): | |
| 178 | cred = HostCred(c) | |
| 179 | key = cred.port | |
| 180 | if not key in self.credsByService: | |
| 181 | self.credsByService[key] = [] | |
| 182 | ||
| 183 | self.credsByService[key].append(cred) | |
| 184 | ||
| 185 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 186 | """ | |
| 187 | Finds a subnode in the host node and the retrieves a value from it. | |
| 188 | ||
| 189 | @return An attribute value | |
| 190 | """ | |
| 191 | sub_node = self.node.find(subnode_xpath_expr) | |
| 192 | if sub_node is not None: | |
| 193 | if sub_node.text is not None: | |
| 194 | return sub_node.text | |
| 195 | ||
| 196 | return None | |
| 197 | ||
| 198 | ||
| 199 | class WebVuln: | |
| 200 | ||
| 201 | def __init__(self, item_node, services): | |
| 202 | self.node = item_node | |
| 203 | self.name = self.get_text_from_subnode('name') | |
| 204 | self.desc = self.get_text_from_subnode('description') | |
| 205 | self.host = self.get_text_from_subnode('vhost') | |
| 206 | self.port = self.get_text_from_subnode('port') | |
| 207 | self.ip = self.get_text_from_subnode('host') | |
| 208 | self.path = self.get_text_from_subnode('path') | |
| 209 | self.method = self.get_text_from_subnode('method') | |
| 210 | self.params = self.get_text_from_subnode('params') | |
| 211 | self.pname = self.get_text_from_subnode('pname') | |
| 212 | self.risk = self.get_text_from_subnode('risk') | |
| 213 | self.confidence = self.get_text_from_subnode('confidence') | |
| 214 | self.query = self.get_text_from_subnode('query') | |
| 215 | self.request = self.get_text_from_subnode('request') | |
| 216 | self.category = self.get_text_from_subnode('category-id') | |
| 217 | self.service_id = services[self.get_text_from_subnode('web-site-id')] | |
| 218 | self.isWeb = True | |
| 219 | ||
| 220 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 221 | """ | |
| 222 | Finds a subnode in the host node and the retrieves a value from it. | |
| 223 | ||
| 224 | @return An attribute value | |
| 225 | """ | |
| 226 | sub_node = self.node.find(subnode_xpath_expr) | |
| 227 | if sub_node is not None: | |
| 228 | if sub_node.text is not None: | |
| 229 | return sub_node.text | |
| 230 | ||
| 231 | return "" | |
| 232 | ||
| 233 | ||
| 234 | class HostNote: | |
| 235 | """ | |
| 236 | An abstract representation of a HostNote | |
| 237 | ||
| 238 | ||
| 239 | @param item_node A item_node taken from an metasploit xml tree | |
| 240 | """ | |
| 241 | ||
| 242 | def __init__(self, item_node): | |
| 243 | self.node = item_node | |
| 244 | self.service_id = self.get_text_from_subnode( | |
| 245 | 'service-id') if not None else "" | |
| 246 | self.host_id = self.get_text_from_subnode('host-id') | |
| 247 | self.ntype = self.get_text_from_subnode('ntype') | |
| 248 | self.data = self.get_text_from_subnode('data') | |
| 249 | ||
| 250 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 251 | """ | |
| 252 | Finds a subnode in the host node and the retrieves a value from it. | |
| 253 | ||
| 254 | @return An attribute value | |
| 255 | """ | |
| 256 | sub_node = self.node.find(subnode_xpath_expr) | |
| 257 | if sub_node is not None: | |
| 258 | if sub_node.text is not None: | |
| 259 | return sub_node.text | |
| 260 | ||
| 261 | return "" | |
| 262 | ||
| 263 | ||
| 264 | class HostCred: | |
| 265 | """ | |
| 266 | An abstract representation of a HostNote | |
| 267 | ||
| 268 | ||
| 269 | @param item_node A item_node taken from an metasploit xml tree | |
| 270 | """ | |
| 271 | ||
| 272 | def __init__(self, item_node): | |
| 273 | self.node = item_node | |
| 274 | self.port = self.get_text_from_subnode('port') | |
| 275 | self.user = self.get_text_from_subnode('user') | |
| 276 | self.passwd = self.get_text_from_subnode('pass') | |
| 277 | self.ptype = self.get_text_from_subnode('ptype') | |
| 278 | self.sname = self.get_text_from_subnode('sname') | |
| 279 | ||
| 280 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 281 | """ | |
| 282 | Finds a subnode in the host node and the retrieves a value from it. | |
| 283 | ||
| 284 | @return An attribute value | |
| 285 | """ | |
| 286 | sub_node = self.node.find(subnode_xpath_expr) | |
| 287 | if sub_node is not None: | |
| 288 | if sub_node.text is not None: | |
| 289 | return sub_node.text | |
| 290 | ||
| 291 | return "" | |
| 292 | ||
| 293 | ||
| 294 | class HostVuln: | |
| 295 | """ | |
| 296 | An abstract representation of a HostVuln | |
| 297 | ||
| 298 | ||
| 299 | @param item_node A item_node taken from an metasploit xml tree | |
| 300 | """ | |
| 301 | ||
| 302 | def __init__(self, item_node): | |
| 303 | self.node = item_node | |
| 304 | self.service_id = self.get_text_from_subnode('service-id') | |
| 305 | self.name = self.get_text_from_subnode('name') | |
| 306 | self.desc = self.get_text_from_subnode('info') | |
| 307 | self.refs = [r.text for r in self.node.findall('refs/ref')] | |
| 308 | self.exploited_date = self.get_text_from_subnode('exploited-at') | |
| 309 | self.exploited = (self.exploited_date != None) | |
| 310 | self.isWeb = False | |
| 311 | ||
| 312 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 313 | """ | |
| 314 | Finds a subnode in the host node and the retrieves a value from it. | |
| 315 | ||
| 316 | @return An attribute value | |
| 317 | """ | |
| 318 | sub_node = self.node.find(subnode_xpath_expr) | |
| 319 | if sub_node is not None: | |
| 320 | if sub_node.text is not None: | |
| 321 | return sub_node.text | |
| 322 | ||
| 323 | return "" | |
| 324 | ||
| 325 | ||
| 326 | class MetasploitPlugin(PluginXMLFormat): | |
| 327 | """ | |
| 328 | Example plugin to parse metasploit output. | |
| 329 | """ | |
| 330 | ||
| 331 | def __init__(self): | |
| 332 | super().__init__() | |
| 333 | self.identifier_tag = ["MetasploitV4", "MetasploitV5"] | |
| 334 | self.id = "Metasploit" | |
| 335 | self.name = "Metasploit XML Output Plugin" | |
| 336 | self.plugin_version = "0.0.1" | |
| 337 | self.version = "4.7.2" | |
| 338 | self.framework_version = "1.0.0" | |
| 339 | self.options = None | |
| 340 | self._current_output = None | |
| 341 | self.target = None | |
| 342 | self._command_regex = re.compile(r'^(metasploit|sudo metasploit|\.\/metasploit).*?') | |
| 343 | ||
| 344 | global current_path | |
| 345 | self._output_file_path = os.path.join(self.data_path, "metasploit_output-%s.xml" % self._rid) | |
| 346 | ||
| 347 | def parseOutputString(self, output, debug=False): | |
| 348 | """ | |
| 349 | This method will discard the output the shell sends, it will read it from | |
| 350 | the xml where it expects it to be present. | |
| 351 | ||
| 352 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 353 | output being sent is valid. | |
| 354 | """ | |
| 355 | ||
| 356 | parser = MetasploitXmlParser(output) | |
| 357 | ||
| 358 | for item in parser.hosts: | |
| 359 | self.hostnames = [] | |
| 360 | if item.host: | |
| 361 | self.hostnames = [item.host] | |
| 362 | ||
| 363 | h_id = self.createAndAddHost(item.ip, os=item.os, hostnames=self.hostnames) | |
| 364 | ||
| 365 | if item.id + "_" in item.notesByService: | |
| 366 | for n in item.notesByService[item.id + "_"]: | |
| 367 | self.createAndAddNoteToHost(h_id, n.ntype, n.data) | |
| 368 | ||
| 369 | for v in item.vulnsByHost: | |
| 370 | v_id = self.createAndAddVulnToHost( | |
| 371 | h_id, v.name, v.desc, ref=v.refs) | |
| 372 | ||
| 373 | for s in item.services: | |
| 374 | s_id = self.createAndAddServiceToHost(h_id, s['name'], | |
| 375 | protocol=s['proto'], | |
| 376 | ports=[s['port']], | |
| 377 | status=s['state'], | |
| 378 | description=s['info']) | |
| 379 | ||
| 380 | if item.id + "_" + s['id'] in item.notesByService: | |
| 381 | for n in item.notesByService[item.id + "_" + s['id']]: | |
| 382 | self.createAndAddNoteToService( | |
| 383 | h_id, s_id, n.ntype, n.data) | |
| 384 | ||
| 385 | if s['port'] in item.credsByService: | |
| 386 | for c in item.credsByService[s['port']]: | |
| 387 | self.createAndAddCredToService( | |
| 388 | h_id, s_id, c.user, c.passwd) | |
| 389 | self.createAndAddVulnToService(h_id, s_id, "Weak Credentials", "[metasploit found the following credentials]\nuser:%s\npass:%s" % ( | |
| 390 | c.user, c.passwd), severity="high") | |
| 391 | ||
| 392 | for v in item.vulnsByService[s['id']]: | |
| 393 | if v.isWeb: | |
| 394 | v_id = self.createAndAddVulnWebToService(h_id, s_id, v.name, v.desc, | |
| 395 | severity=v.risk, website=v.host, | |
| 396 | path=v.path, request=v.request, method=v.method, | |
| 397 | pname=v.pname, params=v.params, query=v.query, | |
| 398 | category=v.category) | |
| 399 | else: | |
| 400 | v_id = self.createAndAddVulnToService( | |
| 401 | h_id, s_id, v.name, v.desc, ref=v.refs) | |
| 402 | ||
| 403 | del parser | |
| 404 | ||
| 405 | def _isIPV4(self, ip): | |
| 406 | if len(ip.split(".")) == 4: | |
| 407 | return True | |
| 408 | else: | |
| 409 | return False | |
| 410 | ||
| 411 | def processCommandString(self, username, current_path, command_string): | |
| 412 | return None | |
| 413 | ||
| 414 | def setHost(self): | |
| 415 | pass | |
| 416 | ||
| 417 | ||
| 418 | def createPlugin(): | |
| 419 | return MetasploitPlugin() | |
| 420 | ||
| 421 | ||
| 422 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | from faraday.client.model import api | |
| 8 | import re | |
| 9 | import os | |
| 10 | import sys | |
| 11 | ||
| 12 | try: | |
| 13 | import psycopg2 | |
| 14 | except ImportError: | |
| 15 | raise Exception("Please install psycopg2 to use plugin: MetasploitOn") | |
| 16 | ||
| 17 | import time | |
| 18 | ||
| 19 | current_path = os.path.abspath(os.getcwd()) | |
| 20 | ||
| 21 | __author__ = "Francisco Amato" | |
| 22 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 23 | __credits__ = ["Francisco Amato"] | |
| 24 | __license__ = "" | |
| 25 | __version__ = "1.0.0" | |
| 26 | __maintainer__ = "Francisco Amato" | |
| 27 | __email__ = "[email protected]" | |
| 28 | __status__ = "Development" | |
| 29 | ||
| 30 | ||
| 31 | class MetasploitOnPlugin(core.PluginBase): | |
| 32 | """ | |
| 33 | Example plugin to parse metasploiton output. | |
| 34 | """ | |
| 35 | ||
| 36 | def __init__(self): | |
| 37 | super().__init__() | |
| 38 | self.id = "MetasploitOn" | |
| 39 | self.name = "Metasploit Online Service Plugin" | |
| 40 | self.plugin_version = "0.0.3" | |
| 41 | self.version = "Metasploit 4.10.0" | |
| 42 | self.framework_version = "1.0.0" | |
| 43 | self.options = None | |
| 44 | self._current_output = None | |
| 45 | self.target = None | |
| 46 | self._command_regex = re.compile( | |
| 47 | r'^(metasploiton|sudo metasploiton|\.\/metasploiton).*?') | |
| 48 | ||
| 49 | global current_path | |
| 50 | ||
| 51 | self.addSetting("Database", str, "db") | |
| 52 | self.addSetting("User", str, "user") | |
| 53 | self.addSetting("Password", str, "pass") | |
| 54 | self.addSetting("Server", str, "localhost") | |
| 55 | self.addSetting("Port", str, "5432") | |
| 56 | ### NOTE: do _not_ correct the typo, it's used by the user.xml | |
| 57 | self.addSetting("Workspace", str, "default") | |
| 58 | self.addSetting("Enable", str, "0") | |
| 59 | ||
| 60 | self._sdate = "" | |
| 61 | self._lsdate = "" | |
| 62 | self._mwhere = "" | |
| 63 | ||
| 64 | def parseOutputString(self, output, debug=False): | |
| 65 | """ | |
| 66 | This method will discard the output the shell sends, it will read it | |
| 67 | from the xml where it expects it to be present. | |
| 68 | ||
| 69 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 70 | output being sent is valid. | |
| 71 | """ | |
| 72 | ||
| 73 | try: | |
| 74 | conn = psycopg2.connect(dbname=self.getSetting("Database"), | |
| 75 | user=self.getSetting("User"), | |
| 76 | password=self.getSetting("Password"), | |
| 77 | host=self.getSetting("Server"), | |
| 78 | port=self.getSetting("Port")) | |
| 79 | ||
| 80 | cur = conn.cursor() | |
| 81 | except Exception as e: | |
| 82 | print("[Faraday - MetasplotiOn] Error Connecting to the database") | |
| 83 | print("[Faraday - MetasplotiOn]Check your metasploit postgresql credentials and server IP/Port") | |
| 84 | print(e) | |
| 85 | return | |
| 86 | ||
| 87 | cur = self._doSql( | |
| 88 | cur, | |
| 89 | "select * from hosts inner join workspaces ON (hosts.workspace_id=workspaces.id) where workspaces.name like '" + self.getSetting("Workspace") + "';") | |
| 90 | if cur is None: | |
| 91 | print("Error getting database data\n") | |
| 92 | return | |
| 93 | ||
| 94 | self.path = self.data_path + "/" + api.getActiveWorkspace().name + \ | |
| 95 | "_metasploit_last" | |
| 96 | ||
| 97 | if os.path.isfile(self.path): | |
| 98 | f = open(self.path, "r") | |
| 99 | self._sdate = f.readline() | |
| 100 | f.close | |
| 101 | ||
| 102 | for h in cur.fetchall(): | |
| 103 | ||
| 104 | h_id = self.createAndAddHost( | |
| 105 | str(h[2]), | |
| 106 | str(h[7])) | |
| 107 | ||
| 108 | if self._isIPV4(str(h[2])): | |
| 109 | ||
| 110 | i_id = self.createAndAddInterface( | |
| 111 | h_id, | |
| 112 | str(h[2]), | |
| 113 | mac=str(h[3]), | |
| 114 | ipv4_address=str(h[2]), | |
| 115 | hostname_resolution=[str(h[5])]) | |
| 116 | else: | |
| 117 | ||
| 118 | i_id = self.createAndAddInterface( | |
| 119 | h_id, | |
| 120 | str(h[2]), | |
| 121 | mac=str(h[3]), | |
| 122 | ipv6_address=str(h[2]), | |
| 123 | hostname_resolution=[str(h[5])]) | |
| 124 | ||
| 125 | self._checkDate(str(h[13])) | |
| 126 | ||
| 127 | cur = self._doSql( | |
| 128 | cur, | |
| 129 | "select * from vulns where host_id=" + str(h[0]) + " and service_id is null" + self._mwhere + ";") | |
| 130 | if cur is None: | |
| 131 | return | |
| 132 | ||
| 133 | for v in cur.fetchall(): | |
| 134 | ||
| 135 | self._checkDate(str(v[5])) | |
| 136 | ||
| 137 | cur = self._doSql( | |
| 138 | cur, | |
| 139 | "select * from vulns_refs inner join refs ON (vulns_refs.id=refs.id) where vulns_refs.vuln_id=" + str(v[0]) + ";") | |
| 140 | if cur is None: | |
| 141 | return | |
| 142 | ||
| 143 | refs = [] | |
| 144 | for r in cur.fetchall(): | |
| 145 | self._checkDate(str(r[5])) | |
| 146 | refs.append(r[6]) | |
| 147 | ||
| 148 | self.createAndAddVulnToHost( | |
| 149 | h_id, | |
| 150 | str(v[4]), | |
| 151 | str(v[6]), | |
| 152 | refs) | |
| 153 | ||
| 154 | cur = self._doSql( | |
| 155 | cur, | |
| 156 | "select * from notes where host_id=" + str(h[0]) + " and service_id is null" + self._mwhere + ";") | |
| 157 | if cur is None: | |
| 158 | return | |
| 159 | ||
| 160 | for n in cur.fetchall(): | |
| 161 | self._checkDate(str(n[6])) | |
| 162 | self.createAndAddNoteToHost( | |
| 163 | h_id, | |
| 164 | str(n[2]), | |
| 165 | str(n[9])) | |
| 166 | ||
| 167 | cur = self._doSql( | |
| 168 | cur, | |
| 169 | "select * from services where host_id=" + str(h[0])) | |
| 170 | if cur is None: | |
| 171 | return | |
| 172 | ||
| 173 | for s in cur.fetchall(): | |
| 174 | ||
| 175 | self._checkDate(str(s[7])) | |
| 176 | s_id = self.createAndAddServiceToInterface( | |
| 177 | h_id, | |
| 178 | i_id, | |
| 179 | name=str(s[6]), | |
| 180 | ports=[str(s[3])], | |
| 181 | protocol=str(s[4]), | |
| 182 | status=str(s[5]), | |
| 183 | description=str(s[8]), | |
| 184 | version=str(s[8])) | |
| 185 | ||
| 186 | cur = self._doSql( | |
| 187 | cur, | |
| 188 | "select * from creds where service_id=" + str(s[0]) + self._mwhere + ";") | |
| 189 | ||
| 190 | if cur is None: | |
| 191 | return | |
| 192 | for c in cur.fetchall(): | |
| 193 | self._checkDate(str(c[3])) | |
| 194 | ||
| 195 | self.createAndAddCredToService( | |
| 196 | h_id, | |
| 197 | s_id, | |
| 198 | c[4], | |
| 199 | c[5]) | |
| 200 | ||
| 201 | self.createAndAddVulnToService( | |
| 202 | h_id, | |
| 203 | s_id, | |
| 204 | "Weak Credentials", | |
| 205 | "[metasploit found the following credentials]\nuser:%s\npass:%s" % (c[4], c[ | |
| 206 | 5]), | |
| 207 | severity="high") | |
| 208 | ||
| 209 | cur = self._doSql( | |
| 210 | cur, | |
| 211 | "select * from vulns where host_id=" + str(h[0]) + " and service_id=" + str(s[0]) + self._mwhere + ";") | |
| 212 | if cur is None: | |
| 213 | return | |
| 214 | ||
| 215 | for v in cur.fetchall(): | |
| 216 | self._checkDate(str(v[5])) | |
| 217 | ||
| 218 | cur = self._doSql( | |
| 219 | cur, | |
| 220 | "select * from vulns_refs inner join refs ON (vulns_refs.id=refs.id) where vulns_refs.vuln_id=" + str(v[0]) + ";") | |
| 221 | if cur is None: | |
| 222 | return | |
| 223 | ||
| 224 | refs = [] | |
| 225 | for r in cur.fetchall(): | |
| 226 | self._checkDate(str(r[5])) | |
| 227 | refs.append(r[6]) | |
| 228 | ||
| 229 | self.createAndAddVulnToService( | |
| 230 | h_id, | |
| 231 | s_id, | |
| 232 | name=str(v[4]), | |
| 233 | desc=str(v[6]), | |
| 234 | ref=refs) | |
| 235 | ||
| 236 | mwhere = re.sub( | |
| 237 | "updated_at", | |
| 238 | "web_vulns.updated_at", | |
| 239 | self._mwhere) | |
| 240 | ||
| 241 | cur = self._doSql( | |
| 242 | cur, | |
| 243 | "select * from web_vulns INNER JOIN web_sites ON (web_vulns.web_site_id=web_sites.id) where web_sites.service_id=" + str(s[0]) + mwhere + ";") | |
| 244 | ||
| 245 | if cur is None: | |
| 246 | return | |
| 247 | ||
| 248 | ||
| 249 | for v in cur.fetchall(): | |
| 250 | self._checkDate(str(v[3])) | |
| 251 | ||
| 252 | #TODO: should be nice to stop hardcoding the positions | |
| 253 | # of the information and instead make it depend | |
| 254 | # on the column name | |
| 255 | ||
| 256 | # beware, next silly coder, the table as it stands | |
| 257 | # right holds information in each position like this: | |
| 258 | # v[0] = id, v[1] = web_site_id, v[2] = created_at | |
| 259 | # v[3] = updated_at, v[4] = path, v[5] = method, | |
| 260 | # v[6] = params, v[7] = pname, v[8] = risk, v[9] = name | |
| 261 | # v[10] = query, v[11] = category, v[12] = confidence, | |
| 262 | # v[13] = description, v[14] = blame, v[15] = request, | |
| 263 | # v[16] = proof, v[17] = owner, v[18] = payload, v[19] = id, | |
| 264 | # v[20] = service_id, v[21] = created_at, v[22] = updated_at | |
| 265 | # v[23] = vhost, v[24] = comments, v[25] = options | |
| 266 | ||
| 267 | # if the plugin breakes, check that everything is in the | |
| 268 | # same position | |
| 269 | ||
| 270 | # metasploit doesn't give us a website, but the vhost + | |
| 271 | # path is kinda the same | |
| 272 | website = str(v[23]) + str(v[4]) | |
| 273 | ||
| 274 | self.createAndAddVulnWebToService( | |
| 275 | h_id, | |
| 276 | s_id, | |
| 277 | name=str(v[9]), | |
| 278 | desc=str(v[13]), | |
| 279 | website=website, | |
| 280 | path=str(v[5]), | |
| 281 | request=str(v[16]), | |
| 282 | method=str(v[6]), | |
| 283 | pname=str(v[8]), | |
| 284 | params=str(v[7]), | |
| 285 | query=str(v[11])) | |
| 286 | ||
| 287 | cur = self._doSql( | |
| 288 | cur, | |
| 289 | "select * from notes where host_id=" + str(h[0]) + " and service_id=" + str(s[0]) + self._mwhere) | |
| 290 | ||
| 291 | if cur is None: | |
| 292 | return | |
| 293 | ||
| 294 | for n in cur.fetchall(): | |
| 295 | ||
| 296 | self._checkDate(str(n[6])) | |
| 297 | ||
| 298 | self.createAndAddNoteToService( | |
| 299 | h_id, | |
| 300 | s_id, | |
| 301 | str(n[2]), | |
| 302 | str(n[9])) | |
| 303 | ||
| 304 | cur = self._doSql( | |
| 305 | cur, | |
| 306 | "select * from web_sites where service_id=" + str(s[0]) + self._mwhere) | |
| 307 | ||
| 308 | for w in cur.fetchall(): | |
| 309 | self._checkDate(str(w[3])) | |
| 310 | ||
| 311 | cur.close() | |
| 312 | conn.close() | |
| 313 | ||
| 314 | def _doSql(self, db, sql): | |
| 315 | try: | |
| 316 | api.devlog("SQL:" + sql) | |
| 317 | db.execute(sql) | |
| 318 | except Exception as e: | |
| 319 | print ("Error SQL[" + e.pgcode + "] - " + e.pgerror) | |
| 320 | return None | |
| 321 | ||
| 322 | return db | |
| 323 | ||
| 324 | def _checkDate(self, rowdate): | |
| 325 | ||
| 326 | mret = True | |
| 327 | msave = True | |
| 328 | ||
| 329 | if not self._lsdate: | |
| 330 | ||
| 331 | if self._sdate: | |
| 332 | self._lsdate = self._sdate | |
| 333 | else: | |
| 334 | self._lsdate = rowdate | |
| 335 | ||
| 336 | if self._cdate(self._lsdate, rowdate): | |
| 337 | msave = False | |
| 338 | ||
| 339 | if self._sdate: | |
| 340 | self._mwhere = " and updated_at > to_timestamp('" + \ | |
| 341 | self._sdate + "','YYYY-MM-DD HH24:MI:SS.US');" | |
| 342 | ||
| 343 | if msave: | |
| 344 | try: | |
| 345 | f = open(self.path, "w") | |
| 346 | f.write(rowdate) | |
| 347 | f.close() | |
| 348 | self._lsdate = rowdate | |
| 349 | except: | |
| 350 | print ("Can't save metasploit lastupdate file") | |
| 351 | return | |
| 352 | ||
| 353 | return mret | |
| 354 | ||
| 355 | def _cdate(self, date1, date2): | |
| 356 | ||
| 357 | mdate = time.strptime(date1.split(".")[0], "%Y-%m-%d %H:%M:%S") | |
| 358 | mdate2 = time.strptime(date2.split(".")[0], "%Y-%m-%d %H:%M:%S") | |
| 359 | ||
| 360 | if mdate > mdate2: | |
| 361 | return True | |
| 362 | else: | |
| 363 | return False | |
| 364 | ||
| 365 | def _isIPV4(self, ip): | |
| 366 | if len(ip.split(".")) == 4: | |
| 367 | return True | |
| 368 | else: | |
| 369 | return False | |
| 370 | ||
| 371 | def processCommandString(self, username, current_path, command_string): | |
| 372 | return None | |
| 373 | ||
| 374 | def setHost(self): | |
| 375 | pass | |
| 376 | ||
| 377 | ||
| 378 | def createPlugin(): | |
| 379 | return MetasploitOnPlugin() | |
| 380 | ||
| 381 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | from faraday.client.model import api | |
| 8 | import re | |
| 9 | ||
| 10 | try: | |
| 11 | import xml.etree.cElementTree as ET | |
| 12 | import xml.etree.ElementTree as ET_ORIG | |
| 13 | except ImportError: | |
| 14 | import xml.etree.ElementTree as ET | |
| 15 | ||
| 16 | __author__ = 'Ezequiel Tavella' | |
| 17 | __copyright__ = 'Copyright (c) 2016, Infobyte LLC' | |
| 18 | __credits__ = ['Ezequiel Tavella'] | |
| 19 | __license__ = '' | |
| 20 | __version__ = '1.0.0' | |
| 21 | __email__ = "[email protected]" | |
| 22 | __status__ = "Development" | |
| 23 | ||
| 24 | ||
| 25 | class NdiffXmlParser(): | |
| 26 | """ | |
| 27 | The objective of this class is to parse an xml file generated by | |
| 28 | the ndiff tool. | |
| 29 | """ | |
| 30 | ||
| 31 | def __init__(self, xmlOutput): | |
| 32 | self.tree = self.parse_xml(xmlOutput) | |
| 33 | ||
| 34 | if self.tree: | |
| 35 | self.hostDiff = self.getHostsDiffs(self.tree) | |
| 36 | else: | |
| 37 | self.hostDiff = [] | |
| 38 | ||
| 39 | def parse_xml(self, xmlOutput): | |
| 40 | ||
| 41 | # Open and parse an xml output | |
| 42 | ||
| 43 | try: | |
| 44 | return ET.fromstring(xmlOutput) | |
| 45 | except SyntaxError as err: | |
| 46 | print("SyntaxError: %s" % err) | |
| 47 | return None | |
| 48 | ||
| 49 | def getHostsDiffs(self, tree): | |
| 50 | """ | |
| 51 | @return hosts A list of HostDiff instances | |
| 52 | """ | |
| 53 | for node in tree.findall('scandiff/hostdiff'): | |
| 54 | yield HostDiff(node) | |
| 55 | ||
| 56 | ||
| 57 | class HostDiff(): | |
| 58 | ||
| 59 | # Abstraction of a Hosts Diff | |
| 60 | # Search for a new host in the second scan and new ports opened or changed | |
| 61 | # of status... | |
| 62 | def __init__(self, hostDiff): | |
| 63 | ||
| 64 | self.isNewHost = False | |
| 65 | self.hostXml = self.getHostXml(hostDiff) | |
| 66 | ||
| 67 | self.ip = self.getIp() | |
| 68 | self.ports = self.getPorts() | |
| 69 | ||
| 70 | def getHostXml(self, hostDiff): | |
| 71 | ||
| 72 | host = hostDiff.find('host') | |
| 73 | if host is not None: | |
| 74 | return host | |
| 75 | else: | |
| 76 | self.isNewHost = True | |
| 77 | return hostDiff.find('b/host') | |
| 78 | ||
| 79 | def getIp(self): | |
| 80 | if self.hostXml is None: | |
| 81 | return None | |
| 82 | return self.hostXml.find('address').get('addr') | |
| 83 | ||
| 84 | def getPorts(self): | |
| 85 | ||
| 86 | ports = [] | |
| 87 | if self.hostXml is None: | |
| 88 | return ports | |
| 89 | ||
| 90 | if self.isNewHost: | |
| 91 | ||
| 92 | for port in self.hostXml.find('ports').findall('port'): | |
| 93 | ports.append( | |
| 94 | [port.get('portid'), port.find('state').get('state')]) | |
| 95 | return ports | |
| 96 | ||
| 97 | else: | |
| 98 | ||
| 99 | for port in self.hostXml.find('ports').findall('portdiff'): | |
| 100 | if port.find('b/port'): | |
| 101 | ports.append([port.find('b/port').get('portid'), | |
| 102 | port.find('b/port/state').get('state')]) | |
| 103 | return ports | |
| 104 | ||
| 105 | ||
| 106 | class CmdNdiffPlugin(core.PluginBase): | |
| 107 | """ | |
| 108 | This plugin handles ndiff command. | |
| 109 | Add a new vuln INFO if detect a new host or a new port .. | |
| 110 | """ | |
| 111 | ||
| 112 | def __init__(self): | |
| 113 | super().__init__() | |
| 114 | self.id = "Ndiff" | |
| 115 | self.name = "ndiff" | |
| 116 | self.plugin_version = "0.0.1" | |
| 117 | self.version = "1.0.0" | |
| 118 | self._command_regex = re.compile(r'^(sudo ndiff|ndiff).*?') | |
| 119 | ||
| 120 | def parseOutputString(self, output, debug=False): | |
| 121 | ||
| 122 | parser = NdiffXmlParser(output) | |
| 123 | ||
| 124 | for host in parser.hostDiff: | |
| 125 | ||
| 126 | if host.ip is None: | |
| 127 | continue | |
| 128 | ||
| 129 | if host.isNewHost: | |
| 130 | hostId = self.createAndAddHost(host.ip, '') | |
| 131 | ||
| 132 | description = '%s is a NEW host active.\n' % host.ip | |
| 133 | for port in host.ports: | |
| 134 | description += 'Port: %s/%s\n' % (port[0], port[1]) | |
| 135 | ||
| 136 | self.createAndAddVulnToHost( | |
| 137 | hostId, | |
| 138 | 'New host active', | |
| 139 | description, | |
| 140 | ['Ndiff tool'], | |
| 141 | 'INFO' | |
| 142 | ) | |
| 143 | else: | |
| 144 | ||
| 145 | if host.ports == []: | |
| 146 | continue | |
| 147 | ||
| 148 | hostId = self.createAndAddHost(host.ip, '') | |
| 149 | ||
| 150 | description = 'New service/s found.\n' | |
| 151 | for port in host.ports: | |
| 152 | description += 'Port: %s/%s\n' % (port[0], port[1]) | |
| 153 | ||
| 154 | self.createAndAddVulnToHost( | |
| 155 | hostId, | |
| 156 | 'New ports actives', | |
| 157 | description, | |
| 158 | ['Ndiff tool'], | |
| 159 | 'INFO' | |
| 160 | ) | |
| 161 | ||
| 162 | def processCommandString(self, username, current_path, command_string): | |
| 163 | if command_string.find('--xml') < 0: | |
| 164 | return command_string + '--xml' | |
| 165 | ||
| 166 | ||
| 167 | def createPlugin(): | |
| 168 | return CmdNdiffPlugin() | |
| 169 | ||
| 170 | ||
| 171 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | # dotnessus_v2.py | |
| 1 | # Python module to deal with Nessus .nessus (v2) files | |
| 2 | # http://code.google.com/p/pynessus/ | |
| 3 | # | |
| 4 | ||
| 5 | # Copyright (C) 2010 Dustin Seibel | |
| 6 | # | |
| 7 | # GNU General Public Licence (GPL) | |
| 8 | # | |
| 9 | # This program is free software; you can redistribute it and/or modify it under | |
| 10 | # the terms of the GNU General Public License as published by the Free Software | |
| 11 | # Foundation; either version 2 of the License, or (at your option) any later | |
| 12 | # version. | |
| 13 | # This program is distributed in the hope that it will be useful, but WITHOUT | |
| 14 | # ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS | |
| 15 | # FOR A PARTICULAR PURPOSE. See the GNU General Public License for more | |
| 16 | # details. | |
| 17 | # You should have received a copy of the GNU General Public License along with | |
| 18 | # this program; if not, write to the Free Software Foundation, Inc., 59 Temple | |
| 19 | # Place, Suite 330, Boston, MA 02111-1307 USA | |
| 20 | # | |
| 21 | # 2011-03-12: 0.1.1: Initial version. | |
| 22 | from __future__ import absolute_import | |
| 23 | ||
| 24 | import sys | |
| 25 | import re | |
| 26 | import xml.etree.ElementTree as ET | |
| 27 | from datetime import datetime | |
| 28 | from io import StringIO, BytesIO | |
| 29 | ||
| 30 | ||
| 31 | # List all nodes in a ReportItem object that can have multiple values | |
| 32 | MULTI_VALUED_ATTS = [ | |
| 33 | 'cve', | |
| 34 | 'bid', | |
| 35 | 'xref', | |
| 36 | 'cvss_base_score' | |
| 37 | ] | |
| 38 | ||
| 39 | # HOST_(START|END) date format | |
| 40 | HOST_DATE_FORMAT = '%a %b %d %H:%M:%S %Y' | |
| 41 | ||
| 42 | # Regex defs | |
| 43 | re_ip = re.compile('\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}') | |
| 44 | re_wmi_ip = re.compile( | |
| 45 | 'IPAddress/IPSubnet.*?(?P<value>\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})', re.I) | |
| 46 | re_wmi_man = re.compile( | |
| 47 | 'Computer Manufacturer : (?P<manufacturer>.*?)\n.*?Computer Model : (?P<model>.*?)\n.*?Computer Memory : (?P<memory>\d+)\s', re.I | re.M | re.S) | |
| 48 | re_shares = re.compile('- (?P<value>.*?)\n', re.I | re.M | re.S) | |
| 49 | re_local_admins = re.compile('- (?P<value>.*?)\s\(', re.I | re.M | re.S) | |
| 50 | re_wsus = re.compile('WUServer: (?P<wsus_server>.*?)\n.*?AUOptions: (?P<wsus_auoption>.*?)\n.*?Detect LastSuccessTime: (?P<wsus_lastdetect>.*?)\n.*?Download LastSuccessTime: (?P<wsus_lastdownload>.*?)\n.*?Install LastSuccessTime: (?P<wsus_lastinstall>.*?)\n.*?RebootRequired: (?P<wsus_rebootneeded>.*?)\n.*?ServiceStatus: (?P<wsus_auenabled>.*?)(\n|$)', re.I | re.M | re.S) | |
| 51 | re_unix_memory = re.compile('Total memory: (?P<memory>\d+)\s', re.I) | |
| 52 | re_unix_model = re.compile( | |
| 53 | 'Serial Number\s+: (?P<serial>.*?)\s.*?\nProduct Name\s+: (?P<model>.*?)(\n|$)', re.I | re.M) | |
| 54 | re_unix_cpu = re.compile('Current Speed\s+: (?P<cpu_speed>.*?)\s*\nManufacturer\s+: (?P<cpu_vendor>.*?)\s*\nFamily\s+: (?P<cpu_model>.*?)\s*\nExternal Clock\s+: (?P<cpu_externalclock>.*?)\s*\nVersion\s+: (?P<cpu_version>.*?)\s*\nType\s+: (?P<cpu_type>.*?)($|\s*\n)', re.I | re.M) | |
| 55 | ||
| 56 | # Plugin to regex map | |
| 57 | # Format is plugin_id: (attribute_name, regex_object, attribute_to_parse, | |
| 58 | # multi_valued) | |
| 59 | REGEX_MAP = { | |
| 60 | '24272': ('ips', re_wmi_ip, 'plugin_output', True), | |
| 61 | '25203': ('ips', re_ip, 'plugin_output', True), | |
| 62 | '24270': ('', re_wmi_man, 'description', False), | |
| 63 | '10395': ('shares', re_shares, 'plugin_output', True), | |
| 64 | '10902': ('local_admins', re_local_admins, 'plugin_output', True), | |
| 65 | '10860': ('local_users', re_local_admins, 'plugin_output', True), | |
| 66 | '55555': ('', re_wsus, 'description', False), | |
| 67 | '45433': ('', re_unix_memory, 'plugin_output', False), | |
| 68 | '35351': ('', re_unix_model, 'plugin_output', False), | |
| 69 | '45432': ('', re_unix_cpu, 'plugin_output', False), | |
| 70 | } | |
| 71 | ||
| 72 | # Local IP list | |
| 73 | LOCAL_IP_LIST = [ | |
| 74 | '0.0.0.0', | |
| 75 | '127.0.0.1', | |
| 76 | ] | |
| 77 | ||
| 78 | ||
| 79 | class Report: | |
| 80 | ||
| 81 | def __init__(self): | |
| 82 | self.name = None | |
| 83 | self.targets = [] | |
| 84 | self.scan_start = None | |
| 85 | self.scan_end = None | |
| 86 | ||
| 87 | def parse(self, xml_file, from_string=False): | |
| 88 | """Import .nessus file""" | |
| 89 | # Parse XML file | |
| 90 | #getLogger(self).debug("Parsing report start") | |
| 91 | if from_string: | |
| 92 | try: | |
| 93 | xml_file = BytesIO(xml_file) | |
| 94 | except Exception as e1: | |
| 95 | try: | |
| 96 | xml_file = StringIO(xml_file) | |
| 97 | except Exception as e2: | |
| 98 | raise Exception(str(e1) + "\n" + str(e2)) | |
| 99 | ||
| 100 | # Iterate through each host scanned and create objects for each | |
| 101 | for event, elem in ET.iterparse(xml_file): | |
| 102 | ||
| 103 | #getLogger(self).debug("Parsing elemn %s" % elem[0:20]) | |
| 104 | # Grab the report name from the Report element | |
| 105 | if event == 'end' and elem.tag == 'Report': | |
| 106 | self.name = elem.attrib.get('name') | |
| 107 | ||
| 108 | # Only process ReportHost elements | |
| 109 | elif event == 'end' and elem.tag != 'ReportHost': | |
| 110 | continue | |
| 111 | ||
| 112 | rh_obj = ReportHost(elem) | |
| 113 | if rh_obj: | |
| 114 | self.targets.append(rh_obj) | |
| 115 | ||
| 116 | # Update Report dates | |
| 117 | if not self.scan_start: | |
| 118 | self.scan_start = rh_obj.host_start | |
| 119 | if not self.scan_end: | |
| 120 | self.scan_end = rh_obj.host_end | |
| 121 | if rh_obj.get('host_start'): | |
| 122 | if rh_obj.host_start < self.scan_start: | |
| 123 | self.scan_start = rh_obj.host_start | |
| 124 | if rh_obj.host_end > self.scan_end: | |
| 125 | self.scan_end = rh_obj.host_end | |
| 126 | ||
| 127 | def __repr__(self): | |
| 128 | return "<Report: %s>" % self.name | |
| 129 | ||
| 130 | def get_target(self, name): | |
| 131 | """Returns a target object given a name""" | |
| 132 | for t in self.targets: | |
| 133 | if name.lower() == t.name.lower(): | |
| 134 | return t | |
| 135 | ||
| 136 | ||
| 137 | class ReportHost: | |
| 138 | ||
| 139 | def __init__(self, xml_report_host): | |
| 140 | self.name = None | |
| 141 | self.dead = False | |
| 142 | self.vulns = [] | |
| 143 | ||
| 144 | # Do a check to make sure it's well formed | |
| 145 | # ... | |
| 146 | ||
| 147 | # Get ReportHost name | |
| 148 | self.name = xml_report_host.attrib.get('name') | |
| 149 | ||
| 150 | # Get HostProperties tags | |
| 151 | for n in xml_report_host.findall('HostProperties/tag'): | |
| 152 | setattr(self, n.attrib.get('name'), n.text) | |
| 153 | ||
| 154 | #getLogger(self).debug("Parsing host start tag") | |
| 155 | tmp = Report() | |
| 156 | # Convert scan dates and check for dead status | |
| 157 | if self.get('HOST_START'): | |
| 158 | ||
| 159 | self.host_start = self.get('HOST_START') | |
| 160 | #getLogger(self).info("Host start found %s" % self.host_start) | |
| 161 | ||
| 162 | #self.host_start = datetime.strptime(self.get('HOST_START'), HOST_DATE_FORMAT) | |
| 163 | else: | |
| 164 | self.dead = True | |
| 165 | self.host_start = None | |
| 166 | self.host_end = self.get('HOST_END') | |
| 167 | #self.host_end = datetime.strptime(self.get('HOST_END'), HOST_DATE_FORMAT) | |
| 168 | ||
| 169 | # Get all ReportItems | |
| 170 | for ri in xml_report_host.findall('ReportItem'): | |
| 171 | ri_obj = ReportItem(ri) | |
| 172 | if ri_obj: | |
| 173 | self.vulns.append(ri_obj) | |
| 174 | xml_report_host.clear() | |
| 175 | ||
| 176 | # Do an additional check for deadness | |
| 177 | for v in self.find_vuln(plugin_id='10180'): | |
| 178 | if 'dead' in str(v.get('plugin_output')): | |
| 179 | self.dead = True | |
| 180 | ||
| 181 | # Parse additional fields into host attributes | |
| 182 | for plugin_id in REGEX_MAP: | |
| 183 | att, regex, dest_att, multi = REGEX_MAP[plugin_id] | |
| 184 | vulns = self.find_vuln(plugin_id=plugin_id) | |
| 185 | ||
| 186 | # If multi flag is set, store results in a dict | |
| 187 | if multi: | |
| 188 | results = [] | |
| 189 | ||
| 190 | # Grab all plugins | |
| 191 | for v in vulns: | |
| 192 | if multi: | |
| 193 | setattr(self, att, regex.findall(v.get(dest_att))) | |
| 194 | else: | |
| 195 | plugin_output = v.get(dest_att) | |
| 196 | if not plugin_output: | |
| 197 | continue | |
| 198 | ||
| 199 | res = regex.search(v.get(dest_att)) | |
| 200 | if not res: | |
| 201 | continue | |
| 202 | ||
| 203 | # Check to see if named fields were given | |
| 204 | if res.groupdict(): | |
| 205 | # Store each named field as an attribute | |
| 206 | for k, v in res.groupdict().items(): | |
| 207 | setattr(self, k, v) | |
| 208 | ||
| 209 | # No named fields, just grab whatever matched | |
| 210 | else: | |
| 211 | setattr(self, att, res.group()) | |
| 212 | ||
| 213 | def __repr__(self): | |
| 214 | return "<ReportHost: %s>" % self.name | |
| 215 | ||
| 216 | def get(self, attr): | |
| 217 | """Returns attribute value if it exists""" | |
| 218 | try: | |
| 219 | return getattr(self, attr) | |
| 220 | except AttributeError: | |
| 221 | return None | |
| 222 | ||
| 223 | def find_vuln(self, **kwargs): | |
| 224 | """Find a ReportItem given the search params""" | |
| 225 | results = [] | |
| 226 | ||
| 227 | # Iterate through preferences | |
| 228 | for r in self.vulns: | |
| 229 | match = True | |
| 230 | # If one of the search criteria doesn't match, set the flag | |
| 231 | for k in kwargs: | |
| 232 | if kwargs.get(k) != r.get(k): | |
| 233 | match = False | |
| 234 | ||
| 235 | # If it's a match, add it to results | |
| 236 | if match: | |
| 237 | results.append(r) | |
| 238 | return results | |
| 239 | ||
| 240 | def get_ips(self, exclude_local=True): | |
| 241 | """Return a list of IPs for host""" | |
| 242 | ip_list = set() | |
| 243 | if re_ip.search(self.name): | |
| 244 | ip_list.add(self.name) | |
| 245 | if self.get('host-ip'): | |
| 246 | ip_list.add(self.get('host-ip')) | |
| 247 | if self.get('ips'): | |
| 248 | ip_list.update(self.ips) | |
| 249 | ||
| 250 | # If exclude_local is set, remove local IPs from list | |
| 251 | if exclude_local: | |
| 252 | for i in LOCAL_IP_LIST: | |
| 253 | if i in ip_list: | |
| 254 | ip_list.remove(i) | |
| 255 | ||
| 256 | return list(ip_list) | |
| 257 | ||
| 258 | def get_open_ports(self): | |
| 259 | """Returns a dict of open ports found""" | |
| 260 | results = {} | |
| 261 | ||
| 262 | # Fetch results | |
| 263 | vulns = self.find_vuln(plugin_id='0') | |
| 264 | ||
| 265 | # For each port, put it in a dict | |
| 266 | for v in vulns: | |
| 267 | proto = v.get('protocol') | |
| 268 | port = v.get('port') | |
| 269 | if proto not in results: | |
| 270 | results[proto] = [] | |
| 271 | results[proto].append(port) | |
| 272 | return results | |
| 273 | ||
| 274 | def get_name(self): | |
| 275 | """Returns a friendly name for host""" | |
| 276 | if re_ip.search(self.name): | |
| 277 | if self.get('netbios-name'): | |
| 278 | return self.get('netbios-name').lower() | |
| 279 | elif self.get('host-fqdn'): | |
| 280 | return self.get('host-fqdn').lower() | |
| 281 | else: | |
| 282 | return self.name | |
| 283 | else: | |
| 284 | return self.name | |
| 285 | ||
| 286 | ||
| 287 | class ReportItem: | |
| 288 | ||
| 289 | def __init__(self, xml_report_item): | |
| 290 | # Make sure object is well formed | |
| 291 | # ... | |
| 292 | ||
| 293 | # Get ReportItem attributes | |
| 294 | self.port = xml_report_item.attrib.get('port') | |
| 295 | self.svc_name = xml_report_item.attrib.get('svc_name') | |
| 296 | self.protocol = xml_report_item.attrib.get('protocol') | |
| 297 | self.severity = xml_report_item.attrib.get('severity') | |
| 298 | self.plugin_id = xml_report_item.attrib.get('pluginID') | |
| 299 | self.plugin_name = xml_report_item.attrib.get('pluginName') | |
| 300 | self.plugin_family = xml_report_item.attrib.get('pluginFamily') | |
| 301 | ||
| 302 | # Create multi-valued atts | |
| 303 | for m in MULTI_VALUED_ATTS: | |
| 304 | setattr(self, m, list()) | |
| 305 | ||
| 306 | # Get optional nodes | |
| 307 | for n in xml_report_item.getchildren(): | |
| 308 | # If it's a multi-valued att, append to list | |
| 309 | if n.tag in MULTI_VALUED_ATTS: | |
| 310 | v = getattr(self, n.tag) | |
| 311 | v.append(n.text.strip()) | |
| 312 | setattr(self, n.tag, v) | |
| 313 | continue | |
| 314 | ||
| 315 | # If it's not a multi-valued att, store it as a string | |
| 316 | if n.text is not None: | |
| 317 | setattr(self, n.tag, n.text.strip()) | |
| 318 | ||
| 319 | xml_report_item.clear() | |
| 320 | ||
| 321 | def __repr__(self): | |
| 322 | return "<ReportItem: %s/%s %s %s>" % (self.port, self.protocol, self.plugin_id, self.plugin_name) | |
| 323 | ||
| 324 | def get(self, attr): | |
| 325 | """Returns attribute value if it exists""" | |
| 326 | try: | |
| 327 | return getattr(self, attr) | |
| 328 | except AttributeError: | |
| 329 | return None | |
| 330 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | ||
| 7 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 8 | import re | |
| 9 | import os | |
| 10 | import socket | |
| 11 | ||
| 12 | import faraday.client.plugins.repo.nessus.dotnessus_v2 as dotnessus_v2 | |
| 13 | ||
| 14 | ||
| 15 | ||
| 16 | current_path = os.path.abspath(os.getcwd()) | |
| 17 | ||
| 18 | __author__ = "Francisco Amato" | |
| 19 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 20 | __credits__ = ["Francisco Amato"] | |
| 21 | __license__ = "" | |
| 22 | __version__ = "1.0.0" | |
| 23 | __maintainer__ = "Francisco Amato" | |
| 24 | __email__ = "[email protected]" | |
| 25 | __status__ = "Development" | |
| 26 | ||
| 27 | ||
| 28 | class NessusParser: | |
| 29 | """ | |
| 30 | The objective of this class is to parse an xml file generated by the nessus tool. | |
| 31 | ||
| 32 | TODO: Handle errors. | |
| 33 | TODO: Test nessus output version. Handle what happens if the parser doesn't support it. | |
| 34 | TODO: Test cases. | |
| 35 | ||
| 36 | @param nessus_filepath A proper simple report generated by nessus | |
| 37 | """ | |
| 38 | ||
| 39 | def __init__(self, output): | |
| 40 | lists = output.split("\r\n") | |
| 41 | i = 0 | |
| 42 | self.items = [] | |
| 43 | if re.search("Could not reach", output) is not None: | |
| 44 | self.fail = True | |
| 45 | return | |
| 46 | ||
| 47 | for line in lists: | |
| 48 | if i > 8: | |
| 49 | item = {'link': line} | |
| 50 | self.items.append(item) | |
| 51 | i = i + 1 | |
| 52 | ||
| 53 | ||
| 54 | class NessusPlugin(PluginXMLFormat): | |
| 55 | """ | |
| 56 | Example plugin to parse nessus output. | |
| 57 | """ | |
| 58 | ||
| 59 | def __init__(self): | |
| 60 | super().__init__() | |
| 61 | self.extension = ".nessus" | |
| 62 | self.identifier_tag = "NessusClientData_v2" | |
| 63 | self.id = "Nessus" | |
| 64 | self.name = "Nessus XML Output Plugin" | |
| 65 | self.plugin_version = "0.0.1" | |
| 66 | self.version = "5.2.4" | |
| 67 | self.framework_version = "1.0.1" | |
| 68 | self.options = None | |
| 69 | self._current_output = None | |
| 70 | self._current_path = None | |
| 71 | self._command_regex = re.compile( | |
| 72 | r'^(nessus|sudo nessus|\.\/nessus).*?') | |
| 73 | self.host = None | |
| 74 | self.port = None | |
| 75 | self.protocol = None | |
| 76 | self.fail = None | |
| 77 | ||
| 78 | global current_path | |
| 79 | self.output_path = os.path.join(self.data_path, "nessus_output-%s.txt" % self._rid) | |
| 80 | ||
| 81 | def canParseCommandString(self, current_input): | |
| 82 | if self._command_regex.match(current_input.strip()): | |
| 83 | return True | |
| 84 | else: | |
| 85 | return False | |
| 86 | ||
| 87 | def parseOutputString(self, output, debug=False): | |
| 88 | """ | |
| 89 | This method will discard the output the shell sends, it will read it from | |
| 90 | the xml where it expects it to be present. | |
| 91 | ||
| 92 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 93 | output being sent is valid. | |
| 94 | """ | |
| 95 | p = dotnessus_v2.Report() | |
| 96 | try: | |
| 97 | p.parse(output, from_string=True) | |
| 98 | except Exception as e: | |
| 99 | self.logger.error("Exception - %s", e) | |
| 100 | ||
| 101 | for t in p.targets: | |
| 102 | mac = "" | |
| 103 | host = "" | |
| 104 | ip = "" | |
| 105 | ||
| 106 | if t.get('mac-address'): | |
| 107 | mac = t.get('mac-address') | |
| 108 | if t.get('host-fqdn'): | |
| 109 | host = t.get('host-fqdn') | |
| 110 | if t.get('host-ip'): | |
| 111 | ip = t.get('host-ip') | |
| 112 | ||
| 113 | if not ip: | |
| 114 | if not t.get_ips(): | |
| 115 | continue | |
| 116 | ip = t.get_ips().pop() | |
| 117 | ||
| 118 | h_id = self.createAndAddHost(ip, t.get('operating-system'), hostnames=[host]) | |
| 119 | ||
| 120 | if self._isIPV4(ip): | |
| 121 | i_id = self.createAndAddInterface( | |
| 122 | h_id, ip, mac, ipv4_address=ip, hostname_resolution=[host]) | |
| 123 | else: | |
| 124 | i_id = self.createAndAddInterface( | |
| 125 | h_id, ip, mac, ipv6_address=ip, hostname_resolution=[host]) | |
| 126 | ||
| 127 | srv = {} | |
| 128 | web = False | |
| 129 | for v in t.vulns: | |
| 130 | external_id = "" | |
| 131 | ||
| 132 | external_id = v.get('plugin_id') | |
| 133 | ||
| 134 | desc = "" | |
| 135 | desc += v.get('description') if v.get('description') else "" | |
| 136 | resolution = "" | |
| 137 | resolution = v.get('solution') if v.get('solution') else "" | |
| 138 | ||
| 139 | data = "\nOutput: " + v.get('plugin_output') if v.get('plugin_output') else "" | |
| 140 | ||
| 141 | ref = [] | |
| 142 | if v.get('cve'): | |
| 143 | cves = v.get('cve') | |
| 144 | for cve in cves: | |
| 145 | #logger.debug('Appending %s', cve.encode("utf-8")) | |
| 146 | ref.append(cve.encode("utf-8").strip()) | |
| 147 | if v.get('bid'): | |
| 148 | bids = v.get('bid') | |
| 149 | for bid in bids: | |
| 150 | #logger.debug('Appending %s', bid.encode("utf-8")) | |
| 151 | ref.append("BID-%s" % bid.encode("utf-8").strip() ) | |
| 152 | if v.get('cvss_base_score'): | |
| 153 | ref.append("CVSS: " + ", ".join(v.get('cvss_base_score'))) | |
| 154 | if v.get('xref'): | |
| 155 | ref.append(", ".join(v.get('xref'))) | |
| 156 | if v.get('svc_name') == "general": | |
| 157 | v_id = self.createAndAddVulnToHost(h_id, v.get('plugin_name'), | |
| 158 | desc=desc, ref=ref, data=data, severity=v.get('severity'), resolution=resolution, external_id=external_id) | |
| 159 | else: | |
| 160 | ||
| 161 | s_id = self.createAndAddServiceToInterface(h_id, i_id, v.get('svc_name'), | |
| 162 | v.get( | |
| 163 | 'protocol'), | |
| 164 | ports=[ | |
| 165 | str(v.get('port'))], | |
| 166 | status="open") | |
| 167 | ||
| 168 | web = re.search(r'^(www|http)', v.get('svc_name')) | |
| 169 | if v.get('svc_name') in srv: | |
| 170 | srv[v.get('svc_name')] = 1 | |
| 171 | ||
| 172 | if web: | |
| 173 | v_id = self.createAndAddVulnWebToService(h_id, s_id, v.get('plugin_name'), | |
| 174 | desc=desc, data=data, website=host, severity=v.get('severity'), | |
| 175 | resolution=resolution, ref=ref, external_id=external_id) | |
| 176 | else: | |
| 177 | v_id = self.createAndAddVulnToService(h_id, s_id, v.get('plugin_name'), | |
| 178 | desc=desc, data=data, severity=v.get('severity'), resolution=resolution, | |
| 179 | ref=ref, external_id=external_id) | |
| 180 | ||
| 181 | def _isIPV4(self, ip): | |
| 182 | if len(ip.split(".")) == 4: | |
| 183 | return True | |
| 184 | else: | |
| 185 | return False | |
| 186 | ||
| 187 | def processCommandString(self, username, current_path, command_string): | |
| 188 | return None | |
| 189 | ||
| 190 | def setHost(self): | |
| 191 | pass | |
| 192 | ||
| 193 | def resolve(self, host): | |
| 194 | try: | |
| 195 | return socket.gethostbyname(host) | |
| 196 | except: | |
| 197 | pass | |
| 198 | return host | |
| 199 | ||
| 200 | ||
| 201 | def createPlugin(): | |
| 202 | return NessusPlugin() | |
| 203 | ||
| 204 | # I'm Py3⏎ |
| 0 | # pynessus.py | |
| 1 | # Python module to interact with a Nessus 4.x scanner via XMLRPC. | |
| 2 | # http://code.google.com/p/pynessus/ | |
| 3 | # | |
| 4 | # Copyright (C) 2010 Dustin Seibel | |
| 5 | # | |
| 6 | # GNU General Public Licence (GPL) | |
| 7 | # | |
| 8 | # This program is free software; you can redistribute it and/or modify it under | |
| 9 | # the terms of the GNU General Public License as published by the Free Software | |
| 10 | # Foundation; either version 2 of the License, or (at your option) any later | |
| 11 | # version. | |
| 12 | # This program is distributed in the hope that it will be useful, but WITHOUT | |
| 13 | # ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS | |
| 14 | # FOR A PARTICULAR PURPOSE. See the GNU General Public License for more | |
| 15 | # details. | |
| 16 | # You should have received a copy of the GNU General Public License along with | |
| 17 | # this program; if not, write to the Free Software Foundation, Inc., 59 Temple | |
| 18 | # Place, Suite 330, Boston, MA 02111-1307 USA | |
| 19 | # | |
| 20 | # 2010-08-12: 0.1.0: Initial version. | |
| 21 | # 2011-03-12: 0.2.1: Added a bunch of methods and robustified everything. | |
| 22 | from __future__ import absolute_import | |
| 23 | from __future__ import print_function | |
| 24 | ||
| 25 | import sys | |
| 26 | try: | |
| 27 | from urllib2 import ProxyHandler, build_opener, urlopen, install_opener | |
| 28 | from urlparse import urljoin | |
| 29 | from urllib import quote | |
| 30 | except ImportError: | |
| 31 | from urllib.request import ProxyHandler, build_opener, urlopen, install_opener | |
| 32 | from urllib.parse import urljoin, quote | |
| 33 | ||
| 34 | import xml.etree.ElementTree as ET | |
| 35 | import re | |
| 36 | import datetime | |
| 37 | import os | |
| 38 | from random import randint | |
| 39 | ||
| 40 | # Regex defs | |
| 41 | re_unix_timestamp = re.compile('^\d{10}$') | |
| 42 | re_unauthorized = re.compile('<title>200 Unauthorized</title>') | |
| 43 | ||
| 44 | TOKEN_FILE = '.nessus_token' | |
| 45 | ||
| 46 | # Plugin multi-value tags | |
| 47 | PLUGIN_MULTI_VAL = [ | |
| 48 | 'bid', | |
| 49 | 'xref', | |
| 50 | 'cve', | |
| 51 | ] | |
| 52 | ||
| 53 | ||
| 54 | class NessusServer: | |
| 55 | ||
| 56 | def __init__(self, server, port, username, password, verbose=False): | |
| 57 | self.server = server | |
| 58 | self.port = port | |
| 59 | self.username = username | |
| 60 | self.password = password | |
| 61 | self.base_url = 'https://%s:%s' % (self.server, self.port) | |
| 62 | self.verbose = verbose | |
| 63 | self.launched_scans = {} | |
| 64 | ||
| 65 | # Force urllib2 to not use a proxy | |
| 66 | hand = ProxyHandler({}) | |
| 67 | opener = build_opener(hand) | |
| 68 | install_opener(opener) | |
| 69 | ||
| 70 | self.login() | |
| 71 | ||
| 72 | # If token file exists, use it | |
| 73 | #self.token = get_token_file() | |
| 74 | # if not self.check_auth(): | |
| 75 | # self.login() | |
| 76 | # success = create_token_file(self.token) | |
| 77 | # # if not success... | |
| 78 | ||
| 79 | def login(self): | |
| 80 | """Login to server""" | |
| 81 | # If token file exists, try to use it | |
| 82 | self.token = get_token_file() | |
| 83 | if self.check_auth(): | |
| 84 | return True | |
| 85 | ||
| 86 | # Make call to server | |
| 87 | data = make_args(login=self.username, password=quote(self.password)) | |
| 88 | resp = self._call('login', data) | |
| 89 | if self.verbose: | |
| 90 | print(resp) | |
| 91 | ||
| 92 | # Parse token | |
| 93 | seq, status, parsed = parse_reply(resp, ['token']) | |
| 94 | if 'token' in parsed: | |
| 95 | self.token = parsed['token'] | |
| 96 | else: | |
| 97 | return False | |
| 98 | ||
| 99 | # Store it on the filesystem | |
| 100 | success = create_token_file(self.token) | |
| 101 | if success: | |
| 102 | return True | |
| 103 | else: | |
| 104 | return False | |
| 105 | ||
| 106 | def logout(self): | |
| 107 | """Logout from server""" | |
| 108 | data = make_args(token=self.token) | |
| 109 | resp = self._call('logout', data) | |
| 110 | self.token = None | |
| 111 | ||
| 112 | def check_auth(self): | |
| 113 | """Does a quick check to make sure token is still valid""" | |
| 114 | if not self.token: | |
| 115 | return False | |
| 116 | data = make_args(token=self.token) | |
| 117 | resp = self._call('scan/list', data) | |
| 118 | if not resp: | |
| 119 | return False | |
| 120 | elif re_unauthorized.search(resp): | |
| 121 | return False | |
| 122 | else: | |
| 123 | return True | |
| 124 | ||
| 125 | def download_plugins(self): | |
| 126 | """Downloads all plugins""" | |
| 127 | data = make_args(token=self.token) | |
| 128 | resp = self._call('plugins/descriptions', data) | |
| 129 | ||
| 130 | # Get parsed data | |
| 131 | keys = [] | |
| 132 | seq, status, parsed = parse_reply( | |
| 133 | resp, keys, uniq='pluginID', start_node='pluginsList') | |
| 134 | return parsed | |
| 135 | ||
| 136 | def download_report(self, uuid, v1=False): | |
| 137 | """Retrieves a report""" | |
| 138 | if v1: | |
| 139 | data = make_args(token=self.token, report=uuid, v1='true') | |
| 140 | else: | |
| 141 | data = make_args(token=self.token, report=uuid) | |
| 142 | url = urljoin(self.base_url, 'file/report/download/?%s' % data) | |
| 143 | req = urlopen(url) | |
| 144 | resp = req.read() | |
| 145 | if not check_auth(resp): | |
| 146 | print("Unauthorized", file=sys.stderr) | |
| 147 | return None | |
| 148 | return resp | |
| 149 | ||
| 150 | def launch_scan(self, name, policy_id, target_list): | |
| 151 | """Launches scan. Returns UUID of scan.""" | |
| 152 | arg_targets = quote('\n'.join(target_list)) | |
| 153 | data = make_args(token=self.token, scan_name=quote( | |
| 154 | name), policy_id=policy_id, target=arg_targets) | |
| 155 | resp = self._call('/scan/new', data) | |
| 156 | if self.verbose: | |
| 157 | print(resp) | |
| 158 | ||
| 159 | # Get parsed data | |
| 160 | keys = ['uuid', 'owner', 'start_time', 'scan_name'] | |
| 161 | seq, status, parsed = parse_reply(resp, keys) | |
| 162 | self.launched_scans[parsed['uuid']] = parsed | |
| 163 | return parsed['uuid'] | |
| 164 | ||
| 165 | def list_plugins(self): | |
| 166 | """List plugins""" | |
| 167 | data = make_args(token=self.token) | |
| 168 | resp = _call('plugins/list', data) | |
| 169 | ||
| 170 | def list_policies(self): | |
| 171 | """List policies""" | |
| 172 | data = make_args(token=self.token) | |
| 173 | resp = self._call('policy/list', data) | |
| 174 | ||
| 175 | # Get parsed data | |
| 176 | seq, status, parsed = parse_reply( | |
| 177 | resp, ['policyName', 'policyOwner', 'policyComments'], uniq='policyID') | |
| 178 | return parsed | |
| 179 | ||
| 180 | def get_policy_id(self, policy_name): | |
| 181 | """Attempts to grab the policy ID for a name""" | |
| 182 | pols = self.list_policies() | |
| 183 | for k, v in pols.items(): | |
| 184 | if v.get('policyName').lower() == policy_name: | |
| 185 | return k | |
| 186 | ||
| 187 | def list_reports(self): | |
| 188 | """List reports""" | |
| 189 | data = make_args(token=self.token) | |
| 190 | resp = self._call('report/list', data) | |
| 191 | ||
| 192 | # Get parsed data | |
| 193 | seq, status, parsed = parse_reply( | |
| 194 | resp, ['name', 'readableName', 'timestamp', 'status'], uniq='name') | |
| 195 | return parsed | |
| 196 | ||
| 197 | def list_scans(self): | |
| 198 | """List scans""" | |
| 199 | data = make_args(token=self.token) | |
| 200 | resp = self._call('scan/list', data) | |
| 201 | ||
| 202 | # Get parsed data | |
| 203 | keys = ['owner', 'start_time', | |
| 204 | 'completion_current', 'completion_total'] | |
| 205 | seq, status, parsed = parse_reply( | |
| 206 | resp, keys, uniq='uuid', start_node='scans/scanList') | |
| 207 | return parsed | |
| 208 | ||
| 209 | def list_hosts(self, report_uuid): | |
| 210 | """List hosts for a given report""" | |
| 211 | data = make_args(token=self.token, report=report_uuid) | |
| 212 | resp = self._call('report/hosts', data) | |
| 213 | ||
| 214 | # Get parsed data | |
| 215 | keys = ['hostname', 'severity'] | |
| 216 | seq, status, parsed = parse_reply( | |
| 217 | resp, keys, uniq='hostname', start_node='hostList') | |
| 218 | return parsed | |
| 219 | ||
| 220 | def list_ports(self, report_uuid, hostname): | |
| 221 | """List hosts for a given report""" | |
| 222 | data = make_args(token=self.token, report=report_uuid, | |
| 223 | hostname=hostname) | |
| 224 | resp = self._call('report/ports', data) | |
| 225 | # return resp | |
| 226 | ||
| 227 | # Get parsed data | |
| 228 | seq, status, parsed = parse_ports(resp) | |
| 229 | return parsed | |
| 230 | ||
| 231 | def list_detail(self, report_uuid, hostname, protocol, port): | |
| 232 | """List details for a given host/protocol/port""" | |
| 233 | data = make_args(token=self.token, report=report_uuid, | |
| 234 | hostname=hostname, protocol=protocol, port=port) | |
| 235 | resp = self._call('report/detail', data) | |
| 236 | # return resp | |
| 237 | ||
| 238 | # Get parsed data | |
| 239 | seq, status, parsed = parse_ports(resp) | |
| 240 | return parsed | |
| 241 | ||
| 242 | def list_tags(self, report_uuid, hostname): | |
| 243 | """List hosts for a given report""" | |
| 244 | data = make_args(token=self.token, report=report_uuid, | |
| 245 | hostname=hostname) | |
| 246 | resp = self._call('report/tags', data) | |
| 247 | # return resp | |
| 248 | ||
| 249 | # Get parsed data | |
| 250 | seq, status, tags = parse_tags(resp) | |
| 251 | return tags | |
| 252 | ||
| 253 | # Template methods | |
| 254 | def create_template(self, name, policy_id, target_list): | |
| 255 | """Creates a new scan template. Returns """ | |
| 256 | arg_targets = quote('\n'.join(target_list)) | |
| 257 | data = make_args(token=self.token, template_name=quote( | |
| 258 | name), policy_id=policy_id, target=arg_targets) | |
| 259 | resp = self._call('/scan/template/new', data) | |
| 260 | ||
| 261 | def edit_template(self, template_id, name, policy_id, target_list): | |
| 262 | """Edits an existing scan template.""" | |
| 263 | arg_targets = quote('\n'.join(target_list)) | |
| 264 | data = make_args(token=self.token, template=template_id, template_name=quote( | |
| 265 | name), policy_id=policy_id, target=arg_targets) | |
| 266 | resp = self._call('/scan/template/edit', data) | |
| 267 | ||
| 268 | def list_templates(self): | |
| 269 | """List templates""" | |
| 270 | data = make_args(token=self.token) | |
| 271 | resp = self._call('scan/list', data) | |
| 272 | ||
| 273 | # Get parsed data | |
| 274 | keys = ['policy_id', 'readableName', 'owner', 'startTime'] | |
| 275 | seq, status, parsed = parse_reply( | |
| 276 | resp, keys, uniq='name', start_node='templates') | |
| 277 | return parsed | |
| 278 | ||
| 279 | def _call(self, func_url, args): | |
| 280 | url = urljoin(self.base_url, func_url) | |
| 281 | if self.verbose: | |
| 282 | print("URL: '%s'" % url) | |
| 283 | print("POST: '%s'" % args) | |
| 284 | req = urlopen(url, args) | |
| 285 | resp = req.read() | |
| 286 | if not check_auth(resp): | |
| 287 | print("200 Unauthorized", file=sys.stderr) | |
| 288 | return resp | |
| 289 | return resp | |
| 290 | ||
| 291 | ||
| 292 | def check_auth(resp_str): | |
| 293 | """Checks for an unauthorized message in HTTP response.""" | |
| 294 | if re_unauthorized.search(resp_str): | |
| 295 | return False | |
| 296 | else: | |
| 297 | return True | |
| 298 | ||
| 299 | ||
| 300 | def create_token_file(token, token_file=TOKEN_FILE): | |
| 301 | """Creates token file""" | |
| 302 | if not token: | |
| 303 | return False | |
| 304 | # Write to file | |
| 305 | try: | |
| 306 | fout = open(token_file, 'w') | |
| 307 | except IOError: | |
| 308 | return False | |
| 309 | fout.write(token) | |
| 310 | fout.close() | |
| 311 | ||
| 312 | # Confirm the file was created and has the right token | |
| 313 | new_token = get_token_file(token_file) | |
| 314 | if new_token != token: | |
| 315 | return False | |
| 316 | else: | |
| 317 | return True | |
| 318 | ||
| 319 | ||
| 320 | def get_token_file(token_file=TOKEN_FILE): | |
| 321 | """Checks token from file""" | |
| 322 | if not os.path.isfile(token_file): | |
| 323 | return False | |
| 324 | fin = open(token_file, 'r') | |
| 325 | token = fin.read() | |
| 326 | fin.close() | |
| 327 | return token | |
| 328 | ||
| 329 | ||
| 330 | def convert_date(unix_timestamp): | |
| 331 | """Converts UNIX timestamp to a datetime object""" | |
| 332 | # try: | |
| 333 | # return datetime.datetime.fromtimestamp(float(unix_timestamp)) | |
| 334 | # except Exception: | |
| 335 | # return unix_timestamp | |
| 336 | return datetime.datetime.fromtimestamp(float(unix_timestamp)) | |
| 337 | ||
| 338 | ||
| 339 | def parse_reply(xml_string, key_list, start_node=None, uniq=None): | |
| 340 | """Gets all key/value pairs from XML""" | |
| 341 | ROOT_NODES = ['seq', 'status', 'contents'] | |
| 342 | if not xml_string: | |
| 343 | return (0, 'Not a valid string', {}) | |
| 344 | ||
| 345 | # Parse xml | |
| 346 | try: | |
| 347 | xml = ET.fromstring(xml_string) | |
| 348 | except ET.ExpatError: | |
| 349 | return (0, 'Cannot parse XML', {}) | |
| 350 | ||
| 351 | # Make sure it looks like what we expect it to be | |
| 352 | if [t.tag for t in xml.getchildren()] != ROOT_NODES: | |
| 353 | return (0, 'XML not formatted correctly', {}) | |
| 354 | ||
| 355 | # Get seq and status | |
| 356 | seq = xml.findtext('seq') | |
| 357 | status = xml.findtext('status') | |
| 358 | ||
| 359 | # If start node was given, append it to contents node | |
| 360 | if start_node: | |
| 361 | start_node = 'contents/%s' % start_node | |
| 362 | else: | |
| 363 | start_node = 'contents' | |
| 364 | if not xml.find(start_node): | |
| 365 | return (seq, 'start_node not found', {}) | |
| 366 | ||
| 367 | # If a unique value was given, make sure it is a valid tag | |
| 368 | if uniq: | |
| 369 | found = False | |
| 370 | for x in xml.find(start_node).getiterator(): | |
| 371 | if x.tag == uniq: | |
| 372 | found = True | |
| 373 | break | |
| 374 | if not found: | |
| 375 | return (seq, 'uniq not a valid tag', {}) | |
| 376 | ||
| 377 | # Parse keys from contents | |
| 378 | d = {} | |
| 379 | for x in xml.find(start_node).getiterator(): | |
| 380 | if uniq: | |
| 381 | # If tag is a unique field, start a new dict | |
| 382 | if x.tag == uniq: | |
| 383 | d[x.text] = {} | |
| 384 | k = x.text | |
| 385 | ||
| 386 | # Store key/value pair if tag is in key list or if no key list was | |
| 387 | # given | |
| 388 | if not x.text: | |
| 389 | continue | |
| 390 | if ((x.tag in key_list) or (not key_list)) and x.text.strip(): | |
| 391 | # If the tag has the word time and the value is a UNIX | |
| 392 | # timestamp, convert it | |
| 393 | if 'time' in x.tag and re_unix_timestamp.search(x.text): | |
| 394 | d[k][x.tag] = convert_date(x.text) | |
| 395 | else: | |
| 396 | # Check to see if this is multi-valued | |
| 397 | if x.tag in PLUGIN_MULTI_VAL: | |
| 398 | if x.tag in d[k]: | |
| 399 | d[k][x.tag].append(x.text) | |
| 400 | else: | |
| 401 | d[k][x.tag] = [x.text] | |
| 402 | else: | |
| 403 | d[k][x.tag] = x.text | |
| 404 | ||
| 405 | else: | |
| 406 | # Store key/value pair if tag is in key list | |
| 407 | if not x.text: | |
| 408 | continue | |
| 409 | if ((x.tag in key_list) or (not key_list)) and x.text.strip(): | |
| 410 | # If the tag has the word time and the value is a UNIX | |
| 411 | # timestamp, convert it | |
| 412 | if 'time' in x.tag and re_unix_timestamp.search(x.text): | |
| 413 | d[x.tag] = convert_date(x.text) | |
| 414 | else: | |
| 415 | d[x.tag] = x.text | |
| 416 | return (seq, status, d) | |
| 417 | ||
| 418 | ||
| 419 | def parse_reply_orig(xml_string, key_list, start_node=None, uniq=None): | |
| 420 | """Gets all key/value pairs from XML""" | |
| 421 | ROOT_NODES = ['seq', 'status', 'contents'] | |
| 422 | if not xml_string: | |
| 423 | return (0, 'Not a valid string', {}) | |
| 424 | ||
| 425 | # Parse xml | |
| 426 | try: | |
| 427 | xml = ET.fromstring(xml_string) | |
| 428 | except ET.ExpatError: | |
| 429 | return (0, 'Cannot parse XML', {}) | |
| 430 | ||
| 431 | # Make sure it looks like what we expect it to be | |
| 432 | if [t.tag for t in xml.getchildren()] != ROOT_NODES: | |
| 433 | return (0, 'XML not formatted correctly', {}) | |
| 434 | ||
| 435 | # Get seq and status | |
| 436 | seq = xml.findtext('seq') | |
| 437 | status = xml.findtext('status') | |
| 438 | ||
| 439 | # If start node was given, append it to contents node | |
| 440 | if start_node: | |
| 441 | start_node = 'contents/%s' % start_node | |
| 442 | else: | |
| 443 | start_node = 'contents' | |
| 444 | if not xml.find(start_node): | |
| 445 | return (seq, 'start_node not found', {}) | |
| 446 | ||
| 447 | # If a unique value was given, make sure it is a valid tag | |
| 448 | if uniq: | |
| 449 | found = False | |
| 450 | for x in xml.find(start_node).getiterator(): | |
| 451 | if x.tag == uniq: | |
| 452 | found = True | |
| 453 | break | |
| 454 | if not found: | |
| 455 | return (seq, 'uniq not a valid tag', {}) | |
| 456 | ||
| 457 | # Parse keys from contents | |
| 458 | d = {} | |
| 459 | for x in xml.find(start_node).getiterator(): | |
| 460 | if uniq: | |
| 461 | # If tag is a unique field, start a new dict | |
| 462 | if x.tag == uniq: | |
| 463 | d[x.text] = {} | |
| 464 | k = x.text | |
| 465 | ||
| 466 | # Store key/value pair if tag is in key list | |
| 467 | if x.tag in key_list: | |
| 468 | # If the tag has the word time and the value is a UNIX | |
| 469 | # timestamp, convert it | |
| 470 | if 'time' in x.tag and re_unix_timestamp.search(x.text): | |
| 471 | d[k][x.tag] = convert_date(x.text) | |
| 472 | else: | |
| 473 | d[k][x.tag] = x.text | |
| 474 | ||
| 475 | else: | |
| 476 | # Store key/value pair if tag is in key list | |
| 477 | if x.tag in key_list: | |
| 478 | # If the tag has the word time and the value is a UNIX | |
| 479 | # timestamp, convert it | |
| 480 | if 'time' in x.tag and re_unix_timestamp.search(x.text): | |
| 481 | d[x.tag] = convert_date(x.text) | |
| 482 | else: | |
| 483 | d[x.tag] = x.text | |
| 484 | return (seq, status, d) | |
| 485 | ||
| 486 | ||
| 487 | def parse_ports(xml_string): | |
| 488 | """Parses ports from report/ports""" | |
| 489 | ROOT_NODES = ['seq', 'status', 'contents'] | |
| 490 | if not xml_string: | |
| 491 | return (0, 'Not a valid string', {}) | |
| 492 | ||
| 493 | # Parse xml | |
| 494 | try: | |
| 495 | xml = ET.fromstring(xml_string) | |
| 496 | except ET.ExpatError: | |
| 497 | return (0, 'Cannot parse XML', {}) | |
| 498 | ||
| 499 | # Make sure it looks like what we expect it to be | |
| 500 | if [t.tag for t in xml.getchildren()] != ROOT_NODES: | |
| 501 | return (0, 'XML not formatted correctly', {}) | |
| 502 | ||
| 503 | # Get seq and status | |
| 504 | seq = xml.findtext('seq') | |
| 505 | status = xml.findtext('status') | |
| 506 | ||
| 507 | # Parse ports | |
| 508 | d = {'tcp': {}, 'udp': {}, 'icmp': {}} | |
| 509 | for t in xml.findall('contents/portList/port'): | |
| 510 | port_d = {} | |
| 511 | prot = t.findtext('protocol') | |
| 512 | num = t.findtext('portNum') | |
| 513 | ||
| 514 | # Get additional attributes | |
| 515 | port_d['severity'] = t.findtext('severity') | |
| 516 | port_d['svcName'] = t.findtext('svcName') | |
| 517 | ||
| 518 | d[prot][num] = port_d | |
| 519 | return (seq, status, d) | |
| 520 | ||
| 521 | ||
| 522 | def parse_tags(xml_string): | |
| 523 | """Parses tags from report/tags""" | |
| 524 | ROOT_NODES = ['seq', 'status', 'contents'] | |
| 525 | if not xml_string: | |
| 526 | return (0, 'Not a valid string', {}) | |
| 527 | ||
| 528 | # Parse xml | |
| 529 | try: | |
| 530 | xml = ET.fromstring(xml_string) | |
| 531 | except ET.ExpatError: | |
| 532 | return (0, 'Cannot parse XML', {}) | |
| 533 | ||
| 534 | # Make sure it looks like what we expect it to be | |
| 535 | if [t.tag for t in xml.getchildren()] != ROOT_NODES: | |
| 536 | return (0, 'XML not formatted correctly', {}) | |
| 537 | ||
| 538 | # Get seq and status | |
| 539 | seq = xml.findtext('seq') | |
| 540 | status = xml.findtext('status') | |
| 541 | ||
| 542 | # Parse tags | |
| 543 | d = {} | |
| 544 | for t in xml.findall('contents/tags/tag'): | |
| 545 | k = t.findtext('name') | |
| 546 | v = t.findtext('value') | |
| 547 | d[k] = v | |
| 548 | return (seq, status, d) | |
| 549 | ||
| 550 | ||
| 551 | def make_args(**kwargs): | |
| 552 | """Returns arg list suitable for GET or POST requests""" | |
| 553 | args = [] | |
| 554 | for k in kwargs: | |
| 555 | args.append('%s=%s' % (k, str(kwargs[k]))) | |
| 556 | ||
| 557 | # Add a random number | |
| 558 | seq = randint(1, 1000) | |
| 559 | args.append('seq=%d' % seq) | |
| 560 | ||
| 561 | return '&'.join(args) | |
| 562 | ||
| 563 | ||
| 564 | def zerome(string): | |
| 565 | # taken from http://www.codexon.com/posts/clearing-passwords-in-memory-with-python | |
| 566 | # to be used to secure the password in memory | |
| 567 | # find the header size with a dummy string | |
| 568 | temp = "finding offset" | |
| 569 | header = ctypes.string_at(id(temp), sys.getsizeof(temp)).find(temp) | |
| 570 | ||
| 571 | location = id(string) + header | |
| 572 | size = sys.getsizeof(string) - header | |
| 573 | ||
| 574 | # Check platform | |
| 575 | if 'windows' in sys.platform.lower(): | |
| 576 | memset = ctypes.cdll.msvcrt.memset | |
| 577 | else: | |
| 578 | # For Linux, use the following. Change the 6 to whatever it is on your | |
| 579 | # computer. | |
| 580 | memset = ctypes.CDLL("libc.so.6").memset | |
| 581 | ||
| 582 | print("Clearing 0x%08x size %i bytes" % (location, size)) | |
| 583 | ||
| 584 | memset(location, 0, size) | |
| 585 | ||
| 586 | ||
| 587 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | from faraday.client.model import api | |
| 8 | import re | |
| 9 | import os | |
| 10 | import socket | |
| 11 | ||
| 12 | __author__ = "Ulisses Albuquerque" | |
| 13 | __copyright__ = "Copyright (c) 2016, Securus Global" | |
| 14 | __credits__ = ["Ulisses Albuquerque"] | |
| 15 | __license__ = "" | |
| 16 | __version__ = "1.0.0" | |
| 17 | __maintainer__ = "Ulisses Albuquerque" | |
| 18 | __email__ = "[email protected]" | |
| 19 | __status__ = "Development" | |
| 20 | ||
| 21 | ||
| 22 | class CmdNetcatPlugin(core.PluginBase): | |
| 23 | """ | |
| 24 | This plugin handles ping command. | |
| 25 | Basically detects if user was able to connect to a device | |
| 26 | """ | |
| 27 | ||
| 28 | def __init__(self): | |
| 29 | super().__init__() | |
| 30 | self.id = "netcat" | |
| 31 | self.name = "Netcat" | |
| 32 | self.plugin_version = "0.0.1" | |
| 33 | self.version = "1.0.0" | |
| 34 | self._command_regex = re.compile( | |
| 35 | r'^(?:.*\|)?\s*(?:nc|netcat|nc.openbsd|nc.traditional)\s+.*$') | |
| 36 | self._completition = { | |
| 37 | "": "[-bhklnrtuvCz] [-c shell] [-e filename] [-g gateway] [-G num] [-i secs] [-o file] [-p port] [-q secs] [-s addr] [-T tos] [-w secs]", | |
| 38 | "-c": "shell", | |
| 39 | "-e": "filename", | |
| 40 | "-b": "allow broadcasts", | |
| 41 | "-g": "gateway", | |
| 42 | "-G": "num", | |
| 43 | "-h": "this cruft", | |
| 44 | "-i": "secs", | |
| 45 | "-k": "set keepalive option on socket", | |
| 46 | "-l": "listen mode, for inbound connects", | |
| 47 | "-n": "numeric-only IP addresses, no DNS", | |
| 48 | "-o": "file", | |
| 49 | "-p": "port", | |
| 50 | "-r": "randomize local and remote ports", | |
| 51 | "-q": "secs", | |
| 52 | "-s": "addr", | |
| 53 | "-T": "tos", | |
| 54 | "-t": "answer TELNET negotiation", | |
| 55 | "-u": "UDP mode", | |
| 56 | "-v": "verbose [use twice to be more verbose]", | |
| 57 | "-w": "secs", | |
| 58 | "-C": "Send CRLF as line-ending", | |
| 59 | "-z": "zero-I/O mode [used for scanning]", | |
| 60 | } | |
| 61 | ||
| 62 | def resolveHost(self, host): | |
| 63 | """ | |
| 64 | The use of gethostbyname/gethostbyaddr here is questionable, but it is | |
| 65 | the easiest way to sort out the discrepancies between the output | |
| 66 | formats of both versions of netcat | |
| 67 | """ | |
| 68 | if re.search(r'^\d{1,3}(?:\.\d{1,3}){3}', host) is not None: | |
| 69 | try: | |
| 70 | result = socket.gethostbyaddr(host) | |
| 71 | return (host, result[0]) | |
| 72 | except: | |
| 73 | return (host, None) | |
| 74 | else: | |
| 75 | try: | |
| 76 | result = socket.gethostbyname(host) | |
| 77 | return (result, host) | |
| 78 | except: | |
| 79 | return (None, host) | |
| 80 | ||
| 81 | def addEntry(self, attr_dict): | |
| 82 | """ | |
| 83 | Because output differs between both versions of netcat, and because | |
| 84 | the user might use the -n parameter which disables name resolution, | |
| 85 | we need to check if the values we are getting are hostnames or IP | |
| 86 | addresses | |
| 87 | """ | |
| 88 | ip_address, hostname = self.resolveHost(attr_dict['host']) | |
| 89 | ||
| 90 | # When service does not match anything in /etc/services, we get those | |
| 91 | if attr_dict['service'] == '*' or attr_dict['service'] == '?' or attr_dict['service'] is None: | |
| 92 | attr_dict['service'] = 'unknown' | |
| 93 | ||
| 94 | if 'protocol' not in attr_dict: | |
| 95 | attr_dict['protocol'] = 'tcp' | |
| 96 | ||
| 97 | h_id = self.createAndAddHost(hostname) | |
| 98 | i_id = self.createAndAddInterface( | |
| 99 | h_id, ip_address, ipv4_address=ip_address) | |
| 100 | s_id = self.createAndAddServiceToInterface(h_id, i_id, attr_dict['service'], | |
| 101 | protocol=attr_dict['protocol'], ports=[int(attr_dict['port'])]) | |
| 102 | ||
| 103 | def matchInOutput(self, regexp, output): | |
| 104 | """ | |
| 105 | We take a split & filter approach to matching our regexps to the | |
| 106 | command output | |
| 107 | """ | |
| 108 | mapped_list = list(map(lambda s: re.search(regexp, s), re.split(r'(\r|\n)', output))) | |
| 109 | filtered_list = list(filter(lambda s: s is not None, mapped_list)) | |
| 110 | ||
| 111 | if len(filtered_list) > 0: | |
| 112 | return filtered_list[0] | |
| 113 | else: | |
| 114 | return None | |
| 115 | ||
| 116 | def parseOutputString(self, output, debug=False): | |
| 117 | """ | |
| 118 | There are at least two variants of netcat, the OpenBSD version and the | |
| 119 | 'traditional' version. The verbose output differs between them, so we | |
| 120 | will try to cover both cases. | |
| 121 | """ | |
| 122 | print(output) | |
| 123 | nc_bsd_rx = re.compile( | |
| 124 | r'^Connection\s+to\s+(?P<host>\S+)\s+(?P<port>\d+)\s+port\s+\[(?P<protocol>tcp|udp)/(?P<service>[^\]]+)\]\s+succeeded.*') | |
| 125 | nc_sys_rx = re.compile( | |
| 126 | r'^(?P<host>\S+)\s+\[(?P<address>[0-9\.]+)\]\s+(?P<port>\d+)(?:\s+\((?P<service>[^)]+)\))?\s+open.*') | |
| 127 | ||
| 128 | nc_bsd_match = self.matchInOutput(nc_bsd_rx, output) | |
| 129 | if nc_bsd_match is not None: | |
| 130 | self.addEntry(nc_bsd_match.groupdict()) | |
| 131 | ||
| 132 | nc_sys_match = self.matchInOutput(nc_sys_rx, output) | |
| 133 | if nc_sys_match is not None: | |
| 134 | self.addEntry(nc_sys_match.groupdict()) | |
| 135 | ||
| 136 | return True | |
| 137 | ||
| 138 | def processCommandString(self, username, current_path, command_string): | |
| 139 | """ | |
| 140 | We need to use '-v' because otherwise netcat does not provide any | |
| 141 | output to indicate whether a connection has been successful; our | |
| 142 | regexp can certainly be improved, because we might get '-v' combined | |
| 143 | with other parameters, like in "nc -nv" | |
| 144 | """ | |
| 145 | if re.search(r'(nc|netcat)[^\d|\|]*-v', command_string) is None: | |
| 146 | return re.sub(r'(nc(?:\.traditional|\.openbsd)?|netcat)', r'\1 -v', command_string) | |
| 147 | ||
| 148 | return command_string | |
| 149 | ||
| 150 | ||
| 151 | def createPlugin(): | |
| 152 | return CmdNetcatPlugin() | |
| 153 | ||
| 154 | ||
| 155 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import core | |
| 6 | import pprint | |
| 7 | import re | |
| 8 | ||
| 9 | __author__ = "Federico Fernandez - @q3rv0" | |
| 10 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 11 | __license__ = "" | |
| 12 | __version__ = "1.0.0" | |
| 13 | __maintainer__ = "Federico Fernandez" | |
| 14 | __email__ = "[email protected]" | |
| 15 | __status__ = "Development" | |
| 16 | ||
| 17 | class NetdiscoverPlugin(core.PluginBase): | |
| 18 | ||
| 19 | def __init__(self): | |
| 20 | super().__init__() | |
| 21 | self.id = "Netdiscover" | |
| 22 | self.name = "netdiscover" | |
| 23 | self.plugin_version = "0.0.1" | |
| 24 | self.version = "1.0.0" | |
| 25 | self._command_regex = re.compile(r'^(sudo netdiscover|netdiscover).*?') | |
| 26 | ||
| 27 | def parseOutputString(self, output, debug=False): | |
| 28 | #regexp get ip, mac and hostname | |
| 29 | reg = re.findall(r"(([0-9]+\.?){4})\s+(([0-9a-f]+\:?){6})((\s+[0-9]+){2})(.*)", output) | |
| 30 | ||
| 31 | if output.find('Finished!') != -1 and len(reg) > 0: | |
| 32 | ||
| 33 | for stdout in reg: | |
| 34 | ip_address = stdout[0] | |
| 35 | mac = stdout[2] | |
| 36 | hostname = stdout[6].strip() | |
| 37 | ||
| 38 | h_id = self.createAndAddHost(ip_address) | |
| 39 | self.createAndAddInterface(h_id, ip_address, ipv4_address=ip_address, mac=mac, hostname_resolution=[hostname]) | |
| 40 | ||
| 41 | return True | |
| 42 | ||
| 43 | def processCommandString(self, username, current_path, command_string): | |
| 44 | return None | |
| 45 | ||
| 46 | ||
| 47 | def createPlugin(): | |
| 48 | return NetdiscoverPlugin() | |
| 49 | ||
| 50 | ||
| 51 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 7 | from faraday.client.model import api | |
| 8 | import re | |
| 9 | import os | |
| 10 | import sys | |
| 11 | import socket | |
| 12 | import urllib | |
| 13 | from bs4 import BeautifulSoup | |
| 14 | ||
| 15 | try: | |
| 16 | import xml.etree.cElementTree as ET | |
| 17 | import xml.etree.ElementTree as ET_ORIG | |
| 18 | ETREE_VERSION = ET_ORIG.VERSION | |
| 19 | except ImportError: | |
| 20 | import xml.etree.ElementTree as ET | |
| 21 | ETREE_VERSION = ET.VERSION | |
| 22 | ||
| 23 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 24 | ||
| 25 | current_path = os.path.abspath(os.getcwd()) | |
| 26 | ||
| 27 | __author__ = "Francisco Amato" | |
| 28 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 29 | __credits__ = ["Francisco Amato"] | |
| 30 | __license__ = "" | |
| 31 | __version__ = "1.0.0" | |
| 32 | __maintainer__ = "Francisco Amato" | |
| 33 | __email__ = "[email protected]" | |
| 34 | __status__ = "Development" | |
| 35 | ||
| 36 | ||
| 37 | class NetsparkerXmlParser: | |
| 38 | """ | |
| 39 | The objective of this class is to parse an xml file generated by the netsparker tool. | |
| 40 | ||
| 41 | TODO: Handle errors. | |
| 42 | TODO: Test netsparker output version. Handle what happens if the parser doesn't support it. | |
| 43 | TODO: Test cases. | |
| 44 | ||
| 45 | @param netsparker_xml_filepath A proper xml generated by netsparker | |
| 46 | """ | |
| 47 | ||
| 48 | def __init__(self, xml_output): | |
| 49 | self.filepath = xml_output | |
| 50 | ||
| 51 | tree = self.parse_xml(xml_output) | |
| 52 | if tree: | |
| 53 | self.items = list(self.get_items(tree)) | |
| 54 | else: | |
| 55 | self.items = [] | |
| 56 | ||
| 57 | def parse_xml(self, xml_output): | |
| 58 | """ | |
| 59 | Open and parse an xml file. | |
| 60 | ||
| 61 | TODO: Write custom parser to just read the nodes that we need instead of | |
| 62 | reading the whole file. | |
| 63 | ||
| 64 | @return xml_tree An xml tree instance. None if error. | |
| 65 | """ | |
| 66 | try: | |
| 67 | tree = ET.fromstring(xml_output) | |
| 68 | except SyntaxError as err: | |
| 69 | self.devlog("SyntaxError: %s. %s" % (err, xml_output)) | |
| 70 | return None | |
| 71 | ||
| 72 | return tree | |
| 73 | ||
| 74 | def get_items(self, tree): | |
| 75 | """ | |
| 76 | @return items A list of Host instances | |
| 77 | """ | |
| 78 | for node in tree.findall("vulnerability"): | |
| 79 | yield Item(node) | |
| 80 | ||
| 81 | ||
| 82 | class Item: | |
| 83 | """ | |
| 84 | An abstract representation of a Item | |
| 85 | ||
| 86 | ||
| 87 | @param item_node A item_node taken from an netsparker xml tree | |
| 88 | """ | |
| 89 | ||
| 90 | def re_map_severity(self, severity): | |
| 91 | if severity == "Important": | |
| 92 | return "high" | |
| 93 | return severity | |
| 94 | ||
| 95 | def __init__(self, item_node, encoding="ascii"): | |
| 96 | self.node = item_node | |
| 97 | self.url = self.get_text_from_subnode("url") | |
| 98 | ||
| 99 | host = re.search( | |
| 100 | "(http|https|ftp)\://([a-zA-Z0-9\.\-]+(\:[a-zA-Z0-9\.&%\$\-]+)*@)*((25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9])\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9]|0)\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9]|0)\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[0-9])|localhost|([a-zA-Z0-9\-]+\.)*[a-zA-Z0-9\-]+\.(com|edu|gov|int|mil|net|org|biz|arpa|info|name|pro|aero|coop|museum|[a-zA-Z]{2}))[\:]*([0-9]+)*([/]*($|[a-zA-Z0-9\.\,\?\'\\\+&%\$#\=~_\-]+)).*?$", self.url) | |
| 101 | ||
| 102 | self.protocol = host.group(1) | |
| 103 | self.hostname = host.group(4) | |
| 104 | self.port = 80 | |
| 105 | ||
| 106 | if self.protocol == 'https': | |
| 107 | self.port = 443 | |
| 108 | if host.group(11) is not None: | |
| 109 | self.port = host.group(11) | |
| 110 | ||
| 111 | self.name = self.get_text_from_subnode("type") | |
| 112 | self.desc = self.get_text_from_subnode("description") | |
| 113 | self.severity = self.re_map_severity(self.get_text_from_subnode("severity")) | |
| 114 | self.certainty = self.get_text_from_subnode("certainty") | |
| 115 | self.method = self.get_text_from_subnode("vulnerableparametertype") | |
| 116 | self.param = self.get_text_from_subnode("vulnerableparameter") | |
| 117 | self.paramval = self.get_text_from_subnode("vulnerableparametervalue") | |
| 118 | self.reference = self.get_text_from_subnode("externalReferences") | |
| 119 | self.resolution = self.get_text_from_subnode("actionsToTake") | |
| 120 | self.request = self.get_text_from_subnode("rawrequest") | |
| 121 | self.response = self.get_text_from_subnode("rawresponse") | |
| 122 | if self.response: | |
| 123 | self.response = self.response.encode(encoding,errors="backslashreplace").decode(encoding) | |
| 124 | if self.request: | |
| 125 | self.request = self.request.encode(encoding,errors="backslashreplace").decode(encoding) | |
| 126 | if self.reference: | |
| 127 | self.reference = self.reference.encode(encoding,errors="backslashreplace").decode(encoding) | |
| 128 | ||
| 129 | ||
| 130 | self.kvulns = [] | |
| 131 | for v in self.node.findall("knownvulnerabilities/knownvulnerability"): | |
| 132 | self.node = v | |
| 133 | self.kvulns.append(self.get_text_from_subnode( | |
| 134 | "severity") + "-" + self.get_text_from_subnode("title")) | |
| 135 | ||
| 136 | self.extra = [] | |
| 137 | for v in item_node.findall("extrainformation/info"): | |
| 138 | self.extra.append(v.get('name') + ":" + v.text) | |
| 139 | ||
| 140 | self.node = item_node | |
| 141 | self.node = item_node.find("classification") | |
| 142 | self.owasp = self.get_text_from_subnode("OWASP") | |
| 143 | self.wasc = self.get_text_from_subnode("WASC") | |
| 144 | self.cwe = self.get_text_from_subnode("CWE") | |
| 145 | self.capec = self.get_text_from_subnode("CAPEC") | |
| 146 | self.pci = self.get_text_from_subnode("PCI") | |
| 147 | self.pci2 = self.get_text_from_subnode("PCI2") | |
| 148 | self.node = item_node.find("classification/CVSS") | |
| 149 | self.cvss = self.get_text_from_subnode("vector") | |
| 150 | ||
| 151 | self.ref = [] | |
| 152 | if self.cwe: | |
| 153 | self.ref.append("CWE-" + self.cwe) | |
| 154 | if self.owasp: | |
| 155 | self.ref.append("OWASP-" + self.owasp) | |
| 156 | if self.reference: | |
| 157 | self.ref.extend(list(set(re.findall('https?://(?:[-\w.]|(?:%[\da-fA-F]{2}))+', self.reference)))) | |
| 158 | if self.cvss: | |
| 159 | self.ref.append(self.cvss) | |
| 160 | ||
| 161 | self.data = "" | |
| 162 | self.data += "\nKnowVulns: " + \ | |
| 163 | "\n".join(self.kvulns) if self.kvulns else "" | |
| 164 | self.data += "\nWASC: " + self.wasc if self.wasc else "" | |
| 165 | self.data += "\nCertainty: " + self.certainty if self.certainty else "" | |
| 166 | self.data += "\nPCI: " + self.pci if self.pci else "" | |
| 167 | self.data += "\nPCI2: " + self.pci2 if self.pci2 else "" | |
| 168 | self.data += "\nCAPEC: " + self.capec if self.capec else "" | |
| 169 | self.data += "\nPARAM: " + self.param if self.param else "" | |
| 170 | self.data += "\nPARAM VAL: " + \ | |
| 171 | repr(self.paramval) if self.paramval else "" | |
| 172 | self.data += "\nExtra: " + "\n".join(self.extra) if self.extra else "" | |
| 173 | ||
| 174 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 175 | """ | |
| 176 | Finds a subnode in the host node and the retrieves a value from it. | |
| 177 | ||
| 178 | @return An attribute value | |
| 179 | """ | |
| 180 | if self.node: | |
| 181 | sub_node = self.node.find(subnode_xpath_expr) | |
| 182 | if sub_node is not None: | |
| 183 | return sub_node.text | |
| 184 | ||
| 185 | return None | |
| 186 | ||
| 187 | ||
| 188 | class NetsparkerPlugin(PluginXMLFormat): | |
| 189 | """ | |
| 190 | Example plugin to parse netsparker output. | |
| 191 | """ | |
| 192 | ||
| 193 | def __init__(self): | |
| 194 | super().__init__() | |
| 195 | self.identifier_tag = "netsparker" | |
| 196 | self.id = "Netsparker" | |
| 197 | self.name = "Netsparker XML Output Plugin" | |
| 198 | self.plugin_version = "0.0.1" | |
| 199 | self.version = "Netsparker 3.1.1.0" | |
| 200 | self.framework_version = "1.0.0" | |
| 201 | self.options = None | |
| 202 | self._current_output = None | |
| 203 | self._command_regex = re.compile( | |
| 204 | r'^(sudo netsparker|\.\/netsparker).*?') | |
| 205 | ||
| 206 | global current_path | |
| 207 | self._output_file_path = os.path.join(self.data_path, "netsparker_output-%s.xml" % self._rid) | |
| 208 | ||
| 209 | def resolve(self, host): | |
| 210 | try: | |
| 211 | return socket.gethostbyname(host) | |
| 212 | except: | |
| 213 | pass | |
| 214 | return host | |
| 215 | ||
| 216 | def parseOutputString(self, output, debug=False): | |
| 217 | ||
| 218 | parser = NetsparkerXmlParser(output) | |
| 219 | first = True | |
| 220 | for i in parser.items: | |
| 221 | if first: | |
| 222 | ip = self.resolve(i.hostname) | |
| 223 | h_id = self.createAndAddHost(ip, hostnames=[ip]) | |
| 224 | ||
| 225 | s_id = self.createAndAddServiceToHost(h_id, str(i.port), | |
| 226 | protocol = str(i.protocol), | |
| 227 | ports=[str(i.port)], | |
| 228 | status="open") | |
| 229 | first = False | |
| 230 | ||
| 231 | v_id = self.createAndAddVulnWebToService(h_id, s_id, i.name, ref=i.ref, website=i.hostname, | |
| 232 | severity=i.severity, desc=BeautifulSoup(i.desc, "lxml").text, | |
| 233 | path=i.url, method=i.method, request=i.request, response=i.response, | |
| 234 | resolution=BeautifulSoup(i.resolution, "lxml").text,pname=i.param, data=i.data) | |
| 235 | ||
| 236 | del parser | |
| 237 | ||
| 238 | def processCommandString(self, username, current_path, command_string): | |
| 239 | return None | |
| 240 | ||
| 241 | ||
| 242 | def createPlugin(): | |
| 243 | return NetsparkerPlugin() | |
| 244 | ||
| 245 | ||
| 246 | ||
| 247 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 7 | from faraday.client.model import api | |
| 8 | import re | |
| 9 | import os | |
| 10 | import sys | |
| 11 | import socket | |
| 12 | ||
| 13 | try: | |
| 14 | import xml.etree.cElementTree as ET | |
| 15 | import xml.etree.ElementTree as ET_ORIG | |
| 16 | ETREE_VERSION = ET_ORIG.VERSION | |
| 17 | except ImportError: | |
| 18 | import xml.etree.ElementTree as ET | |
| 19 | ETREE_VERSION = ET.VERSION | |
| 20 | ||
| 21 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 22 | ||
| 23 | current_path = os.path.abspath(os.getcwd()) | |
| 24 | ||
| 25 | __author__ = "Francisco Amato" | |
| 26 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 27 | __credits__ = ["Francisco Amato"] | |
| 28 | __license__ = "" | |
| 29 | __version__ = "1.0.0" | |
| 30 | __maintainer__ = "Francisco Amato" | |
| 31 | __email__ = "[email protected]" | |
| 32 | __status__ = "Development" | |
| 33 | ||
| 34 | ||
| 35 | def cleaner_unicode(string): | |
| 36 | if string is not None: | |
| 37 | return string.encode('ascii', errors='backslashreplace') | |
| 38 | else: | |
| 39 | return string | |
| 40 | ||
| 41 | def cleaner_results(string): | |
| 42 | ||
| 43 | try: | |
| 44 | q = re.compile(r'<.*?>', re.IGNORECASE) | |
| 45 | return re.sub(q, '', string) | |
| 46 | ||
| 47 | except: | |
| 48 | return '' | |
| 49 | ||
| 50 | def get_urls(string): | |
| 51 | urls = re.findall(r'href=[\'"]?([^\'" >]+)', string) | |
| 52 | return urls | |
| 53 | ||
| 54 | ||
| 55 | class NetsparkerCloudXmlParser: | |
| 56 | """ | |
| 57 | The objective of this class is to parse an xml file generated by the netsparkercloud tool. | |
| 58 | ||
| 59 | TODO: Handle errors. | |
| 60 | TODO: Test netsparkercloud output version. Handle what happens if the parser doesn't support it. | |
| 61 | TODO: Test cases. | |
| 62 | ||
| 63 | @param netsparkercloud_xml_filepath A proper xml generated by netsparkercloud | |
| 64 | """ | |
| 65 | ||
| 66 | def __init__(self, xml_output): | |
| 67 | self.filepath = xml_output | |
| 68 | ||
| 69 | tree = self.parse_xml(xml_output) | |
| 70 | if tree: | |
| 71 | self.items = list(self.get_items(tree)) | |
| 72 | else: | |
| 73 | self.items = [] | |
| 74 | ||
| 75 | def parse_xml(self, xml_output): | |
| 76 | """ | |
| 77 | Open and parse an xml file. | |
| 78 | ||
| 79 | TODO: Write custom parser to just read the nodes that we need instead of | |
| 80 | reading the whole file. | |
| 81 | ||
| 82 | @return xml_tree An xml tree instance. None if error. | |
| 83 | """ | |
| 84 | try: | |
| 85 | tree = ET.fromstring(xml_output) | |
| 86 | except SyntaxError as err: | |
| 87 | self.devlog("SyntaxError: %s. %s" % (err, xml_output)) | |
| 88 | return None | |
| 89 | ||
| 90 | return tree | |
| 91 | ||
| 92 | def get_items(self, tree): | |
| 93 | """ | |
| 94 | @return items A list of Host instances | |
| 95 | """ | |
| 96 | for node in tree.findall("vulnerabilities/vulnerability"): | |
| 97 | yield Item(node) | |
| 98 | ||
| 99 | ||
| 100 | class Item: | |
| 101 | """ | |
| 102 | An abstract representation of a Item | |
| 103 | ||
| 104 | ||
| 105 | @param item_node A item_node taken from an netsparkercloud xml tree | |
| 106 | """ | |
| 107 | def re_map_severity(self, severity): | |
| 108 | if severity == "Important": | |
| 109 | return "high" | |
| 110 | return severity | |
| 111 | ||
| 112 | def __init__(self, item_node): | |
| 113 | self.node = item_node | |
| 114 | self.url = self.get_text_from_subnode("url") | |
| 115 | ||
| 116 | host = re.search( | |
| 117 | "(http|https|ftp)\://([a-zA-Z0-9\.\-]+(\:[a-zA-Z0-9\.&%\$\-]+)*@)*((25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9])\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9]|0)\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9]|0)\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[0-9])|localhost|([a-zA-Z0-9\-]+\.)*[a-zA-Z0-9\-]+\.(com|edu|gov|int|mil|net|org|biz|arpa|info|name|pro|aero|coop|museum|[a-zA-Z]{2}))[\:]*([0-9]+)*([/]*($|[a-zA-Z0-9\.\,\?\'\\\+&%\$#\=~_\-]+)).*?$", self.url) | |
| 118 | ||
| 119 | self.protocol = host.group(1) | |
| 120 | self.hostname = host.group(4) | |
| 121 | self.port = 80 | |
| 122 | ||
| 123 | if self.protocol == 'https': | |
| 124 | self.port = 443 | |
| 125 | if host.group(11) is not None: | |
| 126 | self.port = host.group(11) | |
| 127 | ||
| 128 | self.type = self.get_text_from_subnode("type") | |
| 129 | self.name = self.get_text_from_subnode("name") | |
| 130 | self.severity = self.re_map_severity(self.get_text_from_subnode("severity")) | |
| 131 | self.certainty = self.get_text_from_subnode("certainty") | |
| 132 | ||
| 133 | ||
| 134 | self.node = item_node.find("http-request") | |
| 135 | self.method = self.get_text_from_subnode("method") | |
| 136 | self.request = self.get_text_from_subnode("content") | |
| 137 | ||
| 138 | #print self.node | |
| 139 | self.param = "" | |
| 140 | self.paramval = "" | |
| 141 | for p in self.node.findall("parameters/parameter"): | |
| 142 | self.param = p.get('name') | |
| 143 | self.paramval = p.get('value') | |
| 144 | ||
| 145 | self.node = item_node.find("http-response") | |
| 146 | self.response = self.get_text_from_subnode("content") | |
| 147 | ||
| 148 | self.extra = [] | |
| 149 | for v in item_node.findall("extra-information/info"): | |
| 150 | self.extra.append(v.get('name') + ":" + v.get('value') ) | |
| 151 | ||
| 152 | self.node = item_node.find("classification") | |
| 153 | self.owasp = self.get_text_from_subnode("owasp") | |
| 154 | self.wasc = self.get_text_from_subnode("wasc") | |
| 155 | self.cwe = self.get_text_from_subnode("cwe") | |
| 156 | self.capec = self.get_text_from_subnode("capec") | |
| 157 | self.pci = self.get_text_from_subnode("pci31") | |
| 158 | self.pci2 = self.get_text_from_subnode("pci32") | |
| 159 | self.hipaa = self.get_text_from_subnode("hipaa") | |
| 160 | ||
| 161 | self.ref = [] | |
| 162 | if self.cwe: | |
| 163 | self.ref.append("CWE-" + self.cwe) | |
| 164 | if self.owasp: | |
| 165 | self.ref.append("OWASP-" + self.owasp) | |
| 166 | ||
| 167 | self.node = item_node | |
| 168 | self.remedyreferences = self.get_text_from_subnode("remedy-references") | |
| 169 | self.externalreferences = self.get_text_from_subnode("external-references") | |
| 170 | if self.remedyreferences: | |
| 171 | for u in get_urls(self.remedyreferences): | |
| 172 | self.ref.append(u) | |
| 173 | if self.externalreferences: | |
| 174 | for u in get_urls(self.externalreferences): | |
| 175 | self.ref.append(u) | |
| 176 | ||
| 177 | self.impact = cleaner_results(self.get_text_from_subnode("impact")) | |
| 178 | self.remedialprocedure = cleaner_results(self.get_text_from_subnode("remedial-procedure")) | |
| 179 | self.remedialactions = cleaner_results(self.get_text_from_subnode("remedial-actions")) | |
| 180 | self.exploitationskills = cleaner_results(self.get_text_from_subnode("exploitation-skills")) | |
| 181 | self.proofofconcept = cleaner_results(self.get_text_from_subnode("proof-of-concept")) | |
| 182 | ||
| 183 | self.resolution = self.remedialprocedure | |
| 184 | self.resolution += "\nRemedial Actions: " + self.remedialactions if self.remedialactions is not None else "" | |
| 185 | ||
| 186 | ||
| 187 | self.desc = cleaner_results(self.get_text_from_subnode("description")) | |
| 188 | self.desc += "\nImpact: " + self.impact if self.impact else "" | |
| 189 | self.desc += "\nExploitation Skills: " + self.exploitationskills if self.exploitationskills else "" | |
| 190 | self.desc += "\nProof of concept: " + self.proofofconcept if self.proofofconcept else "" | |
| 191 | self.desc += "\nWASC: " + self.wasc if self.wasc else "" | |
| 192 | self.desc += "\nPCI31: " + self.pci if self.pci else "" | |
| 193 | self.desc += "\nPCI32: " + self.pci2 if self.pci2 else "" | |
| 194 | self.desc += "\nCAPEC: " + self.capec if self.capec else "" | |
| 195 | self.desc += "\nHIPA: " + self.hipaa if self.hipaa else "" | |
| 196 | self.desc += "\nExtra: " + "\n".join(self.extra) if self.extra else "" | |
| 197 | ||
| 198 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 199 | """ | |
| 200 | Finds a subnode in the host node and the retrieves a value from it. | |
| 201 | ||
| 202 | @return An attribute value | |
| 203 | """ | |
| 204 | if self.node: | |
| 205 | sub_node = self.node.find(subnode_xpath_expr) | |
| 206 | if sub_node is not None: | |
| 207 | if sub_node.text is not None: | |
| 208 | return cleaner_unicode(sub_node.text) | |
| 209 | ||
| 210 | return "" | |
| 211 | ||
| 212 | ||
| 213 | class NetsparkerCloudPlugin(PluginXMLFormat): | |
| 214 | """ | |
| 215 | Example plugin to parse netsparkercloud output. | |
| 216 | """ | |
| 217 | ||
| 218 | def __init__(self): | |
| 219 | super().__init__() | |
| 220 | self.identifier_tag = "netsparker-cloud" | |
| 221 | self.id = "NetsparkerCloud" | |
| 222 | self.name = "NetsparkerCloud XML Output Plugin" | |
| 223 | self.plugin_version = "0.0.1" | |
| 224 | self.version = "NetsparkerCloud" | |
| 225 | self.framework_version = "1.0.0" | |
| 226 | self.options = None | |
| 227 | self._current_output = None | |
| 228 | self._command_regex = re.compile( | |
| 229 | r'^(sudo netsparkercloud|\.\/netsparkercloud).*?') | |
| 230 | ||
| 231 | global current_path | |
| 232 | self._output_file_path = os.path.join(self.data_path, | |
| 233 | "netsparkercloud_output-%s.xml" % self._rid) | |
| 234 | ||
| 235 | def resolve(self, host): | |
| 236 | try: | |
| 237 | return socket.gethostbyname(host) | |
| 238 | except: | |
| 239 | pass | |
| 240 | return host | |
| 241 | ||
| 242 | def parseOutputString(self, output, debug=False): | |
| 243 | ||
| 244 | parser = NetsparkerCloudXmlParser(output) | |
| 245 | first = True | |
| 246 | for i in parser.items: | |
| 247 | if first: | |
| 248 | ip = self.resolve(i.hostname) | |
| 249 | h_id = self.createAndAddHost(ip) | |
| 250 | i_id = self.createAndAddInterface( | |
| 251 | h_id, ip, ipv4_address=ip, hostname_resolution=[i.hostname]) | |
| 252 | ||
| 253 | s_id = self.createAndAddServiceToInterface(h_id, i_id, str(i.port), | |
| 254 | str(i.protocol), | |
| 255 | ports=[str(i.port)], | |
| 256 | status="open") | |
| 257 | ||
| 258 | first = False | |
| 259 | ||
| 260 | v_id = self.createAndAddVulnWebToService(h_id, s_id, i.name, ref=i.ref, website=i.hostname, | |
| 261 | severity=i.severity, desc=i.desc, path=i.url, method=i.method, | |
| 262 | request=i.request, response=i.response, resolution=i.resolution, pname=i.param) | |
| 263 | ||
| 264 | del parser | |
| 265 | ||
| 266 | def processCommandString(self, username, current_path, command_string): | |
| 267 | return None | |
| 268 | ||
| 269 | def setHost(self): | |
| 270 | pass | |
| 271 | ||
| 272 | ||
| 273 | def createPlugin(): | |
| 274 | return NetsparkerCloudPlugin() | |
| 275 | ||
| 276 | ||
| 277 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 7 | from faraday.client.model import api | |
| 8 | import re | |
| 9 | import os | |
| 10 | import sys | |
| 11 | ||
| 12 | try: | |
| 13 | import xml.etree.cElementTree as ET | |
| 14 | import xml.etree.ElementTree as ET_ORIG | |
| 15 | ETREE_VERSION = ET_ORIG.VERSION | |
| 16 | except ImportError: | |
| 17 | import xml.etree.ElementTree as ET | |
| 18 | ETREE_VERSION = ET.VERSION | |
| 19 | ||
| 20 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 21 | ||
| 22 | current_path = os.path.abspath(os.getcwd()) | |
| 23 | ||
| 24 | __author__ = "Micaela Ranea Sanchez" | |
| 25 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 26 | __credits__ = ["Francisco Amato", "Federico Kirschbaum", | |
| 27 | "Micaela Ranea Sanchez", "German Riera"] | |
| 28 | __license__ = "" | |
| 29 | __version__ = "1.0.0" | |
| 30 | __maintainer__ = "Micaela Ranea Sanchez" | |
| 31 | __email__ = "[email protected]" | |
| 32 | __status__ = "Development" | |
| 33 | ||
| 34 | ||
| 35 | class NexposeFullXmlParser: | |
| 36 | """ | |
| 37 | The objective of this class is to parse Nexpose's XML 2.0 Report. | |
| 38 | ||
| 39 | TODO: Handle errors. | |
| 40 | TODO: Test nexpose output version. Handle what happens if the parser doesn't support it. | |
| 41 | TODO: Test cases. | |
| 42 | ||
| 43 | @param xml_filepath A proper xml generated by nexpose | |
| 44 | """ | |
| 45 | ||
| 46 | def __init__(self, xml_output): | |
| 47 | tree = self.parse_xml(xml_output) | |
| 48 | self.vulns = self.get_vuln_definitions(tree) | |
| 49 | ||
| 50 | if tree: | |
| 51 | self.items = self.get_items(tree, self.vulns) | |
| 52 | else: | |
| 53 | self.items = [] | |
| 54 | ||
| 55 | def parse_xml(self, xml_output): | |
| 56 | """ | |
| 57 | Open and parse an xml file. | |
| 58 | ||
| 59 | TODO: Write custom parser to just read the nodes that we need instead of | |
| 60 | reading the whole file. | |
| 61 | ||
| 62 | @return xml_tree An xml tree instance. None if error. | |
| 63 | """ | |
| 64 | try: | |
| 65 | tree = ET.fromstring(xml_output) | |
| 66 | except SyntaxError as err: | |
| 67 | print("SyntaxError: %s. %s" % (err, xml_output)) | |
| 68 | return None | |
| 69 | ||
| 70 | return tree | |
| 71 | ||
| 72 | def parse_html_type(self, node: ET.Element) -> str: | |
| 73 | """ | |
| 74 | Parse XML element of type HtmlType | |
| 75 | ||
| 76 | @return ret A string containing the parsed element | |
| 77 | """ | |
| 78 | ret = "" | |
| 79 | tag: str = node.tag.lower() | |
| 80 | if tag == 'containerblockelement': | |
| 81 | if len(list(node)) > 0: | |
| 82 | for child in list(node): | |
| 83 | ret += self.parse_html_type(child) | |
| 84 | else: | |
| 85 | ret += node.text.strip() if node.text else "" | |
| 86 | if tag == 'listitem': | |
| 87 | if len(list(node)) > 0: | |
| 88 | for child in list(node): | |
| 89 | ret += self.parse_html_type(child) | |
| 90 | else: | |
| 91 | ret = node.text.strip() if node.text else "" | |
| 92 | if tag == 'orderedlist': | |
| 93 | i = 1 | |
| 94 | for item in list(node): | |
| 95 | ret += "\t" + str(i) + " " + self.parse_html_type(item) + "\n" | |
| 96 | i += 1 | |
| 97 | if tag == 'paragraph': | |
| 98 | if len(list(node)) > 0: | |
| 99 | for child in list(node): | |
| 100 | ret += self.parse_html_type(child) | |
| 101 | else: | |
| 102 | ret += node.text.strip() if node.text else "" | |
| 103 | if tag == 'unorderedlist': | |
| 104 | for item in list(node): | |
| 105 | ret += "\t" + "* " + self.parse_html_type(item) + "\n" | |
| 106 | if tag == 'urllink': | |
| 107 | if node.get('text'): | |
| 108 | ret += node.text.strip() + " " | |
| 109 | last = "" | |
| 110 | for attr in node.attrib: | |
| 111 | if node.get(attr) and node.get(attr) != node.get(last): | |
| 112 | ret += node.get(attr) + " " | |
| 113 | last = attr | |
| 114 | ||
| 115 | return ret | |
| 116 | ||
| 117 | def parse_tests_type(self, node, vulnsDefinitions): | |
| 118 | """ | |
| 119 | Parse XML element of type TestsType | |
| 120 | ||
| 121 | @return vulns A list of vulnerabilities according to vulnsDefinitions | |
| 122 | """ | |
| 123 | vulns = list() | |
| 124 | ||
| 125 | for tests in node.findall('tests'): | |
| 126 | for test in tests.iter('test'): | |
| 127 | vuln = dict() | |
| 128 | if test.get('id').lower() in vulnsDefinitions: | |
| 129 | vuln = vulnsDefinitions[test.get('id').lower()].copy() | |
| 130 | key = test.get('key', '') | |
| 131 | if key.startswith('/'): | |
| 132 | # It has the path where the vuln was found | |
| 133 | # Example key: "/comments.asp||content" | |
| 134 | vuln['path'] = key[:key.find('|')] | |
| 135 | for desc in list(test): | |
| 136 | vuln['desc'] += self.parse_html_type(desc) | |
| 137 | vulns.append(vuln) | |
| 138 | return vulns | |
| 139 | ||
| 140 | def get_vuln_definitions(self, tree): | |
| 141 | """ | |
| 142 | @returns vulns A dict of Vulnerability Definitions | |
| 143 | """ | |
| 144 | vulns = dict() | |
| 145 | #CVSS V3 | |
| 146 | SEVERITY_MAPPING_DICT = {'0': 'info', '1': 'low', '2': 'low', '3': 'low', '4': 'med', '5': 'med', '6': 'med', | |
| 147 | '7': 'high', '8': 'high', '9': 'critical', '10': 'critical'} | |
| 148 | ||
| 149 | for vulnsDef in tree.iter('VulnerabilityDefinitions'): | |
| 150 | for vulnDef in vulnsDef.iter('vulnerability'): | |
| 151 | vid = vulnDef.get('id').lower() | |
| 152 | vector = vulnDef.get('cvssVector') | |
| 153 | ||
| 154 | vuln = { | |
| 155 | 'desc': "", | |
| 156 | 'name': vulnDef.get('title'), | |
| 157 | 'refs': ["vector: " + vector, vid], | |
| 158 | 'resolution': "", | |
| 159 | 'severity': SEVERITY_MAPPING_DICT[vulnDef.get('severity')], | |
| 160 | 'tags': list(), | |
| 161 | 'is_web': vid.startswith('http-') | |
| 162 | } | |
| 163 | ||
| 164 | for item in list(vulnDef): | |
| 165 | if item.tag == 'description': | |
| 166 | for htmlType in list(item): | |
| 167 | vuln['desc'] += self.parse_html_type(htmlType) | |
| 168 | if item.tag == 'exploits': | |
| 169 | for exploit in list(item): | |
| 170 | if exploit.get('title') and exploit.get('link'): | |
| 171 | title = exploit.get('title').encode( | |
| 172 | "ascii", errors="backslashreplace").strip() | |
| 173 | link = exploit.get('link').encode( | |
| 174 | "ascii", errors="backslashreplace").strip() | |
| 175 | vuln['refs'].append(title + b' ' + link) | |
| 176 | if item.tag == 'references': | |
| 177 | for ref in list(item): | |
| 178 | if ref.text: | |
| 179 | rf = ref.text.encode( | |
| 180 | "ascii", errors="backslashreplace").strip() | |
| 181 | vuln['refs'].append(rf) | |
| 182 | if item.tag == 'solution': | |
| 183 | for htmlType in list(item): | |
| 184 | vuln[ | |
| 185 | 'resolution'] += self.parse_html_type(htmlType) | |
| 186 | """ | |
| 187 | # there is currently no method to register tags in vulns | |
| 188 | if item.tag == 'tags': | |
| 189 | for tag in list(item): | |
| 190 | vuln['tags'].append(tag.text.lower()) | |
| 191 | """ | |
| 192 | vulns[vid] = vuln | |
| 193 | return vulns | |
| 194 | ||
| 195 | def get_items(self, tree, vulns): | |
| 196 | """ | |
| 197 | @return hosts A list of Host instances | |
| 198 | """ | |
| 199 | ||
| 200 | hosts = list() | |
| 201 | ||
| 202 | for nodes in tree.iter('nodes'): | |
| 203 | for node in nodes.iter('node'): | |
| 204 | host = dict() | |
| 205 | host['name'] = node.get('address') | |
| 206 | host['hostnames'] = list() | |
| 207 | host['os'] = "" | |
| 208 | host['services'] = list() | |
| 209 | host['vulns'] = self.parse_tests_type(node, vulns) | |
| 210 | ||
| 211 | for names in node.iter('names'): | |
| 212 | for name in list(names): | |
| 213 | host['hostnames'].append(name.text) | |
| 214 | ||
| 215 | for fingerprints in node.iter('fingerprints'): | |
| 216 | os = fingerprints.find('os') | |
| 217 | if os is not None: | |
| 218 | host['os'] = os.get('product', "") | |
| 219 | if os.get('version') is not None: | |
| 220 | host['os'] += " " + os.get('version') | |
| 221 | ||
| 222 | for endpoints in node.iter('endpoints'): | |
| 223 | for endpoint in list(endpoints): | |
| 224 | svc = { | |
| 225 | 'protocol': endpoint.get('protocol'), | |
| 226 | 'port': endpoint.get('port'), | |
| 227 | 'status': endpoint.get('status'), | |
| 228 | } | |
| 229 | for services in endpoint.iter('services'): | |
| 230 | for service in list(services): | |
| 231 | svc['name'] = service.get('name') | |
| 232 | svc['vulns'] = self.parse_tests_type( | |
| 233 | service, vulns) | |
| 234 | for configs in service.iter('configurations'): | |
| 235 | for config in list(configs): | |
| 236 | if "banner" in config.get('name'): | |
| 237 | svc['version'] = config.get('name') | |
| 238 | ||
| 239 | host['services'].append(svc) | |
| 240 | ||
| 241 | hosts.append(host) | |
| 242 | ||
| 243 | return hosts | |
| 244 | ||
| 245 | ||
| 246 | class NexposeFullPlugin(PluginXMLFormat): | |
| 247 | """ | |
| 248 | Example plugin to parse nexpose output. | |
| 249 | """ | |
| 250 | ||
| 251 | def __init__(self): | |
| 252 | super().__init__() | |
| 253 | self.identifier_tag = "NexposeReport" | |
| 254 | self.id = "NexposeFull" | |
| 255 | self.name = "Nexpose XML 2.0 Report Plugin" | |
| 256 | self.plugin_version = "0.0.1" | |
| 257 | self.version = "Nexpose Enterprise 5.7.19" | |
| 258 | self.framework_version = "1.0.0" | |
| 259 | self.options = None | |
| 260 | self._current_output = None | |
| 261 | self._command_regex = re.compile(r'^(sudo nexpose|\.\/nexpose).*?') | |
| 262 | ||
| 263 | global current_path | |
| 264 | self._output_file_path = os.path.join(self.data_path, | |
| 265 | "nexpose_full_output-%s.xml" % self._rid) | |
| 266 | ||
| 267 | def parseOutputString(self, output, debug=False): | |
| 268 | ||
| 269 | parser = NexposeFullXmlParser(output) | |
| 270 | ||
| 271 | for item in parser.items: | |
| 272 | ||
| 273 | h_id = self.createAndAddHost(item['name'], item['os'], hostnames=item['hostnames']) | |
| 274 | ||
| 275 | i_id = self.createAndAddInterface( | |
| 276 | h_id, | |
| 277 | item['name'], | |
| 278 | ipv4_address=item['name'], | |
| 279 | hostname_resolution=item['hostnames']) | |
| 280 | ||
| 281 | for v in item['vulns']: | |
| 282 | ||
| 283 | v_id = self.createAndAddVulnToHost( | |
| 284 | h_id, | |
| 285 | v['name'], | |
| 286 | v['desc'], | |
| 287 | v['refs'], | |
| 288 | v['severity'], | |
| 289 | v['resolution']) | |
| 290 | ||
| 291 | ||
| 292 | for s in item['services']: | |
| 293 | web = False | |
| 294 | version = s.get("version", "") | |
| 295 | ||
| 296 | s_id = self.createAndAddServiceToInterface( | |
| 297 | h_id, | |
| 298 | i_id, | |
| 299 | s['name'], | |
| 300 | s['protocol'], | |
| 301 | ports=[str(s['port'])], | |
| 302 | status=s['status'], | |
| 303 | version=version) | |
| 304 | ||
| 305 | for v in s['vulns']: | |
| 306 | if v['is_web']: | |
| 307 | v_id = self.createAndAddVulnWebToService( | |
| 308 | h_id, | |
| 309 | s_id, | |
| 310 | v['name'], | |
| 311 | v['desc'], | |
| 312 | v['refs'], | |
| 313 | v['severity'], | |
| 314 | v['resolution'], | |
| 315 | path=v.get('path','')) | |
| 316 | else: | |
| 317 | v_id = self.createAndAddVulnToService( | |
| 318 | h_id, | |
| 319 | s_id, | |
| 320 | v['name'], | |
| 321 | v['desc'], | |
| 322 | v['refs'], | |
| 323 | v['severity'], | |
| 324 | v['resolution']) | |
| 325 | ||
| 326 | del parser | |
| 327 | ||
| 328 | def processCommandString(self, username, current_path, command_string): | |
| 329 | return None | |
| 330 | ||
| 331 | def setHost(self): | |
| 332 | pass | |
| 333 | ||
| 334 | ||
| 335 | def createPlugin(): | |
| 336 | return NexposeFullPlugin() | |
| 337 | ||
| 338 | ||
| 339 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import plugin_utils | |
| 6 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 7 | import re | |
| 8 | import os | |
| 9 | import sys | |
| 10 | import random | |
| 11 | from html.parser import HTMLParser | |
| 12 | ||
| 13 | try: | |
| 14 | import xml.etree.cElementTree as ET | |
| 15 | import xml.etree.ElementTree as ET_ORIG | |
| 16 | ETREE_VERSION = ET_ORIG.VERSION | |
| 17 | except ImportError: | |
| 18 | import xml.etree.ElementTree as ET | |
| 19 | ETREE_VERSION = ET.VERSION | |
| 20 | ||
| 21 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 22 | ||
| 23 | current_path = os.path.abspath(os.getcwd()) | |
| 24 | ||
| 25 | __author__ = "Francisco Amato" | |
| 26 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 27 | __credits__ = ["Facundo de Guzmán", "Francisco Amato"] | |
| 28 | __license__ = "" | |
| 29 | __version__ = "1.0.0" | |
| 30 | __maintainer__ = "Francisco Amato" | |
| 31 | __email__ = "[email protected]" | |
| 32 | __status__ = "Development" | |
| 33 | ||
| 34 | ||
| 35 | class NiktoXmlParser: | |
| 36 | """ | |
| 37 | The objective of this class is to parse an xml file generated by the nikto tool. | |
| 38 | ||
| 39 | TODO: Handle errors. | |
| 40 | TODO: Test nikto output version. Handle what happens if the parser doesn't support it. | |
| 41 | TODO: Test cases. | |
| 42 | ||
| 43 | @param nikto_xml_filepath A proper xml generated by nikto | |
| 44 | """ | |
| 45 | ||
| 46 | def __init__(self, xml_output): | |
| 47 | ||
| 48 | tree = self.parse_xml(xml_output) | |
| 49 | ||
| 50 | if tree: | |
| 51 | self.hosts = list(self.get_hosts(tree)) | |
| 52 | else: | |
| 53 | self.hosts = [] | |
| 54 | ||
| 55 | def parse_xml(self, xml_output): | |
| 56 | """ | |
| 57 | Open and parse an xml file. | |
| 58 | ||
| 59 | TODO: Write custom parser to just read the nodes that we need instead of | |
| 60 | reading the whole file. | |
| 61 | ||
| 62 | @return xml_tree An xml tree instance. None if error. | |
| 63 | """ | |
| 64 | try: | |
| 65 | tree = ET.fromstring(xml_output) | |
| 66 | except SyntaxError as err: | |
| 67 | print("SyntaxError: %s. %s" % (err, xml_output)) | |
| 68 | return None | |
| 69 | ||
| 70 | return tree | |
| 71 | ||
| 72 | def get_hosts(self, tree): | |
| 73 | """ | |
| 74 | @return items A list of Host instances | |
| 75 | """ | |
| 76 | if tree.find('niktoscan'): | |
| 77 | for host_node in tree.find('niktoscan').findall('scandetails'): | |
| 78 | yield Host(host_node) | |
| 79 | else: | |
| 80 | for host_node in tree.findall('scandetails'): | |
| 81 | yield Host(host_node) | |
| 82 | ||
| 83 | ||
| 84 | def get_attrib_from_subnode(xml_node, subnode_xpath_expr, attrib_name): | |
| 85 | """ | |
| 86 | Finds a subnode in the item node and the retrieves a value from it | |
| 87 | ||
| 88 | @return An attribute value | |
| 89 | """ | |
| 90 | global ETREE_VERSION | |
| 91 | node = None | |
| 92 | ||
| 93 | if ETREE_VERSION[0] <= 1 and ETREE_VERSION[1] < 3: | |
| 94 | ||
| 95 | match_obj = re.search( | |
| 96 | "([^\@]+?)\[\@([^=]*?)=\'([^\']*?)\'", subnode_xpath_expr) | |
| 97 | if match_obj is not None: | |
| 98 | ||
| 99 | node_to_find = match_obj.group(1) | |
| 100 | xpath_attrib = match_obj.group(2) | |
| 101 | xpath_value = match_obj.group(3) | |
| 102 | for node_found in xml_node.findall(node_to_find): | |
| 103 | ||
| 104 | if node_found.attrib[xpath_attrib] == xpath_value: | |
| 105 | node = node_found | |
| 106 | break | |
| 107 | else: | |
| 108 | node = xml_node.find(subnode_xpath_expr) | |
| 109 | ||
| 110 | else: | |
| 111 | node = xml_node.find(subnode_xpath_expr) | |
| 112 | ||
| 113 | if node is not None: | |
| 114 | return node.get(attrib_name) | |
| 115 | ||
| 116 | return None | |
| 117 | ||
| 118 | ||
| 119 | class Item: | |
| 120 | """ | |
| 121 | An abstract representation of a Item | |
| 122 | ||
| 123 | TODO: Consider evaluating the attributes lazily | |
| 124 | TODO: Write what's expected to be present in the nodes | |
| 125 | TODO: Refactor both Host and the Port clases? | |
| 126 | ||
| 127 | @param item_node A item_node taken from an nikto xml tree | |
| 128 | """ | |
| 129 | ||
| 130 | def __init__(self, item_node): | |
| 131 | ||
| 132 | self.node = item_node | |
| 133 | ||
| 134 | self.osvdbid = [ | |
| 135 | "OSVDB-ID: " + self.node.get('osvdbid')] if self.node.get('osvdbid') != "0" else [] | |
| 136 | ||
| 137 | self.namelink = self.get_text_from_subnode('namelink') | |
| 138 | self.iplink = self.get_text_from_subnode('iplink') | |
| 139 | ||
| 140 | self.id_nikto = self.node.get('id') | |
| 141 | self.osvdblink = self.node.get('osvdbidlink') | |
| 142 | self.method = self.node.get('method') | |
| 143 | ||
| 144 | self.uri = self.get_uri() | |
| 145 | self.desc = self.get_desc() | |
| 146 | self.params = self.get_params(self.uri) | |
| 147 | ||
| 148 | def get_uri(self): | |
| 149 | ||
| 150 | try: | |
| 151 | ||
| 152 | uri = self.get_text_from_subnode('uri') | |
| 153 | h = HTMLParser.HTMLParser() | |
| 154 | return h.unescape(uri) | |
| 155 | ||
| 156 | except Exception as e: | |
| 157 | return uri | |
| 158 | ||
| 159 | def get_desc(self): | |
| 160 | ||
| 161 | desc = self.get_text_from_subnode('description') | |
| 162 | ||
| 163 | try: | |
| 164 | ||
| 165 | uri_present = desc.split(': ', 1)[0] | |
| 166 | h = HTMLParser.HTMLParser() | |
| 167 | if uri_present == h.unescape(self.uri): | |
| 168 | ||
| 169 | name = desc.split(': ', 1)[1] | |
| 170 | if name is not None and name != '': | |
| 171 | return name | |
| 172 | ||
| 173 | return desc | |
| 174 | ||
| 175 | except Exception as e: | |
| 176 | return desc | |
| 177 | ||
| 178 | def get_params(self, uri): | |
| 179 | """Return the paramethers as a string""" | |
| 180 | try: | |
| 181 | params = uri.split('?')[1].replace('&', ',') | |
| 182 | except Exception as e: | |
| 183 | params = '' | |
| 184 | ||
| 185 | return params | |
| 186 | ||
| 187 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 188 | """ | |
| 189 | Finds a subnode in the host node and the retrieves a value from it. | |
| 190 | ||
| 191 | @return An attribute value | |
| 192 | """ | |
| 193 | sub_node = self.node.find(subnode_xpath_expr) | |
| 194 | if sub_node is not None: | |
| 195 | return sub_node.text | |
| 196 | ||
| 197 | return None | |
| 198 | ||
| 199 | def __str__(self): | |
| 200 | ports = [] | |
| 201 | for port in self.ports: | |
| 202 | var = " %s" % port | |
| 203 | ports.append(var) | |
| 204 | ports = "\n".join(ports) | |
| 205 | ||
| 206 | return "%s, %s, %s [%s], %s\n%s" % (self.hostnames, self.status, | |
| 207 | self.ipv4_address, self.mac_address, self.os, ports) | |
| 208 | ||
| 209 | ||
| 210 | class Host: | |
| 211 | """ | |
| 212 | An abstract representation of a Host | |
| 213 | ||
| 214 | @param host_node A host_node taken from an nmap xml tree | |
| 215 | """ | |
| 216 | ||
| 217 | def __init__(self, host_node): | |
| 218 | ||
| 219 | self.node = host_node | |
| 220 | self.targetip = self.node.get('targetip') | |
| 221 | self.targethostname = self.node.get('targethostname') | |
| 222 | self.port = self.node.get('targetport') | |
| 223 | self.targetbanner = self.node.get('targetbanner') | |
| 224 | self.starttime = self.node.get('starttime') | |
| 225 | self.sitename = self.node.get('sitename') | |
| 226 | self.siteip = self.node.get('hostheader') | |
| 227 | self.items = list(self.get_items()) | |
| 228 | ||
| 229 | def get_items(self): | |
| 230 | """ | |
| 231 | @return items A list of Host instances | |
| 232 | """ | |
| 233 | for item_node in self.node.findall('item'): | |
| 234 | yield Item(item_node) | |
| 235 | ||
| 236 | def __str__(self): | |
| 237 | ports = [] | |
| 238 | for port in self.ports: | |
| 239 | var = " %s" % port | |
| 240 | ports.append(var) | |
| 241 | ports = "\n".join(ports) | |
| 242 | ||
| 243 | return "%s, %s, %s [%s], %s\n%s" % (self.hostnames, self.status, | |
| 244 | self.ipv4_address, self.mac_address, self.os, ports) | |
| 245 | ||
| 246 | ||
| 247 | class NiktoPlugin(PluginXMLFormat): | |
| 248 | """ | |
| 249 | Example plugin to parse nikto output. | |
| 250 | """ | |
| 251 | ||
| 252 | def __init__(self): | |
| 253 | super().__init__() | |
| 254 | self.identifier_tag = "niktoscan" | |
| 255 | self.id = "Nikto" | |
| 256 | self.name = "Nikto XML Output Plugin" | |
| 257 | self.plugin_version = "0.0.2" | |
| 258 | self.version = "2.1.5" | |
| 259 | self.options = None | |
| 260 | self._current_output = None | |
| 261 | self.parent = None | |
| 262 | self._command_regex = re.compile( | |
| 263 | r'^(sudo nikto|nikto|sudo nikto\.pl|nikto\.pl|perl nikto\.pl|\.\/nikto\.pl|\.\/nikto).*?') | |
| 264 | self._completition = { | |
| 265 | "": "", | |
| 266 | "-ask+": "Whether to ask about submitting updates", | |
| 267 | "-Cgidirs+": 'Scan these CGI dirs: "none", "all", or values like "/cgi/ /cgi-a/"', | |
| 268 | "-config+": "Use this config file", | |
| 269 | "-Display+": "Turn on/off display outputs:", | |
| 270 | "-dbcheck": "Check database and other key files for syntax errors", | |
| 271 | "-evasion+": "Encoding technique:", | |
| 272 | "-Format+": "Save file (-o) format:", | |
| 273 | "-Help": "Extended help information", | |
| 274 | "-host+": "Target host", | |
| 275 | "-IgnoreCode": "Ignore Codes--treat as negative responses", | |
| 276 | "-id+": "Host authentication to use, format is id:pass or id:pass:realm", | |
| 277 | "-key+": "Client certificate key file", | |
| 278 | "-list-plugins": "List all available plugins, perform no testing", | |
| 279 | "-maxtime+": "Maximum testing time per host", | |
| 280 | "-mutate+": "Guess additional file names:", | |
| 281 | "-mutate-options": "Provide information for mutates", | |
| 282 | "-nointeractive": "Disables interactive features", | |
| 283 | "-nolookup": "Disables DNS lookups", | |
| 284 | "-nossl": "Disables the use of SSL", | |
| 285 | "-no404": "Disables nikto attempting to guess a 404 page", | |
| 286 | "-output+": "Write output to this file ('.' for auto-name)", | |
| 287 | "-Pause+": "Pause between tests (seconds, integer or float)", | |
| 288 | "-Plugins+": "List of plugins to run (default: ALL)", | |
| 289 | "-port+": "Port to use (default 80)", | |
| 290 | "-RSAcert+": "Client certificate file", | |
| 291 | "-root+": "Prepend root value to all requests, format is /directory", | |
| 292 | "-Save": "Save positive responses to this directory ('.' for auto-name)", | |
| 293 | "-ssl": "Force ssl mode on port", | |
| 294 | "-Tuning+": "Scan tuning:", | |
| 295 | "-timeout+": "Timeout for requests (default 10 seconds)", | |
| 296 | "-Userdbs": "Load only user databases, not the standard databases", | |
| 297 | "-until": "Run until the specified time or duration", | |
| 298 | "-update": "Update databases and plugins from CIRT.net", | |
| 299 | "-useproxy": "Use the proxy defined in nikto.conf", | |
| 300 | "-Version": "Print plugin and database versions", | |
| 301 | "-vhost+": "Virtual host (for Host header)", | |
| 302 | } | |
| 303 | ||
| 304 | global current_path | |
| 305 | self._output_file_path = os.path.join(self.data_path, | |
| 306 | "nikto_output-%s.xml" % self._rid) | |
| 307 | ||
| 308 | def parseOutputString(self, output, debug=False): | |
| 309 | """ | |
| 310 | This method will discard the output the shell sends, it will read it from | |
| 311 | the xml where it expects it to be present. | |
| 312 | ||
| 313 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 314 | output being sent is valid. | |
| 315 | """ | |
| 316 | ||
| 317 | parser = NiktoXmlParser(output) | |
| 318 | ||
| 319 | for host in parser.hosts: | |
| 320 | ||
| 321 | h_id = self.createAndAddHost( | |
| 322 | host.targetip, | |
| 323 | hostnames=[host.targethostname] | |
| 324 | ) | |
| 325 | ||
| 326 | s_id = self.createAndAddServiceToHost( | |
| 327 | h_id, | |
| 328 | "http", | |
| 329 | "tcp", | |
| 330 | ports=[host.port], | |
| 331 | status="open" | |
| 332 | ) | |
| 333 | ||
| 334 | for item in host.items: | |
| 335 | ||
| 336 | v_id = self.createAndAddVulnWebToService( | |
| 337 | h_id, | |
| 338 | s_id, | |
| 339 | name=item.desc, | |
| 340 | ref=item.osvdbid, | |
| 341 | method=item.method, | |
| 342 | params=', '.join(item.params), | |
| 343 | **plugin_utils.get_vulnweb_url_fields(item.namelink) | |
| 344 | ) | |
| 345 | ||
| 346 | del parser | |
| 347 | ||
| 348 | xml_arg_re = re.compile(r"^.*(-output\s*[^\s]+).*$") | |
| 349 | ||
| 350 | def processCommandString(self, username, current_path, command_string): | |
| 351 | """ | |
| 352 | Adds the -oX parameter to get xml output to the command string that the | |
| 353 | user has set. | |
| 354 | """ | |
| 355 | self._output_file_path = os.path.join( | |
| 356 | self.data_path, | |
| 357 | "%s_%s_output-%s.xml" % ( | |
| 358 | self.get_ws(), | |
| 359 | self.id, | |
| 360 | random.uniform(1, 10) | |
| 361 | ) | |
| 362 | ) | |
| 363 | ||
| 364 | arg_match = self.xml_arg_re.match(command_string) | |
| 365 | ||
| 366 | if arg_match is None: | |
| 367 | return re.sub(r"(^.*?nikto(\.pl)?)", | |
| 368 | r"\1 -output %s -Format XML" % self._output_file_path, | |
| 369 | command_string) | |
| 370 | else: | |
| 371 | data = re.sub(" \-Format XML", "", command_string) | |
| 372 | return re.sub(arg_match.group(1), | |
| 373 | r"-output %s -Format XML" % self._output_file_path, | |
| 374 | data) | |
| 375 | ||
| 376 | def setHost(self): | |
| 377 | pass | |
| 378 | ||
| 379 | ||
| 380 | def createPlugin(): | |
| 381 | return NiktoPlugin() | |
| 382 | ||
| 383 | ||
| 384 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | ||
| 7 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 8 | import re | |
| 9 | import os | |
| 10 | import sys | |
| 11 | import random | |
| 12 | ||
| 13 | ||
| 14 | try: | |
| 15 | import xml.etree.cElementTree as ET | |
| 16 | import xml.etree.ElementTree as ET_ORIG | |
| 17 | ETREE_VERSION = ET_ORIG.VERSION | |
| 18 | except ImportError: | |
| 19 | import xml.etree.ElementTree as ET | |
| 20 | ETREE_VERSION = ET.VERSION | |
| 21 | ||
| 22 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 23 | ||
| 24 | current_path = os.path.abspath(os.getcwd()) | |
| 25 | ||
| 26 | ||
| 27 | class NmapXmlParser: | |
| 28 | """ | |
| 29 | The objective of this class is to parse an xml file generated by | |
| 30 | the nmap tool. | |
| 31 | ||
| 32 | TODO: Handle errors. | |
| 33 | TODO: Test nmap output version. Handle what happens if the parser | |
| 34 | doesn't support it. | |
| 35 | TODO: Test cases. | |
| 36 | ||
| 37 | @param nmap_xml_filepath A proper xml generated by nmap | |
| 38 | """ | |
| 39 | ||
| 40 | def __init__(self, xml_output): | |
| 41 | tree = self.parse_xml(xml_output) | |
| 42 | ||
| 43 | if tree: | |
| 44 | self.hosts = list(self.get_hosts(tree)) | |
| 45 | else: | |
| 46 | self.hosts = [] | |
| 47 | ||
| 48 | def parse_xml(self, xml_output): | |
| 49 | """ | |
| 50 | Open and parse an xml file. | |
| 51 | ||
| 52 | TODO: Write custom parser to just read the nodes that we need instead | |
| 53 | of reading the whole file. | |
| 54 | ||
| 55 | @return xml_tree An xml tree instance. None if error. | |
| 56 | """ | |
| 57 | ||
| 58 | try: | |
| 59 | return ET.fromstring(xml_output) | |
| 60 | except SyntaxError as err: | |
| 61 | #logger.error("SyntaxError: %s." % (err)) | |
| 62 | return None | |
| 63 | ||
| 64 | def get_hosts(self, tree): | |
| 65 | """ | |
| 66 | @return hosts A list of Host instances | |
| 67 | """ | |
| 68 | for host_node in tree.findall('host'): | |
| 69 | yield Host(host_node) | |
| 70 | ||
| 71 | ||
| 72 | def get_attrib_from_subnode(xml_node, subnode_xpath_expr, attrib_name): | |
| 73 | """ | |
| 74 | Finds a subnode in the host node and the retrieves a value from it | |
| 75 | ||
| 76 | @return An attribute value | |
| 77 | """ | |
| 78 | global ETREE_VERSION | |
| 79 | node = None | |
| 80 | ||
| 81 | if ETREE_VERSION[0] <= 1 and ETREE_VERSION[1] < 3: | |
| 82 | ||
| 83 | match_obj = re.search( | |
| 84 | "([^\@]+?)\[\@([^=]*?)=\'([^\']*?)\'", | |
| 85 | subnode_xpath_expr) | |
| 86 | ||
| 87 | if match_obj is not None: | |
| 88 | ||
| 89 | node_to_find = match_obj.group(1) | |
| 90 | xpath_attrib = match_obj.group(2) | |
| 91 | xpath_value = match_obj.group(3) | |
| 92 | ||
| 93 | for node_found in xml_node.findall(node_to_find): | |
| 94 | if node_found.attrib[xpath_attrib] == xpath_value: | |
| 95 | node = node_found | |
| 96 | break | |
| 97 | else: | |
| 98 | node = xml_node.find(subnode_xpath_expr) | |
| 99 | ||
| 100 | else: | |
| 101 | node = xml_node.find(subnode_xpath_expr) | |
| 102 | ||
| 103 | if node is not None: | |
| 104 | return node.get(attrib_name) | |
| 105 | ||
| 106 | return None | |
| 107 | ||
| 108 | ||
| 109 | class Host: | |
| 110 | """ | |
| 111 | An abstract representation of a Host | |
| 112 | ||
| 113 | TODO: Consider evaluating the attributes lazily | |
| 114 | TODO: Write what's expected to be present in the nodes | |
| 115 | TODO: Refactor both Host and the Port clases? | |
| 116 | ||
| 117 | @param host_node A host_node taken from an nmap xml tree | |
| 118 | """ | |
| 119 | ||
| 120 | def __init__(self, host_node): | |
| 121 | self.node = host_node | |
| 122 | ||
| 123 | self.hostnames = [hostname[0] for hostname in self.get_hostnames()] | |
| 124 | if len(self.hostnames) != 0: | |
| 125 | self.hostname = self.hostnames[0] | |
| 126 | else: | |
| 127 | self.hostname = 'unknown' | |
| 128 | ||
| 129 | self.hostnames = list(set(self.hostnames)) | |
| 130 | self.status = self.get_status() | |
| 131 | self.ipv4_address = self.get_ipv4_address() | |
| 132 | self.ipv6_address = self.get_ipv6_address() | |
| 133 | self.mac_address = self.get_mac_address() | |
| 134 | self.os_guesses = list(self.get_os_guesses()) | |
| 135 | self.os = self.top_os_guess() | |
| 136 | self.ports = list(self.get_ports()) | |
| 137 | self.vulns = list(self.get_scripts()) | |
| 138 | if self.os != 'unknown': | |
| 139 | for p in self.ports: | |
| 140 | if p.service is not None: | |
| 141 | if p.service.ostype: | |
| 142 | self.os = p.service.ostype | |
| 143 | break | |
| 144 | ||
| 145 | def get_hostnames(self): | |
| 146 | """ | |
| 147 | Expects to find one or more | |
| 148 | '<hostname name="localhost.localdomain" type="PTR"/>' in the host node. | |
| 149 | ||
| 150 | @return A list of (hostname, hostname_type) or None | |
| 151 | """ | |
| 152 | for hostname in self.node.findall('hostnames/hostname'): | |
| 153 | yield (hostname.attrib["name"], hostname.attrib["type"]) | |
| 154 | ||
| 155 | def get_attrib_from_subnode(self, subnode_xpath_expr, attrib_name): | |
| 156 | """ | |
| 157 | Finds a subnode in the host node and the retrieves a value from it | |
| 158 | ||
| 159 | @return An attribute value | |
| 160 | """ | |
| 161 | return get_attrib_from_subnode( | |
| 162 | self.node, | |
| 163 | subnode_xpath_expr, | |
| 164 | attrib_name) | |
| 165 | ||
| 166 | def get_status(self): | |
| 167 | """ | |
| 168 | Expects to find '<status state="up" reason="conn-refused"/>' | |
| 169 | in the node | |
| 170 | TODO: Use 'reason' | |
| 171 | @return An status or 'unknown' | |
| 172 | """ | |
| 173 | status = self.get_attrib_from_subnode('status', 'state') | |
| 174 | ||
| 175 | return status if status else 'unknown' | |
| 176 | ||
| 177 | def get_ipv4_address(self): | |
| 178 | """ | |
| 179 | Expects to find '<address addr="127.0.0.1" addrtype="ipv4"/>' | |
| 180 | in the node | |
| 181 | ||
| 182 | @return ip_address or 'unknown' | |
| 183 | """ | |
| 184 | ip_address = self.get_attrib_from_subnode( | |
| 185 | "address[@addrtype='ipv4']", | |
| 186 | 'addr') | |
| 187 | return ip_address if ip_address else 'unknown' | |
| 188 | ||
| 189 | def get_ipv6_address(self): | |
| 190 | """ | |
| 191 | Expects to find '<address addr="127.0.0.1" addrtype="ipv6"/>' | |
| 192 | in the node | |
| 193 | ||
| 194 | @return ip_address or 'unknown' | |
| 195 | """ | |
| 196 | ip_address = self.get_attrib_from_subnode( | |
| 197 | "address[@addrtype='ipv6']", | |
| 198 | 'addr') | |
| 199 | return ip_address if ip_address else 'unknown' | |
| 200 | ||
| 201 | def get_mac_address(self): | |
| 202 | """ | |
| 203 | Expects to find | |
| 204 | '<address addr="00:08:54:26:A9:E5" addrtype="mac" vendor="Netronix" />' | |
| 205 | in the node | |
| 206 | ||
| 207 | @return mac_address or 'unknown' | |
| 208 | """ | |
| 209 | mac_address = self.get_attrib_from_subnode( | |
| 210 | "address[@addrtype='mac']", | |
| 211 | 'addr') | |
| 212 | return mac_address if mac_address else 'unknown' | |
| 213 | ||
| 214 | def get_os_guesses(self): | |
| 215 | """ | |
| 216 | Expects to find | |
| 217 | '<os>..<osclass type="general purpose" vendor="Microsoft" | |
| 218 | osfamily="Windows" osgen="2003" accuracy="96" />..</os>' in the node | |
| 219 | ||
| 220 | @return A list of (os_vendor_family_gen, accuracy) | |
| 221 | """ | |
| 222 | # OS information about host with great acurracy. | |
| 223 | ||
| 224 | osclasses = self.node.findall('os/osclass') | |
| 225 | if osclasses == []: | |
| 226 | osclasses = self.node.findall('os/osmatch/osclass') | |
| 227 | ||
| 228 | for osclass in osclasses: | |
| 229 | os_vendor = osclass.get("vendor", "unknown") | |
| 230 | os_family = osclass.get("osfamily", "unknown") | |
| 231 | os_gen = osclass.get("osgen", "unknown") | |
| 232 | accuracy = osclass.get("accuracy", "unknown") | |
| 233 | ||
| 234 | yield ("%s %s %s" % (os_vendor, os_family, os_gen), accuracy) | |
| 235 | ||
| 236 | # Os information in services, bad acurracy. | |
| 237 | if osclasses == []: | |
| 238 | services = self.node.findall("ports/port/service") | |
| 239 | for service in services: | |
| 240 | ostype = service.get("ostype", "unknown") | |
| 241 | yield ("%s" % ostype, 0) | |
| 242 | ||
| 243 | ||
| 244 | def top_os_guess(self): | |
| 245 | """ | |
| 246 | @return The most accurate os_guess_id or 'unknown'. | |
| 247 | """ | |
| 248 | return self.os_guesses[0][0] if len(self.os_guesses) != 0 else 'unknown' | |
| 249 | ||
| 250 | def get_scripts(self): | |
| 251 | # Expects to find a scripts in the node. | |
| 252 | for s in self.node.findall('hostscript/script'): | |
| 253 | yield Script(s) | |
| 254 | ||
| 255 | def get_ports(self): | |
| 256 | """ | |
| 257 | Expects to find one or more | |
| 258 | '<port protocol="tcp" portid="631">...</port>' in the node. | |
| 259 | ||
| 260 | @return A list of Port instances or None | |
| 261 | """ | |
| 262 | for port in self.node.findall('ports/port'): | |
| 263 | yield Port(port) | |
| 264 | ||
| 265 | def is_up(self): | |
| 266 | """ | |
| 267 | Returns True if the host is up else False. | |
| 268 | """ | |
| 269 | if self.status == 'up': | |
| 270 | return True | |
| 271 | else: | |
| 272 | return False | |
| 273 | ||
| 274 | def __str__(self): | |
| 275 | ports = [] | |
| 276 | for port in self.ports: | |
| 277 | var = " %s" % port | |
| 278 | ports.append(var) | |
| 279 | ports = "\n".join(ports) | |
| 280 | ||
| 281 | return "%s, %s, %s [%s], %s\n%s" % ( | |
| 282 | self.hostnames, | |
| 283 | self.status, | |
| 284 | self.ipv4_address, | |
| 285 | self.mac_address, | |
| 286 | self.os, ports) | |
| 287 | ||
| 288 | ||
| 289 | class Port: | |
| 290 | """ | |
| 291 | An abstract representation of a Port. | |
| 292 | ||
| 293 | @param port_node A port_node taken from an nmap xml tree | |
| 294 | """ | |
| 295 | ||
| 296 | def __init__(self, port_node): | |
| 297 | self.node = port_node | |
| 298 | ||
| 299 | self.protocol = self.node.get("protocol") | |
| 300 | self.number = self.node.get("portid") | |
| 301 | self.state, self.reason, self.reason_ttl = self.get_state() | |
| 302 | self.service = self.get_service() | |
| 303 | self.vulns = list(self.get_scripts()) | |
| 304 | ||
| 305 | def get_attrib_from_subnode(self, subnode_xpath_expr, attrib_name): | |
| 306 | """ | |
| 307 | Finds a subnode in the host node and the retrieves a value from it. | |
| 308 | ||
| 309 | @return An attribute value | |
| 310 | """ | |
| 311 | return get_attrib_from_subnode( | |
| 312 | self.node, | |
| 313 | subnode_xpath_expr, | |
| 314 | attrib_name) | |
| 315 | ||
| 316 | def get_state(self): | |
| 317 | """ | |
| 318 | Expects to find a | |
| 319 | '<state state="open" reason="syn-ack" reason_ttl="0"/>' in the node. | |
| 320 | ||
| 321 | @return (state, reason, reason_ttl) or ('unknown','unknown','unknown') | |
| 322 | """ | |
| 323 | state = self.get_attrib_from_subnode('state', 'state') | |
| 324 | reason = self.get_attrib_from_subnode('state', 'reason') | |
| 325 | reason_ttl = self.get_attrib_from_subnode('state', 'reason_ttl') | |
| 326 | ||
| 327 | return (state if state else 'unknown', | |
| 328 | reason if reason else 'unknown', | |
| 329 | reason_ttl if reason_ttl else 'unknown') | |
| 330 | ||
| 331 | def get_service(self): | |
| 332 | """ | |
| 333 | Expects to find a service in the node. | |
| 334 | """ | |
| 335 | service_node = self.node.find('service') | |
| 336 | if service_node is not None: | |
| 337 | return Service(service_node) | |
| 338 | ||
| 339 | return None | |
| 340 | ||
| 341 | def get_scripts(self): | |
| 342 | """ | |
| 343 | Expects to find a scripts in the node. | |
| 344 | """ | |
| 345 | for s in self.node.findall('script'): | |
| 346 | yield Script(s) | |
| 347 | ||
| 348 | def __str__(self): | |
| 349 | return "%s, %s, Service: %s" % (self.number, self.state, self.service) | |
| 350 | ||
| 351 | ||
| 352 | class Script: | |
| 353 | """ | |
| 354 | An abstract representation of a Script. | |
| 355 | ||
| 356 | '<script id="http-methods" output="No Allow or Public header in OPTIONS | |
| 357 | response (status code 400)"/><script id="http-title" | |
| 358 | output="Document Error: Unauthorized"><elem key="title"> | |
| 359 | Document Error: Unauthorized</elem></script>' | |
| 360 | ||
| 361 | @param script_node A script_node taken from an nmap xml tree | |
| 362 | """ | |
| 363 | ||
| 364 | def parse_output(self, output): | |
| 365 | block_re = re.compile('^\s{4}References:((?:.|[\r\n])+[\r\n](?:\s{4}\w|\s*$))', re.MULTILINE) | |
| 366 | m1 = block_re.findall(output) | |
| 367 | if len(m1) > 0: | |
| 368 | links_re = re.compile('[ \t]+([^ \t\n\r]+)[ \t]*') | |
| 369 | m2 = links_re.findall(m1[0]) | |
| 370 | return m2 | |
| 371 | return [] | |
| 372 | ||
| 373 | def __init__(self, script_node): | |
| 374 | self.node = script_node | |
| 375 | ||
| 376 | self.name = script_node.get("id") | |
| 377 | self.desc = script_node.get("output") | |
| 378 | self.refs = self.parse_output(self.desc) | |
| 379 | self.response = "" | |
| 380 | for k in script_node.findall("elem"): | |
| 381 | self.response += "\n" + str(k.get('key')) + ": " + str(k.text) | |
| 382 | self.web = re.search("(http-|https-)", self.name) | |
| 383 | ||
| 384 | def __str__(self): | |
| 385 | return "%s, %s, %s" % (self.name, self.product, self.version) | |
| 386 | ||
| 387 | ||
| 388 | class Service: | |
| 389 | """ | |
| 390 | An abstract representation of a Service. | |
| 391 | ||
| 392 | '<service name="ipp" product="CUPS" version="1.4" method="probed" | |
| 393 | conf="10"/>' | |
| 394 | ||
| 395 | @param service_node A service_node taken from an nmap xml tree | |
| 396 | """ | |
| 397 | ||
| 398 | def __init__(self, service_node): | |
| 399 | self.node = service_node | |
| 400 | ||
| 401 | name = service_node.get("name") | |
| 402 | self.name = name if name else 'unknown' | |
| 403 | ||
| 404 | product = service_node.get("product") | |
| 405 | self.product = product if product else 'unknown' | |
| 406 | ||
| 407 | version = service_node.get("version") | |
| 408 | self.version = version if version else 'unknown' | |
| 409 | ||
| 410 | self.method = service_node.get("method") | |
| 411 | self.conf = service_node.get("conf") | |
| 412 | self.ostype = self.node.get("ostype") | |
| 413 | ||
| 414 | def __str__(self): | |
| 415 | return "%s, %s, %s" % (self.name, self.product, self.version) | |
| 416 | ||
| 417 | ||
| 418 | class NmapPlugin(PluginXMLFormat): | |
| 419 | """ | |
| 420 | Example plugin to parse nmap output. | |
| 421 | """ | |
| 422 | ||
| 423 | def __init__(self): | |
| 424 | super().__init__() | |
| 425 | self.identifier_tag = "nmaprun" | |
| 426 | self.id = "Nmap" | |
| 427 | self.name = "Nmap XML Output Plugin" | |
| 428 | self.plugin_version = "0.0.3" | |
| 429 | self.version = "6.40" | |
| 430 | self.framework_version = "1.0.0" | |
| 431 | self.options = None | |
| 432 | self._current_output = None | |
| 433 | self._command_regex = re.compile(r'^(sudo nmap|nmap|\.\/nmap).*?') | |
| 434 | ||
| 435 | global current_path | |
| 436 | self._output_file_path = os.path.join( | |
| 437 | self.data_path, | |
| 438 | "nmap_output-%s.xml" % self._rid) | |
| 439 | ||
| 440 | self.xml_arg_re = re.compile(r"^.*(-oX\s*[^\s]+).*$") | |
| 441 | self.addSetting("Scan Technique", str, "-sS") | |
| 442 | ||
| 443 | def parseOutputString(self, output, debug=False): | |
| 444 | """ | |
| 445 | This method will discard the output the shell sends, it will read it | |
| 446 | from the xml where it expects it to be present. | |
| 447 | ||
| 448 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 449 | output being sent is valid. | |
| 450 | """ | |
| 451 | ||
| 452 | parser = NmapXmlParser(output) | |
| 453 | ||
| 454 | for host in parser.hosts: | |
| 455 | # if not host.is_up(): | |
| 456 | # continue | |
| 457 | ||
| 458 | if host.mac_address == 'unknown': | |
| 459 | host.mac_address = "00:00:00:00:00:00" | |
| 460 | ||
| 461 | if host.ipv4_address != 'unknown': | |
| 462 | minterfase = host.ipv4_address | |
| 463 | h_id = self.createAndAddHost(minterfase, host.os) | |
| 464 | i_id = self.createAndAddInterface( | |
| 465 | h_id, | |
| 466 | minterfase, | |
| 467 | host.mac_address, | |
| 468 | ipv4_address=host.ipv4_address, | |
| 469 | hostname_resolution=host.hostnames) | |
| 470 | else: | |
| 471 | minterfase = host.ipv6_address | |
| 472 | h_id = self.createAndAddHost(minterfase, host.os) | |
| 473 | i_id = self.createAndAddInterface( | |
| 474 | h_id, | |
| 475 | minterfase, | |
| 476 | host.mac_address, | |
| 477 | ipv6_address=host.ipv6_address, | |
| 478 | hostname_resolution=host.hostnames) | |
| 479 | ||
| 480 | for v in host.vulns: | |
| 481 | desc = v.desc | |
| 482 | desc += "\nOutput: " + v.response if v.response else "" | |
| 483 | ||
| 484 | v_id = self.createAndAddVulnToHost( | |
| 485 | h_id, | |
| 486 | v.name, | |
| 487 | desc=v.desc, | |
| 488 | ref=v.refs, | |
| 489 | severity=0, | |
| 490 | external_id=v.name) | |
| 491 | ||
| 492 | for port in host.ports: | |
| 493 | ||
| 494 | srvname = str(port.number) | |
| 495 | srvversion = "unknown" | |
| 496 | if port.service is not None: | |
| 497 | srvname = port.service.name | |
| 498 | srvversion = port.service.product if port.service.product != "unknown" else "" | |
| 499 | srvversion += " " + port.service.version if port.service.version != "unknown" else "" | |
| 500 | ||
| 501 | s_id = self.createAndAddServiceToInterface( | |
| 502 | h_id, | |
| 503 | i_id, | |
| 504 | srvname, | |
| 505 | port.protocol, | |
| 506 | ports=[port.number], | |
| 507 | status=port.state, | |
| 508 | version=srvversion, | |
| 509 | description=srvname) | |
| 510 | ||
| 511 | for v in port.vulns: | |
| 512 | severity = 0 | |
| 513 | desc = v.desc | |
| 514 | refs = v.refs | |
| 515 | ||
| 516 | if re.search(r"VULNERABLE", desc): | |
| 517 | severity = "high" | |
| 518 | if re.search(r"ERROR", desc): | |
| 519 | severity = "unclassified" | |
| 520 | if re.search(r"Couldn't", desc): | |
| 521 | severity = "unclassified" | |
| 522 | if v.web: | |
| 523 | v_id = self.createAndAddVulnWebToService( | |
| 524 | h_id, | |
| 525 | s_id, | |
| 526 | v.name, | |
| 527 | desc=desc, | |
| 528 | response = v.response if v.response else "", | |
| 529 | ref=refs, | |
| 530 | severity=severity, | |
| 531 | website=minterfase, | |
| 532 | external_id=v.name) | |
| 533 | else: | |
| 534 | v_id = self.createAndAddVulnToService( | |
| 535 | h_id, | |
| 536 | s_id, | |
| 537 | v.name, | |
| 538 | desc=v.desc, | |
| 539 | ref=refs, | |
| 540 | severity=severity, | |
| 541 | external_id=v.name) | |
| 542 | del parser | |
| 543 | return True | |
| 544 | ||
| 545 | def processCommandString(self, username, current_path, command_string): | |
| 546 | """ | |
| 547 | Adds the -oX parameter to get xml output to the command string that the | |
| 548 | user has set. | |
| 549 | """ | |
| 550 | ||
| 551 | self._output_file_path = os.path.join( | |
| 552 | self.data_path, | |
| 553 | "%s_%s_output-%s.xml" % ( | |
| 554 | self.get_ws(), | |
| 555 | self.id, | |
| 556 | random.uniform(1, 10)) | |
| 557 | ) | |
| 558 | ||
| 559 | arg_match = self.xml_arg_re.match(command_string) | |
| 560 | ||
| 561 | if arg_match is None: | |
| 562 | return re.sub(r"(^.*?nmap)", | |
| 563 | r"\1 -oX %s" % self._output_file_path, | |
| 564 | command_string) | |
| 565 | else: | |
| 566 | return re.sub(arg_match.group(1), | |
| 567 | r"-oX %s" % self._output_file_path, | |
| 568 | command_string) | |
| 569 | ||
| 570 | def setHost(self): | |
| 571 | pass | |
| 572 | ||
| 573 | ||
| 574 | def createPlugin(): | |
| 575 | return NmapPlugin() | |
| 576 | ||
| 577 | ||
| 578 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | import re | |
| 7 | import os | |
| 8 | from collections import defaultdict | |
| 9 | ||
| 10 | try: | |
| 11 | import xml.etree.cElementTree as ET | |
| 12 | import xml.etree.ElementTree as ET_ORIG | |
| 13 | ETREE_VERSION = ET_ORIG.VERSION | |
| 14 | except ImportError: | |
| 15 | import xml.etree.ElementTree as ET | |
| 16 | ETREE_VERSION = ET.VERSION | |
| 17 | ||
| 18 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 19 | from faraday.client.plugins.plugins_utils import filter_services | |
| 20 | ||
| 21 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 22 | ||
| 23 | current_path = os.path.abspath(os.getcwd()) | |
| 24 | ||
| 25 | __author__ = "Francisco Amato" | |
| 26 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 27 | __credits__ = ["Francisco Amato"] | |
| 28 | __license__ = "" | |
| 29 | __version__ = "1.0.0" | |
| 30 | __maintainer__ = "Francisco Amato" | |
| 31 | __email__ = "[email protected]" | |
| 32 | __status__ = "Development" | |
| 33 | ||
| 34 | ||
| 35 | class OpenvasXmlParser: | |
| 36 | """ | |
| 37 | The objective of this class is to parse an xml file generated by the openvas tool. | |
| 38 | ||
| 39 | TODO: Handle errors. | |
| 40 | TODO: Test openvas output version. Handle what happens if the parser doesn't support it. | |
| 41 | TODO: Test cases. | |
| 42 | ||
| 43 | @param openvas_xml_filepath A proper xml generated by openvas | |
| 44 | """ | |
| 45 | ||
| 46 | def __init__(self, xml_output, logger): | |
| 47 | self.target = None | |
| 48 | self.port = "80" | |
| 49 | self.host = None | |
| 50 | self.logger = logger | |
| 51 | tree = self.parse_xml(xml_output) | |
| 52 | if tree: | |
| 53 | self.hosts = self.get_hosts(tree) | |
| 54 | self.items = list(self.get_items(tree, self.hosts)) | |
| 55 | else: | |
| 56 | self.items = [] | |
| 57 | ||
| 58 | def parse_xml(self, xml_output): | |
| 59 | """ | |
| 60 | Open and parse an xml file. | |
| 61 | ||
| 62 | TODO: Write custom parser to just read the nodes that we need instead of | |
| 63 | reading the whole file. | |
| 64 | ||
| 65 | @return xml_tree An xml tree instance. None if error. | |
| 66 | """ | |
| 67 | try: | |
| 68 | tree = ET.fromstring(xml_output) | |
| 69 | except SyntaxError as err: | |
| 70 | self.logger.error("SyntaxError: %s. %s", err, xml_output) | |
| 71 | return None | |
| 72 | return tree | |
| 73 | ||
| 74 | def get_items(self, tree, hosts): | |
| 75 | """ | |
| 76 | @return items A list of Host instances | |
| 77 | """ | |
| 78 | try: | |
| 79 | report = tree.find('report') | |
| 80 | results = report.findall('results') | |
| 81 | if results: | |
| 82 | nodes = report.findall('results')[0] | |
| 83 | else: | |
| 84 | nodes = tree.findall('result') | |
| 85 | for node in nodes: | |
| 86 | try: | |
| 87 | yield Item(node, hosts) | |
| 88 | except Exception as e: | |
| 89 | self.logger.error("Error generating Item from %s [%s]", node.attrib, e) | |
| 90 | except Exception as e: | |
| 91 | self.logger.error("Tag not found: %s", e) | |
| 92 | ||
| 93 | def get_hosts(self, tree): | |
| 94 | # Hosts are located in: /report/report/host | |
| 95 | # hosts_dict will contain has keys its details and its hostnames | |
| 96 | hosts = tree.findall('report/host') | |
| 97 | hosts_dict = {} | |
| 98 | for host in hosts: | |
| 99 | ip = self.do_clean(host.find('ip').text) | |
| 100 | details = self.get_data_from_detail(host.findall('detail')) | |
| 101 | hosts_dict[ip] = details | |
| 102 | return hosts_dict | |
| 103 | ||
| 104 | def get_data_from_detail(self, details): | |
| 105 | data = {} | |
| 106 | details_data = defaultdict(list) | |
| 107 | hostnames = [] | |
| 108 | for item in details: | |
| 109 | name = self.do_clean(item.find('name').text) | |
| 110 | value = self.do_clean(item.find('value').text) | |
| 111 | if "EXIT" in name: | |
| 112 | continue | |
| 113 | if name == 'hostname': | |
| 114 | hostnames.append(value) | |
| 115 | else: | |
| 116 | details_data[name].append(value) | |
| 117 | data['details'] = details_data | |
| 118 | data['hostnames'] = hostnames | |
| 119 | return data | |
| 120 | ||
| 121 | def do_clean(self, value): | |
| 122 | myreturn = "" | |
| 123 | if value is not None: | |
| 124 | myreturn = re.sub("\s+", " ", value) | |
| 125 | return myreturn.strip() | |
| 126 | ||
| 127 | ||
| 128 | def get_attrib_from_subnode(xml_node, subnode_xpath_expr, attrib_name): | |
| 129 | """ | |
| 130 | Finds a subnode in the item node and the retrieves a value from it | |
| 131 | ||
| 132 | @return An attribute value | |
| 133 | """ | |
| 134 | global ETREE_VERSION | |
| 135 | node = None | |
| 136 | ||
| 137 | if ETREE_VERSION[0] <= 1 and ETREE_VERSION[1] < 3: | |
| 138 | ||
| 139 | match_obj = re.search( | |
| 140 | "([^\@]+?)\[\@([^=]*?)=\'([^\']*?)\'", | |
| 141 | subnode_xpath_expr) | |
| 142 | ||
| 143 | if match_obj is not None: | |
| 144 | node_to_find = match_obj.group(1) | |
| 145 | xpath_attrib = match_obj.group(2) | |
| 146 | xpath_value = match_obj.group(3) | |
| 147 | for node_found in xml_node.findall(node_to_find): | |
| 148 | if node_found.attrib[xpath_attrib] == xpath_value: | |
| 149 | node = node_found | |
| 150 | break | |
| 151 | else: | |
| 152 | node = xml_node.find(subnode_xpath_expr) | |
| 153 | ||
| 154 | else: | |
| 155 | node = xml_node.find(subnode_xpath_expr) | |
| 156 | ||
| 157 | if node is not None: | |
| 158 | return node.get(attrib_name) | |
| 159 | ||
| 160 | return None | |
| 161 | ||
| 162 | ||
| 163 | class Item: | |
| 164 | """ | |
| 165 | An abstract representation of a Item | |
| 166 | @param item_node A item_node taken from an openvas xml tree | |
| 167 | """ | |
| 168 | ||
| 169 | def __init__(self, item_node, hosts): | |
| 170 | self.node = item_node | |
| 171 | self.host = self.get_text_from_subnode('host') | |
| 172 | self.subnet = self.get_text_from_subnode('subnet') | |
| 173 | if self.subnet is '': | |
| 174 | self.subnet = self.host | |
| 175 | self.port = "None" | |
| 176 | self.severity = self.severity_mapper() | |
| 177 | self.service = "Unknown" | |
| 178 | self.protocol = "" | |
| 179 | port = self.get_text_from_subnode('port') | |
| 180 | ||
| 181 | if "general" not in port: | |
| 182 | # service vuln | |
| 183 | info = port.split("/") | |
| 184 | self.port = info[0] | |
| 185 | self.protocol = info[1] | |
| 186 | host_details = hosts[self.host].get('details') | |
| 187 | self.service = self.get_service(port, host_details) | |
| 188 | else: | |
| 189 | # general was found in port data | |
| 190 | # this is a host vuln | |
| 191 | # this case will have item.port = 'None' | |
| 192 | info = port.split("/") | |
| 193 | self.protocol = info[1] | |
| 194 | self.service = info[0] # this value is general | |
| 195 | self.nvt = self.node.findall('nvt')[0] | |
| 196 | self.node = self.nvt | |
| 197 | self.id = self.node.get('oid') | |
| 198 | self.name = self.get_text_from_subnode('name') | |
| 199 | self.cve = self.get_text_from_subnode('cve') if self.get_text_from_subnode('cve') != "NOCVE" else "" | |
| 200 | self.bid = self.get_text_from_subnode('bid') if self.get_text_from_subnode('bid') != "NOBID" else "" | |
| 201 | self.xref = self.get_text_from_subnode('xref') if self.get_text_from_subnode('xref') != "NOXREF" else "" | |
| 202 | self.description = '' | |
| 203 | self.resolution = '' | |
| 204 | self.cvss_vector = '' | |
| 205 | self.tags = self.get_text_from_subnode('tags') | |
| 206 | if self.tags: | |
| 207 | tags_data = self.get_data_from_tags(self.tags) | |
| 208 | self.description = tags_data['description'] | |
| 209 | self.resolution = tags_data['solution'] | |
| 210 | self.cvss_vector = tags_data['cvss_base_vector'] | |
| 211 | ||
| 212 | ||
| 213 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 214 | """ | |
| 215 | Finds a subnode in the host node and the retrieves a value from it. | |
| 216 | ||
| 217 | @return An attribute value | |
| 218 | """ | |
| 219 | sub_node = self.node.find(subnode_xpath_expr) | |
| 220 | if sub_node is not None and sub_node.text is not None: | |
| 221 | return sub_node.text.strip() | |
| 222 | return '' | |
| 223 | ||
| 224 | def severity_mapper(self): | |
| 225 | severity = self.get_text_from_subnode('threat') | |
| 226 | if severity == 'Alarm': | |
| 227 | severity = 'Critical' | |
| 228 | return severity | |
| 229 | ||
| 230 | def get_service(self, port, details_from_host): | |
| 231 | # details_from_host: | |
| 232 | # name: name of detail | |
| 233 | # value: list with the values associated with the name | |
| 234 | for name, value in details_from_host.items(): | |
| 235 | service_detail = self.get_service_from_details(name, value, port) | |
| 236 | if service_detail: | |
| 237 | return service_detail | |
| 238 | # if the service is not in details_from_host, we will search it in | |
| 239 | # the file port_mapper.txt | |
| 240 | services_mapper = filter_services() | |
| 241 | for service in services_mapper: | |
| 242 | if service[0] == port: | |
| 243 | return service[1] | |
| 244 | ||
| 245 | return "Unknown" | |
| 246 | ||
| 247 | def do_clean(self, value): | |
| 248 | myreturn = "" | |
| 249 | if value is not None: | |
| 250 | myreturn = re.sub("\s+", " ", value) | |
| 251 | ||
| 252 | return myreturn.strip() | |
| 253 | ||
| 254 | def get_service_from_details(self, name, value_list, port): | |
| 255 | # detail: | |
| 256 | # name: name of detail | |
| 257 | # value_list: list with the values associated with the name | |
| 258 | res = None | |
| 259 | priority = 0 | |
| 260 | ||
| 261 | for value in value_list: | |
| 262 | if name == 'Services': | |
| 263 | aux_port = port.split('/')[0] | |
| 264 | value_splited = value.split(',') | |
| 265 | if value_splited[0] == aux_port: | |
| 266 | res = value_splited[2] | |
| 267 | priority = 3 | |
| 268 | ||
| 269 | elif '/' in value and priority != 3: | |
| 270 | auxiliar_value = value.split('/')[0] | |
| 271 | if auxiliar_value == port.split('/')[0]: | |
| 272 | res = name | |
| 273 | priority = 2 | |
| 274 | ||
| 275 | elif value.isdigit() and priority == 0: | |
| 276 | if value == port.split('/')[0]: | |
| 277 | res = name | |
| 278 | priority = 1 | |
| 279 | ||
| 280 | elif '::' in value and priority == 0: | |
| 281 | aux_value = value.split('::')[0] | |
| 282 | auxiliar_port = port.split('/')[0] | |
| 283 | if aux_value == auxiliar_port: | |
| 284 | res = name | |
| 285 | return res | |
| 286 | ||
| 287 | def get_data_from_tags(self, tags_text): | |
| 288 | clean_text = self.do_clean(tags_text) | |
| 289 | tags = clean_text.split('|') | |
| 290 | summary = '' | |
| 291 | insight = '' | |
| 292 | data = { | |
| 293 | 'solution': '', | |
| 294 | 'cvss_base_vector': '', | |
| 295 | 'description': '' | |
| 296 | } | |
| 297 | for tag in tags: | |
| 298 | splited_tag = tag.split('=', 1) | |
| 299 | if splited_tag[0] in data.keys(): | |
| 300 | data[splited_tag[0]] = splited_tag[1] | |
| 301 | elif splited_tag[0] == 'summary': | |
| 302 | summary = splited_tag[1] | |
| 303 | elif splited_tag[0] == 'insight': | |
| 304 | insight = splited_tag[1] | |
| 305 | ||
| 306 | data['description'] = ' '.join([summary, insight]).strip() | |
| 307 | ||
| 308 | return data | |
| 309 | ||
| 310 | ||
| 311 | class OpenvasPlugin(PluginXMLFormat): | |
| 312 | """ | |
| 313 | Example plugin to parse openvas output. | |
| 314 | """ | |
| 315 | ||
| 316 | def __init__(self): | |
| 317 | super().__init__() | |
| 318 | self.identifier_tag = "report" | |
| 319 | self.id = "Openvas" | |
| 320 | self.name = "Openvas XML Output Plugin" | |
| 321 | self.plugin_version = "0.3" | |
| 322 | self.version = "9.0.3" | |
| 323 | self.framework_version = "1.0.0" | |
| 324 | self.options = None | |
| 325 | self._current_output = None | |
| 326 | self.target = None | |
| 327 | self._command_regex = re.compile( | |
| 328 | r'^(openvas|sudo openvas|\.\/openvas).*?') | |
| 329 | ||
| 330 | global current_path | |
| 331 | self._output_file_path = os.path.join(self.data_path, "openvas_output-%s.xml" % self._rid) | |
| 332 | ||
| 333 | def report_belongs_to(self, **kwargs): | |
| 334 | if super().report_belongs_to(**kwargs): | |
| 335 | report_path = kwargs.get("report_path", "") | |
| 336 | with open(report_path) as f: | |
| 337 | output = f.read() | |
| 338 | return re.search("OpenVAS", output) is not None or re.search('<omp>', output) is not None | |
| 339 | return False | |
| 340 | ||
| 341 | def parseOutputString(self, output, debug=False): | |
| 342 | """ | |
| 343 | This method will discard the output the shell sends, it will read it | |
| 344 | from the xml where it expects it to be present. | |
| 345 | ||
| 346 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 347 | output being sent is valid. | |
| 348 | """ | |
| 349 | parser = OpenvasXmlParser(output, self.logger) | |
| 350 | web = False | |
| 351 | ids = {} | |
| 352 | # The following threats values will not be taken as vulns | |
| 353 | self.ignored_severities = ['Log', 'Debug'] | |
| 354 | for ip, values in parser.hosts.items(): | |
| 355 | # values contains: ip details and ip hostnames | |
| 356 | h_id = self.createAndAddHost( | |
| 357 | ip, | |
| 358 | hostnames=values['hostnames'] | |
| 359 | ) | |
| 360 | ids[ip] = h_id | |
| 361 | ||
| 362 | for item in parser.items: | |
| 363 | if item.name is not None: | |
| 364 | ref = [] | |
| 365 | if item.cve: | |
| 366 | cves = item.cve.split(',') | |
| 367 | for cve in cves: | |
| 368 | ref.append(cve.encode("utf-8").strip()) | |
| 369 | if item.bid: | |
| 370 | bids = item.bid.split(',') | |
| 371 | for bid in bids: | |
| 372 | ref.append("BID-%s" % bid.encode("utf-8").strip() ) | |
| 373 | if item.xref: | |
| 374 | ref.append(item.xref.encode("utf-8")) | |
| 375 | if item.tags and item.cvss_vector: | |
| 376 | ref.append(item.cvss_vector.encode("utf-8")) | |
| 377 | ||
| 378 | if item.subnet in ids: | |
| 379 | h_id = ids[item.host] | |
| 380 | else: | |
| 381 | h_id = self.createAndAddHost( | |
| 382 | item.subnet, | |
| 383 | hostnames=[item.host]) | |
| 384 | ids[item.subnet] = h_id | |
| 385 | ||
| 386 | if item.port == "None": | |
| 387 | if item.severity not in self.ignored_severities: | |
| 388 | v_id = self.createAndAddVulnToHost( | |
| 389 | h_id, | |
| 390 | item.name, | |
| 391 | desc=item.description, | |
| 392 | severity=item.severity, | |
| 393 | resolution=item.resolution, | |
| 394 | ref=ref, | |
| 395 | external_id=item.id) | |
| 396 | else: | |
| 397 | if item.service: | |
| 398 | web = re.search( | |
| 399 | r'^(www|http)', | |
| 400 | item.service) | |
| 401 | else: | |
| 402 | web = item.port in ('80', '443', '8080') | |
| 403 | ||
| 404 | if item.subnet + "_" + item.port in ids: | |
| 405 | s_id = ids[item.subnet + "_" + item.port] | |
| 406 | else: | |
| 407 | s_id = self.createAndAddServiceToHost( | |
| 408 | h_id, | |
| 409 | item.service, | |
| 410 | item.protocol, | |
| 411 | ports=[str(item.port)] | |
| 412 | ) | |
| 413 | ids[item.subnet + "_" + item.port] = s_id | |
| 414 | if web: | |
| 415 | if item.severity not in self.ignored_severities: | |
| 416 | v_id = self.createAndAddVulnWebToService( | |
| 417 | h_id, | |
| 418 | s_id, | |
| 419 | item.name, | |
| 420 | desc=item.description, | |
| 421 | website=item.host, | |
| 422 | severity=item.severity, | |
| 423 | ref=ref, | |
| 424 | resolution=item.resolution, | |
| 425 | external_id=item.id) | |
| 426 | elif item.severity not in self.ignored_severities: | |
| 427 | self.createAndAddVulnToService( | |
| 428 | h_id, | |
| 429 | s_id, | |
| 430 | item.name, | |
| 431 | desc=item.description, | |
| 432 | severity=item.severity, | |
| 433 | ref=ref, | |
| 434 | resolution=item.resolution, | |
| 435 | external_id=item.id) | |
| 436 | del parser | |
| 437 | ||
| 438 | def _isIPV4(self, ip): | |
| 439 | if len(ip.split(".")) == 4: | |
| 440 | return True | |
| 441 | else: | |
| 442 | return False | |
| 443 | ||
| 444 | def processCommandString(self, username, current_path, command_string): | |
| 445 | return None | |
| 446 | ||
| 447 | def setHost(self): | |
| 448 | pass | |
| 449 | ||
| 450 | ||
| 451 | def createPlugin(): | |
| 452 | return OpenvasPlugin() | |
| 453 | ||
| 454 | ||
| 455 | ||
| 456 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | ||
| 7 | # Author: @EzequielTBH | |
| 8 | from builtins import str | |
| 9 | ||
| 10 | from faraday.client.plugins import core | |
| 11 | import json | |
| 12 | import re | |
| 13 | ||
| 14 | __author__ = "@EzequielTBH" | |
| 15 | __copyright__ = "Copyright 2015, @EzequielTBH" | |
| 16 | __credits__ = "@EzequielTBH" | |
| 17 | __license__ = "GPL v3" | |
| 18 | __version__ = "1.0.0" | |
| 19 | ||
| 20 | ||
| 21 | class pasteAnalyzerPlugin(core.PluginBase): | |
| 22 | ||
| 23 | def __init__(self): | |
| 24 | super().__init__() | |
| 25 | self.id = "pasteAnalyzer" | |
| 26 | self.name = "pasteAnalyzer JSON Output Plugin" | |
| 27 | self.plugin_version = "1.0.0" | |
| 28 | self.command_string = "" | |
| 29 | self.current_path = "" | |
| 30 | self._command_regex = re.compile( | |
| 31 | r'^(pasteAnalyzer|python pasteAnalyzer.py|\./pasteAnalyzer.py|sudo python pasteAnalyzer.py|sudo \./pasteAnalyzer.py).*?') | |
| 32 | ||
| 33 | def parseOutputString(self, output, debug=False): | |
| 34 | ||
| 35 | print("[*]Parsing Output...") | |
| 36 | ||
| 37 | # Generating file name with full path. | |
| 38 | indexStart = self.command_string.find("-j") + 3 | |
| 39 | ||
| 40 | fileJson = self.command_string[ | |
| 41 | indexStart:self.command_string.find(" ", indexStart)] | |
| 42 | ||
| 43 | fileJson = self.current_path + "/" + fileJson | |
| 44 | ||
| 45 | try: | |
| 46 | with open(fileJson, "r") as fileJ: | |
| 47 | results = json.loads(fileJ.read()) | |
| 48 | ||
| 49 | except Exception as e: | |
| 50 | print("\n[!]Exception opening file\n" + str(e)) | |
| 51 | return | |
| 52 | ||
| 53 | if results == []: | |
| 54 | return | |
| 55 | ||
| 56 | print("[*]Results loaded...") | |
| 57 | ||
| 58 | # Configuration initial. | |
| 59 | hostId = self.createAndAddHost("pasteAnalyzer") | |
| 60 | interfaceId = self.createAndAddInterface(hostId, "Results") | |
| 61 | serviceId = self.createAndAddServiceToInterface( | |
| 62 | hostId, | |
| 63 | interfaceId, | |
| 64 | "Web", | |
| 65 | "TcpHTTP", | |
| 66 | ['80'] | |
| 67 | ) | |
| 68 | print("[*]Initial Configuration ready....") | |
| 69 | ||
| 70 | # Loading results. | |
| 71 | for i in range(0, len(results), 2): | |
| 72 | ||
| 73 | data = results[i + 1] | |
| 74 | description = "" | |
| 75 | ||
| 76 | for element in data: | |
| 77 | ||
| 78 | # Is Category | |
| 79 | if type(element) == str: #TODO bte arrray decode | |
| 80 | description += element + ": " | |
| 81 | ||
| 82 | # Is a list with results! | |
| 83 | else: | |
| 84 | for element2 in element: | |
| 85 | description += "\n" + element2 | |
| 86 | ||
| 87 | self.createAndAddVulnWebToService( | |
| 88 | hostId, | |
| 89 | serviceId, | |
| 90 | results[i], | |
| 91 | description | |
| 92 | ) | |
| 93 | ||
| 94 | print("[*]Parse finished, API faraday called...") | |
| 95 | ||
| 96 | def processCommandString(self, username, current_path, command_string): | |
| 97 | ||
| 98 | print("[*]pasteAnalyzer Plugin running...") | |
| 99 | ||
| 100 | if command_string.find("-j") < 0: | |
| 101 | command_string += " -j JSON_OUTPUT " | |
| 102 | ||
| 103 | self.command_string = command_string | |
| 104 | self.current_path = current_path | |
| 105 | ||
| 106 | return command_string | |
| 107 | ||
| 108 | ||
| 109 | def createPlugin(): | |
| 110 | return pasteAnalyzerPlugin() | |
| 111 | ||
| 112 | ||
| 113 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | import re | |
| 6 | import socket | |
| 7 | from os import path | |
| 8 | from faraday.client.plugins import core | |
| 9 | from urllib.parse import urlparse | |
| 10 | ||
| 11 | __author__ = "Andres Tarantini" | |
| 12 | __copyright__ = "Copyright (c) 2015 Andres Tarantini" | |
| 13 | __credits__ = ["Andres Tarantini"] | |
| 14 | __license__ = "MIT" | |
| 15 | __version__ = "0.0.1" | |
| 16 | __maintainer__ = "Andres Tarantini" | |
| 17 | __email__ = "[email protected]" | |
| 18 | __status__ = "Development" | |
| 19 | ||
| 20 | ||
| 21 | class PeepingTomPlugin(core.PluginBase): | |
| 22 | """ | |
| 23 | Handle PeepingTom (https://bitbucket.org/LaNMaSteR53/peepingtom) output | |
| 24 | """ | |
| 25 | ||
| 26 | def __init__(self): | |
| 27 | super().__init__() | |
| 28 | self.id = "peepingtom" | |
| 29 | self.name = "PeepingTom" | |
| 30 | self.plugin_version = "0.0.1" | |
| 31 | self.version = "02.19.15" | |
| 32 | self._command_regex = re.compile( | |
| 33 | r'^(python peepingtom.py|\./peepingtom.py).*?') | |
| 34 | self._path = None | |
| 35 | ||
| 36 | def parseOutputString(self, output): | |
| 37 | # Find data path | |
| 38 | data_path_search = re.search(r"in '(.*)\/'", output) | |
| 39 | print(data_path_search) | |
| 40 | if not data_path_search: | |
| 41 | # No data path found | |
| 42 | return True | |
| 43 | ||
| 44 | # Parse "peepingtom.html" report and extract results | |
| 45 | data_path = data_path_search.groups()[0] | |
| 46 | html = open(path.join(self._path, data_path, "peepingtom.html")).read() | |
| 47 | for url in re.findall(r'href=[\'"]?([^\'" >]+)', html): | |
| 48 | if "://" in url: | |
| 49 | url_parsed = urlparse(url) | |
| 50 | address = socket.gethostbyname(url_parsed.netloc) | |
| 51 | host = self.createAndAddHost(address) | |
| 52 | iface = self.createAndAddInterface( | |
| 53 | host, address, ipv4_address=address) | |
| 54 | service = self.createAndAddServiceToInterface(host, iface, "http", protocol="tcp", ports=[80]) | |
| 55 | self.createAndAddNoteToService( | |
| 56 | host, | |
| 57 | service, | |
| 58 | 'screenshot', | |
| 59 | path.join( | |
| 60 | self._path, | |
| 61 | data_path_search.groups()[0], | |
| 62 | "{}.png".format(url.replace( | |
| 63 | "://", "").replace("/", "").replace(".", "")) | |
| 64 | ) | |
| 65 | ) | |
| 66 | ||
| 67 | return True | |
| 68 | ||
| 69 | def processCommandString(self, username, current_path, command_string): | |
| 70 | self._path = current_path | |
| 71 | ||
| 72 | ||
| 73 | def createPlugin(): | |
| 74 | return PeepingTomPlugin() | |
| 75 | ||
| 76 | ||
| 77 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | import re | |
| 8 | ||
| 9 | __author__ = "Facundo de Guzmán, Esteban Guillardoy" | |
| 10 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 11 | __credits__ = ["Facundo de Guzmán", "Esteban Guillardoy"] | |
| 12 | __license__ = "" | |
| 13 | __version__ = "1.0.0" | |
| 14 | __maintainer__ = "Francisco Amato" | |
| 15 | __email__ = "[email protected]" | |
| 16 | __status__ = "Development" | |
| 17 | ||
| 18 | ||
| 19 | class CmdPingPlugin(core.PluginBase): | |
| 20 | """ | |
| 21 | This plugin handles ping command. | |
| 22 | Basically detects if user was able to connect to a device | |
| 23 | """ | |
| 24 | ||
| 25 | def __init__(self): | |
| 26 | super().__init__() | |
| 27 | self.id = "ping" | |
| 28 | self.name = "Ping" | |
| 29 | self.plugin_version = "0.0.1" | |
| 30 | self.version = "1.0.0" | |
| 31 | self._command_regex = re.compile( | |
| 32 | r'^(sudo ping|ping|sudo ping6|ping6).*?') | |
| 33 | ||
| 34 | def parseOutputString(self, output, debug=False): | |
| 35 | ||
| 36 | reg = re.search(r"PING ([\w\.-:]+)( |)\(([\w\.:]+)\)", output) | |
| 37 | if re.search("0 received|unknown host", output) is None and reg is not None: | |
| 38 | ||
| 39 | ip_address = reg.group(3) | |
| 40 | hostname = reg.group(1) | |
| 41 | ||
| 42 | h_id = self.createAndAddHost(ip_address) | |
| 43 | if self._isIPV4(ip_address): | |
| 44 | i_id = self.createAndAddInterface( | |
| 45 | h_id, ip_address, ipv4_address=ip_address, hostname_resolution=[hostname]) | |
| 46 | else: | |
| 47 | self.createAndAddInterface( | |
| 48 | h_id, ip_address, ipv6_address=ip_address, hostname_resolution=[hostname]) | |
| 49 | ||
| 50 | return True | |
| 51 | ||
| 52 | def _isIPV4(self, ip): | |
| 53 | if len(ip.split(".")) == 4: | |
| 54 | return True | |
| 55 | else: | |
| 56 | return False | |
| 57 | ||
| 58 | def processCommandString(self, username, current_path, command_string): | |
| 59 | """ | |
| 60 | """ | |
| 61 | return None | |
| 62 | ||
| 63 | ||
| 64 | def createPlugin(): | |
| 65 | return CmdPingPlugin() | |
| 66 | ||
| 67 | ||
| 68 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | from faraday.client.model import api | |
| 8 | import re | |
| 9 | ||
| 10 | ||
| 11 | __author__ = "Federico Kirschbaum" | |
| 12 | __copyright__ = "Copyright 2011, Faraday Project" | |
| 13 | __credits__ = ["Federico Kirschbaum"] | |
| 14 | __license__ = "" | |
| 15 | __version__ = "1.0.0" | |
| 16 | __maintainer__ = "Federico Kirschbaum" | |
| 17 | __email__ = "[email protected]" | |
| 18 | __status__ = "Development" | |
| 19 | ||
| 20 | ||
| 21 | class CmdPropeciaPlugin(core.PluginBase): | |
| 22 | """ | |
| 23 | This plugin handles propecia command. | |
| 24 | Basically inserts into the tree the ouput of this tool | |
| 25 | """ | |
| 26 | ||
| 27 | def __init__(self): | |
| 28 | super().__init__() | |
| 29 | self.id = "propecia" | |
| 30 | self.name = "propecia port scanner" | |
| 31 | self.plugin_version = "0.0.1" | |
| 32 | self.version = "1.0" | |
| 33 | self.framework_version = "1.0.0" | |
| 34 | self.options = None | |
| 35 | self._current_output = None | |
| 36 | self._command_regex = re.compile( | |
| 37 | r'^(sudo propecia|\.\/propecia|propecia).*?') | |
| 38 | self._host_ip = None | |
| 39 | self._port = "23" | |
| 40 | ||
| 41 | def parseOutputString(self, output, debug=False): | |
| 42 | ||
| 43 | host_info = re.search( | |
| 44 | r"(\b(?:(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.){3}(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\b)", output) | |
| 45 | ||
| 46 | if host_info is None: | |
| 47 | api.log("No hosts detected") | |
| 48 | else: | |
| 49 | for host in output.splitlines(): | |
| 50 | if host != "": | |
| 51 | h_id = self.createAndAddHost(host) | |
| 52 | i_id = self.createAndAddInterface( | |
| 53 | h_id, host, ipv4_address=host) | |
| 54 | s_id = self.createAndAddServiceToInterface(h_id, i_id, str(self._port), | |
| 55 | "tcp", | |
| 56 | ports=[self._port], | |
| 57 | status="open", | |
| 58 | version="", | |
| 59 | description="") | |
| 60 | if debug is True: | |
| 61 | api.devlog("Debug is active") | |
| 62 | ||
| 63 | return True | |
| 64 | ||
| 65 | def processCommandString(self, username, current_path, command_string): | |
| 66 | """ | |
| 67 | """ | |
| 68 | count_args = command_string.split() | |
| 69 | ||
| 70 | if count_args.__len__() == 3: | |
| 71 | self._port = count_args[2] | |
| 72 | ||
| 73 | ||
| 74 | def createPlugin(): | |
| 75 | return CmdPropeciaPlugin() | |
| 76 | ||
| 77 | ||
| 78 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 6 | import re | |
| 7 | import os | |
| 8 | import sys | |
| 9 | import logging | |
| 10 | ||
| 11 | try: | |
| 12 | import xml.etree.cElementTree as ET | |
| 13 | import xml.etree.ElementTree as ET_ORIG | |
| 14 | ETREE_VERSION = ET_ORIG.VERSION | |
| 15 | except ImportError: | |
| 16 | import xml.etree.ElementTree as ET | |
| 17 | ETREE_VERSION = ET.VERSION | |
| 18 | ||
| 19 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split('.')] | |
| 20 | ||
| 21 | logger = logging.getLogger(__name__) | |
| 22 | ||
| 23 | current_path = os.path.abspath(os.getcwd()) | |
| 24 | ||
| 25 | __author__ = 'Francisco Amato' | |
| 26 | __copyright__ = 'Copyright (c) 2013, Infobyte LLC' | |
| 27 | __credits__ = ['Francisco Amato'] | |
| 28 | __license__ = '' | |
| 29 | __version__ = '1.0.0' | |
| 30 | __maintainer__ = 'Francisco Amato' | |
| 31 | __email__ = '[email protected]' | |
| 32 | __status__ = 'Development' | |
| 33 | ||
| 34 | ||
| 35 | def cleaner_unicode(string): | |
| 36 | if string is not None: | |
| 37 | return string.encode('ascii', errors='backslashreplace') | |
| 38 | else: | |
| 39 | return string | |
| 40 | ||
| 41 | ||
| 42 | def cleaner_results(string): | |
| 43 | ||
| 44 | try: | |
| 45 | result = string.replace('<P>', '').replace('<UL>', ''). \ | |
| 46 | replace('<LI>', '').replace('<BR>', ''). \ | |
| 47 | replace('<A HREF="', '').replace('</A>', ' '). \ | |
| 48 | replace('" TARGET="_blank">', ' ').replace('"', '"') | |
| 49 | return result | |
| 50 | ||
| 51 | except: | |
| 52 | return '' | |
| 53 | ||
| 54 | ||
| 55 | class QualysguardXmlParser(): | |
| 56 | """ | |
| 57 | The objective of this class is to parse an xml file generated by | |
| 58 | the qualysguard tool. | |
| 59 | ||
| 60 | TODO: Handle errors. | |
| 61 | TODO: Test qualysguard output version. Handle what happens if the parser | |
| 62 | doesn't support it. | |
| 63 | TODO: Test cases. | |
| 64 | ||
| 65 | @param qualysguard_xml_filepath A proper xml generated by qualysguard | |
| 66 | """ | |
| 67 | ||
| 68 | def __init__(self, xml_output): | |
| 69 | tree, type_report = self.parse_xml(xml_output) | |
| 70 | ||
| 71 | if not tree or type_report is None: | |
| 72 | self.items = [] | |
| 73 | return | |
| 74 | ||
| 75 | if type_report is 'ASSET_DATA_REPORT': | |
| 76 | self.items = list(self.get_items_asset_report(tree)) | |
| 77 | elif type_report is 'SCAN': | |
| 78 | self.items = list(self.get_items_scan_report(tree)) | |
| 79 | ||
| 80 | def parse_xml(self, xml_output): | |
| 81 | """ | |
| 82 | Open and parse an xml file. | |
| 83 | ||
| 84 | TODO: Write custom parser to just read the nodes that we need instead | |
| 85 | of reading the whole file. | |
| 86 | ||
| 87 | @return xml_tree An xml tree instance. None if error. | |
| 88 | """ | |
| 89 | ||
| 90 | asset_data_report = '<!DOCTYPE ASSET_DATA_REPORT SYSTEM' | |
| 91 | scan_report = '<!DOCTYPE SCAN SYSTEM' | |
| 92 | ||
| 93 | try: | |
| 94 | tree = ET.fromstring(xml_output) | |
| 95 | ||
| 96 | if asset_data_report in xml_output: | |
| 97 | type_report = 'ASSET_DATA_REPORT' | |
| 98 | elif scan_report in xml_output: | |
| 99 | type_report = 'SCAN' | |
| 100 | else: | |
| 101 | type_report = None | |
| 102 | ||
| 103 | except SyntaxError as err: | |
| 104 | logger.error('SyntaxError: %s.' % (err)) | |
| 105 | return None, None | |
| 106 | ||
| 107 | return tree, type_report | |
| 108 | ||
| 109 | def get_items_scan_report(self, tree): | |
| 110 | """ | |
| 111 | @return items A list of Host instances | |
| 112 | """ | |
| 113 | for node in tree.findall('IP'): | |
| 114 | yield ItemScanReport(node) | |
| 115 | ||
| 116 | def get_items_asset_report(self, tree): | |
| 117 | """ | |
| 118 | @return items A list of Host instances | |
| 119 | """ | |
| 120 | for node in tree.find('HOST_LIST').findall('HOST'): | |
| 121 | yield ItemAssetReport(node, tree) | |
| 122 | ||
| 123 | ||
| 124 | class ItemAssetReport(): | |
| 125 | """ | |
| 126 | An abstract representation of a Item (HOST) for a Asset Report. | |
| 127 | @param item_node A item_node taken from an qualysguard xml tree | |
| 128 | """ | |
| 129 | ||
| 130 | def __init__(self, item_node, tree): | |
| 131 | ||
| 132 | self.node = item_node | |
| 133 | self.ip = self.get_text_from_subnode('IP') | |
| 134 | self.hostname = self.get_text_from_subnode('DNS') or '' | |
| 135 | self.os = self.get_text_from_subnode('OPERATING_SYSTEM') | |
| 136 | self.vulns = self.getResults(tree) | |
| 137 | ||
| 138 | def getResults(self, tree): | |
| 139 | ||
| 140 | glossary = tree.find('GLOSSARY/VULN_DETAILS_LIST') | |
| 141 | ||
| 142 | for self.issue in self.node.find('VULN_INFO_LIST'): | |
| 143 | yield ResultsAssetReport(self.issue, glossary) | |
| 144 | ||
| 145 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 146 | """ | |
| 147 | Finds a subnode in the host node and the retrieves a value from it. | |
| 148 | ||
| 149 | @return An attribute value | |
| 150 | """ | |
| 151 | sub_node = self.node.find(subnode_xpath_expr) | |
| 152 | if sub_node is not None: | |
| 153 | return sub_node.text | |
| 154 | ||
| 155 | return None | |
| 156 | ||
| 157 | ||
| 158 | class ResultsAssetReport(): | |
| 159 | """ | |
| 160 | A abstraction of Results for a Asset Report of Qualysguard. | |
| 161 | """ | |
| 162 | ||
| 163 | def __init__(self, issue_node, glossary): | |
| 164 | ||
| 165 | # VULN_INFO ElementTree | |
| 166 | self.node = issue_node | |
| 167 | self.port = self.get_text_from_subnode(self.node, 'PORT') | |
| 168 | self.protocol = self.get_text_from_subnode(self.node, 'PROTOCOL') | |
| 169 | self.name = self.get_text_from_subnode(self.node, 'QID') | |
| 170 | self.external_id = self.name | |
| 171 | self.result = self.get_text_from_subnode(self.node, 'RESULT') | |
| 172 | ||
| 173 | self.severity_dict = { | |
| 174 | '1': 'info', | |
| 175 | '2': 'info', | |
| 176 | '3': 'med', | |
| 177 | '4': 'high', | |
| 178 | '5': 'critical'} | |
| 179 | ||
| 180 | # GLOSSARY TAG | |
| 181 | self.glossary = glossary | |
| 182 | self.severity = self.severity_dict.get( | |
| 183 | self.get_text_from_glossary('SEVERITY'), 'info') | |
| 184 | self.title = self.get_text_from_glossary('TITLE') | |
| 185 | self.cvss = self.get_text_from_glossary('CVSS_SCORE/CVSS_BASE') | |
| 186 | self.pci = self.get_text_from_glossary('PCI_FLAG') | |
| 187 | self.solution = self.get_text_from_glossary('SOLUTION') | |
| 188 | self.impact = self.get_text_from_glossary('IMPACT') | |
| 189 | ||
| 190 | # Description | |
| 191 | self.desc = cleaner_results(self.get_text_from_glossary('THREAT')) | |
| 192 | if not self.desc: | |
| 193 | self.desc = '' | |
| 194 | if self.result: | |
| 195 | self.desc += '\n\nResult: ' + cleaner_results(self.result) | |
| 196 | if self.impact: | |
| 197 | self.desc += '\n\nImpact: ' + cleaner_results(self.impact) | |
| 198 | if self.result: | |
| 199 | self.desc += '\n\nSolution: ' + cleaner_results(self.solution) | |
| 200 | ||
| 201 | # References | |
| 202 | self.ref = [] | |
| 203 | ||
| 204 | cve_id = self.get_text_from_glossary('CVE_ID_LIST/CVE_ID/ID') | |
| 205 | if cve_id: | |
| 206 | self.ref.append(cve_id) | |
| 207 | ||
| 208 | if self.cvss: | |
| 209 | self.ref.append('CVSS SCORE: ' + self.cvss) | |
| 210 | ||
| 211 | if self.pci: | |
| 212 | self.ref.append('PCI: ' + self.pci) | |
| 213 | ||
| 214 | def get_text_from_glossary(self, tag): | |
| 215 | """ | |
| 216 | Finds a subnode in the glossary and retrieves a value of this. | |
| 217 | Filter by QualysId. | |
| 218 | ||
| 219 | @return An attribute value | |
| 220 | """ | |
| 221 | ||
| 222 | for vuln_detail in self.glossary: | |
| 223 | ||
| 224 | id_act = vuln_detail.get('id').strip('qid_') | |
| 225 | if id_act == self.name: | |
| 226 | ||
| 227 | text = vuln_detail.find(tag) | |
| 228 | if text is not None: | |
| 229 | return cleaner_unicode(text.text) | |
| 230 | else: | |
| 231 | return None | |
| 232 | ||
| 233 | def get_text_from_subnode(self, node, subnode_xpath_expr): | |
| 234 | """ | |
| 235 | Finds a subnode in the node and the retrieves a value from it. | |
| 236 | ||
| 237 | @return An attribute value | |
| 238 | """ | |
| 239 | sub_node = node.find(subnode_xpath_expr) | |
| 240 | if sub_node is not None: | |
| 241 | return cleaner_unicode(sub_node.text) | |
| 242 | ||
| 243 | return None | |
| 244 | ||
| 245 | ||
| 246 | class ItemScanReport(): | |
| 247 | """ | |
| 248 | An abstract representation of a Item for a 'SCAN' report of Qualysguard. | |
| 249 | ||
| 250 | @param item_node A item_node taken from an qualysguard xml tree | |
| 251 | """ | |
| 252 | ||
| 253 | def __init__(self, item_node): | |
| 254 | self.node = item_node | |
| 255 | self.ip = item_node.get('value') | |
| 256 | self.os = self.get_text_from_subnode('OS') | |
| 257 | self.hostname = self.get_hostname(item_node) | |
| 258 | self.vulns = self.getResults(item_node) | |
| 259 | ||
| 260 | def getResults(self, tree): | |
| 261 | """ | |
| 262 | :param tree: | |
| 263 | """ | |
| 264 | for self.issues in tree.findall('VULNS/CAT'): | |
| 265 | for v in self.issues.findall('VULN'): | |
| 266 | yield ResultsScanReport(v, self.issues) | |
| 267 | for self.issues in tree.findall('INFOS/CAT'): | |
| 268 | for v in self.issues.findall('INFO'): | |
| 269 | yield ResultsScanReport(v, self.issues) | |
| 270 | for self.issues in tree.findall('SERVICES/CAT'): | |
| 271 | for v in self.issues.findall('SERVICE'): | |
| 272 | yield ResultsScanReport(v, self.issues) | |
| 273 | for self.issues in tree.findall('PRACTICES/CAT'): | |
| 274 | for v in self.issues.findall('PRACTICE'): | |
| 275 | yield ResultsScanReport(v, self.issues) | |
| 276 | ||
| 277 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 278 | """ | |
| 279 | Finds a subnode in the host node and the retrieves a value from it. | |
| 280 | ||
| 281 | @return An attribute value | |
| 282 | """ | |
| 283 | sub_node = self.node.find(subnode_xpath_expr) | |
| 284 | if sub_node is not None: | |
| 285 | return sub_node.text | |
| 286 | ||
| 287 | return None | |
| 288 | ||
| 289 | def get_hostname(self, node): | |
| 290 | hostname = node.get('name') | |
| 291 | ||
| 292 | if hostname == 'No registered hostname': | |
| 293 | return "" | |
| 294 | ||
| 295 | return hostname | |
| 296 | ||
| 297 | ||
| 298 | class ResultsScanReport(): | |
| 299 | """ | |
| 300 | An abstraction of Result for Qualysguard 'SCAN' Report. | |
| 301 | """ | |
| 302 | ||
| 303 | def __init__(self, issue_node, parent): | |
| 304 | self.node = issue_node | |
| 305 | self.port = parent.get('port') | |
| 306 | self.protocol = parent.get('protocol') | |
| 307 | self.name = self.node.get('number') | |
| 308 | self.external_id = self.node.get('number') | |
| 309 | self.title = self.get_text_from_subnode('TITLE') | |
| 310 | self.cvss = self.get_text_from_subnode('CVSS_BASE') | |
| 311 | self.diagnosis = self.get_text_from_subnode('DIAGNOSIS') | |
| 312 | self.solution = self.get_text_from_subnode('SOLUTION') | |
| 313 | self.result = self.get_text_from_subnode('RESULT') | |
| 314 | self.consequence = self.get_text_from_subnode('CONSEQUENCE') | |
| 315 | ||
| 316 | self.severity_dict = { | |
| 317 | '1': 'info', | |
| 318 | '2': 'info', | |
| 319 | '3': 'med', | |
| 320 | '4': 'high', | |
| 321 | '5': 'critical'} | |
| 322 | ||
| 323 | self.severity = self.severity_dict.get(self.node.get('severity'), 'info') | |
| 324 | ||
| 325 | self.desc = cleaner_results(self.diagnosis) | |
| 326 | if self.result: | |
| 327 | self.desc += '\nResult: ' + cleaner_results(self.result) | |
| 328 | else: | |
| 329 | self.desc += '' | |
| 330 | ||
| 331 | if self.consequence: | |
| 332 | self.desc += '\nConsequence: ' + cleaner_results(self.consequence) | |
| 333 | else: | |
| 334 | self.desc += '' | |
| 335 | ||
| 336 | self.ref = [] | |
| 337 | for r in issue_node.findall('CVE_ID_LIST/CVE_ID'): | |
| 338 | self.node = r | |
| 339 | self.ref.append(self.get_text_from_subnode('ID')) | |
| 340 | for r in issue_node.findall('BUGTRAQ_ID_LIST/BUGTRAQ_ID'): | |
| 341 | self.node = r | |
| 342 | self.ref.append('bid-' + self.get_text_from_subnode('ID')) | |
| 343 | ||
| 344 | if self.cvss: | |
| 345 | self.ref.append('CVSS BASE: ' + self.cvss) | |
| 346 | ||
| 347 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 348 | """ | |
| 349 | Finds a subnode in the host node and the retrieves a value from it. | |
| 350 | ||
| 351 | @return An attribute value | |
| 352 | """ | |
| 353 | sub_node = self.node.find(subnode_xpath_expr) | |
| 354 | if sub_node is not None: | |
| 355 | return cleaner_results(cleaner_unicode(sub_node.text)) | |
| 356 | ||
| 357 | return None | |
| 358 | ||
| 359 | ||
| 360 | class QualysguardPlugin(PluginXMLFormat): | |
| 361 | """ | |
| 362 | Example plugin to parse qualysguard output. | |
| 363 | """ | |
| 364 | ||
| 365 | def __init__(self): | |
| 366 | super().__init__() | |
| 367 | self.identifier_tag = ["ASSET_DATA_REPORT", "SCAN"] | |
| 368 | self.id = 'Qualysguard' | |
| 369 | self.name = 'Qualysguard XML Output Plugin' | |
| 370 | self.plugin_version = '0.0.2' | |
| 371 | self.version = 'Qualysguard 8.17.1.0.2' | |
| 372 | self.framework_version = '1.0.0' | |
| 373 | self.options = None | |
| 374 | self._current_output = None | |
| 375 | self._command_regex = re.compile( | |
| 376 | r'^(sudo qualysguard|\.\/qualysguard).*?') | |
| 377 | ||
| 378 | global current_path | |
| 379 | self._output_file_path = os.path.join( | |
| 380 | self.data_path, | |
| 381 | 'qualysguard_output-%s.xml' % self._rid) | |
| 382 | ||
| 383 | def parseOutputString(self, output, debug=False): | |
| 384 | ||
| 385 | parser = QualysguardXmlParser(output) | |
| 386 | ||
| 387 | for item in parser.items: | |
| 388 | h_id = self.createAndAddHost( | |
| 389 | item.ip, | |
| 390 | item.os, | |
| 391 | hostnames=[item.hostname]) | |
| 392 | ||
| 393 | for v in item.vulns: | |
| 394 | if v.port is None: | |
| 395 | self.createAndAddVulnToHost( | |
| 396 | h_id, | |
| 397 | v.title if v.title else v.name, | |
| 398 | ref=v.ref, | |
| 399 | severity=v.severity, | |
| 400 | resolution=v.solution if v.solution else '', | |
| 401 | desc=v.desc, | |
| 402 | external_id=v.external_id) | |
| 403 | ||
| 404 | else: | |
| 405 | ||
| 406 | web = False | |
| 407 | s_id = self.createAndAddServiceToHost( | |
| 408 | h_id, | |
| 409 | v.port, | |
| 410 | v.protocol, | |
| 411 | ports=[str(v.port)], | |
| 412 | status='open') | |
| 413 | ||
| 414 | if v.port in ['80', '443'] or re.search('ssl|http', v.name): | |
| 415 | web = True | |
| 416 | else: | |
| 417 | web = False | |
| 418 | ||
| 419 | if web: | |
| 420 | self.createAndAddVulnWebToService( | |
| 421 | h_id, | |
| 422 | s_id, | |
| 423 | v.title if v.title else v.name, | |
| 424 | ref=v.ref, | |
| 425 | website=item.ip, | |
| 426 | severity=v.severity, | |
| 427 | desc=v.desc, | |
| 428 | resolution=v.solution if v.solution else '', | |
| 429 | external_id=v.external_id) | |
| 430 | ||
| 431 | else: | |
| 432 | self.createAndAddVulnToService( | |
| 433 | h_id, | |
| 434 | s_id, | |
| 435 | v.title if v.title else v.name, | |
| 436 | ref=v.ref, | |
| 437 | severity=v.severity, | |
| 438 | desc=v.desc, | |
| 439 | resolution=v.solution if v.solution else '', | |
| 440 | external_id=v.external_id) | |
| 441 | ||
| 442 | del parser | |
| 443 | ||
| 444 | def processCommandString(self, username, current_path, command_string): | |
| 445 | return None | |
| 446 | ||
| 447 | def setHost(self): | |
| 448 | pass | |
| 449 | ||
| 450 | ||
| 451 | def createPlugin(): | |
| 452 | return QualysguardPlugin() | |
| 453 | ||
| 454 | ||
| 455 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2017 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | import re | |
| 6 | import json | |
| 7 | import socket | |
| 8 | import logging | |
| 9 | try: | |
| 10 | from lxml import etree as ET | |
| 11 | except ImportError: | |
| 12 | import xml.etree.ElementTree as ET | |
| 13 | ||
| 14 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 15 | ||
| 16 | __author__ = 'Leonardo Lazzaro' | |
| 17 | __copyright__ = 'Copyright (c) 2017, Infobyte LLC' | |
| 18 | __credits__ = ['Leonardo Lazzaro'] | |
| 19 | __license__ = '' | |
| 20 | __version__ = '0.1.0' | |
| 21 | __maintainer__ = 'Leonardo Lazzaro' | |
| 22 | __email__ = '[email protected]' | |
| 23 | __status__ = 'Development' | |
| 24 | ||
| 25 | logger = logging.getLogger(__name__) | |
| 26 | ||
| 27 | ||
| 28 | class ReconngParser: | |
| 29 | def __init__(self, output): | |
| 30 | self._format = self.report_format(output) | |
| 31 | self.hosts = [] | |
| 32 | self.vulns = [] | |
| 33 | ||
| 34 | if self._format == 'xml': | |
| 35 | self.parsable_tree = self.get_parseable_xml_output(output) | |
| 36 | self.parse_xml_report(self.parsable_tree) | |
| 37 | ||
| 38 | elif self._format == 'json': | |
| 39 | self.parse_json_report(output) | |
| 40 | ||
| 41 | def report_format(self, output): | |
| 42 | xml_format_regex = re.compile(r'^<(.*?)>') | |
| 43 | json_format_regex = re.compile(r'(^{)') | |
| 44 | ||
| 45 | if xml_format_regex.match(output): | |
| 46 | output_format = 'xml' | |
| 47 | elif json_format_regex.match(output): | |
| 48 | output_format = 'json' | |
| 49 | else: | |
| 50 | return False | |
| 51 | ||
| 52 | return output_format | |
| 53 | ||
| 54 | def get_parseable_xml_output(self, xml_output): | |
| 55 | try: | |
| 56 | tree = ET.fromstring(xml_output) | |
| 57 | return tree | |
| 58 | except IndexError: | |
| 59 | print("Syntax error") | |
| 60 | return None | |
| 61 | ||
| 62 | def parse_xml_report(self, tree): | |
| 63 | hosts_items = tree.xpath('//hosts/item') | |
| 64 | self.hosts_from_report(hosts_items) | |
| 65 | ||
| 66 | vulnerabilities_items = tree.xpath('//vulnerabilities/item') | |
| 67 | self.vulns_from_report(vulnerabilities_items) | |
| 68 | ||
| 69 | def parse_json_report(self, output): | |
| 70 | reconng_data = json.loads(output) | |
| 71 | hosts_items = reconng_data.get('hosts', '') | |
| 72 | self.hosts_from_report(hosts_items) | |
| 73 | ||
| 74 | vulns_items = reconng_data.get('vulnerabilities','') | |
| 75 | self.vulns_from_report(vulns_items) | |
| 76 | ||
| 77 | def hosts_from_report(self, hosts_items): | |
| 78 | for host in hosts_items: | |
| 79 | host_info = self.get_info_from_host_element(host) | |
| 80 | self.hosts.append(host_info) | |
| 81 | ||
| 82 | def vulns_from_report(self, vulns_items): | |
| 83 | for vuln in vulns_items: | |
| 84 | vuln_info = self.get_info_from_vuln_element(vuln) | |
| 85 | self.vulns.append(vuln_info) | |
| 86 | ||
| 87 | def get_info_from_host_element(self, element): | |
| 88 | info = {} | |
| 89 | if self._format == 'xml': | |
| 90 | info['host'] = element.find('host').text | |
| 91 | info['ip'] = element.find('ip_address').text | |
| 92 | ||
| 93 | elif self._format == 'json': | |
| 94 | info['host'] = element['host'] | |
| 95 | info['ip'] = element['ip_address'] | |
| 96 | ||
| 97 | return info | |
| 98 | ||
| 99 | def get_info_from_vuln_element(self, element): | |
| 100 | info = {} | |
| 101 | if self._format == 'xml': | |
| 102 | info['host'] = element.find('host').text | |
| 103 | info['reference'] = element.find('reference').text | |
| 104 | info['module'] = element.find('module').text | |
| 105 | info['example'] = element.find('example').text | |
| 106 | info['category'] = element.find('category').text | |
| 107 | elif self._format == 'json': | |
| 108 | info['category'] = element['category'] | |
| 109 | info['host'] = element['host'] | |
| 110 | info['module'] = element['module'] | |
| 111 | info['reference'] = element['reference'] | |
| 112 | info['example'] = element['example'] | |
| 113 | ||
| 114 | if 'XSS' in info['category']: | |
| 115 | info['severity'] = 'high' | |
| 116 | elif 'SSL' in info['category']: | |
| 117 | info['severity'] = 'med' | |
| 118 | else: | |
| 119 | info['severity'] = 'info' | |
| 120 | ||
| 121 | return info | |
| 122 | ||
| 123 | ||
| 124 | class ReconngPlugin(PluginXMLFormat): | |
| 125 | """ | |
| 126 | Example plugin to parse qualysguard output. | |
| 127 | """ | |
| 128 | ||
| 129 | def __init__(self): | |
| 130 | super().__init__() | |
| 131 | self.identifier_tag = "reconng" | |
| 132 | self.id = 'Reconng' | |
| 133 | self.name = 'Reconng XML Output Plugin' | |
| 134 | self.plugin_version = '0.0.3' | |
| 135 | self.version = '' | |
| 136 | self.framework_version = '' | |
| 137 | self.options = None | |
| 138 | self._current_output = None | |
| 139 | self._command_regex = re.compile( | |
| 140 | r'records added to') | |
| 141 | ||
| 142 | self.host_mapper = {} | |
| 143 | ||
| 144 | def parseOutputString(self, output): | |
| 145 | parser = ReconngParser(output) | |
| 146 | ||
| 147 | for host in parser.hosts: | |
| 148 | h_id = self.createAndAddHost( | |
| 149 | host['ip'], | |
| 150 | hostnames=[host['host']] | |
| 151 | ) | |
| 152 | self.host_mapper[host['host']] = h_id | |
| 153 | for vuln in parser.vulns: | |
| 154 | if vuln['host'] not in list(self.host_mapper.keys()): | |
| 155 | ip = self.resolve_host(vuln['host']) | |
| 156 | h_id = self.createAndAddHost( | |
| 157 | ip, | |
| 158 | hostnames=[vuln['host']] | |
| 159 | ) | |
| 160 | self.host_mapper[vuln['host']] = h_id | |
| 161 | else: | |
| 162 | h_id = self.host_mapper[vuln['host']] | |
| 163 | ||
| 164 | self.createAndAddVulnToHost( | |
| 165 | name='Recon-ng found: ' + vuln['category'] + ' vulnerability', | |
| 166 | desc='Found by module: ' + vuln['module'], | |
| 167 | severity=vuln['severity'], | |
| 168 | ref=[vuln['reference']], | |
| 169 | host_id=h_id, | |
| 170 | data=vuln['example'] | |
| 171 | ) | |
| 172 | ||
| 173 | def processCommandString(self, username, current_path, command_string): | |
| 174 | return | |
| 175 | ||
| 176 | def resolve_host(self, host): | |
| 177 | try: | |
| 178 | return socket.gethostbyname(host) | |
| 179 | except: | |
| 180 | pass | |
| 181 | return host | |
| 182 | ||
| 183 | ||
| 184 | def createPlugin(): | |
| 185 | return ReconngPlugin() | |
| 186 | ||
| 187 | ||
| 188 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 7 | import re | |
| 8 | import os | |
| 9 | import sys | |
| 10 | ||
| 11 | try: | |
| 12 | import xml.etree.cElementTree as ET | |
| 13 | import xml.etree.ElementTree as ET_ORIG | |
| 14 | ETREE_VERSION = ET_ORIG.VERSION | |
| 15 | except ImportError: | |
| 16 | import xml.etree.ElementTree as ET | |
| 17 | ETREE_VERSION = ET.VERSION | |
| 18 | ||
| 19 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 20 | ||
| 21 | current_path = os.path.abspath(os.getcwd()) | |
| 22 | ||
| 23 | __author__ = "Francisco Amato" | |
| 24 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 25 | __credits__ = ["Francisco Amato"] | |
| 26 | __license__ = "" | |
| 27 | __version__ = "1.0.0" | |
| 28 | __maintainer__ = "Francisco Amato" | |
| 29 | __email__ = "[email protected]" | |
| 30 | __status__ = "Development" | |
| 31 | ||
| 32 | ||
| 33 | class RetinaXmlParser: | |
| 34 | """ | |
| 35 | The objective of this class is to parse an xml file generated by the retina tool. | |
| 36 | ||
| 37 | TODO: Handle errors. | |
| 38 | TODO: Test retina output version. Handle what happens if the parser doesn't support it. | |
| 39 | TODO: Test cases. | |
| 40 | ||
| 41 | @param retina_xml_filepath A proper xml generated by retina | |
| 42 | """ | |
| 43 | ||
| 44 | def __init__(self, xml_output): | |
| 45 | tree = self.parse_xml(xml_output) | |
| 46 | if tree: | |
| 47 | self.items = list(self.get_items(tree)) | |
| 48 | else: | |
| 49 | self.items = [] | |
| 50 | ||
| 51 | def parse_xml(self, xml_output): | |
| 52 | """ | |
| 53 | Open and parse an xml file. | |
| 54 | ||
| 55 | TODO: Write custom parser to just read the nodes that we need instead of | |
| 56 | reading the whole file. | |
| 57 | ||
| 58 | @return xml_tree An xml tree instance. None if error. | |
| 59 | """ | |
| 60 | try: | |
| 61 | tree = ET.fromstring(xml_output) | |
| 62 | except SyntaxError as err: | |
| 63 | print("SyntaxError: %s. %s" % (err, xml_output)) | |
| 64 | return None | |
| 65 | ||
| 66 | return tree | |
| 67 | ||
| 68 | def get_items(self, tree): | |
| 69 | """ | |
| 70 | @return items A list of Host instances | |
| 71 | """ | |
| 72 | for node in tree.findall("hosts/host"): | |
| 73 | yield Item(node) | |
| 74 | ||
| 75 | ||
| 76 | class Item: | |
| 77 | """ | |
| 78 | An abstract representation of a Item | |
| 79 | ||
| 80 | ||
| 81 | @param item_node A item_node taken from an retina xml tree | |
| 82 | """ | |
| 83 | ||
| 84 | def __init__(self, item_node): | |
| 85 | self.node = item_node | |
| 86 | self.ip = self.get_text_from_subnode("ip") | |
| 87 | self.hostname = "" if self.get_text_from_subnode( | |
| 88 | "dnsName") == "unknown" else self.get_text_from_subnode("dnsName") | |
| 89 | self.netbiosname = self.get_text_from_subnode("netBIOSName") | |
| 90 | self.netbiosdomain = self.get_text_from_subnode("netBIOSDomain") | |
| 91 | self.os = self.get_text_from_subnode("os") | |
| 92 | self.mac = self.get_text_from_subnode("mac") | |
| 93 | ||
| 94 | self.vulns = self.getResults(item_node) | |
| 95 | self.ports = {} | |
| 96 | for v in self.vulns: | |
| 97 | if not v.port in self.ports: | |
| 98 | self.ports[v.port] = [] | |
| 99 | self.ports[v.port].append(v) | |
| 100 | ||
| 101 | def getResults(self, tree): | |
| 102 | """ | |
| 103 | :param tree: | |
| 104 | """ | |
| 105 | for self.issues in tree.findall("audit"): | |
| 106 | yield Results(self.issues) | |
| 107 | ||
| 108 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 109 | """ | |
| 110 | Finds a subnode in the host node and the retrieves a value from it. | |
| 111 | ||
| 112 | @return An attribute value | |
| 113 | """ | |
| 114 | sub_node = self.node.find(subnode_xpath_expr) | |
| 115 | if sub_node is not None: | |
| 116 | return sub_node.text | |
| 117 | ||
| 118 | return None | |
| 119 | ||
| 120 | ||
| 121 | class Results(): | |
| 122 | ||
| 123 | def __init__(self, issue_node): | |
| 124 | self.node = issue_node | |
| 125 | self.name = self.get_text_from_subnode('name') | |
| 126 | ||
| 127 | self.description = self.get_text_from_subnode('description') | |
| 128 | self.solution = self.get_text_from_subnode('fixInformation') | |
| 129 | self.severity = self.get_text_from_subnode('risk') | |
| 130 | self.cve = "" if self.get_text_from_subnode( | |
| 131 | 'cve') == 'N/A' else self.get_text_from_subnode('cve') | |
| 132 | self.cce = self.get_text_from_subnode('cce') | |
| 133 | self.date = self.get_text_from_subnode('date') | |
| 134 | self.pciLevel = self.get_text_from_subnode('pciLevel') | |
| 135 | self.pciReason = self.get_text_from_subnode('pciReason') | |
| 136 | self.pciPassFail = self.get_text_from_subnode('pciPassFail') | |
| 137 | self.cvssScore = self.get_text_from_subnode('cvssScore') | |
| 138 | self.exploit = self.get_text_from_subnode('exploit') | |
| 139 | self.context = self.get_text_from_subnode('context') | |
| 140 | val = self.context.split(":") | |
| 141 | self.port = "" | |
| 142 | self.protocol = "" | |
| 143 | if len(val) == 2: | |
| 144 | if val[0] in ['TCP', 'UDP']: | |
| 145 | self.protocol = val[0] | |
| 146 | self.port = val[1] | |
| 147 | ||
| 148 | self.desc = self.get_text_from_subnode('description') | |
| 149 | self.solution = self.solution if self.solution else "" | |
| 150 | self.desc += "\nExploit: " + self.exploit if self.exploit else "" | |
| 151 | self.desc += "\ncvssScore: " + self.cvssScore if self.cvssScore else "" | |
| 152 | self.desc += "\nContext: " + self.context if self.context else "" | |
| 153 | ||
| 154 | self.ref = [] | |
| 155 | if self.cve: | |
| 156 | self.ref = self.cve.split(",") | |
| 157 | ||
| 158 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 159 | """ | |
| 160 | Finds a subnode in the host node and the retrieves a value from it. | |
| 161 | ||
| 162 | @return An attribute value | |
| 163 | """ | |
| 164 | sub_node = self.node.find(subnode_xpath_expr) | |
| 165 | if sub_node is not None: | |
| 166 | return sub_node.text | |
| 167 | ||
| 168 | return None | |
| 169 | ||
| 170 | ||
| 171 | class RetinaPlugin(PluginXMLFormat): | |
| 172 | """ | |
| 173 | Example plugin to parse retina output. | |
| 174 | """ | |
| 175 | ||
| 176 | def __init__(self): | |
| 177 | super().__init__() | |
| 178 | self.identifier_tag = "scanJob" | |
| 179 | self.id = "Retina" | |
| 180 | self.name = "Retina XML Output Plugin" | |
| 181 | self.plugin_version = "0.0.1" | |
| 182 | self.version = "Retina Network 5.19.2.2718" | |
| 183 | self.framework_version = "1.0.0" | |
| 184 | self.options = None | |
| 185 | self._current_output = None | |
| 186 | self._command_regex = re.compile(r'^(sudo retina|\.\/retina).*?') | |
| 187 | ||
| 188 | global current_path | |
| 189 | self._output_file_path = os.path.join(self.data_path, | |
| 190 | "retina_output-%s.xml" % self._rid) | |
| 191 | ||
| 192 | def parseOutputString(self, output, debug=False): | |
| 193 | ||
| 194 | parser = RetinaXmlParser(output) | |
| 195 | for item in parser.items: | |
| 196 | h_id = self.createAndAddHost(item.ip, item.os) | |
| 197 | hostname = item.hostname if item.hostname else item.ip | |
| 198 | i_id = self.createAndAddInterface( | |
| 199 | h_id, item.ip, ipv4_address=item.ip, hostname_resolution=[hostname]) | |
| 200 | ||
| 201 | if not item.netbiosname == 'N/A': | |
| 202 | self.createAndAddNoteToHost( | |
| 203 | h_id, "netBIOSName", item.netbiosname) | |
| 204 | ||
| 205 | if not item.netbiosdomain == 'N/A': | |
| 206 | self.createAndAddNoteToHost( | |
| 207 | h_id, "netBIOSDomain", item.netbiosdomain) | |
| 208 | ||
| 209 | for k, vulns in item.ports.items(): | |
| 210 | if k: | |
| 211 | for v in vulns: | |
| 212 | web = False | |
| 213 | s_id = self.createAndAddServiceToInterface(h_id, i_id, 'unknown', | |
| 214 | v.protocol.lower(), | |
| 215 | ports=[str(v.port)], | |
| 216 | status="open") | |
| 217 | ||
| 218 | if v.port in ['80', '443'] or re.search("ssl|http", v.name.lower()): | |
| 219 | web = True | |
| 220 | else: | |
| 221 | web = False | |
| 222 | ||
| 223 | if web: | |
| 224 | v_id = self.createAndAddVulnWebToService(h_id, s_id, v.name.encode( | |
| 225 | "utf-8"), ref=v.ref, website=hostname, severity=v.severity, resolution=v.solution.encode("utf-8"), desc=v.desc.encode("utf-8")) | |
| 226 | else: | |
| 227 | v_id = self.createAndAddVulnToService(h_id, s_id, v.name.encode( | |
| 228 | "utf-8"), ref=v.ref, severity=v.severity, resolution=v.solution.encode("utf-8"), desc=v.desc.encode("utf-8")) | |
| 229 | else: | |
| 230 | for v in vulns: | |
| 231 | v_id = self.createAndAddVulnToHost(h_id, v.name.encode( | |
| 232 | "utf-8"), ref=v.ref, severity=v.severity, resolution=v.solution.encode("utf-8"), desc=v.desc.encode("utf-8")) | |
| 233 | del parser | |
| 234 | ||
| 235 | def processCommandString(self, username, current_path, command_string): | |
| 236 | return None | |
| 237 | ||
| 238 | def setHost(self): | |
| 239 | pass | |
| 240 | ||
| 241 | ||
| 242 | def createPlugin(): | |
| 243 | return RetinaPlugin() | |
| 244 | ||
| 245 | ||
| 246 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | import re | |
| 8 | import os | |
| 9 | import sys | |
| 10 | ||
| 11 | ||
| 12 | current_path = os.path.abspath(os.getcwd()) | |
| 13 | ||
| 14 | __author__ = "Francisco Amato" | |
| 15 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 16 | __credits__ = ["Francisco Amato"] | |
| 17 | __license__ = "" | |
| 18 | __version__ = "1.0.0" | |
| 19 | __maintainer__ = "Francisco Amato" | |
| 20 | __email__ = "[email protected]" | |
| 21 | __status__ = "Development" | |
| 22 | ||
| 23 | ||
| 24 | class ReverseraiderParser: | |
| 25 | """ | |
| 26 | The objective of this class is to parse an xml file generated by the reverseraider tool. | |
| 27 | ||
| 28 | @param reverseraider_filepath A proper simple report generated by reverseraider | |
| 29 | """ | |
| 30 | ||
| 31 | def __init__(self, output): | |
| 32 | ||
| 33 | lists = output.split("\r\n") | |
| 34 | self.items = [] | |
| 35 | ||
| 36 | if re.search("ReverseRaider domain scanner|Error opening", output) is not None: | |
| 37 | return | |
| 38 | ||
| 39 | for line in lists: | |
| 40 | if line != "": | |
| 41 | print("(%s)" % line) | |
| 42 | info = line.split("\t") | |
| 43 | if info.__len__() > 0: | |
| 44 | item = {'host': info[0], 'ip': info[1]} | |
| 45 | print("host = %s, ip = %s" % (info[0], info[1])) | |
| 46 | self.items.append(item) | |
| 47 | ||
| 48 | ||
| 49 | class ReverseraiderPlugin(core.PluginBase): | |
| 50 | """ | |
| 51 | Example plugin to parse reverseraider output. | |
| 52 | """ | |
| 53 | ||
| 54 | def __init__(self): | |
| 55 | super().__init__() | |
| 56 | self.id = "Reverseraider" | |
| 57 | self.name = "Reverseraider XML Output Plugin" | |
| 58 | self.plugin_version = "0.0.1" | |
| 59 | self.version = "0.7.6" | |
| 60 | self.options = None | |
| 61 | self._current_output = None | |
| 62 | self._current_path = None | |
| 63 | self._command_regex = re.compile( | |
| 64 | r'^(sudo \.\/reverseraider|\.\/reverseraider).*?') | |
| 65 | self._completition = { | |
| 66 | "": "reverseraider -d domain | -r range [options]", | |
| 67 | "-r": "range of ipv4 or ipv6 addresses, for reverse scanning", | |
| 68 | "-d": "domain, for wordlist scanning (example google.com)", | |
| 69 | "-w": "wordlist file (see wordlists directory...)", | |
| 70 | "-t": "requests timeout in seconds", | |
| 71 | "-P": "enable numeric permutation on wordlist (default off)", | |
| 72 | "-D": "nameserver to use (default: resolv.conf)", | |
| 73 | "-T": "use TCP queries instead of UDP queries", | |
| 74 | "-R": "don't set the recursion bit on queries", | |
| 75 | } | |
| 76 | ||
| 77 | global current_path | |
| 78 | ||
| 79 | def canParseCommandString(self, current_input): | |
| 80 | if self._command_regex.match(current_input.strip()): | |
| 81 | return True | |
| 82 | else: | |
| 83 | return False | |
| 84 | ||
| 85 | def parseOutputString(self, output, debug=False): | |
| 86 | """ | |
| 87 | This method will discard the output the shell sends, it will read it from | |
| 88 | the xml where it expects it to be present. | |
| 89 | ||
| 90 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 91 | output being sent is valid. | |
| 92 | """ | |
| 93 | ||
| 94 | if debug: | |
| 95 | parser = ReverseraiderParser(output) | |
| 96 | else: | |
| 97 | ||
| 98 | parser = ReverseraiderParser(output) | |
| 99 | ||
| 100 | for item in parser.items: | |
| 101 | h_id = self.createAndAddHost(item['ip']) | |
| 102 | i_id = self.createAndAddInterface( | |
| 103 | h_id, item['ip'], ipv4_address=item['ip']) | |
| 104 | ||
| 105 | del parser | |
| 106 | ||
| 107 | def processCommandString(self, username, current_path, command_string): | |
| 108 | """ | |
| 109 | """ | |
| 110 | return None | |
| 111 | ||
| 112 | ||
| 113 | def createPlugin(): | |
| 114 | return ReverseraiderPlugin() | |
| 115 | ||
| 116 | ||
| 117 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import core | |
| 6 | from faraday.config.configuration import getInstanceConfiguration | |
| 7 | import requests | |
| 8 | import xmlrpc.client | |
| 9 | import json | |
| 10 | import uuid | |
| 11 | import re | |
| 12 | ||
| 13 | __author__ = "Alejandro Parodi" | |
| 14 | __copyright__ = "Copyright (c) 2016, Infobyte LLC" | |
| 15 | __credits__ = ["Parodi, Alejandro Julián"] | |
| 16 | __license__ = "" | |
| 17 | __version__ = "1.0.0" | |
| 18 | __maintainer__ = "Alejandro Parodi" | |
| 19 | __email__ = "[email protected]" | |
| 20 | __status__ = "Development" | |
| 21 | ||
| 22 | ||
| 23 | class SentinelPlugin(core.PluginBase): | |
| 24 | """ | |
| 25 | This plugin get information from Sentinel Tool. | |
| 26 | """ | |
| 27 | ||
| 28 | def __init__(self): | |
| 29 | super().__init__() | |
| 30 | self.id = "Sentinel" | |
| 31 | self.name = "Sentinel Online Plugin" | |
| 32 | self.plugin_version = "0.0.1" | |
| 33 | self.version = "1.0.0" | |
| 34 | self.baseURL = "https://sentinel.whitehatsec.com/api/" | |
| 35 | self.vulnURL = "https://source.whitehatsec.com/site_vuln_detail.html?site_id=" | |
| 36 | ||
| 37 | self.addSetting("Api_key", str, "") | |
| 38 | self.addSetting("Enable", str, "0") | |
| 39 | ||
| 40 | self.faraday_config = 'http://' + getInstanceConfiguration().getApiConInfoHost() + ':' + str(getInstanceConfiguration().getApiConInfoPort()) + '/' | |
| 41 | self.faraday_api = xmlrpc.client.ServerProxy(self.faraday_config) | |
| 42 | self.format = "?format=json&display_all=1&key=" | |
| 43 | self._command_regex = re.compile( | |
| 44 | r'^(sudo sentinel|sentinel).*?') | |
| 45 | ||
| 46 | def parseOutputString(self, output, debug=False): | |
| 47 | ||
| 48 | if self.getSetting("Api_key") == "": | |
| 49 | self.log("Please set Sentinel API in plugin configuration", "ERROR") | |
| 50 | return True | |
| 51 | ||
| 52 | allVulns = self.getAllVulns() | |
| 53 | for element in allVulns['collection']: | |
| 54 | ||
| 55 | vulnClass = element.get('class', "Vuln_Without_Title") | |
| 56 | severity = element.get('severity', "INFO") | |
| 57 | host = element.get('url', 'Unknown Hostname') | |
| 58 | ||
| 59 | hostId = self.faraday_api.createAndAddHost(host, "") | |
| 60 | ||
| 61 | interfaceId = self.faraday_api.createAndAddInterface( | |
| 62 | hostId, | |
| 63 | host, | |
| 64 | '00:00:00:00:00:00', | |
| 65 | '0.0.0.0', | |
| 66 | '0.0.0.0', | |
| 67 | '0.0.0.0', | |
| 68 | [], | |
| 69 | host) | |
| 70 | ||
| 71 | serviceId = self.faraday_api.createAndAddServiceToInterface(hostId, interfaceId, "HTTP") | |
| 72 | vulnData = self.getAttackVector(element.get('href', 'unknown')) | |
| 73 | ||
| 74 | for vuln in vulnData['collection']: | |
| 75 | ||
| 76 | vuln_information = self.getVulnInformation(element.get('href', 'unknown')) | |
| 77 | ||
| 78 | desc = vuln_information.get("description", "").get("description_prepend", "") | |
| 79 | solution = vuln_information.get("solution", "").get("solution_prepend", "") | |
| 80 | siteId = vuln_information.get("site", "Unknown") | |
| 81 | id = vuln_information.get("id", uuid.uuid4()) | |
| 82 | ||
| 83 | vulnUrlComplete = self.vulnURL + siteId + "&vuln_id=" + id | |
| 84 | ||
| 85 | cvss = "CVSS: " + vuln_information.get("cvss_score", "") | |
| 86 | siteName = "Site-Name: " + vuln_information.get("site_name", "Unknown") | |
| 87 | ||
| 88 | found = vuln.get('found', '0000-00-00T00:00:00Z') | |
| 89 | tested = vuln.get('tested', '0000-00-00T00:00:00Z') | |
| 90 | request = vuln.get('request', {})#{} | |
| 91 | ||
| 92 | state = "State: " + vuln.get('state', 'Unknown') | |
| 93 | ||
| 94 | ||
| 95 | if(len(request)>0): | |
| 96 | ||
| 97 | url = request.get('url', "Unknown") | |
| 98 | method = request.get('method', "Unknown") | |
| 99 | headers = request.get("headers", []) | |
| 100 | reqHeader = "" | |
| 101 | ||
| 102 | if(headers == None): | |
| 103 | headers = [] | |
| 104 | ||
| 105 | for parts in headers: | |
| 106 | reqHeader += parts.get("name", "") + ":" + parts.get("value", "")+"\n" | |
| 107 | ||
| 108 | body = request.get("body", {})#{} | |
| 109 | ||
| 110 | if(len(body)>0): | |
| 111 | bodyContent = body.get('content', "") | |
| 112 | ||
| 113 | response = vuln.get('response', {})#{} | |
| 114 | ||
| 115 | if(len(response)>0): | |
| 116 | ||
| 117 | status = str(response.get("status", "")) | |
| 118 | headers = response.get("headers", []) | |
| 119 | resHeader = "" | |
| 120 | ||
| 121 | if (headers == None): | |
| 122 | headers = [] | |
| 123 | ||
| 124 | for parts in headers: | |
| 125 | resHeader += parts.get("name", "") + ":" + parts.get("value", "") + "\n" | |
| 126 | ||
| 127 | resBody = response.get("body", {})#{} | |
| 128 | if(len(resBody)>0): | |
| 129 | resBodyMatch = resBody.get("body_match", {})# | |
| 130 | resBodyContent = resBodyMatch.get("content", "") | |
| 131 | ||
| 132 | data = "\n\nFound: " + found + "\n" + "Tested: " + tested + "\n" + state | |
| 133 | req = "" | |
| 134 | res = "" | |
| 135 | ||
| 136 | if(len(request)>0): | |
| 137 | ||
| 138 | req = method+" "+url+"\n" | |
| 139 | req += reqHeader+"\n" | |
| 140 | req += bodyContent | |
| 141 | ||
| 142 | if (len(response)>0): | |
| 143 | ||
| 144 | res = "Status: "+status+"\n" | |
| 145 | res += resHeader+"\n" | |
| 146 | res += resBodyContent | |
| 147 | ||
| 148 | name = vulnClass+" ID: "+id | |
| 149 | ||
| 150 | self.faraday_api.createAndAddVulnWebToService(hostId, | |
| 151 | serviceId, name, | |
| 152 | desc + data, | |
| 153 | [cvss, state, siteName, vulnUrlComplete], | |
| 154 | severity, solution, url, "", req, res, | |
| 155 | method, "", "", "", "") | |
| 156 | return True | |
| 157 | ||
| 158 | def getAllVulns(self): | |
| 159 | req = self.baseURL+"vuln"+self.format+self.getSetting("Api_key") | |
| 160 | r = requests.get(req) | |
| 161 | return json.loads(r.text) | |
| 162 | ||
| 163 | def getAttackVector(self, path): | |
| 164 | if(path != "unknown"): | |
| 165 | req = self.baseURL + path[5:] + "/attack_vector" +self.format + self.getSetting("Api_key") | |
| 166 | r = requests.get(req) | |
| 167 | return json.loads(r.text) | |
| 168 | else: | |
| 169 | return json.loads("{'colection':[]}") | |
| 170 | ||
| 171 | def getVulnInformation(self, path): | |
| 172 | req = self.baseURL + path[5:] + self.format + self.getSetting("Api_key") + "&display_description=1&display_solution=1&display_cvss=1" | |
| 173 | r = requests.get(req) | |
| 174 | return json.loads(r.text) | |
| 175 | ||
| 176 | def processCommandString(self, username, current_path, command_string): | |
| 177 | return | |
| 178 | ||
| 179 | ||
| 180 | def createPlugin(): | |
| 181 | return SentinelPlugin() | |
| 182 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | import re | |
| 8 | import os | |
| 9 | import sys | |
| 10 | import json | |
| 11 | import socket | |
| 12 | import random | |
| 13 | ||
| 14 | current_path = os.path.abspath(os.getcwd()) | |
| 15 | ||
| 16 | __author__ = "Nicolas Rodriguez" | |
| 17 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 18 | __credits__ = ["Nicolas Rodriguez"] | |
| 19 | __license__ = "" | |
| 20 | __version__ = "1.0.0" | |
| 21 | __maintainer__ = "Francisco Amato" | |
| 22 | __email__ = "[email protected]" | |
| 23 | __status__ = "Development" | |
| 24 | ||
| 25 | ||
| 26 | class SkipfishParser: | |
| 27 | """ | |
| 28 | The objective of this class is to parse an xml file generated by | |
| 29 | the skipfish tool. | |
| 30 | ||
| 31 | TODO: Handle errors. | |
| 32 | TODO: Test skipfish output version. Handle what happens if the parser | |
| 33 | doesn't support it. | |
| 34 | TODO: Test cases. | |
| 35 | ||
| 36 | @param skipfish_filepath A proper xml generated by skipfish | |
| 37 | """ | |
| 38 | ||
| 39 | def __init__(self, skipfish_filepath): | |
| 40 | self.filepath = skipfish_filepath | |
| 41 | ||
| 42 | tmp = open(skipfish_filepath + "/samples.js", "r").read() | |
| 43 | data = self.extract_data( | |
| 44 | tmp, | |
| 45 | "var issue_samples =", "];", | |
| 46 | lambda x: x.replace("'", '"'), | |
| 47 | False, | |
| 48 | False) | |
| 49 | # Escape characters not allowed in JSON, repr fix this with double Escape | |
| 50 | # Also remove \n character and space for have a valid JSON. | |
| 51 | issues = json.loads(repr(data[1]).replace("\\n"," ").replace("'","") + "]") | |
| 52 | ||
| 53 | tmp = open(skipfish_filepath + "/index.html", "r").read() | |
| 54 | err_msg = json.loads( | |
| 55 | self.extract_data( | |
| 56 | tmp, | |
| 57 | "var issue_desc=", | |
| 58 | "};", | |
| 59 | lambda x: self.convert_quotes(x, "'", '"'), | |
| 60 | False, | |
| 61 | False) | |
| 62 | [1] + "}") | |
| 63 | ||
| 64 | self.err_msg = err_msg | |
| 65 | self.issues = issues | |
| 66 | ||
| 67 | def convert_quotes(self, text, quote="'", inside='"'): | |
| 68 | start = 0 | |
| 69 | while True: | |
| 70 | pos = text.find(quote, start) | |
| 71 | ||
| 72 | if pos == -1: | |
| 73 | break | |
| 74 | ||
| 75 | ss = text[:pos - 1] | |
| 76 | quotes = len(ss) - len(ss.replace(inside, "")) | |
| 77 | ||
| 78 | if quotes % 2 == 0: | |
| 79 | text = text[:pos - 1] + "\\" + quote + text[pos + 1:] | |
| 80 | ||
| 81 | start = pos + 1 | |
| 82 | return text | |
| 83 | ||
| 84 | def extract_data(self, samples, start_tag, end_tag, fn=lambda x: x, include_start_tag=True, include_end_tag=True): | |
| 85 | start = samples.find(start_tag) | |
| 86 | ||
| 87 | if start == -1: | |
| 88 | return (-1, None) | |
| 89 | ||
| 90 | end = samples.find(end_tag, start + 1) | |
| 91 | ||
| 92 | if end == -1: | |
| 93 | return (-2, None) | |
| 94 | ||
| 95 | data = samples[start:end + len(end_tag)] | |
| 96 | data = fn(data) | |
| 97 | ||
| 98 | if not include_start_tag: | |
| 99 | data = data[len(start_tag) + 1:] | |
| 100 | ||
| 101 | if not include_end_tag: | |
| 102 | data = data[:-1 * len(end_tag)] | |
| 103 | ||
| 104 | return (0, data) | |
| 105 | ||
| 106 | ||
| 107 | class SkipfishPlugin(core.PluginBase): | |
| 108 | """ | |
| 109 | Example plugin to parse skipfish output. | |
| 110 | """ | |
| 111 | ||
| 112 | def __init__(self): | |
| 113 | super().__init__() | |
| 114 | self.id = "Skipfish" | |
| 115 | self.name = "Skipfish XML Output Plugin" | |
| 116 | self.plugin_version = "0.0.2" | |
| 117 | self.version = "2.1.5" | |
| 118 | self.options = None | |
| 119 | self._current_output = None | |
| 120 | self.parent = None | |
| 121 | self._command_regex = re.compile( | |
| 122 | r'^(sudo skipfish|skipfish|sudo skipfish\.pl|skipfish\.pl|perl skipfish\.pl|\.\/skipfish\.pl|\.\/skipfish).*?') | |
| 123 | global current_path | |
| 124 | ||
| 125 | def parseOutputString(self, output, debug=False): | |
| 126 | """ | |
| 127 | This method will discard the output the shell sends, it will read it | |
| 128 | from the xml where it expects it to be present. | |
| 129 | ||
| 130 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 131 | output being sent is valid. | |
| 132 | """ | |
| 133 | ||
| 134 | if not os.path.exists(self._output_path): | |
| 135 | return False | |
| 136 | ||
| 137 | p = SkipfishParser(self._output_path) | |
| 138 | ||
| 139 | hostc = {} | |
| 140 | port = 80 | |
| 141 | for issue in p.issues: | |
| 142 | req = "" | |
| 143 | res = "" | |
| 144 | for sample in issue["samples"]: | |
| 145 | if not sample["url"] in hostc: | |
| 146 | reg = re.search( | |
| 147 | "(http|https|ftp)\://([a-zA-Z0-9\.\-]+(\:[a-zA-Z0-9\.&%\$\-]+)*@)*((25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9])\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9]|0)\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9]|0)\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[0-9])|localhost|([a-zA-Z0-9\-]+\.)*[a-zA-Z0-9\-]+\.(com|edu|gov|int|mil|net|org|biz|arpa|info|name|pro|aero|coop|museum|[a-zA-Z]{2}))[\:]*([0-9]+)*([/]*($|[a-zA-Z0-9\.\,\?\'\\\+&%\$#\=~_\-]+)).*?$", sample["url"]) | |
| 148 | ||
| 149 | protocol = reg.group(1) | |
| 150 | host = reg.group(4) | |
| 151 | if reg.group(11) is not None: | |
| 152 | port = reg.group(11) | |
| 153 | else: | |
| 154 | port = 443 if protocol == "https" else 80 | |
| 155 | ||
| 156 | ip = self.resolve(host) | |
| 157 | ||
| 158 | h_id = self.createAndAddHost(ip) | |
| 159 | i_id = self.createAndAddInterface( | |
| 160 | h_id, | |
| 161 | ip, | |
| 162 | ipv4_address=ip, | |
| 163 | hostname_resolution=[host]) | |
| 164 | ||
| 165 | s_id = self.createAndAddServiceToInterface( | |
| 166 | h_id, | |
| 167 | i_id, | |
| 168 | "http", | |
| 169 | "tcp", | |
| 170 | ports=[port], | |
| 171 | status="open") | |
| 172 | ||
| 173 | hostc[sample["url"]] = { | |
| 174 | 'h_id': h_id, | |
| 175 | 'ip': ip, | |
| 176 | 'port': port, | |
| 177 | 'host': host, | |
| 178 | 'protocol': protocol, | |
| 179 | 'i_id': i_id, | |
| 180 | 's_id': s_id} | |
| 181 | ||
| 182 | try: | |
| 183 | req = open("%s/request.dat" % sample["dir"], "r").read() | |
| 184 | except: | |
| 185 | pass | |
| 186 | ||
| 187 | try: | |
| 188 | res = open("%s/request.dat" % sample["dir"], "r").read() | |
| 189 | except: | |
| 190 | pass | |
| 191 | ||
| 192 | d = hostc[sample["url"]] | |
| 193 | self.createAndAddVulnWebToService( | |
| 194 | d['h_id'], | |
| 195 | d['s_id'], | |
| 196 | name=p.err_msg[str(issue["type"])], | |
| 197 | desc="Extra: " + sample["extra"], | |
| 198 | website=d['host'], | |
| 199 | path=sample["url"], | |
| 200 | severity=issue["severity"]) | |
| 201 | ||
| 202 | def resolve(self, host): | |
| 203 | try: | |
| 204 | return socket.gethostbyname(host) | |
| 205 | except: | |
| 206 | pass | |
| 207 | return host | |
| 208 | ||
| 209 | xml_arg_re = re.compile(r"^.*(-o\s*[^\s]+).*$") | |
| 210 | ||
| 211 | def processCommandString(self, username, current_path, command_string): | |
| 212 | """ | |
| 213 | Adds the -o parameter to get report of the command string that the | |
| 214 | user has set. | |
| 215 | """ | |
| 216 | arg_match = self.xml_arg_re.match(command_string) | |
| 217 | ||
| 218 | self._output_path = os.path.join( | |
| 219 | self.data_path, | |
| 220 | "skipfish_output-%s" % random.uniform(1, 10)) | |
| 221 | ||
| 222 | if arg_match is None: | |
| 223 | return re.sub( | |
| 224 | r"(^.*?skipfish)", | |
| 225 | r"\1 -o %s" % self._output_path, | |
| 226 | command_string, | |
| 227 | 1) | |
| 228 | else: | |
| 229 | return re.sub( | |
| 230 | arg_match.group(1), | |
| 231 | r"-o %s" % self._output_path, | |
| 232 | command_string, | |
| 233 | 1) | |
| 234 | ||
| 235 | def setHost(self): | |
| 236 | pass | |
| 237 | ||
| 238 | ||
| 239 | def createPlugin(): | |
| 240 | return SkipfishPlugin() | |
| 241 | ||
| 242 | if __name__ == '__main__': | |
| 243 | parser = SkipfishParser(sys.argv[1]) | |
| 244 | for item in parser.items: | |
| 245 | if item.status == 'up': | |
| 246 | print(item) | |
| 247 | ||
| 248 | ||
| 249 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | import argparse | |
| 6 | import base64 | |
| 7 | import hashlib | |
| 8 | import os | |
| 9 | import pickle | |
| 10 | import re | |
| 11 | import shlex | |
| 12 | import socket | |
| 13 | import sqlite3 | |
| 14 | import sys | |
| 15 | from urllib.parse import urlparse | |
| 16 | from io import StringIO | |
| 17 | from http.server import BaseHTTPRequestHandler | |
| 18 | ||
| 19 | from collections import defaultdict | |
| 20 | ||
| 21 | from faraday.client.plugins.plugin import PluginTerminalOutput | |
| 22 | from faraday.client.plugins.plugin_utils import get_vulnweb_url_fields | |
| 23 | ||
| 24 | try: | |
| 25 | import xml.etree.cElementTree as ET | |
| 26 | import xml.etree.ElementTree as ET_ORIG | |
| 27 | ETREE_VERSION = ET_ORIG.VERSION | |
| 28 | except ImportError: | |
| 29 | import xml.etree.ElementTree as ET | |
| 30 | ETREE_VERSION = ET.VERSION | |
| 31 | ||
| 32 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 33 | ||
| 34 | current_path = os.path.abspath(os.getcwd()) | |
| 35 | ||
| 36 | __author__ = "Francisco Amato" | |
| 37 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 38 | __credits__ = ["Francisco Amato"] | |
| 39 | __license__ = "" | |
| 40 | __version__ = "1.0.0" | |
| 41 | __maintainer__ = "Francisco Amato" | |
| 42 | __email__ = "[email protected]" | |
| 43 | __status__ = "Development" | |
| 44 | ||
| 45 | ||
| 46 | # This is the value of the HASHDB_MILESTONE_VALUE constant | |
| 47 | # in the lib/core/settings.py file of sqlmap. | |
| 48 | # If that value is changed in a newer version of SQLMap, it means that the | |
| 49 | # hashdb mechanism has backwards-incompatible changes that probably will | |
| 50 | # break our plugin, so the plugin will show an error and abort | |
| 51 | SUPPORTED_HASHDB_VERSIONS = { | |
| 52 | "dPHoJRQYvs", # 1.0.11 | |
| 53 | "BZzRotigLX", # 1.2.8 | |
| 54 | "OdqjeUpBLc", # 1.3.6..1.3.10 | |
| 55 | } | |
| 56 | ||
| 57 | ||
| 58 | class Database: | |
| 59 | ||
| 60 | def __init__(self, database): | |
| 61 | self.database = database | |
| 62 | ||
| 63 | def connect(self, who="server"): | |
| 64 | ||
| 65 | self.connection = sqlite3.connect( | |
| 66 | self.database, timeout=3, isolation_level=None) | |
| 67 | ||
| 68 | self.cursor = self.connection.cursor() | |
| 69 | ||
| 70 | def disconnect(self): | |
| 71 | self.cursor.close() | |
| 72 | self.connection.close() | |
| 73 | ||
| 74 | def commit(self): | |
| 75 | self.cursor.commit() | |
| 76 | ||
| 77 | def execute(self, statement, arguments=None): | |
| 78 | if arguments: | |
| 79 | self.cursor.execute(statement, arguments) | |
| 80 | else: | |
| 81 | self.cursor.execute(statement) | |
| 82 | ||
| 83 | if statement.lstrip().upper().startswith("SELECT"): | |
| 84 | return self.cursor.fetchall() | |
| 85 | ||
| 86 | ||
| 87 | class SqlmapPlugin(PluginTerminalOutput): | |
| 88 | # Plugin for Sqlmap Tool | |
| 89 | def __init__(self): | |
| 90 | ||
| 91 | PluginTerminalOutput.__init__(self) | |
| 92 | self.id = "Sqlmap" | |
| 93 | self.name = "Sqlmap" | |
| 94 | self.plugin_version = "0.0.3" | |
| 95 | self.version = "1.2.8" | |
| 96 | self.framework_version = "1.0.0" | |
| 97 | self._current_output = None | |
| 98 | self.url = "" | |
| 99 | self.protocol = "" | |
| 100 | self.hostname = "" | |
| 101 | self.port = "80" | |
| 102 | self.params = "" | |
| 103 | self.fullpath = "" | |
| 104 | self.path = "" | |
| 105 | self.ignore_parsing = False | |
| 106 | ||
| 107 | self.addSetting("Sqlmap path", str, "/root/tools/sqlmap") | |
| 108 | ||
| 109 | self.db_port = { | |
| 110 | "MySQL": 3306, "PostgreSQL": "", "Microsoft SQL Server": 1433, | |
| 111 | "Oracle": 1521, "Firebird": 3050, | |
| 112 | "SAP MaxDB": 7210, "Sybase": 5000, | |
| 113 | "IBM DB2": 50000, "HSQLDB": 9001} | |
| 114 | ||
| 115 | self.ptype = { | |
| 116 | 1: "Unescaped numeric", | |
| 117 | 2: "Single quoted string", | |
| 118 | 3: "LIKE single quoted string", | |
| 119 | 4: "Double quoted string", | |
| 120 | 5: "LIKE double quoted string", | |
| 121 | } | |
| 122 | ||
| 123 | self._command_regex = re.compile( | |
| 124 | r'^(python2 ./sqlmap.py|python2.7 ./sqlmap.py|sudo sqlmap|sqlmap|sudo python sqlmap|python sqlmap|\.\/sqlmap).*?') | |
| 125 | ||
| 126 | global current_path | |
| 127 | self._output_path = '' | |
| 128 | ||
| 129 | class HTTPRequest(BaseHTTPRequestHandler): | |
| 130 | ||
| 131 | def __init__(self, request_text): | |
| 132 | super().__init__() | |
| 133 | self.rfile = StringIO(request_text) | |
| 134 | self.raw_requestline = self.rfile.readline() | |
| 135 | self.error_code = self.error_message = None | |
| 136 | self.parse_request() | |
| 137 | ||
| 138 | def send_error(self, code, message): | |
| 139 | self.error_code = code | |
| 140 | self.error_message = message | |
| 141 | ||
| 142 | def hashKey(self, key): | |
| 143 | # from sqlmap/lib/utils/hashdb.py | |
| 144 | import six #pylint: disable=import-error,bad-option-value,import-outside-toplevel | |
| 145 | from lib.core.convert import getBytes #pylint: disable=import-error,bad-option-value,import-outside-toplevel | |
| 146 | key = getBytes(key if isinstance(key, six.text_type) else repr(key)) | |
| 147 | retVal = int(hashlib.md5(key).hexdigest(), 16) & 0x7fffffffffffffff # Reference: http://stackoverflow.com/a/4448400 | |
| 148 | return retVal | |
| 149 | ||
| 150 | def hashDBRetrieve(self, key, unserialize=False, db=False): | |
| 151 | """ | |
| 152 | Helper function for restoring session data from HashDB | |
| 153 | """ | |
| 154 | ||
| 155 | if self.HASHDB_MILESTONE_VALUE == 'dPHoJRQYvs': | |
| 156 | # Support for old SQLMap versions | |
| 157 | key = "%s%s%s" % (self.url or "%s%s" % ( | |
| 158 | self.hostname, self.port), key, self.HASHDB_MILESTONE_VALUE) | |
| 159 | else: | |
| 160 | if not self.url: | |
| 161 | self.log('No URL found while running sqlmap', 'ERROR') | |
| 162 | url = urlparse(self.url) | |
| 163 | key = '|'.join([ | |
| 164 | url.hostname, | |
| 165 | url.path.strip('/'), | |
| 166 | key, | |
| 167 | self.HASHDB_MILESTONE_VALUE | |
| 168 | ]) | |
| 169 | ||
| 170 | retVal = '' | |
| 171 | hash_ = self.hashKey(key) | |
| 172 | ||
| 173 | if not retVal: | |
| 174 | while True: | |
| 175 | try: | |
| 176 | for row in db.execute("SELECT value FROM storage WHERE id=?", (hash_,)): | |
| 177 | retVal = row[0] | |
| 178 | except sqlite3.OperationalError as ex: | |
| 179 | if not 'locked' in ex.message: | |
| 180 | raise | |
| 181 | else: | |
| 182 | break | |
| 183 | return retVal if not unserialize else self.base64unpickle(retVal) | |
| 184 | ||
| 185 | def base64decode(self, value): | |
| 186 | """ | |
| 187 | Decodes string value from Base64 to plain format | |
| 188 | ||
| 189 | >>> base64decode('Zm9vYmFy') | |
| 190 | 'foobar' | |
| 191 | """ | |
| 192 | ||
| 193 | return base64.b64decode(value) | |
| 194 | ||
| 195 | def base64encode(self, value): | |
| 196 | """ | |
| 197 | Encodes string value from plain to Base64 format | |
| 198 | ||
| 199 | >>> base64encode('foobar') | |
| 200 | 'Zm9vYmFy' | |
| 201 | """ | |
| 202 | return base64.b64encode(value)[:-1].replace("\n", "") | |
| 203 | ||
| 204 | def base64unpickle(self, value): | |
| 205 | """ | |
| 206 | Decodes value from Base64 to plain format and deserializes (with pickle) its content | |
| 207 | ||
| 208 | >>> base64unpickle('gAJVBmZvb2JhcnEALg==') | |
| 209 | 'foobar' | |
| 210 | """ | |
| 211 | if value: | |
| 212 | return pickle.loads(self.base64decode(value)) | |
| 213 | ||
| 214 | def xmlvalue(self, db, name, value="query"): | |
| 215 | ||
| 216 | filepath = "%s" % os.path.join( | |
| 217 | current_path, "plugins/repo/sqlmap/queries.xml") | |
| 218 | with open(filepath, "r") as f: | |
| 219 | try: | |
| 220 | tree = ET.fromstring(f.read()) | |
| 221 | except SyntaxError as err: | |
| 222 | self.log("SyntaxError: %s. %s" % (err, filepath), "ERROR") | |
| 223 | return None | |
| 224 | ||
| 225 | for node in tree.findall("dbms[@value='" + db + "']/" + name + ''): | |
| 226 | return node.attrib[value] | |
| 227 | ||
| 228 | def getuser(self, data): | |
| 229 | ||
| 230 | users = re.search( | |
| 231 | r'database management system users \[[\d]+\]:\n((\[\*\] (.*)\n)*)', | |
| 232 | data) | |
| 233 | ||
| 234 | if users: | |
| 235 | return [x.replace("[*] ", "") for x in users.group(1).split("\n")] | |
| 236 | ||
| 237 | def getdbs(self, data): | |
| 238 | ||
| 239 | dbs = re.search( | |
| 240 | r'available databases \[[\d]+\]:\n(((\[\*\] (.*)\n)*))', | |
| 241 | data) | |
| 242 | ||
| 243 | if dbs: | |
| 244 | return [x.replace("[*] ", "") for x in dbs.group(1).split("\n")] | |
| 245 | ||
| 246 | def getpassword(self, data): | |
| 247 | ||
| 248 | users = {} | |
| 249 | ||
| 250 | password = re.findall( | |
| 251 | r"\n\[\*\] (.*) \[\d\]:\n\s*password hash: (.*)", | |
| 252 | data) | |
| 253 | ||
| 254 | if password: | |
| 255 | for credential in password: | |
| 256 | ||
| 257 | user = credential[0] | |
| 258 | mpass = credential[1] | |
| 259 | users[user] = mpass | |
| 260 | ||
| 261 | return users | |
| 262 | ||
| 263 | def _get_log_message(self, line): | |
| 264 | """Return the message of a log line. | |
| 265 | ||
| 266 | If the line isn't from the log it will raise a ValueError | |
| 267 | ||
| 268 | >>> line = '[16:59:03] [INFO] fetching tables' | |
| 269 | >>> self._get_log_message('line') | |
| 270 | 'fetching tables' | |
| 271 | """ | |
| 272 | match = re.match(r'\[[0-9:]+\] \[\w+\] (.+)$', line) | |
| 273 | if match is None: | |
| 274 | raise ValueError('Incorrect format of line') | |
| 275 | return match.group(1) | |
| 276 | ||
| 277 | def _is_log_and_startswith(self, text, line): | |
| 278 | try: | |
| 279 | msg = self._get_log_message(line) | |
| 280 | except ValueError: | |
| 281 | return False | |
| 282 | else: | |
| 283 | return msg.startswith(text) | |
| 284 | ||
| 285 | def _is_tables_log_line(self, line): | |
| 286 | # [16:59:03] [INFO] fetching tables for databases: 'bWAPP, ... | |
| 287 | return self._is_log_and_startswith('fetching tables for databases', | |
| 288 | line) | |
| 289 | ||
| 290 | def _is_columns_log_line(self, line): | |
| 291 | # [16:59:03] [INFO] fetching columns for table ... | |
| 292 | return self._is_log_and_startswith('fetching columns for table ', | |
| 293 | line) | |
| 294 | ||
| 295 | def _match_start_get_remaining(self, start, text): | |
| 296 | """ | |
| 297 | If text starts with start, return text with start stripped. | |
| 298 | ||
| 299 | Return None if it doesn't match. | |
| 300 | """ | |
| 301 | if not text.startswith(start): | |
| 302 | return | |
| 303 | return text[len(start):] | |
| 304 | ||
| 305 | def gettables(self, data): | |
| 306 | """ | |
| 307 | Return enumerated tables of the remote database. | |
| 308 | """ | |
| 309 | tables = defaultdict(list) # Map database names with its tables | |
| 310 | current_database = None | |
| 311 | status = 'find_log_line' | |
| 312 | list_found = False | |
| 313 | for line in data.splitlines(): | |
| 314 | if status == 'find_log_line': | |
| 315 | # Look for the correct log line to start searching databases | |
| 316 | if self._is_tables_log_line(line): | |
| 317 | # Correct line, change status | |
| 318 | status = 'find_dbname' | |
| 319 | elif self._is_log_and_startswith('', line) and list_found: | |
| 320 | # If another log line is reached, stop looking | |
| 321 | break | |
| 322 | elif status == 'find_dbname': | |
| 323 | database = self._match_start_get_remaining('Database: ', line) | |
| 324 | if database is not None: | |
| 325 | current_database = database | |
| 326 | list_found = True | |
| 327 | status = 'find_list_start' | |
| 328 | elif status == 'find_list_start': | |
| 329 | # Find +--------------+ line | |
| 330 | if re.match(r'^\+\-+\+$', line): | |
| 331 | # Line found | |
| 332 | status = 'find_tables' | |
| 333 | elif status == 'find_tables': | |
| 334 | if line.startswith('|') and line.endswith('|'): | |
| 335 | table = line[1:-1].strip() | |
| 336 | tables[current_database].append(table) | |
| 337 | elif re.match(r'^\+\-+\+$', line): | |
| 338 | # Table list for this db ended | |
| 339 | status = 'find_dbname' | |
| 340 | else: | |
| 341 | raise RuntimeError('unknown status') | |
| 342 | return tables | |
| 343 | ||
| 344 | def getcolumns(self, data): | |
| 345 | """ | |
| 346 | Return enumerated columns of the remote database. | |
| 347 | """ | |
| 348 | columns = defaultdict(lambda: defaultdict(list)) | |
| 349 | current_table = current_database = None | |
| 350 | status = 'find_log_line' | |
| 351 | list_start_count = 0 | |
| 352 | list_found = False | |
| 353 | for line in data.splitlines(): | |
| 354 | if status == 'find_log_line': | |
| 355 | if self._is_columns_log_line(line): | |
| 356 | status = 'find_dbname' | |
| 357 | elif self._is_log_and_startswith('', line) and list_found: | |
| 358 | # Don't accept log lines if the DB dump started | |
| 359 | break | |
| 360 | elif status == 'find_dbname': | |
| 361 | database = self._match_start_get_remaining('Database: ', line) | |
| 362 | if database is not None: | |
| 363 | list_found = True | |
| 364 | current_database = database | |
| 365 | status = 'find_table_name' | |
| 366 | elif status == 'find_table_name': | |
| 367 | table = self._match_start_get_remaining('Table: ', line) | |
| 368 | if database is not None: | |
| 369 | current_table = table | |
| 370 | status = 'find_two_list_starts' | |
| 371 | elif status == 'find_two_list_starts': | |
| 372 | if re.match(r'^\+[\-\+]+\+$', line): | |
| 373 | list_start_count += 1 | |
| 374 | if list_start_count == 2: | |
| 375 | # Start fetching columns | |
| 376 | list_start_count = 0 | |
| 377 | status = 'find_columns' | |
| 378 | elif status == 'find_columns': | |
| 379 | if line.startswith('|') and line.endswith('|'): | |
| 380 | (name, type_) = [val.strip() | |
| 381 | for val in line[1:-1].split('|')] | |
| 382 | columns[current_database][current_table].append( | |
| 383 | (name, type_)) | |
| 384 | elif re.match(r'^\+[\-\+]+\+$', line): | |
| 385 | status = 'find_dbname' | |
| 386 | else: | |
| 387 | raise RuntimeError('unknown status') | |
| 388 | return columns | |
| 389 | ||
| 390 | def getAddress(self, hostname): | |
| 391 | """ | |
| 392 | Returns remote IP address from hostname. | |
| 393 | """ | |
| 394 | try: | |
| 395 | return socket.gethostbyname(hostname) | |
| 396 | except socket.error: | |
| 397 | return self.hostname | |
| 398 | ||
| 399 | def parseOutputString(self, output, debug=False): | |
| 400 | """ | |
| 401 | This method will discard the output the shell sends, it will read it from | |
| 402 | the xml where it expects it to be present. | |
| 403 | ||
| 404 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 405 | output being sent is valid. | |
| 406 | """ | |
| 407 | ||
| 408 | if self.ignore_parsing: | |
| 409 | return | |
| 410 | sys.path.append(self.getSetting("Sqlmap path")) | |
| 411 | ||
| 412 | try: | |
| 413 | from lib.core.settings import HASHDB_MILESTONE_VALUE #pylint: disable=import-error,bad-option-value,import-outside-toplevel | |
| 414 | from lib.core.enums import HASHDB_KEYS #pylint: disable=import-error,import-outside-toplevel | |
| 415 | from lib.core.settings import UNICODE_ENCODING #pylint: disable=import-error,import-outside-toplevel | |
| 416 | except: | |
| 417 | self.log('Remember set your Sqlmap Path Setting!... Abort plugin.', 'ERROR') | |
| 418 | return | |
| 419 | ||
| 420 | if HASHDB_MILESTONE_VALUE not in SUPPORTED_HASHDB_VERSIONS: | |
| 421 | self.log( | |
| 422 | "Your version of SQLMap is not supported with this plugin. " | |
| 423 | "Please use an older version of SQLMap (the suggested one " | |
| 424 | "is \"{}\"). Also, we suggest you to open issue in our GitHub " | |
| 425 | "issue tracker: https://github.com/infobyte/faraday/issues/".format(self.version), | |
| 426 | 'ERROR') | |
| 427 | return | |
| 428 | ||
| 429 | self.HASHDB_MILESTONE_VALUE = HASHDB_MILESTONE_VALUE | |
| 430 | self.HASHDB_KEYS = HASHDB_KEYS | |
| 431 | self.UNICODE_ENCODING = UNICODE_ENCODING | |
| 432 | ||
| 433 | password = self.getpassword(output) | |
| 434 | ||
| 435 | webserver = re.search("web application technology: (.*?)\n", output) | |
| 436 | if webserver: | |
| 437 | webserver = webserver.group(1) | |
| 438 | ||
| 439 | users = self.getuser(output) | |
| 440 | dbs = self.getdbs(output) | |
| 441 | tables = self.gettables(output) | |
| 442 | columns = self.getcolumns(output) | |
| 443 | ||
| 444 | db = Database(self._output_path) | |
| 445 | db.connect() | |
| 446 | ||
| 447 | absFilePaths = self.hashDBRetrieve( | |
| 448 | self.HASHDB_KEYS.KB_ABS_FILE_PATHS, True, db) | |
| 449 | ||
| 450 | brute_tables = self.hashDBRetrieve( | |
| 451 | self.HASHDB_KEYS.KB_BRUTE_TABLES, True, db) | |
| 452 | ||
| 453 | brute_columns = self.hashDBRetrieve( | |
| 454 | self.HASHDB_KEYS.KB_BRUTE_COLUMNS, True, db) | |
| 455 | ||
| 456 | xpCmdshellAvailable = self.hashDBRetrieve( | |
| 457 | self.HASHDB_KEYS.KB_XP_CMDSHELL_AVAILABLE, True, db) | |
| 458 | ||
| 459 | dbms_version = self.hashDBRetrieve(self.HASHDB_KEYS.DBMS, False, db) | |
| 460 | ||
| 461 | self.ip = self.getAddress(self.hostname) | |
| 462 | ||
| 463 | h_id = self.createAndAddHost(self.ip) | |
| 464 | ||
| 465 | i_id = self.createAndAddInterface( | |
| 466 | h_id, | |
| 467 | name=self.ip, | |
| 468 | ipv4_address=self.ip, | |
| 469 | hostname_resolution=[self.hostname]) | |
| 470 | ||
| 471 | s_id = self.createAndAddServiceToInterface( | |
| 472 | h_id, | |
| 473 | i_id, | |
| 474 | self.protocol, | |
| 475 | 'tcp', | |
| 476 | [self.port], | |
| 477 | status="open", | |
| 478 | version=webserver) | |
| 479 | ||
| 480 | db_port = 0 | |
| 481 | for item in self.db_port.keys(): | |
| 482 | if dbms_version.find(item) >= 0: | |
| 483 | db_port = self.db_port[item] | |
| 484 | ||
| 485 | s_id2 = self.createAndAddServiceToInterface( | |
| 486 | h_id, | |
| 487 | i_id, | |
| 488 | name=dbms_version, | |
| 489 | protocol="tcp", | |
| 490 | status="closed", | |
| 491 | version=str(dbms_version), | |
| 492 | ports=[str(db_port)], | |
| 493 | description="DB detect by SQLi") | |
| 494 | ||
| 495 | # sqlmap.py --users | |
| 496 | if users: | |
| 497 | for v in users: | |
| 498 | if v: | |
| 499 | self.createAndAddCredToService(h_id, s_id2, v, '') | |
| 500 | ||
| 501 | # sqlmap.py --passwords | |
| 502 | if password: | |
| 503 | for k, v in password.items(): | |
| 504 | self.createAndAddCredToService(h_id, s_id2, k, v) | |
| 505 | ||
| 506 | # sqlmap.py --file-dest | |
| 507 | if absFilePaths: | |
| 508 | self.createAndAddNoteToService( | |
| 509 | h_id, | |
| 510 | s_id2, | |
| 511 | "sqlmap.absFilePaths", | |
| 512 | '\n'.join(absFilePaths)) | |
| 513 | ||
| 514 | # sqlmap.py --common-tables | |
| 515 | if brute_tables: | |
| 516 | for item in brute_tables: | |
| 517 | self.createAndAddNoteToService( | |
| 518 | h_id, | |
| 519 | s_id2, | |
| 520 | "sqlmap.brutetables", | |
| 521 | item[1]) | |
| 522 | ||
| 523 | # sqlmap.py --tables | |
| 524 | if tables: | |
| 525 | table_names = ['{}.{}'.format(db_name, table) | |
| 526 | for (db_name, db_tables) in tables.items() | |
| 527 | for table in db_tables] | |
| 528 | self.createAndAddNoteToService( | |
| 529 | h_id, | |
| 530 | s_id2, | |
| 531 | "sqlmap.tables", | |
| 532 | '\n'.join(table_names) | |
| 533 | ) | |
| 534 | ||
| 535 | # sqlmap.py --columns | |
| 536 | if columns: | |
| 537 | # Create one note per database | |
| 538 | for (database, tables) in columns.items(): | |
| 539 | text = '' | |
| 540 | for (table_name, columns) in tables.items(): | |
| 541 | columns_text = ', '.join( | |
| 542 | '{} {}'.format(col_name, type_) | |
| 543 | for (col_name, type_) in columns) | |
| 544 | text += '{}: {}\n'.format(table_name, columns_text) | |
| 545 | self.createAndAddNoteToService( | |
| 546 | h_id, | |
| 547 | s_id2, | |
| 548 | "sqlmap.columns." + database, | |
| 549 | text) | |
| 550 | ||
| 551 | # sqlmap.py --common-columns | |
| 552 | if brute_columns: | |
| 553 | ||
| 554 | text = ( | |
| 555 | 'Db: ' + brute_columns[0][0] + | |
| 556 | '\nTable: ' + brute_columns[0][1] + | |
| 557 | '\nColumns:') | |
| 558 | ||
| 559 | for element in brute_columns: | |
| 560 | text += str(element[2]) + '\n' | |
| 561 | ||
| 562 | self.createAndAddNoteToService( | |
| 563 | h_id, | |
| 564 | s_id2, | |
| 565 | "sqlmap.brutecolumns", | |
| 566 | text) | |
| 567 | ||
| 568 | # sqlmap.py --os-shell | |
| 569 | if xpCmdshellAvailable: | |
| 570 | self.createAndAddNoteToService( | |
| 571 | h_id, | |
| 572 | s_id2, | |
| 573 | "sqlmap.xpCmdshellAvailable", | |
| 574 | str(xpCmdshellAvailable)) | |
| 575 | ||
| 576 | # sqlmap.py --dbs | |
| 577 | if dbs: | |
| 578 | self.createAndAddNoteToService( | |
| 579 | h_id, | |
| 580 | s_id2, | |
| 581 | "db.databases", | |
| 582 | '\n'.join(dbs)) | |
| 583 | ||
| 584 | for inj in self.hashDBRetrieve(self.HASHDB_KEYS.KB_INJECTIONS, True, db) or []: | |
| 585 | ||
| 586 | for k, v in inj.data.items(): | |
| 587 | self.createAndAddVulnWebToService( | |
| 588 | h_id, | |
| 589 | s_id, | |
| 590 | name=inj.data[k]['title'], | |
| 591 | desc="Payload:" + str(inj.data[k]['payload']) + "\nVector:" + str(inj.data[k]['vector']) + | |
| 592 | "\nParam type:" + str(self.ptype[inj.ptype]), | |
| 593 | ref=[], | |
| 594 | pname=inj.parameter, | |
| 595 | severity="high", | |
| 596 | method=inj.place, | |
| 597 | params=self.params, | |
| 598 | **get_vulnweb_url_fields(self.fullpath)) | |
| 599 | ||
| 600 | def processCommandString(self, username, current_path, command_string): | |
| 601 | ||
| 602 | parser = argparse.ArgumentParser(conflict_handler='resolve') | |
| 603 | ||
| 604 | parser.add_argument('-h') | |
| 605 | parser.add_argument('-u') | |
| 606 | parser.add_argument('-s') | |
| 607 | parser.add_argument('-r') | |
| 608 | ||
| 609 | try: | |
| 610 | args, unknown = parser.parse_known_args( | |
| 611 | shlex.split(re.sub(r'\-h|\-\-help', r'', command_string))) | |
| 612 | except SystemExit: | |
| 613 | pass | |
| 614 | ||
| 615 | if args.r: | |
| 616 | filename = os.path.expanduser(args.r) | |
| 617 | if not os.path.isabs(filename): | |
| 618 | self.log('Please use an absolute path in -r option of sqlmap', 'ERROR') | |
| 619 | self.ignore_parsing = True | |
| 620 | return | |
| 621 | with open(filename, 'r') as f: | |
| 622 | request = self.HTTPRequest(f.read()) | |
| 623 | args.u = "http://" + request.headers['host'] + request.path | |
| 624 | f.close() | |
| 625 | ||
| 626 | if args.u: | |
| 627 | ||
| 628 | if args.u.find('http://') < 0 and args.u.find('https://') < 0: | |
| 629 | urlComponents = urlparse('http://' + args.u) | |
| 630 | else: | |
| 631 | urlComponents = urlparse(args.u) | |
| 632 | ||
| 633 | self.protocol = urlComponents.scheme | |
| 634 | self.hostname = urlComponents.netloc | |
| 635 | ||
| 636 | if urlComponents.port: | |
| 637 | self.port = urlComponents.port | |
| 638 | else: | |
| 639 | self.port = '80' | |
| 640 | ||
| 641 | if urlComponents.query: | |
| 642 | self.path = urlComponents.path | |
| 643 | self.params = urlComponents.query | |
| 644 | ||
| 645 | self.url = self.protocol + "://" + self.hostname + ":" + str(self.port) + self.path | |
| 646 | self.fullpath = self.url + "?" + self.params | |
| 647 | ||
| 648 | self._output_path = "%s%s" % ( | |
| 649 | os.path.join(self.data_path, "sqlmap_output-"), | |
| 650 | re.sub(r'[\n\/]', r'', base64.b64encode(args.u.encode()).strip().decode())) | |
| 651 | ||
| 652 | if not args.s: | |
| 653 | return "%s -s %s" % (command_string, self._output_path) | |
| 654 | ||
| 655 | def setHost(self): | |
| 656 | pass | |
| 657 | ||
| 658 | ||
| 659 | def createPlugin(): | |
| 660 | return SqlmapPlugin() | |
| 661 | ||
| 662 | ||
| 663 | # I'm Py3 |
| 0 | <?xml version="1.0" encoding="UTF-8"?> | |
| 1 | ||
| 2 | <root> | |
| 3 | <!-- MySQL --> | |
| 4 | <dbms value="MySQL"> | |
| 5 | <cast query="CAST(%s AS CHAR)"/> | |
| 6 | <length query="CHAR_LENGTH(%s)"/> | |
| 7 | <isnull query="IFNULL(%s,' ')"/> | |
| 8 | <delimiter query=","/> | |
| 9 | <limit query="LIMIT %d,%d"/> | |
| 10 | <limitregexp query="\s+LIMIT\s+([\d]+)\s*\,\s*([\d]+)" query2="\s+LIMIT\s+([\d]+)"/> | |
| 11 | <limitgroupstart query="1"/> | |
| 12 | <limitgroupstop query="2"/> | |
| 13 | <limitstring query=" LIMIT "/> | |
| 14 | <order query="ORDER BY %s ASC"/> | |
| 15 | <count query="COUNT(%s)"/> | |
| 16 | <comment query="-- " query2="/*" query3="#"/> | |
| 17 | <substring query="MID((%s),%d,%d)"/> | |
| 18 | <concatenate query="CONCAT(%s,%s)"/> | |
| 19 | <case query="SELECT (CASE WHEN (%s) THEN 1 ELSE 0 END)"/> | |
| 20 | <hex query="HEX(%s)"/> | |
| 21 | <inference query="ORD(MID((%s),%d,1))>%d"/> | |
| 22 | <banner query="VERSION()"/> | |
| 23 | <current_user query="CURRENT_USER()"/> | |
| 24 | <current_db query="DATABASE()"/> | |
| 25 | <hostname query="@@HOSTNAME"/> | |
| 26 | <table_comment query="SELECT table_comment FROM INFORMATION_SCHEMA.TABLES WHERE table_schema='%s' AND table_name='%s'"/> | |
| 27 | <column_comment query="SELECT column_comment FROM INFORMATION_SCHEMA.COLUMNS WHERE table_schema='%s' AND table_name='%s' AND column_name='%s'"/> | |
| 28 | <is_dba query="(SELECT super_priv FROM mysql.user WHERE user='%s' LIMIT 0,1)='Y'"/> | |
| 29 | <check_udf query="(SELECT name FROM mysql.func WHERE name='%s' LIMIT 0,1)='%s'"/> | |
| 30 | <users> | |
| 31 | <inband query="SELECT grantee FROM INFORMATION_SCHEMA.USER_PRIVILEGES" query2="SELECT user FROM mysql.user"/> | |
| 32 | <blind query="SELECT DISTINCT(grantee) FROM INFORMATION_SCHEMA.USER_PRIVILEGES LIMIT %d,1" query2="SELECT DISTINCT(user) FROM mysql.user LIMIT %d,1" count="SELECT COUNT(DISTINCT(grantee)) FROM INFORMATION_SCHEMA.USER_PRIVILEGES" count2="SELECT COUNT(DISTINCT(user)) FROM mysql.user"/> | |
| 33 | </users> | |
| 34 | <passwords> | |
| 35 | <inband query="SELECT user,password FROM mysql.user" condition="user"/> | |
| 36 | <blind query="SELECT DISTINCT(password) FROM mysql.user WHERE user='%s' LIMIT %d,1" count="SELECT COUNT(DISTINCT(password)) FROM mysql.user WHERE user='%s'"/> | |
| 37 | </passwords> | |
| 38 | <privileges> | |
| 39 | <inband query="SELECT grantee,privilege_type FROM INFORMATION_SCHEMA.USER_PRIVILEGES" condition="grantee" query2="SELECT user,select_priv,insert_priv,update_priv,delete_priv,create_priv,drop_priv,reload_priv,shutdown_priv,process_priv,file_priv,grant_priv,references_priv,index_priv,alter_priv,show_db_priv,super_priv,create_tmp_table_priv,lock_tables_priv,execute_priv,repl_slave_priv,repl_client_priv,create_view_priv,show_view_priv,create_routine_priv,alter_routine_priv,create_user_priv FROM mysql.user" condition2="user"/> | |
| 40 | <blind query="SELECT DISTINCT(privilege_type) FROM INFORMATION_SCHEMA.USER_PRIVILEGES WHERE grantee%s'%s' LIMIT %d,1" query2="SELECT select_priv,insert_priv,update_priv,delete_priv,create_priv,drop_priv,reload_priv,shutdown_priv,process_priv,file_priv,grant_priv,references_priv,index_priv,alter_priv,show_db_priv,super_priv,create_tmp_table_priv,lock_tables_priv,execute_priv,repl_slave_priv,repl_client_priv,create_view_priv,show_view_priv,create_routine_priv,alter_routine_priv,create_user_priv FROM mysql.user WHERE user='%s' LIMIT %d,1" count="SELECT COUNT(DISTINCT(privilege_type)) FROM INFORMATION_SCHEMA.USER_PRIVILEGES WHERE grantee%s'%s'" count2="SELECT COUNT(*) FROM mysql.user WHERE user='%s'"/> | |
| 41 | </privileges> | |
| 42 | <roles/> | |
| 43 | <dbs> | |
| 44 | <inband query="SELECT schema_name FROM INFORMATION_SCHEMA.SCHEMATA" query2="SELECT db FROM mysql.db"/> | |
| 45 | <blind query="SELECT DISTINCT(schema_name) FROM INFORMATION_SCHEMA.SCHEMATA LIMIT %d,1" query2="SELECT DISTINCT(db) FROM mysql.db LIMIT %d,1" count="SELECT COUNT(DISTINCT(schema_name)) FROM INFORMATION_SCHEMA.SCHEMATA" count2="SELECT COUNT(DISTINCT(db)) FROM mysql.db"/> | |
| 46 | </dbs> | |
| 47 | <tables> | |
| 48 | <inband query="SELECT table_schema,table_name FROM INFORMATION_SCHEMA.TABLES" condition="table_schema"/> | |
| 49 | <blind query="SELECT table_name FROM INFORMATION_SCHEMA.TABLES WHERE table_schema='%s' LIMIT %d,1" count="SELECT COUNT(table_name) FROM INFORMATION_SCHEMA.TABLES WHERE table_schema='%s'"/> | |
| 50 | </tables> | |
| 51 | <columns> | |
| 52 | <inband query="SELECT column_name,column_type FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name='%s' AND table_schema='%s'" condition="column_name"/> | |
| 53 | <blind query="SELECT column_name FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name='%s' AND table_schema='%s'" query2="SELECT column_type FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name='%s' AND column_name='%s' AND table_schema='%s'" count="SELECT COUNT(column_name) FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name='%s' AND table_schema='%s'" condition="column_name"/> | |
| 54 | </columns> | |
| 55 | <dump_table> | |
| 56 | <inband query="SELECT %s FROM %s.%s ORDER BY %s"/> | |
| 57 | <blind query="SELECT %s FROM %s.%s ORDER BY %s LIMIT %d,1" count="SELECT COUNT(*) FROM %s.%s"/> | |
| 58 | </dump_table> | |
| 59 | <search_db> | |
| 60 | <inband query="SELECT schema_name FROM INFORMATION_SCHEMA.SCHEMATA WHERE %s" query2="SELECT db FROM mysql.db WHERE %s" condition="schema_name" condition2="db"/> | |
| 61 | <blind query="SELECT DISTINCT(schema_name) FROM INFORMATION_SCHEMA.SCHEMATA WHERE %s" query2="SELECT DISTINCT(db) FROM mysql.db WHERE %s" count="SELECT COUNT(DISTINCT(schema_name)) FROM INFORMATION_SCHEMA.SCHEMATA WHERE %s" count2="SELECT COUNT(DISTINCT(db)) FROM mysql.db WHERE %s" condition="schema_name" condition2="db"/> | |
| 62 | </search_db> | |
| 63 | <search_table> | |
| 64 | <inband query="SELECT table_schema,table_name FROM INFORMATION_SCHEMA.TABLES WHERE %s" condition="table_name" condition2="table_schema"/> | |
| 65 | <blind query="SELECT DISTINCT(table_schema) FROM INFORMATION_SCHEMA.TABLES WHERE %s" query2="SELECT DISTINCT(table_name) FROM INFORMATION_SCHEMA.TABLES WHERE table_schema='%s'" count="SELECT COUNT(DISTINCT(table_schema)) FROM INFORMATION_SCHEMA.TABLES WHERE %s" count2="SELECT COUNT(DISTINCT(table_name)) FROM INFORMATION_SCHEMA.TABLES WHERE table_schema='%s'" condition="table_name" condition2="table_schema"/> | |
| 66 | </search_table> | |
| 67 | <search_column> | |
| 68 | <inband query="SELECT table_schema,table_name FROM INFORMATION_SCHEMA.COLUMNS WHERE %s" condition="column_name" condition2="table_schema" condition3="table_name"/> | |
| 69 | <blind query="SELECT DISTINCT(table_schema) FROM INFORMATION_SCHEMA.COLUMNS WHERE %s" query2="SELECT DISTINCT(table_name) FROM INFORMATION_SCHEMA.COLUMNS WHERE table_schema='%s'" count="SELECT COUNT(DISTINCT(table_schema)) FROM INFORMATION_SCHEMA.COLUMNS WHERE %s" count2="SELECT COUNT(DISTINCT(table_name)) FROM INFORMATION_SCHEMA.COLUMNS WHERE table_schema='%s'" condition="column_name" condition2="table_schema" condition3="table_name"/> | |
| 70 | </search_column> | |
| 71 | </dbms> | |
| 72 | ||
| 73 | <!-- PostgreSQL --> | |
| 74 | <dbms value="PostgreSQL"> | |
| 75 | <cast query="CAST(%s AS CHARACTER(10000))"/> | |
| 76 | <length query="LENGTH(%s)"/> | |
| 77 | <isnull query="COALESCE(%s,' ')"/> | |
| 78 | <delimiter query="||"/> | |
| 79 | <limit query="OFFSET %d LIMIT %d"/> | |
| 80 | <limitregexp query="\s+OFFSET\s+([\d]+)\s+LIMIT\s+([\d]+)" query2="\s+LIMIT\s+([\d]+)"/> | |
| 81 | <limitgroupstart query="1"/> | |
| 82 | <limitgroupstop query="2"/> | |
| 83 | <limitstring query=" OFFSET "/> | |
| 84 | <order query="ORDER BY %s ASC"/> | |
| 85 | <count query="COUNT(%s)"/> | |
| 86 | <comment query="--" query2="/*"/> | |
| 87 | <substring query="SUBSTRING((%s)::text FROM %d FOR %d)"/> | |
| 88 | <concatenate query="%s||%s"/> | |
| 89 | <case query="SELECT (CASE WHEN (%s) THEN '1' ELSE '0' END)"/> | |
| 90 | <hex query="ENCODE(CONVERT_TO((%s),'UTF8'),'HEX')"/> | |
| 91 | <inference query="ASCII(SUBSTRING((%s)::text FROM %d FOR 1))>%d"/> | |
| 92 | <banner query="VERSION()"/> | |
| 93 | <current_user query="CURRENT_USER"/> | |
| 94 | <current_db query="CURRENT_SCHEMA()"/> | |
| 95 | <hostname/> | |
| 96 | <!--<table_comment query="SELECT pg_catalog.obj_description(c.oid) FROM pg_catalog.pg_class c WHERE c.relname='%s'"/>--> | |
| 97 | <table_comment query="SELECT description FROM pg_description JOIN pg_class ON pg_description.objoid=pg_class.oid JOIN pg_namespace ON pg_class.relnamespace=pg_namespace.oid WHERE nspname='%s' AND relname='%s'"/> | |
| 98 | <column_comment query="SELECT col_description(pg_class.oid,pg_attribute.attnum) FROM pg_class JOIN pg_namespace ON pg_class.relnamespace=pg_namespace.oid JOIN pg_attribute ON pg_class.oid=pg_attribute.attrelid WHERE nspname='%s' AND relname='%s' AND attname='%s'"/> | |
| 99 | <is_dba query="(SELECT usesuper=true FROM pg_user WHERE usename=CURRENT_USER OFFSET 0 LIMIT 1)"/> | |
| 100 | <check_udf query="(SELECT proname='%s' FROM pg_proc WHERE proname='%s' OFFSET 0 LIMIT 1)"/> | |
| 101 | <users> | |
| 102 | <inband query="SELECT usename FROM pg_user"/> | |
| 103 | <blind query="SELECT DISTINCT(usename) FROM pg_user OFFSET %d LIMIT 1" count="SELECT COUNT(DISTINCT(usename)) FROM pg_user"/> | |
| 104 | </users> | |
| 105 | <passwords> | |
| 106 | <inband query="SELECT usename,passwd FROM pg_shadow" condition="usename"/> | |
| 107 | <blind query="SELECT DISTINCT(passwd) FROM pg_shadow WHERE usename='%s' OFFSET %d LIMIT 1" count="SELECT COUNT(DISTINCT(passwd)) FROM pg_shadow WHERE usename='%s'"/> | |
| 108 | </passwords> | |
| 109 | <privileges> | |
| 110 | <inband query="SELECT usename,(CASE WHEN usecreatedb THEN 1 ELSE 0 END),(CASE WHEN usesuper THEN 1 ELSE 0 END),(CASE WHEN usecatupd THEN 1 ELSE 0 END) FROM pg_user" condition="usename"/> | |
| 111 | <blind query="SELECT (CASE WHEN usecreatedb THEN 1 ELSE 0 END),(CASE WHEN usesuper THEN 1 ELSE 0 END),(CASE WHEN usecatupd THEN 1 ELSE 0 END) FROM pg_user WHERE usename='%s' OFFSET %d LIMIT 1" count="SELECT COUNT(DISTINCT(usename)) FROM pg_user WHERE usename='%s'"/> | |
| 112 | </privileges> | |
| 113 | <roles/> | |
| 114 | <dbs> | |
| 115 | <inband query="SELECT schemaname FROM pg_tables"/> | |
| 116 | <blind query="SELECT DISTINCT(schemaname) FROM pg_tables OFFSET %d LIMIT 1" count="SELECT COUNT(DISTINCT(schemaname)) FROM pg_tables"/> | |
| 117 | </dbs> | |
| 118 | <tables> | |
| 119 | <inband query="SELECT schemaname,tablename FROM pg_tables" condition="schemaname"/> | |
| 120 | <blind query="SELECT tablename FROM pg_tables WHERE schemaname='%s' OFFSET %d LIMIT 1" count="SELECT COUNT(tablename) FROM pg_tables WHERE schemaname='%s'"/> | |
| 121 | </tables> | |
| 122 | <columns> | |
| 123 | <inband query="SELECT attname,typname FROM pg_namespace,pg_type,pg_attribute b JOIN pg_class a ON a.oid=b.attrelid WHERE a.relnamespace=pg_namespace.oid AND pg_type.oid=b.atttypid AND attnum>0 AND a.relname='%s' AND nspname='%s'" condition="attname"/> | |
| 124 | <blind query="SELECT attname FROM pg_namespace,pg_type,pg_attribute b JOIN pg_class a ON a.oid=b.attrelid WHERE a.relnamespace=pg_namespace.oid AND pg_type.oid=b.atttypid AND attnum>0 AND a.relname='%s' AND nspname='%s'" query2="SELECT typname FROM pg_namespace,pg_type,pg_attribute b JOIN pg_class a ON a.oid=b.attrelid WHERE a.relname='%s' AND a.relnamespace=pg_namespace.oid AND pg_type.oid=b.atttypid AND attnum>0 AND attname='%s' AND nspname='%s'" count="SELECT COUNT(attname) FROM pg_namespace,pg_type,pg_attribute b JOIN pg_class a ON a.oid=b.attrelid WHERE a.relnamespace=pg_namespace.oid AND pg_type.oid=b.atttypid AND attnum>0 AND a.relname='%s' AND nspname='%s'" condition="attname"/> | |
| 125 | </columns> | |
| 126 | <dump_table> | |
| 127 | <inband query="SELECT %s FROM %s.%s ORDER BY %s"/> | |
| 128 | <blind query="SELECT %s FROM %s.%s ORDER BY %s OFFSET %d LIMIT 1" count="SELECT COUNT(*) FROM %s.%s"/> | |
| 129 | </dump_table> | |
| 130 | <search_db> | |
| 131 | <inband query="SELECT datname FROM pg_database WHERE %s" condition="datname"/> | |
| 132 | <blind query="SELECT DISTINCT(datname) FROM pg_database WHERE %s" count="SELECT COUNT(DISTINCT(datname)) FROM pg_database WHERE %s" condition="datname"/> | |
| 133 | </search_db> | |
| 134 | <search_table> | |
| 135 | <inband query="SELECT schemaname,tablename FROM pg_tables WHERE %s" condition="tablename" condition2="schemaname"/> | |
| 136 | <blind query="SELECT DISTINCT(schemaname) FROM pg_tables WHERE %s" query2="SELECT tablename FROM pg_tables WHERE schemaname='%s'" count="SELECT COUNT(DISTINCT(schemaname)) FROM pg_tables WHERE %s" count2="SELECT COUNT(tablename) FROM pg_tables WHERE schemaname='%s'" condition="tablename" condition2="schemaname"/> | |
| 137 | </search_table> | |
| 138 | <search_column> | |
| 139 | <inband query="SELECT nspname,relname FROM pg_namespace,pg_type,pg_attribute b JOIN pg_class a ON a.oid=b.attrelid WHERE a.relnamespace=pg_namespace.oid AND pg_type.oid=b.atttypid AND attnum>0 AND %s" condition="attname" condition2="nspname" condition3="relname"/> | |
| 140 | <blind query="SELECT DISTINCT(nspname) FROM pg_namespace,pg_type,pg_attribute b JOIN pg_class a ON a.oid=b.attrelid WHERE a.relnamespace=pg_namespace.oid AND pg_type.oid=b.atttypid AND attnum>0 AND %s" query2="SELECT DISTINCT(relname) FROM pg_namespace,pg_type,pg_attribute b JOIN pg_class a ON a.oid=b.attrelid WHERE a.relnamespace=pg_namespace.oid AND pg_type.oid=b.atttypid AND attnum>0 AND nspname='%s'" count="SELECT COUNT(DISTINCT(nspname)) FROM pg_namespace,pg_type,pg_attribute b JOIN pg_class a ON a.oid=b.attrelid WHERE a.relnamespace=pg_namespace.oid AND pg_type.oid=b.atttypid AND attnum>0 AND %s" count2="SELECT COUNT(DISTINCT(relname)) FROM pg_namespace,pg_type,pg_attribute b JOIN pg_class a ON a.oid=b.attrelid WHERE a.relnamespace=pg_namespace.oid AND pg_type.oid=b.atttypid AND attnum>0 AND nspname='%s'" condition="attname" condition2="nspname" condition3="relname"/> | |
| 141 | </search_column> | |
| 142 | </dbms> | |
| 143 | ||
| 144 | <!-- Microsoft SQL Server --> | |
| 145 | <dbms value="Microsoft SQL Server"> | |
| 146 | <cast query="CAST(%s AS NVARCHAR(4000))"/> | |
| 147 | <length query="LTRIM(STR(LEN(%s)))"/> | |
| 148 | <isnull query="ISNULL(%s,' ')"/> | |
| 149 | <delimiter query="+"/> | |
| 150 | <limit query="SELECT TOP %d "/> | |
| 151 | <limitregexp query="TOP\s+([\d]+)\s+.+?\s+FROM\s+.+?\s+WHERE\s+.+?\s+NOT\s+IN\s+\(SELECT\s+TOP\s+([\d]+)\s+"/> | |
| 152 | <limitgroupstart query="2"/> | |
| 153 | <limitgroupstop query="1"/> | |
| 154 | <limitstring/> | |
| 155 | <order query="ORDER BY %s ASC"/> | |
| 156 | <count query="COUNT(%s)"/> | |
| 157 | <comment query="--" query2="/*"/> | |
| 158 | <substring query="SUBSTRING((%s),%d,%d)"/> | |
| 159 | <concatenate query="%s+%s"/> | |
| 160 | <case query="SELECT (CASE WHEN (%s) THEN '1' ELSE '0' END)"/> | |
| 161 | <hex query="master.dbo.fn_varbintohexstr(CAST(%s AS VARBINARY(8000)))"/> | |
| 162 | <inference query="UNICODE(SUBSTRING((%s),%d,1))>%d"/> | |
| 163 | <banner query="SELECT @@VERSION"/> | |
| 164 | <current_user query="SELECT SYSTEM_USER"/> | |
| 165 | <current_db query="SELECT DB_NAME()"/> | |
| 166 | <hostname query="@@SERVERNAME"/> | |
| 167 | <table_comment query="SELECT value FROM fn_listextendedproperty(NULL,'schema','%s','table','%s',NULL,NULL)"/> | |
| 168 | <column_comment query="SELECT value FROM fn_listextendedproperty(NULL,'schema','%s','table','%s','column','%s')"/> | |
| 169 | <is_dba query="IS_SRVROLEMEMBER('sysadmin')=1" query2="IS_SRVROLEMEMBER('sysadmin','%s')=1"/> | |
| 170 | <users> | |
| 171 | <inband query="SELECT name FROM master..syslogins" query2="SELECT name FROM sys.sql_logins"/> | |
| 172 | <!-- NOTE: in NOT IN kind of queries ORDER BY is a must --> | |
| 173 | <blind query="SELECT TOP 1 name FROM master..syslogins WHERE name NOT IN (SELECT TOP %d name FROM master..syslogins ORDER BY name) ORDER BY name" query2="SELECT TOP 1 name FROM sys.sql_logins WHERE name NOT IN (SELECT TOP %d name FROM sys.sql_logins ORDER BY name) ORDER BY name" count="SELECT LTRIM(STR(COUNT(name))) FROM master..syslogins" count2="SELECT LTRIM(STR(COUNT(name))) FROM sys.sql_logins"/> | |
| 174 | </users> | |
| 175 | <passwords> | |
| 176 | <inband query="SELECT name,master.dbo.fn_varbintohexstr(password) FROM master..sysxlogins" query2="SELECT name,master.dbo.fn_varbintohexstr(password_hash) FROM sys.sql_logins" condition="name"/> | |
| 177 | <blind query="SELECT TOP 1 master.dbo.fn_varbintohexstr(password) FROM master..sysxlogins WHERE name='%s' AND password NOT IN (SELECT TOP %d password FROM master..sysxlogins WHERE name='%s' ORDER BY password) ORDER BY password" query2="SELECT TOP 1 master.dbo.fn_varbintohexstr(password_hash) FROM sys.sql_logins WHERE name='%s' AND password_hash NOT IN (SELECT TOP %d password_hash FROM sys.sql_logins WHERE name='%s' ORDER BY password_hash) ORDER BY password_hash" count="SELECT LTRIM(STR(COUNT(password))) FROM master..sysxlogins WHERE name='%s'" count2="SELECT LTRIM(STR(COUNT(password_hash))) FROM sys.sql_logins WHERE name='%s'"/> | |
| 178 | </passwords> | |
| 179 | <!-- NOTE: in Microsoft SQL Server there is no query to enumerate DBMS users privileges --> | |
| 180 | <privileges/> | |
| 181 | <roles/> | |
| 182 | <dbs> | |
| 183 | <inband query="SELECT name FROM master..sysdatabases" query2="SELECT DB_NAME(%d)"/> | |
| 184 | <blind query="SELECT TOP 1 name FROM master..sysdatabases WHERE name NOT IN (SELECT TOP %d name FROM master..sysdatabases ORDER BY name) ORDER BY name" count="SELECT LTRIM(STR(COUNT(name))) FROM master..sysdatabases"/> | |
| 185 | </dbs> | |
| 186 | <tables> | |
| 187 | <inband query="SELECT %s..sysusers.name+'.'+%s..sysobjects.name FROM %s..sysobjects INNER JOIN %s..sysusers ON %s..sysobjects.uid = %s..sysusers.uid WHERE %s..sysobjects.xtype IN ('u','v')" query2="SELECT table_schema+'.'+table_name FROM information_schema.tables WHERE table_catalog='%s'" query3="SELECT name FROM %s..sysobjects WHERE xtype = 'U'"/> | |
| 188 | <blind query="SELECT TOP 1 %s..sysusers.name+'.'+%s..sysobjects.name FROM %s..sysobjects INNER JOIN %s..sysusers ON %s..sysobjects.uid = %s..sysusers.uid WHERE %s..sysobjects.xtype IN ('u','v') AND %s..sysusers.name+'.'+%s..sysobjects.name NOT IN (SELECT TOP %d %s..sysusers.name+'.'+%s..sysobjects.name FROM %s..sysobjects INNER JOIN %s..sysusers ON %s..sysobjects.uid = %s..sysusers.uid WHERE %s..sysobjects.xtype IN ('u','v') ORDER BY %s..sysusers.name+'.'+%s..sysobjects.name) ORDER BY %s..sysusers.name+'.'+%s..sysobjects.name" count="SELECT LTRIM(STR(COUNT(name))) FROM %s..sysobjects WHERE %s..sysobjects.xtype IN ('u','v')" query2="SELECT TOP 1 table_schema+'.'+table_name FROM information_schema.tables WHERE table_catalog='%s' AND table_schema+'.'+table_name NOT IN (SELECT TOP %d table_schema+'.'+table_name FROM information_schema.tables WHERE table_catalog='%s' ORDER BY table_schema+'.'+table_name) ORDER BY table_schema+'.'+table_name" count2="SELECT LTRIM(STR(COUNT(table_name))) FROM information_schema.tables WHERE table_catalog='%s'" query3="SELECT TOP 1 name FROM %s..sysobjects WHERE xtype = 'U' AND name NOT IN (SELECT TOP %d name FROM %s..sysobjects WHERE xtype = 'U' ORDER BY name) ORDER BY name" count3="SELECT COUNT(name) FROM %s..sysobjects WHERE xtype = 'U'"/> | |
| 189 | </tables> | |
| 190 | <columns> | |
| 191 | <inband query="SELECT %s..syscolumns.name,TYPE_NAME(%s..syscolumns.xtype) FROM %s..syscolumns,%s..sysobjects WHERE %s..syscolumns.id=%s..sysobjects.id AND %s..sysobjects.name='%s'" query2="SELECT COL_NAME(OBJECT_ID('%s.%s'),%d)" condition="[DB]..syscolumns.name"/> | |
| 192 | <blind query="SELECT TOP 1 %s..syscolumns.name FROM %s..syscolumns,%s..sysobjects WHERE %s..syscolumns.id=%s..sysobjects.id AND %s..sysobjects.name='%s' AND %s..syscolumns.name NOT IN (SELECT TOP %d %s..syscolumns.name FROM %s..syscolumns,%s..sysobjects WHERE %s..syscolumns.id=%s..sysobjects.id AND %s..sysobjects.name='%s' ORDER BY %s..syscolumns.name) ORDER BY %s..syscolumns.name" query2="SELECT TYPE_NAME(%s..syscolumns.xtype) FROM %s..syscolumns,%s..sysobjects WHERE %s..syscolumns.name='%s' AND %s..syscolumns.id=%s..sysobjects.id AND %s..sysobjects.name='%s'" query3="SELECT COL_NAME(OBJECT_ID('%s.%s'),%d)" count="SELECT LTRIM(STR(COUNT(name))) FROM %s..syscolumns WHERE id=(SELECT id FROM %s..sysobjects WHERE name='%s')" condition="[DB]..syscolumns.name"/> | |
| 193 | </columns> | |
| 194 | <dump_table> | |
| 195 | <inband query="SELECT %s FROM %s.%s"/> | |
| 196 | <blind query="SELECT MIN(%s) FROM %s WHERE CONVERT(NVARCHAR(4000),%s)>'%s'" query2="SELECT MAX(%s) FROM %s WHERE CONVERT(NVARCHAR(4000),%s) LIKE '%s'" count="SELECT LTRIM(STR(COUNT(*))) FROM %s" count2="SELECT LTRIM(STR(COUNT(DISTINCT(%s)))) FROM %s"/> | |
| 197 | </dump_table> | |
| 198 | <search_db> | |
| 199 | <inband query="SELECT name FROM master..sysdatabases WHERE %s" condition="name"/> | |
| 200 | <blind query="SELECT name FROM master..sysdatabases WHERE %s" count="SELECT LTRIM(STR(COUNT(name))) FROM master..sysdatabases WHERE " condition="name"/> | |
| 201 | </search_db> | |
| 202 | <search_table> | |
| 203 | <inband query="SELECT name FROM %s..sysobjects WHERE %s..sysobjects.xtype IN ('u','v') AND " condition="name" condition2="name"/> | |
| 204 | <blind query="SELECT name FROM %s..sysobjects WHERE %s..sysobjects.xtype IN ('u','v') " count="SELECT LTRIM(STR(COUNT(name))) FROM %s..sysobjects WHERE %s..sysobjects.xtype IN ('u','v')" condition="name" condition2="name"/> | |
| 205 | </search_table> | |
| 206 | <search_column> | |
| 207 | <inband query="SELECT %s..sysobjects.name FROM %s..syscolumns,%s..sysobjects WHERE %s..syscolumns.id=%s..sysobjects.id AND %s..sysobjects.xtype IN ('u','v')" condition="[DB]..syscolumns.name" condition2="[DB]..sysobjects.name"/> | |
| 208 | <blind query="SELECT %s..sysobjects.name FROM %s..syscolumns,%s..sysobjects WHERE %s..syscolumns.id=%s..sysobjects.id AND %s..sysobjects.xtype IN ('u','v')" count="SELECT COUNT(%s..sysobjects.name) FROM %s..syscolumns,%s..sysobjects WHERE %s..syscolumns.id=%s..sysobjects.id AND %s..sysobjects.xtype IN ('u','v')" condition="[DB]..syscolumns.name" condition2="[DB]..sysobjects.name"/> | |
| 209 | </search_column> | |
| 210 | </dbms> | |
| 211 | ||
| 212 | <!-- Oracle --> | |
| 213 | <dbms value="Oracle"> | |
| 214 | <cast query="CAST(%s AS VARCHAR(4000))"/> | |
| 215 | <length query="LENGTH(%s)"/> | |
| 216 | <isnull query="NVL(%s,' ')"/> | |
| 217 | <delimiter query="||"/> | |
| 218 | <limit query="ROWNUM AS LIMIT %s) WHERE LIMIT"/> | |
| 219 | <limitregexp query="ROWNUM\s+AS\s+.+?\s+FROM\s+.+?\)\s+WHERE\s+.+?\s*=\s*[\d]+|ROWNUM\s*=\s*[\d]+"/> | |
| 220 | <limitgroupstart/> | |
| 221 | <limitgroupstop/> | |
| 222 | <limitstring/> | |
| 223 | <order query="ORDER BY %s ASC"/> | |
| 224 | <count query="COUNT(%s)"/> | |
| 225 | <comment query="--"/> | |
| 226 | <substring query="SUBSTRC((%s),%d,%d)"/> | |
| 227 | <concatenate query="%s||%s"/> | |
| 228 | <case query="SELECT (CASE WHEN (%s) THEN 1 ELSE 0 END)"/> | |
| 229 | <hex query="RAWTOHEX(%s)"/> | |
| 230 | <inference query="ASCII(SUBSTRC((%s),%d,1))>%d"/> | |
| 231 | <banner query="SELECT banner FROM v$version WHERE ROWNUM=1"/> | |
| 232 | <current_user query="SELECT USER FROM DUAL"/> | |
| 233 | <!-- | |
| 234 | NOTE: current physical DB but not usable for enumeration | |
| 235 | <current_db query="SELECT SYS.DATABASE_NAME FROM DUAL"/> | |
| 236 | --> | |
| 237 | <current_db query="SELECT USER FROM DUAL"/> | |
| 238 | <!-- | |
| 239 | NOTE: in Oracle to check if the session user is DBA you can use: | |
| 240 | SELECT USERENV('ISDBA') FROM DUAL | |
| 241 | --> | |
| 242 | <hostname query="SELECT UTL_INADDR.GET_HOST_NAME FROM DUAL"/> | |
| 243 | <table_comment query="SELECT COMMENTS FROM ALL_TAB_COMMENTS WHERE OWNER='%s' AND TABLE_NAME='%s'"/> | |
| 244 | <column_comment query="SELECT COMMENTS FROM ALL_COL_COMMENTS WHERE OWNER='%s' AND TABLE_NAME='%s' AND COLUMN_NAME='%s'"/> | |
| 245 | <is_dba query="(SELECT GRANTED_ROLE FROM DBA_ROLE_PRIVS WHERE GRANTEE=USER AND GRANTED_ROLE='DBA')='DBA'"/> | |
| 246 | <users> | |
| 247 | <inband query="SELECT USERNAME FROM SYS.ALL_USERS"/> | |
| 248 | <blind query="SELECT USERNAME FROM (SELECT USERNAME,ROWNUM AS LIMIT FROM SYS.ALL_USERS) WHERE LIMIT=%d" count="SELECT COUNT(USERNAME) FROM SYS.ALL_USERS"/> | |
| 249 | </users> | |
| 250 | <passwords> | |
| 251 | <inband query="SELECT NAME,PASSWORD FROM SYS.USER$" condition="NAME"/> | |
| 252 | <blind query="SELECT PASSWORD FROM (SELECT PASSWORD,ROWNUM AS LIMIT FROM SYS.USER$ WHERE NAME='%s') WHERE LIMIT=%d" count="SELECT COUNT(PASSWORD) FROM SYS.USER$ WHERE NAME='%s'"/> | |
| 253 | </passwords> | |
| 254 | <!-- | |
| 255 | NOTE: in Oracle to enumerate the privileges for the session user you can use: | |
| 256 | SELECT * FROM SESSION_PRIVS | |
| 257 | --> | |
| 258 | <privileges> | |
| 259 | <inband query="SELECT GRANTEE,PRIVILEGE FROM DBA_SYS_PRIVS" query2="SELECT USERNAME,PRIVILEGE FROM USER_SYS_PRIVS" condition="GRANTEE" condition2="USERNAME"/> | |
| 260 | <blind query="SELECT PRIVILEGE FROM (SELECT PRIVILEGE,ROWNUM AS LIMIT FROM DBA_SYS_PRIVS WHERE GRANTEE='%s') WHERE LIMIT=%d" query2="SELECT PRIVILEGE FROM (SELECT PRIVILEGE,ROWNUM AS LIMIT FROM USER_SYS_PRIVS WHERE USERNAME='%s') WHERE LIMIT=%d" count="SELECT COUNT(PRIVILEGE) FROM DBA_SYS_PRIVS WHERE GRANTEE='%s'" count2="SELECT COUNT(PRIVILEGE) FROM USER_SYS_PRIVS WHERE USERNAME='%s'"/> | |
| 261 | </privileges> | |
| 262 | <!-- | |
| 263 | NOTE: in Oracle to enumerate the roles for the session user you can use: | |
| 264 | SELECT * FROM SESSION_ROLES | |
| 265 | --> | |
| 266 | <roles> | |
| 267 | <inband query="SELECT GRANTEE,GRANTED_ROLE FROM DBA_ROLE_PRIVS" query2="SELECT USERNAME,GRANTED_ROLE FROM USER_ROLE_PRIVS" condition="GRANTEE" condition2="USERNAME"/> | |
| 268 | <blind query="SELECT GRANTED_ROLE FROM (SELECT GRANTED_ROLE,ROWNUM AS LIMIT FROM DBA_ROLE_PRIVS WHERE GRANTEE='%s') WHERE LIMIT=%d" query2="SELECT GRANTED_ROLE FROM (SELECT GRANTED_ROLE,ROWNUM AS LIMIT FROM USER_ROLE_PRIVS WHERE USERNAME='%s') WHERE LIMIT=%d" count="SELECT COUNT(GRANTED_ROLE) FROM DBA_ROLE_PRIVS WHERE GRANTEE='%s'" count2="SELECT COUNT(GRANTED_ROLE) FROM USER_ROLE_PRIVS WHERE USERNAME='%s'"/> | |
| 269 | </roles> | |
| 270 | <!-- NOTE: in Oracle schema names are the counterpart to database names on other DBMSes --> | |
| 271 | <dbs> | |
| 272 | <inband query="SELECT OWNER FROM (SELECT DISTINCT(OWNER) FROM SYS.ALL_TABLES)"/> | |
| 273 | <blind query="SELECT OWNER FROM (SELECT OWNER,ROWNUM AS LIMIT FROM (SELECT DISTINCT(OWNER) FROM SYS.ALL_TABLES)) WHERE LIMIT=%d" count="SELECT COUNT(DISTINCT(OWNER)) FROM SYS.ALL_TABLES"/> | |
| 274 | </dbs> | |
| 275 | <tables> | |
| 276 | <inband query="SELECT OWNER,TABLE_NAME FROM SYS.ALL_TABLES" condition="OWNER"/> | |
| 277 | <blind query="SELECT TABLE_NAME FROM (SELECT TABLE_NAME,ROWNUM AS LIMIT FROM SYS.ALL_TABLES WHERE OWNER='%s') WHERE LIMIT=%d" count="SELECT COUNT(TABLE_NAME) FROM SYS.ALL_TABLES WHERE OWNER='%s'"/> | |
| 278 | </tables> | |
| 279 | <columns> | |
| 280 | <inband query="SELECT COLUMN_NAME,DATA_TYPE FROM SYS.ALL_TAB_COLUMNS WHERE TABLE_NAME='%s' AND OWNER='%s'" condition="COLUMN_NAME"/> | |
| 281 | <blind query="SELECT COLUMN_NAME FROM SYS.ALL_TAB_COLUMNS WHERE TABLE_NAME='%s' AND OWNER='%s'" query2="SELECT DATA_TYPE FROM SYS.ALL_TAB_COLUMNS WHERE TABLE_NAME='%s' AND COLUMN_NAME='%s' AND OWNER='%s'" count="SELECT COUNT(COLUMN_NAME) FROM SYS.ALL_TAB_COLUMNS WHERE TABLE_NAME='%s' AND OWNER='%s'" condition="COLUMN_NAME"/> | |
| 282 | </columns> | |
| 283 | <dump_table> | |
| 284 | <inband query="SELECT %s FROM %s"/> | |
| 285 | <blind query="SELECT ENTRY_VALUE FROM (SELECT %s AS ENTRY_VALUE,ROWNUM AS LIMIT FROM %s) WHERE LIMIT=%d" count="SELECT COUNT(*) FROM %s"/> | |
| 286 | </dump_table> | |
| 287 | <!-- NOTE: in Oracle schema names are the counterpart to database names on other DBMSes --> | |
| 288 | <search_db> | |
| 289 | <inband query="SELECT OWNER FROM (SELECT DISTINCT(OWNER) FROM SYS.ALL_TABLES) WHERE %s" condition="OWNER"/> | |
| 290 | <blind query="SELECT OWNER FROM (SELECT DISTINCT(OWNER) FROM SYS.ALL_TABLES) WHERE %s" count="SELECT COUNT(DISTINCT(OWNER)) FROM SYS.ALL_TABLES WHERE %s" condition="OWNER"/> | |
| 291 | </search_db> | |
| 292 | <search_table> | |
| 293 | <inband query="SELECT OWNER,TABLE_NAME FROM SYS.ALL_TABLES WHERE %s" condition="TABLE_NAME" condition2="OWNER"/> | |
| 294 | <blind query="SELECT OWNER FROM (SELECT DISTINCT(OWNER) FROM SYS.ALL_TABLES WHERE %s)" query2="SELECT TABLE_NAME FROM (SELECT DISTINCT(TABLE_NAME) FROM SYS.ALL_TABLES WHERE OWNER='%s')" count="SELECT COUNT(DISTINCT(OWNER)) FROM SYS.ALL_TABLES WHERE %s" count2="SELECT COUNT(DISTINCT(TABLE_NAME)) FROM SYS.ALL_TABLES WHERE OWNER='%s'" condition="TABLE_NAME" condition2="OWNER"/> | |
| 295 | </search_table> | |
| 296 | <search_column> | |
| 297 | <inband query="SELECT OWNER,TABLE_NAME FROM SYS.ALL_TAB_COLUMNS WHERE %s" condition="COLUMN_NAME" condition2="OWNER" condition3="TABLE_NAME"/> | |
| 298 | <blind query="SELECT OWNER FROM (SELECT DISTINCT(OWNER) FROM SYS.ALL_TAB_COLUMNS WHERE %s)" query2="SELECT TABLE_NAME FROM (SELECT DISTINCT(TABLE_NAME) FROM SYS.ALL_TAB_COLUMNS WHERE OWNER='%s')" count="SELECT COUNT(DISTINCT(OWNER)) FROM SYS.ALL_TAB_COLUMNS WHERE %s" count2="SELECT COUNT(DISTINCT(TABLE_NAME)) FROM SYS.ALL_TAB_COLUMNS WHERE OWNER='%s'" condition="COLUMN_NAME" condition2="OWNER" condition3="TABLE_NAME"/> | |
| 299 | </search_column> | |
| 300 | </dbms> | |
| 301 | ||
| 302 | <!-- SQLite --> | |
| 303 | <dbms value="SQLite"> | |
| 304 | <cast query="CAST(%s AS TEXT)" dbms_version=">=3.0"/> | |
| 305 | <!-- NOTE: On SQLite version 2 everything is stored as a string (Reference: http://www.mono-project.com/SQLite) --> | |
| 306 | <length query="LENGTH(%s)"/> | |
| 307 | <isnull query="COALESCE(%s,' ')"/> | |
| 308 | <delimiter query="||"/> | |
| 309 | <limit query="LIMIT %d,%d"/> | |
| 310 | <limitregexp query="\s+LIMIT\s+([\d]+)\s*\,\s*([\d]+)" query2="\s+LIMIT\s+([\d]+)"/> | |
| 311 | <limitgroupstart query="1"/> | |
| 312 | <limitgroupstop query="2"/> | |
| 313 | <limitstring query=" LIMIT "/> | |
| 314 | <order query="ORDER BY %s ASC"/> | |
| 315 | <count query="COUNT(%s)"/> | |
| 316 | <comment query="--" query2="/*"/> | |
| 317 | <substring query="SUBSTR((%s),%d,%d)"/> | |
| 318 | <concatenate query="%s||%s"/> | |
| 319 | <case query="SELECT (CASE WHEN (%s) THEN 1 ELSE 0 END)"/> | |
| 320 | <hex query="HEX(%s)"/> | |
| 321 | <inference query="SUBSTR((%s),%d,1)>'%c'"/> | |
| 322 | <banner query="SELECT SQLITE_VERSION()"/> | |
| 323 | <current_user/> | |
| 324 | <current_db/> | |
| 325 | <hostname/> | |
| 326 | <table_comment/> | |
| 327 | <column_comment/> | |
| 328 | <is_dba/> | |
| 329 | <check_udf/> | |
| 330 | <users/> | |
| 331 | <passwords/> | |
| 332 | <privileges/> | |
| 333 | <roles/> | |
| 334 | <dbs/> | |
| 335 | <tables> | |
| 336 | <inband query="SELECT tbl_name FROM sqlite_master WHERE type='table'"/> | |
| 337 | <blind query="SELECT tbl_name FROM sqlite_master WHERE type='table' LIMIT %d,1" count="SELECT COUNT(tbl_name) FROM sqlite_master WHERE type='table'"/> | |
| 338 | </tables> | |
| 339 | <columns> | |
| 340 | <inband query="SELECT MIN(sql) FROM sqlite_master WHERE tbl_name='%s'"/> | |
| 341 | <blind query="SELECT sql FROM sqlite_master WHERE tbl_name='%s' LIMIT 1" condition=""/> | |
| 342 | </columns> | |
| 343 | <dump_table> | |
| 344 | <inband query="SELECT %s FROM %s"/> | |
| 345 | <blind query="SELECT %s FROM %s LIMIT %d,1" count="SELECT COUNT(*) FROM %s"/> | |
| 346 | </dump_table> | |
| 347 | <search_db/> | |
| 348 | <search_table> | |
| 349 | <inband query="SELECT tbl_name FROM sqlite_master WHERE type='table' AND %s" condition="tbl_name" condition2=""/> | |
| 350 | <blind query="" query2="SELECT tbl_name FROM sqlite_master WHERE type='table'" count="" count2="SELECT COUNT(tbl_name) FROM sqlite_master WHERE type='table'" condition="tbl_name" condition2=""/> | |
| 351 | </search_table> | |
| 352 | <search_column/> | |
| 353 | </dbms> | |
| 354 | ||
| 355 | <!-- Microsoft Access --> | |
| 356 | <dbms value="Microsoft Access"> | |
| 357 | <cast query="RTRIM(CVAR(%s))"/> | |
| 358 | <length query="LEN(RTRIM(CVAR(%s)))"/> | |
| 359 | <isnull query="IIF(LEN(%s)=0,' ',%s)"/> | |
| 360 | <delimiter query="&"/> | |
| 361 | <limit query="TOP %d"/> | |
| 362 | <limitregexp query="\s+TOP\s+([\d]+)"/> | |
| 363 | <limitgroupstart query="1"/> | |
| 364 | <limitgroupstop query="1"/> | |
| 365 | <limitstring query=" TOP "/> | |
| 366 | <order query="ORDER BY %s ASC"/> | |
| 367 | <count query="COUNT(%s)"/> | |
| 368 | <comment query="%16" query2="%00"/> | |
| 369 | <substring query="MID((%s),%d,%d)"/> | |
| 370 | <concatenate query="%s&%s"/> | |
| 371 | <case query="SELECT (IIF(%s,1,0))"/> | |
| 372 | <inference query="ASCW(MID((%s),%d,1))>%d"/> | |
| 373 | <banner/> | |
| 374 | <!--CURRENTUSER() is not available outside the MS Access query tool itself--> | |
| 375 | <current_user/> | |
| 376 | <current_db/> | |
| 377 | <hostname/> | |
| 378 | <table_comment/> | |
| 379 | <column_comment/> | |
| 380 | <is_dba/> | |
| 381 | <dbs/> | |
| 382 | <!--MSysObjects have no read permission by default--> | |
| 383 | <tables> | |
| 384 | <inband query="SELECT Name FROM MSysObjects WHERE Type=1"/> | |
| 385 | <blind query="SELECT MIN(Name) FROM MSysObjects WHERE Type=1 AND Name>'%s'" count="SELECT COUNT(Name) FROM MSysObjects WHERE Type=1"/> | |
| 386 | </tables> | |
| 387 | <dump_table> | |
| 388 | <inband query="SELECT %s FROM %s"/> | |
| 389 | <blind query="SELECT MIN(%s) FROM %s WHERE CVAR(%s)>'%s'" query2="SELECT TOP 1 %s FROM %s WHERE CVAR(%s) LIKE '%s'" count="SELECT COUNT(*) FROM %s" count2="SELECT COUNT(*) FROM (SELECT DISTINCT %s FROM %s)"/> | |
| 390 | </dump_table> | |
| 391 | <users/> | |
| 392 | <privileges/> | |
| 393 | <roles/> | |
| 394 | <search_db/> | |
| 395 | <search_table/> | |
| 396 | <search_column/> | |
| 397 | </dbms> | |
| 398 | ||
| 399 | <!-- Firebird --> | |
| 400 | <dbms value="Firebird"> | |
| 401 | <cast query="TRIM(CAST(%s AS VARCHAR(10000)))"/> | |
| 402 | <length query="CHAR_LENGTH(TRIM(%s))"/> | |
| 403 | <delimiter query="||"/> | |
| 404 | <limit query="ROWS %d TO %d"/> | |
| 405 | <limitregexp query="\s+ROWS\s+([\d]+)(\s+\TO\s+([\d]+))?"/> | |
| 406 | <limitgroupstart query="1"/> | |
| 407 | <limitgroupstop query="2"/> | |
| 408 | <limitstring query=" ROWS "/> | |
| 409 | <isnull query="COALESCE(%s,' ')"/> | |
| 410 | <order query="ORDER BY %s ASC"/> | |
| 411 | <comment query="--"/> | |
| 412 | <count query="COUNT(%s)"/> | |
| 413 | <substring query="SUBSTRING((%s) FROM %d FOR %d)"/> | |
| 414 | <concatenate query="%s||%s"/> | |
| 415 | <case query="SELECT IIF(%s,1,0)"/> | |
| 416 | <inference query="ASCII_VAL(SUBSTRING((%s) FROM %d FOR 1))>%d" dbms_version=">=2.1" query2="SUBSTRING((%s) FROM %d FOR 1)>'%c'"/> | |
| 417 | <banner query="SELECT RDB$GET_CONTEXT('SYSTEM','ENGINE_VERSION') FROM RDB$DATABASE" dbms_version=">=2.1"/> | |
| 418 | <current_user query="SELECT CURRENT_USER FROM RDB$DATABASE"/> | |
| 419 | <current_db query="SELECT RDB$GET_CONTEXT('SYSTEM','DB_NAME') FROM RDB$DATABASE"/> | |
| 420 | <hostname/> | |
| 421 | <table_comment/> | |
| 422 | <column_comment/> | |
| 423 | <is_dba query="CURRENT_USER='SYSDBA'"/> | |
| 424 | <users> | |
| 425 | <inband query="SELECT RDB$USER FROM RDB$USER_PRIVILEGES"/> | |
| 426 | <blind query="SELECT FIRST 1 SKIP %d DISTINCT(RDB$USER) FROM RDB$USER_PRIVILEGES" count="SELECT COUNT(DISTINCT(RDB$USER)) FROM RDB$USER_PRIVILEGES"/> | |
| 427 | </users> | |
| 428 | <tables> | |
| 429 | <inband query="SELECT RDB$RELATION_NAME FROM RDB$RELATIONS WHERE RDB$VIEW_BLR IS NULL AND (RDB$SYSTEM_FLAG IS NULL OR RDB$SYSTEM_FLAG = 0)"/> | |
| 430 | <blind query="SELECT FIRST 1 SKIP %d RDB$RELATION_NAME FROM RDB$RELATIONS WHERE RDB$VIEW_BLR IS NULL AND (RDB$SYSTEM_FLAG IS NULL OR RDB$SYSTEM_FLAG = 0)" count="SELECT COUNT(RDB$RELATION_NAME) FROM RDB$RELATIONS WHERE RDB$VIEW_BLR IS NULL AND (RDB$SYSTEM_FLAG IS NULL OR RDB$SYSTEM_FLAG = 0)"/> | |
| 431 | </tables> | |
| 432 | <privileges> | |
| 433 | <inband query="SELECT RDB$USER,RDB$PRIVILEGE FROM RDB$USER_PRIVILEGES" condition="RDB$USER"/> | |
| 434 | <blind query="SELECT FIRST 1 SKIP %d DISTINCT(RDB$PRIVILEGE) FROM RDB$USER_PRIVILEGES WHERE RDB$USER='%s'" count="SELECT COUNT(DISTINCT(RDB$PRIVILEGE)) FROM RDB$USER_PRIVILEGES WHERE RDB$USER='%s'"/> | |
| 435 | </privileges> | |
| 436 | <roles/> | |
| 437 | <dbs/> | |
| 438 | <columns> | |
| 439 | <!--<inband query="SELECT r.RDB$FIELD_NAME,CASE f.RDB$FIELD_TYPE WHEN 261 THEN 'BLOB' WHEN 14 THEN 'CHAR' WHEN 40 THEN 'CSTRING' WHEN 11 THEN 'D_FLOAT' WHEN 27 THEN 'DOUBLE' WHEN 10 THEN 'FLOAT' WHEN 16 THEN 'INT64' WHEN 8 THEN 'INTEGER' WHEN 9 THEN 'QUAD' WHEN 7 THEN 'SMALLINT' WHEN 12 THEN 'DATE' WHEN 13 THEN 'TIME' WHEN 35 THEN 'TIMESTAMP' WHEN 37 THEN 'VARCHAR' ELSE 'UNKNOWN' END AS field_type FROM RDB$RELATION_FIELDS r LEFT JOIN RDB$FIELDS f ON r.RDB$FIELD_SOURCE = f.RDB$FIELD_NAME WHERE r.RDB$RELATION_NAME='%s'"/>--> | |
| 440 | <inband query="SELECT r.RDB$FIELD_NAME,f.RDB$FIELD_TYPE FROM RDB$RELATION_FIELDS r LEFT JOIN RDB$FIELDS f ON r.RDB$FIELD_SOURCE = f.RDB$FIELD_NAME WHERE r.RDB$RELATION_NAME='%s'"/> | |
| 441 | <blind query="SELECT r.RDB$FIELD_NAME FROM RDB$RELATION_FIELDS r LEFT JOIN RDB$FIELDS f ON r.RDB$FIELD_SOURCE = f.RDB$FIELD_NAME WHERE r.RDB$RELATION_NAME='%s'" query2="SELECT f.RDB$FIELD_TYPE FROM RDB$RELATION_FIELDS r LEFT JOIN RDB$FIELDS f ON r.RDB$FIELD_SOURCE = f.RDB$FIELD_NAME WHERE r.RDB$RELATION_NAME='%s' AND r.RDB$FIELD_NAME='%s'" count="SELECT COUNT(r.RDB$FIELD_NAME) FROM RDB$RELATION_FIELDS r LEFT JOIN RDB$FIELDS f ON r.RDB$FIELD_SOURCE = f.RDB$FIELD_NAME WHERE r.RDB$RELATION_NAME='%s'"/> | |
| 442 | </columns> | |
| 443 | <dump_table> | |
| 444 | <inband query="SELECT %s FROM %s"/> | |
| 445 | <blind query="SELECT FIRST 1 SKIP %d %s FROM %s" count="SELECT COUNT(*) FROM %s"/> | |
| 446 | </dump_table> | |
| 447 | <search_db/> | |
| 448 | <search_table> | |
| 449 | <inband query="SELECT RDB$RELATION_NAME FROM RDB$RELATIONS WHERE RDB$VIEW_BLR IS NULL AND (RDB$SYSTEM_FLAG IS NULL OR RDB$SYSTEM_FLAG = 0) AND %s" condition="RDB$RELATION_NAME" condition2=""/> | |
| 450 | <blind query="" query2="SELECT FIRST 1 SKIP %d RDB$RELATION_NAME FROM RDB$RELATIONS WHERE RDB$VIEW_BLR IS NULL AND (RDB$SYSTEM_FLAG IS NULL OR RDB$SYSTEM_FLAG = 0)" count="" count2="SELECT COUNT(RDB$RELATION_NAME) FROM RDB$RELATIONS WHERE RDB$VIEW_BLR IS NULL AND (RDB$SYSTEM_FLAG IS NULL OR RDB$SYSTEM_FLAG = 0)" condition="RDB$RELATION_NAME" condition2=""/> | |
| 451 | </search_table> | |
| 452 | <search_column/> | |
| 453 | </dbms> | |
| 454 | ||
| 455 | <!-- SAP MaxDB --> | |
| 456 | <!-- http://dev.mysql.com/tech-resources/articles/maxdb-php-ready-for-web.html --> | |
| 457 | <!-- http://dev.mysql.com/doc/refman/5.0/es/maxdb-reserved-words.html --> | |
| 458 | <!-- http://maxdb.sap.com/doc/7_6/default.htm --> | |
| 459 | <!-- http://www.sapdb.org/7.4/htmhelp/35/f8823cb7e5d42be10000000a114027/content.htm --> | |
| 460 | <!-- http://www.ximido.de/research/PenTestingMaxDB.pdf --> | |
| 461 | <dbms value="SAP MaxDB"> | |
| 462 | <length query="LENGTH(%s)"/> | |
| 463 | <isnull query="VALUE(%s,' ')" query2="IFNULL(%s,' ')"/> | |
| 464 | <delimiter query=","/> | |
| 465 | <!-- No real cast on SAP MaxDB --> | |
| 466 | <cast query="REPLACE(CHR(%s),' ','_')"/> | |
| 467 | <order query="ORDER BY %s ASC"/> | |
| 468 | <count query="COUNT(%s)"/> | |
| 469 | <comment query="--" query2="#"/> | |
| 470 | <substring query="SUBSTR((%s),%d,%d)"/> | |
| 471 | <concatenate query="CONCAT(%s,%s)"/> | |
| 472 | <case query="SELECT (CASE WHEN (%s) THEN 1 ELSE 0 END)"/> | |
| 473 | <hex query="HEX(%s)"/> | |
| 474 | <inference query="SUBSTR((%s),%d,1)>'%c'"/> | |
| 475 | <banner query="SELECT ID FROM SYSINFO.VERSION"/> | |
| 476 | <current_user query="SELECT USER() FROM DUAL"/> | |
| 477 | <current_db query="SELECT DATABASE() FROM DUAL"/> | |
| 478 | <hostname/> | |
| 479 | <table_comment/> | |
| 480 | <column_comment/> | |
| 481 | <is_dba/> | |
| 482 | <users> | |
| 483 | <inband query="SELECT username FROM domain.users"/> | |
| 484 | <blind query="SELECT MIN(username) FROM domain.users WHERE username>'%s'" count="SELECT CHR(COUNT(*)) FROM domain.users"/> | |
| 485 | </users> | |
| 486 | <columns> | |
| 487 | <inband query="SELECT columnname,datatype,len FROM domain.columns WHERE tablename='%s' AND schemaname=%s"/> | |
| 488 | <blind/> | |
| 489 | </columns> | |
| 490 | <tables> | |
| 491 | <inband query="SELECT tablename FROM domain.tables WHERE schemaname=%s AND type='TABLE'"/> | |
| 492 | <blind/> | |
| 493 | </tables> | |
| 494 | <dbs> | |
| 495 | <inband query="SELECT DISTINCT(schemaname) FROM domain.tables"/> | |
| 496 | <blind/> | |
| 497 | </dbs> | |
| 498 | <roles> | |
| 499 | <inband query="SELECT owner,role FROM domain.roles" condition="owner"/> | |
| 500 | <blind/> | |
| 501 | </roles> | |
| 502 | <dump_table> | |
| 503 | <inband query="SELECT %s FROM %%s"/> | |
| 504 | <blind query="SELECT MIN(%s) FROM %s WHERE CHR(%s)>'%s'" query2="SELECT MAX(%s) FROM %s WHERE CHR(%s) LIKE '%s'" count="SELECT COUNT(*) FROM %s" count2="SELECT COUNT(*) FROM (SELECT DISTINCT %s FROM %s) AS value_table"/> | |
| 505 | </dump_table> | |
| 506 | </dbms> | |
| 507 | ||
| 508 | <!-- Sybase --> | |
| 509 | <dbms value="Sybase"> | |
| 510 | <cast query="CONVERT(NVARCHAR(4000),%s)"/> | |
| 511 | <length query="LTRIM(STR(LEN(%s)))"/> | |
| 512 | <isnull query="ISNULL(%s,' ')"/> | |
| 513 | <delimiter query="+"/> | |
| 514 | <limit query="SELECT TOP %d "/> | |
| 515 | <limitregexp query="TOP\s+([\d]+)\s+.+?\s+FROM\s+.+?\s+WHERE\s+.+?\s+NOT\s+IN\s+\(SELECT\s+TOP\s+([\d]+)\s+"/> | |
| 516 | <limitgroupstart query="2"/> | |
| 517 | <limitgroupstop query="1"/> | |
| 518 | <limitstring/> | |
| 519 | <order query="ORDER BY %s ASC"/> | |
| 520 | <count query="COUNT(%s)"/> | |
| 521 | <comment query="--" query2="/*"/> | |
| 522 | <substring query="SUBSTRING((%s),%d,%d)"/> | |
| 523 | <concatenate query="%s+%s"/> | |
| 524 | <case query="SELECT (CASE WHEN (%s) THEN '1' ELSE '0' END)"/> | |
| 525 | <hex query="BINTOSTR(CONVERT(VARBINARY,%s))"/> | |
| 526 | <inference query="ASCII(SUBSTRING((%s),%d,1))>%d"/> | |
| 527 | <banner query="SELECT @@VERSION"/> | |
| 528 | <current_user query="SELECT SUSER_NAME()"/> | |
| 529 | <current_db query="SELECT DB_NAME()"/> | |
| 530 | <hostname/> | |
| 531 | <table_comment/> | |
| 532 | <column_comment/> | |
| 533 | <is_dba query="PATINDEX('%sa_role%',SHOW_ROLE())>0" query2="EXISTS(SELECT * FROM master..syslogins,master..sysloginroles WHERE srid=0 and name='%s')"/> | |
| 534 | <users> | |
| 535 | <inband query="SELECT name FROM master..syslogins"/> | |
| 536 | <blind/> | |
| 537 | </users> | |
| 538 | <passwords> | |
| 539 | <inband query="SELECT name,password FROM master..syslogins" condition="name"/> | |
| 540 | <blind/> | |
| 541 | </passwords> | |
| 542 | <privileges/> | |
| 543 | <roles> | |
| 544 | <inband query="SELECT name,srid FROM master..syslogins,master..sysloginroles" condition="name"/> | |
| 545 | <blind/> | |
| 546 | </roles> | |
| 547 | <dbs> | |
| 548 | <inband query="SELECT name FROM master..sysdatabases"/> | |
| 549 | <blind/> | |
| 550 | </dbs> | |
| 551 | <tables> | |
| 552 | <inband query="SELECT name FROM %s..sysobjects WHERE type IN ('U')"/> | |
| 553 | <blind/> | |
| 554 | </tables> | |
| 555 | <columns> | |
| 556 | <inband query="SELECT %s..syscolumns.name,%s..syscolumns.usertype FROM %s..syscolumns,%s..sysobjects WHERE %s..syscolumns.id=%s..sysobjects.id AND %s..sysobjects.name='%s'" condition="[DB]..syscolumns.name"/> | |
| 557 | <blind/> | |
| 558 | </columns> | |
| 559 | <dump_table> | |
| 560 | <inband query="SELECT %s FROM %s.%s"/> | |
| 561 | <blind query="SELECT MIN(%s) FROM %s WHERE CONVERT(NVARCHAR(4000),%s)>'%s'" query2="SELECT MAX(%s) FROM %s WHERE CONVERT(NVARCHAR(4000),%s) LIKE '%s'" count="SELECT COUNT(*) FROM %s" count2="SELECT COUNT(*) FROM (SELECT DISTINCT %s FROM %s) AS value_table"/> | |
| 562 | </dump_table> | |
| 563 | <search_db> | |
| 564 | <inband query="SELECT name FROM master..sysdatabases WHERE %s" condition="name"/> | |
| 565 | <blind/> | |
| 566 | </search_db> | |
| 567 | <search_table> | |
| 568 | <inband query="SELECT name FROM %s..sysobjects WHERE type IN ('U') AND " condition="name" condition2="name"/> | |
| 569 | <blind/> | |
| 570 | </search_table> | |
| 571 | <search_column> | |
| 572 | <inband query="SELECT %s..sysobjects.name FROM %s..syscolumns,%s..sysobjects WHERE %s..syscolumns.id=%s..sysobjects.id" condition="[DB]..syscolumns.name" condition2="[DB]..sysobjects.name"/> | |
| 573 | <blind/> | |
| 574 | </search_column> | |
| 575 | </dbms> | |
| 576 | ||
| 577 | <!-- IBM DB2 --> | |
| 578 | <dbms value="IBM DB2"> | |
| 579 | <!-- Casting to varchar does not work with version < v9, so we had to use char(254) instead --> | |
| 580 | <cast query="RTRIM(CAST(%s AS CHAR(254)))"/> | |
| 581 | <length query="LENGTH(RTRIM(CAST(%s AS CHAR(254))))"/> | |
| 582 | <isnull query="COALESCE(%s,' ')"/> | |
| 583 | <delimiter query="||"/> | |
| 584 | <limit query="ROW_NUMBER() OVER () AS LIMIT %s) AS foobar WHERE LIMIT"/> | |
| 585 | <limitregexp query="ROW_NUMBER\(\)\s+OVER\s+\(\)\s+AS\s+.+?\s+FROM\s+.+?\)\s+WHERE\s+.+?\s*=\s*[\d]+"/> | |
| 586 | <limitgroupstart/> | |
| 587 | <limitgroupstop/> | |
| 588 | <limitstring/> | |
| 589 | <order query="ORDER BY %s ASC"/> | |
| 590 | <count query="COUNT(%s)"/> | |
| 591 | <comment query="--"/> | |
| 592 | <!-- TODO --> | |
| 593 | <substring query="SUBSTR((%s),%d,%d)"/> | |
| 594 | <concatenate query="%s||%s"/> | |
| 595 | <case query="SELECT (CASE WHEN (%s) THEN '1' ELSE '0' END) FROM SYSIBM.SYSDUMMY1"/> | |
| 596 | <hex query="HEX(%s)"/> | |
| 597 | <inference query="SUBSTR((%s),%d,1)>'%c'"/> | |
| 598 | <!-- NOTE: We have to use the complicated UDB OLAP functions in query2 because sqlmap injects isnull query inside MAX function, else we would use: SELECT MAX(versionnumber) FROM sysibm.sysversions --> | |
| 599 | <banner query="SELECT service_level FROM TABLE(sysproc.env_get_inst_info())" query2="SELECT versionnumber FROM (SELECT ROW_NUMBER() OVER (ORDER BY versionnumber DESC) AS LIMIT,versionnumber FROM sysibm.sysversions) AS foobar WHERE LIMIT=1"/> | |
| 600 | <current_user query="SELECT user FROM SYSIBM.SYSDUMMY1"/> | |
| 601 | <!-- NOTE: On DB2 we use the current user as default schema (database) --> | |
| 602 | <current_db query="SELECT current server FROM SYSIBM.SYSDUMMY1"/> | |
| 603 | <hostname query="SELECT host_name FROM TABLE(sysproc.env_get_sys_info())"/> | |
| 604 | <table_comment/> | |
| 605 | <column_comment/> | |
| 606 | <is_dba query="(SELECT dbadmauth FROM syscat.dbauth WHERE grantee=current user)='Y'"/> | |
| 607 | <users> | |
| 608 | <inband query="SELECT grantee FROM sysibm.sysdbauth WHERE grantee!='SYSTEM' AND grantee!='PUBLIC'"/> | |
| 609 | <blind query="SELECT grantee FROM (SELECT ROW_NUMBER() OVER () AS LIMIT,grantee FROM sysibm.sysdbauth WHERE grantee!='SYSTEM' AND grantee!='PUBLIC') AS foobar WHERE LIMIT=%d" count="SELECT COUNT(DISTINCT(grantee)) FROM sysibm.sysdbauth WHERE grantee!='SYSTEM' AND grantee!='PUBLIC'"/> | |
| 610 | </users> | |
| 611 | <!-- NOTE: On DB2 it is not possible to list password hashes, since they are handled by the OS --> | |
| 612 | <passwords/> | |
| 613 | <privileges> | |
| 614 | <inband query="SELECT grantee,RTRIM(tabschema)||'.'||tabname||CHR(44)||controlauth||alterauth||deleteauth||indexauth||insertauth||refauth||selectauth||updateauth FROM syscat.tabauth" condition="grantee"/> | |
| 615 | <blind query="SELECT tabschema||'.'||tabname||CHR(44)||controlauth||alterauth||deleteauth||indexauth||insertauth||refauth||selectauth||updateauth FROM (SELECT ROW_NUMBER() OVER () AS LIMIT,syscat.tabauth.* FROM syscat.tabauth WHERE grantee='%s') AS foobar WHERE LIMIT=%d" count="SELECT COUNT(*) FROM syscat.tabauth WHERE grantee='%s'"/> | |
| 616 | </privileges> | |
| 617 | <roles/> | |
| 618 | <!-- NOTE: in DB2 schema names are the counterpart to database names on other DBMSes --> | |
| 619 | <dbs> | |
| 620 | <inband query="SELECT schemaname FROM syscat.schemata"/> | |
| 621 | <blind query="SELECT schemaname FROM (SELECT ROW_NUMBER() OVER () AS LIMIT,schemaname FROM syscat.schemata) AS foobar WHERE LIMIT=%d" count="SELECT COUNT(schemaname) FROM syscat.schemata"/> | |
| 622 | </dbs> | |
| 623 | <tables> | |
| 624 | <inband query="SELECT tabschema,tabname FROM sysstat.tables" condition="tabschema"/> | |
| 625 | <blind query="SELECT tabname FROM (SELECT ROW_NUMBER() OVER () AS LIMIT,tabname FROM sysstat.tables WHERE tabschema='%s') AS foobar WHERE LIMIT=INT('%d')" count="SELECT COUNT(*) FROM sysstat.tables WHERE tabschema='%s'"/> | |
| 626 | </tables> | |
| 627 | <columns> | |
| 628 | <inband query="SELECT name,RTRIM(coltype)||CHR(40)||RTRIM(CAST(length AS CHAR(254)))||CHR(41) FROM sysibm.syscolumns WHERE tbname='%s' AND tbcreator='%s'" condition="name"/> | |
| 629 | <blind query="SELECT name FROM sysibm.syscolumns WHERE tbname='%s' AND tbcreator='%s'" query2="SELECT RTRIM(coltype)||CHR(40)||RTRIM(CAST(length AS CHAR(254)))||CHR(41) FROM sysibm.syscolumns WHERE tbname='%s' AND name='%s' AND tbcreator='%s'" count="SELECT COUNT(name) FROM sysibm.syscolumns WHERE tbname='%s' AND tbcreator='%s'" condition="name"/> | |
| 630 | </columns> | |
| 631 | <dump_table> | |
| 632 | <inband query="SELECT %s FROM %s"/> | |
| 633 | <blind query="SELECT ENTRY_VALUE FROM (SELECT ROW_NUMBER() OVER () AS LIMIT,%s AS ENTRY_VALUE FROM %s) AS foobar WHERE LIMIT=%d" count="SELECT COUNT(*) FROM %s"/> | |
| 634 | </dump_table> | |
| 635 | <search_db> | |
| 636 | <inband query="SELECT schemaname FROM syscat.schemata WHERE %s" condition="schemaname"/> | |
| 637 | <blind query="SELECT schemaname FROM (SELECT DISTINCT(schemaname) FROM syscat.schemata WHERE %s) AS foobar" count="SELECT COUNT(DISTINCT(schemaname)) FROM syscat.schemata WHERE %s" condition="schemaname"/> | |
| 638 | </search_db> | |
| 639 | <search_table> | |
| 640 | <inband query="SELECT tabschema,tabname FROM sysstat.tables WHERE %s" condition="tabname" condition2="tabschema"/> | |
| 641 | <blind query="SELECT tabschema FROM (SELECT DISTINCT(tabschema) FROM sysstat.tables WHERE %s) AS foobar" query2="SELECT DISTINCT(tabname) FROM sysstat.tables WHERE tabschema='%s'" count="SELECT COUNT(DISTINCT(tabschema)) FROM sysstat.tables WHERE %s" count2="SELECT COUNT(tabname) FROM sysstat.tables WHERE tabschema='%s'" condition="tabname" condition2="tabschema"/> | |
| 642 | </search_table> | |
| 643 | <search_column> | |
| 644 | <inband query="SELECT tabschema,tabname FROM sysstat.columns WHERE %s" condition="colname" condition2="tabschema" condition3="tabname"/> | |
| 645 | <blind query="SELECT tabschema FROM (SELECT DISTINCT(tabschema) FROM sysstat.columns WHERE %s) AS foobar" query2="SELECT DISTINCT(tabname) FROM sysstat.columns WHERE tabschema='%s'" count="SELECT COUNT(DISTINCT(tabschema)) FROM sysstat.columns WHERE %s" count2="SELECT COUNT(DISTINCT(tabname)) FROM sysstat.columns WHERE tabschema='%s'" condition="colname" condition2="tabschema" condition3="tabname"/> | |
| 646 | </search_column> | |
| 647 | </dbms> | |
| 648 | ||
| 649 | <dbms value="HSQLDB"> | |
| 650 | <cast query="CAST(%s AS LONGVARCHAR)"/> | |
| 651 | <length query="CHAR_LENGTH(%s)"/> | |
| 652 | <isnull query="IFNULL(%s,' ')"/> | |
| 653 | <delimiter query=","/> | |
| 654 | <limit query="LIMIT %d %d"/> | |
| 655 | <limitregexp query="\s+LIMIT\s+([\d]+)\s*\,\s*([\d]+)" query2="\s+LIMIT\s+([\d]+)"/> | |
| 656 | <limitgroupstart query="1"/> | |
| 657 | <limitgroupstop query="2"/> | |
| 658 | <limitstring query=" LIMIT "/> | |
| 659 | <order query="ORDER BY %s ASC"/> | |
| 660 | <count query="COUNT(%s)"/> | |
| 661 | <comment query="--" query2="/*" query3="//"/> | |
| 662 | <substring query="SUBSTR((%s),%d,%d)"/> | |
| 663 | <concatenate query="CONCAT(%s,%s)"/> | |
| 664 | <case query="SELECT (CASE WHEN (%s) THEN 1 ELSE 0 END)"/> | |
| 665 | <hex query="RAWTOHEX(%s)"/> | |
| 666 | <inference query="ASCII(SUBSTR((%s),%d,1))>%d"/> | |
| 667 | <banner query="DATABASE_VERSION()"/> | |
| 668 | <current_user query="CURRENT_USER"/> | |
| 669 | <current_db query="DATABASE()"/> | |
| 670 | <hostname/> | |
| 671 | <table_comment/> | |
| 672 | <column_comment/> | |
| 673 | <is_dba query="SELECT ADMIN FROM INFORMATION_SCHEMA.SYSTEM_USERS WHERE USER=CURRENT_USER"/> | |
| 674 | <check_udf/> | |
| 675 | <users> | |
| 676 | <inband query="SELECT user FROM INFORMATION_SCHEMA.SYSTEM_USERS"/> | |
| 677 | <!-- LIMIT is needed at start for v1.7 this gets mangled unless no-cast is used --> | |
| 678 | <blind query="SELECT LIMIT %d 1 DISTINCT(user) FROM INFORMATION_SCHEMA.SYSTEM_USERS" count="SELECT COUNT(DISTINCT(user)) FROM INFORMATION_SCHEMA.SYSTEM_USERS"/> | |
| 679 | </users> | |
| 680 | <passwords> | |
| 681 | <!-- Passwords only shown in later versions >=2.0 --> | |
| 682 | <inband query="SELECT user_name,password_digest FROM INFORMATION_SCHEMA.SYSTEM_USERS" condition="user_name"/> | |
| 683 | <blind query="SELECT LIMIT %d 1 DISTINCT(password_digest) FROM INFORMATION_SCHEMA.SYSTEM_USERS WHERE user_name='%s'" count="SELECT COUNT(DISTINCT(password_digest)) FROM INFORMATION_SCHEMA.SYSTEM_USERS WHERE user_name='%s'"/> | |
| 684 | </passwords> | |
| 685 | <privileges/> | |
| 686 | <roles/> | |
| 687 | <dbs> | |
| 688 | <inband query="SELECT table_schem FROM INFORMATION_SCHEMA.SYSTEM_SCHEMAS" /> | |
| 689 | <blind query="SELECT LIMIT %d 1 DISTINCT(table_schem) FROM INFORMATION_SCHEMA.SYSTEM_SCHEMAS" count="SELECT COUNT(table_schem) FROM INFORMATION_SCHEMA.SYSTEM_SCHEMAS"/> | |
| 690 | </dbs> | |
| 691 | <tables> | |
| 692 | <inband query="SELECT table_schem,table_name FROM INFORMATION_SCHEMA.SYSTEM_TABLES" condition="table_schem"/> | |
| 693 | <blind query="SELECT LIMIT %d 1 table_name FROM INFORMATION_SCHEMA.SYSTEM_TABLES WHERE table_schem='%s' " count="SELECT COUNT(table_name) FROM INFORMATION_SCHEMA.SYSTEM_TABLES WHERE table_schem='%s'"/> | |
| 694 | </tables> | |
| 695 | <columns> | |
| 696 | <inband query="SELECT column_name,type_name FROM INFORMATION_SCHEMA.SYSTEM_COLUMNS WHERE table_name='%s' AND table_schem='%s'" condition="column_name"/> | |
| 697 | <blind query="SELECT column_name FROM INFORMATION_SCHEMA.SYSTEM_COLUMNS WHERE table_name='%s' AND table_schem='%s'" query2="SELECT column_type FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name='%s' AND column_name='%s' AND table_schema='%s'" count="SELECT COUNT(column_name) FROM INFORMATION_SCHEMA.COLUMNS WHERE table_name='%s' AND table_schema='%s'" condition="column_name"/> | |
| 698 | </columns> | |
| 699 | <dump_table> | |
| 700 | <inband query="SELECT %s FROM %s.%s ORDER BY %s"/> | |
| 701 | <blind query="SELECT LIMIT %d 1 %s FROM %s.%s ORDER BY %s " count="SELECT COUNT(*) FROM %s.%s"/> | |
| 702 | </dump_table> | |
| 703 | <search_db> | |
| 704 | <inband query="SELECT table_schem FROM INFORMATION_SCHEMA.SYSTEM_SCHEMAS WHERE %s" condition="table_schem"/> | |
| 705 | <blind query="SELECT DISTINCT(table_schem) FROM INFORMATION_SCHEMA.SYSTEM_SCHEMAS WHERE %s" count="SELECT COUNT(DISTINCT(table_schem)) FROM INFORMATION_SCHEMA.SYSTEM_SCHEMAS WHERE %s" condition="table_schem"/> | |
| 706 | </search_db> | |
| 707 | <search_table> | |
| 708 | <inband query="SELECT table_schem,table_name FROM INFORMATION_SCHEMA.SYSTEM_TABLES WHERE %s" condition="table_name" condition2="table_schem"/> | |
| 709 | <blind query="SELECT DISTINCT(table_schem) FROM INFORMATION_SCHEMA.SYSTEM_TABLES WHERE %s" count="SELECT COUNT(DISTINCT(table_schem)) FROM INFORMATION_SCHEMA.SYSTEM_TABLES WHERE %s" condition="table_name" condition2="table_schem"/> | |
| 710 | </search_table> | |
| 711 | <search_column> | |
| 712 | <inband query="SELECT table_schem,table_name FROM INFORMATION_SCHEMA.SYSTEM_COLUMNS WHERE %s" condition="column_name" condition2="table_schem" condition3="table_name"/> | |
| 713 | <blind query="SELECT DISTINCT(table_schem) FROM INFORMATION_SCHEMA.SYSTEM_COLUMNS WHERE %s" count="SELECT COUNT(DISTINCT(table_schem)) FROM INFORMATION_SCHEMA.SYSTEM_COLUMNS WHERE %s" condition="column_name" condition2="table_schem" condition3="table_name"/> | |
| 714 | </search_column> | |
| 715 | </dbms> | |
| 716 | </root> |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import core | |
| 6 | import re | |
| 7 | ||
| 8 | __author__ = "Andres Tarantini" | |
| 9 | __copyright__ = "Copyright (c) 2015 Andres Tarantini" | |
| 10 | __credits__ = ["Andres Tarantini"] | |
| 11 | __license__ = "MIT" | |
| 12 | __version__ = "0.0.1" | |
| 13 | __maintainer__ = "Andres Tarantini" | |
| 14 | __email__ = "[email protected]" | |
| 15 | __status__ = "Development" | |
| 16 | ||
| 17 | ||
| 18 | class SSHDefaultScanPlugin(core.PluginBase): | |
| 19 | """ | |
| 20 | Handle sshdefaultscan (https://github.com/atarantini/sshdefaultscan) output | |
| 21 | using --batch and --batch-template; supports --username and --password | |
| 22 | """ | |
| 23 | ||
| 24 | def __init__(self): | |
| 25 | super().__init__() | |
| 26 | self.id = "sshdefaultscan" | |
| 27 | self.name = "sshdefaultscan" | |
| 28 | self.plugin_version = "0.0.1" | |
| 29 | self.version = "1.0.0" | |
| 30 | self._command_regex = re.compile( | |
| 31 | r'^(python sshdefaultscan.py|\./sshdefaultscan.py).*?') | |
| 32 | self._completition = {"--fast": "Fast scan mode"} | |
| 33 | ||
| 34 | def parseOutputString(self, output, debug=False): | |
| 35 | for line in [l.strip() for l in output.split("\n")]: | |
| 36 | output_rexeg_match = re.match( | |
| 37 | r".*:.*@\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}$", line) | |
| 38 | if output_rexeg_match: | |
| 39 | credentials, address = line.split("@") | |
| 40 | host = self.createAndAddHost(address) | |
| 41 | iface = self.createAndAddInterface( | |
| 42 | host, address, ipv4_address=address) | |
| 43 | service = self.createAndAddServiceToInterface( | |
| 44 | host, iface, "ssh", protocol="tcp", ports=[22] | |
| 45 | ) | |
| 46 | username, password = credentials.split(":") | |
| 47 | cred = self.createAndAddCredToService( | |
| 48 | host, service, username, password) | |
| 49 | vuln = self.createAndAddVulnToService( | |
| 50 | host, | |
| 51 | service, | |
| 52 | "Default credentials", | |
| 53 | desc="The SSH server have default credentials ({username}:{password})".format( | |
| 54 | username=username, | |
| 55 | password=password | |
| 56 | ), | |
| 57 | severity=3 | |
| 58 | ) | |
| 59 | ||
| 60 | return True | |
| 61 | ||
| 62 | def processCommandString(self, username, current_path, command_string): | |
| 63 | if "--batch" not in command_string: | |
| 64 | return "{command} --batch --batch-template {template}".format( | |
| 65 | command=command_string, | |
| 66 | template="{username}:{password}@{host}" | |
| 67 | ) | |
| 68 | ||
| 69 | return None | |
| 70 | ||
| 71 | ||
| 72 | def createPlugin(): | |
| 73 | return SSHDefaultScanPlugin() | |
| 74 | ||
| 75 | ||
| 76 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import core | |
| 6 | import re | |
| 7 | import os | |
| 8 | import sys | |
| 9 | import random | |
| 10 | import tempfile | |
| 11 | ||
| 12 | ||
| 13 | try: | |
| 14 | import xml.etree.cElementTree as ET | |
| 15 | import xml.etree.ElementTree as ET_ORIG | |
| 16 | ETREE_VERSION = ET_ORIG.VERSION | |
| 17 | except ImportError: | |
| 18 | import xml.etree.ElementTree as ET | |
| 19 | ETREE_VERSION = ET.VERSION | |
| 20 | ||
| 21 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 22 | ||
| 23 | current_path = os.path.abspath(os.getcwd()) | |
| 24 | ||
| 25 | __author__ = "Morgan Lemarechal" | |
| 26 | __copyright__ = "Copyright 2014, Faraday Project" | |
| 27 | __credits__ = ["Morgan Lemarechal"] | |
| 28 | __license__ = "" | |
| 29 | __version__ = "1.0.0" | |
| 30 | __maintainer__ = "Morgan Lemarechal" | |
| 31 | __email__ = "[email protected]" | |
| 32 | __status__ = "Development" | |
| 33 | ||
| 34 | ||
| 35 | class SslcheckParser: | |
| 36 | """ | |
| 37 | The objective of this class is to parse an xml file generated by the ssl-check tool. | |
| 38 | TODO: Handle errors. | |
| 39 | TODO: Test ssl-check output version. Handle what happens if the parser doesn't support it. | |
| 40 | TODO: Test cases. | |
| 41 | @param sslcheck_filepath A proper simple report generated by ssl-check | |
| 42 | """ | |
| 43 | ||
| 44 | def __init__(self, output): | |
| 45 | self.hostinfo = {} | |
| 46 | self.result = {} | |
| 47 | tree = ET.parse(output) | |
| 48 | root = tree.getroot() | |
| 49 | for scan in root.findall(".//scan"): | |
| 50 | infos = {} | |
| 51 | for info in scan.attrib: | |
| 52 | infos[info] = scan.attrib[info] | |
| 53 | self.hostinfo[scan.attrib['host']] = infos | |
| 54 | ||
| 55 | item = {} | |
| 56 | for carac in scan: | |
| 57 | item[carac.tag] = carac.text | |
| 58 | self.result[scan.attrib['host']] = item | |
| 59 | ||
| 60 | ||
| 61 | class SslcheckPlugin(core.PluginBase): | |
| 62 | """ | |
| 63 | Example plugin to parse ssl-check output. | |
| 64 | """ | |
| 65 | ||
| 66 | def __init__(self): | |
| 67 | super().__init__() | |
| 68 | self.id = "Sslcheck" | |
| 69 | self.name = "Sslcheck XML Output Plugin" | |
| 70 | self.plugin_version = "0.0.2" | |
| 71 | self.version = "0.30" | |
| 72 | self._completition = { | |
| 73 | "": "ssl-check [-h] [-r {key,ren,sign,serv,cyph,forw,heart,crime,all} [{key,ren,sign,serv,cyph,forw,heart,crime,all} ...]] -host HOST [-port PORT] [--xml] [--version]", | |
| 74 | "-h": "show this help message and exit", | |
| 75 | "-r": "store the scan(s) requested made by the users", | |
| 76 | "-host": "store the target's host address", | |
| 77 | "-port": "store the target's port", | |
| 78 | "--xml": "Enable the XML output", | |
| 79 | "--version": "Show program's version number and exit", | |
| 80 | } | |
| 81 | ||
| 82 | self.options = None | |
| 83 | self._current_output = None | |
| 84 | self.current_path = None | |
| 85 | self._command_regex = re.compile( | |
| 86 | r'^(sudo sslcheck|sslcheck|\.\/sslcheck|sudo \.\/sslcheck|python( *|2|3) sslcheck|sudo python( *|2|3) sslcheck).*?') | |
| 87 | ||
| 88 | global current_path | |
| 89 | self._output_file_path = os.path.join(self.data_path, "%s_%s_output-%s.xml" % (self.get_ws(), | |
| 90 | self.id, | |
| 91 | random.uniform(1, 10))) | |
| 92 | ||
| 93 | def canParseCommandString(self, current_input): | |
| 94 | if self._command_regex.match(current_input.strip()): | |
| 95 | return True | |
| 96 | else: | |
| 97 | return False | |
| 98 | ||
| 99 | def parseOutputString(self, output, debug=False): | |
| 100 | """ | |
| 101 | This method will discard the output the shell sends, it will read it from | |
| 102 | the xml where it expects it to be present. | |
| 103 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 104 | output being sent is valid. | |
| 105 | """ | |
| 106 | if debug: | |
| 107 | parser = SslcheckParser(self._output_file_path) | |
| 108 | else: | |
| 109 | ||
| 110 | if not os.path.exists(self._output_file_path): | |
| 111 | if output: | |
| 112 | temp_file = tempfile.NamedTemporaryFile() | |
| 113 | temp_file.write(output) | |
| 114 | temp_file.flush() | |
| 115 | self._output_file_path = temp_file.name | |
| 116 | else: | |
| 117 | return False | |
| 118 | parser = SslcheckParser(self._output_file_path) | |
| 119 | # print parser.result | |
| 120 | # print parser.hostinfo | |
| 121 | for host in parser.result: | |
| 122 | h_id = self.createAndAddHost(host) | |
| 123 | if(re.match("(^[2][0-5][0-5]|^[1]{0,1}[0-9]{1,2})\.([0-2][0-5][0-5]|[1]{0,1}[0-9]{1,2})\.([0-2][0-5][0-5]|[1]{0,1}[0-9]{1,2})\.([0-2][0-5][0-5]|[1]{0,1}[0-9]{1,2})$", host)): | |
| 124 | i_id = self.createAndAddInterface(h_id, | |
| 125 | host, | |
| 126 | ipv4_address=host, | |
| 127 | hostname_resolution=[parser.hostinfo[host]['hostname']]) | |
| 128 | else: | |
| 129 | i_id = self.createAndAddInterface(h_id, | |
| 130 | host, | |
| 131 | ipv6_address=host) | |
| 132 | ||
| 133 | s_id = self.createAndAddServiceToInterface( | |
| 134 | h_id, i_id, "https", protocol="tcp", ports=int(parser.hostinfo[host]['port'])) | |
| 135 | for carac in parser.result[host]: | |
| 136 | if carac == "key" and int(parser.result[host][carac]) < 2048: | |
| 137 | v_id = self.createAndAddVulnToService( | |
| 138 | h_id, s_id, "Public server key size", desc="Key size = {} bits (2048 bits recommended)".format(parser.result[host][carac]), severity=2) | |
| 139 | continue | |
| 140 | if carac == "renegotiation" and parser.result[host][carac] == "no": | |
| 141 | v_id = self.createAndAddVulnToService( | |
| 142 | h_id, s_id, "Secure renegotiation", desc="Secure renegotiation disabled (recommended: enabled)", severity=1) | |
| 143 | continue | |
| 144 | if carac == "forward_secrecy" and parser.result[host][carac] == "no": | |
| 145 | v_id = self.createAndAddVulnToService( | |
| 146 | h_id, s_id, "Forward Secrecy", desc="Forward secrecy disabled (recommended: enabled)", severity=1) | |
| 147 | continue | |
| 148 | if carac == "heartbeat" and parser.result[host][carac] == "yes": | |
| 149 | v_id = self.createAndAddVulnToService( | |
| 150 | h_id, s_id, "Heartbleed", desc="Heartbeat enabled (recommended: disabled)", severity=4) | |
| 151 | continue | |
| 152 | if carac == "forward_secrecy" and parser.result[host][carac] == "no": | |
| 153 | v_id = self.createAndAddVulnToService( | |
| 154 | h_id, s_id, "CRIME", desc="Potentially vulnerable to CRIME attack", severity=0) | |
| 155 | continue | |
| 156 | if parser.result[host][carac] == "insecure": | |
| 157 | v_id = self.createAndAddVulnToService(h_id, s_id, "Cipher suite {}".format( | |
| 158 | carac), desc="{} enabled (recommended: disabled)".format(parser.result[host][carac]), severity=1) | |
| 159 | continue | |
| 160 | if parser.result[host][carac] == "signature insecure": | |
| 161 | v_id = self.createAndAddVulnToService(h_id, s_id, "Certificate signature cipher suite {}".format(parser.result[host][ | |
| 162 | carac]), desc="{} used (recommended: use a safer one as sha256WithRSAEncryption)".format(parser.result[host][carac]), severity=1) | |
| 163 | continue | |
| 164 | if (carac == "SSLv3" and parser.result[host][carac] == "yes"): | |
| 165 | v_id = self.createAndAddVulnToService( | |
| 166 | h_id, s_id, "SSL3", desc="SSL3 enabled (recommended: disabled)\nSSL3 is broken and should not be used.", severity=2) | |
| 167 | continue | |
| 168 | if (carac == "TLSv1" and parser.result[host][carac] == "yes"): | |
| 169 | v_id = self.createAndAddVulnToService( | |
| 170 | h_id, s_id, "TLSv1.0", desc="TLSv1.0 enabled (recommended: disabled, and to use TLSv1.1 or TLSv1.2)", severity=1) | |
| 171 | continue | |
| 172 | if (carac == "TLSv1.1" and parser.result[host][carac] == "no") or (carac == "TLSv1.2" and parser.result[host][carac] == "no"): | |
| 173 | v_id = self.createAndAddVulnToService(h_id, s_id, parser.result[host][ | |
| 174 | carac], desc="{} disabled (recommended: enabled)".format(parser.result[host][carac]), severity=1) | |
| 175 | continue | |
| 176 | ||
| 177 | del parser | |
| 178 | ||
| 179 | return True | |
| 180 | ||
| 181 | xml_arg_re = re.compile(r"^.*(--xml\s*[^\s]+).*$") | |
| 182 | ||
| 183 | def processCommandString(self, username, current_path, command_string): | |
| 184 | """ | |
| 185 | Adds the parameter to get output to the command string that the | |
| 186 | user has set. | |
| 187 | """ | |
| 188 | ||
| 189 | arg_match = self.xml_arg_re.match(command_string) | |
| 190 | ||
| 191 | if arg_match is None: | |
| 192 | return "%s --xml %s" % (command_string, self._output_file_path) | |
| 193 | else: | |
| 194 | return re.sub(arg_match.group(1), | |
| 195 | r"-xml %s" % self._output_file_path, | |
| 196 | command_string) | |
| 197 | ||
| 198 | ||
| 199 | def createPlugin(): | |
| 200 | return SslcheckPlugin() | |
| 201 | ||
| 202 | # I'm Py3 |
| 0 | import re | |
| 1 | import os | |
| 2 | import random | |
| 3 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 4 | ||
| 5 | try: | |
| 6 | from lxml import etree as ET | |
| 7 | except ImportError: | |
| 8 | import xml.etree.ElementTree as ET | |
| 9 | ||
| 10 | ||
| 11 | WEAK_CIPHER_LIST = [ | |
| 12 | "TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA", | |
| 13 | "TLS_RSA_WITH_AES_128_CBC_SHA", | |
| 14 | "TLS_RSA_WITH_AES_128_CBC_SHA256", | |
| 15 | "TLS_RSA_WITH_AES_128_GCM_SHA256", | |
| 16 | "TLS_RSA_WITH_AES_256_CBC_SHA", | |
| 17 | "TLS_RSA_WITH_AES_256_CBC_SHA256", | |
| 18 | "TLS_RSA_WITH_AES_256_GCM_SHA384", | |
| 19 | "TLS_RSA_WITH_3DES_EDE_CBC_SHA", | |
| 20 | "TLS_RSA_WITH_CAMELLIA_256_CBC_SHA", | |
| 21 | "TLS_RSA_WITH_CAMELLIA_128_CBC_SHA" | |
| 22 | ] | |
| 23 | ||
| 24 | ||
| 25 | class SslyzeXmlParser: | |
| 26 | ||
| 27 | def __init__(self, xml_output): | |
| 28 | self.parser = self.parse_xml(xml_output) | |
| 29 | self.target = self.get_target(self.parser) | |
| 30 | self.certificate = self.get_hostname_validation(self.parser) | |
| 31 | self.cipher_suite = self.get_weak_cipher_suite(self.parser) | |
| 32 | self.heart_bleed = self.get_heartbleed(self.parser) | |
| 33 | self.open_ssl_ccs = self.get_openssl_ccs(self.parser) | |
| 34 | ||
| 35 | def parse_xml(self, xml_output): | |
| 36 | try: | |
| 37 | tree = ET.fromstring(xml_output) | |
| 38 | return tree | |
| 39 | except IndexError: | |
| 40 | print("Syntax error") | |
| 41 | return None | |
| 42 | ||
| 43 | def get_target(self, tree): | |
| 44 | return tree.xpath('//target') | |
| 45 | ||
| 46 | def get_hostname_validation(self, tree): | |
| 47 | return tree.xpath('//hostnameValidation') | |
| 48 | ||
| 49 | def get_protocol_name(self, tree): | |
| 50 | protocol_supported = [] | |
| 51 | protocols = [] | |
| 52 | protocols.append(tree.xpath('//sslv2')) | |
| 53 | protocols.append(tree.xpath('//sslv3')) | |
| 54 | protocols.append(tree.xpath('//tlsv1')) | |
| 55 | protocols.append(tree.xpath('//tlsv1_1')) | |
| 56 | protocols.append(tree.xpath('//tlsv1_2')) | |
| 57 | protocols.append(tree.xpath('//tlsv1_3')) | |
| 58 | ||
| 59 | for protocol in protocols: | |
| 60 | if protocol[0].attrib['isProtocolSupported'] == "True": | |
| 61 | protocol_supported.append(protocol[0]) | |
| 62 | ||
| 63 | return protocol_supported | |
| 64 | ||
| 65 | def get_weak_cipher_suite(self, tree): | |
| 66 | protocols = self.get_protocol_name(tree) | |
| 67 | weak_cipher = {} | |
| 68 | ||
| 69 | for protocol in protocols: | |
| 70 | weak_cipher[protocol.tag] = [] | |
| 71 | for ciphers in protocol: | |
| 72 | if ciphers.tag == 'preferredCipherSuite' or ciphers.tag == 'acceptedCipherSuites': | |
| 73 | for cipher in ciphers: | |
| 74 | if cipher.attrib['name'] in WEAK_CIPHER_LIST: | |
| 75 | if not cipher.attrib['name'] in weak_cipher[protocol.tag]: | |
| 76 | weak_cipher[protocol.tag].append(cipher.attrib['name']) | |
| 77 | ||
| 78 | return weak_cipher | |
| 79 | ||
| 80 | def get_heartbleed(self, tree): | |
| 81 | return tree.xpath('//heartbleed') | |
| 82 | ||
| 83 | def get_openssl_ccs(self, tree): | |
| 84 | return tree.xpath('//openssl_ccs') | |
| 85 | ||
| 86 | ||
| 87 | class SslyzePlugin(PluginXMLFormat): | |
| 88 | ||
| 89 | def __init__(self): | |
| 90 | super().__init__() | |
| 91 | self.identifier_tag = "document" | |
| 92 | self.id = "Sslyze" | |
| 93 | self.name = "Sslyze Plugin" | |
| 94 | self.plugin_version = "0.0.1" | |
| 95 | self.version = "2.0.6" | |
| 96 | self.framework_version = "1.0.0" | |
| 97 | self.options = None | |
| 98 | self._current_output = None | |
| 99 | self._command_regex = re.compile(r'^(sudo sslyze|sslyze|\.\/sslyze).*?') | |
| 100 | self.xml_arg_re = re.compile(r"^.*(--xml_output\s*[^\s]+).*$") | |
| 101 | ||
| 102 | def report_belongs_to(self, **kwargs): | |
| 103 | if super().report_belongs_to(**kwargs): | |
| 104 | report_path = kwargs.get("report_path", "") | |
| 105 | with open(report_path) as f: | |
| 106 | output = f.read() | |
| 107 | return re.search("SSLyzeVersion", output) is not None | |
| 108 | return False | |
| 109 | ||
| 110 | def parseOutputString(self, output, debug=False): | |
| 111 | parser = SslyzeXmlParser(output) | |
| 112 | host = parser.target[0].attrib['host'] | |
| 113 | ip = parser.target[0].attrib['ip'] | |
| 114 | port = parser.target[0].attrib['port'] | |
| 115 | protocol = parser.target[0].attrib['tlsWrappedProtocol'] | |
| 116 | cipher = parser.cipher_suite | |
| 117 | ||
| 118 | # Creating host | |
| 119 | host_id = self.createAndAddHost(ip) | |
| 120 | # Creating service CHANGE NAME | |
| 121 | service_id = self.createAndAddServiceToHost( | |
| 122 | host_id, | |
| 123 | name=protocol, | |
| 124 | protocol=protocol, | |
| 125 | ports=[port], | |
| 126 | ) | |
| 127 | ||
| 128 | # Checking if certificate matches | |
| 129 | certificate = parser.certificate[0].attrib['certificateMatchesServerHostname'] | |
| 130 | server_hostname = parser.certificate[0].attrib['serverHostname'] | |
| 131 | if certificate.lower() == 'false': | |
| 132 | self.createAndAddVulnToService( | |
| 133 | host_id, | |
| 134 | service_id, | |
| 135 | name="Certificate mismatch", | |
| 136 | desc="Certificate does not match server hostname {}".format(server_hostname), | |
| 137 | severity="info") | |
| 138 | #Ciphers | |
| 139 | cipher = parser.cipher_suite | |
| 140 | ||
| 141 | for key in cipher: | |
| 142 | for value in cipher[key]: | |
| 143 | self.createAndAddVulnToService( | |
| 144 | host_id, | |
| 145 | service_id, | |
| 146 | name=value, | |
| 147 | desc="In protocol [{}], weak cipher suite: {}".format(key, value), | |
| 148 | severity="low") | |
| 149 | ||
| 150 | #Heartbleed | |
| 151 | heartbleed = parser.heart_bleed | |
| 152 | ||
| 153 | if heartbleed[0][0].attrib['isVulnerable'].lower() == 'true': | |
| 154 | self.createAndAddVulnToService( | |
| 155 | host_id, | |
| 156 | service_id, | |
| 157 | name="OpenSSL Heartbleed", | |
| 158 | desc="OpenSSL Heartbleed is vulnerable", | |
| 159 | severity="critical") | |
| 160 | ||
| 161 | #OpenSsl CCS Injection | |
| 162 | openssl_ccs = parser.open_ssl_ccs | |
| 163 | ||
| 164 | if openssl_ccs[0][0].attrib['isVulnerable'].lower() == 'true': | |
| 165 | self.createAndAddVulnToService( | |
| 166 | host_id, | |
| 167 | service_id, | |
| 168 | name="OpenSSL CCS Injection", | |
| 169 | desc="OpenSSL CCS Injection is vulnerable", | |
| 170 | severity="medium") | |
| 171 | ||
| 172 | def processCommandString(self, username, current_path, command_string): | |
| 173 | self._output_file_path = os.path.join( | |
| 174 | self.data_path, | |
| 175 | "%s_%s_output-%s.xml" % ( | |
| 176 | self.get_ws(), | |
| 177 | self.id, | |
| 178 | random.uniform(1, 10)) | |
| 179 | ) | |
| 180 | ||
| 181 | arg_match = self.xml_arg_re.match(command_string) | |
| 182 | ||
| 183 | if arg_match is None: | |
| 184 | return re.sub(r"(^.*?sslyze)", | |
| 185 | r"\1 --xml_out %s" % self._output_file_path, | |
| 186 | command_string) | |
| 187 | else: | |
| 188 | return re.sub(arg_match.group(1), | |
| 189 | r"--xml_out %s" % self._output_file_path, | |
| 190 | command_string) | |
| 191 | ||
| 192 | ||
| 193 | def createPlugin(): | |
| 194 | return SslyzePlugin() | |
| 195 | ||
| 196 | ||
| 197 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | import re | |
| 6 | import os | |
| 7 | import shlex | |
| 8 | import socket | |
| 9 | import argparse | |
| 10 | import tempfile | |
| 11 | from faraday.client.plugins.plugin import PluginTerminalOutput | |
| 12 | ||
| 13 | ||
| 14 | __author__ = "Matías Lang" | |
| 15 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 16 | __credits__ = ["Matías Lang"] | |
| 17 | __license__ = "" | |
| 18 | __version__ = "0.0.1" | |
| 19 | __maintainer__ = "Matías Lang" | |
| 20 | __email__ = "[email protected]" | |
| 21 | __status__ = "Development" | |
| 22 | ||
| 23 | ||
| 24 | class Sublist3rPlugin(PluginTerminalOutput): | |
| 25 | def __init__(self): | |
| 26 | super().__init__() | |
| 27 | self.id = "sublist3r" | |
| 28 | self.name = "sublist3r" | |
| 29 | self.plugin_version = "0.0.1" | |
| 30 | self.version = "0.0.1" | |
| 31 | self._command_regex = re.compile( | |
| 32 | r'^(sudo )?(python[0-9\.]? )?sublist3r(\.py)?') | |
| 33 | self.ignore_parsing = False | |
| 34 | self.report_file = None | |
| 35 | ||
| 36 | def parseOutputString(self, output, debug=False): | |
| 37 | if self.ignore_parsing: | |
| 38 | return | |
| 39 | if self.report_file: | |
| 40 | # We ran the plugin via command line | |
| 41 | try: | |
| 42 | fp = open(self.report_file) | |
| 43 | except IOError: | |
| 44 | self.log('Error opening report file {}'.format( | |
| 45 | self.report_file | |
| 46 | ), 'ERROR') | |
| 47 | else: | |
| 48 | self.parse_report(fp.read()) | |
| 49 | if self.remove_report: | |
| 50 | os.unlink(self.report_file) | |
| 51 | else: | |
| 52 | # We are importing a report | |
| 53 | self.parse_report(output) | |
| 54 | ||
| 55 | def resolve(self, domain): | |
| 56 | return socket.gethostbyname(domain) | |
| 57 | ||
| 58 | def parse_report(self, contents): | |
| 59 | for line in contents.splitlines(): | |
| 60 | hostname = line.strip() | |
| 61 | if not hostname: | |
| 62 | continue | |
| 63 | try: | |
| 64 | ip = self.resolve(hostname) | |
| 65 | except socket.gaierror: | |
| 66 | self.log('Error resolving hostname {}. Skipping.'.format( | |
| 67 | hostname | |
| 68 | ), 'ERROR') | |
| 69 | continue | |
| 70 | h_id = self.createAndAddHost(ip) | |
| 71 | ||
| 72 | self.createAndAddInterface( | |
| 73 | h_id, | |
| 74 | name=ip, | |
| 75 | ipv4_address=ip, | |
| 76 | hostname_resolution=[hostname]) | |
| 77 | ||
| 78 | def processCommandString(self, username, current_path, command_string): | |
| 79 | parser = argparse.ArgumentParser(conflict_handler='resolve') | |
| 80 | parser.add_argument('-h', '--help', action='store_true') | |
| 81 | parser.add_argument('-o', '--output') | |
| 82 | args, unknown = parser.parse_known_args(shlex.split(command_string)) | |
| 83 | ||
| 84 | if args.help: | |
| 85 | self.devlog('help detected, ignoring parsing') | |
| 86 | return command_string | |
| 87 | if args.output: | |
| 88 | # The user already defined a path to the report | |
| 89 | self.report_file = args.output | |
| 90 | self.remove_report = False | |
| 91 | return command_string | |
| 92 | else: | |
| 93 | # Use temporal file to save the report data | |
| 94 | self.report_file = tempfile.mktemp( | |
| 95 | prefix="sublist3r_report_", suffix=".txt") | |
| 96 | self.devlog('Setting report file to {}'.format( | |
| 97 | self.report_file)) | |
| 98 | self.remove_report = True | |
| 99 | return '{} --output {}'.format(command_string, | |
| 100 | self.report_file) | |
| 101 | ||
| 102 | ||
| 103 | def createPlugin(): | |
| 104 | return Sublist3rPlugin() | |
| 105 | ||
| 106 | ||
| 107 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | from faraday.client.model import api | |
| 8 | import re | |
| 9 | import os | |
| 10 | import socket | |
| 11 | ||
| 12 | current_path = os.path.abspath(os.getcwd()) | |
| 13 | ||
| 14 | __author__ = "Facundo de Guzmán, Esteban Guillardoy" | |
| 15 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 16 | __credits__ = ["Facundo de Guzmán", "Esteban Guillardoy"] | |
| 17 | __license__ = "" | |
| 18 | __version__ = "1.0.0" | |
| 19 | __maintainer__ = "Facundo de Guzmán" | |
| 20 | __email__ = "[email protected]" | |
| 21 | __status__ = "Development" | |
| 22 | ||
| 23 | ||
| 24 | class TelnetRouterPlugin(core.PluginBase): | |
| 25 | """ | |
| 26 | This plugin handles telnet command. | |
| 27 | Basically detects if user was able to connect to a device | |
| 28 | """ | |
| 29 | ||
| 30 | def __init__(self): | |
| 31 | super().__init__() | |
| 32 | self.id = "Telnet" | |
| 33 | self.name = "Telnet" | |
| 34 | self.plugin_version = "0.0.1" | |
| 35 | self.version = "0.17" | |
| 36 | self.framework_version = "1.0.0" | |
| 37 | self.options = None | |
| 38 | self._current_output = None | |
| 39 | self._command_regex = re.compile(r'^telnet.*?') | |
| 40 | self._host_ip = None | |
| 41 | self._host = [] | |
| 42 | self._port = "23" | |
| 43 | self._completition = { | |
| 44 | "": "telnet [-468ELadr] [-S tos] [-b address] [-e escapechar] [-l user] [-n tracefile] [host [port]]", | |
| 45 | "-4": "Force IPv4 address resolution.", | |
| 46 | "-6": "Force IPv6 address resolution.", | |
| 47 | "-8": "Request 8-bit operation. This causes an attempt to negotiate the TELNET BINARY option for both input and output. By default telnet is not 8-bit clean.", | |
| 48 | "-E": "Disables the escape character functionality; that is, sets the escape character to ``no character''.", | |
| 49 | "-L": "Specifies an 8-bit data path on output. This causes the TELNET BINARY option to be negotiated on just output.", | |
| 50 | "-a": "Attempt automatic login. Currently, this sends the user name via the USER variable of the ENVIRON option if supported by the remote system. The username is retrieved via getlogin(3).", | |
| 51 | "-b": "-b <address> Use bind(2) on the local socket to bind it to a specific local address.", | |
| 52 | "-d": "Sets the initial value of the debug toggle to TRUE.", | |
| 53 | "-r": "Emulate rlogin(1). In this mode, the default escape character is a tilde. Also, the interpretation of the escape character is changed: an escape character followed by a dot causes telnet to disconnect from the remote host. A ^Z instead of a dot suspends telnet, and a ^] (the default telnet escape character) generates a normal telnet prompt. These codes are accepted only at the beginning of a line.", | |
| 54 | "-S": "-S <tos> Sets the IP type-of-service (TOS) option for the telnet connection to the value tos.", | |
| 55 | "-e": "-e <escapechar> Sets the escape character to escapechar. If no character is supplied, no escape character will be used. Entering the escape character while connected causes telnet to drop to command mode.", | |
| 56 | "-l": "-l <user> Specify user as the user to log in as on the remote system. This is accomplished by sending the specified name as the USER environment variable, so it requires that the remote system support the TELNET ENVIRON option. This option implies the -a option, and may also be used with the open command.", | |
| 57 | "-n": "-n <tracefile> Opens tracefile for recording trace information. See the set tracefile command below.", | |
| 58 | } | |
| 59 | ||
| 60 | global current_path | |
| 61 | ||
| 62 | def resolve(self, host): | |
| 63 | try: | |
| 64 | return socket.gethostbyname(host) | |
| 65 | except: | |
| 66 | pass | |
| 67 | return host | |
| 68 | ||
| 69 | def parseOutputString(self, output, debug=False): | |
| 70 | ||
| 71 | host_info = re.search(r"Connected to (.+)\.", output) | |
| 72 | ||
| 73 | hostname = host_info.group(1) | |
| 74 | ip_address = self.resolve(hostname) | |
| 75 | ||
| 76 | if host_info is not None: | |
| 77 | h_id = self.createAndAddHost(ip_address) | |
| 78 | i_id = self.createAndAddInterface( | |
| 79 | h_id, ip_address, ipv4_address=ip_address, hostname_resolution=[hostname]) | |
| 80 | s_id = self.createAndAddServiceToInterface(h_id, i_id, self._port, | |
| 81 | "tcp", | |
| 82 | ports=[self._port], | |
| 83 | status="open") | |
| 84 | return True | |
| 85 | ||
| 86 | def processCommandString(self, username, current_path, command_string): | |
| 87 | ||
| 88 | count_args = command_string.split() | |
| 89 | ||
| 90 | c = count_args.__len__() | |
| 91 | self._port = "23" | |
| 92 | if re.search(r"[\d]+", count_args[c - 1]): | |
| 93 | self._port = count_args[c - 1] | |
| 94 | ||
| 95 | ||
| 96 | def createPlugin(): | |
| 97 | return TelnetRouterPlugin() | |
| 98 | ||
| 99 | ||
| 100 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | import re | |
| 8 | import os | |
| 9 | import sys | |
| 10 | ||
| 11 | ||
| 12 | current_path = os.path.abspath(os.getcwd()) | |
| 13 | ||
| 14 | __author__ = "Francisco Amato" | |
| 15 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 16 | __credits__ = ["Francisco Amato"] | |
| 17 | __license__ = "" | |
| 18 | __version__ = "1.0.0" | |
| 19 | __maintainer__ = "Francisco Amato" | |
| 20 | __email__ = "[email protected]" | |
| 21 | __status__ = "Development" | |
| 22 | ||
| 23 | ||
| 24 | class TheharvesterParser: | |
| 25 | """ | |
| 26 | The objective of this class is to parse an xml file generated by the theharvester tool. | |
| 27 | ||
| 28 | TODO: Handle errors. | |
| 29 | TODO: Test theharvester output version. Handle what happens if the parser doesn't support it. | |
| 30 | TODO: Test cases. | |
| 31 | ||
| 32 | @param theharvester_filepath A proper simple report generated by theharvester | |
| 33 | """ | |
| 34 | ||
| 35 | def __init__(self, output): | |
| 36 | ||
| 37 | self.items = [] | |
| 38 | _hosts, _vhosts = [], [] | |
| 39 | ||
| 40 | mregex = re.search( | |
| 41 | "\[\+\] Hosts found in search engines:[-=\s]+([\w\W]*)\[\+\]", output) | |
| 42 | if mregex is None: | |
| 43 | mregex = re.search( | |
| 44 | "\[\+\] Hosts found in search engines:[-=\s]+([\w\W]*)\n", output) | |
| 45 | mregex2 = re.search("\[\+\] Virtual hosts:[-=\s]+([\w\W]*)\n", output) | |
| 46 | ||
| 47 | if mregex is None and mregex2 is None: | |
| 48 | return | |
| 49 | ||
| 50 | if mregex: | |
| 51 | _hosts = mregex.group(1).strip().split("\n") | |
| 52 | if mregex2: | |
| 53 | _vhosts = mregex2.group(1).strip().split("\n") | |
| 54 | ||
| 55 | for line in _hosts: | |
| 56 | ||
| 57 | info = line.split(":") | |
| 58 | ||
| 59 | if len(info) > 1: | |
| 60 | item = {'host': info[1].strip(), 'ip': info[0].strip()} | |
| 61 | ||
| 62 | self.items.append(item) | |
| 63 | ||
| 64 | for line in _vhosts: | |
| 65 | ||
| 66 | info = line.split() | |
| 67 | if len(info) > 1: | |
| 68 | item = {'host': info[1].strip(), 'ip': info[0].strip()} | |
| 69 | ||
| 70 | self.items.append(item) | |
| 71 | ||
| 72 | ||
| 73 | class TheharvesterPlugin(core.PluginBase): | |
| 74 | """ | |
| 75 | Example plugin to parse theharvester output. | |
| 76 | """ | |
| 77 | ||
| 78 | def __init__(self): | |
| 79 | super().__init__() | |
| 80 | self.id = "Theharvester" | |
| 81 | self.name = "Theharvester XML Output Plugin" | |
| 82 | self.plugin_version = "0.0.1" | |
| 83 | self.version = "2.2a" | |
| 84 | self.options = None | |
| 85 | self._current_output = None | |
| 86 | self._current_path = None | |
| 87 | self._command_regex = re.compile( | |
| 88 | r'^(theharvester|sudo theharvester|sudo theHarvester\.py|theHarvester\.py|python theHarvester\.py|\.\/theHarvester\.py).*?') | |
| 89 | self._completition = { | |
| 90 | "": "Examples:./theharvester.py -d microsoft.com -l 500 -b google", | |
| 91 | "-d": "Domain to search or company name", | |
| 92 | "-b": "Data source (google,bing,bingapi,pgp,linkedin,google-profiles,exalead,all)", | |
| 93 | "-s": "Start in result number X (default 0)", | |
| 94 | "-v": "Verify host name via dns resolution and search for vhosts(basic)", | |
| 95 | "-l": "Limit the number of results to work with(bing goes from 50 to 50 results,", | |
| 96 | "-f": "Save the results into an XML file", | |
| 97 | "-n": "Perform a DNS reverse query on all ranges discovered", | |
| 98 | "-c": "Perform a DNS brute force for the domain name", | |
| 99 | "-t": "Perform a DNS TLD expansion discovery", | |
| 100 | "-e": "Use this DNS server", | |
| 101 | "-h": "use SHODAN database to query discovered hosts. google 100 to 100, and pgp doesn't use this option)", | |
| 102 | } | |
| 103 | ||
| 104 | global current_path | |
| 105 | ||
| 106 | def parseOutputString(self, output, debug=False): | |
| 107 | """ | |
| 108 | This method will discard the output the shell sends, it will read it from | |
| 109 | the xml where it expects it to be present. | |
| 110 | ||
| 111 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 112 | output being sent is valid. | |
| 113 | """ | |
| 114 | ||
| 115 | print("este es el output (%s)" % output) | |
| 116 | ||
| 117 | if debug: | |
| 118 | parser = TheharvesterParser(output) | |
| 119 | else: | |
| 120 | ||
| 121 | parser = TheharvesterParser(output) | |
| 122 | ||
| 123 | print(len(parser.items)) | |
| 124 | for item in parser.items: | |
| 125 | host = [] | |
| 126 | if item['host'] != item['ip']: | |
| 127 | host = [item['host']] | |
| 128 | h_id = self.createAndAddHost(item['ip']) | |
| 129 | i_id = self.createAndAddInterface(h_id, item['ip'], ipv4_address=item[ | |
| 130 | 'ip'], hostname_resolution=host) | |
| 131 | ||
| 132 | del parser | |
| 133 | ||
| 134 | def processCommandString(self, username, current_path, command_string): | |
| 135 | """ | |
| 136 | """ | |
| 137 | return None | |
| 138 | ||
| 139 | ||
| 140 | def createPlugin(): | |
| 141 | return TheharvesterPlugin() | |
| 142 | ||
| 143 | ||
| 144 | ||
| 145 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | import re | |
| 8 | ||
| 9 | __author__ = "Ezequiel Tavella - @EzequielTBH" | |
| 10 | __copyright__ = "Copyright 2015, @EzequielTBH" | |
| 11 | __credits__ = "Ezequiel Tavella - @EzequielTBH" | |
| 12 | __license__ = "GPL v3" | |
| 13 | __version__ = "1.0.0" | |
| 14 | ||
| 15 | ||
| 16 | class traceroutePlugin(core.PluginBase): | |
| 17 | ||
| 18 | def __init__(self): | |
| 19 | super().__init__() | |
| 20 | self.id = "Traceroute" | |
| 21 | self.name = "Traceroute" | |
| 22 | self.plugin_version = "1.0.0" | |
| 23 | self.command_string = "" | |
| 24 | self._command_regex = re.compile( | |
| 25 | r'^(traceroute|traceroute6).*?') | |
| 26 | ||
| 27 | def parseOutputString(self, output, debug=False): | |
| 28 | ||
| 29 | print("[*]Parsing Output...") | |
| 30 | ||
| 31 | # Check no results. | |
| 32 | if output.startswith("traceroute to") == False: | |
| 33 | return | |
| 34 | ||
| 35 | # Check if last parameter is host or ( packetlen or data size). | |
| 36 | parameters = self.command_string.split(' ') | |
| 37 | parameters.reverse() | |
| 38 | hostName = parameters[0] | |
| 39 | ||
| 40 | try: | |
| 41 | int(hostName) | |
| 42 | # No exception => host is the next item. | |
| 43 | hostName = parameters[1] | |
| 44 | except: | |
| 45 | pass | |
| 46 | ||
| 47 | # Add host and note with output of traceroute. | |
| 48 | hostId = self.createAndAddHost(hostName) | |
| 49 | self.createAndAddNoteToHost(hostId, "Traceroute Results", output) | |
| 50 | ||
| 51 | print("[*]Parse finished, API faraday called...") | |
| 52 | ||
| 53 | def processCommandString(self, username, current_path, command_string): | |
| 54 | ||
| 55 | print("[*]traceroute Plugin running...") | |
| 56 | self.command_string = command_string | |
| 57 | return command_string | |
| 58 | ||
| 59 | ||
| 60 | def createPlugin(): | |
| 61 | return traceroutePlugin() | |
| 62 | ||
| 63 | ||
| 64 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | ||
| 7 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 8 | from faraday.client.model import api | |
| 9 | import re | |
| 10 | import os | |
| 11 | import socket | |
| 12 | import pprint | |
| 13 | import sys | |
| 14 | ||
| 15 | try: | |
| 16 | import xml.etree.cElementTree as ET | |
| 17 | import xml.etree.ElementTree as ET_ORIG | |
| 18 | ETREE_VERSION = ET_ORIG.VERSION | |
| 19 | except ImportError: | |
| 20 | import xml.etree.ElementTree as ET | |
| 21 | ETREE_VERSION = ET.VERSION | |
| 22 | ||
| 23 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 24 | ||
| 25 | current_path = os.path.abspath(os.getcwd()) | |
| 26 | ||
| 27 | __author__ = "Francisco Amato" | |
| 28 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 29 | __credits__ = ["Francisco Amato"] | |
| 30 | __license__ = "" | |
| 31 | __version__ = "1.0.0" | |
| 32 | __maintainer__ = "Francisco Amato" | |
| 33 | __email__ = "[email protected]" | |
| 34 | __status__ = "Development" | |
| 35 | ||
| 36 | ||
| 37 | class W3afXmlParser: | |
| 38 | """ | |
| 39 | The objective of this class is to parse an xml file generated by the w3af tool. | |
| 40 | ||
| 41 | TODO: Handle errors. | |
| 42 | TODO: Test w3af output version. Handle what happens if the parser doesn't support it. | |
| 43 | TODO: Test cases. | |
| 44 | ||
| 45 | @param w3af_xml_filepath A proper xml generated by w3af | |
| 46 | """ | |
| 47 | ||
| 48 | def __init__(self, xml_output): | |
| 49 | self.target = None | |
| 50 | self.port = "80" | |
| 51 | self.host = None | |
| 52 | ||
| 53 | tree = self.parse_xml(xml_output) | |
| 54 | ||
| 55 | if tree: | |
| 56 | self.items = list(self.get_items(tree)) | |
| 57 | else: | |
| 58 | self.items = [] | |
| 59 | ||
| 60 | def parse_xml(self, xml_output): | |
| 61 | """ | |
| 62 | Open and parse an xml file. | |
| 63 | ||
| 64 | TODO: Write custom parser to just read the nodes that we need instead of | |
| 65 | reading the whole file. | |
| 66 | ||
| 67 | @return xml_tree An xml tree instance. None if error. | |
| 68 | """ | |
| 69 | try: | |
| 70 | tree = ET.fromstring(xml_output) | |
| 71 | except SyntaxError as err: | |
| 72 | print("SyntaxError: %s. %s" % (err, xml_output)) | |
| 73 | return None | |
| 74 | ||
| 75 | return tree | |
| 76 | ||
| 77 | def get_items(self, tree): | |
| 78 | """ | |
| 79 | @return items A list of Host instances | |
| 80 | """ | |
| 81 | bugtype = "" | |
| 82 | ||
| 83 | if len(tree.findall('scan-info')) == 0: | |
| 84 | scaninfo = tree.findall('scaninfo')[0] | |
| 85 | else: | |
| 86 | scaninfo = tree.findall('scan-info')[0] | |
| 87 | ||
| 88 | self.target = scaninfo.get('target') | |
| 89 | host = re.search( | |
| 90 | "(http|https|ftp)\://([a-zA-Z0-9\.\-]+(\:[a-zA-Z0-9\.&%\$\-]+)*@)*((25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9])\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9]|0)\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9]|0)\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[0-9])|localhost|([a-zA-Z0-9\-]+\.)*[a-zA-Z0-9\-]+\.(com|edu|gov|int|mil|net|org|biz|arpa|info|name|pro|aero|coop|museum|[a-zA-Z]{2}))[\:]*([0-9]+)*([/]*($|[a-zA-Z0-9\.\,\?\'\\\+&%\$#\=~_\-]+)).*?$", self.target) | |
| 91 | ||
| 92 | self.protocol = host.group(1) | |
| 93 | self.host = host.group(4) | |
| 94 | if self.protocol == 'https': | |
| 95 | self.port = 443 | |
| 96 | if host.group(11) is not None: | |
| 97 | self.port = host.group(11) | |
| 98 | ||
| 99 | for node in tree.findall('vulnerability'): | |
| 100 | yield Item(node) | |
| 101 | for node in tree.findall('information'): | |
| 102 | yield Item(node) | |
| 103 | ||
| 104 | ||
| 105 | def get_attrib_from_subnode(xml_node, subnode_xpath_expr, attrib_name): | |
| 106 | """ | |
| 107 | Finds a subnode in the item node and the retrieves a value from it | |
| 108 | ||
| 109 | @return An attribute value | |
| 110 | """ | |
| 111 | global ETREE_VERSION | |
| 112 | node = None | |
| 113 | ||
| 114 | if ETREE_VERSION[0] <= 1 and ETREE_VERSION[1] < 3: | |
| 115 | ||
| 116 | match_obj = re.search( | |
| 117 | "([^\@]+?)\[\@([^=]*?)=\'([^\']*?)\'", subnode_xpath_expr) | |
| 118 | if match_obj is not None: | |
| 119 | node_to_find = match_obj.group(1) | |
| 120 | xpath_attrib = match_obj.group(2) | |
| 121 | xpath_value = match_obj.group(3) | |
| 122 | for node_found in xml_node.findall(node_to_find): | |
| 123 | if node_found.attrib[xpath_attrib] == xpath_value: | |
| 124 | node = node_found | |
| 125 | break | |
| 126 | else: | |
| 127 | node = xml_node.find(subnode_xpath_expr) | |
| 128 | ||
| 129 | else: | |
| 130 | node = xml_node.find(subnode_xpath_expr) | |
| 131 | ||
| 132 | if node is not None: | |
| 133 | return node.get(attrib_name) | |
| 134 | ||
| 135 | return None | |
| 136 | ||
| 137 | ||
| 138 | class Item: | |
| 139 | """ | |
| 140 | An abstract representation of a Item | |
| 141 | ||
| 142 | ||
| 143 | @param item_node A item_node taken from an w3af xml tree | |
| 144 | """ | |
| 145 | ||
| 146 | def __init__(self, item_node): | |
| 147 | self.node = item_node | |
| 148 | ||
| 149 | self.id = self.node.get('id') | |
| 150 | self.name = self.node.get('name') | |
| 151 | self.url = self.node.get('url') | |
| 152 | self.url = self.url if self.url != 'None' else "/" | |
| 153 | self.plugin = self.node.get('plugin') | |
| 154 | self.detail = self.get_text_from_subnode('description') | |
| 155 | self.resolution = self.get_text_from_subnode('fix-guidance') | |
| 156 | self.fix_effort = self.get_text_from_subnode('fix-effort') | |
| 157 | self.longdetail = self.get_text_from_subnode('description') | |
| 158 | self.severity = self.node.get('severity') | |
| 159 | self.method = self.node.get('method') | |
| 160 | self.ref = [] | |
| 161 | self.param = self.node.get('var') if self.node.get( | |
| 162 | 'var') != "None" else "" | |
| 163 | for ref in self.node.findall('references/reference'): | |
| 164 | self.ref.append(ref.get('url')) | |
| 165 | ||
| 166 | self.req = self.resp = '' | |
| 167 | for tx in self.node.findall('http-transactions/http-transaction'): | |
| 168 | if tx.find('http-request'): | |
| 169 | hreq = tx.find('http-request') | |
| 170 | else: | |
| 171 | hreq = tx.find('httprequest') | |
| 172 | ||
| 173 | if tx.find('http-response'): | |
| 174 | hres = tx.find('http-response') | |
| 175 | else: | |
| 176 | hres = tx.find('httpresponse') | |
| 177 | ||
| 178 | self.req = hreq.find('status').text | |
| 179 | for h in hreq.findall('headers/header'): | |
| 180 | self.req += "\n%s: %s" % (h.get('field'), h.get('content')) | |
| 181 | ||
| 182 | self.resp = hres.find('status').text | |
| 183 | for h in hres.findall('headers/header'): | |
| 184 | self.resp += "\n%s: %s" % (h.get('field'), h.get('content')) | |
| 185 | ||
| 186 | if hres.find('body'): | |
| 187 | self.resp += "\n%s" % hres.find('body').text | |
| 188 | ||
| 189 | def do_clean(self, value): | |
| 190 | myreturn = "" | |
| 191 | if value is not None: | |
| 192 | myreturn = re.sub("\n", "", value) | |
| 193 | return myreturn | |
| 194 | ||
| 195 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 196 | """ | |
| 197 | Finds a subnode in the host node and the retrieves a value from it. | |
| 198 | ||
| 199 | @return An attribute value | |
| 200 | """ | |
| 201 | sub_node = self.node.find(subnode_xpath_expr) | |
| 202 | if sub_node is not None: | |
| 203 | return sub_node.text | |
| 204 | ||
| 205 | return None | |
| 206 | ||
| 207 | ||
| 208 | class W3afPlugin(PluginXMLFormat): | |
| 209 | """ | |
| 210 | Example plugin to parse w3af output. | |
| 211 | """ | |
| 212 | ||
| 213 | def __init__(self): | |
| 214 | super().__init__() | |
| 215 | self.identifier_tag = "w3af-run" | |
| 216 | self.id = "W3af" | |
| 217 | self.name = "W3af XML Output Plugin" | |
| 218 | self.plugin_version = "0.0.2" | |
| 219 | self.version = "1.7.6" | |
| 220 | self.framework_version = "1.0.0" | |
| 221 | self.options = None | |
| 222 | self._current_output = None | |
| 223 | self.target = None | |
| 224 | self._command_regex = re.compile(r'^(w3af|sudo w3af|\.\/w3af).*?') | |
| 225 | self._completition = { | |
| 226 | "": "", | |
| 227 | "-h": "Display this help message.", | |
| 228 | } | |
| 229 | ||
| 230 | global current_path | |
| 231 | self._output_file_path = os.path.join(self.data_path, | |
| 232 | "w3af_output-%s.xml" % self._rid) | |
| 233 | ||
| 234 | def parseOutputString(self, output, debug=False): | |
| 235 | ||
| 236 | parser = W3afXmlParser(output) | |
| 237 | ||
| 238 | ip = self.resolve(parser.host) | |
| 239 | h_id = self.createAndAddHost(ip) | |
| 240 | i_id = self.createAndAddInterface( | |
| 241 | h_id, ip, ipv4_address=ip, hostname_resolution=[parser.host]) | |
| 242 | s_id = self.createAndAddServiceToInterface(h_id, i_id, "http", | |
| 243 | "tcp", | |
| 244 | ports=[parser.port], | |
| 245 | status="open") | |
| 246 | ||
| 247 | for item in parser.items: | |
| 248 | v_id = self.createAndAddVulnWebToService(h_id, s_id, item.name, | |
| 249 | item.detail, pname=item.param, path=item.url, website=parser.host, severity=item.severity, | |
| 250 | method=item.method, request=item.req, resolution=item.resolution, ref=item.ref, response=item.resp) | |
| 251 | del parser | |
| 252 | ||
| 253 | def resolve(self, host): | |
| 254 | try: | |
| 255 | return socket.gethostbyname(host) | |
| 256 | except: | |
| 257 | pass | |
| 258 | return host | |
| 259 | ||
| 260 | def processCommandString(self, username, current_path, command_string): | |
| 261 | return None | |
| 262 | ||
| 263 | def setHost(self): | |
| 264 | pass | |
| 265 | ||
| 266 | ||
| 267 | def createPlugin(): | |
| 268 | return W3afPlugin() | |
| 269 | ||
| 270 | ||
| 271 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | import re | |
| 7 | import os | |
| 8 | import socket | |
| 9 | ||
| 10 | from urllib.parse import urlparse | |
| 11 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 12 | try: | |
| 13 | import xml.etree.cElementTree as ET | |
| 14 | import xml.etree.ElementTree as ET_ORIG | |
| 15 | ETREE_VERSION = ET_ORIG.VERSION | |
| 16 | except ImportError: | |
| 17 | import xml.etree.ElementTree as ET | |
| 18 | ETREE_VERSION = ET.VERSION | |
| 19 | ||
| 20 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 21 | ||
| 22 | current_path = os.path.abspath(os.getcwd()) | |
| 23 | ||
| 24 | __author__ = "Francisco Amato" | |
| 25 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 26 | __credits__ = ["Francisco Amato"] | |
| 27 | __license__ = "" | |
| 28 | __version__ = "1.0.0" | |
| 29 | __maintainer__ = "Francisco Amato" | |
| 30 | __email__ = "[email protected]" | |
| 31 | __status__ = "Development" | |
| 32 | ||
| 33 | ||
| 34 | class WapitiXmlParser: | |
| 35 | """ | |
| 36 | The objective of this class is to parse an xml file generated by the wapiti tool. | |
| 37 | ||
| 38 | TODO: Handle errors. | |
| 39 | TODO: Test wapiti output version. Handle what happens if the parser doesn't support it. | |
| 40 | TODO: Test cases. | |
| 41 | ||
| 42 | @param wapiti_xml_filepath A proper xml generated by wapiti | |
| 43 | """ | |
| 44 | ||
| 45 | def __init__(self, xml_output): | |
| 46 | tree = self.parse_xml(xml_output) | |
| 47 | if tree: | |
| 48 | self.items = list(self.get_items(tree)) | |
| 49 | else: | |
| 50 | self.items = [] | |
| 51 | ||
| 52 | def parse_xml(self, xml_output): | |
| 53 | """ | |
| 54 | Open and parse an xml file. | |
| 55 | ||
| 56 | TODO: Write custom parser to just read the nodes that we need instead of | |
| 57 | reading the whole file. | |
| 58 | ||
| 59 | @return xml_tree An xml tree instance. None if error. | |
| 60 | """ | |
| 61 | try: | |
| 62 | tree = ET.fromstring(xml_output) | |
| 63 | except SyntaxError as err: | |
| 64 | print("SyntaxError: %s. %s" % (err, xml_output)) | |
| 65 | return None | |
| 66 | ||
| 67 | return tree | |
| 68 | ||
| 69 | def get_items(self, tree): | |
| 70 | """ | |
| 71 | @return items A list of Host instances | |
| 72 | """ | |
| 73 | ||
| 74 | yield Item(tree) | |
| 75 | ||
| 76 | ||
| 77 | ||
| 78 | def get_attrib_from_subnode(xml_node, subnode_xpath_expr, attrib_name): | |
| 79 | """ | |
| 80 | Finds a subnode in the item node and the retrieves a value from it | |
| 81 | ||
| 82 | @return An attribute value | |
| 83 | """ | |
| 84 | global ETREE_VERSION | |
| 85 | node = None | |
| 86 | ||
| 87 | if ETREE_VERSION[0] <= 1 and ETREE_VERSION[1] < 3: | |
| 88 | match_obj = re.search( | |
| 89 | "([^\@]+?)\[\@([^=]*?)=\'([^\']*?)\'", subnode_xpath_expr) | |
| 90 | if match_obj is not None: | |
| 91 | node_to_find = match_obj.group(1) | |
| 92 | xpath_attrib = match_obj.group(2) | |
| 93 | xpath_value = match_obj.group(3) | |
| 94 | for node_found in xml_node.findall(node_to_find): | |
| 95 | if node_found.attrib[xpath_attrib] == xpath_value: | |
| 96 | node = node_found | |
| 97 | break | |
| 98 | else: | |
| 99 | node = xml_node.find(subnode_xpath_expr) | |
| 100 | else: | |
| 101 | node = xml_node.find(subnode_xpath_expr) | |
| 102 | if node is not None: | |
| 103 | return node.get(attrib_name) | |
| 104 | return None | |
| 105 | ||
| 106 | ||
| 107 | class Item: | |
| 108 | """ | |
| 109 | An abstract representation of a Item | |
| 110 | ||
| 111 | TODO: Consider evaluating the attributes lazily | |
| 112 | TODO: Write what's expected to be present in the nodes | |
| 113 | TODO: Refactor both Host and the Port clases? | |
| 114 | ||
| 115 | @param item_node A item_node taken from an wapiti xml tree | |
| 116 | """ | |
| 117 | ||
| 118 | def __init__(self, item_node): | |
| 119 | self.node = item_node | |
| 120 | self.url = self.get_url(item_node) | |
| 121 | self.ip = socket.gethostbyname(self.url.hostname) | |
| 122 | self.hostname = self.url.hostname | |
| 123 | self.port = self.get_port(self.url) | |
| 124 | self.scheme = self.url.scheme | |
| 125 | self.vulns = self.get_vulns(item_node) | |
| 126 | ||
| 127 | def do_clean(self, value): | |
| 128 | myreturn = "" | |
| 129 | if value is not None: | |
| 130 | myreturn = re.sub("\n", "", value) | |
| 131 | return myreturn | |
| 132 | ||
| 133 | def get_text_from_subnode(self, node, subnode_xpath_expr): | |
| 134 | """ | |
| 135 | Finds a subnode in the host node and the retrieves a value from it. | |
| 136 | ||
| 137 | @return An attribute value | |
| 138 | """ | |
| 139 | sub_node = node.find(subnode_xpath_expr) | |
| 140 | if sub_node is not None: | |
| 141 | return sub_node.text.strip() | |
| 142 | ||
| 143 | return None | |
| 144 | ||
| 145 | def get_url(self, item_node): | |
| 146 | target = self.get_info(item_node,'target') | |
| 147 | return urlparse(target) | |
| 148 | ||
| 149 | def get_info(self, item_node,name): | |
| 150 | path = item_node.findall('report_infos/info') | |
| 151 | ||
| 152 | for item in path: | |
| 153 | if item.attrib['name'] == name: | |
| 154 | return item.text | |
| 155 | ||
| 156 | def get_port(self, url): | |
| 157 | if url.port: | |
| 158 | return url.port | |
| 159 | else: | |
| 160 | if url.scheme == "http": | |
| 161 | return "80" | |
| 162 | elif url.scheme == "https": | |
| 163 | return "443" | |
| 164 | ||
| 165 | def get_vulns(self, item_node): | |
| 166 | vulns_node = item_node.findall('vulnerabilities/vulnerability') | |
| 167 | vulns_list = [] | |
| 168 | ||
| 169 | for vuln in vulns_node: | |
| 170 | vulns_dict = {} | |
| 171 | vulns_dict['id'] = vuln.attrib['name'] | |
| 172 | vulns_dict['description'] = self.get_text_from_subnode(vuln,'description') | |
| 173 | vulns_dict['solution'] = self.get_text_from_subnode(vuln,'solution') | |
| 174 | vulns_dict['references'] = self.get_references(vuln) | |
| 175 | vulns_dict['entries'] = self.get_entries(vuln) | |
| 176 | vulns_list.append(vulns_dict) | |
| 177 | ||
| 178 | return vulns_list | |
| 179 | ||
| 180 | def get_references(self, node): | |
| 181 | refs = node.findall('references/reference') | |
| 182 | references_list = [] | |
| 183 | for ref in refs: | |
| 184 | references_list.append('Title: ' + self.get_text_from_subnode(ref,'title')) | |
| 185 | references_list.append('URL: ' + self.get_text_from_subnode(ref,'url')) | |
| 186 | ||
| 187 | return references_list | |
| 188 | ||
| 189 | def get_entries(self,node): | |
| 190 | entries = node.findall('entries/entry') | |
| 191 | entries_list = [] | |
| 192 | for entry in entries: | |
| 193 | entries_dict = {} | |
| 194 | entries_dict['method'] = self.get_text_from_subnode(entry,'method') | |
| 195 | entries_dict['path'] = self.get_text_from_subnode(entry,'path') | |
| 196 | entries_dict['level'] = self.severity_format(entry) | |
| 197 | entries_dict['parameter'] = self.get_text_from_subnode(entry,'parameter') | |
| 198 | entries_dict['http_request'] = self.get_text_from_subnode(entry,'http_request') | |
| 199 | entries_dict['curl_command'] = self.get_text_from_subnode(entry,'curl_command') | |
| 200 | entries_list.append(entries_dict) | |
| 201 | ||
| 202 | return entries_list | |
| 203 | ||
| 204 | def severity_format(self, node): | |
| 205 | """ | |
| 206 | Convert Nexpose severity format into Faraday API severity format | |
| 207 | ||
| 208 | @return a severity | |
| 209 | """ | |
| 210 | severity = self.get_text_from_subnode(node, 'level') | |
| 211 | ||
| 212 | if severity == '1': | |
| 213 | return 'high' | |
| 214 | elif severity == '2': | |
| 215 | return 'medium' | |
| 216 | elif severity == '3': | |
| 217 | return 'low' | |
| 218 | ||
| 219 | ||
| 220 | class WapitiPlugin(PluginXMLFormat): | |
| 221 | """ | |
| 222 | Example plugin to parse wapiti output. | |
| 223 | """ | |
| 224 | ||
| 225 | def __init__(self): | |
| 226 | super().__init__() | |
| 227 | self.identifier_tag = "report" | |
| 228 | self.id = "Wapiti" | |
| 229 | self.name = "Wapiti XML Output Plugin" | |
| 230 | self.plugin_version = "0.0.1" | |
| 231 | self.version = "2.2.1" | |
| 232 | self.options = None | |
| 233 | self._current_output = None | |
| 234 | self.protocol = None | |
| 235 | self.host = None | |
| 236 | self.port = "80" | |
| 237 | self.xml_arg_re = re.compile(r"^.*(-oX\s*[^\s]+).*$") | |
| 238 | self._command_regex = re.compile( | |
| 239 | r'^(python wapiti|wapiti|sudo wapiti|sudo wapiti\.py|wapiti\.py|python wapiti\.py|\.\/wapiti\.py|wapiti|\.\/wapiti|python wapiti|python \.\/wapiti).*?') | |
| 240 | self._completition = { | |
| 241 | "": "python wapiti.py http://server.com/base/url/ [options]", | |
| 242 | "-s": "<url> ", | |
| 243 | "--start": "<url> ", | |
| 244 | "-x": "<url> ", | |
| 245 | "--exclude": "<url> ", | |
| 246 | "-p": "<url_proxy> ", | |
| 247 | "--proxy": "<url_proxy> ", | |
| 248 | "-c": " -c <cookie_file> ", | |
| 249 | "--cookie": "<cookie_file> ", | |
| 250 | "-t": "<timeout> ", | |
| 251 | "--timeout": "<timeout> ", | |
| 252 | "-a": "<login%password> ", | |
| 253 | "--auth": "<login%password> ", | |
| 254 | "-r": "<parameter_name> ", | |
| 255 | "--remove": "<parameter_name> ", | |
| 256 | "-n": "<limit> ", | |
| 257 | "--nice": "<limit> ", | |
| 258 | "-m": "<module_options> Set the modules and HTTP methods to use for attacks. Example: -m \"-all,xss:get,exec:post\"", | |
| 259 | "--module": "<module_options> Set the modules and HTTP methods to use for attacks. Example: -m \"-all,xss:get,exec:post\"", | |
| 260 | "-u": "Use color to highlight vulnerables parameters in output", | |
| 261 | "--underline": "Use color to highlight vulnerables parameters in output", | |
| 262 | "-v": "<level> ", | |
| 263 | "--verbose": "<level> ", | |
| 264 | "-b": "<scope>", | |
| 265 | "--scope": "<scope>", | |
| 266 | "-f": "<type_file> ", | |
| 267 | "--reportType": "<type_file> ", | |
| 268 | "-o": "<output_file> ", | |
| 269 | "--output": "<output_file> ", | |
| 270 | "-i": "<file>", | |
| 271 | "--continue": "<file>", | |
| 272 | "-k": "<file>", | |
| 273 | "--attack": "<file>", | |
| 274 | "-h": "To print this usage message", | |
| 275 | "--help": "To print this usage message", | |
| 276 | } | |
| 277 | ||
| 278 | global current_path | |
| 279 | self._output_file_path = os.path.join(self.data_path, "wapiti_output-%s.xml" % self._rid) | |
| 280 | ||
| 281 | def report_belongs_to(self, **kwargs): | |
| 282 | if super().report_belongs_to(**kwargs): | |
| 283 | report_path = kwargs.get("report_path", "") | |
| 284 | with open(report_path) as f: | |
| 285 | output = f.read() | |
| 286 | return re.search("Wapiti", output) is not None | |
| 287 | return False | |
| 288 | ||
| 289 | ||
| 290 | def parseOutputString(self, output): | |
| 291 | """ | |
| 292 | This method will discard the output the shell sends, it will read it from | |
| 293 | the xml where it expects it to be present. | |
| 294 | """ | |
| 295 | ||
| 296 | parser = WapitiXmlParser(output) | |
| 297 | for item in parser.items: | |
| 298 | host_id = self.createAndAddHost(item.ip, hostnames=[item.hostname]) | |
| 299 | service_id = self.createAndAddServiceToHost(host_id, item.scheme, protocol='tcp', ports=[item.port]) | |
| 300 | for vuln in item.vulns: | |
| 301 | for entry in vuln['entries']: | |
| 302 | vuln_id = self.createAndAddVulnWebToService(host_id, | |
| 303 | service_id, | |
| 304 | vuln['id'], | |
| 305 | desc=vuln['description'], | |
| 306 | ref=vuln['references'], | |
| 307 | resolution=vuln['solution'], | |
| 308 | severity=entry['level'], | |
| 309 | website=entry['curl_command'], | |
| 310 | path=entry['path'], | |
| 311 | request=entry['http_request'], | |
| 312 | method=entry['method'], | |
| 313 | params=entry['parameter']) | |
| 314 | ||
| 315 | def processCommandString(self, username, current_path, command_string): | |
| 316 | """ | |
| 317 | Adds the -oX parameter to get xml output to the command string that the | |
| 318 | user has set. | |
| 319 | """ | |
| 320 | host = re.search( | |
| 321 | "(http|https|ftp)\://([a-zA-Z0-9\.\-]+(\:[a-zA-Z0-9\.&%\$\-]+)*@)*((25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9])\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9]|0)\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[1-9]|0)\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|[0-9])|localhost|([a-zA-Z0-9\-]+\.)*[a-zA-Z0-9\-]+\.(com|edu|gov|int|mil|net|org|biz|arpa|info|name|pro|aero|coop|museum|[a-zA-Z]{2}))[\:]*([0-9]+)*([/]*($|[a-zA-Z0-9\.\,\?\'\\\+&%\$#\=~_\-]+)).*?$", command_string) | |
| 322 | self.protocol = host.group(1) | |
| 323 | self.host = host.group(4) | |
| 324 | if host.group(11) is not None: | |
| 325 | self.port = host.group(11) | |
| 326 | if self.protocol == 'https': | |
| 327 | self.port = 443 | |
| 328 | self.logger.debug("host = %s, port = %s",self.host, self.port) | |
| 329 | arg_match = self.xml_arg_re.match(command_string) | |
| 330 | return "%s -o %s -f xml \n" % (command_string, self._output_file_path) | |
| 331 | ||
| 332 | def setHost(self): | |
| 333 | pass | |
| 334 | ||
| 335 | ||
| 336 | def createPlugin(): | |
| 337 | return WapitiPlugin() | |
| 338 | ||
| 339 | ||
| 340 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import core | |
| 6 | import re | |
| 7 | import os | |
| 8 | import sys | |
| 9 | import random | |
| 10 | ||
| 11 | try: | |
| 12 | import xml.etree.cElementTree as ET | |
| 13 | import xml.etree.ElementTree as ET_ORIG | |
| 14 | ETREE_VERSION = ET_ORIG.VERSION | |
| 15 | except ImportError: | |
| 16 | import xml.etree.ElementTree as ET | |
| 17 | ETREE_VERSION = ET.VERSION | |
| 18 | ||
| 19 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 20 | ||
| 21 | current_path = os.path.abspath(os.getcwd()) | |
| 22 | ||
| 23 | __author__ = "Morgan Lemarechal" | |
| 24 | __copyright__ = "Copyright 2014, Faraday Project" | |
| 25 | __credits__ = ["Morgan Lemarechal"] | |
| 26 | __license__ = "" | |
| 27 | __version__ = "1.0.0" | |
| 28 | __maintainer__ = "Morgan Lemarechal" | |
| 29 | __email__ = "[email protected]" | |
| 30 | __status__ = "Development" | |
| 31 | ||
| 32 | ||
| 33 | class WcscanParser: | |
| 34 | """ | |
| 35 | The objective of this class is to parse an xml file generated by the wcscan tool. | |
| 36 | TODO: Handle errors. | |
| 37 | TODO: Test wcscan output version. Handle what happens if the parser doesn't support it. | |
| 38 | TODO: Test cases. | |
| 39 | @param wcscan_filepath A proper simple report generated by wcscan | |
| 40 | """ | |
| 41 | ||
| 42 | def __init__(self, output): | |
| 43 | self.scaninfo = {} | |
| 44 | self.result = {} | |
| 45 | tree = ET.parse(output) | |
| 46 | root = tree.getroot() | |
| 47 | for scan in root.findall(".//scan"): | |
| 48 | infos = {} | |
| 49 | for info in scan.attrib: | |
| 50 | infos[info] = scan.attrib[info] | |
| 51 | self.scaninfo[scan.attrib['file']] = infos | |
| 52 | ||
| 53 | item = {} | |
| 54 | if scan.attrib['type'] == "phpini": | |
| 55 | for carac in scan: | |
| 56 | item[carac.tag] = [carac.text, carac.attrib['rec'], ""] | |
| 57 | ||
| 58 | if scan.attrib['type'] == "webconfig": | |
| 59 | id = 0 | |
| 60 | for carac in scan: | |
| 61 | id += 1 | |
| 62 | item[id] = [carac.text, carac.attrib['rec'], | |
| 63 | carac.attrib['option'], carac.tag] | |
| 64 | ||
| 65 | self.result[scan.attrib['file']] = item | |
| 66 | ||
| 67 | ||
| 68 | class WcscanPlugin(core.PluginBase): | |
| 69 | """ | |
| 70 | Example plugin to parse wcscan output. | |
| 71 | """ | |
| 72 | ||
| 73 | def __init__(self): | |
| 74 | super().__init__() | |
| 75 | self.id = "Wcscan" | |
| 76 | self.name = "Wcscan XML Output Plugin" | |
| 77 | self.plugin_version = "0.0.2" | |
| 78 | self.version = "0.30" | |
| 79 | self._completition = { | |
| 80 | "": "wcscan [-h] [-r] [-host HOST] [-port PORT] [--xml XMLOUTPUT] [--version] files [files ...]", | |
| 81 | "-h": "show this help message and exit", | |
| 82 | "-r": "enable the recommendation mode", | |
| 83 | "--host": "to give the IP address of the conf file owner", | |
| 84 | "--port": "to give a associated port", | |
| 85 | "--xml": "enabled the XML output in a specified file", | |
| 86 | "--version": "Show program's version number and exit", | |
| 87 | } | |
| 88 | ||
| 89 | self.options = None | |
| 90 | self._current_output = None | |
| 91 | self.current_path = None | |
| 92 | self._command_regex = re.compile( | |
| 93 | r'^(sudo wcscan|wcscan|\.\/wcscan).*?') | |
| 94 | ||
| 95 | global current_path | |
| 96 | self._output_file_path = os.path.join(self.data_path, "%s_%s_output-%s.xml" % (self.get_ws(), | |
| 97 | self.id, | |
| 98 | random.uniform(1, 10))) | |
| 99 | ||
| 100 | def canParseCommandString(self, current_input): | |
| 101 | if self._command_regex.match(current_input.strip()): | |
| 102 | return True | |
| 103 | else: | |
| 104 | return False | |
| 105 | ||
| 106 | def parseOutputString(self, output, debug=False): | |
| 107 | """ | |
| 108 | This method will discard the output the shell sends, it will read it from | |
| 109 | the xml where it expects it to be present. | |
| 110 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 111 | output being sent is valid. | |
| 112 | """ | |
| 113 | if debug: | |
| 114 | parser = WcscanParser(self._output_file_path) | |
| 115 | else: | |
| 116 | ||
| 117 | if not os.path.exists(self._output_file_path): | |
| 118 | return False | |
| 119 | parser = WcscanParser(self._output_file_path) | |
| 120 | ||
| 121 | for file in parser.scaninfo: | |
| 122 | host = parser.scaninfo[file]['host'] | |
| 123 | port = parser.scaninfo[file]['port'] | |
| 124 | h_id = self.createAndAddHost(host) | |
| 125 | if(re.match("(^[2][0-5][0-5]|^[1]{0,1}[0-9]{1,2})\.([0-2][0-5][0-5]|[1]{0,1}[0-9]{1,2})\.([0-2][0-5][0-5]|[1]{0,1}[0-9]{1,2})\.([0-2][0-5][0-5]|[1]{0,1}[0-9]{1,2})$", host)): | |
| 126 | i_id = self.createAndAddInterface(h_id, | |
| 127 | host, | |
| 128 | ipv4_address=host) | |
| 129 | else: | |
| 130 | i_id = self.createAndAddInterface(h_id, | |
| 131 | host, | |
| 132 | ipv6_address=host) | |
| 133 | ||
| 134 | s_id = self.createAndAddServiceToInterface( | |
| 135 | h_id, i_id, "http", protocol="tcp", ports=port) | |
| 136 | for vuln in parser.result[file]: | |
| 137 | if parser.scaninfo[file]['type'] == "phpini": | |
| 138 | v_id = self.createAndAddVulnToService(h_id, s_id, | |
| 139 | parser.scaninfo[file][ | |
| 140 | 'file'] + ":" + vuln, | |
| 141 | desc="{} : {}\n{}".format(vuln, | |
| 142 | str(parser.result[ | |
| 143 | file][vuln][0]), | |
| 144 | str(parser.result[file][vuln][1])), | |
| 145 | severity=0) | |
| 146 | ||
| 147 | if parser.scaninfo[file]['type'] == "webconfig": | |
| 148 | v_id = self.createAndAddVulnToService(h_id, s_id, | |
| 149 | parser.scaninfo[file][ | |
| 150 | 'file'] + ":" + str(parser.result[file][vuln][3]), | |
| 151 | desc="{} : {} = {}\n{}".format(str(parser.result[file][vuln][3]), | |
| 152 | str(parser.result[ | |
| 153 | file][vuln][2]), | |
| 154 | str(parser.result[ | |
| 155 | file][vuln][0]), | |
| 156 | str(parser.result[file][vuln][1])), | |
| 157 | severity=0) | |
| 158 | del parser | |
| 159 | ||
| 160 | return True | |
| 161 | ||
| 162 | xml_arg_re = re.compile(r"^.*(--xml\s*[^\s]+).*$") | |
| 163 | ||
| 164 | def processCommandString(self, username, current_path, command_string): | |
| 165 | """ | |
| 166 | Adds the parameter to get output to the command string that the | |
| 167 | user has set. | |
| 168 | """ | |
| 169 | ||
| 170 | arg_match = self.xml_arg_re.match(command_string) | |
| 171 | ||
| 172 | if arg_match is None: | |
| 173 | return "%s --xml %s" % (command_string, self._output_file_path) | |
| 174 | else: | |
| 175 | return re.sub(arg_match.group(1), | |
| 176 | r"-xml %s" % self._output_file_path, | |
| 177 | command_string) | |
| 178 | ||
| 179 | ||
| 180 | def createPlugin(): | |
| 181 | return WcscanPlugin() | |
| 182 | ||
| 183 | ||
| 184 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | from faraday.client.model import api | |
| 8 | import re | |
| 9 | import os | |
| 10 | import pprint | |
| 11 | import sys | |
| 12 | ||
| 13 | ||
| 14 | current_path = os.path.abspath(os.getcwd()) | |
| 15 | ||
| 16 | __author__ = "Francisco Amato" | |
| 17 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 18 | __credits__ = ["Francisco Amato"] | |
| 19 | __license__ = "" | |
| 20 | __version__ = "1.0.0" | |
| 21 | __maintainer__ = "Francisco Amato" | |
| 22 | __email__ = "[email protected]" | |
| 23 | __status__ = "Development" | |
| 24 | ||
| 25 | ||
| 26 | class WebfuzzerParser: | |
| 27 | """ | |
| 28 | The objective of this class is to parse an xml file generated by the webfuzzer tool. | |
| 29 | ||
| 30 | TODO: Handle errors. | |
| 31 | TODO: Test webfuzzer output version. Handle what happens if the parser doesn't support it. | |
| 32 | TODO: Test cases. | |
| 33 | ||
| 34 | @param webfuzzer_filepath A proper output generated by webfuzzer | |
| 35 | """ | |
| 36 | ||
| 37 | def __init__(self, webfuzzer_filepath): | |
| 38 | self.filepath = webfuzzer_filepath | |
| 39 | ||
| 40 | with open(self.filepath, "r") as f: | |
| 41 | try: | |
| 42 | data = f.read() | |
| 43 | f.close() | |
| 44 | m = re.search( | |
| 45 | "Scan of ([\w.]+):([\d]+) \[([/\w]+)\] \(([\w.]+)\)", data) | |
| 46 | self.hostname = m.group(1) | |
| 47 | self.port = m.group(2) | |
| 48 | self.uri = m.group(3) | |
| 49 | self.ipaddress = m.group(4) | |
| 50 | ||
| 51 | m = re.search("Server header:\n\n([\w\W]+)\n\n\n", data) | |
| 52 | self.header = m.group(1) | |
| 53 | ||
| 54 | self.items = [] | |
| 55 | ||
| 56 | pattern = r'\((POST|GET)\): ([\w\W]*?) \]--' | |
| 57 | ||
| 58 | for m in re.finditer(pattern, data, re.DOTALL): | |
| 59 | ||
| 60 | method = m.group(1) | |
| 61 | info = re.search( | |
| 62 | "^([\w\W]+)\(([\w\W]+)\)\n--\[ ([\w\W]+)$", m.group(2)) | |
| 63 | ||
| 64 | vuln = {'method': m.group(1), 'desc': info.group( | |
| 65 | 1), 'url': info.group(2), 'resp': info.group(3)} | |
| 66 | self.items.append(vuln) | |
| 67 | ||
| 68 | except SyntaxError as err: | |
| 69 | print("SyntaxError: %s. %s" % (err, self.filepath)) | |
| 70 | return None | |
| 71 | ||
| 72 | ||
| 73 | class WebfuzzerPlugin(core.PluginBase): | |
| 74 | """ | |
| 75 | Example plugin to parse webfuzzer output. | |
| 76 | """ | |
| 77 | ||
| 78 | def __init__(self): | |
| 79 | super().__init__() | |
| 80 | self.id = "Webfuzzer" | |
| 81 | self.name = "Webfuzzer Output Plugin" | |
| 82 | self.plugin_version = "0.0.2" | |
| 83 | self.version = "0.2.0" | |
| 84 | self.options = None | |
| 85 | self._current_output = None | |
| 86 | self.host = None | |
| 87 | self._command_regex = re.compile( | |
| 88 | r'^(sudo webfuzzer|webfuzzer|\.\/webfuzzer).*?') | |
| 89 | self._completition = {'': '__Usage: ./webfuzzer -G|-P URL [OPTIONS]', | |
| 90 | '-G': '<url> get this as starting url (with parameters)', | |
| 91 | '-P': '<url> post this as starting url (with parameters)', | |
| 92 | '-x': 'html output (txt default)', | |
| 93 | '-c': 'use cookies', | |
| 94 | '-C': '<cookies> set this cookie(s) **', | |
| 95 | '-s': 'check for sql, asp, vb, php errors (default)', | |
| 96 | '-d': 'check for directory traversal *', | |
| 97 | '-p': 'check for insecure perl open or xss *', | |
| 98 | '-e': 'check for execution through shell escapes or xss *', | |
| 99 | '-a': 'set all of the above switches on *', | |
| 100 | } | |
| 101 | ||
| 102 | self._output_path = None | |
| 103 | ||
| 104 | def parseOutputString(self, output, debug=False): | |
| 105 | """ | |
| 106 | This method will discard the output the shell sends, it will read it from | |
| 107 | the xml where it expects it to be present. | |
| 108 | ||
| 109 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 110 | output being sent is valid. | |
| 111 | """ | |
| 112 | ||
| 113 | if self._output_path is None: | |
| 114 | return False | |
| 115 | else: | |
| 116 | if not os.path.exists(self._output_path): | |
| 117 | return False | |
| 118 | ||
| 119 | parser = WebfuzzerParser(self._output_path) | |
| 120 | ||
| 121 | h_id = self.createAndAddHost(parser.ipaddress) | |
| 122 | ||
| 123 | i_id = self.createAndAddInterface( | |
| 124 | h_id, parser.ipaddress, ipv4_address=parser.ipaddress, hostname_resolution=[parser.hostname]) | |
| 125 | ||
| 126 | first = True | |
| 127 | for item in parser.items: | |
| 128 | if first: | |
| 129 | s_id = self.createAndAddServiceToInterface(h_id, i_id, parser.port, | |
| 130 | "tcp", | |
| 131 | ports=[parser.port]) | |
| 132 | first = False | |
| 133 | ||
| 134 | v_id = self.createAndAddVulnWebToService(h_id, s_id, name=item['desc'], | |
| 135 | path=item['url'], response=item[ | |
| 136 | 'resp'], | |
| 137 | method=item['method'], website=parser.hostname) | |
| 138 | ||
| 139 | del parser | |
| 140 | ||
| 141 | return True | |
| 142 | ||
| 143 | def processCommandString(self, username, current_path, command_string): | |
| 144 | """ | |
| 145 | """ | |
| 146 | host = re.search("\-([G|P]) ([\w\.\-]+)", command_string) | |
| 147 | ||
| 148 | if host is not None: | |
| 149 | self.host = host.group(2) | |
| 150 | self._output_path = current_path + "/" + self.host + ".txt" | |
| 151 | ||
| 152 | ||
| 153 | def createPlugin(): | |
| 154 | return WebfuzzerPlugin() | |
| 155 | ||
| 156 | ||
| 157 | ||
| 158 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2018 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | from faraday.client.plugins import core | |
| 6 | from faraday.client.plugins.plugin_utils import get_vulnweb_url_fields | |
| 7 | import re | |
| 8 | ||
| 9 | try: | |
| 10 | import xml.etree.ElementTree as ET | |
| 11 | except ImportError: | |
| 12 | import xml.etree.ElementTree as ET | |
| 13 | ||
| 14 | ||
| 15 | def cleanhtml(raw_html): | |
| 16 | cleanr = re.compile('<.*?>') | |
| 17 | cleantext = re.sub(cleanr, '', raw_html) | |
| 18 | return cleantext | |
| 19 | ||
| 20 | ||
| 21 | class WebInspectParser(): | |
| 22 | ||
| 23 | def __init__(self, output): | |
| 24 | self.xml = ET.fromstring(output) | |
| 25 | self.issues = self.xml.findall("Issues/Issue") | |
| 26 | ||
| 27 | def parse_severity(self, severity): | |
| 28 | ||
| 29 | severity_dict = { | |
| 30 | "0": "info", | |
| 31 | "1": "low", | |
| 32 | "2": "med", | |
| 33 | "3": "high", | |
| 34 | "4": "critical"} | |
| 35 | ||
| 36 | result = severity_dict.get(severity) | |
| 37 | if not result: | |
| 38 | return "info" | |
| 39 | else: | |
| 40 | return result | |
| 41 | ||
| 42 | def return_text(self, tag,element): | |
| 43 | try: | |
| 44 | text = element.find(tag).text.encode("ascii", errors="backslashreplace") | |
| 45 | return text | |
| 46 | except: | |
| 47 | return "" | |
| 48 | ||
| 49 | def parse(self): | |
| 50 | ||
| 51 | map_objects_fields = { | |
| 52 | "Name": ["Vuln", "name"], | |
| 53 | "URL": ["Vuln", "website"], | |
| 54 | "Scheme": ["Service", "name"], | |
| 55 | "Host": ["Host", "name"], | |
| 56 | "Port": ["Service", "port"], | |
| 57 | "AttackMethod": ["Vuln", "method"], | |
| 58 | "VulnerableSession": ["Vuln", "request"], | |
| 59 | "VulnerabilityID": ["Vuln", "reference"], | |
| 60 | "RawResponse": ["Vuln", "response"], | |
| 61 | "Summary": ["Vuln", "description"], | |
| 62 | "Implication": ["Vuln", "data"], | |
| 63 | "Fix": ["Vuln", "resolution"], | |
| 64 | "Reference Info": ["Vuln", "reference"], | |
| 65 | "Severity": ["Vuln", "severity"] | |
| 66 | } | |
| 67 | ||
| 68 | result = [] | |
| 69 | for issue in self.issues: | |
| 70 | ||
| 71 | obj = { | |
| 72 | "Host" : {}, | |
| 73 | "Service" : {}, | |
| 74 | "Interface" : {}, | |
| 75 | "Vuln": { | |
| 76 | "reference" : []} | |
| 77 | } | |
| 78 | ||
| 79 | for tag, obj_property in map_objects_fields.items(): | |
| 80 | ||
| 81 | value = self.return_text(tag,issue) | |
| 82 | ||
| 83 | if value != None: | |
| 84 | ||
| 85 | faraday_obj_name = obj_property[0] | |
| 86 | faraday_field = obj_property[1] | |
| 87 | if faraday_field == "reference": | |
| 88 | obj[faraday_obj_name].get("reference").append(value) | |
| 89 | else: | |
| 90 | obj[faraday_obj_name].update({faraday_field:value}) | |
| 91 | ||
| 92 | # This for loads Summary, Implication, Fix and Reference | |
| 93 | for section in issue.findall("ReportSection"): | |
| 94 | ||
| 95 | try: | |
| 96 | field = section.find("Name").text.encode("ascii", errors="backslashreplace") | |
| 97 | value = section.find("SectionText").text.encode("ascii", errors="backslashreplace") | |
| 98 | ||
| 99 | faraday_obj_name = map_objects_fields.get(field)[0] | |
| 100 | faraday_field = map_objects_fields.get(field)[1] | |
| 101 | except: | |
| 102 | continue | |
| 103 | ||
| 104 | if faraday_field == "reference" and value != "": | |
| 105 | obj[faraday_obj_name].get("reference").append(cleanhtml(value)) | |
| 106 | else: | |
| 107 | obj[faraday_obj_name].update({faraday_field:value}) | |
| 108 | ||
| 109 | result.append(obj) | |
| 110 | return result | |
| 111 | ||
| 112 | ||
| 113 | class WebInspectPlugin(core.PluginBase): | |
| 114 | """ | |
| 115 | This plugin handles WebInspect reports. | |
| 116 | """ | |
| 117 | ||
| 118 | def __init__(self): | |
| 119 | super().__init__() | |
| 120 | self.id = "Webinspect" | |
| 121 | self.name = "Webinspect" | |
| 122 | self.plugin_version = "0.0.1" | |
| 123 | self.version = "1.0.0" | |
| 124 | ||
| 125 | def parseOutputString(self, output, debug=False): | |
| 126 | ||
| 127 | parser = WebInspectParser(output) | |
| 128 | vulns = parser.parse() | |
| 129 | ||
| 130 | for vuln in vulns: | |
| 131 | ||
| 132 | host_id = self.createAndAddHost( | |
| 133 | vuln.get("Host").get("name")) | |
| 134 | ||
| 135 | interface_id = self.createAndAddInterface( | |
| 136 | host_id, vuln.get("Host").get("name")) | |
| 137 | ||
| 138 | service_id = self.createAndAddServiceToInterface( | |
| 139 | host_id, interface_id, | |
| 140 | vuln.get("Service").get("name"), | |
| 141 | protocol=vuln.get("Service").get("name"), | |
| 142 | ports=[vuln.get("Service").get("port")]) | |
| 143 | ||
| 144 | self.createAndAddVulnWebToService( | |
| 145 | host_id, service_id, | |
| 146 | vuln.get("Vuln").get("name"), | |
| 147 | website=get_vulnweb_url_fields(vuln.get("Vuln").get("website")).get("website"), | |
| 148 | path=get_vulnweb_url_fields(vuln.get("Vuln").get("website")).get("path"), | |
| 149 | query=get_vulnweb_url_fields(vuln.get("Vuln").get("website")).get("query"), | |
| 150 | method=vuln.get("Vuln").get("method"), | |
| 151 | request=vuln.get("Vuln").get("request"), | |
| 152 | ref=list(filter(None ,vuln.get("Vuln").get("reference"))), | |
| 153 | response=vuln.get("Vuln").get("response"), | |
| 154 | desc=cleanhtml(vuln.get("Vuln").get("description")), | |
| 155 | resolution=cleanhtml(vuln.get("Vuln").get("resolution")), | |
| 156 | severity=parser.parse_severity(vuln.get("Vuln").get("severity")) | |
| 157 | ) | |
| 158 | ||
| 159 | return True | |
| 160 | ||
| 161 | def processCommandString(self, username, current_path, command_string): | |
| 162 | return None | |
| 163 | ||
| 164 | def createPlugin(): | |
| 165 | return WebInspectPlugin() | |
| 166 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | import re | |
| 1 | import string | |
| 2 | from urllib.parse import urljoin, urlparse | |
| 3 | ||
| 4 | from faraday.client.plugins import core | |
| 5 | ||
| 6 | ||
| 7 | class WfuzzPlugin(core.PluginBase): | |
| 8 | ||
| 9 | def __init__(self): | |
| 10 | super().__init__() | |
| 11 | self.id = "Wfuzz" | |
| 12 | self.name = "Wfuzz Plugin" | |
| 13 | self.plugin_version = "0.0.1" | |
| 14 | self.version = "2.2.11" | |
| 15 | self.options = None | |
| 16 | ||
| 17 | self.host = None | |
| 18 | self.port = None | |
| 19 | self.protocol = None | |
| 20 | self.fail = None | |
| 21 | self._command_regex = re.compile( | |
| 22 | r'^(wfuzz).*?') | |
| 23 | ||
| 24 | def parseData(self, output): | |
| 25 | ||
| 26 | data = { | |
| 27 | 'target' : '', | |
| 28 | 'findings' : [] | |
| 29 | } | |
| 30 | for line in output: | |
| 31 | # remove stdout hidden chars | |
| 32 | line = ''.join([char for char in line if char in string.printable]) | |
| 33 | line = line.strip('\r').replace('[0K', '').replace('[0m', '') | |
| 34 | if line.startswith('Target'): | |
| 35 | data['target'] = line[8:].rstrip() | |
| 36 | continue | |
| 37 | if line.startswith('0'): | |
| 38 | aux = line.split(' ') | |
| 39 | res = {} | |
| 40 | for item in aux: | |
| 41 | if 'C=' in item: | |
| 42 | res['response'] = int(item.replace('C=', '')) | |
| 43 | elif 'L' in item and ' ' in item: | |
| 44 | res['lines'] = int(item.replace('L', '')) | |
| 45 | elif 'W' in item and ' ' in item: | |
| 46 | res['words'] = int(item.replace('W', '')) | |
| 47 | elif 'Ch' in item and ' ' in item: | |
| 48 | res['chars'] = int(item.replace('Ch', '')) | |
| 49 | else: | |
| 50 | res['request'] = item.rstrip().replace('"', '') | |
| 51 | data['findings'].append(res) | |
| 52 | ||
| 53 | return data | |
| 54 | ||
| 55 | def parseOutputString(self, output, debug=False): | |
| 56 | output_list = output.split('\n') | |
| 57 | info = self.parseData(output_list) | |
| 58 | ||
| 59 | target = info['target'] | |
| 60 | target_url = urlparse(target) | |
| 61 | port = 80 | |
| 62 | ||
| 63 | if target_url.scheme == 'https': | |
| 64 | port = 443 | |
| 65 | custom_port = target_url.netloc.split(':') | |
| 66 | if len(custom_port) > 1: | |
| 67 | port = custom_port[1] | |
| 68 | ||
| 69 | host_id = self.createAndAddHost(target) | |
| 70 | ||
| 71 | service_id = self.createAndAddServiceToHost(host_id,name="http",protocol="tcp", ports=[port] ) | |
| 72 | ||
| 73 | for item in info['findings']: | |
| 74 | path = item['request'] | |
| 75 | status = item['response'] | |
| 76 | url = urljoin(target, path) | |
| 77 | lines = item['lines'] | |
| 78 | chars = item['chars'] | |
| 79 | words = item['words'] | |
| 80 | name = "Wfuzz found: {path} with status {status} on url {url}".format(path=path, status=status, url=url) | |
| 81 | desc = 'Wfuzz found a response with status {status}. Response contains: \n* {words} words \n* {lines} lines \n* {chars} chars'.format( | |
| 82 | words=words, | |
| 83 | url=url, | |
| 84 | lines=lines, | |
| 85 | chars=chars, | |
| 86 | status=status | |
| 87 | ) | |
| 88 | self.createAndAddVulnWebToService(host_id, | |
| 89 | service_id, | |
| 90 | name, | |
| 91 | desc, | |
| 92 | severity="info", | |
| 93 | website=target, | |
| 94 | path=path | |
| 95 | ) | |
| 96 | ||
| 97 | ||
| 98 | def createPlugin(): | |
| 99 | return WfuzzPlugin() | |
| 100 | ||
| 101 | ||
| 102 | if __name__ == '__main__': | |
| 103 | parser = WfuzzPlugin() | |
| 104 | with open("/home/javier/salida", "r") as report: | |
| 105 | parser.parseOutputString(report.read()) | |
| 106 | ||
| 107 | ||
| 108 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | from faraday.client.model import api | |
| 8 | import re | |
| 9 | import os | |
| 10 | import socket | |
| 11 | import pprint | |
| 12 | current_path = os.path.abspath(os.getcwd()) | |
| 13 | ||
| 14 | __author__ = "Facundo de Guzmán, Esteban Guillardoy" | |
| 15 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 16 | __credits__ = ["Facundo de Guzmán", "Esteban Guillardoy"] | |
| 17 | __license__ = "" | |
| 18 | __version__ = "1.0.0" | |
| 19 | __maintainer__ = "Federico Kirschbaum" | |
| 20 | __email__ = "[email protected]" | |
| 21 | __status__ = "Development" | |
| 22 | ||
| 23 | ||
| 24 | class CmdWhoisPlugin(core.PluginBase): | |
| 25 | """ | |
| 26 | This plugin handles whois command. | |
| 27 | Basically detects if user was able to connect to a device | |
| 28 | """ | |
| 29 | ||
| 30 | def __init__(self): | |
| 31 | super().__init__() | |
| 32 | self.id = "whois" | |
| 33 | self.name = "Whois" | |
| 34 | self.plugin_version = "0.0.1" | |
| 35 | self.version = "5.0.20" | |
| 36 | self.framework_version = "1.0.0" | |
| 37 | self.options = None | |
| 38 | self._current_output = None | |
| 39 | self._command_regex = re.compile(r'^whois.*?') | |
| 40 | self._host_ip = None | |
| 41 | self._info = 0 | |
| 42 | self._completition = { | |
| 43 | "": "whois [OPTION]... OBJECT...", | |
| 44 | "-l": "one level less specific lookup [RPSL only]", | |
| 45 | "-L": "find all Less specific matches", | |
| 46 | "-m": "find first level more specific matches", | |
| 47 | "-M": "find all More specific matches", | |
| 48 | "-c": "find the smallest match containing a mnt-irt attribute", | |
| 49 | "-x": "exact match [RPSL only]", | |
| 50 | "-d": "return DNS reverse delegation objects too [RPSL only]", | |
| 51 | "-i": "-i ATTR[,ATTR]... do an inverse lookup for specified ATTRibutes", | |
| 52 | "-T": "-T TYPE[,TYPE]... only look for objects of TYPE", | |
| 53 | "-K": "only primary keys are returned [RPSL only]", | |
| 54 | "-r": "turn off recursive lookups for contact information", | |
| 55 | "-R": "force to show local copy of the domain object even if it contains referral", | |
| 56 | "-a": "search all databases", | |
| 57 | "-s": "-s SOURCE[,SOURCE]... search the database from SOURCE", | |
| 58 | "-g": "-g SOURCE:FIRST-LAST find updates from SOURCE from serial FIRST to LAST", | |
| 59 | "-t": "-t TYPE request template for object of TYPE", | |
| 60 | "-v": "-v TYPE request verbose template for object of TYPE", | |
| 61 | "-q": "-q [version|sources|types] query specified server info [RPSL only]", | |
| 62 | "-F": "fast raw output (implies -r)", | |
| 63 | "-h": "-h HOST connect to server HOST", | |
| 64 | "-p": "-p PORT connect to PORT", | |
| 65 | "-H": "hide legal disclaimers", | |
| 66 | "--verbose": "explain what is being done", | |
| 67 | "--help": "display this help and exit", | |
| 68 | "--version": "output version information and exit", | |
| 69 | } | |
| 70 | ||
| 71 | global current_path | |
| 72 | ||
| 73 | def resolve(self, host): | |
| 74 | try: | |
| 75 | return socket.gethostbyname(host) | |
| 76 | except: | |
| 77 | pass | |
| 78 | return host | |
| 79 | ||
| 80 | def parseOutputString(self, output, debug=False): | |
| 81 | matches = re.findall("Name Server:\s*(.*)\s*", output) | |
| 82 | for m in matches: | |
| 83 | m = m.strip() | |
| 84 | ip = self.resolve(m) | |
| 85 | h_id = self.createAndAddHost(ip, "os unknown") | |
| 86 | i_id = self.createAndAddInterface( | |
| 87 | h_id, ip, "00:00:00:00:00:00", ip, hostname_resolution=[m]) | |
| 88 | return True | |
| 89 | ||
| 90 | def processCommandString(self, username, current_path, command_string): | |
| 91 | """ | |
| 92 | """ | |
| 93 | return None | |
| 94 | ||
| 95 | ||
| 96 | def createPlugin(): | |
| 97 | return CmdWhoisPlugin() | |
| 98 | ||
| 99 | ||
| 100 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | ||
| 7 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins import core | |
| 7 | import re | |
| 8 | import os | |
| 9 | import socket | |
| 10 | import json | |
| 11 | ||
| 12 | __author__ = "Joaquin L. Pereyra | Federico Fernandez" | |
| 13 | __copyright__ = "Copyright (c) 2016, Infobyte LLC" | |
| 14 | __credits__ = ["Joaquin L. Pereyra"] | |
| 15 | __license__ = "" | |
| 16 | __version__ = "0.0.1" | |
| 17 | __maintainer__ = "Joaquin L. Pereyra" | |
| 18 | __email__ = "[email protected]" | |
| 19 | __status__ = "Development" | |
| 20 | ||
| 21 | ||
| 22 | class WPScanPlugin(core.PluginBase): | |
| 23 | """ Handle the WPScan tool. Detects the output of the tool | |
| 24 | and adds the information to Faraday. | |
| 25 | """ | |
| 26 | ||
| 27 | def __init__(self): | |
| 28 | """Initalizes the plugin with some basic params. | |
| 29 | Right now the plugin doesnt support being executed from another folder, | |
| 30 | like /dir/wpscan.rb | |
| 31 | """ | |
| 32 | super().__init__() | |
| 33 | self.id = "wpscan" | |
| 34 | self.name = "WPscan" | |
| 35 | self.plugin_version = "0.2" | |
| 36 | self.version = "3.4.5" | |
| 37 | self._command_regex = re.compile( | |
| 38 | r"^((sudo )?(ruby )?(\.\/)?(wpscan)(.rb)?)") | |
| 39 | self.wpPath = self.get_wpscan_filepath() | |
| 40 | self.addSetting("WPscan path", str, self.wpPath) | |
| 41 | self.themes = {} | |
| 42 | self.plugins = {} | |
| 43 | self.wpversion = '' | |
| 44 | self.risks = {'AUTHBYPASS': 'high', | |
| 45 | 'BYPASS': 'med', | |
| 46 | 'CSRF': 'med', | |
| 47 | 'DOS': 'med', | |
| 48 | 'FPD': 'info', | |
| 49 | 'LFI': 'high', | |
| 50 | 'MULTI': 'unclassified', | |
| 51 | 'OBJECTINJECTION': 'med', | |
| 52 | 'PRIVESC': 'high', | |
| 53 | 'RCE': 'critical', | |
| 54 | 'REDIRECT': 'low', | |
| 55 | 'RFI': 'critical', | |
| 56 | 'SQLI': 'high', | |
| 57 | 'SSRF': 'med', | |
| 58 | 'UNKNOWN': 'unclassified', | |
| 59 | 'UPLOAD': 'critical', | |
| 60 | 'XSS': 'high', | |
| 61 | 'XXE': 'high'} | |
| 62 | ||
| 63 | def get_wpscan_filepath(self): | |
| 64 | home = os.path.expanduser("~") | |
| 65 | ||
| 66 | wpscan_path = os.path.join(home, '.wpscan') | |
| 67 | if os.path.exists(wpscan_path): | |
| 68 | return wpscan_path | |
| 69 | else: | |
| 70 | return None | |
| 71 | ||
| 72 | def search_file_in_wpscan_folder(self, wp_file): | |
| 73 | db_path = os.path.join(self.wpPath, 'db', wp_file) | |
| 74 | data_path = os.path.join(self.wpPath, 'data', wp_file) | |
| 75 | if os.path.exists(db_path): | |
| 76 | return db_path | |
| 77 | elif os.path.exists(data_path): | |
| 78 | return data_path | |
| 79 | ||
| 80 | def getPort(self, host, proto): | |
| 81 | p = re.search(r"\:([0-9]+)\/", host) | |
| 82 | if p is not None: | |
| 83 | return p.group(1) | |
| 84 | elif proto == 'https': | |
| 85 | return 443 | |
| 86 | else: | |
| 87 | return 80 | |
| 88 | ||
| 89 | def parseOutputWpscan(self, output): | |
| 90 | sp = output.split('0m Name:') # cut by name | |
| 91 | for e in sp: | |
| 92 | if 'Title:' in e: | |
| 93 | if 'WordPress version' in e: | |
| 94 | r = re.search(r'WordPress version (\d.\w)', e) # get wordpress version | |
| 95 | self.wpversion = r.group(1) | |
| 96 | ||
| 97 | elif 'wp-content/themes/' in e: | |
| 98 | name = re.findall(r"Location: .+themes\/(.+)\/", e) # get theme name | |
| 99 | title = re.findall(r"Title: (.+)", e) # get vulnerabilities title | |
| 100 | self.themes[name[0]] = title # insert theme in dicc {'themeName' : ['titles', 'titles']} | |
| 101 | ||
| 102 | else: | |
| 103 | name = re.findall(r"Location: .+plugins\/(.+)\/", e) # get plugin name | |
| 104 | title = re.findall(r"Title: (.+)", e) # get vulnerabilities title | |
| 105 | self.plugins[name[0]] = title # insert plugin in dicc {'plugin' : ['titles', 'titles']} | |
| 106 | ||
| 107 | def addThemesOrPluginsVulns(self, wpscan_db_filename, dic, host_id, serv_id, domain, wp_url, name): | |
| 108 | db_file_path = self.search_file_in_wpscan_folder(wpscan_db_filename) | |
| 109 | with open(db_file_path, "r") as data: | |
| 110 | j = json.load(data) | |
| 111 | for p in dic: | |
| 112 | for title in dic[p]: | |
| 113 | for vuln in j[p]['vulnerabilities']: # iter vulnerabilities | |
| 114 | if vuln['title'] == title: # if output title is equal | |
| 115 | title = vuln['title'] # title | |
| 116 | risk = self.risks[vuln['vuln_type']] # vuln type (xss,rce,lfi,etc) - risk | |
| 117 | location = wp_url+'wp-content/'+name+'/'+p+'/' | |
| 118 | if vuln['references'].has_key('url') == True: # if references | |
| 119 | refs = vuln['references']['url'] #references[] | |
| 120 | else: | |
| 121 | refs = [] # references null | |
| 122 | self.createAndAddVulnWebToService( | |
| 123 | host_id, | |
| 124 | serv_id, | |
| 125 | title, | |
| 126 | severity=risk, | |
| 127 | website=domain, | |
| 128 | ref=refs, | |
| 129 | path=location) | |
| 130 | ||
| 131 | def addWPVulns(self, wpscan_db_filename, version, host_id, serv_id, domain): | |
| 132 | db_file_path = self.search_file_in_wpscan_folder(wpscan_db_filename) | |
| 133 | with open(db_file_path, "r") as data: | |
| 134 | j = json.load(data) | |
| 135 | for vuln in j[version]['vulnerabilities']: # iter vulnerabilities | |
| 136 | title = vuln['title'] # title | |
| 137 | risk = self.risks[vuln['vuln_type']] # vuln type (xss,rce,lfi,etc) - risk | |
| 138 | if vuln['references'].has_key('url') == True: # if references | |
| 139 | refs = vuln['references']['url'] # references[] | |
| 140 | else: | |
| 141 | refs = [] # references null | |
| 142 | self.createAndAddVulnWebToService( | |
| 143 | host_id, | |
| 144 | serv_id, | |
| 145 | title, | |
| 146 | severity=risk, | |
| 147 | website=domain, | |
| 148 | ref=refs) | |
| 149 | ||
| 150 | def parseOutputString(self, output, debug=False): | |
| 151 | """Parses the output given as a string by the wpscan tool and creates | |
| 152 | the appropiate hosts, service and vulnerabilites. Return | |
| 153 | nothing. | |
| 154 | """ | |
| 155 | self.parseOutputWpscan(output) | |
| 156 | wp_url = re.search(r"URL: ((http[s]?)\:\/\/([\w\.]+)[.\S]+)", output) | |
| 157 | service, base_url = self.__get_service_and_url_from_output(output) | |
| 158 | if service and base_url: | |
| 159 | port = self.getPort(wp_url.group(1), service) | |
| 160 | host_ip = socket.gethostbyname_ex(base_url)[2][0] | |
| 161 | host_id = self.createAndAddHost( | |
| 162 | host_ip, | |
| 163 | hostnames=[base_url]) | |
| 164 | ||
| 165 | service_id = self.createAndAddServiceToHost(host_id, | |
| 166 | service, | |
| 167 | "tcp", | |
| 168 | ports=[port]) | |
| 169 | ||
| 170 | potential_vulns = re.findall(r"(\[\!\].*)", output) | |
| 171 | for potential_vuln in potential_vulns: | |
| 172 | vuln_name, severity = self.__get_name_and_severity(potential_vuln) | |
| 173 | if vuln_name is not None: | |
| 174 | vuln = potential_vuln # they grow up so fast | |
| 175 | path = self.__get_path_from_vuln(vuln) | |
| 176 | self.createAndAddVulnWebToService(host_id, service_id, | |
| 177 | name=vuln_name, | |
| 178 | website=base_url, | |
| 179 | path=path, severity=severity) | |
| 180 | ||
| 181 | if len(self.plugins) > 0: | |
| 182 | self.addThemesOrPluginsVulns( | |
| 183 | 'plugins.json', | |
| 184 | self.plugins, | |
| 185 | host_id, | |
| 186 | service_id, | |
| 187 | base_url, | |
| 188 | wp_url.group(1), | |
| 189 | 'plugins') | |
| 190 | ||
| 191 | if len(self.wpversion) > 0: | |
| 192 | self.addWPVulns( | |
| 193 | 'wordpresses.json', | |
| 194 | self.wpversion, | |
| 195 | host_id, | |
| 196 | service_id, | |
| 197 | base_url) | |
| 198 | ||
| 199 | if len(self.themes) > 0: | |
| 200 | self.addThemesOrPluginsVulns( | |
| 201 | 'themes.json', | |
| 202 | self.themes, | |
| 203 | host_id, | |
| 204 | service_id, | |
| 205 | base_url, | |
| 206 | wp_url.group(1), | |
| 207 | 'themes') | |
| 208 | ||
| 209 | def __get_service_and_url_from_output(self, output): | |
| 210 | """ Return the service (http or https) and the base URL (URL without | |
| 211 | protocol) from a given string. In case more than one URL is found, | |
| 212 | return the service and base_url of the first one, ignore others. | |
| 213 | """ | |
| 214 | search_url = re.search(r"URL: ((http[s]?)\:\/\/([\w\.]+)[.\S]+)", output) | |
| 215 | if not search_url: | |
| 216 | return None, None | |
| 217 | else: | |
| 218 | service, base_url = search_url.group(2), search_url.group(3) | |
| 219 | return service, base_url | |
| 220 | ||
| 221 | def __get_name_and_severity(self, potential_vuln): | |
| 222 | """Regex the potential_vuln string against a regex with all | |
| 223 | the vulnerabilities given by WPscan. Returns a regex match object with | |
| 224 | the vulnerability's name and severity if the regex found something | |
| 225 | and (None, None) if the regex found nothing. | |
| 226 | """ | |
| 227 | critical_search = re.search(r"Website is not fully configured|" | |
| 228 | "Debug log file found|" | |
| 229 | "wp-config\.php backup file has been found|" | |
| 230 | "searchreplacedb2.php has been found", | |
| 231 | potential_vuln) | |
| 232 | if critical_search: | |
| 233 | return critical_search.group(0), "critical" | |
| 234 | ||
| 235 | info_search = re.search(r"Directory listing is enabled|" | |
| 236 | "An error_log file has been found|" | |
| 237 | "file exists exposing a version number|" | |
| 238 | "Full Path Disclosure|" | |
| 239 | "Registration is enabled|" | |
| 240 | "(Upload|Includes) directory has directory listing enabled|" | |
| 241 | "Default first Wordpress username 'admin' is still used", | |
| 242 | potential_vuln) | |
| 243 | if info_search: | |
| 244 | return info_search.group(0), "info" | |
| 245 | ||
| 246 | return None, None | |
| 247 | ||
| 248 | def __get_path_from_vuln(self, vuln): | |
| 249 | """Given a vuln as string, return the path as a string (empty string | |
| 250 | for path not found). | |
| 251 | """ | |
| 252 | path_search = re.search("(?P<url>https?://[^\s]+)", vuln) | |
| 253 | path = path_search.group('url') if path_search else "" | |
| 254 | return path | |
| 255 | ||
| 256 | def processCommandString(self, username, current_path, command_string): | |
| 257 | return None | |
| 258 | ||
| 259 | ||
| 260 | def createPlugin(): | |
| 261 | return WPScanPlugin() | |
| 262 | ||
| 263 | ||
| 264 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 7 | from faraday.client.model import api | |
| 8 | import re | |
| 9 | import os | |
| 10 | import sys | |
| 11 | ||
| 12 | try: | |
| 13 | import xml.etree.cElementTree as ET | |
| 14 | import xml.etree.ElementTree as ET_ORIG | |
| 15 | ETREE_VERSION = ET_ORIG.VERSION | |
| 16 | except ImportError: | |
| 17 | import xml.etree.ElementTree as ET | |
| 18 | ETREE_VERSION = ET.VERSION | |
| 19 | ||
| 20 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 21 | ||
| 22 | current_path = os.path.abspath(os.getcwd()) | |
| 23 | ||
| 24 | __author__ = "Francisco Amato" | |
| 25 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 26 | __credits__ = ["Francisco Amato"] | |
| 27 | __license__ = "" | |
| 28 | __version__ = "1.0.0" | |
| 29 | __maintainer__ = "Francisco Amato" | |
| 30 | __email__ = "[email protected]" | |
| 31 | __status__ = "Development" | |
| 32 | ||
| 33 | ||
| 34 | class X1XmlParser: | |
| 35 | """ | |
| 36 | The objective of this class is to parse an xml file generated by the x1 tool. | |
| 37 | ||
| 38 | TODO: Handle errors. | |
| 39 | TODO: Test x1 output version. Handle what happens if the parser doesn't support it. | |
| 40 | TODO: Test cases. | |
| 41 | ||
| 42 | @param x1_xml_filepath A proper xml generated by x1 | |
| 43 | """ | |
| 44 | ||
| 45 | def __init__(self, xml_output): | |
| 46 | ||
| 47 | tree = self.parse_xml(xml_output) | |
| 48 | if tree: | |
| 49 | self.items = list(self.get_items(tree)) | |
| 50 | else: | |
| 51 | self.items = [] | |
| 52 | ||
| 53 | def parse_xml(self, xml_output): | |
| 54 | """ | |
| 55 | Open and parse an xml file. | |
| 56 | ||
| 57 | TODO: Write custom parser to just read the nodes that we need instead of | |
| 58 | reading the whole file. | |
| 59 | ||
| 60 | @return xml_tree An xml tree instance. None if error. | |
| 61 | """ | |
| 62 | try: | |
| 63 | tree = ET.fromstring(xml_output) | |
| 64 | except SyntaxError as err: | |
| 65 | print("SyntaxError: %s. %s" % (err, xml_output)) | |
| 66 | return None | |
| 67 | ||
| 68 | return tree | |
| 69 | ||
| 70 | def get_items(self, tree): | |
| 71 | """ | |
| 72 | @return items A list of Host instances | |
| 73 | """ | |
| 74 | ||
| 75 | for node in tree.findall('results/landscape/system/component'): | |
| 76 | yield Item(node) | |
| 77 | ||
| 78 | ||
| 79 | class Item: | |
| 80 | """ | |
| 81 | An abstract representation of a Item | |
| 82 | ||
| 83 | ||
| 84 | @param item_node A item_node taken from an x1 xml tree | |
| 85 | """ | |
| 86 | ||
| 87 | def __init__(self, item_node): | |
| 88 | self.node = item_node | |
| 89 | ||
| 90 | self.name = self.get_text_from_subnode('name') | |
| 91 | self.host = self.get_text_from_subnode('host') | |
| 92 | self.vclass = self.get_text_from_subnode('class') | |
| 93 | ||
| 94 | self.connector = self.node.find('connector') | |
| 95 | self.cname = self.connector.get('name') | |
| 96 | data = self.cname.split("/") | |
| 97 | self.port, self.protocol = data[0].split() | |
| 98 | self.srvname = data[1] | |
| 99 | ||
| 100 | self.cresults = self.getResults(self.connector) | |
| 101 | self.results = self.getResults(self.node) | |
| 102 | ||
| 103 | def getResults(self, tree): | |
| 104 | """ | |
| 105 | :param tree: | |
| 106 | """ | |
| 107 | for self.issues in tree.findall('modResults/moduleResult'): | |
| 108 | yield Results(self.issues) | |
| 109 | ||
| 110 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 111 | """ | |
| 112 | Finds a subnode in the host node and the retrieves a value from it. | |
| 113 | ||
| 114 | @return An attribute value | |
| 115 | """ | |
| 116 | sub_node = self.node.find(subnode_xpath_expr) | |
| 117 | if sub_node is not None: | |
| 118 | return sub_node.text | |
| 119 | ||
| 120 | return None | |
| 121 | ||
| 122 | ||
| 123 | class Results(): | |
| 124 | ||
| 125 | def __init__(self, issue_node): | |
| 126 | self.node = issue_node | |
| 127 | self.id = self.get_text_from_subnode('id') | |
| 128 | self.name = self.get_text_from_subnode('name') | |
| 129 | ||
| 130 | self.category = self.get_text_from_subnode('category') | |
| 131 | self.trendingStatus = self.get_text_from_subnode('trendingStatus') | |
| 132 | self.description = self.get_text_from_subnode('description') | |
| 133 | self.risk = self.get_text_from_subnode('risk') | |
| 134 | self.resolution = self.get_text_from_subnode('solution') | |
| 135 | self.ref = [] | |
| 136 | for r in issue_node.findall('refs/reference'): | |
| 137 | ||
| 138 | self.ref.append(r.get('type') + "-" + r.get('text')) | |
| 139 | ||
| 140 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 141 | """ | |
| 142 | Finds a subnode in the host node and the retrieves a value from it. | |
| 143 | ||
| 144 | @return An attribute value | |
| 145 | """ | |
| 146 | sub_node = self.node.find(subnode_xpath_expr) | |
| 147 | if sub_node is not None: | |
| 148 | return sub_node.text | |
| 149 | ||
| 150 | return None | |
| 151 | ||
| 152 | ||
| 153 | class X1Plugin(PluginXMLFormat): | |
| 154 | """ | |
| 155 | Example plugin to parse x1 output. | |
| 156 | """ | |
| 157 | ||
| 158 | def __init__(self): | |
| 159 | super().__init__() | |
| 160 | self.identifier_tag = ["session", "landscapePolicy"] | |
| 161 | self.id = "X1" | |
| 162 | self.name = "Onapsis X1 XML Output Plugin" | |
| 163 | self.plugin_version = "0.0.1" | |
| 164 | self.version = "Onapsis X1 2.56" | |
| 165 | self.framework_version = "1.0.0" | |
| 166 | self.options = None | |
| 167 | self._current_output = None | |
| 168 | self._command_regex = re.compile(r'^(sudo x1|\.\/x1).*?') | |
| 169 | ||
| 170 | global current_path | |
| 171 | self._output_file_path = os.path.join(self.data_path, "x1_output-%s.xml" % self._rid) | |
| 172 | ||
| 173 | def parseOutputString(self, output, debug=False): | |
| 174 | ||
| 175 | parser = X1XmlParser(output) | |
| 176 | for item in parser.items: | |
| 177 | h_id = self.createAndAddHost(item.host, item.name) | |
| 178 | i_id = self.createAndAddInterface( | |
| 179 | h_id, item.host, ipv4_address=item.host, hostname_resolution=[item.vclass]) | |
| 180 | s_id = self.createAndAddServiceToInterface(h_id, i_id, item.srvname, | |
| 181 | item.protocol, | |
| 182 | ports=[str(item.port)], | |
| 183 | status="open") | |
| 184 | for v in item.results: | |
| 185 | desc = v.description | |
| 186 | v_id = self.createAndAddVulnToService(h_id, s_id, v.name, desc=desc, | |
| 187 | ref=v.ref, severity=v.risk, resolution=v.resolution) | |
| 188 | ||
| 189 | for v in item.cresults: | |
| 190 | desc = v.description | |
| 191 | v_id = self.createAndAddVulnToService(h_id, s_id, v.name, desc=desc, | |
| 192 | ref=v.ref, severity=v.risk, resolution=v.resolution) | |
| 193 | ||
| 194 | del parser | |
| 195 | ||
| 196 | def processCommandString(self, username, current_path, command_string): | |
| 197 | return None | |
| 198 | ||
| 199 | def setHost(self): | |
| 200 | pass | |
| 201 | ||
| 202 | ||
| 203 | def createPlugin(): | |
| 204 | return X1Plugin() | |
| 205 | ||
| 206 | ||
| 207 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2017 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | import re | |
| 6 | import socket | |
| 7 | from faraday.client.plugins import core | |
| 8 | ||
| 9 | __author__ = "Roberto Focke" | |
| 10 | __copyright__ = "Copyright (c) 2017, Infobyte LLC" | |
| 11 | __license__ = "" | |
| 12 | __version__ = "1.0.0" | |
| 13 | ||
| 14 | ||
| 15 | class xsssniper (core.PluginBase): | |
| 16 | ||
| 17 | def __init__(self): | |
| 18 | super().__init__() | |
| 19 | self.id = "xsssniper" | |
| 20 | self.name = "xsssniper" | |
| 21 | self.plugin_version = "0.0.1" | |
| 22 | self.version = "1.0.0" | |
| 23 | self.protocol="tcp" | |
| 24 | self._command_regex = re.compile(r'^(sudo xsssniper|xsssniper|sudo xsssniper\.py|xsssniper\.py|sudo python xsssniper\.py|.\/xsssniper\.py|python xsssniper\.py)') | |
| 25 | ||
| 26 | def parseOutputString(self, output, debug=False): | |
| 27 | parametro=[] | |
| 28 | lineas = output.split("\n") | |
| 29 | aux = 0 | |
| 30 | for linea in lineas: | |
| 31 | if not linea: | |
| 32 | continue | |
| 33 | linea = linea.lower() | |
| 34 | if ((linea.find("target:")>0)): | |
| 35 | url = re.findall('(?:[-\w.]|(?:%[\da-fA-F]{2}))+', linea) | |
| 36 | host_id = self.createAndAddHost(url[3]) | |
| 37 | address=socket.gethostbyname(url[3]) | |
| 38 | interface_id = self.createAndAddInterface(host_id,address,ipv4_address=address,hostname_resolution=url[3]) | |
| 39 | if ((linea.find("method")>0)): | |
| 40 | list_a = re.findall("\w+", linea) | |
| 41 | metodo= list_a[1] | |
| 42 | if ((linea.find("query string:")>0)): | |
| 43 | lista_parametros=linea.split('=') | |
| 44 | aux=len(lista_parametros) | |
| 45 | if ((linea.find("param:")>0)): | |
| 46 | list2= re.findall("\w+",linea) | |
| 47 | parametro.append(list2[1]) | |
| 48 | service_id = self.createAndAddServiceToInterface(host_id,interface_id,self.protocol,'tcp',ports=['80'],status='Open',version="", description="") | |
| 49 | if aux !=0: | |
| 50 | self.createAndAddVulnWebToService(host_id,service_id,name="xss",desc="XSS",ref='',severity='med',website=url[0],path='',method=metodo,pname='',params=''.join(parametro),request='',response='') | |
| 51 | ||
| 52 | def processCommandString(self, username, current_path, command_string): | |
| 53 | return None | |
| 54 | ||
| 55 | ||
| 56 | def createPlugin(): | |
| 57 | return xsssniper() | |
| 58 | ||
| 59 | ||
| 60 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | /* | |
| 1 | * Zed Attack Proxy (ZAP) and its related class files. | |
| 2 | * | |
| 3 | * ZAP is an HTTP/HTTPS proxy for assessing web application security. | |
| 4 | * | |
| 5 | * Copyright 2018 The ZAP Development Team | |
| 6 | * | |
| 7 | * Licensed under the Apache License, Version 2.0 (the "License"); | |
| 8 | * you may not use this file except in compliance with the License. | |
| 9 | * You may obtain a copy of the License at | |
| 10 | * | |
| 11 | * http://www.apache.org/licenses/LICENSE-2.0 | |
| 12 | * | |
| 13 | * Unless required by applicable law or agreed to in writing, software | |
| 14 | * distributed under the License is distributed on an "AS IS" BASIS, | |
| 15 | * WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. | |
| 16 | * See the License for the specific language governing permissions and | |
| 17 | * limitations under the License. | |
| 18 | */ | |
| 19 | ||
| 20 | package org.zaproxy.zap.extension.faraday; | |
| 21 | ||
| 22 | import org.parosproxy.paros.Constant; | |
| 23 | ||
| 24 | import javax.swing.*; | |
| 25 | import java.io.*; | |
| 26 | import java.util.Properties; | |
| 27 | ||
| 28 | public class Configuration { | |
| 29 | private String server; | |
| 30 | private String user; | |
| 31 | private String password; | |
| 32 | private String session; | |
| 33 | private String workspace; | |
| 34 | private boolean autoImport; | |
| 35 | private static Configuration _instance; | |
| 36 | ||
| 37 | private Configuration() { | |
| 38 | this.user = ""; | |
| 39 | this.password = ""; | |
| 40 | this.server = "http://127.0.0.1:5985/"; | |
| 41 | this.autoImport = false; | |
| 42 | } | |
| 43 | ||
| 44 | public static Configuration getSingleton() { | |
| 45 | if (_instance == null) | |
| 46 | _instance = new Configuration(); | |
| 47 | return _instance; | |
| 48 | } | |
| 49 | ||
| 50 | public boolean save() throws IOException { | |
| 51 | ||
| 52 | Properties prop = new Properties(); | |
| 53 | OutputStream output = null; | |
| 54 | ||
| 55 | String userHome = System.getProperty("user.home"); | |
| 56 | String outputFolder = Constant.getZapHome() + "faraday"; | |
| 57 | File folder = new File(outputFolder); | |
| 58 | if (!folder.exists()) { | |
| 59 | folder.mkdir(); | |
| 60 | } | |
| 61 | ||
| 62 | ||
| 63 | String filePath = outputFolder + File.separator + this.getUser() + ".properties"; | |
| 64 | output = new FileOutputStream(filePath); | |
| 65 | ||
| 66 | // set the properties value | |
| 67 | prop.setProperty("fuser", this.getUser()); | |
| 68 | prop.setProperty("fpassword", this.getPassword()); | |
| 69 | prop.setProperty("fserver", this.getServer()); | |
| 70 | prop.setProperty("fworkspace", this.getWorkspace()); | |
| 71 | prop.setProperty("fsession", this.getSession()); | |
| 72 | ||
| 73 | // save properties to project root folder | |
| 74 | prop.store(output, null); | |
| 75 | ||
| 76 | if (output != null) { | |
| 77 | try { | |
| 78 | output.close(); | |
| 79 | } catch (IOException e) { | |
| 80 | e.printStackTrace(); | |
| 81 | return false; | |
| 82 | } | |
| 83 | } | |
| 84 | ||
| 85 | return true; | |
| 86 | } | |
| 87 | ||
| 88 | ||
| 89 | public void restore(String fUser) throws IOException { | |
| 90 | Properties prop = new Properties(); | |
| 91 | InputStream input = null; | |
| 92 | ||
| 93 | String outputFolder = Constant.getZapHome() + "faraday"; | |
| 94 | String filePath = outputFolder + File.separator + fUser + ".properties"; | |
| 95 | input = new FileInputStream(filePath); | |
| 96 | ||
| 97 | // load a properties file | |
| 98 | prop.load(input); | |
| 99 | ||
| 100 | this.setUser(prop.getProperty("fuser")); | |
| 101 | this.setPassword(prop.getProperty("fpassword")); | |
| 102 | this.setServer(prop.getProperty("fserver")); | |
| 103 | this.setWorkspace(prop.getProperty("fworkspace")); | |
| 104 | ||
| 105 | if (input != null) { | |
| 106 | try { | |
| 107 | input.close(); | |
| 108 | } catch (IOException e) { | |
| 109 | e.printStackTrace(); | |
| 110 | } | |
| 111 | } | |
| 112 | ||
| 113 | } | |
| 114 | ||
| 115 | public String getUser() { | |
| 116 | return user; | |
| 117 | } | |
| 118 | ||
| 119 | public void setUser(String user) { | |
| 120 | this.user = user; | |
| 121 | } | |
| 122 | ||
| 123 | public String getPassword() { | |
| 124 | return password; | |
| 125 | } | |
| 126 | ||
| 127 | public void setPassword(String password) { | |
| 128 | this.password = password; | |
| 129 | } | |
| 130 | ||
| 131 | public String getServer() { | |
| 132 | return server; | |
| 133 | } | |
| 134 | ||
| 135 | public void setServer(String server) { | |
| 136 | this.server = server; | |
| 137 | } | |
| 138 | ||
| 139 | public boolean isAutoImport() { | |
| 140 | return autoImport; | |
| 141 | } | |
| 142 | ||
| 143 | public void setAutoImport(boolean autoImport) { | |
| 144 | this.autoImport = autoImport; | |
| 145 | } | |
| 146 | ||
| 147 | public String getSession() { | |
| 148 | return session; | |
| 149 | } | |
| 150 | ||
| 151 | public void setSession(String session) { | |
| 152 | this.session = session; | |
| 153 | } | |
| 154 | ||
| 155 | public String getWorkspace() { | |
| 156 | return workspace; | |
| 157 | } | |
| 158 | ||
| 159 | public void setWorkspace(String workspace) { | |
| 160 | this.workspace = workspace; | |
| 161 | } | |
| 162 | } |
| 0 | package org.zaproxy.zap.extension.faraday; | |
| 1 | ||
| 2 | ||
| 3 | import org.apache.log4j.Logger; | |
| 4 | import org.parosproxy.paros.Constant; | |
| 5 | ||
| 6 | import javax.swing.*; | |
| 7 | import javax.swing.border.Border; | |
| 8 | import java.awt.*; | |
| 9 | import java.awt.event.*; | |
| 10 | import java.io.*; | |
| 11 | import java.util.ArrayList; | |
| 12 | import java.util.Properties; | |
| 13 | import java.util.ResourceBundle; | |
| 14 | ||
| 15 | public class ConfigurationDialog extends JFrame { | |
| 16 | private static final Logger logger = Logger.getLogger(ConfigurationDialog.class); | |
| 17 | private ResourceBundle messages = null; | |
| 18 | private FaradayClient faradayClient; | |
| 19 | ||
| 20 | private static String LOGIN_BUTTON = "Login"; | |
| 21 | private static String LOGOUT_BUTTON = "Logout"; | |
| 22 | private static String WORKSPACES_FIELD = "Select faraday workspace"; | |
| 23 | private static String IMPORT_NEW_VULNS_FIELD = "Import new vulnerabilities"; | |
| 24 | private static String SET_CONFIG_AS_DEFAULT = "Set this configuration as default"; | |
| 25 | private static String IMPORT_BUTTON = "Import vulnerabilities"; | |
| 26 | private static String REFRESH_BUTTON = "Refresh"; | |
| 27 | private static String RESTORE_BUTTON = "Restore"; | |
| 28 | private static String SAVE_BUTTON = "Save"; | |
| 29 | ||
| 30 | private JTabbedPane tabbedPane; | |
| 31 | private JPanel authPanel; | |
| 32 | private JPanel configPanel; | |
| 33 | ||
| 34 | private JTextField fldUser; | |
| 35 | private JTextField fldPass; | |
| 36 | private JTextField fldServer; | |
| 37 | ||
| 38 | private JComboBox cmbWorkspaces; | |
| 39 | private JCheckBox cboxSetConfigDefault; | |
| 40 | ||
| 41 | ||
| 42 | private JButton loginButton; | |
| 43 | private JButton logoutButton; | |
| 44 | private JButton refreshButton; | |
| 45 | private JButton restoreButton; | |
| 46 | private JButton importButton; | |
| 47 | private JButton saveButton; | |
| 48 | private JButton closeButton; | |
| 49 | ||
| 50 | ||
| 51 | public ConfigurationDialog(String s) throws HeadlessException { | |
| 52 | super(s); | |
| 53 | } | |
| 54 | ||
| 55 | ||
| 56 | public void init() { | |
| 57 | logger.debug("Init Faraday configuration dialog"); | |
| 58 | messages = ResourceBundle.getBundle( | |
| 59 | this.getClass().getPackage().getName() + | |
| 60 | ".Messages", Constant.getLocale()); | |
| 61 | // Setup the content-pane of JFrame in BorderLayout | |
| 62 | Container cp = this.getContentPane(); | |
| 63 | cp.setLayout(new BorderLayout(5, 5)); | |
| 64 | Border padding = BorderFactory.createEmptyBorder(10, 10, 10, 10); | |
| 65 | ||
| 66 | ||
| 67 | String USERNAME_FIELD = messages.getString("faraday.config.dialog.auth.user"); | |
| 68 | String PASS_FIELD = messages.getString("faraday.config.dialog.auth.pass"); | |
| 69 | String SERVER_FIELD = messages.getString("faraday.config.dialog.server"); | |
| 70 | LOGIN_BUTTON = messages.getString("faraday.config.dialog.auth.login"); | |
| 71 | LOGOUT_BUTTON = messages.getString("faraday.config.dialog.auth.logout"); | |
| 72 | WORKSPACES_FIELD = messages.getString("faraday.config.dialog.workspace"); | |
| 73 | IMPORT_NEW_VULNS_FIELD = messages.getString("faraday.config.dialog.import.new"); | |
| 74 | SET_CONFIG_AS_DEFAULT = messages.getString("faraday.config.dialog.default"); | |
| 75 | IMPORT_BUTTON = messages.getString("faraday.config.dialog.import.new"); | |
| 76 | REFRESH_BUTTON = messages.getString("faraday.config.dialog.refresh"); | |
| 77 | RESTORE_BUTTON = messages.getString("faraday.config.dialog.restore"); | |
| 78 | SAVE_BUTTON = messages.getString("faraday.config.dialog.save"); | |
| 79 | tabbedPane = new JTabbedPane(); | |
| 80 | ||
| 81 | JPanel buttonLoginPanel = new JPanel(); | |
| 82 | buttonLoginPanel.setLayout(new FlowLayout(FlowLayout.RIGHT)); | |
| 83 | ||
| 84 | JPanel buttonConfigPanel = new JPanel(); | |
| 85 | buttonConfigPanel.setLayout(new FlowLayout(FlowLayout.RIGHT)); | |
| 86 | ||
| 87 | authPanel = new JPanel(new GridLayout(4, 2, 10, 2)); | |
| 88 | authPanel.setBorder(padding); | |
| 89 | configPanel = new JPanel(new GridLayout(3, 2, 10, 2)); | |
| 90 | configPanel.setBorder(padding); | |
| 91 | ||
| 92 | ||
| 93 | Configuration configuration = Configuration.getSingleton(); | |
| 94 | faradayClient = new FaradayClient(configuration.getServer()); | |
| 95 | ||
| 96 | authPanel.add(new JLabel(USERNAME_FIELD)); | |
| 97 | fldUser = new JTextField(10); | |
| 98 | authPanel.add(fldUser); | |
| 99 | ||
| 100 | authPanel.add(new JLabel(PASS_FIELD)); | |
| 101 | fldPass = new JPasswordField(10); | |
| 102 | authPanel.add(fldPass); | |
| 103 | ||
| 104 | authPanel.add(new JLabel(SERVER_FIELD)); | |
| 105 | fldServer = new JTextField(10); | |
| 106 | fldServer.setText(configuration.getServer()); | |
| 107 | authPanel.add(fldServer); | |
| 108 | ||
| 109 | configPanel.add(getCBoxSetDefaultConfig()); | |
| 110 | ||
| 111 | buttonConfigPanel.add(getCloseButton()); | |
| 112 | buttonConfigPanel.add(getCloseButton()); | |
| 113 | buttonConfigPanel.add(getRefreshButton()); | |
| 114 | buttonConfigPanel.add(getRestoreButton()); | |
| 115 | buttonConfigPanel.add(getSaveButton()); | |
| 116 | // buttonConfigPanel.add(getImportButton()); | |
| 117 | buttonConfigPanel.add(getLoginButton()); | |
| 118 | buttonConfigPanel.add(getLogoutButton()); | |
| 119 | ||
| 120 | ||
| 121 | authPanel.addComponentListener(new ComponentListener() { | |
| 122 | @Override | |
| 123 | public void componentResized(ComponentEvent componentEvent) { | |
| 124 | ||
| 125 | } | |
| 126 | ||
| 127 | @Override | |
| 128 | public void componentMoved(ComponentEvent componentEvent) { | |
| 129 | ||
| 130 | } | |
| 131 | ||
| 132 | @Override | |
| 133 | public void componentShown(ComponentEvent componentEvent) { | |
| 134 | ||
| 135 | refreshButton.setVisible(false); | |
| 136 | restoreButton.setVisible(false); | |
| 137 | // importButton.setVisible(false); | |
| 138 | saveButton.setVisible(false); | |
| 139 | } | |
| 140 | ||
| 141 | @Override | |
| 142 | public void componentHidden(ComponentEvent componentEvent) { | |
| 143 | refreshButton.setVisible(true); | |
| 144 | restoreButton.setVisible(true); | |
| 145 | // importButton.setVisible(true); | |
| 146 | saveButton.setVisible(true); | |
| 147 | } | |
| 148 | }); | |
| 149 | ||
| 150 | configPanel.addComponentListener(new ComponentListener() { | |
| 151 | @Override | |
| 152 | public void componentResized(ComponentEvent componentEvent) { | |
| 153 | ||
| 154 | } | |
| 155 | ||
| 156 | @Override | |
| 157 | public void componentMoved(ComponentEvent componentEvent) { | |
| 158 | ||
| 159 | } | |
| 160 | ||
| 161 | @Override | |
| 162 | public void componentShown(ComponentEvent componentEvent) { | |
| 163 | loginButton.setVisible(false); | |
| 164 | logoutButton.setVisible(false); | |
| 165 | } | |
| 166 | ||
| 167 | @Override | |
| 168 | public void componentHidden(ComponentEvent componentEvent) { | |
| 169 | if (configuration.getSession().equals("")) { | |
| 170 | loginButton.setVisible(true); | |
| 171 | } else { | |
| 172 | logoutButton.setVisible(true); | |
| 173 | } | |
| 174 | } | |
| 175 | }); | |
| 176 | ||
| 177 | tabbedPane.addTab(messages.getString("faraday.config.dialog.tab.auth"), null, authPanel, null); | |
| 178 | tabbedPane.setMnemonicAt(0, KeyEvent.VK_1); | |
| 179 | ||
| 180 | ||
| 181 | tabbedPane.addTab(messages.getString("faraday.config.dialog.tabs.conf"), null, configPanel, null); | |
| 182 | tabbedPane.setMnemonicAt(1, KeyEvent.VK_2); | |
| 183 | ||
| 184 | tabbedPane.setEnabledAt(1, false); | |
| 185 | ||
| 186 | cp.add(tabbedPane, BorderLayout.NORTH); | |
| 187 | cp.add(buttonConfigPanel, BorderLayout.SOUTH); | |
| 188 | ||
| 189 | if (configuration.getSession() != null && !configuration.getSession().equals("")) { | |
| 190 | logoutButton.setVisible(true); | |
| 191 | loginButton.setVisible(false); | |
| 192 | } else { | |
| 193 | loginButton.setVisible(true); | |
| 194 | logoutButton.setVisible(false); | |
| 195 | } | |
| 196 | ||
| 197 | ||
| 198 | if (!configuration.getUser().equals("") && !configuration.getPassword().equals("")) { | |
| 199 | if (faradayClient.Login(configuration.getUser(), configuration.getPassword(), configuration.getServer())) { | |
| 200 | fldUser.setText(configuration.getUser()); | |
| 201 | fldPass.setText(configuration.getPassword()); | |
| 202 | fldServer.setText(configuration.getServer()); | |
| 203 | ||
| 204 | tabbedPane.setEnabledAt(1, true); | |
| 205 | tabbedPane.setSelectedIndex(1); | |
| 206 | ||
| 207 | cboxSetConfigDefault.setSelected(true); | |
| 208 | ||
| 209 | if (cmbWorkspaces == null) { | |
| 210 | configPanel.add(new JLabel(WORKSPACES_FIELD)); | |
| 211 | configPanel.add(getWSComboBox()); | |
| 212 | } | |
| 213 | } | |
| 214 | } | |
| 215 | ||
| 216 | this.setSize(550, 300); | |
| 217 | this.setResizable(false); | |
| 218 | this.setLocationRelativeTo(null); | |
| 219 | this.setVisible(true); | |
| 220 | } | |
| 221 | ||
| 222 | ||
| 223 | private JButton getLoginButton() { | |
| 224 | if (this.loginButton == null) { | |
| 225 | this.loginButton = new JButton(); | |
| 226 | this.loginButton.setText(LOGIN_BUTTON); | |
| 227 | this.loginButton.addActionListener(new ActionListener() { | |
| 228 | public void actionPerformed(ActionEvent e) { | |
| 229 | if (fldUser.getText().equals("") || fldPass.getText().equals("") || fldServer.getText().equals("")) { | |
| 230 | showMessage(messages.getString("faraday.message.invalid.check.credentials"), messages.getString("faraday.dialog.login.title"), JOptionPane.ERROR_MESSAGE); | |
| 231 | } else { | |
| 232 | if (faradayClient.Login(fldUser.getText(), fldPass.getText(), fldServer.getText())) { | |
| 233 | logoutButton.setVisible(true); | |
| 234 | loginButton.setVisible(false); | |
| 235 | if (!tabbedPane.isEnabledAt(1)) { | |
| 236 | tabbedPane.setEnabledAt(1, true); | |
| 237 | } | |
| 238 | tabbedPane.setSelectedIndex(1); | |
| 239 | if (cmbWorkspaces == null) { | |
| 240 | configPanel.add(new JLabel(WORKSPACES_FIELD)); | |
| 241 | configPanel.add(getWSComboBox()); | |
| 242 | } else { | |
| 243 | configPanel.remove(cmbWorkspaces); | |
| 244 | configPanel.add(getWSComboBox()); | |
| 245 | } | |
| 246 | } else { | |
| 247 | showMessage(messages.getString("faraday.message.invalid.credentials"), messages.getString("faraday.dialog.login.title"), JOptionPane.ERROR_MESSAGE); | |
| 248 | } | |
| 249 | } | |
| 250 | ||
| 251 | ||
| 252 | } | |
| 253 | }); | |
| 254 | ||
| 255 | ||
| 256 | } | |
| 257 | ||
| 258 | return this.loginButton; | |
| 259 | } | |
| 260 | ||
| 261 | ||
| 262 | private JButton getLogoutButton() { | |
| 263 | if (this.logoutButton == null) { | |
| 264 | this.logoutButton = new JButton(); | |
| 265 | this.logoutButton.setText(LOGOUT_BUTTON); | |
| 266 | this.logoutButton.addActionListener(new ActionListener() { | |
| 267 | public void actionPerformed(ActionEvent e) { | |
| 268 | Configuration configuration = Configuration.getSingleton(); | |
| 269 | String userTemp = configuration.getUser(); | |
| 270 | if (faradayClient.Logout()) { | |
| 271 | logoutButton.setVisible(false); | |
| 272 | loginButton.setVisible(true); | |
| 273 | ||
| 274 | if (tabbedPane.isEnabledAt(1)) { | |
| 275 | tabbedPane.setEnabledAt(1, false); | |
| 276 | } | |
| 277 | tabbedPane.setSelectedIndex(0); | |
| 278 | ||
| 279 | Properties prop = new Properties(); | |
| 280 | InputStream input = null; | |
| 281 | try { | |
| 282 | String filePath = Constant.getZapHome() + "faraday" + File.separator + "default.properties"; | |
| 283 | input = new FileInputStream(filePath); | |
| 284 | // load a properties file | |
| 285 | prop.load(input); | |
| 286 | // set the properties value | |
| 287 | String fUser = prop.getProperty("default"); | |
| 288 | if (fUser.equals(userTemp)) { | |
| 289 | removeDefaultConfig(); | |
| 290 | } | |
| 291 | ||
| 292 | } catch (IOException io) { | |
| 293 | System.out.println("We can't found default.properties file"); | |
| 294 | } finally { | |
| 295 | if (input != null) { | |
| 296 | try { | |
| 297 | input.close(); | |
| 298 | } catch (IOException er) { | |
| 299 | er.printStackTrace(); | |
| 300 | } | |
| 301 | } | |
| 302 | } | |
| 303 | ||
| 304 | ||
| 305 | showMessage(messages.getString("faraday.dialog.logout.success"), messages.getString("faraday.dialog.logout.title"), JOptionPane.INFORMATION_MESSAGE); | |
| 306 | } else { | |
| 307 | showMessage(messages.getString("faraday.dialog.logout.error"), messages.getString("faraday.dialog.logout.title"), JOptionPane.ERROR_MESSAGE); | |
| 308 | } | |
| 309 | } | |
| 310 | }); | |
| 311 | } | |
| 312 | ||
| 313 | return this.logoutButton; | |
| 314 | } | |
| 315 | ||
| 316 | ||
| 317 | private JButton getRefreshButton() { | |
| 318 | if (this.refreshButton == null) { | |
| 319 | this.refreshButton = new JButton(); | |
| 320 | this.refreshButton.setText(REFRESH_BUTTON); | |
| 321 | this.refreshButton.addActionListener(new ActionListener() { | |
| 322 | public void actionPerformed(ActionEvent e) { | |
| 323 | refreshWorkspaces(true); | |
| 324 | } | |
| 325 | }); | |
| 326 | } | |
| 327 | ||
| 328 | return this.refreshButton; | |
| 329 | } | |
| 330 | ||
| 331 | ||
| 332 | private JButton getCloseButton() { | |
| 333 | if (this.closeButton == null) { | |
| 334 | this.closeButton = new JButton(); | |
| 335 | this.closeButton.setText(messages.getString("faraday.dialog.button.close")); | |
| 336 | this.closeButton.addActionListener(new ActionListener() { | |
| 337 | public void actionPerformed(ActionEvent e) { | |
| 338 | setVisible(false); | |
| 339 | dispose(); | |
| 340 | } | |
| 341 | }); | |
| 342 | } | |
| 343 | ||
| 344 | return this.closeButton; | |
| 345 | } | |
| 346 | ||
| 347 | ||
| 348 | private JButton getRestoreButton() { | |
| 349 | if (this.restoreButton == null) { | |
| 350 | this.restoreButton = new JButton(); | |
| 351 | this.restoreButton.setText(RESTORE_BUTTON); | |
| 352 | this.restoreButton.addActionListener(new ActionListener() { | |
| 353 | public void actionPerformed(ActionEvent e) { | |
| 354 | String fUser = JOptionPane.showInputDialog(messages.getString("faraday.config.dialog.restore"), messages.getString("faraday.dialog.enter.user")); | |
| 355 | if (fUser != null) { | |
| 356 | restoreConfiguration(fUser); | |
| 357 | } | |
| 358 | } | |
| 359 | }); | |
| 360 | } | |
| 361 | ||
| 362 | return this.restoreButton; | |
| 363 | } | |
| 364 | ||
| 365 | ||
| 366 | private JButton getImportButton() { | |
| 367 | if (this.importButton == null) { | |
| 368 | this.importButton = new JButton(); | |
| 369 | this.importButton.setText(IMPORT_BUTTON); | |
| 370 | this.importButton.addActionListener(new ActionListener() { | |
| 371 | public void actionPerformed(ActionEvent e) { | |
| 372 | ||
| 373 | } | |
| 374 | }); | |
| 375 | } | |
| 376 | ||
| 377 | return this.importButton; | |
| 378 | } | |
| 379 | ||
| 380 | ||
| 381 | private JButton getSaveButton() { | |
| 382 | if (this.saveButton == null) { | |
| 383 | this.saveButton = new JButton(); | |
| 384 | this.saveButton.setText(SAVE_BUTTON); | |
| 385 | this.saveButton.addActionListener(new ActionListener() { | |
| 386 | public void actionPerformed(ActionEvent e) { | |
| 387 | saveConfiguration(); | |
| 388 | } | |
| 389 | }); | |
| 390 | } | |
| 391 | ||
| 392 | return this.saveButton; | |
| 393 | } | |
| 394 | ||
| 395 | ||
| 396 | private JComboBox getWSComboBox() { | |
| 397 | Configuration configuration = Configuration.getSingleton(); | |
| 398 | ||
| 399 | ArrayList<String> wsList = faradayClient.GetWorkspaces(); | |
| 400 | String[] workspaces = new String[wsList.size()]; | |
| 401 | for (int i = 0; i < wsList.size(); i++) { | |
| 402 | workspaces[i] = wsList.get(i); | |
| 403 | } | |
| 404 | cmbWorkspaces = new JComboBox(workspaces); | |
| 405 | if (workspaces.length > 0) { | |
| 406 | if (configuration.getWorkspace() != null) { | |
| 407 | cmbWorkspaces.setSelectedItem(configuration.getWorkspace()); | |
| 408 | } else { | |
| 409 | configuration.setWorkspace(workspaces[0]); | |
| 410 | } | |
| 411 | } | |
| 412 | cmbWorkspaces.addActionListener(new ActionListener() { | |
| 413 | @Override | |
| 414 | public void actionPerformed(ActionEvent actionEvent) { | |
| 415 | Configuration.getSingleton().setWorkspace(cmbWorkspaces.getSelectedItem().toString()); | |
| 416 | } | |
| 417 | }); | |
| 418 | ||
| 419 | ||
| 420 | return cmbWorkspaces; | |
| 421 | } | |
| 422 | ||
| 423 | ||
| 424 | private JCheckBox getCBoxSetDefaultConfig() { | |
| 425 | if (this.cboxSetConfigDefault == null) { | |
| 426 | cboxSetConfigDefault = new JCheckBox(SET_CONFIG_AS_DEFAULT, false); | |
| 427 | ||
| 428 | cboxSetConfigDefault.addActionListener(new ActionListener() { | |
| 429 | @Override | |
| 430 | public void actionPerformed(ActionEvent actionEvent) { | |
| 431 | if (cboxSetConfigDefault.isSelected()) { | |
| 432 | setConfigAsDefault(); | |
| 433 | } else { | |
| 434 | removeDefaultConfig(); | |
| 435 | } | |
| 436 | } | |
| 437 | }); | |
| 438 | } | |
| 439 | ||
| 440 | return cboxSetConfigDefault; | |
| 441 | } | |
| 442 | ||
| 443 | ||
| 444 | private void showMessage(String message, String title, int icon) { | |
| 445 | JOptionPane.showMessageDialog( | |
| 446 | this, | |
| 447 | message, | |
| 448 | title, | |
| 449 | icon); | |
| 450 | } | |
| 451 | ||
| 452 | ||
| 453 | private void saveConfiguration() { | |
| 454 | try { | |
| 455 | if (Configuration.getSingleton().save()) { | |
| 456 | JOptionPane.showMessageDialog( | |
| 457 | this, | |
| 458 | messages.getString("faraday.save.config.success"), | |
| 459 | messages.getString("faraday.config.dialog.title"), | |
| 460 | JOptionPane.INFORMATION_MESSAGE); | |
| 461 | } else { | |
| 462 | JOptionPane.showMessageDialog( | |
| 463 | this, | |
| 464 | messages.getString("faraday.save.config.error"), | |
| 465 | messages.getString("faraday.config.dialog.title"), | |
| 466 | JOptionPane.ERROR_MESSAGE); | |
| 467 | ||
| 468 | } | |
| 469 | } catch (IOException io) { | |
| 470 | JOptionPane.showMessageDialog( | |
| 471 | this, | |
| 472 | messages.getString("faraday.save.config.error"), | |
| 473 | messages.getString("faraday.config.dialog.title"), | |
| 474 | JOptionPane.ERROR_MESSAGE); | |
| 475 | io.printStackTrace(); | |
| 476 | ||
| 477 | } | |
| 478 | } | |
| 479 | ||
| 480 | ||
| 481 | private void restoreConfiguration(String fUser) { | |
| 482 | try { | |
| 483 | Configuration configuration = Configuration.getSingleton(); | |
| 484 | configuration.restore(fUser); | |
| 485 | if (faradayClient.Login(configuration.getUser(), configuration.getPassword(), configuration.getServer())) { | |
| 486 | fldUser.setText(configuration.getUser()); | |
| 487 | fldPass.setText(configuration.getPassword()); | |
| 488 | fldServer.setText(configuration.getServer()); | |
| 489 | ||
| 490 | tabbedPane.setEnabledAt(1, true); | |
| 491 | tabbedPane.setSelectedIndex(0); | |
| 492 | ||
| 493 | cboxSetConfigDefault.setSelected(false); | |
| 494 | refreshWorkspaces(false); | |
| 495 | } else { | |
| 496 | JOptionPane.showMessageDialog( | |
| 497 | this, | |
| 498 | messages.getString("faraday.restore.config.error.login"), | |
| 499 | messages.getString("faraday.config.dialog.title"), | |
| 500 | JOptionPane.ERROR_MESSAGE); | |
| 501 | } | |
| 502 | } catch (IOException ex) { | |
| 503 | JOptionPane.showMessageDialog( | |
| 504 | this, | |
| 505 | messages.getString("faraday.restore.config.error"), | |
| 506 | messages.getString("faraday.config.dialog.title"), | |
| 507 | JOptionPane.ERROR_MESSAGE); | |
| 508 | } | |
| 509 | ||
| 510 | } | |
| 511 | ||
| 512 | ||
| 513 | private void setConfigAsDefault() { | |
| 514 | Configuration configuration = Configuration.getSingleton(); | |
| 515 | ||
| 516 | Properties prop = new Properties(); | |
| 517 | OutputStream output = null; | |
| 518 | ||
| 519 | try { | |
| 520 | String outputFolder = Constant.getZapHome() + "faraday"; | |
| 521 | File folder = new File(outputFolder); | |
| 522 | if (!folder.exists()) { | |
| 523 | folder.mkdir(); | |
| 524 | } | |
| 525 | ||
| 526 | String filePath = outputFolder + File.separator + "default.properties"; | |
| 527 | output = new FileOutputStream(filePath); | |
| 528 | ||
| 529 | // set the properties value | |
| 530 | prop.setProperty("default", configuration.getUser()); | |
| 531 | ||
| 532 | // save properties to project root folder | |
| 533 | prop.store(output, null); | |
| 534 | ||
| 535 | } catch (IOException io) { | |
| 536 | JOptionPane.showMessageDialog( | |
| 537 | this, | |
| 538 | messages.getString("faraday.set.default.config.error"), | |
| 539 | messages.getString("faraday.config.dialog.title"), | |
| 540 | JOptionPane.ERROR_MESSAGE); | |
| 541 | io.printStackTrace(); | |
| 542 | } finally { | |
| 543 | if (output != null) { | |
| 544 | try { | |
| 545 | output.close(); | |
| 546 | } catch (IOException e) { | |
| 547 | e.printStackTrace(); | |
| 548 | } | |
| 549 | } | |
| 550 | ||
| 551 | } | |
| 552 | } | |
| 553 | ||
| 554 | ||
| 555 | private void removeDefaultConfig() { | |
| 556 | try { | |
| 557 | ||
| 558 | String filePath = Constant.getZapHome() + "faraday" + File.separator + "default.properties"; | |
| 559 | File file = new File(filePath); | |
| 560 | if (file.delete()) { | |
| 561 | System.out.println(file.getName() + " is deleted!"); | |
| 562 | } else { | |
| 563 | System.out.println("Delete operation is failed."); | |
| 564 | } | |
| 565 | ||
| 566 | } catch (Exception e) { | |
| 567 | ||
| 568 | e.printStackTrace(); | |
| 569 | ||
| 570 | } | |
| 571 | } | |
| 572 | ||
| 573 | ||
| 574 | private void refreshWorkspaces(boolean canShowAlert) { | |
| 575 | if (cmbWorkspaces != null) { | |
| 576 | configPanel.remove(cmbWorkspaces); | |
| 577 | configPanel.add(getWSComboBox()); | |
| 578 | if (canShowAlert) { | |
| 579 | JOptionPane.showMessageDialog( | |
| 580 | this, | |
| 581 | messages.getString("faraday.refresh.workspace.done"), | |
| 582 | messages.getString("faraday.config.dialog.title"), | |
| 583 | JOptionPane.INFORMATION_MESSAGE); | |
| 584 | } | |
| 585 | } | |
| 586 | } | |
| 587 | ||
| 588 | } |
| 0 | package org.zaproxy.zap.extension.faraday; | |
| 1 | ||
| 2 | import net.sf.json.JSONArray; | |
| 3 | import net.sf.json.JSONObject; | |
| 4 | import org.apache.commons.httpclient.URIException; | |
| 5 | import org.apache.commons.httpclient.methods.PostMethod; | |
| 6 | import org.apache.http.HttpEntity; | |
| 7 | import org.apache.http.HttpResponse; | |
| 8 | ||
| 9 | import org.apache.http.client.ClientProtocolException; | |
| 10 | import org.apache.http.client.HttpClient; | |
| 11 | import org.apache.http.entity.StringEntity; | |
| 12 | import org.apache.http.client.entity.UrlEncodedFormEntity; | |
| 13 | import org.apache.http.client.methods.HttpGet; | |
| 14 | import org.apache.http.client.methods.HttpPost; | |
| 15 | import org.apache.http.impl.client.HttpClients; | |
| 16 | import org.apache.http.NameValuePair; | |
| 17 | import org.apache.http.message.BasicNameValuePair; | |
| 18 | import org.apache.http.util.EntityUtils; | |
| 19 | import org.parosproxy.paros.Constant; | |
| 20 | import org.parosproxy.paros.core.scanner.Alert; | |
| 21 | import org.parosproxy.paros.model.HistoryReference; | |
| 22 | ||
| 23 | import java.io.*; | |
| 24 | import java.net.*; | |
| 25 | import java.nio.charset.StandardCharsets; | |
| 26 | import java.sql.Time; | |
| 27 | import java.time.Instant; | |
| 28 | import java.util.*; | |
| 29 | ||
| 30 | ||
| 31 | public class FaradayClient { | |
| 32 | ||
| 33 | private String baseUrl; | |
| 34 | private ResourceBundle messages = null; | |
| 35 | ||
| 36 | public FaradayClient(String baseUrl) { | |
| 37 | this.baseUrl = baseUrl; | |
| 38 | messages = ResourceBundle.getBundle( | |
| 39 | this.getClass().getPackage().getName() + | |
| 40 | ".Messages", Constant.getLocale()); | |
| 41 | ||
| 42 | } | |
| 43 | ||
| 44 | public boolean Login(String username, String password, String server) { | |
| 45 | Logout(); | |
| 46 | HttpClient httpClient = HttpClients.createDefault(); | |
| 47 | String LOGIN_URL = "_api/login"; | |
| 48 | HttpPost httpPost = new HttpPost(server + LOGIN_URL); | |
| 49 | ||
| 50 | // Request parameters and other properties. | |
| 51 | List<BasicNameValuePair> params = new ArrayList<>(2); | |
| 52 | params.add(new BasicNameValuePair("email", username)); | |
| 53 | params.add(new BasicNameValuePair("password", password)); | |
| 54 | ||
| 55 | try { | |
| 56 | httpPost.setEntity(new UrlEncodedFormEntity(params, "UTF-8")); | |
| 57 | HttpResponse response = httpClient.execute(httpPost); | |
| 58 | if (response.getFirstHeader("Set-Cookie") != null) { | |
| 59 | Configuration configuration = Configuration.getSingleton(); | |
| 60 | configuration.setSession(response.getFirstHeader("Set-Cookie").getValue()); | |
| 61 | configuration.setUser(username); | |
| 62 | configuration.setPassword(password); | |
| 63 | configuration.setServer(server); | |
| 64 | setBaseUrl(server); | |
| 65 | return true; | |
| 66 | } else if (response.getStatusLine().getStatusCode() == 302) { | |
| 67 | return true; | |
| 68 | } | |
| 69 | return false; | |
| 70 | } catch (UnsupportedEncodingException e) { | |
| 71 | // writing error to Log | |
| 72 | e.printStackTrace(); | |
| 73 | return false; | |
| 74 | } catch (ClientProtocolException e) { | |
| 75 | e.printStackTrace(); | |
| 76 | return false; | |
| 77 | } catch (IOException e) { | |
| 78 | e.printStackTrace(); | |
| 79 | return false; | |
| 80 | } | |
| 81 | ||
| 82 | } | |
| 83 | ||
| 84 | public boolean Logout() { | |
| 85 | String LOGOUT_URL = "_api/logout"; | |
| 86 | HttpGet httpGet = new HttpGet(this.baseUrl + LOGOUT_URL); | |
| 87 | Configuration configuration = Configuration.getSingleton(); | |
| 88 | ||
| 89 | if (!Objects.equals(configuration.getSession(), "")) { | |
| 90 | httpGet.setHeader("Cookie", configuration.getSession()); | |
| 91 | ||
| 92 | //Execute and get the response. | |
| 93 | HttpResponse response = null; | |
| 94 | ||
| 95 | try { | |
| 96 | HttpClient httpClient = HttpClients.createDefault(); | |
| 97 | response = httpClient.execute(httpGet); | |
| 98 | HttpEntity entity = response.getEntity(); | |
| 99 | if (response.getStatusLine().getStatusCode() == 200) { | |
| 100 | configuration.setSession(""); | |
| 101 | configuration.setUser(""); | |
| 102 | configuration.setPassword(""); | |
| 103 | return true; | |
| 104 | } | |
| 105 | return false; | |
| 106 | } catch (IOException e) { | |
| 107 | e.printStackTrace(); | |
| 108 | return false; | |
| 109 | } | |
| 110 | } | |
| 111 | return true; | |
| 112 | } | |
| 113 | ||
| 114 | public ArrayList<String> GetWorkspaces() { | |
| 115 | ArrayList<String> workspaces = new ArrayList<>(); | |
| 116 | String WORKSPACES_URL = "_api/v2/ws/"; | |
| 117 | HttpGet httpGet = new HttpGet(this.baseUrl + WORKSPACES_URL); | |
| 118 | Configuration configuration = Configuration.getSingleton(); | |
| 119 | ||
| 120 | if (configuration.getSession() != "") { | |
| 121 | httpGet.setHeader("Cookie", configuration.getSession()); | |
| 122 | ||
| 123 | //Execute and get the response. | |
| 124 | HttpResponse response = null; | |
| 125 | InputStream instream = null; | |
| 126 | try { | |
| 127 | HttpClient httpClient = HttpClients.createDefault(); | |
| 128 | response = httpClient.execute(httpGet); | |
| 129 | HttpEntity entity = response.getEntity(); | |
| 130 | ||
| 131 | if (entity != null && response.getStatusLine().getStatusCode() == 200) { | |
| 132 | instream = entity.getContent(); | |
| 133 | ||
| 134 | BufferedReader br = new BufferedReader(new InputStreamReader(instream)); | |
| 135 | String output; | |
| 136 | JSONArray jsonArray = new JSONArray(); | |
| 137 | while ((output = br.readLine()) != null) { | |
| 138 | System.out.println(output); | |
| 139 | jsonArray = JSONArray.fromObject(output); | |
| 140 | } | |
| 141 | ||
| 142 | for (int i = 0; i < jsonArray.size(); i++) { | |
| 143 | JSONObject jsonObject = jsonArray.getJSONObject(i); | |
| 144 | workspaces.add(jsonObject.get("name").toString()); | |
| 145 | } | |
| 146 | } | |
| 147 | } catch (IOException e) { | |
| 148 | e.printStackTrace(); | |
| 149 | } finally { | |
| 150 | try { | |
| 151 | instream.close(); | |
| 152 | } catch (IOException e) { | |
| 153 | e.printStackTrace(); | |
| 154 | } | |
| 155 | } | |
| 156 | } | |
| 157 | ||
| 158 | return workspaces; | |
| 159 | } | |
| 160 | ||
| 161 | ||
| 162 | private int AddCommand(String commandName, String workspace, String session) { | |
| 163 | String COMMAND_URL = "_api/v2/ws/" + workspace + "/commands/"; | |
| 164 | HttpClient httpClient = HttpClients.createDefault(); | |
| 165 | HttpPost httpPost = new HttpPost(this.baseUrl + COMMAND_URL); | |
| 166 | ||
| 167 | try { | |
| 168 | StringEntity stringEntity = new StringEntity(ConvertCommandToParams(commandName).toString()); | |
| 169 | httpPost.setHeader("Cookie", session); | |
| 170 | httpPost.setHeader("Content-Type", "application/json"); | |
| 171 | httpPost.setEntity(stringEntity); | |
| 172 | HttpResponse response = httpClient.execute(httpPost); | |
| 173 | HttpEntity entity = response.getEntity(); | |
| 174 | ||
| 175 | if (response.getStatusLine().getStatusCode() == 200 || response.getStatusLine().getStatusCode() == 201 || response.getStatusLine().getStatusCode() == 409) { | |
| 176 | BufferedReader br = new BufferedReader(new InputStreamReader(entity.getContent())); | |
| 177 | String output; | |
| 178 | JSONObject json; | |
| 179 | String commandStr = "-1"; | |
| 180 | while ((output = br.readLine()) != null) { | |
| 181 | json = JSONObject.fromObject(output); | |
| 182 | if (response.getStatusLine().getStatusCode() == 409) { | |
| 183 | JSONObject jsonObject = JSONObject.fromObject(json.get("object")); | |
| 184 | commandStr = jsonObject.get("_id").toString(); | |
| 185 | } else { | |
| 186 | commandStr = json.get("_id").toString(); | |
| 187 | } | |
| 188 | } | |
| 189 | return Integer.parseInt(commandStr); | |
| 190 | } | |
| 191 | return -1; | |
| 192 | } catch (UnsupportedEncodingException e) { | |
| 193 | // writing error to Log | |
| 194 | e.printStackTrace(); | |
| 195 | return -1; | |
| 196 | } catch (ClientProtocolException e) { | |
| 197 | e.printStackTrace(); | |
| 198 | return -1; | |
| 199 | } catch (IOException e) { | |
| 200 | e.printStackTrace(); | |
| 201 | return -1; | |
| 202 | } | |
| 203 | } | |
| 204 | ||
| 205 | private int AddHost(Alert alert, String workspace, String session) { | |
| 206 | String VULN_URL = "_api/v2/ws/" + workspace + "/hosts/"; | |
| 207 | HttpClient httpClient = HttpClients.createDefault(); | |
| 208 | HttpPost httpPost = new HttpPost(this.baseUrl + VULN_URL); | |
| 209 | ||
| 210 | try { | |
| 211 | StringEntity stringEntity = new StringEntity(ConvertHostToParams(alert).toString()); | |
| 212 | httpPost.setHeader("Cookie", session); | |
| 213 | httpPost.setHeader("Content-Type", "application/json"); | |
| 214 | httpPost.setEntity(stringEntity); | |
| 215 | HttpResponse response = httpClient.execute(httpPost); | |
| 216 | HttpEntity entity = response.getEntity(); | |
| 217 | ||
| 218 | if (response.getStatusLine().getStatusCode() == 200 || response.getStatusLine().getStatusCode() == 201 || response.getStatusLine().getStatusCode() == 409) { | |
| 219 | BufferedReader br = new BufferedReader(new InputStreamReader(entity.getContent())); | |
| 220 | String output; | |
| 221 | JSONObject json; | |
| 222 | String hostStr = "-1"; | |
| 223 | while ((output = br.readLine()) != null) { | |
| 224 | json = JSONObject.fromObject(output); | |
| 225 | if (response.getStatusLine().getStatusCode() == 409) { | |
| 226 | JSONObject jsonObject = JSONObject.fromObject(json.get("object")); | |
| 227 | hostStr = jsonObject.get("id").toString(); | |
| 228 | } else { | |
| 229 | hostStr = json.get("id").toString(); | |
| 230 | } | |
| 231 | } | |
| 232 | return Integer.parseInt(hostStr); | |
| 233 | } | |
| 234 | return -1; | |
| 235 | } catch (UnsupportedEncodingException e) { | |
| 236 | // writing error to Log | |
| 237 | e.printStackTrace(); | |
| 238 | return -1; | |
| 239 | } catch (ClientProtocolException e) { | |
| 240 | e.printStackTrace(); | |
| 241 | return -1; | |
| 242 | } catch (IOException e) { | |
| 243 | e.printStackTrace(); | |
| 244 | return -1; | |
| 245 | } | |
| 246 | } | |
| 247 | ||
| 248 | private int AddService(Alert alert, String workspace, String session, int hostId) { | |
| 249 | String VULN_URL = "_api/v2/ws/" + workspace + "/services/"; | |
| 250 | HttpClient httpClient = HttpClients.createDefault(); | |
| 251 | HttpPost httpPost = new HttpPost(this.baseUrl + VULN_URL); | |
| 252 | ||
| 253 | try { | |
| 254 | StringEntity stringEntity = new StringEntity(ConvertServiceToParams(alert, hostId).toString()); | |
| 255 | httpPost.setHeader("Cookie", session); | |
| 256 | httpPost.setHeader("Content-Type", "application/json"); | |
| 257 | httpPost.setEntity(stringEntity); | |
| 258 | HttpResponse response = httpClient.execute(httpPost); | |
| 259 | HttpEntity entity = response.getEntity(); | |
| 260 | ||
| 261 | BufferedReader br = new BufferedReader(new InputStreamReader(entity.getContent())); | |
| 262 | String output; | |
| 263 | if (response.getStatusLine().getStatusCode() == 200 || response.getStatusLine().getStatusCode() == 201 || response.getStatusLine().getStatusCode() == 409) { | |
| 264 | JSONObject json; | |
| 265 | String serviceStr = "-1"; | |
| 266 | while ((output = br.readLine()) != null) { | |
| 267 | json = JSONObject.fromObject(output); | |
| 268 | if (response.getStatusLine().getStatusCode() == 409) { | |
| 269 | JSONObject jsonObject = JSONObject.fromObject(json.get("object")); | |
| 270 | serviceStr = jsonObject.get("id").toString(); | |
| 271 | } else { | |
| 272 | serviceStr = json.get("id").toString(); | |
| 273 | } | |
| 274 | } | |
| 275 | return Integer.parseInt(serviceStr); | |
| 276 | } else { | |
| 277 | while ((output = br.readLine()) != null) { | |
| 278 | System.out.println(output); | |
| 279 | } | |
| 280 | ||
| 281 | return -1; | |
| 282 | } | |
| 283 | ||
| 284 | } catch (UnsupportedEncodingException e) { | |
| 285 | // writing error to Log | |
| 286 | e.printStackTrace(); | |
| 287 | return -1; | |
| 288 | } catch (ClientProtocolException e) { | |
| 289 | e.printStackTrace(); | |
| 290 | return -1; | |
| 291 | } catch (IOException e) { | |
| 292 | e.printStackTrace(); | |
| 293 | return -1; | |
| 294 | } | |
| 295 | } | |
| 296 | ||
| 297 | public int AddVulnerability(Alert alert, String workspace, String session) { | |
| 298 | int hostId = AddHost(alert, workspace, session); | |
| 299 | if (hostId == -1) { | |
| 300 | return 500; | |
| 301 | } | |
| 302 | ||
| 303 | String parentType = "Service"; | |
| 304 | int serviceId = AddService(alert, workspace, session, hostId); | |
| 305 | if (serviceId == -1) { | |
| 306 | return 500; | |
| 307 | } | |
| 308 | ||
| 309 | ||
| 310 | String commandName = messages.getString("faraday.tool.command.name"); | |
| 311 | int commandId = AddCommand(commandName, workspace, session); | |
| 312 | if (commandId == -1) { | |
| 313 | return 500; | |
| 314 | } | |
| 315 | ||
| 316 | ||
| 317 | String VULN_URL = "_api/v2/ws/" + workspace + "/vulns/?command_id=" + commandId; | |
| 318 | HttpClient httpClient = HttpClients.createDefault(); | |
| 319 | HttpPost httpPost = new HttpPost(this.baseUrl + VULN_URL); | |
| 320 | try { | |
| 321 | ||
| 322 | StringEntity stringEntity = new StringEntity(ConvertAlertToParams(alert, workspace, parentType, serviceId).toString()); | |
| 323 | httpPost.setHeader("Cookie", session); | |
| 324 | httpPost.setHeader("Content-Type", "application/json"); | |
| 325 | httpPost.setEntity(stringEntity); | |
| 326 | HttpResponse response = httpClient.execute(httpPost); | |
| 327 | return response.getStatusLine().getStatusCode(); | |
| 328 | ||
| 329 | } catch (UnsupportedEncodingException e) { | |
| 330 | // writing error to Log | |
| 331 | e.printStackTrace(); | |
| 332 | return 402; | |
| 333 | } catch (ClientProtocolException e) { | |
| 334 | e.printStackTrace(); | |
| 335 | return 402; | |
| 336 | } catch (IOException e) { | |
| 337 | e.printStackTrace(); | |
| 338 | return 402; | |
| 339 | } | |
| 340 | } | |
| 341 | ||
| 342 | private JSONObject ConvertAlertToParams(Alert alert, String workspace, String parentType, int parentId) { | |
| 343 | // Request parameters and other properties. | |
| 344 | JSONObject params = new JSONObject(); | |
| 345 | ||
| 346 | params.put("name", alert.getName()); | |
| 347 | params.put("ws", workspace); | |
| 348 | params.put("request", alert.getMessage().getRequestHeader().toString()); | |
| 349 | params.put("response", alert.getMessage().getResponseHeader().toString()); | |
| 350 | String desc = !alert.getParam().equals("") ? alert.getDescription() + "\nWith parameter: '" + alert.getParam() + "'" : | |
| 351 | alert.getDescription(); | |
| 352 | params.put("desc", desc); | |
| 353 | params.put("resolution", alert.getSolution()); | |
| 354 | params.put("type", "VulnerabilityWeb"); | |
| 355 | params.put("data", alert.getPostData()); | |
| 356 | params.put("policyviolations", "[]"); | |
| 357 | params.put("parent_type", parentType); | |
| 358 | params.put("parent", parentId); | |
| 359 | params.put("params", alert.getParam()); | |
| 360 | ||
| 361 | JSONObject metadata = new JSONObject(); | |
| 362 | metadata.put("creator", "OWASP"); | |
| 363 | params.put("metadata", metadata); | |
| 364 | ||
| 365 | String hostname = alert.getMessage().getRequestHeader().getHostName(); | |
| 366 | String IpAddres = GetIPFromHostname(hostname); | |
| 367 | JSONArray hostNamesArray = new JSONArray(); | |
| 368 | hostNamesArray.add(hostname); | |
| 369 | hostNamesArray.add(IpAddres); | |
| 370 | params.put("hostnames", hostNamesArray); | |
| 371 | params.put("target", IpAddres); | |
| 372 | params.put("website", hostname); | |
| 373 | ||
| 374 | JSONArray refsJsonArray = new JSONArray(); | |
| 375 | String[] resfArray = alert.getReference().split("\n"); | |
| 376 | Collections.addAll(refsJsonArray, resfArray); | |
| 377 | params.put("refs", refsJsonArray); | |
| 378 | ||
| 379 | try { | |
| 380 | params.put("path", alert.getMsgUri().getPath()); | |
| 381 | } catch (URIException e) { | |
| 382 | e.printStackTrace(); | |
| 383 | } | |
| 384 | ||
| 385 | if (alert.getConfidence() == 4) { | |
| 386 | params.put("confirmed", true); | |
| 387 | } | |
| 388 | ||
| 389 | switch (alert.getRisk()) { | |
| 390 | case 0: | |
| 391 | params.put("severity", "informational"); | |
| 392 | break; | |
| 393 | case 1: | |
| 394 | params.put("severity", "low"); | |
| 395 | break; | |
| 396 | case 2: | |
| 397 | params.put("severity", "medium"); | |
| 398 | break; | |
| 399 | case 3: | |
| 400 | params.put("severity", "high"); | |
| 401 | break; | |
| 402 | } | |
| 403 | return params; | |
| 404 | ||
| 405 | } | |
| 406 | ||
| 407 | private JSONObject ConvertHostToParams(Alert alert) { | |
| 408 | // Request parameters and other properties. | |
| 409 | JSONObject params = new JSONObject(); | |
| 410 | ||
| 411 | try { | |
| 412 | String ipAddress = GetIPFromHostname(alert.getMsgUri().getHost()); | |
| 413 | params.put("ip", ipAddress); | |
| 414 | params.put("name", alert.getMsgUri().getName()); | |
| 415 | params.put("os", "Unknown"); | |
| 416 | params.put("description", ""); | |
| 417 | JSONObject metadata = new JSONObject(); | |
| 418 | metadata.put("creator", "Zap"); | |
| 419 | params.put("metadata", metadata); | |
| 420 | ||
| 421 | String hostname = alert.getMessage().getRequestHeader().getHostName(); | |
| 422 | JSONArray hostNamesArray = new JSONArray(); | |
| 423 | hostNamesArray.add(hostname); | |
| 424 | params.put("hostnames", hostNamesArray); | |
| 425 | ||
| 426 | } catch (URIException e) { | |
| 427 | e.printStackTrace(); | |
| 428 | } | |
| 429 | return params; | |
| 430 | } | |
| 431 | ||
| 432 | private JSONObject ConvertServiceToParams(Alert alert, int parentId) { | |
| 433 | // Request parameters and other properties. | |
| 434 | JSONObject params = new JSONObject(); | |
| 435 | JSONArray portsJson = new JSONArray(); | |
| 436 | portsJson.add(alert.getMessage().getRequestHeader().getHostPort()); | |
| 437 | params.put("ports", portsJson); | |
| 438 | params.put("parent", parentId); | |
| 439 | params.put("status", "open"); | |
| 440 | params.put("type", "Service"); | |
| 441 | params.put("description", ""); | |
| 442 | JSONObject metadata = new JSONObject(); | |
| 443 | metadata.put("creator", "OWASP"); | |
| 444 | params.put("metadata", metadata); | |
| 445 | ||
| 446 | switch (alert.getMessage().getRequestHeader().getHostPort()) { | |
| 447 | case 21: | |
| 448 | params.put("name", "FTP"); | |
| 449 | params.put("protocol", "tcp"); | |
| 450 | break; | |
| 451 | case 22: | |
| 452 | params.put("name", "SSH"); | |
| 453 | params.put("protocol", "tcp"); | |
| 454 | break; | |
| 455 | case 23: | |
| 456 | params.put("name", "TELNET"); | |
| 457 | params.put("protocol", "tcp"); | |
| 458 | break; | |
| 459 | case 25: | |
| 460 | params.put("name", "SMTP"); | |
| 461 | params.put("protocol", "tcp"); | |
| 462 | break; | |
| 463 | case 80: | |
| 464 | params.put("name", "HTTP"); | |
| 465 | params.put("protocol", "tcp"); | |
| 466 | break; | |
| 467 | case 110: | |
| 468 | params.put("name", "POP"); | |
| 469 | params.put("protocol", "tcp"); | |
| 470 | break; | |
| 471 | case 443: | |
| 472 | params.put("name", "SSL"); | |
| 473 | params.put("protocol", "tcp"); | |
| 474 | break; | |
| 475 | default: | |
| 476 | params.put("name", "unknown"); | |
| 477 | params.put("protocol", "unknown"); | |
| 478 | break; | |
| 479 | } | |
| 480 | ||
| 481 | return params; | |
| 482 | } | |
| 483 | ||
| 484 | private JSONObject ConvertCommandToParams(String commandName) { | |
| 485 | // Request parameters and other properties. | |
| 486 | JSONObject params = new JSONObject(); | |
| 487 | params.put("itime", Instant.EPOCH.getEpochSecond()); | |
| 488 | params.put("import_source", "shell"); | |
| 489 | params.put("duration", ""); | |
| 490 | params.put("command", "Zap"); | |
| 491 | params.put("tool", commandName); | |
| 492 | return params; | |
| 493 | } | |
| 494 | ||
| 495 | private String GetIPFromHostname(String hostname) { | |
| 496 | try { | |
| 497 | InetAddress inetAddr = InetAddress.getByName(hostname); | |
| 498 | byte[] addr = inetAddr.getAddress(); | |
| 499 | ||
| 500 | // Convert to dot representation | |
| 501 | String ipAddr = ""; | |
| 502 | for (int i = 0; i < addr.length; i++) { | |
| 503 | if (i > 0) { | |
| 504 | ipAddr += "."; | |
| 505 | } | |
| 506 | ||
| 507 | ipAddr += addr[i] & 0xFF; | |
| 508 | } | |
| 509 | ||
| 510 | System.out.println("IP Address: " + ipAddr); | |
| 511 | return ipAddr; | |
| 512 | } catch (UnknownHostException e) { | |
| 513 | System.out.println("Host not found: " + e.getMessage()); | |
| 514 | return ""; | |
| 515 | } | |
| 516 | } | |
| 517 | ||
| 518 | public void setBaseUrl(String baseUrl) { | |
| 519 | this.baseUrl = baseUrl; | |
| 520 | } | |
| 521 | } | |
| 522 | ||
| 523 | ||
| 524 |
| 0 | /* | |
| 1 | * Zed Attack Proxy (ZAP) and its related class files. | |
| 2 | * | |
| 3 | * ZAP is an HTTP/HTTPS proxy for assessing web application security. | |
| 4 | * | |
| 5 | * Licensed under the Apache License, Version 2.0 (the "License"); | |
| 6 | * you may not use this file except in compliance with the License. | |
| 7 | * You may obtain a copy of the License at | |
| 8 | * | |
| 9 | * http://www.apache.org/licenses/LICENSE-2.0 | |
| 10 | * | |
| 11 | * Unless required by applicable law or agreed to in writing, software | |
| 12 | * distributed under the License is distributed on an "AS IS" BASIS, | |
| 13 | * WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. | |
| 14 | * See the License for the specific language governing permissions and | |
| 15 | * limitations under the License. | |
| 16 | */ | |
| 17 | package org.zaproxy.zap.extension.faraday; | |
| 18 | ||
| 19 | import org.apache.log4j.Logger; | |
| 20 | import org.parosproxy.paros.Constant; | |
| 21 | import org.parosproxy.paros.control.Control; | |
| 22 | import org.parosproxy.paros.extension.ExtensionAdaptor; | |
| 23 | import org.parosproxy.paros.extension.ExtensionHook; | |
| 24 | import org.parosproxy.paros.extension.ExtensionPopupMenuItem; | |
| 25 | import org.zaproxy.zap.view.ZapMenuItem; | |
| 26 | ||
| 27 | import javax.swing.*; | |
| 28 | import java.awt.*; | |
| 29 | import java.awt.event.KeyEvent; | |
| 30 | import java.io.*; | |
| 31 | import java.util.Properties; | |
| 32 | import java.util.ResourceBundle; | |
| 33 | ||
| 34 | public class FaradayExtension extends ExtensionAdaptor { | |
| 35 | private static final Logger logger = Logger.getLogger(FaradayExtension.class); | |
| 36 | private ZapMenuItem menuItemFaradayConfig; | |
| 37 | private ConfigurationDialog configurationDialog; | |
| 38 | private PopupMenuItemSendAlert popupMenuItemSendAlert; | |
| 39 | private PopupMenuItemSendRequest popupMenuItemSendRequest; | |
| 40 | private ResourceBundle messages = null; | |
| 41 | ||
| 42 | ||
| 43 | ||
| 44 | public FaradayExtension(String name) { | |
| 45 | super(name); | |
| 46 | } | |
| 47 | ||
| 48 | ||
| 49 | public FaradayExtension() { | |
| 50 | super(); | |
| 51 | initialize(); | |
| 52 | } | |
| 53 | ||
| 54 | ||
| 55 | private void initialize() { | |
| 56 | messages = ResourceBundle.getBundle( | |
| 57 | this.getClass().getPackage().getName() + | |
| 58 | ".Messages", Constant.getLocale()); | |
| 59 | this.setName(messages.getString("faraday.extension.name")); | |
| 60 | this.initConfiguration(); | |
| 61 | } | |
| 62 | ||
| 63 | @Override | |
| 64 | public String getAuthor() { | |
| 65 | return messages.getString("faraday.extension.author"); | |
| 66 | } | |
| 67 | ||
| 68 | @Override | |
| 69 | public void hook(ExtensionHook extensionHook) { | |
| 70 | super.hook(extensionHook); | |
| 71 | ||
| 72 | if (getView() != null) { | |
| 73 | extensionHook.getHookMenu().addToolsMenuItem(getMenuItemFaradayConfig()); | |
| 74 | extensionHook.getHookMenu().addPopupMenuItem(this.getPopupMenuItem()); | |
| 75 | extensionHook.getHookMenu().addPopupMenuItem(this.getPopupMenuItemRequest()); | |
| 76 | } | |
| 77 | } | |
| 78 | ||
| 79 | @Override | |
| 80 | public boolean canUnload() { | |
| 81 | return true; | |
| 82 | } | |
| 83 | ||
| 84 | private ZapMenuItem getMenuItemFaradayConfig() { | |
| 85 | if (menuItemFaradayConfig == null) { | |
| 86 | menuItemFaradayConfig = new ZapMenuItem( | |
| 87 | "faraday.menu.tools.label", | |
| 88 | KeyStroke.getKeyStroke( | |
| 89 | KeyEvent.VK_F, | |
| 90 | Toolkit.getDefaultToolkit().getMenuShortcutKeyMask() | KeyEvent.ALT_DOWN_MASK, | |
| 91 | false)); | |
| 92 | menuItemFaradayConfig.setEnabled(Control.getSingleton().getMode() != Control.Mode.safe); | |
| 93 | ||
| 94 | menuItemFaradayConfig.addActionListener(new java.awt.event.ActionListener() { | |
| 95 | ||
| 96 | @Override | |
| 97 | public void actionPerformed(java.awt.event.ActionEvent e) { | |
| 98 | showConfigurationDialog(); | |
| 99 | } | |
| 100 | }); | |
| 101 | } | |
| 102 | return menuItemFaradayConfig; | |
| 103 | } | |
| 104 | ||
| 105 | ||
| 106 | private void showConfigurationDialog() { | |
| 107 | if (configurationDialog == null) { | |
| 108 | configurationDialog = new ConfigurationDialog(messages.getString("faraday.config.dialog.title")); | |
| 109 | configurationDialog.init(); | |
| 110 | } | |
| 111 | configurationDialog.setVisible(true); | |
| 112 | } | |
| 113 | ||
| 114 | ||
| 115 | private ExtensionPopupMenuItem getPopupMenuItem() { | |
| 116 | if (popupMenuItemSendAlert == null) { | |
| 117 | popupMenuItemSendAlert = new PopupMenuItemSendAlert(messages.getString("faraday.button.send.alert")); | |
| 118 | } | |
| 119 | ||
| 120 | return popupMenuItemSendAlert; | |
| 121 | ||
| 122 | } | |
| 123 | ||
| 124 | ||
| 125 | private ExtensionPopupMenuItem getPopupMenuItemRequest() { | |
| 126 | if (popupMenuItemSendRequest == null) { | |
| 127 | popupMenuItemSendRequest = new PopupMenuItemSendRequest(messages.getString("faraday.button.send.request")); | |
| 128 | } | |
| 129 | ||
| 130 | return popupMenuItemSendRequest; | |
| 131 | ||
| 132 | } | |
| 133 | ||
| 134 | ||
| 135 | private void initConfiguration() { | |
| 136 | Configuration configuration = Configuration.getSingleton(); | |
| 137 | ||
| 138 | Properties prop = new Properties(); | |
| 139 | InputStream input = null; | |
| 140 | ||
| 141 | try { | |
| 142 | String filePath = Constant.getZapHome() + "faraday" + File.separator + "default.properties"; | |
| 143 | input = new FileInputStream(filePath); | |
| 144 | ||
| 145 | // load a properties file | |
| 146 | prop.load(input); | |
| 147 | ||
| 148 | // set the properties value | |
| 149 | String fUser = prop.getProperty("default"); | |
| 150 | configuration.restore(fUser); | |
| 151 | ||
| 152 | } catch (IOException io) { | |
| 153 | System.out.println("We can't found default.properties file"); | |
| 154 | } finally { | |
| 155 | if (input != null) { | |
| 156 | try { | |
| 157 | input.close(); | |
| 158 | } catch (IOException e) { | |
| 159 | e.printStackTrace(); | |
| 160 | } | |
| 161 | } | |
| 162 | ||
| 163 | } | |
| 164 | } | |
| 165 | ||
| 166 | } |
| 0 | # An example ZAP extension which adds a top level menu item. | |
| 1 | # | |
| 2 | # This file defines the default (English) variants of all of the | |
| 3 | ||
| 4 | faraday.extension.name = Faraday Extension | |
| 5 | faraday.extension.author = Jorge Luis Gonzàlez Iznaga | |
| 6 | ||
| 7 | faraday.menu.tools.label = Faraday configuration options | |
| 8 | faraday.config.dialog.title = Faraday configuration | |
| 9 | faraday.config.dialog.tabs.auth = Authorization | |
| 10 | faraday.config.dialog.tabs.conf = Configuration | |
| 11 | faraday.config.dialog.auth.user = Faraday user | |
| 12 | faraday.config.dialog.auth.pass = Faraday password | |
| 13 | faraday.config.dialog.server = Faraday server | |
| 14 | faraday.config.dialog.auth.login = Login | |
| 15 | faraday.config.dialog.auth.logout = Logout | |
| 16 | faraday.config.dialog.import.current = Import current vulnerabilities | |
| 17 | faraday.config.dialog.import.new = Import new vulnerabilities | |
| 18 | faraday.config.dialog.restore = Restore configuration | |
| 19 | faraday.config.dialog.refresh = Refresh | |
| 20 | faraday.config.dialog.save = Save configuration | |
| 21 | faraday.config.dialog.workspace = Select faraday workspace | |
| 22 | faraday.config.dialog.default = Set this configuration as default | |
| 23 | ||
| 24 | faraday.config.dialog.tab.auth = Authorization | |
| 25 | faraday.config.dialog.tab.conf = Configuration | |
| 26 | ||
| 27 | faraday.dialog.enter.user = Please enter your user | |
| 28 | ||
| 29 | ||
| 30 | faraday.button.send.alert = Send alert to Faraday | |
| 31 | faraday.button.send.request = Send request to Faraday | |
| 32 | ||
| 33 | faraday.message.invalid.check.credentials = Please, check your credentials | |
| 34 | faraday.message.invalid.credentials = Invalid credentials | |
| 35 | faraday.dialog.login.title = Faraday login | |
| 36 | faraday.dialog.logout.title = Faraday logout | |
| 37 | faraday.dialog.logout.success = You're logout successfully ! | |
| 38 | faraday.dialog.logout.error = We can't complete logout operation | |
| 39 | ||
| 40 | faraday.dialog.button.close = Close | |
| 41 | ||
| 42 | faraday.save.config.success = Configuration saved successfully | |
| 43 | faraday.save.config.error = We can't save your configuration, please check home ZAP directory | |
| 44 | faraday.restore.config.error = You haven't a configuration saved with this user | |
| 45 | faraday.refresh.workspace.done = Your workspaces are up to date | |
| 46 | faraday.restore.config.error.login = Unable to restore this configuration | |
| 47 | faraday.set.default.config.error = We can't set your configuration | |
| 48 | ||
| 49 | faraday.send.alert.permissions.error = You should check your current workspace and your permissions | |
| 50 | faraday.send.alert.conflict = This alert already exists in Faraday | |
| 51 | faraday.send.request.conflict = This request already exists in Faraday | |
| 52 | faraday.send.alert.success = Alert added successfully | |
| 53 | faraday.send.request.success = Request added successfully | |
| 54 | ||
| 55 | faraday.tool.command.name = OWASP⏎ |
| 0 | package org.zaproxy.zap.extension.faraday; | |
| 1 | ||
| 2 | import org.apache.log4j.Logger; | |
| 3 | import org.parosproxy.paros.Constant; | |
| 4 | import org.parosproxy.paros.core.scanner.Alert; | |
| 5 | import org.parosproxy.paros.view.View; | |
| 6 | import org.zaproxy.zap.extension.alert.AlertNode; | |
| 7 | import org.zaproxy.zap.extension.alert.PopupMenuItemAlert; | |
| 8 | ||
| 9 | import javax.swing.*; | |
| 10 | import java.awt.*; | |
| 11 | import java.util.ResourceBundle; | |
| 12 | ||
| 13 | public class PopupMenuItemSendAlert extends PopupMenuItemAlert { | |
| 14 | private static final Logger logger = Logger.getLogger(PopupMenuItemSendAlert.class); | |
| 15 | private FaradayClient faradayClient; | |
| 16 | private ResourceBundle messages = null; | |
| 17 | private int selectionCount = 0; | |
| 18 | private int totalSelectionCount = 0; | |
| 19 | private boolean treeAlertParentSelected = false; | |
| 20 | ||
| 21 | public PopupMenuItemSendAlert(String label) { | |
| 22 | super(label, true); | |
| 23 | Configuration configuration = Configuration.getSingleton(); | |
| 24 | faradayClient = new FaradayClient(configuration.getServer()); | |
| 25 | messages = ResourceBundle.getBundle( | |
| 26 | this.getClass().getPackage().getName() + | |
| 27 | ".Messages", Constant.getLocale()); | |
| 28 | } | |
| 29 | ||
| 30 | @Override | |
| 31 | protected void performAction(Alert alert) { | |
| 32 | Configuration configuration = Configuration.getSingleton(); | |
| 33 | String workspace = configuration.getWorkspace(); | |
| 34 | String session = configuration.getSession(); | |
| 35 | if (workspace != null && session != null && !workspace.equals("") && !session.equals("")) { | |
| 36 | int responseCode = faradayClient.AddVulnerability(alert, configuration.getWorkspace(), session); | |
| 37 | String message; | |
| 38 | int iconMessage = 1; | |
| 39 | switch (responseCode) { | |
| 40 | case 200: | |
| 41 | case 201: | |
| 42 | case 409: | |
| 43 | message = messages.getString("faraday.send.alert.success"); | |
| 44 | break; | |
| 45 | case 403: | |
| 46 | message = messages.getString("faraday.send.alert.permissions.error"); | |
| 47 | iconMessage = JOptionPane.WARNING_MESSAGE; | |
| 48 | break; | |
| 49 | // case 409: | |
| 50 | // message = messages.getString("faraday.send.alert.conflict"); | |
| 51 | // iconMessage = JOptionPane.WARNING_MESSAGE; | |
| 52 | // break; | |
| 53 | case 400: | |
| 54 | case 500: | |
| 55 | message = "Unable to send " + alert.getName() + " to Faraday"; | |
| 56 | iconMessage = JOptionPane.ERROR_MESSAGE; | |
| 57 | break; | |
| 58 | ||
| 59 | default: | |
| 60 | message = "Unable to send " + alert.getName() + " to Faraday"; | |
| 61 | iconMessage = JOptionPane.ERROR_MESSAGE; | |
| 62 | break; | |
| 63 | } | |
| 64 | ||
| 65 | if (canShowMessageDialog()/*this.selectionCount == 1 && !treeAlertParentSelected*/) { | |
| 66 | JOptionPane.showMessageDialog( | |
| 67 | this, | |
| 68 | message, | |
| 69 | messages.getString("faraday.button.send.alert"), | |
| 70 | iconMessage); | |
| 71 | } | |
| 72 | ||
| 73 | ||
| 74 | logger.error(message); | |
| 75 | if (View.isInitialised()) { | |
| 76 | // Report info to the Output tab | |
| 77 | View.getSingleton().getOutputPanel().append(message + "\n"); | |
| 78 | } | |
| 79 | ||
| 80 | ||
| 81 | } else { | |
| 82 | if (canShowMessageDialog()) { | |
| 83 | JOptionPane.showMessageDialog( | |
| 84 | this, | |
| 85 | messages.getString("faraday.send.alert.permissions.error"), | |
| 86 | messages.getString("faraday.button.send.alert"), | |
| 87 | JOptionPane.ERROR_MESSAGE); | |
| 88 | logger.error(messages.getString("faraday.send.alert.permissions.error")); | |
| 89 | } | |
| 90 | ||
| 91 | ||
| 92 | if (View.isInitialised()) { | |
| 93 | // Report info to the Output tab | |
| 94 | View.getSingleton().getOutputPanel().append(messages.getString("faraday.send.alert.permissions.error") + "\n"); | |
| 95 | } | |
| 96 | } | |
| 97 | ||
| 98 | } | |
| 99 | ||
| 100 | @Override | |
| 101 | public boolean isEnableForComponent(Component invoker) { | |
| 102 | logger.info(invoker.getName()); | |
| 103 | this.totalSelectionCount = 0; | |
| 104 | try { | |
| 105 | if (Configuration.getSingleton().getSession() == null || Configuration.getSingleton().getSession().equals("")) { | |
| 106 | return false; | |
| 107 | } | |
| 108 | treeAlertParentSelected = ((JTree) invoker).isRowSelected(0); | |
| 109 | if (super.isEnableForComponent(invoker) || treeAlertParentSelected) { | |
| 110 | this.selectionCount = ((JTree) invoker).getSelectionCount(); | |
| 111 | for (int i = 0; i < ((JTree) invoker).getSelectionPaths().length; i++) { | |
| 112 | AlertNode nodeTemp = (AlertNode) ((JTree) invoker).getSelectionPaths()[i].getLastPathComponent(); | |
| 113 | this.totalSelectionCount += getTotalAlertsToProcess(nodeTemp); | |
| 114 | } | |
| 115 | ||
| 116 | setEnabled(true); | |
| 117 | return true; | |
| 118 | } | |
| 119 | return false; | |
| 120 | } catch (Exception e) { | |
| 121 | return false; | |
| 122 | } | |
| 123 | } | |
| 124 | ||
| 125 | ||
| 126 | private int getTotalAlertsToProcess(AlertNode node) { | |
| 127 | if (node.getChildCount() > 0) { | |
| 128 | int total = 0; | |
| 129 | for (int i = 0; i < node.getChildCount(); i++) { | |
| 130 | total += getTotalAlertsToProcess(node.getChildAt(i)); | |
| 131 | } | |
| 132 | return total; | |
| 133 | } else { | |
| 134 | return 1; | |
| 135 | } | |
| 136 | ||
| 137 | } | |
| 138 | ||
| 139 | private boolean canShowMessageDialog() { | |
| 140 | this.totalSelectionCount--; | |
| 141 | if (this.treeAlertParentSelected) { | |
| 142 | this.totalSelectionCount = 1; | |
| 143 | this.treeAlertParentSelected = false; | |
| 144 | } | |
| 145 | ||
| 146 | return this.totalSelectionCount == 0; | |
| 147 | } | |
| 148 | } |
| 0 | package org.zaproxy.zap.extension.faraday; | |
| 1 | ||
| 2 | import org.apache.log4j.Logger; | |
| 3 | import org.parosproxy.paros.Constant; | |
| 4 | import org.parosproxy.paros.core.scanner.Alert; | |
| 5 | import org.parosproxy.paros.db.DatabaseException; | |
| 6 | import org.parosproxy.paros.db.RecordAlert; | |
| 7 | import org.parosproxy.paros.model.HistoryReference; | |
| 8 | import org.parosproxy.paros.network.HttpMalformedHeaderException; | |
| 9 | import org.parosproxy.paros.view.View; | |
| 10 | import org.zaproxy.zap.extension.alert.PopupMenuAlert; | |
| 11 | import org.zaproxy.zap.view.messagecontainer.http.HttpMessageContainer; | |
| 12 | import org.zaproxy.zap.view.popup.PopupMenuItemHistoryReferenceContainer; | |
| 13 | ||
| 14 | import javax.swing.*; | |
| 15 | import java.awt.*; | |
| 16 | import java.util.Iterator; | |
| 17 | import java.util.List; | |
| 18 | import java.util.ResourceBundle; | |
| 19 | ||
| 20 | ||
| 21 | public class PopupMenuItemSendRequest extends PopupMenuItemHistoryReferenceContainer { | |
| 22 | private FaradayClient faradayClient; | |
| 23 | private ResourceBundle messages = null; | |
| 24 | private int selectionCount = 0; | |
| 25 | private static final Logger logger = Logger.getLogger(PopupMenuItemSendRequest.class); | |
| 26 | ||
| 27 | ||
| 28 | public PopupMenuItemSendRequest(String label) { | |
| 29 | super(label, true); | |
| 30 | Configuration configuration = Configuration.getSingleton(); | |
| 31 | faradayClient = new FaradayClient(configuration.getServer()); | |
| 32 | messages = ResourceBundle.getBundle( | |
| 33 | this.getClass().getPackage().getName() + | |
| 34 | ".Messages", Constant.getLocale()); | |
| 35 | } | |
| 36 | ||
| 37 | @Override | |
| 38 | public void performAction(HistoryReference href) { | |
| 39 | try { | |
| 40 | Alert alert = new Alert(new RecordAlert(), href); | |
| 41 | alert.setName(href.getSiteNode().getName()); | |
| 42 | alert.setUri(href.getURI().toString()); | |
| 43 | alert.setMessage(href.getHttpMessage()); | |
| 44 | alert.setDescription(""); | |
| 45 | alert.setRiskConfidence(0, 0); | |
| 46 | ||
| 47 | Configuration configuration = Configuration.getSingleton(); | |
| 48 | String workspace = configuration.getWorkspace(); | |
| 49 | String session = configuration.getSession(); | |
| 50 | if (workspace != null && session != null && !workspace.equals("") && !session.equals("")) { | |
| 51 | int responseCode = faradayClient.AddVulnerability(alert, configuration.getWorkspace(), session); | |
| 52 | String message = ""; | |
| 53 | int iconMessage = 1; | |
| 54 | switch (responseCode) { | |
| 55 | case 403: | |
| 56 | message = messages.getString("faraday.send.alert.permissions.error"); | |
| 57 | iconMessage = JOptionPane.WARNING_MESSAGE; | |
| 58 | break; | |
| 59 | case 409: | |
| 60 | message = messages.getString("faraday.send.request.conflict"); | |
| 61 | iconMessage = JOptionPane.WARNING_MESSAGE; | |
| 62 | break; | |
| 63 | case 500: | |
| 64 | message = "Unable to send " + alert.getName() + " to Faraday"; | |
| 65 | iconMessage = JOptionPane.ERROR_MESSAGE; | |
| 66 | break; | |
| 67 | case 201: | |
| 68 | message = messages.getString("faraday.send.request.success"); | |
| 69 | break; | |
| 70 | } | |
| 71 | ||
| 72 | if (this.selectionCount == 1) { | |
| 73 | JOptionPane.showMessageDialog( | |
| 74 | this, | |
| 75 | message, | |
| 76 | messages.getString("faraday.button.send.alert"), | |
| 77 | iconMessage); | |
| 78 | } | |
| 79 | ||
| 80 | logger.error(message); | |
| 81 | if (View.isInitialised()) { | |
| 82 | // Report info to the Output tab | |
| 83 | View.getSingleton().getOutputPanel().append(message + "\n"); | |
| 84 | } | |
| 85 | ||
| 86 | ||
| 87 | } else { | |
| 88 | JOptionPane.showMessageDialog( | |
| 89 | this, | |
| 90 | messages.getString("faraday.send.alert.permissions.error"), | |
| 91 | messages.getString("faraday.button.send.request"), | |
| 92 | JOptionPane.ERROR_MESSAGE); | |
| 93 | ||
| 94 | logger.error(messages.getString("faraday.send.alert.permissions.error")); | |
| 95 | if (View.isInitialised()) { | |
| 96 | // Report info to the Output tab | |
| 97 | View.getSingleton().getOutputPanel().append(messages.getString("faraday.send.alert.permissions.error") + "\n"); | |
| 98 | } | |
| 99 | } | |
| 100 | ||
| 101 | ||
| 102 | } catch (HttpMalformedHeaderException e) { | |
| 103 | e.printStackTrace(); | |
| 104 | } catch (DatabaseException e) { | |
| 105 | e.printStackTrace(); | |
| 106 | } | |
| 107 | } | |
| 108 | ||
| 109 | ||
| 110 | @Override | |
| 111 | public void performHistoryReferenceActions(List<HistoryReference> hrefs) { | |
| 112 | this.selectionCount = hrefs.size(); | |
| 113 | ||
| 114 | for (HistoryReference href : hrefs) { | |
| 115 | this.performAction(href); | |
| 116 | } | |
| 117 | } | |
| 118 | ||
| 119 | @Override | |
| 120 | public boolean isEnableForInvoker(Invoker invoker, HttpMessageContainer httpMessageContainer) { | |
| 121 | if (Configuration.getSingleton().getSession() == null || Configuration.getSingleton().getSession().equals("") || | |
| 122 | invoker.name().equals("ALERTS_PANEL")) { | |
| 123 | return false; | |
| 124 | } | |
| 125 | return super.isEnableForInvoker(invoker, httpMessageContainer); | |
| 126 | } | |
| 127 | ||
| 128 | @Override | |
| 129 | public boolean isButtonEnabledForHistoryReference(HistoryReference href) { | |
| 130 | if (Configuration.getSingleton().getSession() == null || Configuration.getSingleton().getSession().equals("")) { | |
| 131 | return false; | |
| 132 | } | |
| 133 | ||
| 134 | return href.getSiteNode() != null && super.isButtonEnabledForHistoryReference(href); | |
| 135 | } | |
| 136 | }⏎ |
| 0 | <zapaddon> | |
| 1 | <name>Faraday</name> | |
| 2 | <version>1</version> | |
| 3 | <status>release</status> | |
| 4 | <description>This extension integrates ZAP with the Faraday Integrated Penetration-Test Environment</description> | |
| 5 | <author>Jorge Luis González Iznaga</author> | |
| 6 | <extensions> | |
| 7 | <extension>org.zaproxy.zap.extension.faraday.FaradayExtension</extension> | |
| 8 | </extensions> | |
| 9 | <ascanrules/> | |
| 10 | <pscanrules/> | |
| 11 | <not-before-version>2.7.0</not-before-version> | |
| 12 | <not-from-version/> | |
| 13 | </zapaddon> |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | """ | |
| 5 | import re | |
| 6 | import os | |
| 7 | import socket | |
| 8 | import sys | |
| 9 | from faraday.client.plugins.plugin import PluginXMLFormat | |
| 10 | ||
| 11 | ||
| 12 | try: | |
| 13 | import xml.etree.cElementTree as ET | |
| 14 | import xml.etree.ElementTree as ET_ORIG | |
| 15 | ETREE_VERSION = ET_ORIG.VERSION | |
| 16 | ||
| 17 | except ImportError: | |
| 18 | import xml.etree.ElementTree as ET | |
| 19 | ETREE_VERSION = ET.VERSION | |
| 20 | ||
| 21 | ETREE_VERSION = [int(i) for i in ETREE_VERSION.split(".")] | |
| 22 | ||
| 23 | current_path = os.path.abspath(os.getcwd()) | |
| 24 | ||
| 25 | __author__ = "Francisco Amato" | |
| 26 | __copyright__ = "Copyright (c) 2013, Infobyte LLC" | |
| 27 | __credits__ = ["Francisco Amato"] | |
| 28 | __license__ = "" | |
| 29 | __version__ = "1.0.0" | |
| 30 | __maintainer__ = "Francisco Amato" | |
| 31 | __email__ = "[email protected]" | |
| 32 | __status__ = "Development" | |
| 33 | ||
| 34 | ||
| 35 | class ParserEtToAscii(ET_ORIG.TreeBuilder): | |
| 36 | ||
| 37 | def data(self, data): | |
| 38 | self._data.append(data.encode("ascii", errors="backslashreplace")) | |
| 39 | ||
| 40 | ||
| 41 | class ZapXmlParser: | |
| 42 | """ | |
| 43 | The objective of this class is to parse an xml | |
| 44 | file generated by the zap tool. | |
| 45 | ||
| 46 | TODO: Handle errors. | |
| 47 | TODO: Test zap output version. Handle what happens | |
| 48 | if the parser doesn't support it. | |
| 49 | ||
| 50 | TODO: Test cases. | |
| 51 | ||
| 52 | @param zap_xml_filepath A proper xml generated by zap | |
| 53 | """ | |
| 54 | ||
| 55 | def __init__(self, xml_output): | |
| 56 | ||
| 57 | tree = self.parse_xml(xml_output) | |
| 58 | ||
| 59 | if tree is not None: | |
| 60 | self.sites = list(self.get_items(tree)) | |
| 61 | else: | |
| 62 | self.sites = [] | |
| 63 | ||
| 64 | def parse_xml(self, xml_output): | |
| 65 | """ | |
| 66 | Open and parse an xml file. | |
| 67 | ||
| 68 | TODO: Write custom parser to just read the nodes that we need instead of | |
| 69 | reading the whole file. | |
| 70 | ||
| 71 | @return xml_tree An xml tree instance. None if error. | |
| 72 | """ | |
| 73 | try: | |
| 74 | parser = ET_ORIG.XMLParser(target=ParserEtToAscii()) | |
| 75 | parser.feed(xml_output) | |
| 76 | tree = parser.close() | |
| 77 | ||
| 78 | except SyntaxError as err: | |
| 79 | print("SyntaxError: %s. %s" % (err, xml_output)) | |
| 80 | return None | |
| 81 | ||
| 82 | return tree | |
| 83 | ||
| 84 | def get_items(self, tree): | |
| 85 | """ | |
| 86 | @return items A list of Host instances | |
| 87 | """ | |
| 88 | for node in tree.findall('site'): | |
| 89 | yield Site(node) | |
| 90 | ||
| 91 | ||
| 92 | def get_attrib_from_subnode(xml_node, subnode_xpath_expr, attrib_name): | |
| 93 | """ | |
| 94 | Finds a subnode in the item node and the retrieves a value from it | |
| 95 | ||
| 96 | @return An attribute value | |
| 97 | """ | |
| 98 | global ETREE_VERSION | |
| 99 | node = None | |
| 100 | ||
| 101 | if ETREE_VERSION[0] <= 1 and ETREE_VERSION[1] < 3: | |
| 102 | ||
| 103 | match_obj = re.search( | |
| 104 | "([^\@]+?)\[\@([^=]*?)=\'([^\']*?)\'", | |
| 105 | subnode_xpath_expr) | |
| 106 | ||
| 107 | if match_obj is not None: | |
| 108 | ||
| 109 | node_to_find = match_obj.group(1) | |
| 110 | xpath_attrib = match_obj.group(2) | |
| 111 | xpath_value = match_obj.group(3) | |
| 112 | ||
| 113 | for node_found in xml_node.findall(node_to_find): | |
| 114 | ||
| 115 | if node_found.attrib[xpath_attrib] == xpath_value: | |
| 116 | node = node_found | |
| 117 | break | |
| 118 | else: | |
| 119 | node = xml_node.find(subnode_xpath_expr) | |
| 120 | ||
| 121 | else: | |
| 122 | node = xml_node.find(subnode_xpath_expr) | |
| 123 | ||
| 124 | if node is not None: | |
| 125 | return node.get(attrib_name) | |
| 126 | ||
| 127 | return None | |
| 128 | ||
| 129 | ||
| 130 | class Site: | |
| 131 | ||
| 132 | def __init__(self, item_node): | |
| 133 | ||
| 134 | self.node = item_node | |
| 135 | ||
| 136 | self.host = self.node.get('host') | |
| 137 | self.ip = self.resolve(self.host) | |
| 138 | self.port = self.node.get('port') | |
| 139 | ||
| 140 | self.items = [] | |
| 141 | for alert in self.node.findall('alerts/alertitem'): | |
| 142 | self.items.append(Item(alert)) | |
| 143 | ||
| 144 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 145 | """ | |
| 146 | Finds a subnode in the host node and the retrieves a value from it. | |
| 147 | ||
| 148 | @return An attribute value | |
| 149 | """ | |
| 150 | sub_node = self.node.find(subnode_xpath_expr) | |
| 151 | if sub_node is not None: | |
| 152 | return sub_node.text | |
| 153 | return None | |
| 154 | ||
| 155 | def resolve(self, host): | |
| 156 | ||
| 157 | try: | |
| 158 | return socket.gethostbyname(host) | |
| 159 | except: | |
| 160 | pass | |
| 161 | ||
| 162 | return host | |
| 163 | ||
| 164 | ||
| 165 | class Item: | |
| 166 | """ | |
| 167 | An abstract representation of a Item | |
| 168 | ||
| 169 | ||
| 170 | @param item_node A item_node taken from an zap xml tree | |
| 171 | """ | |
| 172 | ||
| 173 | def __init__(self, item_node): | |
| 174 | ||
| 175 | self.node = item_node | |
| 176 | self.id = self.get_text_from_subnode('pluginid') | |
| 177 | self.name = self.get_text_from_subnode('alert') | |
| 178 | self.severity = self.get_text_from_subnode('riskcode') | |
| 179 | self.desc = self.get_text_from_subnode('desc') | |
| 180 | ||
| 181 | if self.get_text_from_subnode('solution'): | |
| 182 | self.resolution = self.get_text_from_subnode('solution') | |
| 183 | else: | |
| 184 | self.resolution = '' | |
| 185 | ||
| 186 | if self.get_text_from_subnode('reference'): | |
| 187 | self.desc += '\nReference: ' + \ | |
| 188 | self.get_text_from_subnode('reference') | |
| 189 | ||
| 190 | self.ref = [] | |
| 191 | if self.get_text_from_subnode('cweid'): | |
| 192 | self.ref.append("CWE-" + self.get_text_from_subnode('cweid')) | |
| 193 | ||
| 194 | self.items = [] | |
| 195 | ||
| 196 | if item_node.find('instances'): | |
| 197 | arr = item_node.find('instances') | |
| 198 | else: | |
| 199 | arr = [item_node] | |
| 200 | ||
| 201 | for elem in arr: | |
| 202 | uri = elem.find('uri').text | |
| 203 | self.parse_uri(uri) | |
| 204 | ||
| 205 | self.requests = "\n".join([i['uri'] for i in self.items]) | |
| 206 | ||
| 207 | def parse_uri(self, uri): | |
| 208 | mregex = re.search( | |
| 209 | "(http|https|ftp)\://([a-zA-Z0-9\.\-]+(\:[a-zA-Z0-9\.&" | |
| 210 | ";%\$\-]+)*@)*((25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]" | |
| 211 | "{1}|[1-9])\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}" | |
| 212 | "|[1-9]|0)\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}" | |
| 213 | "|[1-9]|0)\.(25[0-5]|2[0-4][0-9]|[0-1]{1}[0-9]{2}|[1-9]{1}[0-9]{1}|" | |
| 214 | "[0-9])|localhost|([a-zA-Z0-9\-]+\.)*[a-zA-Z0-9\-]+\.(com|edu|gov|" | |
| 215 | "int|mil|net|org|biz|arpa|info|name|pro|aero|coop|museum|[a-zA-Z]{2" | |
| 216 | "}))[\:]*([0-9]+)*([/]*($|[a-zA-Z0-9\.\,\?\'\\\+&%\$#\=~_\-]+))" | |
| 217 | ".*?$", | |
| 218 | uri) | |
| 219 | ||
| 220 | protocol = mregex.group(1) | |
| 221 | host = mregex.group(4) | |
| 222 | port = 80 | |
| 223 | if protocol == 'https': | |
| 224 | port = 443 | |
| 225 | if mregex.group(11) is not None: | |
| 226 | port = mregex.group(11) | |
| 227 | ||
| 228 | try: | |
| 229 | params = [i.split('=')[0] | |
| 230 | for i in uri.split('?')[1].split('&')] | |
| 231 | except Exception as e: | |
| 232 | params = '' | |
| 233 | ||
| 234 | item = { | |
| 235 | 'uri': uri, | |
| 236 | 'params': ', '.join(params), | |
| 237 | 'host': host, | |
| 238 | 'protocol': protocol, | |
| 239 | 'port': port | |
| 240 | } | |
| 241 | self.items.append(item) | |
| 242 | ||
| 243 | ||
| 244 | def get_text_from_subnode(self, subnode_xpath_expr): | |
| 245 | """ | |
| 246 | Finds a subnode in the host node and the retrieves a value from it. | |
| 247 | ||
| 248 | @return An attribute value | |
| 249 | """ | |
| 250 | sub_node = self.node.find(subnode_xpath_expr) | |
| 251 | if sub_node is not None: | |
| 252 | return sub_node.text | |
| 253 | ||
| 254 | return None | |
| 255 | ||
| 256 | ||
| 257 | class ZapPlugin(PluginXMLFormat): | |
| 258 | """ | |
| 259 | Example plugin to parse zap output. | |
| 260 | """ | |
| 261 | ||
| 262 | def __init__(self): | |
| 263 | super().__init__() | |
| 264 | self.identifier_tag = "OWASPZAPReport" | |
| 265 | self.id = "Zap" | |
| 266 | self.name = "Zap XML Output Plugin" | |
| 267 | self.plugin_version = "0.0.3" | |
| 268 | self.version = "2.4.3" | |
| 269 | self.framework_version = "1.0.0" | |
| 270 | self.options = None | |
| 271 | self._current_output = None | |
| 272 | self.target = None | |
| 273 | self._command_regex = re.compile(r'^(zap|sudo zap|\.\/zap).*?') | |
| 274 | ||
| 275 | global current_path | |
| 276 | ||
| 277 | self._output_file_path = os.path.join(self.data_path, "zap_output-%s.xml" % self._rid) | |
| 278 | ||
| 279 | def parseOutputString(self, output, debug=False): | |
| 280 | """ | |
| 281 | This method will discard the output the shell sends, it will read it | |
| 282 | from the xml where it expects it to be present. | |
| 283 | ||
| 284 | NOTE: if 'debug' is true then it is being run from a test case and the | |
| 285 | output being sent is valid. | |
| 286 | """ | |
| 287 | ||
| 288 | parser = ZapXmlParser(output) | |
| 289 | ||
| 290 | for site in parser.sites: | |
| 291 | ||
| 292 | host = [] | |
| 293 | if site.host != site.ip: | |
| 294 | host = [site.host] | |
| 295 | ||
| 296 | h_id = self.createAndAddHost(site.ip) | |
| 297 | ||
| 298 | i_id = self.createAndAddInterface( | |
| 299 | h_id, | |
| 300 | site.ip, | |
| 301 | ipv4_address=site.ip, | |
| 302 | hostname_resolution=host | |
| 303 | ) | |
| 304 | ||
| 305 | s_id = self.createAndAddServiceToInterface( | |
| 306 | h_id, | |
| 307 | i_id, | |
| 308 | "http", | |
| 309 | "tcp", | |
| 310 | ports=[site.port], | |
| 311 | status='open' | |
| 312 | ) | |
| 313 | ||
| 314 | for item in site.items: | |
| 315 | v_id = self.createAndAddVulnWebToService( | |
| 316 | h_id, | |
| 317 | s_id, | |
| 318 | item.name, | |
| 319 | item.desc, | |
| 320 | website=site.host, | |
| 321 | severity=item.severity, | |
| 322 | path=item.items[0]['uri'], | |
| 323 | params=item.items[0]['params'], | |
| 324 | request=item.requests, | |
| 325 | ref=item.ref, | |
| 326 | resolution=item.resolution | |
| 327 | ) | |
| 328 | ||
| 329 | del parser | |
| 330 | ||
| 331 | def processCommandString(self, username, current_path, command_string): | |
| 332 | return None | |
| 333 | ||
| 334 | def setHost(self): | |
| 335 | pass | |
| 336 | ||
| 337 | ||
| 338 | def createPlugin(): | |
| 339 | return ZapPlugin() | |
| 340 | ||
| 341 | ||
| 342 | ||
| 343 | # I'm Py3 |
| 0 | <?xml version="1.0" encoding="UTF-8"?><report> | |
| 1 | Report generated at Tue, 12 Jul 2011 08:32:22. | |
| 2 | <alertitem> | |
| 3 | <pluginid>40000</pluginid> | |
| 4 | <alert>Cookie set without HttpOnly flag</alert> | |
| 5 | <riskcode>1</riskcode> | |
| 6 | <reliability>2</reliability> | |
| 7 | <riskdesc>Low (Warning)</riskdesc> | |
| 8 | <desc>A cookie has been set without the HttpOnly flag, which means that the cookie can be accessed by JavaScript. If a malicious script can be run on this page then the cookie will be accessible and can be transmitted to another site. If this is a session cookie then session hijacking may be possible. | |
| 9 | </desc> | |
| 10 | <uri>http://192.168.1.100/</uri> | |
| 11 | <param>ASPSESSIONIDQSDRBCRQ=EEFHJOACLHOKLJHFNAFBBECK; path=/</param> | |
| 12 | <otherinfo/> | |
| 13 | <uri>http://www.web3.com.ar/ServFotoPorNoticia.asp</uri> | |
| 14 | <param>ASPSESSIONIDCQATADBB=LMFPHGLBHIIEDFILGFJEJNGE; path=/</param> | |
| 15 | <otherinfo/> | |
| 16 | <uri>http://www.web1.com.ar/acceso/include/valida.asp</uri> | |
| 17 | <param>ASPSESSIONIDSCBABSTB=MNPOKADDPAIDCDNBPGFDHGBF; path=/</param> | |
| 18 | <otherinfo/> | |
| 19 | <uri>http://www.web3.com.ar/files/</uri> | |
| 20 | <param>ASPSESSIONIDCSCTCABB=HFCNOPJBMNJEAHDHMCKAHOBN; path=/</param> | |
| 21 | <otherinfo/> | |
| 22 | <uri>http://www.web2.com.ar/acceso/include/valida.asp</uri> | |
| 23 | <param>ASPSESSIONIDQAASDACB=HADJFCIBOIANGBGNAOIDBGIL; path=/</param> | |
| 24 | <otherinfo/> | |
| 25 | <uri>http://www.web3.com.ar/</uri> | |
| 26 | <param>ASPSESSIONIDSABQACDB=PAJBMJHBLOFELCIKBNLAAKKJ; path=/</param> | |
| 27 | <otherinfo/> | |
| 28 | <solution>Ensure that the HttpOnly flag is set for all cookies. | |
| 29 | </solution> | |
| 30 | <reference>www.owasp.org/index.php/HttpOnly | |
| 31 | </reference> | |
| 32 | </alertitem> | |
| 33 | <alertitem> | |
| 34 | <pluginid>40001</pluginid> | |
| 35 | <alert>Password Autocomplete in browser</alert> | |
| 36 | <riskcode>1</riskcode> | |
| 37 | <reliability>2</reliability> | |
| 38 | <riskdesc>Low (Warning)</riskdesc> | |
| 39 | <desc>AUTOCOMPLETE attribute is not disabled in HTML FORM/INPUT element containing password type input. Passwords may be stored in browsers and retrieved. | |
| 40 | </desc> | |
| 41 | <uri>http://192.168.1.100/</uri> | |
| 42 | <param>input</param> | |
| 43 | <otherinfo/> | |
| 44 | <uri>http://www.web3.com.ar/</uri> | |
| 45 | <param>input</param> | |
| 46 | <otherinfo/> | |
| 47 | <uri>http://www.web3.com.ar/default.asp?errsession=1</uri> | |
| 48 | <param>input</param> | |
| 49 | <otherinfo/> | |
| 50 | <uri>http://www.web3.com.ar/</uri> | |
| 51 | <param>input</param> | |
| 52 | <otherinfo/> | |
| 53 | <uri>http://www.web3.com.ar/</uri> | |
| 54 | <param>input</param> | |
| 55 | <otherinfo/> | |
| 56 | <uri>http://www.web2.com.ar/dealers.htm</uri> | |
| 57 | <param>input</param> | |
| 58 | <otherinfo/> | |
| 59 | <uri>http://www.web3.com.ar/</uri> | |
| 60 | <param>input</param> | |
| 61 | <otherinfo/> | |
| 62 | <solution>Turn off AUTOCOMPLETE attribute in form or individual input elements containing password by using AUTOCOMPLETE='OFF' | |
| 63 | </solution> | |
| 64 | <reference>http://msdn.microsoft.com/library/default.asp?url=/workshop/author/forms/autocomplete_ovr.asp | |
| 65 | </reference> | |
| 66 | </alertitem> | |
| 67 | <alertitem> | |
| 68 | <pluginid>40003</pluginid> | |
| 69 | <alert>Cross site scripting</alert> | |
| 70 | <riskcode>3</riskcode> | |
| 71 | <reliability>2</reliability> | |
| 72 | <riskdesc>High (Warning)</riskdesc> | |
| 73 | <desc>Cross-site scripting or HTML injection is possible. Malicious script may be injected into the browser which appeared to be genuine content from the original site. These scripts can be used to execute arbitrary code or steal customer sensitive information such as user password or cookies. | |
| 74 | Very often this is in the form of a hyperlink with the injected script embeded in the query strings. However, XSS is possible via FORM POST data, cookies, user data sent from another user or shared data retrieved from database. | |
| 75 | Currently this check does not verify XSS from cookie or database. They should be checked manually if the application retrieve database records from another user's input. | |
| 76 | </desc> | |
| 77 | <uri>http://www.web3.com.ar/Mes.asp?hhFrm=frm&hhDia=DiaF&hhMes=MesF&hhAnno=%3CSCRIPT%3Ealert(%22OWASP%20ZAP%22);%3C/SCRIPT%3E</uri> | |
| 78 | <param>hhAnno=<SCRIPT>alert("OWASP ZAP");</SCRIPT></param> | |
| 79 | <otherinfo/> | |
| 80 | <uri>http://www.web3.com.ar/Mes.asp?hhFrm=frm&hhDia=DiaF&hhMes=%3CSCRIPT%3Ealert(%22OWASP%20ZAP%22);%3C/SCRIPT%3E&hhAnno=AnnoF</uri> | |
| 81 | <param>hhMes=<SCRIPT>alert("OWASP ZAP");</SCRIPT></param> | |
| 82 | <otherinfo/> | |
| 83 | <uri>http://www.web3.com.ar/Mes.asp?hhFrm=frm&hhDia=%3CSCRIPT%3Ealert(%22OWASP%20ZAP%22);%3C/SCRIPT%3E&hhMes=MesF&hhAnno=AnnoF</uri> | |
| 84 | <param>hhDia=<SCRIPT>alert("OWASP ZAP");</SCRIPT></param> | |
| 85 | <otherinfo/> | |
| 86 | <uri>http://www.web3.com.ar/Mes.asp?hhFrm=%3CSCRIPT%3Ealert(%22OWASP%20ZAP%22);%3C/SCRIPT%3E&hhDia=DiaF&hhMes=MesF&hhAnno=AnnoF</uri> | |
| 87 | <param>hhFrm=<SCRIPT>alert("OWASP ZAP");</SCRIPT></param> | |
| 88 | <otherinfo/> | |
| 89 | <solution>Do not trust client side input even if there is client side validation. Sanitize potentially danger characters in the server side. Very often filtering the <, >, " characters prevented injected script to be executed in most cases. However, sometimes other danger meta-characters such as ' , (, ), /, &, ; etc are also needed. | |
| 90 | In addition (or if these characters are needed), HTML encode meta-characters in the response. For example, encode < as &lt; | |
| 91 | ||
| 92 | </solution> | |
| 93 | <reference>The OWASP guide at http://www.owasp.org/documentation/guide | |
| 94 | http://www.technicalinfo.net/papers/CSS.html | |
| 95 | http://www.cgisecurity.org/articles/xss-faq.shtml | |
| 96 | http://www.cert.org/tech_tips/malicious_code_FAQ.html | |
| 97 | http://sandsprite.com/Sleuth/papers/RealWorld_XSS_1.html | |
| 98 | ||
| 99 | </reference> | |
| 100 | </alertitem> | |
| 101 | <alertitem> | |
| 102 | <pluginid>40004</pluginid> | |
| 103 | <alert>Cross site scripting without brackets</alert> | |
| 104 | <riskcode>3</riskcode> | |
| 105 | <reliability>1</reliability> | |
| 106 | <riskdesc>High (Suspicious)</riskdesc> | |
| 107 | <desc>Cross-site scripting or HTML injection is possible without '<' and '>'. Malicious script may be injected into the browser which appeared to be genuine content from the original site. These scripts can be used to execute arbitrary code or steal customer sensitive information such as user password or cookies. | |
| 108 | Very often this is in the form of a hyperlink with the injected script embeded in the query strings. However, XSS is possible via FORM POST data, cookies, user data sent from another user or shared data retrieved from database. | |
| 109 | Currently this check does not verify XSS from cookie or database. They should be checked manually if the application retrieve database records from another user's input. | |
| 110 | </desc> | |
| 111 | <uri>http://www.web3.com.ar/Mes.asp?hhFrm=frm&hhDia=DiaF&hhMes=MesF&hhAnno=paros%22%20style=%22background:url(javascript:alert('OWASP%20ZAP'))</uri> | |
| 112 | <param>hhAnno=paros" style="background:url(javascript:alert('OWASP ZAP'))</param> | |
| 113 | <otherinfo/> | |
| 114 | <uri>http://www.web3.com.ar/Mes.asp?hhFrm=frm&hhDia=DiaF&hhMes=paros%22%20style=%22background:url(javascript:alert('OWASP%20ZAP'))&hhAnno=%3CSCRIPT%3Ealert(%22OWASP%20ZAP%22);%3C/SCRIPT%3E</uri> | |
| 115 | <param>hhMes=paros" style="background:url(javascript:alert('OWASP ZAP'))</param> | |
| 116 | <otherinfo/> | |
| 117 | <uri>http://www.web3.com.ar/Mes.asp?hhFrm=frm&hhDia=paros%22%20style=%22background:url(javascript:alert('OWASP%20ZAP'))&hhMes=MesF&hhAnno=%3CSCRIPT%3Ealert(%22OWASP%20ZAP%22);%3C/SCRIPT%3E</uri> | |
| 118 | <param>hhDia=paros" style="background:url(javascript:alert('OWASP ZAP'))</param> | |
| 119 | <otherinfo/> | |
| 120 | <uri>http://www.web3.com.ar/Mes.asp?hhFrm=paros%22%20style=%22background:url(javascript:alert('OWASP%20ZAP'))&hhDia=DiaF&hhMes=MesF&hhAnno=%3CSCRIPT%3Ealert(%22OWASP%20ZAP%22);%3C/SCRIPT%3E</uri> | |
| 121 | <param>hhFrm=paros" style="background:url(javascript:alert('OWASP ZAP'))</param> | |
| 122 | <otherinfo/> | |
| 123 | <solution>Do not trust client side input even if there is client side validation. Sanitize potentially danger characters in the server side. Very often filtering the <, >, " characters prevented injected script to be executed in most cases. However, sometimes other danger meta-characters such as ' , (, ), /, &, ; etc are also needed. | |
| 124 | In addition (or if these characters are needed), HTML encode meta-characters in the response. For example, encode < as &lt; | |
| 125 | ||
| 126 | </solution> | |
| 127 | <reference>The OWASP guide at http://www.owasp.org/documentation/guide | |
| 128 | http://www.technicalinfo.net/papers/CSS.html | |
| 129 | http://www.cgisecurity.org/articles/xss-faq.shtml | |
| 130 | http://www.cert.org/tech_tips/malicious_code_FAQ.html | |
| 131 | http://sandsprite.com/Sleuth/papers/RealWorld_XSS_1.html | |
| 132 | ||
| 133 | </reference> | |
| 134 | </alertitem> | |
| 135 | <alertitem> | |
| 136 | <pluginid>40030</pluginid> | |
| 137 | <alert>SQL Injection</alert> | |
| 138 | <riskcode>3</riskcode> | |
| 139 | <reliability>2</reliability> | |
| 140 | <riskdesc>High (Warning)</riskdesc> | |
| 141 | <desc>SQL injection is possible. User parameters submitted will be formulated into a SQL query for database processing. If the query is built by simple 'string concatenation', it is possible to modify the meaning of the query by carefully crafting the parameters. Depending on the access right and type of database used, tampered query can be used to retrieve sensitive information from the database or execute arbitrary code. MS SQL and PostGreSQL, which supports multiple statements, may be exploited if the database access right is more powerful. | |
| 142 | This can occur in URL query strings, POST paramters or even cookies. Currently check on cookie is not supported by Paros. You should check SQL injection manually as well as some blind SQL injection areas cannot be discovered by this check. | |
| 143 | </desc> | |
| 144 | <uri>http://www.web3.com.ar/buscador.asp</uri> | |
| 145 | <param>hId=&hAreturn=&hAccion=OK&txtBuscar=test&x=0&y=0%27+AND+%271%27%3D%271</param> | |
| 146 | <otherinfo/> | |
| 147 | <uri>http://www.web3.com.ar/buscador.asp</uri> | |
| 148 | <param>hId=&hAreturn=&hAccion=OK%22+OR+%221%22%3D%221&txtBuscar=test&x=0&y=0</param> | |
| 149 | <otherinfo/> | |
| 150 | <solution>Do not trust client side input even if there is client side validation. In general, If the input string is numeric, type check it. | |
| 151 | If the application used JDBC, use PreparedStatement or CallableStatement with parameters passed by '?' | |
| 152 | If the application used ASP, use ADO Command Objects with strong type checking and parameterized query. | |
| 153 | If stored procedure or bind variables can be used, use it for parameter passing into query. Do not just concatenate string into query in the stored procedure! | |
| 154 | Do not create dynamic SQL query by simple string concatentation. | |
| 155 | Use minimum database user privilege for the application. This does not eliminate SQL injection but minimize its damage. Eg if the application require reading one table only, grant such access to the application. Avoid using 'sa' or 'db-owner'. | |
| 156 | ||
| 157 | </solution> | |
| 158 | <reference>The OWASP guide at http://www.owasp.org/documentation/guide | |
| 159 | http://www.sqlsecurity.com/DesktopDefault.aspx?tabid=23 | |
| 160 | http://www.spidynamics.com/whitepapers/WhitepaperSQLInjection.pdf | |
| 161 | For Oracle database, refer to http://www.integrigy.com/info/IntegrigyIntrotoSQLInjectionAttacks.pdf | |
| 162 | ||
| 163 | </reference> | |
| 164 | </alertitem> | |
| 165 | </report>⏎ |
| 0 | #!/usr/bin/env python3 | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2018 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | """ | |
| 6 | ||
| 7 | from __future__ import absolute_import | |
| 8 | from __future__ import print_function | |
| 9 | ||
| 10 | from builtins import input | |
| 11 | ||
| 12 | import os | |
| 13 | import sys | |
| 14 | import imp | |
| 15 | import shutil | |
| 16 | import getpass | |
| 17 | import argparse | |
| 18 | import requests | |
| 19 | import requests.exceptions | |
| 20 | import logging | |
| 21 | ||
| 22 | from faraday.config.configuration import getInstanceConfiguration | |
| 23 | from faraday.config.constant import ( | |
| 24 | CONST_USER_HOME, | |
| 25 | CONST_FARADAY_PLUGINS_PATH, | |
| 26 | CONST_FARADAY_PLUGINS_REPO_PATH, | |
| 27 | CONST_FARADAY_IMAGES, | |
| 28 | CONST_FARADAY_USER_CFG, | |
| 29 | CONST_FARADAY_BASE_CFG, | |
| 30 | CONST_USER_ZSHRC, | |
| 31 | CONST_FARADAY_ZSHRC, | |
| 32 | CONST_ZSH_PATH, | |
| 33 | CONST_FARADAY_ZSH_FARADAY, | |
| 34 | CONST_REQUIREMENTS_FILE, | |
| 35 | CONST_FARADAY_FOLDER_LIST, | |
| 36 | ) | |
| 37 | ||
| 38 | CONST_FARADAY_HOME_PATH = os.path.expanduser('~/.faraday') | |
| 39 | from faraday.utils import dependencies | |
| 40 | from faraday.server.utils.logger import get_logger, set_logging_level | |
| 41 | from faraday.utils.user_input import query_yes_no | |
| 42 | ||
| 43 | from faraday import __version__ as f_version | |
| 44 | from faraday.client.persistence.server import server | |
| 45 | from faraday.client.persistence.server.server import login_user, get_user_info | |
| 46 | ||
| 47 | import faraday | |
| 48 | ||
| 49 | from colorama import Fore, Back, Style | |
| 50 | ||
| 51 | USER_HOME = os.path.expanduser(CONST_USER_HOME) | |
| 52 | # find_module returns if search is successful, the return value is a 3-element tuple (file, pathname, description): | |
| 53 | FARADAY_BASE = os.path.dirname(faraday.__file__) | |
| 54 | os.path.dirname(os.path.dirname(os.path.realpath(__file__))) # Use double dirname to obtain parent directory | |
| 55 | FARADAY_CLIENT_BASE = os.path.join(FARADAY_BASE, 'client') | |
| 56 | ||
| 57 | FARADAY_USER_HOME = os.path.expanduser(CONST_FARADAY_HOME_PATH) | |
| 58 | ||
| 59 | FARADAY_PLUGINS_PATH = os.path.join(FARADAY_USER_HOME, CONST_FARADAY_PLUGINS_PATH) | |
| 60 | ||
| 61 | FARADAY_PLUGINS_BASEPATH = os.path.join(FARADAY_CLIENT_BASE, CONST_FARADAY_PLUGINS_REPO_PATH) | |
| 62 | ||
| 63 | FARADAY_BASE_IMAGES = os.path.join(FARADAY_CLIENT_BASE, "data", CONST_FARADAY_IMAGES) | |
| 64 | ||
| 65 | FARADAY_USER_CONFIG_XML = os.path.join(FARADAY_USER_HOME, CONST_FARADAY_USER_CFG) | |
| 66 | ||
| 67 | FARADAY_BASE_CONFIG_XML = os.path.join(FARADAY_BASE, CONST_FARADAY_BASE_CFG) | |
| 68 | ||
| 69 | USER_ZSHRC = os.path.expanduser(CONST_USER_ZSHRC) | |
| 70 | ||
| 71 | FARADAY_USER_IMAGES = os.path.join(FARADAY_USER_HOME, CONST_FARADAY_IMAGES) | |
| 72 | ||
| 73 | FARADAY_USER_ZSHRC = os.path.join(FARADAY_USER_HOME, CONST_FARADAY_ZSHRC) | |
| 74 | FARADAY_USER_ZSH_PATH = os.path.join(FARADAY_USER_HOME, CONST_ZSH_PATH) | |
| 75 | FARADAY_BASE_ZSH = os.path.join(FARADAY_CLIENT_BASE, CONST_FARADAY_ZSH_FARADAY) | |
| 76 | ||
| 77 | FARADAY_REQUIREMENTS_FILE = os.path.join(FARADAY_BASE, CONST_REQUIREMENTS_FILE) | |
| 78 | ||
| 79 | REQUESTS_CA_BUNDLE_VAR = "REQUESTS_CA_BUNDLE" | |
| 80 | FARADAY_DEFAULT_PORT_XMLRPC = 9876 | |
| 81 | FARADAY_DEFAULT_PORT_REST = 9977 | |
| 82 | FARADAY_DEFAULT_HOST = "localhost" | |
| 83 | ||
| 84 | logger = logging.getLogger(__name__) | |
| 85 | ||
| 86 | ||
| 87 | def getParserArgs(): | |
| 88 | """ | |
| 89 | Parser setup for faraday launcher arguments. | |
| 90 | """ | |
| 91 | ||
| 92 | parser = argparse.ArgumentParser( | |
| 93 | description="Faraday's launcher parser.", | |
| 94 | fromfile_prefix_chars='@') | |
| 95 | ||
| 96 | parser_connection = parser.add_argument_group('connection') | |
| 97 | ||
| 98 | parser_connection.add_argument('-n', '--hostname', | |
| 99 | action="store", | |
| 100 | dest="host", | |
| 101 | default=None, | |
| 102 | help="The hostname where both server APIs will listen (XMLRPC and RESTful). Default = localhost") | |
| 103 | ||
| 104 | parser_connection.add_argument('-px', | |
| 105 | '--port-xmlrpc', | |
| 106 | action="store", | |
| 107 | dest="port_xmlrpc", | |
| 108 | default=None, | |
| 109 | type=int, | |
| 110 | help="Sets the port where the API XMLRPC Server will listen. Default = 9876") | |
| 111 | ||
| 112 | parser_connection.add_argument('-pr', | |
| 113 | '--port-rest', | |
| 114 | action="store", | |
| 115 | dest="port_rest", | |
| 116 | default=None, | |
| 117 | type=int, | |
| 118 | help="Sets the port where the API RESTful Server will listen. Default = 9977") | |
| 119 | ||
| 120 | parser.add_argument('--disable-excepthook', | |
| 121 | action="store_true", | |
| 122 | dest="disable_excepthook", | |
| 123 | default=False, | |
| 124 | help="Disable the application exception hook that allows to send error reports to developers.") | |
| 125 | ||
| 126 | parser.add_argument('--login', | |
| 127 | action="store_true", | |
| 128 | dest="login", | |
| 129 | default=False, | |
| 130 | help="Enable prompt for authentication Database credentials") | |
| 131 | ||
| 132 | parser.add_argument('--dev-mode', | |
| 133 | action="store_true", | |
| 134 | dest="dev_mode", | |
| 135 | default=False, | |
| 136 | help="Enable dev mode. This will use the user config and plugin folder.") | |
| 137 | ||
| 138 | parser.add_argument('--cert', | |
| 139 | action="store", | |
| 140 | dest="cert_path", | |
| 141 | default=None, | |
| 142 | help="Path to the valid Faraday server certificate") | |
| 143 | ||
| 144 | parser.add_argument('--gui', | |
| 145 | action="store", | |
| 146 | dest="gui", | |
| 147 | default="gtk", | |
| 148 | help="Select interface to start Faraday. Supported values are 'gtk' and 'no' (no GUI at all). Defaults to GTK") | |
| 149 | ||
| 150 | parser.add_argument('--cli', | |
| 151 | action="store_true", | |
| 152 | dest="cli", | |
| 153 | default=False, | |
| 154 | help="Set this flag to avoid GUI and use Faraday as a CLI.") | |
| 155 | ||
| 156 | parser.add_argument('-w', | |
| 157 | '--workspace', | |
| 158 | action="store", | |
| 159 | dest="workspace", | |
| 160 | default=None, | |
| 161 | help="Workspace to be opened") | |
| 162 | ||
| 163 | parser.add_argument('-r', | |
| 164 | '--report', | |
| 165 | action="store", | |
| 166 | dest="filename", | |
| 167 | default=None, | |
| 168 | help="Report to be parsed by the CLI") | |
| 169 | ||
| 170 | parser.add_argument('-d', | |
| 171 | '--debug', | |
| 172 | action="store_true", | |
| 173 | default=False, | |
| 174 | help="Enables debug mode. Default = disabled") | |
| 175 | ||
| 176 | parser.add_argument('--creds-file', | |
| 177 | action="store", | |
| 178 | dest="creds_file", | |
| 179 | default=None, | |
| 180 | help="File containing user's credentials to be used in CLI mode") | |
| 181 | ||
| 182 | parser.add_argument('--nodeps', | |
| 183 | action="store_true", | |
| 184 | help='Skip dependency check') | |
| 185 | parser.add_argument('--keep-old', action='store_true', help='Keep old object in CLI mode if Faraday find a conflict') | |
| 186 | parser.add_argument('--keep-new', action='store_true', help='Keep new object in CLI mode if Faraday find a conflict (DEFAULT ACTION)') | |
| 187 | ||
| 188 | parser.add_argument('-v', '--version', action='version', | |
| 189 | version='Faraday v{version}'.format(version=f_version)) | |
| 190 | ||
| 191 | return parser.parse_args() | |
| 192 | ||
| 193 | ||
| 194 | def check_dependencies_or_exit(): | |
| 195 | """ | |
| 196 | Dependency resolver based on a previously specified CONST_REQUIREMENTS_FILE. | |
| 197 | Currently checks a list of dependencies from a file and exits if they are not met. | |
| 198 | """ | |
| 199 | ||
| 200 | installed_deps, missing_deps, conflict_deps = dependencies.check_dependencies(requirements_file=FARADAY_REQUIREMENTS_FILE) | |
| 201 | ||
| 202 | logger.info("Checking dependencies...") | |
| 203 | ||
| 204 | if conflict_deps: | |
| 205 | logger.info("Some dependencies are old. Update them with \"pip install -r requirements_server.txt -U\"") | |
| 206 | ||
| 207 | if missing_deps: | |
| 208 | ||
| 209 | install_deps = query_yes_no("Do you want to install them?", default="no") | |
| 210 | ||
| 211 | if install_deps: | |
| 212 | dependencies.install_packages(missing_deps) | |
| 213 | logger.info("Dependencies installed. Please launch Faraday Server again.") | |
| 214 | sys.exit(0) | |
| 215 | else: | |
| 216 | logger.error("Dependencies not met. Please refer to the documentation in order to install them. [%s]", | |
| 217 | ", ".join(missing_deps)) | |
| 218 | sys.exit(1) | |
| 219 | ||
| 220 | logger.info("Dependencies met") | |
| 221 | ||
| 222 | def setConf(): | |
| 223 | """ | |
| 224 | User configuration management and instantiation. | |
| 225 | Setting framework configuration based either on previously user saved | |
| 226 | settings or default ones. | |
| 227 | """ | |
| 228 | ||
| 229 | logger.info("Setting configuration.") | |
| 230 | ||
| 231 | CONF = getInstanceConfiguration() | |
| 232 | CONF.setDebugStatus(args.debug) | |
| 233 | if args.debug: | |
| 234 | set_logging_level(logging.DEBUG) | |
| 235 | ||
| 236 | host = CONF.getApiConInfoHost() if str(CONF.getApiConInfoHost()) != "None" else FARADAY_DEFAULT_HOST | |
| 237 | port_xmlrpc = CONF.getApiConInfoPort() if str(CONF.getApiConInfoPort()) != "None" else FARADAY_DEFAULT_PORT_XMLRPC | |
| 238 | port_rest = CONF.getApiRestfulConInfoPort() if str( | |
| 239 | CONF.getApiRestfulConInfoPort()) != "None" else FARADAY_DEFAULT_PORT_REST | |
| 240 | ||
| 241 | host = args.host if args.host else host | |
| 242 | port_xmlrpc = args.port_xmlrpc if args.port_xmlrpc else port_xmlrpc | |
| 243 | port_rest = args.port_rest if args.port_rest else port_rest | |
| 244 | ||
| 245 | CONF.setApiConInfoHost(host) | |
| 246 | CONF.setApiConInfoPort(port_xmlrpc) | |
| 247 | CONF.setApiRestfulConInfoPort(port_rest) | |
| 248 | ||
| 249 | ||
| 250 | def startFaraday(): | |
| 251 | """Application startup. | |
| 252 | ||
| 253 | Starts a MainApplication with the previously parsed arguments, and handles | |
| 254 | a profiler if requested. | |
| 255 | ||
| 256 | Returns application status. | |
| 257 | ||
| 258 | """ | |
| 259 | from faraday.client.model.application import MainApplication # pylint:disable=import-outside-toplevel | |
| 260 | ||
| 261 | logger.info("All done. Opening environment.") | |
| 262 | # TODO: Handle args in CONF and send only necessary ones. | |
| 263 | ||
| 264 | main_app = MainApplication(args) | |
| 265 | ||
| 266 | if not args.disable_excepthook: | |
| 267 | logger.info("Main application ExceptHook enabled.") | |
| 268 | main_app.enableExceptHook() | |
| 269 | ||
| 270 | logger.info("Starting main application.") | |
| 271 | start = main_app.start | |
| 272 | ||
| 273 | serverURL = getInstanceConfiguration().getServerURI() | |
| 274 | if serverURL: | |
| 275 | url = "%s/_ui" % serverURL | |
| 276 | print(Fore.WHITE + Style.BRIGHT + "\n* " + "Faraday UI is ready") | |
| 277 | print( | |
| 278 | Fore.WHITE + Style.BRIGHT + "Point your browser to: \n[%s]" % url) | |
| 279 | ||
| 280 | print(Fore.RESET + Back.RESET + Style.RESET_ALL) | |
| 281 | ||
| 282 | exit_status = start() | |
| 283 | ||
| 284 | return exit_status | |
| 285 | ||
| 286 | ||
| 287 | def setupPlugins(dev_mode=False): | |
| 288 | """ | |
| 289 | Checks and handles Faraday's plugin status. | |
| 290 | ||
| 291 | When dev_mode is True, the user enters in development mode and the plugins | |
| 292 | will be replaced with the latest ones. | |
| 293 | ||
| 294 | Otherwise, it checks if the plugin folders exists or not, and creates it | |
| 295 | with its content. | |
| 296 | ||
| 297 | TODO: When dependencies are not satisfied ask user if he wants to try and | |
| 298 | run faraday with a inestability warning. | |
| 299 | """ | |
| 300 | ||
| 301 | if dev_mode: | |
| 302 | logger.warning("Running under plugin development mode!") | |
| 303 | logger.warning("Using user plugins folder") | |
| 304 | else: | |
| 305 | if os.path.isdir(FARADAY_PLUGINS_PATH): | |
| 306 | logger.info("Removing old plugins folder.") | |
| 307 | shutil.rmtree(FARADAY_PLUGINS_PATH) | |
| 308 | else: | |
| 309 | logger.info("No plugins folder detected. Creating new one.") | |
| 310 | ||
| 311 | shutil.copytree(FARADAY_PLUGINS_BASEPATH, FARADAY_PLUGINS_PATH) | |
| 312 | ||
| 313 | ||
| 314 | def setupZSH(): | |
| 315 | """ | |
| 316 | Checks and handles Faraday's integration with ZSH. | |
| 317 | ||
| 318 | If the user has a .zshrc file, it gets copied and integrated with | |
| 319 | faraday's zsh plugin. | |
| 320 | """ | |
| 321 | ||
| 322 | if os.path.isfile(USER_ZSHRC): | |
| 323 | shutil.copy(USER_ZSHRC, FARADAY_USER_ZSHRC) | |
| 324 | else: | |
| 325 | open(FARADAY_USER_ZSHRC, 'w').close() | |
| 326 | ||
| 327 | with open(FARADAY_USER_ZSHRC, "r+") as f: | |
| 328 | content = f.read() | |
| 329 | f.seek(0, 0) | |
| 330 | f.write('ZDOTDIR=$OLDZDOTDIR' + '\n' + content) | |
| 331 | with open(FARADAY_USER_ZSHRC, "a") as f: | |
| 332 | f.write("source \"%s\"" % FARADAY_BASE_ZSH) | |
| 333 | shutil.copy(FARADAY_BASE_ZSH, FARADAY_USER_ZSH_PATH) | |
| 334 | ||
| 335 | ||
| 336 | def setupXMLConfig(): | |
| 337 | """ | |
| 338 | Checks user configuration file status. | |
| 339 | ||
| 340 | If there is no custom config the default one will be copied as a default. | |
| 341 | """ | |
| 342 | ||
| 343 | if not os.path.isfile(FARADAY_USER_CONFIG_XML): | |
| 344 | logger.info("Copying default configuration from project.") | |
| 345 | shutil.copy(FARADAY_BASE_CONFIG_XML, FARADAY_USER_CONFIG_XML) | |
| 346 | else: | |
| 347 | logger.info("Using custom user configuration.") | |
| 348 | ||
| 349 | ||
| 350 | def setupImages(): | |
| 351 | """ | |
| 352 | Copy png icons | |
| 353 | """ | |
| 354 | if os.path.exists(FARADAY_USER_IMAGES): | |
| 355 | shutil.rmtree(FARADAY_USER_IMAGES) | |
| 356 | shutil.copytree(FARADAY_BASE_IMAGES, FARADAY_USER_IMAGES) | |
| 357 | ||
| 358 | ||
| 359 | def checkConfiguration(gui_type): | |
| 360 | """ | |
| 361 | Checks if the environment is ready to run Faraday. | |
| 362 | ||
| 363 | Checks different environment requirements and sets them before starting | |
| 364 | Faraday. This includes checking for plugin folders, libraries, | |
| 365 | and ZSH integration. | |
| 366 | """ | |
| 367 | logger.info("Checking configuration.") | |
| 368 | logger.info("Setting up plugins.") | |
| 369 | setupPlugins(args.dev_mode) | |
| 370 | logger.info("Setting up ZSH integration.") | |
| 371 | setupZSH() | |
| 372 | logger.info("Setting up user configuration.") | |
| 373 | setupXMLConfig() | |
| 374 | logger.info("Setting up icons for GTK interface.") | |
| 375 | setupImages() | |
| 376 | ||
| 377 | ||
| 378 | def setupFolders(folderlist): | |
| 379 | """ | |
| 380 | Checks if a list of folders exists and creates them otherwise. | |
| 381 | """ | |
| 382 | ||
| 383 | for folder in folderlist: | |
| 384 | fp_folder = os.path.join(FARADAY_USER_HOME, folder) | |
| 385 | checkFolder(fp_folder) | |
| 386 | ||
| 387 | ||
| 388 | def checkFolder(folder): | |
| 389 | """ | |
| 390 | Checks whether a folder exists and creates it if it doesn't. | |
| 391 | """ | |
| 392 | ||
| 393 | if not os.path.isdir(folder): | |
| 394 | if logger: | |
| 395 | logger.info("Creating %s" % folder) | |
| 396 | os.makedirs(folder) | |
| 397 | ||
| 398 | ||
| 399 | def printBanner(): | |
| 400 | """ | |
| 401 | Prints Faraday's ascii banner. | |
| 402 | """ | |
| 403 | print (Fore.RED + """ | |
| 404 | _____ .___ | |
| 405 | _/ ____\_____ ____________ __| _/_____ ___.__. | |
| 406 | \ __\ \__ \ \_ __ \__ \ / __ | \__ \ < | | | |
| 407 | | | / __ \_| | \// __ \_/ /_/ | / __ \_\___ | | |
| 408 | |__| (____ /|__| (____ /\____ | (____ // ____| | |
| 409 | \/ \/ \/ \/ \/ | |
| 410 | """) | |
| 411 | ||
| 412 | print(Fore.WHITE + Back.RED + Style.BRIGHT + "[*[ Open Source Penetration Test IDE ]*]") | |
| 413 | print(Back.RESET + " Where pwnage goes multiplayer") | |
| 414 | print(Fore.RESET + Back.RESET + Style.RESET_ALL) | |
| 415 | logger.info("Starting Faraday IDE.") | |
| 416 | ||
| 417 | ||
| 418 | def checkUpdates(): | |
| 419 | uri = getInstanceConfiguration().getUpdatesUri() | |
| 420 | resp = u"OK" | |
| 421 | try: | |
| 422 | ||
| 423 | getInstanceConfiguration().setVersion(f_version) | |
| 424 | getInstanceConfiguration().setAppname("Faraday - Penetration Test IDE Community") | |
| 425 | parameter = {"version": getInstanceConfiguration().getVersion()} | |
| 426 | ||
| 427 | resp = requests.get(uri, params=parameter, timeout=1, verify=True) | |
| 428 | resp = resp.text.strip() | |
| 429 | except Exception as e: | |
| 430 | logger.error(e) | |
| 431 | version = getInstanceConfiguration().getVersion() | |
| 432 | if 'b' in version.split("+")[0]: | |
| 433 | return | |
| 434 | if not resp == u'OK': | |
| 435 | logger.info("You have available updates. Run ./faraday.py --update to catchup!") | |
| 436 | else: | |
| 437 | logger.info("No updates available, enjoy Faraday.") | |
| 438 | ||
| 439 | ||
| 440 | def check_faraday_version(): | |
| 441 | try: | |
| 442 | server.check_faraday_version() | |
| 443 | except RuntimeError: | |
| 444 | get_logger("launcher").error( | |
| 445 | "The server is running a different Faraday version than the client you are running. Version numbers must match!") | |
| 446 | ||
| 447 | ||
| 448 | def try_login_user(server_uri, api_username, api_password): | |
| 449 | ||
| 450 | try: | |
| 451 | session_cookie = login_user(server_uri, api_username, api_password) | |
| 452 | return session_cookie | |
| 453 | except requests.exceptions.SSLError: | |
| 454 | print("SSL certificate validation failed.\nYou can use the --cert option in Faraday to set the path of the cert") | |
| 455 | sys.exit(-1) | |
| 456 | except requests.exceptions.MissingSchema: | |
| 457 | print("The Faraday Server URL is incorrect, please try again.") | |
| 458 | sys.exit(-2) | |
| 459 | ||
| 460 | ||
| 461 | def doLoginLoop(force_login=False): | |
| 462 | """ | |
| 463 | Sets the username and passwords from the command line. | |
| 464 | If --login flag is set then username and password is set | |
| 465 | """ | |
| 466 | ||
| 467 | try: | |
| 468 | ||
| 469 | CONF = getInstanceConfiguration() | |
| 470 | old_server_url = CONF.getAPIUrl() | |
| 471 | api_username = CONF.getAPIUsername() | |
| 472 | api_password = CONF.getAPIPassword() | |
| 473 | if old_server_url and api_username and api_password and not force_login: | |
| 474 | return | |
| 475 | ||
| 476 | if old_server_url is None: | |
| 477 | new_server_url = input( | |
| 478 | "\nPlease enter the Faraday Server URL (Press enter for http://localhost:5985): ") or "http://localhost:5985" | |
| 479 | else: | |
| 480 | new_server_url = input( | |
| 481 | "\nPlease enter the Faraday Server URL (Press enter for last used: {}): ".format(old_server_url)) or old_server_url | |
| 482 | ||
| 483 | CONF.setAPIUrl(new_server_url) | |
| 484 | ||
| 485 | print("""\nTo login please provide your valid Faraday credentials.\nYou have 3 attempts.""") | |
| 486 | ||
| 487 | for attempt in range(1, 4): | |
| 488 | ||
| 489 | api_username = input("Username (press enter for faraday): ") or "faraday" | |
| 490 | api_password = getpass.getpass('Password: ') | |
| 491 | ||
| 492 | session_cookie = try_login_user(new_server_url, api_username, api_password) | |
| 493 | ||
| 494 | if session_cookie: | |
| 495 | ||
| 496 | CONF.setAPIUsername(api_username) | |
| 497 | CONF.setAPIPassword(api_password) | |
| 498 | CONF.setDBSessionCookies(session_cookie) | |
| 499 | CONF.saveConfig() | |
| 500 | ||
| 501 | user_info = get_user_info() | |
| 502 | if (user_info is None) or (not user_info) or ('username' not in user_info): | |
| 503 | print('Login failed, please try again. You have %d more attempts' % (3 - attempt)) | |
| 504 | continue | |
| 505 | ||
| 506 | logger.info('Login successful: {0}'.format(api_username)) | |
| 507 | break | |
| 508 | ||
| 509 | print('Login failed, please try again. You have %d more attempts' % (3 - attempt)) | |
| 510 | ||
| 511 | else: | |
| 512 | logger.fatal('Invalid credentials, 3 attempts failed. Quitting Faraday...') | |
| 513 | sys.exit(-1) | |
| 514 | ||
| 515 | except KeyboardInterrupt: | |
| 516 | sys.exit(0) | |
| 517 | ||
| 518 | ||
| 519 | def login(forced_login): | |
| 520 | ||
| 521 | CONF = getInstanceConfiguration() | |
| 522 | server_uri = CONF.getServerURI() | |
| 523 | api_username = CONF.getAPIUsername() | |
| 524 | api_password = CONF.getAPIPassword() | |
| 525 | ||
| 526 | if forced_login: | |
| 527 | doLoginLoop(forced_login) | |
| 528 | return | |
| 529 | ||
| 530 | if server_uri and api_username and api_password: | |
| 531 | ||
| 532 | session_cookie = try_login_user(server_uri, api_username, api_password) | |
| 533 | ||
| 534 | if session_cookie: | |
| 535 | CONF.setDBSessionCookies(session_cookie) | |
| 536 | logger.info('Login successful: {0}'.format(api_username)) | |
| 537 | return | |
| 538 | ||
| 539 | doLoginLoop() | |
| 540 | ||
| 541 | ||
| 542 | def main(): | |
| 543 | """ | |
| 544 | Main function for launcher. | |
| 545 | """ | |
| 546 | global args | |
| 547 | ||
| 548 | args = getParserArgs() | |
| 549 | setupFolders(CONST_FARADAY_FOLDER_LIST) | |
| 550 | printBanner() | |
| 551 | if args.cert_path: | |
| 552 | os.environ[REQUESTS_CA_BUNDLE_VAR] = args.cert_path | |
| 553 | checkConfiguration(args.gui) | |
| 554 | setConf() | |
| 555 | login(args.login) | |
| 556 | check_faraday_version() | |
| 557 | checkUpdates() | |
| 558 | startFaraday() | |
| 559 | ||
| 560 | ||
| 561 | if __name__ == '__main__': | |
| 562 | main() | |
| 563 | ||
| 564 | ||
| 565 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env zsh | |
| 1 | ||
| 2 | ### | |
| 3 | ## Faraday Penetration Test IDE | |
| 4 | ## Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 5 | ## See the file 'doc/LICENSE' for the license information | |
| 6 | ### | |
| 7 | ||
| 8 | #ZDOTDIR="~/.faraday/zsh/" /bin/zsh | |
| 9 | FARADAY_ZSH_RPORT="9977" | |
| 10 | FARADAY_ZSH_HOST="127.0.0.1" | |
| 11 | if [ $# -eq 2 ]; then | |
| 12 | FARADAY_ZSH_HOST=$1 | |
| 13 | FARADAY_ZSH_RPORT=$2 | |
| 14 | else | |
| 15 | if [ $# -gt 2 ] || [ $# -eq 1 ]; then | |
| 16 | echo "[*] Usage $0 host port" | |
| 17 | echo "[*] Usage $0 127.0.0.1 9977" | |
| 18 | exit | |
| 19 | else | |
| 20 | echo "[!] Using default configuration" $FARADAY_ZSH_HOST:$FARADAY_ZSH_RPORT | |
| 21 | fi | |
| 22 | fi | |
| 23 | ||
| 24 | export FARADAY_ZSH_RPORT | |
| 25 | export FARADAY_ZSH_HOST | |
| 26 | FARADAYZDOTDIR="$HOME/.faraday/zsh/" | |
| 27 | OLDZDOTDIR=$ZDOTDIR | |
| 28 | ZDOTDIR=$FARADAYZDOTDIR /usr/bin/env zsh | |
| 29 | ||
| 30 | #source ~/.faraday/zsh/.zshrc |
| 0 | #''' | |
| 1 | #Faraday Penetration Test IDE | |
| 2 | #Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | #See the file 'doc/LICENSE' for the license information | |
| 4 | # | |
| 5 | #''' | |
| 6 | ||
| 7 | WORKSPACE=`cat $HOME/.faraday/config/user.xml | grep '<last_workspace' | cut -d '>' -f 2 | cut -d '<' -f 1` | |
| 8 | STATUS=`curl -s $FARADAY_ZSH_HOST:$FARADAY_ZSH_RPORT/status/check | sed "s/[^0-9]//g" | grep -v '^[[:space:]]*$'` | |
| 9 | USERPS1=$PS1 | |
| 10 | PS1="%{${fg_bold[red]}%}[faraday]($WORKSPACE)%{${reset_color}%} $USERPS1" | |
| 11 | export FARADAY_OUTPUT= | |
| 12 | export FARADAY_PLUGIN= | |
| 13 | alias faraday_b64='base64 -w 0' | |
| 14 | ||
| 15 | if [[ $(uname) == 'Darwin' ]]; then | |
| 16 | alias faraday_b64='base64' | |
| 17 | fi | |
| 18 | ||
| 19 | echo ">>> WELCOME TO FARADAY" | |
| 20 | echo "[+] Current Workspace: $WORKSPACE" | |
| 21 | if [[ -z $STATUS ]]; then | |
| 22 | echo "[-] API: Warning API unreachable" | |
| 23 | ||
| 24 | elif [[ $STATUS == "200" ]]; then | |
| 25 | echo "[+] API: OK" | |
| 26 | else | |
| 27 | echo "[!] API: $STATUS" | |
| 28 | ||
| 29 | fi | |
| 30 | ||
| 31 | setopt multios | |
| 32 | setopt histignorespace | |
| 33 | ||
| 34 | old_cmd= | |
| 35 | ||
| 36 | function add-output() { | |
| 37 | old_cmd=$BUFFER | |
| 38 | FARADAY_PLUGIN= | |
| 39 | FARADAY_OUTPUT= | |
| 40 | pwd_actual=$(printf "%s" "$(pwd)"| faraday_b64) | |
| 41 | cmd_encoded=$(printf "%s" "$BUFFER"| faraday_b64) | |
| 42 | json_response=`curl -s -X POST -H "Content-Type: application/json" -d "{\"cmd\": \"$cmd_encoded\", \"pid\": $$, \"pwd\": \"$pwd_actual\"}" http://$FARADAY_ZSH_HOST:$FARADAY_ZSH_RPORT/cmd/input` | |
| 43 | if [[ $? -eq 0 ]]; then | |
| 44 | code=`echo $json_response|env python3 -c "import sys, json;print(json.load(sys.stdin)[\"code\"])"` | |
| 45 | if [[ "$code" == "200" ]]; then | |
| 46 | FARADAY_PLUGIN=`echo $json_response | env python3 -c "import sys, json; print(json.load(sys.stdin)[\"plugin\"])"` | |
| 47 | new_cmd=`echo $json_response | env python3 -c "import sys, json; print(json.load(sys.stdin)[\"cmd\"])"` | |
| 48 | if [[ "$new_cmd" != "None" ]]; then | |
| 49 | BUFFER=" $new_cmd" | |
| 50 | fi | |
| 51 | FARADAY_OUTPUT=`mktemp tmp.XXXXXXXXXXXXXXXXXXXXXXXXXXXXX` | |
| 52 | BUFFER="$BUFFER 2>&1 | tee -a $FARADAY_OUTPUT" | |
| 53 | fi | |
| 54 | fi | |
| 55 | zle .accept-line "$@" | |
| 56 | } | |
| 57 | ||
| 58 | function send-output() { | |
| 59 | if [ ! -z "$FARADAY_PLUGIN" ]; then | |
| 60 | output=`base64 "$FARADAY_OUTPUT"` | |
| 61 | temp_file=`mktemp tmp.XXXXXXXXXXXXXXXXXXXXXXXXXXXXX` | |
| 62 | echo "{\"exit_code\": $?, \"pid\": $$, \"output\": \"$output\" }" >> $temp_file | |
| 63 | curl=`curl -s -X POST -H "Content-Type: application/json" -d @$temp_file http://$FARADAY_ZSH_HOST:$FARADAY_ZSH_RPORT/cmd/output` | |
| 64 | rm -f $temp_file | |
| 65 | fi | |
| 66 | if [ -f $FARADAY_OUTPUT ];then | |
| 67 | rm -f $FARADAY_OUTPUT | |
| 68 | fi | |
| 69 | FARADAY_OUTPUT= | |
| 70 | FARADAY_PLUGIN= | |
| 71 | } | |
| 72 | ||
| 73 | zshaddhistory() { | |
| 74 | emulate -L zsh | |
| 75 | print -sr -- "$old_cmd" | |
| 76 | fc -p | |
| 77 | return 1 | |
| 78 | } | |
| 79 | ||
| 80 | precmd() { | |
| 81 | send-output | |
| 82 | WORKSPACE=`cat $HOME/.faraday/config/user.xml | grep '<last_workspace' | cut -d '>' -f 2 | cut -d '<' -f 1` | |
| 83 | PS1="%{${fg_bold[red]}%}[faraday]($WORKSPACE)%{${reset_color}%} $USERPS1" | |
| 84 | return 0 | |
| 85 | } | |
| 86 | ||
| 87 | zshexit() { | |
| 88 | send-output | |
| 89 | } | |
| 90 | ||
| 91 | if [ -n "${FARADAY_PATH+x}" ]; then | |
| 92 | echo "[+] Faraday path set. Aliasing fplugin" | |
| 93 | ||
| 94 | function fplugin() { | |
| 95 | python "$FARADAY_PATH/client/bin/fplugin.py" $*; | |
| 96 | } | |
| 97 | else | |
| 98 | ||
| 99 | if [ -s "./faraday-server.py" ]; then | |
| 100 | echo "[+] Faraday path not set, but server found. Aliasing fplugin" | |
| 101 | function fplugin() { | |
| 102 | "./bin/fplugin" $*; | |
| 103 | } | |
| 104 | else | |
| 105 | ||
| 106 | echo "[-] Faraday path not set" | |
| 107 | fi | |
| 108 | ||
| 109 | fi | |
| 110 | ||
| 111 | zle -N accept-line add-output |
| 0 | #!/usr/bin/env python3 | |
| 1 | """ | |
| 2 | Faraday Penetration Test IDE | |
| 3 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | """ | |
| 7 | from __future__ import absolute_import | |
| 8 | from __future__ import print_function | |
| 9 | ||
| 10 | import json | |
| 11 | import requests | |
| 12 | import sys | |
| 13 | import uuid | |
| 14 | import os | |
| 15 | import base64 | |
| 16 | ||
| 17 | #TODO: load output dir from faraday config | |
| 18 | #check if output dir already exists, otherwise create it | |
| 19 | file_path = os.path.realpath(__file__) | |
| 20 | output_folder = "%s/output" % os.path.dirname(file_path) | |
| 21 | if not os.path.exists(output_folder): | |
| 22 | os.mkdir(output_folder) | |
| 23 | ||
| 24 | host = os.environ["FARADAY_ZSH_HOST"] | |
| 25 | port = int(os.environ["FARADAY_ZSH_RPORT"]) | |
| 26 | ||
| 27 | url_input = "http://%s:%d/cmd/input" % (host, port) | |
| 28 | url_output = "http://%s:%d/cmd/output" % (host, port) | |
| 29 | url_active_plugins = "http://%s:%d/cmd/active-plugins" % (host, port) | |
| 30 | headers = {'Content-type': 'application/json', 'Accept': 'application/json'} | |
| 31 | ||
| 32 | ||
| 33 | def send_cmd(pid, cmd): | |
| 34 | ||
| 35 | data = {'pid': pid, 'cmd': cmd} | |
| 36 | new_cmd = cmd | |
| 37 | response = '' | |
| 38 | ||
| 39 | try: | |
| 40 | request = requests.post( | |
| 41 | url_input, | |
| 42 | data=json.dumps(data), | |
| 43 | headers=headers) | |
| 44 | ||
| 45 | if request.status_code == 200: | |
| 46 | ||
| 47 | response = request.json() | |
| 48 | if response.get("cmd") is not None: | |
| 49 | new_cmd = response.get("cmd") | |
| 50 | ||
| 51 | output_file = "%s/%s%s.output" % ( | |
| 52 | output_folder, data['pid'], uuid.uuid4()) | |
| 53 | ||
| 54 | new_cmd += " >&1 > %s" % output_file | |
| 55 | except: | |
| 56 | response = '' | |
| 57 | finally: | |
| 58 | print(response) | |
| 59 | return 0 | |
| 60 | ||
| 61 | def gen_output(pid): | |
| 62 | print("%s/%s.%s.output" % (output_folder, pid, uuid.uuid4())) | |
| 63 | return 0 | |
| 64 | ||
| 65 | def send_output(pid, exit_code, output_file): | |
| 66 | output_file = open(output_file) | |
| 67 | output = output_file.read() | |
| 68 | ||
| 69 | data = { | |
| 70 | 'pid': pid, | |
| 71 | 'exit_code': exit_code, | |
| 72 | 'output': base64.b64encode(output) | |
| 73 | } | |
| 74 | ||
| 75 | response = requests.post(url_output, | |
| 76 | data=json.dumps(data), | |
| 77 | headers=headers) | |
| 78 | if response.status_code != 200: | |
| 79 | print(response.json()) | |
| 80 | return -1 | |
| 81 | return 0 | |
| 82 | ||
| 83 | ||
| 84 | def main(argv): | |
| 85 | if len(argv) < 2: | |
| 86 | sys.exit(0) | |
| 87 | ||
| 88 | action = argv[1] | |
| 89 | ||
| 90 | # dispatcher = { | |
| 91 | # 'send_cmd': send_cmd, | |
| 92 | # 'send_output': send_output, | |
| 93 | # 'gen_output': gen_output} | |
| 94 | ||
| 95 | if action == 'send_cmd' and len(argv[2:]) == 2: | |
| 96 | send_cmd(argv[2], argv[3]) | |
| 97 | if action == 'send_output' and len(argv[2:]) == 3: | |
| 98 | send_cmd(argv[2], argv[3], argv[4]) | |
| 99 | if action == 'gen_output' and len(argv[2:]) == 1: | |
| 100 | send_cmd(argv[2]) | |
| 101 | ||
| 102 | # if action in dispatcher.keys(): | |
| 103 | # if len(argv[2:]) > 0: | |
| 104 | # dispatcher[action](*argv[2:]) | |
| 105 | ||
| 106 | ||
| 107 | if __name__ == '__main__': | |
| 108 | main(sys.argv) | |
| 109 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | __all__ = [] | |
| 7 | # I'm Py3⏎ |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | import os | |
| 7 | import json | |
| 8 | import shutil | |
| 9 | ||
| 10 | from faraday.config.constant import CONST_FARADAY_HOME_PATH | |
| 11 | ||
| 12 | try: | |
| 13 | import xml.etree.cElementTree as ET | |
| 14 | from xml.etree.cElementTree import Element, ElementTree | |
| 15 | except ImportError: | |
| 16 | import xml.etree.ElementTree as ET | |
| 17 | from xml.etree.ElementTree import Element, ElementTree | |
| 18 | ||
| 19 | ||
| 20 | the_config = None | |
| 21 | ||
| 22 | CONST_API_CON_INFO = "api_con_info" | |
| 23 | CONST_API_CON_INFO_HOST = "api_con_info_host" | |
| 24 | CONST_API_CON_INFO_PORT = "api_con_info_port" | |
| 25 | CONST_API_RESTFUL_CON_INFO_PORT = "api_restful_con_info_port" | |
| 26 | CONST_APPNAME = "appname" | |
| 27 | CONST_AUTH = "auth" | |
| 28 | CONST_AUTO_SHARE_WORKSPACE = "auto_share_workspace" | |
| 29 | CONST_CONFIG_PATH = "config_path" | |
| 30 | CONST_DATA_PATH = "data_path" | |
| 31 | CONST_DEBUG_STATUS = "debug_status" | |
| 32 | CONST_DEFAULT_CATEGORY = "default_category" | |
| 33 | CONST_DEFAULT_TEMP_PATH = "default_temp_path" | |
| 34 | CONST_FONT = "font" | |
| 35 | CONST_HOME_PATH = "home_path" | |
| 36 | CONST_HOST_TREE_TOGGLE = "host_tree_toggle" | |
| 37 | CONST_HSTACTIONS_PATH = "hstactions_path" | |
| 38 | CONST_ICONS_PATH = "icons_path" | |
| 39 | CONST_IMAGE_PATH = "image_path" | |
| 40 | CONST_LOG_CONSOLE_TOGGLE = "log_console_toggle" | |
| 41 | CONST_NETWORK_LOCATION = "network_location" | |
| 42 | CONST_PERSISTENCE_PATH = "persistence_path" | |
| 43 | CONST_PERSPECTIVE_VIEW = "perspective_view" | |
| 44 | CONST_REPO_PASSWORD = "repo_password" | |
| 45 | CONST_API_URL = "api_url" | |
| 46 | CONST_API_USERNAME = "api_username" | |
| 47 | CONST_API_PASSWORD = "api_password" | |
| 48 | CONST_COUCH_URI = "couch_uri" | |
| 49 | CONST_COUCH_REPLICS = "couch_replics" | |
| 50 | CONST_COUCH_ISREPLICATED = "couch_is_replicated" | |
| 51 | CONST_REPO_URL = "repo_url" | |
| 52 | CONST_REPO_USER = "repo_user" | |
| 53 | CONST_REPORT_PATH = "report_path" | |
| 54 | CONST_SHELL_MAXIMIZED = "shell_maximized" | |
| 55 | CONST_VERSION = "version" | |
| 56 | CONST_UPDATEURI = "updates_uri" | |
| 57 | CONST_TKTURI = "tickets_uri" | |
| 58 | CONST_TKTAPIPARAMS = "tickets_api" | |
| 59 | CONST_TKTTEMPLATE = "tickets_template" | |
| 60 | CONST_OSINT = "osint" | |
| 61 | ||
| 62 | CONST_LAST_WORKSPACE = "last_workspace" | |
| 63 | CONST_PLUGIN_SETTINGS = "plugin_settings" | |
| 64 | ||
| 65 | ||
| 66 | DEFAULT_XML = os.path.dirname(__file__) + "/default.xml" | |
| 67 | DEFAULT_SERVER_INI = os.path.join(os.path.dirname(__file__), "..", "server", "default.ini") | |
| 68 | ||
| 69 | ||
| 70 | class Configuration: | |
| 71 | ||
| 72 | def __init__(self, xml_file=DEFAULT_XML): | |
| 73 | """ Initializer that handles a configuration automagically. """ | |
| 74 | ||
| 75 | self.filepath = xml_file | |
| 76 | self._api_con_info = '' | |
| 77 | ||
| 78 | if self._isConfig(): | |
| 79 | self._getConfig() | |
| 80 | ||
| 81 | def _isConfig(self): | |
| 82 | """ Checks whether the given file exists and belongs | |
| 83 | to faraday's configuration syntax""" | |
| 84 | ||
| 85 | root = f = None | |
| 86 | ||
| 87 | try: | |
| 88 | f = open(self.filepath, 'rb') | |
| 89 | try: | |
| 90 | for event, elem in ET.iterparse(f, ('start', )): | |
| 91 | root = elem.tag | |
| 92 | break | |
| 93 | except SyntaxError as err: | |
| 94 | print("Not an xml file.\n %s" % (err)) | |
| 95 | return False | |
| 96 | ||
| 97 | except IOError as err: | |
| 98 | print("Error while opening file.\n%s. %s" % (err, self.filepath)) | |
| 99 | return False | |
| 100 | ||
| 101 | finally: | |
| 102 | if f: | |
| 103 | f.close() | |
| 104 | ||
| 105 | return (root == "faraday") | |
| 106 | ||
| 107 | def _getTree(self): | |
| 108 | """ Returns an XML tree read from file. """ | |
| 109 | ||
| 110 | f = open(self.filepath) | |
| 111 | try: | |
| 112 | tree = ET.fromstring(f.read()) | |
| 113 | except SyntaxError as err: | |
| 114 | print("SyntaxError: %s. %s" % (err, self.filepath)) | |
| 115 | return None | |
| 116 | return tree | |
| 117 | ||
| 118 | def _getValue(self, tree, var, default=None): | |
| 119 | """ Returns generic value from a variable on an XML tree. """ | |
| 120 | ||
| 121 | elem = tree.findall(var) | |
| 122 | if not(elem): | |
| 123 | return default | |
| 124 | ||
| 125 | return elem[0].text | |
| 126 | ||
| 127 | def _getConfig(self): | |
| 128 | """ Gathers all configuration data from self.filepath, and | |
| 129 | completes private attributes with such information. """ | |
| 130 | ||
| 131 | tree = self._getTree() | |
| 132 | if tree: | |
| 133 | self._api_con_info_host = self._getValue(tree, CONST_API_CON_INFO_HOST) | |
| 134 | self._api_con_info_port = self._getValue(tree, CONST_API_CON_INFO_PORT) | |
| 135 | self._api_restful_con_info_port = self._getValue(tree, CONST_API_RESTFUL_CON_INFO_PORT) | |
| 136 | self._api_con_info = self._getValue(tree, CONST_API_CON_INFO) | |
| 137 | self._appname = self._getValue(tree, CONST_APPNAME) | |
| 138 | self._auth = self._getValue(tree, CONST_AUTH) | |
| 139 | self._auto_share_workspace = self._getValue(tree, CONST_AUTO_SHARE_WORKSPACE) | |
| 140 | self._config_path = self._getValue(tree, CONST_CONFIG_PATH) | |
| 141 | self._data_path = self._getValue(tree, CONST_DATA_PATH) | |
| 142 | self._debug_status = self._getValue(tree, CONST_DEBUG_STATUS) | |
| 143 | self._default_category = self._getValue(tree, CONST_DEFAULT_CATEGORY) | |
| 144 | self._default_temp_path = self._getValue(tree, CONST_DEFAULT_TEMP_PATH) | |
| 145 | self._font = self._getValue(tree, CONST_FONT) | |
| 146 | self._home_path = self._getValue(tree, CONST_HOME_PATH) | |
| 147 | self._host_tree_toggle = self._getValue(tree, CONST_HOST_TREE_TOGGLE) | |
| 148 | self._hsactions_path = self._getValue(tree, CONST_HSTACTIONS_PATH) | |
| 149 | self._icons_path = self._getValue(tree, CONST_ICONS_PATH) | |
| 150 | self._image_path = self._getValue(tree, CONST_IMAGE_PATH) | |
| 151 | self._log_console_toggle = self._getValue(tree, CONST_LOG_CONSOLE_TOGGLE) | |
| 152 | self._network_location = self._getValue(tree, CONST_NETWORK_LOCATION) | |
| 153 | self._persistence_path = self._getValue(tree, CONST_PERSISTENCE_PATH) | |
| 154 | self._perspective_view = self._getValue(tree, CONST_PERSISTENCE_PATH) | |
| 155 | self._repo_password = self._getValue(tree, CONST_REPO_PASSWORD) | |
| 156 | self._api_url = self._getValue(tree, CONST_API_URL) | |
| 157 | self._api_username = self._getValue(tree, CONST_API_USERNAME) | |
| 158 | self._api_password = self._getValue(tree, CONST_API_PASSWORD) | |
| 159 | self._couch_uri = self._getValue(tree, CONST_COUCH_URI, default = "") | |
| 160 | self._couch_replics = self._getValue(tree, CONST_COUCH_REPLICS, default = "") | |
| 161 | self._couch_is_replicated = bool(self._getValue(tree, CONST_COUCH_ISREPLICATED, default = False)) | |
| 162 | self._repo_url = self._getValue(tree, CONST_REPO_URL) | |
| 163 | self._repo_user = self._getValue(tree, CONST_REPO_USER) | |
| 164 | self._report_path = self._getValue(tree, CONST_REPORT_PATH) | |
| 165 | self._shell_maximized = self._getValue(tree, CONST_SHELL_MAXIMIZED) | |
| 166 | self._version = self._getValue(tree, CONST_VERSION) | |
| 167 | self._last_workspace = self._getValue(tree, CONST_LAST_WORKSPACE, default = "untitled") | |
| 168 | self._plugin_settings = json.loads(self._getValue(tree, CONST_PLUGIN_SETTINGS, default = "{}")) | |
| 169 | self._osint = json.loads(self._getValue(tree, CONST_OSINT, default = "{\"host\": \"shodan.io\",\"icon\": \"shodan\",\"label\": \"Shodan\", \"prefix\": \"/search?query=\", \"suffix\": \"\", \"use_external_icon\": false}")) | |
| 170 | ||
| 171 | self._db_user = "" | |
| 172 | self._session_cookies = {} | |
| 173 | ||
| 174 | self._updates_uri = self._getValue(tree, CONST_UPDATEURI, default = "https://www.faradaysec.com/scripts/updates.php") | |
| 175 | self._tkts_uri = self._getValue(tree, CONST_TKTURI,default = "https://www.faradaysec.com/scripts/listener.php") | |
| 176 | self._tkt_api_params = self._getValue(tree, CONST_TKTAPIPARAMS,default ="{}") | |
| 177 | self._tkt_template = self._getValue(tree, CONST_TKTTEMPLATE,default ="{}") | |
| 178 | ||
| 179 | self._merge_strategy = None | |
| 180 | ||
| 181 | def getApiConInfo(self): | |
| 182 | if str(self._api_con_info_host) == "None" or str(self._api_con_info_port) == "None": | |
| 183 | return None | |
| 184 | return self._api_con_info_host, int(self._api_con_info_port) | |
| 185 | ||
| 186 | def getApiRestfulConInfo(self): | |
| 187 | if str(self._api_con_info_host) == "None" or str(self._api_restful_con_info_port) == "None": | |
| 188 | return None | |
| 189 | return self._api_con_info_host, int(self._api_restful_con_info_port) | |
| 190 | ||
| 191 | def getApiConInfoHost(self): | |
| 192 | return self._api_con_info_host | |
| 193 | ||
| 194 | def getApiConInfoPort(self): | |
| 195 | if str(self._api_con_info_port) == "None": | |
| 196 | return None | |
| 197 | return int(self._api_con_info_port) | |
| 198 | ||
| 199 | def getApiRestfulConInfoPort(self): | |
| 200 | if str(self._api_restful_con_info_port) == "None": | |
| 201 | return None | |
| 202 | return int(self._api_restful_con_info_port) | |
| 203 | ||
| 204 | def getAppname(self): | |
| 205 | return self._appname | |
| 206 | ||
| 207 | def getAuth(self): | |
| 208 | return self._auth | |
| 209 | ||
| 210 | def getAutoShareWorkspace(self): | |
| 211 | return self._auto_share_workspace | |
| 212 | ||
| 213 | def getConfigPath(self): | |
| 214 | if not self._config_path: | |
| 215 | self._config_path = CONST_FARADAY_HOME_PATH | |
| 216 | return self._config_path | |
| 217 | ||
| 218 | def getDataPath(self): | |
| 219 | if not self._data_path: | |
| 220 | self._data_path = os.path.join(CONST_FARADAY_HOME_PATH,'data') | |
| 221 | return self._data_path | |
| 222 | ||
| 223 | def getDebugStatus(self): | |
| 224 | return int(self._debug_status) | |
| 225 | ||
| 226 | def getDefaultCategory(self): | |
| 227 | return self._default_category | |
| 228 | ||
| 229 | def getDefaultTempPath(self): | |
| 230 | if not self._default_temp_path: | |
| 231 | self._default_temp_path = os.path.join(CONST_FARADAY_HOME_PATH,'temp') | |
| 232 | return self._default_temp_path | |
| 233 | ||
| 234 | def getFont(self): | |
| 235 | return self._font | |
| 236 | ||
| 237 | def getHomePath(self): | |
| 238 | if not self._home_path: | |
| 239 | self._home_path = CONST_FARADAY_HOME_PATH | |
| 240 | return self._home_path | |
| 241 | ||
| 242 | def getHostTreeToggle(self): | |
| 243 | return self._host_tree_toggle | |
| 244 | ||
| 245 | def getHsactionsPath(self): | |
| 246 | if not self._hsactions_path: | |
| 247 | self._hsactions_path = os.path.join(CONST_FARADAY_HOME_PATH, 'hstactions.dat') | |
| 248 | return self._hsactions_path | |
| 249 | ||
| 250 | def getIconsPath(self): | |
| 251 | if not self._icons_path: | |
| 252 | self._icons_path = os.path.join(CONST_FARADAY_HOME_PATH, 'images', 'icons') | |
| 253 | return self._icons_path | |
| 254 | ||
| 255 | def getImagePath(self): | |
| 256 | if not self._image_path: | |
| 257 | self._image_path = os.path.join(CONST_FARADAY_HOME_PATH,'images') | |
| 258 | return self._image_path | |
| 259 | ||
| 260 | def getLogConsoleToggle(self): | |
| 261 | return self._log_console_toggle | |
| 262 | ||
| 263 | def getNetworkLocation(self): | |
| 264 | return self._network_location | |
| 265 | ||
| 266 | def getPersistencePath(self): | |
| 267 | if not self._persistence_path: | |
| 268 | self._persistence_path = os.path.join(CONST_FARADAY_HOME_PATH,'persistence') | |
| 269 | return self._persistence_path | |
| 270 | ||
| 271 | def getPerspectiveView(self): | |
| 272 | return self._perspective_view | |
| 273 | ||
| 274 | def getServerURI(self): | |
| 275 | return self._api_url | |
| 276 | ||
| 277 | def getDBSessionCookies(self): | |
| 278 | return self._session_cookies | |
| 279 | ||
| 280 | def getDBUser(self): | |
| 281 | return self._db_user | |
| 282 | ||
| 283 | def getRepoPassword(self): | |
| 284 | return self._repo_password | |
| 285 | ||
| 286 | def getRepoUrl(self): | |
| 287 | return self._repo_url | |
| 288 | ||
| 289 | def getRepoUser(self): | |
| 290 | return self._repo_user | |
| 291 | ||
| 292 | def getReportPath(self): | |
| 293 | if not self._report_path: | |
| 294 | self._report_path = os.path.join(CONST_FARADAY_HOME_PATH,"report") | |
| 295 | return self._report_path | |
| 296 | ||
| 297 | def getShellMaximized(self): | |
| 298 | return self._shell_maximized | |
| 299 | ||
| 300 | def getVersion(self): | |
| 301 | return self._version | |
| 302 | ||
| 303 | def getLastWorkspace(self): | |
| 304 | return self._last_workspace | |
| 305 | ||
| 306 | def getPluginSettings(self): | |
| 307 | return self._plugin_settings | |
| 308 | ||
| 309 | def getOsint(self): | |
| 310 | return self._osint | |
| 311 | ||
| 312 | def getUpdatesUri(self): | |
| 313 | return self._updates_uri | |
| 314 | ||
| 315 | def getTktPostUri(self): | |
| 316 | return self._tkts_uri | |
| 317 | ||
| 318 | def getApiParams(self): | |
| 319 | return self._tkt_api_params | |
| 320 | ||
| 321 | def getTktTemplate(self): | |
| 322 | return self._tkt_template | |
| 323 | ||
| 324 | def getMergeStrategy(self): | |
| 325 | return self._merge_strategy | |
| 326 | ||
| 327 | def getAPIUrl(self): | |
| 328 | return self._api_url | |
| 329 | ||
| 330 | def getAPIUsername(self): | |
| 331 | return self._api_username | |
| 332 | ||
| 333 | def getAPIPassword(self): | |
| 334 | return self._api_password | |
| 335 | ||
| 336 | def getCouchURI(self): | |
| 337 | if self._couch_uri and self._couch_uri.endswith('/'): | |
| 338 | return self._couch_uri[:-1] | |
| 339 | else: | |
| 340 | return self._couch_uri | |
| 341 | ||
| 342 | def getCouchReplics(self): | |
| 343 | return self._couch_replics | |
| 344 | ||
| 345 | def getCouchIsReplicated(self): | |
| 346 | return self._couch_is_replicated | |
| 347 | ||
| 348 | def setLastWorkspace(self, workspaceName): | |
| 349 | self._last_workspace = workspaceName | |
| 350 | ||
| 351 | def setApiConInfo(self, val1, val2): | |
| 352 | self._api_con_info = val1, val2 | |
| 353 | self.setApiConInfoHost(val1) | |
| 354 | self.setApiConInfoPort(val2) | |
| 355 | ||
| 356 | def setApiRestfulConInfo(self, val1, val2): | |
| 357 | self._api_con_info = val1, val2 | |
| 358 | self.setApiConInfoHost(val1) | |
| 359 | self.setApiRestfulConInfoPort(val2) | |
| 360 | ||
| 361 | def setApiConInfoHost(self, val): | |
| 362 | self._api_con_info_host = val | |
| 363 | ||
| 364 | def setApiConInfoPort(self, val): | |
| 365 | self._api_con_info_port = str(val) | |
| 366 | ||
| 367 | def setApiRestfulConInfoPort(self, val): | |
| 368 | self._api_restful_con_info_port = str(val) | |
| 369 | ||
| 370 | def setAppname(self, val): | |
| 371 | self._appname = val | |
| 372 | ||
| 373 | def setAuth(self, val): | |
| 374 | self._auth = val | |
| 375 | ||
| 376 | def setAutoShareWorkspace(self, val): | |
| 377 | self._auto_share_workspace = val | |
| 378 | ||
| 379 | def setConfigPath(self, val): | |
| 380 | self._config_path = val | |
| 381 | ||
| 382 | def setDataPath(self, val): | |
| 383 | self._data_path = val | |
| 384 | ||
| 385 | def setDebugStatus(self, val): | |
| 386 | self._debug_status = int(val) | |
| 387 | ||
| 388 | def setDefaultCategory(self, val): | |
| 389 | self._default_category = val | |
| 390 | ||
| 391 | def setDefaultTempPath(self, val): | |
| 392 | self._default_temp_path = val | |
| 393 | ||
| 394 | def setFont(self, val): | |
| 395 | self._font = val | |
| 396 | ||
| 397 | def setHomePath(self, val): | |
| 398 | self._home_path = val | |
| 399 | ||
| 400 | def setHostTreeToggle(self, val): | |
| 401 | self._host_tree_toggle = val | |
| 402 | ||
| 403 | def setHsactionsPath(self, val): | |
| 404 | self._hsactions_path = val | |
| 405 | ||
| 406 | def setIconsPath(self, val): | |
| 407 | self._icons_path = val | |
| 408 | ||
| 409 | def setImagePath(self, val): | |
| 410 | self._image_path = val | |
| 411 | ||
| 412 | def setLogConsoleToggle(self, val): | |
| 413 | self._log_console_toggle = val | |
| 414 | ||
| 415 | def setNetworkLocation(self, val): | |
| 416 | self._network_location = val | |
| 417 | ||
| 418 | def setPersistencePath(self, val): | |
| 419 | self._persistence_path = val | |
| 420 | ||
| 421 | def setPerspectiveView(self, val): | |
| 422 | self._perspective_view = val | |
| 423 | ||
| 424 | def setDBSessionCookies(self, val=None): | |
| 425 | self._session_cookies = val | |
| 426 | ||
| 427 | def setDBUser(self, val=None): | |
| 428 | self._db_user = val | |
| 429 | ||
| 430 | def setRepoPassword(self, val): | |
| 431 | self._repo_password = val | |
| 432 | ||
| 433 | def setRepoUrl(self, val): | |
| 434 | self._repo_url = val | |
| 435 | ||
| 436 | def setRepoUser(self, val): | |
| 437 | self._repo_user = val | |
| 438 | ||
| 439 | def setReportPath(self, val): | |
| 440 | self._report_path = val | |
| 441 | ||
| 442 | def setShellMaximized(self, val): | |
| 443 | self._shell_maximized = val | |
| 444 | ||
| 445 | def setVersion(self, val): | |
| 446 | self._version = val | |
| 447 | ||
| 448 | def setAPIUrl(self, url): | |
| 449 | self._api_url = url | |
| 450 | ||
| 451 | def setAPIUsername(self, username): | |
| 452 | self._api_username = username | |
| 453 | ||
| 454 | def setAPIPassword(self, password): | |
| 455 | self._api_password = password | |
| 456 | ||
| 457 | def setCouchUri(self, uri): | |
| 458 | self._couch_uri = uri | |
| 459 | ||
| 460 | def setCouchIsReplicated(self, is_it): | |
| 461 | self._couch_is_replicated = is_it | |
| 462 | ||
| 463 | def setCouchReplics(self, urls): | |
| 464 | self._couch_replics = urls | |
| 465 | ||
| 466 | def setPluginSettings(self, settings): | |
| 467 | self._plugin_settings = settings | |
| 468 | ||
| 469 | def setOsint(self, config): | |
| 470 | self._osint = config | |
| 471 | ||
| 472 | def setMergeStrategy(self, strategy): | |
| 473 | self._merge_strategy = strategy | |
| 474 | ||
| 475 | def indent(self, elem, level=0): | |
| 476 | """ Indents the tree to make a pretty view of it. """ | |
| 477 | ||
| 478 | i = "\n" + level*" " | |
| 479 | if len(elem): | |
| 480 | if not elem.text or not elem.text.strip(): | |
| 481 | elem.text = i + " " | |
| 482 | if not elem.tail or not elem.tail.strip(): | |
| 483 | elem.tail = i | |
| 484 | for elem in elem: | |
| 485 | self.indent(elem, level+1) | |
| 486 | if not elem.tail or not elem.tail.strip(): | |
| 487 | elem.tail = i | |
| 488 | else: | |
| 489 | if level and (not elem.tail or not elem.tail.strip()): | |
| 490 | elem.tail = i | |
| 491 | ||
| 492 | def saveConfig(self, xml_file=None): | |
| 493 | """ Saves XML config on new file. """ | |
| 494 | ||
| 495 | ROOT = Element("faraday") | |
| 496 | ||
| 497 | tree = self._getTree() | |
| 498 | ||
| 499 | API_CON_INFO_HOST = Element(CONST_API_CON_INFO_HOST) | |
| 500 | #API_CON_INFO_HOST.text = self._getValue(tree, CONST_API_CON_INFO_HOST) | |
| 501 | API_CON_INFO_HOST.text = self.getApiConInfoHost() | |
| 502 | ROOT.append(API_CON_INFO_HOST) | |
| 503 | ||
| 504 | API_CON_INFO_PORT = Element(CONST_API_CON_INFO_PORT) | |
| 505 | #API_CON_INFO_PORT.text = self._getValue(tree, CONST_API_CON_INFO_PORT) | |
| 506 | API_CON_INFO_PORT.text = str(self.getApiConInfoPort()) | |
| 507 | ROOT.append(API_CON_INFO_PORT) | |
| 508 | ||
| 509 | API_RESTFUL_CON_INFO_PORT = Element(CONST_API_RESTFUL_CON_INFO_PORT) | |
| 510 | #API_RESTFUL_CON_INFO_PORT.text = self._getValue(tree, CONST_API_RESTFUL_CON_INFO_PORT) | |
| 511 | API_RESTFUL_CON_INFO_PORT.text = str(self.getApiRestfulConInfoPort()) | |
| 512 | ROOT.append(API_RESTFUL_CON_INFO_PORT) | |
| 513 | ||
| 514 | APPNAME = Element(CONST_APPNAME) | |
| 515 | APPNAME.text = self.getAppname() | |
| 516 | ROOT.append(APPNAME) | |
| 517 | ||
| 518 | AUTH = Element(CONST_AUTH, encrypted="no", algorithm="OTR") | |
| 519 | AUTH.text = self.getAuth() | |
| 520 | ROOT.append(AUTH) | |
| 521 | ||
| 522 | AUTO_SHARE_WORKSPACE = Element(CONST_AUTO_SHARE_WORKSPACE) | |
| 523 | AUTO_SHARE_WORKSPACE.text = self.getAutoShareWorkspace() | |
| 524 | ROOT.append(AUTO_SHARE_WORKSPACE) | |
| 525 | ||
| 526 | CONFIG_PATH = Element(CONST_CONFIG_PATH) | |
| 527 | CONFIG_PATH.text = self.getConfigPath() | |
| 528 | ROOT.append(CONFIG_PATH) | |
| 529 | ||
| 530 | DATA_PATH = Element(CONST_DATA_PATH) | |
| 531 | DATA_PATH.text = self.getDataPath() | |
| 532 | ROOT.append(DATA_PATH) | |
| 533 | ||
| 534 | DEBUG_STATUS = Element(CONST_DEBUG_STATUS) | |
| 535 | DEBUG_STATUS.text = str(self.getDebugStatus()) | |
| 536 | ROOT.append(DEBUG_STATUS) | |
| 537 | ||
| 538 | DEFAULT_CATEGORY = Element(CONST_DEFAULT_CATEGORY) | |
| 539 | DEFAULT_CATEGORY.text = self.getDefaultCategory() | |
| 540 | ROOT.append(DEFAULT_CATEGORY) | |
| 541 | ||
| 542 | DEFAULT_TEMP_PATH = Element(CONST_DEFAULT_TEMP_PATH) | |
| 543 | DEFAULT_TEMP_PATH.text = self.getDefaultTempPath() | |
| 544 | ROOT.append(DEFAULT_TEMP_PATH) | |
| 545 | ||
| 546 | FONT = Element(CONST_FONT) | |
| 547 | FONT.text = self.getFont() | |
| 548 | ROOT.append(FONT) | |
| 549 | ||
| 550 | HOME_PATH = Element(CONST_HOME_PATH) | |
| 551 | HOME_PATH.text = self.getHomePath() | |
| 552 | ROOT.append(HOME_PATH) | |
| 553 | ||
| 554 | HOST_TREE_TOGGLE = Element(CONST_HOST_TREE_TOGGLE) | |
| 555 | HOST_TREE_TOGGLE.text = self.getHostTreeToggle() | |
| 556 | ROOT.append(HOST_TREE_TOGGLE) | |
| 557 | ||
| 558 | HSTACTIONS_PATH = Element(CONST_HSTACTIONS_PATH) | |
| 559 | HSTACTIONS_PATH.text = self.getHsactionsPath() | |
| 560 | ROOT.append(HSTACTIONS_PATH) | |
| 561 | ||
| 562 | ICONS_PATH = Element(CONST_ICONS_PATH) | |
| 563 | ICONS_PATH.text = self.getIconsPath() | |
| 564 | ROOT.append(ICONS_PATH) | |
| 565 | ||
| 566 | IMAGE_PATH = Element(CONST_IMAGE_PATH) | |
| 567 | IMAGE_PATH.text = self.getImagePath() | |
| 568 | ROOT.append(IMAGE_PATH) | |
| 569 | ||
| 570 | LOG_CONSOLE_TOGGLE = Element(CONST_LOG_CONSOLE_TOGGLE) | |
| 571 | LOG_CONSOLE_TOGGLE.text = self.getLogConsoleToggle() | |
| 572 | ROOT.append(LOG_CONSOLE_TOGGLE) | |
| 573 | ||
| 574 | NETWORK_LOCATION = Element(CONST_NETWORK_LOCATION) | |
| 575 | NETWORK_LOCATION.text = self.getNetworkLocation() | |
| 576 | ROOT.append(NETWORK_LOCATION) | |
| 577 | ||
| 578 | PERSISTENCE_PATH = Element(CONST_PERSISTENCE_PATH) | |
| 579 | PERSISTENCE_PATH.text = self.getPersistencePath() | |
| 580 | ROOT.append(PERSISTENCE_PATH) | |
| 581 | ||
| 582 | PERSPECTIVE_VIEW = Element(CONST_PERSPECTIVE_VIEW) | |
| 583 | PERSPECTIVE_VIEW.text = self.getPerspectiveView() | |
| 584 | ROOT.append(PERSPECTIVE_VIEW) | |
| 585 | ||
| 586 | REPO_PASSWORD = Element(CONST_REPO_PASSWORD) | |
| 587 | REPO_PASSWORD.text = self.getRepoPassword() | |
| 588 | ROOT.append(REPO_PASSWORD) | |
| 589 | ||
| 590 | REPO_URL = Element(CONST_REPO_URL, type="SVN") | |
| 591 | REPO_URL.text = self.getRepoUrl() | |
| 592 | ROOT.append(REPO_URL) | |
| 593 | ||
| 594 | REPO_USER = Element(CONST_REPO_USER) | |
| 595 | REPO_USER.text = self.getRepoUser() | |
| 596 | ROOT.append(REPO_USER) | |
| 597 | ||
| 598 | REPORT_PATH = Element(CONST_REPORT_PATH) | |
| 599 | REPORT_PATH.text = self.getReportPath() | |
| 600 | ROOT.append(REPORT_PATH) | |
| 601 | ||
| 602 | SHELL_MAXIMIZED = Element(CONST_SHELL_MAXIMIZED) | |
| 603 | SHELL_MAXIMIZED.text = self.getShellMaximized() | |
| 604 | ROOT.append(SHELL_MAXIMIZED) | |
| 605 | ||
| 606 | LAST_WORKSPACE = Element(CONST_LAST_WORKSPACE) | |
| 607 | LAST_WORKSPACE.text = self.getLastWorkspace() | |
| 608 | ROOT.append(LAST_WORKSPACE) | |
| 609 | ||
| 610 | SERVER_URL = Element(CONST_API_URL) | |
| 611 | SERVER_URL.text = self.getServerURI() | |
| 612 | ROOT.append(SERVER_URL) | |
| 613 | ||
| 614 | SERVER_USERNAME = Element(CONST_API_USERNAME) | |
| 615 | SERVER_USERNAME.text = self.getAPIUsername() | |
| 616 | ROOT.append(SERVER_USERNAME) | |
| 617 | ||
| 618 | SERVER_PASSWORD = Element(CONST_API_PASSWORD) | |
| 619 | SERVER_PASSWORD.text = self.getAPIPassword() | |
| 620 | ROOT.append(SERVER_PASSWORD) | |
| 621 | ||
| 622 | COUCH_URI = Element(CONST_COUCH_URI) | |
| 623 | COUCH_URI.text = self.getCouchURI() | |
| 624 | ROOT.append(COUCH_URI) | |
| 625 | ||
| 626 | COUCH_IS_REPLICATED = Element(CONST_COUCH_ISREPLICATED) | |
| 627 | COUCH_IS_REPLICATED.text = str(self.getCouchIsReplicated()) | |
| 628 | ROOT.append(COUCH_IS_REPLICATED) | |
| 629 | ||
| 630 | COUCH_REPLICS = Element(CONST_COUCH_REPLICS) | |
| 631 | COUCH_REPLICS.text = self.getCouchReplics() | |
| 632 | ROOT.append(COUCH_REPLICS) | |
| 633 | ||
| 634 | VERSION = Element(CONST_VERSION) | |
| 635 | VERSION.text = self.getVersion() | |
| 636 | ROOT.append(VERSION) | |
| 637 | ||
| 638 | PLUGIN_SETTINGS = Element(CONST_PLUGIN_SETTINGS) | |
| 639 | PLUGIN_SETTINGS.text = json.dumps(self.getPluginSettings()) | |
| 640 | ROOT.append(PLUGIN_SETTINGS) | |
| 641 | ||
| 642 | OSINT = Element(CONST_OSINT) | |
| 643 | OSINT.text = json.dumps(self.getOsint()) | |
| 644 | ROOT.append(OSINT) | |
| 645 | ||
| 646 | UPDATE_URI = Element(CONST_UPDATEURI) | |
| 647 | UPDATE_URI.text = self.getUpdatesUri() | |
| 648 | ROOT.append(UPDATE_URI) | |
| 649 | ||
| 650 | TKT_URI = Element(CONST_TKTURI) | |
| 651 | TKT_URI.text = self.getTktPostUri() | |
| 652 | ROOT.append(TKT_URI) | |
| 653 | ||
| 654 | TKT_APIPARAMS = Element(CONST_TKTAPIPARAMS) | |
| 655 | TKT_APIPARAMS.text = self.getApiParams() | |
| 656 | ROOT.append(TKT_APIPARAMS) | |
| 657 | ||
| 658 | TKT_TEMPLATE = Element(CONST_TKTTEMPLATE) | |
| 659 | TKT_TEMPLATE.text = self.getTktTemplate() | |
| 660 | ROOT.append(TKT_TEMPLATE) | |
| 661 | ||
| 662 | self.indent(ROOT, 0) | |
| 663 | ||
| 664 | if not xml_file: | |
| 665 | xml_file = os.path.expanduser(os.path.join(CONST_FARADAY_HOME_PATH, 'config/user.xml')) | |
| 666 | ||
| 667 | if xml_file.startswith('~'): | |
| 668 | xml_file = os.path.expanduser(xml_file) | |
| 669 | ||
| 670 | ElementTree(ROOT).write(xml_file) | |
| 671 | ||
| 672 | ||
| 673 | def getInstanceConfiguration(): | |
| 674 | # TODO: move this to the client and stop using this on the server. | |
| 675 | global the_config | |
| 676 | if the_config is None: | |
| 677 | faraday_dir = CONST_FARADAY_HOME_PATH | |
| 678 | if not os.path.exists(faraday_dir): | |
| 679 | os.mkdir(faraday_dir) | |
| 680 | config_dir = os.path.join(faraday_dir, 'config') | |
| 681 | if not os.path.exists(config_dir): | |
| 682 | os.mkdir(config_dir) | |
| 683 | ||
| 684 | faraday_server_config = os.path.join(config_dir, "server.ini") | |
| 685 | if not os.path.isfile(faraday_server_config): | |
| 686 | shutil.copy(DEFAULT_SERVER_INI, faraday_server_config) | |
| 687 | ||
| 688 | faraday_user_config = os.path.join(config_dir, "user.xml") | |
| 689 | if not os.path.isfile(faraday_user_config): | |
| 690 | shutil.copy(DEFAULT_XML, faraday_user_config) | |
| 691 | ||
| 692 | if os.path.exists(os.path.join(config_dir, "user.xml")): | |
| 693 | the_config = Configuration(os.path.join(config_dir, "user.xml")) | |
| 694 | else: | |
| 695 | the_config = Configuration(os.path.join(config_dir, "config.xml")) | |
| 696 | return the_config | |
| 697 | ||
| 698 | ||
| 699 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2014 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | import os | |
| 7 | ||
| 8 | CONST_REQUIREMENTS_FILE = 'requirements.txt' | |
| 9 | CONST_FARADAY_HOME_PATH = os.path.join(os.getenv('FARADAY_HOME', os.path.expanduser('~/')), '.faraday') | |
| 10 | CONST_FARADAY_PLUGINS_PATH = 'plugins' | |
| 11 | CONST_FARADAY_PLUGINS_REPO_PATH = 'plugins/repo' | |
| 12 | CONST_FARADAY_IMAGES = 'images/' | |
| 13 | CONST_FARADAY_LOGS_PATH = 'logs/' | |
| 14 | CONST_FARADAY_FOLDER_LIST = [ "config", "data", "images", | |
| 15 | "persistence", "plugins", | |
| 16 | "report", "temp", "zsh", "logs" ] | |
| 17 | ||
| 18 | ||
| 19 | CONST_FARADAY_ZSHRC = "zsh/.zshrc" | |
| 20 | CONST_FARADAY_ZSH_FARADAY = "zsh/faraday.zsh" | |
| 21 | CONST_FARADAY_ZSH_OUTPUT_PATH = "zsh/output" | |
| 22 | CONST_FARADAY_BASE_CFG = "config/default.xml" | |
| 23 | CONST_FARADAY_USER_CFG = "config/config.xml" | |
| 24 | CONST_LICENSES_DB = "faraday_licenses" | |
| 25 | CONST_VULN_MODEL_DB = "cwe" | |
| 26 | CONST_BLACKDBS = ('cwe','reports', CONST_LICENSES_DB) | |
| 27 | ||
| 28 | CONST_USER_HOME = "~" | |
| 29 | CONST_USER_ZSHRC = "~/.zshrc" | |
| 30 | CONST_ZSH_PATH = "zsh" | |
| 31 | ||
| 32 | ||
| 33 | # I'm Py3 |
| 0 | <?xml version="1.0"?> | |
| 1 | <faraday> | |
| 2 | ||
| 3 | <appname>Faraday - Penetration Test IDE</appname> | |
| 4 | <version>3.10.2</version> | |
| 5 | <debug_status>0</debug_status> | |
| 6 | <font>-Misc-Fixed-medium-r-normal-*-12-100-100-100-c-70-iso8859-1</font> | |
| 7 | <home_path></home_path> | |
| 8 | <image_path></image_path>> | |
| 9 | <icons_path></icons_path> | |
| 10 | <data_path></data_path> | |
| 11 | <config_path></config_path> | |
| 12 | <default_temp_path></default_temp_path> | |
| 13 | <persistence_path></persistence_path> | |
| 14 | <report_path></report_path> | |
| 15 | <hstactions_path></hstactions_path> | |
| 16 | ||
| 17 | <default_category>General</default_category> | |
| 18 | <auto_share_workspace>1</auto_share_workspace> | |
| 19 | <network_location>LAN</network_location> | |
| 20 | <perspective_view>Hosts</perspective_view> | |
| 21 | <log_console_toggle></log_console_toggle> | |
| 22 | <shell_maximized>0</shell_maximized> | |
| 23 | <host_tree_toggle></host_tree_toggle> | |
| 24 | ||
| 25 | <api_con_info>None</api_con_info> | |
| 26 | <api_con_info_host>None</api_con_info_host> | |
| 27 | <api_con_info_port>None</api_con_info_port> | |
| 28 | <auth encrypted="no" algorithm="OTR">0</auth> | |
| 29 | <repo_url type="svn"></repo_url> | |
| 30 | <repo_user>u</repo_user> | |
| 31 | <repo_password></repo_password> | |
| 32 | <couch_uri>http://127.0.0.1:5985</couch_uri> | |
| 33 | <couch_is_replicated/> | |
| 34 | <couch_replics/> | |
| 35 | ||
| 36 | <updates_uri>https://www.faradaysec.com/scripts/updates.php</updates_uri> | |
| 37 | <tickets_uri>https://www.faradaysec.com/scripts/listener.php</tickets_uri> | |
| 38 | <tickets_template>{}</tickets_template> | |
| 39 | <tickets_api>{}</tickets_api> | |
| 40 | ||
| 41 | ||
| 42 | </faraday> |
| 29 | 29 | import requests |
| 30 | 30 | import alembic.command |
| 31 | 31 | from pgcli.main import PGCli |
| 32 | from requests import ConnectionError | |
| 33 | 32 | from urllib.parse import urlparse |
| 34 | 33 | from alembic.config import Config |
| 35 | 34 | from sqlalchemy.exc import ProgrammingError, OperationalError |
| 36 | 35 | |
| 37 | 36 | import faraday.server.config |
| 38 | 37 | from faraday.server.config import FARADAY_BASE |
| 39 | from faraday.client.persistence.server.server import _conf, FARADAY_UP, SERVER_URL | |
| 40 | from faraday.client.start_client import FARADAY_PLUGINS_BASEPATH | |
| 41 | 38 | from faraday.server.commands.initdb import InitDB |
| 42 | 39 | from faraday.server.commands.faraday_schema_display import DatabaseSchema |
| 43 | 40 | from faraday.server.commands.app_urls import show_all_urls |
| 41 | from faraday.server.commands.app_urls import openapi_format | |
| 44 | 42 | from faraday.server.commands import status_check as status_check_functions |
| 45 | 43 | from faraday.server.commands import change_password as change_pass |
| 46 | 44 | from faraday.server.commands.custom_fields import add_custom_field_main, delete_custom_field_main |
| 48 | 46 | from faraday.server.commands import change_username |
| 49 | 47 | from faraday.server.models import db, User |
| 50 | 48 | from faraday.server.web import app |
| 49 | from faraday_plugins.plugins.manager import PluginsManager | |
| 51 | 50 | |
| 52 | 51 | CONTEXT_SETTINGS = dict(help_option_names=['-h', '--help']) |
| 53 | 52 | |
| 54 | logger = logging.getLogger(__name__) | |
| 53 | #logger = logging.getLogger(__name__) | |
| 55 | 54 | |
| 56 | 55 | @click.group(context_settings=CONTEXT_SETTINGS) |
| 57 | 56 | def cli(): |
| 65 | 64 | @click.command(help="Show all URLs in Faraday Server API") |
| 66 | 65 | def show_urls(): |
| 67 | 66 | show_all_urls() |
| 67 | ||
| 68 | ||
| 69 | @click.command(help="Show all URLs in OPENAPI format") | |
| 70 | def openapi_yaml(): | |
| 71 | openapi_format() | |
| 72 | ||
| 68 | 73 | |
| 69 | 74 | @click.command(help="Create Faraday DB in Postgresql, also tables and indexes") |
| 70 | 75 | @click.option( |
| 156 | 161 | |
| 157 | 162 | @click.command(help="List Available Plugins") |
| 158 | 163 | def list_plugins(): |
| 159 | plugins_list = [name for name in os.listdir(FARADAY_PLUGINS_BASEPATH) | |
| 160 | if os.path.isdir(os.path.join(FARADAY_PLUGINS_BASEPATH, name))] | |
| 161 | print('\n'.join(sorted(plugins_list))) | |
| 164 | plugins_manager = PluginsManager() | |
| 165 | for _, plugin in plugins_manager.get_plugins(): | |
| 166 | click.echo(f"{plugin.id}") | |
| 162 | 167 | |
| 163 | 168 | @click.command(help="Create ADMIN user for Faraday application") |
| 164 | 169 | @click.option('--username', prompt=True, callback=validate_user_unique_field) |
| 212 | 217 | required=False, |
| 213 | 218 | ) |
| 214 | 219 | def migrate(downgrade, revision): |
| 215 | logger.info("Running migrations") | |
| 216 | 220 | try: |
| 217 | 221 | revision = revision or ("-1" if downgrade else "head") |
| 218 | 222 | config = Config(os.path.join(FARADAY_BASE,"alembic.ini")) |
| 222 | 226 | else: |
| 223 | 227 | alembic.command.upgrade(config, revision) |
| 224 | 228 | except OperationalError as e: |
| 229 | logger = logging.getLogger(__name__) | |
| 225 | 230 | logger.error("Migration Error: %s", e) |
| 231 | logger.exception(e) | |
| 226 | 232 | print('Please verify your configuration on server.ini or the hba configuration!') |
| 227 | 233 | except Exception as e: |
| 228 | logger.exception("Migration Error: %s", e) | |
| 229 | print('Migration failed! Please check the logs') | |
| 234 | logger = logging.getLogger(__name__) | |
| 235 | logger.error("Migration Error: %s", e) | |
| 236 | print('Migration failed!', e) | |
| 230 | 237 | sys.exit(1) |
| 231 | else: | |
| 232 | logger.info("Migrations finished") | |
| 233 | 238 | |
| 234 | 239 | |
| 235 | 240 | @click.command(help='Custom field wizard') |
| 267 | 272 | cli.add_command(support) |
| 268 | 273 | cli.add_command(list_plugins) |
| 269 | 274 | cli.add_command(rename_user) |
| 275 | cli.add_command(openapi_yaml) | |
| 270 | 276 | |
| 271 | 277 | if __name__ == '__main__': |
| 272 | 278 | |
| 26 | 26 | target_metadata = db.metadata |
| 27 | 27 | alembic_logger = logging.getLogger('alembic.runtime.migration') |
| 28 | 28 | LOG_FILE = os.path.expanduser(os.path.join( |
| 29 | faraday.server.config.CONSTANTS.CONST_FARADAY_HOME_PATH, | |
| 30 | faraday.server.config.CONSTANTS.CONST_FARADAY_LOGS_PATH, 'alembic.log')) | |
| 29 | faraday.server.config.CONST_FARADAY_HOME_PATH, | |
| 30 | 'logs', 'alembic.log')) | |
| 31 | 31 | fh = logging.FileHandler(LOG_FILE) |
| 32 | 32 | fh.setLevel(logging.INFO) |
| 33 | 33 | alembic_logger.addHandler(fh) |
| 0 | """empty message | |
| 1 | ||
| 2 | Revision ID: 282ac9b6569f | |
| 3 | Revises: 84f266a05be3 | |
| 4 | Create Date: 2020-03-27 05:37:11.000671+00:00 | |
| 5 | ||
| 6 | """ | |
| 7 | from alembic import op | |
| 8 | import sqlalchemy as sa | |
| 9 | from faraday.server.models import Command | |
| 10 | ||
| 11 | ||
| 12 | # revision identifiers, used by Alembic. | |
| 13 | revision = '282ac9b6569f' | |
| 14 | down_revision = '84f266a05be3' | |
| 15 | branch_labels = None | |
| 16 | depends_on = None | |
| 17 | ||
| 18 | ||
| 19 | old_types = Command.IMPORT_SOURCE.remove('agent') | |
| 20 | new_types = list(set(Command.IMPORT_SOURCE + ['agent'])) | |
| 21 | new_options = sorted(new_types) | |
| 22 | ||
| 23 | old_type = sa.Enum(*Command.IMPORT_SOURCE, name='import_source_enum') | |
| 24 | new_type = sa.Enum(*new_options, name='import_source_enum') | |
| 25 | tmp_type = sa.Enum(*new_options, name='_import_source_enum') | |
| 26 | ||
| 27 | cmd = sa.sql.table('command', | |
| 28 | sa.Column('import_source', new_type, nullable=True)) | |
| 29 | ||
| 30 | ||
| 31 | def upgrade(): | |
| 32 | tmp_type.create(op.get_bind(), checkfirst=False) | |
| 33 | op.execute('ALTER TABLE command ALTER COLUMN import_source TYPE _import_source_enum' | |
| 34 | ' USING import_source::text::_import_source_enum') | |
| 35 | old_type.drop(op.get_bind(), checkfirst=False) | |
| 36 | # Create and convert to the "new" status type | |
| 37 | new_type.create(op.get_bind(), checkfirst=False) | |
| 38 | op.execute('ALTER TABLE command ALTER COLUMN import_source TYPE import_source_enum' | |
| 39 | ' USING import_source::text::import_source_enum') | |
| 40 | tmp_type.drop(op.get_bind(), checkfirst=False) | |
| 41 | ||
| 42 | ||
| 43 | def downgrade(): | |
| 44 | # Convert 'asset_owner' status into 'client' | |
| 45 | op.execute(cmd.update().where(cmd.c.import_source == u'agent') | |
| 46 | .values(import_source=None)) | |
| 47 | # Create a temporary "_role" type, convert and drop the "new" type | |
| 48 | tmp_type.create(op.get_bind(), checkfirst=False) | |
| 49 | op.execute('ALTER TABLE command ALTER COLUMN import_source TYPE _import_source_enum' | |
| 50 | ' USING import_source::text::_import_source_enum') | |
| 51 | new_type.drop(op.get_bind(), checkfirst=False) | |
| 52 | # Create and convert to the "old" role type | |
| 53 | old_type.create(op.get_bind(), checkfirst=False) | |
| 54 | op.execute('ALTER TABLE command ALTER COLUMN import_source TYPE import_source_enum' | |
| 55 | ' USING import_source::text::import_source_enum') | |
| 56 | tmp_type.drop(op.get_bind(), checkfirst=False) |
| 0 | """add tool column to vuln | |
| 1 | ||
| 2 | Revision ID: 84f266a05be3 | |
| 3 | Revises: 2a0de6132377 | |
| 4 | Create Date: 2019-11-28 15:19:31.097481+00:00 | |
| 5 | ||
| 6 | """ | |
| 7 | from alembic import op | |
| 8 | import sqlalchemy as sa | |
| 9 | ||
| 10 | ||
| 11 | # revision identifiers, used by Alembic. | |
| 12 | revision = '84f266a05be3' | |
| 13 | down_revision = 'a39a3a6e3f99' | |
| 14 | branch_labels = None | |
| 15 | depends_on = None | |
| 16 | ||
| 17 | ||
| 18 | def upgrade(): | |
| 19 | op.add_column('vulnerability', sa.Column( | |
| 20 | 'tool', | |
| 21 | sa.Text(), | |
| 22 | nullable=False, | |
| 23 | server_default="" | |
| 24 | ) | |
| 25 | ) | |
| 26 | conn = op.get_bind() | |
| 27 | conn.execute("""UPDATE vulnerability | |
| 28 | SET tool=SUBQUERY.tool | |
| 29 | FROM (select v.id, c.tool from vulnerability v, command_object co, command c where v.id = co.object_id and co.object_type = 'vulnerability' and co.command_id = c.id) AS SUBQUERY | |
| 30 | WHERE vulnerability.id=SUBQUERY.id""") | |
| 31 | conn.execute("UPDATE vulnerability set tool='Web UI' where tool=''") | |
| 32 | ||
| 33 | ||
| 34 | def downgrade(): | |
| 35 | op.drop_column('vulnerability','tool') | |
| 36 |
| 0 | """add enabled field to rule | |
| 1 | ||
| 2 | Revision ID: 9c678c44aa61 | |
| 3 | Revises: 282ac9b6569f | |
| 4 | Create Date: 2020-04-08 18:11:04.761114+00:00 | |
| 5 | ||
| 6 | """ | |
| 7 | from alembic import op | |
| 8 | import sqlalchemy as sa | |
| 9 | ||
| 10 | ||
| 11 | # revision identifiers, used by Alembic. | |
| 12 | revision = '9c678c44aa61' | |
| 13 | down_revision = 'b1d15a55556d' | |
| 14 | branch_labels = None | |
| 15 | depends_on = None | |
| 16 | ||
| 17 | ||
| 18 | def upgrade(): | |
| 19 | op.add_column('rule', sa.Column('enabled', sa.Boolean, default=True, nullable=False, server_default='True')) | |
| 20 | ||
| 21 | ||
| 22 | def downgrade(): | |
| 23 | op.drop_column('rule', 'enabled') |
| 0 | """create user preferences column | |
| 1 | ||
| 2 | Revision ID: a39a3a6e3f99 | |
| 3 | Revises: 904a517a2f0c | |
| 4 | Create Date: 2020-02-04 15:28:09.796949+00:00 | |
| 5 | ||
| 6 | """ | |
| 7 | from alembic import op | |
| 8 | ||
| 9 | ||
| 10 | # revision identifiers, used by Alembic. | |
| 11 | revision = 'a39a3a6e3f99' | |
| 12 | down_revision = '904a517a2f0c' | |
| 13 | branch_labels = None | |
| 14 | depends_on = None | |
| 15 | ||
| 16 | ||
| 17 | def upgrade(): | |
| 18 | conn = op.get_bind() | |
| 19 | conn.execute("ALTER TABLE faraday_user ADD COLUMN preferences jsonb not null default '{}'::jsonb") | |
| 20 | ||
| 21 | ||
| 22 | def downgrade(): | |
| 23 | conn = op.get_bind() | |
| 24 | conn.execute('ALTER TABLE faraday_user DROP COLUMN "preferences"') |
| 0 | """remove ticketing tools credentials | |
| 1 | ||
| 2 | Revision ID: b1d15a55556d | |
| 3 | Revises: f00247a92a14 | |
| 4 | Create Date: 2020-04-02 20:41:41.083048+00:00 | |
| 5 | ||
| 6 | """ | |
| 7 | from alembic import op | |
| 8 | import sqlalchemy as sa | |
| 9 | ||
| 10 | from faraday.server.config import LOCAL_CONFIG_FILE | |
| 11 | from configparser import ConfigParser, NoSectionError | |
| 12 | ||
| 13 | ||
| 14 | # revision identifiers, used by Alembic. | |
| 15 | revision = 'b1d15a55556d' | |
| 16 | down_revision = 'f00247a92a14' | |
| 17 | branch_labels = None | |
| 18 | depends_on = None | |
| 19 | ||
| 20 | ||
| 21 | def upgrade(): | |
| 22 | try: | |
| 23 | config = ConfigParser() | |
| 24 | config.read(LOCAL_CONFIG_FILE) | |
| 25 | config.remove_option('ticketing_tool', 'tool_username') | |
| 26 | config.remove_option('ticketing_tool', 'tool_password') | |
| 27 | ||
| 28 | with open(LOCAL_CONFIG_FILE, 'w') as configfile: | |
| 29 | config.write(configfile) | |
| 30 | except NoSectionError: | |
| 31 | pass | |
| 32 | ||
| 33 | ||
| 34 | def downgrade(): | |
| 35 | pass |
| 0 | """Add Agent execution data | |
| 1 | ||
| 2 | Revision ID: f00247a92a14 | |
| 3 | Revises: 282ac9b6569f | |
| 4 | Create Date: 2020-04-01 18:51:29.071191+00:00 | |
| 5 | ||
| 6 | """ | |
| 7 | from alembic import op | |
| 8 | import sqlalchemy as sa | |
| 9 | ||
| 10 | ||
| 11 | # revision identifiers, used by Alembic. | |
| 12 | revision = 'f00247a92a14' | |
| 13 | down_revision = '282ac9b6569f' | |
| 14 | branch_labels = None | |
| 15 | depends_on = None | |
| 16 | ||
| 17 | ||
| 18 | def upgrade(): | |
| 19 | op.add_column( | |
| 20 | 'agent_execution', | |
| 21 | sa.Column( | |
| 22 | 'parameters_data', | |
| 23 | sa.JSON(), | |
| 24 | nullable=False, | |
| 25 | default=lambda: {}, | |
| 26 | server_default="{}" | |
| 27 | ) | |
| 28 | ) | |
| 29 | ||
| 30 | ||
| 31 | def downgrade(): | |
| 32 | op.drop_column( | |
| 33 | 'agent_execution', | |
| 34 | 'parameters_data', | |
| 35 | ) |
| 16 | 16 | branch_labels = None |
| 17 | 17 | depends_on = None |
| 18 | 18 | |
| 19 | old_types = User.ROLES.remove('asset_owner') | |
| 20 | new_types = list(set(User.ROLES + ['asset_owner'])) | |
| 21 | new_options = sorted(new_types) | |
| 22 | ||
| 23 | old_type = sa.Enum(*User.ROLES, name='user_roles') | |
| 24 | new_type = sa.Enum(*new_options, name='user_roles') | |
| 25 | tmp_type = sa.Enum(*new_options, name='_user_roles') | |
| 26 | ||
| 27 | tcr = sa.sql.table('faraday_user', | |
| 28 | sa.Column('role', new_type, nullable=False)) | |
| 29 | ||
| 30 | 19 | |
| 31 | 20 | def upgrade(): |
| 21 | old_type = sa.Enum(*User.ROLES, name='user_roles') | |
| 22 | ||
| 23 | new_types = list(set(User.ROLES + ['asset_owner'])) | |
| 24 | new_options = sorted(new_types) | |
| 25 | new_type = sa.Enum(*new_options, name='user_roles') | |
| 26 | ||
| 27 | tmp_type = sa.Enum(*new_options, name='_user_roles') | |
| 28 | ||
| 32 | 29 | tmp_type.create(op.get_bind(), checkfirst=False) |
| 33 | 30 | op.execute('ALTER TABLE faraday_user ALTER COLUMN role TYPE _user_roles' |
| 34 | 31 | ' USING role::text::_user_roles') |
| 41 | 38 | |
| 42 | 39 | |
| 43 | 40 | def downgrade(): |
| 41 | new_types = list(set(User.ROLES + ['asset_owner'])) | |
| 42 | new_options = sorted(new_types) | |
| 43 | new_type = sa.Enum(*new_options, name='user_roles') | |
| 44 | ||
| 45 | tmp_type = sa.Enum(*new_options, name='_user_roles') | |
| 46 | ||
| 47 | tcr = sa.sql.table('faraday_user', | |
| 48 | sa.Column('role', new_type, nullable=False)) | |
| 49 | ||
| 50 | old_type = sa.Enum(*User.ROLES, name='user_roles') | |
| 51 | ||
| 44 | 52 | # Convert 'asset_owner' status into 'client' |
| 45 | 53 | op.execute(tcr.update().where(tcr.c.role == u'asset_owner') |
| 46 | 54 | .values(status='client')) |
| 9 | 9 | from __future__ import print_function |
| 10 | 10 | from __future__ import division |
| 11 | 11 | from builtins import str |
| 12 | from imp import reload | |
| 13 | 12 | |
| 14 | 13 | import ast |
| 15 | 14 | import json |
| 148 | 147 | def process_models_by_similarity(api, _models, rule, mail_notificacion): |
| 149 | 148 | logger.debug("--> Start Process models by similarity") |
| 150 | 149 | for index_m1, m1 in zip(list(range(len(_models) - 1)), _models): |
| 151 | for index_m2, m2 in zip(list(range(index_m1 + 1, len(_models))), _models[index_m1 + 1:]): | |
| 150 | for _, m2 in zip(list(range(index_m1 + 1, len(_models))), _models[index_m1 + 1:]): | |
| 152 | 151 | if m1.id != m2.id and is_same_level(m1, m2): |
| 153 | 152 | if equals(m1, m2, rule): |
| 154 | 153 | environment = [m1, m2] |
| 433 | 432 | return 'informational' |
| 434 | 433 | if value == 'med': |
| 435 | 434 | return 'medium' |
| 435 | value = value.replace('%', ' ') | |
| 436 | 436 | return value |
| 437 | 437 | |
| 438 | 438 | |
| 440 | 440 | os.remove(".lock.pod") |
| 441 | 441 | logger.info('Killed') |
| 442 | 442 | sys.exit(0) |
| 443 | ||
| 443 | 444 | |
| 444 | 445 | class Searcher: |
| 445 | 446 | def __init__(self, api, mail_notification=None, tool_name='Searcher'): |
| 446 | 447 | self.tool_name = tool_name |
| 447 | 448 | self.api = api |
| 448 | 449 | self.mail_notification = mail_notification |
| 450 | self.rules = [] | |
| 449 | 451 | |
| 450 | 452 | def process(self, rules): |
| 451 | 453 | if rules and validate_rules(rules): |
| 452 | self.rules = rules | |
| 453 | ||
| 454 | self._process_vulnerabilities(rules) | |
| 455 | self._process_services(rules) | |
| 456 | self._process_hosts(rules) | |
| 454 | self.rules = [rule for rule in rules if 'disabled' not in rule or not rule['disabled']] | |
| 455 | ||
| 456 | self._process_vulnerabilities(self.rules) | |
| 457 | self._process_services(self.rules) | |
| 458 | self._process_hosts(self.rules) | |
| 457 | 459 | # TODO: FIX THIS |
| 458 | 460 | |
| 459 | 461 | def _process_vulnerabilities(self, rules): |
| 826 | 828 | def _process_models_by_similarity(self, _models, rule): |
| 827 | 829 | logger.debug("--> Start Process models by similarity") |
| 828 | 830 | for index_m1, m1 in zip(list(range(len(_models) - 1)), _models): |
| 829 | for index_m2, m2 in zip(list(range(index_m1 + 1, len(_models))), _models[index_m1 + 1:]): | |
| 831 | for _, m2 in zip(list(range(index_m1 + 1, len(_models))), _models[index_m1 + 1:]): | |
| 830 | 832 | if m1.id != m2.id and is_same_level(m1, m2): |
| 831 | 833 | if equals(m1, m2, rule): |
| 832 | 834 | environment = [m1, m2] |
| 97 | 97 | templates.distinct(Host.id)] |
| 98 | 98 | return templates |
| 99 | 99 | |
| 100 | def _filter_vulns(self, vulnerability_object, **kwargs): | |
| 101 | vulnerabilities = [] | |
| 102 | vulnerabilities_query = self.session. \ | |
| 103 | query(vulnerability_object). \ | |
| 104 | join(vulnerability_object.workspace). \ | |
| 105 | filter(Workspace.name == self.workspace.name) | |
| 106 | for attr, value in kwargs.items(): | |
| 107 | if attr == 'regex': | |
| 108 | vulnerabilities_query = vulnerabilities_query.filter(vulnerability_object.name.op('~')(value)) | |
| 109 | vulnerabilities = vulnerabilities_query.all() | |
| 110 | elif hasattr(vulnerability_object, attr): | |
| 111 | filter_attr = getattr(vulnerability_object, attr) | |
| 112 | if hasattr(getattr(vulnerability_object, attr).prop, 'entity'): | |
| 113 | map_attr = { | |
| 114 | 'creator': 'username' | |
| 115 | } | |
| 116 | filter_attr = getattr(filter_attr.comparator.entity.class_, map_attr.get(attr, attr)) | |
| 117 | vulnerabilities_query = vulnerabilities_query.filter(filter_attr == str(value)) | |
| 118 | vulnerabilities = vulnerabilities_query.all() | |
| 119 | return vulnerabilities | |
| 120 | ||
| 100 | 121 | def filter_vulnerabilities(self, **kwargs): |
| 101 | vulnerabilities = [] | |
| 102 | vulnerabilities_query = self.session.query(Vulnerability, Workspace.id).join(Workspace).filter( | |
| 103 | Workspace.name == self.workspace.name) | |
| 104 | for attr, value in kwargs.items(): | |
| 105 | if attr == 'regex': | |
| 106 | vulnerabilities_query = vulnerabilities_query.filter(Vulnerability.name.op('~')(value)) | |
| 107 | vulnerabilities = [vulnerability for vulnerability, pos in | |
| 108 | vulnerabilities_query.distinct(Vulnerability.id)] | |
| 109 | elif hasattr(Vulnerability, attr): | |
| 110 | vulnerabilities_query = vulnerabilities_query.filter(getattr(Vulnerability, attr) == str(value)) | |
| 111 | vulnerabilities = [vulnerability for vulnerability, pos in | |
| 112 | vulnerabilities_query.distinct(Vulnerability.id)] | |
| 113 | ||
| 114 | web_vulnerabilities = [] | |
| 115 | web_vulnerabilities_query = self.session.query(VulnerabilityWeb, Workspace.id).join(Workspace).filter( | |
| 116 | Workspace.name == self.workspace.name) | |
| 117 | for attr, value in kwargs.items(): | |
| 118 | if attr == 'regex': | |
| 119 | web_vulnerabilities_query = web_vulnerabilities_query.filter(VulnerabilityWeb.name.op('~')(value)) | |
| 120 | web_vulnerabilities = [web_vulnerability for web_vulnerability, pos in | |
| 121 | web_vulnerabilities_query.distinct(VulnerabilityWeb.id)] | |
| 122 | elif hasattr(VulnerabilityWeb, attr): | |
| 123 | web_vulnerabilities_query = web_vulnerabilities_query.filter(getattr(VulnerabilityWeb, attr) == str(value)) | |
| 124 | web_vulnerabilities = [web_vulnerability for web_vulnerability, pos in | |
| 125 | web_vulnerabilities_query.distinct(VulnerabilityWeb.id)] | |
| 126 | ||
| 122 | vulnerabilities = self._filter_vulns(Vulnerability, **kwargs) | |
| 123 | web_vulnerabilities = self._filter_vulns(VulnerabilityWeb, **kwargs) | |
| 127 | 124 | return list(set(vulnerabilities + web_vulnerabilities)) |
| 128 | 125 | |
| 129 | 126 | def filter_services(self, **kwargs): |
| 0 | # Faraday Penetration Test IDE | |
| 1 | # Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) | |
| 2 | # See the file 'doc/LICENSE' for the license information | |
| 3 | import logging | |
| 4 | import threading | |
| 5 | from time import sleep | |
| 6 | 0 | |
| 7 | import requests | |
| 8 | ||
| 9 | import faraday | |
| 10 | ||
| 11 | logger = logging.getLogger(__name__) | |
| 12 | ||
| 13 | ||
| 14 | class TimerClass(threading.Thread): | |
| 15 | def __init__(self): | |
| 16 | super().__init__(name="TimerClassThread") | |
| 17 | self.__event = threading.Event() | |
| 18 | ||
| 19 | def run(self): | |
| 20 | while not self.__event.is_set(): | |
| 21 | try: | |
| 22 | sleep(5) | |
| 23 | res = requests.get("https://portal.faradaysec.com/api/v1/license_check", | |
| 24 | params={'version': faraday.__version__, 'key': 'white'}, | |
| 25 | timeout=1, | |
| 26 | verify=True) | |
| 27 | logger.info('License status {0}'.format(res.json().get('license_status', 'FAILED!'))) | |
| 28 | except Exception as ex: | |
| 29 | logger.exception(ex) | |
| 30 | logger.warn( | |
| 31 | "NEWS: Can't connect to faradaysec.com...") | |
| 32 | ||
| 33 | self.__event.wait(43200) | |
| 34 | ||
| 35 | def stop(self): | |
| 36 | self.__event.set() |
| 8 | 8 | |
| 9 | 9 | import flask |
| 10 | 10 | import sqlalchemy |
| 11 | from collections import defaultdict | |
| 11 | 12 | from flask import g |
| 12 | 13 | from flask_classful import FlaskView |
| 13 | 14 | from sqlalchemy.orm import joinedload, undefer |
| 14 | 15 | from sqlalchemy.orm.exc import NoResultFound, ObjectDeletedError |
| 15 | 16 | from sqlalchemy.inspection import inspect |
| 16 | from sqlalchemy import func | |
| 17 | from sqlalchemy import func, desc, asc | |
| 17 | 18 | from marshmallow import Schema |
| 18 | 19 | from marshmallow.compat import with_metaclass |
| 19 | 20 | from marshmallow.validate import Length |
| 29 | 30 | ) |
| 30 | 31 | |
| 31 | 32 | from faraday.server.utils.py3 import BytesJSONEncoder |
| 33 | from faraday.server.config import faraday_server | |
| 32 | 34 | |
| 33 | 35 | logger = logging.getLogger(__name__) |
| 34 | 36 | |
| 79 | 81 | |
| 80 | 82 | #: **Required**. The class of the SQLAlchemy model this view will handle |
| 81 | 83 | model_class = None |
| 82 | ||
| 83 | 84 | #: **Required** (unless _get_schema_class is overwritten). |
| 84 | 85 | #: A subclass of `marshmallow.Schema` to serialize and deserialize the |
| 85 | 86 | #: data provided by the user |
| 302 | 303 | super(GenericView, cls).register(app, *args, **kwargs) |
| 303 | 304 | |
| 304 | 305 | @app.errorhandler(422) |
| 305 | def handle_error(err): | |
| 306 | def handle_error(err): # pylint: disable=unused-variable | |
| 306 | 307 | # webargs attaches additional metadata to the `data` attribute |
| 307 | 308 | exc = getattr(err, 'exc') |
| 308 | 309 | if exc: |
| 315 | 316 | }), 400 |
| 316 | 317 | |
| 317 | 318 | @app.errorhandler(409) |
| 318 | def handle_conflict(err): | |
| 319 | def handle_conflict(err): # pylint: disable=unused-variable | |
| 319 | 320 | # webargs attaches additional metadata to the `data` attribute |
| 320 | 321 | exc = getattr(err, 'exc', None) or getattr(err, 'description', None) |
| 321 | 322 | if exc: |
| 326 | 327 | return flask.jsonify(messages), 409 |
| 327 | 328 | |
| 328 | 329 | @app.errorhandler(InvalidUsage) |
| 329 | def handle_invalid_usage(error): | |
| 330 | def handle_invalid_usage(error): # pylint: disable=unused-variable | |
| 330 | 331 | response = flask.jsonify(error.to_dict()) |
| 331 | 332 | response.status_code = error.status_code |
| 332 | 333 | return response |
| 333 | 334 | |
| 335 | # @app.errorhandler(404) | |
| 336 | def handle_not_found(err): # pylint: disable=unused-variable | |
| 337 | response = {'success': False, 'message': err.description if faraday_server.debug else err.name} | |
| 338 | return flask.jsonify(response), 404 | |
| 339 | ||
| 340 | @app.errorhandler(500) | |
| 341 | def handle_server_error(err): # pylint: disable=unused-variable | |
| 342 | response = {'success': False, 'message': f"Exception: {err.original_exception}" if faraday_server.debug else 'Internal Server Error'} | |
| 343 | return flask.jsonify(response), 500 | |
| 334 | 344 | |
| 335 | 345 | class GenericWorkspacedView(GenericView): |
| 336 | 346 | """Abstract class for a view that depends on the workspace, that is |
| 575 | 585 | """Add GET /<id>/ route""" |
| 576 | 586 | |
| 577 | 587 | def get(self, object_id, **kwargs): |
| 588 | """ | |
| 589 | --- | |
| 590 | tags: ["{tag_name}"] | |
| 591 | summary: Retrieves {class_model} | |
| 592 | parameters: | |
| 593 | - in: path | |
| 594 | name: object_id | |
| 595 | required: true | |
| 596 | schema: | |
| 597 | type: integer | |
| 598 | responses: | |
| 599 | 200: | |
| 600 | description: Ok | |
| 601 | content: | |
| 602 | application/json: | |
| 603 | schema: {schema_class} | |
| 604 | """ | |
| 578 | 605 | return self._dump(self._get_object(object_id, eagerload=True, |
| 579 | 606 | **kwargs), kwargs) |
| 580 | 607 | |
| 583 | 610 | """Add GET /<workspace_name>/<route_base>/<id>/ route""" |
| 584 | 611 | # There are no differences with the non-workspaced implementations. The code |
| 585 | 612 | # inside the view generic methods is enough |
| 613 | def get(self, object_id, workspace_name=None): | |
| 614 | """ | |
| 615 | --- | |
| 616 | tags: ["{tag_name}"] | |
| 617 | summary: Retrieves {class_model} | |
| 618 | parameters: | |
| 619 | - in: path | |
| 620 | name: object_id | |
| 621 | required: true | |
| 622 | schema: | |
| 623 | type: integer | |
| 624 | - in: path | |
| 625 | name: workspace_name | |
| 626 | required: true | |
| 627 | schema: | |
| 628 | type: string | |
| 629 | responses: | |
| 630 | 200: | |
| 631 | description: Ok | |
| 632 | content: | |
| 633 | application/json: | |
| 634 | schema: {schema_class} | |
| 635 | """ | |
| 636 | return super(RetrieveWorkspacedMixin, self).get(object_id, workspace_name=workspace_name) | |
| 586 | 637 | |
| 587 | 638 | |
| 588 | 639 | class ReadOnlyView(SortableMixin, |
| 610 | 661 | """Add POST / route""" |
| 611 | 662 | |
| 612 | 663 | def post(self, **kwargs): |
| 664 | """ | |
| 665 | --- | |
| 666 | tags: ["{tag_name}"] | |
| 667 | summary: Creates {class_model} | |
| 668 | requestBody: | |
| 669 | required: true | |
| 670 | content: | |
| 671 | application/json: | |
| 672 | schema: {schema_class} | |
| 673 | responses: | |
| 674 | 201: | |
| 675 | description: Created | |
| 676 | content: | |
| 677 | application/json: | |
| 678 | schema: {schema_class} | |
| 679 | 409: | |
| 680 | description: Duplicated key found | |
| 681 | content: | |
| 682 | application/json: | |
| 683 | schema: {schema_class} | |
| 684 | """ | |
| 613 | 685 | context = {'updating': False} |
| 614 | 686 | |
| 615 | 687 | data = self._parse_data(self._get_schema_instance(kwargs, context=context), |
| 700 | 772 | the database. |
| 701 | 773 | """ |
| 702 | 774 | |
| 775 | def post(self, workspace_name=None): | |
| 776 | """ | |
| 777 | --- | |
| 778 | tags: ["{tag_name}"] | |
| 779 | summary: Creates {class_model} | |
| 780 | parameters: | |
| 781 | - in: path | |
| 782 | name: workspace_name | |
| 783 | required: true | |
| 784 | schema: | |
| 785 | type: string | |
| 786 | requestBody: | |
| 787 | required: true | |
| 788 | content: | |
| 789 | application/json: | |
| 790 | schema: {schema_class} | |
| 791 | responses: | |
| 792 | 201: | |
| 793 | description: Created | |
| 794 | content: | |
| 795 | application/json: | |
| 796 | schema: {schema_class} | |
| 797 | 409: | |
| 798 | description: Duplicated key found | |
| 799 | content: | |
| 800 | application/json: | |
| 801 | schema: {schema_class} | |
| 802 | """ | |
| 803 | return super(CreateWorkspacedMixin, self).post(workspace_name=workspace_name) | |
| 804 | ||
| 703 | 805 | def _perform_create(self, data, workspace_name): |
| 704 | 806 | assert not db.session.new |
| 705 | 807 | workspace = self._get_workspace(workspace_name) |
| 734 | 836 | """Add PUT /<id>/ route""" |
| 735 | 837 | |
| 736 | 838 | def put(self, object_id, **kwargs): |
| 839 | """ | |
| 840 | --- | |
| 841 | tags: ["{tag_name}"] | |
| 842 | summary: Updates {class_model} | |
| 843 | parameters: | |
| 844 | - in: path | |
| 845 | name: object_id | |
| 846 | required: true | |
| 847 | schema: | |
| 848 | type: integer | |
| 849 | requestBody: | |
| 850 | required: true | |
| 851 | content: | |
| 852 | application/json: | |
| 853 | schema: {schema_class} | |
| 854 | responses: | |
| 855 | 200: | |
| 856 | description: Ok | |
| 857 | content: | |
| 858 | application/json: | |
| 859 | schema: {schema_class} | |
| 860 | 409: | |
| 861 | description: Duplicated key found | |
| 862 | content: | |
| 863 | application/json: | |
| 864 | schema: {schema_class} | |
| 865 | """ | |
| 866 | ||
| 737 | 867 | obj = self._get_object(object_id, **kwargs) |
| 738 | 868 | context = {'updating': True, 'object': obj} |
| 739 | 869 | data = self._parse_data(self._get_schema_instance(kwargs, context=context), |
| 792 | 922 | the database. |
| 793 | 923 | """ |
| 794 | 924 | |
| 925 | def put(self, object_id, workspace_name=None): | |
| 926 | """ | |
| 927 | --- | |
| 928 | tags: ["{tag_name}"] | |
| 929 | summary: Updates {class_model} | |
| 930 | parameters: | |
| 931 | - in: path | |
| 932 | name: object_id | |
| 933 | required: true | |
| 934 | schema: | |
| 935 | type: integer | |
| 936 | - in: path | |
| 937 | name: workspace_name | |
| 938 | required: true | |
| 939 | schema: | |
| 940 | type: string | |
| 941 | requestBody: | |
| 942 | required: true | |
| 943 | content: | |
| 944 | application/json: | |
| 945 | schema: {schema_class} | |
| 946 | responses: | |
| 947 | 200: | |
| 948 | description: Ok | |
| 949 | content: | |
| 950 | application/json: | |
| 951 | schema: {schema_class} | |
| 952 | 409: | |
| 953 | description: Duplicated key found | |
| 954 | content: | |
| 955 | application/json: | |
| 956 | schema: {schema_class} | |
| 957 | """ | |
| 958 | return super(UpdateWorkspacedMixin, self).put(object_id, workspace_name=workspace_name) | |
| 959 | ||
| 795 | 960 | def _perform_update(self, object_id, obj, data, workspace_name=None): |
| 796 | 961 | # # Make sure that if I created new objects, I had properly commited them |
| 797 | 962 | # assert not db.session.new |
| 807 | 972 | class DeleteMixin: |
| 808 | 973 | """Add DELETE /<id>/ route""" |
| 809 | 974 | def delete(self, object_id, **kwargs): |
| 975 | """ | |
| 976 | --- | |
| 977 | tags: ["{tag_name}"] | |
| 978 | summary: Deletes {class_model} | |
| 979 | parameters: | |
| 980 | - in: path | |
| 981 | name: object_id | |
| 982 | required: true | |
| 983 | schema: | |
| 984 | type: integer | |
| 985 | responses: | |
| 986 | 204: | |
| 987 | description: The resource was deleted successfully | |
| 988 | """ | |
| 810 | 989 | obj = self._get_object(object_id, **kwargs) |
| 811 | 990 | self._perform_delete(obj, **kwargs) |
| 812 | 991 | return None, 204 |
| 818 | 997 | |
| 819 | 998 | class DeleteWorkspacedMixin(DeleteMixin): |
| 820 | 999 | """Add DELETE /<workspace_name>/<route_base>/<id>/ route""" |
| 1000 | def delete(self, object_id, workspace_name=None): | |
| 1001 | ||
| 1002 | """ | |
| 1003 | --- | |
| 1004 | tags: ["{tag_name}"] | |
| 1005 | summary: Deletes {class_model} | |
| 1006 | parameters: | |
| 1007 | - in: path | |
| 1008 | name: object_id | |
| 1009 | required: true | |
| 1010 | schema: | |
| 1011 | type: integer | |
| 1012 | - in: path | |
| 1013 | name: workspace_name | |
| 1014 | required: true | |
| 1015 | schema: | |
| 1016 | type: string | |
| 1017 | responses: | |
| 1018 | 204: | |
| 1019 | description: The resource was deleted successfully | |
| 1020 | """ | |
| 1021 | return super(DeleteWorkspacedMixin, self).delete(object_id, workspace_name=workspace_name) | |
| 821 | 1022 | |
| 822 | 1023 | def _perform_delete(self, obj, workspace_name=None): |
| 823 | 1024 | with db.session.no_autoflush: |
| 848 | 1049 | 'total_count': 0 |
| 849 | 1050 | } |
| 850 | 1051 | group_by = flask.request.args.get('group_by', None) |
| 1052 | sort_dir = flask.request.args.get('order', "asc").lower() | |
| 1053 | ||
| 851 | 1054 | # TODO migration: whitelist fields to avoid leaking a confidential |
| 852 | 1055 | # field's value. |
| 853 | 1056 | # Example: /users/count/?group_by=password |
| 854 | 1057 | # Also we should check that the field exists in the db and isn't, for |
| 855 | 1058 | # example, a relationship |
| 856 | 1059 | if not group_by or group_by not in inspect(self.model_class).attrs: |
| 857 | flask.abort(404) | |
| 1060 | flask.abort(400, {"message": "group_by is a required parameter"}) | |
| 1061 | ||
| 1062 | if sort_dir and sort_dir not in ('asc', 'desc'): | |
| 1063 | flask.abort(400, {"message": "order must be 'desc' or 'asc'"}) | |
| 858 | 1064 | |
| 859 | 1065 | workspace_name = kwargs.pop('workspace_name') |
| 860 | 1066 | # using format is not a great practice. |
| 868 | 1074 | .group_by(group_by) |
| 869 | 1075 | .filter(Workspace.name == workspace_name, |
| 870 | 1076 | *self.count_extra_filters)) |
| 1077 | ||
| 1078 | #order | |
| 1079 | order_by = group_by | |
| 1080 | if sort_dir == 'desc': | |
| 1081 | count = count.order_by(desc(order_by)) | |
| 1082 | else: | |
| 1083 | count = count.order_by(asc(order_by)) | |
| 1084 | ||
| 871 | 1085 | for key, count in count.values(group_by, func.count(group_by)): |
| 872 | 1086 | res['groups'].append( |
| 873 | 1087 | {'count': count, |
| 880 | 1094 | return res |
| 881 | 1095 | |
| 882 | 1096 | |
| 1097 | class CountMultiWorkspacedMixin: | |
| 1098 | """Add GET /<workspace_name>/<route_base>/count_multi_workspace/ route | |
| 1099 | ||
| 1100 | Receives a list of workspaces separated by comma in the workspaces | |
| 1101 | GET parameter. | |
| 1102 | If no workspace is specified, the view will return a 400 error. | |
| 1103 | ||
| 1104 | Group objects by the field set in the group_by GET parameter. If it | |
| 1105 | isn't specified, the view will return a 400 error. For each group, | |
| 1106 | show the count of elements and its value. | |
| 1107 | ||
| 1108 | This view is often used by some parts of the web UI. It was designed | |
| 1109 | to keep backwards compatibility with the count endpoint of Faraday | |
| 1110 | v2. | |
| 1111 | """ | |
| 1112 | ||
| 1113 | #: List of SQLAlchemy query filters to apply when counting | |
| 1114 | count_extra_filters = [] | |
| 1115 | ||
| 1116 | def count_multi_workspace(self, **kwargs): | |
| 1117 | res = { | |
| 1118 | 'groups': defaultdict(dict), | |
| 1119 | 'total_count': 0 | |
| 1120 | } | |
| 1121 | ||
| 1122 | workspace_names_list = flask.request.args.get('workspaces', None) | |
| 1123 | ||
| 1124 | if not workspace_names_list: | |
| 1125 | flask.abort(400, {"message": "workspaces is a required parameter"}) | |
| 1126 | ||
| 1127 | workspace_names_list = workspace_names_list.split(',') | |
| 1128 | ||
| 1129 | # Enforce workspace permission checking for each workspace | |
| 1130 | for workspace_name in workspace_names_list: | |
| 1131 | self._get_workspace(workspace_name) | |
| 1132 | ||
| 1133 | group_by = flask.request.args.get('group_by', None) | |
| 1134 | sort_dir = flask.request.args.get('order', "asc").lower() | |
| 1135 | ||
| 1136 | # TODO migration: whitelist fields to avoid leaking a confidential | |
| 1137 | # field's value. | |
| 1138 | # Example: /users/count/?group_by=password | |
| 1139 | # Also we should check that the field exists in the db and isn't, for | |
| 1140 | # example, a relationship | |
| 1141 | if not group_by or group_by not in inspect(self.model_class).attrs: | |
| 1142 | flask.abort(400, {"message": "group_by is a required parameter"}) | |
| 1143 | ||
| 1144 | if sort_dir and sort_dir not in ('asc', 'desc'): | |
| 1145 | flask.abort(400, {"message": "order must be 'desc' or 'asc'"}) | |
| 1146 | ||
| 1147 | grouped_attr = getattr(self.model_class, group_by) | |
| 1148 | ||
| 1149 | q = db.session.query( | |
| 1150 | Workspace.name, | |
| 1151 | grouped_attr, | |
| 1152 | func.count(grouped_attr) | |
| 1153 | )\ | |
| 1154 | .join(Workspace)\ | |
| 1155 | .group_by(grouped_attr, Workspace.name)\ | |
| 1156 | .filter(Workspace.name.in_(workspace_names_list)) | |
| 1157 | ||
| 1158 | #order | |
| 1159 | order_by = grouped_attr | |
| 1160 | if sort_dir == 'desc': | |
| 1161 | q = q.order_by(desc(Workspace.name), desc(order_by)) | |
| 1162 | else: | |
| 1163 | q = q.order_by(asc(Workspace.name), asc(order_by)) | |
| 1164 | ||
| 1165 | for workspace, key, count in q.all(): | |
| 1166 | res['groups'][workspace][key] = count | |
| 1167 | res['total_count'] += count | |
| 1168 | ||
| 1169 | return res | |
| 1170 | ||
| 1171 | ||
| 883 | 1172 | class ReadWriteView(CreateMixin, |
| 884 | 1173 | UpdateMixin, |
| 885 | 1174 | DeleteMixin, |
| 953 | 1242 | """Base Meta class of FilterSet objects""" |
| 954 | 1243 | parser = parser_imported |
| 955 | 1244 | converter = FilterAlchemyModelConverter() |
| 1245 | ||
| 1246 | ||
| 1247 | def get_user_permissions(user): | |
| 1248 | permissions = defaultdict(dict) | |
| 1249 | ||
| 1250 | # Hardcode all permisions to allowed | |
| 1251 | ALLOWED = {'allowed': True, 'reason': None} | |
| 1252 | ||
| 1253 | # TODO schema | |
| 1254 | generic_entities = { | |
| 1255 | 'licences', 'methodology_templates', 'task_templates', 'users', | |
| 1256 | 'vulnerability_template', 'workspaces', | |
| 1257 | 'agents', 'agents_schedules', 'commands', 'comments', 'hosts', | |
| 1258 | 'executive_reports', 'services', 'methodologies', 'tasks', 'vulns', | |
| 1259 | 'credentials', | |
| 1260 | } | |
| 1261 | ||
| 1262 | for entity in generic_entities: | |
| 1263 | permissions[entity]['view'] = ALLOWED | |
| 1264 | permissions[entity]['create'] = ALLOWED | |
| 1265 | permissions[entity]['update'] = ALLOWED | |
| 1266 | permissions[entity]['delete'] = ALLOWED | |
| 1267 | ||
| 1268 | extra_permissions = { | |
| 1269 | 'vulns.status_change', | |
| 1270 | 'settings.view', | |
| 1271 | 'settings.update', | |
| 1272 | 'ticketing.jira', | |
| 1273 | 'ticketing.servicenow', | |
| 1274 | 'bulk_create.bulk_create', | |
| 1275 | 'agents.run', | |
| 1276 | 'workspace_comparison.compare', | |
| 1277 | 'data_analysis.view', | |
| 1278 | } | |
| 1279 | ||
| 1280 | for permission in extra_permissions: | |
| 1281 | (entity, action) = permission.split('.') | |
| 1282 | permissions[entity][action] = ALLOWED | |
| 1283 | ||
| 1284 | return permissions | |
| 0 | 0 | # Faraday Penetration Test IDE |
| 1 | 1 | # Copyright (C) 2019 Infobyte LLC (http://www.infobytesec.com/) |
| 2 | 2 | # See the file 'doc/LICENSE' for the license information |
| 3 | import json | |
| 4 | ||
| 5 | 3 | import flask |
| 6 | import wtforms | |
| 4 | import logging | |
| 7 | 5 | |
| 8 | 6 | from flask import Blueprint, abort, request |
| 9 | 7 | from flask_classful import route |
| 10 | from flask_wtf.csrf import validate_csrf | |
| 11 | 8 | from marshmallow import fields, Schema |
| 9 | from sqlalchemy.orm.exc import NoResultFound | |
| 10 | ||
| 12 | 11 | |
| 13 | 12 | from faraday.server.api.base import (AutoSchema, UpdateWorkspacedMixin, DeleteWorkspacedMixin, |
| 14 | 13 | CountWorkspacedMixin, ReadOnlyWorkspacedView, CreateWorkspacedMixin, |
| 15 | 14 | GenericWorkspacedView) |
| 16 | from faraday.server.models import Agent, Executor | |
| 17 | from faraday.server.schemas import PrimaryKeyRelatedField, MutableField, SelfNestedField | |
| 15 | from faraday.server.models import Agent, Executor, AgentExecution, db | |
| 16 | from faraday.server.schemas import PrimaryKeyRelatedField | |
| 18 | 17 | from faraday.server.config import faraday_server |
| 19 | 18 | from faraday.server.events import changes_queue |
| 20 | 19 | |
| 21 | 20 | agent_api = Blueprint('agent_api', __name__) |
| 22 | 21 | |
| 22 | logger = logging.getLogger(__name__) | |
| 23 | 23 | |
| 24 | 24 | class ExecutorSchema(AutoSchema): |
| 25 | 25 | |
| 72 | 72 | |
| 73 | 73 | |
| 74 | 74 | class AgentCreationView(GenericWorkspacedView, CreateWorkspacedMixin): |
| 75 | """ | |
| 76 | --- | |
| 77 | tags: ["Agent"] | |
| 78 | description: Creates an agent | |
| 79 | responses: | |
| 80 | 201: | |
| 81 | description: Ok | |
| 82 | content: | |
| 83 | application/json: | |
| 84 | schema: AgentCreationSchema | |
| 85 | 401: | |
| 86 | description: Invalid token | |
| 87 | """ | |
| 75 | 88 | route_base = 'agent_registration' |
| 76 | 89 | model_class = Agent |
| 77 | 90 | schema_class = AgentCreationSchema |
| 109 | 122 | |
| 110 | 123 | @route('/<int:agent_id>/run/', methods=['POST']) |
| 111 | 124 | def run_agent(self, workspace_name, agent_id): |
| 125 | """ | |
| 126 | --- | |
| 127 | tags: ["Agent"] | |
| 128 | description: Runs an agent | |
| 129 | responses: | |
| 130 | 400: | |
| 131 | description: Bad request | |
| 132 | 201: | |
| 133 | description: Ok | |
| 134 | content: | |
| 135 | application/json: | |
| 136 | schema: AgentSchema | |
| 137 | """ | |
| 112 | 138 | if flask.request.content_type != 'application/json': |
| 113 | 139 | abort(400, "Only application/json is a valid content-type") |
| 114 | 140 | data = self._parse_data(AgentRunSchema(strict=True), request) |
| 115 | 141 | agent = self._get_object(agent_id, workspace_name) |
| 116 | 142 | executor_data = data['executorData'] |
| 117 | changes_queue.put({ | |
| 118 | 'agent_id': agent.id, | |
| 119 | 'action': 'RUN', | |
| 120 | "executor": executor_data.get('executor'), | |
| 121 | "args": executor_data.get('args') | |
| 122 | }) | |
| 143 | ||
| 144 | try: | |
| 145 | executor = Executor.query.filter(Executor.name == executor_data['executor'], | |
| 146 | Executor.agent_id == agent_id).one() | |
| 147 | ||
| 148 | agent_execution = AgentExecution( | |
| 149 | running=None, | |
| 150 | successful=None, | |
| 151 | message='', | |
| 152 | executor=executor, | |
| 153 | workspace_id=executor.agent.workspace_id, | |
| 154 | parameters_data=executor_data["args"] | |
| 155 | ) | |
| 156 | db.session.add(agent_execution) | |
| 157 | db.session.commit() | |
| 158 | ||
| 159 | changes_queue.put({ | |
| 160 | 'execution_id': agent_execution.id, | |
| 161 | 'agent_id': agent.id, | |
| 162 | 'action': 'RUN', | |
| 163 | "executor": executor_data.get('executor'), | |
| 164 | "args": executor_data.get('args') | |
| 165 | }) | |
| 166 | except NoResultFound as e: | |
| 167 | logger.exception(e) | |
| 168 | abort(400, "Can not find an agent execution with that id") | |
| 169 | ||
| 123 | 170 | return flask.jsonify({ |
| 124 | 171 | 'successful': True, |
| 125 | 172 | }) |
| 0 | import logging | |
| 1 | from datetime import datetime, timedelta | |
| 0 | 2 | import flask |
| 1 | 3 | import sqlalchemy |
| 4 | from sqlalchemy.orm.exc import NoResultFound | |
| 2 | 5 | from marshmallow import ( |
| 3 | 6 | fields, |
| 4 | 7 | post_load, |
| 17 | 20 | Service, |
| 18 | 21 | Vulnerability, |
| 19 | 22 | VulnerabilityWeb, |
| 20 | ) | |
| 23 | AgentExecution) | |
| 21 | 24 | from faraday.server.utils.database import ( |
| 22 | 25 | get_conflict_object, |
| 23 | 26 | is_unique_constraint_violation, |
| 29 | 32 | ) |
| 30 | 33 | from faraday.server.api.base import AutoSchema, GenericWorkspacedView |
| 31 | 34 | from faraday.server.api.modules.websocket_auth import require_agent_token |
| 35 | from faraday.server.utils.bulk_create import add_creator | |
| 32 | 36 | |
| 33 | 37 | bulk_create_api = flask.Blueprint('bulk_create_api', __name__) |
| 38 | ||
| 39 | logger = logging.getLogger(__name__) | |
| 34 | 40 | |
| 35 | 41 | class VulnerabilitySchema(vulns.VulnerabilitySchema): |
| 36 | 42 | class Meta(vulns.VulnerabilitySchema.Meta): |
| 43 | extra_fields = ('run_date',) | |
| 37 | 44 | fields = tuple( |
| 38 | field_name for field_name in vulns.VulnerabilitySchema.Meta.fields | |
| 45 | field_name for field_name in (vulns.VulnerabilitySchema.Meta.fields + extra_fields) | |
| 39 | 46 | if field_name not in ('parent', 'parent_type') |
| 40 | 47 | ) |
| 41 | 48 | |
| 42 | 49 | |
| 43 | class VulnerabilityWebSchema(vulns.VulnerabilityWebSchema): | |
| 50 | class BulkVulnerabilityWebSchema(vulns.VulnerabilityWebSchema): | |
| 44 | 51 | class Meta(vulns.VulnerabilityWebSchema.Meta): |
| 52 | extra_fields = ('run_date',) | |
| 45 | 53 | fields = tuple( |
| 46 | field_name for field_name in vulns.VulnerabilityWebSchema.Meta.fields | |
| 54 | field_name for field_name in (vulns.VulnerabilityWebSchema.Meta.fields + extra_fields) | |
| 47 | 55 | if field_name not in ('parent', 'parent_type') |
| 48 | 56 | ) |
| 49 | 57 | |
| 55 | 63 | super(PolymorphicVulnerabilityField, self).__init__(*args, **kwargs) |
| 56 | 64 | self.many = kwargs.get('many', False) |
| 57 | 65 | self.vuln_schema = VulnerabilitySchema(strict=True) |
| 58 | self.vulnweb_schema = VulnerabilityWebSchema(strict=True) | |
| 66 | self.vulnweb_schema = BulkVulnerabilityWebSchema(strict=True) | |
| 59 | 67 | |
| 60 | 68 | def _deserialize(self, value, attr, data): |
| 61 | 69 | if self.many and not utils.is_collection(value): |
| 78 | 86 | return schema.load(value).data |
| 79 | 87 | |
| 80 | 88 | |
| 81 | class CredentialSchema(AutoSchema): | |
| 89 | class BulkCredentialSchema(AutoSchema): | |
| 82 | 90 | class Meta: |
| 83 | 91 | model = Credential |
| 84 | 92 | fields = ('username', 'password', 'description', 'name') |
| 85 | 93 | |
| 86 | 94 | |
| 87 | class ServiceSchema(services.ServiceSchema): | |
| 95 | class BulkServiceSchema(services.ServiceSchema): | |
| 88 | 96 | """It's like the original service schema, but now it only uses port |
| 89 | 97 | instead of ports (a single integer array). That field was only used |
| 90 | 98 | to keep backwards compatibility with the Web UI""" |
| 96 | 104 | missing=[], |
| 97 | 105 | ) |
| 98 | 106 | credentials = fields.Nested( |
| 99 | CredentialSchema(many=True), | |
| 107 | BulkCredentialSchema(many=True), | |
| 100 | 108 | many=True, |
| 101 | 109 | missing=[], |
| 102 | 110 | ) |
| 112 | 120 | ) + ('vulnerabilities',) |
| 113 | 121 | |
| 114 | 122 | |
| 115 | class HostSchema(hosts.HostSchema): | |
| 123 | class HostBulkSchema(hosts.HostSchema): | |
| 116 | 124 | ip = fields.String(required=True) |
| 117 | 125 | services = fields.Nested( |
| 118 | ServiceSchema(many=True, context={'updating': False}), | |
| 126 | BulkServiceSchema(many=True, context={'updating': False}), | |
| 119 | 127 | many=True, |
| 120 | 128 | missing=[], |
| 121 | 129 | ) |
| 125 | 133 | missing=[], |
| 126 | 134 | ) |
| 127 | 135 | credentials = fields.Nested( |
| 128 | CredentialSchema(many=True), | |
| 136 | BulkCredentialSchema(many=True), | |
| 129 | 137 | many=True, |
| 130 | 138 | missing=[], |
| 131 | 139 | ) |
| 134 | 142 | fields = hosts.HostSchema.Meta.fields + ('services', 'vulnerabilities') |
| 135 | 143 | |
| 136 | 144 | |
| 137 | class CommandSchema(AutoSchema): | |
| 145 | class BulkCommandSchema(AutoSchema): | |
| 138 | 146 | """The schema of faraday/server/api/modules/commandsrun.py has a lot |
| 139 | 147 | of ugly things because of the Web UI backwards compatibility. |
| 140 | 148 | |
| 157 | 165 | |
| 158 | 166 | class BulkCreateSchema(Schema): |
| 159 | 167 | hosts = fields.Nested( |
| 160 | HostSchema(many=True), | |
| 168 | HostBulkSchema(many=True), | |
| 161 | 169 | many=True, |
| 162 | 170 | required=True, |
| 163 | 171 | ) |
| 164 | 172 | command = fields.Nested( |
| 165 | CommandSchema(), | |
| 173 | BulkCommandSchema(), | |
| 166 | 174 | required=False, |
| 167 | 175 | ) |
| 176 | execution_id = fields.Integer(attribute='execution_id') | |
| 168 | 177 | |
| 169 | 178 | |
| 170 | 179 | def get_or_create(ws, model_class, data): |
| 270 | 279 | assert 'host' in kwargs or 'service' in kwargs |
| 271 | 280 | assert not ('host' in kwargs and 'service' in kwargs) |
| 272 | 281 | |
| 273 | attachments = vuln_data.pop('_attachments', {}) | |
| 282 | vuln_data.pop('_attachments', {}) | |
| 274 | 283 | references = vuln_data.pop('references', []) |
| 275 | 284 | policyviolations = vuln_data.pop('policy_violations', []) |
| 276 | 285 | |
| 284 | 293 | model_class = VulnerabilityWeb |
| 285 | 294 | else: |
| 286 | 295 | raise ValidationError("unknown type") |
| 287 | ||
| 296 | tool = vuln_data.get('tool', '') | |
| 297 | if not tool: | |
| 298 | if command: | |
| 299 | vuln_data['tool'] = command.tool | |
| 300 | else: | |
| 301 | vuln_data['tool'] = 'Web UI' | |
| 302 | ||
| 303 | run_date_string = vuln_data.pop('run_date', None) | |
| 304 | if run_date_string: | |
| 305 | try: | |
| 306 | run_timestamp = float(run_date_string) | |
| 307 | run_date = datetime.utcfromtimestamp(run_timestamp) | |
| 308 | if run_date < datetime.now() + timedelta(hours=24): | |
| 309 | logger.debug("Valid run date") | |
| 310 | else: | |
| 311 | run_date = None | |
| 312 | logger.debug("Run date (%s) is greater than allowed", run_date) | |
| 313 | except ValueError: | |
| 314 | logger.error("Error converting run_date to a valid date") | |
| 315 | flask.abort(400, "Invalid run_date") | |
| 316 | else: | |
| 317 | run_date = None | |
| 288 | 318 | (created, vuln) = get_or_create(ws, model_class, vuln_data) |
| 289 | db.session.commit() | |
| 319 | if created and run_date: | |
| 320 | logger.debug("Apply run date to vuln") | |
| 321 | vuln.create_date = run_date | |
| 322 | db.session.commit() | |
| 290 | 323 | |
| 291 | 324 | if command is not None: |
| 292 | 325 | _create_command_object_for(ws, created, vuln, command) |
| 293 | 326 | |
| 294 | 327 | def update_vuln(policyviolations, references, vuln): |
| 295 | 328 | vuln.references = references |
| 296 | vuln.policyviolations = policyviolations | |
| 329 | vuln.policy_violations = policyviolations | |
| 297 | 330 | # TODO attachments |
| 298 | 331 | db.session.add(vuln) |
| 299 | 332 | db.session.commit() |
| 328 | 361 | schema_class = BulkCreateSchema |
| 329 | 362 | |
| 330 | 363 | def post(self, workspace_name): |
| 364 | """ | |
| 365 | --- | |
| 366 | tags: ["Bulk"] | |
| 367 | description: Creates all faraday objects in bulk for a workspace | |
| 368 | requestBody: | |
| 369 | required: true | |
| 370 | content: | |
| 371 | application/json: | |
| 372 | schema: BulkCreateSchema | |
| 373 | responses: | |
| 374 | 201:tags: | |
| 375 | description: Created | |
| 376 | content: | |
| 377 | application/json: | |
| 378 | schema: BulkCreateSchema | |
| 379 | 403: | |
| 380 | description: Disabled workspace | |
| 381 | 404: | |
| 382 | description: Workspace not found | |
| 383 | """ | |
| 384 | data = self._parse_data(self._get_schema_instance({}), flask.request) | |
| 385 | ||
| 331 | 386 | if flask.g.user is None: |
| 332 | 387 | agent = require_agent_token() |
| 333 | 388 | workspace = agent.workspace |
| 334 | assert workspace.name | |
| 335 | if workspace_name != workspace.name: | |
| 389 | ||
| 390 | if not workspace or workspace_name != workspace.name: | |
| 336 | 391 | flask.abort(404, "No such workspace: %s" % workspace_name) |
| 392 | ||
| 393 | if "execution_id" not in data: | |
| 394 | flask.abort(400, "'execution_id' argument expected") | |
| 395 | ||
| 396 | execution_id = data["execution_id"] | |
| 397 | ||
| 398 | agent_execution = AgentExecution.query.filter( | |
| 399 | AgentExecution.id == execution_id | |
| 400 | ).one_or_none() | |
| 401 | ||
| 402 | if agent_execution is None: | |
| 403 | logger.exception( | |
| 404 | NoResultFound( | |
| 405 | f"No row was found for agent executor id {execution_id}") | |
| 406 | ) | |
| 407 | flask.abort(400, "Can not find an agent execution with that id") | |
| 408 | ||
| 409 | if workspace_name != agent_execution.workspace.name: | |
| 410 | logger.exception( | |
| 411 | ValueError(f"The {agent.name} agent has permission to workspace {workspace_name} and ask to write " | |
| 412 | f"to workspace {agent_execution.workspace.name}") | |
| 413 | ) | |
| 414 | flask.abort(400, "Trying to write to the incorrect workspace") | |
| 415 | ||
| 416 | now = datetime.now() | |
| 417 | ||
| 418 | params_data = agent_execution.parameters_data | |
| 419 | params = ', '.join([f'{key}={value}' for (key, value) in params_data.items()]) | |
| 420 | ||
| 421 | ||
| 422 | data["command"] = { | |
| 423 | 'tool': agent.name, # Agent name | |
| 424 | 'command': agent_execution.executor.name, | |
| 425 | 'user': '', | |
| 426 | 'hostname': '', | |
| 427 | 'params': params, | |
| 428 | 'import_source': 'agent', | |
| 429 | 'start_date': (data["command"].get("start_date") or now) if "command" in data else now, #Now or when received run | |
| 430 | 'end_date': (data["command"].get("start_date") or now) if "command" in data else now, #Now or when received run | |
| 431 | } | |
| 337 | 432 | else: |
| 338 | 433 | workspace = self._get_workspace(workspace_name) |
| 339 | data = self._parse_data(self._get_schema_instance({}), flask.request) | |
| 434 | creator_user = flask.g.user | |
| 435 | data = add_creator(data,creator_user) | |
| 436 | ||
| 340 | 437 | bulk_create(workspace, data, True) |
| 341 | 438 | return "Created", 201 |
| 342 | 439 | |
| 345 | 442 | BulkCreateView.register(bulk_create_api) |
| 346 | 443 | |
| 347 | 444 | |
| 348 | # I'm Py3 | |
| 2 | 2 | # See the file 'doc/LICENSE' for the license information |
| 3 | 3 | from flask import Blueprint |
| 4 | 4 | from marshmallow import fields, post_load, ValidationError, validate |
| 5 | from filteralchemy import FilterSet, operators | |
| 5 | from filteralchemy import FilterSet, operators # pylint:disable=unused-import | |
| 6 | 6 | from sqlalchemy.orm.exc import NoResultFound |
| 7 | 7 | |
| 8 | 8 | from faraday.server.api.base import ( |
| 37 | 37 | default=None) |
| 38 | 38 | service_name = fields.String(dump_only=True, attribute="service.name", |
| 39 | 39 | default=None) |
| 40 | target = fields.Method('get_target', dump_only=True) | |
| 40 | target = fields.String(dump_only=True, attribute="target_ip") | |
| 41 | 41 | |
| 42 | 42 | # for filtering |
| 43 | 43 | host_id = fields.Integer(load_only=True) |
| 62 | 62 | fields = ('id', '_id', "_rev", 'parent', 'username', 'description', |
| 63 | 63 | 'name', 'password', 'owner', 'owned', 'couchdbid', 'parent', |
| 64 | 64 | 'parent_type', 'metadata', 'host_ip', 'service_name', |
| 65 | 'target') | |
| 65 | 'target', | |
| 66 | ) | |
| 66 | 67 | |
| 67 | 68 | @post_load |
| 68 | 69 | def set_parent(self, data): |
| 97 | 98 | 'name', |
| 98 | 99 | 'username', |
| 99 | 100 | 'host_id', |
| 100 | 'service_id' | |
| 101 | 'service_id', | |
| 101 | 102 | ) |
| 102 | ||
| 103 | 103 | default_operator = operators.Equal |
| 104 | 104 | operators = (operators.Equal, ) |
| 105 | 105 | |
| 126 | 126 | |
| 127 | 127 | |
| 128 | 128 | CredentialView.register(credentials_api) |
| 129 | # I'm Py3⏎ | |
| 129 | # I'm Py3 | |
| 0 | ||
| 1 | import logging | |
| 2 | from io import BytesIO | |
| 3 | from lxml.etree import Element, SubElement, tostring | |
| 4 | from flask import Blueprint, request, abort, send_file | |
| 5 | ||
| 6 | from faraday.server.models import Workspace | |
| 7 | ||
| 8 | export_data_api = Blueprint('export_data_api', __name__) | |
| 9 | ||
| 10 | logger = logging.getLogger(__name__) | |
| 11 | ||
| 12 | ||
| 13 | @export_data_api.route('/v2/ws/<workspace_name>/export_data', methods=['GET']) | |
| 14 | def export_data(workspace_name): | |
| 15 | workspace = Workspace.query.filter_by(name=workspace_name).first() | |
| 16 | if not workspace: | |
| 17 | logger.error("No such workspace. Please, specify a valid workspace.") | |
| 18 | abort(404, "No such workspace: %s" % workspace_name) | |
| 19 | ||
| 20 | export_format = request.args.get('format', '') | |
| 21 | if not export_format: | |
| 22 | logger.error("No format specified. Please, specify the format to export the data.") | |
| 23 | abort(400, "No format specified.") | |
| 24 | ||
| 25 | if export_format == 'xml_metasploit': | |
| 26 | memory_file = xml_metasploit_format(workspace) | |
| 27 | return send_file( | |
| 28 | memory_file, | |
| 29 | attachment_filename="Faraday-%s-data.xml" % workspace_name, | |
| 30 | as_attachment=True, | |
| 31 | cache_timeout=-1 | |
| 32 | ) | |
| 33 | else: | |
| 34 | logger.error("Invalid format. Please, specify a valid format.") | |
| 35 | abort(400, "Invalid format.") | |
| 36 | ||
| 37 | ||
| 38 | def xml_metasploit_format(workspace): | |
| 39 | root = Element('MetasploitV4') | |
| 40 | hosts_tag = SubElement(root, 'hosts') | |
| 41 | services_tag = SubElement(root, 'services') # Element's parent is root | |
| 42 | websites_tag = SubElement(root, 'web_sites') | |
| 43 | web_vulns_tag = SubElement(root, 'web_vulns') | |
| 44 | web_services = set() | |
| 45 | for host in workspace.hosts: | |
| 46 | host_tag = SubElement(hosts_tag, 'host') | |
| 47 | _build_host_element(host, host_tag) | |
| 48 | ||
| 49 | host_services_tag = SubElement(host_tag, 'services') # Element's parent is host | |
| 50 | vulns_tag = SubElement(host_tag, 'vulns') | |
| 51 | for service in host.services: | |
| 52 | host_service_tag = SubElement(host_services_tag, 'service') | |
| 53 | _build_service_element(service, host_service_tag) | |
| 54 | ||
| 55 | service_tag = SubElement(services_tag, 'service') | |
| 56 | _build_service_element(service, service_tag) | |
| 57 | for vuln in service.vulnerabilities: | |
| 58 | vuln_tag = SubElement(vulns_tag, 'vuln') | |
| 59 | _build_vuln_element(vuln, vuln_tag) | |
| 60 | ||
| 61 | for vuln_web in service.vulnerabilities_web: | |
| 62 | web_services.add(vuln_web.service) | |
| 63 | web_vuln_tag = SubElement(web_vulns_tag, 'web_vuln') | |
| 64 | _build_vuln_web_element(vuln_web, web_vuln_tag) | |
| 65 | ||
| 66 | ||
| 67 | for vuln in host.vulnerabilities: | |
| 68 | vuln_tag = SubElement(vulns_tag, 'vuln') | |
| 69 | _build_vuln_element(vuln, vuln_tag) | |
| 70 | ||
| 71 | _build_websites_element(web_services, websites_tag) | |
| 72 | ||
| 73 | memory_file = BytesIO() | |
| 74 | memory_file.write(tostring(root, xml_declaration=True, encoding="utf-8", pretty_print=True)) | |
| 75 | memory_file.seek(0) | |
| 76 | return memory_file | |
| 77 | ||
| 78 | ||
| 79 | def _build_host_element(host, host_tag): | |
| 80 | host_id = SubElement(host_tag, 'id') | |
| 81 | host_id.text = str(host.id) | |
| 82 | create_date = SubElement(host_tag, 'created-at') | |
| 83 | create_date.text = host.create_date.strftime("%Y-%m-%d %H:%M:%S") | |
| 84 | address = SubElement(host_tag, 'address') | |
| 85 | address.text = host.ip | |
| 86 | mac_address = SubElement(host_tag, 'mac') | |
| 87 | mac_address.text = host.mac | |
| 88 | name = SubElement(host_tag, 'name') | |
| 89 | name.text = ','.join([hostname.name for hostname in host.hostnames]) | |
| 90 | os = SubElement(host_tag, 'os-name') | |
| 91 | os.text = host.os | |
| 92 | update_date = SubElement(host_tag, 'updated-at') | |
| 93 | update_date.text = host.update_date.strftime("%Y-%m-%d %H:%M:%S") | |
| 94 | host_description = SubElement(host_tag, 'comments') | |
| 95 | host_description.text = host.description | |
| 96 | vuln_count = SubElement(host_tag, 'vuln-count') | |
| 97 | vuln_count.text = str(len(host.vulnerabilities)) | |
| 98 | service_count = SubElement(host_tag, 'service-count') | |
| 99 | service_count.text = str(len(host.services)) | |
| 100 | _build_host_empty_fields(host_tag) | |
| 101 | ||
| 102 | ||
| 103 | def _build_host_empty_fields(host_tag): | |
| 104 | empty_fields = ["comm", "state", "os-flavor", "os-sp", "os-lang", "purpose"] | |
| 105 | for field in empty_fields: | |
| 106 | SubElement(host_tag, field) | |
| 107 | ||
| 108 | ||
| 109 | def _build_service_element(service, service_tag): | |
| 110 | service_id = SubElement(service_tag, 'id') | |
| 111 | service_id.text = str(service.id) | |
| 112 | create_date = SubElement(service_tag, 'created-at') | |
| 113 | create_date.text = service.create_date.strftime("%Y-%m-%d %H:%M:%S") | |
| 114 | host_id = SubElement(service_tag, 'host-id') | |
| 115 | host_id.text = str(service.host_id) | |
| 116 | port = SubElement(service_tag, 'port') | |
| 117 | port.text = str(service.port) | |
| 118 | protocol = SubElement(service_tag, 'proto') | |
| 119 | protocol.text = service.protocol | |
| 120 | status = SubElement(service_tag, 'state') | |
| 121 | status.text = service.status | |
| 122 | service_name = SubElement(service_tag, 'name') | |
| 123 | service_name.text = service.name | |
| 124 | update_date = SubElement(service_tag, 'updated-at') | |
| 125 | update_date.text = service.update_date.strftime("%Y-%m-%d %H:%M:%S") | |
| 126 | service_version = SubElement(service_tag, 'info') | |
| 127 | service_version.text = service.version | |
| 128 | ||
| 129 | ||
| 130 | def _build_vuln_element(vuln, vuln_tag): | |
| 131 | vuln_id = SubElement(vuln_tag, 'id') | |
| 132 | vuln_id.text = str(vuln.id) | |
| 133 | if vuln.service: | |
| 134 | host_id = SubElement(vuln_tag, 'host-id') | |
| 135 | host_id.text = str(vuln.service.host_id) | |
| 136 | service_id = SubElement(vuln_tag, 'service-id') | |
| 137 | service_id.text = str(vuln.service_id) | |
| 138 | website_id = SubElement(vuln_tag, 'web-site-id') | |
| 139 | website_id.text = str(vuln.service_id) | |
| 140 | else: | |
| 141 | host_id = SubElement(vuln_tag, 'host-id') | |
| 142 | host_id.text = str(vuln.host_id) | |
| 143 | vuln_name = SubElement(vuln_tag, 'name') | |
| 144 | vuln_name.text = vuln.name | |
| 145 | vuln_info = SubElement(vuln_tag, 'info') | |
| 146 | vuln_info.text = vuln.description | |
| 147 | vuln_refs_tag = SubElement(vuln_tag, 'refs') | |
| 148 | for ref in vuln.references: | |
| 149 | vuln_ref = SubElement(vuln_refs_tag, 'ref') | |
| 150 | vuln_ref.text = ref | |
| 151 | ||
| 152 | ||
| 153 | def _build_vuln_web_element(vuln, vuln_tag): | |
| 154 | vuln_id = SubElement(vuln_tag, 'id') | |
| 155 | vuln_id.text = str(vuln.id) | |
| 156 | ||
| 157 | website_id = SubElement(vuln_tag, 'web-site-id') | |
| 158 | website_id.text = str(vuln.service_id) | |
| 159 | ||
| 160 | create_date = SubElement(vuln_tag, 'created-at') | |
| 161 | create_date.text = vuln.update_date.strftime("%Y-%m-%d %H:%M:%S") | |
| 162 | update_date = SubElement(vuln_tag, 'updated-at') | |
| 163 | update_date.text = vuln.update_date.strftime("%Y-%m-%d %H:%M:%S") | |
| 164 | ||
| 165 | vuln_name = SubElement(vuln_tag, 'name') | |
| 166 | vuln_name.text = vuln.name | |
| 167 | vuln_desc = SubElement(vuln_tag, 'description') | |
| 168 | vuln_desc.text = vuln.description | |
| 169 | risk = SubElement(vuln_tag, 'risk') | |
| 170 | risk.text = map_severity(vuln.severity) | |
| 171 | legacy_category = SubElement(vuln_tag, 'legacy-category') | |
| 172 | legacy_category.text = "Faraday" | |
| 173 | ||
| 174 | path = SubElement(vuln_tag, 'path') | |
| 175 | path.text = vuln.path or "/" | |
| 176 | method = SubElement(vuln_tag, 'method') | |
| 177 | method.text = vuln.method or "GET" | |
| 178 | params = SubElement(vuln_tag, 'params') | |
| 179 | params.text = '' | |
| 180 | pname = SubElement(vuln_tag, 'pname') | |
| 181 | pname.text = vuln.parameter_name | |
| 182 | query = SubElement(vuln_tag, 'query') | |
| 183 | query.text = vuln.query_string | |
| 184 | request = SubElement(vuln_tag, 'request') | |
| 185 | request.text = vuln.request | |
| 186 | ||
| 187 | vhost = SubElement(vuln_tag, 'vhost') | |
| 188 | vhost.text = str(vuln.service.host.ip) | |
| 189 | host = SubElement(vuln_tag, 'host') | |
| 190 | host.text = str(vuln.service.host.ip) | |
| 191 | port = SubElement(vuln_tag, 'port') | |
| 192 | port.text = str(vuln.service.port) | |
| 193 | ssl = SubElement(vuln_tag, 'ssl') | |
| 194 | ssl.text = 'true' if vuln.service.port == 443 else '' | |
| 195 | ||
| 196 | confidence = SubElement(vuln_tag, 'confidence') | |
| 197 | confidence.text = '' | |
| 198 | ||
| 199 | ||
| 200 | def map_severity(severity): | |
| 201 | risk = '1' | |
| 202 | if severity in ['high', 'critical']: | |
| 203 | risk = '5' | |
| 204 | elif severity == 'medium': | |
| 205 | risk = '4' | |
| 206 | elif severity == 'low': | |
| 207 | risk = '3' | |
| 208 | elif severity == 'informational': | |
| 209 | risk = '2' | |
| 210 | ||
| 211 | return risk | |
| 212 | ||
| 213 | ||
| 214 | def _build_websites_element(web_services, websites_tag): | |
| 215 | for web_service in web_services: | |
| 216 | web_site_tag = SubElement(websites_tag, 'web_site') | |
| 217 | website_id = SubElement(web_site_tag, 'id') | |
| 218 | website_id.text = str(web_service.id) | |
| 219 | website_service_id = SubElement(web_site_tag, 'service-id') | |
| 220 | website_service_id.text = str(web_service.id) | |
| 221 | ||
| 222 | website_vhost = SubElement(web_site_tag, 'vhost') | |
| 223 | website_vhost.text = str(web_service.host.ip) | |
| 224 | website_host = SubElement(web_site_tag, 'host') | |
| 225 | website_host.text = str(web_service.host.ip) | |
| 226 | website_port = SubElement(web_site_tag, 'port') | |
| 227 | website_port.text = str(web_service.port) | |
| 228 | ||
| 229 | create_date = SubElement(web_site_tag, 'created-at') | |
| 230 | create_date.text = web_service.create_date.strftime("%Y-%m-%d %H:%M:%S") | |
| 231 | update_date = SubElement(web_site_tag, 'updated-at') | |
| 232 | update_date.text = web_service.update_date.strftime("%Y-%m-%d %H:%M:%S") | |
| 233 | ||
| 234 | website_comments = SubElement(web_site_tag, 'comments') | |
| 235 | website_comments.text = str(web_service.description) | |
| 236 | ||
| 237 | website_options = SubElement(web_site_tag, 'options') | |
| 238 | website_options.text = '' | |
| 239 | ||
| 240 | website_ssl = SubElement(web_site_tag, 'ssl') | |
| 241 | website_ssl.text = 'true' if web_service.port == 443 else '' |
| 42 | 42 | class HostSchema(AutoSchema): |
| 43 | 43 | _id = fields.Integer(dump_only=True, attribute='id') |
| 44 | 44 | id = fields.Integer() |
| 45 | _rev = fields.String(default='') | |
| 45 | _rev = fields.String(default='', dump_only=True) | |
| 46 | 46 | ip = fields.String(default='') |
| 47 | 47 | description = fields.String(required=True) # Explicitly set required=True |
| 48 | 48 | default_gateway = NullToBlankString( |
| 143 | 143 | |
| 144 | 144 | @route('/bulk_create/', methods=['POST']) |
| 145 | 145 | def bulk_create(self, workspace_name): |
| 146 | """ | |
| 147 | --- | |
| 148 | post: | |
| 149 | tags: ["Vulns"] | |
| 150 | description: Creates hosts in bulk | |
| 151 | responses: | |
| 152 | 201: | |
| 153 | description: Created | |
| 154 | content: | |
| 155 | application/json: | |
| 156 | schema: HostSchema | |
| 157 | 400: | |
| 158 | description: Bad request | |
| 159 | 403: | |
| 160 | description: Forbidden | |
| 161 | """ | |
| 146 | 162 | try: |
| 147 | 163 | validate_csrf(flask.request.form.get('csrf_token')) |
| 148 | 164 | except wtforms.ValidationError: |
| 196 | 212 | |
| 197 | 213 | @route('/countVulns/') |
| 198 | 214 | def count_vulns(self, workspace_name): |
| 215 | """ | |
| 216 | --- | |
| 217 | get: | |
| 218 | tags: ["Hosts"] | |
| 219 | summary: Counts Vulnerabilities per host | |
| 220 | responses: | |
| 221 | 200: | |
| 222 | description: Ok | |
| 223 | content: | |
| 224 | application/json: | |
| 225 | schema: HostCountSchema | |
| 226 | """ | |
| 199 | 227 | host_ids = flask.request.args.get('hosts', None) |
| 200 | 228 | if host_ids: |
| 201 | 229 | host_id_list = host_ids.split(',') |
| 202 | 230 | else: |
| 203 | 231 | host_id_list = None |
| 204 | 232 | |
| 205 | res_dict = {'hosts':{}} | |
| 233 | res_dict = {'hosts': {}} | |
| 206 | 234 | |
| 207 | 235 | host_count_schema = HostCountSchema() |
| 208 | 236 | host_count = Host.query_with_count(None, host_id_list, workspace_name) |
| 224 | 252 | result = query.all() |
| 225 | 253 | res_dict = {'tools': []} |
| 226 | 254 | for row in result: |
| 227 | host, command = row | |
| 255 | _, command = row | |
| 228 | 256 | res_dict['tools'].append({'command': command.tool, 'user': command.user, 'params': command.params, 'command_id': command.id, 'create_date': command.create_date.replace(tzinfo=pytz.utc).strftime("%c")}) |
| 229 | 257 | return res_dict |
| 230 | 258 | |
| 280 | 308 | or len(hosts)), |
| 281 | 309 | } |
| 282 | 310 | |
| 311 | @route('bulk_delete/', methods=['DELETE']) | |
| 312 | def bulk_delete(self, workspace_name): | |
| 313 | workspace = self._get_workspace(workspace_name) | |
| 314 | json_request = flask.request.get_json() | |
| 315 | if not json_request: | |
| 316 | flask.abort(400, 'Invalid request. Check the request data or the content type of the request') | |
| 317 | hosts_ids = json_request.get('hosts_ids', []) | |
| 318 | hosts_ids = [host_id for host_id in hosts_ids if isinstance(host_id, int)] | |
| 319 | deleted_hosts = 0 | |
| 320 | if hosts_ids: | |
| 321 | deleted_hosts = Host.query.filter( | |
| 322 | Host.id.in_(hosts_ids), | |
| 323 | Host.workspace_id == workspace.id).delete(synchronize_session='fetch') | |
| 324 | else: | |
| 325 | flask.abort(400, "Invalid request") | |
| 326 | ||
| 327 | db.session.commit() | |
| 328 | response = {'deleted_hosts': deleted_hosts} | |
| 329 | return flask.jsonify(response) | |
| 330 | ||
| 283 | 331 | |
| 284 | 332 | HostsView.register(host_api) |
| 285 | # I'm Py3⏎ | |
| 333 | # I'm Py3 | |
| 0 | from faraday.server.api.base import GenericView | |
| 1 | from faraday.server.models import User, db | |
| 2 | from flask import Blueprint, request, jsonify, g, abort | |
| 3 | ||
| 4 | preferences_api = Blueprint('preferences_api', __name__) | |
| 5 | ||
| 6 | ||
| 7 | class PreferencesView(GenericView): | |
| 8 | model_class = User | |
| 9 | route_base = 'preferences' | |
| 10 | ||
| 11 | def post(self): | |
| 12 | user = g.user | |
| 13 | ||
| 14 | if request.json and 'preferences' not in request.json: | |
| 15 | abort(400) | |
| 16 | ||
| 17 | preferences = request.json.get('preferences', {}) | |
| 18 | user.preferences = preferences | |
| 19 | ||
| 20 | db.session.commit() | |
| 21 | ||
| 22 | return jsonify(''), 200 | |
| 23 | ||
| 24 | def get(self): | |
| 25 | return jsonify({'preferences': g.user.preferences}), 200 | |
| 26 | ||
| 27 | PreferencesView.register(preferences_api) |
| 1 | 1 | # Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) |
| 2 | 2 | # See the file 'doc/LICENSE' for the license information |
| 3 | 3 | from flask import Blueprint, abort, make_response, jsonify |
| 4 | from filteralchemy import FilterSet, operators | |
| 4 | from filteralchemy import FilterSet, operators # pylint:disable=unused-import | |
| 5 | 5 | from marshmallow import fields, post_load, ValidationError |
| 6 | 6 | from marshmallow.validate import OneOf, Range |
| 7 | 7 | from sqlalchemy.orm.exc import NoResultFound |
| 104 | 104 | |
| 105 | 105 | |
| 106 | 106 | class ServiceView(FilterAlchemyMixin, ReadWriteWorkspacedView): |
| 107 | ||
| 107 | 108 | route_base = 'services' |
| 108 | 109 | model_class = Service |
| 109 | 110 | schema_class = ServiceSchema |
| 131 | 132 | return super(ServiceView, self)._perform_create(data, **kwargs) |
| 132 | 133 | |
| 133 | 134 | ServiceView.register(services_api) |
| 134 | # I'm Py3⏎ | |
| 135 | # I'm Py3 | |
| 5 | 5 | """ |
| 6 | 6 | from flask import jsonify, session, Blueprint, current_app |
| 7 | 7 | from flask_wtf.csrf import generate_csrf |
| 8 | from faraday.server.api.base import get_user_permissions | |
| 8 | 9 | |
| 9 | 10 | session_api = Blueprint('session_api', __name__) |
| 10 | 11 | |
| 13 | 14 | user = current_app.user_datastore.get_user(session['user_id']) |
| 14 | 15 | data = user.get_security_payload() |
| 15 | 16 | data['csrf_token'] = generate_csrf() |
| 17 | data['preferences'] = user.preferences | |
| 18 | data['permissions'] = get_user_permissions(user) | |
| 16 | 19 | return jsonify(data) |
| 17 | # I'm Py3⏎ | |
| 20 | # I'm Py3 | |
| 4 | 4 | import string |
| 5 | 5 | import random |
| 6 | 6 | import logging |
| 7 | ||
| 8 | from faraday.server.config import CONST_FARADAY_HOME_PATH | |
| 7 | 9 | from faraday.server.threads.reports_processor import REPORTS_QUEUE |
| 8 | 10 | from flask import ( |
| 9 | 11 | request, |
| 12 | 14 | jsonify, |
| 13 | 15 | Blueprint, |
| 14 | 16 | ) |
| 17 | import flask | |
| 15 | 18 | |
| 16 | 19 | from flask_wtf.csrf import validate_csrf |
| 17 | 20 | from werkzeug.utils import secure_filename |
| 19 | 22 | |
| 20 | 23 | from faraday.server.utils.web import gzipped |
| 21 | 24 | from faraday.server.models import Workspace |
| 22 | from faraday.config.configuration import getInstanceConfiguration | |
| 23 | 25 | |
| 24 | CONF = getInstanceConfiguration() | |
| 25 | 26 | upload_api = Blueprint('upload_reports', __name__) |
| 26 | 27 | |
| 27 | 28 | logger = logging.getLogger(__name__) |
| 57 | 58 | raw_report_filename = '{0}_{1}'.format(random_prefix, secure_filename(report_file.filename)) |
| 58 | 59 | |
| 59 | 60 | try: |
| 60 | file_path = os.path.join(CONF.getConfigPath(), 'uploaded_reports', raw_report_filename) | |
| 61 | file_path = os.path.join(CONST_FARADAY_HOME_PATH, 'uploaded_reports', raw_report_filename) | |
| 61 | 62 | with open(file_path, 'wb') as output: |
| 62 | 63 | output.write(report_file.read()) |
| 63 | 64 | except AttributeError: |
| 65 | 66 | "Upload reports in WEB-UI not configurated, run Faraday client and try again...") |
| 66 | 67 | abort(make_response(jsonify(message="Upload reports not configurated: Run faraday client and start Faraday server again"), 500)) |
| 67 | 68 | else: |
| 68 | REPORTS_QUEUE.put((workspace, file_path)) | |
| 69 | REPORTS_QUEUE.put((workspace, file_path, flask.g.user)) | |
| 69 | 70 | return make_response(jsonify(message="ok"), 200) |
| 70 | 71 | else: |
| 71 | 72 | abort(make_response(jsonify(message="Missing report file"), 400)) |
| 73 | # I'm Py3 | |
| 189 | 189 | }, 'policyviolations': [], "refs": [], "resolution": "", "type": "vulnerability_template"} |
| 190 | 190 | vuln_dict.update(other_fields) |
| 191 | 191 | vuln_schema = schema.load(vuln_dict) |
| 192 | vuln_template = super(VulnerabilityTemplateView, self)._perform_create(vuln_schema.data) | |
| 192 | super(VulnerabilityTemplateView, self)._perform_create(vuln_schema.data) | |
| 193 | 193 | db.session.commit() |
| 194 | 194 | except Exception as e: |
| 195 | 195 | logger.error("Error creating vuln (%s)", e) |
| 0 | 0 | # Faraday Penetration Test IDE |
| 1 | 1 | # Copyright (C) 2016 Infobyte LLC (http://www.infobytesec.com/) |
| 2 | 2 | # See the file 'doc/LICENSE' for the license information |
| 3 | from builtins import str | |
| 4 | 3 | |
| 5 | 4 | import os |
| 6 | 5 | import io |
| 29 | 28 | FilterSetMeta, |
| 30 | 29 | PaginatedMixin, |
| 31 | 30 | ReadWriteWorkspacedView, |
| 32 | InvalidUsage) | |
| 31 | InvalidUsage, | |
| 32 | CountMultiWorkspacedMixin) | |
| 33 | 33 | from faraday.server.fields import FaradayUploadedFile |
| 34 | 34 | from faraday.server.models import ( |
| 35 | 35 | db, |
| 96 | 96 | creator = fields.Method('get_creator', dump_only=True) |
| 97 | 97 | |
| 98 | 98 | def get_creator(self, obj): |
| 99 | return obj.creator_command_tool or 'Web UI' | |
| 99 | if obj.tool: | |
| 100 | return obj.tool | |
| 101 | else: | |
| 102 | return obj.creator_command_tool or 'Web UI' | |
| 100 | 103 | |
| 101 | 104 | |
| 102 | 105 | class VulnerabilitySchema(AutoSchema): |
| 113 | 116 | attribute='policy_violations') |
| 114 | 117 | refs = fields.List(fields.String(), attribute='references') |
| 115 | 118 | issuetracker = fields.Method(serialize='get_issuetracker', dump_only=True) |
| 119 | tool = fields.String(attribute='tool') | |
| 116 | 120 | parent = fields.Method(serialize='get_parent', deserialize='load_parent', required=True) |
| 117 | 121 | parent_type = MutableField(fields.Method('get_parent_type'), |
| 118 | 122 | fields.String(), |
| 156 | 160 | 'service', 'obj_id', 'type', 'policyviolations', |
| 157 | 161 | '_attachments', |
| 158 | 162 | 'target', 'host_os', 'resolution', 'metadata', |
| 159 | 'custom_fields', 'external_id') | |
| 163 | 'custom_fields', 'external_id', 'tool') | |
| 160 | 164 | |
| 161 | 165 | def get_type(self, obj): |
| 162 | 166 | return obj.__class__.__name__ |
| 280 | 284 | 'service', 'obj_id', 'type', 'policyviolations', |
| 281 | 285 | 'request', '_attachments', 'params', |
| 282 | 286 | 'target', 'host_os', 'resolution', 'method', 'metadata', |
| 283 | 'status_code', 'custom_fields', 'external_id' | |
| 287 | 'status_code', 'custom_fields', 'external_id', 'tool' | |
| 284 | 288 | ) |
| 285 | 289 | |
| 286 | 290 | |
| 371 | 375 | "parameters", "params", "resolution", "ease_of_resolution", |
| 372 | 376 | "description", "command_id", "target", "creator", "method", |
| 373 | 377 | "easeofresolution", "query_string", "parameter_name", "service_id", |
| 374 | "status_code" | |
| 378 | "status_code", "tool", | |
| 375 | 379 | ) |
| 376 | 380 | |
| 377 | 381 | strict_fields = ( |
| 426 | 430 | |
| 427 | 431 | class VulnerabilityView(PaginatedMixin, |
| 428 | 432 | FilterAlchemyMixin, |
| 429 | ReadWriteWorkspacedView): | |
| 433 | ReadWriteWorkspacedView, | |
| 434 | CountMultiWorkspacedMixin): | |
| 435 | ||
| 430 | 436 | route_base = 'vulns' |
| 431 | 437 | filterset_class = VulnerabilityFilterSet |
| 432 | 438 | sort_model_class = VulnerabilityWeb # It has all the fields |
| 469 | 475 | attachments = data.pop('_attachments', {}) |
| 470 | 476 | references = data.pop('references', []) |
| 471 | 477 | policyviolations = data.pop('policy_violations', []) |
| 472 | ||
| 473 | 478 | try: |
| 474 | 479 | obj = super(VulnerabilityView, self)._perform_create(data, **kwargs) |
| 475 | 480 | except TypeError: |
| 479 | 484 | |
| 480 | 485 | obj.references = references |
| 481 | 486 | obj.policy_violations = policyviolations |
| 487 | if not obj.tool: | |
| 488 | if obj.creator_command_tool: | |
| 489 | obj.tool = obj.creator_command_tool | |
| 490 | else: | |
| 491 | obj.tool = "Web UI" | |
| 482 | 492 | db.session.commit() |
| 483 | 493 | self._process_attachments(obj, attachments) |
| 484 | 494 | return obj |
| 504 | 514 | |
| 505 | 515 | def _update_object(self, obj, data): |
| 506 | 516 | data.pop('type') # It's forbidden to change vuln type! |
| 517 | data.pop('tool', '') | |
| 507 | 518 | return super(VulnerabilityView, self)._update_object(obj, data) |
| 508 | 519 | |
| 509 | 520 | def _perform_update(self, object_id, obj, data, workspace_name): |
| 612 | 623 | |
| 613 | 624 | @route('/<int:vuln_id>/attachment/', methods=['POST']) |
| 614 | 625 | def post_attachment(self, workspace_name, vuln_id): |
| 626 | ||
| 615 | 627 | try: |
| 616 | 628 | validate_csrf(request.form.get('csrf_token')) |
| 617 | 629 | except wtforms.ValidationError: |
| 768 | 780 | |
| 769 | 781 | @route('/<int:vuln_id>/attachments/', methods=['GET']) |
| 770 | 782 | def get_attachments_by_vuln(self, workspace_name, vuln_id): |
| 783 | """ | |
| 784 | --- | |
| 785 | get: | |
| 786 | tags: ["Vulns"] | |
| 787 | description: Gets an attachment for a vulnerability | |
| 788 | responses: | |
| 789 | 200: | |
| 790 | description: Ok | |
| 791 | content: | |
| 792 | application/json: | |
| 793 | schema: EvidenceSchema | |
| 794 | 403: | |
| 795 | description: Workspace disabled or no permission | |
| 796 | 404: | |
| 797 | description: Not Found | |
| 798 | """ | |
| 771 | 799 | workspace = self._get_workspace(workspace_name) |
| 772 | 800 | vuln_workspace_check = db.session.query(VulnerabilityGeneric, Workspace.id).join( |
| 773 | 801 | Workspace).filter(VulnerabilityGeneric.id == vuln_id, |
| 821 | 849 | attachment_filename="Faraday-SR-%s.csv" % workspace_name, |
| 822 | 850 | as_attachment=True, |
| 823 | 851 | cache_timeout=-1) |
| 852 | ||
| 824 | 853 | |
| 825 | 854 | @route('bulk_delete/', methods=['DELETE']) |
| 826 | 855 | def bulk_delete(self, workspace_name): |
| 49 | 49 | salt="websocket_agent") |
| 50 | 50 | try: |
| 51 | 51 | agent_id = signer.unsign(token, max_age=60).decode('utf-8') |
| 52 | except BadData as e: | |
| 52 | except BadData: | |
| 53 | 53 | raise ValueError("Invalid Token") |
| 54 | 54 | agent = Agent.query.get(agent_id) |
| 55 | 55 | if agent is None: |
| 2 | 2 | # See the file 'doc/LICENSE' for the license information |
| 3 | 3 | from builtins import str |
| 4 | 4 | |
| 5 | import os | |
| 6 | 5 | import json |
| 7 | 6 | import logging |
| 8 | 7 | |
| 24 | 23 | SelfNestedField, |
| 25 | 24 | ) |
| 26 | 25 | from faraday.server.api.base import ReadWriteView, AutoSchema |
| 27 | from faraday.config.configuration import getInstanceConfiguration | |
| 28 | 26 | |
| 29 | 27 | logger = logging.getLogger(__name__) |
| 30 | 28 | |
| 103 | 101 | objects = [] |
| 104 | 102 | for workspace_stat in query: |
| 105 | 103 | workspace_stat_dict = dict(workspace_stat) |
| 106 | for key, value in list(workspace_stat_dict.items()): | |
| 104 | for key, _ in list(workspace_stat_dict.items()): | |
| 107 | 105 | if key.startswith('workspace_'): |
| 108 | 106 | new_key = key.replace('workspace_', '') |
| 109 | 107 | workspace_stat_dict[new_key] = workspace_stat_dict[key] |
| 192 | 190 | db.session.commit() |
| 193 | 191 | return workspace |
| 194 | 192 | |
| 195 | def _createWorkspaceFolder(self, name): | |
| 196 | CONF = getInstanceConfiguration() | |
| 197 | self._report_path = os.path.join(CONF.getReportPath(), name) | |
| 198 | self._report_ppath = os.path.join(self._report_path, "process") | |
| 199 | self._report_upath = os.path.join(self._report_path, "unprocessed") | |
| 200 | ||
| 201 | if not os.path.exists(CONF.getReportPath()): | |
| 202 | os.mkdir(CONF.getReportPath()) | |
| 203 | ||
| 204 | if not os.path.exists(self._report_path): | |
| 205 | os.mkdir(self._report_path) | |
| 206 | ||
| 207 | if not os.path.exists(self._report_ppath): | |
| 208 | os.mkdir(self._report_ppath) | |
| 209 | ||
| 210 | if not os.path.exists(self._report_upath): | |
| 211 | os.mkdir(self._report_upath) | |
| 212 | ||
| 213 | 193 | def _update_object(self, obj, data): |
| 214 | 194 | scope = data.pop('scope', []) |
| 215 | 195 | obj.set_scope(scope) |
| 4 | 4 | import os |
| 5 | 5 | import string |
| 6 | 6 | import datetime |
| 7 | ||
| 8 | import requests | |
| 7 | 9 | from itsdangerous import TimedJSONWebSignatureSerializer, SignatureExpired, BadSignature |
| 8 | 10 | from os.path import join |
| 9 | 11 | from random import SystemRandom |
| 13 | 15 | from configparser import ConfigParser, NoSectionError, NoOptionError, DuplicateSectionError |
| 14 | 16 | |
| 15 | 17 | import flask |
| 16 | from flask import Flask, session, g | |
| 18 | from flask import Flask, session, g, request | |
| 17 | 19 | from flask.json import JSONEncoder |
| 18 | 20 | from flask_sqlalchemy import get_debug_queries |
| 19 | 21 | from flask_security import ( |
| 29 | 31 | from flask_kvsession import KVSessionExtension |
| 30 | 32 | from simplekv.fs import FilesystemStore |
| 31 | 33 | from simplekv.decorator import PrefixDecorator |
| 32 | from flask_login import user_logged_out | |
| 34 | from flask_login import user_logged_out, user_logged_in | |
| 33 | 35 | from nplusone.ext.flask_sqlalchemy import NPlusOne |
| 34 | 36 | from depot.manager import DepotManager |
| 35 | 37 | |
| 38 | 40 | import faraday.server.events |
| 39 | 41 | from faraday.server.utils.logger import LOGGING_HANDLERS |
| 40 | 42 | from faraday.server.utils.invalid_chars import remove_null_caracters |
| 41 | from faraday.config.constant import CONST_FARADAY_HOME_PATH | |
| 43 | from faraday.server.config import CONST_FARADAY_HOME_PATH | |
| 42 | 44 | |
| 43 | 45 | |
| 44 | 46 | logger = logging.getLogger(__name__) |
| 86 | 88 | from faraday.server.api.modules.bulk_create import bulk_create_api # pylint:disable=import-outside-toplevel |
| 87 | 89 | from faraday.server.api.modules.token import token_api # pylint:disable=import-outside-toplevel |
| 88 | 90 | from faraday.server.api.modules.search_filter import searchfilter_api # pylint:disable=import-outside-toplevel |
| 91 | from faraday.server.api.modules.preferences import preferences_api # pylint:disable=import-outside-toplevel | |
| 92 | from faraday.server.api.modules.export_data import export_data_api # pylint:disable=import-outside-toplevel | |
| 89 | 93 | |
| 90 | 94 | app.register_blueprint(commandsrun_api) |
| 91 | 95 | app.register_blueprint(activityfeed_api) |
| 109 | 113 | app.register_blueprint(bulk_create_api) |
| 110 | 114 | app.register_blueprint(token_api) |
| 111 | 115 | app.register_blueprint(searchfilter_api) |
| 116 | app.register_blueprint(preferences_api) | |
| 117 | app.register_blueprint(export_data_api) | |
| 112 | 118 | |
| 113 | 119 | |
| 114 | 120 | def check_testing_configuration(testing, app): |
| 125 | 131 | # We are exposing a RESTful API, so don't redirect a user to a login page in |
| 126 | 132 | # case of being unauthorized, raise a 403 error instead |
| 127 | 133 | @app.login_manager.unauthorized_handler |
| 128 | def unauthorized(): | |
| 134 | def unauthorized(): # pylint:disable=unused-variable | |
| 129 | 135 | flask.abort(403) |
| 130 | 136 | |
| 131 | 137 | def verify_token(token): |
| 145 | 151 | |
| 146 | 152 | |
| 147 | 153 | @app.before_request |
| 148 | def default_login_required(): | |
| 154 | def default_login_required(): # pylint:disable=unused-variable | |
| 149 | 155 | view = app.view_functions.get(flask.request.endpoint) |
| 150 | 156 | |
| 151 | 157 | if app.config['SECURITY_TOKEN_AUTHENTICATION_HEADER'] in flask.request.headers: |
| 192 | 198 | return |
| 193 | 199 | |
| 194 | 200 | @app.before_request |
| 195 | def load_g_custom_fields(): | |
| 201 | def load_g_custom_fields(): # pylint:disable=unused-variable | |
| 196 | 202 | g.custom_fields = {} |
| 197 | 203 | |
| 198 | 204 | @app.after_request |
| 199 | def log_queries_count(response): | |
| 205 | def log_queries_count(response): # pylint:disable=unused-variable | |
| 200 | 206 | if flask.request.method not in ['GET', 'HEAD']: |
| 201 | 207 | # We did most optimizations for read only endpoints |
| 202 | 208 | # TODO migrations: improve optimization and remove this if |
| 247 | 253 | session.destroy() |
| 248 | 254 | KVSessionExtension(app=app).cleanup_sessions(app) |
| 249 | 255 | |
| 256 | ||
| 257 | def user_logged_in_succesfull(app, user): | |
| 258 | user_agent = request.headers.get('User-Agent') | |
| 259 | if user_agent.startswith('faraday-client/'): | |
| 260 | HOME_URL = "https://portal.faradaysec.com/api/v1/license_check" | |
| 261 | params = {'version': faraday.__version__, 'key': 'white', 'client': user_agent} | |
| 262 | try: | |
| 263 | logger.debug('Send Faraday-Client license_check') | |
| 264 | res = requests.get(HOME_URL, params=params, timeout=1, verify=True) | |
| 265 | logger.debug("Faraday-Client license_check response: %s", res.text) | |
| 266 | except Exception as e: | |
| 267 | logger.warning("Error sending client license_check [%s]", e) | |
| 250 | 268 | |
| 251 | 269 | def create_app(db_connection_string=None, testing=None): |
| 252 | 270 | app = Flask(__name__) |
| 310 | 328 | store = FilesystemStore(app.config['SESSION_FILE_DIR']) |
| 311 | 329 | prefixed_store = PrefixDecorator('sessions_', store) |
| 312 | 330 | KVSessionExtension(prefixed_store, app) |
| 331 | user_logged_in.connect(user_logged_in_succesfull, app) | |
| 313 | 332 | user_logged_out.connect(expire_session, app) |
| 314 | 333 | |
| 315 | 334 | storage_path = faraday.server.config.storage.path |
| 357 | 376 | |
| 358 | 377 | for handler in LOGGING_HANDLERS: |
| 359 | 378 | app.logger.addHandler(handler) |
| 360 | ||
| 379 | app.logger.propagate = False | |
| 361 | 380 | register_blueprints(app) |
| 362 | 381 | register_handlers(app) |
| 363 | 382 | |
| 3 | 3 | See the file 'doc/LICENSE' for the license information |
| 4 | 4 | |
| 5 | 5 | """ |
| 6 | from apispec import APISpec | |
| 7 | from apispec.ext.marshmallow import MarshmallowPlugin | |
| 6 | 8 | from faraday.server.web import app |
| 9 | from faraday import __version__ as f_version | |
| 10 | import json | |
| 11 | ||
| 12 | from faraday.utils.faraday_openapi_plugin import FaradayAPIPlugin | |
| 13 | ||
| 14 | ||
| 15 | def openapi_format(format="yaml"): | |
| 16 | ||
| 17 | spec = APISpec( | |
| 18 | title="Faraday API", | |
| 19 | version="2", | |
| 20 | openapi_version="3.0.2", | |
| 21 | plugins=[FaradayAPIPlugin(), MarshmallowPlugin()], | |
| 22 | info={'description': 'The Faraday server API'}, | |
| 23 | ) | |
| 24 | ||
| 25 | with app.test_request_context(): | |
| 26 | for endpoint in app.view_functions: | |
| 27 | spec.path(view=app.view_functions[endpoint], app=app) | |
| 28 | if format.lower() == "yaml": | |
| 29 | print(spec.to_yaml()) | |
| 30 | else: | |
| 31 | print(json.dumps(spec.to_dict(), indent=2)) | |
| 7 | 32 | |
| 8 | 33 | |
| 9 | 34 | def show_all_urls(): |
| 10 | 35 | print(app.url_map) |
| 11 | # I'm Py3⏎ |
| 5 | 5 | """ |
| 6 | 6 | import sys |
| 7 | 7 | from sqlalchemy import MetaData |
| 8 | try: | |
| 9 | from sqlalchemy_schemadisplay import create_schema_graph | |
| 10 | from sqlalchemy_schemadisplay import create_uml_graph | |
| 11 | except ImportError: | |
| 12 | print('Please install sqlalchemy_schemadisplay with "pip install sqlalchemy_schemadisplay"') | |
| 13 | sys.exit(1) | |
| 14 | 8 | from sqlalchemy.orm import class_mapper |
| 15 | 9 | |
| 16 | 10 | from faraday.server import models |
| 29 | 23 | |
| 30 | 24 | def _draw_entity_diagrama(self): |
| 31 | 25 | # create the pydot graph object by autoloading all tables via a bound metadata object |
| 26 | try: | |
| 27 | from sqlalchemy_schemadisplay import create_schema_graph # pylint:disable=import-outside-toplevel | |
| 28 | except ImportError: | |
| 29 | print('Please install sqlalchemy_schemadisplay with "pip install sqlalchemy_schemadisplay"') | |
| 30 | sys.exit(1) | |
| 32 | 31 | graph = create_schema_graph( |
| 33 | 32 | metadata=MetaData(faraday.server.config.database.connection_string.strip("'")), |
| 34 | 33 | show_datatypes=False, # The image would get nasty big if we'd show the datatypes |
| 47 | 46 | |
| 48 | 47 | def _draw_uml_class_diagram(self): |
| 49 | 48 | # lets find all the mappers in our model |
| 49 | try: | |
| 50 | from sqlalchemy_schemadisplay import create_uml_graph # pylint:disable=import-outside-toplevel | |
| 51 | except ImportError: | |
| 52 | print('Please install sqlalchemy_schemadisplay with "pip install sqlalchemy_schemadisplay"') | |
| 53 | sys.exit(1) | |
| 50 | 54 | mappers = [] |
| 51 | 55 | for attr in dir(models): |
| 52 | 56 | if attr[0] == '_': |
| 54 | 58 | try: |
| 55 | 59 | cls = getattr(models, attr) |
| 56 | 60 | mappers.append(class_mapper(cls)) |
| 57 | except: | |
| 58 | pass | |
| 61 | except Exception as ex: | |
| 62 | print(ex) | |
| 59 | 63 | |
| 60 | 64 | # pass them to the function and set some formatting options |
| 61 | 65 | graph = create_uml_graph( |
| 66 | 70 | ) |
| 67 | 71 | graph.write_png('uml_schema.png') # write out the file |
| 68 | 72 | print("Graph written to fle uml_schema.png") |
| 69 | # I'm Py3⏎ | |
| 73 | # I'm Py3 | |
| 6 | 6 | from builtins import input |
| 7 | 7 | |
| 8 | 8 | import getpass |
| 9 | import shutil | |
| 10 | 9 | import string |
| 11 | 10 | |
| 12 | 11 | import os |
| 22 | 21 | import sqlalchemy |
| 23 | 22 | from sqlalchemy import create_engine |
| 24 | 23 | |
| 25 | from faraday.config.configuration import Configuration | |
| 26 | from faraday.client.start_client import ( # TODO load this from other place | |
| 27 | FARADAY_BASE_CONFIG_XML, | |
| 28 | FARADAY_BASE, | |
| 29 | ) | |
| 30 | 24 | from faraday.server.utils.database import is_unique_constraint_violation |
| 31 | 25 | |
| 32 | 26 | from configparser import ConfigParser, NoSectionError |
| 37 | 31 | from sqlalchemy.exc import OperationalError, ProgrammingError |
| 38 | 32 | |
| 39 | 33 | import faraday.server.config |
| 40 | from faraday.config.constant import CONST_FARADAY_HOME_PATH | |
| 41 | from faraday.server.config import LOCAL_CONFIG_FILE | |
| 34 | from faraday.server.config import CONST_FARADAY_HOME_PATH | |
| 35 | from faraday.server.config import LOCAL_CONFIG_FILE, FARADAY_BASE | |
| 36 | ||
| 42 | 37 | init() |
| 43 | 38 | |
| 44 | 39 | |
| 98 | 93 | current_psql_output.close() |
| 99 | 94 | conn_string = self._save_config(config, username, password, database_name, hostname) |
| 100 | 95 | self._create_tables(conn_string) |
| 101 | couchdb_config_present = faraday.server.config.couchdb | |
| 102 | if not (couchdb_config_present and couchdb_config_present.user and couchdb_config_present.password): | |
| 103 | self._create_admin_user(conn_string, choose_password) | |
| 104 | else: | |
| 105 | print('Skipping new admin creation since couchdb configuration was found.') | |
| 96 | self._create_admin_user(conn_string, choose_password) | |
| 106 | 97 | except KeyboardInterrupt: |
| 107 | 98 | current_psql_output.close() |
| 108 | 99 | print('User cancelled.') |
| 136 | 127 | print( |
| 137 | 128 | "{yellow}WARNING{white}: Can't create administrator user.".format( |
| 138 | 129 | yellow=Fore.YELLOW, white=Fore.WHITE)) |
| 139 | raise | |
| 130 | raise | |
| 140 | 131 | if not already_created: |
| 141 | ||
| 142 | self._save_user_xml(random_password) | |
| 143 | 132 | print("Admin user created with \n\n{red}username: {white}faraday \n" |
| 144 | 133 | "{red}password:{white} {" |
| 145 | 134 | "random_password} \n".format(random_password=random_password, |
| 146 | white=Fore.WHITE, red=Fore.RED)) | |
| 147 | print("{yellow}WARNING{white}: If you are going to execute couchdb importer you must use the couchdb password for faraday user.".format(white=Fore.WHITE, yellow=Fore.YELLOW)) | |
| 148 | ||
| 149 | def _save_user_xml(self, random_password): | |
| 150 | user_xml = os.path.join(CONST_FARADAY_HOME_PATH, "config", "user.xml") | |
| 151 | if not os.path.exists(user_xml): | |
| 152 | shutil.copy(FARADAY_BASE_CONFIG_XML, user_xml) | |
| 153 | conf = Configuration(user_xml) | |
| 154 | conf.setAPIUrl('http://localhost:5985') | |
| 155 | conf.setAPIUsername('faraday') | |
| 156 | conf.setAPIPassword(random_password) | |
| 157 | conf.saveConfig(user_xml) | |
| 135 | white=Fore.WHITE, red=Fore.RED)) | |
| 158 | 136 | |
| 159 | 137 | def _configure_existing_postgres_user(self): |
| 160 | 138 | username = input('Please enter the postgresql username: ') |
| 23 | 23 | 'faraday_user'): |
| 24 | 24 | try: |
| 25 | 25 | db.engine.execute('DROP TABLE {} CASCADE'.format(table)) |
| 26 | except: | |
| 27 | pass | |
| 26 | except Exception as ex: | |
| 27 | print(ex) | |
| 28 | 28 | db.drop_all() |
| 29 | 29 | |
| 30 | 30 | # db.create_all() |
| 6 | 6 | import os |
| 7 | 7 | import socket |
| 8 | 8 | |
| 9 | import requests | |
| 10 | 9 | import sqlalchemy |
| 11 | 10 | from colorama import init |
| 12 | 11 | from colorama import Fore |
| 13 | from requests.exceptions import InvalidURL, ConnectionError | |
| 14 | 12 | |
| 15 | 13 | import faraday.server.config |
| 16 | from faraday.config import constant as CONSTANTS | |
| 17 | from faraday.config.configuration import getInstanceConfiguration | |
| 18 | 14 | from faraday.server.web import app |
| 19 | 15 | from faraday.server.models import db |
| 20 | from faraday.server.config import FARADAY_BASE | |
| 16 | from faraday.server.config import CONST_FARADAY_HOME_PATH | |
| 21 | 17 | from faraday.server.utils.daemonize import is_server_running |
| 22 | from faraday.utils import dependencies | |
| 23 | ||
| 24 | ||
| 25 | CONF = getInstanceConfiguration() | |
| 18 | import faraday_plugins | |
| 26 | 19 | |
| 27 | 20 | init() |
| 28 | 21 | |
| 101 | 94 | return None |
| 102 | 95 | |
| 103 | 96 | |
| 104 | def check_client(): | |
| 105 | ||
| 106 | port_rest = CONF.getApiRestfulConInfoPort() | |
| 107 | ||
| 108 | if port_rest is None: | |
| 109 | port_rest = "9977" | |
| 110 | try: | |
| 111 | response_rest = requests.get('http://{}:{}/status/check'.format(faraday.server.config.faraday_server.bind_address,port_rest)) | |
| 112 | return True | |
| 113 | except ConnectionError: | |
| 114 | return False | |
| 115 | except InvalidURL: | |
| 116 | return False | |
| 117 | ||
| 118 | ||
| 119 | def check_server_dependencies(): | |
| 120 | ||
| 121 | requirements_file=os.path.join(FARADAY_BASE,'requirements_server.txt') | |
| 122 | installed_deps, missing_deps, conflict_deps = dependencies.check_dependencies( | |
| 123 | requirements_file=requirements_file) | |
| 124 | ||
| 125 | if conflict_deps: | |
| 126 | return True, conflict_deps | |
| 127 | ||
| 128 | if missing_deps: | |
| 129 | return 0, missing_deps | |
| 130 | ||
| 131 | if not conflict_deps and not missing_deps: | |
| 132 | return None, None | |
| 133 | ||
| 134 | ||
| 135 | def check_client_dependencies(): | |
| 136 | ||
| 137 | requirements_file=os.path.join(FARADAY_BASE,'requirements.txt') | |
| 138 | installed_deps, missing_deps, conflict_deps = dependencies.check_dependencies( | |
| 139 | requirements_file=requirements_file) | |
| 140 | ||
| 141 | if 'argparse' in conflict_deps: | |
| 142 | conflict_deps.remove('argparse') | |
| 143 | ||
| 144 | if conflict_deps: | |
| 145 | return True, conflict_deps | |
| 146 | ||
| 147 | if missing_deps: | |
| 148 | return 0, missing_deps | |
| 149 | ||
| 150 | if not conflict_deps and not missing_deps: | |
| 151 | return None, None | |
| 152 | ||
| 153 | ||
| 154 | def check_credentials(): | |
| 155 | ||
| 156 | api_username = CONF.getAPIUsername() | |
| 157 | api_password = CONF.getAPIPassword() | |
| 158 | ||
| 159 | address = faraday.server.config.faraday_server.bind_address | |
| 160 | port = int(faraday.server.config.faraday_server.port) | |
| 161 | ||
| 162 | values = {'email': api_username , 'password': api_password} | |
| 163 | ||
| 164 | try: | |
| 165 | r = requests.post('http://{ADDRESS}:{PORT}/_api/login'.format(ADDRESS=address,PORT=port), json=values) | |
| 166 | ||
| 167 | if r.status_code == 200 and 'user' in r.json()['response']: | |
| 168 | return 200 | |
| 169 | elif r.status_code == 400: | |
| 170 | return 400 | |
| 171 | elif r.status_code == 500: | |
| 172 | return 500 | |
| 173 | ||
| 174 | except ConnectionError: | |
| 175 | return None | |
| 176 | ||
| 177 | ||
| 178 | 97 | def check_storage_permission(): |
| 179 | 98 | |
| 180 | path = os.path.join(CONSTANTS.CONST_FARADAY_HOME_PATH,'storage/test') | |
| 99 | path = os.path.join(CONST_FARADAY_HOME_PATH, 'storage', 'test') | |
| 181 | 100 | |
| 182 | 101 | try: |
| 183 | 102 | os.mkdir(path) |
| 185 | 104 | return True |
| 186 | 105 | except OSError: |
| 187 | 106 | return None |
| 107 | ||
| 108 | ||
| 109 | def print_config_info(): | |
| 110 | print('\n{white}Showing faraday server configuration'.format(white=Fore.WHITE)) | |
| 111 | print('{blue} {KEY}: {white}{VALUE}'. | |
| 112 | format(KEY='version', VALUE=faraday.__version__, white=Fore.WHITE, blue=Fore.BLUE)) | |
| 113 | ||
| 114 | data_keys = ['bind_address', 'port', 'websocket_port', 'debug'] | |
| 115 | for key in data_keys: | |
| 116 | print('{blue} {KEY}: {white}{VALUE}'. | |
| 117 | format(KEY=key, VALUE=getattr(faraday.server.config.faraday_server, key), white=Fore.WHITE, blue=Fore.BLUE)) | |
| 118 | ||
| 119 | print('\n{white}Showing faraday plugins data'.format(white=Fore.WHITE)) | |
| 120 | print('{blue} {KEY}: {white}{VALUE}'. | |
| 121 | format(KEY='version', VALUE=faraday_plugins.__version__, white=Fore.WHITE, blue=Fore.BLUE)) | |
| 122 | ||
| 123 | print('\n{white}Showing dashboard configuration'.format(white=Fore.WHITE)) | |
| 124 | data_keys = ['show_vulns_by_price'] | |
| 125 | for key in data_keys: | |
| 126 | print('{blue} {KEY}: {white}{VALUE}'. | |
| 127 | format(KEY=key, VALUE=getattr(faraday.server.config.dashboard, key), white=Fore.WHITE, blue=Fore.BLUE)) | |
| 128 | ||
| 129 | print('\n{white}Showing storage configuration'.format(white=Fore.WHITE)) | |
| 130 | data_keys = ['path'] | |
| 131 | for key in data_keys: | |
| 132 | print('{blue} {KEY}: {white}{VALUE}'. | |
| 133 | format(KEY=key, VALUE=getattr(faraday.server.config.storage, key), white=Fore.WHITE, blue=Fore.BLUE)) | |
| 188 | 134 | |
| 189 | 135 | |
| 190 | 136 | def print_postgresql_status(): |
| 235 | 181 | |
| 236 | 182 | |
| 237 | 183 | def print_faraday_status(): |
| 238 | """Prints Status of farday using check_server_running() and check_client""" | |
| 184 | """Prints Status of farday using check_server_running() """ | |
| 239 | 185 | |
| 240 | 186 | #Prints Status of the server using check_server_running() |
| 241 | 187 | pid = check_server_running() |
| 246 | 192 | print('[{red}-{white}] Faraday Server is not running {white} \ |
| 247 | 193 | '.format(red=Fore.RED, white=Fore.WHITE)) |
| 248 | 194 | |
| 249 | #Prints Status of the client using check_client() | |
| 250 | if check_client(): | |
| 251 | print('[{green}+{white}] Faraday GTK is running'.\ | |
| 252 | format(green=Fore.GREEN, white=Fore.WHITE)) | |
| 253 | else: | |
| 254 | print('[{yellow}-{white}] Faraday GTK is not running'\ | |
| 255 | .format(yellow=Fore.YELLOW, white=Fore.WHITE)) | |
| 256 | ||
| 257 | ||
| 258 | def print_depencencies_status(): | |
| 259 | """Prints Status of the dependencies using check_server_dependencies() and check_client_dependencies()""" | |
| 260 | ||
| 261 | status, server_dep = check_server_dependencies() | |
| 262 | red = Fore.RED | |
| 263 | white = Fore.WHITE | |
| 264 | green = Fore.GREEN | |
| 265 | if status == True: | |
| 266 | print(f"[{red}-{white}] Some server dependencies are old: [{', '.join(server_dep)}']. Update them with \"pip install -r requirements_server.txt -U\"") | |
| 267 | ||
| 268 | elif status == 0: | |
| 269 | print(f"[{red}-{white}] Client dependencies not met: [{', '.join(server_dep)}'] Install them with \"pip install -r requirements_server.txt -U\"") | |
| 270 | ||
| 271 | else: | |
| 272 | print(f'[{green}+{white}] Server dependencies met') | |
| 273 | ||
| 274 | status, client_dep = check_client_dependencies() | |
| 275 | if status == True: | |
| 276 | print(f"[{red}-{white}] Some client dependencies are old: [{', '.join(client_dep)}]. Update them with \"pip install -r requirements.txt -U\"") | |
| 277 | ||
| 278 | elif status == 0: | |
| 279 | print(f"[{red}-{white}] Client dependencies not met: [{', '.join(client_dep)}]. Install them with \"pip install -r requirements.txt -U\"") | |
| 280 | ||
| 281 | else: | |
| 282 | print(f'[{green}+{white}] Client dependencies met') | |
| 283 | ||
| 284 | 195 | |
| 285 | 196 | def print_config_status(): |
| 286 | 197 | """Prints Status of the configuration using check_credentials(), check_storage_permission() and check_open_ports()""" |
| 287 | 198 | |
| 288 | pid = check_server_running() | |
| 289 | result = check_postgres() | |
| 290 | if pid and result: | |
| 291 | status_code = check_credentials() | |
| 292 | if status_code == 200: | |
| 293 | print('[{green}+{white}] Credentials matched'.format(green=Fore.GREEN, white=Fore.WHITE)) | |
| 294 | elif status_code == 400: | |
| 295 | print('[{red}-{white}] Error. Credentials does not match' \ | |
| 296 | .format(red=Fore.RED, white=Fore.WHITE)) | |
| 297 | else: | |
| 298 | print('[{red}-{white}] Credentials can not be checked. Either Faraday Server not running or database not working'.format(red=Fore.RED, white=Fore.WHITE)) | |
| 199 | check_server_running() | |
| 200 | check_postgres() | |
| 299 | 201 | |
| 300 | 202 | if check_storage_permission(): |
| 301 | 203 | print('[{green}+{white}] /.faraday/storage -> Permission accepted' \ |
| 313 | 215 | |
| 314 | 216 | |
| 315 | 217 | def full_status_check(): |
| 218 | print_config_info() | |
| 219 | ||
| 316 | 220 | print('\n{white}Checking if postgreSQL is running...'.format(white=Fore.WHITE)) |
| 317 | 221 | print_postgresql_status() |
| 318 | 222 | print_postgresql_other_status() |
| 320 | 224 | print('\n{white}Checking if Faraday is running...'.format(white=Fore.WHITE)) |
| 321 | 225 | print_faraday_status() |
| 322 | 226 | |
| 323 | print('\n{white}Checking Faraday dependencies...'.format(white=Fore.WHITE)) | |
| 324 | print_depencencies_status() | |
| 325 | ||
| 326 | 227 | print('\n{white}Checking Faraday config...{white}'.format(white=Fore.WHITE)) |
| 327 | 228 | print_config_status() |
| 328 | # I'm Py3⏎ | |
| 7 | 7 | |
| 8 | 8 | import distro |
| 9 | 9 | |
| 10 | try: | |
| 11 | from pip._internal.operations import freeze | |
| 12 | except ImportError: # pip < 10.0 | |
| 13 | from pip.operations import freeze | |
| 10 | from faraday.server.config import CONST_FARADAY_HOME_PATH | |
| 14 | 11 | |
| 15 | import faraday.config.constant as constants | |
| 16 | 12 | from faraday.server.commands import status_check |
| 17 | 13 | |
| 18 | 14 | init() |
| 34 | 30 | sys.stdout = original_stdout |
| 35 | 31 | |
| 36 | 32 | |
| 37 | def get_pip_freeze(path): | |
| 38 | #Executes pip freeze internally and saves the info a pip_freeze.txt file | |
| 39 | pip_freeze = freeze.freeze() | |
| 40 | pip_file = open(path + '/pip_freeze.txt', 'a') | |
| 41 | for line in pip_freeze: | |
| 42 | pip_file.write(line) | |
| 43 | pip_file.write('\n') | |
| 44 | pip_file.close() | |
| 45 | ||
| 46 | ||
| 47 | 33 | def get_logs(path): |
| 48 | 34 | #Copies the logs using the logs path saved on constants |
| 49 | orig_path = os.path.join(constants.CONST_FARADAY_HOME_PATH, 'logs') | |
| 35 | orig_path = os.path.join(CONST_FARADAY_HOME_PATH, 'logs') | |
| 50 | 36 | dst_path = os.path.join(path, 'logs') |
| 51 | 37 | shutil.copytree(orig_path, dst_path, ignore=shutil.ignore_patterns('access*.*')) |
| 52 | 38 | |
| 70 | 56 | pbar.update(1) |
| 71 | 57 | get_logs(path) |
| 72 | 58 | pbar.update(1) |
| 73 | get_pip_freeze(path) | |
| 74 | 59 | pbar.update(1) |
| 75 | 60 | revise_os(path) |
| 76 | 61 | pbar.update(1) |
| 80 | 65 | pbar.update(1) |
| 81 | 66 | |
| 82 | 67 | print('[{green}+{white}] Process Completed. A {bright}faraday_support.zip{normal} was generated' |
| 83 | .format(green=Fore.GREEN, white=Fore.WHITE, bright=Style.BRIGHT, normal=Style.NORMAL))# I'm Py3⏎ | |
| 68 | .format(green=Fore.GREEN, white=Fore.WHITE, bright=Style.BRIGHT, normal=Style.NORMAL))# I'm Py3 | |
| 11 | 11 | INFO, |
| 12 | 12 | ) |
| 13 | 13 | from faraday import __license_version__ as license_version |
| 14 | from faraday.config import constant as CONSTANTS | |
| 15 | from faraday.config.configuration import getInstanceConfiguration | |
| 14 | ||
| 15 | CONST_FARADAY_HOME_PATH = os.path.join(os.getenv('FARADAY_HOME', os.path.expanduser('~/')), '.faraday') | |
| 16 | 16 | |
| 17 | 17 | LOGGING_LEVEL = INFO |
| 18 | 18 | |
| 19 | 19 | FARADAY_BASE = os.path.abspath(os.path.join(os.path.dirname(__file__), '..')) |
| 20 | FARADAY_SERVER_SESSIONS_DIR = os.path.join(CONSTANTS.CONST_FARADAY_HOME_PATH, 'session') | |
| 21 | if not os.path.exists(CONSTANTS.CONST_FARADAY_HOME_PATH): | |
| 22 | os.mkdir(CONSTANTS.CONST_FARADAY_HOME_PATH) | |
| 20 | FARADAY_SERVER_SESSIONS_DIR = os.path.join(CONST_FARADAY_HOME_PATH, 'session') | |
| 21 | if not os.path.exists(CONST_FARADAY_HOME_PATH): | |
| 22 | os.mkdir(CONST_FARADAY_HOME_PATH) | |
| 23 | 23 | if not os.path.exists(FARADAY_SERVER_SESSIONS_DIR): |
| 24 | 24 | # Temporary hack, remove me |
| 25 | 25 | os.mkdir(FARADAY_SERVER_SESSIONS_DIR) |
| 26 | 26 | FARADAY_SERVER_PID_FILE = os.path.join( |
| 27 | CONSTANTS.CONST_FARADAY_HOME_PATH, 'faraday-server-port-{0}.pid') | |
| 28 | REQUIREMENTS_FILE = os.path.join(FARADAY_BASE, 'requirements_server.txt') | |
| 27 | CONST_FARADAY_HOME_PATH, 'faraday-server-port-{0}.pid') | |
| 28 | REQUIREMENTS_FILE = os.path.join(FARADAY_BASE, 'requirements.txt') | |
| 29 | 29 | DEFAULT_CONFIG_FILE = os.path.join(FARADAY_BASE, 'server/default.ini') |
| 30 | 30 | REPORTS_VIEWS_DIR = os.path.join(FARADAY_BASE, 'views/reports') |
| 31 | 31 | LOCAL_CONFIG_FILE = os.path.expanduser( |
| 32 | os.path.join(CONSTANTS.CONST_FARADAY_HOME_PATH, 'config/server.ini')) | |
| 32 | os.path.join(CONST_FARADAY_HOME_PATH, 'config/server.ini')) | |
| 33 | 33 | LOCAL_REPORTS_FOLDER = os.path.expanduser( |
| 34 | os.path.join(CONSTANTS.CONST_FARADAY_HOME_PATH, 'uploaded_reports/')) | |
| 34 | os.path.join(CONST_FARADAY_HOME_PATH, 'uploaded_reports/')) | |
| 35 | 35 | |
| 36 | 36 | CONFIG_FILES = [DEFAULT_CONFIG_FILE, LOCAL_CONFIG_FILE] |
| 37 | WS_BLACKLIST = CONSTANTS.CONST_BLACKDBS | |
| 37 | CONST_LICENSES_DB = 'faraday_licenses' | |
| 38 | CONST_VULN_MODEL_DB = 'cwe' | |
| 38 | 39 | |
| 39 | 40 | if not os.path.exists(LOCAL_REPORTS_FOLDER): |
| 40 | 41 | try: |
| 73 | 74 | ConfigSection.parse_section(section_name, __parser._sections[section_name]) |
| 74 | 75 | |
| 75 | 76 | |
| 76 | def __get_osint(): | |
| 77 | try: | |
| 78 | return getInstanceConfiguration().getOsint() | |
| 79 | except: | |
| 80 | return '' | |
| 81 | ||
| 82 | ||
| 83 | 77 | def is_debug_mode(): |
| 84 | 78 | return LOGGING_LEVEL is DEBUG |
| 85 | 79 | |
| 87 | 81 | class ConfigSection: |
| 88 | 82 | def parse(self, __parser): |
| 89 | 83 | for att in self.__dict__: |
| 84 | value = __parser.get(att) | |
| 90 | 85 | if isinstance(self.__dict__[att], bool): |
| 91 | value = __parser.get(att) | |
| 92 | 86 | if value in ("yes", "true", "t", "1", "True"): |
| 93 | 87 | self.__setattr__(att, True) |
| 94 | 88 | else: |
| 95 | 89 | self.__setattr__(att, False) |
| 96 | ||
| 97 | 90 | else: |
| 98 | self.__setattr__(att, __parser.get(att)) | |
| 91 | if value: | |
| 92 | self.__setattr__(att, value) | |
| 99 | 93 | |
| 100 | 94 | @staticmethod |
| 101 | 95 | def parse_section(section_name, __parser): |
| 102 | 96 | section = None |
| 103 | if section_name == 'couchdb': | |
| 104 | section = couchdb | |
| 105 | elif section_name == 'database': | |
| 97 | if section_name == 'database': | |
| 106 | 98 | section = database |
| 107 | 99 | elif section_name == 'dashboard': |
| 108 | 100 | section = dashboard |
| 123 | 115 | section.parse(__parser) |
| 124 | 116 | |
| 125 | 117 | |
| 126 | class CouchDBConfigObject(ConfigSection): | |
| 127 | def __init__(self): | |
| 128 | self.host = None | |
| 129 | self.password = None | |
| 130 | self.port = None | |
| 131 | self.protocol = None | |
| 132 | self.ssl_port = None | |
| 133 | self.user = None | |
| 134 | ||
| 135 | ||
| 136 | 118 | class DatabaseConfigObject(ConfigSection): |
| 137 | 119 | def __init__(self): |
| 138 | 120 | self.connection_string = None |
| 153 | 135 | self.agent_token = None |
| 154 | 136 | self.debug = False |
| 155 | 137 | self.custom_plugins_folder = None |
| 138 | ||
| 156 | 139 | |
| 157 | 140 | class LDAPConfigObject(ConfigSection): |
| 158 | 141 | def __init__(self): |
| 192 | 175 | def __init__(self): |
| 193 | 176 | self.use_rfc5424_formatter = False |
| 194 | 177 | |
| 195 | couchdb = CouchDBConfigObject() | |
| 196 | 178 | database = DatabaseConfigObject() |
| 197 | 179 | dashboard = DashboardConfigObject() |
| 198 | 180 | faraday_server = FaradayServerConfigObject() |
| 210 | 192 | # authenticated user. Don't add sensitive information here. |
| 211 | 193 | doc = { |
| 212 | 194 | 'ver': license_version, |
| 213 | 'lic_db': CONSTANTS.CONST_LICENSES_DB, | |
| 214 | "osint": __get_osint(), | |
| 215 | 'vuln_model_db': CONSTANTS.CONST_VULN_MODEL_DB, | |
| 195 | 'lic_db': CONST_LICENSES_DB, | |
| 196 | 'vuln_model_db': CONST_VULN_MODEL_DB, | |
| 216 | 197 | 'show_vulns_by_price': dashboard.show_vulns_by_price, |
| 217 | 198 | 'websocket_ssl': websocket_ssl.enabled, |
| 218 | 199 | 'websocket_port': faraday_server.websocket_port, |
| 219 | 200 | } |
| 220 | 201 | return doc |
| 221 | ||
| 222 | ||
| 223 | # I'm Py3⏎ | |
| 58 | 58 | content = file_from_content(content) |
| 59 | 59 | try: |
| 60 | 60 | uploaded_image = Image.open(content) |
| 61 | except: | |
| 61 | except Exception: | |
| 62 | 62 | flask.abort(400, ValidationError( |
| 63 | 63 | { |
| 64 | 64 | 'message': 'File Format', |
| 82 | 82 | |
| 83 | 83 | |
| 84 | 84 | class CustomEngineConnector(_EngineConnector): |
| 85 | """Used by overrided SQLAlchemy class to fix rollback issues. | |
| 85 | """Used by overridden SQLAlchemy class to fix rollback issues. | |
| 86 | 86 | |
| 87 | 87 | Also set case sensitive likes (in SQLite there are case |
| 88 | 88 | insensitive by default)""" |
| 99 | 99 | if uri.startswith('sqlite://'): |
| 100 | 100 | with self._lock: |
| 101 | 101 | @event.listens_for(rv, "connect") |
| 102 | def do_connect(dbapi_connection, connection_record): | |
| 102 | def do_connect(dbapi_connection, connection_record): # pylint:disable=unused-variable | |
| 103 | 103 | # disable pysqlite's emitting of the BEGIN statement |
| 104 | 104 | # entirely. also stops it from emitting COMMIT before any |
| 105 | 105 | # DDL. |
| 109 | 109 | cursor.close() |
| 110 | 110 | |
| 111 | 111 | @event.listens_for(rv, "begin") |
| 112 | def do_begin(conn): | |
| 112 | def do_begin(conn): # pylint:disable=unused-variable | |
| 113 | 113 | # emit our own BEGIN |
| 114 | 114 | conn.execute("BEGIN") |
| 115 | 115 | return rv |
| 781 | 781 | IMPORT_SOURCE = [ |
| 782 | 782 | 'report', # all the files the tools export and faraday imports it from the resports directory, gtk manual import or web import. |
| 783 | 783 | 'shell', # command executed on the shell or webshell with hooks connected to faraday. |
| 784 | 'agent' | |
| 784 | 785 | ] |
| 785 | 786 | |
| 786 | 787 | __tablename__ = 'command' |
| 838 | 839 | issuetracker = BlankColumn(Text) |
| 839 | 840 | association_date = Column(DateTime, nullable=True) |
| 840 | 841 | disassociated_manually = Column(Boolean, nullable=False, default=False) |
| 842 | tool = BlankColumn(Text, nullable=False) | |
| 841 | 843 | |
| 842 | 844 | vulnerability_duplicate_id = Column( |
| 843 | 845 | Integer, |
| 1271 | 1273 | backref=backref('credentials', cascade="all, delete-orphan"), |
| 1272 | 1274 | foreign_keys=[workspace_id], |
| 1273 | 1275 | ) |
| 1276 | ||
| 1277 | _host_ip_query = ( | |
| 1278 | select([Host.ip]) | |
| 1279 | .where(text('credential.host_id = host.id')) | |
| 1280 | ) | |
| 1281 | ||
| 1282 | _service_ip_query = ( | |
| 1283 | select([text('host_inner.ip || \'/\' || service.name')]) | |
| 1284 | .select_from(text('host as host_inner, service')) | |
| 1285 | .where(text('credential.service_id = service.id and ' | |
| 1286 | 'host_inner.id = service.host_id')) | |
| 1287 | ) | |
| 1288 | ||
| 1289 | target_ip = column_property( | |
| 1290 | case([ | |
| 1291 | (text('credential.host_id IS NOT null'), | |
| 1292 | _host_ip_query.as_scalar()), | |
| 1293 | (text('credential.service_id IS NOT null'), | |
| 1294 | _service_ip_query.as_scalar()) | |
| 1295 | ]), | |
| 1296 | deferred=True | |
| 1297 | ) | |
| 1298 | ||
| 1274 | 1299 | |
| 1275 | 1300 | __table_args__ = ( |
| 1276 | 1301 | CheckConstraint('(host_id IS NULL AND service_id IS NOT NULL) OR ' |
| 1545 | 1570 | String(16), |
| 1546 | 1571 | name="otp_secret", nullable=True) |
| 1547 | 1572 | state_otp = Column(Enum(*OTP_STATES, name='user_otp_states'), nullable=False, default="disabled") |
| 1573 | preferences = Column(JSONType, nullable=True, default={}) | |
| 1548 | 1574 | |
| 1549 | 1575 | # TODO: add many to many relationship to add permission to workspace |
| 1550 | 1576 | |
| 1904 | 1930 | |
| 1905 | 1931 | class Rule(Metadata): |
| 1906 | 1932 | __tablename__ = 'rule' |
| 1907 | ||
| 1908 | 1933 | id = Column(Integer, primary_key=True) |
| 1909 | 1934 | model = Column(String, nullable=False) |
| 1910 | 1935 | object_parent = Column(String, nullable=True) |
| 1911 | 1936 | fields = Column(JSONType, nullable=True) |
| 1912 | 1937 | object = Column(JSONType, nullable=False) |
| 1938 | enabled = Column(Boolean, nullable=False, default=True) | |
| 1913 | 1939 | actions = relationship("Action", secondary="rule_action", backref=backref("rules")) |
| 1914 | 1940 | workspace_id = Column(Integer, ForeignKey('workspace.id'), index=True, nullable=False) |
| 1915 | 1941 | workspace = relationship('Workspace', backref=backref('rules', cascade="all, delete-orphan")) |
| 1942 | ||
| 1943 | @property | |
| 1944 | def parent(self): | |
| 1945 | return | |
| 1946 | ||
| 1947 | @property | |
| 1948 | def disabled(self): | |
| 1949 | return not self.enabled | |
| 1950 | ||
| 1951 | @disabled.setter | |
| 1952 | def disabled(self, value): | |
| 1953 | self.enabled = not value | |
| 1916 | 1954 | |
| 1917 | 1955 | |
| 1918 | 1956 | class Action(Metadata): |
| 2030 | 2068 | 'Workspace', |
| 2031 | 2069 | backref=backref('agent_executions', cascade="all, delete-orphan"), |
| 2032 | 2070 | ) |
| 2071 | parameters_data = Column(JSONType, nullable=False) | |
| 2033 | 2072 | |
| 2034 | 2073 | @property |
| 2035 | 2074 | def parent(self): |
| 2118 | 2157 | ) |
| 2119 | 2158 | |
| 2120 | 2159 | # We have to import this after all models are defined |
| 2121 | import faraday.server.events | |
| 2122 | # I'm Py3⏎ | |
| 2160 | import faraday.server.events # pylint: disable=unused-import | |
| 3 | 3 | See the file 'doc/LICENSE' for the license information |
| 4 | 4 | |
| 5 | 5 | """ |
| 6 | import json | |
| 6 | 7 | import time |
| 7 | 8 | import datetime |
| 8 | 9 | from flask import g |
| 9 | from marshmallow import fields, Schema | |
| 10 | from marshmallow import fields, Schema, post_dump | |
| 10 | 11 | from marshmallow.exceptions import ValidationError |
| 12 | from marshmallow.utils import missing | |
| 11 | 13 | from dateutil.tz import tzutc |
| 12 | 14 | |
| 13 | 15 | from faraday.server.models import ( |
| 223 | 225 | def deserialize(self, value, attr=None, data=None): |
| 224 | 226 | # Validate required fields, deserialize, then validate |
| 225 | 227 | # deserialized value |
| 226 | if value: | |
| 227 | value = value.replace('\0', | |
| 228 | '') # Postgres does not allow nul 0x00 in the strings. | |
| 228 | if isinstance(value, str): | |
| 229 | value = value.replace('\0', '') # Postgres does not allow nul 0x00 in the strings. | |
| 230 | elif value is not None and value != missing: | |
| 231 | raise ValidationError("Deserializing a non string field when expected") | |
| 229 | 232 | self._validate_missing(value) |
| 230 | 233 | if getattr(self, 'allow_none', False) is True and value is None: |
| 231 | 234 | return '' |
| 277 | 280 | date.astimezone(tzutc()) |
| 278 | 281 | date = date.replace(tzinfo=None) |
| 279 | 282 | return date |
| 283 | ||
| 284 | ||
| 285 | class WorkerActionSchema(Schema): | |
| 286 | action = fields.Method('get_command') | |
| 287 | ||
| 288 | def get_command(self, obj): | |
| 289 | if obj.command == 'UPDATE': | |
| 290 | return "--{command}:{field}={value}".format(command=obj.command, field=obj.field, value=obj.value) | |
| 291 | if obj.command in ['DELETE', 'REMOVE']: | |
| 292 | return "--DELETE:" | |
| 293 | if obj.command == 'ALERT': | |
| 294 | return "--{command}:{value}".format(command=obj.command, value=obj.value) | |
| 295 | ||
| 296 | raise ValidationError("Command {} not supported.".format(obj.command)) | |
| 297 | ||
| 298 | ||
| 299 | class WorkerConditionSchema(Schema): | |
| 300 | condition = fields.Method('get_condition') | |
| 301 | ||
| 302 | def get_condition(self, obj): | |
| 303 | if obj.operator == "equals": | |
| 304 | operator = "=" | |
| 305 | else: | |
| 306 | raise ValidationError("Condition operator {} not support.".format(obj.operator)) | |
| 307 | return '{field}{operator}{value}'.format(field=obj.field, operator=operator, value=obj.value) | |
| 308 | ||
| 309 | ||
| 310 | class WorkerRuleSchema(Schema): | |
| 311 | id = fields.Integer() | |
| 312 | model = fields.String() | |
| 313 | object = fields.Method('get_object') | |
| 314 | actions = fields.Nested(WorkerActionSchema, attribute='actions', many=True) | |
| 315 | conditions = fields.Nested(WorkerConditionSchema, attribute='conditions', many=True) | |
| 316 | parent = fields.String(allow_none=False, attribute='object_parent') | |
| 317 | disabled = fields.Boolean(allow_none=True, attribute='disabled') | |
| 318 | fields = fields.String(allow_none=False) | |
| 319 | ||
| 320 | def get_object(self, rule): | |
| 321 | try: | |
| 322 | object_rules = json.loads(rule.object) | |
| 323 | except ValueError: | |
| 324 | rule_name, value = rule.object.split('=') | |
| 325 | object_rules = [{rule_name: value}] | |
| 326 | ||
| 327 | for object_rule in object_rules: | |
| 328 | for object_rule_name, value in object_rule.items(): | |
| 329 | if value == 'informational': | |
| 330 | value = 'info' | |
| 331 | if value == 'medium': | |
| 332 | value = 'med' | |
| 333 | return '{}={}'.format(object_rule_name, value) | |
| 334 | ||
| 335 | @post_dump | |
| 336 | def remove_none_values(self, data): | |
| 337 | actions = [] | |
| 338 | conditions = [] | |
| 339 | for action in data['actions']: | |
| 340 | actions.append(action['action']) | |
| 341 | for condition in data['conditions']: | |
| 342 | conditions.append(condition['condition']) | |
| 343 | ||
| 344 | data['actions'] = actions | |
| 345 | data['conditions'] = conditions | |
| 346 | ||
| 347 | return { | |
| 348 | key: value for key, value in data.items() | |
| 349 | if value | |
| 350 | } | |
| 351 | ||
| 280 | 352 | # I'm Py3⏎ |
| 0 | import logging | |
| 1 | import threading | |
| 2 | import requests | |
| 3 | import faraday | |
| 4 | ||
| 5 | logger = logging.getLogger(__name__) | |
| 6 | ||
| 7 | RUN_INTERVAL = 43200 | |
| 8 | HOME_URL = "https://portal.faradaysec.com/api/v1/license_check" | |
| 9 | ||
| 10 | ||
| 11 | class PingHomeThread(threading.Thread): | |
| 12 | def __init__(self): | |
| 13 | super().__init__(name="PingHomeThread") | |
| 14 | self.__event = threading.Event() | |
| 15 | ||
| 16 | def run(self): | |
| 17 | while not self.__event.is_set(): | |
| 18 | try: | |
| 19 | res = requests.get(HOME_URL, params={'version': faraday.__version__, 'key': 'white'}, | |
| 20 | timeout=1, verify=True) | |
| 21 | if res.status_code != 200: | |
| 22 | logger.error("Invalid response from portal") | |
| 23 | else: | |
| 24 | logger.debug("Ping Home") | |
| 25 | except Exception as ex: | |
| 26 | logger.exception(ex) | |
| 27 | logger.warning("Can't connect to portal...") | |
| 28 | self.__event.wait(RUN_INTERVAL) | |
| 29 | ||
| 30 | def stop(self): | |
| 31 | self.__event.set() |
| 3 | 3 | import time |
| 4 | 4 | import os |
| 5 | 5 | from faraday_plugins.plugins.manager import PluginsManager, ReportAnalyzer |
| 6 | from faraday.server.api.modules.bulk_create import bulk_create | |
| 6 | from faraday.server.api.modules.bulk_create import bulk_create, BulkCreateSchema | |
| 7 | 7 | |
| 8 | 8 | from faraday.server.models import Workspace |
| 9 | from faraday.server.utils.bulk_create import add_creator | |
| 9 | 10 | |
| 10 | 11 | logger = logging.getLogger(__name__) |
| 11 | 12 | |
| 25 | 26 | logger.debug("Stop Reports Manager") |
| 26 | 27 | self._must_stop = True |
| 27 | 28 | |
| 28 | def send_report_request(self, workspace_name, report_json): | |
| 29 | def send_report_request(self, workspace_name, report_json, user): | |
| 29 | 30 | logger.info("Send Report data to workspace [%s]", workspace_name) |
| 30 | 31 | from faraday.server.web import app # pylint:disable=import-outside-toplevel |
| 31 | 32 | with app.app_context(): |
| 32 | 33 | ws = Workspace.query.filter_by(name=workspace_name).one() |
| 33 | bulk_create(ws, report_json, False) | |
| 34 | schema = BulkCreateSchema(strict=True) | |
| 35 | data = schema.load(report_json).data | |
| 36 | data = add_creator(data, user) | |
| 37 | bulk_create(ws, data, True) | |
| 34 | 38 | |
| 35 | def process_report(self, workspace, file_path): | |
| 39 | def process_report(self, workspace, file_path, user): | |
| 36 | 40 | report_analyzer = ReportAnalyzer(self.plugins_manager) |
| 37 | 41 | plugin = report_analyzer.get_plugin(file_path) |
| 38 | 42 | if plugin: |
| 45 | 49 | logger.exception(e) |
| 46 | 50 | else: |
| 47 | 51 | try: |
| 48 | self.send_report_request(workspace, vulns_data) | |
| 52 | self.send_report_request(workspace, vulns_data, user) | |
| 49 | 53 | logger.info("Report processing finished") |
| 50 | 54 | except Exception as e: |
| 51 | 55 | logger.exception(e) |
| 57 | 61 | logger.debug("Start Reports Manager") |
| 58 | 62 | while not self._must_stop: |
| 59 | 63 | try: |
| 60 | workspace, file_path = self.upload_reports_queue.get(False, timeout=0.1) | |
| 64 | workspace, file_path, user = self.upload_reports_queue.get(False, timeout=0.1) | |
| 61 | 65 | logger.info("Processing raw report %s", file_path) |
| 62 | 66 | if os.path.isfile(file_path): |
| 63 | self.process_report(workspace, file_path) | |
| 67 | self.process_report(workspace, file_path, user) | |
| 64 | 68 | else: |
| 65 | 69 | logger.warning("Report file [%s] don't exists", file_path) |
| 66 | 70 | except Empty: |
| 0 | # Faraday Penetration Test IDE | |
| 1 | # Copyright (C) 2020 Infobyte LLC (http://www.infobytesec.com/) | |
| 2 | # See the file 'doc/LICENSE' for the license information | |
| 3 | ||
| 4 | import logging | |
| 5 | ||
| 6 | logger = logging.getLogger(__name__) | |
| 7 | ||
| 8 | ||
| 9 | def add_creator(data, creator_user): | |
| 10 | hosts_ = [] | |
| 11 | for host in data["hosts"]: | |
| 12 | host["creator_id"] = creator_user.id | |
| 13 | for service in host["services"]: | |
| 14 | service["creator_id"] = creator_user.id | |
| 15 | for vuln in service["vulnerabilities"]: | |
| 16 | vuln["creator_id"] = creator_user.id | |
| 17 | for vuln in host["vulnerabilities"]: | |
| 18 | vuln["creator_id"] = creator_user.id | |
| 19 | for cred in host["credentials"]: | |
| 20 | cred["creator_id"] = creator_user.id | |
| 21 | hosts_.append(host) | |
| 22 | ||
| 23 | response = dict(hosts=hosts_) | |
| 24 | if "command" in data: | |
| 25 | command = data['command'] | |
| 26 | command["creator_id"] = creator_user.id | |
| 27 | response["command"] = command | |
| 28 | ||
| 29 | return response |
| 136 | 136 | |
| 137 | 137 | def start_server(): |
| 138 | 138 | logger.info('Running as a daemon') |
| 139 | WORKDIR = faraday.server.config.FARADAY_BASE | |
| 139 | WORKDIR = faraday.server.config.FARADAY_BASE # pylint:disable=unused-variable | |
| 140 | 140 | createDaemon() |
| 141 | 141 | |
| 142 | 142 | |
| 217 | 217 | def get_ports_running(): |
| 218 | 218 | ports = [] |
| 219 | 219 | re_string = re.escape(faraday.server.config.FARADAY_SERVER_PID_FILE) |
| 220 | re_string = re_string.replace("\{0\}","[0-9]+") | |
| 221 | home_dir = os.listdir(faraday.server.config.CONSTANTS.CONST_FARADAY_HOME_PATH) | |
| 220 | re_string = re_string.replace("\{0\}", "[0-9]+") | |
| 221 | home_dir = os.listdir(faraday.server.config.CONST_FARADAY_HOME_PATH) | |
| 222 | 222 | |
| 223 | 223 | for path in home_dir: |
| 224 | path = faraday.server.config.CONSTANTS.CONST_FARADAY_HOME_PATH + "/" + path | |
| 225 | if re.match(re_string,path): | |
| 224 | path = faraday.server.config.CONST_FARADAY_HOME_PATH + "/" + path | |
| 225 | if re.match(re_string, path): | |
| 226 | 226 | port = path.split("-")[-1].split(".")[0] |
| 227 | 227 | ports.append(int(port)) |
| 228 | 228 | |
| 229 | 229 | return ports |
| 230 | # I'm Py3⏎ | |
| 4 | 4 | |
| 5 | 5 | from faraday.server.models import ( |
| 6 | 6 | db, |
| 7 | Comment | |
| 7 | Comment, | |
| 8 | Host, | |
| 9 | Service | |
| 8 | 10 | ) |
| 9 | 11 | |
| 10 | 12 | logger = logging.getLogger(__name__) |
| 11 | 13 | |
| 14 | ||
| 12 | 15 | def export_vulns_to_csv(vulns, custom_fields_columns=None): |
| 16 | buffer = StringIO() | |
| 17 | ||
| 18 | vuln_headers = [ | |
| 19 | "confirmed", "id", "date", "name", "severity", "service", | |
| 20 | "target", "desc", "status", "hostnames", "comments", "owner", | |
| 21 | "os", "resolution", "refs", "easeofresolution", "web_vulnerability", | |
| 22 | "data", "website", "path", "status_code", "request", "response", "method", | |
| 23 | "params", "pname", "query", "policyviolations", "external_id", "impact_confidentiality", | |
| 24 | "impact_integrity", "impact_availability", "impact_accountability", "update_date" | |
| 25 | ] | |
| 26 | ||
| 13 | 27 | if custom_fields_columns is None: |
| 14 | 28 | custom_fields_columns = [] |
| 15 | buffer = StringIO() | |
| 16 | headers = [ | |
| 17 | "confirmed", "id", "date", "name", "severity", "service", | |
| 18 | "target", "desc", "status", "hostnames", "comments", "owner", "os", "resolution", "easeofresolution", "web_vulnerability", | |
| 19 | "data", "website", "path", "status_code", "request", "method", "params", "pname", "query", | |
| 20 | "policyviolations", "external_id", "impact_confidentiality", "impact_integrity", "impact_availability", | |
| 21 | "impact_accountability", "update_date" | |
| 29 | vuln_headers += custom_fields_columns | |
| 30 | ||
| 31 | headers = vuln_headers + [ | |
| 32 | "host_id", "host_description", "mac", | |
| 33 | "host_owned", "host_creator_id", "host_date", "host_update_date", | |
| 34 | "service_id", "service_name", "service_description", "service_owned", | |
| 35 | "port", "protocol", "summary", "version", "service_status", | |
| 36 | "service_creator_id", "service_date", "service_update_date", "service_parent_id" | |
| 22 | 37 | ] |
| 23 | headers += custom_fields_columns | |
| 38 | ||
| 24 | 39 | writer = csv.DictWriter(buffer, fieldnames=headers) |
| 25 | 40 | writer.writeheader() |
| 41 | ||
| 42 | hosts_data = {} | |
| 43 | services_data = {} | |
| 26 | 44 | for vuln in vulns: |
| 27 | comments = [] | |
| 28 | for comment in db.session.query(Comment).filter_by(object_type='vulnerability', object_id=vuln['_id']).all(): | |
| 29 | comments.append(comment.text) | |
| 30 | vuln_description = re.sub(' +', ' ', vuln['description'].strip().replace("\n", "")) | |
| 31 | vuln_date = vuln['metadata']['create_time'] | |
| 32 | if vuln['service']: | |
| 33 | service_fields = ["status", "protocol", "name", "summary", "version", "ports"] | |
| 34 | service_fields_values = ["%s:%s" % (field, vuln['service'][field]) for field in service_fields] | |
| 35 | vuln_service = " - ".join(service_fields_values) | |
| 36 | else: | |
| 37 | vuln_service = "" | |
| 38 | if all(isinstance(hostname, str) for hostname in vuln['hostnames']): | |
| 39 | vuln_hostnames = vuln['hostnames'] | |
| 40 | else: | |
| 41 | vuln_hostnames = [str(hostname['name']) for hostname in vuln['hostnames']] | |
| 45 | vuln_data = _build_vuln_data(vuln, custom_fields_columns) | |
| 46 | if vuln['parent_type'] == 'Host': | |
| 47 | host_id = vuln['parent'] | |
| 48 | if host_id in hosts_data: | |
| 49 | host_data = hosts_data[host_id] | |
| 50 | else: | |
| 51 | host_data = _build_host_data(host_id) | |
| 52 | hosts_data[host_id] = host_data | |
| 53 | row = {**vuln_data, **host_data} | |
| 54 | elif vuln['parent_type'] == 'Service': | |
| 55 | service_id = vuln['parent'] | |
| 56 | if service_id in services_data: | |
| 57 | service_data = services_data[service_id] | |
| 58 | else: | |
| 59 | service_data = _build_service_data(service_id) | |
| 60 | services_data[service_id] = service_data | |
| 61 | host_id = service_data['service_parent_id'] | |
| 62 | if host_id in hosts_data: | |
| 63 | host_data = hosts_data[host_id] | |
| 64 | else: | |
| 65 | host_data = _build_host_data(host_id) | |
| 66 | hosts_data[host_id] = host_data | |
| 67 | row = {**vuln_data, **host_data, **service_data} | |
| 42 | 68 | |
| 43 | vuln_dict = {"confirmed": vuln['confirmed'], | |
| 44 | "id": vuln.get('_id', None), | |
| 45 | "date": vuln_date, | |
| 46 | "update_date": vuln['metadata']['update_time'], | |
| 47 | "severity": vuln.get('severity', None), | |
| 48 | "target": vuln.get('target', None), | |
| 49 | "status": vuln.get('status', None), | |
| 50 | "hostnames": vuln_hostnames, | |
| 51 | "desc": vuln_description, | |
| 52 | "name": vuln.get('name', None), | |
| 53 | "service": vuln_service, | |
| 54 | "comments": comments, | |
| 55 | "owner": vuln.get('owner', None), | |
| 56 | "os": vuln.get('host_os', None), | |
| 57 | "resolution": vuln.get('resolution', None), | |
| 58 | "easeofresolution": vuln.get('easeofresolution', None), | |
| 59 | "data": vuln.get('data', None), | |
| 60 | "website": vuln.get('website', None), | |
| 61 | "path": vuln.get('path', None), | |
| 62 | "status_code": vuln.get('status_code', None), | |
| 63 | "request": vuln.get('request', None), | |
| 64 | "method": vuln.get('method', None), | |
| 65 | "params": vuln.get('params', None), | |
| 66 | "pname": vuln.get('pname', None), | |
| 67 | "query": vuln.get('query', None), | |
| 68 | "policyviolations": vuln.get('policyviolations', None), | |
| 69 | "external_id": vuln.get('external_id', None), | |
| 70 | "impact_confidentiality": vuln["impact"]["confidentiality"], | |
| 71 | "impact_integrity": vuln["impact"]["integrity"], | |
| 72 | "impact_availability": vuln["impact"]["availability"], | |
| 73 | "impact_accountability": vuln["impact"]["accountability"], | |
| 74 | "web_vulnerability": vuln['type'] == "VulnerabilityWeb" | |
| 75 | } | |
| 76 | if vuln['custom_fields']: | |
| 77 | for field_name, value in vuln['custom_fields'].items(): | |
| 78 | if field_name in custom_fields_columns: | |
| 79 | vuln_dict.update({field_name: value}) | |
| 80 | writer.writerow(vuln_dict) | |
| 69 | writer.writerow(row) | |
| 70 | ||
| 81 | 71 | memory_file = BytesIO() |
| 82 | 72 | memory_file.write(buffer.getvalue().encode('utf8')) |
| 83 | 73 | memory_file.seek(0) |
| 84 | 74 | return memory_file |
| 85 | 75 | |
| 76 | ||
| 77 | def _build_host_data(host_id): | |
| 78 | host = db.session.query(Host)\ | |
| 79 | .filter(Host.id == host_id).one() | |
| 80 | ||
| 81 | host_data = { | |
| 82 | "host_id": host.id, | |
| 83 | "host_description": host.description, | |
| 84 | "mac": host.mac, | |
| 85 | "host_owned": host.owned, | |
| 86 | "host_creator_id": host.creator_id, | |
| 87 | "host_date": host.create_date, | |
| 88 | "host_update_date": host.update_date, | |
| 89 | } | |
| 90 | ||
| 91 | return host_data | |
| 92 | ||
| 93 | ||
| 94 | def _build_service_data(service_id): | |
| 95 | service = db.session.query(Service)\ | |
| 96 | .filter(Service.id == service_id).one() | |
| 97 | service_data = { | |
| 98 | "service_id": service.id, | |
| 99 | "service_name": service.name, | |
| 100 | "service_description": service.description, | |
| 101 | "service_owned": service.owned, | |
| 102 | "port": service.port, | |
| 103 | "protocol": service.protocol, | |
| 104 | "summary": service.summary, | |
| 105 | "version": service.version, | |
| 106 | "service_status": service.status, | |
| 107 | "service_creator_id": service.creator_id, | |
| 108 | "service_date": service.create_date, | |
| 109 | "service_update_date": service.update_date, | |
| 110 | "service_parent_id": service.host_id, | |
| 111 | } | |
| 112 | ||
| 113 | return service_data | |
| 114 | ||
| 115 | ||
| 116 | def _build_vuln_data(vuln, custom_fields_columns): | |
| 117 | comments_list = [] | |
| 118 | comments = db.session.query(Comment).filter_by( | |
| 119 | object_type='vulnerability', | |
| 120 | object_id=vuln['_id']).all() | |
| 121 | for comment in comments: | |
| 122 | comments_list.append(comment.text) | |
| 123 | vuln_description = re.sub(' +', ' ', vuln['description'].strip().replace("\n", "")) | |
| 124 | vuln_date = vuln['metadata']['create_time'] | |
| 125 | if vuln['service']: | |
| 126 | service_fields = ["status", "protocol", "name", "summary", "version", "ports"] | |
| 127 | service_fields_values = ["%s:%s" % (field, vuln['service'][field]) for field in service_fields] | |
| 128 | vuln_service = " - ".join(service_fields_values) | |
| 129 | else: | |
| 130 | vuln_service = "" | |
| 131 | ||
| 132 | if all(isinstance(hostname, str) for hostname in vuln['hostnames']): | |
| 133 | vuln_hostnames = vuln['hostnames'] | |
| 134 | else: | |
| 135 | vuln_hostnames = [str(hostname['name']) for hostname in vuln['hostnames']] | |
| 136 | ||
| 137 | vuln_data = { | |
| 138 | "confirmed": vuln['confirmed'], | |
| 139 | "id": vuln.get('_id', None), | |
| 140 | "date": vuln_date, | |
| 141 | "name": vuln.get('name', None), | |
| 142 | "severity": vuln.get('severity', None), | |
| 143 | "service": vuln_service, | |
| 144 | "target": vuln.get('target', None), | |
| 145 | "desc": vuln_description, | |
| 146 | "status": vuln.get('status', None), | |
| 147 | "hostnames": vuln_hostnames, | |
| 148 | "comments": comments_list, | |
| 149 | "owner": vuln.get('owner', None), | |
| 150 | "os": vuln.get('host_os', None), | |
| 151 | "resolution": vuln.get('resolution', None), | |
| 152 | "refs": vuln.get('refs', None), | |
| 153 | "easeofresolution": vuln.get('easeofresolution', None), | |
| 154 | "web_vulnerability": vuln['type'] == "VulnerabilityWeb", | |
| 155 | "data": vuln.get('data', None), | |
| 156 | "website": vuln.get('website', None), | |
| 157 | "path": vuln.get('path', None), | |
| 158 | "status_code": vuln.get('status_code', None), | |
| 159 | "request": vuln.get('request', None), | |
| 160 | "response": vuln.get('response', None), | |
| 161 | "method": vuln.get('method', None), | |
| 162 | "params": vuln.get('params', None), | |
| 163 | "pname": vuln.get('pname', None), | |
| 164 | "query": vuln.get('query', None), | |
| 165 | "policyviolations": vuln.get('policyviolations', None), | |
| 166 | "external_id": vuln.get('external_id', None), | |
| 167 | "impact_confidentiality": vuln["impact"]["confidentiality"], | |
| 168 | "impact_integrity": vuln["impact"]["integrity"], | |
| 169 | "impact_availability": vuln["impact"]["availability"], | |
| 170 | "impact_accountability": vuln["impact"]["accountability"], | |
| 171 | "update_date": vuln['metadata'].get('update_time', None), | |
| 172 | } | |
| 173 | if vuln['custom_fields']: | |
| 174 | for field_name, value in vuln['custom_fields'].items(): | |
| 175 | if field_name in custom_fields_columns: | |
| 176 | vuln_data.update({field_name: value}) | |
| 177 | ||
| 178 | vuln_data = csv_escape(vuln_data) | |
| 179 | return vuln_data | |
| 180 | ||
| 181 | ||
| 182 | # Patch possible formula injection attacks | |
| 183 | def csv_escape(vuln_dict): | |
| 184 | for key,value in vuln_dict.items(): | |
| 185 | if str(value).startswith('=') or str(value).startswith('+') or str(value).startswith('-') or str(value).startswith('@'): | |
| 186 | # Convert value to str just in case is has another type (like a list or | |
| 187 | # dict). This would be done anyway by the csv writer. | |
| 188 | vuln_dict[key] = "'" + str(value) | |
| 189 | return vuln_dict |
| 9 | 9 | from syslog_rfc5424_formatter import RFC5424Formatter |
| 10 | 10 | |
| 11 | 11 | LOG_FILE = os.path.expanduser(os.path.join( |
| 12 | faraday.server.config.CONSTANTS.CONST_FARADAY_HOME_PATH, | |
| 13 | faraday.server.config.CONSTANTS.CONST_FARADAY_LOGS_PATH, 'faraday-server.log')) | |
| 12 | faraday.server.config.CONST_FARADAY_HOME_PATH, | |
| 13 | 'logs', | |
| 14 | 'faraday-server.log')) | |
| 14 | 15 | |
| 15 | 16 | MAX_LOG_FILE_SIZE = 5 * 1024 * 1024 # 5 MB |
| 16 | 17 | MAX_LOG_FILE_BACKUP_COUNT = 5 |
| 18 | LOG_FORMAT = '%(asctime)s - %(name)s - %(levelname)s {%(threadName)s} [%(filename)s:%(lineno)s - %(funcName)s()] %(message)s' | |
| 19 | LOG_DATE_FORMAT = '%Y-%m-%dT%H:%M:%S%z' | |
| 17 | 20 | ROOT_LOGGER = u'faraday' |
| 18 | 21 | LOGGING_HANDLERS = [] |
| 19 | 22 | LVL_SETTABLE_HANDLERS = [] |
| 27 | 30 | if faraday.server.config.logger_config.use_rfc5424_formatter: |
| 28 | 31 | formatter = RFC5424Formatter() |
| 29 | 32 | else: |
| 30 | formatter = logging.Formatter( | |
| 31 | '%(asctime)s - %(name)s - %(levelname)s {%(threadName)s} [%(filename)s:%(lineno)s - %(funcName)s()] %(message)s') | |
| 33 | ||
| 34 | formatter = logging.Formatter(LOG_FORMAT, LOG_DATE_FORMAT) | |
| 32 | 35 | setup_console_logging(formatter) |
| 33 | 36 | setup_file_logging(formatter) |
| 34 | 37 | |
| 42 | 42 | @functools.wraps(f) |
| 43 | 43 | def view_func(*args, **kwargs): |
| 44 | 44 | @after_this_request |
| 45 | def zipper(response): | |
| 45 | def zipper(response): # pylint:disable=unused-variable | |
| 46 | 46 | accept_encoding = request.headers.get('Accept-Encoding', '') |
| 47 | 47 | |
| 48 | 48 | if 'gzip' not in accept_encoding.lower(): |
| 22 | 22 | |
| 23 | 23 | import faraday.server.config |
| 24 | 24 | |
| 25 | from faraday.config.constant import CONST_FARADAY_HOME_PATH | |
| 26 | from faraday.server import TimerClass | |
| 25 | from faraday.server.config import CONST_FARADAY_HOME_PATH | |
| 27 | 26 | from faraday.server.utils import logger |
| 28 | 27 | from faraday.server.threads.reports_processor import ReportsManager, REPORTS_QUEUE |
| 28 | from faraday.server.threads.ping_home import PingHomeThread | |
| 29 | 29 | from faraday.server.app import create_app |
| 30 | 30 | from faraday.server.websocket_factories import ( |
| 31 | 31 | WorkspaceServerFactory, |
| 73 | 73 | API_URL_PATH = b'_api' |
| 74 | 74 | WEB_UI_LOCAL_PATH = os.path.join(faraday.server.config.FARADAY_BASE, 'server/www') |
| 75 | 75 | |
| 76 | def __init__(self, enable_ssl=False): | |
| 77 | logger.info('Starting web server at {}://{}:{}/'.format( | |
| 78 | 'https' if enable_ssl else 'http', | |
| 76 | def __init__(self): | |
| 77 | self.__ssl_enabled = faraday.server.config.ssl.enabled | |
| 78 | logger.info('Starting web server at %s://%s:%s/', | |
| 79 | 'https' if self.__ssl_enabled else 'http', | |
| 79 | 80 | faraday.server.config.faraday_server.bind_address, |
| 80 | faraday.server.config.faraday_server.port)) | |
| 81 | self.__ssl_enabled = enable_ssl | |
| 81 | faraday.server.config.ssl.port if self.__ssl_enabled else faraday.server.config.faraday_server.port) | |
| 82 | 82 | self.__websocket_ssl_enabled = faraday.server.config.websocket_ssl.enabled |
| 83 | 83 | self.__websocket_port = faraday.server.config.faraday_server.websocket_port or 9000 |
| 84 | 84 | self.__config_server() |
| 86 | 86 | |
| 87 | 87 | def __config_server(self): |
| 88 | 88 | self.__bind_address = faraday.server.config.faraday_server.bind_address |
| 89 | self.__listen_port = int(faraday.server.config.faraday_server.port) | |
| 90 | 89 | if self.__ssl_enabled: |
| 91 | 90 | self.__listen_port = int(faraday.server.config.ssl.port) |
| 91 | else: | |
| 92 | self.__listen_port = int(faraday.server.config.faraday_server.port) | |
| 92 | 93 | |
| 93 | 94 | def __load_ssl_certs(self): |
| 94 | 95 | certs = (faraday.server.config.ssl.keyfile, faraday.server.config.ssl.certificate) |
| 115 | 116 | |
| 116 | 117 | def __build_websockets_resource(self): |
| 117 | 118 | websocket_port = int(faraday.server.config.faraday_server.websocket_port) |
| 118 | url = '{0}:{1}'.format(self.__bind_address, websocket_port) | |
| 119 | url = '{0}:{1}/websockets'.format(self.__bind_address, websocket_port) | |
| 119 | 120 | if self.__websocket_ssl_enabled: |
| 120 | 121 | url = 'wss://' + url |
| 121 | 122 | else: |
| 143 | 144 | # teardown() |
| 144 | 145 | if self.raw_report_processor.isAlive(): |
| 145 | 146 | self.raw_report_processor.stop() |
| 146 | self.timer.stop() | |
| 147 | self.ping_home_thread.stop() | |
| 147 | 148 | |
| 148 | 149 | log_path = os.path.join(CONST_FARADAY_HOME_PATH, 'logs', 'access-logging.log') |
| 149 | 150 | site = twisted.web.server.Site(self.__root_resource, |
| 163 | 164 | # start threads and processes |
| 164 | 165 | self.raw_report_processor = ReportsManager(REPORTS_QUEUE, name="ReportsManager-Thread", daemon=True) |
| 165 | 166 | self.raw_report_processor.start() |
| 166 | self.timer = TimerClass() | |
| 167 | self.timer.start() | |
| 167 | self.ping_home_thread = PingHomeThread() | |
| 168 | self.ping_home_thread.start() | |
| 168 | 169 | # web and static content |
| 169 | 170 | self.__listen_func( |
| 170 | 171 | self.__listen_port, site, |
| 181 | 182 | listenWS(self.__build_websockets_resource(), interface=self.__bind_address, contextFactory=contextFactory) |
| 182 | 183 | |
| 183 | 184 | except SSLError as e: |
| 184 | logger.error('Could not start websockets due to a SSL Config error. Some web functionality will not be available') | |
| 185 | logger.error('Could not start websockets due to a SSL Config error. Some web functionality will not be available') | |
| 185 | 186 | except error.CannotListenError: |
| 186 | 187 | logger.warn('Could not start websockets, address already open. This is ok is you wan to run multiple instances.') |
| 187 | 188 | except Exception as ex: |
| 203 | 204 | |
| 204 | 205 | |
| 205 | 206 | except Exception as e: |
| 206 | logger.error('Something went wrong when trying to setup the Web UI') | |
| 207 | logger.exception(e) | |
| 207 | logger.exception('Something went wrong when trying to setup the Web UI') | |
| 208 | 208 | sys.exit(1) |
| 209 | 209 | # I'm Py3 |
| 19 | 19 | |
| 20 | 20 | from autobahn.websocket.protocol import WebSocketProtocol |
| 21 | 21 | from twisted.internet import reactor |
| 22 | from sqlalchemy.orm.exc import NoResultFound | |
| 22 | 23 | |
| 23 | 24 | from autobahn.twisted.websocket import ( |
| 24 | 25 | WebSocketServerFactory, |
| 141 | 142 | ] |
| 142 | 143 | agent = Agent.query.get(agent_id) |
| 143 | 144 | assert agent is not None # TODO the agent could be deleted here |
| 144 | executor = Executor.query.filter(Executor.name == message['executor_name'], | |
| 145 | Executor.agent_id == agent_id).first() | |
| 146 | if executor: | |
| 147 | successful = message.get('successful', None) | |
| 148 | running = message.get('running', None) | |
| 149 | msg = message['message'] | |
| 150 | agent_execution = AgentExecution( | |
| 151 | running=running, | |
| 152 | successful=successful, | |
| 153 | message=msg, | |
| 154 | executor=executor, | |
| 155 | workspace_id=executor.agent.workspace_id | |
| 156 | ) | |
| 157 | db.session.add(agent_execution) | |
| 158 | db.session.commit() | |
| 145 | ||
| 146 | execution_id = message.get('execution_id', None) | |
| 147 | assert execution_id is not None | |
| 148 | agent_execution = AgentExecution.query.filter(AgentExecution.id == execution_id).first() | |
| 149 | if agent_execution: | |
| 150 | ||
| 151 | if agent.workspace.name != agent_execution.workspace.name: | |
| 152 | logger.exception( | |
| 153 | ValueError(f"The {agent.name} agent has permission to workspace {agent.workspace.name} " | |
| 154 | f"and ask to write to workspace {agent_execution.workspace.name}") | |
| 155 | ) | |
| 156 | else: | |
| 157 | agent_execution.successful = message.get('successful', None) | |
| 158 | agent_execution.running = message.get('running', None) | |
| 159 | agent_execution.message = message.get('message','') | |
| 160 | db.session.commit() | |
| 161 | else: | |
| 162 | logger.exception( | |
| 163 | NoResultFound(f"No row was found for agent executor id {execution_id}")) | |
| 159 | 164 | |
| 160 | 165 | def connectionLost(self, reason): |
| 161 | 166 | WebSocketServerProtocol.connectionLost(self, reason) |
| 171 | 176 | for raw_executor in executors: |
| 172 | 177 | if 'executor_name' not in raw_executor or 'args' not in raw_executor: |
| 173 | 178 | continue |
| 174 | executor, created = get_or_create( | |
| 179 | executor, _ = get_or_create( | |
| 175 | 180 | db.session, |
| 176 | 181 | Executor, |
| 177 | 182 | **{ |
| 1402 | 1402 | padding-bottom: 0px !important; |
| 1403 | 1403 | margin-bottom: 15px; |
| 1404 | 1404 | } |
| 1405 | .no-padding{ | |
| 1406 | padding: 0 !important; | |
| 1407 | } | |
| 1408 | .responsive_agent_command{ | |
| 1409 | width: 30em; | |
| 1410 | white-space: nowrap; | |
| 1411 | text-overflow: ellipsis; | |
| 1412 | overflow: hidden; | |
| 1413 | }⏎ |
| 0 | <?xml version="1.0" encoding="utf-8"?> | |
| 1 | <svg version="1.1" id="Capa_1" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" x="0px" y="0px" | |
| 2 | viewBox="0 0 16 16" style="enable-background:new 0 0 16 16;" xml:space="preserve"> | |
| 3 | <style type="text/css"> | |
| 4 | .st0{fill:#DEF1FE;} | |
| 5 | .st1{fill:#1C87C3;} | |
| 6 | </style> | |
| 7 | <path class="st0" d="M8,15.4c-4.1,0-7.4-3.3-7.4-7.4S3.9,0.6,8,0.6s7.4,3.3,7.4,7.4S12.1,15.4,8,15.4z"/> | |
| 8 | <path class="st1" d="M8,0.8c4,0,7.2,3.2,7.2,7.2S12,15.2,8,15.2S0.8,12,0.8,8S4,0.8,8,0.8 M8,0.4C3.8,0.4,0.4,3.8,0.4,8 | |
| 9 | s3.4,7.6,7.6,7.6s7.6-3.4,7.6-7.6S12.2,0.4,8,0.4L8,0.4z"/> | |
| 10 | </svg> |
| 0 | <svg xmlns="http://www.w3.org/2000/svg" viewBox="0 0 40 40" width="16px" height="16px"><path fill="#bae0bd" d="M20,38.5C9.799,38.5,1.5,30.201,1.5,20S9.799,1.5,20,1.5S38.5,9.799,38.5,20S30.201,38.5,20,38.5z"/><path fill="#5e9c76" d="M20,2c9.925,0,18,8.075,18,18s-8.075,18-18,18S2,29.925,2,20S10.075,2,20,2 M20,1 C9.507,1,1,9.507,1,20s8.507,19,19,19s19-8.507,19-19S30.493,1,20,1L20,1z"/><path fill="none" stroke="#fff" stroke-miterlimit="10" stroke-width="2" d="M11 20L17 26 30 13"/></svg>⏎ |
| 0 | <?xml version="1.0" encoding="utf-8"?> | |
| 1 | <!-- Generator: Adobe Illustrator 24.1.1, SVG Export Plug-In . SVG Version: 6.00 Build 0) --> | |
| 2 | <svg version="1.1" id="Capa_1" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" x="0px" y="0px" | |
| 3 | viewBox="0 0 39 46.9" style="enable-background:new 0 0 39 46.9;" xml:space="preserve"> | |
| 4 | <style type="text/css"> | |
| 5 | .st0{fill:#DEF1FE;} | |
| 6 | .st1{fill:none;stroke:#1C87C3;stroke-width:1.6;stroke-linecap:round;stroke-miterlimit:10;} | |
| 7 | .st2{fill:#1C87C3;} | |
| 8 | </style> | |
| 9 | <rect x="1.7" y="17.9" class="st0" width="36" height="28"/> | |
| 10 | <path class="st1" d="M3.7,45.9c-1.1,0-2-0.9-2-2v-24c0-1.1,0.9-2,2-2h32c1.1,0,2,0.9,2,2v24c0,1.1-0.9,2-2,2H3.7z"/> | |
| 11 | <path class="st1" d="M30.7,17.6c0,0,0-3.8,0-4.5c0-6.2-4.8-10.7-11-10.7c-6.1,0-10.9,4.4-10.9,10.7c0.1,0.7,0,3.3,0,4.8"/> | |
| 12 | <path class="st2" d="M22.7,29.9c0-1.7-1.3-3-3-3s-3,1.3-3,3c0,0.9,0.4,1.7,1,2.2v2.8c0,1.1,0.9,2,2,2s2-0.9,2-2v-2.8 | |
| 13 | C22.3,31.6,22.7,30.8,22.7,29.9z"/> | |
| 14 | </svg> |
| 0 | <?xml version="1.0" encoding="utf-8"?> | |
| 1 | <!-- Generator: Adobe Illustrator 24.1.1, SVG Export Plug-In . SVG Version: 6.00 Build 0) --> | |
| 2 | <svg version="1.1" id="Capa_1" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink" x="0px" y="0px" | |
| 3 | viewBox="0 0 50 50" style="enable-background:new 0 0 50 50;" xml:space="preserve"> | |
| 4 | <style type="text/css"> | |
| 5 | .st0{fill:#DEF1FE;} | |
| 6 | .st1{fill:none;stroke:#1C87C3;stroke-width:1.6;stroke-linecap:round;stroke-miterlimit:10;} | |
| 7 | .st2{fill:#1C87C3;} | |
| 8 | </style> | |
| 9 | <rect x="7" y="21" class="st0" width="36" height="28"/> | |
| 10 | <path class="st1" d="M9,49c-1.1,0-2-0.9-2-2V23c0-1.1,0.9-2,2-2h32c1.1,0,2,0.9,2,2v24c0,1.1-0.9,2-2,2H9z M34.6,13.1 | |
| 11 | c0,0-1.1-3.6-1.3-4.3c-1.8-5.8-8-9.1-13.8-7.3s-9.1,8-7.3,13.8C12.6,16.4,14,21,14,21"/> | |
| 12 | <path class="st2" d="M28,33c0-1.7-1.3-3-3-3s-3,1.3-3,3c0,0.9,0.4,1.7,1,2.2V38c0,1.1,0.9,2,2,2s2-0.9,2-2v-2.8 | |
| 13 | C27.6,34.7,28,33.9,28,33z"/> | |
| 14 | </svg> |
| 4 | 4 | */ |
| 5 | 5 | |
| 6 | 6 | table.rz-table { |
| 7 | table-layout: fixed; | |
| 7 | /*table-layout: fixed;*/ | |
| 8 | 8 | border-collapse: collapse; |
| 9 | 9 | } |
| 10 | 10 |
| 2251 | 2251 | 'zzz':'\ud83d\udca4', |
| 2252 | 2252 | |
| 2253 | 2253 | /* special emojis :P */ |
| 2254 | 'octocat': '<img width="20" height="20" align="absmiddle" src="https://assets-cdn.github.com/images/icons/emoji/octocat.png">', | |
| 2254 | /* 'octocat': '<img width="20" height="20" align="absmiddle" src="https://assets-cdn.github.com/images/icons/emoji/octocat.png">',*/ | |
| 2255 | 2255 | 'showdown': '<img width="20" height="20" align="absmiddle" src="data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAEAAAABACAMAAACdt4HsAAAAS1BMVEX///8jJS0jJS0jJS0jJS0jJS0jJS0jJS0jJS0jJS0jJS0jJS0jJS0jJS0jJS0jJS0jJS3b1q3b1q3b1q3b1q3b1q3b1q3b1q3b1q0565CIAAAAGXRSTlMAQHCAYCCw/+DQwPCQUBAwoHCAEP+wwFBgS2fvBgAAAUZJREFUeAHs1cGy7BAUheFFsEDw/k97VTq3T6ge2EmdM+pvrP6Iwd74XV9Kb52xuMU4/uc1YNgZLFOeV8FGdhGrNk5SEgUyPxAEdj4LlMRDyhVAMVEa2M7TBSeVZAFPdqHgzSZJwPKgcLFLAooHDJo4EDCw4gAtBoJA5UFj4Ng5LOGLwVXZuoIlji/jeQHFk7+baHxrCjeUwB9+s88KndvlhcyBN5BSkYNQIVVb4pV+Npm7hhuKDs/uMP5KxT3WzSNNLIuuoDpMmuAVMruMSeDyQBi24DTr43LAY7ILA1QYaWkgfHzFthYYzg67SQsCbB8GhJUEGCtO9n0rSaCLxgJQjS/JSgMTg2eBDEHAJ+H350AsjYNYscrErgI2e/l+mdR967TCX/v6N0EhPECYCP0i+IAoYQOE8BogNhQMEMdrgAQWHaMAAGi5I5euoY9NAAAAAElFTkSuQmCC">' |
| 2256 | 2256 | }; |
| 2257 | 2257 |
| 11 | 11 | <span class="glyphicon glyphicon-question-sign margin-right-15px" |
| 12 | 12 | title="To register a new agent you should enter the current token"></span> |
| 13 | 13 | |
| 14 | <button type="button" class="btn btn-success" | |
| 14 | <button type="button" class="btn btn-info" | |
| 15 | 15 | title="A new token will be shown and the current token will be lost" |
| 16 | 16 | ng-click="refreshToken()"> |
| 17 | 17 | <i class="fa fa-refresh"></i> New Token |
| 93 | 93 | <button type="button" class="btn btn-info" |
| 94 | 94 | ng-click="selectAgent(agent)" |
| 95 | 95 | title="Run Agent" |
| 96 | data-toggle="modal" data-target="#selectExecutorModal-{{agent.id}}" ng-disabled="!agent.active || disableExecute"> | |
| 96 | data-toggle="modal" data-target="#selectExecutorModal-{{agent.id}}" ng-disabled="!agent.active || disableExecute || agent.status=='offline'"> | |
| 97 | 97 | Execute |
| 98 | 98 | </button> |
| 99 | 99 | <button type="button" class="btn" |
| 100 | 100 | ng-class="{'btn-danger': agent.active, 'btn-success': !agent.active}" |
| 101 | 101 | title="{{agent.active?'Pause Agent': 'Unpause Agent'}}" |
| 102 | ng-click="changeStatusAgent(agent)"> | |
| 102 | ng-click="changeStatusAgent(agent)" | |
| 103 | ng-disabled="agent.status=='offline'"> | |
| 103 | 104 | <span ng-bind="agent.active ?'Pause': 'Unpause'"></span> |
| 104 | 105 | </button> |
| 105 | 106 | <button type="button" class="btn btn-danger" title="Remove Agent" ng-click="removeAgent(agent.id)"> |
| 141 | 142 | </div> |
| 142 | 143 | |
| 143 | 144 | <div class="var-item margin-top-65px row"> |
| 144 | <div class="form-group col-md-6" ng-repeat="parameter in data.selectedExecutor.parameters_metadata"> | |
| 145 | <label for="paramName">{{parameter.name}}</label> | |
| 146 | <input type="text" class="form-control" id="paramName" placeholder="{{parameter.name}}" ng-model="data.selectedExecutor.parameters_values[parameter.name]" ng-required="parameter.isRequired"> | |
| 145 | <div class="form-group col-md-6" ng-repeat="parameter in data.selectedExecutor.parameters_metadata" ng-class="{'has-error': form[$index].$invalid}"> | |
| 146 | <label for="paramName" ng-class="{'text-danger': form[$index].$invalid}">{{parameter.name}} <span ng-if="parameter.isRequired">*</span></label> | |
| 147 | <input type="text" class="form-control" name="{{$index}}" id="paramName" placeholder="{{parameter.name}}" ng-model="data.selectedExecutor.parameters_values[parameter.name]" ng-required="parameter.isRequired"> | |
| 147 | 148 | </div> |
| 148 | 149 | </div> |
| 149 | 150 | </div> |
| 97 | 97 | }); |
| 98 | 98 | $routeProvider. |
| 99 | 99 | when('/', { |
| 100 | redirectTo: "/dashboard/ws/:wsId" | |
| 100 | redirectTo: "/workspaces" | |
| 101 | 101 | }). |
| 102 | 102 | when('/dashboard/ws/:wsId', { |
| 103 | 103 | templateUrl: 'scripts/dashboard/partials/dashboard.html', |
| 105 | 105 | title: 'Dashboard | ' |
| 106 | 106 | }). |
| 107 | 107 | when('/dashboard/ws', { |
| 108 | templateUrl: 'scripts/commons/partials/workspaces.html', | |
| 108 | templateUrl: 'scripts/workspaces/partials/list.html', | |
| 109 | 109 | controller: 'workspacesCtrl', |
| 110 | 110 | title: 'Dashboard | ' |
| 111 | 111 | }). |
| 112 | 112 | when('/dashboard', { |
| 113 | templateUrl: 'scripts/commons/partials/workspaces.html', | |
| 113 | templateUrl: 'scripts/workspaces/partials/list.html', | |
| 114 | 114 | controller: 'workspacesCtrl', |
| 115 | 115 | title: 'Dashboard | ' |
| 116 | 116 | }). |
| 134 | 134 | title: 'Hosts | ' |
| 135 | 135 | }). |
| 136 | 136 | when('/hosts/ws', { |
| 137 | templateUrl: 'scripts/commons/partials/workspaces.html', | |
| 137 | templateUrl: 'scripts/workspaces/partials/list.html', | |
| 138 | 138 | controller: 'workspacesCtrl', |
| 139 | 139 | title: 'Hosts | ' |
| 140 | 140 | }). |
| 149 | 149 | title: 'Host and services | ' |
| 150 | 150 | }). |
| 151 | 151 | when('/hosts', { |
| 152 | templateUrl: 'scripts/commons/partials/workspaces.html', | |
| 152 | templateUrl: 'scripts/workspaces/partials/list.html', | |
| 153 | 153 | controller: 'workspacesCtrl', |
| 154 | 154 | title: 'Hosts | ' |
| 155 | 155 | }). |
| 257 | 257 | } |
| 258 | 258 | }). |
| 259 | 259 | when('/status/ws', { |
| 260 | templateUrl: 'scripts/commons/partials/workspaces.html', | |
| 260 | templateUrl: 'scripts/workspaces/partials/list.html', | |
| 261 | 261 | controller: 'workspacesCtrl', |
| 262 | 262 | title: 'Status Report | ', |
| 263 | 263 | resolve: { |
| 267 | 267 | } |
| 268 | 268 | }). |
| 269 | 269 | when('/status', { |
| 270 | templateUrl: 'scripts/commons/partials/workspaces.html', | |
| 270 | templateUrl: 'scripts/workspaces/partials/list.html', | |
| 271 | 271 | controller: 'workspacesCtrl', |
| 272 | 272 | title: 'Status Report | ' |
| 273 | 273 | }). |
| 315 | 315 | title: 'Credentials | ' |
| 316 | 316 | }). |
| 317 | 317 | when('/credentials/ws', { |
| 318 | templateUrl: 'scripts/commons/partials/workspaces.html', | |
| 318 | templateUrl: 'scripts/workspaces/partials/list.html', | |
| 319 | 319 | controller: 'workspacesCtrl', |
| 320 | 320 | title: 'Credentials | ' |
| 321 | 321 | }). |
| 20 | 20 | $scope.login = function(){ |
| 21 | 21 | if ($scope.data.user && $scope.data.pass){ |
| 22 | 22 | loginSrv.login($scope.data.user, $scope.data.pass).then(function(user){ |
| 23 | var currentUrl = "/dashboard/ws"; | |
| 23 | var currentUrl = "/workspaces"; | |
| 24 | 24 | if($cookies.currentUrl != undefined) { |
| 25 | 25 | currentUrl = $cookies.currentUrl; |
| 26 | 26 | } |
| 66 | 66 | $scope.logout = function(){ |
| 67 | 67 | loginSrv.logout().then(function(){ |
| 68 | 68 | $location.path('/login'); |
| 69 | $cookies.currentUrl = "/dashboard/ws"; | |
| 69 | $cookies.currentUrl = "/workspaces"; | |
| 70 | 70 | }); |
| 71 | 71 | }; |
| 72 | 72 | |
| 0 | 0 | <div class="faraday-page-header" class="clearfix"> |
| 1 | 1 | <div class="head"> |
| 2 | <a href="#/" class="ws-dashboard" uib-tooltip="{{version}}" tooltip-placement="bottom" style="margin-right: 20px;"> | |
| 2 | <a href="#/workspaces" class="ws-dashboard" uib-tooltip="{{version}}" tooltip-placement="bottom" style="margin-right: 20px;"> | |
| 3 | 3 | <img class="" style="margin: 0.5rem;" src="../../../images/logo-faraday-blanco.svg" alt="Faraday home | WS Dashboard"/> |
| 4 | 4 | </a> |
| 5 | 5 | </div> |
| 24 | 24 | <td class="wrapword"> |
| 25 | 25 | <span ng-if="cmd.import_source == 'report'">Import {{(cmd.tool == 'unknown' ? cmd.command : cmd.tool)}}</span> |
| 26 | 26 | <span ng-if="cmd.import_source == 'shell'">{{cmd.command + ' ' + cmd.params}}</span> |
| 27 | <span ng-if="cmd.import_source == 'agent'"> | |
| 28 | <p class="responsive_agent_command"> | |
| 29 | {{cmd.tool + ' executor: ' + cmd.command + ' ' + cmd.params}} | |
| 30 | </p> | |
| 31 | </span> | |
| 27 | 32 | </td> |
| 28 | 33 | <td am-time-ago="cmd.date" am-preprocess="utc"></td> |
| 29 | 34 | <td ng-bind="cmd.duration || 'undefined'"></td> |
| 303 | 303 | "query": false, |
| 304 | 304 | "response": false, |
| 305 | 305 | "web": false, |
| 306 | "creator": false, | |
| 306 | "tool": false, | |
| 307 | 307 | "policyviolations": false, |
| 308 | 308 | "external_id": false |
| 309 | 309 | }; |
| 337 | 337 | "query": "100", |
| 338 | 338 | "response": "90", |
| 339 | 339 | "web": "80", |
| 340 | "metadata.creator": "100", | |
| 340 | "tool": "100", | |
| 341 | 341 | "policyviolations": "100" |
| 342 | 342 | }; |
| 343 | 343 | } |
| 620 | 620 | visible: $scope.columns["web"] |
| 621 | 621 | }); |
| 622 | 622 | $scope.gridOptions.columnDefs.push({ name : 'metadata.creator', |
| 623 | displayName : "creator", | |
| 623 | displayName : "tool", | |
| 624 | 624 | cellTemplate: 'scripts/statusReport/partials/ui-grid/columns/creatorcolumn.html', |
| 625 | 625 | headerCellTemplate: header, |
| 626 | sort: getColumnSort('metadata.creator'), | |
| 627 | visible: $scope.columns["creator"] | |
| 626 | sort: getColumnSort('tool'), | |
| 627 | visible: $scope.columns["tool"] | |
| 628 | 628 | }); |
| 629 | 629 | $scope.gridOptions.columnDefs.push({ name : 'policyviolations', |
| 630 | 630 | // The following line breaks the remembering of the field (i.e. |
| 1230 | 1230 | if ($scope.propertyFilterConfirmed === 'Unconfirmed'){ |
| 1231 | 1231 | searchFilter.confirmed = false; |
| 1232 | 1232 | } |
| 1233 | ||
| 1234 | if(paginationOptions.sortColumn == "metadata.creator") | |
| 1235 | paginationOptions.sortColumn = "tool"; | |
| 1233 | 1236 | // load all vulnerabilities |
| 1234 | 1237 | vulnsManager.getVulns($scope.workspace, |
| 1235 | 1238 | paginationOptions.page, |
| 0 | 0 | <div ng-if="row.entity._id != undefined"> |
| 1 | <div ng-if="!col.grouping || col.grouping.groupPriority === undefined || col.grouping.groupPriority === null || ( row.groupHeader && col.grouping.groupPriority === row.treeLevel )" class="ui-grid-cell-contents white-space" uib-tooltip="{{COL_FIELD}}"><a href='{{grid.appScope.hash}}/search/creator={{grid.appScope.encodeUrl(row.entity.metadata.creator)}}' append-search-param="creator={{grid.appScope.encodeUrl(row.entity.metadata.creator)}}">{{COL_FIELD CUSTOM_FILTERS}}</a></div> | |
| 1 | <div ng-if="!col.grouping || col.grouping.groupPriority === undefined || col.grouping.groupPriority === null || ( row.groupHeader && col.grouping.groupPriority === row.treeLevel )" class="ui-grid-cell-contents white-space" uib-tooltip="{{COL_FIELD}}"><a href='{{grid.appScope.hash}}/search/tool={{grid.appScope.encodeUrl(row.entity.metadata.creator)}}' append-search-param="creator={{grid.appScope.encodeUrl(row.entity.metadata.creator)}}">{{COL_FIELD CUSTOM_FILTERS}}</a></div> | |
| 2 | 2 | </div> |
| 3 | 3 | <div ng-if="row.groupHeader && col.grouping.groupPriority !== undefined" class="ui-grid-cell-contents white-space">{{COL_FIELD.split("(")[0] !== " " ? COL_FIELD : "EMPTY" + COL_FIELD}}</div>⏎ |
| 69 | 69 | <input type="checkbox" ng-model="selectall" ng-click="disabledClick || checkAll()"/> |
| 70 | 70 | </th> |
| 71 | 71 | <th class="ui-grid-cell-contents ui-grid-header-cell"> |
| 72 | <span ng-click="toggleSort('name')">Name</span> | |
| 72 | <span ng-click="toggleSort('name')">Template Name</span> | |
| 73 | 73 | </th> |
| 74 | 74 | <th class="ui-grid-cell-contents ui-grid-header-cell"> |
| 75 | 75 | <span ng-click="toggleSort('description')">Description</span> |
| 76 | </th> | |
| 77 | <th class="ui-grid-cell-contents ui-grid-header-cell"> | |
| 78 | <span ng-click="toggleSort('description')">External ID</span> | |
| 79 | 76 | </th> |
| 80 | 77 | <th class="ui-grid-cell-contents ui-grid-header-cell"> |
| 81 | 78 | <span ng-click="toggleSort('references')">References</span> |
| 82 | 79 | </th> |
| 83 | 80 | <th class="ui-grid-cell-contents ui-grid-header-cell"> |
| 84 | <span ng-click="toggleSort('data')">Data</span> | |
| 85 | </th> | |
| 86 | <th class="ui-grid-cell-contents ui-grid-header-cell"> | |
| 87 | 81 | <span ng-click="toggleSort('resolution')">Resolution</span> |
| 88 | 82 | </th> |
| 89 | 83 | <th class="ui-grid-cell-contents ui-grid-header-cell"> |
| 90 | <span ng-click="toggleSort('impact')">Impact</span> | |
| 91 | </th> | |
| 92 | <th class="ui-grid-cell-contents ui-grid-header-cell"> | |
| 93 | 84 | <span ng-click="toggleSort('exploitation')">Severity</span> |
| 94 | </th> | |
| 95 | <th class="ui-grid-cell-contents ui-grid-header-cell"> | |
| 96 | <span ng-click="toggleSort('easeofresolution')">Ease of Resolution</span> | |
| 97 | 85 | </th> |
| 98 | 86 | <th class="ui-grid-cell-contents ui-grid-header-cell"> |
| 99 | 87 | <span ng-click="toggleSort('policyviolations')">Policy Violations</span> |
| 113 | 101 | selection-model-selected-class="multi-selected" |
| 114 | 102 | selection-model-on-change="selectedModels()"> |
| 115 | 103 | <td class="checkbox-select"><input type="checkbox" name="{{model._id}}"/></td> |
| 116 | <td>{{model.name}}</td> | |
| 117 | <td>{{model.description}}</td> | |
| 118 | <td>{{model.external_id}}</td> | |
| 119 | <td><div ng-repeat="ref in model.refs">{{ref}}</div></td> | |
| 120 | <td>{{model.data}}</td> | |
| 121 | <td>{{model.resolution}}</td> | |
| 122 | <td><div ng-repeat="(key, value) in model.impact" ng-if="value == true">{{key}}</div></td> | |
| 104 | <td class="ui-grid-cell-contents" style="max-width: 20vw;">{{model.name}}</td> | |
| 105 | <td class="ui-grid-cell-contents" style="max-width: 20vw;">{{model.description}}</td> | |
| 106 | <td><div ng-repeat="ref in model.refs|limitTo:4" class="ui-grid-cell-contents no-padding" style="max-width: 15vw;">{{ref}}</div></td> | |
| 107 | <td class="ui-grid-cell-contents no-padding" style="max-width: 10vw;">{{model.resolution}}</td> | |
| 123 | 108 | <td>{{model.exploitation}}</td> |
| 124 | <td>{{model.easeofresolution}}</td> | |
| 125 | <td><div ng-repeat="policy in model.policyviolations">{{policy}}</div></td> | |
| 126 | <td>{{model.creator}}</td> | |
| 109 | <td><div ng-repeat="policy in model.policyviolations|limitTo:4" class="ui-grid-cell-contents no-padding" style="max-width: 10vw;">{{policy}}</div></td> | |
| 110 | <td style="max-width: 10vw;">{{model.creator}}</td> | |
| 127 | 111 | <td><p ng-bind="model.create_at | date:'MM/dd/yyyy'"></p></td> |
| 128 | 112 | </tr> |
| 129 | 113 | </tbody> |
| 217 | 217 | |
| 218 | 218 | $scope.edit = function () { |
| 219 | 219 | var workspace; |
| 220 | ||
| 220 | 221 | $scope.workspaces.forEach(function (w) { |
| 221 | 222 | if (w.selected) { |
| 222 | 223 | workspace = w; |
| 49 | 49 | <table class="table-v3 table table-responsive"> |
| 50 | 50 | <thead> |
| 51 | 51 | <tr class="ui-grid-header"> |
| 52 | <th class="ui-grid-cell-contents ui-grid-header-cell">Read only</th> | |
| 53 | <th class="ui-grid-cell-contents ui-grid-header-cell">Active</th> | |
| 54 | 52 | <th class="ui-grid-cell-contents ui-grid-header-cell"> |
| 55 | 53 | <a href="" ng-click="toggleSort('name')">Name</a> |
| 56 | 54 | </th> |
| 60 | 58 | <th class="ui-grid-cell-contents ui-grid-header-cell">Hosts</th> |
| 61 | 59 | <th class="ui-grid-cell-contents ui-grid-header-cell">Services</th> |
| 62 | 60 | <th class="ui-grid-cell-contents ui-grid-header-cell">Last Modified</th> |
| 61 | <th class="ui-grid-cell-contents ui-grid-header-cell">Active</th> | |
| 62 | <th class="ui-grid-cell-contents ui-grid-header-cell">Read only</th> | |
| 63 | 63 | </tr> |
| 64 | 64 | </thead> |
| 65 | 65 | <tbody> |
| 66 | 66 | <tr ng-repeat="ws in workspaces | filter:query | filter:search | filter:{active:archived == false? true : undefined} | orderBy:sortField:reverse" |
| 67 | 67 | selection-model selection-model-selected-class="multi-selected"> |
| 68 | ||
| 69 | <td class="ui-grid-cell-contents active-toggle"> | |
| 70 | <div class="toogle-img-container"> | |
| 71 | <span ng-click="readonlyToggle(ws)" class="active-toggle-container" ng-class="{ disabled:ws.readonly === false }" uib-tooltip="{{(ws.readonly === false) ? 'Workspace with all permissions' : 'Workspace read only'}}" tooltip-placement="right"> | |
| 72 | <img ng-src="{{ (ws.readonly == true) ? 'images/icon-list-confirmed.svg' : 'images/icon-list-notconfirmed.svg'}}" class="confirm-icon" ng-style="{ 'opacity': (ws.readonly === true) ? '1' : '0.7' }" /> | |
| 73 | </span> | |
| 74 | </div> | |
| 75 | </td> | |
| 76 | ||
| 77 | <td class="ui-grid-cell-contents active-toggle"> | |
| 78 | <div class="toogle-img-container"> | |
| 79 | <span ng-click="activeToggle(ws)" class="active-toggle-container" ng-class="{ disabled:ws.active === false }" uib-tooltip="{{(ws.active === true) ? 'Disable workspace' : 'Enable workspace'}}" tooltip-placement="right"> | |
| 80 | <img ng-src="{{ (ws.active) ? 'images/icon-list-confirmed.svg' : 'images/icon-list-notconfirmed.svg'}}" class="confirm-icon" ng-style="{ 'opacity': (ws.active === true) ? '1' : '0.7' }" /> | |
| 81 | </span> | |
| 82 | </div> | |
| 83 | </td> | |
| 84 | 68 | <td class="ui-grid-cell-contents"> |
| 85 | 69 | <span class="onhover upsize" ng-click="dashboardRedirect(ws.name)"> |
| 86 | 70 | <b>{{ws.name}}</b> |
| 87 | 71 | </span> |
| 88 | 72 | </td> |
| 89 | <td class="ui-grid-cell-contents" ng-bind="ws.duration.start_date | amUtc | amDateFormat:'MM/DD/YYYY'"></td> | |
| 90 | <td class="ui-grid-cell-contents" ng-bind="ws.duration.end_date | amUtc | amDateFormat:'MM/DD/YYYY'"></td> | |
| 73 | <td class="ui-grid-cell-contents" ng-if="ws.duration.start_date" ng-bind="ws.duration.start_date | amTimeAgo"></td> | |
| 74 | <td class="ui-grid-cell-contents" ng-if="!ws.duration.start_date">-</td> | |
| 75 | <td class="ui-grid-cell-contents" ng-if="ws.duration.end_date" ng-bind="ws.duration.end_date | amTimeAgo"></td> | |
| 76 | <td class="ui-grid-cell-contents" ng-if="!ws.duration.end_date">-</td> | |
| 91 | 77 | <td class="ui-grid-cell-contents"><a href="#/status/ws/{{ws.name}}">{{objects[ws.name]['total_vulns']}}</a></td> |
| 92 | 78 | <td class="ui-grid-cell-contents"><a href="#/hosts/ws/{{ws.name}}">{{objects[ws.name]['hosts']}}</a></td> |
| 93 | 79 | <td class="ui-grid-cell-contents" ng-bind="objects[ws.name]['services']"></td> |
| 94 | <td class="ui-grid-cell-contents" ng-bind="ws.last_modified | amUtc | amDateFormat:'MM/DD/YYYY'"></td> | |
| 80 | <td class="ui-grid-cell-contents" ng-bind="ws.update_date | amTimeAgo"></td> | |
| 81 | <td class="ui-grid-cell-contents active-toggle"> | |
| 82 | <div class="toogle-img-container"> | |
| 83 | <span ng-click="activeToggle(ws)" class="active-toggle-container" ng-class="{ disabled:ws.active === false }" uib-tooltip="{{(ws.active === true) ? 'Disable workspace' : 'Enable workspace'}}" tooltip-placement="right"> | |
| 84 | <img ng-src="{{ (ws.active) ? 'images/ok-active.svg' : 'images/active.svg'}}" class="confirm-icon" ng-style="{ 'opacity': (ws.active === true) ? '1' : '0.7' }" /> | |
| 85 | </span> | |
| 86 | </div> | |
| 87 | </td> | |
| 88 | <td class="ui-grid-cell-contents active-toggle"> | |
| 89 | <div class="toogle-img-container"> | |
| 90 | <span ng-click="readonlyToggle(ws)" class="active-toggle-container" ng-class="{ disabled:ws.readonly === false }" uib-tooltip="{{(ws.readonly === false) ? 'Workspace with all permissions' : 'Workspace read only'}}" tooltip-placement="right"> | |
| 91 | <img ng-src="{{ (ws.readonly == true) ? 'images/padlock_closed.svg' : 'images/padlock_open.svg'}}" class="confirm-icon" ng-style="{ 'opacity': (ws.readonly === true) ? '1' : '0.7' }" /> | |
| 92 | </span> | |
| 93 | </div> | |
| 94 | </td> | |
| 95 | 95 | </tr> |
| 96 | 96 | </tbody> |
| 97 | 97 | </table><!-- #hosts --> |
| 5 | 5 | import glob |
| 6 | 6 | import socket |
| 7 | 7 | import argparse |
| 8 | import subprocess | |
| 9 | 8 | |
| 10 | from faraday.server import TimerClass | |
| 9 | from alembic.runtime.migration import MigrationContext | |
| 11 | 10 | |
| 12 | try: | |
| 13 | from colorama import init, Fore | |
| 14 | import sqlalchemy | |
| 15 | import faraday.server.config | |
| 16 | import faraday.server.utils.logger | |
| 17 | import faraday.server.web | |
| 18 | from faraday.server.models import db, Workspace | |
| 19 | from faraday.server.utils import daemonize | |
| 20 | from faraday.server.web import app | |
| 21 | from faraday.utils import dependencies | |
| 22 | from faraday.server.config import FARADAY_BASE | |
| 23 | from alembic.script import ScriptDirectory | |
| 24 | from alembic.config import Config | |
| 25 | from alembic.migration import MigrationContext | |
| 26 | except ImportError as ex: | |
| 27 | print(ex) | |
| 28 | print('Missing dependencies.\nPlease execute: pip install -r requirements_server.txt') | |
| 29 | sys.exit(1) | |
| 11 | from colorama import init, Fore | |
| 12 | import sqlalchemy | |
| 13 | import faraday.server.config | |
| 14 | import faraday.server.utils.logger | |
| 15 | import faraday.server.web | |
| 16 | from faraday.server.models import db, Workspace | |
| 17 | from faraday.server.utils import daemonize | |
| 18 | from faraday.server.web import app | |
| 19 | from alembic.script import ScriptDirectory | |
| 20 | from alembic.config import Config | |
| 21 | ||
| 30 | 22 | logger = faraday.server.utils.logger.get_logger(faraday.server.utils.logger.ROOT_LOGGER) |
| 31 | 23 | |
| 32 | 24 | init() |
| 35 | 27 | def setup_environment(check_deps=False): |
| 36 | 28 | # Configuration files generation |
| 37 | 29 | faraday.server.config.copy_default_config_to_local() |
| 38 | if check_deps: | |
| 39 | # Check dependencies | |
| 40 | installed_deps, missing_deps, conflict_deps = dependencies.check_dependencies( | |
| 41 | requirements_file=faraday.server.config.REQUIREMENTS_FILE) | |
| 42 | logger.info("Checking dependencies...") | |
| 43 | if conflict_deps: | |
| 44 | logger.info("Some dependencies are old. Update them with \"pip install -r requirements_server.txt -U\"") | |
| 45 | logger.info("Dependencies met") | |
| 46 | 30 | # Web configuration file generation |
| 47 | 31 | faraday.server.config.gen_web_config() |
| 48 | ||
| 49 | ||
| 50 | def stop_server(port): | |
| 51 | if not daemonize.stop_server(port): | |
| 52 | # Exists with an error if it couldn't close the server | |
| 53 | return False | |
| 54 | else: | |
| 55 | return True | |
| 56 | 32 | |
| 57 | 33 | |
| 58 | 34 | def is_server_running(port): |
| 65 | 41 | |
| 66 | 42 | |
| 67 | 43 | def run_server(args): |
| 68 | web_server = faraday.server.web.WebServer(enable_ssl=args.ssl) | |
| 44 | web_server = faraday.server.web.WebServer() | |
| 69 | 45 | daemonize.create_pid_file(args.port) |
| 70 | 46 | web_server.run() |
| 71 | ||
| 72 | ||
| 73 | def restart_server(args_port): | |
| 74 | devnull = open('/dev/null', 'w') | |
| 75 | if args_port: | |
| 76 | ports = [args_port] | |
| 77 | else: | |
| 78 | ports = daemonize.get_ports_running() | |
| 79 | if not ports: | |
| 80 | logger.error('Faraday Server is not running') | |
| 81 | sys.exit(1) | |
| 82 | for port in ports: | |
| 83 | stop_server(port) | |
| 84 | params = ['/usr/bin/env', 'python3', # TODO que hacemos con esto??? | |
| 85 | os.path.join(faraday.server.config.FARADAY_BASE, __file__), '--no-setup', '--port', str(port)] | |
| 86 | logger.info('Restarting Faraday Server...') | |
| 87 | subprocess.Popen(params, stdout=devnull, stderr=devnull) | |
| 88 | logger.info('Faraday Server is running as a daemon in port {}'.format(port)) | |
| 89 | 47 | |
| 90 | 48 | |
| 91 | 49 | def check_postgresql(): |
| 92 | 50 | with app.app_context(): |
| 93 | 51 | try: |
| 94 | 52 | if not db.session.query(Workspace).count(): |
| 95 | logger.warn('No workspaces found. Remember to execute CouchDB importer') | |
| 53 | logger.warn('No workspaces found') | |
| 96 | 54 | except sqlalchemy.exc.ArgumentError: |
| 97 | 55 | logger.error( |
| 98 | 56 | '\n\b{RED}Please check your PostgreSQL connection string in the file ~/.faraday/config/server.ini on your home directory.{WHITE} \n'.format(RED=Fore.RED, WHITE=Fore.WHITE) |
| 102 | 60 | logger.error( |
| 103 | 61 | '\n\n{RED}Could not connect to PostgreSQL.\n{WHITE}Please check: \n{YELLOW} * if database is running \n * configuration settings are correct. \n\n{WHITE}For first time installations execute{WHITE}: \n\n {GREEN} faraday-manage initdb\n\n'.format(GREEN=Fore.GREEN, YELLOW=Fore.YELLOW, WHITE=Fore.WHITE, RED=Fore.RED)) |
| 104 | 62 | sys.exit(1) |
| 105 | except sqlalchemy.exc.ProgrammingError as e: | |
| 63 | except sqlalchemy.exc.ProgrammingError: | |
| 106 | 64 | logger.error( |
| 107 | '\n\nn{WHITE}Missing migrations, please execute: \n\nfaraday-manage migrate'.format(WHITE=Fore.WHITE, RED=Fore.RED)) | |
| 65 | '\n\nn{WHITE}Missing migrations, please execute: \n\nfaraday-manage migrate'.format(WHITE=Fore.WHITE)) | |
| 108 | 66 | sys.exit(1) |
| 109 | 67 | |
| 110 | 68 | |
| 117 | 75 | with app.app_context(): |
| 118 | 76 | try: |
| 119 | 77 | conn = db.session.connection() |
| 120 | except ImportError as ex: | |
| 78 | except ImportError: | |
| 121 | 79 | if not faraday.server.config.database.connection_string: |
| 122 | 80 | print("\n\nNo database configuration found. Did you execute \"faraday-manage initdb\"? \n\n") |
| 123 | 81 | sys.exit(1) |
| 124 | except sqlalchemy.exc.OperationalError as ex: | |
| 82 | except sqlalchemy.exc.OperationalError: | |
| 125 | 83 | print("Bad Credentials, please check the .faraday/config/server.ini") |
| 126 | 84 | sys.exit(1) |
| 127 | 85 | |
| 129 | 87 | |
| 130 | 88 | current_revision = context.get_current_revision() |
| 131 | 89 | if head_revision != current_revision: |
| 132 | if glob.glob(os.path.join(FARADAY_BASE, 'migrations', 'versions', | |
| 90 | if glob.glob(os.path.join(faraday.server.config.FARADAY_BASE, 'migrations', 'versions', | |
| 133 | 91 | '{}_*.py'.format(current_revision))): |
| 134 | 92 | print('--' * 20) |
| 135 | 93 | print('Missing migrations, please execute: \n\n') |
| 144 | 102 | ) |
| 145 | 103 | |
| 146 | 104 | def main(): |
| 147 | os.chdir(FARADAY_BASE) | |
| 105 | os.chdir(faraday.server.config.FARADAY_BASE) | |
| 148 | 106 | check_alembic_version() |
| 149 | 107 | check_postgresql() |
| 150 | 108 | parser = argparse.ArgumentParser() |
| 151 | parser.add_argument('--ssl', action='store_true', help='enable HTTPS') | |
| 152 | 109 | parser.add_argument('--debug', action='store_true', help='run Faraday Server in debug mode') |
| 153 | parser.add_argument('--start', action='store_true', help='run Faraday Server in background') | |
| 154 | parser.add_argument('--stop', action='store_true', help='stop Faraday Server') | |
| 155 | parser.add_argument('--restart', action='store_true', help='Restart Faraday Server') | |
| 156 | 110 | parser.add_argument('--nodeps', action='store_true', help='Skip dependency check') |
| 157 | 111 | parser.add_argument('--no-setup', action='store_true', help=argparse.SUPPRESS) |
| 158 | 112 | parser.add_argument('--port', help='Overides server.ini port configuration') |
| 163 | 117 | args = parser.parse_args() |
| 164 | 118 | if args.debug or faraday.server.config.faraday_server.debug: |
| 165 | 119 | faraday.server.utils.logger.set_logging_level(faraday.server.config.DEBUG) |
| 166 | if args.restart: | |
| 167 | restart_server(args.port) | |
| 168 | sys.exit() | |
| 169 | if args.stop: | |
| 170 | if args.port: | |
| 171 | sys.exit(0 if stop_server(args.port) else 1) | |
| 172 | else: | |
| 173 | ports = daemonize.get_ports_running() | |
| 174 | if not ports: | |
| 175 | logger.info('Faraday Server is not running') | |
| 176 | exit_code = 0 | |
| 177 | for port in ports: | |
| 178 | exit_code += 0 if stop_server(port) else 1 | |
| 179 | sys.exit(exit_code) | |
| 180 | else: | |
| 181 | if not args.port: | |
| 182 | args.port = '5985' | |
| 120 | args.port = faraday.server.config.faraday_server.port = args.port or \ | |
| 121 | faraday.server.config.faraday_server.port or '5985' | |
| 122 | if args.bind_address: | |
| 123 | faraday.server.config.faraday_server.bind_address = args.bind_address | |
| 124 | ||
| 183 | 125 | sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM) |
| 184 | 126 | result = sock.connect_ex((args.bind_address or faraday.server.config.faraday_server.bind_address, |
| 185 | 127 | int(args.port or faraday.server.config.faraday_server.port))) |
| 188 | 130 | if result == 0: |
| 189 | 131 | logger.error("Faraday Server port in use. Check your processes and run the server again...") |
| 190 | 132 | sys.exit(1) |
| 191 | # Overwrites config option if SSL is set by argument | |
| 192 | if args.ssl: | |
| 193 | faraday.server.config.ssl.enabled = 'true' | |
| 194 | 133 | if not args.no_setup: |
| 195 | 134 | setup_environment(not args.nodeps) |
| 196 | if args.port: | |
| 197 | faraday.server.config.faraday_server.port = args.port | |
| 198 | if args.bind_address: | |
| 199 | faraday.server.config.faraday_server.bind_address = args.bind_address | |
| 200 | 135 | if args.websocket_port: |
| 201 | 136 | faraday.server.config.faraday_server.websocket_port = args.websocket_port |
| 202 | if args.start: | |
| 203 | # Starts a new process on background with --ignore-setup | |
| 204 | # and without --start nor --stop | |
| 205 | devnull = open('/dev/null', 'w') | |
| 206 | params = ['/usr/bin/env', 'python3', os.path.join(faraday.server.config.FARADAY_BASE, __file__), '--no-setup'] | |
| 207 | arg_dict = vars(args) | |
| 208 | for arg in arg_dict: | |
| 209 | if arg not in ["start", "stop"] and arg_dict[arg]: | |
| 210 | params.append('--'+arg) | |
| 211 | if not arg_dict[arg]: | |
| 212 | params.append(arg_dict[arg]) | |
| 213 | logger.info('Faraday Server is running as a daemon') | |
| 214 | subprocess.Popen(params, stdout=devnull, stderr=devnull) | |
| 215 | elif not args.start: | |
| 216 | run_server(args) | |
| 217 | 137 | |
| 218 | if __name__ == '__main__': # TODO Borrar??? | |
| 138 | run_server(args) | |
| 139 | ||
| 140 | ||
| 141 | if __name__ == '__main__': # Don't delete. this is used for dev | |
| 219 | 142 | main() |
| 220 | # I'm Py3⏎ | |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | import hashlib | |
| 7 | import uuid | |
| 8 | import socket | |
| 9 | import struct | |
| 10 | import sys | |
| 11 | import requests | |
| 12 | ||
| 13 | def sha1OfFile(filepath): | |
| 14 | with open(filepath, 'rb') as f: | |
| 15 | return hashlib.sha1(f.read()).hexdigest() | |
| 16 | ||
| 17 | def sha1OfStr(strvalue): | |
| 18 | return hashlib.sha1(strvalue).hexdigest() | |
| 19 | ||
| 20 | def get_hash(parts): | |
| 21 | return hashlib.sha1("._.".join(parts)).hexdigest() | |
| 22 | ||
| 23 | def new_id(): | |
| 24 | return uuid.uuid4() | |
| 25 | ||
| 26 | def get_macaddress(host): | |
| 27 | if sys.platform in ['linux','linux2']: | |
| 28 | with open("/proc/net/arp") as fh: | |
| 29 | for line in fh: | |
| 30 | fields = line.strip().split() | |
| 31 | if fields[0] == host: | |
| 32 | return fields[3] | |
| 33 | else: | |
| 34 | return None | |
| 35 | ||
| 36 | def gateway(): | |
| 37 | ip="" | |
| 38 | if sys.platform in ['linux','linux2']: | |
| 39 | with open("/proc/net/route") as fh: | |
| 40 | for line in fh: | |
| 41 | fields = line.strip().split() | |
| 42 | if fields[1] != '00000000' or not int(fields[3], 16) & 2: | |
| 43 | continue | |
| 44 | ip=socket.inet_ntoa(struct.pack("<L", int(fields[2], 16))) | |
| 45 | mac=get_macaddress(ip) | |
| 46 | return [str(ip),str(mac)] | |
| 47 | elif sys.platform in ['darwin']: | |
| 48 | ||
| 49 | return None | |
| 50 | else: | |
| 51 | return None | |
| 52 | ||
| 53 | ||
| 54 | def checkSSL(uri): | |
| 55 | """ | |
| 56 | This method checks SSL validation | |
| 57 | It only returns True if the certificate is valid | |
| 58 | and the http server returned a 200 OK | |
| 59 | """ | |
| 60 | try: | |
| 61 | res = requests.get(uri, timeout=5) | |
| 62 | return res.ok | |
| 63 | except Exception: | |
| 64 | return False | |
| 65 | ||
| 66 | ||
| 67 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2014 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | import sys | |
| 7 | try: | |
| 8 | from pip import main | |
| 9 | except ImportError: | |
| 10 | # pip 10 compat | |
| 11 | from pip._internal import main | |
| 12 | import pkg_resources | |
| 13 | ||
| 14 | ||
| 15 | def check_dependencies(requirements_file='requirements.txt'): | |
| 16 | dependencies_file = open(requirements_file, 'r') | |
| 17 | filtered_deps = [x for x in dependencies_file.readlines() if not | |
| 18 | x.startswith('git+')] | |
| 19 | ||
| 20 | requirements = list(pkg_resources.parse_requirements(filtered_deps)) | |
| 21 | ||
| 22 | installed = [] | |
| 23 | missing = [] | |
| 24 | conflict = [] | |
| 25 | ||
| 26 | for package in requirements: | |
| 27 | try: | |
| 28 | pkg_resources.working_set.resolve([package]) | |
| 29 | installed += [package] | |
| 30 | except pkg_resources.DistributionNotFound: | |
| 31 | missing += [package.key] | |
| 32 | except pkg_resources.VersionConflict: | |
| 33 | conflict += [package.key] | |
| 34 | ||
| 35 | return installed, missing, conflict | |
| 36 | ||
| 37 | ||
| 38 | def install_packages(packages): | |
| 39 | for package in packages: | |
| 40 | pip_cmd = ['install', package, '-U'] | |
| 41 | if not hasattr(sys, 'real_prefix'): | |
| 42 | pip_cmd.append('--user') | |
| 43 | main(pip_cmd) | |
| 44 | ||
| 45 | ||
| 46 | # I'm Py3 |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | """ | |
| 7 | This module will help us to retrieve information | |
| 8 | about the app state and system information and | |
| 9 | report it to developers to be able to get information about | |
| 10 | a crash or bug | |
| 11 | """ | |
| 12 | import sys | |
| 13 | import traceback | |
| 14 | import threading | |
| 15 | import requests | |
| 16 | import hashlib | |
| 17 | import platform | |
| 18 | import faraday.client.model.guiapi | |
| 19 | from io import StringIO | |
| 20 | from faraday.client.gui.customevents import ShowExceptionCustomEvent | |
| 21 | from faraday.config.configuration import getInstanceConfiguration | |
| 22 | import json | |
| 23 | import time | |
| 24 | ||
| 25 | try: | |
| 26 | import pip | |
| 27 | except ImportError: | |
| 28 | pass | |
| 29 | ||
| 30 | CONF = getInstanceConfiguration() | |
| 31 | ||
| 32 | ||
| 33 | def get_crash_log(): | |
| 34 | pass | |
| 35 | ||
| 36 | def get_system_info(): | |
| 37 | pass | |
| 38 | ||
| 39 | ||
| 40 | def exception_handler(type, value, tb): | |
| 41 | """ | |
| 42 | This is a custom exception handler to replace the python original one. | |
| 43 | The idea is to show the user a dialog with the information and let him/her | |
| 44 | decide wether to send the developers a report with additional info. | |
| 45 | The report is created and sent using the callback. | |
| 46 | Since this handler may be called from threads, the dialog must be created | |
| 47 | using gtk idle_add or signals to avoid issues. | |
| 48 | """ | |
| 49 | ||
| 50 | text = StringIO() | |
| 51 | traceback.print_exception(type, value, tb, file=text) | |
| 52 | error_name = text.getvalue().split('\n')[-2] | |
| 53 | ||
| 54 | excepts = """ | |
| 55 | Traceback: %s | |
| 56 | """ % (text.getvalue() ) | |
| 57 | ||
| 58 | exception_hash = hashlib.sha256(excepts).hexdigest() | |
| 59 | os_dist = " ".join(platform.dist()) | |
| 60 | python_version = platform.python_version() | |
| 61 | faraday_version = CONF.getVersion() | |
| 62 | ||
| 63 | modules_info = "" | |
| 64 | try: | |
| 65 | modules_info = ",".join([ "%s=%s" % (x.key, x.version) | |
| 66 | for x in pip.get_installed_distributions()]) | |
| 67 | except (ImportError, AttributeError): | |
| 68 | pass | |
| 69 | ||
| 70 | ||
| 71 | python_dist = "Python %s \n Modules: [ %s ]" % (python_version, modules_info) | |
| 72 | ||
| 73 | description = """ | |
| 74 | Exception: %s | |
| 75 | Identifier: %s | |
| 76 | Versions: OS: %s, | |
| 77 | Faraday Version: %s | |
| 78 | Python Versions: %s | |
| 79 | """ % (excepts, exception_hash, os_dist, faraday_version, python_dist) | |
| 80 | ||
| 81 | ||
| 82 | ||
| 83 | event = ShowExceptionCustomEvent(description, reportToDevelopers, error_name) | |
| 84 | faraday.client.model.guiapi.postCustomEvent(event) | |
| 85 | text.seek(0) | |
| 86 | text.truncate() | |
| 87 | del text | |
| 88 | ||
| 89 | ||
| 90 | def reportToDevelopers(name=None, *description): | |
| 91 | try: | |
| 92 | ||
| 93 | uri = CONF.getTktPostUri() | |
| 94 | headers = json.loads(CONF.getApiParams()) | |
| 95 | params = json.loads(CONF.getApiParams()) | |
| 96 | ||
| 97 | params['description'] = description[1] | |
| 98 | ||
| 99 | if name is not None: | |
| 100 | params['summary'] = name | |
| 101 | else: | |
| 102 | params['summary'] = 'autoreport %s' % time.time() | |
| 103 | ||
| 104 | resp = requests.post(uri, | |
| 105 | headers = headers, | |
| 106 | data = params, timeout = 1, verify=True) | |
| 107 | ||
| 108 | model.api.devlog("Report sent to faraday server") | |
| 109 | ||
| 110 | except Exception as e: | |
| 111 | model.api.devlog("Error reporting to developers:") | |
| 112 | model.api.devlog(e) | |
| 113 | ||
| 114 | def installThreadExcepthook(): | |
| 115 | """ | |
| 116 | Workaround for sys.excepthook thread bug from | |
| 117 | http://spyced.blogspot.com/2007/06/workaround-for-sysexcepthook-bug.html | |
| 118 | (https://sourceforge.net/tracker/?func=detail&atid=105470&aid=1230540&group_id=5470). | |
| 119 | Call once from __main__ before creating any threads. | |
| 120 | If using psyco, call psyco.cannotcompile(threading.Thread.run) | |
| 121 | since this replaces a new-style class method. | |
| 122 | """ | |
| 123 | init_old = threading.Thread.__init__ | |
| 124 | def init(self, *args, **kwargs): | |
| 125 | init_old(self, *args, **kwargs) | |
| 126 | run_old = self.run | |
| 127 | def run_with_except_hook(*args, **kw): | |
| 128 | try: | |
| 129 | run_old(*args, **kw) | |
| 130 | except Exception as e: | |
| 131 | if isinstance(e, (KeyboardInterrupt, SystemExit)): | |
| 132 | raise | |
| 133 | sys.excepthook(*sys.exc_info()) | |
| 134 | self.run = run_with_except_hook | |
| 135 | threading.Thread.__init__ = init | |
| 136 | ||
| 137 | ||
| 138 | # I'm Py3 |
| 0 | """Flask plugin. Includes a path helper that allows you to pass a view | |
| 1 | function to `path`. Inspects URL rules and view docstrings. | |
| 2 | ||
| 3 | Passing a view function:: | |
| 4 | ||
| 5 | from flask import Flask | |
| 6 | ||
| 7 | app = Flask(__name__) | |
| 8 | ||
| 9 | @app.route('/gists/<gist_id>') | |
| 10 | def gist_detail(gist_id): | |
| 11 | '''Gist detail view. | |
| 12 | --- | |
| 13 | x-extension: metadata | |
| 14 | get: | |
| 15 | responses: | |
| 16 | 200: | |
| 17 | schema: | |
| 18 | $ref: '#/definitions/Gist' | |
| 19 | ''' | |
| 20 | return 'detail for gist {}'.format(gist_id) | |
| 21 | ||
| 22 | with app.test_request_context(): | |
| 23 | spec.path(view=gist_detail) | |
| 24 | print(spec.to_dict()['paths']) | |
| 25 | # {'/gists/{gist_id}': {'get': {'responses': {200: {'schema': {'$ref': '#/definitions/Gist'}}}}, | |
| 26 | # 'x-extension': 'metadata'}} | |
| 27 | ||
| 28 | Passing a method view function:: | |
| 29 | ||
| 30 | from flask import Flask | |
| 31 | from flask.views import MethodView | |
| 32 | ||
| 33 | app = Flask(__name__) | |
| 34 | ||
| 35 | class GistApi(MethodView): | |
| 36 | '''Gist API. | |
| 37 | --- | |
| 38 | x-extension: metadata | |
| 39 | ''' | |
| 40 | def get(self): | |
| 41 | '''Gist view | |
| 42 | --- | |
| 43 | responses: | |
| 44 | 200: | |
| 45 | schema: | |
| 46 | $ref: '#/definitions/Gist' | |
| 47 | ''' | |
| 48 | pass | |
| 49 | ||
| 50 | def post(self): | |
| 51 | pass | |
| 52 | ||
| 53 | method_view = GistApi.as_view('gists') | |
| 54 | app.add_url_rule("/gists", view_func=method_view) | |
| 55 | with app.test_request_context(): | |
| 56 | spec.path(view=method_view) | |
| 57 | ||
| 58 | # Alternatively, pass in an app object as a kwarg | |
| 59 | # spec.path(view=method_view, app=app) | |
| 60 | ||
| 61 | print(spec.to_dict()['paths']) | |
| 62 | # {'/gists': {'get': {'responses': {200: {'schema': {'$ref': '#/definitions/Gist'}}}}, | |
| 63 | # 'post': {}, | |
| 64 | # 'x-extension': 'metadata'}} | |
| 65 | ||
| 66 | ||
| 67 | """ | |
| 68 | import re | |
| 69 | ||
| 70 | from flask import current_app | |
| 71 | ||
| 72 | from apispec import BasePlugin, yaml_utils | |
| 73 | from apispec.exceptions import APISpecError | |
| 74 | ||
| 75 | from flask.views import MethodView | |
| 76 | ||
| 77 | from faraday.server.api.base import GenericView | |
| 78 | ||
| 79 | RE_URL = re.compile(r"<(?:[^:<>]+:)?([^<>]+)>") | |
| 80 | ||
| 81 | ||
| 82 | class FaradayAPIPlugin(BasePlugin): | |
| 83 | """APISpec plugin for Flask""" | |
| 84 | ||
| 85 | @staticmethod | |
| 86 | def flaskpath2openapi(path): | |
| 87 | """Convert a Flask URL rule to an OpenAPI-compliant path. | |
| 88 | ||
| 89 | :param str path: Flask path template. | |
| 90 | """ | |
| 91 | return RE_URL.sub(r"{\1}", path) | |
| 92 | ||
| 93 | @staticmethod | |
| 94 | def _rule_for_view(view, app=None): | |
| 95 | if app is None: | |
| 96 | app = current_app | |
| 97 | ||
| 98 | view_funcs = app.view_functions | |
| 99 | endpoint = None | |
| 100 | for ept, view_func in view_funcs.items(): | |
| 101 | if view_func == view: | |
| 102 | endpoint = ept | |
| 103 | if not endpoint: | |
| 104 | raise APISpecError(f"Could not find endpoint for view {view}") | |
| 105 | ||
| 106 | # WARNING: Assume 1 rule per view function for now | |
| 107 | rule = app.url_map._rules_by_endpoint[endpoint][0] | |
| 108 | return rule | |
| 109 | ||
| 110 | def path_helper(self, operations, *, view, app=None, **kwargs): | |
| 111 | """Path helper that allows passing a Flask view function.""" | |
| 112 | rule = self._rule_for_view(view, app=app) | |
| 113 | if '.' not in view.__qualname__: | |
| 114 | return self.flaskpath2openapi(rule.rule) | |
| 115 | view_name = view.__qualname__.split('.')[1] | |
| 116 | if view.__closure__ is None: | |
| 117 | return self.flaskpath2openapi(rule.rule) | |
| 118 | view_instance = next(cl.cell_contents for cl in view.__closure__ if isinstance(cl.cell_contents, GenericView)) | |
| 119 | if view_name in ['get', 'put', 'post', 'delete']: | |
| 120 | ||
| 121 | if view.__doc__: | |
| 122 | if hasattr(view_instance.model_class, "__name__"): | |
| 123 | class_model = view_instance.model_class.__name__ | |
| 124 | else: | |
| 125 | class_model = 'No name' | |
| 126 | operations[view_name] = yaml_utils.load_yaml_from_docstring( | |
| 127 | view.__doc__.format(schema_class=view_instance._get_schema_class().__name__, class_model=class_model, tag_name=class_model) | |
| 128 | ) | |
| 129 | ||
| 130 | if hasattr(view, "view_class") and issubclass(view.view_class, MethodView): | |
| 131 | for method in view.methods: | |
| 132 | if method in rule.methods: | |
| 133 | method_name = method.lower() | |
| 134 | method = getattr(view.view_class, method_name) | |
| 135 | operations[method_name] = yaml_utils.load_yaml_from_docstring( | |
| 136 | method.__doc__ | |
| 137 | ) | |
| 138 | return self.flaskpath2openapi(rule.rule) |
| 0 | """ | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | """ | |
| 6 | import sys | |
| 7 | ||
| 8 | def query_yes_no(question, default="yes"): | |
| 9 | """Ask a yes/no question via raw_input() and return their answer. | |
| 10 | ||
| 11 | "question" is a string that is presented to the user. | |
| 12 | "default" is the presumed answer if the user just hits <Enter>. | |
| 13 | It must be "yes" (the default), "no" or None (meaning | |
| 14 | an answer is required of the user). | |
| 15 | ||
| 16 | The "answer" return value is one of "yes" or "no". | |
| 17 | """ | |
| 18 | valid = {"yes": True, "y": True, "ye": True, | |
| 19 | "no": False, "n": False} | |
| 20 | if default is None: | |
| 21 | prompt = " [y/n] " | |
| 22 | elif default == "yes": | |
| 23 | prompt = " [Y/n] " | |
| 24 | elif default == "no": | |
| 25 | prompt = " [y/N] " | |
| 26 | else: | |
| 27 | raise ValueError("invalid default answer: '%s'" % default) | |
| 28 | ||
| 29 | while True: | |
| 30 | sys.stdout.write(question + prompt) | |
| 31 | choice = input().lower() | |
| 32 | if default is not None and choice == '': | |
| 33 | return valid[default] | |
| 34 | elif choice in valid: | |
| 35 | return valid[choice] | |
| 36 | else: | |
| 37 | sys.stdout.write("Please respond with 'yes' or 'no' " | |
| 38 | "(or 'y' or 'n').\n") | |
| 39 | ||
| 40 | ||
| 41 | ||
| 42 | # I'm Py3 |
| 0 | #!/usr/bin/env python | |
| 1 | ||
| 2 | # Faraday Penetration Test IDE | |
| 3 | # Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | # See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | # Developers: the code for faraday-server is located in faraday/start_server.py | |
| 7 | from __future__ import absolute_import | |
| 8 | ||
| 9 | from __future__ import print_function | |
| 10 | import sys | |
| 11 | ||
| 12 | print( | |
| 13 | "From Faraday v3.8 onwards, running ./faraday-server.py doesn't work " | |
| 14 | "anymore. You should run faraday-server instead.\n\n" | |
| 15 | ||
| 16 | "This allows users to put the faraday-server script in any directory " | |
| 17 | "(like /usr/local/bin) and to run it from anywhere, with no need of " | |
| 18 | "switching to the Faraday directory.", | |
| 19 | ||
| 20 | file=sys.stderr | |
| 21 | ) | |
| 22 | ||
| 23 | sys.exit(1) | |
| 24 | ||
| 25 | ||
| 26 | # I'm Py3 |
| 0 | # -*- mode: python ; coding: utf-8 -*- | |
| 1 | ||
| 2 | block_cipher = None | |
| 3 | ||
| 4 | ||
| 5 | a = Analysis(['faraday/client/bin/fplugin.py'], | |
| 6 | pathex=['/Users/lcubo/workspace/faraday'], | |
| 7 | binaries=[], | |
| 8 | datas=[('faraday', 'faraday')], | |
| 9 | hiddenimports=[], | |
| 10 | hookspath=[], | |
| 11 | runtime_hooks=[], | |
| 12 | excludes=[], | |
| 13 | win_no_prefer_redirects=False, | |
| 14 | win_private_assemblies=False, | |
| 15 | cipher=block_cipher, | |
| 16 | noarchive=False) | |
| 17 | pyz = PYZ(a.pure, a.zipped_data, | |
| 18 | cipher=block_cipher) | |
| 19 | exe = EXE(pyz, | |
| 20 | a.scripts, | |
| 21 | a.binaries, | |
| 22 | a.zipfiles, | |
| 23 | a.datas, | |
| 24 | [], | |
| 25 | name='fplugin', | |
| 26 | debug=False, | |
| 27 | bootloader_ignore_signals=False, | |
| 28 | strip=False, | |
| 29 | upx=True, | |
| 30 | runtime_tmpdir=None, | |
| 31 | console=False ) | |
| 32 | app = BUNDLE(exe, | |
| 33 | name='fplugin.app', | |
| 34 | icon=None, | |
| 35 | bundle_identifier=None) |
| 0 | # -*- mode: python ; coding: utf-8 -*- | |
| 1 | ||
| 2 | block_cipher = None | |
| 3 | ||
| 4 | ||
| 5 | a = Analysis(['faraday/manage.py'], | |
| 6 | pathex=['/home/faraday/faraday'], | |
| 7 | binaries=[], | |
| 8 | datas=[('faraday', 'faraday')], | |
| 9 | hiddenimports=['sqlalchemy.sql.default_comparator', 'backports.functools_lru_cache', 'depot.io.local', 'passlib.handlers.bcrypt', 'passlib.handlers.pbkdf2', 'passlib.handlers.misc', 'passlib.handlers.sha2_crypt', 'passlib.handlers.digests', 'text_unidecode'], | |
| 10 | hookspath=[], | |
| 11 | runtime_hooks=[], | |
| 12 | excludes=[], | |
| 13 | win_no_prefer_redirects=False, | |
| 14 | win_private_assemblies=False, | |
| 15 | cipher=block_cipher, | |
| 16 | noarchive=False) | |
| 17 | pyz = PYZ(a.pure, a.zipped_data, | |
| 18 | cipher=block_cipher) | |
| 19 | exe = EXE(pyz, | |
| 20 | a.scripts, | |
| 21 | a.binaries, | |
| 22 | a.zipfiles, | |
| 23 | a.datas, | |
| 24 | [], | |
| 25 | name='manage', | |
| 26 | debug=False, | |
| 27 | bootloader_ignore_signals=False, | |
| 28 | strip=False, | |
| 29 | upx=True, | |
| 30 | runtime_tmpdir=None, | |
| 31 | console=False ) |
| 0 | #!/usr/bin/env python3 | |
| 1 | ||
| 2 | # Faraday Penetration Test IDE | |
| 3 | # Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | # See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | ''' | |
| 7 | Internal script used to detect merge conflicts to branch with | |
| 8 | our propiertary code. Not useful if you don't have access to | |
| 9 | the code of Faraday Professional or Faraday Corporate | |
| 10 | ''' | |
| 11 | from __future__ import absolute_import | |
| 12 | from __future__ import print_function | |
| 13 | ||
| 14 | import os | |
| 15 | import re | |
| 16 | import sys | |
| 17 | import subprocess | |
| 18 | import logging | |
| 19 | import argparse | |
| 20 | from contextlib import contextmanager | |
| 21 | from tempfile import mkdtemp | |
| 22 | from shutil import rmtree | |
| 23 | ||
| 24 | VERSIONS = ['white', 'pink', 'black'] | |
| 25 | BRANCH_FORMAT = 'origin/{}/dev' | |
| 26 | ||
| 27 | @contextmanager | |
| 28 | def chdir(directory): | |
| 29 | """Context manager to work in the specified directory""" | |
| 30 | current = os.getcwd() | |
| 31 | os.chdir(directory) | |
| 32 | yield | |
| 33 | os.chdir(current) | |
| 34 | ||
| 35 | @contextmanager | |
| 36 | def temp_worktree(branch=None): | |
| 37 | """Context manager that creates a temporal worktree and | |
| 38 | changes the current working directory, and when finished | |
| 39 | removes the dir and runs a git worktree prune""" | |
| 40 | directory = mkdtemp() | |
| 41 | cmd = ["git", "worktree", "add", directory] | |
| 42 | if branch is not None: | |
| 43 | cmd.append(branch) | |
| 44 | subprocess.check_output(cmd) | |
| 45 | with chdir(directory): | |
| 46 | yield | |
| 47 | rmtree(directory) | |
| 48 | subprocess.check_output(['git', 'worktree', 'prune']) | |
| 49 | ||
| 50 | def check_merge(dst_branch, cur_branch='HEAD'): | |
| 51 | """Return a boolean indicating if the merge from cur_branch | |
| 52 | to dst_branch will merge without causing conflicts that need | |
| 53 | manual resolution""" | |
| 54 | # https://stackoverflow.com/questions/501407/is-there-a-git-merge-dry-run-option | |
| 55 | with temp_worktree(dst_branch): | |
| 56 | exit_code = subprocess.call( | |
| 57 | ['git', 'merge', '--no-commit', '--no-ff', cur_branch]) | |
| 58 | # Use call because it will have exit code 128 when there is nothing to | |
| 59 | # abort | |
| 60 | subprocess.call(['git', 'merge', '--abort']) | |
| 61 | return exit_code == 0 | |
| 62 | ||
| 63 | ||
| 64 | def get_current_branch(): | |
| 65 | """Return the current branch of the current workspace""" | |
| 66 | # https://stackoverflow.com/questions/6245570/how-to-get-the-current-branch-name-in-git | |
| 67 | branch = subprocess.check_output( | |
| 68 | ['git', 'rev-parse', '--abbrev-ref', 'HEAD']).decode().strip() | |
| 69 | if branch == 'HEAD': | |
| 70 | # Probably in a detached state inside gitlab CI | |
| 71 | # Fallback to the branch name defined in an env var | |
| 72 | branch = 'origin/' + os.environ['CI_COMMIT_REF_NAME'] | |
| 73 | return branch | |
| 74 | ||
| 75 | ||
| 76 | def branch_exists(branch_name): | |
| 77 | exit_code = subprocess.call( | |
| 78 | ['git', 'rev-parse', '--verify', '--quiet', branch_name]) | |
| 79 | if exit_code == 0: | |
| 80 | return True | |
| 81 | elif exit_code == 1: | |
| 82 | return False | |
| 83 | else: | |
| 84 | raise ValueError('Error when checking for branch existence') | |
| 85 | ||
| 86 | ||
| 87 | def version_of_branch(branch_name): | |
| 88 | """ | |
| 89 | >>> version_of_branch('tkt_white_this_is_not_a_pink_branch') | |
| 90 | 'white' | |
| 91 | """ | |
| 92 | positions = {version: branch_name.find(version) | |
| 93 | for version in VERSIONS} | |
| 94 | if all((pos < 0) for pos in positions.values()): | |
| 95 | # The branch name doesn't contain white, pink or black | |
| 96 | return | |
| 97 | positions = {version: pos | |
| 98 | for (version, pos) in positions.items() | |
| 99 | if pos >= 0} | |
| 100 | return min(positions.keys(), key=positions.get) | |
| 101 | ||
| 102 | ||
| 103 | def main(branch): | |
| 104 | logging.getLogger().setLevel(getattr(logging, args.log_level.upper())) | |
| 105 | logger = logging # TODO FIXME | |
| 106 | logger.info('Checking merge conflicts for branch %s', branch) | |
| 107 | version = version_of_branch(branch) | |
| 108 | if version is None: | |
| 109 | logger.error('Unknown version name. Exiting') | |
| 110 | sys.exit(-1) | |
| 111 | ||
| 112 | versions_to_test = VERSIONS[VERSIONS.index(version):] | |
| 113 | branches_to_test = [] | |
| 114 | for target_version in versions_to_test: | |
| 115 | overriden_branch = branch.replace(version, target_version) | |
| 116 | if target_version != version and \ | |
| 117 | branch_exists(overriden_branch): | |
| 118 | branches_to_test.append(overriden_branch) | |
| 119 | # break # Uncomment if want to cut the checker on merging to black if has overridden pink branch | |
| 120 | else: | |
| 121 | branches_to_test.append(BRANCH_FORMAT.format(target_version)) | |
| 122 | ||
| 123 | logging.info('Testing merges in branches %s' % branches_to_test) | |
| 124 | ||
| 125 | success = True | |
| 126 | cur_branch = branch | |
| 127 | for dst_branch in branches_to_test: | |
| 128 | result = check_merge(dst_branch, cur_branch) | |
| 129 | if result: | |
| 130 | logger.info("Merge into %s succeeded!", dst_branch) | |
| 131 | else: | |
| 132 | success = False | |
| 133 | logger.error("Merge into %s failed :(", dst_branch) | |
| 134 | print() | |
| 135 | print() | |
| 136 | ||
| 137 | if not success: | |
| 138 | sys.exit(1) | |
| 139 | ||
| 140 | ||
| 141 | if __name__ == "__main__": | |
| 142 | parser = argparse.ArgumentParser() | |
| 143 | parser.add_argument('-b', '--branch', default=get_current_branch()) | |
| 144 | parser.add_argument('-l', '--log-level', default='debug') | |
| 145 | args = parser.parse_args() | |
| 146 | main(args.branch) | |
| 147 | ||
| 148 | ||
| 149 | # I'm Py3 |
| 0 | #!/usr/bin/env python3 | |
| 1 | ||
| 2 | # Faraday Penetration Test IDE | |
| 3 | # Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | # See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | ''' | |
| 7 | Internal script used to detect merge conflicts to branch with | |
| 8 | our propiertary code. Not useful if you don't have access to | |
| 9 | the code of Faraday Professional or Faraday Corporate | |
| 10 | ''' | |
| 11 | from __future__ import absolute_import | |
| 12 | from __future__ import print_function | |
| 13 | ||
| 14 | import os | |
| 15 | import re | |
| 16 | import sys | |
| 17 | import subprocess | |
| 18 | import logging | |
| 19 | import argparse | |
| 20 | from contextlib import contextmanager | |
| 21 | from tempfile import mkdtemp | |
| 22 | from shutil import rmtree | |
| 23 | ||
| 24 | VERSIONS = ['white', 'pink', 'black'] | |
| 25 | BRANCH_FORMAT = 'origin/{}3/dev' | |
| 26 | ||
| 27 | @contextmanager | |
| 28 | def chdir(directory): | |
| 29 | """Context manager to work in the specified directory""" | |
| 30 | current = os.getcwd() | |
| 31 | os.chdir(directory) | |
| 32 | yield | |
| 33 | os.chdir(current) | |
| 34 | ||
| 35 | @contextmanager | |
| 36 | def temp_worktree(branch=None): | |
| 37 | """Context manager that creates a temporal worktree and | |
| 38 | changes the current working directory, and when finished | |
| 39 | removes the dir and runs a git worktree prune""" | |
| 40 | directory = mkdtemp() | |
| 41 | cmd = ["git", "worktree", "add", directory] | |
| 42 | if branch is not None: | |
| 43 | cmd.append(branch) | |
| 44 | subprocess.check_output(cmd) | |
| 45 | with chdir(directory): | |
| 46 | yield | |
| 47 | rmtree(directory) | |
| 48 | subprocess.check_output(['git', 'worktree', 'prune']) | |
| 49 | ||
| 50 | def check_merge(dst_branch, cur_branch='HEAD'): | |
| 51 | """Return a boolean indicating if the merge from cur_branch | |
| 52 | to dst_branch will merge without causing conflicts that need | |
| 53 | manual resolution""" | |
| 54 | # https://stackoverflow.com/questions/501407/is-there-a-git-merge-dry-run-option | |
| 55 | with temp_worktree(dst_branch): | |
| 56 | exit_code = subprocess.call( | |
| 57 | ['git', 'merge', '--no-commit', '--no-ff', cur_branch]) | |
| 58 | # Use call because it will have exit code 128 when there is nothing to | |
| 59 | # abort | |
| 60 | subprocess.call(['git', 'merge', '--abort']) | |
| 61 | return exit_code == 0 | |
| 62 | ||
| 63 | ||
| 64 | def get_current_branch(): | |
| 65 | """Return the current branch of the current workspace""" | |
| 66 | # https://stackoverflow.com/questions/6245570/how-to-get-the-current-branch-name-in-git | |
| 67 | branch = subprocess.check_output( | |
| 68 | ['git', 'rev-parse', '--abbrev-ref', 'HEAD']).decode().strip() | |
| 69 | if branch == 'HEAD': | |
| 70 | # Probably in a detached state inside gitlab CI | |
| 71 | # Fallback to the branch name defined in an env var | |
| 72 | branch = 'origin/' + os.environ['CI_COMMIT_REF_NAME'] | |
| 73 | return branch | |
| 74 | ||
| 75 | ||
| 76 | def branch_exists(branch_name): | |
| 77 | exit_code = subprocess.call( | |
| 78 | ['git', 'rev-parse', '--verify', '--quiet', branch_name]) | |
| 79 | if exit_code == 0: | |
| 80 | return True | |
| 81 | elif exit_code == 1: | |
| 82 | return False | |
| 83 | else: | |
| 84 | raise ValueError('Error when checking for branch existence') | |
| 85 | ||
| 86 | ||
| 87 | def version_of_branch(branch_name): | |
| 88 | """ | |
| 89 | >>> version_of_branch('tkt_white_this_is_not_a_pink_branch') | |
| 90 | 'white' | |
| 91 | """ | |
| 92 | positions = {version: branch_name.find(version) | |
| 93 | for version in VERSIONS} | |
| 94 | if all((pos < 0) for pos in positions.values()): | |
| 95 | # The branch name doesn't contain white, pink or black | |
| 96 | return | |
| 97 | positions = {version: pos | |
| 98 | for (version, pos) in positions.items() | |
| 99 | if pos >= 0} | |
| 100 | return min(positions.keys(), key=positions.get) | |
| 101 | ||
| 102 | ||
| 103 | def main(branch): | |
| 104 | logging.getLogger().setLevel(getattr(logging, args.log_level.upper())) | |
| 105 | logger = logging # TODO FIXME | |
| 106 | logger.info('Checking merge conflicts for branch %s', branch) | |
| 107 | version = version_of_branch(branch) | |
| 108 | if version is None: | |
| 109 | logger.error('Unknown version name. Exiting') | |
| 110 | sys.exit(-1) | |
| 111 | ||
| 112 | versions_to_test = VERSIONS[VERSIONS.index(version):] | |
| 113 | branches_to_test = [] | |
| 114 | for target_version in versions_to_test: | |
| 115 | overriden_branch = branch.replace(version, target_version) | |
| 116 | if target_version != version and \ | |
| 117 | branch_exists(overriden_branch): | |
| 118 | branches_to_test.append(overriden_branch) | |
| 119 | # break # Uncomment if want to cut the checker on merging to black if has overridden pink branch | |
| 120 | else: | |
| 121 | branches_to_test.append(BRANCH_FORMAT.format(target_version)) | |
| 122 | ||
| 123 | logging.info('Testing merges in branches %s' % branches_to_test) | |
| 124 | ||
| 125 | success = True | |
| 126 | cur_branch = branch | |
| 127 | for dst_branch in branches_to_test: | |
| 128 | result = check_merge(dst_branch, cur_branch) | |
| 129 | if result: | |
| 130 | logger.info("Merge into %s succeeded!", dst_branch) | |
| 131 | else: | |
| 132 | success = False | |
| 133 | logger.error("Merge into %s failed :(", dst_branch) | |
| 134 | print() | |
| 135 | print() | |
| 136 | ||
| 137 | if not success: | |
| 138 | sys.exit(1) | |
| 139 | ||
| 140 | ||
| 141 | if __name__ == "__main__": | |
| 142 | parser = argparse.ArgumentParser() | |
| 143 | parser.add_argument('-b', '--branch', default=get_current_branch()) | |
| 144 | parser.add_argument('-l', '--log-level', default='debug') | |
| 145 | args = parser.parse_args() | |
| 146 | main(args.branch) | |
| 147 | ||
| 148 | ||
| 149 | # I'm Py3 |
| 0 | #!/usr/bin/env python3 | |
| 1 | ||
| 2 | # Faraday Penetration Test IDE | |
| 3 | # Copyright (C) 2019 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | # See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | """ | |
| 7 | Internal script used to detect if the auto-claimer v3 python files | |
| 8 | are actually executable with python3 | |
| 9 | """ | |
| 10 | from __future__ import absolute_import | |
| 11 | from __future__ import print_function | |
| 12 | from __future__ import division | |
| 13 | ||
| 14 | import argparse | |
| 15 | import logging | |
| 16 | import os | |
| 17 | import re | |
| 18 | ||
| 19 | from pylint import epylint as lint | |
| 20 | ||
| 21 | BLACK_LIST = ["build"] | |
| 22 | ||
| 23 | ||
| 24 | # Pylint code Message Final return code | |
| 25 | # 0 Ok 0 | |
| 26 | # 1 Fatal message issued 1 | |
| 27 | # 2 Error message issued 0 | |
| 28 | # 4 Warning message issued 0 | |
| 29 | # 8 Refactor message issued 0 | |
| 30 | # 16 Convention message issued 0 | |
| 31 | # 32 Usage error 1 | |
| 32 | OK = 0 | |
| 33 | FATAL = 1 | |
| 34 | ERROR = 2 | |
| 35 | WARNING = 4 | |
| 36 | REFACTOR = 8 | |
| 37 | CONVENTION = 16 | |
| 38 | USAGE = 32 | |
| 39 | ||
| 40 | PY3_MSG = r"# I'm Py3" | |
| 41 | ||
| 42 | ||
| 43 | def find_py3_msg(path): | |
| 44 | with open(path) as origin_file: | |
| 45 | for line in origin_file: | |
| 46 | line = re.search(PY3_MSG, line) | |
| 47 | if line: | |
| 48 | return True | |
| 49 | return False | |
| 50 | ||
| 51 | class Analyser: | |
| 52 | ||
| 53 | def __init__(self): | |
| 54 | logging.getLogger().setLevel(getattr(logging, args.log_level.upper())) | |
| 55 | self.logger = logging # TODO FIXME | |
| 56 | ||
| 57 | def analyse_file(self, path): | |
| 58 | if path[-3:] != ".py": | |
| 59 | return 0, 0, [], [] | |
| 60 | ||
| 61 | find_py3_ok_result = find_py3_msg(path) | |
| 62 | lint_ok_result = lint.lint(path, ["--py3k"]) in [OK] | |
| 63 | error_list = [] | |
| 64 | if find_py3_ok_result and not lint_ok_result: | |
| 65 | self.logger.error("The auto-claimed python file {path} as python is not python3".format(path=path)) | |
| 66 | error_list.append(path) | |
| 67 | if not find_py3_ok_result and lint_ok_result: | |
| 68 | self.logger.info("The file {path} is python3, adding the signature comment in the last line".format(path=path)) | |
| 69 | with open(path,"a+") as py3_file: | |
| 70 | py3_file.writelines(["\n\n", PY3_MSG, "\n"]) | |
| 71 | ||
| 72 | if not lint_ok_result: | |
| 73 | self.logger.info("The file {path} is python2".format(path=path)) | |
| 74 | return 1 if lint_ok_result else 0, 1, [], error_list | |
| 75 | ||
| 76 | def analyse_folder(self, parent_path): | |
| 77 | are3, total, strs, error_files = 0, 0, [], [] | |
| 78 | for subpath in os.listdir(parent_path): | |
| 79 | if subpath[0] != '.' and subpath not in BLACK_LIST: | |
| 80 | path = os.path.join(parent_path, subpath) | |
| 81 | s_are3, s_total, s_strs, s_error_files = \ | |
| 82 | self.analyse_folder(path) \ | |
| 83 | if not os.path.isfile(path) \ | |
| 84 | else self.analyse_file(path) | |
| 85 | are3 += s_are3 | |
| 86 | total += s_total | |
| 87 | strs.extend(s_strs) | |
| 88 | error_files.extend(s_error_files) | |
| 89 | if are3 != total and total > 0: | |
| 90 | prtg = 100.0*are3/total | |
| 91 | strs.append('Analysed {path}, {are3}/{total} {prtg}%' | |
| 92 | .format(path=parent_path, are3=are3, total=total, prtg=prtg)) | |
| 93 | return are3, total, strs, error_files | |
| 94 | ||
| 95 | def run(self): | |
| 96 | are3, total, strs, error_files = self.analyse_folder(os.getcwd()) | |
| 97 | for s in strs: | |
| 98 | self.logger.info(s) | |
| 99 | if len(error_files) > 0: | |
| 100 | for error_file in error_files: | |
| 101 | self.logger.error("The auto-claimed python file {path} as python is not python3".format(path=error_file)) | |
| 102 | raise Exception("One or more auto-claimed python file(s) as python is(are) not python3") | |
| 103 | if are3 == total: | |
| 104 | print("100% coverage") | |
| 105 | ||
| 106 | ||
| 107 | def main(filename): | |
| 108 | PYTLINT = ".pylintrc" | |
| 109 | RENAMED = ".to_be_renamed" | |
| 110 | os.rename(PYTLINT, RENAMED) | |
| 111 | ||
| 112 | if filename: | |
| 113 | import sys | |
| 114 | sys.stdout = open(filename, 'w') | |
| 115 | try: | |
| 116 | Analyser().run() | |
| 117 | finally: | |
| 118 | os.rename(RENAMED, PYTLINT) | |
| 119 | ||
| 120 | if __name__ == "__main__": | |
| 121 | parser = argparse.ArgumentParser() | |
| 122 | parser.add_argument('-c', '--only-coverage', default=False) | |
| 123 | parser.add_argument('-l', '--log-level', default='debug') | |
| 124 | parser.add_argument('-o', '--output-file', dest='filename', default=None) | |
| 125 | args = parser.parse_args() | |
| 126 | import time | |
| 127 | t = time.time() | |
| 128 | main(args.filename) | |
| 129 | print(t - time.time()) | |
| 130 | ||
| 131 | ||
| 132 | # pylint --py3k⏎ |
| 0 | { overlays ? [ ], ... }@args: | |
| 1 | let | |
| 2 | pypi2nixOverlay = self: super: { | |
| 3 | python3 = super.python3.override { inherit packageOverrides; }; | |
| 4 | }; | |
| 5 | ||
| 6 | nixpkgs = builtins.fetchTarball { | |
| 7 | url = | |
| 8 | "https://github.com/nixos/nixpkgs/archive/91c43a9dc822da30cf3cd2908891edddcea482f2.tar.gz"; | |
| 9 | sha256 = "06ikg56ifx57b0n9yqa9szipbsswn98gz5zszi8nsqd7d4p4l3y4"; | |
| 10 | }; | |
| 11 | ||
| 12 | packageOverrides = self: super: { | |
| 13 | ||
| 14 | faradaysec = self.callPackage ./packages/faradaysec.nix { }; | |
| 15 | ||
| 16 | flask = self.callPackage ./packages/flask.nix { }; | |
| 17 | ||
| 18 | flask-classful = self.callPackage ./packages/flask-classful.nix { }; | |
| 19 | ||
| 20 | flask-security = self.callPackage ./packages/flask-security.nix { }; | |
| 21 | ||
| 22 | flask-babelex = self.callPackage ./packages/flask-babelex.nix { }; | |
| 23 | ||
| 24 | pgcli = self.callPackage ./packages/pgcli.nix { }; | |
| 25 | ||
| 26 | webargs = self.callPackage ./packages/webargs.nix { }; | |
| 27 | ||
| 28 | marshmallow-sqlalchemy = | |
| 29 | self.callPackage ./packages/marshmallow-sqlalchemy.nix { }; | |
| 30 | ||
| 31 | filteralchemy-fork = self.callPackage ./packages/filteralchemy-fork.nix { }; | |
| 32 | ||
| 33 | filedepot = self.callPackage ./packages/filedepot.nix { }; | |
| 34 | ||
| 35 | nplusone = self.callPackage ./packages/nplusone.nix { }; | |
| 36 | ||
| 37 | flask-restless = self.callPackage ./packages/flask-restless.nix { }; | |
| 38 | ||
| 39 | mimerender = self.callPackage ./packages/mimerender.nix { }; | |
| 40 | ||
| 41 | syslog-rfc5424-formatter = | |
| 42 | self.callPackage ./packages/syslog-rfc5424-formatter.nix { }; | |
| 43 | ||
| 44 | simplekv = self.callPackage ./packages/simplekv.nix { }; | |
| 45 | ||
| 46 | flask-kvsession-fork = | |
| 47 | self.callPackage ./packages/flask-kvsession-fork.nix { }; | |
| 48 | ||
| 49 | faraday-plugins = self.callPackage ./packages/faraday-plugins.nix { }; | |
| 50 | ||
| 51 | apispec-webframeworks = | |
| 52 | self.callPackage ./packages/apispec-webframeworks.nix { }; | |
| 53 | ||
| 54 | pytest-factoryboy = self.callPackage ./packages/pytest-factoryboy.nix { }; | |
| 55 | ||
| 56 | }; | |
| 57 | in import nixpkgs (args // { overlays = [ pypi2nixOverlay ] ++ overlays; }) |
| 0 | { apispec, buildPythonPackage, fetchPypi, lib }: | |
| 1 | buildPythonPackage rec { | |
| 2 | pname = "apispec-webframeworks"; | |
| 3 | version = "0.5.2"; | |
| 4 | ||
| 5 | src = builtins.fetchurl { | |
| 6 | url = | |
| 7 | "https://files.pythonhosted.org/packages/bd/35/a1eb70cd9eaee7400941ca01acff9b593a12a558031f62332927970ee400/apispec-webframeworks-0.5.2.tar.gz"; | |
| 8 | sha256 = "1wyw30402xq2a8icrsjmy9v43jyvawcjd85ccb2zicqlg4k5pcqd"; | |
| 9 | }; | |
| 10 | ||
| 11 | # TODO FIXME | |
| 12 | doCheck = false; | |
| 13 | ||
| 14 | buildInputs = [ ]; | |
| 15 | propagatedBuildInputs = [ apispec ]; | |
| 16 | } |
| 0 | { beautifulsoup4, buildPythonPackage, click, dateutil, fetchPypi, html2text, lib | |
| 1 | , lxml, pytz, requests, simplejson }: | |
| 2 | buildPythonPackage rec { | |
| 3 | pname = "faraday-plugins"; | |
| 4 | version = "1.1"; | |
| 5 | ||
| 6 | src = builtins.fetchurl { | |
| 7 | url = | |
| 8 | "https://files.pythonhosted.org/packages/3f/63/59fdcf2f6bc0f309fcc46b8ca58990ad84ef37d1db1b78f8a04523d52369/faraday-plugins-1.1.tar.gz"; | |
| 9 | sha256 = "0hzlymg318j78fpfrscszsfxrs21ikxy49bx91yc77b42vf73y4f"; | |
| 10 | }; | |
| 11 | ||
| 12 | # TODO FIXME | |
| 13 | doCheck = false; | |
| 14 | ||
| 15 | buildInputs = [ ]; | |
| 16 | propagatedBuildInputs = | |
| 17 | [ click simplejson requests lxml html2text beautifulsoup4 pytz dateutil ]; | |
| 18 | } |
| 0 | { alembic, apispec, apispec-webframeworks, autobahn, bcrypt, buildPythonPackage | |
| 1 | , click, colorama, dateutil, distro, faraday-plugins, fetchPypi, filedepot | |
| 2 | , filteralchemy-fork, flask, flask-classful, flask-kvsession-fork | |
| 3 | , flask-restless, flask-security, flask_login, flask_sqlalchemy, lib | |
| 4 | , marshmallow, marshmallow-sqlalchemy, nplusone, pgcli, pillow, psycopg2, pyasn1 | |
| 5 | , pyopenssl, pytestrunner, requests, service-identity, simplejson, simplekv | |
| 6 | , sqlalchemy, syslog-rfc5424-formatter, tqdm, twisted, webargs, werkzeug }: | |
| 7 | buildPythonPackage rec { | |
| 8 | pname = "faradaysec"; | |
| 9 | version = "0.1dev"; | |
| 10 | ||
| 11 | src = lib.cleanSource ../..; | |
| 12 | ||
| 13 | # TODO FIXME | |
| 14 | doCheck = false; | |
| 15 | ||
| 16 | buildInputs = [ pytestrunner ]; | |
| 17 | propagatedBuildInputs = [ | |
| 18 | werkzeug | |
| 19 | autobahn | |
| 20 | alembic | |
| 21 | bcrypt | |
| 22 | colorama | |
| 23 | click | |
| 24 | flask | |
| 25 | flask_sqlalchemy | |
| 26 | flask-classful | |
| 27 | flask_login | |
| 28 | flask-security | |
| 29 | marshmallow | |
| 30 | pillow | |
| 31 | psycopg2 | |
| 32 | pgcli | |
| 33 | pyopenssl | |
| 34 | dateutil | |
| 35 | requests | |
| 36 | pyasn1 | |
| 37 | service-identity | |
| 38 | sqlalchemy | |
| 39 | tqdm | |
| 40 | twisted | |
| 41 | webargs | |
| 42 | marshmallow-sqlalchemy | |
| 43 | filteralchemy-fork | |
| 44 | filedepot | |
| 45 | nplusone | |
| 46 | flask-restless | |
| 47 | simplejson | |
| 48 | syslog-rfc5424-formatter | |
| 49 | simplekv | |
| 50 | flask-kvsession-fork | |
| 51 | distro | |
| 52 | faraday-plugins | |
| 53 | apispec | |
| 54 | apispec-webframeworks | |
| 55 | ]; | |
| 56 | } |
| 0 | { buildPythonPackage, fetchPypi, lib, unidecode }: | |
| 1 | buildPythonPackage rec { | |
| 2 | pname = "filedepot"; | |
| 3 | version = "0.7.1"; | |
| 4 | ||
| 5 | src = builtins.fetchurl { | |
| 6 | url = | |
| 7 | "https://files.pythonhosted.org/packages/56/40/8755419cb2cd1be41690a5c15694c738c67ea84a84ad9128222c7a4477c1/filedepot-0.7.1.tar.gz"; | |
| 8 | sha256 = "1rhyhr9d4ypb7qai8rgi7h2ikyiwmx7ib6xlqid1kbg0l22j1g4k"; | |
| 9 | }; | |
| 10 | ||
| 11 | # TODO FIXME | |
| 12 | doCheck = false; | |
| 13 | ||
| 14 | buildInputs = [ ]; | |
| 15 | propagatedBuildInputs = [ unidecode ]; | |
| 16 | } |
| 0 | { buildPythonPackage, fetchPypi, lib, marshmallow-sqlalchemy, six, webargs }: | |
| 1 | buildPythonPackage rec { | |
| 2 | pname = "filteralchemy-fork"; | |
| 3 | version = "0.1.0"; | |
| 4 | ||
| 5 | src = builtins.fetchurl { | |
| 6 | url = | |
| 7 | "https://files.pythonhosted.org/packages/ba/79/4b39ef7e32e610e789aa987a4ae1723a937cd1cbf16a0ac5865b37dd6ca3/filteralchemy-fork-0.1.0.tar.gz"; | |
| 8 | sha256 = "1lssfgz7vlsvyl9kpcmdjndfklyb3nkxyyqwf2jwzd8zpv9cbwvs"; | |
| 9 | }; | |
| 10 | ||
| 11 | # TODO FIXME | |
| 12 | doCheck = false; | |
| 13 | ||
| 14 | buildInputs = [ ]; | |
| 15 | propagatedBuildInputs = [ six webargs marshmallow-sqlalchemy ]; | |
| 16 | } |
| 0 | { Babel, buildPythonPackage, fetchPypi, flask, jinja2, lib, speaklater }: | |
| 1 | buildPythonPackage rec { | |
| 2 | pname = "flask-babelex"; | |
| 3 | version = "0.9.4"; | |
| 4 | ||
| 5 | src = builtins.fetchurl { | |
| 6 | url = | |
| 7 | "https://files.pythonhosted.org/packages/85/e7/217fb37ccd4bd93cd0f002028fb7c5fdf6ee0063a6beb83e43cd903da46e/Flask-BabelEx-0.9.4.tar.gz"; | |
| 8 | sha256 = "09yfr8hlwvpgvq8kp1y7qbnnl0q28hi0348bv199ssiqx779r99r"; | |
| 9 | }; | |
| 10 | ||
| 11 | # TODO FIXME | |
| 12 | doCheck = false; | |
| 13 | ||
| 14 | buildInputs = [ ]; | |
| 15 | propagatedBuildInputs = [ flask Babel speaklater jinja2 ]; | |
| 16 | } |
| 0 | { buildPythonPackage, fetchPypi, flask, lib }: | |
| 1 | buildPythonPackage rec { | |
| 2 | pname = "flask-classful"; | |
| 3 | version = "0.14.2"; | |
| 4 | ||
| 5 | src = builtins.fetchurl { | |
| 6 | url = | |
| 7 | "https://files.pythonhosted.org/packages/aa/f5/c79cb4b711a76a0fad1b464b5e77b1786c8630783226f9e90f6060e63db0/Flask-Classful-0.14.2.tar.gz"; | |
| 8 | sha256 = "1xxzwhv09l8j8qmww2ps9cj7fm9s5n3507zk7gdic7lyyv9sn35f"; | |
| 9 | }; | |
| 10 | ||
| 11 | # TODO FIXME | |
| 12 | doCheck = false; | |
| 13 | ||
| 14 | buildInputs = [ ]; | |
| 15 | propagatedBuildInputs = [ flask ]; | |
| 16 | } |
| 0 | { buildPythonPackage, fetchPypi, flask, itsdangerous, lib, simplekv, six | |
| 1 | , werkzeug }: | |
| 2 | buildPythonPackage rec { | |
| 3 | pname = "flask-kvsession-fork"; | |
| 4 | version = "0.6.3"; | |
| 5 | ||
| 6 | src = builtins.fetchurl { | |
| 7 | url = | |
| 8 | "https://files.pythonhosted.org/packages/9e/0e/c15210cae6741d1b6c663944126ed3949ca6600df5844093ca70521bb5ed/Flask-KVSession-fork-0.6.3.tar.gz"; | |
| 9 | sha256 = "0j5ncqb2kwigs2h12vd5jwhj11ma2igw35yz9l79h2q2gg38nn8l"; | |
| 10 | }; | |
| 11 | ||
| 12 | # TODO FIXME | |
| 13 | doCheck = false; | |
| 14 | ||
| 15 | buildInputs = [ ]; | |
| 16 | propagatedBuildInputs = [ flask simplekv werkzeug itsdangerous six ]; | |
| 17 | } |
| 0 | { buildPythonPackage, dateutil, fetchPypi, flask, lib, mimerender, sqlalchemy }: | |
| 1 | buildPythonPackage rec { | |
| 2 | pname = "flask-restless"; | |
| 3 | version = "0.17.0"; | |
| 4 | ||
| 5 | src = builtins.fetchurl { | |
| 6 | url = | |
| 7 | "https://files.pythonhosted.org/packages/ae/ad/14eee74ef110f2bd8641de98675037f037dd06d614f7c435671be66a55c7/Flask-Restless-0.17.0.tar.gz"; | |
| 8 | sha256 = "1dn2g3qkgvbbs4165hng82gkplm1bnxf010qkaf26ixx1bl7zr0x"; | |
| 9 | }; | |
| 10 | ||
| 11 | # TODO FIXME | |
| 12 | doCheck = false; | |
| 13 | ||
| 14 | buildInputs = [ ]; | |
| 15 | propagatedBuildInputs = [ flask sqlalchemy dateutil mimerender ]; | |
| 16 | } |
| 0 | { Babel, buildPythonPackage, fetchPypi, flask, flask-babelex, flask_login | |
| 1 | , flask_mail, flask_principal, flask_wtf, itsdangerous, lib, passlib | |
| 2 | , pytestrunner }: | |
| 3 | buildPythonPackage rec { | |
| 4 | pname = "flask-security"; | |
| 5 | version = "3.0.0"; | |
| 6 | ||
| 7 | src = builtins.fetchurl { | |
| 8 | url = | |
| 9 | "https://files.pythonhosted.org/packages/ba/c1/16e460fec7961509b10aaf8cc986fa7a1df5dced2844f42cd46732621211/Flask-Security-3.0.0.tar.gz"; | |
| 10 | sha256 = "0ck4ybpppka56cqv0s26h1jjq6sqvwmqfm85ylq9zy28b9gsl7fn"; | |
| 11 | }; | |
| 12 | ||
| 13 | # TODO FIXME | |
| 14 | doCheck = false; | |
| 15 | ||
| 16 | buildInputs = [ Babel pytestrunner ]; | |
| 17 | propagatedBuildInputs = [ | |
| 18 | flask | |
| 19 | flask_login | |
| 20 | flask_mail | |
| 21 | flask_principal | |
| 22 | flask_wtf | |
| 23 | flask-babelex | |
| 24 | itsdangerous | |
| 25 | passlib | |
| 26 | ]; | |
| 27 | } |
| 0 | { buildPythonPackage, click, fetchPypi, itsdangerous, jinja2, lib, werkzeug }: | |
| 1 | buildPythonPackage rec { | |
| 2 | pname = "flask"; | |
| 3 | version = "1.1.2"; | |
| 4 | ||
| 5 | src = builtins.fetchurl { | |
| 6 | url = | |
| 7 | "https://files.pythonhosted.org/packages/4e/0b/cb02268c90e67545a0e3a37ea1ca3d45de3aca43ceb7dbf1712fb5127d5d/Flask-1.1.2.tar.gz"; | |
| 8 | sha256 = "0q3h295izcil7lswkzfnyg3k5gq4hpmqmpl6i7s5m1n9szi1myjf"; | |
| 9 | }; | |
| 10 | ||
| 11 | # TODO FIXME | |
| 12 | doCheck = false; | |
| 13 | ||
| 14 | buildInputs = [ ]; | |
| 15 | propagatedBuildInputs = [ werkzeug jinja2 itsdangerous click ]; | |
| 16 | } |
| 0 | { buildPythonPackage, fetchPypi, lib, marshmallow, sqlalchemy }: | |
| 1 | buildPythonPackage rec { | |
| 2 | pname = "marshmallow-sqlalchemy"; | |
| 3 | version = "0.15.0"; | |
| 4 | ||
| 5 | src = builtins.fetchurl { | |
| 6 | url = | |
| 7 | "https://files.pythonhosted.org/packages/fe/d2/de4f83721cddc2f4f9525efe916c4e87d54ca00aa678098d9d5bcdfcf966/marshmallow-sqlalchemy-0.15.0.tar.gz"; | |
| 8 | sha256 = "1phqbbrq1xjvc7cwasy5zws4bdb050qikfp1qg8f1hqhmipkpiaz"; | |
| 9 | }; | |
| 10 | ||
| 11 | # TODO FIXME | |
| 12 | doCheck = false; | |
| 13 | ||
| 14 | buildInputs = [ ]; | |
| 15 | propagatedBuildInputs = [ marshmallow sqlalchemy ]; | |
| 16 | } |
| 0 | { buildPythonPackage, fetchPypi, lib, python_mimeparse }: | |
| 1 | buildPythonPackage rec { | |
| 2 | pname = "mimerender"; | |
| 3 | version = "0.6.0"; | |
| 4 | ||
| 5 | src = builtins.fetchurl { | |
| 6 | url = | |
| 7 | "https://files.pythonhosted.org/packages/90/93/04da69a3a9adae4aae66cf9884f09d82e318018673ba9193a593db01e0ee/mimerender-0.6.0.tar.gz"; | |
| 8 | sha256 = "1imim78dypbl9fvrz21j8f13q8i96dx90m7f5ib3z371zrz3gwg7"; | |
| 9 | }; | |
| 10 | ||
| 11 | # TODO FIXME | |
| 12 | doCheck = false; | |
| 13 | ||
| 14 | buildInputs = [ ]; | |
| 15 | propagatedBuildInputs = [ python_mimeparse ]; | |
| 16 | } |
| 0 | { blinker, buildPythonPackage, fetchPypi, lib, six }: | |
| 1 | buildPythonPackage rec { | |
| 2 | pname = "nplusone"; | |
| 3 | version = "1.0.0"; | |
| 4 | ||
| 5 | src = builtins.fetchurl { | |
| 6 | url = | |
| 7 | "https://files.pythonhosted.org/packages/26/da/663f551cdda166eaf75a564f64d022c6eb03c710ba83c3fb0f4ac664ebde/nplusone-1.0.0.tar.gz"; | |
| 8 | sha256 = "0lanbbpi5gfwjy6rlwlxw9z6nyzr5y4b4kg20jxym9qa1jhw09hp"; | |
| 9 | }; | |
| 10 | ||
| 11 | # TODO FIXME | |
| 12 | doCheck = false; | |
| 13 | ||
| 14 | buildInputs = [ ]; | |
| 15 | propagatedBuildInputs = [ six blinker ]; | |
| 16 | } |
| 0 | { buildPythonPackage, cli-helpers, click, configobj, fetchPypi, humanize, lib | |
| 1 | , pgspecial, prompt_toolkit, psycopg2, pygments, setproctitle, sqlparse }: | |
| 2 | buildPythonPackage rec { | |
| 3 | pname = "pgcli"; | |
| 4 | version = "2.1.0"; | |
| 5 | ||
| 6 | src = builtins.fetchurl { | |
| 7 | url = | |
| 8 | "https://files.pythonhosted.org/packages/ed/90/c8d33a8be3d85347a23ccd5663b8a2e82f6c79b75eb2fd9339371a9f1284/pgcli-2.1.0.tar.gz"; | |
| 9 | sha256 = "0p60297ppljc2nyqfchzcc17ls4m5841i7gyzqags0j8fg3s749p"; | |
| 10 | }; | |
| 11 | ||
| 12 | # TODO FIXME | |
| 13 | doCheck = false; | |
| 14 | ||
| 15 | buildInputs = [ ]; | |
| 16 | propagatedBuildInputs = [ | |
| 17 | pgspecial | |
| 18 | click | |
| 19 | pygments | |
| 20 | prompt_toolkit | |
| 21 | psycopg2 | |
| 22 | sqlparse | |
| 23 | configobj | |
| 24 | humanize | |
| 25 | cli-helpers | |
| 26 | setproctitle | |
| 27 | ]; | |
| 28 | } |
| 0 | { buildPythonPackage, factory_boy, fetchPypi, inflection, lib, pytest }: | |
| 1 | buildPythonPackage rec { | |
| 2 | pname = "pytest-factoryboy"; | |
| 3 | version = "2.0.3"; | |
| 4 | ||
| 5 | src = builtins.fetchurl { | |
| 6 | url = | |
| 7 | "https://files.pythonhosted.org/packages/77/8b/ec891cea6f61ac849bd68ff677ee2176eaec606fa1b7a7a4a80fa17ce6b1/pytest-factoryboy-2.0.3.tar.gz"; | |
| 8 | sha256 = "06js78jshf81i2nqgf2svb8z68wh4m34hcqdvz9rj4pcvnvkzvzz"; | |
| 9 | }; | |
| 10 | ||
| 11 | # TODO FIXME | |
| 12 | doCheck = false; | |
| 13 | ||
| 14 | buildInputs = [ ]; | |
| 15 | propagatedBuildInputs = [ inflection factory_boy pytest ]; | |
| 16 | } |
| 0 | { buildPythonPackage, fetchPypi, lib }: | |
| 1 | buildPythonPackage rec { | |
| 2 | pname = "simplekv"; | |
| 3 | version = "0.13.0"; | |
| 4 | ||
| 5 | src = builtins.fetchurl { | |
| 6 | url = | |
| 7 | "https://files.pythonhosted.org/packages/42/8e/4f96c4038d966bafbe020c36770599ce4e0f0ccbb7b93437d7742a952e03/simplekv-0.13.0.tar.gz"; | |
| 8 | sha256 = "01iw920m8aaak3dp0y61ny7vin5yizm55h9i2vwgkv0qhvsfhlmf"; | |
| 9 | }; | |
| 10 | ||
| 11 | # TODO FIXME | |
| 12 | doCheck = false; | |
| 13 | ||
| 14 | buildInputs = [ ]; | |
| 15 | propagatedBuildInputs = [ ]; | |
| 16 | } |
| 0 | { buildPythonPackage, fetchPypi, lib }: | |
| 1 | buildPythonPackage rec { | |
| 2 | pname = "syslog-rfc5424-formatter"; | |
| 3 | version = "1.2.2"; | |
| 4 | ||
| 5 | src = builtins.fetchurl { | |
| 6 | url = | |
| 7 | "https://files.pythonhosted.org/packages/45/75/95ca5b9fbc31f850a2f84da8302cc0eca1420e12c7e6064dda1569d5882e/syslog-rfc5424-formatter-1.2.2.tar.gz"; | |
| 8 | sha256 = "113fc9wbsbb63clw74f7riyv37ar1131x8lc32q2cvqd523jqsns"; | |
| 9 | }; | |
| 10 | ||
| 11 | # TODO FIXME | |
| 12 | doCheck = false; | |
| 13 | ||
| 14 | buildInputs = [ ]; | |
| 15 | propagatedBuildInputs = [ ]; | |
| 16 | } |
| 0 | { buildPythonPackage, fetchPypi, lib, marshmallow }: | |
| 1 | buildPythonPackage rec { | |
| 2 | pname = "webargs"; | |
| 3 | version = "5.5.3"; | |
| 4 | ||
| 5 | src = builtins.fetchurl { | |
| 6 | url = | |
| 7 | "https://files.pythonhosted.org/packages/5a/46/72d3c7e0acbdb9c79caf7e03835cd7f77163026811855b59a1eaf6c0c2e5/webargs-5.5.3.tar.gz"; | |
| 8 | sha256 = "16pjzc265yx579ijz5scffyfd1vsmi87fdcgnzaj2by6w2i445l7"; | |
| 9 | }; | |
| 10 | ||
| 11 | # TODO FIXME | |
| 12 | doCheck = false; | |
| 13 | ||
| 14 | buildInputs = [ ]; | |
| 15 | propagatedBuildInputs = [ marshmallow ]; | |
| 16 | } |
| 0 | websocket-client>=0.54.0 | |
| 0 | werkzeug<1.0.0 | |
| 1 | 1 | autobahn>=17.10.1 |
| 2 | alembic>=0.9.9 | |
| 3 | bcrypt>=3.1.4 | |
| 2 | 4 | colorama>=0.3.9 |
| 3 | deprecation>=1.0.1 | |
| 4 | flask>=1.0 | |
| 5 | IPy>=0.83 | |
| 6 | mockito>=1.0.12 | |
| 7 | pgcli>=1.8.2 | |
| 5 | click>=5.1 | |
| 6 | flask>=1.1 | |
| 7 | Flask-SQLAlchemy>=2.3.1 | |
| 8 | flask-classful>=0.14 | |
| 9 | flask-login<0.5.0 | |
| 10 | Flask-Security>=3.0.0 | |
| 11 | marshmallow<3.0.0 | |
| 12 | Pillow>=4.2.1 | |
| 13 | psycopg2==2.7.7 | |
| 14 | pgcli==2.1.0 | |
| 15 | pyopenssl>=17.2.0 | |
| 16 | python-dateutil>=2.6.0 | |
| 8 | 17 | requests>=2.18.4 |
| 9 | tornado>=5.0.0 | |
| 18 | pyasn1 | |
| 19 | service_identity>=17.0.0 | |
| 20 | SQLAlchemy>=1.2.0b2 | |
| 10 | 21 | tqdm>=4.15.0 |
| 11 | whoosh>=2.7.4 | |
| 12 | cairocffi==0.9.0 | |
| 13 | pycairo==1.18.1 | |
| 14 | PyGObject==3.32.1 | |
| 15 | lxml==4.3.3 | |
| 16 | html2text==2019.8.11 | |
| 22 | twisted>=18.9.0 | |
| 23 | webargs>=5.1.0,<6.0.0 | |
| 24 | marshmallow-sqlalchemy==0.15.0 | |
| 25 | filteralchemy-fork | |
| 26 | filedepot>=0.5.0 | |
| 27 | nplusone>=0.8.1 | |
| 28 | Flask-Restless==0.17.0 | |
| 29 | simplejson>=3.16.0 | |
| 30 | syslog-rfc5424-formatter>=1.1.1 | |
| 31 | simplekv==0.13.0 | |
| 32 | Flask-KVSession-fork>=0.6.3 | |
| 33 | distro>=1.4.0 | |
| 34 | faraday-plugins>=1.0.1,<2.0.0 | |
| 35 | apispec>=3.0.0 | |
| 36 | apispec-webframeworks>=0.5.0 |
| 0 | autobahn>=17.10.1 | |
| 1 | alembic>=0.9.9 | |
| 2 | bcrypt>=3.1.4 | |
| 3 | colorama>=0.3.9 | |
| 4 | click>=5.1 | |
| 5 | Flask-SQLAlchemy>=2.3.1 | |
| 6 | flask-classful>=0.14 | |
| 7 | Flask-Security>=3.0.0 | |
| 8 | flask-session>=0.3.1 | |
| 9 | flask>=1.1 | |
| 10 | future>=0.17.1 | |
| 11 | IPy>=0.83 | |
| 12 | marshmallow<3.0.0 | |
| 13 | Pillow>=4.2.1 | |
| 14 | pgcli==2.1.1 | |
| 15 | psycopg2-binary==2.8.4 | |
| 16 | pyasn1-modules>=0.0.11 | |
| 17 | pyopenssl>=17.2.0 | |
| 18 | python-dateutil>=2.6.0 | |
| 19 | requests>=2.18.4 | |
| 20 | service_identity>=17.0.0 | |
| 21 | SQLAlchemy>=1.2.0b2 | |
| 22 | sqlalchemy_schemadisplay>=1.3 | |
| 23 | tqdm>=4.15.0 | |
| 24 | twisted>=18.9.0 | |
| 25 | webargs>=5.1.0,<6.0.0 | |
| 26 | marshmallow-sqlalchemy==0.15.0 | |
| 27 | filteralchemy-fork | |
| 28 | filedepot>=0.5.0 | |
| 29 | nplusone>=0.8.1 | |
| 30 | deprecation>=1.0.1 | |
| 31 | websocket-client>=0.46.0 | |
| 32 | attrs>=17.4.0 | |
| 33 | Flask-Restless==0.17.0 | |
| 34 | simplejson>=3.16.0 | |
| 35 | syslog-rfc5424-formatter==1.1.1 | |
| 36 | beautifulsoup4==4.7.1 | |
| 37 | Flask-KVSession-fork>=0.6.3 | |
| 38 | simplekv==0.13.0 | |
| 39 | pypcapfile==0.12.0 | |
| 40 | html2text==2019.8.11 | |
| 41 | distro==1.4.0 | |
| 42 | faraday-plugins>=1.0.1,<2.0.0 |
| 0 | #!/usr/bin/env python3 | |
| 1 | ||
| 2 | # Faraday Penetration Test IDE | |
| 3 | # Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 4 | # See the file 'doc/LICENSE' for the license information | |
| 5 | ||
| 6 | ''' | |
| 7 | Internal script used to detect merge conflicts to branch with | |
| 8 | our propiertary code. Not useful if you don't have access to | |
| 9 | the code of Faraday Professional or Faraday Corporate | |
| 10 | ''' | |
| 11 | from __future__ import absolute_import | |
| 12 | from __future__ import print_function | |
| 13 | ||
| 14 | import os | |
| 15 | import re | |
| 16 | import sys | |
| 17 | import subprocess | |
| 18 | import logging | |
| 19 | import argparse | |
| 20 | from contextlib import contextmanager | |
| 21 | from tempfile import mkdtemp | |
| 22 | from shutil import rmtree | |
| 23 | ||
| 24 | VERSIONS = ['white', 'pink', 'black'] | |
| 25 | BRANCH_FORMAT = 'origin/{}/dev' | |
| 26 | ||
| 27 | @contextmanager | |
| 28 | def chdir(directory): | |
| 29 | """Context manager to work in the specified directory""" | |
| 30 | current = os.getcwd() | |
| 31 | os.chdir(directory) | |
| 32 | yield | |
| 33 | os.chdir(current) | |
| 34 | ||
| 35 | @contextmanager | |
| 36 | def temp_worktree(branch=None): | |
| 37 | """Context manager that creates a temporal worktree and | |
| 38 | changes the current working directory, and when finished | |
| 39 | removes the dir and runs a git worktree prune""" | |
| 40 | directory = mkdtemp() | |
| 41 | cmd = ["git", "worktree", "add", directory] | |
| 42 | if branch is not None: | |
| 43 | cmd.append(branch) | |
| 44 | subprocess.check_output(cmd) | |
| 45 | with chdir(directory): | |
| 46 | yield | |
| 47 | rmtree(directory) | |
| 48 | subprocess.check_output(['git', 'worktree', 'prune']) | |
| 49 | ||
| 50 | def check_merge(dst_branch, cur_branch='HEAD'): | |
| 51 | """Return a boolean indicating if the merge from cur_branch | |
| 52 | to dst_branch will merge without causing conflicts that need | |
| 53 | manual resolution""" | |
| 54 | # https://stackoverflow.com/questions/501407/is-there-a-git-merge-dry-run-option | |
| 55 | with temp_worktree(dst_branch): | |
| 56 | exit_code = subprocess.call( | |
| 57 | ['git', 'merge', '--no-commit', '--no-ff', cur_branch]) | |
| 58 | # Use call because it will have exit code 128 when there is nothing to | |
| 59 | # abort | |
| 60 | subprocess.call(['git', 'merge', '--abort']) | |
| 61 | return exit_code == 0 | |
| 62 | ||
| 63 | ||
| 64 | def get_current_branch(): | |
| 65 | """Return the current branch of the current workspace""" | |
| 66 | # https://stackoverflow.com/questions/6245570/how-to-get-the-current-branch-name-in-git | |
| 67 | branch = subprocess.check_output( | |
| 68 | ['git', 'rev-parse', '--abbrev-ref', 'HEAD']).decode().strip() | |
| 69 | if branch == 'HEAD': | |
| 70 | # Probably in a detached state inside gitlab CI | |
| 71 | # Fallback to the branch name defined in an env var | |
| 72 | branch = 'origin/' + os.environ['CI_COMMIT_REF_NAME'] | |
| 73 | return branch | |
| 74 | ||
| 75 | ||
| 76 | def branch_exists(branch_name): | |
| 77 | exit_code = subprocess.call( | |
| 78 | ['git', 'rev-parse', '--verify', '--quiet', branch_name]) | |
| 79 | if exit_code == 0: | |
| 80 | return True | |
| 81 | elif exit_code == 1: | |
| 82 | return False | |
| 83 | else: | |
| 84 | raise ValueError('Error when checking for branch existence') | |
| 85 | ||
| 86 | ||
| 87 | def version_of_branch(branch_name): | |
| 88 | """ | |
| 89 | >>> version_of_branch('tkt_white_this_is_not_a_pink_branch') | |
| 90 | 'white' | |
| 91 | """ | |
| 92 | positions = {version: branch_name.find(version) | |
| 93 | for version in VERSIONS} | |
| 94 | if all((pos < 0) for pos in positions.values()): | |
| 95 | # The branch name doesn't contain white, pink or black | |
| 96 | return | |
| 97 | positions = {version: pos | |
| 98 | for (version, pos) in positions.items() | |
| 99 | if pos >= 0} | |
| 100 | return min(positions.keys(), key=positions.get) | |
| 101 | ||
| 102 | ||
| 103 | def main(branch): | |
| 104 | logging.getLogger().setLevel(getattr(logging, args.log_level.upper())) | |
| 105 | logger = logging # TODO FIXME | |
| 106 | logger.info('Checking merge conflicts for branch %s', branch) | |
| 107 | version = version_of_branch(branch) | |
| 108 | if version is None: | |
| 109 | logger.error('Unknown version name. Exiting') | |
| 110 | sys.exit(-1) | |
| 111 | ||
| 112 | versions_to_test = VERSIONS[VERSIONS.index(version):] | |
| 113 | branches_to_test = [] | |
| 114 | for target_version in versions_to_test: | |
| 115 | overriden_branch = branch.replace(version, target_version) | |
| 116 | if target_version != version and \ | |
| 117 | branch_exists(overriden_branch): | |
| 118 | branches_to_test.append(overriden_branch) | |
| 119 | # break # Uncomment if want to cut the checker on merging to black if has overridden pink branch | |
| 120 | else: | |
| 121 | branches_to_test.append(BRANCH_FORMAT.format(target_version)) | |
| 122 | ||
| 123 | logging.info('Testing merges in branches %s' % branches_to_test) | |
| 124 | ||
| 125 | success = True | |
| 126 | cur_branch = branch | |
| 127 | for dst_branch in branches_to_test: | |
| 128 | result = check_merge(dst_branch, cur_branch) | |
| 129 | if result: | |
| 130 | logger.info("Merge into %s succeeded!", dst_branch) | |
| 131 | else: | |
| 132 | success = False | |
| 133 | logger.error("Merge into %s failed :(", dst_branch) | |
| 134 | print() | |
| 135 | print() | |
| 136 | ||
| 137 | if not success: | |
| 138 | sys.exit(1) | |
| 139 | ||
| 140 | ||
| 141 | if __name__ == "__main__": | |
| 142 | parser = argparse.ArgumentParser() | |
| 143 | parser.add_argument('-b', '--branch', default=get_current_branch()) | |
| 144 | parser.add_argument('-l', '--log-level', default='debug') | |
| 145 | args = parser.parse_args() | |
| 146 | main(args.branch) | |
| 147 | ||
| 148 | ||
| 149 | # I'm Py3 | |
| 150 |
| 0 | # -*- mode: python ; coding: utf-8 -*- | |
| 1 | ||
| 2 | block_cipher = None | |
| 3 | ||
| 4 | ||
| 5 | a = Analysis(['faraday/searcher/searcher.py', 'searcher.spec'], | |
| 6 | binaries=[], | |
| 7 | datas=[], | |
| 8 | hiddenimports=[], | |
| 9 | hookspath=[], | |
| 10 | runtime_hooks=[], | |
| 11 | excludes=[], | |
| 12 | win_no_prefer_redirects=False, | |
| 13 | win_private_assemblies=False, | |
| 14 | cipher=block_cipher, | |
| 15 | noarchive=False) | |
| 16 | pyz = PYZ(a.pure, a.zipped_data, | |
| 17 | cipher=block_cipher) | |
| 18 | exe = EXE(pyz, | |
| 19 | a.scripts, | |
| 20 | a.binaries, | |
| 21 | a.zipfiles, | |
| 22 | a.datas, | |
| 23 | [], | |
| 24 | name='searcher', | |
| 25 | debug=False, | |
| 26 | bootloader_ignore_signals=False, | |
| 27 | strip=False, | |
| 28 | upx=True, | |
| 29 | runtime_tmpdir=None, | |
| 30 | console=False , icon='faraday/faraday/server/www/favicon.ico') | |
| 31 | app = BUNDLE(exe, | |
| 32 | name='searcher.app', | |
| 33 | icon='faraday/faraday/server/www/favicon.ico', | |
| 34 | bundle_identifier=None) |
| 32 | 32 | version = search(r'__version__ = \'(.*?)\'', f.read()).group(1) |
| 33 | 33 | |
| 34 | 34 | # Taken from https://stackoverflow.com/questions/14399534/reference-requirements-txt-for-the-install-requires-kwarg-in-setuptools-setup-py/14399775#14399775 |
| 35 | with open('requirements_server.txt') as fp: | |
| 35 | with open('requirements.txt') as fp: | |
| 36 | 36 | required = fp.read().splitlines() |
| 37 | required.reverse() | |
| 38 | 37 | |
| 39 | 38 | with open('requirements_dev.txt') as fp: |
| 40 | 39 | dev_required = fp.read().splitlines() |
| 210 | 209 | # MANIFEST.in as well. |
| 211 | 210 | include_package_data=True, |
| 212 | 211 | package_data={ # Optional |
| 213 | '': ['requirements.txt', | |
| 214 | 'requirements_server.txt'], | |
| 212 | '': ['requirements.txt',], | |
| 215 | 213 | }, |
| 216 | 214 | |
| 217 | 215 | # Although 'package_data' is the preferred approach, in some case you may |
| 232 | 230 | entry_points={ # Optional |
| 233 | 231 | 'console_scripts': [ |
| 234 | 232 | 'faraday-server=faraday.start_server:main', |
| 235 | 'faraday-client=faraday.client.start_client:main', | |
| 236 | 'fplugin=faraday.client.bin.fplugin:main', | |
| 237 | 233 | 'faraday-manage=faraday.manage:cli', |
| 238 | 234 | 'faraday-searcher=faraday.searcher.searcher:main' |
| 239 | 235 | ], |
| 0 | with (import <nixpkgs> {}); | |
| 1 | mkShell { | |
| 2 | buildInputs = [pandoc] ++ (with python3Packages; | |
| 3 | [virtualenv pyopenssl psycopg2 pillow pygobject3 pynacl matplotlib lxml ldap autobahn | |
| 4 | gobjectIntrospection gtk3 gnome3.vte gssapi pykerberos | |
| 5 | ]); | |
| 6 | shellHook = '' | |
| 7 | unset SOURCE_DATE_EPOCH # Required to make pip work | |
| 8 | ||
| 9 | VENV_PATH=.venv-white | |
| 10 | [[ -f faraday/server/api/modules/reports.py ]] && VENV_PATH=.venv-pink | |
| 11 | [[ -f faraday/server/api/modules/jira.py ]] && VENV_PATH=.venv-black | |
| 12 | ||
| 13 | mkvirtualenv(){ | |
| 14 | # Reset previous virtualenv | |
| 15 | type -t deactivate && deactivate | |
| 16 | rm -rf $VENV_PATH | |
| 17 | ||
| 18 | # Build new virtualenv with system packages | |
| 19 | virtualenv --system-site-packages $VENV_PATH | |
| 20 | source $VENV_PATH/bin/activate | |
| 21 | python setup.py develop | |
| 22 | # pip install -r requirements_server.txt | |
| 23 | # pip install -r requirements.txt | |
| 24 | pip install -r requirements_dev.txt | |
| 25 | } | |
| 26 | ||
| 27 | if [[ -d $VENV_PATH ]]; then | |
| 28 | source $VENV_PATH/bin/activate | |
| 29 | else | |
| 30 | echo Creating new virtualenv | |
| 31 | mkvirtualenv | |
| 32 | fi | |
| 33 | ||
| 34 | # Without this, the import report dialog of the client breaks | |
| 35 | # Taken from https://github.com/NixOS/nixpkgs/pull/26614 | |
| 36 | export XDG_DATA_DIRS=$XDG_ICON_DIRS:$GSETTINGS_SCHEMAS_PATH\''${XDG_DATA_DIRS:+:}\$XDG_DATA_DIRS | |
| 37 | ''; | |
| 38 | } | |
| 0 | (import ./default.nix).overrideAttrs (_: { | |
| 1 | doCheck = true; | |
| 2 | checkPhase = "true"; | |
| 3 | checkInputs = with (import ./pypi2nixpkgs/nixpkgs.nix { }).python3.pkgs; [ | |
| 4 | pylint | |
| 5 | factory_boy | |
| 6 | pytest | |
| 7 | pytest-factoryboy | |
| 8 | responses | |
| 9 | hypothesis | |
| 10 | sphinx | |
| 11 | pytestcov | |
| 12 | ]; | |
| 13 | }) |
| 0 | # -*- mode: python ; coding: utf-8 -*- | |
| 1 | ||
| 2 | block_cipher = None | |
| 3 | ||
| 4 | ||
| 5 | a = Analysis(['faraday/client/start_client.py'], | |
| 6 | pathex=['/home/faraday/faraday'], | |
| 7 | binaries=[], | |
| 8 | datas=[('faraday', 'faraday')], | |
| 9 | hiddenimports=[ | |
| 10 | 'sqlalchemy.sql.default_comparator', | |
| 11 | 'backports.functools_lru_cache', | |
| 12 | 'depot.io.local', | |
| 13 | 'passlib.handlers.bcrypt', | |
| 14 | 'passlib.handlers.pbkdf2', | |
| 15 | 'passlib.handlers.misc', | |
| 16 | 'passlib.handlers.sha2_crypt', | |
| 17 | 'passlib.handlers.digests', | |
| 18 | 'tornado', | |
| 19 | 'faraday.client.plugins.core', | |
| 20 | 'pipes', | |
| 21 | 'xml.sax.drivers', | |
| 22 | 'xml.sax.drivers2', | |
| 23 | 'tqdm', | |
| 24 | 'dateutil', | |
| 25 | ], | |
| 26 | hookspath=[], | |
| 27 | runtime_hooks=[], | |
| 28 | excludes=[], | |
| 29 | win_no_prefer_redirects=False, | |
| 30 | win_private_assemblies=False, | |
| 31 | cipher=block_cipher, | |
| 32 | noarchive=False) | |
| 33 | pyz = PYZ(a.pure, a.zipped_data, | |
| 34 | cipher=block_cipher) | |
| 35 | exe = EXE(pyz, | |
| 36 | a.scripts, | |
| 37 | a.binaries, | |
| 38 | a.zipfiles, | |
| 39 | a.datas, | |
| 40 | [], | |
| 41 | name='start_client', | |
| 42 | debug=False, | |
| 43 | bootloader_ignore_signals=False, | |
| 44 | strip=False, | |
| 45 | upx=True, | |
| 46 | runtime_tmpdir=None, | |
| 47 | console=False ) |
| 0 | # -*- mode: python ; coding: utf-8 -*- | |
| 1 | ||
| 2 | block_cipher = None | |
| 3 | ||
| 4 | ||
| 5 | a = Analysis(['faraday/start_server.py'], | |
| 6 | pathex=['/home/faraday/faraday'], | |
| 7 | binaries=[], | |
| 8 | datas=[('faraday', 'faraday')], | |
| 9 | hiddenimports=['sqlalchemy.sql.default_comparator', 'backports.functools_lru_cache', 'depot.io.local', 'passlib.handlers.bcrypt', 'passlib.handlers.pbkdf2', 'passlib.handlers.misc', 'passlib.handlers.sha2_crypt', 'passlib.handlers.digests', 'xml.sax.xmlreader', 'xml.sax.expatreader', 'sqlalchemy.ext.baked', 'faraday.client.plugins.core'], | |
| 10 | hookspath=[], | |
| 11 | runtime_hooks=[], | |
| 12 | excludes=[], | |
| 13 | win_no_prefer_redirects=False, | |
| 14 | win_private_assemblies=False, | |
| 15 | cipher=block_cipher, | |
| 16 | noarchive=False) | |
| 17 | pyz = PYZ(a.pure, a.zipped_data, | |
| 18 | cipher=block_cipher) | |
| 19 | exe = EXE(pyz, | |
| 20 | a.scripts, | |
| 21 | a.binaries, | |
| 22 | a.zipfiles, | |
| 23 | a.datas, | |
| 24 | [], | |
| 25 | name='start_server', | |
| 26 | debug=False, | |
| 27 | bootloader_ignore_signals=False, | |
| 28 | strip=False, | |
| 29 | upx=True, | |
| 30 | runtime_tmpdir=None, | |
| 31 | console=False ) |
| 0 | <?xml version='1.0' encoding='utf-8'?> | |
| 1 | <MetasploitV4> | |
| 2 | <hosts> | |
| 3 | <host> | |
| 4 | <id>44155</id> | |
| 5 | <created-at>2020-04-17 15:18:07</created-at> | |
| 6 | <address>127.0.0.1</address> | |
| 7 | <mac>30-65-EC-6F-C4-58</mac> | |
| 8 | <name>test,localhost</name> | |
| 9 | <os-name>Linux</os-name> | |
| 10 | <updated-at>2020-04-17 15:28:08</updated-at> | |
| 11 | <comments>Host for test purposes</comments> | |
| 12 | <vuln-count>1</vuln-count> | |
| 13 | <service-count>1</service-count> | |
| 14 | <comm/> | |
| 15 | <state/> | |
| 16 | <os-flavor/> | |
| 17 | <os-sp/> | |
| 18 | <os-lang/> | |
| 19 | <purpose/> | |
| 20 | <services> | |
| 21 | <service> | |
| 22 | <id>23547</id> | |
| 23 | <created-at>2020-04-17 15:18:07</created-at> | |
| 24 | <host-id>44155</host-id> | |
| 25 | <port>8080</port> | |
| 26 | <proto>tcp</proto> | |
| 27 | <state>open</state> | |
| 28 | <name>Test service</name> | |
| 29 | <updated-at>2020-04-17 15:28:38</updated-at> | |
| 30 | <info>5.0</info> | |
| 31 | </service> | |
| 32 | </services> | |
| 33 | <vulns> | |
| 34 | <vuln> | |
| 35 | <id>24713</id> | |
| 36 | <host-id>44155</host-id> | |
| 37 | <name>Vulnerability test</name> | |
| 38 | <info>Desc for testing</info> | |
| 39 | <refs> | |
| 40 | <ref>ref1</ref> | |
| 41 | <ref>ref2</ref> | |
| 42 | </refs> | |
| 43 | </vuln> | |
| 44 | </vulns> | |
| 45 | </host> | |
| 46 | </hosts> | |
| 47 | <services> | |
| 48 | <service> | |
| 49 | <id>23547</id> | |
| 50 | <created-at>2020-04-17 15:18:07</created-at> | |
| 51 | <host-id>44155</host-id> | |
| 52 | <port>8080</port> | |
| 53 | <proto>tcp</proto> | |
| 54 | <state>open</state> | |
| 55 | <name>Test service</name> | |
| 56 | <updated-at>2020-04-17 15:28:38</updated-at> | |
| 57 | <info>5.0</info> | |
| 58 | </service> | |
| 59 | </services> | |
| 60 | <web_sites> | |
| 61 | <web_site> | |
| 62 | <id>23547</id> | |
| 63 | <service-id>23547</service-id> | |
| 64 | <vhost>127.0.0.1</vhost> | |
| 65 | <host>127.0.0.1</host> | |
| 66 | <port>8080</port> | |
| 67 | <created-at>2020-04-17 15:18:07</created-at> | |
| 68 | <updated-at>2020-04-17 15:28:38</updated-at> | |
| 69 | <comments>Description for service</comments> | |
| 70 | <options></options> | |
| 71 | <ssl></ssl> | |
| 72 | </web_site> | |
| 73 | </web_sites> | |
| 74 | <web_vulns> | |
| 75 | <web_vuln> | |
| 76 | <id>24714</id> | |
| 77 | <web-site-id>23547</web-site-id> | |
| 78 | <created-at>2020-04-17 15:20:57</created-at> | |
| 79 | <updated-at>2020-04-17 15:20:57</updated-at> | |
| 80 | <name>Vulnerability Web test</name> | |
| 81 | <description>Desc for testing web vuln</description> | |
| 82 | <risk>5</risk> | |
| 83 | <legacy-category>Faraday</legacy-category> | |
| 84 | <path>faraday.com</path> | |
| 85 | <method>GET</method> | |
| 86 | <params></params> | |
| 87 | <pname>qwerty</pname> | |
| 88 | <query>query for vuln</query> | |
| 89 | <request>GET for vuln</request> | |
| 90 | <vhost>127.0.0.1</vhost> | |
| 91 | <host>127.0.0.1</host> | |
| 92 | <port>8080</port> | |
| 93 | <ssl></ssl> | |
| 94 | <confidence></confidence> | |
| 95 | </web_vuln> | |
| 96 | </web_vulns> | |
| 97 | </MetasploitV4>⏎ |
| 44 | 44 | Comment, |
| 45 | 45 | CustomFieldsSchema, |
| 46 | 46 | Agent, |
| 47 | SearchFilter, Executor) | |
| 47 | AgentExecution, | |
| 48 | SearchFilter, | |
| 49 | Executor, | |
| 50 | Rule, | |
| 51 | Action, | |
| 52 | RuleAction) | |
| 48 | 53 | |
| 49 | 54 | # Make partials for start and end date. End date must be after start date |
| 50 | 55 | FuzzyStartTime = lambda: ( |
| 442 | 447 | class ExecutorFactory(FaradayFactory): |
| 443 | 448 | name = FuzzyText() |
| 444 | 449 | agent = factory.SubFactory(AgentFactory) |
| 445 | ||
| 450 | parameters_metadata = factory.LazyAttribute( | |
| 451 | lambda e: str({"param_name": False}) | |
| 452 | ) | |
| 446 | 453 | class Meta: |
| 447 | 454 | model = Executor |
| 448 | 455 | sqlalchemy_session = db.session |
| 456 | ||
| 457 | ||
| 458 | class AgentExecutionFactory(WorkspaceObjectFactory): | |
| 459 | executor = factory.SubFactory( | |
| 460 | ExecutorFactory, | |
| 461 | ) | |
| 462 | parameters_data = factory.LazyAttribute( | |
| 463 | lambda _: {"param_name": "param_value"} | |
| 464 | ) | |
| 465 | workspace = factory.SelfAttribute('executor.agent.workspace') | |
| 466 | ||
| 467 | class Meta: | |
| 468 | model = AgentExecution | |
| 469 | sqlalchemy_session = db.session | |
| 470 | ||
| 449 | 471 | |
| 450 | 472 | |
| 451 | 473 | class SearchFilterFactory(FaradayFactory): |
| 461 | 483 | sqlalchemy_session = db.session |
| 462 | 484 | |
| 463 | 485 | |
| 486 | class ActionFactory(FaradayFactory): | |
| 487 | name = FuzzyText() | |
| 488 | command = FuzzyChoice(['UPDATE', 'DELETE', 'ALERT']) | |
| 489 | field = 'severity' | |
| 490 | value = 'informational' | |
| 491 | ||
| 492 | class Meta: | |
| 493 | model = Action | |
| 494 | sqlalchemy_session = db.session | |
| 495 | ||
| 496 | ||
| 497 | class RuleFactory(WorkspaceObjectFactory): | |
| 498 | model = 'Vulnerability' | |
| 499 | object = "severity=low", | |
| 500 | disabled = FuzzyChoice([True, False]) | |
| 501 | workspace = factory.SubFactory(WorkspaceFactory) | |
| 502 | ||
| 503 | class Meta: | |
| 504 | model = Rule | |
| 505 | # sqlalchemy_session = db.session | |
| 506 | ||
| 507 | ||
| 508 | class RuleActionFactory(FaradayFactory): | |
| 509 | rule = factory.SubFactory(RuleFactory) | |
| 510 | action = factory.SubFactory(ActionFactory) | |
| 511 | ||
| 512 | class Meta: | |
| 513 | model = RuleAction | |
| 514 | sqlalchemy_session = db.session | |
| 515 | ||
| 464 | 516 | # I'm Py3 |
| 0 | <?xml version="1.0"?> | |
| 1 | <ScanGroup ExportedOn="14/11/2013, 11:36"> | |
| 2 | <Scan> | |
| 3 | <Name><![CDATA[Scan Thread 1 ( http://testaspnet.vulnweb.com:80/ )]]></Name> | |
| 4 | <ShortName><![CDATA[Scan Thread 1]]></ShortName> | |
| 5 | <StartURL><![CDATA[http://testaspnet.vulnweb.com:80/]]></StartURL> | |
| 6 | <StartTime><![CDATA[14/11/2013, 11:30:14]]></StartTime> | |
| 7 | <FinishTime><![CDATA[14/11/2013, 11:34:08]]></FinishTime> | |
| 8 | <ScanTime><![CDATA[3 minutes, 55 seconds]]></ScanTime> | |
| 9 | <Aborted><![CDATA[True]]></Aborted> | |
| 10 | <Responsive><![CDATA[True]]></Responsive> | |
| 11 | <Banner><![CDATA[Microsoft-IIS/6.0]]></Banner> | |
| 12 | <Os><![CDATA[Windows]]></Os> | |
| 13 | <WebServer><![CDATA[IIS 6.0]]></WebServer> | |
| 14 | <Technologies><![CDATA[ASP.NET]]></Technologies> | |
| 15 | <Crawler StartUrl="http://testaspnet.vulnweb.com/"> | |
| 16 | <LoginSequence> | |
| 17 | </LoginSequence> | |
| 18 | <Cookies> | |
| 19 | <Variable Name="ASP.NET_SessionId" Type="Cookie"> | |
| 20 | </Variable> | |
| 21 | </Cookies> | |
| 22 | <SiteFiles> | |
| 23 | <SiteFile id="1"> | |
| 24 | <Name></Name> | |
| 25 | <URL>/</URL> | |
| 26 | <FullURL>http://testaspnet.vulnweb.com/</FullURL> | |
| 27 | <Inputs> | |
| 28 | <Variable Name="/" Type="Path Fragment (suffix .aspx)"> | |
| 29 | </Variable> | |
| 30 | </Inputs> | |
| 31 | <Variations> | |
| 32 | </Variations> | |
| 33 | </SiteFile> | |
| 34 | <SiteFile id="2"> | |
| 35 | <Name>default.aspx</Name> | |
| 36 | <URL>/default.aspx</URL> | |
| 37 | <FullURL>http://testaspnet.vulnweb.com/default.aspx</FullURL> | |
| 38 | <Inputs> | |
| 39 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 40 | </Variable> | |
| 41 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 42 | </Variable> | |
| 43 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 44 | </Variable> | |
| 45 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 46 | </Variable> | |
| 47 | <Variable Name="delete" Type="URL encoded GET"> | |
| 48 | </Variable> | |
| 49 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 50 | </Variable> | |
| 51 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 52 | </Variable> | |
| 53 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 54 | </Variable> | |
| 55 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 56 | </Variable> | |
| 57 | <Variable Name="__EVENTTARGET" Type="URL encoded GET"> | |
| 58 | </Variable> | |
| 59 | </Inputs> | |
| 60 | <Variations> | |
| 61 | <Variation> | |
| 62 | <URL>http://testaspnet.vulnweb.com/default.aspx</URL> | |
| 63 | <PostData><![CDATA[__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWVwLYpJyYAwKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IM2hPdJHXXMZ9eiMzbVXhkJFAWyDk%3d&__VIEWSTATE=/wEPDwUKLTEwNTI0MjkwNQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkZDUAskqLyfS1MBsZINJY6LpGzdzU]]></PostData> | |
| 64 | </Variation> | |
| 65 | </Variations> | |
| 66 | </SiteFile> | |
| 67 | <SiteFile id="3"> | |
| 68 | <Name>about.aspx</Name> | |
| 69 | <URL>/about.aspx</URL> | |
| 70 | <FullURL>http://testaspnet.vulnweb.com/about.aspx</FullURL> | |
| 71 | <Inputs> | |
| 72 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 73 | </Variable> | |
| 74 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 75 | </Variable> | |
| 76 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 77 | </Variable> | |
| 78 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 79 | </Variable> | |
| 80 | </Inputs> | |
| 81 | <Variations> | |
| 82 | <Variation> | |
| 83 | <URL>http://testaspnet.vulnweb.com/about.aspx</URL> | |
| 84 | <PostData><![CDATA[__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWVwKNioOoAwKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMioFdCiszghoRRSqYTihftirSM2E%3d&__VIEWSTATE=/wEPDwUKLTEwNTI0MjkwNQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkZCUArJ3C1Fln0zT65m8W%2b6wYPSdL]]></PostData> | |
| 85 | </Variation> | |
| 86 | </Variations> | |
| 87 | </SiteFile> | |
| 88 | <SiteFile id="4"> | |
| 89 | <Name>login.aspx</Name> | |
| 90 | <URL>/login.aspx</URL> | |
| 91 | <FullURL>http://testaspnet.vulnweb.com/login.aspx</FullURL> | |
| 92 | <Inputs> | |
| 93 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 94 | </Variable> | |
| 95 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 96 | </Variable> | |
| 97 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 98 | </Variable> | |
| 99 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 100 | </Variable> | |
| 101 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 102 | </Variable> | |
| 103 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 104 | </Variable> | |
| 105 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 106 | </Variable> | |
| 107 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 108 | </Variable> | |
| 109 | <Variable Name="ReturnUrl" Type="URL encoded GET"> | |
| 110 | </Variable> | |
| 111 | <Variable Name="ReturnUrl" Type="URL encoded GET"> | |
| 112 | </Variable> | |
| 113 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 114 | </Variable> | |
| 115 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 116 | </Variable> | |
| 117 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 118 | </Variable> | |
| 119 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 120 | </Variable> | |
| 121 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 122 | </Variable> | |
| 123 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 124 | </Variable> | |
| 125 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 126 | </Variable> | |
| 127 | <Variable Name="btnLogin" Type="URL encoded POST"> | |
| 128 | </Variable> | |
| 129 | </Inputs> | |
| 130 | <Variations> | |
| 131 | <Variation> | |
| 132 | <URL>http://testaspnet.vulnweb.com/login.aspx</URL> | |
| 133 | <PostData><![CDATA[btnLogin=Login&cbPersistCookie=on&tbPassword=g00dPa%24%24w0rD&tbUsername=ljmrwpfo&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></PostData> | |
| 134 | </Variation> | |
| 135 | <Variation> | |
| 136 | <URL>http://testaspnet.vulnweb.com/login.aspx</URL> | |
| 137 | <PostData><![CDATA[btnLogin=Login&tbPassword=g00dPa%24%24w0rD&tbUsername=fyjmttcx&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></PostData> | |
| 138 | </Variation> | |
| 139 | <Variation> | |
| 140 | <URL>http://testaspnet.vulnweb.com/login.aspx?ReturnUrl=/logout.aspx</URL> | |
| 141 | <PostData><![CDATA[]]></PostData> | |
| 142 | </Variation> | |
| 143 | <Variation> | |
| 144 | <URL>http://testaspnet.vulnweb.com/login.aspx?ReturnUrl=/postnews.aspx</URL> | |
| 145 | <PostData><![CDATA[]]></PostData> | |
| 146 | </Variation> | |
| 147 | <Variation> | |
| 148 | <URL>http://testaspnet.vulnweb.com/login.aspx?ReturnUrl=/logout.aspx</URL> | |
| 149 | <PostData><![CDATA[btnLogin=Login&cbPersistCookie=on&tbPassword=g00dPa%24%24w0rD&tbUsername=riqcjwfs&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></PostData> | |
| 150 | </Variation> | |
| 151 | <Variation> | |
| 152 | <URL>http://testaspnet.vulnweb.com/login.aspx?ReturnUrl=/logout.aspx</URL> | |
| 153 | <PostData><![CDATA[btnLogin=Login&tbPassword=g00dPa%24%24w0rD&tbUsername=hjhhosnx&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></PostData> | |
| 154 | </Variation> | |
| 155 | <Variation> | |
| 156 | <URL>http://testaspnet.vulnweb.com/login.aspx?ReturnUrl=/postnews.aspx</URL> | |
| 157 | <PostData><![CDATA[btnLogin=Login&cbPersistCookie=on&tbPassword=g00dPa%24%24w0rD&tbUsername=usighdix&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></PostData> | |
| 158 | </Variation> | |
| 159 | <Variation> | |
| 160 | <URL>http://testaspnet.vulnweb.com/login.aspx?ReturnUrl=/postnews.aspx</URL> | |
| 161 | <PostData><![CDATA[btnLogin=Login&tbPassword=g00dPa%24%24w0rD&tbUsername=vpustxlw&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></PostData> | |
| 162 | </Variation> | |
| 163 | <Variation> | |
| 164 | <URL>http://testaspnet.vulnweb.com/login.aspx</URL> | |
| 165 | <PostData><![CDATA[btnLogin=Login&cbPersistCookie=e&tbPassword=g00dPa%24%24w0rD&tbUsername=xeitiyuu&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></PostData> | |
| 166 | </Variation> | |
| 167 | </Variations> | |
| 168 | </SiteFile> | |
| 169 | <SiteFile id="5"> | |
| 170 | <Name>styles.css</Name> | |
| 171 | <URL>/styles.css</URL> | |
| 172 | <FullURL>http://testaspnet.vulnweb.com/styles.css</FullURL> | |
| 173 | <Inputs> | |
| 174 | </Inputs> | |
| 175 | <Variations> | |
| 176 | </Variations> | |
| 177 | </SiteFile> | |
| 178 | <SiteFile id="6"> | |
| 179 | <Name>signup.aspx</Name> | |
| 180 | <URL>/signup.aspx</URL> | |
| 181 | <FullURL>http://testaspnet.vulnweb.com/signup.aspx</FullURL> | |
| 182 | <Inputs> | |
| 183 | <Variable Name="btnSignup" Type="URL encoded POST"> | |
| 184 | </Variable> | |
| 185 | <Variable Name="btnSignup" Type="URL encoded POST"> | |
| 186 | </Variable> | |
| 187 | <Variable Name="btnSignup" Type="URL encoded POST"> | |
| 188 | </Variable> | |
| 189 | <Variable Name="btnSignup" Type="URL encoded POST"> | |
| 190 | </Variable> | |
| 191 | <Variable Name="btnSignup" Type="URL encoded POST"> | |
| 192 | </Variable> | |
| 193 | <Variable Name="btnSignup" Type="URL encoded POST"> | |
| 194 | </Variable> | |
| 195 | <Variable Name="btnSignup" Type="URL encoded POST"> | |
| 196 | </Variable> | |
| 197 | </Inputs> | |
| 198 | <Variations> | |
| 199 | <Variation> | |
| 200 | <URL>http://testaspnet.vulnweb.com/signup.aspx</URL> | |
| 201 | <PostData><![CDATA[btnSignup=Sign%20me%20up&tbPassword=g00dPa%24%24w0rD&tbUsername=paucanor&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWgKJ%2b8rsBQLStq24BwK3jsrkBALF97vxAQKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMe7zvcGDW1XEmT%2bKc/cai9hiHVyk%3d&__VIEWSTATE=/wEPDwUKLTY0MzI4NjU4Mw9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkZHEZ3VN6SP/C2xESDN/Y3p8zhfSB]]></PostData> | |
| 202 | </Variation> | |
| 203 | </Variations> | |
| 204 | </SiteFile> | |
| 205 | <SiteFile id="7"> | |
| 206 | <Name>rssfeed.aspx</Name> | |
| 207 | <URL>/rssfeed.aspx</URL> | |
| 208 | <FullURL>http://testaspnet.vulnweb.com/rssfeed.aspx</FullURL> | |
| 209 | <Inputs> | |
| 210 | </Inputs> | |
| 211 | <Variations> | |
| 212 | </Variations> | |
| 213 | </SiteFile> | |
| 214 | <SiteFile id="8"> | |
| 215 | <Name>readnews.aspx</Name> | |
| 216 | <URL>/readnews.aspx</URL> | |
| 217 | <FullURL>http://testaspnet.vulnweb.com/readnews.aspx</FullURL> | |
| 218 | <Inputs> | |
| 219 | <Variable Name="id" Type="URL encoded GET"> | |
| 220 | </Variable> | |
| 221 | <Variable Name="id" Type="URL encoded GET"> | |
| 222 | </Variable> | |
| 223 | <Variable Name="id" Type="URL encoded GET"> | |
| 224 | </Variable> | |
| 225 | <Variable Name="id" Type="URL encoded GET"> | |
| 226 | </Variable> | |
| 227 | <Variable Name="id" Type="URL encoded GET"> | |
| 228 | </Variable> | |
| 229 | <Variable Name="NewsAd" Type="URL encoded POST"> | |
| 230 | </Variable> | |
| 231 | <Variable Name="NewsAd" Type="URL encoded POST"> | |
| 232 | </Variable> | |
| 233 | <Variable Name="NewsAd" Type="URL encoded POST"> | |
| 234 | </Variable> | |
| 235 | <Variable Name="NewsAd" Type="URL encoded POST"> | |
| 236 | </Variable> | |
| 237 | <Variable Name="id" Type="URL encoded GET"> | |
| 238 | </Variable> | |
| 239 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 240 | </Variable> | |
| 241 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 242 | </Variable> | |
| 243 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 244 | </Variable> | |
| 245 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 246 | </Variable> | |
| 247 | </Inputs> | |
| 248 | <Variations> | |
| 249 | <Variation> | |
| 250 | <URL>http://testaspnet.vulnweb.com/readnews.aspx?id=2&NewsAd=ads/def.html</URL> | |
| 251 | <PostData><![CDATA[]]></PostData> | |
| 252 | </Variation> | |
| 253 | <Variation> | |
| 254 | <URL>http://testaspnet.vulnweb.com/readnews.aspx?id=0&NewsAd=ads/def.html</URL> | |
| 255 | <PostData><![CDATA[]]></PostData> | |
| 256 | </Variation> | |
| 257 | <Variation> | |
| 258 | <URL>http://testaspnet.vulnweb.com/readnews.aspx?id=3&NewsAd=ads/def.html</URL> | |
| 259 | <PostData><![CDATA[]]></PostData> | |
| 260 | </Variation> | |
| 261 | <Variation> | |
| 262 | <URL>http://testaspnet.vulnweb.com/readnews.aspx?id=2&NewsAd=ads/def.html</URL> | |
| 263 | <PostData><![CDATA[__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWVwKO/ffgDgKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMTuBuYk15KvnzAGnqqPk6tDbzR0Y%3d&__VIEWSTATE=/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc%2bYWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNToyMiBBTWQCBQ8WAh8BBTxXZWIgYXR0YWNrcyAtIGNhbiB5b3VyIHdlYiBhcHBsaWNhdGlvbnMgd2l0aHN0YW5kIHRoZSBmb3JjZT9kAgcPFgIfAQWuNzxwPjxzdHJvbmc%2bQWN1bmV0aXggY29tYmF0cyByaXNlIGluIHdlYiBhdHRhY2tzIHdpdGggQWN1bmV0aXggICAgICAgICAgICAgICAgICAgICAgICAgICAgV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAyIDwvc3Ryb25nPjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD4yMSBKdWx5IDIwMDUgLSA8c3Ryb25nPlN0YXJ0LXVwIGNvbXBhbnkgQWN1bmV0aXggcmVsZWFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lcjogYSB0b29sIHRvIGF1dG9tYXRpY2FsbHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXVkaXQgd2Vic2l0ZSBzZWN1cml0eS4gQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAgICAgICAgICAgICAgICAgICAgICAgICAgICAyIGNyYXdscyBhbiBlbnRpcmUgd2Vic2l0ZSwgbGF1bmNoZXMgcG9wdWxhciB3ZWIgYXR0YWNrcyAgICAgICAgICAgICAgICAgICAgICAgICAgICAoU1FMIEluamVjdGlvbiBldGMuKSBhbmQgaWRlbnRpZmllcyB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdGhhdCBuZWVkIHRvIGJlIGZpeGVkLjwvc3Ryb25nPiA8L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5TZWN1cmluZyB5b3VyIHdlYnNpdGUgc2hvdWxkIGJlIHlvdXIgbnVtYmVyIG9uZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjb25jZXJuPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgSGFja2VycyBhcmUgY29uY2VudHJhdGluZyB0aGVpciBlZmZvcnRzIG9uIHdlYi1iYXNlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBhcHBsaWNhdGlvbnMgLSA3NSUgb2YgY3liZXIgYXR0YWNrcyBhcmUgZG9uZSBhdCB0aGUgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGxldmVsLCBhIEdhcnRuZXIgR3JvdXAgc3R1ZHkgaGFzIHJldmVhbGVkLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBXZWIgYXBwbGljYXRpb25zIGFyZSBhY2Nlc3NpYmxlIDI0IGhvdXJzIGEgZGF5LCA3IGRheXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgYSB3ZWVrIGFuZCBjb250cm9sIHZhbHVhYmxlIGRhdGEgc3VjaCBhcyBjdXN0b21lciBpbmZvcm1hdGlvbiwgICAgICAgICAgICAgICAgICAgICAgICAgICAgdHJhbnNhY3Rpb24gaW5mb3JtYXRpb24gYW5kIGV2ZW4gcHJvcHJpZXRhcnkgY29ycG9yYXRlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGEuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bNTAwLDAwMCBjdXN0b21lciBjcmVkaXQgY2FyZCBudW1iZXJzIG9idGFpbmVkIHZpYSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhIHdlYiBhdHRhY2s8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBXZWxsLWtub3duIHNpdGVzIHRoYXQgd2VyZSBvcGVuIHRvIHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGluY2x1ZGUgZmFzaGlvbiBsYWJlbCBHdWVzcyBhbmQgcGV0IHN1cHBseSByZXRhaWxlciAgICAgICAgICAgICAgICAgICAgICAgICAgICBQZXRDby5jb20gd2hvIHdlcmUgbm90b3Jpb3VzbHkgZm91bmQgdG8gYmUgdnVsbmVyYWJsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB0byB0aGUgU1FMIGluamVjdGlvbiB2dWxuZXJhYmlsaXR5IChKdW5lIDIwMDMpLiBUaGlzICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJlc3VsdGVkIGluIFBldENvIGxlYXZpbmcgYXMgbWFueSBhcyA1MDAsMDAwIGNyZWRpdCAgICAgICAgICAgICAgICAgICAgICAgICAgICBjYXJkIG51bWJlcnMgb3BlbiB0byBhbnlvbmUgYWJsZSB0byBjb25zdHJ1Y3QgdGhpcyBzcGVjaWFsbHktY3JhZnRlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBVUkwuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bRmlyZXdhbGxzLCBTU0wgYW5kIGxvY2tlZC1kb3duIHNlcnZlcnMgYXJlIGZ1dGlsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBoYWNraW5nPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQW55IGRlZmVuc2UgYXQgbmV0d29yayBzZWN1cml0eSBsZXZlbCB3aWxsIHByb3ZpZGUgbm8gICAgICAgICAgICAgICAgICAgICAgICAgICAgcHJvdGVjdGlvbiBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzIHNpbmNlIHRoZXkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXJlIGxhdW5jaGVkIG9uIHBvcnQgODAgLSB3aGljaCBoYXMgdG8gcmVtYWluIG9wZW4uICAgICAgICAgICAgICAgICAgICAgICAgICAgIEluIGFkZGl0aW9uLCB3ZWIgYXBwbGljYXRpb25zIChjdXN0b21lciBhcmVhcywgc2hvcHBpbmcgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FydHMgZXRjLikgYXJlIG9mdGVuIHRhaWxvci1tYWRlLCBpbnZhcmlhYmx5IHRlc3RlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBsZXNzIHRoYW4gb2ZmLXRoZS1zaGVsZiBzb2Z0d2FyZSBhbmQgYXJlIHRoZXJlZm9yZSBtb3JlICAgICAgICAgICAgICAgICAgICAgICAgICAgIHN1c2NlcHRpYmxlIHRvIGF0dGFjay48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bJnF1b3Q7Q29tcGFuaWVzIGhhdmUgaW1wbGVtZW50ZWQgbmV0d29yay1sZXZlbCBzZWN1cml0eSwgICAgICAgICAgICAgICAgICAgICAgICAgICAgaG93ZXZlciB0aGV5IGZhaWwgdG8gYXVkaXQgYW5kIHNlY3VyZSB0aGVpciB3ZWIgYXBwbGljYXRpb25zLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBUaGVzZSBhcHBsaWNhdGlvbnMgaGF2ZSBhY2Nlc3MgdG8gc2Vuc2l0aXZlIGRhdGEgYW5kICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFyZSBhIGhhY2tlcidzIHByaW1lIHRhcmdldCwmcXVvdDsgc2FpZCBOaWNrIEdhbGVhLCAgICAgICAgICAgICAgICAgICAgICAgICAgICBDRU8gb2YgQWN1bmV0aXguICZxdW90O0F1ZGl0aW5nIG9uZSdzIHdlYiBhcHBzIHNob3VsZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBiZSB0aGUgbnVtYmVyIG9uZSBzZWN1cml0eSBjb25jZXJuLiZxdW90OzwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlRoZSBuZWVkIGZvciBhbiBhdXRvbWF0ZWQgd2ViIGFwcGxpY2F0aW9uIHZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgc2Nhbm5lcjwvc3Ryb25nPjxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIE1hbnVhbGx5IGF1ZGl0aW5nIGEgd2ViIGFwcGxpY2F0aW9uIGZvciB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdG8gU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiAgICAgICAgICAgICAgICAgICAgICAgICAgICBhdHRhY2tzIGlzIHZpcnR1YWxseSBpbXBvc3NpYmxlLiBXaXRoIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5ICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNjYW5uZXIgdGhlIHByb2Nlc3Mgb2YgYXVkaXRpbmcgd2ViIGFwcGxpY2F0aW9ucyBzdWNoICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFzIHNob3BwaW5nIGNhcnRzIGFuZCBmb3JtcywgY2FuIGJlIGVhc2lseSBhdXRvbWF0ZWQuICAgICAgICAgICAgICAgICAgICAgICAgICAgIFdoYXQncyBtb3JlLCB0aGUgc2VjdXJpdHkgY2hlY2tzIGNhbiBlYXNpbHkgYmUgcmUtbGF1bmNoZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGVhY2ggYXBwbGljYXRpb24gdXBkYXRlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkhvdyBBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIHdvcmtzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGZpcnN0IGNyYXdscyB0aGUgd2hvbGUgd2Vic2l0ZSwgYW5hbHl6ZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgaW4tZGVwdGggZWFjaCBmaWxlIGl0IGZpbmRzLCBhbmQgZGlzcGxheXMgdGhlIGVudGlyZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB3ZWJzaXRlIHN0cnVjdHVyZS4gQWZ0ZXIgdGhpcyBkaXNjb3Zlcnkgc3RhZ2UsIGl0IHBlcmZvcm1zICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFuIGF1dG9tYXRpYyBhdWRpdCBmb3IgY29tbW9uIHNlY3VyaXR5IHZ1bG5lcmFiaWxpdGllcy48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BdXRvbWF0aWNhbGx5IGRldGVjdHMgU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiB2dWxuZXJhYmlsaXRpZXM8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBTUUwgaW5qZWN0aW9uIGlzIGEgaGFja2luZyB0ZWNobmlxdWUgd2hpY2ggbW9kaWZpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgU1FMIGNvbW1hbmRzIGluIG9yZGVyIHRvIGdhaW4gYWNjZXNzIHRvIGRhdGEgaW4gdGhlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGFiYXNlLiBDcm9zcyBzaXRlIHNjcmlwdGluZyBhdHRhY2tzIGFsbG93IGEgaGFja2VyICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRvIGV4ZWN1dGUgYSBtYWxpY2lvdXMgc2NyaXB0IG9uIHlvdXIgdmlzaXRvcnMnIGJyb3dzZXIuICAgICAgICAgICAgICAgICAgICAgICAgICAgIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgY2FuIGNoZWNrIGlmIHlvdXIgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGlzIHZ1bG5lcmFibGUgdG8gYm90aCBvZiB0aGVzZSBhdHRhY2tzLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBNb3JlIGluZm9ybWF0aW9uIGFib3V0IGNyb3NzIHNpdGUgc2NyaXB0aW5nICZhbXA7IFNRTCAgICAgICAgICAgICAgICAgICAgICAgICAgICBpbmplY3Rpb24gYXQgb3VyIHdlYnNpdGUgc2VjdXJpdHkgaW5mbyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgYWxzbyBjaGVja3MgZm9yICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRoZSBmb2xsb3dpbmcgd2ViIGF0dGFja3M6PC9zdHJvbmc%2bPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDx1bD4gPGxpPkNSTEYgaW5qZWN0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5Db2RlIGV4ZWN1dGlvbiBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRGlyZWN0b3J5IHRyYXZlcnNhbCBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRmlsZSBpbmNsdXNpb24gYXR0YWNrczxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvbGk%2bPGxpPiBJbnB1dCB2YWxpZGF0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5BdXRoZW50aWNhdGlvbiBhdHRhY2tzLjwvbGk%2bIDwvdWw%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BZHZhbmNlZCBwZW5ldHJhdGlvbiB0ZXN0aW5nIHRvb2xzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGFsc28gaW5jbHVkZXMgdG9vbHMgc3VjaCBhcyBhbiBIVFRQIGVkaXRvciAgICAgICAgICAgICAgICAgICAgICAgICAgICAmYW1wOyBIVFRQIHNuaWZmZXIgdG8gYWxsb3cgY3VzdG9taXphdGlvbiBvZiB3ZWIgdnVsbmVyYWJpbGl0eSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjaGVja3MuIFVzaW5nIHRoZSBWdWxuZXJhYmlsaXR5IGVkaXRvciwgbmV3IGF0dGFja3MgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FuIGVhc2lseSBiZSBjcmVhdGVkLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlByaWNpbmcgJmFtcDsgYXZhaWxhYmlsaXR5PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGlzIGF2YWlsYWJsZSBhcyBhbiBlbnRlcnByaXNlIG9yIGFzIGEgY29uc3VsdGFudCAgICAgICAgICAgICAgICAgICAgICAgICAgICB2ZXJzaW9uLiBBIHN1YnNjcmlwdGlvbiBiYXNlZCBsaWNlbnNlIGNhbiBiZSBwdXJjaGFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGFzIGxpdHRsZSBhcyAkMzk1LCB3aGVyZWFzIGEgcGVycGV0dWFsIGxpY2Vuc2Ugc3RhcnRzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGF0ICQyOTk1LiBGb3IgbW9yZSBpbmZvcm1hdGlvbiB2aXNpdCBvdXIgcHJpY2luZyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFib3V0IEFjdW5ldGl4PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggd2FzIGZvdW5kZWQgdG8gY29tYmF0IHRoZSBhbGFybWluZyByaXNlIGluICAgICAgICAgICAgICAgICAgICAgICAgICAgIHdlYiBhdHRhY2tzLiBJdHMgZmxhZ3NoaXAgcHJvZHVjdCwgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgU2Nhbm5lciwgaXMgdGhlIHJlc3VsdCBvZiBzZXZlcmFsIHllYXJzIG9mIGRldmVsb3BtZW50ICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJ5IGEgdGVhbSBvZiBoaWdobHkgZXhwZXJpZW5jZWQgc2VjdXJpdHkgZGV2ZWxvcGVycy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggaXMgYSBwcml2YXRlbHkgaGVsZCBjb21wYW55IHdpdGggaGVhZHF1YXJ0ZXJzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJhc2VkIGluIEV1cm9wZSAoTWFsdGEpIHdpdGggaXRzIE5ldyBZb3JrIFVTIG9mZmljZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY2hlZHVsZWQgdG8gb3BlbiBpbiBRMyBvZiAyMDA1LiA8L3A%2bIGQCCQ8PFgIeC05hdmlnYXRlVXJsBRJDb21tZW50cy5hc3B4P2lkPTJkZAILDxYCHgNzcmMFDGFkcy9kZWYuaHRtbGRkNCSZh%2buMoCTcXGDfVu5D5CfxA7Y%3d]]></PostData> | |
| 264 | </Variation> | |
| 265 | <Variation> | |
| 266 | <URL>http://testaspnet.vulnweb.com/readnews.aspx?id=2</URL> | |
| 267 | <PostData><![CDATA[]]></PostData> | |
| 268 | </Variation> | |
| 269 | <Variation> | |
| 270 | <URL>http://testaspnet.vulnweb.com/readnews.aspx?id=0&NewsAd=ads/def.html</URL> | |
| 271 | <PostData><![CDATA[__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWVwKO/ffgDgKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMTuBuYk15KvnzAGnqqPk6tDbzR0Y%3d&__VIEWSTATE=/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc%2bYWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNToyMiBBTWQCBQ8WAh8BBTxXZWIgYXR0YWNrcyAtIGNhbiB5b3VyIHdlYiBhcHBsaWNhdGlvbnMgd2l0aHN0YW5kIHRoZSBmb3JjZT9kAgcPFgIfAQWuNzxwPjxzdHJvbmc%2bQWN1bmV0aXggY29tYmF0cyByaXNlIGluIHdlYiBhdHRhY2tzIHdpdGggQWN1bmV0aXggICAgICAgICAgICAgICAgICAgICAgICAgICAgV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAyIDwvc3Ryb25nPjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD4yMSBKdWx5IDIwMDUgLSA8c3Ryb25nPlN0YXJ0LXVwIGNvbXBhbnkgQWN1bmV0aXggcmVsZWFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lcjogYSB0b29sIHRvIGF1dG9tYXRpY2FsbHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXVkaXQgd2Vic2l0ZSBzZWN1cml0eS4gQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAgICAgICAgICAgICAgICAgICAgICAgICAgICAyIGNyYXdscyBhbiBlbnRpcmUgd2Vic2l0ZSwgbGF1bmNoZXMgcG9wdWxhciB3ZWIgYXR0YWNrcyAgICAgICAgICAgICAgICAgICAgICAgICAgICAoU1FMIEluamVjdGlvbiBldGMuKSBhbmQgaWRlbnRpZmllcyB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdGhhdCBuZWVkIHRvIGJlIGZpeGVkLjwvc3Ryb25nPiA8L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5TZWN1cmluZyB5b3VyIHdlYnNpdGUgc2hvdWxkIGJlIHlvdXIgbnVtYmVyIG9uZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjb25jZXJuPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgSGFja2VycyBhcmUgY29uY2VudHJhdGluZyB0aGVpciBlZmZvcnRzIG9uIHdlYi1iYXNlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBhcHBsaWNhdGlvbnMgLSA3NSUgb2YgY3liZXIgYXR0YWNrcyBhcmUgZG9uZSBhdCB0aGUgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGxldmVsLCBhIEdhcnRuZXIgR3JvdXAgc3R1ZHkgaGFzIHJldmVhbGVkLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBXZWIgYXBwbGljYXRpb25zIGFyZSBhY2Nlc3NpYmxlIDI0IGhvdXJzIGEgZGF5LCA3IGRheXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgYSB3ZWVrIGFuZCBjb250cm9sIHZhbHVhYmxlIGRhdGEgc3VjaCBhcyBjdXN0b21lciBpbmZvcm1hdGlvbiwgICAgICAgICAgICAgICAgICAgICAgICAgICAgdHJhbnNhY3Rpb24gaW5mb3JtYXRpb24gYW5kIGV2ZW4gcHJvcHJpZXRhcnkgY29ycG9yYXRlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGEuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bNTAwLDAwMCBjdXN0b21lciBjcmVkaXQgY2FyZCBudW1iZXJzIG9idGFpbmVkIHZpYSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhIHdlYiBhdHRhY2s8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBXZWxsLWtub3duIHNpdGVzIHRoYXQgd2VyZSBvcGVuIHRvIHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGluY2x1ZGUgZmFzaGlvbiBsYWJlbCBHdWVzcyBhbmQgcGV0IHN1cHBseSByZXRhaWxlciAgICAgICAgICAgICAgICAgICAgICAgICAgICBQZXRDby5jb20gd2hvIHdlcmUgbm90b3Jpb3VzbHkgZm91bmQgdG8gYmUgdnVsbmVyYWJsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB0byB0aGUgU1FMIGluamVjdGlvbiB2dWxuZXJhYmlsaXR5IChKdW5lIDIwMDMpLiBUaGlzICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJlc3VsdGVkIGluIFBldENvIGxlYXZpbmcgYXMgbWFueSBhcyA1MDAsMDAwIGNyZWRpdCAgICAgICAgICAgICAgICAgICAgICAgICAgICBjYXJkIG51bWJlcnMgb3BlbiB0byBhbnlvbmUgYWJsZSB0byBjb25zdHJ1Y3QgdGhpcyBzcGVjaWFsbHktY3JhZnRlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBVUkwuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bRmlyZXdhbGxzLCBTU0wgYW5kIGxvY2tlZC1kb3duIHNlcnZlcnMgYXJlIGZ1dGlsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBoYWNraW5nPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQW55IGRlZmVuc2UgYXQgbmV0d29yayBzZWN1cml0eSBsZXZlbCB3aWxsIHByb3ZpZGUgbm8gICAgICAgICAgICAgICAgICAgICAgICAgICAgcHJvdGVjdGlvbiBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzIHNpbmNlIHRoZXkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXJlIGxhdW5jaGVkIG9uIHBvcnQgODAgLSB3aGljaCBoYXMgdG8gcmVtYWluIG9wZW4uICAgICAgICAgICAgICAgICAgICAgICAgICAgIEluIGFkZGl0aW9uLCB3ZWIgYXBwbGljYXRpb25zIChjdXN0b21lciBhcmVhcywgc2hvcHBpbmcgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FydHMgZXRjLikgYXJlIG9mdGVuIHRhaWxvci1tYWRlLCBpbnZhcmlhYmx5IHRlc3RlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBsZXNzIHRoYW4gb2ZmLXRoZS1zaGVsZiBzb2Z0d2FyZSBhbmQgYXJlIHRoZXJlZm9yZSBtb3JlICAgICAgICAgICAgICAgICAgICAgICAgICAgIHN1c2NlcHRpYmxlIHRvIGF0dGFjay48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bJnF1b3Q7Q29tcGFuaWVzIGhhdmUgaW1wbGVtZW50ZWQgbmV0d29yay1sZXZlbCBzZWN1cml0eSwgICAgICAgICAgICAgICAgICAgICAgICAgICAgaG93ZXZlciB0aGV5IGZhaWwgdG8gYXVkaXQgYW5kIHNlY3VyZSB0aGVpciB3ZWIgYXBwbGljYXRpb25zLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBUaGVzZSBhcHBsaWNhdGlvbnMgaGF2ZSBhY2Nlc3MgdG8gc2Vuc2l0aXZlIGRhdGEgYW5kICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFyZSBhIGhhY2tlcidzIHByaW1lIHRhcmdldCwmcXVvdDsgc2FpZCBOaWNrIEdhbGVhLCAgICAgICAgICAgICAgICAgICAgICAgICAgICBDRU8gb2YgQWN1bmV0aXguICZxdW90O0F1ZGl0aW5nIG9uZSdzIHdlYiBhcHBzIHNob3VsZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBiZSB0aGUgbnVtYmVyIG9uZSBzZWN1cml0eSBjb25jZXJuLiZxdW90OzwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlRoZSBuZWVkIGZvciBhbiBhdXRvbWF0ZWQgd2ViIGFwcGxpY2F0aW9uIHZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgc2Nhbm5lcjwvc3Ryb25nPjxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIE1hbnVhbGx5IGF1ZGl0aW5nIGEgd2ViIGFwcGxpY2F0aW9uIGZvciB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdG8gU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiAgICAgICAgICAgICAgICAgICAgICAgICAgICBhdHRhY2tzIGlzIHZpcnR1YWxseSBpbXBvc3NpYmxlLiBXaXRoIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5ICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNjYW5uZXIgdGhlIHByb2Nlc3Mgb2YgYXVkaXRpbmcgd2ViIGFwcGxpY2F0aW9ucyBzdWNoICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFzIHNob3BwaW5nIGNhcnRzIGFuZCBmb3JtcywgY2FuIGJlIGVhc2lseSBhdXRvbWF0ZWQuICAgICAgICAgICAgICAgICAgICAgICAgICAgIFdoYXQncyBtb3JlLCB0aGUgc2VjdXJpdHkgY2hlY2tzIGNhbiBlYXNpbHkgYmUgcmUtbGF1bmNoZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGVhY2ggYXBwbGljYXRpb24gdXBkYXRlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkhvdyBBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIHdvcmtzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGZpcnN0IGNyYXdscyB0aGUgd2hvbGUgd2Vic2l0ZSwgYW5hbHl6ZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgaW4tZGVwdGggZWFjaCBmaWxlIGl0IGZpbmRzLCBhbmQgZGlzcGxheXMgdGhlIGVudGlyZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB3ZWJzaXRlIHN0cnVjdHVyZS4gQWZ0ZXIgdGhpcyBkaXNjb3Zlcnkgc3RhZ2UsIGl0IHBlcmZvcm1zICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFuIGF1dG9tYXRpYyBhdWRpdCBmb3IgY29tbW9uIHNlY3VyaXR5IHZ1bG5lcmFiaWxpdGllcy48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BdXRvbWF0aWNhbGx5IGRldGVjdHMgU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiB2dWxuZXJhYmlsaXRpZXM8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBTUUwgaW5qZWN0aW9uIGlzIGEgaGFja2luZyB0ZWNobmlxdWUgd2hpY2ggbW9kaWZpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgU1FMIGNvbW1hbmRzIGluIG9yZGVyIHRvIGdhaW4gYWNjZXNzIHRvIGRhdGEgaW4gdGhlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGFiYXNlLiBDcm9zcyBzaXRlIHNjcmlwdGluZyBhdHRhY2tzIGFsbG93IGEgaGFja2VyICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRvIGV4ZWN1dGUgYSBtYWxpY2lvdXMgc2NyaXB0IG9uIHlvdXIgdmlzaXRvcnMnIGJyb3dzZXIuICAgICAgICAgICAgICAgICAgICAgICAgICAgIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgY2FuIGNoZWNrIGlmIHlvdXIgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGlzIHZ1bG5lcmFibGUgdG8gYm90aCBvZiB0aGVzZSBhdHRhY2tzLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBNb3JlIGluZm9ybWF0aW9uIGFib3V0IGNyb3NzIHNpdGUgc2NyaXB0aW5nICZhbXA7IFNRTCAgICAgICAgICAgICAgICAgICAgICAgICAgICBpbmplY3Rpb24gYXQgb3VyIHdlYnNpdGUgc2VjdXJpdHkgaW5mbyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgYWxzbyBjaGVja3MgZm9yICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRoZSBmb2xsb3dpbmcgd2ViIGF0dGFja3M6PC9zdHJvbmc%2bPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDx1bD4gPGxpPkNSTEYgaW5qZWN0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5Db2RlIGV4ZWN1dGlvbiBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRGlyZWN0b3J5IHRyYXZlcnNhbCBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRmlsZSBpbmNsdXNpb24gYXR0YWNrczxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvbGk%2bPGxpPiBJbnB1dCB2YWxpZGF0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5BdXRoZW50aWNhdGlvbiBhdHRhY2tzLjwvbGk%2bIDwvdWw%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BZHZhbmNlZCBwZW5ldHJhdGlvbiB0ZXN0aW5nIHRvb2xzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGFsc28gaW5jbHVkZXMgdG9vbHMgc3VjaCBhcyBhbiBIVFRQIGVkaXRvciAgICAgICAgICAgICAgICAgICAgICAgICAgICAmYW1wOyBIVFRQIHNuaWZmZXIgdG8gYWxsb3cgY3VzdG9taXphdGlvbiBvZiB3ZWIgdnVsbmVyYWJpbGl0eSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjaGVja3MuIFVzaW5nIHRoZSBWdWxuZXJhYmlsaXR5IGVkaXRvciwgbmV3IGF0dGFja3MgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FuIGVhc2lseSBiZSBjcmVhdGVkLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlByaWNpbmcgJmFtcDsgYXZhaWxhYmlsaXR5PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGlzIGF2YWlsYWJsZSBhcyBhbiBlbnRlcnByaXNlIG9yIGFzIGEgY29uc3VsdGFudCAgICAgICAgICAgICAgICAgICAgICAgICAgICB2ZXJzaW9uLiBBIHN1YnNjcmlwdGlvbiBiYXNlZCBsaWNlbnNlIGNhbiBiZSBwdXJjaGFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGFzIGxpdHRsZSBhcyAkMzk1LCB3aGVyZWFzIGEgcGVycGV0dWFsIGxpY2Vuc2Ugc3RhcnRzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGF0ICQyOTk1LiBGb3IgbW9yZSBpbmZvcm1hdGlvbiB2aXNpdCBvdXIgcHJpY2luZyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFib3V0IEFjdW5ldGl4PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggd2FzIGZvdW5kZWQgdG8gY29tYmF0IHRoZSBhbGFybWluZyByaXNlIGluICAgICAgICAgICAgICAgICAgICAgICAgICAgIHdlYiBhdHRhY2tzLiBJdHMgZmxhZ3NoaXAgcHJvZHVjdCwgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgU2Nhbm5lciwgaXMgdGhlIHJlc3VsdCBvZiBzZXZlcmFsIHllYXJzIG9mIGRldmVsb3BtZW50ICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJ5IGEgdGVhbSBvZiBoaWdobHkgZXhwZXJpZW5jZWQgc2VjdXJpdHkgZGV2ZWxvcGVycy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggaXMgYSBwcml2YXRlbHkgaGVsZCBjb21wYW55IHdpdGggaGVhZHF1YXJ0ZXJzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJhc2VkIGluIEV1cm9wZSAoTWFsdGEpIHdpdGggaXRzIE5ldyBZb3JrIFVTIG9mZmljZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY2hlZHVsZWQgdG8gb3BlbiBpbiBRMyBvZiAyMDA1LiA8L3A%2bIGQCCQ8PFgIeC05hdmlnYXRlVXJsBRJDb21tZW50cy5hc3B4P2lkPTJkZAILDxYCHgNzcmMFDGFkcy9kZWYuaHRtbGRkNCSZh%2buMoCTcXGDfVu5D5CfxA7Y%3d]]></PostData> | |
| 272 | </Variation> | |
| 273 | <Variation> | |
| 274 | <URL>http://testaspnet.vulnweb.com/readnews.aspx?id=3&NewsAd=ads/def.html</URL> | |
| 275 | <PostData><![CDATA[__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWVwKO/ffgDgKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMTuBuYk15KvnzAGnqqPk6tDbzR0Y%3d&__VIEWSTATE=/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc%2bYWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNToyMiBBTWQCBQ8WAh8BBTxXZWIgYXR0YWNrcyAtIGNhbiB5b3VyIHdlYiBhcHBsaWNhdGlvbnMgd2l0aHN0YW5kIHRoZSBmb3JjZT9kAgcPFgIfAQWuNzxwPjxzdHJvbmc%2bQWN1bmV0aXggY29tYmF0cyByaXNlIGluIHdlYiBhdHRhY2tzIHdpdGggQWN1bmV0aXggICAgICAgICAgICAgICAgICAgICAgICAgICAgV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAyIDwvc3Ryb25nPjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD4yMSBKdWx5IDIwMDUgLSA8c3Ryb25nPlN0YXJ0LXVwIGNvbXBhbnkgQWN1bmV0aXggcmVsZWFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lcjogYSB0b29sIHRvIGF1dG9tYXRpY2FsbHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXVkaXQgd2Vic2l0ZSBzZWN1cml0eS4gQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAgICAgICAgICAgICAgICAgICAgICAgICAgICAyIGNyYXdscyBhbiBlbnRpcmUgd2Vic2l0ZSwgbGF1bmNoZXMgcG9wdWxhciB3ZWIgYXR0YWNrcyAgICAgICAgICAgICAgICAgICAgICAgICAgICAoU1FMIEluamVjdGlvbiBldGMuKSBhbmQgaWRlbnRpZmllcyB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdGhhdCBuZWVkIHRvIGJlIGZpeGVkLjwvc3Ryb25nPiA8L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5TZWN1cmluZyB5b3VyIHdlYnNpdGUgc2hvdWxkIGJlIHlvdXIgbnVtYmVyIG9uZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjb25jZXJuPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgSGFja2VycyBhcmUgY29uY2VudHJhdGluZyB0aGVpciBlZmZvcnRzIG9uIHdlYi1iYXNlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBhcHBsaWNhdGlvbnMgLSA3NSUgb2YgY3liZXIgYXR0YWNrcyBhcmUgZG9uZSBhdCB0aGUgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGxldmVsLCBhIEdhcnRuZXIgR3JvdXAgc3R1ZHkgaGFzIHJldmVhbGVkLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBXZWIgYXBwbGljYXRpb25zIGFyZSBhY2Nlc3NpYmxlIDI0IGhvdXJzIGEgZGF5LCA3IGRheXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgYSB3ZWVrIGFuZCBjb250cm9sIHZhbHVhYmxlIGRhdGEgc3VjaCBhcyBjdXN0b21lciBpbmZvcm1hdGlvbiwgICAgICAgICAgICAgICAgICAgICAgICAgICAgdHJhbnNhY3Rpb24gaW5mb3JtYXRpb24gYW5kIGV2ZW4gcHJvcHJpZXRhcnkgY29ycG9yYXRlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGEuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bNTAwLDAwMCBjdXN0b21lciBjcmVkaXQgY2FyZCBudW1iZXJzIG9idGFpbmVkIHZpYSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhIHdlYiBhdHRhY2s8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBXZWxsLWtub3duIHNpdGVzIHRoYXQgd2VyZSBvcGVuIHRvIHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGluY2x1ZGUgZmFzaGlvbiBsYWJlbCBHdWVzcyBhbmQgcGV0IHN1cHBseSByZXRhaWxlciAgICAgICAgICAgICAgICAgICAgICAgICAgICBQZXRDby5jb20gd2hvIHdlcmUgbm90b3Jpb3VzbHkgZm91bmQgdG8gYmUgdnVsbmVyYWJsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB0byB0aGUgU1FMIGluamVjdGlvbiB2dWxuZXJhYmlsaXR5IChKdW5lIDIwMDMpLiBUaGlzICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJlc3VsdGVkIGluIFBldENvIGxlYXZpbmcgYXMgbWFueSBhcyA1MDAsMDAwIGNyZWRpdCAgICAgICAgICAgICAgICAgICAgICAgICAgICBjYXJkIG51bWJlcnMgb3BlbiB0byBhbnlvbmUgYWJsZSB0byBjb25zdHJ1Y3QgdGhpcyBzcGVjaWFsbHktY3JhZnRlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBVUkwuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bRmlyZXdhbGxzLCBTU0wgYW5kIGxvY2tlZC1kb3duIHNlcnZlcnMgYXJlIGZ1dGlsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBoYWNraW5nPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQW55IGRlZmVuc2UgYXQgbmV0d29yayBzZWN1cml0eSBsZXZlbCB3aWxsIHByb3ZpZGUgbm8gICAgICAgICAgICAgICAgICAgICAgICAgICAgcHJvdGVjdGlvbiBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzIHNpbmNlIHRoZXkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXJlIGxhdW5jaGVkIG9uIHBvcnQgODAgLSB3aGljaCBoYXMgdG8gcmVtYWluIG9wZW4uICAgICAgICAgICAgICAgICAgICAgICAgICAgIEluIGFkZGl0aW9uLCB3ZWIgYXBwbGljYXRpb25zIChjdXN0b21lciBhcmVhcywgc2hvcHBpbmcgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FydHMgZXRjLikgYXJlIG9mdGVuIHRhaWxvci1tYWRlLCBpbnZhcmlhYmx5IHRlc3RlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBsZXNzIHRoYW4gb2ZmLXRoZS1zaGVsZiBzb2Z0d2FyZSBhbmQgYXJlIHRoZXJlZm9yZSBtb3JlICAgICAgICAgICAgICAgICAgICAgICAgICAgIHN1c2NlcHRpYmxlIHRvIGF0dGFjay48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bJnF1b3Q7Q29tcGFuaWVzIGhhdmUgaW1wbGVtZW50ZWQgbmV0d29yay1sZXZlbCBzZWN1cml0eSwgICAgICAgICAgICAgICAgICAgICAgICAgICAgaG93ZXZlciB0aGV5IGZhaWwgdG8gYXVkaXQgYW5kIHNlY3VyZSB0aGVpciB3ZWIgYXBwbGljYXRpb25zLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBUaGVzZSBhcHBsaWNhdGlvbnMgaGF2ZSBhY2Nlc3MgdG8gc2Vuc2l0aXZlIGRhdGEgYW5kICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFyZSBhIGhhY2tlcidzIHByaW1lIHRhcmdldCwmcXVvdDsgc2FpZCBOaWNrIEdhbGVhLCAgICAgICAgICAgICAgICAgICAgICAgICAgICBDRU8gb2YgQWN1bmV0aXguICZxdW90O0F1ZGl0aW5nIG9uZSdzIHdlYiBhcHBzIHNob3VsZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBiZSB0aGUgbnVtYmVyIG9uZSBzZWN1cml0eSBjb25jZXJuLiZxdW90OzwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlRoZSBuZWVkIGZvciBhbiBhdXRvbWF0ZWQgd2ViIGFwcGxpY2F0aW9uIHZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgc2Nhbm5lcjwvc3Ryb25nPjxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIE1hbnVhbGx5IGF1ZGl0aW5nIGEgd2ViIGFwcGxpY2F0aW9uIGZvciB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdG8gU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiAgICAgICAgICAgICAgICAgICAgICAgICAgICBhdHRhY2tzIGlzIHZpcnR1YWxseSBpbXBvc3NpYmxlLiBXaXRoIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5ICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNjYW5uZXIgdGhlIHByb2Nlc3Mgb2YgYXVkaXRpbmcgd2ViIGFwcGxpY2F0aW9ucyBzdWNoICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFzIHNob3BwaW5nIGNhcnRzIGFuZCBmb3JtcywgY2FuIGJlIGVhc2lseSBhdXRvbWF0ZWQuICAgICAgICAgICAgICAgICAgICAgICAgICAgIFdoYXQncyBtb3JlLCB0aGUgc2VjdXJpdHkgY2hlY2tzIGNhbiBlYXNpbHkgYmUgcmUtbGF1bmNoZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGVhY2ggYXBwbGljYXRpb24gdXBkYXRlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkhvdyBBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIHdvcmtzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGZpcnN0IGNyYXdscyB0aGUgd2hvbGUgd2Vic2l0ZSwgYW5hbHl6ZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgaW4tZGVwdGggZWFjaCBmaWxlIGl0IGZpbmRzLCBhbmQgZGlzcGxheXMgdGhlIGVudGlyZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB3ZWJzaXRlIHN0cnVjdHVyZS4gQWZ0ZXIgdGhpcyBkaXNjb3Zlcnkgc3RhZ2UsIGl0IHBlcmZvcm1zICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFuIGF1dG9tYXRpYyBhdWRpdCBmb3IgY29tbW9uIHNlY3VyaXR5IHZ1bG5lcmFiaWxpdGllcy48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BdXRvbWF0aWNhbGx5IGRldGVjdHMgU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiB2dWxuZXJhYmlsaXRpZXM8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBTUUwgaW5qZWN0aW9uIGlzIGEgaGFja2luZyB0ZWNobmlxdWUgd2hpY2ggbW9kaWZpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgU1FMIGNvbW1hbmRzIGluIG9yZGVyIHRvIGdhaW4gYWNjZXNzIHRvIGRhdGEgaW4gdGhlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGFiYXNlLiBDcm9zcyBzaXRlIHNjcmlwdGluZyBhdHRhY2tzIGFsbG93IGEgaGFja2VyICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRvIGV4ZWN1dGUgYSBtYWxpY2lvdXMgc2NyaXB0IG9uIHlvdXIgdmlzaXRvcnMnIGJyb3dzZXIuICAgICAgICAgICAgICAgICAgICAgICAgICAgIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgY2FuIGNoZWNrIGlmIHlvdXIgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGlzIHZ1bG5lcmFibGUgdG8gYm90aCBvZiB0aGVzZSBhdHRhY2tzLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBNb3JlIGluZm9ybWF0aW9uIGFib3V0IGNyb3NzIHNpdGUgc2NyaXB0aW5nICZhbXA7IFNRTCAgICAgICAgICAgICAgICAgICAgICAgICAgICBpbmplY3Rpb24gYXQgb3VyIHdlYnNpdGUgc2VjdXJpdHkgaW5mbyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgYWxzbyBjaGVja3MgZm9yICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRoZSBmb2xsb3dpbmcgd2ViIGF0dGFja3M6PC9zdHJvbmc%2bPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDx1bD4gPGxpPkNSTEYgaW5qZWN0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5Db2RlIGV4ZWN1dGlvbiBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRGlyZWN0b3J5IHRyYXZlcnNhbCBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRmlsZSBpbmNsdXNpb24gYXR0YWNrczxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvbGk%2bPGxpPiBJbnB1dCB2YWxpZGF0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5BdXRoZW50aWNhdGlvbiBhdHRhY2tzLjwvbGk%2bIDwvdWw%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BZHZhbmNlZCBwZW5ldHJhdGlvbiB0ZXN0aW5nIHRvb2xzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGFsc28gaW5jbHVkZXMgdG9vbHMgc3VjaCBhcyBhbiBIVFRQIGVkaXRvciAgICAgICAgICAgICAgICAgICAgICAgICAgICAmYW1wOyBIVFRQIHNuaWZmZXIgdG8gYWxsb3cgY3VzdG9taXphdGlvbiBvZiB3ZWIgdnVsbmVyYWJpbGl0eSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjaGVja3MuIFVzaW5nIHRoZSBWdWxuZXJhYmlsaXR5IGVkaXRvciwgbmV3IGF0dGFja3MgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FuIGVhc2lseSBiZSBjcmVhdGVkLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlByaWNpbmcgJmFtcDsgYXZhaWxhYmlsaXR5PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGlzIGF2YWlsYWJsZSBhcyBhbiBlbnRlcnByaXNlIG9yIGFzIGEgY29uc3VsdGFudCAgICAgICAgICAgICAgICAgICAgICAgICAgICB2ZXJzaW9uLiBBIHN1YnNjcmlwdGlvbiBiYXNlZCBsaWNlbnNlIGNhbiBiZSBwdXJjaGFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGFzIGxpdHRsZSBhcyAkMzk1LCB3aGVyZWFzIGEgcGVycGV0dWFsIGxpY2Vuc2Ugc3RhcnRzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGF0ICQyOTk1LiBGb3IgbW9yZSBpbmZvcm1hdGlvbiB2aXNpdCBvdXIgcHJpY2luZyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFib3V0IEFjdW5ldGl4PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggd2FzIGZvdW5kZWQgdG8gY29tYmF0IHRoZSBhbGFybWluZyByaXNlIGluICAgICAgICAgICAgICAgICAgICAgICAgICAgIHdlYiBhdHRhY2tzLiBJdHMgZmxhZ3NoaXAgcHJvZHVjdCwgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgU2Nhbm5lciwgaXMgdGhlIHJlc3VsdCBvZiBzZXZlcmFsIHllYXJzIG9mIGRldmVsb3BtZW50ICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJ5IGEgdGVhbSBvZiBoaWdobHkgZXhwZXJpZW5jZWQgc2VjdXJpdHkgZGV2ZWxvcGVycy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggaXMgYSBwcml2YXRlbHkgaGVsZCBjb21wYW55IHdpdGggaGVhZHF1YXJ0ZXJzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJhc2VkIGluIEV1cm9wZSAoTWFsdGEpIHdpdGggaXRzIE5ldyBZb3JrIFVTIG9mZmljZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY2hlZHVsZWQgdG8gb3BlbiBpbiBRMyBvZiAyMDA1LiA8L3A%2bIGQCCQ8PFgIeC05hdmlnYXRlVXJsBRJDb21tZW50cy5hc3B4P2lkPTJkZAILDxYCHgNzcmMFDGFkcy9kZWYuaHRtbGRkNCSZh%2buMoCTcXGDfVu5D5CfxA7Y%3d]]></PostData> | |
| 276 | </Variation> | |
| 277 | <Variation> | |
| 278 | <URL>http://testaspnet.vulnweb.com/readnews.aspx?id=3</URL> | |
| 279 | <PostData><![CDATA[]]></PostData> | |
| 280 | </Variation> | |
| 281 | <Variation> | |
| 282 | <URL>http://testaspnet.vulnweb.com/readnews.aspx?id=2</URL> | |
| 283 | <PostData><![CDATA[__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWVwK0ovnWBgKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IM%2blktliK1xNDntOrRvIod2XbGitg%3d&__VIEWSTATE=/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc%2bYWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNToyMiBBTWQCBQ8WAh8BBTxXZWIgYXR0YWNrcyAtIGNhbiB5b3VyIHdlYiBhcHBsaWNhdGlvbnMgd2l0aHN0YW5kIHRoZSBmb3JjZT9kAgcPFgIfAQWuNzxwPjxzdHJvbmc%2bQWN1bmV0aXggY29tYmF0cyByaXNlIGluIHdlYiBhdHRhY2tzIHdpdGggQWN1bmV0aXggICAgICAgICAgICAgICAgICAgICAgICAgICAgV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAyIDwvc3Ryb25nPjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD4yMSBKdWx5IDIwMDUgLSA8c3Ryb25nPlN0YXJ0LXVwIGNvbXBhbnkgQWN1bmV0aXggcmVsZWFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lcjogYSB0b29sIHRvIGF1dG9tYXRpY2FsbHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXVkaXQgd2Vic2l0ZSBzZWN1cml0eS4gQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAgICAgICAgICAgICAgICAgICAgICAgICAgICAyIGNyYXdscyBhbiBlbnRpcmUgd2Vic2l0ZSwgbGF1bmNoZXMgcG9wdWxhciB3ZWIgYXR0YWNrcyAgICAgICAgICAgICAgICAgICAgICAgICAgICAoU1FMIEluamVjdGlvbiBldGMuKSBhbmQgaWRlbnRpZmllcyB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdGhhdCBuZWVkIHRvIGJlIGZpeGVkLjwvc3Ryb25nPiA8L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5TZWN1cmluZyB5b3VyIHdlYnNpdGUgc2hvdWxkIGJlIHlvdXIgbnVtYmVyIG9uZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjb25jZXJuPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgSGFja2VycyBhcmUgY29uY2VudHJhdGluZyB0aGVpciBlZmZvcnRzIG9uIHdlYi1iYXNlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBhcHBsaWNhdGlvbnMgLSA3NSUgb2YgY3liZXIgYXR0YWNrcyBhcmUgZG9uZSBhdCB0aGUgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGxldmVsLCBhIEdhcnRuZXIgR3JvdXAgc3R1ZHkgaGFzIHJldmVhbGVkLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBXZWIgYXBwbGljYXRpb25zIGFyZSBhY2Nlc3NpYmxlIDI0IGhvdXJzIGEgZGF5LCA3IGRheXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgYSB3ZWVrIGFuZCBjb250cm9sIHZhbHVhYmxlIGRhdGEgc3VjaCBhcyBjdXN0b21lciBpbmZvcm1hdGlvbiwgICAgICAgICAgICAgICAgICAgICAgICAgICAgdHJhbnNhY3Rpb24gaW5mb3JtYXRpb24gYW5kIGV2ZW4gcHJvcHJpZXRhcnkgY29ycG9yYXRlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGEuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bNTAwLDAwMCBjdXN0b21lciBjcmVkaXQgY2FyZCBudW1iZXJzIG9idGFpbmVkIHZpYSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhIHdlYiBhdHRhY2s8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBXZWxsLWtub3duIHNpdGVzIHRoYXQgd2VyZSBvcGVuIHRvIHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGluY2x1ZGUgZmFzaGlvbiBsYWJlbCBHdWVzcyBhbmQgcGV0IHN1cHBseSByZXRhaWxlciAgICAgICAgICAgICAgICAgICAgICAgICAgICBQZXRDby5jb20gd2hvIHdlcmUgbm90b3Jpb3VzbHkgZm91bmQgdG8gYmUgdnVsbmVyYWJsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB0byB0aGUgU1FMIGluamVjdGlvbiB2dWxuZXJhYmlsaXR5IChKdW5lIDIwMDMpLiBUaGlzICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJlc3VsdGVkIGluIFBldENvIGxlYXZpbmcgYXMgbWFueSBhcyA1MDAsMDAwIGNyZWRpdCAgICAgICAgICAgICAgICAgICAgICAgICAgICBjYXJkIG51bWJlcnMgb3BlbiB0byBhbnlvbmUgYWJsZSB0byBjb25zdHJ1Y3QgdGhpcyBzcGVjaWFsbHktY3JhZnRlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBVUkwuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bRmlyZXdhbGxzLCBTU0wgYW5kIGxvY2tlZC1kb3duIHNlcnZlcnMgYXJlIGZ1dGlsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBoYWNraW5nPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQW55IGRlZmVuc2UgYXQgbmV0d29yayBzZWN1cml0eSBsZXZlbCB3aWxsIHByb3ZpZGUgbm8gICAgICAgICAgICAgICAgICAgICAgICAgICAgcHJvdGVjdGlvbiBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzIHNpbmNlIHRoZXkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXJlIGxhdW5jaGVkIG9uIHBvcnQgODAgLSB3aGljaCBoYXMgdG8gcmVtYWluIG9wZW4uICAgICAgICAgICAgICAgICAgICAgICAgICAgIEluIGFkZGl0aW9uLCB3ZWIgYXBwbGljYXRpb25zIChjdXN0b21lciBhcmVhcywgc2hvcHBpbmcgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FydHMgZXRjLikgYXJlIG9mdGVuIHRhaWxvci1tYWRlLCBpbnZhcmlhYmx5IHRlc3RlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBsZXNzIHRoYW4gb2ZmLXRoZS1zaGVsZiBzb2Z0d2FyZSBhbmQgYXJlIHRoZXJlZm9yZSBtb3JlICAgICAgICAgICAgICAgICAgICAgICAgICAgIHN1c2NlcHRpYmxlIHRvIGF0dGFjay48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bJnF1b3Q7Q29tcGFuaWVzIGhhdmUgaW1wbGVtZW50ZWQgbmV0d29yay1sZXZlbCBzZWN1cml0eSwgICAgICAgICAgICAgICAgICAgICAgICAgICAgaG93ZXZlciB0aGV5IGZhaWwgdG8gYXVkaXQgYW5kIHNlY3VyZSB0aGVpciB3ZWIgYXBwbGljYXRpb25zLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBUaGVzZSBhcHBsaWNhdGlvbnMgaGF2ZSBhY2Nlc3MgdG8gc2Vuc2l0aXZlIGRhdGEgYW5kICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFyZSBhIGhhY2tlcidzIHByaW1lIHRhcmdldCwmcXVvdDsgc2FpZCBOaWNrIEdhbGVhLCAgICAgICAgICAgICAgICAgICAgICAgICAgICBDRU8gb2YgQWN1bmV0aXguICZxdW90O0F1ZGl0aW5nIG9uZSdzIHdlYiBhcHBzIHNob3VsZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBiZSB0aGUgbnVtYmVyIG9uZSBzZWN1cml0eSBjb25jZXJuLiZxdW90OzwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlRoZSBuZWVkIGZvciBhbiBhdXRvbWF0ZWQgd2ViIGFwcGxpY2F0aW9uIHZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgc2Nhbm5lcjwvc3Ryb25nPjxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIE1hbnVhbGx5IGF1ZGl0aW5nIGEgd2ViIGFwcGxpY2F0aW9uIGZvciB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdG8gU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiAgICAgICAgICAgICAgICAgICAgICAgICAgICBhdHRhY2tzIGlzIHZpcnR1YWxseSBpbXBvc3NpYmxlLiBXaXRoIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5ICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNjYW5uZXIgdGhlIHByb2Nlc3Mgb2YgYXVkaXRpbmcgd2ViIGFwcGxpY2F0aW9ucyBzdWNoICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFzIHNob3BwaW5nIGNhcnRzIGFuZCBmb3JtcywgY2FuIGJlIGVhc2lseSBhdXRvbWF0ZWQuICAgICAgICAgICAgICAgICAgICAgICAgICAgIFdoYXQncyBtb3JlLCB0aGUgc2VjdXJpdHkgY2hlY2tzIGNhbiBlYXNpbHkgYmUgcmUtbGF1bmNoZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGVhY2ggYXBwbGljYXRpb24gdXBkYXRlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkhvdyBBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIHdvcmtzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGZpcnN0IGNyYXdscyB0aGUgd2hvbGUgd2Vic2l0ZSwgYW5hbHl6ZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgaW4tZGVwdGggZWFjaCBmaWxlIGl0IGZpbmRzLCBhbmQgZGlzcGxheXMgdGhlIGVudGlyZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB3ZWJzaXRlIHN0cnVjdHVyZS4gQWZ0ZXIgdGhpcyBkaXNjb3Zlcnkgc3RhZ2UsIGl0IHBlcmZvcm1zICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFuIGF1dG9tYXRpYyBhdWRpdCBmb3IgY29tbW9uIHNlY3VyaXR5IHZ1bG5lcmFiaWxpdGllcy48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BdXRvbWF0aWNhbGx5IGRldGVjdHMgU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiB2dWxuZXJhYmlsaXRpZXM8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBTUUwgaW5qZWN0aW9uIGlzIGEgaGFja2luZyB0ZWNobmlxdWUgd2hpY2ggbW9kaWZpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgU1FMIGNvbW1hbmRzIGluIG9yZGVyIHRvIGdhaW4gYWNjZXNzIHRvIGRhdGEgaW4gdGhlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGFiYXNlLiBDcm9zcyBzaXRlIHNjcmlwdGluZyBhdHRhY2tzIGFsbG93IGEgaGFja2VyICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRvIGV4ZWN1dGUgYSBtYWxpY2lvdXMgc2NyaXB0IG9uIHlvdXIgdmlzaXRvcnMnIGJyb3dzZXIuICAgICAgICAgICAgICAgICAgICAgICAgICAgIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgY2FuIGNoZWNrIGlmIHlvdXIgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGlzIHZ1bG5lcmFibGUgdG8gYm90aCBvZiB0aGVzZSBhdHRhY2tzLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBNb3JlIGluZm9ybWF0aW9uIGFib3V0IGNyb3NzIHNpdGUgc2NyaXB0aW5nICZhbXA7IFNRTCAgICAgICAgICAgICAgICAgICAgICAgICAgICBpbmplY3Rpb24gYXQgb3VyIHdlYnNpdGUgc2VjdXJpdHkgaW5mbyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgYWxzbyBjaGVja3MgZm9yICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRoZSBmb2xsb3dpbmcgd2ViIGF0dGFja3M6PC9zdHJvbmc%2bPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDx1bD4gPGxpPkNSTEYgaW5qZWN0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5Db2RlIGV4ZWN1dGlvbiBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRGlyZWN0b3J5IHRyYXZlcnNhbCBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRmlsZSBpbmNsdXNpb24gYXR0YWNrczxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvbGk%2bPGxpPiBJbnB1dCB2YWxpZGF0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5BdXRoZW50aWNhdGlvbiBhdHRhY2tzLjwvbGk%2bIDwvdWw%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BZHZhbmNlZCBwZW5ldHJhdGlvbiB0ZXN0aW5nIHRvb2xzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGFsc28gaW5jbHVkZXMgdG9vbHMgc3VjaCBhcyBhbiBIVFRQIGVkaXRvciAgICAgICAgICAgICAgICAgICAgICAgICAgICAmYW1wOyBIVFRQIHNuaWZmZXIgdG8gYWxsb3cgY3VzdG9taXphdGlvbiBvZiB3ZWIgdnVsbmVyYWJpbGl0eSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjaGVja3MuIFVzaW5nIHRoZSBWdWxuZXJhYmlsaXR5IGVkaXRvciwgbmV3IGF0dGFja3MgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FuIGVhc2lseSBiZSBjcmVhdGVkLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlByaWNpbmcgJmFtcDsgYXZhaWxhYmlsaXR5PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGlzIGF2YWlsYWJsZSBhcyBhbiBlbnRlcnByaXNlIG9yIGFzIGEgY29uc3VsdGFudCAgICAgICAgICAgICAgICAgICAgICAgICAgICB2ZXJzaW9uLiBBIHN1YnNjcmlwdGlvbiBiYXNlZCBsaWNlbnNlIGNhbiBiZSBwdXJjaGFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGFzIGxpdHRsZSBhcyAkMzk1LCB3aGVyZWFzIGEgcGVycGV0dWFsIGxpY2Vuc2Ugc3RhcnRzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGF0ICQyOTk1LiBGb3IgbW9yZSBpbmZvcm1hdGlvbiB2aXNpdCBvdXIgcHJpY2luZyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFib3V0IEFjdW5ldGl4PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggd2FzIGZvdW5kZWQgdG8gY29tYmF0IHRoZSBhbGFybWluZyByaXNlIGluICAgICAgICAgICAgICAgICAgICAgICAgICAgIHdlYiBhdHRhY2tzLiBJdHMgZmxhZ3NoaXAgcHJvZHVjdCwgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgU2Nhbm5lciwgaXMgdGhlIHJlc3VsdCBvZiBzZXZlcmFsIHllYXJzIG9mIGRldmVsb3BtZW50ICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJ5IGEgdGVhbSBvZiBoaWdobHkgZXhwZXJpZW5jZWQgc2VjdXJpdHkgZGV2ZWxvcGVycy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggaXMgYSBwcml2YXRlbHkgaGVsZCBjb21wYW55IHdpdGggaGVhZHF1YXJ0ZXJzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJhc2VkIGluIEV1cm9wZSAoTWFsdGEpIHdpdGggaXRzIE5ldyBZb3JrIFVTIG9mZmljZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY2hlZHVsZWQgdG8gb3BlbiBpbiBRMyBvZiAyMDA1LiA8L3A%2bIGQCCQ8PFgIeC05hdmlnYXRlVXJsBRJDb21tZW50cy5hc3B4P2lkPTJkZAILDxYCHgNzcmNkZGS78tg0yYdYIrm%2b7bJhr2ToTj/BEA%3d%3d]]></PostData> | |
| 284 | </Variation> | |
| 285 | <Variation> | |
| 286 | <URL>http://testaspnet.vulnweb.com/readnews.aspx?id=3</URL> | |
| 287 | <PostData><![CDATA[__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWVwK0ovnWBgKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IM%2blktliK1xNDntOrRvIod2XbGitg%3d&__VIEWSTATE=/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc%2bYWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNToyMiBBTWQCBQ8WAh8BBTxXZWIgYXR0YWNrcyAtIGNhbiB5b3VyIHdlYiBhcHBsaWNhdGlvbnMgd2l0aHN0YW5kIHRoZSBmb3JjZT9kAgcPFgIfAQWuNzxwPjxzdHJvbmc%2bQWN1bmV0aXggY29tYmF0cyByaXNlIGluIHdlYiBhdHRhY2tzIHdpdGggQWN1bmV0aXggICAgICAgICAgICAgICAgICAgICAgICAgICAgV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAyIDwvc3Ryb25nPjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD4yMSBKdWx5IDIwMDUgLSA8c3Ryb25nPlN0YXJ0LXVwIGNvbXBhbnkgQWN1bmV0aXggcmVsZWFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lcjogYSB0b29sIHRvIGF1dG9tYXRpY2FsbHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXVkaXQgd2Vic2l0ZSBzZWN1cml0eS4gQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAgICAgICAgICAgICAgICAgICAgICAgICAgICAyIGNyYXdscyBhbiBlbnRpcmUgd2Vic2l0ZSwgbGF1bmNoZXMgcG9wdWxhciB3ZWIgYXR0YWNrcyAgICAgICAgICAgICAgICAgICAgICAgICAgICAoU1FMIEluamVjdGlvbiBldGMuKSBhbmQgaWRlbnRpZmllcyB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdGhhdCBuZWVkIHRvIGJlIGZpeGVkLjwvc3Ryb25nPiA8L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5TZWN1cmluZyB5b3VyIHdlYnNpdGUgc2hvdWxkIGJlIHlvdXIgbnVtYmVyIG9uZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjb25jZXJuPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgSGFja2VycyBhcmUgY29uY2VudHJhdGluZyB0aGVpciBlZmZvcnRzIG9uIHdlYi1iYXNlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBhcHBsaWNhdGlvbnMgLSA3NSUgb2YgY3liZXIgYXR0YWNrcyBhcmUgZG9uZSBhdCB0aGUgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGxldmVsLCBhIEdhcnRuZXIgR3JvdXAgc3R1ZHkgaGFzIHJldmVhbGVkLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBXZWIgYXBwbGljYXRpb25zIGFyZSBhY2Nlc3NpYmxlIDI0IGhvdXJzIGEgZGF5LCA3IGRheXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgYSB3ZWVrIGFuZCBjb250cm9sIHZhbHVhYmxlIGRhdGEgc3VjaCBhcyBjdXN0b21lciBpbmZvcm1hdGlvbiwgICAgICAgICAgICAgICAgICAgICAgICAgICAgdHJhbnNhY3Rpb24gaW5mb3JtYXRpb24gYW5kIGV2ZW4gcHJvcHJpZXRhcnkgY29ycG9yYXRlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGEuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bNTAwLDAwMCBjdXN0b21lciBjcmVkaXQgY2FyZCBudW1iZXJzIG9idGFpbmVkIHZpYSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhIHdlYiBhdHRhY2s8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBXZWxsLWtub3duIHNpdGVzIHRoYXQgd2VyZSBvcGVuIHRvIHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGluY2x1ZGUgZmFzaGlvbiBsYWJlbCBHdWVzcyBhbmQgcGV0IHN1cHBseSByZXRhaWxlciAgICAgICAgICAgICAgICAgICAgICAgICAgICBQZXRDby5jb20gd2hvIHdlcmUgbm90b3Jpb3VzbHkgZm91bmQgdG8gYmUgdnVsbmVyYWJsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB0byB0aGUgU1FMIGluamVjdGlvbiB2dWxuZXJhYmlsaXR5IChKdW5lIDIwMDMpLiBUaGlzICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJlc3VsdGVkIGluIFBldENvIGxlYXZpbmcgYXMgbWFueSBhcyA1MDAsMDAwIGNyZWRpdCAgICAgICAgICAgICAgICAgICAgICAgICAgICBjYXJkIG51bWJlcnMgb3BlbiB0byBhbnlvbmUgYWJsZSB0byBjb25zdHJ1Y3QgdGhpcyBzcGVjaWFsbHktY3JhZnRlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBVUkwuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bRmlyZXdhbGxzLCBTU0wgYW5kIGxvY2tlZC1kb3duIHNlcnZlcnMgYXJlIGZ1dGlsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBoYWNraW5nPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQW55IGRlZmVuc2UgYXQgbmV0d29yayBzZWN1cml0eSBsZXZlbCB3aWxsIHByb3ZpZGUgbm8gICAgICAgICAgICAgICAgICAgICAgICAgICAgcHJvdGVjdGlvbiBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzIHNpbmNlIHRoZXkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXJlIGxhdW5jaGVkIG9uIHBvcnQgODAgLSB3aGljaCBoYXMgdG8gcmVtYWluIG9wZW4uICAgICAgICAgICAgICAgICAgICAgICAgICAgIEluIGFkZGl0aW9uLCB3ZWIgYXBwbGljYXRpb25zIChjdXN0b21lciBhcmVhcywgc2hvcHBpbmcgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FydHMgZXRjLikgYXJlIG9mdGVuIHRhaWxvci1tYWRlLCBpbnZhcmlhYmx5IHRlc3RlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBsZXNzIHRoYW4gb2ZmLXRoZS1zaGVsZiBzb2Z0d2FyZSBhbmQgYXJlIHRoZXJlZm9yZSBtb3JlICAgICAgICAgICAgICAgICAgICAgICAgICAgIHN1c2NlcHRpYmxlIHRvIGF0dGFjay48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bJnF1b3Q7Q29tcGFuaWVzIGhhdmUgaW1wbGVtZW50ZWQgbmV0d29yay1sZXZlbCBzZWN1cml0eSwgICAgICAgICAgICAgICAgICAgICAgICAgICAgaG93ZXZlciB0aGV5IGZhaWwgdG8gYXVkaXQgYW5kIHNlY3VyZSB0aGVpciB3ZWIgYXBwbGljYXRpb25zLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBUaGVzZSBhcHBsaWNhdGlvbnMgaGF2ZSBhY2Nlc3MgdG8gc2Vuc2l0aXZlIGRhdGEgYW5kICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFyZSBhIGhhY2tlcidzIHByaW1lIHRhcmdldCwmcXVvdDsgc2FpZCBOaWNrIEdhbGVhLCAgICAgICAgICAgICAgICAgICAgICAgICAgICBDRU8gb2YgQWN1bmV0aXguICZxdW90O0F1ZGl0aW5nIG9uZSdzIHdlYiBhcHBzIHNob3VsZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBiZSB0aGUgbnVtYmVyIG9uZSBzZWN1cml0eSBjb25jZXJuLiZxdW90OzwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlRoZSBuZWVkIGZvciBhbiBhdXRvbWF0ZWQgd2ViIGFwcGxpY2F0aW9uIHZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgc2Nhbm5lcjwvc3Ryb25nPjxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIE1hbnVhbGx5IGF1ZGl0aW5nIGEgd2ViIGFwcGxpY2F0aW9uIGZvciB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdG8gU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiAgICAgICAgICAgICAgICAgICAgICAgICAgICBhdHRhY2tzIGlzIHZpcnR1YWxseSBpbXBvc3NpYmxlLiBXaXRoIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5ICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNjYW5uZXIgdGhlIHByb2Nlc3Mgb2YgYXVkaXRpbmcgd2ViIGFwcGxpY2F0aW9ucyBzdWNoICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFzIHNob3BwaW5nIGNhcnRzIGFuZCBmb3JtcywgY2FuIGJlIGVhc2lseSBhdXRvbWF0ZWQuICAgICAgICAgICAgICAgICAgICAgICAgICAgIFdoYXQncyBtb3JlLCB0aGUgc2VjdXJpdHkgY2hlY2tzIGNhbiBlYXNpbHkgYmUgcmUtbGF1bmNoZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGVhY2ggYXBwbGljYXRpb24gdXBkYXRlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkhvdyBBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIHdvcmtzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGZpcnN0IGNyYXdscyB0aGUgd2hvbGUgd2Vic2l0ZSwgYW5hbHl6ZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgaW4tZGVwdGggZWFjaCBmaWxlIGl0IGZpbmRzLCBhbmQgZGlzcGxheXMgdGhlIGVudGlyZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB3ZWJzaXRlIHN0cnVjdHVyZS4gQWZ0ZXIgdGhpcyBkaXNjb3Zlcnkgc3RhZ2UsIGl0IHBlcmZvcm1zICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFuIGF1dG9tYXRpYyBhdWRpdCBmb3IgY29tbW9uIHNlY3VyaXR5IHZ1bG5lcmFiaWxpdGllcy48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BdXRvbWF0aWNhbGx5IGRldGVjdHMgU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiB2dWxuZXJhYmlsaXRpZXM8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBTUUwgaW5qZWN0aW9uIGlzIGEgaGFja2luZyB0ZWNobmlxdWUgd2hpY2ggbW9kaWZpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgU1FMIGNvbW1hbmRzIGluIG9yZGVyIHRvIGdhaW4gYWNjZXNzIHRvIGRhdGEgaW4gdGhlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGFiYXNlLiBDcm9zcyBzaXRlIHNjcmlwdGluZyBhdHRhY2tzIGFsbG93IGEgaGFja2VyICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRvIGV4ZWN1dGUgYSBtYWxpY2lvdXMgc2NyaXB0IG9uIHlvdXIgdmlzaXRvcnMnIGJyb3dzZXIuICAgICAgICAgICAgICAgICAgICAgICAgICAgIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgY2FuIGNoZWNrIGlmIHlvdXIgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGlzIHZ1bG5lcmFibGUgdG8gYm90aCBvZiB0aGVzZSBhdHRhY2tzLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBNb3JlIGluZm9ybWF0aW9uIGFib3V0IGNyb3NzIHNpdGUgc2NyaXB0aW5nICZhbXA7IFNRTCAgICAgICAgICAgICAgICAgICAgICAgICAgICBpbmplY3Rpb24gYXQgb3VyIHdlYnNpdGUgc2VjdXJpdHkgaW5mbyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgYWxzbyBjaGVja3MgZm9yICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRoZSBmb2xsb3dpbmcgd2ViIGF0dGFja3M6PC9zdHJvbmc%2bPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDx1bD4gPGxpPkNSTEYgaW5qZWN0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5Db2RlIGV4ZWN1dGlvbiBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRGlyZWN0b3J5IHRyYXZlcnNhbCBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRmlsZSBpbmNsdXNpb24gYXR0YWNrczxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvbGk%2bPGxpPiBJbnB1dCB2YWxpZGF0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5BdXRoZW50aWNhdGlvbiBhdHRhY2tzLjwvbGk%2bIDwvdWw%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BZHZhbmNlZCBwZW5ldHJhdGlvbiB0ZXN0aW5nIHRvb2xzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGFsc28gaW5jbHVkZXMgdG9vbHMgc3VjaCBhcyBhbiBIVFRQIGVkaXRvciAgICAgICAgICAgICAgICAgICAgICAgICAgICAmYW1wOyBIVFRQIHNuaWZmZXIgdG8gYWxsb3cgY3VzdG9taXphdGlvbiBvZiB3ZWIgdnVsbmVyYWJpbGl0eSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjaGVja3MuIFVzaW5nIHRoZSBWdWxuZXJhYmlsaXR5IGVkaXRvciwgbmV3IGF0dGFja3MgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FuIGVhc2lseSBiZSBjcmVhdGVkLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlByaWNpbmcgJmFtcDsgYXZhaWxhYmlsaXR5PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGlzIGF2YWlsYWJsZSBhcyBhbiBlbnRlcnByaXNlIG9yIGFzIGEgY29uc3VsdGFudCAgICAgICAgICAgICAgICAgICAgICAgICAgICB2ZXJzaW9uLiBBIHN1YnNjcmlwdGlvbiBiYXNlZCBsaWNlbnNlIGNhbiBiZSBwdXJjaGFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGFzIGxpdHRsZSBhcyAkMzk1LCB3aGVyZWFzIGEgcGVycGV0dWFsIGxpY2Vuc2Ugc3RhcnRzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGF0ICQyOTk1LiBGb3IgbW9yZSBpbmZvcm1hdGlvbiB2aXNpdCBvdXIgcHJpY2luZyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFib3V0IEFjdW5ldGl4PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggd2FzIGZvdW5kZWQgdG8gY29tYmF0IHRoZSBhbGFybWluZyByaXNlIGluICAgICAgICAgICAgICAgICAgICAgICAgICAgIHdlYiBhdHRhY2tzLiBJdHMgZmxhZ3NoaXAgcHJvZHVjdCwgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgU2Nhbm5lciwgaXMgdGhlIHJlc3VsdCBvZiBzZXZlcmFsIHllYXJzIG9mIGRldmVsb3BtZW50ICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJ5IGEgdGVhbSBvZiBoaWdobHkgZXhwZXJpZW5jZWQgc2VjdXJpdHkgZGV2ZWxvcGVycy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggaXMgYSBwcml2YXRlbHkgaGVsZCBjb21wYW55IHdpdGggaGVhZHF1YXJ0ZXJzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJhc2VkIGluIEV1cm9wZSAoTWFsdGEpIHdpdGggaXRzIE5ldyBZb3JrIFVTIG9mZmljZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY2hlZHVsZWQgdG8gb3BlbiBpbiBRMyBvZiAyMDA1LiA8L3A%2bIGQCCQ8PFgIeC05hdmlnYXRlVXJsBRJDb21tZW50cy5hc3B4P2lkPTJkZAILDxYCHgNzcmNkZGS78tg0yYdYIrm%2b7bJhr2ToTj/BEA%3d%3d]]></PostData> | |
| 288 | </Variation> | |
| 289 | </Variations> | |
| 290 | </SiteFile> | |
| 291 | <SiteFile id="9"> | |
| 292 | <Name>comments.aspx</Name> | |
| 293 | <URL>/comments.aspx</URL> | |
| 294 | <FullURL>http://testaspnet.vulnweb.com/comments.aspx</FullURL> | |
| 295 | <Inputs> | |
| 296 | <Variable Name="id" Type="URL encoded GET"> | |
| 297 | </Variable> | |
| 298 | <Variable Name="id" Type="URL encoded GET"> | |
| 299 | </Variable> | |
| 300 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 301 | </Variable> | |
| 302 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 303 | </Variable> | |
| 304 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 305 | </Variable> | |
| 306 | <Variable Name="__EVENTARGUMENT" Type="URL encoded POST"> | |
| 307 | </Variable> | |
| 308 | <Variable Name="id" Type="URL encoded GET"> | |
| 309 | </Variable> | |
| 310 | <Variable Name="btnSend" Type="URL encoded POST"> | |
| 311 | </Variable> | |
| 312 | <Variable Name="btnSend" Type="URL encoded POST"> | |
| 313 | </Variable> | |
| 314 | <Variable Name="btnSend" Type="URL encoded POST"> | |
| 315 | </Variable> | |
| 316 | <Variable Name="btnSend" Type="URL encoded POST"> | |
| 317 | </Variable> | |
| 318 | <Variable Name="btnSend" Type="URL encoded POST"> | |
| 319 | </Variable> | |
| 320 | <Variable Name="btnSend" Type="URL encoded POST"> | |
| 321 | </Variable> | |
| 322 | </Inputs> | |
| 323 | <Variations> | |
| 324 | <Variation> | |
| 325 | <URL>http://testaspnet.vulnweb.com/comments.aspx?id=2</URL> | |
| 326 | <PostData><![CDATA[]]></PostData> | |
| 327 | </Variation> | |
| 328 | <Variation> | |
| 329 | <URL>http://testaspnet.vulnweb.com/comments.aspx?id=0</URL> | |
| 330 | <PostData><![CDATA[]]></PostData> | |
| 331 | </Variation> | |
| 332 | <Variation> | |
| 333 | <URL>http://testaspnet.vulnweb.com/comments.aspx?id=3</URL> | |
| 334 | <PostData><![CDATA[]]></PostData> | |
| 335 | </Variation> | |
| 336 | <Variation> | |
| 337 | <URL>http://testaspnet.vulnweb.com/comments.aspx?id=2</URL> | |
| 338 | <PostData><![CDATA[__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWQLhxPPJAwKAgcfvBQKFzrr8AQKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMTN/AvEAAOD%2bI818GCE7TFNsXr%2bM%3d&__VIEWSTATE=/wEPDwUKLTg2MjcwMzE2Mg9kFgICAQ9kFgoCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc%2bYWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNToyMiBBTWQCBQ8WBB8BBTxXZWIgYXR0YWNrcyAtIGNhbiB5b3VyIHdlYiBhcHBsaWNhdGlvbnMgd2l0aHN0YW5kIHRoZSBmb3JjZT8fAAUSUmVhZE5ld3MuYXNweD9pZD0yZAIHDxYCHwEFrAIyMSBKdWx5IDIwMDUgLSBTdGFydC11cCBjb21wYW55IEFjdW5ldGl4IHJlbGVhc2VkIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXI6IGEgdG9vbCB0byBhdXRvbWF0aWNhbGx5IGF1ZGl0IHdlYnNpdGUgc2VjdXJpdHkuIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgMiBjcmF3bHMgYW4gZW50aXJlIHdlYnNpdGUsIGxhdW5jaGVzIHBvcHVsYXIgd2ViIGF0dGFja3MgKFNRTCBJbmplY3Rpb24gZXRjLikgYW5kIGlkZW50aWZpZXMgdnVsbmVyYWJpbGl0aWVzIHRoYXQgbmVlZCB0byBiZSBmaXhlZC5kAgkPZBYCAgEPZBZUZg9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAgEPZBYCZg8WAh4FY2xhc3MFB0NvbW1lbnRkAgIPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAgMPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIED2QWAmYPFgIfAwUHQ29tbWVudGQCBQ9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCBg9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAgcPZBYCZg8WAh8DBQdDb21tZW50ZAIID2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIJD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCCg9kFgJmDxYCHwMFB0NvbW1lbnRkAgsPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAgwPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIND2QWAmYPFgIfAwUHQ29tbWVudGQCDg9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCDw9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAhAPZBYCZg8WAh8DBQdDb21tZW50ZAIRD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAISD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCEw9kFgJmDxYCHwMFB0NvbW1lbnRkAhQPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAhUPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIWD2QWAmYPFgIfAwUHQ29tbWVudGQCFw9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCGA9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAhkPZBYCZg8WAh8DBQdDb21tZW50ZAIaD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIbD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCHA9kFgJmDxYCHwMFB0NvbW1lbnRkAh0PZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAh4PZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIfD2QWAmYPFgIfAwUHQ29tbWVudGQCIA9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCIQ9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAiIPZBYCZg8WAh8DBQdDb21tZW50ZAIjD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIkD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCJQ9kFgJmDxYCHwMFB0NvbW1lbnRkAiYPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAicPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIoD2QWAmYPFgIfAwUHQ29tbWVudGQCKQ9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmRkLb6CUW1qfx56qAx2J/B/XMdFeyU%3d]]></PostData> | |
| 339 | </Variation> | |
| 340 | <Variation> | |
| 341 | <URL>http://testaspnet.vulnweb.com/comments.aspx?id=3</URL> | |
| 342 | <PostData><![CDATA[btnSend=Send%20comment&tbComment=1&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWQKGnd2qBAKAgcfvBQKFzrr8AQKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IM6/7zO/iGsX28uMOhuqkE9gRbREU%3d&__VIEWSTATE=/wEPDwUKLTg2MjcwMzE2Mg9kFgICAQ9kFgoCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc%2bYWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNzozNSBBTWQCBQ8WBB8BBTFBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIGJldGEgcmVsZWFzZWQhHwAFElJlYWROZXdzLmFzcHg/aWQ9M2QCBw8WAh8BBagBMjYgSmFudWFyeSAyMDA1IC0gQSBiZXRhIHZlcnNpb24gb2YgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciBoYXMgYmVlbiByZWxlYXNlZCB0b2RheS4gVGhlIGJldGEgaXMgYXZhaWxhYmxlIGZvciBkb3dubG9hZCBhdCBodHRwOi8vd3d3LmFjdW5ldGl4LmNvbS9kb3dubG9hZC8uZAIJD2QWAgIBD2QWcmYPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIBD2QWAmYPFgIeBWNsYXNzBQdDb21tZW50ZAICD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIDD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCBA9kFgJmDxYCHwMFB0NvbW1lbnRkAgUPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAgYPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIHD2QWAmYPFgIfAwUHQ29tbWVudGQCCA9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCCQ9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAgoPZBYCZg8WAh8DBQdDb21tZW50ZAILD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIMD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCDQ9kFgJmDxYCHwMFB0NvbW1lbnRkAg4PZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAg8PZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIQD2QWAmYPFgIfAwUHQ29tbWVudGQCEQ9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCEg9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAhMPZBYCZg8WAh8DBQdDb21tZW50ZAIUD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIVD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCFg9kFgJmDxYCHwMFB0NvbW1lbnRkAhcPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAhgPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIZD2QWAmYPFgIfAwUHQ29tbWVudGQCGg9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCGw9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAhwPZBYCZg8WAh8DBQdDb21tZW50ZAIdD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIeD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCHw9kFgJmDxYCHwMFB0NvbW1lbnRkAiAPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAiEPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIiD2QWAmYPFgIfAwUHQ29tbWVudGQCIw9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCJA9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAiUPZBYCZg8WAh8DBQdDb21tZW50ZAImD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAInD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCKA9kFgJmDxYCHwMFB0NvbW1lbnRkAikPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAioPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIrD2QWAmYPFgIfAwUHQ29tbWVudGQCLA9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCLQ9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAi4PZBYCZg8WAh8DBQdDb21tZW50ZAIvD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIwD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCMQ9kFgJmDxYCHwMFB0NvbW1lbnRkAjIPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAjMPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAI0D2QWAmYPFgIfAwUHQ29tbWVudGQCNQ9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCNg9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAjcPZBYCZg8WAh8DBQdDb21tZW50ZAI4D2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZGRbXMsd1lEmXls/MPIgqXEnJDtSHQ%3d%3d]]></PostData> | |
| 343 | </Variation> | |
| 344 | <Variation> | |
| 345 | <URL>http://testaspnet.vulnweb.com/comments.aspx?id=0</URL> | |
| 346 | <PostData><![CDATA[btnSend=Send%20comment&tbComment=1&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWQKGnd2qBAKAgcfvBQKFzrr8AQKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IM6/7zO/iGsX28uMOhuqkE9gRbREU%3d&__VIEWSTATE=/wEPDwUKLTg2MjcwMzE2Mg9kFgICAQ9kFgoCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc%2bYWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNzozNSBBTWQCBQ8WBB8BBTFBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIGJldGEgcmVsZWFzZWQhHwAFElJlYWROZXdzLmFzcHg/aWQ9M2QCBw8WAh8BBagBMjYgSmFudWFyeSAyMDA1IC0gQSBiZXRhIHZlcnNpb24gb2YgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciBoYXMgYmVlbiByZWxlYXNlZCB0b2RheS4gVGhlIGJldGEgaXMgYXZhaWxhYmxlIGZvciBkb3dubG9hZCBhdCBodHRwOi8vd3d3LmFjdW5ldGl4LmNvbS9kb3dubG9hZC8uZAIJD2QWAgIBD2QWcmYPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIBD2QWAmYPFgIeBWNsYXNzBQdDb21tZW50ZAICD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIDD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCBA9kFgJmDxYCHwMFB0NvbW1lbnRkAgUPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAgYPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIHD2QWAmYPFgIfAwUHQ29tbWVudGQCCA9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCCQ9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAgoPZBYCZg8WAh8DBQdDb21tZW50ZAILD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIMD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCDQ9kFgJmDxYCHwMFB0NvbW1lbnRkAg4PZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAg8PZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIQD2QWAmYPFgIfAwUHQ29tbWVudGQCEQ9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCEg9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAhMPZBYCZg8WAh8DBQdDb21tZW50ZAIUD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIVD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCFg9kFgJmDxYCHwMFB0NvbW1lbnRkAhcPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAhgPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIZD2QWAmYPFgIfAwUHQ29tbWVudGQCGg9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCGw9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAhwPZBYCZg8WAh8DBQdDb21tZW50ZAIdD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIeD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCHw9kFgJmDxYCHwMFB0NvbW1lbnRkAiAPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAiEPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIiD2QWAmYPFgIfAwUHQ29tbWVudGQCIw9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCJA9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAiUPZBYCZg8WAh8DBQdDb21tZW50ZAImD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAInD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCKA9kFgJmDxYCHwMFB0NvbW1lbnRkAikPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAioPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIrD2QWAmYPFgIfAwUHQ29tbWVudGQCLA9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCLQ9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAi4PZBYCZg8WAh8DBQdDb21tZW50ZAIvD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIwD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCMQ9kFgJmDxYCHwMFB0NvbW1lbnRkAjIPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAjMPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAI0D2QWAmYPFgIfAwUHQ29tbWVudGQCNQ9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCNg9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAjcPZBYCZg8WAh8DBQdDb21tZW50ZAI4D2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZGRbXMsd1lEmXls/MPIgqXEnJDtSHQ%3d%3d]]></PostData> | |
| 347 | </Variation> | |
| 348 | <Variation> | |
| 349 | <URL>http://testaspnet.vulnweb.com/comments.aspx?id=2</URL> | |
| 350 | <PostData><![CDATA[btnSend=Send%20comment&tbComment=1&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWQKGnd2qBAKAgcfvBQKFzrr8AQKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IM6/7zO/iGsX28uMOhuqkE9gRbREU%3d&__VIEWSTATE=/wEPDwUKLTg2MjcwMzE2Mg9kFgICAQ9kFgoCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc%2bYWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNzozNSBBTWQCBQ8WBB8BBTFBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIGJldGEgcmVsZWFzZWQhHwAFElJlYWROZXdzLmFzcHg/aWQ9M2QCBw8WAh8BBagBMjYgSmFudWFyeSAyMDA1IC0gQSBiZXRhIHZlcnNpb24gb2YgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciBoYXMgYmVlbiByZWxlYXNlZCB0b2RheS4gVGhlIGJldGEgaXMgYXZhaWxhYmxlIGZvciBkb3dubG9hZCBhdCBodHRwOi8vd3d3LmFjdW5ldGl4LmNvbS9kb3dubG9hZC8uZAIJD2QWAgIBD2QWcmYPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIBD2QWAmYPFgIeBWNsYXNzBQdDb21tZW50ZAICD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIDD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCBA9kFgJmDxYCHwMFB0NvbW1lbnRkAgUPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAgYPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIHD2QWAmYPFgIfAwUHQ29tbWVudGQCCA9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCCQ9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAgoPZBYCZg8WAh8DBQdDb21tZW50ZAILD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIMD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCDQ9kFgJmDxYCHwMFB0NvbW1lbnRkAg4PZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAg8PZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIQD2QWAmYPFgIfAwUHQ29tbWVudGQCEQ9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCEg9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAhMPZBYCZg8WAh8DBQdDb21tZW50ZAIUD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIVD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCFg9kFgJmDxYCHwMFB0NvbW1lbnRkAhcPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAhgPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIZD2QWAmYPFgIfAwUHQ29tbWVudGQCGg9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCGw9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAhwPZBYCZg8WAh8DBQdDb21tZW50ZAIdD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIeD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCHw9kFgJmDxYCHwMFB0NvbW1lbnRkAiAPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAiEPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIiD2QWAmYPFgIfAwUHQ29tbWVudGQCIw9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCJA9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAiUPZBYCZg8WAh8DBQdDb21tZW50ZAImD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAInD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCKA9kFgJmDxYCHwMFB0NvbW1lbnRkAikPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAioPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAIrD2QWAmYPFgIfAwUHQ29tbWVudGQCLA9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCLQ9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAi4PZBYCZg8WAh8DBQdDb21tZW50ZAIvD2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZAIwD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWJlZm9yZS5naWYiPmQCMQ9kFgJmDxYCHwMFB0NvbW1lbnRkAjIPZBYCZg8WAh8BBSQ8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYWZ0ZXIuZ2lmIj5kAjMPZBYCZg8WAh8BBSU8SU1HIHNyYz0iaW1hZ2VzL2NvbW1lbnQtYmVmb3JlLmdpZiI%2bZAI0D2QWAmYPFgIfAwUHQ29tbWVudGQCNQ9kFgJmDxYCHwEFJDxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1hZnRlci5naWYiPmQCNg9kFgJmDxYCHwEFJTxJTUcgc3JjPSJpbWFnZXMvY29tbWVudC1iZWZvcmUuZ2lmIj5kAjcPZBYCZg8WAh8DBQdDb21tZW50ZAI4D2QWAmYPFgIfAQUkPElNRyBzcmM9ImltYWdlcy9jb21tZW50LWFmdGVyLmdpZiI%2bZGRbXMsd1lEmXls/MPIgqXEnJDtSHQ%3d%3d]]></PostData> | |
| 351 | </Variation> | |
| 352 | </Variations> | |
| 353 | </SiteFile> | |
| 354 | <SiteFile id="10"> | |
| 355 | <Name>images</Name> | |
| 356 | <URL>/images/</URL> | |
| 357 | <FullURL>http://testaspnet.vulnweb.com/images/</FullURL> | |
| 358 | <Inputs> | |
| 359 | </Inputs> | |
| 360 | <Variations> | |
| 361 | </Variations> | |
| 362 | </SiteFile> | |
| 363 | <SiteFile id="11"> | |
| 364 | <Name>ads</Name> | |
| 365 | <URL>/ads/</URL> | |
| 366 | <FullURL>http://testaspnet.vulnweb.com/ads/</FullURL> | |
| 367 | <Inputs> | |
| 368 | </Inputs> | |
| 369 | <Variations> | |
| 370 | </Variations> | |
| 371 | </SiteFile> | |
| 372 | <SiteFile id="12"> | |
| 373 | <Name>def.html</Name> | |
| 374 | <URL>/ads/def.html</URL> | |
| 375 | <FullURL>http://testaspnet.vulnweb.com/ads/def.html</FullURL> | |
| 376 | <Inputs> | |
| 377 | </Inputs> | |
| 378 | <Variations> | |
| 379 | </Variations> | |
| 380 | </SiteFile> | |
| 381 | <SiteFile id="13"> | |
| 382 | <Name>aspnet_client</Name> | |
| 383 | <URL>/aspnet_client/</URL> | |
| 384 | <FullURL>http://testaspnet.vulnweb.com/aspnet_client/</FullURL> | |
| 385 | <Inputs> | |
| 386 | </Inputs> | |
| 387 | <Variations> | |
| 388 | </Variations> | |
| 389 | </SiteFile> | |
| 390 | <SiteFile id="14"> | |
| 391 | <Name>system_web</Name> | |
| 392 | <URL>/aspnet_client/system_web/</URL> | |
| 393 | <FullURL>http://testaspnet.vulnweb.com/aspnet_client/system_web/</FullURL> | |
| 394 | <Inputs> | |
| 395 | </Inputs> | |
| 396 | <Variations> | |
| 397 | </Variations> | |
| 398 | </SiteFile> | |
| 399 | <SiteFile id="15"> | |
| 400 | <Name>2_0_50727</Name> | |
| 401 | <URL>/aspnet_client/system_web/2_0_50727/</URL> | |
| 402 | <FullURL>http://testaspnet.vulnweb.com/aspnet_client/system_web/2_0_50727/</FullURL> | |
| 403 | <Inputs> | |
| 404 | </Inputs> | |
| 405 | <Variations> | |
| 406 | </Variations> | |
| 407 | </SiteFile> | |
| 408 | <SiteFile id="16"> | |
| 409 | <Name>bin</Name> | |
| 410 | <URL>/bin/</URL> | |
| 411 | <FullURL>http://testaspnet.vulnweb.com/bin/</FullURL> | |
| 412 | <Inputs> | |
| 413 | </Inputs> | |
| 414 | <Variations> | |
| 415 | </Variations> | |
| 416 | </SiteFile> | |
| 417 | <SiteFile id="17"> | |
| 418 | <Name>acublog.dll</Name> | |
| 419 | <URL>/bin/acublog.dll</URL> | |
| 420 | <FullURL>http://testaspnet.vulnweb.com/bin/acublog.dll</FullURL> | |
| 421 | <Inputs> | |
| 422 | </Inputs> | |
| 423 | <Variations> | |
| 424 | </Variations> | |
| 425 | </SiteFile> | |
| 426 | <SiteFile id="18"> | |
| 427 | <Name>acublog.dll.bak</Name> | |
| 428 | <URL>/bin/acublog.dll.bak</URL> | |
| 429 | <FullURL>http://testaspnet.vulnweb.com/bin/acublog.dll.bak</FullURL> | |
| 430 | <Inputs> | |
| 431 | </Inputs> | |
| 432 | <Variations> | |
| 433 | </Variations> | |
| 434 | </SiteFile> | |
| 435 | <SiteFile id="19"> | |
| 436 | <Name>acublog.pdb</Name> | |
| 437 | <URL>/bin/acublog.pdb</URL> | |
| 438 | <FullURL>http://testaspnet.vulnweb.com/bin/acublog.pdb</FullURL> | |
| 439 | <Inputs> | |
| 440 | </Inputs> | |
| 441 | <Variations> | |
| 442 | </Variations> | |
| 443 | </SiteFile> | |
| 444 | <SiteFile id="20"> | |
| 445 | <Name>acuweaver.dll</Name> | |
| 446 | <URL>/bin/acuweaver.dll</URL> | |
| 447 | <FullURL>http://testaspnet.vulnweb.com/bin/acuweaver.dll</FullURL> | |
| 448 | <Inputs> | |
| 449 | </Inputs> | |
| 450 | <Variations> | |
| 451 | </Variations> | |
| 452 | </SiteFile> | |
| 453 | <SiteFile id="21"> | |
| 454 | <Name>jscripts</Name> | |
| 455 | <URL>/jscripts/</URL> | |
| 456 | <FullURL>http://testaspnet.vulnweb.com/jscripts/</FullURL> | |
| 457 | <Inputs> | |
| 458 | </Inputs> | |
| 459 | <Variations> | |
| 460 | </Variations> | |
| 461 | </SiteFile> | |
| 462 | <SiteFile id="22"> | |
| 463 | <Name>tiny_mce</Name> | |
| 464 | <URL>/jscripts/tiny_mce/</URL> | |
| 465 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/</FullURL> | |
| 466 | <Inputs> | |
| 467 | </Inputs> | |
| 468 | <Variations> | |
| 469 | </Variations> | |
| 470 | </SiteFile> | |
| 471 | <SiteFile id="23"> | |
| 472 | <Name>langs</Name> | |
| 473 | <URL>/jscripts/tiny_mce/langs/</URL> | |
| 474 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/langs/</FullURL> | |
| 475 | <Inputs> | |
| 476 | </Inputs> | |
| 477 | <Variations> | |
| 478 | </Variations> | |
| 479 | </SiteFile> | |
| 480 | <SiteFile id="24"> | |
| 481 | <Name>en.js</Name> | |
| 482 | <URL>/jscripts/tiny_mce/langs/en.js</URL> | |
| 483 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/langs/en.js</FullURL> | |
| 484 | <Inputs> | |
| 485 | </Inputs> | |
| 486 | <Variations> | |
| 487 | </Variations> | |
| 488 | </SiteFile> | |
| 489 | <SiteFile id="25"> | |
| 490 | <Name>themes</Name> | |
| 491 | <URL>/jscripts/tiny_mce/themes/</URL> | |
| 492 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/themes/</FullURL> | |
| 493 | <Inputs> | |
| 494 | </Inputs> | |
| 495 | <Variations> | |
| 496 | </Variations> | |
| 497 | </SiteFile> | |
| 498 | <SiteFile id="26"> | |
| 499 | <Name>simple</Name> | |
| 500 | <URL>/jscripts/tiny_mce/themes/simple/</URL> | |
| 501 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/themes/simple/</FullURL> | |
| 502 | <Inputs> | |
| 503 | </Inputs> | |
| 504 | <Variations> | |
| 505 | </Variations> | |
| 506 | </SiteFile> | |
| 507 | <SiteFile id="27"> | |
| 508 | <Name>css</Name> | |
| 509 | <URL>/jscripts/tiny_mce/themes/simple/css/</URL> | |
| 510 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/themes/simple/css/</FullURL> | |
| 511 | <Inputs> | |
| 512 | </Inputs> | |
| 513 | <Variations> | |
| 514 | </Variations> | |
| 515 | </SiteFile> | |
| 516 | <SiteFile id="28"> | |
| 517 | <Name>editor_content.css</Name> | |
| 518 | <URL>/jscripts/tiny_mce/themes/simple/css/editor_content.css</URL> | |
| 519 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/themes/simple/css/editor_content.css</FullURL> | |
| 520 | <Inputs> | |
| 521 | </Inputs> | |
| 522 | <Variations> | |
| 523 | </Variations> | |
| 524 | </SiteFile> | |
| 525 | <SiteFile id="29"> | |
| 526 | <Name>editor_popup.css</Name> | |
| 527 | <URL>/jscripts/tiny_mce/themes/simple/css/editor_popup.css</URL> | |
| 528 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/themes/simple/css/editor_popup.css</FullURL> | |
| 529 | <Inputs> | |
| 530 | </Inputs> | |
| 531 | <Variations> | |
| 532 | </Variations> | |
| 533 | </SiteFile> | |
| 534 | <SiteFile id="30"> | |
| 535 | <Name>editor_ui.css</Name> | |
| 536 | <URL>/jscripts/tiny_mce/themes/simple/css/editor_ui.css</URL> | |
| 537 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/themes/simple/css/editor_ui.css</FullURL> | |
| 538 | <Inputs> | |
| 539 | </Inputs> | |
| 540 | <Variations> | |
| 541 | </Variations> | |
| 542 | </SiteFile> | |
| 543 | <SiteFile id="31"> | |
| 544 | <Name>images</Name> | |
| 545 | <URL>/jscripts/tiny_mce/themes/simple/images/</URL> | |
| 546 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/themes/simple/images/</FullURL> | |
| 547 | <Inputs> | |
| 548 | </Inputs> | |
| 549 | <Variations> | |
| 550 | </Variations> | |
| 551 | </SiteFile> | |
| 552 | <SiteFile id="32"> | |
| 553 | <Name>editor_template.js</Name> | |
| 554 | <URL>/jscripts/tiny_mce/themes/simple/editor_template.js</URL> | |
| 555 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/themes/simple/editor_template.js</FullURL> | |
| 556 | <Inputs> | |
| 557 | </Inputs> | |
| 558 | <Variations> | |
| 559 | </Variations> | |
| 560 | </SiteFile> | |
| 561 | <SiteFile id="33"> | |
| 562 | <Name>editor_template_src.js</Name> | |
| 563 | <URL>/jscripts/tiny_mce/themes/simple/editor_template_src.js</URL> | |
| 564 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/themes/simple/editor_template_src.js</FullURL> | |
| 565 | <Inputs> | |
| 566 | </Inputs> | |
| 567 | <Variations> | |
| 568 | </Variations> | |
| 569 | </SiteFile> | |
| 570 | <SiteFile id="34"> | |
| 571 | <Name>utils</Name> | |
| 572 | <URL>/jscripts/tiny_mce/utils/</URL> | |
| 573 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/utils/</FullURL> | |
| 574 | <Inputs> | |
| 575 | </Inputs> | |
| 576 | <Variations> | |
| 577 | </Variations> | |
| 578 | </SiteFile> | |
| 579 | <SiteFile id="35"> | |
| 580 | <Name>form_utils.js</Name> | |
| 581 | <URL>/jscripts/tiny_mce/utils/form_utils.js</URL> | |
| 582 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/utils/form_utils.js</FullURL> | |
| 583 | <Inputs> | |
| 584 | </Inputs> | |
| 585 | <Variations> | |
| 586 | </Variations> | |
| 587 | </SiteFile> | |
| 588 | <SiteFile id="36"> | |
| 589 | <Name>mctabs.js</Name> | |
| 590 | <URL>/jscripts/tiny_mce/utils/mctabs.js</URL> | |
| 591 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/utils/mctabs.js</FullURL> | |
| 592 | <Inputs> | |
| 593 | </Inputs> | |
| 594 | <Variations> | |
| 595 | </Variations> | |
| 596 | </SiteFile> | |
| 597 | <SiteFile id="37"> | |
| 598 | <Name>validate.js</Name> | |
| 599 | <URL>/jscripts/tiny_mce/utils/validate.js</URL> | |
| 600 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/utils/validate.js</FullURL> | |
| 601 | <Inputs> | |
| 602 | </Inputs> | |
| 603 | <Variations> | |
| 604 | </Variations> | |
| 605 | </SiteFile> | |
| 606 | <SiteFile id="38"> | |
| 607 | <Name>blank.htm</Name> | |
| 608 | <URL>/jscripts/tiny_mce/blank.htm</URL> | |
| 609 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/blank.htm</FullURL> | |
| 610 | <Inputs> | |
| 611 | </Inputs> | |
| 612 | <Variations> | |
| 613 | </Variations> | |
| 614 | </SiteFile> | |
| 615 | <SiteFile id="39"> | |
| 616 | <Name>license.txt</Name> | |
| 617 | <URL>/jscripts/tiny_mce/license.txt</URL> | |
| 618 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/license.txt</FullURL> | |
| 619 | <Inputs> | |
| 620 | </Inputs> | |
| 621 | <Variations> | |
| 622 | </Variations> | |
| 623 | </SiteFile> | |
| 624 | <SiteFile id="40"> | |
| 625 | <Name>tiny_mce.js</Name> | |
| 626 | <URL>/jscripts/tiny_mce/tiny_mce.js</URL> | |
| 627 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/tiny_mce.js</FullURL> | |
| 628 | <Inputs> | |
| 629 | </Inputs> | |
| 630 | <Variations> | |
| 631 | </Variations> | |
| 632 | </SiteFile> | |
| 633 | <SiteFile id="41"> | |
| 634 | <Name>tiny_mce_popup.js</Name> | |
| 635 | <URL>/jscripts/tiny_mce/tiny_mce_popup.js</URL> | |
| 636 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/tiny_mce_popup.js</FullURL> | |
| 637 | <Inputs> | |
| 638 | </Inputs> | |
| 639 | <Variations> | |
| 640 | </Variations> | |
| 641 | </SiteFile> | |
| 642 | <SiteFile id="42"> | |
| 643 | <Name>tiny_mce_src.js</Name> | |
| 644 | <URL>/jscripts/tiny_mce/tiny_mce_src.js</URL> | |
| 645 | <FullURL>http://testaspnet.vulnweb.com/jscripts/tiny_mce/tiny_mce_src.js</FullURL> | |
| 646 | <Inputs> | |
| 647 | </Inputs> | |
| 648 | <Variations> | |
| 649 | </Variations> | |
| 650 | </SiteFile> | |
| 651 | <SiteFile id="43"> | |
| 652 | <Name>temp</Name> | |
| 653 | <URL>/temp/</URL> | |
| 654 | <FullURL>http://testaspnet.vulnweb.com/temp/</FullURL> | |
| 655 | <Inputs> | |
| 656 | </Inputs> | |
| 657 | <Variations> | |
| 658 | </Variations> | |
| 659 | </SiteFile> | |
| 660 | <SiteFile id="44"> | |
| 661 | <Name>.rnd</Name> | |
| 662 | <URL>/temp/.rnd</URL> | |
| 663 | <FullURL>http://testaspnet.vulnweb.com/temp/.rnd</FullURL> | |
| 664 | <Inputs> | |
| 665 | </Inputs> | |
| 666 | <Variations> | |
| 667 | </Variations> | |
| 668 | </SiteFile> | |
| 669 | <SiteFile id="45"> | |
| 670 | <Name>utils</Name> | |
| 671 | <URL>/utils/</URL> | |
| 672 | <FullURL>http://testaspnet.vulnweb.com/utils/</FullURL> | |
| 673 | <Inputs> | |
| 674 | </Inputs> | |
| 675 | <Variations> | |
| 676 | </Variations> | |
| 677 | </SiteFile> | |
| 678 | <SiteFile id="46"> | |
| 679 | <Name>usermanager.cs</Name> | |
| 680 | <URL>/utils/usermanager.cs</URL> | |
| 681 | <FullURL>http://testaspnet.vulnweb.com/utils/usermanager.cs</FullURL> | |
| 682 | <Inputs> | |
| 683 | </Inputs> | |
| 684 | <Variations> | |
| 685 | </Variations> | |
| 686 | </SiteFile> | |
| 687 | <SiteFile id="47"> | |
| 688 | <Name>_vti_cnf</Name> | |
| 689 | <URL>/_vti_cnf/</URL> | |
| 690 | <FullURL>http://testaspnet.vulnweb.com/_vti_cnf/</FullURL> | |
| 691 | <Inputs> | |
| 692 | </Inputs> | |
| 693 | <Variations> | |
| 694 | </Variations> | |
| 695 | </SiteFile> | |
| 696 | <SiteFile id="48"> | |
| 697 | <Name>acublog.csproj</Name> | |
| 698 | <URL>/_vti_cnf/acublog.csproj</URL> | |
| 699 | <FullURL>http://testaspnet.vulnweb.com/_vti_cnf/acublog.csproj</FullURL> | |
| 700 | <Inputs> | |
| 701 | </Inputs> | |
| 702 | <Variations> | |
| 703 | </Variations> | |
| 704 | </SiteFile> | |
| 705 | <SiteFile id="49"> | |
| 706 | <Name>acublog.csproj.webinfo</Name> | |
| 707 | <URL>/_vti_cnf/acublog.csproj.webinfo</URL> | |
| 708 | <FullURL>http://testaspnet.vulnweb.com/_vti_cnf/acublog.csproj.webinfo</FullURL> | |
| 709 | <Inputs> | |
| 710 | </Inputs> | |
| 711 | <Variations> | |
| 712 | </Variations> | |
| 713 | </SiteFile> | |
| 714 | <SiteFile id="50"> | |
| 715 | <Name>about.aspx.cs</Name> | |
| 716 | <URL>/about.aspx.cs</URL> | |
| 717 | <FullURL>http://testaspnet.vulnweb.com/about.aspx.cs</FullURL> | |
| 718 | <Inputs> | |
| 719 | </Inputs> | |
| 720 | <Variations> | |
| 721 | </Variations> | |
| 722 | </SiteFile> | |
| 723 | <SiteFile id="51"> | |
| 724 | <Name>about.aspx.resx</Name> | |
| 725 | <URL>/about.aspx.resx</URL> | |
| 726 | <FullURL>http://testaspnet.vulnweb.com/about.aspx.resx</FullURL> | |
| 727 | <Inputs> | |
| 728 | </Inputs> | |
| 729 | <Variations> | |
| 730 | </Variations> | |
| 731 | </SiteFile> | |
| 732 | <SiteFile id="52"> | |
| 733 | <Name>acublog.csproj</Name> | |
| 734 | <URL>/acublog.csproj</URL> | |
| 735 | <FullURL>http://testaspnet.vulnweb.com/acublog.csproj</FullURL> | |
| 736 | <Inputs> | |
| 737 | </Inputs> | |
| 738 | <Variations> | |
| 739 | </Variations> | |
| 740 | </SiteFile> | |
| 741 | <SiteFile id="53"> | |
| 742 | <Name>acublog.csproj.webinfo</Name> | |
| 743 | <URL>/acublog.csproj.webinfo</URL> | |
| 744 | <FullURL>http://testaspnet.vulnweb.com/acublog.csproj.webinfo</FullURL> | |
| 745 | <Inputs> | |
| 746 | </Inputs> | |
| 747 | <Variations> | |
| 748 | </Variations> | |
| 749 | </SiteFile> | |
| 750 | <SiteFile id="54"> | |
| 751 | <Name>assemblyinfo.cs</Name> | |
| 752 | <URL>/assemblyinfo.cs</URL> | |
| 753 | <FullURL>http://testaspnet.vulnweb.com/assemblyinfo.cs</FullURL> | |
| 754 | <Inputs> | |
| 755 | </Inputs> | |
| 756 | <Variations> | |
| 757 | </Variations> | |
| 758 | </SiteFile> | |
| 759 | <SiteFile id="55"> | |
| 760 | <Name>comments.aspx.cs</Name> | |
| 761 | <URL>/comments.aspx.cs</URL> | |
| 762 | <FullURL>http://testaspnet.vulnweb.com/comments.aspx.cs</FullURL> | |
| 763 | <Inputs> | |
| 764 | </Inputs> | |
| 765 | <Variations> | |
| 766 | </Variations> | |
| 767 | </SiteFile> | |
| 768 | <SiteFile id="56"> | |
| 769 | <Name>comments.aspx.resx</Name> | |
| 770 | <URL>/comments.aspx.resx</URL> | |
| 771 | <FullURL>http://testaspnet.vulnweb.com/comments.aspx.resx</FullURL> | |
| 772 | <Inputs> | |
| 773 | </Inputs> | |
| 774 | <Variations> | |
| 775 | </Variations> | |
| 776 | </SiteFile> | |
| 777 | <SiteFile id="57"> | |
| 778 | <Name>default.aspx.cs</Name> | |
| 779 | <URL>/default.aspx.cs</URL> | |
| 780 | <FullURL>http://testaspnet.vulnweb.com/default.aspx.cs</FullURL> | |
| 781 | <Inputs> | |
| 782 | </Inputs> | |
| 783 | <Variations> | |
| 784 | </Variations> | |
| 785 | </SiteFile> | |
| 786 | <SiteFile id="58"> | |
| 787 | <Name>default.aspx.resx</Name> | |
| 788 | <URL>/default.aspx.resx</URL> | |
| 789 | <FullURL>http://testaspnet.vulnweb.com/default.aspx.resx</FullURL> | |
| 790 | <Inputs> | |
| 791 | </Inputs> | |
| 792 | <Variations> | |
| 793 | </Variations> | |
| 794 | </SiteFile> | |
| 795 | <SiteFile id="59"> | |
| 796 | <Name>global.asax</Name> | |
| 797 | <URL>/global.asax</URL> | |
| 798 | <FullURL>http://testaspnet.vulnweb.com/global.asax</FullURL> | |
| 799 | <Inputs> | |
| 800 | </Inputs> | |
| 801 | <Variations> | |
| 802 | </Variations> | |
| 803 | </SiteFile> | |
| 804 | <SiteFile id="60"> | |
| 805 | <Name>global.asax.cs</Name> | |
| 806 | <URL>/global.asax.cs</URL> | |
| 807 | <FullURL>http://testaspnet.vulnweb.com/global.asax.cs</FullURL> | |
| 808 | <Inputs> | |
| 809 | </Inputs> | |
| 810 | <Variations> | |
| 811 | </Variations> | |
| 812 | </SiteFile> | |
| 813 | <SiteFile id="61"> | |
| 814 | <Name>global.asax.resx</Name> | |
| 815 | <URL>/global.asax.resx</URL> | |
| 816 | <FullURL>http://testaspnet.vulnweb.com/global.asax.resx</FullURL> | |
| 817 | <Inputs> | |
| 818 | </Inputs> | |
| 819 | <Variations> | |
| 820 | </Variations> | |
| 821 | </SiteFile> | |
| 822 | <SiteFile id="62"> | |
| 823 | <Name>login.aspx.cs</Name> | |
| 824 | <URL>/login.aspx.cs</URL> | |
| 825 | <FullURL>http://testaspnet.vulnweb.com/login.aspx.cs</FullURL> | |
| 826 | <Inputs> | |
| 827 | </Inputs> | |
| 828 | <Variations> | |
| 829 | </Variations> | |
| 830 | </SiteFile> | |
| 831 | <SiteFile id="63"> | |
| 832 | <Name>login.aspx.resx</Name> | |
| 833 | <URL>/login.aspx.resx</URL> | |
| 834 | <FullURL>http://testaspnet.vulnweb.com/login.aspx.resx</FullURL> | |
| 835 | <Inputs> | |
| 836 | </Inputs> | |
| 837 | <Variations> | |
| 838 | </Variations> | |
| 839 | </SiteFile> | |
| 840 | <SiteFile id="64"> | |
| 841 | <Name>logout.aspx</Name> | |
| 842 | <URL>/logout.aspx</URL> | |
| 843 | <FullURL>http://testaspnet.vulnweb.com/logout.aspx</FullURL> | |
| 844 | <Inputs> | |
| 845 | </Inputs> | |
| 846 | <Variations> | |
| 847 | </Variations> | |
| 848 | </SiteFile> | |
| 849 | <SiteFile id="65"> | |
| 850 | <Name>logout.aspx.cs</Name> | |
| 851 | <URL>/logout.aspx.cs</URL> | |
| 852 | <FullURL>http://testaspnet.vulnweb.com/logout.aspx.cs</FullURL> | |
| 853 | <Inputs> | |
| 854 | </Inputs> | |
| 855 | <Variations> | |
| 856 | </Variations> | |
| 857 | </SiteFile> | |
| 858 | <SiteFile id="66"> | |
| 859 | <Name>logout.aspx.resx</Name> | |
| 860 | <URL>/logout.aspx.resx</URL> | |
| 861 | <FullURL>http://testaspnet.vulnweb.com/logout.aspx.resx</FullURL> | |
| 862 | <Inputs> | |
| 863 | </Inputs> | |
| 864 | <Variations> | |
| 865 | </Variations> | |
| 866 | </SiteFile> | |
| 867 | <SiteFile id="67"> | |
| 868 | <Name>mainmenu.ascx</Name> | |
| 869 | <URL>/mainmenu.ascx</URL> | |
| 870 | <FullURL>http://testaspnet.vulnweb.com/mainmenu.ascx</FullURL> | |
| 871 | <Inputs> | |
| 872 | </Inputs> | |
| 873 | <Variations> | |
| 874 | </Variations> | |
| 875 | </SiteFile> | |
| 876 | <SiteFile id="68"> | |
| 877 | <Name>mainmenu.ascx.cs</Name> | |
| 878 | <URL>/mainmenu.ascx.cs</URL> | |
| 879 | <FullURL>http://testaspnet.vulnweb.com/mainmenu.ascx.cs</FullURL> | |
| 880 | <Inputs> | |
| 881 | </Inputs> | |
| 882 | <Variations> | |
| 883 | </Variations> | |
| 884 | </SiteFile> | |
| 885 | <SiteFile id="69"> | |
| 886 | <Name>mainmenu.ascx.resx</Name> | |
| 887 | <URL>/mainmenu.ascx.resx</URL> | |
| 888 | <FullURL>http://testaspnet.vulnweb.com/mainmenu.ascx.resx</FullURL> | |
| 889 | <Inputs> | |
| 890 | </Inputs> | |
| 891 | <Variations> | |
| 892 | </Variations> | |
| 893 | </SiteFile> | |
| 894 | <SiteFile id="70"> | |
| 895 | <Name>postnews.aspx</Name> | |
| 896 | <URL>/postnews.aspx</URL> | |
| 897 | <FullURL>http://testaspnet.vulnweb.com/postnews.aspx</FullURL> | |
| 898 | <Inputs> | |
| 899 | </Inputs> | |
| 900 | <Variations> | |
| 901 | </Variations> | |
| 902 | </SiteFile> | |
| 903 | <SiteFile id="71"> | |
| 904 | <Name>postnews.aspx.cs</Name> | |
| 905 | <URL>/postnews.aspx.cs</URL> | |
| 906 | <FullURL>http://testaspnet.vulnweb.com/postnews.aspx.cs</FullURL> | |
| 907 | <Inputs> | |
| 908 | </Inputs> | |
| 909 | <Variations> | |
| 910 | </Variations> | |
| 911 | </SiteFile> | |
| 912 | <SiteFile id="72"> | |
| 913 | <Name>postnews.aspx.resx</Name> | |
| 914 | <URL>/postnews.aspx.resx</URL> | |
| 915 | <FullURL>http://testaspnet.vulnweb.com/postnews.aspx.resx</FullURL> | |
| 916 | <Inputs> | |
| 917 | </Inputs> | |
| 918 | <Variations> | |
| 919 | </Variations> | |
| 920 | </SiteFile> | |
| 921 | <SiteFile id="73"> | |
| 922 | <Name>readnews.aspx.cs</Name> | |
| 923 | <URL>/readnews.aspx.cs</URL> | |
| 924 | <FullURL>http://testaspnet.vulnweb.com/readnews.aspx.cs</FullURL> | |
| 925 | <Inputs> | |
| 926 | </Inputs> | |
| 927 | <Variations> | |
| 928 | </Variations> | |
| 929 | </SiteFile> | |
| 930 | <SiteFile id="74"> | |
| 931 | <Name>readnews.aspx.resx</Name> | |
| 932 | <URL>/readnews.aspx.resx</URL> | |
| 933 | <FullURL>http://testaspnet.vulnweb.com/readnews.aspx.resx</FullURL> | |
| 934 | <Inputs> | |
| 935 | </Inputs> | |
| 936 | <Variations> | |
| 937 | </Variations> | |
| 938 | </SiteFile> | |
| 939 | <SiteFile id="75"> | |
| 940 | <Name>rightpanel.ascx</Name> | |
| 941 | <URL>/rightpanel.ascx</URL> | |
| 942 | <FullURL>http://testaspnet.vulnweb.com/rightpanel.ascx</FullURL> | |
| 943 | <Inputs> | |
| 944 | </Inputs> | |
| 945 | <Variations> | |
| 946 | </Variations> | |
| 947 | </SiteFile> | |
| 948 | <SiteFile id="76"> | |
| 949 | <Name>rightpanel.ascx.cs</Name> | |
| 950 | <URL>/rightpanel.ascx.cs</URL> | |
| 951 | <FullURL>http://testaspnet.vulnweb.com/rightpanel.ascx.cs</FullURL> | |
| 952 | <Inputs> | |
| 953 | </Inputs> | |
| 954 | <Variations> | |
| 955 | </Variations> | |
| 956 | </SiteFile> | |
| 957 | <SiteFile id="77"> | |
| 958 | <Name>rightpanel.ascx.resx</Name> | |
| 959 | <URL>/rightpanel.ascx.resx</URL> | |
| 960 | <FullURL>http://testaspnet.vulnweb.com/rightpanel.ascx.resx</FullURL> | |
| 961 | <Inputs> | |
| 962 | </Inputs> | |
| 963 | <Variations> | |
| 964 | </Variations> | |
| 965 | </SiteFile> | |
| 966 | <SiteFile id="78"> | |
| 967 | <Name>rssfeed.aspx.cs</Name> | |
| 968 | <URL>/rssfeed.aspx.cs</URL> | |
| 969 | <FullURL>http://testaspnet.vulnweb.com/rssfeed.aspx.cs</FullURL> | |
| 970 | <Inputs> | |
| 971 | </Inputs> | |
| 972 | <Variations> | |
| 973 | </Variations> | |
| 974 | </SiteFile> | |
| 975 | <SiteFile id="79"> | |
| 976 | <Name>rssfeed.aspx.resx</Name> | |
| 977 | <URL>/rssfeed.aspx.resx</URL> | |
| 978 | <FullURL>http://testaspnet.vulnweb.com/rssfeed.aspx.resx</FullURL> | |
| 979 | <Inputs> | |
| 980 | </Inputs> | |
| 981 | <Variations> | |
| 982 | </Variations> | |
| 983 | </SiteFile> | |
| 984 | <SiteFile id="80"> | |
| 985 | <Name>signup.aspx.cs</Name> | |
| 986 | <URL>/signup.aspx.cs</URL> | |
| 987 | <FullURL>http://testaspnet.vulnweb.com/signup.aspx.cs</FullURL> | |
| 988 | <Inputs> | |
| 989 | </Inputs> | |
| 990 | <Variations> | |
| 991 | </Variations> | |
| 992 | </SiteFile> | |
| 993 | <SiteFile id="81"> | |
| 994 | <Name>signup.aspx.resx</Name> | |
| 995 | <URL>/signup.aspx.resx</URL> | |
| 996 | <FullURL>http://testaspnet.vulnweb.com/signup.aspx.resx</FullURL> | |
| 997 | <Inputs> | |
| 998 | </Inputs> | |
| 999 | <Variations> | |
| 1000 | </Variations> | |
| 1001 | </SiteFile> | |
| 1002 | <SiteFile id="82"> | |
| 1003 | <Name>test.txt</Name> | |
| 1004 | <URL>/test.txt</URL> | |
| 1005 | <FullURL>http://testaspnet.vulnweb.com/test.txt</FullURL> | |
| 1006 | <Inputs> | |
| 1007 | </Inputs> | |
| 1008 | <Variations> | |
| 1009 | </Variations> | |
| 1010 | </SiteFile> | |
| 1011 | <SiteFile id="83"> | |
| 1012 | <Name>web.config</Name> | |
| 1013 | <URL>/web.config</URL> | |
| 1014 | <FullURL>http://testaspnet.vulnweb.com/web.config</FullURL> | |
| 1015 | <Inputs> | |
| 1016 | </Inputs> | |
| 1017 | <Variations> | |
| 1018 | </Variations> | |
| 1019 | </SiteFile> | |
| 1020 | <SiteFile id="84"> | |
| 1021 | <Name>robots.txt</Name> | |
| 1022 | <URL>/robots.txt</URL> | |
| 1023 | <FullURL>http://testaspnet.vulnweb.com/robots.txt</FullURL> | |
| 1024 | <Inputs> | |
| 1025 | </Inputs> | |
| 1026 | <Variations> | |
| 1027 | </Variations> | |
| 1028 | </SiteFile> | |
| 1029 | </SiteFiles> | |
| 1030 | </Crawler> | |
| 1031 | <ReportItems> | |
| 1032 | ||
| 1033 | <ReportItem id="0" color="orange"> | |
| 1034 | <Name><![CDATA[ASP.NET error message]]></Name> | |
| 1035 | <ModuleName><![CDATA[Scripting (ASP_NET_Error_Message.script)]]></ModuleName> | |
| 1036 | <Details><![CDATA[Error message pattern found: <font color="dark"><title>Illegal characters in path.</title></font><br/>Version information found: <font color="dark">Microsoft .NET Framework Version:2.0.50727.3053; ASP.NET Version:2.0.50727.3053 ⏎ | |
| 1037 | </font>]]></Details> | |
| 1038 | <Affects><![CDATA[Web Server]]></Affects> | |
| 1039 | <Parameter><![CDATA[]]></Parameter> | |
| 1040 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1041 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1042 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1043 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1044 | <Severity><![CDATA[medium]]></Severity> | |
| 1045 | <Type><![CDATA[Validation]]></Type> | |
| 1046 | <Impact><![CDATA[The error messages may disclose sensitive information. This information can be used to launch further attacks.]]></Impact> | |
| 1047 | <Description><![CDATA[By requesting a specially crafted URL is possible to generate an ASP.NET error message. The message contains the complete stack trace and Microsoft .NET Framework Version.<br/><br/> | |
| 1048 | ]]></Description> | |
| 1049 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1050 | <Recommendation><![CDATA[Adjust web.config to enable custom errors for remote clients. Set <b>customErrors</b> mode to <b>Off</b> or <b>RemoteOnly</b>. customErrors is part of system.web Element. RemoteOnly specifies that custom errors are shown only to the remote clients, and that ASP.NET errors are shown to the local host. This is the default value. <br/> | |
| 1051 | ||
| 1052 | <pre wrap="virtual"> | |
| 1053 | <configuration> | |
| 1054 | <system.web> | |
| 1055 | <customErrors mode="RemoteOnly" /> | |
| 1056 | </system.web> | |
| 1057 | </configuration> | |
| 1058 | </pre>]]></Recommendation> | |
| 1059 | <TechnicalDetails> | |
| 1060 | <Request><![CDATA[GET /|~.aspx HTTP/1.1 | |
| 1061 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1062 | Host: testaspnet.vulnweb.com | |
| 1063 | Connection: Keep-alive | |
| 1064 | Accept-Encoding: gzip,deflate | |
| 1065 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1066 | Accept: */* | |
| 1067 | ||
| 1068 | ]]></Request> | |
| 1069 | <Response><![CDATA[HTTP/1.1 500 Internal Server Error | |
| 1070 | Date: Thu, 14 Nov 2013 14:26:33 GMT | |
| 1071 | Server: Microsoft-IIS/6.0 | |
| 1072 | X-Powered-By: ASP.NET | |
| 1073 | X-AspNet-Version: 2.0.50727 | |
| 1074 | Cache-Control: private | |
| 1075 | Content-Type: text/html; charset=utf-8 | |
| 1076 | Content-Length: 3670 | |
| 1077 | ]]></Response> | |
| 1078 | </TechnicalDetails> | |
| 1079 | <References> | |
| 1080 | <Reference> | |
| 1081 | <Database><![CDATA[customErrors Element (ASP.NET Settings Schema)]]></Database> | |
| 1082 | <URL><![CDATA[http://msdn.microsoft.com/en-us/library/vstudio/h0hfz6fc%28v=vs.100%29.aspx]]></URL> | |
| 1083 | </Reference> | |
| 1084 | </References> | |
| 1085 | </ReportItem> | |
| 1086 | ||
| 1087 | <ReportItem id="1" color="orange"> | |
| 1088 | <Name><![CDATA[Unencrypted __VIEWSTATE parameter]]></Name> | |
| 1089 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 1090 | <Details><![CDATA[form name: <font color="dark">"Form1"</font><br/>form action: <font color="dark">"Default.aspx"</font><br/>VIEWSTATE: <font color="dark">"/wEPDwUKLTEwNTI0MjkwNQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkZDUAskqLyfS1MBsZINJY6LpGzdzU"</font><br/>VIEWSTATE decoded: <font color="dark">"##### | |
| 1091 | -105242905#d#####d#####d#########href# | |
| 1092 | login.aspx# innerhtml##logind#######d##Visiblehdd5##J####0## #X##F###"</font><br/>]]></Details> | |
| 1093 | <Affects><![CDATA[/]]></Affects> | |
| 1094 | <Parameter><![CDATA[]]></Parameter> | |
| 1095 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1096 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1097 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1098 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1099 | <Severity><![CDATA[medium]]></Severity> | |
| 1100 | <Type><![CDATA[Informational]]></Type> | |
| 1101 | <Impact><![CDATA[Possible sensitive information disclosure.]]></Impact> | |
| 1102 | <Description><![CDATA[The __VIEWSTATE parameter is not encrypted. To reduce the chance of someone intercepting the information stored in the ViewState, it is good design to encrypt the ViewState. To do this, set the machineKey validation type to 3DES. This instructs ASP.NET to encrypt the ViewState value using the Triple DES symmetric encryption algorithm.]]></Description> | |
| 1103 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1104 | <Recommendation><![CDATA[Open <font color="dark"><b>Web.Config</b></font> and add the following line under the <font color="dark"><b><system.web></b></font> element: <br/><pre wrap="virtual"><machineKey validation="3DES"/> </pre>]]></Recommendation> | |
| 1105 | <TechnicalDetails> | |
| 1106 | <Request><![CDATA[GET / HTTP/1.1 | |
| 1107 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1108 | Host: testaspnet.vulnweb.com | |
| 1109 | Connection: Keep-alive | |
| 1110 | Accept-Encoding: gzip,deflate | |
| 1111 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1112 | Accept: */* | |
| 1113 | ||
| 1114 | ]]></Request> | |
| 1115 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 1116 | Date: Thu, 14 Nov 2013 14:26:34 GMT | |
| 1117 | Server: Microsoft-IIS/6.0 | |
| 1118 | X-Powered-By: ASP.NET | |
| 1119 | X-AspNet-Version: 2.0.50727 | |
| 1120 | Cache-Control: private | |
| 1121 | Content-Type: text/html; charset=utf-8 | |
| 1122 | Content-Length: 12967 | |
| 1123 | ]]></Response> | |
| 1124 | </TechnicalDetails> | |
| 1125 | <References></References> | |
| 1126 | </ReportItem> | |
| 1127 | ||
| 1128 | <ReportItem id="2" color="blue"> | |
| 1129 | <Name><![CDATA[Clickjacking: X-Frame-Options header missing]]></Name> | |
| 1130 | <ModuleName><![CDATA[Scripting (Clickjacking_X_Frame_Options.script)]]></ModuleName> | |
| 1131 | <Details><![CDATA[No details are available.]]></Details> | |
| 1132 | <Affects><![CDATA[Web Server]]></Affects> | |
| 1133 | <Parameter><![CDATA[]]></Parameter> | |
| 1134 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1135 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1136 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1137 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1138 | <Severity><![CDATA[low]]></Severity> | |
| 1139 | <Type><![CDATA[Configuration]]></Type> | |
| 1140 | <Impact><![CDATA[The impact depends on the affected web application. ]]></Impact> | |
| 1141 | <Description><![CDATA[Clickjacking (User Interface redress attack, UI redress attack, UI redressing) is a malicious technique of tricking a Web user into clicking on something different from what the user perceives they are clicking on, thus potentially revealing confidential information or taking control of their computer while clicking on seemingly innocuous web pages. <br/><br/> | |
| 1142 | The server didn't return an <b>X-Frame-Options</b> header which means that this website could be at risk of a clickjacking attack. The X-Frame-Options HTTP response header can be used to indicate whether or not a browser should be allowed to render a page in a <frame> or <iframe>. Sites can use this to avoid clickjacking attacks, by ensuring that their content is not embedded into other sites. | |
| 1143 | ]]></Description> | |
| 1144 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1145 | <Recommendation><![CDATA[Configure your web server to include an X-Frame-Options header. Consult Web references for more information about the possible values for this header.]]></Recommendation> | |
| 1146 | <TechnicalDetails> | |
| 1147 | <Request><![CDATA[GET / HTTP/1.1 | |
| 1148 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1149 | Host: testaspnet.vulnweb.com | |
| 1150 | Connection: Keep-alive | |
| 1151 | Accept-Encoding: gzip,deflate | |
| 1152 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1153 | Accept: */* | |
| 1154 | ||
| 1155 | ]]></Request> | |
| 1156 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 1157 | Date: Thu, 14 Nov 2013 14:26:34 GMT | |
| 1158 | Server: Microsoft-IIS/6.0 | |
| 1159 | X-Powered-By: ASP.NET | |
| 1160 | X-AspNet-Version: 2.0.50727 | |
| 1161 | Cache-Control: private | |
| 1162 | Content-Type: text/html; charset=utf-8 | |
| 1163 | Content-Length: 12967 | |
| 1164 | ]]></Response> | |
| 1165 | </TechnicalDetails> | |
| 1166 | <References> | |
| 1167 | <Reference> | |
| 1168 | <Database><![CDATA[The X-Frame-Options response header]]></Database> | |
| 1169 | <URL><![CDATA[https://developer.mozilla.org/en-US/docs/HTTP/X-Frame-Options]]></URL> | |
| 1170 | </Reference> | |
| 1171 | <Reference> | |
| 1172 | <Database><![CDATA[Clickjacking]]></Database> | |
| 1173 | <URL><![CDATA[http://en.wikipedia.org/wiki/Clickjacking]]></URL> | |
| 1174 | </Reference> | |
| 1175 | <Reference> | |
| 1176 | <Database><![CDATA[Original Clickjacking paper]]></Database> | |
| 1177 | <URL><![CDATA[http://www.sectheory.com/clickjacking.htm]]></URL> | |
| 1178 | </Reference> | |
| 1179 | </References> | |
| 1180 | </ReportItem> | |
| 1181 | ||
| 1182 | <ReportItem id="3" color="orange"> | |
| 1183 | <Name><![CDATA[Unencrypted __VIEWSTATE parameter]]></Name> | |
| 1184 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 1185 | <Details><![CDATA[form name: <font color="dark">"Form1"</font><br/>form action: <font color="dark">"about.aspx"</font><br/>VIEWSTATE: <font color="dark">"/wEPDwUKLTEwNTI0MjkwNQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkZCUArJ3C1Fln0zT65m8W+6wYPSdL"</font><br/>VIEWSTATE decoded: <font color="dark">"##### | |
| 1186 | -105242905#d#####d#####d#########href# | |
| 1187 | login.aspx# innerhtml##logind#######d##Visiblehdd%#####Yg#4##o####='K"</font><br/>]]></Details> | |
| 1188 | <Affects><![CDATA[/about.aspx]]></Affects> | |
| 1189 | <Parameter><![CDATA[]]></Parameter> | |
| 1190 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1191 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1192 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1193 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1194 | <Severity><![CDATA[medium]]></Severity> | |
| 1195 | <Type><![CDATA[Informational]]></Type> | |
| 1196 | <Impact><![CDATA[Possible sensitive information disclosure.]]></Impact> | |
| 1197 | <Description><![CDATA[The __VIEWSTATE parameter is not encrypted. To reduce the chance of someone intercepting the information stored in the ViewState, it is good design to encrypt the ViewState. To do this, set the machineKey validation type to 3DES. This instructs ASP.NET to encrypt the ViewState value using the Triple DES symmetric encryption algorithm.]]></Description> | |
| 1198 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1199 | <Recommendation><![CDATA[Open <font color="dark"><b>Web.Config</b></font> and add the following line under the <font color="dark"><b><system.web></b></font> element: <br/><pre wrap="virtual"><machineKey validation="3DES"/> </pre>]]></Recommendation> | |
| 1200 | <TechnicalDetails> | |
| 1201 | <Request><![CDATA[GET /about.aspx HTTP/1.1 | |
| 1202 | Pragma: no-cache | |
| 1203 | Cache-Control: no-cache | |
| 1204 | Referer: http://testaspnet.vulnweb.com/ | |
| 1205 | Acunetix-Aspect: enabled | |
| 1206 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1207 | Acunetix-Aspect-Queries: aspectalerts | |
| 1208 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1209 | Host: testaspnet.vulnweb.com | |
| 1210 | Connection: Keep-alive | |
| 1211 | Accept-Encoding: gzip,deflate | |
| 1212 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1213 | Accept: */* | |
| 1214 | ||
| 1215 | ]]></Request> | |
| 1216 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 1217 | Date: Thu, 14 Nov 2013 14:26:35 GMT | |
| 1218 | Server: Microsoft-IIS/6.0 | |
| 1219 | X-Powered-By: ASP.NET | |
| 1220 | X-AspNet-Version: 2.0.50727 | |
| 1221 | Cache-Control: private | |
| 1222 | Content-Type: text/html; charset=utf-8 | |
| 1223 | Content-Length: 13528 | |
| 1224 | ]]></Response> | |
| 1225 | </TechnicalDetails> | |
| 1226 | <References></References> | |
| 1227 | </ReportItem> | |
| 1228 | ||
| 1229 | <ReportItem id="4" color="green"> | |
| 1230 | <Name><![CDATA[Password type input with auto-complete enabled]]></Name> | |
| 1231 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 1232 | <Details><![CDATA[Password type input named <b><font color="dark">tbPassword</font></b> from form named <b>frmLogin</b> with action <b>login.aspx</b> has autocomplete enabled.]]></Details> | |
| 1233 | <Affects><![CDATA[/login.aspx]]></Affects> | |
| 1234 | <Parameter><![CDATA[]]></Parameter> | |
| 1235 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1236 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1237 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1238 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1239 | <Severity><![CDATA[info]]></Severity> | |
| 1240 | <Type><![CDATA[Informational]]></Type> | |
| 1241 | <Impact><![CDATA[Possible sensitive information disclosure]]></Impact> | |
| 1242 | <Description><![CDATA[When a new name and password is entered in a form and the form is submitted, the browser asks if the password should be saved. Thereafter when the form is displayed, the name and password are filled in automatically or are completed as the name is entered. An attacker with local access could obtain the cleartext password from the browser cache.]]></Description> | |
| 1243 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1244 | <Recommendation><![CDATA[The password auto-complete should be disabled in sensitive applications. <br/>To disable auto-complete, you may use a code similar to: <pre wrap="virtual"><code><INPUT TYPE="password" AUTOCOMPLETE="off"></code></pre>]]></Recommendation> | |
| 1245 | <TechnicalDetails> | |
| 1246 | <Request><![CDATA[GET /login.aspx HTTP/1.1 | |
| 1247 | Pragma: no-cache | |
| 1248 | Cache-Control: no-cache | |
| 1249 | Referer: http://testaspnet.vulnweb.com/ | |
| 1250 | Acunetix-Aspect: enabled | |
| 1251 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1252 | Acunetix-Aspect-Queries: aspectalerts | |
| 1253 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1254 | Host: testaspnet.vulnweb.com | |
| 1255 | Connection: Keep-alive | |
| 1256 | Accept-Encoding: gzip,deflate | |
| 1257 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1258 | Accept: */* | |
| 1259 | ||
| 1260 | ]]></Request> | |
| 1261 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 1262 | Date: Thu, 14 Nov 2013 14:26:35 GMT | |
| 1263 | Server: Microsoft-IIS/6.0 | |
| 1264 | X-Powered-By: ASP.NET | |
| 1265 | X-AspNet-Version: 2.0.50727 | |
| 1266 | Cache-Control: private | |
| 1267 | Content-Type: text/html; charset=utf-8 | |
| 1268 | Content-Length: 12329 | |
| 1269 | ]]></Response> | |
| 1270 | </TechnicalDetails> | |
| 1271 | <References></References> | |
| 1272 | </ReportItem> | |
| 1273 | ||
| 1274 | <ReportItem id="5" color="orange"> | |
| 1275 | <Name><![CDATA[User credentials are sent in clear text]]></Name> | |
| 1276 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 1277 | <Details><![CDATA[Form name: <font color="navy">frmLogin</font><br/>Form action: <font color="navy">http://testaspnet.vulnweb.com/login.aspx</font><br/>Form method: <font color="navy">POST</font><br/><br/>Form inputs:<br/><ul><li>__EVENTTARGET [Hidden]</li><li>__EVENTARGUMENT [Hidden]</li><li>__VIEWSTATE [Hidden]</li><li>__EVENTVALIDATION [Hidden]</li><li>tbUsername [Text]</li><li>tbPassword [Password]</li><li>cbPersistCookie [Checkbox]</li><li>btnLogin [Submit]</li></ul>]]></Details> | |
| 1278 | <Affects><![CDATA[/login.aspx]]></Affects> | |
| 1279 | <Parameter><![CDATA[]]></Parameter> | |
| 1280 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1281 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1282 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1283 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1284 | <Severity><![CDATA[medium]]></Severity> | |
| 1285 | <Type><![CDATA[Informational]]></Type> | |
| 1286 | <Impact><![CDATA[A third party may be able to read the user credentials by intercepting an unencrypted HTTP connection.]]></Impact> | |
| 1287 | <Description><![CDATA[User credentials are transmitted over an unencrypted channel. This information should always be transferred via an encrypted channel (HTTPS) to avoid being intercepted by malicious users.]]></Description> | |
| 1288 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1289 | <Recommendation><![CDATA[Because user credentials are considered sensitive information, should always be transferred to the server over an encrypted connection (HTTPS).]]></Recommendation> | |
| 1290 | <TechnicalDetails> | |
| 1291 | <Request><![CDATA[GET /login.aspx HTTP/1.1 | |
| 1292 | Pragma: no-cache | |
| 1293 | Cache-Control: no-cache | |
| 1294 | Referer: http://testaspnet.vulnweb.com/ | |
| 1295 | Acunetix-Aspect: enabled | |
| 1296 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1297 | Acunetix-Aspect-Queries: aspectalerts | |
| 1298 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1299 | Host: testaspnet.vulnweb.com | |
| 1300 | Connection: Keep-alive | |
| 1301 | Accept-Encoding: gzip,deflate | |
| 1302 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1303 | Accept: */* | |
| 1304 | ||
| 1305 | ]]></Request> | |
| 1306 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 1307 | Date: Thu, 14 Nov 2013 14:26:35 GMT | |
| 1308 | Server: Microsoft-IIS/6.0 | |
| 1309 | X-Powered-By: ASP.NET | |
| 1310 | X-AspNet-Version: 2.0.50727 | |
| 1311 | Cache-Control: private | |
| 1312 | Content-Type: text/html; charset=utf-8 | |
| 1313 | Content-Length: 12329 | |
| 1314 | ]]></Response> | |
| 1315 | </TechnicalDetails> | |
| 1316 | <References></References> | |
| 1317 | </ReportItem> | |
| 1318 | ||
| 1319 | <ReportItem id="6" color="orange"> | |
| 1320 | <Name><![CDATA[Unencrypted __VIEWSTATE parameter]]></Name> | |
| 1321 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 1322 | <Details><![CDATA[form name: <font color="dark">"frmLogin"</font><br/>form action: <font color="dark">"login.aspx"</font><br/>VIEWSTATE: <font color="dark">"/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W+w+8Zj9n0mGriLs0UbfzYNdg=="</font><br/>VIEWSTATE decoded: <font color="dark">"##### | |
| 1323 | -223969811#d#####d#####d#########href# | |
| 1324 | login.aspx# innerhtml##logind#######d##Visiblehd####__ControlsRequirePostBackKey__####cbPersistCookie##o###c#}&####E#6 ⏎ | |
| 1325 | v"</font><br/>]]></Details> | |
| 1326 | <Affects><![CDATA[/login.aspx]]></Affects> | |
| 1327 | <Parameter><![CDATA[]]></Parameter> | |
| 1328 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1329 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1330 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1331 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1332 | <Severity><![CDATA[medium]]></Severity> | |
| 1333 | <Type><![CDATA[Informational]]></Type> | |
| 1334 | <Impact><![CDATA[Possible sensitive information disclosure.]]></Impact> | |
| 1335 | <Description><![CDATA[The __VIEWSTATE parameter is not encrypted. To reduce the chance of someone intercepting the information stored in the ViewState, it is good design to encrypt the ViewState. To do this, set the machineKey validation type to 3DES. This instructs ASP.NET to encrypt the ViewState value using the Triple DES symmetric encryption algorithm.]]></Description> | |
| 1336 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1337 | <Recommendation><![CDATA[Open <font color="dark"><b>Web.Config</b></font> and add the following line under the <font color="dark"><b><system.web></b></font> element: <br/><pre wrap="virtual"><machineKey validation="3DES"/> </pre>]]></Recommendation> | |
| 1338 | <TechnicalDetails> | |
| 1339 | <Request><![CDATA[GET /login.aspx HTTP/1.1 | |
| 1340 | Pragma: no-cache | |
| 1341 | Cache-Control: no-cache | |
| 1342 | Referer: http://testaspnet.vulnweb.com/ | |
| 1343 | Acunetix-Aspect: enabled | |
| 1344 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1345 | Acunetix-Aspect-Queries: aspectalerts | |
| 1346 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1347 | Host: testaspnet.vulnweb.com | |
| 1348 | Connection: Keep-alive | |
| 1349 | Accept-Encoding: gzip,deflate | |
| 1350 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1351 | Accept: */* | |
| 1352 | ||
| 1353 | ]]></Request> | |
| 1354 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 1355 | Date: Thu, 14 Nov 2013 14:26:35 GMT | |
| 1356 | Server: Microsoft-IIS/6.0 | |
| 1357 | X-Powered-By: ASP.NET | |
| 1358 | X-AspNet-Version: 2.0.50727 | |
| 1359 | Cache-Control: private | |
| 1360 | Content-Type: text/html; charset=utf-8 | |
| 1361 | Content-Length: 12329 | |
| 1362 | ]]></Response> | |
| 1363 | </TechnicalDetails> | |
| 1364 | <References></References> | |
| 1365 | </ReportItem> | |
| 1366 | ||
| 1367 | <ReportItem id="7" color="green"> | |
| 1368 | <Name><![CDATA[GHDB: Typical login page]]></Name> | |
| 1369 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 1370 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">inurl:login.asp</font></pre>]]></Details> | |
| 1371 | <Affects><![CDATA[/login.aspx]]></Affects> | |
| 1372 | <Parameter><![CDATA[]]></Parameter> | |
| 1373 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1374 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1375 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1376 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1377 | <Severity><![CDATA[info]]></Severity> | |
| 1378 | <Type><![CDATA[Informational]]></Type> | |
| 1379 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 1380 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Pages containing login portals</font><br/><br/>This is a typical login page. It has recently become a target for SQL injection. Comsec's article at http://www.governmentsecurity.org/articles/SQLinjectionBasicTutorial.php brought this to my attention.<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 1381 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1382 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 1383 | <TechnicalDetails> | |
| 1384 | <Request><![CDATA[GET /login.aspx HTTP/1.1 | |
| 1385 | Pragma: no-cache | |
| 1386 | Cache-Control: no-cache | |
| 1387 | Referer: http://testaspnet.vulnweb.com/ | |
| 1388 | Acunetix-Aspect: enabled | |
| 1389 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1390 | Acunetix-Aspect-Queries: aspectalerts | |
| 1391 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1392 | Host: testaspnet.vulnweb.com | |
| 1393 | Connection: Keep-alive | |
| 1394 | Accept-Encoding: gzip,deflate | |
| 1395 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1396 | Accept: */* | |
| 1397 | ||
| 1398 | ]]></Request> | |
| 1399 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 1400 | Date: Thu, 14 Nov 2013 14:26:35 GMT | |
| 1401 | Server: Microsoft-IIS/6.0 | |
| 1402 | X-Powered-By: ASP.NET | |
| 1403 | X-AspNet-Version: 2.0.50727 | |
| 1404 | Cache-Control: private | |
| 1405 | Content-Type: text/html; charset=utf-8 | |
| 1406 | Content-Length: 12329 | |
| 1407 | ]]></Response> | |
| 1408 | </TechnicalDetails> | |
| 1409 | <References> | |
| 1410 | <Reference> | |
| 1411 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 1412 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 1413 | </Reference> | |
| 1414 | <Reference> | |
| 1415 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 1416 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 1417 | </Reference> | |
| 1418 | </References> | |
| 1419 | </ReportItem> | |
| 1420 | ||
| 1421 | <ReportItem id="8" color="green"> | |
| 1422 | <Name><![CDATA[Password type input with auto-complete enabled]]></Name> | |
| 1423 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 1424 | <Details><![CDATA[Password type input named <b><font color="dark">tbPassword</font></b> from form named <b>Form1</b> with action <b>signup.aspx</b> has autocomplete enabled.]]></Details> | |
| 1425 | <Affects><![CDATA[/signup.aspx]]></Affects> | |
| 1426 | <Parameter><![CDATA[]]></Parameter> | |
| 1427 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1428 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1429 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1430 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1431 | <Severity><![CDATA[info]]></Severity> | |
| 1432 | <Type><![CDATA[Informational]]></Type> | |
| 1433 | <Impact><![CDATA[Possible sensitive information disclosure]]></Impact> | |
| 1434 | <Description><![CDATA[When a new name and password is entered in a form and the form is submitted, the browser asks if the password should be saved. Thereafter when the form is displayed, the name and password are filled in automatically or are completed as the name is entered. An attacker with local access could obtain the cleartext password from the browser cache.]]></Description> | |
| 1435 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1436 | <Recommendation><![CDATA[The password auto-complete should be disabled in sensitive applications. <br/>To disable auto-complete, you may use a code similar to: <pre wrap="virtual"><code><INPUT TYPE="password" AUTOCOMPLETE="off"></code></pre>]]></Recommendation> | |
| 1437 | <TechnicalDetails> | |
| 1438 | <Request><![CDATA[GET /signup.aspx HTTP/1.1 | |
| 1439 | Pragma: no-cache | |
| 1440 | Cache-Control: no-cache | |
| 1441 | Referer: http://testaspnet.vulnweb.com/ | |
| 1442 | Acunetix-Aspect: enabled | |
| 1443 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1444 | Acunetix-Aspect-Queries: aspectalerts | |
| 1445 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1446 | Host: testaspnet.vulnweb.com | |
| 1447 | Connection: Keep-alive | |
| 1448 | Accept-Encoding: gzip,deflate | |
| 1449 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1450 | Accept: */* | |
| 1451 | ||
| 1452 | ]]></Request> | |
| 1453 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 1454 | Date: Thu, 14 Nov 2013 14:26:35 GMT | |
| 1455 | Server: Microsoft-IIS/6.0 | |
| 1456 | X-Powered-By: ASP.NET | |
| 1457 | X-AspNet-Version: 2.0.50727 | |
| 1458 | Cache-Control: private | |
| 1459 | Content-Type: text/html; charset=utf-8 | |
| 1460 | Content-Length: 12014 | |
| 1461 | ]]></Response> | |
| 1462 | </TechnicalDetails> | |
| 1463 | <References></References> | |
| 1464 | </ReportItem> | |
| 1465 | ||
| 1466 | <ReportItem id="9" color="orange"> | |
| 1467 | <Name><![CDATA[User credentials are sent in clear text]]></Name> | |
| 1468 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 1469 | <Details><![CDATA[Form name: <font color="navy">Form1</font><br/>Form action: <font color="navy">http://testaspnet.vulnweb.com/signup.aspx</font><br/>Form method: <font color="navy">POST</font><br/><br/>Form inputs:<br/><ul><li>__EVENTTARGET [Hidden]</li><li>__EVENTARGUMENT [Hidden]</li><li>__VIEWSTATE [Hidden]</li><li>__EVENTVALIDATION [Hidden]</li><li>tbUsername [Text]</li><li>tbPassword [Password]</li><li>btnSignup [Submit]</li></ul>]]></Details> | |
| 1470 | <Affects><![CDATA[/signup.aspx]]></Affects> | |
| 1471 | <Parameter><![CDATA[]]></Parameter> | |
| 1472 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1473 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1474 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1475 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1476 | <Severity><![CDATA[medium]]></Severity> | |
| 1477 | <Type><![CDATA[Informational]]></Type> | |
| 1478 | <Impact><![CDATA[A third party may be able to read the user credentials by intercepting an unencrypted HTTP connection.]]></Impact> | |
| 1479 | <Description><![CDATA[User credentials are transmitted over an unencrypted channel. This information should always be transferred via an encrypted channel (HTTPS) to avoid being intercepted by malicious users.]]></Description> | |
| 1480 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1481 | <Recommendation><![CDATA[Because user credentials are considered sensitive information, should always be transferred to the server over an encrypted connection (HTTPS).]]></Recommendation> | |
| 1482 | <TechnicalDetails> | |
| 1483 | <Request><![CDATA[GET /signup.aspx HTTP/1.1 | |
| 1484 | Pragma: no-cache | |
| 1485 | Cache-Control: no-cache | |
| 1486 | Referer: http://testaspnet.vulnweb.com/ | |
| 1487 | Acunetix-Aspect: enabled | |
| 1488 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1489 | Acunetix-Aspect-Queries: aspectalerts | |
| 1490 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1491 | Host: testaspnet.vulnweb.com | |
| 1492 | Connection: Keep-alive | |
| 1493 | Accept-Encoding: gzip,deflate | |
| 1494 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1495 | Accept: */* | |
| 1496 | ||
| 1497 | ]]></Request> | |
| 1498 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 1499 | Date: Thu, 14 Nov 2013 14:26:35 GMT | |
| 1500 | Server: Microsoft-IIS/6.0 | |
| 1501 | X-Powered-By: ASP.NET | |
| 1502 | X-AspNet-Version: 2.0.50727 | |
| 1503 | Cache-Control: private | |
| 1504 | Content-Type: text/html; charset=utf-8 | |
| 1505 | Content-Length: 12014 | |
| 1506 | ]]></Response> | |
| 1507 | </TechnicalDetails> | |
| 1508 | <References></References> | |
| 1509 | </ReportItem> | |
| 1510 | ||
| 1511 | <ReportItem id="10" color="orange"> | |
| 1512 | <Name><![CDATA[Unencrypted __VIEWSTATE parameter]]></Name> | |
| 1513 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 1514 | <Details><![CDATA[form name: <font color="dark">"Form1"</font><br/>form action: <font color="dark">"signup.aspx"</font><br/>VIEWSTATE: <font color="dark">"/wEPDwUKLTY0MzI4NjU4Mw9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkZHEZ3VN6SP/C2xESDN/Y3p8zhfSB"</font><br/>VIEWSTATE decoded: <font color="dark">"##### | |
| 1515 | -643286583#d#####d#####d#########href# | |
| 1516 | login.aspx# innerhtml##logind#######d##Visiblehddq##SzH##########3###"</font><br/>]]></Details> | |
| 1517 | <Affects><![CDATA[/signup.aspx]]></Affects> | |
| 1518 | <Parameter><![CDATA[]]></Parameter> | |
| 1519 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1520 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1521 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1522 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1523 | <Severity><![CDATA[medium]]></Severity> | |
| 1524 | <Type><![CDATA[Informational]]></Type> | |
| 1525 | <Impact><![CDATA[Possible sensitive information disclosure.]]></Impact> | |
| 1526 | <Description><![CDATA[The __VIEWSTATE parameter is not encrypted. To reduce the chance of someone intercepting the information stored in the ViewState, it is good design to encrypt the ViewState. To do this, set the machineKey validation type to 3DES. This instructs ASP.NET to encrypt the ViewState value using the Triple DES symmetric encryption algorithm.]]></Description> | |
| 1527 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1528 | <Recommendation><![CDATA[Open <font color="dark"><b>Web.Config</b></font> and add the following line under the <font color="dark"><b><system.web></b></font> element: <br/><pre wrap="virtual"><machineKey validation="3DES"/> </pre>]]></Recommendation> | |
| 1529 | <TechnicalDetails> | |
| 1530 | <Request><![CDATA[GET /signup.aspx HTTP/1.1 | |
| 1531 | Pragma: no-cache | |
| 1532 | Cache-Control: no-cache | |
| 1533 | Referer: http://testaspnet.vulnweb.com/ | |
| 1534 | Acunetix-Aspect: enabled | |
| 1535 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1536 | Acunetix-Aspect-Queries: aspectalerts | |
| 1537 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1538 | Host: testaspnet.vulnweb.com | |
| 1539 | Connection: Keep-alive | |
| 1540 | Accept-Encoding: gzip,deflate | |
| 1541 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1542 | Accept: */* | |
| 1543 | ||
| 1544 | ]]></Request> | |
| 1545 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 1546 | Date: Thu, 14 Nov 2013 14:26:35 GMT | |
| 1547 | Server: Microsoft-IIS/6.0 | |
| 1548 | X-Powered-By: ASP.NET | |
| 1549 | X-AspNet-Version: 2.0.50727 | |
| 1550 | Cache-Control: private | |
| 1551 | Content-Type: text/html; charset=utf-8 | |
| 1552 | Content-Length: 12014 | |
| 1553 | ]]></Response> | |
| 1554 | </TechnicalDetails> | |
| 1555 | <References></References> | |
| 1556 | </ReportItem> | |
| 1557 | ||
| 1558 | <ReportItem id="11" color="orange"> | |
| 1559 | <Name><![CDATA[Unencrypted __VIEWSTATE parameter]]></Name> | |
| 1560 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 1561 | <Details><![CDATA[form name: <font color="dark">"Form1"</font><br/>form action: <font color="dark">"readnews.aspx?id=2&NewsAd=ads%2fdef.html"</font><br/>VIEWSTATE: <font color="dark">"/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc+YWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNToyMiBBTWQCBQ8WAh8BBTxXZWIgYXR0YWNrcyAtIGNhbiB5b3VyIHdlYiBhcHBsaWNhdGlvbnMgd2l0aHN0YW5kIHRoZSBmb3JjZT9kAgcPFgIfAQWuNzxwPjxzdHJvbmc+QWN1bmV0aXggY29tYmF0cyByaXNlIGluIHdlYiBhdHRhY2tzIHdpdGggQWN1bmV0aXggICAgICAgICAgICAgICAgICAgICAgICAgICAgV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAyIDwvc3Ryb25nPjwv"</font><br/>VIEWSTATE decoded: <font color="dark">"##### | |
| 1562 | -352232569#d#####d#####d#########href# | |
| 1563 | login.aspx# innerhtml##logind#######d##Visiblehd########Iposted by <strong>admin </strong>11/8/2005 11:35:22 AMd########<Web attacks - can your web applications withstand the force?d#########7<p><strong>Acunetix combats rise in web attacks with Acunetix Web Vulnerability Scanner 2 </strong></p> <p>21 July 2005 - <strong>Start-up company Acunetix released Acunetix We"</font><br/>]]></Details> | |
| 1564 | <Affects><![CDATA[/readnews.aspx (f6272bf70dcf239f162f7915a4e4b3b8)]]></Affects> | |
| 1565 | <Parameter><![CDATA[]]></Parameter> | |
| 1566 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1567 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1568 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1569 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1570 | <Severity><![CDATA[medium]]></Severity> | |
| 1571 | <Type><![CDATA[Informational]]></Type> | |
| 1572 | <Impact><![CDATA[Possible sensitive information disclosure.]]></Impact> | |
| 1573 | <Description><![CDATA[The __VIEWSTATE parameter is not encrypted. To reduce the chance of someone intercepting the information stored in the ViewState, it is good design to encrypt the ViewState. To do this, set the machineKey validation type to 3DES. This instructs ASP.NET to encrypt the ViewState value using the Triple DES symmetric encryption algorithm.]]></Description> | |
| 1574 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1575 | <Recommendation><![CDATA[Open <font color="dark"><b>Web.Config</b></font> and add the following line under the <font color="dark"><b><system.web></b></font> element: <br/><pre wrap="virtual"><machineKey validation="3DES"/> </pre>]]></Recommendation> | |
| 1576 | <TechnicalDetails> | |
| 1577 | <Request><![CDATA[GET /readnews.aspx?id=2&NewsAd=ads/def.html HTTP/1.1 | |
| 1578 | Pragma: no-cache | |
| 1579 | Cache-Control: no-cache | |
| 1580 | Referer: http://testaspnet.vulnweb.com/ | |
| 1581 | Acunetix-Aspect: enabled | |
| 1582 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1583 | Acunetix-Aspect-Queries: aspectalerts | |
| 1584 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1585 | Host: testaspnet.vulnweb.com | |
| 1586 | Connection: Keep-alive | |
| 1587 | Accept-Encoding: gzip,deflate | |
| 1588 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1589 | Accept: */* | |
| 1590 | ||
| 1591 | ]]></Request> | |
| 1592 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 1593 | Date: Thu, 14 Nov 2013 14:26:35 GMT | |
| 1594 | Server: Microsoft-IIS/6.0 | |
| 1595 | X-Powered-By: ASP.NET | |
| 1596 | X-AspNet-Version: 2.0.50727 | |
| 1597 | Cache-Control: private | |
| 1598 | Content-Type: text/html; charset=utf-8 | |
| 1599 | Content-Length: 29264 | |
| 1600 | ]]></Response> | |
| 1601 | </TechnicalDetails> | |
| 1602 | <References></References> | |
| 1603 | </ReportItem> | |
| 1604 | ||
| 1605 | <ReportItem id="12" color="orange"> | |
| 1606 | <Name><![CDATA[Unencrypted __VIEWSTATE parameter]]></Name> | |
| 1607 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 1608 | <Details><![CDATA[form name: <font color="dark">"Form1"</font><br/>form action: <font color="dark">"comments.aspx?id=2"</font><br/>VIEWSTATE: <font color="dark">"/wEPDwUKLTg2MjcwMzE2Mg9kFgICAQ9kFgoCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc+YWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNToyMiBBTWQCBQ8WBB8BBTxXZWIgYXR0YWNrcyAtIGNhbiB5b3VyIHdlYiBhcHBsaWNhdGlvbnMgd2l0aHN0YW5kIHRoZSBmb3JjZT8fAAUSUmVhZE5ld3MuYXNweD9pZD0yZAIHDxYCHwEFrAIyMSBKdWx5IDIwMDUgLSBTdGFydC11cCBjb21wYW55IEFjdW5ldGl4IHJlbGVhc2VkIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXI6IGEgdG9vbCB0byBhdXRvbWF0aWNh"</font><br/>VIEWSTATE decoded: <font color="dark">"##### | |
| 1609 | -862703162#d#####d# | |
| 1610 | ###d#########href# | |
| 1611 | login.aspx# innerhtml##logind#######d##Visiblehd########Iposted by <strong>admin </strong>11/8/2005 11:35:22 AMd########<Web attacks - can your web applications withstand the force?####ReadNews.aspx?id=2d##########21 July 2005 - Start-up company Acunetix released Acunetix Web Vulnerability Scanner: a tool to automatically audit website security. Acunetix Web Vulnerability Scanner 2 crawls an entire website, launches popular web attacks (SQL Inj"</font><br/>]]></Details> | |
| 1612 | <Affects><![CDATA[/comments.aspx (cfbc7026028fd30e88c94fcdc534d6ba)]]></Affects> | |
| 1613 | <Parameter><![CDATA[]]></Parameter> | |
| 1614 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1615 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1616 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1617 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1618 | <Severity><![CDATA[medium]]></Severity> | |
| 1619 | <Type><![CDATA[Informational]]></Type> | |
| 1620 | <Impact><![CDATA[Possible sensitive information disclosure.]]></Impact> | |
| 1621 | <Description><![CDATA[The __VIEWSTATE parameter is not encrypted. To reduce the chance of someone intercepting the information stored in the ViewState, it is good design to encrypt the ViewState. To do this, set the machineKey validation type to 3DES. This instructs ASP.NET to encrypt the ViewState value using the Triple DES symmetric encryption algorithm.]]></Description> | |
| 1622 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1623 | <Recommendation><![CDATA[Open <font color="dark"><b>Web.Config</b></font> and add the following line under the <font color="dark"><b><system.web></b></font> element: <br/><pre wrap="virtual"><machineKey validation="3DES"/> </pre>]]></Recommendation> | |
| 1624 | <TechnicalDetails> | |
| 1625 | <Request><![CDATA[GET /comments.aspx?id=2 HTTP/1.1 | |
| 1626 | Pragma: no-cache | |
| 1627 | Cache-Control: no-cache | |
| 1628 | Referer: http://testaspnet.vulnweb.com/ | |
| 1629 | Acunetix-Aspect: enabled | |
| 1630 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1631 | Acunetix-Aspect-Queries: aspectalerts | |
| 1632 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1633 | Host: testaspnet.vulnweb.com | |
| 1634 | Connection: Keep-alive | |
| 1635 | Accept-Encoding: gzip,deflate | |
| 1636 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1637 | Accept: */* | |
| 1638 | ||
| 1639 | ]]></Request> | |
| 1640 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 1641 | Date: Thu, 14 Nov 2013 14:26:35 GMT | |
| 1642 | Server: Microsoft-IIS/6.0 | |
| 1643 | X-Powered-By: ASP.NET | |
| 1644 | X-AspNet-Version: 2.0.50727 | |
| 1645 | Cache-Control: private | |
| 1646 | Content-Type: text/html; charset=utf-8 | |
| 1647 | Content-Length: 20197 | |
| 1648 | ]]></Response> | |
| 1649 | </TechnicalDetails> | |
| 1650 | <References></References> | |
| 1651 | </ReportItem> | |
| 1652 | ||
| 1653 | <ReportItem id="13" color="orange"> | |
| 1654 | <Name><![CDATA[Unencrypted __VIEWSTATE parameter]]></Name> | |
| 1655 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 1656 | <Details><![CDATA[form name: <font color="dark">"Form1"</font><br/>form action: <font color="dark">"readnews.aspx?id=0&NewsAd=ads%2fdef.html"</font><br/>VIEWSTATE: <font color="dark">"/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc+YWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozMjozMCBBTWQCBQ8WAh8BBT1XYXRjaGZpcmUgTGljZW5zZXMgUGF0ZW50ZWQgSW50ZWxsZWN0dWFsIFByb3BlcnR5IHRvIEFjdW5ldGl4ZAIHDxYCHwEFwSQgICAgICAgICAgICAgICAgICAgICAgICAgICAxNCBTZXB0ZW1iZXIgMjAwNSAtIFdhdGNoZmlyZSwgYSBwcm92aWRlciBvZiBzb2Z0d2FyZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhbmQgc2VydmljZXMgdG8gbWFu"</font><br/>VIEWSTATE decoded: <font color="dark">"##### | |
| 1657 | -352232569#d#####d#####d#########href# | |
| 1658 | login.aspx# innerhtml##logind#######d##Visiblehd########Iposted by <strong>admin </strong>11/8/2005 11:32:30 AMd########=Watchfire Licenses Patented Intellectual Property to Acunetixd#########$ 14 September 2005 - Watchfire, a provider of software and services to manage online risk, and Acunetix, provider of the Acunetix Web Vulnerability Scanner, today announced "</font><br/>]]></Details> | |
| 1659 | <Affects><![CDATA[/readnews.aspx (54db37c887f8663f3ac272fd57842c59)]]></Affects> | |
| 1660 | <Parameter><![CDATA[]]></Parameter> | |
| 1661 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1662 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1663 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1664 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1665 | <Severity><![CDATA[medium]]></Severity> | |
| 1666 | <Type><![CDATA[Informational]]></Type> | |
| 1667 | <Impact><![CDATA[Possible sensitive information disclosure.]]></Impact> | |
| 1668 | <Description><![CDATA[The __VIEWSTATE parameter is not encrypted. To reduce the chance of someone intercepting the information stored in the ViewState, it is good design to encrypt the ViewState. To do this, set the machineKey validation type to 3DES. This instructs ASP.NET to encrypt the ViewState value using the Triple DES symmetric encryption algorithm.]]></Description> | |
| 1669 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1670 | <Recommendation><![CDATA[Open <font color="dark"><b>Web.Config</b></font> and add the following line under the <font color="dark"><b><system.web></b></font> element: <br/><pre wrap="virtual"><machineKey validation="3DES"/> </pre>]]></Recommendation> | |
| 1671 | <TechnicalDetails> | |
| 1672 | <Request><![CDATA[GET /readnews.aspx?id=0&NewsAd=ads/def.html HTTP/1.1 | |
| 1673 | Pragma: no-cache | |
| 1674 | Cache-Control: no-cache | |
| 1675 | Referer: http://testaspnet.vulnweb.com/ | |
| 1676 | Acunetix-Aspect: enabled | |
| 1677 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1678 | Acunetix-Aspect-Queries: aspectalerts | |
| 1679 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1680 | Host: testaspnet.vulnweb.com | |
| 1681 | Connection: Keep-alive | |
| 1682 | Accept-Encoding: gzip,deflate | |
| 1683 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1684 | Accept: */* | |
| 1685 | ||
| 1686 | ]]></Request> | |
| 1687 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 1688 | Date: Thu, 14 Nov 2013 14:26:35 GMT | |
| 1689 | Server: Microsoft-IIS/6.0 | |
| 1690 | X-Powered-By: ASP.NET | |
| 1691 | X-AspNet-Version: 2.0.50727 | |
| 1692 | Cache-Control: private | |
| 1693 | Content-Type: text/html; charset=utf-8 | |
| 1694 | Content-Length: 23636 | |
| 1695 | ]]></Response> | |
| 1696 | </TechnicalDetails> | |
| 1697 | <References></References> | |
| 1698 | </ReportItem> | |
| 1699 | ||
| 1700 | <ReportItem id="14" color="orange"> | |
| 1701 | <Name><![CDATA[Unencrypted __VIEWSTATE parameter]]></Name> | |
| 1702 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 1703 | <Details><![CDATA[form name: <font color="dark">"Form1"</font><br/>form action: <font color="dark">"comments.aspx?id=0"</font><br/>VIEWSTATE: <font color="dark">"/wEPDwUKLTg2MjcwMzE2Mg9kFgICAQ9kFgoCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc+YWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozMjozMCBBTWQCBQ8WBB8BBT1XYXRjaGZpcmUgTGljZW5zZXMgUGF0ZW50ZWQgSW50ZWxsZWN0dWFsIFByb3BlcnR5IHRvIEFjdW5ldGl4HwAFElJlYWROZXdzLmFzcHg/aWQ9MGQCBw8WAh8BBT5XYXRjaGZpcmUgYW5kIEFjdW5ldGl4IEFsc28gRW50ZXIgaW50byBDcm9zcy1MaWNlbnNlIEFncmVlbWVudGQCCQ9kFgICAQ9kFhJmD2QWAmYPFgIfAQUlPElNRyBzcmM9ImltYWdlcy9j"</font><br/>VIEWSTATE decoded: <font color="dark">"##### | |
| 1704 | -862703162#d#####d# | |
| 1705 | ###d#########href# | |
| 1706 | login.aspx# innerhtml##logind#######d##Visiblehd########Iposted by <strong>admin </strong>11/8/2005 11:32:30 AMd########=Watchfire Licenses Patented Intellectual Property to Acunetix####ReadNews.aspx?id=0d########>Watchfire and Acunetix Also Enter into Cross-License Agreementd# #d#####d##f#d##f######%<IMG src="images/comment-before.gif">d###d##f#####class##Commentd###d##f######$<IMG src="images/comment-after.gif">d###d##f######%<IMG src="images"</font><br/>]]></Details> | |
| 1707 | <Affects><![CDATA[/comments.aspx (3cff0a3b9e9e434739b9c4da2938e086)]]></Affects> | |
| 1708 | <Parameter><![CDATA[]]></Parameter> | |
| 1709 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1710 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1711 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1712 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1713 | <Severity><![CDATA[medium]]></Severity> | |
| 1714 | <Type><![CDATA[Informational]]></Type> | |
| 1715 | <Impact><![CDATA[Possible sensitive information disclosure.]]></Impact> | |
| 1716 | <Description><![CDATA[The __VIEWSTATE parameter is not encrypted. To reduce the chance of someone intercepting the information stored in the ViewState, it is good design to encrypt the ViewState. To do this, set the machineKey validation type to 3DES. This instructs ASP.NET to encrypt the ViewState value using the Triple DES symmetric encryption algorithm.]]></Description> | |
| 1717 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1718 | <Recommendation><![CDATA[Open <font color="dark"><b>Web.Config</b></font> and add the following line under the <font color="dark"><b><system.web></b></font> element: <br/><pre wrap="virtual"><machineKey validation="3DES"/> </pre>]]></Recommendation> | |
| 1719 | <TechnicalDetails> | |
| 1720 | <Request><![CDATA[GET /comments.aspx?id=0 HTTP/1.1 | |
| 1721 | Pragma: no-cache | |
| 1722 | Cache-Control: no-cache | |
| 1723 | Referer: http://testaspnet.vulnweb.com/ | |
| 1724 | Acunetix-Aspect: enabled | |
| 1725 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1726 | Acunetix-Aspect-Queries: aspectalerts | |
| 1727 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1728 | Host: testaspnet.vulnweb.com | |
| 1729 | Connection: Keep-alive | |
| 1730 | Accept-Encoding: gzip,deflate | |
| 1731 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1732 | Accept: */* | |
| 1733 | ||
| 1734 | ]]></Request> | |
| 1735 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 1736 | Date: Thu, 14 Nov 2013 14:26:36 GMT | |
| 1737 | Server: Microsoft-IIS/6.0 | |
| 1738 | X-Powered-By: ASP.NET | |
| 1739 | X-AspNet-Version: 2.0.50727 | |
| 1740 | Cache-Control: private | |
| 1741 | Content-Type: text/html; charset=utf-8 | |
| 1742 | Content-Length: 14197 | |
| 1743 | ]]></Response> | |
| 1744 | </TechnicalDetails> | |
| 1745 | <References></References> | |
| 1746 | </ReportItem> | |
| 1747 | ||
| 1748 | <ReportItem id="15" color="green"> | |
| 1749 | <Name><![CDATA[GHDB: Frontpage extensions for Unix]]></Name> | |
| 1750 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 1751 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">allinurl:("/*/_vti_pvt/" | "/*/_vti_cnf/")</font></pre>]]></Details> | |
| 1752 | <Affects><![CDATA[/_vti_cnf]]></Affects> | |
| 1753 | <Parameter><![CDATA[]]></Parameter> | |
| 1754 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1755 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1756 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1757 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1758 | <Severity><![CDATA[info]]></Severity> | |
| 1759 | <Type><![CDATA[Informational]]></Type> | |
| 1760 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 1761 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Sensitive Directories</font><br/><br/>Frontpage extensions for Unix ? So be it..<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 1762 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1763 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 1764 | <TechnicalDetails> | |
| 1765 | <Request><![CDATA[GET /_vti_cnf/ HTTP/1.1 | |
| 1766 | Pragma: no-cache | |
| 1767 | Cache-Control: no-cache | |
| 1768 | Referer: http://testaspnet.vulnweb.com/Default.aspx | |
| 1769 | Acunetix-Aspect: enabled | |
| 1770 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1771 | Acunetix-Aspect-Queries: aspectalerts | |
| 1772 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1773 | Host: testaspnet.vulnweb.com | |
| 1774 | Connection: Keep-alive | |
| 1775 | Accept-Encoding: gzip,deflate | |
| 1776 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1777 | Accept: */* | |
| 1778 | ||
| 1779 | ]]></Request> | |
| 1780 | <Response><![CDATA[HTTP/1.1 403 Forbidden | |
| 1781 | Content-Length: 218 | |
| 1782 | Content-Type: text/html | |
| 1783 | Server: Microsoft-IIS/6.0 | |
| 1784 | X-Powered-By: ASP.NET | |
| 1785 | Date: Thu, 14 Nov 2013 14:26:37 GMT | |
| 1786 | ]]></Response> | |
| 1787 | </TechnicalDetails> | |
| 1788 | <References> | |
| 1789 | <Reference> | |
| 1790 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 1791 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 1792 | </Reference> | |
| 1793 | <Reference> | |
| 1794 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 1795 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 1796 | </Reference> | |
| 1797 | </References> | |
| 1798 | </ReportItem> | |
| 1799 | ||
| 1800 | <ReportItem id="16" color="green"> | |
| 1801 | <Name><![CDATA[GHDB: Frontpage extensions for Unix]]></Name> | |
| 1802 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 1803 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">allinurl:("/*/_vti_pvt/" | "/*/_vti_cnf/")</font></pre>]]></Details> | |
| 1804 | <Affects><![CDATA[/_vti_cnf/acublog.csproj]]></Affects> | |
| 1805 | <Parameter><![CDATA[]]></Parameter> | |
| 1806 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1807 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1808 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1809 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1810 | <Severity><![CDATA[info]]></Severity> | |
| 1811 | <Type><![CDATA[Informational]]></Type> | |
| 1812 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 1813 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Sensitive Directories</font><br/><br/>Frontpage extensions for Unix ? So be it..<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 1814 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1815 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 1816 | <TechnicalDetails> | |
| 1817 | <Request><![CDATA[GET /_vti_cnf/acublog.csproj HTTP/1.1 | |
| 1818 | Pragma: no-cache | |
| 1819 | Cache-Control: no-cache | |
| 1820 | Referer: http://testaspnet.vulnweb.com/Default.aspx | |
| 1821 | Acunetix-Aspect: enabled | |
| 1822 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1823 | Acunetix-Aspect-Queries: aspectalerts | |
| 1824 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1825 | Host: testaspnet.vulnweb.com | |
| 1826 | Connection: Keep-alive | |
| 1827 | Accept-Encoding: gzip,deflate | |
| 1828 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1829 | Accept: */* | |
| 1830 | ||
| 1831 | ]]></Request> | |
| 1832 | <Response><![CDATA[HTTP/1.1 403 Forbidden | |
| 1833 | Date: Thu, 14 Nov 2013 14:26:38 GMT | |
| 1834 | Server: Microsoft-IIS/6.0 | |
| 1835 | X-Powered-By: ASP.NET | |
| 1836 | X-AspNet-Version: 2.0.50727 | |
| 1837 | Cache-Control: private | |
| 1838 | Content-Type: text/html; charset=utf-8 | |
| 1839 | Content-Length: 2358 | |
| 1840 | ]]></Response> | |
| 1841 | </TechnicalDetails> | |
| 1842 | <References> | |
| 1843 | <Reference> | |
| 1844 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 1845 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 1846 | </Reference> | |
| 1847 | <Reference> | |
| 1848 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 1849 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 1850 | </Reference> | |
| 1851 | </References> | |
| 1852 | </ReportItem> | |
| 1853 | ||
| 1854 | <ReportItem id="17" color="green"> | |
| 1855 | <Name><![CDATA[GHDB: Frontpage extensions for Unix]]></Name> | |
| 1856 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 1857 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">allinurl:("/*/_vti_pvt/" | "/*/_vti_cnf/")</font></pre>]]></Details> | |
| 1858 | <Affects><![CDATA[/_vti_cnf/acublog.csproj.webinfo]]></Affects> | |
| 1859 | <Parameter><![CDATA[]]></Parameter> | |
| 1860 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1861 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1862 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1863 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1864 | <Severity><![CDATA[info]]></Severity> | |
| 1865 | <Type><![CDATA[Informational]]></Type> | |
| 1866 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 1867 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Sensitive Directories</font><br/><br/>Frontpage extensions for Unix ? So be it..<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 1868 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1869 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 1870 | <TechnicalDetails> | |
| 1871 | <Request><![CDATA[GET /_vti_cnf/acublog.csproj.webinfo HTTP/1.1 | |
| 1872 | Pragma: no-cache | |
| 1873 | Cache-Control: no-cache | |
| 1874 | Referer: http://testaspnet.vulnweb.com/Default.aspx | |
| 1875 | Acunetix-Aspect: enabled | |
| 1876 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1877 | Acunetix-Aspect-Queries: aspectalerts | |
| 1878 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1879 | Host: testaspnet.vulnweb.com | |
| 1880 | Connection: Keep-alive | |
| 1881 | Accept-Encoding: gzip,deflate | |
| 1882 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1883 | Accept: */* | |
| 1884 | ||
| 1885 | ]]></Request> | |
| 1886 | <Response><![CDATA[HTTP/1.1 403 Forbidden | |
| 1887 | Date: Thu, 14 Nov 2013 14:26:38 GMT | |
| 1888 | Server: Microsoft-IIS/6.0 | |
| 1889 | X-Powered-By: ASP.NET | |
| 1890 | X-AspNet-Version: 2.0.50727 | |
| 1891 | Cache-Control: private | |
| 1892 | Content-Type: text/html; charset=utf-8 | |
| 1893 | Content-Length: 2375 | |
| 1894 | ]]></Response> | |
| 1895 | </TechnicalDetails> | |
| 1896 | <References> | |
| 1897 | <Reference> | |
| 1898 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 1899 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 1900 | </Reference> | |
| 1901 | <Reference> | |
| 1902 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 1903 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 1904 | </Reference> | |
| 1905 | </References> | |
| 1906 | </ReportItem> | |
| 1907 | ||
| 1908 | <ReportItem id="18" color="green"> | |
| 1909 | <Name><![CDATA[GHDB: Typical login page]]></Name> | |
| 1910 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 1911 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">inurl:login.asp</font></pre>]]></Details> | |
| 1912 | <Affects><![CDATA[/login.aspx.cs]]></Affects> | |
| 1913 | <Parameter><![CDATA[]]></Parameter> | |
| 1914 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1915 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1916 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1917 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1918 | <Severity><![CDATA[info]]></Severity> | |
| 1919 | <Type><![CDATA[Informational]]></Type> | |
| 1920 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 1921 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Pages containing login portals</font><br/><br/>This is a typical login page. It has recently become a target for SQL injection. Comsec's article at http://www.governmentsecurity.org/articles/SQLinjectionBasicTutorial.php brought this to my attention.<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 1922 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1923 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 1924 | <TechnicalDetails> | |
| 1925 | <Request><![CDATA[GET /login.aspx.cs HTTP/1.1 | |
| 1926 | Pragma: no-cache | |
| 1927 | Cache-Control: no-cache | |
| 1928 | Referer: http://testaspnet.vulnweb.com/Default.aspx | |
| 1929 | Acunetix-Aspect: enabled | |
| 1930 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1931 | Acunetix-Aspect-Queries: aspectalerts | |
| 1932 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1933 | Host: testaspnet.vulnweb.com | |
| 1934 | Connection: Keep-alive | |
| 1935 | Accept-Encoding: gzip,deflate | |
| 1936 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1937 | Accept: */* | |
| 1938 | ||
| 1939 | ]]></Request> | |
| 1940 | <Response><![CDATA[HTTP/1.1 403 Forbidden | |
| 1941 | Date: Thu, 14 Nov 2013 14:26:39 GMT | |
| 1942 | Server: Microsoft-IIS/6.0 | |
| 1943 | X-Powered-By: ASP.NET | |
| 1944 | X-AspNet-Version: 2.0.50727 | |
| 1945 | Cache-Control: private | |
| 1946 | Content-Type: text/html; charset=utf-8 | |
| 1947 | Content-Length: 2334 | |
| 1948 | ]]></Response> | |
| 1949 | </TechnicalDetails> | |
| 1950 | <References> | |
| 1951 | <Reference> | |
| 1952 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 1953 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 1954 | </Reference> | |
| 1955 | <Reference> | |
| 1956 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 1957 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 1958 | </Reference> | |
| 1959 | </References> | |
| 1960 | </ReportItem> | |
| 1961 | ||
| 1962 | <ReportItem id="19" color="green"> | |
| 1963 | <Name><![CDATA[GHDB: Typical login page]]></Name> | |
| 1964 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 1965 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">inurl:login.asp</font></pre>]]></Details> | |
| 1966 | <Affects><![CDATA[/login.aspx.resx]]></Affects> | |
| 1967 | <Parameter><![CDATA[]]></Parameter> | |
| 1968 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 1969 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 1970 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 1971 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 1972 | <Severity><![CDATA[info]]></Severity> | |
| 1973 | <Type><![CDATA[Informational]]></Type> | |
| 1974 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 1975 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Pages containing login portals</font><br/><br/>This is a typical login page. It has recently become a target for SQL injection. Comsec's article at http://www.governmentsecurity.org/articles/SQLinjectionBasicTutorial.php brought this to my attention.<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 1976 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 1977 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 1978 | <TechnicalDetails> | |
| 1979 | <Request><![CDATA[GET /login.aspx.resx HTTP/1.1 | |
| 1980 | Pragma: no-cache | |
| 1981 | Cache-Control: no-cache | |
| 1982 | Referer: http://testaspnet.vulnweb.com/Default.aspx | |
| 1983 | Acunetix-Aspect: enabled | |
| 1984 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 1985 | Acunetix-Aspect-Queries: aspectalerts | |
| 1986 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 1987 | Host: testaspnet.vulnweb.com | |
| 1988 | Connection: Keep-alive | |
| 1989 | Accept-Encoding: gzip,deflate | |
| 1990 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 1991 | Accept: */* | |
| 1992 | ||
| 1993 | ]]></Request> | |
| 1994 | <Response><![CDATA[HTTP/1.1 403 Forbidden | |
| 1995 | Date: Thu, 14 Nov 2013 14:26:39 GMT | |
| 1996 | Server: Microsoft-IIS/6.0 | |
| 1997 | X-Powered-By: ASP.NET | |
| 1998 | X-AspNet-Version: 2.0.50727 | |
| 1999 | Cache-Control: private | |
| 2000 | Content-Type: text/html; charset=utf-8 | |
| 2001 | Content-Length: 2340 | |
| 2002 | ]]></Response> | |
| 2003 | </TechnicalDetails> | |
| 2004 | <References> | |
| 2005 | <Reference> | |
| 2006 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 2007 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 2008 | </Reference> | |
| 2009 | <Reference> | |
| 2010 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 2011 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 2012 | </Reference> | |
| 2013 | </References> | |
| 2014 | </ReportItem> | |
| 2015 | ||
| 2016 | <ReportItem id="20" color="green"> | |
| 2017 | <Name><![CDATA[GHDB: Possible ASP.NET sensitive file (web.config)]]></Name> | |
| 2018 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 2019 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">filetype:config web.config -CVS</font></pre>]]></Details> | |
| 2020 | <Affects><![CDATA[/web.config]]></Affects> | |
| 2021 | <Parameter><![CDATA[]]></Parameter> | |
| 2022 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2023 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2024 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2025 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2026 | <Severity><![CDATA[info]]></Severity> | |
| 2027 | <Type><![CDATA[Informational]]></Type> | |
| 2028 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 2029 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Files containing juicy info</font><br/><br/>Through Web.config an IIS adminstrator can specify settings like custom 404 error pages, authentication and authorization settings for the Web site. | |
| 2030 | ||
| 2031 | This file can hold a plaintext password in the worst case or just reveil the full path info on a 404 error.<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 2032 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2033 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 2034 | <TechnicalDetails> | |
| 2035 | <Request><![CDATA[GET /web.config HTTP/1.1 | |
| 2036 | Pragma: no-cache | |
| 2037 | Cache-Control: no-cache | |
| 2038 | Referer: http://testaspnet.vulnweb.com/Default.aspx | |
| 2039 | Acunetix-Aspect: enabled | |
| 2040 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2041 | Acunetix-Aspect-Queries: aspectalerts | |
| 2042 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2043 | Host: testaspnet.vulnweb.com | |
| 2044 | Connection: Keep-alive | |
| 2045 | Accept-Encoding: gzip,deflate | |
| 2046 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2047 | Accept: */* | |
| 2048 | ||
| 2049 | ]]></Request> | |
| 2050 | <Response><![CDATA[HTTP/1.1 403 Forbidden | |
| 2051 | Date: Thu, 14 Nov 2013 14:26:40 GMT | |
| 2052 | Server: Microsoft-IIS/6.0 | |
| 2053 | X-Powered-By: ASP.NET | |
| 2054 | X-AspNet-Version: 2.0.50727 | |
| 2055 | Cache-Control: private | |
| 2056 | Content-Type: text/html; charset=utf-8 | |
| 2057 | Content-Length: 2332 | |
| 2058 | ]]></Response> | |
| 2059 | </TechnicalDetails> | |
| 2060 | <References> | |
| 2061 | <Reference> | |
| 2062 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 2063 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 2064 | </Reference> | |
| 2065 | <Reference> | |
| 2066 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 2067 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 2068 | </Reference> | |
| 2069 | </References> | |
| 2070 | </ReportItem> | |
| 2071 | ||
| 2072 | <ReportItem id="21" color="blue"> | |
| 2073 | <Name><![CDATA[OPTIONS method is enabled]]></Name> | |
| 2074 | <ModuleName><![CDATA[Scripting (Options_Server_Method.script)]]></ModuleName> | |
| 2075 | <Details><![CDATA[Methods allowed: <font color="dark"><b>OPTIONS, TRACE, GET, HEAD</b></font>]]></Details> | |
| 2076 | <Affects><![CDATA[Web Server]]></Affects> | |
| 2077 | <Parameter><![CDATA[]]></Parameter> | |
| 2078 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2079 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2080 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2081 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2082 | <Severity><![CDATA[low]]></Severity> | |
| 2083 | <Type><![CDATA[Validation]]></Type> | |
| 2084 | <Impact><![CDATA[The OPTIONS method may expose sensitive information that may help an malicious user to prepare more advanced attacks.]]></Impact> | |
| 2085 | <Description><![CDATA[HTTP OPTIONS method is enabled on this web server. The OPTIONS method provides a list of the methods that are supported by the web server, it represents a request for information about the communication options available on the request/response chain identified by the Request-URI. ]]></Description> | |
| 2086 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2087 | <Recommendation><![CDATA[It's recommended to disable OPTIONS Method on the web server.]]></Recommendation> | |
| 2088 | <TechnicalDetails> | |
| 2089 | <Request><![CDATA[OPTIONS / HTTP/1.1 | |
| 2090 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2091 | Host: testaspnet.vulnweb.com | |
| 2092 | Connection: Keep-alive | |
| 2093 | Accept-Encoding: gzip,deflate | |
| 2094 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2095 | Accept: */* | |
| 2096 | ||
| 2097 | ]]></Request> | |
| 2098 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2099 | Allow: OPTIONS, TRACE, GET, HEAD | |
| 2100 | Content-Length: 0 | |
| 2101 | Server: Microsoft-IIS/6.0 | |
| 2102 | Public: OPTIONS, TRACE, GET, HEAD, POST | |
| 2103 | X-Powered-By: ASP.NET | |
| 2104 | Date: Thu, 14 Nov 2013 14:26:40 GMT | |
| 2105 | ]]></Response> | |
| 2106 | </TechnicalDetails> | |
| 2107 | <References> | |
| 2108 | <Reference> | |
| 2109 | <Database><![CDATA[Testing for HTTP Methods and XST (OWASP-CM-008)]]></Database> | |
| 2110 | <URL><![CDATA[https://www.owasp.org/index.php/Testing_for_HTTP_Methods_and_XST_(OWASP-CM-008)]]></URL> | |
| 2111 | </Reference> | |
| 2112 | </References> | |
| 2113 | </ReportItem> | |
| 2114 | ||
| 2115 | <ReportItem id="22" color="green"> | |
| 2116 | <Name><![CDATA[GHDB: Typical login page]]></Name> | |
| 2117 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 2118 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">inurl:login.asp</font></pre>]]></Details> | |
| 2119 | <Affects><![CDATA[/login.aspx (534f1aa002ea6e0e6ca3cd0a64bb17bd)]]></Affects> | |
| 2120 | <Parameter><![CDATA[]]></Parameter> | |
| 2121 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2122 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2123 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2124 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2125 | <Severity><![CDATA[info]]></Severity> | |
| 2126 | <Type><![CDATA[Informational]]></Type> | |
| 2127 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 2128 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Pages containing login portals</font><br/><br/>This is a typical login page. It has recently become a target for SQL injection. Comsec's article at http://www.governmentsecurity.org/articles/SQLinjectionBasicTutorial.php brought this to my attention.<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 2129 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2130 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 2131 | <TechnicalDetails> | |
| 2132 | <Request><![CDATA[POST /login.aspx HTTP/1.1 | |
| 2133 | Pragma: no-cache | |
| 2134 | Cache-Control: no-cache | |
| 2135 | Referer: http://testaspnet.vulnweb.com/login.aspx | |
| 2136 | Content-Length: 1142 | |
| 2137 | Content-Type: application/x-www-form-urlencoded | |
| 2138 | Acunetix-Aspect: enabled | |
| 2139 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2140 | Acunetix-Aspect-Queries: aspectalerts | |
| 2141 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2142 | Host: testaspnet.vulnweb.com | |
| 2143 | Connection: Keep-alive | |
| 2144 | Accept-Encoding: gzip,deflate | |
| 2145 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2146 | Accept: */* | |
| 2147 | ||
| 2148 | btnLogin=Login&tbPassword=g00dPa%24%24w0rD&tbUsername=fyjmttcx&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></Request> | |
| 2149 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2150 | Date: Thu, 14 Nov 2013 14:26:41 GMT | |
| 2151 | Server: Microsoft-IIS/6.0 | |
| 2152 | X-Powered-By: ASP.NET | |
| 2153 | X-AspNet-Version: 2.0.50727 | |
| 2154 | Cache-Control: private | |
| 2155 | Content-Type: text/html; charset=utf-8 | |
| 2156 | Content-Length: 12328 | |
| 2157 | ]]></Response> | |
| 2158 | </TechnicalDetails> | |
| 2159 | <References> | |
| 2160 | <Reference> | |
| 2161 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 2162 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 2163 | </Reference> | |
| 2164 | <Reference> | |
| 2165 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 2166 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 2167 | </Reference> | |
| 2168 | </References> | |
| 2169 | </ReportItem> | |
| 2170 | ||
| 2171 | <ReportItem id="23" color="orange"> | |
| 2172 | <Name><![CDATA[Unencrypted __VIEWSTATE parameter]]></Name> | |
| 2173 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 2174 | <Details><![CDATA[form name: <font color="dark">"Form1"</font><br/>form action: <font color="dark">"readnews.aspx?id=3&NewsAd=ads%2fdef.html"</font><br/>VIEWSTATE: <font color="dark">"/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc+YWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNzozNSBBTWQCBQ8WAh8BBTFBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIGJldGEgcmVsZWFzZWQhZAIHDxYCHwEF8Q08cD5EdXJpbmcgdGhlIGJldGEgcGhhc2UsIGJ1aWxkcyBhcmUgcmVsZWFzZWQgZnJlcXVlbnRseSwgICAgICAgICAgICAgICAgICAgICAgICAgICAgdGhlcmVmb3JlIGl0IGlzIG5vdCByZWNvbW1lbmRlZCB0aGF0IHRoZSBzYW1lIGJldGEgdmVy"</font><br/>VIEWSTATE decoded: <font color="dark">"##### | |
| 2175 | -352232569#d#####d#####d#########href# | |
| 2176 | login.aspx# innerhtml##logind#######d##Visiblehd########Iposted by <strong>admin </strong>11/8/2005 11:37:35 AMd########1Acunetix Web Vulnerability Scanner beta released!d######### ⏎ | |
| 2177 | <p>During the beta phase, builds are released frequently, therefore it is not recommended that the same beta version is used for more than 30 days. To beta-test beyond 30 days, users sho"</font><br/>]]></Details> | |
| 2178 | <Affects><![CDATA[/readnews.aspx (e4657a51a6805d9d37502f831ddc19c6)]]></Affects> | |
| 2179 | <Parameter><![CDATA[]]></Parameter> | |
| 2180 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2181 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2182 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2183 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2184 | <Severity><![CDATA[medium]]></Severity> | |
| 2185 | <Type><![CDATA[Informational]]></Type> | |
| 2186 | <Impact><![CDATA[Possible sensitive information disclosure.]]></Impact> | |
| 2187 | <Description><![CDATA[The __VIEWSTATE parameter is not encrypted. To reduce the chance of someone intercepting the information stored in the ViewState, it is good design to encrypt the ViewState. To do this, set the machineKey validation type to 3DES. This instructs ASP.NET to encrypt the ViewState value using the Triple DES symmetric encryption algorithm.]]></Description> | |
| 2188 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2189 | <Recommendation><![CDATA[Open <font color="dark"><b>Web.Config</b></font> and add the following line under the <font color="dark"><b><system.web></b></font> element: <br/><pre wrap="virtual"><machineKey validation="3DES"/> </pre>]]></Recommendation> | |
| 2190 | <TechnicalDetails> | |
| 2191 | <Request><![CDATA[POST /readnews.aspx?id=3&NewsAd=ads/def.html HTTP/1.1 | |
| 2192 | Pragma: no-cache | |
| 2193 | Cache-Control: no-cache | |
| 2194 | Referer: http://testaspnet.vulnweb.com/readnews.aspx | |
| 2195 | Content-Length: 10791 | |
| 2196 | Content-Type: application/x-www-form-urlencoded | |
| 2197 | Acunetix-Aspect: enabled | |
| 2198 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2199 | Acunetix-Aspect-Queries: aspectalerts | |
| 2200 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2201 | Host: testaspnet.vulnweb.com | |
| 2202 | Connection: Keep-alive | |
| 2203 | Accept-Encoding: gzip,deflate | |
| 2204 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2205 | Accept: */* | |
| 2206 | ||
| 2207 | __EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWVwKO/ffgDgKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMTuBuYk15KvnzAGnqqPk6tDbzR0Y%3d&__VIEWSTATE=/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc%2bYWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNToyMiBBTWQCBQ8WAh8BBTxXZWIgYXR0YWNrcyAtIGNhbiB5b3VyIHdlYiBhcHBsaWNhdGlvbnMgd2l0aHN0YW5kIHRoZSBmb3JjZT9kAgcPFgIfAQWuNzxwPjxzdHJvbmc%2bQWN1bmV0aXggY29tYmF0cyByaXNlIGluIHdlYiBhdHRhY2tzIHdpdGggQWN1bmV0aXggICAgICAgICAgICAgICAgICAgICAgICAgICAgV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAyIDwvc3Ryb25nPjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD4yMSBKdWx5IDIwMDUgLSA8c3Ryb25nPlN0YXJ0LXVwIGNvbXBhbnkgQWN1bmV0aXggcmVsZWFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lcjogYSB0b29sIHRvIGF1dG9tYXRpY2FsbHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXVkaXQgd2Vic2l0ZSBzZWN1cml0eS4gQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAgICAgICAgICAgICAgICAgICAgICAgICAgICAyIGNyYXdscyBhbiBlbnRpcmUgd2Vic2l0ZSwgbGF1bmNoZXMgcG9wdWxhciB3ZWIgYXR0YWNrcyAgICAgICAgICAgICAgICAgICAgICAgICAgICAoU1FMIEluamVjdGlvbiBldGMuKSBhbmQgaWRlbnRpZmllcyB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdGhhdCBuZWVkIHRvIGJlIGZpeGVkLjwvc3Ryb25nPiA8L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5TZWN1cmluZyB5b3VyIHdlYnNpdGUgc2hvdWxkIGJlIHlvdXIgbnVtYmVyIG9uZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjb25jZXJuPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgSGFja2VycyBhcmUgY29uY2VudHJhdGluZyB0aGVpciBlZmZvcnRzIG9uIHdlYi1iYXNlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBhcHBsaWNhdGlvbnMgLSA3NSUgb2YgY3liZXIgYXR0YWNrcyBhcmUgZG9uZSBhdCB0aGUgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGxldmVsLCBhIEdhcnRuZXIgR3JvdXAgc3R1ZHkgaGFzIHJldmVhbGVkLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBXZWIgYXBwbGljYXRpb25zIGFyZSBhY2Nlc3NpYmxlIDI0IGhvdXJzIGEgZGF5LCA3IGRheXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgYSB3ZWVrIGFuZCBjb250cm9sIHZhbHVhYmxlIGRhdGEgc3VjaCBhcyBjdXN0b21lciBpbmZvcm1hdGlvbiwgICAgICAgICAgICAgICAgICAgICAgICAgICAgdHJhbnNhY3Rpb24gaW5mb3JtYXRpb24gYW5kIGV2ZW4gcHJvcHJpZXRhcnkgY29ycG9yYXRlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGEuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bNTAwLDAwMCBjdXN0b21lciBjcmVkaXQgY2FyZCBudW1iZXJzIG9idGFpbmVkIHZpYSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhIHdlYiBhdHRhY2s8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBXZWxsLWtub3duIHNpdGVzIHRoYXQgd2VyZSBvcGVuIHRvIHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGluY2x1ZGUgZmFzaGlvbiBsYWJlbCBHdWVzcyBhbmQgcGV0IHN1cHBseSByZXRhaWxlciAgICAgICAgICAgICAgICAgICAgICAgICAgICBQZXRDby5jb20gd2hvIHdlcmUgbm90b3Jpb3VzbHkgZm91bmQgdG8gYmUgdnVsbmVyYWJsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB0byB0aGUgU1FMIGluamVjdGlvbiB2dWxuZXJhYmlsaXR5IChKdW5lIDIwMDMpLiBUaGlzICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJlc3VsdGVkIGluIFBldENvIGxlYXZpbmcgYXMgbWFueSBhcyA1MDAsMDAwIGNyZWRpdCAgICAgICAgICAgICAgICAgICAgICAgICAgICBjYXJkIG51bWJlcnMgb3BlbiB0byBhbnlvbmUgYWJsZSB0byBjb25zdHJ1Y3QgdGhpcyBzcGVjaWFsbHktY3JhZnRlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBVUkwuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bRmlyZXdhbGxzLCBTU0wgYW5kIGxvY2tlZC1kb3duIHNlcnZlcnMgYXJlIGZ1dGlsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBoYWNraW5nPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQW55IGRlZmVuc2UgYXQgbmV0d29yayBzZWN1cml0eSBsZXZlbCB3aWxsIHByb3ZpZGUgbm8gICAgICAgICAgICAgICAgICAgICAgICAgICAgcHJvdGVjdGlvbiBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzIHNpbmNlIHRoZXkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXJlIGxhdW5jaGVkIG9uIHBvcnQgODAgLSB3aGljaCBoYXMgdG8gcmVtYWluIG9wZW4uICAgICAgICAgICAgICAgICAgICAgICAgICAgIEluIGFkZGl0aW9uLCB3ZWIgYXBwbGljYXRpb25zIChjdXN0b21lciBhcmVhcywgc2hvcHBpbmcgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FydHMgZXRjLikgYXJlIG9mdGVuIHRhaWxvci1tYWRlLCBpbnZhcmlhYmx5IHRlc3RlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBsZXNzIHRoYW4gb2ZmLXRoZS1zaGVsZiBzb2Z0d2FyZSBhbmQgYXJlIHRoZXJlZm9yZSBtb3JlICAgICAgICAgICAgICAgICAgICAgICAgICAgIHN1c2NlcHRpYmxlIHRvIGF0dGFjay48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bJnF1b3Q7Q29tcGFuaWVzIGhhdmUgaW1wbGVtZW50ZWQgbmV0d29yay1sZXZlbCBzZWN1cml0eSwgICAgICAgICAgICAgICAgICAgICAgICAgICAgaG93ZXZlciB0aGV5IGZhaWwgdG8gYXVkaXQgYW5kIHNlY3VyZSB0aGVpciB3ZWIgYXBwbGljYXRpb25zLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBUaGVzZSBhcHBsaWNhdGlvbnMgaGF2ZSBhY2Nlc3MgdG8gc2Vuc2l0aXZlIGRhdGEgYW5kICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFyZSBhIGhhY2tlcidzIHByaW1lIHRhcmdldCwmcXVvdDsgc2FpZCBOaWNrIEdhbGVhLCAgICAgICAgICAgICAgICAgICAgICAgICAgICBDRU8gb2YgQWN1bmV0aXguICZxdW90O0F1ZGl0aW5nIG9uZSdzIHdlYiBhcHBzIHNob3VsZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBiZSB0aGUgbnVtYmVyIG9uZSBzZWN1cml0eSBjb25jZXJuLiZxdW90OzwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlRoZSBuZWVkIGZvciBhbiBhdXRvbWF0ZWQgd2ViIGFwcGxpY2F0aW9uIHZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgc2Nhbm5lcjwvc3Ryb25nPjxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIE1hbnVhbGx5IGF1ZGl0aW5nIGEgd2ViIGFwcGxpY2F0aW9uIGZvciB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdG8gU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiAgICAgICAgICAgICAgICAgICAgICAgICAgICBhdHRhY2tzIGlzIHZpcnR1YWxseSBpbXBvc3NpYmxlLiBXaXRoIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5ICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNjYW5uZXIgdGhlIHByb2Nlc3Mgb2YgYXVkaXRpbmcgd2ViIGFwcGxpY2F0aW9ucyBzdWNoICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFzIHNob3BwaW5nIGNhcnRzIGFuZCBmb3JtcywgY2FuIGJlIGVhc2lseSBhdXRvbWF0ZWQuICAgICAgICAgICAgICAgICAgICAgICAgICAgIFdoYXQncyBtb3JlLCB0aGUgc2VjdXJpdHkgY2hlY2tzIGNhbiBlYXNpbHkgYmUgcmUtbGF1bmNoZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGVhY2ggYXBwbGljYXRpb24gdXBkYXRlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkhvdyBBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIHdvcmtzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGZpcnN0IGNyYXdscyB0aGUgd2hvbGUgd2Vic2l0ZSwgYW5hbHl6ZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgaW4tZGVwdGggZWFjaCBmaWxlIGl0IGZpbmRzLCBhbmQgZGlzcGxheXMgdGhlIGVudGlyZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB3ZWJzaXRlIHN0cnVjdHVyZS4gQWZ0ZXIgdGhpcyBkaXNjb3Zlcnkgc3RhZ2UsIGl0IHBlcmZvcm1zICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFuIGF1dG9tYXRpYyBhdWRpdCBmb3IgY29tbW9uIHNlY3VyaXR5IHZ1bG5lcmFiaWxpdGllcy48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BdXRvbWF0aWNhbGx5IGRldGVjdHMgU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiB2dWxuZXJhYmlsaXRpZXM8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBTUUwgaW5qZWN0aW9uIGlzIGEgaGFja2luZyB0ZWNobmlxdWUgd2hpY2ggbW9kaWZpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgU1FMIGNvbW1hbmRzIGluIG9yZGVyIHRvIGdhaW4gYWNjZXNzIHRvIGRhdGEgaW4gdGhlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGFiYXNlLiBDcm9zcyBzaXRlIHNjcmlwdGluZyBhdHRhY2tzIGFsbG93IGEgaGFja2VyICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRvIGV4ZWN1dGUgYSBtYWxpY2lvdXMgc2NyaXB0IG9uIHlvdXIgdmlzaXRvcnMnIGJyb3dzZXIuICAgICAgICAgICAgICAgICAgICAgICAgICAgIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgY2FuIGNoZWNrIGlmIHlvdXIgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGlzIHZ1bG5lcmFibGUgdG8gYm90aCBvZiB0aGVzZSBhdHRhY2tzLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBNb3JlIGluZm9ybWF0aW9uIGFib3V0IGNyb3NzIHNpdGUgc2NyaXB0aW5nICZhbXA7IFNRTCAgICAgICAgICAgICAgICAgICAgICAgICAgICBpbmplY3Rpb24gYXQgb3VyIHdlYnNpdGUgc2VjdXJpdHkgaW5mbyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgYWxzbyBjaGVja3MgZm9yICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRoZSBmb2xsb3dpbmcgd2ViIGF0dGFja3M6PC9zdHJvbmc%2bPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDx1bD4gPGxpPkNSTEYgaW5qZWN0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5Db2RlIGV4ZWN1dGlvbiBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRGlyZWN0b3J5IHRyYXZlcnNhbCBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRmlsZSBpbmNsdXNpb24gYXR0YWNrczxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvbGk%2bPGxpPiBJbnB1dCB2YWxpZGF0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5BdXRoZW50aWNhdGlvbiBhdHRhY2tzLjwvbGk%2bIDwvdWw%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BZHZhbmNlZCBwZW5ldHJhdGlvbiB0ZXN0aW5nIHRvb2xzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGFsc28gaW5jbHVkZXMgdG9vbHMgc3VjaCBhcyBhbiBIVFRQIGVkaXRvciAgICAgICAgICAgICAgICAgICAgICAgICAgICAmYW1wOyBIVFRQIHNuaWZmZXIgdG8gYWxsb3cgY3VzdG9taXphdGlvbiBvZiB3ZWIgdnVsbmVyYWJpbGl0eSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjaGVja3MuIFVzaW5nIHRoZSBWdWxuZXJhYmlsaXR5IGVkaXRvciwgbmV3IGF0dGFja3MgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FuIGVhc2lseSBiZSBjcmVhdGVkLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlByaWNpbmcgJmFtcDsgYXZhaWxhYmlsaXR5PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGlzIGF2YWlsYWJsZSBhcyBhbiBlbnRlcnByaXNlIG9yIGFzIGEgY29uc3VsdGFudCAgICAgICAgICAgICAgICAgICAgICAgICAgICB2ZXJzaW9uLiBBIHN1YnNjcmlwdGlvbiBiYXNlZCBsaWNlbnNlIGNhbiBiZSBwdXJjaGFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGFzIGxpdHRsZSBhcyAkMzk1LCB3aGVyZWFzIGEgcGVycGV0dWFsIGxpY2Vuc2Ugc3RhcnRzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGF0ICQyOTk1LiBGb3IgbW9yZSBpbmZvcm1hdGlvbiB2aXNpdCBvdXIgcHJpY2luZyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFib3V0IEFjdW5ldGl4PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggd2FzIGZvdW5kZWQgdG8gY29tYmF0IHRoZSBhbGFybWluZyByaXNlIGluICAgICAgICAgICAgICAgICAgICAgICAgICAgIHdlYiBhdHRhY2tzLiBJdHMgZmxhZ3NoaXAgcHJvZHVjdCwgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgU2Nhbm5lciwgaXMgdGhlIHJlc3VsdCBvZiBzZXZlcmFsIHllYXJzIG9mIGRldmVsb3BtZW50ICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJ5IGEgdGVhbSBvZiBoaWdobHkgZXhwZXJpZW5jZWQgc2VjdXJpdHkgZGV2ZWxvcGVycy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggaXMgYSBwcml2YXRlbHkgaGVsZCBjb21wYW55IHdpdGggaGVhZHF1YXJ0ZXJzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJhc2VkIGluIEV1cm9wZSAoTWFsdGEpIHdpdGggaXRzIE5ldyBZb3JrIFVTIG9mZmljZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY2hlZHVsZWQgdG8gb3BlbiBpbiBRMyBvZiAyMDA1LiA8L3A%2bIGQCCQ8PFgIeC05hdmlnYXRlVXJsBRJDb21tZW50cy5hc3B4P2lkPTJkZAILDxYCHgNzcmMFDGFkcy9kZWYuaHRtbGRkNCSZh%2buMoCTcXGDfVu5D5CfxA7Y%3d]]></Request> | |
| 2208 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2209 | Date: Thu, 14 Nov 2013 14:26:41 GMT | |
| 2210 | Server: Microsoft-IIS/6.0 | |
| 2211 | X-Powered-By: ASP.NET | |
| 2212 | X-AspNet-Version: 2.0.50727 | |
| 2213 | Cache-Control: private | |
| 2214 | Content-Type: text/html; charset=utf-8 | |
| 2215 | Content-Length: 16884 | |
| 2216 | ]]></Response> | |
| 2217 | </TechnicalDetails> | |
| 2218 | <References></References> | |
| 2219 | </ReportItem> | |
| 2220 | ||
| 2221 | <ReportItem id="24" color="orange"> | |
| 2222 | <Name><![CDATA[Unencrypted __VIEWSTATE parameter]]></Name> | |
| 2223 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 2224 | <Details><![CDATA[form name: <font color="dark">"Form1"</font><br/>form action: <font color="dark">"readnews.aspx?id=3"</font><br/>VIEWSTATE: <font color="dark">"/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc+YWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNzozNSBBTWQCBQ8WAh8BBTFBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIGJldGEgcmVsZWFzZWQhZAIHDxYCHwEF8Q08cD5EdXJpbmcgdGhlIGJldGEgcGhhc2UsIGJ1aWxkcyBhcmUgcmVsZWFzZWQgZnJlcXVlbnRseSwgICAgICAgICAgICAgICAgICAgICAgICAgICAgdGhlcmVmb3JlIGl0IGlzIG5vdCByZWNvbW1lbmRlZCB0aGF0IHRoZSBzYW1lIGJldGEgdmVy"</font><br/>VIEWSTATE decoded: <font color="dark">"##### | |
| 2225 | -352232569#d#####d#####d#########href# | |
| 2226 | login.aspx# innerhtml##logind#######d##Visiblehd########Iposted by <strong>admin </strong>11/8/2005 11:37:35 AMd########1Acunetix Web Vulnerability Scanner beta released!d######### ⏎ | |
| 2227 | <p>During the beta phase, builds are released frequently, therefore it is not recommended that the same beta version is used for more than 30 days. To beta-test beyond 30 days, users sho"</font><br/>]]></Details> | |
| 2228 | <Affects><![CDATA[/readnews.aspx (2ae3ef37ff42a40617d25a9c1c42559d)]]></Affects> | |
| 2229 | <Parameter><![CDATA[]]></Parameter> | |
| 2230 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2231 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2232 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2233 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2234 | <Severity><![CDATA[medium]]></Severity> | |
| 2235 | <Type><![CDATA[Informational]]></Type> | |
| 2236 | <Impact><![CDATA[Possible sensitive information disclosure.]]></Impact> | |
| 2237 | <Description><![CDATA[The __VIEWSTATE parameter is not encrypted. To reduce the chance of someone intercepting the information stored in the ViewState, it is good design to encrypt the ViewState. To do this, set the machineKey validation type to 3DES. This instructs ASP.NET to encrypt the ViewState value using the Triple DES symmetric encryption algorithm.]]></Description> | |
| 2238 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2239 | <Recommendation><![CDATA[Open <font color="dark"><b>Web.Config</b></font> and add the following line under the <font color="dark"><b><system.web></b></font> element: <br/><pre wrap="virtual"><machineKey validation="3DES"/> </pre>]]></Recommendation> | |
| 2240 | <TechnicalDetails> | |
| 2241 | <Request><![CDATA[GET /readnews.aspx?id=3 HTTP/1.1 | |
| 2242 | Pragma: no-cache | |
| 2243 | Cache-Control: no-cache | |
| 2244 | Referer: http://testaspnet.vulnweb.com/comments.aspx | |
| 2245 | Acunetix-Aspect: enabled | |
| 2246 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2247 | Acunetix-Aspect-Queries: aspectalerts | |
| 2248 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2249 | Host: testaspnet.vulnweb.com | |
| 2250 | Connection: Keep-alive | |
| 2251 | Accept-Encoding: gzip,deflate | |
| 2252 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2253 | Accept: */* | |
| 2254 | ||
| 2255 | ]]></Request> | |
| 2256 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2257 | Date: Thu, 14 Nov 2013 14:26:42 GMT | |
| 2258 | Server: Microsoft-IIS/6.0 | |
| 2259 | X-Powered-By: ASP.NET | |
| 2260 | X-AspNet-Version: 2.0.50727 | |
| 2261 | Cache-Control: private | |
| 2262 | Content-Type: text/html; charset=utf-8 | |
| 2263 | Content-Length: 16787 | |
| 2264 | ]]></Response> | |
| 2265 | </TechnicalDetails> | |
| 2266 | <References></References> | |
| 2267 | </ReportItem> | |
| 2268 | ||
| 2269 | <ReportItem id="25" color="green"> | |
| 2270 | <Name><![CDATA[Error page web server version disclosure]]></Name> | |
| 2271 | <ModuleName><![CDATA[Scripting (Error_Page_Path_Disclosure.script)]]></ModuleName> | |
| 2272 | <Details><![CDATA[Information disclosure pattern found: <font color="dark">Microsoft .NET Framework Version:2.0.50727.3053; ASP.NET Version:2.0.50727.3053</font>]]></Details> | |
| 2273 | <Affects><![CDATA[Web Server]]></Affects> | |
| 2274 | <Parameter><![CDATA[]]></Parameter> | |
| 2275 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2276 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2277 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2278 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2279 | <Severity><![CDATA[info]]></Severity> | |
| 2280 | <Type><![CDATA[Configuration]]></Type> | |
| 2281 | <Impact><![CDATA[Possible sensitive information disclosure.]]></Impact> | |
| 2282 | <Description><![CDATA[By requesting a page that doesn't exist, an error page was returned. This error page contains the web server version number and a list of modules enabled on this server. This information can be used to conduct further attacks.]]></Description> | |
| 2283 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2284 | <Recommendation><![CDATA[If you are using Apache, you can setup a custom 404 page by following the instructions provided in the References section.]]></Recommendation> | |
| 2285 | <TechnicalDetails> | |
| 2286 | <Request><![CDATA[GET /R9bwZuGkQ0.aspx HTTP/1.1 | |
| 2287 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2288 | Host: testaspnet.vulnweb.com | |
| 2289 | Connection: Keep-alive | |
| 2290 | Accept-Encoding: gzip,deflate | |
| 2291 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2292 | Accept: */* | |
| 2293 | ||
| 2294 | ]]></Request> | |
| 2295 | <Response><![CDATA[HTTP/1.1 404 Not Found | |
| 2296 | Date: Thu, 14 Nov 2013 14:26:42 GMT | |
| 2297 | Server: Microsoft-IIS/6.0 | |
| 2298 | X-Powered-By: ASP.NET | |
| 2299 | X-AspNet-Version: 2.0.50727 | |
| 2300 | Cache-Control: private | |
| 2301 | Content-Type: text/html; charset=utf-8 | |
| 2302 | Content-Length: 3347 | |
| 2303 | ]]></Response> | |
| 2304 | </TechnicalDetails> | |
| 2305 | <References> | |
| 2306 | <Reference> | |
| 2307 | <Database><![CDATA[Custom error responses]]></Database> | |
| 2308 | <URL><![CDATA[http://httpd.apache.org/docs/1.3/custom-error.html]]></URL> | |
| 2309 | </Reference> | |
| 2310 | <Reference> | |
| 2311 | <Database><![CDATA[Creating Custom Error Pages on Apache Servers]]></Database> | |
| 2312 | <URL><![CDATA[http://www.webreference.com/programming/apache_errors/]]></URL> | |
| 2313 | </Reference> | |
| 2314 | </References> | |
| 2315 | </ReportItem> | |
| 2316 | ||
| 2317 | <ReportItem id="26" color="green"> | |
| 2318 | <Name><![CDATA[GHDB: Typical login page]]></Name> | |
| 2319 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 2320 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">inurl:login.asp</font></pre>]]></Details> | |
| 2321 | <Affects><![CDATA[/login.aspx (79ea5a36a5cedd4ac82ab5b64fe8ad28)]]></Affects> | |
| 2322 | <Parameter><![CDATA[]]></Parameter> | |
| 2323 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2324 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2325 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2326 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2327 | <Severity><![CDATA[info]]></Severity> | |
| 2328 | <Type><![CDATA[Informational]]></Type> | |
| 2329 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 2330 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Pages containing login portals</font><br/><br/>This is a typical login page. It has recently become a target for SQL injection. Comsec's article at http://www.governmentsecurity.org/articles/SQLinjectionBasicTutorial.php brought this to my attention.<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 2331 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2332 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 2333 | <TechnicalDetails> | |
| 2334 | <Request><![CDATA[POST /login.aspx HTTP/1.1 | |
| 2335 | Pragma: no-cache | |
| 2336 | Cache-Control: no-cache | |
| 2337 | Referer: http://testaspnet.vulnweb.com/login.aspx | |
| 2338 | Content-Length: 1161 | |
| 2339 | Content-Type: application/x-www-form-urlencoded | |
| 2340 | Acunetix-Aspect: enabled | |
| 2341 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2342 | Acunetix-Aspect-Queries: aspectalerts | |
| 2343 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2344 | Host: testaspnet.vulnweb.com | |
| 2345 | Connection: Keep-alive | |
| 2346 | Accept-Encoding: gzip,deflate | |
| 2347 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2348 | Accept: */* | |
| 2349 | ||
| 2350 | btnLogin=Login&cbPersistCookie=on&tbPassword=g00dPa%24%24w0rD&tbUsername=ljmrwpfo&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></Request> | |
| 2351 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2352 | Date: Thu, 14 Nov 2013 14:26:42 GMT | |
| 2353 | Server: Microsoft-IIS/6.0 | |
| 2354 | X-Powered-By: ASP.NET | |
| 2355 | X-AspNet-Version: 2.0.50727 | |
| 2356 | Cache-Control: private | |
| 2357 | Content-Type: text/html; charset=utf-8 | |
| 2358 | Content-Length: 12346 | |
| 2359 | ]]></Response> | |
| 2360 | </TechnicalDetails> | |
| 2361 | <References> | |
| 2362 | <Reference> | |
| 2363 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 2364 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 2365 | </Reference> | |
| 2366 | <Reference> | |
| 2367 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 2368 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 2369 | </Reference> | |
| 2370 | </References> | |
| 2371 | </ReportItem> | |
| 2372 | ||
| 2373 | <ReportItem id="27" color="green"> | |
| 2374 | <Name><![CDATA[Password type input with auto-complete enabled]]></Name> | |
| 2375 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 2376 | <Details><![CDATA[Password type input named <b><font color="dark">tbPassword</font></b> from form named <b>frmLogin</b> with action <b>login.aspx?ReturnUrl=%2flogout.aspx</b> has autocomplete enabled.]]></Details> | |
| 2377 | <Affects><![CDATA[/login.aspx (2cf4e729ea10427a01c01f366190f25a)]]></Affects> | |
| 2378 | <Parameter><![CDATA[]]></Parameter> | |
| 2379 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2380 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2381 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2382 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2383 | <Severity><![CDATA[info]]></Severity> | |
| 2384 | <Type><![CDATA[Informational]]></Type> | |
| 2385 | <Impact><![CDATA[Possible sensitive information disclosure]]></Impact> | |
| 2386 | <Description><![CDATA[When a new name and password is entered in a form and the form is submitted, the browser asks if the password should be saved. Thereafter when the form is displayed, the name and password are filled in automatically or are completed as the name is entered. An attacker with local access could obtain the cleartext password from the browser cache.]]></Description> | |
| 2387 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2388 | <Recommendation><![CDATA[The password auto-complete should be disabled in sensitive applications. <br/>To disable auto-complete, you may use a code similar to: <pre wrap="virtual"><code><INPUT TYPE="password" AUTOCOMPLETE="off"></code></pre>]]></Recommendation> | |
| 2389 | <TechnicalDetails> | |
| 2390 | <Request><![CDATA[GET /login.aspx?ReturnUrl=/logout.aspx HTTP/1.1 | |
| 2391 | Pragma: no-cache | |
| 2392 | Cache-Control: no-cache | |
| 2393 | Referer: http://testaspnet.vulnweb.com/logout.aspx | |
| 2394 | Acunetix-Aspect: enabled | |
| 2395 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2396 | Acunetix-Aspect-Queries: aspectalerts | |
| 2397 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2398 | Host: testaspnet.vulnweb.com | |
| 2399 | Connection: Keep-alive | |
| 2400 | Accept-Encoding: gzip,deflate | |
| 2401 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2402 | Accept: */* | |
| 2403 | ||
| 2404 | ]]></Request> | |
| 2405 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2406 | Date: Thu, 14 Nov 2013 14:26:42 GMT | |
| 2407 | Server: Microsoft-IIS/6.0 | |
| 2408 | X-Powered-By: ASP.NET | |
| 2409 | X-AspNet-Version: 2.0.50727 | |
| 2410 | Cache-Control: private | |
| 2411 | Content-Type: text/html; charset=utf-8 | |
| 2412 | Content-Length: 12354 | |
| 2413 | ]]></Response> | |
| 2414 | </TechnicalDetails> | |
| 2415 | <References></References> | |
| 2416 | </ReportItem> | |
| 2417 | ||
| 2418 | <ReportItem id="28" color="orange"> | |
| 2419 | <Name><![CDATA[Unencrypted __VIEWSTATE parameter]]></Name> | |
| 2420 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 2421 | <Details><![CDATA[form name: <font color="dark">"frmLogin"</font><br/>form action: <font color="dark">"login.aspx?ReturnUrl=%2flogout.aspx"</font><br/>VIEWSTATE: <font color="dark">"/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W+w+8Zj9n0mGriLs0UbfzYNdg=="</font><br/>VIEWSTATE decoded: <font color="dark">"##### | |
| 2422 | -223969811#d#####d#####d#########href# | |
| 2423 | login.aspx# innerhtml##logind#######d##Visiblehd####__ControlsRequirePostBackKey__####cbPersistCookie##o###c#}&####E#6 ⏎ | |
| 2424 | v"</font><br/>]]></Details> | |
| 2425 | <Affects><![CDATA[/login.aspx (2cf4e729ea10427a01c01f366190f25a)]]></Affects> | |
| 2426 | <Parameter><![CDATA[]]></Parameter> | |
| 2427 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2428 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2429 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2430 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2431 | <Severity><![CDATA[medium]]></Severity> | |
| 2432 | <Type><![CDATA[Informational]]></Type> | |
| 2433 | <Impact><![CDATA[Possible sensitive information disclosure.]]></Impact> | |
| 2434 | <Description><![CDATA[The __VIEWSTATE parameter is not encrypted. To reduce the chance of someone intercepting the information stored in the ViewState, it is good design to encrypt the ViewState. To do this, set the machineKey validation type to 3DES. This instructs ASP.NET to encrypt the ViewState value using the Triple DES symmetric encryption algorithm.]]></Description> | |
| 2435 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2436 | <Recommendation><![CDATA[Open <font color="dark"><b>Web.Config</b></font> and add the following line under the <font color="dark"><b><system.web></b></font> element: <br/><pre wrap="virtual"><machineKey validation="3DES"/> </pre>]]></Recommendation> | |
| 2437 | <TechnicalDetails> | |
| 2438 | <Request><![CDATA[GET /login.aspx?ReturnUrl=/logout.aspx HTTP/1.1 | |
| 2439 | Pragma: no-cache | |
| 2440 | Cache-Control: no-cache | |
| 2441 | Referer: http://testaspnet.vulnweb.com/logout.aspx | |
| 2442 | Acunetix-Aspect: enabled | |
| 2443 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2444 | Acunetix-Aspect-Queries: aspectalerts | |
| 2445 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2446 | Host: testaspnet.vulnweb.com | |
| 2447 | Connection: Keep-alive | |
| 2448 | Accept-Encoding: gzip,deflate | |
| 2449 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2450 | Accept: */* | |
| 2451 | ||
| 2452 | ]]></Request> | |
| 2453 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2454 | Date: Thu, 14 Nov 2013 14:26:42 GMT | |
| 2455 | Server: Microsoft-IIS/6.0 | |
| 2456 | X-Powered-By: ASP.NET | |
| 2457 | X-AspNet-Version: 2.0.50727 | |
| 2458 | Cache-Control: private | |
| 2459 | Content-Type: text/html; charset=utf-8 | |
| 2460 | Content-Length: 12354 | |
| 2461 | ]]></Response> | |
| 2462 | </TechnicalDetails> | |
| 2463 | <References></References> | |
| 2464 | </ReportItem> | |
| 2465 | ||
| 2466 | <ReportItem id="29" color="green"> | |
| 2467 | <Name><![CDATA[GHDB: Typical login page]]></Name> | |
| 2468 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 2469 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">inurl:login.asp</font></pre>]]></Details> | |
| 2470 | <Affects><![CDATA[/login.aspx (2cf4e729ea10427a01c01f366190f25a)]]></Affects> | |
| 2471 | <Parameter><![CDATA[]]></Parameter> | |
| 2472 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2473 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2474 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2475 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2476 | <Severity><![CDATA[info]]></Severity> | |
| 2477 | <Type><![CDATA[Informational]]></Type> | |
| 2478 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 2479 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Pages containing login portals</font><br/><br/>This is a typical login page. It has recently become a target for SQL injection. Comsec's article at http://www.governmentsecurity.org/articles/SQLinjectionBasicTutorial.php brought this to my attention.<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 2480 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2481 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 2482 | <TechnicalDetails> | |
| 2483 | <Request><![CDATA[GET /login.aspx?ReturnUrl=/logout.aspx HTTP/1.1 | |
| 2484 | Pragma: no-cache | |
| 2485 | Cache-Control: no-cache | |
| 2486 | Referer: http://testaspnet.vulnweb.com/logout.aspx | |
| 2487 | Acunetix-Aspect: enabled | |
| 2488 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2489 | Acunetix-Aspect-Queries: aspectalerts | |
| 2490 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2491 | Host: testaspnet.vulnweb.com | |
| 2492 | Connection: Keep-alive | |
| 2493 | Accept-Encoding: gzip,deflate | |
| 2494 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2495 | Accept: */* | |
| 2496 | ||
| 2497 | ]]></Request> | |
| 2498 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2499 | Date: Thu, 14 Nov 2013 14:26:42 GMT | |
| 2500 | Server: Microsoft-IIS/6.0 | |
| 2501 | X-Powered-By: ASP.NET | |
| 2502 | X-AspNet-Version: 2.0.50727 | |
| 2503 | Cache-Control: private | |
| 2504 | Content-Type: text/html; charset=utf-8 | |
| 2505 | Content-Length: 12354 | |
| 2506 | ]]></Response> | |
| 2507 | </TechnicalDetails> | |
| 2508 | <References> | |
| 2509 | <Reference> | |
| 2510 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 2511 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 2512 | </Reference> | |
| 2513 | <Reference> | |
| 2514 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 2515 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 2516 | </Reference> | |
| 2517 | </References> | |
| 2518 | </ReportItem> | |
| 2519 | ||
| 2520 | <ReportItem id="30" color="green"> | |
| 2521 | <Name><![CDATA[Password type input with auto-complete enabled]]></Name> | |
| 2522 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 2523 | <Details><![CDATA[Password type input named <b><font color="dark">tbPassword</font></b> from form named <b>frmLogin</b> with action <b>login.aspx?ReturnUrl=%2fpostnews.aspx</b> has autocomplete enabled.]]></Details> | |
| 2524 | <Affects><![CDATA[/login.aspx (7dd31244ca65de83cf0faf8d8fc754b2)]]></Affects> | |
| 2525 | <Parameter><![CDATA[]]></Parameter> | |
| 2526 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2527 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2528 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2529 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2530 | <Severity><![CDATA[info]]></Severity> | |
| 2531 | <Type><![CDATA[Informational]]></Type> | |
| 2532 | <Impact><![CDATA[Possible sensitive information disclosure]]></Impact> | |
| 2533 | <Description><![CDATA[When a new name and password is entered in a form and the form is submitted, the browser asks if the password should be saved. Thereafter when the form is displayed, the name and password are filled in automatically or are completed as the name is entered. An attacker with local access could obtain the cleartext password from the browser cache.]]></Description> | |
| 2534 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2535 | <Recommendation><![CDATA[The password auto-complete should be disabled in sensitive applications. <br/>To disable auto-complete, you may use a code similar to: <pre wrap="virtual"><code><INPUT TYPE="password" AUTOCOMPLETE="off"></code></pre>]]></Recommendation> | |
| 2536 | <TechnicalDetails> | |
| 2537 | <Request><![CDATA[GET /login.aspx?ReturnUrl=/postnews.aspx HTTP/1.1 | |
| 2538 | Pragma: no-cache | |
| 2539 | Cache-Control: no-cache | |
| 2540 | Referer: http://testaspnet.vulnweb.com/postnews.aspx | |
| 2541 | Acunetix-Aspect: enabled | |
| 2542 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2543 | Acunetix-Aspect-Queries: aspectalerts | |
| 2544 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2545 | Host: testaspnet.vulnweb.com | |
| 2546 | Connection: Keep-alive | |
| 2547 | Accept-Encoding: gzip,deflate | |
| 2548 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2549 | Accept: */* | |
| 2550 | ||
| 2551 | ]]></Request> | |
| 2552 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2553 | Date: Thu, 14 Nov 2013 14:26:42 GMT | |
| 2554 | Server: Microsoft-IIS/6.0 | |
| 2555 | X-Powered-By: ASP.NET | |
| 2556 | X-AspNet-Version: 2.0.50727 | |
| 2557 | Cache-Control: private | |
| 2558 | Content-Type: text/html; charset=utf-8 | |
| 2559 | Content-Length: 12356 | |
| 2560 | ]]></Response> | |
| 2561 | </TechnicalDetails> | |
| 2562 | <References></References> | |
| 2563 | </ReportItem> | |
| 2564 | ||
| 2565 | <ReportItem id="31" color="orange"> | |
| 2566 | <Name><![CDATA[Unencrypted __VIEWSTATE parameter]]></Name> | |
| 2567 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 2568 | <Details><![CDATA[form name: <font color="dark">"frmLogin"</font><br/>form action: <font color="dark">"login.aspx?ReturnUrl=%2fpostnews.aspx"</font><br/>VIEWSTATE: <font color="dark">"/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W+w+8Zj9n0mGriLs0UbfzYNdg=="</font><br/>VIEWSTATE decoded: <font color="dark">"##### | |
| 2569 | -223969811#d#####d#####d#########href# | |
| 2570 | login.aspx# innerhtml##logind#######d##Visiblehd####__ControlsRequirePostBackKey__####cbPersistCookie##o###c#}&####E#6 ⏎ | |
| 2571 | v"</font><br/>]]></Details> | |
| 2572 | <Affects><![CDATA[/login.aspx (7dd31244ca65de83cf0faf8d8fc754b2)]]></Affects> | |
| 2573 | <Parameter><![CDATA[]]></Parameter> | |
| 2574 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2575 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2576 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2577 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2578 | <Severity><![CDATA[medium]]></Severity> | |
| 2579 | <Type><![CDATA[Informational]]></Type> | |
| 2580 | <Impact><![CDATA[Possible sensitive information disclosure.]]></Impact> | |
| 2581 | <Description><![CDATA[The __VIEWSTATE parameter is not encrypted. To reduce the chance of someone intercepting the information stored in the ViewState, it is good design to encrypt the ViewState. To do this, set the machineKey validation type to 3DES. This instructs ASP.NET to encrypt the ViewState value using the Triple DES symmetric encryption algorithm.]]></Description> | |
| 2582 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2583 | <Recommendation><![CDATA[Open <font color="dark"><b>Web.Config</b></font> and add the following line under the <font color="dark"><b><system.web></b></font> element: <br/><pre wrap="virtual"><machineKey validation="3DES"/> </pre>]]></Recommendation> | |
| 2584 | <TechnicalDetails> | |
| 2585 | <Request><![CDATA[GET /login.aspx?ReturnUrl=/postnews.aspx HTTP/1.1 | |
| 2586 | Pragma: no-cache | |
| 2587 | Cache-Control: no-cache | |
| 2588 | Referer: http://testaspnet.vulnweb.com/postnews.aspx | |
| 2589 | Acunetix-Aspect: enabled | |
| 2590 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2591 | Acunetix-Aspect-Queries: aspectalerts | |
| 2592 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2593 | Host: testaspnet.vulnweb.com | |
| 2594 | Connection: Keep-alive | |
| 2595 | Accept-Encoding: gzip,deflate | |
| 2596 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2597 | Accept: */* | |
| 2598 | ||
| 2599 | ]]></Request> | |
| 2600 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2601 | Date: Thu, 14 Nov 2013 14:26:42 GMT | |
| 2602 | Server: Microsoft-IIS/6.0 | |
| 2603 | X-Powered-By: ASP.NET | |
| 2604 | X-AspNet-Version: 2.0.50727 | |
| 2605 | Cache-Control: private | |
| 2606 | Content-Type: text/html; charset=utf-8 | |
| 2607 | Content-Length: 12356 | |
| 2608 | ]]></Response> | |
| 2609 | </TechnicalDetails> | |
| 2610 | <References></References> | |
| 2611 | </ReportItem> | |
| 2612 | ||
| 2613 | <ReportItem id="32" color="green"> | |
| 2614 | <Name><![CDATA[GHDB: Typical login page]]></Name> | |
| 2615 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 2616 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">inurl:login.asp</font></pre>]]></Details> | |
| 2617 | <Affects><![CDATA[/login.aspx (7dd31244ca65de83cf0faf8d8fc754b2)]]></Affects> | |
| 2618 | <Parameter><![CDATA[]]></Parameter> | |
| 2619 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2620 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2621 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2622 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2623 | <Severity><![CDATA[info]]></Severity> | |
| 2624 | <Type><![CDATA[Informational]]></Type> | |
| 2625 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 2626 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Pages containing login portals</font><br/><br/>This is a typical login page. It has recently become a target for SQL injection. Comsec's article at http://www.governmentsecurity.org/articles/SQLinjectionBasicTutorial.php brought this to my attention.<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 2627 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2628 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 2629 | <TechnicalDetails> | |
| 2630 | <Request><![CDATA[GET /login.aspx?ReturnUrl=/postnews.aspx HTTP/1.1 | |
| 2631 | Pragma: no-cache | |
| 2632 | Cache-Control: no-cache | |
| 2633 | Referer: http://testaspnet.vulnweb.com/postnews.aspx | |
| 2634 | Acunetix-Aspect: enabled | |
| 2635 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2636 | Acunetix-Aspect-Queries: aspectalerts | |
| 2637 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2638 | Host: testaspnet.vulnweb.com | |
| 2639 | Connection: Keep-alive | |
| 2640 | Accept-Encoding: gzip,deflate | |
| 2641 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2642 | Accept: */* | |
| 2643 | ||
| 2644 | ]]></Request> | |
| 2645 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2646 | Date: Thu, 14 Nov 2013 14:26:42 GMT | |
| 2647 | Server: Microsoft-IIS/6.0 | |
| 2648 | X-Powered-By: ASP.NET | |
| 2649 | X-AspNet-Version: 2.0.50727 | |
| 2650 | Cache-Control: private | |
| 2651 | Content-Type: text/html; charset=utf-8 | |
| 2652 | Content-Length: 12356 | |
| 2653 | ]]></Response> | |
| 2654 | </TechnicalDetails> | |
| 2655 | <References> | |
| 2656 | <Reference> | |
| 2657 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 2658 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 2659 | </Reference> | |
| 2660 | <Reference> | |
| 2661 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 2662 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 2663 | </Reference> | |
| 2664 | </References> | |
| 2665 | </ReportItem> | |
| 2666 | ||
| 2667 | <ReportItem id="33" color="orange"> | |
| 2668 | <Name><![CDATA[Unencrypted __VIEWSTATE parameter]]></Name> | |
| 2669 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 2670 | <Details><![CDATA[form name: <font color="dark">"Form1"</font><br/>form action: <font color="dark">"readnews.aspx?id=2"</font><br/>VIEWSTATE: <font color="dark">"/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc+YWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNToyMiBBTWQCBQ8WAh8BBTxXZWIgYXR0YWNrcyAtIGNhbiB5b3VyIHdlYiBhcHBsaWNhdGlvbnMgd2l0aHN0YW5kIHRoZSBmb3JjZT9kAgcPFgIfAQWuNzxwPjxzdHJvbmc+QWN1bmV0aXggY29tYmF0cyByaXNlIGluIHdlYiBhdHRhY2tzIHdpdGggQWN1bmV0aXggICAgICAgICAgICAgICAgICAgICAgICAgICAgV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAyIDwvc3Ryb25nPjwv"</font><br/>VIEWSTATE decoded: <font color="dark">"##### | |
| 2671 | -352232569#d#####d#####d#########href# | |
| 2672 | login.aspx# innerhtml##logind#######d##Visiblehd########Iposted by <strong>admin </strong>11/8/2005 11:35:22 AMd########<Web attacks - can your web applications withstand the force?d#########7<p><strong>Acunetix combats rise in web attacks with Acunetix Web Vulnerability Scanner 2 </strong></p> <p>21 July 2005 - <strong>Start-up company Acunetix released Acunetix We"</font><br/>]]></Details> | |
| 2673 | <Affects><![CDATA[/readnews.aspx (93588f630275abc47ac25455f074741b)]]></Affects> | |
| 2674 | <Parameter><![CDATA[]]></Parameter> | |
| 2675 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2676 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2677 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2678 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2679 | <Severity><![CDATA[medium]]></Severity> | |
| 2680 | <Type><![CDATA[Informational]]></Type> | |
| 2681 | <Impact><![CDATA[Possible sensitive information disclosure.]]></Impact> | |
| 2682 | <Description><![CDATA[The __VIEWSTATE parameter is not encrypted. To reduce the chance of someone intercepting the information stored in the ViewState, it is good design to encrypt the ViewState. To do this, set the machineKey validation type to 3DES. This instructs ASP.NET to encrypt the ViewState value using the Triple DES symmetric encryption algorithm.]]></Description> | |
| 2683 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2684 | <Recommendation><![CDATA[Open <font color="dark"><b>Web.Config</b></font> and add the following line under the <font color="dark"><b><system.web></b></font> element: <br/><pre wrap="virtual"><machineKey validation="3DES"/> </pre>]]></Recommendation> | |
| 2685 | <TechnicalDetails> | |
| 2686 | <Request><![CDATA[POST /readnews.aspx?id=2 HTTP/1.1 | |
| 2687 | Pragma: no-cache | |
| 2688 | Cache-Control: no-cache | |
| 2689 | Referer: http://testaspnet.vulnweb.com/readnews.aspx | |
| 2690 | Content-Length: 10779 | |
| 2691 | Content-Type: application/x-www-form-urlencoded | |
| 2692 | Acunetix-Aspect: enabled | |
| 2693 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2694 | Acunetix-Aspect-Queries: aspectalerts | |
| 2695 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2696 | Host: testaspnet.vulnweb.com | |
| 2697 | Connection: Keep-alive | |
| 2698 | Accept-Encoding: gzip,deflate | |
| 2699 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2700 | Accept: */* | |
| 2701 | ||
| 2702 | __EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWVwK0ovnWBgKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IM%2blktliK1xNDntOrRvIod2XbGitg%3d&__VIEWSTATE=/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc%2bYWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNToyMiBBTWQCBQ8WAh8BBTxXZWIgYXR0YWNrcyAtIGNhbiB5b3VyIHdlYiBhcHBsaWNhdGlvbnMgd2l0aHN0YW5kIHRoZSBmb3JjZT9kAgcPFgIfAQWuNzxwPjxzdHJvbmc%2bQWN1bmV0aXggY29tYmF0cyByaXNlIGluIHdlYiBhdHRhY2tzIHdpdGggQWN1bmV0aXggICAgICAgICAgICAgICAgICAgICAgICAgICAgV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAyIDwvc3Ryb25nPjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD4yMSBKdWx5IDIwMDUgLSA8c3Ryb25nPlN0YXJ0LXVwIGNvbXBhbnkgQWN1bmV0aXggcmVsZWFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lcjogYSB0b29sIHRvIGF1dG9tYXRpY2FsbHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXVkaXQgd2Vic2l0ZSBzZWN1cml0eS4gQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAgICAgICAgICAgICAgICAgICAgICAgICAgICAyIGNyYXdscyBhbiBlbnRpcmUgd2Vic2l0ZSwgbGF1bmNoZXMgcG9wdWxhciB3ZWIgYXR0YWNrcyAgICAgICAgICAgICAgICAgICAgICAgICAgICAoU1FMIEluamVjdGlvbiBldGMuKSBhbmQgaWRlbnRpZmllcyB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdGhhdCBuZWVkIHRvIGJlIGZpeGVkLjwvc3Ryb25nPiA8L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5TZWN1cmluZyB5b3VyIHdlYnNpdGUgc2hvdWxkIGJlIHlvdXIgbnVtYmVyIG9uZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjb25jZXJuPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgSGFja2VycyBhcmUgY29uY2VudHJhdGluZyB0aGVpciBlZmZvcnRzIG9uIHdlYi1iYXNlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBhcHBsaWNhdGlvbnMgLSA3NSUgb2YgY3liZXIgYXR0YWNrcyBhcmUgZG9uZSBhdCB0aGUgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGxldmVsLCBhIEdhcnRuZXIgR3JvdXAgc3R1ZHkgaGFzIHJldmVhbGVkLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBXZWIgYXBwbGljYXRpb25zIGFyZSBhY2Nlc3NpYmxlIDI0IGhvdXJzIGEgZGF5LCA3IGRheXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgYSB3ZWVrIGFuZCBjb250cm9sIHZhbHVhYmxlIGRhdGEgc3VjaCBhcyBjdXN0b21lciBpbmZvcm1hdGlvbiwgICAgICAgICAgICAgICAgICAgICAgICAgICAgdHJhbnNhY3Rpb24gaW5mb3JtYXRpb24gYW5kIGV2ZW4gcHJvcHJpZXRhcnkgY29ycG9yYXRlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGEuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bNTAwLDAwMCBjdXN0b21lciBjcmVkaXQgY2FyZCBudW1iZXJzIG9idGFpbmVkIHZpYSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhIHdlYiBhdHRhY2s8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBXZWxsLWtub3duIHNpdGVzIHRoYXQgd2VyZSBvcGVuIHRvIHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGluY2x1ZGUgZmFzaGlvbiBsYWJlbCBHdWVzcyBhbmQgcGV0IHN1cHBseSByZXRhaWxlciAgICAgICAgICAgICAgICAgICAgICAgICAgICBQZXRDby5jb20gd2hvIHdlcmUgbm90b3Jpb3VzbHkgZm91bmQgdG8gYmUgdnVsbmVyYWJsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB0byB0aGUgU1FMIGluamVjdGlvbiB2dWxuZXJhYmlsaXR5IChKdW5lIDIwMDMpLiBUaGlzICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJlc3VsdGVkIGluIFBldENvIGxlYXZpbmcgYXMgbWFueSBhcyA1MDAsMDAwIGNyZWRpdCAgICAgICAgICAgICAgICAgICAgICAgICAgICBjYXJkIG51bWJlcnMgb3BlbiB0byBhbnlvbmUgYWJsZSB0byBjb25zdHJ1Y3QgdGhpcyBzcGVjaWFsbHktY3JhZnRlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBVUkwuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bRmlyZXdhbGxzLCBTU0wgYW5kIGxvY2tlZC1kb3duIHNlcnZlcnMgYXJlIGZ1dGlsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBoYWNraW5nPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQW55IGRlZmVuc2UgYXQgbmV0d29yayBzZWN1cml0eSBsZXZlbCB3aWxsIHByb3ZpZGUgbm8gICAgICAgICAgICAgICAgICAgICAgICAgICAgcHJvdGVjdGlvbiBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzIHNpbmNlIHRoZXkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXJlIGxhdW5jaGVkIG9uIHBvcnQgODAgLSB3aGljaCBoYXMgdG8gcmVtYWluIG9wZW4uICAgICAgICAgICAgICAgICAgICAgICAgICAgIEluIGFkZGl0aW9uLCB3ZWIgYXBwbGljYXRpb25zIChjdXN0b21lciBhcmVhcywgc2hvcHBpbmcgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FydHMgZXRjLikgYXJlIG9mdGVuIHRhaWxvci1tYWRlLCBpbnZhcmlhYmx5IHRlc3RlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBsZXNzIHRoYW4gb2ZmLXRoZS1zaGVsZiBzb2Z0d2FyZSBhbmQgYXJlIHRoZXJlZm9yZSBtb3JlICAgICAgICAgICAgICAgICAgICAgICAgICAgIHN1c2NlcHRpYmxlIHRvIGF0dGFjay48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bJnF1b3Q7Q29tcGFuaWVzIGhhdmUgaW1wbGVtZW50ZWQgbmV0d29yay1sZXZlbCBzZWN1cml0eSwgICAgICAgICAgICAgICAgICAgICAgICAgICAgaG93ZXZlciB0aGV5IGZhaWwgdG8gYXVkaXQgYW5kIHNlY3VyZSB0aGVpciB3ZWIgYXBwbGljYXRpb25zLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBUaGVzZSBhcHBsaWNhdGlvbnMgaGF2ZSBhY2Nlc3MgdG8gc2Vuc2l0aXZlIGRhdGEgYW5kICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFyZSBhIGhhY2tlcidzIHByaW1lIHRhcmdldCwmcXVvdDsgc2FpZCBOaWNrIEdhbGVhLCAgICAgICAgICAgICAgICAgICAgICAgICAgICBDRU8gb2YgQWN1bmV0aXguICZxdW90O0F1ZGl0aW5nIG9uZSdzIHdlYiBhcHBzIHNob3VsZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBiZSB0aGUgbnVtYmVyIG9uZSBzZWN1cml0eSBjb25jZXJuLiZxdW90OzwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlRoZSBuZWVkIGZvciBhbiBhdXRvbWF0ZWQgd2ViIGFwcGxpY2F0aW9uIHZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgc2Nhbm5lcjwvc3Ryb25nPjxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIE1hbnVhbGx5IGF1ZGl0aW5nIGEgd2ViIGFwcGxpY2F0aW9uIGZvciB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdG8gU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiAgICAgICAgICAgICAgICAgICAgICAgICAgICBhdHRhY2tzIGlzIHZpcnR1YWxseSBpbXBvc3NpYmxlLiBXaXRoIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5ICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNjYW5uZXIgdGhlIHByb2Nlc3Mgb2YgYXVkaXRpbmcgd2ViIGFwcGxpY2F0aW9ucyBzdWNoICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFzIHNob3BwaW5nIGNhcnRzIGFuZCBmb3JtcywgY2FuIGJlIGVhc2lseSBhdXRvbWF0ZWQuICAgICAgICAgICAgICAgICAgICAgICAgICAgIFdoYXQncyBtb3JlLCB0aGUgc2VjdXJpdHkgY2hlY2tzIGNhbiBlYXNpbHkgYmUgcmUtbGF1bmNoZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGVhY2ggYXBwbGljYXRpb24gdXBkYXRlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkhvdyBBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIHdvcmtzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGZpcnN0IGNyYXdscyB0aGUgd2hvbGUgd2Vic2l0ZSwgYW5hbHl6ZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgaW4tZGVwdGggZWFjaCBmaWxlIGl0IGZpbmRzLCBhbmQgZGlzcGxheXMgdGhlIGVudGlyZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB3ZWJzaXRlIHN0cnVjdHVyZS4gQWZ0ZXIgdGhpcyBkaXNjb3Zlcnkgc3RhZ2UsIGl0IHBlcmZvcm1zICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFuIGF1dG9tYXRpYyBhdWRpdCBmb3IgY29tbW9uIHNlY3VyaXR5IHZ1bG5lcmFiaWxpdGllcy48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BdXRvbWF0aWNhbGx5IGRldGVjdHMgU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiB2dWxuZXJhYmlsaXRpZXM8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBTUUwgaW5qZWN0aW9uIGlzIGEgaGFja2luZyB0ZWNobmlxdWUgd2hpY2ggbW9kaWZpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgU1FMIGNvbW1hbmRzIGluIG9yZGVyIHRvIGdhaW4gYWNjZXNzIHRvIGRhdGEgaW4gdGhlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGFiYXNlLiBDcm9zcyBzaXRlIHNjcmlwdGluZyBhdHRhY2tzIGFsbG93IGEgaGFja2VyICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRvIGV4ZWN1dGUgYSBtYWxpY2lvdXMgc2NyaXB0IG9uIHlvdXIgdmlzaXRvcnMnIGJyb3dzZXIuICAgICAgICAgICAgICAgICAgICAgICAgICAgIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgY2FuIGNoZWNrIGlmIHlvdXIgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGlzIHZ1bG5lcmFibGUgdG8gYm90aCBvZiB0aGVzZSBhdHRhY2tzLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBNb3JlIGluZm9ybWF0aW9uIGFib3V0IGNyb3NzIHNpdGUgc2NyaXB0aW5nICZhbXA7IFNRTCAgICAgICAgICAgICAgICAgICAgICAgICAgICBpbmplY3Rpb24gYXQgb3VyIHdlYnNpdGUgc2VjdXJpdHkgaW5mbyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgYWxzbyBjaGVja3MgZm9yICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRoZSBmb2xsb3dpbmcgd2ViIGF0dGFja3M6PC9zdHJvbmc%2bPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDx1bD4gPGxpPkNSTEYgaW5qZWN0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5Db2RlIGV4ZWN1dGlvbiBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRGlyZWN0b3J5IHRyYXZlcnNhbCBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRmlsZSBpbmNsdXNpb24gYXR0YWNrczxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvbGk%2bPGxpPiBJbnB1dCB2YWxpZGF0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5BdXRoZW50aWNhdGlvbiBhdHRhY2tzLjwvbGk%2bIDwvdWw%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BZHZhbmNlZCBwZW5ldHJhdGlvbiB0ZXN0aW5nIHRvb2xzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGFsc28gaW5jbHVkZXMgdG9vbHMgc3VjaCBhcyBhbiBIVFRQIGVkaXRvciAgICAgICAgICAgICAgICAgICAgICAgICAgICAmYW1wOyBIVFRQIHNuaWZmZXIgdG8gYWxsb3cgY3VzdG9taXphdGlvbiBvZiB3ZWIgdnVsbmVyYWJpbGl0eSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjaGVja3MuIFVzaW5nIHRoZSBWdWxuZXJhYmlsaXR5IGVkaXRvciwgbmV3IGF0dGFja3MgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FuIGVhc2lseSBiZSBjcmVhdGVkLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlByaWNpbmcgJmFtcDsgYXZhaWxhYmlsaXR5PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGlzIGF2YWlsYWJsZSBhcyBhbiBlbnRlcnByaXNlIG9yIGFzIGEgY29uc3VsdGFudCAgICAgICAgICAgICAgICAgICAgICAgICAgICB2ZXJzaW9uLiBBIHN1YnNjcmlwdGlvbiBiYXNlZCBsaWNlbnNlIGNhbiBiZSBwdXJjaGFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGFzIGxpdHRsZSBhcyAkMzk1LCB3aGVyZWFzIGEgcGVycGV0dWFsIGxpY2Vuc2Ugc3RhcnRzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGF0ICQyOTk1LiBGb3IgbW9yZSBpbmZvcm1hdGlvbiB2aXNpdCBvdXIgcHJpY2luZyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFib3V0IEFjdW5ldGl4PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggd2FzIGZvdW5kZWQgdG8gY29tYmF0IHRoZSBhbGFybWluZyByaXNlIGluICAgICAgICAgICAgICAgICAgICAgICAgICAgIHdlYiBhdHRhY2tzLiBJdHMgZmxhZ3NoaXAgcHJvZHVjdCwgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgU2Nhbm5lciwgaXMgdGhlIHJlc3VsdCBvZiBzZXZlcmFsIHllYXJzIG9mIGRldmVsb3BtZW50ICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJ5IGEgdGVhbSBvZiBoaWdobHkgZXhwZXJpZW5jZWQgc2VjdXJpdHkgZGV2ZWxvcGVycy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggaXMgYSBwcml2YXRlbHkgaGVsZCBjb21wYW55IHdpdGggaGVhZHF1YXJ0ZXJzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJhc2VkIGluIEV1cm9wZSAoTWFsdGEpIHdpdGggaXRzIE5ldyBZb3JrIFVTIG9mZmljZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY2hlZHVsZWQgdG8gb3BlbiBpbiBRMyBvZiAyMDA1LiA8L3A%2bIGQCCQ8PFgIeC05hdmlnYXRlVXJsBRJDb21tZW50cy5hc3B4P2lkPTJkZAILDxYCHgNzcmNkZGS78tg0yYdYIrm%2b7bJhr2ToTj/BEA%3d%3d]]></Request> | |
| 2703 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2704 | Date: Thu, 14 Nov 2013 14:26:43 GMT | |
| 2705 | Server: Microsoft-IIS/6.0 | |
| 2706 | X-Powered-By: ASP.NET | |
| 2707 | X-AspNet-Version: 2.0.50727 | |
| 2708 | Cache-Control: private | |
| 2709 | Content-Type: text/html; charset=utf-8 | |
| 2710 | Content-Length: 29235 | |
| 2711 | ]]></Response> | |
| 2712 | </TechnicalDetails> | |
| 2713 | <References></References> | |
| 2714 | </ReportItem> | |
| 2715 | ||
| 2716 | <ReportItem id="34" color="green"> | |
| 2717 | <Name><![CDATA[GHDB: Typical login page]]></Name> | |
| 2718 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 2719 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">inurl:login.asp</font></pre>]]></Details> | |
| 2720 | <Affects><![CDATA[/login.aspx (2be6e0f4b01a065da1815689302d0b54)]]></Affects> | |
| 2721 | <Parameter><![CDATA[]]></Parameter> | |
| 2722 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2723 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2724 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2725 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2726 | <Severity><![CDATA[info]]></Severity> | |
| 2727 | <Type><![CDATA[Informational]]></Type> | |
| 2728 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 2729 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Pages containing login portals</font><br/><br/>This is a typical login page. It has recently become a target for SQL injection. Comsec's article at http://www.governmentsecurity.org/articles/SQLinjectionBasicTutorial.php brought this to my attention.<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 2730 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2731 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 2732 | <TechnicalDetails> | |
| 2733 | <Request><![CDATA[POST /login.aspx?ReturnUrl=/logout.aspx HTTP/1.1 | |
| 2734 | Pragma: no-cache | |
| 2735 | Cache-Control: no-cache | |
| 2736 | Referer: http://testaspnet.vulnweb.com/login.aspx | |
| 2737 | Content-Length: 1161 | |
| 2738 | Content-Type: application/x-www-form-urlencoded | |
| 2739 | Acunetix-Aspect: enabled | |
| 2740 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2741 | Acunetix-Aspect-Queries: aspectalerts | |
| 2742 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2743 | Host: testaspnet.vulnweb.com | |
| 2744 | Connection: Keep-alive | |
| 2745 | Accept-Encoding: gzip,deflate | |
| 2746 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2747 | Accept: */* | |
| 2748 | ||
| 2749 | btnLogin=Login&cbPersistCookie=on&tbPassword=g00dPa%24%24w0rD&tbUsername=riqcjwfs&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></Request> | |
| 2750 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2751 | Date: Thu, 14 Nov 2013 14:26:44 GMT | |
| 2752 | Server: Microsoft-IIS/6.0 | |
| 2753 | X-Powered-By: ASP.NET | |
| 2754 | X-AspNet-Version: 2.0.50727 | |
| 2755 | Cache-Control: private | |
| 2756 | Content-Type: text/html; charset=utf-8 | |
| 2757 | Content-Length: 12371 | |
| 2758 | ]]></Response> | |
| 2759 | </TechnicalDetails> | |
| 2760 | <References> | |
| 2761 | <Reference> | |
| 2762 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 2763 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 2764 | </Reference> | |
| 2765 | <Reference> | |
| 2766 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 2767 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 2768 | </Reference> | |
| 2769 | </References> | |
| 2770 | </ReportItem> | |
| 2771 | ||
| 2772 | <ReportItem id="35" color="green"> | |
| 2773 | <Name><![CDATA[GHDB: Typical login page]]></Name> | |
| 2774 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 2775 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">inurl:login.asp</font></pre>]]></Details> | |
| 2776 | <Affects><![CDATA[/login.aspx (81f0efe3f5d1c23f8cdff40bfe50b960)]]></Affects> | |
| 2777 | <Parameter><![CDATA[]]></Parameter> | |
| 2778 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2779 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2780 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2781 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2782 | <Severity><![CDATA[info]]></Severity> | |
| 2783 | <Type><![CDATA[Informational]]></Type> | |
| 2784 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 2785 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Pages containing login portals</font><br/><br/>This is a typical login page. It has recently become a target for SQL injection. Comsec's article at http://www.governmentsecurity.org/articles/SQLinjectionBasicTutorial.php brought this to my attention.<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 2786 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2787 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 2788 | <TechnicalDetails> | |
| 2789 | <Request><![CDATA[POST /login.aspx?ReturnUrl=/logout.aspx HTTP/1.1 | |
| 2790 | Pragma: no-cache | |
| 2791 | Cache-Control: no-cache | |
| 2792 | Referer: http://testaspnet.vulnweb.com/login.aspx | |
| 2793 | Content-Length: 1142 | |
| 2794 | Content-Type: application/x-www-form-urlencoded | |
| 2795 | Acunetix-Aspect: enabled | |
| 2796 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2797 | Acunetix-Aspect-Queries: aspectalerts | |
| 2798 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2799 | Host: testaspnet.vulnweb.com | |
| 2800 | Connection: Keep-alive | |
| 2801 | Accept-Encoding: gzip,deflate | |
| 2802 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2803 | Accept: */* | |
| 2804 | ||
| 2805 | btnLogin=Login&tbPassword=g00dPa%24%24w0rD&tbUsername=hjhhosnx&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></Request> | |
| 2806 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2807 | Date: Thu, 14 Nov 2013 14:26:44 GMT | |
| 2808 | Server: Microsoft-IIS/6.0 | |
| 2809 | X-Powered-By: ASP.NET | |
| 2810 | X-AspNet-Version: 2.0.50727 | |
| 2811 | Cache-Control: private | |
| 2812 | Content-Type: text/html; charset=utf-8 | |
| 2813 | Content-Length: 12353 | |
| 2814 | ]]></Response> | |
| 2815 | </TechnicalDetails> | |
| 2816 | <References> | |
| 2817 | <Reference> | |
| 2818 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 2819 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 2820 | </Reference> | |
| 2821 | <Reference> | |
| 2822 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 2823 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 2824 | </Reference> | |
| 2825 | </References> | |
| 2826 | </ReportItem> | |
| 2827 | ||
| 2828 | <ReportItem id="36" color="green"> | |
| 2829 | <Name><![CDATA[GHDB: Typical login page]]></Name> | |
| 2830 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 2831 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">inurl:login.asp</font></pre>]]></Details> | |
| 2832 | <Affects><![CDATA[/login.aspx (56d7c30dbfad941e90adb621920d0432)]]></Affects> | |
| 2833 | <Parameter><![CDATA[]]></Parameter> | |
| 2834 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2835 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2836 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2837 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2838 | <Severity><![CDATA[info]]></Severity> | |
| 2839 | <Type><![CDATA[Informational]]></Type> | |
| 2840 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 2841 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Pages containing login portals</font><br/><br/>This is a typical login page. It has recently become a target for SQL injection. Comsec's article at http://www.governmentsecurity.org/articles/SQLinjectionBasicTutorial.php brought this to my attention.<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 2842 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2843 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 2844 | <TechnicalDetails> | |
| 2845 | <Request><![CDATA[POST /login.aspx?ReturnUrl=/postnews.aspx HTTP/1.1 | |
| 2846 | Pragma: no-cache | |
| 2847 | Cache-Control: no-cache | |
| 2848 | Referer: http://testaspnet.vulnweb.com/login.aspx | |
| 2849 | Content-Length: 1142 | |
| 2850 | Content-Type: application/x-www-form-urlencoded | |
| 2851 | Acunetix-Aspect: enabled | |
| 2852 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2853 | Acunetix-Aspect-Queries: aspectalerts | |
| 2854 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2855 | Host: testaspnet.vulnweb.com | |
| 2856 | Connection: Keep-alive | |
| 2857 | Accept-Encoding: gzip,deflate | |
| 2858 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2859 | Accept: */* | |
| 2860 | ||
| 2861 | btnLogin=Login&tbPassword=g00dPa%24%24w0rD&tbUsername=vpustxlw&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></Request> | |
| 2862 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2863 | Date: Thu, 14 Nov 2013 14:26:44 GMT | |
| 2864 | Server: Microsoft-IIS/6.0 | |
| 2865 | X-Powered-By: ASP.NET | |
| 2866 | X-AspNet-Version: 2.0.50727 | |
| 2867 | Cache-Control: private | |
| 2868 | Content-Type: text/html; charset=utf-8 | |
| 2869 | Content-Length: 12355 | |
| 2870 | ]]></Response> | |
| 2871 | </TechnicalDetails> | |
| 2872 | <References> | |
| 2873 | <Reference> | |
| 2874 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 2875 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 2876 | </Reference> | |
| 2877 | <Reference> | |
| 2878 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 2879 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 2880 | </Reference> | |
| 2881 | </References> | |
| 2882 | </ReportItem> | |
| 2883 | ||
| 2884 | <ReportItem id="37" color="green"> | |
| 2885 | <Name><![CDATA[GHDB: Typical login page]]></Name> | |
| 2886 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 2887 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">inurl:login.asp</font></pre>]]></Details> | |
| 2888 | <Affects><![CDATA[/login.aspx (faf66eb1993c2a83f6af89ad50fbd4fd)]]></Affects> | |
| 2889 | <Parameter><![CDATA[]]></Parameter> | |
| 2890 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2891 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2892 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2893 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2894 | <Severity><![CDATA[info]]></Severity> | |
| 2895 | <Type><![CDATA[Informational]]></Type> | |
| 2896 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 2897 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Pages containing login portals</font><br/><br/>This is a typical login page. It has recently become a target for SQL injection. Comsec's article at http://www.governmentsecurity.org/articles/SQLinjectionBasicTutorial.php brought this to my attention.<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 2898 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2899 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 2900 | <TechnicalDetails> | |
| 2901 | <Request><![CDATA[POST /login.aspx?ReturnUrl=/postnews.aspx HTTP/1.1 | |
| 2902 | Pragma: no-cache | |
| 2903 | Cache-Control: no-cache | |
| 2904 | Referer: http://testaspnet.vulnweb.com/login.aspx | |
| 2905 | Content-Length: 1161 | |
| 2906 | Content-Type: application/x-www-form-urlencoded | |
| 2907 | Acunetix-Aspect: enabled | |
| 2908 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2909 | Acunetix-Aspect-Queries: aspectalerts | |
| 2910 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2911 | Host: testaspnet.vulnweb.com | |
| 2912 | Connection: Keep-alive | |
| 2913 | Accept-Encoding: gzip,deflate | |
| 2914 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2915 | Accept: */* | |
| 2916 | ||
| 2917 | btnLogin=Login&cbPersistCookie=on&tbPassword=g00dPa%24%24w0rD&tbUsername=usighdix&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></Request> | |
| 2918 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2919 | Date: Thu, 14 Nov 2013 14:26:44 GMT | |
| 2920 | Server: Microsoft-IIS/6.0 | |
| 2921 | X-Powered-By: ASP.NET | |
| 2922 | X-AspNet-Version: 2.0.50727 | |
| 2923 | Cache-Control: private | |
| 2924 | Content-Type: text/html; charset=utf-8 | |
| 2925 | Content-Length: 12373 | |
| 2926 | ]]></Response> | |
| 2927 | </TechnicalDetails> | |
| 2928 | <References> | |
| 2929 | <Reference> | |
| 2930 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 2931 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 2932 | </Reference> | |
| 2933 | <Reference> | |
| 2934 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 2935 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 2936 | </Reference> | |
| 2937 | </References> | |
| 2938 | </ReportItem> | |
| 2939 | ||
| 2940 | <ReportItem id="38" color="orange"> | |
| 2941 | <Name><![CDATA[User credentials are sent in clear text]]></Name> | |
| 2942 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 2943 | <Details><![CDATA[Form name: <font color="navy">frmLogin</font><br/>Form action: <font color="navy">http://testaspnet.vulnweb.com/login.aspx</font><br/>Form method: <font color="navy">POST</font><br/><br/>Form inputs:<br/><ul><li>__EVENTTARGET [Hidden]</li><li>__EVENTARGUMENT [Hidden]</li><li>__VIEWSTATE [Hidden]</li><li>__EVENTVALIDATION [Hidden]</li><li>tbUsername [Text]</li><li>tbPassword [Password]</li><li>cbPersistCookie [Checkbox]</li><li>btnLogin [Submit]</li></ul>]]></Details> | |
| 2944 | <Affects><![CDATA[/login.aspx]]></Affects> | |
| 2945 | <Parameter><![CDATA[]]></Parameter> | |
| 2946 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2947 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2948 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2949 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2950 | <Severity><![CDATA[medium]]></Severity> | |
| 2951 | <Type><![CDATA[Informational]]></Type> | |
| 2952 | <Impact><![CDATA[A third party may be able to read the user credentials by intercepting an unencrypted HTTP connection.]]></Impact> | |
| 2953 | <Description><![CDATA[User credentials are transmitted over an unencrypted channel. This information should always be transferred via an encrypted channel (HTTPS) to avoid being intercepted by malicious users.]]></Description> | |
| 2954 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 2955 | <Recommendation><![CDATA[Because user credentials are considered sensitive information, should always be transferred to the server over an encrypted connection (HTTPS).]]></Recommendation> | |
| 2956 | <TechnicalDetails> | |
| 2957 | <Request><![CDATA[GET /login.aspx HTTP/1.1 | |
| 2958 | Pragma: no-cache | |
| 2959 | Cache-Control: no-cache | |
| 2960 | Referer: http://testaspnet.vulnweb.com/ | |
| 2961 | Acunetix-Aspect: enabled | |
| 2962 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 2963 | Acunetix-Aspect-Queries: aspectalerts | |
| 2964 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 2965 | Host: testaspnet.vulnweb.com | |
| 2966 | Connection: Keep-alive | |
| 2967 | Accept-Encoding: gzip,deflate | |
| 2968 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 2969 | Accept: */* | |
| 2970 | ||
| 2971 | ]]></Request> | |
| 2972 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 2973 | Date: Thu, 14 Nov 2013 14:26:35 GMT | |
| 2974 | Server: Microsoft-IIS/6.0 | |
| 2975 | X-Powered-By: ASP.NET | |
| 2976 | X-AspNet-Version: 2.0.50727 | |
| 2977 | Cache-Control: private | |
| 2978 | Content-Type: text/html; charset=utf-8 | |
| 2979 | Content-Length: 12329 | |
| 2980 | ]]></Response> | |
| 2981 | </TechnicalDetails> | |
| 2982 | <References></References> | |
| 2983 | </ReportItem> | |
| 2984 | ||
| 2985 | <ReportItem id="39" color="green"> | |
| 2986 | <Name><![CDATA[GHDB: Typical login page]]></Name> | |
| 2987 | <ModuleName><![CDATA[GHDB]]></ModuleName> | |
| 2988 | <Details><![CDATA[We found <pre wrap="virtual"><font color="blue">inurl:login.asp</font></pre>]]></Details> | |
| 2989 | <Affects><![CDATA[/login.aspx (239d6b360bee5200c1daef0c8f58c779)]]></Affects> | |
| 2990 | <Parameter><![CDATA[]]></Parameter> | |
| 2991 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 2992 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 2993 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 2994 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 2995 | <Severity><![CDATA[info]]></Severity> | |
| 2996 | <Type><![CDATA[Informational]]></Type> | |
| 2997 | <Impact><![CDATA[Not available. Check description.]]></Impact> | |
| 2998 | <Description><![CDATA[ <div class="coolbox"><font color="dark">The description for this alert is contributed by the GHDB community, it may contain inappropriate language.</font></div><br/><font color="navy">Category : Pages containing login portals</font><br/><br/>This is a typical login page. It has recently become a target for SQL injection. Comsec's article at http://www.governmentsecurity.org/articles/SQLinjectionBasicTutorial.php brought this to my attention.<br/><br/>The Google Hacking Database (GHDB) appears courtesy of the Google Hacking community.]]></Description> | |
| 2999 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 3000 | <Recommendation><![CDATA[Not available. Check description.]]></Recommendation> | |
| 3001 | <TechnicalDetails> | |
| 3002 | <Request><![CDATA[POST /login.aspx HTTP/1.1 | |
| 3003 | Pragma: no-cache | |
| 3004 | Cache-Control: no-cache | |
| 3005 | Referer: http://testaspnet.vulnweb.com/login.aspx | |
| 3006 | Content-Length: 1160 | |
| 3007 | Content-Type: application/x-www-form-urlencoded | |
| 3008 | Acunetix-Aspect: enabled | |
| 3009 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 3010 | Acunetix-Aspect-Queries: aspectalerts | |
| 3011 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 3012 | Host: testaspnet.vulnweb.com | |
| 3013 | Connection: Keep-alive | |
| 3014 | Accept-Encoding: gzip,deflate | |
| 3015 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 3016 | Accept: */* | |
| 3017 | ||
| 3018 | btnLogin=Login&cbPersistCookie=e&tbPassword=g00dPa%24%24w0rD&tbUsername=xeitiyuu&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></Request> | |
| 3019 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 3020 | Date: Thu, 14 Nov 2013 14:26:59 GMT | |
| 3021 | Server: Microsoft-IIS/6.0 | |
| 3022 | X-Powered-By: ASP.NET | |
| 3023 | X-AspNet-Version: 2.0.50727 | |
| 3024 | Cache-Control: private | |
| 3025 | Content-Type: text/html; charset=utf-8 | |
| 3026 | Content-Length: 12346 | |
| 3027 | ]]></Response> | |
| 3028 | </TechnicalDetails> | |
| 3029 | <References> | |
| 3030 | <Reference> | |
| 3031 | <Database><![CDATA[The Google Hacking Database (GHDB) community]]></Database> | |
| 3032 | <URL><![CDATA[http://johnny.ihackstuff.com/]]></URL> | |
| 3033 | </Reference> | |
| 3034 | <Reference> | |
| 3035 | <Database><![CDATA[Acunetix Google hacking]]></Database> | |
| 3036 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/google-hacking.htm]]></URL> | |
| 3037 | </Reference> | |
| 3038 | </References> | |
| 3039 | </ReportItem> | |
| 3040 | ||
| 3041 | <ReportItem id="40" color="blue"> | |
| 3042 | <Name><![CDATA[Session Cookie without Secure flag set]]></Name> | |
| 3043 | <ModuleName><![CDATA[Crawler]]></ModuleName> | |
| 3044 | <Details><![CDATA[Cookie name: <font color="dark">"ASP.NET_SessionId"</font><br/>Cookie domain: <font color="dark">"testaspnet.vulnweb.com"</font><br/>]]></Details> | |
| 3045 | <Affects><![CDATA[/]]></Affects> | |
| 3046 | <Parameter><![CDATA[]]></Parameter> | |
| 3047 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 3048 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 3049 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 3050 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 3051 | <Severity><![CDATA[low]]></Severity> | |
| 3052 | <Type><![CDATA[Informational]]></Type> | |
| 3053 | <Impact><![CDATA[None]]></Impact> | |
| 3054 | <Description><![CDATA[This cookie does not have the Secure flag set. When a cookie is set with the Secure flag, it instructs the browser that the cookie can only be accessed over secure SSL channels. This is an important security protection for session cookies.]]></Description> | |
| 3055 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 3056 | <Recommendation><![CDATA[If possible, you should set the Secure flag for this cookie.]]></Recommendation> | |
| 3057 | <TechnicalDetails> | |
| 3058 | <Request><![CDATA[GET / HTTP/1.1 | |
| 3059 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 3060 | Host: testaspnet.vulnweb.com | |
| 3061 | Connection: Keep-alive | |
| 3062 | Accept-Encoding: gzip,deflate | |
| 3063 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 3064 | Accept: */* | |
| 3065 | ||
| 3066 | ]]></Request> | |
| 3067 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 3068 | Date: Thu, 14 Nov 2013 14:26:34 GMT | |
| 3069 | Server: Microsoft-IIS/6.0 | |
| 3070 | X-Powered-By: ASP.NET | |
| 3071 | X-AspNet-Version: 2.0.50727 | |
| 3072 | Cache-Control: private | |
| 3073 | Content-Type: text/html; charset=utf-8 | |
| 3074 | Content-Length: 12967 | |
| 3075 | ]]></Response> | |
| 3076 | </TechnicalDetails> | |
| 3077 | <References></References> | |
| 3078 | </ReportItem> | |
| 3079 | ||
| 3080 | <ReportItem id="41" color="red"> | |
| 3081 | <Name><![CDATA[SQL injection (verified)]]></Name> | |
| 3082 | <ModuleName><![CDATA[Scripting (Sql_Injection.script)]]></ModuleName> | |
| 3083 | <Details><![CDATA[URL encoded GET input <b><font color="dark">id</font></b> was set to <b><font color="dark">1ACUSTART'"JufNHACUEND</font></b>]]></Details> | |
| 3084 | <Affects><![CDATA[/comments.aspx]]></Affects> | |
| 3085 | <Parameter><![CDATA[id]]></Parameter> | |
| 3086 | <AOP_SourceFile><![CDATA[C:\Websites\AspNet\comments.aspx]]></AOP_SourceFile> | |
| 3087 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 3088 | <AOP_Additional><![CDATA[SQL query: SELECT NewsDate, NewsTitle, NewsShort, AuthorId, NewsId FROM news WHERE NewsId=1ACUSTART'"JufNHACUEND | |
| 3089 | ||
| 3090 | Stack trace: | |
| 3091 | Method: Void ReadData() | |
| 3092 | Method: Void OnLoad(System.EventArgs) | |
| 3093 | Method: Void LoadRecursive() | |
| 3094 | Method: Void ProcessRequestMain(Boolean, Boolean) | |
| 3095 | Method: Void ProcessRequest(Boolean, Boolean) | |
| 3096 | Method: Void ProcessRequest() | |
| 3097 | Method: Void ProcessRequest(System.Web.HttpContext) | |
| 3098 | Method: Void ProcessRequest(System.Web.HttpContext) | |
| 3099 | Method: Void System.Web.HttpApplication.IExecutionStep.Execute() | |
| 3100 | Method: System.Exception ExecuteStep(IExecutionStep, Boolean ByRef) | |
| 3101 | Method: Void ResumeSteps(System.Exception) | |
| 3102 | Method: System.IAsyncResult System.Web.IHttpAsyncHandler.BeginProcessRequest(System.Web.HttpContext, System.AsyncCallback, System.Object) | |
| 3103 | Method: Void ProcessRequestInternal(System.Web.HttpWorkerRequest) | |
| 3104 | Method: Void ProcessRequestNoDemand(System.Web.HttpWorkerRequest) | |
| 3105 | Method: Int32 ProcessRequest(IntPtr, Int32)]]></AOP_Additional> | |
| 3106 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 3107 | <Severity><![CDATA[high]]></Severity> | |
| 3108 | <Type><![CDATA[Validation]]></Type> | |
| 3109 | <Impact><![CDATA[An attacker may execute arbitrary SQL statements on the vulnerable system. This may compromise the integrity of your database and/or expose sensitive information. <br/><br/>Depending on the back-end database in use, SQL injection vulnerabilities lead to varying levels of data/system access for the attacker. It may be possible to not only manipulate existing queries, but to UNION in arbitrary data, use sub selects, or append additional queries. In some cases, it may be possible to read in or write out to files, or to execute shell commands on the underlying operating system.<br/><br/>Certain SQL Servers such as Microsoft SQL Server contain stored and extended procedures (database server functions). If an attacker can obtain access to these procedures it may be possible to compromise the entire machine.]]></Impact> | |
| 3110 | <Description><![CDATA[This script is possibly vulnerable to SQL Injection attacks.<br/><br/> | |
| 3111 | SQL injection is a vulnerability that allows an attacker to alter back-end SQL statements by manipulating the user input. An SQL injection occurs when web applications accept user input that is directly placed into a SQL statement and doesn't properly filter out dangerous characters. <br/> <br/> This is one of the most common application layer attacks currently being used on the Internet. Despite the fact that it is relatively easy to protect against, there is a large number of web applications vulnerable.]]></Description> | |
| 3112 | <DetailedInformation><![CDATA[<i>Quote from SQL Injection Attacks by Example - http://www.unixwiz.net/techtips/sql-injection.html</i> | |
| 3113 | <h2>SQL injection mitigations</h2> | |
| 3114 | ||
| 3115 | <p>We believe that web application developers often simply do not think about "surprise inputs", but security people do (including the bad guys), so there are three broad approaches that can be applied here.</p> | |
| 3116 | ||
| 3117 | <h2>Sanitize the input</h2> | |
| 3118 | <p>It's absolutely vital to sanitize user inputs to insure that they do not contain dangerous codes, whether to the SQL server or to HTML itself. One's first idea is to strip out "bad stuff", such as quotes or semicolons or escapes, but this is a misguided attempt. Though it's easy to point out some dangerous characters, it's harder to point to all of them.</p> | |
| 3119 | <p>The language of the web is full of special characters and strange markup (including alternate ways of representing the same characters), and efforts to authoritatively identify all "bad stuff" are unlikely to be successful.</p> | |
| 3120 | <p>Instead, rather than "remove known bad data", it's better to "remove everything but known good data": this distinction is crucial. Since - in our example - an email address can contain only these characters: </p> | |
| 3121 | <code><pre wrap="virtual"> | |
| 3122 | abcdefghijklmnopqrstuvwxyz | |
| 3123 | ABCDEFGHIJKLMNOPQRSTUVWXYZ | |
| 3124 | 0123456789 | |
| 3125 | @.-_+ | |
| 3126 | </pre></code> | |
| 3127 | ||
| 3128 | <p>There is really no benefit in allowing characters that could not be valid, and rejecting them early - presumably with an error message - not only helps forestall SQL Injection, but also catches mere typos early rather than stores them into the database. </p> | |
| 3129 | ||
| 3130 | <p>Be aware that "sanitizing the input" doesn't mean merely "remove the quotes", because even "regular" characters can be troublesome. In an example where an integer ID value is being compared against the user input (say, a numeric PIN): </p> | |
| 3131 | <code><pre wrap="virtual"> | |
| 3132 | SELECT fieldlist | |
| 3133 | FROM table | |
| 3134 | WHERE id = 23 OR 1=1; -- Boom! Always matches! | |
| 3135 | </pre></code> | |
| 3136 | <p>In practice, however, this approach is highly limited because there are so few fields for which it's possible to outright exclude many of the dangerous characters. For "dates" or "email addresses" or "integers" it may have merit, but for any kind of real application, one simply cannot avoid the other mitigations. </p> | |
| 3137 | ||
| 3138 | <h2>Escape/Quotesafe the input</h2> | |
| 3139 | <p>Even if one might be able to sanitize a phone number or email address, one cannot take this approach with a "name" field lest one wishes to exclude the likes of Bill O'Reilly from one's application: a quote is simply a valid character for this field.</p> | |
| 3140 | <p>One includes an actual single quote in an SQL string by putting two of them together, so this suggests the obvious - but wrong! - technique of preprocessing every string to replicate the single quotes:</p> | |
| 3141 | <code><pre wrap="virtual"> | |
| 3142 | SELECT fieldlist | |
| 3143 | FROM customers | |
| 3144 | WHERE name = 'Bill O''Reilly'; -- works OK | |
| 3145 | </pre></code> | |
| 3146 | <p>However, this naive approach can be beaten because most databases support other string escape mechanisms. MySQL, for instance, also permits \' to escape a quote, so after input of \'; DROP TABLE users; -- is "protected" by doubling the quotes, we get: </p> | |
| 3147 | <code><pre wrap="virtual"> | |
| 3148 | SELECT fieldlist | |
| 3149 | FROM customers | |
| 3150 | WHERE name = '\''; DROP TABLE users; --'; -- Boom! | |
| 3151 | </pre></code> | |
| 3152 | <p>The expression '\'' is a complete string (containing just one single quote), and the usual SQL shenanigans follow. It doesn't stop with backslashes either: there is Unicode, other encodings, and parsing oddities all hiding in the weeds to trip up the application designer.</p> | |
| 3153 | <p>Getting quotes right is notoriously difficult, which is why many database interface languages provide a function that does it for you. When the same internal code is used for "string quoting" and "string parsing", it's much more likely that the process will be done properly and safely.</p> | |
| 3154 | <p>Some examples are the MySQL function <b>mysql_real_escape_string()</b> and perl DBD method <b>$dbh->quote($value)</b>. These methods must be used. </p> | |
| 3155 | ||
| 3156 | <h2>Use bound parameters (the PREPARE statement)</h2> | |
| 3157 | <p>Though quotesafing is a good mechanism, we're still in the area of "considering user input as SQL", and a much better approach exists: bound parameters, which are supported by essentially all database programming interfaces. In this technique, an SQL statement string is created with placeholders - a question mark for each parameter - and it's compiled ("prepared", in SQL parlance) into an internal form. Later, this prepared query is "executed" with a list of parameters: </p> | |
| 3158 | ||
| 3159 | <b>Example in perl</b> | |
| 3160 | <code><pre wrap="virtual"> $sth = $dbh->prepare("SELECT email, userid FROM members WHERE email = ?;"); | |
| 3161 | $sth->execute($email); | |
| 3162 | </pre></code> | |
| 3163 | <p>Thanks to Stefan Wagner, this demonstrates bound parameters in Java: </p> | |
| 3164 | ||
| 3165 | <b>Insecure version</b> | |
| 3166 | <code><pre wrap="virtual"> Statement s = connection.createStatement(); | |
| 3167 | ResultSet rs = s.executeQuery("SELECT email FROM member WHERE name = " | |
| 3168 | + formField); // *boom* | |
| 3169 | </pre></code> | |
| 3170 | ||
| 3171 | <p><b>Secure version</b></p> | |
| 3172 | <code><pre wrap="virtual"> PreparedStatement ps = connection.prepareStatement( | |
| 3173 | "SELECT email FROM member WHERE name = ?"); | |
| 3174 | ps.setString(1, formField); | |
| 3175 | ResultSet rs = ps.executeQuery(); | |
| 3176 | </pre></code> | |
| 3177 | ||
| 3178 | <p>Here, $email is the data obtained from the user's form, and it is passed as positional parameter #1 (the first question mark), and at no point do the contents of this variable have anything to do with SQL statement parsing. Quotes, semicolons, backslashes, SQL comment notation - none of this has any impact, because it's "just data". There simply is nothing to subvert, so the application is be largely immune to SQL injection attacks.</p> | |
| 3179 | ||
| 3180 | <p>There also may be some performance benefits if this prepared query is reused multiple times (it only has to be parsed once), but this is minor compared to the enormous security benefits. This is probably the single most important step one can take to secure a web application. </p> | |
| 3181 | ||
| 3182 | <h2>Limit database permissions and segregate users</h2> | |
| 3183 | <p>In the case at hand, we observed just two interactions that are made not in the context of a logged-in user: "log in" and "send me password". The web application ought to use a database connection with the most limited rights possible: query-only access to the members table, and no access to any other table.</p> | |
| 3184 | <p>The effect here is that even a "successful" SQL injection attack is going to have much more limited success. Here, we'd not have been able to do the UPDATE request that ultimately granted us access, so we'd have had to resort to other avenues.</p> | |
| 3185 | <p>Once the web application determined that a set of valid credentials had been passed via the login form, it would then switch that session to a database connection with more rights.</p> | |
| 3186 | <p>It should go almost without saying that sa rights should never be used for any web-based application.</p> | |
| 3187 | ||
| 3188 | <h2>Use stored procedures for database access</h2> | |
| 3189 | <p>When the database server supports them, use stored procedures for performing access on the application's behalf, which can eliminate SQL entirely (assuming the stored procedures themselves are written properly). </p> | |
| 3190 | <p>By encapsulating the rules for a certain action - query, update, delete, etc. - into a single procedure, it can be tested and documented on a standalone basis and business rules enforced (for instance, the "add new order" procedure might reject that order if the customer were over his credit limit). </p> | |
| 3191 | <p>For simple queries this might be only a minor benefit, but as the operations become more complicated (or are used in more than one place), having a single definition for the operation means it's going to be more robust and easier to maintain. </p> | |
| 3192 | <p><i>Note: </i>it's always possible to write a stored procedure that itself constructs a query dynamically: this provides no protection against SQL Injection - it's only proper binding with prepare/execute or direct SQL statements with bound variables that provide this protection. </p> | |
| 3193 | ||
| 3194 | <h2>Isolate the webserver</h2> | |
| 3195 | <p>Even having taken all these mitigation steps, it's nevertheless still possible to miss something and leave the server open to compromise. One ought to design the network infrastructure to assume that the bad guy will have full administrator access to the machine, and then attempt to limit how that can be leveraged to compromise other things. </p> | |
| 3196 | <p>For instance, putting the machine in a DMZ with extremely limited pinholes "inside" the network means that even getting complete control of the webserver doesn't automatically grant full access to everything else. This won't stop everything, of course, but it makes it a lot harder. </p> | |
| 3197 | ||
| 3198 | <h2>Configure error reporting</h2> | |
| 3199 | <p>The default error reporting for some frameworks includes developer debugging information, and this cannot be shown to outside users. Imagine how much easier a time it makes for an attacker if the full query is shown, pointing to the syntax error involved. </p> | |
| 3200 | <p>This information is useful to developers, but it should be restricted - if possible - to just internal users. </p>]]></DetailedInformation> | |
| 3201 | <Recommendation><![CDATA[Your script should filter metacharacters from user input. <br/>Check detailed information for more information about fixing this vulnerability.]]></Recommendation> | |
| 3202 | <TechnicalDetails> | |
| 3203 | <Request><![CDATA[GET /comments.aspx?id=1ACUSTART'%22JufNHACUEND HTTP/1.1 | |
| 3204 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 3205 | Acunetix-Aspect: enabled | |
| 3206 | Referer: http://testaspnet.vulnweb.com:80/ | |
| 3207 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 3208 | Host: testaspnet.vulnweb.com | |
| 3209 | Connection: Keep-alive | |
| 3210 | Accept-Encoding: gzip,deflate | |
| 3211 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 3212 | Accept: */* | |
| 3213 | ||
| 3214 | ]]></Request> | |
| 3215 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 3216 | Date: Thu, 14 Nov 2013 14:27:02 GMT | |
| 3217 | Server: Microsoft-IIS/6.0 | |
| 3218 | X-Powered-By: ASP.NET | |
| 3219 | X-AspNet-Version: 2.0.50727 | |
| 3220 | Cache-Control: private | |
| 3221 | Content-Type: text/html; charset=utf-8 | |
| 3222 | Content-Length: 13233 | |
| 3223 | ]]></Response> | |
| 3224 | </TechnicalDetails> | |
| 3225 | <References> | |
| 3226 | <Reference> | |
| 3227 | <Database><![CDATA[Acunetix SQL Injection Attack]]></Database> | |
| 3228 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/sql-injection.htm]]></URL> | |
| 3229 | </Reference> | |
| 3230 | <Reference> | |
| 3231 | <Database><![CDATA[VIDEO: SQL Injection tutorial]]></Database> | |
| 3232 | <URL><![CDATA[http://www.acunetix.com/blog/web-security-zone/video-sql-injection-tutorial/]]></URL> | |
| 3233 | </Reference> | |
| 3234 | <Reference> | |
| 3235 | <Database><![CDATA[OWASP Injection Flaws]]></Database> | |
| 3236 | <URL><![CDATA[http://www.owasp.org/index.php/Injection_Flaws]]></URL> | |
| 3237 | </Reference> | |
| 3238 | <Reference> | |
| 3239 | <Database><![CDATA[How to check for SQL injection vulnerabilities]]></Database> | |
| 3240 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/sql-injection2/]]></URL> | |
| 3241 | </Reference> | |
| 3242 | <Reference> | |
| 3243 | <Database><![CDATA[SQL Injection Walkthrough]]></Database> | |
| 3244 | <URL><![CDATA[http://www.securiteam.com/securityreviews/5DP0N1P76E.html]]></URL> | |
| 3245 | </Reference> | |
| 3246 | <Reference> | |
| 3247 | <Database><![CDATA[OWASP PHP Top 5]]></Database> | |
| 3248 | <URL><![CDATA[http://www.owasp.org/index.php/PHP_Top_5]]></URL> | |
| 3249 | </Reference> | |
| 3250 | </References> | |
| 3251 | </ReportItem> | |
| 3252 | ||
| 3253 | <ReportItem id="42" color="red"> | |
| 3254 | <Name><![CDATA[Blind SQL Injection]]></Name> | |
| 3255 | <ModuleName><![CDATA[Scripting (Blind_Sql_Injection.script)]]></ModuleName> | |
| 3256 | <Details><![CDATA[URL encoded GET input <b><font color="dark">id</font></b> was set to <b><font color="dark">3/**/AND/**/382=382</font></b><br/><br/>Tests performed: <ul><li>0+0+0+3 => <b>TRUE</b></li><li>0+382*377+3 => <b>FALSE</b></li><li>13-5-2-999 => <b>FALSE</b></li><li>13-5-2-3 => <b>TRUE</b></li><li>13-2*5+0+0+1-1 => <b>TRUE</b></li><li>13-2*6+0+0+1-1 => <b>FALSE</b></li><li>3 AND 2+1-1-1=1 AND 382=382 => <b>TRUE</b></li><li>3 AND 3+1-1-1=1 AND 382=382 => <b>FALSE</b></li><li>3 AND 3*2<5 AND 382=382 => <b>FALSE</b></li><li>3 AND 3*2>5 AND 382=382 => <b>TRUE</b></li><li>3/**/AND/**/0=1/**/AND/**/382=382 => <b>FALSE</b></li><li>3/**/AND/**/382=382 => <b>TRUE</b></li></ul><br/> Original value: <b>3</b>]]></Details> | |
| 3257 | <Affects><![CDATA[/comments.aspx]]></Affects> | |
| 3258 | <Parameter><![CDATA[id]]></Parameter> | |
| 3259 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 3260 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 3261 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 3262 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 3263 | <Severity><![CDATA[high]]></Severity> | |
| 3264 | <Type><![CDATA[Validation]]></Type> | |
| 3265 | <Impact><![CDATA[An attacker may execute arbitrary SQL statements on the vulnerable system. This may compromise the integrity of your database and/or expose sensitive information. <br/><br/>Depending on the back-end database in use, SQL injection vulnerabilities lead to varying levels of data/system access for the attacker. It may be possible to not only manipulate existing queries, but to UNION in arbitrary data, use sub selects, or append additional queries. In some cases, it may be possible to read in or write out to files, or to execute shell commands on the underlying operating system.<br/><br/>Certain SQL Servers such as Microsoft SQL Server contain stored and extended procedures (database server functions). If an attacker can obtain access to these procedures it may be possible to compromise the entire machine.]]></Impact> | |
| 3266 | <Description><![CDATA[This script is possibly vulnerable to SQL Injection attacks.<br/><br/> | |
| 3267 | SQL injection is a vulnerability that allows an attacker to alter back-end SQL statements by manipulating the user input. An SQL injection occurs when web applications accept user input that is directly placed into a SQL statement and doesn't properly filter out dangerous characters. <br/> <br/> This is one of the most common application layer attacks currently being used on the Internet. Despite the fact that it is relatively easy to protect against, there is a large number of web applications vulnerable.]]></Description> | |
| 3268 | <DetailedInformation><![CDATA[<i>Quote from SQL Injection Attacks by Example - http://www.unixwiz.net/techtips/sql-injection.html</i> | |
| 3269 | <h2>SQL injection mitigations</h2> | |
| 3270 | ||
| 3271 | <p>We believe that web application developers often simply do not think about "surprise inputs", but security people do (including the bad guys), so there are three broad approaches that can be applied here.</p> | |
| 3272 | ||
| 3273 | <h2>Sanitize the input</h2> | |
| 3274 | <p>It's absolutely vital to sanitize user inputs to insure that they do not contain dangerous codes, whether to the SQL server or to HTML itself. One's first idea is to strip out "bad stuff", such as quotes or semicolons or escapes, but this is a misguided attempt. Though it's easy to point out some dangerous characters, it's harder to point to all of them.</p> | |
| 3275 | <p>The language of the web is full of special characters and strange markup (including alternate ways of representing the same characters), and efforts to authoritatively identify all "bad stuff" are unlikely to be successful.</p> | |
| 3276 | <p>Instead, rather than "remove known bad data", it's better to "remove everything but known good data": this distinction is crucial. Since - in our example - an email address can contain only these characters: </p> | |
| 3277 | <code><pre wrap="virtual"> | |
| 3278 | abcdefghijklmnopqrstuvwxyz | |
| 3279 | ABCDEFGHIJKLMNOPQRSTUVWXYZ | |
| 3280 | 0123456789 | |
| 3281 | @.-_+ | |
| 3282 | </pre></code> | |
| 3283 | ||
| 3284 | <p>There is really no benefit in allowing characters that could not be valid, and rejecting them early - presumably with an error message - not only helps forestall SQL Injection, but also catches mere typos early rather than stores them into the database. </p> | |
| 3285 | ||
| 3286 | <p>Be aware that "sanitizing the input" doesn't mean merely "remove the quotes", because even "regular" characters can be troublesome. In an example where an integer ID value is being compared against the user input (say, a numeric PIN): </p> | |
| 3287 | <code><pre wrap="virtual"> | |
| 3288 | SELECT fieldlist | |
| 3289 | FROM table | |
| 3290 | WHERE id = 23 OR 1=1; -- Boom! Always matches! | |
| 3291 | </pre></code> | |
| 3292 | <p>In practice, however, this approach is highly limited because there are so few fields for which it's possible to outright exclude many of the dangerous characters. For "dates" or "email addresses" or "integers" it may have merit, but for any kind of real application, one simply cannot avoid the other mitigations. </p> | |
| 3293 | ||
| 3294 | <h2>Escape/Quotesafe the input</h2> | |
| 3295 | <p>Even if one might be able to sanitize a phone number or email address, one cannot take this approach with a "name" field lest one wishes to exclude the likes of Bill O'Reilly from one's application: a quote is simply a valid character for this field.</p> | |
| 3296 | <p>One includes an actual single quote in an SQL string by putting two of them together, so this suggests the obvious - but wrong! - technique of preprocessing every string to replicate the single quotes:</p> | |
| 3297 | <code><pre wrap="virtual"> | |
| 3298 | SELECT fieldlist | |
| 3299 | FROM customers | |
| 3300 | WHERE name = 'Bill O''Reilly'; -- works OK | |
| 3301 | </pre></code> | |
| 3302 | <p>However, this naive approach can be beaten because most databases support other string escape mechanisms. MySQL, for instance, also permits \' to escape a quote, so after input of \'; DROP TABLE users; -- is "protected" by doubling the quotes, we get: </p> | |
| 3303 | <code><pre wrap="virtual"> | |
| 3304 | SELECT fieldlist | |
| 3305 | FROM customers | |
| 3306 | WHERE name = '\''; DROP TABLE users; --'; -- Boom! | |
| 3307 | </pre></code> | |
| 3308 | <p>The expression '\'' is a complete string (containing just one single quote), and the usual SQL shenanigans follow. It doesn't stop with backslashes either: there is Unicode, other encodings, and parsing oddities all hiding in the weeds to trip up the application designer.</p> | |
| 3309 | <p>Getting quotes right is notoriously difficult, which is why many database interface languages provide a function that does it for you. When the same internal code is used for "string quoting" and "string parsing", it's much more likely that the process will be done properly and safely.</p> | |
| 3310 | <p>Some examples are the MySQL function <b>mysql_real_escape_string()</b> and perl DBD method <b>$dbh->quote($value)</b>. These methods must be used. </p> | |
| 3311 | ||
| 3312 | <h2>Use bound parameters (the PREPARE statement)</h2> | |
| 3313 | <p>Though quotesafing is a good mechanism, we're still in the area of "considering user input as SQL", and a much better approach exists: bound parameters, which are supported by essentially all database programming interfaces. In this technique, an SQL statement string is created with placeholders - a question mark for each parameter - and it's compiled ("prepared", in SQL parlance) into an internal form. Later, this prepared query is "executed" with a list of parameters: </p> | |
| 3314 | ||
| 3315 | <b>Example in perl</b> | |
| 3316 | <code><pre wrap="virtual"> $sth = $dbh->prepare("SELECT email, userid FROM members WHERE email = ?;"); | |
| 3317 | $sth->execute($email); | |
| 3318 | </pre></code> | |
| 3319 | <p>Thanks to Stefan Wagner, this demonstrates bound parameters in Java: </p> | |
| 3320 | ||
| 3321 | <b>Insecure version</b> | |
| 3322 | <code><pre wrap="virtual"> Statement s = connection.createStatement(); | |
| 3323 | ResultSet rs = s.executeQuery("SELECT email FROM member WHERE name = " | |
| 3324 | + formField); // *boom* | |
| 3325 | </pre></code> | |
| 3326 | ||
| 3327 | <p><b>Secure version</b></p> | |
| 3328 | <code><pre wrap="virtual"> PreparedStatement ps = connection.prepareStatement( | |
| 3329 | "SELECT email FROM member WHERE name = ?"); | |
| 3330 | ps.setString(1, formField); | |
| 3331 | ResultSet rs = ps.executeQuery(); | |
| 3332 | </pre></code> | |
| 3333 | ||
| 3334 | <p>Here, $email is the data obtained from the user's form, and it is passed as positional parameter #1 (the first question mark), and at no point do the contents of this variable have anything to do with SQL statement parsing. Quotes, semicolons, backslashes, SQL comment notation - none of this has any impact, because it's "just data". There simply is nothing to subvert, so the application is be largely immune to SQL injection attacks.</p> | |
| 3335 | ||
| 3336 | <p>There also may be some performance benefits if this prepared query is reused multiple times (it only has to be parsed once), but this is minor compared to the enormous security benefits. This is probably the single most important step one can take to secure a web application. </p> | |
| 3337 | ||
| 3338 | <h2>Limit database permissions and segregate users</h2> | |
| 3339 | <p>In the case at hand, we observed just two interactions that are made not in the context of a logged-in user: "log in" and "send me password". The web application ought to use a database connection with the most limited rights possible: query-only access to the members table, and no access to any other table.</p> | |
| 3340 | <p>The effect here is that even a "successful" SQL injection attack is going to have much more limited success. Here, we'd not have been able to do the UPDATE request that ultimately granted us access, so we'd have had to resort to other avenues.</p> | |
| 3341 | <p>Once the web application determined that a set of valid credentials had been passed via the login form, it would then switch that session to a database connection with more rights.</p> | |
| 3342 | <p>It should go almost without saying that sa rights should never be used for any web-based application.</p> | |
| 3343 | ||
| 3344 | <h2>Use stored procedures for database access</h2> | |
| 3345 | <p>When the database server supports them, use stored procedures for performing access on the application's behalf, which can eliminate SQL entirely (assuming the stored procedures themselves are written properly). </p> | |
| 3346 | <p>By encapsulating the rules for a certain action - query, update, delete, etc. - into a single procedure, it can be tested and documented on a standalone basis and business rules enforced (for instance, the "add new order" procedure might reject that order if the customer were over his credit limit). </p> | |
| 3347 | <p>For simple queries this might be only a minor benefit, but as the operations become more complicated (or are used in more than one place), having a single definition for the operation means it's going to be more robust and easier to maintain. </p> | |
| 3348 | <p><i>Note: </i>it's always possible to write a stored procedure that itself constructs a query dynamically: this provides no protection against SQL Injection - it's only proper binding with prepare/execute or direct SQL statements with bound variables that provide this protection. </p> | |
| 3349 | ||
| 3350 | <h2>Isolate the webserver</h2> | |
| 3351 | <p>Even having taken all these mitigation steps, it's nevertheless still possible to miss something and leave the server open to compromise. One ought to design the network infrastructure to assume that the bad guy will have full administrator access to the machine, and then attempt to limit how that can be leveraged to compromise other things. </p> | |
| 3352 | <p>For instance, putting the machine in a DMZ with extremely limited pinholes "inside" the network means that even getting complete control of the webserver doesn't automatically grant full access to everything else. This won't stop everything, of course, but it makes it a lot harder. </p> | |
| 3353 | ||
| 3354 | <h2>Configure error reporting</h2> | |
| 3355 | <p>The default error reporting for some frameworks includes developer debugging information, and this cannot be shown to outside users. Imagine how much easier a time it makes for an attacker if the full query is shown, pointing to the syntax error involved. </p> | |
| 3356 | <p>This information is useful to developers, but it should be restricted - if possible - to just internal users. </p>]]></DetailedInformation> | |
| 3357 | <Recommendation><![CDATA[Your script should filter metacharacters from user input. <br/>Check detailed information for more information about fixing this vulnerability.]]></Recommendation> | |
| 3358 | <TechnicalDetails> | |
| 3359 | <Request><![CDATA[GET /comments.aspx?id=3/**/AND/**/382%3d382 HTTP/1.1 | |
| 3360 | X-Requested-With: XMLHttpRequest | |
| 3361 | Referer: http://testaspnet.vulnweb.com:80/ | |
| 3362 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 3363 | Host: testaspnet.vulnweb.com | |
| 3364 | Connection: Keep-alive | |
| 3365 | Accept-Encoding: gzip,deflate | |
| 3366 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 3367 | Accept: */* | |
| 3368 | ||
| 3369 | ]]></Request> | |
| 3370 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 3371 | Date: Thu, 14 Nov 2013 14:27:09 GMT | |
| 3372 | Server: Microsoft-IIS/6.0 | |
| 3373 | X-Powered-By: ASP.NET | |
| 3374 | X-AspNet-Version: 2.0.50727 | |
| 3375 | Cache-Control: private | |
| 3376 | Content-Type: text/html; charset=utf-8 | |
| 3377 | Content-Length: 22650 | |
| 3378 | ]]></Response> | |
| 3379 | </TechnicalDetails> | |
| 3380 | <References> | |
| 3381 | <Reference> | |
| 3382 | <Database><![CDATA[Acunetix SQL Injection Attack]]></Database> | |
| 3383 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/sql-injection.htm]]></URL> | |
| 3384 | </Reference> | |
| 3385 | <Reference> | |
| 3386 | <Database><![CDATA[VIDEO: SQL Injection tutorial]]></Database> | |
| 3387 | <URL><![CDATA[http://www.acunetix.com/blog/web-security-zone/video-sql-injection-tutorial/]]></URL> | |
| 3388 | </Reference> | |
| 3389 | <Reference> | |
| 3390 | <Database><![CDATA[OWASP Injection Flaws]]></Database> | |
| 3391 | <URL><![CDATA[http://www.owasp.org/index.php/Injection_Flaws]]></URL> | |
| 3392 | </Reference> | |
| 3393 | <Reference> | |
| 3394 | <Database><![CDATA[How to check for SQL injection vulnerabilities]]></Database> | |
| 3395 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/sql-injection2/]]></URL> | |
| 3396 | </Reference> | |
| 3397 | <Reference> | |
| 3398 | <Database><![CDATA[SQL Injection Walkthrough]]></Database> | |
| 3399 | <URL><![CDATA[http://www.securiteam.com/securityreviews/5DP0N1P76E.html]]></URL> | |
| 3400 | </Reference> | |
| 3401 | <Reference> | |
| 3402 | <Database><![CDATA[OWASP PHP Top 5]]></Database> | |
| 3403 | <URL><![CDATA[http://www.owasp.org/index.php/PHP_Top_5]]></URL> | |
| 3404 | </Reference> | |
| 3405 | </References> | |
| 3406 | </ReportItem> | |
| 3407 | ||
| 3408 | <ReportItem id="43" color="blue"> | |
| 3409 | <Name><![CDATA[Login page password-guessing attack]]></Name> | |
| 3410 | <ModuleName><![CDATA[Scripting (Html_Authentication_Audit.script)]]></ModuleName> | |
| 3411 | <Details><![CDATA[The scanner tested 10 invalid credentials and no account lockout was detected.]]></Details> | |
| 3412 | <Affects><![CDATA[/login.aspx]]></Affects> | |
| 3413 | <Parameter><![CDATA[]]></Parameter> | |
| 3414 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 3415 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 3416 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 3417 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 3418 | <Severity><![CDATA[low]]></Severity> | |
| 3419 | <Type><![CDATA[Validation]]></Type> | |
| 3420 | <Impact><![CDATA[An attacker may attempt to discover a weak password by systematically trying every possible combination of letters, numbers, and symbols until it discovers the one correct combination that works.]]></Impact> | |
| 3421 | <Description><![CDATA[A common threat web developers face is a password-guessing attack known as a brute force attack. A brute-force attack is an attempt to discover a password by systematically trying every possible combination of letters, numbers, and symbols until you discover the one correct combination that works. <br/><br/> | |
| 3422 | ||
| 3423 | This login page doesn't have any protection against password-guessing attacks (brute force attacks). It's recommended to implement some type of account lockout after a defined number of incorrect password attempts. Consult Web references for more information about fixing this problem. ]]></Description> | |
| 3424 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 3425 | <Recommendation><![CDATA[It's recommended to implement some type of account lockout after a defined number of incorrect password attempts. ]]></Recommendation> | |
| 3426 | <TechnicalDetails> | |
| 3427 | <Request><![CDATA[POST /login.aspx HTTP/1.1 | |
| 3428 | Content-Length: 1152 | |
| 3429 | Content-Type: application/x-www-form-urlencoded | |
| 3430 | Referer: http://testaspnet.vulnweb.com:80/ | |
| 3431 | Host: testaspnet.vulnweb.com | |
| 3432 | Connection: Keep-alive | |
| 3433 | Accept-Encoding: gzip,deflate | |
| 3434 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 3435 | Accept: */* | |
| 3436 | ||
| 3437 | btnLogin=Login&cbPersistCookie=e&tbPassword=SnfMQ6nv&tbUsername=s71nc2IH&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></Request> | |
| 3438 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 3439 | Date: Thu, 14 Nov 2013 14:27:42 GMT | |
| 3440 | Server: Microsoft-IIS/6.0 | |
| 3441 | X-Powered-By: ASP.NET | |
| 3442 | X-AspNet-Version: 2.0.50727 | |
| 3443 | Set-Cookie: ASP.NET_SessionId=ua4kaq55jbok4b45bo0lnw55; path=/; HttpOnly | |
| 3444 | Cache-Control: private | |
| 3445 | Content-Type: text/html; charset=utf-8 | |
| 3446 | Content-Length: 12346 | |
| 3447 | ]]></Response> | |
| 3448 | </TechnicalDetails> | |
| 3449 | <References> | |
| 3450 | <Reference> | |
| 3451 | <Database><![CDATA[Blocking Brute Force Attacks]]></Database> | |
| 3452 | <URL><![CDATA[http://www.owasp.org/index.php/Blocking_Brute_Force_Attacks]]></URL> | |
| 3453 | </Reference> | |
| 3454 | </References> | |
| 3455 | </ReportItem> | |
| 3456 | ||
| 3457 | <ReportItem id="44" color="red"> | |
| 3458 | <Name><![CDATA[Blind SQL Injection]]></Name> | |
| 3459 | <ModuleName><![CDATA[Scripting (Blind_Sql_Injection.script)]]></ModuleName> | |
| 3460 | <Details><![CDATA[URL encoded POST input <b><font color="dark">tbUsername</font></b> was set to <b><font color="dark">CeNM62R3'; waitfor delay '0:0:0' -- </font></b><br/><br/>Tests performed: <ul><li>DsQdToog'; waitfor delay '0:0:6' -- => <b>6.911 s</b></li><li>dnDk3cZE'; waitfor delay '0:0:3' -- => <b>3.728 s</b></li><li>822Z2llJ'; waitfor delay '0:0:9' -- => <b>9.734 s</b></li><li>z6HEOzaP'; waitfor delay '0:0:0' -- => <b>1.248 s</b></li><li>4RemiJv6'; waitfor delay '0:0:0' -- => <b>1.248 s</b></li><li>i7Mo5Sw8'; waitfor delay '0:0:0' -- => <b>0.718 s</b></li><li>WRV67kph'; waitfor delay '0:0:0' -- => <b>0.671 s</b></li><li>wdZzXouP'; waitfor delay '0:0:6' -- => <b>6.676 s</b></li><li>CeNM62R3'; waitfor delay '0:0:0' -- => <b>0.686 s</b></li></ul><br/> Original value: <b>kjhxcchf</b>]]></Details> | |
| 3461 | <Affects><![CDATA[/login.aspx]]></Affects> | |
| 3462 | <Parameter><![CDATA[tbUsername]]></Parameter> | |
| 3463 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 3464 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 3465 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 3466 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 3467 | <Severity><![CDATA[high]]></Severity> | |
| 3468 | <Type><![CDATA[Validation]]></Type> | |
| 3469 | <Impact><![CDATA[An attacker may execute arbitrary SQL statements on the vulnerable system. This may compromise the integrity of your database and/or expose sensitive information. <br/><br/>Depending on the back-end database in use, SQL injection vulnerabilities lead to varying levels of data/system access for the attacker. It may be possible to not only manipulate existing queries, but to UNION in arbitrary data, use sub selects, or append additional queries. In some cases, it may be possible to read in or write out to files, or to execute shell commands on the underlying operating system.<br/><br/>Certain SQL Servers such as Microsoft SQL Server contain stored and extended procedures (database server functions). If an attacker can obtain access to these procedures it may be possible to compromise the entire machine.]]></Impact> | |
| 3470 | <Description><![CDATA[This script is possibly vulnerable to SQL Injection attacks.<br/><br/> | |
| 3471 | SQL injection is a vulnerability that allows an attacker to alter back-end SQL statements by manipulating the user input. An SQL injection occurs when web applications accept user input that is directly placed into a SQL statement and doesn't properly filter out dangerous characters. <br/> <br/> This is one of the most common application layer attacks currently being used on the Internet. Despite the fact that it is relatively easy to protect against, there is a large number of web applications vulnerable.]]></Description> | |
| 3472 | <DetailedInformation><![CDATA[<i>Quote from SQL Injection Attacks by Example - http://www.unixwiz.net/techtips/sql-injection.html</i> | |
| 3473 | <h2>SQL injection mitigations</h2> | |
| 3474 | ||
| 3475 | <p>We believe that web application developers often simply do not think about "surprise inputs", but security people do (including the bad guys), so there are three broad approaches that can be applied here.</p> | |
| 3476 | ||
| 3477 | <h2>Sanitize the input</h2> | |
| 3478 | <p>It's absolutely vital to sanitize user inputs to insure that they do not contain dangerous codes, whether to the SQL server or to HTML itself. One's first idea is to strip out "bad stuff", such as quotes or semicolons or escapes, but this is a misguided attempt. Though it's easy to point out some dangerous characters, it's harder to point to all of them.</p> | |
| 3479 | <p>The language of the web is full of special characters and strange markup (including alternate ways of representing the same characters), and efforts to authoritatively identify all "bad stuff" are unlikely to be successful.</p> | |
| 3480 | <p>Instead, rather than "remove known bad data", it's better to "remove everything but known good data": this distinction is crucial. Since - in our example - an email address can contain only these characters: </p> | |
| 3481 | <code><pre wrap="virtual"> | |
| 3482 | abcdefghijklmnopqrstuvwxyz | |
| 3483 | ABCDEFGHIJKLMNOPQRSTUVWXYZ | |
| 3484 | 0123456789 | |
| 3485 | @.-_+ | |
| 3486 | </pre></code> | |
| 3487 | ||
| 3488 | <p>There is really no benefit in allowing characters that could not be valid, and rejecting them early - presumably with an error message - not only helps forestall SQL Injection, but also catches mere typos early rather than stores them into the database. </p> | |
| 3489 | ||
| 3490 | <p>Be aware that "sanitizing the input" doesn't mean merely "remove the quotes", because even "regular" characters can be troublesome. In an example where an integer ID value is being compared against the user input (say, a numeric PIN): </p> | |
| 3491 | <code><pre wrap="virtual"> | |
| 3492 | SELECT fieldlist | |
| 3493 | FROM table | |
| 3494 | WHERE id = 23 OR 1=1; -- Boom! Always matches! | |
| 3495 | </pre></code> | |
| 3496 | <p>In practice, however, this approach is highly limited because there are so few fields for which it's possible to outright exclude many of the dangerous characters. For "dates" or "email addresses" or "integers" it may have merit, but for any kind of real application, one simply cannot avoid the other mitigations. </p> | |
| 3497 | ||
| 3498 | <h2>Escape/Quotesafe the input</h2> | |
| 3499 | <p>Even if one might be able to sanitize a phone number or email address, one cannot take this approach with a "name" field lest one wishes to exclude the likes of Bill O'Reilly from one's application: a quote is simply a valid character for this field.</p> | |
| 3500 | <p>One includes an actual single quote in an SQL string by putting two of them together, so this suggests the obvious - but wrong! - technique of preprocessing every string to replicate the single quotes:</p> | |
| 3501 | <code><pre wrap="virtual"> | |
| 3502 | SELECT fieldlist | |
| 3503 | FROM customers | |
| 3504 | WHERE name = 'Bill O''Reilly'; -- works OK | |
| 3505 | </pre></code> | |
| 3506 | <p>However, this naive approach can be beaten because most databases support other string escape mechanisms. MySQL, for instance, also permits \' to escape a quote, so after input of \'; DROP TABLE users; -- is "protected" by doubling the quotes, we get: </p> | |
| 3507 | <code><pre wrap="virtual"> | |
| 3508 | SELECT fieldlist | |
| 3509 | FROM customers | |
| 3510 | WHERE name = '\''; DROP TABLE users; --'; -- Boom! | |
| 3511 | </pre></code> | |
| 3512 | <p>The expression '\'' is a complete string (containing just one single quote), and the usual SQL shenanigans follow. It doesn't stop with backslashes either: there is Unicode, other encodings, and parsing oddities all hiding in the weeds to trip up the application designer.</p> | |
| 3513 | <p>Getting quotes right is notoriously difficult, which is why many database interface languages provide a function that does it for you. When the same internal code is used for "string quoting" and "string parsing", it's much more likely that the process will be done properly and safely.</p> | |
| 3514 | <p>Some examples are the MySQL function <b>mysql_real_escape_string()</b> and perl DBD method <b>$dbh->quote($value)</b>. These methods must be used. </p> | |
| 3515 | ||
| 3516 | <h2>Use bound parameters (the PREPARE statement)</h2> | |
| 3517 | <p>Though quotesafing is a good mechanism, we're still in the area of "considering user input as SQL", and a much better approach exists: bound parameters, which are supported by essentially all database programming interfaces. In this technique, an SQL statement string is created with placeholders - a question mark for each parameter - and it's compiled ("prepared", in SQL parlance) into an internal form. Later, this prepared query is "executed" with a list of parameters: </p> | |
| 3518 | ||
| 3519 | <b>Example in perl</b> | |
| 3520 | <code><pre wrap="virtual"> $sth = $dbh->prepare("SELECT email, userid FROM members WHERE email = ?;"); | |
| 3521 | $sth->execute($email); | |
| 3522 | </pre></code> | |
| 3523 | <p>Thanks to Stefan Wagner, this demonstrates bound parameters in Java: </p> | |
| 3524 | ||
| 3525 | <b>Insecure version</b> | |
| 3526 | <code><pre wrap="virtual"> Statement s = connection.createStatement(); | |
| 3527 | ResultSet rs = s.executeQuery("SELECT email FROM member WHERE name = " | |
| 3528 | + formField); // *boom* | |
| 3529 | </pre></code> | |
| 3530 | ||
| 3531 | <p><b>Secure version</b></p> | |
| 3532 | <code><pre wrap="virtual"> PreparedStatement ps = connection.prepareStatement( | |
| 3533 | "SELECT email FROM member WHERE name = ?"); | |
| 3534 | ps.setString(1, formField); | |
| 3535 | ResultSet rs = ps.executeQuery(); | |
| 3536 | </pre></code> | |
| 3537 | ||
| 3538 | <p>Here, $email is the data obtained from the user's form, and it is passed as positional parameter #1 (the first question mark), and at no point do the contents of this variable have anything to do with SQL statement parsing. Quotes, semicolons, backslashes, SQL comment notation - none of this has any impact, because it's "just data". There simply is nothing to subvert, so the application is be largely immune to SQL injection attacks.</p> | |
| 3539 | ||
| 3540 | <p>There also may be some performance benefits if this prepared query is reused multiple times (it only has to be parsed once), but this is minor compared to the enormous security benefits. This is probably the single most important step one can take to secure a web application. </p> | |
| 3541 | ||
| 3542 | <h2>Limit database permissions and segregate users</h2> | |
| 3543 | <p>In the case at hand, we observed just two interactions that are made not in the context of a logged-in user: "log in" and "send me password". The web application ought to use a database connection with the most limited rights possible: query-only access to the members table, and no access to any other table.</p> | |
| 3544 | <p>The effect here is that even a "successful" SQL injection attack is going to have much more limited success. Here, we'd not have been able to do the UPDATE request that ultimately granted us access, so we'd have had to resort to other avenues.</p> | |
| 3545 | <p>Once the web application determined that a set of valid credentials had been passed via the login form, it would then switch that session to a database connection with more rights.</p> | |
| 3546 | <p>It should go almost without saying that sa rights should never be used for any web-based application.</p> | |
| 3547 | ||
| 3548 | <h2>Use stored procedures for database access</h2> | |
| 3549 | <p>When the database server supports them, use stored procedures for performing access on the application's behalf, which can eliminate SQL entirely (assuming the stored procedures themselves are written properly). </p> | |
| 3550 | <p>By encapsulating the rules for a certain action - query, update, delete, etc. - into a single procedure, it can be tested and documented on a standalone basis and business rules enforced (for instance, the "add new order" procedure might reject that order if the customer were over his credit limit). </p> | |
| 3551 | <p>For simple queries this might be only a minor benefit, but as the operations become more complicated (or are used in more than one place), having a single definition for the operation means it's going to be more robust and easier to maintain. </p> | |
| 3552 | <p><i>Note: </i>it's always possible to write a stored procedure that itself constructs a query dynamically: this provides no protection against SQL Injection - it's only proper binding with prepare/execute or direct SQL statements with bound variables that provide this protection. </p> | |
| 3553 | ||
| 3554 | <h2>Isolate the webserver</h2> | |
| 3555 | <p>Even having taken all these mitigation steps, it's nevertheless still possible to miss something and leave the server open to compromise. One ought to design the network infrastructure to assume that the bad guy will have full administrator access to the machine, and then attempt to limit how that can be leveraged to compromise other things. </p> | |
| 3556 | <p>For instance, putting the machine in a DMZ with extremely limited pinholes "inside" the network means that even getting complete control of the webserver doesn't automatically grant full access to everything else. This won't stop everything, of course, but it makes it a lot harder. </p> | |
| 3557 | ||
| 3558 | <h2>Configure error reporting</h2> | |
| 3559 | <p>The default error reporting for some frameworks includes developer debugging information, and this cannot be shown to outside users. Imagine how much easier a time it makes for an attacker if the full query is shown, pointing to the syntax error involved. </p> | |
| 3560 | <p>This information is useful to developers, but it should be restricted - if possible - to just internal users. </p>]]></DetailedInformation> | |
| 3561 | <Recommendation><![CDATA[Your script should filter metacharacters from user input. <br/>Check detailed information for more information about fixing this vulnerability.]]></Recommendation> | |
| 3562 | <TechnicalDetails> | |
| 3563 | <Request><![CDATA[POST /login.aspx HTTP/1.1 | |
| 3564 | Content-Length: 1199 | |
| 3565 | Content-Type: application/x-www-form-urlencoded | |
| 3566 | X-Requested-With: XMLHttpRequest | |
| 3567 | Referer: http://testaspnet.vulnweb.com:80/ | |
| 3568 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 3569 | Host: testaspnet.vulnweb.com | |
| 3570 | Connection: Keep-alive | |
| 3571 | Accept-Encoding: gzip,deflate | |
| 3572 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 3573 | Accept: */* | |
| 3574 | ||
| 3575 | btnLogin=Login&cbPersistCookie=on&tbPassword=g00dPa%24%24w0rD&tbUsername=CeNM62R3';%20waitfor%20delay%20'0:0:0'%20--%20&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></Request> | |
| 3576 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 3577 | Date: Thu, 14 Nov 2013 14:28:45 GMT | |
| 3578 | Server: Microsoft-IIS/6.0 | |
| 3579 | X-Powered-By: ASP.NET | |
| 3580 | X-AspNet-Version: 2.0.50727 | |
| 3581 | Cache-Control: private | |
| 3582 | Content-Type: text/html; charset=utf-8 | |
| 3583 | Content-Length: 12374 | |
| 3584 | ]]></Response> | |
| 3585 | </TechnicalDetails> | |
| 3586 | <References> | |
| 3587 | <Reference> | |
| 3588 | <Database><![CDATA[Acunetix SQL Injection Attack]]></Database> | |
| 3589 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/sql-injection.htm]]></URL> | |
| 3590 | </Reference> | |
| 3591 | <Reference> | |
| 3592 | <Database><![CDATA[VIDEO: SQL Injection tutorial]]></Database> | |
| 3593 | <URL><![CDATA[http://www.acunetix.com/blog/web-security-zone/video-sql-injection-tutorial/]]></URL> | |
| 3594 | </Reference> | |
| 3595 | <Reference> | |
| 3596 | <Database><![CDATA[OWASP Injection Flaws]]></Database> | |
| 3597 | <URL><![CDATA[http://www.owasp.org/index.php/Injection_Flaws]]></URL> | |
| 3598 | </Reference> | |
| 3599 | <Reference> | |
| 3600 | <Database><![CDATA[How to check for SQL injection vulnerabilities]]></Database> | |
| 3601 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/sql-injection2/]]></URL> | |
| 3602 | </Reference> | |
| 3603 | <Reference> | |
| 3604 | <Database><![CDATA[SQL Injection Walkthrough]]></Database> | |
| 3605 | <URL><![CDATA[http://www.securiteam.com/securityreviews/5DP0N1P76E.html]]></URL> | |
| 3606 | </Reference> | |
| 3607 | <Reference> | |
| 3608 | <Database><![CDATA[OWASP PHP Top 5]]></Database> | |
| 3609 | <URL><![CDATA[http://www.owasp.org/index.php/PHP_Top_5]]></URL> | |
| 3610 | </Reference> | |
| 3611 | </References> | |
| 3612 | </ReportItem> | |
| 3613 | ||
| 3614 | <ReportItem id="45" color="red"> | |
| 3615 | <Name><![CDATA[SQL injection (verified)]]></Name> | |
| 3616 | <ModuleName><![CDATA[Scripting (Sql_Injection.script)]]></ModuleName> | |
| 3617 | <Details><![CDATA[URL encoded POST input <b><font color="dark">tbUsername</font></b> was set to <b><font color="dark">1ACUSTART'"7SbaMACUEND</font></b>]]></Details> | |
| 3618 | <Affects><![CDATA[/login.aspx]]></Affects> | |
| 3619 | <Parameter><![CDATA[tbUsername]]></Parameter> | |
| 3620 | <AOP_SourceFile><![CDATA[C:\Websites\AspNet\login.aspx]]></AOP_SourceFile> | |
| 3621 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 3622 | <AOP_Additional><![CDATA[SQL query: SELECT uname, alevel FROM users WHERE uname='1ACUSTART'"7SbaMACUEND' AND upass='32cc5886dc1fa8c106a02056292c4654' | |
| 3623 | ||
| 3624 | Stack trace: | |
| 3625 | Method: Boolean Authenticate(System.String ByRef, System.String, Int32 ByRef) | |
| 3626 | Method: Void btnLogin_Click(System.Object, System.EventArgs) | |
| 3627 | Method: Void OnClick(System.EventArgs) | |
| 3628 | Method: Void RaisePostBackEvent(System.String) | |
| 3629 | Method: Void RaisePostBackEvent(System.Web.UI.IPostBackEventHandler, System.String) | |
| 3630 | Method: Void ProcessRequestMain(Boolean, Boolean) | |
| 3631 | Method: Void ProcessRequest(Boolean, Boolean) | |
| 3632 | Method: Void ProcessRequest() | |
| 3633 | Method: Void ProcessRequest(System.Web.HttpContext) | |
| 3634 | Method: Void ProcessRequest(System.Web.HttpContext) | |
| 3635 | Method: Void System.Web.HttpApplication.IExecutionStep.Execute() | |
| 3636 | Method: System.Exception ExecuteStep(IExecutionStep, Boolean ByRef) | |
| 3637 | Method: Void ResumeSteps(System.Exception) | |
| 3638 | Method: Void ResumeStepsFromThreadPoolThread(System.Exception) | |
| 3639 | Method: Void ResumeStepsWithAssert(System.Exception) | |
| 3640 | Method: Void OnAsyncEventCompletion(System.IAsyncResult) | |
| 3641 | Method: Void Complete(Boolean, System.Object, System.Exception, System.Web.RequestNotificationStatus) | |
| 3642 | Method: Void PollLockedSessionCallback(System.Object) | |
| 3643 | Method: Void runTryCode(System.Object) | |
| 3644 | Method: Void ExecuteCodeWithGuaranteedCleanup(TryCode, CleanupCode, System.Object) | |
| 3645 | Method: Void Run(System.Threading.ExecutionContext, System.Threading.ContextCallback, System.Object) | |
| 3646 | Method: Void PerformTimerCallback(System.Object)]]></AOP_Additional> | |
| 3647 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 3648 | <Severity><![CDATA[high]]></Severity> | |
| 3649 | <Type><![CDATA[Validation]]></Type> | |
| 3650 | <Impact><![CDATA[An attacker may execute arbitrary SQL statements on the vulnerable system. This may compromise the integrity of your database and/or expose sensitive information. <br/><br/>Depending on the back-end database in use, SQL injection vulnerabilities lead to varying levels of data/system access for the attacker. It may be possible to not only manipulate existing queries, but to UNION in arbitrary data, use sub selects, or append additional queries. In some cases, it may be possible to read in or write out to files, or to execute shell commands on the underlying operating system.<br/><br/>Certain SQL Servers such as Microsoft SQL Server contain stored and extended procedures (database server functions). If an attacker can obtain access to these procedures it may be possible to compromise the entire machine.]]></Impact> | |
| 3651 | <Description><![CDATA[This script is possibly vulnerable to SQL Injection attacks.<br/><br/> | |
| 3652 | SQL injection is a vulnerability that allows an attacker to alter back-end SQL statements by manipulating the user input. An SQL injection occurs when web applications accept user input that is directly placed into a SQL statement and doesn't properly filter out dangerous characters. <br/> <br/> This is one of the most common application layer attacks currently being used on the Internet. Despite the fact that it is relatively easy to protect against, there is a large number of web applications vulnerable.]]></Description> | |
| 3653 | <DetailedInformation><![CDATA[<i>Quote from SQL Injection Attacks by Example - http://www.unixwiz.net/techtips/sql-injection.html</i> | |
| 3654 | <h2>SQL injection mitigations</h2> | |
| 3655 | ||
| 3656 | <p>We believe that web application developers often simply do not think about "surprise inputs", but security people do (including the bad guys), so there are three broad approaches that can be applied here.</p> | |
| 3657 | ||
| 3658 | <h2>Sanitize the input</h2> | |
| 3659 | <p>It's absolutely vital to sanitize user inputs to insure that they do not contain dangerous codes, whether to the SQL server or to HTML itself. One's first idea is to strip out "bad stuff", such as quotes or semicolons or escapes, but this is a misguided attempt. Though it's easy to point out some dangerous characters, it's harder to point to all of them.</p> | |
| 3660 | <p>The language of the web is full of special characters and strange markup (including alternate ways of representing the same characters), and efforts to authoritatively identify all "bad stuff" are unlikely to be successful.</p> | |
| 3661 | <p>Instead, rather than "remove known bad data", it's better to "remove everything but known good data": this distinction is crucial. Since - in our example - an email address can contain only these characters: </p> | |
| 3662 | <code><pre wrap="virtual"> | |
| 3663 | abcdefghijklmnopqrstuvwxyz | |
| 3664 | ABCDEFGHIJKLMNOPQRSTUVWXYZ | |
| 3665 | 0123456789 | |
| 3666 | @.-_+ | |
| 3667 | </pre></code> | |
| 3668 | ||
| 3669 | <p>There is really no benefit in allowing characters that could not be valid, and rejecting them early - presumably with an error message - not only helps forestall SQL Injection, but also catches mere typos early rather than stores them into the database. </p> | |
| 3670 | ||
| 3671 | <p>Be aware that "sanitizing the input" doesn't mean merely "remove the quotes", because even "regular" characters can be troublesome. In an example where an integer ID value is being compared against the user input (say, a numeric PIN): </p> | |
| 3672 | <code><pre wrap="virtual"> | |
| 3673 | SELECT fieldlist | |
| 3674 | FROM table | |
| 3675 | WHERE id = 23 OR 1=1; -- Boom! Always matches! | |
| 3676 | </pre></code> | |
| 3677 | <p>In practice, however, this approach is highly limited because there are so few fields for which it's possible to outright exclude many of the dangerous characters. For "dates" or "email addresses" or "integers" it may have merit, but for any kind of real application, one simply cannot avoid the other mitigations. </p> | |
| 3678 | ||
| 3679 | <h2>Escape/Quotesafe the input</h2> | |
| 3680 | <p>Even if one might be able to sanitize a phone number or email address, one cannot take this approach with a "name" field lest one wishes to exclude the likes of Bill O'Reilly from one's application: a quote is simply a valid character for this field.</p> | |
| 3681 | <p>One includes an actual single quote in an SQL string by putting two of them together, so this suggests the obvious - but wrong! - technique of preprocessing every string to replicate the single quotes:</p> | |
| 3682 | <code><pre wrap="virtual"> | |
| 3683 | SELECT fieldlist | |
| 3684 | FROM customers | |
| 3685 | WHERE name = 'Bill O''Reilly'; -- works OK | |
| 3686 | </pre></code> | |
| 3687 | <p>However, this naive approach can be beaten because most databases support other string escape mechanisms. MySQL, for instance, also permits \' to escape a quote, so after input of \'; DROP TABLE users; -- is "protected" by doubling the quotes, we get: </p> | |
| 3688 | <code><pre wrap="virtual"> | |
| 3689 | SELECT fieldlist | |
| 3690 | FROM customers | |
| 3691 | WHERE name = '\''; DROP TABLE users; --'; -- Boom! | |
| 3692 | </pre></code> | |
| 3693 | <p>The expression '\'' is a complete string (containing just one single quote), and the usual SQL shenanigans follow. It doesn't stop with backslashes either: there is Unicode, other encodings, and parsing oddities all hiding in the weeds to trip up the application designer.</p> | |
| 3694 | <p>Getting quotes right is notoriously difficult, which is why many database interface languages provide a function that does it for you. When the same internal code is used for "string quoting" and "string parsing", it's much more likely that the process will be done properly and safely.</p> | |
| 3695 | <p>Some examples are the MySQL function <b>mysql_real_escape_string()</b> and perl DBD method <b>$dbh->quote($value)</b>. These methods must be used. </p> | |
| 3696 | ||
| 3697 | <h2>Use bound parameters (the PREPARE statement)</h2> | |
| 3698 | <p>Though quotesafing is a good mechanism, we're still in the area of "considering user input as SQL", and a much better approach exists: bound parameters, which are supported by essentially all database programming interfaces. In this technique, an SQL statement string is created with placeholders - a question mark for each parameter - and it's compiled ("prepared", in SQL parlance) into an internal form. Later, this prepared query is "executed" with a list of parameters: </p> | |
| 3699 | ||
| 3700 | <b>Example in perl</b> | |
| 3701 | <code><pre wrap="virtual"> $sth = $dbh->prepare("SELECT email, userid FROM members WHERE email = ?;"); | |
| 3702 | $sth->execute($email); | |
| 3703 | </pre></code> | |
| 3704 | <p>Thanks to Stefan Wagner, this demonstrates bound parameters in Java: </p> | |
| 3705 | ||
| 3706 | <b>Insecure version</b> | |
| 3707 | <code><pre wrap="virtual"> Statement s = connection.createStatement(); | |
| 3708 | ResultSet rs = s.executeQuery("SELECT email FROM member WHERE name = " | |
| 3709 | + formField); // *boom* | |
| 3710 | </pre></code> | |
| 3711 | ||
| 3712 | <p><b>Secure version</b></p> | |
| 3713 | <code><pre wrap="virtual"> PreparedStatement ps = connection.prepareStatement( | |
| 3714 | "SELECT email FROM member WHERE name = ?"); | |
| 3715 | ps.setString(1, formField); | |
| 3716 | ResultSet rs = ps.executeQuery(); | |
| 3717 | </pre></code> | |
| 3718 | ||
| 3719 | <p>Here, $email is the data obtained from the user's form, and it is passed as positional parameter #1 (the first question mark), and at no point do the contents of this variable have anything to do with SQL statement parsing. Quotes, semicolons, backslashes, SQL comment notation - none of this has any impact, because it's "just data". There simply is nothing to subvert, so the application is be largely immune to SQL injection attacks.</p> | |
| 3720 | ||
| 3721 | <p>There also may be some performance benefits if this prepared query is reused multiple times (it only has to be parsed once), but this is minor compared to the enormous security benefits. This is probably the single most important step one can take to secure a web application. </p> | |
| 3722 | ||
| 3723 | <h2>Limit database permissions and segregate users</h2> | |
| 3724 | <p>In the case at hand, we observed just two interactions that are made not in the context of a logged-in user: "log in" and "send me password". The web application ought to use a database connection with the most limited rights possible: query-only access to the members table, and no access to any other table.</p> | |
| 3725 | <p>The effect here is that even a "successful" SQL injection attack is going to have much more limited success. Here, we'd not have been able to do the UPDATE request that ultimately granted us access, so we'd have had to resort to other avenues.</p> | |
| 3726 | <p>Once the web application determined that a set of valid credentials had been passed via the login form, it would then switch that session to a database connection with more rights.</p> | |
| 3727 | <p>It should go almost without saying that sa rights should never be used for any web-based application.</p> | |
| 3728 | ||
| 3729 | <h2>Use stored procedures for database access</h2> | |
| 3730 | <p>When the database server supports them, use stored procedures for performing access on the application's behalf, which can eliminate SQL entirely (assuming the stored procedures themselves are written properly). </p> | |
| 3731 | <p>By encapsulating the rules for a certain action - query, update, delete, etc. - into a single procedure, it can be tested and documented on a standalone basis and business rules enforced (for instance, the "add new order" procedure might reject that order if the customer were over his credit limit). </p> | |
| 3732 | <p>For simple queries this might be only a minor benefit, but as the operations become more complicated (or are used in more than one place), having a single definition for the operation means it's going to be more robust and easier to maintain. </p> | |
| 3733 | <p><i>Note: </i>it's always possible to write a stored procedure that itself constructs a query dynamically: this provides no protection against SQL Injection - it's only proper binding with prepare/execute or direct SQL statements with bound variables that provide this protection. </p> | |
| 3734 | ||
| 3735 | <h2>Isolate the webserver</h2> | |
| 3736 | <p>Even having taken all these mitigation steps, it's nevertheless still possible to miss something and leave the server open to compromise. One ought to design the network infrastructure to assume that the bad guy will have full administrator access to the machine, and then attempt to limit how that can be leveraged to compromise other things. </p> | |
| 3737 | <p>For instance, putting the machine in a DMZ with extremely limited pinholes "inside" the network means that even getting complete control of the webserver doesn't automatically grant full access to everything else. This won't stop everything, of course, but it makes it a lot harder. </p> | |
| 3738 | ||
| 3739 | <h2>Configure error reporting</h2> | |
| 3740 | <p>The default error reporting for some frameworks includes developer debugging information, and this cannot be shown to outside users. Imagine how much easier a time it makes for an attacker if the full query is shown, pointing to the syntax error involved. </p> | |
| 3741 | <p>This information is useful to developers, but it should be restricted - if possible - to just internal users. </p>]]></DetailedInformation> | |
| 3742 | <Recommendation><![CDATA[Your script should filter metacharacters from user input. <br/>Check detailed information for more information about fixing this vulnerability.]]></Recommendation> | |
| 3743 | <TechnicalDetails> | |
| 3744 | <Request><![CDATA[POST /login.aspx HTTP/1.1 | |
| 3745 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 3746 | Acunetix-Aspect: enabled | |
| 3747 | Content-Length: 1177 | |
| 3748 | Content-Type: application/x-www-form-urlencoded | |
| 3749 | Referer: http://testaspnet.vulnweb.com:80/ | |
| 3750 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 3751 | Host: testaspnet.vulnweb.com | |
| 3752 | Connection: Keep-alive | |
| 3753 | Accept-Encoding: gzip,deflate | |
| 3754 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 3755 | Accept: */* | |
| 3756 | ||
| 3757 | btnLogin=Login&cbPersistCookie=on&tbPassword=g00dPa%24%24w0rD&tbUsername=1ACUSTART'%227SbaMACUEND&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></Request> | |
| 3758 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 3759 | Date: Thu, 14 Nov 2013 14:28:46 GMT | |
| 3760 | Server: Microsoft-IIS/6.0 | |
| 3761 | X-Powered-By: ASP.NET | |
| 3762 | X-AspNet-Version: 2.0.50727 | |
| 3763 | Cache-Control: private | |
| 3764 | Content-Type: text/html; charset=utf-8 | |
| 3765 | Content-Length: 12365 | |
| 3766 | ]]></Response> | |
| 3767 | </TechnicalDetails> | |
| 3768 | <References> | |
| 3769 | <Reference> | |
| 3770 | <Database><![CDATA[Acunetix SQL Injection Attack]]></Database> | |
| 3771 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/sql-injection.htm]]></URL> | |
| 3772 | </Reference> | |
| 3773 | <Reference> | |
| 3774 | <Database><![CDATA[VIDEO: SQL Injection tutorial]]></Database> | |
| 3775 | <URL><![CDATA[http://www.acunetix.com/blog/web-security-zone/video-sql-injection-tutorial/]]></URL> | |
| 3776 | </Reference> | |
| 3777 | <Reference> | |
| 3778 | <Database><![CDATA[OWASP Injection Flaws]]></Database> | |
| 3779 | <URL><![CDATA[http://www.owasp.org/index.php/Injection_Flaws]]></URL> | |
| 3780 | </Reference> | |
| 3781 | <Reference> | |
| 3782 | <Database><![CDATA[How to check for SQL injection vulnerabilities]]></Database> | |
| 3783 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/sql-injection2/]]></URL> | |
| 3784 | </Reference> | |
| 3785 | <Reference> | |
| 3786 | <Database><![CDATA[SQL Injection Walkthrough]]></Database> | |
| 3787 | <URL><![CDATA[http://www.securiteam.com/securityreviews/5DP0N1P76E.html]]></URL> | |
| 3788 | </Reference> | |
| 3789 | <Reference> | |
| 3790 | <Database><![CDATA[OWASP PHP Top 5]]></Database> | |
| 3791 | <URL><![CDATA[http://www.owasp.org/index.php/PHP_Top_5]]></URL> | |
| 3792 | </Reference> | |
| 3793 | </References> | |
| 3794 | </ReportItem> | |
| 3795 | ||
| 3796 | <ReportItem id="46" color="blue"> | |
| 3797 | <Name><![CDATA[Login page password-guessing attack]]></Name> | |
| 3798 | <ModuleName><![CDATA[Scripting (Html_Authentication_Audit.script)]]></ModuleName> | |
| 3799 | <Details><![CDATA[The scanner tested 10 invalid credentials and no account lockout was detected.]]></Details> | |
| 3800 | <Affects><![CDATA[/signup.aspx]]></Affects> | |
| 3801 | <Parameter><![CDATA[]]></Parameter> | |
| 3802 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 3803 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 3804 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 3805 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 3806 | <Severity><![CDATA[low]]></Severity> | |
| 3807 | <Type><![CDATA[Validation]]></Type> | |
| 3808 | <Impact><![CDATA[An attacker may attempt to discover a weak password by systematically trying every possible combination of letters, numbers, and symbols until it discovers the one correct combination that works.]]></Impact> | |
| 3809 | <Description><![CDATA[A common threat web developers face is a password-guessing attack known as a brute force attack. A brute-force attack is an attempt to discover a password by systematically trying every possible combination of letters, numbers, and symbols until you discover the one correct combination that works. <br/><br/> | |
| 3810 | ||
| 3811 | This login page doesn't have any protection against password-guessing attacks (brute force attacks). It's recommended to implement some type of account lockout after a defined number of incorrect password attempts. Consult Web references for more information about fixing this problem. ]]></Description> | |
| 3812 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 3813 | <Recommendation><![CDATA[It's recommended to implement some type of account lockout after a defined number of incorrect password attempts. ]]></Recommendation> | |
| 3814 | <TechnicalDetails> | |
| 3815 | <Request><![CDATA[POST /signup.aspx HTTP/1.1 | |
| 3816 | Content-Length: 1060 | |
| 3817 | Content-Type: application/x-www-form-urlencoded | |
| 3818 | Referer: http://testaspnet.vulnweb.com:80/ | |
| 3819 | Host: testaspnet.vulnweb.com | |
| 3820 | Connection: Keep-alive | |
| 3821 | Accept-Encoding: gzip,deflate | |
| 3822 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 3823 | Accept: */* | |
| 3824 | ||
| 3825 | btnSignup=Sign%20me%20up&tbPassword=wIwclpQE&tbUsername=XRr9zg25&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWgKJ%2b8rsBQLStq24BwK3jsrkBALF97vxAQKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMe7zvcGDW1XEmT%2bKc/cai9hiHVyk%3d&__VIEWSTATE=/wEPDwUKLTY0MzI4NjU4Mw9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkZHEZ3VN6SP/C2xESDN/Y3p8zhfSB]]></Request> | |
| 3826 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 3827 | Date: Thu, 14 Nov 2013 14:29:02 GMT | |
| 3828 | Server: Microsoft-IIS/6.0 | |
| 3829 | X-Powered-By: ASP.NET | |
| 3830 | X-AspNet-Version: 2.0.50727 | |
| 3831 | Set-Cookie: ASP.NET_SessionId=tbbbkxq40eiyvn45c0scehya; path=/; HttpOnly | |
| 3832 | Cache-Control: private | |
| 3833 | Content-Type: text/html; charset=utf-8 | |
| 3834 | Content-Length: 12242 | |
| 3835 | ]]></Response> | |
| 3836 | </TechnicalDetails> | |
| 3837 | <References> | |
| 3838 | <Reference> | |
| 3839 | <Database><![CDATA[Blocking Brute Force Attacks]]></Database> | |
| 3840 | <URL><![CDATA[http://www.owasp.org/index.php/Blocking_Brute_Force_Attacks]]></URL> | |
| 3841 | </Reference> | |
| 3842 | </References> | |
| 3843 | </ReportItem> | |
| 3844 | ||
| 3845 | <ReportItem id="47" color="red"> | |
| 3846 | <Name><![CDATA[SQL injection (verified)]]></Name> | |
| 3847 | <ModuleName><![CDATA[Scripting (Sql_Injection.script)]]></ModuleName> | |
| 3848 | <Details><![CDATA[URL encoded GET input <b><font color="dark">id</font></b> was set to <b><font color="dark">1ACUSTART'"tR4ngACUEND</font></b>]]></Details> | |
| 3849 | <Affects><![CDATA[/readnews.aspx]]></Affects> | |
| 3850 | <Parameter><![CDATA[id]]></Parameter> | |
| 3851 | <AOP_SourceFile><![CDATA[C:\Websites\AspNet\readnews.aspx]]></AOP_SourceFile> | |
| 3852 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 3853 | <AOP_Additional><![CDATA[SQL query: SELECT NewsDate, NewsTitle, NewsLong, AuthorId FROM news WHERE NewsId=1ACUSTART'"tR4ngACUEND | |
| 3854 | ||
| 3855 | Stack trace: | |
| 3856 | Method: Void Page_Load(System.Object, System.EventArgs) | |
| 3857 | Method: Void OnLoad(System.EventArgs) | |
| 3858 | Method: Void LoadRecursive() | |
| 3859 | Method: Void ProcessRequestMain(Boolean, Boolean) | |
| 3860 | Method: Void ProcessRequest(Boolean, Boolean) | |
| 3861 | Method: Void ProcessRequest() | |
| 3862 | Method: Void ProcessRequest(System.Web.HttpContext) | |
| 3863 | Method: Void ProcessRequest(System.Web.HttpContext) | |
| 3864 | Method: Void System.Web.HttpApplication.IExecutionStep.Execute() | |
| 3865 | Method: System.Exception ExecuteStep(IExecutionStep, Boolean ByRef) | |
| 3866 | Method: Void ResumeSteps(System.Exception) | |
| 3867 | Method: System.IAsyncResult System.Web.IHttpAsyncHandler.BeginProcessRequest(System.Web.HttpContext, System.AsyncCallback, System.Object) | |
| 3868 | Method: Void ProcessRequestInternal(System.Web.HttpWorkerRequest) | |
| 3869 | Method: Void ProcessRequestNoDemand(System.Web.HttpWorkerRequest) | |
| 3870 | Method: Int32 ProcessRequest(IntPtr, Int32)]]></AOP_Additional> | |
| 3871 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 3872 | <Severity><![CDATA[high]]></Severity> | |
| 3873 | <Type><![CDATA[Validation]]></Type> | |
| 3874 | <Impact><![CDATA[An attacker may execute arbitrary SQL statements on the vulnerable system. This may compromise the integrity of your database and/or expose sensitive information. <br/><br/>Depending on the back-end database in use, SQL injection vulnerabilities lead to varying levels of data/system access for the attacker. It may be possible to not only manipulate existing queries, but to UNION in arbitrary data, use sub selects, or append additional queries. In some cases, it may be possible to read in or write out to files, or to execute shell commands on the underlying operating system.<br/><br/>Certain SQL Servers such as Microsoft SQL Server contain stored and extended procedures (database server functions). If an attacker can obtain access to these procedures it may be possible to compromise the entire machine.]]></Impact> | |
| 3875 | <Description><![CDATA[This script is possibly vulnerable to SQL Injection attacks.<br/><br/> | |
| 3876 | SQL injection is a vulnerability that allows an attacker to alter back-end SQL statements by manipulating the user input. An SQL injection occurs when web applications accept user input that is directly placed into a SQL statement and doesn't properly filter out dangerous characters. <br/> <br/> This is one of the most common application layer attacks currently being used on the Internet. Despite the fact that it is relatively easy to protect against, there is a large number of web applications vulnerable.]]></Description> | |
| 3877 | <DetailedInformation><![CDATA[<i>Quote from SQL Injection Attacks by Example - http://www.unixwiz.net/techtips/sql-injection.html</i> | |
| 3878 | <h2>SQL injection mitigations</h2> | |
| 3879 | ||
| 3880 | <p>We believe that web application developers often simply do not think about "surprise inputs", but security people do (including the bad guys), so there are three broad approaches that can be applied here.</p> | |
| 3881 | ||
| 3882 | <h2>Sanitize the input</h2> | |
| 3883 | <p>It's absolutely vital to sanitize user inputs to insure that they do not contain dangerous codes, whether to the SQL server or to HTML itself. One's first idea is to strip out "bad stuff", such as quotes or semicolons or escapes, but this is a misguided attempt. Though it's easy to point out some dangerous characters, it's harder to point to all of them.</p> | |
| 3884 | <p>The language of the web is full of special characters and strange markup (including alternate ways of representing the same characters), and efforts to authoritatively identify all "bad stuff" are unlikely to be successful.</p> | |
| 3885 | <p>Instead, rather than "remove known bad data", it's better to "remove everything but known good data": this distinction is crucial. Since - in our example - an email address can contain only these characters: </p> | |
| 3886 | <code><pre wrap="virtual"> | |
| 3887 | abcdefghijklmnopqrstuvwxyz | |
| 3888 | ABCDEFGHIJKLMNOPQRSTUVWXYZ | |
| 3889 | 0123456789 | |
| 3890 | @.-_+ | |
| 3891 | </pre></code> | |
| 3892 | ||
| 3893 | <p>There is really no benefit in allowing characters that could not be valid, and rejecting them early - presumably with an error message - not only helps forestall SQL Injection, but also catches mere typos early rather than stores them into the database. </p> | |
| 3894 | ||
| 3895 | <p>Be aware that "sanitizing the input" doesn't mean merely "remove the quotes", because even "regular" characters can be troublesome. In an example where an integer ID value is being compared against the user input (say, a numeric PIN): </p> | |
| 3896 | <code><pre wrap="virtual"> | |
| 3897 | SELECT fieldlist | |
| 3898 | FROM table | |
| 3899 | WHERE id = 23 OR 1=1; -- Boom! Always matches! | |
| 3900 | </pre></code> | |
| 3901 | <p>In practice, however, this approach is highly limited because there are so few fields for which it's possible to outright exclude many of the dangerous characters. For "dates" or "email addresses" or "integers" it may have merit, but for any kind of real application, one simply cannot avoid the other mitigations. </p> | |
| 3902 | ||
| 3903 | <h2>Escape/Quotesafe the input</h2> | |
| 3904 | <p>Even if one might be able to sanitize a phone number or email address, one cannot take this approach with a "name" field lest one wishes to exclude the likes of Bill O'Reilly from one's application: a quote is simply a valid character for this field.</p> | |
| 3905 | <p>One includes an actual single quote in an SQL string by putting two of them together, so this suggests the obvious - but wrong! - technique of preprocessing every string to replicate the single quotes:</p> | |
| 3906 | <code><pre wrap="virtual"> | |
| 3907 | SELECT fieldlist | |
| 3908 | FROM customers | |
| 3909 | WHERE name = 'Bill O''Reilly'; -- works OK | |
| 3910 | </pre></code> | |
| 3911 | <p>However, this naive approach can be beaten because most databases support other string escape mechanisms. MySQL, for instance, also permits \' to escape a quote, so after input of \'; DROP TABLE users; -- is "protected" by doubling the quotes, we get: </p> | |
| 3912 | <code><pre wrap="virtual"> | |
| 3913 | SELECT fieldlist | |
| 3914 | FROM customers | |
| 3915 | WHERE name = '\''; DROP TABLE users; --'; -- Boom! | |
| 3916 | </pre></code> | |
| 3917 | <p>The expression '\'' is a complete string (containing just one single quote), and the usual SQL shenanigans follow. It doesn't stop with backslashes either: there is Unicode, other encodings, and parsing oddities all hiding in the weeds to trip up the application designer.</p> | |
| 3918 | <p>Getting quotes right is notoriously difficult, which is why many database interface languages provide a function that does it for you. When the same internal code is used for "string quoting" and "string parsing", it's much more likely that the process will be done properly and safely.</p> | |
| 3919 | <p>Some examples are the MySQL function <b>mysql_real_escape_string()</b> and perl DBD method <b>$dbh->quote($value)</b>. These methods must be used. </p> | |
| 3920 | ||
| 3921 | <h2>Use bound parameters (the PREPARE statement)</h2> | |
| 3922 | <p>Though quotesafing is a good mechanism, we're still in the area of "considering user input as SQL", and a much better approach exists: bound parameters, which are supported by essentially all database programming interfaces. In this technique, an SQL statement string is created with placeholders - a question mark for each parameter - and it's compiled ("prepared", in SQL parlance) into an internal form. Later, this prepared query is "executed" with a list of parameters: </p> | |
| 3923 | ||
| 3924 | <b>Example in perl</b> | |
| 3925 | <code><pre wrap="virtual"> $sth = $dbh->prepare("SELECT email, userid FROM members WHERE email = ?;"); | |
| 3926 | $sth->execute($email); | |
| 3927 | </pre></code> | |
| 3928 | <p>Thanks to Stefan Wagner, this demonstrates bound parameters in Java: </p> | |
| 3929 | ||
| 3930 | <b>Insecure version</b> | |
| 3931 | <code><pre wrap="virtual"> Statement s = connection.createStatement(); | |
| 3932 | ResultSet rs = s.executeQuery("SELECT email FROM member WHERE name = " | |
| 3933 | + formField); // *boom* | |
| 3934 | </pre></code> | |
| 3935 | ||
| 3936 | <p><b>Secure version</b></p> | |
| 3937 | <code><pre wrap="virtual"> PreparedStatement ps = connection.prepareStatement( | |
| 3938 | "SELECT email FROM member WHERE name = ?"); | |
| 3939 | ps.setString(1, formField); | |
| 3940 | ResultSet rs = ps.executeQuery(); | |
| 3941 | </pre></code> | |
| 3942 | ||
| 3943 | <p>Here, $email is the data obtained from the user's form, and it is passed as positional parameter #1 (the first question mark), and at no point do the contents of this variable have anything to do with SQL statement parsing. Quotes, semicolons, backslashes, SQL comment notation - none of this has any impact, because it's "just data". There simply is nothing to subvert, so the application is be largely immune to SQL injection attacks.</p> | |
| 3944 | ||
| 3945 | <p>There also may be some performance benefits if this prepared query is reused multiple times (it only has to be parsed once), but this is minor compared to the enormous security benefits. This is probably the single most important step one can take to secure a web application. </p> | |
| 3946 | ||
| 3947 | <h2>Limit database permissions and segregate users</h2> | |
| 3948 | <p>In the case at hand, we observed just two interactions that are made not in the context of a logged-in user: "log in" and "send me password". The web application ought to use a database connection with the most limited rights possible: query-only access to the members table, and no access to any other table.</p> | |
| 3949 | <p>The effect here is that even a "successful" SQL injection attack is going to have much more limited success. Here, we'd not have been able to do the UPDATE request that ultimately granted us access, so we'd have had to resort to other avenues.</p> | |
| 3950 | <p>Once the web application determined that a set of valid credentials had been passed via the login form, it would then switch that session to a database connection with more rights.</p> | |
| 3951 | <p>It should go almost without saying that sa rights should never be used for any web-based application.</p> | |
| 3952 | ||
| 3953 | <h2>Use stored procedures for database access</h2> | |
| 3954 | <p>When the database server supports them, use stored procedures for performing access on the application's behalf, which can eliminate SQL entirely (assuming the stored procedures themselves are written properly). </p> | |
| 3955 | <p>By encapsulating the rules for a certain action - query, update, delete, etc. - into a single procedure, it can be tested and documented on a standalone basis and business rules enforced (for instance, the "add new order" procedure might reject that order if the customer were over his credit limit). </p> | |
| 3956 | <p>For simple queries this might be only a minor benefit, but as the operations become more complicated (or are used in more than one place), having a single definition for the operation means it's going to be more robust and easier to maintain. </p> | |
| 3957 | <p><i>Note: </i>it's always possible to write a stored procedure that itself constructs a query dynamically: this provides no protection against SQL Injection - it's only proper binding with prepare/execute or direct SQL statements with bound variables that provide this protection. </p> | |
| 3958 | ||
| 3959 | <h2>Isolate the webserver</h2> | |
| 3960 | <p>Even having taken all these mitigation steps, it's nevertheless still possible to miss something and leave the server open to compromise. One ought to design the network infrastructure to assume that the bad guy will have full administrator access to the machine, and then attempt to limit how that can be leveraged to compromise other things. </p> | |
| 3961 | <p>For instance, putting the machine in a DMZ with extremely limited pinholes "inside" the network means that even getting complete control of the webserver doesn't automatically grant full access to everything else. This won't stop everything, of course, but it makes it a lot harder. </p> | |
| 3962 | ||
| 3963 | <h2>Configure error reporting</h2> | |
| 3964 | <p>The default error reporting for some frameworks includes developer debugging information, and this cannot be shown to outside users. Imagine how much easier a time it makes for an attacker if the full query is shown, pointing to the syntax error involved. </p> | |
| 3965 | <p>This information is useful to developers, but it should be restricted - if possible - to just internal users. </p>]]></DetailedInformation> | |
| 3966 | <Recommendation><![CDATA[Your script should filter metacharacters from user input. <br/>Check detailed information for more information about fixing this vulnerability.]]></Recommendation> | |
| 3967 | <TechnicalDetails> | |
| 3968 | <Request><![CDATA[POST /readnews.aspx?id=1ACUSTART'%22tR4ngACUEND&NewsAd=ads/def.html HTTP/1.1 | |
| 3969 | Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c | |
| 3970 | Acunetix-Aspect: enabled | |
| 3971 | Content-Length: 10791 | |
| 3972 | Content-Type: application/x-www-form-urlencoded | |
| 3973 | Referer: http://testaspnet.vulnweb.com:80/ | |
| 3974 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 3975 | Host: testaspnet.vulnweb.com | |
| 3976 | Connection: Keep-alive | |
| 3977 | Accept-Encoding: gzip,deflate | |
| 3978 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 3979 | Accept: */* | |
| 3980 | ||
| 3981 | __EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWVwKO/ffgDgKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMTuBuYk15KvnzAGnqqPk6tDbzR0Y%3d&__VIEWSTATE=/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc%2bYWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNToyMiBBTWQCBQ8WAh8BBTxXZWIgYXR0YWNrcyAtIGNhbiB5b3VyIHdlYiBhcHBsaWNhdGlvbnMgd2l0aHN0YW5kIHRoZSBmb3JjZT9kAgcPFgIfAQWuNzxwPjxzdHJvbmc%2bQWN1bmV0aXggY29tYmF0cyByaXNlIGluIHdlYiBhdHRhY2tzIHdpdGggQWN1bmV0aXggICAgICAgICAgICAgICAgICAgICAgICAgICAgV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAyIDwvc3Ryb25nPjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD4yMSBKdWx5IDIwMDUgLSA8c3Ryb25nPlN0YXJ0LXVwIGNvbXBhbnkgQWN1bmV0aXggcmVsZWFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lcjogYSB0b29sIHRvIGF1dG9tYXRpY2FsbHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXVkaXQgd2Vic2l0ZSBzZWN1cml0eS4gQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAgICAgICAgICAgICAgICAgICAgICAgICAgICAyIGNyYXdscyBhbiBlbnRpcmUgd2Vic2l0ZSwgbGF1bmNoZXMgcG9wdWxhciB3ZWIgYXR0YWNrcyAgICAgICAgICAgICAgICAgICAgICAgICAgICAoU1FMIEluamVjdGlvbiBldGMuKSBhbmQgaWRlbnRpZmllcyB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdGhhdCBuZWVkIHRvIGJlIGZpeGVkLjwvc3Ryb25nPiA8L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5TZWN1cmluZyB5b3VyIHdlYnNpdGUgc2hvdWxkIGJlIHlvdXIgbnVtYmVyIG9uZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjb25jZXJuPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgSGFja2VycyBhcmUgY29uY2VudHJhdGluZyB0aGVpciBlZmZvcnRzIG9uIHdlYi1iYXNlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBhcHBsaWNhdGlvbnMgLSA3NSUgb2YgY3liZXIgYXR0YWNrcyBhcmUgZG9uZSBhdCB0aGUgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGxldmVsLCBhIEdhcnRuZXIgR3JvdXAgc3R1ZHkgaGFzIHJldmVhbGVkLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBXZWIgYXBwbGljYXRpb25zIGFyZSBhY2Nlc3NpYmxlIDI0IGhvdXJzIGEgZGF5LCA3IGRheXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgYSB3ZWVrIGFuZCBjb250cm9sIHZhbHVhYmxlIGRhdGEgc3VjaCBhcyBjdXN0b21lciBpbmZvcm1hdGlvbiwgICAgICAgICAgICAgICAgICAgICAgICAgICAgdHJhbnNhY3Rpb24gaW5mb3JtYXRpb24gYW5kIGV2ZW4gcHJvcHJpZXRhcnkgY29ycG9yYXRlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGEuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bNTAwLDAwMCBjdXN0b21lciBjcmVkaXQgY2FyZCBudW1iZXJzIG9idGFpbmVkIHZpYSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhIHdlYiBhdHRhY2s8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBXZWxsLWtub3duIHNpdGVzIHRoYXQgd2VyZSBvcGVuIHRvIHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGluY2x1ZGUgZmFzaGlvbiBsYWJlbCBHdWVzcyBhbmQgcGV0IHN1cHBseSByZXRhaWxlciAgICAgICAgICAgICAgICAgICAgICAgICAgICBQZXRDby5jb20gd2hvIHdlcmUgbm90b3Jpb3VzbHkgZm91bmQgdG8gYmUgdnVsbmVyYWJsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB0byB0aGUgU1FMIGluamVjdGlvbiB2dWxuZXJhYmlsaXR5IChKdW5lIDIwMDMpLiBUaGlzICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJlc3VsdGVkIGluIFBldENvIGxlYXZpbmcgYXMgbWFueSBhcyA1MDAsMDAwIGNyZWRpdCAgICAgICAgICAgICAgICAgICAgICAgICAgICBjYXJkIG51bWJlcnMgb3BlbiB0byBhbnlvbmUgYWJsZSB0byBjb25zdHJ1Y3QgdGhpcyBzcGVjaWFsbHktY3JhZnRlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBVUkwuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bRmlyZXdhbGxzLCBTU0wgYW5kIGxvY2tlZC1kb3duIHNlcnZlcnMgYXJlIGZ1dGlsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBoYWNraW5nPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQW55IGRlZmVuc2UgYXQgbmV0d29yayBzZWN1cml0eSBsZXZlbCB3aWxsIHByb3ZpZGUgbm8gICAgICAgICAgICAgICAgICAgICAgICAgICAgcHJvdGVjdGlvbiBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzIHNpbmNlIHRoZXkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXJlIGxhdW5jaGVkIG9uIHBvcnQgODAgLSB3aGljaCBoYXMgdG8gcmVtYWluIG9wZW4uICAgICAgICAgICAgICAgICAgICAgICAgICAgIEluIGFkZGl0aW9uLCB3ZWIgYXBwbGljYXRpb25zIChjdXN0b21lciBhcmVhcywgc2hvcHBpbmcgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FydHMgZXRjLikgYXJlIG9mdGVuIHRhaWxvci1tYWRlLCBpbnZhcmlhYmx5IHRlc3RlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBsZXNzIHRoYW4gb2ZmLXRoZS1zaGVsZiBzb2Z0d2FyZSBhbmQgYXJlIHRoZXJlZm9yZSBtb3JlICAgICAgICAgICAgICAgICAgICAgICAgICAgIHN1c2NlcHRpYmxlIHRvIGF0dGFjay48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bJnF1b3Q7Q29tcGFuaWVzIGhhdmUgaW1wbGVtZW50ZWQgbmV0d29yay1sZXZlbCBzZWN1cml0eSwgICAgICAgICAgICAgICAgICAgICAgICAgICAgaG93ZXZlciB0aGV5IGZhaWwgdG8gYXVkaXQgYW5kIHNlY3VyZSB0aGVpciB3ZWIgYXBwbGljYXRpb25zLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBUaGVzZSBhcHBsaWNhdGlvbnMgaGF2ZSBhY2Nlc3MgdG8gc2Vuc2l0aXZlIGRhdGEgYW5kICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFyZSBhIGhhY2tlcidzIHByaW1lIHRhcmdldCwmcXVvdDsgc2FpZCBOaWNrIEdhbGVhLCAgICAgICAgICAgICAgICAgICAgICAgICAgICBDRU8gb2YgQWN1bmV0aXguICZxdW90O0F1ZGl0aW5nIG9uZSdzIHdlYiBhcHBzIHNob3VsZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBiZSB0aGUgbnVtYmVyIG9uZSBzZWN1cml0eSBjb25jZXJuLiZxdW90OzwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlRoZSBuZWVkIGZvciBhbiBhdXRvbWF0ZWQgd2ViIGFwcGxpY2F0aW9uIHZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgc2Nhbm5lcjwvc3Ryb25nPjxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIE1hbnVhbGx5IGF1ZGl0aW5nIGEgd2ViIGFwcGxpY2F0aW9uIGZvciB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdG8gU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiAgICAgICAgICAgICAgICAgICAgICAgICAgICBhdHRhY2tzIGlzIHZpcnR1YWxseSBpbXBvc3NpYmxlLiBXaXRoIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5ICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNjYW5uZXIgdGhlIHByb2Nlc3Mgb2YgYXVkaXRpbmcgd2ViIGFwcGxpY2F0aW9ucyBzdWNoICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFzIHNob3BwaW5nIGNhcnRzIGFuZCBmb3JtcywgY2FuIGJlIGVhc2lseSBhdXRvbWF0ZWQuICAgICAgICAgICAgICAgICAgICAgICAgICAgIFdoYXQncyBtb3JlLCB0aGUgc2VjdXJpdHkgY2hlY2tzIGNhbiBlYXNpbHkgYmUgcmUtbGF1bmNoZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGVhY2ggYXBwbGljYXRpb24gdXBkYXRlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkhvdyBBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIHdvcmtzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGZpcnN0IGNyYXdscyB0aGUgd2hvbGUgd2Vic2l0ZSwgYW5hbHl6ZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgaW4tZGVwdGggZWFjaCBmaWxlIGl0IGZpbmRzLCBhbmQgZGlzcGxheXMgdGhlIGVudGlyZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB3ZWJzaXRlIHN0cnVjdHVyZS4gQWZ0ZXIgdGhpcyBkaXNjb3Zlcnkgc3RhZ2UsIGl0IHBlcmZvcm1zICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFuIGF1dG9tYXRpYyBhdWRpdCBmb3IgY29tbW9uIHNlY3VyaXR5IHZ1bG5lcmFiaWxpdGllcy48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BdXRvbWF0aWNhbGx5IGRldGVjdHMgU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiB2dWxuZXJhYmlsaXRpZXM8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBTUUwgaW5qZWN0aW9uIGlzIGEgaGFja2luZyB0ZWNobmlxdWUgd2hpY2ggbW9kaWZpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgU1FMIGNvbW1hbmRzIGluIG9yZGVyIHRvIGdhaW4gYWNjZXNzIHRvIGRhdGEgaW4gdGhlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGFiYXNlLiBDcm9zcyBzaXRlIHNjcmlwdGluZyBhdHRhY2tzIGFsbG93IGEgaGFja2VyICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRvIGV4ZWN1dGUgYSBtYWxpY2lvdXMgc2NyaXB0IG9uIHlvdXIgdmlzaXRvcnMnIGJyb3dzZXIuICAgICAgICAgICAgICAgICAgICAgICAgICAgIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgY2FuIGNoZWNrIGlmIHlvdXIgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGlzIHZ1bG5lcmFibGUgdG8gYm90aCBvZiB0aGVzZSBhdHRhY2tzLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBNb3JlIGluZm9ybWF0aW9uIGFib3V0IGNyb3NzIHNpdGUgc2NyaXB0aW5nICZhbXA7IFNRTCAgICAgICAgICAgICAgICAgICAgICAgICAgICBpbmplY3Rpb24gYXQgb3VyIHdlYnNpdGUgc2VjdXJpdHkgaW5mbyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgYWxzbyBjaGVja3MgZm9yICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRoZSBmb2xsb3dpbmcgd2ViIGF0dGFja3M6PC9zdHJvbmc%2bPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDx1bD4gPGxpPkNSTEYgaW5qZWN0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5Db2RlIGV4ZWN1dGlvbiBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRGlyZWN0b3J5IHRyYXZlcnNhbCBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRmlsZSBpbmNsdXNpb24gYXR0YWNrczxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvbGk%2bPGxpPiBJbnB1dCB2YWxpZGF0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5BdXRoZW50aWNhdGlvbiBhdHRhY2tzLjwvbGk%2bIDwvdWw%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BZHZhbmNlZCBwZW5ldHJhdGlvbiB0ZXN0aW5nIHRvb2xzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGFsc28gaW5jbHVkZXMgdG9vbHMgc3VjaCBhcyBhbiBIVFRQIGVkaXRvciAgICAgICAgICAgICAgICAgICAgICAgICAgICAmYW1wOyBIVFRQIHNuaWZmZXIgdG8gYWxsb3cgY3VzdG9taXphdGlvbiBvZiB3ZWIgdnVsbmVyYWJpbGl0eSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjaGVja3MuIFVzaW5nIHRoZSBWdWxuZXJhYmlsaXR5IGVkaXRvciwgbmV3IGF0dGFja3MgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FuIGVhc2lseSBiZSBjcmVhdGVkLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlByaWNpbmcgJmFtcDsgYXZhaWxhYmlsaXR5PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGlzIGF2YWlsYWJsZSBhcyBhbiBlbnRlcnByaXNlIG9yIGFzIGEgY29uc3VsdGFudCAgICAgICAgICAgICAgICAgICAgICAgICAgICB2ZXJzaW9uLiBBIHN1YnNjcmlwdGlvbiBiYXNlZCBsaWNlbnNlIGNhbiBiZSBwdXJjaGFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGFzIGxpdHRsZSBhcyAkMzk1LCB3aGVyZWFzIGEgcGVycGV0dWFsIGxpY2Vuc2Ugc3RhcnRzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGF0ICQyOTk1LiBGb3IgbW9yZSBpbmZvcm1hdGlvbiB2aXNpdCBvdXIgcHJpY2luZyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFib3V0IEFjdW5ldGl4PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggd2FzIGZvdW5kZWQgdG8gY29tYmF0IHRoZSBhbGFybWluZyByaXNlIGluICAgICAgICAgICAgICAgICAgICAgICAgICAgIHdlYiBhdHRhY2tzLiBJdHMgZmxhZ3NoaXAgcHJvZHVjdCwgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgU2Nhbm5lciwgaXMgdGhlIHJlc3VsdCBvZiBzZXZlcmFsIHllYXJzIG9mIGRldmVsb3BtZW50ICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJ5IGEgdGVhbSBvZiBoaWdobHkgZXhwZXJpZW5jZWQgc2VjdXJpdHkgZGV2ZWxvcGVycy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggaXMgYSBwcml2YXRlbHkgaGVsZCBjb21wYW55IHdpdGggaGVhZHF1YXJ0ZXJzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJhc2VkIGluIEV1cm9wZSAoTWFsdGEpIHdpdGggaXRzIE5ldyBZb3JrIFVTIG9mZmljZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY2hlZHVsZWQgdG8gb3BlbiBpbiBRMyBvZiAyMDA1LiA8L3A%2bIGQCCQ8PFgIeC05hdmlnYXRlVXJsBRJDb21tZW50cy5hc3B4P2lkPTJkZAILDxYCHgNzcmMFDGFkcy9kZWYuaHRtbGRkNCSZh%2buMoCTcXGDfVu5D5CfxA7Y%3d]]></Request> | |
| 3982 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 3983 | Date: Thu, 14 Nov 2013 14:29:34 GMT | |
| 3984 | Server: Microsoft-IIS/6.0 | |
| 3985 | X-Powered-By: ASP.NET | |
| 3986 | X-AspNet-Version: 2.0.50727 | |
| 3987 | Cache-Control: private | |
| 3988 | Content-Type: text/html; charset=utf-8 | |
| 3989 | Content-Length: 29377 | |
| 3990 | ]]></Response> | |
| 3991 | </TechnicalDetails> | |
| 3992 | <References> | |
| 3993 | <Reference> | |
| 3994 | <Database><![CDATA[Acunetix SQL Injection Attack]]></Database> | |
| 3995 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/sql-injection.htm]]></URL> | |
| 3996 | </Reference> | |
| 3997 | <Reference> | |
| 3998 | <Database><![CDATA[VIDEO: SQL Injection tutorial]]></Database> | |
| 3999 | <URL><![CDATA[http://www.acunetix.com/blog/web-security-zone/video-sql-injection-tutorial/]]></URL> | |
| 4000 | </Reference> | |
| 4001 | <Reference> | |
| 4002 | <Database><![CDATA[OWASP Injection Flaws]]></Database> | |
| 4003 | <URL><![CDATA[http://www.owasp.org/index.php/Injection_Flaws]]></URL> | |
| 4004 | </Reference> | |
| 4005 | <Reference> | |
| 4006 | <Database><![CDATA[How to check for SQL injection vulnerabilities]]></Database> | |
| 4007 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/sql-injection2/]]></URL> | |
| 4008 | </Reference> | |
| 4009 | <Reference> | |
| 4010 | <Database><![CDATA[SQL Injection Walkthrough]]></Database> | |
| 4011 | <URL><![CDATA[http://www.securiteam.com/securityreviews/5DP0N1P76E.html]]></URL> | |
| 4012 | </Reference> | |
| 4013 | <Reference> | |
| 4014 | <Database><![CDATA[OWASP PHP Top 5]]></Database> | |
| 4015 | <URL><![CDATA[http://www.owasp.org/index.php/PHP_Top_5]]></URL> | |
| 4016 | </Reference> | |
| 4017 | </References> | |
| 4018 | </ReportItem> | |
| 4019 | ||
| 4020 | <ReportItem id="48" color="red"> | |
| 4021 | <Name><![CDATA[Blind SQL Injection]]></Name> | |
| 4022 | <ModuleName><![CDATA[Scripting (Blind_Sql_Injection.script)]]></ModuleName> | |
| 4023 | <Details><![CDATA[URL encoded GET input <b><font color="dark">id</font></b> was set to <b><font color="dark">-1; waitfor delay '0:0:0' -- </font></b><br/><br/>Tests performed: <ul><li>-1; waitfor delay '0:0:6' -- => <b>6.271 s</b></li><li>-1; waitfor delay '0:0:3' -- => <b>3.276 s</b></li><li>-1; waitfor delay '0:0:0' -- => <b>0.39 s</b></li><li>-1; waitfor delay '0:0:9' -- => <b>9.282 s</b></li><li>-1; waitfor delay '0:0:0' -- => <b>0.265 s</b></li><li>-1; waitfor delay '0:0:0' -- => <b>0.265 s</b></li><li>-1; waitfor delay '0:0:0' -- => <b>0.281 s</b></li><li>-1; waitfor delay '0:0:6' -- => <b>6.755 s</b></li><li>-1; waitfor delay '0:0:0' -- => <b>0.764 s</b></li></ul><br/> Original value: <b>2</b>]]></Details> | |
| 4024 | <Affects><![CDATA[/readnews.aspx]]></Affects> | |
| 4025 | <Parameter><![CDATA[id]]></Parameter> | |
| 4026 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 4027 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 4028 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 4029 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 4030 | <Severity><![CDATA[high]]></Severity> | |
| 4031 | <Type><![CDATA[Validation]]></Type> | |
| 4032 | <Impact><![CDATA[An attacker may execute arbitrary SQL statements on the vulnerable system. This may compromise the integrity of your database and/or expose sensitive information. <br/><br/>Depending on the back-end database in use, SQL injection vulnerabilities lead to varying levels of data/system access for the attacker. It may be possible to not only manipulate existing queries, but to UNION in arbitrary data, use sub selects, or append additional queries. In some cases, it may be possible to read in or write out to files, or to execute shell commands on the underlying operating system.<br/><br/>Certain SQL Servers such as Microsoft SQL Server contain stored and extended procedures (database server functions). If an attacker can obtain access to these procedures it may be possible to compromise the entire machine.]]></Impact> | |
| 4033 | <Description><![CDATA[This script is possibly vulnerable to SQL Injection attacks.<br/><br/> | |
| 4034 | SQL injection is a vulnerability that allows an attacker to alter back-end SQL statements by manipulating the user input. An SQL injection occurs when web applications accept user input that is directly placed into a SQL statement and doesn't properly filter out dangerous characters. <br/> <br/> This is one of the most common application layer attacks currently being used on the Internet. Despite the fact that it is relatively easy to protect against, there is a large number of web applications vulnerable.]]></Description> | |
| 4035 | <DetailedInformation><![CDATA[<i>Quote from SQL Injection Attacks by Example - http://www.unixwiz.net/techtips/sql-injection.html</i> | |
| 4036 | <h2>SQL injection mitigations</h2> | |
| 4037 | ||
| 4038 | <p>We believe that web application developers often simply do not think about "surprise inputs", but security people do (including the bad guys), so there are three broad approaches that can be applied here.</p> | |
| 4039 | ||
| 4040 | <h2>Sanitize the input</h2> | |
| 4041 | <p>It's absolutely vital to sanitize user inputs to insure that they do not contain dangerous codes, whether to the SQL server or to HTML itself. One's first idea is to strip out "bad stuff", such as quotes or semicolons or escapes, but this is a misguided attempt. Though it's easy to point out some dangerous characters, it's harder to point to all of them.</p> | |
| 4042 | <p>The language of the web is full of special characters and strange markup (including alternate ways of representing the same characters), and efforts to authoritatively identify all "bad stuff" are unlikely to be successful.</p> | |
| 4043 | <p>Instead, rather than "remove known bad data", it's better to "remove everything but known good data": this distinction is crucial. Since - in our example - an email address can contain only these characters: </p> | |
| 4044 | <code><pre wrap="virtual"> | |
| 4045 | abcdefghijklmnopqrstuvwxyz | |
| 4046 | ABCDEFGHIJKLMNOPQRSTUVWXYZ | |
| 4047 | 0123456789 | |
| 4048 | @.-_+ | |
| 4049 | </pre></code> | |
| 4050 | ||
| 4051 | <p>There is really no benefit in allowing characters that could not be valid, and rejecting them early - presumably with an error message - not only helps forestall SQL Injection, but also catches mere typos early rather than stores them into the database. </p> | |
| 4052 | ||
| 4053 | <p>Be aware that "sanitizing the input" doesn't mean merely "remove the quotes", because even "regular" characters can be troublesome. In an example where an integer ID value is being compared against the user input (say, a numeric PIN): </p> | |
| 4054 | <code><pre wrap="virtual"> | |
| 4055 | SELECT fieldlist | |
| 4056 | FROM table | |
| 4057 | WHERE id = 23 OR 1=1; -- Boom! Always matches! | |
| 4058 | </pre></code> | |
| 4059 | <p>In practice, however, this approach is highly limited because there are so few fields for which it's possible to outright exclude many of the dangerous characters. For "dates" or "email addresses" or "integers" it may have merit, but for any kind of real application, one simply cannot avoid the other mitigations. </p> | |
| 4060 | ||
| 4061 | <h2>Escape/Quotesafe the input</h2> | |
| 4062 | <p>Even if one might be able to sanitize a phone number or email address, one cannot take this approach with a "name" field lest one wishes to exclude the likes of Bill O'Reilly from one's application: a quote is simply a valid character for this field.</p> | |
| 4063 | <p>One includes an actual single quote in an SQL string by putting two of them together, so this suggests the obvious - but wrong! - technique of preprocessing every string to replicate the single quotes:</p> | |
| 4064 | <code><pre wrap="virtual"> | |
| 4065 | SELECT fieldlist | |
| 4066 | FROM customers | |
| 4067 | WHERE name = 'Bill O''Reilly'; -- works OK | |
| 4068 | </pre></code> | |
| 4069 | <p>However, this naive approach can be beaten because most databases support other string escape mechanisms. MySQL, for instance, also permits \' to escape a quote, so after input of \'; DROP TABLE users; -- is "protected" by doubling the quotes, we get: </p> | |
| 4070 | <code><pre wrap="virtual"> | |
| 4071 | SELECT fieldlist | |
| 4072 | FROM customers | |
| 4073 | WHERE name = '\''; DROP TABLE users; --'; -- Boom! | |
| 4074 | </pre></code> | |
| 4075 | <p>The expression '\'' is a complete string (containing just one single quote), and the usual SQL shenanigans follow. It doesn't stop with backslashes either: there is Unicode, other encodings, and parsing oddities all hiding in the weeds to trip up the application designer.</p> | |
| 4076 | <p>Getting quotes right is notoriously difficult, which is why many database interface languages provide a function that does it for you. When the same internal code is used for "string quoting" and "string parsing", it's much more likely that the process will be done properly and safely.</p> | |
| 4077 | <p>Some examples are the MySQL function <b>mysql_real_escape_string()</b> and perl DBD method <b>$dbh->quote($value)</b>. These methods must be used. </p> | |
| 4078 | ||
| 4079 | <h2>Use bound parameters (the PREPARE statement)</h2> | |
| 4080 | <p>Though quotesafing is a good mechanism, we're still in the area of "considering user input as SQL", and a much better approach exists: bound parameters, which are supported by essentially all database programming interfaces. In this technique, an SQL statement string is created with placeholders - a question mark for each parameter - and it's compiled ("prepared", in SQL parlance) into an internal form. Later, this prepared query is "executed" with a list of parameters: </p> | |
| 4081 | ||
| 4082 | <b>Example in perl</b> | |
| 4083 | <code><pre wrap="virtual"> $sth = $dbh->prepare("SELECT email, userid FROM members WHERE email = ?;"); | |
| 4084 | $sth->execute($email); | |
| 4085 | </pre></code> | |
| 4086 | <p>Thanks to Stefan Wagner, this demonstrates bound parameters in Java: </p> | |
| 4087 | ||
| 4088 | <b>Insecure version</b> | |
| 4089 | <code><pre wrap="virtual"> Statement s = connection.createStatement(); | |
| 4090 | ResultSet rs = s.executeQuery("SELECT email FROM member WHERE name = " | |
| 4091 | + formField); // *boom* | |
| 4092 | </pre></code> | |
| 4093 | ||
| 4094 | <p><b>Secure version</b></p> | |
| 4095 | <code><pre wrap="virtual"> PreparedStatement ps = connection.prepareStatement( | |
| 4096 | "SELECT email FROM member WHERE name = ?"); | |
| 4097 | ps.setString(1, formField); | |
| 4098 | ResultSet rs = ps.executeQuery(); | |
| 4099 | </pre></code> | |
| 4100 | ||
| 4101 | <p>Here, $email is the data obtained from the user's form, and it is passed as positional parameter #1 (the first question mark), and at no point do the contents of this variable have anything to do with SQL statement parsing. Quotes, semicolons, backslashes, SQL comment notation - none of this has any impact, because it's "just data". There simply is nothing to subvert, so the application is be largely immune to SQL injection attacks.</p> | |
| 4102 | ||
| 4103 | <p>There also may be some performance benefits if this prepared query is reused multiple times (it only has to be parsed once), but this is minor compared to the enormous security benefits. This is probably the single most important step one can take to secure a web application. </p> | |
| 4104 | ||
| 4105 | <h2>Limit database permissions and segregate users</h2> | |
| 4106 | <p>In the case at hand, we observed just two interactions that are made not in the context of a logged-in user: "log in" and "send me password". The web application ought to use a database connection with the most limited rights possible: query-only access to the members table, and no access to any other table.</p> | |
| 4107 | <p>The effect here is that even a "successful" SQL injection attack is going to have much more limited success. Here, we'd not have been able to do the UPDATE request that ultimately granted us access, so we'd have had to resort to other avenues.</p> | |
| 4108 | <p>Once the web application determined that a set of valid credentials had been passed via the login form, it would then switch that session to a database connection with more rights.</p> | |
| 4109 | <p>It should go almost without saying that sa rights should never be used for any web-based application.</p> | |
| 4110 | ||
| 4111 | <h2>Use stored procedures for database access</h2> | |
| 4112 | <p>When the database server supports them, use stored procedures for performing access on the application's behalf, which can eliminate SQL entirely (assuming the stored procedures themselves are written properly). </p> | |
| 4113 | <p>By encapsulating the rules for a certain action - query, update, delete, etc. - into a single procedure, it can be tested and documented on a standalone basis and business rules enforced (for instance, the "add new order" procedure might reject that order if the customer were over his credit limit). </p> | |
| 4114 | <p>For simple queries this might be only a minor benefit, but as the operations become more complicated (or are used in more than one place), having a single definition for the operation means it's going to be more robust and easier to maintain. </p> | |
| 4115 | <p><i>Note: </i>it's always possible to write a stored procedure that itself constructs a query dynamically: this provides no protection against SQL Injection - it's only proper binding with prepare/execute or direct SQL statements with bound variables that provide this protection. </p> | |
| 4116 | ||
| 4117 | <h2>Isolate the webserver</h2> | |
| 4118 | <p>Even having taken all these mitigation steps, it's nevertheless still possible to miss something and leave the server open to compromise. One ought to design the network infrastructure to assume that the bad guy will have full administrator access to the machine, and then attempt to limit how that can be leveraged to compromise other things. </p> | |
| 4119 | <p>For instance, putting the machine in a DMZ with extremely limited pinholes "inside" the network means that even getting complete control of the webserver doesn't automatically grant full access to everything else. This won't stop everything, of course, but it makes it a lot harder. </p> | |
| 4120 | ||
| 4121 | <h2>Configure error reporting</h2> | |
| 4122 | <p>The default error reporting for some frameworks includes developer debugging information, and this cannot be shown to outside users. Imagine how much easier a time it makes for an attacker if the full query is shown, pointing to the syntax error involved. </p> | |
| 4123 | <p>This information is useful to developers, but it should be restricted - if possible - to just internal users. </p>]]></DetailedInformation> | |
| 4124 | <Recommendation><![CDATA[Your script should filter metacharacters from user input. <br/>Check detailed information for more information about fixing this vulnerability.]]></Recommendation> | |
| 4125 | <TechnicalDetails> | |
| 4126 | <Request><![CDATA[POST /readnews.aspx?id=-1;%20waitfor%20delay%20'0:0:0'%20--%20&NewsAd=ads/def.html HTTP/1.1 | |
| 4127 | Content-Length: 10791 | |
| 4128 | Content-Type: application/x-www-form-urlencoded | |
| 4129 | X-Requested-With: XMLHttpRequest | |
| 4130 | Referer: http://testaspnet.vulnweb.com:80/ | |
| 4131 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 4132 | Host: testaspnet.vulnweb.com | |
| 4133 | Connection: Keep-alive | |
| 4134 | Accept-Encoding: gzip,deflate | |
| 4135 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 4136 | Accept: */* | |
| 4137 | ||
| 4138 | __EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWVwKO/ffgDgKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMTuBuYk15KvnzAGnqqPk6tDbzR0Y%3d&__VIEWSTATE=/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc%2bYWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNToyMiBBTWQCBQ8WAh8BBTxXZWIgYXR0YWNrcyAtIGNhbiB5b3VyIHdlYiBhcHBsaWNhdGlvbnMgd2l0aHN0YW5kIHRoZSBmb3JjZT9kAgcPFgIfAQWuNzxwPjxzdHJvbmc%2bQWN1bmV0aXggY29tYmF0cyByaXNlIGluIHdlYiBhdHRhY2tzIHdpdGggQWN1bmV0aXggICAgICAgICAgICAgICAgICAgICAgICAgICAgV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAyIDwvc3Ryb25nPjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD4yMSBKdWx5IDIwMDUgLSA8c3Ryb25nPlN0YXJ0LXVwIGNvbXBhbnkgQWN1bmV0aXggcmVsZWFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lcjogYSB0b29sIHRvIGF1dG9tYXRpY2FsbHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXVkaXQgd2Vic2l0ZSBzZWN1cml0eS4gQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAgICAgICAgICAgICAgICAgICAgICAgICAgICAyIGNyYXdscyBhbiBlbnRpcmUgd2Vic2l0ZSwgbGF1bmNoZXMgcG9wdWxhciB3ZWIgYXR0YWNrcyAgICAgICAgICAgICAgICAgICAgICAgICAgICAoU1FMIEluamVjdGlvbiBldGMuKSBhbmQgaWRlbnRpZmllcyB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdGhhdCBuZWVkIHRvIGJlIGZpeGVkLjwvc3Ryb25nPiA8L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5TZWN1cmluZyB5b3VyIHdlYnNpdGUgc2hvdWxkIGJlIHlvdXIgbnVtYmVyIG9uZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjb25jZXJuPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgSGFja2VycyBhcmUgY29uY2VudHJhdGluZyB0aGVpciBlZmZvcnRzIG9uIHdlYi1iYXNlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBhcHBsaWNhdGlvbnMgLSA3NSUgb2YgY3liZXIgYXR0YWNrcyBhcmUgZG9uZSBhdCB0aGUgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGxldmVsLCBhIEdhcnRuZXIgR3JvdXAgc3R1ZHkgaGFzIHJldmVhbGVkLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBXZWIgYXBwbGljYXRpb25zIGFyZSBhY2Nlc3NpYmxlIDI0IGhvdXJzIGEgZGF5LCA3IGRheXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgYSB3ZWVrIGFuZCBjb250cm9sIHZhbHVhYmxlIGRhdGEgc3VjaCBhcyBjdXN0b21lciBpbmZvcm1hdGlvbiwgICAgICAgICAgICAgICAgICAgICAgICAgICAgdHJhbnNhY3Rpb24gaW5mb3JtYXRpb24gYW5kIGV2ZW4gcHJvcHJpZXRhcnkgY29ycG9yYXRlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGEuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bNTAwLDAwMCBjdXN0b21lciBjcmVkaXQgY2FyZCBudW1iZXJzIG9idGFpbmVkIHZpYSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhIHdlYiBhdHRhY2s8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBXZWxsLWtub3duIHNpdGVzIHRoYXQgd2VyZSBvcGVuIHRvIHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGluY2x1ZGUgZmFzaGlvbiBsYWJlbCBHdWVzcyBhbmQgcGV0IHN1cHBseSByZXRhaWxlciAgICAgICAgICAgICAgICAgICAgICAgICAgICBQZXRDby5jb20gd2hvIHdlcmUgbm90b3Jpb3VzbHkgZm91bmQgdG8gYmUgdnVsbmVyYWJsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB0byB0aGUgU1FMIGluamVjdGlvbiB2dWxuZXJhYmlsaXR5IChKdW5lIDIwMDMpLiBUaGlzICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJlc3VsdGVkIGluIFBldENvIGxlYXZpbmcgYXMgbWFueSBhcyA1MDAsMDAwIGNyZWRpdCAgICAgICAgICAgICAgICAgICAgICAgICAgICBjYXJkIG51bWJlcnMgb3BlbiB0byBhbnlvbmUgYWJsZSB0byBjb25zdHJ1Y3QgdGhpcyBzcGVjaWFsbHktY3JhZnRlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBVUkwuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bRmlyZXdhbGxzLCBTU0wgYW5kIGxvY2tlZC1kb3duIHNlcnZlcnMgYXJlIGZ1dGlsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBoYWNraW5nPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQW55IGRlZmVuc2UgYXQgbmV0d29yayBzZWN1cml0eSBsZXZlbCB3aWxsIHByb3ZpZGUgbm8gICAgICAgICAgICAgICAgICAgICAgICAgICAgcHJvdGVjdGlvbiBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzIHNpbmNlIHRoZXkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXJlIGxhdW5jaGVkIG9uIHBvcnQgODAgLSB3aGljaCBoYXMgdG8gcmVtYWluIG9wZW4uICAgICAgICAgICAgICAgICAgICAgICAgICAgIEluIGFkZGl0aW9uLCB3ZWIgYXBwbGljYXRpb25zIChjdXN0b21lciBhcmVhcywgc2hvcHBpbmcgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FydHMgZXRjLikgYXJlIG9mdGVuIHRhaWxvci1tYWRlLCBpbnZhcmlhYmx5IHRlc3RlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBsZXNzIHRoYW4gb2ZmLXRoZS1zaGVsZiBzb2Z0d2FyZSBhbmQgYXJlIHRoZXJlZm9yZSBtb3JlICAgICAgICAgICAgICAgICAgICAgICAgICAgIHN1c2NlcHRpYmxlIHRvIGF0dGFjay48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bJnF1b3Q7Q29tcGFuaWVzIGhhdmUgaW1wbGVtZW50ZWQgbmV0d29yay1sZXZlbCBzZWN1cml0eSwgICAgICAgICAgICAgICAgICAgICAgICAgICAgaG93ZXZlciB0aGV5IGZhaWwgdG8gYXVkaXQgYW5kIHNlY3VyZSB0aGVpciB3ZWIgYXBwbGljYXRpb25zLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBUaGVzZSBhcHBsaWNhdGlvbnMgaGF2ZSBhY2Nlc3MgdG8gc2Vuc2l0aXZlIGRhdGEgYW5kICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFyZSBhIGhhY2tlcidzIHByaW1lIHRhcmdldCwmcXVvdDsgc2FpZCBOaWNrIEdhbGVhLCAgICAgICAgICAgICAgICAgICAgICAgICAgICBDRU8gb2YgQWN1bmV0aXguICZxdW90O0F1ZGl0aW5nIG9uZSdzIHdlYiBhcHBzIHNob3VsZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBiZSB0aGUgbnVtYmVyIG9uZSBzZWN1cml0eSBjb25jZXJuLiZxdW90OzwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlRoZSBuZWVkIGZvciBhbiBhdXRvbWF0ZWQgd2ViIGFwcGxpY2F0aW9uIHZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgc2Nhbm5lcjwvc3Ryb25nPjxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIE1hbnVhbGx5IGF1ZGl0aW5nIGEgd2ViIGFwcGxpY2F0aW9uIGZvciB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdG8gU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiAgICAgICAgICAgICAgICAgICAgICAgICAgICBhdHRhY2tzIGlzIHZpcnR1YWxseSBpbXBvc3NpYmxlLiBXaXRoIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5ICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNjYW5uZXIgdGhlIHByb2Nlc3Mgb2YgYXVkaXRpbmcgd2ViIGFwcGxpY2F0aW9ucyBzdWNoICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFzIHNob3BwaW5nIGNhcnRzIGFuZCBmb3JtcywgY2FuIGJlIGVhc2lseSBhdXRvbWF0ZWQuICAgICAgICAgICAgICAgICAgICAgICAgICAgIFdoYXQncyBtb3JlLCB0aGUgc2VjdXJpdHkgY2hlY2tzIGNhbiBlYXNpbHkgYmUgcmUtbGF1bmNoZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGVhY2ggYXBwbGljYXRpb24gdXBkYXRlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkhvdyBBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIHdvcmtzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGZpcnN0IGNyYXdscyB0aGUgd2hvbGUgd2Vic2l0ZSwgYW5hbHl6ZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgaW4tZGVwdGggZWFjaCBmaWxlIGl0IGZpbmRzLCBhbmQgZGlzcGxheXMgdGhlIGVudGlyZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB3ZWJzaXRlIHN0cnVjdHVyZS4gQWZ0ZXIgdGhpcyBkaXNjb3Zlcnkgc3RhZ2UsIGl0IHBlcmZvcm1zICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFuIGF1dG9tYXRpYyBhdWRpdCBmb3IgY29tbW9uIHNlY3VyaXR5IHZ1bG5lcmFiaWxpdGllcy48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BdXRvbWF0aWNhbGx5IGRldGVjdHMgU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiB2dWxuZXJhYmlsaXRpZXM8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBTUUwgaW5qZWN0aW9uIGlzIGEgaGFja2luZyB0ZWNobmlxdWUgd2hpY2ggbW9kaWZpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgU1FMIGNvbW1hbmRzIGluIG9yZGVyIHRvIGdhaW4gYWNjZXNzIHRvIGRhdGEgaW4gdGhlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGFiYXNlLiBDcm9zcyBzaXRlIHNjcmlwdGluZyBhdHRhY2tzIGFsbG93IGEgaGFja2VyICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRvIGV4ZWN1dGUgYSBtYWxpY2lvdXMgc2NyaXB0IG9uIHlvdXIgdmlzaXRvcnMnIGJyb3dzZXIuICAgICAgICAgICAgICAgICAgICAgICAgICAgIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgY2FuIGNoZWNrIGlmIHlvdXIgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGlzIHZ1bG5lcmFibGUgdG8gYm90aCBvZiB0aGVzZSBhdHRhY2tzLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBNb3JlIGluZm9ybWF0aW9uIGFib3V0IGNyb3NzIHNpdGUgc2NyaXB0aW5nICZhbXA7IFNRTCAgICAgICAgICAgICAgICAgICAgICAgICAgICBpbmplY3Rpb24gYXQgb3VyIHdlYnNpdGUgc2VjdXJpdHkgaW5mbyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgYWxzbyBjaGVja3MgZm9yICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRoZSBmb2xsb3dpbmcgd2ViIGF0dGFja3M6PC9zdHJvbmc%2bPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDx1bD4gPGxpPkNSTEYgaW5qZWN0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5Db2RlIGV4ZWN1dGlvbiBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRGlyZWN0b3J5IHRyYXZlcnNhbCBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRmlsZSBpbmNsdXNpb24gYXR0YWNrczxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvbGk%2bPGxpPiBJbnB1dCB2YWxpZGF0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5BdXRoZW50aWNhdGlvbiBhdHRhY2tzLjwvbGk%2bIDwvdWw%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BZHZhbmNlZCBwZW5ldHJhdGlvbiB0ZXN0aW5nIHRvb2xzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGFsc28gaW5jbHVkZXMgdG9vbHMgc3VjaCBhcyBhbiBIVFRQIGVkaXRvciAgICAgICAgICAgICAgICAgICAgICAgICAgICAmYW1wOyBIVFRQIHNuaWZmZXIgdG8gYWxsb3cgY3VzdG9taXphdGlvbiBvZiB3ZWIgdnVsbmVyYWJpbGl0eSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjaGVja3MuIFVzaW5nIHRoZSBWdWxuZXJhYmlsaXR5IGVkaXRvciwgbmV3IGF0dGFja3MgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FuIGVhc2lseSBiZSBjcmVhdGVkLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlByaWNpbmcgJmFtcDsgYXZhaWxhYmlsaXR5PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGlzIGF2YWlsYWJsZSBhcyBhbiBlbnRlcnByaXNlIG9yIGFzIGEgY29uc3VsdGFudCAgICAgICAgICAgICAgICAgICAgICAgICAgICB2ZXJzaW9uLiBBIHN1YnNjcmlwdGlvbiBiYXNlZCBsaWNlbnNlIGNhbiBiZSBwdXJjaGFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGFzIGxpdHRsZSBhcyAkMzk1LCB3aGVyZWFzIGEgcGVycGV0dWFsIGxpY2Vuc2Ugc3RhcnRzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGF0ICQyOTk1LiBGb3IgbW9yZSBpbmZvcm1hdGlvbiB2aXNpdCBvdXIgcHJpY2luZyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFib3V0IEFjdW5ldGl4PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggd2FzIGZvdW5kZWQgdG8gY29tYmF0IHRoZSBhbGFybWluZyByaXNlIGluICAgICAgICAgICAgICAgICAgICAgICAgICAgIHdlYiBhdHRhY2tzLiBJdHMgZmxhZ3NoaXAgcHJvZHVjdCwgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgU2Nhbm5lciwgaXMgdGhlIHJlc3VsdCBvZiBzZXZlcmFsIHllYXJzIG9mIGRldmVsb3BtZW50ICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJ5IGEgdGVhbSBvZiBoaWdobHkgZXhwZXJpZW5jZWQgc2VjdXJpdHkgZGV2ZWxvcGVycy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggaXMgYSBwcml2YXRlbHkgaGVsZCBjb21wYW55IHdpdGggaGVhZHF1YXJ0ZXJzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJhc2VkIGluIEV1cm9wZSAoTWFsdGEpIHdpdGggaXRzIE5ldyBZb3JrIFVTIG9mZmljZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY2hlZHVsZWQgdG8gb3BlbiBpbiBRMyBvZiAyMDA1LiA8L3A%2bIGQCCQ8PFgIeC05hdmlnYXRlVXJsBRJDb21tZW50cy5hc3B4P2lkPTJkZAILDxYCHgNzcmMFDGFkcy9kZWYuaHRtbGRkNCSZh%2buMoCTcXGDfVu5D5CfxA7Y%3d]]></Request> | |
| 4139 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 4140 | Date: Thu, 14 Nov 2013 14:29:42 GMT | |
| 4141 | Server: Microsoft-IIS/6.0 | |
| 4142 | X-Powered-By: ASP.NET | |
| 4143 | X-AspNet-Version: 2.0.50727 | |
| 4144 | Cache-Control: private | |
| 4145 | Content-Type: text/html; charset=utf-8 | |
| 4146 | Content-Length: 29398 | |
| 4147 | ]]></Response> | |
| 4148 | </TechnicalDetails> | |
| 4149 | <References> | |
| 4150 | <Reference> | |
| 4151 | <Database><![CDATA[Acunetix SQL Injection Attack]]></Database> | |
| 4152 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/sql-injection.htm]]></URL> | |
| 4153 | </Reference> | |
| 4154 | <Reference> | |
| 4155 | <Database><![CDATA[VIDEO: SQL Injection tutorial]]></Database> | |
| 4156 | <URL><![CDATA[http://www.acunetix.com/blog/web-security-zone/video-sql-injection-tutorial/]]></URL> | |
| 4157 | </Reference> | |
| 4158 | <Reference> | |
| 4159 | <Database><![CDATA[OWASP Injection Flaws]]></Database> | |
| 4160 | <URL><![CDATA[http://www.owasp.org/index.php/Injection_Flaws]]></URL> | |
| 4161 | </Reference> | |
| 4162 | <Reference> | |
| 4163 | <Database><![CDATA[How to check for SQL injection vulnerabilities]]></Database> | |
| 4164 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/sql-injection2/]]></URL> | |
| 4165 | </Reference> | |
| 4166 | <Reference> | |
| 4167 | <Database><![CDATA[SQL Injection Walkthrough]]></Database> | |
| 4168 | <URL><![CDATA[http://www.securiteam.com/securityreviews/5DP0N1P76E.html]]></URL> | |
| 4169 | </Reference> | |
| 4170 | <Reference> | |
| 4171 | <Database><![CDATA[OWASP PHP Top 5]]></Database> | |
| 4172 | <URL><![CDATA[http://www.owasp.org/index.php/PHP_Top_5]]></URL> | |
| 4173 | </Reference> | |
| 4174 | </References> | |
| 4175 | </ReportItem> | |
| 4176 | ||
| 4177 | <ReportItem id="49" color="orange"> | |
| 4178 | <Name><![CDATA[Cross frame scripting]]></Name> | |
| 4179 | <ModuleName><![CDATA[Scripting (XFS_and_Redir.script)]]></ModuleName> | |
| 4180 | <Details><![CDATA[URL encoded GET input <b><font color="dark">NewsAd</font></b> was set to <b><font color="dark">http://www.acunetix.tst</font></b>]]></Details> | |
| 4181 | <Affects><![CDATA[/readnews.aspx]]></Affects> | |
| 4182 | <Parameter><![CDATA[NewsAd]]></Parameter> | |
| 4183 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 4184 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 4185 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 4186 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 4187 | <Severity><![CDATA[medium]]></Severity> | |
| 4188 | <Type><![CDATA[Validation]]></Type> | |
| 4189 | <Impact><![CDATA[Malicious users may poison a frame allowing them to conduct phishing attacks.]]></Impact> | |
| 4190 | <Description><![CDATA[This script is possibly vulnerable to Cross Frame Scripting (XFS) attacks.<br/><br/>This is an attack technique used to trick a user into thinking that fake web site content is legitimate data. ]]></Description> | |
| 4191 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 4192 | <Recommendation><![CDATA[Your script should filter metacharacters from user input.]]></Recommendation> | |
| 4193 | <TechnicalDetails> | |
| 4194 | <Request><![CDATA[POST /readnews.aspx?id=2&NewsAd=http://www.acunetix.tst HTTP/1.1 | |
| 4195 | Content-Length: 10791 | |
| 4196 | Content-Type: application/x-www-form-urlencoded | |
| 4197 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 4198 | Host: testaspnet.vulnweb.com | |
| 4199 | Connection: Keep-alive | |
| 4200 | Accept-Encoding: gzip,deflate | |
| 4201 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 4202 | Accept: */* | |
| 4203 | ||
| 4204 | __EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWVwKO/ffgDgKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMTuBuYk15KvnzAGnqqPk6tDbzR0Y%3d&__VIEWSTATE=/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc%2bYWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNToyMiBBTWQCBQ8WAh8BBTxXZWIgYXR0YWNrcyAtIGNhbiB5b3VyIHdlYiBhcHBsaWNhdGlvbnMgd2l0aHN0YW5kIHRoZSBmb3JjZT9kAgcPFgIfAQWuNzxwPjxzdHJvbmc%2bQWN1bmV0aXggY29tYmF0cyByaXNlIGluIHdlYiBhdHRhY2tzIHdpdGggQWN1bmV0aXggICAgICAgICAgICAgICAgICAgICAgICAgICAgV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAyIDwvc3Ryb25nPjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD4yMSBKdWx5IDIwMDUgLSA8c3Ryb25nPlN0YXJ0LXVwIGNvbXBhbnkgQWN1bmV0aXggcmVsZWFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lcjogYSB0b29sIHRvIGF1dG9tYXRpY2FsbHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXVkaXQgd2Vic2l0ZSBzZWN1cml0eS4gQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAgICAgICAgICAgICAgICAgICAgICAgICAgICAyIGNyYXdscyBhbiBlbnRpcmUgd2Vic2l0ZSwgbGF1bmNoZXMgcG9wdWxhciB3ZWIgYXR0YWNrcyAgICAgICAgICAgICAgICAgICAgICAgICAgICAoU1FMIEluamVjdGlvbiBldGMuKSBhbmQgaWRlbnRpZmllcyB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdGhhdCBuZWVkIHRvIGJlIGZpeGVkLjwvc3Ryb25nPiA8L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5TZWN1cmluZyB5b3VyIHdlYnNpdGUgc2hvdWxkIGJlIHlvdXIgbnVtYmVyIG9uZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjb25jZXJuPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgSGFja2VycyBhcmUgY29uY2VudHJhdGluZyB0aGVpciBlZmZvcnRzIG9uIHdlYi1iYXNlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBhcHBsaWNhdGlvbnMgLSA3NSUgb2YgY3liZXIgYXR0YWNrcyBhcmUgZG9uZSBhdCB0aGUgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGxldmVsLCBhIEdhcnRuZXIgR3JvdXAgc3R1ZHkgaGFzIHJldmVhbGVkLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBXZWIgYXBwbGljYXRpb25zIGFyZSBhY2Nlc3NpYmxlIDI0IGhvdXJzIGEgZGF5LCA3IGRheXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgYSB3ZWVrIGFuZCBjb250cm9sIHZhbHVhYmxlIGRhdGEgc3VjaCBhcyBjdXN0b21lciBpbmZvcm1hdGlvbiwgICAgICAgICAgICAgICAgICAgICAgICAgICAgdHJhbnNhY3Rpb24gaW5mb3JtYXRpb24gYW5kIGV2ZW4gcHJvcHJpZXRhcnkgY29ycG9yYXRlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGEuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bNTAwLDAwMCBjdXN0b21lciBjcmVkaXQgY2FyZCBudW1iZXJzIG9idGFpbmVkIHZpYSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhIHdlYiBhdHRhY2s8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBXZWxsLWtub3duIHNpdGVzIHRoYXQgd2VyZSBvcGVuIHRvIHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGluY2x1ZGUgZmFzaGlvbiBsYWJlbCBHdWVzcyBhbmQgcGV0IHN1cHBseSByZXRhaWxlciAgICAgICAgICAgICAgICAgICAgICAgICAgICBQZXRDby5jb20gd2hvIHdlcmUgbm90b3Jpb3VzbHkgZm91bmQgdG8gYmUgdnVsbmVyYWJsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB0byB0aGUgU1FMIGluamVjdGlvbiB2dWxuZXJhYmlsaXR5IChKdW5lIDIwMDMpLiBUaGlzICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJlc3VsdGVkIGluIFBldENvIGxlYXZpbmcgYXMgbWFueSBhcyA1MDAsMDAwIGNyZWRpdCAgICAgICAgICAgICAgICAgICAgICAgICAgICBjYXJkIG51bWJlcnMgb3BlbiB0byBhbnlvbmUgYWJsZSB0byBjb25zdHJ1Y3QgdGhpcyBzcGVjaWFsbHktY3JhZnRlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBVUkwuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bRmlyZXdhbGxzLCBTU0wgYW5kIGxvY2tlZC1kb3duIHNlcnZlcnMgYXJlIGZ1dGlsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBoYWNraW5nPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQW55IGRlZmVuc2UgYXQgbmV0d29yayBzZWN1cml0eSBsZXZlbCB3aWxsIHByb3ZpZGUgbm8gICAgICAgICAgICAgICAgICAgICAgICAgICAgcHJvdGVjdGlvbiBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzIHNpbmNlIHRoZXkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXJlIGxhdW5jaGVkIG9uIHBvcnQgODAgLSB3aGljaCBoYXMgdG8gcmVtYWluIG9wZW4uICAgICAgICAgICAgICAgICAgICAgICAgICAgIEluIGFkZGl0aW9uLCB3ZWIgYXBwbGljYXRpb25zIChjdXN0b21lciBhcmVhcywgc2hvcHBpbmcgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FydHMgZXRjLikgYXJlIG9mdGVuIHRhaWxvci1tYWRlLCBpbnZhcmlhYmx5IHRlc3RlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBsZXNzIHRoYW4gb2ZmLXRoZS1zaGVsZiBzb2Z0d2FyZSBhbmQgYXJlIHRoZXJlZm9yZSBtb3JlICAgICAgICAgICAgICAgICAgICAgICAgICAgIHN1c2NlcHRpYmxlIHRvIGF0dGFjay48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bJnF1b3Q7Q29tcGFuaWVzIGhhdmUgaW1wbGVtZW50ZWQgbmV0d29yay1sZXZlbCBzZWN1cml0eSwgICAgICAgICAgICAgICAgICAgICAgICAgICAgaG93ZXZlciB0aGV5IGZhaWwgdG8gYXVkaXQgYW5kIHNlY3VyZSB0aGVpciB3ZWIgYXBwbGljYXRpb25zLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBUaGVzZSBhcHBsaWNhdGlvbnMgaGF2ZSBhY2Nlc3MgdG8gc2Vuc2l0aXZlIGRhdGEgYW5kICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFyZSBhIGhhY2tlcidzIHByaW1lIHRhcmdldCwmcXVvdDsgc2FpZCBOaWNrIEdhbGVhLCAgICAgICAgICAgICAgICAgICAgICAgICAgICBDRU8gb2YgQWN1bmV0aXguICZxdW90O0F1ZGl0aW5nIG9uZSdzIHdlYiBhcHBzIHNob3VsZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBiZSB0aGUgbnVtYmVyIG9uZSBzZWN1cml0eSBjb25jZXJuLiZxdW90OzwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlRoZSBuZWVkIGZvciBhbiBhdXRvbWF0ZWQgd2ViIGFwcGxpY2F0aW9uIHZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgc2Nhbm5lcjwvc3Ryb25nPjxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIE1hbnVhbGx5IGF1ZGl0aW5nIGEgd2ViIGFwcGxpY2F0aW9uIGZvciB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdG8gU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiAgICAgICAgICAgICAgICAgICAgICAgICAgICBhdHRhY2tzIGlzIHZpcnR1YWxseSBpbXBvc3NpYmxlLiBXaXRoIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5ICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNjYW5uZXIgdGhlIHByb2Nlc3Mgb2YgYXVkaXRpbmcgd2ViIGFwcGxpY2F0aW9ucyBzdWNoICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFzIHNob3BwaW5nIGNhcnRzIGFuZCBmb3JtcywgY2FuIGJlIGVhc2lseSBhdXRvbWF0ZWQuICAgICAgICAgICAgICAgICAgICAgICAgICAgIFdoYXQncyBtb3JlLCB0aGUgc2VjdXJpdHkgY2hlY2tzIGNhbiBlYXNpbHkgYmUgcmUtbGF1bmNoZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGVhY2ggYXBwbGljYXRpb24gdXBkYXRlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkhvdyBBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIHdvcmtzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGZpcnN0IGNyYXdscyB0aGUgd2hvbGUgd2Vic2l0ZSwgYW5hbHl6ZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgaW4tZGVwdGggZWFjaCBmaWxlIGl0IGZpbmRzLCBhbmQgZGlzcGxheXMgdGhlIGVudGlyZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB3ZWJzaXRlIHN0cnVjdHVyZS4gQWZ0ZXIgdGhpcyBkaXNjb3Zlcnkgc3RhZ2UsIGl0IHBlcmZvcm1zICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFuIGF1dG9tYXRpYyBhdWRpdCBmb3IgY29tbW9uIHNlY3VyaXR5IHZ1bG5lcmFiaWxpdGllcy48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BdXRvbWF0aWNhbGx5IGRldGVjdHMgU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiB2dWxuZXJhYmlsaXRpZXM8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBTUUwgaW5qZWN0aW9uIGlzIGEgaGFja2luZyB0ZWNobmlxdWUgd2hpY2ggbW9kaWZpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgU1FMIGNvbW1hbmRzIGluIG9yZGVyIHRvIGdhaW4gYWNjZXNzIHRvIGRhdGEgaW4gdGhlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGFiYXNlLiBDcm9zcyBzaXRlIHNjcmlwdGluZyBhdHRhY2tzIGFsbG93IGEgaGFja2VyICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRvIGV4ZWN1dGUgYSBtYWxpY2lvdXMgc2NyaXB0IG9uIHlvdXIgdmlzaXRvcnMnIGJyb3dzZXIuICAgICAgICAgICAgICAgICAgICAgICAgICAgIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgY2FuIGNoZWNrIGlmIHlvdXIgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGlzIHZ1bG5lcmFibGUgdG8gYm90aCBvZiB0aGVzZSBhdHRhY2tzLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBNb3JlIGluZm9ybWF0aW9uIGFib3V0IGNyb3NzIHNpdGUgc2NyaXB0aW5nICZhbXA7IFNRTCAgICAgICAgICAgICAgICAgICAgICAgICAgICBpbmplY3Rpb24gYXQgb3VyIHdlYnNpdGUgc2VjdXJpdHkgaW5mbyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgYWxzbyBjaGVja3MgZm9yICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRoZSBmb2xsb3dpbmcgd2ViIGF0dGFja3M6PC9zdHJvbmc%2bPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDx1bD4gPGxpPkNSTEYgaW5qZWN0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5Db2RlIGV4ZWN1dGlvbiBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRGlyZWN0b3J5IHRyYXZlcnNhbCBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRmlsZSBpbmNsdXNpb24gYXR0YWNrczxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvbGk%2bPGxpPiBJbnB1dCB2YWxpZGF0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5BdXRoZW50aWNhdGlvbiBhdHRhY2tzLjwvbGk%2bIDwvdWw%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BZHZhbmNlZCBwZW5ldHJhdGlvbiB0ZXN0aW5nIHRvb2xzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGFsc28gaW5jbHVkZXMgdG9vbHMgc3VjaCBhcyBhbiBIVFRQIGVkaXRvciAgICAgICAgICAgICAgICAgICAgICAgICAgICAmYW1wOyBIVFRQIHNuaWZmZXIgdG8gYWxsb3cgY3VzdG9taXphdGlvbiBvZiB3ZWIgdnVsbmVyYWJpbGl0eSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjaGVja3MuIFVzaW5nIHRoZSBWdWxuZXJhYmlsaXR5IGVkaXRvciwgbmV3IGF0dGFja3MgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FuIGVhc2lseSBiZSBjcmVhdGVkLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlByaWNpbmcgJmFtcDsgYXZhaWxhYmlsaXR5PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGlzIGF2YWlsYWJsZSBhcyBhbiBlbnRlcnByaXNlIG9yIGFzIGEgY29uc3VsdGFudCAgICAgICAgICAgICAgICAgICAgICAgICAgICB2ZXJzaW9uLiBBIHN1YnNjcmlwdGlvbiBiYXNlZCBsaWNlbnNlIGNhbiBiZSBwdXJjaGFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGFzIGxpdHRsZSBhcyAkMzk1LCB3aGVyZWFzIGEgcGVycGV0dWFsIGxpY2Vuc2Ugc3RhcnRzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGF0ICQyOTk1LiBGb3IgbW9yZSBpbmZvcm1hdGlvbiB2aXNpdCBvdXIgcHJpY2luZyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFib3V0IEFjdW5ldGl4PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggd2FzIGZvdW5kZWQgdG8gY29tYmF0IHRoZSBhbGFybWluZyByaXNlIGluICAgICAgICAgICAgICAgICAgICAgICAgICAgIHdlYiBhdHRhY2tzLiBJdHMgZmxhZ3NoaXAgcHJvZHVjdCwgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgU2Nhbm5lciwgaXMgdGhlIHJlc3VsdCBvZiBzZXZlcmFsIHllYXJzIG9mIGRldmVsb3BtZW50ICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJ5IGEgdGVhbSBvZiBoaWdobHkgZXhwZXJpZW5jZWQgc2VjdXJpdHkgZGV2ZWxvcGVycy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggaXMgYSBwcml2YXRlbHkgaGVsZCBjb21wYW55IHdpdGggaGVhZHF1YXJ0ZXJzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJhc2VkIGluIEV1cm9wZSAoTWFsdGEpIHdpdGggaXRzIE5ldyBZb3JrIFVTIG9mZmljZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY2hlZHVsZWQgdG8gb3BlbiBpbiBRMyBvZiAyMDA1LiA8L3A%2bIGQCCQ8PFgIeC05hdmlnYXRlVXJsBRJDb21tZW50cy5hc3B4P2lkPTJkZAILDxYCHgNzcmMFDGFkcy9kZWYuaHRtbGRkNCSZh%2buMoCTcXGDfVu5D5CfxA7Y%3d]]></Request> | |
| 4205 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 4206 | Date: Thu, 14 Nov 2013 14:29:42 GMT | |
| 4207 | Server: Microsoft-IIS/6.0 | |
| 4208 | X-Powered-By: ASP.NET | |
| 4209 | X-AspNet-Version: 2.0.50727 | |
| 4210 | Cache-Control: private | |
| 4211 | Content-Type: text/html; charset=utf-8 | |
| 4212 | Content-Length: 29338 | |
| 4213 | ]]></Response> | |
| 4214 | </TechnicalDetails> | |
| 4215 | <References> | |
| 4216 | <Reference> | |
| 4217 | <Database><![CDATA[Cross Frame Scripting]]></Database> | |
| 4218 | <URL><![CDATA[https://www.owasp.org/index.php/Cross_Frame_Scripting]]></URL> | |
| 4219 | </Reference> | |
| 4220 | </References> | |
| 4221 | </ReportItem> | |
| 4222 | ||
| 4223 | <ReportItem id="50" color="red"> | |
| 4224 | <Name><![CDATA[Cross site scripting (verified)]]></Name> | |
| 4225 | <ModuleName><![CDATA[Scripting (XSS.script)]]></ModuleName> | |
| 4226 | <Details><![CDATA[URL encoded GET input <b><font color="dark">NewsAd</font></b> was set to <b><font color="dark">javascript:prompt(974652);</font></b><br/>The input is reflected inside A tag href parameter, a FORM tag action parameter or (I)FRAME src parameter.<br/>]]></Details> | |
| 4227 | <Affects><![CDATA[/readnews.aspx]]></Affects> | |
| 4228 | <Parameter><![CDATA[NewsAd]]></Parameter> | |
| 4229 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 4230 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 4231 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 4232 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 4233 | <Severity><![CDATA[high]]></Severity> | |
| 4234 | <Type><![CDATA[Validation]]></Type> | |
| 4235 | <Impact><![CDATA[Malicious users may inject JavaScript, VBScript, ActiveX, HTML or Flash into a vulnerable application to fool a user in order to gather data from them. | |
| 4236 | An attacker can steal the session cookie and take over the account, impersonating the user. | |
| 4237 | It is also possible to modify the content of the page presented to the user. | |
| 4238 | ]]></Impact> | |
| 4239 | <Description><![CDATA[This script is possibly vulnerable to Cross Site Scripting (XSS) attacks.<br/><br/> | |
| 4240 | Cross site scripting (also referred to as XSS) is a vulnerability that allows an attacker to send malicious code (usually in the form of Javascript) to another user. | |
| 4241 | Because a browser cannot know if the script should be trusted or not, it will execute the script in the user context allowing the attacker to access any cookies or session tokens retained by the browser. ]]></Description> | |
| 4242 | <DetailedInformation><![CDATA[<i>Quote from The Cross Site Scripting FAQ - http://www.cgisecurity.com/articles/xss-faq.shtml </i> | |
| 4243 | ||
| 4244 | <h2>Introduction</h2> | |
| 4245 | ||
| 4246 | <p>Websites today are more complex than ever, containing a lot of dynamic content making the experience for the user more enjoyable. Dynamic content is achieved through the use of web applications which can deliver different output to a user depending on their settings and needs. Dynamic websites suffer from a threat that static websites don't, called "Cross Site Scripting" (or XSS dubbed by other security professionals). Currently small informational tidbits about Cross Site Scripting holes exist but none really explain them to an average person or administrator. This FAQ was written to provide a better understanding of this emerging threat, and to give guidance on detection and prevention.</p> | |
| 4247 | ||
| 4248 | <h2>"What is Cross Site Scripting?"</h2> | |
| 4249 | ||
| 4250 | <p>Cross site scripting (also known as XSS) occurs when a web application gathers malicious data from a user. The data is usually gathered in the form of a hyperlink which contains malicious content within it. The user will most likely click on this link from another website, instant message, or simply just reading a web board or email message. Usually the attacker will encode the malicious portion of the link to the site in HEX (or other encoding methods) so the request is less suspicious looking to the user when clicked on. After the data is collected by the web application, it creates an output page for the user containing the malicious data that was originally sent to it, but in a manner to make it appear as valid content from the website. Many popular guestbook and forum programs allow users to submit posts with html and javascript embedded in them. If for example I was logged in as "john" and read a message by "joe" that contained malicious javascript in it, then it may be possible for "joe" to hijack my session just by reading his bulletin board post. Further details on how attacks like this are accomplished via "cookie theft" are explained in detail below.</p> | |
| 4251 | ||
| 4252 | <h2>"What does XSS and CSS mean?"</h2> | |
| 4253 | ||
| 4254 | <p>Often people refer to Cross Site Scripting as CSS. There has been a lot of confusion with Cascading Style Sheets (CSS) and cross site scripting. Some security people refer to Cross Site Scripting as XSS. If you hear someone say "I found a XSS hole", they are talking about Cross Site Scripting for certain.</p> | |
| 4255 | ||
| 4256 | ||
| 4257 | <h2>"What are the threats of Cross Site Scripting?"</h2> | |
| 4258 | ||
| 4259 | <p>Often attackers will inject JavaScript, VBScript, ActiveX, HTML, or Flash into a vulnerable application to fool a user (Read below for further details) in order to gather data from them. Everything from account hijacking, changing of user settings, cookie theft/poisoning, or false advertising is possible. New malicious uses are being found every day for XSS attacks. The post below by Brett Moore brings up a good point with regard to "Denial Of Service", and potential "auto-attacking" of hosts if a user simply reads a post on a message board.</p> | |
| 4260 | ||
| 4261 | <h2>"What can I do to protect myself as a vendor?"</h2> | |
| 4262 | ||
| 4263 | <p>This is a simple answer. Never trust user input and always filter metacharacters. This will eliminate the majority of XSS attacks. Converting < and > to &lt; and &gt; is also suggested when it comes to script output. Remember XSS holes can be damaging and costly to your business if abused. Often attackers will disclose these holes to the public, which can erode customer and public confidence in the security and privacy of your organization's site. Filtering < and > alone will not solve all cross site scripting attacks and it is suggested you also attempt to filter out ( and ) by translating them to &#40; and &#41;, and also # and & by translating them to &#35 (#) and &#38 (&).</p> | |
| 4264 | ||
| 4265 | <h2>"What can I do to protect myself as a user?"</h2> | |
| 4266 | ||
| 4267 | <p>The easiest way to protect yourself as a user is to only follow links from the main website you wish to view. If you visit one website and it links to CNN for example, instead of clicking on it visit CNN's main site and use its search engine to find the content. This will probably eliminate ninety percent of the problem. Sometimes XSS can be executed automatically when you open an email, email attachment, read a guestbook, or bulletin board post. If you plan on opening an email, or reading a post on a public board from a person you don't know BE CAREFUL. One of the best ways to protect yourself is to turn off Javascript in your browser settings. In IE turn your security settings to high. This can prevent cookie theft, and in general is a safer thing to do.</p> | |
| 4268 | ||
| 4269 | <h2>"How common are XSS holes?"</h2> | |
| 4270 | ||
| 4271 | <p>Cross site scripting holes are gaining popularity among hackers as easy holes to find in large websites. Websites from FBI.gov, CNN.com, Time.com, Ebay, Yahoo, Apple computer, Microsoft, Zdnet, Wired, and Newsbytes have all had one form or another of XSS bugs.</p> | |
| 4272 | ||
| 4273 | <p>Every month roughly 10-25 XSS holes are found in commercial products and advisories are published explaining the threat.</p> | |
| 4274 | ||
| 4275 | ||
| 4276 | <h2>"Does encryption protect me?"</h2> | |
| 4277 | ||
| 4278 | <p>Websites that use SSL (https) are in no way more protected than websites that are not encrypted. The web applications work the same way as before, except the attack is taking place in an encrypted connection. People often think that because they see the lock on their browser it means everything is secure. This just isn't the case.</p> | |
| 4279 | ||
| 4280 | ||
| 4281 | <h2>"Can XSS holes allow command execution?"</h2> | |
| 4282 | ||
| 4283 | <p>XSS holes can allow Javascript insertion, which may allow for limited execution. If an attacker were to exploit a browser flaw (browser hole) it could then be possible to execute commands on the client's side. If command execution were possible it would only be possible on the client side. In simple terms XSS holes can be used to help exploit other holes that may exist in your browser.</p> | |
| 4284 | ||
| 4285 | ||
| 4286 | <h2>"What if I don't feel like fixing a CSS/XSS Hole?"</h2> | |
| 4287 | ||
| 4288 | <p>By not fixing an XSS hole this could allow possible user account compromise in portions of your site as they get added or updated. Cross Site Scripting has been found in various large sites recently and have been widely publicized. Left unrepaired, someone may discover it and publish a warning about your company. This may damage your company's reputation, depicting it as being lax on security matters. This of course also sends the message to your clients that you aren't dealing with every problem that arises, which turns into a trust issue. If your client doesn't trust you why would they wish to do business with you?</p>]]></DetailedInformation> | |
| 4289 | <Recommendation><![CDATA[Your script should filter metacharacters from user input.]]></Recommendation> | |
| 4290 | <TechnicalDetails> | |
| 4291 | <Request><![CDATA[POST /readnews.aspx?id=2&NewsAd=javascript:prompt(974652); HTTP/1.1 | |
| 4292 | Content-Length: 10791 | |
| 4293 | Content-Type: application/x-www-form-urlencoded | |
| 4294 | Referer: http://testaspnet.vulnweb.com:80/ | |
| 4295 | Cookie: ASP.NET_SessionId=h40t2vqojkvypzbut2jnhbeh | |
| 4296 | Host: testaspnet.vulnweb.com | |
| 4297 | Connection: Keep-alive | |
| 4298 | Accept-Encoding: gzip,deflate | |
| 4299 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 4300 | Accept: */* | |
| 4301 | ||
| 4302 | __EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWVwKO/ffgDgKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMTuBuYk15KvnzAGnqqPk6tDbzR0Y%3d&__VIEWSTATE=/wEPDwUKLTM1MjIzMjU2OQ9kFgICAQ9kFgwCAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkAgMPFgIfAQVJcG9zdGVkIGJ5IDxzdHJvbmc%2bYWRtaW4gICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjExLzgvMjAwNSAxMTozNToyMiBBTWQCBQ8WAh8BBTxXZWIgYXR0YWNrcyAtIGNhbiB5b3VyIHdlYiBhcHBsaWNhdGlvbnMgd2l0aHN0YW5kIHRoZSBmb3JjZT9kAgcPFgIfAQWuNzxwPjxzdHJvbmc%2bQWN1bmV0aXggY29tYmF0cyByaXNlIGluIHdlYiBhdHRhY2tzIHdpdGggQWN1bmV0aXggICAgICAgICAgICAgICAgICAgICAgICAgICAgV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAyIDwvc3Ryb25nPjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD4yMSBKdWx5IDIwMDUgLSA8c3Ryb25nPlN0YXJ0LXVwIGNvbXBhbnkgQWN1bmV0aXggcmVsZWFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lcjogYSB0b29sIHRvIGF1dG9tYXRpY2FsbHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXVkaXQgd2Vic2l0ZSBzZWN1cml0eS4gQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgU2Nhbm5lciAgICAgICAgICAgICAgICAgICAgICAgICAgICAyIGNyYXdscyBhbiBlbnRpcmUgd2Vic2l0ZSwgbGF1bmNoZXMgcG9wdWxhciB3ZWIgYXR0YWNrcyAgICAgICAgICAgICAgICAgICAgICAgICAgICAoU1FMIEluamVjdGlvbiBldGMuKSBhbmQgaWRlbnRpZmllcyB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdGhhdCBuZWVkIHRvIGJlIGZpeGVkLjwvc3Ryb25nPiA8L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5TZWN1cmluZyB5b3VyIHdlYnNpdGUgc2hvdWxkIGJlIHlvdXIgbnVtYmVyIG9uZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjb25jZXJuPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgSGFja2VycyBhcmUgY29uY2VudHJhdGluZyB0aGVpciBlZmZvcnRzIG9uIHdlYi1iYXNlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBhcHBsaWNhdGlvbnMgLSA3NSUgb2YgY3liZXIgYXR0YWNrcyBhcmUgZG9uZSBhdCB0aGUgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGxldmVsLCBhIEdhcnRuZXIgR3JvdXAgc3R1ZHkgaGFzIHJldmVhbGVkLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBXZWIgYXBwbGljYXRpb25zIGFyZSBhY2Nlc3NpYmxlIDI0IGhvdXJzIGEgZGF5LCA3IGRheXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgYSB3ZWVrIGFuZCBjb250cm9sIHZhbHVhYmxlIGRhdGEgc3VjaCBhcyBjdXN0b21lciBpbmZvcm1hdGlvbiwgICAgICAgICAgICAgICAgICAgICAgICAgICAgdHJhbnNhY3Rpb24gaW5mb3JtYXRpb24gYW5kIGV2ZW4gcHJvcHJpZXRhcnkgY29ycG9yYXRlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGEuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bNTAwLDAwMCBjdXN0b21lciBjcmVkaXQgY2FyZCBudW1iZXJzIG9idGFpbmVkIHZpYSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhIHdlYiBhdHRhY2s8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBXZWxsLWtub3duIHNpdGVzIHRoYXQgd2VyZSBvcGVuIHRvIHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGluY2x1ZGUgZmFzaGlvbiBsYWJlbCBHdWVzcyBhbmQgcGV0IHN1cHBseSByZXRhaWxlciAgICAgICAgICAgICAgICAgICAgICAgICAgICBQZXRDby5jb20gd2hvIHdlcmUgbm90b3Jpb3VzbHkgZm91bmQgdG8gYmUgdnVsbmVyYWJsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB0byB0aGUgU1FMIGluamVjdGlvbiB2dWxuZXJhYmlsaXR5IChKdW5lIDIwMDMpLiBUaGlzICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJlc3VsdGVkIGluIFBldENvIGxlYXZpbmcgYXMgbWFueSBhcyA1MDAsMDAwIGNyZWRpdCAgICAgICAgICAgICAgICAgICAgICAgICAgICBjYXJkIG51bWJlcnMgb3BlbiB0byBhbnlvbmUgYWJsZSB0byBjb25zdHJ1Y3QgdGhpcyBzcGVjaWFsbHktY3JhZnRlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBVUkwuPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzdHJvbmc%2bRmlyZXdhbGxzLCBTU0wgYW5kIGxvY2tlZC1kb3duIHNlcnZlcnMgYXJlIGZ1dGlsZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBoYWNraW5nPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQW55IGRlZmVuc2UgYXQgbmV0d29yayBzZWN1cml0eSBsZXZlbCB3aWxsIHByb3ZpZGUgbm8gICAgICAgICAgICAgICAgICAgICAgICAgICAgcHJvdGVjdGlvbiBhZ2FpbnN0IHdlYiBhcHBsaWNhdGlvbiBhdHRhY2tzIHNpbmNlIHRoZXkgICAgICAgICAgICAgICAgICAgICAgICAgICAgYXJlIGxhdW5jaGVkIG9uIHBvcnQgODAgLSB3aGljaCBoYXMgdG8gcmVtYWluIG9wZW4uICAgICAgICAgICAgICAgICAgICAgICAgICAgIEluIGFkZGl0aW9uLCB3ZWIgYXBwbGljYXRpb25zIChjdXN0b21lciBhcmVhcywgc2hvcHBpbmcgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FydHMgZXRjLikgYXJlIG9mdGVuIHRhaWxvci1tYWRlLCBpbnZhcmlhYmx5IHRlc3RlZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBsZXNzIHRoYW4gb2ZmLXRoZS1zaGVsZiBzb2Z0d2FyZSBhbmQgYXJlIHRoZXJlZm9yZSBtb3JlICAgICAgICAgICAgICAgICAgICAgICAgICAgIHN1c2NlcHRpYmxlIHRvIGF0dGFjay48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bJnF1b3Q7Q29tcGFuaWVzIGhhdmUgaW1wbGVtZW50ZWQgbmV0d29yay1sZXZlbCBzZWN1cml0eSwgICAgICAgICAgICAgICAgICAgICAgICAgICAgaG93ZXZlciB0aGV5IGZhaWwgdG8gYXVkaXQgYW5kIHNlY3VyZSB0aGVpciB3ZWIgYXBwbGljYXRpb25zLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBUaGVzZSBhcHBsaWNhdGlvbnMgaGF2ZSBhY2Nlc3MgdG8gc2Vuc2l0aXZlIGRhdGEgYW5kICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFyZSBhIGhhY2tlcidzIHByaW1lIHRhcmdldCwmcXVvdDsgc2FpZCBOaWNrIEdhbGVhLCAgICAgICAgICAgICAgICAgICAgICAgICAgICBDRU8gb2YgQWN1bmV0aXguICZxdW90O0F1ZGl0aW5nIG9uZSdzIHdlYiBhcHBzIHNob3VsZCAgICAgICAgICAgICAgICAgICAgICAgICAgICBiZSB0aGUgbnVtYmVyIG9uZSBzZWN1cml0eSBjb25jZXJuLiZxdW90OzwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlRoZSBuZWVkIGZvciBhbiBhdXRvbWF0ZWQgd2ViIGFwcGxpY2F0aW9uIHZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgc2Nhbm5lcjwvc3Ryb25nPjxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIE1hbnVhbGx5IGF1ZGl0aW5nIGEgd2ViIGFwcGxpY2F0aW9uIGZvciB2dWxuZXJhYmlsaXRpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgdG8gU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiAgICAgICAgICAgICAgICAgICAgICAgICAgICBhdHRhY2tzIGlzIHZpcnR1YWxseSBpbXBvc3NpYmxlLiBXaXRoIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5ICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNjYW5uZXIgdGhlIHByb2Nlc3Mgb2YgYXVkaXRpbmcgd2ViIGFwcGxpY2F0aW9ucyBzdWNoICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFzIHNob3BwaW5nIGNhcnRzIGFuZCBmb3JtcywgY2FuIGJlIGVhc2lseSBhdXRvbWF0ZWQuICAgICAgICAgICAgICAgICAgICAgICAgICAgIFdoYXQncyBtb3JlLCB0aGUgc2VjdXJpdHkgY2hlY2tzIGNhbiBlYXNpbHkgYmUgcmUtbGF1bmNoZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGVhY2ggYXBwbGljYXRpb24gdXBkYXRlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkhvdyBBY3VuZXRpeCBXZWIgVnVsbmVyYWJpbGl0eSBTY2FubmVyIHdvcmtzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGZpcnN0IGNyYXdscyB0aGUgd2hvbGUgd2Vic2l0ZSwgYW5hbHl6ZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgaW4tZGVwdGggZWFjaCBmaWxlIGl0IGZpbmRzLCBhbmQgZGlzcGxheXMgdGhlIGVudGlyZSAgICAgICAgICAgICAgICAgICAgICAgICAgICB3ZWJzaXRlIHN0cnVjdHVyZS4gQWZ0ZXIgdGhpcyBkaXNjb3Zlcnkgc3RhZ2UsIGl0IHBlcmZvcm1zICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFuIGF1dG9tYXRpYyBhdWRpdCBmb3IgY29tbW9uIHNlY3VyaXR5IHZ1bG5lcmFiaWxpdGllcy48L3A%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BdXRvbWF0aWNhbGx5IGRldGVjdHMgU1FMIGluamVjdGlvbiwgY3Jvc3Mgc2l0ZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY3JpcHRpbmcgYW5kIG90aGVyIHdlYiB2dWxuZXJhYmlsaXRpZXM8L3N0cm9uZz48YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICBTUUwgaW5qZWN0aW9uIGlzIGEgaGFja2luZyB0ZWNobmlxdWUgd2hpY2ggbW9kaWZpZXMgICAgICAgICAgICAgICAgICAgICAgICAgICAgU1FMIGNvbW1hbmRzIGluIG9yZGVyIHRvIGdhaW4gYWNjZXNzIHRvIGRhdGEgaW4gdGhlICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRhdGFiYXNlLiBDcm9zcyBzaXRlIHNjcmlwdGluZyBhdHRhY2tzIGFsbG93IGEgaGFja2VyICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRvIGV4ZWN1dGUgYSBtYWxpY2lvdXMgc2NyaXB0IG9uIHlvdXIgdmlzaXRvcnMnIGJyb3dzZXIuICAgICAgICAgICAgICAgICAgICAgICAgICAgIEFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgY2FuIGNoZWNrIGlmIHlvdXIgICAgICAgICAgICAgICAgICAgICAgICAgICAgd2ViIGFwcGxpY2F0aW9uIGlzIHZ1bG5lcmFibGUgdG8gYm90aCBvZiB0aGVzZSBhdHRhY2tzLiAgICAgICAgICAgICAgICAgICAgICAgICAgICBNb3JlIGluZm9ybWF0aW9uIGFib3V0IGNyb3NzIHNpdGUgc2NyaXB0aW5nICZhbXA7IFNRTCAgICAgICAgICAgICAgICAgICAgICAgICAgICBpbmplY3Rpb24gYXQgb3VyIHdlYnNpdGUgc2VjdXJpdHkgaW5mbyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFjdW5ldGl4IFdlYiBWdWxuZXJhYmlsaXR5IFNjYW5uZXIgYWxzbyBjaGVja3MgZm9yICAgICAgICAgICAgICAgICAgICAgICAgICAgIHRoZSBmb2xsb3dpbmcgd2ViIGF0dGFja3M6PC9zdHJvbmc%2bPC9wPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDx1bD4gPGxpPkNSTEYgaW5qZWN0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5Db2RlIGV4ZWN1dGlvbiBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRGlyZWN0b3J5IHRyYXZlcnNhbCBhdHRhY2tzPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9saT48bGk%2bRmlsZSBpbmNsdXNpb24gYXR0YWNrczxiciAvPiAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvbGk%2bPGxpPiBJbnB1dCB2YWxpZGF0aW9uIGF0dGFja3M8YnIgLz4gICAgICAgICAgICAgICAgICAgICAgICAgICA8L2xpPjxsaT5BdXRoZW50aWNhdGlvbiBhdHRhY2tzLjwvbGk%2bIDwvdWw%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA%2bPHN0cm9uZz5BZHZhbmNlZCBwZW5ldHJhdGlvbiB0ZXN0aW5nIHRvb2xzPC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGFsc28gaW5jbHVkZXMgdG9vbHMgc3VjaCBhcyBhbiBIVFRQIGVkaXRvciAgICAgICAgICAgICAgICAgICAgICAgICAgICAmYW1wOyBIVFRQIHNuaWZmZXIgdG8gYWxsb3cgY3VzdG9taXphdGlvbiBvZiB3ZWIgdnVsbmVyYWJpbGl0eSAgICAgICAgICAgICAgICAgICAgICAgICAgICBjaGVja3MuIFVzaW5nIHRoZSBWdWxuZXJhYmlsaXR5IGVkaXRvciwgbmV3IGF0dGFja3MgICAgICAgICAgICAgICAgICAgICAgICAgICAgY2FuIGVhc2lseSBiZSBjcmVhdGVkLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPlByaWNpbmcgJmFtcDsgYXZhaWxhYmlsaXR5PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggV1ZTIGlzIGF2YWlsYWJsZSBhcyBhbiBlbnRlcnByaXNlIG9yIGFzIGEgY29uc3VsdGFudCAgICAgICAgICAgICAgICAgICAgICAgICAgICB2ZXJzaW9uLiBBIHN1YnNjcmlwdGlvbiBiYXNlZCBsaWNlbnNlIGNhbiBiZSBwdXJjaGFzZWQgICAgICAgICAgICAgICAgICAgICAgICAgICAgZm9yIGFzIGxpdHRsZSBhcyAkMzk1LCB3aGVyZWFzIGEgcGVycGV0dWFsIGxpY2Vuc2Ugc3RhcnRzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGF0ICQyOTk1LiBGb3IgbW9yZSBpbmZvcm1hdGlvbiB2aXNpdCBvdXIgcHJpY2luZyBwYWdlLjwvcD4gICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c3Ryb25nPkFib3V0IEFjdW5ldGl4PC9zdHJvbmc%2bPGJyIC8%2bICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggd2FzIGZvdW5kZWQgdG8gY29tYmF0IHRoZSBhbGFybWluZyByaXNlIGluICAgICAgICAgICAgICAgICAgICAgICAgICAgIHdlYiBhdHRhY2tzLiBJdHMgZmxhZ3NoaXAgcHJvZHVjdCwgQWN1bmV0aXggV2ViIFZ1bG5lcmFiaWxpdHkgICAgICAgICAgICAgICAgICAgICAgICAgICAgU2Nhbm5lciwgaXMgdGhlIHJlc3VsdCBvZiBzZXZlcmFsIHllYXJzIG9mIGRldmVsb3BtZW50ICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJ5IGEgdGVhbSBvZiBoaWdobHkgZXhwZXJpZW5jZWQgc2VjdXJpdHkgZGV2ZWxvcGVycy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgQWN1bmV0aXggaXMgYSBwcml2YXRlbHkgaGVsZCBjb21wYW55IHdpdGggaGVhZHF1YXJ0ZXJzICAgICAgICAgICAgICAgICAgICAgICAgICAgIGJhc2VkIGluIEV1cm9wZSAoTWFsdGEpIHdpdGggaXRzIE5ldyBZb3JrIFVTIG9mZmljZSAgICAgICAgICAgICAgICAgICAgICAgICAgICBzY2hlZHVsZWQgdG8gb3BlbiBpbiBRMyBvZiAyMDA1LiA8L3A%2bIGQCCQ8PFgIeC05hdmlnYXRlVXJsBRJDb21tZW50cy5hc3B4P2lkPTJkZAILDxYCHgNzcmMFDGFkcy9kZWYuaHRtbGRkNCSZh%2buMoCTcXGDfVu5D5CfxA7Y%3d]]></Request> | |
| 4303 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 4304 | Date: Thu, 14 Nov 2013 14:29:49 GMT | |
| 4305 | Server: Microsoft-IIS/6.0 | |
| 4306 | X-Powered-By: ASP.NET | |
| 4307 | X-AspNet-Version: 2.0.50727 | |
| 4308 | Cache-Control: private | |
| 4309 | Content-Type: text/html; charset=utf-8 | |
| 4310 | Content-Length: 29346 | |
| 4311 | ]]></Response> | |
| 4312 | </TechnicalDetails> | |
| 4313 | <References> | |
| 4314 | <Reference> | |
| 4315 | <Database><![CDATA[Acunetix Cross Site Scripting Attack]]></Database> | |
| 4316 | <URL><![CDATA[http://www.acunetix.com/websitesecurity/cross-site-scripting.htm]]></URL> | |
| 4317 | </Reference> | |
| 4318 | <Reference> | |
| 4319 | <Database><![CDATA[VIDEO: How Cross-Site Scripting (XSS) Works]]></Database> | |
| 4320 | <URL><![CDATA[http://www.acunetix.com/blog/web-security-zone/video-how-cross-site-scripting-xss-works/]]></URL> | |
| 4321 | </Reference> | |
| 4322 | <Reference> | |
| 4323 | <Database><![CDATA[The Cross Site Scripting Faq]]></Database> | |
| 4324 | <URL><![CDATA[http://www.cgisecurity.com/xss-faq.html]]></URL> | |
| 4325 | </Reference> | |
| 4326 | <Reference> | |
| 4327 | <Database><![CDATA[OWASP Cross Site Scripting]]></Database> | |
| 4328 | <URL><![CDATA[http://www.owasp.org/index.php/Cross_Site_Scripting]]></URL> | |
| 4329 | </Reference> | |
| 4330 | <Reference> | |
| 4331 | <Database><![CDATA[XSS Annihilation]]></Database> | |
| 4332 | <URL><![CDATA[http://ha.ckers.org/blog/20060602/xss-annihilation/]]></URL> | |
| 4333 | </Reference> | |
| 4334 | <Reference> | |
| 4335 | <Database><![CDATA[XSS Filter Evasion Cheat Sheet]]></Database> | |
| 4336 | <URL><![CDATA[https://www.owasp.org/index.php/XSS_Filter_Evasion_Cheat_Sheet]]></URL> | |
| 4337 | </Reference> | |
| 4338 | <Reference> | |
| 4339 | <Database><![CDATA[Cross site scripting]]></Database> | |
| 4340 | <URL><![CDATA[http://en.wikipedia.org/wiki/Cross-site_scripting ]]></URL> | |
| 4341 | </Reference> | |
| 4342 | <Reference> | |
| 4343 | <Database><![CDATA[OWASP PHP Top 5]]></Database> | |
| 4344 | <URL><![CDATA[http://www.owasp.org/index.php/PHP_Top_5]]></URL> | |
| 4345 | </Reference> | |
| 4346 | <Reference> | |
| 4347 | <Database><![CDATA[How To: Prevent Cross-Site Scripting in ASP.NET]]></Database> | |
| 4348 | <URL><![CDATA[http://msdn.microsoft.com/en-us/library/ms998274.aspx]]></URL> | |
| 4349 | </Reference> | |
| 4350 | </References> | |
| 4351 | </ReportItem> | |
| 4352 | ||
| 4353 | <ReportItem id="51" color="blue"> | |
| 4354 | <Name><![CDATA[Login page password-guessing attack]]></Name> | |
| 4355 | <ModuleName><![CDATA[Scripting (Html_Authentication_Audit.script)]]></ModuleName> | |
| 4356 | <Details><![CDATA[The scanner tested 10 invalid credentials and no account lockout was detected.]]></Details> | |
| 4357 | <Affects><![CDATA[/login.aspx]]></Affects> | |
| 4358 | <Parameter><![CDATA[]]></Parameter> | |
| 4359 | <AOP_SourceFile><![CDATA[]]></AOP_SourceFile> | |
| 4360 | <AOP_SourceLine>0</AOP_SourceLine> | |
| 4361 | <AOP_Additional><![CDATA[]]></AOP_Additional> | |
| 4362 | <IsFalsePositive><![CDATA[False]]></IsFalsePositive> | |
| 4363 | <Severity><![CDATA[low]]></Severity> | |
| 4364 | <Type><![CDATA[Validation]]></Type> | |
| 4365 | <Impact><![CDATA[An attacker may attempt to discover a weak password by systematically trying every possible combination of letters, numbers, and symbols until it discovers the one correct combination that works.]]></Impact> | |
| 4366 | <Description><![CDATA[A common threat web developers face is a password-guessing attack known as a brute force attack. A brute-force attack is an attempt to discover a password by systematically trying every possible combination of letters, numbers, and symbols until you discover the one correct combination that works. <br/><br/> | |
| 4367 | ||
| 4368 | This login page doesn't have any protection against password-guessing attacks (brute force attacks). It's recommended to implement some type of account lockout after a defined number of incorrect password attempts. Consult Web references for more information about fixing this problem. ]]></Description> | |
| 4369 | <DetailedInformation><![CDATA[]]></DetailedInformation> | |
| 4370 | <Recommendation><![CDATA[It's recommended to implement some type of account lockout after a defined number of incorrect password attempts. ]]></Recommendation> | |
| 4371 | <TechnicalDetails> | |
| 4372 | <Request><![CDATA[POST /login.aspx?ReturnUrl=/postnews.aspx HTTP/1.1 | |
| 4373 | Content-Length: 1134 | |
| 4374 | Content-Type: application/x-www-form-urlencoded | |
| 4375 | Referer: http://testaspnet.vulnweb.com:80/ | |
| 4376 | Host: testaspnet.vulnweb.com | |
| 4377 | Connection: Keep-alive | |
| 4378 | Accept-Encoding: gzip,deflate | |
| 4379 | User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36 | |
| 4380 | Accept: */* | |
| 4381 | ||
| 4382 | btnLogin=Login&tbPassword=TKVH3aFE&tbUsername=P4aR2fQn&__EVENTARGUMENT=&__EVENTTARGET=&__EVENTVALIDATION=/wEWWwLeys6NCALStq24BwK3jsrkBALtuvfLDQKC3IeGDAKt3MH6DgKi3JnqBwL0pMmsCQL0pMmsCQL0pP3DAgL0pP3DAgLJy8/oBQLJy8/oBQLJy%2bOPDQLJy%2bOPDQLJy5eiBgLJy5eiBgLJy4v5DwLJy4v5DwLJy7%2bcBwLJy7%2bcBwLJy9MwAsnL0zACycvH1wkCycvH1wkCycv76gICycv76gICycuv0g8Cycuv0g8CycvD9ggCycvD9ggCotKtngoCotKtngoCotLBsgMCotLBsgMCotL1yQwCotL1yQwCotLp7AUCotLp7AUCotKdgw0CotKdgw0CotKxpgYCotKxpgYCotKl/Q8CotKl/Q8CotLZkQcCotLZkQcCotKN%2bQUCotKN%2bQUCotKhnA0CotKhnA0Ch/mzBQKH%2bbMFAof5p9gJAof5p9gJAof52/wCAof52/wCAof5z5MKAof5z5MKAof547YDAof547YDAof5l80MAof5l80MAof5i%2bAFAof5i%2bAFAof5v4cNAof5v4cNAof5k%2bwLAof5k%2bwLAof5h4MDAof5h4MDAqiT88QJAqiT88QJAqiT55sBAqiT55sBAqiTm74KAqiTm74KAqiTj9UDAqiTj9UDAqiTo%2bgMAqiTo%2bgMAqiT14wEAqiT14wEAqiTy6MNAqiTy6MNAqiT/8YGAqiT/8YGAqiT068DAqiT068DAqiTx8IMAqiTx8IMvX3f25exzUvBo2CmzE01Tn1QOss%3d&__VIEWSTATE=/wEPDwUKLTIyMzk2OTgxMQ9kFgICAQ9kFgICAQ9kFgQCAQ8WBB4EaHJlZgUKbG9naW4uYXNweB4JaW5uZXJodG1sBQVsb2dpbmQCAw8WBB8AZB4HVmlzaWJsZWhkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYBBQ9jYlBlcnNpc3RDb29raWWL1W%2bw%2b8Zj9n0mGriLs0UbfzYNdg%3d%3d]]></Request> | |
| 4383 | <Response><![CDATA[HTTP/1.1 200 OK | |
| 4384 | Date: Thu, 14 Nov 2013 14:30:12 GMT | |
| 4385 | Server: Microsoft-IIS/6.0 | |
| 4386 | X-Powered-By: ASP.NET | |
| 4387 | X-AspNet-Version: 2.0.50727 | |
| 4388 | Set-Cookie: ASP.NET_SessionId=o1beqzbkvjzjod55ou10xuna; path=/; HttpOnly | |
| 4389 | Cache-Control: private | |
| 4390 | Content-Type: text/html; charset=utf-8 | |
| 4391 | Content-Length: 12355 | |
| 4392 | ]]></Response> | |
| 4393 | </TechnicalDetails> | |
| 4394 | <References> | |
| 4395 | <Reference> | |
| 4396 | <Database><![CDATA[Blocking Brute Force Attacks]]></Database> | |
| 4397 | <URL><![CDATA[http://www.owasp.org/index.php/Blocking_Brute_Force_Attacks]]></URL> | |
| 4398 | </Reference> | |
| 4399 | </References> | |
| 4400 | </ReportItem> | |
| 4401 | </ReportItems> | |
| 4402 | </Scan> | |
| 4403 | </ScanGroup> |
| 0 | <?xml version="1.0"?> | |
| 1 | <!DOCTYPE issues [ | |
| 2 | <!ELEMENT issues (issue*)> | |
| 3 | <!ATTLIST issues burpVersion CDATA ""> | |
| 4 | <!ATTLIST issues exportTime CDATA ""> | |
| 5 | <!ELEMENT issue (serialNumber, type, name, host, path, location, severity, confidence, issueBackground?, remediationBackground?, issueDetail?, remediationDetail?, requestresponse*)> | |
| 6 | <!ELEMENT serialNumber (#PCDATA)> | |
| 7 | <!ELEMENT type (#PCDATA)> | |
| 8 | <!ELEMENT name (#PCDATA)> | |
| 9 | <!ELEMENT host (#PCDATA)> | |
| 10 | <!ATTLIST host ip CDATA ""> | |
| 11 | <!ELEMENT path (#PCDATA)> | |
| 12 | <!ELEMENT location (#PCDATA)> | |
| 13 | <!ELEMENT severity (#PCDATA)> | |
| 14 | <!ELEMENT confidence (#PCDATA)> | |
| 15 | <!ELEMENT issueBackground (#PCDATA)> | |
| 16 | <!ELEMENT remediationBackground (#PCDATA)> | |
| 17 | <!ELEMENT issueDetail (#PCDATA)> | |
| 18 | <!ELEMENT remediationDetail (#PCDATA)> | |
| 19 | <!ELEMENT requestresponse (request?, response?, responseRedirected?)> | |
| 20 | <!ELEMENT request (#PCDATA)> | |
| 21 | <!ATTLIST request base64 (true|false) "false"> | |
| 22 | <!ELEMENT response (#PCDATA)> | |
| 23 | <!ATTLIST response base64 (true|false) "false"> | |
| 24 | <!ELEMENT responseRedirected (#PCDATA)> | |
| 25 | ]> | |
| 26 | <issues burpVersion="1.5.18" exportTime="Thu Nov 07 15:19:06 GMT-03:00 2013"> | |
| 27 | <issue> | |
| 28 | <serialNumber>382887018676354048</serialNumber> | |
| 29 | <type>3145984</type> | |
| 30 | <name>Cleartext submission of password</name> | |
| 31 | <host ip="200.20.20.201">http://www.example.org.ar</host> | |
| 32 | <path><![CDATA[/index.php]]></path> | |
| 33 | <location><![CDATA[/index.php]]></location> | |
| 34 | <severity>High</severity> | |
| 35 | <confidence>Certain</confidence> | |
| 36 | <issueBackground><![CDATA[Passwords submitted over an unencrypted connection are vulnerable to capture by an attacker who is suitably positioned on the network. This includes any malicious party located on the user's own network, within their ISP, within the ISP used by the application, and within the application's hosting infrastructure. Even if switched networks are employed at some of these locations, techniques exist to circumvent this defense and monitor the traffic passing through switches. ]]></issueBackground> | |
| 37 | <remediationBackground><![CDATA[The application should use transport-level encryption (SSL or TLS) to protect all sensitive communications passing between the client and the server. Communications that should be protected include the login mechanism and related functionality, and any functions where sensitive data can be accessed or privileged actions can be performed. These areas of the application should employ their own session handling mechanism, and the session tokens used should never be transmitted over unencrypted communications. If HTTP cookies are used for transmitting session tokens, then the secure flag should be set to prevent transmission over clear-text HTTP.]]></remediationBackground> | |
| 38 | <issueDetail><![CDATA[The page contains a form with the following action URL, which is submitted over clear-text HTTP:<ul><li>http://www.example.org.ar/login.php</li></ul>The form contains the following password field:<ul><li>pass</li></ul>]]></issueDetail> | |
| 39 | <requestresponse> | |
| 40 | <request base64="true"><![CDATA[R0VUIC9pbmRleC5waHAgSFRUUC8xLjENCkhvc3Q6IHd3dy5zYWx1ZGFjdGl2YS5vcmcuYXINCkFjY2VwdDogKi8qDQpBY2NlcHQtTGFuZ3VhZ2U6IGVuDQpVc2VyLUFnZW50OiBNb3ppbGxhLzUuMCAoY29tcGF0aWJsZTsgTVNJRSA5LjA7IFdpbmRvd3MgTlQgNi4xOyBXaW42NDsgeDY0OyBUcmlkZW50LzUuMCkNCkNvbm5lY3Rpb246IGNsb3NlDQoNCg==]]></request> | |
| 41 | <response base64="true"><![CDATA[SFRUUC8xLjEgMjAwIE9LDQpEYXRlOiBUaHUsIDA3IE5vdiAyMDEzIDE3OjE0OjA1IEdNVA0KU2VydmVyOiBBcGFjaGUvMi4yLjIzIChVbml4KSBtb2Rfc3NsLzIuMi4yMyBPcGVuU1NMLzAuOS44ZS1maXBzLXJoZWw1DQpYLVBvd2VyZWQtQnk6IFBIUC81LjIuMTcNCkV4cGlyZXM6IFRodSwgMTkgTm92IDE5ODEgMDg6NTI6MDAgR01UDQpDYWNoZS1Db250cm9sOiBuby1zdG9yZSwgbm8tY2FjaGUsIG11c3QtcmV2YWxpZGF0ZSwgcG9zdC1jaGVjaz0wLCBwcmUtY2hlY2s9MA0KUHJhZ21hOiBuby1jYWNoZQ0KQ29ubmVjdGlvbjogY2xvc2UNCkNvbnRlbnQtVHlwZTogdGV4dC9odG1sDQpDb250ZW50LUxlbmd0aDogNjA2MDYNCg0KIDxoZWFkPgo8bWV0YSBodHRwLWVxdWl2PSJDb250ZW50LVR5cGUiIGNvbnRlbnQ9InRleHQvaHRtbDsgY2hhcnNldD1pc28tODg1OS0xIiAvPgo8dGl0bGU+U2FsdWQgQWN0aXZhIC0gQWJ1c28gdmlvbGVuY2lhIHkgbWFsdHJhdG88L3RpdGxlPgoKPHNjcmlwdD4gCiAgICAvL2VzdG8gcGFyYSBwYXNhcmxlIGFsIGZsYXNoIGxhcyB2YXJpYWxiZXMgZGVsIHBocAogCQoKCXZhciBib3Q9Jyc7Ci8vYWxlcnQodmFyaWFibGVTZXJ2aWRvcik7Cjwvc2NyaXB0Pgo8c2NyaXB0IGxhbmd1YWdlPSJKYXZhU2NyaXB0IiB0eXBlPSJ0ZXh0L0phdmFTY3JpcHQiPgo8IS0tCmZ1bmN0aW9uIE1NX3ByZWxvYWRJbWFnZXMoKSB7IC8vdjMuMAogIHZhciBkPWRvY3VtZW50OyBpZihkLmltYWdlcyl7IGlmKCFkLk1NX3ApIGQuTU1fcD1uZXcgQXJyYXkoKTsKICAgIHZhciBpLGo9ZC5NTV9wLmxlbmd0aCxhPU1NX3ByZWxvYWRJbWFnZXMuYXJndW1lbnRzOyBmb3IoaT0wOyBpPGEubGVuZ3RoOyBpKyspCiAgICBpZiAoYVtpXS5pbmRleE9mKCIjIikhPTApeyBkLk1NX3Bbal09bmV3IEltYWdlOyBkLk1NX3BbaisrXS5zcmM9YVtpXTt9fQp9Ci8vLS0+Cjwvc2NyaXB0Pgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KCjwvaGVhZD4KCjxzY3JpcHQgbGFuZ3VhZ2U9IkphdmFTY3JpcHQiIHR5cGU9InRleHQvSmF2YVNjcmlwdCI+CjwhLS0KZnVuY3Rpb24gTU1fcmVsb2FkUGFnZShpbml0KSB7ICAvL3JlbG9hZHMgdGhlIHdpbmRvdyBpZiBOYXY0IHJlc2l6ZWQKICBpZiAoaW5pdD09dHJ1ZSkgd2l0aCAobmF2aWdhdG9yKSB7aWYgKChhcHBOYW1lPT0iTmV0c2NhcGUiKSYmKHBhcnNlSW50KGFwcFZlcnNpb24pPT00KSkgewogICAgZG9jdW1lbnQuTU1fcGdXPWlubmVyV2lkdGg7IGRvY3VtZW50Lk1NX3BnSD1pbm5lckhlaWdodDsgb25yZXNpemU9TU1fcmVsb2FkUGFnZTsgfX0KICBlbHNlIGlmIChpbm5lcldpZHRoIT1kb2N1bWVudC5NTV9wZ1cgfHwgaW5uZXJIZWlnaHQhPWRvY3VtZW50Lk1NX3BnSCkgbG9jYXRpb24ucmVsb2FkKCk7Cn0KTU1fcmVsb2FkUGFnZSh0cnVlKTsKLy8tLT4KCjwvc2NyaXB0Pgo8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoKCjwvaGVhZD4KCjxib2R5IGJhY2tncm91bmQ9ImltZy9mb25kb19kZWdyYWRlLmpwZyIgdG9wbWFyZ2luPSIwIj4KPHRhYmxlIHdpZHRoPSIxMDA1IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgPHRyPiAKICAgIDx0ZCB3aWR0aD0iOTYiPjxpbWcgc3JjPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzBfMDEuanBnIiB3aWR0aD0iOTYiIGhlaWdodD0iMjA4IiAvPjwvdGQ+CiAgICA8dGQgd2lkdGg9IjgwOSI+IDxzY3JpcHQgdHlwZT0idGV4dC9qYXZhc2NyaXB0Ij4KQUNfRkxfUnVuQ29udGVudCggJ2NvZGViYXNlJywnaHR0cDovL2Rvd25sb2FkLm1hY3JvbWVkaWEuY29tL3B1Yi9zaG9ja3dhdmUvY2Ficy9mbGFzaC9zd2ZsYXNoLmNhYiN2ZXJzaW9uPTcsMCwxOSwwJywnd2lkdGgnLCc4MDknLCdoZWlnaHQnLCcyMDgnLCdzcmMnLCdzd2YvaGVhZGVyJywncXVhbGl0eScsJ2hpZ2gnLCdwbHVnaW5zcGFnZScsJ2h0dHA6Ly93d3cubWFjcm9tZWRpYS5jb20vZ28vZ2V0Zmxhc2hwbGF5ZXInLCdtb3ZpZScsJ3N3Zi9oZWFkZXInICk7IC8vZW5kIEFDIGNvZGUKPC9zY3JpcHQ+IDxub3NjcmlwdD4KICAgICAgPG9iamVjdCBjbGFzc2lkPSJjbHNpZDpEMjdDREI2RS1BRTZELTExY2YtOTZCOC00NDQ1NTM1NDAwMDAiIGNvZGViYXNlPSJodHRwOi8vZG93bmxvYWQubWFjcm9tZWRpYS5jb20vcHViL3Nob2Nrd2F2ZS9jYWJzL2ZsYXNoL3N3Zmxhc2guY2FiI3ZlcnNpb249NywwLDE5LDAiIHdpZHRoPSI4MDkiIGhlaWdodD0iMjA4Ij4KICAgICAgICA8cGFyYW0gbmFtZT0ibW92aWUiIHZhbHVlPSJzd2YvaGVhZGVyLnN3ZiIgLz4KICAgICAgICA8cGFyYW0gbmFtZT0icXVhbGl0eSIgdmFsdWU9ImhpZ2giIC8+CiAgICAgICAgPGVtYmVkIHNyYz0ic3dmL2hlYWRlci5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9IjgwOSIgaGVpZ2h0PSIyMDgiPjwvZW1iZWQ+IAogICAgICA8L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIHdpZHRoPSIxMiUiIHJvd3NwYW49IjUiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iIzAwMDAwMCI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI0NjEiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmFja2dyb3VuZD0iaW1nL1F1aWVuZXNTb21vc19BMl8wXzEzLmpwZyI+IAogICAgICA8c2NyaXB0IHR5cGU9InRleHQvamF2YXNjcmlwdCI+CkFDX0ZMX1J1bkNvbnRlbnQoICdjb2RlYmFzZScsJ2h0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCcsJ3dpZHRoJywnOTYnLCdoZWlnaHQnLCc0NjEnLCdzcmMnLCdzd2Yvc3VibWVudScsJ3F1YWxpdHknLCdoaWdoJywncGx1Z2luc3BhZ2UnLCdodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyJywnbW92aWUnLCdzd2Yvc3VibWVudScgKTsgLy9lbmQgQUMgY29kZQo8L3NjcmlwdD4gPG5vc2NyaXB0PgogICAgICA8b2JqZWN0IGNsYXNzaWQ9ImNsc2lkOkQyN0NEQjZFLUFFNkQtMTFjZi05NkI4LTQ0NDU1MzU0MDAwMCIgY29kZWJhc2U9Imh0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+CiAgICAgICAgPHBhcmFtIG5hbWU9Im1vdmllIiB2YWx1ZT0ic3dmL3N1Ym1lbnUuc3dmIiAvPgogICAgICAgIDxwYXJhbSBuYW1lPSJxdWFsaXR5IiB2YWx1ZT0iaGlnaCIgLz4KICAgICAgICA8ZW1iZWQgc3JjPSJzd2Yvc3VibWVudS5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+PC9lbWJlZD48L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCIgYmdjb2xvcj0iI0ZGRkZGRiI+CiAgICAgICAgPHRyPiAKICAgICAgICAgIDx0ZCB3aWR0aD0iMTciIHJvd3NwYW49IjciPjxwPiZuYnNwOzwvcD48L3RkPgogICAgICAgICAgPHRkIHdpZHRoPSIxNzIiIGFsaWduPSJjZW50ZXIiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxpbWcgc3JjPSJpbWcvM3B4LmpwZyIgd2lkdGg9IjUiIGhlaWdodD0iNSI+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciI+PGxpbmsgaHJlZj0iLi4vZXN0aWxvcy5jc3MiIHJlbD0ic3R5bGVzaGVldCIgdHlwZT0idGV4dC9jc3MiIC8+Cjxib2R5IGJnY29sb3I9IiNDQ0NDQ0MiIHRvcG1hcmdpbj0iNiBweCI+PHRhYmxlIHdpZHRoPSIxNjUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIzIiBiZ2NvbG9yPSIjRkZGRkZGIj4KPHRyPgogICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTkxIiBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiAgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MThfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+SG9tZTwvYT48L3RkPgogIDwvdHI+Cjx0cj4KICA8dGQgaGVpZ2h0PSIyOCIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj4mbmJzcDsmbmJzcDtOb3RpY2lhczwvYT48L3RkPgo8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJkb25hY2lvbmVzLyIgdGFyZ2V0PSJfYmxhbmsiIGNsYXNzPSJmb25kb2JvdG9uIj5Eb25hY2lvbmVzPC9hPjwvdGQ+CiAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciICB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yM19uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5IaXN0b3JpYWwgZGUgbmV3c2xldHRlcnM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTEzYSIgY2xhc3M9ImZvbmRvYm90b24iPkVudmlhciBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yNl9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5WZXIgdHJhYmFqb3MgZGUgdXN1YXJpb3M8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MTZfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+U2FsdWQgQWN0aXZhIHByZW5zYTwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJtYWlsdG86c2FsdWRhY3RpdmFAc2FsdWRhY3RpdmEub3JnLmFyIiBjbGFzcz0iZm9uZG9ib3RvbiI+TWFuZCZhYWN1dGU7IHR1IEMuVi48L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgIHdpZHRoPSI2ImhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTIxX25ldyIgY2xhc3M9ImZvbmRvYm90b24iPkluZm9ybWFjaSZvYWN1dGU7biBkZSBpbnRlciZlYWN1dGU7czwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyI+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiBoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xMF80IiBjbGFzcz0iZm9uZG9ib3RvbiI+Q29uZ3Jlc29zCiAgICAgICAgICAgICAgICAgIHkgSm9ybmFkYXM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTExIiBjbGFzcz0iZm9uZG9ib3RvbiI+UmVnaXN0cmFjaSZvYWN1dGU7bjwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgCiAgICAgICAgICA8L3RhYmxlPgo8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNSIgdGFyZ2V0PSJfYmxhbmsiPjxicj4KICAgICAgICAgICAgICAgICAgPGltZyBzcmM9ImltZy9iYW5uZXJfZG9uYWNpb25lcy5qcGciIHdpZHRoPSIxNjIiIGhlaWdodD0iMTIwIiBib3JkZXI9IjAiPjxicj4KICAgICAgICAgICAgICAgICAgPGJyPgogICAgICAgICAgICAgICAgICA8aW1nIHNyYz0iaW1nL2JvdG9uRm9yby5naWYiIHdpZHRoPSIxNzIiIGhlaWdodD0iMTE3IiBib3JkZXI9IjAiPjwvYT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTY3IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjkiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzAzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iOSIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTQ5IiBiYWNrZ3JvdW5kPSJpbWcvY2hpY29zX3BlcmRpZG9zXzA1LmdpZiI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDUuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMCI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDcuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMi5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEyLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9InNyYy9pbWdfdXAvMjMwODIwMTIuMS5qcGciIHdpZHRoPSIxNDkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMy5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNi5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iNSIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTcuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNy5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgYmdjb2xvcj0iI0ZFRTdDRiIgY2xhc3M9InRpdHVsb2hvbWU1Ij48c3Ryb25nPk5pJm50aWxkZTtvcyBwZXJkaWRvczxicj4KICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0yOSIgY2xhc3M9ImJvdG9uIj5bVmVyIG0mYWFjdXRlO3NdPC9hPjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTkuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xOS5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18yMC5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iMjUiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4NCgkJCQkNCgkJCQk8Zm9ybSBhY3Rpb249ImluZGV4LnBocD9pZD0xMSIgIG1ldGhvZD0icG9zdCI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9penExLmpwZyIgd2lkdGg9IjEyIiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9hcnJpYmEuanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9kZXIxLmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgIDwvdHI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiIgdmFsaWduPSJ0b3AiIGNsYXNzPSJyZWdGb25kbzEiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9penEuanBnIiB3aWR0aD0iMTIiIGhlaWdodD0iMTIiIC8+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSI5NCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV90aXQuanBnIiB3aWR0aD0iNjYiIGhlaWdodD0iMjMiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSI1MCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJyZWdpc3RyYXJzZSI+SW5ncmVzJmFhY3V0ZTsgDQogICAgICAgICAgICAgIHR1cyBkYXRvcyB5IHJlY2liJmlhY3V0ZTsgbGEgbWVqb3IgaW5mb3JtYWNpJm9hY3V0ZTtuIGEgdHJhdiZlYWN1dGU7cyANCiAgICAgICAgICAgICAgZGUgbnVlc3RybzxzdHJvbmc+IE5ld3NsZXR0ZXI8L3N0cm9uZz4uIDxzdHJvbmc+PHNwYW4gY2xhc3M9ImdyYXRpcyI+R3JhdGlzITwvc3Bhbj48L3N0cm9uZz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI1IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9InRyYWJTRUNDSU9OIj5Ob21icmU8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBjbGFzcz0icmVnQ0VMREEiPjxpbnB1dCBuYW1lPSJub21icmUiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0ibm9tYnJlIiAvPjwvdGQ+DQogICAgICAgICAgPC90cj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0idHJhYlNFQ0NJT04iPkFwZWxsaWRvPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iYXBlbGxpZG8iIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iYXBlbGxpZG8iIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJ0cmFiU0VDQ0lPTiI+RS1tYWlsPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iZW1haWwiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iZW1haWwiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InRyYWJTRUNDSU9OIj4mbmJzcDs8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idHJhYlNFQ0NJT04iPjxpbnB1dCB0eXBlPSJpbWFnZSIgc3JjPSJpbWcvcmVnaXN0cmF0ZV9ib3Rvbi5qcGciIHdpZHRoPSIxMTciIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgIDwvdGFibGU+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE0IiB2YWxpZ249InRvcCIgY2xhc3M9InJlZ0ZvbmRvMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2Rlci5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIxNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KICAgICAgICAgICAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTIiIGhlaWdodD0iMjQiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfaXpxMi5qcGciIHdpZHRoPSIxMiIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI0Ij48aW1nIHNyYz0iaW1nL3JlZ2lzdHJhdGVfYWJham8uanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjI0IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfZGVyMi5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KCQkJCQkNCgkJCQkJPC9mb3JtPg0KICAgICAgICAgICAgICAgICAgPC90YWJsZT4NCjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPiAKICAgICAgICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTcwIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUyIj4KCQkJCQkJCQkJCQkJCQkJCTwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9jbGF1ZGlhMl8wMy5qcGciIHdpZHRoPSIxNzQiIGhlaWdodD0iMjUwIiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcCI+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICA8dGQgcm93c3Bhbj0iNyIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nLzV4NS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjciPjwvdGQ+CiAgICAgICAgICA8dGQgY29sc3Bhbj0iMiIgcm93c3Bhbj0iNCIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPGZvcm0gYWN0aW9uPSJsb2dpbi5waHAiIG1ldGhvZD0icG9zdCIgbmFtZT0iZm9ybTIiPgoKICAgICAgICAgICAgICA8dHI+IAogICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgY29sc3Bhbj0iMiIgYWxpZ249ImxlZnQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIiA+IAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8c3Ryb25nPlVzdWFyaW8gbm8gcmVnaXN0cmFkbzwvc3Ryb25nPiAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9mb250PiA8L3N0cm9uZz4gCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDkiIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPlVzdWFyaW8mbmJzcDsmbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzOSIgdmFsaWduPSJtaWRkbGUiPjxpbnB1dCBuYW1lPSJ1c3VhcmlvIiB0eXBlPSJ0ZXh0IiBjbGFzcz0icmVnIiBpZD0idXN1YXJpbyIgc2l6ZT0iNyI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjciIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPkNvbnRyYXNlJm50aWxkZTthJm5ic3A7Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzkiIHZhbGlnbj0ibWlkZGxlIj48aW5wdXQgbmFtZT0icGFzcyIgdHlwZT0icGFzc3dvcmQiIGNsYXNzPSJyZWciIGlkPSJwYXNzIiBzaXplPSI3Ij48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiIgYWxpZ249InJpZ2h0IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9ImJvdG9uIj48aW5wdXQgdHlwZT0iaW1hZ2UiIHNyYz0iaW1nL3JlZy5qcGciIHdpZHRoPSI1OCIgaGVpZ2h0PSIzMCI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjciIGhlaWdodD0iMTkiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgPjxhIGhyZWY9Imh0dHA6Ly93d3cuZmFjZWJvb2suY29tL2hvbWUucGhwPyMhL3BhZ2VzL01lcmxvLUFyZ2VudGluYS9TQUxVRC1BQ1RJVkEvMTAwNTgzNTQzMzE3MzIyP3JlZj10cyZhamF4cGlwZT0xJl9fYT03IiB0YXJnZXQ9Il9ibGFuayI+PGltZyBzcmM9ImltZy9mYWNlYm9vay5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzExIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj48ZGl2IGFsaWduPSJsZWZ0Ij48YSBocmVmPSJodHRwOi8vdHdpdHRlci5jb20vU2FsdWRBY3RpdmFPTkciIHRhcmdldD0iX2JsYW5rIj48aW1nIHNyYz0iaW1nL3R3aXRlci5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC9kaXY+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSI1IiBhbGlnbj0icmlnaHQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIj48bGFiZWw+PGZvbnQgc2l6ZT0iLTYiPlNpCiAgICAgICAgICAgICAgICAgICAgICAgdG9kYXYmaWFjdXRlO2Egbm8gZXMgdXN1YXJpbyA8L2ZvbnQ+IDxhIGhyZWY9ImluZGV4LnBocD9pZD0xMSIgY2xhc3M9ImJvdG9uIj48Zm9udCBzaXplPSItNiI+cmVnJmlhY3V0ZTtzdHJlc2UKICAgICAgICAgICAgICAgICAgICAgICAgYXF1JmlhY3V0ZTsgPGZvbnQgY29sb3I9IiM2NjY2NjYiPiYjODIyNjs8L2ZvbnQ+PC9mb250PjwvYT4gPGEgaHJlZj0iaW5kZXgucGhwP2lkPTEyIiBjbGFzcz0iYm90b24xIj48Zm9udCBzaXplPSItNiI+b2x2aWRlIG1pIGNvbnRyYXNlJm50aWxkZTthPC9mb250PjwvYT48L2xhYmVsPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE3Ij4mbmJzcDsgPC90ZD4KICAgICAgICAgICAgICA8L3RyPgoJCQkgIDwvZm9ybT4KCiAgICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgICA8IURPQ1RZUEUgaHRtbCBQVUJMSUMgIi0vL1czQy8vRFREIFhIVE1MIDEuMCBUcmFuc2l0aW9uYWwvL0VOIiAiaHR0cDovL3d3dy53My5vcmcvVFIveGh0bWwxL0RURC94aHRtbDEtdHJhbnNpdGlvbmFsLmR0ZCI+CjxodG1sIHhtbG5zPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hodG1sIj4KPGhlYWQ+CjxtZXRhIGh0dHAtZXF1aXY9IkNvbnRlbnQtVHlwZSIgY29udGVudD0idGV4dC9odG1sOyBjaGFyc2V0PWlzby04ODU5LTEiIC8+Cjx0aXRsZT5Eb2N1bWVudG8gc2luIHQmaWFjdXRlO3R1bG88L3RpdGxlPgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KPHNjcmlwdCBsYW5ndWFnZT0iSmF2YVNjcmlwdCIgdHlwZT0idGV4dC9KYXZhU2NyaXB0Ij4KPCEtLQpmdW5jdGlvbiBNTV9yZWxvYWRQYWdlKGluaXQpIHsgIC8vcmVsb2FkcyB0aGUgd2luZG93IGlmIE5hdjQgcmVzaXplZAogIGlmIChpbml0PT10cnVlKSB3aXRoIChuYXZpZ2F0b3IpIHtpZiAoKGFwcE5hbWU9PSJOZXRzY2FwZSIpJiYocGFyc2VJbnQoYXBwVmVyc2lvbik9PTQpKSB7CiAgICBkb2N1bWVudC5NTV9wZ1c9aW5uZXJXaWR0aDsgZG9jdW1lbnQuTU1fcGdIPWlubmVySGVpZ2h0OyBvbnJlc2l6ZT1NTV9yZWxvYWRQYWdlOyB9fQogIGVsc2UgaWYgKGlubmVyV2lkdGghPWRvY3VtZW50Lk1NX3BnVyB8fCBpbm5lckhlaWdodCE9ZG9jdW1lbnQuTU1fcGdIKSBsb2NhdGlvbi5yZWxvYWQoKTsKfQpNTV9yZWxvYWRQYWdlKHRydWUpOwoKZnVuY3Rpb24gTU1fcHJlbG9hZEltYWdlcygpIHsgLy92My4wCiAgdmFyIGQ9ZG9jdW1lbnQ7IGlmKGQuaW1hZ2VzKXsgaWYoIWQuTU1fcCkgZC5NTV9wPW5ldyBBcnJheSgpOwogICAgdmFyIGksaj1kLk1NX3AubGVuZ3RoLGE9TU1fcHJlbG9hZEltYWdlcy5hcmd1bWVudHM7IGZvcihpPTA7IGk8YS5sZW5ndGg7IGkrKykKICAgIGlmIChhW2ldLmluZGV4T2YoIiMiKSE9MCl7IGQuTU1fcFtqXT1uZXcgSW1hZ2U7IGQuTU1fcFtqKytdLnNyYz1hW2ldO319Cn0KLy8tLT4KPC9zY3JpcHQ+CiAgICAgICAgICAgICA8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoJCQkgCjxzdHlsZSB0eXBlPSJ0ZXh0L2NzcyI+CjwhLS0KI0xheWVyMSB7Cglwb3NpdGlvbjphYnNvbHV0ZTsKCXdpZHRoOjY1MXB4OwoJaGVpZ2h0OjIxOHB4OwoJei1pbmRleDoxOwp9CiNMYXllcjIgewoJcG9zaXRpb246YWJzb2x1dGU7Cgl3aWR0aDoyMDBweDsKCWhlaWdodDoxMTVweDsKCXotaW5kZXg6MTsKCXZpc2liaWxpdHk6IHZpc2libGU7Cn0KLkVzdGlsbzEgewoJZm9udC1zaXplOiAxOHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzIgewoJZm9udC1zaXplOiAxNHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzMge2NvbG9yOiAjNTA2OTkwOyBsaW5lLWhlaWdodDogMTJweDsgdGV4dC1kZWNvcmF0aW9uOiBub25lOyBmb250LWZhbWlseTogVGFob21hO30KLS0+Cjwvc3R5bGU+CjwvaGVhZD4KCjxib2R5IGxlZnRtYXJnaW49IjIiIG1hcmdpbndpZHRoPSIyIj4KPHRhYmxlIHdpZHRoPSI2MDgiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICA8dHI+CiAgICA8dGQgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCB3aWR0aD0iMiUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzA3LmpwZyIgd2lkdGg9IjI0IiBoZWlnaHQ9IjE0IiAvPjwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI5MCUiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18wNy5qcGciPiZuYnNwOzwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI4JSIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wOS5qcGciIHdpZHRoPSI0NSIgaGVpZ2h0PSIxNyIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogIDwvdHI+CiAgPHRyPgogICAgPHRkIGNvbHNwYW49IjQiPjxiciAvPgogICAgICA8dGFibGUgd2lkdGg9Ijk4JSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICA8dHI+CiAgICAgICAgPHRkIHdpZHRoPSIyJSI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgICA8dGQgd2lkdGg9IjkzJSI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CjwhLS0gSU5JQ0lPIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzIzMDQyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjIvMTEvMjAxMzwvc3Bhbj48YnI+SVYgQ29uZ3Jlc28gSW50ZXJuYWNpb25hbCB2aW9sZW5jaWEsIG1hbHRyYXRvIHkgYWJ1c288L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxzdHJvbmc+MTQsIDE1IHkgMTYgZGUgTm92aWVtYnJlIEFCSUVSVEEgTEEgSU5TQ1JJUENJJk9hY3V0ZTtOISAoY29uIGRlc2N1ZW50byBoYXN0YSBlbCAyNy84KTxiciAvPjwvc3Ryb25nPjwvcD4NCjxwPjxzdHJvbmc+QUJJRVJUQSBMQSBSRUNFUENJJk9hY3V0ZTtOIERFIFRSQUJBSk88YSBocmVmPSJodHRwOi8vd3d3LmNvbmdyZXNvdmlvbGVuY2lhLmNvbS9pbmRleC5waHA/aWQ9bW9kYWxpZGFkZXMiIHRhcmdldD0iX2JsYW5rIj4gKG1hcyBpbmZvKTwvYT48L3N0cm9uZz48L3A+DQo8cD48c3BhbiBzdHlsZT0iY29sb3I6ICNmZjY2MDA7Ij48c3Ryb25nPk9yZ2FuaXphOiBTYWx1ZCBBY3RpdmE8L3N0cm9uZz48L3NwYW4+PC9wPg0KPHA+PHNwYW4gc3R5bGU9ImNvbG9yOiAjZmY2NjAwOyI+SW5jcmlwdG9zIGFsIFBvcnRhbCBkZSBTYWx1ZCBBY3RpdmEsIGltcG9ydGFudGVzIGRlc2N1ZW50b3MhPGJyIC8+PC9zcGFuPjwvcD4NCjxwPkx1Z2FyIGRlIFJlYWxpemFjaSZvYWN1dGU7biB5IGNvbGFib3JhY2lvbjogVW5pdmVyc2lkYWQgZGVsIEVzdGUsIExhIFBsYXRhIEJ1ZW5vcyBBaXJlczwvcD4NCjxwPk1hcyBkZSAxNTAgdHJhYmFqb3MgcHJlc2VudGFkb3MsIHVsdGltb3MgZGlhcyBwYXJhIGluc2NyaWJpcnNlIGNvbiBkZXNjdWVudG8hITwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPkluc2NyaWJpcnNlPC9hPjwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPjxiciAvPjwvYT48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAxIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDEiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MDQvMTEvMjAxMzwvc3Bhbj48YnI+RWwgY29sZWdpbyBkZSBQc2lj82xvZ29zIGRlIEPzcmRvYmEgc2UgcHJvbnVuY2lhIGVuIHJlbGFjafNuIGFsIFNBUCB5IGVuIGNvbmNvcmRhbmNpYSBjb24gbG8gZXhwcmVzYWRvIHBvciBlbCBDb2xlZ2lvIGRlIFBzaWPzbG9nb3MgZGUgTWFyIGRlbCBQbGF0YSB5IGVsIENvbGVnaW8gZGUgUHNpY/Nsb2dvcyBkZSBsYSAgUHJvdmluY2lhIGRlIEJ1ZW5vcyBBaXJlczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+Jm5ic3A7PC9wPg0KPHA+TGFzIGNvbnRyb3ZlcnNpYXMgZ2VuZXJhZGFzIGVuIHJlbGFjaSZvYWN1dGU7biBhbCAic2luZHJvbWUgZGUgYWxpZW5hY2kmb2FjdXRlO24gcGFyZW50YSIgU0FQLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMxMCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzEwIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzE2MTAyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTYvMTAvMjAxMzwvc3Bhbj48YnI+U2FsdWQgQWN0aXZhIG90b3JnYSBtZWRpYXMgYmVjYXMgcGFyYSBlbCBJViBDb25ncmVzbyBJbnRlcm5hY2lvbmFsLCBWIE5hY2lvbmFsLCBWSSBSZWdpb25hbCBWaW9sZW5jaWEsIE1hbHRyYXRvIHkgQWJ1c28uPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD4mbmJzcDs8L3A+DQo8cD5TZXImYWFjdXRlO24gb3RvcmdhZGFzIDUwIG1lZGlhcyBiZWNhcywgcXVlZGFuIHBvY2FzISEhIGNvbmRpY2lvbjo8L3A+DQo8cD5QZXJ0ZW5lY2VyIGFsIGFtYml0byBwdWJsaWNvIG8gYSBPTkcsIHNlIGNvbnNpZGVyYSB0YW1iaWVuIGxhIGRpc3RhbmNpYSBhbCBsdWdhciBkZWwgZXZlbnRvISEhIGVzIG11eSBzZW5jaWxsbywgc29sbyBkZWJlcyBlbnZpYXIgdW4gZW1haWwuLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwOSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA5Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjI0LzA3LzIwMTM8L3NwYW4+PGJyPk5FQ0VTSVRBTU9TIERFIFNVIFNPTElEQVJJREFEIEhBQ0lBIExPUyBOSdFPUyBZIE5J0UFTISEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPlBST0dSQU1BIEZBTUlMSUFTIFNPTElEQVJJQVM8L3NwYW4+PC9zdHJvbmc+PC9wPg0KPHA+PHN0cm9uZz5DQU1CSU8gREUgU0VERTwvc3Ryb25nPjwvcD4NCjxwPkxhIGNhcGFjaXRhY2kmb2FjdXRlO24gcGFyYSBsYSBwdWVzdGEgZW4gbWFyY2hhIGRlbCA8c3Ryb25nPlByb2dyYW1hIEZhbWlsaWFzIFNvbGlkYXJpYXM8L3N0cm9uZz4gc2UgcmVhbGl6YXImYWFjdXRlOyBlbiBsYSBsb2NhbGlkYWQgZGUgPHN0cm9uZz5OYXZhcnJvPC9zdHJvbmc+IHBhcmEgdG9kbyBlbCBjb3JyZWRvciBkZSBsYSBSdXRhIDQwLjwvcD4NCjxwPkluaWNpbyA8c3Ryb25nPk1pJmVhY3V0ZTtyY29sZXMgMjggZGUgYWdvc3RvIGEgbGFzIDE0IGhvcmFzLiZuYnNwOzwvc3Ryb25nPjwvcD4NCjxwPlNlZGU6IDxzdHJvbmc+U2FsJm9hY3V0ZTtuIE11bmljaXBhbCBlbiBsYSBjYWxsZSAxMDcgZXNxdWluYSAyMiAtIE5hdmFycm88L3N0cm9uZz48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA4Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTIwNzIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xMi8wNy8yMDEzPC9zcGFuPjxicj5TQUxVRCBBQ1RJVkEgaGEgc2lkbyBlbGVnaWRhIHBvciBzZWd1bmRhIHZleiBjb25zZWN1dGl2YSBjb21vIHVubyBkZSBsb3MgZ2FuYWRvcmVzIGRlbCBDdWFydG8gQ29uY3Vyc28gZGUgUHJveWVjdG9zIFNvY2lhbGVzIGRlIFBldHJvYnJhczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+RW4gZWwgbWFyY28gZGVsIEN1YXJ0byBDb25jdXJzbyBkZSBQcm95ZWN0b3MgU29jaWFsZXMgZGUgUGV0cm9icmFzLCANCm51ZXN0cmEgSW5zdGl0dWNpJm9hY3V0ZTtuIFNBTFVEIEFDVElWQSBoYSBzaWRvIGVsZWdpZGEgcG9yIHNlZ3VuZGEgdmV6IA0KY29uc2VjdXRpdmEgY29tbyB1bm8gZGUgbG9zIGdhbmFkb3JlcyBkZSBkaWNobyBjb25jdXJzby48YnIgLz5FbiBlc3RhIA0KZWRpY2kmb2FjdXRlO24gZWwgcHJveWVjdG8gcXVlIGhhIHNpZG8gZWxlZ2lkbyBlcyBlbCAmbGRxdW87UHJvZ3JhbWEgZGUgRmFtaWxpYXMgDQpTb2xpZGFyaWFzJnJkcXVvOyBzaWVuZG8gc3UgJmFhY3V0ZTtyZWEgZGUgaW1wbGVtZW50YWNpJm9hY3V0ZTtuIGxvcyBNdW5pY2lwaW9zIGRlIE5hdmFycm8sIA0KR3JhbC4gTGFzIEhlcmFzLCBNYXJjb3MgUGF6LCB5IE1lcmxvPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAyLzA3LzIwMTM8L3NwYW4+PGJyPk/tciBvIGVzY3VjaGFyPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Qb3IgQ2FybG9zIFJvemFuc2tpICo8L3A+DQo8cD5BIGxvIGxhcmdvIGRlIGxvcyBzaWdsb3MsIGxhcyBuaSZudGlsZGU7YXMsIG5pJm50aWxkZTtvcyB5IGFkb2xlc2NlbnRlcyBoYW4gc2lkbyBtYWx0cmF0YWRvcyB5IGFidXNhZG9zIHNpbiBxdWUgYSBsYSBjb211bmlkYWQgbGUgaW50ZXJlc2FyYSBuaSBzaXF1aWVyYSBlc2N1Y2hhcmxvcyBjdWFuZG8gaGFjJmlhY3V0ZTthbiBzYWJlciBkZSBhbGd1bmEgZm9ybWEgbG9zIHN1ZnJpbWllbnRvcyBxdWUgcGFkZWMmaWFjdXRlO2FuLiBFbiAxODc0LCBlbiBFc3RhZG9zIFVuaWRvcywgZnVlIGxhIHByaW1lcmEgdmV6IHF1ZSBlbCBFc3RhZG8gaW50ZXJ2aW5vIGVuIHVuIGNhc28gZGUgbWFsdHJhdG8geSBhYnVzby4uLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDYiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4wMi8wNy8yMDEzPC9zcGFuPjxicj5FbCBkZXJlY2hvIGRlIGxvcyBuafFvcyBhIHNlciBlc2N1Y2hhZG9zPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5VbiBob21icmUgYWN1c2FkbyBkZSBoYWJlciBhYnVzYWRvIGRlIHN1cyBoaWpvcyBoYWImaWFjdXRlO2Egc2lkbyBzb2JyZXNlJmlhY3V0ZTtkbyBkb3MgdmVjZXMgcG9yIGxhIEp1c3RpY2lhLiBQZXJvIGFob3JhLCBsYSBDJmFhY3V0ZTttYXJhIGRlIENhc2FjaSZvYWN1dGU7biByZXZvYyZvYWN1dGU7IGVzYSBkZWNpc2kmb2FjdXRlO24gcG9ycXVlIGVuIGxhIGludmVzdGlnYWNpJm9hY3V0ZTtuIGVsIGp1ZXogbnVuY2EgaGFiJmlhY3V0ZTthIGVzY3VjaGFkbyBhIGxvcyBjaGljb3MuIFkgb3JkZW4mb2FjdXRlOyBxdWUgdGVuZ2EgZW4gY3VlbnRhIGxvIHF1ZSBkaWNlbi48L3A+DQo8cD5Qb3IgTWFyaWFuYSBDYXJiYWphbDwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDUiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE1NiIgcm93c3Bhbj0iMiIgdmFsaWduPSJ0b3AiPgoJCQkJCgkJCQk8dGFibGUgd2lkdGg9IjMyJSIgYm9yZGVyPSIxIiBjZWxsc3BhY2luZz0iMyIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48aW1nIHNyYz0ic3JjL2ltZ191cC8wNjA2MjAxMy4xLmpwZyIgd2lkdGg9IjE0NiIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT4KCQkJCQkJCQk8L3RkPiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjA2LzA2LzIwMTM8L3NwYW4+PGJyPkFidXNvIHNleHVhbCBpbmZhbnRpbC4gRGVzYWZpb3MgZGUgbGEgY2xpbmljYSBhY3R1YWw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkFiaWVydGEgbGEgaW5zY3JpcGNpb248L3A+DQo8cD5Eb2NlbnRlczogTGljLiBNYXJpYSBCZWF0cml6IE0mdXVtbDtsbGVyLiBMaWMuIFBhb2xhIE11Jm50aWxkZTtveiBEdWFydGU8L3A+DQo8cD5JbmljaW86IE1pZXJjb2xlcyAxOSBkZSBKdW5pbzwvcD4NCjxwPkZyZWN1ZW5jaWE6IFNlbWFuYWw8L3A+DQo8cD5Nb2RhbGlkYWQ6IEludGVuc2l2YTwvcD4NCjxwPkNvbnRlbmlkb3M6ICZuYnNwOyBFc3RhIGRlc3RpbmFkbyBhIHRvZG9zIGxvcyBwcm9mZXNpb25hbGVzIGNvbXByb21ldGlkb3MgY29uIGxhIHRlbWF0aWNhIGRlbCBhYnVzbyBpbmZhbnRpbCBxdWUgcXVpZXJhbiBhY3R1YWxpemFyc2UgZSBpbnRlcmNhbWJpYXIgZXhwZXJpZW5jaWFzIGRlIHRyYWJham8uLi48L3A+DQo8cD4mbmJzcDs8L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA0Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDQiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTYwNTIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xNi8wNS8yMDEzPC9zcGFuPjxicj5TYWx1ZCBBY3RpdmEgbmVjZXNpdGEgZGUgdHUgYXl1ZGEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5UcmFiYWphbW9zIGNvbW8gcG9kZW1vczogYmEmbnRpbGRlO29zIHJvdG9zLCBzdXNwZW5zaSZvYWN1dGU7biBkZSByZXVuaW9uZXMgcG9yIGNvcnRlcyBkZSBsdXogeSBhZ3VhLCBqdWd1ZXRlcyB2aWVqb3MsIG1lc2VzIGRlIGF0cmFzbyBlbiBlbCBwYWdvIGRlIHN1cyBwcm9mZXNpb25hbGVzIGRlIGxhIHNhbHVkLiBSZWNpZW50ZW1lbnRlIHR1dmltb3MgcXVlIGNlcnJhciBudWVzdHJvIHF1ZXJpZG8gSG9nYXI6ICZsZHF1bztNZXRhbW9yZm9zaXMmcmRxdW87IGVyYSBlbCBsdWdhciBxdWUgc3VwbyBjb250ZW5lciBhIG5pJm50aWxkZTthcyB5IGomb2FjdXRlO3ZlbmVzIHJlc2NhdGFkYSBkZSByZWRlcyBkZSB0cmF0YSBvIHYmaWFjdXRlO2N0aW1hcyBkZSBhYnVzbyBpbnRyYWZhbWlsaWFyLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAzIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAzLzA1LzIwMTM8L3NwYW4+PGJyPlJFUFVESU8gQSBMQSBQUkVTRU5DSUEgRU4gTEEgRkVSSUEgREVMIExJQlJPIERFIFVOIEVYIEpVRVogQUNVU0FETyBERSBBQlVTTyBTRVhVQUw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkZ1ZSBjYW1hcmlzdGEgZW4gTWFyIGRlbCBQbGF0YSBkdXJhbnRlIGxhIGRpY3RhZHVyYS4gSGFjZSBhJm50aWxkZTtvcywgdmFyaWFzIG11amVyZXMgbG8gYWN1c2Fyb24gZGUgaGFiZXIgYWJ1c2FkbyBkZSBlbGxhcyBjdWFuZG8gZXJhbiBuaSZudGlsZGU7YXMuIExhIGNhdXNhIHByZXNjcmliaSZvYWN1dGU7IHkgbm8gaHVibyBjb25kZW5hLiBNYSZudGlsZGU7YW5hIHRpZW5lIHByZXZpc3RvIGZpcm1hciBzdSBsaWJyby4gRXNhcyBtaXNtYXMgbXVqZXJlcyBwaWRlbiBxdWUgbm8gc2VhIGFkbWl0aWRvIGVuIGxhIGZlcmlhLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDIiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgIDwhLS0gRklOIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgIDwvdGFibGU+ICAgICAgICA8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iNSUiIGFsaWduPSJyaWdodCI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgPC90cj4KICAgIDwvdGFibGU+PC90ZD4KICA8L3RyPgogIDx0cj4KICAgIDx0ZCB3aWR0aD0iMSUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiIgYWxpZ249ImNlbnRlciI+Jm5ic3A7PC90ZD4KICAgIDx0ZCB3aWR0aD0iMiUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgPC90cj4KICAKICA8dGQ+CiAgPHRyPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0ciBhbGlnbj0iY2VudGVyIj4KICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgPHRkIHdpZHRoPSI5NyIgY29sc3Bhbj0iMiIgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iNTQ2IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idGl0dWxvaG9tZTIiPjx0YWJsZSB3aWR0aD0iIiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYWxpZ249ImxlZnQiIHZhbGlnbj0iYm90dG9tIiBjbGFzcz0idGl0dWxvaG9tZTIiPlJhbmtpbmc8L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSIgY2xhc3M9InRpdHVsb2hvbWUyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iIiBoZWlnaHQ9IjM1IiBhbGlnbj0ibGVmdCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPiZidWxsO0xhcyBtJmFhY3V0ZTtzIGxlaWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGNsYXNzPSJjb250ZW5pZG9ob21lIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBjbGFzcz0iY29udGVuaWRvaG9tZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+JmJ1bGw7TGFzIG0mYWFjdXRlO3MgY29tZW50YWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTHVkb3RlY2EgR2FyYWJhdG8gLSBQcm95ZWN0byBzYWx1ZGFjdGl2YSwgUG9yIHVuYSBpbmZhbmNpYSBmZWxpeiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iOSUiIGJnY29sb3I9IiNFRkVGRUYiPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzJSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xNjIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDUlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTE2MiIgY2xhc3M9ImJvdG9uIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBDdXJzbyBJbnRlbnNpdm8gZGUgb3BlcmFkb3IgdGVyYXBldXRpY28gZXNwZWNpYWxpemFkbyBlbiBlbCBhYm9yZGFqZSBkZWwgYWJ1c28sIGxhIHZpb2xlbmNpYSB5IGVsIG1hbHRyYXRvIGluZmFudGlsICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgUFJPR1JBTUEgTEFTIFZJQ1RJTUFTIENPTlRSQSBMQVMgVklPTEVOQ0lBUyAgTWluaXN0ZXJpbyBkZSBKdXN0aWNpYSB5IERlcmVjaG9zIEh1bWFub3MgZGUgbGEgTmFjafNuICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI5JSIgYmdjb2xvcj0iI0VGRUZFRiI+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjMlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTI1NSIgY2xhc3M9ImJvdG9uIj48aW1nIHNyYz0iaW1nL2ZsZWNoYW5hcmFuamFmZ3Jpc18yNC5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSI3IiBib3JkZXI9IjAiIGFsaWduPSJhYnNtaWRkbGUiIC8+PC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI0NSUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MjU1IiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIERpcGxvbWF0dXJhIGVuIEFib3JkYWplIGludGVyZGlzY2lwbGluYXJpbyBkZWwgbWFsdHJhdG8sIGxhIHZpb2xlbmNpYSB5IGVsIGFidXNvIHNleHVhbCBpbmZhbnRpbCAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyJSIgaGVpZ2h0PSIyMCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQxJSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNhbHVkIEFjdGl2YSBuZWNlc2l0YSBkZSB0dSBheXVkYSEgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjklIiBiZ2NvbG9yPSIjRUZFRkVGIj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMyUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MTA0IiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQ1JSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xMDQiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTGxhbWFkbyBwYXJhIHByZXNlbnRhY2nzbiBkZSB0cmFiYWpvcy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjIwIiBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyMCIgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGJnY29sb3I9IiNGRkZGRkYiIGNsYXNzPSJ0ZXh0b251ZXZvIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPgogICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iIyIgY2xhc3M9ImJvdG9uIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgPC90YWJsZT48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj4mbmJzcDs8L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBJTklDSU8gbm90YSBjb211biAtLT4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTUvMDQvMjAxMjwvc3Bhbj48YnI+T3JnYW5pemFuIGpvcm5hZGEgc29icmUgdmlvbGVuY2lhPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPlNlIGNlbnRyYXImYWFjdXRlOyBlbiBsb3MgZmVuJm9hY3V0ZTttZW5vcyBxdWUgYWZlY3RhbiBhIGxhIGZhbWlsaWEgeSBlbiBsbyBxdWUgb2N1cnJlIGVuIGxhcyBlc2N1ZWxhcy48YnIgLz4gU2UgbGxldmFyJmFhY3V0ZTsgYSBjYWJvIGVsIGx1bmVzIDIzLCBlbiBlbCBDZW50cm8gQ3VsdHVyYWwgZGUgVG9zY2hpIHkgVHJlcyANCkFycm95b3MsIHVuYSBqb3JuYWRhIGRlIHJlZmxleGkmb2FjdXRlO24geSBkZWJhdGUgYWJpZXJ0YSBhIGxhIGNvbXVuaWRhZCBzb2JyZSANCiZsZHF1bztWaW9sZW5jaWEgZW4gbGEgZmFtaWxpYSB5IGVuIGxhIGVzY3VlbGEgeSBzdSByZWxhY2kmb2FjdXRlO24gY29uIGVsIGZyYWNhc28gDQplc2NvbGFyJnJkcXVvOywgb3JnYW5pemFkYSBwb3IgbGEgQXNvY2lhY2kmb2FjdXRlO24gQ2l2aWwgQ2VudHJvIEFydCZlYWN1dGU7bWlkZXMgeSBsYSANCk11bmljaXBhbGlkYWQgZGUgQ2lwb2xsZXR0aS5TZSBjZW50cmFyJmFhY3V0ZTsgZW4gbG9zIGZlbiZvYWN1dGU7bWVub3MgcXVlIGFmZWN0YW4gYSBsYSBmYW1pbGlhIHkgZW4gbG8gcXVlIG9jdXJyZSBlbiBsYXMgZXNjdWVsYXMuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjMwLzAzLzIwMTI8L3NwYW4+PGJyPkNhcnRhIGRlIEFTQVBNSSAtIEFzb2NpYWNp824gQXJnZW50aW5hIGRlIFByZXZlbmNp824gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbDwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjE1IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSIxNSIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjgwIiBjb2xzcGFuPSI0IiBhbGlnbj0ibGVmdCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Mb3MgaW50ZWdyYW50ZXMgZGUgbGEgQ29taXNpJm9hY3V0ZTtuIERpcmVjdGl2YSBkZSBBU0FQTUkgLSBBc29jaWFjaSZvYWN1dGU7biBBcmdlbnRpbmEgZGUgUHJldmVuY2kmb2FjdXRlO24gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbCwgYXNvY2lhZGEgYSBsYSBJbnRlcm5hdGlvbmFsIFNvY2lldHkgZm9yIFByZXZlbnRpb24gb2YgQ2hpbGQgQWJ1c2UgYW5kIE5lZ2xlY3QgKElTUENBTikgLSwgdGVuZW1vcyBlbCBhZ3JhZG8gZGUgZGlyaWdpcm5vcyBhIFVzdGVkIHBhcmEgdHJhc21pdGlybGUgbnVlc3RyYSBwcm9mdW5kYSAmbmJzcDt5IGhvbmRhIHByZW9jdXBhY2kmb2FjdXRlO24gcG9yIGxhIHBvc3R1cmEgcXVlIHZpZW5lbiBhc3VtaWVuZG8gZW4gZm9ybWEgY29udGludWFkYSBhbGd1bm9zIGNvbGVnaW9zIGRlIHBzaWMmb2FjdXRlO2xvZ29zLCBlc3BlY2lhbG1lbnRlIGRlIGxhIHByb3ZpbmNpYSBkZSBCdWVub3MgQWlyZXMsIGVuIHJlbGFjaSZvYWN1dGU7biBhbCB0cmF0YW1pZW50byBwb2NvIHNlcmlvIHkgY29tcHJvbWV0aWRvIHF1ZSBzZSBsZXMgb3RvcmdhIGEgbGFzIGRlbnVuY2lhcyBlZmVjdHVhZGFzIGNvbnRyYSBwcm9mZXNpb25hbGVzIHBzaWMmb2FjdXRlO2xvZ29zLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjAvMDMvMjAxMjwvc3Bhbj48YnI+TEEgVklPTEVOQ0lBIFNFWFVBTCBDT05UUkEgTknRT1MgWSBOSdFBUyBFTiBDSUZSQVM8L3RkPgogICAgICAgICAgPC90cj4KICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkIHdpZHRoPSIxNSIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4MCIgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+UmFkaW9ncmFmJmlhY3V0ZTthIGRlIHVuIHByb2JsZW1hPC9wPg0KPHA+RGUgbG9zIG4mdWFjdXRlO21lcm9zIGNvbXBpbGFkb3MgcG9yIGRvcyBlcXVpcG9zIGRlbCBNaW5pc3RlcmlvIGRlIEp1c3RpY2lhLCBsYQ0KIGF1dG9yYSB0b21hIGxvcyBkZSBsYSBjaXVkYWQgZGUgQnVlbm9zIEFpcmVzIHBhcmEgdHJhemFyIHVuIHBhcmFkaWdtYSANCmRlIGxvcyBkZWxpdG9zIGNvbnRyYSBsYSBpbnRlZ3JpZGFkIHNleHVhbCBlbiBlbCBwYSZpYWN1dGU7cyB5IHNvYnJlIHN1IA0KYXRlbmNpJm9hY3V0ZTtuLjxiciAvPiA8YnIgLz4gJm5ic3A7UG9yIEV2YSBHaWJlcnRpPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2MCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjAiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjE1LzAzLzIwMTI8L3NwYW4+PGJyPkZBTExPIERFIExBIENPUlRFIFNVUFJFTUEgU09CUkUgTEEgTk8gSlVESUNJQUxJWkFDSU9OIERFTCBBQk9SVE8gRU4gQ0FTT1MgREUgVklPTEFDSU9OPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxiciAvPiBKVVJJU0RJQ0NJT046IE5BQ0lPTkFMPGJyIC8+IE1BVEVSSUE6IEFCT1JUTy48YnIgLz4gVFJJQlVOQUw6IENvcnRlIFN1cHJlbWEgZGUgSnVzdGljaWEgZGUgbGEgTmFjaSZvYWN1dGU7bi48YnIgLz4gQVVUT1M6IEYuLCBBLiBMLiBzLyBtZWRpZGEgYXV0b3NhdGlzZmFjdGl2YS48YnIgLz4gRkVDSEE6IDEzLzAzLzIwMTIuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI1OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNTkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBGSU4gbm90YSBjb211biAtLT4KPC90YWJsZT4KPG1hcCBuYW1lPSJNYXBNYXAiIGlkPSJNYXBNYXAiPjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjE0NCw0LDIxNCwzNiIgaHJlZj0iaW5kZXgucGhwP2lkPTE0IiAvPgo8L21hcD4KPG1hcCBuYW1lPSJNYXAyTWFwMiIgaWQ9Ik1hcDJNYXAyIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIxNDcsNCwyMjAsMzYiIGhyZWY9ImluZGV4LnBocD9pZD0xNGEiIC8+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcDMiIGlkPSJNYXAzIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIzNjMsMyw0MzYsMzkiIGhyZWY9ImluZGV4LnBocD9pZD0xNGIiIC8+CjwvbWFwPgo8L2h0bWw+CjwvdGQ+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gICAgICAgICAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFM0UzRTMiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSI3MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNiUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9kZWNpbG9fYmllbl9mdWVydGUxLmpwZyIgd2lkdGg9IjEyMCIgaGVpZ2h0PSIxMTIiPjwvdGQ+CiAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiA+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTI0IiBjbGFzcz0iYm90b24xIj5bK10gTSZhYWN1dGU7cyBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0UzRTNFMyI+ICAgICAgICA8L3RyPgogICAgICAgIDx0cj4gCiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj4mbmJzcDs8L3RkPgogICAgICAgIDwvdHI+CiAgICA8L3RhYmxlPjwvdGQ+CiAgPC90cj4KICA8dHI+IAogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSI+PGltZyBzcmM9ImltZy9penExLmpwZyIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjExNCIgLz48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9RdWllbmVzU29tb3NfQTJfMF8yNS5qcGciIHdpZHRoPSI4MDkiIGhlaWdodD0iMTE0IiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcDIiIC8+PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI1MCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiYWNrZ3JvdW5kPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzE4XzE4LmpwZyI+Jm5ic3A7PC90ZD4KICAgIDx0ZCBoZWlnaHQ9IjUwIiBjbGFzcz0iZm9uZG9ib3R0b20iPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2l0ZWkuY29tLmFyLyI+PGltZyBzcmM9ImltZy9laV9jb2xvci5wbmciIGFsdD0iZXNwYWNpb3MgZGUgaW1hZ2luYWNpb24sIGRlc2Fycm9sbG9zIGludGVyYWN0aXZvcywgY3JlYXRpdmlkYWQsIGRpc2XxbyIgd2lkdGg9IjI3IiBoZWlnaHQ9IjE1IiBib3JkZXI9IjAiPjwvYT4gPHNwYW4gY2xhc3M9ImVpIj48YSBocmVmPSJodHRwOi8vd3d3LnNpdGVpLmNvbS5hci8iIHNwYW4gY2xhc3M9ImVpIj5kaXNlJm50aWxkZTtvICsgY29tdW5pY2FjaSZvYWN1dGU7bjwvYT48L3NwYW4+PGVtPiZuYnNwOzwvZW0+PC9zcGFuPjxzcGFuIGNsYXNzPSJibGFuY28xIj48ZW0+Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7PC9lbT48L3NwYW4+PC90ZD4KICA8L3RyPgo8L3RhYmxlPgoKCjxtYXAgbmFtZT0iTWFwMiI+PGFyZWEgc2hhcGU9InJlY3QiIGNvb3Jkcz0iMjQ3LDY5LDQxNCw4MiIgaHJlZj0ibWFpbHRvOnNhbHVkYWN0aXZhQHNhbHVkYWN0aXZvLm9yZy5hciI+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcCI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM2LDE0MiwxNDksMTUyIiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MiI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM0LDE4NiwxNTAsMTk2IiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MCI+CjwvbWFwPgo8L2JvZHk+CjwvaHRtbD4K]]></response> | |
| 42 | <responseRedirected>false</responseRedirected> | |
| 43 | </requestresponse> | |
| 44 | </issue> | |
| 45 | <issue> | |
| 46 | <serialNumber>7694445463187357696</serialNumber> | |
| 47 | <type>3145984</type> | |
| 48 | <name>Cleartext submission of password</name> | |
| 49 | <host ip="200.20.20.201">http://www.example.org.ar</host> | |
| 50 | <path><![CDATA[/]]></path> | |
| 51 | <location><![CDATA[/]]></location> | |
| 52 | <severity>High</severity> | |
| 53 | <confidence>Certain</confidence> | |
| 54 | <issueBackground><![CDATA[Passwords submitted over an unencrypted connection are vulnerable to capture by an attacker who is suitably positioned on the network. This includes any malicious party located on the user's own network, within their ISP, within the ISP used by the application, and within the application's hosting infrastructure. Even if switched networks are employed at some of these locations, techniques exist to circumvent this defense and monitor the traffic passing through switches. ]]></issueBackground> | |
| 55 | <remediationBackground><![CDATA[The application should use transport-level encryption (SSL or TLS) to protect all sensitive communications passing between the client and the server. Communications that should be protected include the login mechanism and related functionality, and any functions where sensitive data can be accessed or privileged actions can be performed. These areas of the application should employ their own session handling mechanism, and the session tokens used should never be transmitted over unencrypted communications. If HTTP cookies are used for transmitting session tokens, then the secure flag should be set to prevent transmission over clear-text HTTP.]]></remediationBackground> | |
| 56 | <issueDetail><![CDATA[The page contains a form with the following action URL, which is submitted over clear-text HTTP:<ul><li>http://www.example.org.ar/login.php</li></ul>The form contains the following password field:<ul><li>pass</li></ul>]]></issueDetail> | |
| 57 | <requestresponse> | |
| 58 | <request base64="true"><![CDATA[R0VUIC8gSFRUUC8xLjENCkhvc3Q6IHd3dy5zYWx1ZGFjdGl2YS5vcmcuYXINClVzZXItQWdlbnQ6IE1vemlsbGEvNS4wIChNYWNpbnRvc2g7IEludGVsIE1hYyBPUyBYIDEwLjg7IHJ2OjIzLjApIEdlY2tvLzIwMTAwMTAxIEZpcmVmb3gvMjMuMA0KQWNjZXB0OiB0ZXh0L2h0bWwsYXBwbGljYXRpb24veGh0bWwreG1sLGFwcGxpY2F0aW9uL3htbDtxPTAuOSwqLyo7cT0wLjgNCkFjY2VwdC1MYW5ndWFnZTogZW4tVVMsZW47cT0wLjUNCkFjY2VwdC1FbmNvZGluZzogZ3ppcCwgZGVmbGF0ZQ0KQ29ubmVjdGlvbjoga2VlcC1hbGl2ZQ0KDQo=]]></request> | |
| 59 | <response base64="true"><![CDATA[SFRUUC8xLjEgMjAwIE9LDQpEYXRlOiBUaHUsIDA3IE5vdiAyMDEzIDE3OjEyOjAyIEdNVA0KU2VydmVyOiBBcGFjaGUvMi4yLjIzIChVbml4KSBtb2Rfc3NsLzIuMi4yMyBPcGVuU1NMLzAuOS44ZS1maXBzLXJoZWw1DQpYLVBvd2VyZWQtQnk6IFBIUC81LjIuMTcNCkV4cGlyZXM6IFRodSwgMTkgTm92IDE5ODEgMDg6NTI6MDAgR01UDQpDYWNoZS1Db250cm9sOiBuby1zdG9yZSwgbm8tY2FjaGUsIG11c3QtcmV2YWxpZGF0ZSwgcG9zdC1jaGVjaz0wLCBwcmUtY2hlY2s9MA0KUHJhZ21hOiBuby1jYWNoZQ0KU2V0LUNvb2tpZTogUEhQU0VTU0lEPTk0NTg1YWEwYzExY2YyZTg2NGQ4M2UyNDY3OGI5ODY1OyBwYXRoPS8NCktlZXAtQWxpdmU6IHRpbWVvdXQ9MjAsIG1heD0yMDANCkNvbm5lY3Rpb246IEtlZXAtQWxpdmUNCkNvbnRlbnQtVHlwZTogdGV4dC9odG1sDQpDb250ZW50LUxlbmd0aDogNjA2MDYNCg0KIDxoZWFkPgo8bWV0YSBodHRwLWVxdWl2PSJDb250ZW50LVR5cGUiIGNvbnRlbnQ9InRleHQvaHRtbDsgY2hhcnNldD1pc28tODg1OS0xIiAvPgo8dGl0bGU+U2FsdWQgQWN0aXZhIC0gQWJ1c28gdmlvbGVuY2lhIHkgbWFsdHJhdG88L3RpdGxlPgoKPHNjcmlwdD4gCiAgICAvL2VzdG8gcGFyYSBwYXNhcmxlIGFsIGZsYXNoIGxhcyB2YXJpYWxiZXMgZGVsIHBocAogCQoKCXZhciBib3Q9Jyc7Ci8vYWxlcnQodmFyaWFibGVTZXJ2aWRvcik7Cjwvc2NyaXB0Pgo8c2NyaXB0IGxhbmd1YWdlPSJKYXZhU2NyaXB0IiB0eXBlPSJ0ZXh0L0phdmFTY3JpcHQiPgo8IS0tCmZ1bmN0aW9uIE1NX3ByZWxvYWRJbWFnZXMoKSB7IC8vdjMuMAogIHZhciBkPWRvY3VtZW50OyBpZihkLmltYWdlcyl7IGlmKCFkLk1NX3ApIGQuTU1fcD1uZXcgQXJyYXkoKTsKICAgIHZhciBpLGo9ZC5NTV9wLmxlbmd0aCxhPU1NX3ByZWxvYWRJbWFnZXMuYXJndW1lbnRzOyBmb3IoaT0wOyBpPGEubGVuZ3RoOyBpKyspCiAgICBpZiAoYVtpXS5pbmRleE9mKCIjIikhPTApeyBkLk1NX3Bbal09bmV3IEltYWdlOyBkLk1NX3BbaisrXS5zcmM9YVtpXTt9fQp9Ci8vLS0+Cjwvc2NyaXB0Pgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KCjwvaGVhZD4KCjxzY3JpcHQgbGFuZ3VhZ2U9IkphdmFTY3JpcHQiIHR5cGU9InRleHQvSmF2YVNjcmlwdCI+CjwhLS0KZnVuY3Rpb24gTU1fcmVsb2FkUGFnZShpbml0KSB7ICAvL3JlbG9hZHMgdGhlIHdpbmRvdyBpZiBOYXY0IHJlc2l6ZWQKICBpZiAoaW5pdD09dHJ1ZSkgd2l0aCAobmF2aWdhdG9yKSB7aWYgKChhcHBOYW1lPT0iTmV0c2NhcGUiKSYmKHBhcnNlSW50KGFwcFZlcnNpb24pPT00KSkgewogICAgZG9jdW1lbnQuTU1fcGdXPWlubmVyV2lkdGg7IGRvY3VtZW50Lk1NX3BnSD1pbm5lckhlaWdodDsgb25yZXNpemU9TU1fcmVsb2FkUGFnZTsgfX0KICBlbHNlIGlmIChpbm5lcldpZHRoIT1kb2N1bWVudC5NTV9wZ1cgfHwgaW5uZXJIZWlnaHQhPWRvY3VtZW50Lk1NX3BnSCkgbG9jYXRpb24ucmVsb2FkKCk7Cn0KTU1fcmVsb2FkUGFnZSh0cnVlKTsKLy8tLT4KCjwvc2NyaXB0Pgo8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoKCjwvaGVhZD4KCjxib2R5IGJhY2tncm91bmQ9ImltZy9mb25kb19kZWdyYWRlLmpwZyIgdG9wbWFyZ2luPSIwIj4KPHRhYmxlIHdpZHRoPSIxMDA1IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgPHRyPiAKICAgIDx0ZCB3aWR0aD0iOTYiPjxpbWcgc3JjPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzBfMDEuanBnIiB3aWR0aD0iOTYiIGhlaWdodD0iMjA4IiAvPjwvdGQ+CiAgICA8dGQgd2lkdGg9IjgwOSI+IDxzY3JpcHQgdHlwZT0idGV4dC9qYXZhc2NyaXB0Ij4KQUNfRkxfUnVuQ29udGVudCggJ2NvZGViYXNlJywnaHR0cDovL2Rvd25sb2FkLm1hY3JvbWVkaWEuY29tL3B1Yi9zaG9ja3dhdmUvY2Ficy9mbGFzaC9zd2ZsYXNoLmNhYiN2ZXJzaW9uPTcsMCwxOSwwJywnd2lkdGgnLCc4MDknLCdoZWlnaHQnLCcyMDgnLCdzcmMnLCdzd2YvaGVhZGVyJywncXVhbGl0eScsJ2hpZ2gnLCdwbHVnaW5zcGFnZScsJ2h0dHA6Ly93d3cubWFjcm9tZWRpYS5jb20vZ28vZ2V0Zmxhc2hwbGF5ZXInLCdtb3ZpZScsJ3N3Zi9oZWFkZXInICk7IC8vZW5kIEFDIGNvZGUKPC9zY3JpcHQ+IDxub3NjcmlwdD4KICAgICAgPG9iamVjdCBjbGFzc2lkPSJjbHNpZDpEMjdDREI2RS1BRTZELTExY2YtOTZCOC00NDQ1NTM1NDAwMDAiIGNvZGViYXNlPSJodHRwOi8vZG93bmxvYWQubWFjcm9tZWRpYS5jb20vcHViL3Nob2Nrd2F2ZS9jYWJzL2ZsYXNoL3N3Zmxhc2guY2FiI3ZlcnNpb249NywwLDE5LDAiIHdpZHRoPSI4MDkiIGhlaWdodD0iMjA4Ij4KICAgICAgICA8cGFyYW0gbmFtZT0ibW92aWUiIHZhbHVlPSJzd2YvaGVhZGVyLnN3ZiIgLz4KICAgICAgICA8cGFyYW0gbmFtZT0icXVhbGl0eSIgdmFsdWU9ImhpZ2giIC8+CiAgICAgICAgPGVtYmVkIHNyYz0ic3dmL2hlYWRlci5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9IjgwOSIgaGVpZ2h0PSIyMDgiPjwvZW1iZWQ+IAogICAgICA8L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIHdpZHRoPSIxMiUiIHJvd3NwYW49IjUiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iIzAwMDAwMCI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI0NjEiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmFja2dyb3VuZD0iaW1nL1F1aWVuZXNTb21vc19BMl8wXzEzLmpwZyI+IAogICAgICA8c2NyaXB0IHR5cGU9InRleHQvamF2YXNjcmlwdCI+CkFDX0ZMX1J1bkNvbnRlbnQoICdjb2RlYmFzZScsJ2h0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCcsJ3dpZHRoJywnOTYnLCdoZWlnaHQnLCc0NjEnLCdzcmMnLCdzd2Yvc3VibWVudScsJ3F1YWxpdHknLCdoaWdoJywncGx1Z2luc3BhZ2UnLCdodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyJywnbW92aWUnLCdzd2Yvc3VibWVudScgKTsgLy9lbmQgQUMgY29kZQo8L3NjcmlwdD4gPG5vc2NyaXB0PgogICAgICA8b2JqZWN0IGNsYXNzaWQ9ImNsc2lkOkQyN0NEQjZFLUFFNkQtMTFjZi05NkI4LTQ0NDU1MzU0MDAwMCIgY29kZWJhc2U9Imh0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+CiAgICAgICAgPHBhcmFtIG5hbWU9Im1vdmllIiB2YWx1ZT0ic3dmL3N1Ym1lbnUuc3dmIiAvPgogICAgICAgIDxwYXJhbSBuYW1lPSJxdWFsaXR5IiB2YWx1ZT0iaGlnaCIgLz4KICAgICAgICA8ZW1iZWQgc3JjPSJzd2Yvc3VibWVudS5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+PC9lbWJlZD48L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCIgYmdjb2xvcj0iI0ZGRkZGRiI+CiAgICAgICAgPHRyPiAKICAgICAgICAgIDx0ZCB3aWR0aD0iMTciIHJvd3NwYW49IjciPjxwPiZuYnNwOzwvcD48L3RkPgogICAgICAgICAgPHRkIHdpZHRoPSIxNzIiIGFsaWduPSJjZW50ZXIiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxpbWcgc3JjPSJpbWcvM3B4LmpwZyIgd2lkdGg9IjUiIGhlaWdodD0iNSI+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciI+PGxpbmsgaHJlZj0iLi4vZXN0aWxvcy5jc3MiIHJlbD0ic3R5bGVzaGVldCIgdHlwZT0idGV4dC9jc3MiIC8+Cjxib2R5IGJnY29sb3I9IiNDQ0NDQ0MiIHRvcG1hcmdpbj0iNiBweCI+PHRhYmxlIHdpZHRoPSIxNjUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIzIiBiZ2NvbG9yPSIjRkZGRkZGIj4KPHRyPgogICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTkxIiBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiAgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MThfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+SG9tZTwvYT48L3RkPgogIDwvdHI+Cjx0cj4KICA8dGQgaGVpZ2h0PSIyOCIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj4mbmJzcDsmbmJzcDtOb3RpY2lhczwvYT48L3RkPgo8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJkb25hY2lvbmVzLyIgdGFyZ2V0PSJfYmxhbmsiIGNsYXNzPSJmb25kb2JvdG9uIj5Eb25hY2lvbmVzPC9hPjwvdGQ+CiAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciICB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yM19uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5IaXN0b3JpYWwgZGUgbmV3c2xldHRlcnM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTEzYSIgY2xhc3M9ImZvbmRvYm90b24iPkVudmlhciBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yNl9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5WZXIgdHJhYmFqb3MgZGUgdXN1YXJpb3M8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MTZfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+U2FsdWQgQWN0aXZhIHByZW5zYTwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJtYWlsdG86c2FsdWRhY3RpdmFAc2FsdWRhY3RpdmEub3JnLmFyIiBjbGFzcz0iZm9uZG9ib3RvbiI+TWFuZCZhYWN1dGU7IHR1IEMuVi48L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgIHdpZHRoPSI2ImhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTIxX25ldyIgY2xhc3M9ImZvbmRvYm90b24iPkluZm9ybWFjaSZvYWN1dGU7biBkZSBpbnRlciZlYWN1dGU7czwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyI+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiBoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xMF80IiBjbGFzcz0iZm9uZG9ib3RvbiI+Q29uZ3Jlc29zCiAgICAgICAgICAgICAgICAgIHkgSm9ybmFkYXM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTExIiBjbGFzcz0iZm9uZG9ib3RvbiI+UmVnaXN0cmFjaSZvYWN1dGU7bjwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgCiAgICAgICAgICA8L3RhYmxlPgo8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNSIgdGFyZ2V0PSJfYmxhbmsiPjxicj4KICAgICAgICAgICAgICAgICAgPGltZyBzcmM9ImltZy9iYW5uZXJfZG9uYWNpb25lcy5qcGciIHdpZHRoPSIxNjIiIGhlaWdodD0iMTIwIiBib3JkZXI9IjAiPjxicj4KICAgICAgICAgICAgICAgICAgPGJyPgogICAgICAgICAgICAgICAgICA8aW1nIHNyYz0iaW1nL2JvdG9uRm9yby5naWYiIHdpZHRoPSIxNzIiIGhlaWdodD0iMTE3IiBib3JkZXI9IjAiPjwvYT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTY3IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjkiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzAzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iOSIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTQ5IiBiYWNrZ3JvdW5kPSJpbWcvY2hpY29zX3BlcmRpZG9zXzA1LmdpZiI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDUuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMCI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDcuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMi5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEyLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9InNyYy9pbWdfdXAvMjMwODIwMTIuMS5qcGciIHdpZHRoPSIxNDkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMy5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNi5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iNSIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTcuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNy5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgYmdjb2xvcj0iI0ZFRTdDRiIgY2xhc3M9InRpdHVsb2hvbWU1Ij48c3Ryb25nPk5pJm50aWxkZTtvcyBwZXJkaWRvczxicj4KICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0yOSIgY2xhc3M9ImJvdG9uIj5bVmVyIG0mYWFjdXRlO3NdPC9hPjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTkuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xOS5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18yMC5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iMjUiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4NCgkJCQkNCgkJCQk8Zm9ybSBhY3Rpb249ImluZGV4LnBocD9pZD0xMSIgIG1ldGhvZD0icG9zdCI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9penExLmpwZyIgd2lkdGg9IjEyIiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9hcnJpYmEuanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9kZXIxLmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgIDwvdHI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiIgdmFsaWduPSJ0b3AiIGNsYXNzPSJyZWdGb25kbzEiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9penEuanBnIiB3aWR0aD0iMTIiIGhlaWdodD0iMTIiIC8+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSI5NCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV90aXQuanBnIiB3aWR0aD0iNjYiIGhlaWdodD0iMjMiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSI1MCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJyZWdpc3RyYXJzZSI+SW5ncmVzJmFhY3V0ZTsgDQogICAgICAgICAgICAgIHR1cyBkYXRvcyB5IHJlY2liJmlhY3V0ZTsgbGEgbWVqb3IgaW5mb3JtYWNpJm9hY3V0ZTtuIGEgdHJhdiZlYWN1dGU7cyANCiAgICAgICAgICAgICAgZGUgbnVlc3RybzxzdHJvbmc+IE5ld3NsZXR0ZXI8L3N0cm9uZz4uIDxzdHJvbmc+PHNwYW4gY2xhc3M9ImdyYXRpcyI+R3JhdGlzITwvc3Bhbj48L3N0cm9uZz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI1IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9InRyYWJTRUNDSU9OIj5Ob21icmU8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBjbGFzcz0icmVnQ0VMREEiPjxpbnB1dCBuYW1lPSJub21icmUiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0ibm9tYnJlIiAvPjwvdGQ+DQogICAgICAgICAgPC90cj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0idHJhYlNFQ0NJT04iPkFwZWxsaWRvPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iYXBlbGxpZG8iIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iYXBlbGxpZG8iIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJ0cmFiU0VDQ0lPTiI+RS1tYWlsPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iZW1haWwiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iZW1haWwiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InRyYWJTRUNDSU9OIj4mbmJzcDs8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idHJhYlNFQ0NJT04iPjxpbnB1dCB0eXBlPSJpbWFnZSIgc3JjPSJpbWcvcmVnaXN0cmF0ZV9ib3Rvbi5qcGciIHdpZHRoPSIxMTciIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgIDwvdGFibGU+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE0IiB2YWxpZ249InRvcCIgY2xhc3M9InJlZ0ZvbmRvMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2Rlci5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIxNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KICAgICAgICAgICAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTIiIGhlaWdodD0iMjQiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfaXpxMi5qcGciIHdpZHRoPSIxMiIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI0Ij48aW1nIHNyYz0iaW1nL3JlZ2lzdHJhdGVfYWJham8uanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjI0IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfZGVyMi5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KCQkJCQkNCgkJCQkJPC9mb3JtPg0KICAgICAgICAgICAgICAgICAgPC90YWJsZT4NCjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPiAKICAgICAgICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTcwIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUyIj4KCQkJCQkJCQkJCQkJCQkJCTwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9jbGF1ZGlhMl8wMy5qcGciIHdpZHRoPSIxNzQiIGhlaWdodD0iMjUwIiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcCI+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICA8dGQgcm93c3Bhbj0iNyIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nLzV4NS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjciPjwvdGQ+CiAgICAgICAgICA8dGQgY29sc3Bhbj0iMiIgcm93c3Bhbj0iNCIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPGZvcm0gYWN0aW9uPSJsb2dpbi5waHAiIG1ldGhvZD0icG9zdCIgbmFtZT0iZm9ybTIiPgoKICAgICAgICAgICAgICA8dHI+IAogICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgY29sc3Bhbj0iMiIgYWxpZ249ImxlZnQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIiA+IAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8c3Ryb25nPlVzdWFyaW8gbm8gcmVnaXN0cmFkbzwvc3Ryb25nPiAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9mb250PiA8L3N0cm9uZz4gCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDkiIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPlVzdWFyaW8mbmJzcDsmbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzOSIgdmFsaWduPSJtaWRkbGUiPjxpbnB1dCBuYW1lPSJ1c3VhcmlvIiB0eXBlPSJ0ZXh0IiBjbGFzcz0icmVnIiBpZD0idXN1YXJpbyIgc2l6ZT0iNyI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjciIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPkNvbnRyYXNlJm50aWxkZTthJm5ic3A7Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzkiIHZhbGlnbj0ibWlkZGxlIj48aW5wdXQgbmFtZT0icGFzcyIgdHlwZT0icGFzc3dvcmQiIGNsYXNzPSJyZWciIGlkPSJwYXNzIiBzaXplPSI3Ij48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiIgYWxpZ249InJpZ2h0IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9ImJvdG9uIj48aW5wdXQgdHlwZT0iaW1hZ2UiIHNyYz0iaW1nL3JlZy5qcGciIHdpZHRoPSI1OCIgaGVpZ2h0PSIzMCI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjciIGhlaWdodD0iMTkiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgPjxhIGhyZWY9Imh0dHA6Ly93d3cuZmFjZWJvb2suY29tL2hvbWUucGhwPyMhL3BhZ2VzL01lcmxvLUFyZ2VudGluYS9TQUxVRC1BQ1RJVkEvMTAwNTgzNTQzMzE3MzIyP3JlZj10cyZhamF4cGlwZT0xJl9fYT03IiB0YXJnZXQ9Il9ibGFuayI+PGltZyBzcmM9ImltZy9mYWNlYm9vay5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzExIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj48ZGl2IGFsaWduPSJsZWZ0Ij48YSBocmVmPSJodHRwOi8vdHdpdHRlci5jb20vU2FsdWRBY3RpdmFPTkciIHRhcmdldD0iX2JsYW5rIj48aW1nIHNyYz0iaW1nL3R3aXRlci5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC9kaXY+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSI1IiBhbGlnbj0icmlnaHQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIj48bGFiZWw+PGZvbnQgc2l6ZT0iLTYiPlNpCiAgICAgICAgICAgICAgICAgICAgICAgdG9kYXYmaWFjdXRlO2Egbm8gZXMgdXN1YXJpbyA8L2ZvbnQ+IDxhIGhyZWY9ImluZGV4LnBocD9pZD0xMSIgY2xhc3M9ImJvdG9uIj48Zm9udCBzaXplPSItNiI+cmVnJmlhY3V0ZTtzdHJlc2UKICAgICAgICAgICAgICAgICAgICAgICAgYXF1JmlhY3V0ZTsgPGZvbnQgY29sb3I9IiM2NjY2NjYiPiYjODIyNjs8L2ZvbnQ+PC9mb250PjwvYT4gPGEgaHJlZj0iaW5kZXgucGhwP2lkPTEyIiBjbGFzcz0iYm90b24xIj48Zm9udCBzaXplPSItNiI+b2x2aWRlIG1pIGNvbnRyYXNlJm50aWxkZTthPC9mb250PjwvYT48L2xhYmVsPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE3Ij4mbmJzcDsgPC90ZD4KICAgICAgICAgICAgICA8L3RyPgoJCQkgIDwvZm9ybT4KCiAgICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgICA8IURPQ1RZUEUgaHRtbCBQVUJMSUMgIi0vL1czQy8vRFREIFhIVE1MIDEuMCBUcmFuc2l0aW9uYWwvL0VOIiAiaHR0cDovL3d3dy53My5vcmcvVFIveGh0bWwxL0RURC94aHRtbDEtdHJhbnNpdGlvbmFsLmR0ZCI+CjxodG1sIHhtbG5zPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hodG1sIj4KPGhlYWQ+CjxtZXRhIGh0dHAtZXF1aXY9IkNvbnRlbnQtVHlwZSIgY29udGVudD0idGV4dC9odG1sOyBjaGFyc2V0PWlzby04ODU5LTEiIC8+Cjx0aXRsZT5Eb2N1bWVudG8gc2luIHQmaWFjdXRlO3R1bG88L3RpdGxlPgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KPHNjcmlwdCBsYW5ndWFnZT0iSmF2YVNjcmlwdCIgdHlwZT0idGV4dC9KYXZhU2NyaXB0Ij4KPCEtLQpmdW5jdGlvbiBNTV9yZWxvYWRQYWdlKGluaXQpIHsgIC8vcmVsb2FkcyB0aGUgd2luZG93IGlmIE5hdjQgcmVzaXplZAogIGlmIChpbml0PT10cnVlKSB3aXRoIChuYXZpZ2F0b3IpIHtpZiAoKGFwcE5hbWU9PSJOZXRzY2FwZSIpJiYocGFyc2VJbnQoYXBwVmVyc2lvbik9PTQpKSB7CiAgICBkb2N1bWVudC5NTV9wZ1c9aW5uZXJXaWR0aDsgZG9jdW1lbnQuTU1fcGdIPWlubmVySGVpZ2h0OyBvbnJlc2l6ZT1NTV9yZWxvYWRQYWdlOyB9fQogIGVsc2UgaWYgKGlubmVyV2lkdGghPWRvY3VtZW50Lk1NX3BnVyB8fCBpbm5lckhlaWdodCE9ZG9jdW1lbnQuTU1fcGdIKSBsb2NhdGlvbi5yZWxvYWQoKTsKfQpNTV9yZWxvYWRQYWdlKHRydWUpOwoKZnVuY3Rpb24gTU1fcHJlbG9hZEltYWdlcygpIHsgLy92My4wCiAgdmFyIGQ9ZG9jdW1lbnQ7IGlmKGQuaW1hZ2VzKXsgaWYoIWQuTU1fcCkgZC5NTV9wPW5ldyBBcnJheSgpOwogICAgdmFyIGksaj1kLk1NX3AubGVuZ3RoLGE9TU1fcHJlbG9hZEltYWdlcy5hcmd1bWVudHM7IGZvcihpPTA7IGk8YS5sZW5ndGg7IGkrKykKICAgIGlmIChhW2ldLmluZGV4T2YoIiMiKSE9MCl7IGQuTU1fcFtqXT1uZXcgSW1hZ2U7IGQuTU1fcFtqKytdLnNyYz1hW2ldO319Cn0KLy8tLT4KPC9zY3JpcHQ+CiAgICAgICAgICAgICA8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoJCQkgCjxzdHlsZSB0eXBlPSJ0ZXh0L2NzcyI+CjwhLS0KI0xheWVyMSB7Cglwb3NpdGlvbjphYnNvbHV0ZTsKCXdpZHRoOjY1MXB4OwoJaGVpZ2h0OjIxOHB4OwoJei1pbmRleDoxOwp9CiNMYXllcjIgewoJcG9zaXRpb246YWJzb2x1dGU7Cgl3aWR0aDoyMDBweDsKCWhlaWdodDoxMTVweDsKCXotaW5kZXg6MTsKCXZpc2liaWxpdHk6IHZpc2libGU7Cn0KLkVzdGlsbzEgewoJZm9udC1zaXplOiAxOHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzIgewoJZm9udC1zaXplOiAxNHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzMge2NvbG9yOiAjNTA2OTkwOyBsaW5lLWhlaWdodDogMTJweDsgdGV4dC1kZWNvcmF0aW9uOiBub25lOyBmb250LWZhbWlseTogVGFob21hO30KLS0+Cjwvc3R5bGU+CjwvaGVhZD4KCjxib2R5IGxlZnRtYXJnaW49IjIiIG1hcmdpbndpZHRoPSIyIj4KPHRhYmxlIHdpZHRoPSI2MDgiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICA8dHI+CiAgICA8dGQgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCB3aWR0aD0iMiUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzA3LmpwZyIgd2lkdGg9IjI0IiBoZWlnaHQ9IjE0IiAvPjwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI5MCUiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18wNy5qcGciPiZuYnNwOzwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI4JSIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wOS5qcGciIHdpZHRoPSI0NSIgaGVpZ2h0PSIxNyIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogIDwvdHI+CiAgPHRyPgogICAgPHRkIGNvbHNwYW49IjQiPjxiciAvPgogICAgICA8dGFibGUgd2lkdGg9Ijk4JSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICA8dHI+CiAgICAgICAgPHRkIHdpZHRoPSIyJSI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgICA8dGQgd2lkdGg9IjkzJSI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CjwhLS0gSU5JQ0lPIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzIzMDQyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjIvMTEvMjAxMzwvc3Bhbj48YnI+SVYgQ29uZ3Jlc28gSW50ZXJuYWNpb25hbCB2aW9sZW5jaWEsIG1hbHRyYXRvIHkgYWJ1c288L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxzdHJvbmc+MTQsIDE1IHkgMTYgZGUgTm92aWVtYnJlIEFCSUVSVEEgTEEgSU5TQ1JJUENJJk9hY3V0ZTtOISAoY29uIGRlc2N1ZW50byBoYXN0YSBlbCAyNy84KTxiciAvPjwvc3Ryb25nPjwvcD4NCjxwPjxzdHJvbmc+QUJJRVJUQSBMQSBSRUNFUENJJk9hY3V0ZTtOIERFIFRSQUJBSk88YSBocmVmPSJodHRwOi8vd3d3LmNvbmdyZXNvdmlvbGVuY2lhLmNvbS9pbmRleC5waHA/aWQ9bW9kYWxpZGFkZXMiIHRhcmdldD0iX2JsYW5rIj4gKG1hcyBpbmZvKTwvYT48L3N0cm9uZz48L3A+DQo8cD48c3BhbiBzdHlsZT0iY29sb3I6ICNmZjY2MDA7Ij48c3Ryb25nPk9yZ2FuaXphOiBTYWx1ZCBBY3RpdmE8L3N0cm9uZz48L3NwYW4+PC9wPg0KPHA+PHNwYW4gc3R5bGU9ImNvbG9yOiAjZmY2NjAwOyI+SW5jcmlwdG9zIGFsIFBvcnRhbCBkZSBTYWx1ZCBBY3RpdmEsIGltcG9ydGFudGVzIGRlc2N1ZW50b3MhPGJyIC8+PC9zcGFuPjwvcD4NCjxwPkx1Z2FyIGRlIFJlYWxpemFjaSZvYWN1dGU7biB5IGNvbGFib3JhY2lvbjogVW5pdmVyc2lkYWQgZGVsIEVzdGUsIExhIFBsYXRhIEJ1ZW5vcyBBaXJlczwvcD4NCjxwPk1hcyBkZSAxNTAgdHJhYmFqb3MgcHJlc2VudGFkb3MsIHVsdGltb3MgZGlhcyBwYXJhIGluc2NyaWJpcnNlIGNvbiBkZXNjdWVudG8hITwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPkluc2NyaWJpcnNlPC9hPjwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPjxiciAvPjwvYT48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAxIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDEiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MDQvMTEvMjAxMzwvc3Bhbj48YnI+RWwgY29sZWdpbyBkZSBQc2lj82xvZ29zIGRlIEPzcmRvYmEgc2UgcHJvbnVuY2lhIGVuIHJlbGFjafNuIGFsIFNBUCB5IGVuIGNvbmNvcmRhbmNpYSBjb24gbG8gZXhwcmVzYWRvIHBvciBlbCBDb2xlZ2lvIGRlIFBzaWPzbG9nb3MgZGUgTWFyIGRlbCBQbGF0YSB5IGVsIENvbGVnaW8gZGUgUHNpY/Nsb2dvcyBkZSBsYSAgUHJvdmluY2lhIGRlIEJ1ZW5vcyBBaXJlczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+Jm5ic3A7PC9wPg0KPHA+TGFzIGNvbnRyb3ZlcnNpYXMgZ2VuZXJhZGFzIGVuIHJlbGFjaSZvYWN1dGU7biBhbCAic2luZHJvbWUgZGUgYWxpZW5hY2kmb2FjdXRlO24gcGFyZW50YSIgU0FQLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMxMCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzEwIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzE2MTAyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTYvMTAvMjAxMzwvc3Bhbj48YnI+U2FsdWQgQWN0aXZhIG90b3JnYSBtZWRpYXMgYmVjYXMgcGFyYSBlbCBJViBDb25ncmVzbyBJbnRlcm5hY2lvbmFsLCBWIE5hY2lvbmFsLCBWSSBSZWdpb25hbCBWaW9sZW5jaWEsIE1hbHRyYXRvIHkgQWJ1c28uPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD4mbmJzcDs8L3A+DQo8cD5TZXImYWFjdXRlO24gb3RvcmdhZGFzIDUwIG1lZGlhcyBiZWNhcywgcXVlZGFuIHBvY2FzISEhIGNvbmRpY2lvbjo8L3A+DQo8cD5QZXJ0ZW5lY2VyIGFsIGFtYml0byBwdWJsaWNvIG8gYSBPTkcsIHNlIGNvbnNpZGVyYSB0YW1iaWVuIGxhIGRpc3RhbmNpYSBhbCBsdWdhciBkZWwgZXZlbnRvISEhIGVzIG11eSBzZW5jaWxsbywgc29sbyBkZWJlcyBlbnZpYXIgdW4gZW1haWwuLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwOSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA5Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjI0LzA3LzIwMTM8L3NwYW4+PGJyPk5FQ0VTSVRBTU9TIERFIFNVIFNPTElEQVJJREFEIEhBQ0lBIExPUyBOSdFPUyBZIE5J0UFTISEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPlBST0dSQU1BIEZBTUlMSUFTIFNPTElEQVJJQVM8L3NwYW4+PC9zdHJvbmc+PC9wPg0KPHA+PHN0cm9uZz5DQU1CSU8gREUgU0VERTwvc3Ryb25nPjwvcD4NCjxwPkxhIGNhcGFjaXRhY2kmb2FjdXRlO24gcGFyYSBsYSBwdWVzdGEgZW4gbWFyY2hhIGRlbCA8c3Ryb25nPlByb2dyYW1hIEZhbWlsaWFzIFNvbGlkYXJpYXM8L3N0cm9uZz4gc2UgcmVhbGl6YXImYWFjdXRlOyBlbiBsYSBsb2NhbGlkYWQgZGUgPHN0cm9uZz5OYXZhcnJvPC9zdHJvbmc+IHBhcmEgdG9kbyBlbCBjb3JyZWRvciBkZSBsYSBSdXRhIDQwLjwvcD4NCjxwPkluaWNpbyA8c3Ryb25nPk1pJmVhY3V0ZTtyY29sZXMgMjggZGUgYWdvc3RvIGEgbGFzIDE0IGhvcmFzLiZuYnNwOzwvc3Ryb25nPjwvcD4NCjxwPlNlZGU6IDxzdHJvbmc+U2FsJm9hY3V0ZTtuIE11bmljaXBhbCBlbiBsYSBjYWxsZSAxMDcgZXNxdWluYSAyMiAtIE5hdmFycm88L3N0cm9uZz48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA4Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTIwNzIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xMi8wNy8yMDEzPC9zcGFuPjxicj5TQUxVRCBBQ1RJVkEgaGEgc2lkbyBlbGVnaWRhIHBvciBzZWd1bmRhIHZleiBjb25zZWN1dGl2YSBjb21vIHVubyBkZSBsb3MgZ2FuYWRvcmVzIGRlbCBDdWFydG8gQ29uY3Vyc28gZGUgUHJveWVjdG9zIFNvY2lhbGVzIGRlIFBldHJvYnJhczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+RW4gZWwgbWFyY28gZGVsIEN1YXJ0byBDb25jdXJzbyBkZSBQcm95ZWN0b3MgU29jaWFsZXMgZGUgUGV0cm9icmFzLCANCm51ZXN0cmEgSW5zdGl0dWNpJm9hY3V0ZTtuIFNBTFVEIEFDVElWQSBoYSBzaWRvIGVsZWdpZGEgcG9yIHNlZ3VuZGEgdmV6IA0KY29uc2VjdXRpdmEgY29tbyB1bm8gZGUgbG9zIGdhbmFkb3JlcyBkZSBkaWNobyBjb25jdXJzby48YnIgLz5FbiBlc3RhIA0KZWRpY2kmb2FjdXRlO24gZWwgcHJveWVjdG8gcXVlIGhhIHNpZG8gZWxlZ2lkbyBlcyBlbCAmbGRxdW87UHJvZ3JhbWEgZGUgRmFtaWxpYXMgDQpTb2xpZGFyaWFzJnJkcXVvOyBzaWVuZG8gc3UgJmFhY3V0ZTtyZWEgZGUgaW1wbGVtZW50YWNpJm9hY3V0ZTtuIGxvcyBNdW5pY2lwaW9zIGRlIE5hdmFycm8sIA0KR3JhbC4gTGFzIEhlcmFzLCBNYXJjb3MgUGF6LCB5IE1lcmxvPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAyLzA3LzIwMTM8L3NwYW4+PGJyPk/tciBvIGVzY3VjaGFyPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Qb3IgQ2FybG9zIFJvemFuc2tpICo8L3A+DQo8cD5BIGxvIGxhcmdvIGRlIGxvcyBzaWdsb3MsIGxhcyBuaSZudGlsZGU7YXMsIG5pJm50aWxkZTtvcyB5IGFkb2xlc2NlbnRlcyBoYW4gc2lkbyBtYWx0cmF0YWRvcyB5IGFidXNhZG9zIHNpbiBxdWUgYSBsYSBjb211bmlkYWQgbGUgaW50ZXJlc2FyYSBuaSBzaXF1aWVyYSBlc2N1Y2hhcmxvcyBjdWFuZG8gaGFjJmlhY3V0ZTthbiBzYWJlciBkZSBhbGd1bmEgZm9ybWEgbG9zIHN1ZnJpbWllbnRvcyBxdWUgcGFkZWMmaWFjdXRlO2FuLiBFbiAxODc0LCBlbiBFc3RhZG9zIFVuaWRvcywgZnVlIGxhIHByaW1lcmEgdmV6IHF1ZSBlbCBFc3RhZG8gaW50ZXJ2aW5vIGVuIHVuIGNhc28gZGUgbWFsdHJhdG8geSBhYnVzby4uLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDYiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4wMi8wNy8yMDEzPC9zcGFuPjxicj5FbCBkZXJlY2hvIGRlIGxvcyBuafFvcyBhIHNlciBlc2N1Y2hhZG9zPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5VbiBob21icmUgYWN1c2FkbyBkZSBoYWJlciBhYnVzYWRvIGRlIHN1cyBoaWpvcyBoYWImaWFjdXRlO2Egc2lkbyBzb2JyZXNlJmlhY3V0ZTtkbyBkb3MgdmVjZXMgcG9yIGxhIEp1c3RpY2lhLiBQZXJvIGFob3JhLCBsYSBDJmFhY3V0ZTttYXJhIGRlIENhc2FjaSZvYWN1dGU7biByZXZvYyZvYWN1dGU7IGVzYSBkZWNpc2kmb2FjdXRlO24gcG9ycXVlIGVuIGxhIGludmVzdGlnYWNpJm9hY3V0ZTtuIGVsIGp1ZXogbnVuY2EgaGFiJmlhY3V0ZTthIGVzY3VjaGFkbyBhIGxvcyBjaGljb3MuIFkgb3JkZW4mb2FjdXRlOyBxdWUgdGVuZ2EgZW4gY3VlbnRhIGxvIHF1ZSBkaWNlbi48L3A+DQo8cD5Qb3IgTWFyaWFuYSBDYXJiYWphbDwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDUiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE1NiIgcm93c3Bhbj0iMiIgdmFsaWduPSJ0b3AiPgoJCQkJCgkJCQk8dGFibGUgd2lkdGg9IjMyJSIgYm9yZGVyPSIxIiBjZWxsc3BhY2luZz0iMyIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48aW1nIHNyYz0ic3JjL2ltZ191cC8wNjA2MjAxMy4xLmpwZyIgd2lkdGg9IjE0NiIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT4KCQkJCQkJCQk8L3RkPiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjA2LzA2LzIwMTM8L3NwYW4+PGJyPkFidXNvIHNleHVhbCBpbmZhbnRpbC4gRGVzYWZpb3MgZGUgbGEgY2xpbmljYSBhY3R1YWw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkFiaWVydGEgbGEgaW5zY3JpcGNpb248L3A+DQo8cD5Eb2NlbnRlczogTGljLiBNYXJpYSBCZWF0cml6IE0mdXVtbDtsbGVyLiBMaWMuIFBhb2xhIE11Jm50aWxkZTtveiBEdWFydGU8L3A+DQo8cD5JbmljaW86IE1pZXJjb2xlcyAxOSBkZSBKdW5pbzwvcD4NCjxwPkZyZWN1ZW5jaWE6IFNlbWFuYWw8L3A+DQo8cD5Nb2RhbGlkYWQ6IEludGVuc2l2YTwvcD4NCjxwPkNvbnRlbmlkb3M6ICZuYnNwOyBFc3RhIGRlc3RpbmFkbyBhIHRvZG9zIGxvcyBwcm9mZXNpb25hbGVzIGNvbXByb21ldGlkb3MgY29uIGxhIHRlbWF0aWNhIGRlbCBhYnVzbyBpbmZhbnRpbCBxdWUgcXVpZXJhbiBhY3R1YWxpemFyc2UgZSBpbnRlcmNhbWJpYXIgZXhwZXJpZW5jaWFzIGRlIHRyYWJham8uLi48L3A+DQo8cD4mbmJzcDs8L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA0Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDQiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTYwNTIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xNi8wNS8yMDEzPC9zcGFuPjxicj5TYWx1ZCBBY3RpdmEgbmVjZXNpdGEgZGUgdHUgYXl1ZGEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5UcmFiYWphbW9zIGNvbW8gcG9kZW1vczogYmEmbnRpbGRlO29zIHJvdG9zLCBzdXNwZW5zaSZvYWN1dGU7biBkZSByZXVuaW9uZXMgcG9yIGNvcnRlcyBkZSBsdXogeSBhZ3VhLCBqdWd1ZXRlcyB2aWVqb3MsIG1lc2VzIGRlIGF0cmFzbyBlbiBlbCBwYWdvIGRlIHN1cyBwcm9mZXNpb25hbGVzIGRlIGxhIHNhbHVkLiBSZWNpZW50ZW1lbnRlIHR1dmltb3MgcXVlIGNlcnJhciBudWVzdHJvIHF1ZXJpZG8gSG9nYXI6ICZsZHF1bztNZXRhbW9yZm9zaXMmcmRxdW87IGVyYSBlbCBsdWdhciBxdWUgc3VwbyBjb250ZW5lciBhIG5pJm50aWxkZTthcyB5IGomb2FjdXRlO3ZlbmVzIHJlc2NhdGFkYSBkZSByZWRlcyBkZSB0cmF0YSBvIHYmaWFjdXRlO2N0aW1hcyBkZSBhYnVzbyBpbnRyYWZhbWlsaWFyLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAzIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAzLzA1LzIwMTM8L3NwYW4+PGJyPlJFUFVESU8gQSBMQSBQUkVTRU5DSUEgRU4gTEEgRkVSSUEgREVMIExJQlJPIERFIFVOIEVYIEpVRVogQUNVU0FETyBERSBBQlVTTyBTRVhVQUw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkZ1ZSBjYW1hcmlzdGEgZW4gTWFyIGRlbCBQbGF0YSBkdXJhbnRlIGxhIGRpY3RhZHVyYS4gSGFjZSBhJm50aWxkZTtvcywgdmFyaWFzIG11amVyZXMgbG8gYWN1c2Fyb24gZGUgaGFiZXIgYWJ1c2FkbyBkZSBlbGxhcyBjdWFuZG8gZXJhbiBuaSZudGlsZGU7YXMuIExhIGNhdXNhIHByZXNjcmliaSZvYWN1dGU7IHkgbm8gaHVibyBjb25kZW5hLiBNYSZudGlsZGU7YW5hIHRpZW5lIHByZXZpc3RvIGZpcm1hciBzdSBsaWJyby4gRXNhcyBtaXNtYXMgbXVqZXJlcyBwaWRlbiBxdWUgbm8gc2VhIGFkbWl0aWRvIGVuIGxhIGZlcmlhLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDIiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgIDwhLS0gRklOIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgIDwvdGFibGU+ICAgICAgICA8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iNSUiIGFsaWduPSJyaWdodCI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgPC90cj4KICAgIDwvdGFibGU+PC90ZD4KICA8L3RyPgogIDx0cj4KICAgIDx0ZCB3aWR0aD0iMSUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiIgYWxpZ249ImNlbnRlciI+Jm5ic3A7PC90ZD4KICAgIDx0ZCB3aWR0aD0iMiUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgPC90cj4KICAKICA8dGQ+CiAgPHRyPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0ciBhbGlnbj0iY2VudGVyIj4KICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgPHRkIHdpZHRoPSI5NyIgY29sc3Bhbj0iMiIgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iNTQ2IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idGl0dWxvaG9tZTIiPjx0YWJsZSB3aWR0aD0iIiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYWxpZ249ImxlZnQiIHZhbGlnbj0iYm90dG9tIiBjbGFzcz0idGl0dWxvaG9tZTIiPlJhbmtpbmc8L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSIgY2xhc3M9InRpdHVsb2hvbWUyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iIiBoZWlnaHQ9IjM1IiBhbGlnbj0ibGVmdCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPiZidWxsO0xhcyBtJmFhY3V0ZTtzIGxlaWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGNsYXNzPSJjb250ZW5pZG9ob21lIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBjbGFzcz0iY29udGVuaWRvaG9tZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+JmJ1bGw7TGFzIG0mYWFjdXRlO3MgY29tZW50YWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTHVkb3RlY2EgR2FyYWJhdG8gLSBQcm95ZWN0byBzYWx1ZGFjdGl2YSwgUG9yIHVuYSBpbmZhbmNpYSBmZWxpeiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iOSUiIGJnY29sb3I9IiNFRkVGRUYiPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzJSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xNjIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDUlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTE2MiIgY2xhc3M9ImJvdG9uIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBDdXJzbyBJbnRlbnNpdm8gZGUgb3BlcmFkb3IgdGVyYXBldXRpY28gZXNwZWNpYWxpemFkbyBlbiBlbCBhYm9yZGFqZSBkZWwgYWJ1c28sIGxhIHZpb2xlbmNpYSB5IGVsIG1hbHRyYXRvIGluZmFudGlsICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgUFJPR1JBTUEgTEFTIFZJQ1RJTUFTIENPTlRSQSBMQVMgVklPTEVOQ0lBUyAgTWluaXN0ZXJpbyBkZSBKdXN0aWNpYSB5IERlcmVjaG9zIEh1bWFub3MgZGUgbGEgTmFjafNuICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI5JSIgYmdjb2xvcj0iI0VGRUZFRiI+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjMlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTI1NSIgY2xhc3M9ImJvdG9uIj48aW1nIHNyYz0iaW1nL2ZsZWNoYW5hcmFuamFmZ3Jpc18yNC5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSI3IiBib3JkZXI9IjAiIGFsaWduPSJhYnNtaWRkbGUiIC8+PC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI0NSUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MjU1IiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIERpcGxvbWF0dXJhIGVuIEFib3JkYWplIGludGVyZGlzY2lwbGluYXJpbyBkZWwgbWFsdHJhdG8sIGxhIHZpb2xlbmNpYSB5IGVsIGFidXNvIHNleHVhbCBpbmZhbnRpbCAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyJSIgaGVpZ2h0PSIyMCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQxJSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNhbHVkIEFjdGl2YSBuZWNlc2l0YSBkZSB0dSBheXVkYSEgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjklIiBiZ2NvbG9yPSIjRUZFRkVGIj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMyUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MTA0IiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQ1JSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xMDQiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTGxhbWFkbyBwYXJhIHByZXNlbnRhY2nzbiBkZSB0cmFiYWpvcy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjIwIiBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyMCIgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGJnY29sb3I9IiNGRkZGRkYiIGNsYXNzPSJ0ZXh0b251ZXZvIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPgogICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iIyIgY2xhc3M9ImJvdG9uIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgPC90YWJsZT48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj4mbmJzcDs8L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBJTklDSU8gbm90YSBjb211biAtLT4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTUvMDQvMjAxMjwvc3Bhbj48YnI+T3JnYW5pemFuIGpvcm5hZGEgc29icmUgdmlvbGVuY2lhPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPlNlIGNlbnRyYXImYWFjdXRlOyBlbiBsb3MgZmVuJm9hY3V0ZTttZW5vcyBxdWUgYWZlY3RhbiBhIGxhIGZhbWlsaWEgeSBlbiBsbyBxdWUgb2N1cnJlIGVuIGxhcyBlc2N1ZWxhcy48YnIgLz4gU2UgbGxldmFyJmFhY3V0ZTsgYSBjYWJvIGVsIGx1bmVzIDIzLCBlbiBlbCBDZW50cm8gQ3VsdHVyYWwgZGUgVG9zY2hpIHkgVHJlcyANCkFycm95b3MsIHVuYSBqb3JuYWRhIGRlIHJlZmxleGkmb2FjdXRlO24geSBkZWJhdGUgYWJpZXJ0YSBhIGxhIGNvbXVuaWRhZCBzb2JyZSANCiZsZHF1bztWaW9sZW5jaWEgZW4gbGEgZmFtaWxpYSB5IGVuIGxhIGVzY3VlbGEgeSBzdSByZWxhY2kmb2FjdXRlO24gY29uIGVsIGZyYWNhc28gDQplc2NvbGFyJnJkcXVvOywgb3JnYW5pemFkYSBwb3IgbGEgQXNvY2lhY2kmb2FjdXRlO24gQ2l2aWwgQ2VudHJvIEFydCZlYWN1dGU7bWlkZXMgeSBsYSANCk11bmljaXBhbGlkYWQgZGUgQ2lwb2xsZXR0aS5TZSBjZW50cmFyJmFhY3V0ZTsgZW4gbG9zIGZlbiZvYWN1dGU7bWVub3MgcXVlIGFmZWN0YW4gYSBsYSBmYW1pbGlhIHkgZW4gbG8gcXVlIG9jdXJyZSBlbiBsYXMgZXNjdWVsYXMuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjMwLzAzLzIwMTI8L3NwYW4+PGJyPkNhcnRhIGRlIEFTQVBNSSAtIEFzb2NpYWNp824gQXJnZW50aW5hIGRlIFByZXZlbmNp824gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbDwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjE1IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSIxNSIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjgwIiBjb2xzcGFuPSI0IiBhbGlnbj0ibGVmdCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Mb3MgaW50ZWdyYW50ZXMgZGUgbGEgQ29taXNpJm9hY3V0ZTtuIERpcmVjdGl2YSBkZSBBU0FQTUkgLSBBc29jaWFjaSZvYWN1dGU7biBBcmdlbnRpbmEgZGUgUHJldmVuY2kmb2FjdXRlO24gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbCwgYXNvY2lhZGEgYSBsYSBJbnRlcm5hdGlvbmFsIFNvY2lldHkgZm9yIFByZXZlbnRpb24gb2YgQ2hpbGQgQWJ1c2UgYW5kIE5lZ2xlY3QgKElTUENBTikgLSwgdGVuZW1vcyBlbCBhZ3JhZG8gZGUgZGlyaWdpcm5vcyBhIFVzdGVkIHBhcmEgdHJhc21pdGlybGUgbnVlc3RyYSBwcm9mdW5kYSAmbmJzcDt5IGhvbmRhIHByZW9jdXBhY2kmb2FjdXRlO24gcG9yIGxhIHBvc3R1cmEgcXVlIHZpZW5lbiBhc3VtaWVuZG8gZW4gZm9ybWEgY29udGludWFkYSBhbGd1bm9zIGNvbGVnaW9zIGRlIHBzaWMmb2FjdXRlO2xvZ29zLCBlc3BlY2lhbG1lbnRlIGRlIGxhIHByb3ZpbmNpYSBkZSBCdWVub3MgQWlyZXMsIGVuIHJlbGFjaSZvYWN1dGU7biBhbCB0cmF0YW1pZW50byBwb2NvIHNlcmlvIHkgY29tcHJvbWV0aWRvIHF1ZSBzZSBsZXMgb3RvcmdhIGEgbGFzIGRlbnVuY2lhcyBlZmVjdHVhZGFzIGNvbnRyYSBwcm9mZXNpb25hbGVzIHBzaWMmb2FjdXRlO2xvZ29zLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjAvMDMvMjAxMjwvc3Bhbj48YnI+TEEgVklPTEVOQ0lBIFNFWFVBTCBDT05UUkEgTknRT1MgWSBOSdFBUyBFTiBDSUZSQVM8L3RkPgogICAgICAgICAgPC90cj4KICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkIHdpZHRoPSIxNSIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4MCIgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+UmFkaW9ncmFmJmlhY3V0ZTthIGRlIHVuIHByb2JsZW1hPC9wPg0KPHA+RGUgbG9zIG4mdWFjdXRlO21lcm9zIGNvbXBpbGFkb3MgcG9yIGRvcyBlcXVpcG9zIGRlbCBNaW5pc3RlcmlvIGRlIEp1c3RpY2lhLCBsYQ0KIGF1dG9yYSB0b21hIGxvcyBkZSBsYSBjaXVkYWQgZGUgQnVlbm9zIEFpcmVzIHBhcmEgdHJhemFyIHVuIHBhcmFkaWdtYSANCmRlIGxvcyBkZWxpdG9zIGNvbnRyYSBsYSBpbnRlZ3JpZGFkIHNleHVhbCBlbiBlbCBwYSZpYWN1dGU7cyB5IHNvYnJlIHN1IA0KYXRlbmNpJm9hY3V0ZTtuLjxiciAvPiA8YnIgLz4gJm5ic3A7UG9yIEV2YSBHaWJlcnRpPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2MCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjAiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjE1LzAzLzIwMTI8L3NwYW4+PGJyPkZBTExPIERFIExBIENPUlRFIFNVUFJFTUEgU09CUkUgTEEgTk8gSlVESUNJQUxJWkFDSU9OIERFTCBBQk9SVE8gRU4gQ0FTT1MgREUgVklPTEFDSU9OPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxiciAvPiBKVVJJU0RJQ0NJT046IE5BQ0lPTkFMPGJyIC8+IE1BVEVSSUE6IEFCT1JUTy48YnIgLz4gVFJJQlVOQUw6IENvcnRlIFN1cHJlbWEgZGUgSnVzdGljaWEgZGUgbGEgTmFjaSZvYWN1dGU7bi48YnIgLz4gQVVUT1M6IEYuLCBBLiBMLiBzLyBtZWRpZGEgYXV0b3NhdGlzZmFjdGl2YS48YnIgLz4gRkVDSEE6IDEzLzAzLzIwMTIuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI1OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNTkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBGSU4gbm90YSBjb211biAtLT4KPC90YWJsZT4KPG1hcCBuYW1lPSJNYXBNYXAiIGlkPSJNYXBNYXAiPjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjE0NCw0LDIxNCwzNiIgaHJlZj0iaW5kZXgucGhwP2lkPTE0IiAvPgo8L21hcD4KPG1hcCBuYW1lPSJNYXAyTWFwMiIgaWQ9Ik1hcDJNYXAyIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIxNDcsNCwyMjAsMzYiIGhyZWY9ImluZGV4LnBocD9pZD0xNGEiIC8+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcDMiIGlkPSJNYXAzIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIzNjMsMyw0MzYsMzkiIGhyZWY9ImluZGV4LnBocD9pZD0xNGIiIC8+CjwvbWFwPgo8L2h0bWw+CjwvdGQ+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gICAgICAgICAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFM0UzRTMiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSI3MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNiUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9kZWNpbG9fYmllbl9mdWVydGUxLmpwZyIgd2lkdGg9IjEyMCIgaGVpZ2h0PSIxMTIiPjwvdGQ+CiAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiA+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTI0IiBjbGFzcz0iYm90b24xIj5bK10gTSZhYWN1dGU7cyBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0UzRTNFMyI+ICAgICAgICA8L3RyPgogICAgICAgIDx0cj4gCiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj4mbmJzcDs8L3RkPgogICAgICAgIDwvdHI+CiAgICA8L3RhYmxlPjwvdGQ+CiAgPC90cj4KICA8dHI+IAogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSI+PGltZyBzcmM9ImltZy9penExLmpwZyIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjExNCIgLz48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9RdWllbmVzU29tb3NfQTJfMF8yNS5qcGciIHdpZHRoPSI4MDkiIGhlaWdodD0iMTE0IiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcDIiIC8+PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI1MCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiYWNrZ3JvdW5kPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzE4XzE4LmpwZyI+Jm5ic3A7PC90ZD4KICAgIDx0ZCBoZWlnaHQ9IjUwIiBjbGFzcz0iZm9uZG9ib3R0b20iPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2l0ZWkuY29tLmFyLyI+PGltZyBzcmM9ImltZy9laV9jb2xvci5wbmciIGFsdD0iZXNwYWNpb3MgZGUgaW1hZ2luYWNpb24sIGRlc2Fycm9sbG9zIGludGVyYWN0aXZvcywgY3JlYXRpdmlkYWQsIGRpc2XxbyIgd2lkdGg9IjI3IiBoZWlnaHQ9IjE1IiBib3JkZXI9IjAiPjwvYT4gPHNwYW4gY2xhc3M9ImVpIj48YSBocmVmPSJodHRwOi8vd3d3LnNpdGVpLmNvbS5hci8iIHNwYW4gY2xhc3M9ImVpIj5kaXNlJm50aWxkZTtvICsgY29tdW5pY2FjaSZvYWN1dGU7bjwvYT48L3NwYW4+PGVtPiZuYnNwOzwvZW0+PC9zcGFuPjxzcGFuIGNsYXNzPSJibGFuY28xIj48ZW0+Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7PC9lbT48L3NwYW4+PC90ZD4KICA8L3RyPgo8L3RhYmxlPgoKCjxtYXAgbmFtZT0iTWFwMiI+PGFyZWEgc2hhcGU9InJlY3QiIGNvb3Jkcz0iMjQ3LDY5LDQxNCw4MiIgaHJlZj0ibWFpbHRvOnNhbHVkYWN0aXZhQHNhbHVkYWN0aXZvLm9yZy5hciI+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcCI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM2LDE0MiwxNDksMTUyIiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MiI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM0LDE4NiwxNTAsMTk2IiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MCI+CjwvbWFwPgo8L2JvZHk+CjwvaHRtbD4K]]></response> | |
| 60 | <responseRedirected>false</responseRedirected> | |
| 61 | </requestresponse> | |
| 62 | </issue> | |
| 63 | <issue> | |
| 64 | <serialNumber>3831322476981454848</serialNumber> | |
| 65 | <type>5244928</type> | |
| 66 | <name>Password field with autocomplete enabled</name> | |
| 67 | <host ip="200.20.20.201">http://www.example.org.ar</host> | |
| 68 | <path><![CDATA[/]]></path> | |
| 69 | <location><![CDATA[/]]></location> | |
| 70 | <severity>Low</severity> | |
| 71 | <confidence>Certain</confidence> | |
| 72 | <issueBackground><![CDATA[Most browsers have a facility to remember user credentials that are entered into HTML forms. This function can be configured by the user and also by applications which employ user credentials. If the function is enabled, then credentials entered by the user are stored on their local computer and retrieved by the browser on future visits to the same application.<br><br>The stored credentials can be captured by an attacker who gains access to the computer, either locally or through some remote compromise. Further, methods have existed whereby a malicious web site can retrieve the stored credentials for other applications, by exploiting browser vulnerabilities or through application-level cross-domain attacks. ]]></issueBackground> | |
| 73 | <remediationBackground><![CDATA[To prevent browsers from storing credentials entered into HTML forms, you should include the attribute <b>autocomplete="off"</b> within the FORM tag (to protect all form fields) or within the relevant INPUT tags (to protect specific individual fields).]]></remediationBackground> | |
| 74 | <issueDetail><![CDATA[The page contains a form with the following action URL:<ul><li>http://www.example.org.ar/login.php</li></ul>The form contains the following password field with autocomplete enabled:<ul><li>pass</li></ul>]]></issueDetail> | |
| 75 | <requestresponse> | |
| 76 | <request base64="true"><![CDATA[R0VUIC8gSFRUUC8xLjENCkhvc3Q6IHd3dy5zYWx1ZGFjdGl2YS5vcmcuYXINClVzZXItQWdlbnQ6IE1vemlsbGEvNS4wIChNYWNpbnRvc2g7IEludGVsIE1hYyBPUyBYIDEwLjg7IHJ2OjIzLjApIEdlY2tvLzIwMTAwMTAxIEZpcmVmb3gvMjMuMA0KQWNjZXB0OiB0ZXh0L2h0bWwsYXBwbGljYXRpb24veGh0bWwreG1sLGFwcGxpY2F0aW9uL3htbDtxPTAuOSwqLyo7cT0wLjgNCkFjY2VwdC1MYW5ndWFnZTogZW4tVVMsZW47cT0wLjUNCkFjY2VwdC1FbmNvZGluZzogZ3ppcCwgZGVmbGF0ZQ0KQ29ubmVjdGlvbjoga2VlcC1hbGl2ZQ0KDQo=]]></request> | |
| 77 | <response base64="true"><![CDATA[SFRUUC8xLjEgMjAwIE9LDQpEYXRlOiBUaHUsIDA3IE5vdiAyMDEzIDE3OjEyOjAyIEdNVA0KU2VydmVyOiBBcGFjaGUvMi4yLjIzIChVbml4KSBtb2Rfc3NsLzIuMi4yMyBPcGVuU1NMLzAuOS44ZS1maXBzLXJoZWw1DQpYLVBvd2VyZWQtQnk6IFBIUC81LjIuMTcNCkV4cGlyZXM6IFRodSwgMTkgTm92IDE5ODEgMDg6NTI6MDAgR01UDQpDYWNoZS1Db250cm9sOiBuby1zdG9yZSwgbm8tY2FjaGUsIG11c3QtcmV2YWxpZGF0ZSwgcG9zdC1jaGVjaz0wLCBwcmUtY2hlY2s9MA0KUHJhZ21hOiBuby1jYWNoZQ0KU2V0LUNvb2tpZTogUEhQU0VTU0lEPTk0NTg1YWEwYzExY2YyZTg2NGQ4M2UyNDY3OGI5ODY1OyBwYXRoPS8NCktlZXAtQWxpdmU6IHRpbWVvdXQ9MjAsIG1heD0yMDANCkNvbm5lY3Rpb246IEtlZXAtQWxpdmUNCkNvbnRlbnQtVHlwZTogdGV4dC9odG1sDQpDb250ZW50LUxlbmd0aDogNjA2MDYNCg0KIDxoZWFkPgo8bWV0YSBodHRwLWVxdWl2PSJDb250ZW50LVR5cGUiIGNvbnRlbnQ9InRleHQvaHRtbDsgY2hhcnNldD1pc28tODg1OS0xIiAvPgo8dGl0bGU+U2FsdWQgQWN0aXZhIC0gQWJ1c28gdmlvbGVuY2lhIHkgbWFsdHJhdG88L3RpdGxlPgoKPHNjcmlwdD4gCiAgICAvL2VzdG8gcGFyYSBwYXNhcmxlIGFsIGZsYXNoIGxhcyB2YXJpYWxiZXMgZGVsIHBocAogCQoKCXZhciBib3Q9Jyc7Ci8vYWxlcnQodmFyaWFibGVTZXJ2aWRvcik7Cjwvc2NyaXB0Pgo8c2NyaXB0IGxhbmd1YWdlPSJKYXZhU2NyaXB0IiB0eXBlPSJ0ZXh0L0phdmFTY3JpcHQiPgo8IS0tCmZ1bmN0aW9uIE1NX3ByZWxvYWRJbWFnZXMoKSB7IC8vdjMuMAogIHZhciBkPWRvY3VtZW50OyBpZihkLmltYWdlcyl7IGlmKCFkLk1NX3ApIGQuTU1fcD1uZXcgQXJyYXkoKTsKICAgIHZhciBpLGo9ZC5NTV9wLmxlbmd0aCxhPU1NX3ByZWxvYWRJbWFnZXMuYXJndW1lbnRzOyBmb3IoaT0wOyBpPGEubGVuZ3RoOyBpKyspCiAgICBpZiAoYVtpXS5pbmRleE9mKCIjIikhPTApeyBkLk1NX3Bbal09bmV3IEltYWdlOyBkLk1NX3BbaisrXS5zcmM9YVtpXTt9fQp9Ci8vLS0+Cjwvc2NyaXB0Pgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KCjwvaGVhZD4KCjxzY3JpcHQgbGFuZ3VhZ2U9IkphdmFTY3JpcHQiIHR5cGU9InRleHQvSmF2YVNjcmlwdCI+CjwhLS0KZnVuY3Rpb24gTU1fcmVsb2FkUGFnZShpbml0KSB7ICAvL3JlbG9hZHMgdGhlIHdpbmRvdyBpZiBOYXY0IHJlc2l6ZWQKICBpZiAoaW5pdD09dHJ1ZSkgd2l0aCAobmF2aWdhdG9yKSB7aWYgKChhcHBOYW1lPT0iTmV0c2NhcGUiKSYmKHBhcnNlSW50KGFwcFZlcnNpb24pPT00KSkgewogICAgZG9jdW1lbnQuTU1fcGdXPWlubmVyV2lkdGg7IGRvY3VtZW50Lk1NX3BnSD1pbm5lckhlaWdodDsgb25yZXNpemU9TU1fcmVsb2FkUGFnZTsgfX0KICBlbHNlIGlmIChpbm5lcldpZHRoIT1kb2N1bWVudC5NTV9wZ1cgfHwgaW5uZXJIZWlnaHQhPWRvY3VtZW50Lk1NX3BnSCkgbG9jYXRpb24ucmVsb2FkKCk7Cn0KTU1fcmVsb2FkUGFnZSh0cnVlKTsKLy8tLT4KCjwvc2NyaXB0Pgo8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoKCjwvaGVhZD4KCjxib2R5IGJhY2tncm91bmQ9ImltZy9mb25kb19kZWdyYWRlLmpwZyIgdG9wbWFyZ2luPSIwIj4KPHRhYmxlIHdpZHRoPSIxMDA1IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgPHRyPiAKICAgIDx0ZCB3aWR0aD0iOTYiPjxpbWcgc3JjPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzBfMDEuanBnIiB3aWR0aD0iOTYiIGhlaWdodD0iMjA4IiAvPjwvdGQ+CiAgICA8dGQgd2lkdGg9IjgwOSI+IDxzY3JpcHQgdHlwZT0idGV4dC9qYXZhc2NyaXB0Ij4KQUNfRkxfUnVuQ29udGVudCggJ2NvZGViYXNlJywnaHR0cDovL2Rvd25sb2FkLm1hY3JvbWVkaWEuY29tL3B1Yi9zaG9ja3dhdmUvY2Ficy9mbGFzaC9zd2ZsYXNoLmNhYiN2ZXJzaW9uPTcsMCwxOSwwJywnd2lkdGgnLCc4MDknLCdoZWlnaHQnLCcyMDgnLCdzcmMnLCdzd2YvaGVhZGVyJywncXVhbGl0eScsJ2hpZ2gnLCdwbHVnaW5zcGFnZScsJ2h0dHA6Ly93d3cubWFjcm9tZWRpYS5jb20vZ28vZ2V0Zmxhc2hwbGF5ZXInLCdtb3ZpZScsJ3N3Zi9oZWFkZXInICk7IC8vZW5kIEFDIGNvZGUKPC9zY3JpcHQ+IDxub3NjcmlwdD4KICAgICAgPG9iamVjdCBjbGFzc2lkPSJjbHNpZDpEMjdDREI2RS1BRTZELTExY2YtOTZCOC00NDQ1NTM1NDAwMDAiIGNvZGViYXNlPSJodHRwOi8vZG93bmxvYWQubWFjcm9tZWRpYS5jb20vcHViL3Nob2Nrd2F2ZS9jYWJzL2ZsYXNoL3N3Zmxhc2guY2FiI3ZlcnNpb249NywwLDE5LDAiIHdpZHRoPSI4MDkiIGhlaWdodD0iMjA4Ij4KICAgICAgICA8cGFyYW0gbmFtZT0ibW92aWUiIHZhbHVlPSJzd2YvaGVhZGVyLnN3ZiIgLz4KICAgICAgICA8cGFyYW0gbmFtZT0icXVhbGl0eSIgdmFsdWU9ImhpZ2giIC8+CiAgICAgICAgPGVtYmVkIHNyYz0ic3dmL2hlYWRlci5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9IjgwOSIgaGVpZ2h0PSIyMDgiPjwvZW1iZWQ+IAogICAgICA8L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIHdpZHRoPSIxMiUiIHJvd3NwYW49IjUiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iIzAwMDAwMCI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI0NjEiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmFja2dyb3VuZD0iaW1nL1F1aWVuZXNTb21vc19BMl8wXzEzLmpwZyI+IAogICAgICA8c2NyaXB0IHR5cGU9InRleHQvamF2YXNjcmlwdCI+CkFDX0ZMX1J1bkNvbnRlbnQoICdjb2RlYmFzZScsJ2h0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCcsJ3dpZHRoJywnOTYnLCdoZWlnaHQnLCc0NjEnLCdzcmMnLCdzd2Yvc3VibWVudScsJ3F1YWxpdHknLCdoaWdoJywncGx1Z2luc3BhZ2UnLCdodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyJywnbW92aWUnLCdzd2Yvc3VibWVudScgKTsgLy9lbmQgQUMgY29kZQo8L3NjcmlwdD4gPG5vc2NyaXB0PgogICAgICA8b2JqZWN0IGNsYXNzaWQ9ImNsc2lkOkQyN0NEQjZFLUFFNkQtMTFjZi05NkI4LTQ0NDU1MzU0MDAwMCIgY29kZWJhc2U9Imh0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+CiAgICAgICAgPHBhcmFtIG5hbWU9Im1vdmllIiB2YWx1ZT0ic3dmL3N1Ym1lbnUuc3dmIiAvPgogICAgICAgIDxwYXJhbSBuYW1lPSJxdWFsaXR5IiB2YWx1ZT0iaGlnaCIgLz4KICAgICAgICA8ZW1iZWQgc3JjPSJzd2Yvc3VibWVudS5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+PC9lbWJlZD48L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCIgYmdjb2xvcj0iI0ZGRkZGRiI+CiAgICAgICAgPHRyPiAKICAgICAgICAgIDx0ZCB3aWR0aD0iMTciIHJvd3NwYW49IjciPjxwPiZuYnNwOzwvcD48L3RkPgogICAgICAgICAgPHRkIHdpZHRoPSIxNzIiIGFsaWduPSJjZW50ZXIiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxpbWcgc3JjPSJpbWcvM3B4LmpwZyIgd2lkdGg9IjUiIGhlaWdodD0iNSI+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciI+PGxpbmsgaHJlZj0iLi4vZXN0aWxvcy5jc3MiIHJlbD0ic3R5bGVzaGVldCIgdHlwZT0idGV4dC9jc3MiIC8+Cjxib2R5IGJnY29sb3I9IiNDQ0NDQ0MiIHRvcG1hcmdpbj0iNiBweCI+PHRhYmxlIHdpZHRoPSIxNjUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIzIiBiZ2NvbG9yPSIjRkZGRkZGIj4KPHRyPgogICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTkxIiBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiAgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MThfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+SG9tZTwvYT48L3RkPgogIDwvdHI+Cjx0cj4KICA8dGQgaGVpZ2h0PSIyOCIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj4mbmJzcDsmbmJzcDtOb3RpY2lhczwvYT48L3RkPgo8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJkb25hY2lvbmVzLyIgdGFyZ2V0PSJfYmxhbmsiIGNsYXNzPSJmb25kb2JvdG9uIj5Eb25hY2lvbmVzPC9hPjwvdGQ+CiAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciICB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yM19uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5IaXN0b3JpYWwgZGUgbmV3c2xldHRlcnM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTEzYSIgY2xhc3M9ImZvbmRvYm90b24iPkVudmlhciBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yNl9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5WZXIgdHJhYmFqb3MgZGUgdXN1YXJpb3M8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MTZfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+U2FsdWQgQWN0aXZhIHByZW5zYTwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJtYWlsdG86c2FsdWRhY3RpdmFAc2FsdWRhY3RpdmEub3JnLmFyIiBjbGFzcz0iZm9uZG9ib3RvbiI+TWFuZCZhYWN1dGU7IHR1IEMuVi48L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgIHdpZHRoPSI2ImhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTIxX25ldyIgY2xhc3M9ImZvbmRvYm90b24iPkluZm9ybWFjaSZvYWN1dGU7biBkZSBpbnRlciZlYWN1dGU7czwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyI+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiBoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xMF80IiBjbGFzcz0iZm9uZG9ib3RvbiI+Q29uZ3Jlc29zCiAgICAgICAgICAgICAgICAgIHkgSm9ybmFkYXM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTExIiBjbGFzcz0iZm9uZG9ib3RvbiI+UmVnaXN0cmFjaSZvYWN1dGU7bjwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgCiAgICAgICAgICA8L3RhYmxlPgo8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNSIgdGFyZ2V0PSJfYmxhbmsiPjxicj4KICAgICAgICAgICAgICAgICAgPGltZyBzcmM9ImltZy9iYW5uZXJfZG9uYWNpb25lcy5qcGciIHdpZHRoPSIxNjIiIGhlaWdodD0iMTIwIiBib3JkZXI9IjAiPjxicj4KICAgICAgICAgICAgICAgICAgPGJyPgogICAgICAgICAgICAgICAgICA8aW1nIHNyYz0iaW1nL2JvdG9uRm9yby5naWYiIHdpZHRoPSIxNzIiIGhlaWdodD0iMTE3IiBib3JkZXI9IjAiPjwvYT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTY3IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjkiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzAzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iOSIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTQ5IiBiYWNrZ3JvdW5kPSJpbWcvY2hpY29zX3BlcmRpZG9zXzA1LmdpZiI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDUuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMCI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDcuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMi5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEyLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9InNyYy9pbWdfdXAvMjMwODIwMTIuMS5qcGciIHdpZHRoPSIxNDkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMy5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNi5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iNSIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTcuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNy5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgYmdjb2xvcj0iI0ZFRTdDRiIgY2xhc3M9InRpdHVsb2hvbWU1Ij48c3Ryb25nPk5pJm50aWxkZTtvcyBwZXJkaWRvczxicj4KICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0yOSIgY2xhc3M9ImJvdG9uIj5bVmVyIG0mYWFjdXRlO3NdPC9hPjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTkuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xOS5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18yMC5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iMjUiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4NCgkJCQkNCgkJCQk8Zm9ybSBhY3Rpb249ImluZGV4LnBocD9pZD0xMSIgIG1ldGhvZD0icG9zdCI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9penExLmpwZyIgd2lkdGg9IjEyIiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9hcnJpYmEuanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9kZXIxLmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgIDwvdHI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiIgdmFsaWduPSJ0b3AiIGNsYXNzPSJyZWdGb25kbzEiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9penEuanBnIiB3aWR0aD0iMTIiIGhlaWdodD0iMTIiIC8+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSI5NCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV90aXQuanBnIiB3aWR0aD0iNjYiIGhlaWdodD0iMjMiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSI1MCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJyZWdpc3RyYXJzZSI+SW5ncmVzJmFhY3V0ZTsgDQogICAgICAgICAgICAgIHR1cyBkYXRvcyB5IHJlY2liJmlhY3V0ZTsgbGEgbWVqb3IgaW5mb3JtYWNpJm9hY3V0ZTtuIGEgdHJhdiZlYWN1dGU7cyANCiAgICAgICAgICAgICAgZGUgbnVlc3RybzxzdHJvbmc+IE5ld3NsZXR0ZXI8L3N0cm9uZz4uIDxzdHJvbmc+PHNwYW4gY2xhc3M9ImdyYXRpcyI+R3JhdGlzITwvc3Bhbj48L3N0cm9uZz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI1IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9InRyYWJTRUNDSU9OIj5Ob21icmU8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBjbGFzcz0icmVnQ0VMREEiPjxpbnB1dCBuYW1lPSJub21icmUiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0ibm9tYnJlIiAvPjwvdGQ+DQogICAgICAgICAgPC90cj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0idHJhYlNFQ0NJT04iPkFwZWxsaWRvPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iYXBlbGxpZG8iIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iYXBlbGxpZG8iIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJ0cmFiU0VDQ0lPTiI+RS1tYWlsPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iZW1haWwiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iZW1haWwiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InRyYWJTRUNDSU9OIj4mbmJzcDs8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idHJhYlNFQ0NJT04iPjxpbnB1dCB0eXBlPSJpbWFnZSIgc3JjPSJpbWcvcmVnaXN0cmF0ZV9ib3Rvbi5qcGciIHdpZHRoPSIxMTciIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgIDwvdGFibGU+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE0IiB2YWxpZ249InRvcCIgY2xhc3M9InJlZ0ZvbmRvMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2Rlci5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIxNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KICAgICAgICAgICAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTIiIGhlaWdodD0iMjQiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfaXpxMi5qcGciIHdpZHRoPSIxMiIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI0Ij48aW1nIHNyYz0iaW1nL3JlZ2lzdHJhdGVfYWJham8uanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjI0IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfZGVyMi5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KCQkJCQkNCgkJCQkJPC9mb3JtPg0KICAgICAgICAgICAgICAgICAgPC90YWJsZT4NCjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPiAKICAgICAgICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTcwIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUyIj4KCQkJCQkJCQkJCQkJCQkJCTwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9jbGF1ZGlhMl8wMy5qcGciIHdpZHRoPSIxNzQiIGhlaWdodD0iMjUwIiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcCI+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICA8dGQgcm93c3Bhbj0iNyIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nLzV4NS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjciPjwvdGQ+CiAgICAgICAgICA8dGQgY29sc3Bhbj0iMiIgcm93c3Bhbj0iNCIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPGZvcm0gYWN0aW9uPSJsb2dpbi5waHAiIG1ldGhvZD0icG9zdCIgbmFtZT0iZm9ybTIiPgoKICAgICAgICAgICAgICA8dHI+IAogICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgY29sc3Bhbj0iMiIgYWxpZ249ImxlZnQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIiA+IAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8c3Ryb25nPlVzdWFyaW8gbm8gcmVnaXN0cmFkbzwvc3Ryb25nPiAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9mb250PiA8L3N0cm9uZz4gCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDkiIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPlVzdWFyaW8mbmJzcDsmbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzOSIgdmFsaWduPSJtaWRkbGUiPjxpbnB1dCBuYW1lPSJ1c3VhcmlvIiB0eXBlPSJ0ZXh0IiBjbGFzcz0icmVnIiBpZD0idXN1YXJpbyIgc2l6ZT0iNyI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjciIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPkNvbnRyYXNlJm50aWxkZTthJm5ic3A7Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzkiIHZhbGlnbj0ibWlkZGxlIj48aW5wdXQgbmFtZT0icGFzcyIgdHlwZT0icGFzc3dvcmQiIGNsYXNzPSJyZWciIGlkPSJwYXNzIiBzaXplPSI3Ij48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiIgYWxpZ249InJpZ2h0IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9ImJvdG9uIj48aW5wdXQgdHlwZT0iaW1hZ2UiIHNyYz0iaW1nL3JlZy5qcGciIHdpZHRoPSI1OCIgaGVpZ2h0PSIzMCI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjciIGhlaWdodD0iMTkiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgPjxhIGhyZWY9Imh0dHA6Ly93d3cuZmFjZWJvb2suY29tL2hvbWUucGhwPyMhL3BhZ2VzL01lcmxvLUFyZ2VudGluYS9TQUxVRC1BQ1RJVkEvMTAwNTgzNTQzMzE3MzIyP3JlZj10cyZhamF4cGlwZT0xJl9fYT03IiB0YXJnZXQ9Il9ibGFuayI+PGltZyBzcmM9ImltZy9mYWNlYm9vay5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzExIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj48ZGl2IGFsaWduPSJsZWZ0Ij48YSBocmVmPSJodHRwOi8vdHdpdHRlci5jb20vU2FsdWRBY3RpdmFPTkciIHRhcmdldD0iX2JsYW5rIj48aW1nIHNyYz0iaW1nL3R3aXRlci5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC9kaXY+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSI1IiBhbGlnbj0icmlnaHQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIj48bGFiZWw+PGZvbnQgc2l6ZT0iLTYiPlNpCiAgICAgICAgICAgICAgICAgICAgICAgdG9kYXYmaWFjdXRlO2Egbm8gZXMgdXN1YXJpbyA8L2ZvbnQ+IDxhIGhyZWY9ImluZGV4LnBocD9pZD0xMSIgY2xhc3M9ImJvdG9uIj48Zm9udCBzaXplPSItNiI+cmVnJmlhY3V0ZTtzdHJlc2UKICAgICAgICAgICAgICAgICAgICAgICAgYXF1JmlhY3V0ZTsgPGZvbnQgY29sb3I9IiM2NjY2NjYiPiYjODIyNjs8L2ZvbnQ+PC9mb250PjwvYT4gPGEgaHJlZj0iaW5kZXgucGhwP2lkPTEyIiBjbGFzcz0iYm90b24xIj48Zm9udCBzaXplPSItNiI+b2x2aWRlIG1pIGNvbnRyYXNlJm50aWxkZTthPC9mb250PjwvYT48L2xhYmVsPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE3Ij4mbmJzcDsgPC90ZD4KICAgICAgICAgICAgICA8L3RyPgoJCQkgIDwvZm9ybT4KCiAgICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgICA8IURPQ1RZUEUgaHRtbCBQVUJMSUMgIi0vL1czQy8vRFREIFhIVE1MIDEuMCBUcmFuc2l0aW9uYWwvL0VOIiAiaHR0cDovL3d3dy53My5vcmcvVFIveGh0bWwxL0RURC94aHRtbDEtdHJhbnNpdGlvbmFsLmR0ZCI+CjxodG1sIHhtbG5zPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hodG1sIj4KPGhlYWQ+CjxtZXRhIGh0dHAtZXF1aXY9IkNvbnRlbnQtVHlwZSIgY29udGVudD0idGV4dC9odG1sOyBjaGFyc2V0PWlzby04ODU5LTEiIC8+Cjx0aXRsZT5Eb2N1bWVudG8gc2luIHQmaWFjdXRlO3R1bG88L3RpdGxlPgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KPHNjcmlwdCBsYW5ndWFnZT0iSmF2YVNjcmlwdCIgdHlwZT0idGV4dC9KYXZhU2NyaXB0Ij4KPCEtLQpmdW5jdGlvbiBNTV9yZWxvYWRQYWdlKGluaXQpIHsgIC8vcmVsb2FkcyB0aGUgd2luZG93IGlmIE5hdjQgcmVzaXplZAogIGlmIChpbml0PT10cnVlKSB3aXRoIChuYXZpZ2F0b3IpIHtpZiAoKGFwcE5hbWU9PSJOZXRzY2FwZSIpJiYocGFyc2VJbnQoYXBwVmVyc2lvbik9PTQpKSB7CiAgICBkb2N1bWVudC5NTV9wZ1c9aW5uZXJXaWR0aDsgZG9jdW1lbnQuTU1fcGdIPWlubmVySGVpZ2h0OyBvbnJlc2l6ZT1NTV9yZWxvYWRQYWdlOyB9fQogIGVsc2UgaWYgKGlubmVyV2lkdGghPWRvY3VtZW50Lk1NX3BnVyB8fCBpbm5lckhlaWdodCE9ZG9jdW1lbnQuTU1fcGdIKSBsb2NhdGlvbi5yZWxvYWQoKTsKfQpNTV9yZWxvYWRQYWdlKHRydWUpOwoKZnVuY3Rpb24gTU1fcHJlbG9hZEltYWdlcygpIHsgLy92My4wCiAgdmFyIGQ9ZG9jdW1lbnQ7IGlmKGQuaW1hZ2VzKXsgaWYoIWQuTU1fcCkgZC5NTV9wPW5ldyBBcnJheSgpOwogICAgdmFyIGksaj1kLk1NX3AubGVuZ3RoLGE9TU1fcHJlbG9hZEltYWdlcy5hcmd1bWVudHM7IGZvcihpPTA7IGk8YS5sZW5ndGg7IGkrKykKICAgIGlmIChhW2ldLmluZGV4T2YoIiMiKSE9MCl7IGQuTU1fcFtqXT1uZXcgSW1hZ2U7IGQuTU1fcFtqKytdLnNyYz1hW2ldO319Cn0KLy8tLT4KPC9zY3JpcHQ+CiAgICAgICAgICAgICA8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoJCQkgCjxzdHlsZSB0eXBlPSJ0ZXh0L2NzcyI+CjwhLS0KI0xheWVyMSB7Cglwb3NpdGlvbjphYnNvbHV0ZTsKCXdpZHRoOjY1MXB4OwoJaGVpZ2h0OjIxOHB4OwoJei1pbmRleDoxOwp9CiNMYXllcjIgewoJcG9zaXRpb246YWJzb2x1dGU7Cgl3aWR0aDoyMDBweDsKCWhlaWdodDoxMTVweDsKCXotaW5kZXg6MTsKCXZpc2liaWxpdHk6IHZpc2libGU7Cn0KLkVzdGlsbzEgewoJZm9udC1zaXplOiAxOHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzIgewoJZm9udC1zaXplOiAxNHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzMge2NvbG9yOiAjNTA2OTkwOyBsaW5lLWhlaWdodDogMTJweDsgdGV4dC1kZWNvcmF0aW9uOiBub25lOyBmb250LWZhbWlseTogVGFob21hO30KLS0+Cjwvc3R5bGU+CjwvaGVhZD4KCjxib2R5IGxlZnRtYXJnaW49IjIiIG1hcmdpbndpZHRoPSIyIj4KPHRhYmxlIHdpZHRoPSI2MDgiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICA8dHI+CiAgICA8dGQgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCB3aWR0aD0iMiUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzA3LmpwZyIgd2lkdGg9IjI0IiBoZWlnaHQ9IjE0IiAvPjwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI5MCUiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18wNy5qcGciPiZuYnNwOzwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI4JSIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wOS5qcGciIHdpZHRoPSI0NSIgaGVpZ2h0PSIxNyIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogIDwvdHI+CiAgPHRyPgogICAgPHRkIGNvbHNwYW49IjQiPjxiciAvPgogICAgICA8dGFibGUgd2lkdGg9Ijk4JSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICA8dHI+CiAgICAgICAgPHRkIHdpZHRoPSIyJSI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgICA8dGQgd2lkdGg9IjkzJSI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CjwhLS0gSU5JQ0lPIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzIzMDQyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjIvMTEvMjAxMzwvc3Bhbj48YnI+SVYgQ29uZ3Jlc28gSW50ZXJuYWNpb25hbCB2aW9sZW5jaWEsIG1hbHRyYXRvIHkgYWJ1c288L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxzdHJvbmc+MTQsIDE1IHkgMTYgZGUgTm92aWVtYnJlIEFCSUVSVEEgTEEgSU5TQ1JJUENJJk9hY3V0ZTtOISAoY29uIGRlc2N1ZW50byBoYXN0YSBlbCAyNy84KTxiciAvPjwvc3Ryb25nPjwvcD4NCjxwPjxzdHJvbmc+QUJJRVJUQSBMQSBSRUNFUENJJk9hY3V0ZTtOIERFIFRSQUJBSk88YSBocmVmPSJodHRwOi8vd3d3LmNvbmdyZXNvdmlvbGVuY2lhLmNvbS9pbmRleC5waHA/aWQ9bW9kYWxpZGFkZXMiIHRhcmdldD0iX2JsYW5rIj4gKG1hcyBpbmZvKTwvYT48L3N0cm9uZz48L3A+DQo8cD48c3BhbiBzdHlsZT0iY29sb3I6ICNmZjY2MDA7Ij48c3Ryb25nPk9yZ2FuaXphOiBTYWx1ZCBBY3RpdmE8L3N0cm9uZz48L3NwYW4+PC9wPg0KPHA+PHNwYW4gc3R5bGU9ImNvbG9yOiAjZmY2NjAwOyI+SW5jcmlwdG9zIGFsIFBvcnRhbCBkZSBTYWx1ZCBBY3RpdmEsIGltcG9ydGFudGVzIGRlc2N1ZW50b3MhPGJyIC8+PC9zcGFuPjwvcD4NCjxwPkx1Z2FyIGRlIFJlYWxpemFjaSZvYWN1dGU7biB5IGNvbGFib3JhY2lvbjogVW5pdmVyc2lkYWQgZGVsIEVzdGUsIExhIFBsYXRhIEJ1ZW5vcyBBaXJlczwvcD4NCjxwPk1hcyBkZSAxNTAgdHJhYmFqb3MgcHJlc2VudGFkb3MsIHVsdGltb3MgZGlhcyBwYXJhIGluc2NyaWJpcnNlIGNvbiBkZXNjdWVudG8hITwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPkluc2NyaWJpcnNlPC9hPjwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPjxiciAvPjwvYT48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAxIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDEiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MDQvMTEvMjAxMzwvc3Bhbj48YnI+RWwgY29sZWdpbyBkZSBQc2lj82xvZ29zIGRlIEPzcmRvYmEgc2UgcHJvbnVuY2lhIGVuIHJlbGFjafNuIGFsIFNBUCB5IGVuIGNvbmNvcmRhbmNpYSBjb24gbG8gZXhwcmVzYWRvIHBvciBlbCBDb2xlZ2lvIGRlIFBzaWPzbG9nb3MgZGUgTWFyIGRlbCBQbGF0YSB5IGVsIENvbGVnaW8gZGUgUHNpY/Nsb2dvcyBkZSBsYSAgUHJvdmluY2lhIGRlIEJ1ZW5vcyBBaXJlczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+Jm5ic3A7PC9wPg0KPHA+TGFzIGNvbnRyb3ZlcnNpYXMgZ2VuZXJhZGFzIGVuIHJlbGFjaSZvYWN1dGU7biBhbCAic2luZHJvbWUgZGUgYWxpZW5hY2kmb2FjdXRlO24gcGFyZW50YSIgU0FQLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMxMCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzEwIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzE2MTAyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTYvMTAvMjAxMzwvc3Bhbj48YnI+U2FsdWQgQWN0aXZhIG90b3JnYSBtZWRpYXMgYmVjYXMgcGFyYSBlbCBJViBDb25ncmVzbyBJbnRlcm5hY2lvbmFsLCBWIE5hY2lvbmFsLCBWSSBSZWdpb25hbCBWaW9sZW5jaWEsIE1hbHRyYXRvIHkgQWJ1c28uPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD4mbmJzcDs8L3A+DQo8cD5TZXImYWFjdXRlO24gb3RvcmdhZGFzIDUwIG1lZGlhcyBiZWNhcywgcXVlZGFuIHBvY2FzISEhIGNvbmRpY2lvbjo8L3A+DQo8cD5QZXJ0ZW5lY2VyIGFsIGFtYml0byBwdWJsaWNvIG8gYSBPTkcsIHNlIGNvbnNpZGVyYSB0YW1iaWVuIGxhIGRpc3RhbmNpYSBhbCBsdWdhciBkZWwgZXZlbnRvISEhIGVzIG11eSBzZW5jaWxsbywgc29sbyBkZWJlcyBlbnZpYXIgdW4gZW1haWwuLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwOSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA5Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjI0LzA3LzIwMTM8L3NwYW4+PGJyPk5FQ0VTSVRBTU9TIERFIFNVIFNPTElEQVJJREFEIEhBQ0lBIExPUyBOSdFPUyBZIE5J0UFTISEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPlBST0dSQU1BIEZBTUlMSUFTIFNPTElEQVJJQVM8L3NwYW4+PC9zdHJvbmc+PC9wPg0KPHA+PHN0cm9uZz5DQU1CSU8gREUgU0VERTwvc3Ryb25nPjwvcD4NCjxwPkxhIGNhcGFjaXRhY2kmb2FjdXRlO24gcGFyYSBsYSBwdWVzdGEgZW4gbWFyY2hhIGRlbCA8c3Ryb25nPlByb2dyYW1hIEZhbWlsaWFzIFNvbGlkYXJpYXM8L3N0cm9uZz4gc2UgcmVhbGl6YXImYWFjdXRlOyBlbiBsYSBsb2NhbGlkYWQgZGUgPHN0cm9uZz5OYXZhcnJvPC9zdHJvbmc+IHBhcmEgdG9kbyBlbCBjb3JyZWRvciBkZSBsYSBSdXRhIDQwLjwvcD4NCjxwPkluaWNpbyA8c3Ryb25nPk1pJmVhY3V0ZTtyY29sZXMgMjggZGUgYWdvc3RvIGEgbGFzIDE0IGhvcmFzLiZuYnNwOzwvc3Ryb25nPjwvcD4NCjxwPlNlZGU6IDxzdHJvbmc+U2FsJm9hY3V0ZTtuIE11bmljaXBhbCBlbiBsYSBjYWxsZSAxMDcgZXNxdWluYSAyMiAtIE5hdmFycm88L3N0cm9uZz48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA4Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTIwNzIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xMi8wNy8yMDEzPC9zcGFuPjxicj5TQUxVRCBBQ1RJVkEgaGEgc2lkbyBlbGVnaWRhIHBvciBzZWd1bmRhIHZleiBjb25zZWN1dGl2YSBjb21vIHVubyBkZSBsb3MgZ2FuYWRvcmVzIGRlbCBDdWFydG8gQ29uY3Vyc28gZGUgUHJveWVjdG9zIFNvY2lhbGVzIGRlIFBldHJvYnJhczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+RW4gZWwgbWFyY28gZGVsIEN1YXJ0byBDb25jdXJzbyBkZSBQcm95ZWN0b3MgU29jaWFsZXMgZGUgUGV0cm9icmFzLCANCm51ZXN0cmEgSW5zdGl0dWNpJm9hY3V0ZTtuIFNBTFVEIEFDVElWQSBoYSBzaWRvIGVsZWdpZGEgcG9yIHNlZ3VuZGEgdmV6IA0KY29uc2VjdXRpdmEgY29tbyB1bm8gZGUgbG9zIGdhbmFkb3JlcyBkZSBkaWNobyBjb25jdXJzby48YnIgLz5FbiBlc3RhIA0KZWRpY2kmb2FjdXRlO24gZWwgcHJveWVjdG8gcXVlIGhhIHNpZG8gZWxlZ2lkbyBlcyBlbCAmbGRxdW87UHJvZ3JhbWEgZGUgRmFtaWxpYXMgDQpTb2xpZGFyaWFzJnJkcXVvOyBzaWVuZG8gc3UgJmFhY3V0ZTtyZWEgZGUgaW1wbGVtZW50YWNpJm9hY3V0ZTtuIGxvcyBNdW5pY2lwaW9zIGRlIE5hdmFycm8sIA0KR3JhbC4gTGFzIEhlcmFzLCBNYXJjb3MgUGF6LCB5IE1lcmxvPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAyLzA3LzIwMTM8L3NwYW4+PGJyPk/tciBvIGVzY3VjaGFyPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Qb3IgQ2FybG9zIFJvemFuc2tpICo8L3A+DQo8cD5BIGxvIGxhcmdvIGRlIGxvcyBzaWdsb3MsIGxhcyBuaSZudGlsZGU7YXMsIG5pJm50aWxkZTtvcyB5IGFkb2xlc2NlbnRlcyBoYW4gc2lkbyBtYWx0cmF0YWRvcyB5IGFidXNhZG9zIHNpbiBxdWUgYSBsYSBjb211bmlkYWQgbGUgaW50ZXJlc2FyYSBuaSBzaXF1aWVyYSBlc2N1Y2hhcmxvcyBjdWFuZG8gaGFjJmlhY3V0ZTthbiBzYWJlciBkZSBhbGd1bmEgZm9ybWEgbG9zIHN1ZnJpbWllbnRvcyBxdWUgcGFkZWMmaWFjdXRlO2FuLiBFbiAxODc0LCBlbiBFc3RhZG9zIFVuaWRvcywgZnVlIGxhIHByaW1lcmEgdmV6IHF1ZSBlbCBFc3RhZG8gaW50ZXJ2aW5vIGVuIHVuIGNhc28gZGUgbWFsdHJhdG8geSBhYnVzby4uLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDYiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4wMi8wNy8yMDEzPC9zcGFuPjxicj5FbCBkZXJlY2hvIGRlIGxvcyBuafFvcyBhIHNlciBlc2N1Y2hhZG9zPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5VbiBob21icmUgYWN1c2FkbyBkZSBoYWJlciBhYnVzYWRvIGRlIHN1cyBoaWpvcyBoYWImaWFjdXRlO2Egc2lkbyBzb2JyZXNlJmlhY3V0ZTtkbyBkb3MgdmVjZXMgcG9yIGxhIEp1c3RpY2lhLiBQZXJvIGFob3JhLCBsYSBDJmFhY3V0ZTttYXJhIGRlIENhc2FjaSZvYWN1dGU7biByZXZvYyZvYWN1dGU7IGVzYSBkZWNpc2kmb2FjdXRlO24gcG9ycXVlIGVuIGxhIGludmVzdGlnYWNpJm9hY3V0ZTtuIGVsIGp1ZXogbnVuY2EgaGFiJmlhY3V0ZTthIGVzY3VjaGFkbyBhIGxvcyBjaGljb3MuIFkgb3JkZW4mb2FjdXRlOyBxdWUgdGVuZ2EgZW4gY3VlbnRhIGxvIHF1ZSBkaWNlbi48L3A+DQo8cD5Qb3IgTWFyaWFuYSBDYXJiYWphbDwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDUiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE1NiIgcm93c3Bhbj0iMiIgdmFsaWduPSJ0b3AiPgoJCQkJCgkJCQk8dGFibGUgd2lkdGg9IjMyJSIgYm9yZGVyPSIxIiBjZWxsc3BhY2luZz0iMyIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48aW1nIHNyYz0ic3JjL2ltZ191cC8wNjA2MjAxMy4xLmpwZyIgd2lkdGg9IjE0NiIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT4KCQkJCQkJCQk8L3RkPiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjA2LzA2LzIwMTM8L3NwYW4+PGJyPkFidXNvIHNleHVhbCBpbmZhbnRpbC4gRGVzYWZpb3MgZGUgbGEgY2xpbmljYSBhY3R1YWw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkFiaWVydGEgbGEgaW5zY3JpcGNpb248L3A+DQo8cD5Eb2NlbnRlczogTGljLiBNYXJpYSBCZWF0cml6IE0mdXVtbDtsbGVyLiBMaWMuIFBhb2xhIE11Jm50aWxkZTtveiBEdWFydGU8L3A+DQo8cD5JbmljaW86IE1pZXJjb2xlcyAxOSBkZSBKdW5pbzwvcD4NCjxwPkZyZWN1ZW5jaWE6IFNlbWFuYWw8L3A+DQo8cD5Nb2RhbGlkYWQ6IEludGVuc2l2YTwvcD4NCjxwPkNvbnRlbmlkb3M6ICZuYnNwOyBFc3RhIGRlc3RpbmFkbyBhIHRvZG9zIGxvcyBwcm9mZXNpb25hbGVzIGNvbXByb21ldGlkb3MgY29uIGxhIHRlbWF0aWNhIGRlbCBhYnVzbyBpbmZhbnRpbCBxdWUgcXVpZXJhbiBhY3R1YWxpemFyc2UgZSBpbnRlcmNhbWJpYXIgZXhwZXJpZW5jaWFzIGRlIHRyYWJham8uLi48L3A+DQo8cD4mbmJzcDs8L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA0Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDQiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTYwNTIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xNi8wNS8yMDEzPC9zcGFuPjxicj5TYWx1ZCBBY3RpdmEgbmVjZXNpdGEgZGUgdHUgYXl1ZGEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5UcmFiYWphbW9zIGNvbW8gcG9kZW1vczogYmEmbnRpbGRlO29zIHJvdG9zLCBzdXNwZW5zaSZvYWN1dGU7biBkZSByZXVuaW9uZXMgcG9yIGNvcnRlcyBkZSBsdXogeSBhZ3VhLCBqdWd1ZXRlcyB2aWVqb3MsIG1lc2VzIGRlIGF0cmFzbyBlbiBlbCBwYWdvIGRlIHN1cyBwcm9mZXNpb25hbGVzIGRlIGxhIHNhbHVkLiBSZWNpZW50ZW1lbnRlIHR1dmltb3MgcXVlIGNlcnJhciBudWVzdHJvIHF1ZXJpZG8gSG9nYXI6ICZsZHF1bztNZXRhbW9yZm9zaXMmcmRxdW87IGVyYSBlbCBsdWdhciBxdWUgc3VwbyBjb250ZW5lciBhIG5pJm50aWxkZTthcyB5IGomb2FjdXRlO3ZlbmVzIHJlc2NhdGFkYSBkZSByZWRlcyBkZSB0cmF0YSBvIHYmaWFjdXRlO2N0aW1hcyBkZSBhYnVzbyBpbnRyYWZhbWlsaWFyLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAzIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAzLzA1LzIwMTM8L3NwYW4+PGJyPlJFUFVESU8gQSBMQSBQUkVTRU5DSUEgRU4gTEEgRkVSSUEgREVMIExJQlJPIERFIFVOIEVYIEpVRVogQUNVU0FETyBERSBBQlVTTyBTRVhVQUw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkZ1ZSBjYW1hcmlzdGEgZW4gTWFyIGRlbCBQbGF0YSBkdXJhbnRlIGxhIGRpY3RhZHVyYS4gSGFjZSBhJm50aWxkZTtvcywgdmFyaWFzIG11amVyZXMgbG8gYWN1c2Fyb24gZGUgaGFiZXIgYWJ1c2FkbyBkZSBlbGxhcyBjdWFuZG8gZXJhbiBuaSZudGlsZGU7YXMuIExhIGNhdXNhIHByZXNjcmliaSZvYWN1dGU7IHkgbm8gaHVibyBjb25kZW5hLiBNYSZudGlsZGU7YW5hIHRpZW5lIHByZXZpc3RvIGZpcm1hciBzdSBsaWJyby4gRXNhcyBtaXNtYXMgbXVqZXJlcyBwaWRlbiBxdWUgbm8gc2VhIGFkbWl0aWRvIGVuIGxhIGZlcmlhLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDIiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgIDwhLS0gRklOIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgIDwvdGFibGU+ICAgICAgICA8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iNSUiIGFsaWduPSJyaWdodCI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgPC90cj4KICAgIDwvdGFibGU+PC90ZD4KICA8L3RyPgogIDx0cj4KICAgIDx0ZCB3aWR0aD0iMSUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiIgYWxpZ249ImNlbnRlciI+Jm5ic3A7PC90ZD4KICAgIDx0ZCB3aWR0aD0iMiUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgPC90cj4KICAKICA8dGQ+CiAgPHRyPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0ciBhbGlnbj0iY2VudGVyIj4KICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgPHRkIHdpZHRoPSI5NyIgY29sc3Bhbj0iMiIgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iNTQ2IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idGl0dWxvaG9tZTIiPjx0YWJsZSB3aWR0aD0iIiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYWxpZ249ImxlZnQiIHZhbGlnbj0iYm90dG9tIiBjbGFzcz0idGl0dWxvaG9tZTIiPlJhbmtpbmc8L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSIgY2xhc3M9InRpdHVsb2hvbWUyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iIiBoZWlnaHQ9IjM1IiBhbGlnbj0ibGVmdCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPiZidWxsO0xhcyBtJmFhY3V0ZTtzIGxlaWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGNsYXNzPSJjb250ZW5pZG9ob21lIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBjbGFzcz0iY29udGVuaWRvaG9tZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+JmJ1bGw7TGFzIG0mYWFjdXRlO3MgY29tZW50YWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTHVkb3RlY2EgR2FyYWJhdG8gLSBQcm95ZWN0byBzYWx1ZGFjdGl2YSwgUG9yIHVuYSBpbmZhbmNpYSBmZWxpeiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iOSUiIGJnY29sb3I9IiNFRkVGRUYiPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzJSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xNjIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDUlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTE2MiIgY2xhc3M9ImJvdG9uIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBDdXJzbyBJbnRlbnNpdm8gZGUgb3BlcmFkb3IgdGVyYXBldXRpY28gZXNwZWNpYWxpemFkbyBlbiBlbCBhYm9yZGFqZSBkZWwgYWJ1c28sIGxhIHZpb2xlbmNpYSB5IGVsIG1hbHRyYXRvIGluZmFudGlsICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgUFJPR1JBTUEgTEFTIFZJQ1RJTUFTIENPTlRSQSBMQVMgVklPTEVOQ0lBUyAgTWluaXN0ZXJpbyBkZSBKdXN0aWNpYSB5IERlcmVjaG9zIEh1bWFub3MgZGUgbGEgTmFjafNuICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI5JSIgYmdjb2xvcj0iI0VGRUZFRiI+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjMlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTI1NSIgY2xhc3M9ImJvdG9uIj48aW1nIHNyYz0iaW1nL2ZsZWNoYW5hcmFuamFmZ3Jpc18yNC5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSI3IiBib3JkZXI9IjAiIGFsaWduPSJhYnNtaWRkbGUiIC8+PC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI0NSUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MjU1IiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIERpcGxvbWF0dXJhIGVuIEFib3JkYWplIGludGVyZGlzY2lwbGluYXJpbyBkZWwgbWFsdHJhdG8sIGxhIHZpb2xlbmNpYSB5IGVsIGFidXNvIHNleHVhbCBpbmZhbnRpbCAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyJSIgaGVpZ2h0PSIyMCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQxJSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNhbHVkIEFjdGl2YSBuZWNlc2l0YSBkZSB0dSBheXVkYSEgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjklIiBiZ2NvbG9yPSIjRUZFRkVGIj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMyUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MTA0IiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQ1JSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xMDQiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTGxhbWFkbyBwYXJhIHByZXNlbnRhY2nzbiBkZSB0cmFiYWpvcy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjIwIiBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyMCIgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGJnY29sb3I9IiNGRkZGRkYiIGNsYXNzPSJ0ZXh0b251ZXZvIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPgogICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iIyIgY2xhc3M9ImJvdG9uIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgPC90YWJsZT48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj4mbmJzcDs8L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBJTklDSU8gbm90YSBjb211biAtLT4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTUvMDQvMjAxMjwvc3Bhbj48YnI+T3JnYW5pemFuIGpvcm5hZGEgc29icmUgdmlvbGVuY2lhPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPlNlIGNlbnRyYXImYWFjdXRlOyBlbiBsb3MgZmVuJm9hY3V0ZTttZW5vcyBxdWUgYWZlY3RhbiBhIGxhIGZhbWlsaWEgeSBlbiBsbyBxdWUgb2N1cnJlIGVuIGxhcyBlc2N1ZWxhcy48YnIgLz4gU2UgbGxldmFyJmFhY3V0ZTsgYSBjYWJvIGVsIGx1bmVzIDIzLCBlbiBlbCBDZW50cm8gQ3VsdHVyYWwgZGUgVG9zY2hpIHkgVHJlcyANCkFycm95b3MsIHVuYSBqb3JuYWRhIGRlIHJlZmxleGkmb2FjdXRlO24geSBkZWJhdGUgYWJpZXJ0YSBhIGxhIGNvbXVuaWRhZCBzb2JyZSANCiZsZHF1bztWaW9sZW5jaWEgZW4gbGEgZmFtaWxpYSB5IGVuIGxhIGVzY3VlbGEgeSBzdSByZWxhY2kmb2FjdXRlO24gY29uIGVsIGZyYWNhc28gDQplc2NvbGFyJnJkcXVvOywgb3JnYW5pemFkYSBwb3IgbGEgQXNvY2lhY2kmb2FjdXRlO24gQ2l2aWwgQ2VudHJvIEFydCZlYWN1dGU7bWlkZXMgeSBsYSANCk11bmljaXBhbGlkYWQgZGUgQ2lwb2xsZXR0aS5TZSBjZW50cmFyJmFhY3V0ZTsgZW4gbG9zIGZlbiZvYWN1dGU7bWVub3MgcXVlIGFmZWN0YW4gYSBsYSBmYW1pbGlhIHkgZW4gbG8gcXVlIG9jdXJyZSBlbiBsYXMgZXNjdWVsYXMuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjMwLzAzLzIwMTI8L3NwYW4+PGJyPkNhcnRhIGRlIEFTQVBNSSAtIEFzb2NpYWNp824gQXJnZW50aW5hIGRlIFByZXZlbmNp824gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbDwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjE1IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSIxNSIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjgwIiBjb2xzcGFuPSI0IiBhbGlnbj0ibGVmdCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Mb3MgaW50ZWdyYW50ZXMgZGUgbGEgQ29taXNpJm9hY3V0ZTtuIERpcmVjdGl2YSBkZSBBU0FQTUkgLSBBc29jaWFjaSZvYWN1dGU7biBBcmdlbnRpbmEgZGUgUHJldmVuY2kmb2FjdXRlO24gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbCwgYXNvY2lhZGEgYSBsYSBJbnRlcm5hdGlvbmFsIFNvY2lldHkgZm9yIFByZXZlbnRpb24gb2YgQ2hpbGQgQWJ1c2UgYW5kIE5lZ2xlY3QgKElTUENBTikgLSwgdGVuZW1vcyBlbCBhZ3JhZG8gZGUgZGlyaWdpcm5vcyBhIFVzdGVkIHBhcmEgdHJhc21pdGlybGUgbnVlc3RyYSBwcm9mdW5kYSAmbmJzcDt5IGhvbmRhIHByZW9jdXBhY2kmb2FjdXRlO24gcG9yIGxhIHBvc3R1cmEgcXVlIHZpZW5lbiBhc3VtaWVuZG8gZW4gZm9ybWEgY29udGludWFkYSBhbGd1bm9zIGNvbGVnaW9zIGRlIHBzaWMmb2FjdXRlO2xvZ29zLCBlc3BlY2lhbG1lbnRlIGRlIGxhIHByb3ZpbmNpYSBkZSBCdWVub3MgQWlyZXMsIGVuIHJlbGFjaSZvYWN1dGU7biBhbCB0cmF0YW1pZW50byBwb2NvIHNlcmlvIHkgY29tcHJvbWV0aWRvIHF1ZSBzZSBsZXMgb3RvcmdhIGEgbGFzIGRlbnVuY2lhcyBlZmVjdHVhZGFzIGNvbnRyYSBwcm9mZXNpb25hbGVzIHBzaWMmb2FjdXRlO2xvZ29zLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjAvMDMvMjAxMjwvc3Bhbj48YnI+TEEgVklPTEVOQ0lBIFNFWFVBTCBDT05UUkEgTknRT1MgWSBOSdFBUyBFTiBDSUZSQVM8L3RkPgogICAgICAgICAgPC90cj4KICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkIHdpZHRoPSIxNSIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4MCIgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+UmFkaW9ncmFmJmlhY3V0ZTthIGRlIHVuIHByb2JsZW1hPC9wPg0KPHA+RGUgbG9zIG4mdWFjdXRlO21lcm9zIGNvbXBpbGFkb3MgcG9yIGRvcyBlcXVpcG9zIGRlbCBNaW5pc3RlcmlvIGRlIEp1c3RpY2lhLCBsYQ0KIGF1dG9yYSB0b21hIGxvcyBkZSBsYSBjaXVkYWQgZGUgQnVlbm9zIEFpcmVzIHBhcmEgdHJhemFyIHVuIHBhcmFkaWdtYSANCmRlIGxvcyBkZWxpdG9zIGNvbnRyYSBsYSBpbnRlZ3JpZGFkIHNleHVhbCBlbiBlbCBwYSZpYWN1dGU7cyB5IHNvYnJlIHN1IA0KYXRlbmNpJm9hY3V0ZTtuLjxiciAvPiA8YnIgLz4gJm5ic3A7UG9yIEV2YSBHaWJlcnRpPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2MCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjAiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjE1LzAzLzIwMTI8L3NwYW4+PGJyPkZBTExPIERFIExBIENPUlRFIFNVUFJFTUEgU09CUkUgTEEgTk8gSlVESUNJQUxJWkFDSU9OIERFTCBBQk9SVE8gRU4gQ0FTT1MgREUgVklPTEFDSU9OPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxiciAvPiBKVVJJU0RJQ0NJT046IE5BQ0lPTkFMPGJyIC8+IE1BVEVSSUE6IEFCT1JUTy48YnIgLz4gVFJJQlVOQUw6IENvcnRlIFN1cHJlbWEgZGUgSnVzdGljaWEgZGUgbGEgTmFjaSZvYWN1dGU7bi48YnIgLz4gQVVUT1M6IEYuLCBBLiBMLiBzLyBtZWRpZGEgYXV0b3NhdGlzZmFjdGl2YS48YnIgLz4gRkVDSEE6IDEzLzAzLzIwMTIuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI1OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNTkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBGSU4gbm90YSBjb211biAtLT4KPC90YWJsZT4KPG1hcCBuYW1lPSJNYXBNYXAiIGlkPSJNYXBNYXAiPjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjE0NCw0LDIxNCwzNiIgaHJlZj0iaW5kZXgucGhwP2lkPTE0IiAvPgo8L21hcD4KPG1hcCBuYW1lPSJNYXAyTWFwMiIgaWQ9Ik1hcDJNYXAyIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIxNDcsNCwyMjAsMzYiIGhyZWY9ImluZGV4LnBocD9pZD0xNGEiIC8+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcDMiIGlkPSJNYXAzIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIzNjMsMyw0MzYsMzkiIGhyZWY9ImluZGV4LnBocD9pZD0xNGIiIC8+CjwvbWFwPgo8L2h0bWw+CjwvdGQ+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gICAgICAgICAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFM0UzRTMiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSI3MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNiUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9kZWNpbG9fYmllbl9mdWVydGUxLmpwZyIgd2lkdGg9IjEyMCIgaGVpZ2h0PSIxMTIiPjwvdGQ+CiAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiA+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTI0IiBjbGFzcz0iYm90b24xIj5bK10gTSZhYWN1dGU7cyBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0UzRTNFMyI+ICAgICAgICA8L3RyPgogICAgICAgIDx0cj4gCiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj4mbmJzcDs8L3RkPgogICAgICAgIDwvdHI+CiAgICA8L3RhYmxlPjwvdGQ+CiAgPC90cj4KICA8dHI+IAogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSI+PGltZyBzcmM9ImltZy9penExLmpwZyIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjExNCIgLz48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9RdWllbmVzU29tb3NfQTJfMF8yNS5qcGciIHdpZHRoPSI4MDkiIGhlaWdodD0iMTE0IiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcDIiIC8+PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI1MCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiYWNrZ3JvdW5kPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzE4XzE4LmpwZyI+Jm5ic3A7PC90ZD4KICAgIDx0ZCBoZWlnaHQ9IjUwIiBjbGFzcz0iZm9uZG9ib3R0b20iPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2l0ZWkuY29tLmFyLyI+PGltZyBzcmM9ImltZy9laV9jb2xvci5wbmciIGFsdD0iZXNwYWNpb3MgZGUgaW1hZ2luYWNpb24sIGRlc2Fycm9sbG9zIGludGVyYWN0aXZvcywgY3JlYXRpdmlkYWQsIGRpc2XxbyIgd2lkdGg9IjI3IiBoZWlnaHQ9IjE1IiBib3JkZXI9IjAiPjwvYT4gPHNwYW4gY2xhc3M9ImVpIj48YSBocmVmPSJodHRwOi8vd3d3LnNpdGVpLmNvbS5hci8iIHNwYW4gY2xhc3M9ImVpIj5kaXNlJm50aWxkZTtvICsgY29tdW5pY2FjaSZvYWN1dGU7bjwvYT48L3NwYW4+PGVtPiZuYnNwOzwvZW0+PC9zcGFuPjxzcGFuIGNsYXNzPSJibGFuY28xIj48ZW0+Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7PC9lbT48L3NwYW4+PC90ZD4KICA8L3RyPgo8L3RhYmxlPgoKCjxtYXAgbmFtZT0iTWFwMiI+PGFyZWEgc2hhcGU9InJlY3QiIGNvb3Jkcz0iMjQ3LDY5LDQxNCw4MiIgaHJlZj0ibWFpbHRvOnNhbHVkYWN0aXZhQHNhbHVkYWN0aXZvLm9yZy5hciI+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcCI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM2LDE0MiwxNDksMTUyIiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MiI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM0LDE4NiwxNTAsMTk2IiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MCI+CjwvbWFwPgo8L2JvZHk+CjwvaHRtbD4K]]></response> | |
| 78 | <responseRedirected>false</responseRedirected> | |
| 79 | </requestresponse> | |
| 80 | </issue> | |
| 81 | <issue> | |
| 82 | <serialNumber>5107728146274449408</serialNumber> | |
| 83 | <type>5243904</type> | |
| 84 | <name>Cross-domain Referer leakage</name> | |
| 85 | <host ip="200.20.20.201">http://www.example.org.ar</host> | |
| 86 | <path><![CDATA[/index.php]]></path> | |
| 87 | <location><![CDATA[/index.php]]></location> | |
| 88 | <severity>Information</severity> | |
| 89 | <confidence>Certain</confidence> | |
| 90 | <issueBackground><![CDATA[When a web browser makes a request for a resource, it typically adds an HTTP header, called the "Referer" header, indicating the URL of the resource from which the request originated. This occurs in numerous situations, for example when a web page loads an image or script, or when a user clicks on a link or submits a form.<br><br>If the resource being requested resides on a different domain, then the Referer header is still generally included in the cross-domain request. If the originating URL contains any sensitive information within its query string, such as a session token, then this information will be transmitted to the other domain. If the other domain is not fully trusted by the application, then this may lead to a security compromise.<br><br>You should review the contents of the information being transmitted to other domains, and also determine whether those domains are fully trusted by the originating application.<br><br>Today's browsers may withhold the Referer header in some situations (for example, when loading a non-HTTPS resource from a page that was loaded over HTTPS, or when a Refresh directive is issued), but this behavior should not be relied upon to protect the originating URL from disclosure.<br><br>Note also that if users can author content within the application then an attacker may be able to inject links referring to a domain they control in order to capture data from URLs used within the application.]]></issueBackground> | |
| 91 | <remediationBackground><![CDATA[The application should never transmit any sensitive information within the URL query string. In addition to being leaked in the Referer header, such information may be logged in various locations and may be visible on-screen to untrusted parties.]]></remediationBackground> | |
| 92 | <issueDetail><![CDATA[The page was loaded from a URL containing a query string:<ul><li>http://www.example.org.ar/index.php?id=14_new&nota=301</li></ul>The response contains the following links to other domains:<ul><li>http://download.macromedia.com/pub/shockwave/cabs/flash/swflash.cab</li><li>http://twitter.com/exampleONG</li><li>http://www.congresoviolencia.com/</li><li>http://www.facebook.com/home.php?</li><li>http://www.sitei.com.ar/</li></ul>]]></issueDetail> | |
| 93 | <requestresponse> | |
| 94 | <request base64="true"><![CDATA[R0VUIC9pbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAxIEhUVFAvMS4xDQpIb3N0OiB3d3cuc2FsdWRhY3RpdmEub3JnLmFyDQpBY2NlcHQ6ICovKg0KQWNjZXB0LUxhbmd1YWdlOiBlbg0KVXNlci1BZ2VudDogTW96aWxsYS81LjAgKGNvbXBhdGlibGU7IE1TSUUgOS4wOyBXaW5kb3dzIE5UIDYuMTsgV2luNjQ7IHg2NDsgVHJpZGVudC81LjApDQpDb25uZWN0aW9uOiBjbG9zZQ0KDQo=]]></request> | |
| 95 | <response base64="true"><![CDATA[SFRUUC8xLjEgMjAwIE9LDQpEYXRlOiBUaHUsIDA3IE5vdiAyMDEzIDE3OjE0OjA1IEdNVA0KU2VydmVyOiBBcGFjaGUvMi4yLjIzIChVbml4KSBtb2Rfc3NsLzIuMi4yMyBPcGVuU1NMLzAuOS44ZS1maXBzLXJoZWw1DQpYLVBvd2VyZWQtQnk6IFBIUC81LjIuMTcNCkV4cGlyZXM6IFRodSwgMTkgTm92IDE5ODEgMDg6NTI6MDAgR01UDQpDYWNoZS1Db250cm9sOiBuby1zdG9yZSwgbm8tY2FjaGUsIG11c3QtcmV2YWxpZGF0ZSwgcG9zdC1jaGVjaz0wLCBwcmUtY2hlY2s9MA0KUHJhZ21hOiBuby1jYWNoZQ0KQ29ubmVjdGlvbjogY2xvc2UNCkNvbnRlbnQtVHlwZTogdGV4dC9odG1sDQpDb250ZW50LUxlbmd0aDogNTAzMTMNCg0KIDxoZWFkPgo8bWV0YSBodHRwLWVxdWl2PSJDb250ZW50LVR5cGUiIGNvbnRlbnQ9InRleHQvaHRtbDsgY2hhcnNldD1pc28tODg1OS0xIiAvPgo8dGl0bGU+U2FsdWQgQWN0aXZhIC0gQWJ1c28gdmlvbGVuY2lhIHkgbWFsdHJhdG88L3RpdGxlPgoKPHNjcmlwdD4gCiAgICAvL2VzdG8gcGFyYSBwYXNhcmxlIGFsIGZsYXNoIGxhcyB2YXJpYWxiZXMgZGVsIHBocAogCQoKCXZhciBib3Q9Jyc7Ci8vYWxlcnQodmFyaWFibGVTZXJ2aWRvcik7Cjwvc2NyaXB0Pgo8c2NyaXB0IGxhbmd1YWdlPSJKYXZhU2NyaXB0IiB0eXBlPSJ0ZXh0L0phdmFTY3JpcHQiPgo8IS0tCmZ1bmN0aW9uIE1NX3ByZWxvYWRJbWFnZXMoKSB7IC8vdjMuMAogIHZhciBkPWRvY3VtZW50OyBpZihkLmltYWdlcyl7IGlmKCFkLk1NX3ApIGQuTU1fcD1uZXcgQXJyYXkoKTsKICAgIHZhciBpLGo9ZC5NTV9wLmxlbmd0aCxhPU1NX3ByZWxvYWRJbWFnZXMuYXJndW1lbnRzOyBmb3IoaT0wOyBpPGEubGVuZ3RoOyBpKyspCiAgICBpZiAoYVtpXS5pbmRleE9mKCIjIikhPTApeyBkLk1NX3Bbal09bmV3IEltYWdlOyBkLk1NX3BbaisrXS5zcmM9YVtpXTt9fQp9Ci8vLS0+Cjwvc2NyaXB0Pgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KCjwvaGVhZD4KCjxzY3JpcHQgbGFuZ3VhZ2U9IkphdmFTY3JpcHQiIHR5cGU9InRleHQvSmF2YVNjcmlwdCI+CjwhLS0KZnVuY3Rpb24gTU1fcmVsb2FkUGFnZShpbml0KSB7ICAvL3JlbG9hZHMgdGhlIHdpbmRvdyBpZiBOYXY0IHJlc2l6ZWQKICBpZiAoaW5pdD09dHJ1ZSkgd2l0aCAobmF2aWdhdG9yKSB7aWYgKChhcHBOYW1lPT0iTmV0c2NhcGUiKSYmKHBhcnNlSW50KGFwcFZlcnNpb24pPT00KSkgewogICAgZG9jdW1lbnQuTU1fcGdXPWlubmVyV2lkdGg7IGRvY3VtZW50Lk1NX3BnSD1pbm5lckhlaWdodDsgb25yZXNpemU9TU1fcmVsb2FkUGFnZTsgfX0KICBlbHNlIGlmIChpbm5lcldpZHRoIT1kb2N1bWVudC5NTV9wZ1cgfHwgaW5uZXJIZWlnaHQhPWRvY3VtZW50Lk1NX3BnSCkgbG9jYXRpb24ucmVsb2FkKCk7Cn0KTU1fcmVsb2FkUGFnZSh0cnVlKTsKLy8tLT4KCjwvc2NyaXB0Pgo8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoKCjwvaGVhZD4KCjxib2R5IGJhY2tncm91bmQ9ImltZy9mb25kb19kZWdyYWRlLmpwZyIgdG9wbWFyZ2luPSIwIj4KPHRhYmxlIHdpZHRoPSIxMDA1IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgPHRyPiAKICAgIDx0ZCB3aWR0aD0iOTYiPjxpbWcgc3JjPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzBfMDEuanBnIiB3aWR0aD0iOTYiIGhlaWdodD0iMjA4IiAvPjwvdGQ+CiAgICA8dGQgd2lkdGg9IjgwOSI+IDxzY3JpcHQgdHlwZT0idGV4dC9qYXZhc2NyaXB0Ij4KQUNfRkxfUnVuQ29udGVudCggJ2NvZGViYXNlJywnaHR0cDovL2Rvd25sb2FkLm1hY3JvbWVkaWEuY29tL3B1Yi9zaG9ja3dhdmUvY2Ficy9mbGFzaC9zd2ZsYXNoLmNhYiN2ZXJzaW9uPTcsMCwxOSwwJywnd2lkdGgnLCc4MDknLCdoZWlnaHQnLCcyMDgnLCdzcmMnLCdzd2YvaGVhZGVyJywncXVhbGl0eScsJ2hpZ2gnLCdwbHVnaW5zcGFnZScsJ2h0dHA6Ly93d3cubWFjcm9tZWRpYS5jb20vZ28vZ2V0Zmxhc2hwbGF5ZXInLCdtb3ZpZScsJ3N3Zi9oZWFkZXInICk7IC8vZW5kIEFDIGNvZGUKPC9zY3JpcHQ+IDxub3NjcmlwdD4KICAgICAgPG9iamVjdCBjbGFzc2lkPSJjbHNpZDpEMjdDREI2RS1BRTZELTExY2YtOTZCOC00NDQ1NTM1NDAwMDAiIGNvZGViYXNlPSJodHRwOi8vZG93bmxvYWQubWFjcm9tZWRpYS5jb20vcHViL3Nob2Nrd2F2ZS9jYWJzL2ZsYXNoL3N3Zmxhc2guY2FiI3ZlcnNpb249NywwLDE5LDAiIHdpZHRoPSI4MDkiIGhlaWdodD0iMjA4Ij4KICAgICAgICA8cGFyYW0gbmFtZT0ibW92aWUiIHZhbHVlPSJzd2YvaGVhZGVyLnN3ZiIgLz4KICAgICAgICA8cGFyYW0gbmFtZT0icXVhbGl0eSIgdmFsdWU9ImhpZ2giIC8+CiAgICAgICAgPGVtYmVkIHNyYz0ic3dmL2hlYWRlci5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9IjgwOSIgaGVpZ2h0PSIyMDgiPjwvZW1iZWQ+IAogICAgICA8L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIHdpZHRoPSIxMiUiIHJvd3NwYW49IjUiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iIzAwMDAwMCI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI0NjEiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmFja2dyb3VuZD0iaW1nL1F1aWVuZXNTb21vc19BMl8wXzEzLmpwZyI+IAogICAgICA8c2NyaXB0IHR5cGU9InRleHQvamF2YXNjcmlwdCI+CkFDX0ZMX1J1bkNvbnRlbnQoICdjb2RlYmFzZScsJ2h0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCcsJ3dpZHRoJywnOTYnLCdoZWlnaHQnLCc0NjEnLCdzcmMnLCdzd2Yvc3VibWVudScsJ3F1YWxpdHknLCdoaWdoJywncGx1Z2luc3BhZ2UnLCdodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyJywnbW92aWUnLCdzd2Yvc3VibWVudScgKTsgLy9lbmQgQUMgY29kZQo8L3NjcmlwdD4gPG5vc2NyaXB0PgogICAgICA8b2JqZWN0IGNsYXNzaWQ9ImNsc2lkOkQyN0NEQjZFLUFFNkQtMTFjZi05NkI4LTQ0NDU1MzU0MDAwMCIgY29kZWJhc2U9Imh0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+CiAgICAgICAgPHBhcmFtIG5hbWU9Im1vdmllIiB2YWx1ZT0ic3dmL3N1Ym1lbnUuc3dmIiAvPgogICAgICAgIDxwYXJhbSBuYW1lPSJxdWFsaXR5IiB2YWx1ZT0iaGlnaCIgLz4KICAgICAgICA8ZW1iZWQgc3JjPSJzd2Yvc3VibWVudS5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+PC9lbWJlZD48L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCIgYmdjb2xvcj0iI0ZGRkZGRiI+CiAgICAgICAgPHRyPiAKICAgICAgICAgIDx0ZCB3aWR0aD0iMTciIHJvd3NwYW49IjciPjxwPiZuYnNwOzwvcD48L3RkPgogICAgICAgICAgPHRkIHdpZHRoPSIxNzIiIGFsaWduPSJjZW50ZXIiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxpbWcgc3JjPSJpbWcvM3B4LmpwZyIgd2lkdGg9IjUiIGhlaWdodD0iNSI+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciI+PGxpbmsgaHJlZj0iLi4vZXN0aWxvcy5jc3MiIHJlbD0ic3R5bGVzaGVldCIgdHlwZT0idGV4dC9jc3MiIC8+Cjxib2R5IGJnY29sb3I9IiNDQ0NDQ0MiIHRvcG1hcmdpbj0iNiBweCI+PHRhYmxlIHdpZHRoPSIxNjUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIzIiBiZ2NvbG9yPSIjRkZGRkZGIj4KPHRyPgogICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTkxIiBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiAgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MThfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+SG9tZTwvYT48L3RkPgogIDwvdHI+Cjx0cj4KICA8dGQgaGVpZ2h0PSIyOCIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj4mbmJzcDsmbmJzcDtOb3RpY2lhczwvYT48L3RkPgo8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJkb25hY2lvbmVzLyIgdGFyZ2V0PSJfYmxhbmsiIGNsYXNzPSJmb25kb2JvdG9uIj5Eb25hY2lvbmVzPC9hPjwvdGQ+CiAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciICB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yM19uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5IaXN0b3JpYWwgZGUgbmV3c2xldHRlcnM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTEzYSIgY2xhc3M9ImZvbmRvYm90b24iPkVudmlhciBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yNl9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5WZXIgdHJhYmFqb3MgZGUgdXN1YXJpb3M8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MTZfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+U2FsdWQgQWN0aXZhIHByZW5zYTwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJtYWlsdG86c2FsdWRhY3RpdmFAc2FsdWRhY3RpdmEub3JnLmFyIiBjbGFzcz0iZm9uZG9ib3RvbiI+TWFuZCZhYWN1dGU7IHR1IEMuVi48L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgIHdpZHRoPSI2ImhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTIxX25ldyIgY2xhc3M9ImZvbmRvYm90b24iPkluZm9ybWFjaSZvYWN1dGU7biBkZSBpbnRlciZlYWN1dGU7czwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyI+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiBoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xMF80IiBjbGFzcz0iZm9uZG9ib3RvbiI+Q29uZ3Jlc29zCiAgICAgICAgICAgICAgICAgIHkgSm9ybmFkYXM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTExIiBjbGFzcz0iZm9uZG9ib3RvbiI+UmVnaXN0cmFjaSZvYWN1dGU7bjwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgCiAgICAgICAgICA8L3RhYmxlPgo8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNSIgdGFyZ2V0PSJfYmxhbmsiPjxicj4KICAgICAgICAgICAgICAgICAgPGltZyBzcmM9ImltZy9iYW5uZXJfZG9uYWNpb25lcy5qcGciIHdpZHRoPSIxNjIiIGhlaWdodD0iMTIwIiBib3JkZXI9IjAiPjxicj4KICAgICAgICAgICAgICAgICAgPGJyPgogICAgICAgICAgICAgICAgICA8aW1nIHNyYz0iaW1nL2JvdG9uRm9yby5naWYiIHdpZHRoPSIxNzIiIGhlaWdodD0iMTE3IiBib3JkZXI9IjAiPjwvYT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTY3IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjkiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzAzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iOSIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTQ5IiBiYWNrZ3JvdW5kPSJpbWcvY2hpY29zX3BlcmRpZG9zXzA1LmdpZiI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDUuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMCI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDcuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMi5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEyLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9InNyYy9pbWdfdXAvMjMwODIwMTIuMS5qcGciIHdpZHRoPSIxNDkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMy5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNi5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iNSIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTcuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNy5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgYmdjb2xvcj0iI0ZFRTdDRiIgY2xhc3M9InRpdHVsb2hvbWU1Ij48c3Ryb25nPk5pJm50aWxkZTtvcyBwZXJkaWRvczxicj4KICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0yOSIgY2xhc3M9ImJvdG9uIj5bVmVyIG0mYWFjdXRlO3NdPC9hPjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTkuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xOS5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18yMC5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iMjUiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4NCgkJCQkNCgkJCQk8Zm9ybSBhY3Rpb249ImluZGV4LnBocD9pZD0xMSIgIG1ldGhvZD0icG9zdCI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9penExLmpwZyIgd2lkdGg9IjEyIiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9hcnJpYmEuanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9kZXIxLmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgIDwvdHI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiIgdmFsaWduPSJ0b3AiIGNsYXNzPSJyZWdGb25kbzEiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9penEuanBnIiB3aWR0aD0iMTIiIGhlaWdodD0iMTIiIC8+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSI5NCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV90aXQuanBnIiB3aWR0aD0iNjYiIGhlaWdodD0iMjMiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSI1MCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJyZWdpc3RyYXJzZSI+SW5ncmVzJmFhY3V0ZTsgDQogICAgICAgICAgICAgIHR1cyBkYXRvcyB5IHJlY2liJmlhY3V0ZTsgbGEgbWVqb3IgaW5mb3JtYWNpJm9hY3V0ZTtuIGEgdHJhdiZlYWN1dGU7cyANCiAgICAgICAgICAgICAgZGUgbnVlc3RybzxzdHJvbmc+IE5ld3NsZXR0ZXI8L3N0cm9uZz4uIDxzdHJvbmc+PHNwYW4gY2xhc3M9ImdyYXRpcyI+R3JhdGlzITwvc3Bhbj48L3N0cm9uZz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI1IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9InRyYWJTRUNDSU9OIj5Ob21icmU8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBjbGFzcz0icmVnQ0VMREEiPjxpbnB1dCBuYW1lPSJub21icmUiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0ibm9tYnJlIiAvPjwvdGQ+DQogICAgICAgICAgPC90cj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0idHJhYlNFQ0NJT04iPkFwZWxsaWRvPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iYXBlbGxpZG8iIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iYXBlbGxpZG8iIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJ0cmFiU0VDQ0lPTiI+RS1tYWlsPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iZW1haWwiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iZW1haWwiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InRyYWJTRUNDSU9OIj4mbmJzcDs8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idHJhYlNFQ0NJT04iPjxpbnB1dCB0eXBlPSJpbWFnZSIgc3JjPSJpbWcvcmVnaXN0cmF0ZV9ib3Rvbi5qcGciIHdpZHRoPSIxMTciIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgIDwvdGFibGU+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE0IiB2YWxpZ249InRvcCIgY2xhc3M9InJlZ0ZvbmRvMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2Rlci5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIxNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KICAgICAgICAgICAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTIiIGhlaWdodD0iMjQiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfaXpxMi5qcGciIHdpZHRoPSIxMiIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI0Ij48aW1nIHNyYz0iaW1nL3JlZ2lzdHJhdGVfYWJham8uanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjI0IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfZGVyMi5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KCQkJCQkNCgkJCQkJPC9mb3JtPg0KICAgICAgICAgICAgICAgICAgPC90YWJsZT4NCjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPiAKICAgICAgICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTcwIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUyIj4KCQkJCQkJCQkJCQkJCQkJCTwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9jbGF1ZGlhMl8wMy5qcGciIHdpZHRoPSIxNzQiIGhlaWdodD0iMjUwIiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcCI+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICA8dGQgcm93c3Bhbj0iNyIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nLzV4NS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjciPjwvdGQ+CiAgICAgICAgICA8dGQgY29sc3Bhbj0iMiIgcm93c3Bhbj0iNCIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPGZvcm0gYWN0aW9uPSJsb2dpbi5waHAiIG1ldGhvZD0icG9zdCIgbmFtZT0iZm9ybTIiPgoKICAgICAgICAgICAgICA8dHI+IAogICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgY29sc3Bhbj0iMiIgYWxpZ249ImxlZnQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIiA+IAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8c3Ryb25nPlVzdWFyaW8gbm8gcmVnaXN0cmFkbzwvc3Ryb25nPiAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9mb250PiA8L3N0cm9uZz4gCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDkiIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPlVzdWFyaW8mbmJzcDsmbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzOSIgdmFsaWduPSJtaWRkbGUiPjxpbnB1dCBuYW1lPSJ1c3VhcmlvIiB0eXBlPSJ0ZXh0IiBjbGFzcz0icmVnIiBpZD0idXN1YXJpbyIgc2l6ZT0iNyI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjciIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPkNvbnRyYXNlJm50aWxkZTthJm5ic3A7Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzkiIHZhbGlnbj0ibWlkZGxlIj48aW5wdXQgbmFtZT0icGFzcyIgdHlwZT0icGFzc3dvcmQiIGNsYXNzPSJyZWciIGlkPSJwYXNzIiBzaXplPSI3Ij48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiIgYWxpZ249InJpZ2h0IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9ImJvdG9uIj48aW5wdXQgdHlwZT0iaW1hZ2UiIHNyYz0iaW1nL3JlZy5qcGciIHdpZHRoPSI1OCIgaGVpZ2h0PSIzMCI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjciIGhlaWdodD0iMTkiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgPjxhIGhyZWY9Imh0dHA6Ly93d3cuZmFjZWJvb2suY29tL2hvbWUucGhwPyMhL3BhZ2VzL01lcmxvLUFyZ2VudGluYS9TQUxVRC1BQ1RJVkEvMTAwNTgzNTQzMzE3MzIyP3JlZj10cyZhamF4cGlwZT0xJl9fYT03IiB0YXJnZXQ9Il9ibGFuayI+PGltZyBzcmM9ImltZy9mYWNlYm9vay5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzExIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj48ZGl2IGFsaWduPSJsZWZ0Ij48YSBocmVmPSJodHRwOi8vdHdpdHRlci5jb20vU2FsdWRBY3RpdmFPTkciIHRhcmdldD0iX2JsYW5rIj48aW1nIHNyYz0iaW1nL3R3aXRlci5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC9kaXY+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSI1IiBhbGlnbj0icmlnaHQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIj48bGFiZWw+PGZvbnQgc2l6ZT0iLTYiPlNpCiAgICAgICAgICAgICAgICAgICAgICAgdG9kYXYmaWFjdXRlO2Egbm8gZXMgdXN1YXJpbyA8L2ZvbnQ+IDxhIGhyZWY9ImluZGV4LnBocD9pZD0xMSIgY2xhc3M9ImJvdG9uIj48Zm9udCBzaXplPSItNiI+cmVnJmlhY3V0ZTtzdHJlc2UKICAgICAgICAgICAgICAgICAgICAgICAgYXF1JmlhY3V0ZTsgPGZvbnQgY29sb3I9IiM2NjY2NjYiPiYjODIyNjs8L2ZvbnQ+PC9mb250PjwvYT4gPGEgaHJlZj0iaW5kZXgucGhwP2lkPTEyIiBjbGFzcz0iYm90b24xIj48Zm9udCBzaXplPSItNiI+b2x2aWRlIG1pIGNvbnRyYXNlJm50aWxkZTthPC9mb250PjwvYT48L2xhYmVsPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE3Ij4mbmJzcDsgPC90ZD4KICAgICAgICAgICAgICA8L3RyPgoJCQkgIDwvZm9ybT4KCiAgICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgICA8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyI+CjxTQ1JJUFQgTEFOR1VBR0U9IkphdmFTY3JpcHQiPgpmdW5jdGlvbiBpc0VtcHR5KHMpIHsKICByZXR1cm4gKChzID09IG51bGwpIHx8IChzLmxlbmd0aCA9PSAwKSkKfQoKZnVuY3Rpb24gaXNFbWFpbEFkZHJlc3MocykgewoJLy92YXIgZmlsdGVyPS9eW0EtWmEtel1bQS1aYS16MC05X10qQFtBLVphLXowLTlfXStcLltBLVphLXowLTlfLl0rW0EtemEtel0kLzsKCXZhciBmaWx0ZXI9L15cdysoW1wuLV0/XHcrKSpAXHcrKFtcLi1dP1x3KykqKFwuXHd7MiwzfSkrJC87CglpZiAocy5sZW5ndGggPT0gMCApIHJldHVybiB0cnVlOwoJaWYgKGZpbHRlci50ZXN0KHMpKSB7CgkJcmV0dXJuIHRydWU7Cgl9IGVsc2UgewoJCXJldHVybiBmYWxzZTsKCX0KfQoKZnVuY3Rpb24gdmFsaWRhcihvYmopIHsKICAgCiAgICBlcnJvcnMgPSAiIjsKICAgIAogICAgLy9Ob21icmUKICAgIGlmIChpc0VtcHR5KG9iai5ub21icmUudmFsdWUpKSB7CiAgICAgIGVycm9ycyArPSAiXG4tIEVsIE5vbWJyZSBlc3RhIHZhY2lvIjsKICAgIH0KCS8vRW1haWwKICAgIGlmIChpc0VtcHR5KG9iai5lbWFpbC52YWx1ZSkpIHsKICAgICAgZXJyb3JzICs9ICJcbi0gRWwgRW1haWwgZXN0YSB2YWNpbyI7CiAgICB9IGVsc2UgewoJCWlmIChpc0VtYWlsQWRkcmVzcyhvYmouZW1haWwudmFsdWUpID09IGZhbHNlKSB7CgkJCWVycm9ycyArPSAiXG4tIEVsIEVtYWlsIGluZ3Jlc2FkbyBlcyBpbmNvcnJlY3RvIjsKCQl9Cgl9CiAgICAvL0NvbWVudGFyaW8KICAgIGlmIChpc0VtcHR5KG9iai5jb21lbnRhcmlvLnZhbHVlKSkgewogICAgICBlcnJvcnMgKz0gIlxuLSBFbCBDb21lbnRhcmlvIGVzdGEgdmFjaW8iOwogICAgfQogICAgCiAgICBpZiAoIShlcnJvcnM9PSIiKSl7CgkJbXNnID0gIl9fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX1xuXG5MYSByZWdpc3RyYWNp824gbm8gZnVlIGxsZXZhZGEgYSBjYWJvIHBvciBjYXVzYSBkZSBsb3Mgc2lndWllbnRlcyBlcnJvcmVzLlxuUG9yIGZhdm9yLCBjb3Jy7WphbG9zIHkgdnVlbHZhIGEgZW52aWFyLlxuX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fX19fXG4iOwoJCWlmIChlcnJvcnMhPSIiKXsKCQkJbXNnICs9IGVycm9yczsKCQl9CgkJYWxlcnQobXNnKTsKCQlyZXR1cm4gZmFsc2U7Cgl9ZWxzZXsKCSAgCgkgIG9iai5yZWNhcHRjaGFfY2hhbGxlbmdlX2ZpZWxkX2QudmFsdWUgPSBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgncmVjYXB0Y2hhX2NoYWxsZW5nZV9maWVsZCcpLnZhbHVlOwoJICBvYmoucmVjYXB0Y2hhX3Jlc3BvbnNlX2ZpZWxkX2QudmFsdWUgPSBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgncmVjYXB0Y2hhX3Jlc3BvbnNlX2ZpZWxkJykudmFsdWU7CgkgIAoJICByZXR1cm4gdHJ1ZTsKCX0KfQo8L1NDUklQVD4KPHN0eWxlPgojYXBlbGxpZG8gewogICAgZGlzcGxheTogbm9uZTsKfQojYWRkcmVzcyB7CiAgICBkaXNwbGF5OiBub25lOwp9Cjwvc3R5bGU+Cjx0YWJsZSB3aWR0aD0iNTk2IiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+Cjx0ciBhbGlnbj0iY2VudGVyIj4KICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMiI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMDcuanBnIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzUlIiBhbGlnbj0iY2VudGVyIj48YSBocmVmPSJqYXZhc2NyaXB0OjsiIG9uQ2xpY2s9IndpbmRvdy5vcGVuKCdpbXByaW1pci5waHA/bm90YT0zMDEnLCAnbm90YV9pbXByaW1pcicsICdyZXNpemFibGU9MSxzY3JvbGxiYXJzPTEnKSI+PGltZyBzcmM9ImltZy9pY29ub3Mtbm90YV8wOC5qcGciIHdpZHRoPSI5OCIgaGVpZ2h0PSI0NCIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzMiUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNyZhbXA7aWRwYWc9MTQiPjxpbWcgc3JjPSJpbWcvaWNvbm9zLW5vdGFfMDUuanBnIiB3aWR0aD0iMTIzIiBoZWlnaHQ9IjQ3IiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjMzJSI+PGltZyBzcmM9ImltZy9pY29ub3Mtbm90YV8wMy5qcGciIHdpZHRoPSIxMDgiIGhlaWdodD0iNDgiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDwvdHI+CgkJCQkgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciI+PGltZyBzcmM9InNyYy9pbWdfdXAvMjMwNDIwMTMuMS5qcGciIHdpZHRoPSI0MjAiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPC90cj4KCQkJCSAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+CiAgICAgICAgICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMTUiPgogICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4yMi8xMS8yMDEzPGJyPjxzcGFuIGNsYXNzPSJ0cmFiVElUIj48Zm9udCBmYWNlPSJHZW9yZ2lhLCBUaW1lcyBOZXcgUm9tYW4sIFRpbWVzLCBzZXJpZiI+SVYgQ29uZ3Jlc28gSW50ZXJuYWNpb25hbCB2aW9sZW5jaWEsIG1hbHRyYXRvIHkgYWJ1c288L2ZvbnQ+PGJyIC8+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHNwYW4gY2xhc3M9ImNvbnRlbmlkbyI+PHN0cm9uZz48Zm9udCBzaXplPSIxIj5WaWN0aW1vbG9n7WEsIENyaW1pbm9sb2ftYSB5IEfpbmVyby4gVW5hIHRyaWxvZ+1hIGNvbXBsZWphPC9mb250Pjwvc3Ryb25nPjwvc3Bhbj48L3NwYW4+PC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkPjxkaXYgY2xhc3M9ImRlc3RhY2Fkb3MiPjxwPiZuYnNwOzwvcD4NCjxwPjE0LCAxNSB5IDE2IGRlIE5vdmllbWJyZTwvcD4NCjxwPjxzdHJvbmc+PHNwYW4gc3R5bGU9ImNvbG9yOiAjZmY2NjAwOyI+T3JnYW5pemE6IFNhbHVkIEFjdGl2YTwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3BhbiBzdHlsZT0iY29sb3I6ICNmZjY2MDA7Ij5BcXVlbGxvcyBpbnNjcmlwdG9zIGFsIHBvcnRhbCBkZSBTYWx1ZCBBY3RpdmEsIGhhc3RhIGVsIDMwLzA1LzIwMTMsIHB1ZGVuIGFjY2VkZXIgYSBpbXBvcnRhbnRlcyBkZXNjdWVudG9zIGVuIGxhIGluc2NyaXBjaSZvYWN1dGU7biBkZWwgY29uZ3Jlc28uPGJyIC8+PC9zcGFuPjwvcD4NCjxwPkx1Z2FyIGRlIFJlYWxpemFjaSZvYWN1dGU7biB5IGNvbGFib3JhY2kmb2FjdXRlO246IFVuaXZlcnNpZGFkIGRlbCBFc3RlLCBDYWxsZSAyIE4mb3JkbTsgNjg0LCBMYSBQbGF0YSwgQnVlbm9zIEFpcmVzPC9wPg0KPHA+PHN0cm9uZz48c3BhbiBzdHlsZT0iY29sb3I6ICNmZjAwMDA7Ij48c3BhbiBzdHlsZT0iZm9udC1zaXplOiB4LXNtYWxsOyI+SU5TQ1JJUENJT05FUyBDT04gREVTQ1VFTlRPIEhBU1RBIEVMIDI3IERFIEFHT1NUTyEhISE8L3NwYW4+PC9zcGFuPjwvc3Ryb25nPjwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tIiB0YXJnZXQ9Il9ibGFuayI+bWFzIGluZm9ybWFjaW9uPC9hPjwvcD4NCjxwPiZuYnNwOzwvcD48L2Rpdj4gPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgIAkJCQkJCiAgICAJCQkJCSAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjQyMCIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iNCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDYiIHZhbGlnbj0iYm90dG9tIj4KCQkJCQkgIAkJCQkJICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzMTMiIHZhbGlnbj0ibWlkZGxlIj4KCQkJCQkgIAkJCQkJICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgPHRkIGFsaWduPSJyaWdodCIgdmFsaWduPSJib3R0b20iPjxhIGhyZWY9ImluZGV4LnBocCIgY2xhc3M9ImJvdG9uIj4mbHQ7Jmx0O1ZPTFZFUjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgPHRkID48L3RkPgogICAgICAgICAgICAgICAgPC90cj4KCgkJCQk8Zm9ybSBuYW1lPSJmb3JtdV9jb21lbnRhcmlvIiBhY3Rpb249Imd1YXJkYXJfZGFuaS5waHAiIG1ldGhvZD0icG9zdCIgb25TdWJtaXQ9InJldHVybiB2YWxpZGFyKHRoaXMpOyI+CgkJCQk8aW5wdXQgdHlwZT0iaGlkZGVuIiBuYW1lPSJhY2MiIHZhbHVlPSJndWFyZGFyX2NvbWVudGFyaW8iPgoJCQkJPGlucHV0IHR5cGU9ImhpZGRlbiIgbmFtZT0ibm90YSIgdmFsdWU9IjMwMSI+CgkJCQkKCQkJCTxpbnB1dCB0eXBlPSJoaWRkZW4iIG5hbWU9InJlY2FwdGNoYV9jaGFsbGVuZ2VfZmllbGRfZCIgdmFsdWU9IiI+CgkJCQk8aW5wdXQgdHlwZT0iaGlkZGVuIiBuYW1lPSJyZWNhcHRjaGFfcmVzcG9uc2VfZmllbGRfZCIgdmFsdWU9IiI+CiAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9Ijg1JSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRyYWJUSVQiPjxmb250IGZhY2U9Ikdlb3JnaWEsIFRpbWVzIE5ldyBSb21hbiwgVGltZXMsIHNlcmlmIj5Db21lbnRhcmlvczwvZm9udD48L3RkPgogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMSUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAJCQkJCTx0cj4KICAgICAgICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMzAiIGNsYXNzPSJib3JkZWFycmliYSI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSI3IiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgYWxpZ249InJpZ2h0IiBjbGFzcz0iY29udGVuaWRvaG9tZSI+PHN0cm9uZz5Ob21icmU6PC9zdHJvbmc+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYyJSI+PHNwYW4gY2xhc3M9ImNvbnRlbmlkbyI+T2ZlbGlhIERlbCBDYXJtZW4gIE1pbGxhIDwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTglIiBjbGFzcz0iZGVzdGFjYWRvcyI+PHN0cm9uZz4wOS8wNi8yMDEzICAgICAgICAgICAgICAgICAgICAgICAgICA8L3N0cm9uZz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGFsaWduPSJyaWdodCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPkNvbWVudGFyaW86PC9zdHJvbmc+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMiI+PHNwYW4gY2xhc3M9InRleHRvbnVldm8iPk11eSBJbnRlcmVzYW50ZSBsYSBwcm9wdWVzdGEhISEgcGFydGljaXBlIGRlIGxhIGpvcm5hZGFzIGRlIEFydGVtaWRlcyBlbiBjaXBvbGxldHRpIHlvIHNveSBkZSBBbGxlbiAsQWNvbXBh8WFudGUgVGVyYXDpdXRpY2EgeVByb2Zlc29yYSBFbnNl8WFuemEgUHJpbWFyaWEudHViZSBsYSBvcG9ydHVuaWRhZCBjb25vY2VyIGEgQmVhdHJpeiBNdWxsZXI8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CgkJCQkJCQkJCQk8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjMwIiBjbGFzcz0iYm9yZGVhcnJpYmEiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iNyIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIGFsaWduPSJyaWdodCIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+Tm9tYnJlOjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiUiPjxzcGFuIGNsYXNzPSJjb250ZW5pZG8iPkFkcmlhbmEgY2FybGEgR29ybGVybzwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTglIiBjbGFzcz0iZGVzdGFjYWRvcyI+PHN0cm9uZz4xNS8wNi8yMDEzICAgICAgICAgICAgICAgICAgICAgICAgICA8L3N0cm9uZz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGFsaWduPSJyaWdodCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPkNvbWVudGFyaW86PC9zdHJvbmc+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMiI+PHNwYW4gY2xhc3M9InRleHRvbnVldm8iPlNveSB0ZXNpc3RhIGRlIGFudHJvcCBzb2MsIHkgY3JlZSAgdW4gcHJvZ3JhbWEgZGUiQ29udGVuY2lvbiB5IGZvcnRhbGVjaW1pZW50byBwYXJhIHBlcnNvbmFzIGVuIHNpdHVhY2lvbiBkZSB2aW9sZW5jaWEscXVlIHNlIGltcGxlbWVudGEgZGVzZGUgZWwgYfFvIDIwMTEuIFJlY2liZW4gcG9uZW5jaWFzPyBtdWNoYXMgZ3JhY2lhcyA8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CgkJCQkJCQkJCQk8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjMwIiBjbGFzcz0iYm9yZGVhcnJpYmEiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iNyIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIGFsaWduPSJyaWdodCIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+Tm9tYnJlOjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiUiPjxzcGFuIGNsYXNzPSJjb250ZW5pZG8iPkxlb25vcjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTglIiBjbGFzcz0iZGVzdGFjYWRvcyI+PHN0cm9uZz4yNy8wNi8yMDEzICAgICAgICAgICAgICAgICAgICAgICAgICA8L3N0cm9uZz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGFsaWduPSJyaWdodCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPkNvbWVudGFyaW86PC9zdHJvbmc+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMiI+PHNwYW4gY2xhc3M9InRleHRvbnVldm8iPkdyYWNpYXMgcG9yIGVzdGUgY29uZ3Jlc28gdGFuIGltcG9ydGFudGUuIENvbW8gZnV0dXJhIFByb2Zlc29yYSBlbiBDcy4gZGUgbGEgRWR1Y2FjafNuIHkgT3BlcmFkb3JhIGVuIFBzLiBTYyBtZSBpbnRlcmVzYSB0cmFiYWphciBlc3RvcyB0ZW1hcy5Fc3Blcm8gY29uIGFuc2lhcyBwb2RlciBhc2lzdGlyIDwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KCQkJCQkJCQkJCTx0cj4KICAgICAgICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMzAiIGNsYXNzPSJib3JkZWFycmliYSI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSI3IiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgYWxpZ249InJpZ2h0IiBjbGFzcz0iY29udGVuaWRvaG9tZSI+PHN0cm9uZz5Ob21icmU6PC9zdHJvbmc+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYyJSI+PHNwYW4gY2xhc3M9ImNvbnRlbmlkbyI+RGVuaXNzZTwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTglIiBjbGFzcz0iZGVzdGFjYWRvcyI+PHN0cm9uZz4wNS8wOC8yMDEzICAgICAgICAgICAgICAgICAgICAgICAgICA8L3N0cm9uZz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGFsaWduPSJyaWdodCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPkNvbWVudGFyaW86PC9zdHJvbmc+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMiI+PHNwYW4gY2xhc3M9InRleHRvbnVldm8iPr9Db21vIGhhZ28gcGFyYSBpbnNjcmliaXJtZT88L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CgkJCQkJCQkJCQk8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjMwIiBjbGFzcz0iYm9yZGVhcnJpYmEiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iNyIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIGFsaWduPSJyaWdodCIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+Tm9tYnJlOjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiUiPjxzcGFuIGNsYXNzPSJjb250ZW5pZG8iPnNhbmRyYSB2YWxkZXo8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE4JSIgY2xhc3M9ImRlc3RhY2Fkb3MiPjxzdHJvbmc+MjEvMDgvMjAxMyAgICAgICAgICAgICAgICAgICAgICAgICAgPC9zdHJvbmc+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIiBjbGFzcz0iY29udGVuaWRvaG9tZSI+PHN0cm9uZz5Db21lbnRhcmlvOjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjIiPjxzcGFuIGNsYXNzPSJ0ZXh0b251ZXZvIj5lc3RveSBpbnRlcmVzYWRhIGVuIGNvbm9jZXIgbWFzIGFjZXJjYSBkZSBlc3RhIGpvcm5hZGEuIFByb2dyYW1hLCBwcmVjaW8gZXRjLiBQb2RyaWFuIGVudmlhciBlc3RhIGluZm9ybWFjaW9uLiBEZXNkZSB5YSBtdWhjYXMgZ3JhY2lhcyA8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CgkJCQkJCQkJCQk8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjMwIiBjbGFzcz0iYm9yZGVhcnJpYmEiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iNyIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIGFsaWduPSJyaWdodCIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+Tm9tYnJlOjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiUiPjxzcGFuIGNsYXNzPSJjb250ZW5pZG8iPmdyYWNpZWxhIGxpbGlhbmEga2FlbXBmZm1hbm48L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE4JSIgY2xhc3M9ImRlc3RhY2Fkb3MiPjxzdHJvbmc+MTAvMDkvMjAxMyAgICAgICAgICAgICAgICAgICAgICAgICAgPC9zdHJvbmc+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIiBjbGFzcz0iY29udGVuaWRvaG9tZSI+PHN0cm9uZz5Db21lbnRhcmlvOjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjIiPjxzcGFuIGNsYXNzPSJ0ZXh0b251ZXZvIj5NZSBpbnRlcmVzYSBlc3RlIENvbmdyZXNvLCB5YSBxdWUgdHJhYmFqbyBjb21vIHRlY25pY2EgZW4gbGEgdW5pZGFkIGVqZWN1dG9yYSBkZSB2aW9sZW5jaWEgZmFtaWxpYXIsIGVuIGxhIGNpdWRhZCBkZSBHZW5lcmFsIFJvY2EsIFLtbyBOZWdybywgcXVpc2llcmEgc2FiZXIgc2kgZXhpc3RlIGFsZ/puIGNvbnZlbmlvIGNvbiBsYSBwcm92aW5jaWEuIDwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KCQkJCQkJCQkJCTx0cj4KICAgICAgICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMzAiIGNsYXNzPSJib3JkZWFycmliYSI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSI3IiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgYWxpZ249InJpZ2h0IiBjbGFzcz0iY29udGVuaWRvaG9tZSI+PHN0cm9uZz5Ob21icmU6PC9zdHJvbmc+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYyJSI+PHNwYW4gY2xhc3M9ImNvbnRlbmlkbyI+TWF0aWxkZSBNYW5nZTwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTglIiBjbGFzcz0iZGVzdGFjYWRvcyI+PHN0cm9uZz4xNy8wOS8yMDEzICAgICAgICAgICAgICAgICAgICAgICAgICA8L3N0cm9uZz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGFsaWduPSJyaWdodCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPkNvbWVudGFyaW86PC9zdHJvbmc+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMiI+PHNwYW4gY2xhc3M9InRleHRvbnVldm8iPlF1ZSBs4XN0aW1hIHJlY2npbiBtZSBlbnRlcm8uIFlhIGVzIHRhcmRlIHBhcmEgdG9tYXJtZSBsb3MgZO1hcy4gPC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgoJCQkJCQkJCQkJPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIzMCIgY2xhc3M9ImJvcmRlYXJyaWJhIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjciIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiBhbGlnbj0icmlnaHQiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPk5vbWJyZTo8L3N0cm9uZz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjIlIj48c3BhbiBjbGFzcz0iY29udGVuaWRvIj5QYXRyaWNpYSBNYXJ0aW48L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE4JSIgY2xhc3M9ImRlc3RhY2Fkb3MiPjxzdHJvbmc+MjAvMDkvMjAxMyAgICAgICAgICAgICAgICAgICAgICAgICAgPC9zdHJvbmc+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIiBjbGFzcz0iY29udGVuaWRvaG9tZSI+PHN0cm9uZz5Db21lbnRhcmlvOjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjIiPjxzcGFuIGNsYXNzPSJ0ZXh0b251ZXZvIj5UcmFiYWphbW9zIGVuIGVsIFByb2dyYW1hIFByb3ZpbmNpYWwgZGUgQXRlbmNp824geSBQcmV2ZW5jafNuIGFsIE1hbHRyYXRvIEluZmFudGlsLCBlbiBzZW5kb3MgY2Fzb3MgaGFjZSBt4XMgZGUgZGlleiBh8W9zLiBEZXNlYXLtYW1vcyBzYWJlciBsbyByZWxhdGl2byBhIGJlY2FzLiBHcmFjaWFzPC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgoJCQkJCQkJCQkJPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIzMCIgY2xhc3M9ImJvcmRlYXJyaWJhIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjciIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiBhbGlnbj0icmlnaHQiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPk5vbWJyZTo8L3N0cm9uZz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjIlIj48c3BhbiBjbGFzcz0iY29udGVuaWRvIj5BREVMQSBiZWF0cml6IGtvaGFuPC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOCUiIGNsYXNzPSJkZXN0YWNhZG9zIj48c3Ryb25nPjIyLzA5LzIwMTMgICAgICAgICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+Q29tZW50YXJpbzo8L3N0cm9uZz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIyIj48c3BhbiBjbGFzcz0idGV4dG9udWV2byI+dm95IGEgcGFydGljaXBhcixleGNlbGVudGUgcHJvcHVlc3RhPC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgoJCQkJCQkJCQkJPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIzMCIgY2xhc3M9ImJvcmRlYXJyaWJhIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjciIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiBhbGlnbj0icmlnaHQiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPk5vbWJyZTo8L3N0cm9uZz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjIlIj48c3BhbiBjbGFzcz0iY29udGVuaWRvIj5NYXRpbGRlIE1hbmdlPC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOCUiIGNsYXNzPSJkZXN0YWNhZG9zIj48c3Ryb25nPjMwLzA5LzIwMTMgICAgICAgICAgICAgICAgICAgICAgICAgIDwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+Q29tZW50YXJpbzo8L3N0cm9uZz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIyIj48c3BhbiBjbGFzcz0idGV4dG9udWV2byI+v1B1ZWRvIGluc2NyaWJpcm1lIGFsIGxsZWdhcj8gTm8gbWUgaGFuIGNvbnRlc3RhZG8gc2kgbWUgZGFuIGxvcyBk7WFzIHBhcmEgZWwgQ29uZ3Jlc28uIEdyYWNpYXM8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CgkJCQkJCQkJCQk8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjMwIiBjbGFzcz0iYm9yZGVhcnJpYmEiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iNyIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIGFsaWduPSJyaWdodCIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+Tm9tYnJlOjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiUiPjxzcGFuIGNsYXNzPSJjb250ZW5pZG8iPnNhbmRyYSBwZXJlejwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTglIiBjbGFzcz0iZGVzdGFjYWRvcyI+PHN0cm9uZz4wNC8xMC8yMDEzICAgICAgICAgICAgICAgICAgICAgICAgICA8L3N0cm9uZz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGFsaWduPSJyaWdodCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPkNvbWVudGFyaW86PC9zdHJvbmc+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMiI+PHNwYW4gY2xhc3M9InRleHRvbnVldm8iPnF1aXNpZXJhIHNhYmVyIHNpIGVzdGUgY29uZ3Jlc28gdGllbmUgUmVzb2x1Y2lvbiBkZWwgbWluaXN0ZXJpbyBkZSBlZHVjYWNpb24gZGUgbGEgUHJvdi4gZGUgQnVlbm9zIEFpcmVzIFNpIGVzIGFzaSBzb2xpY2l0byBzaSBwdWVkZW4gZW52aWFybWUgZWwgbnJvLkdyYWNpYXM8YnIgLz4NCjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KCQkJCQkJCQkJCTx0cj4KCQkJCQkgIDx0ZD4mbmJzcDs8L3RkPgoJCQkJCSAgPHRkIGhlaWdodD0iMzAiIGNsYXNzPSJib3JkZWFycmliYSI+Jm5ic3A7PC90ZD4KCQkJCQkgIDx0ZD4mbmJzcDs8L3RkPgoJCQkJICAgIDwvdHI+CgkJCQkJPHRyPgoJCQkJCSAgPHRkPiZuYnNwOzwvdGQ+CgkJCQkJICA8dGQgaGVpZ2h0PSIzMCIgPjxzcGFuIGNsYXNzPSJ0cmFiVElUIj48Zm9udCBmYWNlPSJHZW9yZ2lhLCBUaW1lcyBOZXcgUm9tYW4sIFRpbWVzLCBzZXJpZiIgPkNvbWVudGFyaW9zPC9mb250Pjwvc3Bhbj48L3RkPgoJCQkJCSAgPHRkPiZuYnNwOzwvdGQ+CgkJCQkgICAgPC90cj4KCQkJCQk8dHI+CgkJCQkJICA8dGQ+Jm5ic3A7PC90ZD4KCQkJCQkgIDx0ZCBoZWlnaHQ9IjMwIiBjbGFzcz0iYm9yZGVhcnJpYmEiPjxzdHJvbmc+JmJ1bGw7PHNwYW4gY2xhc3M9ImNvbnRlbmlkb2hvbWUiPkluZ3Jlc2UKCQkJICAgICAgICBzdXMgZGF0b3MgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvc3Bhbj48L3N0cm9uZz48L3RkPgoJCQkJCSAgPHRkPiZuYnNwOzwvdGQ+CgkJCQkgICAgPC90cj4KCQkJCQk8dHI+CgkJCQkJICA8dGQ+Jm5ic3A7PC90ZD4KCQkJCQkgIDx0ZCBoZWlnaHQ9IjMwIiA+CgkJCQkJICAgIDxpbnB1dCBuYW1lPSJub21icmUiIHR5cGU9InRleHQiIGNsYXNzPSJjZWxkYWZvcm0iIGlkPSJub21icmUiIHNpemU9IjQwIiB2YWx1ZT0iIiAvPgoJCQkJCSAgICA8aW5wdXQgbmFtZT0iYXBlbGxpZG8iIHR5cGU9InRleHQiIGNsYXNzPSJjZWxkYWZvcm0iIGlkPSJhcGVsbGlkbyIgc2l6ZT0iNDAiIHZhbHVlPSIiIC8+CgkJCQkgICAgICA8c3BhbiBjbGFzcz0iY29udGVuaWRvaG9tZSI+Tm9tYnJlPC9zcGFuPgkJCQkJICA8L3RkPgoJCQkJCSAgPHRkPiZuYnNwOzwvdGQ+CgkJCQkgICAgPC90cj4KCQkJCQk8dHI+CgkJCQkJICA8dGQ+Jm5ic3A7PC90ZD4KCQkJCQkgIDx0ZCBoZWlnaHQ9IjMwIiA+PGlucHV0IG5hbWU9ImVtYWlsIiB0eXBlPSJ0ZXh0IiBjbGFzcz0iY2VsZGFmb3JtIiBpZD0iZW1haWwiIHNpemU9IjQwIiB2YWx1ZT0iIiAvPgoJCQkJCSAgICA8aW5wdXQgbmFtZT0iYWRkcmVzcyIgdHlwZT0idGV4dCIgY2xhc3M9ImNlbGRhZm9ybSIgaWQ9ImFkZHJlc3MiIHNpemU9IjQwIiB2YWx1ZT0iIiAvPgogICAgICAgICAgICAgICAgICAgICAgICA8c3BhbiBjbGFzcz0iY29udGVuaWRvaG9tZSI+RW1haWw8L3NwYW4+PC90ZD4KCQkJCQkgIDx0ZD4mbmJzcDs8L3RkPgoJCQkJICAgIDwvdHI+CgkJCQkJPHRyPgoJCQkJCSAgPHRkIGhlaWdodD0iMzAiPjxzcGFuIGNsYXNzPSJjb250ZW5pZG9ob21lIj48L3NwYW4+PC90ZD4KCQkJCQkgIDx0ZCBoZWlnaHQ9IjMwIj48c3BhbiBjbGFzcz0iY29udGVuaWRvaG9tZSI+PHN0cm9uZz4mYnVsbDtEZWplIHN1IGNvbWVudGFyaW8KCQkJICAgICAgICBzb2JyZSBsYSBub3RhICht4XhpbW8gMjAwIGNhcmFjdGVyZXMpCgkJCQkJICA8dGQ+Jm5ic3A7PC90ZD4KCQkJCSAgICA8L3RyPgoJCQkJCTx0cj4KCQkJCQkgIDx0ZD4mbmJzcDs8L3RkPgoJCQkJCSAgPHRkIGhlaWdodD0iMzAiPgoJCQkJCSAgICA8c2NyaXB0PgoJCQkJCSAgICBmdW5jdGlvbiBtYXhpbW9zQ2FyYWN0ZXJlcyhteWZpZWxkLGUsbWF4aW1vKSB7CiAgICAgICAgICAgICAgICAgICAgICAgIAl2YXIga2V5Y29kZTsKICAgICAgICAgICAgICAgICAgICAgICAgCWlmICh3aW5kb3cuZXZlbnQpIHsKICAgICAgICAgICAgICAgICAgICAgICAgCSAgICBrZXljb2RlID0gd2luZG93LmV2ZW50LmtleUNvZGU7CiAgICAgICAgICAgICAgICAgICAgICAgIAl9IGVsc2UgewogICAgICAgICAgICAgICAgICAgICAgICAJICAgIGlmIChlKSB7CiAgICAgICAgICAgICAgICAgICAgICAgIAkgICAgICAgIGtleWNvZGUgPSBlLndoaWNoOwogICAgICAgICAgICAgICAgICAgICAgICAJICAgIH0gZWxzZSB7CiAgICAgICAgICAgICAgICAgICAgICAgIAkgICAgICAgIHJldHVybiB0cnVlOwogICAgICAgICAgICAgICAgICAgICAgICAJICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgCX0KICAgICAgICAgICAgICAgICAgICAgICAgCWlmIChteWZpZWxkLnZhbHVlLmxlbmd0aCA8IG1heGltbyB8fCAoa2V5Y29kZT09MCkgfHwgKGtleWNvZGU9PTgpKSB7CiAgICAgICAgICAgICAgICAgICAgICAgIAkgICAgcmV0dXJuIHRydWU7IAogICAgICAgICAgICAgICAgICAgICAgICAJfSBlbHNlIHsKICAgICAgICAgICAgICAgICAgICAgICAgCSAgICByZXR1cm4gZmFsc2U7CiAgICAgICAgICAgICAgICAgICAgICAgIAl9CiAgICAgICAgICAgICAgICAgICAgICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgPC9zY3JpcHQ+CgkJCQkJICAgIDx0ZXh0YXJlYSBuYW1lPSJjb21lbnRhcmlvIiBjb2xzPSI0NSIgcm93cz0iNSIgY2xhc3M9InNjcm9sbDEiIGlkPSJjb21lbnRhcmlvIiBvbktleVByZXNzPSJyZXR1cm4gbWF4aW1vc0NhcmFjdGVyZXModGhpcywgZXZlbnQsIDIwMCkiPjwvdGV4dGFyZWE+PC90ZD4KCQkJCQkgIDx0ZD4mbmJzcDs8L3RkPgoJCQkJICAgIDwvdHI+CgkJCQkgICAgPHRyPgoJCQkJCSAgPHRkIGhlaWdodD0iMzAiPjxzcGFuIGNsYXNzPSJjb250ZW5pZG9ob21lIj48L3NwYW4+PC90ZD4KCQkJCQkgIDx0ZCBoZWlnaHQ9IjMwIj48c3BhbiBjbGFzcz0iY29udGVuaWRvaG9tZSI+PHN0cm9uZz4mYnVsbDtFc2NyaWJhIGVsIEPzZGlnbyBkZSBTZWd1cmlkYWQgcXVlIGFwYXJlY2UgYSBjb250aW51YWNp8248L3N0cm9uZz48L3NwYW4+PC90ZD4KCQkJCQkgIDx0ZD4mbmJzcDs8L3RkPgoJCQkJICAgIDwvdHI+CgkJCQkgICAgPHRyPgoJCQkJCSAgPHRkPiZuYnNwOzwvdGQ+CgkJCQkJICA8dGQgaGVpZ2h0PSIzMCI+CgkJCQkJICAgIDxhIG5hbWU9ImNvZGlnb19zZWd1cmlkYWQiPjwvYT4KCQkJCQkgICAgPGltZyBzcmM9InNlY3VyaW1hZ2Vfc2hvdy5waHA/c2lkPTM5OGI2NTBmODdhY2Y1NTQ2NjE2YzllYmQ4YjUyMjc0Ij48YnIgLz4KCQkJCQkgICAgPGlucHV0IG5hbWU9ImNvZGUiIHR5cGU9ImNvZGUiIGNsYXNzPSJjZWxkYWZvcm0iIGlkPSJjb2RlIiBzaXplPSI0MCIgLz4KCQkJCQkgIDwvdGQ+CgkJCQkJICA8dGQ+Jm5ic3A7PC90ZD4KCQkJCSAgICA8L3RyPgoJCQkJICAgIDwhLS0KCQkJCSAgICA8dHI+CgkJCQkgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgoJCQkJICAgICAgICA8dGQ+CgkJCQkgICAgICAgICAgICA8c2NyaXB0IHR5cGU9InRleHQvamF2YXNjcmlwdCIgc3JjPSJodHRwOi8vd3d3Lmdvb2dsZS5jb20vcmVjYXB0Y2hhL2FwaS9jaGFsbGVuZ2U/az02TGRYTDhvU0FBQUFBT3VtZnN3YmI5TTdMSEVHVHhjbjBjUkN2V3ZiIj48L3NjcmlwdD4KCgk8bm9zY3JpcHQ+CiAgCQk8aWZyYW1lIHNyYz0iaHR0cDovL3d3dy5nb29nbGUuY29tL3JlY2FwdGNoYS9hcGkvbm9zY3JpcHQ/az02TGRYTDhvU0FBQUFBT3VtZnN3YmI5TTdMSEVHVHhjbjBjUkN2V3ZiIiBoZWlnaHQ9IjMwMCIgd2lkdGg9IjUwMCIgZnJhbWVib3JkZXI9IjAiPjwvaWZyYW1lPjxici8+CiAgCQk8dGV4dGFyZWEgbmFtZT0icmVjYXB0Y2hhX2NoYWxsZW5nZV9maWVsZCIgcm93cz0iMyIgY29scz0iNDAiPjwvdGV4dGFyZWE+CiAgCQk8aW5wdXQgdHlwZT0iaGlkZGVuIiBuYW1lPSJyZWNhcHRjaGFfcmVzcG9uc2VfZmllbGQiIHZhbHVlPSJtYW51YWxfY2hhbGxlbmdlIi8+Cgk8L25vc2NyaXB0PgkJCQkgICAgICAgIDwvdGQ+CgkJCQkgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgoJCQkJICAgIDwvdHI+CgkJCQkgICAgLS0+CgkJCQkJPHRyPgoJCQkJCSAgPHRkPiZuYnNwOzwvdGQ+CgkJCQkJICA8dGQgaGVpZ2h0PSIzMCIgPjxpbnB1dCBuYW1lPSJidXR0b24iIHR5cGU9InN1Ym1pdCIgY2xhc3M9ImNlbGRhZm9ybSIgaWQ9ImJ1dHRvbjIiIHZhbHVlPSJFbnZpYXIiIC8+PC90ZD4KCQkJCQkgIDx0ZD4mbmJzcDs8L3RkPgoJCQkJICAgIDwvdHI+CgkJCQkJCiAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgIDwvdHI+CgkJCQkKCQkJCTwvZm9ybT4KCQkJCQogICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgPHRkIHJvd3NwYW49IjIiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE3MCIgcm93c3Bhbj0iMiIgYWxpZ249ImNlbnRlciIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFRkVGRUYiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICA8dGQgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzA3LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wOS5qcGciIHdpZHRoPSI0NSIgaGVpZ2h0PSIxNyIgLz48L3RkPgogICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iNjkiIGFsaWduPSJjZW50ZXIiIHZhbGlnbj0ibWlkZGxlIiBiZ2NvbG9yPSIjRkZGRkZGIj48c3Ryb25nIGNsYXNzPSJ0aXR1bG9ob21lMiI+PGZvbnQgc2l6ZT0iMSIgZmFjZT0iR2VvcmdpYSwgVGltZXMgTmV3IFJvbWFuLCBUaW1lcywgc2VyaWYiPkNhbnRpZGFkIGRlIGxlY3R1cmFzOiA8Zm9udCBjb2xvcj0iI0ZGOTI0MSIgc2l6ZT0iMiI+MjI5PC9mb250PjwvZm9udD48L3N0cm9uZz48L3RkPgogICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNzAiIGFsaWduPSJjZW50ZXIiIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjE1MCIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjMiIGNsYXNzPSJib3JkZSI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIiBiZ2NvbG9yPSIjRkZGRkZGIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYWxpZ249ImxlZnQiIHZhbGlnbj0iYm90dG9tIiBjbGFzcz0idGl0dWxvaG9tZTIiPk90cmFzIG5vdGFzPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBhbGlnbj0ibGVmdCIgdmFsaWduPSJib3R0b20iIGNsYXNzPSJ0aXR1bG9ob21lMiI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iIiBoZWlnaHQ9IjM1IiBhbGlnbj0ibGVmdCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIGNsYXNzPSJjb250ZW5pZG9ob21lIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIGNvbHNwYW49IjMiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPjxhIGhyZWY9ImphdmFzY3JpcHQ6OyIgY2xhc3M9ImRlc3RhY2Fkb3MiPklWIENvbmdyZXNvIEludGVybmFjaW9uYWwgdmlvbGVuY2lhLCBtYWx0cmF0byB5IGFidXNvPC9hPjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQlIiBjb2xzcGFuPSIzIiByb3dzcGFuPSI0IiBjbGFzcz0iY29udGVuaWRvaG9tZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIAkJCQkJCQkJCSAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI0JSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJtaWRkbGUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzJSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNFRkVGRUYiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIzMCIgY29sc3Bhbj0iMiIgYWxpZ249ImxlZnQiIHZhbGlnbj0ibWlkZGxlIiBiZ2NvbG9yPSIjRUZFRkVGIiBjbGFzcz0iY29udGVuaWRvaG9tZSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMxMCIgY2xhc3M9ImJvdG9uIj48c3Ryb25nPkVsIGNvbGVnaW8gZGUgUHNpY/Nsb2dvcyBkZSBD83Jkb2JhIHNlIHByb251bmNpYSBlbiByZWxhY2nzbiBhbCBTQVAgeSBlbiBjb25jb3JkYW5jaWEgY29uIGxvIGV4cHJlc2FkbyBwb3IgZWwgQ29sZWdpbyBkZSBQc2lj82xvZ29zIGRlIE1hciBkZWwgUGxhdGEgeSBlbCBDb2xlZ2lvIGRlIFBzaWPzbG9nb3MgZGUgbGEgIFByb3ZpbmNpYSBkZSBCdWVub3MgQWlyZXM8L3N0cm9uZz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgoJCQkJCQkJCQkgIAkJCQkJCQkJCSAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI0JSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJtaWRkbGUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzJSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNGRkZGRkYiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIzMCIgY29sc3Bhbj0iMiIgYWxpZ249ImxlZnQiIHZhbGlnbj0ibWlkZGxlIiBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0iY29udGVuaWRvaG9tZSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwOSIgY2xhc3M9ImJvdG9uIj48c3Ryb25nPlNhbHVkIEFjdGl2YSBvdG9yZ2EgbWVkaWFzIGJlY2FzIHBhcmEgZWwgSVYgQ29uZ3Jlc28gSW50ZXJuYWNpb25hbCwgViBOYWNpb25hbCwgVkkgUmVnaW9uYWwgVmlvbGVuY2lhLCBNYWx0cmF0byB5IEFidXNvLjwvc3Ryb25nPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CgkJCQkJCQkJCSAgCQkJCQkJCQkJICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQlIiBoZWlnaHQ9IjMwIiB2YWxpZ249Im1pZGRsZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMlIiBoZWlnaHQ9IjMwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjMwIiBjb2xzcGFuPSIyIiBhbGlnbj0ibGVmdCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNFRkVGRUYiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA4IiBjbGFzcz0iYm90b24iPjxzdHJvbmc+TkVDRVNJVEFNT1MgREUgU1UgU09MSURBUklEQUQgSEFDSUEgTE9TIE5J0U9TIFkgTknRQVMhISE8L3N0cm9uZz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgoJCQkJCQkJCQkgIAkJCQkJCQkJCSAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI0JSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJtaWRkbGUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzJSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNGRkZGRkYiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIzMCIgY29sc3Bhbj0iMiIgYWxpZ249ImxlZnQiIHZhbGlnbj0ibWlkZGxlIiBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0iY29udGVuaWRvaG9tZSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNyIgY2xhc3M9ImJvdG9uIj48c3Ryb25nPlNBTFVEIEFDVElWQSBoYSBzaWRvIGVsZWdpZGEgcG9yIHNlZ3VuZGEgdmV6IGNvbnNlY3V0aXZhIGNvbW8gdW5vIGRlIGxvcyBnYW5hZG9yZXMgZGVsIEN1YXJ0byBDb25jdXJzbyBkZSBQcm95ZWN0b3MgU29jaWFsZXMgZGUgUGV0cm9icmFzPC9zdHJvbmc+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KCQkJCQkJCQkJICAJCQkJCQkJCQkgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNCUiIGhlaWdodD0iMzAiIHZhbGlnbj0ibWlkZGxlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyUiIGhlaWdodD0iMzAiIHZhbGlnbj0ibWlkZGxlIiBiZ2NvbG9yPSIjRUZFRkVGIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMzAiIGNvbHNwYW49IjIiIGFsaWduPSJsZWZ0IiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDYiIGNsYXNzPSJib3RvbiI+PHN0cm9uZz5P7XIgbyBlc2N1Y2hhcjwvc3Ryb25nPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CgkJCQkJCQkJCSAgCQkJCQkJCQkJICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQlIiBoZWlnaHQ9IjMwIiB2YWxpZ249Im1pZGRsZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMlIiBoZWlnaHQ9IjMwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0ZGRkZGRiI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjMwIiBjb2xzcGFuPSIyIiBhbGlnbj0ibGVmdCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNGRkZGRkYiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA1IiBjbGFzcz0iYm90b24iPjxzdHJvbmc+RWwgZGVyZWNobyBkZSBsb3Mgbmnxb3MgYSBzZXIgZXNjdWNoYWRvczwvc3Ryb25nPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CgkJCQkJCQkJCSAgCQkJCQkJCQkJICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQlIiBoZWlnaHQ9IjMwIiB2YWxpZ249Im1pZGRsZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMlIiBoZWlnaHQ9IjMwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjMwIiBjb2xzcGFuPSIyIiBhbGlnbj0ibGVmdCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNFRkVGRUYiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA0IiBjbGFzcz0iYm90b24iPjxzdHJvbmc+QWJ1c28gc2V4dWFsIGluZmFudGlsLiBEZXNhZmlvcyBkZSBsYSBjbGluaWNhIGFjdHVhbDwvc3Ryb25nPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CgkJCQkJCQkJCSAgCQkJCQkJCQkJICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQlIiBoZWlnaHQ9IjMwIiB2YWxpZ249Im1pZGRsZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMlIiBoZWlnaHQ9IjMwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0ZGRkZGRiI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjMwIiBjb2xzcGFuPSIyIiBhbGlnbj0ibGVmdCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNGRkZGRkYiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAzIiBjbGFzcz0iYm90b24iPjxzdHJvbmc+U2FsdWQgQWN0aXZhIG5lY2VzaXRhIGRlIHR1IGF5dWRhITwvc3Ryb25nPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CgkJCQkJCQkJCSAgCQkJCQkJCQkJICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQlIiBoZWlnaHQ9IjMwIiB2YWxpZ249Im1pZGRsZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMlIiBoZWlnaHQ9IjMwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjMwIiBjb2xzcGFuPSIyIiBhbGlnbj0ibGVmdCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNFRkVGRUYiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAyIiBjbGFzcz0iYm90b24iPjxzdHJvbmc+UkVQVURJTyBBIExBIFBSRVNFTkNJQSBFTiBMQSBGRVJJQSBERUwgTElCUk8gREUgVU4gRVggSlVFWiBBQ1VTQURPIERFIEFCVVNPIFNFWFVBTDwvc3Ryb25nPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CgkJCQkJCQkJCSAgCQkJCQkJCQkJICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQlIiBoZWlnaHQ9IjMwIiB2YWxpZ249Im1pZGRsZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMlIiBoZWlnaHQ9IjMwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0ZGRkZGRiI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjMwIiBjb2xzcGFuPSIyIiBhbGlnbj0ibGVmdCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNGRkZGRkYiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAwIiBjbGFzcz0iYm90b24iPjxzdHJvbmc+VU5BIEpVRVpBIERFIFZJTExBIEdFU0VMTCBSRUNIQVpPIEVMIFBFRElETyBERSBVTiBQQURSRSBRVUUgU0UgQVBPWUFCQSBFTiBFTCBTQVAsIERFTlVOQ0lBRE8gUE9SIEFCVVNBUiBERSBTVSBISUpPPC9zdHJvbmc+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KCQkJCQkJCQkJICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjIwIiBjb2xzcGFuPSI3IiBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3X3RvZGFzIiBjbGFzcz0iYm90b24iPjxzdHJvbmc+VmVyIFRvZGFzIGxhcyBOb3RpY2lhczwvc3Ryb25nPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogIDwvdHI+CjwvdGFibGU+CjwvdGQ+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gICAgICAgICAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFM0UzRTMiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSI3MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNiUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9kZWNpbG9fYmllbl9mdWVydGUxLmpwZyIgd2lkdGg9IjEyMCIgaGVpZ2h0PSIxMTIiPjwvdGQ+CiAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiA+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTI0IiBjbGFzcz0iYm90b24xIj5bK10gTSZhYWN1dGU7cyBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0UzRTNFMyI+ICAgICAgICA8L3RyPgogICAgICAgIDx0cj4gCiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj4mbmJzcDs8L3RkPgogICAgICAgIDwvdHI+CiAgICA8L3RhYmxlPjwvdGQ+CiAgPC90cj4KICA8dHI+IAogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSI+PGltZyBzcmM9ImltZy9penExLmpwZyIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjExNCIgLz48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9RdWllbmVzU29tb3NfQTJfMF8yNS5qcGciIHdpZHRoPSI4MDkiIGhlaWdodD0iMTE0IiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcDIiIC8+PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI1MCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiYWNrZ3JvdW5kPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzE4XzE4LmpwZyI+Jm5ic3A7PC90ZD4KICAgIDx0ZCBoZWlnaHQ9IjUwIiBjbGFzcz0iZm9uZG9ib3R0b20iPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2l0ZWkuY29tLmFyLyI+PGltZyBzcmM9ImltZy9laV9jb2xvci5wbmciIGFsdD0iZXNwYWNpb3MgZGUgaW1hZ2luYWNpb24sIGRlc2Fycm9sbG9zIGludGVyYWN0aXZvcywgY3JlYXRpdmlkYWQsIGRpc2XxbyIgd2lkdGg9IjI3IiBoZWlnaHQ9IjE1IiBib3JkZXI9IjAiPjwvYT4gPHNwYW4gY2xhc3M9ImVpIj48YSBocmVmPSJodHRwOi8vd3d3LnNpdGVpLmNvbS5hci8iIHNwYW4gY2xhc3M9ImVpIj5kaXNlJm50aWxkZTtvICsgY29tdW5pY2FjaSZvYWN1dGU7bjwvYT48L3NwYW4+PGVtPiZuYnNwOzwvZW0+PC9zcGFuPjxzcGFuIGNsYXNzPSJibGFuY28xIj48ZW0+Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7PC9lbT48L3NwYW4+PC90ZD4KICA8L3RyPgo8L3RhYmxlPgoKCjxtYXAgbmFtZT0iTWFwMiI+PGFyZWEgc2hhcGU9InJlY3QiIGNvb3Jkcz0iMjQ3LDY5LDQxNCw4MiIgaHJlZj0ibWFpbHRvOnNhbHVkYWN0aXZhQHNhbHVkYWN0aXZvLm9yZy5hciI+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcCI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM2LDE0MiwxNDksMTUyIiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MiI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM0LDE4NiwxNTAsMTk2IiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MCI+CjwvbWFwPgo8L2JvZHk+CjwvaHRtbD4K]]></response> | |
| 96 | <responseRedirected>false</responseRedirected> | |
| 97 | </requestresponse> | |
| 98 | </issue> | |
| 99 | <issue> | |
| 100 | <serialNumber>6589706705335705600</serialNumber> | |
| 101 | <type>5244928</type> | |
| 102 | <name>Password field with autocomplete enabled</name> | |
| 103 | <host ip="200.20.20.201">http://www.example.org.ar</host> | |
| 104 | <path><![CDATA[/index.php]]></path> | |
| 105 | <location><![CDATA[/index.php]]></location> | |
| 106 | <severity>Low</severity> | |
| 107 | <confidence>Certain</confidence> | |
| 108 | <issueBackground><![CDATA[Most browsers have a facility to remember user credentials that are entered into HTML forms. This function can be configured by the user and also by applications which employ user credentials. If the function is enabled, then credentials entered by the user are stored on their local computer and retrieved by the browser on future visits to the same application.<br><br>The stored credentials can be captured by an attacker who gains access to the computer, either locally or through some remote compromise. Further, methods have existed whereby a malicious web site can retrieve the stored credentials for other applications, by exploiting browser vulnerabilities or through application-level cross-domain attacks. ]]></issueBackground> | |
| 109 | <remediationBackground><![CDATA[To prevent browsers from storing credentials entered into HTML forms, you should include the attribute <b>autocomplete="off"</b> within the FORM tag (to protect all form fields) or within the relevant INPUT tags (to protect specific individual fields).]]></remediationBackground> | |
| 110 | <issueDetail><![CDATA[The page contains a form with the following action URL:<ul><li>http://www.example.org.ar/login.php</li></ul>The form contains the following password field with autocomplete enabled:<ul><li>pass</li></ul>]]></issueDetail> | |
| 111 | <requestresponse> | |
| 112 | <request base64="true"><![CDATA[R0VUIC9pbmRleC5waHAgSFRUUC8xLjENCkhvc3Q6IHd3dy5zYWx1ZGFjdGl2YS5vcmcuYXINCkFjY2VwdDogKi8qDQpBY2NlcHQtTGFuZ3VhZ2U6IGVuDQpVc2VyLUFnZW50OiBNb3ppbGxhLzUuMCAoY29tcGF0aWJsZTsgTVNJRSA5LjA7IFdpbmRvd3MgTlQgNi4xOyBXaW42NDsgeDY0OyBUcmlkZW50LzUuMCkNCkNvbm5lY3Rpb246IGNsb3NlDQoNCg==]]></request> | |
| 113 | <response base64="true"><![CDATA[SFRUUC8xLjEgMjAwIE9LDQpEYXRlOiBUaHUsIDA3IE5vdiAyMDEzIDE3OjE0OjA1IEdNVA0KU2VydmVyOiBBcGFjaGUvMi4yLjIzIChVbml4KSBtb2Rfc3NsLzIuMi4yMyBPcGVuU1NMLzAuOS44ZS1maXBzLXJoZWw1DQpYLVBvd2VyZWQtQnk6IFBIUC81LjIuMTcNCkV4cGlyZXM6IFRodSwgMTkgTm92IDE5ODEgMDg6NTI6MDAgR01UDQpDYWNoZS1Db250cm9sOiBuby1zdG9yZSwgbm8tY2FjaGUsIG11c3QtcmV2YWxpZGF0ZSwgcG9zdC1jaGVjaz0wLCBwcmUtY2hlY2s9MA0KUHJhZ21hOiBuby1jYWNoZQ0KQ29ubmVjdGlvbjogY2xvc2UNCkNvbnRlbnQtVHlwZTogdGV4dC9odG1sDQpDb250ZW50LUxlbmd0aDogNjA2MDYNCg0KIDxoZWFkPgo8bWV0YSBodHRwLWVxdWl2PSJDb250ZW50LVR5cGUiIGNvbnRlbnQ9InRleHQvaHRtbDsgY2hhcnNldD1pc28tODg1OS0xIiAvPgo8dGl0bGU+U2FsdWQgQWN0aXZhIC0gQWJ1c28gdmlvbGVuY2lhIHkgbWFsdHJhdG88L3RpdGxlPgoKPHNjcmlwdD4gCiAgICAvL2VzdG8gcGFyYSBwYXNhcmxlIGFsIGZsYXNoIGxhcyB2YXJpYWxiZXMgZGVsIHBocAogCQoKCXZhciBib3Q9Jyc7Ci8vYWxlcnQodmFyaWFibGVTZXJ2aWRvcik7Cjwvc2NyaXB0Pgo8c2NyaXB0IGxhbmd1YWdlPSJKYXZhU2NyaXB0IiB0eXBlPSJ0ZXh0L0phdmFTY3JpcHQiPgo8IS0tCmZ1bmN0aW9uIE1NX3ByZWxvYWRJbWFnZXMoKSB7IC8vdjMuMAogIHZhciBkPWRvY3VtZW50OyBpZihkLmltYWdlcyl7IGlmKCFkLk1NX3ApIGQuTU1fcD1uZXcgQXJyYXkoKTsKICAgIHZhciBpLGo9ZC5NTV9wLmxlbmd0aCxhPU1NX3ByZWxvYWRJbWFnZXMuYXJndW1lbnRzOyBmb3IoaT0wOyBpPGEubGVuZ3RoOyBpKyspCiAgICBpZiAoYVtpXS5pbmRleE9mKCIjIikhPTApeyBkLk1NX3Bbal09bmV3IEltYWdlOyBkLk1NX3BbaisrXS5zcmM9YVtpXTt9fQp9Ci8vLS0+Cjwvc2NyaXB0Pgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KCjwvaGVhZD4KCjxzY3JpcHQgbGFuZ3VhZ2U9IkphdmFTY3JpcHQiIHR5cGU9InRleHQvSmF2YVNjcmlwdCI+CjwhLS0KZnVuY3Rpb24gTU1fcmVsb2FkUGFnZShpbml0KSB7ICAvL3JlbG9hZHMgdGhlIHdpbmRvdyBpZiBOYXY0IHJlc2l6ZWQKICBpZiAoaW5pdD09dHJ1ZSkgd2l0aCAobmF2aWdhdG9yKSB7aWYgKChhcHBOYW1lPT0iTmV0c2NhcGUiKSYmKHBhcnNlSW50KGFwcFZlcnNpb24pPT00KSkgewogICAgZG9jdW1lbnQuTU1fcGdXPWlubmVyV2lkdGg7IGRvY3VtZW50Lk1NX3BnSD1pbm5lckhlaWdodDsgb25yZXNpemU9TU1fcmVsb2FkUGFnZTsgfX0KICBlbHNlIGlmIChpbm5lcldpZHRoIT1kb2N1bWVudC5NTV9wZ1cgfHwgaW5uZXJIZWlnaHQhPWRvY3VtZW50Lk1NX3BnSCkgbG9jYXRpb24ucmVsb2FkKCk7Cn0KTU1fcmVsb2FkUGFnZSh0cnVlKTsKLy8tLT4KCjwvc2NyaXB0Pgo8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoKCjwvaGVhZD4KCjxib2R5IGJhY2tncm91bmQ9ImltZy9mb25kb19kZWdyYWRlLmpwZyIgdG9wbWFyZ2luPSIwIj4KPHRhYmxlIHdpZHRoPSIxMDA1IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgPHRyPiAKICAgIDx0ZCB3aWR0aD0iOTYiPjxpbWcgc3JjPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzBfMDEuanBnIiB3aWR0aD0iOTYiIGhlaWdodD0iMjA4IiAvPjwvdGQ+CiAgICA8dGQgd2lkdGg9IjgwOSI+IDxzY3JpcHQgdHlwZT0idGV4dC9qYXZhc2NyaXB0Ij4KQUNfRkxfUnVuQ29udGVudCggJ2NvZGViYXNlJywnaHR0cDovL2Rvd25sb2FkLm1hY3JvbWVkaWEuY29tL3B1Yi9zaG9ja3dhdmUvY2Ficy9mbGFzaC9zd2ZsYXNoLmNhYiN2ZXJzaW9uPTcsMCwxOSwwJywnd2lkdGgnLCc4MDknLCdoZWlnaHQnLCcyMDgnLCdzcmMnLCdzd2YvaGVhZGVyJywncXVhbGl0eScsJ2hpZ2gnLCdwbHVnaW5zcGFnZScsJ2h0dHA6Ly93d3cubWFjcm9tZWRpYS5jb20vZ28vZ2V0Zmxhc2hwbGF5ZXInLCdtb3ZpZScsJ3N3Zi9oZWFkZXInICk7IC8vZW5kIEFDIGNvZGUKPC9zY3JpcHQ+IDxub3NjcmlwdD4KICAgICAgPG9iamVjdCBjbGFzc2lkPSJjbHNpZDpEMjdDREI2RS1BRTZELTExY2YtOTZCOC00NDQ1NTM1NDAwMDAiIGNvZGViYXNlPSJodHRwOi8vZG93bmxvYWQubWFjcm9tZWRpYS5jb20vcHViL3Nob2Nrd2F2ZS9jYWJzL2ZsYXNoL3N3Zmxhc2guY2FiI3ZlcnNpb249NywwLDE5LDAiIHdpZHRoPSI4MDkiIGhlaWdodD0iMjA4Ij4KICAgICAgICA8cGFyYW0gbmFtZT0ibW92aWUiIHZhbHVlPSJzd2YvaGVhZGVyLnN3ZiIgLz4KICAgICAgICA8cGFyYW0gbmFtZT0icXVhbGl0eSIgdmFsdWU9ImhpZ2giIC8+CiAgICAgICAgPGVtYmVkIHNyYz0ic3dmL2hlYWRlci5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9IjgwOSIgaGVpZ2h0PSIyMDgiPjwvZW1iZWQ+IAogICAgICA8L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIHdpZHRoPSIxMiUiIHJvd3NwYW49IjUiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iIzAwMDAwMCI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI0NjEiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmFja2dyb3VuZD0iaW1nL1F1aWVuZXNTb21vc19BMl8wXzEzLmpwZyI+IAogICAgICA8c2NyaXB0IHR5cGU9InRleHQvamF2YXNjcmlwdCI+CkFDX0ZMX1J1bkNvbnRlbnQoICdjb2RlYmFzZScsJ2h0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCcsJ3dpZHRoJywnOTYnLCdoZWlnaHQnLCc0NjEnLCdzcmMnLCdzd2Yvc3VibWVudScsJ3F1YWxpdHknLCdoaWdoJywncGx1Z2luc3BhZ2UnLCdodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyJywnbW92aWUnLCdzd2Yvc3VibWVudScgKTsgLy9lbmQgQUMgY29kZQo8L3NjcmlwdD4gPG5vc2NyaXB0PgogICAgICA8b2JqZWN0IGNsYXNzaWQ9ImNsc2lkOkQyN0NEQjZFLUFFNkQtMTFjZi05NkI4LTQ0NDU1MzU0MDAwMCIgY29kZWJhc2U9Imh0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+CiAgICAgICAgPHBhcmFtIG5hbWU9Im1vdmllIiB2YWx1ZT0ic3dmL3N1Ym1lbnUuc3dmIiAvPgogICAgICAgIDxwYXJhbSBuYW1lPSJxdWFsaXR5IiB2YWx1ZT0iaGlnaCIgLz4KICAgICAgICA8ZW1iZWQgc3JjPSJzd2Yvc3VibWVudS5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+PC9lbWJlZD48L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCIgYmdjb2xvcj0iI0ZGRkZGRiI+CiAgICAgICAgPHRyPiAKICAgICAgICAgIDx0ZCB3aWR0aD0iMTciIHJvd3NwYW49IjciPjxwPiZuYnNwOzwvcD48L3RkPgogICAgICAgICAgPHRkIHdpZHRoPSIxNzIiIGFsaWduPSJjZW50ZXIiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxpbWcgc3JjPSJpbWcvM3B4LmpwZyIgd2lkdGg9IjUiIGhlaWdodD0iNSI+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciI+PGxpbmsgaHJlZj0iLi4vZXN0aWxvcy5jc3MiIHJlbD0ic3R5bGVzaGVldCIgdHlwZT0idGV4dC9jc3MiIC8+Cjxib2R5IGJnY29sb3I9IiNDQ0NDQ0MiIHRvcG1hcmdpbj0iNiBweCI+PHRhYmxlIHdpZHRoPSIxNjUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIzIiBiZ2NvbG9yPSIjRkZGRkZGIj4KPHRyPgogICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTkxIiBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiAgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MThfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+SG9tZTwvYT48L3RkPgogIDwvdHI+Cjx0cj4KICA8dGQgaGVpZ2h0PSIyOCIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj4mbmJzcDsmbmJzcDtOb3RpY2lhczwvYT48L3RkPgo8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJkb25hY2lvbmVzLyIgdGFyZ2V0PSJfYmxhbmsiIGNsYXNzPSJmb25kb2JvdG9uIj5Eb25hY2lvbmVzPC9hPjwvdGQ+CiAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciICB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yM19uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5IaXN0b3JpYWwgZGUgbmV3c2xldHRlcnM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTEzYSIgY2xhc3M9ImZvbmRvYm90b24iPkVudmlhciBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yNl9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5WZXIgdHJhYmFqb3MgZGUgdXN1YXJpb3M8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MTZfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+U2FsdWQgQWN0aXZhIHByZW5zYTwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJtYWlsdG86c2FsdWRhY3RpdmFAc2FsdWRhY3RpdmEub3JnLmFyIiBjbGFzcz0iZm9uZG9ib3RvbiI+TWFuZCZhYWN1dGU7IHR1IEMuVi48L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgIHdpZHRoPSI2ImhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTIxX25ldyIgY2xhc3M9ImZvbmRvYm90b24iPkluZm9ybWFjaSZvYWN1dGU7biBkZSBpbnRlciZlYWN1dGU7czwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyI+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiBoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xMF80IiBjbGFzcz0iZm9uZG9ib3RvbiI+Q29uZ3Jlc29zCiAgICAgICAgICAgICAgICAgIHkgSm9ybmFkYXM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTExIiBjbGFzcz0iZm9uZG9ib3RvbiI+UmVnaXN0cmFjaSZvYWN1dGU7bjwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgCiAgICAgICAgICA8L3RhYmxlPgo8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNSIgdGFyZ2V0PSJfYmxhbmsiPjxicj4KICAgICAgICAgICAgICAgICAgPGltZyBzcmM9ImltZy9iYW5uZXJfZG9uYWNpb25lcy5qcGciIHdpZHRoPSIxNjIiIGhlaWdodD0iMTIwIiBib3JkZXI9IjAiPjxicj4KICAgICAgICAgICAgICAgICAgPGJyPgogICAgICAgICAgICAgICAgICA8aW1nIHNyYz0iaW1nL2JvdG9uRm9yby5naWYiIHdpZHRoPSIxNzIiIGhlaWdodD0iMTE3IiBib3JkZXI9IjAiPjwvYT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTY3IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjkiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzAzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iOSIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTQ5IiBiYWNrZ3JvdW5kPSJpbWcvY2hpY29zX3BlcmRpZG9zXzA1LmdpZiI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDUuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMCI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDcuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMi5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEyLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9InNyYy9pbWdfdXAvMjMwODIwMTIuMS5qcGciIHdpZHRoPSIxNDkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMy5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNi5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iNSIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTcuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNy5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgYmdjb2xvcj0iI0ZFRTdDRiIgY2xhc3M9InRpdHVsb2hvbWU1Ij48c3Ryb25nPk5pJm50aWxkZTtvcyBwZXJkaWRvczxicj4KICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0yOSIgY2xhc3M9ImJvdG9uIj5bVmVyIG0mYWFjdXRlO3NdPC9hPjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTkuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xOS5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18yMC5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iMjUiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4NCgkJCQkNCgkJCQk8Zm9ybSBhY3Rpb249ImluZGV4LnBocD9pZD0xMSIgIG1ldGhvZD0icG9zdCI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9penExLmpwZyIgd2lkdGg9IjEyIiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9hcnJpYmEuanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9kZXIxLmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgIDwvdHI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiIgdmFsaWduPSJ0b3AiIGNsYXNzPSJyZWdGb25kbzEiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9penEuanBnIiB3aWR0aD0iMTIiIGhlaWdodD0iMTIiIC8+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSI5NCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV90aXQuanBnIiB3aWR0aD0iNjYiIGhlaWdodD0iMjMiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSI1MCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJyZWdpc3RyYXJzZSI+SW5ncmVzJmFhY3V0ZTsgDQogICAgICAgICAgICAgIHR1cyBkYXRvcyB5IHJlY2liJmlhY3V0ZTsgbGEgbWVqb3IgaW5mb3JtYWNpJm9hY3V0ZTtuIGEgdHJhdiZlYWN1dGU7cyANCiAgICAgICAgICAgICAgZGUgbnVlc3RybzxzdHJvbmc+IE5ld3NsZXR0ZXI8L3N0cm9uZz4uIDxzdHJvbmc+PHNwYW4gY2xhc3M9ImdyYXRpcyI+R3JhdGlzITwvc3Bhbj48L3N0cm9uZz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI1IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9InRyYWJTRUNDSU9OIj5Ob21icmU8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBjbGFzcz0icmVnQ0VMREEiPjxpbnB1dCBuYW1lPSJub21icmUiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0ibm9tYnJlIiAvPjwvdGQ+DQogICAgICAgICAgPC90cj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0idHJhYlNFQ0NJT04iPkFwZWxsaWRvPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iYXBlbGxpZG8iIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iYXBlbGxpZG8iIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJ0cmFiU0VDQ0lPTiI+RS1tYWlsPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iZW1haWwiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iZW1haWwiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InRyYWJTRUNDSU9OIj4mbmJzcDs8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idHJhYlNFQ0NJT04iPjxpbnB1dCB0eXBlPSJpbWFnZSIgc3JjPSJpbWcvcmVnaXN0cmF0ZV9ib3Rvbi5qcGciIHdpZHRoPSIxMTciIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgIDwvdGFibGU+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE0IiB2YWxpZ249InRvcCIgY2xhc3M9InJlZ0ZvbmRvMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2Rlci5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIxNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KICAgICAgICAgICAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTIiIGhlaWdodD0iMjQiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfaXpxMi5qcGciIHdpZHRoPSIxMiIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI0Ij48aW1nIHNyYz0iaW1nL3JlZ2lzdHJhdGVfYWJham8uanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjI0IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfZGVyMi5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KCQkJCQkNCgkJCQkJPC9mb3JtPg0KICAgICAgICAgICAgICAgICAgPC90YWJsZT4NCjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPiAKICAgICAgICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTcwIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUyIj4KCQkJCQkJCQkJCQkJCQkJCTwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9jbGF1ZGlhMl8wMy5qcGciIHdpZHRoPSIxNzQiIGhlaWdodD0iMjUwIiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcCI+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICA8dGQgcm93c3Bhbj0iNyIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nLzV4NS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjciPjwvdGQ+CiAgICAgICAgICA8dGQgY29sc3Bhbj0iMiIgcm93c3Bhbj0iNCIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPGZvcm0gYWN0aW9uPSJsb2dpbi5waHAiIG1ldGhvZD0icG9zdCIgbmFtZT0iZm9ybTIiPgoKICAgICAgICAgICAgICA8dHI+IAogICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgY29sc3Bhbj0iMiIgYWxpZ249ImxlZnQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIiA+IAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8c3Ryb25nPlVzdWFyaW8gbm8gcmVnaXN0cmFkbzwvc3Ryb25nPiAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9mb250PiA8L3N0cm9uZz4gCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDkiIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPlVzdWFyaW8mbmJzcDsmbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzOSIgdmFsaWduPSJtaWRkbGUiPjxpbnB1dCBuYW1lPSJ1c3VhcmlvIiB0eXBlPSJ0ZXh0IiBjbGFzcz0icmVnIiBpZD0idXN1YXJpbyIgc2l6ZT0iNyI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjciIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPkNvbnRyYXNlJm50aWxkZTthJm5ic3A7Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzkiIHZhbGlnbj0ibWlkZGxlIj48aW5wdXQgbmFtZT0icGFzcyIgdHlwZT0icGFzc3dvcmQiIGNsYXNzPSJyZWciIGlkPSJwYXNzIiBzaXplPSI3Ij48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiIgYWxpZ249InJpZ2h0IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9ImJvdG9uIj48aW5wdXQgdHlwZT0iaW1hZ2UiIHNyYz0iaW1nL3JlZy5qcGciIHdpZHRoPSI1OCIgaGVpZ2h0PSIzMCI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjciIGhlaWdodD0iMTkiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgPjxhIGhyZWY9Imh0dHA6Ly93d3cuZmFjZWJvb2suY29tL2hvbWUucGhwPyMhL3BhZ2VzL01lcmxvLUFyZ2VudGluYS9TQUxVRC1BQ1RJVkEvMTAwNTgzNTQzMzE3MzIyP3JlZj10cyZhamF4cGlwZT0xJl9fYT03IiB0YXJnZXQ9Il9ibGFuayI+PGltZyBzcmM9ImltZy9mYWNlYm9vay5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzExIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj48ZGl2IGFsaWduPSJsZWZ0Ij48YSBocmVmPSJodHRwOi8vdHdpdHRlci5jb20vU2FsdWRBY3RpdmFPTkciIHRhcmdldD0iX2JsYW5rIj48aW1nIHNyYz0iaW1nL3R3aXRlci5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC9kaXY+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSI1IiBhbGlnbj0icmlnaHQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIj48bGFiZWw+PGZvbnQgc2l6ZT0iLTYiPlNpCiAgICAgICAgICAgICAgICAgICAgICAgdG9kYXYmaWFjdXRlO2Egbm8gZXMgdXN1YXJpbyA8L2ZvbnQ+IDxhIGhyZWY9ImluZGV4LnBocD9pZD0xMSIgY2xhc3M9ImJvdG9uIj48Zm9udCBzaXplPSItNiI+cmVnJmlhY3V0ZTtzdHJlc2UKICAgICAgICAgICAgICAgICAgICAgICAgYXF1JmlhY3V0ZTsgPGZvbnQgY29sb3I9IiM2NjY2NjYiPiYjODIyNjs8L2ZvbnQ+PC9mb250PjwvYT4gPGEgaHJlZj0iaW5kZXgucGhwP2lkPTEyIiBjbGFzcz0iYm90b24xIj48Zm9udCBzaXplPSItNiI+b2x2aWRlIG1pIGNvbnRyYXNlJm50aWxkZTthPC9mb250PjwvYT48L2xhYmVsPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE3Ij4mbmJzcDsgPC90ZD4KICAgICAgICAgICAgICA8L3RyPgoJCQkgIDwvZm9ybT4KCiAgICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgICA8IURPQ1RZUEUgaHRtbCBQVUJMSUMgIi0vL1czQy8vRFREIFhIVE1MIDEuMCBUcmFuc2l0aW9uYWwvL0VOIiAiaHR0cDovL3d3dy53My5vcmcvVFIveGh0bWwxL0RURC94aHRtbDEtdHJhbnNpdGlvbmFsLmR0ZCI+CjxodG1sIHhtbG5zPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hodG1sIj4KPGhlYWQ+CjxtZXRhIGh0dHAtZXF1aXY9IkNvbnRlbnQtVHlwZSIgY29udGVudD0idGV4dC9odG1sOyBjaGFyc2V0PWlzby04ODU5LTEiIC8+Cjx0aXRsZT5Eb2N1bWVudG8gc2luIHQmaWFjdXRlO3R1bG88L3RpdGxlPgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KPHNjcmlwdCBsYW5ndWFnZT0iSmF2YVNjcmlwdCIgdHlwZT0idGV4dC9KYXZhU2NyaXB0Ij4KPCEtLQpmdW5jdGlvbiBNTV9yZWxvYWRQYWdlKGluaXQpIHsgIC8vcmVsb2FkcyB0aGUgd2luZG93IGlmIE5hdjQgcmVzaXplZAogIGlmIChpbml0PT10cnVlKSB3aXRoIChuYXZpZ2F0b3IpIHtpZiAoKGFwcE5hbWU9PSJOZXRzY2FwZSIpJiYocGFyc2VJbnQoYXBwVmVyc2lvbik9PTQpKSB7CiAgICBkb2N1bWVudC5NTV9wZ1c9aW5uZXJXaWR0aDsgZG9jdW1lbnQuTU1fcGdIPWlubmVySGVpZ2h0OyBvbnJlc2l6ZT1NTV9yZWxvYWRQYWdlOyB9fQogIGVsc2UgaWYgKGlubmVyV2lkdGghPWRvY3VtZW50Lk1NX3BnVyB8fCBpbm5lckhlaWdodCE9ZG9jdW1lbnQuTU1fcGdIKSBsb2NhdGlvbi5yZWxvYWQoKTsKfQpNTV9yZWxvYWRQYWdlKHRydWUpOwoKZnVuY3Rpb24gTU1fcHJlbG9hZEltYWdlcygpIHsgLy92My4wCiAgdmFyIGQ9ZG9jdW1lbnQ7IGlmKGQuaW1hZ2VzKXsgaWYoIWQuTU1fcCkgZC5NTV9wPW5ldyBBcnJheSgpOwogICAgdmFyIGksaj1kLk1NX3AubGVuZ3RoLGE9TU1fcHJlbG9hZEltYWdlcy5hcmd1bWVudHM7IGZvcihpPTA7IGk8YS5sZW5ndGg7IGkrKykKICAgIGlmIChhW2ldLmluZGV4T2YoIiMiKSE9MCl7IGQuTU1fcFtqXT1uZXcgSW1hZ2U7IGQuTU1fcFtqKytdLnNyYz1hW2ldO319Cn0KLy8tLT4KPC9zY3JpcHQ+CiAgICAgICAgICAgICA8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoJCQkgCjxzdHlsZSB0eXBlPSJ0ZXh0L2NzcyI+CjwhLS0KI0xheWVyMSB7Cglwb3NpdGlvbjphYnNvbHV0ZTsKCXdpZHRoOjY1MXB4OwoJaGVpZ2h0OjIxOHB4OwoJei1pbmRleDoxOwp9CiNMYXllcjIgewoJcG9zaXRpb246YWJzb2x1dGU7Cgl3aWR0aDoyMDBweDsKCWhlaWdodDoxMTVweDsKCXotaW5kZXg6MTsKCXZpc2liaWxpdHk6IHZpc2libGU7Cn0KLkVzdGlsbzEgewoJZm9udC1zaXplOiAxOHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzIgewoJZm9udC1zaXplOiAxNHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzMge2NvbG9yOiAjNTA2OTkwOyBsaW5lLWhlaWdodDogMTJweDsgdGV4dC1kZWNvcmF0aW9uOiBub25lOyBmb250LWZhbWlseTogVGFob21hO30KLS0+Cjwvc3R5bGU+CjwvaGVhZD4KCjxib2R5IGxlZnRtYXJnaW49IjIiIG1hcmdpbndpZHRoPSIyIj4KPHRhYmxlIHdpZHRoPSI2MDgiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICA8dHI+CiAgICA8dGQgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCB3aWR0aD0iMiUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzA3LmpwZyIgd2lkdGg9IjI0IiBoZWlnaHQ9IjE0IiAvPjwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI5MCUiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18wNy5qcGciPiZuYnNwOzwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI4JSIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wOS5qcGciIHdpZHRoPSI0NSIgaGVpZ2h0PSIxNyIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogIDwvdHI+CiAgPHRyPgogICAgPHRkIGNvbHNwYW49IjQiPjxiciAvPgogICAgICA8dGFibGUgd2lkdGg9Ijk4JSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICA8dHI+CiAgICAgICAgPHRkIHdpZHRoPSIyJSI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgICA8dGQgd2lkdGg9IjkzJSI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CjwhLS0gSU5JQ0lPIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzIzMDQyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjIvMTEvMjAxMzwvc3Bhbj48YnI+SVYgQ29uZ3Jlc28gSW50ZXJuYWNpb25hbCB2aW9sZW5jaWEsIG1hbHRyYXRvIHkgYWJ1c288L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxzdHJvbmc+MTQsIDE1IHkgMTYgZGUgTm92aWVtYnJlIEFCSUVSVEEgTEEgSU5TQ1JJUENJJk9hY3V0ZTtOISAoY29uIGRlc2N1ZW50byBoYXN0YSBlbCAyNy84KTxiciAvPjwvc3Ryb25nPjwvcD4NCjxwPjxzdHJvbmc+QUJJRVJUQSBMQSBSRUNFUENJJk9hY3V0ZTtOIERFIFRSQUJBSk88YSBocmVmPSJodHRwOi8vd3d3LmNvbmdyZXNvdmlvbGVuY2lhLmNvbS9pbmRleC5waHA/aWQ9bW9kYWxpZGFkZXMiIHRhcmdldD0iX2JsYW5rIj4gKG1hcyBpbmZvKTwvYT48L3N0cm9uZz48L3A+DQo8cD48c3BhbiBzdHlsZT0iY29sb3I6ICNmZjY2MDA7Ij48c3Ryb25nPk9yZ2FuaXphOiBTYWx1ZCBBY3RpdmE8L3N0cm9uZz48L3NwYW4+PC9wPg0KPHA+PHNwYW4gc3R5bGU9ImNvbG9yOiAjZmY2NjAwOyI+SW5jcmlwdG9zIGFsIFBvcnRhbCBkZSBTYWx1ZCBBY3RpdmEsIGltcG9ydGFudGVzIGRlc2N1ZW50b3MhPGJyIC8+PC9zcGFuPjwvcD4NCjxwPkx1Z2FyIGRlIFJlYWxpemFjaSZvYWN1dGU7biB5IGNvbGFib3JhY2lvbjogVW5pdmVyc2lkYWQgZGVsIEVzdGUsIExhIFBsYXRhIEJ1ZW5vcyBBaXJlczwvcD4NCjxwPk1hcyBkZSAxNTAgdHJhYmFqb3MgcHJlc2VudGFkb3MsIHVsdGltb3MgZGlhcyBwYXJhIGluc2NyaWJpcnNlIGNvbiBkZXNjdWVudG8hITwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPkluc2NyaWJpcnNlPC9hPjwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPjxiciAvPjwvYT48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAxIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDEiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MDQvMTEvMjAxMzwvc3Bhbj48YnI+RWwgY29sZWdpbyBkZSBQc2lj82xvZ29zIGRlIEPzcmRvYmEgc2UgcHJvbnVuY2lhIGVuIHJlbGFjafNuIGFsIFNBUCB5IGVuIGNvbmNvcmRhbmNpYSBjb24gbG8gZXhwcmVzYWRvIHBvciBlbCBDb2xlZ2lvIGRlIFBzaWPzbG9nb3MgZGUgTWFyIGRlbCBQbGF0YSB5IGVsIENvbGVnaW8gZGUgUHNpY/Nsb2dvcyBkZSBsYSAgUHJvdmluY2lhIGRlIEJ1ZW5vcyBBaXJlczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+Jm5ic3A7PC9wPg0KPHA+TGFzIGNvbnRyb3ZlcnNpYXMgZ2VuZXJhZGFzIGVuIHJlbGFjaSZvYWN1dGU7biBhbCAic2luZHJvbWUgZGUgYWxpZW5hY2kmb2FjdXRlO24gcGFyZW50YSIgU0FQLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMxMCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzEwIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzE2MTAyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTYvMTAvMjAxMzwvc3Bhbj48YnI+U2FsdWQgQWN0aXZhIG90b3JnYSBtZWRpYXMgYmVjYXMgcGFyYSBlbCBJViBDb25ncmVzbyBJbnRlcm5hY2lvbmFsLCBWIE5hY2lvbmFsLCBWSSBSZWdpb25hbCBWaW9sZW5jaWEsIE1hbHRyYXRvIHkgQWJ1c28uPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD4mbmJzcDs8L3A+DQo8cD5TZXImYWFjdXRlO24gb3RvcmdhZGFzIDUwIG1lZGlhcyBiZWNhcywgcXVlZGFuIHBvY2FzISEhIGNvbmRpY2lvbjo8L3A+DQo8cD5QZXJ0ZW5lY2VyIGFsIGFtYml0byBwdWJsaWNvIG8gYSBPTkcsIHNlIGNvbnNpZGVyYSB0YW1iaWVuIGxhIGRpc3RhbmNpYSBhbCBsdWdhciBkZWwgZXZlbnRvISEhIGVzIG11eSBzZW5jaWxsbywgc29sbyBkZWJlcyBlbnZpYXIgdW4gZW1haWwuLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwOSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA5Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjI0LzA3LzIwMTM8L3NwYW4+PGJyPk5FQ0VTSVRBTU9TIERFIFNVIFNPTElEQVJJREFEIEhBQ0lBIExPUyBOSdFPUyBZIE5J0UFTISEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPlBST0dSQU1BIEZBTUlMSUFTIFNPTElEQVJJQVM8L3NwYW4+PC9zdHJvbmc+PC9wPg0KPHA+PHN0cm9uZz5DQU1CSU8gREUgU0VERTwvc3Ryb25nPjwvcD4NCjxwPkxhIGNhcGFjaXRhY2kmb2FjdXRlO24gcGFyYSBsYSBwdWVzdGEgZW4gbWFyY2hhIGRlbCA8c3Ryb25nPlByb2dyYW1hIEZhbWlsaWFzIFNvbGlkYXJpYXM8L3N0cm9uZz4gc2UgcmVhbGl6YXImYWFjdXRlOyBlbiBsYSBsb2NhbGlkYWQgZGUgPHN0cm9uZz5OYXZhcnJvPC9zdHJvbmc+IHBhcmEgdG9kbyBlbCBjb3JyZWRvciBkZSBsYSBSdXRhIDQwLjwvcD4NCjxwPkluaWNpbyA8c3Ryb25nPk1pJmVhY3V0ZTtyY29sZXMgMjggZGUgYWdvc3RvIGEgbGFzIDE0IGhvcmFzLiZuYnNwOzwvc3Ryb25nPjwvcD4NCjxwPlNlZGU6IDxzdHJvbmc+U2FsJm9hY3V0ZTtuIE11bmljaXBhbCBlbiBsYSBjYWxsZSAxMDcgZXNxdWluYSAyMiAtIE5hdmFycm88L3N0cm9uZz48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA4Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTIwNzIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xMi8wNy8yMDEzPC9zcGFuPjxicj5TQUxVRCBBQ1RJVkEgaGEgc2lkbyBlbGVnaWRhIHBvciBzZWd1bmRhIHZleiBjb25zZWN1dGl2YSBjb21vIHVubyBkZSBsb3MgZ2FuYWRvcmVzIGRlbCBDdWFydG8gQ29uY3Vyc28gZGUgUHJveWVjdG9zIFNvY2lhbGVzIGRlIFBldHJvYnJhczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+RW4gZWwgbWFyY28gZGVsIEN1YXJ0byBDb25jdXJzbyBkZSBQcm95ZWN0b3MgU29jaWFsZXMgZGUgUGV0cm9icmFzLCANCm51ZXN0cmEgSW5zdGl0dWNpJm9hY3V0ZTtuIFNBTFVEIEFDVElWQSBoYSBzaWRvIGVsZWdpZGEgcG9yIHNlZ3VuZGEgdmV6IA0KY29uc2VjdXRpdmEgY29tbyB1bm8gZGUgbG9zIGdhbmFkb3JlcyBkZSBkaWNobyBjb25jdXJzby48YnIgLz5FbiBlc3RhIA0KZWRpY2kmb2FjdXRlO24gZWwgcHJveWVjdG8gcXVlIGhhIHNpZG8gZWxlZ2lkbyBlcyBlbCAmbGRxdW87UHJvZ3JhbWEgZGUgRmFtaWxpYXMgDQpTb2xpZGFyaWFzJnJkcXVvOyBzaWVuZG8gc3UgJmFhY3V0ZTtyZWEgZGUgaW1wbGVtZW50YWNpJm9hY3V0ZTtuIGxvcyBNdW5pY2lwaW9zIGRlIE5hdmFycm8sIA0KR3JhbC4gTGFzIEhlcmFzLCBNYXJjb3MgUGF6LCB5IE1lcmxvPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAyLzA3LzIwMTM8L3NwYW4+PGJyPk/tciBvIGVzY3VjaGFyPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Qb3IgQ2FybG9zIFJvemFuc2tpICo8L3A+DQo8cD5BIGxvIGxhcmdvIGRlIGxvcyBzaWdsb3MsIGxhcyBuaSZudGlsZGU7YXMsIG5pJm50aWxkZTtvcyB5IGFkb2xlc2NlbnRlcyBoYW4gc2lkbyBtYWx0cmF0YWRvcyB5IGFidXNhZG9zIHNpbiBxdWUgYSBsYSBjb211bmlkYWQgbGUgaW50ZXJlc2FyYSBuaSBzaXF1aWVyYSBlc2N1Y2hhcmxvcyBjdWFuZG8gaGFjJmlhY3V0ZTthbiBzYWJlciBkZSBhbGd1bmEgZm9ybWEgbG9zIHN1ZnJpbWllbnRvcyBxdWUgcGFkZWMmaWFjdXRlO2FuLiBFbiAxODc0LCBlbiBFc3RhZG9zIFVuaWRvcywgZnVlIGxhIHByaW1lcmEgdmV6IHF1ZSBlbCBFc3RhZG8gaW50ZXJ2aW5vIGVuIHVuIGNhc28gZGUgbWFsdHJhdG8geSBhYnVzby4uLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDYiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4wMi8wNy8yMDEzPC9zcGFuPjxicj5FbCBkZXJlY2hvIGRlIGxvcyBuafFvcyBhIHNlciBlc2N1Y2hhZG9zPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5VbiBob21icmUgYWN1c2FkbyBkZSBoYWJlciBhYnVzYWRvIGRlIHN1cyBoaWpvcyBoYWImaWFjdXRlO2Egc2lkbyBzb2JyZXNlJmlhY3V0ZTtkbyBkb3MgdmVjZXMgcG9yIGxhIEp1c3RpY2lhLiBQZXJvIGFob3JhLCBsYSBDJmFhY3V0ZTttYXJhIGRlIENhc2FjaSZvYWN1dGU7biByZXZvYyZvYWN1dGU7IGVzYSBkZWNpc2kmb2FjdXRlO24gcG9ycXVlIGVuIGxhIGludmVzdGlnYWNpJm9hY3V0ZTtuIGVsIGp1ZXogbnVuY2EgaGFiJmlhY3V0ZTthIGVzY3VjaGFkbyBhIGxvcyBjaGljb3MuIFkgb3JkZW4mb2FjdXRlOyBxdWUgdGVuZ2EgZW4gY3VlbnRhIGxvIHF1ZSBkaWNlbi48L3A+DQo8cD5Qb3IgTWFyaWFuYSBDYXJiYWphbDwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDUiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE1NiIgcm93c3Bhbj0iMiIgdmFsaWduPSJ0b3AiPgoJCQkJCgkJCQk8dGFibGUgd2lkdGg9IjMyJSIgYm9yZGVyPSIxIiBjZWxsc3BhY2luZz0iMyIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48aW1nIHNyYz0ic3JjL2ltZ191cC8wNjA2MjAxMy4xLmpwZyIgd2lkdGg9IjE0NiIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT4KCQkJCQkJCQk8L3RkPiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjA2LzA2LzIwMTM8L3NwYW4+PGJyPkFidXNvIHNleHVhbCBpbmZhbnRpbC4gRGVzYWZpb3MgZGUgbGEgY2xpbmljYSBhY3R1YWw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkFiaWVydGEgbGEgaW5zY3JpcGNpb248L3A+DQo8cD5Eb2NlbnRlczogTGljLiBNYXJpYSBCZWF0cml6IE0mdXVtbDtsbGVyLiBMaWMuIFBhb2xhIE11Jm50aWxkZTtveiBEdWFydGU8L3A+DQo8cD5JbmljaW86IE1pZXJjb2xlcyAxOSBkZSBKdW5pbzwvcD4NCjxwPkZyZWN1ZW5jaWE6IFNlbWFuYWw8L3A+DQo8cD5Nb2RhbGlkYWQ6IEludGVuc2l2YTwvcD4NCjxwPkNvbnRlbmlkb3M6ICZuYnNwOyBFc3RhIGRlc3RpbmFkbyBhIHRvZG9zIGxvcyBwcm9mZXNpb25hbGVzIGNvbXByb21ldGlkb3MgY29uIGxhIHRlbWF0aWNhIGRlbCBhYnVzbyBpbmZhbnRpbCBxdWUgcXVpZXJhbiBhY3R1YWxpemFyc2UgZSBpbnRlcmNhbWJpYXIgZXhwZXJpZW5jaWFzIGRlIHRyYWJham8uLi48L3A+DQo8cD4mbmJzcDs8L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA0Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDQiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTYwNTIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xNi8wNS8yMDEzPC9zcGFuPjxicj5TYWx1ZCBBY3RpdmEgbmVjZXNpdGEgZGUgdHUgYXl1ZGEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5UcmFiYWphbW9zIGNvbW8gcG9kZW1vczogYmEmbnRpbGRlO29zIHJvdG9zLCBzdXNwZW5zaSZvYWN1dGU7biBkZSByZXVuaW9uZXMgcG9yIGNvcnRlcyBkZSBsdXogeSBhZ3VhLCBqdWd1ZXRlcyB2aWVqb3MsIG1lc2VzIGRlIGF0cmFzbyBlbiBlbCBwYWdvIGRlIHN1cyBwcm9mZXNpb25hbGVzIGRlIGxhIHNhbHVkLiBSZWNpZW50ZW1lbnRlIHR1dmltb3MgcXVlIGNlcnJhciBudWVzdHJvIHF1ZXJpZG8gSG9nYXI6ICZsZHF1bztNZXRhbW9yZm9zaXMmcmRxdW87IGVyYSBlbCBsdWdhciBxdWUgc3VwbyBjb250ZW5lciBhIG5pJm50aWxkZTthcyB5IGomb2FjdXRlO3ZlbmVzIHJlc2NhdGFkYSBkZSByZWRlcyBkZSB0cmF0YSBvIHYmaWFjdXRlO2N0aW1hcyBkZSBhYnVzbyBpbnRyYWZhbWlsaWFyLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAzIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAzLzA1LzIwMTM8L3NwYW4+PGJyPlJFUFVESU8gQSBMQSBQUkVTRU5DSUEgRU4gTEEgRkVSSUEgREVMIExJQlJPIERFIFVOIEVYIEpVRVogQUNVU0FETyBERSBBQlVTTyBTRVhVQUw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkZ1ZSBjYW1hcmlzdGEgZW4gTWFyIGRlbCBQbGF0YSBkdXJhbnRlIGxhIGRpY3RhZHVyYS4gSGFjZSBhJm50aWxkZTtvcywgdmFyaWFzIG11amVyZXMgbG8gYWN1c2Fyb24gZGUgaGFiZXIgYWJ1c2FkbyBkZSBlbGxhcyBjdWFuZG8gZXJhbiBuaSZudGlsZGU7YXMuIExhIGNhdXNhIHByZXNjcmliaSZvYWN1dGU7IHkgbm8gaHVibyBjb25kZW5hLiBNYSZudGlsZGU7YW5hIHRpZW5lIHByZXZpc3RvIGZpcm1hciBzdSBsaWJyby4gRXNhcyBtaXNtYXMgbXVqZXJlcyBwaWRlbiBxdWUgbm8gc2VhIGFkbWl0aWRvIGVuIGxhIGZlcmlhLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDIiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgIDwhLS0gRklOIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgIDwvdGFibGU+ICAgICAgICA8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iNSUiIGFsaWduPSJyaWdodCI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgPC90cj4KICAgIDwvdGFibGU+PC90ZD4KICA8L3RyPgogIDx0cj4KICAgIDx0ZCB3aWR0aD0iMSUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiIgYWxpZ249ImNlbnRlciI+Jm5ic3A7PC90ZD4KICAgIDx0ZCB3aWR0aD0iMiUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgPC90cj4KICAKICA8dGQ+CiAgPHRyPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0ciBhbGlnbj0iY2VudGVyIj4KICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgPHRkIHdpZHRoPSI5NyIgY29sc3Bhbj0iMiIgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iNTQ2IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idGl0dWxvaG9tZTIiPjx0YWJsZSB3aWR0aD0iIiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYWxpZ249ImxlZnQiIHZhbGlnbj0iYm90dG9tIiBjbGFzcz0idGl0dWxvaG9tZTIiPlJhbmtpbmc8L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSIgY2xhc3M9InRpdHVsb2hvbWUyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iIiBoZWlnaHQ9IjM1IiBhbGlnbj0ibGVmdCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPiZidWxsO0xhcyBtJmFhY3V0ZTtzIGxlaWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGNsYXNzPSJjb250ZW5pZG9ob21lIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBjbGFzcz0iY29udGVuaWRvaG9tZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+JmJ1bGw7TGFzIG0mYWFjdXRlO3MgY29tZW50YWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTHVkb3RlY2EgR2FyYWJhdG8gLSBQcm95ZWN0byBzYWx1ZGFjdGl2YSwgUG9yIHVuYSBpbmZhbmNpYSBmZWxpeiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iOSUiIGJnY29sb3I9IiNFRkVGRUYiPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzJSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xNjIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDUlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTE2MiIgY2xhc3M9ImJvdG9uIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBDdXJzbyBJbnRlbnNpdm8gZGUgb3BlcmFkb3IgdGVyYXBldXRpY28gZXNwZWNpYWxpemFkbyBlbiBlbCBhYm9yZGFqZSBkZWwgYWJ1c28sIGxhIHZpb2xlbmNpYSB5IGVsIG1hbHRyYXRvIGluZmFudGlsICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgUFJPR1JBTUEgTEFTIFZJQ1RJTUFTIENPTlRSQSBMQVMgVklPTEVOQ0lBUyAgTWluaXN0ZXJpbyBkZSBKdXN0aWNpYSB5IERlcmVjaG9zIEh1bWFub3MgZGUgbGEgTmFjafNuICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI5JSIgYmdjb2xvcj0iI0VGRUZFRiI+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjMlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTI1NSIgY2xhc3M9ImJvdG9uIj48aW1nIHNyYz0iaW1nL2ZsZWNoYW5hcmFuamFmZ3Jpc18yNC5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSI3IiBib3JkZXI9IjAiIGFsaWduPSJhYnNtaWRkbGUiIC8+PC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI0NSUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MjU1IiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIERpcGxvbWF0dXJhIGVuIEFib3JkYWplIGludGVyZGlzY2lwbGluYXJpbyBkZWwgbWFsdHJhdG8sIGxhIHZpb2xlbmNpYSB5IGVsIGFidXNvIHNleHVhbCBpbmZhbnRpbCAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyJSIgaGVpZ2h0PSIyMCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQxJSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNhbHVkIEFjdGl2YSBuZWNlc2l0YSBkZSB0dSBheXVkYSEgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjklIiBiZ2NvbG9yPSIjRUZFRkVGIj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMyUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MTA0IiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQ1JSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xMDQiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTGxhbWFkbyBwYXJhIHByZXNlbnRhY2nzbiBkZSB0cmFiYWpvcy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjIwIiBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyMCIgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGJnY29sb3I9IiNGRkZGRkYiIGNsYXNzPSJ0ZXh0b251ZXZvIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPgogICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iIyIgY2xhc3M9ImJvdG9uIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgPC90YWJsZT48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj4mbmJzcDs8L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBJTklDSU8gbm90YSBjb211biAtLT4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTUvMDQvMjAxMjwvc3Bhbj48YnI+T3JnYW5pemFuIGpvcm5hZGEgc29icmUgdmlvbGVuY2lhPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPlNlIGNlbnRyYXImYWFjdXRlOyBlbiBsb3MgZmVuJm9hY3V0ZTttZW5vcyBxdWUgYWZlY3RhbiBhIGxhIGZhbWlsaWEgeSBlbiBsbyBxdWUgb2N1cnJlIGVuIGxhcyBlc2N1ZWxhcy48YnIgLz4gU2UgbGxldmFyJmFhY3V0ZTsgYSBjYWJvIGVsIGx1bmVzIDIzLCBlbiBlbCBDZW50cm8gQ3VsdHVyYWwgZGUgVG9zY2hpIHkgVHJlcyANCkFycm95b3MsIHVuYSBqb3JuYWRhIGRlIHJlZmxleGkmb2FjdXRlO24geSBkZWJhdGUgYWJpZXJ0YSBhIGxhIGNvbXVuaWRhZCBzb2JyZSANCiZsZHF1bztWaW9sZW5jaWEgZW4gbGEgZmFtaWxpYSB5IGVuIGxhIGVzY3VlbGEgeSBzdSByZWxhY2kmb2FjdXRlO24gY29uIGVsIGZyYWNhc28gDQplc2NvbGFyJnJkcXVvOywgb3JnYW5pemFkYSBwb3IgbGEgQXNvY2lhY2kmb2FjdXRlO24gQ2l2aWwgQ2VudHJvIEFydCZlYWN1dGU7bWlkZXMgeSBsYSANCk11bmljaXBhbGlkYWQgZGUgQ2lwb2xsZXR0aS5TZSBjZW50cmFyJmFhY3V0ZTsgZW4gbG9zIGZlbiZvYWN1dGU7bWVub3MgcXVlIGFmZWN0YW4gYSBsYSBmYW1pbGlhIHkgZW4gbG8gcXVlIG9jdXJyZSBlbiBsYXMgZXNjdWVsYXMuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjMwLzAzLzIwMTI8L3NwYW4+PGJyPkNhcnRhIGRlIEFTQVBNSSAtIEFzb2NpYWNp824gQXJnZW50aW5hIGRlIFByZXZlbmNp824gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbDwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjE1IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSIxNSIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjgwIiBjb2xzcGFuPSI0IiBhbGlnbj0ibGVmdCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Mb3MgaW50ZWdyYW50ZXMgZGUgbGEgQ29taXNpJm9hY3V0ZTtuIERpcmVjdGl2YSBkZSBBU0FQTUkgLSBBc29jaWFjaSZvYWN1dGU7biBBcmdlbnRpbmEgZGUgUHJldmVuY2kmb2FjdXRlO24gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbCwgYXNvY2lhZGEgYSBsYSBJbnRlcm5hdGlvbmFsIFNvY2lldHkgZm9yIFByZXZlbnRpb24gb2YgQ2hpbGQgQWJ1c2UgYW5kIE5lZ2xlY3QgKElTUENBTikgLSwgdGVuZW1vcyBlbCBhZ3JhZG8gZGUgZGlyaWdpcm5vcyBhIFVzdGVkIHBhcmEgdHJhc21pdGlybGUgbnVlc3RyYSBwcm9mdW5kYSAmbmJzcDt5IGhvbmRhIHByZW9jdXBhY2kmb2FjdXRlO24gcG9yIGxhIHBvc3R1cmEgcXVlIHZpZW5lbiBhc3VtaWVuZG8gZW4gZm9ybWEgY29udGludWFkYSBhbGd1bm9zIGNvbGVnaW9zIGRlIHBzaWMmb2FjdXRlO2xvZ29zLCBlc3BlY2lhbG1lbnRlIGRlIGxhIHByb3ZpbmNpYSBkZSBCdWVub3MgQWlyZXMsIGVuIHJlbGFjaSZvYWN1dGU7biBhbCB0cmF0YW1pZW50byBwb2NvIHNlcmlvIHkgY29tcHJvbWV0aWRvIHF1ZSBzZSBsZXMgb3RvcmdhIGEgbGFzIGRlbnVuY2lhcyBlZmVjdHVhZGFzIGNvbnRyYSBwcm9mZXNpb25hbGVzIHBzaWMmb2FjdXRlO2xvZ29zLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjAvMDMvMjAxMjwvc3Bhbj48YnI+TEEgVklPTEVOQ0lBIFNFWFVBTCBDT05UUkEgTknRT1MgWSBOSdFBUyBFTiBDSUZSQVM8L3RkPgogICAgICAgICAgPC90cj4KICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkIHdpZHRoPSIxNSIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4MCIgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+UmFkaW9ncmFmJmlhY3V0ZTthIGRlIHVuIHByb2JsZW1hPC9wPg0KPHA+RGUgbG9zIG4mdWFjdXRlO21lcm9zIGNvbXBpbGFkb3MgcG9yIGRvcyBlcXVpcG9zIGRlbCBNaW5pc3RlcmlvIGRlIEp1c3RpY2lhLCBsYQ0KIGF1dG9yYSB0b21hIGxvcyBkZSBsYSBjaXVkYWQgZGUgQnVlbm9zIEFpcmVzIHBhcmEgdHJhemFyIHVuIHBhcmFkaWdtYSANCmRlIGxvcyBkZWxpdG9zIGNvbnRyYSBsYSBpbnRlZ3JpZGFkIHNleHVhbCBlbiBlbCBwYSZpYWN1dGU7cyB5IHNvYnJlIHN1IA0KYXRlbmNpJm9hY3V0ZTtuLjxiciAvPiA8YnIgLz4gJm5ic3A7UG9yIEV2YSBHaWJlcnRpPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2MCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjAiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjE1LzAzLzIwMTI8L3NwYW4+PGJyPkZBTExPIERFIExBIENPUlRFIFNVUFJFTUEgU09CUkUgTEEgTk8gSlVESUNJQUxJWkFDSU9OIERFTCBBQk9SVE8gRU4gQ0FTT1MgREUgVklPTEFDSU9OPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxiciAvPiBKVVJJU0RJQ0NJT046IE5BQ0lPTkFMPGJyIC8+IE1BVEVSSUE6IEFCT1JUTy48YnIgLz4gVFJJQlVOQUw6IENvcnRlIFN1cHJlbWEgZGUgSnVzdGljaWEgZGUgbGEgTmFjaSZvYWN1dGU7bi48YnIgLz4gQVVUT1M6IEYuLCBBLiBMLiBzLyBtZWRpZGEgYXV0b3NhdGlzZmFjdGl2YS48YnIgLz4gRkVDSEE6IDEzLzAzLzIwMTIuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI1OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNTkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBGSU4gbm90YSBjb211biAtLT4KPC90YWJsZT4KPG1hcCBuYW1lPSJNYXBNYXAiIGlkPSJNYXBNYXAiPjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjE0NCw0LDIxNCwzNiIgaHJlZj0iaW5kZXgucGhwP2lkPTE0IiAvPgo8L21hcD4KPG1hcCBuYW1lPSJNYXAyTWFwMiIgaWQ9Ik1hcDJNYXAyIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIxNDcsNCwyMjAsMzYiIGhyZWY9ImluZGV4LnBocD9pZD0xNGEiIC8+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcDMiIGlkPSJNYXAzIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIzNjMsMyw0MzYsMzkiIGhyZWY9ImluZGV4LnBocD9pZD0xNGIiIC8+CjwvbWFwPgo8L2h0bWw+CjwvdGQ+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gICAgICAgICAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFM0UzRTMiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSI3MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNiUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9kZWNpbG9fYmllbl9mdWVydGUxLmpwZyIgd2lkdGg9IjEyMCIgaGVpZ2h0PSIxMTIiPjwvdGQ+CiAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiA+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTI0IiBjbGFzcz0iYm90b24xIj5bK10gTSZhYWN1dGU7cyBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0UzRTNFMyI+ICAgICAgICA8L3RyPgogICAgICAgIDx0cj4gCiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj4mbmJzcDs8L3RkPgogICAgICAgIDwvdHI+CiAgICA8L3RhYmxlPjwvdGQ+CiAgPC90cj4KICA8dHI+IAogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSI+PGltZyBzcmM9ImltZy9penExLmpwZyIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjExNCIgLz48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9RdWllbmVzU29tb3NfQTJfMF8yNS5qcGciIHdpZHRoPSI4MDkiIGhlaWdodD0iMTE0IiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcDIiIC8+PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI1MCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiYWNrZ3JvdW5kPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzE4XzE4LmpwZyI+Jm5ic3A7PC90ZD4KICAgIDx0ZCBoZWlnaHQ9IjUwIiBjbGFzcz0iZm9uZG9ib3R0b20iPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2l0ZWkuY29tLmFyLyI+PGltZyBzcmM9ImltZy9laV9jb2xvci5wbmciIGFsdD0iZXNwYWNpb3MgZGUgaW1hZ2luYWNpb24sIGRlc2Fycm9sbG9zIGludGVyYWN0aXZvcywgY3JlYXRpdmlkYWQsIGRpc2XxbyIgd2lkdGg9IjI3IiBoZWlnaHQ9IjE1IiBib3JkZXI9IjAiPjwvYT4gPHNwYW4gY2xhc3M9ImVpIj48YSBocmVmPSJodHRwOi8vd3d3LnNpdGVpLmNvbS5hci8iIHNwYW4gY2xhc3M9ImVpIj5kaXNlJm50aWxkZTtvICsgY29tdW5pY2FjaSZvYWN1dGU7bjwvYT48L3NwYW4+PGVtPiZuYnNwOzwvZW0+PC9zcGFuPjxzcGFuIGNsYXNzPSJibGFuY28xIj48ZW0+Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7PC9lbT48L3NwYW4+PC90ZD4KICA8L3RyPgo8L3RhYmxlPgoKCjxtYXAgbmFtZT0iTWFwMiI+PGFyZWEgc2hhcGU9InJlY3QiIGNvb3Jkcz0iMjQ3LDY5LDQxNCw4MiIgaHJlZj0ibWFpbHRvOnNhbHVkYWN0aXZhQHNhbHVkYWN0aXZvLm9yZy5hciI+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcCI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM2LDE0MiwxNDksMTUyIiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MiI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM0LDE4NiwxNTAsMTk2IiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MCI+CjwvbWFwPgo8L2JvZHk+CjwvaHRtbD4K]]></response> | |
| 114 | <responseRedirected>false</responseRedirected> | |
| 115 | </requestresponse> | |
| 116 | </issue> | |
| 117 | <issue> | |
| 118 | <serialNumber>3685188967706670080</serialNumber> | |
| 119 | <type>5245440</type> | |
| 120 | <name>TRACE method is enabled</name> | |
| 121 | <host ip="200.20.20.201">http://www.example.org.ar</host> | |
| 122 | <path><![CDATA[/]]></path> | |
| 123 | <location><![CDATA[/]]></location> | |
| 124 | <severity>Information</severity> | |
| 125 | <confidence>Certain</confidence> | |
| 126 | <issueBackground><![CDATA[The TRACE method is designed for diagnostic purposes. If enabled, the web server will respond to requests which use the TRACE method by echoing in its response the exact request which was received.<br><br>Although this behavior is apparently harmless in itself, it can sometimes be leveraged to support attacks against other application users. If an attacker can find a way of causing a user to make a TRACE request, and can retrieve the response to that request, then the attacker will be able to capture any sensitive data which is included in the request by the user's browser, for example session cookies or credentials for platform-level authentication. This may exacerbate the impact of other vulnerabilities, such as cross-site scripting.]]></issueBackground> | |
| 127 | <remediationBackground><![CDATA[The TRACE method should be disabled on the web server.]]></remediationBackground> | |
| 128 | <requestresponse> | |
| 129 | <request base64="true"><![CDATA[VFJBQ0UgLyBIVFRQLzEuMA0KSG9zdDogd3d3LnNhbHVkYWN0aXZhLm9yZy5hcg0KQ29va2llOiBhYzMyNzQ2YjdhYzA2YzE5DQoNCg==]]></request> | |
| 130 | <response base64="true"><![CDATA[SFRUUC8xLjEgMjAwIE9LDQpEYXRlOiBUaHUsIDA3IE5vdiAyMDEzIDE3OjE0OjA2IEdNVA0KU2VydmVyOiBBcGFjaGUvMi4yLjIzIChVbml4KSBtb2Rfc3NsLzIuMi4yMyBPcGVuU1NMLzAuOS44ZS1maXBzLXJoZWw1DQpDb25uZWN0aW9uOiBjbG9zZQ0KQ29udGVudC1UeXBlOiBtZXNzYWdlL2h0dHANCg0KVFJBQ0UgLyBIVFRQLzEuMA0KSG9zdDogd3d3LnNhbHVkYWN0aXZhLm9yZy5hcg0KQ29va2llOiBhYzMyNzQ2YjdhYzA2YzE5OyBQSFBTRVNTSUQ9OTQ1ODVhYTBjMTFjZjJlODY0ZDgzZTI0Njc4Yjk4NjUNCg0K]]></response> | |
| 131 | <responseRedirected>false</responseRedirected> | |
| 132 | </requestresponse> | |
| 133 | </issue> | |
| 134 | <issue> | |
| 135 | <serialNumber>739390687228795904</serialNumber> | |
| 136 | <type>5245344</type> | |
| 137 | <name>Frameable response (potential Clickjacking)</name> | |
| 138 | <host ip="200.20.20.201">http://www.example.org.ar</host> | |
| 139 | <path><![CDATA[/]]></path> | |
| 140 | <location><![CDATA[/]]></location> | |
| 141 | <severity>Information</severity> | |
| 142 | <confidence>Firm</confidence> | |
| 143 | <issueBackground><![CDATA[It might be possible for a web page controlled by an attacker to load the content of this response within an iframe on the attacker's page. This may enable a "clickjacking" attack, in which the attacker's page overlays the target application's interface with a different interface provided by the attacker. By inducing victim users to perform actions such as mouse clicks and keystrokes, the attacker can cause them to unwittingly carry out actions within the application that is being targeted. This technique allows the attacker to circumvent defenses against cross-site request forgery, and may result in unauthorized actions.<br><br>Note that this issue is being reported because the application's response does not set a suitable <b>X-Frame-Options</b> header in order to prevent framing attacks. Some applications attempt to prevent these attacks from within the HTML page itself, using "framebusting" code. However, this type of defense is normally ineffective and can usually be circumvented by a skilled attacker.]]></issueBackground> | |
| 144 | <remediationBackground><![CDATA[You should review the application functions that are accessible from within the response, and determine whether they can be used by application users to perform any sensitive actions within the application. If so, then a framing attack targeting this response may result in unauthorized actions.<br><br>To effectively prevent framing attacks, the application should return a response header with the name <b>X-Frame-Options</b> and the value <b>DENY</b> to prevent framing altogether, or the value <b>SAMEORIGIN</b> to allow framing only by pages on the same origin as the response itself.]]></remediationBackground> | |
| 145 | <requestresponse> | |
| 146 | <request base64="true"><![CDATA[R0VUIC8gSFRUUC8xLjENCkhvc3Q6IHd3dy5zYWx1ZGFjdGl2YS5vcmcuYXINClVzZXItQWdlbnQ6IE1vemlsbGEvNS4wIChNYWNpbnRvc2g7IEludGVsIE1hYyBPUyBYIDEwLjg7IHJ2OjIzLjApIEdlY2tvLzIwMTAwMTAxIEZpcmVmb3gvMjMuMA0KQWNjZXB0OiB0ZXh0L2h0bWwsYXBwbGljYXRpb24veGh0bWwreG1sLGFwcGxpY2F0aW9uL3htbDtxPTAuOSwqLyo7cT0wLjgNCkFjY2VwdC1MYW5ndWFnZTogZW4tVVMsZW47cT0wLjUNCkFjY2VwdC1FbmNvZGluZzogZ3ppcCwgZGVmbGF0ZQ0KQ29ubmVjdGlvbjoga2VlcC1hbGl2ZQ0KDQo=]]></request> | |
| 147 | <response base64="true"><![CDATA[SFRUUC8xLjEgMjAwIE9LDQpEYXRlOiBUaHUsIDA3IE5vdiAyMDEzIDE3OjEyOjAyIEdNVA0KU2VydmVyOiBBcGFjaGUvMi4yLjIzIChVbml4KSBtb2Rfc3NsLzIuMi4yMyBPcGVuU1NMLzAuOS44ZS1maXBzLXJoZWw1DQpYLVBvd2VyZWQtQnk6IFBIUC81LjIuMTcNCkV4cGlyZXM6IFRodSwgMTkgTm92IDE5ODEgMDg6NTI6MDAgR01UDQpDYWNoZS1Db250cm9sOiBuby1zdG9yZSwgbm8tY2FjaGUsIG11c3QtcmV2YWxpZGF0ZSwgcG9zdC1jaGVjaz0wLCBwcmUtY2hlY2s9MA0KUHJhZ21hOiBuby1jYWNoZQ0KU2V0LUNvb2tpZTogUEhQU0VTU0lEPTk0NTg1YWEwYzExY2YyZTg2NGQ4M2UyNDY3OGI5ODY1OyBwYXRoPS8NCktlZXAtQWxpdmU6IHRpbWVvdXQ9MjAsIG1heD0yMDANCkNvbm5lY3Rpb246IEtlZXAtQWxpdmUNCkNvbnRlbnQtVHlwZTogdGV4dC9odG1sDQpDb250ZW50LUxlbmd0aDogNjA2MDYNCg0KIDxoZWFkPgo8bWV0YSBodHRwLWVxdWl2PSJDb250ZW50LVR5cGUiIGNvbnRlbnQ9InRleHQvaHRtbDsgY2hhcnNldD1pc28tODg1OS0xIiAvPgo8dGl0bGU+U2FsdWQgQWN0aXZhIC0gQWJ1c28gdmlvbGVuY2lhIHkgbWFsdHJhdG88L3RpdGxlPgoKPHNjcmlwdD4gCiAgICAvL2VzdG8gcGFyYSBwYXNhcmxlIGFsIGZsYXNoIGxhcyB2YXJpYWxiZXMgZGVsIHBocAogCQoKCXZhciBib3Q9Jyc7Ci8vYWxlcnQodmFyaWFibGVTZXJ2aWRvcik7Cjwvc2NyaXB0Pgo8c2NyaXB0IGxhbmd1YWdlPSJKYXZhU2NyaXB0IiB0eXBlPSJ0ZXh0L0phdmFTY3JpcHQiPgo8IS0tCmZ1bmN0aW9uIE1NX3ByZWxvYWRJbWFnZXMoKSB7IC8vdjMuMAogIHZhciBkPWRvY3VtZW50OyBpZihkLmltYWdlcyl7IGlmKCFkLk1NX3ApIGQuTU1fcD1uZXcgQXJyYXkoKTsKICAgIHZhciBpLGo9ZC5NTV9wLmxlbmd0aCxhPU1NX3ByZWxvYWRJbWFnZXMuYXJndW1lbnRzOyBmb3IoaT0wOyBpPGEubGVuZ3RoOyBpKyspCiAgICBpZiAoYVtpXS5pbmRleE9mKCIjIikhPTApeyBkLk1NX3Bbal09bmV3IEltYWdlOyBkLk1NX3BbaisrXS5zcmM9YVtpXTt9fQp9Ci8vLS0+Cjwvc2NyaXB0Pgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KCjwvaGVhZD4KCjxzY3JpcHQgbGFuZ3VhZ2U9IkphdmFTY3JpcHQiIHR5cGU9InRleHQvSmF2YVNjcmlwdCI+CjwhLS0KZnVuY3Rpb24gTU1fcmVsb2FkUGFnZShpbml0KSB7ICAvL3JlbG9hZHMgdGhlIHdpbmRvdyBpZiBOYXY0IHJlc2l6ZWQKICBpZiAoaW5pdD09dHJ1ZSkgd2l0aCAobmF2aWdhdG9yKSB7aWYgKChhcHBOYW1lPT0iTmV0c2NhcGUiKSYmKHBhcnNlSW50KGFwcFZlcnNpb24pPT00KSkgewogICAgZG9jdW1lbnQuTU1fcGdXPWlubmVyV2lkdGg7IGRvY3VtZW50Lk1NX3BnSD1pbm5lckhlaWdodDsgb25yZXNpemU9TU1fcmVsb2FkUGFnZTsgfX0KICBlbHNlIGlmIChpbm5lcldpZHRoIT1kb2N1bWVudC5NTV9wZ1cgfHwgaW5uZXJIZWlnaHQhPWRvY3VtZW50Lk1NX3BnSCkgbG9jYXRpb24ucmVsb2FkKCk7Cn0KTU1fcmVsb2FkUGFnZSh0cnVlKTsKLy8tLT4KCjwvc2NyaXB0Pgo8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoKCjwvaGVhZD4KCjxib2R5IGJhY2tncm91bmQ9ImltZy9mb25kb19kZWdyYWRlLmpwZyIgdG9wbWFyZ2luPSIwIj4KPHRhYmxlIHdpZHRoPSIxMDA1IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgPHRyPiAKICAgIDx0ZCB3aWR0aD0iOTYiPjxpbWcgc3JjPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzBfMDEuanBnIiB3aWR0aD0iOTYiIGhlaWdodD0iMjA4IiAvPjwvdGQ+CiAgICA8dGQgd2lkdGg9IjgwOSI+IDxzY3JpcHQgdHlwZT0idGV4dC9qYXZhc2NyaXB0Ij4KQUNfRkxfUnVuQ29udGVudCggJ2NvZGViYXNlJywnaHR0cDovL2Rvd25sb2FkLm1hY3JvbWVkaWEuY29tL3B1Yi9zaG9ja3dhdmUvY2Ficy9mbGFzaC9zd2ZsYXNoLmNhYiN2ZXJzaW9uPTcsMCwxOSwwJywnd2lkdGgnLCc4MDknLCdoZWlnaHQnLCcyMDgnLCdzcmMnLCdzd2YvaGVhZGVyJywncXVhbGl0eScsJ2hpZ2gnLCdwbHVnaW5zcGFnZScsJ2h0dHA6Ly93d3cubWFjcm9tZWRpYS5jb20vZ28vZ2V0Zmxhc2hwbGF5ZXInLCdtb3ZpZScsJ3N3Zi9oZWFkZXInICk7IC8vZW5kIEFDIGNvZGUKPC9zY3JpcHQ+IDxub3NjcmlwdD4KICAgICAgPG9iamVjdCBjbGFzc2lkPSJjbHNpZDpEMjdDREI2RS1BRTZELTExY2YtOTZCOC00NDQ1NTM1NDAwMDAiIGNvZGViYXNlPSJodHRwOi8vZG93bmxvYWQubWFjcm9tZWRpYS5jb20vcHViL3Nob2Nrd2F2ZS9jYWJzL2ZsYXNoL3N3Zmxhc2guY2FiI3ZlcnNpb249NywwLDE5LDAiIHdpZHRoPSI4MDkiIGhlaWdodD0iMjA4Ij4KICAgICAgICA8cGFyYW0gbmFtZT0ibW92aWUiIHZhbHVlPSJzd2YvaGVhZGVyLnN3ZiIgLz4KICAgICAgICA8cGFyYW0gbmFtZT0icXVhbGl0eSIgdmFsdWU9ImhpZ2giIC8+CiAgICAgICAgPGVtYmVkIHNyYz0ic3dmL2hlYWRlci5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9IjgwOSIgaGVpZ2h0PSIyMDgiPjwvZW1iZWQ+IAogICAgICA8L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIHdpZHRoPSIxMiUiIHJvd3NwYW49IjUiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iIzAwMDAwMCI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI0NjEiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmFja2dyb3VuZD0iaW1nL1F1aWVuZXNTb21vc19BMl8wXzEzLmpwZyI+IAogICAgICA8c2NyaXB0IHR5cGU9InRleHQvamF2YXNjcmlwdCI+CkFDX0ZMX1J1bkNvbnRlbnQoICdjb2RlYmFzZScsJ2h0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCcsJ3dpZHRoJywnOTYnLCdoZWlnaHQnLCc0NjEnLCdzcmMnLCdzd2Yvc3VibWVudScsJ3F1YWxpdHknLCdoaWdoJywncGx1Z2luc3BhZ2UnLCdodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyJywnbW92aWUnLCdzd2Yvc3VibWVudScgKTsgLy9lbmQgQUMgY29kZQo8L3NjcmlwdD4gPG5vc2NyaXB0PgogICAgICA8b2JqZWN0IGNsYXNzaWQ9ImNsc2lkOkQyN0NEQjZFLUFFNkQtMTFjZi05NkI4LTQ0NDU1MzU0MDAwMCIgY29kZWJhc2U9Imh0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+CiAgICAgICAgPHBhcmFtIG5hbWU9Im1vdmllIiB2YWx1ZT0ic3dmL3N1Ym1lbnUuc3dmIiAvPgogICAgICAgIDxwYXJhbSBuYW1lPSJxdWFsaXR5IiB2YWx1ZT0iaGlnaCIgLz4KICAgICAgICA8ZW1iZWQgc3JjPSJzd2Yvc3VibWVudS5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+PC9lbWJlZD48L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCIgYmdjb2xvcj0iI0ZGRkZGRiI+CiAgICAgICAgPHRyPiAKICAgICAgICAgIDx0ZCB3aWR0aD0iMTciIHJvd3NwYW49IjciPjxwPiZuYnNwOzwvcD48L3RkPgogICAgICAgICAgPHRkIHdpZHRoPSIxNzIiIGFsaWduPSJjZW50ZXIiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxpbWcgc3JjPSJpbWcvM3B4LmpwZyIgd2lkdGg9IjUiIGhlaWdodD0iNSI+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciI+PGxpbmsgaHJlZj0iLi4vZXN0aWxvcy5jc3MiIHJlbD0ic3R5bGVzaGVldCIgdHlwZT0idGV4dC9jc3MiIC8+Cjxib2R5IGJnY29sb3I9IiNDQ0NDQ0MiIHRvcG1hcmdpbj0iNiBweCI+PHRhYmxlIHdpZHRoPSIxNjUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIzIiBiZ2NvbG9yPSIjRkZGRkZGIj4KPHRyPgogICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTkxIiBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiAgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MThfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+SG9tZTwvYT48L3RkPgogIDwvdHI+Cjx0cj4KICA8dGQgaGVpZ2h0PSIyOCIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj4mbmJzcDsmbmJzcDtOb3RpY2lhczwvYT48L3RkPgo8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJkb25hY2lvbmVzLyIgdGFyZ2V0PSJfYmxhbmsiIGNsYXNzPSJmb25kb2JvdG9uIj5Eb25hY2lvbmVzPC9hPjwvdGQ+CiAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciICB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yM19uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5IaXN0b3JpYWwgZGUgbmV3c2xldHRlcnM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTEzYSIgY2xhc3M9ImZvbmRvYm90b24iPkVudmlhciBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yNl9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5WZXIgdHJhYmFqb3MgZGUgdXN1YXJpb3M8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MTZfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+U2FsdWQgQWN0aXZhIHByZW5zYTwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJtYWlsdG86c2FsdWRhY3RpdmFAc2FsdWRhY3RpdmEub3JnLmFyIiBjbGFzcz0iZm9uZG9ib3RvbiI+TWFuZCZhYWN1dGU7IHR1IEMuVi48L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgIHdpZHRoPSI2ImhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTIxX25ldyIgY2xhc3M9ImZvbmRvYm90b24iPkluZm9ybWFjaSZvYWN1dGU7biBkZSBpbnRlciZlYWN1dGU7czwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyI+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiBoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xMF80IiBjbGFzcz0iZm9uZG9ib3RvbiI+Q29uZ3Jlc29zCiAgICAgICAgICAgICAgICAgIHkgSm9ybmFkYXM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTExIiBjbGFzcz0iZm9uZG9ib3RvbiI+UmVnaXN0cmFjaSZvYWN1dGU7bjwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgCiAgICAgICAgICA8L3RhYmxlPgo8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNSIgdGFyZ2V0PSJfYmxhbmsiPjxicj4KICAgICAgICAgICAgICAgICAgPGltZyBzcmM9ImltZy9iYW5uZXJfZG9uYWNpb25lcy5qcGciIHdpZHRoPSIxNjIiIGhlaWdodD0iMTIwIiBib3JkZXI9IjAiPjxicj4KICAgICAgICAgICAgICAgICAgPGJyPgogICAgICAgICAgICAgICAgICA8aW1nIHNyYz0iaW1nL2JvdG9uRm9yby5naWYiIHdpZHRoPSIxNzIiIGhlaWdodD0iMTE3IiBib3JkZXI9IjAiPjwvYT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTY3IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjkiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzAzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iOSIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTQ5IiBiYWNrZ3JvdW5kPSJpbWcvY2hpY29zX3BlcmRpZG9zXzA1LmdpZiI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDUuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMCI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDcuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMi5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEyLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9InNyYy9pbWdfdXAvMjMwODIwMTIuMS5qcGciIHdpZHRoPSIxNDkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMy5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNi5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iNSIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTcuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNy5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgYmdjb2xvcj0iI0ZFRTdDRiIgY2xhc3M9InRpdHVsb2hvbWU1Ij48c3Ryb25nPk5pJm50aWxkZTtvcyBwZXJkaWRvczxicj4KICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0yOSIgY2xhc3M9ImJvdG9uIj5bVmVyIG0mYWFjdXRlO3NdPC9hPjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTkuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xOS5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18yMC5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iMjUiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4NCgkJCQkNCgkJCQk8Zm9ybSBhY3Rpb249ImluZGV4LnBocD9pZD0xMSIgIG1ldGhvZD0icG9zdCI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9penExLmpwZyIgd2lkdGg9IjEyIiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9hcnJpYmEuanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9kZXIxLmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgIDwvdHI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiIgdmFsaWduPSJ0b3AiIGNsYXNzPSJyZWdGb25kbzEiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9penEuanBnIiB3aWR0aD0iMTIiIGhlaWdodD0iMTIiIC8+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSI5NCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV90aXQuanBnIiB3aWR0aD0iNjYiIGhlaWdodD0iMjMiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSI1MCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJyZWdpc3RyYXJzZSI+SW5ncmVzJmFhY3V0ZTsgDQogICAgICAgICAgICAgIHR1cyBkYXRvcyB5IHJlY2liJmlhY3V0ZTsgbGEgbWVqb3IgaW5mb3JtYWNpJm9hY3V0ZTtuIGEgdHJhdiZlYWN1dGU7cyANCiAgICAgICAgICAgICAgZGUgbnVlc3RybzxzdHJvbmc+IE5ld3NsZXR0ZXI8L3N0cm9uZz4uIDxzdHJvbmc+PHNwYW4gY2xhc3M9ImdyYXRpcyI+R3JhdGlzITwvc3Bhbj48L3N0cm9uZz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI1IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9InRyYWJTRUNDSU9OIj5Ob21icmU8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBjbGFzcz0icmVnQ0VMREEiPjxpbnB1dCBuYW1lPSJub21icmUiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0ibm9tYnJlIiAvPjwvdGQ+DQogICAgICAgICAgPC90cj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0idHJhYlNFQ0NJT04iPkFwZWxsaWRvPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iYXBlbGxpZG8iIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iYXBlbGxpZG8iIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJ0cmFiU0VDQ0lPTiI+RS1tYWlsPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iZW1haWwiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iZW1haWwiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InRyYWJTRUNDSU9OIj4mbmJzcDs8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idHJhYlNFQ0NJT04iPjxpbnB1dCB0eXBlPSJpbWFnZSIgc3JjPSJpbWcvcmVnaXN0cmF0ZV9ib3Rvbi5qcGciIHdpZHRoPSIxMTciIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgIDwvdGFibGU+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE0IiB2YWxpZ249InRvcCIgY2xhc3M9InJlZ0ZvbmRvMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2Rlci5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIxNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KICAgICAgICAgICAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTIiIGhlaWdodD0iMjQiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfaXpxMi5qcGciIHdpZHRoPSIxMiIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI0Ij48aW1nIHNyYz0iaW1nL3JlZ2lzdHJhdGVfYWJham8uanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjI0IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfZGVyMi5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KCQkJCQkNCgkJCQkJPC9mb3JtPg0KICAgICAgICAgICAgICAgICAgPC90YWJsZT4NCjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPiAKICAgICAgICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTcwIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUyIj4KCQkJCQkJCQkJCQkJCQkJCTwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9jbGF1ZGlhMl8wMy5qcGciIHdpZHRoPSIxNzQiIGhlaWdodD0iMjUwIiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcCI+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICA8dGQgcm93c3Bhbj0iNyIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nLzV4NS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjciPjwvdGQ+CiAgICAgICAgICA8dGQgY29sc3Bhbj0iMiIgcm93c3Bhbj0iNCIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPGZvcm0gYWN0aW9uPSJsb2dpbi5waHAiIG1ldGhvZD0icG9zdCIgbmFtZT0iZm9ybTIiPgoKICAgICAgICAgICAgICA8dHI+IAogICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgY29sc3Bhbj0iMiIgYWxpZ249ImxlZnQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIiA+IAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8c3Ryb25nPlVzdWFyaW8gbm8gcmVnaXN0cmFkbzwvc3Ryb25nPiAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9mb250PiA8L3N0cm9uZz4gCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDkiIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPlVzdWFyaW8mbmJzcDsmbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzOSIgdmFsaWduPSJtaWRkbGUiPjxpbnB1dCBuYW1lPSJ1c3VhcmlvIiB0eXBlPSJ0ZXh0IiBjbGFzcz0icmVnIiBpZD0idXN1YXJpbyIgc2l6ZT0iNyI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjciIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPkNvbnRyYXNlJm50aWxkZTthJm5ic3A7Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzkiIHZhbGlnbj0ibWlkZGxlIj48aW5wdXQgbmFtZT0icGFzcyIgdHlwZT0icGFzc3dvcmQiIGNsYXNzPSJyZWciIGlkPSJwYXNzIiBzaXplPSI3Ij48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiIgYWxpZ249InJpZ2h0IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9ImJvdG9uIj48aW5wdXQgdHlwZT0iaW1hZ2UiIHNyYz0iaW1nL3JlZy5qcGciIHdpZHRoPSI1OCIgaGVpZ2h0PSIzMCI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjciIGhlaWdodD0iMTkiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgPjxhIGhyZWY9Imh0dHA6Ly93d3cuZmFjZWJvb2suY29tL2hvbWUucGhwPyMhL3BhZ2VzL01lcmxvLUFyZ2VudGluYS9TQUxVRC1BQ1RJVkEvMTAwNTgzNTQzMzE3MzIyP3JlZj10cyZhamF4cGlwZT0xJl9fYT03IiB0YXJnZXQ9Il9ibGFuayI+PGltZyBzcmM9ImltZy9mYWNlYm9vay5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzExIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj48ZGl2IGFsaWduPSJsZWZ0Ij48YSBocmVmPSJodHRwOi8vdHdpdHRlci5jb20vU2FsdWRBY3RpdmFPTkciIHRhcmdldD0iX2JsYW5rIj48aW1nIHNyYz0iaW1nL3R3aXRlci5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC9kaXY+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSI1IiBhbGlnbj0icmlnaHQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIj48bGFiZWw+PGZvbnQgc2l6ZT0iLTYiPlNpCiAgICAgICAgICAgICAgICAgICAgICAgdG9kYXYmaWFjdXRlO2Egbm8gZXMgdXN1YXJpbyA8L2ZvbnQ+IDxhIGhyZWY9ImluZGV4LnBocD9pZD0xMSIgY2xhc3M9ImJvdG9uIj48Zm9udCBzaXplPSItNiI+cmVnJmlhY3V0ZTtzdHJlc2UKICAgICAgICAgICAgICAgICAgICAgICAgYXF1JmlhY3V0ZTsgPGZvbnQgY29sb3I9IiM2NjY2NjYiPiYjODIyNjs8L2ZvbnQ+PC9mb250PjwvYT4gPGEgaHJlZj0iaW5kZXgucGhwP2lkPTEyIiBjbGFzcz0iYm90b24xIj48Zm9udCBzaXplPSItNiI+b2x2aWRlIG1pIGNvbnRyYXNlJm50aWxkZTthPC9mb250PjwvYT48L2xhYmVsPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE3Ij4mbmJzcDsgPC90ZD4KICAgICAgICAgICAgICA8L3RyPgoJCQkgIDwvZm9ybT4KCiAgICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgICA8IURPQ1RZUEUgaHRtbCBQVUJMSUMgIi0vL1czQy8vRFREIFhIVE1MIDEuMCBUcmFuc2l0aW9uYWwvL0VOIiAiaHR0cDovL3d3dy53My5vcmcvVFIveGh0bWwxL0RURC94aHRtbDEtdHJhbnNpdGlvbmFsLmR0ZCI+CjxodG1sIHhtbG5zPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hodG1sIj4KPGhlYWQ+CjxtZXRhIGh0dHAtZXF1aXY9IkNvbnRlbnQtVHlwZSIgY29udGVudD0idGV4dC9odG1sOyBjaGFyc2V0PWlzby04ODU5LTEiIC8+Cjx0aXRsZT5Eb2N1bWVudG8gc2luIHQmaWFjdXRlO3R1bG88L3RpdGxlPgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KPHNjcmlwdCBsYW5ndWFnZT0iSmF2YVNjcmlwdCIgdHlwZT0idGV4dC9KYXZhU2NyaXB0Ij4KPCEtLQpmdW5jdGlvbiBNTV9yZWxvYWRQYWdlKGluaXQpIHsgIC8vcmVsb2FkcyB0aGUgd2luZG93IGlmIE5hdjQgcmVzaXplZAogIGlmIChpbml0PT10cnVlKSB3aXRoIChuYXZpZ2F0b3IpIHtpZiAoKGFwcE5hbWU9PSJOZXRzY2FwZSIpJiYocGFyc2VJbnQoYXBwVmVyc2lvbik9PTQpKSB7CiAgICBkb2N1bWVudC5NTV9wZ1c9aW5uZXJXaWR0aDsgZG9jdW1lbnQuTU1fcGdIPWlubmVySGVpZ2h0OyBvbnJlc2l6ZT1NTV9yZWxvYWRQYWdlOyB9fQogIGVsc2UgaWYgKGlubmVyV2lkdGghPWRvY3VtZW50Lk1NX3BnVyB8fCBpbm5lckhlaWdodCE9ZG9jdW1lbnQuTU1fcGdIKSBsb2NhdGlvbi5yZWxvYWQoKTsKfQpNTV9yZWxvYWRQYWdlKHRydWUpOwoKZnVuY3Rpb24gTU1fcHJlbG9hZEltYWdlcygpIHsgLy92My4wCiAgdmFyIGQ9ZG9jdW1lbnQ7IGlmKGQuaW1hZ2VzKXsgaWYoIWQuTU1fcCkgZC5NTV9wPW5ldyBBcnJheSgpOwogICAgdmFyIGksaj1kLk1NX3AubGVuZ3RoLGE9TU1fcHJlbG9hZEltYWdlcy5hcmd1bWVudHM7IGZvcihpPTA7IGk8YS5sZW5ndGg7IGkrKykKICAgIGlmIChhW2ldLmluZGV4T2YoIiMiKSE9MCl7IGQuTU1fcFtqXT1uZXcgSW1hZ2U7IGQuTU1fcFtqKytdLnNyYz1hW2ldO319Cn0KLy8tLT4KPC9zY3JpcHQ+CiAgICAgICAgICAgICA8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoJCQkgCjxzdHlsZSB0eXBlPSJ0ZXh0L2NzcyI+CjwhLS0KI0xheWVyMSB7Cglwb3NpdGlvbjphYnNvbHV0ZTsKCXdpZHRoOjY1MXB4OwoJaGVpZ2h0OjIxOHB4OwoJei1pbmRleDoxOwp9CiNMYXllcjIgewoJcG9zaXRpb246YWJzb2x1dGU7Cgl3aWR0aDoyMDBweDsKCWhlaWdodDoxMTVweDsKCXotaW5kZXg6MTsKCXZpc2liaWxpdHk6IHZpc2libGU7Cn0KLkVzdGlsbzEgewoJZm9udC1zaXplOiAxOHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzIgewoJZm9udC1zaXplOiAxNHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzMge2NvbG9yOiAjNTA2OTkwOyBsaW5lLWhlaWdodDogMTJweDsgdGV4dC1kZWNvcmF0aW9uOiBub25lOyBmb250LWZhbWlseTogVGFob21hO30KLS0+Cjwvc3R5bGU+CjwvaGVhZD4KCjxib2R5IGxlZnRtYXJnaW49IjIiIG1hcmdpbndpZHRoPSIyIj4KPHRhYmxlIHdpZHRoPSI2MDgiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICA8dHI+CiAgICA8dGQgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCB3aWR0aD0iMiUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzA3LmpwZyIgd2lkdGg9IjI0IiBoZWlnaHQ9IjE0IiAvPjwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI5MCUiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18wNy5qcGciPiZuYnNwOzwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI4JSIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wOS5qcGciIHdpZHRoPSI0NSIgaGVpZ2h0PSIxNyIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogIDwvdHI+CiAgPHRyPgogICAgPHRkIGNvbHNwYW49IjQiPjxiciAvPgogICAgICA8dGFibGUgd2lkdGg9Ijk4JSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICA8dHI+CiAgICAgICAgPHRkIHdpZHRoPSIyJSI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgICA8dGQgd2lkdGg9IjkzJSI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CjwhLS0gSU5JQ0lPIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzIzMDQyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjIvMTEvMjAxMzwvc3Bhbj48YnI+SVYgQ29uZ3Jlc28gSW50ZXJuYWNpb25hbCB2aW9sZW5jaWEsIG1hbHRyYXRvIHkgYWJ1c288L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxzdHJvbmc+MTQsIDE1IHkgMTYgZGUgTm92aWVtYnJlIEFCSUVSVEEgTEEgSU5TQ1JJUENJJk9hY3V0ZTtOISAoY29uIGRlc2N1ZW50byBoYXN0YSBlbCAyNy84KTxiciAvPjwvc3Ryb25nPjwvcD4NCjxwPjxzdHJvbmc+QUJJRVJUQSBMQSBSRUNFUENJJk9hY3V0ZTtOIERFIFRSQUJBSk88YSBocmVmPSJodHRwOi8vd3d3LmNvbmdyZXNvdmlvbGVuY2lhLmNvbS9pbmRleC5waHA/aWQ9bW9kYWxpZGFkZXMiIHRhcmdldD0iX2JsYW5rIj4gKG1hcyBpbmZvKTwvYT48L3N0cm9uZz48L3A+DQo8cD48c3BhbiBzdHlsZT0iY29sb3I6ICNmZjY2MDA7Ij48c3Ryb25nPk9yZ2FuaXphOiBTYWx1ZCBBY3RpdmE8L3N0cm9uZz48L3NwYW4+PC9wPg0KPHA+PHNwYW4gc3R5bGU9ImNvbG9yOiAjZmY2NjAwOyI+SW5jcmlwdG9zIGFsIFBvcnRhbCBkZSBTYWx1ZCBBY3RpdmEsIGltcG9ydGFudGVzIGRlc2N1ZW50b3MhPGJyIC8+PC9zcGFuPjwvcD4NCjxwPkx1Z2FyIGRlIFJlYWxpemFjaSZvYWN1dGU7biB5IGNvbGFib3JhY2lvbjogVW5pdmVyc2lkYWQgZGVsIEVzdGUsIExhIFBsYXRhIEJ1ZW5vcyBBaXJlczwvcD4NCjxwPk1hcyBkZSAxNTAgdHJhYmFqb3MgcHJlc2VudGFkb3MsIHVsdGltb3MgZGlhcyBwYXJhIGluc2NyaWJpcnNlIGNvbiBkZXNjdWVudG8hITwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPkluc2NyaWJpcnNlPC9hPjwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPjxiciAvPjwvYT48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAxIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDEiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MDQvMTEvMjAxMzwvc3Bhbj48YnI+RWwgY29sZWdpbyBkZSBQc2lj82xvZ29zIGRlIEPzcmRvYmEgc2UgcHJvbnVuY2lhIGVuIHJlbGFjafNuIGFsIFNBUCB5IGVuIGNvbmNvcmRhbmNpYSBjb24gbG8gZXhwcmVzYWRvIHBvciBlbCBDb2xlZ2lvIGRlIFBzaWPzbG9nb3MgZGUgTWFyIGRlbCBQbGF0YSB5IGVsIENvbGVnaW8gZGUgUHNpY/Nsb2dvcyBkZSBsYSAgUHJvdmluY2lhIGRlIEJ1ZW5vcyBBaXJlczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+Jm5ic3A7PC9wPg0KPHA+TGFzIGNvbnRyb3ZlcnNpYXMgZ2VuZXJhZGFzIGVuIHJlbGFjaSZvYWN1dGU7biBhbCAic2luZHJvbWUgZGUgYWxpZW5hY2kmb2FjdXRlO24gcGFyZW50YSIgU0FQLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMxMCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzEwIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzE2MTAyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTYvMTAvMjAxMzwvc3Bhbj48YnI+U2FsdWQgQWN0aXZhIG90b3JnYSBtZWRpYXMgYmVjYXMgcGFyYSBlbCBJViBDb25ncmVzbyBJbnRlcm5hY2lvbmFsLCBWIE5hY2lvbmFsLCBWSSBSZWdpb25hbCBWaW9sZW5jaWEsIE1hbHRyYXRvIHkgQWJ1c28uPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD4mbmJzcDs8L3A+DQo8cD5TZXImYWFjdXRlO24gb3RvcmdhZGFzIDUwIG1lZGlhcyBiZWNhcywgcXVlZGFuIHBvY2FzISEhIGNvbmRpY2lvbjo8L3A+DQo8cD5QZXJ0ZW5lY2VyIGFsIGFtYml0byBwdWJsaWNvIG8gYSBPTkcsIHNlIGNvbnNpZGVyYSB0YW1iaWVuIGxhIGRpc3RhbmNpYSBhbCBsdWdhciBkZWwgZXZlbnRvISEhIGVzIG11eSBzZW5jaWxsbywgc29sbyBkZWJlcyBlbnZpYXIgdW4gZW1haWwuLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwOSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA5Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjI0LzA3LzIwMTM8L3NwYW4+PGJyPk5FQ0VTSVRBTU9TIERFIFNVIFNPTElEQVJJREFEIEhBQ0lBIExPUyBOSdFPUyBZIE5J0UFTISEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPlBST0dSQU1BIEZBTUlMSUFTIFNPTElEQVJJQVM8L3NwYW4+PC9zdHJvbmc+PC9wPg0KPHA+PHN0cm9uZz5DQU1CSU8gREUgU0VERTwvc3Ryb25nPjwvcD4NCjxwPkxhIGNhcGFjaXRhY2kmb2FjdXRlO24gcGFyYSBsYSBwdWVzdGEgZW4gbWFyY2hhIGRlbCA8c3Ryb25nPlByb2dyYW1hIEZhbWlsaWFzIFNvbGlkYXJpYXM8L3N0cm9uZz4gc2UgcmVhbGl6YXImYWFjdXRlOyBlbiBsYSBsb2NhbGlkYWQgZGUgPHN0cm9uZz5OYXZhcnJvPC9zdHJvbmc+IHBhcmEgdG9kbyBlbCBjb3JyZWRvciBkZSBsYSBSdXRhIDQwLjwvcD4NCjxwPkluaWNpbyA8c3Ryb25nPk1pJmVhY3V0ZTtyY29sZXMgMjggZGUgYWdvc3RvIGEgbGFzIDE0IGhvcmFzLiZuYnNwOzwvc3Ryb25nPjwvcD4NCjxwPlNlZGU6IDxzdHJvbmc+U2FsJm9hY3V0ZTtuIE11bmljaXBhbCBlbiBsYSBjYWxsZSAxMDcgZXNxdWluYSAyMiAtIE5hdmFycm88L3N0cm9uZz48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA4Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTIwNzIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xMi8wNy8yMDEzPC9zcGFuPjxicj5TQUxVRCBBQ1RJVkEgaGEgc2lkbyBlbGVnaWRhIHBvciBzZWd1bmRhIHZleiBjb25zZWN1dGl2YSBjb21vIHVubyBkZSBsb3MgZ2FuYWRvcmVzIGRlbCBDdWFydG8gQ29uY3Vyc28gZGUgUHJveWVjdG9zIFNvY2lhbGVzIGRlIFBldHJvYnJhczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+RW4gZWwgbWFyY28gZGVsIEN1YXJ0byBDb25jdXJzbyBkZSBQcm95ZWN0b3MgU29jaWFsZXMgZGUgUGV0cm9icmFzLCANCm51ZXN0cmEgSW5zdGl0dWNpJm9hY3V0ZTtuIFNBTFVEIEFDVElWQSBoYSBzaWRvIGVsZWdpZGEgcG9yIHNlZ3VuZGEgdmV6IA0KY29uc2VjdXRpdmEgY29tbyB1bm8gZGUgbG9zIGdhbmFkb3JlcyBkZSBkaWNobyBjb25jdXJzby48YnIgLz5FbiBlc3RhIA0KZWRpY2kmb2FjdXRlO24gZWwgcHJveWVjdG8gcXVlIGhhIHNpZG8gZWxlZ2lkbyBlcyBlbCAmbGRxdW87UHJvZ3JhbWEgZGUgRmFtaWxpYXMgDQpTb2xpZGFyaWFzJnJkcXVvOyBzaWVuZG8gc3UgJmFhY3V0ZTtyZWEgZGUgaW1wbGVtZW50YWNpJm9hY3V0ZTtuIGxvcyBNdW5pY2lwaW9zIGRlIE5hdmFycm8sIA0KR3JhbC4gTGFzIEhlcmFzLCBNYXJjb3MgUGF6LCB5IE1lcmxvPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAyLzA3LzIwMTM8L3NwYW4+PGJyPk/tciBvIGVzY3VjaGFyPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Qb3IgQ2FybG9zIFJvemFuc2tpICo8L3A+DQo8cD5BIGxvIGxhcmdvIGRlIGxvcyBzaWdsb3MsIGxhcyBuaSZudGlsZGU7YXMsIG5pJm50aWxkZTtvcyB5IGFkb2xlc2NlbnRlcyBoYW4gc2lkbyBtYWx0cmF0YWRvcyB5IGFidXNhZG9zIHNpbiBxdWUgYSBsYSBjb211bmlkYWQgbGUgaW50ZXJlc2FyYSBuaSBzaXF1aWVyYSBlc2N1Y2hhcmxvcyBjdWFuZG8gaGFjJmlhY3V0ZTthbiBzYWJlciBkZSBhbGd1bmEgZm9ybWEgbG9zIHN1ZnJpbWllbnRvcyBxdWUgcGFkZWMmaWFjdXRlO2FuLiBFbiAxODc0LCBlbiBFc3RhZG9zIFVuaWRvcywgZnVlIGxhIHByaW1lcmEgdmV6IHF1ZSBlbCBFc3RhZG8gaW50ZXJ2aW5vIGVuIHVuIGNhc28gZGUgbWFsdHJhdG8geSBhYnVzby4uLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDYiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4wMi8wNy8yMDEzPC9zcGFuPjxicj5FbCBkZXJlY2hvIGRlIGxvcyBuafFvcyBhIHNlciBlc2N1Y2hhZG9zPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5VbiBob21icmUgYWN1c2FkbyBkZSBoYWJlciBhYnVzYWRvIGRlIHN1cyBoaWpvcyBoYWImaWFjdXRlO2Egc2lkbyBzb2JyZXNlJmlhY3V0ZTtkbyBkb3MgdmVjZXMgcG9yIGxhIEp1c3RpY2lhLiBQZXJvIGFob3JhLCBsYSBDJmFhY3V0ZTttYXJhIGRlIENhc2FjaSZvYWN1dGU7biByZXZvYyZvYWN1dGU7IGVzYSBkZWNpc2kmb2FjdXRlO24gcG9ycXVlIGVuIGxhIGludmVzdGlnYWNpJm9hY3V0ZTtuIGVsIGp1ZXogbnVuY2EgaGFiJmlhY3V0ZTthIGVzY3VjaGFkbyBhIGxvcyBjaGljb3MuIFkgb3JkZW4mb2FjdXRlOyBxdWUgdGVuZ2EgZW4gY3VlbnRhIGxvIHF1ZSBkaWNlbi48L3A+DQo8cD5Qb3IgTWFyaWFuYSBDYXJiYWphbDwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDUiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE1NiIgcm93c3Bhbj0iMiIgdmFsaWduPSJ0b3AiPgoJCQkJCgkJCQk8dGFibGUgd2lkdGg9IjMyJSIgYm9yZGVyPSIxIiBjZWxsc3BhY2luZz0iMyIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48aW1nIHNyYz0ic3JjL2ltZ191cC8wNjA2MjAxMy4xLmpwZyIgd2lkdGg9IjE0NiIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT4KCQkJCQkJCQk8L3RkPiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjA2LzA2LzIwMTM8L3NwYW4+PGJyPkFidXNvIHNleHVhbCBpbmZhbnRpbC4gRGVzYWZpb3MgZGUgbGEgY2xpbmljYSBhY3R1YWw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkFiaWVydGEgbGEgaW5zY3JpcGNpb248L3A+DQo8cD5Eb2NlbnRlczogTGljLiBNYXJpYSBCZWF0cml6IE0mdXVtbDtsbGVyLiBMaWMuIFBhb2xhIE11Jm50aWxkZTtveiBEdWFydGU8L3A+DQo8cD5JbmljaW86IE1pZXJjb2xlcyAxOSBkZSBKdW5pbzwvcD4NCjxwPkZyZWN1ZW5jaWE6IFNlbWFuYWw8L3A+DQo8cD5Nb2RhbGlkYWQ6IEludGVuc2l2YTwvcD4NCjxwPkNvbnRlbmlkb3M6ICZuYnNwOyBFc3RhIGRlc3RpbmFkbyBhIHRvZG9zIGxvcyBwcm9mZXNpb25hbGVzIGNvbXByb21ldGlkb3MgY29uIGxhIHRlbWF0aWNhIGRlbCBhYnVzbyBpbmZhbnRpbCBxdWUgcXVpZXJhbiBhY3R1YWxpemFyc2UgZSBpbnRlcmNhbWJpYXIgZXhwZXJpZW5jaWFzIGRlIHRyYWJham8uLi48L3A+DQo8cD4mbmJzcDs8L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA0Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDQiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTYwNTIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xNi8wNS8yMDEzPC9zcGFuPjxicj5TYWx1ZCBBY3RpdmEgbmVjZXNpdGEgZGUgdHUgYXl1ZGEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5UcmFiYWphbW9zIGNvbW8gcG9kZW1vczogYmEmbnRpbGRlO29zIHJvdG9zLCBzdXNwZW5zaSZvYWN1dGU7biBkZSByZXVuaW9uZXMgcG9yIGNvcnRlcyBkZSBsdXogeSBhZ3VhLCBqdWd1ZXRlcyB2aWVqb3MsIG1lc2VzIGRlIGF0cmFzbyBlbiBlbCBwYWdvIGRlIHN1cyBwcm9mZXNpb25hbGVzIGRlIGxhIHNhbHVkLiBSZWNpZW50ZW1lbnRlIHR1dmltb3MgcXVlIGNlcnJhciBudWVzdHJvIHF1ZXJpZG8gSG9nYXI6ICZsZHF1bztNZXRhbW9yZm9zaXMmcmRxdW87IGVyYSBlbCBsdWdhciBxdWUgc3VwbyBjb250ZW5lciBhIG5pJm50aWxkZTthcyB5IGomb2FjdXRlO3ZlbmVzIHJlc2NhdGFkYSBkZSByZWRlcyBkZSB0cmF0YSBvIHYmaWFjdXRlO2N0aW1hcyBkZSBhYnVzbyBpbnRyYWZhbWlsaWFyLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAzIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAzLzA1LzIwMTM8L3NwYW4+PGJyPlJFUFVESU8gQSBMQSBQUkVTRU5DSUEgRU4gTEEgRkVSSUEgREVMIExJQlJPIERFIFVOIEVYIEpVRVogQUNVU0FETyBERSBBQlVTTyBTRVhVQUw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkZ1ZSBjYW1hcmlzdGEgZW4gTWFyIGRlbCBQbGF0YSBkdXJhbnRlIGxhIGRpY3RhZHVyYS4gSGFjZSBhJm50aWxkZTtvcywgdmFyaWFzIG11amVyZXMgbG8gYWN1c2Fyb24gZGUgaGFiZXIgYWJ1c2FkbyBkZSBlbGxhcyBjdWFuZG8gZXJhbiBuaSZudGlsZGU7YXMuIExhIGNhdXNhIHByZXNjcmliaSZvYWN1dGU7IHkgbm8gaHVibyBjb25kZW5hLiBNYSZudGlsZGU7YW5hIHRpZW5lIHByZXZpc3RvIGZpcm1hciBzdSBsaWJyby4gRXNhcyBtaXNtYXMgbXVqZXJlcyBwaWRlbiBxdWUgbm8gc2VhIGFkbWl0aWRvIGVuIGxhIGZlcmlhLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDIiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgIDwhLS0gRklOIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgIDwvdGFibGU+ICAgICAgICA8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iNSUiIGFsaWduPSJyaWdodCI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgPC90cj4KICAgIDwvdGFibGU+PC90ZD4KICA8L3RyPgogIDx0cj4KICAgIDx0ZCB3aWR0aD0iMSUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiIgYWxpZ249ImNlbnRlciI+Jm5ic3A7PC90ZD4KICAgIDx0ZCB3aWR0aD0iMiUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgPC90cj4KICAKICA8dGQ+CiAgPHRyPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0ciBhbGlnbj0iY2VudGVyIj4KICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgPHRkIHdpZHRoPSI5NyIgY29sc3Bhbj0iMiIgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iNTQ2IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idGl0dWxvaG9tZTIiPjx0YWJsZSB3aWR0aD0iIiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYWxpZ249ImxlZnQiIHZhbGlnbj0iYm90dG9tIiBjbGFzcz0idGl0dWxvaG9tZTIiPlJhbmtpbmc8L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSIgY2xhc3M9InRpdHVsb2hvbWUyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iIiBoZWlnaHQ9IjM1IiBhbGlnbj0ibGVmdCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPiZidWxsO0xhcyBtJmFhY3V0ZTtzIGxlaWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGNsYXNzPSJjb250ZW5pZG9ob21lIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBjbGFzcz0iY29udGVuaWRvaG9tZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+JmJ1bGw7TGFzIG0mYWFjdXRlO3MgY29tZW50YWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTHVkb3RlY2EgR2FyYWJhdG8gLSBQcm95ZWN0byBzYWx1ZGFjdGl2YSwgUG9yIHVuYSBpbmZhbmNpYSBmZWxpeiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iOSUiIGJnY29sb3I9IiNFRkVGRUYiPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzJSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xNjIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDUlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTE2MiIgY2xhc3M9ImJvdG9uIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBDdXJzbyBJbnRlbnNpdm8gZGUgb3BlcmFkb3IgdGVyYXBldXRpY28gZXNwZWNpYWxpemFkbyBlbiBlbCBhYm9yZGFqZSBkZWwgYWJ1c28sIGxhIHZpb2xlbmNpYSB5IGVsIG1hbHRyYXRvIGluZmFudGlsICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgUFJPR1JBTUEgTEFTIFZJQ1RJTUFTIENPTlRSQSBMQVMgVklPTEVOQ0lBUyAgTWluaXN0ZXJpbyBkZSBKdXN0aWNpYSB5IERlcmVjaG9zIEh1bWFub3MgZGUgbGEgTmFjafNuICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI5JSIgYmdjb2xvcj0iI0VGRUZFRiI+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjMlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTI1NSIgY2xhc3M9ImJvdG9uIj48aW1nIHNyYz0iaW1nL2ZsZWNoYW5hcmFuamFmZ3Jpc18yNC5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSI3IiBib3JkZXI9IjAiIGFsaWduPSJhYnNtaWRkbGUiIC8+PC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI0NSUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MjU1IiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIERpcGxvbWF0dXJhIGVuIEFib3JkYWplIGludGVyZGlzY2lwbGluYXJpbyBkZWwgbWFsdHJhdG8sIGxhIHZpb2xlbmNpYSB5IGVsIGFidXNvIHNleHVhbCBpbmZhbnRpbCAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyJSIgaGVpZ2h0PSIyMCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQxJSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNhbHVkIEFjdGl2YSBuZWNlc2l0YSBkZSB0dSBheXVkYSEgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjklIiBiZ2NvbG9yPSIjRUZFRkVGIj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMyUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MTA0IiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQ1JSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xMDQiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTGxhbWFkbyBwYXJhIHByZXNlbnRhY2nzbiBkZSB0cmFiYWpvcy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjIwIiBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyMCIgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGJnY29sb3I9IiNGRkZGRkYiIGNsYXNzPSJ0ZXh0b251ZXZvIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPgogICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iIyIgY2xhc3M9ImJvdG9uIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgPC90YWJsZT48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj4mbmJzcDs8L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBJTklDSU8gbm90YSBjb211biAtLT4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTUvMDQvMjAxMjwvc3Bhbj48YnI+T3JnYW5pemFuIGpvcm5hZGEgc29icmUgdmlvbGVuY2lhPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPlNlIGNlbnRyYXImYWFjdXRlOyBlbiBsb3MgZmVuJm9hY3V0ZTttZW5vcyBxdWUgYWZlY3RhbiBhIGxhIGZhbWlsaWEgeSBlbiBsbyBxdWUgb2N1cnJlIGVuIGxhcyBlc2N1ZWxhcy48YnIgLz4gU2UgbGxldmFyJmFhY3V0ZTsgYSBjYWJvIGVsIGx1bmVzIDIzLCBlbiBlbCBDZW50cm8gQ3VsdHVyYWwgZGUgVG9zY2hpIHkgVHJlcyANCkFycm95b3MsIHVuYSBqb3JuYWRhIGRlIHJlZmxleGkmb2FjdXRlO24geSBkZWJhdGUgYWJpZXJ0YSBhIGxhIGNvbXVuaWRhZCBzb2JyZSANCiZsZHF1bztWaW9sZW5jaWEgZW4gbGEgZmFtaWxpYSB5IGVuIGxhIGVzY3VlbGEgeSBzdSByZWxhY2kmb2FjdXRlO24gY29uIGVsIGZyYWNhc28gDQplc2NvbGFyJnJkcXVvOywgb3JnYW5pemFkYSBwb3IgbGEgQXNvY2lhY2kmb2FjdXRlO24gQ2l2aWwgQ2VudHJvIEFydCZlYWN1dGU7bWlkZXMgeSBsYSANCk11bmljaXBhbGlkYWQgZGUgQ2lwb2xsZXR0aS5TZSBjZW50cmFyJmFhY3V0ZTsgZW4gbG9zIGZlbiZvYWN1dGU7bWVub3MgcXVlIGFmZWN0YW4gYSBsYSBmYW1pbGlhIHkgZW4gbG8gcXVlIG9jdXJyZSBlbiBsYXMgZXNjdWVsYXMuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjMwLzAzLzIwMTI8L3NwYW4+PGJyPkNhcnRhIGRlIEFTQVBNSSAtIEFzb2NpYWNp824gQXJnZW50aW5hIGRlIFByZXZlbmNp824gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbDwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjE1IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSIxNSIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjgwIiBjb2xzcGFuPSI0IiBhbGlnbj0ibGVmdCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Mb3MgaW50ZWdyYW50ZXMgZGUgbGEgQ29taXNpJm9hY3V0ZTtuIERpcmVjdGl2YSBkZSBBU0FQTUkgLSBBc29jaWFjaSZvYWN1dGU7biBBcmdlbnRpbmEgZGUgUHJldmVuY2kmb2FjdXRlO24gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbCwgYXNvY2lhZGEgYSBsYSBJbnRlcm5hdGlvbmFsIFNvY2lldHkgZm9yIFByZXZlbnRpb24gb2YgQ2hpbGQgQWJ1c2UgYW5kIE5lZ2xlY3QgKElTUENBTikgLSwgdGVuZW1vcyBlbCBhZ3JhZG8gZGUgZGlyaWdpcm5vcyBhIFVzdGVkIHBhcmEgdHJhc21pdGlybGUgbnVlc3RyYSBwcm9mdW5kYSAmbmJzcDt5IGhvbmRhIHByZW9jdXBhY2kmb2FjdXRlO24gcG9yIGxhIHBvc3R1cmEgcXVlIHZpZW5lbiBhc3VtaWVuZG8gZW4gZm9ybWEgY29udGludWFkYSBhbGd1bm9zIGNvbGVnaW9zIGRlIHBzaWMmb2FjdXRlO2xvZ29zLCBlc3BlY2lhbG1lbnRlIGRlIGxhIHByb3ZpbmNpYSBkZSBCdWVub3MgQWlyZXMsIGVuIHJlbGFjaSZvYWN1dGU7biBhbCB0cmF0YW1pZW50byBwb2NvIHNlcmlvIHkgY29tcHJvbWV0aWRvIHF1ZSBzZSBsZXMgb3RvcmdhIGEgbGFzIGRlbnVuY2lhcyBlZmVjdHVhZGFzIGNvbnRyYSBwcm9mZXNpb25hbGVzIHBzaWMmb2FjdXRlO2xvZ29zLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjAvMDMvMjAxMjwvc3Bhbj48YnI+TEEgVklPTEVOQ0lBIFNFWFVBTCBDT05UUkEgTknRT1MgWSBOSdFBUyBFTiBDSUZSQVM8L3RkPgogICAgICAgICAgPC90cj4KICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkIHdpZHRoPSIxNSIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4MCIgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+UmFkaW9ncmFmJmlhY3V0ZTthIGRlIHVuIHByb2JsZW1hPC9wPg0KPHA+RGUgbG9zIG4mdWFjdXRlO21lcm9zIGNvbXBpbGFkb3MgcG9yIGRvcyBlcXVpcG9zIGRlbCBNaW5pc3RlcmlvIGRlIEp1c3RpY2lhLCBsYQ0KIGF1dG9yYSB0b21hIGxvcyBkZSBsYSBjaXVkYWQgZGUgQnVlbm9zIEFpcmVzIHBhcmEgdHJhemFyIHVuIHBhcmFkaWdtYSANCmRlIGxvcyBkZWxpdG9zIGNvbnRyYSBsYSBpbnRlZ3JpZGFkIHNleHVhbCBlbiBlbCBwYSZpYWN1dGU7cyB5IHNvYnJlIHN1IA0KYXRlbmNpJm9hY3V0ZTtuLjxiciAvPiA8YnIgLz4gJm5ic3A7UG9yIEV2YSBHaWJlcnRpPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2MCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjAiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjE1LzAzLzIwMTI8L3NwYW4+PGJyPkZBTExPIERFIExBIENPUlRFIFNVUFJFTUEgU09CUkUgTEEgTk8gSlVESUNJQUxJWkFDSU9OIERFTCBBQk9SVE8gRU4gQ0FTT1MgREUgVklPTEFDSU9OPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxiciAvPiBKVVJJU0RJQ0NJT046IE5BQ0lPTkFMPGJyIC8+IE1BVEVSSUE6IEFCT1JUTy48YnIgLz4gVFJJQlVOQUw6IENvcnRlIFN1cHJlbWEgZGUgSnVzdGljaWEgZGUgbGEgTmFjaSZvYWN1dGU7bi48YnIgLz4gQVVUT1M6IEYuLCBBLiBMLiBzLyBtZWRpZGEgYXV0b3NhdGlzZmFjdGl2YS48YnIgLz4gRkVDSEE6IDEzLzAzLzIwMTIuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI1OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNTkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBGSU4gbm90YSBjb211biAtLT4KPC90YWJsZT4KPG1hcCBuYW1lPSJNYXBNYXAiIGlkPSJNYXBNYXAiPjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjE0NCw0LDIxNCwzNiIgaHJlZj0iaW5kZXgucGhwP2lkPTE0IiAvPgo8L21hcD4KPG1hcCBuYW1lPSJNYXAyTWFwMiIgaWQ9Ik1hcDJNYXAyIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIxNDcsNCwyMjAsMzYiIGhyZWY9ImluZGV4LnBocD9pZD0xNGEiIC8+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcDMiIGlkPSJNYXAzIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIzNjMsMyw0MzYsMzkiIGhyZWY9ImluZGV4LnBocD9pZD0xNGIiIC8+CjwvbWFwPgo8L2h0bWw+CjwvdGQ+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gICAgICAgICAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFM0UzRTMiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSI3MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNiUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9kZWNpbG9fYmllbl9mdWVydGUxLmpwZyIgd2lkdGg9IjEyMCIgaGVpZ2h0PSIxMTIiPjwvdGQ+CiAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiA+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTI0IiBjbGFzcz0iYm90b24xIj5bK10gTSZhYWN1dGU7cyBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0UzRTNFMyI+ICAgICAgICA8L3RyPgogICAgICAgIDx0cj4gCiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj4mbmJzcDs8L3RkPgogICAgICAgIDwvdHI+CiAgICA8L3RhYmxlPjwvdGQ+CiAgPC90cj4KICA8dHI+IAogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSI+PGltZyBzcmM9ImltZy9penExLmpwZyIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjExNCIgLz48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9RdWllbmVzU29tb3NfQTJfMF8yNS5qcGciIHdpZHRoPSI4MDkiIGhlaWdodD0iMTE0IiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcDIiIC8+PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI1MCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiYWNrZ3JvdW5kPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzE4XzE4LmpwZyI+Jm5ic3A7PC90ZD4KICAgIDx0ZCBoZWlnaHQ9IjUwIiBjbGFzcz0iZm9uZG9ib3R0b20iPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2l0ZWkuY29tLmFyLyI+PGltZyBzcmM9ImltZy9laV9jb2xvci5wbmciIGFsdD0iZXNwYWNpb3MgZGUgaW1hZ2luYWNpb24sIGRlc2Fycm9sbG9zIGludGVyYWN0aXZvcywgY3JlYXRpdmlkYWQsIGRpc2XxbyIgd2lkdGg9IjI3IiBoZWlnaHQ9IjE1IiBib3JkZXI9IjAiPjwvYT4gPHNwYW4gY2xhc3M9ImVpIj48YSBocmVmPSJodHRwOi8vd3d3LnNpdGVpLmNvbS5hci8iIHNwYW4gY2xhc3M9ImVpIj5kaXNlJm50aWxkZTtvICsgY29tdW5pY2FjaSZvYWN1dGU7bjwvYT48L3NwYW4+PGVtPiZuYnNwOzwvZW0+PC9zcGFuPjxzcGFuIGNsYXNzPSJibGFuY28xIj48ZW0+Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7PC9lbT48L3NwYW4+PC90ZD4KICA8L3RyPgo8L3RhYmxlPgoKCjxtYXAgbmFtZT0iTWFwMiI+PGFyZWEgc2hhcGU9InJlY3QiIGNvb3Jkcz0iMjQ3LDY5LDQxNCw4MiIgaHJlZj0ibWFpbHRvOnNhbHVkYWN0aXZhQHNhbHVkYWN0aXZvLm9yZy5hciI+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcCI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM2LDE0MiwxNDksMTUyIiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MiI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM0LDE4NiwxNTAsMTk2IiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MCI+CjwvbWFwPgo8L2JvZHk+CjwvaHRtbD4K]]></response> | |
| 148 | <responseRedirected>false</responseRedirected> | |
| 149 | </requestresponse> | |
| 150 | </issue> | |
| 151 | <issue> | |
| 152 | <serialNumber>3368157477358873600</serialNumber> | |
| 153 | <type>5245344</type> | |
| 154 | <name>Frameable response (potential Clickjacking)</name> | |
| 155 | <host ip="200.20.20.201">http://www.example.org.ar</host> | |
| 156 | <path><![CDATA[/index.php]]></path> | |
| 157 | <location><![CDATA[/index.php]]></location> | |
| 158 | <severity>Information</severity> | |
| 159 | <confidence>Firm</confidence> | |
| 160 | <issueBackground><![CDATA[It might be possible for a web page controlled by an attacker to load the content of this response within an iframe on the attacker's page. This may enable a "clickjacking" attack, in which the attacker's page overlays the target application's interface with a different interface provided by the attacker. By inducing victim users to perform actions such as mouse clicks and keystrokes, the attacker can cause them to unwittingly carry out actions within the application that is being targeted. This technique allows the attacker to circumvent defenses against cross-site request forgery, and may result in unauthorized actions.<br><br>Note that this issue is being reported because the application's response does not set a suitable <b>X-Frame-Options</b> header in order to prevent framing attacks. Some applications attempt to prevent these attacks from within the HTML page itself, using "framebusting" code. However, this type of defense is normally ineffective and can usually be circumvented by a skilled attacker.]]></issueBackground> | |
| 161 | <remediationBackground><![CDATA[You should review the application functions that are accessible from within the response, and determine whether they can be used by application users to perform any sensitive actions within the application. If so, then a framing attack targeting this response may result in unauthorized actions.<br><br>To effectively prevent framing attacks, the application should return a response header with the name <b>X-Frame-Options</b> and the value <b>DENY</b> to prevent framing altogether, or the value <b>SAMEORIGIN</b> to allow framing only by pages on the same origin as the response itself.]]></remediationBackground> | |
| 162 | <requestresponse> | |
| 163 | <request base64="true"><![CDATA[R0VUIC9pbmRleC5waHAgSFRUUC8xLjENCkhvc3Q6IHd3dy5zYWx1ZGFjdGl2YS5vcmcuYXINCkFjY2VwdDogKi8qDQpBY2NlcHQtTGFuZ3VhZ2U6IGVuDQpVc2VyLUFnZW50OiBNb3ppbGxhLzUuMCAoY29tcGF0aWJsZTsgTVNJRSA5LjA7IFdpbmRvd3MgTlQgNi4xOyBXaW42NDsgeDY0OyBUcmlkZW50LzUuMCkNCkNvbm5lY3Rpb246IGNsb3NlDQoNCg==]]></request> | |
| 164 | <response base64="true"><![CDATA[SFRUUC8xLjEgMjAwIE9LDQpEYXRlOiBUaHUsIDA3IE5vdiAyMDEzIDE3OjE0OjA1IEdNVA0KU2VydmVyOiBBcGFjaGUvMi4yLjIzIChVbml4KSBtb2Rfc3NsLzIuMi4yMyBPcGVuU1NMLzAuOS44ZS1maXBzLXJoZWw1DQpYLVBvd2VyZWQtQnk6IFBIUC81LjIuMTcNCkV4cGlyZXM6IFRodSwgMTkgTm92IDE5ODEgMDg6NTI6MDAgR01UDQpDYWNoZS1Db250cm9sOiBuby1zdG9yZSwgbm8tY2FjaGUsIG11c3QtcmV2YWxpZGF0ZSwgcG9zdC1jaGVjaz0wLCBwcmUtY2hlY2s9MA0KUHJhZ21hOiBuby1jYWNoZQ0KQ29ubmVjdGlvbjogY2xvc2UNCkNvbnRlbnQtVHlwZTogdGV4dC9odG1sDQpDb250ZW50LUxlbmd0aDogNjA2MDYNCg0KIDxoZWFkPgo8bWV0YSBodHRwLWVxdWl2PSJDb250ZW50LVR5cGUiIGNvbnRlbnQ9InRleHQvaHRtbDsgY2hhcnNldD1pc28tODg1OS0xIiAvPgo8dGl0bGU+U2FsdWQgQWN0aXZhIC0gQWJ1c28gdmlvbGVuY2lhIHkgbWFsdHJhdG88L3RpdGxlPgoKPHNjcmlwdD4gCiAgICAvL2VzdG8gcGFyYSBwYXNhcmxlIGFsIGZsYXNoIGxhcyB2YXJpYWxiZXMgZGVsIHBocAogCQoKCXZhciBib3Q9Jyc7Ci8vYWxlcnQodmFyaWFibGVTZXJ2aWRvcik7Cjwvc2NyaXB0Pgo8c2NyaXB0IGxhbmd1YWdlPSJKYXZhU2NyaXB0IiB0eXBlPSJ0ZXh0L0phdmFTY3JpcHQiPgo8IS0tCmZ1bmN0aW9uIE1NX3ByZWxvYWRJbWFnZXMoKSB7IC8vdjMuMAogIHZhciBkPWRvY3VtZW50OyBpZihkLmltYWdlcyl7IGlmKCFkLk1NX3ApIGQuTU1fcD1uZXcgQXJyYXkoKTsKICAgIHZhciBpLGo9ZC5NTV9wLmxlbmd0aCxhPU1NX3ByZWxvYWRJbWFnZXMuYXJndW1lbnRzOyBmb3IoaT0wOyBpPGEubGVuZ3RoOyBpKyspCiAgICBpZiAoYVtpXS5pbmRleE9mKCIjIikhPTApeyBkLk1NX3Bbal09bmV3IEltYWdlOyBkLk1NX3BbaisrXS5zcmM9YVtpXTt9fQp9Ci8vLS0+Cjwvc2NyaXB0Pgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KCjwvaGVhZD4KCjxzY3JpcHQgbGFuZ3VhZ2U9IkphdmFTY3JpcHQiIHR5cGU9InRleHQvSmF2YVNjcmlwdCI+CjwhLS0KZnVuY3Rpb24gTU1fcmVsb2FkUGFnZShpbml0KSB7ICAvL3JlbG9hZHMgdGhlIHdpbmRvdyBpZiBOYXY0IHJlc2l6ZWQKICBpZiAoaW5pdD09dHJ1ZSkgd2l0aCAobmF2aWdhdG9yKSB7aWYgKChhcHBOYW1lPT0iTmV0c2NhcGUiKSYmKHBhcnNlSW50KGFwcFZlcnNpb24pPT00KSkgewogICAgZG9jdW1lbnQuTU1fcGdXPWlubmVyV2lkdGg7IGRvY3VtZW50Lk1NX3BnSD1pbm5lckhlaWdodDsgb25yZXNpemU9TU1fcmVsb2FkUGFnZTsgfX0KICBlbHNlIGlmIChpbm5lcldpZHRoIT1kb2N1bWVudC5NTV9wZ1cgfHwgaW5uZXJIZWlnaHQhPWRvY3VtZW50Lk1NX3BnSCkgbG9jYXRpb24ucmVsb2FkKCk7Cn0KTU1fcmVsb2FkUGFnZSh0cnVlKTsKLy8tLT4KCjwvc2NyaXB0Pgo8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoKCjwvaGVhZD4KCjxib2R5IGJhY2tncm91bmQ9ImltZy9mb25kb19kZWdyYWRlLmpwZyIgdG9wbWFyZ2luPSIwIj4KPHRhYmxlIHdpZHRoPSIxMDA1IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgPHRyPiAKICAgIDx0ZCB3aWR0aD0iOTYiPjxpbWcgc3JjPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzBfMDEuanBnIiB3aWR0aD0iOTYiIGhlaWdodD0iMjA4IiAvPjwvdGQ+CiAgICA8dGQgd2lkdGg9IjgwOSI+IDxzY3JpcHQgdHlwZT0idGV4dC9qYXZhc2NyaXB0Ij4KQUNfRkxfUnVuQ29udGVudCggJ2NvZGViYXNlJywnaHR0cDovL2Rvd25sb2FkLm1hY3JvbWVkaWEuY29tL3B1Yi9zaG9ja3dhdmUvY2Ficy9mbGFzaC9zd2ZsYXNoLmNhYiN2ZXJzaW9uPTcsMCwxOSwwJywnd2lkdGgnLCc4MDknLCdoZWlnaHQnLCcyMDgnLCdzcmMnLCdzd2YvaGVhZGVyJywncXVhbGl0eScsJ2hpZ2gnLCdwbHVnaW5zcGFnZScsJ2h0dHA6Ly93d3cubWFjcm9tZWRpYS5jb20vZ28vZ2V0Zmxhc2hwbGF5ZXInLCdtb3ZpZScsJ3N3Zi9oZWFkZXInICk7IC8vZW5kIEFDIGNvZGUKPC9zY3JpcHQ+IDxub3NjcmlwdD4KICAgICAgPG9iamVjdCBjbGFzc2lkPSJjbHNpZDpEMjdDREI2RS1BRTZELTExY2YtOTZCOC00NDQ1NTM1NDAwMDAiIGNvZGViYXNlPSJodHRwOi8vZG93bmxvYWQubWFjcm9tZWRpYS5jb20vcHViL3Nob2Nrd2F2ZS9jYWJzL2ZsYXNoL3N3Zmxhc2guY2FiI3ZlcnNpb249NywwLDE5LDAiIHdpZHRoPSI4MDkiIGhlaWdodD0iMjA4Ij4KICAgICAgICA8cGFyYW0gbmFtZT0ibW92aWUiIHZhbHVlPSJzd2YvaGVhZGVyLnN3ZiIgLz4KICAgICAgICA8cGFyYW0gbmFtZT0icXVhbGl0eSIgdmFsdWU9ImhpZ2giIC8+CiAgICAgICAgPGVtYmVkIHNyYz0ic3dmL2hlYWRlci5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9IjgwOSIgaGVpZ2h0PSIyMDgiPjwvZW1iZWQ+IAogICAgICA8L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIHdpZHRoPSIxMiUiIHJvd3NwYW49IjUiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iIzAwMDAwMCI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI0NjEiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmFja2dyb3VuZD0iaW1nL1F1aWVuZXNTb21vc19BMl8wXzEzLmpwZyI+IAogICAgICA8c2NyaXB0IHR5cGU9InRleHQvamF2YXNjcmlwdCI+CkFDX0ZMX1J1bkNvbnRlbnQoICdjb2RlYmFzZScsJ2h0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCcsJ3dpZHRoJywnOTYnLCdoZWlnaHQnLCc0NjEnLCdzcmMnLCdzd2Yvc3VibWVudScsJ3F1YWxpdHknLCdoaWdoJywncGx1Z2luc3BhZ2UnLCdodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyJywnbW92aWUnLCdzd2Yvc3VibWVudScgKTsgLy9lbmQgQUMgY29kZQo8L3NjcmlwdD4gPG5vc2NyaXB0PgogICAgICA8b2JqZWN0IGNsYXNzaWQ9ImNsc2lkOkQyN0NEQjZFLUFFNkQtMTFjZi05NkI4LTQ0NDU1MzU0MDAwMCIgY29kZWJhc2U9Imh0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+CiAgICAgICAgPHBhcmFtIG5hbWU9Im1vdmllIiB2YWx1ZT0ic3dmL3N1Ym1lbnUuc3dmIiAvPgogICAgICAgIDxwYXJhbSBuYW1lPSJxdWFsaXR5IiB2YWx1ZT0iaGlnaCIgLz4KICAgICAgICA8ZW1iZWQgc3JjPSJzd2Yvc3VibWVudS5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+PC9lbWJlZD48L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCIgYmdjb2xvcj0iI0ZGRkZGRiI+CiAgICAgICAgPHRyPiAKICAgICAgICAgIDx0ZCB3aWR0aD0iMTciIHJvd3NwYW49IjciPjxwPiZuYnNwOzwvcD48L3RkPgogICAgICAgICAgPHRkIHdpZHRoPSIxNzIiIGFsaWduPSJjZW50ZXIiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxpbWcgc3JjPSJpbWcvM3B4LmpwZyIgd2lkdGg9IjUiIGhlaWdodD0iNSI+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciI+PGxpbmsgaHJlZj0iLi4vZXN0aWxvcy5jc3MiIHJlbD0ic3R5bGVzaGVldCIgdHlwZT0idGV4dC9jc3MiIC8+Cjxib2R5IGJnY29sb3I9IiNDQ0NDQ0MiIHRvcG1hcmdpbj0iNiBweCI+PHRhYmxlIHdpZHRoPSIxNjUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIzIiBiZ2NvbG9yPSIjRkZGRkZGIj4KPHRyPgogICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTkxIiBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiAgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MThfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+SG9tZTwvYT48L3RkPgogIDwvdHI+Cjx0cj4KICA8dGQgaGVpZ2h0PSIyOCIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj4mbmJzcDsmbmJzcDtOb3RpY2lhczwvYT48L3RkPgo8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJkb25hY2lvbmVzLyIgdGFyZ2V0PSJfYmxhbmsiIGNsYXNzPSJmb25kb2JvdG9uIj5Eb25hY2lvbmVzPC9hPjwvdGQ+CiAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciICB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yM19uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5IaXN0b3JpYWwgZGUgbmV3c2xldHRlcnM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTEzYSIgY2xhc3M9ImZvbmRvYm90b24iPkVudmlhciBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yNl9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5WZXIgdHJhYmFqb3MgZGUgdXN1YXJpb3M8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MTZfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+U2FsdWQgQWN0aXZhIHByZW5zYTwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJtYWlsdG86c2FsdWRhY3RpdmFAc2FsdWRhY3RpdmEub3JnLmFyIiBjbGFzcz0iZm9uZG9ib3RvbiI+TWFuZCZhYWN1dGU7IHR1IEMuVi48L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgIHdpZHRoPSI2ImhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTIxX25ldyIgY2xhc3M9ImZvbmRvYm90b24iPkluZm9ybWFjaSZvYWN1dGU7biBkZSBpbnRlciZlYWN1dGU7czwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyI+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiBoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xMF80IiBjbGFzcz0iZm9uZG9ib3RvbiI+Q29uZ3Jlc29zCiAgICAgICAgICAgICAgICAgIHkgSm9ybmFkYXM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTExIiBjbGFzcz0iZm9uZG9ib3RvbiI+UmVnaXN0cmFjaSZvYWN1dGU7bjwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgCiAgICAgICAgICA8L3RhYmxlPgo8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNSIgdGFyZ2V0PSJfYmxhbmsiPjxicj4KICAgICAgICAgICAgICAgICAgPGltZyBzcmM9ImltZy9iYW5uZXJfZG9uYWNpb25lcy5qcGciIHdpZHRoPSIxNjIiIGhlaWdodD0iMTIwIiBib3JkZXI9IjAiPjxicj4KICAgICAgICAgICAgICAgICAgPGJyPgogICAgICAgICAgICAgICAgICA8aW1nIHNyYz0iaW1nL2JvdG9uRm9yby5naWYiIHdpZHRoPSIxNzIiIGhlaWdodD0iMTE3IiBib3JkZXI9IjAiPjwvYT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTY3IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjkiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzAzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iOSIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTQ5IiBiYWNrZ3JvdW5kPSJpbWcvY2hpY29zX3BlcmRpZG9zXzA1LmdpZiI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDUuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMCI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDcuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMi5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEyLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9InNyYy9pbWdfdXAvMjMwODIwMTIuMS5qcGciIHdpZHRoPSIxNDkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMy5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNi5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iNSIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTcuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNy5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgYmdjb2xvcj0iI0ZFRTdDRiIgY2xhc3M9InRpdHVsb2hvbWU1Ij48c3Ryb25nPk5pJm50aWxkZTtvcyBwZXJkaWRvczxicj4KICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0yOSIgY2xhc3M9ImJvdG9uIj5bVmVyIG0mYWFjdXRlO3NdPC9hPjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTkuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xOS5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18yMC5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iMjUiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4NCgkJCQkNCgkJCQk8Zm9ybSBhY3Rpb249ImluZGV4LnBocD9pZD0xMSIgIG1ldGhvZD0icG9zdCI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9penExLmpwZyIgd2lkdGg9IjEyIiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9hcnJpYmEuanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9kZXIxLmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgIDwvdHI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiIgdmFsaWduPSJ0b3AiIGNsYXNzPSJyZWdGb25kbzEiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9penEuanBnIiB3aWR0aD0iMTIiIGhlaWdodD0iMTIiIC8+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSI5NCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV90aXQuanBnIiB3aWR0aD0iNjYiIGhlaWdodD0iMjMiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSI1MCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJyZWdpc3RyYXJzZSI+SW5ncmVzJmFhY3V0ZTsgDQogICAgICAgICAgICAgIHR1cyBkYXRvcyB5IHJlY2liJmlhY3V0ZTsgbGEgbWVqb3IgaW5mb3JtYWNpJm9hY3V0ZTtuIGEgdHJhdiZlYWN1dGU7cyANCiAgICAgICAgICAgICAgZGUgbnVlc3RybzxzdHJvbmc+IE5ld3NsZXR0ZXI8L3N0cm9uZz4uIDxzdHJvbmc+PHNwYW4gY2xhc3M9ImdyYXRpcyI+R3JhdGlzITwvc3Bhbj48L3N0cm9uZz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI1IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9InRyYWJTRUNDSU9OIj5Ob21icmU8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBjbGFzcz0icmVnQ0VMREEiPjxpbnB1dCBuYW1lPSJub21icmUiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0ibm9tYnJlIiAvPjwvdGQ+DQogICAgICAgICAgPC90cj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0idHJhYlNFQ0NJT04iPkFwZWxsaWRvPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iYXBlbGxpZG8iIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iYXBlbGxpZG8iIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJ0cmFiU0VDQ0lPTiI+RS1tYWlsPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iZW1haWwiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iZW1haWwiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InRyYWJTRUNDSU9OIj4mbmJzcDs8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idHJhYlNFQ0NJT04iPjxpbnB1dCB0eXBlPSJpbWFnZSIgc3JjPSJpbWcvcmVnaXN0cmF0ZV9ib3Rvbi5qcGciIHdpZHRoPSIxMTciIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgIDwvdGFibGU+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE0IiB2YWxpZ249InRvcCIgY2xhc3M9InJlZ0ZvbmRvMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2Rlci5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIxNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KICAgICAgICAgICAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTIiIGhlaWdodD0iMjQiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfaXpxMi5qcGciIHdpZHRoPSIxMiIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI0Ij48aW1nIHNyYz0iaW1nL3JlZ2lzdHJhdGVfYWJham8uanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjI0IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfZGVyMi5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KCQkJCQkNCgkJCQkJPC9mb3JtPg0KICAgICAgICAgICAgICAgICAgPC90YWJsZT4NCjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPiAKICAgICAgICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTcwIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUyIj4KCQkJCQkJCQkJCQkJCQkJCTwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9jbGF1ZGlhMl8wMy5qcGciIHdpZHRoPSIxNzQiIGhlaWdodD0iMjUwIiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcCI+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICA8dGQgcm93c3Bhbj0iNyIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nLzV4NS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjciPjwvdGQ+CiAgICAgICAgICA8dGQgY29sc3Bhbj0iMiIgcm93c3Bhbj0iNCIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPGZvcm0gYWN0aW9uPSJsb2dpbi5waHAiIG1ldGhvZD0icG9zdCIgbmFtZT0iZm9ybTIiPgoKICAgICAgICAgICAgICA8dHI+IAogICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgY29sc3Bhbj0iMiIgYWxpZ249ImxlZnQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIiA+IAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8c3Ryb25nPlVzdWFyaW8gbm8gcmVnaXN0cmFkbzwvc3Ryb25nPiAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9mb250PiA8L3N0cm9uZz4gCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDkiIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPlVzdWFyaW8mbmJzcDsmbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzOSIgdmFsaWduPSJtaWRkbGUiPjxpbnB1dCBuYW1lPSJ1c3VhcmlvIiB0eXBlPSJ0ZXh0IiBjbGFzcz0icmVnIiBpZD0idXN1YXJpbyIgc2l6ZT0iNyI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjciIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPkNvbnRyYXNlJm50aWxkZTthJm5ic3A7Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzkiIHZhbGlnbj0ibWlkZGxlIj48aW5wdXQgbmFtZT0icGFzcyIgdHlwZT0icGFzc3dvcmQiIGNsYXNzPSJyZWciIGlkPSJwYXNzIiBzaXplPSI3Ij48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiIgYWxpZ249InJpZ2h0IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9ImJvdG9uIj48aW5wdXQgdHlwZT0iaW1hZ2UiIHNyYz0iaW1nL3JlZy5qcGciIHdpZHRoPSI1OCIgaGVpZ2h0PSIzMCI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjciIGhlaWdodD0iMTkiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgPjxhIGhyZWY9Imh0dHA6Ly93d3cuZmFjZWJvb2suY29tL2hvbWUucGhwPyMhL3BhZ2VzL01lcmxvLUFyZ2VudGluYS9TQUxVRC1BQ1RJVkEvMTAwNTgzNTQzMzE3MzIyP3JlZj10cyZhamF4cGlwZT0xJl9fYT03IiB0YXJnZXQ9Il9ibGFuayI+PGltZyBzcmM9ImltZy9mYWNlYm9vay5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzExIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj48ZGl2IGFsaWduPSJsZWZ0Ij48YSBocmVmPSJodHRwOi8vdHdpdHRlci5jb20vU2FsdWRBY3RpdmFPTkciIHRhcmdldD0iX2JsYW5rIj48aW1nIHNyYz0iaW1nL3R3aXRlci5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC9kaXY+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSI1IiBhbGlnbj0icmlnaHQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIj48bGFiZWw+PGZvbnQgc2l6ZT0iLTYiPlNpCiAgICAgICAgICAgICAgICAgICAgICAgdG9kYXYmaWFjdXRlO2Egbm8gZXMgdXN1YXJpbyA8L2ZvbnQ+IDxhIGhyZWY9ImluZGV4LnBocD9pZD0xMSIgY2xhc3M9ImJvdG9uIj48Zm9udCBzaXplPSItNiI+cmVnJmlhY3V0ZTtzdHJlc2UKICAgICAgICAgICAgICAgICAgICAgICAgYXF1JmlhY3V0ZTsgPGZvbnQgY29sb3I9IiM2NjY2NjYiPiYjODIyNjs8L2ZvbnQ+PC9mb250PjwvYT4gPGEgaHJlZj0iaW5kZXgucGhwP2lkPTEyIiBjbGFzcz0iYm90b24xIj48Zm9udCBzaXplPSItNiI+b2x2aWRlIG1pIGNvbnRyYXNlJm50aWxkZTthPC9mb250PjwvYT48L2xhYmVsPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE3Ij4mbmJzcDsgPC90ZD4KICAgICAgICAgICAgICA8L3RyPgoJCQkgIDwvZm9ybT4KCiAgICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgICA8IURPQ1RZUEUgaHRtbCBQVUJMSUMgIi0vL1czQy8vRFREIFhIVE1MIDEuMCBUcmFuc2l0aW9uYWwvL0VOIiAiaHR0cDovL3d3dy53My5vcmcvVFIveGh0bWwxL0RURC94aHRtbDEtdHJhbnNpdGlvbmFsLmR0ZCI+CjxodG1sIHhtbG5zPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hodG1sIj4KPGhlYWQ+CjxtZXRhIGh0dHAtZXF1aXY9IkNvbnRlbnQtVHlwZSIgY29udGVudD0idGV4dC9odG1sOyBjaGFyc2V0PWlzby04ODU5LTEiIC8+Cjx0aXRsZT5Eb2N1bWVudG8gc2luIHQmaWFjdXRlO3R1bG88L3RpdGxlPgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KPHNjcmlwdCBsYW5ndWFnZT0iSmF2YVNjcmlwdCIgdHlwZT0idGV4dC9KYXZhU2NyaXB0Ij4KPCEtLQpmdW5jdGlvbiBNTV9yZWxvYWRQYWdlKGluaXQpIHsgIC8vcmVsb2FkcyB0aGUgd2luZG93IGlmIE5hdjQgcmVzaXplZAogIGlmIChpbml0PT10cnVlKSB3aXRoIChuYXZpZ2F0b3IpIHtpZiAoKGFwcE5hbWU9PSJOZXRzY2FwZSIpJiYocGFyc2VJbnQoYXBwVmVyc2lvbik9PTQpKSB7CiAgICBkb2N1bWVudC5NTV9wZ1c9aW5uZXJXaWR0aDsgZG9jdW1lbnQuTU1fcGdIPWlubmVySGVpZ2h0OyBvbnJlc2l6ZT1NTV9yZWxvYWRQYWdlOyB9fQogIGVsc2UgaWYgKGlubmVyV2lkdGghPWRvY3VtZW50Lk1NX3BnVyB8fCBpbm5lckhlaWdodCE9ZG9jdW1lbnQuTU1fcGdIKSBsb2NhdGlvbi5yZWxvYWQoKTsKfQpNTV9yZWxvYWRQYWdlKHRydWUpOwoKZnVuY3Rpb24gTU1fcHJlbG9hZEltYWdlcygpIHsgLy92My4wCiAgdmFyIGQ9ZG9jdW1lbnQ7IGlmKGQuaW1hZ2VzKXsgaWYoIWQuTU1fcCkgZC5NTV9wPW5ldyBBcnJheSgpOwogICAgdmFyIGksaj1kLk1NX3AubGVuZ3RoLGE9TU1fcHJlbG9hZEltYWdlcy5hcmd1bWVudHM7IGZvcihpPTA7IGk8YS5sZW5ndGg7IGkrKykKICAgIGlmIChhW2ldLmluZGV4T2YoIiMiKSE9MCl7IGQuTU1fcFtqXT1uZXcgSW1hZ2U7IGQuTU1fcFtqKytdLnNyYz1hW2ldO319Cn0KLy8tLT4KPC9zY3JpcHQ+CiAgICAgICAgICAgICA8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoJCQkgCjxzdHlsZSB0eXBlPSJ0ZXh0L2NzcyI+CjwhLS0KI0xheWVyMSB7Cglwb3NpdGlvbjphYnNvbHV0ZTsKCXdpZHRoOjY1MXB4OwoJaGVpZ2h0OjIxOHB4OwoJei1pbmRleDoxOwp9CiNMYXllcjIgewoJcG9zaXRpb246YWJzb2x1dGU7Cgl3aWR0aDoyMDBweDsKCWhlaWdodDoxMTVweDsKCXotaW5kZXg6MTsKCXZpc2liaWxpdHk6IHZpc2libGU7Cn0KLkVzdGlsbzEgewoJZm9udC1zaXplOiAxOHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzIgewoJZm9udC1zaXplOiAxNHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzMge2NvbG9yOiAjNTA2OTkwOyBsaW5lLWhlaWdodDogMTJweDsgdGV4dC1kZWNvcmF0aW9uOiBub25lOyBmb250LWZhbWlseTogVGFob21hO30KLS0+Cjwvc3R5bGU+CjwvaGVhZD4KCjxib2R5IGxlZnRtYXJnaW49IjIiIG1hcmdpbndpZHRoPSIyIj4KPHRhYmxlIHdpZHRoPSI2MDgiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICA8dHI+CiAgICA8dGQgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCB3aWR0aD0iMiUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzA3LmpwZyIgd2lkdGg9IjI0IiBoZWlnaHQ9IjE0IiAvPjwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI5MCUiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18wNy5qcGciPiZuYnNwOzwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI4JSIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wOS5qcGciIHdpZHRoPSI0NSIgaGVpZ2h0PSIxNyIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogIDwvdHI+CiAgPHRyPgogICAgPHRkIGNvbHNwYW49IjQiPjxiciAvPgogICAgICA8dGFibGUgd2lkdGg9Ijk4JSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICA8dHI+CiAgICAgICAgPHRkIHdpZHRoPSIyJSI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgICA8dGQgd2lkdGg9IjkzJSI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CjwhLS0gSU5JQ0lPIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzIzMDQyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjIvMTEvMjAxMzwvc3Bhbj48YnI+SVYgQ29uZ3Jlc28gSW50ZXJuYWNpb25hbCB2aW9sZW5jaWEsIG1hbHRyYXRvIHkgYWJ1c288L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxzdHJvbmc+MTQsIDE1IHkgMTYgZGUgTm92aWVtYnJlIEFCSUVSVEEgTEEgSU5TQ1JJUENJJk9hY3V0ZTtOISAoY29uIGRlc2N1ZW50byBoYXN0YSBlbCAyNy84KTxiciAvPjwvc3Ryb25nPjwvcD4NCjxwPjxzdHJvbmc+QUJJRVJUQSBMQSBSRUNFUENJJk9hY3V0ZTtOIERFIFRSQUJBSk88YSBocmVmPSJodHRwOi8vd3d3LmNvbmdyZXNvdmlvbGVuY2lhLmNvbS9pbmRleC5waHA/aWQ9bW9kYWxpZGFkZXMiIHRhcmdldD0iX2JsYW5rIj4gKG1hcyBpbmZvKTwvYT48L3N0cm9uZz48L3A+DQo8cD48c3BhbiBzdHlsZT0iY29sb3I6ICNmZjY2MDA7Ij48c3Ryb25nPk9yZ2FuaXphOiBTYWx1ZCBBY3RpdmE8L3N0cm9uZz48L3NwYW4+PC9wPg0KPHA+PHNwYW4gc3R5bGU9ImNvbG9yOiAjZmY2NjAwOyI+SW5jcmlwdG9zIGFsIFBvcnRhbCBkZSBTYWx1ZCBBY3RpdmEsIGltcG9ydGFudGVzIGRlc2N1ZW50b3MhPGJyIC8+PC9zcGFuPjwvcD4NCjxwPkx1Z2FyIGRlIFJlYWxpemFjaSZvYWN1dGU7biB5IGNvbGFib3JhY2lvbjogVW5pdmVyc2lkYWQgZGVsIEVzdGUsIExhIFBsYXRhIEJ1ZW5vcyBBaXJlczwvcD4NCjxwPk1hcyBkZSAxNTAgdHJhYmFqb3MgcHJlc2VudGFkb3MsIHVsdGltb3MgZGlhcyBwYXJhIGluc2NyaWJpcnNlIGNvbiBkZXNjdWVudG8hITwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPkluc2NyaWJpcnNlPC9hPjwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPjxiciAvPjwvYT48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAxIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDEiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MDQvMTEvMjAxMzwvc3Bhbj48YnI+RWwgY29sZWdpbyBkZSBQc2lj82xvZ29zIGRlIEPzcmRvYmEgc2UgcHJvbnVuY2lhIGVuIHJlbGFjafNuIGFsIFNBUCB5IGVuIGNvbmNvcmRhbmNpYSBjb24gbG8gZXhwcmVzYWRvIHBvciBlbCBDb2xlZ2lvIGRlIFBzaWPzbG9nb3MgZGUgTWFyIGRlbCBQbGF0YSB5IGVsIENvbGVnaW8gZGUgUHNpY/Nsb2dvcyBkZSBsYSAgUHJvdmluY2lhIGRlIEJ1ZW5vcyBBaXJlczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+Jm5ic3A7PC9wPg0KPHA+TGFzIGNvbnRyb3ZlcnNpYXMgZ2VuZXJhZGFzIGVuIHJlbGFjaSZvYWN1dGU7biBhbCAic2luZHJvbWUgZGUgYWxpZW5hY2kmb2FjdXRlO24gcGFyZW50YSIgU0FQLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMxMCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzEwIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzE2MTAyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTYvMTAvMjAxMzwvc3Bhbj48YnI+U2FsdWQgQWN0aXZhIG90b3JnYSBtZWRpYXMgYmVjYXMgcGFyYSBlbCBJViBDb25ncmVzbyBJbnRlcm5hY2lvbmFsLCBWIE5hY2lvbmFsLCBWSSBSZWdpb25hbCBWaW9sZW5jaWEsIE1hbHRyYXRvIHkgQWJ1c28uPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD4mbmJzcDs8L3A+DQo8cD5TZXImYWFjdXRlO24gb3RvcmdhZGFzIDUwIG1lZGlhcyBiZWNhcywgcXVlZGFuIHBvY2FzISEhIGNvbmRpY2lvbjo8L3A+DQo8cD5QZXJ0ZW5lY2VyIGFsIGFtYml0byBwdWJsaWNvIG8gYSBPTkcsIHNlIGNvbnNpZGVyYSB0YW1iaWVuIGxhIGRpc3RhbmNpYSBhbCBsdWdhciBkZWwgZXZlbnRvISEhIGVzIG11eSBzZW5jaWxsbywgc29sbyBkZWJlcyBlbnZpYXIgdW4gZW1haWwuLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwOSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA5Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjI0LzA3LzIwMTM8L3NwYW4+PGJyPk5FQ0VTSVRBTU9TIERFIFNVIFNPTElEQVJJREFEIEhBQ0lBIExPUyBOSdFPUyBZIE5J0UFTISEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPlBST0dSQU1BIEZBTUlMSUFTIFNPTElEQVJJQVM8L3NwYW4+PC9zdHJvbmc+PC9wPg0KPHA+PHN0cm9uZz5DQU1CSU8gREUgU0VERTwvc3Ryb25nPjwvcD4NCjxwPkxhIGNhcGFjaXRhY2kmb2FjdXRlO24gcGFyYSBsYSBwdWVzdGEgZW4gbWFyY2hhIGRlbCA8c3Ryb25nPlByb2dyYW1hIEZhbWlsaWFzIFNvbGlkYXJpYXM8L3N0cm9uZz4gc2UgcmVhbGl6YXImYWFjdXRlOyBlbiBsYSBsb2NhbGlkYWQgZGUgPHN0cm9uZz5OYXZhcnJvPC9zdHJvbmc+IHBhcmEgdG9kbyBlbCBjb3JyZWRvciBkZSBsYSBSdXRhIDQwLjwvcD4NCjxwPkluaWNpbyA8c3Ryb25nPk1pJmVhY3V0ZTtyY29sZXMgMjggZGUgYWdvc3RvIGEgbGFzIDE0IGhvcmFzLiZuYnNwOzwvc3Ryb25nPjwvcD4NCjxwPlNlZGU6IDxzdHJvbmc+U2FsJm9hY3V0ZTtuIE11bmljaXBhbCBlbiBsYSBjYWxsZSAxMDcgZXNxdWluYSAyMiAtIE5hdmFycm88L3N0cm9uZz48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA4Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTIwNzIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xMi8wNy8yMDEzPC9zcGFuPjxicj5TQUxVRCBBQ1RJVkEgaGEgc2lkbyBlbGVnaWRhIHBvciBzZWd1bmRhIHZleiBjb25zZWN1dGl2YSBjb21vIHVubyBkZSBsb3MgZ2FuYWRvcmVzIGRlbCBDdWFydG8gQ29uY3Vyc28gZGUgUHJveWVjdG9zIFNvY2lhbGVzIGRlIFBldHJvYnJhczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+RW4gZWwgbWFyY28gZGVsIEN1YXJ0byBDb25jdXJzbyBkZSBQcm95ZWN0b3MgU29jaWFsZXMgZGUgUGV0cm9icmFzLCANCm51ZXN0cmEgSW5zdGl0dWNpJm9hY3V0ZTtuIFNBTFVEIEFDVElWQSBoYSBzaWRvIGVsZWdpZGEgcG9yIHNlZ3VuZGEgdmV6IA0KY29uc2VjdXRpdmEgY29tbyB1bm8gZGUgbG9zIGdhbmFkb3JlcyBkZSBkaWNobyBjb25jdXJzby48YnIgLz5FbiBlc3RhIA0KZWRpY2kmb2FjdXRlO24gZWwgcHJveWVjdG8gcXVlIGhhIHNpZG8gZWxlZ2lkbyBlcyBlbCAmbGRxdW87UHJvZ3JhbWEgZGUgRmFtaWxpYXMgDQpTb2xpZGFyaWFzJnJkcXVvOyBzaWVuZG8gc3UgJmFhY3V0ZTtyZWEgZGUgaW1wbGVtZW50YWNpJm9hY3V0ZTtuIGxvcyBNdW5pY2lwaW9zIGRlIE5hdmFycm8sIA0KR3JhbC4gTGFzIEhlcmFzLCBNYXJjb3MgUGF6LCB5IE1lcmxvPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAyLzA3LzIwMTM8L3NwYW4+PGJyPk/tciBvIGVzY3VjaGFyPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Qb3IgQ2FybG9zIFJvemFuc2tpICo8L3A+DQo8cD5BIGxvIGxhcmdvIGRlIGxvcyBzaWdsb3MsIGxhcyBuaSZudGlsZGU7YXMsIG5pJm50aWxkZTtvcyB5IGFkb2xlc2NlbnRlcyBoYW4gc2lkbyBtYWx0cmF0YWRvcyB5IGFidXNhZG9zIHNpbiBxdWUgYSBsYSBjb211bmlkYWQgbGUgaW50ZXJlc2FyYSBuaSBzaXF1aWVyYSBlc2N1Y2hhcmxvcyBjdWFuZG8gaGFjJmlhY3V0ZTthbiBzYWJlciBkZSBhbGd1bmEgZm9ybWEgbG9zIHN1ZnJpbWllbnRvcyBxdWUgcGFkZWMmaWFjdXRlO2FuLiBFbiAxODc0LCBlbiBFc3RhZG9zIFVuaWRvcywgZnVlIGxhIHByaW1lcmEgdmV6IHF1ZSBlbCBFc3RhZG8gaW50ZXJ2aW5vIGVuIHVuIGNhc28gZGUgbWFsdHJhdG8geSBhYnVzby4uLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDYiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4wMi8wNy8yMDEzPC9zcGFuPjxicj5FbCBkZXJlY2hvIGRlIGxvcyBuafFvcyBhIHNlciBlc2N1Y2hhZG9zPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5VbiBob21icmUgYWN1c2FkbyBkZSBoYWJlciBhYnVzYWRvIGRlIHN1cyBoaWpvcyBoYWImaWFjdXRlO2Egc2lkbyBzb2JyZXNlJmlhY3V0ZTtkbyBkb3MgdmVjZXMgcG9yIGxhIEp1c3RpY2lhLiBQZXJvIGFob3JhLCBsYSBDJmFhY3V0ZTttYXJhIGRlIENhc2FjaSZvYWN1dGU7biByZXZvYyZvYWN1dGU7IGVzYSBkZWNpc2kmb2FjdXRlO24gcG9ycXVlIGVuIGxhIGludmVzdGlnYWNpJm9hY3V0ZTtuIGVsIGp1ZXogbnVuY2EgaGFiJmlhY3V0ZTthIGVzY3VjaGFkbyBhIGxvcyBjaGljb3MuIFkgb3JkZW4mb2FjdXRlOyBxdWUgdGVuZ2EgZW4gY3VlbnRhIGxvIHF1ZSBkaWNlbi48L3A+DQo8cD5Qb3IgTWFyaWFuYSBDYXJiYWphbDwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDUiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE1NiIgcm93c3Bhbj0iMiIgdmFsaWduPSJ0b3AiPgoJCQkJCgkJCQk8dGFibGUgd2lkdGg9IjMyJSIgYm9yZGVyPSIxIiBjZWxsc3BhY2luZz0iMyIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48aW1nIHNyYz0ic3JjL2ltZ191cC8wNjA2MjAxMy4xLmpwZyIgd2lkdGg9IjE0NiIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT4KCQkJCQkJCQk8L3RkPiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjA2LzA2LzIwMTM8L3NwYW4+PGJyPkFidXNvIHNleHVhbCBpbmZhbnRpbC4gRGVzYWZpb3MgZGUgbGEgY2xpbmljYSBhY3R1YWw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkFiaWVydGEgbGEgaW5zY3JpcGNpb248L3A+DQo8cD5Eb2NlbnRlczogTGljLiBNYXJpYSBCZWF0cml6IE0mdXVtbDtsbGVyLiBMaWMuIFBhb2xhIE11Jm50aWxkZTtveiBEdWFydGU8L3A+DQo8cD5JbmljaW86IE1pZXJjb2xlcyAxOSBkZSBKdW5pbzwvcD4NCjxwPkZyZWN1ZW5jaWE6IFNlbWFuYWw8L3A+DQo8cD5Nb2RhbGlkYWQ6IEludGVuc2l2YTwvcD4NCjxwPkNvbnRlbmlkb3M6ICZuYnNwOyBFc3RhIGRlc3RpbmFkbyBhIHRvZG9zIGxvcyBwcm9mZXNpb25hbGVzIGNvbXByb21ldGlkb3MgY29uIGxhIHRlbWF0aWNhIGRlbCBhYnVzbyBpbmZhbnRpbCBxdWUgcXVpZXJhbiBhY3R1YWxpemFyc2UgZSBpbnRlcmNhbWJpYXIgZXhwZXJpZW5jaWFzIGRlIHRyYWJham8uLi48L3A+DQo8cD4mbmJzcDs8L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA0Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDQiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTYwNTIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xNi8wNS8yMDEzPC9zcGFuPjxicj5TYWx1ZCBBY3RpdmEgbmVjZXNpdGEgZGUgdHUgYXl1ZGEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5UcmFiYWphbW9zIGNvbW8gcG9kZW1vczogYmEmbnRpbGRlO29zIHJvdG9zLCBzdXNwZW5zaSZvYWN1dGU7biBkZSByZXVuaW9uZXMgcG9yIGNvcnRlcyBkZSBsdXogeSBhZ3VhLCBqdWd1ZXRlcyB2aWVqb3MsIG1lc2VzIGRlIGF0cmFzbyBlbiBlbCBwYWdvIGRlIHN1cyBwcm9mZXNpb25hbGVzIGRlIGxhIHNhbHVkLiBSZWNpZW50ZW1lbnRlIHR1dmltb3MgcXVlIGNlcnJhciBudWVzdHJvIHF1ZXJpZG8gSG9nYXI6ICZsZHF1bztNZXRhbW9yZm9zaXMmcmRxdW87IGVyYSBlbCBsdWdhciBxdWUgc3VwbyBjb250ZW5lciBhIG5pJm50aWxkZTthcyB5IGomb2FjdXRlO3ZlbmVzIHJlc2NhdGFkYSBkZSByZWRlcyBkZSB0cmF0YSBvIHYmaWFjdXRlO2N0aW1hcyBkZSBhYnVzbyBpbnRyYWZhbWlsaWFyLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAzIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAzLzA1LzIwMTM8L3NwYW4+PGJyPlJFUFVESU8gQSBMQSBQUkVTRU5DSUEgRU4gTEEgRkVSSUEgREVMIExJQlJPIERFIFVOIEVYIEpVRVogQUNVU0FETyBERSBBQlVTTyBTRVhVQUw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkZ1ZSBjYW1hcmlzdGEgZW4gTWFyIGRlbCBQbGF0YSBkdXJhbnRlIGxhIGRpY3RhZHVyYS4gSGFjZSBhJm50aWxkZTtvcywgdmFyaWFzIG11amVyZXMgbG8gYWN1c2Fyb24gZGUgaGFiZXIgYWJ1c2FkbyBkZSBlbGxhcyBjdWFuZG8gZXJhbiBuaSZudGlsZGU7YXMuIExhIGNhdXNhIHByZXNjcmliaSZvYWN1dGU7IHkgbm8gaHVibyBjb25kZW5hLiBNYSZudGlsZGU7YW5hIHRpZW5lIHByZXZpc3RvIGZpcm1hciBzdSBsaWJyby4gRXNhcyBtaXNtYXMgbXVqZXJlcyBwaWRlbiBxdWUgbm8gc2VhIGFkbWl0aWRvIGVuIGxhIGZlcmlhLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDIiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgIDwhLS0gRklOIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgIDwvdGFibGU+ICAgICAgICA8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iNSUiIGFsaWduPSJyaWdodCI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgPC90cj4KICAgIDwvdGFibGU+PC90ZD4KICA8L3RyPgogIDx0cj4KICAgIDx0ZCB3aWR0aD0iMSUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiIgYWxpZ249ImNlbnRlciI+Jm5ic3A7PC90ZD4KICAgIDx0ZCB3aWR0aD0iMiUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgPC90cj4KICAKICA8dGQ+CiAgPHRyPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0ciBhbGlnbj0iY2VudGVyIj4KICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgPHRkIHdpZHRoPSI5NyIgY29sc3Bhbj0iMiIgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iNTQ2IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idGl0dWxvaG9tZTIiPjx0YWJsZSB3aWR0aD0iIiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYWxpZ249ImxlZnQiIHZhbGlnbj0iYm90dG9tIiBjbGFzcz0idGl0dWxvaG9tZTIiPlJhbmtpbmc8L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSIgY2xhc3M9InRpdHVsb2hvbWUyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iIiBoZWlnaHQ9IjM1IiBhbGlnbj0ibGVmdCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPiZidWxsO0xhcyBtJmFhY3V0ZTtzIGxlaWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGNsYXNzPSJjb250ZW5pZG9ob21lIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBjbGFzcz0iY29udGVuaWRvaG9tZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+JmJ1bGw7TGFzIG0mYWFjdXRlO3MgY29tZW50YWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTHVkb3RlY2EgR2FyYWJhdG8gLSBQcm95ZWN0byBzYWx1ZGFjdGl2YSwgUG9yIHVuYSBpbmZhbmNpYSBmZWxpeiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iOSUiIGJnY29sb3I9IiNFRkVGRUYiPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzJSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xNjIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDUlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTE2MiIgY2xhc3M9ImJvdG9uIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBDdXJzbyBJbnRlbnNpdm8gZGUgb3BlcmFkb3IgdGVyYXBldXRpY28gZXNwZWNpYWxpemFkbyBlbiBlbCBhYm9yZGFqZSBkZWwgYWJ1c28sIGxhIHZpb2xlbmNpYSB5IGVsIG1hbHRyYXRvIGluZmFudGlsICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgUFJPR1JBTUEgTEFTIFZJQ1RJTUFTIENPTlRSQSBMQVMgVklPTEVOQ0lBUyAgTWluaXN0ZXJpbyBkZSBKdXN0aWNpYSB5IERlcmVjaG9zIEh1bWFub3MgZGUgbGEgTmFjafNuICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI5JSIgYmdjb2xvcj0iI0VGRUZFRiI+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjMlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTI1NSIgY2xhc3M9ImJvdG9uIj48aW1nIHNyYz0iaW1nL2ZsZWNoYW5hcmFuamFmZ3Jpc18yNC5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSI3IiBib3JkZXI9IjAiIGFsaWduPSJhYnNtaWRkbGUiIC8+PC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI0NSUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MjU1IiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIERpcGxvbWF0dXJhIGVuIEFib3JkYWplIGludGVyZGlzY2lwbGluYXJpbyBkZWwgbWFsdHJhdG8sIGxhIHZpb2xlbmNpYSB5IGVsIGFidXNvIHNleHVhbCBpbmZhbnRpbCAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyJSIgaGVpZ2h0PSIyMCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQxJSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNhbHVkIEFjdGl2YSBuZWNlc2l0YSBkZSB0dSBheXVkYSEgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjklIiBiZ2NvbG9yPSIjRUZFRkVGIj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMyUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MTA0IiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQ1JSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xMDQiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTGxhbWFkbyBwYXJhIHByZXNlbnRhY2nzbiBkZSB0cmFiYWpvcy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjIwIiBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyMCIgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGJnY29sb3I9IiNGRkZGRkYiIGNsYXNzPSJ0ZXh0b251ZXZvIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPgogICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iIyIgY2xhc3M9ImJvdG9uIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgPC90YWJsZT48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj4mbmJzcDs8L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBJTklDSU8gbm90YSBjb211biAtLT4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTUvMDQvMjAxMjwvc3Bhbj48YnI+T3JnYW5pemFuIGpvcm5hZGEgc29icmUgdmlvbGVuY2lhPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPlNlIGNlbnRyYXImYWFjdXRlOyBlbiBsb3MgZmVuJm9hY3V0ZTttZW5vcyBxdWUgYWZlY3RhbiBhIGxhIGZhbWlsaWEgeSBlbiBsbyBxdWUgb2N1cnJlIGVuIGxhcyBlc2N1ZWxhcy48YnIgLz4gU2UgbGxldmFyJmFhY3V0ZTsgYSBjYWJvIGVsIGx1bmVzIDIzLCBlbiBlbCBDZW50cm8gQ3VsdHVyYWwgZGUgVG9zY2hpIHkgVHJlcyANCkFycm95b3MsIHVuYSBqb3JuYWRhIGRlIHJlZmxleGkmb2FjdXRlO24geSBkZWJhdGUgYWJpZXJ0YSBhIGxhIGNvbXVuaWRhZCBzb2JyZSANCiZsZHF1bztWaW9sZW5jaWEgZW4gbGEgZmFtaWxpYSB5IGVuIGxhIGVzY3VlbGEgeSBzdSByZWxhY2kmb2FjdXRlO24gY29uIGVsIGZyYWNhc28gDQplc2NvbGFyJnJkcXVvOywgb3JnYW5pemFkYSBwb3IgbGEgQXNvY2lhY2kmb2FjdXRlO24gQ2l2aWwgQ2VudHJvIEFydCZlYWN1dGU7bWlkZXMgeSBsYSANCk11bmljaXBhbGlkYWQgZGUgQ2lwb2xsZXR0aS5TZSBjZW50cmFyJmFhY3V0ZTsgZW4gbG9zIGZlbiZvYWN1dGU7bWVub3MgcXVlIGFmZWN0YW4gYSBsYSBmYW1pbGlhIHkgZW4gbG8gcXVlIG9jdXJyZSBlbiBsYXMgZXNjdWVsYXMuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjMwLzAzLzIwMTI8L3NwYW4+PGJyPkNhcnRhIGRlIEFTQVBNSSAtIEFzb2NpYWNp824gQXJnZW50aW5hIGRlIFByZXZlbmNp824gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbDwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjE1IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSIxNSIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjgwIiBjb2xzcGFuPSI0IiBhbGlnbj0ibGVmdCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Mb3MgaW50ZWdyYW50ZXMgZGUgbGEgQ29taXNpJm9hY3V0ZTtuIERpcmVjdGl2YSBkZSBBU0FQTUkgLSBBc29jaWFjaSZvYWN1dGU7biBBcmdlbnRpbmEgZGUgUHJldmVuY2kmb2FjdXRlO24gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbCwgYXNvY2lhZGEgYSBsYSBJbnRlcm5hdGlvbmFsIFNvY2lldHkgZm9yIFByZXZlbnRpb24gb2YgQ2hpbGQgQWJ1c2UgYW5kIE5lZ2xlY3QgKElTUENBTikgLSwgdGVuZW1vcyBlbCBhZ3JhZG8gZGUgZGlyaWdpcm5vcyBhIFVzdGVkIHBhcmEgdHJhc21pdGlybGUgbnVlc3RyYSBwcm9mdW5kYSAmbmJzcDt5IGhvbmRhIHByZW9jdXBhY2kmb2FjdXRlO24gcG9yIGxhIHBvc3R1cmEgcXVlIHZpZW5lbiBhc3VtaWVuZG8gZW4gZm9ybWEgY29udGludWFkYSBhbGd1bm9zIGNvbGVnaW9zIGRlIHBzaWMmb2FjdXRlO2xvZ29zLCBlc3BlY2lhbG1lbnRlIGRlIGxhIHByb3ZpbmNpYSBkZSBCdWVub3MgQWlyZXMsIGVuIHJlbGFjaSZvYWN1dGU7biBhbCB0cmF0YW1pZW50byBwb2NvIHNlcmlvIHkgY29tcHJvbWV0aWRvIHF1ZSBzZSBsZXMgb3RvcmdhIGEgbGFzIGRlbnVuY2lhcyBlZmVjdHVhZGFzIGNvbnRyYSBwcm9mZXNpb25hbGVzIHBzaWMmb2FjdXRlO2xvZ29zLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjAvMDMvMjAxMjwvc3Bhbj48YnI+TEEgVklPTEVOQ0lBIFNFWFVBTCBDT05UUkEgTknRT1MgWSBOSdFBUyBFTiBDSUZSQVM8L3RkPgogICAgICAgICAgPC90cj4KICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkIHdpZHRoPSIxNSIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4MCIgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+UmFkaW9ncmFmJmlhY3V0ZTthIGRlIHVuIHByb2JsZW1hPC9wPg0KPHA+RGUgbG9zIG4mdWFjdXRlO21lcm9zIGNvbXBpbGFkb3MgcG9yIGRvcyBlcXVpcG9zIGRlbCBNaW5pc3RlcmlvIGRlIEp1c3RpY2lhLCBsYQ0KIGF1dG9yYSB0b21hIGxvcyBkZSBsYSBjaXVkYWQgZGUgQnVlbm9zIEFpcmVzIHBhcmEgdHJhemFyIHVuIHBhcmFkaWdtYSANCmRlIGxvcyBkZWxpdG9zIGNvbnRyYSBsYSBpbnRlZ3JpZGFkIHNleHVhbCBlbiBlbCBwYSZpYWN1dGU7cyB5IHNvYnJlIHN1IA0KYXRlbmNpJm9hY3V0ZTtuLjxiciAvPiA8YnIgLz4gJm5ic3A7UG9yIEV2YSBHaWJlcnRpPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2MCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjAiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjE1LzAzLzIwMTI8L3NwYW4+PGJyPkZBTExPIERFIExBIENPUlRFIFNVUFJFTUEgU09CUkUgTEEgTk8gSlVESUNJQUxJWkFDSU9OIERFTCBBQk9SVE8gRU4gQ0FTT1MgREUgVklPTEFDSU9OPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxiciAvPiBKVVJJU0RJQ0NJT046IE5BQ0lPTkFMPGJyIC8+IE1BVEVSSUE6IEFCT1JUTy48YnIgLz4gVFJJQlVOQUw6IENvcnRlIFN1cHJlbWEgZGUgSnVzdGljaWEgZGUgbGEgTmFjaSZvYWN1dGU7bi48YnIgLz4gQVVUT1M6IEYuLCBBLiBMLiBzLyBtZWRpZGEgYXV0b3NhdGlzZmFjdGl2YS48YnIgLz4gRkVDSEE6IDEzLzAzLzIwMTIuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI1OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNTkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBGSU4gbm90YSBjb211biAtLT4KPC90YWJsZT4KPG1hcCBuYW1lPSJNYXBNYXAiIGlkPSJNYXBNYXAiPjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjE0NCw0LDIxNCwzNiIgaHJlZj0iaW5kZXgucGhwP2lkPTE0IiAvPgo8L21hcD4KPG1hcCBuYW1lPSJNYXAyTWFwMiIgaWQ9Ik1hcDJNYXAyIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIxNDcsNCwyMjAsMzYiIGhyZWY9ImluZGV4LnBocD9pZD0xNGEiIC8+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcDMiIGlkPSJNYXAzIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIzNjMsMyw0MzYsMzkiIGhyZWY9ImluZGV4LnBocD9pZD0xNGIiIC8+CjwvbWFwPgo8L2h0bWw+CjwvdGQ+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gICAgICAgICAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFM0UzRTMiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSI3MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNiUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9kZWNpbG9fYmllbl9mdWVydGUxLmpwZyIgd2lkdGg9IjEyMCIgaGVpZ2h0PSIxMTIiPjwvdGQ+CiAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiA+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTI0IiBjbGFzcz0iYm90b24xIj5bK10gTSZhYWN1dGU7cyBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0UzRTNFMyI+ICAgICAgICA8L3RyPgogICAgICAgIDx0cj4gCiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj4mbmJzcDs8L3RkPgogICAgICAgIDwvdHI+CiAgICA8L3RhYmxlPjwvdGQ+CiAgPC90cj4KICA8dHI+IAogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSI+PGltZyBzcmM9ImltZy9penExLmpwZyIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjExNCIgLz48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9RdWllbmVzU29tb3NfQTJfMF8yNS5qcGciIHdpZHRoPSI4MDkiIGhlaWdodD0iMTE0IiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcDIiIC8+PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI1MCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiYWNrZ3JvdW5kPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzE4XzE4LmpwZyI+Jm5ic3A7PC90ZD4KICAgIDx0ZCBoZWlnaHQ9IjUwIiBjbGFzcz0iZm9uZG9ib3R0b20iPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2l0ZWkuY29tLmFyLyI+PGltZyBzcmM9ImltZy9laV9jb2xvci5wbmciIGFsdD0iZXNwYWNpb3MgZGUgaW1hZ2luYWNpb24sIGRlc2Fycm9sbG9zIGludGVyYWN0aXZvcywgY3JlYXRpdmlkYWQsIGRpc2XxbyIgd2lkdGg9IjI3IiBoZWlnaHQ9IjE1IiBib3JkZXI9IjAiPjwvYT4gPHNwYW4gY2xhc3M9ImVpIj48YSBocmVmPSJodHRwOi8vd3d3LnNpdGVpLmNvbS5hci8iIHNwYW4gY2xhc3M9ImVpIj5kaXNlJm50aWxkZTtvICsgY29tdW5pY2FjaSZvYWN1dGU7bjwvYT48L3NwYW4+PGVtPiZuYnNwOzwvZW0+PC9zcGFuPjxzcGFuIGNsYXNzPSJibGFuY28xIj48ZW0+Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7PC9lbT48L3NwYW4+PC90ZD4KICA8L3RyPgo8L3RhYmxlPgoKCjxtYXAgbmFtZT0iTWFwMiI+PGFyZWEgc2hhcGU9InJlY3QiIGNvb3Jkcz0iMjQ3LDY5LDQxNCw4MiIgaHJlZj0ibWFpbHRvOnNhbHVkYWN0aXZhQHNhbHVkYWN0aXZvLm9yZy5hciI+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcCI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM2LDE0MiwxNDksMTUyIiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MiI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM0LDE4NiwxNTAsMTk2IiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MCI+CjwvbWFwPgo8L2JvZHk+CjwvaHRtbD4K]]></response> | |
| 165 | <responseRedirected>false</responseRedirected> | |
| 166 | </requestresponse> | |
| 167 | </issue> | |
| 168 | <issue> | |
| 169 | <serialNumber>8637745207739944960</serialNumber> | |
| 170 | <type>6291968</type> | |
| 171 | <name>Email addresses disclosed</name> | |
| 172 | <host ip="200.20.20.201">http://www.example.org.ar</host> | |
| 173 | <path><![CDATA[/index.php]]></path> | |
| 174 | <location><![CDATA[/index.php]]></location> | |
| 175 | <severity>Information</severity> | |
| 176 | <confidence>Certain</confidence> | |
| 177 | <issueBackground><![CDATA[The presence of email addresses within application responses does not necessarily constitute a security vulnerability. Email addresses may appear intentionally within contact information, and many applications (such as web mail) include arbitrary third-party email addresses within their core content.<br><br>However, email addresses of developers and other individuals (whether appearing on-screen or hidden within page source) may disclose information that is useful to an attacker; for example, they may represent usernames that can be used at the application's login, and they may be used in social engineering attacks against the organization's personnel. Unnecessary or excessive disclosure of email addresses may also lead to an increase in the volume of spam email received.]]></issueBackground> | |
| 178 | <remediationBackground><![CDATA[You should review the email addresses being disclosed by the application, and consider removing any that are unnecessary, or replacing personal addresses with anonymous mailbox addresses (such as [email protected]).]]></remediationBackground> | |
| 179 | <issueDetail><![CDATA[The following email addresses were disclosed in the response:<ul><li>[email protected]</li><li>[email protected]</li></ul>]]></issueDetail> | |
| 180 | <requestresponse> | |
| 181 | <request base64="true"><![CDATA[R0VUIC9pbmRleC5waHAgSFRUUC8xLjENCkhvc3Q6IHd3dy5zYWx1ZGFjdGl2YS5vcmcuYXINCkFjY2VwdDogKi8qDQpBY2NlcHQtTGFuZ3VhZ2U6IGVuDQpVc2VyLUFnZW50OiBNb3ppbGxhLzUuMCAoY29tcGF0aWJsZTsgTVNJRSA5LjA7IFdpbmRvd3MgTlQgNi4xOyBXaW42NDsgeDY0OyBUcmlkZW50LzUuMCkNCkNvbm5lY3Rpb246IGNsb3NlDQoNCg==]]></request> | |
| 182 | <response base64="true"><![CDATA[SFRUUC8xLjEgMjAwIE9LDQpEYXRlOiBUaHUsIDA3IE5vdiAyMDEzIDE3OjE0OjA1IEdNVA0KU2VydmVyOiBBcGFjaGUvMi4yLjIzIChVbml4KSBtb2Rfc3NsLzIuMi4yMyBPcGVuU1NMLzAuOS44ZS1maXBzLXJoZWw1DQpYLVBvd2VyZWQtQnk6IFBIUC81LjIuMTcNCkV4cGlyZXM6IFRodSwgMTkgTm92IDE5ODEgMDg6NTI6MDAgR01UDQpDYWNoZS1Db250cm9sOiBuby1zdG9yZSwgbm8tY2FjaGUsIG11c3QtcmV2YWxpZGF0ZSwgcG9zdC1jaGVjaz0wLCBwcmUtY2hlY2s9MA0KUHJhZ21hOiBuby1jYWNoZQ0KQ29ubmVjdGlvbjogY2xvc2UNCkNvbnRlbnQtVHlwZTogdGV4dC9odG1sDQpDb250ZW50LUxlbmd0aDogNjA2MDYNCg0KIDxoZWFkPgo8bWV0YSBodHRwLWVxdWl2PSJDb250ZW50LVR5cGUiIGNvbnRlbnQ9InRleHQvaHRtbDsgY2hhcnNldD1pc28tODg1OS0xIiAvPgo8dGl0bGU+U2FsdWQgQWN0aXZhIC0gQWJ1c28gdmlvbGVuY2lhIHkgbWFsdHJhdG88L3RpdGxlPgoKPHNjcmlwdD4gCiAgICAvL2VzdG8gcGFyYSBwYXNhcmxlIGFsIGZsYXNoIGxhcyB2YXJpYWxiZXMgZGVsIHBocAogCQoKCXZhciBib3Q9Jyc7Ci8vYWxlcnQodmFyaWFibGVTZXJ2aWRvcik7Cjwvc2NyaXB0Pgo8c2NyaXB0IGxhbmd1YWdlPSJKYXZhU2NyaXB0IiB0eXBlPSJ0ZXh0L0phdmFTY3JpcHQiPgo8IS0tCmZ1bmN0aW9uIE1NX3ByZWxvYWRJbWFnZXMoKSB7IC8vdjMuMAogIHZhciBkPWRvY3VtZW50OyBpZihkLmltYWdlcyl7IGlmKCFkLk1NX3ApIGQuTU1fcD1uZXcgQXJyYXkoKTsKICAgIHZhciBpLGo9ZC5NTV9wLmxlbmd0aCxhPU1NX3ByZWxvYWRJbWFnZXMuYXJndW1lbnRzOyBmb3IoaT0wOyBpPGEubGVuZ3RoOyBpKyspCiAgICBpZiAoYVtpXS5pbmRleE9mKCIjIikhPTApeyBkLk1NX3Bbal09bmV3IEltYWdlOyBkLk1NX3BbaisrXS5zcmM9YVtpXTt9fQp9Ci8vLS0+Cjwvc2NyaXB0Pgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KCjwvaGVhZD4KCjxzY3JpcHQgbGFuZ3VhZ2U9IkphdmFTY3JpcHQiIHR5cGU9InRleHQvSmF2YVNjcmlwdCI+CjwhLS0KZnVuY3Rpb24gTU1fcmVsb2FkUGFnZShpbml0KSB7ICAvL3JlbG9hZHMgdGhlIHdpbmRvdyBpZiBOYXY0IHJlc2l6ZWQKICBpZiAoaW5pdD09dHJ1ZSkgd2l0aCAobmF2aWdhdG9yKSB7aWYgKChhcHBOYW1lPT0iTmV0c2NhcGUiKSYmKHBhcnNlSW50KGFwcFZlcnNpb24pPT00KSkgewogICAgZG9jdW1lbnQuTU1fcGdXPWlubmVyV2lkdGg7IGRvY3VtZW50Lk1NX3BnSD1pbm5lckhlaWdodDsgb25yZXNpemU9TU1fcmVsb2FkUGFnZTsgfX0KICBlbHNlIGlmIChpbm5lcldpZHRoIT1kb2N1bWVudC5NTV9wZ1cgfHwgaW5uZXJIZWlnaHQhPWRvY3VtZW50Lk1NX3BnSCkgbG9jYXRpb24ucmVsb2FkKCk7Cn0KTU1fcmVsb2FkUGFnZSh0cnVlKTsKLy8tLT4KCjwvc2NyaXB0Pgo8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoKCjwvaGVhZD4KCjxib2R5IGJhY2tncm91bmQ9ImltZy9mb25kb19kZWdyYWRlLmpwZyIgdG9wbWFyZ2luPSIwIj4KPHRhYmxlIHdpZHRoPSIxMDA1IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgPHRyPiAKICAgIDx0ZCB3aWR0aD0iOTYiPjxpbWcgc3JjPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzBfMDEuanBnIiB3aWR0aD0iOTYiIGhlaWdodD0iMjA4IiAvPjwvdGQ+CiAgICA8dGQgd2lkdGg9IjgwOSI+IDxzY3JpcHQgdHlwZT0idGV4dC9qYXZhc2NyaXB0Ij4KQUNfRkxfUnVuQ29udGVudCggJ2NvZGViYXNlJywnaHR0cDovL2Rvd25sb2FkLm1hY3JvbWVkaWEuY29tL3B1Yi9zaG9ja3dhdmUvY2Ficy9mbGFzaC9zd2ZsYXNoLmNhYiN2ZXJzaW9uPTcsMCwxOSwwJywnd2lkdGgnLCc4MDknLCdoZWlnaHQnLCcyMDgnLCdzcmMnLCdzd2YvaGVhZGVyJywncXVhbGl0eScsJ2hpZ2gnLCdwbHVnaW5zcGFnZScsJ2h0dHA6Ly93d3cubWFjcm9tZWRpYS5jb20vZ28vZ2V0Zmxhc2hwbGF5ZXInLCdtb3ZpZScsJ3N3Zi9oZWFkZXInICk7IC8vZW5kIEFDIGNvZGUKPC9zY3JpcHQ+IDxub3NjcmlwdD4KICAgICAgPG9iamVjdCBjbGFzc2lkPSJjbHNpZDpEMjdDREI2RS1BRTZELTExY2YtOTZCOC00NDQ1NTM1NDAwMDAiIGNvZGViYXNlPSJodHRwOi8vZG93bmxvYWQubWFjcm9tZWRpYS5jb20vcHViL3Nob2Nrd2F2ZS9jYWJzL2ZsYXNoL3N3Zmxhc2guY2FiI3ZlcnNpb249NywwLDE5LDAiIHdpZHRoPSI4MDkiIGhlaWdodD0iMjA4Ij4KICAgICAgICA8cGFyYW0gbmFtZT0ibW92aWUiIHZhbHVlPSJzd2YvaGVhZGVyLnN3ZiIgLz4KICAgICAgICA8cGFyYW0gbmFtZT0icXVhbGl0eSIgdmFsdWU9ImhpZ2giIC8+CiAgICAgICAgPGVtYmVkIHNyYz0ic3dmL2hlYWRlci5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9IjgwOSIgaGVpZ2h0PSIyMDgiPjwvZW1iZWQ+IAogICAgICA8L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIHdpZHRoPSIxMiUiIHJvd3NwYW49IjUiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iIzAwMDAwMCI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI0NjEiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmFja2dyb3VuZD0iaW1nL1F1aWVuZXNTb21vc19BMl8wXzEzLmpwZyI+IAogICAgICA8c2NyaXB0IHR5cGU9InRleHQvamF2YXNjcmlwdCI+CkFDX0ZMX1J1bkNvbnRlbnQoICdjb2RlYmFzZScsJ2h0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCcsJ3dpZHRoJywnOTYnLCdoZWlnaHQnLCc0NjEnLCdzcmMnLCdzd2Yvc3VibWVudScsJ3F1YWxpdHknLCdoaWdoJywncGx1Z2luc3BhZ2UnLCdodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyJywnbW92aWUnLCdzd2Yvc3VibWVudScgKTsgLy9lbmQgQUMgY29kZQo8L3NjcmlwdD4gPG5vc2NyaXB0PgogICAgICA8b2JqZWN0IGNsYXNzaWQ9ImNsc2lkOkQyN0NEQjZFLUFFNkQtMTFjZi05NkI4LTQ0NDU1MzU0MDAwMCIgY29kZWJhc2U9Imh0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+CiAgICAgICAgPHBhcmFtIG5hbWU9Im1vdmllIiB2YWx1ZT0ic3dmL3N1Ym1lbnUuc3dmIiAvPgogICAgICAgIDxwYXJhbSBuYW1lPSJxdWFsaXR5IiB2YWx1ZT0iaGlnaCIgLz4KICAgICAgICA8ZW1iZWQgc3JjPSJzd2Yvc3VibWVudS5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+PC9lbWJlZD48L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCIgYmdjb2xvcj0iI0ZGRkZGRiI+CiAgICAgICAgPHRyPiAKICAgICAgICAgIDx0ZCB3aWR0aD0iMTciIHJvd3NwYW49IjciPjxwPiZuYnNwOzwvcD48L3RkPgogICAgICAgICAgPHRkIHdpZHRoPSIxNzIiIGFsaWduPSJjZW50ZXIiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxpbWcgc3JjPSJpbWcvM3B4LmpwZyIgd2lkdGg9IjUiIGhlaWdodD0iNSI+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciI+PGxpbmsgaHJlZj0iLi4vZXN0aWxvcy5jc3MiIHJlbD0ic3R5bGVzaGVldCIgdHlwZT0idGV4dC9jc3MiIC8+Cjxib2R5IGJnY29sb3I9IiNDQ0NDQ0MiIHRvcG1hcmdpbj0iNiBweCI+PHRhYmxlIHdpZHRoPSIxNjUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIzIiBiZ2NvbG9yPSIjRkZGRkZGIj4KPHRyPgogICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTkxIiBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiAgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MThfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+SG9tZTwvYT48L3RkPgogIDwvdHI+Cjx0cj4KICA8dGQgaGVpZ2h0PSIyOCIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj4mbmJzcDsmbmJzcDtOb3RpY2lhczwvYT48L3RkPgo8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJkb25hY2lvbmVzLyIgdGFyZ2V0PSJfYmxhbmsiIGNsYXNzPSJmb25kb2JvdG9uIj5Eb25hY2lvbmVzPC9hPjwvdGQ+CiAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciICB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yM19uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5IaXN0b3JpYWwgZGUgbmV3c2xldHRlcnM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTEzYSIgY2xhc3M9ImZvbmRvYm90b24iPkVudmlhciBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yNl9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5WZXIgdHJhYmFqb3MgZGUgdXN1YXJpb3M8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MTZfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+U2FsdWQgQWN0aXZhIHByZW5zYTwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJtYWlsdG86c2FsdWRhY3RpdmFAc2FsdWRhY3RpdmEub3JnLmFyIiBjbGFzcz0iZm9uZG9ib3RvbiI+TWFuZCZhYWN1dGU7IHR1IEMuVi48L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgIHdpZHRoPSI2ImhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTIxX25ldyIgY2xhc3M9ImZvbmRvYm90b24iPkluZm9ybWFjaSZvYWN1dGU7biBkZSBpbnRlciZlYWN1dGU7czwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyI+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiBoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xMF80IiBjbGFzcz0iZm9uZG9ib3RvbiI+Q29uZ3Jlc29zCiAgICAgICAgICAgICAgICAgIHkgSm9ybmFkYXM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTExIiBjbGFzcz0iZm9uZG9ib3RvbiI+UmVnaXN0cmFjaSZvYWN1dGU7bjwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgCiAgICAgICAgICA8L3RhYmxlPgo8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNSIgdGFyZ2V0PSJfYmxhbmsiPjxicj4KICAgICAgICAgICAgICAgICAgPGltZyBzcmM9ImltZy9iYW5uZXJfZG9uYWNpb25lcy5qcGciIHdpZHRoPSIxNjIiIGhlaWdodD0iMTIwIiBib3JkZXI9IjAiPjxicj4KICAgICAgICAgICAgICAgICAgPGJyPgogICAgICAgICAgICAgICAgICA8aW1nIHNyYz0iaW1nL2JvdG9uRm9yby5naWYiIHdpZHRoPSIxNzIiIGhlaWdodD0iMTE3IiBib3JkZXI9IjAiPjwvYT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTY3IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjkiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzAzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iOSIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTQ5IiBiYWNrZ3JvdW5kPSJpbWcvY2hpY29zX3BlcmRpZG9zXzA1LmdpZiI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDUuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMCI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDcuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMi5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEyLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9InNyYy9pbWdfdXAvMjMwODIwMTIuMS5qcGciIHdpZHRoPSIxNDkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMy5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNi5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iNSIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTcuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNy5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgYmdjb2xvcj0iI0ZFRTdDRiIgY2xhc3M9InRpdHVsb2hvbWU1Ij48c3Ryb25nPk5pJm50aWxkZTtvcyBwZXJkaWRvczxicj4KICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0yOSIgY2xhc3M9ImJvdG9uIj5bVmVyIG0mYWFjdXRlO3NdPC9hPjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTkuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xOS5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18yMC5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iMjUiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4NCgkJCQkNCgkJCQk8Zm9ybSBhY3Rpb249ImluZGV4LnBocD9pZD0xMSIgIG1ldGhvZD0icG9zdCI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9penExLmpwZyIgd2lkdGg9IjEyIiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9hcnJpYmEuanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9kZXIxLmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgIDwvdHI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiIgdmFsaWduPSJ0b3AiIGNsYXNzPSJyZWdGb25kbzEiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9penEuanBnIiB3aWR0aD0iMTIiIGhlaWdodD0iMTIiIC8+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSI5NCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV90aXQuanBnIiB3aWR0aD0iNjYiIGhlaWdodD0iMjMiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSI1MCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJyZWdpc3RyYXJzZSI+SW5ncmVzJmFhY3V0ZTsgDQogICAgICAgICAgICAgIHR1cyBkYXRvcyB5IHJlY2liJmlhY3V0ZTsgbGEgbWVqb3IgaW5mb3JtYWNpJm9hY3V0ZTtuIGEgdHJhdiZlYWN1dGU7cyANCiAgICAgICAgICAgICAgZGUgbnVlc3RybzxzdHJvbmc+IE5ld3NsZXR0ZXI8L3N0cm9uZz4uIDxzdHJvbmc+PHNwYW4gY2xhc3M9ImdyYXRpcyI+R3JhdGlzITwvc3Bhbj48L3N0cm9uZz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI1IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9InRyYWJTRUNDSU9OIj5Ob21icmU8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBjbGFzcz0icmVnQ0VMREEiPjxpbnB1dCBuYW1lPSJub21icmUiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0ibm9tYnJlIiAvPjwvdGQ+DQogICAgICAgICAgPC90cj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0idHJhYlNFQ0NJT04iPkFwZWxsaWRvPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iYXBlbGxpZG8iIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iYXBlbGxpZG8iIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJ0cmFiU0VDQ0lPTiI+RS1tYWlsPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iZW1haWwiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iZW1haWwiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InRyYWJTRUNDSU9OIj4mbmJzcDs8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idHJhYlNFQ0NJT04iPjxpbnB1dCB0eXBlPSJpbWFnZSIgc3JjPSJpbWcvcmVnaXN0cmF0ZV9ib3Rvbi5qcGciIHdpZHRoPSIxMTciIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgIDwvdGFibGU+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE0IiB2YWxpZ249InRvcCIgY2xhc3M9InJlZ0ZvbmRvMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2Rlci5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIxNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KICAgICAgICAgICAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTIiIGhlaWdodD0iMjQiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfaXpxMi5qcGciIHdpZHRoPSIxMiIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI0Ij48aW1nIHNyYz0iaW1nL3JlZ2lzdHJhdGVfYWJham8uanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjI0IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfZGVyMi5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KCQkJCQkNCgkJCQkJPC9mb3JtPg0KICAgICAgICAgICAgICAgICAgPC90YWJsZT4NCjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPiAKICAgICAgICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTcwIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUyIj4KCQkJCQkJCQkJCQkJCQkJCTwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9jbGF1ZGlhMl8wMy5qcGciIHdpZHRoPSIxNzQiIGhlaWdodD0iMjUwIiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcCI+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICA8dGQgcm93c3Bhbj0iNyIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nLzV4NS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjciPjwvdGQ+CiAgICAgICAgICA8dGQgY29sc3Bhbj0iMiIgcm93c3Bhbj0iNCIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPGZvcm0gYWN0aW9uPSJsb2dpbi5waHAiIG1ldGhvZD0icG9zdCIgbmFtZT0iZm9ybTIiPgoKICAgICAgICAgICAgICA8dHI+IAogICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgY29sc3Bhbj0iMiIgYWxpZ249ImxlZnQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIiA+IAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8c3Ryb25nPlVzdWFyaW8gbm8gcmVnaXN0cmFkbzwvc3Ryb25nPiAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9mb250PiA8L3N0cm9uZz4gCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDkiIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPlVzdWFyaW8mbmJzcDsmbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzOSIgdmFsaWduPSJtaWRkbGUiPjxpbnB1dCBuYW1lPSJ1c3VhcmlvIiB0eXBlPSJ0ZXh0IiBjbGFzcz0icmVnIiBpZD0idXN1YXJpbyIgc2l6ZT0iNyI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjciIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPkNvbnRyYXNlJm50aWxkZTthJm5ic3A7Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzkiIHZhbGlnbj0ibWlkZGxlIj48aW5wdXQgbmFtZT0icGFzcyIgdHlwZT0icGFzc3dvcmQiIGNsYXNzPSJyZWciIGlkPSJwYXNzIiBzaXplPSI3Ij48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiIgYWxpZ249InJpZ2h0IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9ImJvdG9uIj48aW5wdXQgdHlwZT0iaW1hZ2UiIHNyYz0iaW1nL3JlZy5qcGciIHdpZHRoPSI1OCIgaGVpZ2h0PSIzMCI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjciIGhlaWdodD0iMTkiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgPjxhIGhyZWY9Imh0dHA6Ly93d3cuZmFjZWJvb2suY29tL2hvbWUucGhwPyMhL3BhZ2VzL01lcmxvLUFyZ2VudGluYS9TQUxVRC1BQ1RJVkEvMTAwNTgzNTQzMzE3MzIyP3JlZj10cyZhamF4cGlwZT0xJl9fYT03IiB0YXJnZXQ9Il9ibGFuayI+PGltZyBzcmM9ImltZy9mYWNlYm9vay5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzExIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj48ZGl2IGFsaWduPSJsZWZ0Ij48YSBocmVmPSJodHRwOi8vdHdpdHRlci5jb20vU2FsdWRBY3RpdmFPTkciIHRhcmdldD0iX2JsYW5rIj48aW1nIHNyYz0iaW1nL3R3aXRlci5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC9kaXY+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSI1IiBhbGlnbj0icmlnaHQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIj48bGFiZWw+PGZvbnQgc2l6ZT0iLTYiPlNpCiAgICAgICAgICAgICAgICAgICAgICAgdG9kYXYmaWFjdXRlO2Egbm8gZXMgdXN1YXJpbyA8L2ZvbnQ+IDxhIGhyZWY9ImluZGV4LnBocD9pZD0xMSIgY2xhc3M9ImJvdG9uIj48Zm9udCBzaXplPSItNiI+cmVnJmlhY3V0ZTtzdHJlc2UKICAgICAgICAgICAgICAgICAgICAgICAgYXF1JmlhY3V0ZTsgPGZvbnQgY29sb3I9IiM2NjY2NjYiPiYjODIyNjs8L2ZvbnQ+PC9mb250PjwvYT4gPGEgaHJlZj0iaW5kZXgucGhwP2lkPTEyIiBjbGFzcz0iYm90b24xIj48Zm9udCBzaXplPSItNiI+b2x2aWRlIG1pIGNvbnRyYXNlJm50aWxkZTthPC9mb250PjwvYT48L2xhYmVsPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE3Ij4mbmJzcDsgPC90ZD4KICAgICAgICAgICAgICA8L3RyPgoJCQkgIDwvZm9ybT4KCiAgICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgICA8IURPQ1RZUEUgaHRtbCBQVUJMSUMgIi0vL1czQy8vRFREIFhIVE1MIDEuMCBUcmFuc2l0aW9uYWwvL0VOIiAiaHR0cDovL3d3dy53My5vcmcvVFIveGh0bWwxL0RURC94aHRtbDEtdHJhbnNpdGlvbmFsLmR0ZCI+CjxodG1sIHhtbG5zPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hodG1sIj4KPGhlYWQ+CjxtZXRhIGh0dHAtZXF1aXY9IkNvbnRlbnQtVHlwZSIgY29udGVudD0idGV4dC9odG1sOyBjaGFyc2V0PWlzby04ODU5LTEiIC8+Cjx0aXRsZT5Eb2N1bWVudG8gc2luIHQmaWFjdXRlO3R1bG88L3RpdGxlPgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KPHNjcmlwdCBsYW5ndWFnZT0iSmF2YVNjcmlwdCIgdHlwZT0idGV4dC9KYXZhU2NyaXB0Ij4KPCEtLQpmdW5jdGlvbiBNTV9yZWxvYWRQYWdlKGluaXQpIHsgIC8vcmVsb2FkcyB0aGUgd2luZG93IGlmIE5hdjQgcmVzaXplZAogIGlmIChpbml0PT10cnVlKSB3aXRoIChuYXZpZ2F0b3IpIHtpZiAoKGFwcE5hbWU9PSJOZXRzY2FwZSIpJiYocGFyc2VJbnQoYXBwVmVyc2lvbik9PTQpKSB7CiAgICBkb2N1bWVudC5NTV9wZ1c9aW5uZXJXaWR0aDsgZG9jdW1lbnQuTU1fcGdIPWlubmVySGVpZ2h0OyBvbnJlc2l6ZT1NTV9yZWxvYWRQYWdlOyB9fQogIGVsc2UgaWYgKGlubmVyV2lkdGghPWRvY3VtZW50Lk1NX3BnVyB8fCBpbm5lckhlaWdodCE9ZG9jdW1lbnQuTU1fcGdIKSBsb2NhdGlvbi5yZWxvYWQoKTsKfQpNTV9yZWxvYWRQYWdlKHRydWUpOwoKZnVuY3Rpb24gTU1fcHJlbG9hZEltYWdlcygpIHsgLy92My4wCiAgdmFyIGQ9ZG9jdW1lbnQ7IGlmKGQuaW1hZ2VzKXsgaWYoIWQuTU1fcCkgZC5NTV9wPW5ldyBBcnJheSgpOwogICAgdmFyIGksaj1kLk1NX3AubGVuZ3RoLGE9TU1fcHJlbG9hZEltYWdlcy5hcmd1bWVudHM7IGZvcihpPTA7IGk8YS5sZW5ndGg7IGkrKykKICAgIGlmIChhW2ldLmluZGV4T2YoIiMiKSE9MCl7IGQuTU1fcFtqXT1uZXcgSW1hZ2U7IGQuTU1fcFtqKytdLnNyYz1hW2ldO319Cn0KLy8tLT4KPC9zY3JpcHQ+CiAgICAgICAgICAgICA8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoJCQkgCjxzdHlsZSB0eXBlPSJ0ZXh0L2NzcyI+CjwhLS0KI0xheWVyMSB7Cglwb3NpdGlvbjphYnNvbHV0ZTsKCXdpZHRoOjY1MXB4OwoJaGVpZ2h0OjIxOHB4OwoJei1pbmRleDoxOwp9CiNMYXllcjIgewoJcG9zaXRpb246YWJzb2x1dGU7Cgl3aWR0aDoyMDBweDsKCWhlaWdodDoxMTVweDsKCXotaW5kZXg6MTsKCXZpc2liaWxpdHk6IHZpc2libGU7Cn0KLkVzdGlsbzEgewoJZm9udC1zaXplOiAxOHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzIgewoJZm9udC1zaXplOiAxNHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzMge2NvbG9yOiAjNTA2OTkwOyBsaW5lLWhlaWdodDogMTJweDsgdGV4dC1kZWNvcmF0aW9uOiBub25lOyBmb250LWZhbWlseTogVGFob21hO30KLS0+Cjwvc3R5bGU+CjwvaGVhZD4KCjxib2R5IGxlZnRtYXJnaW49IjIiIG1hcmdpbndpZHRoPSIyIj4KPHRhYmxlIHdpZHRoPSI2MDgiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICA8dHI+CiAgICA8dGQgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCB3aWR0aD0iMiUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzA3LmpwZyIgd2lkdGg9IjI0IiBoZWlnaHQ9IjE0IiAvPjwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI5MCUiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18wNy5qcGciPiZuYnNwOzwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI4JSIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wOS5qcGciIHdpZHRoPSI0NSIgaGVpZ2h0PSIxNyIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogIDwvdHI+CiAgPHRyPgogICAgPHRkIGNvbHNwYW49IjQiPjxiciAvPgogICAgICA8dGFibGUgd2lkdGg9Ijk4JSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICA8dHI+CiAgICAgICAgPHRkIHdpZHRoPSIyJSI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgICA8dGQgd2lkdGg9IjkzJSI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CjwhLS0gSU5JQ0lPIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzIzMDQyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjIvMTEvMjAxMzwvc3Bhbj48YnI+SVYgQ29uZ3Jlc28gSW50ZXJuYWNpb25hbCB2aW9sZW5jaWEsIG1hbHRyYXRvIHkgYWJ1c288L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxzdHJvbmc+MTQsIDE1IHkgMTYgZGUgTm92aWVtYnJlIEFCSUVSVEEgTEEgSU5TQ1JJUENJJk9hY3V0ZTtOISAoY29uIGRlc2N1ZW50byBoYXN0YSBlbCAyNy84KTxiciAvPjwvc3Ryb25nPjwvcD4NCjxwPjxzdHJvbmc+QUJJRVJUQSBMQSBSRUNFUENJJk9hY3V0ZTtOIERFIFRSQUJBSk88YSBocmVmPSJodHRwOi8vd3d3LmNvbmdyZXNvdmlvbGVuY2lhLmNvbS9pbmRleC5waHA/aWQ9bW9kYWxpZGFkZXMiIHRhcmdldD0iX2JsYW5rIj4gKG1hcyBpbmZvKTwvYT48L3N0cm9uZz48L3A+DQo8cD48c3BhbiBzdHlsZT0iY29sb3I6ICNmZjY2MDA7Ij48c3Ryb25nPk9yZ2FuaXphOiBTYWx1ZCBBY3RpdmE8L3N0cm9uZz48L3NwYW4+PC9wPg0KPHA+PHNwYW4gc3R5bGU9ImNvbG9yOiAjZmY2NjAwOyI+SW5jcmlwdG9zIGFsIFBvcnRhbCBkZSBTYWx1ZCBBY3RpdmEsIGltcG9ydGFudGVzIGRlc2N1ZW50b3MhPGJyIC8+PC9zcGFuPjwvcD4NCjxwPkx1Z2FyIGRlIFJlYWxpemFjaSZvYWN1dGU7biB5IGNvbGFib3JhY2lvbjogVW5pdmVyc2lkYWQgZGVsIEVzdGUsIExhIFBsYXRhIEJ1ZW5vcyBBaXJlczwvcD4NCjxwPk1hcyBkZSAxNTAgdHJhYmFqb3MgcHJlc2VudGFkb3MsIHVsdGltb3MgZGlhcyBwYXJhIGluc2NyaWJpcnNlIGNvbiBkZXNjdWVudG8hITwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPkluc2NyaWJpcnNlPC9hPjwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPjxiciAvPjwvYT48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAxIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDEiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MDQvMTEvMjAxMzwvc3Bhbj48YnI+RWwgY29sZWdpbyBkZSBQc2lj82xvZ29zIGRlIEPzcmRvYmEgc2UgcHJvbnVuY2lhIGVuIHJlbGFjafNuIGFsIFNBUCB5IGVuIGNvbmNvcmRhbmNpYSBjb24gbG8gZXhwcmVzYWRvIHBvciBlbCBDb2xlZ2lvIGRlIFBzaWPzbG9nb3MgZGUgTWFyIGRlbCBQbGF0YSB5IGVsIENvbGVnaW8gZGUgUHNpY/Nsb2dvcyBkZSBsYSAgUHJvdmluY2lhIGRlIEJ1ZW5vcyBBaXJlczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+Jm5ic3A7PC9wPg0KPHA+TGFzIGNvbnRyb3ZlcnNpYXMgZ2VuZXJhZGFzIGVuIHJlbGFjaSZvYWN1dGU7biBhbCAic2luZHJvbWUgZGUgYWxpZW5hY2kmb2FjdXRlO24gcGFyZW50YSIgU0FQLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMxMCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzEwIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzE2MTAyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTYvMTAvMjAxMzwvc3Bhbj48YnI+U2FsdWQgQWN0aXZhIG90b3JnYSBtZWRpYXMgYmVjYXMgcGFyYSBlbCBJViBDb25ncmVzbyBJbnRlcm5hY2lvbmFsLCBWIE5hY2lvbmFsLCBWSSBSZWdpb25hbCBWaW9sZW5jaWEsIE1hbHRyYXRvIHkgQWJ1c28uPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD4mbmJzcDs8L3A+DQo8cD5TZXImYWFjdXRlO24gb3RvcmdhZGFzIDUwIG1lZGlhcyBiZWNhcywgcXVlZGFuIHBvY2FzISEhIGNvbmRpY2lvbjo8L3A+DQo8cD5QZXJ0ZW5lY2VyIGFsIGFtYml0byBwdWJsaWNvIG8gYSBPTkcsIHNlIGNvbnNpZGVyYSB0YW1iaWVuIGxhIGRpc3RhbmNpYSBhbCBsdWdhciBkZWwgZXZlbnRvISEhIGVzIG11eSBzZW5jaWxsbywgc29sbyBkZWJlcyBlbnZpYXIgdW4gZW1haWwuLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwOSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA5Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjI0LzA3LzIwMTM8L3NwYW4+PGJyPk5FQ0VTSVRBTU9TIERFIFNVIFNPTElEQVJJREFEIEhBQ0lBIExPUyBOSdFPUyBZIE5J0UFTISEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPlBST0dSQU1BIEZBTUlMSUFTIFNPTElEQVJJQVM8L3NwYW4+PC9zdHJvbmc+PC9wPg0KPHA+PHN0cm9uZz5DQU1CSU8gREUgU0VERTwvc3Ryb25nPjwvcD4NCjxwPkxhIGNhcGFjaXRhY2kmb2FjdXRlO24gcGFyYSBsYSBwdWVzdGEgZW4gbWFyY2hhIGRlbCA8c3Ryb25nPlByb2dyYW1hIEZhbWlsaWFzIFNvbGlkYXJpYXM8L3N0cm9uZz4gc2UgcmVhbGl6YXImYWFjdXRlOyBlbiBsYSBsb2NhbGlkYWQgZGUgPHN0cm9uZz5OYXZhcnJvPC9zdHJvbmc+IHBhcmEgdG9kbyBlbCBjb3JyZWRvciBkZSBsYSBSdXRhIDQwLjwvcD4NCjxwPkluaWNpbyA8c3Ryb25nPk1pJmVhY3V0ZTtyY29sZXMgMjggZGUgYWdvc3RvIGEgbGFzIDE0IGhvcmFzLiZuYnNwOzwvc3Ryb25nPjwvcD4NCjxwPlNlZGU6IDxzdHJvbmc+U2FsJm9hY3V0ZTtuIE11bmljaXBhbCBlbiBsYSBjYWxsZSAxMDcgZXNxdWluYSAyMiAtIE5hdmFycm88L3N0cm9uZz48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA4Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTIwNzIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xMi8wNy8yMDEzPC9zcGFuPjxicj5TQUxVRCBBQ1RJVkEgaGEgc2lkbyBlbGVnaWRhIHBvciBzZWd1bmRhIHZleiBjb25zZWN1dGl2YSBjb21vIHVubyBkZSBsb3MgZ2FuYWRvcmVzIGRlbCBDdWFydG8gQ29uY3Vyc28gZGUgUHJveWVjdG9zIFNvY2lhbGVzIGRlIFBldHJvYnJhczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+RW4gZWwgbWFyY28gZGVsIEN1YXJ0byBDb25jdXJzbyBkZSBQcm95ZWN0b3MgU29jaWFsZXMgZGUgUGV0cm9icmFzLCANCm51ZXN0cmEgSW5zdGl0dWNpJm9hY3V0ZTtuIFNBTFVEIEFDVElWQSBoYSBzaWRvIGVsZWdpZGEgcG9yIHNlZ3VuZGEgdmV6IA0KY29uc2VjdXRpdmEgY29tbyB1bm8gZGUgbG9zIGdhbmFkb3JlcyBkZSBkaWNobyBjb25jdXJzby48YnIgLz5FbiBlc3RhIA0KZWRpY2kmb2FjdXRlO24gZWwgcHJveWVjdG8gcXVlIGhhIHNpZG8gZWxlZ2lkbyBlcyBlbCAmbGRxdW87UHJvZ3JhbWEgZGUgRmFtaWxpYXMgDQpTb2xpZGFyaWFzJnJkcXVvOyBzaWVuZG8gc3UgJmFhY3V0ZTtyZWEgZGUgaW1wbGVtZW50YWNpJm9hY3V0ZTtuIGxvcyBNdW5pY2lwaW9zIGRlIE5hdmFycm8sIA0KR3JhbC4gTGFzIEhlcmFzLCBNYXJjb3MgUGF6LCB5IE1lcmxvPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAyLzA3LzIwMTM8L3NwYW4+PGJyPk/tciBvIGVzY3VjaGFyPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Qb3IgQ2FybG9zIFJvemFuc2tpICo8L3A+DQo8cD5BIGxvIGxhcmdvIGRlIGxvcyBzaWdsb3MsIGxhcyBuaSZudGlsZGU7YXMsIG5pJm50aWxkZTtvcyB5IGFkb2xlc2NlbnRlcyBoYW4gc2lkbyBtYWx0cmF0YWRvcyB5IGFidXNhZG9zIHNpbiBxdWUgYSBsYSBjb211bmlkYWQgbGUgaW50ZXJlc2FyYSBuaSBzaXF1aWVyYSBlc2N1Y2hhcmxvcyBjdWFuZG8gaGFjJmlhY3V0ZTthbiBzYWJlciBkZSBhbGd1bmEgZm9ybWEgbG9zIHN1ZnJpbWllbnRvcyBxdWUgcGFkZWMmaWFjdXRlO2FuLiBFbiAxODc0LCBlbiBFc3RhZG9zIFVuaWRvcywgZnVlIGxhIHByaW1lcmEgdmV6IHF1ZSBlbCBFc3RhZG8gaW50ZXJ2aW5vIGVuIHVuIGNhc28gZGUgbWFsdHJhdG8geSBhYnVzby4uLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDYiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4wMi8wNy8yMDEzPC9zcGFuPjxicj5FbCBkZXJlY2hvIGRlIGxvcyBuafFvcyBhIHNlciBlc2N1Y2hhZG9zPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5VbiBob21icmUgYWN1c2FkbyBkZSBoYWJlciBhYnVzYWRvIGRlIHN1cyBoaWpvcyBoYWImaWFjdXRlO2Egc2lkbyBzb2JyZXNlJmlhY3V0ZTtkbyBkb3MgdmVjZXMgcG9yIGxhIEp1c3RpY2lhLiBQZXJvIGFob3JhLCBsYSBDJmFhY3V0ZTttYXJhIGRlIENhc2FjaSZvYWN1dGU7biByZXZvYyZvYWN1dGU7IGVzYSBkZWNpc2kmb2FjdXRlO24gcG9ycXVlIGVuIGxhIGludmVzdGlnYWNpJm9hY3V0ZTtuIGVsIGp1ZXogbnVuY2EgaGFiJmlhY3V0ZTthIGVzY3VjaGFkbyBhIGxvcyBjaGljb3MuIFkgb3JkZW4mb2FjdXRlOyBxdWUgdGVuZ2EgZW4gY3VlbnRhIGxvIHF1ZSBkaWNlbi48L3A+DQo8cD5Qb3IgTWFyaWFuYSBDYXJiYWphbDwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDUiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE1NiIgcm93c3Bhbj0iMiIgdmFsaWduPSJ0b3AiPgoJCQkJCgkJCQk8dGFibGUgd2lkdGg9IjMyJSIgYm9yZGVyPSIxIiBjZWxsc3BhY2luZz0iMyIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48aW1nIHNyYz0ic3JjL2ltZ191cC8wNjA2MjAxMy4xLmpwZyIgd2lkdGg9IjE0NiIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT4KCQkJCQkJCQk8L3RkPiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjA2LzA2LzIwMTM8L3NwYW4+PGJyPkFidXNvIHNleHVhbCBpbmZhbnRpbC4gRGVzYWZpb3MgZGUgbGEgY2xpbmljYSBhY3R1YWw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkFiaWVydGEgbGEgaW5zY3JpcGNpb248L3A+DQo8cD5Eb2NlbnRlczogTGljLiBNYXJpYSBCZWF0cml6IE0mdXVtbDtsbGVyLiBMaWMuIFBhb2xhIE11Jm50aWxkZTtveiBEdWFydGU8L3A+DQo8cD5JbmljaW86IE1pZXJjb2xlcyAxOSBkZSBKdW5pbzwvcD4NCjxwPkZyZWN1ZW5jaWE6IFNlbWFuYWw8L3A+DQo8cD5Nb2RhbGlkYWQ6IEludGVuc2l2YTwvcD4NCjxwPkNvbnRlbmlkb3M6ICZuYnNwOyBFc3RhIGRlc3RpbmFkbyBhIHRvZG9zIGxvcyBwcm9mZXNpb25hbGVzIGNvbXByb21ldGlkb3MgY29uIGxhIHRlbWF0aWNhIGRlbCBhYnVzbyBpbmZhbnRpbCBxdWUgcXVpZXJhbiBhY3R1YWxpemFyc2UgZSBpbnRlcmNhbWJpYXIgZXhwZXJpZW5jaWFzIGRlIHRyYWJham8uLi48L3A+DQo8cD4mbmJzcDs8L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA0Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDQiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTYwNTIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xNi8wNS8yMDEzPC9zcGFuPjxicj5TYWx1ZCBBY3RpdmEgbmVjZXNpdGEgZGUgdHUgYXl1ZGEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5UcmFiYWphbW9zIGNvbW8gcG9kZW1vczogYmEmbnRpbGRlO29zIHJvdG9zLCBzdXNwZW5zaSZvYWN1dGU7biBkZSByZXVuaW9uZXMgcG9yIGNvcnRlcyBkZSBsdXogeSBhZ3VhLCBqdWd1ZXRlcyB2aWVqb3MsIG1lc2VzIGRlIGF0cmFzbyBlbiBlbCBwYWdvIGRlIHN1cyBwcm9mZXNpb25hbGVzIGRlIGxhIHNhbHVkLiBSZWNpZW50ZW1lbnRlIHR1dmltb3MgcXVlIGNlcnJhciBudWVzdHJvIHF1ZXJpZG8gSG9nYXI6ICZsZHF1bztNZXRhbW9yZm9zaXMmcmRxdW87IGVyYSBlbCBsdWdhciBxdWUgc3VwbyBjb250ZW5lciBhIG5pJm50aWxkZTthcyB5IGomb2FjdXRlO3ZlbmVzIHJlc2NhdGFkYSBkZSByZWRlcyBkZSB0cmF0YSBvIHYmaWFjdXRlO2N0aW1hcyBkZSBhYnVzbyBpbnRyYWZhbWlsaWFyLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAzIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAzLzA1LzIwMTM8L3NwYW4+PGJyPlJFUFVESU8gQSBMQSBQUkVTRU5DSUEgRU4gTEEgRkVSSUEgREVMIExJQlJPIERFIFVOIEVYIEpVRVogQUNVU0FETyBERSBBQlVTTyBTRVhVQUw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkZ1ZSBjYW1hcmlzdGEgZW4gTWFyIGRlbCBQbGF0YSBkdXJhbnRlIGxhIGRpY3RhZHVyYS4gSGFjZSBhJm50aWxkZTtvcywgdmFyaWFzIG11amVyZXMgbG8gYWN1c2Fyb24gZGUgaGFiZXIgYWJ1c2FkbyBkZSBlbGxhcyBjdWFuZG8gZXJhbiBuaSZudGlsZGU7YXMuIExhIGNhdXNhIHByZXNjcmliaSZvYWN1dGU7IHkgbm8gaHVibyBjb25kZW5hLiBNYSZudGlsZGU7YW5hIHRpZW5lIHByZXZpc3RvIGZpcm1hciBzdSBsaWJyby4gRXNhcyBtaXNtYXMgbXVqZXJlcyBwaWRlbiBxdWUgbm8gc2VhIGFkbWl0aWRvIGVuIGxhIGZlcmlhLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDIiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgIDwhLS0gRklOIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgIDwvdGFibGU+ICAgICAgICA8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iNSUiIGFsaWduPSJyaWdodCI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgPC90cj4KICAgIDwvdGFibGU+PC90ZD4KICA8L3RyPgogIDx0cj4KICAgIDx0ZCB3aWR0aD0iMSUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiIgYWxpZ249ImNlbnRlciI+Jm5ic3A7PC90ZD4KICAgIDx0ZCB3aWR0aD0iMiUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgPC90cj4KICAKICA8dGQ+CiAgPHRyPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0ciBhbGlnbj0iY2VudGVyIj4KICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgPHRkIHdpZHRoPSI5NyIgY29sc3Bhbj0iMiIgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iNTQ2IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idGl0dWxvaG9tZTIiPjx0YWJsZSB3aWR0aD0iIiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYWxpZ249ImxlZnQiIHZhbGlnbj0iYm90dG9tIiBjbGFzcz0idGl0dWxvaG9tZTIiPlJhbmtpbmc8L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSIgY2xhc3M9InRpdHVsb2hvbWUyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iIiBoZWlnaHQ9IjM1IiBhbGlnbj0ibGVmdCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPiZidWxsO0xhcyBtJmFhY3V0ZTtzIGxlaWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGNsYXNzPSJjb250ZW5pZG9ob21lIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBjbGFzcz0iY29udGVuaWRvaG9tZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+JmJ1bGw7TGFzIG0mYWFjdXRlO3MgY29tZW50YWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTHVkb3RlY2EgR2FyYWJhdG8gLSBQcm95ZWN0byBzYWx1ZGFjdGl2YSwgUG9yIHVuYSBpbmZhbmNpYSBmZWxpeiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iOSUiIGJnY29sb3I9IiNFRkVGRUYiPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzJSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xNjIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDUlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTE2MiIgY2xhc3M9ImJvdG9uIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBDdXJzbyBJbnRlbnNpdm8gZGUgb3BlcmFkb3IgdGVyYXBldXRpY28gZXNwZWNpYWxpemFkbyBlbiBlbCBhYm9yZGFqZSBkZWwgYWJ1c28sIGxhIHZpb2xlbmNpYSB5IGVsIG1hbHRyYXRvIGluZmFudGlsICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgUFJPR1JBTUEgTEFTIFZJQ1RJTUFTIENPTlRSQSBMQVMgVklPTEVOQ0lBUyAgTWluaXN0ZXJpbyBkZSBKdXN0aWNpYSB5IERlcmVjaG9zIEh1bWFub3MgZGUgbGEgTmFjafNuICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI5JSIgYmdjb2xvcj0iI0VGRUZFRiI+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjMlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTI1NSIgY2xhc3M9ImJvdG9uIj48aW1nIHNyYz0iaW1nL2ZsZWNoYW5hcmFuamFmZ3Jpc18yNC5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSI3IiBib3JkZXI9IjAiIGFsaWduPSJhYnNtaWRkbGUiIC8+PC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI0NSUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MjU1IiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIERpcGxvbWF0dXJhIGVuIEFib3JkYWplIGludGVyZGlzY2lwbGluYXJpbyBkZWwgbWFsdHJhdG8sIGxhIHZpb2xlbmNpYSB5IGVsIGFidXNvIHNleHVhbCBpbmZhbnRpbCAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyJSIgaGVpZ2h0PSIyMCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQxJSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNhbHVkIEFjdGl2YSBuZWNlc2l0YSBkZSB0dSBheXVkYSEgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjklIiBiZ2NvbG9yPSIjRUZFRkVGIj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMyUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MTA0IiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQ1JSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xMDQiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTGxhbWFkbyBwYXJhIHByZXNlbnRhY2nzbiBkZSB0cmFiYWpvcy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjIwIiBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyMCIgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGJnY29sb3I9IiNGRkZGRkYiIGNsYXNzPSJ0ZXh0b251ZXZvIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPgogICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iIyIgY2xhc3M9ImJvdG9uIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgPC90YWJsZT48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj4mbmJzcDs8L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBJTklDSU8gbm90YSBjb211biAtLT4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTUvMDQvMjAxMjwvc3Bhbj48YnI+T3JnYW5pemFuIGpvcm5hZGEgc29icmUgdmlvbGVuY2lhPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPlNlIGNlbnRyYXImYWFjdXRlOyBlbiBsb3MgZmVuJm9hY3V0ZTttZW5vcyBxdWUgYWZlY3RhbiBhIGxhIGZhbWlsaWEgeSBlbiBsbyBxdWUgb2N1cnJlIGVuIGxhcyBlc2N1ZWxhcy48YnIgLz4gU2UgbGxldmFyJmFhY3V0ZTsgYSBjYWJvIGVsIGx1bmVzIDIzLCBlbiBlbCBDZW50cm8gQ3VsdHVyYWwgZGUgVG9zY2hpIHkgVHJlcyANCkFycm95b3MsIHVuYSBqb3JuYWRhIGRlIHJlZmxleGkmb2FjdXRlO24geSBkZWJhdGUgYWJpZXJ0YSBhIGxhIGNvbXVuaWRhZCBzb2JyZSANCiZsZHF1bztWaW9sZW5jaWEgZW4gbGEgZmFtaWxpYSB5IGVuIGxhIGVzY3VlbGEgeSBzdSByZWxhY2kmb2FjdXRlO24gY29uIGVsIGZyYWNhc28gDQplc2NvbGFyJnJkcXVvOywgb3JnYW5pemFkYSBwb3IgbGEgQXNvY2lhY2kmb2FjdXRlO24gQ2l2aWwgQ2VudHJvIEFydCZlYWN1dGU7bWlkZXMgeSBsYSANCk11bmljaXBhbGlkYWQgZGUgQ2lwb2xsZXR0aS5TZSBjZW50cmFyJmFhY3V0ZTsgZW4gbG9zIGZlbiZvYWN1dGU7bWVub3MgcXVlIGFmZWN0YW4gYSBsYSBmYW1pbGlhIHkgZW4gbG8gcXVlIG9jdXJyZSBlbiBsYXMgZXNjdWVsYXMuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjMwLzAzLzIwMTI8L3NwYW4+PGJyPkNhcnRhIGRlIEFTQVBNSSAtIEFzb2NpYWNp824gQXJnZW50aW5hIGRlIFByZXZlbmNp824gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbDwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjE1IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSIxNSIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjgwIiBjb2xzcGFuPSI0IiBhbGlnbj0ibGVmdCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Mb3MgaW50ZWdyYW50ZXMgZGUgbGEgQ29taXNpJm9hY3V0ZTtuIERpcmVjdGl2YSBkZSBBU0FQTUkgLSBBc29jaWFjaSZvYWN1dGU7biBBcmdlbnRpbmEgZGUgUHJldmVuY2kmb2FjdXRlO24gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbCwgYXNvY2lhZGEgYSBsYSBJbnRlcm5hdGlvbmFsIFNvY2lldHkgZm9yIFByZXZlbnRpb24gb2YgQ2hpbGQgQWJ1c2UgYW5kIE5lZ2xlY3QgKElTUENBTikgLSwgdGVuZW1vcyBlbCBhZ3JhZG8gZGUgZGlyaWdpcm5vcyBhIFVzdGVkIHBhcmEgdHJhc21pdGlybGUgbnVlc3RyYSBwcm9mdW5kYSAmbmJzcDt5IGhvbmRhIHByZW9jdXBhY2kmb2FjdXRlO24gcG9yIGxhIHBvc3R1cmEgcXVlIHZpZW5lbiBhc3VtaWVuZG8gZW4gZm9ybWEgY29udGludWFkYSBhbGd1bm9zIGNvbGVnaW9zIGRlIHBzaWMmb2FjdXRlO2xvZ29zLCBlc3BlY2lhbG1lbnRlIGRlIGxhIHByb3ZpbmNpYSBkZSBCdWVub3MgQWlyZXMsIGVuIHJlbGFjaSZvYWN1dGU7biBhbCB0cmF0YW1pZW50byBwb2NvIHNlcmlvIHkgY29tcHJvbWV0aWRvIHF1ZSBzZSBsZXMgb3RvcmdhIGEgbGFzIGRlbnVuY2lhcyBlZmVjdHVhZGFzIGNvbnRyYSBwcm9mZXNpb25hbGVzIHBzaWMmb2FjdXRlO2xvZ29zLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjAvMDMvMjAxMjwvc3Bhbj48YnI+TEEgVklPTEVOQ0lBIFNFWFVBTCBDT05UUkEgTknRT1MgWSBOSdFBUyBFTiBDSUZSQVM8L3RkPgogICAgICAgICAgPC90cj4KICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkIHdpZHRoPSIxNSIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4MCIgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+UmFkaW9ncmFmJmlhY3V0ZTthIGRlIHVuIHByb2JsZW1hPC9wPg0KPHA+RGUgbG9zIG4mdWFjdXRlO21lcm9zIGNvbXBpbGFkb3MgcG9yIGRvcyBlcXVpcG9zIGRlbCBNaW5pc3RlcmlvIGRlIEp1c3RpY2lhLCBsYQ0KIGF1dG9yYSB0b21hIGxvcyBkZSBsYSBjaXVkYWQgZGUgQnVlbm9zIEFpcmVzIHBhcmEgdHJhemFyIHVuIHBhcmFkaWdtYSANCmRlIGxvcyBkZWxpdG9zIGNvbnRyYSBsYSBpbnRlZ3JpZGFkIHNleHVhbCBlbiBlbCBwYSZpYWN1dGU7cyB5IHNvYnJlIHN1IA0KYXRlbmNpJm9hY3V0ZTtuLjxiciAvPiA8YnIgLz4gJm5ic3A7UG9yIEV2YSBHaWJlcnRpPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2MCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjAiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjE1LzAzLzIwMTI8L3NwYW4+PGJyPkZBTExPIERFIExBIENPUlRFIFNVUFJFTUEgU09CUkUgTEEgTk8gSlVESUNJQUxJWkFDSU9OIERFTCBBQk9SVE8gRU4gQ0FTT1MgREUgVklPTEFDSU9OPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxiciAvPiBKVVJJU0RJQ0NJT046IE5BQ0lPTkFMPGJyIC8+IE1BVEVSSUE6IEFCT1JUTy48YnIgLz4gVFJJQlVOQUw6IENvcnRlIFN1cHJlbWEgZGUgSnVzdGljaWEgZGUgbGEgTmFjaSZvYWN1dGU7bi48YnIgLz4gQVVUT1M6IEYuLCBBLiBMLiBzLyBtZWRpZGEgYXV0b3NhdGlzZmFjdGl2YS48YnIgLz4gRkVDSEE6IDEzLzAzLzIwMTIuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI1OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNTkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBGSU4gbm90YSBjb211biAtLT4KPC90YWJsZT4KPG1hcCBuYW1lPSJNYXBNYXAiIGlkPSJNYXBNYXAiPjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjE0NCw0LDIxNCwzNiIgaHJlZj0iaW5kZXgucGhwP2lkPTE0IiAvPgo8L21hcD4KPG1hcCBuYW1lPSJNYXAyTWFwMiIgaWQ9Ik1hcDJNYXAyIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIxNDcsNCwyMjAsMzYiIGhyZWY9ImluZGV4LnBocD9pZD0xNGEiIC8+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcDMiIGlkPSJNYXAzIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIzNjMsMyw0MzYsMzkiIGhyZWY9ImluZGV4LnBocD9pZD0xNGIiIC8+CjwvbWFwPgo8L2h0bWw+CjwvdGQ+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gICAgICAgICAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFM0UzRTMiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSI3MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNiUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9kZWNpbG9fYmllbl9mdWVydGUxLmpwZyIgd2lkdGg9IjEyMCIgaGVpZ2h0PSIxMTIiPjwvdGQ+CiAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiA+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTI0IiBjbGFzcz0iYm90b24xIj5bK10gTSZhYWN1dGU7cyBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0UzRTNFMyI+ICAgICAgICA8L3RyPgogICAgICAgIDx0cj4gCiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj4mbmJzcDs8L3RkPgogICAgICAgIDwvdHI+CiAgICA8L3RhYmxlPjwvdGQ+CiAgPC90cj4KICA8dHI+IAogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSI+PGltZyBzcmM9ImltZy9penExLmpwZyIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjExNCIgLz48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9RdWllbmVzU29tb3NfQTJfMF8yNS5qcGciIHdpZHRoPSI4MDkiIGhlaWdodD0iMTE0IiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcDIiIC8+PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI1MCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiYWNrZ3JvdW5kPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzE4XzE4LmpwZyI+Jm5ic3A7PC90ZD4KICAgIDx0ZCBoZWlnaHQ9IjUwIiBjbGFzcz0iZm9uZG9ib3R0b20iPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2l0ZWkuY29tLmFyLyI+PGltZyBzcmM9ImltZy9laV9jb2xvci5wbmciIGFsdD0iZXNwYWNpb3MgZGUgaW1hZ2luYWNpb24sIGRlc2Fycm9sbG9zIGludGVyYWN0aXZvcywgY3JlYXRpdmlkYWQsIGRpc2XxbyIgd2lkdGg9IjI3IiBoZWlnaHQ9IjE1IiBib3JkZXI9IjAiPjwvYT4gPHNwYW4gY2xhc3M9ImVpIj48YSBocmVmPSJodHRwOi8vd3d3LnNpdGVpLmNvbS5hci8iIHNwYW4gY2xhc3M9ImVpIj5kaXNlJm50aWxkZTtvICsgY29tdW5pY2FjaSZvYWN1dGU7bjwvYT48L3NwYW4+PGVtPiZuYnNwOzwvZW0+PC9zcGFuPjxzcGFuIGNsYXNzPSJibGFuY28xIj48ZW0+Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7PC9lbT48L3NwYW4+PC90ZD4KICA8L3RyPgo8L3RhYmxlPgoKCjxtYXAgbmFtZT0iTWFwMiI+PGFyZWEgc2hhcGU9InJlY3QiIGNvb3Jkcz0iMjQ3LDY5LDQxNCw4MiIgaHJlZj0ibWFpbHRvOnNhbHVkYWN0aXZhQHNhbHVkYWN0aXZvLm9yZy5hciI+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcCI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM2LDE0MiwxNDksMTUyIiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MiI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM0LDE4NiwxNTAsMTk2IiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MCI+CjwvbWFwPgo8L2JvZHk+CjwvaHRtbD4K]]></response> | |
| 183 | <responseRedirected>false</responseRedirected> | |
| 184 | </requestresponse> | |
| 185 | </issue> | |
| 186 | <issue> | |
| 187 | <serialNumber>2348918843333562368</serialNumber> | |
| 188 | <type>6291968</type> | |
| 189 | <name>Email addresses disclosed</name> | |
| 190 | <host ip="200.20.20.201">http://www.example.org.ar</host> | |
| 191 | <path><![CDATA[/]]></path> | |
| 192 | <location><![CDATA[/]]></location> | |
| 193 | <severity>Information</severity> | |
| 194 | <confidence>Certain</confidence> | |
| 195 | <issueBackground><![CDATA[The presence of email addresses within application responses does not necessarily constitute a security vulnerability. Email addresses may appear intentionally within contact information, and many applications (such as web mail) include arbitrary third-party email addresses within their core content.<br><br>However, email addresses of developers and other individuals (whether appearing on-screen or hidden within page source) may disclose information that is useful to an attacker; for example, they may represent usernames that can be used at the application's login, and they may be used in social engineering attacks against the organization's personnel. Unnecessary or excessive disclosure of email addresses may also lead to an increase in the volume of spam email received.]]></issueBackground> | |
| 196 | <remediationBackground><![CDATA[You should review the email addresses being disclosed by the application, and consider removing any that are unnecessary, or replacing personal addresses with anonymous mailbox addresses (such as [email protected]).]]></remediationBackground> | |
| 197 | <issueDetail><![CDATA[The following email addresses were disclosed in the response:<ul><li>[email protected]</li><li>[email protected]</li></ul>]]></issueDetail> | |
| 198 | <requestresponse> | |
| 199 | <request base64="true"><![CDATA[R0VUIC8gSFRUUC8xLjENCkhvc3Q6IHd3dy5zYWx1ZGFjdGl2YS5vcmcuYXINClVzZXItQWdlbnQ6IE1vemlsbGEvNS4wIChNYWNpbnRvc2g7IEludGVsIE1hYyBPUyBYIDEwLjg7IHJ2OjIzLjApIEdlY2tvLzIwMTAwMTAxIEZpcmVmb3gvMjMuMA0KQWNjZXB0OiB0ZXh0L2h0bWwsYXBwbGljYXRpb24veGh0bWwreG1sLGFwcGxpY2F0aW9uL3htbDtxPTAuOSwqLyo7cT0wLjgNCkFjY2VwdC1MYW5ndWFnZTogZW4tVVMsZW47cT0wLjUNCkFjY2VwdC1FbmNvZGluZzogZ3ppcCwgZGVmbGF0ZQ0KQ29ubmVjdGlvbjoga2VlcC1hbGl2ZQ0KDQo=]]></request> | |
| 200 | <response base64="true"><![CDATA[SFRUUC8xLjEgMjAwIE9LDQpEYXRlOiBUaHUsIDA3IE5vdiAyMDEzIDE3OjEyOjAyIEdNVA0KU2VydmVyOiBBcGFjaGUvMi4yLjIzIChVbml4KSBtb2Rfc3NsLzIuMi4yMyBPcGVuU1NMLzAuOS44ZS1maXBzLXJoZWw1DQpYLVBvd2VyZWQtQnk6IFBIUC81LjIuMTcNCkV4cGlyZXM6IFRodSwgMTkgTm92IDE5ODEgMDg6NTI6MDAgR01UDQpDYWNoZS1Db250cm9sOiBuby1zdG9yZSwgbm8tY2FjaGUsIG11c3QtcmV2YWxpZGF0ZSwgcG9zdC1jaGVjaz0wLCBwcmUtY2hlY2s9MA0KUHJhZ21hOiBuby1jYWNoZQ0KU2V0LUNvb2tpZTogUEhQU0VTU0lEPTk0NTg1YWEwYzExY2YyZTg2NGQ4M2UyNDY3OGI5ODY1OyBwYXRoPS8NCktlZXAtQWxpdmU6IHRpbWVvdXQ9MjAsIG1heD0yMDANCkNvbm5lY3Rpb246IEtlZXAtQWxpdmUNCkNvbnRlbnQtVHlwZTogdGV4dC9odG1sDQpDb250ZW50LUxlbmd0aDogNjA2MDYNCg0KIDxoZWFkPgo8bWV0YSBodHRwLWVxdWl2PSJDb250ZW50LVR5cGUiIGNvbnRlbnQ9InRleHQvaHRtbDsgY2hhcnNldD1pc28tODg1OS0xIiAvPgo8dGl0bGU+U2FsdWQgQWN0aXZhIC0gQWJ1c28gdmlvbGVuY2lhIHkgbWFsdHJhdG88L3RpdGxlPgoKPHNjcmlwdD4gCiAgICAvL2VzdG8gcGFyYSBwYXNhcmxlIGFsIGZsYXNoIGxhcyB2YXJpYWxiZXMgZGVsIHBocAogCQoKCXZhciBib3Q9Jyc7Ci8vYWxlcnQodmFyaWFibGVTZXJ2aWRvcik7Cjwvc2NyaXB0Pgo8c2NyaXB0IGxhbmd1YWdlPSJKYXZhU2NyaXB0IiB0eXBlPSJ0ZXh0L0phdmFTY3JpcHQiPgo8IS0tCmZ1bmN0aW9uIE1NX3ByZWxvYWRJbWFnZXMoKSB7IC8vdjMuMAogIHZhciBkPWRvY3VtZW50OyBpZihkLmltYWdlcyl7IGlmKCFkLk1NX3ApIGQuTU1fcD1uZXcgQXJyYXkoKTsKICAgIHZhciBpLGo9ZC5NTV9wLmxlbmd0aCxhPU1NX3ByZWxvYWRJbWFnZXMuYXJndW1lbnRzOyBmb3IoaT0wOyBpPGEubGVuZ3RoOyBpKyspCiAgICBpZiAoYVtpXS5pbmRleE9mKCIjIikhPTApeyBkLk1NX3Bbal09bmV3IEltYWdlOyBkLk1NX3BbaisrXS5zcmM9YVtpXTt9fQp9Ci8vLS0+Cjwvc2NyaXB0Pgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KCjwvaGVhZD4KCjxzY3JpcHQgbGFuZ3VhZ2U9IkphdmFTY3JpcHQiIHR5cGU9InRleHQvSmF2YVNjcmlwdCI+CjwhLS0KZnVuY3Rpb24gTU1fcmVsb2FkUGFnZShpbml0KSB7ICAvL3JlbG9hZHMgdGhlIHdpbmRvdyBpZiBOYXY0IHJlc2l6ZWQKICBpZiAoaW5pdD09dHJ1ZSkgd2l0aCAobmF2aWdhdG9yKSB7aWYgKChhcHBOYW1lPT0iTmV0c2NhcGUiKSYmKHBhcnNlSW50KGFwcFZlcnNpb24pPT00KSkgewogICAgZG9jdW1lbnQuTU1fcGdXPWlubmVyV2lkdGg7IGRvY3VtZW50Lk1NX3BnSD1pbm5lckhlaWdodDsgb25yZXNpemU9TU1fcmVsb2FkUGFnZTsgfX0KICBlbHNlIGlmIChpbm5lcldpZHRoIT1kb2N1bWVudC5NTV9wZ1cgfHwgaW5uZXJIZWlnaHQhPWRvY3VtZW50Lk1NX3BnSCkgbG9jYXRpb24ucmVsb2FkKCk7Cn0KTU1fcmVsb2FkUGFnZSh0cnVlKTsKLy8tLT4KCjwvc2NyaXB0Pgo8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoKCjwvaGVhZD4KCjxib2R5IGJhY2tncm91bmQ9ImltZy9mb25kb19kZWdyYWRlLmpwZyIgdG9wbWFyZ2luPSIwIj4KPHRhYmxlIHdpZHRoPSIxMDA1IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgPHRyPiAKICAgIDx0ZCB3aWR0aD0iOTYiPjxpbWcgc3JjPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzBfMDEuanBnIiB3aWR0aD0iOTYiIGhlaWdodD0iMjA4IiAvPjwvdGQ+CiAgICA8dGQgd2lkdGg9IjgwOSI+IDxzY3JpcHQgdHlwZT0idGV4dC9qYXZhc2NyaXB0Ij4KQUNfRkxfUnVuQ29udGVudCggJ2NvZGViYXNlJywnaHR0cDovL2Rvd25sb2FkLm1hY3JvbWVkaWEuY29tL3B1Yi9zaG9ja3dhdmUvY2Ficy9mbGFzaC9zd2ZsYXNoLmNhYiN2ZXJzaW9uPTcsMCwxOSwwJywnd2lkdGgnLCc4MDknLCdoZWlnaHQnLCcyMDgnLCdzcmMnLCdzd2YvaGVhZGVyJywncXVhbGl0eScsJ2hpZ2gnLCdwbHVnaW5zcGFnZScsJ2h0dHA6Ly93d3cubWFjcm9tZWRpYS5jb20vZ28vZ2V0Zmxhc2hwbGF5ZXInLCdtb3ZpZScsJ3N3Zi9oZWFkZXInICk7IC8vZW5kIEFDIGNvZGUKPC9zY3JpcHQ+IDxub3NjcmlwdD4KICAgICAgPG9iamVjdCBjbGFzc2lkPSJjbHNpZDpEMjdDREI2RS1BRTZELTExY2YtOTZCOC00NDQ1NTM1NDAwMDAiIGNvZGViYXNlPSJodHRwOi8vZG93bmxvYWQubWFjcm9tZWRpYS5jb20vcHViL3Nob2Nrd2F2ZS9jYWJzL2ZsYXNoL3N3Zmxhc2guY2FiI3ZlcnNpb249NywwLDE5LDAiIHdpZHRoPSI4MDkiIGhlaWdodD0iMjA4Ij4KICAgICAgICA8cGFyYW0gbmFtZT0ibW92aWUiIHZhbHVlPSJzd2YvaGVhZGVyLnN3ZiIgLz4KICAgICAgICA8cGFyYW0gbmFtZT0icXVhbGl0eSIgdmFsdWU9ImhpZ2giIC8+CiAgICAgICAgPGVtYmVkIHNyYz0ic3dmL2hlYWRlci5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9IjgwOSIgaGVpZ2h0PSIyMDgiPjwvZW1iZWQ+IAogICAgICA8L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIHdpZHRoPSIxMiUiIHJvd3NwYW49IjUiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iIzAwMDAwMCI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI0NjEiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmFja2dyb3VuZD0iaW1nL1F1aWVuZXNTb21vc19BMl8wXzEzLmpwZyI+IAogICAgICA8c2NyaXB0IHR5cGU9InRleHQvamF2YXNjcmlwdCI+CkFDX0ZMX1J1bkNvbnRlbnQoICdjb2RlYmFzZScsJ2h0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCcsJ3dpZHRoJywnOTYnLCdoZWlnaHQnLCc0NjEnLCdzcmMnLCdzd2Yvc3VibWVudScsJ3F1YWxpdHknLCdoaWdoJywncGx1Z2luc3BhZ2UnLCdodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyJywnbW92aWUnLCdzd2Yvc3VibWVudScgKTsgLy9lbmQgQUMgY29kZQo8L3NjcmlwdD4gPG5vc2NyaXB0PgogICAgICA8b2JqZWN0IGNsYXNzaWQ9ImNsc2lkOkQyN0NEQjZFLUFFNkQtMTFjZi05NkI4LTQ0NDU1MzU0MDAwMCIgY29kZWJhc2U9Imh0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+CiAgICAgICAgPHBhcmFtIG5hbWU9Im1vdmllIiB2YWx1ZT0ic3dmL3N1Ym1lbnUuc3dmIiAvPgogICAgICAgIDxwYXJhbSBuYW1lPSJxdWFsaXR5IiB2YWx1ZT0iaGlnaCIgLz4KICAgICAgICA8ZW1iZWQgc3JjPSJzd2Yvc3VibWVudS5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+PC9lbWJlZD48L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCIgYmdjb2xvcj0iI0ZGRkZGRiI+CiAgICAgICAgPHRyPiAKICAgICAgICAgIDx0ZCB3aWR0aD0iMTciIHJvd3NwYW49IjciPjxwPiZuYnNwOzwvcD48L3RkPgogICAgICAgICAgPHRkIHdpZHRoPSIxNzIiIGFsaWduPSJjZW50ZXIiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxpbWcgc3JjPSJpbWcvM3B4LmpwZyIgd2lkdGg9IjUiIGhlaWdodD0iNSI+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciI+PGxpbmsgaHJlZj0iLi4vZXN0aWxvcy5jc3MiIHJlbD0ic3R5bGVzaGVldCIgdHlwZT0idGV4dC9jc3MiIC8+Cjxib2R5IGJnY29sb3I9IiNDQ0NDQ0MiIHRvcG1hcmdpbj0iNiBweCI+PHRhYmxlIHdpZHRoPSIxNjUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIzIiBiZ2NvbG9yPSIjRkZGRkZGIj4KPHRyPgogICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTkxIiBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiAgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MThfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+SG9tZTwvYT48L3RkPgogIDwvdHI+Cjx0cj4KICA8dGQgaGVpZ2h0PSIyOCIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj4mbmJzcDsmbmJzcDtOb3RpY2lhczwvYT48L3RkPgo8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJkb25hY2lvbmVzLyIgdGFyZ2V0PSJfYmxhbmsiIGNsYXNzPSJmb25kb2JvdG9uIj5Eb25hY2lvbmVzPC9hPjwvdGQ+CiAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciICB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yM19uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5IaXN0b3JpYWwgZGUgbmV3c2xldHRlcnM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTEzYSIgY2xhc3M9ImZvbmRvYm90b24iPkVudmlhciBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yNl9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5WZXIgdHJhYmFqb3MgZGUgdXN1YXJpb3M8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MTZfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+U2FsdWQgQWN0aXZhIHByZW5zYTwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJtYWlsdG86c2FsdWRhY3RpdmFAc2FsdWRhY3RpdmEub3JnLmFyIiBjbGFzcz0iZm9uZG9ib3RvbiI+TWFuZCZhYWN1dGU7IHR1IEMuVi48L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgIHdpZHRoPSI2ImhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTIxX25ldyIgY2xhc3M9ImZvbmRvYm90b24iPkluZm9ybWFjaSZvYWN1dGU7biBkZSBpbnRlciZlYWN1dGU7czwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyI+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiBoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xMF80IiBjbGFzcz0iZm9uZG9ib3RvbiI+Q29uZ3Jlc29zCiAgICAgICAgICAgICAgICAgIHkgSm9ybmFkYXM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTExIiBjbGFzcz0iZm9uZG9ib3RvbiI+UmVnaXN0cmFjaSZvYWN1dGU7bjwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgCiAgICAgICAgICA8L3RhYmxlPgo8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNSIgdGFyZ2V0PSJfYmxhbmsiPjxicj4KICAgICAgICAgICAgICAgICAgPGltZyBzcmM9ImltZy9iYW5uZXJfZG9uYWNpb25lcy5qcGciIHdpZHRoPSIxNjIiIGhlaWdodD0iMTIwIiBib3JkZXI9IjAiPjxicj4KICAgICAgICAgICAgICAgICAgPGJyPgogICAgICAgICAgICAgICAgICA8aW1nIHNyYz0iaW1nL2JvdG9uRm9yby5naWYiIHdpZHRoPSIxNzIiIGhlaWdodD0iMTE3IiBib3JkZXI9IjAiPjwvYT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTY3IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjkiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzAzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iOSIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTQ5IiBiYWNrZ3JvdW5kPSJpbWcvY2hpY29zX3BlcmRpZG9zXzA1LmdpZiI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDUuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMCI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDcuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMi5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEyLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9InNyYy9pbWdfdXAvMjMwODIwMTIuMS5qcGciIHdpZHRoPSIxNDkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMy5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNi5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iNSIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTcuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNy5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgYmdjb2xvcj0iI0ZFRTdDRiIgY2xhc3M9InRpdHVsb2hvbWU1Ij48c3Ryb25nPk5pJm50aWxkZTtvcyBwZXJkaWRvczxicj4KICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0yOSIgY2xhc3M9ImJvdG9uIj5bVmVyIG0mYWFjdXRlO3NdPC9hPjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTkuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xOS5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18yMC5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iMjUiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4NCgkJCQkNCgkJCQk8Zm9ybSBhY3Rpb249ImluZGV4LnBocD9pZD0xMSIgIG1ldGhvZD0icG9zdCI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9penExLmpwZyIgd2lkdGg9IjEyIiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9hcnJpYmEuanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9kZXIxLmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgIDwvdHI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiIgdmFsaWduPSJ0b3AiIGNsYXNzPSJyZWdGb25kbzEiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9penEuanBnIiB3aWR0aD0iMTIiIGhlaWdodD0iMTIiIC8+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSI5NCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV90aXQuanBnIiB3aWR0aD0iNjYiIGhlaWdodD0iMjMiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSI1MCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJyZWdpc3RyYXJzZSI+SW5ncmVzJmFhY3V0ZTsgDQogICAgICAgICAgICAgIHR1cyBkYXRvcyB5IHJlY2liJmlhY3V0ZTsgbGEgbWVqb3IgaW5mb3JtYWNpJm9hY3V0ZTtuIGEgdHJhdiZlYWN1dGU7cyANCiAgICAgICAgICAgICAgZGUgbnVlc3RybzxzdHJvbmc+IE5ld3NsZXR0ZXI8L3N0cm9uZz4uIDxzdHJvbmc+PHNwYW4gY2xhc3M9ImdyYXRpcyI+R3JhdGlzITwvc3Bhbj48L3N0cm9uZz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI1IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9InRyYWJTRUNDSU9OIj5Ob21icmU8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBjbGFzcz0icmVnQ0VMREEiPjxpbnB1dCBuYW1lPSJub21icmUiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0ibm9tYnJlIiAvPjwvdGQ+DQogICAgICAgICAgPC90cj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0idHJhYlNFQ0NJT04iPkFwZWxsaWRvPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iYXBlbGxpZG8iIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iYXBlbGxpZG8iIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJ0cmFiU0VDQ0lPTiI+RS1tYWlsPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iZW1haWwiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iZW1haWwiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InRyYWJTRUNDSU9OIj4mbmJzcDs8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idHJhYlNFQ0NJT04iPjxpbnB1dCB0eXBlPSJpbWFnZSIgc3JjPSJpbWcvcmVnaXN0cmF0ZV9ib3Rvbi5qcGciIHdpZHRoPSIxMTciIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgIDwvdGFibGU+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE0IiB2YWxpZ249InRvcCIgY2xhc3M9InJlZ0ZvbmRvMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2Rlci5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIxNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KICAgICAgICAgICAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTIiIGhlaWdodD0iMjQiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfaXpxMi5qcGciIHdpZHRoPSIxMiIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI0Ij48aW1nIHNyYz0iaW1nL3JlZ2lzdHJhdGVfYWJham8uanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjI0IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfZGVyMi5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KCQkJCQkNCgkJCQkJPC9mb3JtPg0KICAgICAgICAgICAgICAgICAgPC90YWJsZT4NCjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPiAKICAgICAgICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTcwIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUyIj4KCQkJCQkJCQkJCQkJCQkJCTwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9jbGF1ZGlhMl8wMy5qcGciIHdpZHRoPSIxNzQiIGhlaWdodD0iMjUwIiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcCI+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICA8dGQgcm93c3Bhbj0iNyIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nLzV4NS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjciPjwvdGQ+CiAgICAgICAgICA8dGQgY29sc3Bhbj0iMiIgcm93c3Bhbj0iNCIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPGZvcm0gYWN0aW9uPSJsb2dpbi5waHAiIG1ldGhvZD0icG9zdCIgbmFtZT0iZm9ybTIiPgoKICAgICAgICAgICAgICA8dHI+IAogICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgY29sc3Bhbj0iMiIgYWxpZ249ImxlZnQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIiA+IAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8c3Ryb25nPlVzdWFyaW8gbm8gcmVnaXN0cmFkbzwvc3Ryb25nPiAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9mb250PiA8L3N0cm9uZz4gCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDkiIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPlVzdWFyaW8mbmJzcDsmbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzOSIgdmFsaWduPSJtaWRkbGUiPjxpbnB1dCBuYW1lPSJ1c3VhcmlvIiB0eXBlPSJ0ZXh0IiBjbGFzcz0icmVnIiBpZD0idXN1YXJpbyIgc2l6ZT0iNyI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjciIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPkNvbnRyYXNlJm50aWxkZTthJm5ic3A7Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzkiIHZhbGlnbj0ibWlkZGxlIj48aW5wdXQgbmFtZT0icGFzcyIgdHlwZT0icGFzc3dvcmQiIGNsYXNzPSJyZWciIGlkPSJwYXNzIiBzaXplPSI3Ij48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiIgYWxpZ249InJpZ2h0IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9ImJvdG9uIj48aW5wdXQgdHlwZT0iaW1hZ2UiIHNyYz0iaW1nL3JlZy5qcGciIHdpZHRoPSI1OCIgaGVpZ2h0PSIzMCI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjciIGhlaWdodD0iMTkiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgPjxhIGhyZWY9Imh0dHA6Ly93d3cuZmFjZWJvb2suY29tL2hvbWUucGhwPyMhL3BhZ2VzL01lcmxvLUFyZ2VudGluYS9TQUxVRC1BQ1RJVkEvMTAwNTgzNTQzMzE3MzIyP3JlZj10cyZhamF4cGlwZT0xJl9fYT03IiB0YXJnZXQ9Il9ibGFuayI+PGltZyBzcmM9ImltZy9mYWNlYm9vay5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzExIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj48ZGl2IGFsaWduPSJsZWZ0Ij48YSBocmVmPSJodHRwOi8vdHdpdHRlci5jb20vU2FsdWRBY3RpdmFPTkciIHRhcmdldD0iX2JsYW5rIj48aW1nIHNyYz0iaW1nL3R3aXRlci5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC9kaXY+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSI1IiBhbGlnbj0icmlnaHQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIj48bGFiZWw+PGZvbnQgc2l6ZT0iLTYiPlNpCiAgICAgICAgICAgICAgICAgICAgICAgdG9kYXYmaWFjdXRlO2Egbm8gZXMgdXN1YXJpbyA8L2ZvbnQ+IDxhIGhyZWY9ImluZGV4LnBocD9pZD0xMSIgY2xhc3M9ImJvdG9uIj48Zm9udCBzaXplPSItNiI+cmVnJmlhY3V0ZTtzdHJlc2UKICAgICAgICAgICAgICAgICAgICAgICAgYXF1JmlhY3V0ZTsgPGZvbnQgY29sb3I9IiM2NjY2NjYiPiYjODIyNjs8L2ZvbnQ+PC9mb250PjwvYT4gPGEgaHJlZj0iaW5kZXgucGhwP2lkPTEyIiBjbGFzcz0iYm90b24xIj48Zm9udCBzaXplPSItNiI+b2x2aWRlIG1pIGNvbnRyYXNlJm50aWxkZTthPC9mb250PjwvYT48L2xhYmVsPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE3Ij4mbmJzcDsgPC90ZD4KICAgICAgICAgICAgICA8L3RyPgoJCQkgIDwvZm9ybT4KCiAgICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgICA8IURPQ1RZUEUgaHRtbCBQVUJMSUMgIi0vL1czQy8vRFREIFhIVE1MIDEuMCBUcmFuc2l0aW9uYWwvL0VOIiAiaHR0cDovL3d3dy53My5vcmcvVFIveGh0bWwxL0RURC94aHRtbDEtdHJhbnNpdGlvbmFsLmR0ZCI+CjxodG1sIHhtbG5zPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hodG1sIj4KPGhlYWQ+CjxtZXRhIGh0dHAtZXF1aXY9IkNvbnRlbnQtVHlwZSIgY29udGVudD0idGV4dC9odG1sOyBjaGFyc2V0PWlzby04ODU5LTEiIC8+Cjx0aXRsZT5Eb2N1bWVudG8gc2luIHQmaWFjdXRlO3R1bG88L3RpdGxlPgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KPHNjcmlwdCBsYW5ndWFnZT0iSmF2YVNjcmlwdCIgdHlwZT0idGV4dC9KYXZhU2NyaXB0Ij4KPCEtLQpmdW5jdGlvbiBNTV9yZWxvYWRQYWdlKGluaXQpIHsgIC8vcmVsb2FkcyB0aGUgd2luZG93IGlmIE5hdjQgcmVzaXplZAogIGlmIChpbml0PT10cnVlKSB3aXRoIChuYXZpZ2F0b3IpIHtpZiAoKGFwcE5hbWU9PSJOZXRzY2FwZSIpJiYocGFyc2VJbnQoYXBwVmVyc2lvbik9PTQpKSB7CiAgICBkb2N1bWVudC5NTV9wZ1c9aW5uZXJXaWR0aDsgZG9jdW1lbnQuTU1fcGdIPWlubmVySGVpZ2h0OyBvbnJlc2l6ZT1NTV9yZWxvYWRQYWdlOyB9fQogIGVsc2UgaWYgKGlubmVyV2lkdGghPWRvY3VtZW50Lk1NX3BnVyB8fCBpbm5lckhlaWdodCE9ZG9jdW1lbnQuTU1fcGdIKSBsb2NhdGlvbi5yZWxvYWQoKTsKfQpNTV9yZWxvYWRQYWdlKHRydWUpOwoKZnVuY3Rpb24gTU1fcHJlbG9hZEltYWdlcygpIHsgLy92My4wCiAgdmFyIGQ9ZG9jdW1lbnQ7IGlmKGQuaW1hZ2VzKXsgaWYoIWQuTU1fcCkgZC5NTV9wPW5ldyBBcnJheSgpOwogICAgdmFyIGksaj1kLk1NX3AubGVuZ3RoLGE9TU1fcHJlbG9hZEltYWdlcy5hcmd1bWVudHM7IGZvcihpPTA7IGk8YS5sZW5ndGg7IGkrKykKICAgIGlmIChhW2ldLmluZGV4T2YoIiMiKSE9MCl7IGQuTU1fcFtqXT1uZXcgSW1hZ2U7IGQuTU1fcFtqKytdLnNyYz1hW2ldO319Cn0KLy8tLT4KPC9zY3JpcHQ+CiAgICAgICAgICAgICA8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoJCQkgCjxzdHlsZSB0eXBlPSJ0ZXh0L2NzcyI+CjwhLS0KI0xheWVyMSB7Cglwb3NpdGlvbjphYnNvbHV0ZTsKCXdpZHRoOjY1MXB4OwoJaGVpZ2h0OjIxOHB4OwoJei1pbmRleDoxOwp9CiNMYXllcjIgewoJcG9zaXRpb246YWJzb2x1dGU7Cgl3aWR0aDoyMDBweDsKCWhlaWdodDoxMTVweDsKCXotaW5kZXg6MTsKCXZpc2liaWxpdHk6IHZpc2libGU7Cn0KLkVzdGlsbzEgewoJZm9udC1zaXplOiAxOHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzIgewoJZm9udC1zaXplOiAxNHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzMge2NvbG9yOiAjNTA2OTkwOyBsaW5lLWhlaWdodDogMTJweDsgdGV4dC1kZWNvcmF0aW9uOiBub25lOyBmb250LWZhbWlseTogVGFob21hO30KLS0+Cjwvc3R5bGU+CjwvaGVhZD4KCjxib2R5IGxlZnRtYXJnaW49IjIiIG1hcmdpbndpZHRoPSIyIj4KPHRhYmxlIHdpZHRoPSI2MDgiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICA8dHI+CiAgICA8dGQgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCB3aWR0aD0iMiUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzA3LmpwZyIgd2lkdGg9IjI0IiBoZWlnaHQ9IjE0IiAvPjwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI5MCUiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18wNy5qcGciPiZuYnNwOzwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI4JSIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wOS5qcGciIHdpZHRoPSI0NSIgaGVpZ2h0PSIxNyIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogIDwvdHI+CiAgPHRyPgogICAgPHRkIGNvbHNwYW49IjQiPjxiciAvPgogICAgICA8dGFibGUgd2lkdGg9Ijk4JSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICA8dHI+CiAgICAgICAgPHRkIHdpZHRoPSIyJSI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgICA8dGQgd2lkdGg9IjkzJSI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CjwhLS0gSU5JQ0lPIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzIzMDQyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjIvMTEvMjAxMzwvc3Bhbj48YnI+SVYgQ29uZ3Jlc28gSW50ZXJuYWNpb25hbCB2aW9sZW5jaWEsIG1hbHRyYXRvIHkgYWJ1c288L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxzdHJvbmc+MTQsIDE1IHkgMTYgZGUgTm92aWVtYnJlIEFCSUVSVEEgTEEgSU5TQ1JJUENJJk9hY3V0ZTtOISAoY29uIGRlc2N1ZW50byBoYXN0YSBlbCAyNy84KTxiciAvPjwvc3Ryb25nPjwvcD4NCjxwPjxzdHJvbmc+QUJJRVJUQSBMQSBSRUNFUENJJk9hY3V0ZTtOIERFIFRSQUJBSk88YSBocmVmPSJodHRwOi8vd3d3LmNvbmdyZXNvdmlvbGVuY2lhLmNvbS9pbmRleC5waHA/aWQ9bW9kYWxpZGFkZXMiIHRhcmdldD0iX2JsYW5rIj4gKG1hcyBpbmZvKTwvYT48L3N0cm9uZz48L3A+DQo8cD48c3BhbiBzdHlsZT0iY29sb3I6ICNmZjY2MDA7Ij48c3Ryb25nPk9yZ2FuaXphOiBTYWx1ZCBBY3RpdmE8L3N0cm9uZz48L3NwYW4+PC9wPg0KPHA+PHNwYW4gc3R5bGU9ImNvbG9yOiAjZmY2NjAwOyI+SW5jcmlwdG9zIGFsIFBvcnRhbCBkZSBTYWx1ZCBBY3RpdmEsIGltcG9ydGFudGVzIGRlc2N1ZW50b3MhPGJyIC8+PC9zcGFuPjwvcD4NCjxwPkx1Z2FyIGRlIFJlYWxpemFjaSZvYWN1dGU7biB5IGNvbGFib3JhY2lvbjogVW5pdmVyc2lkYWQgZGVsIEVzdGUsIExhIFBsYXRhIEJ1ZW5vcyBBaXJlczwvcD4NCjxwPk1hcyBkZSAxNTAgdHJhYmFqb3MgcHJlc2VudGFkb3MsIHVsdGltb3MgZGlhcyBwYXJhIGluc2NyaWJpcnNlIGNvbiBkZXNjdWVudG8hITwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPkluc2NyaWJpcnNlPC9hPjwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPjxiciAvPjwvYT48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAxIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDEiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MDQvMTEvMjAxMzwvc3Bhbj48YnI+RWwgY29sZWdpbyBkZSBQc2lj82xvZ29zIGRlIEPzcmRvYmEgc2UgcHJvbnVuY2lhIGVuIHJlbGFjafNuIGFsIFNBUCB5IGVuIGNvbmNvcmRhbmNpYSBjb24gbG8gZXhwcmVzYWRvIHBvciBlbCBDb2xlZ2lvIGRlIFBzaWPzbG9nb3MgZGUgTWFyIGRlbCBQbGF0YSB5IGVsIENvbGVnaW8gZGUgUHNpY/Nsb2dvcyBkZSBsYSAgUHJvdmluY2lhIGRlIEJ1ZW5vcyBBaXJlczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+Jm5ic3A7PC9wPg0KPHA+TGFzIGNvbnRyb3ZlcnNpYXMgZ2VuZXJhZGFzIGVuIHJlbGFjaSZvYWN1dGU7biBhbCAic2luZHJvbWUgZGUgYWxpZW5hY2kmb2FjdXRlO24gcGFyZW50YSIgU0FQLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMxMCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzEwIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzE2MTAyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTYvMTAvMjAxMzwvc3Bhbj48YnI+U2FsdWQgQWN0aXZhIG90b3JnYSBtZWRpYXMgYmVjYXMgcGFyYSBlbCBJViBDb25ncmVzbyBJbnRlcm5hY2lvbmFsLCBWIE5hY2lvbmFsLCBWSSBSZWdpb25hbCBWaW9sZW5jaWEsIE1hbHRyYXRvIHkgQWJ1c28uPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD4mbmJzcDs8L3A+DQo8cD5TZXImYWFjdXRlO24gb3RvcmdhZGFzIDUwIG1lZGlhcyBiZWNhcywgcXVlZGFuIHBvY2FzISEhIGNvbmRpY2lvbjo8L3A+DQo8cD5QZXJ0ZW5lY2VyIGFsIGFtYml0byBwdWJsaWNvIG8gYSBPTkcsIHNlIGNvbnNpZGVyYSB0YW1iaWVuIGxhIGRpc3RhbmNpYSBhbCBsdWdhciBkZWwgZXZlbnRvISEhIGVzIG11eSBzZW5jaWxsbywgc29sbyBkZWJlcyBlbnZpYXIgdW4gZW1haWwuLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwOSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA5Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjI0LzA3LzIwMTM8L3NwYW4+PGJyPk5FQ0VTSVRBTU9TIERFIFNVIFNPTElEQVJJREFEIEhBQ0lBIExPUyBOSdFPUyBZIE5J0UFTISEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPlBST0dSQU1BIEZBTUlMSUFTIFNPTElEQVJJQVM8L3NwYW4+PC9zdHJvbmc+PC9wPg0KPHA+PHN0cm9uZz5DQU1CSU8gREUgU0VERTwvc3Ryb25nPjwvcD4NCjxwPkxhIGNhcGFjaXRhY2kmb2FjdXRlO24gcGFyYSBsYSBwdWVzdGEgZW4gbWFyY2hhIGRlbCA8c3Ryb25nPlByb2dyYW1hIEZhbWlsaWFzIFNvbGlkYXJpYXM8L3N0cm9uZz4gc2UgcmVhbGl6YXImYWFjdXRlOyBlbiBsYSBsb2NhbGlkYWQgZGUgPHN0cm9uZz5OYXZhcnJvPC9zdHJvbmc+IHBhcmEgdG9kbyBlbCBjb3JyZWRvciBkZSBsYSBSdXRhIDQwLjwvcD4NCjxwPkluaWNpbyA8c3Ryb25nPk1pJmVhY3V0ZTtyY29sZXMgMjggZGUgYWdvc3RvIGEgbGFzIDE0IGhvcmFzLiZuYnNwOzwvc3Ryb25nPjwvcD4NCjxwPlNlZGU6IDxzdHJvbmc+U2FsJm9hY3V0ZTtuIE11bmljaXBhbCBlbiBsYSBjYWxsZSAxMDcgZXNxdWluYSAyMiAtIE5hdmFycm88L3N0cm9uZz48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA4Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTIwNzIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xMi8wNy8yMDEzPC9zcGFuPjxicj5TQUxVRCBBQ1RJVkEgaGEgc2lkbyBlbGVnaWRhIHBvciBzZWd1bmRhIHZleiBjb25zZWN1dGl2YSBjb21vIHVubyBkZSBsb3MgZ2FuYWRvcmVzIGRlbCBDdWFydG8gQ29uY3Vyc28gZGUgUHJveWVjdG9zIFNvY2lhbGVzIGRlIFBldHJvYnJhczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+RW4gZWwgbWFyY28gZGVsIEN1YXJ0byBDb25jdXJzbyBkZSBQcm95ZWN0b3MgU29jaWFsZXMgZGUgUGV0cm9icmFzLCANCm51ZXN0cmEgSW5zdGl0dWNpJm9hY3V0ZTtuIFNBTFVEIEFDVElWQSBoYSBzaWRvIGVsZWdpZGEgcG9yIHNlZ3VuZGEgdmV6IA0KY29uc2VjdXRpdmEgY29tbyB1bm8gZGUgbG9zIGdhbmFkb3JlcyBkZSBkaWNobyBjb25jdXJzby48YnIgLz5FbiBlc3RhIA0KZWRpY2kmb2FjdXRlO24gZWwgcHJveWVjdG8gcXVlIGhhIHNpZG8gZWxlZ2lkbyBlcyBlbCAmbGRxdW87UHJvZ3JhbWEgZGUgRmFtaWxpYXMgDQpTb2xpZGFyaWFzJnJkcXVvOyBzaWVuZG8gc3UgJmFhY3V0ZTtyZWEgZGUgaW1wbGVtZW50YWNpJm9hY3V0ZTtuIGxvcyBNdW5pY2lwaW9zIGRlIE5hdmFycm8sIA0KR3JhbC4gTGFzIEhlcmFzLCBNYXJjb3MgUGF6LCB5IE1lcmxvPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAyLzA3LzIwMTM8L3NwYW4+PGJyPk/tciBvIGVzY3VjaGFyPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Qb3IgQ2FybG9zIFJvemFuc2tpICo8L3A+DQo8cD5BIGxvIGxhcmdvIGRlIGxvcyBzaWdsb3MsIGxhcyBuaSZudGlsZGU7YXMsIG5pJm50aWxkZTtvcyB5IGFkb2xlc2NlbnRlcyBoYW4gc2lkbyBtYWx0cmF0YWRvcyB5IGFidXNhZG9zIHNpbiBxdWUgYSBsYSBjb211bmlkYWQgbGUgaW50ZXJlc2FyYSBuaSBzaXF1aWVyYSBlc2N1Y2hhcmxvcyBjdWFuZG8gaGFjJmlhY3V0ZTthbiBzYWJlciBkZSBhbGd1bmEgZm9ybWEgbG9zIHN1ZnJpbWllbnRvcyBxdWUgcGFkZWMmaWFjdXRlO2FuLiBFbiAxODc0LCBlbiBFc3RhZG9zIFVuaWRvcywgZnVlIGxhIHByaW1lcmEgdmV6IHF1ZSBlbCBFc3RhZG8gaW50ZXJ2aW5vIGVuIHVuIGNhc28gZGUgbWFsdHJhdG8geSBhYnVzby4uLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDYiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4wMi8wNy8yMDEzPC9zcGFuPjxicj5FbCBkZXJlY2hvIGRlIGxvcyBuafFvcyBhIHNlciBlc2N1Y2hhZG9zPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5VbiBob21icmUgYWN1c2FkbyBkZSBoYWJlciBhYnVzYWRvIGRlIHN1cyBoaWpvcyBoYWImaWFjdXRlO2Egc2lkbyBzb2JyZXNlJmlhY3V0ZTtkbyBkb3MgdmVjZXMgcG9yIGxhIEp1c3RpY2lhLiBQZXJvIGFob3JhLCBsYSBDJmFhY3V0ZTttYXJhIGRlIENhc2FjaSZvYWN1dGU7biByZXZvYyZvYWN1dGU7IGVzYSBkZWNpc2kmb2FjdXRlO24gcG9ycXVlIGVuIGxhIGludmVzdGlnYWNpJm9hY3V0ZTtuIGVsIGp1ZXogbnVuY2EgaGFiJmlhY3V0ZTthIGVzY3VjaGFkbyBhIGxvcyBjaGljb3MuIFkgb3JkZW4mb2FjdXRlOyBxdWUgdGVuZ2EgZW4gY3VlbnRhIGxvIHF1ZSBkaWNlbi48L3A+DQo8cD5Qb3IgTWFyaWFuYSBDYXJiYWphbDwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDUiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE1NiIgcm93c3Bhbj0iMiIgdmFsaWduPSJ0b3AiPgoJCQkJCgkJCQk8dGFibGUgd2lkdGg9IjMyJSIgYm9yZGVyPSIxIiBjZWxsc3BhY2luZz0iMyIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48aW1nIHNyYz0ic3JjL2ltZ191cC8wNjA2MjAxMy4xLmpwZyIgd2lkdGg9IjE0NiIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT4KCQkJCQkJCQk8L3RkPiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjA2LzA2LzIwMTM8L3NwYW4+PGJyPkFidXNvIHNleHVhbCBpbmZhbnRpbC4gRGVzYWZpb3MgZGUgbGEgY2xpbmljYSBhY3R1YWw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkFiaWVydGEgbGEgaW5zY3JpcGNpb248L3A+DQo8cD5Eb2NlbnRlczogTGljLiBNYXJpYSBCZWF0cml6IE0mdXVtbDtsbGVyLiBMaWMuIFBhb2xhIE11Jm50aWxkZTtveiBEdWFydGU8L3A+DQo8cD5JbmljaW86IE1pZXJjb2xlcyAxOSBkZSBKdW5pbzwvcD4NCjxwPkZyZWN1ZW5jaWE6IFNlbWFuYWw8L3A+DQo8cD5Nb2RhbGlkYWQ6IEludGVuc2l2YTwvcD4NCjxwPkNvbnRlbmlkb3M6ICZuYnNwOyBFc3RhIGRlc3RpbmFkbyBhIHRvZG9zIGxvcyBwcm9mZXNpb25hbGVzIGNvbXByb21ldGlkb3MgY29uIGxhIHRlbWF0aWNhIGRlbCBhYnVzbyBpbmZhbnRpbCBxdWUgcXVpZXJhbiBhY3R1YWxpemFyc2UgZSBpbnRlcmNhbWJpYXIgZXhwZXJpZW5jaWFzIGRlIHRyYWJham8uLi48L3A+DQo8cD4mbmJzcDs8L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA0Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDQiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTYwNTIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xNi8wNS8yMDEzPC9zcGFuPjxicj5TYWx1ZCBBY3RpdmEgbmVjZXNpdGEgZGUgdHUgYXl1ZGEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5UcmFiYWphbW9zIGNvbW8gcG9kZW1vczogYmEmbnRpbGRlO29zIHJvdG9zLCBzdXNwZW5zaSZvYWN1dGU7biBkZSByZXVuaW9uZXMgcG9yIGNvcnRlcyBkZSBsdXogeSBhZ3VhLCBqdWd1ZXRlcyB2aWVqb3MsIG1lc2VzIGRlIGF0cmFzbyBlbiBlbCBwYWdvIGRlIHN1cyBwcm9mZXNpb25hbGVzIGRlIGxhIHNhbHVkLiBSZWNpZW50ZW1lbnRlIHR1dmltb3MgcXVlIGNlcnJhciBudWVzdHJvIHF1ZXJpZG8gSG9nYXI6ICZsZHF1bztNZXRhbW9yZm9zaXMmcmRxdW87IGVyYSBlbCBsdWdhciBxdWUgc3VwbyBjb250ZW5lciBhIG5pJm50aWxkZTthcyB5IGomb2FjdXRlO3ZlbmVzIHJlc2NhdGFkYSBkZSByZWRlcyBkZSB0cmF0YSBvIHYmaWFjdXRlO2N0aW1hcyBkZSBhYnVzbyBpbnRyYWZhbWlsaWFyLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAzIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAzLzA1LzIwMTM8L3NwYW4+PGJyPlJFUFVESU8gQSBMQSBQUkVTRU5DSUEgRU4gTEEgRkVSSUEgREVMIExJQlJPIERFIFVOIEVYIEpVRVogQUNVU0FETyBERSBBQlVTTyBTRVhVQUw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkZ1ZSBjYW1hcmlzdGEgZW4gTWFyIGRlbCBQbGF0YSBkdXJhbnRlIGxhIGRpY3RhZHVyYS4gSGFjZSBhJm50aWxkZTtvcywgdmFyaWFzIG11amVyZXMgbG8gYWN1c2Fyb24gZGUgaGFiZXIgYWJ1c2FkbyBkZSBlbGxhcyBjdWFuZG8gZXJhbiBuaSZudGlsZGU7YXMuIExhIGNhdXNhIHByZXNjcmliaSZvYWN1dGU7IHkgbm8gaHVibyBjb25kZW5hLiBNYSZudGlsZGU7YW5hIHRpZW5lIHByZXZpc3RvIGZpcm1hciBzdSBsaWJyby4gRXNhcyBtaXNtYXMgbXVqZXJlcyBwaWRlbiBxdWUgbm8gc2VhIGFkbWl0aWRvIGVuIGxhIGZlcmlhLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDIiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgIDwhLS0gRklOIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgIDwvdGFibGU+ICAgICAgICA8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iNSUiIGFsaWduPSJyaWdodCI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgPC90cj4KICAgIDwvdGFibGU+PC90ZD4KICA8L3RyPgogIDx0cj4KICAgIDx0ZCB3aWR0aD0iMSUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiIgYWxpZ249ImNlbnRlciI+Jm5ic3A7PC90ZD4KICAgIDx0ZCB3aWR0aD0iMiUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgPC90cj4KICAKICA8dGQ+CiAgPHRyPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0ciBhbGlnbj0iY2VudGVyIj4KICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgPHRkIHdpZHRoPSI5NyIgY29sc3Bhbj0iMiIgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iNTQ2IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idGl0dWxvaG9tZTIiPjx0YWJsZSB3aWR0aD0iIiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYWxpZ249ImxlZnQiIHZhbGlnbj0iYm90dG9tIiBjbGFzcz0idGl0dWxvaG9tZTIiPlJhbmtpbmc8L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSIgY2xhc3M9InRpdHVsb2hvbWUyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iIiBoZWlnaHQ9IjM1IiBhbGlnbj0ibGVmdCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPiZidWxsO0xhcyBtJmFhY3V0ZTtzIGxlaWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGNsYXNzPSJjb250ZW5pZG9ob21lIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBjbGFzcz0iY29udGVuaWRvaG9tZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+JmJ1bGw7TGFzIG0mYWFjdXRlO3MgY29tZW50YWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTHVkb3RlY2EgR2FyYWJhdG8gLSBQcm95ZWN0byBzYWx1ZGFjdGl2YSwgUG9yIHVuYSBpbmZhbmNpYSBmZWxpeiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iOSUiIGJnY29sb3I9IiNFRkVGRUYiPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzJSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xNjIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDUlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTE2MiIgY2xhc3M9ImJvdG9uIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBDdXJzbyBJbnRlbnNpdm8gZGUgb3BlcmFkb3IgdGVyYXBldXRpY28gZXNwZWNpYWxpemFkbyBlbiBlbCBhYm9yZGFqZSBkZWwgYWJ1c28sIGxhIHZpb2xlbmNpYSB5IGVsIG1hbHRyYXRvIGluZmFudGlsICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgUFJPR1JBTUEgTEFTIFZJQ1RJTUFTIENPTlRSQSBMQVMgVklPTEVOQ0lBUyAgTWluaXN0ZXJpbyBkZSBKdXN0aWNpYSB5IERlcmVjaG9zIEh1bWFub3MgZGUgbGEgTmFjafNuICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI5JSIgYmdjb2xvcj0iI0VGRUZFRiI+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjMlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTI1NSIgY2xhc3M9ImJvdG9uIj48aW1nIHNyYz0iaW1nL2ZsZWNoYW5hcmFuamFmZ3Jpc18yNC5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSI3IiBib3JkZXI9IjAiIGFsaWduPSJhYnNtaWRkbGUiIC8+PC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI0NSUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MjU1IiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIERpcGxvbWF0dXJhIGVuIEFib3JkYWplIGludGVyZGlzY2lwbGluYXJpbyBkZWwgbWFsdHJhdG8sIGxhIHZpb2xlbmNpYSB5IGVsIGFidXNvIHNleHVhbCBpbmZhbnRpbCAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyJSIgaGVpZ2h0PSIyMCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQxJSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNhbHVkIEFjdGl2YSBuZWNlc2l0YSBkZSB0dSBheXVkYSEgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjklIiBiZ2NvbG9yPSIjRUZFRkVGIj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMyUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MTA0IiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQ1JSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xMDQiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTGxhbWFkbyBwYXJhIHByZXNlbnRhY2nzbiBkZSB0cmFiYWpvcy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjIwIiBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyMCIgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGJnY29sb3I9IiNGRkZGRkYiIGNsYXNzPSJ0ZXh0b251ZXZvIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPgogICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iIyIgY2xhc3M9ImJvdG9uIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgPC90YWJsZT48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj4mbmJzcDs8L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBJTklDSU8gbm90YSBjb211biAtLT4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTUvMDQvMjAxMjwvc3Bhbj48YnI+T3JnYW5pemFuIGpvcm5hZGEgc29icmUgdmlvbGVuY2lhPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPlNlIGNlbnRyYXImYWFjdXRlOyBlbiBsb3MgZmVuJm9hY3V0ZTttZW5vcyBxdWUgYWZlY3RhbiBhIGxhIGZhbWlsaWEgeSBlbiBsbyBxdWUgb2N1cnJlIGVuIGxhcyBlc2N1ZWxhcy48YnIgLz4gU2UgbGxldmFyJmFhY3V0ZTsgYSBjYWJvIGVsIGx1bmVzIDIzLCBlbiBlbCBDZW50cm8gQ3VsdHVyYWwgZGUgVG9zY2hpIHkgVHJlcyANCkFycm95b3MsIHVuYSBqb3JuYWRhIGRlIHJlZmxleGkmb2FjdXRlO24geSBkZWJhdGUgYWJpZXJ0YSBhIGxhIGNvbXVuaWRhZCBzb2JyZSANCiZsZHF1bztWaW9sZW5jaWEgZW4gbGEgZmFtaWxpYSB5IGVuIGxhIGVzY3VlbGEgeSBzdSByZWxhY2kmb2FjdXRlO24gY29uIGVsIGZyYWNhc28gDQplc2NvbGFyJnJkcXVvOywgb3JnYW5pemFkYSBwb3IgbGEgQXNvY2lhY2kmb2FjdXRlO24gQ2l2aWwgQ2VudHJvIEFydCZlYWN1dGU7bWlkZXMgeSBsYSANCk11bmljaXBhbGlkYWQgZGUgQ2lwb2xsZXR0aS5TZSBjZW50cmFyJmFhY3V0ZTsgZW4gbG9zIGZlbiZvYWN1dGU7bWVub3MgcXVlIGFmZWN0YW4gYSBsYSBmYW1pbGlhIHkgZW4gbG8gcXVlIG9jdXJyZSBlbiBsYXMgZXNjdWVsYXMuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjMwLzAzLzIwMTI8L3NwYW4+PGJyPkNhcnRhIGRlIEFTQVBNSSAtIEFzb2NpYWNp824gQXJnZW50aW5hIGRlIFByZXZlbmNp824gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbDwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjE1IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSIxNSIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjgwIiBjb2xzcGFuPSI0IiBhbGlnbj0ibGVmdCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Mb3MgaW50ZWdyYW50ZXMgZGUgbGEgQ29taXNpJm9hY3V0ZTtuIERpcmVjdGl2YSBkZSBBU0FQTUkgLSBBc29jaWFjaSZvYWN1dGU7biBBcmdlbnRpbmEgZGUgUHJldmVuY2kmb2FjdXRlO24gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbCwgYXNvY2lhZGEgYSBsYSBJbnRlcm5hdGlvbmFsIFNvY2lldHkgZm9yIFByZXZlbnRpb24gb2YgQ2hpbGQgQWJ1c2UgYW5kIE5lZ2xlY3QgKElTUENBTikgLSwgdGVuZW1vcyBlbCBhZ3JhZG8gZGUgZGlyaWdpcm5vcyBhIFVzdGVkIHBhcmEgdHJhc21pdGlybGUgbnVlc3RyYSBwcm9mdW5kYSAmbmJzcDt5IGhvbmRhIHByZW9jdXBhY2kmb2FjdXRlO24gcG9yIGxhIHBvc3R1cmEgcXVlIHZpZW5lbiBhc3VtaWVuZG8gZW4gZm9ybWEgY29udGludWFkYSBhbGd1bm9zIGNvbGVnaW9zIGRlIHBzaWMmb2FjdXRlO2xvZ29zLCBlc3BlY2lhbG1lbnRlIGRlIGxhIHByb3ZpbmNpYSBkZSBCdWVub3MgQWlyZXMsIGVuIHJlbGFjaSZvYWN1dGU7biBhbCB0cmF0YW1pZW50byBwb2NvIHNlcmlvIHkgY29tcHJvbWV0aWRvIHF1ZSBzZSBsZXMgb3RvcmdhIGEgbGFzIGRlbnVuY2lhcyBlZmVjdHVhZGFzIGNvbnRyYSBwcm9mZXNpb25hbGVzIHBzaWMmb2FjdXRlO2xvZ29zLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjAvMDMvMjAxMjwvc3Bhbj48YnI+TEEgVklPTEVOQ0lBIFNFWFVBTCBDT05UUkEgTknRT1MgWSBOSdFBUyBFTiBDSUZSQVM8L3RkPgogICAgICAgICAgPC90cj4KICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkIHdpZHRoPSIxNSIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4MCIgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+UmFkaW9ncmFmJmlhY3V0ZTthIGRlIHVuIHByb2JsZW1hPC9wPg0KPHA+RGUgbG9zIG4mdWFjdXRlO21lcm9zIGNvbXBpbGFkb3MgcG9yIGRvcyBlcXVpcG9zIGRlbCBNaW5pc3RlcmlvIGRlIEp1c3RpY2lhLCBsYQ0KIGF1dG9yYSB0b21hIGxvcyBkZSBsYSBjaXVkYWQgZGUgQnVlbm9zIEFpcmVzIHBhcmEgdHJhemFyIHVuIHBhcmFkaWdtYSANCmRlIGxvcyBkZWxpdG9zIGNvbnRyYSBsYSBpbnRlZ3JpZGFkIHNleHVhbCBlbiBlbCBwYSZpYWN1dGU7cyB5IHNvYnJlIHN1IA0KYXRlbmNpJm9hY3V0ZTtuLjxiciAvPiA8YnIgLz4gJm5ic3A7UG9yIEV2YSBHaWJlcnRpPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2MCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjAiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjE1LzAzLzIwMTI8L3NwYW4+PGJyPkZBTExPIERFIExBIENPUlRFIFNVUFJFTUEgU09CUkUgTEEgTk8gSlVESUNJQUxJWkFDSU9OIERFTCBBQk9SVE8gRU4gQ0FTT1MgREUgVklPTEFDSU9OPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxiciAvPiBKVVJJU0RJQ0NJT046IE5BQ0lPTkFMPGJyIC8+IE1BVEVSSUE6IEFCT1JUTy48YnIgLz4gVFJJQlVOQUw6IENvcnRlIFN1cHJlbWEgZGUgSnVzdGljaWEgZGUgbGEgTmFjaSZvYWN1dGU7bi48YnIgLz4gQVVUT1M6IEYuLCBBLiBMLiBzLyBtZWRpZGEgYXV0b3NhdGlzZmFjdGl2YS48YnIgLz4gRkVDSEE6IDEzLzAzLzIwMTIuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI1OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNTkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBGSU4gbm90YSBjb211biAtLT4KPC90YWJsZT4KPG1hcCBuYW1lPSJNYXBNYXAiIGlkPSJNYXBNYXAiPjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjE0NCw0LDIxNCwzNiIgaHJlZj0iaW5kZXgucGhwP2lkPTE0IiAvPgo8L21hcD4KPG1hcCBuYW1lPSJNYXAyTWFwMiIgaWQ9Ik1hcDJNYXAyIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIxNDcsNCwyMjAsMzYiIGhyZWY9ImluZGV4LnBocD9pZD0xNGEiIC8+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcDMiIGlkPSJNYXAzIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIzNjMsMyw0MzYsMzkiIGhyZWY9ImluZGV4LnBocD9pZD0xNGIiIC8+CjwvbWFwPgo8L2h0bWw+CjwvdGQ+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gICAgICAgICAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFM0UzRTMiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSI3MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNiUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9kZWNpbG9fYmllbl9mdWVydGUxLmpwZyIgd2lkdGg9IjEyMCIgaGVpZ2h0PSIxMTIiPjwvdGQ+CiAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiA+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTI0IiBjbGFzcz0iYm90b24xIj5bK10gTSZhYWN1dGU7cyBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0UzRTNFMyI+ICAgICAgICA8L3RyPgogICAgICAgIDx0cj4gCiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj4mbmJzcDs8L3RkPgogICAgICAgIDwvdHI+CiAgICA8L3RhYmxlPjwvdGQ+CiAgPC90cj4KICA8dHI+IAogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSI+PGltZyBzcmM9ImltZy9penExLmpwZyIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjExNCIgLz48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9RdWllbmVzU29tb3NfQTJfMF8yNS5qcGciIHdpZHRoPSI4MDkiIGhlaWdodD0iMTE0IiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcDIiIC8+PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI1MCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiYWNrZ3JvdW5kPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzE4XzE4LmpwZyI+Jm5ic3A7PC90ZD4KICAgIDx0ZCBoZWlnaHQ9IjUwIiBjbGFzcz0iZm9uZG9ib3R0b20iPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2l0ZWkuY29tLmFyLyI+PGltZyBzcmM9ImltZy9laV9jb2xvci5wbmciIGFsdD0iZXNwYWNpb3MgZGUgaW1hZ2luYWNpb24sIGRlc2Fycm9sbG9zIGludGVyYWN0aXZvcywgY3JlYXRpdmlkYWQsIGRpc2XxbyIgd2lkdGg9IjI3IiBoZWlnaHQ9IjE1IiBib3JkZXI9IjAiPjwvYT4gPHNwYW4gY2xhc3M9ImVpIj48YSBocmVmPSJodHRwOi8vd3d3LnNpdGVpLmNvbS5hci8iIHNwYW4gY2xhc3M9ImVpIj5kaXNlJm50aWxkZTtvICsgY29tdW5pY2FjaSZvYWN1dGU7bjwvYT48L3NwYW4+PGVtPiZuYnNwOzwvZW0+PC9zcGFuPjxzcGFuIGNsYXNzPSJibGFuY28xIj48ZW0+Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7PC9lbT48L3NwYW4+PC90ZD4KICA8L3RyPgo8L3RhYmxlPgoKCjxtYXAgbmFtZT0iTWFwMiI+PGFyZWEgc2hhcGU9InJlY3QiIGNvb3Jkcz0iMjQ3LDY5LDQxNCw4MiIgaHJlZj0ibWFpbHRvOnNhbHVkYWN0aXZhQHNhbHVkYWN0aXZvLm9yZy5hciI+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcCI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM2LDE0MiwxNDksMTUyIiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MiI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM0LDE4NiwxNTAsMTk2IiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MCI+CjwvbWFwPgo8L2JvZHk+CjwvaHRtbD4K]]></response> | |
| 201 | <responseRedirected>false</responseRedirected> | |
| 202 | </requestresponse> | |
| 203 | </issue> | |
| 204 | <issue> | |
| 205 | <serialNumber>3742539495863584768</serialNumber> | |
| 206 | <type>5243904</type> | |
| 207 | <name>Cross-domain Referer leakage</name> | |
| 208 | <host ip="200.20.20.201">http://www.example.org.ar</host> | |
| 209 | <path><![CDATA[/index.php]]></path> | |
| 210 | <location><![CDATA[/index.php]]></location> | |
| 211 | <severity>Information</severity> | |
| 212 | <confidence>Certain</confidence> | |
| 213 | <issueBackground><![CDATA[When a web browser makes a request for a resource, it typically adds an HTTP header, called the "Referer" header, indicating the URL of the resource from which the request originated. This occurs in numerous situations, for example when a web page loads an image or script, or when a user clicks on a link or submits a form.<br><br>If the resource being requested resides on a different domain, then the Referer header is still generally included in the cross-domain request. If the originating URL contains any sensitive information within its query string, such as a session token, then this information will be transmitted to the other domain. If the other domain is not fully trusted by the application, then this may lead to a security compromise.<br><br>You should review the contents of the information being transmitted to other domains, and also determine whether those domains are fully trusted by the originating application.<br><br>Today's browsers may withhold the Referer header in some situations (for example, when loading a non-HTTPS resource from a page that was loaded over HTTPS, or when a Refresh directive is issued), but this behavior should not be relied upon to protect the originating URL from disclosure.<br><br>Note also that if users can author content within the application then an attacker may be able to inject links referring to a domain they control in order to capture data from URLs used within the application.]]></issueBackground> | |
| 214 | <remediationBackground><![CDATA[The application should never transmit any sensitive information within the URL query string. In addition to being leaked in the Referer header, such information may be logged in various locations and may be visible on-screen to untrusted parties.]]></remediationBackground> | |
| 215 | <issueDetail><![CDATA[The page was loaded from a URL containing a query string:<ul><li>http://www.example.org.ar/index.php?id=18_new</li></ul>The response contains the following links to other domains:<ul><li>http://download.macromedia.com/pub/shockwave/cabs/flash/swflash.cab</li><li>http://twitter.com/exampleONG</li><li>http://www.congresoviolencia.com/index.php?id=inscripcion</li><li>http://www.congresoviolencia.com/index.php?id=modalidades</li><li>http://www.facebook.com/home.php?</li><li>http://www.sitei.com.ar/</li></ul>]]></issueDetail> | |
| 216 | <requestresponse> | |
| 217 | <request base64="true"><![CDATA[R0VUIC9pbmRleC5waHA/aWQ9MThfbmV3IEhUVFAvMS4xDQpIb3N0OiB3d3cuc2FsdWRhY3RpdmEub3JnLmFyDQpBY2NlcHQ6ICovKg0KQWNjZXB0LUxhbmd1YWdlOiBlbg0KVXNlci1BZ2VudDogTW96aWxsYS81LjAgKGNvbXBhdGlibGU7IE1TSUUgOS4wOyBXaW5kb3dzIE5UIDYuMTsgV2luNjQ7IHg2NDsgVHJpZGVudC81LjApDQpDb25uZWN0aW9uOiBjbG9zZQ0KDQo=]]></request> | |
| 218 | <response base64="true"><![CDATA[SFRUUC8xLjEgMjAwIE9LDQpEYXRlOiBUaHUsIDA3IE5vdiAyMDEzIDE3OjE0OjA1IEdNVA0KU2VydmVyOiBBcGFjaGUvMi4yLjIzIChVbml4KSBtb2Rfc3NsLzIuMi4yMyBPcGVuU1NMLzAuOS44ZS1maXBzLXJoZWw1DQpYLVBvd2VyZWQtQnk6IFBIUC81LjIuMTcNCkV4cGlyZXM6IFRodSwgMTkgTm92IDE5ODEgMDg6NTI6MDAgR01UDQpDYWNoZS1Db250cm9sOiBuby1zdG9yZSwgbm8tY2FjaGUsIG11c3QtcmV2YWxpZGF0ZSwgcG9zdC1jaGVjaz0wLCBwcmUtY2hlY2s9MA0KUHJhZ21hOiBuby1jYWNoZQ0KQ29ubmVjdGlvbjogY2xvc2UNCkNvbnRlbnQtVHlwZTogdGV4dC9odG1sDQpDb250ZW50LUxlbmd0aDogNjA2MDYNCg0KIDxoZWFkPgo8bWV0YSBodHRwLWVxdWl2PSJDb250ZW50LVR5cGUiIGNvbnRlbnQ9InRleHQvaHRtbDsgY2hhcnNldD1pc28tODg1OS0xIiAvPgo8dGl0bGU+U2FsdWQgQWN0aXZhIC0gQWJ1c28gdmlvbGVuY2lhIHkgbWFsdHJhdG88L3RpdGxlPgoKPHNjcmlwdD4gCiAgICAvL2VzdG8gcGFyYSBwYXNhcmxlIGFsIGZsYXNoIGxhcyB2YXJpYWxiZXMgZGVsIHBocAogCQoKCXZhciBib3Q9Jyc7Ci8vYWxlcnQodmFyaWFibGVTZXJ2aWRvcik7Cjwvc2NyaXB0Pgo8c2NyaXB0IGxhbmd1YWdlPSJKYXZhU2NyaXB0IiB0eXBlPSJ0ZXh0L0phdmFTY3JpcHQiPgo8IS0tCmZ1bmN0aW9uIE1NX3ByZWxvYWRJbWFnZXMoKSB7IC8vdjMuMAogIHZhciBkPWRvY3VtZW50OyBpZihkLmltYWdlcyl7IGlmKCFkLk1NX3ApIGQuTU1fcD1uZXcgQXJyYXkoKTsKICAgIHZhciBpLGo9ZC5NTV9wLmxlbmd0aCxhPU1NX3ByZWxvYWRJbWFnZXMuYXJndW1lbnRzOyBmb3IoaT0wOyBpPGEubGVuZ3RoOyBpKyspCiAgICBpZiAoYVtpXS5pbmRleE9mKCIjIikhPTApeyBkLk1NX3Bbal09bmV3IEltYWdlOyBkLk1NX3BbaisrXS5zcmM9YVtpXTt9fQp9Ci8vLS0+Cjwvc2NyaXB0Pgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KCjwvaGVhZD4KCjxzY3JpcHQgbGFuZ3VhZ2U9IkphdmFTY3JpcHQiIHR5cGU9InRleHQvSmF2YVNjcmlwdCI+CjwhLS0KZnVuY3Rpb24gTU1fcmVsb2FkUGFnZShpbml0KSB7ICAvL3JlbG9hZHMgdGhlIHdpbmRvdyBpZiBOYXY0IHJlc2l6ZWQKICBpZiAoaW5pdD09dHJ1ZSkgd2l0aCAobmF2aWdhdG9yKSB7aWYgKChhcHBOYW1lPT0iTmV0c2NhcGUiKSYmKHBhcnNlSW50KGFwcFZlcnNpb24pPT00KSkgewogICAgZG9jdW1lbnQuTU1fcGdXPWlubmVyV2lkdGg7IGRvY3VtZW50Lk1NX3BnSD1pbm5lckhlaWdodDsgb25yZXNpemU9TU1fcmVsb2FkUGFnZTsgfX0KICBlbHNlIGlmIChpbm5lcldpZHRoIT1kb2N1bWVudC5NTV9wZ1cgfHwgaW5uZXJIZWlnaHQhPWRvY3VtZW50Lk1NX3BnSCkgbG9jYXRpb24ucmVsb2FkKCk7Cn0KTU1fcmVsb2FkUGFnZSh0cnVlKTsKLy8tLT4KCjwvc2NyaXB0Pgo8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoKCjwvaGVhZD4KCjxib2R5IGJhY2tncm91bmQ9ImltZy9mb25kb19kZWdyYWRlLmpwZyIgdG9wbWFyZ2luPSIwIj4KPHRhYmxlIHdpZHRoPSIxMDA1IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgPHRyPiAKICAgIDx0ZCB3aWR0aD0iOTYiPjxpbWcgc3JjPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzBfMDEuanBnIiB3aWR0aD0iOTYiIGhlaWdodD0iMjA4IiAvPjwvdGQ+CiAgICA8dGQgd2lkdGg9IjgwOSI+IDxzY3JpcHQgdHlwZT0idGV4dC9qYXZhc2NyaXB0Ij4KQUNfRkxfUnVuQ29udGVudCggJ2NvZGViYXNlJywnaHR0cDovL2Rvd25sb2FkLm1hY3JvbWVkaWEuY29tL3B1Yi9zaG9ja3dhdmUvY2Ficy9mbGFzaC9zd2ZsYXNoLmNhYiN2ZXJzaW9uPTcsMCwxOSwwJywnd2lkdGgnLCc4MDknLCdoZWlnaHQnLCcyMDgnLCdzcmMnLCdzd2YvaGVhZGVyJywncXVhbGl0eScsJ2hpZ2gnLCdwbHVnaW5zcGFnZScsJ2h0dHA6Ly93d3cubWFjcm9tZWRpYS5jb20vZ28vZ2V0Zmxhc2hwbGF5ZXInLCdtb3ZpZScsJ3N3Zi9oZWFkZXInICk7IC8vZW5kIEFDIGNvZGUKPC9zY3JpcHQ+IDxub3NjcmlwdD4KICAgICAgPG9iamVjdCBjbGFzc2lkPSJjbHNpZDpEMjdDREI2RS1BRTZELTExY2YtOTZCOC00NDQ1NTM1NDAwMDAiIGNvZGViYXNlPSJodHRwOi8vZG93bmxvYWQubWFjcm9tZWRpYS5jb20vcHViL3Nob2Nrd2F2ZS9jYWJzL2ZsYXNoL3N3Zmxhc2guY2FiI3ZlcnNpb249NywwLDE5LDAiIHdpZHRoPSI4MDkiIGhlaWdodD0iMjA4Ij4KICAgICAgICA8cGFyYW0gbmFtZT0ibW92aWUiIHZhbHVlPSJzd2YvaGVhZGVyLnN3ZiIgLz4KICAgICAgICA8cGFyYW0gbmFtZT0icXVhbGl0eSIgdmFsdWU9ImhpZ2giIC8+CiAgICAgICAgPGVtYmVkIHNyYz0ic3dmL2hlYWRlci5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9IjgwOSIgaGVpZ2h0PSIyMDgiPjwvZW1iZWQ+IAogICAgICA8L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIHdpZHRoPSIxMiUiIHJvd3NwYW49IjUiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iIzAwMDAwMCI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI0NjEiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmFja2dyb3VuZD0iaW1nL1F1aWVuZXNTb21vc19BMl8wXzEzLmpwZyI+IAogICAgICA8c2NyaXB0IHR5cGU9InRleHQvamF2YXNjcmlwdCI+CkFDX0ZMX1J1bkNvbnRlbnQoICdjb2RlYmFzZScsJ2h0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCcsJ3dpZHRoJywnOTYnLCdoZWlnaHQnLCc0NjEnLCdzcmMnLCdzd2Yvc3VibWVudScsJ3F1YWxpdHknLCdoaWdoJywncGx1Z2luc3BhZ2UnLCdodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyJywnbW92aWUnLCdzd2Yvc3VibWVudScgKTsgLy9lbmQgQUMgY29kZQo8L3NjcmlwdD4gPG5vc2NyaXB0PgogICAgICA8b2JqZWN0IGNsYXNzaWQ9ImNsc2lkOkQyN0NEQjZFLUFFNkQtMTFjZi05NkI4LTQ0NDU1MzU0MDAwMCIgY29kZWJhc2U9Imh0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+CiAgICAgICAgPHBhcmFtIG5hbWU9Im1vdmllIiB2YWx1ZT0ic3dmL3N1Ym1lbnUuc3dmIiAvPgogICAgICAgIDxwYXJhbSBuYW1lPSJxdWFsaXR5IiB2YWx1ZT0iaGlnaCIgLz4KICAgICAgICA8ZW1iZWQgc3JjPSJzd2Yvc3VibWVudS5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+PC9lbWJlZD48L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCIgYmdjb2xvcj0iI0ZGRkZGRiI+CiAgICAgICAgPHRyPiAKICAgICAgICAgIDx0ZCB3aWR0aD0iMTciIHJvd3NwYW49IjciPjxwPiZuYnNwOzwvcD48L3RkPgogICAgICAgICAgPHRkIHdpZHRoPSIxNzIiIGFsaWduPSJjZW50ZXIiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxpbWcgc3JjPSJpbWcvM3B4LmpwZyIgd2lkdGg9IjUiIGhlaWdodD0iNSI+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciI+PGxpbmsgaHJlZj0iLi4vZXN0aWxvcy5jc3MiIHJlbD0ic3R5bGVzaGVldCIgdHlwZT0idGV4dC9jc3MiIC8+Cjxib2R5IGJnY29sb3I9IiNDQ0NDQ0MiIHRvcG1hcmdpbj0iNiBweCI+PHRhYmxlIHdpZHRoPSIxNjUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIzIiBiZ2NvbG9yPSIjRkZGRkZGIj4KPHRyPgogICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTkxIiBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiAgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MThfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+SG9tZTwvYT48L3RkPgogIDwvdHI+Cjx0cj4KICA8dGQgaGVpZ2h0PSIyOCIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj4mbmJzcDsmbmJzcDtOb3RpY2lhczwvYT48L3RkPgo8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJkb25hY2lvbmVzLyIgdGFyZ2V0PSJfYmxhbmsiIGNsYXNzPSJmb25kb2JvdG9uIj5Eb25hY2lvbmVzPC9hPjwvdGQ+CiAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciICB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yM19uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5IaXN0b3JpYWwgZGUgbmV3c2xldHRlcnM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTEzYSIgY2xhc3M9ImZvbmRvYm90b24iPkVudmlhciBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yNl9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5WZXIgdHJhYmFqb3MgZGUgdXN1YXJpb3M8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MTZfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+U2FsdWQgQWN0aXZhIHByZW5zYTwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJtYWlsdG86c2FsdWRhY3RpdmFAc2FsdWRhY3RpdmEub3JnLmFyIiBjbGFzcz0iZm9uZG9ib3RvbiI+TWFuZCZhYWN1dGU7IHR1IEMuVi48L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgIHdpZHRoPSI2ImhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTIxX25ldyIgY2xhc3M9ImZvbmRvYm90b24iPkluZm9ybWFjaSZvYWN1dGU7biBkZSBpbnRlciZlYWN1dGU7czwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyI+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiBoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xMF80IiBjbGFzcz0iZm9uZG9ib3RvbiI+Q29uZ3Jlc29zCiAgICAgICAgICAgICAgICAgIHkgSm9ybmFkYXM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTExIiBjbGFzcz0iZm9uZG9ib3RvbiI+UmVnaXN0cmFjaSZvYWN1dGU7bjwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgCiAgICAgICAgICA8L3RhYmxlPgo8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNSIgdGFyZ2V0PSJfYmxhbmsiPjxicj4KICAgICAgICAgICAgICAgICAgPGltZyBzcmM9ImltZy9iYW5uZXJfZG9uYWNpb25lcy5qcGciIHdpZHRoPSIxNjIiIGhlaWdodD0iMTIwIiBib3JkZXI9IjAiPjxicj4KICAgICAgICAgICAgICAgICAgPGJyPgogICAgICAgICAgICAgICAgICA8aW1nIHNyYz0iaW1nL2JvdG9uRm9yby5naWYiIHdpZHRoPSIxNzIiIGhlaWdodD0iMTE3IiBib3JkZXI9IjAiPjwvYT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTY3IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjkiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzAzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iOSIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTQ5IiBiYWNrZ3JvdW5kPSJpbWcvY2hpY29zX3BlcmRpZG9zXzA1LmdpZiI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDUuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMCI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDcuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMi5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEyLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9InNyYy9pbWdfdXAvMjMwODIwMTIuMS5qcGciIHdpZHRoPSIxNDkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMy5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNi5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iNSIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTcuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNy5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgYmdjb2xvcj0iI0ZFRTdDRiIgY2xhc3M9InRpdHVsb2hvbWU1Ij48c3Ryb25nPk5pJm50aWxkZTtvcyBwZXJkaWRvczxicj4KICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0yOSIgY2xhc3M9ImJvdG9uIj5bVmVyIG0mYWFjdXRlO3NdPC9hPjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTkuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xOS5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18yMC5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iMjUiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4NCgkJCQkNCgkJCQk8Zm9ybSBhY3Rpb249ImluZGV4LnBocD9pZD0xMSIgIG1ldGhvZD0icG9zdCI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9penExLmpwZyIgd2lkdGg9IjEyIiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9hcnJpYmEuanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9kZXIxLmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgIDwvdHI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiIgdmFsaWduPSJ0b3AiIGNsYXNzPSJyZWdGb25kbzEiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9penEuanBnIiB3aWR0aD0iMTIiIGhlaWdodD0iMTIiIC8+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSI5NCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV90aXQuanBnIiB3aWR0aD0iNjYiIGhlaWdodD0iMjMiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSI1MCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJyZWdpc3RyYXJzZSI+SW5ncmVzJmFhY3V0ZTsgDQogICAgICAgICAgICAgIHR1cyBkYXRvcyB5IHJlY2liJmlhY3V0ZTsgbGEgbWVqb3IgaW5mb3JtYWNpJm9hY3V0ZTtuIGEgdHJhdiZlYWN1dGU7cyANCiAgICAgICAgICAgICAgZGUgbnVlc3RybzxzdHJvbmc+IE5ld3NsZXR0ZXI8L3N0cm9uZz4uIDxzdHJvbmc+PHNwYW4gY2xhc3M9ImdyYXRpcyI+R3JhdGlzITwvc3Bhbj48L3N0cm9uZz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI1IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9InRyYWJTRUNDSU9OIj5Ob21icmU8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBjbGFzcz0icmVnQ0VMREEiPjxpbnB1dCBuYW1lPSJub21icmUiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0ibm9tYnJlIiAvPjwvdGQ+DQogICAgICAgICAgPC90cj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0idHJhYlNFQ0NJT04iPkFwZWxsaWRvPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iYXBlbGxpZG8iIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iYXBlbGxpZG8iIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJ0cmFiU0VDQ0lPTiI+RS1tYWlsPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iZW1haWwiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iZW1haWwiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InRyYWJTRUNDSU9OIj4mbmJzcDs8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idHJhYlNFQ0NJT04iPjxpbnB1dCB0eXBlPSJpbWFnZSIgc3JjPSJpbWcvcmVnaXN0cmF0ZV9ib3Rvbi5qcGciIHdpZHRoPSIxMTciIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgIDwvdGFibGU+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE0IiB2YWxpZ249InRvcCIgY2xhc3M9InJlZ0ZvbmRvMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2Rlci5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIxNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KICAgICAgICAgICAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTIiIGhlaWdodD0iMjQiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfaXpxMi5qcGciIHdpZHRoPSIxMiIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI0Ij48aW1nIHNyYz0iaW1nL3JlZ2lzdHJhdGVfYWJham8uanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjI0IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfZGVyMi5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KCQkJCQkNCgkJCQkJPC9mb3JtPg0KICAgICAgICAgICAgICAgICAgPC90YWJsZT4NCjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPiAKICAgICAgICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTcwIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUyIj4KCQkJCQkJCQkJCQkJCQkJCTwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9jbGF1ZGlhMl8wMy5qcGciIHdpZHRoPSIxNzQiIGhlaWdodD0iMjUwIiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcCI+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICA8dGQgcm93c3Bhbj0iNyIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nLzV4NS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjciPjwvdGQ+CiAgICAgICAgICA8dGQgY29sc3Bhbj0iMiIgcm93c3Bhbj0iNCIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPGZvcm0gYWN0aW9uPSJsb2dpbi5waHAiIG1ldGhvZD0icG9zdCIgbmFtZT0iZm9ybTIiPgoKICAgICAgICAgICAgICA8dHI+IAogICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgY29sc3Bhbj0iMiIgYWxpZ249ImxlZnQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIiA+IAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8c3Ryb25nPlVzdWFyaW8gbm8gcmVnaXN0cmFkbzwvc3Ryb25nPiAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9mb250PiA8L3N0cm9uZz4gCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDkiIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPlVzdWFyaW8mbmJzcDsmbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzOSIgdmFsaWduPSJtaWRkbGUiPjxpbnB1dCBuYW1lPSJ1c3VhcmlvIiB0eXBlPSJ0ZXh0IiBjbGFzcz0icmVnIiBpZD0idXN1YXJpbyIgc2l6ZT0iNyI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjciIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPkNvbnRyYXNlJm50aWxkZTthJm5ic3A7Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzkiIHZhbGlnbj0ibWlkZGxlIj48aW5wdXQgbmFtZT0icGFzcyIgdHlwZT0icGFzc3dvcmQiIGNsYXNzPSJyZWciIGlkPSJwYXNzIiBzaXplPSI3Ij48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiIgYWxpZ249InJpZ2h0IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9ImJvdG9uIj48aW5wdXQgdHlwZT0iaW1hZ2UiIHNyYz0iaW1nL3JlZy5qcGciIHdpZHRoPSI1OCIgaGVpZ2h0PSIzMCI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjciIGhlaWdodD0iMTkiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgPjxhIGhyZWY9Imh0dHA6Ly93d3cuZmFjZWJvb2suY29tL2hvbWUucGhwPyMhL3BhZ2VzL01lcmxvLUFyZ2VudGluYS9TQUxVRC1BQ1RJVkEvMTAwNTgzNTQzMzE3MzIyP3JlZj10cyZhamF4cGlwZT0xJl9fYT03IiB0YXJnZXQ9Il9ibGFuayI+PGltZyBzcmM9ImltZy9mYWNlYm9vay5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzExIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj48ZGl2IGFsaWduPSJsZWZ0Ij48YSBocmVmPSJodHRwOi8vdHdpdHRlci5jb20vU2FsdWRBY3RpdmFPTkciIHRhcmdldD0iX2JsYW5rIj48aW1nIHNyYz0iaW1nL3R3aXRlci5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC9kaXY+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSI1IiBhbGlnbj0icmlnaHQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIj48bGFiZWw+PGZvbnQgc2l6ZT0iLTYiPlNpCiAgICAgICAgICAgICAgICAgICAgICAgdG9kYXYmaWFjdXRlO2Egbm8gZXMgdXN1YXJpbyA8L2ZvbnQ+IDxhIGhyZWY9ImluZGV4LnBocD9pZD0xMSIgY2xhc3M9ImJvdG9uIj48Zm9udCBzaXplPSItNiI+cmVnJmlhY3V0ZTtzdHJlc2UKICAgICAgICAgICAgICAgICAgICAgICAgYXF1JmlhY3V0ZTsgPGZvbnQgY29sb3I9IiM2NjY2NjYiPiYjODIyNjs8L2ZvbnQ+PC9mb250PjwvYT4gPGEgaHJlZj0iaW5kZXgucGhwP2lkPTEyIiBjbGFzcz0iYm90b24xIj48Zm9udCBzaXplPSItNiI+b2x2aWRlIG1pIGNvbnRyYXNlJm50aWxkZTthPC9mb250PjwvYT48L2xhYmVsPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE3Ij4mbmJzcDsgPC90ZD4KICAgICAgICAgICAgICA8L3RyPgoJCQkgIDwvZm9ybT4KCiAgICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgICA8IURPQ1RZUEUgaHRtbCBQVUJMSUMgIi0vL1czQy8vRFREIFhIVE1MIDEuMCBUcmFuc2l0aW9uYWwvL0VOIiAiaHR0cDovL3d3dy53My5vcmcvVFIveGh0bWwxL0RURC94aHRtbDEtdHJhbnNpdGlvbmFsLmR0ZCI+CjxodG1sIHhtbG5zPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hodG1sIj4KPGhlYWQ+CjxtZXRhIGh0dHAtZXF1aXY9IkNvbnRlbnQtVHlwZSIgY29udGVudD0idGV4dC9odG1sOyBjaGFyc2V0PWlzby04ODU5LTEiIC8+Cjx0aXRsZT5Eb2N1bWVudG8gc2luIHQmaWFjdXRlO3R1bG88L3RpdGxlPgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KPHNjcmlwdCBsYW5ndWFnZT0iSmF2YVNjcmlwdCIgdHlwZT0idGV4dC9KYXZhU2NyaXB0Ij4KPCEtLQpmdW5jdGlvbiBNTV9yZWxvYWRQYWdlKGluaXQpIHsgIC8vcmVsb2FkcyB0aGUgd2luZG93IGlmIE5hdjQgcmVzaXplZAogIGlmIChpbml0PT10cnVlKSB3aXRoIChuYXZpZ2F0b3IpIHtpZiAoKGFwcE5hbWU9PSJOZXRzY2FwZSIpJiYocGFyc2VJbnQoYXBwVmVyc2lvbik9PTQpKSB7CiAgICBkb2N1bWVudC5NTV9wZ1c9aW5uZXJXaWR0aDsgZG9jdW1lbnQuTU1fcGdIPWlubmVySGVpZ2h0OyBvbnJlc2l6ZT1NTV9yZWxvYWRQYWdlOyB9fQogIGVsc2UgaWYgKGlubmVyV2lkdGghPWRvY3VtZW50Lk1NX3BnVyB8fCBpbm5lckhlaWdodCE9ZG9jdW1lbnQuTU1fcGdIKSBsb2NhdGlvbi5yZWxvYWQoKTsKfQpNTV9yZWxvYWRQYWdlKHRydWUpOwoKZnVuY3Rpb24gTU1fcHJlbG9hZEltYWdlcygpIHsgLy92My4wCiAgdmFyIGQ9ZG9jdW1lbnQ7IGlmKGQuaW1hZ2VzKXsgaWYoIWQuTU1fcCkgZC5NTV9wPW5ldyBBcnJheSgpOwogICAgdmFyIGksaj1kLk1NX3AubGVuZ3RoLGE9TU1fcHJlbG9hZEltYWdlcy5hcmd1bWVudHM7IGZvcihpPTA7IGk8YS5sZW5ndGg7IGkrKykKICAgIGlmIChhW2ldLmluZGV4T2YoIiMiKSE9MCl7IGQuTU1fcFtqXT1uZXcgSW1hZ2U7IGQuTU1fcFtqKytdLnNyYz1hW2ldO319Cn0KLy8tLT4KPC9zY3JpcHQ+CiAgICAgICAgICAgICA8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoJCQkgCjxzdHlsZSB0eXBlPSJ0ZXh0L2NzcyI+CjwhLS0KI0xheWVyMSB7Cglwb3NpdGlvbjphYnNvbHV0ZTsKCXdpZHRoOjY1MXB4OwoJaGVpZ2h0OjIxOHB4OwoJei1pbmRleDoxOwp9CiNMYXllcjIgewoJcG9zaXRpb246YWJzb2x1dGU7Cgl3aWR0aDoyMDBweDsKCWhlaWdodDoxMTVweDsKCXotaW5kZXg6MTsKCXZpc2liaWxpdHk6IHZpc2libGU7Cn0KLkVzdGlsbzEgewoJZm9udC1zaXplOiAxOHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzIgewoJZm9udC1zaXplOiAxNHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzMge2NvbG9yOiAjNTA2OTkwOyBsaW5lLWhlaWdodDogMTJweDsgdGV4dC1kZWNvcmF0aW9uOiBub25lOyBmb250LWZhbWlseTogVGFob21hO30KLS0+Cjwvc3R5bGU+CjwvaGVhZD4KCjxib2R5IGxlZnRtYXJnaW49IjIiIG1hcmdpbndpZHRoPSIyIj4KPHRhYmxlIHdpZHRoPSI2MDgiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICA8dHI+CiAgICA8dGQgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCB3aWR0aD0iMiUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzA3LmpwZyIgd2lkdGg9IjI0IiBoZWlnaHQ9IjE0IiAvPjwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI5MCUiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18wNy5qcGciPiZuYnNwOzwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI4JSIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wOS5qcGciIHdpZHRoPSI0NSIgaGVpZ2h0PSIxNyIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogIDwvdHI+CiAgPHRyPgogICAgPHRkIGNvbHNwYW49IjQiPjxiciAvPgogICAgICA8dGFibGUgd2lkdGg9Ijk4JSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICA8dHI+CiAgICAgICAgPHRkIHdpZHRoPSIyJSI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgICA8dGQgd2lkdGg9IjkzJSI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CjwhLS0gSU5JQ0lPIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzIzMDQyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjIvMTEvMjAxMzwvc3Bhbj48YnI+SVYgQ29uZ3Jlc28gSW50ZXJuYWNpb25hbCB2aW9sZW5jaWEsIG1hbHRyYXRvIHkgYWJ1c288L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxzdHJvbmc+MTQsIDE1IHkgMTYgZGUgTm92aWVtYnJlIEFCSUVSVEEgTEEgSU5TQ1JJUENJJk9hY3V0ZTtOISAoY29uIGRlc2N1ZW50byBoYXN0YSBlbCAyNy84KTxiciAvPjwvc3Ryb25nPjwvcD4NCjxwPjxzdHJvbmc+QUJJRVJUQSBMQSBSRUNFUENJJk9hY3V0ZTtOIERFIFRSQUJBSk88YSBocmVmPSJodHRwOi8vd3d3LmNvbmdyZXNvdmlvbGVuY2lhLmNvbS9pbmRleC5waHA/aWQ9bW9kYWxpZGFkZXMiIHRhcmdldD0iX2JsYW5rIj4gKG1hcyBpbmZvKTwvYT48L3N0cm9uZz48L3A+DQo8cD48c3BhbiBzdHlsZT0iY29sb3I6ICNmZjY2MDA7Ij48c3Ryb25nPk9yZ2FuaXphOiBTYWx1ZCBBY3RpdmE8L3N0cm9uZz48L3NwYW4+PC9wPg0KPHA+PHNwYW4gc3R5bGU9ImNvbG9yOiAjZmY2NjAwOyI+SW5jcmlwdG9zIGFsIFBvcnRhbCBkZSBTYWx1ZCBBY3RpdmEsIGltcG9ydGFudGVzIGRlc2N1ZW50b3MhPGJyIC8+PC9zcGFuPjwvcD4NCjxwPkx1Z2FyIGRlIFJlYWxpemFjaSZvYWN1dGU7biB5IGNvbGFib3JhY2lvbjogVW5pdmVyc2lkYWQgZGVsIEVzdGUsIExhIFBsYXRhIEJ1ZW5vcyBBaXJlczwvcD4NCjxwPk1hcyBkZSAxNTAgdHJhYmFqb3MgcHJlc2VudGFkb3MsIHVsdGltb3MgZGlhcyBwYXJhIGluc2NyaWJpcnNlIGNvbiBkZXNjdWVudG8hITwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPkluc2NyaWJpcnNlPC9hPjwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPjxiciAvPjwvYT48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAxIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDEiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MDQvMTEvMjAxMzwvc3Bhbj48YnI+RWwgY29sZWdpbyBkZSBQc2lj82xvZ29zIGRlIEPzcmRvYmEgc2UgcHJvbnVuY2lhIGVuIHJlbGFjafNuIGFsIFNBUCB5IGVuIGNvbmNvcmRhbmNpYSBjb24gbG8gZXhwcmVzYWRvIHBvciBlbCBDb2xlZ2lvIGRlIFBzaWPzbG9nb3MgZGUgTWFyIGRlbCBQbGF0YSB5IGVsIENvbGVnaW8gZGUgUHNpY/Nsb2dvcyBkZSBsYSAgUHJvdmluY2lhIGRlIEJ1ZW5vcyBBaXJlczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+Jm5ic3A7PC9wPg0KPHA+TGFzIGNvbnRyb3ZlcnNpYXMgZ2VuZXJhZGFzIGVuIHJlbGFjaSZvYWN1dGU7biBhbCAic2luZHJvbWUgZGUgYWxpZW5hY2kmb2FjdXRlO24gcGFyZW50YSIgU0FQLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMxMCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzEwIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzE2MTAyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTYvMTAvMjAxMzwvc3Bhbj48YnI+U2FsdWQgQWN0aXZhIG90b3JnYSBtZWRpYXMgYmVjYXMgcGFyYSBlbCBJViBDb25ncmVzbyBJbnRlcm5hY2lvbmFsLCBWIE5hY2lvbmFsLCBWSSBSZWdpb25hbCBWaW9sZW5jaWEsIE1hbHRyYXRvIHkgQWJ1c28uPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD4mbmJzcDs8L3A+DQo8cD5TZXImYWFjdXRlO24gb3RvcmdhZGFzIDUwIG1lZGlhcyBiZWNhcywgcXVlZGFuIHBvY2FzISEhIGNvbmRpY2lvbjo8L3A+DQo8cD5QZXJ0ZW5lY2VyIGFsIGFtYml0byBwdWJsaWNvIG8gYSBPTkcsIHNlIGNvbnNpZGVyYSB0YW1iaWVuIGxhIGRpc3RhbmNpYSBhbCBsdWdhciBkZWwgZXZlbnRvISEhIGVzIG11eSBzZW5jaWxsbywgc29sbyBkZWJlcyBlbnZpYXIgdW4gZW1haWwuLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwOSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA5Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjI0LzA3LzIwMTM8L3NwYW4+PGJyPk5FQ0VTSVRBTU9TIERFIFNVIFNPTElEQVJJREFEIEhBQ0lBIExPUyBOSdFPUyBZIE5J0UFTISEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPlBST0dSQU1BIEZBTUlMSUFTIFNPTElEQVJJQVM8L3NwYW4+PC9zdHJvbmc+PC9wPg0KPHA+PHN0cm9uZz5DQU1CSU8gREUgU0VERTwvc3Ryb25nPjwvcD4NCjxwPkxhIGNhcGFjaXRhY2kmb2FjdXRlO24gcGFyYSBsYSBwdWVzdGEgZW4gbWFyY2hhIGRlbCA8c3Ryb25nPlByb2dyYW1hIEZhbWlsaWFzIFNvbGlkYXJpYXM8L3N0cm9uZz4gc2UgcmVhbGl6YXImYWFjdXRlOyBlbiBsYSBsb2NhbGlkYWQgZGUgPHN0cm9uZz5OYXZhcnJvPC9zdHJvbmc+IHBhcmEgdG9kbyBlbCBjb3JyZWRvciBkZSBsYSBSdXRhIDQwLjwvcD4NCjxwPkluaWNpbyA8c3Ryb25nPk1pJmVhY3V0ZTtyY29sZXMgMjggZGUgYWdvc3RvIGEgbGFzIDE0IGhvcmFzLiZuYnNwOzwvc3Ryb25nPjwvcD4NCjxwPlNlZGU6IDxzdHJvbmc+U2FsJm9hY3V0ZTtuIE11bmljaXBhbCBlbiBsYSBjYWxsZSAxMDcgZXNxdWluYSAyMiAtIE5hdmFycm88L3N0cm9uZz48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA4Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTIwNzIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xMi8wNy8yMDEzPC9zcGFuPjxicj5TQUxVRCBBQ1RJVkEgaGEgc2lkbyBlbGVnaWRhIHBvciBzZWd1bmRhIHZleiBjb25zZWN1dGl2YSBjb21vIHVubyBkZSBsb3MgZ2FuYWRvcmVzIGRlbCBDdWFydG8gQ29uY3Vyc28gZGUgUHJveWVjdG9zIFNvY2lhbGVzIGRlIFBldHJvYnJhczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+RW4gZWwgbWFyY28gZGVsIEN1YXJ0byBDb25jdXJzbyBkZSBQcm95ZWN0b3MgU29jaWFsZXMgZGUgUGV0cm9icmFzLCANCm51ZXN0cmEgSW5zdGl0dWNpJm9hY3V0ZTtuIFNBTFVEIEFDVElWQSBoYSBzaWRvIGVsZWdpZGEgcG9yIHNlZ3VuZGEgdmV6IA0KY29uc2VjdXRpdmEgY29tbyB1bm8gZGUgbG9zIGdhbmFkb3JlcyBkZSBkaWNobyBjb25jdXJzby48YnIgLz5FbiBlc3RhIA0KZWRpY2kmb2FjdXRlO24gZWwgcHJveWVjdG8gcXVlIGhhIHNpZG8gZWxlZ2lkbyBlcyBlbCAmbGRxdW87UHJvZ3JhbWEgZGUgRmFtaWxpYXMgDQpTb2xpZGFyaWFzJnJkcXVvOyBzaWVuZG8gc3UgJmFhY3V0ZTtyZWEgZGUgaW1wbGVtZW50YWNpJm9hY3V0ZTtuIGxvcyBNdW5pY2lwaW9zIGRlIE5hdmFycm8sIA0KR3JhbC4gTGFzIEhlcmFzLCBNYXJjb3MgUGF6LCB5IE1lcmxvPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAyLzA3LzIwMTM8L3NwYW4+PGJyPk/tciBvIGVzY3VjaGFyPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Qb3IgQ2FybG9zIFJvemFuc2tpICo8L3A+DQo8cD5BIGxvIGxhcmdvIGRlIGxvcyBzaWdsb3MsIGxhcyBuaSZudGlsZGU7YXMsIG5pJm50aWxkZTtvcyB5IGFkb2xlc2NlbnRlcyBoYW4gc2lkbyBtYWx0cmF0YWRvcyB5IGFidXNhZG9zIHNpbiBxdWUgYSBsYSBjb211bmlkYWQgbGUgaW50ZXJlc2FyYSBuaSBzaXF1aWVyYSBlc2N1Y2hhcmxvcyBjdWFuZG8gaGFjJmlhY3V0ZTthbiBzYWJlciBkZSBhbGd1bmEgZm9ybWEgbG9zIHN1ZnJpbWllbnRvcyBxdWUgcGFkZWMmaWFjdXRlO2FuLiBFbiAxODc0LCBlbiBFc3RhZG9zIFVuaWRvcywgZnVlIGxhIHByaW1lcmEgdmV6IHF1ZSBlbCBFc3RhZG8gaW50ZXJ2aW5vIGVuIHVuIGNhc28gZGUgbWFsdHJhdG8geSBhYnVzby4uLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDYiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4wMi8wNy8yMDEzPC9zcGFuPjxicj5FbCBkZXJlY2hvIGRlIGxvcyBuafFvcyBhIHNlciBlc2N1Y2hhZG9zPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5VbiBob21icmUgYWN1c2FkbyBkZSBoYWJlciBhYnVzYWRvIGRlIHN1cyBoaWpvcyBoYWImaWFjdXRlO2Egc2lkbyBzb2JyZXNlJmlhY3V0ZTtkbyBkb3MgdmVjZXMgcG9yIGxhIEp1c3RpY2lhLiBQZXJvIGFob3JhLCBsYSBDJmFhY3V0ZTttYXJhIGRlIENhc2FjaSZvYWN1dGU7biByZXZvYyZvYWN1dGU7IGVzYSBkZWNpc2kmb2FjdXRlO24gcG9ycXVlIGVuIGxhIGludmVzdGlnYWNpJm9hY3V0ZTtuIGVsIGp1ZXogbnVuY2EgaGFiJmlhY3V0ZTthIGVzY3VjaGFkbyBhIGxvcyBjaGljb3MuIFkgb3JkZW4mb2FjdXRlOyBxdWUgdGVuZ2EgZW4gY3VlbnRhIGxvIHF1ZSBkaWNlbi48L3A+DQo8cD5Qb3IgTWFyaWFuYSBDYXJiYWphbDwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDUiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE1NiIgcm93c3Bhbj0iMiIgdmFsaWduPSJ0b3AiPgoJCQkJCgkJCQk8dGFibGUgd2lkdGg9IjMyJSIgYm9yZGVyPSIxIiBjZWxsc3BhY2luZz0iMyIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48aW1nIHNyYz0ic3JjL2ltZ191cC8wNjA2MjAxMy4xLmpwZyIgd2lkdGg9IjE0NiIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT4KCQkJCQkJCQk8L3RkPiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjA2LzA2LzIwMTM8L3NwYW4+PGJyPkFidXNvIHNleHVhbCBpbmZhbnRpbC4gRGVzYWZpb3MgZGUgbGEgY2xpbmljYSBhY3R1YWw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkFiaWVydGEgbGEgaW5zY3JpcGNpb248L3A+DQo8cD5Eb2NlbnRlczogTGljLiBNYXJpYSBCZWF0cml6IE0mdXVtbDtsbGVyLiBMaWMuIFBhb2xhIE11Jm50aWxkZTtveiBEdWFydGU8L3A+DQo8cD5JbmljaW86IE1pZXJjb2xlcyAxOSBkZSBKdW5pbzwvcD4NCjxwPkZyZWN1ZW5jaWE6IFNlbWFuYWw8L3A+DQo8cD5Nb2RhbGlkYWQ6IEludGVuc2l2YTwvcD4NCjxwPkNvbnRlbmlkb3M6ICZuYnNwOyBFc3RhIGRlc3RpbmFkbyBhIHRvZG9zIGxvcyBwcm9mZXNpb25hbGVzIGNvbXByb21ldGlkb3MgY29uIGxhIHRlbWF0aWNhIGRlbCBhYnVzbyBpbmZhbnRpbCBxdWUgcXVpZXJhbiBhY3R1YWxpemFyc2UgZSBpbnRlcmNhbWJpYXIgZXhwZXJpZW5jaWFzIGRlIHRyYWJham8uLi48L3A+DQo8cD4mbmJzcDs8L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA0Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDQiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTYwNTIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xNi8wNS8yMDEzPC9zcGFuPjxicj5TYWx1ZCBBY3RpdmEgbmVjZXNpdGEgZGUgdHUgYXl1ZGEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5UcmFiYWphbW9zIGNvbW8gcG9kZW1vczogYmEmbnRpbGRlO29zIHJvdG9zLCBzdXNwZW5zaSZvYWN1dGU7biBkZSByZXVuaW9uZXMgcG9yIGNvcnRlcyBkZSBsdXogeSBhZ3VhLCBqdWd1ZXRlcyB2aWVqb3MsIG1lc2VzIGRlIGF0cmFzbyBlbiBlbCBwYWdvIGRlIHN1cyBwcm9mZXNpb25hbGVzIGRlIGxhIHNhbHVkLiBSZWNpZW50ZW1lbnRlIHR1dmltb3MgcXVlIGNlcnJhciBudWVzdHJvIHF1ZXJpZG8gSG9nYXI6ICZsZHF1bztNZXRhbW9yZm9zaXMmcmRxdW87IGVyYSBlbCBsdWdhciBxdWUgc3VwbyBjb250ZW5lciBhIG5pJm50aWxkZTthcyB5IGomb2FjdXRlO3ZlbmVzIHJlc2NhdGFkYSBkZSByZWRlcyBkZSB0cmF0YSBvIHYmaWFjdXRlO2N0aW1hcyBkZSBhYnVzbyBpbnRyYWZhbWlsaWFyLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAzIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAzLzA1LzIwMTM8L3NwYW4+PGJyPlJFUFVESU8gQSBMQSBQUkVTRU5DSUEgRU4gTEEgRkVSSUEgREVMIExJQlJPIERFIFVOIEVYIEpVRVogQUNVU0FETyBERSBBQlVTTyBTRVhVQUw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkZ1ZSBjYW1hcmlzdGEgZW4gTWFyIGRlbCBQbGF0YSBkdXJhbnRlIGxhIGRpY3RhZHVyYS4gSGFjZSBhJm50aWxkZTtvcywgdmFyaWFzIG11amVyZXMgbG8gYWN1c2Fyb24gZGUgaGFiZXIgYWJ1c2FkbyBkZSBlbGxhcyBjdWFuZG8gZXJhbiBuaSZudGlsZGU7YXMuIExhIGNhdXNhIHByZXNjcmliaSZvYWN1dGU7IHkgbm8gaHVibyBjb25kZW5hLiBNYSZudGlsZGU7YW5hIHRpZW5lIHByZXZpc3RvIGZpcm1hciBzdSBsaWJyby4gRXNhcyBtaXNtYXMgbXVqZXJlcyBwaWRlbiBxdWUgbm8gc2VhIGFkbWl0aWRvIGVuIGxhIGZlcmlhLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDIiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgIDwhLS0gRklOIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgIDwvdGFibGU+ICAgICAgICA8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iNSUiIGFsaWduPSJyaWdodCI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgPC90cj4KICAgIDwvdGFibGU+PC90ZD4KICA8L3RyPgogIDx0cj4KICAgIDx0ZCB3aWR0aD0iMSUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiIgYWxpZ249ImNlbnRlciI+Jm5ic3A7PC90ZD4KICAgIDx0ZCB3aWR0aD0iMiUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgPC90cj4KICAKICA8dGQ+CiAgPHRyPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0ciBhbGlnbj0iY2VudGVyIj4KICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgPHRkIHdpZHRoPSI5NyIgY29sc3Bhbj0iMiIgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iNTQ2IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idGl0dWxvaG9tZTIiPjx0YWJsZSB3aWR0aD0iIiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYWxpZ249ImxlZnQiIHZhbGlnbj0iYm90dG9tIiBjbGFzcz0idGl0dWxvaG9tZTIiPlJhbmtpbmc8L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSIgY2xhc3M9InRpdHVsb2hvbWUyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iIiBoZWlnaHQ9IjM1IiBhbGlnbj0ibGVmdCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPiZidWxsO0xhcyBtJmFhY3V0ZTtzIGxlaWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGNsYXNzPSJjb250ZW5pZG9ob21lIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBjbGFzcz0iY29udGVuaWRvaG9tZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+JmJ1bGw7TGFzIG0mYWFjdXRlO3MgY29tZW50YWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTHVkb3RlY2EgR2FyYWJhdG8gLSBQcm95ZWN0byBzYWx1ZGFjdGl2YSwgUG9yIHVuYSBpbmZhbmNpYSBmZWxpeiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iOSUiIGJnY29sb3I9IiNFRkVGRUYiPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzJSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xNjIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDUlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTE2MiIgY2xhc3M9ImJvdG9uIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBDdXJzbyBJbnRlbnNpdm8gZGUgb3BlcmFkb3IgdGVyYXBldXRpY28gZXNwZWNpYWxpemFkbyBlbiBlbCBhYm9yZGFqZSBkZWwgYWJ1c28sIGxhIHZpb2xlbmNpYSB5IGVsIG1hbHRyYXRvIGluZmFudGlsICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgUFJPR1JBTUEgTEFTIFZJQ1RJTUFTIENPTlRSQSBMQVMgVklPTEVOQ0lBUyAgTWluaXN0ZXJpbyBkZSBKdXN0aWNpYSB5IERlcmVjaG9zIEh1bWFub3MgZGUgbGEgTmFjafNuICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI5JSIgYmdjb2xvcj0iI0VGRUZFRiI+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjMlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTI1NSIgY2xhc3M9ImJvdG9uIj48aW1nIHNyYz0iaW1nL2ZsZWNoYW5hcmFuamFmZ3Jpc18yNC5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSI3IiBib3JkZXI9IjAiIGFsaWduPSJhYnNtaWRkbGUiIC8+PC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI0NSUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MjU1IiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIERpcGxvbWF0dXJhIGVuIEFib3JkYWplIGludGVyZGlzY2lwbGluYXJpbyBkZWwgbWFsdHJhdG8sIGxhIHZpb2xlbmNpYSB5IGVsIGFidXNvIHNleHVhbCBpbmZhbnRpbCAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyJSIgaGVpZ2h0PSIyMCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQxJSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNhbHVkIEFjdGl2YSBuZWNlc2l0YSBkZSB0dSBheXVkYSEgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjklIiBiZ2NvbG9yPSIjRUZFRkVGIj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMyUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MTA0IiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQ1JSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xMDQiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTGxhbWFkbyBwYXJhIHByZXNlbnRhY2nzbiBkZSB0cmFiYWpvcy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjIwIiBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyMCIgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGJnY29sb3I9IiNGRkZGRkYiIGNsYXNzPSJ0ZXh0b251ZXZvIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPgogICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iIyIgY2xhc3M9ImJvdG9uIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgPC90YWJsZT48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj4mbmJzcDs8L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBJTklDSU8gbm90YSBjb211biAtLT4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTUvMDQvMjAxMjwvc3Bhbj48YnI+T3JnYW5pemFuIGpvcm5hZGEgc29icmUgdmlvbGVuY2lhPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPlNlIGNlbnRyYXImYWFjdXRlOyBlbiBsb3MgZmVuJm9hY3V0ZTttZW5vcyBxdWUgYWZlY3RhbiBhIGxhIGZhbWlsaWEgeSBlbiBsbyBxdWUgb2N1cnJlIGVuIGxhcyBlc2N1ZWxhcy48YnIgLz4gU2UgbGxldmFyJmFhY3V0ZTsgYSBjYWJvIGVsIGx1bmVzIDIzLCBlbiBlbCBDZW50cm8gQ3VsdHVyYWwgZGUgVG9zY2hpIHkgVHJlcyANCkFycm95b3MsIHVuYSBqb3JuYWRhIGRlIHJlZmxleGkmb2FjdXRlO24geSBkZWJhdGUgYWJpZXJ0YSBhIGxhIGNvbXVuaWRhZCBzb2JyZSANCiZsZHF1bztWaW9sZW5jaWEgZW4gbGEgZmFtaWxpYSB5IGVuIGxhIGVzY3VlbGEgeSBzdSByZWxhY2kmb2FjdXRlO24gY29uIGVsIGZyYWNhc28gDQplc2NvbGFyJnJkcXVvOywgb3JnYW5pemFkYSBwb3IgbGEgQXNvY2lhY2kmb2FjdXRlO24gQ2l2aWwgQ2VudHJvIEFydCZlYWN1dGU7bWlkZXMgeSBsYSANCk11bmljaXBhbGlkYWQgZGUgQ2lwb2xsZXR0aS5TZSBjZW50cmFyJmFhY3V0ZTsgZW4gbG9zIGZlbiZvYWN1dGU7bWVub3MgcXVlIGFmZWN0YW4gYSBsYSBmYW1pbGlhIHkgZW4gbG8gcXVlIG9jdXJyZSBlbiBsYXMgZXNjdWVsYXMuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjMwLzAzLzIwMTI8L3NwYW4+PGJyPkNhcnRhIGRlIEFTQVBNSSAtIEFzb2NpYWNp824gQXJnZW50aW5hIGRlIFByZXZlbmNp824gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbDwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjE1IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSIxNSIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjgwIiBjb2xzcGFuPSI0IiBhbGlnbj0ibGVmdCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Mb3MgaW50ZWdyYW50ZXMgZGUgbGEgQ29taXNpJm9hY3V0ZTtuIERpcmVjdGl2YSBkZSBBU0FQTUkgLSBBc29jaWFjaSZvYWN1dGU7biBBcmdlbnRpbmEgZGUgUHJldmVuY2kmb2FjdXRlO24gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbCwgYXNvY2lhZGEgYSBsYSBJbnRlcm5hdGlvbmFsIFNvY2lldHkgZm9yIFByZXZlbnRpb24gb2YgQ2hpbGQgQWJ1c2UgYW5kIE5lZ2xlY3QgKElTUENBTikgLSwgdGVuZW1vcyBlbCBhZ3JhZG8gZGUgZGlyaWdpcm5vcyBhIFVzdGVkIHBhcmEgdHJhc21pdGlybGUgbnVlc3RyYSBwcm9mdW5kYSAmbmJzcDt5IGhvbmRhIHByZW9jdXBhY2kmb2FjdXRlO24gcG9yIGxhIHBvc3R1cmEgcXVlIHZpZW5lbiBhc3VtaWVuZG8gZW4gZm9ybWEgY29udGludWFkYSBhbGd1bm9zIGNvbGVnaW9zIGRlIHBzaWMmb2FjdXRlO2xvZ29zLCBlc3BlY2lhbG1lbnRlIGRlIGxhIHByb3ZpbmNpYSBkZSBCdWVub3MgQWlyZXMsIGVuIHJlbGFjaSZvYWN1dGU7biBhbCB0cmF0YW1pZW50byBwb2NvIHNlcmlvIHkgY29tcHJvbWV0aWRvIHF1ZSBzZSBsZXMgb3RvcmdhIGEgbGFzIGRlbnVuY2lhcyBlZmVjdHVhZGFzIGNvbnRyYSBwcm9mZXNpb25hbGVzIHBzaWMmb2FjdXRlO2xvZ29zLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjAvMDMvMjAxMjwvc3Bhbj48YnI+TEEgVklPTEVOQ0lBIFNFWFVBTCBDT05UUkEgTknRT1MgWSBOSdFBUyBFTiBDSUZSQVM8L3RkPgogICAgICAgICAgPC90cj4KICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkIHdpZHRoPSIxNSIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4MCIgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+UmFkaW9ncmFmJmlhY3V0ZTthIGRlIHVuIHByb2JsZW1hPC9wPg0KPHA+RGUgbG9zIG4mdWFjdXRlO21lcm9zIGNvbXBpbGFkb3MgcG9yIGRvcyBlcXVpcG9zIGRlbCBNaW5pc3RlcmlvIGRlIEp1c3RpY2lhLCBsYQ0KIGF1dG9yYSB0b21hIGxvcyBkZSBsYSBjaXVkYWQgZGUgQnVlbm9zIEFpcmVzIHBhcmEgdHJhemFyIHVuIHBhcmFkaWdtYSANCmRlIGxvcyBkZWxpdG9zIGNvbnRyYSBsYSBpbnRlZ3JpZGFkIHNleHVhbCBlbiBlbCBwYSZpYWN1dGU7cyB5IHNvYnJlIHN1IA0KYXRlbmNpJm9hY3V0ZTtuLjxiciAvPiA8YnIgLz4gJm5ic3A7UG9yIEV2YSBHaWJlcnRpPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2MCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjAiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjE1LzAzLzIwMTI8L3NwYW4+PGJyPkZBTExPIERFIExBIENPUlRFIFNVUFJFTUEgU09CUkUgTEEgTk8gSlVESUNJQUxJWkFDSU9OIERFTCBBQk9SVE8gRU4gQ0FTT1MgREUgVklPTEFDSU9OPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxiciAvPiBKVVJJU0RJQ0NJT046IE5BQ0lPTkFMPGJyIC8+IE1BVEVSSUE6IEFCT1JUTy48YnIgLz4gVFJJQlVOQUw6IENvcnRlIFN1cHJlbWEgZGUgSnVzdGljaWEgZGUgbGEgTmFjaSZvYWN1dGU7bi48YnIgLz4gQVVUT1M6IEYuLCBBLiBMLiBzLyBtZWRpZGEgYXV0b3NhdGlzZmFjdGl2YS48YnIgLz4gRkVDSEE6IDEzLzAzLzIwMTIuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI1OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNTkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBGSU4gbm90YSBjb211biAtLT4KPC90YWJsZT4KPG1hcCBuYW1lPSJNYXBNYXAiIGlkPSJNYXBNYXAiPjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjE0NCw0LDIxNCwzNiIgaHJlZj0iaW5kZXgucGhwP2lkPTE0IiAvPgo8L21hcD4KPG1hcCBuYW1lPSJNYXAyTWFwMiIgaWQ9Ik1hcDJNYXAyIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIxNDcsNCwyMjAsMzYiIGhyZWY9ImluZGV4LnBocD9pZD0xNGEiIC8+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcDMiIGlkPSJNYXAzIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIzNjMsMyw0MzYsMzkiIGhyZWY9ImluZGV4LnBocD9pZD0xNGIiIC8+CjwvbWFwPgo8L2h0bWw+CjwvdGQ+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gICAgICAgICAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFM0UzRTMiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSI3MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNiUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9kZWNpbG9fYmllbl9mdWVydGUxLmpwZyIgd2lkdGg9IjEyMCIgaGVpZ2h0PSIxMTIiPjwvdGQ+CiAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiA+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTI0IiBjbGFzcz0iYm90b24xIj5bK10gTSZhYWN1dGU7cyBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0UzRTNFMyI+ICAgICAgICA8L3RyPgogICAgICAgIDx0cj4gCiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj4mbmJzcDs8L3RkPgogICAgICAgIDwvdHI+CiAgICA8L3RhYmxlPjwvdGQ+CiAgPC90cj4KICA8dHI+IAogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSI+PGltZyBzcmM9ImltZy9penExLmpwZyIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjExNCIgLz48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9RdWllbmVzU29tb3NfQTJfMF8yNS5qcGciIHdpZHRoPSI4MDkiIGhlaWdodD0iMTE0IiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcDIiIC8+PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI1MCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiYWNrZ3JvdW5kPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzE4XzE4LmpwZyI+Jm5ic3A7PC90ZD4KICAgIDx0ZCBoZWlnaHQ9IjUwIiBjbGFzcz0iZm9uZG9ib3R0b20iPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2l0ZWkuY29tLmFyLyI+PGltZyBzcmM9ImltZy9laV9jb2xvci5wbmciIGFsdD0iZXNwYWNpb3MgZGUgaW1hZ2luYWNpb24sIGRlc2Fycm9sbG9zIGludGVyYWN0aXZvcywgY3JlYXRpdmlkYWQsIGRpc2XxbyIgd2lkdGg9IjI3IiBoZWlnaHQ9IjE1IiBib3JkZXI9IjAiPjwvYT4gPHNwYW4gY2xhc3M9ImVpIj48YSBocmVmPSJodHRwOi8vd3d3LnNpdGVpLmNvbS5hci8iIHNwYW4gY2xhc3M9ImVpIj5kaXNlJm50aWxkZTtvICsgY29tdW5pY2FjaSZvYWN1dGU7bjwvYT48L3NwYW4+PGVtPiZuYnNwOzwvZW0+PC9zcGFuPjxzcGFuIGNsYXNzPSJibGFuY28xIj48ZW0+Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7PC9lbT48L3NwYW4+PC90ZD4KICA8L3RyPgo8L3RhYmxlPgoKCjxtYXAgbmFtZT0iTWFwMiI+PGFyZWEgc2hhcGU9InJlY3QiIGNvb3Jkcz0iMjQ3LDY5LDQxNCw4MiIgaHJlZj0ibWFpbHRvOnNhbHVkYWN0aXZhQHNhbHVkYWN0aXZvLm9yZy5hciI+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcCI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM2LDE0MiwxNDksMTUyIiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MiI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM0LDE4NiwxNTAsMTk2IiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MCI+CjwvbWFwPgo8L2JvZHk+CjwvaHRtbD4K]]></response> | |
| 219 | <responseRedirected>false</responseRedirected> | |
| 220 | </requestresponse> | |
| 221 | </issue> | |
| 222 | <issue> | |
| 223 | <serialNumber>3820606740865266688</serialNumber> | |
| 224 | <type>5245344</type> | |
| 225 | <name>Frameable response (potential Clickjacking)</name> | |
| 226 | <host ip="200.20.20.201">http://www.example.org.ar</host> | |
| 227 | <path><![CDATA[/donaciones/]]></path> | |
| 228 | <location><![CDATA[/donaciones/]]></location> | |
| 229 | <severity>Information</severity> | |
| 230 | <confidence>Firm</confidence> | |
| 231 | <issueBackground><![CDATA[It might be possible for a web page controlled by an attacker to load the content of this response within an iframe on the attacker's page. This may enable a "clickjacking" attack, in which the attacker's page overlays the target application's interface with a different interface provided by the attacker. By inducing victim users to perform actions such as mouse clicks and keystrokes, the attacker can cause them to unwittingly carry out actions within the application that is being targeted. This technique allows the attacker to circumvent defenses against cross-site request forgery, and may result in unauthorized actions.<br><br>Note that this issue is being reported because the application's response does not set a suitable <b>X-Frame-Options</b> header in order to prevent framing attacks. Some applications attempt to prevent these attacks from within the HTML page itself, using "framebusting" code. However, this type of defense is normally ineffective and can usually be circumvented by a skilled attacker.]]></issueBackground> | |
| 232 | <remediationBackground><![CDATA[You should review the application functions that are accessible from within the response, and determine whether they can be used by application users to perform any sensitive actions within the application. If so, then a framing attack targeting this response may result in unauthorized actions.<br><br>To effectively prevent framing attacks, the application should return a response header with the name <b>X-Frame-Options</b> and the value <b>DENY</b> to prevent framing altogether, or the value <b>SAMEORIGIN</b> to allow framing only by pages on the same origin as the response itself.]]></remediationBackground> | |
| 233 | <requestresponse> | |
| 234 | <request base64="true"><![CDATA[R0VUIC9kb25hY2lvbmVzLyBIVFRQLzEuMQ0KSG9zdDogd3d3LnNhbHVkYWN0aXZhLm9yZy5hcg0KQWNjZXB0OiAqLyoNCkFjY2VwdC1MYW5ndWFnZTogZW4NClVzZXItQWdlbnQ6IE1vemlsbGEvNS4wIChjb21wYXRpYmxlOyBNU0lFIDkuMDsgV2luZG93cyBOVCA2LjE7IFdpbjY0OyB4NjQ7IFRyaWRlbnQvNS4wKQ0KQ29ubmVjdGlvbjogY2xvc2UNCg0K]]></request> | |
| 235 | <response base64="true"><![CDATA[SFRUUC8xLjEgMjAwIE9LDQpEYXRlOiBUaHUsIDA3IE5vdiAyMDEzIDE3OjE0OjA2IEdNVA0KU2VydmVyOiBBcGFjaGUvMi4yLjIzIChVbml4KSBtb2Rfc3NsLzIuMi4yMyBPcGVuU1NMLzAuOS44ZS1maXBzLXJoZWw1DQpMYXN0LU1vZGlmaWVkOiBXZWQsIDAzIEp1bCAyMDEzIDEzOjQ4OjMwIEdNVA0KRVRhZzogImFhZDk2Ny03MTI5LTRlMDliYjc3ZmM3ODAiDQpBY2NlcHQtUmFuZ2VzOiBieXRlcw0KQ29udGVudC1MZW5ndGg6IDI4OTY5DQpDb25uZWN0aW9uOiBjbG9zZQ0KQ29udGVudC1UeXBlOiB0ZXh0L2h0bWwNCg0KPCFET0NUWVBFIGh0bWwgUFVCTElDICItLy9XM0MvL0RURCBYSFRNTCAxLjAgVHJhbnNpdGlvbmFsLy9FTiIgImh0dHA6Ly93d3cudzMub3JnL1RSL3hodG1sMS9EVEQveGh0bWwxLXRyYW5zaXRpb25hbC5kdGQiPgo8aHRtbCB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMTk5OS94aHRtbCI+CjxoZWFkPgo8bWV0YSBodHRwLWVxdWl2PSJDb250ZW50LVR5cGUiIGNvbnRlbnQ9InRleHQvaHRtbDsgY2hhcnNldD1VVEYtOCIgLz4KPHRpdGxlPlNhbHVkIEFjdGl2YTwvdGl0bGU+CjxsaW5rIGhyZWY9ImVzdGlsb3MuY3NzIiByZWw9InN0eWxlc2hlZXQiIHR5cGU9InRleHQvY3NzIiAvPgo8bGluayBocmVmPSJmb3JtX2ZpbGVzL2VzdGlsb3MuY3NzIiByZWw9InN0eWxlc2hlZXQiIHR5cGU9InRleHQvY3NzIj4KPCEtLVtpZiBJRSA2XT4KCQkJPHN0eWxlIHR5cGU9InRleHQvY3NzIj4KCQkJIEBpbXBvcnQgdXJsKGllNi5jc3MpOwoJCQk8L3N0eWxlPiAKCQk8IVtlbmRpZl0tLT4KPHNjcmlwdCB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiIHNyYz0ianMvanF1ZXJ5Lm1pbi5qcyI+PC9zY3JpcHQ+CjxzY3JpcHQgc3JjPSJTY3JpcHRzL3N3Zm9iamVjdF9tb2RpZmllZC5qcyIgdHlwZT0idGV4dC9qYXZhc2NyaXB0Ij48L3NjcmlwdD4KPHNjcmlwdCB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiIHNyYz0ianMvanF1ZXJ5LmN5Y2xlLmFsbC4yLjc0LmpzIj48L3NjcmlwdD4gCjxzY3JpcHQgdHlwZT0idGV4dC9qYXZhc2NyaXB0Ij4KJChkb2N1bWVudCkucmVhZHkoZnVuY3Rpb24oKSB7CgkkKCcjc2xpZGUnKS5jeWNsZSh7IAogICAgCWZ4OiAgICAgJ3Njcm9sbExlZnQnLCAKICAgCSAJc3BlZWQ6ICAxNTAwLCAKICAgIAl0aW1lb3V0OiA2MDAwICwKCQluZXh0OiAgICcjbmV4dCcsIAogICAgCXByZXY6ICAgJyNwcmV2JwoJfSk7Cn0pOwokKGZ1bmN0aW9uKCkKewovL2JvdG9uMQokKCIjYm90b24xIikuY2xpY2soZnVuY3Rpb24oZXZlbnQpIHsKZXZlbnQucHJldmVudERlZmF1bHQoKTsKJCgiI2NvbnRlbmlkbzEiKS5zbGlkZVRvZ2dsZSgpOwokKCIjY29udGVuaWRvMiwgI2NvbnRlbmlkbzMsICNjb250ZW5pZG80LCAjY29udGVuaWRvNSIpLnNsaWRlVXAoKTsKJCgiI2JvdG9uMSIpLnJlbW92ZUNsYXNzKCdub3NlbGVjdCcpLmFkZENsYXNzKCdzZWxlY3QnKTsKLy8kKCIjYm90b24yLCAjYm90b24zLCAjYm90b240LCAjYm90b241IikucmVtb3ZlQ2xhc3MoJ3NlbGVjdCcpLmFkZENsYXNzKCdub3NlbGVjdCcpOwp9KTsKCi8vYm90b24yCiQoIiNib3RvbjIiKS5jbGljayhmdW5jdGlvbihldmVudCkgewpldmVudC5wcmV2ZW50RGVmYXVsdCgpOwokKCIjY29udGVuaWRvMiIpLnNsaWRlVG9nZ2xlKCk7CiQoIiNjb250ZW5pZG8xLCAjY29udGVuaWRvMywgI2NvbnRlbmlkbzQsICNjb250ZW5pZG81Iikuc2xpZGVVcCgpOwokKCIjYm90b24yIikucmVtb3ZlQ2xhc3MoJ25vc2VsZWN0JykuYWRkQ2xhc3MoJ3NlbGVjdCcpOwovLyQoIiNib3RvbjEsICNib3RvbjMsICNib3RvbjQsICNib3RvbjUiKS5yZW1vdmVDbGFzcygnc2VsZWN0JykuYWRkQ2xhc3MoJ25vc2VsZWN0Jyk7Cn0pOwoKLy9ib3RvbjMKJCgiI2JvdG9uMyIpLmNsaWNrKGZ1bmN0aW9uKGV2ZW50KSB7CmV2ZW50LnByZXZlbnREZWZhdWx0KCk7CiQoIiNjb250ZW5pZG8zIikuc2xpZGVUb2dnbGUoKTsKJCgiI2NvbnRlbmlkbzEsICNjb250ZW5pZG8yLCAjY29udGVuaWRvNCwgI2NvbnRlbmlkbzUiKS5zbGlkZVVwKCk7CiQoIiNib3RvbjMiKS5yZW1vdmVDbGFzcygnbm9zZWxlY3QnKS5hZGRDbGFzcygnc2VsZWN0Jyk7Ci8vJCgiI2JvdG9uMiwgI2JvdG9uMSwgI2JvdG9uNCwgI2JvdG9uNSIpLnJlbW92ZUNsYXNzKCdzZWxlY3QnKS5hZGRDbGFzcygnbm9zZWxlY3QnKTsKfSk7CgovL2JvdG9uNAokKCIjYm90b240IikuY2xpY2soZnVuY3Rpb24oZXZlbnQpIHsKZXZlbnQucHJldmVudERlZmF1bHQoKTsKJCgiI2NvbnRlbmlkbzQiKS5zbGlkZVRvZ2dsZSgpOwokKCIjY29udGVuaWRvMSwgI2NvbnRlbmlkbzMsICNjb250ZW5pZG8yLCAjY29udGVuaWRvNSIpLnNsaWRlVXAoKTsKJCgiI2JvdG9uNCIpLnJlbW92ZUNsYXNzKCdub3NlbGVjdCcpLmFkZENsYXNzKCdzZWxlY3QnKTsKJCgiI2JvdG9uMiwgI2JvdG9uMywgI2JvdG9uMSwgI2JvdG9uNSIpLnJlbW92ZUNsYXNzKCdzZWxlY3QnKS5hZGRDbGFzcygnbm9zZWxlY3QnKTsKfSk7CgovL2JvdG9uNQokKCIjYm90b241IikuY2xpY2soZnVuY3Rpb24oZXZlbnQpIHsKZXZlbnQucHJldmVudERlZmF1bHQoKTsKJCgiI2NvbnRlbmlkbzUiKS5zbGlkZVRvZ2dsZSgpOwokKCIjY29udGVuaWRvMSwgI2NvbnRlbmlkbzMsICNjb250ZW5pZG8yLCAjY29udGVuaWRvNCIpLnNsaWRlVXAoKTsKJCgiI2JvdG9uNSIpLnJlbW92ZUNsYXNzKCdub3NlbGVjdCcpLmFkZENsYXNzKCdzZWxlY3QnKTsKJCgiI2JvdG9uMiwgI2JvdG9uMywgI2JvdG9uMSwgI2JvdG9uNCIpLnJlbW92ZUNsYXNzKCdzZWxlY3QnKS5hZGRDbGFzcygnbm9zZWxlY3QnKTsKfSk7Cn0pOwo8L3NjcmlwdD4KCgo8L2hlYWQ+Cgo8Ym9keT4KPGRpdiBpZD0iY29udGVuZWRvciI+CjxkaXYgaWQ9ImhlYWRlciI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgPHRyPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249Im1pZGRsZSI+PGltZyBzcmM9ImltYWdlcy9oZWFkZXIuanBnIiBuYW1lPSJib3RvbjQiIHdpZHRoPSI5MzMiIGhlaWdodD0iMTI5IiBpZD0iYm90b240Ii8+PC90ZD4KICAgPCEtLSA8dGQgdmFsaWduPSJtaWRkbGUiPjxhIGhyZWY9ImluZm8uZG9jIiB0YXJnZXQ9Il9ibGFuayI+PGltZyBzcmM9ImltYWdlcy9oZWFkZXJtYzEuanBnIiBuYW1lPSJkZXNjYXJnYSIgd2lkdGg9Ijg0NSIgaGVpZ2h0PSIxMTAiIGJvcmRlcj0iMCIgIGlkPSJkZXNjYXJnYSIvPi0tPgo8L2E+PC90ZD4KICA8L3RyPgo8L3RhYmxlPgo8L2Rpdj4gPCEtLWVuZCBvZiBIRUFERVIgLS0+CiAgICA8ZGl2IGlkPSJpbWFnZW5lcyI+CiAgICAgIDxkaXYgaWQ9InNsaWRlciI+CiAgIAkgIDxkaXY+CiAgIAkJPGltZyBzcmM9ImltYWdlcy9iYW5uZXJfaG9tZS5qcGciIHdpZHRoPSI5MzUiIGhlaWdodD0iMzA5IiAvPjwvZGl2PiAKICAgCSAgPCEtLWVuZCBvZiBTTElERSAtLT4KICAgICAgPC9kaXY+IAogICAgICA8IS0tZW5kIG9mIFNMSURFUiAtLT4KPC9kaXY+IAogICAgPCEtLWVuZCBvZiBJTUFHRU5FUyAtLT4gICAgCjxkaXYgaWQ9ImJvdG9uZXJhIj4KICAgIAk8dWw+CiAgICAgICAgCTxsaSBjbGFzcz0ibm9zZWxlY3QxIiBpZD0iYm90b24yIj48L2xpPgogICAgICAgICAgICA8bGkgY2xhc3M9Im5vc2VsZWN0MiIgaWQ9ImJvdG9uMSI+PC9saT4KICAgICAgICAgIDxhIGhyZWY9ImphdmFzY3JpcHQ6IHZvaWQobyk7IiBvbmNsaWNrPSJ3aW5kb3cub3BlbignaHR0cDovL3d3dy5mYWNlYm9vay5jb20vc2hhcmVyLnBocD91PWh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2RvbmFjaW9uZXMvJywndmVudGFuYWNvbXBhcnRpcicsICd0b29sYmFyPTAsIHN0YXR1cz0wLCB3aWR0aD02NTAsIGhlaWdodD00NTAnKTsiPgogICAgICAgIDxsaSBjbGFzcz0ibm9zZWxlY3QzIj48L2xpPgogICAgICAgICAgICA8L2E+CiAgICAgICAgICAgIDwhLS08bGkgY2xhc3M9Im5vc2VsZWN0IiBpZD0iYm90b240Ij5JTkZPUk1BQ0nDk04gREUgQ09NUFJBUzwvbGk+LS0+CiAgICAgICAgICA8IS0tIDxsaSBjbGFzcz0ibm9zZWxlY3QiIGlkPSJib3RvbjUiPkNPTUVSQ0lBTCBERSBUVjwvbGk+IC0tPgogICAgICAgIDwvdWw+CiAgICAgPC9kaXY+ICAgICAgIAogICAgIDwvZGl2Pgo8IS0tZW5kIG9mIEJPVE9ORVJBIC0tPgogICAgCjxkaXYgY2xhc3M9ImNvbnRlbmlkbyIgaWQ9ImNvbnRlbmlkbzEiPgoKPCEtLUNPTlRFTklETyAxZXIgQk9UT04gLS0+CiAKPGRpdiBjbGFzcz0iZm9uZG9fY29udDQiPgoKPGRpdiBjbGFzcz0idGV4dG8iPgo8cD4mbmJzcDs8L3A+CjxwPiZuYnNwOzwvcD4KPHA+PHNwYW4gY2xhc3M9ImgxIj48Yj5TYWx1ZCBBY3RpdmE8L2I+PC9zcGFuPjwvcD4KICAgIAo8cD48c3BhbiBjbGFzcz0iaDIiPlNhbHVkIEFjdGl2YSBlcyB1bmEgb3JnYW5pemFjacOzbiBzaW4gZmluZXMgZGUgbHVjcm8gcXVlIGluaWNpw7Mgc3UgdHJhYmFqbyBhIHByaW5jaXBpb3MgZGVsIGHDsW8gMTk5OS48L3NwYW4+PC9wPgoKPHA+PHNwYW4gY2xhc3M9ImgzIj4KPHN0cm9uZyBzdHlsZT0iZm9udC13ZWlnaHQ6Ym9sZDsiPjxiciAvPgpIb3kgZXN0YW1vcyB0cmFiYWphbmRvIGVuIGVzdGUgcHJveWVjdG86PC9zdHJvbmc+PGJyIC8+CjxhIGhyZWY9Imh0dHA6Ly9pc3N1dS5jb20vZWkuZXN0dWRpby9kb2NzL3NhbHVkYWN0aXZhLWx1ZG90ZWNhP21vZGU9d2luZG93IiB0YXJnZXQ9Il9ibGFuayI+PGltZyBzcmM9ImltYWdlcy9HYXJhYmF0b0x1ZG90ZWNhXzUwMHB4LmpwZyIgd2lkdGg9IjUwMCIgaGVpZ2h0PSIxMTMiIGJvcmRlcj0iMCIgLz48L2E+Cgo8YnIgLz4KPGEgaHJlZj0iUHJveWVjdG9MdWRvdGVjYUNvbXBsZXRvLnBkZiIgdGFyZ2V0PSJfYmxhbmsiIHN0eWxlPSJjb2xvcjojRjYwOyI+VmVyIHByb3llY3RvIGNvbXBsZXRvPC9hPjxiciAvPgo8c3Ryb25nPjxiciAvPgo8L3N0cm9uZz48L3NwYW4+PHN0cm9uZyBzdHlsZT0iZm9udC13ZWlnaHQ6Ym9sZDsiPlVuIHBvY28gZGUgaGlzdG9yaWE8L3N0cm9uZz48ZW0+OjwvZW0+PC9wPgo8cD48c3BhbiBjbGFzcz0iaDMiPkN1YW5kbyBpbmljaWFtb3MgZXN0ZSBjYW1pbm8gdGVuw61hbW9zIHVuYSBwcmVvY3VwYWNpw7NuLCBsb3MgcHNpY8OzbG9nb3MgeSBwc2ljw7Nsb2dhcyBjdWFuZG8gc2UgcmVjaWLDrWFuIHRlbsOtYW4gcXVlIGNvbWVuemFyIGEgZWplcmNlciB5IHNlIGVuZnJlbnRhYmFuIGEgdW5hIHNlcmllIGRlIHByb2JsZW1hcywgZW50cmUgZWxsb3MgbGEgZGlmZXJlbmNpYSBlbnRyZSBsbyBxdWUgYXByZW5kw61hbiAoeSBhcHJlbmRlbikgZW4gbGEgRmFjdWx0YWQgKHNlYSBsYSBxdWUgc2VhKSB5IGxhIHJlYWxpZGFkIGRlbCBzdWZyaW1pZW50byBkZSBsYSBnZW50ZS4gCiAgRWwgb3RybyBwcm9ibGVtYSBjb24gZWwgcXVlIHNlIHRvcGFiYW4gZXMgbGEgaW5leGlzdGVuY2lhIGRlIGx1Z2FyZXMgZG9uZGUgcmVhbGl6YXIgcHLDoWN0aWNhcywgZG9uZGUgYXByZW5kZXIgYSBhdGVuZGVyIHBhY2llbnRlcywgY29tbyBzZXIgcHNpY8OzbG9nb3MgeSBwc2ljw7Nsb2dhcyBlbiBsYSByZWFsaWRhZCBkZWwgY29udXJiYW5vIGJvbmFlcmVuc2XigKYgPGJyIC8+PGJyIC8+CiAgRXNhcyBwcmVvY3VwYWNpb25lcyBzZSBkZXNwcmVuZGllcm9uIGRlIGRpZXogYcOxb3MgZGUgZnVuY2lvbmFtaWVudG8gY29tbyBpbnN0aXR1Y2nDs24gcHNpY29sw7NnaWNhLCBlbCBDSUFQU0kgKENlbnRybyBkZSBJbnZlc3RpZ2FjacOzbiB5IEFzaXN0ZW5jaWEgUHNpY29zb23DoXRpY2EgZnVuZGFkbyBlbiAxOTg5KSB5IGEgbGEgcXVlIGNvbnZvY2Ftb3MgYSBtdWNob3MgeSBtdWNoYXMgasOzdmVuZXMgY29sZWdhcyBxdWUgc3VmcsOtYW4gZXN0YXMgZG9zIGNhcmVuY2lhcyBiw6FzaWNhcyBlbiBzdSBmb3JtYWNpw7NuLiBDb24gZXN0ZSBlc3DDrXJpdHUgZGUgZm9ybWFjacOzbiBwcm9mZXNpb25hbCBjb21lbnphbW9zIG51ZXN0cm8gY2FtaW5vIGNvbiBTYWx1ZCBBY3RpdmEsIGV4YWN0YW1lbnRlIGVsIDkgZGUgYWJyaWwgZGVsIDk5LCBtZWRpYW50ZSBsYSBpbXBsZW1lbnRhY2nDs24gZGVsIFByb2dyYW1hIEFzaXRpci4gQ29udm9jYW1vcyBhIGxvcyBwcm9mZXNpb25hbGVzIHJlY2nDqW4gcmVjaWJpZG9zIGEgcmVhbGl6YXIgZXN0YSBmb3JtYWNpw7NuIHByb2Zlc2lvbmFsIHRlw7NyaWNvLXByw6FjdGljYSBkZSBtYW5lcmEgZ3JhdHVpdGEgeSBxdWUgaW5jbHXDrWEgbGEgc3VwZXJ2aXNpw7NuIGNsw61uaWNhIGRlIGxvcyBwYWNpZW50ZXMgdGFtYmnDqW4gZGUgbWFuZXJhIGdyYXR1aXRhLiAKICA8YnIgLz48YnIgLz4KICBQYXJhIGdlbmVyYXIgbG9zIGVzcGFjaW9zIGRlIGxhIHByw6FjdGljYSBpbnZpdGFtb3MgYSBsYSBjb211bmlkYWQgY2VyY2FuYSBhIHBhcnRpY2lwYXIgZGUgZXN0YSBwb3NpYmlsaWRhZDogYXNpc3RlbmNpYSBwc2ljb2zDs2dpY2EgZ3JhdHVpdGEgbyBtZWRpYW50ZSBlbCBwYWdvIGRlIHVuIG3DrW5pbW8gYm9ubyBjb250cmlidWNpw7Nu4oCmCiAgPGJyIC8+PGJyIC8+CiAgUHJpbWVybyBmdWVyb24gbGFzIGVzY3VlbGFzIGRlIG51ZXN0cm8gcGFydGlkbywgcG9kcsOhbiBpbWFnaW5hcnNlIHF1ZSBsYSBwcmltZXJhIHJlYWNjacOzbiBmdWUgZGUgYXNvbWJybyB5IGRlc2NvbmZpYW56YSwgbGFzIGRpcmVjdG9yYXMgeSBlcXVpcG9zIHTDqWNuaWNvcyBjb21lbnphcm9uIGEgbGxhbWFyIHBvciB0ZWzDqWZvbm8sIHNlIGZ1ZXJvbiBhY2VyY2FuZG8geSBsZXMgZXhwbGljw6FiYW1vcyBjdWFsZXMgZXJhbiBudWVzdHJvcyBvYmpldGl2b3M6IGZvcm1hciBwcm9mZXNpb25hbGVzIHkgcGVybWl0aXIgYSBtw6FzIGdlbnRlIHBvZGVyIGFjY2VkZXIgYSBsYSBhc2lzdGVuY2lhIHBzaWNvbMOzZ2ljYS4gQXPDrSBwbGFudGVhZG8gZW1wZXphcm9uIGEgbGxlZ2FyIGxhcyBwcmltZXJhcyBkZXJpdmFjaW9uZXM6IG5pw7FvcywgbmnDsWFzIHkgYWRvbGVzY2VudGVzIHF1ZSB0dXZpZXJhbiBkaWZpY3VsdGFkZXMgbyBwcm9ibGVtYXMgZW4gbGEgZXNjdWVsYSwgeSBxdWUgbGEgZXNjdWVsYSBzZSBjb21wcm9tZXRpZXJhIGEKICB0cmFiYWphciBqdW50byBhIG5vc290cm9zIGVuIGxhIHByb2JsZW3DoXRpY2EgZGVsIG5pw7FvIG8gbmnDsWEuCiAgUXVlIGZ1ZSBsbyBxdWUgb2N1cnJpw7PigKZsYSBtYXlvcsOtYSBkZSBsYXMgZGVyaXZhY2lvbmVzIGVzdGFiYW4gdmluY3VsYWRhcyBhbCBtYWx0cmF0byAsIGEgbGEgdmlvbGVuY2lhIHkgYWwgYWJ1c28gaW5mYW50aWwuIAogIDxiciAvPjxiciAvPgogIEp1c3RhbWVudGUgcG9yIHVuIGNhc28gZGUgYWJ1c28gc2V4dWFsIGluZmFudGlsIGZ1aW1vcyBjb252b2NhZG9zIHBvciB1bm8gZGUgbG9zIFRyaWJ1bmFsZXMgZGUgRmFtaWxpYSBkZSBNb3LDs24sIGVsIG7CuiAxIHBhcmEgc2VyIG3DoXMgZXhhY3RvcyBlbiBkb25kZSBjb21lbnphYmEgYSBmdW5jaW9uYXIgdW4gZXNwYWNpbyBpbm5vdmFkb3IgcGFyYSBhcXVlbCBtb21lbnRvLCBub3ZpZW1icmUgZGVsIDk5LCAgbGEgUmVkIGRlIEZhbWlsaWEgZGVsIE9lc3RlLCBjcmVhZGEgcG9yIHVuIEp1ZXogZWwgRHIuIENhcmxvcyBSb21hbm8sIHZpc2lvbmFyaW8gc29icmUgbGEgZm9ybWEgZW4gbGEgcXVlIHNlIGRlYmVuIHRyYWJhamFyIGxvcyB0ZW1hcyBkZSB2aW9sZW5jaWEsIG1hbHRyYXRvIHkgYWJ1c286IGVuIHJlZCwgYXJ0aWN1bGFuZG8sCiAgbXVsdGlkaXNjaXBsaW5hcmlhbWVudGUsIHBlbnNhbmRvIGp1bnRvcywgc2llbmRvIGNyZWF0aXZvc+KApgogIDxiciAvPjxiciAvPgogIE5vcyBhdXRvIGZvcm1hbW9zLCBpbnZlc3RpZ2Ftb3MsIGNvbnN0aXR1aW1vcyBncnVwb3MgZGUgZXN0dWRpbywgbm9zIGNhcGFjaXRhbW9zLCB5IG5vcyBlc3BlY2lhbGl6YW1vcy4KICBTaWVtcHJlIGRlY2ltb3MgcXVlIG5vc290cm9zIG5vIGVsZWdpbW9zIGhhY2VyIGVzdG8sIGxhIHJlYWxpZGFkIHNlIG5vcyBpbXB1c28geSBzZW50aW1vcyBxdWUgZXJhIG51ZXN0cm8gZGViZXIgcmVzcG9uZGVyIGEgbG8gcXVlIG5hZGllIHJlc3BvbmRlLCBhY29tcGHDsWFyIGxvIHF1ZSBuYWRpZSBhY29tcGHDsWEsIHkgcG9yIHNvYnJlIHRvZG8gaGFjZXLigKYsIHRyYXRhciBxdWUgZWwgcXVlIGVzdMOhIHN1ZnJpZW5kbyB0ZW5nYSBsYSBvcG9ydHVuaWRhZCBkZSBlbGVnaXIgb3RyYSBjb3NhLCB0ZW5nYSBsYSBwb3NpYmlsaWRhZCBkZSBtZWpvcmFyLCBkZSBjYW1iaWFyIHN1IGRlc3Rpbm/igKYKICA8YnIgLz48YnIgLz4KICBFbiBlc2UgY2FtaW5vIGZ1aW1vcyBoYWNpZW5kbywgbG9zIENvbmdyZXNvcywgbGFzIEpvcm5hZGFzLCBsYXMgY2FwYWNpdGFjaW9uZXMgZXh0ZXJuYXMgeSBmb3JtYW1vcyBtdWNob3MsIHBlcm8gbXVjaG9zIHByb2Zlc2lvbmFsZXPigKZudW5jYSB0dXZpbW9zIGVsIHRpZW1wbyB5IGVsIGRpbmVybyBwYXJhIHNpc3RlbWF0aXphciBsYSBpbmZvcm1hY2nDs24geSBwb2RlciBjb250YXIgY29uIGVzdGFkw61zdGljYXMgcG9ycXVlIGVsIHRpZW1wbyB5IGVsIHBvY28gZGluZXJvIGxvIHVzYW1vcyBwYXJhIGFsaXZpYXIgZWwgc3VmcmltaWVudG8gZGUgbG9zIHBhY2llbnRlcyBxdWUgcmVjdXJyZW4gYSBub3NvdHJvcy4KICA8YnIgLz48YnIgLz4KICBUYW1iacOpbiBub3MgZGltb3MgY3VlbnRhIHF1ZSBlbiBtdWNob3MgbW9tZW50b3MgZGUgbGEgdmlkYSBkZSBsb3MgbmnDsW9zIHkgbmnDsWFzIG5vIGFsY2FuemEgY29uIGVsIHRyYXRhbWllbnRvIGVuIHVuIGNvbnN1bHRvcmlvLCBwb3JxdWUgbGFzIHByb2JsZW3DoXRpY2FzIHNlIGNvbXBsZWppemFuLCBsYXMgc2l0dWFjaW9uZXMgc2UgYWdyYXZhbiB5IHNlbnRpbW9zIHF1ZSB0ZW7DrWFtb3MgcXVlIGhhY2VyIGFsZ28gbcOhc+KApgogIEFzw60gbmFjZSBudWVzdHJvIFByb2dyYW1hIE1ldGFtb3Jmb3NpcywgdW4gZXNwYWNpbyBkZSB0cmF0YW1pZW50byBpbnRlZ3JhbCBjb24gaW50ZXJuYWNpw7NuIHBhcmEgYWRvbGVzY2VudGVzIG11amVyZXMgdsOtY3RpbWFzIGRlIGFidXNvIHNleHVhbCwgZGUgdmlvbGVuY2lhLCBkZSB0cmF0YeKAplRhbWJpw6luIGluaWNpYW1vcyBudWVzdHJvcyBwcm9ncmFtYXMgQ29uc3RydXllbmRvIHkgQXByZW5kZXIgYSB2b2xhciwgZGVzdGluYWRvIGEgYWRvbGVzY2VudGVzIGVuIGNvbmZsaWN0byBjb24gbGEgbGV5IHBlbmFsLCAgcHVuaWJsZXMgeSBubyBwdW5pYmxlcyByZXNwZWN0aXZhbWVudGUsIAogIGFsZ28gYWx0ZXJuYXRpdm8gYSBsYSBpbnRlcm5hY2nDs27igKYKICA8YnIgLz48YnIgLz4KICBBIGxvIGxhcmdvIGRlIGVzdG9zIGHDsW9zIGhlbW9zIGRlc2Fycm9sbGFkbyBtdWNob3MgcHJvZ3JhbWFzLCBxdWUgdHV2aWVyb24gcXVlIGRpc2NvbnRpbnVhcnNlIGRlYmlkbyBhIGxhIGZhbHRhIGRlIHJlY3Vyc29zIGVjb27Ds21pY29zLCBsYSB2ZXJkYWQgZXMgcXVlIG51bmNhIGhheSBkaW5lcm8gcGFyYSBlc3RvcyB0ZW1hcywgYSBwZXNhciBkZSBxdWUgdG9kbyBlbCBtdW5kbyBzZSBsYSBwYXNhIGhhYmxhbmRvIGRlIGVsbG9zLCBwZXJvIGhhYmxhbiwgc29sbyBoYWJsYW7igKYKICA8YnIgLz48YnIgLz4KICBIb3kgbm9zIGVuY29udHJhbW9zIGVuIGVzdGUgbW9tZW50bywgZW4gZG9uZGUgU2FsdWQgQWN0aXZhIHNlIGVuY3VlbnRyYSBlbiBjcmlzaXPigKYKICBOdWVzdHJhIMO6bmljYSBmdWVudGUgZGUgZmluYW5jaWFtaWVudG8gcGFyZWNlIHF1ZSB0YW1iacOpbiBlc3TDoSBlbiBjcmlzaXMsIG5vcyBlbmNvbnRyYW1vcyBlbiB1bmEgZW5jcnVjaWphZGEsIG5lY2VzaXRhbW9zIGRlIGxhIGF5dWRhIGRlIHVzdGVkZXPigKZTaSBsZXMgcGFyZWNlIHF1ZSBlc3RhbW9zIGhhY2llbmRvIGFsZ28gYnVlbm8gcGFyYSBsYSBnZW50ZSBsb3MgaW52aXRhbW9zIGEgcXVlIHNlIGFzb2NpZW4gYSBub3NvdHJvcyBtZWRpYW50ZSBlbCBwYWdvIGRlIHVuYSBwZXF1ZcOxYSBjb250cmlidWNpw7NuIG1lbnN1YWwgcXVlIHNlIGRlYml0YXLDoSBkZSBzdSB0YXJqZXRhIAogIGRlIGNyw6lkaXRvLCB0b2RhIGNvbGFib3JhY2nDs24gcG9yIHBlcXVlw7FhIHF1ZSBzZWEgbm9zIGF5dWRhcsOhCiAgPGJyIC8+PGJyIC8+CiAgQWNvbXBhw7FlbiBlc3RhIHRhcmVhIHF1ZSBkZXNlYW1vcyBzZWd1aXIgaGFjaWVuZG/igKYKPC9zcGFuPjwvcD4KPC9kaXY+CgkJCjwvZGl2PgogICAgPGRpdiBjbGFzcz0iZm9vdGVyIj48aW1nIHNyYz0iaW1hZ2VzL2Zvb3Rlci5qcGciIHdpZHRoPSI5MzUiIGhlaWdodD0iODciIC8+PC9kaXY+Cgo8L2Rpdj4KICAgICA8IS0tZW5kIG9mIENPTlRFTklETzEgLS0+CiAgICAKICAgIDxkaXYgY2xhc3M9ImNvbnRlbmlkbzIiIGlkPSJjb250ZW5pZG8yIj4KICAgIDwhLS1DT05URU5JRE8gMmRvIEJPVE9OICAtLT4KICAgIAoKPGRpdiBjbGFzcz0iZm9uZG9fY29udDIiPgoKPGRpdiBjbGFzcz0iZm9ybSI+CiAgPGRpdiBjbGFzcz0idGV4dG8iPgogICAgPHA+Jm5ic3A7PC9wPgogICAgPHA+Jm5ic3A7PC9wPgo8cD48c3BhbiBjbGFzcz0idGl0dWxvX2Zvcm0iPjxiPkRBVE9TIFBFUlNPTkFMRVM8L2I+PC9zcGFuPgogICAgPHNwYW4gY2xhc3M9InRpdHVsb19mb3JtMiI+KEVzIG9ibGlnYXRvcmlvIHJlbGxlbmFyIGxvcyBjYW1wb3MgCiAgICAgICAgICAgICAgICBpbmRpY2Fkb3MgY29uICopPC9zcGFuPjwvcD4KICAgIDxkaXYgaWQ9ImJsb3F1ZV9penFfMDMiPgogICAgCQk8ZGl2IGlkPSJibG9xdWVfaXpxXzAzX3RleHRvIj4KICAgICAgICAgICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgICAgICAgICAgIDxzY3JpcHQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICBmdW5jdGlvbiB2YWxpZGFyRW1haWwoZW1haWwpIHsgCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgdmFyIHJlICA9IC9eKFthLXpBLVowLTlfLi1dKStAKChbYS16QS1aMC05LV0pKy4pKyhbYS16QS1aMC05XXsyLDR9KSskLzsgCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgaWYgKCFyZS50ZXN0KGVtYWlsKSkgeyAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgcmV0dXJuIGZhbHNlOyAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICB9IAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJldHVybiB0cnVlOyAKICAgICAgICAgICAgICAgICAgICAgICAgICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgZnVuY3Rpb24gdmFsaWRhcihvYmopIHsKICAgICAgICAgICAgICAgICAgICAgICAgICAgIGlmIChvYmoubm9tYnJlLnZhbHVlID09ICcnKSB7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgYWxlcnQoIkRlYmUgaW5ncmVzYXIgc3Ugbm9tYnJlIik7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgb2JqLm5vbWJyZS5mb2N1cygpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJldHVybiBmYWxzZTsKICAgICAgICAgICAgICAgICAgICAgICAgICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgICAgIGlmIChvYmouYXBlbGxpZG8udmFsdWUgPT0gJycpIHsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBhbGVydCgiRGViZSBpbmdyZXNhciBzdSBhcGVsbGlkbyIpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIG9iai5hcGVsbGlkby5mb2N1cygpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJldHVybiBmYWxzZTsKICAgICAgICAgICAgICAgICAgICAgICAgICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgICAgIGlmIChvYmoudGVsZWZvbm8udmFsdWUgPT0gJycpIHsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBhbGVydCgiRGViZSBpbmdyZXNhciBzdSB0ZWxlZm9ubyIpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIG9iai50ZWxlZm9uby5mb2N1cygpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJldHVybiBmYWxzZTsKICAgICAgICAgICAgICAgICAgICAgICAgICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgICAgIGlmIChvYmouZW1haWwudmFsdWUgPT0gJycpIHsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBhbGVydCgiRGViZSBpbmdyZXNhciBzdSBlbWFpbCIpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIG9iai5lbWFpbC5mb2N1cygpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJldHVybiBmYWxzZTsKICAgICAgICAgICAgICAgICAgICAgICAgICAgIH0gZWxzZSB7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgaWYgKHZhbGlkYXJFbWFpbChvYmouZW1haWwudmFsdWUpID09IGZhbHNlKSB7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFsZXJ0KCJFbCBlbWFpbCBpbmdyZXNhZG8gZXMgaW5jb3JyZWN0byIpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBvYmouZW1haWwuZm9jdXMoKTsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgcmV0dXJuIGZhbHNlOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgICAgIGlmIChvYmoudGVybWlub3MuY2hlY2tlZCAhPSB0cnVlKSB7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgYWxlcnQoIkRlYmUgYWNlcHRhciBsb3MgdMOpcm1pbm9zIHkgY29uZGljaW9uZXMiKTsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBvYmoudGVybWlub3MuZm9jdXMoKTsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICByZXR1cm4gZmFsc2U7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICB9CiAgICAgICAgICAgICAgICAgICAgICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgPC9zY3JpcHQ+CiAgICAgICAgICAgICAgICAgICAgICAgIAogICAgICAgICAgICAgICAgICAgICAgICA8Zm9ybSBuYW1lPSJjb250YWN0IiBtZXRob2Q9IlBPU1QiIGFjdGlvbj0iZW52aW8ucGhwIiBvblN1Ym1pdD0icmV0dXJuIHZhbGlkYXIodGhpcykiPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgICAgICAgICAgPGRpdiBpZD0iYmxvcXVlX2l6cV8wMiI+CjxoMT5Ob21icmU8Zm9udCBjb2xvcj0iI0ZGNjYwMCI+KjwvZm9udD48L2gxPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxoMT5BcGVsbGlkbzxmb250IGNvbG9yPSIjRkY2NjAwIj4qPC9mb250PjwvaDE+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGgxPlByb2Zlc2nDs248L2gxPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxoMT5MdWdhciBkZSB0cmFiYWpvPC9oMT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8aDE+VGVsw6lmb25vPGZvbnQgY29sb3I9IiNGRjY2MDAiPio8L2ZvbnQ+PC9oMT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8aDE+RW1haWw8Zm9udCBjb2xvcj0iI0ZGNjYwMCI+KjwvZm9udD48L2gxPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxiciAvPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxiciAvPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwhLS0gPGgxPk5yby4gZGUgVGFyamV0YTxmb250IGNvbG9yPSIjRkY2NjAwIj4qPC9mb250PjwvaDE+IC0tPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxoMT5Nb250bzxmb250IGNvbG9yPSIjRkY2NjAwIj4qPC9mb250PjwvaDE+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGgxPlRpcG8gZGUgT3BlcmFjacOzbjxmb250IGNvbG9yPSIjRkY2NjAwIj4qPC9mb250PjwvaDE+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGgxIGlkPSJoMV90YXJqZXRhIj5UYXJqZXRhPGZvbnQgY29sb3I9IiNGRjY2MDAiPio8L2ZvbnQ+PC9oMT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8aDEgaWQ9ImgxX2ZyZWN1ZW5jaWEiPkZyZWN1ZW5jaWE8Zm9udCBjb2xvcj0iI0ZGNjYwMCI+KjwvZm9udD48L2gxPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9kaXY+CiAgICAgICAgICAgICAgICAgICAJCSAgPGZpZWxkc2V0PgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48YnIgLz4KICAgICAgICAgICAgICAgICAgICAgICAgICA8aW5wdXQgbmFtZT0ibm9tYnJlIiBjbGFzcz0icmVnMSIgc2l6ZT0iMTUiIHdpZHRoPSIxMDUiIGlkPSJub21icmUiIHR5cGU9InRleHQiPjwvcD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGgxPjwvaDE+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxpbnB1dCBuYW1lPSJhcGVsbGlkbyIgY2xhc3M9InJlZzEiIHNpemU9IjE1IiB3aWR0aD0iMTA1IiBpZD0iYXBlbGxpZG8iIHR5cGU9InRleHQiPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3A+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxoMT48L2gxPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48aW5wdXQgbmFtZT0icHJvZmVzaW9uIiBjbGFzcz0icmVnMSIgc2l6ZT0iMTUiIHdpZHRoPSIxMDUiIGlkPSJwcm9mZXNpb24iIHR5cGU9InRleHQiPjwvcD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGgxPjwvaDE+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxpbnB1dCBuYW1lPSJ0cmFiYWpvIiBjbGFzcz0icmVnMSIgc2l6ZT0iMTUiIHdpZHRoPSIxMDUiIGlkPSJ0cmFiYWpvIiB0eXBlPSJ0ZXh0Ij48L3A+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxoMT48L2gxPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48aW5wdXQgbmFtZT0idGVsZWZvbm8iIGNsYXNzPSJyZWcxIiBzaXplPSIxNSIgd2lkdGg9IjEwNSIgaWQ9InRlbGVmb25vIiB0eXBlPSJ0ZXh0Ij48L3A+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxoMT48L2gxPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48aW5wdXQgbmFtZT0iZW1haWwiIGNsYXNzPSJyZWcxIiBzaXplPSIxNSIgd2lkdGg9IjEwNSIgaWQ9ImVtYWlsIiB0eXBlPSJ0ZXh0Ij48L3A+PGJyIC8+CgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA+PHNwYW4gY2xhc3M9InRpdHVsb19mb3JtIj48Yj5ET05BQ0lPTkVTPC9iPjwvc3Bhbj48L3A+ICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjwvcD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwhLS0gPHA+PGlucHV0IG5hbWU9InRhcmpldGEiIGNsYXNzPSJyZWcxIiBzaXplPSIxNSIgd2lkdGg9IjEwNSIgaWQ9InRhcmpldGEiIHR5cGU9InRleHQiPjwvcD4gLS0+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c2VsZWN0IG5hbWU9Im1vbnRvIiBjbGFzcz0icmVnMiIgaWQ9Im1vbnRvIiBvbkNoYW5nZT0iaWYgKHRoaXMudmFsdWUgPT0gJy0xJykgeyBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgndHh0bW9udG8nKS5zdHlsZS5kaXNwbGF5PScnOyB9IGVsc2UgeyBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgndHh0bW9udG8nKS5zdHlsZS5kaXNwbGF5PSdub25lJzsgfSAiPgogICAgICAgICAgICAgICAgICAgICAgPG9wdGlvbiB2YWx1ZT0iNTAiPiQgNTA8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjEwMCI+JCAxMDA8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjE1MCI+JCAxNTA8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjIwMCI+JCAyMDA8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9Ii0xIj5PdHJvLCBpbmdyZXNlIHZhbG9yPC9vcHRpb24+CiAgICAgICAgICAgICAgICAgICAgPC9zZWxlY3Q+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8c2NyaXB0PgogICAgICAgICAgICAgICAgICAgICAgICAgICAgZnVuY3Rpb24gc29sb051bWVyb3MobXlmaWVsZCxlKSB7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAJdmFyIGtleWNvZGU7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAJaWYgKHdpbmRvdy5ldmVudCkgewogICAgICAgICAgICAgICAgICAgICAgICAgICAgCSAgICBrZXljb2RlID0gd2luZG93LmV2ZW50LmtleUNvZGU7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAJfSBlbHNlIHsKICAgICAgICAgICAgICAgICAgICAgICAgICAgIAkgICAgaWYgKGUpIHsKICAgICAgICAgICAgICAgICAgICAgICAgICAgIAkgICAgICAgIGtleWNvZGUgPSBlLndoaWNoOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgCSAgICB9IGVsc2UgewogICAgICAgICAgICAgICAgICAgICAgICAgICAgCSAgICAgICAgcmV0dXJuIHRydWU7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAJICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgICAgIAl9CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAJaWYgKCgoa2V5Y29kZT40NykgJiYgKGtleWNvZGU8NTgpKSAgfHwgKGtleWNvZGU9PTgpKSB7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAJICAgIHJldHVybiB0cnVlOyAKICAgICAgICAgICAgICAgICAgICAgICAgICAgIAl9IGVsc2UgewogICAgICAgICAgICAgICAgICAgICAgICAgICAgCSAgICByZXR1cm4gZmFsc2U7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAJfQogICAgICAgICAgICAgICAgICAgICAgICAgICAgfQogICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9zY3JpcHQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8aW5wdXQgbmFtZT0idHh0bW9udG8iIGNsYXNzPSJyZWcxIiBzaXplPSIxNSIgd2lkdGg9IjIwIiBpZD0idHh0bW9udG8iIHR5cGU9InRleHQiIG1heGxlbmd0aD0iNyIgb25LZXlQcmVzcz0icmV0dXJuIHNvbG9OdW1lcm9zKHRoaXMsIGV2ZW50KTsiIHN0eWxlPSJkaXNwbGF5Om5vbmUiPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9wPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPHNjcmlwdD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgIGZ1bmN0aW9uIG11ZXN0cmFGb3JtYVBhZ28odmFsb3IpIHsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBpZiAodmFsb3IgPT0gMikgewogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgncF9tZWRpb3BhZ28nKS5zdHlsZS5kaXNwbGF5ID0gJ25vbmUnOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgncF9jdW90YXMnKS5zdHlsZS5kaXNwbGF5ID0gJ25vbmUnOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgncF9mb3JtYXBhZ29vdHJvJykuc3R5bGUuZGlzcGxheSA9ICcnOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgnaDFfdGFyamV0YScpLmlubmVySFRNTCA9ICdGb3JtYSBkZSBQYWdvPGZvbnQgY29sb3I9IiNGRjY2MDAiPio8L2ZvbnQ+JzsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgZG9jdW1lbnQuZ2V0RWxlbWVudEJ5SWQoJ2gxX2ZyZWN1ZW5jaWEnKS5pbm5lckhUTUwgPSAnJzsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICB9IGVsc2UgewogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgncF9tZWRpb3BhZ28nKS5zdHlsZS5kaXNwbGF5ID0gJyc7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRvY3VtZW50LmdldEVsZW1lbnRCeUlkKCdwX2N1b3RhcycpLnN0eWxlLmRpc3BsYXkgPSAnJzsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgZG9jdW1lbnQuZ2V0RWxlbWVudEJ5SWQoJ3BfZm9ybWFwYWdvb3RybycpLnN0eWxlLmRpc3BsYXkgPSAnbm9uZSc7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRvY3VtZW50LmdldEVsZW1lbnRCeUlkKCdoMV90YXJqZXRhJykuaW5uZXJIVE1MID0gJ1RhcmpldGE8Zm9udCBjb2xvcj0iI0ZGNjYwMCI+KjwvZm9udD4nOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgnaDFfZnJlY3VlbmNpYScpLmlubmVySFRNTCA9ICdGcmVjdWVuY2lhPGZvbnQgY29sb3I9IiNGRjY2MDAiPio8L2ZvbnQ+JzsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICB9CiAgICAgICAgICAgICAgICAgICAgICAgICAgICB9CiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3NjcmlwdD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzZWxlY3QgbmFtZT0iZm9ybWFwYWdvIiBjbGFzcz0icmVnMiIgaWQ9ImZvcm1hcGFnbyIgb25DaGFuZ2U9Im11ZXN0cmFGb3JtYVBhZ28odGhpcy52YWx1ZSkiIHN0eWxlPSJwb3NpdGlvbjpyZWxhdGl2ZTsgdG9wOjVweDsiPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8b3B0aW9uIHZhbHVlPSIxIj5UYXJqZXRhIGRlIENyw6lkaXRvPC9vcHRpb24+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjIiPkVmZWN0aXZvICjDum5pY2EgdmV6KTwvb3B0aW9uPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9zZWxlY3Q+PC9wPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPHAgaWQ9InBfbWVkaW9wYWdvIiBzdHlsZT0iZGlzcGxheTpub25lIj48c2VsZWN0IG5hbWU9Im1lZGlvcGFnbyIgY2xhc3M9InJlZzIiIGlkPSJtZWRpb3BhZ28iIHN0eWxlPSJwb3NpdGlvbjpyZWxhdGl2ZTsgdG9wOjZweDsiPgogICAgICAgICAgICAgICAgICAgICAgPG9wdGlvbiB2YWx1ZT0iMTUiPk1hc3RlcmNhcmQ8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjEiPlZpc2E8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjYiPkFtZXJpY2FuIEV4cHJlc3M8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICA8L3NlbGVjdD48L3A+CiAgICAgICAgICAgICAgICAgICAgIDxwIGlkPSJwX2N1b3RhcyIgc3R5bGU9ImRpc3BsYXk6bm9uZSI+PHNlbGVjdCBuYW1lPSJjdW90YXMiIGNsYXNzPSJyZWcyIiBpZD0iY3VvdGFzIiBzdHlsZT0icG9zaXRpb246cmVsYXRpdmU7IHRvcDo3cHg7Ij4KICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjEiPkQmZWFjdXRlO2JpdG8gQXV0b20mYWFjdXRlO3RpY28gKHRvZG9zIGxvcyBtZXNlcyk8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjIiPsOabmljYSB2ZXo8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8L3NlbGVjdD48L3A+CiAgICAgICAgICAgICAgICAgICAgPHAgaWQ9InBfZm9ybWFwYWdvb3RybyIgc3R5bGU9ImRpc3BsYXk6bm9uZSI+PHNlbGVjdCBuYW1lPSJmb3JtYXBhZ29vdHJvIiBjbGFzcz0icmVnMiIgaWQ9ImZvcm1hcGFnb290cm8iIHN0eWxlPSJwb3NpdGlvbjpyZWxhdGl2ZTsgdG9wOjdweDsiPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPG9wdGlvbiB2YWx1ZT0iOTk3Ij5EZXBvc2l0byBCYW5jYXJpbzwvb3B0aW9uPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPG9wdGlvbiB2YWx1ZT0iOTk4Ij5QYWdvIGVuIEVmZWN0aXZvPC9vcHRpb24+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8b3B0aW9uIHZhbHVlPSI5OTkiPkRpbmVyb01haWw8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8L3NlbGVjdD48L3A+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA+ICAgCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxiciAvPiAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxpbnB1dCBuYW1lPSJyZWNpYmlyIiBpZD0iY2hlY2siIHR5cGU9ImNoZWNrYm94IiBjaGVja2VkPSJ0cnVlIiB2YWx1ZT0iU2kiIC8+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIFMmaWFjdXRlOywgZGVzZW8gcmVjaWJpciAKICAgICAgICAgICAgICAgIGluZm9ybWFjaSZvYWN1dGU7biBwZXJpJm9hY3V0ZTtkaWNhIGRlIFNhbHVkIEFjdGl2YSB5IAogICAgICAgICAgICAgICAgc3VzIFByb3llY3RvcyBkZSBEZXNhcnJvbGxvLiAgICAgICAgICAgICAgICA8L3A+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxpbnB1dCBuYW1lPSJsaXN0YSIgaWQ9ImNoZWNrIiB0eXBlPSJjaGVja2JveCIgY2hlY2tlZD0idHJ1ZSIgdmFsdWU9IlNpIiAvPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNpIGRlc2VvIGFwYXJlY2VyIGVuIGxhIGxpc3RhIGRlIGRvbmFjaW9uZXMgaW5kaXZpZHVhbGVzLiAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBBcGFyZWNlciZhYWN1dGU7IHN1IG5vbWJyZSBlbiBsYSBsaXN0YSBkZWwgcG9ydGFsIGRlIFNhbHVkIAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICBBY3RpdmEuPC9wPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8cD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8aW5wdXQgbmFtZT0idGVybWlub3MiIGlkPSJ0ZXJtaW5vcyIgdHlwZT0iY2hlY2tib3giIHZhbHVlPSJTaSIgLz4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBBY2VwdG8gbG9zIHTDqXJtaW5vcyB5IGNvbmRpY2lvbmVzLjwvcD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgQWRlbcOhcywgY29uIHR1IGRvbmFjacOzbiwgb2J0ZW7DqXMgZGVzY3VlbnRvcyBlbiB0b2RhcyBsYXMgYWN0aXZpZGFkZXMgZGUgU2FsdWQgQWN0aXZhOiBjdXJzb3MsIGpvcm5hZGFzLCBjb25ncmVzb3MuPC9wPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8cD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxpbnB1dCBuYW1lPSJpbWFnZSIgc3JjPSJmb3JtX2ZpbGVzL0ZPUk1VTEFSSU9fMTUuanBnIiBoZWlnaHQ9IjM4IiB0eXBlPSJpbWFnZSIgd2lkdGg9IjExNSI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGltZyBvbkNsaWNrPSJyZXR1cm4gcmVzZXQoKTsiIHNyYz0iZm9ybV9maWxlcy9ib3Rvbi1jYW5jZWxfMTUuanBnIiBoZWlnaHQ9IjM4IiB3aWR0aD0iMTE1Ij48L3A+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPC9maWVsZHNldD4KCiAgPC9mb3JtPgogIAogIDxiciAvPgo8YnIgLz4KCgoKPHRhYmxlIHdpZHRoPSI2MzMiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjAiIGFsaWduPSJsZWZ0IiBiZ2NvbG9yPSIjMjY1MjE3IiBjbGFzcz0iaDMiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMTAiIGNlbGxwYWRkaW5nPSI3Ij4KICAgICAgPHRyPgogICAgICAgIDx0ZCBjbGFzcz0iaDUiPkZPUk1BUyBERSBQQUdPPC90ZD4KICAgICAgPC90cj4KICAgIDwvdGFibGU+CiAgICAgIDxzcGFuIGNsYXNzPSJoNCI+CiAgICA8L3NwYW4+PC90ZD4KICA8L3RyPgogIDx0cj4KICAgIDx0ZCBiZ2NvbG9yPSIjQ0NDQ0NDIj48YnIgLz4KICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIxMCIgY2VsbHNwYWNpbmc9IjUiPgogICAgICA8dHI+CiAgICAgICAgPHRkIGJnY29sb3I9IiNlMDY3MGEiPiZuYnNwOyZuYnNwOzxzcGFuIGNsYXNzPSJoNSI+VGFyamV0YSBkZSBDUsOJRElUTyAocG9yIGTDqWJpdG8gYXV0b23DoXRpY28pPC9zcGFuPjwvdGQ+CiAgICAgIDwvdHI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSIxODUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkIHdpZHRoPSIxMCI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTAiPjxpbWcgc3JjPSJpbWFnZXMvdmlzYW1hc3RlcmFtZS5qcGciICB3aWR0aD0iMjM2IiBoZWlnaHQ9IjYwIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CiAgICAgICAgICA8dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjciIGNlbGxwYWRkaW5nPSI1Ij4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPlNlIGxlIGRlYml0YXLDoSBkZSBzdSBjdWVudGEsIHRvZG9zIGxvcyBtZXNlcy4gTGUgcmVjb3JkYW1vcyBxdWUgZWwgZMOpYml0byBhdXRvbcOhdGljbyBkZSBzdSB0YXJqZXRhIGRlIGNyw6lkaXRvIHVzdGVkIGxvIHB1ZWRlIGNhbmNlbGFyIGVuIGVsIG1vbWVudG8gcXVlIGxvIGRlc2VlIGNvbXVuaWPDoW5kb3NlIGNvbiBub3NvdHJvczwvc3Bhbj48L3RkPgogICAgICAgICAgICA8L3RyPgogICAgICAgICAgPC90YWJsZT4KICAgICAgICAgIDxwPgogICAgICAgICAgPC9wPjwvdGQ+CiAgICAgIDwvdHI+CiAgICA8L3RhYmxlPgogICAgICA8cD4mbmJzcDs8L3A+CiAgICAgIDx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBhbGlnbj0iY2VudGVyIiBjZWxscGFkZGluZz0iMTAiIGNlbGxzcGFjaW5nPSI1Ij4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYmdjb2xvcj0iI2UwNjcwYSI+Jm5ic3A7IDxzcGFuIGNsYXNzPSJoNSI+RUZFQ1RJVk8gcG9yIMO6bmljYSB2ZXogPC9zcGFuPjwvdGQ+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSI3IiBjZWxscGFkZGluZz0iNSI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+PHNwYW4gY2xhc3M9ImgzIj48ZW0+VXN0ZWQgcmVhbGl6YXLDoSBsYSBkb25hY2nDs24gcG9yIMO6bmljYSB2ZXouIFB1ZWRlIGRvbmFyIGxhcyB2ZWNlcyBxdWUgcXVpZXJhLCBjb21wbGV0YW5kbyBudWV2YW1lbnRlIGVzdGUgZm9ybXVsYXJpbyBlIGluZ3Jlc2FuZG8gZWwgbW9udG8gZGVzZWFkby48L2VtPjwvc3Bhbj48L3RkPgogICAgICAgICAgICA8L3RyPgogICAgICAgICAgPC90YWJsZT4KICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSI3IiBjZWxscGFkZGluZz0iNSI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGJnY29sb3I9IiNDQ0NDQ0MiPjxzcGFuIGNsYXNzPSJoMiI+PHN0cm9uZz5Qb3IgIHRyYW5zZmVyZW5jaWEgYmFuY2FyaWEgbyBkZXDDs3NpdG88L3N0cm9uZz4gPC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT4KICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSI3IiBjZWxscGFkZGluZz0iNSI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNSUiPjxzcGFuIGNsYXNzPSJoMyI+QVJHRU5USU5BPC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9Ijg1JSI+PHNwYW4gY2xhc3M9ImgzIj48aW1nIHNyYz0iaW1hZ2VzL2dhbGljaWEuanBnIiB3aWR0aD0iMTA3IiBoZWlnaHQ9IjE5IiBhbGlnbj0ibWlkZGxlIiAvPjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjIiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMiIgY2VsbHBhZGRpbmc9IjciPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjIiPjxzcGFuIGNsYXNzPSJoMyI+RGF0b3MgcGFyYSBkZXDDs3NpdG9zIHkvbyB0cmFuc2ZlcmVuY2lhOjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIxJSI+PHNwYW4gY2xhc3M9ImgzIj5FbnRpZGFkIEJhbmNhcmlhOiA8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9Ijc5JSI+PHNwYW4gY2xhc3M9ImgzIj5CYW5jbyBHYWxpY2lhPC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQ+PHNwYW4gY2xhc3M9ImgzIj5UaXR1bGFyIGRlIEN1ZW50YTo8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQ+PHNwYW4gY2xhc3M9ImgzIj5TYWx1ZCBBY3RpdmE8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPlRpcG8gZGUgY3VlbnRhOjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPkN1ZW50YSBDb3JyaWVudGUgZW4gcGVzb3M8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPk7Dum1lcm8gZGUgY3VlbnRhOjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPjU1MTctOCAwNTktNDwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkPjxzcGFuIGNsYXNzPSJoMyI+Q0JVOjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPjAwNzAwNTk3MjAwMDAwMDU1MTc4NDY8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPkNVSVQ6PC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkPjxzcGFuIGNsYXNzPSJoMyI+MzAtNzA4MDE0NjMtNjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjIiIGNsYXNzPSJoMyI+UkVTVE8gREVMIE1VTkRPPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIyIiBjbGFzcz0iaDMiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMiIgY2VsbHBhZGRpbmc9IjciPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjIiPjxzcGFuIGNsYXNzPSJoMyI+RGF0b3MgcGFyYSBkZXDDs3NpdG9zIHkvbyB0cmFuc2ZlcmVuY2lhOjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMSUiPjxzcGFuIGNsYXNzPSJoMyI+RW50aWRhZCBCYW5jYXJpYTogPC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI3OSUiPjxzcGFuIGNsYXNzPSJoMyI+V2FjaG92aWEgQmFuayBOLkEuIC0gTmV3IFlvcms8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPlN3aWZ0IEFkZHJlc3M6PC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkPjxzcGFuIGNsYXNzPSJoMyI+UE5CUFVTM05OWUM8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPkZlZHdpcmU6PC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkPjxzcGFuIGNsYXNzPSJoMyI+MDI2MDA1MDkyPC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT4KICAgICAgICAgICAgPHA+PC9wPgogICAgICAgICAgICA8dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjciIGNlbGxwYWRkaW5nPSI1Ij4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0NDQ0NDQyI+PHNwYW4gY2xhc3M9ImgyIj5BY2Vyw6FuZG9zZSBhIG51ZXN0cmEgZW50aWRhZDwvc3Bhbj48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgICAgIDx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBhbGlnbj0iY2VudGVyIiBjZWxscGFkZGluZz0iMTAiIGNlbGxzcGFjaW5nPSI1Ij4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgIAogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGJnY29sb3I9IiNGRkZGRkYiPjx0YWJsZSB3aWR0aD0iMzAwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7Jm5ic3A7PGltZyBzcmM9ImltYWdlcy9zYWx1ZC5qcGciIHdpZHRoPSIxNTQiIGhlaWdodD0iMzkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT4KICAgICAgICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSI3IiBjZWxscGFkZGluZz0iNSI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkIGNsYXNzPSJoMyI+RGlyZWNjaW9uOiBBdi4gUHRlIFBlcsOzbiAoZXggUml2YWRhdmlhKSAyNTE0MC4gTWVybG8gQnMuIEFzLjxiciAvPgogICAgICAgICAgICAgICAgICAgICAgICBUZWwuOiAwMjIwIDQ4Mjg0MTggLyA0ODYxMTgwPGJyIC8+CiAgICAgICAgICAgICAgICAgICAgICAgIEUtbWFpbDogc2FsdWRhY3RpdmFAc2FsdWRhY3RpdmEub3JnLmFyPC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8L3RhYmxlPgogICAgICAgICAgICAgICAgICA8cD48L3A+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPgogICAgICAgICAgICA8dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjciIGNlbGxwYWRkaW5nPSI1Ij4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0NDQ0NDQyIgY2xhc3M9ImgyIj5ESU5FUk8gTUFJTDwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT4KICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIxMCIgY2VsbHNwYWNpbmc9IjUiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSIzMDAiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTAiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyOTAiPjxpbWcgc3JjPSJpbWFnZXMvZGluZXJvbWFpbC5qcGciIHdpZHRoPSI0MTEiIGhlaWdodD0iNTAiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgICAgICAgICAgIDx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iNyIgY2VsbHBhZGRpbmc9IjUiPgogICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBjbGFzcz0iaDMiPkltcHJpbWEgZWwgY3Vww7NuIHkgZGlyw61qYXNlIGEgbGFzIHN1Y3Vyc2FsZXMgaGFiaWxpdGFkYXMgcGFyYSByZWFsaXphciBlbCBwYWdvLiBMdWVnbyBww7NuZ2FzZSBlbiBjb250YWN0byBjb24gbm9zb3Ryb3MgcGFyYSBpbmZvcm1hcm5vcyBkZSBsYSBvcGVyYWNpw7NuLjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPC90YWJsZT4KICAgICAgICAgICAgICAgICAgPHA+PC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICA8L3RyPgogICAgICA8L3RhYmxlPgogICAgICA8cD48YnIgLz4KICAgIDwvcD48L3RkPgogIDwvdHI+CjwvdGFibGU+CgoKICAgICAKPC9kaXY+CgoKPCEtLWVuZCBvZiBDT05URU5JRE8yIC0tPgogICAgCiAgICA8ZGl2IGNsYXNzPSJjb250ZW5pZG8iIGlkPSJjb250ZW5pZG8zIj4KCgogICAgPC9kaXY+IDwhLS1lbmQgb2YgQ09OVEVOSURPMyAtLT4KICAgIAogICAgPGRpdiBjbGFzcz0iY29udGVuaWRvIiBpZD0iY29udGVuaWRvNCI+CiAgICAKICAgIDwvZGl2PiA8IS0tZW5kIG9mIENPTlRFTklETzQgLS0+CiAgICAKPGJyIC8+ICAgIAo8YnIgLz4KPGRpdiBjbGFzcz0iY29udGVuaWRvMiIgaWQ9ImNvbnRlbmlkbzUiIGFsaWduPSJjZW50ZXIiPjwvZGl2Pgo8cD4KICA8IS0tZW5kIG9mIENPTlRFTklETzQgLS0+CiAgPCEtLWVuZCBvZiBDT05URU5FRE9SIC0tPgo8L3A+Cgo8c2NyaXB0Pm11ZXN0cmFGb3JtYVBhZ28oZG9jdW1lbnQuZ2V0RWxlbWVudEJ5SWQoJ2Zvcm1hcGFnbycpLnZhbHVlKTwvc2NyaXB0Pgo8L2JvZHk+Cgo8L2h0bWw+Cg==]]></response> | |
| 236 | <responseRedirected>false</responseRedirected> | |
| 237 | </requestresponse> | |
| 238 | </issue> | |
| 239 | <issue> | |
| 240 | <serialNumber>3260534830746413056</serialNumber> | |
| 241 | <type>5244416</type> | |
| 242 | <name>Cookie without HttpOnly flag set</name> | |
| 243 | <host ip="200.20.20.201">http://www.example.org.ar</host> | |
| 244 | <path><![CDATA[/]]></path> | |
| 245 | <location><![CDATA[/]]></location> | |
| 246 | <severity>Low</severity> | |
| 247 | <confidence>Firm</confidence> | |
| 248 | <issueBackground><![CDATA[If the HttpOnly attribute is set on a cookie, then the cookie's value cannot be read or set by client-side JavaScript. This measure can prevent certain client-side attacks, such as cross-site scripting, from trivially capturing the cookie's value via an injected script.]]></issueBackground> | |
| 249 | <remediationBackground><![CDATA[There is usually no good reason not to set the HttpOnly flag on all cookies. Unless you specifically require legitimate client-side scripts within your application to read or set a cookie's value, you should set the HttpOnly flag by including this attribute within the relevant Set-cookie directive.<br><br>You should be aware that the restrictions imposed by the HttpOnly flag can potentially be circumvented in some circumstances, and that numerous other serious attacks can be delivered by client-side script injection, aside from simple cookie stealing.]]></remediationBackground> | |
| 250 | <issueDetail><![CDATA[The following cookie was issued by the application and does not have the HttpOnly flag set:<ul><li><b>PHPSESSID=94585aa0c11cf2e864d83e24678b9865; path=/</b></li></ul>The cookie appears to contain a session token, which may increase the risk associated with this issue. You should review the contents of the cookie to determine its function.]]></issueDetail> | |
| 251 | <requestresponse> | |
| 252 | <request base64="true"><![CDATA[R0VUIC8gSFRUUC8xLjENCkhvc3Q6IHd3dy5zYWx1ZGFjdGl2YS5vcmcuYXINClVzZXItQWdlbnQ6IE1vemlsbGEvNS4wIChNYWNpbnRvc2g7IEludGVsIE1hYyBPUyBYIDEwLjg7IHJ2OjIzLjApIEdlY2tvLzIwMTAwMTAxIEZpcmVmb3gvMjMuMA0KQWNjZXB0OiB0ZXh0L2h0bWwsYXBwbGljYXRpb24veGh0bWwreG1sLGFwcGxpY2F0aW9uL3htbDtxPTAuOSwqLyo7cT0wLjgNCkFjY2VwdC1MYW5ndWFnZTogZW4tVVMsZW47cT0wLjUNCkFjY2VwdC1FbmNvZGluZzogZ3ppcCwgZGVmbGF0ZQ0KQ29ubmVjdGlvbjoga2VlcC1hbGl2ZQ0KDQo=]]></request> | |
| 253 | <response base64="true"><![CDATA[SFRUUC8xLjEgMjAwIE9LDQpEYXRlOiBUaHUsIDA3IE5vdiAyMDEzIDE3OjEyOjAyIEdNVA0KU2VydmVyOiBBcGFjaGUvMi4yLjIzIChVbml4KSBtb2Rfc3NsLzIuMi4yMyBPcGVuU1NMLzAuOS44ZS1maXBzLXJoZWw1DQpYLVBvd2VyZWQtQnk6IFBIUC81LjIuMTcNCkV4cGlyZXM6IFRodSwgMTkgTm92IDE5ODEgMDg6NTI6MDAgR01UDQpDYWNoZS1Db250cm9sOiBuby1zdG9yZSwgbm8tY2FjaGUsIG11c3QtcmV2YWxpZGF0ZSwgcG9zdC1jaGVjaz0wLCBwcmUtY2hlY2s9MA0KUHJhZ21hOiBuby1jYWNoZQ0KU2V0LUNvb2tpZTogUEhQU0VTU0lEPTk0NTg1YWEwYzExY2YyZTg2NGQ4M2UyNDY3OGI5ODY1OyBwYXRoPS8NCktlZXAtQWxpdmU6IHRpbWVvdXQ9MjAsIG1heD0yMDANCkNvbm5lY3Rpb246IEtlZXAtQWxpdmUNCkNvbnRlbnQtVHlwZTogdGV4dC9odG1sDQpDb250ZW50LUxlbmd0aDogNjA2MDYNCg0KIDxoZWFkPgo8bWV0YSBodHRwLWVxdWl2PSJDb250ZW50LVR5cGUiIGNvbnRlbnQ9InRleHQvaHRtbDsgY2hhcnNldD1pc28tODg1OS0xIiAvPgo8dGl0bGU+U2FsdWQgQWN0aXZhIC0gQWJ1c28gdmlvbGVuY2lhIHkgbWFsdHJhdG88L3RpdGxlPgoKPHNjcmlwdD4gCiAgICAvL2VzdG8gcGFyYSBwYXNhcmxlIGFsIGZsYXNoIGxhcyB2YXJpYWxiZXMgZGVsIHBocAogCQoKCXZhciBib3Q9Jyc7Ci8vYWxlcnQodmFyaWFibGVTZXJ2aWRvcik7Cjwvc2NyaXB0Pgo8c2NyaXB0IGxhbmd1YWdlPSJKYXZhU2NyaXB0IiB0eXBlPSJ0ZXh0L0phdmFTY3JpcHQiPgo8IS0tCmZ1bmN0aW9uIE1NX3ByZWxvYWRJbWFnZXMoKSB7IC8vdjMuMAogIHZhciBkPWRvY3VtZW50OyBpZihkLmltYWdlcyl7IGlmKCFkLk1NX3ApIGQuTU1fcD1uZXcgQXJyYXkoKTsKICAgIHZhciBpLGo9ZC5NTV9wLmxlbmd0aCxhPU1NX3ByZWxvYWRJbWFnZXMuYXJndW1lbnRzOyBmb3IoaT0wOyBpPGEubGVuZ3RoOyBpKyspCiAgICBpZiAoYVtpXS5pbmRleE9mKCIjIikhPTApeyBkLk1NX3Bbal09bmV3IEltYWdlOyBkLk1NX3BbaisrXS5zcmM9YVtpXTt9fQp9Ci8vLS0+Cjwvc2NyaXB0Pgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KCjwvaGVhZD4KCjxzY3JpcHQgbGFuZ3VhZ2U9IkphdmFTY3JpcHQiIHR5cGU9InRleHQvSmF2YVNjcmlwdCI+CjwhLS0KZnVuY3Rpb24gTU1fcmVsb2FkUGFnZShpbml0KSB7ICAvL3JlbG9hZHMgdGhlIHdpbmRvdyBpZiBOYXY0IHJlc2l6ZWQKICBpZiAoaW5pdD09dHJ1ZSkgd2l0aCAobmF2aWdhdG9yKSB7aWYgKChhcHBOYW1lPT0iTmV0c2NhcGUiKSYmKHBhcnNlSW50KGFwcFZlcnNpb24pPT00KSkgewogICAgZG9jdW1lbnQuTU1fcGdXPWlubmVyV2lkdGg7IGRvY3VtZW50Lk1NX3BnSD1pbm5lckhlaWdodDsgb25yZXNpemU9TU1fcmVsb2FkUGFnZTsgfX0KICBlbHNlIGlmIChpbm5lcldpZHRoIT1kb2N1bWVudC5NTV9wZ1cgfHwgaW5uZXJIZWlnaHQhPWRvY3VtZW50Lk1NX3BnSCkgbG9jYXRpb24ucmVsb2FkKCk7Cn0KTU1fcmVsb2FkUGFnZSh0cnVlKTsKLy8tLT4KCjwvc2NyaXB0Pgo8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoKCjwvaGVhZD4KCjxib2R5IGJhY2tncm91bmQ9ImltZy9mb25kb19kZWdyYWRlLmpwZyIgdG9wbWFyZ2luPSIwIj4KPHRhYmxlIHdpZHRoPSIxMDA1IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgPHRyPiAKICAgIDx0ZCB3aWR0aD0iOTYiPjxpbWcgc3JjPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzBfMDEuanBnIiB3aWR0aD0iOTYiIGhlaWdodD0iMjA4IiAvPjwvdGQ+CiAgICA8dGQgd2lkdGg9IjgwOSI+IDxzY3JpcHQgdHlwZT0idGV4dC9qYXZhc2NyaXB0Ij4KQUNfRkxfUnVuQ29udGVudCggJ2NvZGViYXNlJywnaHR0cDovL2Rvd25sb2FkLm1hY3JvbWVkaWEuY29tL3B1Yi9zaG9ja3dhdmUvY2Ficy9mbGFzaC9zd2ZsYXNoLmNhYiN2ZXJzaW9uPTcsMCwxOSwwJywnd2lkdGgnLCc4MDknLCdoZWlnaHQnLCcyMDgnLCdzcmMnLCdzd2YvaGVhZGVyJywncXVhbGl0eScsJ2hpZ2gnLCdwbHVnaW5zcGFnZScsJ2h0dHA6Ly93d3cubWFjcm9tZWRpYS5jb20vZ28vZ2V0Zmxhc2hwbGF5ZXInLCdtb3ZpZScsJ3N3Zi9oZWFkZXInICk7IC8vZW5kIEFDIGNvZGUKPC9zY3JpcHQ+IDxub3NjcmlwdD4KICAgICAgPG9iamVjdCBjbGFzc2lkPSJjbHNpZDpEMjdDREI2RS1BRTZELTExY2YtOTZCOC00NDQ1NTM1NDAwMDAiIGNvZGViYXNlPSJodHRwOi8vZG93bmxvYWQubWFjcm9tZWRpYS5jb20vcHViL3Nob2Nrd2F2ZS9jYWJzL2ZsYXNoL3N3Zmxhc2guY2FiI3ZlcnNpb249NywwLDE5LDAiIHdpZHRoPSI4MDkiIGhlaWdodD0iMjA4Ij4KICAgICAgICA8cGFyYW0gbmFtZT0ibW92aWUiIHZhbHVlPSJzd2YvaGVhZGVyLnN3ZiIgLz4KICAgICAgICA8cGFyYW0gbmFtZT0icXVhbGl0eSIgdmFsdWU9ImhpZ2giIC8+CiAgICAgICAgPGVtYmVkIHNyYz0ic3dmL2hlYWRlci5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9IjgwOSIgaGVpZ2h0PSIyMDgiPjwvZW1iZWQ+IAogICAgICA8L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIHdpZHRoPSIxMiUiIHJvd3NwYW49IjUiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iIzAwMDAwMCI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI0NjEiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmFja2dyb3VuZD0iaW1nL1F1aWVuZXNTb21vc19BMl8wXzEzLmpwZyI+IAogICAgICA8c2NyaXB0IHR5cGU9InRleHQvamF2YXNjcmlwdCI+CkFDX0ZMX1J1bkNvbnRlbnQoICdjb2RlYmFzZScsJ2h0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCcsJ3dpZHRoJywnOTYnLCdoZWlnaHQnLCc0NjEnLCdzcmMnLCdzd2Yvc3VibWVudScsJ3F1YWxpdHknLCdoaWdoJywncGx1Z2luc3BhZ2UnLCdodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyJywnbW92aWUnLCdzd2Yvc3VibWVudScgKTsgLy9lbmQgQUMgY29kZQo8L3NjcmlwdD4gPG5vc2NyaXB0PgogICAgICA8b2JqZWN0IGNsYXNzaWQ9ImNsc2lkOkQyN0NEQjZFLUFFNkQtMTFjZi05NkI4LTQ0NDU1MzU0MDAwMCIgY29kZWJhc2U9Imh0dHA6Ly9kb3dubG9hZC5tYWNyb21lZGlhLmNvbS9wdWIvc2hvY2t3YXZlL2NhYnMvZmxhc2gvc3dmbGFzaC5jYWIjdmVyc2lvbj02LDAsMjksMCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+CiAgICAgICAgPHBhcmFtIG5hbWU9Im1vdmllIiB2YWx1ZT0ic3dmL3N1Ym1lbnUuc3dmIiAvPgogICAgICAgIDxwYXJhbSBuYW1lPSJxdWFsaXR5IiB2YWx1ZT0iaGlnaCIgLz4KICAgICAgICA8ZW1iZWQgc3JjPSJzd2Yvc3VibWVudS5zd2YiIHF1YWxpdHk9ImhpZ2giIHBsdWdpbnNwYWdlPSJodHRwOi8vd3d3Lm1hY3JvbWVkaWEuY29tL2dvL2dldGZsYXNocGxheWVyIiB0eXBlPSJhcHBsaWNhdGlvbi94LXNob2Nrd2F2ZS1mbGFzaCIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjQ2MSI+PC9lbWJlZD48L29iamVjdD4KICAgICAgPC9ub3NjcmlwdD48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCIgYmdjb2xvcj0iI0ZGRkZGRiI+CiAgICAgICAgPHRyPiAKICAgICAgICAgIDx0ZCB3aWR0aD0iMTciIHJvd3NwYW49IjciPjxwPiZuYnNwOzwvcD48L3RkPgogICAgICAgICAgPHRkIHdpZHRoPSIxNzIiIGFsaWduPSJjZW50ZXIiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxpbWcgc3JjPSJpbWcvM3B4LmpwZyIgd2lkdGg9IjUiIGhlaWdodD0iNSI+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciI+PGxpbmsgaHJlZj0iLi4vZXN0aWxvcy5jc3MiIHJlbD0ic3R5bGVzaGVldCIgdHlwZT0idGV4dC9jc3MiIC8+Cjxib2R5IGJnY29sb3I9IiNDQ0NDQ0MiIHRvcG1hcmdpbj0iNiBweCI+PHRhYmxlIHdpZHRoPSIxNjUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIzIiBiZ2NvbG9yPSIjRkZGRkZGIj4KPHRyPgogICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTkxIiBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiAgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MThfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+SG9tZTwvYT48L3RkPgogIDwvdHI+Cjx0cj4KICA8dGQgaGVpZ2h0PSIyOCIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj4mbmJzcDsmbmJzcDtOb3RpY2lhczwvYT48L3RkPgo8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJkb25hY2lvbmVzLyIgdGFyZ2V0PSJfYmxhbmsiIGNsYXNzPSJmb25kb2JvdG9uIj5Eb25hY2lvbmVzPC9hPjwvdGQ+CiAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI4IiBiYWNrZ3JvdW5kPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiA+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciICB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yM19uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5IaXN0b3JpYWwgZGUgbmV3c2xldHRlcnM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjgiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTEzYSIgY2xhc3M9ImZvbmRvYm90b24iPkVudmlhciBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiJoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0yNl9uZXciIGNsYXNzPSJmb25kb2JvdG9uIj5WZXIgdHJhYmFqb3MgZGUgdXN1YXJpb3M8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJpbmRleC5waHA/aWQ9MTZfbmV3IiBjbGFzcz0iZm9uZG9ib3RvbiI+U2FsdWQgQWN0aXZhIHByZW5zYTwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgPjxpbWcgc3JjPSIuLi9pbWcvcmVkaXNlbm9fMTEuanBnIiB3aWR0aD0iNiIgaGVpZ2h0PSIyOCIgYWxpZ249ImFic21pZGRsZSIgLz48YSBocmVmPSJtYWlsdG86c2FsdWRhY3RpdmFAc2FsdWRhY3RpdmEub3JnLmFyIiBjbGFzcz0iZm9uZG9ib3RvbiI+TWFuZCZhYWN1dGU7IHR1IEMuVi48L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgIHdpZHRoPSI2ImhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTIxX25ldyIgY2xhc3M9ImZvbmRvYm90b24iPkluZm9ybWFjaSZvYWN1dGU7biBkZSBpbnRlciZlYWN1dGU7czwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgYmFja2dyb3VuZD0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyI+PGltZyBzcmM9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciIHdpZHRoPSI2IiBoZWlnaHQ9IjI4IiBhbGlnbj0iYWJzbWlkZGxlIiAvPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xMF80IiBjbGFzcz0iZm9uZG9ib3RvbiI+Q29uZ3Jlc29zCiAgICAgICAgICAgICAgICAgIHkgSm9ybmFkYXM8L2E+PC90ZD4KICA8L3RyPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMTkiIGJhY2tncm91bmQ9Ii4uL2ltZy9yZWRpc2Vub18xMS5qcGciID48aW1nIHNyYz0iLi4vaW1nL3JlZGlzZW5vXzExLmpwZyIgd2lkdGg9IjYiIGhlaWdodD0iMjgiIGFsaWduPSJhYnNtaWRkbGUiIC8+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTExIiBjbGFzcz0iZm9uZG9ib3RvbiI+UmVnaXN0cmFjaSZvYWN1dGU7bjwvYT48L3RkPgogIDwvdHI+CiAgICAgICAgICAgCiAgICAgICAgICA8L3RhYmxlPgo8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGFsaWduPSJjZW50ZXIiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNSIgdGFyZ2V0PSJfYmxhbmsiPjxicj4KICAgICAgICAgICAgICAgICAgPGltZyBzcmM9ImltZy9iYW5uZXJfZG9uYWNpb25lcy5qcGciIHdpZHRoPSIxNjIiIGhlaWdodD0iMTIwIiBib3JkZXI9IjAiPjxicj4KICAgICAgICAgICAgICAgICAgPGJyPgogICAgICAgICAgICAgICAgICA8aW1nIHNyYz0iaW1nL2JvdG9uRm9yby5naWYiIHdpZHRoPSIxNzIiIGhlaWdodD0iMTE3IiBib3JkZXI9IjAiPjwvYT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTY3IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjkiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzAzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iOSIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTQ5IiBiYWNrZ3JvdW5kPSJpbWcvY2hpY29zX3BlcmRpZG9zXzA1LmdpZiI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDUuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMCI+PGltZyBzcmM9ImltZy9jaGljb3NfcGVyZGlkb3NfMDcuZ2lmIiB3aWR0aD0iOSIgaGVpZ2h0PSI5IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMi5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEyLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9InNyYy9pbWdfdXAvMjMwODIwMTIuMS5qcGciIHdpZHRoPSIxNDkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYmFja2dyb3VuZD0iaW1nL2NoaWNvc19wZXJkaWRvc18xMy5naWYiPjxpbWcgc3JjPSJpbWcvY2hpY29zX3BlcmRpZG9zXzEzLmdpZiIgd2lkdGg9IjkiIGhlaWdodD0iMTEiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNi5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iNSIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTcuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xNy5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgYmdjb2xvcj0iI0ZFRTdDRiIgY2xhc3M9InRpdHVsb2hvbWU1Ij48c3Ryb25nPk5pJm50aWxkZTtvcyBwZXJkaWRvczxicj4KICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0yOSIgY2xhc3M9ImJvdG9uIj5bVmVyIG0mYWFjdXRlO3NdPC9hPjwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIGJhY2tncm91bmQ9ImltZy9jaGljb3NfcGVyZGlkb3NfMTkuZ2lmIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18xOS5naWYiIHdpZHRoPSI5IiBoZWlnaHQ9IjkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIj48aW1nIHNyYz0iaW1nL2NoaWNvc19wZXJkaWRvc18yMC5naWYiIHdpZHRoPSIxNjciIGhlaWdodD0iMjUiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4NCgkJCQkNCgkJCQk8Zm9ybSBhY3Rpb249ImluZGV4LnBocD9pZD0xMSIgIG1ldGhvZD0icG9zdCI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9penExLmpwZyIgd2lkdGg9IjEyIiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9hcnJpYmEuanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2VzcV9kZXIxLmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjQ4IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgIDwvdHI+DQogICAgICAgICAgICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMiIgdmFsaWduPSJ0b3AiIGNsYXNzPSJyZWdGb25kbzEiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9penEuanBnIiB3aWR0aD0iMTIiIGhlaWdodD0iMTIiIC8+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSI5NCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV90aXQuanBnIiB3aWR0aD0iNjYiIGhlaWdodD0iMjMiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSI1MCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJyZWdpc3RyYXJzZSI+SW5ncmVzJmFhY3V0ZTsgDQogICAgICAgICAgICAgIHR1cyBkYXRvcyB5IHJlY2liJmlhY3V0ZTsgbGEgbWVqb3IgaW5mb3JtYWNpJm9hY3V0ZTtuIGEgdHJhdiZlYWN1dGU7cyANCiAgICAgICAgICAgICAgZGUgbnVlc3RybzxzdHJvbmc+IE5ld3NsZXR0ZXI8L3N0cm9uZz4uIDxzdHJvbmc+PHNwYW4gY2xhc3M9ImdyYXRpcyI+R3JhdGlzITwvc3Bhbj48L3N0cm9uZz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI1IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9InRyYWJTRUNDSU9OIj5Ob21icmU8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBjbGFzcz0icmVnQ0VMREEiPjxpbnB1dCBuYW1lPSJub21icmUiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0ibm9tYnJlIiAvPjwvdGQ+DQogICAgICAgICAgPC90cj4NCiAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0idHJhYlNFQ0NJT04iPkFwZWxsaWRvPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iYXBlbGxpZG8iIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iYXBlbGxpZG8iIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJ0cmFiU0VDQ0lPTiI+RS1tYWlsPC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InJlZ0NFTERBIj48aW5wdXQgbmFtZT0iZW1haWwiIHR5cGU9InRleHQiIGNsYXNzPSJyZWdDRUxEQWlucHV0IiBpZD0iZW1haWwiIC8+PC90ZD4NCiAgICAgICAgICA8L3RyPg0KICAgICAgICAgIDx0cj4gDQogICAgICAgICAgICA8dGQgY2xhc3M9InRyYWJTRUNDSU9OIj4mbmJzcDs8L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgICAgPHRyPiANCiAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idHJhYlNFQ0NJT04iPjxpbnB1dCB0eXBlPSJpbWFnZSIgc3JjPSJpbWcvcmVnaXN0cmF0ZV9ib3Rvbi5qcGciIHdpZHRoPSIxMTciIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L3RkPg0KICAgICAgICAgIDwvdHI+DQogICAgICAgIDwvdGFibGU+PC90ZD4NCiAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE0IiB2YWxpZ249InRvcCIgY2xhc3M9InJlZ0ZvbmRvMiI+PGltZyBzcmM9ImltZy9yZWdpc3RyYXRlX2Rlci5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIxNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KICAgICAgICAgICAgICAgICAgICA8dHI+IA0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTIiIGhlaWdodD0iMjQiPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfaXpxMi5qcGciIHdpZHRoPSIxMiIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjI0Ij48aW1nIHNyYz0iaW1nL3JlZ2lzdHJhdGVfYWJham8uanBnIiB3aWR0aD0iMTQ2IiBoZWlnaHQ9IjI0IiAvPjwvdGQ+DQogICAgICAgICAgICAgICAgICAgICAgPHRkPjxpbWcgc3JjPSJpbWcvcmVnaXN0cmF0ZV9lc3FfZGVyMi5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSIyNCIgLz48L3RkPg0KICAgICAgICAgICAgICAgICAgICA8L3RyPg0KCQkJCQkNCgkJCQkJPC9mb3JtPg0KICAgICAgICAgICAgICAgICAgPC90YWJsZT4NCjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4gCiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPiAKICAgICAgICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTcwIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUyIj4KCQkJCQkJCQkJCQkJCQkJCTwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9jbGF1ZGlhMl8wMy5qcGciIHdpZHRoPSIxNzQiIGhlaWdodD0iMjUwIiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcCI+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8L3RhYmxlPiAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICA8dGQgcm93c3Bhbj0iNyIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nLzV4NS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjciPjwvdGQ+CiAgICAgICAgICA8dGQgY29sc3Bhbj0iMiIgcm93c3Bhbj0iNCIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPGZvcm0gYWN0aW9uPSJsb2dpbi5waHAiIG1ldGhvZD0icG9zdCIgbmFtZT0iZm9ybTIiPgoKICAgICAgICAgICAgICA8dHI+IAogICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIxOSIgY29sc3Bhbj0iMiIgYWxpZ249ImxlZnQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIiA+IAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8c3Ryb25nPlVzdWFyaW8gbm8gcmVnaXN0cmFkbzwvc3Ryb25nPiAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9mb250PiA8L3N0cm9uZz4gCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDkiIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPlVzdWFyaW8mbmJzcDsmbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzOSIgdmFsaWduPSJtaWRkbGUiPjxpbnB1dCBuYW1lPSJ1c3VhcmlvIiB0eXBlPSJ0ZXh0IiBjbGFzcz0icmVnIiBpZD0idXN1YXJpbyIgc2l6ZT0iNyI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjciIGFsaWduPSJyaWdodCIgdmFsaWduPSJtaWRkbGUiIGNsYXNzPSJjb250ZW5pZG8iPkNvbnRyYXNlJm50aWxkZTthJm5ic3A7Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzkiIHZhbGlnbj0ibWlkZGxlIj48aW5wdXQgbmFtZT0icGFzcyIgdHlwZT0icGFzc3dvcmQiIGNsYXNzPSJyZWciIGlkPSJwYXNzIiBzaXplPSI3Ij48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MiIgYWxpZ249InJpZ2h0IiB2YWxpZ249Im1pZGRsZSIgY2xhc3M9ImJvdG9uIj48aW5wdXQgdHlwZT0iaW1hZ2UiIHNyYz0iaW1nL3JlZy5qcGciIHdpZHRoPSI1OCIgaGVpZ2h0PSIzMCI+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPiAKICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjciIGhlaWdodD0iMTkiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgPjxhIGhyZWY9Imh0dHA6Ly93d3cuZmFjZWJvb2suY29tL2hvbWUucGhwPyMhL3BhZ2VzL01lcmxvLUFyZ2VudGluYS9TQUxVRC1BQ1RJVkEvMTAwNTgzNTQzMzE3MzIyP3JlZj10cyZhamF4cGlwZT0xJl9fYT03IiB0YXJnZXQ9Il9ibGFuayI+PGltZyBzcmM9ImltZy9mYWNlYm9vay5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzExIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj48ZGl2IGFsaWduPSJsZWZ0Ij48YSBocmVmPSJodHRwOi8vdHdpdHRlci5jb20vU2FsdWRBY3RpdmFPTkciIHRhcmdldD0iX2JsYW5rIj48aW1nIHNyYz0iaW1nL3R3aXRlci5qcGciIHdpZHRoPSIyMCIgaGVpZ2h0PSIyMCIgYm9yZGVyPSIwIj48L2E+PC9kaXY+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSI1IiBhbGlnbj0icmlnaHQiIHZhbGlnbj0ibWlkZGxlIiBjbGFzcz0iY29udGVuaWRvIj48bGFiZWw+PGZvbnQgc2l6ZT0iLTYiPlNpCiAgICAgICAgICAgICAgICAgICAgICAgdG9kYXYmaWFjdXRlO2Egbm8gZXMgdXN1YXJpbyA8L2ZvbnQ+IDxhIGhyZWY9ImluZGV4LnBocD9pZD0xMSIgY2xhc3M9ImJvdG9uIj48Zm9udCBzaXplPSItNiI+cmVnJmlhY3V0ZTtzdHJlc2UKICAgICAgICAgICAgICAgICAgICAgICAgYXF1JmlhY3V0ZTsgPGZvbnQgY29sb3I9IiM2NjY2NjYiPiYjODIyNjs8L2ZvbnQ+PC9mb250PjwvYT4gPGEgaHJlZj0iaW5kZXgucGhwP2lkPTEyIiBjbGFzcz0iYm90b24xIj48Zm9udCBzaXplPSItNiI+b2x2aWRlIG1pIGNvbnRyYXNlJm50aWxkZTthPC9mb250PjwvYT48L2xhYmVsPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE3Ij4mbmJzcDsgPC90ZD4KICAgICAgICAgICAgICA8L3RyPgoJCQkgIDwvZm9ybT4KCiAgICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgICA8IURPQ1RZUEUgaHRtbCBQVUJMSUMgIi0vL1czQy8vRFREIFhIVE1MIDEuMCBUcmFuc2l0aW9uYWwvL0VOIiAiaHR0cDovL3d3dy53My5vcmcvVFIveGh0bWwxL0RURC94aHRtbDEtdHJhbnNpdGlvbmFsLmR0ZCI+CjxodG1sIHhtbG5zPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5L3hodG1sIj4KPGhlYWQ+CjxtZXRhIGh0dHAtZXF1aXY9IkNvbnRlbnQtVHlwZSIgY29udGVudD0idGV4dC9odG1sOyBjaGFyc2V0PWlzby04ODU5LTEiIC8+Cjx0aXRsZT5Eb2N1bWVudG8gc2luIHQmaWFjdXRlO3R1bG88L3RpdGxlPgo8bGluayBocmVmPSJlc3RpbG9zLmNzcyIgcmVsPSJzdHlsZXNoZWV0IiB0eXBlPSJ0ZXh0L2NzcyIgLz4KPHNjcmlwdCBsYW5ndWFnZT0iSmF2YVNjcmlwdCIgdHlwZT0idGV4dC9KYXZhU2NyaXB0Ij4KPCEtLQpmdW5jdGlvbiBNTV9yZWxvYWRQYWdlKGluaXQpIHsgIC8vcmVsb2FkcyB0aGUgd2luZG93IGlmIE5hdjQgcmVzaXplZAogIGlmIChpbml0PT10cnVlKSB3aXRoIChuYXZpZ2F0b3IpIHtpZiAoKGFwcE5hbWU9PSJOZXRzY2FwZSIpJiYocGFyc2VJbnQoYXBwVmVyc2lvbik9PTQpKSB7CiAgICBkb2N1bWVudC5NTV9wZ1c9aW5uZXJXaWR0aDsgZG9jdW1lbnQuTU1fcGdIPWlubmVySGVpZ2h0OyBvbnJlc2l6ZT1NTV9yZWxvYWRQYWdlOyB9fQogIGVsc2UgaWYgKGlubmVyV2lkdGghPWRvY3VtZW50Lk1NX3BnVyB8fCBpbm5lckhlaWdodCE9ZG9jdW1lbnQuTU1fcGdIKSBsb2NhdGlvbi5yZWxvYWQoKTsKfQpNTV9yZWxvYWRQYWdlKHRydWUpOwoKZnVuY3Rpb24gTU1fcHJlbG9hZEltYWdlcygpIHsgLy92My4wCiAgdmFyIGQ9ZG9jdW1lbnQ7IGlmKGQuaW1hZ2VzKXsgaWYoIWQuTU1fcCkgZC5NTV9wPW5ldyBBcnJheSgpOwogICAgdmFyIGksaj1kLk1NX3AubGVuZ3RoLGE9TU1fcHJlbG9hZEltYWdlcy5hcmd1bWVudHM7IGZvcihpPTA7IGk8YS5sZW5ndGg7IGkrKykKICAgIGlmIChhW2ldLmluZGV4T2YoIiMiKSE9MCl7IGQuTU1fcFtqXT1uZXcgSW1hZ2U7IGQuTU1fcFtqKytdLnNyYz1hW2ldO319Cn0KLy8tLT4KPC9zY3JpcHQ+CiAgICAgICAgICAgICA8c2NyaXB0IHNyYz0iU2NyaXB0cy9BQ19SdW5BY3RpdmVDb250ZW50LmpzIiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPjwvc2NyaXB0PgoJCQkgCjxzdHlsZSB0eXBlPSJ0ZXh0L2NzcyI+CjwhLS0KI0xheWVyMSB7Cglwb3NpdGlvbjphYnNvbHV0ZTsKCXdpZHRoOjY1MXB4OwoJaGVpZ2h0OjIxOHB4OwoJei1pbmRleDoxOwp9CiNMYXllcjIgewoJcG9zaXRpb246YWJzb2x1dGU7Cgl3aWR0aDoyMDBweDsKCWhlaWdodDoxMTVweDsKCXotaW5kZXg6MTsKCXZpc2liaWxpdHk6IHZpc2libGU7Cn0KLkVzdGlsbzEgewoJZm9udC1zaXplOiAxOHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzIgewoJZm9udC1zaXplOiAxNHB4OwoJZm9udC13ZWlnaHQ6IGJvbGQ7Cn0KLkVzdGlsbzMge2NvbG9yOiAjNTA2OTkwOyBsaW5lLWhlaWdodDogMTJweDsgdGV4dC1kZWNvcmF0aW9uOiBub25lOyBmb250LWZhbWlseTogVGFob21hO30KLS0+Cjwvc3R5bGU+CjwvaGVhZD4KCjxib2R5IGxlZnRtYXJnaW49IjIiIG1hcmdpbndpZHRoPSIyIj4KPHRhYmxlIHdpZHRoPSI2MDgiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICA8dHI+CiAgICA8dGQgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCB3aWR0aD0iMiUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzA3LmpwZyIgd2lkdGg9IjI0IiBoZWlnaHQ9IjE0IiAvPjwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI5MCUiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18wNy5qcGciPiZuYnNwOzwvdGQ+CiAgICAgICAgPHRkIHdpZHRoPSI4JSIgYWxpZ249InJpZ2h0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wOS5qcGciIHdpZHRoPSI0NSIgaGVpZ2h0PSIxNyIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogIDwvdHI+CiAgPHRyPgogICAgPHRkIGNvbHNwYW49IjQiPjxiciAvPgogICAgICA8dGFibGUgd2lkdGg9Ijk4JSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICA8dHI+CiAgICAgICAgPHRkIHdpZHRoPSIyJSI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgICA8dGQgd2lkdGg9IjkzJSI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CjwhLS0gSU5JQ0lPIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzIzMDQyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjIvMTEvMjAxMzwvc3Bhbj48YnI+SVYgQ29uZ3Jlc28gSW50ZXJuYWNpb25hbCB2aW9sZW5jaWEsIG1hbHRyYXRvIHkgYWJ1c288L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxzdHJvbmc+MTQsIDE1IHkgMTYgZGUgTm92aWVtYnJlIEFCSUVSVEEgTEEgSU5TQ1JJUENJJk9hY3V0ZTtOISAoY29uIGRlc2N1ZW50byBoYXN0YSBlbCAyNy84KTxiciAvPjwvc3Ryb25nPjwvcD4NCjxwPjxzdHJvbmc+QUJJRVJUQSBMQSBSRUNFUENJJk9hY3V0ZTtOIERFIFRSQUJBSk88YSBocmVmPSJodHRwOi8vd3d3LmNvbmdyZXNvdmlvbGVuY2lhLmNvbS9pbmRleC5waHA/aWQ9bW9kYWxpZGFkZXMiIHRhcmdldD0iX2JsYW5rIj4gKG1hcyBpbmZvKTwvYT48L3N0cm9uZz48L3A+DQo8cD48c3BhbiBzdHlsZT0iY29sb3I6ICNmZjY2MDA7Ij48c3Ryb25nPk9yZ2FuaXphOiBTYWx1ZCBBY3RpdmE8L3N0cm9uZz48L3NwYW4+PC9wPg0KPHA+PHNwYW4gc3R5bGU9ImNvbG9yOiAjZmY2NjAwOyI+SW5jcmlwdG9zIGFsIFBvcnRhbCBkZSBTYWx1ZCBBY3RpdmEsIGltcG9ydGFudGVzIGRlc2N1ZW50b3MhPGJyIC8+PC9zcGFuPjwvcD4NCjxwPkx1Z2FyIGRlIFJlYWxpemFjaSZvYWN1dGU7biB5IGNvbGFib3JhY2lvbjogVW5pdmVyc2lkYWQgZGVsIEVzdGUsIExhIFBsYXRhIEJ1ZW5vcyBBaXJlczwvcD4NCjxwPk1hcyBkZSAxNTAgdHJhYmFqb3MgcHJlc2VudGFkb3MsIHVsdGltb3MgZGlhcyBwYXJhIGluc2NyaWJpcnNlIGNvbiBkZXNjdWVudG8hITwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPkluc2NyaWJpcnNlPC9hPjwvcD4NCjxwPjxhIGhyZWY9Imh0dHA6Ly93d3cuY29uZ3Jlc292aW9sZW5jaWEuY29tL2luZGV4LnBocD9pZD1pbnNjcmlwY2lvbiIgdGFyZ2V0PSJfYmxhbmsiPjxiciAvPjwvYT48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAxIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDEiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MDQvMTEvMjAxMzwvc3Bhbj48YnI+RWwgY29sZWdpbyBkZSBQc2lj82xvZ29zIGRlIEPzcmRvYmEgc2UgcHJvbnVuY2lhIGVuIHJlbGFjafNuIGFsIFNBUCB5IGVuIGNvbmNvcmRhbmNpYSBjb24gbG8gZXhwcmVzYWRvIHBvciBlbCBDb2xlZ2lvIGRlIFBzaWPzbG9nb3MgZGUgTWFyIGRlbCBQbGF0YSB5IGVsIENvbGVnaW8gZGUgUHNpY/Nsb2dvcyBkZSBsYSAgUHJvdmluY2lhIGRlIEJ1ZW5vcyBBaXJlczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+Jm5ic3A7PC9wPg0KPHA+TGFzIGNvbnRyb3ZlcnNpYXMgZ2VuZXJhZGFzIGVuIHJlbGFjaSZvYWN1dGU7biBhbCAic2luZHJvbWUgZGUgYWxpZW5hY2kmb2FjdXRlO24gcGFyZW50YSIgU0FQLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMxMCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzEwIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTU2IiByb3dzcGFuPSIyIiB2YWxpZ249InRvcCI+CgkJCQkKCQkJCTx0YWJsZSB3aWR0aD0iMzIlIiBib3JkZXI9IjEiIGNlbGxzcGFjaW5nPSIzIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJzcmMvaW1nX3VwLzE2MTAyMDEzLjAuanBnIiB3aWR0aD0iMTQ2IiAvPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPgoJCQkJCQkJCTwvdGQ+ICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTYvMTAvMjAxMzwvc3Bhbj48YnI+U2FsdWQgQWN0aXZhIG90b3JnYSBtZWRpYXMgYmVjYXMgcGFyYSBlbCBJViBDb25ncmVzbyBJbnRlcm5hY2lvbmFsLCBWIE5hY2lvbmFsLCBWSSBSZWdpb25hbCBWaW9sZW5jaWEsIE1hbHRyYXRvIHkgQWJ1c28uPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD4mbmJzcDs8L3A+DQo8cD5TZXImYWFjdXRlO24gb3RvcmdhZGFzIDUwIG1lZGlhcyBiZWNhcywgcXVlZGFuIHBvY2FzISEhIGNvbmRpY2lvbjo8L3A+DQo8cD5QZXJ0ZW5lY2VyIGFsIGFtYml0byBwdWJsaWNvIG8gYSBPTkcsIHNlIGNvbnNpZGVyYSB0YW1iaWVuIGxhIGRpc3RhbmNpYSBhbCBsdWdhciBkZWwgZXZlbnRvISEhIGVzIG11eSBzZW5jaWxsbywgc29sbyBkZWJlcyBlbnZpYXIgdW4gZW1haWwuLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwOSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA5Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjI0LzA3LzIwMTM8L3NwYW4+PGJyPk5FQ0VTSVRBTU9TIERFIFNVIFNPTElEQVJJREFEIEhBQ0lBIExPUyBOSdFPUyBZIE5J0UFTISEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPjxiciAvPjwvc3Bhbj48L3N0cm9uZz48L3A+DQo8cD48c3Ryb25nPjxzcGFuIHN0eWxlPSJ0ZXh0LWRlY29yYXRpb246IHVuZGVybGluZTsiPlBST0dSQU1BIEZBTUlMSUFTIFNPTElEQVJJQVM8L3NwYW4+PC9zdHJvbmc+PC9wPg0KPHA+PHN0cm9uZz5DQU1CSU8gREUgU0VERTwvc3Ryb25nPjwvcD4NCjxwPkxhIGNhcGFjaXRhY2kmb2FjdXRlO24gcGFyYSBsYSBwdWVzdGEgZW4gbWFyY2hhIGRlbCA8c3Ryb25nPlByb2dyYW1hIEZhbWlsaWFzIFNvbGlkYXJpYXM8L3N0cm9uZz4gc2UgcmVhbGl6YXImYWFjdXRlOyBlbiBsYSBsb2NhbGlkYWQgZGUgPHN0cm9uZz5OYXZhcnJvPC9zdHJvbmc+IHBhcmEgdG9kbyBlbCBjb3JyZWRvciBkZSBsYSBSdXRhIDQwLjwvcD4NCjxwPkluaWNpbyA8c3Ryb25nPk1pJmVhY3V0ZTtyY29sZXMgMjggZGUgYWdvc3RvIGEgbGFzIDE0IGhvcmFzLiZuYnNwOzwvc3Ryb25nPjwvcD4NCjxwPlNlZGU6IDxzdHJvbmc+U2FsJm9hY3V0ZTtuIE11bmljaXBhbCBlbiBsYSBjYWxsZSAxMDcgZXNxdWluYSAyMiAtIE5hdmFycm88L3N0cm9uZz48L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA4Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTIwNzIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xMi8wNy8yMDEzPC9zcGFuPjxicj5TQUxVRCBBQ1RJVkEgaGEgc2lkbyBlbGVnaWRhIHBvciBzZWd1bmRhIHZleiBjb25zZWN1dGl2YSBjb21vIHVubyBkZSBsb3MgZ2FuYWRvcmVzIGRlbCBDdWFydG8gQ29uY3Vyc28gZGUgUHJveWVjdG9zIFNvY2lhbGVzIGRlIFBldHJvYnJhczwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSI3IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODUiIGNvbHNwYW49IjQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+RW4gZWwgbWFyY28gZGVsIEN1YXJ0byBDb25jdXJzbyBkZSBQcm95ZWN0b3MgU29jaWFsZXMgZGUgUGV0cm9icmFzLCANCm51ZXN0cmEgSW5zdGl0dWNpJm9hY3V0ZTtuIFNBTFVEIEFDVElWQSBoYSBzaWRvIGVsZWdpZGEgcG9yIHNlZ3VuZGEgdmV6IA0KY29uc2VjdXRpdmEgY29tbyB1bm8gZGUgbG9zIGdhbmFkb3JlcyBkZSBkaWNobyBjb25jdXJzby48YnIgLz5FbiBlc3RhIA0KZWRpY2kmb2FjdXRlO24gZWwgcHJveWVjdG8gcXVlIGhhIHNpZG8gZWxlZ2lkbyBlcyBlbCAmbGRxdW87UHJvZ3JhbWEgZGUgRmFtaWxpYXMgDQpTb2xpZGFyaWFzJnJkcXVvOyBzaWVuZG8gc3UgJmFhY3V0ZTtyZWEgZGUgaW1wbGVtZW50YWNpJm9hY3V0ZTtuIGxvcyBNdW5pY2lwaW9zIGRlIE5hdmFycm8sIA0KR3JhbC4gTGFzIEhlcmFzLCBNYXJjb3MgUGF6LCB5IE1lcmxvPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAyLzA3LzIwMTM8L3NwYW4+PGJyPk/tciBvIGVzY3VjaGFyPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Qb3IgQ2FybG9zIFJvemFuc2tpICo8L3A+DQo8cD5BIGxvIGxhcmdvIGRlIGxvcyBzaWdsb3MsIGxhcyBuaSZudGlsZGU7YXMsIG5pJm50aWxkZTtvcyB5IGFkb2xlc2NlbnRlcyBoYW4gc2lkbyBtYWx0cmF0YWRvcyB5IGFidXNhZG9zIHNpbiBxdWUgYSBsYSBjb211bmlkYWQgbGUgaW50ZXJlc2FyYSBuaSBzaXF1aWVyYSBlc2N1Y2hhcmxvcyBjdWFuZG8gaGFjJmlhY3V0ZTthbiBzYWJlciBkZSBhbGd1bmEgZm9ybWEgbG9zIHN1ZnJpbWllbnRvcyBxdWUgcGFkZWMmaWFjdXRlO2FuLiBFbiAxODc0LCBlbiBFc3RhZG9zIFVuaWRvcywgZnVlIGxhIHByaW1lcmEgdmV6IHF1ZSBlbCBFc3RhZG8gaW50ZXJ2aW5vIGVuIHVuIGNhc28gZGUgbWFsdHJhdG8geSBhYnVzby4uLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDYiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4wMi8wNy8yMDEzPC9zcGFuPjxicj5FbCBkZXJlY2hvIGRlIGxvcyBuafFvcyBhIHNlciBlc2N1Y2hhZG9zPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5VbiBob21icmUgYWN1c2FkbyBkZSBoYWJlciBhYnVzYWRvIGRlIHN1cyBoaWpvcyBoYWImaWFjdXRlO2Egc2lkbyBzb2JyZXNlJmlhY3V0ZTtkbyBkb3MgdmVjZXMgcG9yIGxhIEp1c3RpY2lhLiBQZXJvIGFob3JhLCBsYSBDJmFhY3V0ZTttYXJhIGRlIENhc2FjaSZvYWN1dGU7biByZXZvYyZvYWN1dGU7IGVzYSBkZWNpc2kmb2FjdXRlO24gcG9ycXVlIGVuIGxhIGludmVzdGlnYWNpJm9hY3V0ZTtuIGVsIGp1ZXogbnVuY2EgaGFiJmlhY3V0ZTthIGVzY3VjaGFkbyBhIGxvcyBjaGljb3MuIFkgb3JkZW4mb2FjdXRlOyBxdWUgdGVuZ2EgZW4gY3VlbnRhIGxvIHF1ZSBkaWNlbi48L3A+DQo8cD5Qb3IgTWFyaWFuYSBDYXJiYWphbDwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDUiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwNSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZD48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE1NiIgcm93c3Bhbj0iMiIgdmFsaWduPSJ0b3AiPgoJCQkJCgkJCQk8dGFibGUgd2lkdGg9IjMyJSIgYm9yZGVyPSIxIiBjZWxsc3BhY2luZz0iMyIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48aW1nIHNyYz0ic3JjL2ltZ191cC8wNjA2MjAxMy4xLmpwZyIgd2lkdGg9IjE0NiIgLz48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT4KCQkJCQkJCQk8L3RkPiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjA2LzA2LzIwMTM8L3NwYW4+PGJyPkFidXNvIHNleHVhbCBpbmZhbnRpbC4gRGVzYWZpb3MgZGUgbGEgY2xpbmljYSBhY3R1YWw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkFiaWVydGEgbGEgaW5zY3JpcGNpb248L3A+DQo8cD5Eb2NlbnRlczogTGljLiBNYXJpYSBCZWF0cml6IE0mdXVtbDtsbGVyLiBMaWMuIFBhb2xhIE11Jm50aWxkZTtveiBEdWFydGU8L3A+DQo8cD5JbmljaW86IE1pZXJjb2xlcyAxOSBkZSBKdW5pbzwvcD4NCjxwPkZyZWN1ZW5jaWE6IFNlbWFuYWw8L3A+DQo8cD5Nb2RhbGlkYWQ6IEludGVuc2l2YTwvcD4NCjxwPkNvbnRlbmlkb3M6ICZuYnNwOyBFc3RhIGRlc3RpbmFkbyBhIHRvZG9zIGxvcyBwcm9mZXNpb25hbGVzIGNvbXByb21ldGlkb3MgY29uIGxhIHRlbWF0aWNhIGRlbCBhYnVzbyBpbmZhbnRpbCBxdWUgcXVpZXJhbiBhY3R1YWxpemFyc2UgZSBpbnRlcmNhbWJpYXIgZXhwZXJpZW5jaWFzIGRlIHRyYWJham8uLi48L3A+DQo8cD4mbmJzcDs8L3A+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTklIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzA0Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzE5LmpwZyIgd2lkdGg9Ijc1IiBoZWlnaHQ9IjQxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2luZGV4LnBocD9pZD0xNyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMS5qcGciIHdpZHRoPSI1MyIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48YSBocmVmPSIjIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDQiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIzIiBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgIDwvdHI+CgkJICAgICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTYiIHJvd3NwYW49IjIiIHZhbGlnbj0idG9wIj4KCQkJCQoJCQkJPHRhYmxlIHdpZHRoPSIzMiUiIGJvcmRlcj0iMSIgY2VsbHNwYWNpbmc9IjMiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PGltZyBzcmM9InNyYy9pbWdfdXAvMTYwNTIwMTMuMC5qcGciIHdpZHRoPSIxNDYiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CgkJCQkJCQkJPC90ZD4gICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBjbGFzcz0idGl0dWxvaG9tZTEiPjxzcGFuIGNsYXNzPSJkZXN0YWNhZG9zIj4xNi8wNS8yMDEzPC9zcGFuPjxicj5TYWx1ZCBBY3RpdmEgbmVjZXNpdGEgZGUgdHUgYXl1ZGEhPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjciIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4NSIgY29sc3Bhbj0iNCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5UcmFiYWphbW9zIGNvbW8gcG9kZW1vczogYmEmbnRpbGRlO29zIHJvdG9zLCBzdXNwZW5zaSZvYWN1dGU7biBkZSByZXVuaW9uZXMgcG9yIGNvcnRlcyBkZSBsdXogeSBhZ3VhLCBqdWd1ZXRlcyB2aWVqb3MsIG1lc2VzIGRlIGF0cmFzbyBlbiBlbCBwYWdvIGRlIHN1cyBwcm9mZXNpb25hbGVzIGRlIGxhIHNhbHVkLiBSZWNpZW50ZW1lbnRlIHR1dmltb3MgcXVlIGNlcnJhciBudWVzdHJvIHF1ZXJpZG8gSG9nYXI6ICZsZHF1bztNZXRhbW9yZm9zaXMmcmRxdW87IGVyYSBlbCBsdWdhciBxdWUgc3VwbyBjb250ZW5lciBhIG5pJm50aWxkZTthcyB5IGomb2FjdXRlO3ZlbmVzIHJlc2NhdGFkYSBkZSByZWRlcyBkZSB0cmF0YSBvIHYmaWFjdXRlO2N0aW1hcyBkZSBhYnVzbyBpbnRyYWZhbWlsaWFyLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18xOS5qcGciIHdpZHRoPSI3NSIgaGVpZ2h0PSI0MSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNjAlIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMSUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJodHRwOi8vd3d3LnNhbHVkYWN0aXZhLm9yZy5hci9pbmRleC5waHA/aWQ9MTciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjEuanBnIiB3aWR0aD0iNTMiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PGEgaHJlZj0iIyI+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMCUiIHZhbGlnbj0idG9wIj48YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3Jm5vdGE9MzAzIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIyLmpwZyIgd2lkdGg9Ijc4IiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYmFja2dyb3VuZD0iaW1nL3JlZGlzZW5vXzI2LmpwZyI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yNi5qcGciIHdpZHRoPSIyIiBoZWlnaHQ9IjIiIC8+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgoJCSAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzODEiIGhlaWdodD0iMzAiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjAzLzA1LzIwMTM8L3NwYW4+PGJyPlJFUFVESU8gQSBMQSBQUkVTRU5DSUEgRU4gTEEgRkVSSUEgREVMIExJQlJPIERFIFVOIEVYIEpVRVogQUNVU0FETyBERSBBQlVTTyBTRVhVQUw8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxMyIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iNyIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9Ijg1IiBjb2xzcGFuPSI0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPkZ1ZSBjYW1hcmlzdGEgZW4gTWFyIGRlbCBQbGF0YSBkdXJhbnRlIGxhIGRpY3RhZHVyYS4gSGFjZSBhJm50aWxkZTtvcywgdmFyaWFzIG11amVyZXMgbG8gYWN1c2Fyb24gZGUgaGFiZXIgYWJ1c2FkbyBkZSBlbGxhcyBjdWFuZG8gZXJhbiBuaSZudGlsZGU7YXMuIExhIGNhdXNhIHByZXNjcmliaSZvYWN1dGU7IHkgbm8gaHVibyBjb25kZW5hLiBNYSZudGlsZGU7YW5hIHRpZW5lIHByZXZpc3RvIGZpcm1hciBzdSBsaWJyby4gRXNhcyBtaXNtYXMgbXVqZXJlcyBwaWRlbiBxdWUgbm8gc2VhIGFkbWl0aWRvIGVuIGxhIGZlcmlhLjwvcD48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxOSUiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0zMDIiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMTkuanBnIiB3aWR0aD0iNzUiIGhlaWdodD0iNDEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjYwJSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjxhIGhyZWY9IiMiPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjAlIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTMwMiI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18yMi5qcGciIHdpZHRoPSI3OCIgaGVpZ2h0PSIyMSIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGJhY2tncm91bmQ9ImltZy9yZWRpc2Vub18yNi5qcGciPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjYuanBnIiB3aWR0aD0iMiIgaGVpZ2h0PSIyIiAvPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgPC90cj4KCQkgIDwhLS0gRklOIG5vdGEgZGVzdGFjYWRhIC0tPgogICAgICAgIDwvdGFibGU+ICAgICAgICA8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iNSUiIGFsaWduPSJyaWdodCI+PGltZyBzcmM9ImltZy81eDUuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iMTUiIC8+PC90ZD4KICAgICAgPC90cj4KICAgIDwvdGFibGU+PC90ZD4KICA8L3RyPgogIDx0cj4KICAgIDx0ZCB3aWR0aD0iMSUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiIgYWxpZ249ImNlbnRlciI+Jm5ic3A7PC90ZD4KICAgIDx0ZCB3aWR0aD0iMiUiPjxpbWcgc3JjPSJpbWcvNXg1LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjE1IiAvPjwvdGQ+CiAgPC90cj4KICAKICA8dGQ+CiAgPHRyPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgICA8dGQgY29sc3Bhbj0iMiI+Jm5ic3A7PC90ZD4KICA8L3RyPgogIDx0ciBhbGlnbj0iY2VudGVyIj4KICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgPHRkIHdpZHRoPSI5NyIgY29sc3Bhbj0iMiIgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iNTQ2IiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMyIgY2xhc3M9ImJvcmRlIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCA+PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiBjbGFzcz0idGl0dWxvaG9tZTIiPjx0YWJsZSB3aWR0aD0iIiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgY29sc3Bhbj0iMyIgYWxpZ249ImxlZnQiIHZhbGlnbj0iYm90dG9tIiBjbGFzcz0idGl0dWxvaG9tZTIiPlJhbmtpbmc8L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjMiIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSIgY2xhc3M9InRpdHVsb2hvbWUyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iIiBoZWlnaHQ9IjM1IiBhbGlnbj0ibGVmdCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyNSIgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iMjUiIGNsYXNzPSJjb250ZW5pZG9ob21lIj48c3Ryb25nPiZidWxsO0xhcyBtJmFhY3V0ZTtzIGxlaWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGNsYXNzPSJjb250ZW5pZG9ob21lIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBjbGFzcz0iY29udGVuaWRvaG9tZSI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgY2xhc3M9ImNvbnRlbmlkb2hvbWUiPjxzdHJvbmc+JmJ1bGw7TGFzIG0mYWFjdXRlO3MgY29tZW50YWRhczwvc3Ryb25nPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yOTgiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTHVkb3RlY2EgR2FyYWJhdG8gLSBQcm95ZWN0byBzYWx1ZGFjdGl2YSwgUG9yIHVuYSBpbmZhbmNpYSBmZWxpeiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iOSUiIGJnY29sb3I9IiNFRkVGRUYiPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIzJSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xNjIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDUlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTE2MiIgY2xhc3M9ImJvdG9uIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBDdXJzbyBJbnRlbnNpdm8gZGUgb3BlcmFkb3IgdGVyYXBldXRpY28gZXNwZWNpYWxpemFkbyBlbiBlbCBhYm9yZGFqZSBkZWwgYWJ1c28sIGxhIHZpb2xlbmNpYSB5IGVsIG1hbHRyYXRvIGluZmFudGlsICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIlIiBoZWlnaHQ9IjIwIiB2YWxpZ249Im1pZGRsZSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+PGltZyBzcmM9ImltZy9mbGVjaGFuYXJhbmphZmdyaXNfMjQuanBnIiB3aWR0aD0iMTQiIGhlaWdodD0iNyIgYm9yZGVyPSIwIiBhbGlnbj0iYWJzbWlkZGxlIiAvPjwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iNDElIiBoZWlnaHQ9IjMwIiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0yNDIiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgUFJPR1JBTUEgTEFTIFZJQ1RJTUFTIENPTlRSQSBMQVMgVklPTEVOQ0lBUyAgTWluaXN0ZXJpbyBkZSBKdXN0aWNpYSB5IERlcmVjaG9zIEh1bWFub3MgZGUgbGEgTmFjafNuICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI5JSIgYmdjb2xvcj0iI0VGRUZFRiI+PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjMlIiBiZ2NvbG9yPSIjRUZFRkVGIj4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8YSBocmVmPSJpbmRleC5waHA/aWQ9MTRfbmV3JmFtcDtub3RhPTI1NSIgY2xhc3M9ImJvdG9uIj48aW1nIHNyYz0iaW1nL2ZsZWNoYW5hcmFuamFmZ3Jpc18yNC5qcGciIHdpZHRoPSIxNCIgaGVpZ2h0PSI3IiBib3JkZXI9IjAiIGFsaWduPSJhYnNtaWRkbGUiIC8+PC9hPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI0NSUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MjU1IiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIERpcGxvbWF0dXJhIGVuIEFib3JkYWplIGludGVyZGlzY2lwbGluYXJpbyBkZWwgbWFsdHJhdG8sIGxhIHZpb2xlbmNpYSB5IGVsIGFidXNvIHNleHVhbCBpbmZhbnRpbCAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyJSIgaGVpZ2h0PSIyMCIgdmFsaWduPSJtaWRkbGUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQxJSIgaGVpZ2h0PSIzMCIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MzAzIiBjbGFzcz0iYm90b24iPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNhbHVkIEFjdGl2YSBuZWNlc2l0YSBkZSB0dSBheXVkYSEgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjklIiBiZ2NvbG9yPSIjRUZFRkVGIj48L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMyUiIGJnY29sb3I9IiNFRkVGRUYiPiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmYW1wO25vdGE9MTA0IiBjbGFzcz0iYm90b24iPjxpbWcgc3JjPSJpbWcvZmxlY2hhbmFyYW5qYWZncmlzXzI0LmpwZyIgd2lkdGg9IjE0IiBoZWlnaHQ9IjciIGJvcmRlcj0iMCIgYWxpZ249ImFic21pZGRsZSIgLz48L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjQ1JSIgYmdjb2xvcj0iI0VGRUZFRiI+ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZhbXA7bm90YT0xMDQiIGNsYXNzPSJib3RvbiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgTGxhbWFkbyBwYXJhIHByZXNlbnRhY2nzbiBkZSB0cmFiYWpvcy4gICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2E+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjIwIiBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSIyMCIgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPHRkIGJnY29sb3I9IiNGRkZGRkYiIGNsYXNzPSJ0ZXh0b251ZXZvIj4mbmJzcDs8L3RkPgogICAgICAgICAgICAgICAgICAgICAgICAgIDx0ZCBiZ2NvbG9yPSIjRkZGRkZGIiBjbGFzcz0idGV4dG9udWV2byI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiIgY2xhc3M9InRleHRvbnVldm8iPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgICAgICA8L3RhYmxlPgogICAgICAgICAgICAgICAgICAgICAgPGEgaHJlZj0iIyIgY2xhc3M9ImJvdG9uIj48L2E+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgPC90YWJsZT48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj4mbmJzcDs8L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBJTklDSU8gbm90YSBjb211biAtLT4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MTUvMDQvMjAxMjwvc3Bhbj48YnI+T3JnYW5pemFuIGpvcm5hZGEgc29icmUgdmlvbGVuY2lhPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPlNlIGNlbnRyYXImYWFjdXRlOyBlbiBsb3MgZmVuJm9hY3V0ZTttZW5vcyBxdWUgYWZlY3RhbiBhIGxhIGZhbWlsaWEgeSBlbiBsbyBxdWUgb2N1cnJlIGVuIGxhcyBlc2N1ZWxhcy48YnIgLz4gU2UgbGxldmFyJmFhY3V0ZTsgYSBjYWJvIGVsIGx1bmVzIDIzLCBlbiBlbCBDZW50cm8gQ3VsdHVyYWwgZGUgVG9zY2hpIHkgVHJlcyANCkFycm95b3MsIHVuYSBqb3JuYWRhIGRlIHJlZmxleGkmb2FjdXRlO24geSBkZWJhdGUgYWJpZXJ0YSBhIGxhIGNvbXVuaWRhZCBzb2JyZSANCiZsZHF1bztWaW9sZW5jaWEgZW4gbGEgZmFtaWxpYSB5IGVuIGxhIGVzY3VlbGEgeSBzdSByZWxhY2kmb2FjdXRlO24gY29uIGVsIGZyYWNhc28gDQplc2NvbGFyJnJkcXVvOywgb3JnYW5pemFkYSBwb3IgbGEgQXNvY2lhY2kmb2FjdXRlO24gQ2l2aWwgQ2VudHJvIEFydCZlYWN1dGU7bWlkZXMgeSBsYSANCk11bmljaXBhbGlkYWQgZGUgQ2lwb2xsZXR0aS5TZSBjZW50cmFyJmFhY3V0ZTsgZW4gbG9zIGZlbiZvYWN1dGU7bWVub3MgcXVlIGFmZWN0YW4gYSBsYSBmYW1pbGlhIHkgZW4gbG8gcXVlIG9jdXJyZSBlbiBsYXMgZXNjdWVsYXMuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjMwLzAzLzIwMTI8L3NwYW4+PGJyPkNhcnRhIGRlIEFTQVBNSSAtIEFzb2NpYWNp824gQXJnZW50aW5hIGRlIFByZXZlbmNp824gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbDwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjE1IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18wMV8xOS5qcGciIHdpZHRoPSIxNSIgaGVpZ2h0PSI3MSIgLz48L3RkPgogICAgICAgICAgICA8dGQgdmFsaWduPSJ0b3AiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBoZWlnaHQ9IjgwIiBjb2xzcGFuPSI0IiBhbGlnbj0ibGVmdCIgdmFsaWduPSJ0b3AiIGNsYXNzPSJ0ZXh0b251ZXZvIj48cD5Mb3MgaW50ZWdyYW50ZXMgZGUgbGEgQ29taXNpJm9hY3V0ZTtuIERpcmVjdGl2YSBkZSBBU0FQTUkgLSBBc29jaWFjaSZvYWN1dGU7biBBcmdlbnRpbmEgZGUgUHJldmVuY2kmb2FjdXRlO24gZGVsIE1hbHRyYXRvIEluZmFudG8tSnV2ZW5pbCwgYXNvY2lhZGEgYSBsYSBJbnRlcm5hdGlvbmFsIFNvY2lldHkgZm9yIFByZXZlbnRpb24gb2YgQ2hpbGQgQWJ1c2UgYW5kIE5lZ2xlY3QgKElTUENBTikgLSwgdGVuZW1vcyBlbCBhZ3JhZG8gZGUgZGlyaWdpcm5vcyBhIFVzdGVkIHBhcmEgdHJhc21pdGlybGUgbnVlc3RyYSBwcm9mdW5kYSAmbmJzcDt5IGhvbmRhIHByZW9jdXBhY2kmb2FjdXRlO24gcG9yIGxhIHBvc3R1cmEgcXVlIHZpZW5lbiBhc3VtaWVuZG8gZW4gZm9ybWEgY29udGludWFkYSBhbGd1bm9zIGNvbGVnaW9zIGRlIHBzaWMmb2FjdXRlO2xvZ29zLCBlc3BlY2lhbG1lbnRlIGRlIGxhIHByb3ZpbmNpYSBkZSBCdWVub3MgQWlyZXMsIGVuIHJlbGFjaSZvYWN1dGU7biBhbCB0cmF0YW1pZW50byBwb2NvIHNlcmlvIHkgY29tcHJvbWV0aWRvIHF1ZSBzZSBsZXMgb3RvcmdhIGEgbGFzIGRlbnVuY2lhcyBlZmVjdHVhZGFzIGNvbnRyYSBwcm9mZXNpb25hbGVzIHBzaWMmb2FjdXRlO2xvZ29zLi4uPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2OCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjgiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgIDx0ZCBjb2xzcGFuPSIyIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgPHRyPgogICAgICAgIDx0ZCBiYWNrZ3JvdW5kPSJpbWcvcmVkaXNlbm9fMjYuanBnIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzI2LmpwZyIgd2lkdGg9IjIiIGhlaWdodD0iMiIgLz48L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjElIj4mbmJzcDs8L3RkPgogICAgPHRkIGNvbHNwYW49IjIiIGFsaWduPSJjZW50ZXIiPjx0YWJsZSB3aWR0aD0iNTQwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgd2lkdGg9IjI3MCIgdmFsaWduPSJ0b3AiPgoJCQkJPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxwYWRkaW5nPSIwIiBjZWxsc3BhY2luZz0iMCI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTMiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMzgxIiBoZWlnaHQ9IjMwIiBhbGlnbj0ibGVmdCIgY2xhc3M9InRpdHVsb2hvbWUxIj48c3BhbiBjbGFzcz0iZGVzdGFjYWRvcyI+MjAvMDMvMjAxMjwvc3Bhbj48YnI+TEEgVklPTEVOQ0lBIFNFWFVBTCBDT05UUkEgTknRT1MgWSBOSdFBUyBFTiBDSUZSQVM8L3RkPgogICAgICAgICAgPC90cj4KICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkIHdpZHRoPSIxNSIgdmFsaWduPSJ0b3AiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMDFfMTkuanBnIiB3aWR0aD0iMTUiIGhlaWdodD0iNzEiIC8+PC90ZD4KICAgICAgICAgICAgPHRkIHZhbGlnbj0idG9wIj48dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgaGVpZ2h0PSI4MCIgY29sc3Bhbj0iNCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBjbGFzcz0idGV4dG9udWV2byI+PHA+UmFkaW9ncmFmJmlhY3V0ZTthIGRlIHVuIHByb2JsZW1hPC9wPg0KPHA+RGUgbG9zIG4mdWFjdXRlO21lcm9zIGNvbXBpbGFkb3MgcG9yIGRvcyBlcXVpcG9zIGRlbCBNaW5pc3RlcmlvIGRlIEp1c3RpY2lhLCBsYQ0KIGF1dG9yYSB0b21hIGxvcyBkZSBsYSBjaXVkYWQgZGUgQnVlbm9zIEFpcmVzIHBhcmEgdHJhemFyIHVuIHBhcmFkaWdtYSANCmRlIGxvcyBkZWxpdG9zIGNvbnRyYSBsYSBpbnRlZ3JpZGFkIHNleHVhbCBlbiBlbCBwYSZpYWN1dGU7cyB5IHNvYnJlIHN1IA0KYXRlbmNpJm9hY3V0ZTtuLjxiciAvPiA8YnIgLz4gJm5ic3A7UG9yIEV2YSBHaWJlcnRpPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI2MCI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNjAiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICAgIDx0ZCB3aWR0aD0iMjcwIiBhbGlnbj0icmlnaHQiIHZhbGlnbj0idG9wIj4KCQkJCTx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxscGFkZGluZz0iMCIgY2VsbHNwYWNpbmc9IjAiPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQgd2lkdGg9IjEzIj4mbmJzcDs8L3RkPgogICAgICAgICAgICA8dGQgd2lkdGg9IjM4MSIgaGVpZ2h0PSIzMCIgYWxpZ249ImxlZnQiIGNsYXNzPSJ0aXR1bG9ob21lMSI+PHNwYW4gY2xhc3M9ImRlc3RhY2Fkb3MiPjE1LzAzLzIwMTI8L3NwYW4+PGJyPkZBTExPIERFIExBIENPUlRFIFNVUFJFTUEgU09CUkUgTEEgTk8gSlVESUNJQUxJWkFDSU9OIERFTCBBQk9SVE8gRU4gQ0FTT1MgREUgVklPTEFDSU9OPC90ZD4KICAgICAgICAgIDwvdHI+CiAgICAgICAgICA8dHI+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTUiIHZhbGlnbj0idG9wIj48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzAxXzE5LmpwZyIgd2lkdGg9IjE1IiBoZWlnaHQ9IjcxIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB2YWxpZ249InRvcCI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGhlaWdodD0iODAiIGNvbHNwYW49IjQiIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgY2xhc3M9InRleHRvbnVldm8iPjxwPjxiciAvPiBKVVJJU0RJQ0NJT046IE5BQ0lPTkFMPGJyIC8+IE1BVEVSSUE6IEFCT1JUTy48YnIgLz4gVFJJQlVOQUw6IENvcnRlIFN1cHJlbWEgZGUgSnVzdGljaWEgZGUgbGEgTmFjaSZvYWN1dGU7bi48YnIgLz4gQVVUT1M6IEYuLCBBLiBMLiBzLyBtZWRpZGEgYXV0b3NhdGlzZmFjdGl2YS48YnIgLz4gRkVDSEE6IDEzLzAzLzIwMTIuPC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjE5JSI+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTE0X25ldyZub3RhPTI1OSI+PGltZyBzcmM9ImltZy9yZWRpc2Vub18zMy5qcGciIHdpZHRoPSI2NiIgaGVpZ2h0PSIyNyIgYm9yZGVyPSIwIiAvPjwvYT48L3RkPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI2MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjElIiB2YWxpZ249InRvcCI+PGEgaHJlZj0iaHR0cDovL3d3dy5zYWx1ZGFjdGl2YS5vcmcuYXIvaW5kZXgucGhwP2lkPTE3Ij48aW1nIHNyYz0iaW1nL3JlZGlzZW5vXzIxLmpwZyIgd2lkdGg9IjUzIiBoZWlnaHQ9IjIxIiBib3JkZXI9IjAiIC8+PC9hPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIwJSIgdmFsaWduPSJ0b3AiPjxhIGhyZWY9ImluZGV4LnBocD9pZD0xNF9uZXcmbm90YT0yNTkiPjxpbWcgc3JjPSJpbWcvcmVkaXNlbm9fMjIuanBnIiB3aWR0aD0iNzgiIGhlaWdodD0iMjEiIGJvcmRlcj0iMCIgLz48L2E+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgICAgPHRyPgogICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CgkJCQk8L3RkPgogICAgICA8L3RyPgogICAgPC90YWJsZT48L3RkPgogICAgPHRkPiZuYnNwOzwvdGQ+CiAgPC90cj4KPCEtLSBGSU4gbm90YSBjb211biAtLT4KPC90YWJsZT4KPG1hcCBuYW1lPSJNYXBNYXAiIGlkPSJNYXBNYXAiPjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjE0NCw0LDIxNCwzNiIgaHJlZj0iaW5kZXgucGhwP2lkPTE0IiAvPgo8L21hcD4KPG1hcCBuYW1lPSJNYXAyTWFwMiIgaWQ9Ik1hcDJNYXAyIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIxNDcsNCwyMjAsMzYiIGhyZWY9ImluZGV4LnBocD9pZD0xNGEiIC8+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcDMiIGlkPSJNYXAzIj48YXJlYSBzaGFwZT0icmVjdCIgY29vcmRzPSIzNjMsMyw0MzYsMzkiIGhyZWY9ImluZGV4LnBocD9pZD0xNGIiIC8+CjwvbWFwPgo8L2h0bWw+CjwvdGQ+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiZ2NvbG9yPSIjRTNFM0UzIj4gICAgICAgICAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYWxpZ249ImNlbnRlciIgdmFsaWduPSJ0b3AiIGJnY29sb3I9IiNFM0UzRTMiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMCIgY2VsbHBhZGRpbmc9IjAiPgogICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSI3MCUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNiUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+PGltZyBzcmM9ImltZy9kZWNpbG9fYmllbl9mdWVydGUxLmpwZyIgd2lkdGg9IjEyMCIgaGVpZ2h0PSIxMTIiPjwvdGQ+CiAgICAgICAgICAgICAgPHRkPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZD4mbmJzcDs8L3RkPgogICAgICAgICAgICAgIDx0ZCBhbGlnbj0iY2VudGVyIiA+PGEgaHJlZj0iaW5kZXgucGhwP2lkPTI0IiBjbGFzcz0iYm90b24xIj5bK10gTSZhYWN1dGU7cyBpbmZvcm1hY2kmb2FjdXRlO248L2E+PC90ZD4KICAgICAgICAgICAgICA8dGQ+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPC90cj4KICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCIgYmdjb2xvcj0iI0UzRTNFMyI+ICAgICAgICA8L3RyPgogICAgICAgIDx0cj4gCiAgICAgICAgICA8dGQgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIj4mbmJzcDs8L3RkPgogICAgICAgIDwvdHI+CiAgICA8L3RhYmxlPjwvdGQ+CiAgPC90cj4KICA8dHI+IAogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249ImJvdHRvbSI+PGltZyBzcmM9ImltZy9penExLmpwZyIgd2lkdGg9Ijk2IiBoZWlnaHQ9IjExNCIgLz48L3RkPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249InRvcCI+PGltZyBzcmM9ImltZy9RdWllbmVzU29tb3NfQTJfMF8yNS5qcGciIHdpZHRoPSI4MDkiIGhlaWdodD0iMTE0IiBib3JkZXI9IjAiIHVzZW1hcD0iI01hcDIiIC8+PC90ZD4KICA8L3RyPgogIDx0cj4gCiAgICA8dGQgaGVpZ2h0PSI1MCIgYWxpZ249ImxlZnQiIHZhbGlnbj0idG9wIiBiYWNrZ3JvdW5kPSJpbWcvUXVpZW5lc1NvbW9zX0EyXzE4XzE4LmpwZyI+Jm5ic3A7PC90ZD4KICAgIDx0ZCBoZWlnaHQ9IjUwIiBjbGFzcz0iZm9uZG9ib3R0b20iPjxhIGhyZWY9Imh0dHA6Ly93d3cuc2l0ZWkuY29tLmFyLyI+PGltZyBzcmM9ImltZy9laV9jb2xvci5wbmciIGFsdD0iZXNwYWNpb3MgZGUgaW1hZ2luYWNpb24sIGRlc2Fycm9sbG9zIGludGVyYWN0aXZvcywgY3JlYXRpdmlkYWQsIGRpc2XxbyIgd2lkdGg9IjI3IiBoZWlnaHQ9IjE1IiBib3JkZXI9IjAiPjwvYT4gPHNwYW4gY2xhc3M9ImVpIj48YSBocmVmPSJodHRwOi8vd3d3LnNpdGVpLmNvbS5hci8iIHNwYW4gY2xhc3M9ImVpIj5kaXNlJm50aWxkZTtvICsgY29tdW5pY2FjaSZvYWN1dGU7bjwvYT48L3NwYW4+PGVtPiZuYnNwOzwvZW0+PC9zcGFuPjxzcGFuIGNsYXNzPSJibGFuY28xIj48ZW0+Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7Jm5ic3A7PC9lbT48L3NwYW4+PC90ZD4KICA8L3RyPgo8L3RhYmxlPgoKCjxtYXAgbmFtZT0iTWFwMiI+PGFyZWEgc2hhcGU9InJlY3QiIGNvb3Jkcz0iMjQ3LDY5LDQxNCw4MiIgaHJlZj0ibWFpbHRvOnNhbHVkYWN0aXZhQHNhbHVkYWN0aXZvLm9yZy5hciI+CjwvbWFwPgo8bWFwIG5hbWU9Ik1hcCI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM2LDE0MiwxNDksMTUyIiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MiI+CjxhcmVhIHNoYXBlPSJyZWN0IiBjb29yZHM9IjM0LDE4NiwxNTAsMTk2IiBocmVmPSJpbmRleC5waHA/aWQ9OF92ZXIyJmNvbmY9MCI+CjwvbWFwPgo8L2JvZHk+CjwvaHRtbD4K]]></response> | |
| 254 | <responseRedirected>false</responseRedirected> | |
| 255 | </requestresponse> | |
| 256 | </issue> | |
| 257 | <issue> | |
| 258 | <serialNumber>497905397226519552</serialNumber> | |
| 259 | <type>6291968</type> | |
| 260 | <name>Email addresses disclosed</name> | |
| 261 | <host ip="200.20.20.201">http://www.example.org.ar</host> | |
| 262 | <path><![CDATA[/donaciones/]]></path> | |
| 263 | <location><![CDATA[/donaciones/]]></location> | |
| 264 | <severity>Information</severity> | |
| 265 | <confidence>Certain</confidence> | |
| 266 | <issueBackground><![CDATA[The presence of email addresses within application responses does not necessarily constitute a security vulnerability. Email addresses may appear intentionally within contact information, and many applications (such as web mail) include arbitrary third-party email addresses within their core content.<br><br>However, email addresses of developers and other individuals (whether appearing on-screen or hidden within page source) may disclose information that is useful to an attacker; for example, they may represent usernames that can be used at the application's login, and they may be used in social engineering attacks against the organization's personnel. Unnecessary or excessive disclosure of email addresses may also lead to an increase in the volume of spam email received.]]></issueBackground> | |
| 267 | <remediationBackground><![CDATA[You should review the email addresses being disclosed by the application, and consider removing any that are unnecessary, or replacing personal addresses with anonymous mailbox addresses (such as [email protected]).]]></remediationBackground> | |
| 268 | <issueDetail><![CDATA[The following email address was disclosed in the response:<ul><li>[email protected]</li></ul>]]></issueDetail> | |
| 269 | <requestresponse> | |
| 270 | <request base64="true"><![CDATA[R0VUIC9kb25hY2lvbmVzLyBIVFRQLzEuMQ0KSG9zdDogd3d3LnNhbHVkYWN0aXZhLm9yZy5hcg0KQWNjZXB0OiAqLyoNCkFjY2VwdC1MYW5ndWFnZTogZW4NClVzZXItQWdlbnQ6IE1vemlsbGEvNS4wIChjb21wYXRpYmxlOyBNU0lFIDkuMDsgV2luZG93cyBOVCA2LjE7IFdpbjY0OyB4NjQ7IFRyaWRlbnQvNS4wKQ0KQ29ubmVjdGlvbjogY2xvc2UNCg0K]]></request> | |
| 271 | <response base64="true"><![CDATA[SFRUUC8xLjEgMjAwIE9LDQpEYXRlOiBUaHUsIDA3IE5vdiAyMDEzIDE3OjE0OjA2IEdNVA0KU2VydmVyOiBBcGFjaGUvMi4yLjIzIChVbml4KSBtb2Rfc3NsLzIuMi4yMyBPcGVuU1NMLzAuOS44ZS1maXBzLXJoZWw1DQpMYXN0LU1vZGlmaWVkOiBXZWQsIDAzIEp1bCAyMDEzIDEzOjQ4OjMwIEdNVA0KRVRhZzogImFhZDk2Ny03MTI5LTRlMDliYjc3ZmM3ODAiDQpBY2NlcHQtUmFuZ2VzOiBieXRlcw0KQ29udGVudC1MZW5ndGg6IDI4OTY5DQpDb25uZWN0aW9uOiBjbG9zZQ0KQ29udGVudC1UeXBlOiB0ZXh0L2h0bWwNCg0KPCFET0NUWVBFIGh0bWwgUFVCTElDICItLy9XM0MvL0RURCBYSFRNTCAxLjAgVHJhbnNpdGlvbmFsLy9FTiIgImh0dHA6Ly93d3cudzMub3JnL1RSL3hodG1sMS9EVEQveGh0bWwxLXRyYW5zaXRpb25hbC5kdGQiPgo8aHRtbCB4bWxucz0iaHR0cDovL3d3dy53My5vcmcvMTk5OS94aHRtbCI+CjxoZWFkPgo8bWV0YSBodHRwLWVxdWl2PSJDb250ZW50LVR5cGUiIGNvbnRlbnQ9InRleHQvaHRtbDsgY2hhcnNldD1VVEYtOCIgLz4KPHRpdGxlPlNhbHVkIEFjdGl2YTwvdGl0bGU+CjxsaW5rIGhyZWY9ImVzdGlsb3MuY3NzIiByZWw9InN0eWxlc2hlZXQiIHR5cGU9InRleHQvY3NzIiAvPgo8bGluayBocmVmPSJmb3JtX2ZpbGVzL2VzdGlsb3MuY3NzIiByZWw9InN0eWxlc2hlZXQiIHR5cGU9InRleHQvY3NzIj4KPCEtLVtpZiBJRSA2XT4KCQkJPHN0eWxlIHR5cGU9InRleHQvY3NzIj4KCQkJIEBpbXBvcnQgdXJsKGllNi5jc3MpOwoJCQk8L3N0eWxlPiAKCQk8IVtlbmRpZl0tLT4KPHNjcmlwdCB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiIHNyYz0ianMvanF1ZXJ5Lm1pbi5qcyI+PC9zY3JpcHQ+CjxzY3JpcHQgc3JjPSJTY3JpcHRzL3N3Zm9iamVjdF9tb2RpZmllZC5qcyIgdHlwZT0idGV4dC9qYXZhc2NyaXB0Ij48L3NjcmlwdD4KPHNjcmlwdCB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiIHNyYz0ianMvanF1ZXJ5LmN5Y2xlLmFsbC4yLjc0LmpzIj48L3NjcmlwdD4gCjxzY3JpcHQgdHlwZT0idGV4dC9qYXZhc2NyaXB0Ij4KJChkb2N1bWVudCkucmVhZHkoZnVuY3Rpb24oKSB7CgkkKCcjc2xpZGUnKS5jeWNsZSh7IAogICAgCWZ4OiAgICAgJ3Njcm9sbExlZnQnLCAKICAgCSAJc3BlZWQ6ICAxNTAwLCAKICAgIAl0aW1lb3V0OiA2MDAwICwKCQluZXh0OiAgICcjbmV4dCcsIAogICAgCXByZXY6ICAgJyNwcmV2JwoJfSk7Cn0pOwokKGZ1bmN0aW9uKCkKewovL2JvdG9uMQokKCIjYm90b24xIikuY2xpY2soZnVuY3Rpb24oZXZlbnQpIHsKZXZlbnQucHJldmVudERlZmF1bHQoKTsKJCgiI2NvbnRlbmlkbzEiKS5zbGlkZVRvZ2dsZSgpOwokKCIjY29udGVuaWRvMiwgI2NvbnRlbmlkbzMsICNjb250ZW5pZG80LCAjY29udGVuaWRvNSIpLnNsaWRlVXAoKTsKJCgiI2JvdG9uMSIpLnJlbW92ZUNsYXNzKCdub3NlbGVjdCcpLmFkZENsYXNzKCdzZWxlY3QnKTsKLy8kKCIjYm90b24yLCAjYm90b24zLCAjYm90b240LCAjYm90b241IikucmVtb3ZlQ2xhc3MoJ3NlbGVjdCcpLmFkZENsYXNzKCdub3NlbGVjdCcpOwp9KTsKCi8vYm90b24yCiQoIiNib3RvbjIiKS5jbGljayhmdW5jdGlvbihldmVudCkgewpldmVudC5wcmV2ZW50RGVmYXVsdCgpOwokKCIjY29udGVuaWRvMiIpLnNsaWRlVG9nZ2xlKCk7CiQoIiNjb250ZW5pZG8xLCAjY29udGVuaWRvMywgI2NvbnRlbmlkbzQsICNjb250ZW5pZG81Iikuc2xpZGVVcCgpOwokKCIjYm90b24yIikucmVtb3ZlQ2xhc3MoJ25vc2VsZWN0JykuYWRkQ2xhc3MoJ3NlbGVjdCcpOwovLyQoIiNib3RvbjEsICNib3RvbjMsICNib3RvbjQsICNib3RvbjUiKS5yZW1vdmVDbGFzcygnc2VsZWN0JykuYWRkQ2xhc3MoJ25vc2VsZWN0Jyk7Cn0pOwoKLy9ib3RvbjMKJCgiI2JvdG9uMyIpLmNsaWNrKGZ1bmN0aW9uKGV2ZW50KSB7CmV2ZW50LnByZXZlbnREZWZhdWx0KCk7CiQoIiNjb250ZW5pZG8zIikuc2xpZGVUb2dnbGUoKTsKJCgiI2NvbnRlbmlkbzEsICNjb250ZW5pZG8yLCAjY29udGVuaWRvNCwgI2NvbnRlbmlkbzUiKS5zbGlkZVVwKCk7CiQoIiNib3RvbjMiKS5yZW1vdmVDbGFzcygnbm9zZWxlY3QnKS5hZGRDbGFzcygnc2VsZWN0Jyk7Ci8vJCgiI2JvdG9uMiwgI2JvdG9uMSwgI2JvdG9uNCwgI2JvdG9uNSIpLnJlbW92ZUNsYXNzKCdzZWxlY3QnKS5hZGRDbGFzcygnbm9zZWxlY3QnKTsKfSk7CgovL2JvdG9uNAokKCIjYm90b240IikuY2xpY2soZnVuY3Rpb24oZXZlbnQpIHsKZXZlbnQucHJldmVudERlZmF1bHQoKTsKJCgiI2NvbnRlbmlkbzQiKS5zbGlkZVRvZ2dsZSgpOwokKCIjY29udGVuaWRvMSwgI2NvbnRlbmlkbzMsICNjb250ZW5pZG8yLCAjY29udGVuaWRvNSIpLnNsaWRlVXAoKTsKJCgiI2JvdG9uNCIpLnJlbW92ZUNsYXNzKCdub3NlbGVjdCcpLmFkZENsYXNzKCdzZWxlY3QnKTsKJCgiI2JvdG9uMiwgI2JvdG9uMywgI2JvdG9uMSwgI2JvdG9uNSIpLnJlbW92ZUNsYXNzKCdzZWxlY3QnKS5hZGRDbGFzcygnbm9zZWxlY3QnKTsKfSk7CgovL2JvdG9uNQokKCIjYm90b241IikuY2xpY2soZnVuY3Rpb24oZXZlbnQpIHsKZXZlbnQucHJldmVudERlZmF1bHQoKTsKJCgiI2NvbnRlbmlkbzUiKS5zbGlkZVRvZ2dsZSgpOwokKCIjY29udGVuaWRvMSwgI2NvbnRlbmlkbzMsICNjb250ZW5pZG8yLCAjY29udGVuaWRvNCIpLnNsaWRlVXAoKTsKJCgiI2JvdG9uNSIpLnJlbW92ZUNsYXNzKCdub3NlbGVjdCcpLmFkZENsYXNzKCdzZWxlY3QnKTsKJCgiI2JvdG9uMiwgI2JvdG9uMywgI2JvdG9uMSwgI2JvdG9uNCIpLnJlbW92ZUNsYXNzKCdzZWxlY3QnKS5hZGRDbGFzcygnbm9zZWxlY3QnKTsKfSk7Cn0pOwo8L3NjcmlwdD4KCgo8L2hlYWQ+Cgo8Ym9keT4KPGRpdiBpZD0iY29udGVuZWRvciI+CjxkaXYgaWQ9ImhlYWRlciI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgPHRyPgogICAgPHRkIGFsaWduPSJsZWZ0IiB2YWxpZ249Im1pZGRsZSI+PGltZyBzcmM9ImltYWdlcy9oZWFkZXIuanBnIiBuYW1lPSJib3RvbjQiIHdpZHRoPSI5MzMiIGhlaWdodD0iMTI5IiBpZD0iYm90b240Ii8+PC90ZD4KICAgPCEtLSA8dGQgdmFsaWduPSJtaWRkbGUiPjxhIGhyZWY9ImluZm8uZG9jIiB0YXJnZXQ9Il9ibGFuayI+PGltZyBzcmM9ImltYWdlcy9oZWFkZXJtYzEuanBnIiBuYW1lPSJkZXNjYXJnYSIgd2lkdGg9Ijg0NSIgaGVpZ2h0PSIxMTAiIGJvcmRlcj0iMCIgIGlkPSJkZXNjYXJnYSIvPi0tPgo8L2E+PC90ZD4KICA8L3RyPgo8L3RhYmxlPgo8L2Rpdj4gPCEtLWVuZCBvZiBIRUFERVIgLS0+CiAgICA8ZGl2IGlkPSJpbWFnZW5lcyI+CiAgICAgIDxkaXYgaWQ9InNsaWRlciI+CiAgIAkgIDxkaXY+CiAgIAkJPGltZyBzcmM9ImltYWdlcy9iYW5uZXJfaG9tZS5qcGciIHdpZHRoPSI5MzUiIGhlaWdodD0iMzA5IiAvPjwvZGl2PiAKICAgCSAgPCEtLWVuZCBvZiBTTElERSAtLT4KICAgICAgPC9kaXY+IAogICAgICA8IS0tZW5kIG9mIFNMSURFUiAtLT4KPC9kaXY+IAogICAgPCEtLWVuZCBvZiBJTUFHRU5FUyAtLT4gICAgCjxkaXYgaWQ9ImJvdG9uZXJhIj4KICAgIAk8dWw+CiAgICAgICAgCTxsaSBjbGFzcz0ibm9zZWxlY3QxIiBpZD0iYm90b24yIj48L2xpPgogICAgICAgICAgICA8bGkgY2xhc3M9Im5vc2VsZWN0MiIgaWQ9ImJvdG9uMSI+PC9saT4KICAgICAgICAgIDxhIGhyZWY9ImphdmFzY3JpcHQ6IHZvaWQobyk7IiBvbmNsaWNrPSJ3aW5kb3cub3BlbignaHR0cDovL3d3dy5mYWNlYm9vay5jb20vc2hhcmVyLnBocD91PWh0dHA6Ly93d3cuc2FsdWRhY3RpdmEub3JnLmFyL2RvbmFjaW9uZXMvJywndmVudGFuYWNvbXBhcnRpcicsICd0b29sYmFyPTAsIHN0YXR1cz0wLCB3aWR0aD02NTAsIGhlaWdodD00NTAnKTsiPgogICAgICAgIDxsaSBjbGFzcz0ibm9zZWxlY3QzIj48L2xpPgogICAgICAgICAgICA8L2E+CiAgICAgICAgICAgIDwhLS08bGkgY2xhc3M9Im5vc2VsZWN0IiBpZD0iYm90b240Ij5JTkZPUk1BQ0nDk04gREUgQ09NUFJBUzwvbGk+LS0+CiAgICAgICAgICA8IS0tIDxsaSBjbGFzcz0ibm9zZWxlY3QiIGlkPSJib3RvbjUiPkNPTUVSQ0lBTCBERSBUVjwvbGk+IC0tPgogICAgICAgIDwvdWw+CiAgICAgPC9kaXY+ICAgICAgIAogICAgIDwvZGl2Pgo8IS0tZW5kIG9mIEJPVE9ORVJBIC0tPgogICAgCjxkaXYgY2xhc3M9ImNvbnRlbmlkbyIgaWQ9ImNvbnRlbmlkbzEiPgoKPCEtLUNPTlRFTklETyAxZXIgQk9UT04gLS0+CiAKPGRpdiBjbGFzcz0iZm9uZG9fY29udDQiPgoKPGRpdiBjbGFzcz0idGV4dG8iPgo8cD4mbmJzcDs8L3A+CjxwPiZuYnNwOzwvcD4KPHA+PHNwYW4gY2xhc3M9ImgxIj48Yj5TYWx1ZCBBY3RpdmE8L2I+PC9zcGFuPjwvcD4KICAgIAo8cD48c3BhbiBjbGFzcz0iaDIiPlNhbHVkIEFjdGl2YSBlcyB1bmEgb3JnYW5pemFjacOzbiBzaW4gZmluZXMgZGUgbHVjcm8gcXVlIGluaWNpw7Mgc3UgdHJhYmFqbyBhIHByaW5jaXBpb3MgZGVsIGHDsW8gMTk5OS48L3NwYW4+PC9wPgoKPHA+PHNwYW4gY2xhc3M9ImgzIj4KPHN0cm9uZyBzdHlsZT0iZm9udC13ZWlnaHQ6Ym9sZDsiPjxiciAvPgpIb3kgZXN0YW1vcyB0cmFiYWphbmRvIGVuIGVzdGUgcHJveWVjdG86PC9zdHJvbmc+PGJyIC8+CjxhIGhyZWY9Imh0dHA6Ly9pc3N1dS5jb20vZWkuZXN0dWRpby9kb2NzL3NhbHVkYWN0aXZhLWx1ZG90ZWNhP21vZGU9d2luZG93IiB0YXJnZXQ9Il9ibGFuayI+PGltZyBzcmM9ImltYWdlcy9HYXJhYmF0b0x1ZG90ZWNhXzUwMHB4LmpwZyIgd2lkdGg9IjUwMCIgaGVpZ2h0PSIxMTMiIGJvcmRlcj0iMCIgLz48L2E+Cgo8YnIgLz4KPGEgaHJlZj0iUHJveWVjdG9MdWRvdGVjYUNvbXBsZXRvLnBkZiIgdGFyZ2V0PSJfYmxhbmsiIHN0eWxlPSJjb2xvcjojRjYwOyI+VmVyIHByb3llY3RvIGNvbXBsZXRvPC9hPjxiciAvPgo8c3Ryb25nPjxiciAvPgo8L3N0cm9uZz48L3NwYW4+PHN0cm9uZyBzdHlsZT0iZm9udC13ZWlnaHQ6Ym9sZDsiPlVuIHBvY28gZGUgaGlzdG9yaWE8L3N0cm9uZz48ZW0+OjwvZW0+PC9wPgo8cD48c3BhbiBjbGFzcz0iaDMiPkN1YW5kbyBpbmljaWFtb3MgZXN0ZSBjYW1pbm8gdGVuw61hbW9zIHVuYSBwcmVvY3VwYWNpw7NuLCBsb3MgcHNpY8OzbG9nb3MgeSBwc2ljw7Nsb2dhcyBjdWFuZG8gc2UgcmVjaWLDrWFuIHRlbsOtYW4gcXVlIGNvbWVuemFyIGEgZWplcmNlciB5IHNlIGVuZnJlbnRhYmFuIGEgdW5hIHNlcmllIGRlIHByb2JsZW1hcywgZW50cmUgZWxsb3MgbGEgZGlmZXJlbmNpYSBlbnRyZSBsbyBxdWUgYXByZW5kw61hbiAoeSBhcHJlbmRlbikgZW4gbGEgRmFjdWx0YWQgKHNlYSBsYSBxdWUgc2VhKSB5IGxhIHJlYWxpZGFkIGRlbCBzdWZyaW1pZW50byBkZSBsYSBnZW50ZS4gCiAgRWwgb3RybyBwcm9ibGVtYSBjb24gZWwgcXVlIHNlIHRvcGFiYW4gZXMgbGEgaW5leGlzdGVuY2lhIGRlIGx1Z2FyZXMgZG9uZGUgcmVhbGl6YXIgcHLDoWN0aWNhcywgZG9uZGUgYXByZW5kZXIgYSBhdGVuZGVyIHBhY2llbnRlcywgY29tbyBzZXIgcHNpY8OzbG9nb3MgeSBwc2ljw7Nsb2dhcyBlbiBsYSByZWFsaWRhZCBkZWwgY29udXJiYW5vIGJvbmFlcmVuc2XigKYgPGJyIC8+PGJyIC8+CiAgRXNhcyBwcmVvY3VwYWNpb25lcyBzZSBkZXNwcmVuZGllcm9uIGRlIGRpZXogYcOxb3MgZGUgZnVuY2lvbmFtaWVudG8gY29tbyBpbnN0aXR1Y2nDs24gcHNpY29sw7NnaWNhLCBlbCBDSUFQU0kgKENlbnRybyBkZSBJbnZlc3RpZ2FjacOzbiB5IEFzaXN0ZW5jaWEgUHNpY29zb23DoXRpY2EgZnVuZGFkbyBlbiAxOTg5KSB5IGEgbGEgcXVlIGNvbnZvY2Ftb3MgYSBtdWNob3MgeSBtdWNoYXMgasOzdmVuZXMgY29sZWdhcyBxdWUgc3VmcsOtYW4gZXN0YXMgZG9zIGNhcmVuY2lhcyBiw6FzaWNhcyBlbiBzdSBmb3JtYWNpw7NuLiBDb24gZXN0ZSBlc3DDrXJpdHUgZGUgZm9ybWFjacOzbiBwcm9mZXNpb25hbCBjb21lbnphbW9zIG51ZXN0cm8gY2FtaW5vIGNvbiBTYWx1ZCBBY3RpdmEsIGV4YWN0YW1lbnRlIGVsIDkgZGUgYWJyaWwgZGVsIDk5LCBtZWRpYW50ZSBsYSBpbXBsZW1lbnRhY2nDs24gZGVsIFByb2dyYW1hIEFzaXRpci4gQ29udm9jYW1vcyBhIGxvcyBwcm9mZXNpb25hbGVzIHJlY2nDqW4gcmVjaWJpZG9zIGEgcmVhbGl6YXIgZXN0YSBmb3JtYWNpw7NuIHByb2Zlc2lvbmFsIHRlw7NyaWNvLXByw6FjdGljYSBkZSBtYW5lcmEgZ3JhdHVpdGEgeSBxdWUgaW5jbHXDrWEgbGEgc3VwZXJ2aXNpw7NuIGNsw61uaWNhIGRlIGxvcyBwYWNpZW50ZXMgdGFtYmnDqW4gZGUgbWFuZXJhIGdyYXR1aXRhLiAKICA8YnIgLz48YnIgLz4KICBQYXJhIGdlbmVyYXIgbG9zIGVzcGFjaW9zIGRlIGxhIHByw6FjdGljYSBpbnZpdGFtb3MgYSBsYSBjb211bmlkYWQgY2VyY2FuYSBhIHBhcnRpY2lwYXIgZGUgZXN0YSBwb3NpYmlsaWRhZDogYXNpc3RlbmNpYSBwc2ljb2zDs2dpY2EgZ3JhdHVpdGEgbyBtZWRpYW50ZSBlbCBwYWdvIGRlIHVuIG3DrW5pbW8gYm9ubyBjb250cmlidWNpw7Nu4oCmCiAgPGJyIC8+PGJyIC8+CiAgUHJpbWVybyBmdWVyb24gbGFzIGVzY3VlbGFzIGRlIG51ZXN0cm8gcGFydGlkbywgcG9kcsOhbiBpbWFnaW5hcnNlIHF1ZSBsYSBwcmltZXJhIHJlYWNjacOzbiBmdWUgZGUgYXNvbWJybyB5IGRlc2NvbmZpYW56YSwgbGFzIGRpcmVjdG9yYXMgeSBlcXVpcG9zIHTDqWNuaWNvcyBjb21lbnphcm9uIGEgbGxhbWFyIHBvciB0ZWzDqWZvbm8sIHNlIGZ1ZXJvbiBhY2VyY2FuZG8geSBsZXMgZXhwbGljw6FiYW1vcyBjdWFsZXMgZXJhbiBudWVzdHJvcyBvYmpldGl2b3M6IGZvcm1hciBwcm9mZXNpb25hbGVzIHkgcGVybWl0aXIgYSBtw6FzIGdlbnRlIHBvZGVyIGFjY2VkZXIgYSBsYSBhc2lzdGVuY2lhIHBzaWNvbMOzZ2ljYS4gQXPDrSBwbGFudGVhZG8gZW1wZXphcm9uIGEgbGxlZ2FyIGxhcyBwcmltZXJhcyBkZXJpdmFjaW9uZXM6IG5pw7FvcywgbmnDsWFzIHkgYWRvbGVzY2VudGVzIHF1ZSB0dXZpZXJhbiBkaWZpY3VsdGFkZXMgbyBwcm9ibGVtYXMgZW4gbGEgZXNjdWVsYSwgeSBxdWUgbGEgZXNjdWVsYSBzZSBjb21wcm9tZXRpZXJhIGEKICB0cmFiYWphciBqdW50byBhIG5vc290cm9zIGVuIGxhIHByb2JsZW3DoXRpY2EgZGVsIG5pw7FvIG8gbmnDsWEuCiAgUXVlIGZ1ZSBsbyBxdWUgb2N1cnJpw7PigKZsYSBtYXlvcsOtYSBkZSBsYXMgZGVyaXZhY2lvbmVzIGVzdGFiYW4gdmluY3VsYWRhcyBhbCBtYWx0cmF0byAsIGEgbGEgdmlvbGVuY2lhIHkgYWwgYWJ1c28gaW5mYW50aWwuIAogIDxiciAvPjxiciAvPgogIEp1c3RhbWVudGUgcG9yIHVuIGNhc28gZGUgYWJ1c28gc2V4dWFsIGluZmFudGlsIGZ1aW1vcyBjb252b2NhZG9zIHBvciB1bm8gZGUgbG9zIFRyaWJ1bmFsZXMgZGUgRmFtaWxpYSBkZSBNb3LDs24sIGVsIG7CuiAxIHBhcmEgc2VyIG3DoXMgZXhhY3RvcyBlbiBkb25kZSBjb21lbnphYmEgYSBmdW5jaW9uYXIgdW4gZXNwYWNpbyBpbm5vdmFkb3IgcGFyYSBhcXVlbCBtb21lbnRvLCBub3ZpZW1icmUgZGVsIDk5LCAgbGEgUmVkIGRlIEZhbWlsaWEgZGVsIE9lc3RlLCBjcmVhZGEgcG9yIHVuIEp1ZXogZWwgRHIuIENhcmxvcyBSb21hbm8sIHZpc2lvbmFyaW8gc29icmUgbGEgZm9ybWEgZW4gbGEgcXVlIHNlIGRlYmVuIHRyYWJhamFyIGxvcyB0ZW1hcyBkZSB2aW9sZW5jaWEsIG1hbHRyYXRvIHkgYWJ1c286IGVuIHJlZCwgYXJ0aWN1bGFuZG8sCiAgbXVsdGlkaXNjaXBsaW5hcmlhbWVudGUsIHBlbnNhbmRvIGp1bnRvcywgc2llbmRvIGNyZWF0aXZvc+KApgogIDxiciAvPjxiciAvPgogIE5vcyBhdXRvIGZvcm1hbW9zLCBpbnZlc3RpZ2Ftb3MsIGNvbnN0aXR1aW1vcyBncnVwb3MgZGUgZXN0dWRpbywgbm9zIGNhcGFjaXRhbW9zLCB5IG5vcyBlc3BlY2lhbGl6YW1vcy4KICBTaWVtcHJlIGRlY2ltb3MgcXVlIG5vc290cm9zIG5vIGVsZWdpbW9zIGhhY2VyIGVzdG8sIGxhIHJlYWxpZGFkIHNlIG5vcyBpbXB1c28geSBzZW50aW1vcyBxdWUgZXJhIG51ZXN0cm8gZGViZXIgcmVzcG9uZGVyIGEgbG8gcXVlIG5hZGllIHJlc3BvbmRlLCBhY29tcGHDsWFyIGxvIHF1ZSBuYWRpZSBhY29tcGHDsWEsIHkgcG9yIHNvYnJlIHRvZG8gaGFjZXLigKYsIHRyYXRhciBxdWUgZWwgcXVlIGVzdMOhIHN1ZnJpZW5kbyB0ZW5nYSBsYSBvcG9ydHVuaWRhZCBkZSBlbGVnaXIgb3RyYSBjb3NhLCB0ZW5nYSBsYSBwb3NpYmlsaWRhZCBkZSBtZWpvcmFyLCBkZSBjYW1iaWFyIHN1IGRlc3Rpbm/igKYKICA8YnIgLz48YnIgLz4KICBFbiBlc2UgY2FtaW5vIGZ1aW1vcyBoYWNpZW5kbywgbG9zIENvbmdyZXNvcywgbGFzIEpvcm5hZGFzLCBsYXMgY2FwYWNpdGFjaW9uZXMgZXh0ZXJuYXMgeSBmb3JtYW1vcyBtdWNob3MsIHBlcm8gbXVjaG9zIHByb2Zlc2lvbmFsZXPigKZudW5jYSB0dXZpbW9zIGVsIHRpZW1wbyB5IGVsIGRpbmVybyBwYXJhIHNpc3RlbWF0aXphciBsYSBpbmZvcm1hY2nDs24geSBwb2RlciBjb250YXIgY29uIGVzdGFkw61zdGljYXMgcG9ycXVlIGVsIHRpZW1wbyB5IGVsIHBvY28gZGluZXJvIGxvIHVzYW1vcyBwYXJhIGFsaXZpYXIgZWwgc3VmcmltaWVudG8gZGUgbG9zIHBhY2llbnRlcyBxdWUgcmVjdXJyZW4gYSBub3NvdHJvcy4KICA8YnIgLz48YnIgLz4KICBUYW1iacOpbiBub3MgZGltb3MgY3VlbnRhIHF1ZSBlbiBtdWNob3MgbW9tZW50b3MgZGUgbGEgdmlkYSBkZSBsb3MgbmnDsW9zIHkgbmnDsWFzIG5vIGFsY2FuemEgY29uIGVsIHRyYXRhbWllbnRvIGVuIHVuIGNvbnN1bHRvcmlvLCBwb3JxdWUgbGFzIHByb2JsZW3DoXRpY2FzIHNlIGNvbXBsZWppemFuLCBsYXMgc2l0dWFjaW9uZXMgc2UgYWdyYXZhbiB5IHNlbnRpbW9zIHF1ZSB0ZW7DrWFtb3MgcXVlIGhhY2VyIGFsZ28gbcOhc+KApgogIEFzw60gbmFjZSBudWVzdHJvIFByb2dyYW1hIE1ldGFtb3Jmb3NpcywgdW4gZXNwYWNpbyBkZSB0cmF0YW1pZW50byBpbnRlZ3JhbCBjb24gaW50ZXJuYWNpw7NuIHBhcmEgYWRvbGVzY2VudGVzIG11amVyZXMgdsOtY3RpbWFzIGRlIGFidXNvIHNleHVhbCwgZGUgdmlvbGVuY2lhLCBkZSB0cmF0YeKAplRhbWJpw6luIGluaWNpYW1vcyBudWVzdHJvcyBwcm9ncmFtYXMgQ29uc3RydXllbmRvIHkgQXByZW5kZXIgYSB2b2xhciwgZGVzdGluYWRvIGEgYWRvbGVzY2VudGVzIGVuIGNvbmZsaWN0byBjb24gbGEgbGV5IHBlbmFsLCAgcHVuaWJsZXMgeSBubyBwdW5pYmxlcyByZXNwZWN0aXZhbWVudGUsIAogIGFsZ28gYWx0ZXJuYXRpdm8gYSBsYSBpbnRlcm5hY2nDs27igKYKICA8YnIgLz48YnIgLz4KICBBIGxvIGxhcmdvIGRlIGVzdG9zIGHDsW9zIGhlbW9zIGRlc2Fycm9sbGFkbyBtdWNob3MgcHJvZ3JhbWFzLCBxdWUgdHV2aWVyb24gcXVlIGRpc2NvbnRpbnVhcnNlIGRlYmlkbyBhIGxhIGZhbHRhIGRlIHJlY3Vyc29zIGVjb27Ds21pY29zLCBsYSB2ZXJkYWQgZXMgcXVlIG51bmNhIGhheSBkaW5lcm8gcGFyYSBlc3RvcyB0ZW1hcywgYSBwZXNhciBkZSBxdWUgdG9kbyBlbCBtdW5kbyBzZSBsYSBwYXNhIGhhYmxhbmRvIGRlIGVsbG9zLCBwZXJvIGhhYmxhbiwgc29sbyBoYWJsYW7igKYKICA8YnIgLz48YnIgLz4KICBIb3kgbm9zIGVuY29udHJhbW9zIGVuIGVzdGUgbW9tZW50bywgZW4gZG9uZGUgU2FsdWQgQWN0aXZhIHNlIGVuY3VlbnRyYSBlbiBjcmlzaXPigKYKICBOdWVzdHJhIMO6bmljYSBmdWVudGUgZGUgZmluYW5jaWFtaWVudG8gcGFyZWNlIHF1ZSB0YW1iacOpbiBlc3TDoSBlbiBjcmlzaXMsIG5vcyBlbmNvbnRyYW1vcyBlbiB1bmEgZW5jcnVjaWphZGEsIG5lY2VzaXRhbW9zIGRlIGxhIGF5dWRhIGRlIHVzdGVkZXPigKZTaSBsZXMgcGFyZWNlIHF1ZSBlc3RhbW9zIGhhY2llbmRvIGFsZ28gYnVlbm8gcGFyYSBsYSBnZW50ZSBsb3MgaW52aXRhbW9zIGEgcXVlIHNlIGFzb2NpZW4gYSBub3NvdHJvcyBtZWRpYW50ZSBlbCBwYWdvIGRlIHVuYSBwZXF1ZcOxYSBjb250cmlidWNpw7NuIG1lbnN1YWwgcXVlIHNlIGRlYml0YXLDoSBkZSBzdSB0YXJqZXRhIAogIGRlIGNyw6lkaXRvLCB0b2RhIGNvbGFib3JhY2nDs24gcG9yIHBlcXVlw7FhIHF1ZSBzZWEgbm9zIGF5dWRhcsOhCiAgPGJyIC8+PGJyIC8+CiAgQWNvbXBhw7FlbiBlc3RhIHRhcmVhIHF1ZSBkZXNlYW1vcyBzZWd1aXIgaGFjaWVuZG/igKYKPC9zcGFuPjwvcD4KPC9kaXY+CgkJCjwvZGl2PgogICAgPGRpdiBjbGFzcz0iZm9vdGVyIj48aW1nIHNyYz0iaW1hZ2VzL2Zvb3Rlci5qcGciIHdpZHRoPSI5MzUiIGhlaWdodD0iODciIC8+PC9kaXY+Cgo8L2Rpdj4KICAgICA8IS0tZW5kIG9mIENPTlRFTklETzEgLS0+CiAgICAKICAgIDxkaXYgY2xhc3M9ImNvbnRlbmlkbzIiIGlkPSJjb250ZW5pZG8yIj4KICAgIDwhLS1DT05URU5JRE8gMmRvIEJPVE9OICAtLT4KICAgIAoKPGRpdiBjbGFzcz0iZm9uZG9fY29udDIiPgoKPGRpdiBjbGFzcz0iZm9ybSI+CiAgPGRpdiBjbGFzcz0idGV4dG8iPgogICAgPHA+Jm5ic3A7PC9wPgogICAgPHA+Jm5ic3A7PC9wPgo8cD48c3BhbiBjbGFzcz0idGl0dWxvX2Zvcm0iPjxiPkRBVE9TIFBFUlNPTkFMRVM8L2I+PC9zcGFuPgogICAgPHNwYW4gY2xhc3M9InRpdHVsb19mb3JtMiI+KEVzIG9ibGlnYXRvcmlvIHJlbGxlbmFyIGxvcyBjYW1wb3MgCiAgICAgICAgICAgICAgICBpbmRpY2Fkb3MgY29uICopPC9zcGFuPjwvcD4KICAgIDxkaXYgaWQ9ImJsb3F1ZV9penFfMDMiPgogICAgCQk8ZGl2IGlkPSJibG9xdWVfaXpxXzAzX3RleHRvIj4KICAgICAgICAgICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgICAgICAgICAgIDxzY3JpcHQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICBmdW5jdGlvbiB2YWxpZGFyRW1haWwoZW1haWwpIHsgCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgdmFyIHJlICA9IC9eKFthLXpBLVowLTlfLi1dKStAKChbYS16QS1aMC05LV0pKy4pKyhbYS16QS1aMC05XXsyLDR9KSskLzsgCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgaWYgKCFyZS50ZXN0KGVtYWlsKSkgeyAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgcmV0dXJuIGZhbHNlOyAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICB9IAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJldHVybiB0cnVlOyAKICAgICAgICAgICAgICAgICAgICAgICAgICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgZnVuY3Rpb24gdmFsaWRhcihvYmopIHsKICAgICAgICAgICAgICAgICAgICAgICAgICAgIGlmIChvYmoubm9tYnJlLnZhbHVlID09ICcnKSB7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgYWxlcnQoIkRlYmUgaW5ncmVzYXIgc3Ugbm9tYnJlIik7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgb2JqLm5vbWJyZS5mb2N1cygpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJldHVybiBmYWxzZTsKICAgICAgICAgICAgICAgICAgICAgICAgICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgICAgIGlmIChvYmouYXBlbGxpZG8udmFsdWUgPT0gJycpIHsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBhbGVydCgiRGViZSBpbmdyZXNhciBzdSBhcGVsbGlkbyIpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIG9iai5hcGVsbGlkby5mb2N1cygpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJldHVybiBmYWxzZTsKICAgICAgICAgICAgICAgICAgICAgICAgICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgICAgIGlmIChvYmoudGVsZWZvbm8udmFsdWUgPT0gJycpIHsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBhbGVydCgiRGViZSBpbmdyZXNhciBzdSB0ZWxlZm9ubyIpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIG9iai50ZWxlZm9uby5mb2N1cygpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJldHVybiBmYWxzZTsKICAgICAgICAgICAgICAgICAgICAgICAgICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgICAgIGlmIChvYmouZW1haWwudmFsdWUgPT0gJycpIHsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBhbGVydCgiRGViZSBpbmdyZXNhciBzdSBlbWFpbCIpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIG9iai5lbWFpbC5mb2N1cygpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIHJldHVybiBmYWxzZTsKICAgICAgICAgICAgICAgICAgICAgICAgICAgIH0gZWxzZSB7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgaWYgKHZhbGlkYXJFbWFpbChvYmouZW1haWwudmFsdWUpID09IGZhbHNlKSB7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIGFsZXJ0KCJFbCBlbWFpbCBpbmdyZXNhZG8gZXMgaW5jb3JyZWN0byIpOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBvYmouZW1haWwuZm9jdXMoKTsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgcmV0dXJuIGZhbHNlOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgICAgIGlmIChvYmoudGVybWlub3MuY2hlY2tlZCAhPSB0cnVlKSB7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgYWxlcnQoIkRlYmUgYWNlcHRhciBsb3MgdMOpcm1pbm9zIHkgY29uZGljaW9uZXMiKTsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBvYmoudGVybWlub3MuZm9jdXMoKTsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICByZXR1cm4gZmFsc2U7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICB9CiAgICAgICAgICAgICAgICAgICAgICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgPC9zY3JpcHQ+CiAgICAgICAgICAgICAgICAgICAgICAgIAogICAgICAgICAgICAgICAgICAgICAgICA8Zm9ybSBuYW1lPSJjb250YWN0IiBtZXRob2Q9IlBPU1QiIGFjdGlvbj0iZW52aW8ucGhwIiBvblN1Ym1pdD0icmV0dXJuIHZhbGlkYXIodGhpcykiPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgICAgICAgICAgPGRpdiBpZD0iYmxvcXVlX2l6cV8wMiI+CjxoMT5Ob21icmU8Zm9udCBjb2xvcj0iI0ZGNjYwMCI+KjwvZm9udD48L2gxPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxoMT5BcGVsbGlkbzxmb250IGNvbG9yPSIjRkY2NjAwIj4qPC9mb250PjwvaDE+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGgxPlByb2Zlc2nDs248L2gxPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxoMT5MdWdhciBkZSB0cmFiYWpvPC9oMT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8aDE+VGVsw6lmb25vPGZvbnQgY29sb3I9IiNGRjY2MDAiPio8L2ZvbnQ+PC9oMT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8aDE+RW1haWw8Zm9udCBjb2xvcj0iI0ZGNjYwMCI+KjwvZm9udD48L2gxPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxiciAvPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxiciAvPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwhLS0gPGgxPk5yby4gZGUgVGFyamV0YTxmb250IGNvbG9yPSIjRkY2NjAwIj4qPC9mb250PjwvaDE+IC0tPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxoMT5Nb250bzxmb250IGNvbG9yPSIjRkY2NjAwIj4qPC9mb250PjwvaDE+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGgxPlRpcG8gZGUgT3BlcmFjacOzbjxmb250IGNvbG9yPSIjRkY2NjAwIj4qPC9mb250PjwvaDE+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGgxIGlkPSJoMV90YXJqZXRhIj5UYXJqZXRhPGZvbnQgY29sb3I9IiNGRjY2MDAiPio8L2ZvbnQ+PC9oMT4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8aDEgaWQ9ImgxX2ZyZWN1ZW5jaWEiPkZyZWN1ZW5jaWE8Zm9udCBjb2xvcj0iI0ZGNjYwMCI+KjwvZm9udD48L2gxPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9kaXY+CiAgICAgICAgICAgICAgICAgICAJCSAgPGZpZWxkc2V0PgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48YnIgLz4KICAgICAgICAgICAgICAgICAgICAgICAgICA8aW5wdXQgbmFtZT0ibm9tYnJlIiBjbGFzcz0icmVnMSIgc2l6ZT0iMTUiIHdpZHRoPSIxMDUiIGlkPSJub21icmUiIHR5cGU9InRleHQiPjwvcD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGgxPjwvaDE+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxpbnB1dCBuYW1lPSJhcGVsbGlkbyIgY2xhc3M9InJlZzEiIHNpemU9IjE1IiB3aWR0aD0iMTA1IiBpZD0iYXBlbGxpZG8iIHR5cGU9InRleHQiPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3A+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxoMT48L2gxPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48aW5wdXQgbmFtZT0icHJvZmVzaW9uIiBjbGFzcz0icmVnMSIgc2l6ZT0iMTUiIHdpZHRoPSIxMDUiIGlkPSJwcm9mZXNpb24iIHR5cGU9InRleHQiPjwvcD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGgxPjwvaDE+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxpbnB1dCBuYW1lPSJ0cmFiYWpvIiBjbGFzcz0icmVnMSIgc2l6ZT0iMTUiIHdpZHRoPSIxMDUiIGlkPSJ0cmFiYWpvIiB0eXBlPSJ0ZXh0Ij48L3A+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxoMT48L2gxPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48aW5wdXQgbmFtZT0idGVsZWZvbm8iIGNsYXNzPSJyZWcxIiBzaXplPSIxNSIgd2lkdGg9IjEwNSIgaWQ9InRlbGVmb25vIiB0eXBlPSJ0ZXh0Ij48L3A+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxoMT48L2gxPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48aW5wdXQgbmFtZT0iZW1haWwiIGNsYXNzPSJyZWcxIiBzaXplPSIxNSIgd2lkdGg9IjEwNSIgaWQ9ImVtYWlsIiB0eXBlPSJ0ZXh0Ij48L3A+PGJyIC8+CgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA+PHNwYW4gY2xhc3M9InRpdHVsb19mb3JtIj48Yj5ET05BQ0lPTkVTPC9iPjwvc3Bhbj48L3A+ICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjwvcD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwhLS0gPHA+PGlucHV0IG5hbWU9InRhcmpldGEiIGNsYXNzPSJyZWcxIiBzaXplPSIxNSIgd2lkdGg9IjEwNSIgaWQ9InRhcmpldGEiIHR5cGU9InRleHQiPjwvcD4gLS0+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8cD48c2VsZWN0IG5hbWU9Im1vbnRvIiBjbGFzcz0icmVnMiIgaWQ9Im1vbnRvIiBvbkNoYW5nZT0iaWYgKHRoaXMudmFsdWUgPT0gJy0xJykgeyBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgndHh0bW9udG8nKS5zdHlsZS5kaXNwbGF5PScnOyB9IGVsc2UgeyBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgndHh0bW9udG8nKS5zdHlsZS5kaXNwbGF5PSdub25lJzsgfSAiPgogICAgICAgICAgICAgICAgICAgICAgPG9wdGlvbiB2YWx1ZT0iNTAiPiQgNTA8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjEwMCI+JCAxMDA8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjE1MCI+JCAxNTA8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjIwMCI+JCAyMDA8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9Ii0xIj5PdHJvLCBpbmdyZXNlIHZhbG9yPC9vcHRpb24+CiAgICAgICAgICAgICAgICAgICAgPC9zZWxlY3Q+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8c2NyaXB0PgogICAgICAgICAgICAgICAgICAgICAgICAgICAgZnVuY3Rpb24gc29sb051bWVyb3MobXlmaWVsZCxlKSB7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAJdmFyIGtleWNvZGU7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAJaWYgKHdpbmRvdy5ldmVudCkgewogICAgICAgICAgICAgICAgICAgICAgICAgICAgCSAgICBrZXljb2RlID0gd2luZG93LmV2ZW50LmtleUNvZGU7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAJfSBlbHNlIHsKICAgICAgICAgICAgICAgICAgICAgICAgICAgIAkgICAgaWYgKGUpIHsKICAgICAgICAgICAgICAgICAgICAgICAgICAgIAkgICAgICAgIGtleWNvZGUgPSBlLndoaWNoOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgCSAgICB9IGVsc2UgewogICAgICAgICAgICAgICAgICAgICAgICAgICAgCSAgICAgICAgcmV0dXJuIHRydWU7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAJICAgIH0KICAgICAgICAgICAgICAgICAgICAgICAgICAgIAl9CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAJaWYgKCgoa2V5Y29kZT40NykgJiYgKGtleWNvZGU8NTgpKSAgfHwgKGtleWNvZGU9PTgpKSB7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAJICAgIHJldHVybiB0cnVlOyAKICAgICAgICAgICAgICAgICAgICAgICAgICAgIAl9IGVsc2UgewogICAgICAgICAgICAgICAgICAgICAgICAgICAgCSAgICByZXR1cm4gZmFsc2U7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAJfQogICAgICAgICAgICAgICAgICAgICAgICAgICAgfQogICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9zY3JpcHQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8aW5wdXQgbmFtZT0idHh0bW9udG8iIGNsYXNzPSJyZWcxIiBzaXplPSIxNSIgd2lkdGg9IjIwIiBpZD0idHh0bW9udG8iIHR5cGU9InRleHQiIG1heGxlbmd0aD0iNyIgb25LZXlQcmVzcz0icmV0dXJuIHNvbG9OdW1lcm9zKHRoaXMsIGV2ZW50KTsiIHN0eWxlPSJkaXNwbGF5Om5vbmUiPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9wPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPHNjcmlwdD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgIGZ1bmN0aW9uIG11ZXN0cmFGb3JtYVBhZ28odmFsb3IpIHsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBpZiAodmFsb3IgPT0gMikgewogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgncF9tZWRpb3BhZ28nKS5zdHlsZS5kaXNwbGF5ID0gJ25vbmUnOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgncF9jdW90YXMnKS5zdHlsZS5kaXNwbGF5ID0gJ25vbmUnOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgncF9mb3JtYXBhZ29vdHJvJykuc3R5bGUuZGlzcGxheSA9ICcnOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgnaDFfdGFyamV0YScpLmlubmVySFRNTCA9ICdGb3JtYSBkZSBQYWdvPGZvbnQgY29sb3I9IiNGRjY2MDAiPio8L2ZvbnQ+JzsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgZG9jdW1lbnQuZ2V0RWxlbWVudEJ5SWQoJ2gxX2ZyZWN1ZW5jaWEnKS5pbm5lckhUTUwgPSAnJzsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICB9IGVsc2UgewogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgncF9tZWRpb3BhZ28nKS5zdHlsZS5kaXNwbGF5ID0gJyc7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRvY3VtZW50LmdldEVsZW1lbnRCeUlkKCdwX2N1b3RhcycpLnN0eWxlLmRpc3BsYXkgPSAnJzsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgZG9jdW1lbnQuZ2V0RWxlbWVudEJ5SWQoJ3BfZm9ybWFwYWdvb3RybycpLnN0eWxlLmRpc3BsYXkgPSAnbm9uZSc7CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIGRvY3VtZW50LmdldEVsZW1lbnRCeUlkKCdoMV90YXJqZXRhJykuaW5uZXJIVE1MID0gJ1RhcmpldGE8Zm9udCBjb2xvcj0iI0ZGNjYwMCI+KjwvZm9udD4nOwogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBkb2N1bWVudC5nZXRFbGVtZW50QnlJZCgnaDFfZnJlY3VlbmNpYScpLmlubmVySFRNTCA9ICdGcmVjdWVuY2lhPGZvbnQgY29sb3I9IiNGRjY2MDAiPio8L2ZvbnQ+JzsKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICB9CiAgICAgICAgICAgICAgICAgICAgICAgICAgICB9CiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L3NjcmlwdD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPjxzZWxlY3QgbmFtZT0iZm9ybWFwYWdvIiBjbGFzcz0icmVnMiIgaWQ9ImZvcm1hcGFnbyIgb25DaGFuZ2U9Im11ZXN0cmFGb3JtYVBhZ28odGhpcy52YWx1ZSkiIHN0eWxlPSJwb3NpdGlvbjpyZWxhdGl2ZTsgdG9wOjVweDsiPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8b3B0aW9uIHZhbHVlPSIxIj5UYXJqZXRhIGRlIENyw6lkaXRvPC9vcHRpb24+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjIiPkVmZWN0aXZvICjDum5pY2EgdmV6KTwvb3B0aW9uPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9zZWxlY3Q+PC9wPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPHAgaWQ9InBfbWVkaW9wYWdvIiBzdHlsZT0iZGlzcGxheTpub25lIj48c2VsZWN0IG5hbWU9Im1lZGlvcGFnbyIgY2xhc3M9InJlZzIiIGlkPSJtZWRpb3BhZ28iIHN0eWxlPSJwb3NpdGlvbjpyZWxhdGl2ZTsgdG9wOjZweDsiPgogICAgICAgICAgICAgICAgICAgICAgPG9wdGlvbiB2YWx1ZT0iMTUiPk1hc3RlcmNhcmQ8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjEiPlZpc2E8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjYiPkFtZXJpY2FuIEV4cHJlc3M8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICA8L3NlbGVjdD48L3A+CiAgICAgICAgICAgICAgICAgICAgIDxwIGlkPSJwX2N1b3RhcyIgc3R5bGU9ImRpc3BsYXk6bm9uZSI+PHNlbGVjdCBuYW1lPSJjdW90YXMiIGNsYXNzPSJyZWcyIiBpZD0iY3VvdGFzIiBzdHlsZT0icG9zaXRpb246cmVsYXRpdmU7IHRvcDo3cHg7Ij4KICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjEiPkQmZWFjdXRlO2JpdG8gQXV0b20mYWFjdXRlO3RpY28gKHRvZG9zIGxvcyBtZXNlcyk8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxvcHRpb24gdmFsdWU9IjIiPsOabmljYSB2ZXo8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8L3NlbGVjdD48L3A+CiAgICAgICAgICAgICAgICAgICAgPHAgaWQ9InBfZm9ybWFwYWdvb3RybyIgc3R5bGU9ImRpc3BsYXk6bm9uZSI+PHNlbGVjdCBuYW1lPSJmb3JtYXBhZ29vdHJvIiBjbGFzcz0icmVnMiIgaWQ9ImZvcm1hcGFnb290cm8iIHN0eWxlPSJwb3NpdGlvbjpyZWxhdGl2ZTsgdG9wOjdweDsiPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPG9wdGlvbiB2YWx1ZT0iOTk3Ij5EZXBvc2l0byBCYW5jYXJpbzwvb3B0aW9uPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgPG9wdGlvbiB2YWx1ZT0iOTk4Ij5QYWdvIGVuIEVmZWN0aXZvPC9vcHRpb24+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8b3B0aW9uIHZhbHVlPSI5OTkiPkRpbmVyb01haWw8L29wdGlvbj4KICAgICAgICAgICAgICAgICAgICAgICAgICA8L3NlbGVjdD48L3A+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA+ICAgCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxiciAvPiAgICAgICAgICAgICAgICAgICAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxpbnB1dCBuYW1lPSJyZWNpYmlyIiBpZD0iY2hlY2siIHR5cGU9ImNoZWNrYm94IiBjaGVja2VkPSJ0cnVlIiB2YWx1ZT0iU2kiIC8+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIFMmaWFjdXRlOywgZGVzZW8gcmVjaWJpciAKICAgICAgICAgICAgICAgIGluZm9ybWFjaSZvYWN1dGU7biBwZXJpJm9hY3V0ZTtkaWNhIGRlIFNhbHVkIEFjdGl2YSB5IAogICAgICAgICAgICAgICAgc3VzIFByb3llY3RvcyBkZSBEZXNhcnJvbGxvLiAgICAgICAgICAgICAgICA8L3A+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxwPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxpbnB1dCBuYW1lPSJsaXN0YSIgaWQ9ImNoZWNrIiB0eXBlPSJjaGVja2JveCIgY2hlY2tlZD0idHJ1ZSIgdmFsdWU9IlNpIiAvPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIFNpIGRlc2VvIGFwYXJlY2VyIGVuIGxhIGxpc3RhIGRlIGRvbmFjaW9uZXMgaW5kaXZpZHVhbGVzLiAKICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBBcGFyZWNlciZhYWN1dGU7IHN1IG5vbWJyZSBlbiBsYSBsaXN0YSBkZWwgcG9ydGFsIGRlIFNhbHVkIAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICBBY3RpdmEuPC9wPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8cD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8aW5wdXQgbmFtZT0idGVybWlub3MiIGlkPSJ0ZXJtaW5vcyIgdHlwZT0iY2hlY2tib3giIHZhbHVlPSJTaSIgLz4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBBY2VwdG8gbG9zIHTDqXJtaW5vcyB5IGNvbmRpY2lvbmVzLjwvcD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPHA+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgQWRlbcOhcywgY29uIHR1IGRvbmFjacOzbiwgb2J0ZW7DqXMgZGVzY3VlbnRvcyBlbiB0b2RhcyBsYXMgYWN0aXZpZGFkZXMgZGUgU2FsdWQgQWN0aXZhOiBjdXJzb3MsIGpvcm5hZGFzLCBjb25ncmVzb3MuPC9wPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8cD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIAogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxpbnB1dCBuYW1lPSJpbWFnZSIgc3JjPSJmb3JtX2ZpbGVzL0ZPUk1VTEFSSU9fMTUuanBnIiBoZWlnaHQ9IjM4IiB0eXBlPSJpbWFnZSIgd2lkdGg9IjExNSI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGltZyBvbkNsaWNrPSJyZXR1cm4gcmVzZXQoKTsiIHNyYz0iZm9ybV9maWxlcy9ib3Rvbi1jYW5jZWxfMTUuanBnIiBoZWlnaHQ9IjM4IiB3aWR0aD0iMTE1Ij48L3A+CiAgICAgICAgICAgICAgICAgICAgICAgICAgPC9maWVsZHNldD4KCiAgPC9mb3JtPgogIAogIDxiciAvPgo8YnIgLz4KCgoKPHRhYmxlIHdpZHRoPSI2MzMiIGJvcmRlcj0iMCIgYWxpZ249ImNlbnRlciIgY2VsbHBhZGRpbmc9IjAiIGNlbGxzcGFjaW5nPSIwIj4KICA8dHI+CiAgICA8dGQgd2lkdGg9IjAiIGFsaWduPSJsZWZ0IiBiZ2NvbG9yPSIjMjY1MjE3IiBjbGFzcz0iaDMiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMTAiIGNlbGxwYWRkaW5nPSI3Ij4KICAgICAgPHRyPgogICAgICAgIDx0ZCBjbGFzcz0iaDUiPkZPUk1BUyBERSBQQUdPPC90ZD4KICAgICAgPC90cj4KICAgIDwvdGFibGU+CiAgICAgIDxzcGFuIGNsYXNzPSJoNCI+CiAgICA8L3NwYW4+PC90ZD4KICA8L3RyPgogIDx0cj4KICAgIDx0ZCBiZ2NvbG9yPSIjQ0NDQ0NDIj48YnIgLz4KICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIxMCIgY2VsbHNwYWNpbmc9IjUiPgogICAgICA8dHI+CiAgICAgICAgPHRkIGJnY29sb3I9IiNlMDY3MGEiPiZuYnNwOyZuYnNwOzxzcGFuIGNsYXNzPSJoNSI+VGFyamV0YSBkZSBDUsOJRElUTyAocG9yIGTDqWJpdG8gYXV0b23DoXRpY28pPC9zcGFuPjwvdGQ+CiAgICAgIDwvdHI+CiAgICAgIDx0cj4KICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSIxODUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgIDx0cj4KICAgICAgICAgICAgPHRkIHdpZHRoPSIxMCI+Jm5ic3A7PC90ZD4KICAgICAgICAgICAgPHRkIHdpZHRoPSIxNTAiPjxpbWcgc3JjPSJpbWFnZXMvdmlzYW1hc3RlcmFtZS5qcGciICB3aWR0aD0iMjM2IiBoZWlnaHQ9IjYwIiAvPjwvdGQ+CiAgICAgICAgICAgIDx0ZCB3aWR0aD0iMjUiPiZuYnNwOzwvdGQ+CiAgICAgICAgICA8L3RyPgogICAgICAgIDwvdGFibGU+CiAgICAgICAgICA8dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjciIGNlbGxwYWRkaW5nPSI1Ij4KICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPlNlIGxlIGRlYml0YXLDoSBkZSBzdSBjdWVudGEsIHRvZG9zIGxvcyBtZXNlcy4gTGUgcmVjb3JkYW1vcyBxdWUgZWwgZMOpYml0byBhdXRvbcOhdGljbyBkZSBzdSB0YXJqZXRhIGRlIGNyw6lkaXRvIHVzdGVkIGxvIHB1ZWRlIGNhbmNlbGFyIGVuIGVsIG1vbWVudG8gcXVlIGxvIGRlc2VlIGNvbXVuaWPDoW5kb3NlIGNvbiBub3NvdHJvczwvc3Bhbj48L3RkPgogICAgICAgICAgICA8L3RyPgogICAgICAgICAgPC90YWJsZT4KICAgICAgICAgIDxwPgogICAgICAgICAgPC9wPjwvdGQ+CiAgICAgIDwvdHI+CiAgICA8L3RhYmxlPgogICAgICA8cD4mbmJzcDs8L3A+CiAgICAgIDx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBhbGlnbj0iY2VudGVyIiBjZWxscGFkZGluZz0iMTAiIGNlbGxzcGFjaW5nPSI1Ij4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYmdjb2xvcj0iI2UwNjcwYSI+Jm5ic3A7IDxzcGFuIGNsYXNzPSJoNSI+RUZFQ1RJVk8gcG9yIMO6bmljYSB2ZXogPC9zcGFuPjwvdGQ+CiAgICAgICAgPC90cj4KICAgICAgICA8dHI+CiAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSI3IiBjZWxscGFkZGluZz0iNSI+CiAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICA8dGQ+PHNwYW4gY2xhc3M9ImgzIj48ZW0+VXN0ZWQgcmVhbGl6YXLDoSBsYSBkb25hY2nDs24gcG9yIMO6bmljYSB2ZXouIFB1ZWRlIGRvbmFyIGxhcyB2ZWNlcyBxdWUgcXVpZXJhLCBjb21wbGV0YW5kbyBudWV2YW1lbnRlIGVzdGUgZm9ybXVsYXJpbyBlIGluZ3Jlc2FuZG8gZWwgbW9udG8gZGVzZWFkby48L2VtPjwvc3Bhbj48L3RkPgogICAgICAgICAgICA8L3RyPgogICAgICAgICAgPC90YWJsZT4KICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSI3IiBjZWxscGFkZGluZz0iNSI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGJnY29sb3I9IiNDQ0NDQ0MiPjxzcGFuIGNsYXNzPSJoMiI+PHN0cm9uZz5Qb3IgIHRyYW5zZmVyZW5jaWEgYmFuY2FyaWEgbyBkZXDDs3NpdG88L3N0cm9uZz4gPC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT4KICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSI3IiBjZWxscGFkZGluZz0iNSI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIxNSUiPjxzcGFuIGNsYXNzPSJoMyI+QVJHRU5USU5BPC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICA8dGQgd2lkdGg9Ijg1JSI+PHNwYW4gY2xhc3M9ImgzIj48aW1nIHNyYz0iaW1hZ2VzL2dhbGljaWEuanBnIiB3aWR0aD0iMTA3IiBoZWlnaHQ9IjE5IiBhbGlnbj0ibWlkZGxlIiAvPjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjIiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMiIgY2VsbHBhZGRpbmc9IjciPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjIiPjxzcGFuIGNsYXNzPSJoMyI+RGF0b3MgcGFyYSBkZXDDs3NpdG9zIHkvbyB0cmFuc2ZlcmVuY2lhOjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9IjIxJSI+PHNwYW4gY2xhc3M9ImgzIj5FbnRpZGFkIEJhbmNhcmlhOiA8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQgd2lkdGg9Ijc5JSI+PHNwYW4gY2xhc3M9ImgzIj5CYW5jbyBHYWxpY2lhPC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQ+PHNwYW4gY2xhc3M9ImgzIj5UaXR1bGFyIGRlIEN1ZW50YTo8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8dGQ+PHNwYW4gY2xhc3M9ImgzIj5TYWx1ZCBBY3RpdmE8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPlRpcG8gZGUgY3VlbnRhOjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPkN1ZW50YSBDb3JyaWVudGUgZW4gcGVzb3M8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPk7Dum1lcm8gZGUgY3VlbnRhOjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPjU1MTctOCAwNTktNDwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkPjxzcGFuIGNsYXNzPSJoMyI+Q0JVOjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPjAwNzAwNTk3MjAwMDAwMDU1MTc4NDY8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPkNVSVQ6PC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkPjxzcGFuIGNsYXNzPSJoMyI+MzAtNzA4MDE0NjMtNjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjIiIGNsYXNzPSJoMyI+UkVTVE8gREVMIE1VTkRPPC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgIDx0ZCBjb2xzcGFuPSIyIiBjbGFzcz0iaDMiPjx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iMiIgY2VsbHBhZGRpbmc9IjciPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIGNvbHNwYW49IjIiPjxzcGFuIGNsYXNzPSJoMyI+RGF0b3MgcGFyYSBkZXDDs3NpdG9zIHkvbyB0cmFuc2ZlcmVuY2lhOjwvc3Bhbj48L3RkPgogICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyMSUiPjxzcGFuIGNsYXNzPSJoMyI+RW50aWRhZCBCYW5jYXJpYTogPC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSI3OSUiPjxzcGFuIGNsYXNzPSJoMyI+V2FjaG92aWEgQmFuayBOLkEuIC0gTmV3IFlvcms8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPlN3aWZ0IEFkZHJlc3M6PC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkPjxzcGFuIGNsYXNzPSJoMyI+UE5CUFVTM05OWUM8L3NwYW4+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZD48c3BhbiBjbGFzcz0iaDMiPkZlZHdpcmU6PC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkPjxzcGFuIGNsYXNzPSJoMyI+MDI2MDA1MDkyPC9zcGFuPjwvdGQ+CiAgICAgICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgICA8L3RhYmxlPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT4KICAgICAgICAgICAgPHA+PC9wPgogICAgICAgICAgICA8dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjciIGNlbGxwYWRkaW5nPSI1Ij4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0NDQ0NDQyI+PHNwYW4gY2xhc3M9ImgyIj5BY2Vyw6FuZG9zZSBhIG51ZXN0cmEgZW50aWRhZDwvc3Bhbj48L3RkPgogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgICAgIDx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBhbGlnbj0iY2VudGVyIiBjZWxscGFkZGluZz0iMTAiIGNlbGxzcGFjaW5nPSI1Ij4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgIAogICAgICAgICAgICAgIDwvdHI+CiAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgPHRkIGJnY29sb3I9IiNGRkZGRkYiPjx0YWJsZSB3aWR0aD0iMzAwIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSIwIiBjZWxscGFkZGluZz0iMCI+CiAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICA8dGQ+Jm5ic3A7Jm5ic3A7PGltZyBzcmM9ImltYWdlcy9zYWx1ZC5qcGciIHdpZHRoPSIxNTQiIGhlaWdodD0iMzkiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgPC90YWJsZT4KICAgICAgICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGNlbGxzcGFjaW5nPSI3IiBjZWxscGFkZGluZz0iNSI+CiAgICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgICAgPHRkIGNsYXNzPSJoMyI+RGlyZWNjaW9uOiBBdi4gUHRlIFBlcsOzbiAoZXggUml2YWRhdmlhKSAyNTE0MC4gTWVybG8gQnMuIEFzLjxiciAvPgogICAgICAgICAgICAgICAgICAgICAgICBUZWwuOiAwMjIwIDQ4Mjg0MTggLyA0ODYxMTgwPGJyIC8+CiAgICAgICAgICAgICAgICAgICAgICAgIEUtbWFpbDogc2FsdWRhY3RpdmFAc2FsdWRhY3RpdmEub3JnLmFyPC90ZD4KICAgICAgICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICAgICAgICA8L3RhYmxlPgogICAgICAgICAgICAgICAgICA8cD48L3A+PC90ZD4KICAgICAgICAgICAgICA8L3RyPgogICAgICAgICAgICA8L3RhYmxlPgogICAgICAgICAgICA8dGFibGUgd2lkdGg9IjEwMCUiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjciIGNlbGxwYWRkaW5nPSI1Ij4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0NDQ0NDQyIgY2xhc3M9ImgyIj5ESU5FUk8gTUFJTDwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgPC90YWJsZT4KICAgICAgICAgICAgPHRhYmxlIHdpZHRoPSIxMDAlIiBib3JkZXI9IjAiIGFsaWduPSJjZW50ZXIiIGNlbGxwYWRkaW5nPSIxMCIgY2VsbHNwYWNpbmc9IjUiPgogICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgCiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICA8dHI+CiAgICAgICAgICAgICAgICA8dGQgYmdjb2xvcj0iI0ZGRkZGRiI+PHRhYmxlIHdpZHRoPSIzMDAiIGJvcmRlcj0iMCIgY2VsbHNwYWNpbmc9IjAiIGNlbGxwYWRkaW5nPSIwIj4KICAgICAgICAgICAgICAgICAgPHRyPgogICAgICAgICAgICAgICAgICAgIDx0ZCB3aWR0aD0iMTAiPiZuYnNwOzwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPHRkIHdpZHRoPSIyOTAiPjxpbWcgc3JjPSJpbWFnZXMvZGluZXJvbWFpbC5qcGciIHdpZHRoPSI0MTEiIGhlaWdodD0iNTAiIC8+PC90ZD4KICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgIDwvdGFibGU+CiAgICAgICAgICAgICAgICAgIDx0YWJsZSB3aWR0aD0iMTAwJSIgYm9yZGVyPSIwIiBjZWxsc3BhY2luZz0iNyIgY2VsbHBhZGRpbmc9IjUiPgogICAgICAgICAgICAgICAgICAgIDx0cj4KICAgICAgICAgICAgICAgICAgICAgIDx0ZCBjbGFzcz0iaDMiPkltcHJpbWEgZWwgY3Vww7NuIHkgZGlyw61qYXNlIGEgbGFzIHN1Y3Vyc2FsZXMgaGFiaWxpdGFkYXMgcGFyYSByZWFsaXphciBlbCBwYWdvLiBMdWVnbyBww7NuZ2FzZSBlbiBjb250YWN0byBjb24gbm9zb3Ryb3MgcGFyYSBpbmZvcm1hcm5vcyBkZSBsYSBvcGVyYWNpw7NuLjwvdGQ+CiAgICAgICAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgICAgICAgICAgPC90YWJsZT4KICAgICAgICAgICAgICAgICAgPHA+PC9wPjwvdGQ+CiAgICAgICAgICAgICAgPC90cj4KICAgICAgICAgIDwvdGFibGU+PC90ZD4KICAgICAgICA8L3RyPgogICAgICA8L3RhYmxlPgogICAgICA8cD48YnIgLz4KICAgIDwvcD48L3RkPgogIDwvdHI+CjwvdGFibGU+CgoKICAgICAKPC9kaXY+CgoKPCEtLWVuZCBvZiBDT05URU5JRE8yIC0tPgogICAgCiAgICA8ZGl2IGNsYXNzPSJjb250ZW5pZG8iIGlkPSJjb250ZW5pZG8zIj4KCgogICAgPC9kaXY+IDwhLS1lbmQgb2YgQ09OVEVOSURPMyAtLT4KICAgIAogICAgPGRpdiBjbGFzcz0iY29udGVuaWRvIiBpZD0iY29udGVuaWRvNCI+CiAgICAKICAgIDwvZGl2PiA8IS0tZW5kIG9mIENPTlRFTklETzQgLS0+CiAgICAKPGJyIC8+ICAgIAo8YnIgLz4KPGRpdiBjbGFzcz0iY29udGVuaWRvMiIgaWQ9ImNvbnRlbmlkbzUiIGFsaWduPSJjZW50ZXIiPjwvZGl2Pgo8cD4KICA8IS0tZW5kIG9mIENPTlRFTklETzQgLS0+CiAgPCEtLWVuZCBvZiBDT05URU5FRE9SIC0tPgo8L3A+Cgo8c2NyaXB0Pm11ZXN0cmFGb3JtYVBhZ28oZG9jdW1lbnQuZ2V0RWxlbWVudEJ5SWQoJ2Zvcm1hcGFnbycpLnZhbHVlKTwvc2NyaXB0Pgo8L2JvZHk+Cgo8L2h0bWw+Cg==]]></response> | |
| 272 | <responseRedirected>false</responseRedirected> | |
| 273 | </requestresponse> | |
| 274 | </issue> | |
| 275 | </issues> |
| 0 | <?xml version="1.0" ?> | |
| 1 | <NessusClientData_v2> | |
| 2 | <Policy><policyName>Web App Tests</policyName> | |
| 3 | <Preferences><ServerPreferences><preference><name>max_simult_tcp_sessions</name> | |
| 4 | <value>unlimited</value> | |
| 5 | </preference> | |
| 6 | <preference><name>use_mac_addr</name> | |
| 7 | <value>no</value> | |
| 8 | </preference> | |
| 9 | <preference><name>plugin_set</name> | |
| 10 | <value>16775;16066;25451;54191;60374;55364;61980;33572;12878;24384;43101;40715;26256;27362;57439;66560;21828;64849;39419;32080;65025;64615;28457;55991;38878;40003;40295;16700;14933;66924;19111;15882;36867;63797;24446;34096;34617;23116;27863;56309;23189;32964;50088;53469;34145;32085;27877;18919;60594;62734;42311;19973;31892;36886;38403;55257;25995;52440;31436;17166;65244;19388;27965;15393;26515;28262;16773;62047;20539;35893;59532;15649;23796;58710;11594;45524;33408;39771;29306;14951;63816;58325;31734;38307;32903;56742;22288;56843;34309;39792;19670;14569;56779;25131;51561;20609;40921;25266;29615;63994;58162;10204;53864;14546;22930;60854;25068;23322;16312;19085;44745;50674;44799;24139;12202;36772;18138;52867;55000;62536;16658;38123;34019;55904;40427;44045;38321;24327;62205;20432;23952;38236;21636;28106;36662;43573;55879;43474;51875;11729;13663;42859;56810;65485;47696;31561;47282;45832;53105;13247;56184;57113;11739;58678;27884;29860;51053;57103;46951;15171;14227;17165;20428;52632;41600;15266;16025;46105;51858;46237;39113;16893;22762;40250;51698;33691;42641;33700;54546;21258;58145;16638;63985;22868;49610;56746;52661;48874;51900;47041;24200;21571;66365;11943;20180;14171;10154;47806;62875;22482;45201;50431;30320;66411;28749;16299;22434;57250;51598;37120;45164;34660;29451;29617;49560;41594;59710;24867;48889;41944;43520;15774;54143;47460;49908;39636;49216;19225;49646;64778;42547;21541;57938;61559;18062;26524;38588;11272;21078;62583;60028;31067;37086;51363;15225;28696;20845;66903;16810;21701;66938;13008;15401;26081;51606;37106;37750;41013;20616;45996;53256;53194;24486;19214;10917;15378;54564;40520;27011;38990;19278;44149;55221;49975;43197;34147;32120;53066;33034;20189;61512;47009;55122;48195;51146;28485;24597;59787;24508;36760;20284;49322;40251;14441;25657;50355;30048;17716;59389;16967;36481;43373;60386;29491;38942;39491;37062;34111;54514;59702;12239;59574;20381;30751;24278;21000;41693;11941;54910;30073;28949;37389;40461;14315;10662;24806;14421;41100;26083;60317;22418;18129;32960;54316;45293;33282;63888;49382;25608;33820;12631;39693;59652;60850;46413;14781;60396;39705;17727;17426;64519;50675;10806;61239;20993;52205;42101;41218;16156;17053;25173;57840;51387;47451;11412;52770;10142;13207;37128;61996;27465;39296;49170;37769;29553;62985;38125;53435;53953;39482;29555;10005;15457;53021;33578;37474;20817;41795;20895;14788;19279;38643;47254;11370;18105;17676;14416;21002;39355;33000;30892;28206;50090;20345;22594;66573;53826;42459;19081;64084;63498;22829;39738;24054;37622;64018;31870;51369;10177;24577;14932;58389;45216;20406;65644;17277;25542;45615;31043;60619;15574;40887;22928;55048;10056;12252;36575;55774;52443;16894;40435;57020;25647;18618;25867;48891;18568;23509;32432;64128;40938;40964;36774;41656;54189;46755;34555;30819;14901;35624;31690;24442;39508;31017;66747;44910;24860;66726;26286;50212;34673;31837;53986;62223;12651;62597;11578;59925;28355;29359;17337;36753;42317;40747;22475;31811;49125;12217;57435;45150;50413;23691;29318;30543;64980;30717;54490;14590;56258;32092;35005;27058;63682;44878;34414;24479;19538;48351;20875;41702;20745;21460;53349;18604;63413;32031;31095;18493;33276;25231;13575;59411;13254;27641;24185;10728;42031;10509;15840;51593;39822;62915;43163;13600;52919;43765;62348;33759;62572;47784;35547;46362;12460;18058;59077;39266;65377;36671;53590;23588;36876;42538;28111;34519;15385;12791;49555;36275;10919;61384;37468;43972;37561;21368;38075;46049;65350;35176;45488;21860;45110;50531;58464;58041;53828;63141;37472;63036;60172;17071;41114;14931;59747;28638;54145;41520;44769;56847;31608;55045;20762;35022;41923;11245;14860;32854;19321;32687;42111;11443;39582;33385;38237;41105;65107;22860;64140;27061;42214;32717;53184;61441;23506;64376;33983;61050;19433;49821;24782;51774;21050;30977;50529;43066;35416;43307;65437;60770;49557;21178;62951;22336;53819;20653;45475;32808;30205;26929;39087;57575;25795;43669;50136;50635;29169;56044;64935;51248;63439;35292;65819;19276;33227;33468;55659;22413;50564;49335;56225;50940;11835;17312;44596;45350;50824;27851;27615;42051;60260;52980;13754;45371;49535;37287;50372;66798;65098;52118;46809;40916;61022;59507;10487;19584;42068;62333;39780;63440;47277;49386;16800;42439;19562;42422;40569;38296;58709;19101;33964;27934;50182;18477;31952;36996;61138;38756;44398;26914;44535;22302;22028;65355;33100;63222;43799;65393;33932;50485;28260;46277;18173;66809;47534;39752;60939;33256;13128;37404;42722;27748;23869;28637;35269;20006;19946;50710;36634;55495;19375;34331;34221;49683;23298;38821;57541;62192;55753;63185;61706;53618;59164;15021;22516;39253;60321;33009;44987;13572;11785;38740;22859;24335;57301;51549;13760;13629;58404;45841;34029;38889;11692;63168;44968;46739;18364;29423;31411;36936;42982;35083;52427;23972;27605;49771;57409;18506;21795;47364;55064;57124;21437;30557;63199;49058;63681;56704;13868;25172;49119;36118;62431;46763;27947;38440;60871;22736;50343;17518;28241;21685;64991;30877;65564;26075;64588;31292;27043;46326;51069;11882;28862;27312;55305;52119;39956;25539;32901;17283;37313;20482;16599;63869;18279;52999;58775;58925;31682;61762;47069;55992;51474;52120;19630;30133;29840;44698;63871;47549;11416;55092;30006;48518;19610;64232;17248;27507;65634;32913;36222;65030;53996;66837;47527;12066;43406;54840;48815;59208;66081;58477;23992;25082;36021;44848;60582;27244;38962;62147;46051;21145;51870;43396;17379;44959;15508;25749;41317;11939;28038;64030;22472;32775;32720;20661;60829;20478;65888;48975;20312;55736;47280;27368;21614;49621;14346;66705;16885;14990;40590;17341;16964;20537;63547;28024;52969;29552;22512;62391;29089;34985;11641;43809;19325;30063;28871;11083;51404;27623;38653;12591;47626;56106;13109;40597;28254;65197;62272;47195;13581;66079;57513;28656;51299;33961;30925;57380;49263;24402;52165;37217;14422;38193;56954;21935;17020;15816;61572;25924;44436;37002;17026;14778;18098;16208;65240;24886;49160;62318;62207;38251;11236;63680;41957;17821;54933;23081;16748;13836;27752;26339;26438;21042;33272;49930;11127;19945;35432;29117;54469;14629;44747;13295;16719;64494;51225;34427;17326;63290;38303;33640;38057;26792;33861;45029;11552;60343;24570;41673;51009;22602;23407;17351;23668;27482;65727;54713;30243;10529;29956;41096;40662;36505;20088;19047;10725;51001;55501;32772;53676;29442;10099;53759;52916;10757;52955;13406;45138;59824;18185;38919;31469;51505;55848;41273;19626;38636;37651;44516;25456;28809;40372;61213;18223;13036;34789;14155;33835;25476;59936;33819;55516;28108;21030;62988;65896;43038;18885;37022;44895;45625;38855;60721;26499;22110;26226;11327;10528;45246;22024;32658;24390;62492;21584;22653;45507;49412;46922;15609;48854;57207;56630;60357;30509;60709;17749;10496;64046;66410;53522;60772;29063;23459;28630;48276;28029;31726;64657;18670;24134;18176;53411;48570;61524;55917;66541;52382;25559;43142;34024;27028;22203;46331;63838;33087;51251;44651;39221;36605;26317;41449;43886;22937;43057;29396;20059;28849;17834;47061;50704;14127;45577;40259;59535;25971;11382;52653;44635;59506;38373;21538;50867;58272;15325;51334;29492;20960;48174;45747;48383;47102;11037;46449;53015;21226;13300;42375;11730;23877;35569;21007;24687;34066;27672;31231;56102;55400;38760;55789;60585;48811;13069;55306;44414;50853;55834;50950;17637;18421;53716;23325;65973;52191;48640;38050;16374;59123;41433;14379;46226;55859;17057;32179;62678;62279;58133;35156;35739;30910;25862;16620;17989;56086;39684;52356;23620;41384;10492;46561;36896;28527;34621;46839;31446;63114;17336;33978;63696;57393;40414;18442;22374;50265;30849;58937;21870;42833;26678;51226;34273;31366;40105;19559;59469;34363;38477;29915;10268;36362;21771;40188;19387;41442;52809;12235;40209;59134;62246;23204;61370;42494;54698;43086;29789;49710;15898;61995;54592;12444;23285;42106;64668;50098;23201;38968;44479;49130;40254;21858;44875;10392;43716;65781;44423;65190;44123;51124;35367;20316;60319;11021;65138;55640;49954;46005;29071;55322;16313;46205;51710;32981;19355;59850;60117;30972;29444;54926;59723;39015;25312;19490;54058;61158;64926;10673;63004;43687;33319;23625;42677;37753;61864;60737;36932;50884;19774;27393;23855;27432;36660;16221;22558;66921;37251;34773;57328;47119;40280;52219;42449;12287;58575;45074;12839;13814;38804;31773;12015;28424;39590;27145;58702;13537;58462;53240;14786;42138;51323;63894;15748;62968;32164;49071;17713;65573;63643;22528;56009;38506;61118;31617;24616;45768;24511;37845;66813;38412;27716;28151;56567;64799;29855;41945;44181;62309;23453;30547;62773;22174;18332;59957;43425;31792;60603;52133;22525;18991;63446;66647;63980;11702;58679;32697;57723;55095;54790;36982;18346;39996;66928;64660;44048;26735;59891;34239;40592;13311;56932;22289;53286;59428;26324;36805;13862;35895;34142;46860;46585;63381;42299;23786;54723;31471;20113;23449;38220;36695;42984;25656;18483;37281;20569;61528;11066;52960;58568;10911;11337;10573;60670;55587;53683;44505;25025;34872;12928;30072;25146;28962;51352;57659;46386;41339;14713;16827;37978;39575;53026;16098;49580;55024;34344;55885;65226;55726;34917;24761;61258;52891;17671;64723;59049;63861;32295;59792;26343;27278;52907;64774;25985;54495;54260;33335;65555;17085;46321;38478;42297;37500;53927;47407;12111;24559;52829;59736;49945;66574;16501;30991;33442;49566;61376;13227;66556;43701;24676;17599;57144;15970;56168;21280;59910;53622;14897;18823;49759;38446;36319;14596;32784;28896;14511;48237;36920;15699;13090;18348;60614;44614;19356;13726;45516;13696;15222;52441;56984;25406;12232;60570;35900;21392;45595;41987;20130;34192;39787;14332;55626;49110;23624;40830;52492;26345;13464;21054;26501;26084;19654;16923;46109;36761;26687;62762;25609;29109;61372;16315;37636;28225;57487;18226;13997;34669;31706;19074;52790;28025;63969;58209;56568;57021;50794;42558;15444;29187;54812;63495;28671;64096;27908;64653;15734;58698;16220;14551;34233;21328;49729;60200;31181;38535;14720;50006;35002;53884;43232;55399;22023;35199;64781;62519;61318;30126;55527;53386;28286;13268;35138;59822;42263;44522;37730;14974;27973;21248;49779;37366;27549;19597;36288;42785;27398;43394;43736;47638;28384;42113;59006;26012;51538;39119;33168;58616;24455;53124;36196;60064;17077;14658;37656;53236;27987;50690;60171;65825;16484;14670;46519;44454;17791;17445;55285;61127;57143;21214;12906;15780;56723;24491;40311;26974;43881;33450;14787;12804;27256;32593;61977;65544;14399;18993;34347;22391;51955;23395;50707;58540;31423;23621;50049;16291;56535;45604;59203;50919;43906;36594;26070;11290;61037;41515;61733;48647;44313;36612;64941;61989;30725;13049;35537;25235;24636;40977;32859;47846;13753;15878;15196;37503;60855;30018;17171;47270;59027;11026;46430;41841;26444;47378;60484;56493;64342;15109;34367;14733;56754;26938;11985;44750;52739;61747;40129;47386;51321;30897;14013;53474;26021;38161;10970;56239;27533;38798;54387;14303;33571;12921;33587;12503;23784;16443;44427;57549;43145;61310;23097;57175;55208;26448;30417;44018;59534;43872;51202;60618;26465;24685;33584;11714;46667;50643;20831;47111;51975;14337;32591;46358;36527;10947;22782;33384;15095;52180;34851;66126;54203;34149;25160;60383;58842;26138;60044;52944;39820;51925;12736;44553;20387;13427;24057;41470;32966;37377;52954;56649;15676;66950;59041;41281;59047;60336;38995;48287;61423;45817;29854;15621;14985;28989;52808;21052;62399;24602;14092;36347;50631;36673;38194;49833;35888;19154;61013;62289;46576;21831;29435;46659;40391;12536;58040;61701;28408;66255;39601;13071;32185;38309;46384;49390;24114;61869;48773;53955;62316;66119;40239;35572;24917;63349;19846;33715;15268;64544;47028;30968;65664;32235;44071;45162;41880;14342;16655;44037;29285;47066;44625;47298;59338;24992;47668;17717;38580;10666;65401;25418;55403;43522;14795;26449;48689;18690;28081;25948;45363;55733;46152;20900;32692;15688;17174;36035;65351;20304;28471;25250;42082;35306;46666;40332;34572;11474;50411;26953;33678;49982;28838;26643;35550;50544;45795;10913;26017;33375;63543;43723;31780;27349;51717;28587;41759;62805;35686;64298;42267;21937;41498;18983;57878;65289;47136;31538;33699;64712;43051;21574;13692;11757;29834;44573;14184;53778;42541;13282;42094;42652;43751;23652;15899;31527;36504;51485;53727;43102;38382;30312;18852;48742;15389;36601;40235;49304;27686;51186;18895;16349;35602;41185;12673;46909;13253;22485;45906;53707;32985;35026;36345;13333;48940;28655;40737;16297;23528;37362;18657;65567;65261;20149;45517;40252;12584;64764;48916;56005;42857;62619;26373;39620;34310;58880;22012;24938;65200;53515;66361;65911;57685;64828;62506;58072;37485;55077;61874;16248;17710;29632;59923;65196;60467;14604;60385;64056;22456;43471;39027;35800;55175;24255;47063;38593;54551;61148;28978;24222;66299;15541;12399;32910;47441;44998;33170;13750;47728;32197;52578;35652;35581;28026;51235;51074;25877;60842;43829;46559;62792;43753;22963;64596;18443;19764;18229;37416;38758;30142;62146;57504;50907;14187;51528;35552;47258;36623;45305;34421;32339;65071;66226;10859;23963;46878;56002;33501;47861;49532;29971;55664;29065;15597;23198;20580;32399;21379;23555;36135;40302;41631;15102;38763;28118;35324;61764;56219;22721;41090;13719;25908;54041;29043;13446;60863;26162;59201;43794;56415;26656;24904;15677;66851;63493;30573;47095;39250;53315;32038;50823;14809;27122;26022;54335;39189;39182;38534;33879;59245;44729;31155;34771;38547;66391;26150;63828;15620;50259;35679;20871;61556;64184;26201;62836;60371;59372;57552;19689;52166;58521;18160;34460;33064;38574;66611;62764;51542;44183;29110;47794;28539;13704;20626;28334;64301;38748;47689;10670;19453;21011;56133;41328;37760;28074;50759;63927;58874;14174;65939;46558;37092;13033;37535;22998;51075;38916;27270;43260;45281;15674;16509;54940;26798;57075;12439;60098;12471;19875;47715;32978;44452;44114;27474;33542;55178;57656;20805;65447;45638;35633;17272;55902;29008;45463;50123;58665;53502;27492;42411;25750;30095;55402;41828;51930;35722;17376;11649;28430;58608;51289;59728;36010;38449;23941;33885;39100;56937;22784;34164;47359;18512;17504;49270;16200;56419;66827;33742;15506;22807;17625;10273;27501;15794;31661;33803;45789;43267;44272;60209;47297;51388;11063;14052;48721;32690;23320;37397;19409;52991;11658;50314;46220;45180;27829;43333;66242;49220;52712;34710;42260;66349;14076;45169;48505;38575;18978;54503;62368;26440;54064;34064;61888;24275;48950;33077;55380;59785;16765;29001;28548;52733;46917;35454;53231;41094;25137;17689;20819;10296;15138;33539;38829;64851;18389;58030;45426;29532;62035;48683;55811;64389;55415;54421;43578;61577;51375;12120;51458;52283;51778;20300;42117;44956;31102;52573;23244;22267;41812;26862;66635;61253;13633;21001;21842;13617;30762;38551;51221;33506;59071;50227;49225;36397;27966;30636;38632;60264;27077;60097;11054;56361;21905;15921;19937;49228;30974;23059;49326;38199;26208;18518;38903;13953;66940;15418;11131;45551;31192;25627;43914;38337;35253;11469;46438;26709;18951;42977;56873;11758;33832;44434;54036;29913;28145;24348;57110;39023;36140;18497;46317;22078;56578;20843;13847;60873;36552;39891;64755;20689;11828;29596;56051;60170;38838;21274;31104;54513;54720;48814;16464;12458;27097;50518;21022;42615;60864;46235;35428;57961;24425;34956;56097;52680;24313;62470;63066;11396;43490;55330;21362;49343;22502;44301;53603;57480;33138;34056;62338;37333;33299;32536;56132;55662;49611;23005;44320;39006;26175;12977;38729;24874;32948;38379;48862;41525;12118;41888;24277;40054;52677;10491;65752;15858;48229;25800;37407;56397;12979;12457;34044;48216;45099;53538;33946;42742;37703;37932;31243;47248;65699;40212;13913;18772;56247;26992;29272;29329;28411;60410;57429;20602;53783;48461;26124;42739;59772;60512;63964;43417;14153;18532;14406;10555;24593;59547;14998;39517;49725;55190;23580;61119;46293;37504;64181;31037;54909;39472;18283;39455;47447;24252;43181;27812;21175;28463;31158;55110;60122;36003;53838;33165;39703;40482;63667;10019;64748;27135;57106;58514;60137;60299;30315;64692;25419;10923;58939;51452;18121;45739;36457;25344;12820;40298;45388;43652;37619;63415;66451;42080;58723;19163;26205;60568;55901;21510;63204;59025;38941;64994;21302;39618;54209;26893;16240;47050;63819;36281;36270;55680;32739;51802;20864;31230;21140;39001;23188;47439;32503;19824;11984;40849;60096;47272;47847;60287;31035;21555;49698;46745;35927;53559;54993;47584;57013;29167;38569;26919;63979;20257;44374;11779;27161;26469;16709;30576;48920;65853;30324;45134;22326;62345;20120;40194;52295;43713;58544;32618;34898;26811;52422;50432;22870;21727;37020;21032;26609;10860;54157;45847;21522;63092;26274;45330;32002;19273;19146;44571;47222;25296;46267;32590;54768;19410;42910;26848;24070;33927;36553;28782;12807;13976;18684;57039;42965;65702;41293;62306;30959;60080;59090;39988;48167;19460;32596;40939;30141;58783;40810;46357;12246;13032;16980;14085;29837;27723;35272;44778;10526;16624;55227;63538;41815;26778;12620;23348;43819;58347;38831;38710;65993;41680;30527;53880;55355;58265;18333;11588;31641;40911;66707;50568;53519;66920;28370;35364;22923;66603;41752;21365;18831;61521;12427;11506;14906;52865;46404;60263;60014;11518;27677;40257;32684;15427;31679;32492;32527;15417;39325;21966;61058;21154;55730;10833;61731;26335;31545;33871;48731;10119;10377;11667;39908;60786;45890;60397;52051;58200;66001;50308;10763;61330;14032;35396;47538;46002;49589;37521;49151;37668;15874;64458;61432;61527;30368;20914;52459;36216;63116;57606;62871;52262;40301;64020;47850;43172;57729;41696;64950;32116;66975;32849;37653;25011;53645;24254;45684;55710;43321;28819;51338;40050;50770;52272;51242;23950;53216;19255;18366;66558;51301;57036;49334;59148;26647;18205;42415;19618;23301;54013;54750;39441;63025;20785;38462;38628;51819;34308;60253;17670;65397;16377;22962;11395;11666;46028;37884;22691;49015;27137;37374;12690;46374;42125;29303;17300;29965;30294;53722;53752;20994;13091;38871;23923;39279;37569;13583;44806;49857;30495;36828;42947;13857;20504;56463;51518;66570;37903;51038;19260;56658;35289;26237;56963;41692;19891;46823;55074;22034;19785;41753;14444;56681;13579;16264;66774;47462;44238;13593;35806;53689;48225;61958;22769;39783;18961;42230;51903;66820;55909;15537;22803;41461;52506;41890;57176;52981;40092;47488;10450;49414;16821;25710;41993;31800;32332;34965;44338;52224;40788;24569;32738;40572;19790;34868;24686;66138;28506;64782;48551;41784;26490;46389;38849;40012;31295;54429;17587;15907;37447;18362;13689;43722;42110;49632;54271;58159;43666;12300;12858;42716;25791;61919;64254;35610;63249;13892;56150;32317;31863;33647;15112;53787;34353;44709;61178;63153;24007;35033;60297;38645;14063;37705;43159;39981;43166;47262;66357;18821;56206;58077;60657;36263;24627;62580;13278;17014;17789;57177;14073;54102;13747;39110;13447;46289;23700;58354;56670;24015;35455;46751;64208;61131;29591;40004;53019;21864;33136;20952;42860;46639;14158;24869;52626;30783;21082;17225;14363;48173;35388;21401;43454;28476;65183;47178;32873;20818;27803;54448;50061;16480;13016;25377;30253;51576;65055;38541;40237;66776;27295;42399;44765;60866;21855;37580;19148;29085;60013;19167;32976;46758;24954;63175;45105;42186;14374;52766;24967;40878;38074;56925;47624;36439;40462;39481;44513;59045;54742;12901;63923;45576;48516;10730;63773;50368;42518;56859;52408;18997;37097;27346;30800;18217;11440;20872;15554;56928;26683;31042;28406;17152;12864;44980;64768;41133;49961;29966;50042;29384;32013;14823;55248;21205;58071;22631;66339;33596;48601;29301;21834;51707;52953;22650;40631;46216;16909;16963;40655;30199;30390;43880;46164;43556;55636;51325;63876;46101;12338;45803;54879;49156;50753;40431;39444;53581;16329;49369;13379;27958;24304;56187;65480;11478;50730;11088;63856;65435;64529;27876;54033;25360;46330;35912;40725;39055;34561;45864;62538;17773;30035;44346;34974;35505;42676;65442;29430;21269;52245;54110;64402;36143;35139;54494;32568;42016;44126;13560;44817;50083;48246;11418;39778;35908;24422;15976;48953;36318;40369;17038;20210;58748;42550;48460;25398;30609;28499;37533;27595;60529;41069;24291;46465;37133;39071;15760;64882;37881;56893;20680;53638;37345;32517;32040;25341;64393;34944;59493;34148;52236;56944;25855;21904;45335;44160;55663;18507;38081;55044;24908;56609;35319;56448;29975;14278;39235;27956;64493;55315;47821;40873;10800;47588;50561;59135;17486;62748;15540;17294;16532;63971;16747;37818;63451;62412;29797;38596;30300;27588;61885;21291;20481;26450;10437;57812;52081;31514;51935;11125;60694;39391;42322;54155;64889;28561;42535;38883;52785;60859;58446;44642;30934;47867;34479;14992;55945;23731;34206;66476;47214;30695;20013;20606;31128;62713;46043;32204;19570;63970;16449;10989;62534;53774;41810;60942;61583;18329;24012;50782;52252;51255;17566;35423;41062;52946;63230;44768;21894;51098;42032;21128;54267;45011;44294;63155;66271;34046;11724;61171;21594;16840;45468;18437;33090;26607;46300;65108;62285;52889;26702;13326;25817;63683;63992;39122;53924;24507;29054;44866;16294;60985;63085;25578;21649;46411;55546;62511;10412;25015;33499;24319;46707;11646;60983;32066;44760;10369;48543;34518;40952;61514;61313;66596;28783;45537;48905;66908;61324;57709;45586;58688;53521;55776;65441;29199;62118;36133;65068;16077;22891;31263;61001;58096;30301;36883;44391;38278;66044;19062;19676;66017;60778;27506;59062;53486;16378;49637;24791;52832;49383;21940;18745;39398;56528;31027;15239;44716;31028;28593;18729;15800;59343;41921;43989;41954;35314;41345;62482;23346;42424;22235;53602;20204;34912;56037;64009;37456;10846;15595;20479;30409;58419;62552;21228;18166;12097;54180;17645;44795;16393;43083;24757;36860;49554;52791;54673;12205;16201;61492;16403;11212;17278;56688;61721;27541;49182;54153;62984;40366;20951;12589;15419;63508;61735;62610;24800;44531;58006;62563;33265;11331;36840;56425;35966;51918;49865;38275;15664;13875;41192;51383;62353;33515;42134;11154;29891;46324;45682;45165;53093;58282;51758;64648;24544;38242;35574;51535;24664;17737;40198;15020;20341;27654;12601;58327;17044;59918;37273;47826;16870;17736;64248;33850;59108;17707;38606;44610;66372;30329;46020;29293;31838;21006;38518;34927;35125;19385;59298;17117;18330;15271;31464;26215;10689;53888;50275;65628;17177;43790;56191;36248;18865;49987;24234;33935;20617;50462;57828;46669;23032;46047;65761;26379;15149;32858;36479;52353;58010;42520;39881;45049;65128;56697;51976;21664;25858;13337;61666;18843;21516;21906;44772;66130;61678;65857;43933;11431;30631;64743;34593;22404;64012;16873;15340;42657;13562;58712;53904;25932;48725;65969;44554;13978;14460;55700;12728;52250;33643;64073;38814;14101;53429;50694;36131;38690;18679;25229;62819;56212;59555;33821;32016;27334;15986;62938;22208;40464;26472;61499;57226;28359;31047;40090;17309;44796;55618;66336;23293;28212;30658;63120;62879;52418;22576;13484;35242;62430;59456;33206;13844;48467;53881;35132;12598;65093;64490;46996;47088;29302;57344;20883;12058;11848;22177;51399;55762;21561;25258;54419;18687;63889;58860;41990;42143;35775;54011;35897;51831;42139;60510;50740;63624;28123;34776;16710;44700;18319;13554;50499;53892;51184;64903;16847;15602;65789;14423;24810;22426;44086;56303;34087;39012;28658;66676;42034;44543;23561;28303;57054;53510;35058;27098;60869;37797;42035;16735;41152;51893;37226;53981;40970;50246;41559;52852;51654;17441;40038;20470;43380;10017;45622;62230;44360;42978;35787;43565;13024;50945;36209;58819;29357;41341;64124;36750;56708;27223;59828;53303;17236;47856;11348;13352;40323;47253;56000;22618;10568;66313;35920;20305;52487;39495;38053;30194;55503;59666;24297;36370;62495;53928;62981;62354;56048;26361;66658;47081;24224;36827;19264;21170;10316;47499;65738;40641;59504;15093;14233;39175;51231;54228;46451;29408;46622;19581;15997;19975;42296;44898;30216;14049;66273;33735;37566;64909;54480;14188;32483;65590;64722;66427;46913;19050;32514;28903;23262;18563;55062;12576;10935;38922;55484;55386;27475;12209;47770;66431;29170;48439;58300;54595;34752;62681;18314;62704;38522;48451;18587;39940;52679;42537;54851;40513;19806;48774;20515;60026;51020;24849;10580;66910;34137;57174;49381;19593;57919;28442;30010;50241;47710;10823;16607;35692;45257;46228;50127;23970;18370;32444;64877;20974;53013;30545;47647;22306;19092;37923;49624;43680;41830;59640;62378;30340;66831;20489;65905;42824;14913;35305;22935;15902;20402;60413;36624;30064;62890;60978;27885;56001;34653;58751;57451;38094;17813;52509;11602;62643;14718;35149;48951;20505;12034;25345;51155;43503;53958;62882;31453;20507;54867;61724;36309;44417;35534;29321;16431;12346;18971;34999;34038;65912;53120;24362;51739;36364;25701;13332;33015;66563;46834;21264;64932;58191;20935;45365;47580;28659;27002;26942;41001;21605;51617;14579;54783;41819;17787;49158;60199;63535;56122;28446;14963;52208;26466;33689;43177;38540;58998;13548;11686;33278;55172;49605;48650;50647;48466;46985;37901;58317;34089;51199;57896;24219;22412;44197;28901;57795;64908;55356;59323;53068;63623;38579;40763;22301;62815;66315;56359;12432;16486;59820;40735;65338;15796;56165;60024;53059;31269;60893;14686;37855;33505;52075;43395;62775;18018;66046;21492;44450;54641;27526;29238;43127;49817;24805;51354;42261;29844;29795;12863;12055;44378;44365;58231;60305;12695;41306;35681;61224;29405;14274;38281;54412;61846;24701;22076;22508;61464;15433;66882;27781;35917;18282;19887;64165;61461;62540;23928;49079;20241;26736;66503;63258;62682;44880;35669;25934;27148;58801;35170;46798;26485;38101;24283;60615;60061;22705;43810;35903;64628;24078;63841;35096;20758;50296;41541;37058;52255;47737;51523;41199;34584;64867;32429;52521;46993;30167;61389;49106;58548;23326;61667;57596;57764;14288;39598;42542;30184;32059;64469;25002;44228;52281;28492;33082;15127;61063;21120;26161;37142;42171;45230;17247;18833;14594;48154;50194;65966;53457;15231;52697;64627;51904;28390;21724;15350;35604;23919;30426;16568;26217;18695;10428;20043;19552;45764;24629;11636;60952;33652;29352;32280;11765;54282;58518;64264;23777;64726;34153;27127;43140;24804;18228;58648;10431;20431;11070;55457;55015;42095;35576;56738;42058;33154;64161;26789;39034;37306;39543;49726;18812;57305;47450;62800;19230;22117;10675;12581;34302;21691;54072;38148;18720;28569;21733;20757;14968;35683;63447;62910;61700;33846;37821;27522;14135;38877;54314;57281;12726;11392;62501;36405;33213;36579;50287;12336;10514;66009;45605;65779;32036;28583;54633;31108;25530;52582;36557;38681;49784;39388;12089;48416;56659;25400;43224;46052;30094;44847;43699;26377;28288;64865;65583;16858;41930;30287;18050;12855;37574;46600;27124;32553;42994;44696;28991;54475;45100;28851;20002;32795;63032;33645;29091;65630;42464;63039;31557;33604;53643;53781;27935;62277;11857;66029;42689;47568;13107;50926;45582;18873;28447;43019;64233;36358;64305;19002;33936;29612;53400;52958;55525;58642;60606;52157;59709;62154;21911;14541;56373;43766;12383;21430;38811;23707;23876;65047;58803;64863;47210;15121;40799;19740;53089;62760;10464;12527;61242;31438;14397;52364;34911;51466;10118;22844;26439;41543;33349;26451;13401;25594;31372;14751;18784;51645;44096;25526;50562;22127;38897;45223;33268;36265;66487;45166;13477;45650;18940;21944;27583;53293;66957;20925;18382;61782;45208;66677;24013;32735;50279;18775;56384;30699;49888;47244;56920;62855;28061;47676;63808;43602;10360;33440;30262;46162;42220;17251;64509;57998;40856;38762;53144;23403;63217;14851;22488;45448;11248;38376;24796;27765;39465;30807;30839;63671;24558;13516;39576;33623;62657;61089;46061;37342;36490;64737;24682;61924;63016;63394;50333;22743;13179;18019;28566;22965;58753;57019;52333;38869;28575;38820;23562;19639;28617;37127;35954;14413;52719;50683;21633;26460;47535;31050;41052;37207;48455;55537;12828;24879;61095;20876;42650;65530;10481;62721;53866;42971;55055;11885;46799;54823;19615;26642;59074;28090;14907;21177;29841;45189;49013;16590;37431;24464;45599;13711;16284;41368;61998;44563;40402;50795;34128;58935;25205;62105;35283;27118;31500;55251;38184;44788;41011;57446;59804;40835;34699;12688;33769;52480;21748;47669;29668;61027;18603;28725;27705;22601;12023;55147;48274;14330;25294;57749;21200;11408;66232;30375;17202;29336;39422;33548;19748;53141;33180;52777;39980;41443;41506;54612;12225;57277;29105;45104;10926;49839;34326;22903;39111;11889;27644;29666;52478;52147;14749;18966;41208;47187;42908;20918;40260;41139;36513;53696;48210;55523;53335;64153;23020;27140;49078;63720;58690;56459;14212;21699;17505;35687;26839;51253;29631;36849;30824;41765;31756;44965;41508;41606;62418;27838;22059;56798;27087;54686;10934;26976;42407;52168;44376;29703;32572;62374;33058;40596;21261;40243;51992;46679;28354;30032;64690;16653;34840;31750;63263;32489;53337;59032;17021;40547;27111;52235;16530;23327;58288;64062;37776;43424;27611;39606;32210;27159;49404;54697;38311;53234;65282;45406;23718;65019;36039;13312;25302;28271;64543;43572;43787;54080;29143;40443;55647;30153;15698;36240;25414;33179;33481;14799;48436;36110;57856;66106;24018;41932;62739;60767;36902;52618;29674;56594;23872;41677;51997;23310;20686;59371;39722;28879;49783;40381;31474;33010;15090;51479;24092;26359;23263;27167;39663;33016;66848;52554;56108;59932;32414;40853;27903;10682;20227;34327;39142;15411;13039;38699;30639;53401;56177;33150;61526;58264;65227;57960;42801;23960;23484;63523;24588;62647;13838;15357;27659;16373;37960;26347;14855;10942;12714;15980;50701;35623;45446;61302;14041;65689;19623;41337;52016;25440;30817;35771;22761;65594;31513;36261;22929;40734;36645;17996;52204;50964;63345;30710;53836;38706;30482;60236;30121;50124;28681;33863;49376;31741;13452;62693;20719;38725;22009;42682;49190;57468;51693;40423;52331;48488;30092;16941;18216;64847;31671;15873;51784;39614;60023;55510;34246;39214;65415;35672;13830;12902;49981;46007;16603;27180;56566;35466;28933;52358;49798;52363;48284;17831;42923;55559;52901;64911;25392;28610;66694;36127;17290;11215;63275;35750;61141;35118;64542;35419;12408;61772;47699;18237;43665;21618;30612;55963;40760;63198;28719;37867;39955;48168;53726;30787;47266;62515;65996;37698;32236;53447;30446;62842;19112;25110;53434;60403;50165;52906;16252;28891;30283;24942;23728;26718;61675;46965;34646;23639;29987;26960;58626;49087;22838;57954;25582;48801;51272;63550;52282;61909;25180;61906;42367;10796;21854;25619;51827;35632;17435;47674;28733;11324;57211;53987;52805;30366;10083;50808;13486;16309;37394;54987;30790;44560;43047;55851;20418;44518;65974;10943;12518;47161;49996;49585;51133;28606;25990;26785;13382;21265;17781;24723;58814;18169;32183;28649;57098;41723;18944;20644;31859;43963;42017;36974;39125;13409;54067;64171;31076;29587;19245;56066;49859;38350;57986;48632;59717;50077;48934;36684;16345;59835;50235;53106;23513;31167;64638;22337;39579;63548;29513;37554;17423;51616;65389;32388;25904;63157;53666;12942;41948;18781;39308;22419;45436;20119;36780;34017;47350;27019;36506;38776;44329;62215;59815;32155;27964;16721;24085;20916;54418;61656;26297;64674;53489;36967;14666;47413;56375;34320;18555;34294;65823;13434;28608;55602;44000;19996;50638;60367;18805;13650;64361;63993;55244;36121;26599;38095;50825;20767;22221;56424;59335;64227;41015;49293;49994;58726;13272;36507;40135;41190;27897;47815;57939;54057;22686;50335;29732;24775;30767;40872;24166;14770;17520;49464;53338;51410;31141;32571;49819;41298;36766;22340;29368;14377;49402;19791;51002;49971;45056;56321;54623;57573;58114;15434;19955;35852;19590;17998;28115;13192;54941;61003;14622;29222;53229;20732;46946;53104;58173;24721;37183;21131;43530;12953;46586;12219;26541;47351;35025;38297;63018;44142;55292;38630;58634;26480;17402;36205;45736;38730;41484;35880;19390;63996;40253;45833;21985;28555;29264;27511;49490;35556;43084;32733;33875;52392;15208;37721;61604;23154;65085;53929;60183;46029;20838;29988;33530;20380;41177;58822;10761;37023;31813;42523;29134;13429;30704;44354;41521;16000;13979;54105;49033;12350;43485;10469;55270;62330;33187;55165;62059;34068;56969;51680;60581;61103;51752;34755;53993;28777;41964;39535;38848;16679;35685;59755;19577;28534;18238;34383;55654;45130;13536;38471;28568;63860;13889;41002;46633;11334;25036;19681;62213;39503;38745;65720;60650;47394;12647;60925;16984;63594;55783;61112;53230;42024;37099;55161;38832;34482;18013;51730;46540;31610;16134;24232;64937;64771;29586;41779;22178;39097;13373;13283;16600;34014;35449;32181;15670;29949;58673;64976;28216;28523;34124;14084;40559;22423;41428;25483;52748;37850;18962;15758;49746;38549;17742;57217;55678;63687;27136;42476;33940;17741;36359;14634;29097;52526;15375;19099;11685;30314;28570;15025;21176;27375;54692;11347;62712;15848;36618;58543;50406;12885;14888;58569;51256;35566;10847;31278;18365;33789;42572;53153;45264;17819;59035;14287;54998;20359;32440;49086;31256;18877;45143;58043;22598;17301;62089;63375;40353;63358;16281;15074;32041;55368;20704;52636;14592;22319;55716;53287;22794;26802;51117;21545;17603;12799;64741;41388;29778;34622;66146;45198;24050;23879;51128;29361;34638;38711;64667;15924;44804;29284;28683;62101;54870;36251;27732;60398;27678;39534;46697;32047;58802;38020;37686;63960;29457;55632;24345;27508;50171;53824;54902;10565;12355;64459;26231;64421;35769;20289;10380;66632;64951;17293;60288;57821;54890;64059;60148;54963;27874;37426;17658;51470;47174;11110;63163;60794;53060;24827;28582;66550;15182;21647;49666;41294;60518;12049;27054;34745;62750;18658;64551;34855;34808;29118;66886;37349;35249;11756;37152;34715;41019;33561;65488;18660;39747;58221;58951;22801;55653;40515;52015;58171;56818;51134;64553;45155;51570;31943;66096;57953;23093;60074;47544;66674;11847;64082;25469;36790;32909;33322;51065;19280;17013;11383;44214;12431;57551;61167;51443;19500;27222;29680;10644;22093;65971;34016;26812;23023;49115;53833;25845;40352;26158;18930;25017;56741;28272;63299;19363;17723;34826;61790;25962;10632;33666;57744;62874;57642;18920;46042;25623;32575;18257;50881;19141;34687;22344;39919;20447;12742;26362;34120;58875;37515;63214;31190;15571;40459;58185;50473;23990;26742;44213;38923;16836;46032;13197;23890;15823;12524;41653;12498;11515;47217;64823;39080;28992;52813;63352;28186;31760;51818;18769;29191;64188;28057;46655;15739;64907;58140;49871;41769;61743;52794;20776;12384;34287;36049;34922;65596;16828;22415;60022;29456;66880;31121;26247;62274;28924;20911;36095;11593;65586;38042;20098;52095;49097;35069;32834;48573;64089;65078;36670;26872;19963;13492;17634;13028;17533;30691;22585;48631;43028;29261;42079;34116;35972;30584;17173;24251;63271;25602;37415;43469;31449;49718;42310;38254;15234;35065;53630;38818;38939;64538;21099;35478;36029;46589;13702;23237;30615;51629;56800;42149;61045;59455;11487;10538;52423;40852;29310;16488;41793;40234;13658;14456;64831;23089;26879;14068;46428;35661;41909;52761;45592;53943;64021;11603;51126;33782;13903;44736;45493;50482;54074;11743;36796;24417;54251;20636;64830;28317;34800;65411;28469;37093;55336;51874;17415;29210;52917;57183;14867;38846;16544;15438;54202;48812;45124;19514;39611;53813;63807;30361;12341;66419;34354;32956;11107;43808;57760;47199;22285;60668;23530;44371;40430;57771;13322;20222;25411;57457;12859;39784;44097;56464;49213;33962;52824;14927;43900;45748;42496;48345;47884;14605;15927;30478;50979;37068;36656;28495;65726;27842;61438;14556;33984;61531;19345;31904;34109;19606;26312;34514;33503;41353;37000;18822;12362;56443;14580;29725;41652;58517;25220;46506;12600;36163;59737;33401;32327;41376;21694;38552;56840;29994;31222;40060;29796;49128;11769;52013;23309;37318;57711;62722;41194;30682;52088;59236;51019;32621;59461;26984;52159;24437;29465;45019;58738;38787;51956;45322;29295;52239;63646;48910;17428;20737;51366;33148;44547;44467;34368;61927;34536;20584;43570;59707;45387;38189;42556;21136;31678;14410;26352;25069;22624;28375;16837;54358;65757;16054;65983;11161;15409;66438;56677;60175;20825;31490;26125;55408;17541;55921;25188;61099;56152;21916;16169;19462;29338;43568;42876;32541;26151;14902;40534;48847;40663;19550;43491;57236;16969;66624;39627;40472;56885;43320;19485;66360;27847;27709;46046;60466;50905;37403;24717;56672;41138;49349;56526;62907;53382;27604;58895;33910;26969;12660;51828;40350;53834;15486;25951;50233;46294;54408;31386;42747;24990;10802;15512;12803;46265;32237;52400;32937;26427;29879;26331;60550;28395;19921;59805;12426;51732;53897;20707;40276;45487;58459;50426;66830;17413;65461;57292;52237;41861;23045;49361;37600;61248;66763;42532;21951;31696;61816;13902;13859;26583;61071;60215;38372;23417;48819;53591;37123;23785;17841;36400;21721;13771;41413;13954;63989;31130;31632;31139;13855;45655;57269;65945;50388;21035;57808;35790;41197;18592;23299;27397;57358;62062;62547;55341;31277;34742;24117;29427;30488;62578;48249;55854;20261;44474;13782;46966;16339;42564;35001;43558;19667;66421;34698;44029;32576;54679;54354;40314;18413;51878;22004;17318;41127;46333;56790;26999;33500;53847;15075;57546;45025;49775;28544;32866;47717;26686;10936;42454;44033;50125;20854;60762;42444;50999;35447;20544;42039;43584;47155;13786;63274;27792;36034;23630;10282;34603;63424;42300;26582;20476;49109;53264;33387;35522;36328;39974;22143;66386;61986;26182;32669;44283;21110;49083;44289;48266;50879;33598;48933;51630;45648;48806;48813;45065;53660;11821;41982;58086;22438;42456;18318;50796;35218;32305;14772;50587;41727;11213;45286;24412;66074;30730;13897;14168;11457;18591;44645;63506;11737;36421;22291;65637;63017;37969;37839;35507;11006;21688;42544;56621;61522;21745;54675;43449;63565;37396;57166;26961;44347;16802;44919;61746;26105;18111;54883;47412;16869;44789;34335;56614;24987;65673;64050;38428;66879;24137;12663;48935;29712;32867;26905;19305;44420;62889;14636;41735;45342;52833;48779;10969;57842;13230;35044;55309;46695;51993;22831;39199;23194;63545;30011;15652;64804;53297;23479;15814;39067;42217;17981;42906;34403;60381;17982;49200;29542;25639;43026;39754;49179;14637;36027;48404;25599;15622;20749;13939;27688;16734;61630;22725;57350;24919;14295;43598;55864;57863;48198;18174;22315;20408;47877;15663;32174;49845;59277;26011;23629;13519;45039;43324;26710;16368;56639;20956;47327;36981;27839;13809;26142;37809;12849;14498;33051;10652;20503;25672;53405;12295;64763;62020;25291;55327;40168;54704;29941;62019;56006;54329;54533;46657;39607;37906;44060;64817;33008;62473;32191;17461;42435;31220;45846;45044;36549;44733;34393;20513;20551;34022;24426;22952;33941;55139;22146;30927;22795;16013;20438;48747;66963;64698;25658;57092;42274;16338;34762;14982;63574;37822;56054;49603;18530;24333;34793;55949;64814;57445;17162;52642;33786;62950;52949;17655;49423;39457;46144;24843;13927;21256;25150;16490;64360;17091;63920;61561;63338;54068;23654;50447;41806;29874;35091;33497;53414;40379;62491;32936;22085;43222;36508;59973;55670;46133;52709;53588;13108;45758;51036;63690;59857;61633;65658;61190;43444;31163;11738;35558;16400;65046;43939;11536;42732;65264;15000;25289;33248;64431;26397;51807;45640;55433;18730;60469;12525;30069;30279;51471;54236;48155;21192;32158;57073;49934;51808;20183;42247;40385;65512;57454;26874;31002;13706;47438;21143;49143;12821;36219;64866;43381;22022;14039;27833;14320;12207;13074;59983;34816;59948;36030;46978;33906;62099;32885;29688;27078;53273;15918;51407;32907;56013;26303;13405;32124;16184;18748;54527;22175;64634;45451;43115;62175;46635;53575;43208;60150;48247;32152;10269;65026;32554;15487;46779;23912;27798;66739;16944;14934;49284;55138;38453;10539;30852;64378;42548;45010;55586;22042;55440;14341;49227;25748;54014;23738;27593;12897;17762;20094;31240;61893;13052;41285;15569;29517;48737;28033;13471;18201;22071;65687;20012;13549;49598;59005;13202;38964;25293;65053;66615;66562;51120;10461;25274;41934;30842;28977;16901;15517;46322;19588;53887;39018;16236;62058;58532;39914;20497;39741;20830;27778;65587;60271;58094;57586;49937;20364;19884;46026;57993;16079;56173;10653;43241;57616;36225;51330;66859;54541;25033;19306;26089;55276;62199;63926;64800;39121;32320;30907;49948;40841;47193;28121;31996;17311;15307;61805;25319;16745;22766;28218;50535;49777;36628;61297;40647;47396;43988;29496;33458;16881;46023;63459;64200;65245;56322;24460;51297;39716;40983;31728;57319;64262;20448;20181;29801;15281;40884;40416;42733;48795;43133;21416;57784;58652;53631;63340;23296;35898;22316;34921;21247;13712;28344;44514;57981;62825;64547;26540;45478;40053;60903;53714;29878;10199;60769;64222;42226;30166;36675;30071;29469;30660;54370;48599;53782;41614;53646;35424;30441;51519;64104;55994;19153;27598;32144;26989;55488;51769;65532;46637;17786;55411;31995;63285;18435;62696;35482;48476;56129;61301;50206;15964;58274;27814;17083;50487;15177;58055;62006;32713;62838;45018;30701;61758;26368;43801;24920;42073;59977;46141;13331;10444;60451;58553;43124;46971;61053;45102;15830;58664;10546;51472;65960;63830;57647;31554;23460;43712;10552;51949;60896;59687;22648;40061;33897;15952;28763;32607;15332;30626;37450;66509;13374;12961;24884;39400;33580;61753;48639;45822;27891;25347;62014;34465;34362;25787;29381;60365;40152;59731;49085;43609;11082;64406;59365;19712;39775;61887;13142;63001;54724;26733;34734;60763;28768;23432;55093;25997;33436;62063;10575;56727;63616;42376;60569;48667;56518;32230;22752;64968;47681;24988;15286;15524;13664;23571;31669;10981;23207;20439;23227;20393;52615;16180;30476;42944;49001;61227;51765;47906;28987;45564;40941;10111;53632;66409;21830;50466;44459;61320;42074;43407;28884;23240;59952;55810;62811;24614;38173;17111;54045;34151;30503;30885;61024;32267;22123;39983;11180;43265;13065;61060;57006;17595;30302;52071;26684;37989;15219;60720;45456;65536;10457;11747;39277;50039;51294;57141;58980;62052;54128;40397;45630;23868;14878;40623;55121;51713;27976;14999;61399;56756;51530;23314;56964;24910;32742;63689;49515;39737;14539;48231;47823;19852;20712;64787;48738;53738;45533;52875;55499;27550;54531;39158;26827;57890;11364;31714;52310;38363;58151;53475;38257;57070;62455;33185;16863;50807;65810;15756;30155;60217;25005;29740;27675;21478;24130;12303;62782;35892;59370;24970;52181;30328;44448;61547;15358;12646;22874;66900;56089;21783;11615;24284;45256;11229;20486;26314;57205;13442;18554;50190;49892;61057;31291;65773;59330;51014;53030;16095;25277;29630;59635;64546;52749;34472;66054;20771;44204;18674;47108;49447;38564;61637;59513;42293;64255;60705;18021;40838;60302;11367;58914;51699;14848;14369;27528;12406;42202;15637;57077;62415;56172;54094;40437;51475;45106;56595;17675;14896;21920;63482;65121;66657;53259;21454;53460;44852;63054;25284;34663;44900;60564;58777;27813;38444;43635;54703;10272;57507;10912;58955;34274;22210;21517;23898;59257;24956;43223;14272;52633;58225;30735;24979;60560;54476;47334;47739;14891;59026;61725;10135;59654;26258;61546;22628;65048;64967;46626;60573;44305;26491;18011;30998;19700;52657;21081;60629;45792;10146;64609;56901;23102;35916;18845;28480;14119;26544;33298;23368;58109;55605;18184;43169;22139;56398;27564;44286;12989;25876;18487;40676;64580;52335;63963;25394;55372;13280;28825;14536;62104;11326;28039;45929;37757;49713;48956;21684;16706;55827;16637;38513;25138;64975;47094;27174;66341;24366;19986;31829;27480;19226;49644;33734;48699;35099;65280;21820;11309;18399;25945;23283;62924;19543;37136;57547;53366;26152;24606;29209;39180;50017;15669;40803;12016;15546;46353;16500;43992;64435;10353;38210;32776;66799;38873;12398;49918;57310;14793;18452;39127;34706;38697;40564;15718;65841;12071;37289;40573;36324;30960;40731;39875;27726;40789;59606;57272;18271;54122;62669;44580;26270;39990;15797;42166;46260;51378;18502;66884;66849;53907;26454;19716;15229;57093;16189;17395;58809;31018;44469;28930;32831;41926;28119;22089;50418;59396;55677;34404;36189;62785;18923;63540;64189;42153;16285;30134;54005;61661;52050;14993;14022;66176;35271;24483;57303;32033;36702;31876;13566;42590;13912;39213;32999;52787;33781;13058;39546;66853;52349;25279;24705;29931;58259;55910;49537;57995;47769;31868;25094;31616;17639;24076;12388;16515;16307;51817;25486;32793;37449;10622;55583;42165;58520;30895;19311;51984;29328;19668;34658;22668;66109;18496;33762;62694;16379;15073;32239;62341;24498;27807;13185;50284;27144;39782;50766;57133;39159;58576;22424;61538;21399;25860;51924;36990;40055;11678;22645;11001;51108;10838;27345;27428;22644;21900;64836;35402;66422;19132;18369;55646;35342;47060;50112;63316;16556;14271;59682;34176;57657;47695;56850;57274;31960;20746;10171;39928;30769;14053;60496;14850;62408;48332;63768;12910;51078;17046;48930;51906;34055;33807;28050;15301;35976;47332;33389;62840;29022;44487;27420;19951;54736;14940;26085;13569;37393;48340;11676;55219;13870;19301;28067;54849;21556;45485;47793;16290;60239;11555;64970;52143;33665;42864;52393;25020;17784;64307;41549;43587;40516;45855;10421;48979;27990;30175;53394;58268;32870;32045;53937;22925;13721;58597;57186;66500;19078;52006;47480;41758;23349;28094;18559;56127;36001;38659;42087;62520;14261;28505;23230;57251;20496;34193;36006;56125;47516;41153;11341;63117;11671;53917;47036;30008;59588;16705;47805;36514;43342;66392;43643;42768;18038;23521;56888;54606;23913;56193;58066;60554;48171;63317;27027;10223;29426;19296;50094;20090;57984;54195;13922;13304;43805;63786;53585;61691;33841;39252;51311;65104;33985;57561;43672;15006;19624;27348;11935;39773;51618;58934;19369;33926;66871;55422;30729;60141;25265;12088;15727;43539;63273;52580;61508;63998;54477;19959;60354;48223;12654;52708;37189;50717;40928;52503;43440;30749;62718;39191;51597;55243;37477;21929;25203;19097;12521;18689;66197;23186;21848;41454;50013;19013;59130;51091;15012;19053;42791;60960;53687;38144;39751;63630;37830;11742;29204;42508;11427;23790;51496;29766;27650;10807;59093;55870;26952;66450;34123;56842;62424;60213;60664;56731;58537;14965;51898;35311;29820;28574;60294;61582;19509;33711;53404;32680;40635;42591;48538;40317;21740;60583;22240;10271;56748;17317;39039;18465;63422;26705;10929;16835;42245;40130;23930;19059;13718;34196;49399;38854;21232;41162;54321;29726;39176;11951;56094;16074;53737;54626;59639;50214;15135;40182;34268;61973;42819;21045;19954;33737;59122;66891;56400;14852;53004;38464;29159;60961;64590;57386;34129;10885;66591;59029;32225;64174;37612;40826;61705;55458;55297;27831;20429;11937;19876;29812;38167;26964;52873;62013;26068;15251;40608;25960;62369;38204;11855;27149;66032;12789;33815;18810;25232;41242;21489;48718;49223;26296;10206;44957;40997;41872;40560;24280;20255;59449;13882;61380;18193;21862;16793;55982;43534;17233;55439;27711;13222;39743;26250;23788;24784;23034;19217;63221;42078;60695;36976;47288;20358;61575;37413;59447;30906;35854;40283;52776;49590;26078;51160;62904;20342;39921;28431;24603;21961;51526;50603;50318;48610;23547;24140;44830;41119;33886;54415;22381;63647;26519;33795;19205;49453;33053;54959;49350;15482;16553;44519;22976;35594;28647;41655;21899;31930;19064;53379;22006;49829;13917;15954;18031;37594;65407;12069;19789;54323;24962;34107;31878;48472;46719;24789;42213;14941;41460;61307;36727;25182;30642;14069;64809;46375;30999;45469;45461;15072;10307;60326;21370;63122;17222;64192;20669;37247;43097;28170;16851;13543;53547;15215;26118;66944;16433;40548;33054;26266;19450;14881;33899;19190;38898;12263;18379;19809;11417;24370;32410;18899;48638;49488;52056;38809;32691;28969;54603;33188;27493;53406;39624;65688;20357;45087;20718;62419;64963;37401;49526;48971;39641;31559;48839;31920;45811;30455;27249;33958;55835;47894;38819;31894;55875;46440;41295;18109;36971;16548;65860;60827;56698;64699;34534;11715;37739;12718;33025;60211;26600;18747;27035;27315;24557;27221;54383;13271;52939;52774;11360;55217;59560;59562;66537;34389;58480;18857;49066;49121;62605;22035;23753;55065;55843;22361;56059;12121;26837;66701;61844;11912;11613;34557;58959;14762;43575;13547;57419;37959;41228;31444;24080;40452;45109;35519;38404;13767;47372;55574;60430;13683;35776;38728;43252;39832;36924;60678;35010;62823;38524;54745;15282;15647;36644;18447;55599;21998;65031;37831;31227;48762;54240;58483;18428;57767;62400;62273;42828;13727;32782;46017;23953;62793;19781;10946;35227;19883;31673;14812;17582;11789;38427;26228;30740;64269;62429;66883;20983;59801;10053;25204;52782;30114;13124;19682;56169;16405;33226;26713;50688;47348;47740;60965;23664;27481;15855;64578;30062;25269;27638;51972;43130;11638;28963;29218;28207;15304;57080;44223;61463;34231;44618;62134;62849;64901;61286;46401;20001;59290;23846;54496;58930;41808;60835;61155;25029;50876;24731;42790;57432;52556;60637;13459;18287;34062;11580;50143;38288;65772;44146;45389;11126;35195;51219;61270;52481;22951;54857;52913;51170;10311;48554;61539;58457;30101;61901;43739;63749;62145;66819;23839;42467;10441;41714;49727;50654;38344;13829;63566;36979;14714;14518;58627;11617;24457;20177;41540;29521;32071;60707;62494;47176;10081;55504;17993;18164;16317;44243;16444;39151;36641;42390;43315;57284;57827;33613;31656;42275;41182;37677;51923;41904;22258;17619;63941;54135;22408;47052;21980;50376;17025;66171;50664;55357;29479;18116;51672;18806;65657;58668;42469;64135;51861;21938;64646;61823;65010;21420;55419;43667;37748;59788;41745;58098;33030;54889;59364;30827;46900;39163;51500;38716;28613;50135;56341;23231;32478;65764;31415;39803;65328;61953;33774;66640;41045;26196;55052;63161;16659;64263;61647;59470;50869;57142;40668;34336;19775;50248;24258;58845;17731;16415;18402;31484;37492;62382;40681;56521;36444;31791;59339;14909;20586;18798;24999;22215;28486;21587;62658;19738;50395;46491;53470;31618;64137;39373;55660;50541;38285;24322;64453;14520;35016;40554;27967;14996;39656;34032;14828;41217;57374;51010;14028;28815;47212;14440;12374;27873;46269;30318;15123;59353;31319;35947;57155;18340;42779;22075;45344;34508;22920;22677;61549;61043;41766;45234;49687;54000;46861;55639;45285;33285;22942;62576;37282;57099;54309;25798;41308;30590;45249;11419;35196;10454;61505;45973;30967;43331;63172;57363;48723;24386;24167;32869;62821;59575;52115;13164;28640;11093;22137;65465;63514;14945;59764;51885;14082;41462;51787;61483;43414;29529;33247;20394;60364;16912;23733;54530;13027;40620;66714;65561;48435;35067;15313;26782;13907;19039;51420;21268;11721;18538;14467;19804;14846;44141;15634;61783;45653;30932;21747;41557;54296;12558;61382;36350;60392;20067;39432;29221;61928;41683;33260;37223;55213;36303;35276;60195;18588;52092;28084;32330;28567;60519;21802;21776;58018;60682;48850;30750;60035;35145;58079;45544;44501;13376;12386;36192;65105;46504;43506;29407;50959;53221;31466;40519;29792;15226;42417;62567;33698;64008;63040;49422;28399;48178;27888;57787;32851;30034;26107;24608;49496;15441;55102;64410;62324;59369;43216;22856;43870;15931;13968;37616;47575;46222;13930;15949;47000;53190;61029;28059;26120;63814;49282;12027;38172;42536;40697;14820;45984;36154;38680;41778;40741;18619;18918;29502;43262;16726;38345;48265;23609;47896;42006;64120;37553;38443;33562;48730;26825;40875;29087;39521;40980;46593;10964;30778;26931;55016;50983;36214;18557;57031;39413;14724;14930;62487;29086;50648;56796;30316;38452;20731;33858;55056;43202;40100;46424;18312;35923;60393;13810;45881;46532;26680;46443;28394;25920;10597;48227;29473;48170;10358;31188;16123;28758;63504;61162;12847;49545;24694;58971;65161;23389;12208;62833;48684;48641;16070;41253;57592;61972;37609;19477;11486;37245;18758;29024;35595;48480;32559;57493;55370;40673;54735;51201;31739;32531;30450;43079;56667;63388;30372;41291;60730;64447;12683;29108;21296;22588;59845;64092;30996;12603;66539;23165;48954;44932;11645;50240;46234;49883;53279;58261;23926;30580;14114;43561;25587;57629;55869;63095;61959;18087;60578;42746;52736;63330;65387;58843;63662;58367;34408;65348;50573;31226;36062;25111;38437;60602;21986;56787;65839;61614;19847;16808;26436;33839;38542;35383;52077;31160;51512;12095;62634;66041;27699;31476;25909;51932;27743;64201;20844;19949;39037;27632;12240;19661;29884;56203;52040;47525;26615;10488;54264;56711;16394;24228;58355;54174;46122;49872;44735;56050;28685;55468;44731;51510;56501;57582;37482;10208;60623;65316;36646;27870;31248;19220;63976;35498;41487;14409;25695;56948;56198;14207;10077;48401;39247;56226;61712;17066;51123;30908;54599;54782;64593;38523;30980;46156;55825;65142;29377;46856;55520;10324;58574;50916;10560;37417;18846;26446;48968;54751;25790;53464;31720;23206;52386;28781;22145;37238;65975;32520;47792;35461;23961;20981;41707;20594;45022;62179;28299;39433;28013;11198;20547;51829;46472;52968;49357;11108;26954;43657;61173;25634;65077;48582;32935;32458;42250;62342;46366;13299;47573;27086;32921;66414;52484;47302;60651;10639;65537;34566;56777;44949;60340;20151;37071;37918;33259;29828;50693;17547;59827;35952;34577;53090;18773;27680;26771;25976;37723;39947;35500;47478;52746;47839;11733;11225;40746;29079;19813;65756;20036;34838;19848;31997;42089;60847;58461;16116;51487;23605;47015;35955;66680;40629;58177;24716;64168;46625;22312;26532;50703;36111;30564;46712;50998;22466;30618;27319;50975;54116;41440;36073;63351;40425;30847;33133;30425;51379;32579;32485;60534;60717;56974;38967;39268;63796;62936;31684;54605;28976;29516;61223;65958;25564;13458;54407;56574;61914;27406;50069;56072;21208;60086;23182;60805;33838;66565;24144;29962;41379;32685;41874;64923;14811;46664;56319;41717;31974;30002;24802;32698;53479;61741;20597;42928;66100;20546;34619;65405;56287;10325;58833;12818;26246;48212;50166;34938;32608;58301;62095;17817;18907;66275;66521;29641;44921;17701;64398;41367;32029;58329;32550;47530;64139;62826;43107;51737;55421;51602;26323;42156;41056;20038;44446;41726;50196;22038;34168;42206;58932;33884;39643;61490;12844;45749;57411;12443;35282;52929;35106;17550;30169;66672;53348;58973;36782;57721;64790;61515;17480;26091;62407;41750;58442;65957;16826;21878;17195;66039;25362;31693;28326;35958;52491;52231;34796;15795;18782;10515;30260;66218;54711;57710;18869;65670;26640;16094;10070;54730;66970;59644;31003;51081;66582;46407;44468;48984;65162;48835;13403;23732;50530;51667;42832;49740;61104;41313;32397;17744;51931;51886;11827;42161;49465;19574;20687;56404;35562;66454;51796;16512;35935;65444;58926;41499;60640;19434;19609;39212;48165;20285;30496;43301;53607;58725;46825;17755;44720;22147;51209;17552;28981;47729;34224;23457;62214;14094;20493;36853;19498;16408;59380;42283;64036;31194;37185;32461;60115;24321;48771;41785;39384;12835;40535;65022;34228;37675;10956;55028;16787;61870;27033;18249;60038;43080;36921;24087;45885;15116;48424;65499;33487;23996;35405;49753;62790;48752;10595;32569;28235;45233;48328;40756;11831;35945;53788;29292;10570;65359;48809;28278;58901;15205;10197;54640;17631;47887;21696;65483;54973;47338;15966;57109;57514;60874;20399;13106;23364;42233;34953;12813;51200;25925;54263;59106;42109;66727;55800;31840;52971;52132;34121;42152;47055;16960;38978;11085;17759;53092;58772;48219;21918;50553;32632;15454;28432;21589;50622;61488;64368;51615;36380;36626;66198;26411;15241;51596;15668;59430;43640;44936;29747;49758;10251;37467;43970;37817;49730;11151;20217;47091;43063;22282;24294;61979;39580;54373;20154;57517;43002;48483;59406;66812;13072;20224;58186;33601;65014;31429;54468;16513;63127;41044;11477;34664;15575;31148;39725;32321;51971;57922;48473;51460;15633;51780;43579;45151;66022;46715;56438;48445;17481;23485;19027;63805;57595;66810;27046;11471;13341;55483;42939;25368;43399;33938;11164;66346;62917;49973;55712;65357;31245;58684;18280;14008;61617;21070;26537;29052;40497;26780;29053;45397;39497;48263;18601;29573;31060;18589;24008;49185;36201;29588;22111;56855;36363;28743;27464;18764;13756;37291;58904;13584;45462;19686;43263;12116;16348;41346;13324;27991;29719;38364;31020;48207;24536;60090;27869;61993;25528;32883;50031;26459;42705;43542;64314;20531;16684;11393;23477;22256;53341;31638;48945;40614;29041;61670;62286;44687;63174;60994;14492;39454;13221;12877;11544;22671;29414;63401;16542;45209;17629;44248;40723;39479;11316;14033;15615;61685;33023;63721;63553;60149;50374;23906;65676;53084;35751;50158;58756;26186;10958;28786;44978;35247;49480;15778;20138;65180;30629;38713;47690;32387;11303;48350;45362;27255;41089;48508;46623;31029;16597;40820;23468;41166;11550;31966;49720;23037;43679;20554;52268;53831;25563;63595;55125;59320;26273;54237;65607;58778;63502;40814;52516;57353;44582;28290;48244;53330;28158;18939;21345;27673;40316;63201;25183;22623;35207;61558;26422;64566;28644;50772;27837;50779;29611;64924;43138;63279;21502;45361;38436;25885;27304;53613;40364;10390;54798;46114;54665;48300;32768;52396;36819;26225;34154;11607;33252;20806;52344;11448;65283;14757;12237;36895;42872;22196;52297;18385;60635;60039;60192;13525;36132;38008;45030;25841;22625;55267;15292;30845;59078;55275;53863;45754;25145;61139;64920;49246;65880;35336;12597;37430;63488;65007;55424;28878;34651;56559;23255;35126;59782;53669;29371;22949;61571;53999;13941;35810;36510;60760;38920;38077;26854;45298;28136;65451;37259;21891;53002;29120;57579;54230;11267;50301;47369;18732;44035;48869;41598;22201;24652;38484;63542;63315;51265;41946;50064;18078;46163;20706;22667;40203;64853;36332;45091;40351;60736;53452;24996;42474;42098;21755;53312;10073;42515;61601;58672;66720;43577;45742;27071;27779;56638;63150;65192;28520;40181;21810;24209;33967;51953;45258;29154;39238;50470;53255;54456;44380;48497;53492;52651;38999;19889;46812;14450;20343;54120;60033;58100;19777;45606;21123;30291;61482;23054;66751;43122;40233;39065;48926;34467;22663;33461;25097;11183;53132;16938;21331;34379;40744;13139;26679;33721;26146;23762;65426;66538;18368;49437;17100;60765;12533;49938;47679;16879;56860;29935;40966;11622;42560;40111;43139;42655;39655;26498;57448;51083;36129;35008;20107;41679;12451;47761;53421;66652;47907;36277;52612;53096;56444;27786;15175;59443;58315;49731;45733;58312;50078;15491;14544;36190;53298;40059;43442;59569;20356;51687;24768;56921;26366;27285;17743;33758;58878;15060;10455;57506;14515;13444;60206;40637;14036;20750;35159;29536;44938;17244;12377;51663;64808;43690;17382;17738;47260;49873;59520;19441;32269;28066;66400;66600;48602;29267;39077;53111;49500;56080;21523;30484;25008;22909;11523;24303;39085;60425;23111;50322;20975;55043;35862;30268;53589;16460;50458;53561;26987;66105;37795;45710;51761;19988;10805;61374;27309;39836;58667;35104;15314;10646;22994;57973;39013;12410;37210;25963;62153;33570;10482;18614;21273;48622;28005;11915;26280;31614;44066;27606;28464;33707;35570;28795;34023;65095;16576;66297;34893;35320;18858;42357;62969;16783;57267;53712;59358;64212;50377;51473;19495;28502;23162;53064;50550;49592;25491;63587;17366;19066;16623;44291;16155;32162;22320;28512;51488;50865;38500;64942;10278;38129;15068;60140;11488;46437;33235;43650;45780;57532;46001;25531;26951;40333;48661;66379;44185;42014;45059;52212;10110;65496;29481;47402;63974;25751;39193;14189;55665;18076;26915;64158;11946;51012;21255;18664;28015;11783;11695;54205;21686;36341;12455;35240;29164;15583;21465;15103;13529;29195;13541;14211;10025;27250;36002;53918;43538;44974;65233;26587;56028;23482;42100;41849;54622;63196;62433;13970;16176;58101;12435;55936;22474;62652;14953;37083;26555;12920;15270;39287;20331;32955;14568;62060;50751;35224;26940;44993;42891;18639;66380;47454;19191;13785;27762;30856;45583;50756;26402;31885;27736;41587;22394;63119;18630;44275;65520;23118;23751;63610;55273;29445;30222;23607;59937;27655;66838;16109;53088;61373;51594;55803;61010;25543;15803;58720;19698;63558;59919;31666;36449;66612;13694;11233;20890;41319;45919;10613;63937;54576;21493;52323;10537;66575;26558;16998;54177;52928;41468;37874;14573;44842;45354;51913;65674;54636;24103;50897;52681;36959;20729;40101;12502;45913;23250;56386;15088;56634;45251;34377;50864;50073;38046;33674;64603;48191;30208;22217;55899;45767;60269;46904;45215;22122;19478;56556;38505;35607;34990;29694;29009;61174;18036;59492;41239;37908;38067;46341;14279;12693;58831;66948;35293;43893;47029;44170;42495;32401;18290;60395;36758;38212;65843;23628;12661;29406;27912;34318;12682;66092;19507;21382;63307;12446;58620;62588;20109;30572;37358;32344;13789;43450;40524;37541;13329;65543;58432;11654;15498;47375;28928;47240;63377;61081;22252;57848;58335;55088;17153;46416;23603;18424;16631;61709;39453;55320;51849;24670;44447;40999;53108;47130;37489;28308;64014;34076;38884;43367;41026;55004;44738;29029;16071;35095;12865;47796;32983;48397;55692;52291;66965;40943;59283;45421;24779;37105;59705;34546;10261;29289;13498;64397;59757;64179;47273;35212;61776;37913;36074;10892;22987;51781;53413;18374;50640;66190;18712;39354;65008;16459;38071;34731;65920;18598;20400;12506;15690;20574;52446;60325;66832;19666;26957;25846;46906;60734;42137;47269;59008;40358;43741;66155;60508;18876;44127;10720;50692;23491;55860;30031;14439;25680;15024;19228;53113;22849;31975;23290;39259;11373;35404;52613;45324;32206;63288;13439;33312;37696;65818;46941;60752;60696;33320;12229;49451;10665;25827;31338;27018;58513;33970;44826;61212;65002;43726;11097;20412;50113;46245;28164;36101;16905;47471;10520;41962;35779;41169;34537;11980;39062;64288;42423;17549;35820;60001;10194;52482;12627;34361;41400;33616;34935;55185;54930;54975;53623;12081;57370;46166;21744;25369;29499;23155;54906;14647;47572;40767;17493;63412;60473;59014;24421;66021;25359;32678;27401;31722;21513;24883;50180;58559;61660;15742;46377;59539;21624;61032;37759;18152;64098;33881;15822;52160;20213;56915;46273;61042;31558;25523;40834;44364;40199;49147;33526;64981;48797;10400;30003;22809;12477;35267;13992;42616;30412;43468;53282;40241;42618;22503;47315;65069;40528;56793;49045;10759;53557;46863;53100;25728;30764;62365;65067;33514;33245;60693;55545;40410;42999;41740;62663;57791;50943;39134;66588;42717;65395;23113;12952;62046;40584;40831;37899;34165;41703;48379;56857;20092;18643;11952;56092;18110;44674;57307;16314;13345;61883;48918;33849;66770;35108;27534;14648;12569;16384;66559;44315;11563;37611;63138;29710;61108;28578;63552;13162;29742;34264;34266;18449;46857;44502;42090;44688;57318;36466;11299;60861;15504;61487;44247;15725;58408;44483;49482;41732;63812;15693;50015;18256;41501;14334;29938;32740;13700;14892;23516;24858;13026;31778;62564;41809;25040;13723;54031;44326;25206;21642;48427;12657;63101;10980;20560;65460;17069;38135;50176;44813;18770;19714;20659;58167;54687;43431;16615;11547;24334;41148;66494;16822;45147;14517;44703;51679;49841;16945;50941;53225;57190;53534;35848;45496;61795;59280;27801;30360;47470;18099;27085;28684;20739;61468;57152;56021;22130;40354;23542;53518;44504;39153;12490;64107;53966;51852;30183;49265;12712;66643;49623;39347;63582;22755;44532;50872;59846;38512;63953;30212;14825;21677;24056;17463;39584;42522;55001;53997;59829;52817;22751;66520;33371;20889;44955;10788;57704;27630;63665;28459;42009;46486;64001;66598;13160;33452;23697;29213;45094;21474;38926;16375;60549;42177;29276;50311;46876;30952;44670;35034;31518;21211;11703;24829;54051;16575;16262;28070;55934;37288;63291;12515;21922;19952;20056;55846;18620;35377;28841;50378;56302;14585;15132;45593;12748;31006;28460;63522;66481;21407;49181;11470;53025;42916;42210;50607;31246;39510;57631;60520;34785;36518;29432;40193;19976;38492;63765;62183;30644;60628;56529;43604;45351;17462;47464;56866;21167;18122;27553;44444;31455;41297;54443;66274;13542;10320;23981;30112;18586;32688;44982;30674;14147;32474;19003;66012;34339;31364;57243;52890;45077;39002;39890;47251;27336;56227;56947;18132;12735;59111;37309;39499;40667;64170;37851;13021;25650;52745;16981;12356;59224;25547;10066;31866;57151;44606;46829;22818;17700;15067;31985;15451;66183;19865;13597;19664;21563;60922;45261;23171;40839;45971;48523;25357;53323;66259;38936;16712;35175;53031;16791;37659;23324;12573;62332;23496;35467;12213;41592;47555;12822;58111;15789;11206;28054;49409;45228;37025;33443;27710;61548;44370;13490;49366;35638;36343;66309;63266;17142;19037;64964;20485;15563;23222;32241;53442;34919;36863;35740;51416;23940;15706;31437;65953;49828;57059;16756;34000;40320;64424;63398;59401;66270;35341;20041;25049;18220;11567;14917;45504;63319;45542;12266;37490;38166;59498;64474;58215;21890;25810;66943;66858;15264;20330;66492;58424;30707;29438;43605;55099;45569;44179;51760;10475;13845;51417;45708;28468;31550;18594;35720;63013;52874;39057;44829;15567;42932;53253;29094;10011;17472;58588;48186;59612;63455;46459;32624;46814;42726;54172;10026;17079;13054;30890;14247;49670;55619;33343;29236;20829;32744;62791;31541;38451;10863;60538;21155;39210;19168;59604;34885;61143;43923;59345;58172;45540;61965;33003;39770;66449;31735;47398;64019;45961;26153;15790;65769;23024;11572;59138;30949;28343;54557;57923;16742;45529;61467;36430;42765;37014;38473;38521;45088;51218;14516;61730;33377;58033;46325;18958;30826;65277;35310;25407;61715;29970;64331;30147;56613;50617;51894;39912;56997;13873;12922;40879;36004;42661;24285;50465;58737;66335;66490;56076;27279;38626;19794;55054;50721;54766;37704;34671;56084;53344;55253;42222;25520;33405;54091;48807;40042;37486;35671;32794;20367;23601;32649;22479;39853;14570;66369;56476;16673;51499;41855;35568;28234;27356;63777;53514;15065;66338;30595;19957;10180;22828;61306;45495;47383;33772;26835;44771;14454;14773;27067;34538;57210;44439;32570;17583;33792;31630;38456;27476;27879;24286;23297;26673;24411;53692;17350;45175;31414;61251;10478;30753;34505;57004;54071;30203;59010;50329;65079;28530;66483;43020;33634;38901;13888;52001;29070;15953;24719;31694;30538;20275;19981;60822;42169;20623;54743;12046;23415;10723;52518;31867;27558;28112;47409;33743;34466;35307;23480;27625;33126;46409;42406;51723;52903;59241;10994;45239;29709;66069;25167;63813;59012;31012;59696;20248;44718;48236;24964;44164;63629;49904;44683;20924;37902;62075;21126;64126;51189;44555;45480;32022;31511;19833;16654;38048;27047;66703;22941;32009;21229;55268;21409;46573;16356;22728;20444;36145;46893;25432;54712;37464;63012;44946;51661;50336;42488;30555;27968;36999;30202;57058;45259;31832;12986;42920;32629;25734;38617;24997;58280;25878;62178;59730;61101;60216;66971;36517;36484;32704;26421;46412;62732;55837;57581;46059;21579;65063;45064;36105;41436;23123;50446;54332;49519;55274;27437;57915;52685;19308;10299;39007;12393;25884;25355;18310;13610;30343;59929;65438;25969;49038;44981;34920;60881;17554;34187;42729;23900;17699;65371;61991;58948;35309;40296;59072;19886;39257;64503;33232;40348;52346;14711;24506;51351;18505;51595;36892;31506;56632;49429;43698;36933;51513;54290;63793;59104;61064;58036;53391;11118;55500;52483;16205;33730;46092;33498;23597;18626;27093;33336;24184;52303;44337;58333;17999;63568;66585;29171;14643;23199;56908;25772;31940;44163;10647;29128;63788;27109;31236;49009;19940;49372;27794;60186;35066;62925;19309;58771;59759;34092;60977;61653;43007;32984;16015;19568;28093;26832;25700;48688;16665;55384;36247;22499;50616;29298;66888;41864;35148;64270;62771;38406;63353;52750;60880;51763;55878;56079;54401;59101;51974;15646;51601;56447;23276;35970;64706;25158;44845;37720;30403;57315;10499;59643;15296;12417;58484;14755;50508;58572;55114;26060;21287;36406;41749;62688;24646;13790;24793;52060;59834;57908;66742;57200;15817;28172;22489;26399;25422;34049;32972;11439;36616;66295;64587;60862;16398;63255;57528;10024;49803;29533;35412;29212;63211;30532;20286;37779;52713;51772;27914;56601;62322;47184;52940;53040;29528;12436;15711;24020;52467;23103;20027;53195;62417;46159;51348;58038;56679;22783;28961;23492;33195;36668;45405;64473;64576;47124;18813;34006;32480;39448;19397;16933;57112;19635;59079;14173;57400;58897;55280;50251;52672;18054;29100;15630;53979;58331;26128;32992;23433;59832;58469;45260;28627;34263;10703;57818;38951;29480;53098;14108;58251;37125;19933;46768;54624;64829;20885;29716;13523;22410;47128;50255;18075;15505;22826;23190;38868;30592;58374;56968;26221;43822;61777;13167;58863;45770;21220;19287;30497;31903;65642;14091;37188;42546;11371;46484;61136;33043;24643;25894;65713;15448;32926;55616;26111;58441;15056;10497;49907;41545;50942;10106;59819;30434;38545;30802;21191;34539;61455;18196;23586;22674;47901;66137;66646;61774;39635;44843;30944;50280;27302;52253;44595;12405;61160;32279;52603;10207;36128;20579;60406;53652;15692;52309;42843;16063;14838;35089;23969;59414;49789;29889;22095;60417;41288;17501;27957;17156;66115;28076;12607;16646;42450;14109;55689;66214;65904;66814;61147;32518;29643;41927;48669;27586;11476;57518;48671;23356;35765;24093;11753;12248;16779;58961;65847;35781;32987;30406;24984;31522;25686;28556;63957;21494;12871;53501;27578;53508;53815;51317;17499;65134;38138;60996;25348;45338;12238;64746;54917;33670;50243;39629;42570;12570;32228;45004;62970;18686;32747;54695;10466;34753;29936;22732;33883;43021;40132;30939;40897;55334;61517;34396;49105;65889;57931;48820;53201;17340;34683;62251;59519;39074;21036;29468;54632;60179;41951;19858;43155;11423;11909;24797;61303;17593;52877;12667;41260;31809;20632;30107;14505;60975;55447;53512;24014;31058;53653;57461;42736;29541;18596;57820;59926;38001;23750;34918;62559;54816;20634;17810;48224;30452;63250;22836;13570;37997;57365;35142;34591;18197;21990;36166;28150;64579;63069;26463;23078;27082;48973;20252;19987;25216;65947;44863;41008;28960;54582;38773;57275;53528;47211;30774;17991;25566;29096;37587;33663;44079;26754;57746;50324;14176;28660;10966;52617;32809;30627;59261;64206;37871;61860;21529;57687;57258;62194;23956;66622;48337;32918;14698;40377;21024;41859;15968;10724;62457;53398;58821;29265;37346;53713;33810;56992;64727;43361;17630;13270;43954;29341;26145;54939;61403;60712;52501;34319;41243;49906;29374;40058;27056;57088;46910;24399;61763;51973;53720;47858;31534;33947;49054;28273;56151;53238;55715;50592;54818;13372;52920;57366;33675;38608;33928;36834;25387;48846;62533;51220;43290;66669;16946;44742;32601;65979;43291;19268;38700;66470;51478;26195;32439;45688;21431;28764;25633;34748;23069;35626;41209;66080;45707;31624;61385;21209;55752;31779;17997;63192;52844;11623;26744;65367;16113;65909;22077;31504;15586;28083;25193;13861;49504;44611;19068;55177;57620;47323;48693;50610;21165;24547;11878;54991;24198;30935;66896;30652;24435;57022;38475;48760;25382;38637;33311;33329;34689;36138;60742;45188;33451;13733;33676;10871;32501;30185;56071;11368;13168;54841;64316;66350;32101;26203;33629;56604;27458;24741;57403;40758;27539;62190;34265;63038;53331;39683;28650;57214;49368;61739;13653;46012;43171;34448;20293;47599;29206;31998;53296;33918;55764;56687;28174;19739;65278;54457;34470;18608;37242;63764;54946;32791;50620;62140;25900;39408;16850;29675;45596;11062;34418;38595;46642;41444;42624;66182;55070;21622;21879;32812;52628;44570;43067;12445;12862;30367;42995;21926;10925;60771;47543;14245;62049;16150;42686;49690;12698;23759;66114;24907;21969;60441;54275;16992;61342;14418;21876;66280;40263;32243;44784;27032;54659;62159;60414;30269;24985;45932;59393;54929;14743;28477;19415;25967;58311;54359;60394;21737;63792;37935;50802;39369;22183;20937;10260;43743;44824;58947;54232;31697;59586;23195;49540;64897;50783;12312;44672;18875;27584;24059;39694;62489;43803;14523;26371;20526;60114;50379;20446;64251;36390;40268;25014;26001;47238;56278;41160;25496;36337;31395;51727;64736;63895;27121;40612;23386;50572;21410;48828;17032;45991;65215;45763;63669;46408;53625;47871;51620;56365;21113;31788;26357;41854;52769;17210;31225;52676;24971;30286;49162;34949;51086;25464;30981;27670;54379;24834;26170;23831;49534;24660;57854;29960;17588;52717;10363;13781;55882;31969;34888;25253;29175;35693;10582;61550;52966;43755;31146;55281;40422;47542;40154;15984;37637;52477;12083;36441;46003;25501;15277;57132;31882;21144;44076;17772;10853;57898;61197;33105;38058;46248;12365;39745;47541;38782;47517;29373;56527;62015;52463;62829;32477;38983;13509;48892;24977;23180;54683;40934;56767;16636;56357;24298;22657;45766;46006;40585;55996;20996;48587;54035;49268;47003;19679;55770;46493;15299;48636;15124;22661;12809;49081;36791;34258;53562;52457;37836;58856;63139;39240;17442;32594;15943;32125;50557;53268;30459;19760;42142;39192;46113;13596;48832;61187;21093;44028;37624;19389;62346;57538;15007;45374;14486;50918;10963;48902;12720;18072;42216;56712;52751;54715;60207;61650;11554;62206;16153;14488;23978;63555;35189;29959;22961;63331;20803;23619;12825;42851;30705;46475;28381;12623;44780;17465;16036;40958;14196;60957;60841;19753;24591;22709;50927;37606;63480;52101;32219;56057;25682;22983;46937;43317;32109;58766;65850;47239;42940;53389;24204;65722;31379;19421;32562;17088;57853;42629;31264;64309;13174;49878;17536;29250;40136;66444;59582;52583;15288;55538;26944;38315;60447;23091;63955;57118;51396;66561;12965;32821;24678;16075;36236;37909;38661;12970;30837;32138;33198;57406;65257;53168;55739;23722;21376;65148;23532;66110;23564;31336;40359;62671;22072;54248;50362;26076;54300;25731;51428;64602;22070;19555;60404;55638;22693;34765;49286;25364;43840;26743;61176;33650;15048;18546;10359;12643;34870;20756;36169;42437;39128;29682;35133;61006;54684;54722;38859;46817;60660;34285;37252;51854;28491;55314;20280;55146;47414;37496;22088;43043;10974;45927;64217;33898;38306;49573;38590;65934;62359;59921;15330;44026;47287;22764;18815;18633;49642;64679;19782;55724;10439;38723;55556;12115;26219;25830;42540;61677;15523;25236;49047;48449;15290;29060;64320;36388;51880;65921;10191;53126;18863;18525;63026;59387;30246;18998;49999;44103;45455;37363;28639;45994;56293;48277;47494;66458;63244;28514;21956;53963;35213;44986;59732;19072;51631;45073;57529;62055;50400;62697;38694;15590;50141;66189;28926;32132;32024;14606;13044;64235;39669;25742;64228;34522;24801;63588;37778;15352;20003;41157;44455;56038;36841;60257;21790;58211;39140;41892;10398;30498;35592;66217;37962;12284;10091;46920;64559;24837;23247;56255;49793;39942;12588;13126;47859;59495;31031;20188;32425;28304;41270;16457;65592;50186;39141;43929;66868;64365;40191;26015;16086;41445;31908;37517;50781;62177;48939;29914;64925;27856;31819;42316;29867;16970;53374;28240;47365;13190;52318;62886;65872;28179;54772;33068;43827;11134;44316;29512;27236;63453;48577;66301;62225;22238;17339;55299;57219;28700;61216;14494;21933;64744;10857;65879;20187;35166;53797;29255;22548;17601;62375;21752;65170;53080;25390;50117;32378;15247;27883;18826;39072;21434;64147;40349;16541;56492;20045;36495;27846;30130;47606;50108;31337;40225;54361;64842;10280;46879;62817;32476;47107;56283;52768;13384;58164;40505;35950;58970;15558;65285;43495;27559;15061;13428;11586;43338;44044;63324;18539;18411;66147;31742;50421;11784;42871;61319;18254;64452;31976;48517;32156;27521;24848;52840;66973;43725;29486;38568;23643;20811;58306;46888;40683;27683;19737;63740;22905;12314;53634;19885;53258;46221;29589;51632;65754;10896;11920;57613;52825;52836;14588;54726;46299;36799;25361;23833;16243;56179;54996;45385;37074;24433;60420;54672;52044;45321;38509;31677;51655;19056;59756;17315;54284;24230;30470;63341;36357;64987;51860;29644;51237;26295;13327;58107;32063;21656;51246;15993;27338;30997;19969;27269;25586;56292;40802;21127;62635;11890;28800;62701;29178;60697;45021;38062;46279;35867;15533;65980;48696;36308;18342;58278;40322;25494;20670;64113;13086;49214;28673;31958;23758;52597;11887;64582;51673;55644;47762;15064;19900;28698;66256;61074;43206;47495;63147;31465;32510;29350;19116;26533;21610;58013;17003;39883;21569;33333;21965;52495;51580;28748;48539;10951;61818;66019;25455;57477;60107;23573;13722;39834;24101;62252;26429;32148;60830;65898;36783;57067;26586;54397;35380;54597;43201;32284;53112;41483;40008;43296;47664;43531;61435;35037;10727;12941;52403;29550;17034;50346;15159;28211;30889;42314;45554;53159;48396;24338;65091;10530;40216;33321;41036;12765;24625;56589;36392;54381;58562;44075;26008;53649;23549;60692;57983;52814;12788;42642;33874;42911;27901;31461;34903;56917;23129;64518;14479;45570;49628;37824;24175;59013;33071;64971;26608;47250;22848;33574;66446;19382;31664;55771;55361;10395;40678;61703;30383;15808;11508;29538;28153;59417;40248;51032;53367;10979;52864;34905;42822;16780;35518;39423;35725;38149;21575;66926;30336;53143;13885;31746;46033;11340;29872;14491;21651;19338;29893;15355;39861;61566;65004;34629;62500;41794;46429;10721;19113;41805;30667;43887;24953;30915;27561;32074;27490;63704;17585;46206;60774;25323;46907;49320;16690;32359;42842;33055;42738;22532;64259;15660;48853;50315;46932;14463;23724;10716;16440;32737;56480;14001;18275;20920;25380;35791;58630;23357;42846;27340;23797;39852;57943;59171;31990;16929;55928;57066;53641;57895;32123;26052;27845;21518;19908;60656;47207;30504;32837;28022;29296;47400;38987;64697;13531;42921;12057;50391;43003;37829;44422;66396;40821;24831;31340;45341;40695;44299;51786;27495;20603;40155;56027;24127;20379;23606;61092;66388;54970;46939;53425;13314;13842;53154;21354;23367;46892;47291;31526;62166;43412;65728;61051;45474;51403;44876;33264;17616;46271;35761;60000;20753;58421;48716;52514;27768;60155;29049;14966;45651;20441;24657;64652;33006;65666;26692;12705;39179;58950;20549;39961;36566;35232;51821;54740;32176;14103;28345;21763;59672;20199;66750;59693;21216;25821;25743;53274;62078;52023;39645;52285;51332;52912;45963;50193;51433;21620;60333;19271;66033;20039;34364;29699;33746;12689;58267;66549;43372;39762;13422;23772;27355;45853;35514;52319;49230;66028;49619;34156;33316;48201;54272;51486;31406;59489;59133;48810;50403;25372;49805;48656;32544;26747;30835;62281;51966;56183;31440;64400;22789;61395;49647;66008;11840;19347;22290;35977;55740;66648;59410;32746;11507;19358;39564;25281;20927;49743;14616;54048;54563;17730;59615;48776;21130;35777;12554;60907;26776;28767;21782;10584;33755;66802;53506;25570;32548;13334;40967;38347;50007;28774;34241;35279;26051;22889;29139;50748;50930;40300;34906;31098;58479;23757;48711;47760;56576;36289;31745;17345;37158;47321;48802;50589;13252;61039;13703;48475;30433;55313;63086;59228;55872;66786;25010;44382;27656;16874;48422;55344;50105;42191;61094;66283;46284;48579;57091;19773;58769;53116;31603;36948;48694;40336;53309;52590;54146;17803;36091;24315;17809;59473;64673;26082;44905;19669;63933;61152;53672;25139;17600;41256;29829;53610;60556;36824;51587;61079;27283;55903;34639;63226;48769;27941;35665;44116;42249;34262;58617;36613;43547;13649;49697;53487;14538;35597;16103;12731;58130;47156;29217;63782;45940;54709;46496;32254;36674;62930;30761;46543;28680;42290;41305;18880;39681;56597;14266;46470;55179;36217;55588;29505;29864;15601;27933;62106;56453;24658;61848;59610;15101;62000;12330;56804;65777;23082;20824;28284;39818;44542;33167;40768;38559;19221;49674;40409;54252;35553;25197;36547;61226;32674;49211;45992;11155;40825;63640;48817;33540;23254;11539;63605;53017;23259;18281;42281;26055;15904;32645;11480;60868;49572;57563;29813;40023;14628;42038;30506;20736;14601;35654;28711;51551;27076;47653;44250;52137;41916;20541;43566;15958;54088;29144;61054;41961;65288;26433;31001;27104;41691;11366;59291;64661;12549;39335;10362;27107;12594;40052;27566;28645;46601;28889;49174;57536;29251;61707;65153;51495;53580;20624;34648;40901;53560;39856;65714;13193;46536;59297;25047;42743;37454;48347;33996;19659;44659;35217;47842;44740;45952;42416;52830;62165;48414;60234;45624;63378;38885;43132;63281;61256;53642;30611;28097;62631;57499;64334;64131;49134;35060;44517;44812;63809;56088;65149;62026;59125;19070;50002;21539;58341;23151;48448;13226;58476;41912;58717;53232;61431;25854;58153;43214;64190;17314;35635;27943;13364;10882;26918;26549;33756;12082;53317;50713;21954;51944;32175;59995;63987;63539;27272;42007;27313;15228;18948;39967;57556;25910;49703;11899;36832;13518;62042;54218;50968;14741;20297;38837;63747;47032;51380;56467;52140;59120;64586;44265;29822;48836;31928;39168;22814;46963;38738;25723;36460;43842;27758;18635;15079;62182;62737;25871;20522;17734;48976;57223;23853;15069;55005;63672;22715;15328;44967;61843;26004;22349;64129;53952;51749;21873;22115;25087;28586;58454;58816;50326;25562;63107;30982;61200;15015;48285;44296;61970;58024;30670;13149;36061;10195;53289;10423;10596;29686;20205;18470;64099;12848;66473;57755;61346;51694;61440;65693;52820;47389;19025;18947;23613;24513;32995;27214;56124;59143;14967;50110;18023;61348;48993;34452;56499;31891;30348;49077;21118;33162;55369;53180;34775;50726;54942;26044;20463;59626;52127;41589;14316;28313;66736;30759;27012;60130;61076;25136;15310;58377;40269;33537;60453;39847;60041;63240;28540;38021;55390;42066;11002;24164;63911;17243;35153;61290;63983;40492;21723;28863;64855;60946;39431;29775;63675;13448;58214;60741;35859;65216;26065;42463;11844;44704;23105;26214;30407;57678;63961;58643;13911;54343;38215;63575;34215;21317;10215;42588;65935;40950;16287;28105;38348;57590;27073;35372;50528;24372;43513;42925;33550;49472;54820;52792;22704;18248;63006;29896;24966;17770;53436;10022;59591;58577;57246;46406;63118;10826;41332;26575;27760;61202;35767;14958;37965;20645;18233;57773;26374;62397;60953;59947;64471;14124;16050;54402;33197;59232;62848;42858;38224;66055;29099;27500;35354;53769;63438;56049;17437;36302;45407;60821;31065;50549;47342;51411;34857;25190;28874;52091;61067;50780;33205;20765;42919;41522;38600;49302;37679;43752;40771;66344;64711;20985;14657;37027;52064;12936;36706;14942;22165;41731;14674;22947;29428;55880;57391;62554;53198;23451;41321;42714;41771;51413;24187;30164;22701;33518;43402;17401;36764;58763;51847;64069;55808;13967;57776;33341;15477;10961;16951;50115;31797;32567;50291;16119;13770;13316;28236;43340;66691;39076;40361;54451;22269;63737;13788;38413;36910;12041;20437;20882;14813;35889;52274;61100;18337;42694;60527;23420;41494;57839;27579;36808;38583;19151;21094;15617;16215;50084;60653;30448;34009;54628;11044;34728;28510;36280;50422;58492;32342;62767;16487;36445;17155;57026;66163;18970;42162;16743;46850;61163;46306;33853;21428;58805;33435;38159;31265;60708;41591;56296;35932;66153;36731;53640;58694;42937;18728;43951;29853;15691;20858;19604;31954;52193;21270;32160;15223;52227;26983;18504;42724;43072;65208;52726;49995;59383;49396;48549;11230;59052;63695;17975;39509;42019;12339;63466;18788;64577;30984;19591;44411;66228;17516;36188;50178;28315;29412;36379;41661;32823;30673;21874;15255;40961;28522;19272;52100;36051;45532;15010;24314;19956;50634;11441;21106;15082;60344;49196;36312;10188;37211;18198;56878;29149;36000;62948;56254;28102;49339;18617;63776;42303;34526;46171;25096;30760;20449;48840;57797;58655;58163;58658;20656;66485;38282;14794;20082;21251;32841;15559;13869;48887;39161;15169;11484;29903;55833;29126;46636;18685;59349;40817;15509;28693;55688;42286;20390;64880;29290;17506;40208;30661;31462;27560;64794;38938;47005;62392;38197;53441;52811;52842;22542;21486;10107;64527;32032;35121;61602;46009;42901;55272;25631;62076;45600;25287;64032;35038;19734;57459;11936;26594;54579;26734;61922;37134;48608;24645;20370;35371;41988;65051;41802;26520;43864;49562;62053;18189;63382;27179;55429;63641;28865;24945;27469;64784;25527;22105;34569;64637;13742;24595;54614;43215;56391;57001;65739;27849;31481;36759;21661;61186;44453;35077;12342;55990;53990;51151;17204;58089;23393;11087;27331;39382;49586;23921;17647;16786;54375;24494;55652;32564;53974;46665;15192;59708;50929;47151;17387;16686;25000;24943;59754;17245;54800;13661;30378;52647;21102;35004;59159;29827;64478;60561;66875;54657;21033;11822;46024;23328;22610;50204;25257;15768;46107;22639;21700;20566;62868;42062;58685;30891;15134;52458;24058;49108;43764;55661;30833;17976;57540;38459;59508;36202;24156;26786;57639;51622;54669;56562;58792;37391;52703;41251;33621;35155;39333;35600;37141;23483;22498;28545;39715;47379;54897;34306;16172;60232;33013;10640;10163;58852;58826;33281;24432;26301;46487;39682;34542;41899;54908;12293;12958;48778;10055;50044;32209;15596;24389;50718;30229;37236;29064;29023;26389;24466;20362;54731;62184;44827;51652;47788;24675;11450;33208;31644;14822;14839;65873;65648;35397;66543;14745;46620;46365;44287;63496;58382;43125;49029;14003;42896;34415;47574;48758;30559;43779;64068;59688;20346;32143;13811;16167;55323;19783;38731;59637;20054;46500;58318;48317;28361;52714;11124;59898;66445;38000;13105;55547;24777;29610;53213;53214;17796;28373;14668;11716;28232;51628;27297;62582;42200;41903;22568;31725;56987;34401;12469;43095;27311;43917;15799;63515;62012;37683;63278;22688;66715;48872;21356;65859;21129;64872;18760;56858;55925;12308;48583;47285;44575;27092;60662;13239;65560;40671;57609;28296;15851;47411;55953;64102;27737;19362;28200;66131;60986;39473;20102;28778;25616;39219;10679;40022;57780;64434;42104;46501;30603;15510;29565;45681;49333;41277;23136;39993;65469;38816;65937;13066;32763;56828;24189;47139;54856;36158;44855;35015;28910;63215;17632;30080;63021;40816;34662;33465;26425;59076;21101;12080;41340;42638;29658;29181;35564;28203;14804;28440;13577;65784;28536;26202;11708;55193;29458;65661;31182;43482;24318;32676;57011;33254;46010;42664;52451;38293;49283;56347;12032;15374;21456;30589;24662;18182;24376;41797;66523;51136;38836;50483;11278;47048;27664;34897;14426;10246;37631;38997;17368;17703;15392;63464;16871;24590;26143;15879;42369;63336;65795;62384;16289;65040;23030;12545;50655;45244;66617;48378;48288;18397;28041;50201;57676;50385;60501;36666;18574;25597;13641;59838;42862;55765;18800;12373;22454;24440;60997;27983;18627;55865;25935;56967;51116;12020;26474;66404;57806;43936;10287;13111;41336;20117;38195;43997;33471;51810;61016;62933;21867;19035;29132;19471;65646;37754;64274;23332;60298;29398;47405;54190;24112;60970;41564;26966;38415;48556;19518;54815;58650;43243;63445;12815;11846;47904;65518;22148;64548;49486;40032;46183;47024;12430;32469;48654;27825;28904;27924;60358;51483;31752;57852;66633;23371;54670;64892;16311;22706;18030;24128;14305;43514;63967;10027;48658;32749;23690;47353;13307;53424;26564;47661;39523;35625;55396;36153;65608;61448;51666;19765;46749;47448;56497;35254;35497;24148;22443;40071;21151;65826;32871;53110;41360;55709;27376;44091;24493;31814;25499;39164;63712;29028;36498;64266;48580;28453;18439;56571;25966;55413;23053;27954;32335;42915;52176;44186;63803;25209;19407;49199;15191;57889;60904;10717;13946;15762;25194;61419;17468;65057;11210;45751;37571;58604;40557;50789;22446;19834;47444;46340;18706;34082;15083;61241;28199;11862;50080;26507;40922;45125;12868;47020;61217;59650;40294;57510;42792;50312;31807;53062;58706;48911;34521;15946;61850;22698;59793;21348;48535;31744;13135;27347;10960;22776;35215;21383;28806;51228;32968;36917;33274;48992;47204;18883;23838;49510;51910;61520;50479;18952;51329;31137;19463;57683;19248;63973;45791;23471;49180;54192;65865;18212;32341;12053;63146;17029;63435;41032;62029;60876;41996;62590;15416;13910;14926;25055;26147;51753;63725;42308;42231;50271;40645;43812;32188;37043;26415;32927;53166;52807;59843;63441;58383;33060;39514;34540;61401;47540;38099;43365;39528;55621;39496;45943;62113;54759;23124;66728;37716;45161;53357;12860;15735;60349;49493;15323;54337;43774;56880;53944;49672;35353;55759;14532;43336;52341;40500;32630;33637;60931;62920;32693;20899;34560;54903;11527;41667;50935;38455;17349;54104;15989;51754;19520;65052;63414;21805;19079;63356;29957;49440;56673;46369;39099;47508;46542;42654;38972;34876;66441;49860;52616;16212;59016;41983;46063;28268;47623;10678;23927;13699;52097;26131;26479;66376;43617;64508;32507;25699;12833;63766;43768;64340;34692;12586;29749;59721;65759;60562;46901;58638;17649;10253;24309;32094;42545;43466;43065;51271;42503;59939;23337;14324;43420;47650;12585;32319;56334;46706;51890;35113;18985;40865;28736;47059;45531;29568;13433;19763;38377;31547;13420;64394;40468;57140;26634;22999;52675;13896;58057;63306;44339;16087;62394;52630;61540;59357;37509;31417;19177;33544;32044;61641;30516;19292;36736;59102;13797;30812;23760;25178;13155;10092;31994;23397;41997;32546;54565;34714;37494;15334;11251;24199;49850;49458;17139;27197;50014;21096;47121;10924;61720;56590;52702;35244;55449;37328;29655;12425;13138;57134;33694;50256;62516;46815;65125;33891;32315;51293;36258;32675;26892;53061;65032;10594;34301;30084;56645;53894;27631;59997;64388;28420;50686;25556;66857;14234;50848;11701;21527;23381;38771;51077;56305;15777;19890;36313;46740;49926;37724;17234;46923;34850;22630;64550;60372;58992;20966;35440;15335;35070;26222;65597;61598;24216;10701;23581;27975;24571;23127;32217;34930;58989;11604;11461;47051;56778;15238;32765;61613;28722;57169;31078;11782;19165;65241;15053;16910;23365;64287;45957;63714;26813;19556;24896;24259;55477;22439;49131;30675;34858;32974;25551;16704;11273;40733;55249;58539;65515;41800;12824;64822;40179;32797;15825;13467;17191;52882;53281;17615;31982;62537;17623;46538;22852;38121;48547;22873;11257;58828;26478;54545;13397;17419;44034;34378;35370;11011;62452;45349;54981;60300;29995;35009;45931;19076;52510;57735;34103;64604;66649;41107;18260;32719;43960;10602;36968;53076;53427;23864;35382;39559;54348;46508;27010;29951;13588;47007;20553;52146;16657;47610;49509;18208;19181;14199;59769;60286;19898;63642;49692;56454;29912;44172;66245;37340;10283;20910;16664;32408;17836;17123;22331;57562;24579;10547;50119;48553;31723;13290;34674;10365;12037;33407;26622;12353;66730;34682;21886;43919;59153;24640;13431;21254;53651;23110;44637;11098;19178;17510;58647;50174;61568;35742;20976;57822;47408;28881;33300;54765;31284;56062;40424;42602;55528;56852;57748;51141;55311;20141;42155;48492;51959;66958;34563;14132;31766;34854;60611;40710;54486;29672;56763;17227;19300;30733;60792;31698;34506;30993;37764;20538;22778;45033;31150;43205;57783;25671;18704;31846;14935;51920;61397;29026;28911;38164;34736;13224;52932;31640;48653;64724;64670;17285;51131;41936;20570;32908;30089;22469;15071;43058;31424;38405;42381;38414;43979;46681;21746;41070;26413;45728;22417;33859;23943;44798;65439;48722;13424;47833;33594;41301;57283;13137;49651;20763;19121;13461;65086;47698;60442;65572;10620;44565;64244;25921;48754;62814;53051;32887;52577;18301;47200;12127;47234;35674;58510;59024;57645;50582;23122;46872;14681;43700;39251;61808;45170;40822;15732;42893;23566;46290;48374;21631;44903;18556;27156;61643;29257;18799;54441;50412;60101;45998;65041;64708;48572;37325;62756;25769;14237;59758;52530;13602;57479;53052;41829;35434;66581;32605;32263;55418;32655;60438;59441;62604;60359;49426;55354;57209;57584;15613;14764;41876;44270;55844;49898;21057;66169;35281;60370;53139;53615;20856;45236;48320;65876;49388;45400;31388;16864;34530;33037;36374;49866;36226;15651;65320;51889;65493;40159;63673;21405;10712;20591;36555;66241;36986;44402;12485;53329;53266;60045;29592;27601;54901;36292;25938;37956;10828;26171;52527;18547;34407;62530;27931;56121;22908;24195;40433;26013;35073;32333;41544;66243;33398;35914;20108;63475;55838;49543;41227;33434;42445;66735;16685;29819;56069;60951;41149;26883;59432;64654;64240;56814;62509;41675;17733;19449;20576;60791;17776;56931;12675;11720;65875;54406;62565;20647;44484;24102;56517;28028;49037;24878;64226;37644;42551;27720;21341;49502;33373;62761;35918;42899;33914;45771;16550;64506;58861;18195;61017;32382;11156;50205;49309;45804;10068;49608;59215;50896;63657;13215;47706;28571;39838;11752;29393;13893;28016;13037;29160;38511;23272;45242;43636;12061;30853;66664;13603;51427;56416;27460;18740;39223;28496;63965;11922;56976;48777;66240;45262;12778;11591;25429;35143;18801;19080;12226;33390;25911;64335;66393;29880;51183;15467;40327;12382;27299;59211;24770;33944;13686;28195;51626;41387;21617;54707;56270;13173;11924;56171;46810;48312;19156;41801;15420;49676;62618;63469;25693;63395;60157;59475;31082;20607;39269;55343;34343;27023;26638;10563;62999;21467;11628;66767;35557;48322;23576;10133;11466;51179;61349;14477;14209;34655;25614;11640;50365;58595;65737;25763;59124;32614;66636;38612;22979;29233;11159;66209;25466;11682;18380;21711;30551;55915;10104;56189;25074;59720;58879;42631;41131;42355;32240;40994;25545;40712;14380;13931;47057;65840;42195;36256;43853;20725;17683;64076;29370;60433;19126;49920;39911;32508;36949;53432;34188;41021;30696;59959;43480;25856;11763;36716;20709;24959;18046;53127;21519;17559;51114;44711;60783;19814;25912;40116;34772;46858;58622;27824;24937;58178;65354;66909;48707;56966;39160;25016;57060;30832;16423;17663;18790;53731;51269;53922;43796;35055;36410;34720;37260;11865;17267;39403;20550;63176;25493;25041;29807;46304;43550;40040;35363;50563;60686;63688;26606;40793;48545;15209;20769;39608;52072;56806;32348;34475;34567;39879;55184;52656;41335;52497;20701;20839;45172;60834;37910;31993;46663;23025;22745;63059;56557;25555;53582;30945;24355;17978;64928;60169;10424;28340;18186;10626;31918;44440;25275;10372;55250;17429;53302;63664;33305;10076;12894;32052;30855;41446;56846;24763;27320;43010;40451;55335;10535;43448;14175;39835;26864;41438;65364;28227;42913;19277;23138;49330;25351;52169;16577;42242;65575;18838;17190;16280;32989;59497;61837;21260;38198;34641;42974;52213;58063;26293;65601;58002;50509;39487;47711;47137;49155;40639;53785;21705;52099;48808;54449;62328;22676;42478;27997;33975;59499;33356;63465;63089;44657;14782;23164;16626;34923;29121;29278;40517;11854;13023;44578;29692;34716;28672;21147;38255;42763;58979;19483;21948;18422;64075;40405;60304;49780;34583;48459;11075;47683;50521;36269;38646;20155;15792;65710;21358;33444;57071;20420;29651;31893;49060;66842;14405;57157;35901;49269;59844;66401;65150;17230;62976;15901;12204;34767;27911;18221;54646;66841;35491;25725;60274;45695;25237;53535;59760;37507;59817;38949;47324;58452;54627;18537;28790;60803;29836;39519;64775;53763;21648;14837;46034;45553;33687;48452;45858;40625;57466;42772;61025;17385;28765;50839;29723;30548;44579;43785;10124;46921;32604;28661;40699;26481;51933;22136;12717;57568;52379;25915;53960;39346;55748;63829;25898;16990;22186;33826;33909;19795;40523;59186;45334;19150;18776;42530;38424;29972;59174;65972;32838;16320;55745;64973;42960;30323;34908;62036;12766;59694;33065;21069;26019;13056;57673;49218;60246;47226;13294;64512;12850;58812;37049;15051;48241;12641;57079;60384;62666;45287;63407;37973;48533;44869;60644;58125;47551;56146;62087;50729;58993;18161;35766;53450;62426;39794;28805;58075;17035;56620;27667;37013;23523;55115;38582;44152;16949;16429;10812;60475;29309;40617;28147;24975;51041;43759;21644;63684;39205;61759;15333;58083;40954;51954;63128;22975;13538;34705;58471;25764;29277;55304;55245;33606;36777;55856;62107;23302;63256;52828;57867;38656;58770;58887;29260;15754;61963;53458;62892;49806;43631;19752;48629;32166;26719;64858;35560;64460;27679;56825;53041;49684;24138;42378;24663;18840;11191;21184;28546;41300;13802;39394;29753;48744;21086;16586;27219;20577;11072;11668;53633;12900;48213;15070;27183;38566;38087;40057;48621;52448;23101;38687;63618;54594;35871;42873;20303;18010;17546;11221;19840;44046;45466;34865;21857;40264;40083;52068;54893;56849;58091;65457;52359;30776;59596;64289;27547;42594;29098;32884;28321;24063;32781;56747;63400;57991;17783;41630;35048;20963;63049;28126;54974;25301;27900;45186;61788;63817;40738;20837;46539;51719;31643;19634;62025;32223;43081;39876;47865;58060;57415;52870;10134;24119;26375;31556;18074;60106;46648;22158;16917;19551;10378;19134;44585;59181;26487;40085;53620;26282;31512;62636;36570;58008;29894;17357;44785;21788;14432;20922;30055;30556;58968;15679;50512;11078;50347;33890;66167;40634;44552;35450;54631;20276;30483;55076;34199;25399;57888;16080;53711;49491;29774;18292;48962;36469;17590;59812;64537;29282;34578;52302;42574;45597;49387;28975;36431;25994;28632;18811;55526;32252;45671;65539;53806;60513;22278;39941;27155;40985;63355;38352;34184;41588;61059;19831;45194;66426;22131;52795;59426;18915;35697;24414;23117;65867;39026;44929;50101;15640;57815;58869;12609;21299;24332;12375;29068;22025;31174;49764;15982;14012;45441;34429;46510;26588;25039;20398;61624;34761;62957;24450;42347;30828;13485;10318;20782;35463;59088;54793;16261;10128;18278;64041;49139;47080;22858;11463;62031;41489;25703;38381;33951;13512;59097;13284;14375;19708;40455;64569;41402;15259;13395;26488;47756;16868;33104;50906;33808;57571;14466;13381;23922;55066;31805;53747;64203;42352;18792;14972;21398;63784;19000;45623;46230;59084;22270;62561;63028;63314;60375;39720;55498;44349;39653;42404;44010;29466;11790;20942;37100;27775;37186;14559;34380;24993;61478;19169;14704;25070;37405;38605;53592;11282;59525;24190;58152;21778;50657;62820;38622;17644;20588;34307;58435;49039;49439;13668;23662;23713;58349;52942;36183;27852;65058;59503;49267;59790;50716;15471;63956;48380;39426;42510;56417;17110;25949;32892;53393;41685;27645;25839;65862;20459;11089;21896;51785;27022;17726;59692;33893;35580;38476;27253;52472;30033;56470;40883;34817;21137;58486;55927;50286;66038;49203;26602;20022;45007;20759;46977;34323;18425;62284;34436;58609;13113;18472;10589;55817;33088;27172;44529;11853;63527;40927;13713;43436;12905;62556;62551;14276;64719;22048;55339;37774;34792;16298;28351;55514;17257;18904;22303;13935;35745;36563;61838;44960;54571;22821;17226;28040;60482;23568;30958;23641;53545;59847;43198;21224;28183;52082;17361;63105;61023;64501;19977;27907;22036;64816;11690;45132;44510;34977;46619;22249;11643;46185;64984;26445;40565;15469;50285;21528;16943;24902;14504;58504;16255;40140;30971;58724;27602;51659;27715;28557;54681;66846;18347;39562;53103;23968;60915;25465;36262;50111;19991;11311;36200;51555;34807;15462;12616;43708;43363;63046;35993;39837;58586;11188;60131;48743;15887;62320;27280;45280;14688;14345;16346;40522;39797;66364;20711;27382;38425;39744;55979;10746;37390;64715;14226;13534;59139;11271;33987;19768;38880;18927;20433;62444;32356;61631;31691;16888;12537;52337;30706;64403;35453;55508;65353;27013;58423;63191;14055;10160;49186;54779;50542;35286;55188;44399;49420;19184;45224;25154;26794;37860;24218;34203;62651;41404;42486;54666;15044;10671;61625;29317;63136;15599;25245;12396;22614;42029;59767;46434;59416;55920;27536;44815;53136;46685;24443;24100;35468;25027;34747;16543;33956;30075;20780;62459;58412;45759;64143;22562;33191;55595;47252;11820;23363;25106;35608;32056;12548;38474;57733;66015;61634;28056;56275;54755;62224;22797;51006;11929;31841;29436;61840;32355;35345;11595;42255;41725;14125;46076;55627;36525;29157;12040;41531;45037;35511;17291;45574;52926;59658;24951;40972;30282;54710;61262;39436;14201;32346;64761;46232;41532;64749;50565;64169;19034;31604;22029;23061;57150;63801;24621;25829;49626;28138;25333;21791;41146;19359;60796;44752;66645;21692;12956;54747;64589;32773;45289;24986;54108;12638;39679;12772;10145;65096;54380;31767;22356;62438;61544;38751;44177;32190;65866;27215;27722;48958;47140;33847;37921;14735;37351;14655;41908;22662;61048;24248;34054;30880;23779;50810;62660;34220;31905;55067;60962;25028;53480;56827;16118;21646;47797;60926;39975;43366;53609;39190;17667;66086;36414;29696;21238;13367;18535;11709;33768;31560;12924;39892;51745;51709;22506;28155;55658;65791;63045;52324;12245;24004;31574;25690;45424;25561;37647;10012;31282;43624;38340;44985;46867;25753;14311;42396;14465;46933;18027;25644;22636;10430;17540;56611;17507;42258;34194;48382;37898;41299;41575;60241;51055;11829;45375;62168;38908;40163;62112;58985;66261;31580;29254;66296;24651;38332;14356;22665;39078;53122;40648;61259;45830;46425;13972;14087;53343;32446;63460;20581;16325;22486;15327;39970;39896;20798;17832;20046;63597;18835;12856;45732;50858;25770;30591;52188;46347;17118;51212;55441;33611;41721;26062;59168;54090;10894;10130;44426;16571;32832;12313;38386;22683;46698;62189;51704;55011;10886;28003;23677;56490;34398;33044;31948;10601;23527;62687;61858;47427;34970;13734;61420;33255;60853;43921;30672;46019;43655;64564;24711;34544;23236;49931;58987;57531;25318;28488;58610;15525;64517;56077;56182;10248;54509;48321;39588;51692;54801;45366;41940;17450;56231;51675;33588;29673;40006;52779;51400;35808;66370;33099;15283;21984;30914;59091;18558;26511;37365;21507;32023;63030;51515;40329;13914;62340;13580;44809;59184;29648;25668;31655;41054;56730;37150;59142;56736;11256;33644;54864;60621;47257;36603;15398;48477;50059;50644;16662;40882;15791;37082;42869;61414;19501;61470;40652;51213;52062;30702;38857;28940;62991;21134;24481;37623;11244;41072;23115;11992;43388;31642;27823;37421;46178;12419;44375;34329;18351;46130;35469;59545;15995;36367;55900;64442;39467;36461;61884;33388;16362;53077;43731;15395;49966;15367;35663;13594;18432;56128;41862;44237;61314;48486;64358;36573;14964;41636;33977;18267;44786;21785;19058;47173;57739;29471;16204;32728;39361;65167;35374;42777;65141;27527;65016;10684;12800;46956;47748;21943;15914;11813;16606;44241;22140;61836;35525;35992;20097;34106;57811;21092;47607;15425;11153;55814;28676;14051;10581;42241;20477;42711;58175;56244;21775;49752;59419;48751;15413;29378;18135;38996;62313;58269;26360;10702;11688;44219;20936;43656;54491;60111;56157;54293;15538;19405;38238;19897;47001;20247;21423;60154;36161;55521;14468;51690;21286;57509;30553;56245;39227;43293;26005;59598;43070;47046;17421;11873;32877;49691;44971;55983;59968;15094;29051;21660;63709;12112;30325;56989;47259;50559;51584;20389;66529;61437;12668;40728;53327;41441;31010;54484;44791;58613;25937;14824;61902;40278;37019;32251;55220;26475;19970;18029;46596;47113;47419;59623;28666;39371;65450;21351;34510;38652;23717;41902;46898;51060;29342;38895;50630;33052;42135;13582;63903;24268;15461;46395;50289;42193;40833;55316;44192;57905;48215;66030;55255;48936;28754;12437;62451;22189;35495;55993;52611;37953;15245;41275;59098;27761;14875;24269;42534;61545;56330;51908;66468;41359;61771;28688;62079;47162;32417;60262;24865;56053;31409;57313;51187;35565;53045;66168;54234;53311;56794;56277;38619;37384;50514;47422;50612;31369;45828;56276;54328;66416;37116;18864;36443;18391;13292;48966;46439;19175;57761;23663;49723;23947;47320;43470;54256;51644;59067;21599;16666;40153;64339;55592;63251;33911;18485;65165;65805;15489;29165;39985;31090;12612;26529;41894;28675;45798;22079;34842;65623;57045;46711;27724;55307;53721;54616;31374;35234;45978;28643;65955;62867;61485;50163;38783;54727;23552;23423;55009;31956;66180;58872;17828;61114;53117;57408;64315;60669;40787;47654;44699;14899;58229;41482;65653;26254;16627;40962;14948;38420;10677;53540;41826;27896;11280;42573;34295;23197;15834;34303;49401;49007;49682;44039;58118;56942;31125;34847;62749;19638;43704;24803;64160;21843;25417;57997;26922;45824;22948;47589;61309;51715;47134;13530;55410;23832;54507;27557;16088;13709;53314;10893;30313;47150;20329;47585;41764;60401;52956;38384;50030;57508;17539;41465;61920;34607;11748;60838;16257;29690;36586;43445;52238;20978;43035;66595;44619;29564;62894;20194;37157;62589;38963;41975;58339;11994;19223;35315;43297;16165;13793;40536;14004;50026;20988;23084;41425;42276;42926;33844;31309;35078;35007;20608;14632;19187;59774;16601;28850;15089;55347;19529;35102;63227;46748;46527;62310;42825;57738;26329;62302;22400;29019;14692;34356;58213;44770;35051;17433;23551;11923;31441;66484;46146;36136;61506;12669;26912;14361;51685;18032;46118;12412;14290;66855;13655;16049;37350;30519;46833;27932;11434;41984;60198;27000;43256;55540;34503;50472;21592;16841;33134;46182;16977;21756;30976;51392;16321;52105;19368;64837;24145;49649;26574;34599;65924;48987;66788;17262;29400;46394;38678;37725;64921;52998;44581;29845;44067;36409;17304;18489;46613;11076;11285;15371;25719;14886;14753;34805;27692;35857;46603;35729;50819;58097;41212;38088;31667;28605;52644;59738;18615;12285;19374;49978;21499;28579;65256;40095;65833;19383;34457;61284;51872;11178;20058;55668;12056;51734;66469;18774;15415;59860;51722;56715;11374;43832;48293;60316;66773;33379;43938;15992;63567;10449;53661;27503;63322;60528;49558;22108;15681;28428;65432;36602;17500;55533;32270;53073;40858;49963;60103;47306;37629;52502;33894;32565;16755;46871;57587;13507;33415;38240;46732;27740;16142;56291;38905;18859;53364;50633;28189;53010;23896;56770;30000;65832;14113;42181;10034;37218;53532;44368;12606;37862;37866;32540;50888;59712;58657;44345;18126;28270;65949;26130;41204;51090;19576;37876;15173;39960;22360;41626;54149;58481;39857;26369;36914;49722;42313;53867;18960;53018;45989;52810;61612;46239;39149;53467;63754;22658;49953;27519;40806;15737;57910;61915;46788;24441;27246;34827;50025;42961;45959;43364;38037;17483;22944;23636;29177;27681;46397;63511;63609;58475;20820;47692;33920;40558;29030;26509;14826;45325;24584;64757;52660;14298;19443;15532;64676;52312;36897;29077;57082;11704;22654;11600;10856;15503;24771;15813;25061;14255;66186;60831;41851;37761;66631;48912;48402;31066;28633;49627;28088;65443;18673;17217;45301;34866;56717;33538;39054;21064;23875;53222;48166;39677;39982;46621;51833;15300;49419;14859;45095;41085;32189;48162;12224;62114;47702;13141;61244;25758;47764;17538;44277;19044;24681;16059;34700;53962;42837;45575;58150;52701;15473;43270;11013;33110;40363;24088;32293;14803;35662;43308;28804;66127;18008;66499;55929;18352;37354;14633;57630;15682;49551;49064;16265;40201;59675;30957;24151;12546;57320;42933;22241;40229;45697;44861;15909;62410;49059;44173;14461;27617;22462;46918;38127;21074;16932;31621;40507;21473;11745;40324;26755;11850;31795;57385;49696;57886;59083;61080;61105;21004;18519;66107;64121;17369;21669;56651;43426;37165;27425;46743;17052;15345;31877;49295;11868;17551;55732;61955;19258;34803;61225;31187;66511;25824;52646;13157;49178;16361;16764;31421;46675;21010;17078;26311;39625;40948;17055;18219;46746;17624;48994;66604;62992;66229;58405;31864;13720;24210;24380;34642;15861;64631;51701;40666;27228;39702;40563;56200;25217;47022;30102;43275;19237;63151;37425;20157;43112;48200;64284;42687;24887;46744;15436;28788;52185;31709;61274;21585;17082;63487;49791;28146;17660;66026;56729;48877;35112;10314;10418;41517;57643;61028;19944;47116;39750;31099;52385;65176;62765;56663;22483;36141;27890;12685;35392;30044;41136;63337;66725;30581;60078;19215;59584;65675;33690;14317;25270;27629;20069;24382;41302;40015;20892;49550;64454;53278;25447;37618;29590;57974;11545;38248;35963;25084;11735;18501;52399;14088;41386;15037;45936;44121;23413;62466;57680;59613;20353;39063;31092;49887;62955;27634;40415;46962;35924;37826;25435;32004;25606;24205;39756;63261;18817;55686;41406;50133;37770;50071;29748;34015;13698;13864;46587;25031;31896;51883;45995;63759;15773;61477;59085;44389;58406;15996;61815;29299;37529;56510;19651;64049;17735;37323;14984;62698;19596;11298;62735;46580;44032;29441;61570;50262;32457;48624;13029;27537;39851;40401;22800;31855;38391;13784;53407;13691;43391;56918;20093;49351;23711;14384;49527;10735;35646;26979;37356;64513;62989;45219;37409;17801;45645;31448;12873;59149;19587;17708;54588;14761;56205;43845;54791;62812;57816;46405;17430;46466;16639;33495;29498;24395;13438;47205;25737;33907;23447;41767;15431;59684;35287;61405;38985;14832;32843;49171;14977;13276;14350;61407;18056;59488;18153;53014;16238;65337;41104;33648;60277;50065;30988;21907;33086;60191;44038;46990;29115;23892;10164;28210;11736;33811;46964;64182;32686;29607;59050;28143;55926;32664;33845;59221;47509;35726;66722;13895;20612;10452;40467;37161;26539;54028;18884;60950;48267;56886;18990;66442;21245;27384;45526;32969;27627;38618;38538;58401;26531;51736;42505;36119;42656;38016;13136;17476;17482;37215;56573;14719;29463;15468;55941;15763;47047;54758;57633;17199;30188;40072;48443;37751;11475;21967;21675;26064;32173;23497;58915;65342;29038;42855;25721;34382;32753;35300;60755;53901;37674;45202;33011;33857;30992;22767;42562;56676;31272;27858;30124;42839;17310;26737;16425;25370;53693;13612;31495;35230;40195;50316;45017;42174;29314;58663;40693;24397;33895;15218;41361;21710;47618;32277;30240;60898;56282;34230;35421;12787;23993;20419;24581;59543;11540;32711;49830;49327;10158;42382;57809;61229;17400;26355;38354;18544;40903;43660;23454;59189;39665;19815;16456;31459;50567;56338;56310;23141;50525;53849;13014;27440;27790;42273;19913;11635;45950;45955;16587;35666;51442;65212;44544;39916;56936;41262;57167;60197;37765;13540;15388;25797;33668;47164;26933;24604;53001;58701;54070;23871;35861;65868;51061;20168;53742;28784;57691;29083;42013;64557;34987;20178;53049;46015;41423;45381;36348;56689;50757;15761;63197;13455;21871;34822;62211;40027;37734;61896;23036;11672;18542;18878;47777;33414;38343;30052;27371;55749;38487;22727;54056;56836;62891;11732;59196;34768;13618;48313;60624;59600;21451;65446;14554;45071;17490;61113;65733;54517;34968;16585;65861;47310;30860;59823;30946;20014;60930;48502;37607;62201;50203;21839;37711;30358;26101;32260;34864;19517;51668;66201;63601;36866;42460;56927;27204;11817;52347;38322;66291;22617;29600;62387;20262;32250;12551;32246;25982;50731;42042;37841;13245;14078;44911;41265;32484;62427;41678;44117;16245;63287;57491;14659;54873;42412;23187;28990;63845;46099;18654;47586;35838;49069;28159;41701;50852;40940;25043;58920;52967;27986;53844;12428;10374;60240;45438;49222;26552;42973;41078;30526;11818;66011;18395;30264;16817;13315;44489;65335;34212;46688;10836;27005;54158;55150;56775;25917;13298;19968;52846;16045;49441;31087;61811;35326;64466;52752;64718;50558;55031;57548;33960;36493;46129;26277;42586;51261;51556;13241;26249;54140;35996;31701;59740;56817;28529;32666;22420;62480;20667;60531;20703;44015;27322;25981;14250;62290;16185;34741;29364;19994;12122;26199;22555;20472;66932;57193;55371;28519;56735;64234;29963;24206;25165;24842;38260;25659;62856;12618;60689;65476;27739;58785;45070;38722;47767;34048;57025;31408;48635;13826;47175;32819;14252;13321;25600;35280;33093;60050;42559;44914;12298;42745;54994;39102;21425;40718;48648;63037;60547;49949;60781;66254;27784;54187;50556;18894;13920;11655;62786;22931;21689;64245;58799;51529;65913;66005;65306;13281;54355;50309;52720;12919;13995;26787;35186;58230;30954;21221;43031;45876;45867;10921;26112;24704;66861;64080;33630;57800;66175;19561;25776;19274;10756;33793;29252;18488;35667;25093;37147;48897;34346;36432;44410;48429;58232;10317;52450;56486;57646;64938;56099;50282;63873;63276;65482;29663;42620;54664;51731;64332;37813;36939;18946;52910;15142;28803;27308;27505;62303;38958;40680;26538;37113;40477;25424;58996;25621;52070;42443;24856;52927;54674;51490;53325;33269;61021;33517;49750;23726;44108;56833;16179;63734;40347;53919;65315;62599;33592;11656;15351;65356;16939;52696;48264;62001;22590;20246;17474;29870;58600;16972;47366;27188;19136;35437;42105;44148;34365;30720;41137;66808;25191;13791;51508;42043;28481;46181;23291;31523;29231;11792;51292;50811;55349;29738;21481;12987;16344;11305;52601;43428;20271;17276;33523;51426;13616;11891;35092;37060;18286;59486;44231;27844;14530;19049;11777;28599;64353;51941;62271;21463;52539;39340;35884;50146;58534;18154;35544;54410;15481;54124;28691;21300;42049;23120;34616;11246;39206;43850;28899;64081;25509;22984;61497;35512;15359;53385;62715;26093;56596;60587;44593;64381;16472;29954;42484;46992;39589;30577;51241;40626;12681;10668;45920;39567;47194;17169;11717;10262;36580;31839;44961;21602;55461;37966;56821;37766;59220;43718;17979;65097;28291;64411;22936;35967;62311;23003;55750;65998;59980;66818;64916;46955;29761;41009;39842;18632;65606;42434;32754;63981;30157;46363;40640;51298;63631;66571;21796;24714;57333;47790;50804;54004;24599;12721;43121;40024;17208;31433;55671;14639;12456;66534;64132;20699;26923;29824;39073;19881;49552;29717;57930;57383;40267;16596;16108;35147;10151;58963;63202;41154;10193;34035;44834;54810;16833;24253;56149;31407;35088;10375;38543;12709;36987;22877;61106;26349;36087;36664;48943;53284;55986;14900;41641;44104;42517;48591;19673;51711;45392;58371;47341;28620;33306;65388;11147;55486;51583;11234;42958;59942;63901;29619;18123;16235;25214;39165;56090;58314;54470;33908;49840;48540;21553;56196;59753;63968;63248;62665;32019;66803;42606;35063;19508;62517;36916;55938;33007;32895;65463;19912;44279;49424;43526;53155;42688;64539;40173;18662;29440;64057;40628;20532;10820;35386;19603;22538;28524;56268;27413;41267;27745;55962;63851;29993;16583;35438;23611;35080;31442;55083;25054;56110;55985;11833;33638;30098;45410;44229;51062;28943;29695;19816;45093;19719;17176;25391;12322;29507;24529;64792;21548;17432;17517;59199;43015;53131;31201;61835;57501;40246;47579;43274;36726;24634;12592;37741;22275;19578;38607;22886;44138;65507;55569;17812;21535;16340;44999;45974;32017;35987;44303;32882;66343;37955;52474;25873;49172;45886;30514;64974;29750;60311;27780;39675;31274;63293;62781;60667;26941;55049;51504;43174;42489;18524;26990;55182;38887;14754;36416;31136;35295;21424;54492;30840;18743;34095;43615;57081;30144;48729;48393;35673;62072;24750;16446;40166;66531;49192;31749;39312;24267;45122;32902;63613;26283;61708;33315;35794;40099;10586;19084;12879;40769;45142;12817;30938;47429;14042;61356;14126;64488;32303;16014;55558;56841;27366;43384;36050;58050;45113;24972;40845;57975;39805;45534;21735;14621;41643;46008;48310;50684;41546;46862;32602;58782;48239;32097;26326;61289;50785;42603;66765;19040;42047;48214;45333;36800;23268;44664;36076;26822;35643;10006;29078;23416;16217;64348;41042;59438;29585;47271;10808;22897;30624;19521;16044;60483;43937;15809;40542;32411;35014;24173;14558;58005;51391;63170;62331;31217;50210;24815;11633;32922;10818;24042;19754;41312;29390;34333;13466;11295;34860;11060;32996;27040;59158;60679;59807;33994;60376;50642;24496;23131;44526;49795;12216;64671;39009;65723;41896;48262;44884;58195;33005;48974;23226;50992;42816;61964;34764;24353;54077;59657;38207;35886;32583;26775;18959;61336;21275;26292;34862;65179;48741;28310;59326;33725;53664;30816;30380;20212;65821;31872;17622;60218;17197;63580;49410;41437;56745;47014;35657;59421;66906;46064;15623;63572;40720;16276;30850;24743;52384;21135;45295;63417;37887;58463;62235;25083;24326;21241;21578;18900;44641;33040;61442;16335;62921;46786;11029;32584;46287;28847;59322;66679;18230;36354;31688;48856;49802;58508;10618;10899;34021;39171;65236;64101;44155;21768;46835;61543;49836;54133;56474;55794;18103;38943;25408;32724;48617;27417;31759;58560;11670;62010;45238;59195;39757;57270;22236;40450;52273;22265;23170;31992;22719;20169;33773;19640;28687;18937;48208;13217;55984;51194;35629;44927;31942;42708;62661;24863;52621;43187;30867;35758;21021;23440;49699;25684;10054;46121;32167;62267;30818;58313;52307;36994;60687;42433;58359;15043;49217;17464;43393;13156;27969;11597;54601;54676;40062;24933;65487;16052;38686;47256;17266;32878;66762;51669;46125;29366;54199;39488;23703;66224;16921;40398;41873;11881;38634;57700;23936;54084;43305;29578;30061;25373;44036;66682;25761;32466;47889;11080;14690;20336;38601;34902;13228;10116;20139;61533;36067;58646;57935;15440;15165;29263;28009;10592;10416;38283;52162;54685;34515;45027;45711;40020;55988;27651;16854;30619;22000;25242;35214;40644;51873;26129;23490;37763;65012;27377;35509;20460;36899;25176;31753;58837;23748;45358;26067;22066;23507;36743;17398;11363;28728;35490;50932;51415;52564;48983;57296;32796;18967;64277;55812;45196;62067;42651;43782;58014;22441;21808;11665;25625;64649;22985;32427;38419;14736;10861;21840;11401;12884;38080;30718;42731;38685;40441;58502;11566;26209;25119;26819;31663;62171;18824;65762;55226;36191;40383;63862;28436;19888;51327;32127;36025;33917;15452;63823;11876;28362;41644;13506;48798;38035;66121;21836;64405;32232;64117;40104;13942;26910;23916;32929;28607;41583;53147;53612;22478;47533;28513;37520;21531;22958;10061;14995;53451;57489;34102;45901;58297;32828;36165;25461;49882;58007;15542;57100;45340;40184;42934;18373;63390;46767;37240;65219;45701;63706;23737;66354;16151;32771;32084;54085;40880;51059;24756;25585;43606;12992;20571;56381;13147;26913;21673;36708;34036;13080;40650;55610;51066;26500;35427;37958;14908;33292;50397;65524;61769;36889;23066;42521;60944;44859;23773;21172;60787;30083;24515;46337;19145;12719;55551;63052;59914;26163;53530;42119;31275;59700;32227;62472;59150;65942;63010;45997;62336;17764;61117;47736;33437;29397;39547;10867;57936;25718;57238;61935;31808;25120;40995;55388;57956;52455;10991;48525;40740;39978;53462;10239;40473;39267;21521;33125;25444;44990;66497;41362;10519;61573;21272;39042;27552;31483;46661;52990;13631;23680;10038;41628;14563;25881;47311;23282;32493;53659;11834;61752;61541;29148;66941;45873;11995;59496;61377;57028;25799;58281;66628;25591;34011;37527;48343;27404;63890;13977;53688;11238;36104;12128;23719;35919;66540;22737;66098;37154;26627;21400;44713;33270;56776;50288;55772;66876;18291;26455;45610;28957;18665;36911;30922;43455;64728;58994;23437;50667;33632;28686;54842;39459;26995;62228;52722;43487;28740;15975;63626;37030;39088;52756;11706;52938;55119;32881;25866;44805;37630;13411;31967;58392;56234;11313;10046;12304;58364;34628;42359;44877;25512;40106;22939;57121;22334;50033;14708;20696;61665;20905;26290;62723;41248;34198;24931;36931;50711;32437;49256;58700;66342;58386;37227;43113;49656;21560;45117;25521;22773;47138;11050;54382;63472;11426;28239;41650;38154;13987;17748;50991;54553;32848;21532;23274;59331;56648;61269;59590;13159;13250;58385;22827;40271;22357;13731;51264;18602;60267;10279;50254;47804;65970;54396;22206;29185;11452;53048;22163;12077;14260;26917;18582;12729;17570;43554;39807;43590;29890;13125;12315;24105;31016;10540;53326;34370;65729;62725;21252;37039;60505;59053;60339;23094;36016;36533;40956;23794;55231;47565;17477;44730;51846;31021;21139;23600;39480;34986;58902;45566;20744;45887;23763;27062;55194;17008;16713;58369;61215;34939;65585;35360;28592;19330;31736;49880;58124;66489;18202;41620;38537;59802;22531;50045;45668;51230;29790;10267;31599;54858;14056;43717;65230;57282;17302;10975;11301;49428;39840;62008;27265;55204;24826;44665;11409;58287;24289;37265;34931;42413;52727;60885;52187;36492;42272;23185;35843;10472;37985;12917;45782;54555;39341;48411;14357;26407;38658;23982;38719;35236;20682;61621;15539;30119;23347;53137;59180;22094;14876;54022;54539;16518;10067;64359;27271;49749;30544;47583;19810;44330;48970;43055;32039;21386;52821;62073;58338;29270;61345;31298;29131;46687;54453;57321;54294;14289;65834;33121;60634;32213;30861;16493;16466;41168;25590;26876;36729;30741;32202;56958;23011;45714;63837;39220;57836;12113;41935;31315;61590;29848;24215;62959;41967;62180;12215;10799;19159;36785;30129;33972;19974;63789;44710;55239;54219;39530;60043;13264;21500;25944;63569;64230;44030;43859;25179;37261;42262;25653;55420;61168;37192;26799;60455;47519;60897;63699;13410;63497;29721;20957;63756;44763;65006;22305;63751;32430;23602;13062;65292;23050;49450;34125;54302;43409;13573;27141;57524;30708;55529;43895;38965;32714;44840;45815;13389;45377;57869;14973;27946;49645;36381;18307;56953;56580;15407;19844;61853;22317;23665;36682;30149;42823;17526;37697;10162;53219;13342;21645;46450;21687;20249;63893;56266;51249;12108;58044;38174;52837;40417;53484;29526;35362;53995;24500;49505;53710;30270;52858;21952;32311;57866;43306;58379;47814;43401;41991;62326;49571;33246;35347;59691;64052;39898;53275;44856;34059;39583;42452;51358;50639;11115;21662;59579;12996;49241;23712;35865;44196;13673;24600;29382;41879;29771;51590;20648;27445;58910;37945;56797;54024;63456;22386;60722;29433;23706;19505;36543;22180;39714;31270;32442;47044;48294;25162;14321;25660;16030;15140;59341;35559;65135;23686;13362;41741;25993;23212;27399;26245;22355;46482;40056;65416;37846;13950;66286;21285;34352;41220;22133;30060;60144;30683;50687;14043;25459;38450;62386;31285;26220;62160;37078;37254;55262;16001;65890;19133;64639;20360;37873;49046;64555;35109;20733;61153;36792;60427;52113;60674;27764;48390;28154;51130;55425;31127;29286;30779;42425;16699;34678;15683;54861;24487;42669;51703;65106;15632;62677;35974;39651;29401;45297;43192;54761;42619;34242;43254;24444;30178;34925;14562;48184;17081;45773;66325;11436;47663;38993;50223;27955;62409;66634;33212;30085;51747;39303;21919;16641;31014;11553;65346;14034;14771;66578;52666;50016;53539;46653;66708;30687;44359;42737;22297;49237;27037;55003;65783;26395;20567;27571;17237;34634;10649;47201;52952;64714;38683;59230;28187;26584;65704;52233;21267;38644;29728;42658;28251;59924;64636;38827;49867;25463;20061;41573;63082;33729;22138;48175;28256;62169;18795;19377;64463;32951;26970;59226;61945;59409;50967;59935;43382;51559;13647;45893;35700;19947;54655;63599;39170;28215;28265;23899;24846;64565;55553;59852;45084;49837;29036;38649;59899;62468;38824;39511;19929;56055;22702;38892;32304;28709;39813;24330;38796;52565;66192;11294;43738;28837;17509;54832;23177;41943;17592;32481;25064;33455;34305;59895;10900;56633;20196;64220;39872;37540;30479;64621;12026;16146;55097;53729;38614;34061;58825;11390;14019;37367;63409;12691;66231;11195;56824;16570;59121;52202;34248;10680;60249;37137;37564;57955;28925;42754;40282;55181;64295;10285;29133;63130;34951;54229;31331;61275;17456;58695;28367;16738;46771;37920;25610;47233;55505;49890;33682;54214;55694;65577;36545;24948;36044;58675;35755;34456;22119;34713;58049;47181;35571;42358;25870;31573;42866;14038;47524;35064;26305;13261;18258;63179;62307;59776;40009;43098;17602;24171;66430;32195;48275;36436;17194;29346;44937;65790;25071;30918;56396;60312;12497;13749;35834;35746;57625;24157;36120;35294;49776;41642;35084;66084;65732;55777;35493;34428;44844;48876;31912;21868;59210;22805;40400;59481;14470;17620;30686;49234;59309;24816;33069;35219;45442;64983;54384;28341;62899;59145;56864;31687;60672;33318;32331;50198;63858;33723;35664;16988;16926;32736;27467;17328;62706;50375;61978;31418;64063;22324;42625;47903;47569;61755;31430;32357;24126;33766;56919;30864;53604;60894;34780;21947;25457;14501;31118;29459;31764;30093;59529;21253;52182;41412;47511;37208;27016;52524;50628;23983;53874;17344;65611;60127;17362;49446;62592;35130;29320;56141;53624;39808;55729;29770;15213;39638;58394;48463;44390;30445;58923;61925;44885;36559;48724;27396;15717;56251;46079;56865;60913;42036;15766;21146;24982;52594;33804;25192;41315;39416;15998;62982;53493;41356;65717;20121;59061;13816;15150;14684;22057;22033;23557;52365;27731;31132;18490;41276;56333;35874;20243;23563;35190;62009;64827;42021;45825;34993;57985;11101;27108;42159;59611;20018;47518;14746;37710;44409;25117;42302;49832;43024;59273;59484;42583;44143;47237;33381;61786;33302;20281;41287;48536;20203;11464;39261;14476;50067;32551;49091;34740;14701;33397;40143;16913;42748;51154;27791;28253;52431;20266;43607;34845;39587;35303;43593;12938;20270;39364;37749;66078;39855;45501;24000;40126;38358;40646;48196;19721;40479;40861;65144;18084;56560;50834;65433;14836;42697;38032;38673;47236;65321;19919;14083;33017;59348;51376;35926;53840;43527;54388;23146;64606;41627;34812;16326;51768;33625;33825;47445;62448;13798;42345;20086;62167;36327;61943;49103;62123;13807;46381;42108;39256;53854;25023;52256;66066;55550;40408;18987;56131;24213;18227;42008;21306;41426;57467;28572;45546;37575;33217;13387;16027;39045;66276;51308;31594;41269;29899;56075;61354;15648;20134;56261;31425;43626;55155;11874;20309;10137;10357;59595;62314;13962;22311;34824;61362;50673;20755;46198;11389;43153;50467;49363;24220;45331;31549;26365;57520;22322;19063;40982;47038;20841;20469;60790;50330;51393;51999;18127;31147;23159;51566;40310;39532;34579;38717;13578;61917;43918;12311;13388;36052;15944;14296;23112;39817;35516;18417;64644;11010;55298;53891;15023;17491;46213;64961;24401;11700;29279;50290;45204;56627;61472;29917;57801;29437;33915;33089;18796;24936;10364;38517;22092;46410;41570;43348;37859;63490;31581;33867;27608;45916;19656;31171;53249;42132;16934;37187;38244;42663;12898;57580;38847;60620;63187;49356;46302;36447;58395;52848;45449;17192;54520;32137;60988;33183;60428;35846;42336;26997;25735;58168;12752;35546;63519;48185;13919;65489;19990;41526;66461;48144;18600;45545;18834;26275;34718;19983;11356;35117;58884;26494;16769;14721;35833;30809;43497;26605;49824;34097;25788;12866;48487;46014;46320;45550;59021;31048;59294;51502;24968;13929;60810;29877;46131;31046;62117;26772;57203;12470;43014;27254;15316;55216;42212;12976;65276;23152;44011;49957;56340;17018;56376;37264;32512;14116;13187;56603;21639;32428;32028;18522;23666;49976;40609;57302;43729;60431;62828;18973;23539;10634;20950;30474;36788;39334;57015;39689;42699;57483;35986;63325;16940;42529;57410;60813;37178;11501;65380;66140;42041;54403;16618;18097;63660;49896;26573;28472;25889;56411;14378;51994;56553;33066;47628;15627;49173;63334;32142;58015;26649;48271;10708;61956;17974;40784;59509;33662;51948;58378;64423;40125;23795;12379;62905;33791;21801;50456;19855;41112;24981;11445;13166;29090;49074;66555;48362;11214;62831;65352;61129;52220;42945;56752;65692;31451;56389;64324;44318;18999;43413;46954;24820;11886;49281;41883;15847;47809;44963;40384;27886;43912;33457;27455;45666;28274;40525;44379;39736;26611;42898;66428;43955;19257;53053;50952;19045;17299;31400;50341;62560;14943;26109;63165;34332;34291;38864;13325;48646;62373;30931;50047;54270;25175;34725;42827;10247;48879;33131;63772;45002;45489;44499;23725;12484;21719;40836;21665;28036;38411;61969;54488;25872;46445;21514;18124;18243;14763;61729;14144;47245;29659;65263;13318;52296;20787;54360;49197;45842;17184;59934;33661;60363;46334;47751;51503;36599;47485;16762;14760;30187;33182;61479;48194;51697;42946;40231;44774;60146;61391;44406;34141;51543;62018;58402;63235;36528;43459;41178;51015;10522;29720;25283;53523;66644;25863;20676;47352;53205;49594;19762;20773;56017;59813;29281;15667;42715;42083;65964;23387;38539;33513;24835;30163;32799;59351;35653;55240;31401;40481;65528;42720;34553;52744;44433;42950;36314;33147;65940;17677;37439;16160;27895;52136;43056;58190;34774;54061;42895;41852;35330;18637;46915;10903;27555;28761;19334;53050;32706;39793;12447;24239;60004;11104;13146;45836;57970;20783;35748;65379;35811;48750;38408;51764;30477;40395;21780;48187;11046;58117;49959;45861;39435;48800;20792;38495;65182;51896;33080;19236;40900;53074;28694;47763;39299;54450;34679;20132;56545;22779;56808;43727;14980;64210;19014;53593;28823;66794;17693;64489;16288;55145;59789;63242;57712;27940;64902;15476;37568;31492;28591;32061;34020;23286;63839;51138;42696;26010;50863;13688;28678;14482;28616;13145;21683;31019;28827;35011;49274;57064;59982;20174;54949;49596;65511;15478;44388;35708;10604;45090;22411;19823;20720;28068;57608;20019;49788;63507;49512;54394;12940;42228;53967;58455;65038;45508;15324;32880;59030;48292;22141;34478;61857;55620;23083;52305;43676;60932;11451;45083;21713;37101;23007;36732;37237;14923;43968;49852;49925;66885;14404;11546;48890;33240;32598;34820;60596;20099;52371;21923;35642;61360;40458;63959;21670;13986;33106;66496;33591;51977;56456;52607;50790;10971;57849;48576;37977;23355;49564;64311;63193;18244;34225;17353;37173;57570;29755;33710;44445;54047;61093;56902;63863;54183;45467;22913;35442;51563;52110;15913;15003;19627;38313;60147;65631;22272;25947;14131;53733;18448;33422;39742;44850;47219;28306;33636;44226;50618;41694;50914;40265;29376;20083;44257;42690;17728;11530;59647;27577;21212;60665;33286;34889;14058;19830;47640;52183;24594;62265;34130;20195;22656;55134;30215;48596;21210;49591;54299;13351;61381;35823;40881;57803;32566;57032;37882;13423;62615;41558;44748;13472;29743;42001;44790;34884;25558;43826;36915;63391;20592;40661;55798;10341;51950;40487;55802;33949;37537;26823;14785;62614;42553;24394;49365;24524;21728;56209;65228;40664;63200;46078;36711;15757;24383;50722;32923;49389;27484;48552;36100;43724;64945;24891;55593;52438;14503;18548;59367;16564;17125;66387;23708;11468;51987;13609;53899;19444;46959;61722;61761;49516;27066;11094;53662;29783;33012;21505;52011;59114;56686;11497;10485;55741;19539;24293;11192;49667;16479;51143;57044;38399;54900;63852;53868;10082;64595;49373;65074;56288;26859;29411;43582;64878;64988;21215;49599;17289;12978;51142;24049;32612;45639;36658;54206;53449;23249;46045;51102;50574;65323;31204;34618;51196;15709;37102;34480;10719;12523;23277;54196;30469;61447;24890;18119;44969;20112;30170;49336;25626;25571;15370;40777;35426;66865;23068;20741;21049;30077;24226;48709;21547;10379;34778;11057;54482;14162;21312;45412;24550;61116;18171;40196;54734;61997;12465;36577;30904;63158;63554;24520;42580;14903;12463;20405;12696;54098;30116;33327;50765;61350;57279;62017;33020;62070;43120;46794;21471;40868;13940;51845;20525;31112;64524;49567;54150;43146;48243;55725;50695;35174;62869;23861;50691;26660;49989;23598;20688;10408;24276;51268;64005;26844;37129;31777;42885;24526;62037;35243;46595;64898;29683;50520;15923;42003;49148;61951;18384;54725;24998;56217;41292;51695;31472;63238;60135;35191;34300;17099;57965;56653;53930;39005;31008;15530;28615;35129;39424;24025;50591;52368;32276;21027;19052;66420;17239;51315;10839;20986;35649;13133;38230;17271;25593;44767;59476;58589;13787;35053;40490;15151;26191;24877;22834;42649;29485;35670;21417;27470;39830;15736;27937;23315;28882;62249;60220;45616;65701;44222;44897;25244;50679;45345;45848;19055;33287;35845;58121;38235;27806;48833;43836;38973;19210;41590;22724;58438;55398;61179;51099;40859;49138;61639;31349;54427;66417;35475;45844;64470;50356;26930;19335;51541;41576;14246;13465;26216;62411;64780;13923;52326;35439;31517;25774;32904;59851;18360;53208;16210;59468;57023;62471;62846;56835;20915;13494;19869;31172;42122;60165;49811;41536;26838;19722;41117;26556;55956;50706;59676;55174;62980;57107;44944;38267;16241;61288;33843;48764;47621;45818;58305;35738;63722;38530;34932;27449;58871;32916;29780;47898;44119;47295;63364;32701;35589;14134;60718;22587;45243;16209;44050;23429;47202;61430;60472;64929;38913;12198;25535;37941;16347;63717;21736;26653;35144;47263;26967;49433;57149;36989;47318;27668;61619;19480;51907;51374;58984;15608;63073;60448;62958;53594;18889;12421;61714;20104;10458;59439;16327;42307;51682;43998;50669;56781;55519;57473;21342;56466;51361;45884;20967;63384;42741;20017;13945;21013;16948;64658;14707;20320;47148;44130;38701;66584;14313;63882;31276;45979;40870;25505;52925;20455;62041;56410;11954;36181;27339;43196;61263;11838;45735;59454;15810;59206;66397;45860;34189;55197;19778;56353;43085;15373;52547;46885;14915;63880;39254;12541;13291;33993;30565;45621;37028;54862;41609;15969;26172;29316;62581;41086;61233;27026;65164;27025;42707;38367;29888;54288;24197;27224;64500;30492;46214;15551;10356;59752;30888;45781;58511;22924;32000;22251;60648;52545;29911;30510;47818;28089;11201;22250;20605;19569;61780;53248;31468;15377;44655;33137;57096;21992;25233;61809;41915;57359;22696;57766;11483;61751;44557;26971;49862;26850;17688;25541;39999;51684;23510;52354;27573;66912;44340;22921;52762;22407;38603;39081;51936;20797;57405;52293;22839;42770;55922;46875;55117;36655;17446;30950;49259;12843;26007;52145;11023;40167;41817;21213;42011;11767;36635;66141;25579;28336;66551;57298;38025;19558;44151;37476;17618;18545;50777;13901;30030;27301;52485;35678;12281;22264;11328;18513;40138;26881;27498;16781;22205;20807;55767;44120;60477;21164;47652;40175;53942;31086;28329;31826;54836;58940;66113;37595;15645;22313;54007;51449;21406;64954;52533;11532;16778;14675;63991;13114;11648;17610;61392;62003;66403;12892;55840;65383;42028;37162;27878;63011;35035;54705;39768;43973;51939;21751;63243;35727;16617;62672;12903;62600;38291;54767;42728;36837;15635;10676;53283;53841;20595;18359;63216;44293;40591;24666;57572;17209;33619;56418;56602;36195;32581;47357;56452;61009;12454;46775;18265;27889;56457;21824;20403;48628;45678;14054;55734;66050;10123;62173;11325;43432;55957;59689;46103;23280;33475;45888;43620;48627;36531;32807;41416;23019;66448;48855;14060;11802;44367;62591;57381;18533;19861;41511;24398;11059;65112;39390;48712;52161;48791;63103;49673;38211;56383;45949;53516;40951;52894;18288;58332;19424;51205;12954;23183;16517;29092;13832;61847;38252;46442;20599;63950;57681;15568;56739;58656;37691;36534;37834;39273;34191;19511;51575;30280;30305;16360;23987;48657;18157;14097;50835;11749;49539;65018;50416;33778;18006;41380;50696;57216;65214;48159;12810;41049;29230;31732;54784;39249;19867;54042;43950;20325;53675;18819;44472;31024;23556;39061;48868;51082;25901;44461;65474;40986;20291;54786;46132;64461;46548;59763;31257;23752;14697;54544;48410;54794;51158;31567;28309;56534;55832;50057;20435;34585;54570;16732;18777;44385;19534;34067;30213;37376;58669;66082;22723;60307;58719;46108;45958;24799;19800;47500;34676;11884;14728;13302;38786;19051;63945;20450;10814;63102;39701;27245;52780;16608;27402;13171;41529;13659;29999;49787;15606;21487;51197;64065;60879;25412;52922;57278;64195;47188;35555;38647;37634;39739;36598;55111;16295;50087;15828;32347;20999;33059;19281;66202;25874;21301;26086;62502;24342;17249;28532;34995;52090;37743;60916;41697;66377;17664;53811;60998;45337;65588;18896;25736;55735;24700;39924;30766;66602;29525;52243;36748;31751;55950;39326;16468;46217;53991;44456;37670;18112;62866;13006;40603;26589;28750;37714;47421;56903;15892;32651;19262;23213;54589;31381;19160;36755;11795;50488;61361;44302;63269;47065;16682;18836;52439;63850;30621;66466;20528;55058;33981;61828;24589;12257;58323;11772;60798;42067;11877;44872;13555;65115;61646;41651;58876;57730;57338;48626;38316;35346;57663;12628;31062;59780;53765;56519;26020;24434;50507;59051;32475;50555;45541;65785;30274;62103;59169;43797;52313;22086;40630;36458;64196;52014;20789;62949;36829;31705;22308;57916;22579;66698;26973;45522;43460;35277;36735;15536;55241;19860;25222;58824;17348;12279;48941;61214;30127;63649;22118;28487;48841;51406;50434;53605;44576;24074;66623;11938;22074;66501;31932;36014;38082;42224;65995;41027;39513;64919;36417;59217;20051;59175;20523;55105;44008;48772;65072;64689;31312;33512;27607;54499;10638;51049;58705;20665;44005;63420;14243;21063;47170;48386;38950;22934;65814;37079;25613;36882;19416;35003;37336;24930;32471;14545;22198;54015;64906;29487;59445;14130;34592;31925;50189;21207;57260;19364;33323;47707;14438;41254;40307;62040;66616;52970;49431;51557;34502;59913;12467;55200;39952;26006;18486;38216;60612;61535;49370;16695;15306;29649;45126;57972;22371;28692;57041;26676;51313;11039;15353;59264;46202;36349;12915;65753;34003;63220;18678;14023;58456;45235;16494;22037;16614;28323;32788;45430;53152;58545;55641;40807;31457;16834;29982;17037;19367;38486;64626;17129;54238;39568;30638;34650;46720;66320;34657;35343;42361;33522;40889;50754;62356;52292;27446;12806;19077;29515;28799;54431;46781;62421;32857;11620;30886;27240;57237;37483;62066;32114;22013;29973;51748;60584;28289;53365;24019;59546;31587;13527;59040;61982;62349;51657;52662;39028;33351;26962;36746;45609;43087;63129;16796;34315;35203;12423;28261;25959;56564;43358;41363;56324;35445;42936;29910;63231;65250;24638;12571;34135;52803;14035;51397;27929;56228;15550;51899;28905;58144;58854;26855;60509;27669;59578;52815;18708;18841;54446;58516;14256;38844;56703;66252;29016;35905;32445;35586;60166;27741;56378;62601;25295;20862;45416;44161;16194;23426;10087;65529;26820;50860;13819;55325;59462;36316;27756;61451;26039;15916;62298;53932;29905;51165;41409;41601;32486;33184;41006;24107;11910;45454;29842;25765;21629;45962;26784;63855;39304;28422;50258;52704;62514;64468;27451;62174;19655;60126;50092;17157;10051;56710;40638;59901;63061;42880;30377;15172;30739;49231;49436;22876;27422;14583;62730;27257;66260;40864;54923;35807;52232;53418;26418;37232;49714;32110;47892;21678;23929;45868;19683;51331;41038;29902;50575;52430;10035;66956;29817;35021;59100;15885;31162;56113;51892;66811;61523;27898;46117;42219;63723;17657;21293;24766;21319;56719;32505;46618;36116;56485;27049;62024;37928;16273;22938;60331;64047;44137;61676;27261;11473;62816;43327;52551;43831;26593;66304;35979;43356;53483;54936;34686;14232;27418;29977;28974;36412;16521;13266;58582;37475;64522;35181;15846;15117;38156;50996;20028;53794;38510;12043;65065;56977;63929;53526;23538;19197;30250;54566;48366;14025;15317;50598;59070;45308;32207;54162;36477;12440;34492;40082;60759;35891;56642;29297;56640;49772;32802;21995;25895;29736;19923;34516;23934;17695;45159;43350;30143;19235;12060;52758;18041;53162;17646;19856;38562;57262;15170;60515;16427;19290;43323;21613;41394;51639;46229;46041;29847;43131;30647;41435;10089;56301;44941;48550;26980;21903;29081;14589;22879;11430;24462;63761;43668;32369;14582;25977;30525;29304;52366;57830;13440;44823;17240;33464;45229;63479;48520;42962;29958;51638;57038;26836;54461;40297;58156;39604;55768;59197;25477;45783;35409;16267;46106;38341;19466;25353;61710;66960;46272;16136;19527;13068;59043;58509;25906;51877;23074;53438;31426;31367;43075;60047;53555;21014;42798;47290;28242;26993;26738;37437;12694;17380;20064;22825;54142;15456;52772;30970;59009;19820;58573;53954;18204;55603;38416;52729;40160;25428;28982;19448;35805;61219;61282;66279;63900;27802;64616;47458;58500;53196;40711;16343;27684;38226;28706;34201;18328;23574;14327;30226;41807;59225;58143;44466;14487;35747;59112;27836;21880;52975;17763;37385;23472;13117;27633;20850;20442;33796;49950;47232;54643;54245;16303;34613;58346;34216;60366;53751;64677;64779;21133;27291;57833;36178;18143;44485;18480;56972;32824;27217;65440;48188;32783;31412;46983;25326;31145;66308;52558;20173;62736;21893;60801;54289;52555;13456;19019;30520;36213;62898;48882;23591;51757;11403;17705;29906;49371;55942;56733;23910;11509;20454;17971;45076;26223;40453;35255;52216;65662;49183;16183;17662;25475;18584;19971;46477;12397;14027;20559;36279;16216;54027;46498;59246;58749;23873;40174;50619;24032;18094;54773;48713;34002;30057;26080;53319;66800;65270;43885;59554;53749;45924;15174;50053;59668;22030;40917;66122;51767;27510;23486;37462;50035;56210;22379;40601;58487;14608;12797;14613;55124;44249;35770;39704;65578;16278;59516;55416;52694;12272;44271;39315;11289;56563;61682;43064;49528;59302;61903;23540;51172;35702;65989;17760;60949;34304;24470;50225;29811;66311;46874;21009;34907;32069;59634;42203;40218;54050;30813;42091;46927;54078;57494;63347;47225;40759;14740;42811;21447;43540;66399;19553;28875;32617;41799;12404;51857;29944;59993;53397;26677;23638;61450;56970;16229;19106;54500;36009;63503;44019;60185;35676;41966;17391;38480;20122;60652;41742;61855;13632;32511;39466;41246;16667;24647;43642;55284;36838;33688;34594;43347;38893;53352;40362;50321;51444;25747;51681;42229;13994;23040;10347;20948;46149;30251;61055;52856;59795;10810;16628;65413;65793;24734;41016;32574;11197;22759;11632;20715;29784;19960;61077;58903;20328;30303;29831;52025;10382;25141;15785;28132;62727;57768;57230;16919;54787;27282;11793;52624;40113;12596;66095;19102;65581;25100;38004;63718;17329;60380;42845;14139;10507;37792;62244;39050;63611;59281;57255;64650;60886;65419;45706;14937;44070;20929;21554;56112;16816;30081;58536;34358;13642;38040;13189;60706;24669;55350;33002;55442;12887;64261;15552;59713;55788;52665;11762;55383;35209;50469;59334;21882;14768;35913;51520;58538;24282;27074;53673;33403;36978;48753;17605;47634;11243;35733;50593;12747;39823;53263;13344;63068;56264;15938;12838;53988;12370;66671;44442;41748;20982;37035;11184;12278;28053;38454;17399;59999;44085;61557;46826;47101;43772;65744;26139;37593;23699;16191;35460;64343;43496;44054;57604;37341;46291;57655;44334;20859;48305;47587;56265;15776;51498;63106;14224;27894;56496;62453;21630;63444;28014;15703;56615;52631;57488;44970;35308;30549;25992;43663;32296;56154;15724;20672;55863;48686;35817;64766;12724;15948;59645;63628;52614;14831;38232;29280;21786;61412;40069;63846;45043;45925;17835;14435;13357;10386;18717;15959;65021;44195;10829;36881;40643;49813;55151;44262;44568;10771;45729;22260;42076;43452;32291;31890;63842;47281;50870;34450;15185;46403;35721;62162;35658;38705;25826;55612;52178;40142;21426;17373;20466;62918;27477;35251;35684;23865;47168;26950;43562;37301;59896;21488;12449;22748;20821;20221;55563;61878;25048;54340;48866;66475;59861;13277;14654;22577;22607;32899;15745;66593;53845;42280;44854;19942;64915;14603;62343;50832;12995;27963;54154;17140;62416;60108;21902;57395;20422;14192;52276;25331;23383;13238;36282;23305;55394;49522;42526;45292;18037;30614;55061;54990;19684;36752;45512;32528;21485;17280;11114;21612;33156;18451;14110;49781;19115;27795;64643;42685;34760;45801;39901;52214;21046;24396;62733;28559;41187;22692;14396;16032;62200;34581;11043;19522;35441;62278;24684;64213;18652;42429;39485;42055;29325;28814;19491;21732;24639;54984;19580;52336;15548;17016;53346;65378;52369;10435;32431;48623;11007;48566;63188;44348;37314;19103;57949;24522;38508;27008;62927;57212;60504;54459;18363;48532;43000;10945;25350;42834;51101;66298;47870;28813;11355;31535;46480;32949;54164;55560;35883;27822;62971;26885;34915;37602;55824;61078;45053;28821;52859;54167;36338;30513;52974;10411;14508;29018;36571;66902;30225;38937;66099;62919;63132;39105;37047;50727;47117;15148;55673;36336;18460;43709;35352;65109;24449;64891;63711;54899;60673;20832;66323;31543;30909;27514;36048;52731;24697;43475;31185;61410;16584;64558;53217;65492;45883;51048;30404;25338;59849;34166;26308;31600;60728;61944;46789;39378;10572;56020;37360;27981;51986;15111;49838;62986;40846;35052;58611;21484;47393;62436;44394;48952;45727;65122;18321;57883;54422;53807;12808;28419;21043;57007;16961;14742;31009;19696;60558;62742;22612;15233;12975;11652;41224;22554;21955;59185;46844;60548;34410;27721;42461;38498;29354;58827;13370;36408;59991;23409;42340;58212;56619;44893;35250;13758;50109;35223;36385;47326;42331;50910;16588;45903;65612;40860;56307;28279;11000;36894;18376;39084;16900;16966;50344;20813;54463;23144;40719;25264;16861;13751;38668;18115;57628;19430;24367;17127;56579;55580;24212;58253;28634;52257;66592;19419;35057;41823;42325;45538;60194;26189;48870;35760;63270;47719;40751;11398;47481;32020;66257;52918;45327;11788;44692;28445;19693;18661;15435;59734;54792;29183;33531;30978;29558;52976;23076;28689;12658;12380;49310;17543;60956;54017;16814;63283;40716;66867;30457;35340;19692;25857;27267;63135;17711;43250;12614;22742;36854;14373;60454;46805;50548;63346;16820;31584;26841;45669;36333;40137;48606;30218;30911;54281;64694;38286;22214;26716;44835;44203;20273;28008;22615;62526;19487;65899;50604;36151;32249;46188;64869;33014;55868;32628;56514;66048;48318;64138;18809;14868;57578;52271;23313;17661;57533;51438;15099;64879;22690;55611;13457;55153;24746;66590;64806;53745;19872;14819;15052;19540;22902;40429;57624;55968;31244;43371;42604;21098;16342;43408;35508;15211;13205;58933;16417;11024;64438;42301;14086;19404;19164;53912;30719;37516;40748;20369;41604;33555;53509;53949;66310;38132;30752;45193;46583;18613;56628;38666;34667;42054;65571;23052;62804;61066;57674;44324;36047;19647;34887;30151;13567;23541;50373;55452;40158;27757;35937;37495;31955;27115;13860;36560;61581;28677;27176;13975;10249;61452;26198;59033;36215;35476;11041;21794;33107;48921;40249;41025;33862;56899;23798;31531;36272;11264;29852;34545;54389;13414;64972;61949;21537;58061;56955;65333;25500;16149;12665;36066;66235;32631;15853;20236;52984;53161;20238;16566;50001;21289;12555;41847;55839;19523;40141;22757;18361;30863;57160;41093;60323;63236;60511;11565;63767;37371;64811;30784;27525;35694;66840;13348;25730;32549;32556;16754;21230;48739;31902;15017;37274;14047;40895;50153;16736;46882;18140;43851;62077;58277;10387;26092;18520;51056;34170;28483;38532;12402;44668;15217;18053;47390;16097;40812;60905;56765;52289;53336;35616;33214;16350;54693;36669;38726;31820;41524;51726;44996;59471;32761;62233;36305;36415;17672;62002;48409;39945;65262;44350;53931;46200;62594;26169;21313;50074;33998;23676;58056;23593;46027;15747;52522;53627;43564;19850;57115;25834;62557;21109;17766;17107;30862;45326;60593;23681;11137;19628;55507;35205;35959;14807;33480;23015;58467;29153;52986;40960;39613;38274;53681;56541;19365;46073;55469;34652;29104;40902;57443;41527;20930;13343;39019;66524;39147;29593;17687;62352;54385;44524;22780;46631;28100;51714;41981;64199;39957;28721;35744;34991;26766;20879;32413;25943;25692;40001;28951;31290;28944;62787;40066;40016;48541;62607;42820;59954;30026;22155;31339;27961;37337;53667;31572;29667;63162;37355;62913;63408;43945;39306;21458;64319;26547;12526;45255;13003;31919;42385;24246;63999;26704;25248;22563;26726;66526;59922;64321;14284;20026;51546;47819;65491;43835;65147;55401;56978;48157;25813;55974;10794;28401;60184;14011;17638;16206;63142;21029;60231;18079;50503;43343;17561;33391;30082;37863;30546;50027;29353;10711;64857;15827;15869;66504;47198;21917;14195;23379;46461;15057;16902;23271;53784;31847;64914;50066;29404;16525;45276;56313;13336;37814;63501;13640;48914;65776;56304;21759;47333;39563;33732;28402;48947;12318;11415;12886;54607;44991;28127;48389;61871;44052;44537;40217;54619;35715;51493;35333;60439;34442;31253;51162;49715;13188;41485;64535;28906;46630;22669;35318;56259;42282;37176;30219;33904;61890;21963;13960;50898;31382;17746;17372;61396;17120;37856;63268;30562;54944;25670;65349;37304;49916;44775;45373;61072;66108;49021;50621;16125;36046;24762;29802;41933;17161;48745;66486;34703;44646;13729;51263;19736;41978;38292;52184;21415;26394;52058;31200;66456;12522;46154;41061;24585;58197;20334;13218;17313;46610;16824;33568;30131;33817;42582;27192;39824;53992;57996;40586;62096;51871;49017;44607;35208;40483;25032;21758;10419;48818;49939;52087;53670;12776;64333;41122;14214;34797;49739;34513;32407;66695;42713;32364;61698;15940;50851;57125;36926;32177;12733;41347;26791;49195;65918;31683;40752;53574;59858;40808;52104;17525;56744;11402;61525;60245;15262;52698;59392;15166;44477;28331;30569;33788;57453;10096;18398;57245;41432;60685;47160;12916;60517;13909;20115;50608;50497;15405;12269;53823;17087;13743;21550;35981;31061;55475;28427;19213;40165;14738;45114;37111;56144;19821;61806;36242;18372;22731;24325;34631;36207;37084;13880;63743;31737;25980;38833;15421;32650;36386;45933;64387;22497;21994;42131;26268;43986;66104;41352;55892;62972;62308;47443;20724;31972;57722;25259;16442;23544;24623;63079;51492;17692;19922;22091;34967;10657;18146;59214;50892;18383;16753;10001;64783;59903;12741;38186;24051;22730;37597;65131;51068;22157;35749;62109;58275;56163;54039;56078;28320;18055;58728;23655;52036;12466;19432;48597;27318;37220;44782;24932;34394;40502;52388;66733;53285;53453;29574;51167;10227;46460;56202;40331;16253;11084;13672;54986;44828;21823;60027;62425;16300;30645;26847;58729;35714;59137;31515;46261;11226;47820;21056;15875;25330;45192;51521;52715;58293;11035;15442;32294;25129;61632;61608;54639;41513;32088;51800;12796;36106;47132;51771;24106;34737;54966;13646;34126;60076;55342;15566;31321;20473;32112;24610;57650;16145;38648;28712;52222;28504;37907;27609;61238;60219;53741;57632;30177;17408;65774;41787;15930;59786;62832;38491;48190;16406;46371;66822;25524;57666;51096;36957;49427;37228;49248;53118;62558;46392;32329;30115;46776;64796;51461;53445;30620;12946;11381;17798;31810;32343;12052;57990;43806;16083;15445;35931;25314;53934;15900;33032;33767;27370;19646;64592;40529;28169;33445;35962;25756;47123;45473;59096;26795;16812;13545;61702;48929;52378;36797;66327;26664;62361;41757;34702;31672;38214;42900;55999;10471;11774;52868;10114;45115;10149;48714;32633;30259;50763;39849;61358;60971;13989;44387;60622;64962;50151;27880;56370;25450;38663;14323;24769;40686;26088;55431;17807;35784;28622;56242;46591;36550;33738;62292;25880;54830;46054;53616;39124;57046;44766;40406;36123;19829;43993;26875;59949;13163;43976;50268;15584;42648;32806;39336;38361;65747;11696;35075;16965;65267;27186;36539;54044;20382;18179;41561;22274;65421;59176;21195;61321;30711;30440;39492;35930;52548;56325;61592;16497;37842;42852;52754;56477;19583;29535;66463;33402;30554;48254;53304;44896;11113;57063;35941;13984;39049;23380;46088;61719;54945;52332;32076;46821;35778;23443;28392;46677;19386;20643;16111;22637;19853;46495;35297;22917;57553;16355;50459;38882;42253;50534;22907;14959;13094;31509;41760;36595;38830;56939;66253;28202;12629;25822;19393;25984;34139;47491;58123;25502;34374;20292;46654;53680;56911;22259;53261;16067;56826;25617;34733;55575;60270;59515;41382;16133;42836;44225;47791;53134;34417;39612;36376;56555;58496;55524;28318;46995;46066;16648;32358;55295;32245;21866;44966;32827;66936;13047;33667;30788;33749;19643;11807;19174;44493;29152;59317;57525;49678;24163;54805;49761;46193;51353;50820;24456;41200;11538;57474;63433;23166;62579;23791;55842;16916;50402;41848;24545;24885;62642;34649;17597;41417;62212;65468;11504;11573;37689;56262;18052;30400;10368;21089;16578;19067;12029;31419;14481;65527;52066;22496;23585;10884;65892;56690;24650;49460;23047;52155;64729;10042;45167;15464;30350;33753;20944;55763;24404;25715;31347;37640;45731;41474;55943;50208;18117;52529;65672;52587;12755;63232;54719;42632;31493;49249;39954;25337;26458;19832;37972;66112;41676;10157;35216;35221;10349;58919;48664;45954;12918;26765;44954;56060;36179;11014;25012;33039;50880;27048;16922;49501;31105;46831;44989;28418;39874;65174;11012;28475;61369;38662;31074;34250;41373;62135;54921;62650;64337;62231;41333;41075;50676;63509;30351;10767;49025;60444;57413;62344;55471;37248;66974;36569;36084;32730;30518;33097;59511;55816;10062;13601;41818;43536;21059;60666;66213;20766;15437;28629;61334;10803;44165;19675;53006;19935;52627;18070;13559;49032;35393;18156;38850;10132;37755;64701;19427;45146;57719;61149;15910;49462;42617;38351;13233;33049;20335;14767;55301;48149;37746;52055;15610;63978;60912;51000;60073;36754;10950;58747;38853;53569;16950;17098;30763;58302;39108;11780;49542;22107;23592;16152;10785;57280;15315;29685;46756;62288;17641;49027;55728;30392;44721;10631;37974;17795;43117;16166;17769;22445;47328;55254;60982;21774;44849;35123;29556;46418;18853;57920;51008;47665;60991;66844;21413;22120;61861;42436;48783;20660;48849;63790;29799;57653;64429;49072;16958;35735;29881;15272;66314;63094;12556;44787;53121;52267;47030;59587;42808;23167;18989;63654;40337;63875;50990;35260;57291;23893;38019;58266;27893;53961;51398;56656;56034;42812;35329;44158;14529;29047;54701;58425;27734;49804;42821;28834;65691;25371;20987;58913;16528;54176;45672;17006;57747;41917;12494;33783;62335;55633;18418;52139;28839;29886;23995;27231;33229;14459;55561;10129;16435;63160;46346;62203;18065;10080;28037;38369;31755;27499;34841;21148;34589;51207;16382;52747;54121;63361;53566;53192;40380;17255;44886;31117;43285;63113;53378;19648;51553;19566;14922;36722;11102;60034;39602;20808;29794;60443;41792;41331;23384;21619;59156;46766;18445;46646;24062;23957;53412;32165;52247;51565;55144;50882;47545;55222;32585;32352;65339;26770;58862;60935;18245;57736;55515;46199;12896;47314;41289;37983;20068;49844;24582;31941;26821;32374;38360;45793;17015;66212;38089;53691;56584;49530;24531;44068;20063;42555;51284;60290;56772;60387;52620;15494;26409;57945;57373;51539;38969;10167;58849;42287;27868;22981;14115;32447;29387;65649;16352;59412;29919;44145;39899;15344;63267;41451;37964;43322;16784;46928;47118;59969;34488;65513;63280;30668;57906;39004;57418;47742;38026;40394;40659;10731;64412;61756;22543;64347;59821;59703;48491;59994;30571;53552;36339;28194;47268;39475;44530;56585;33693;52380;59998;45066;20714;62664;19193;22559;53830;46588;29602;52375;17586;63691;25409;21503;38271;57204;61606;11208;65780;54400;46944;66621;48303;45127;36770;65595;34875;16609;12908;28983;22068;61792;12764;64477;29814;30171;47854;13040;16129;51439;50350;24221;31311;65445;16819;59347;66312;61797;58674;26947;52447;47126;59127;16498;57727;53499;49767;66265;22153;52730;43694;36497;22586;49194;28000;14381;55142;17231;40847;61738;45060;35677;46143;38317;31861;50342;38553;47425;53328;28873;31439;12411;43638;39229;30384;42680;27134;16239;59415;61757;48226;46727;49307;63982;22294;35792;60356;15820;45911;10308;48946;11217;24484;64366;59044;59398;64685;50292;40619;14880;56981;65501;31387;10888;49395;65884;42387;27039;42943;46355;39673;65534;24225;60046;27565;56435;14981;10039;36315;38169;64835;66775;55022;57341;62695;39556;61773;11824;35668;33966;40890;55007;47691;65392;18739;41480;38171;47300;40081;58558;35361;35651;62437;56436;55543;34471;58003;59191;28461;15294;33196;43793;23038;12945;23318;60481;29147;22714;24952;57992;51043;25762;31219;42854;60077;61911;39758;45364;20458;42601;31871;53482;32018;61312;34424;17712;53257;47855;49895;62586;44975;40857;21281;49024;30105;32372;36995;14185;21934;53005;28267;10608;25272;27069;55940;17178;29818;30528;64647;51355;15119;10636;35940;13478;30342;37352;32083;10760;54838;17768;38872;45907;38055;39626;30755;43090;44211;46093;36643;13565;55363;17980;64370;30029;53202;45964;30267;33797;24067;37300;46987;38671;36689;65885;20804;15592;30096;64027;18262;29597;11608;26396;35177;29275;29757;40368;19636;59614;21163;50222;14449;26878;51206;51109;38110;28986;22505;47114;30198;42749;54474;12725;27139;16989;52835;15564;17321;33400;50253;40434;14304;38715;16272;11091;21462;36322;50451;46842;42236;18336;42773;53635;40501;52284;41033;28298;26328;59680;43730;37021;44268;52659;41191;54019;39362;14159;31708;58418;16996;33589;34101;59490;34181;61341;27194;65509;14326;41534;31914;45497;19357;49742;27793;52488;25536;31771;61841;41464;54850;25436;24724;24146;20565;27325;57670;48405;34444;27128;42504;45005;27674;57172;34211;43419;28948;23727;14924;63943;15978;38934;45807;23476;16772;45206;19703;39864;23894;53799;29056;19896;44176;46354;54125;47888;34491;22561;38103;40701;55225;31289;27782;46873;55359;21595;16522;58527;35339;31376;63245;49150;65651;36576;24211;65494;64481;64303;56546;60948;38616;46170;51279;57498;62250;27380;53055;19874;10897;34458;52902;25919;10933;33609;29698;66892;11562;38006;22182;54762;43677;21418;42758;28263;27273;30499;11503;50009;51524;23284;29904;24862;11819;49927;24299;30345;53776;20931;46970;35317;48927;10030;35351;52149;34081;15361;66901;23870;60804;17690;30355;55154;25489;10065;13079;30894;27811;29939;39789;36904;53498;19909;53875;59034;47286;38660;34069;36238;29044;25395;53503;54222;11634;31716;31352;55642;55797;14976;17023;16068;30369;14183;27206;40150;31177;54537;63874;15932;26590;36705;56624;59800;23905;41754;56961;60457;40306;33968;10376;34028;26907;51838;19878;18102;39734;17697;15926;54130;52721;10147;10459;33296;28985;60817;29711;60639;32647;52908;25974;31539;17673;16689;35334;15919;18984;64275;52263;64934;31041;10095;51947;31595;22740;37012;42207;17135;46254;39008;31989;62510;42480;45947;21695;58430;43646;43647;47807;62071;55326;46292;21023;51450;38775;22519;13521;51067;27089;31836;13915;30473;33559;47808;31229;22375;58703;45458;52405;27160;66135;34157;65910;14142;50486;12505;43750;14928;21813;24698;54615;56458;43632;19599;42877;37063;13176;35030;23499;60542;18263;18716;11663;56004;12234;46604;35990;13615;29583;39866;25767;42421;58564;64354;17564;26367;24628;46089;47249;37081;44496;38736;32681;39232;22463;12874;59463;40117;51180;39068;66700;24807;13504;53858;61967;38310;30605;19331;11308;47058;39397;29367;50453;50576;16082;46518;27268;57114;64776;26610;13744;20411;40832;10041;26306;42967;17022;24611;13354;25243;54390;27152;64883;18484;53848;34979;66205;17186;28866;19506;10532;36751;62088;26385;22436;22069;12767;24223;47463;30789;53175;11947;42528;25875;17154;48342;61315;60927;47694;65938;12110;30608;61416;15730;26024;62934;39338;34574;32917;30550;42803;30811;46011;61075;51394;66716;26103;43517;64053;64432;53965;51558;56713;61195;25021;35641;34721;57266;37216;42288;56874;51522;40749;50131;31913;27563;38695;35785;56399;51144;54049;11533;47183;26632;60391;55600;35357;46385;39889;50842;26236;57108;29569;48858;57384;38677;46469;29638;21841;20633;66749;66835;44621;64042;40636;49375;32487;61775;29661;55333;36193;30016;48464;52996;55923;22726;29810;60552;61873;60121;56201;26668;14665;29453;56875;20462;28625;38205;17146;53708;53650;17223;11090;66453;12973;32419;49849;14048;10987;35849;11254;43313;44717;38229;13210;22239;39946;26207;19801;16175;39697;15298;44147;28494;59129;12840;44074;27391;15235;34112;64852;10468;61511;15714;17682;46731;29190;49766;31266;61552;60125;19437;14895;24710;61597;22263;36144;38183;18820;60799;20077;12395;56223;32900;58807;15257;22855;56031;18236;18040;45490;13894;66070;17556;52537;22511;38485;45399;31761;54478;29737;33722;42088;36197;49331;35379;16789;22440;46305;40722;53085;50234;15267;20146;25050;27660;65224;59985;12486;18677;55131;34871;37934;45857;30617;53191;14555;54433;66712;58752;59655;46627;31334;26384;41216;53978;58352;56531;63448;24838;37785;21061;24707;22982;26364;26307;33869;15782;62132;33194;46526;47824;61180;59548;12831;16131;55614;39038;24499;64004;19546;48325;65956;61199;13194;25452;34207;46035;26502;65770;18551;44490;27887;48875;26667;21709;28046;46390;64013;32822;14841;36814;59971;63348;45514;16794;39059;62100;29192;15341;64918;12107;61913;24079;61504;14586;55494;20150;16214;22694;23307;14547;34914;34152;66738;56348;29450;56320;66517;45945;26657;43710;52563;46608;34763;49894;34975;12014;30449;40200;26144;63182;24084;60462;24927;10060;11315;58216;56583;37687;52355;24521;12566;21037;21958;48959;31303;14220;58865;34727;45009;55976;37344;59848;54839;52195;19286;44950;51004;11481;50191;38202;19241;29652;28890;64986;62945;21580;41791;38822;44227;35169;25443;22039;32090;31036;49983;62685;36535;37737;31529;22853;14400;29454;14156;21787;40339;39197;64492;66359;50142;49101;21041;30505;64813;63100;42761;25760;30781;18404;46899;54968;34226;20322;51088;27243;52436;19694;63513;26800;45898;47521;32093;17686;42894;60919;59256;36676;50392;41060;29113;21653;14702;56233;49855;31762;62885;41681;58334;20857;13445;16182;24113;24356;13237;43009;42473;46212;31196;11135;17576;55841;43621;64445;15059;44341;31134;61640;22584;51018;17138;21680;12909;62548;28770;60105;58262;50476;20710;59240;21797;32216;42904;45184;45851;57671;35012;65310;43697;24653;48255;26711;30161;45658;66306;33363;18042;56900;35819;26426;36516;60318;12529;42360;31906;53803;36723;65202;14946;19155;16260;66717;14830;60129;30132;17790;24519;37015;56344;49607;44059;12621;63087;42408;38469;25208;50500;13469;24023;16270;57814;14231;42712;45762;36284;55905;59616;18629;21008;63121;49657;36394;21572;33290;19127;53718;32516;14645;13353;36089;49010;65766;19879;57790;20575;16485;19455;41897;25256;40474;26768;51867;64256;39512;45352;15705;55648;38143;38357;54814;59234;55169;22746;55446;64584;64356;61087;24912;41095;56952;10186;25678;23986;50381;58764;52150;38896;34909;63485;34413;16115;39605;45788;35764;65936;51996;14148;59198;20698;46192;42710;63995;10953;36908;45687;28434;66150;34668;28342;44773;14576;15715;27773;18756;62413;27671;42388;34496;27239;56631;40210;63286;48708;61102;22606;19563;49922;11806;64607;37181;30423;27169;32529;20110;55857;24574;16477;44014;29760;54268;44369;20540;36749;60610;65206;19024;50920;23567;38870;44310;25714;46195;46793;13216;66535;43134;21957;25903;37292;50560;22799;39401;31591;31530;62617;20191;11265;21374;21616;13626;44080;57254;25442;26322;63474;51349;13669;44431;17747;53906;65503;56358;32932;51825;57137;55038;29676;41839;39203;24774;41396;53375;32309;21725;28787;66713;11361;27712;20619;56831;47493;20955;65247;16792;18509;13358;10165;31652;61406;40407;31924;63350;52261;60390;62261;53477;37244;26616;15181;31881;24191;25716;47501;61649;39846;21964;60636;14242;31895;25953;54896;65801;39211;37197;48611;65238;17443;64598;45835;62366;14389;42270;32253;55164;43597;32683;30419;43339;66230;17469;64088;12334;64943;58126;13522;38398;16158;18158;49167;24168;34843;47785;28162;27195;66847;51766;47743;61966;39343;51280;60201;52199;38359;22067;57909;26506;39389;49244;30387;31828;12753;50351;23931;19131;28365;16187;33614;61322;54188;47795;42197;10131;17614;30714;47235;56412;41882;28727;41971;21557;39804;11105;23632;16537;23935;66437;18235;32135;47492;20664;47750;33022;53494;61732;35527;38024;24861;36714;50155;16020;52797;61359;30306;44814;42391;57969;11900;30872;62806;13526;16017;40907;50060;55819;65775;54629;25927;61565;65103;12559;14564;41836;34340;48258;65146;64205;29670;20153;54785;24387;48842;31308;30871;63111;48406;30122;27980;50300;18625;20578;32147;38458;25886;29518;10342;20902;40717;64894;12442;25632;39949;22666;50895;48633;52871;51054;23345;25282;29269;25958;15285;11414;53970;52442;44739;62164;23973;62993;40776;26740;65807;49992;12676;37548;13468;20734;60764;19663;41654;39332;55898;58918;33576;41574;36344;10315;61807;46567;17411;37643;40073;66090;30241;12260;49354;58276;49092;23734;21838;28063;55554;23139;48341;32894;25801;56598;58384;40854;10281;50957;43823;39986;37131;23147;25663;63836;43167;12801;60309;11616;29455;46868;20693;15237;27277;23217;52941;63366;64290;65417;38788;47474;34973;53779;38175;17263;58474;61609;39642;50038;54898;45409;58615;35712;15908;55713;42343;34666;31313;63634;48757;62632;63644;58321;23546;42046;25638;56910;46191;19622;62068;41020;17381;13732;15694;32282;57372;39327;66710;42018;60029;38911;32450;18802;35956;10155;23382;37879;20060;22255;56117;66434;16461;23021;23029;16041;52061;21439;50162;33367;57703;46818;27126;45659;21566;49517;54813;10351;33116;12547;50606;65928;56314;23991;33204;31789;65736;49053;62845;51422;59131;26882;20378;47825;52228;45730;33096;54317;43314;42371;34834;34455;61635;51648;34474;48242;52520;58254;36177;61812;34438;66317;18511;23856;18576;45317;37599;12564;12816;53402;22806;59263;34297;34313;24476;59307;62893;49716;42427;19400;62483;56246;36233;25288;31806;66143;48423;30120;59242;65620;64237;44093;57519;42566;46123;38991;38799;26613;21080;50522;42565;47339;58997;23039;23425;55871;28785;13679;29830;41881;20332;46095;42636;58447;54008;25661;18725;50682;43221;49080;58907;51712;48799;46754;34693;14898;10309;31815;41622;28843;50627;32456;29773;28403;18020;21741;22681;46710;46233;53941;33228;53648;61519;66637;34269;42366;21690;57963;45854;25480;52373;65954;55703;15273;25883;38056;10918;25228;30277;18356;58585;35456;64239;61503;56740;56039;37892;11169;61418;49378;30036;42702;29650;27247;13662;11940;39404;64765;37808;54982;31011;46549;19157;40204;63090;58141;48673;38743;16039;43644;48395;23964;59775;51259;35124;54424;52325;19244;33965;19402;50809;39903;60161;31281;27112;33557;23694;16757;54951;52210;51835;14412;49062;64197;56867;63362;31501;65856;56003;12895;64362;56832;47289;48240;50539;61409;59423;58911;32539;10202;44732;24410;49912;33153;13060;24116;13339;60902;64327;65522;31685;23099;58180;61918;44193;50457;25066;49915;60196;17558;59099;13396;22383;39490;55867;63537;53235;45254;16174;33739;16089;13854;65414;63284;33600;39929;13848;45802;61065;21395;21663;56042;13390;36019;34487;35451;14398;20552;31116;53497;35296;18296;62347;43860;54398;61125;49800;52935;11942;32226;41226;28609;32557;49546;33727;54501;61745;59200;39654;53308;24231;26621;13076;11354;30628;36134;22765;45062;22501;17017;56257;12028;52515;20283;25057;24227;14307;19275;43685;54965;61644;17473;39906;55149;43959;22099;23756;37151;18611;65398;34169;36453;25019;25177;11167;23531;14575;40866;24365;49946;41303;57846;22253;64982;22199;39029;22432;55362;34432;62193;50812;14017;16708;11837;55539;53798;59260;63783;64202;65579;66316;66821;58780;41371;25989;20775;55487;42725;17607;52561;18375;40850;48919;16526;64785;62383;36142;43595;42384;53305;52799;28973;54148;65886;53247;60933;26354;47215;27296;20424;31184;50028;37526;21115;31119;32661;16547;52200;65448;52834;48495;56273;39806;57452;40426;31261;44811;15221;53086;36221;27621;21945;42002;59011;44697;28156;49161;43319;56959;57398;33092;49206;11281;45226;42128;26096;19086;53772;64430;39659;19366;43592;28818;31607;58990;44478;59046;12890;53009;58654;37767;14540;23016;53332;33438;58839;19172;63944;54855;28149;39177;35266;48145;39895;12347;23783;48289;23984;27882;56617;14789;24260;41816;32897;25837;31680;66318;10343;53856;40460;64395;37820;48353;11560;38217;38431;18516;49118;55667;22150;43194;63228;10187;61652;17394;59609;27529;56950;36011;57090;30297;27694;58440;48980;47684;13823;55209;43863;20742;19854;46030;11522;58205;65260;18969;32153;50599;10612;41249;65158;58146;60788;49899;21182;16672;13030;18861;58142;47343;14167;49650;30354;57873;10831;54667;36728;33919;20200;43499;64087;29582;64207;62245;11482;30382;44492;42849;42328;59233;51319;61932;25254;38468;28163;35894;65943;43922;53546;32865;65073;11061;35411;17200;33360;25890;47726;15022;46161;47582;37412;57256;31195;43238;21495;64534;23406;31551;44702;46673;64323;56894;48925;53461;64067;44520;43465;21047;23917;14251;18931;39376;65797;55606;65372;59725;62377;40446;22741;28826;12927;21730;65113;45069;13122;16178;45149;43630;38022;59057;29909;25247;55223;11983;57705;14431;47010;34065;13804;29511;24542;17390;45140;31383;65734;44913;48710;54671;50629;35994;40119;20118;57521;57199;51150;12117;28917;28062;22926;65137;60160;63425;59619;52453;52710;30540;18043;35801;62568;40227;45794;66251;28697;54732;28932;62710;64399;13140;64854;57043;39926;29706;36230;48961;10928;15956;12368;44089;65225;20483;27866;49435;37294;46432;31887;46991;55585;34895;52804;53138;34729;49985;63578;27663;41405;13415;26804;44361;23046;16582;31715;25462;19828;21672;56342;42975;17598;40498;66062;57966;19851;26604;26662;44397;46270;16823;53342;19452;33369;14458;23515;14448;59313;27546;42783;64341;39515;65363;18566;39173;55831;45154;10777;14050;38904;31763;62304;19185;20784;49031;41528;54303;28498;63300;18024;37784;56083;60087;55454;30568;39870;47442;25792;34342;41939;63065;11842;51073;26748;45869;38759;28389;32804;55132;34799;47483;15188;14729;34245;49008;52496;51465;16426;26572;48430;64885;66642;57950;30293;25957;46988;50609;18917;51277;42988;26663;13648;35561;64786;41955;11660;59494;30309;35237;42289;49240;51637;28704;15198;32370;10797;15027;48816;24091;65545;51007;60980;27687;62659;60346;19836;11433;31197;20009;64740;27589;52042;42578;30961;40321;20512;42350;19472;52078;42333;38733;15658;13421;34236;11990;59190;47344;57222;26672;58279;30078;33651;52265;19631;30321;22389;66193;39276;23375;17425;21847;30490;41132;65694;13660;56599;61586;13476;42507;61819;20728;20388;21970;48413;10674;58677;21067;64985;50430;34590;28397;58916;54432;40261;17454;57837;25327;53022;46725;35844;42909;16952;34952;50615;20253;29434;35471;31489;63593;18752;15655;57861;45401;11875;30486;40221;30447;60355;62295;18190;47045;63308;18642;11003;45418;47745;25655;55265;11142;59830;58290;27945;11196;64995;64888;26183;46656;39181;11712;56022;20898;43504;27459;27015;46414;37132;23614;55850;24165;38933;40509;41551;29869;66154;60601;60844;51702;18316;45179;60750;17698;53339;63311;51340;37465;16157;43693;40046;11674;60943;42627;39992;32755;36963;62447;43330;65941;41135;62830;19204;40792;54962;41820;24880;26041;62788;55106;42045;56700;34976;41326;30671;12997;53859;34030;18247;46645;56720;65101;28553;13416;23648;20909;56484;29244;45263;40005;59314;48780;50361;32459;52028;64499;54992;55624;10686;16114;21640;11744;32003;35551;31131;54464;43118;45845;66072;19294;64818;27542;10074;63912;16337;26681;12258;44587;28137;54647;39777;57065;28449;57397;31333;32920;44311;25784;63186;61946;57195;41786;33565;14769;32801;36057;21997;63524;56143;20277;49693;53087;56118;40919;58397;25961;28631;54156;42611;53125;21558;14149;36817;61801;31786;63246;11811;25240;26517;38992;26042;56983;22405;51258;55513;62962;66187;45079;53740;28338;31096;52164;31420;47017;37632;44184;27373;10641;39759;38761;12039;58628;29772;37378;42081;29660;32595;64375;34891;45453;15039;51421;59719;19238;45432;64887;25567;44819;27001;60445;63881;63329;54211;23533;65011;43943;33427;15406;56669;65427;32707;45693;25928;33905;62243;18206;48675;59271;62367;35812;32662;61454;10257;41924;40480;27407;51756;58326;20534;15203;43837;35822;45689;55895;27504;21988;65981;63892;34275;66745;27292;10480;45663;51957;39735;16225;42721;36954;57438;25439;36583;15947;62839;59512;42757;34685;11787;15522;52209;51912;29010;22409;58905;58699;28993;55435;39687;36180;63359;34996;55453;15880;62798;32473;44598;51013;38856;14140;51664;17753;26698;10870;11581;30311;40815;66530;44546;13177;31391;17992;23140;61799;25713;30266;22397;22682;14947;29011;53677;60273;27832;36255;58415;46315;37588;57753;18517;41530;57247;61992;16473;26259;49098;40041;52126;39260;39933;42830;56056;41005;61877;59966;59407;34532;55818;49910;45960;41099;38289;63607;11266;49745;31947;10327;19625;18387;32856;16891;33660;26633;46474;11556;63041;14473;31730;39187;44239;47337;16727;34596;62402;52395;44594;35984;24726;54938;44051;65792;12999;51981;61516;34113;16341;44159;24947;21015;45686;20752;47367;26388;59327;26614;58846;41034;38810;51636;36007;38769;43957;47649;23148;14525;32769;55051;48997;54682;50714;57569;34252;50168;30053;50519;40236;19519;39387;18394;24439;44889;36086;37883;53890;62136;22894;27640;54357;57253;29724;62822;22851;65999;23989;66381;38727;11557;18118;48391;62327;42294;17628;49463;56354;47299;34558;13426;34901;13973;21119;34573;29472;49792;48749;15460;43682;50477;63431;60945;51705;15713;66459;13623;49924;39950;32844;29107;39079;36139;32759;31827;16647;57796;50425;25322;46194;32725;33770;13110;61555;20694;58857;30929;64183;20849;29626;37667;11067;23615;32944;39058;40923;23849;65696;58345;63149;62744;54194;54881;21352;59207;58426;50646;38263;34517;22342;12853;23837;65080;66293;44144;44491;64281;65535;61904;60164;43141;18259;59231;44612;42993;10600;55107;39412;24300;26405;66522;60118;29623;22634;27103;52997;14100;42232;18624;64172;58004;44259;64874;10910;48581;30197;56829;44280;39292;57017;44512;40905;43807;15040;29111;37194;53340;58637;28812;60968;36718;19805;61737;62675;42976;23253;33072;61156;24781;12929;40877;38044;61480;65203;38629;14347;39647;11283;11574;23577;44797;58396;21621;19339;63771;50653;26994;49082;53695;22156;40829;61426;49355;35885;48158;38060;57988;31874;34672;64145;26241;27080;21346;33283;16318;65059;35173;41516;30109;24659;39118;26896;37085;49430;31368;52148;47230;61278;42552;38078;64038;38422;17757;28669;28307;64709;15303;62741;45585;58023;43119;15372;40315;66863;16268;29678;39370;24028;41130;31582;58740;41893;28509;19827;47037;26774;30758;22878;22887;40605;12104;17668;20673;58659;45740;43871;63924;12981;47734;14874;62131;65102;40973;60230;16749;20355;30979;24978;59630;44870;53682;27369;25707;12935;35045;26336;63898;14241;25651;31889;15042;16768;56537;39860;46866;16914;42392;14146;46380;23202;30009;60085;36149;14524;29348;13991;58330;30017;34520;37469;24955;56440;54144;43213;29102;39708;28734;59248;10858;40447;54733;29002;54569;65931;65133;27213;19379;14561;21707;32126;17033;28543;47068;31660;32644;41821;46136;64028;57847;45457;17973;66010;42279;32609;48474;27394;43866;57798;39114;50260;18724;53420;31598;50452;13725;64702;45580;58048;50938;28099;35094;53531;26300;55738;18567;10479;27717;62851;23294;40340;55853;51459;60040;45712;44077;50883;29420;31215;49041;55224;38122;56323;15274;36956;14105;64003;57057;34489;40577;11689;37532;45676;56683;61931;33913;31785;35929;55496;57558;26045;47465;55881;24921;50536;55278;48147;27772;24250;30346;34483;28349;13470;25842;39236;20065;33851;12579;40412;59577;63483;50954;64862;28435;40998;26603;56623;55801;61636;59592;30574;63369;61243;39577;29045;18320;25460;55377;61030;17075;43749;36677;62628;14057;50720;14651;35768;57173;18942;25601;24503;41128;44677;48995;45598;56379;16846;51148;59194;40580;43165;47593;14725;47489;37518;30757;58965;16038;33736;34272;46128;26927;32145;33924;31623;11379;18061;45431;13552;61827;15557;47079;33135;38185;50382;20000;20185;29395;61443;49570;49191;25891;31088;43748;46215;57165;16076;11691;24374;61316;49801;18100;31039;30884;62260;35828;10904;27478;39155;54367;40228;30804;61337;43907;17560;21615;22605;38935;48964;29510;31346;65923;28958;47274;14815;38790;12888;56538;15991;47082;26601;48871;18324;39910;63928;35486;54777;40290;13209;15826;16559;54668;66567;30416;11568;13203;51456;54107;52279;60036;59028;16838;57511;64216;36807;36335;23518;60102;49893;16021;15514;55719;46564;27220;13488;13766;60958;32659;52005;11017;62351;51037;65110;65680;52407;60782;13150;29858;15643;11453;29758;36763;15488;31038;13757;62692;57627;38795;36298;44202;54466;51795;16877;13599;47129;52895;11863;36249;44244;19398;53657;60079;52579;66052;18808;16785;38874;42653;13796;26631;52985;43287;51794;26911;46457;54985;16630;23678;36186;51436;41304;65187;29490;52138;12068;40102;56081;24556;59324;11880;41504;20901;40575;42514;17306;57559;22892;35789;17418;62808;10190;50263;56095;53224;49070;25201;55041;52462;65828;39241;61386;53038;58810;40499;25441;45171;48569;60595;10669;30782;50988;62004;39740;52827;43251;27949;14890;29127;63658;65643;18575;54885;30468;33267;37639;43795;63468;60632;42753;13783;56872;36081;47834;31628;56362;26398;26921;46085;44592;32362;34025;38465;42679;59466;37649;35358;58704;64567;64845;32384;31075;46310;53157;56483;56856;53433;59517;20287;39507;19877;36691;13524;58380;25478;50440;46179;28287;59333;29734;28955;59855;16132;45908;46734;32298;48307;44021;16478;35301;38948;15786;18130;16968;34735;60424;65237;20572;45312;33339;53351;20867;27178;30391;11073;39920;47227;50257;10310;51250;65484;62039;34345;17752;37585;31301;49479;45491;17478;36075;10931;26304;53621;46668;18155;35120;54578;65706;19741;61473;31159;57481;32792;11768;22832;22229;12635;14864;23210;25309;61663;57925;60523;33525;12697;48334;41245;18593;42929;36700;40583;58945;60754;57660;59550;28071;20501;10136;46517;34390;65730;12106;19324;39595;20913;21971;66288;65549;39427;50297;58139;40780;36536;11852;66599;63405;62440;61466;55445;50313;28470;13587;64802;52763;63653;47755;17019;36122;46301;39112;54924;46830;15199;64304;31615;63896;12307;59981;26626;26851;26936;32925;43995;53801;16889;25224;21812;61668;49258;36474;22003;35074;59576;30815;38323;63481;51468;12267;35193;55873;11263;15579;17771;18750;64793;54481;59617;32770;22476;35204;35387;18759;65217;42868;17977;37098;31126;20514;22510;63109;57688;21655;62404;33453;33901;57495;66117;40726;44332;24504;13231;30224;63627;52197;29385;25307;64881;49497;63385;47566;63318;15256;61542;23428;61267;49377;44476;56147;15973;21508;38977;23988;16269;18893;57000;63811;30882;13598;48585;24894;53879;66507;14077;13454;35103;18253;26192;34136;54560;62952;21227;66305;28455;50242;59054;32103;14806;19953;25973;52541;37174;13019;38362;31080;29635;13398;40842;12474;11879;50089;22080;38433;66083;17537;36631;40356;32652;32426;58337;55897;66817;43824;65976;37327;48924;47514;55148;63621;48192;43737;46512;25153;16561;57012;66382;24696;65409;46807;18461;43533;15570;22045;63678;39395;45343;57005;34665;35783;16499;54185;35128;60655;11306;51031;19948;40632;31394;33431;31103;48615;12802;12400;39844;40556;15842;64801;49469;28295;54714;22812;28888;54163;49579;10174;37255;66895;55714;11870;28909;27447;12716;56508;66583;11240;25506;18830;56207;12271;58433;35291;43515;22471;23333;42409;35344;54333;59518;45353;10075;21149;25332;25448;37971;22388;37054;41690;40892;15158;56962;48494;25782;62843;40192;16862;29034;66457;25694;40679;29403;60476;65659;61620;29722;65024;13097;12990;61689;15598;41994;18315;49239;61295;65369;41910;16978;58081;28753;63713;52711;29705;19061;15318;20084;19130;56801;16991;14737;29389;18856;53606;56250;47686;22173;25843;41101;33680;16925;63058;59549;41234;48720;33210;28703;59986;56934;33234;30511;61250;51611;63312;45856;47329;58759;39998;33361;27952;44216;27177;25356;17591;61347;62943;60089;46672;62994;40549;40051;24755;19327;29669;27915;28060;18508;30025;18028;18913;13665;36565;23378;26790;32743;48883;23239;25092;53210;11932;45556;22729;20193;16974;47899;26508;15939;20350;35407;57342;58956;29446;40795;41845;26717;14814;20874;22490;17779;35226;42481;55459;23683;39909;16843;13359;32281;50435;49525;27693;48896;30771;55506;10866;14500;30876;36740;47596;17827;28892;17574;30512;38423;37762;50493;54445;25709;37498;37064;41266;16422;66508;28859;10286;27430;38228;26372;47642;66389;13591;66480;40475;28915;46803;59018;66718;38909;42118;43616;14734;48434;16353;13684;26119;20801;64541;32297;49782;22922;45082;13225;24730;59552;25118;46201;32941;42755;38960;23495;51603;36991;26483;54848;40021;41747;34334;23977;37947;40798;58161;21453;54081;31965;51370;39200;35290;20855;54350;34090;26948;49958;36637;15369;25379;45445;62170;52424;15062;45956;43244;60627;39090;53099;51851;63053;18464;52490;17378;15895;11145;34759;40439;65235;38702;22583;41144;44473;14472;21161;66854;50577;18908;58283;24094;61323;60133;64733;15616;17460;28493;16811;45840;64759;15662;23644;59472;17319;29093;29308;64515;11040;47192;25533;52570;35071;60963;53882;22459;32660;64328;29188;63223;42432;46388;40007;16503;51531;43276;64742;66258;42767;49969;42451;15507;23000;51145;20313;35615;19418;47127;58631;25170;31748;16448;38102;42265;24637;15184;41000;14577;52933;23163;44115;26417;59897;34321;32509;55971;29489;64864;51806;18529;63083;45141;18766;17045;61034;22842;54053;30237;34039;10611;39650;32500;61408;24944;66185;64070;14578;41822;39474;20219;44701;38126;13849;33142;14133;25086;48761;13244;47077;34446;23354;55623;40546;49034;24841;38002;45874;21490;39086;28968;54954;30186;16867;26341;10576;28971;18222;59673;62450;21433;14879;38434;32257;57050;23049;31110;31499;54386;12617;33103;51437;65809;59602;25720;42942;29577;32709;21851;65171;15386;55955;43778;26920;14791;39827;57136;59565;46624;51647;20870;26149;61458;44230;34449;12200;61355;40214;47432;14388;14358;51368;52217;40121;19695;57180;63005;19532;15788;65424;10606;10691;22566;42319;30646;65812;27662;36592;22673;18466;54161;13748;18585;38707;19054;37694;17581;53455;20860;63676;45897;64344;61398;63738;55192;38463;30487;21044;20868;21552;39937;30359;44064;17497;32716;43855;61615;36291;64325;14072;18141;18410;45210;40274;15990;64873;13557;10064;57181;46975;53428;61084;33094;49145;42285;10463;39972;12483;45827;24323;31835;50755;18581;24369;42802;19315;14955;17719;44199;35855;32367;44779;45829;64803;44384;38611;15258;63815;39878;31781;43858;33258;26551;19048;39594;65817;30228;42719;61750;54699;37026;57016;53416;40587;24667;46464;53975;59042;65929;28110;10977;51408;63577;35647;26725;59467;20631;45318;36130;23525;39678;40730;30594;64166;38079;24562;14961;14870;15432;51537;62684;53790;49675;36520;63840;23043;52321;47423;50741;13949;48604;19006;50408;27496;42470;46726;19732;22376;21019;28368;48837;14869;53500;65808;61588;43001;58760;18051;62150;26330;65695;11596;28596;65189;44372;60776;59342;50034;30068;25329;40161;51670;47196;28885;31833;46151;39630;26924;51815;32552;26176;21194;38739;22596;40287;47641;14496;23410;57794;14775;10758;31030;12704;66547;65313;63154;38572;28369;29984;65870;48375;59809;16903;57999;35554;26234;41407;13038;33238;45272;32888;54313;55212;59295;13035;18672;34018;41476;61971;17626;62074;22609;13473;43711;11512;49188;40677;39761;25396;65750;64745;18870;25675;18270;41734;45465;27859;40078;32756;32215;49019;18676;43645;27497;15581;10998;60555;60826;12926;14602;31322;37522;42774;12582;60128;23583;16860;66852;13450;15412;19857;58102;21117;60308;35473;41041;47171;27619;46382;12513;58946;12344;36494;19572;19212;32997;64713;35479;22341;21525;21278;34746;31546;19733;21978;59116;10409;30606;57781;38514;30722;12950;42935;33876;11310;63386;46097;60347;19413;35535;24016;24632;50437;25529;40855;24950;59605;33380;63376;27119;24903;19075;64416;15625;54216;64753;43247;38116;59202;35545;29809;19735;24033;62364;49936;45320;28511;47110;40238;55804;46147;19399;15186;43337;50855;46544;51107;15176;55237;63917;19526;56807;52327;60500;56692;63373;18975;33558;14024;48304;55541;22544;20052;24727;33230;47567;34037;34235;57288;18636;34425;49262;29283;52038;48555;60502;58835;52063;49056;62903;21204;12044;54854;32970;45641;24925;42164;12830;51797;66620;35630;34214;41672;62376;48909;50611;21103;65458;34010;51346;52728;30427;10258;50732;13891;28238;45843;20465;51240;45951;54099;58848;57887;21526;40247;36096;54452;16395;17196;56211;36730;63402;60418;33980;27697;10300;55206;20692;31689;30244;28387;64678;24133;26869;37448;30579;65249;61988;34531;14766;65275;38392;63055;34637;31378;26248;32199;34960;60775;16441;59621;34477;57944;50157;65721;56949;34172;49315;66208;20223;22435;47027;20675;24371;62269;47346;41568;15394;35696;24350;52988;48740;20211;61150;12544;13279;23398;49114;10619;27661;52008;13012;57153;38380;19653;11675;62266;66683;50585;16986;22793;11975;45895;41173;41619;44094;20415;36568;49219;54536;61090;58422;40959;59711;10557;45889;48619;24859;22134;10502;62434;57693;57694;50887;20998;57102;49816;25384;40403;21279;48211;62728;47180;19513;32256;36874;26946;20164;35373;54353;18431;16192;25343;28870;64966;59541;65655;55737;30873;22822;17706;37844;15963;53698;55961;26503;14840;33765;35949;21872;61618;55367;61880;64502;64369;55338;23966;16884;22754;15639;47303;14682;27652;25808;22293;24172;18142;66654;26721;20590;40675;38407;37558;28581;56626;39652;19964;36878;29245;32214;44675;61603;50623;46507;53746;55566;50554;33359;17093;11966;30327;35321;43783;36909;19497;35068;53762;15339;65570;49531;29791;56520;26651;17206;61699;43762;31267;19999;14910;42180;32136;44188;24249;35430;66699;45571;50734;46772;29687;51039;62689;30337;61400;27909;58053;57261;42531;52796;11727;14393;14253;18646;26434;21450;48156;47531;52759;12798;26468;51605;49342;59337;18420;45814;43229;12501;26378;46399;54371;25706;51656;36680;26061;13508;17567;44511;32846;16130;43258;38604;62219;15719;10817;36629;51805;66845;18647;44295;22954;62195;41571;47774;35313;23642;10821;45386;27698;55607;40068;54327;29142;42394;11794;33428;20921;57597;11056;56791;63212;20407;14208;49055;45837;48756;30803;19371;13441;24312;17802;27727;58065;29220;56861;45275;40345;66161;11109;60976;66347;43675;27854;20298;41322;30522;37153;52435;31373;66302;49809;44297;35316;57047;46415;17568;66670;59328;41768;54892;57076;36440;17141;28699;63470;37889;54437;61018;37967;36107;62127;54100;64594;29868;14493;30051;63897;38825;54137;36491;63531;58157;27367;43875;65622;23902;22651;53067;11162;19149;65254;11291;56879;47780;66961;10569;11549;34809;33605;36064;38318;52872;45875;51440;35076;32231;18134;12479;24892;36526;57008;50917;33627;60999;59943;31487;14696;27457;17651;20374;52572;20893;25255;47731;18736;21976;10489;11277;52301;27421;40123;44572;14527;43981;13517;61518;16982;41495;35462;52734;30399;50244;30388;46547;30937;11800;10590;63693;63843;18578;66460;23766;29776;47779;32705;25598;57557;50800;19776;56999;65322;47157;48278;48526;12889;45415;63033;21461;44475;13103;31175;57049;28180;43781;54928;13959;11437;54611;38669;38858;60320;46072;30951;17005;47371;49478;36148;43613;57577;13017;48527;46890;16993;56702;55502;65160;33912;25930;55675;58718;65061;38479;31404;43962;49374;29679;41447;31358;66580;33494;13121;21738;65314;49492;34280;50121;30898;57248;66385;65473;32421;63583;19515;49518;10683;49243;39724;20302;45644;24038;24158;56374;30593;66748;15844;25130;54907;34060;19246;16141;37032;65300;28002;39538;32422;27805;61781;36918;66689;57034;17750;54988;16365;61899;32065;66103;55933;24693;60350;47420;17751;17392;32498;39115;20861;32051;40783;49476;22212;27200;60747;12762;24272;33831;37277;46112;21760;33293;64415;60091;43472;35960;29754;23774;14887;66223;65786;45993;39709;59938;14452;21087;11797;42948;20308;56478;56643;57725;17714;43683;65724;41314;14678;10415;50475;46155;51532;12832;55548;40704;11404;49820;19342;38774;62575;19243;50491;13020;18638;16716;46091;16621;15349;43283;25513;22414;52669;36885;52320;62297;40273;44589;16906;29634;20029;19749;34292;12706;41434;34825;12492;38665;15475;46342;20543;34355;60006;18002;21511;59306;50438;29330;30230;39505;33459;55886;51746;51106;55085;39897;18719;11047;54618;57717;34284;48238;53119;36600;35762;34163;12385;16959;15868;42158;20423;33824;17449;18977;34247;56811;19699;38959;53685;66093;37339;26200;64485;23421;57752;63411;58183;36422;19195;22791;60002;66789;63208;31922;45834;20160;27928;48681;14873;26868;41323;54895;21852;16407;16551;44284;57792;66075;49260;57617;49769;19927;36211;58028;38598;47185;31699;61255;24120;64002;35921;24818;59825;19510;65994;19095;41867;15114;56139;65930;48860;65778;63492;36478;29421;44577;39421;15888;41958;45988;18851;63650;20023;10156;47456;64622;36855;46065;24514;29424;46343;45434;29323;23672;25852;50908;17220;26512;41068;19417;27004;22232;27648;48150;47054;15063;47505;12420;56135;63178;65569;56033;42254;34756;59448;56271;34454;51822;11182;53948;31590;60003;15831;64773;19458;11614;52420;53355;24375;32898;63834;63703;64419;26470;28872;59551;33524;60456;58052;24630;35116;19674;46822;62152;25741;31776;19428;32200;63392;66697;33074;53353;33161;33152;28731;20880;28538;52841;11590;38018;55448;55855;41115;45020;17187;53431;63617;26620;16283;59192;36252;51288;28707;48365;38472;51544;63156;16409;37222;22352;21271;23778;44201;60100;50401;35323;60522;23442;61916;25313;18350;22393;37322;36665;18541;41087;50649;50230;39616;62045;49655;24672;55822;12280;17170;24889;59669;60646;65140;13799;53280;45691;66904;65907;12072;32345;24308;31176;66569;59735;27405;48323;17265;19176;54886;26648;14975;17720;16037;57087;31845;43477;33271;29595;15720;18671;31970;17167;56052;49065;39711;58095;15912;21324;14661;25116;10811;52376;24002;58877;25897;34223;33683;65199;11421;10410;39339;58189;22857;25998;44725;25101;51161;25115;40543;52589;27353;35773;56337;20467;57309;66796;48283;65504;17095;58158;20319;33528;58757;22007;15490;64893;63865;18741;27853;63450;38886;51568;58841;63014;38749;64859;52329;47416;31068;40761;22044;29704;38213;11194;15527;28188;14411;12343;13048;58110;49768;11808;11609;63770;44907;47106;13089;61817;42622;20256;16034;61133;50139;52037;46616;27820;48151;15837;41431;31396;33681;10915;35502;16644;38835;40388;36433;61015;13853;43248;39633;25122;65768;54914;16332;58453;14182;14808;22348;59970;59060;33412;52904;43277;62834;41031;40689;47787;47008;45217;30773;21682;42194;54417;47829;12007;26671;38899;58800;30304;34178;63064;29315;33399;21240;66351;38349;22720;30456;45303;58375;25124;24359;56155;44055;24792;42794;60729;37065;34001;55075;45823;45413;46448;55432;39815;29007;39561;58029;55430;60779;61329;34988;64890;46524;30049;65505;19310;20414;52286;10323;19372;59402;23589;30679;63726;13993;18510;21443;42882;39348;26845;11520;30059;63467;13175;34270;34047;27572;62895;64731;37570;59305;63067;33631;33439;54943;37094;35991;44604;60860;25922;26104;37954;26888;16942;57535;12947;25009;47627;25196;45439;52668;19256;18441;15396;28237;49923;43405;33618;56351;21604;27916;13951;59424;50543;39285;10769;20310;47406;64103;40949;51534;47625;65425;59399;36704;30056;27361;44246;16730;60704;32451;43225;41053;17405;24177;41728;26212;10453;26591;32129;35056;18914;46259;66792;36274;34108;36564;40642;18218;32642;31757;25468;22854;21468;62776;18897;40809;17113;45038;49814;57926;42466;55034;48674;13761;63824;53761;33251;27153;64465;23847;43814;21925;25445;19173;51773;34928;14336;53473;58795;44377;63310;32643;22128;47120;56680;20339;56047;60178;32105;45692;32710;14280;32193;42952;23107;27871;22200;46098;22735;56019;45987;61651;35480;16717;13933;55781;50159;38587;64163;34045;52878;10021;39030;43947;14627;46190;66937;33714;26773;60987;31314;49618;19925;31467;31460;38314;47637;65175;43335;23914;23220;49212;51304;14075;20333;53220;26408;10503;58120;49706;40702;33338;48503;32561;58561;20628;58206;66464;41141;54803;48788;49634;13313;18440;54642;43013;16223;15920;64086;53926;35268;11647;12966;60327;38342;13801;26521;25473;65990;21419;25213;31569;52655;23933;27151;34831;43508;41581;64750;55366;49470;24783;33309;50594;51371;59624;19451;49960;25704;27733;62380;10628;56236;28017;14344;29616;36678;37786;20847;56119;30780;39498;15644;34782;39429;48315;23228;52886;11181;12619;10545;43857;18536;49352;41030;32287;58368;18305;63342;24448;61532;64085;57156;52764;22129;31101;20973;51836;46359;54602;10072;30285;48510;52743;33424;11279;26289;52445;44081;27835;48759;43546;55133;64574;43076;33242;17529;19598;41028;11384;52124;64846;34896;35804;54825;56980;59286;12047;57672;55935;15999;15657;48415;55340;56498;26400;51533;13695;57422;18552;34484;58977;32990;26267;50637;21051;21814;36094;34405;65221;54630;53251;41638;26739;57911;64571;14302;52242;12394;50353;65635;37499;55012;55891;66790;46513;15496;23504;57699;44825;14403;66930;62262;51052;48938;12064;21246;35391;50427;63520;20074;37722;39194;43608;11726;49774;24423;28842;43242;28454;16363;38284;29166;57357;31533;59161;20903;28228;64797;46780;24328;31769;43502;66929;57078;53272;20081;66433;60458;24633;45158;15078;49970;41663;57276;26561;38778;28358;58284;47011;34406;60758;61679;58391;63904;16447;32169;46327;18645;45756;34237;34229;30128;49587;51306;41843;10914;19108;44221;29243;17322;62923;34088;66618;43389;14557;46135;49459;64007;32328;53094;41914;47067;35017;28226;35933;40801;32299;60068;51571;13378;65703;48789;66824;18412;65901;66781;18651;36952;12750;27324;32055;49921;34146;42418;30799;49466;48687;13363;46187;37678;24379;32104;16148;65682;57605;50394;60094;48678;24870;25865;56854;21337;20912;25635;24913;64556;14202;22845;54062;30401;53872;49449;29700;47387;60726;56513;11699;57441;29803;40503;46081;45357;37900;42673;48634;65746;11510;22722;56405;10855;43179;66771;21381;14093;24409;35262;40828;21570;17571;63757;40442;31692;51295;47293;25573;21141;15950;42184;55656;13705;50380;18787;13417;10663;29713;55261;15573;41596;58409;13871;37552;58353;27409;37939;12580;36587;19128;44992;22910;27603;42446;14154;55565;33328;66744;23622;44132;16688;24654;16924;63295;19124;26337;51122;29005;62768;14638;18848;48485;57785;53617;48676;28652;46578;21908;51058;14553;51991;44441;50276;18723;18523;18786;13070;26023;62300;61576;42163;39309;57484;45240;13143;41860;57505;58011;13057;20237;20326;29570;29035;31986;25498;16084;34784;39943;48509;57769;15721;44808;22495;64428;65718;17797;28716;64549;65358;53409;57433;49403;66663;49485;60229;61474;58524;12656;37635;30738;13827;18491;56390;50091;49455;56414;33079;27146;51024;44527;61209;63313;61110;44242;55493;41420;22164;55159;26801;23135;49204;66766;37471;12854;14002;25665;55073;13551;61672;34160;24759;66024;65376;48985;43523;13025;54003;27099;24960;34159;26098;53207;60167;48544;61276;22392;62946;13242;17147;56369;18200;50602;10396;50697;62142;28824;12048;43329;34602;20646;19411;64876;19727;52401;12812;64444;30331;30210;14244;39056;47581;56063;20904;16987;47644;11258;20684;52172;50913;21753;19746;18667;32393;48496;14446;50997;65665;48418;30795;53133;33047;48594;47810;63919;44092;42610;29871;15784;21638;22813;43189;13776;21815;43586;33563;55849;53789;49341;37184;22202;53291;28255;14584;62584;65312;57257;19252;60132;23172;42490;31542;46986;39894;14141;45549;55170;61421;52610;16124;11681;15360;23884;27488;46281;43999;57544;55032;36366;57555;53786;19069;35995;59172;45572;46841;41898;38527;26087;42672;11099;59810;31796;28372;46869;26796;41203;17150;40990;44588;38560;45680;14417;12328;36476;14747;23745;34981;57917;59276;25589;61413;40139;54596;25738;14170;45670;36993;16106;50805;26959;15087;31473;64417;60266;29862;58791;18768;58042;25263;46931;26646;63544;54109;46658;24742;51127;13671;28623;48388;45001;25078;34806;60761;20299;10306;24310;22950;24586;61826;46308;43404;18844;40562;45760;39502;52760;47866;61388;20564;23086;28122;34461;45891;41188;29066;54874;27365;49003;46283;37811;57330;66472;31611;44304;23669;36719;60849;18561;29701;65517;37583;41900;32172;55279;14074;20144;23100;22980;42751;63031;53020;42607;37104;53495;27984;16046;52466;42704;50423;41029;58067;42640;17061;52039;65268;26233;29618;49615;24099;31210;65231;25195;33479;34507;17048;51448;20315;52973;45904;48732;63557;32578;19554;28953;18033;29402;50075;54378;57879;41665;51599;63560;33128;55828;49127;41238;23537;18086;60938;16852;26049;13010;54524;32708;64520;54677;30352;55796;20723;62390;64472;54756;16555;31653;12761;10798;60514;18980;48440;22429;51157;56253;18976;23997;56799;45942;36311;20984;13115;32247;54462;44260;32212;11741;54213;30174;45633;18943;14800;44027;22195;37823;17115;41832;12763;66367;58136;48990;43219;36125;35183;54561;14107;20165;17374;29050;34179;58742;32879;49454;41244;48605;35752;41165;57147;47019;40721;28462;63724;59797;43052;28718;28732;31665;27326;61824;23604;51057;59080;48368;52640;42342;35706;20158;10747;40504;27770;60740;60250;19862;31818;21055;15607;50856;33073;64164;46718;43246;45922;12199;32376;28332;61897;17407;29926;46528;36043;34431;28964;46671;18714;12358;62094;43421;33535;43188;57364;50161;66144;29021;28176;23211;29608;10498;23319;13369;38098;22956;41931;19007;61294;45543;37059;63934;27489;32102;22515;37042;23174;15708;30206;32463;22430;49367;22247;12869;30491;30234;53637;39070;20697;42146;29823;10625;46148;59183;36257;33129;62395;52634;33896;42953;63209;10615;45590;60471;59933;35275;61502;26703;44481;51578;20965;11138;50149;65804;41519;64946;39044;64108;26674;40219;55861;63034;17448;42170;35410;66554;58692;66101;52593;28854;12473;37870;64739;12349;17838;65132;56395;27747;45785;39570;17327;55858;56674;14273;43614;10256;15466;61272;10434;61793;53525;37006;24974;49048;49719;60119;27787;33581;46994;18979;23715;39286;25896;47319;63471;43884;48672;29524;57412;36286;53324;51343;50250;64427;55571;16777;24525;63452;45232;53998;31602;62503;33655;47209;42204;56471;60055;49287;22863;48652;44615;60846;37293;63679;39020;49094;56783;37316;29702;24046;60807;63866;18454;12811;61111;27582;26342;21053;22640;49601;30037;13607;23133;56495;46116;42980;59262;59391;44098;61181;44395;28880;60882;13460;21105;39648;12983;23939;11100;58936;25286;51527;17635;40779;64948;58943;13656;21826;45067;20445;11816;54829;25063;58137;25825;12251;66787;53177;38368;13383;32412;18580;37572;61264;45477;58832;66236;59440;48209;57460;55517;26887;66734;61387;33794;33355;10361;25346;33922;38808;38483;15741;17124;55972;36922;29388;64949;60238;30989;58546;62256;29934;12367;63778;48437;65301;31235;47844;18935;53016;25430;44344;59646;13872;55046;49654;59081;31052;65062;57444;34253;29620;56812;21166;33366;26858;50200;27657;21476;45813;17133;44958;52215;32057;62092;15164;46124;27123;18818;20923;45253;64422;46644;15876;62355;34074;52206;53805;47675;64446;25472;28600;15081;57515;62294;52076;26173;58745;66945;31478;33829;59505;46590;29103;46104;49073;16062;26404;16414;22451;23948;17393;16907;35591;59648;22872;10263;32787;48272;48852;33109;24043;58490;30921;23179;46018;15308;25164;66227;54638;62148;46926;65988;38277;54574;29520;30258;37620;49280;37738;59204;58899;46662;20311;58218;20627;18001;33211;61981;52567;43599;13905;30822;33301;44558;62612;15702;58786;42069;22480;59066;29604;62956;65627;41634;50788;58501;64426;22428;50184;21803;16481;47177;52625;62570;14414;55444;16391;52700;50236;23720;56352;23376;10305;49689;17837;52057;31658;60168;15214;25238;11925;49521;62598;51029;59905;39979;14650;40706;43273;55263;10511;41507;50974;10504;15600;46566;36402;58551;36847;34289;23391;17183;41057;54097;63659;53187;39271;54598;11343;43903;39425;32286;49099;11377;23857;25669;59065;31939;30227;64625;32588;53408;46929;16003;30663;52116;50417;35688;32316;12018;58721;55702;47224;59678;22914;36164;33873;48537;24344;59950;28769;32140;48735;47758;13443;64856;34835;42084;63962;30962;12480;29537;56913;43004;66784;63434;49875;14150;38223;51641;28339;50093;38696;58128;47838;58414;34635;23439;55191;39600;39918;59531;55779;60600;29058;30192;12091;38003;33552;22672;30541;63015;58062;56188;39130;45034;33368;10284;38789;12944;31178;25803;35853;51985;52034;41584;52251;52314;41790;35201;48715;14574;45547;13501;63887;29997;52339;18996;54912;51359;50678;24178;42985;46760;18847;21875;53459;54356;15410;60544;13338;31157;13246;57052;62449;58645;28131;43569;48372;47453;34786;24518;25113;26188;50023;20869;14776;30834;19758;18929;50086;31743;37557;52945;63731;58618;14694;30508;54525;52562;58929;59686;61990;40707;58708;42335;47595;44009;23330;37381;29785;40790;47633;35876;35741;24900;46177;41772;24468;29762;64601;62176;12785;23908;11378;16674;33061;25052;33641;54426;23143;52419;35711;64350;65686;42326;29249;19158;56862;29311;21762;64798;11759;12674;58924;40974;54804;64561;24352;38781;11673;43861;15829;32634;21095;46713;64017;48844;50986;14989;66225;31816;44648;13865;41080;10295;48355;64560;43544;21983;53964;37445;32835;50658;20127;39064;33771;62916;52934;23251;24320;65516;57537;66002;13449;43433;36023;48698;26779;63853;19617;51751;35660;10518;40551;65671;59437;13824;15672;65991;23489;29291;42064;55806;54891;24242;65894;20593;57242;13201;32014;26576;43834;18468;12054;13087;14821;47040;19650;16856;51071;14102;24642;38387;38627;60214;40144;34197;51840;16424;40289;14098;35090;30529;42344;65422;13533;37676;19717;55954;45612;29305;59478;52735;52328;37451;44122;50181;25246;22509;17487;47440;60526;37880;41553;33219;48250;16798;16886;31707;16381;10490;41533;15326;51820;37041;11322;60626;11321;25018;55331;32534;43707;34791;43312;48468;45515;41429;46674;19200;15483;45160;20327;57593;56957;14863;34549;57881;36463;66089;55319;31120;56214;38266;39380;10476;26036;54515;44633;25553;29076;35716;64886;20812;33127;16915;28248;47197;24339;57198;53292;61718;26860;13590;17047;20548;15243;51979;53520;12042;35036;19083;19542;34654;34879;29908;10125;57456;21355;45910;51864;10697;59238;32930;45006;24537;49163;26527;12499;40732;42814;45368;61236;26863;65849;28831;59289;19440;45948;23524;35757;58788;58566;35796;54888;31140;52086;38623;22713;60243;13936;13319;35753;18612;60964;34547;39195;62818;33877;24129;62458;35178;44124;61404;50345;11583;60203;63908;43721;51405;54967;20494;38800;58286;42706;31434;15701;27769;55137;11710;62111;33510;41240;15865;49444;43543;59132;28120;16645;32255;64871;46077;39692;24976;49000;45403;61245;23264;41372;56329;43272;39632;29969;33536;14387;23065;19807;31397;15348;50586;43255;14020;48205;62428;18874;12453;54935;59537;30200;26230;45359;30465;56130;48399;59988;34012;45535;60228;36567;66913;34420;64812;53817;59831;31328;24566;53976;28937;61879;57130;26029;27701;53925;17112;49757;52186;36962;27700;58830;37875;48937;28657;27031;52930;60434;31034;45395;13876;30021;13098;51040;22101;44622;50862;44640;43828;10843;35043;36941;50546;42218;43158;50709;56343;54351;41891;45567;32448;37163;30146;59964;65799;50854;22160;61231;54297;14672;47656;14591;10429;57192;13399;62504;36831;38091;18572;57745;21186;41565;57314;29197;51464;16671;33695;54904;60818;49577;33325;64386;19282;51050;51964;46090;66366;30770;25056;19594;39900;29326;30389;57040;53883;32468;29976;42799;64238;66244;15556;61983;35517;44168;45394;16266;19028;23626;46897;41463;14652;27064;26781;55981;14217;27065;41145;39270;10391;51177;22359;62654;10020;24549;20790;37610;41878;60208;62754;55135;42990;22659;23980;17284;37145;44743;16135;19340;16476;16546;47646;64363;29547;51072;44235;41255;52600;19649;25388;48670;20279;20371;65915;45584;20802;66067;22363;13794;51837;56105;60680;37077;17808;51793;40863;13199;27702;45314;24196;34186;24183;11292;45654;45935;57589;44523;26072;51381;47349;18300;32543;54953;55576;46716;64820;65683;21236;27101;55300;60116;32366;43143;39504;15455;62319;63327;60436;11754;13377;59319;33344;43398;35872;66843;62187;52691;10809;19772;17984;11642;64456;30930;23840;18623;38092;23985;28113;44215;35131;62593;65557;55374;29503;25267;19015;66964;17412;42205;11472;22717;50971;29129;32613;50685;64157;37888;35185;59566;12268;60557;54498;32852;41439;59636;46376;22204;22798;12590;29508;48354;49049;19036;25221;40510;56668;13180;27431;25045;54937;54920;55617;18178;36757;20828;17134;62996;33934;22670;38533;58813;60981;12264;54001;22242;22031;37419;60575;61875;57377;65279;58892;65685;29689;48923;51621;19396;35533;24316;36058;58870;56647;63190;31212;32265;19302;17578;12636;30640;11241;33658;36806;62709;60123;30563;29409;32337;38239;14061;61296;33216;48180;24186;44890;54436;23334;23402;61587;47459;56516;60025;52352;50651;53758;47678;32390;30983;27154;43742;40476;32134;54613;29312;22967;62998;22368;32326;19001;60795;57937;31525;33067;12530;41705;49902;32928;55912;45866;66655;29337;64280;59359;57086;16763;30065;34659;27423;60851;34278;60837;14810;37190;39031;49305;46207;54259;21652;33684;64215;49808;66027;65287;38206;17696;16211;14264;24036;65015;50150;27094;41547;13998;25550;39873;51028;28554;27962;20989;20307;64436;34886;42735;24909;62532;28178;24871;40819;22861;41401;20884;13232;45629;46531;33313;10733;12415;18860;48571;56788;11860;29182;40840;53541;43555;31704;14983;48734;45521;62606;50893;39786;13436;43268;55120;65396;44691;31957;47645;45278;49662;12680;65088;59544;63561;17767;40933;53422;24601;48663;13736;43695;29629;34122;65933;55511;19711;65533;51084;61765;28737;11227;34823;44681;57360;30829;10614;65767;61444;49604;14844;19756;20209;49606;33382;24635;49129;14257;49885;21544;23710;20410;37775;14979;38805;33122;24143;22461;51316;20361;16751;18005;28490;13716;34387;63184;32336;62975;52298;26986;13852;29765;49834;52134;34867;58058;52806;24244;24041;47031;52374;34371;61868;37591;11332;16483;66250;10752;39859;17580;10554;66488;58411;31886;53852;64268;39156;58376;53946;19332;12991;22823;16725;20964;49068;65697;34210;39123;48564;17089;59023;44584;10627;35631;64224;17331;55412;24060;33244;37267;31979;23329;28198;36042;59017;30690;48845;55103;39661;38147;52475;61367;31033;51945;39438;54016;48794;62268;57957;22575;12360;10322;18403;44741;37788;44821;58619;41895;47539;63436;13262;58806;41264;15338;47836;28702;51476;58873;20244;20809;13004;12320;63254;54254;30726;22395;58733;57778;61616;44251;18682;21623;35100;25783;43516;44838;22102;38613;57265;39566;23787;53723;26958;28072;64035;50994;16729;43967;35257;20971;33484;24274;45213;55704;32184;29031;64686;55883;52123;25421;36331;30943;61394;66290;11803;36997;23137;52857;10687;49095;47685;28489;38262;60048;37709;60254;33474;40255;19135;53169;16328;16574;12550;32958;15707;31879;62258;39096;16508;16482;55890;22390;45619;45972;58295;47247;29627;15422;14015;26998;49575;42927;17839;61014;66455;63044;40463;46060;46000;22027;41040;62638;15560;39414;18807;24482;15034;55039;28330;46257;59386;61204;64824;10109;30973;22321;33828;17064;19818;36473;26380;17523;45055;52670;46219;60352;33705;21953;14510;29345;41825;49835;43784;15801;59912;33541;33823;43735;38109;56784;20834;45378;48666;28302;64884;45131;32961;54173;39685;60833;22517;35944;26714;25773;32072;58565;20314;12565;62700;64769;48339;45008;45578;64167;14194;27041;66626;65967;19839;45153;65963;44352;25075;58639;45212;13293;19125;54069;63134;54221;13874;26261;40754;62125;41567;62325;43800;57698;23835;46037;32012;31142;12740;32762;40242;17130;49523;17521;27298;26945;16218;12880;37650;34359;65521;62488;39539;60173;50845;46820;49717;17001;34267;59941;26382;15343;14485;41658;24512;29924;65471;19905;41580;65917;15697;47218;39318;22753;42938;54368;63233;21364;16296;35488;59641;64282;29653;21628;54212;61975;15922;65742;23132;12568;23295;27538;33639;15113;22365;24973;20234;21913;55189;19247;32455;50600;53980;37458;57131;60936;58587;21704;11339;25431;65185;41408;50551;31648;30424;38785;48308;61886;38250;25681;35422;55215;62524;13904;56869;34249;28931;41023;66610;38554;45591;25334;63423;28294;31015;40438;28069;34392;48908;65464;21446;58344;16731;17252;60588;28636;61298;17347;60777;39578;13154;66764;59457;17416;63252;60292;65143;54558;50192;38013;23022;44209;16616;40930;11864;25544;60296;47213;25577;43953;47073;13553;31207;19811;24817;62038;41003;47292;44317;29452;19291;60159;57035;54516;49022;34942;24068;28597;56355;65827;24748;42643;52177;26659;61834;21174;53101;27616;18992;46417;17724;39529;33432;49544;27696;40937;39305;27636;47832;52096;61184;44061;22527;47782;53940;47428;13198;39471;20995;30858;38178;66502;61378;28452;57845;51592;27354;50980;48531;34288;32623;58207;34994;39185;43351;35842;55089;33624;64772;64791;51755;22660;10044;41309;57158;59055;16691;29464;52012;65598;39469;52098;53947;28952;59697;50857;43168;34440;58549;34463;19093;12114;29928;21601;50769;33181;12819;31721;14626;41329;35780;15167;18902;59842;10170;47498;24341;10383;65741;61690;41684;54911;51779;54573;35443;41344;53750;64905;58170;27258;41925;42571;35971;35085;61962;44198;35046;37308;15329;36438;64322;54934;57002;30643;51016;21038;21892;44139;30256;60815;15624;42211;45765;65070;21506;52643;48522;49416;11304;17544;11907;56433;34810;12098;23466;21390;32774;40030;24995;24980;16072;39288;22135;50097;39932;58298;41047;62350;32825;58223;60110;19105;15695;56802;22518;20143;16761;55162;57455;38488;12511;53791;54774;38961;61655;33785;13489;49612;12491;13223;44327;11856;53969;14080;13614;50725;51735;30912;57614;14499;46173;46733;58555;16770;28997;42346;52605;43585;28980;35961;46660;64276;16878;50764;22465;47835;22550;66609;57375;23361;65887;55474;47882;11981;12096;45741;19194;13628;59836;27317;51386;54276;22549;26985;22626;22231;50202;39148;42093;13088;18703;37576;44171;40843;33556;41383;25729;59742;10501;51270;64372;48768;26722;57030;41999;14625;53356;37837;57732;39869;59115;41645;34399;58407;45163;20786;34541;36946;39440;30195;21363;22427;59094;64134;11346;55758;52270;66136;27881;63104;52755;43458;29380;49688;15336;30747;27953;45176;16412;54716;56834;28079;55168;33314;56504;60279;65854;50871;32682;39649;60143;37579;62995;49932;49602;13493;25565;50063;30344;52304;33787;63753;31508;56426;53481;61798;27060;16358;33488;39674;39437;45207;20124;54808;15500;27130;62007;33119;58981;57897;30362;53057;48498;16310;14427;35997;44109;42321;63986;60725;39046;48901;43902;18016;23543;61950;27387;16258;43744;40075;35603;35869;57885;66478;41662;56965;13170;57962;54593;18607;36846;31486;56475;43501;21729;53933;27647;23279;14889;66211;26204;37124;61279;56764;48316;24048;19548;66006;10329;53959;62137;57048;39324;34298;23976;60984;51149;49090;46980;31341;56046;27751;27227;51477;42099;10561;14885;20254;22364;42883;43942;43661;22467;29883;52207;42575;58864;40097;48333;17067;46895;24081;36588;34894;12757;22915;22063;30104;11997;18803;44356;58025;14671;36454;49136;37148;14457;45190;39712;13792;20666;55210;29567;41605;12038;51244;34091;45499;33470;47657;53083;34739;11293;13966;38246;22883;46741;60335;16650;20427;61820;22387;43346;44500;43760;39888;66768;15449;36998;18339;39449;38300;44415;11399;53313;33827;10927;26148;17235;36393;28205;11976;10551;45930;38793;43633;53551;12008;64952;54822;13347;46169;44613;37249;22001;28371;51283;40976;33386;61188;65303;62719;20031;43500;13407;13843;39377;15426;38259;26630;25674;62496;19503;26968;30964;65563;16581;28086;15689;15077;10085;46759;62758;15983;16510;56306;10451;13214;63859;15585;11771;40588;52360;40489;65265;33151;44253;31754;63864;52229;40392;54983;59355;54434;51223;12236;13184;19706;46958;46516;23450;26623;43733;12025;34749;54311;23267;62264;10543;15155;30467;66688;29319;53091;37312;52683;15254;53971;19621;36812;56423;19298;35418;24075;16758;63229;43050;38875;11424;29545;37916;42567;35622;18783;20640;56335;25691;45152;49620;18828;30067;47424;63752;13589;64016;37212;62686;51646;51982;35179;48873;60324;36220;33048;18922;25059;45323;28129;11861;63194;58525;32118;33421;26619;25308;18779;57355;66378;39443;12051;19170;39428;55706;25114;38180;26484;32886;23959;44013;65820;52024;61984;63477;16171;15026;41804;44833;28466;40118;52505;63305;62027;59594;15091;23400;10685;10513;65553;44660;38862;24473;17732;47781;19926;54947;54746;18881;31399;22647;28916;11253;26428;11839;50829;21378;17830;61693;55916;15242;51335;24357;64385;61305;24459;41514;48989;52737;46329;40049;11683;41621;41585;40786;25752;17534;27548;55830;38218;49344;49468;60174;41250;56876;35160;51389;12745;52664;58735;60180;20778;48704;13851;26833;12758;25838;62334;20042;54811;11170;62236;46435;53699;11095;34077;37177;14067;11042;54510;40197;13622;55705;54046;54440;62947;61760;55020;44069;55128;43437;54960;63097;42810;25252;35611;62097;19166;10650;36591;20625;32836;55395;60224;17281;15561;54552;32979;54661;13938;62130;29122;15994;36448;59162;61462;55742;51252;45128;30422;21153;29980;40736;16259;46680;32803;31503;56023;17246;53614;38334;22680;54775;42647;22599;29174;21225;34161;54877;50137;59118;42248;39670;49664;20395;43659;38704;55601;41928;14685;61804;53744;35899;52531;39052;41282;37233;66303;54435;33709;61669;20242;18407;22396;50145;50939;42130;50911;18579;54609;51865;26525;48282;42667;31981;14364;43369;57872;23374;30223;20506;15463;54505;27429;44562;53678;30439;39545;63633;27042;62603;49762;19152;18463;14597;63296;61930;40393;45078;60188;64250;54220;42240;45786;36152;33392;19120;33520;56655;52898;53485;59773;52740;63484;36901;26865;48885;34468;32058;49582;64762;40653;62291;34094;31123;45277;20295;32436;58105;30330;65811;34183;66807;61056;60732;57565;15207;60521;43390;20137;21770;10289;54326;13608;57436;31348;45665;59990;47078;47609;60303;29228;29826;23216;24408;24553;48446;22448;60011;15018;33478;52391;11128;33394;12700;54224;39951;45185;30883;40096;26071;36789;21304;18476;28967;24243;43423;63166;36852;52413;62850;61842;47900;34605;20091;46250;37119;56180;39225;48358;25549;25187;27543;11728;47636;21449;17970;23780;43505;29324;15531;21360;39825;10906;43230;27970;51649;28573;22613;66519;34279;24039;59911;45568;13899;52135;39217;63638;57119;41886;25641;36365;58522;36115;26761;11432;29825;23008;57583;23342;22333;23545;16552;64642;19406;16774;46246;26134;16104;40893;65284;11775;31040;53181;16660;37029;33330;11351;23553;60226;47084;44178;18794;57825;58320;36264;31646;28516;24388;20233;23883;50454;18882;26745;39307;17002;40561;55655;66887;22687;53318;59781;31884;16293;20421;39609;30734;33334;15080;39850;15383;40036;21158;12962;41235;27045;12294;19394;54776;66881;53237;33712;25979;47528;52433;44157;55590;32815;45990;51025;58494;64373;36561;28412;20968;45061;54310;60494;26043;25642;50414;30255;28107;25311;14987;18599;16438;32154;35866;33275;56542;29202;58296;51716;19284;19251;49669;24573;33117;53889;63002;48176;41259;33649;53684;32198;38879;37980;64562;35969;42966;49159;20228;17579;32586;40969;45513;18886;45414;16428;13059;24786;62299;23173;56115;56029;39154;37444;44994;24302;27305;41649;12475;31945;18080;51651;23176;24649;15125;52687;66601;60507;58285;33019;64072;43705;61130;61695;20495;15577;34608;26688;23487;28497;14026;36742;20192;38954;30684;55205;29839;58289;62745;56816;41777;52221;55348;11335;44351;57734;56035;25615;25511;27998;19688;55156;64122;33532;56586;28518;18471;24739;41518;32423;54010;27113;66769;46598;15836;21800;36810;54458;63735;20344;19032;26706;64349;43089;32889;64710;50005;12512;17036;50478;42121;45181;34836;23770;19504;30041;49659;25211;24855;33157;12968;65633;46069;27774;20894;39667;27360;34040;62911;32310;66040;28528;47026;41733;36960;49853;31044;58691;29718;61489;54217;23634;41730;38279;46393;24488;24607;41719;15767;44871;58557;22597;38927;24176;37160;29151;27372;53390;19104;58388;34369;66528;22280;27444;11092;12495;41193;33995;23645;25952;62090;49385;41738;21309;55332;20760;21034;43185;29636;38051;63952;33953;54414;23303;17815;19179;20907;26909;50776;45902;11027;21769;17553;51585;46275;36767;19910;29351;39984;22444;64031;35200;40935;55579;22533;31249;16911;34568;60162;51121;39162;10113;66330;37828;14433;22103;31356;59927;44057;29805;34630;44658;46761;64293;59479;34084;19658;59796;36488;57527;51030;61402;44926;23887;32526;44599;16092;53690;48575;25956;46530;55884;38146;47042;37017;57503;42703;45746;64486;43481;40593;62562;50737;39717;13131;23739;36124;34877;13005;13350;46367;15347;43935;65619;29494;24576;39411;14228;10972;43034;10023;15305;27202;24136;47484;29474;41110;62544;47590;54247;19482;49724;21020;38714;34859;17273;62484;41010;20457;44129;18954;56605;23248;63732;25492;27855;29892;26260;46836;17316;13000;66510;22552;10659;43649;39103;51094;51169;35140;64693;18264;56819;12519;38467;20225;43956;58012;55027;16643;43930;29495;49275;17104;35398;46314;29798;56032;56437;46038;27207;33751;37525;43334;60256;55743;56718;58413;60474;52203;35000;15843;28374;60858;17643;63719;45307;47614;49600;13670;12593;58420;65755;15833;64401;11228;36259;10948;39222;26461;40128;49084;30179;15641;55318;32121;44125;64528;37275;24031;39644;45391;10181;55392;20123;18735;30397;56612;52855;64896;29155;21520;26840;32653;19680;12931;49935;45173;52416;34873;40684;45098;13777;39280;36232;30451;46396;36980;28197;28624;38900;55629;46948;47092;41938;13148;30100;21784;49944;57396;18367;42112;42587;42179;31681;59523;38481;10512;39755;32001;52350;44912;54334;17039;31497;26016;12448;15354;17149;51917;66826;57823;28752;27690;20906;15860;57750;46801;61498;55701;27562;25159;22593;50836;63762;47098;46736;31563;24429;57882;35258;42338;38638;47666;11564;45744;66627;46974;19344;26826;60877;47891;55635;55939;48630;24071;65838;22749;51188;12036;62912;32760;22230;25166;64382;51336;26327;35782;38918;24958;54365;23414;15642;65708;18309;19341;23270;46398;39139;24850;10700;54073;16670;14703;29506;34738;13077;29563;57458;55098;22329;58444;31593;38041;37231;44757;54235;27036;65475;23949;56286;23092;58373;42208;44667;11048;35184;34451;51988;52775;66548;34971;61645;11843;51210;19033;41827;32233;48888;55669;30501;46889;61862;10121;33948;21028;13328;54249;41496;19496;31606;35150;59157;63080;55130;66780;39301;61192;35717;52308;33954;17063;41201;58578;44006;50004;45013;42809;38330;36377;53905;50915;64632;30534;15605;45360;41167;46979;54169;32779;42609;26452;33140;30444;10558;38592;21077;41837;47479;19316;27622;55141;60713;43511;56577;53821;19144;59152;33266;51469;41773;32637;65281;39458;38689;45211;15614;51803;53358;14117;22571;50982;40622;64618;56678;35403;18727;48546;33426;47611;39791;24561;43137;12949;11927;51665;17825;23569;57146;66415;53193;61740;11934;29335;64495;31934;37257;53597;22338;46025;53347;37285;45157;42870;38828;19882;17203;43492;30254;25290;46142;26592;23063;53046;22756;36744;36237;10709;31059;59726;38615;22643;39591;31380;26154;25819;26432;24916;31202;61363;45372;33102;24735;51431;10781;48432;48766;60571;11859;10103;52638;39733;36420;58982;27614;33547;27388;65743;33189;41121;17515;37511;55476;18327;21885;13879;37660;50068;63635;44381;26424;54021;61900;38894;24538;60332;40098;11220;41918;42244;15013;41403;42442;23946;38924;48377;36168;30087;61434;39248;25474;56694;36223;48346;51174;55252;40272;59695;64162;10094;60345;54542;36452;36609;59477;33101;65576;56380;53206;36424;62293;39723;19320;22224;49581;22556;30271;51623;21483;47468;60802;55893;52692;25080;45283;27919;64861;20962;36382;12779;34571;49215;36384;54837;47522;26977;18500;18371;66165;20318;65547;49818;58623;19567;34033;61185;15626;18172;24400;43302;57424;19161;13479;45268;41686;20080;66047;38594;63707;33277;50175;53491;39016;40107;31853;49093;43703;36418;16413;62626;27006;25853;53511;25090;18616;66746;51445;33943;11697;19995;27307;44671;28465;51998;41370;46168;34397;60479;38558;22192;57042;17375;40088;62939;49340;17367;15376;64055;45435;51296;63656;53218;50547;16805;54781;65900;34998;20681;41211;14322;48690;16563;42561;56737;22279;16744;31169;65429;14646;20426;50793;42320;20317;25630;19932;58602;47033;62862;49863;33748;26618;14715;66402;12253;26340;22114;64955;25833;49012;22646;44366;36150;15612;36803;29391;42092;31959;62050;17511;52394;62011;57757;16411;39188;58883;32302;51021;26988;32111;45494;16610;62928;17218;25249;41472;27100;45470;32911;48823;14849;64623;17471;35847;40357;42569;15492;54763;66447;44041;28065;37542;55684;46266;35536;32994;38693;36167;22018;23169;38112;60452;17659;21625;27948;46378;27530;66931;56192;35425;64302;15136;19614;38930;59699;11751;37320;32731;27718;19071;23434;60419;30791;19436;46870;65172;34624;49028;51262;43387;57394;28856;65951;19370;27754;61536;17794;31637;36045;32833;13764;24236;21973;64484;45656;65616;10302;36159;38182;31675;31564;60222;12306;15118;31071;28034;19253;34586;52598;62388;57902;18274;16330;25504;58037;41358;44416;11222;66916;13685;19188;59771;49140;46209;56665;42568;56294;30600;44758;43032;63056;41043;30242;14037;26269;11725;24245;23845;42386;36361;58711;22271;41959;14197;36958;31676;32712;32087;27055;50019;58512;35939;20863;35047;21340;10127;62865;50517;61770;52084;50085;10148;53140;28458;38974;54497;45777;30613;62061;64597;14759;43817;50708;18004;64408;36821;52568;48986;66544;22734;35650;22955;13858;13520;10536;39958;59972;20265;40914;45290;12939;31657;50363;16366;21116;19724;19873;37331;24329;42804;32182;66128;66493;51554;11631;60104;62881;65308;23044;42227;32798;63399;59255;33491;10401;14792;37621;46400;65205;40399;32767;11028;32496;39662;54927;19662;31079;54845;63525;17427;36157;59597;64023;17212;22890;31622;27327;52896;14765;23090;60432;43184;20958;19259;37466;36625;32266;33704;23193;60037;59837;24480;10274;45265;44407;33626;17811;49658;49257;42243;47283;29764;37584;42025;52294;58088;37505;36923;39533;11845;50197;52317;10905;26597;51236;56377;28441;65173;47594;31280;63949;16954;43049;30928;25280;22513;66795;50238;54568;43813;22572;53513;45790;51911;15447;56661;46936;61766;50987;31712;45068;26243;29501;58660;51888;26299;27531;19575;65679;33144;65166;53536;35040;55760;32752;47086;52170;66337;40303;43461;38718;24469;34529;58303;42389;48453;28231;11505;65027;41491;19803;23214;65735;23744;50489;20943;65798;31023;17214;51776;66425;45481;28747;63397;56511;27612;34550;62595;31477;21203;65130;13856;23740;62861;53037;20873;11760;30823;17485;17060;52652;10045;47312;19350;34527;50448;21276;55674;65229;62030;62667;63463;63779;40981;17215;59350;27771;21111;61265;40266;58403;61800;31674;43769;28416;28405;36640;62098;54969;37368;13073;46499;34422;13840;39157;36472;61942;56982;36887;18849;30180;29150;14348;14612;10298;64364;45880;17043;46520;45120;21833;52860;10967;32721;30376;47603;20596;12429;37827;28350;33763;34078;35868;44549;60566;38586;43453;47872;13151;13999;52429;34395;32011;62668;52847;24097;20131;52818;38460;45620;20214;32278;54322;26729;49864;38633;53736;37480;36530;18252;57332;19380;16162;61905;33046;59036;16760;28031;27105;23014;43756;25128;63947;62493;26344;11897;66353;32855;30088;59095;38684;54656;19792;39931;59642;30801;28141;44882;15450;39671;44322;51203;11069;10692;12507;53174;54141;26514;45425;28379;12934;58179;59285;64511;51914;40131;51832;52595;23119;24073;34144;43920;11498;53636;36685;41083;40169;32977;45225;37452;59167;40773;46838;47578;23017;66685;59628;63437;28064;30221;31271;24857;59087;38570;51125;27666;39760;65403;51591;56488;58224;34443;47189;52226;14722;63241;60940;11336;47261;32893;20366;59904;61120;15604;23863;29885;23653;46345;13361;54391;18668;59632;42471;29288;60617;25785;57667;33241;41175;51104;43349;39713;56328;49332;43890;49483;58032;37070;21190;28723;37854;52351;27861;30680;64629;54178;25733;21350;44756;64193;31113;37075;30097;14120;42000;33425;36843;31165;13275;29046;26026;27918;41877;57311;52866;55784;22343;18968;15252;52476;38907;61353;40698;39965;57414;45111;63795;51227;13996;39228;63936;26496;53171;17788;59627;34684;26749;47577;48471;27917;46268;36540;43856;14193;62229;66779;64221;57164;25812;50132;12786;47109;17259;35528;57648;63173;24240;63645;37868;11972;58307;50199;34093;30806;65621;38234;41756;58047;10517;37040;21132;47361;37225;12645;56087;62609;46694;15619;43175;21634;39930;25850;26363;30189;12957;34131;52121;61839;39198;35151;47878;50758;38265;58308;12846;27942;60261;21658;16065;19474;64061;23962;64552;18067;27435;16207;27971;34348;66263;65878;19224;18955;32573;58697;27520;26166;33083;48568;52584;29130;62370;23594;48567;11974;44047;41624;52007;18742;44888;13042;16316;37199;40275;35705;56393;27191;18757;40313;53265;26843;56637;13425;57576;34730;13924;29004;16683;50504;59117;47725;27639;47709;28019;28148;12634;45581;24478;37213;49393;19140;33974;64380;62028;27294;40694;42168;40318;42077;13916;24808;66219;23743;64441;42188;30868;56548;27985;13883;50126;26935;60053;52863;60789;56960;52470;60506;48586;32107;13514;61041;61132;54438;55426;24407;15278;22621;28886;43879;24764;26315;18285;47356;47104;43160;33158;41803;19117;13257;20604;54797;26978;10637;33393;16694;23500;26240;19435;18199;42881;34878;17011;23321;15032;16399;53403;37067;30135;21681;24564;54208;34433;52911;51412;15297;24745;23503;50773;10214;63123;16351;44723;27864;49744;59533;20721;46175;53728;20147;32875;23258;23002;11032;44263;51742;12702;47730;53595;40308;24141;53973;29952;16060;23682;14483;55072;11287;13009;46186;65117;55375;63685;10047;18113;28386;19353;18355;13255;55290;63637;14293;53070;59404;53345;45267;13571;55780;50364;41481;56716;44883;46981;11896;48408;21806;38029;49345;28972;10016;63494;17826;51905;18177;17308;10593;65705;32606;65490;34750;46764;49928;66872;24543;56367;56582;35365;39145;66238;10079;50334;43830;16520;55303;24505;43008;33585;64418;42182;62900;53160;24311;12834;16445;10436;24306;59395;39829;26661;37603;22008;53478;27950;46311;32748;55717;23599;62708;62720;54413;13779;54580;38328;12488;65188;24915;40987;30694;43074;21031;15580;19122;63632;25299;64904;20251;59553;52853;53804;19295;57807;52604;56618;58399;17180;53165;38721;57472;43928;39450;53419;44401;47115;47571;27872;64956;38516;61280;41578;49868;41538;29125;44764;66666;25892;36092;33992;31516;59265;22843;23418;57215;26110;54087;35680;62753;52937;41512;18974;31528;52532;32636;21085;20770;44486;47135;40824;46158;19206;18550;47643;53267;21921;54865;28011;61794;33854;52957;53898;45101;61727;49856;43889;32046;60969;52130;30191;10510;65034;65731;46525;26746;50933;21124;15802;34372;20535;60780;52031;23478;19864;53629;57976;58437;27735;59474;18933;19582;34565;51326;15588;10117;22109;63902;58894;41202;48511;59346;16376;18014;35433;29647;34804;27719;35584;19384;47721;52083;30794;37266;17780;57496;31900;45796;57851;49481;40669;39915;57542;40326;39284;54769;63810;21183;47504;22547;64443;63906;46297;32789;60328;19993;43257;20705;48563;38565;37735;45168;20007;14007;54127;43077;35499;60470;41004;58505;40654;30299;21180;31548;24532;34282;35322;29246;22918;11618;15275;54246;19808;53564;56905;61940;35698;36815;56107;29234;54392;49846;54511;64530;44942;52557;29214;38470;16112;42173;53415;15603;36905;52266;55436;35299;10440;58122;22433;28946;64619;12982;15130;66413;49364;47370;36038;57430;34485;56671;55793;46204;31651;58893;42269;62914;60738;66724;59667;32560;39746;56142;42902;11411;33186;30319;23335;53368;42693;18583;39258;60605;18349;53619;16994;26114;23671;22786;51564;62317;16286;56446;51804;44400;22589;55456;29677;58542;36060;66557;63990;37927;58988;28297;35111;18250;56468;52043;29544;38366;33354;44449;21991;16529;30341;65897;17254;44951;15035;55747;24502;61207;41907;21982;25525;11120;22875;23362;12324;45870;39845;62442;50736;61551;21414;55463;21546;56041;60498;43318;37051;60909;25814;33303;59450;51345;61726;32242;43488;11796;36502;47547;49271;58666;43467;46651;15759;66962;11165;17829;12653;14818;55708;31154;50104;25144;25490;34119;60676;25044;59961;60422;60480;49432;39922;55116;30413;15108;12516;58227;30046;47497;32800;25941;66215;17410;51940;19303;38221;44669;47619;26528;66210;39923;23535;24281;38015;42986;55604;41422;23684;20810;42189;16680;62129;19930;51928;66514;32638;33159;27226;48917;50349;43648;50445;59768;66967;49870;29386;25174;33777;22971;65986;16904;37380;32524;21968;50008;25950;65449;43854;39396;23907;58836;60990;64910;56280;27580;31510;24729;63589;26598;51290;59397;49360;20926;26625;41660;59538;62522;36203;64572;26696;12361;13539;28858;45698;62979;58754;18867;35248;57239;63181;25849;51166;61247;27830;17371;33701;31377;44559;12650;49633;16127;28938;50100;26167;58134;57376;41762;34447;52211;48454;22457;33466;15686;19645;45476;37414;43128;11722;59783;36227;54346;37201;60683;26596;52437;58612;24926;50219;10705;38441;21326;64404;25304;30625;28942;24180;44930;40660;19010;61694;66711;57159;47720;42595;29777;13921;50583;26462;64312;59542;27208;53754;46973;63592;27821;46021;32790;38410;22104;21432;26891;40365;46984;39094;10198;19907;60661;42879;50302;11928;30596;49474;26495;45422;29664;27238;26048;58372;44800;19162;46478;58113;19138;62155;29657;12672;32324;52654;23998;49913;48363;25163;51238;38181;57295;28283;11207;46115;57636;50670;32919;33472;50209;64105;58847;44881;33370;22841;41535;29161;32234;36661;44266;37310;25740;13219;41247;13496;41597;41035;25519;43559;14912;14469;39365;60007;26712;52000;19183;14709;39558;64868;12845;36836;66142;31410;14664;25711;51995;22787;46286;52950;44931;59352;11867;21975;39501;39418;55687;48298;56830;11203;13564;30028;66390;64839;44694;44200;65678;34100;30347;31532;54887;42256;33365;51017;26441;55718;36611;24064;28114;43430;56230;47410;20524;56540;35627;16788;62210;37117;32062;27486;57857;41327;39272;59659;34790;36156;26493;55766;13576;61428;52963;49556;55443;22090;59310;57056;61036;28010;39323;38031;60591;22524;45050;47827;21635;25404;26803;66467;20826;50698;61222;52334;42223;13349;59431;51276;63625;40334;35194;52465;31579;66723;36756;50249;35146;63603;16005;22416;61859;34801;25546;43876;37911;28209;34926;10484;55937;15106;33573;57354;52102;36210;41875;51418;16489;46252;47778;46383;16198;26467;44088;45054;22904;35298;36546;53957;46552;24364;29362;22016;29624;38036;30110;59064;61952;53033;36462;48848;14157;44333;46553;40281;40690;34366;48662;34910;54075;45016;27535;25386;54644;14756;32434;29339;54652;27116;13772;62757;27936;59522;60360;24072;35809;61736;35172;35032;53496;18669;66034;37917;37693;46692;55247;40319;59818;32380;22351;36795;44025;53466;55472;33177;15342;62513;42178;28665;57369;10245;21977;49576;41775;62144;42853;22632;21249;20363;23441;51185;16031;18003;33358;31077;63454;56407;41492;48603;54020;11627;12401;28051;50000;30296;53023;44276;11386;41427;35634;33942;44753;66755;26901;35814;27328;41142;11791;29916;13034;51881;50846;65641;13878;54054;11809;17049;23427;40112;37995;25189;61486;65950;37321;51970;28780;34853;13800;43103;50331;12699;25676;42829;33957;33263;28409;56016;23106;29419;65932;25058;59270;65640;50841;41320;29875;46456;15881;49303;64116;64819;13402;54255;15484;21588;51577;25149;51489;44746;36435;16882;21380;13867;58986;62467;55567;52179;40389;28443;11385;18762;65360;54425;37681;13499;10579;18749;61937;57470;27926;52523;41523;53709;26431;46599;66088;49988;18753;41776;40089;63418;26543;48559;54658;50900;33050;20583;43376;62880;51619;20779;14971;55289;30838;13220;64695;26179;41058;44498;26580;18414;32070;28560;28144;41375;19715;34680;36940;50213;48295;11513;31491;18311;33035;28407;19307;61779;63357;38691;13104;26897;14434;34811;43352;13437;61070;26294;47415;11394;59540;27512;66003;15480;64218;17414;52085;31293;19759;55947;39541;57835;35704;39107;26645;14016;51429;47766;18341;61600;56758;10456;27414;22372;39350;47512;66102;20555;41066;18446;39966;21697;64734;39316;60278;44983;50306;29478;25487;32699;30688;64725;37615;60093;50700;46511;58076;50024;51859;47016;21403;19633;36325;62545;21498;28679;61091;24795;23265;60265;51600;22811;35759;34795;15740;33175;51740;53871;14079;43896;57967;62287;49568;19652;15618;46827;60954;43294;50581;61500;58908;14882;66572;51683;64788;46319;49663;37586;32064;19100;45573;12364;65252;61182;38692;31719;31389;34202;34611;49379;63857;43892;52822;33889;31710;12534;31144;55234;50828;41222;32954;18528;31413;57607;19605;54286;60310;42397;42235;61595;13956;25775;45121;64176;55358;39402;41901;64525;33653;34296;36005;59791;45753;43869;64825;33529;50441;27635;14512;46036;28219;29998;66966;34114;29948;33410;55805;53764;50393;58530;41318;49874;13678;47816;39953;37981;43811;12723;30024;45398;65716;48373;34349;55787;21088;58358;39184;16467;58651;40633;58350;16558;11136;57779;10902;35127;22957;60113;56153;53537;19709;36266;55029;34941;33760;12031;60989;60757;24546;32314;20073;22960;64258;45183;10516;66553;40729;21475;29548;33989;10433;10293;20671;48359;25453;18903;42740;64119;58182;18159;34004;15628;42605;57259;52839;18945;52486;39209;54585;24918;40494;22504;12045;10766;45045;64033;31205;57201;64352;25581;28192;57751;40312;43023;58838;52278;59564;63907;14883;25698;62766;35824;35082;14843;41014;18302;23955;33567;39169;40177;26624;33225;21440;53215;34373;49198;19980;22162;27904;21231;26037;55173;61802;49107;18565;65076;48281;45632;10583;45332;20516;45816;43541;46307;49561;63003;31258;59113;20639;56170;43110;20231;12230;44832;38910;63694;22733;27576;62571;50652;22010;24752;48203;26034;35567;32086;38201;56769;31294;34604;49909;18622;51467;51232;29176;41164;44245;25215;63027;61210;46094;58683;35813;48805;52793;21396;65207;51481;43771;14319;43044;19902;54239;38581;57900;27237;30808;13463;47335;20700;50449;16580;42107;44727;33200;11919;40770;23067;10172;48169;40404;58528;18924;38577;54160;40120;45896;55434;14798;54306;14299;23241;53584;54223;63145;53363;31647;19998;41343;61366;65802;58294;45319;55896;32462;21950;64039;27286;38497;63997;36187;46537;26193;28695;24179;43451;56018;53307;19984;47724;49457;35501;29399;66709;18721;28708;62022;42684;28184;24193;65145;16632;19934;47223;34913;62034;53362;13746;18816;44090;20800;42844;57317;15528;63099;15404;35231;51341;48705;44836;42440;24690;33551;23698;25013;63620;32037;58713;43295;66955;46859;55596;54079;21524;57971;25688;32522;32538;22777;54833;40800;58154;38989;43355;38301;18921;46111;19573;29584;17175;39622;43298;24351;49264;31842;28832;28835;58092;23455;35863;13481;31650;50723;42890;42145;34848;13846;57033;59154;35743;15244;24403;42428;49613;20301;63383;27410;54876;23945;18767;41237;63549;16254;58583;62196;40627;27523;43934;52067;24821;63510;40382;63755;19089;57345;21369;33812;33417;21457;41055;17680;64225;49272;54227;24819;44353;18026;13563;62877;65191;44062;21422;31521;30402;32670;14997;27922;35335;56215;26187;63700;14372;25510;29850;27289;34959;62202;15458;58343;41280;61717;53777;60193;57325;62841;43068;29032;27218;60937;57168;54344;22881;36927;57437;61560;36184;44837;21237;65787;63309;17656;32030;30466;34830;48529;17814;50750;40621;18763;49254;50827;21792;40555;42847;20545;18832;22268;10052;35803;44818;19431;62270;52540;65803;43622;64357;14833;35470;51497;21568;26291;33209;65829;12659;62608;52786;14343;41381;14420;34837;11462;12297;41325;20087;66184;40011;47071;52125;52017;51435;66237;66418;50384;37949;21530;11329;37536;14395;52111;62381;62044;52674;16718;46729;11300;43422;26095;52153;62185;58070;57664;18746;20679;20519;33976;15750;56451;39959;12392;65305;28058;32078;19107;33449;31520;44650;66690;37605;55564;29923;37024;31612;25905;33848;33750;10982;41098;27540;44001;15139;46753;36884;39639;23736;61579;21766;39917;60973;52606;15180;40093;53756;44639;36859;47513;33143;23377;34610;43061;63966;42127;30298;18064;57716;38641;40202;42063;27491;45024;10690;11187;63785;22112;23128;41084;22477;20095;46240;18297;37279;44947;33420;44608;15031;45302;35369;29857;13850;34360;49417;54717;21715;61960;10983;42176;10405;54347;32115;16829;41081;63802;54126;51926;40034;37334;11601;17806;11045;59239;64833;22382;51960;46999;31662;43757;25321;42554;40918;56815;49861;24605;63009;47849;64958;36068;10321;44058;58507;14618;39623;32149;13605;27841;13611;13964;35188;60373;51430;25777;63529;62847;26925;36632;64040;10944;48786;49968;53935;46075;46167;63074;14623;38378;31631;25780;51718;66740;49686;28914;14858;24235;66037;13886;20324;34798;43156;38929;43303;50443;18995;46433;25646;38986;64810;25148;56073;38261;15961;41889;48306;57714;47701;22763;28756;34937;24897;24578;48680;26807;33677;53373;42671;10057;19779;40355;57696;20386;11592;63207;11444;54060;28947;18854;26562;23994;50130;57161;12754;47830;65650;34597;31191;30634;34328;40550;61948;20340;26727;52741;36935;16557;14611;39293;64917;48804;42148;15004;20610;17260;60643;13229;46370;56469;14565;63077;64391;29493;32905;21193;60493;65084;18540;38866;56536;36953;65399;23958;23862;55952;29576;40134;20866;39585;46084;14893;26557;30458;33021;16402;30431;66203;46351;63736;42805;10534;14265;38117;22058;51217;44761;66527;61019;51328;17555;36942;63224;21761;22345;35489;44541;45273;13412;36512;25584;56465;19352;24045;23742;16728;16064;47384;53035;57421;66248;62549;55852;66893;24626;45108;44133;28923;18381;51395;12604;56058;19008;11185;17296;16117;29983;53107;64930;58744;60828;28730;18344;50719;56449;41475;58974;58954;54922;43434;38294;30012;34509;63727;21764;45498;54423;13260;35965;47426;44421;31122;22529;56650;35359;13701;13356;17569;32100;20264;49461;43905;39699;24083;20162;27682;36558;20044;45408;62422;64127;35042;54269;13120;11193;45980;66207;43036;62476;10071;12756;31385;38863;28319;43178;18224;22223;52112;33607;20278;10564;60017;66949;61584;43104;56428;60576;56441;38461;25778;30278;30001;63925;10949;12461;43473;63639;60900;51848;44556;62254;19691;42501;48160;54894;30857;56608;36823;60247;17406;16896;56064;38815;65220;65436;21445;32379;16496;51572;23608;37538;31149;39800;19802;40456;40944;41195;42295;34945;13635;65311;56093;41419;60158;50874;42623;66132;28533;56120;59567;65580;51775;25458;66651;14726;29943;25779;30597;38417;40896;54549;62623;63847;14267;23352;52504;17535;12325;16511;51216;24451;65788;22011;46912;25869;61333;40338;25051;32338;54964;57640;27848;49851;36407;34190;31063;13480;49296;36155;20182;58689;26443;37453;29645;66927;23730;36654;25488;65760;21679;28161;27749;47231;56760;34462;17678;53472;48969;15793;19465;54771;42377;62596;27300;24773;11330;38061;66031;64735;13707;55069;48613;16085;62859;61912;16333;35162;58054;37777;18409;41338;19470;32786;28507;32813;11798;13132;19849;30756;30521;55799;11719;36913;55482;24899;59451;24674;29200;64286;66172;34821;23924;25916;14095;44623;47477;19541;16011;44831;22911;31724;46454;49700;48904;65318;59514;51042;58084;22100;47401;33190;16416;56136;32108;24317;26707;14419;64608;58184;23673;28897;43239;42129;52299;40344;61254;17228;31498;25081;34598;56951;28352;50733;63534;29470;19697;53226;43309;63071;22788;37501;25285;11770;17404;58360;31049;19537;59213;25416;49323;12781;51214;49290;16848;42264;40170;18912;53842;42327;46714;28333;19788;58387;48428;31571;35312;47083;56241;54430;45012;40552;19641;40610;64998;65669;35472;43012;44451;30566;33635;22916;51079;15230;14180;42874;34670;35628;65478;27185;18277;12687;56420;35601;51720;25030;39215;52972;51743;36597;45284;27350;25239;44601;48499;42912;39290;25471;25705;30748;60735;37807;46769;60553;34924;15925;64815;43310;10014;56750;56240;16593;22425;45015;53044;15216;24828;40176;61338;48465;40553;53288;14223;43441;12441;44915;55100;49889;13828;32622;22318;45627;54608;52311;45452;27676;50540;28894;11065;66839;63648;24273;15671;49680;40750;38621;36175;40544;58165;49169;23512;15293;55199;28515;54119;29697;32113;60421;65136;23481;30263;32170;11019;47417;45205;15201;42592;30019;37061;20650;58116;21865;28135;41831;28311;24533;23721;13769;40025;43553;43654;35401;64464;34601;12930;32027;11895;52781;32453;43415;66179;53114;53437;65846;30536;32021;11832;46458;36285;28811;58503;30428;63023;10126;56897;56300;58599;48574;13204;35395;36320;18139;61999;38225;65329;35799;22906;13502;21714;46096;20748;37853;56103;59336;11140;37690;33042;22521;58556;32523;38119;14676;22707;50474;32667;22052;33511;53956;12872;52585;40215;60225;48588;60058;19087;27466;65654;16470;48644;16890;48369;43560;36372;60793;66266;65294;63636;53476;42050;40205;27462;66706;26665;30887;12493;43862;57027;35496;47875;29061;57526;26861;39854;59287;51314;53577;13320;13051;16322;59179;66177;52223;14401;45647;15863;60258;45370;19677;14359;37263;41763;38429;23175;47811;24363;20079;31765;54882;10143;34783;16143;30290;56174;61475;18423;25053;46953;24668;28247;16122;12971;20035;53392;52725;35709;56569;31927;60272;54976;64345;22233;29932;24592;65374;49903;62198;31626;48181;19208;35636;66262;29640;35481;58319;48719;22050;35164;10562;45872;43088;60773;49622;54175;50429;50699;50925;57485;37858;48217;25879;57122;20677;23575;53829;23012;21017;22353;16454;64457;15379;11871;51963;55518;63098;42968;43282;34869;40724;32119;35385;29355;41579;22171;17377;20738;65042;55060;35802;51777;28035;52033;60008;51424;60840;36088;41713;57170;56472;38584;42778;15815;37463;14865;63942;34325;44654;61934;34098;16244;64026;43825;22373;17102;17457;13884;57416;34779;14200;62546;10196;63586;33692;26102;55907;42730;22281;52264;37685;29730;40885;63219;15036;47635;60914;28324;39363;18855;22277;65502;51463;55492;24270;26526;62204;30013;33111;20600;57089;48269;55160;62937;47418;20128;25689;45737;21750;53179;65239;64681;62259;59329;18147;26670;19967;45000;37018;32810;21702;45778;43901;27210;46545;45072;11086;54754;19787;47141;43786;17434;41469;41751;37434;30204;25939;63486;11694;26353;36459;32060;27804;56339;26211;46792;63546;41706;27091;20004;35081;42167;24720;61164;25835;25554;35521;40376;43259;34587;11064;14096;60753;54728;27819;14163;21739;32301;12256;20589;51980;57741;37719;19218;15280;15850;11542;13558;33166;65700;35202;48349;58021;65334;25611;25592;42884;37046;31636;26141;48442;18744;38881;60289;60746;23431;18148;49141;16430;30339;23667;61484;50955;50948;38176;48438;29543;23675;36970;20887;15402;25991;57154;13297;10176;37423;59996;23010;28421;44712;31775;40688;44583;60658;14464;49778;56289;20651;52241;54528;65845;44810;11500;55405;36231;62858;43226;41051;47435;29333;50671;57728;54538;37555;12738;33776;14784;26695;27993;38709;14706;54721;61825;40906;28970;13092;58470;66222;58680;12655;24261;31262;51700;24181;61002;55645;35165;23073;39867;38011;60235;23714;25207;55756;51579;42972;60489;20103;28364;48645;22850;30437;41989;47482;60134;18240;38247;26090;54258;42332;47172;62021;57469;48825;66532;61852;53270;49786;24911;53262;20620;12759;18653;50310;24620;11587;33780;65514;23396;16462;18353;12514;26032;57651;15680;17822;34787;23505;57980;52738;16173;62648;43217;36398;39237;23208;16669;49498;52645;38059;14283;64933;22064;18194;53130;32764;16975;45806;58365;43029;45779;17424;63063;59989;30284;29027;30875;16562;46236;44744;57611;23888;43149;22500;64476;38635;16813;56252;44822;16883;19109;61157;25225;47377;29138;50614;18553;30159;66061;15819;39138;47112;20461;51762;49113;12496;43715;31286;16465;57300;33441;14122;39573;17799;12744;51990;15731;50660;58603;60139;39446;43571;31234;30005;52225;55544;15967;59665;10722;36541;17754;26177;29219;45139;21804;44240;37230;21372;60503;57218;20229;18268;32208;31629;19704;12508;63171;58590;41351;65384;25103;23055;61716;21590;30070;42766;63849;30395;44673;18401;56408;34316;13675;64294;29967;34819;42298;26569;26635;26281;11199;11459;30209;46453;64688;26908;55582;53504;21325;26700;32089;11866;46431;39691;38489;30139;32409;10660;25859;47190;63705;13161;66607;18354;44515;58445;50129;10891;17024;60675;39196;55573;40778;26094;41374;61249;25438;57392;10743;51801;56494;39311;17295;27860;56316;32963;43996;28745;25538;18570;45486;58361;59618;57401;16471;12094;21895;18298;35957;40606;53527;30956;52027;14905;65632;54280;46709;39728;24331;66398;56877;41478;47515;49405;28264;37229;59177;52343;27203;62158;22300;13306;58761;37857;57880;16696;58567;56509;13256;27556;61593;35152;19464;39597;30235;63282;11175;17189;25954;51927;52316;28921;40145;24142;32365;36801;55090;33284;33041;23006;41366;42992;23260;19842;25481;29417;20618;57946;32026;14507;53069;12249;42199;29546;63820;55126;58859;19231;40745;44323;65340;48245;10827;22211;32499;36870;45649;39968;44887;58972;14526;15520;20167;62901;58201;44435;56065;31983;27951;12310;46485;61137;41700;57462;29172;36387;22354;50152;41539;11639;63939;21789;62312;40871;40127;40309;44693;14300;32323;28233;44561;15977;54114;53167;33527;16554;51446;63899;28124;23723;66754;48152;48311;33463;46352;45914;42185;21242;44167;58155;24208;10898;50207;35538;46949;17286;13503;16707;16845;20939;50229;18393;25972;34588;41257;23841;43509;58270;49741;35492;57737;31109;18473;17557;61433;25354;54093;50506;59082;53656;46274;58621;22744;21412;49312;14723;59580;19202;53950;15856;10693;56973;28388;23205;36765;39060;60684;59425;49685;38767;15096;39871;46670;10591;47803;21218;30745;22880;34711;30902;39106;24061;13101;37560;64136;14137;39136;39886;37633;54132;39014;47035;45719;61285;29180;10750;30099;23514;42015;44043;45674;23771;19446;57870;48425;14916;36176;44934;66199;28603;30027;30539;33423;49088;44488;47502;44574;43728;32424;18691;36109;20635;22747;55889;15974;11801;16203;20391;37364;64575;55406;34723;14921;13643;22901;49617;24928;48782;48824;59816;50668;20288;55379;27274;52074;41737;26758;35840;47331;59770;24471;64037;29895;43839;36544;49974;12434;53563;26133;14950;23874;60872;25612;30248;27789;66474;43494;43234;30830;12335;26965;29179;51287;15168;10996;57221;59420;44105;59704;64051;38865;40805;43410;51650;15518;39893;66495;46140;49831;49020;60095;62960;57713;31069;40230;12476;56100;59458;56413;16387;14210;40953;25095;30429;41118;37283;51093;13586;56544;54472;50571;54250;26788;66268;30173;25426;59992;48955;22161;51921;19966;43628;44224;63748;58928;37497;14710;22287;57312;27999;57294;61175;27624;46068;52410;57610;22592;30716;45675;33798;54405;11781;25152;46813;55522;46348;25975;45097;63326;46541;28883;32785;39828;65877;49737;31241;37278;63612;60530;33837;66220;27068;54547;52538;31923;62747;49881;47548;22655;56922;22055;58715;16263;52914;24096;58482;64229;50866;29955;41223;24534;50404;19612;25378;23661;19018;24428;34794;43775;55196;24161;39763;37235;23895;52569;56161;32558;54835;30472;26637;57145;57918;14918;32657;12539;51266;48327;31297;39698;64927;49398;10849;56040;32186;56123;56570;65317;52979;63571;22081;52684;33507;10973;46602;10166;42760;25902;46316;57074;22541;40545;34947;63500;49166;20125;47557;11707;31801;39417;61220;58203;65325;42337;49503;28177;49964;19479;54979;51876;57928;32495;53843;14624;61415;62255;66659;15382;55167;14717;27515;62197;58563;31357;52707;43865;30936;56482;58342;46210;27344;41071;63835;50595;45245;19985;28001;64130;37988;28836;46902;18335;41369;51137;35695;17358;24009;55324;28988;49308;58964;51092;40581;40335;19046;24418;60924;61031;60825;37926;17800;38329;21470;31143;16697;34351;21318;62784;31938;29331;30901;58591;57826;62069;40002;55676;12615;31375;60532;48381;53920;14312;52026;34962;30502;15852;28724;49311;66545;52801;52054;40284;18273;38331;47476;32180;19020;63332;53109;50338;30535;31609;33543;17298;40178;64521;24852;64246;28954;64990;31057;16380;27329;35598;29369;43610;38688;63234;55187;34138;60124;65156;18941;25219;60488;52029;60437;35619;63530;19924;40149;56491;42455;45594;59296;51887;23559;51168;65677;11786;22536;18462;44567;66515;25482;16222;13763;52461;28073;36360;13812;18025;66933;64118;14739;43271;52500;28726;46795;29123;53276;26164;32416;52757;32751;56892;29519;25042;39399;29449;23266;49668;53380;19447;13937;11130;17513;57775;54572;62389;65454;17563;64899;11410;24082;66834;25820;14462;30881;62151;15770;41311;32727;40488;55685;25628;25815;57862;39964;60151;28213;28792;48907;50745;55269;30641;24169;22172;57178;24034;30712;44634;19744;21850;45915;13096;65390;41554;52566;29901;13018;15883;13095;36403;45369;38915;38153;55911;10654;60719;51300;63804;62977;38155;58817;45667;15728;10907;28357;61331;61787;13813;60059;18251;19442;64687;57417;65908;42086;36865;61196;62621;44312;47461;49529;65626;20397;59436;10895;29992;33747;12933;19110;43758;63872;27766;23456;61206;46535;58889;26370;52921;39172;32820;24445;62240;37276;25818;36659;53176;18590;49165;28855;43891;10651;41471;64318;14123;11362;43100;18408;33726;33413;22864;28246;12610;15279;62296;54523;29476;37262;32817;19289;47301;30851;46790;27389;40753;25375;34115;35506;50774;37994;48702;11454;12652;49984;35797;54590;63093;15397;61882;38457;47526;54859;63602;24024;40448;37033;24174;15055;55101;10816;57858;15687;31544;32308;64510;63564;45380;46700;18304;43740;63060;49785;53945;39415;66018;36437;41479;13980;58730;40156;60244;29733;43211;63652;45909;52909;53295;38115;38980;32718;43994;58966;16277;21773;19613;54131;43114;40484;59344;40521;48830;66157;31055;23746;62769;46251;31306;31963;25677;41392;46489;56884;46628;31831;26777;21811;48784;44194;38245;50837;66174;42659;45673;52773;12737;46942;16012;12438;30552;63668;37825;59909;58898;45878;19751;56267;48291;16565;23158;28012;61456;38750;20354;66239;44309;26628;13513;37388;47090;30693;50738;45928;61563;54123;66564;45203;41221;22328;53705;13158;62625;52596;30651;59677;41486;18083;37121;46640;40035;62827;62941;27173;41279;34071;40658;52723;12241;12842;46309;26996;13022;13258;14203;24122;40540;32934;42878;13778;43069;33545;31432;17370;23880;64913;47704;20500;48197;66533;65036;27810;45506;27448;44715;22053;23493;42886;50965;63000;57731;39381;15331;21515;57018;35587;59465;37011;64611;51063;36489;47754;53007;17584;36653;39520;26276;66946;62363;11734;62774;39631;14705;66282;48507;30616;25340;48392;26194;44154;12011;59146;52546;36693;48803;40133;43600;48419;25169;12925;14152;43464;39668;20947;62602;50003;14258;38654;28157;60402;35059;65652;11174;53185;53701;57622;37998;15942;66384;10420;35446;45850;21898;38650;62339;30435;50022;52508;30076;12771;39555;52544;60889;21671;58196;28171;24688;22276;58942;43883;40813;15047;21716;10105;50325;37307;52381;34177;20835;12876;13475;18467;62629;27288;12309;27306;12124;24027;62172;33702;54170;32361;58260;13818;40656;34243;22083;36033;38931;50283;16908;10993;39283;64000;21169;35620;50436;65645;62731;49154;46728;37930;13045;51171;26652;62523;56332;55414;31824;17364;10762;66471;16897;65591;65881;32626;36260;57838;16053;26420;14269;52989;27341;33031;64371;65558;49030;44924;54009;65223;63799;17494;46752;40346;59631;27052;10250;37662;40114;53596;34580;27713;40757;29475;15733;46935;58299;56606;56530;24708;56803;63210;63321;63183;52845;27665;58533;60072;32400;53228;22273;17475;62362;38338;10754;42922;32203;17168;30865;42596;37045;38005;53809;11499;61513;39987;53310;56116;50128;42201;49036;43904;29256;13639;55260;44962;58593;66071;53148;25754;46062;66158;51688;19535;65615;23358;60711;47153;66753;11996;60911;38302;24202;60604;13630;56523;65114;21332;14845;29141;18564;25328;44545;31350;22227;53730;58466;58188;48161;27264;36604;48232;52053;43129;38400;37657;46402;20268;19422;45347;21632;62779;17164;54884;45986;63225;35079;62662;63844;42140;46242;65546;43686;37224;20891;52269;30825;20434;58529;54082;41466;56360;38165;14478;62978;60109;57921;28772;35583;50771;62276;54860;39554;47632;31588;43619;61947;25161;64048;60631;16450;58670;37268;27590;52609;43041;20649;39098;12583;49292;52129;42431;48748;16625;53570;51853;41746;35375;54487;26641;39166;12409;50079;44314;17297;30831;20156;41648;53658;40713;35028;37299;36639;17994;57352;40947;36304;59126;57402;57051;22040;37608;25722;43240;28393;50936;19585;24089;54853;56924;43990;38276;55681;61449;59151;43908;47452;62835;61713;27383;33801;51318;14314;35384;28830;52534;31206;49636;24155;58515;47680;13172;43777;53381;61335;26003;43952;56956;48234;43847;25073;50037;31899;33855;16619;25446;35136;23026;39043;48728;39053;12770;50215;46087;37789;50147;31668;15666;38272;23858;38797;35856;41711;15841;65039;20384;49919;61936;29522;17207;31857;22154;15988;61308;33004;66073;65556;26099;47486;32555;41391;25868;19038;40495;35585;32847;52705;26916;33669;33331;61046;29646;66284;49233;45700;56853;20171;26682;57271;62065;20716;64754;44187;44232;60540;52885;56845;40436;30117;10493;58640;59205;47562;42863;16323;63239;32313;30471;40527;42374;61867;14620;42502;47831;36638;48717;41079;15085;18426;23729;12899;13380;29173;14994;25102;57434;33171;53082;32861;42150;22332;23351;36663;25768;46762;45662;43486;63698;42485;57702;52789;53565;14640;22896;24941;20114;39075;65045;47677;66355;23494;48384;41974;34105;56979;24728;64433;45677;33062;15905;37805;20655;56515;61007;58882;64449;36984;37706;57399;47457;27463;65258;43111;21393;29136;59976;40511;44891;64383;22225;15429;34576;27818;26650;25425;10681;46490;66352;21827;32375;34330;25262;61177;50650;40651;28300;10049;35732;42633;53079;32600;48899;49100;59660;34564;56229;58606;33599;65043;51866;15178;30307;40764;37645;44419;49063;42700;21822;60533;52542;59608;37297;57189;15346;49126;31168;65157;40649;49578;29621;29707;46632;57427;31589;47667;43691;51365;22846;25607;20005;60490;47801;12366;42644;66889;40157;47727;25583;13550;15911;54506;47322;36229;11492;50532;53869;11687;64185;16572;43681;17492;60464;21222;62124;22142;31081;19685;43909;59187;26675;10252;39748;31916;49294;23637;44984;30893;66915;42892;21512;48336;55542;23909;55874;38327;14944;64959;37440;50387;43037;42695;53146;65916;50786;59741;19467;27351;42160;65498;13835;30814;15152;22808;20502;44737;37491;38177;16985;36346;47228;24661;41505;59762;24044;20888;46855;29271;43924;61748;18165;52080;59690;23695;34322;63661;11096;64377;45316;20106;42930;47276;46577;33163;65000;41556;17292;30692;15866;44793;13932;14165;39091;24949;65345;42234;27646;51307;52899;19637;56991;22234;54428;43946;55887;49917;43874;10097;41213;66408;20941;23062;23269;49702;27992;55079;57229;11117;22616;21173;64617;33560;12707;33419;19211;32438;54866;66051;32053;62406;18128;47146;34899;10443;29017;13118;40963;13013;37979;62611;11157;43535;49631;53034;18131;33231;60416;58909;36396;14560;26190;22243;13451;54817;13627;16081;12553;41952;20498;63206;19299;16711;38906;11460;33112;61908;14549;56887;55876;31051;48915;20100;63421;61364;12777;54504;53700;49825;25088;29294;59808;53417;37411;48260;40743;46004;43353;29112;40616;53244;14797;52412;44708;20961;31326;31254;44906;27685;17725;36253;53039;25802;15128;60399;59442;36012;15877;46295;28562;36371;58366;55008;58304;11746;59589;32482;63916;50993;34412;17386;28007;48895;20184;22367;49135;37167;53994;36103;49353;16675;56728;46373;31568;43653;22378;15086;42339;12805;53910;25929;21125;22403;31625;28500;25809;36419;24517;48273;57924;62393;56345;33406;28920;66741;29015;57196;38017;36321;18641;15156;64675;24881;20815;63885;64805;28956;22534;16634;66124;50801;12775;33224;21946;38945;21482;61061;63029;54971;52107;19678;27689;24824;15593;56635;33999;11030;33900;25278;61968;51674;31405;26298;21779;18125;12577;27150;25241;52951;29851;34600;40084;40091;20208;54089;38014;43249;39542;64214;37702;22520;49348;24539;42251;27643;66605;23340;33628;17121;58001;12972;32672;43261;16506;50390;38270;12331;52943;42991;36614;61654;50873;64204;32912;28301;30436;46797;41633;58039;33288;35406;52444;49313;51044;40703;37816;29863;59022;30220;15408;21188;42500;37545;32015;27452;61863;62641;25648;66783;23649;17782;49635;44460;31973;57361;52574;31856;20491;59794;57055;31273;25218;22989;19323;56432;36198;40567;15312;45565;34041;26178;29106;64504;41956;36294;59103;19180;25046;51164;32322;63443;58443;30703;38984;19817;55460;14081;58112;38388;65269;13775;14680;37727;26546;20877;51517;42383;50410;28829;60463;41349;57979;26926;41022;61097;17073;33253;55376;46555;32221;34966;65075;23126;25198;60901;66116;55317;61221;43941;65836;18163;34244;35054;49901;50264;11242;24392;44536;61696;65028;59312;15565;62897;53985;23087;22096;26238;11260;62674;10531;25955;55746;61033;56622;19414;36945;18733;11144;35355;25109;44507;55948;35154;39313;12743;47853;26805;59766;25316;10941;21598;64425;23013;10844;13961;53260;35210;64257;35906;57707;48182;33430;25098;49337;31552;36500;30357;41835;39971;31296;44684;62633;36610;25796;28353;28259;59907;27454;39152;52277;19726;15319;52249;21565;19261;33489;59292;62807;42957;20338;58416;19232;22179;25401;47893;33026;10616;40014;59209;16514;37872;32095;28229;20451;53097;51678;58917;23203;22716;55531;61681;59237;33202;17729;30765;58881;19090;41180;54305;64514;41024;51536;45923;60176;62973;56489;53360;46808;52658;47158;40039;18988;23401;19129;56364;22899;57407;22327;64066;43684;60499;60739;11914;16831;41635;41007;41788;23245;11345;23860;32283;45784;20136;16663;39302;12913;28789;22402;16458;66898;31129;28907;42144;54151;24192;17031;39231;36036;25786;22126;56823;50894;37549;10932;12608;10506;63791;18842;41316;33868;30507;10840;49494;17640;17840;34034;66681;39810;41682;65874;37919;58257;20057;65962;63909;59193;15805;54932;24162;42634;32264;12478;61938;40285;46263;58949;43233;60282;61277;26991;24454;60625;36906;26889;27017;56222;27276;27400;41497;50419;52426;26030;23885;53599;31393;12354;10648;51567;55775;39569;59282;15049;25771;49112;33633;23308;24288;43186;15611;26387;63821;32587;21336;19142;42103;51215;38891;26401;24077;51192;60824;34441;27189;38794;23390;43210;39707;29930;31452;37072;20601;29861;16250;50962;48700;55166;49489;66850;42403;18107;62789;38402;42198;22675;33215;41953;66118;35259;55845;48385;49122;48329;12468;43911;22969;18936;41017;29741;40942;50114;11624;41230;56272;39658;44902;37661;54198;21277;43747;60082;11906;60435;63304;57482;21244;36137;60054;29340;27038;20509;19914;30043;38496;21832;64329;35710;64242;24957;18515;61501;13908;42221;17080;62743;53320;40220;54395;40037;50055;11931;55202;46705;62909;60806;20637;56625;49061;33564;24612;46615;22124;61393;61237;17995;63320;38346;24336;23789;31817;46356;35836;17103;10578;16505;51089;35902;42795;42903;60836;29379;64044;28450;55581;53820;25470;36642;50455;55346;34132;43843;58552;49279;44003;56208;60460;51132;40886;58436;55423;45199;29838;19755;30754;23385;55997;20992;44892;52175;53151;19979;37744;26654;45523;62064;65273;36146;29945;45123;15321;24154;33971;46778;54925;61683;64756;30118;43969;54577;28224;31216;47537;31907;48426;13100;22213;29266;14145;32290;26056;40183;39811;26127;39230;63744;56701;29025;44208;16853;55353;24391;32506;36712;17403;37109;60597;21659;46643;23275;65204;14653;32938;34271;58662;62082;14847;37324;52671;38333;10656;34053;42225;57777;22514;61607;52108;53909;15197;14497;16771;51965;43791;41761;22840;11524;35465;28423;24415;51942;16213;61941;53921;40579;57817;43696;49184;52151;21698;54455;51357;39137;32394;11239;35503;14360;28208;24489;54266;43092;61339;12482;20111;41969;42637;61659;24847;31911;36773;50798;33220;21016;17453;46463;39995;42964;54115;30363;63938;61594;33114;57932;46774;43641;48903;51484;13974;56889;42304;35013;16962;60071;15812;58820;25964;13303;19632;50062;61599;16421;44995;46462;57516;55930;41960;34724;14391;39477;65968;22912;41129;54955;16091;52667;19866;11599;27473;24845;66498;49547;25624;62896;38925;10695;24866;57053;64437;40419;25317;28109;56114;60966;26834;23399;64993;15955;43877;35675;59524;36652;34283;49467;49812;31991;65815;63022;29488;64054;41348;47857;43545;27591;36147;20197;33842;59251;42402;50958;27171;30281;41674;57686;62161;24914;32986;50138;61429;11605;31555;25923;20260;57440;46924;53814;63167;29534;51193;34839;32946;10426;21308;28400;65255;44636;53715;36667;11388;18868;62763;42175;24812;55683;21421;55693;61495;22084;62371;31022;66505;22540;60577;25887;23072;52167;31359;15193;44437;47851;21025;59413;47506;65211;36907;49297;16519;14683;38325;55919;58722;11911;57658;10715;35590;46638;22781;58547;43199;15854;45440;10297;28165;58629;25847;12340;17417;45279;22619;12001;24677;12255;18326;26057;21477;49096;40989;44020;62133;33091;56263;65816;65864;43841;19326;36013;35577;21091;38083;46737;61228;19171;29603;12369;26797;39904;43099;10696;51111;21509;19705;55310;39353;26955;40582;29996;60291;29073;42970;46650;14801;65883;14509;38747;42453;55534;30140;61232;33802;57594;33612;36581;41919;38421;13099;26982;26059;66060;11358;17467;39765;27083;34086;11051;22151;51163;60865;58465;59572;59563;54872;32350;28913;13234;50298;23200;55437;36503;15356;52489;49425;60306;66120;54298;62301;24424;21667;17596;40172;14030;12126;29013;44682;60378;41566;28473;19094;59750;17354;61425;64838;48218;29074;39328;51047;27381;58999;12363;66542;10916;24733;50744;42997;41377;49236;36848;26180;45144;56782;19401;19797;51100;36174;36734;53936;24241;20511;20215;15160;26815;45174;36833;30272;58458;35041;16642;31365;48998;25503;15591;47099;66091;63935;14216;33429;20796;40931;58115;29751;65500;35097;55809;30848;29642;43971;58104;50923;62653;24123;20202;61866;35265;22867;56591;66704;41833;19819;28565;45750;49201;24467;33199;41189;34814;27211;18104;39447;22560;17542;18648;37470;56503;30480;40013;21856;22385;16750;47490;34143;50464;54806;18663;48991;36024;24115;66613;44728;26842;54559;60599;30137;40466;48829;50102;58840;42209;32840;30585;45187;28828;25273;25517;60784;44462;54159;59765;49671;56532;50886;21469;56387;29363;38397;30136;11139;64612;54479;37781;19060;53598;22481;37037;21322;52300;24381;24563;19043;35261;55143;25522;55087;28994;27843;20049;30310;14750;65992;35390;11577;34769;60301;41252;52591;65181;50496;52389;46864;44073;23075;49484;29235;66829;15659;57182;48659;65066;11908;26053;60485;65709;30047;26690;44412;43457;31268;60546;11152;19312;48701;26271;21910;30697;34524;51811;14566;16016;50813;32391;37931;41548;15555;41715;64497;60525;25077;37975;59058;62529;28190;34688;51525;51401;31605;30353;46332;12333;47313;49584;32396;37200;53558;18225;27453;44432;53252;40965;25212;24814;24580;64283;49205;52498;54331;21438;22366;22041;28414;32513;10371;12572;40047;30805;63922;36083;27729;64310;55387;36585;37280;29735;25732;27335;43949;16371;40103;36955;56349;57423;33350;28793;50899;27029;37804;64367;21472;20542;61145;35515;22816;56148;46584;56561;58781;31844;14218;30007;12951;48843;60663;27763;14309;40189;53204;53158;65824;16651;28588;65467;21722;38432;37613;23257;54409;53299;26629;39000;54980;31124;54760;18137;64821;66660;46556;61453;24679;11766;50323;35614;18543;32353;63674;62961;57662;25931;31738;30846;25135;19222;44328;51364;55786;52275;54129;45145;24292;40444;59739;18081;50495;61723;36844;40486;18644;39320;52983;44282;23467;33362;16605;32340;37001;37577;58160;57994;22815;31203;34453;28584;64717;55473;18073;24737;59165;14229;27592;32677;47395;10901;62656;18044;30942;18057;49843;24416;59724;44600;23517;17633;12630;34227;21676;55622;63489;66793;52428;56914;45937;43658;30111;11261;32398;36114;50947;63164;57763;11375;46218;12993;25024;39066;10152;52588;55238;22185;57179;55407;62803;12923;14338;13762;12605;13863;44874;29918;33063;50211;43964;34964;34726;35368;14428;45443;10002;12891;26595;40851;17532;47601;12826;32620;38708;66324;22051;42628;21846;54635;65251;52812;50058;65925;23225;41666;53322;52831;26108;53505;18269;61371;54807;33950;24691;18981;55877;65064;61252;45026;27075;36411;46702;57069;20510;59701;30462;16251;47070;16029;23903;50177;13568;47800;44719;11176;46467;66923;50195;63091;43483;26579;35523;52686;50661;51547;33294;37168;35825;16612;32695;63457;66064;21039;26391;41789;56592;12407;10985;42114;43627;50012;42123;36713;57324;40206;20662;25560;36399;65418;55157;54274;44609;59299;37435;34554;45505;31901;46894;54352;41724;44087;63763;41077;23754;30632;19016;12784;28810;62460;41542;13621;60136;54473;39593;13806;42215;29343;57644;60743;31897;46594;14936;53923;48637;36686;40862;65698;58601;53183;58390;45137;30275;25970;35337;50269;10577;50450;43688;48248;14662;60702;22460;34409;29759;39470;13491;26612;19901;23971;29907;51696;21743;60608;25230;39452;15936;23536;65129;55512;65331;42800;14802;51414;48433;36234;55862;34261;17288;39132;59784;32349;54586;11619;35998;66063;52879;17070;63449;11612;23702;39040;42060;53760;17282;33085;12988;58108;51224;66873;59069;14062;43763;31053;23647;32872;49695;35531;30050;63367;32099;66678;14531;45941;36871;47179;11526;64758;21608;58473;31834;60042;30963;20352;31189;56881;37438;43940;45589;33348;58336;22380;43662;18549;42630;42635;30723;66743;56600;63081;28766;16385;24296;42581;15824;15430;31064;63371;15265;22015;26899;60120;34357;25793;11629;30630;15534;33098;56439;30854;14366;60379;46550;13178;36529;64841;63708;18681;44136;35510;30607;55195;57061;51273;10790;38160;41572;17074;50978;29262;51112;45116;28282;31239;21909;44308;43767;45479;21121;53939;58983;19189;12912;41389;22121;47556;41922;44602;47523;12911;65382;13453;64659;32464;56809;66164;58526;10346;63301;65336;22790;49630;45776;16033;16971;32668;37793;57978;62676;10744;25516;46110;47220;48793;50768;47072;41774;10462;35831;19469;17122;37944;49979;64944;46554;53000;12625;17650;11022;51303;64979;15131;52404;38356;26636;47615;60572;13708;32049;50931;40971;25618;16613;38249;23300;35973;28042;36464;29067;54139;44865;44175;40687;43253;41613;65324;19017;43980;24378;52869;30623;49471;10402;21310;19420;60066;60875;57323;46783;43476;29968;60934;48590;52069;15246;52142;28934;17275;18785;47673;23938;43176;32845;57286;43594;58641;31085;16809;38086;28410;22065;60814;16995;19620;11764;23741;65997;13682;26318;16591;17761;29572;52073;58226;62518;44644;34644;42482;32696;51178;27095;12959;37271;15129;19608;30919;62702;53655;65852;22020;43611;15872;16955;49738;16319;28552;56644;50216;63775;60633;48506;53808;53611;33979;24104;62403;38519;41196;23079;24001;64482;23098;66053;50011;58147;59984;54295;11160;50953;14191;21693;53893;15893;40837;30561;14610;42954;23470;65822;32975;13737;47399;43692;42865;64187;57567;51356;47768;20159;26939;38375;55464;56232;61205;60870;42291;25495;11255;46419;20135;14090;41150;55980;36745;20568;18683;31865;62080;35376;12633;58460;28433;55094;26666;10957;26756;14104;57148;38066;49187;48513;39129;23438;45809;34200;20480;36786;19182;47747;58891;45859;56160;25125;29240;15472;20016;14292;44189;41258;42660;15862;58138;42769;46617;55127;62931;21353;20751;50903;57356;21263;62141;39610;39092;11297;22919;21586;48767;61791;55807;64480;28478;32874;66267;62057;52022;39672;31089;40765;24343;64850;27212;44012;20897;63218;48763;57834;14911;36692;62799;35968;41783;32318;42133;16048;18255;13624;65863;33033;16741;48183;56445;17027;18482;40796;50122;62751;61481;35877;45900;60248;61686;50360;21726;13881;34963;22685;26880;55960;20250;54166;43116;13957;24523;22718;56904;30058;53012;37700;22796;18761;23001;42354;37493;44922;54957;24969;50164;55259;59363;30913;44343;61662;46914;51915;34846;36297;59300;30252;52982;56238;37897;36864;15653;23793;53743;54972;31619;52174;30160;30292;38319;40256;25926;11465;23716;29145;42506;13001;19297;11872;29681;17805;27828;59833;20611;41124;24876;23640;27599;30217;22299;46943;13795;34312;50715;41577;25532;34972;45985;61845;16815;13965;48999;55682;45040;30743;44540;10422;29782;63975;33963;38256;47034;29625;26554;58793;63710;39963;50046;66166;35841;31822;33078;59007;53647;30653;28651;35656;49443;14956;12746;30257;54729;65944;45032;47817;22835;45558;60923;36330;12101;39557;17172;40674;41688;36647;35541;50424;59272;26877;47616;10264;27939;37951;34802;53748;44107;11442;66307;17609;64969;19917;27363;53170;25596;47629;50036;49597;63075;50252;34707;42577;24572;61895;24551;13323;44408;15001;54204;40794;25107;12372;37387;48682;19457;56290;24257;53388;45800;39345;29429;36395;41012;12123;16186;13393;39330;58773;51211;19687;65083;50320;59743;65985;24671;62497;60491;35302;43362;47169;53377;34063;65272;21979;66160;35936;31999;12010;20663;38914;53793;11449;60314;47651;45525;65159;62755;22580;58488;64665;13309;31228;32128;28049;12722;65984;10542;51377;18791;54012;28277;33969;46563;42059;31435;19536;29745;22125;16432;40185;46057;26904;45745;14744;36093;15665;17179;29933;31330;11606;25794;48206;20321;46832;31949;15818;34562;13958;18713;23051;32860;18754;64133;59039;59166;14862;20562;51003;53371;57249;44264;32853;13759;63848;10432;24809;13963;50735;49847;19672;55086;50743;13129;32864;65341;20323;15857;61189;35504;60449;13822;15011;30700;55438;58855;31260;42040;31238;12509;22296;47265;40029;30530;25654;51310;15414;48746;49153;22553;49448;64832;11711;13926;65871;26423;28979;15896;26457;40240;37139;32168;66675;59955;62084;22458;18416;31323;24767;55707;65851;65893;12265;13510;45156;35829;25831;56487;61974;44210;35718;57637;58592;63576;15248;15014;46546;49748;57813;18956;27175;31953;37303;28739;12715;48233;39766;46976;33575;35141;46048;39461;55965;44679;62121;66516;10203;44220;54243;16439;22837;14308;41225;30156;61553;61728;14502;44022;31135;34240;33852;35793;11270;38383;35975;62305;57135;24420;33416;51281;47631;20652;52525;41838;64523;27106;10345;18405;30601;16190;15236;35304;36077;19904;11020;59967;66188;13990;59811;52240;10040;63559;61596;66004;65412;18871;18034;25037;43987;43228;42277;42813;49763;20417;49797;21104;37270;51514;55296;15224;61627;46865;61460;62486;22073;62329;23288;15260;39885;31733;54489;45772;14005;54411;23881;12963;55570;38529;63794;17818;23692;32931;41986;56394;39133;39518;43529;23522;28654;53982;62005;27642;29080;27487;23096;24340;59715;51005;54279;12087;31601;66667;54345;14514;15133;16825;17148;48481;57241;11286;18755;42457;58194;55393;28564;57388;66277;61375;47550;61496;43878;64844;18181;45528;16832;54637;55123;57273;65385;43518;33396;56074;24823;42479;32532;25739;34640;58696;28690;35229;13497;12861;65565;30393;54404;29425;38299;22966;29598;35605;12829;13934;60878;13988;46241;20740;15194;57492;32363;26545;59570;37326;52306;64760;12329;25397;21234;51922;32839;66436;41158;19642;61957;58944;60843;15685;66577;34552;14856;50767;59163;55698;26548;50277;65667;47532;27816;45657;59366;17068;43596;29158;45291;44605;41091;24868;36112;12403;18150;24287;59418;47021;32178;57665;21703;62852;48441;53102;45557;34058;51706;36845;11190;65152;14780;45129;17611;41102;44726;53876;64581;62690;53269;54186;25540;60535;58746;22222;36519;56025;45148;52753;39265;62443;36182;45975;43507;19863;52706;45812;65959;42252;43548;56429;25112;48251;65855;39686;35910;27053;40785;66294;28098;39798;22700;41103;20794;42475;63370;33326;24641;55365;21442;35167;40292;11541;46997;54002;65213;51285;62555;37531;44857;20365;49640;52602;54442;61126;59444;57669;66650;61088;41842;44049;60015;18659;23660;42420;18534;40602;33145;50040;45086;18640;36584;44754;40532;65013;42398;65806;56199;22833;11894;29633;42192;56868;28713;19728;22608;14285;35911;46387;47264;62716;29715;29744;40469;40070;23623;19494;50516;11731;43304;39207;11521;40190;43927;64338;53468;59916;15210;28021;32952;17338;42670;55649;52742;54165;26867;20372;63343;44525;11494;47630;39795;33084;23057;40908;46945;48963;38134;14642;62016;22431;34559;30334;48512;62864;45304;57793;65420;41215;13206;50266;38624;44762;18095;47520;61564;40742;60065;25645;39101;19216;45626;63516;60929;57127;18378;31917;40682;37370;34218;40396;47765;13418;38304;15884;44053;49815;21540;42309;28714;22570;59915;21235;66594;31427;23768;32050;16495;39516;27989;55489;51260;58093;53665;44319;31843;14938;46652;47659;62456;34961;11610;54147;10037;14609;39790;66333;37729;57951;40910;57626;19096;49124;52397;43623;17685;60592;49559;66272;21720;60955;37961;38734;15110;50739;21637;33203;40109;19042;28893;29946;18345;56279;48960;30108;28140;36486;29012;32220;23219;50247;41108;37284;53197;34281;44413;16722;53300;28595;56213;46896;35890;35483;62587;43173;25576;46676;22629;61417;61744;48153;38034;45444;31575;15543;17062;29978;47655;36879;55109;44533;12504;48598;15126;13346;65286;44695;33608;40804;37582;13677;40223;29665;11249;47433;32525;11750;31782;23633;29215;54875;24017;37936;45294;58059;56759;14513;56366;61260;27287;42027;33257;24040;18323;36228;44392;32991;27797;28377;38393;58324;44678;16801;54905;29793;48665;58204;27972;28912;59223;31242;44470;38803;46197;66890;40449;66939;58202;62705;51770;27205;52783;21853;16976;35457;30879;12510;35798;58649;32392;51462;51139;29460;49679;35896;58716;24598;49876;15723;11008;45227;59360;58129;17086;25757;66007;49707;47662;29808;44973;12686;10704;23584;66145;24833;10313;20517;63563;21627;48932;61073;56870;55815;53350;59944;40026;17409;41739;32091;44233;46249;49152;49291;66597;37512;30138;38741;35093;25515;52823;65624;66429;62357;52383;27920;29656;46523;39430;20409;42010;19730;63237;31317;49507;48600;59487;30785;24709;58410;60409;30489;31883;31100;33882;13495;48479;39884;63253;59003;12611;15783;40279;36329;53488;66673;46176;13288;24794;17778;11651;29768;22062;47591;35618;63780;54444;25276;64600;37055;56311;11387;31770;30732;66058;52171;22453;22537;39178;57213;39927;43005;46701;40286;42239;22865;26309;39282;53583;30074;21501;28710;53855;59258;11584;17270;16023;34882;21949;29900;29048;23233;64536;15775;60187;46887;59583;45912;48838;44909;44424;40146;12074;63932;11626;51604;31980;40373;16436;60020;59332;56392;62983;34533;66935;60756;54778;15744;60389;26767;43944;19972;18331;12998;66196;50877;58633;44722;31933;42549;50672;57231;33376;30940;45051;18180;57316;21593;51434;57029;27216;17109;51721;21974;22309;47722;39729;48642;22032;59671;33395;15765;45492;56988;34861;55010;11071;50281;57404;57420;17097;52432;24788;34751;64260;45384;44899;64420;47897;51095;35858;61311;44102;58472;24022;33509;41885;38817;51879;17589;14777;50934;60152;53851;13474;50989;42727;35408;60724;39816;43761;47697;11237;17652;56318;11447;24121;65831;20561;42368;33870;34863;54550;32141;56607;32950;48519;57603;57829;33118;50220;61872;26184;53770;20207;28541;41046;20791;36069;57502;61987;49641;38531;58489;28626;35737;32646;29462;38957;21314;14455;34133;42998;40574;34636;55018;45977;17524;23534;14774;45965;10159;60733;65124;31496;17360;14445;45646;31812;66737;36690;40077;44285;60293;49235;15544;18022;25108;22785;48357;10183;10139;24006;26123;30020;65304;35122;28757;33708;48906;61657;63205;42856;15962;27233;30214;12984;21181;62280;65100;37849;59902;32406;61365;62574;58431;61142;63264;56505;47703;19989;44656;16830;60659;22649;44464;63581;36861;40454;36241;57899;54634;63702;43868;50787;57690;42979;35563;23975;37524;53717;34259;36224;56863;17498;21371;20730;63604;22964;41074;35062;61383;34337;65639;54113;51045;12433;58322;43815;21303;28635;19731;53578;64390;65081;53239;27759;48257;42268;65347;48500;57188;17642;13152;39489;10312;62469;41039;41207;63379;45694;61976;31233;21939;42612;18609;27337;15806;63047;26516;33372;60361;46312;59435;45112;20919;54913;42585;17213;34695;13730;41324;26639;39506;45306;13687;38070;61507;54708;66247;12732;51274;15183;28055;55597;24452;53626;29527;37642;60407;47025;28335;55246;66087;36703;63374;66016;46581;52117;27703;28160;42608;30079;21138;34997;39727;52519;44236;57329;42750;34992;57875;19571;10389;16790;11805;33482;35474;19114;40411;19822;39753;55792;44363;50156;32067;59267;63328;66056;11428;48790;61891;51938;36194;24256;21189;22595;17793;17028;48470;65961;53359;15972;42683;33433;30709;35713;14046;39726;22220;16589;22464;64640;33646;63686;33324;27938;23843;45683;55308;20464;14318;37382;17740;25484;63798;43033;13055;58888;48444;24413;60251;17253;66139;38426;62726;18306;30182;38947;32224;63677;39392;63260;14957;29887;43332;53827;50806;34818;49229;58762;58906;37164;59092;65479;64516;40618;60917;48865;64175;63247;32288;38746;64326;48831;64247;58976;15629;13212;55129;66823;19771;65381;26058;16818;22772;64505;19349;28444;36356;39208;34338;17346;18610;56743;20852;63984;58995;27164;18091;46436;37009;39010;49911;10556;32547;10388;63125;33603;29530;21962;65234;55312;53938;31787;10003;30798;10465;23018;54554;51507;66462;12790;16839;14014;47006;13408;34099;31851;37638;24477;15675;27996;12622;26227;55785;29300;39603;42681;50154;44873;55397;64870;37745;43027;42419;26723;52767;54043;53792;13738;35786;29114;49765;15465;41310;32274;19939;40926;18688;12481;29731;62810;12125;42126;16918;53703;20034;53554;14731;31494;39331;20799;23366;43588;18778;24217;45892;14542;41846;19425;12017;32360;49137;13083;65319;60221;59315;49319;48898;29201;55778;37987;23904;52592;65307;30289;35818;17438;18188;42116;63380;56699;47905;31403;52553;34008;62093;30537;38546;45092;56792;44591;17116;23181;31717;22019;10161;22996;54997;26530;30575;40823;37940;50663;34110;27753;11933;58896;52194;17092;17458;65902;13084;55228;50337;52689;19313;36724;33713;33222;46223;36762;53384;26416;24490;35637;27658;39907;35724;24587;32418;26028;27982;26757;60382;64605;36171;56185;14732;34117;25605;17084;38610;38219;29227;38703;17143;57297;27133;64106;63742;43443;57982;26895;43792;24003;51677;66191;59056;32745;52390;47783;32075;58166;25006;62929;63277;20490;28482;49583;21881;48931;11211;65186;19920;61569;39812;53372;62091;19718;26063;25091;53542;34632;50217;55203;46845;49879;55232;64407;47672;50597;61379;59110;17330;47639;24527;26383;51863;55754;28325;32292;10778;46160;60112;29253;15289;13735;39434;52009;36839;24778;39522;42645;41970;26760;21367;10930;48589;41965;64860;42380;20846;13081;57476;25320;16093;17264;41037;21408;56707;46476;55481;26476;45921;42931;49384;10474;52093;42796;65508;58022;26890;58732;26414;19351;39204;40440;49661;41870;34934;60992;24749;54847;54821;51453;14669;17355;32967;30103;18797;47376;15981;10978;62714;35332;41355;32945;56175;50921;33549;37149;47862;11252;64507;28048;47712;16999;12711;27132;35024;39048;23436;56610;66911;66579;21359;44099;60280;22061;64599;42426;11979;66870;29372;39120;29042;30731;10058;39592;16935;62081;22638;18455;23463;42115;56186;65368;63131;31951;56714;38556;25434;45715;32218;34675;39234;43984;64123;22695;30172;46227;52372;32460;39024;47733;62954;41629;33595;30405;58292;61368;31026;50317;54231;27020;55360;29580;20683;60233;61283;30878;51978;22535;62809;29020;46940;25199;51516;51267;59746;45820;51034;66897;28426;19786;34980;47191;18531;11166;17653;33880;48524;58187;41973;11955;59510;16887;48593;33304;26505;57334;30442;66340;53128;37392;60541;26430;54654;34005;53951;46765;27714;36925;62461;48787;32726;42187;37929;53027;50849;34989;61814;34625;43109;49164;41488;18909;50742;43374;55959;57964;58912;31237;29422;60852;47895;25415;44864;12063;46611;38430;13925;52409;48861;15137;40493;54439;23317;34411;21404;49810;66423;12985;56706;55480;24618;18700;38438;59304;45221;31213;47864;38602;41782;31283;10610;50228;56660;17136;61813;23659;65362;19671;34770;38448;62878;37905;30821;31988;62940;46336;46572;34609;55264;55288;23705;29273;37427;57014;50409;54689;22738;46479;11009;32619;37087;34255;58348;51373;38998;24207;62703;12093;41857;66619;56581;32404;14164;49040;65548;19750;60019;11913;19207;28738;42033;50103;56554;11625;30420;52114;57850;38394;12870;35788;36271;19982;19531;42246;15661;43852;34856;26351;45734;47013;47221;44935;45679;56933;55006;32582;41459;35542;59965;44939;15849;24237;13765;32603;22188;28166;39526;64249;59378;32106;40110;61107;65895;49035;48781;18294;13595;64807;45799;22358;19729;39935;23915;55002;21071;53628;50909;50185;27131;31731;48493;43078;52784;16161;40018;59222;34042;22622;65375;21542;57619;29637;23306;28621;46444;61961;14328;59293;14817;14138;32306;10192;38812;49316;28314;62953;23755;66653;54393;60018;63533;21284;12730;21075;65977;66951;45520;29950;62385;66918;50951;35458;16714;34013;44307;35851;19143;29208;11888;39997;53227;20969;56636;34464;41689;39801;17126;53553;10169;57306;34311;35477;30933;35444;11202;44298;65663;53277;63323;24934;38187;60888;21497;43916;60060;30985;17691;12035;39500;39944;19528;56138;13697;19742;30371;59651;20702;11969;26852;37780;61044;41156;33830;41670;47142;43204;63619;63878;22298;64498;41992;66300;60081;48420;48863;57235;44862;47203;66866;28585;45559;44331;61352;64300;19333;17333;13592;56473;38981;48651;42709;27323;51337;52052;24086;27090;63432;53271;18707;43563;15673;27424;27009;49614;45652;46244;17545;12841;27628;45222;25946;49207;34500;16927;11776;12670;45918;58045;24813;21959;11077;63832;55790;38447;20691;23867;32729;15700;62122;54242;21297;21159;66023;50169;47732;54752;46058;35274;25696;21233;47687;60313;34155;41467;33146;19564;37963;12671;33149;32268;16876;13432;26871;13971;12679;32325;26155;62646;27343;57894;32533;21107;65201;59853;13717;41140;53674;18911;65001;49133;57512;58790;20096;57187;45459;28168;63203;29974;66035;14914;50762;57585;37912;18722;13944;47147;20376;33139;22792;15253;26137;20172;46757;16928;13063;29925;45081;61856;17715;36912;54620;34052;20865;28417;60189;52629;11259;41170;63591;65982;28101;21928;62932;60545;65090;46074;55615;28104;43532;22257;27385;63518;62163;35691;46426;18106;48697;13948;64392;25352;19229;22678;43359;29003;29876;39634;35288;18183;66439;18932;25079;41458;28305;24170;28653;49487;64149;61357;40186;29961;33569;66552;60486;54292;29207;38133;61642;23519;21142;14619;47317;34495;34701;62691;65459;18569;12624;19644;17216;21912;37369;24615;41869;56385;29614;46296;37379;40293;10367;36078;42519;27862;15058;29815;38374;16649;33921;53163;53639;21206;35878;16383;23901;65758;16766;52552;11948;42395;12327;27415;58328;57379;15545;53524;45863;35835;65625;27281;48900;30681;57876;18276;65462;65684;44162;55381;15204;65099;24354;27826;57111;38917;16369;50018;59141;28075;28580;30746;44024;41399;53579;36487;65668;31370;45968;34615;42037;12326;14475;48286;27796;25393;48189;17785;52411;35119;40600;10822;15038;25664;28175;56455;62414;16523;65472;56726;26000;37968;65765;36811;28316;12059;17182;20621;46189;25123;16392;23372;32722;37122;44794;34661;29986;13078;26025;64111;45310;33297;11705;37878;60295;13365;48534;43591;31774;62315;21972;34080;12574;44867;45419;23153;47741;25022;35464;16018;17444;12348;66568;12701;26902;61469;12532;51856;28082;50641;23502;54285;20263;20743;53914;38912;51046;58255;36032;56082;53983;29365;29356;24683;58851;41562;21100;23866;34007;43193;43207;31639;66506;23627;65618;28521;42762;26884;59178;17065;35263;65749;36212;65430;33720;38674;29739;17681;23474;52512;18825;18388;53587;38744;11372;27419;40657;62542;22082;14172;66833;44802;62323;43370;45852;32971;24118;39298;31713;33892;54363;32194;33028;55021;34528;10277;40909;21448;20990;33533;55040;17484;11158;13289;15363;55282;64110;31344;16504;33860;33731;24780;25687;60070;34350;35256;53755;24548;11224;54026;61851;23508;58393;63741;23554;65919;18241;63368;56156;57543;41018;37206;45417;55450;56761;27944;41659;30415;42662;37359;66412;61605;64531;16739;51344;55888;45423;58506;52513;37728;24160;43512;33485;52002;43618;62446;19906;14402;27051;40848;22567;42306;43789;22442;39809;30414;52893;16028;18656;38504;44685;12076;49157;30662;49701;50389;63573;26473;14779;57123;62481;31170;15092;51660;30364;13985;23550;57264;33076;56479;16139;42759;48348;48501;36117;31968;23488;31727;61821;19757;23077;10566;55059;40978;47133;61674;36880;30196;49991;14306;34209;14451;40418;21861;18649;61704;40262;40341;13181;17565;58434;54136;47431;51033;43316;54023;34497;50444;10635;41106;19439;15263;18892;11296;53835;41210;27988;46502;24965;17765;20764;30669;59561;18595;45724;44463;35922;63051;26122;55562;36596;61218;38324;22491;14029;55913;23674;47841;12960;32163;62360;61122;15870;57675;63745;44666;37433;39003;51257;37885;55235;50120;42838;34182;35135;65327;61436;46492;16656;16930;34900;28936;65184;59279;47648;43060;12378;46678;34681;14429;44292;26898;56181;50705;60459;32863;40611;59729;22578;50272;38555;37708;29268;65605;19288;14677;27201;55497;29662;44686;43447;51070;47404;16359;34430;39263;41456;52128;13123;46571;29979;62253;66322;36455;26783;66321;20066;43341;25755;14667;24263;30583;65410;59814;35238;22953;28853;25604;11662;60681;52800;41097;53294;57304;52109;54040;31371;23339;48528;64939;41824;41364;41780;19481;34647;38631;11611;49648;18928;10483;34435;31318;58291;25004;35645;11052;19560;26348;33657;38264;55258;30793;22406;66586;35690;52259;42826;40920;26140;19329;27263;56104;19021;44300;38651;48548;35137;26069;50398;55628;60808;27433;11993;49168;24765;19250;66246;12005;27461;56285;66729;36451;53182;51550;10486;28996;27193;63692;43200;39680;61011;47554;55918;61742;32805;60723;28594;30014;38528;59001;66363;34026;47229;48922;49897;49677;24472;13236;63078;31450;14335;60797;16759;35907;52248;14333;27143;56705;14548;41241;62209;14827;16006;16956;22218;46717;11841;54262;12560;31654;57692;31987;42781;50537;11111;50890;62942;50632;40755;54460;45660;51153;26534;27234;64209;43220;11058;37443;12626;13061;12418;15041;11657;21311;41453;16224;25140;62157;41155;20142;55637;20475;61271;46253;22237;25363;61246;58823;34195;45871;51372;52479;66334;46013;47053;47507;14430;11406;45376;45699;46883;18059;24540;32933;30374;57641;44807;41290;27030;54753;27138;14919;15549;57083;14920;32826;29947;20938;18317;56382;13690;42775;21391;20021;20972;51862;36683;63701;21334;60030;49245;54283;18434;59859;65120;23028;24624;34426;31944;65082;27266;56923;45382;54244;50847;57550;12642;55666;12703;50875;56126;39544;35399;28266;64440;42330;23776;43629;23445;23658;11307;31592;53644;28852;32734;29349;35870;29239;31821;31670;23229;39731;65111;28845;57268;19147;33176;65725;37112;29069;62884;36771;55352;36243;10120;45713;61343;35049;46785;32068;52377;56762;43123;34213;28429;45450;40589;22895;45966;60181;26356;56162;52089;35734;31164;60067;59761;39314;61778;39821;41698;64219;45402;26320;21941;16545;28939;58051;66234;58605;53164;35827;62234;26846;54819;18804;27468;53861;46579;29540;14000;51322;17324;64834;61411;52887;21607;45685;35989;21981;35182;23582;54600;33418;48857;56587;28820;20030;49002;40074;49406;64278;41607;59974;39337;22978;10069;14376;15029;14679;52348;19270;65830;66025;61822;12296;50332;26814;51635;60845;43773;21429;64895;51609;42362;14436;20258;55829;20240;20430;35964;38609;43378;15945;48679;57695;33108;27379;32449;37056;30481;64079;28258;36317;45721;56331;37473;33579;33346;42493;10438;46972;33986;42056;32368;50328;36794;48394;63354;14442;54324;49418;60749;64475;36041;56693;48557;27827;66629;16357;14758;35180;28895;54112;44860;60338;48982;21321;16475;18850;56430;25413;11119;28128;15638;38298;23446;46551;26513;10086;28887;28984;26412;16752;44534;56940;35596;39281;64025;48146;25552;34511;17101;40672;40526;55967;19524;31740;64022;39297;43580;20668;55256;17242;16110;32816;42448;15753;17096;24509;47837;16652;54824;45036;41720;41334;27596;23979;17617;23688;39843;24262;42012;41743;22248;38578;17056;64409;56085;52888;20842;66287;36070;18827;25427;62620;23651;15738;47749;38269;61510;46134;43456;31747;35225;52290;21781;39356;16226;57789;25724;29964;44624;32580;59218;37110;47564;16892;30201;49057;10404;59745;41704;66752;18299;16232;41911;38209;13681;20373;28257;63977;54977;53306;38494;52338;52234;22973;37991;35599;12883;31936;48530;29482;21436;49884;56695;48562;37680;33744;14952;66123;27707;62873;47876;44564;21479;53172;18771;60645;54950;32479;31565;16842;46127;15391;43150;64015;33775;28508;26116;49705;32829;13561;42525;35350;39764;20747;26685;40876;30039;66085;63070;46847;14790;15987;32758;13866;45282;64173;58069;61040;64568;22712;44418;60285;41395;17440;23041;19525;56406;19484;15381;38445;35875;60334;49146;45718;46690;50970;26453;63461;14382;21844;43551;23918;59433;48620;49051;37742;27390;57958;52650;15115;11116;30578;23897;37348;60202;39599;36296;33724;50656;55466;28816;22557;29594;65477;57701;54349;37772;23134;49998;32876;62585;56237;19240;52663;63913;27610;34828;23781;14829;34633;11905;14599;41595;46722;63746;52936;43549;11209;16733;45722;25888;57824;32519;28091;12357;56525;28385;59530;62717;14693;25603;28217;53972;20527;24266;66206;24840;54171;33508;36113;64439;16531;54181;24854;28243;54273;26769;13195;41569;58381;57940;34525;11778;24994;46724;13269;65054;19030;49514;11397;23411;53024;48643;60426;36947;17009;58808;57085;42315;36391;27196;34256;55163;56220;55651;33617;26310;47145;31214;26810;58519;50095;25816;38807;57128;53075;18879;43157;36630;35689;47089;61332;48834;39344;59368;53423;54653;22194;20848;43045;54006;60487;12595;37924;16418;10495;40330;29418;28563;50889;18151;24182;59890;51573;47576;16635;34079;13317;11350;28223;66049;31327;51367;29571;30715;10189;57346;25402;64583;31850;18012;18492;26550;41159;27232;47437;47863;60227;45447;18705;56558;19004;34982;26113;49588;14489;60337;46534;52550;27438;53430;53471;53725;27785;65299;26886;34732;66332;18085;40019;61062;37080;54795;21708;14572;58834;45218;29821;45118;58755;27653;40328;23042;25234;61865;22323;65154;53071;45048;28598;32542;42026;59288;20282;44269;16008;34606;56941;18239;60906;44734;41354;38365;55532;53387;18499;21018;27777;60539;20347;19928;40957;30232;47241;31537;10059;15906;66899;43135;26390;46372;53448;47510;50081;23999;62922;55657;61115;59453;64141;18514;40028;31553;15470;60586;53735;19545;30836;46708;13780;33291;57206;25185;35723;66587;29729;16137;16120;62883;58309;49980;41668;28999;31475;10088;29467;58921;46471;38157;43899;43867;12065;44256;27995;46288;48649;18429;27321;53600;53773;27594;51176;26870;42372;60145;56766;49400;52892;11569;13419;64999;12100;20654;10210;32405;24644;27293;17158;18479;62239;18438;55643;50861;20129;46126;63262;14970;33865;22699;17684;25171;45080;30040;22254;39776;58017;64231;41236;28908;18162;49261;10937;15250;62102;31702;16937;28808;61161;15364;17181;49289;42787;54868;44647;40164;15511;34234;12794;57003;58027;28927;48290;17739;24393;60891;29037;65763;36888;60536;27799;30689;27230;15269;63404;35526;46804;60883;38520;16401;47362;63426;19557;39676;66806;24150;12795;54526;21536;49149;11644;56539;64198;28018;15227;43961;19592;43093;58493;64613;15163;31798;65266;59806;54543;57623;61849;17004;26523;65523;63344;60242;64194;25143;37214;48202;27906;43484;59906;31106;18427;66702;58829;19997;46957;24565;20695;14018;65271;47360;48821;27284;55201;33752;47002;53008;40033;36170;50533;23218;45241;36017;58491;51895;40207;50134;42701;34829;43411;38557;17051;64672;43071;49977;28618;41929;33806;46514;62630;64156;35448;12270;59622;45636;63715;20468;57337;15066;26741;32814;43754;60330;51798;35795;15002;39146;56985;22810;10259;49005;53029;14310;23570;25423;13392;29708;16579;59962;40445;16859;18680;15232;45136;22310;18814;65922;20642;47597;19461;28044;39011;22990;29307;12563;16953;51198;18406;61876;40984;13243;50167;49711;27426;29484;18390;52560;40325;13710;58428;41284;62490;43519;32096;33997;13375;51419;30986;64752;33546;23596;23461;27251;24131;46828;44839;62801;56481;23311;16105;63108;55091;41865;51824;35579;57197;11031;21559;54915;48977;47186;31056;34158;16720;25335;45178;39035;25836;14281;20456;19412;58219;24613;16078;45052;44278;36681;20226;45643;60032;46846;30168;66326;14394;34575;32201;41430;21936;40791;10959;12528;26381;53446;36244;38502;25595;35736;20979;33317;30333;28798;21987;22487;17986;43344;26477;23792;52173;42897;47705;49747;23304;28589;50366;60052;46050;35850;60638;58736;13745;49524;26159;44690;21643;40277;59308;54083;36206;14805;58087;41123;35107;66614;24011;66816;62707;55283;31458;13834;60839;10965;52370;13515;59160;42266;63112;16855;61287;55744;28293;32312;21084;27374;15387;47144;60816;28181;38010;26752;27875;41602;53036;40148;59340;37733;48376;59216;37886;43498;39863;63088;48736;55998;66686;43357;59979;27262;63360;13085;19029;30154;52861;38139;42070;14617;54277;40378;66285;58960;24098;23234;27072;60092;24822;10015;20484;14118;44841;52535;49338;63213;38418;11173;12552;61154;47043;38280;62963;29767;27199;24153;28360;30438;33113;60642;46969;39383;53739;66630;20878;32467;64308;27079;28201;11970;26257;15764;36102;42462;30239;11918;27411;35087;45617;22047;49732;17466;62435;23430;66195;21058;45107;60461;65298;23458;26252;54700;44403;18242;37135;48344;20886;20198;50912;22603;20076;11516;66292;52330;17388;39802;12227;28619;39581;17756;65198;30381;30737;42756;19199;29756;32373;27441;31363;46696;32389;22181;41963;30308;51333;22116;20368;36071;17193;47397;44383;27545;56043;17665;46276;18459;28322;41161;56178;17105;21108;30396;58222;28479;47880;50420;44638;22604;65169;12684;52141;49751;32741;34180;31596;19011;47700;27330;61257;56434;66077;18214;46256;38179;51441;14519;53250;24111;21577;30656;34556;32616;12969;49052;48949;59144;39406;46328;12904;32395;15678;39095;39478;13248;25805;22804;57742;23224;32982;55755;31183;35532;20259;22350;32610;60369;25683;18215;26567;56552;44661;42005;54989;30797;13196;36830;21583;46699;47345;47182;38768;55036;20793;33516;36818;59633;38312;52154;59663;38023;32386;49442;45003;17256;39405;33233;14407;64414;24368;11585;40108;56045;18266;15284;63416;38442;10370;26568;26763;28760;19139;18234;16804;14031;51051;66148;30288;29223;15864;62644;21887;20245;27575;54215;49826;14988;51540;59464;45404;49434;56194;55096;43576;23646;63826;31223;57116;60049;12086;10467;47449;34958;65600;49616;19201;28439;50116;21626;63579;18560;34890;17488;51686;25569;13535;36053;34476;53903;50859;17983;45738;29248;16740;27358;30869;11664;37461;48655;23891;19186;54330;42341;20557;23246;40624;43062;21576;46203;58046;58580;23344;21003;20075;34437;24247;46344;32906;55378;26751;28250;57855;53768;62974;55037;34940;24839;25508;11338;62935;19454;54796;51152;55112;38273;27746;24699;17108;28611;32285;66395;43325;21754;36368;52581;17718;34073;59384;59269;57234;46165;27120;13947;51159;33784;55964;37057;17072;28822;55084;53242;52819;28366;26235;38395;21757;65914;62507;52152;49955;36898;54339;59917;40932;62794;45938;63298;16234;23951;40568;23088;13413;44755;60329;62508;57486;62138;53063;43982;54508;58686;35278;51586;33822;41184;66076;11575;39104;17114;61146;44952;18136;56218;32351;10141;53571;17777;17261;41272;65550;56929;16899;17577;19547;18133;14215;57097;60714;13043;36208;36246;45270;52201;43091;34204;34708;26253;24747;22959;40762;20105;30125;51509;61567;20840;35031;24575;11495;49318;11150;56502;59400;45500;38902;41278;20959;27170;63822;60563;63670;48703;37130;15807;45427;55409;19475;33741;10184;29196;41502;45819;12943;58398;20499;50144;35774;63930;11033;45220;41710;41365;43345;25366;50963;23595;21863;25534;49956;36890;38801;42498;17119;32842;49553;19690;22190;11537;35436;32641;32133;65210;47813;40604;10655;18481;60967;64306;50294;23704;17575;32993;18289;52528;19192;33364;39799;64144;44901;20190;11548;50662;12760;41092;27974;49891;38550;12489;38940;59798;10350;24851;37652;21305;42053;24567;13267;57772;30792;59268;22898;10304;21402;26244;65965;54168;17221;26332;47660;53211;45826;37170;31858;35356;33024;53065;41632;29014;32081;58310;17496;60275;23520;27704;29205;24617;62553;34543;51026;58890;11534;49123;38258;56248;60163;41593;53200;49569;30633;49475;25060;10525;56010;65386;28004;27959;23469;35728;27436;51035;34381;21821;18573;52362;52883;29198;16274;25223;55598;18765;49276;22049;64451;18906;56751;50056;26419;19859;60654;11901;37008;56666;41968;44792;47330;28642;48893;65610;45879;23558;65690;54802;55242;23104;57534;66878;59155;54364;35839;24836;56543;13532;16492;10527;22399;45393;61140;14151;30604;51574;14009;35837;15161;64996;46231;12301;40705;25292;13511;28173;63877;66057;29146;50937;33120;37241;41708;43746;19799;42365;13064;26824;29606;18207;21048;24906;31931;49273;58681;12875;65748;25383;41599;58644;31888;26809;29599;30004;59526;60751;15576;45075;15582;50354;16090;49300;31218;47105;54518;12782;28167;34057;38063;41858;10381;66149;27567;20563;60715;54834;62944;61068;52246;39041;46641;64180;33075;39033;36018;47243;61086;44362;41271;24124;14484;43985;64090;20953;62432;59674;45608;56243;32891;27168;42718;45085;56308;42323;44508;43400;38571;49314;60440;32130;16633;35072;29985;13366;59212;32959;63910;31659;47746;64097;51286;25479;63541;38370;48299;27613;27403;61697;10999;57425;34781;53463;13817;34722;57024;34954;13741;35270;49652;46614;23341;49574;10603;15362;34027;16807;33706;27865;47852;16602;19841;64154;56030;34134;28720;66947;10629;54200;55071;27921;11171;27007;57431;34983;61829;38114;20232;57240;50588;20008;17363;31173;27544;31305;29639;47381;39779;10442;16797;40470;61445;15729;33237;35389;31304;25537;36404;46961;30920;47382;45047;39948;64704;34127;64789;42626;15769;13544;29211;13041;28846;53354;62926;27314;60677;41500;56036;66772;17128;41985;57654;28535;64540;19209;24495;66732;11570;26213;57615;62257;24689;62191;27840;18793;47166;19602;27450;30676;42533;25548;34490;45588;24535;22401;24029;64656;47307;55696;46947;52196;65796;14796;51254;60921;11930;44174;30721;16107;31505;49177;59020;25882;20853;46421;54535;59900;41457;42071;65538;58734;45661;39445;54625;48578;11219;47012;24438;26510;62218;64947;43802;37140;56844;16396;45628;59259;63655;25151;41378;43915;19978;61554;36929;43974;36450;26753;54341;26160;40991;44153;65584;48256;56356;36306;52699;22770;21930;13918;56507;58119;14700;49210;44002;27034;20629;57184;29225;31570;44853;63728;57139;23316;20053;37641;64700;50803;17106;25420;31107;31151;64029;65552;50747;10144;27597;25339;49639;16233;42665;36524;59048;52880;52622;35366;25708;51103;32222;44207;60559;60492;58975;31335;38113;35187;43589;42598;41976;29232;31873;34694;39047;51233;19931;11250;42918;38724;10090;57868;23579;11106;22871;28744;24898;32043;55180;57378;47553;21435;44306;42465;21112;22591;43203;64957;23462;48356;20488;33486;23572;24718;14286;56943;33656;53556;29560;23350;12664;40305;46908;64253;44156;58256;22197;37646;39617;34459;63868;39342;54540;40578;41342;64641;63335;14071;47688;37089;64151;42324;38241;37701;55014;17232;14331;11435;49972;41998;27691;33754;27059;45328;36977;55924;29448;24648;22775;66281;46723;33916;38439;43581;48319;18114;46770;65613;31620;62550;19769;10830;38105;20613;66178;16386;52850;55769;49499;24552;21444;38675;41639;23027;50278;29274;21298;50792;42981;57788;54764;58103;21079;15143;43612;29410;60348;52192;53334;23071;15122;60744;60005;24405;17389;29332;65782;23925;60237;45482;15187;26018;60823;43846;49321;12575;15499;46318;36300;37159;35114;54650;30685;37428;49044;37565;21927;65087;32470;43279;15838;63806;23685;30650;17666;39660;42666;40874;24882;53857;54575;57062;47605;51282;31700;61292;15562;15890;56882;39833;21097;66200;36617;17160;62569;44820;38097;26853;26386;18456;36468;55530;11349;25034;50961;28929;24095;44254;15162;28701;49660;33236;47074;25996;65745;47336;43524;34844;43096;10417;60138;64241;27925;41729;26262;13898;51640;47152;60647;44217;65402;54591;41537;17527;64554;10658;62987;12994;39379;21217;66133;66760;52849;34167;36738;13768;23080;30649;27333;58731;37203;26239;21072;40094;63884;50319;56140;23168;16397;34904;45838;65428;24147;19009;58922;16271;60630;45177;46574;37865;15276;52156;28796;23405;42483;50041;41884;26435;36657;28006;23612;31470;56786;15028;40714;23657;64666;30211;33988;60579;21924;24963;13213;66319;46840;34050;30905;39275;30460;57952;39772;17269;22900;40912;59733;15146;57232;49807;25126;30261;10544;57947;10266;12337;65151;15960;49347;20598;52322;21427;62746;47772;61134;57756;56350;38320;58967;66638;35220;23009;66518;22314;26699;35573;29504;57336;43292;56757;44205;61390;39317;32656;32139;52978;50712;66566;61465;38561;55791;28922;31803;12332;58357;65568;41205;37799;31862;59390;55291;30106;17562;55568;41863;24740;38806;20933;33027;29033;12006;34754;56996;24754;25666;64083;47436;34439;28249;65629;54065;26943;65092;33602;44894;57322;59483;13208;50173;24065;11851;52032;19346;29140;26489;22635;44430;53870;40413;41398;40045;28363;64043;23610;52254;43289;16701;13667;24301;15287;29101;29483;22539;42516;30941;32703;47713;53886;56137;39531;16573;22545;26132;45288;62139;46791;37664;36769;54111;14270;20175;51382;65531;28550;36699;35171;17745;39991;11204;54737;11413;37484;60468;51447;28941;22569;43601;15403;26288;51588;14368;63596;31287;62188;52258;11018;42782;16539;55552;34162;22106;41510;13877;25365;41563;31133;23701;61985;33310;39887;17137;34075;34892;44506;33728;66662;62477;12359;50636;35578;50944;24695;52452;64912;57387;48324;21339;36426;53173;11163;24152;11621;42044;27581;21168;43673;54063;27708;42674;24035;43882;55382;49394;57126;30113;25893;31115;16073;21199;34704;60362;46607;18358;41147;12414;22149;35593;11579;20404;38946;28746;15654;53376;34238;37861;17470;48367;61692;11973;21202;31392;33250;55271;28096;47744;40782;65119;13310;12677;14390;47430;24830;60142;34386;38876;64155;42196;43603;26079;35285;24461;41283;46787;24692;30145;15519;45503;50370;62226;43574;16196;47216;30158;29088;30900;18458;18436;53028;31977;66221;22679;30926;12206;54690;51229;51733;64940;25385;19403;51855;59382;46031;53550;20536;48706;44113;40342;29124;26121;63257;26106;20945;41687;27978;55894;54617;52003;12389;46423;24305;50515;53567;23942;45031;27184;11456;66825;17439;33411;47018;26279;27788;24893;62543;40946;16126;66129;30370;59940;55023;48625;65406;11559;54827;36710;42271;44776;53058;35222;53370;28840;53895;52106;23242;30090;59638;47536;11589;25374;46208;32530;21335;45023;43180;43046;59683;24307;22470;48851;28902;52543;51097;23323;63462;33833;14521;39456;25305;19611;31583;45808;54706;33460;22384;31094;33521;59603;35826;48691;24149;27626;24665;22005;11425;56785;18839;42120;25507;44396;42141;55731;44425;28185;13805;44072;12578;10445;41397;42807;28020;59716;10173;37343;53361;56158;44846;20351;53576;47469;40465;47693;25127;18631;48403;10508;15779;20425;42524;20823;58198;27857;52244;51724;41871;62770;64953;52923;58776;60745;54253;30843;35881;23656;66278;45250;21239;49905;19336;21597;10729;53081;57368;30542;50179;42065;43236;43164;51607;27439;41586;47354;20788;61047;37420;56938;28501;30736;43983;12561;65290;57068;23121;17455;46379;10009;51658;25310;32275;64292;62465;39718;22144;43873;39226;59521;24811;18090;51239;55286;52977;48484;41709;66512;53156;56654;31114;46703;48792;13825;19057;40080;30666;21731;12932;47467;43583;15428;16195;18526;19265;64060;54018;57117;19770;61789;53989;56317;30866;53316;18071;59059;51983;48482;16698;59086;51868;16803;17198;13286;36310;29866;58570;57652;62119;44135;15957;49324;35161;17334;65248;62853;18009;36862;52673;39848;29237;22526;32273;14235;60056;26728;54534;19123;46824;15965;44586;52843;57904;45383;49728;60616;35325;29816;63879;39218;40766;57588;60995;22335;38861;15479;51506;57774;26808;42353;51115;66894;24295;10984;57475;61328;53767;58535;40929;31507;20290;19322;35273;45614;34691;63393;15497;44653;20816;44933;13625;11582;47773;35682;36097;40180;32146;55108;26934;55847;45755;63600;20585;32381;31431;23709;46016;41625;29226;57621;62051;44482;19361;46040;32639;32005;17268;33903;12967;64721;15084;47503;35988;57715;16534;13093;29497;23261;10031;46777;14425;64374;18926;20754;41555;28877;16692;39938;21327;24419;18891;51952;40432;42472;11168;56795;16857;61052;30247;10500;55451;46488;21562;56500;56015;17604;59727;49224;52345;61684;64336;50659;57442;54420;40244;63133;49877;22819;40288;10714;65497;52876;53188;41411;53254;50724;39393;18175;62860;58523;28542;49952;56593;26928;41699;33132;61004;65037;52716;64252;26492;25726;50369;62876;64313;59664;35816;62780;46647;55536;57959;35999;38944;24923;14567;31921;33337;15726;44101;47708;51320;28030;32648;52771;42784;32766;66356;28080;54118;51929;64094;29921;22620;11528;41134;51480;34173;65551;42951;17356;31597;18048;12062;26287;24655;57290;64024;16936;39245;34290;64467;63615;27163;14691;27867;32943;26346;41640;64191;14656;39989;32262;30066;10473;44920;29059;13259;56249;23435;28413;23689;64177;21799;66181;58858;65638;56646;43438;32890;22992;19249;43734;26035;51190;65434;50850;37400;45717;44539;26518;57726;42963;63948;50020;45296;19899;50625;52434;18498;38243;58900;62216;32402;15971;30859;38780;21343;54369;58035;26156;25643;61580;45411;45511;53865;32334;65948;40124;25744;44042;13943;63043;64223;53241;54372;12793;27994;29942;52688;41716;48864;63297;62217;55053;30022;47828;41219;16611;26031;16622;47612;28437;57539;37810;31627;18213;32196;58787;61169;13487;44336;37243;51891;23191;45862;65589;51291;58016;35105;15261;57252;17572;41781;56014;36373;38585;26578;24214;63787;41126;65155;30965;48297;40945;29561;14437;41853;10550;12774;52965;53054;47385;53178;11511;12751;47786;50524;12218;22295;64125;30411;58579;37096;29557;37796;14089;22304;34388;66804;33193;15107;51548;57101;62116;47771;22697;62321;63169;15016;31362;39858;41163;45339;12464;28935;45300;31199;42477;35027;33374;30485;14059;53802;50797;54718;28741;50371;65740;39349;26658;13676;31790;14443;46952;25325;59946;66264;52449;62535;55914;26097;52190;24324;64533;12713;39877;52678;23394;49413;45271;31971;59408;54651;32377;63585;15200;51943;50761;41183;30238;65481;24037;65003;10018;56256;32947;64078;37627;60252;58707;53732;26403;28794;41612;56145;29193;50463;23932;34043;52494;31964;66942;50831;18965;32211;48179;22633;29800;12316;23235;31869;15104;13144;17258;66864;43493;59629;46503;35524;23130;32671;20179;44509;53072;28230;38525;32371;42815;37375;17303;60785;28742;66424;48457;15547;19476;41452;64178;12352;39051;33597;62908;58085;32098;46368;52045;15145;38371;17674;16737;29347;14106;27303;36964;50784;57612;21915;21349;48489;44438;43833;17627;49346;28396;59854;21777;55294;47125;33477;57348;37915;46056;37459;23616;65056;17530;63072;23223;51305;24264;56204;20377;15935;56068;30245;17479;51245;47798;40708;16336;15295;41646;62221;40258;61325;26818;55509;57084;42905;33615;41073;52690;61000;47752;33160;63062;64279;65246;59354;56822;40913;52471;21829;13112;35659;53586;10609;44056;40115;56284;52854;21869;36778;63195;18168;26906;27850;26046;26669;16799;24901;52473;55625;30728;10004;63303;31802;45472;54610;66693;34777;14339;10835;46570;31482;51961;23312;42875;46806;54465;63499;26560;48252;63265;34384;53011;49770;52260;25983;29671;64573;33045;58636;12424;27229;64960;11917;16724;19607;23473;60057;47670;40491;38192;52018;52619;54995;46884;24066;34766;65486;56838;15835;58068;21389;32034;66968;49929;25261;16516;21734;45274;55995;44004;45135;58252;49232;41232;27513;46172;40818;24346;25336;43126;34314;41174;64186;56297;35882;49914;34620;30570;59799;41856;23256;33249;66151;49144;48881;62238;19619;31635;26900;57447;33378;55427;11049;25518;18007;38039;48172;51409;37578;48668;51627;59000;28092;16102;50778;47363;46335;52019;61638;27551;28663;48978;48462;13821;54831;12980;58693;64614;44267;52189;27923;57635;61281;58653;55158;20070;53507;14064;26393;42096;41669;59839;28959;65291;27927;26027;19838;17495;20050;39934;21496;43770;33172;53608;53968;24758;14834;47714;35414;49075;30724;59593;28043;62640;46303;26358;12837;41813;19196;56299;25789;45970;56363;21411;60021;14325;63918;17548;25449;19269;39902;11825;23775;55761;26644;47723;57805;10908;14816;43674;35938;28383;43446;43284;17274;21290;40147;26617;29168;63606;36608;62115;20048;51173;53115;44110;32818;66094;33982;51113;53395;24961;20641;47840;16047;30454;65837;29622;41214;14978;35613;55389;22447;52010;35098;14297;39439;10226;35415;24736;11323;56281;50439;61424;29156;10804;15535;29057;33130;65127;28347;57564;17775;51027;11815;52499;37088;54152;17531;62110;27755;20713;27386;15941;59714;64413;49756;42841;42468;21877;15443;51788;14727;14385;28503;48827;41798;48967;60607;23287;60341;59394;11121;19837;45944;10291;10470;46916;29084;33642;31536;66625;46649;55650;29413;60598;39493;43328;41274;33081;49285;17229;17144;10084;39310;49255;64563;32258;14219;52361;65209;53032;31153;60009;30379;48259;21062;27088;50966;20761;48867;40541;14282;25697;20722;33490;33878;22377;15368;23156;31823;27485;27044;36822;55081;22710;18396;45396;30874;40598;22771;44676;64624;60450;38670;34085;28398;64532;19233;57327;23782;47718;54662;14534;45420;13240;17238;39144;12210;23842;14752;27416;58868;63536;37338;65559;56813;54210;12543;16536;45035;11661;15097;12345;37787;51844;57901;34031;36951;14552;22484;60268;45248;42509;49609;11479;62573;16292;34943;49773;39486;19408;11502;22946;45642;28860;41671;54338;61166;64093;40709;49445;22689;57762;51181;28526;49506;21397;53697;30664;58767;65366;42257;52357;57263;33056;58000;27899;21377;20529;21609;59653;35928;17522;57389;37803;39322;14842;63914;43212;28844;23281;43383;21223;29897;25864;44777;44140;16844;55944;60153;15474;28032;49848;29322;27960;13165;20062;21375;39143;29258;35582;54096;16661;52280;55557;45723;11903;49799;18017;11916;43152;15189;28558;60819;60613;59779;54880;46968;23687;20269;11275;23184;63180;11200;10352;36633;23954;60069;17459;42593;54660;52778;33502;13652;45946;24924;56657;49549;10397;41972;42278;45709;30236;66513;61796;10848;18829;59585;65094;28966;32862;21819;27742;45934;61768;45014;27817;44548;12540;60947;59681;25210;14528;45200;55068;64491;51614;22888;48542;65525;38124;12305;57285;32307;55277;52414;46819;54749;44528;49014;65574;47902;56371;28356;33679;24715;58941;18726;30654;16419;11535;41415;30276;58581;25588;14371;25574;20071;46338;37819;39295;42579;43377;63951;29566;64767;30494;47208;46562;11493;54748;22847;60342;61085;31054;47374;23767;39826;64738;30727;32715;57977;57865;33001;40420;33447;40696;36245;45839;14453;46686;59266;26157;55404;21388;40518;56506;35821;17050;53771;61626;52122;41455;40017;20908;29843;19868;22132;50304;48607;64900;54512;63886;11723;43720;56662;52608;16898;43965;52094;19328;40739;19871;50070;17041;11081;53396;18715;23578;50340;35163;42678;42941;14254;58584;45705;54696;62247;65707;39294;16527;12520;43435;21889;24787;20614;59482;60353;39025;55782;33990;47023;51813;25746;48981;61810;50605;28425;45539;34955;36988;49016;13355;11892;59275;63512;22564;14111;23031;27114;49359;25851;23243;39657;65253;65470;59429;27316;36521;35699;38845;17519;27570;18077;59679;21114;24935;39036;10150;24431;23343;57560;15400;20055;54138;51110;60857;11133;47466;46730;47735;52288;54741;24680;63940;57844;34504;60700;60908;32354;17824;40888;34222;12562;17325;13462;66000;64664;48584;64091;49452;22060;38784;42030;65506;37712;25485;39525;38152;39183;50821;13435;27516;13391;13500;11148;49288;29575;35864;65510;46802;10108;10997;22565;20630;15587;58031;53290;53706;32079;59778;19426;13666;49721;28801;23511;21160;46529;20518;35860;54694;38737;43218;25268;16324;10852;34205;61083;13634;34324;15787;54799;41448;57864;28919;17502;27260;51582;12090;31255;27443;15098;28577;42379;58779;26210;59661;24055;25514;47163;43528;24047;33697;35331;26571;24555;61327;34219;66721;44234;33124;23944;41424;14225;33888;10688;21455;42441;10667;57689;65023;58208;13739;19720;35612;28612;64526;46693;29119;39628;63143;36099;27800;66465;21196;28045;27125;33685;31962;52623;45635;65391;63663;31830;39135;11438;55351;61049;61208;57293;13715;48609;47296;66125;50689;43311;19488;40390;42744;63387;14598;15979;44007;17489;65519;28182;65178;54225;28802;47775;16455;53410;13274;54193;37193;56572;29539;22054;40245;63289;35982;59571;19918;52639;15195;48592;28327;53775;14221;45299;33095;54038;28682;44538;30181;13404;49900;10100;22551;40171;20163;38233;48352;58370;51634;49965;65123;63096;66777;46568;51191;26694;51962;50367;15502;42698;35197;33716;23587;32515;13116;29392;30713;35575;60703;11718;53047;19767;28103;23289;40000;14066;61892;54101;29786;36022;58078;49111;22945;10954;57347;36218;18231;38389;47122;38589;66731;42597;19893;64989;44597;35985;38140;16364;66546;41172;33345;28116;24989;54399;62220;16668;48164;62208;23844;57843;35459;57574;50590;31456;53454;20814;27744;53822;38231;55591;61623;64243;40512;53686;46891;18469;25405;17702;21357;18170;58080;47154;26559;18334;64663;55820;10122;66778;20997;26047;32640;26278;19961;21330;45509;10521;64450;33357;52131;29846;15839;18066;34174;21283;56422;19601;58026;56091;48944;42848;48595;47100;23161;35639;42600;30515;11302;31848;56891;59956;23848;46934;12662;56946;22995;59147;54467;53795;39560;19118;59953;58468;33973;63115;63292;53908;35719;50960;45191;29203;29953;66905;28771;44218;27834;51581;34486;15917;27554;24568;58850;51728;24194;18045;33937;14571;66383;23974;19041;50826;30768;20727;29832;48822;23388;60731;18621;44904;21288;44031;46483;46420;48957;20836;16598;60543;16237;44851;26806;24712;59452;47886;23465;62624;12085;17985;37038;56724;14689;62372;36972;44321;19337;38336;48942;37848;53529;49325;40063;61529;22611;27725;47738;33409;45428;24360;39246;35245;11998;48928;51076;18605;36615;10854;18308;57463;18628;25745;36401;42183;53812;50054;59229;13249;15891;31259;30531;24271;31950;40428;65891;20556;65842;61680;19903;10185;32545;33864;53671;50981;15929;57799;29040;54567;51902;33779;61183;38295;13585;23452;46925;49221;29849;50043;28474;11353;38128;18082;22802;20678;42613;38792;47873;63008;45775;56442;64114;52695;46258;15871;43025;28751;21150;65033;51347;56551;54916;15202;38401;61537;26136;53369;56990;56682;11247;18789;30322;55050;26437;56549;65293;50231;64211;10784;39841;20690;55978;56789;27157;31332;45926;58750;52900;15951;53149;61767;33554;25358;26691;39552;45579;48560;12708;62966;18650;46750;39939;53439;55757;31000;27471;49132;55183;16895;47316;33945;27259;36283;29509;38932;20657;57948;25155;21197;11455;26302;23444;11314;37717;28945;50626;35192;10549;49043;47881;43820;24447;31929;60748;19895;27524;13183;34376;56197;62887;40291;22166;26168;47097;62863;41718;28348;11112;25085;36875;57877;12823;62997;21198;27021;59573;56388;63152;32537;22664;29833;49011;41059;30332;38033;31784;28668;31111;64291;55042;50270;28087;25988;39574;22450;63666;30969;11288;55866;58250;12413;16957;38227;14991;50613;27014;51234;48270;22421;13046;51118;21122;34171;33805;43048;17573;62906;24053;22191;52948;15594;41050;48447;31252;25271;55490;33717;50032;57912;18655;31093;38567;46903;25168;20977;61921;31852;19438;25300;46919;43637;54532;46738;45046;62613;62637;23125;30386;36919;21654;43975;51390;29334;49712;46044;49997;57129;42589;21060;55082;24825;21090;17508;45269;37502;31729;17094;42370;38672;16367;49681;55594;10920;14533;21666;15650;39289;31860;26849;51182;54025;38770;42020;11630;47671;58258;19880;52079;15712;29137;54770;65719;32757;52851;29940;61193;36856;58794;18957;60567;24436;21066;18450;32271;39700;50221;40570;21989;21073;46282;19710;35284;43418;46533;50348;31634;49120;36820;23911;42157;18887;19091;55321;22970;39017;41067;31910;32689;10275;34936;64071;25832;51750;44290;21250;57684;25142;57225;46067;36054;65617;52367;17059;14474;35101;39586;47159;58497;61803;42052;35543;66665;37103;14179;54648;19723;45182;15144;14248;16776;44979;22468;34815;41603;31329;47546;26265;22546;21888;58632;40421;48331;45536;21292;27472;21315;48514;38642;50428;50840;12019;27392;55908;58263;39462;15845;51782;43082;52456;65423;66134;56109;61471;16746;31004;49102;10406;58478;19793;27378;25965;43478;32122;46592;35485;65800;47620;19376;11485;21807;50946;30917;11653;49018;64045;27902;26218;44494;24030;14871;24373;25105;35029;33173;48193;60177;35763;31898;35530;53704;38482;13728;26857;62248;14190;66162;57464;46446;45103;54376;30123;56096;22017;34375;12948;24560;61230;39375;59422;21466;45119;45787;19473;30610;31479;43702;11359;59777;53734;33659;41906;12852;65242;26693;41712;13952;63733;61172;30810;19565;33672;37948;66954;61121;25861;42072;29781;60212;53209;41664;58135;10007;15384;62740;30231;20274;42334;25575;41868;58148;37441;20186;48412;55958;12783;21295;57591;12542;22184;47552;31577;42959;24706;61749;20521;31576;21993;30091;45696;41231;37713;33610;32673;18666;30947;14447;57497;28604;21717;46055;54581;33261;18430;63259;35832;28517;15572;29072;38548;41076;27728;32915;45982;24349;14954;22652;29727;25389;60609;10138;60400;35640;18866;49495;12851;42527;35134;55969;24201;54958;49993;59037;23392;56975;46684;33262;24530;38499;28628;60537;54052;39476;61299;22226;55047;21076;57782;47149;51919;66856;30637;22943;38955;31193;54184;54678;10101;36842;14166;25026;13360;57941;52398;26014;29693;44258;25804;63729;66216;15867;51958;39664;51222;55549;34391;53860;57244;27235;61268;29991;59958;43151;24497;29477;23836;14949;32008;36900;18120;50239;59073;16002;28867;53900;28729;58978;43732;23693;46243;12004;59015;66358;10801;30349;39774;57095;54843;15100;28134;61994;31566;33383;57478;22824;33476;11810;14712;46704;35435;33664;49536;58362;16061;51729;61291;25572;54201;41198;64150;60205;63294;13969;49438;50107;38679;30786;15380;60892;46796;49754;50460;10633;16147;50188;50815;43288;54584;62232;34813;48261;61854;57465;64267;31937;64010;61610;15439;46950;23142;51839;62156;50415;14929;25828;48886;30165;21316;26565;63406;38027;13235;56098;42351;60315;61159;56664;30317;60590;38639;31454;20047;23196;30249;27050;35529;31443;65274;29579;63651;21706;34874;30148;40685;61585;52507;43932;33718;13340;42147;32577;27618;41850;53825;59318;27738;43552;54871;46180;34118;54320;29224;52315;61317;64635;36694;37418;37604;29605;19512;41111;60727;58199;20772;28415;34551;36383;56709;17503;48618;34627;34445;28245;66719;55672;46557;17185;51432;62699;29415;50261;36020;21749;10008;44393;11659;35873;43670;35338;21219;14301;56675;24656;10559;22286;32635;64273;42771;48302;36287;41181;60010;25260;43671;61754;39216;10050;12119;62086;23035;59362;44603;38888;24238;27649;47064;13386;12881;19098;35815;15120;17131;23650;61439;18284;11576;50924;44724;21534;23565;65259;22642;59182;57706;39089;30777;33799;45471;43354;40915;45761;63050;27024;66606;63042;20201;47789;19395;63905;43780;12964;45390;41410;27442;22176;27357;58957;59109;21282;19119;50498;44858;50928;11814;34833;19894;48775;42764;18101;24798;17594;43664;17512;46138;14065;43300;64732;31915;20385;57759;14415;17163;25065;17076;61005;44274;55328;33308;31251;37773;25568;20152;42401;57661;20216;20622;49242;55211;50822;16404;25807;30176;53832;61026;20949;33192;16230;19812;39710;30335;43958;47570;14367;57331;53850;55391;41414;47278;56024;15179;49477;28662;55679;59244;66914;31166;19026;17721;14239;21942;51087;62683;60701;41116;16681;46612;38326;14143;65373;21809;29691;13301;40299;31186;27241;18503;62283;29287;19549;40530;50760;25226;26829;64115;28404;22641;19499;15050;16009;64148;46145;55634;58316;22292;38208;58687;36551;18634;24188;55589;45953;46930;29882;49328;37372;24940;30648;62358;25649;42172;40076;61629;31342;48521;55104;61109;21266;40374;51814;13803;26932;55608;48972;66862;59920;58273;20674;12632;43006;37335;38515;37626;41920;28378;66152;46606;16866;24673;50140;14716;53490;53766;57522;39913;13015;44620;35915;39468;38191;21742;52163;27776;60899;33123;12462;40827;41473;24406;34416;62729;54852;39936;35349;19707;11921;39831;27502;50468;63035;15322;17452;51633;54447;46468;40576;10036;12050;26720;11650;29559;24265;16306;28715;34852;61830;27162;14040;21657;62854;13153;54261;47062;22266;10294;26456;34140;44252;61574;58661;51989;22283;36185;52802;45726;46225;66345;18916;51869;42776;18457;17188;41647;53246;47085;31302;44943;40993;34880;36872;44680;13546;34385;50273;66869;47890;33955;41695;23696;44569;41913;15019;39596;22168;43191;32035;46497;23965;18272;42924;16453;51759;31320;30659;65604;28027;28705;34969;47325;50749;36295;63019;35617;49277;13182;26471;51119;43030;24337;51653;20272;12867;26762;42867;46022;12599;12321;41623;34548;28382;26185;58541;25306;49541;31224;40343;55033;23209;55345;65751;50237;52884;46086;33866;25007;15811;46255;45969;28900;22768;52924;24732;54869;12727;40867;13308;25629;16502;40924;10607;23215;16452;12203;39976;10768;43386;49625;53301;58624;23635;19254;48417;30924;55932;17201;45752;53780;53694;14128;49563;60351;53702;60890;48727;60031;43966;65903;56327;56008;20020;26497;15054;30193;19843;37996;17621;39540;21835;47563;15553;21611;34175;52030;31097;15154;66068;38640;15704;57871;63760;42430;40533;34185;60255;38928;27364;51642;55951;13638;49796;55373;26073;31645;41418;13430;13285;44940;55171;62396;30162;32973;63048;21582;22216;30586;21718;20040;63521;48222;62824;65660;42305;33856;37894;36627;38396;23631;38764;50901;18474;42818;62462;12416;17332;10548;42723;20085;32490;37946;50677;56820;11446;54828;42983;46224;38667;10567;24090;21845;53203;18527;57308;56533;58220;18047;49411;40955;42831;39730;57754;55214;61785;31007;22219;12261;11849;28755;58853;63389;21333;56026;49142;16629;21793;12067;60895;27165;47131;39553;42400;16463;10661;25202;59356;17451;13251;54521;50976;31613;31161;20851;48469;64751;25121;59607;11317;35158;63505;19826;51741;50545;62673;36465;23331;13714;41657;43931;56421;65044;17774;30598;45703;27142;19915;22492;39224;20928;12557;12254;27905;35020;63339;22986;26504;54336;38599;22530;46634;38339;55821;55118;65232;23735;44471;28670;43821;41977;23070;42817;25766;63372;10976;22507;18357;44358;17669;35756;24069;14695;35830;12075;57765;52387;61082;12487;45548;44166;43910;32723;62143;14136;62033;51783;55030;52287;16305;37950;59893;27081;24203;37036;36428;52897;12749;28438;35548;54918;52469;33622;58498;32504;59536;20833;42284;52586;48796;12814;13841;14861;28590;10494;58429;16767;40151;47206;62844;46360;41109;15365;49362;11318;22758;39666;32054;40506;20267;20932;62837;25840;55691;19911;14480;45057;43042;52987;54086;62275;56616;33273;49704;41082;48515;58149;28547;33872;36697;20296;66482;11068;22884;17608;52517;37115;21187;13305;39083;55186;18261;16354;51342;19005;59599;35115;50172;12323;46848;37800;44063;20015;16595;19459;48884;43913;56221;35394;14129;40360;44689;31325;65906;46560;32454;37361;19616;59119;55337;34499;46150;33446;40514;37625;22703;61293;28220;17224;62227;24427;50799;25349;32007;11422;37984;15493;30207;38049;43898;20615;48695;47883;56409;38507;14614;54182;12974;28537;30338;33036;48314;66013;43991;11902;15933;27084;49473;61509;58798;46280;46569;34070;53440;33352;50513;46683;20401;55931;39524;50891;65017;65771;29358;44977;47860;33141;23937;34257;11369;61688;25940;12739;57390;45704;62645;62085;54621;39814;32625;23353;52559;19283;35235;49408;61671;49209;51022;66692;19456;28077;16524;31711;33991;49208;66443;44118;36301;48148;53757;50305;18246;62237;25454;54366;36485;24021;58867;13755;45877;21294;23145;28047;53123;53212;62525;39537;24159;55013;58034;51302;21083;38503;28328;63140;54878;25702;18093;42492;44928;36037;51812;52788;25942;28614;55218;43231;11999;40270;23273;43844;49004;55491;65332;64684;59931;16507;25324;33473;56067;20471;49967;24052;27187;65177;66959;30398;59219;32679;32433;37663;24430;40044;48677;38120;29929;39706;45237;45429;39621;63473;54257;39640;19198;33492;64977;57335;39925;54999;19317;37806;50076;60182;65848;66661;58765;38131;46247;34916;59459;11232;39291;49565;66589;20206;16370;59841;47308;21798;66042;54485;29186;55578;41550;43416;51671;19293;20492;13482;26701;46629;38222;30665;33593;61687;18343;55455;26264;24229;56749;66452;15302;64285;14206;64705;15141;44706;25315;56070;52536;32599;51569;16973;13082;11561;24785;18837;51897;32615;29383;47496;35252;40772;40386;15390;36589;14986;20573;18096;50048;48685;11836;51909;22582;42136;52198;32385;45042;49533;32010;35023;53443;22046;35487;42190;15513;34677;31307;60276;33740;58743;66373;60972;58784;37146;50681;36059;29654;32702;34276;18068;17792;61833;47347;59140;54377;38655;51842;56326;18934;49947;18577;40700;50299;66043;35934;19219;39201;42075;26050;16567;38779;50985;11531;55266;30953;24109;16715;39374;57668;52218;60641;66407;53753;28918;47434;38308;55946;34978;62531;50505;65614;43427;29551;12450;29062;38435;54325;16849;36434;66877;42797;41233;66170;27706;43948;47076;53135;43286;11141;24832;58714;36323;64997;51423;36969;22988;47868;57786;36733;49226;49643;22362;39865;51816;44150;31880;30655;11149;38466;26816;56012;34717;34757;48338;56805;38573;10990;52635;22159;59625;64931;51809;19845;49317;10270;33496;38732;55113;16604;64479;54233;51140;10115;44945;47004;19381;46742;46441;66687;59751;57634;48458;31649;62870;21504;27587;43154;66394;63084;57220;33923;10340;56780;52838;27750;63833;22968;51884;11015;45311;65218;45502;35348;46039;17422;21262;48456;54502;17320;55198;20954;56269;20024;12531;26750;35754;43978;38757;41286;60551;15309;13831;63137;60377;58064;43054;66696;39274;64271;35539;44206;24772;18905;32131;36593;57449;61170;50601;63144;46264;32006;25717;22193;22882;49238;21931;25636;16703;37684;15033;59379;57770;39695;10995;54454;29581;42956;43209;48431;22972;17636;54961;45725;52549;25298;34498;65343;55609;21307;52464;51826;64346;31250;50160;32491;33289;22167;47812;50245;19701;14186;25072;50170;29787;17384;53129;55470;20294;17250;23424;62263;53679;37005;23033;13983;37658;64662;34473;56685;58815;37847;33800;23160;63988;21179;31360;13606;51156;57841;11004;49940;33733;26689;36098;31562;25133;62048;34719;54522;47622;16228;39021;60012;12893;52862;65927;63476;21606;61123;51204;44751;47885;39186;11231;42238;36950;31072;26447;38657;21817;32441;33671;50072;33686;20896;22284;30657;53003;51064;16154;64691;45716;42356;23448;43463;14600;57987;24528;29927;50969;32150;50752;31351;12003;18494;26831;55555;59381;36055;10541;12000;28193;26830;53654;11123;27129;61530;56930;45252;42734;53800;51901;12387;36090;44551;42914;30150;35655;21459;30602;60690;42364;27930;28275;61898;49391;13287;42097;58962;10862;30742;21999;39032;54688;26224;18597;42646;22940;22885;42237;10425;24991;66432;56971;49392;28312;18419;35648;27275;53333;61881;39420;59803;31070;34984;38493;64651;37783;25673;62054;40226;47529;42614;22449;42675;15859;23412;44134;45552;45560;33353;23192;18950;47255;44180;28857;37695;39174;13263;35417;10736;65882;59960;16256;31978;21549;25899;25433;34232;39565;62043;11319;37893;52816;54788;55721;32778;21259;20582;12535;15589;26100;12002;57471;64159;14866;64645;55485;35413;57740;56167;46153;34083;57933;12102;40691;24474;14181;13130;59670;36199;60979;38591;35264;16687;43237;10292;14424;56460;10427;44714;25620;32048;40367;10043;46849;49175;35110;22866;10664;58682;11519;14550;20166;47056;53853;50274;46120;39962;21320;26054;41125;17606;15423;34494;54095;38802;54103;33469;18925;64770;26117;39463;55233;25104;10288;11146;34744;60478;38664;31156;33757;37182;37692;64384;65455;16035;62512;15722;39788;62888;57677;50099;55287;41450;12452;44997;13693;14631;52641;41509;19825;50052;19530;43264;12390;56837;64006;55699;53796;61910;64655;33218;27913;56890;44373;46102;13011;45484;37573;15157;61622;23761;54519;35879;49986;14121;30430;47304;46447;29990;11320;28292;51243;47602;11352;30385;51725;27117;66491;11365;10319;28717;57708;28125;23859;33959;29746;64620;21591;43776;18433;29082;61534;16676;50596;29375;34317;16055;56274;17090;15212;24554;29562;17722;46521;14644;44281;33332;61191;30870;55385;48755;38028;33279;50830;56871;59002;57819;58927;57638;26338;54844;55478;25156;62783;63148;16246;21065;11830;53663;39202;24609;33933;38200;14230;66801;61923;39069;21491;11274;48309;57934;50010;25986;25712;64355;65302;61628;18521;51129;18377;64351;50814;31013;35431;18953;49869;31279;50527;42497;14853;17758;32830;10962;43280;62474;42949;34697;66362;60016;54587;18562;45894;23060;15755;65647;38145;44566;48878;21897;62128;19992;47358;52021;40371;15153;62622;26392;63870;36026;43537;20768;59987;63697;28735;56403;21373;26542;21767;21596;27892;13296;24631;50232;29075;27252;13619;32521;13505;57914;48364;19766;66440;31084;61304;63159;12955;30500;30744;34286;15529;56986;35006;40898;45831;53885;57892;29531;11400;56575;14939;14383;42691;61926;54029;40048;34150;38069;27352;60051;50386;52468;57371;11467;54207;34570;47843;59170;25622;14925;58090;51247;10940;26242;33836;36429;59601;26255;62186;35018;20348;22869;57566;46238;61326;26894;11677;34423;30356;59656;25685;27585;53846;32780;27209;21005;55826;20726;31783;17396;43144;29609;26321;55293;16420;38335;22820;55727;19234;10254;52718;52765;49104;18444;55467;38268;31502;37993;35549;20133;22684;61832;59254;22187;55751;23085;32383;23419;57724;33583;33925;54702;33582;50021;51309;16007;28269;17151;60800;30533;19343;48326;10399;13906;60918;24753;65681;19073;47373;46735;49790;20658;43094;32750;58217;42806;11558;10413;44357;18386;14370;35420;42048;60408;57720;35239;32939;18392;30994;31488;25157;33038;31854;38290;55176;34260;10819;64680;46905;17305;36781;16538;43403;54809;59128;37943;42576;11376;59963;65540;38196;35494;20795;13075;22307;62120;31083;60283;12734;14495;21564;21901;15804;51278;25679;53816;32980;23221;66111;45214;13265;28095;21394;58427;19354;43375;48253;31480;14969;16026;35039;28674;34208;14386;63931;44976;64843;34104;32494;28276;61038;44925;56721;45899;51482;59620;42491;54744;23278;53426;49247;34832;62627;14635;62181;18890;47592;18295;66668;37563;29937;20383;18303;63124;22113;25667;17816;31540;41980;56111;36869;15501;24463;26828;24492;19239;38137;63551;28549;43059;29898;39781;48558;21347;37976;28869;61144;42151;22398;50885;55977;24233;32965;46880;38791;26206;61929;27910;21385;63730;36342;59107;12259;41490;11458;34299;37986;29523;23109;48765;31519;47355;56935;43266;61664;16678;59856;59227;56691;28776;60716;35948;32962;64077;48826;47165;36031;36072;23526;50383;14894;54265;60768;41796;61591;45041;45634;33454;57450;24703;61933;55140;27479;66925;52342;50396;38501;45702;29461;42793;35520;27518;26272;61648;48370;46682;38742;42599;66435;38093;45774;52931;36499;26981;23114;65296;66097;38100;39300;42987;19743;58844;52041;36471;47267;54374;31825;16302;13368;15076;26325;30567;14660;63608;40979;35241;56926;37298;26319;14962;49990;55063;46843;50538;10851;12302;26764;51823;32117;36636;36725;41722;42438;26033;10883;18144;45348;35701;37209;33207;25987;17211;39372;50728;29447;19936;50973;22830;44342;57208;36809;28142;23501;31794;22325;19533;33448;27102;16782;18982;59274;43745;57227;48387;63532;46364;39243;49520;57530;42512;37195;59019;41179;34595;60710;54312;59321;15009;30635;12422;13574;19958;16880;49508;14854;11333;41171;65139;54032;60688;20822;48450;25001;62759;42996;64299;60495;17988;52460;51691;59649;27456;30558;59840;11177;56768;21201;55417;54789;10200;20980;26975;47103;44550;42907;47848;46982;60856;25403;15459;65582;24844;29259;62441;24622;48301;29055;29920;48177;40508;48859;18972;20934;21344;25844;22056;35731;32403;45981;55584;65295;39548;44405;44182;31232;66375;64922;48733;34643;28602;12538;51625;29769;43804;55987;25251;50584;48204;26232;56134;45555;66014;39721;32157;62577;38982;52798;20349;14649;53095;61235;37332;56848;17040;61266;65554;62454;58417;23882;41151;19088;11713;50407;60204;54529;41736;24485;27359;47294;59928;14490;28052;16193;51080;31390;19665;14748;50494;58174;66797;24873;42563;61831;36768;39109;39796;30587;40894;32700;18108;18862;32415;17359;28864;32151;21712;12033;64570;33586;40224;40613;58363;50878;26655;62857;14607;51455;65542;58931;20474;66576;38390;27532;36717;11693;40222;33164;49548;18780;23252;22228;15147;12459;51425;56368;37726;28139;43714;20239;59748;57929;45849;65712;25227;23920;53818;38151;39126;50977;33057;14021;37654;55017;21323;58789;46481;24939;48770;36389;50511;44016;29360;61457;23886;44428;12013;11380;51608;25913;53383;47776;48235;17352;54030;66641;20170;41947;18203;58340;54179;30923;48726;58804;16019;25038;28281;14641;64058;57104;12827;66907;60809;41552;25099;21567;37386;65116;15772;41350;23048;66477;59004;59253;45797;53042;60910;18039;49407;62772;37357;42154;42539;11276;21825;30273;11669;30295;27695;38355;13674;24875;21366;49415;63177;33654;46278;47242;39483;57009;33719;17823;21849;63333;18872;31578;21185;65946;14099;48228;39242;37562;35953;47392;17007;53601;51850;32248;20708;53984;24290;64720;17241;18313;57545;39646;30796;15631;38305;62479;26486;17987;29216;36943;45197;28085;56336;38130;28773;39637;21960;16474;30622;34933;41637;51613;37295;47096;13200;31152;39619;38772;17709;47391;63758;52511;64152;55813;36532;66536;12637;46211;52103;22369;55577;38620;32259;39239;24135;63410;21600;49629;44707;27198;27434;12517;10698;29763;45613;29806;11038;45195;54863;32159;10699;66972;58351;27182;25303;45805;27620;57202;37513;39994;24983;30995;33566;59405;54562;47167;66036;61907;36204;20101;25781;17704;25132;41840;49026;43281;40670;43299;33340;23108;16677;15985;31718;57810;44816;49050;22244;20638;43525;22422;43689;18232;11496;54948;35588;64875;36961;16693;63491;30464;47757;33174;60671;40571;55229;22932;14960;24929;58625;19950;37016;32171;19486;33553;47822;36607;42004;52599;23464;41307;59894;50995;32563;33404;23157;17679;58727;14044;26482;28448;22600;46837;12836;56945;64483;17307;35772;20508;35400;31695;46339;64848;56312;37269;59173;34743;31221;66860;61198;60099;58127;10533;58774;27166;38952;33519;20717;41811;61069;15889;28191;44465;36741;60281;20116;30410;58635;35206;24108;58074;59945;18069;51454;31343;45967;46911;44458;66331;54342;36701;64707;28244;58671;32988;41844;36938;65711;19796;46773;57105;29394;65813;26759;39407;55465;13528;63584;31875;32289;12288;59316;64100;26731;16099;44078;26963;13774;34849;41385;31211;63478;21152;48614;22774;22708;54691;44783;28648;56007;53145;13651;33307;11262;48221;42458;43925;24744;46473;16535;17447;19870;63272;37050;38526;19065;54066;37567;15578;52964;35980;47487;40162;40899;26406;22473;46609;63954;64330;63189;44255;53243;51841;42349;58676;65163;56216;22330;42329;63403;12212;42102;11926;38823;26077;40304;59706;42840;54604;45999;23232;30899;56195;12317;66045;44288;33939;42850;10460;37794;26285;57162;52493;45810;61273;30903;63825;14581;10865;43385;43147;50218;49842;39233;41493;60928;37076;29500;28876;64074;61096;52425;18000;10394;40607;55302;32244;60190;27070;63915;34434;60574;17397;19378;61427;50645;18089;58598;46071;53911;57893;43170;60691;22977;36857;35233;60429;34645;52421;15928;46082;17058;50523;20337;36063;62505;45637;13031;19657;37479;57072;25497;52915;16983;65526;18571;45355;19725;14471;34051;44759;47473;35061;20230;19713;65869;53902;42057;44480;11223;55479;42023;43567;38045;10078;52571;45313;47753;20735;20520;14349;35452;46509;15485;66815;45096;21932;31585;50399;50949;47275;37395;34623;26956;11129;57120;62379;59434;26442;57037;32665;59930;33887;42393;26263;12613;16865;24516;12012;14522;56462;25936;24453;47716;66953;51494;20777;16795;28456;15220;48504;33223;45527;42363;55695;44617;63419;61300;26570;54308;50224;21452;50775;22043;42955;19391;57697;33840;25181;24583;22370;16920;23851;60884;32073;40797;36538;44335;22760;57228;14872;64669;44705;51023;58885;63126;11761;63598;21996;29095;28525;20436;22993;42259;32205;41887;58019;26730;56895;13837;11490;19227;26937;28807;33834;21068;56732;55966;12882;35050;47340;32535;38536;40904;15190;45976;39696;21581;41834;30086;31804;65309;62777;20145;29184;37832;66173;30582;60075;12937;28023;62083;49266;13007;10028;21040;29989;39278;13620;11391;63363;56235;11218;57968;12084;51147;26536;47682;14006;51552;52724;25467;31422;31926;63458;13330;32627;41503;37547;19429;58886;66156;20487;62872;13955;20533;48880;57185;15249;29922;65562;14291;19023;21837;65168;24465;43678;59485;22097;13645;45865;17431;33493;30475;24125;59038;30844;38170;41065;14593;33673;59718;48230;11898;11755;64696;30023;29514;19319;50791;35707;48163;40043;60565;29000;26856;48407;31984;40615;34696;48561;62738;65365;43510;24776;63396;50526;62649;13833;43706;42511;16301;46800;32611;40774;63883;59063;15005;29439;19798;23292;25914;17383;43053;58554;16872;39527;54134;46575;38994;61784;37406;48612;34788;22098;30463;63057;11893;15008;58969;15046;37398;20126;35228;10786;20413;45563;50833;45315;26715;23360;53456;17365;66233;12319;59480;43926;43894;66368;37914;44803;32497;28078;27158;26165;33462;49397;59491;24619;27063;11489;51610;43379;30493;25848;18994;66348;13815;65005;62149;11429;48965;42639;19489;55462;26873;30698;18478;39882;64978;59361;26115;43245;28762;48616;20452;34656;45433;44643;43368;64396;19348;54483;44017;45309;58739;32502;36687;48660;62724;23747;19916;12692;16040;25134;39839;48692;33029;51511;17804;47087;36056;27509;22974;54556;13680;23765;38625;42292;52693;48220;37833;31909;29189;49886;50307;20396;53186;56011;35609;34501;31447;12243;49511;21765;38409;28898;62420;58818;23834;53977;25076;49042;15746;30966;27310;18415;18949;61261;38188;11357;23475;17820;30432;19314;42861;57942;50481;49755;64730;29416;29431;21668;17514;13657;41582;46100;64826;50096;41942;24853;43521;52575;27427;66874;59075;15446;45769;12351;29162;36085;38966;61008;45664;58866;33764;63526;14595;35983;41608;43269;31361;54307;17010;30560;42752;15240;30233;17287;41995;66608;33347;22346;46816;25342;37329;57362;28775;43489;21162;34254;23679;38544;36239;13820;51969;66919;20443;43462;64462;65243;59581;60993;18963;49176;44169;39022;29116;61012;54319;26313;19965;37408;48400;34950;23150;58741;29554;10447;66159;56722;63946;63517;31324;36108;40213;27057;12092;48361;50844;40087;55973;20392;40086;43022;30841;18751;57523;44988;13604;16592;55428;27110;57343;46422;60867;23617;59749;55795;44495;37422;45089;58768;18049;59311;29194;40387;28797;16997;23064;47403;65456;57649;14392;46515;26135;57289;63867;46989;46349;35943;27815;23889;56755;26251;55720;50118;54780;56629;39732;26174;40031;47309;58550;17030;26732;55035;66374;34535;46784;52158;46070;47279;44908;61422;36172;59385;11637;25978;62539;51612;13637;66639;52732;43439;14730;52682;34758;49202;27574;35019;66249;44497;31703;57326;34612;13981;28759;31209;15045;42780;41744;30408;39329;50295;14699;32850;44386;19203;57804;25437;42499;58531;31091;39973;45379;39494;53142;20011;49117;26553;36080;27332;28667;11698;32025;33243;60368;20917;54956;55690;21384;37666;20025;19745;51135;55697;34957;10523;46323;55230;47658;53862;40478;47874;40067;10585;11074;26581;39536;10048;29779;29601;10574;26949;58938;47143;22021;61673;10553;35703;25968;41261;51562;36537;45743;60887;36985;32077;32694;29856;37544;66782;14535;10850;60223;44443;28861;31138;11005;52340;56295;22581;64379;28551;43018;29613;39571;41263;50956;46139;51946;29873;65049;46691;52065;29135;39082;23373;31586;30373;44095;49301;31416;20781;20416;14615;42989;50510;33115;26577;62528;37843;24385;48478;54362;65035;60465;27242;36992;44128;57138;39244;49456;59235;54826;63739;28204;66479;66269;19835;26002;57679;31398;54092;51457;17012;39905;30987;15399;26350;19784;66065;18293;35606;27412;30015;15320;32443;20218;29714;50461;50492;16875;47845;61128;39150;43148;38988;22493;21883;50843;49854;66328;39451;55970;20881;42124;20530;59662;11235;17000;61340;37543;11812;22522;27569;19373;27248;62405;19544;36173;61211;47869;16197;60446;45530;56883;57351;33018;38777;37219;55080;36779;57891;32488;41937;26410;43788;19502;17972;30820;25640;65020;24541;57428;49329;22862;43557;29859;46452;18088;16249;43625;60405;44065;46582;42447;59301;62670;23769;21641;51624;18338;51362;42348;19242;46881;26464;43195;50484;16138;66952;11514;18325;28337;60524;54931;27003;30677;22991;27977;15424;43634;53043;25652;60210;47284;57163;22209;37937;28995;65400;66836;61165;64142;41393;33467;21914;15526;24501;46597;19137;28451;45882;53078;45757;45690;25759;28965;62813;58952;13371;58131;65361;33295;14506;53465;30948;29327;58009;63769;36307;24005;15105;16334;61124;62241;49709;15696;27190;37315;10063;26817;24010;19392;39868;45460;16434;40968;64011;39767;62282;61894;19516;35484;41186;35086;52454;46137;51402;36276;35246;32924;35925;33483;58099;51916;20032;51501;41120;45939;35909;58485;10301;26697;43108;22452;42786;56431;53719;66684;15206;61240;61954;57682;14294;14160;35429;26229;30054;59698;48894;61135;39749;49067;22014;50029;60820;61562;48565;47049;10179;10477;32452;56101;45247;28467;65326;63110;28646;60580;45510;37771;32161;65222;60848;52020;22339;36515;27147;34690;10303;65330;16219;62337;63020;46361;31445;46080;38073;66371;66204;54663;19579;16979;55572;54117;23404;65297;12768;31073;55078;59826;44749;62108;15366;34512;62639;26316;21329;56916;13127;14161;47305;52905;58594;15903;13900;21859;54919;46811;46967;42557;25297;32192;43161;48296;54978;57233;28376;21884;58106;45917;29313;34946;60423;16170;19589;45983;46119;59908;50106;47613;12678;56176;43190;60698;32435;43429;17279;38735;62521;10205;64064;15495;14543;41866;12233;41905;61711;36425;43227;15886;54037;33620;16491;51643;38826;58356;16096;28214;40566;18734;53150;26074;19941;63921;21012;47604;60259;32472;15521;64265;60388;21650;34523;57349;46427;34881;16469;31758;35378;34626;37740;30453;37253;14198;42312;24751;20220;44023;37052;56524;56164;55723;18606;28817;51339;23370;23238;52035;12857;27809;20946;65636;47802;18901;46494;39093;12030;48785;43651;23095;13102;57287;62967;23670;41477;13773;61658;63528;44879;36008;65541;14240;30365;36267;37992;50187;13186;55989;19304;28868;58169;12371;60516;30990;10645;51208;65466;56907;50838;53533;32465;16331;10986;65394;38563;33239;23529;25184;41390;62802;39262;64777;61098;42410;18475;27730;31310;42022;61589;16144;46505;47093;28196;59068;47368;53839;25200;59136;45483;43888;16451;38971;16372;10393;44404;38576;58495;51545;13394;37933;61151;64703;65715;13211;51312;25186;47446;32957;22152;34402;32420;23878;62056;23498;59188;65126;62752;17648;60156;62423;39131;49593;33790;35621;57224;27096;51324;59568;38597;42668;55906;18731;12376;44521;19629;14340;38287;63854;61035;29752;13385;24458;27408;11679;34948;51834;36040;56260;44111;50433;35887;65344;32272;57718;31772;40975;64591;16282;34582;22169;10029;63781;45329;26522;25727;19031;12201;37546;36720;30418;18910;44964;61734;22494;58082;43479;40992;30678;65009;47598;54241;26866;40665;16004;19318;18675;54318;15684;15453;38956;18495;58020;46350;41268;64585;30524;57743;62242;17145;23149;22573;30265;34614;19938;30916;14630;37175;22245;59744;34493;16560;16140;15291;31032;30443;65118;16540;18938;52637;11143;52947;57802;63622;21441;57874;47039;28641;42085;36160;11740;48988;49006;31799;63442;13335;66194;16702;23590;25806;13613;35942;25637;30975;56061;27783;13982;63590;48490;47879;28664;22739;48360;37982;33577;50922;41814;30421;56315;51175;31316;10815;58181;40496;41610;25907;19267;44616;36893;22246;56522;16058;20010;65453;36126;15311;24377;32942;35211;18964;37488;10881;14213;18035;14112;45356;10734;44106;65370;33070;60832;14249;39977;45561;18898;53056;64610;14408;19660;56753;45464;40187;47475;59031;11053;35540;31524;15030;18986;24475;28848;38953;23338;15781;43838;27517;66922;33745;44212;24132;60699;32597;39688;53399;64109;27290;58271;22893;59685;26038;49189;62616;49858;10922;19285;38353;56734;58571;62398;56547;28791;34709;13556;44191;39690;31402;47380;24110;46782;30326;24358;41113;31633;62711;20072;42373;12769;17420;29549;54548;23359;45821;62990;38676;59460;10988;60284;17833;19600;25003;54106;65452;54076;53321;58210;64965;62464;63007;21603;25933;10968;20140;23369;32998;11205;22002;55535;16931;44190;42487;33155;36369;44273;32592;14365;21818;62485;50082;35513;54757;46877;40010;11684;26708;42318;41560;33280;38118;43977;61203;52417;62475;12381;30955;63891;52881;15710;41296;49595;66020;22261;20176;59247;16723;16410;15937;51275;52406;60415;29344;26793;28280;61491;21243;30152;58228;33761;60411;51451;24026;16640;16181;54952;48330;57299;25811;25823;29981;31485;65060;23004;44261;51744;40122;10366;33696;37436;62463;63024;10939;15337;11598;20078;37156;26563;28833;56898;21533;23336;14329;51011;60941;57859;49358;43897;26972;64795;57903;54649;33342;51882;49933;21573;28601;47608;16202;10112;19468;55019;38890;55975;35168;31768;56346;53873;64545;43235;63800;59089;13724;12710;11344;12914;42692;58811;46938;61939;44652;20558;19360;53233;63831;35198;65926;50442;39116;32777;14857;58499;49076;63818;58607;51589;37114;24922;50480;54583;27494;50984;10783;43397;66656;58073;54301;40485;65978;64496;43719;31288;41176;50293;61351;24361;12073;33952;12099;25999;63774;49827;10407;39719;53189;40925;26284;15771;60412;56851;54226;61476;37234;54738;21338;28484;47075;46455;54304;53668;59978;63302;32187;55722;64936;56565;34400;12907;45133;14178;13050;43326;63827;64840;34251;60812;32589;10605;49513;45631;65566;13273;26126;65404;31299;51560;49380;39880;27637;50490;55836;56773;46565;49708;56450;55136;23056;20774;19012;56896;32811;60322;26181;61344;55711;25381;25557;59722;46053;16437;29229;14904;63076;30775;38867;14045;27342;24279;39255;52230;66785;42414;16304;44801;16188;59951;30042;51830;49951;41357;59388;63562;41229;66969;50972;38158;51689;50624;60088;35904;33703;63614;33178;16159;25580;64317;31180;64034;37673;24713;22207;22574;32654;56839;57500;29039;56588;25376;48280;31208;63750;43360;46886;17205;49538;14537;32940;44457;46157;37896;33221;63556;30038;49306;50226;20161;12666;30394;23178;60497;64112;53544;43278;58958;40064;26535;50902;22347;57382;13808;60766;40370;39117;62778;45611;20453;28346;60589;58400;21543;17528;66791;57171;65408;56641;36079;47246;19892;50904;16242;27395;59446;62445;31961;26903;18453;16594;21772;40727;35951;61578;22437;46998;62478;40891;26040;42621;20827;13400;22627;35730;41088;10093;11407;63570;30599;30772;61889;36162;28252;57194;30517;31793;55057;46747;65858;25062;62655;28380;12262;50746;52415;10276;60649;60063;14070;22455;20440;45231;53810;34469;59403;51738;54034;38712;13890;66828;51708;51491;45437;36065;28133;55236;19423;20991;22927;45603;16128;35978;57913;27600;17694;40996;66329;40079;45266;21551;28779;45607;62401;36015;31946;18322;45367;24790;47617;45720;65609;40599;12567;16275;15743;44948;12587;19962;17342;54846;31384;11284;36606;56166;33456;59427;20587;57907;50267;37302;41206;53724;14268;26009;49760;64236;16010;45336;33504;40211;15934;41330;16533;28285;26585;25067;41755;29443;56652;47799;16390;14222;46721;46196;36082;20033;28130;23854;29835;28998;11799;34293;64747;50148;43798;24510;28152;56906;44649;27483;36509;59250;41143;47455;30588;30523;25089;35327;12773;60811;20235;29684;25662;61446;20940;32229;55152;25367;65844;19022;12780;18060;54059;51934;64146;24702;53915;57094;36851;30461;27808;13740;63958;18888;43136;41611;54197;34481;46391;31247;39819;61611;16569;40988;15656;32663;38168;16051;43639;60062;62541;36501;38490;46522;33813;40375;14673;11989;23058;59243;56190;32868;46298;16549;21480;46605;20037;63365;49023;34341;51799;33902;21171;50552;13053;59975;39167;24722;26724;20375;24895;52144;29865;23852;53245;38253;28576;41421;65050;44781;17219;17654;52959;21464;13169;19780;22523;13002;50183;13134;20685;11420;15915;18400;32300;12391;25918;10182;32082;13191;61020;50566;19082;13887;63972;41770;52004;13483;30896;48268;30045;49962;28950;40844;48913;21387;44503;15636;33534;31198;31005;54416;44131;53916;22817;64448;44868;54055;47388;65431;18145;13928;29628;39862;24905;16163;27568;47472;60974;39969;62902;54471;64633;39264;65593;64272;60920;66525;12500;16806;65599;21816;49421;61234;56912;24596;32238;10588;20148;55207;17054;27767;44429;31179;16199;58596;35328;44112;11804;12472;13067;24347;24864;63716;24946;47600;65794;17436;40232;12602;29163;57989;19747;66917;65089;46960;50680;46285;28531;23850;31428;28117;21257;31355;22170;56998;53517;31935;57367;10153;65495;34712;22711;20306;27979;37617;64992;54739;45905;34883;26376;29006;65029;38720;14877;23749;15894;61459;54680;26566;33809;49823;20089;31345;59278;16947;34217;42543;66059;66289;49193;21674;42584;52402;62126;19943;14010;35157;32914;20970;48199;48948;65952;56696;26197;56684;62023;65835;22750;32042;14177;40531;62222;50327;10505;40065;37801;27225;25410;56512;56771;56224;32896;32261;24888;61201;52826;19702;34929;35946;46083;27181;28391;46313;12792;13119;54493;45346;54278;42513;48996;32953;35381;64716;38385;62527;34419;61194;32732;34072;10938;65987;49089;53896;43011;10837;55329;17042;57191;53199;60959;54315;</value> | |
| 11 | </preference> | |
| 12 | <preference><name>TARGET</name> | |
| 13 | <value>preprod.boardvantage.net</value> | |
| 14 | </preference> | |
| 15 | <preference><name>throttle_scan</name> | |
| 16 | <value>yes</value> | |
| 17 | </preference> | |
| 18 | <preference><name>listen_address</name> | |
| 19 | <value>0.0.0.0</value> | |
| 20 | </preference> | |
| 21 | <preference><name>non_simult_ports</name> | |
| 22 | <value>139, 445, 3389</value> | |
| 23 | </preference> | |
| 24 | <preference><name>slice_network_addresses</name> | |
| 25 | <value>no</value> | |
| 26 | </preference> | |
| 27 | <preference><name>max_checks</name> | |
| 28 | <value>5</value> | |
| 29 | </preference> | |
| 30 | <preference><name>stop_scan_on_disconnect</name> | |
| 31 | <value>no</value> | |
| 32 | </preference> | |
| 33 | <preference><name>host.max_simult_tcp_sessions</name> | |
| 34 | <value>unlimited</value> | |
| 35 | </preference> | |
| 36 | <preference><name>report_crashes</name> | |
| 37 | <value>yes</value> | |
| 38 | </preference> | |
| 39 | <preference><name>xmlrpc_listen_port</name> | |
| 40 | <value>8834</value> | |
| 41 | </preference> | |
| 42 | <preference><name>whoami</name> | |
| 43 | <value>famato</value> | |
| 44 | </preference> | |
| 45 | <preference><name>audit_trail</name> | |
| 46 | <value>no</value> | |
| 47 | </preference> | |
| 48 | <preference><name>policy_uuid</name> | |
| 49 | <value>D2A991B9-F116-4540-90DC-97BFA7DE615E</value> | |
| 50 | </preference> | |
| 51 | <preference><name>reverse_lookup</name> | |
| 52 | <value>no</value> | |
| 53 | </preference> | |
| 54 | <preference><name>optimize_test</name> | |
| 55 | <value>yes</value> | |
| 56 | </preference> | |
| 57 | <preference><name>log_whole_attack</name> | |
| 58 | <value>no</value> | |
| 59 | </preference> | |
| 60 | <preference><name>ssl_cipher_list</name> | |
| 61 | <value>strong</value> | |
| 62 | </preference> | |
| 63 | <preference><name>cgi_path</name> | |
| 64 | <value>/cgi-bin:/scripts</value> | |
| 65 | </preference> | |
| 66 | <preference><name>unscanned_closed</name> | |
| 67 | <value>no</value> | |
| 68 | </preference> | |
| 69 | <preference><name>save_knowledge_base</name> | |
| 70 | <value>no</value> | |
| 71 | </preference> | |
| 72 | <preference><name>xmlrpc_no_referrer_check</name> | |
| 73 | <value>yes</value> | |
| 74 | </preference> | |
| 75 | <preference><name>use_kernel_congestion_detection</name> | |
| 76 | <value>no</value> | |
| 77 | </preference> | |
| 78 | <preference><name>listen_port</name> | |
| 79 | <value>1241</value> | |
| 80 | </preference> | |
| 81 | <preference><name>auto_update</name> | |
| 82 | <value>yes</value> | |
| 83 | </preference> | |
| 84 | <preference><name>checks_read_timeout</name> | |
| 85 | <value>5</value> | |
| 86 | </preference> | |
| 87 | <preference><name>plugins_timeout</name> | |
| 88 | <value>320</value> | |
| 89 | </preference> | |
| 90 | <preference><name>auto_enable_dependencies</name> | |
| 91 | <value>yes</value> | |
| 92 | </preference> | |
| 93 | <preference><name>safe_checks</name> | |
| 94 | <value>yes</value> | |
| 95 | </preference> | |
| 96 | <preference><name>report_task_id</name> | |
| 97 | <value>8c306ca5-5314-476a-34a6-d66657c2b837c62dc0206bd28ea3</value> | |
| 98 | </preference> | |
| 99 | <preference><name>allow_post_scan_editing</name> | |
| 100 | <value>yes</value> | |
| 101 | </preference> | |
| 102 | <preference><name>stop_scan_on_hang</name> | |
| 103 | <value>no</value> | |
| 104 | </preference> | |
| 105 | <preference><name>max_hosts</name> | |
| 106 | <value>80</value> | |
| 107 | </preference> | |
| 108 | <preference><name>plugin_upload</name> | |
| 109 | <value>yes</value> | |
| 110 | </preference> | |
| 111 | <preference><name>reduce_connections_on_congestion</name> | |
| 112 | <value>no</value> | |
| 113 | </preference> | |
| 114 | <preference><name>feed_type</name> | |
| 115 | <value>HomeFeed</value> | |
| 116 | </preference> | |
| 117 | <preference><name>silent_dependencies</name> | |
| 118 | <value>yes</value> | |
| 119 | </preference> | |
| 120 | <preference><name>port_range</name> | |
| 121 | <value>default</value> | |
| 122 | </preference> | |
| 123 | </ServerPreferences> | |
| 124 | <PluginsPreferences><item><pluginName>amap (NASL wrapper)</pluginName> | |
| 125 | <pluginId>14663</pluginId> | |
| 126 | <fullName>amap (NASL wrapper)[file]:File containing machine readable results :</fullName> | |
| 127 | <preferenceName>File containing machine readable results :</preferenceName> | |
| 128 | <preferenceType>file</preferenceType> | |
| 129 | <preferenceValues></preferenceValues> | |
| 130 | <selectedValue></selectedValue> | |
| 131 | </item> | |
| 132 | <item><pluginName>amap (NASL wrapper)</pluginName> | |
| 133 | <pluginId>14663</pluginId> | |
| 134 | <fullName>amap (NASL wrapper)[radio]:Mode</fullName> | |
| 135 | <preferenceName>Mode</preferenceName> | |
| 136 | <preferenceType>radio</preferenceType> | |
| 137 | <preferenceValues>Map applications;Just grab banners;Port scan only</preferenceValues> | |
| 138 | <selectedValue>Map applications;Just grab banners;Port scan only</selectedValue> | |
| 139 | </item> | |
| 140 | <item><pluginName>amap (NASL wrapper)</pluginName> | |
| 141 | <pluginId>14663</pluginId> | |
| 142 | <fullName>amap (NASL wrapper)[checkbox]:Quicker</fullName> | |
| 143 | <preferenceName>Quicker</preferenceName> | |
| 144 | <preferenceType>checkbox</preferenceType> | |
| 145 | <preferenceValues>no</preferenceValues> | |
| 146 | <selectedValue>no</selectedValue> | |
| 147 | </item> | |
| 148 | <item><pluginName>amap (NASL wrapper)</pluginName> | |
| 149 | <pluginId>14663</pluginId> | |
| 150 | <fullName>amap (NASL wrapper)[checkbox]:UDP scan (disabled in safe_checks)</fullName> | |
| 151 | <preferenceName>UDP scan (disabled in safe_checks)</preferenceName> | |
| 152 | <preferenceType>checkbox</preferenceType> | |
| 153 | <preferenceValues>no</preferenceValues> | |
| 154 | <selectedValue>no</selectedValue> | |
| 155 | </item> | |
| 156 | <item><pluginName>amap (NASL wrapper)</pluginName> | |
| 157 | <pluginId>14663</pluginId> | |
| 158 | <fullName>amap (NASL wrapper)[checkbox]:SSL (disabled in safe_checks)</fullName> | |
| 159 | <preferenceName>SSL (disabled in safe_checks)</preferenceName> | |
| 160 | <preferenceType>checkbox</preferenceType> | |
| 161 | <preferenceValues>yes</preferenceValues> | |
| 162 | <selectedValue>yes</selectedValue> | |
| 163 | </item> | |
| 164 | <item><pluginName>amap (NASL wrapper)</pluginName> | |
| 165 | <pluginId>14663</pluginId> | |
| 166 | <fullName>amap (NASL wrapper)[checkbox]:RPC (disabled in safe_checks)</fullName> | |
| 167 | <preferenceName>RPC (disabled in safe_checks)</preferenceName> | |
| 168 | <preferenceType>checkbox</preferenceType> | |
| 169 | <preferenceValues>yes</preferenceValues> | |
| 170 | <selectedValue>yes</selectedValue> | |
| 171 | </item> | |
| 172 | <item><pluginName>amap (NASL wrapper)</pluginName> | |
| 173 | <pluginId>14663</pluginId> | |
| 174 | <fullName>amap (NASL wrapper)[entry]:Parallel tasks</fullName> | |
| 175 | <preferenceName>Parallel tasks</preferenceName> | |
| 176 | <preferenceType>entry</preferenceType> | |
| 177 | <preferenceValues></preferenceValues> | |
| 178 | <selectedValue></selectedValue> | |
| 179 | </item> | |
| 180 | <item><pluginName>amap (NASL wrapper)</pluginName> | |
| 181 | <pluginId>14663</pluginId> | |
| 182 | <fullName>amap (NASL wrapper)[entry]:Connection retries</fullName> | |
| 183 | <preferenceName>Connection retries</preferenceName> | |
| 184 | <preferenceType>entry</preferenceType> | |
| 185 | <preferenceValues></preferenceValues> | |
| 186 | <selectedValue></selectedValue> | |
| 187 | </item> | |
| 188 | <item><pluginName>amap (NASL wrapper)</pluginName> | |
| 189 | <pluginId>14663</pluginId> | |
| 190 | <fullName>amap (NASL wrapper)[entry]:Connection timeout</fullName> | |
| 191 | <preferenceName>Connection timeout</preferenceName> | |
| 192 | <preferenceType>entry</preferenceType> | |
| 193 | <preferenceValues></preferenceValues> | |
| 194 | <selectedValue></selectedValue> | |
| 195 | </item> | |
| 196 | <item><pluginName>amap (NASL wrapper)</pluginName> | |
| 197 | <pluginId>14663</pluginId> | |
| 198 | <fullName>amap (NASL wrapper)[entry]:Read timeout</fullName> | |
| 199 | <preferenceName>Read timeout</preferenceName> | |
| 200 | <preferenceType>entry</preferenceType> | |
| 201 | <preferenceValues></preferenceValues> | |
| 202 | <selectedValue></selectedValue> | |
| 203 | </item> | |
| 204 | <item><pluginName>SNMP settings</pluginName> | |
| 205 | <pluginId>19762</pluginId> | |
| 206 | <fullName>SNMP settings[entry]:Community name :</fullName> | |
| 207 | <preferenceName>Community name :</preferenceName> | |
| 208 | <preferenceType>entry</preferenceType> | |
| 209 | <preferenceValues>public</preferenceValues> | |
| 210 | <selectedValue>public</selectedValue> | |
| 211 | </item> | |
| 212 | <item><pluginName>SNMP settings</pluginName> | |
| 213 | <pluginId>19762</pluginId> | |
| 214 | <fullName>SNMP settings[entry]:Community name (1) :</fullName> | |
| 215 | <preferenceName>Community name (1) :</preferenceName> | |
| 216 | <preferenceType>entry</preferenceType> | |
| 217 | <preferenceValues></preferenceValues> | |
| 218 | <selectedValue></selectedValue> | |
| 219 | </item> | |
| 220 | <item><pluginName>SNMP settings</pluginName> | |
| 221 | <pluginId>19762</pluginId> | |
| 222 | <fullName>SNMP settings[entry]:Community name (2) :</fullName> | |
| 223 | <preferenceName>Community name (2) :</preferenceName> | |
| 224 | <preferenceType>entry</preferenceType> | |
| 225 | <preferenceValues></preferenceValues> | |
| 226 | <selectedValue></selectedValue> | |
| 227 | </item> | |
| 228 | <item><pluginName>SNMP settings</pluginName> | |
| 229 | <pluginId>19762</pluginId> | |
| 230 | <fullName>SNMP settings[entry]:Community name (3) :</fullName> | |
| 231 | <preferenceName>Community name (3) :</preferenceName> | |
| 232 | <preferenceType>entry</preferenceType> | |
| 233 | <preferenceValues></preferenceValues> | |
| 234 | <selectedValue></selectedValue> | |
| 235 | </item> | |
| 236 | <item><pluginName>SNMP settings</pluginName> | |
| 237 | <pluginId>19762</pluginId> | |
| 238 | <fullName>SNMP settings[entry]:UDP port :</fullName> | |
| 239 | <preferenceName>UDP port :</preferenceName> | |
| 240 | <preferenceType>entry</preferenceType> | |
| 241 | <preferenceValues>161</preferenceValues> | |
| 242 | <selectedValue>161</selectedValue> | |
| 243 | </item> | |
| 244 | <item><pluginName>SNMP settings</pluginName> | |
| 245 | <pluginId>19762</pluginId> | |
| 246 | <fullName>SNMP settings[entry]:SNMPv3 user name :</fullName> | |
| 247 | <preferenceName>SNMPv3 user name :</preferenceName> | |
| 248 | <preferenceType>entry</preferenceType> | |
| 249 | <preferenceValues></preferenceValues> | |
| 250 | <selectedValue></selectedValue> | |
| 251 | </item> | |
| 252 | <item><pluginName>SNMP settings</pluginName> | |
| 253 | <pluginId>19762</pluginId> | |
| 254 | <fullName>SNMP settings[password]:SNMPv3 authentication password :</fullName> | |
| 255 | <preferenceName>SNMPv3 authentication password :</preferenceName> | |
| 256 | <preferenceType>password</preferenceType> | |
| 257 | <preferenceValues></preferenceValues> | |
| 258 | <selectedValue></selectedValue> | |
| 259 | </item> | |
| 260 | <item><pluginName>SNMP settings</pluginName> | |
| 261 | <pluginId>19762</pluginId> | |
| 262 | <fullName>SNMP settings[radio]:SNMPv3 authentication algorithm :</fullName> | |
| 263 | <preferenceName>SNMPv3 authentication algorithm :</preferenceName> | |
| 264 | <preferenceType>radio</preferenceType> | |
| 265 | <preferenceValues>MD5;SHA1</preferenceValues> | |
| 266 | <selectedValue>MD5;SHA1</selectedValue> | |
| 267 | </item> | |
| 268 | <item><pluginName>SNMP settings</pluginName> | |
| 269 | <pluginId>19762</pluginId> | |
| 270 | <fullName>SNMP settings[password]:SNMPv3 privacy password :</fullName> | |
| 271 | <preferenceName>SNMPv3 privacy password :</preferenceName> | |
| 272 | <preferenceType>password</preferenceType> | |
| 273 | <preferenceValues></preferenceValues> | |
| 274 | <selectedValue></selectedValue> | |
| 275 | </item> | |
| 276 | <item><pluginName>SNMP settings</pluginName> | |
| 277 | <pluginId>19762</pluginId> | |
| 278 | <fullName>SNMP settings[radio]:SNMPv3 privacy algorithm :</fullName> | |
| 279 | <preferenceName>SNMPv3 privacy algorithm :</preferenceName> | |
| 280 | <preferenceType>radio</preferenceType> | |
| 281 | <preferenceValues>DES</preferenceValues> | |
| 282 | <selectedValue>DES</selectedValue> | |
| 283 | </item> | |
| 284 | <item><pluginName>Good MDM Settings</pluginName> | |
| 285 | <pluginId>66963</pluginId> | |
| 286 | <fullName>Good MDM Settings[entry]:GMC Server :</fullName> | |
| 287 | <preferenceName>GMC Server :</preferenceName> | |
| 288 | <preferenceType>entry</preferenceType> | |
| 289 | <preferenceValues></preferenceValues> | |
| 290 | <selectedValue></selectedValue> | |
| 291 | </item> | |
| 292 | <item><pluginName>Good MDM Settings</pluginName> | |
| 293 | <pluginId>66963</pluginId> | |
| 294 | <fullName>Good MDM Settings[entry]:Port :</fullName> | |
| 295 | <preferenceName>Port :</preferenceName> | |
| 296 | <preferenceType>entry</preferenceType> | |
| 297 | <preferenceValues></preferenceValues> | |
| 298 | <selectedValue></selectedValue> | |
| 299 | </item> | |
| 300 | <item><pluginName>Good MDM Settings</pluginName> | |
| 301 | <pluginId>66963</pluginId> | |
| 302 | <fullName>Good MDM Settings[entry]:Domain :</fullName> | |
| 303 | <preferenceName>Domain :</preferenceName> | |
| 304 | <preferenceType>entry</preferenceType> | |
| 305 | <preferenceValues></preferenceValues> | |
| 306 | <selectedValue></selectedValue> | |
| 307 | </item> | |
| 308 | <item><pluginName>Good MDM Settings</pluginName> | |
| 309 | <pluginId>66963</pluginId> | |
| 310 | <fullName>Good MDM Settings[entry]:Username :</fullName> | |
| 311 | <preferenceName>Username :</preferenceName> | |
| 312 | <preferenceType>entry</preferenceType> | |
| 313 | <preferenceValues></preferenceValues> | |
| 314 | <selectedValue></selectedValue> | |
| 315 | </item> | |
| 316 | <item><pluginName>Good MDM Settings</pluginName> | |
| 317 | <pluginId>66963</pluginId> | |
| 318 | <fullName>Good MDM Settings[password]:Password :</fullName> | |
| 319 | <preferenceName>Password :</preferenceName> | |
| 320 | <preferenceType>password</preferenceType> | |
| 321 | <preferenceValues></preferenceValues> | |
| 322 | <selectedValue></selectedValue> | |
| 323 | </item> | |
| 324 | <item><pluginName>Good MDM Settings</pluginName> | |
| 325 | <pluginId>66963</pluginId> | |
| 326 | <fullName>Good MDM Settings[checkbox]:SSL :</fullName> | |
| 327 | <preferenceName>SSL :</preferenceName> | |
| 328 | <preferenceType>checkbox</preferenceType> | |
| 329 | <preferenceValues>yes</preferenceValues> | |
| 330 | <selectedValue>yes</selectedValue> | |
| 331 | </item> | |
| 332 | <item><pluginName>Good MDM Settings</pluginName> | |
| 333 | <pluginId>66963</pluginId> | |
| 334 | <fullName>Good MDM Settings[checkbox]:Verify SSL Certificate :</fullName> | |
| 335 | <preferenceName>Verify SSL Certificate :</preferenceName> | |
| 336 | <preferenceType>checkbox</preferenceType> | |
| 337 | <preferenceValues>no</preferenceValues> | |
| 338 | <selectedValue>no</selectedValue> | |
| 339 | </item> | |
| 340 | <item><pluginName>SSH settings</pluginName> | |
| 341 | <pluginId>14273</pluginId> | |
| 342 | <fullName>SSH settings[entry]:SSH user name :</fullName> | |
| 343 | <preferenceName>SSH user name :</preferenceName> | |
| 344 | <preferenceType>entry</preferenceType> | |
| 345 | <preferenceValues>root</preferenceValues> | |
| 346 | <selectedValue>root</selectedValue> | |
| 347 | </item> | |
| 348 | <item><pluginName>SSH settings</pluginName> | |
| 349 | <pluginId>14273</pluginId> | |
| 350 | <fullName>SSH settings[password]:SSH password (unsafe!) :</fullName> | |
| 351 | <preferenceName>SSH password (unsafe!) :</preferenceName> | |
| 352 | <preferenceType>password</preferenceType> | |
| 353 | <preferenceValues></preferenceValues> | |
| 354 | <selectedValue></selectedValue> | |
| 355 | </item> | |
| 356 | <item><pluginName>SSH settings</pluginName> | |
| 357 | <pluginId>14273</pluginId> | |
| 358 | <fullName>SSH settings[file]:SSH public key to use :</fullName> | |
| 359 | <preferenceName>SSH public key to use :</preferenceName> | |
| 360 | <preferenceType>file</preferenceType> | |
| 361 | <preferenceValues></preferenceValues> | |
| 362 | <selectedValue></selectedValue> | |
| 363 | </item> | |
| 364 | <item><pluginName>SSH settings</pluginName> | |
| 365 | <pluginId>14273</pluginId> | |
| 366 | <fullName>SSH settings[file]:SSH private key to use :</fullName> | |
| 367 | <preferenceName>SSH private key to use :</preferenceName> | |
| 368 | <preferenceType>file</preferenceType> | |
| 369 | <preferenceValues></preferenceValues> | |
| 370 | <selectedValue></selectedValue> | |
| 371 | </item> | |
| 372 | <item><pluginName>SSH settings</pluginName> | |
| 373 | <pluginId>14273</pluginId> | |
| 374 | <fullName>SSH settings[password]:Passphrase for SSH key :</fullName> | |
| 375 | <preferenceName>Passphrase for SSH key :</preferenceName> | |
| 376 | <preferenceType>password</preferenceType> | |
| 377 | <preferenceValues></preferenceValues> | |
| 378 | <selectedValue></selectedValue> | |
| 379 | </item> | |
| 380 | <item><pluginName>SSH settings</pluginName> | |
| 381 | <pluginId>14273</pluginId> | |
| 382 | <fullName>SSH settings[radio]:Elevate privileges with :</fullName> | |
| 383 | <preferenceName>Elevate privileges with :</preferenceName> | |
| 384 | <preferenceType>radio</preferenceType> | |
| 385 | <preferenceValues>Nothing;sudo;su;su+sudo;dzdo;pbrun;Cisco 'enable'</preferenceValues> | |
| 386 | <selectedValue>Nothing;sudo;su;su+sudo;Cisco 'enable'</selectedValue> | |
| 387 | </item> | |
| 388 | <item><pluginName>SSH settings</pluginName> | |
| 389 | <pluginId>14273</pluginId> | |
| 390 | <fullName>SSH settings[entry]:Privilege elevation binary path (directory) :</fullName> | |
| 391 | <preferenceName>Privilege elevation binary path (directory) :</preferenceName> | |
| 392 | <preferenceType>entry</preferenceType> | |
| 393 | <preferenceValues></preferenceValues> | |
| 394 | <selectedValue></selectedValue> | |
| 395 | </item> | |
| 396 | <item><pluginName>SSH settings</pluginName> | |
| 397 | <pluginId>14273</pluginId> | |
| 398 | <fullName>SSH settings[entry]:su login :</fullName> | |
| 399 | <preferenceName>su login :</preferenceName> | |
| 400 | <preferenceType>entry</preferenceType> | |
| 401 | <preferenceValues></preferenceValues> | |
| 402 | <selectedValue></selectedValue> | |
| 403 | </item> | |
| 404 | <item><pluginName>SSH settings</pluginName> | |
| 405 | <pluginId>14273</pluginId> | |
| 406 | <fullName>SSH settings[entry]:Escalation account :</fullName> | |
| 407 | <preferenceName>Escalation account :</preferenceName> | |
| 408 | <preferenceType>entry</preferenceType> | |
| 409 | <preferenceValues>root</preferenceValues> | |
| 410 | <selectedValue>root</selectedValue> | |
| 411 | </item> | |
| 412 | <item><pluginName>SSH settings</pluginName> | |
| 413 | <pluginId>14273</pluginId> | |
| 414 | <fullName>SSH settings[password]:Escalation password :</fullName> | |
| 415 | <preferenceName>Escalation password :</preferenceName> | |
| 416 | <preferenceType>password</preferenceType> | |
| 417 | <preferenceValues></preferenceValues> | |
| 418 | <selectedValue></selectedValue> | |
| 419 | </item> | |
| 420 | <item><pluginName>SSH settings</pluginName> | |
| 421 | <pluginId>14273</pluginId> | |
| 422 | <fullName>SSH settings[file]:SSH known_hosts file :</fullName> | |
| 423 | <preferenceName>SSH known_hosts file :</preferenceName> | |
| 424 | <preferenceType>file</preferenceType> | |
| 425 | <preferenceValues></preferenceValues> | |
| 426 | <selectedValue></selectedValue> | |
| 427 | </item> | |
| 428 | <item><pluginName>SSH settings</pluginName> | |
| 429 | <pluginId>14273</pluginId> | |
| 430 | <fullName>SSH settings[entry]:Preferred SSH port :</fullName> | |
| 431 | <preferenceName>Preferred SSH port :</preferenceName> | |
| 432 | <preferenceType>entry</preferenceType> | |
| 433 | <preferenceValues>22</preferenceValues> | |
| 434 | <selectedValue>22</selectedValue> | |
| 435 | </item> | |
| 436 | <item><pluginName>SSH settings</pluginName> | |
| 437 | <pluginId>14273</pluginId> | |
| 438 | <fullName>SSH settings[entry]:Client version :</fullName> | |
| 439 | <preferenceName>Client version :</preferenceName> | |
| 440 | <preferenceType>entry</preferenceType> | |
| 441 | <preferenceValues>OpenSSH_5.0</preferenceValues> | |
| 442 | <selectedValue>OpenSSH_5.0</selectedValue> | |
| 443 | </item> | |
| 444 | <item><pluginName>SSH settings</pluginName> | |
| 445 | <pluginId>14273</pluginId> | |
| 446 | <fullName>SSH settings[entry]:Additional SSH user name (1) :</fullName> | |
| 447 | <preferenceName>Additional SSH user name (1) :</preferenceName> | |
| 448 | <preferenceType>entry</preferenceType> | |
| 449 | <preferenceValues></preferenceValues> | |
| 450 | <selectedValue></selectedValue> | |
| 451 | </item> | |
| 452 | <item><pluginName>SSH settings</pluginName> | |
| 453 | <pluginId>14273</pluginId> | |
| 454 | <fullName>SSH settings[password]:Additional SSH password (1) :</fullName> | |
| 455 | <preferenceName>Additional SSH password (1) :</preferenceName> | |
| 456 | <preferenceType>password</preferenceType> | |
| 457 | <preferenceValues></preferenceValues> | |
| 458 | <selectedValue></selectedValue> | |
| 459 | </item> | |
| 460 | <item><pluginName>SSH settings</pluginName> | |
| 461 | <pluginId>14273</pluginId> | |
| 462 | <fullName>SSH settings[entry]:Additional SSH user name (2) :</fullName> | |
| 463 | <preferenceName>Additional SSH user name (2) :</preferenceName> | |
| 464 | <preferenceType>entry</preferenceType> | |
| 465 | <preferenceValues></preferenceValues> | |
| 466 | <selectedValue></selectedValue> | |
| 467 | </item> | |
| 468 | <item><pluginName>SSH settings</pluginName> | |
| 469 | <pluginId>14273</pluginId> | |
| 470 | <fullName>SSH settings[password]:Additional SSH password (2) :</fullName> | |
| 471 | <preferenceName>Additional SSH password (2) :</preferenceName> | |
| 472 | <preferenceType>password</preferenceType> | |
| 473 | <preferenceValues></preferenceValues> | |
| 474 | <selectedValue></selectedValue> | |
| 475 | </item> | |
| 476 | <item><pluginName>SSH settings</pluginName> | |
| 477 | <pluginId>14273</pluginId> | |
| 478 | <fullName>SSH settings[entry]:Additional SSH user name (3) :</fullName> | |
| 479 | <preferenceName>Additional SSH user name (3) :</preferenceName> | |
| 480 | <preferenceType>entry</preferenceType> | |
| 481 | <preferenceValues></preferenceValues> | |
| 482 | <selectedValue></selectedValue> | |
| 483 | </item> | |
| 484 | <item><pluginName>SSH settings</pluginName> | |
| 485 | <pluginId>14273</pluginId> | |
| 486 | <fullName>SSH settings[password]:Additional SSH password (3) :</fullName> | |
| 487 | <preferenceName>Additional SSH password (3) :</preferenceName> | |
| 488 | <preferenceType>password</preferenceType> | |
| 489 | <preferenceValues></preferenceValues> | |
| 490 | <selectedValue></selectedValue> | |
| 491 | </item> | |
| 492 | <item><pluginName>SSH settings</pluginName> | |
| 493 | <pluginId>14273</pluginId> | |
| 494 | <fullName>SSH settings[entry]:Additional SSH user name (4) :</fullName> | |
| 495 | <preferenceName>Additional SSH user name (4) :</preferenceName> | |
| 496 | <preferenceType>entry</preferenceType> | |
| 497 | <preferenceValues></preferenceValues> | |
| 498 | <selectedValue></selectedValue> | |
| 499 | </item> | |
| 500 | <item><pluginName>SSH settings</pluginName> | |
| 501 | <pluginId>14273</pluginId> | |
| 502 | <fullName>SSH settings[password]:Additional SSH password (4) :</fullName> | |
| 503 | <preferenceName>Additional SSH password (4) :</preferenceName> | |
| 504 | <preferenceType>password</preferenceType> | |
| 505 | <preferenceValues></preferenceValues> | |
| 506 | <selectedValue></selectedValue> | |
| 507 | </item> | |
| 508 | <item><pluginName>SSH settings</pluginName> | |
| 509 | <pluginId>14273</pluginId> | |
| 510 | <fullName>SSH settings[entry]:Additional SSH user name (5) :</fullName> | |
| 511 | <preferenceName>Additional SSH user name (5) :</preferenceName> | |
| 512 | <preferenceType>entry</preferenceType> | |
| 513 | <preferenceValues></preferenceValues> | |
| 514 | <selectedValue></selectedValue> | |
| 515 | </item> | |
| 516 | <item><pluginName>SSH settings</pluginName> | |
| 517 | <pluginId>14273</pluginId> | |
| 518 | <fullName>SSH settings[password]:Additional SSH password (5) :</fullName> | |
| 519 | <preferenceName>Additional SSH password (5) :</preferenceName> | |
| 520 | <preferenceType>password</preferenceType> | |
| 521 | <preferenceValues></preferenceValues> | |
| 522 | <selectedValue></selectedValue> | |
| 523 | </item> | |
| 524 | <item><pluginName>Hydra: LDAP</pluginName> | |
| 525 | <pluginId>15877</pluginId> | |
| 526 | <fullName>Hydra: LDAP[entry]:DN :</fullName> | |
| 527 | <preferenceName>DN :</preferenceName> | |
| 528 | <preferenceType>entry</preferenceType> | |
| 529 | <preferenceValues></preferenceValues> | |
| 530 | <selectedValue></selectedValue> | |
| 531 | </item> | |
| 532 | <item><pluginName>Apple Profile Manager API Settings</pluginName> | |
| 533 | <pluginId>60032</pluginId> | |
| 534 | <fullName>Apple Profile Manager API Settings[entry]:Apple Profile Manager server :</fullName> | |
| 535 | <preferenceName>Apple Profile Manager server :</preferenceName> | |
| 536 | <preferenceType>entry</preferenceType> | |
| 537 | <preferenceValues></preferenceValues> | |
| 538 | <selectedValue></selectedValue> | |
| 539 | </item> | |
| 540 | <item><pluginName>Apple Profile Manager API Settings</pluginName> | |
| 541 | <pluginId>60032</pluginId> | |
| 542 | <fullName>Apple Profile Manager API Settings[entry]:Apple Profile Manager port :</fullName> | |
| 543 | <preferenceName>Apple Profile Manager port :</preferenceName> | |
| 544 | <preferenceType>entry</preferenceType> | |
| 545 | <preferenceValues>443</preferenceValues> | |
| 546 | <selectedValue>443</selectedValue> | |
| 547 | </item> | |
| 548 | <item><pluginName>Apple Profile Manager API Settings</pluginName> | |
| 549 | <pluginId>60032</pluginId> | |
| 550 | <fullName>Apple Profile Manager API Settings[entry]:Apple Profile Manager username :</fullName> | |
| 551 | <preferenceName>Apple Profile Manager username :</preferenceName> | |
| 552 | <preferenceType>entry</preferenceType> | |
| 553 | <preferenceValues></preferenceValues> | |
| 554 | <selectedValue></selectedValue> | |
| 555 | </item> | |
| 556 | <item><pluginName>Apple Profile Manager API Settings</pluginName> | |
| 557 | <pluginId>60032</pluginId> | |
| 558 | <fullName>Apple Profile Manager API Settings[password]:Apple Profile Manager password :</fullName> | |
| 559 | <preferenceName>Apple Profile Manager password :</preferenceName> | |
| 560 | <preferenceType>password</preferenceType> | |
| 561 | <preferenceValues></preferenceValues> | |
| 562 | <selectedValue></selectedValue> | |
| 563 | </item> | |
| 564 | <item><pluginName>Apple Profile Manager API Settings</pluginName> | |
| 565 | <pluginId>60032</pluginId> | |
| 566 | <fullName>Apple Profile Manager API Settings[checkbox]:SSL :</fullName> | |
| 567 | <preferenceName>SSL :</preferenceName> | |
| 568 | <preferenceType>checkbox</preferenceType> | |
| 569 | <preferenceValues>yes</preferenceValues> | |
| 570 | <selectedValue>yes</selectedValue> | |
| 571 | </item> | |
| 572 | <item><pluginName>Apple Profile Manager API Settings</pluginName> | |
| 573 | <pluginId>60032</pluginId> | |
| 574 | <fullName>Apple Profile Manager API Settings[checkbox]:Verify SSL Certificate :</fullName> | |
| 575 | <preferenceName>Verify SSL Certificate :</preferenceName> | |
| 576 | <preferenceType>checkbox</preferenceType> | |
| 577 | <preferenceValues>no</preferenceValues> | |
| 578 | <selectedValue>no</selectedValue> | |
| 579 | </item> | |
| 580 | <item><pluginName>Apple Profile Manager API Settings</pluginName> | |
| 581 | <pluginId>60032</pluginId> | |
| 582 | <fullName>Apple Profile Manager API Settings[checkbox]:Force Device Updates :</fullName> | |
| 583 | <preferenceName>Force Device Updates :</preferenceName> | |
| 584 | <preferenceType>checkbox</preferenceType> | |
| 585 | <preferenceValues>yes</preferenceValues> | |
| 586 | <selectedValue>yes</selectedValue> | |
| 587 | </item> | |
| 588 | <item><pluginName>Apple Profile Manager API Settings</pluginName> | |
| 589 | <pluginId>60032</pluginId> | |
| 590 | <fullName>Apple Profile Manager API Settings[entry]:Device Update Timeout (Minutes) :</fullName> | |
| 591 | <preferenceName>Device Update Timeout (Minutes) :</preferenceName> | |
| 592 | <preferenceType>entry</preferenceType> | |
| 593 | <preferenceValues>5</preferenceValues> | |
| 594 | <selectedValue>5</selectedValue> | |
| 595 | </item> | |
| 596 | <item><pluginName>Remote web server screenshot</pluginName> | |
| 597 | <pluginId>59861</pluginId> | |
| 598 | <fullName>Remote web server screenshot[checkbox]:Allow Nessus to connect to the cloud to take a screenshot of the public targets</fullName> | |
| 599 | <preferenceName>Allow Nessus to connect to the cloud to take a screenshot of the public targets</preferenceName> | |
| 600 | <preferenceType>checkbox</preferenceType> | |
| 601 | <preferenceValues>no</preferenceValues> | |
| 602 | <selectedValue>no</selectedValue> | |
| 603 | </item> | |
| 604 | <item><pluginName>Patch Management: Red Hat Satellite Server Settings</pluginName> | |
| 605 | <pluginId>57063</pluginId> | |
| 606 | <fullName>Patch Management: Red Hat Satellite Server Settings[entry]:Red Hat Satellite server(s) [separated w/ semicolons] :</fullName> | |
| 607 | <preferenceName>Red Hat Satellite server(s) [separated w/ semicolons] :</preferenceName> | |
| 608 | <preferenceType>entry</preferenceType> | |
| 609 | <preferenceValues></preferenceValues> | |
| 610 | <selectedValue></selectedValue> | |
| 611 | </item> | |
| 612 | <item><pluginName>Patch Management: Red Hat Satellite Server Settings</pluginName> | |
| 613 | <pluginId>57063</pluginId> | |
| 614 | <fullName>Patch Management: Red Hat Satellite Server Settings[entry]:Red Hat Satellite port(s) :</fullName> | |
| 615 | <preferenceName>Red Hat Satellite port(s) :</preferenceName> | |
| 616 | <preferenceType>entry</preferenceType> | |
| 617 | <preferenceValues>443</preferenceValues> | |
| 618 | <selectedValue>443</selectedValue> | |
| 619 | </item> | |
| 620 | <item><pluginName>Patch Management: Red Hat Satellite Server Settings</pluginName> | |
| 621 | <pluginId>57063</pluginId> | |
| 622 | <fullName>Patch Management: Red Hat Satellite Server Settings[checkbox]:Verify SSL certificates :</fullName> | |
| 623 | <preferenceName>Verify SSL certificates :</preferenceName> | |
| 624 | <preferenceType>checkbox</preferenceType> | |
| 625 | <preferenceValues>no</preferenceValues> | |
| 626 | <selectedValue>no</selectedValue> | |
| 627 | </item> | |
| 628 | <item><pluginName>Patch Management: Red Hat Satellite Server Settings</pluginName> | |
| 629 | <pluginId>57063</pluginId> | |
| 630 | <fullName>Patch Management: Red Hat Satellite Server Settings[entry]:Red Hat Satellite username(s) :</fullName> | |
| 631 | <preferenceName>Red Hat Satellite username(s) :</preferenceName> | |
| 632 | <preferenceType>entry</preferenceType> | |
| 633 | <preferenceValues></preferenceValues> | |
| 634 | <selectedValue></selectedValue> | |
| 635 | </item> | |
| 636 | <item><pluginName>Patch Management: Red Hat Satellite Server Settings</pluginName> | |
| 637 | <pluginId>57063</pluginId> | |
| 638 | <fullName>Patch Management: Red Hat Satellite Server Settings[password]:Red Hat Satellite password(s) :</fullName> | |
| 639 | <preferenceName>Red Hat Satellite password(s) :</preferenceName> | |
| 640 | <preferenceType>password</preferenceType> | |
| 641 | <preferenceValues></preferenceValues> | |
| 642 | <selectedValue></selectedValue> | |
| 643 | </item> | |
| 644 | <item><pluginName>Hydra: HTTP</pluginName> | |
| 645 | <pluginId>15873</pluginId> | |
| 646 | <fullName>Hydra: HTTP[entry]:Web page :</fullName> | |
| 647 | <preferenceName>Web page :</preferenceName> | |
| 648 | <preferenceType>entry</preferenceType> | |
| 649 | <preferenceValues></preferenceValues> | |
| 650 | <selectedValue></selectedValue> | |
| 651 | </item> | |
| 652 | <item><pluginName>SMB Scope</pluginName> | |
| 653 | <pluginId>10917</pluginId> | |
| 654 | <fullName>SMB Scope[checkbox]:Request information about the domain</fullName> | |
| 655 | <preferenceName>Request information about the domain</preferenceName> | |
| 656 | <preferenceType>checkbox</preferenceType> | |
| 657 | <preferenceValues>yes</preferenceValues> | |
| 658 | <selectedValue>yes</selectedValue> | |
| 659 | </item> | |
| 660 | <item><pluginName>VMware SOAP API Settings</pluginName> | |
| 661 | <pluginId>57395</pluginId> | |
| 662 | <fullName>VMware SOAP API Settings[entry]:VMware user name :</fullName> | |
| 663 | <preferenceName>VMware user name :</preferenceName> | |
| 664 | <preferenceType>entry</preferenceType> | |
| 665 | <preferenceValues></preferenceValues> | |
| 666 | <selectedValue></selectedValue> | |
| 667 | </item> | |
| 668 | <item><pluginName>VMware SOAP API Settings</pluginName> | |
| 669 | <pluginId>57395</pluginId> | |
| 670 | <fullName>VMware SOAP API Settings[password]:VMware password :</fullName> | |
| 671 | <preferenceName>VMware password :</preferenceName> | |
| 672 | <preferenceType>password</preferenceType> | |
| 673 | <preferenceValues></preferenceValues> | |
| 674 | <selectedValue></selectedValue> | |
| 675 | </item> | |
| 676 | <item><pluginName>VMware SOAP API Settings</pluginName> | |
| 677 | <pluginId>57395</pluginId> | |
| 678 | <fullName>VMware SOAP API Settings[checkbox]:Ignore SSL Certificate :</fullName> | |
| 679 | <preferenceName>Ignore SSL Certificate :</preferenceName> | |
| 680 | <preferenceType>checkbox</preferenceType> | |
| 681 | <preferenceValues>no</preferenceValues> | |
| 682 | <selectedValue>no</selectedValue> | |
| 683 | </item> | |
| 684 | <item><pluginName>Login configurations</pluginName> | |
| 685 | <pluginId>10870</pluginId> | |
| 686 | <fullName>Login configurations[entry]:HTTP account :</fullName> | |
| 687 | <preferenceName>HTTP account :</preferenceName> | |
| 688 | <preferenceType>entry</preferenceType> | |
| 689 | <preferenceValues></preferenceValues> | |
| 690 | <selectedValue></selectedValue> | |
| 691 | </item> | |
| 692 | <item><pluginName>Login configurations</pluginName> | |
| 693 | <pluginId>10870</pluginId> | |
| 694 | <fullName>Login configurations[password]:HTTP password (sent in clear) :</fullName> | |
| 695 | <preferenceName>HTTP password (sent in clear) :</preferenceName> | |
| 696 | <preferenceType>password</preferenceType> | |
| 697 | <preferenceValues></preferenceValues> | |
| 698 | <selectedValue></selectedValue> | |
| 699 | </item> | |
| 700 | <item><pluginName>Login configurations</pluginName> | |
| 701 | <pluginId>10870</pluginId> | |
| 702 | <fullName>Login configurations[entry]:NNTP account :</fullName> | |
| 703 | <preferenceName>NNTP account :</preferenceName> | |
| 704 | <preferenceType>entry</preferenceType> | |
| 705 | <preferenceValues></preferenceValues> | |
| 706 | <selectedValue></selectedValue> | |
| 707 | </item> | |
| 708 | <item><pluginName>Login configurations</pluginName> | |
| 709 | <pluginId>10870</pluginId> | |
| 710 | <fullName>Login configurations[password]:NNTP password (sent in clear) :</fullName> | |
| 711 | <preferenceName>NNTP password (sent in clear) :</preferenceName> | |
| 712 | <preferenceType>password</preferenceType> | |
| 713 | <preferenceValues></preferenceValues> | |
| 714 | <selectedValue></selectedValue> | |
| 715 | </item> | |
| 716 | <item><pluginName>Login configurations</pluginName> | |
| 717 | <pluginId>10870</pluginId> | |
| 718 | <fullName>Login configurations[entry]:FTP account :</fullName> | |
| 719 | <preferenceName>FTP account :</preferenceName> | |
| 720 | <preferenceType>entry</preferenceType> | |
| 721 | <preferenceValues>anonymous</preferenceValues> | |
| 722 | <selectedValue>anonymous</selectedValue> | |
| 723 | </item> | |
| 724 | <item><pluginName>Login configurations</pluginName> | |
| 725 | <pluginId>10870</pluginId> | |
| 726 | <fullName>Login configurations[password]:FTP password (sent in clear) :</fullName> | |
| 727 | <preferenceName>FTP password (sent in clear) :</preferenceName> | |
| 728 | <preferenceType>password</preferenceType> | |
| 729 | <preferenceValues>[email protected]</preferenceValues> | |
| 730 | <selectedValue>*********</selectedValue> | |
| 731 | </item> | |
| 732 | <item><pluginName>Login configurations</pluginName> | |
| 733 | <pluginId>10870</pluginId> | |
| 734 | <fullName>Login configurations[entry]:FTP writeable directory :</fullName> | |
| 735 | <preferenceName>FTP writeable directory :</preferenceName> | |
| 736 | <preferenceType>entry</preferenceType> | |
| 737 | <preferenceValues>/incoming</preferenceValues> | |
| 738 | <selectedValue>/incoming</selectedValue> | |
| 739 | </item> | |
| 740 | <item><pluginName>Login configurations</pluginName> | |
| 741 | <pluginId>10870</pluginId> | |
| 742 | <fullName>Login configurations[entry]:POP2 account :</fullName> | |
| 743 | <preferenceName>POP2 account :</preferenceName> | |
| 744 | <preferenceType>entry</preferenceType> | |
| 745 | <preferenceValues></preferenceValues> | |
| 746 | <selectedValue></selectedValue> | |
| 747 | </item> | |
| 748 | <item><pluginName>Login configurations</pluginName> | |
| 749 | <pluginId>10870</pluginId> | |
| 750 | <fullName>Login configurations[password]:POP2 password (sent in clear) :</fullName> | |
| 751 | <preferenceName>POP2 password (sent in clear) :</preferenceName> | |
| 752 | <preferenceType>password</preferenceType> | |
| 753 | <preferenceValues></preferenceValues> | |
| 754 | <selectedValue></selectedValue> | |
| 755 | </item> | |
| 756 | <item><pluginName>Login configurations</pluginName> | |
| 757 | <pluginId>10870</pluginId> | |
| 758 | <fullName>Login configurations[entry]:POP3 account :</fullName> | |
| 759 | <preferenceName>POP3 account :</preferenceName> | |
| 760 | <preferenceType>entry</preferenceType> | |
| 761 | <preferenceValues></preferenceValues> | |
| 762 | <selectedValue></selectedValue> | |
| 763 | </item> | |
| 764 | <item><pluginName>Login configurations</pluginName> | |
| 765 | <pluginId>10870</pluginId> | |
| 766 | <fullName>Login configurations[password]:POP3 password (sent in clear) :</fullName> | |
| 767 | <preferenceName>POP3 password (sent in clear) :</preferenceName> | |
| 768 | <preferenceType>password</preferenceType> | |
| 769 | <preferenceValues></preferenceValues> | |
| 770 | <selectedValue></selectedValue> | |
| 771 | </item> | |
| 772 | <item><pluginName>Login configurations</pluginName> | |
| 773 | <pluginId>10870</pluginId> | |
| 774 | <fullName>Login configurations[entry]:IMAP account :</fullName> | |
| 775 | <preferenceName>IMAP account :</preferenceName> | |
| 776 | <preferenceType>entry</preferenceType> | |
| 777 | <preferenceValues></preferenceValues> | |
| 778 | <selectedValue></selectedValue> | |
| 779 | </item> | |
| 780 | <item><pluginName>Login configurations</pluginName> | |
| 781 | <pluginId>10870</pluginId> | |
| 782 | <fullName>Login configurations[password]:IMAP password (sent in clear) :</fullName> | |
| 783 | <preferenceName>IMAP password (sent in clear) :</preferenceName> | |
| 784 | <preferenceType>password</preferenceType> | |
| 785 | <preferenceValues></preferenceValues> | |
| 786 | <selectedValue></selectedValue> | |
| 787 | </item> | |
| 788 | <item><pluginName>Login configurations</pluginName> | |
| 789 | <pluginId>10870</pluginId> | |
| 790 | <fullName>Login configurations[entry]:SMB account :</fullName> | |
| 791 | <preferenceName>SMB account :</preferenceName> | |
| 792 | <preferenceType>entry</preferenceType> | |
| 793 | <preferenceValues></preferenceValues> | |
| 794 | <selectedValue></selectedValue> | |
| 795 | </item> | |
| 796 | <item><pluginName>Login configurations</pluginName> | |
| 797 | <pluginId>10870</pluginId> | |
| 798 | <fullName>Login configurations[password]:SMB password :</fullName> | |
| 799 | <preferenceName>SMB password :</preferenceName> | |
| 800 | <preferenceType>password</preferenceType> | |
| 801 | <preferenceValues></preferenceValues> | |
| 802 | <selectedValue></selectedValue> | |
| 803 | </item> | |
| 804 | <item><pluginName>Login configurations</pluginName> | |
| 805 | <pluginId>10870</pluginId> | |
| 806 | <fullName>Login configurations[entry]:SMB domain (optional) :</fullName> | |
| 807 | <preferenceName>SMB domain (optional) :</preferenceName> | |
| 808 | <preferenceType>entry</preferenceType> | |
| 809 | <preferenceValues></preferenceValues> | |
| 810 | <selectedValue></selectedValue> | |
| 811 | </item> | |
| 812 | <item><pluginName>Login configurations</pluginName> | |
| 813 | <pluginId>10870</pluginId> | |
| 814 | <fullName>Login configurations[radio]:SMB password type :</fullName> | |
| 815 | <preferenceName>SMB password type :</preferenceName> | |
| 816 | <preferenceType>radio</preferenceType> | |
| 817 | <preferenceValues>Password;LM Hash;NTLM Hash</preferenceValues> | |
| 818 | <selectedValue>Password;LM Hash;NTLM Hash</selectedValue> | |
| 819 | </item> | |
| 820 | <item><pluginName>Login configurations</pluginName> | |
| 821 | <pluginId>10870</pluginId> | |
| 822 | <fullName>Login configurations[entry]:Additional SMB account (1) :</fullName> | |
| 823 | <preferenceName>Additional SMB account (1) :</preferenceName> | |
| 824 | <preferenceType>entry</preferenceType> | |
| 825 | <preferenceValues></preferenceValues> | |
| 826 | <selectedValue></selectedValue> | |
| 827 | </item> | |
| 828 | <item><pluginName>Login configurations</pluginName> | |
| 829 | <pluginId>10870</pluginId> | |
| 830 | <fullName>Login configurations[password]:Additional SMB password (1) :</fullName> | |
| 831 | <preferenceName>Additional SMB password (1) :</preferenceName> | |
| 832 | <preferenceType>password</preferenceType> | |
| 833 | <preferenceValues></preferenceValues> | |
| 834 | <selectedValue></selectedValue> | |
| 835 | </item> | |
| 836 | <item><pluginName>Login configurations</pluginName> | |
| 837 | <pluginId>10870</pluginId> | |
| 838 | <fullName>Login configurations[entry]:Additional SMB domain (optional) (1) :</fullName> | |
| 839 | <preferenceName>Additional SMB domain (optional) (1) :</preferenceName> | |
| 840 | <preferenceType>entry</preferenceType> | |
| 841 | <preferenceValues></preferenceValues> | |
| 842 | <selectedValue></selectedValue> | |
| 843 | </item> | |
| 844 | <item><pluginName>Login configurations</pluginName> | |
| 845 | <pluginId>10870</pluginId> | |
| 846 | <fullName>Login configurations[entry]:Additional SMB account (2) :</fullName> | |
| 847 | <preferenceName>Additional SMB account (2) :</preferenceName> | |
| 848 | <preferenceType>entry</preferenceType> | |
| 849 | <preferenceValues></preferenceValues> | |
| 850 | <selectedValue></selectedValue> | |
| 851 | </item> | |
| 852 | <item><pluginName>Login configurations</pluginName> | |
| 853 | <pluginId>10870</pluginId> | |
| 854 | <fullName>Login configurations[password]:Additional SMB password (2) :</fullName> | |
| 855 | <preferenceName>Additional SMB password (2) :</preferenceName> | |
| 856 | <preferenceType>password</preferenceType> | |
| 857 | <preferenceValues></preferenceValues> | |
| 858 | <selectedValue></selectedValue> | |
| 859 | </item> | |
| 860 | <item><pluginName>Login configurations</pluginName> | |
| 861 | <pluginId>10870</pluginId> | |
| 862 | <fullName>Login configurations[entry]:Additional SMB domain (optional) (2) :</fullName> | |
| 863 | <preferenceName>Additional SMB domain (optional) (2) :</preferenceName> | |
| 864 | <preferenceType>entry</preferenceType> | |
| 865 | <preferenceValues></preferenceValues> | |
| 866 | <selectedValue></selectedValue> | |
| 867 | </item> | |
| 868 | <item><pluginName>Login configurations</pluginName> | |
| 869 | <pluginId>10870</pluginId> | |
| 870 | <fullName>Login configurations[entry]:Additional SMB account (3) :</fullName> | |
| 871 | <preferenceName>Additional SMB account (3) :</preferenceName> | |
| 872 | <preferenceType>entry</preferenceType> | |
| 873 | <preferenceValues></preferenceValues> | |
| 874 | <selectedValue></selectedValue> | |
| 875 | </item> | |
| 876 | <item><pluginName>Login configurations</pluginName> | |
| 877 | <pluginId>10870</pluginId> | |
| 878 | <fullName>Login configurations[password]:Additional SMB password (3) :</fullName> | |
| 879 | <preferenceName>Additional SMB password (3) :</preferenceName> | |
| 880 | <preferenceType>password</preferenceType> | |
| 881 | <preferenceValues></preferenceValues> | |
| 882 | <selectedValue></selectedValue> | |
| 883 | </item> | |
| 884 | <item><pluginName>Login configurations</pluginName> | |
| 885 | <pluginId>10870</pluginId> | |
| 886 | <fullName>Login configurations[entry]:Additional SMB domain (optional) (3) :</fullName> | |
| 887 | <preferenceName>Additional SMB domain (optional) (3) :</preferenceName> | |
| 888 | <preferenceType>entry</preferenceType> | |
| 889 | <preferenceValues></preferenceValues> | |
| 890 | <selectedValue></selectedValue> | |
| 891 | </item> | |
| 892 | <item><pluginName>Login configurations</pluginName> | |
| 893 | <pluginId>10870</pluginId> | |
| 894 | <fullName>Login configurations[checkbox]:Never send SMB credentials in clear text</fullName> | |
| 895 | <preferenceName>Never send SMB credentials in clear text</preferenceName> | |
| 896 | <preferenceType>checkbox</preferenceType> | |
| 897 | <preferenceValues>yes</preferenceValues> | |
| 898 | <selectedValue>yes</selectedValue> | |
| 899 | </item> | |
| 900 | <item><pluginName>Login configurations</pluginName> | |
| 901 | <pluginId>10870</pluginId> | |
| 902 | <fullName>Login configurations[checkbox]:Only use NTLMv2</fullName> | |
| 903 | <preferenceName>Only use NTLMv2</preferenceName> | |
| 904 | <preferenceType>checkbox</preferenceType> | |
| 905 | <preferenceValues>no</preferenceValues> | |
| 906 | <selectedValue>no</selectedValue> | |
| 907 | </item> | |
| 908 | <item><pluginName>Login configurations</pluginName> | |
| 909 | <pluginId>10870</pluginId> | |
| 910 | <fullName>Login configurations[checkbox]:Only use Kerberos authentication for SMB</fullName> | |
| 911 | <preferenceName>Only use Kerberos authentication for SMB</preferenceName> | |
| 912 | <preferenceType>checkbox</preferenceType> | |
| 913 | <preferenceValues>no</preferenceValues> | |
| 914 | <selectedValue>no</selectedValue> | |
| 915 | </item> | |
| 916 | <item><pluginName>SMB Registry : Start the Registry Service during the scan</pluginName> | |
| 917 | <pluginId>35703</pluginId> | |
| 918 | <fullName>SMB Registry : Start the Registry Service during the scan[checkbox]:Start the registry service during the scan</fullName> | |
| 919 | <preferenceName>Start the registry service during the scan</preferenceName> | |
| 920 | <preferenceType>checkbox</preferenceType> | |
| 921 | <preferenceValues>no</preferenceValues> | |
| 922 | <selectedValue>no</selectedValue> | |
| 923 | </item> | |
| 924 | <item><pluginName>SMB Registry : Start the Registry Service during the scan</pluginName> | |
| 925 | <pluginId>35703</pluginId> | |
| 926 | <fullName>SMB Registry : Start the Registry Service during the scan[checkbox]:Enable administrative shares during the scan</fullName> | |
| 927 | <preferenceName>Enable administrative shares during the scan</preferenceName> | |
| 928 | <preferenceType>checkbox</preferenceType> | |
| 929 | <preferenceValues>no</preferenceValues> | |
| 930 | <selectedValue>no</selectedValue> | |
| 931 | </item> | |
| 932 | <item><pluginName>Hydra: SMB</pluginName> | |
| 933 | <pluginId>15884</pluginId> | |
| 934 | <fullName>Hydra: SMB[radio]:Check local / domain accounts</fullName> | |
| 935 | <preferenceName>Check local / domain accounts</preferenceName> | |
| 936 | <preferenceType>radio</preferenceType> | |
| 937 | <preferenceValues>Local accounts; Domain Accounts; Either</preferenceValues> | |
| 938 | <selectedValue>Local accounts; Domain Accounts; Either</selectedValue> | |
| 939 | </item> | |
| 940 | <item><pluginName>Hydra: SMB</pluginName> | |
| 941 | <pluginId>15884</pluginId> | |
| 942 | <fullName>Hydra: SMB[checkbox]:Interpret passwords as NTLM hashes</fullName> | |
| 943 | <preferenceName>Interpret passwords as NTLM hashes</preferenceName> | |
| 944 | <preferenceType>checkbox</preferenceType> | |
| 945 | <preferenceValues>no</preferenceValues> | |
| 946 | <selectedValue>no</selectedValue> | |
| 947 | </item> | |
| 948 | <item><pluginName>Patch Management: SCCM Server Settings</pluginName> | |
| 949 | <pluginId>57029</pluginId> | |
| 950 | <fullName>Patch Management: SCCM Server Settings[entry]:SCCM Server :</fullName> | |
| 951 | <preferenceName>SCCM Server :</preferenceName> | |
| 952 | <preferenceType>entry</preferenceType> | |
| 953 | <preferenceValues></preferenceValues> | |
| 954 | <selectedValue></selectedValue> | |
| 955 | </item> | |
| 956 | <item><pluginName>Patch Management: SCCM Server Settings</pluginName> | |
| 957 | <pluginId>57029</pluginId> | |
| 958 | <fullName>Patch Management: SCCM Server Settings[entry]:SCCM Domain :</fullName> | |
| 959 | <preferenceName>SCCM Domain :</preferenceName> | |
| 960 | <preferenceType>entry</preferenceType> | |
| 961 | <preferenceValues></preferenceValues> | |
| 962 | <selectedValue></selectedValue> | |
| 963 | </item> | |
| 964 | <item><pluginName>Patch Management: SCCM Server Settings</pluginName> | |
| 965 | <pluginId>57029</pluginId> | |
| 966 | <fullName>Patch Management: SCCM Server Settings[entry]:SCCM Username :</fullName> | |
| 967 | <preferenceName>SCCM Username :</preferenceName> | |
| 968 | <preferenceType>entry</preferenceType> | |
| 969 | <preferenceValues></preferenceValues> | |
| 970 | <selectedValue></selectedValue> | |
| 971 | </item> | |
| 972 | <item><pluginName>Patch Management: SCCM Server Settings</pluginName> | |
| 973 | <pluginId>57029</pluginId> | |
| 974 | <fullName>Patch Management: SCCM Server Settings[password]:SCCM Password :</fullName> | |
| 975 | <preferenceName>SCCM Password :</preferenceName> | |
| 976 | <preferenceType>password</preferenceType> | |
| 977 | <preferenceValues></preferenceValues> | |
| 978 | <selectedValue></selectedValue> | |
| 979 | </item> | |
| 980 | <item><pluginName>Palo Alto Networks PAN-OS Settings</pluginName> | |
| 981 | <pluginId>64286</pluginId> | |
| 982 | <fullName>Palo Alto Networks PAN-OS Settings[entry]:Palo Alto Username :</fullName> | |
| 983 | <preferenceName>Palo Alto Username :</preferenceName> | |
| 984 | <preferenceType>entry</preferenceType> | |
| 985 | <preferenceValues></preferenceValues> | |
| 986 | <selectedValue></selectedValue> | |
| 987 | </item> | |
| 988 | <item><pluginName>Palo Alto Networks PAN-OS Settings</pluginName> | |
| 989 | <pluginId>64286</pluginId> | |
| 990 | <fullName>Palo Alto Networks PAN-OS Settings[password]:Palo Alto Password :</fullName> | |
| 991 | <preferenceName>Palo Alto Password :</preferenceName> | |
| 992 | <preferenceType>password</preferenceType> | |
| 993 | <preferenceValues></preferenceValues> | |
| 994 | <selectedValue></selectedValue> | |
| 995 | </item> | |
| 996 | <item><pluginName>Palo Alto Networks PAN-OS Settings</pluginName> | |
| 997 | <pluginId>64286</pluginId> | |
| 998 | <fullName>Palo Alto Networks PAN-OS Settings[entry]:Palo Alto Port :</fullName> | |
| 999 | <preferenceName>Palo Alto Port :</preferenceName> | |
| 1000 | <preferenceType>entry</preferenceType> | |
| 1001 | <preferenceValues>443</preferenceValues> | |
| 1002 | <selectedValue>443</selectedValue> | |
| 1003 | </item> | |
| 1004 | <item><pluginName>Palo Alto Networks PAN-OS Settings</pluginName> | |
| 1005 | <pluginId>64286</pluginId> | |
| 1006 | <fullName>Palo Alto Networks PAN-OS Settings[checkbox]:Verify SSL Certificate :</fullName> | |
| 1007 | <preferenceName>Verify SSL Certificate :</preferenceName> | |
| 1008 | <preferenceType>checkbox</preferenceType> | |
| 1009 | <preferenceValues>no</preferenceValues> | |
| 1010 | <selectedValue>no</selectedValue> | |
| 1011 | </item> | |
| 1012 | <item><pluginName>Port scanners settings</pluginName> | |
| 1013 | <pluginId>33812</pluginId> | |
| 1014 | <fullName>Port scanners settings[checkbox]:Check open TCP ports found by local port enumerators</fullName> | |
| 1015 | <preferenceName>Check open TCP ports found by local port enumerators</preferenceName> | |
| 1016 | <preferenceType>checkbox</preferenceType> | |
| 1017 | <preferenceValues>no</preferenceValues> | |
| 1018 | <selectedValue>no</selectedValue> | |
| 1019 | </item> | |
| 1020 | <item><pluginName>Port scanners settings</pluginName> | |
| 1021 | <pluginId>33812</pluginId> | |
| 1022 | <fullName>Port scanners settings[checkbox]:Only run network port scanners if local port enumeration failed</fullName> | |
| 1023 | <preferenceName>Only run network port scanners if local port enumeration failed</preferenceName> | |
| 1024 | <preferenceType>checkbox</preferenceType> | |
| 1025 | <preferenceValues>yes</preferenceValues> | |
| 1026 | <selectedValue>yes</selectedValue> | |
| 1027 | </item> | |
| 1028 | <item><pluginName>VMware vCenter SOAP API Settings</pluginName> | |
| 1029 | <pluginId>63060</pluginId> | |
| 1030 | <fullName>VMware vCenter SOAP API Settings[entry]:VMware vCenter host :</fullName> | |
| 1031 | <preferenceName>VMware vCenter host :</preferenceName> | |
| 1032 | <preferenceType>entry</preferenceType> | |
| 1033 | <preferenceValues></preferenceValues> | |
| 1034 | <selectedValue></selectedValue> | |
| 1035 | </item> | |
| 1036 | <item><pluginName>VMware vCenter SOAP API Settings</pluginName> | |
| 1037 | <pluginId>63060</pluginId> | |
| 1038 | <fullName>VMware vCenter SOAP API Settings[entry]:VMware vCenter port :</fullName> | |
| 1039 | <preferenceName>VMware vCenter port :</preferenceName> | |
| 1040 | <preferenceType>entry</preferenceType> | |
| 1041 | <preferenceValues>443</preferenceValues> | |
| 1042 | <selectedValue>443</selectedValue> | |
| 1043 | </item> | |
| 1044 | <item><pluginName>VMware vCenter SOAP API Settings</pluginName> | |
| 1045 | <pluginId>63060</pluginId> | |
| 1046 | <fullName>VMware vCenter SOAP API Settings[entry]:VMware vCenter user name :</fullName> | |
| 1047 | <preferenceName>VMware vCenter user name :</preferenceName> | |
| 1048 | <preferenceType>entry</preferenceType> | |
| 1049 | <preferenceValues></preferenceValues> | |
| 1050 | <selectedValue></selectedValue> | |
| 1051 | </item> | |
| 1052 | <item><pluginName>VMware vCenter SOAP API Settings</pluginName> | |
| 1053 | <pluginId>63060</pluginId> | |
| 1054 | <fullName>VMware vCenter SOAP API Settings[password]:VMware vCenter password :</fullName> | |
| 1055 | <preferenceName>VMware vCenter password :</preferenceName> | |
| 1056 | <preferenceType>password</preferenceType> | |
| 1057 | <preferenceValues></preferenceValues> | |
| 1058 | <selectedValue></selectedValue> | |
| 1059 | </item> | |
| 1060 | <item><pluginName>VMware vCenter SOAP API Settings</pluginName> | |
| 1061 | <pluginId>63060</pluginId> | |
| 1062 | <fullName>VMware vCenter SOAP API Settings[checkbox]:SSL :</fullName> | |
| 1063 | <preferenceName>SSL :</preferenceName> | |
| 1064 | <preferenceType>checkbox</preferenceType> | |
| 1065 | <preferenceValues>yes</preferenceValues> | |
| 1066 | <selectedValue>yes</selectedValue> | |
| 1067 | </item> | |
| 1068 | <item><pluginName>VMware vCenter SOAP API Settings</pluginName> | |
| 1069 | <pluginId>63060</pluginId> | |
| 1070 | <fullName>VMware vCenter SOAP API Settings[checkbox]:Verify SSL Certificate :</fullName> | |
| 1071 | <preferenceName>Verify SSL Certificate :</preferenceName> | |
| 1072 | <preferenceType>checkbox</preferenceType> | |
| 1073 | <preferenceValues>no</preferenceValues> | |
| 1074 | <selectedValue>no</selectedValue> | |
| 1075 | </item> | |
| 1076 | <item><pluginName>Patch Management: VMware Go Server Settings</pluginName> | |
| 1077 | <pluginId>57026</pluginId> | |
| 1078 | <fullName>Patch Management: VMware Go Server Settings[entry]:Host :</fullName> | |
| 1079 | <preferenceName>Host :</preferenceName> | |
| 1080 | <preferenceType>entry</preferenceType> | |
| 1081 | <preferenceValues>services.shavlik.com</preferenceValues> | |
| 1082 | <selectedValue>services.shavlik.com</selectedValue> | |
| 1083 | </item> | |
| 1084 | <item><pluginName>Patch Management: VMware Go Server Settings</pluginName> | |
| 1085 | <pluginId>57026</pluginId> | |
| 1086 | <fullName>Patch Management: VMware Go Server Settings[entry]:Port :</fullName> | |
| 1087 | <preferenceName>Port :</preferenceName> | |
| 1088 | <preferenceType>entry</preferenceType> | |
| 1089 | <preferenceValues>443</preferenceValues> | |
| 1090 | <selectedValue>443</selectedValue> | |
| 1091 | </item> | |
| 1092 | <item><pluginName>Patch Management: VMware Go Server Settings</pluginName> | |
| 1093 | <pluginId>57026</pluginId> | |
| 1094 | <fullName>Patch Management: VMware Go Server Settings[entry]:Username :</fullName> | |
| 1095 | <preferenceName>Username :</preferenceName> | |
| 1096 | <preferenceType>entry</preferenceType> | |
| 1097 | <preferenceValues></preferenceValues> | |
| 1098 | <selectedValue></selectedValue> | |
| 1099 | </item> | |
| 1100 | <item><pluginName>Patch Management: VMware Go Server Settings</pluginName> | |
| 1101 | <pluginId>57026</pluginId> | |
| 1102 | <fullName>Patch Management: VMware Go Server Settings[password]:Password :</fullName> | |
| 1103 | <preferenceName>Password :</preferenceName> | |
| 1104 | <preferenceType>password</preferenceType> | |
| 1105 | <preferenceValues></preferenceValues> | |
| 1106 | <selectedValue></selectedValue> | |
| 1107 | </item> | |
| 1108 | <item><pluginName>Patch Management: VMware Go Server Settings</pluginName> | |
| 1109 | <pluginId>57026</pluginId> | |
| 1110 | <fullName>Patch Management: VMware Go Server Settings[entry]:Domain :</fullName> | |
| 1111 | <preferenceName>Domain :</preferenceName> | |
| 1112 | <preferenceType>entry</preferenceType> | |
| 1113 | <preferenceValues></preferenceValues> | |
| 1114 | <selectedValue></selectedValue> | |
| 1115 | </item> | |
| 1116 | <item><pluginName>Patch Management: VMware Go Server Settings</pluginName> | |
| 1117 | <pluginId>57026</pluginId> | |
| 1118 | <fullName>Patch Management: VMware Go Server Settings[entry]:API path :</fullName> | |
| 1119 | <preferenceName>API path :</preferenceName> | |
| 1120 | <preferenceType>entry</preferenceType> | |
| 1121 | <preferenceValues>/api/authenticationbroker/account/httpIssue.svc/</preferenceValues> | |
| 1122 | <selectedValue>/api/authenticationbroker/account/httpIssue.svc/</selectedValue> | |
| 1123 | </item> | |
| 1124 | <item><pluginName>Patch Management: VMware Go Server Settings</pluginName> | |
| 1125 | <pluginId>57026</pluginId> | |
| 1126 | <fullName>Patch Management: VMware Go Server Settings[entry]:Authentication realm :</fullName> | |
| 1127 | <preferenceName>Authentication realm :</preferenceName> | |
| 1128 | <preferenceType>entry</preferenceType> | |
| 1129 | <preferenceValues>https://services.shavlik.com/api/dataservices/v1r1/default.aspx</preferenceValues> | |
| 1130 | <selectedValue>https://services.shavlik.com/api/dataservices/v1r1/default.aspx</selectedValue> | |
| 1131 | </item> | |
| 1132 | <item><pluginName>Patch Management: VMware Go Server Settings</pluginName> | |
| 1133 | <pluginId>57026</pluginId> | |
| 1134 | <fullName>Patch Management: VMware Go Server Settings[entry]:Service path :</fullName> | |
| 1135 | <preferenceName>Service path :</preferenceName> | |
| 1136 | <preferenceType>entry</preferenceType> | |
| 1137 | <preferenceValues>/api/dataservices/v1r1/OData.svc/</preferenceValues> | |
| 1138 | <selectedValue>/api/dataservices/v1r1/OData.svc/</selectedValue> | |
| 1139 | </item> | |
| 1140 | <item><pluginName>HTTP cookies import</pluginName> | |
| 1141 | <pluginId>42893</pluginId> | |
| 1142 | <fullName>HTTP cookies import[file]:Cookies file :</fullName> | |
| 1143 | <preferenceName>Cookies file :</preferenceName> | |
| 1144 | <preferenceType>file</preferenceType> | |
| 1145 | <preferenceValues></preferenceValues> | |
| 1146 | <selectedValue></selectedValue> | |
| 1147 | </item> | |
| 1148 | <item><pluginName>Ping the remote host</pluginName> | |
| 1149 | <pluginId>10180</pluginId> | |
| 1150 | <fullName>Ping the remote host[entry]:TCP ping destination port(s) :</fullName> | |
| 1151 | <preferenceName>TCP ping destination port(s) :</preferenceName> | |
| 1152 | <preferenceType>entry</preferenceType> | |
| 1153 | <preferenceValues>built-in</preferenceValues> | |
| 1154 | <selectedValue>built-in</selectedValue> | |
| 1155 | </item> | |
| 1156 | <item><pluginName>Ping the remote host</pluginName> | |
| 1157 | <pluginId>10180</pluginId> | |
| 1158 | <fullName>Ping the remote host[checkbox]:Do an ARP ping</fullName> | |
| 1159 | <preferenceName>Do an ARP ping</preferenceName> | |
| 1160 | <preferenceType>checkbox</preferenceType> | |
| 1161 | <preferenceValues>yes</preferenceValues> | |
| 1162 | <selectedValue>yes</selectedValue> | |
| 1163 | </item> | |
| 1164 | <item><pluginName>Ping the remote host</pluginName> | |
| 1165 | <pluginId>10180</pluginId> | |
| 1166 | <fullName>Ping the remote host[checkbox]:Do a TCP ping</fullName> | |
| 1167 | <preferenceName>Do a TCP ping</preferenceName> | |
| 1168 | <preferenceType>checkbox</preferenceType> | |
| 1169 | <preferenceValues>yes</preferenceValues> | |
| 1170 | <selectedValue>yes</selectedValue> | |
| 1171 | </item> | |
| 1172 | <item><pluginName>Ping the remote host</pluginName> | |
| 1173 | <pluginId>10180</pluginId> | |
| 1174 | <fullName>Ping the remote host[checkbox]:Do an ICMP ping</fullName> | |
| 1175 | <preferenceName>Do an ICMP ping</preferenceName> | |
| 1176 | <preferenceType>checkbox</preferenceType> | |
| 1177 | <preferenceValues>yes</preferenceValues> | |
| 1178 | <selectedValue>yes</selectedValue> | |
| 1179 | </item> | |
| 1180 | <item><pluginName>Ping the remote host</pluginName> | |
| 1181 | <pluginId>10180</pluginId> | |
| 1182 | <fullName>Ping the remote host[entry]:Number of retries (ICMP) :</fullName> | |
| 1183 | <preferenceName>Number of retries (ICMP) :</preferenceName> | |
| 1184 | <preferenceType>entry</preferenceType> | |
| 1185 | <preferenceValues>2</preferenceValues> | |
| 1186 | <selectedValue>2</selectedValue> | |
| 1187 | </item> | |
| 1188 | <item><pluginName>Ping the remote host</pluginName> | |
| 1189 | <pluginId>10180</pluginId> | |
| 1190 | <fullName>Ping the remote host[checkbox]:Do an applicative UDP ping (DNS,RPC...)</fullName> | |
| 1191 | <preferenceName>Do an applicative UDP ping (DNS,RPC...)</preferenceName> | |
| 1192 | <preferenceType>checkbox</preferenceType> | |
| 1193 | <preferenceValues>no</preferenceValues> | |
| 1194 | <selectedValue>no</selectedValue> | |
| 1195 | </item> | |
| 1196 | <item><pluginName>Ping the remote host</pluginName> | |
| 1197 | <pluginId>10180</pluginId> | |
| 1198 | <fullName>Ping the remote host[checkbox]:Make the dead hosts appear in the report</fullName> | |
| 1199 | <preferenceName>Make the dead hosts appear in the report</preferenceName> | |
| 1200 | <preferenceType>checkbox</preferenceType> | |
| 1201 | <preferenceValues>no</preferenceValues> | |
| 1202 | <selectedValue>no</selectedValue> | |
| 1203 | </item> | |
| 1204 | <item><pluginName>Ping the remote host</pluginName> | |
| 1205 | <pluginId>10180</pluginId> | |
| 1206 | <fullName>Ping the remote host[checkbox]:Log live hosts in the report</fullName> | |
| 1207 | <preferenceName>Log live hosts in the report</preferenceName> | |
| 1208 | <preferenceType>checkbox</preferenceType> | |
| 1209 | <preferenceValues>no</preferenceValues> | |
| 1210 | <selectedValue>no</selectedValue> | |
| 1211 | </item> | |
| 1212 | <item><pluginName>Ping the remote host</pluginName> | |
| 1213 | <pluginId>10180</pluginId> | |
| 1214 | <fullName>Ping the remote host[checkbox]:Test the local Nessus host</fullName> | |
| 1215 | <preferenceName>Test the local Nessus host</preferenceName> | |
| 1216 | <preferenceType>checkbox</preferenceType> | |
| 1217 | <preferenceValues>yes</preferenceValues> | |
| 1218 | <selectedValue>yes</selectedValue> | |
| 1219 | </item> | |
| 1220 | <item><pluginName>Ping the remote host</pluginName> | |
| 1221 | <pluginId>10180</pluginId> | |
| 1222 | <fullName>Ping the remote host[checkbox]:Fast network discovery</fullName> | |
| 1223 | <preferenceName>Fast network discovery</preferenceName> | |
| 1224 | <preferenceType>checkbox</preferenceType> | |
| 1225 | <preferenceValues>no</preferenceValues> | |
| 1226 | <selectedValue>no</selectedValue> | |
| 1227 | </item> | |
| 1228 | <item><pluginName>LDAP 'Domain Admins' Group Membership Enumeration</pluginName> | |
| 1229 | <pluginId>58038</pluginId> | |
| 1230 | <fullName>LDAP 'Domain Admins' Group Membership Enumeration[entry]:LDAP user :</fullName> | |
| 1231 | <preferenceName>LDAP user :</preferenceName> | |
| 1232 | <preferenceType>entry</preferenceType> | |
| 1233 | <preferenceValues></preferenceValues> | |
| 1234 | <selectedValue></selectedValue> | |
| 1235 | </item> | |
| 1236 | <item><pluginName>LDAP 'Domain Admins' Group Membership Enumeration</pluginName> | |
| 1237 | <pluginId>58038</pluginId> | |
| 1238 | <fullName>LDAP 'Domain Admins' Group Membership Enumeration[password]:LDAP password :</fullName> | |
| 1239 | <preferenceName>LDAP password :</preferenceName> | |
| 1240 | <preferenceType>password</preferenceType> | |
| 1241 | <preferenceValues></preferenceValues> | |
| 1242 | <selectedValue></selectedValue> | |
| 1243 | </item> | |
| 1244 | <item><pluginName>LDAP 'Domain Admins' Group Membership Enumeration</pluginName> | |
| 1245 | <pluginId>58038</pluginId> | |
| 1246 | <fullName>LDAP 'Domain Admins' Group Membership Enumeration[entry]:Max results :</fullName> | |
| 1247 | <preferenceName>Max results :</preferenceName> | |
| 1248 | <preferenceType>entry</preferenceType> | |
| 1249 | <preferenceValues>1000</preferenceValues> | |
| 1250 | <selectedValue>1000</selectedValue> | |
| 1251 | </item> | |
| 1252 | <item><pluginName>Global variable settings</pluginName> | |
| 1253 | <pluginId>12288</pluginId> | |
| 1254 | <fullName>Global variable settings[checkbox]:Probe services on every port</fullName> | |
| 1255 | <preferenceName>Probe services on every port</preferenceName> | |
| 1256 | <preferenceType>checkbox</preferenceType> | |
| 1257 | <preferenceValues>yes</preferenceValues> | |
| 1258 | <selectedValue>yes</selectedValue> | |
| 1259 | </item> | |
| 1260 | <item><pluginName>Global variable settings</pluginName> | |
| 1261 | <pluginId>12288</pluginId> | |
| 1262 | <fullName>Global variable settings[checkbox]:Do not log in with user accounts not specified in the policy</fullName> | |
| 1263 | <preferenceName>Do not log in with user accounts not specified in the policy</preferenceName> | |
| 1264 | <preferenceType>checkbox</preferenceType> | |
| 1265 | <preferenceValues>no</preferenceValues> | |
| 1266 | <selectedValue>no</selectedValue> | |
| 1267 | </item> | |
| 1268 | <item><pluginName>Global variable settings</pluginName> | |
| 1269 | <pluginId>12288</pluginId> | |
| 1270 | <fullName>Global variable settings[checkbox]:Enable CGI scanning</fullName> | |
| 1271 | <preferenceName>Enable CGI scanning</preferenceName> | |
| 1272 | <preferenceType>checkbox</preferenceType> | |
| 1273 | <preferenceValues>no</preferenceValues> | |
| 1274 | <selectedValue>yes</selectedValue> | |
| 1275 | </item> | |
| 1276 | <item><pluginName>Global variable settings</pluginName> | |
| 1277 | <pluginId>12288</pluginId> | |
| 1278 | <fullName>Global variable settings[radio]:Network type</fullName> | |
| 1279 | <preferenceName>Network type</preferenceName> | |
| 1280 | <preferenceType>radio</preferenceType> | |
| 1281 | <preferenceValues>Mixed (use RFC 1918);Private LAN;Public WAN (Internet)</preferenceValues> | |
| 1282 | <selectedValue>Mixed (use RFC 1918)</selectedValue> | |
| 1283 | </item> | |
| 1284 | <item><pluginName>Global variable settings</pluginName> | |
| 1285 | <pluginId>12288</pluginId> | |
| 1286 | <fullName>Global variable settings[checkbox]:Enable experimental scripts</fullName> | |
| 1287 | <preferenceName>Enable experimental scripts</preferenceName> | |
| 1288 | <preferenceType>checkbox</preferenceType> | |
| 1289 | <preferenceValues>no</preferenceValues> | |
| 1290 | <selectedValue>no</selectedValue> | |
| 1291 | </item> | |
| 1292 | <item><pluginName>Global variable settings</pluginName> | |
| 1293 | <pluginId>12288</pluginId> | |
| 1294 | <fullName>Global variable settings[checkbox]:Thorough tests (slow)</fullName> | |
| 1295 | <preferenceName>Thorough tests (slow)</preferenceName> | |
| 1296 | <preferenceType>checkbox</preferenceType> | |
| 1297 | <preferenceValues>no</preferenceValues> | |
| 1298 | <selectedValue>no</selectedValue> | |
| 1299 | </item> | |
| 1300 | <item><pluginName>Global variable settings</pluginName> | |
| 1301 | <pluginId>12288</pluginId> | |
| 1302 | <fullName>Global variable settings[radio]:Report verbosity</fullName> | |
| 1303 | <preferenceName>Report verbosity</preferenceName> | |
| 1304 | <preferenceType>radio</preferenceType> | |
| 1305 | <preferenceValues>Normal;Quiet;Verbose</preferenceValues> | |
| 1306 | <selectedValue>Normal</selectedValue> | |
| 1307 | </item> | |
| 1308 | <item><pluginName>Global variable settings</pluginName> | |
| 1309 | <pluginId>12288</pluginId> | |
| 1310 | <fullName>Global variable settings[radio]:Report paranoia</fullName> | |
| 1311 | <preferenceName>Report paranoia</preferenceName> | |
| 1312 | <preferenceType>radio</preferenceType> | |
| 1313 | <preferenceValues>Normal;Avoid false alarms;Paranoid (more false alarms)</preferenceValues> | |
| 1314 | <selectedValue>Normal</selectedValue> | |
| 1315 | </item> | |
| 1316 | <item><pluginName>Global variable settings</pluginName> | |
| 1317 | <pluginId>12288</pluginId> | |
| 1318 | <fullName>Global variable settings[entry]:HTTP User-Agent</fullName> | |
| 1319 | <preferenceName>HTTP User-Agent</preferenceName> | |
| 1320 | <preferenceType>entry</preferenceType> | |
| 1321 | <preferenceValues>Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0)</preferenceValues> | |
| 1322 | <selectedValue>Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0)</selectedValue> | |
| 1323 | </item> | |
| 1324 | <item><pluginName>Global variable settings</pluginName> | |
| 1325 | <pluginId>12288</pluginId> | |
| 1326 | <fullName>Global variable settings[file]:SSL certificate to use :</fullName> | |
| 1327 | <preferenceName>SSL certificate to use :</preferenceName> | |
| 1328 | <preferenceType>file</preferenceType> | |
| 1329 | <preferenceValues></preferenceValues> | |
| 1330 | <selectedValue></selectedValue> | |
| 1331 | </item> | |
| 1332 | <item><pluginName>Global variable settings</pluginName> | |
| 1333 | <pluginId>12288</pluginId> | |
| 1334 | <fullName>Global variable settings[file]:SSL CA to trust :</fullName> | |
| 1335 | <preferenceName>SSL CA to trust :</preferenceName> | |
| 1336 | <preferenceType>file</preferenceType> | |
| 1337 | <preferenceValues></preferenceValues> | |
| 1338 | <selectedValue></selectedValue> | |
| 1339 | </item> | |
| 1340 | <item><pluginName>Global variable settings</pluginName> | |
| 1341 | <pluginId>12288</pluginId> | |
| 1342 | <fullName>Global variable settings[file]:SSL key to use :</fullName> | |
| 1343 | <preferenceName>SSL key to use :</preferenceName> | |
| 1344 | <preferenceType>file</preferenceType> | |
| 1345 | <preferenceValues></preferenceValues> | |
| 1346 | <selectedValue></selectedValue> | |
| 1347 | </item> | |
| 1348 | <item><pluginName>Global variable settings</pluginName> | |
| 1349 | <pluginId>12288</pluginId> | |
| 1350 | <fullName>Global variable settings[password]:SSL password for SSL key :</fullName> | |
| 1351 | <preferenceName>SSL password for SSL key :</preferenceName> | |
| 1352 | <preferenceType>password</preferenceType> | |
| 1353 | <preferenceValues></preferenceValues> | |
| 1354 | <selectedValue></selectedValue> | |
| 1355 | </item> | |
| 1356 | <item><pluginName>Hydra: SAP R3</pluginName> | |
| 1357 | <pluginId>15883</pluginId> | |
| 1358 | <fullName>Hydra: SAP R3[entry]:Client ID (between 0 and 99) :</fullName> | |
| 1359 | <preferenceName>Client ID (between 0 and 99) :</preferenceName> | |
| 1360 | <preferenceType>entry</preferenceType> | |
| 1361 | <preferenceValues></preferenceValues> | |
| 1362 | <selectedValue></selectedValue> | |
| 1363 | </item> | |
| 1364 | <item><pluginName>Cleartext protocols settings</pluginName> | |
| 1365 | <pluginId>21744</pluginId> | |
| 1366 | <fullName>Cleartext protocols settings[entry]:User name :</fullName> | |
| 1367 | <preferenceName>User name :</preferenceName> | |
| 1368 | <preferenceType>entry</preferenceType> | |
| 1369 | <preferenceValues></preferenceValues> | |
| 1370 | <selectedValue></selectedValue> | |
| 1371 | </item> | |
| 1372 | <item><pluginName>Cleartext protocols settings</pluginName> | |
| 1373 | <pluginId>21744</pluginId> | |
| 1374 | <fullName>Cleartext protocols settings[password]:Password (unsafe!) :</fullName> | |
| 1375 | <preferenceName>Password (unsafe!) :</preferenceName> | |
| 1376 | <preferenceType>password</preferenceType> | |
| 1377 | <preferenceValues></preferenceValues> | |
| 1378 | <selectedValue></selectedValue> | |
| 1379 | </item> | |
| 1380 | <item><pluginName>Cleartext protocols settings</pluginName> | |
| 1381 | <pluginId>21744</pluginId> | |
| 1382 | <fullName>Cleartext protocols settings[checkbox]:Try to perform patch level checks over telnet</fullName> | |
| 1383 | <preferenceName>Try to perform patch level checks over telnet</preferenceName> | |
| 1384 | <preferenceType>checkbox</preferenceType> | |
| 1385 | <preferenceValues>no</preferenceValues> | |
| 1386 | <selectedValue>no</selectedValue> | |
| 1387 | </item> | |
| 1388 | <item><pluginName>Cleartext protocols settings</pluginName> | |
| 1389 | <pluginId>21744</pluginId> | |
| 1390 | <fullName>Cleartext protocols settings[checkbox]:Try to perform patch level checks over rsh</fullName> | |
| 1391 | <preferenceName>Try to perform patch level checks over rsh</preferenceName> | |
| 1392 | <preferenceType>checkbox</preferenceType> | |
| 1393 | <preferenceValues>no</preferenceValues> | |
| 1394 | <selectedValue>no</selectedValue> | |
| 1395 | </item> | |
| 1396 | <item><pluginName>Cleartext protocols settings</pluginName> | |
| 1397 | <pluginId>21744</pluginId> | |
| 1398 | <fullName>Cleartext protocols settings[checkbox]:Try to perform patch level checks over rexec</fullName> | |
| 1399 | <preferenceName>Try to perform patch level checks over rexec</preferenceName> | |
| 1400 | <preferenceType>checkbox</preferenceType> | |
| 1401 | <preferenceValues>no</preferenceValues> | |
| 1402 | <selectedValue>no</selectedValue> | |
| 1403 | </item> | |
| 1404 | <item><pluginName>IBM iSeries Credentials</pluginName> | |
| 1405 | <pluginId>57861</pluginId> | |
| 1406 | <fullName>IBM iSeries Credentials[entry]:Login :</fullName> | |
| 1407 | <preferenceName>Login :</preferenceName> | |
| 1408 | <preferenceType>entry</preferenceType> | |
| 1409 | <preferenceValues></preferenceValues> | |
| 1410 | <selectedValue></selectedValue> | |
| 1411 | </item> | |
| 1412 | <item><pluginName>IBM iSeries Credentials</pluginName> | |
| 1413 | <pluginId>57861</pluginId> | |
| 1414 | <fullName>IBM iSeries Credentials[password]:Password :</fullName> | |
| 1415 | <preferenceName>Password :</preferenceName> | |
| 1416 | <preferenceType>password</preferenceType> | |
| 1417 | <preferenceValues></preferenceValues> | |
| 1418 | <selectedValue></selectedValue> | |
| 1419 | </item> | |
| 1420 | <item><pluginName>SMB Use Domain SID to Enumerate Users</pluginName> | |
| 1421 | <pluginId>10399</pluginId> | |
| 1422 | <fullName>SMB Use Domain SID to Enumerate Users[entry]:Start UID :</fullName> | |
| 1423 | <preferenceName>Start UID :</preferenceName> | |
| 1424 | <preferenceType>entry</preferenceType> | |
| 1425 | <preferenceValues>1000</preferenceValues> | |
| 1426 | <selectedValue>1000</selectedValue> | |
| 1427 | </item> | |
| 1428 | <item><pluginName>SMB Use Domain SID to Enumerate Users</pluginName> | |
| 1429 | <pluginId>10399</pluginId> | |
| 1430 | <fullName>SMB Use Domain SID to Enumerate Users[entry]:End UID :</fullName> | |
| 1431 | <preferenceName>End UID :</preferenceName> | |
| 1432 | <preferenceType>entry</preferenceType> | |
| 1433 | <preferenceValues>1200</preferenceValues> | |
| 1434 | <selectedValue>1200</selectedValue> | |
| 1435 | </item> | |
| 1436 | <item><pluginName>Do not scan fragile devices</pluginName> | |
| 1437 | <pluginId>22481</pluginId> | |
| 1438 | <fullName>Do not scan fragile devices[checkbox]:Scan Network Printers</fullName> | |
| 1439 | <preferenceName>Scan Network Printers</preferenceName> | |
| 1440 | <preferenceType>checkbox</preferenceType> | |
| 1441 | <preferenceValues>no</preferenceValues> | |
| 1442 | <selectedValue>no</selectedValue> | |
| 1443 | </item> | |
| 1444 | <item><pluginName>Do not scan fragile devices</pluginName> | |
| 1445 | <pluginId>22481</pluginId> | |
| 1446 | <fullName>Do not scan fragile devices[checkbox]:Scan Novell Netware hosts</fullName> | |
| 1447 | <preferenceName>Scan Novell Netware hosts</preferenceName> | |
| 1448 | <preferenceType>checkbox</preferenceType> | |
| 1449 | <preferenceValues>no</preferenceValues> | |
| 1450 | <selectedValue>no</selectedValue> | |
| 1451 | </item> | |
| 1452 | <item><pluginName>Hydra: HTTP proxy</pluginName> | |
| 1453 | <pluginId>15874</pluginId> | |
| 1454 | <fullName>Hydra: HTTP proxy[entry]:Web site (optional) :</fullName> | |
| 1455 | <preferenceName>Web site (optional) :</preferenceName> | |
| 1456 | <preferenceType>entry</preferenceType> | |
| 1457 | <preferenceValues></preferenceValues> | |
| 1458 | <selectedValue></selectedValue> | |
| 1459 | </item> | |
| 1460 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1461 | <pluginId>14260</pluginId> | |
| 1462 | <fullName>Nikto (NASL wrapper)[checkbox]:Enable Nikto</fullName> | |
| 1463 | <preferenceName>Enable Nikto</preferenceName> | |
| 1464 | <preferenceType>checkbox</preferenceType> | |
| 1465 | <preferenceValues>no</preferenceValues> | |
| 1466 | <selectedValue>no</selectedValue> | |
| 1467 | </item> | |
| 1468 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1469 | <pluginId>14260</pluginId> | |
| 1470 | <fullName>Nikto (NASL wrapper)[checkbox]:Disable if server never replies 404</fullName> | |
| 1471 | <preferenceName>Disable if server never replies 404</preferenceName> | |
| 1472 | <preferenceType>checkbox</preferenceType> | |
| 1473 | <preferenceValues>yes</preferenceValues> | |
| 1474 | <selectedValue>yes</selectedValue> | |
| 1475 | </item> | |
| 1476 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1477 | <pluginId>14260</pluginId> | |
| 1478 | <fullName>Nikto (NASL wrapper)[entry]:Root directory</fullName> | |
| 1479 | <preferenceName>Root directory</preferenceName> | |
| 1480 | <preferenceType>entry</preferenceType> | |
| 1481 | <preferenceValues></preferenceValues> | |
| 1482 | <selectedValue></selectedValue> | |
| 1483 | </item> | |
| 1484 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1485 | <pluginId>14260</pluginId> | |
| 1486 | <fullName>Nikto (NASL wrapper)[entry]:Pause between tests (s)</fullName> | |
| 1487 | <preferenceName>Pause between tests (s)</preferenceName> | |
| 1488 | <preferenceType>entry</preferenceType> | |
| 1489 | <preferenceValues></preferenceValues> | |
| 1490 | <selectedValue></selectedValue> | |
| 1491 | </item> | |
| 1492 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1493 | <pluginId>14260</pluginId> | |
| 1494 | <fullName>Nikto (NASL wrapper)[radio]:Scan CGI directories</fullName> | |
| 1495 | <preferenceName>Scan CGI directories</preferenceName> | |
| 1496 | <preferenceType>radio</preferenceType> | |
| 1497 | <preferenceValues>User supplied;All;None</preferenceValues> | |
| 1498 | <selectedValue>User supplied;All;None</selectedValue> | |
| 1499 | </item> | |
| 1500 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1501 | <pluginId>14260</pluginId> | |
| 1502 | <fullName>Nikto (NASL wrapper)[checkbox]:Display: 1 Show redirects</fullName> | |
| 1503 | <preferenceName>Display: 1 Show redirects</preferenceName> | |
| 1504 | <preferenceType>checkbox</preferenceType> | |
| 1505 | <preferenceValues>no</preferenceValues> | |
| 1506 | <selectedValue>no</selectedValue> | |
| 1507 | </item> | |
| 1508 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1509 | <pluginId>14260</pluginId> | |
| 1510 | <fullName>Nikto (NASL wrapper)[checkbox]:Display: 2 Show cookies received</fullName> | |
| 1511 | <preferenceName>Display: 2 Show cookies received</preferenceName> | |
| 1512 | <preferenceType>checkbox</preferenceType> | |
| 1513 | <preferenceValues>no</preferenceValues> | |
| 1514 | <selectedValue>no</selectedValue> | |
| 1515 | </item> | |
| 1516 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1517 | <pluginId>14260</pluginId> | |
| 1518 | <fullName>Nikto (NASL wrapper)[checkbox]:Display: 3 Show all 200/OK responses</fullName> | |
| 1519 | <preferenceName>Display: 3 Show all 200/OK responses</preferenceName> | |
| 1520 | <preferenceType>checkbox</preferenceType> | |
| 1521 | <preferenceValues>no</preferenceValues> | |
| 1522 | <selectedValue>no</selectedValue> | |
| 1523 | </item> | |
| 1524 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1525 | <pluginId>14260</pluginId> | |
| 1526 | <fullName>Nikto (NASL wrapper)[checkbox]:Display: 4 Show URLs which require authentication</fullName> | |
| 1527 | <preferenceName>Display: 4 Show URLs which require authentication</preferenceName> | |
| 1528 | <preferenceType>checkbox</preferenceType> | |
| 1529 | <preferenceValues>no</preferenceValues> | |
| 1530 | <selectedValue>no</selectedValue> | |
| 1531 | </item> | |
| 1532 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1533 | <pluginId>14260</pluginId> | |
| 1534 | <fullName>Nikto (NASL wrapper)[checkbox]:Display: V Verbose Output</fullName> | |
| 1535 | <preferenceName>Display: V Verbose Output</preferenceName> | |
| 1536 | <preferenceType>checkbox</preferenceType> | |
| 1537 | <preferenceValues>no</preferenceValues> | |
| 1538 | <selectedValue>no</selectedValue> | |
| 1539 | </item> | |
| 1540 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1541 | <pluginId>14260</pluginId> | |
| 1542 | <fullName>Nikto (NASL wrapper)[checkbox]:Tuning: 1 Interesting File / Seen in logs</fullName> | |
| 1543 | <preferenceName>Tuning: 1 Interesting File / Seen in logs</preferenceName> | |
| 1544 | <preferenceType>checkbox</preferenceType> | |
| 1545 | <preferenceValues>no</preferenceValues> | |
| 1546 | <selectedValue>no</selectedValue> | |
| 1547 | </item> | |
| 1548 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1549 | <pluginId>14260</pluginId> | |
| 1550 | <fullName>Nikto (NASL wrapper)[checkbox]:Tuning: 2 Misconfiguration / Default File</fullName> | |
| 1551 | <preferenceName>Tuning: 2 Misconfiguration / Default File</preferenceName> | |
| 1552 | <preferenceType>checkbox</preferenceType> | |
| 1553 | <preferenceValues>no</preferenceValues> | |
| 1554 | <selectedValue>no</selectedValue> | |
| 1555 | </item> | |
| 1556 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1557 | <pluginId>14260</pluginId> | |
| 1558 | <fullName>Nikto (NASL wrapper)[checkbox]:Tuning: 3 Information Disclosure</fullName> | |
| 1559 | <preferenceName>Tuning: 3 Information Disclosure</preferenceName> | |
| 1560 | <preferenceType>checkbox</preferenceType> | |
| 1561 | <preferenceValues>no</preferenceValues> | |
| 1562 | <selectedValue>no</selectedValue> | |
| 1563 | </item> | |
| 1564 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1565 | <pluginId>14260</pluginId> | |
| 1566 | <fullName>Nikto (NASL wrapper)[checkbox]:Tuning: 4 Injection (XSS/Script/HTML)</fullName> | |
| 1567 | <preferenceName>Tuning: 4 Injection (XSS/Script/HTML)</preferenceName> | |
| 1568 | <preferenceType>checkbox</preferenceType> | |
| 1569 | <preferenceValues>no</preferenceValues> | |
| 1570 | <selectedValue>no</selectedValue> | |
| 1571 | </item> | |
| 1572 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1573 | <pluginId>14260</pluginId> | |
| 1574 | <fullName>Nikto (NASL wrapper)[checkbox]:Tuning: 5 Remote File Retrieval - Inside Web Root</fullName> | |
| 1575 | <preferenceName>Tuning: 5 Remote File Retrieval - Inside Web Root</preferenceName> | |
| 1576 | <preferenceType>checkbox</preferenceType> | |
| 1577 | <preferenceValues>no</preferenceValues> | |
| 1578 | <selectedValue>no</selectedValue> | |
| 1579 | </item> | |
| 1580 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1581 | <pluginId>14260</pluginId> | |
| 1582 | <fullName>Nikto (NASL wrapper)[checkbox]:Tuning: 6 Denial of Service</fullName> | |
| 1583 | <preferenceName>Tuning: 6 Denial of Service</preferenceName> | |
| 1584 | <preferenceType>checkbox</preferenceType> | |
| 1585 | <preferenceValues>no</preferenceValues> | |
| 1586 | <selectedValue>no</selectedValue> | |
| 1587 | </item> | |
| 1588 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1589 | <pluginId>14260</pluginId> | |
| 1590 | <fullName>Nikto (NASL wrapper)[checkbox]:Tuning: 7 Remote File Retrieval - Server Wide</fullName> | |
| 1591 | <preferenceName>Tuning: 7 Remote File Retrieval - Server Wide</preferenceName> | |
| 1592 | <preferenceType>checkbox</preferenceType> | |
| 1593 | <preferenceValues>no</preferenceValues> | |
| 1594 | <selectedValue>no</selectedValue> | |
| 1595 | </item> | |
| 1596 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1597 | <pluginId>14260</pluginId> | |
| 1598 | <fullName>Nikto (NASL wrapper)[checkbox]:Tuning: 8 Command Execution / Remote Shell</fullName> | |
| 1599 | <preferenceName>Tuning: 8 Command Execution / Remote Shell</preferenceName> | |
| 1600 | <preferenceType>checkbox</preferenceType> | |
| 1601 | <preferenceValues>no</preferenceValues> | |
| 1602 | <selectedValue>no</selectedValue> | |
| 1603 | </item> | |
| 1604 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1605 | <pluginId>14260</pluginId> | |
| 1606 | <fullName>Nikto (NASL wrapper)[checkbox]:Tuning: 9 SQL Injection</fullName> | |
| 1607 | <preferenceName>Tuning: 9 SQL Injection</preferenceName> | |
| 1608 | <preferenceType>checkbox</preferenceType> | |
| 1609 | <preferenceValues>no</preferenceValues> | |
| 1610 | <selectedValue>no</selectedValue> | |
| 1611 | </item> | |
| 1612 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1613 | <pluginId>14260</pluginId> | |
| 1614 | <fullName>Nikto (NASL wrapper)[checkbox]:Tuning: 0 File Upload</fullName> | |
| 1615 | <preferenceName>Tuning: 0 File Upload</preferenceName> | |
| 1616 | <preferenceType>checkbox</preferenceType> | |
| 1617 | <preferenceValues>no</preferenceValues> | |
| 1618 | <selectedValue>no</selectedValue> | |
| 1619 | </item> | |
| 1620 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1621 | <pluginId>14260</pluginId> | |
| 1622 | <fullName>Nikto (NASL wrapper)[checkbox]:Tuning: a Authentication Bypass</fullName> | |
| 1623 | <preferenceName>Tuning: a Authentication Bypass</preferenceName> | |
| 1624 | <preferenceType>checkbox</preferenceType> | |
| 1625 | <preferenceValues>no</preferenceValues> | |
| 1626 | <selectedValue>no</selectedValue> | |
| 1627 | </item> | |
| 1628 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1629 | <pluginId>14260</pluginId> | |
| 1630 | <fullName>Nikto (NASL wrapper)[checkbox]:Tuning: b Software Identification</fullName> | |
| 1631 | <preferenceName>Tuning: b Software Identification</preferenceName> | |
| 1632 | <preferenceType>checkbox</preferenceType> | |
| 1633 | <preferenceValues>no</preferenceValues> | |
| 1634 | <selectedValue>no</selectedValue> | |
| 1635 | </item> | |
| 1636 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1637 | <pluginId>14260</pluginId> | |
| 1638 | <fullName>Nikto (NASL wrapper)[checkbox]:Tuning: c Remote Source Inclusion</fullName> | |
| 1639 | <preferenceName>Tuning: c Remote Source Inclusion</preferenceName> | |
| 1640 | <preferenceType>checkbox</preferenceType> | |
| 1641 | <preferenceValues>no</preferenceValues> | |
| 1642 | <selectedValue>no</selectedValue> | |
| 1643 | </item> | |
| 1644 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1645 | <pluginId>14260</pluginId> | |
| 1646 | <fullName>Nikto (NASL wrapper)[checkbox]:Tuning: x Reverse Tuning Options (i.e., include all except specified)</fullName> | |
| 1647 | <preferenceName>Tuning: x Reverse Tuning Options (i.e., include all except specified)</preferenceName> | |
| 1648 | <preferenceType>checkbox</preferenceType> | |
| 1649 | <preferenceValues>no</preferenceValues> | |
| 1650 | <selectedValue>no</selectedValue> | |
| 1651 | </item> | |
| 1652 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1653 | <pluginId>14260</pluginId> | |
| 1654 | <fullName>Nikto (NASL wrapper)[checkbox]:Mutate: 1 Test all files with all root directories</fullName> | |
| 1655 | <preferenceName>Mutate: 1 Test all files with all root directories</preferenceName> | |
| 1656 | <preferenceType>checkbox</preferenceType> | |
| 1657 | <preferenceValues>no</preferenceValues> | |
| 1658 | <selectedValue>no</selectedValue> | |
| 1659 | </item> | |
| 1660 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1661 | <pluginId>14260</pluginId> | |
| 1662 | <fullName>Nikto (NASL wrapper)[checkbox]:Mutate: 2 Guess for password file names</fullName> | |
| 1663 | <preferenceName>Mutate: 2 Guess for password file names</preferenceName> | |
| 1664 | <preferenceType>checkbox</preferenceType> | |
| 1665 | <preferenceValues>no</preferenceValues> | |
| 1666 | <selectedValue>no</selectedValue> | |
| 1667 | </item> | |
| 1668 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1669 | <pluginId>14260</pluginId> | |
| 1670 | <fullName>Nikto (NASL wrapper)[checkbox]:Mutate: 3 Enumerate user names via Apache (/~user type requests)</fullName> | |
| 1671 | <preferenceName>Mutate: 3 Enumerate user names via Apache (/~user type requests)</preferenceName> | |
| 1672 | <preferenceType>checkbox</preferenceType> | |
| 1673 | <preferenceValues>no</preferenceValues> | |
| 1674 | <selectedValue>no</selectedValue> | |
| 1675 | </item> | |
| 1676 | <item><pluginName>Nikto (NASL wrapper)</pluginName> | |
| 1677 | <pluginId>14260</pluginId> | |
| 1678 | <fullName>Nikto (NASL wrapper)[checkbox]:Mutate: 4 Enumerate user names via cgiwrap (/cgi-bin/cgiwrap/~user type requests)</fullName> | |
| 1679 | <preferenceName>Mutate: 4 Enumerate user names via cgiwrap (/cgi-bin/cgiwrap/~user type requests)</preferenceName> | |
| 1680 | <preferenceType>checkbox</preferenceType> | |
| 1681 | <preferenceValues>no</preferenceValues> | |
| 1682 | <selectedValue>no</selectedValue> | |
| 1683 | </item> | |
| 1684 | <item><pluginName>Oracle Settings</pluginName> | |
| 1685 | <pluginId>22076</pluginId> | |
| 1686 | <fullName>Oracle Settings[entry]:Oracle SID :</fullName> | |
| 1687 | <preferenceName>Oracle SID :</preferenceName> | |
| 1688 | <preferenceType>entry</preferenceType> | |
| 1689 | <preferenceValues></preferenceValues> | |
| 1690 | <selectedValue></selectedValue> | |
| 1691 | </item> | |
| 1692 | <item><pluginName>Oracle Settings</pluginName> | |
| 1693 | <pluginId>22076</pluginId> | |
| 1694 | <fullName>Oracle Settings[checkbox]:Test default accounts (slow)</fullName> | |
| 1695 | <preferenceName>Test default accounts (slow)</preferenceName> | |
| 1696 | <preferenceType>checkbox</preferenceType> | |
| 1697 | <preferenceValues>no</preferenceValues> | |
| 1698 | <selectedValue>no</selectedValue> | |
| 1699 | </item> | |
| 1700 | <item><pluginName>Web Application Tests Settings</pluginName> | |
| 1701 | <pluginId>39471</pluginId> | |
| 1702 | <fullName>Web Application Tests Settings[checkbox]:Enable web applications tests</fullName> | |
| 1703 | <preferenceName>Enable web applications tests</preferenceName> | |
| 1704 | <preferenceType>checkbox</preferenceType> | |
| 1705 | <preferenceValues>no</preferenceValues> | |
| 1706 | <selectedValue>yes</selectedValue> | |
| 1707 | </item> | |
| 1708 | <item><pluginName>Web Application Tests Settings</pluginName> | |
| 1709 | <pluginId>39471</pluginId> | |
| 1710 | <fullName>Web Application Tests Settings[entry]:Maximum run time (min) :</fullName> | |
| 1711 | <preferenceName>Maximum run time (min) :</preferenceName> | |
| 1712 | <preferenceType>entry</preferenceType> | |
| 1713 | <preferenceValues>60</preferenceValues> | |
| 1714 | <selectedValue>60</selectedValue> | |
| 1715 | </item> | |
| 1716 | <item><pluginName>Web Application Tests Settings</pluginName> | |
| 1717 | <pluginId>39471</pluginId> | |
| 1718 | <fullName>Web Application Tests Settings[checkbox]:Try all HTTP methods</fullName> | |
| 1719 | <preferenceName>Try all HTTP methods</preferenceName> | |
| 1720 | <preferenceType>checkbox</preferenceType> | |
| 1721 | <preferenceValues>no</preferenceValues> | |
| 1722 | <selectedValue>no</selectedValue> | |
| 1723 | </item> | |
| 1724 | <item><pluginName>Web Application Tests Settings</pluginName> | |
| 1725 | <pluginId>39471</pluginId> | |
| 1726 | <fullName>Web Application Tests Settings[radio]:Combinations of arguments values</fullName> | |
| 1727 | <preferenceName>Combinations of arguments values</preferenceName> | |
| 1728 | <preferenceType>radio</preferenceType> | |
| 1729 | <preferenceValues>one value;some pairs;all pairs (slower but efficient);some combinations;all combinations (extremely slow)</preferenceValues> | |
| 1730 | <selectedValue>some pairs</selectedValue> | |
| 1731 | </item> | |
| 1732 | <item><pluginName>Web Application Tests Settings</pluginName> | |
| 1733 | <pluginId>39471</pluginId> | |
| 1734 | <fullName>Web Application Tests Settings[checkbox]:HTTP Parameter Pollution</fullName> | |
| 1735 | <preferenceName>HTTP Parameter Pollution</preferenceName> | |
| 1736 | <preferenceType>checkbox</preferenceType> | |
| 1737 | <preferenceValues>no</preferenceValues> | |
| 1738 | <selectedValue>no</selectedValue> | |
| 1739 | </item> | |
| 1740 | <item><pluginName>Web Application Tests Settings</pluginName> | |
| 1741 | <pluginId>39471</pluginId> | |
| 1742 | <fullName>Web Application Tests Settings[radio]:Stop at first flaw</fullName> | |
| 1743 | <preferenceName>Stop at first flaw</preferenceName> | |
| 1744 | <preferenceType>radio</preferenceType> | |
| 1745 | <preferenceValues>per CGI;per port (quicker);per parameter (slow);look for all flaws (slower)</preferenceValues> | |
| 1746 | <selectedValue>per CGI</selectedValue> | |
| 1747 | </item> | |
| 1748 | <item><pluginName>Web Application Tests Settings</pluginName> | |
| 1749 | <pluginId>39471</pluginId> | |
| 1750 | <fullName>Web Application Tests Settings[checkbox]:Test embedded web servers</fullName> | |
| 1751 | <preferenceName>Test embedded web servers</preferenceName> | |
| 1752 | <preferenceType>checkbox</preferenceType> | |
| 1753 | <preferenceValues>no</preferenceValues> | |
| 1754 | <selectedValue>no</selectedValue> | |
| 1755 | </item> | |
| 1756 | <item><pluginName>Web Application Tests Settings</pluginName> | |
| 1757 | <pluginId>39471</pluginId> | |
| 1758 | <fullName>Web Application Tests Settings[entry]:URL for Remote File Inclusion :</fullName> | |
| 1759 | <preferenceName>URL for Remote File Inclusion :</preferenceName> | |
| 1760 | <preferenceType>entry</preferenceType> | |
| 1761 | <preferenceValues>http://rfi.nessus.org/rfi.txt</preferenceValues> | |
| 1762 | <selectedValue>http://rfi.nessus.org/rfi.txt</selectedValue> | |
| 1763 | </item> | |
| 1764 | <item><pluginName>Nessus TCP scanner</pluginName> | |
| 1765 | <pluginId>10335</pluginId> | |
| 1766 | <fullName>Nessus TCP scanner[radio]:Firewall detection :</fullName> | |
| 1767 | <preferenceName>Firewall detection :</preferenceName> | |
| 1768 | <preferenceType>radio</preferenceType> | |
| 1769 | <preferenceValues>Automatic (normal);Disabled (softer);Do not detect RST rate limitation (soft);Ignore closed ports (aggressive)</preferenceValues> | |
| 1770 | <selectedValue>Automatic (normal);Disabled (softer);Do not detect RST rate limitation (soft);Ignore closed ports (aggressive)</selectedValue> | |
| 1771 | </item> | |
| 1772 | <item><pluginName>HTTP login page</pluginName> | |
| 1773 | <pluginId>11149</pluginId> | |
| 1774 | <fullName>HTTP login page[entry]:Login page :</fullName> | |
| 1775 | <preferenceName>Login page :</preferenceName> | |
| 1776 | <preferenceType>entry</preferenceType> | |
| 1777 | <preferenceValues>/</preferenceValues> | |
| 1778 | <selectedValue>/</selectedValue> | |
| 1779 | </item> | |
| 1780 | <item><pluginName>HTTP login page</pluginName> | |
| 1781 | <pluginId>11149</pluginId> | |
| 1782 | <fullName>HTTP login page[entry]:Login form :</fullName> | |
| 1783 | <preferenceName>Login form :</preferenceName> | |
| 1784 | <preferenceType>entry</preferenceType> | |
| 1785 | <preferenceValues></preferenceValues> | |
| 1786 | <selectedValue></selectedValue> | |
| 1787 | </item> | |
| 1788 | <item><pluginName>HTTP login page</pluginName> | |
| 1789 | <pluginId>11149</pluginId> | |
| 1790 | <fullName>HTTP login page[entry]:Login form fields :</fullName> | |
| 1791 | <preferenceName>Login form fields :</preferenceName> | |
| 1792 | <preferenceType>entry</preferenceType> | |
| 1793 | <preferenceValues>user=%USER%&pass=%PASS%</preferenceValues> | |
| 1794 | <selectedValue>user=%USER%&pass=%PASS%</selectedValue> | |
| 1795 | </item> | |
| 1796 | <item><pluginName>HTTP login page</pluginName> | |
| 1797 | <pluginId>11149</pluginId> | |
| 1798 | <fullName>HTTP login page[radio]:Login form method :</fullName> | |
| 1799 | <preferenceName>Login form method :</preferenceName> | |
| 1800 | <preferenceType>radio</preferenceType> | |
| 1801 | <preferenceValues>POST;GET</preferenceValues> | |
| 1802 | <selectedValue>POST;GET</selectedValue> | |
| 1803 | </item> | |
| 1804 | <item><pluginName>HTTP login page</pluginName> | |
| 1805 | <pluginId>11149</pluginId> | |
| 1806 | <fullName>HTTP login page[checkbox]:Automated login page search</fullName> | |
| 1807 | <preferenceName>Automated login page search</preferenceName> | |
| 1808 | <preferenceType>checkbox</preferenceType> | |
| 1809 | <preferenceValues>no</preferenceValues> | |
| 1810 | <selectedValue>no</selectedValue> | |
| 1811 | </item> | |
| 1812 | <item><pluginName>HTTP login page</pluginName> | |
| 1813 | <pluginId>11149</pluginId> | |
| 1814 | <fullName>HTTP login page[entry]:Re-authenticate delay (seconds) :</fullName> | |
| 1815 | <preferenceName>Re-authenticate delay (seconds) :</preferenceName> | |
| 1816 | <preferenceType>entry</preferenceType> | |
| 1817 | <preferenceValues></preferenceValues> | |
| 1818 | <selectedValue></selectedValue> | |
| 1819 | </item> | |
| 1820 | <item><pluginName>HTTP login page</pluginName> | |
| 1821 | <pluginId>11149</pluginId> | |
| 1822 | <fullName>HTTP login page[entry]:Check authentication on page :</fullName> | |
| 1823 | <preferenceName>Check authentication on page :</preferenceName> | |
| 1824 | <preferenceType>entry</preferenceType> | |
| 1825 | <preferenceValues></preferenceValues> | |
| 1826 | <selectedValue></selectedValue> | |
| 1827 | </item> | |
| 1828 | <item><pluginName>HTTP login page</pluginName> | |
| 1829 | <pluginId>11149</pluginId> | |
| 1830 | <fullName>HTTP login page[entry]:Follow 30x redirections (# of levels) :</fullName> | |
| 1831 | <preferenceName>Follow 30x redirections (# of levels) :</preferenceName> | |
| 1832 | <preferenceType>entry</preferenceType> | |
| 1833 | <preferenceValues>2</preferenceValues> | |
| 1834 | <selectedValue>2</selectedValue> | |
| 1835 | </item> | |
| 1836 | <item><pluginName>HTTP login page</pluginName> | |
| 1837 | <pluginId>11149</pluginId> | |
| 1838 | <fullName>HTTP login page[entry]:Authenticated regex :</fullName> | |
| 1839 | <preferenceName>Authenticated regex :</preferenceName> | |
| 1840 | <preferenceType>entry</preferenceType> | |
| 1841 | <preferenceValues></preferenceValues> | |
| 1842 | <selectedValue></selectedValue> | |
| 1843 | </item> | |
| 1844 | <item><pluginName>HTTP login page</pluginName> | |
| 1845 | <pluginId>11149</pluginId> | |
| 1846 | <fullName>HTTP login page[checkbox]:Invert test (disconnected if regex matches)</fullName> | |
| 1847 | <preferenceName>Invert test (disconnected if regex matches)</preferenceName> | |
| 1848 | <preferenceType>checkbox</preferenceType> | |
| 1849 | <preferenceValues>no</preferenceValues> | |
| 1850 | <selectedValue>no</selectedValue> | |
| 1851 | </item> | |
| 1852 | <item><pluginName>HTTP login page</pluginName> | |
| 1853 | <pluginId>11149</pluginId> | |
| 1854 | <fullName>HTTP login page[checkbox]:Match regex on HTTP headers</fullName> | |
| 1855 | <preferenceName>Match regex on HTTP headers</preferenceName> | |
| 1856 | <preferenceType>checkbox</preferenceType> | |
| 1857 | <preferenceValues>no</preferenceValues> | |
| 1858 | <selectedValue>no</selectedValue> | |
| 1859 | </item> | |
| 1860 | <item><pluginName>HTTP login page</pluginName> | |
| 1861 | <pluginId>11149</pluginId> | |
| 1862 | <fullName>HTTP login page[checkbox]:Case insensitive regex</fullName> | |
| 1863 | <preferenceName>Case insensitive regex</preferenceName> | |
| 1864 | <preferenceType>checkbox</preferenceType> | |
| 1865 | <preferenceValues>no</preferenceValues> | |
| 1866 | <selectedValue>no</selectedValue> | |
| 1867 | </item> | |
| 1868 | <item><pluginName>HTTP login page</pluginName> | |
| 1869 | <pluginId>11149</pluginId> | |
| 1870 | <fullName>HTTP login page[checkbox]:Abort web application tests if login fails</fullName> | |
| 1871 | <preferenceName>Abort web application tests if login fails</preferenceName> | |
| 1872 | <preferenceType>checkbox</preferenceType> | |
| 1873 | <preferenceValues>no</preferenceValues> | |
| 1874 | <selectedValue>no</selectedValue> | |
| 1875 | </item> | |
| 1876 | <item><pluginName>Patch Management: IBM Tivoli Endpoint Manager Server Settings</pluginName> | |
| 1877 | <pluginId>62558</pluginId> | |
| 1878 | <fullName>Patch Management: IBM Tivoli Endpoint Manager Server Settings[entry]:Web Reports Server :</fullName> | |
| 1879 | <preferenceName>Web Reports Server :</preferenceName> | |
| 1880 | <preferenceType>entry</preferenceType> | |
| 1881 | <preferenceValues></preferenceValues> | |
| 1882 | <selectedValue></selectedValue> | |
| 1883 | </item> | |
| 1884 | <item><pluginName>Patch Management: IBM Tivoli Endpoint Manager Server Settings</pluginName> | |
| 1885 | <pluginId>62558</pluginId> | |
| 1886 | <fullName>Patch Management: IBM Tivoli Endpoint Manager Server Settings[entry]:Web Reports Port :</fullName> | |
| 1887 | <preferenceName>Web Reports Port :</preferenceName> | |
| 1888 | <preferenceType>entry</preferenceType> | |
| 1889 | <preferenceValues></preferenceValues> | |
| 1890 | <selectedValue></selectedValue> | |
| 1891 | </item> | |
| 1892 | <item><pluginName>Patch Management: IBM Tivoli Endpoint Manager Server Settings</pluginName> | |
| 1893 | <pluginId>62558</pluginId> | |
| 1894 | <fullName>Patch Management: IBM Tivoli Endpoint Manager Server Settings[entry]:Web Reports Username :</fullName> | |
| 1895 | <preferenceName>Web Reports Username :</preferenceName> | |
| 1896 | <preferenceType>entry</preferenceType> | |
| 1897 | <preferenceValues></preferenceValues> | |
| 1898 | <selectedValue></selectedValue> | |
| 1899 | </item> | |
| 1900 | <item><pluginName>Patch Management: IBM Tivoli Endpoint Manager Server Settings</pluginName> | |
| 1901 | <pluginId>62558</pluginId> | |
| 1902 | <fullName>Patch Management: IBM Tivoli Endpoint Manager Server Settings[password]:Web Reports Password :</fullName> | |
| 1903 | <preferenceName>Web Reports Password :</preferenceName> | |
| 1904 | <preferenceType>password</preferenceType> | |
| 1905 | <preferenceValues></preferenceValues> | |
| 1906 | <selectedValue></selectedValue> | |
| 1907 | </item> | |
| 1908 | <item><pluginName>Patch Management: IBM Tivoli Endpoint Manager Server Settings</pluginName> | |
| 1909 | <pluginId>62558</pluginId> | |
| 1910 | <fullName>Patch Management: IBM Tivoli Endpoint Manager Server Settings[checkbox]:SSL :</fullName> | |
| 1911 | <preferenceName>SSL :</preferenceName> | |
| 1912 | <preferenceType>checkbox</preferenceType> | |
| 1913 | <preferenceValues>no</preferenceValues> | |
| 1914 | <selectedValue>no</selectedValue> | |
| 1915 | </item> | |
| 1916 | <item><pluginName>Patch Management: IBM Tivoli Endpoint Manager Server Settings</pluginName> | |
| 1917 | <pluginId>62558</pluginId> | |
| 1918 | <fullName>Patch Management: IBM Tivoli Endpoint Manager Server Settings[checkbox]:Verify SSL Certificate :</fullName> | |
| 1919 | <preferenceName>Verify SSL Certificate :</preferenceName> | |
| 1920 | <preferenceType>checkbox</preferenceType> | |
| 1921 | <preferenceValues>no</preferenceValues> | |
| 1922 | <selectedValue>no</selectedValue> | |
| 1923 | </item> | |
| 1924 | <item><pluginName>Patch Report</pluginName> | |
| 1925 | <pluginId>66334</pluginId> | |
| 1926 | <fullName>Patch Report[checkbox]:Display the superseded patches in the report</fullName> | |
| 1927 | <preferenceName>Display the superseded patches in the report</preferenceName> | |
| 1928 | <preferenceType>checkbox</preferenceType> | |
| 1929 | <preferenceValues>yes</preferenceValues> | |
| 1930 | <selectedValue>yes</selectedValue> | |
| 1931 | </item> | |
| 1932 | <item><pluginName>Hydra (NASL wrappers options)</pluginName> | |
| 1933 | <pluginId>15868</pluginId> | |
| 1934 | <fullName>Hydra (NASL wrappers options)[checkbox]:Always enable Hydra (slow)</fullName> | |
| 1935 | <preferenceName>Always enable Hydra (slow)</preferenceName> | |
| 1936 | <preferenceType>checkbox</preferenceType> | |
| 1937 | <preferenceValues>no</preferenceValues> | |
| 1938 | <selectedValue>no</selectedValue> | |
| 1939 | </item> | |
| 1940 | <item><pluginName>Hydra (NASL wrappers options)</pluginName> | |
| 1941 | <pluginId>15868</pluginId> | |
| 1942 | <fullName>Hydra (NASL wrappers options)[file]:Logins file :</fullName> | |
| 1943 | <preferenceName>Logins file :</preferenceName> | |
| 1944 | <preferenceType>file</preferenceType> | |
| 1945 | <preferenceValues></preferenceValues> | |
| 1946 | <selectedValue></selectedValue> | |
| 1947 | </item> | |
| 1948 | <item><pluginName>Hydra (NASL wrappers options)</pluginName> | |
| 1949 | <pluginId>15868</pluginId> | |
| 1950 | <fullName>Hydra (NASL wrappers options)[file]:Passwords file :</fullName> | |
| 1951 | <preferenceName>Passwords file :</preferenceName> | |
| 1952 | <preferenceType>file</preferenceType> | |
| 1953 | <preferenceValues></preferenceValues> | |
| 1954 | <selectedValue></selectedValue> | |
| 1955 | </item> | |
| 1956 | <item><pluginName>Hydra (NASL wrappers options)</pluginName> | |
| 1957 | <pluginId>15868</pluginId> | |
| 1958 | <fullName>Hydra (NASL wrappers options)[entry]:Number of parallel tasks :</fullName> | |
| 1959 | <preferenceName>Number of parallel tasks :</preferenceName> | |
| 1960 | <preferenceType>entry</preferenceType> | |
| 1961 | <preferenceValues>16</preferenceValues> | |
| 1962 | <selectedValue>16</selectedValue> | |
| 1963 | </item> | |
| 1964 | <item><pluginName>Hydra (NASL wrappers options)</pluginName> | |
| 1965 | <pluginId>15868</pluginId> | |
| 1966 | <fullName>Hydra (NASL wrappers options)[entry]:Timeout (in seconds) :</fullName> | |
| 1967 | <preferenceName>Timeout (in seconds) :</preferenceName> | |
| 1968 | <preferenceType>entry</preferenceType> | |
| 1969 | <preferenceValues>30</preferenceValues> | |
| 1970 | <selectedValue>30</selectedValue> | |
| 1971 | </item> | |
| 1972 | <item><pluginName>Hydra (NASL wrappers options)</pluginName> | |
| 1973 | <pluginId>15868</pluginId> | |
| 1974 | <fullName>Hydra (NASL wrappers options)[checkbox]:Try empty passwords</fullName> | |
| 1975 | <preferenceName>Try empty passwords</preferenceName> | |
| 1976 | <preferenceType>checkbox</preferenceType> | |
| 1977 | <preferenceValues>yes</preferenceValues> | |
| 1978 | <selectedValue>yes</selectedValue> | |
| 1979 | </item> | |
| 1980 | <item><pluginName>Hydra (NASL wrappers options)</pluginName> | |
| 1981 | <pluginId>15868</pluginId> | |
| 1982 | <fullName>Hydra (NASL wrappers options)[checkbox]:Try login as password</fullName> | |
| 1983 | <preferenceName>Try login as password</preferenceName> | |
| 1984 | <preferenceType>checkbox</preferenceType> | |
| 1985 | <preferenceValues>yes</preferenceValues> | |
| 1986 | <selectedValue>yes</selectedValue> | |
| 1987 | </item> | |
| 1988 | <item><pluginName>Hydra (NASL wrappers options)</pluginName> | |
| 1989 | <pluginId>15868</pluginId> | |
| 1990 | <fullName>Hydra (NASL wrappers options)[checkbox]:Exit as soon as an account is found</fullName> | |
| 1991 | <preferenceName>Exit as soon as an account is found</preferenceName> | |
| 1992 | <preferenceType>checkbox</preferenceType> | |
| 1993 | <preferenceValues>no</preferenceValues> | |
| 1994 | <selectedValue>no</selectedValue> | |
| 1995 | </item> | |
| 1996 | <item><pluginName>Hydra (NASL wrappers options)</pluginName> | |
| 1997 | <pluginId>15868</pluginId> | |
| 1998 | <fullName>Hydra (NASL wrappers options)[checkbox]:Add accounts found by other plugins to login file</fullName> | |
| 1999 | <preferenceName>Add accounts found by other plugins to login file</preferenceName> | |
| 2000 | <preferenceType>checkbox</preferenceType> | |
| 2001 | <preferenceValues>yes</preferenceValues> | |
| 2002 | <selectedValue>yes</selectedValue> | |
| 2003 | </item> | |
| 2004 | <item><pluginName>Wake-on-LAN</pluginName> | |
| 2005 | <pluginId>52616</pluginId> | |
| 2006 | <fullName>Wake-on-LAN[file]:List of MAC addresses for Wake-on-LAN:</fullName> | |
| 2007 | <preferenceName>List of MAC addresses for Wake-on-LAN:</preferenceName> | |
| 2008 | <preferenceType>file</preferenceType> | |
| 2009 | <preferenceValues></preferenceValues> | |
| 2010 | <selectedValue></selectedValue> | |
| 2011 | </item> | |
| 2012 | <item><pluginName>Wake-on-LAN</pluginName> | |
| 2013 | <pluginId>52616</pluginId> | |
| 2014 | <fullName>Wake-on-LAN[entry]:Time to wait (in minutes) for the systems to boot:</fullName> | |
| 2015 | <preferenceName>Time to wait (in minutes) for the systems to boot:</preferenceName> | |
| 2016 | <preferenceType>entry</preferenceType> | |
| 2017 | <preferenceValues>5</preferenceValues> | |
| 2018 | <selectedValue>5</selectedValue> | |
| 2019 | </item> | |
| 2020 | <item><pluginName>ADSI Settings</pluginName> | |
| 2021 | <pluginId>60024</pluginId> | |
| 2022 | <fullName>ADSI Settings[entry]:Domain Controller :</fullName> | |
| 2023 | <preferenceName>Domain Controller :</preferenceName> | |
| 2024 | <preferenceType>entry</preferenceType> | |
| 2025 | <preferenceValues></preferenceValues> | |
| 2026 | <selectedValue></selectedValue> | |
| 2027 | </item> | |
| 2028 | <item><pluginName>ADSI Settings</pluginName> | |
| 2029 | <pluginId>60024</pluginId> | |
| 2030 | <fullName>ADSI Settings[entry]:Domain :</fullName> | |
| 2031 | <preferenceName>Domain :</preferenceName> | |
| 2032 | <preferenceType>entry</preferenceType> | |
| 2033 | <preferenceValues></preferenceValues> | |
| 2034 | <selectedValue></selectedValue> | |
| 2035 | </item> | |
| 2036 | <item><pluginName>ADSI Settings</pluginName> | |
| 2037 | <pluginId>60024</pluginId> | |
| 2038 | <fullName>ADSI Settings[entry]:Domain Username :</fullName> | |
| 2039 | <preferenceName>Domain Username :</preferenceName> | |
| 2040 | <preferenceType>entry</preferenceType> | |
| 2041 | <preferenceValues></preferenceValues> | |
| 2042 | <selectedValue></selectedValue> | |
| 2043 | </item> | |
| 2044 | <item><pluginName>ADSI Settings</pluginName> | |
| 2045 | <pluginId>60024</pluginId> | |
| 2046 | <fullName>ADSI Settings[password]:Domain Password :</fullName> | |
| 2047 | <preferenceName>Domain Password :</preferenceName> | |
| 2048 | <preferenceType>password</preferenceType> | |
| 2049 | <preferenceValues></preferenceValues> | |
| 2050 | <selectedValue></selectedValue> | |
| 2051 | </item> | |
| 2052 | <item><pluginName>ADSI Settings</pluginName> | |
| 2053 | <pluginId>60024</pluginId> | |
| 2054 | <fullName>ADSI Settings[entry]:Domain Controller 2:</fullName> | |
| 2055 | <preferenceName>Domain Controller 2:</preferenceName> | |
| 2056 | <preferenceType>entry</preferenceType> | |
| 2057 | <preferenceValues></preferenceValues> | |
| 2058 | <selectedValue></selectedValue> | |
| 2059 | </item> | |
| 2060 | <item><pluginName>ADSI Settings</pluginName> | |
| 2061 | <pluginId>60024</pluginId> | |
| 2062 | <fullName>ADSI Settings[entry]:Domain 2:</fullName> | |
| 2063 | <preferenceName>Domain 2:</preferenceName> | |
| 2064 | <preferenceType>entry</preferenceType> | |
| 2065 | <preferenceValues></preferenceValues> | |
| 2066 | <selectedValue></selectedValue> | |
| 2067 | </item> | |
| 2068 | <item><pluginName>ADSI Settings</pluginName> | |
| 2069 | <pluginId>60024</pluginId> | |
| 2070 | <fullName>ADSI Settings[entry]:Domain Username 2:</fullName> | |
| 2071 | <preferenceName>Domain Username 2:</preferenceName> | |
| 2072 | <preferenceType>entry</preferenceType> | |
| 2073 | <preferenceValues></preferenceValues> | |
| 2074 | <selectedValue></selectedValue> | |
| 2075 | </item> | |
| 2076 | <item><pluginName>ADSI Settings</pluginName> | |
| 2077 | <pluginId>60024</pluginId> | |
| 2078 | <fullName>ADSI Settings[password]:Domain Password 2:</fullName> | |
| 2079 | <preferenceName>Domain Password 2:</preferenceName> | |
| 2080 | <preferenceType>password</preferenceType> | |
| 2081 | <preferenceValues></preferenceValues> | |
| 2082 | <selectedValue></selectedValue> | |
| 2083 | </item> | |
| 2084 | <item><pluginName>ADSI Settings</pluginName> | |
| 2085 | <pluginId>60024</pluginId> | |
| 2086 | <fullName>ADSI Settings[entry]:Domain Controller 3:</fullName> | |
| 2087 | <preferenceName>Domain Controller 3:</preferenceName> | |
| 2088 | <preferenceType>entry</preferenceType> | |
| 2089 | <preferenceValues></preferenceValues> | |
| 2090 | <selectedValue></selectedValue> | |
| 2091 | </item> | |
| 2092 | <item><pluginName>ADSI Settings</pluginName> | |
| 2093 | <pluginId>60024</pluginId> | |
| 2094 | <fullName>ADSI Settings[entry]:Domain 3:</fullName> | |
| 2095 | <preferenceName>Domain 3:</preferenceName> | |
| 2096 | <preferenceType>entry</preferenceType> | |
| 2097 | <preferenceValues></preferenceValues> | |
| 2098 | <selectedValue></selectedValue> | |
| 2099 | </item> | |
| 2100 | <item><pluginName>ADSI Settings</pluginName> | |
| 2101 | <pluginId>60024</pluginId> | |
| 2102 | <fullName>ADSI Settings[entry]:Domain Username 3:</fullName> | |
| 2103 | <preferenceName>Domain Username 3:</preferenceName> | |
| 2104 | <preferenceType>entry</preferenceType> | |
| 2105 | <preferenceValues></preferenceValues> | |
| 2106 | <selectedValue></selectedValue> | |
| 2107 | </item> | |
| 2108 | <item><pluginName>ADSI Settings</pluginName> | |
| 2109 | <pluginId>60024</pluginId> | |
| 2110 | <fullName>ADSI Settings[password]:Domain Password 3:</fullName> | |
| 2111 | <preferenceName>Domain Password 3:</preferenceName> | |
| 2112 | <preferenceType>password</preferenceType> | |
| 2113 | <preferenceValues></preferenceValues> | |
| 2114 | <selectedValue></selectedValue> | |
| 2115 | </item> | |
| 2116 | <item><pluginName>ADSI Settings</pluginName> | |
| 2117 | <pluginId>60024</pluginId> | |
| 2118 | <fullName>ADSI Settings[entry]:Domain Controller 4:</fullName> | |
| 2119 | <preferenceName>Domain Controller 4:</preferenceName> | |
| 2120 | <preferenceType>entry</preferenceType> | |
| 2121 | <preferenceValues></preferenceValues> | |
| 2122 | <selectedValue></selectedValue> | |
| 2123 | </item> | |
| 2124 | <item><pluginName>ADSI Settings</pluginName> | |
| 2125 | <pluginId>60024</pluginId> | |
| 2126 | <fullName>ADSI Settings[entry]:Domain 4:</fullName> | |
| 2127 | <preferenceName>Domain 4:</preferenceName> | |
| 2128 | <preferenceType>entry</preferenceType> | |
| 2129 | <preferenceValues></preferenceValues> | |
| 2130 | <selectedValue></selectedValue> | |
| 2131 | </item> | |
| 2132 | <item><pluginName>ADSI Settings</pluginName> | |
| 2133 | <pluginId>60024</pluginId> | |
| 2134 | <fullName>ADSI Settings[entry]:Domain Username 4:</fullName> | |
| 2135 | <preferenceName>Domain Username 4:</preferenceName> | |
| 2136 | <preferenceType>entry</preferenceType> | |
| 2137 | <preferenceValues></preferenceValues> | |
| 2138 | <selectedValue></selectedValue> | |
| 2139 | </item> | |
| 2140 | <item><pluginName>ADSI Settings</pluginName> | |
| 2141 | <pluginId>60024</pluginId> | |
| 2142 | <fullName>ADSI Settings[password]:Domain Password 4:</fullName> | |
| 2143 | <preferenceName>Domain Password 4:</preferenceName> | |
| 2144 | <preferenceType>password</preferenceType> | |
| 2145 | <preferenceValues></preferenceValues> | |
| 2146 | <selectedValue></selectedValue> | |
| 2147 | </item> | |
| 2148 | <item><pluginName>ADSI Settings</pluginName> | |
| 2149 | <pluginId>60024</pluginId> | |
| 2150 | <fullName>ADSI Settings[entry]:Domain Controller 5:</fullName> | |
| 2151 | <preferenceName>Domain Controller 5:</preferenceName> | |
| 2152 | <preferenceType>entry</preferenceType> | |
| 2153 | <preferenceValues></preferenceValues> | |
| 2154 | <selectedValue></selectedValue> | |
| 2155 | </item> | |
| 2156 | <item><pluginName>ADSI Settings</pluginName> | |
| 2157 | <pluginId>60024</pluginId> | |
| 2158 | <fullName>ADSI Settings[entry]:Domain 5:</fullName> | |
| 2159 | <preferenceName>Domain 5:</preferenceName> | |
| 2160 | <preferenceType>entry</preferenceType> | |
| 2161 | <preferenceValues></preferenceValues> | |
| 2162 | <selectedValue></selectedValue> | |
| 2163 | </item> | |
| 2164 | <item><pluginName>ADSI Settings</pluginName> | |
| 2165 | <pluginId>60024</pluginId> | |
| 2166 | <fullName>ADSI Settings[entry]:Domain Username 5:</fullName> | |
| 2167 | <preferenceName>Domain Username 5:</preferenceName> | |
| 2168 | <preferenceType>entry</preferenceType> | |
| 2169 | <preferenceValues></preferenceValues> | |
| 2170 | <selectedValue></selectedValue> | |
| 2171 | </item> | |
| 2172 | <item><pluginName>ADSI Settings</pluginName> | |
| 2173 | <pluginId>60024</pluginId> | |
| 2174 | <fullName>ADSI Settings[password]:Domain Password 5:</fullName> | |
| 2175 | <preferenceName>Domain Password 5:</preferenceName> | |
| 2176 | <preferenceType>password</preferenceType> | |
| 2177 | <preferenceValues></preferenceValues> | |
| 2178 | <selectedValue></selectedValue> | |
| 2179 | </item> | |
| 2180 | <item><pluginName>Hydra: PostgreSQL</pluginName> | |
| 2181 | <pluginId>18660</pluginId> | |
| 2182 | <fullName>Hydra: PostgreSQL[entry]:Database name (optional) :</fullName> | |
| 2183 | <preferenceName>Database name (optional) :</preferenceName> | |
| 2184 | <preferenceType>entry</preferenceType> | |
| 2185 | <preferenceValues></preferenceValues> | |
| 2186 | <selectedValue></selectedValue> | |
| 2187 | </item> | |
| 2188 | <item><pluginName>Hydra: Cisco enable</pluginName> | |
| 2189 | <pluginId>15870</pluginId> | |
| 2190 | <fullName>Hydra: Cisco enable[entry]:Logon password :</fullName> | |
| 2191 | <preferenceName>Logon password :</preferenceName> | |
| 2192 | <preferenceType>entry</preferenceType> | |
| 2193 | <preferenceValues></preferenceValues> | |
| 2194 | <selectedValue></selectedValue> | |
| 2195 | </item> | |
| 2196 | <item><pluginName>Database settings</pluginName> | |
| 2197 | <pluginId>33815</pluginId> | |
| 2198 | <fullName>Database settings[entry]:Login :</fullName> | |
| 2199 | <preferenceName>Login :</preferenceName> | |
| 2200 | <preferenceType>entry</preferenceType> | |
| 2201 | <preferenceValues></preferenceValues> | |
| 2202 | <selectedValue></selectedValue> | |
| 2203 | </item> | |
| 2204 | <item><pluginName>Database settings</pluginName> | |
| 2205 | <pluginId>33815</pluginId> | |
| 2206 | <fullName>Database settings[password]:Password :</fullName> | |
| 2207 | <preferenceName>Password :</preferenceName> | |
| 2208 | <preferenceType>password</preferenceType> | |
| 2209 | <preferenceValues></preferenceValues> | |
| 2210 | <selectedValue></selectedValue> | |
| 2211 | </item> | |
| 2212 | <item><pluginName>Database settings</pluginName> | |
| 2213 | <pluginId>33815</pluginId> | |
| 2214 | <fullName>Database settings[radio]:DB Type :</fullName> | |
| 2215 | <preferenceName>DB Type :</preferenceName> | |
| 2216 | <preferenceType>radio</preferenceType> | |
| 2217 | <preferenceValues>Oracle;SQL Server;MySQL;DB2;Informix/DRDA;PostgreSQL</preferenceValues> | |
| 2218 | <selectedValue>Oracle;SQL Server;MySQL;DB2;Informix/DRDA;PostgreSQL</selectedValue> | |
| 2219 | </item> | |
| 2220 | <item><pluginName>Database settings</pluginName> | |
| 2221 | <pluginId>33815</pluginId> | |
| 2222 | <fullName>Database settings[entry]:Database SID :</fullName> | |
| 2223 | <preferenceName>Database SID :</preferenceName> | |
| 2224 | <preferenceType>entry</preferenceType> | |
| 2225 | <preferenceValues></preferenceValues> | |
| 2226 | <selectedValue></selectedValue> | |
| 2227 | </item> | |
| 2228 | <item><pluginName>Database settings</pluginName> | |
| 2229 | <pluginId>33815</pluginId> | |
| 2230 | <fullName>Database settings[entry]:Database port to use :</fullName> | |
| 2231 | <preferenceName>Database port to use :</preferenceName> | |
| 2232 | <preferenceType>entry</preferenceType> | |
| 2233 | <preferenceValues></preferenceValues> | |
| 2234 | <selectedValue></selectedValue> | |
| 2235 | </item> | |
| 2236 | <item><pluginName>Database settings</pluginName> | |
| 2237 | <pluginId>33815</pluginId> | |
| 2238 | <fullName>Database settings[radio]:Oracle auth type:</fullName> | |
| 2239 | <preferenceName>Oracle auth type:</preferenceName> | |
| 2240 | <preferenceType>radio</preferenceType> | |
| 2241 | <preferenceValues>NORMAL;SYSOPER;SYSDBA</preferenceValues> | |
| 2242 | <selectedValue>NORMAL;SYSOPER;SYSDBA</selectedValue> | |
| 2243 | </item> | |
| 2244 | <item><pluginName>Database settings</pluginName> | |
| 2245 | <pluginId>33815</pluginId> | |
| 2246 | <fullName>Database settings[radio]:SQL Server auth type:</fullName> | |
| 2247 | <preferenceName>SQL Server auth type:</preferenceName> | |
| 2248 | <preferenceType>radio</preferenceType> | |
| 2249 | <preferenceValues>Windows;SQL</preferenceValues> | |
| 2250 | <selectedValue>Windows;SQL</selectedValue> | |
| 2251 | </item> | |
| 2252 | <item><pluginName>Service Detection</pluginName> | |
| 2253 | <pluginId>22964</pluginId> | |
| 2254 | <fullName>Service Detection[radio]:Test SSL based services</fullName> | |
| 2255 | <preferenceName>Test SSL based services</preferenceName> | |
| 2256 | <preferenceType>radio</preferenceType> | |
| 2257 | <preferenceValues>Known SSL ports;All;None</preferenceValues> | |
| 2258 | <selectedValue>Known SSL ports;All;None</selectedValue> | |
| 2259 | </item> | |
| 2260 | <item><pluginName>Kerberos configuration</pluginName> | |
| 2261 | <pluginId>17351</pluginId> | |
| 2262 | <fullName>Kerberos configuration[entry]:Kerberos Key Distribution Center (KDC) :</fullName> | |
| 2263 | <preferenceName>Kerberos Key Distribution Center (KDC) :</preferenceName> | |
| 2264 | <preferenceType>entry</preferenceType> | |
| 2265 | <preferenceValues></preferenceValues> | |
| 2266 | <selectedValue></selectedValue> | |
| 2267 | </item> | |
| 2268 | <item><pluginName>Kerberos configuration</pluginName> | |
| 2269 | <pluginId>17351</pluginId> | |
| 2270 | <fullName>Kerberos configuration[entry]:Kerberos KDC Port :</fullName> | |
| 2271 | <preferenceName>Kerberos KDC Port :</preferenceName> | |
| 2272 | <preferenceType>entry</preferenceType> | |
| 2273 | <preferenceValues>88</preferenceValues> | |
| 2274 | <selectedValue>88</selectedValue> | |
| 2275 | </item> | |
| 2276 | <item><pluginName>Kerberos configuration</pluginName> | |
| 2277 | <pluginId>17351</pluginId> | |
| 2278 | <fullName>Kerberos configuration[radio]:Kerberos KDC Transport :</fullName> | |
| 2279 | <preferenceName>Kerberos KDC Transport :</preferenceName> | |
| 2280 | <preferenceType>radio</preferenceType> | |
| 2281 | <preferenceValues>udp;tcp</preferenceValues> | |
| 2282 | <selectedValue>udp;tcp</selectedValue> | |
| 2283 | </item> | |
| 2284 | <item><pluginName>Kerberos configuration</pluginName> | |
| 2285 | <pluginId>17351</pluginId> | |
| 2286 | <fullName>Kerberos configuration[entry]:Kerberos Realm (SSH only) :</fullName> | |
| 2287 | <preferenceName>Kerberos Realm (SSH only) :</preferenceName> | |
| 2288 | <preferenceType>entry</preferenceType> | |
| 2289 | <preferenceValues></preferenceValues> | |
| 2290 | <selectedValue></selectedValue> | |
| 2291 | </item> | |
| 2292 | <item><pluginName>Malicious Process Detection</pluginName> | |
| 2293 | <pluginId>59275</pluginId> | |
| 2294 | <fullName>Malicious Process Detection[file]:Additional MD5 hashes (optional) :</fullName> | |
| 2295 | <preferenceName>Additional MD5 hashes (optional) :</preferenceName> | |
| 2296 | <preferenceType>file</preferenceType> | |
| 2297 | <preferenceValues></preferenceValues> | |
| 2298 | <selectedValue></selectedValue> | |
| 2299 | </item> | |
| 2300 | <item><pluginName>Patch Management: WSUS Server Settings</pluginName> | |
| 2301 | <pluginId>57031</pluginId> | |
| 2302 | <fullName>Patch Management: WSUS Server Settings[entry]:WSUS Server :</fullName> | |
| 2303 | <preferenceName>WSUS Server :</preferenceName> | |
| 2304 | <preferenceType>entry</preferenceType> | |
| 2305 | <preferenceValues></preferenceValues> | |
| 2306 | <selectedValue></selectedValue> | |
| 2307 | </item> | |
| 2308 | <item><pluginName>Patch Management: WSUS Server Settings</pluginName> | |
| 2309 | <pluginId>57031</pluginId> | |
| 2310 | <fullName>Patch Management: WSUS Server Settings[entry]:WSUS Port :</fullName> | |
| 2311 | <preferenceName>WSUS Port :</preferenceName> | |
| 2312 | <preferenceType>entry</preferenceType> | |
| 2313 | <preferenceValues></preferenceValues> | |
| 2314 | <selectedValue></selectedValue> | |
| 2315 | </item> | |
| 2316 | <item><pluginName>Patch Management: WSUS Server Settings</pluginName> | |
| 2317 | <pluginId>57031</pluginId> | |
| 2318 | <fullName>Patch Management: WSUS Server Settings[entry]:WSUS Username :</fullName> | |
| 2319 | <preferenceName>WSUS Username :</preferenceName> | |
| 2320 | <preferenceType>entry</preferenceType> | |
| 2321 | <preferenceValues></preferenceValues> | |
| 2322 | <selectedValue></selectedValue> | |
| 2323 | </item> | |
| 2324 | <item><pluginName>Patch Management: WSUS Server Settings</pluginName> | |
| 2325 | <pluginId>57031</pluginId> | |
| 2326 | <fullName>Patch Management: WSUS Server Settings[password]:WSUS Password :</fullName> | |
| 2327 | <preferenceName>WSUS Password :</preferenceName> | |
| 2328 | <preferenceType>password</preferenceType> | |
| 2329 | <preferenceValues></preferenceValues> | |
| 2330 | <selectedValue></selectedValue> | |
| 2331 | </item> | |
| 2332 | <item><pluginName>Patch Management: WSUS Server Settings</pluginName> | |
| 2333 | <pluginId>57031</pluginId> | |
| 2334 | <fullName>Patch Management: WSUS Server Settings[checkbox]:SSL :</fullName> | |
| 2335 | <preferenceName>SSL :</preferenceName> | |
| 2336 | <preferenceType>checkbox</preferenceType> | |
| 2337 | <preferenceValues>no</preferenceValues> | |
| 2338 | <selectedValue>no</selectedValue> | |
| 2339 | </item> | |
| 2340 | <item><pluginName>Patch Management: WSUS Server Settings</pluginName> | |
| 2341 | <pluginId>57031</pluginId> | |
| 2342 | <fullName>Patch Management: WSUS Server Settings[checkbox]:Verify SSL Certificate :</fullName> | |
| 2343 | <preferenceName>Verify SSL Certificate :</preferenceName> | |
| 2344 | <preferenceType>checkbox</preferenceType> | |
| 2345 | <preferenceValues>no</preferenceValues> | |
| 2346 | <selectedValue>no</selectedValue> | |
| 2347 | </item> | |
| 2348 | <item><pluginName>Nessus SYN scanner</pluginName> | |
| 2349 | <pluginId>11219</pluginId> | |
| 2350 | <fullName>Nessus SYN scanner[radio]:Firewall detection :</fullName> | |
| 2351 | <preferenceName>Firewall detection :</preferenceName> | |
| 2352 | <preferenceType>radio</preferenceType> | |
| 2353 | <preferenceValues>Automatic (normal);Disabled (softer);Do not detect RST rate limitation (soft);Ignore closed ports (aggressive)</preferenceValues> | |
| 2354 | <selectedValue>Automatic (normal);Disabled (softer);Do not detect RST rate limitation (soft);Ignore closed ports (aggressive)</selectedValue> | |
| 2355 | </item> | |
| 2356 | <item><pluginName>SMTP settings</pluginName> | |
| 2357 | <pluginId>11038</pluginId> | |
| 2358 | <fullName>SMTP settings[entry]:Third party domain :</fullName> | |
| 2359 | <preferenceName>Third party domain :</preferenceName> | |
| 2360 | <preferenceType>entry</preferenceType> | |
| 2361 | <preferenceValues>example.com</preferenceValues> | |
| 2362 | <selectedValue>example.com</selectedValue> | |
| 2363 | </item> | |
| 2364 | <item><pluginName>SMTP settings</pluginName> | |
| 2365 | <pluginId>11038</pluginId> | |
| 2366 | <fullName>SMTP settings[entry]:From address :</fullName> | |
| 2367 | <preferenceName>From address :</preferenceName> | |
| 2368 | <preferenceType>entry</preferenceType> | |
| 2369 | <preferenceValues>[email protected]</preferenceValues> | |
| 2370 | <selectedValue>[email protected]</selectedValue> | |
| 2371 | </item> | |
| 2372 | <item><pluginName>SMTP settings</pluginName> | |
| 2373 | <pluginId>11038</pluginId> | |
| 2374 | <fullName>SMTP settings[entry]:To address :</fullName> | |
| 2375 | <preferenceName>To address :</preferenceName> | |
| 2376 | <preferenceType>entry</preferenceType> | |
| 2377 | <preferenceValues>postmaster@[AUTO_REPLACED_IP]</preferenceValues> | |
| 2378 | <selectedValue>postmaster@[AUTO_REPLACED_IP]</selectedValue> | |
| 2379 | </item> | |
| 2380 | <item><pluginName>SMB Use Host SID to Enumerate Local Users</pluginName> | |
| 2381 | <pluginId>10860</pluginId> | |
| 2382 | <fullName>SMB Use Host SID to Enumerate Local Users[entry]:Start UID :</fullName> | |
| 2383 | <preferenceName>Start UID :</preferenceName> | |
| 2384 | <preferenceType>entry</preferenceType> | |
| 2385 | <preferenceValues>1000</preferenceValues> | |
| 2386 | <selectedValue>1000</selectedValue> | |
| 2387 | </item> | |
| 2388 | <item><pluginName>SMB Use Host SID to Enumerate Local Users</pluginName> | |
| 2389 | <pluginId>10860</pluginId> | |
| 2390 | <fullName>SMB Use Host SID to Enumerate Local Users[entry]:End UID :</fullName> | |
| 2391 | <preferenceName>End UID :</preferenceName> | |
| 2392 | <preferenceType>entry</preferenceType> | |
| 2393 | <preferenceValues>1200</preferenceValues> | |
| 2394 | <selectedValue>1200</selectedValue> | |
| 2395 | </item> | |
| 2396 | <item><pluginName>Web mirroring</pluginName> | |
| 2397 | <pluginId>10662</pluginId> | |
| 2398 | <fullName>Web mirroring[entry]:Number of pages to mirror :</fullName> | |
| 2399 | <preferenceName>Number of pages to mirror :</preferenceName> | |
| 2400 | <preferenceType>entry</preferenceType> | |
| 2401 | <preferenceValues>1000</preferenceValues> | |
| 2402 | <selectedValue>1000</selectedValue> | |
| 2403 | </item> | |
| 2404 | <item><pluginName>Web mirroring</pluginName> | |
| 2405 | <pluginId>10662</pluginId> | |
| 2406 | <fullName>Web mirroring[entry]:Maximum depth :</fullName> | |
| 2407 | <preferenceName>Maximum depth :</preferenceName> | |
| 2408 | <preferenceType>entry</preferenceType> | |
| 2409 | <preferenceValues>6</preferenceValues> | |
| 2410 | <selectedValue>6</selectedValue> | |
| 2411 | </item> | |
| 2412 | <item><pluginName>Web mirroring</pluginName> | |
| 2413 | <pluginId>10662</pluginId> | |
| 2414 | <fullName>Web mirroring[entry]:Start page :</fullName> | |
| 2415 | <preferenceName>Start page :</preferenceName> | |
| 2416 | <preferenceType>entry</preferenceType> | |
| 2417 | <preferenceValues>/</preferenceValues> | |
| 2418 | <selectedValue>/</selectedValue> | |
| 2419 | </item> | |
| 2420 | <item><pluginName>Web mirroring</pluginName> | |
| 2421 | <pluginId>10662</pluginId> | |
| 2422 | <fullName>Web mirroring[entry]:Excluded items regex :</fullName> | |
| 2423 | <preferenceName>Excluded items regex :</preferenceName> | |
| 2424 | <preferenceType>entry</preferenceType> | |
| 2425 | <preferenceValues>/server_privileges\.php|logout</preferenceValues> | |
| 2426 | <selectedValue>/server_privileges\.php|logout</selectedValue> | |
| 2427 | </item> | |
| 2428 | <item><pluginName>Web mirroring</pluginName> | |
| 2429 | <pluginId>10662</pluginId> | |
| 2430 | <fullName>Web mirroring[checkbox]:Follow dynamic pages :</fullName> | |
| 2431 | <preferenceName>Follow dynamic pages :</preferenceName> | |
| 2432 | <preferenceType>checkbox</preferenceType> | |
| 2433 | <preferenceValues>no</preferenceValues> | |
| 2434 | <selectedValue>yes</selectedValue> | |
| 2435 | </item> | |
| 2436 | </PluginsPreferences> | |
| 2437 | </Preferences> | |
| 2438 | <FamilySelection><FamilyItem><FamilyName>MacOS X Local Security Checks</FamilyName> | |
| 2439 | <Status>enabled</Status> | |
| 2440 | </FamilyItem> | |
| 2441 | <FamilyItem><FamilyName>DNS</FamilyName> | |
| 2442 | <Status>enabled</Status> | |
| 2443 | </FamilyItem> | |
| 2444 | <FamilyItem><FamilyName>Gain a shell remotely</FamilyName> | |
| 2445 | <Status>enabled</Status> | |
| 2446 | </FamilyItem> | |
| 2447 | <FamilyItem><FamilyName>Solaris Local Security Checks</FamilyName> | |
| 2448 | <Status>enabled</Status> | |
| 2449 | </FamilyItem> | |
| 2450 | <FamilyItem><FamilyName>Port scanners</FamilyName> | |
| 2451 | <Status>mixed</Status> | |
| 2452 | </FamilyItem> | |
| 2453 | <FamilyItem><FamilyName>Web Servers</FamilyName> | |
| 2454 | <Status>enabled</Status> | |
| 2455 | </FamilyItem> | |
| 2456 | <FamilyItem><FamilyName>SMTP problems</FamilyName> | |
| 2457 | <Status>enabled</Status> | |
| 2458 | </FamilyItem> | |
| 2459 | <FamilyItem><FamilyName>Service detection</FamilyName> | |
| 2460 | <Status>enabled</Status> | |
| 2461 | </FamilyItem> | |
| 2462 | <FamilyItem><FamilyName>CGI abuses : XSS</FamilyName> | |
| 2463 | <Status>enabled</Status> | |
| 2464 | </FamilyItem> | |
| 2465 | <FamilyItem><FamilyName>Debian Local Security Checks</FamilyName> | |
| 2466 | <Status>enabled</Status> | |
| 2467 | </FamilyItem> | |
| 2468 | <FamilyItem><FamilyName>Databases</FamilyName> | |
| 2469 | <Status>enabled</Status> | |
| 2470 | </FamilyItem> | |
| 2471 | <FamilyItem><FamilyName>Mandriva Local Security Checks</FamilyName> | |
| 2472 | <Status>enabled</Status> | |
| 2473 | </FamilyItem> | |
| 2474 | <FamilyItem><FamilyName>Default Unix Accounts</FamilyName> | |
| 2475 | <Status>enabled</Status> | |
| 2476 | </FamilyItem> | |
| 2477 | <FamilyItem><FamilyName>Denial of Service</FamilyName> | |
| 2478 | <Status>enabled</Status> | |
| 2479 | </FamilyItem> | |
| 2480 | <FamilyItem><FamilyName>Settings</FamilyName> | |
| 2481 | <Status>enabled</Status> | |
| 2482 | </FamilyItem> | |
| 2483 | <FamilyItem><FamilyName>Backdoors</FamilyName> | |
| 2484 | <Status>enabled</Status> | |
| 2485 | </FamilyItem> | |
| 2486 | <FamilyItem><FamilyName>HP-UX Local Security Checks</FamilyName> | |
| 2487 | <Status>enabled</Status> | |
| 2488 | </FamilyItem> | |
| 2489 | <FamilyItem><FamilyName>VMware ESX Local Security Checks</FamilyName> | |
| 2490 | <Status>enabled</Status> | |
| 2491 | </FamilyItem> | |
| 2492 | <FamilyItem><FamilyName>SCADA</FamilyName> | |
| 2493 | <Status>enabled</Status> | |
| 2494 | </FamilyItem> | |
| 2495 | <FamilyItem><FamilyName>General</FamilyName> | |
| 2496 | <Status>enabled</Status> | |
| 2497 | </FamilyItem> | |
| 2498 | <FamilyItem><FamilyName>Red Hat Local Security Checks</FamilyName> | |
| 2499 | <Status>enabled</Status> | |
| 2500 | </FamilyItem> | |
| 2501 | <FamilyItem><FamilyName>FreeBSD Local Security Checks</FamilyName> | |
| 2502 | <Status>enabled</Status> | |
| 2503 | </FamilyItem> | |
| 2504 | <FamilyItem><FamilyName>CGI abuses</FamilyName> | |
| 2505 | <Status>enabled</Status> | |
| 2506 | </FamilyItem> | |
| 2507 | <FamilyItem><FamilyName>Netware</FamilyName> | |
| 2508 | <Status>enabled</Status> | |
| 2509 | </FamilyItem> | |
| 2510 | <FamilyItem><FamilyName>Windows : User management</FamilyName> | |
| 2511 | <Status>enabled</Status> | |
| 2512 | </FamilyItem> | |
| 2513 | <FamilyItem><FamilyName>Peer-To-Peer File Sharing</FamilyName> | |
| 2514 | <Status>enabled</Status> | |
| 2515 | </FamilyItem> | |
| 2516 | <FamilyItem><FamilyName>Slackware Local Security Checks</FamilyName> | |
| 2517 | <Status>enabled</Status> | |
| 2518 | </FamilyItem> | |
| 2519 | <FamilyItem><FamilyName>SNMP</FamilyName> | |
| 2520 | <Status>enabled</Status> | |
| 2521 | </FamilyItem> | |
| 2522 | <FamilyItem><FamilyName>Gentoo Local Security Checks</FamilyName> | |
| 2523 | <Status>enabled</Status> | |
| 2524 | </FamilyItem> | |
| 2525 | <FamilyItem><FamilyName>Fedora Local Security Checks</FamilyName> | |
| 2526 | <Status>enabled</Status> | |
| 2527 | </FamilyItem> | |
| 2528 | <FamilyItem><FamilyName>Misc.</FamilyName> | |
| 2529 | <Status>enabled</Status> | |
| 2530 | </FamilyItem> | |
| 2531 | <FamilyItem><FamilyName>Ubuntu Local Security Checks</FamilyName> | |
| 2532 | <Status>enabled</Status> | |
| 2533 | </FamilyItem> | |
| 2534 | <FamilyItem><FamilyName>FTP</FamilyName> | |
| 2535 | <Status>enabled</Status> | |
| 2536 | </FamilyItem> | |
| 2537 | <FamilyItem><FamilyName>Firewalls</FamilyName> | |
| 2538 | <Status>enabled</Status> | |
| 2539 | </FamilyItem> | |
| 2540 | <FamilyItem><FamilyName>Windows : Microsoft Bulletins</FamilyName> | |
| 2541 | <Status>enabled</Status> | |
| 2542 | </FamilyItem> | |
| 2543 | <FamilyItem><FamilyName>SuSE Local Security Checks</FamilyName> | |
| 2544 | <Status>enabled</Status> | |
| 2545 | </FamilyItem> | |
| 2546 | <FamilyItem><FamilyName>Policy Compliance</FamilyName> | |
| 2547 | <Status>enabled</Status> | |
| 2548 | </FamilyItem> | |
| 2549 | <FamilyItem><FamilyName>Windows</FamilyName> | |
| 2550 | <Status>enabled</Status> | |
| 2551 | </FamilyItem> | |
| 2552 | <FamilyItem><FamilyName>RPC</FamilyName> | |
| 2553 | <Status>enabled</Status> | |
| 2554 | </FamilyItem> | |
| 2555 | <FamilyItem><FamilyName>Finger abuses</FamilyName> | |
| 2556 | <Status>enabled</Status> | |
| 2557 | </FamilyItem> | |
| 2558 | <FamilyItem><FamilyName>CentOS Local Security Checks</FamilyName> | |
| 2559 | <Status>enabled</Status> | |
| 2560 | </FamilyItem> | |
| 2561 | <FamilyItem><FamilyName>AIX Local Security Checks</FamilyName> | |
| 2562 | <Status>enabled</Status> | |
| 2563 | </FamilyItem> | |
| 2564 | <FamilyItem><FamilyName>CISCO</FamilyName> | |
| 2565 | <Status>enabled</Status> | |
| 2566 | </FamilyItem> | |
| 2567 | <FamilyItem><FamilyName>Junos Local Security Checks</FamilyName> | |
| 2568 | <Status>enabled</Status> | |
| 2569 | </FamilyItem> | |
| 2570 | <FamilyItem><FamilyName>Mobile Devices</FamilyName> | |
| 2571 | <Status>enabled</Status> | |
| 2572 | </FamilyItem> | |
| 2573 | <FamilyItem><FamilyName>Scientific Linux Local Security Checks</FamilyName> | |
| 2574 | <Status>enabled</Status> | |
| 2575 | </FamilyItem> | |
| 2576 | <FamilyItem><FamilyName>Brute force attacks</FamilyName> | |
| 2577 | <Status>enabled</Status> | |
| 2578 | </FamilyItem> | |
| 2579 | </FamilySelection> | |
| 2580 | <IndividualPluginSelection><PluginItem><PluginId>34220</PluginId> | |
| 2581 | <PluginName>Netstat Portscanner (WMI)</PluginName> | |
| 2582 | <Family>Port scanners</Family> | |
| 2583 | <Status>enabled</Status> | |
| 2584 | </PluginItem> | |
| 2585 | <PluginItem><PluginId>14274</PluginId> | |
| 2586 | <PluginName>Nessus SNMP Scanner</PluginName> | |
| 2587 | <Family>Port scanners</Family> | |
| 2588 | <Status>enabled</Status> | |
| 2589 | </PluginItem> | |
| 2590 | <PluginItem><PluginId>14272</PluginId> | |
| 2591 | <PluginName>netstat portscanner (SSH)</PluginName> | |
| 2592 | <Family>Port scanners</Family> | |
| 2593 | <Status>enabled</Status> | |
| 2594 | </PluginItem> | |
| 2595 | <PluginItem><PluginId>10180</PluginId> | |
| 2596 | <PluginName>Ping the remote host</PluginName> | |
| 2597 | <Family>Port scanners</Family> | |
| 2598 | <Status>enabled</Status> | |
| 2599 | </PluginItem> | |
| 2600 | <PluginItem><PluginId>11219</PluginId> | |
| 2601 | <PluginName>Nessus SYN scanner</PluginName> | |
| 2602 | <Family>Port scanners</Family> | |
| 2603 | <Status>enabled</Status> | |
| 2604 | </PluginItem> | |
| 2605 | </IndividualPluginSelection> | |
| 2606 | </Policy> | |
| 2607 | <Report name="Remote" xmlns:cm="http://www.nessus.org/cm"> | |
| 2608 | <ReportHost name="preprod.boardvantage.net"><HostProperties> | |
| 2609 | <tag name="HOST_END">Tue Jun 25 10:39:42 2013</tag> | |
| 2610 | <tag name="patch-summary-total-cves">0</tag> | |
| 2611 | <tag name="system-type">firewall</tag> | |
| 2612 | <tag name="operating-system">CISCO PIX 7.0</tag> | |
| 2613 | <tag name="host-ip">12.233.108.201</tag> | |
| 2614 | <tag name="host-fqdn">preprod.boardvantage.net</tag> | |
| 2615 | <tag name="HOST_START">Tue Jun 25 10:32:42 2013</tag> | |
| 2616 | </HostProperties> | |
| 2617 | <ReportItem port="0" svc_name="general" protocol="tcp" severity="0" pluginID="19506" pluginName="Nessus Scan Information" pluginFamily="Settings"> | |
| 2618 | <description>This script displays, for each tested host, information about the scan itself : | |
| 2619 | ||
| 2620 | - The version of the plugin set | |
| 2621 | - The type of plugin feed (HomeFeed or ProfessionalFeed) | |
| 2622 | - The version of the Nessus Engine | |
| 2623 | - The port scanner(s) used | |
| 2624 | - The port range scanned | |
| 2625 | - Whether credentialed or third-party patch management checks are possible | |
| 2626 | - The date of the scan | |
| 2627 | - The duration of the scan | |
| 2628 | - The number of hosts scanned in parallel | |
| 2629 | - The number of checks done in parallel</description> | |
| 2630 | <fname>scan_info.nasl</fname> | |
| 2631 | <plugin_modification_date>2013/05/31</plugin_modification_date> | |
| 2632 | <plugin_name>Nessus Scan Information</plugin_name> | |
| 2633 | <plugin_publication_date>2005/08/26</plugin_publication_date> | |
| 2634 | <plugin_type>summary</plugin_type> | |
| 2635 | <risk_factor>None</risk_factor> | |
| 2636 | <script_version>$Revision: 1.59 $</script_version> | |
| 2637 | <solution>n/a</solution> | |
| 2638 | <synopsis>Information about the Nessus scan.</synopsis> | |
| 2639 | <plugin_output>Information about this scan : | |
| 2640 | ||
| 2641 | Nessus version : 5.2.1 | |
| 2642 | Plugin feed version : 201306251015 | |
| 2643 | Type of plugin feed : HomeFeed (Non-commercial use only) | |
| 2644 | Scanner IP : 172.16.138.167 | |
| 2645 | Port scanner(s) : nessus_syn_scanner | |
| 2646 | Port range : default | |
| 2647 | Thorough tests : no | |
| 2648 | Experimental tests : no | |
| 2649 | Paranoia level : 1 | |
| 2650 | Report Verbosity : 1 | |
| 2651 | Safe checks : yes | |
| 2652 | Optimize the test : yes | |
| 2653 | Credentialed checks : no | |
| 2654 | Patch management checks : None | |
| 2655 | CGI scanning : enabled | |
| 2656 | Web application tests : enabled | |
| 2657 | Web app tests - Test mode : some_pairs | |
| 2658 | Web app tests - Try all HTTP methods : no | |
| 2659 | Web app tests - Maximum run time : 60 minutes. | |
| 2660 | Web app tests - Stop at first flaw : CGI | |
| 2661 | Max hosts : 80 | |
| 2662 | Max checks : 5 | |
| 2663 | Recv timeout : 5 | |
| 2664 | Backports : None | |
| 2665 | Allow post-scan editing: Yes | |
| 2666 | Scan Start Date : 2013/6/25 10:32 | |
| 2667 | Scan duration : 416 sec | |
| 2668 | </plugin_output> | |
| 2669 | </ReportItem> | |
| 2670 | <ReportItem port="0" svc_name="general" protocol="tcp" severity="0" pluginID="54615" pluginName="Device Type" pluginFamily="General"> | |
| 2671 | <description>Based on the remote operating system, it is possible to determine what the remote system type is (eg: a printer, router, general-purpose computer, etc).</description> | |
| 2672 | <fname>device_type.nasl</fname> | |
| 2673 | <plugin_modification_date>2011/05/23</plugin_modification_date> | |
| 2674 | <plugin_name>Device Type</plugin_name> | |
| 2675 | <plugin_publication_date>2011/05/23</plugin_publication_date> | |
| 2676 | <plugin_type>combined</plugin_type> | |
| 2677 | <risk_factor>None</risk_factor> | |
| 2678 | <script_version>$Revision: 1.1 $</script_version> | |
| 2679 | <solution>n/a</solution> | |
| 2680 | <synopsis>It is possible to guess the remote device type.</synopsis> | |
| 2681 | <plugin_output>Remote device type : firewall | |
| 2682 | Confidence level : 70 | |
| 2683 | </plugin_output> | |
| 2684 | </ReportItem> | |
| 2685 | <ReportItem port="0" svc_name="general" protocol="tcp" severity="0" pluginID="45590" pluginName="Common Platform Enumeration (CPE)" pluginFamily="General"> | |
| 2686 | <description>By using information obtained from a Nessus scan, this plugin reports CPE (Common Platform Enumeration) matches for various hardware and software products found on a host. | |
| 2687 | ||
| 2688 | Note that if an official CPE is not available for the product, this plugin computes the best possible CPE based on the information available from the scan.</description> | |
| 2689 | <fname>cpe.nbin</fname> | |
| 2690 | <plugin_modification_date>2013/05/13</plugin_modification_date> | |
| 2691 | <plugin_name>Common Platform Enumeration (CPE)</plugin_name> | |
| 2692 | <plugin_publication_date>2010/04/21</plugin_publication_date> | |
| 2693 | <plugin_type>local</plugin_type> | |
| 2694 | <risk_factor>None</risk_factor> | |
| 2695 | <script_version>$Revision: 1.19 $</script_version> | |
| 2696 | <see_also>http://cpe.mitre.org/</see_also> | |
| 2697 | <solution>n/a</solution> | |
| 2698 | <synopsis>It is possible to enumerate CPE names that matched on the remote system.</synopsis> | |
| 2699 | <plugin_output> | |
| 2700 | The remote operating system matched the following CPE : | |
| 2701 | ||
| 2702 | cpe:/o:cisco:pix_firewall:7.0 | |
| 2703 | </plugin_output> | |
| 2704 | </ReportItem> | |
| 2705 | <ReportItem port="0" svc_name="general" protocol="tcp" severity="0" pluginID="11936" pluginName="OS Identification" pluginFamily="General"> | |
| 2706 | <description>Using a combination of remote probes (TCP/IP, SMB, HTTP, NTP, SNMP, etc...), it is possible to guess the name of the remote operating system in use. It is also sometimes possible to guess the version of the operating system.</description> | |
| 2707 | <fname>os_fingerprint.nasl</fname> | |
| 2708 | <plugin_modification_date>2013/04/01</plugin_modification_date> | |
| 2709 | <plugin_name>OS Identification</plugin_name> | |
| 2710 | <plugin_publication_date>2003/12/09</plugin_publication_date> | |
| 2711 | <plugin_type>combined</plugin_type> | |
| 2712 | <risk_factor>None</risk_factor> | |
| 2713 | <script_version>$Revision: 2.34 $</script_version> | |
| 2714 | <solution>n/a</solution> | |
| 2715 | <synopsis>It is possible to guess the remote operating system.</synopsis> | |
| 2716 | <plugin_output> | |
| 2717 | Remote operating system : CISCO PIX 7.0 | |
| 2718 | Confidence Level : 70 | |
| 2719 | Method : SinFP | |
| 2720 | ||
| 2721 | ||
| 2722 | The remote host is running CISCO PIX 7.0</plugin_output> | |
| 2723 | </ReportItem> | |
| 2724 | <ReportItem port="0" svc_name="general" protocol="tcp" severity="0" pluginID="12053" pluginName="Host Fully Qualified Domain Name (FQDN) Resolution" pluginFamily="General"> | |
| 2725 | <description>Nessus was able to resolve the FQDN of the remote host.</description> | |
| 2726 | <fname>fqdn.nasl</fname> | |
| 2727 | <plugin_modification_date>2012/09/28</plugin_modification_date> | |
| 2728 | <plugin_name>Host Fully Qualified Domain Name (FQDN) Resolution</plugin_name> | |
| 2729 | <plugin_publication_date>2004/02/11</plugin_publication_date> | |
| 2730 | <plugin_type>remote</plugin_type> | |
| 2731 | <risk_factor>None</risk_factor> | |
| 2732 | <script_version>$Revision: 1.12 $</script_version> | |
| 2733 | <solution>n/a</solution> | |
| 2734 | <synopsis>It was possible to resolve the name of the remote host.</synopsis> | |
| 2735 | <plugin_output> | |
| 2736 | 12.233.108.201 resolves as preprod.boardvantage.net. | |
| 2737 | </plugin_output> | |
| 2738 | </ReportItem> | |
| 2739 | <ReportItem port="443" svc_name="https?" protocol="tcp" severity="0" pluginID="11219" pluginName="Nessus SYN scanner" pluginFamily="Port scanners"> | |
| 2740 | <description>This plugin is a SYN 'half-open' port scanner. | |
| 2741 | It shall be reasonably quick even against a firewalled target. | |
| 2742 | ||
| 2743 | Note that SYN scanners are less intrusive than TCP (full connect) scanners against broken services, but they might kill lame misconfigured firewalls. They might also leave unclosed connections on the remote target, if the network is loaded.</description> | |
| 2744 | <fname>nessus_syn_scanner.nbin</fname> | |
| 2745 | <plugin_modification_date>2011/04/05</plugin_modification_date> | |
| 2746 | <plugin_name>Nessus SYN scanner</plugin_name> | |
| 2747 | <plugin_type>remote</plugin_type> | |
| 2748 | <risk_factor>None</risk_factor> | |
| 2749 | <script_version>$Revision: 1.14 $</script_version> | |
| 2750 | <solution>Protect your target with an IP filter.</solution> | |
| 2751 | <synopsis>It is possible to determine which TCP ports are open.</synopsis> | |
| 2752 | <plugin_output>Port 443/tcp was found to be open</plugin_output> | |
| 2753 | </ReportItem> | |
| 2754 | </ReportHost> | |
| 2755 | </Report> | |
| 2756 | </NessusClientData_v2> |
| 0 | <NexposeReport version="1.0"> | |
| 1 | <scans> | |
| 2 | <scan id="1" name="Localhost" startTime="20131127T050242739" endTime="20131127T115513233" status="stopped"/> | |
| 3 | </scans><nodes> | |
| 4 | <node address="192.168.1.1" status="alive" device-id="7"> | |
| 5 | <fingerprints> | |
| 6 | <os certainty="0.70" device-class="General" vendor="Linux" family="Linux" product="Linux" version="2.6.9"/> | |
| 7 | </fingerprints> | |
| 8 | <tests> | |
| 9 | <test id="tcp-seq-num-approximation" status="vulnerable-exploited"> | |
| 10 | ||
| 11 | <Paragraph> | |
| 12 | <Paragraph>TCP reset with incorrect sequence number triggered this fault on 192.168.1.1:21: Connection reset by peer</Paragraph></Paragraph> | |
| 13 | </test> | |
| 14 | ||
| 15 | <test id="generic-icmp-netmask" status="not-vulnerable"> | |
| 16 | ||
| 17 | <Paragraph> | |
| 18 | <Paragraph>No response</Paragraph></Paragraph> | |
| 19 | </test> | |
| 20 | ||
| 21 | <test id="generic-icmp-timestamp" status="vulnerable-exploited"> | |
| 22 | ||
| 23 | <Paragraph> | |
| 24 | <Paragraph>Remote system time: 03:49:09.250 UTC</Paragraph></Paragraph> | |
| 25 | </test> | |
| 26 | ||
| 27 | <test id="generic-tcp-timestamp" status="vulnerable-exploited"> | |
| 28 | ||
| 29 | <Paragraph> | |
| 30 | <Paragraph>Apparent system boot time: Wed Nov 27 00:21:55 UTC 2013</Paragraph></Paragraph> | |
| 31 | </test> | |
| 32 | </tests> | |
| 33 | <endpoints> | |
| 34 | <endpoint protocol="tcp" port="21" status="open"> | |
| 35 | <services> | |
| 36 | <service name="FTP"> | |
| 37 | <configuration> | |
| 38 | <config name="ftp.banner">220 Welcome to TBS FTP Server.</config> | |
| 39 | </configuration> | |
| 40 | <tests> | |
| 41 | <test id="ftp-anonymous-writeable-directories" status="error"> | |
| 42 | ||
| 43 | <Paragraph> | |
| 44 | <Paragraph>Could not connect to endpoint with any known anonymous credentials</Paragraph></Paragraph> | |
| 45 | </test> | |
| 46 | ||
| 47 | <test id="ftp-proftpd-1-3-3c-backdoor" status="not-vulnerable"> | |
| 48 | ||
| 49 | <Paragraph> | |
| 50 | <Paragraph>Returned the following is a result to executing 'id;uname -a;': 202 Command not implemented, superfluous at this site.</Paragraph></Paragraph> | |
| 51 | </test> | |
| 52 | ||
| 53 | <test id="ftp-default-login-admin-null" status="not-vulnerable"> | |
| 54 | ||
| 55 | <Paragraph> | |
| 56 | <Paragraph>Running vulnerable FTP service.</Paragraph>Was not able to authenticate to the FTP service with no credentials.</Paragraph> | |
| 57 | </test> | |
| 58 | ||
| 59 | <test id="ftp-default-login-admin-passwd" status="not-vulnerable"> | |
| 60 | ||
| 61 | <Paragraph> | |
| 62 | <Paragraph>Running vulnerable FTP service.</Paragraph>Was not able to authenticate to the FTP service with no credentials.</Paragraph> | |
| 63 | </test> | |
| 64 | ||
| 65 | <test id="ftp-default-login-admin-password" status="not-vulnerable"> | |
| 66 | ||
| 67 | <Paragraph> | |
| 68 | <Paragraph>Running vulnerable FTP service.</Paragraph>Was not able to authenticate to the FTP service with no credentials.</Paragraph> | |
| 69 | </test> | |
| 70 | ||
| 71 | <test id="ftp-default-login-administrator-null" status="not-vulnerable"> | |
| 72 | ||
| 73 | <Paragraph> | |
| 74 | <Paragraph>Running vulnerable FTP service.</Paragraph>Was not able to authenticate to the FTP service with no credentials.</Paragraph> | |
| 75 | </test> | |
| 76 | ||
| 77 | <test id="ftp-default-login-administrator-passwd" status="not-vulnerable"> | |
| 78 | ||
| 79 | <Paragraph> | |
| 80 | <Paragraph>Running vulnerable FTP service.</Paragraph>Was not able to authenticate to the FTP service with no credentials.</Paragraph> | |
| 81 | </test> | |
| 82 | ||
| 83 | <test id="ftp-default-login-administrator-password" status="not-vulnerable"> | |
| 84 | ||
| 85 | <Paragraph> | |
| 86 | <Paragraph>Running vulnerable FTP service.</Paragraph>Was not able to authenticate to the FTP service with no credentials.</Paragraph> | |
| 87 | </test> | |
| 88 | ||
| 89 | <test id="ftp-generic-0007" status="not-vulnerable"> | |
| 90 | ||
| 91 | <Paragraph> | |
| 92 | <Paragraph>Server supports AUTH mechanism TLS</Paragraph></Paragraph> | |
| 93 | </test> | |
| 94 | ||
| 95 | <test id="ftp-generic-0001" status="not-vulnerable"> | |
| 96 | ||
| 97 | <Paragraph> | |
| 98 | <Paragraph>Running vulnerable FTP service.</Paragraph>Was not able to authenticate to the FTP service with no credentials.</Paragraph> | |
| 99 | </test> | |
| 100 | ||
| 101 | <test id="ftp-generic-0002" status="not-vulnerable"> | |
| 102 | ||
| 103 | <Paragraph> | |
| 104 | <Paragraph>Running vulnerable FTP service.</Paragraph>Was not able to authenticate to the FTP service with no credentials.</Paragraph> | |
| 105 | </test> | |
| 106 | ||
| 107 | <test id="ftp-generic-0003" status="not-vulnerable"> | |
| 108 | ||
| 109 | <Paragraph> | |
| 110 | <Paragraph>Running vulnerable FTP service.</Paragraph>Was not able to authenticate to the FTP service with no credentials.</Paragraph> | |
| 111 | </test> | |
| 112 | ||
| 113 | <test id="ftp-generic-0004" status="not-vulnerable"> | |
| 114 | ||
| 115 | <Paragraph> | |
| 116 | <Paragraph>Running vulnerable FTP service.</Paragraph>Was not able to authenticate to the FTP service with no credentials.</Paragraph> | |
| 117 | </test> | |
| 118 | ||
| 119 | <test id="ftp-generic-0005" status="not-vulnerable"> | |
| 120 | ||
| 121 | <Paragraph> | |
| 122 | <Paragraph>Running vulnerable FTP service.</Paragraph>Was not able to authenticate to the FTP service with no credentials.</Paragraph> | |
| 123 | </test> | |
| 124 | ||
| 125 | <test id="ftp-generic-0006" status="not-vulnerable"> | |
| 126 | ||
| 127 | <Paragraph> | |
| 128 | <Paragraph>Running vulnerable FTP service.</Paragraph>Was not able to authenticate to the FTP service with no credentials.</Paragraph> | |
| 129 | </test> | |
| 130 | </tests> | |
| 131 | </service> | |
| 132 | </services> | |
| 133 | </endpoint> | |
| 134 | ||
| 135 | <endpoint protocol="tcp" port="22" status="open"> | |
| 136 | <services> | |
| 137 | <service name="SSH"> | |
| 138 | <fingerprints> | |
| 139 | <fingerprint certainty="0.90" family="Dropbear" product="Dropbear" version="0.51"/> | |
| 140 | </fingerprints> | |
| 141 | <configuration> | |
| 142 | <config name="ssh.banner">SSH-2.0-dropbear_0.51</config> | |
| 143 | <config name="ssh.protocol.version">2.0</config> | |
| 144 | <config name="ssh.rsa.pubkey.fingerprint">6305014FCD096DADED95AE89192CB8BC</config> | |
| 145 | </configuration> | |
| 146 | <tests> | |
| 147 | <test id="ssh-default-account-admin-password-admin" status="not-vulnerable"> | |
| 148 | ||
| 149 | <Paragraph> | |
| 150 | <Paragraph>Running vulnerable SSH service.</Paragraph>Was not able to authenticate to the SSH service with no credentials.</Paragraph> | |
| 151 | </test> | |
| 152 | ||
| 153 | <test id="ssh-default-account-admin-password-password" status="not-vulnerable"> | |
| 154 | ||
| 155 | <Paragraph> | |
| 156 | <Paragraph>Running vulnerable SSH service.</Paragraph>Was not able to authenticate to the SSH service with no credentials.</Paragraph> | |
| 157 | </test> | |
| 158 | ||
| 159 | <test id="ssh-default-account-root-no-password" status="not-vulnerable"> | |
| 160 | ||
| 161 | <Paragraph> | |
| 162 | <Paragraph>Running vulnerable SSH service.</Paragraph>Was not able to authenticate to the SSH service with no credentials.</Paragraph> | |
| 163 | </test> | |
| 164 | ||
| 165 | <test id="ssh-default-account-root-password-password" status="not-vulnerable"> | |
| 166 | ||
| 167 | <Paragraph> | |
| 168 | <Paragraph>Running vulnerable SSH service.</Paragraph>Was not able to authenticate to the SSH service with no credentials.</Paragraph> | |
| 169 | </test> | |
| 170 | ||
| 171 | <test id="ssh-default-account-root-password-root" status="vulnerable-exploited"> | |
| 172 | ||
| 173 | <Paragraph> | |
| 174 | <Paragraph>Running vulnerable SSH service.</Paragraph>Successfully authenticated to the SSH service with credentials: uid[root] pw[root] realm[null]</Paragraph> | |
| 175 | </test> | |
| 176 | ||
| 177 | <test id="ssh-default-account-root-password-toor" status="not-vulnerable"> | |
| 178 | ||
| 179 | <Paragraph> | |
| 180 | <Paragraph>Running vulnerable SSH service.</Paragraph>Was not able to authenticate to the SSH service with no credentials.</Paragraph> | |
| 181 | </test> | |
| 182 | ||
| 183 | <test id="ssh-generic-0003" status="skipped-version"> | |
| 184 | ||
| 185 | <Paragraph> | |
| 186 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 187 | </test> | |
| 188 | ||
| 189 | <test id="ssh-iphone-default-account-root-password-alpine" status="not-vulnerable"> | |
| 190 | ||
| 191 | <Paragraph> | |
| 192 | <Paragraph>Running vulnerable SSH service.</Paragraph>Was not able to authenticate to the SSH service with no credentials.</Paragraph> | |
| 193 | </test> | |
| 194 | ||
| 195 | <test id="ssh-iphone-default-account-root-password-dottie" status="not-vulnerable"> | |
| 196 | ||
| 197 | <Paragraph> | |
| 198 | <Paragraph>Running vulnerable SSH service.</Paragraph>Was not able to authenticate to the SSH service with no credentials.</Paragraph> | |
| 199 | </test> | |
| 200 | ||
| 201 | <test id="ssh-openssh-0001" status="skipped-version"> | |
| 202 | ||
| 203 | <Paragraph> | |
| 204 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 205 | </test> | |
| 206 | ||
| 207 | <test id="ssh-openssh-0006" status="skipped-version"> | |
| 208 | ||
| 209 | <Paragraph> | |
| 210 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 211 | </test> | |
| 212 | ||
| 213 | <test id="ssh-openssh-0007" status="skipped-version"> | |
| 214 | ||
| 215 | <Paragraph> | |
| 216 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 217 | </test> | |
| 218 | ||
| 219 | <test id="ssh-openssh-0010" status="skipped-version"> | |
| 220 | ||
| 221 | <Paragraph> | |
| 222 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 223 | </test> | |
| 224 | ||
| 225 | <test id="ssh-pragma-sshredder-overflow" status="skipped-version"> | |
| 226 | ||
| 227 | <Paragraph> | |
| 228 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 229 | </test> | |
| 230 | ||
| 231 | <test id="ssh-suse-default-account-suse-gm-password-123456" status="not-vulnerable"> | |
| 232 | ||
| 233 | <Paragraph> | |
| 234 | <Paragraph>Running vulnerable SSH service.</Paragraph>Was not able to authenticate to the SSH service with no credentials.</Paragraph> | |
| 235 | </test> | |
| 236 | ||
| 237 | <test id="ssh-openssh-pam-multiple-vulns" status="skipped-version"> | |
| 238 | ||
| 239 | <Paragraph> | |
| 240 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 241 | </test> | |
| 242 | ||
| 243 | <test id="openssl-debian-weak-keys" status="not-vulnerable"> | |
| 244 | ||
| 245 | <Paragraph> | |
| 246 | <Paragraph>SSH public key with fingerprint 6305014FCD096DADED95AE89192CB8BC is not a known weak key</Paragraph></Paragraph> | |
| 247 | </test> | |
| 248 | ||
| 249 | <test id="ssh-default-account-guest-password-guest" status="not-vulnerable"> | |
| 250 | ||
| 251 | <Paragraph> | |
| 252 | <Paragraph>Running vulnerable SSH service.</Paragraph>Was not able to authenticate to the SSH service with no credentials.</Paragraph> | |
| 253 | </test> | |
| 254 | ||
| 255 | <test id="ssh-default-account-vmware-password-vmware" status="not-vulnerable"> | |
| 256 | ||
| 257 | <Paragraph> | |
| 258 | <Paragraph>Running vulnerable SSH service.</Paragraph>Was not able to authenticate to the SSH service with no credentials.</Paragraph> | |
| 259 | </test> | |
| 260 | ||
| 261 | <test id="ssh-openssh-0003" status="skipped-version"> | |
| 262 | ||
| 263 | <Paragraph> | |
| 264 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 265 | </test> | |
| 266 | ||
| 267 | <test id="ssh-openssh-0005" status="skipped-version"> | |
| 268 | ||
| 269 | <Paragraph> | |
| 270 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 271 | </test> | |
| 272 | ||
| 273 | <test id="ssh-openssh-0008" status="skipped-version"> | |
| 274 | ||
| 275 | <Paragraph> | |
| 276 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 277 | </test> | |
| 278 | ||
| 279 | <test id="ssh-openssh-0009" status="skipped-version"> | |
| 280 | ||
| 281 | <Paragraph> | |
| 282 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 283 | </test> | |
| 284 | ||
| 285 | <test id="ssh-sshinc-0002" status="skipped-version"> | |
| 286 | ||
| 287 | <Paragraph> | |
| 288 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 289 | </test> | |
| 290 | ||
| 291 | <test id="ssh-sshinc-0007" status="skipped-version"> | |
| 292 | ||
| 293 | <Paragraph> | |
| 294 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 295 | </test> | |
| 296 | ||
| 297 | <test id="ssh-v1-supported" status="skipped-version"> | |
| 298 | ||
| 299 | <Paragraph> | |
| 300 | <Paragraph>Running not-vulnerable SSH service.</Paragraph></Paragraph> | |
| 301 | </test> | |
| 302 | ||
| 303 | <test id="ssh-openssh-0002" status="skipped-version"> | |
| 304 | ||
| 305 | <Paragraph> | |
| 306 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 307 | </test> | |
| 308 | ||
| 309 | <test id="ssh-openssh-0004" status="skipped-version"> | |
| 310 | ||
| 311 | <Paragraph> | |
| 312 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 313 | </test> | |
| 314 | ||
| 315 | <test id="ssh-sshinc-0001" status="skipped-version"> | |
| 316 | ||
| 317 | <Paragraph> | |
| 318 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 319 | </test> | |
| 320 | ||
| 321 | <test id="ssh-sshinc-0005" status="skipped-version"> | |
| 322 | ||
| 323 | <Paragraph> | |
| 324 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 325 | </test> | |
| 326 | ||
| 327 | <test id="ssh-sshinc-0006" status="skipped-version"> | |
| 328 | ||
| 329 | <Paragraph> | |
| 330 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 331 | </test> | |
| 332 | ||
| 333 | <test id="ssh-sshinc-getlogin-spoof-privilege-escalation" status="skipped-version"> | |
| 334 | ||
| 335 | <Paragraph> | |
| 336 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 337 | </test> | |
| 338 | ||
| 339 | <test id="ssh-sshinc-rsa-signature-forging" status="skipped-version"> | |
| 340 | ||
| 341 | <Paragraph> | |
| 342 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 343 | </test> | |
| 344 | ||
| 345 | <test id="ssh-openssh-valid-username-info-leak" status="skipped-version"> | |
| 346 | ||
| 347 | <Paragraph> | |
| 348 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 349 | </test> | |
| 350 | ||
| 351 | <test id="ssh-sshinc-0004" status="skipped-version"> | |
| 352 | ||
| 353 | <Paragraph> | |
| 354 | <Paragraph>Running not-vulnerable SSH service: Dropbear 0.51.</Paragraph></Paragraph> | |
| 355 | </test> | |
| 356 | </tests> | |
| 357 | </service> | |
| 358 | </services> | |
| 359 | </endpoint> | |
| 360 | ||
| 361 | <endpoint protocol="tcp" port="23" status="open"> | |
| 362 | <services> | |
| 363 | <service name="Telnet"> | |
| 364 | <tests> | |
| 365 | <test id="telnet-avaya-default-login-diag" status="not-vulnerable"> | |
| 366 | ||
| 367 | <Paragraph> | |
| 368 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 369 | </test> | |
| 370 | ||
| 371 | <test id="telnet-avaya-default-login-manuf" status="not-vulnerable"> | |
| 372 | ||
| 373 | <Paragraph> | |
| 374 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 375 | </test> | |
| 376 | ||
| 377 | <test id="telnet-default-account-admin-password-password" status="not-vulnerable"> | |
| 378 | ||
| 379 | <Paragraph> | |
| 380 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 381 | </test> | |
| 382 | ||
| 383 | <test id="telnet-default-account-root-password-password" status="not-vulnerable"> | |
| 384 | ||
| 385 | <Paragraph> | |
| 386 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 387 | </test> | |
| 388 | ||
| 389 | <test id="telnet-generic-0001" status="not-vulnerable"> | |
| 390 | ||
| 391 | <Paragraph> | |
| 392 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 393 | </test> | |
| 394 | ||
| 395 | <test id="telnet-generic-0002" status="not-vulnerable"> | |
| 396 | ||
| 397 | <Paragraph> | |
| 398 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 399 | </test> | |
| 400 | ||
| 401 | <test id="telnet-generic-0003" status="not-vulnerable"> | |
| 402 | ||
| 403 | <Paragraph> | |
| 404 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 405 | </test> | |
| 406 | ||
| 407 | <test id="telnet-generic-0004" status="not-vulnerable"> | |
| 408 | ||
| 409 | <Paragraph> | |
| 410 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 411 | </test> | |
| 412 | ||
| 413 | <test id="telnet-generic-0005" status="not-vulnerable"> | |
| 414 | ||
| 415 | <Paragraph> | |
| 416 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 417 | </test> | |
| 418 | ||
| 419 | <test id="telnet-netscreen-default-netscreen-netscreen" status="not-vulnerable"> | |
| 420 | ||
| 421 | <Paragraph> | |
| 422 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 423 | </test> | |
| 424 | ||
| 425 | <test id="telnet-db2-default-login-db2as" status="not-vulnerable"> | |
| 426 | ||
| 427 | <Paragraph> | |
| 428 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 429 | </test> | |
| 430 | ||
| 431 | <test id="telnet-db2-default-login-db2fenc1" status="not-vulnerable"> | |
| 432 | ||
| 433 | <Paragraph> | |
| 434 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 435 | </test> | |
| 436 | ||
| 437 | <test id="telnet-db2-default-login-db2inst1" status="not-vulnerable"> | |
| 438 | ||
| 439 | <Paragraph> | |
| 440 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 441 | </test> | |
| 442 | ||
| 443 | <test id="telnet-open-port" status="vulnerable-version"> | |
| 444 | ||
| 445 | <Paragraph> | |
| 446 | <Paragraph>Running vulnerable Telnet service.</Paragraph></Paragraph> | |
| 447 | </test> | |
| 448 | </tests> | |
| 449 | </service> | |
| 450 | </services> | |
| 451 | </endpoint> | |
| 452 | ||
| 453 | <endpoint protocol="tcp" port="80" status="open"> | |
| 454 | <services> | |
| 455 | <service name="HTTP"> | |
| 456 | <fingerprints> | |
| 457 | <fingerprint certainty="0.90" vendor="ACME Laboratories" family="mini_httpd" product="mini_httpd" version="1.19"/> | |
| 458 | </fingerprints> | |
| 459 | <configuration> | |
| 460 | <config name="http.banner">mini_httpd/1.19 19dec2003</config> | |
| 461 | <config name="http.banner.server">mini_httpd/1.19 19dec2003</config> | |
| 462 | </configuration> | |
| 463 | <tests> | |
| 464 | <test id="adobe-apsb13-03-cve-2013-0632" key="/CFIDE/adminapi/administrator.cfc?" status="not-vulnerable"> | |
| 465 | ||
| 466 | <Paragraph> | |
| 467 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 468 | <Paragraph> | |
| 469 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 470 | </test> | |
| 471 | ||
| 472 | <test id="adobe-apsb13-13-cve-2013-1389" status="skipped-version"> | |
| 473 | ||
| 474 | <Paragraph> | |
| 475 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 476 | <Paragraph>Based on the result of the "APSB13-13: Security updates available for Adobe ColdFusion (CVE-2013-3336)" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 477 | </test> | |
| 478 | ||
| 479 | <test id="http-3com-wap-default-admin-password" key="/index.htm" status="not-vulnerable"> | |
| 480 | ||
| 481 | <Paragraph> | |
| 482 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 483 | <Paragraph> | |
| 484 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 485 | </test> | |
| 486 | ||
| 487 | <test id="http-drac-default-login" status="not-vulnerable"> | |
| 488 | ||
| 489 | <Paragraph> | |
| 490 | <Paragraph>Server responded with an HTTP 404 to a request to /cgi-bin/webcgi/login</Paragraph></Paragraph> | |
| 491 | </test> | |
| 492 | ||
| 493 | <test id="http-drac-default-login" key="/data/login" status="not-vulnerable"> | |
| 494 | ||
| 495 | <Paragraph> | |
| 496 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 497 | <Paragraph> | |
| 498 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 499 | </test> | |
| 500 | ||
| 501 | <test id="http-drac-default-login" key="/cgi/login" status="not-vulnerable"> | |
| 502 | ||
| 503 | <Paragraph> | |
| 504 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 505 | <Paragraph> | |
| 506 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 507 | </test> | |
| 508 | ||
| 509 | <test id="http-glassfish-default-admin-password" key="/common/index.jsf" status="not-vulnerable"> | |
| 510 | ||
| 511 | <Paragraph> | |
| 512 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 513 | <Paragraph> | |
| 514 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 515 | </test> | |
| 516 | ||
| 517 | <test id="http-nokia-firewall-default-admin-password" key="/cgi-bin/home.tcl" status="not-vulnerable"> | |
| 518 | ||
| 519 | <Paragraph> | |
| 520 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 521 | <Paragraph> | |
| 522 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 523 | </test> | |
| 524 | ||
| 525 | <test id="http-phpmyadmin-account-pma-password-empty" key="/phpmyadmin/" status="not-vulnerable"> | |
| 526 | ||
| 527 | <Paragraph> | |
| 528 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 529 | <Paragraph> | |
| 530 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 531 | </test> | |
| 532 | ||
| 533 | <test id="apache-struts-cve-2013-2251" key="/struts2-showcase/employee/save.action" status="not-vulnerable"> | |
| 534 | ||
| 535 | <Paragraph> | |
| 536 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 537 | <Paragraph> | |
| 538 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 539 | </test> | |
| 540 | ||
| 541 | <test id="apache-struts-cve-2013-2251" key="/struts2-blank/example/HelloWorld.action" status="not-vulnerable"> | |
| 542 | ||
| 543 | <Paragraph> | |
| 544 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 545 | <Paragraph> | |
| 546 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 547 | </test> | |
| 548 | ||
| 549 | <test id="checkpoint-ess-info-disclosure-sk57881" key="/conf/ssl/apache/integrity.key" status="not-vulnerable"> | |
| 550 | ||
| 551 | <Paragraph> | |
| 552 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 553 | <Paragraph> | |
| 554 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 555 | </test> | |
| 556 | ||
| 557 | <test id="http-thttpd-obsolete" status="skipped-version"> | |
| 558 | ||
| 559 | <Paragraph> | |
| 560 | <Paragraph>Running not-vulnerable HTTP service: ACME Laboratories mini_httpd 1.19.</Paragraph></Paragraph> | |
| 561 | </test> | |
| 562 | ||
| 563 | <test id="http-unrestricted-webdav-put-delete" status="not-vulnerable"> | |
| 564 | ||
| 565 | <Paragraph> | |
| 566 | <Paragraph>/r7.txt was not successfully PUT on the server.</Paragraph></Paragraph> | |
| 567 | </test> | |
| 568 | ||
| 569 | <test id="adobe-apsb10-18-cve-2010-2861" key="/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en" status="not-vulnerable"> | |
| 570 | ||
| 571 | <Paragraph> | |
| 572 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 573 | <Paragraph> | |
| 574 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 575 | </test> | |
| 576 | ||
| 577 | <test id="http-awstats-remote-code-execution" key="/cgi-bin/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" status="not-vulnerable"> | |
| 578 | ||
| 579 | <Paragraph> | |
| 580 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 581 | <Paragraph> | |
| 582 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 583 | </test> | |
| 584 | ||
| 585 | <test id="http-cgi-faxsurvey-command-execution" key="/cgi-bin/faxsurvey?/bin/cat%20/etc/passwd" status="not-vulnerable"> | |
| 586 | ||
| 587 | <Paragraph> | |
| 588 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 589 | <Paragraph> | |
| 590 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 591 | </test> | |
| 592 | ||
| 593 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/servermanager/" status="not-vulnerable"> | |
| 594 | ||
| 595 | <Paragraph> | |
| 596 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 597 | <Paragraph> | |
| 598 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 599 | </test> | |
| 600 | ||
| 601 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/adminapi/base.cfc?wsdl" status="not-vulnerable"> | |
| 602 | ||
| 603 | <Paragraph> | |
| 604 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 605 | <Paragraph> | |
| 606 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 607 | </test> | |
| 608 | ||
| 609 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/adminiapi/" status="not-vulnerable"> | |
| 610 | ||
| 611 | <Paragraph> | |
| 612 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 613 | <Paragraph> | |
| 614 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 615 | </test> | |
| 616 | ||
| 617 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/administrator/" status="not-vulnerable"> | |
| 618 | ||
| 619 | <Paragraph> | |
| 620 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 621 | <Paragraph> | |
| 622 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 623 | </test> | |
| 624 | ||
| 625 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/AIR/" status="not-vulnerable"> | |
| 626 | ||
| 627 | <Paragraph> | |
| 628 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 629 | <Paragraph> | |
| 630 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 631 | </test> | |
| 632 | ||
| 633 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/appdeployment/" status="not-vulnerable"> | |
| 634 | ||
| 635 | <Paragraph> | |
| 636 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 637 | <Paragraph> | |
| 638 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 639 | </test> | |
| 640 | ||
| 641 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/componentutils/" status="not-vulnerable"> | |
| 642 | ||
| 643 | <Paragraph> | |
| 644 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 645 | <Paragraph> | |
| 646 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 647 | </test> | |
| 648 | ||
| 649 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/orm/" status="not-vulnerable"> | |
| 650 | ||
| 651 | <Paragraph> | |
| 652 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 653 | <Paragraph> | |
| 654 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 655 | </test> | |
| 656 | ||
| 657 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/portlets/" status="not-vulnerable"> | |
| 658 | ||
| 659 | <Paragraph> | |
| 660 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 661 | <Paragraph> | |
| 662 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 663 | </test> | |
| 664 | ||
| 665 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/scheduler/" status="not-vulnerable"> | |
| 666 | ||
| 667 | <Paragraph> | |
| 668 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 669 | <Paragraph> | |
| 670 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 671 | </test> | |
| 672 | ||
| 673 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/services/" status="not-vulnerable"> | |
| 674 | ||
| 675 | <Paragraph> | |
| 676 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 677 | <Paragraph> | |
| 678 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 679 | </test> | |
| 680 | ||
| 681 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/websocket/" status="not-vulnerable"> | |
| 682 | ||
| 683 | <Paragraph> | |
| 684 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 685 | <Paragraph> | |
| 686 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 687 | </test> | |
| 688 | ||
| 689 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/wizards/common/" status="not-vulnerable"> | |
| 690 | ||
| 691 | <Paragraph> | |
| 692 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 693 | <Paragraph> | |
| 694 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 695 | </test> | |
| 696 | ||
| 697 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=localhost&vport=22&vstart=&vusername=&vpassword=&returnformat=json" status="not-vulnerable"> | |
| 698 | ||
| 699 | <Paragraph> | |
| 700 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 701 | <Paragraph> | |
| 702 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 703 | </test> | |
| 704 | ||
| 705 | <test id="http-frontpage-unprotected" key="/_vti_bin/_vti_aut/author.dll" status="not-vulnerable"> | |
| 706 | ||
| 707 | <Paragraph> | |
| 708 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 709 | <Paragraph> | |
| 710 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 711 | </test> | |
| 712 | ||
| 713 | <test id="http-php-xmlrpc-code-injection" key="/xmlrpc.php" status="not-vulnerable"> | |
| 714 | ||
| 715 | <Paragraph> | |
| 716 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 717 | <Paragraph> | |
| 718 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 719 | </test> | |
| 720 | ||
| 721 | <test id="adobe-apsb13-03-cve-2013-0625" status="skipped-version"> | |
| 722 | ||
| 723 | <Paragraph> | |
| 724 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 725 | <Paragraph>Based on the result of the "APSB13-03: Security updates available for Adobe ColdFusion (CVE-2013-0629)" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 726 | </test> | |
| 727 | ||
| 728 | <test id="http-basic-auth-cleartext" key="/" status="not-vulnerable"> | |
| 729 | ||
| 730 | <Paragraph> | |
| 731 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 732 | <Paragraph> | |
| 733 | <ContainerBlockElement> | |
| 734 | <ContainerBlockElement> | |
| 735 | <Paragraph>HTTP GET request to | |
| 736 | <URLLink LinkURL="http://192.168.1.1/" LinkTitle="http://192.168.1.1/"></URLLink></Paragraph>HTTP response code was 200 but expected 401</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 737 | </test> | |
| 738 | ||
| 739 | <test id="http-iis-0014" status="not-vulnerable"> | |
| 740 | ||
| 741 | <Paragraph> | |
| 742 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 743 | <Paragraph>Based on the following 3 results: | |
| 744 | <OrderedList> | |
| 745 | <ListItem> | |
| 746 | <Paragraph> | |
| 747 | <ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem> | |
| 748 | <ListItem> | |
| 749 | <Paragraph> | |
| 750 | <ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem> | |
| 751 | <ListItem> | |
| 752 | <Paragraph> | |
| 753 | <ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem></OrderedList></Paragraph></Paragraph> | |
| 754 | </test> | |
| 755 | ||
| 756 | <test id="http-cgi-viewsource-arbitrary-file-access" key="/cgi-bin/view-source?../../../../../../../etc/passwd" status="not-vulnerable"> | |
| 757 | ||
| 758 | <Paragraph> | |
| 759 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 760 | <Paragraph> | |
| 761 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 762 | </test> | |
| 763 | ||
| 764 | <test id="http-trace-method-enabled" key="/" status="not-vulnerable"> | |
| 765 | ||
| 766 | <Paragraph> | |
| 767 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 768 | <Paragraph> | |
| 769 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 770 | </test> | |
| 771 | ||
| 772 | <test id="http-track-method-enabled" key="/" status="not-vulnerable"> | |
| 773 | ||
| 774 | <Paragraph> | |
| 775 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 776 | <Paragraph> | |
| 777 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 778 | </test> | |
| 779 | ||
| 780 | <test id="spider-adobe-flash-permissive-crossdomain-xml" key="/crossdomain.xml" status="not-vulnerable"> | |
| 781 | ||
| 782 | <Paragraph> | |
| 783 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 784 | <Paragraph> | |
| 785 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 786 | </test> | |
| 787 | ||
| 788 | <test id="adobe-apsb13-03-cve-2013-0631" key="/CFIDE/adminapi/customtags/fusebox.cfm" status="not-vulnerable"> | |
| 789 | ||
| 790 | <Paragraph> | |
| 791 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 792 | <Paragraph> | |
| 793 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 794 | </test> | |
| 795 | ||
| 796 | <test id="adobe-apsb13-13-cve-2013-3336" key="/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charse" status="not-vulnerable"> | |
| 797 | ||
| 798 | <Paragraph> | |
| 799 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 800 | <Paragraph> | |
| 801 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 802 | </test> | |
| 803 | ||
| 804 | <test id="http-awstats-debug-information-disclosure" key="/cgi-bin/awstats.pl?debug=1" status="not-vulnerable"> | |
| 805 | ||
| 806 | <Paragraph> | |
| 807 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 808 | <Paragraph> | |
| 809 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 810 | </test> | |
| 811 | ||
| 812 | <test id="http-bigbrother-accessible" key="/bb/" status="not-vulnerable"> | |
| 813 | ||
| 814 | <Paragraph> | |
| 815 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 816 | <Paragraph> | |
| 817 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 818 | </test> | |
| 819 | ||
| 820 | <test id="http-cgi-htdig-arbitrary-file-access" key="/cgi-bin/htsearch?Exclude=%60/etc/passwd%60" status="not-vulnerable"> | |
| 821 | ||
| 822 | <Paragraph> | |
| 823 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 824 | <Paragraph> | |
| 825 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 826 | </test> | |
| 827 | ||
| 828 | <test id="http-cgi-htgrep-arbitrary-file-access" key="/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd" status="not-vulnerable"> | |
| 829 | ||
| 830 | <Paragraph> | |
| 831 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 832 | <Paragraph> | |
| 833 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 834 | </test> | |
| 835 | ||
| 836 | <test id="http-cgi-htmlscript-arbitrary-file-access" key="/cgi-bin/htmlscript?../../../../../../../etc/passwd" status="not-vulnerable"> | |
| 837 | ||
| 838 | <Paragraph> | |
| 839 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 840 | <Paragraph> | |
| 841 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 842 | </test> | |
| 843 | ||
| 844 | <test id="http-cgi-testcgi-file-listing" key="/cgi-bin/test-cgi" status="not-vulnerable"> | |
| 845 | ||
| 846 | <Paragraph> | |
| 847 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 848 | <Paragraph> | |
| 849 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 850 | </test> | |
| 851 | ||
| 852 | <test id="http-cookie-http-only-flag" key="/cgi-bin/webproc" status="vulnerable-exploited"> | |
| 853 | ||
| 854 | <Paragraph> | |
| 855 | <ContainerBlockElement> | |
| 856 | <Paragraph>Cookie is not marked as HttpOnly: 'sessionid=7d7130f3; path=/cgi-bin; domain=192.168.1.1'</Paragraph> | |
| 857 | <Paragraph>URL: | |
| 858 | <URLLink LinkURL="http://192.168.1.1/cgi-bin/webproc" LinkTitle="http://192.168.1.1/cgi-bin/webproc"></URLLink></Paragraph></ContainerBlockElement></Paragraph> | |
| 859 | </test> | |
| 860 | ||
| 861 | <test id="http-generic-propfind-dir-browsing" status="skipped-version"> | |
| 862 | ||
| 863 | <Paragraph> | |
| 864 | <Paragraph> | |
| 865 | <ContainerBlockElement> | |
| 866 | <Paragraph>HTTP request to | |
| 867 | <URLLink LinkURL="http://192.168.1.1/html/" LinkTitle="http://192.168.1.1/html/"></URLLink></Paragraph></ContainerBlockElement></Paragraph> | |
| 868 | <Paragraph>Server did not respond with a valid XML document.</Paragraph> | |
| 869 | <Paragraph>Based on the result of the "WebDAV Extensions are Enabled" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 870 | </test> | |
| 871 | ||
| 872 | <test id="http-generic-propfind-dir-browsing" status="skipped-version"> | |
| 873 | ||
| 874 | <Paragraph> | |
| 875 | <Paragraph> | |
| 876 | <ContainerBlockElement> | |
| 877 | <Paragraph>HTTP request to | |
| 878 | <URLLink LinkURL="http://192.168.1.1/" LinkTitle="http://192.168.1.1/"></URLLink></Paragraph></ContainerBlockElement></Paragraph> | |
| 879 | <Paragraph>Server did not respond with a valid XML document.</Paragraph> | |
| 880 | <Paragraph>Based on the result of the "WebDAV Extensions are Enabled" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 881 | </test> | |
| 882 | ||
| 883 | <test id="http-lighttpd-mod_userdir-info-discl" key="/~bin/true" status="not-vulnerable"> | |
| 884 | ||
| 885 | <Paragraph> | |
| 886 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 887 | <Paragraph> | |
| 888 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 889 | </test> | |
| 890 | ||
| 891 | <test id="http-open-proxy" key="http://www.google.com:80/" status="not-vulnerable"> | |
| 892 | ||
| 893 | <Paragraph> | |
| 894 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 895 | <Paragraph> | |
| 896 | <ContainerBlockElement> | |
| 897 | <ContainerBlockElement> | |
| 898 | <Paragraph>HTTP HEAD request to | |
| 899 | <URLLink LinkURL="http://www.google.com/" LinkTitle="http://www.google.com/"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 900 | </test> | |
| 901 | ||
| 902 | <test id="http-php-ini-file-exposed" key="/cgi-bin/php.ini" status="not-vulnerable"> | |
| 903 | ||
| 904 | <Paragraph> | |
| 905 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 906 | <Paragraph> | |
| 907 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 908 | </test> | |
| 909 | ||
| 910 | <test id="http-symantec-scan-engine-file-disclosure" key="/README.txt" status="not-vulnerable"> | |
| 911 | ||
| 912 | <Paragraph> | |
| 913 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 914 | <Paragraph> | |
| 915 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 916 | </test> | |
| 917 | ||
| 918 | <test id="http-tomcat-jkstatus-accessible" key="/jkstatus/" status="not-vulnerable"> | |
| 919 | ||
| 920 | <Paragraph> | |
| 921 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 922 | <Paragraph> | |
| 923 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 924 | </test> | |
| 925 | ||
| 926 | <test id="http-vignette-app-portal-diag" status="not-vulnerable"> | |
| 927 | ||
| 928 | <Paragraph> | |
| 929 | <Paragraph>Diagnostics page not returned</Paragraph></Paragraph> | |
| 930 | </test> | |
| 931 | ||
| 932 | <test id="adobe-apsb13-03-cve-2013-0629" key="/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../license.txt" status="not-vulnerable"> | |
| 933 | ||
| 934 | <Paragraph> | |
| 935 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 936 | <Paragraph> | |
| 937 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 938 | </test> | |
| 939 | ||
| 940 | <test id="apache-httpd-cve-2008-0005" key="ftp://ftp.kernel.org/;utf7xss" status="not-vulnerable"> | |
| 941 | ||
| 942 | <Paragraph> | |
| 943 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 944 | <Paragraph> | |
| 945 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 946 | </test> | |
| 947 | ||
| 948 | <test id="apache-httpd-cve-2008-0005" key="ftp://ftp.kernel.org/;utf7xss" status="not-vulnerable"> | |
| 949 | ||
| 950 | <Paragraph> | |
| 951 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 952 | <Paragraph> | |
| 953 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 954 | </test> | |
| 955 | ||
| 956 | <test id="apache-httpd-cve-2008-2939" key="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" status="not-vulnerable"> | |
| 957 | ||
| 958 | <Paragraph> | |
| 959 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 960 | <Paragraph> | |
| 961 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 962 | </test> | |
| 963 | ||
| 964 | <test id="apache-httpd-cve-2008-2939" key="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" status="not-vulnerable"> | |
| 965 | ||
| 966 | <Paragraph> | |
| 967 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 968 | <Paragraph> | |
| 969 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 970 | </test> | |
| 971 | ||
| 972 | <test id="http-adobe-amf-gateway-xxe-cve-2009-3960" key="/flex2gateway/http" status="not-vulnerable"> | |
| 973 | ||
| 974 | <Paragraph> | |
| 975 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 976 | <Paragraph> | |
| 977 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 978 | </test> | |
| 979 | </tests> | |
| 980 | </service> | |
| 981 | </services> | |
| 982 | </endpoint> | |
| 983 | </endpoints> | |
| 984 | </node> | |
| 985 | ||
| 986 | <node address="192.168.1.18" status="alive" device-id="6"> | |
| 987 | <fingerprints> | |
| 988 | <os certainty="0.70" device-class="WAP" vendor="Linux" family="Linux" product="Linux" version="2.4.20"/> | |
| 989 | </fingerprints> | |
| 990 | <tests> | |
| 991 | <test id="tcp-seq-num-approximation" status="vulnerable-exploited"> | |
| 992 | ||
| 993 | <Paragraph> | |
| 994 | <Paragraph>TCP reset with incorrect sequence number triggered this fault on 192.168.1.18:23: Connection reset by peer</Paragraph></Paragraph> | |
| 995 | </test> | |
| 996 | ||
| 997 | <test id="generic-icmp-netmask" status="not-vulnerable"> | |
| 998 | ||
| 999 | <Paragraph> | |
| 1000 | <Paragraph>No response</Paragraph></Paragraph> | |
| 1001 | </test> | |
| 1002 | ||
| 1003 | <test id="generic-icmp-timestamp" status="vulnerable-exploited"> | |
| 1004 | ||
| 1005 | <Paragraph> | |
| 1006 | <Paragraph>Remote system time: 06:05:56.324 UTC</Paragraph></Paragraph> | |
| 1007 | </test> | |
| 1008 | ||
| 1009 | <test id="generic-tcp-timestamp" status="vulnerable-exploited"> | |
| 1010 | ||
| 1011 | <Paragraph> | |
| 1012 | <Paragraph>Apparent system boot time: Wed Nov 27 00:16:51 UTC 2013</Paragraph></Paragraph> | |
| 1013 | </test> | |
| 1014 | </tests> | |
| 1015 | <endpoints> | |
| 1016 | <endpoint protocol="tcp" port="23" status="open"> | |
| 1017 | <services> | |
| 1018 | <service name="Telnet"> | |
| 1019 | <tests> | |
| 1020 | <test id="telnet-avaya-default-login-diag" status="not-vulnerable"> | |
| 1021 | ||
| 1022 | <Paragraph> | |
| 1023 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 1024 | </test> | |
| 1025 | ||
| 1026 | <test id="telnet-avaya-default-login-manuf" status="not-vulnerable"> | |
| 1027 | ||
| 1028 | <Paragraph> | |
| 1029 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 1030 | </test> | |
| 1031 | ||
| 1032 | <test id="telnet-default-account-admin-password-password" status="not-vulnerable"> | |
| 1033 | ||
| 1034 | <Paragraph> | |
| 1035 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 1036 | </test> | |
| 1037 | ||
| 1038 | <test id="telnet-default-account-root-password-password" status="not-vulnerable"> | |
| 1039 | ||
| 1040 | <Paragraph> | |
| 1041 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 1042 | </test> | |
| 1043 | ||
| 1044 | <test id="telnet-generic-0001" status="not-vulnerable"> | |
| 1045 | ||
| 1046 | <Paragraph> | |
| 1047 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 1048 | </test> | |
| 1049 | ||
| 1050 | <test id="telnet-generic-0002" status="not-vulnerable"> | |
| 1051 | ||
| 1052 | <Paragraph> | |
| 1053 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 1054 | </test> | |
| 1055 | ||
| 1056 | <test id="telnet-generic-0003" status="not-vulnerable"> | |
| 1057 | ||
| 1058 | <Paragraph> | |
| 1059 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 1060 | </test> | |
| 1061 | ||
| 1062 | <test id="telnet-generic-0004" status="not-vulnerable"> | |
| 1063 | ||
| 1064 | <Paragraph> | |
| 1065 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 1066 | </test> | |
| 1067 | ||
| 1068 | <test id="telnet-generic-0005" status="not-vulnerable"> | |
| 1069 | ||
| 1070 | <Paragraph> | |
| 1071 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 1072 | </test> | |
| 1073 | ||
| 1074 | <test id="telnet-netscreen-default-netscreen-netscreen" status="not-vulnerable"> | |
| 1075 | ||
| 1076 | <Paragraph> | |
| 1077 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 1078 | </test> | |
| 1079 | ||
| 1080 | <test id="telnet-db2-default-login-db2as" status="not-vulnerable"> | |
| 1081 | ||
| 1082 | <Paragraph> | |
| 1083 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 1084 | </test> | |
| 1085 | ||
| 1086 | <test id="telnet-db2-default-login-db2fenc1" status="not-vulnerable"> | |
| 1087 | ||
| 1088 | <Paragraph> | |
| 1089 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 1090 | </test> | |
| 1091 | ||
| 1092 | <test id="telnet-db2-default-login-db2inst1" status="not-vulnerable"> | |
| 1093 | ||
| 1094 | <Paragraph> | |
| 1095 | <Paragraph>Running vulnerable Telnet service.</Paragraph>Was not able to authenticate to the Telnet service with no credentials.</Paragraph> | |
| 1096 | </test> | |
| 1097 | ||
| 1098 | <test id="telnet-open-port" status="vulnerable-version"> | |
| 1099 | ||
| 1100 | <Paragraph> | |
| 1101 | <Paragraph>Running vulnerable Telnet service.</Paragraph></Paragraph> | |
| 1102 | </test> | |
| 1103 | </tests> | |
| 1104 | </service> | |
| 1105 | </services> | |
| 1106 | </endpoint> | |
| 1107 | ||
| 1108 | <endpoint protocol="tcp" port="53" status="open"> | |
| 1109 | <services> | |
| 1110 | <service name="DNS-TCP"> | |
| 1111 | <tests> | |
| 1112 | <test id="dns-allows-cache-snooping" status="error"> | |
| 1113 | ||
| 1114 | <Paragraph> | |
| 1115 | <Paragraph>java.io.EOFException</Paragraph></Paragraph> | |
| 1116 | </test> | |
| 1117 | ||
| 1118 | <test id="dns-processes-recursive-queries" status="not-vulnerable"> | |
| 1119 | ||
| 1120 | <Paragraph> | |
| 1121 | <Paragraph>Nameserver did not resolve test host.</Paragraph></Paragraph> | |
| 1122 | </test> | |
| 1123 | ||
| 1124 | <test id="dns-unrestricted-reverse-zone-transfer" status="error"> | |
| 1125 | ||
| 1126 | <Paragraph> | |
| 1127 | <Paragraph>java.io.EOFException</Paragraph></Paragraph> | |
| 1128 | </test> | |
| 1129 | ||
| 1130 | <test id="dns-0004" status="not-vulnerable"> | |
| 1131 | ||
| 1132 | <Paragraph> | |
| 1133 | <Paragraph>The zone data was not transferred.</Paragraph></Paragraph> | |
| 1134 | </test> | |
| 1135 | </tests> | |
| 1136 | </service> | |
| 1137 | </services> | |
| 1138 | </endpoint> | |
| 1139 | ||
| 1140 | <endpoint protocol="tcp" port="80" status="open"> | |
| 1141 | <services> | |
| 1142 | <service name="HTTP"> | |
| 1143 | <fingerprints> | |
| 1144 | <fingerprint certainty="0.75" product="httpd"/> | |
| 1145 | </fingerprints> | |
| 1146 | <configuration> | |
| 1147 | <config name="http.banner">httpd</config> | |
| 1148 | <config name="http.banner.server">httpd</config> | |
| 1149 | </configuration> | |
| 1150 | <tests> | |
| 1151 | <test id="adobe-apsb13-03-cve-2013-0632" key="/CFIDE/adminapi/administrator.cfc?" status="not-vulnerable"> | |
| 1152 | ||
| 1153 | <Paragraph> | |
| 1154 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1155 | <Paragraph> | |
| 1156 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1157 | </test> | |
| 1158 | ||
| 1159 | <test id="adobe-apsb13-13-cve-2013-1389" status="skipped-version"> | |
| 1160 | ||
| 1161 | <Paragraph> | |
| 1162 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1163 | <Paragraph>Based on the result of the "APSB13-13: Security updates available for Adobe ColdFusion (CVE-2013-3336)" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 1164 | </test> | |
| 1165 | ||
| 1166 | <test id="http-3com-wap-default-admin-password" key="/index.htm" status="not-vulnerable"> | |
| 1167 | ||
| 1168 | <Paragraph> | |
| 1169 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1170 | <Paragraph> | |
| 1171 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1172 | </test> | |
| 1173 | ||
| 1174 | <test id="http-drac-default-login" key="/data/login" status="not-vulnerable"> | |
| 1175 | ||
| 1176 | <Paragraph> | |
| 1177 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1178 | <Paragraph> | |
| 1179 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1180 | </test> | |
| 1181 | ||
| 1182 | <test id="http-drac-default-login" key="/cgi/login" status="not-vulnerable"> | |
| 1183 | ||
| 1184 | <Paragraph> | |
| 1185 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1186 | <Paragraph> | |
| 1187 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1188 | </test> | |
| 1189 | ||
| 1190 | <test id="http-drac-default-login" status="not-vulnerable"> | |
| 1191 | ||
| 1192 | <Paragraph> | |
| 1193 | <Paragraph>Server responded with an HTTP 401 to a request to /cgi-bin/webcgi/login</Paragraph></Paragraph> | |
| 1194 | </test> | |
| 1195 | ||
| 1196 | <test id="http-glassfish-default-admin-password" key="/common/index.jsf" status="not-vulnerable"> | |
| 1197 | ||
| 1198 | <Paragraph> | |
| 1199 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1200 | <Paragraph> | |
| 1201 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1202 | </test> | |
| 1203 | ||
| 1204 | <test id="http-nokia-firewall-default-admin-password" key="/cgi-bin/home.tcl" status="not-vulnerable"> | |
| 1205 | ||
| 1206 | <Paragraph> | |
| 1207 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1208 | <Paragraph> | |
| 1209 | <ContainerBlockElement> | |
| 1210 | <ContainerBlockElement> | |
| 1211 | <Paragraph>HTTP POST request to | |
| 1212 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/home.tcl" LinkTitle="http://192.168.1.18/cgi-bin/home.tcl"></URLLink></Paragraph>HTTP response code was 401 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1213 | </test> | |
| 1214 | ||
| 1215 | <test id="http-phpmyadmin-account-pma-password-empty" key="/phpmyadmin/" status="not-vulnerable"> | |
| 1216 | ||
| 1217 | <Paragraph> | |
| 1218 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1219 | <Paragraph> | |
| 1220 | <ContainerBlockElement> | |
| 1221 | <ContainerBlockElement> | |
| 1222 | <Paragraph>HTTP GET request to | |
| 1223 | <URLLink LinkURL="http://192.168.1.18/phpmyadmin/" LinkTitle="http://192.168.1.18/phpmyadmin/"></URLLink></Paragraph>HTTP response code was 200 but expected 401</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1224 | </test> | |
| 1225 | ||
| 1226 | <test id="apache-struts-cve-2013-2251" key="/struts2-showcase/employee/save.action" status="not-vulnerable"> | |
| 1227 | ||
| 1228 | <Paragraph> | |
| 1229 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1230 | <Paragraph> | |
| 1231 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1232 | </test> | |
| 1233 | ||
| 1234 | <test id="apache-struts-cve-2013-2251" key="/struts2-blank/example/HelloWorld.action" status="not-vulnerable"> | |
| 1235 | ||
| 1236 | <Paragraph> | |
| 1237 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1238 | <Paragraph> | |
| 1239 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1240 | </test> | |
| 1241 | ||
| 1242 | <test id="checkpoint-ess-info-disclosure-sk57881" key="/conf/ssl/apache/integrity.key" status="not-vulnerable"> | |
| 1243 | ||
| 1244 | <Paragraph> | |
| 1245 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1246 | <Paragraph> | |
| 1247 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1248 | </test> | |
| 1249 | ||
| 1250 | <test id="http-thttpd-obsolete" status="skipped-version"> | |
| 1251 | ||
| 1252 | <Paragraph> | |
| 1253 | <Paragraph>Running not-vulnerable HTTP service: httpd.</Paragraph></Paragraph> | |
| 1254 | </test> | |
| 1255 | ||
| 1256 | <test id="http-unrestricted-webdav-put-delete" status="not-vulnerable"> | |
| 1257 | ||
| 1258 | <Paragraph> | |
| 1259 | <Paragraph>/r7.txt was not successfully PUT on the server.</Paragraph></Paragraph> | |
| 1260 | </test> | |
| 1261 | ||
| 1262 | <test id="adobe-apsb10-18-cve-2010-2861" key="/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en" status="not-vulnerable"> | |
| 1263 | ||
| 1264 | <Paragraph> | |
| 1265 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1266 | <Paragraph> | |
| 1267 | <ContainerBlockElement> | |
| 1268 | <ContainerBlockElement> | |
| 1269 | <Paragraph>HTTP GET request to | |
| 1270 | <URLLink LinkURL="http://192.168.1.18/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en" LinkTitle="http://192.168.1.18/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en"></URLLink></Paragraph>HTTP response code was 400 but expected 200HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1271 | </test> | |
| 1272 | ||
| 1273 | <test id="http-awstats-remote-code-execution" key="/cgi-bin/awstats/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" status="not-vulnerable"> | |
| 1274 | ||
| 1275 | <Paragraph> | |
| 1276 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1277 | <Paragraph> | |
| 1278 | <ContainerBlockElement> | |
| 1279 | <ContainerBlockElement> | |
| 1280 | <Paragraph>HTTP GET request to | |
| 1281 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" LinkTitle="http://192.168.1.18/cgi-bin/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;"></URLLink></Paragraph>HTTP response code was 401 but expected 200</ContainerBlockElement> | |
| 1282 | <ContainerBlockElement> | |
| 1283 | <Paragraph>HTTP GET request to | |
| 1284 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/awstats/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" LinkTitle="http://192.168.1.18/cgi-bin/awstats/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;"></URLLink></Paragraph>HTTP response code was 401 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1285 | </test> | |
| 1286 | ||
| 1287 | <test id="http-cgi-faxsurvey-command-execution" key="/cgi-bin/faxquery?/bin/cat%20/etc/passwd" status="not-vulnerable"> | |
| 1288 | ||
| 1289 | <Paragraph> | |
| 1290 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1291 | <Paragraph> | |
| 1292 | <ContainerBlockElement> | |
| 1293 | <ContainerBlockElement> | |
| 1294 | <Paragraph>HTTP GET request to | |
| 1295 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/faxsurvey?/bin/cat%20/etc/passwd" LinkTitle="http://192.168.1.18/cgi-bin/faxsurvey?/bin/cat%20/etc/passwd"></URLLink></Paragraph>HTTP response code was 401 but expected 200</ContainerBlockElement> | |
| 1296 | <ContainerBlockElement> | |
| 1297 | <Paragraph>HTTP GET request to | |
| 1298 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/faxquery?/bin/cat%20/etc/passwd" LinkTitle="http://192.168.1.18/cgi-bin/faxquery?/bin/cat%20/etc/passwd"></URLLink></Paragraph>HTTP response code was 401 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1299 | </test> | |
| 1300 | ||
| 1301 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/AIR/" status="not-vulnerable"> | |
| 1302 | ||
| 1303 | <Paragraph> | |
| 1304 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1305 | <Paragraph> | |
| 1306 | <ContainerBlockElement> | |
| 1307 | <ContainerBlockElement> | |
| 1308 | <Paragraph>HTTP GET request to | |
| 1309 | <URLLink LinkURL="http://192.168.1.18/CFIDE/AIR/" LinkTitle="http://192.168.1.18/CFIDE/AIR/"></URLLink></Paragraph>HTTP response code was an expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1310 | </test> | |
| 1311 | ||
| 1312 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=localhost&vport=22&vstart=&vusername=&vpassword=&returnformat=json" status="not-vulnerable"> | |
| 1313 | ||
| 1314 | <Paragraph> | |
| 1315 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1316 | <Paragraph> | |
| 1317 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1318 | </test> | |
| 1319 | ||
| 1320 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/wizards/common/" status="not-vulnerable"> | |
| 1321 | ||
| 1322 | <Paragraph> | |
| 1323 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1324 | <Paragraph> | |
| 1325 | <ContainerBlockElement> | |
| 1326 | <ContainerBlockElement> | |
| 1327 | <Paragraph>HTTP GET request to | |
| 1328 | <URLLink LinkURL="http://192.168.1.18/CFIDE/wizards/common/" LinkTitle="http://192.168.1.18/CFIDE/wizards/common/"></URLLink></Paragraph>HTTP response code was an expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1329 | </test> | |
| 1330 | ||
| 1331 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/websocket/" status="not-vulnerable"> | |
| 1332 | ||
| 1333 | <Paragraph> | |
| 1334 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1335 | <Paragraph> | |
| 1336 | <ContainerBlockElement> | |
| 1337 | <ContainerBlockElement> | |
| 1338 | <Paragraph>HTTP GET request to | |
| 1339 | <URLLink LinkURL="http://192.168.1.18/CFIDE/websocket/" LinkTitle="http://192.168.1.18/CFIDE/websocket/"></URLLink></Paragraph>HTTP response code was an expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1340 | </test> | |
| 1341 | ||
| 1342 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/services/" status="not-vulnerable"> | |
| 1343 | ||
| 1344 | <Paragraph> | |
| 1345 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1346 | <Paragraph> | |
| 1347 | <ContainerBlockElement> | |
| 1348 | <ContainerBlockElement> | |
| 1349 | <Paragraph>HTTP GET request to | |
| 1350 | <URLLink LinkURL="http://192.168.1.18/CFIDE/services/" LinkTitle="http://192.168.1.18/CFIDE/services/"></URLLink></Paragraph>HTTP response code was an expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1351 | </test> | |
| 1352 | ||
| 1353 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/servermanager/" status="not-vulnerable"> | |
| 1354 | ||
| 1355 | <Paragraph> | |
| 1356 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1357 | <Paragraph> | |
| 1358 | <ContainerBlockElement> | |
| 1359 | <ContainerBlockElement> | |
| 1360 | <Paragraph>HTTP GET request to | |
| 1361 | <URLLink LinkURL="http://192.168.1.18/CFIDE/servermanager/" LinkTitle="http://192.168.1.18/CFIDE/servermanager/"></URLLink></Paragraph>HTTP response code was an expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1362 | </test> | |
| 1363 | ||
| 1364 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/scheduler/" status="not-vulnerable"> | |
| 1365 | ||
| 1366 | <Paragraph> | |
| 1367 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1368 | <Paragraph> | |
| 1369 | <ContainerBlockElement> | |
| 1370 | <ContainerBlockElement> | |
| 1371 | <Paragraph>HTTP GET request to | |
| 1372 | <URLLink LinkURL="http://192.168.1.18/CFIDE/scheduler/" LinkTitle="http://192.168.1.18/CFIDE/scheduler/"></URLLink></Paragraph>HTTP response code was an expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1373 | </test> | |
| 1374 | ||
| 1375 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/portlets/" status="not-vulnerable"> | |
| 1376 | ||
| 1377 | <Paragraph> | |
| 1378 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1379 | <Paragraph> | |
| 1380 | <ContainerBlockElement> | |
| 1381 | <ContainerBlockElement> | |
| 1382 | <Paragraph>HTTP GET request to | |
| 1383 | <URLLink LinkURL="http://192.168.1.18/CFIDE/portlets/" LinkTitle="http://192.168.1.18/CFIDE/portlets/"></URLLink></Paragraph>HTTP response code was an expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1384 | </test> | |
| 1385 | ||
| 1386 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/orm/" status="not-vulnerable"> | |
| 1387 | ||
| 1388 | <Paragraph> | |
| 1389 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1390 | <Paragraph> | |
| 1391 | <ContainerBlockElement> | |
| 1392 | <ContainerBlockElement> | |
| 1393 | <Paragraph>HTTP GET request to | |
| 1394 | <URLLink LinkURL="http://192.168.1.18/CFIDE/orm/" LinkTitle="http://192.168.1.18/CFIDE/orm/"></URLLink></Paragraph>HTTP response code was an expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1395 | </test> | |
| 1396 | ||
| 1397 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/componentutils/" status="not-vulnerable"> | |
| 1398 | ||
| 1399 | <Paragraph> | |
| 1400 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1401 | <Paragraph> | |
| 1402 | <ContainerBlockElement> | |
| 1403 | <ContainerBlockElement> | |
| 1404 | <Paragraph>HTTP GET request to | |
| 1405 | <URLLink LinkURL="http://192.168.1.18/CFIDE/componentutils/" LinkTitle="http://192.168.1.18/CFIDE/componentutils/"></URLLink></Paragraph>HTTP response code was an expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1406 | </test> | |
| 1407 | ||
| 1408 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/appdeployment/" status="not-vulnerable"> | |
| 1409 | ||
| 1410 | <Paragraph> | |
| 1411 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1412 | <Paragraph> | |
| 1413 | <ContainerBlockElement> | |
| 1414 | <ContainerBlockElement> | |
| 1415 | <Paragraph>HTTP GET request to | |
| 1416 | <URLLink LinkURL="http://192.168.1.18/CFIDE/appdeployment/" LinkTitle="http://192.168.1.18/CFIDE/appdeployment/"></URLLink></Paragraph>HTTP response code was an expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1417 | </test> | |
| 1418 | ||
| 1419 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/administrator/enter.cfm" status="not-vulnerable"> | |
| 1420 | ||
| 1421 | <Paragraph> | |
| 1422 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1423 | <Paragraph> | |
| 1424 | <ContainerBlockElement> | |
| 1425 | <ContainerBlockElement> | |
| 1426 | <Paragraph>HTTP GET request to | |
| 1427 | <URLLink LinkURL="http://192.168.1.18/CFIDE/administrator/" LinkTitle="http://192.168.1.18/CFIDE/administrator/"></URLLink></Paragraph>HTTP response code was an expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1428 | </test> | |
| 1429 | ||
| 1430 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/adminiapi/" status="not-vulnerable"> | |
| 1431 | ||
| 1432 | <Paragraph> | |
| 1433 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1434 | <Paragraph> | |
| 1435 | <ContainerBlockElement> | |
| 1436 | <ContainerBlockElement> | |
| 1437 | <Paragraph>HTTP GET request to | |
| 1438 | <URLLink LinkURL="http://192.168.1.18/CFIDE/adminiapi/" LinkTitle="http://192.168.1.18/CFIDE/adminiapi/"></URLLink></Paragraph>HTTP response code was an expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1439 | </test> | |
| 1440 | ||
| 1441 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/adminapi/base.cfc?wsdl" status="not-vulnerable"> | |
| 1442 | ||
| 1443 | <Paragraph> | |
| 1444 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1445 | <Paragraph> | |
| 1446 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1447 | </test> | |
| 1448 | ||
| 1449 | <test id="http-dd-wrt-remote-command-execution" status="vulnerable-exploited"> | |
| 1450 | ||
| 1451 | <Paragraph> | |
| 1452 | <Paragraph>Sleep command executed (Round-trip times: 10428ms, 92ms, 10100ms, 364ms)</Paragraph></Paragraph> | |
| 1453 | </test> | |
| 1454 | ||
| 1455 | <test id="http-frontpage-unprotected" key="/_vti_bin/_vti_aut/author.dll" status="not-vulnerable"> | |
| 1456 | ||
| 1457 | <Paragraph> | |
| 1458 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1459 | <Paragraph> | |
| 1460 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1461 | </test> | |
| 1462 | ||
| 1463 | <test id="http-php-xmlrpc-code-injection" key="/xmlrpc.php" status="not-vulnerable"> | |
| 1464 | ||
| 1465 | <Paragraph> | |
| 1466 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1467 | <Paragraph> | |
| 1468 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1469 | </test> | |
| 1470 | ||
| 1471 | <test id="adobe-apsb13-03-cve-2013-0625" status="skipped-version"> | |
| 1472 | ||
| 1473 | <Paragraph> | |
| 1474 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1475 | <Paragraph>Based on the result of the "APSB13-03: Security updates available for Adobe ColdFusion (CVE-2013-0629)" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 1476 | </test> | |
| 1477 | ||
| 1478 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Management.asp" status="vulnerable-exploited"> | |
| 1479 | ||
| 1480 | <Paragraph> | |
| 1481 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1482 | <Paragraph> | |
| 1483 | <ContainerBlockElement> | |
| 1484 | <Paragraph>HTTP request to | |
| 1485 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Management.asp" LinkTitle="http://192.168.1.18/cgi-bin/Management.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1486 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1487 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1488 | </test> | |
| 1489 | ||
| 1490 | <test id="http-basic-auth-cleartext" key="/" status="not-vulnerable"> | |
| 1491 | ||
| 1492 | <Paragraph> | |
| 1493 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1494 | <Paragraph> | |
| 1495 | <ContainerBlockElement> | |
| 1496 | <ContainerBlockElement> | |
| 1497 | <Paragraph>HTTP GET request to | |
| 1498 | <URLLink LinkURL="http://192.168.1.18/" LinkTitle="http://192.168.1.18/"></URLLink></Paragraph>HTTP response code was 200 but expected 401</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 1499 | </test> | |
| 1500 | ||
| 1501 | <test id="http-basic-auth-cleartext" key="/cgi-bin/images/apply.cgi" status="vulnerable-exploited"> | |
| 1502 | ||
| 1503 | <Paragraph> | |
| 1504 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1505 | <Paragraph> | |
| 1506 | <ContainerBlockElement> | |
| 1507 | <Paragraph>HTTP request to | |
| 1508 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/images/apply.cgi" LinkTitle="http://192.168.1.18/cgi-bin/images/apply.cgi"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1509 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1510 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1511 | </test> | |
| 1512 | ||
| 1513 | <test id="http-basic-auth-cleartext" key="/cgi-bin/images/index.asp" status="vulnerable-exploited"> | |
| 1514 | ||
| 1515 | <Paragraph> | |
| 1516 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1517 | <Paragraph> | |
| 1518 | <ContainerBlockElement> | |
| 1519 | <Paragraph>HTTP request to | |
| 1520 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/images/index.asp" LinkTitle="http://192.168.1.18/cgi-bin/images/index.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1521 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1522 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1523 | </test> | |
| 1524 | ||
| 1525 | <test id="http-basic-auth-cleartext" key="/cgi-bin/images/Info.live.htm" status="vulnerable-exploited"> | |
| 1526 | ||
| 1527 | <Paragraph> | |
| 1528 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1529 | <Paragraph> | |
| 1530 | <ContainerBlockElement> | |
| 1531 | <Paragraph>HTTP request to | |
| 1532 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/images/Info.live.htm" LinkTitle="http://192.168.1.18/cgi-bin/images/Info.live.htm"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1533 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1534 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1535 | </test> | |
| 1536 | ||
| 1537 | <test id="http-basic-auth-cleartext" key="/cgi-bin/images/style/elegant/style.css" status="vulnerable-exploited"> | |
| 1538 | ||
| 1539 | <Paragraph> | |
| 1540 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1541 | <Paragraph> | |
| 1542 | <ContainerBlockElement> | |
| 1543 | <Paragraph>HTTP request to | |
| 1544 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/images/style/elegant/style.css" LinkTitle="http://192.168.1.18/cgi-bin/images/style/elegant/style.css"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1545 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1546 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1547 | </test> | |
| 1548 | ||
| 1549 | <test id="http-basic-auth-cleartext" key="/cgi-bin/index.asp/<script>xss</script>" status="vulnerable-exploited"> | |
| 1550 | ||
| 1551 | <Paragraph> | |
| 1552 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1553 | <Paragraph> | |
| 1554 | <ContainerBlockElement> | |
| 1555 | <Paragraph>HTTP request to | |
| 1556 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.asp/<script>xss</script>" LinkTitle="http://192.168.1.18/cgi-bin/index.asp/<script>xss</script>"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1557 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1558 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1559 | </test> | |
| 1560 | ||
| 1561 | <test id="http-basic-auth-cleartext" key="/cgi-bin/index.bak" status="vulnerable-exploited"> | |
| 1562 | ||
| 1563 | <Paragraph> | |
| 1564 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1565 | <Paragraph> | |
| 1566 | <ContainerBlockElement> | |
| 1567 | <Paragraph>HTTP request to | |
| 1568 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.bak" LinkTitle="http://192.168.1.18/cgi-bin/index.bak"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1569 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1570 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1571 | </test> | |
| 1572 | ||
| 1573 | <test id="http-basic-auth-cleartext" key="/cgi-bin/index.chtml" status="vulnerable-exploited"> | |
| 1574 | ||
| 1575 | <Paragraph> | |
| 1576 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1577 | <Paragraph> | |
| 1578 | <ContainerBlockElement> | |
| 1579 | <Paragraph>HTTP request to | |
| 1580 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.chtml" LinkTitle="http://192.168.1.18/cgi-bin/index.chtml"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1581 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1582 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1583 | </test> | |
| 1584 | ||
| 1585 | <test id="http-basic-auth-cleartext" key="/cgi-bin/index.htm" status="vulnerable-exploited"> | |
| 1586 | ||
| 1587 | <Paragraph> | |
| 1588 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1589 | <Paragraph> | |
| 1590 | <ContainerBlockElement> | |
| 1591 | <Paragraph>HTTP request to | |
| 1592 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.htm" LinkTitle="http://192.168.1.18/cgi-bin/index.htm"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1593 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1594 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1595 | </test> | |
| 1596 | ||
| 1597 | <test id="http-basic-auth-cleartext" key="/cgi-bin/index.html" status="vulnerable-exploited"> | |
| 1598 | ||
| 1599 | <Paragraph> | |
| 1600 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1601 | <Paragraph> | |
| 1602 | <ContainerBlockElement> | |
| 1603 | <Paragraph>HTTP request to | |
| 1604 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.html" LinkTitle="http://192.168.1.18/cgi-bin/index.html"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1605 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1606 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1607 | </test> | |
| 1608 | ||
| 1609 | <test id="http-basic-auth-cleartext" key="/cgi-bin/index.old" status="vulnerable-exploited"> | |
| 1610 | ||
| 1611 | <Paragraph> | |
| 1612 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1613 | <Paragraph> | |
| 1614 | <ContainerBlockElement> | |
| 1615 | <Paragraph>HTTP request to | |
| 1616 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.old" LinkTitle="http://192.168.1.18/cgi-bin/index.old"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1617 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1618 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1619 | </test> | |
| 1620 | ||
| 1621 | <test id="http-basic-auth-cleartext" key="/cgi-bin/index.swf" status="vulnerable-exploited"> | |
| 1622 | ||
| 1623 | <Paragraph> | |
| 1624 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1625 | <Paragraph> | |
| 1626 | <ContainerBlockElement> | |
| 1627 | <Paragraph>HTTP request to | |
| 1628 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.swf" LinkTitle="http://192.168.1.18/cgi-bin/index.swf"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1629 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1630 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1631 | </test> | |
| 1632 | ||
| 1633 | <test id="http-basic-auth-cleartext" key="/cgi-bin/[email protected]" status="vulnerable-exploited"> | |
| 1634 | ||
| 1635 | <Paragraph> | |
| 1636 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1637 | <Paragraph> | |
| 1638 | <ContainerBlockElement> | |
| 1639 | <Paragraph>HTTP request to | |
| 1640 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/[email protected]" LinkTitle="http://192.168.1.18/cgi-bin/[email protected]"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1641 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1642 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1643 | </test> | |
| 1644 | ||
| 1645 | <test id="http-basic-auth-cleartext" key="/cgi-bin/readme.txt" status="vulnerable-exploited"> | |
| 1646 | ||
| 1647 | <Paragraph> | |
| 1648 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1649 | <Paragraph> | |
| 1650 | <ContainerBlockElement> | |
| 1651 | <Paragraph>HTTP request to | |
| 1652 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/readme.txt" LinkTitle="http://192.168.1.18/cgi-bin/readme.txt"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1653 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1654 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1655 | </test> | |
| 1656 | ||
| 1657 | <test id="http-basic-auth-cleartext" key="/cgi-bin/style/elegant/style.css" status="vulnerable-exploited"> | |
| 1658 | ||
| 1659 | <Paragraph> | |
| 1660 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1661 | <Paragraph> | |
| 1662 | <ContainerBlockElement> | |
| 1663 | <Paragraph>HTTP request to | |
| 1664 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/style.css" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/style.css"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1665 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1666 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1667 | </test> | |
| 1668 | ||
| 1669 | <test id="http-basic-auth-cleartext" key="/cgi-bin/lang_pack/common.js" status="vulnerable-exploited"> | |
| 1670 | ||
| 1671 | <Paragraph> | |
| 1672 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1673 | <Paragraph> | |
| 1674 | <ContainerBlockElement> | |
| 1675 | <Paragraph>HTTP request to | |
| 1676 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/lang_pack/common.js" LinkTitle="http://192.168.1.18/cgi-bin/lang_pack/common.js"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1677 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1678 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1679 | </test> | |
| 1680 | ||
| 1681 | <test id="http-basic-auth-cleartext" key="/cgi-bin/lang_pack/lang_pack/english.js" status="vulnerable-exploited"> | |
| 1682 | ||
| 1683 | <Paragraph> | |
| 1684 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1685 | <Paragraph> | |
| 1686 | <ContainerBlockElement> | |
| 1687 | <Paragraph>HTTP request to | |
| 1688 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/lang_pack/lang_pack/english.js" LinkTitle="http://192.168.1.18/cgi-bin/lang_pack/lang_pack/english.js"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1689 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1690 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1691 | </test> | |
| 1692 | ||
| 1693 | <test id="http-basic-auth-cleartext" key="/cgi-bin/lang_pack/Filters.asp" status="vulnerable-exploited"> | |
| 1694 | ||
| 1695 | <Paragraph> | |
| 1696 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1697 | <Paragraph> | |
| 1698 | <ContainerBlockElement> | |
| 1699 | <Paragraph>HTTP request to | |
| 1700 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/lang_pack/Filters.asp" LinkTitle="http://192.168.1.18/cgi-bin/lang_pack/Filters.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1701 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1702 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1703 | </test> | |
| 1704 | ||
| 1705 | <test id="http-basic-auth-cleartext" key="/cgi-bin/lang_pack/Firewall.asp" status="vulnerable-exploited"> | |
| 1706 | ||
| 1707 | <Paragraph> | |
| 1708 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1709 | <Paragraph> | |
| 1710 | <ContainerBlockElement> | |
| 1711 | <Paragraph>HTTP request to | |
| 1712 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/lang_pack/Firewall.asp" LinkTitle="http://192.168.1.18/cgi-bin/lang_pack/Firewall.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1713 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1714 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1715 | </test> | |
| 1716 | ||
| 1717 | <test id="http-basic-auth-cleartext" key="/cgi-bin/lang_pack/ForwardSpec.asp" status="vulnerable-exploited"> | |
| 1718 | ||
| 1719 | <Paragraph> | |
| 1720 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1721 | <Paragraph> | |
| 1722 | <ContainerBlockElement> | |
| 1723 | <Paragraph>HTTP request to | |
| 1724 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/lang_pack/ForwardSpec.asp" LinkTitle="http://192.168.1.18/cgi-bin/lang_pack/ForwardSpec.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1725 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1726 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1727 | </test> | |
| 1728 | ||
| 1729 | <test id="http-basic-auth-cleartext" key="/cgi-bin/style/elegant/common.js" status="vulnerable-exploited"> | |
| 1730 | ||
| 1731 | <Paragraph> | |
| 1732 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1733 | <Paragraph> | |
| 1734 | <ContainerBlockElement> | |
| 1735 | <Paragraph>HTTP request to | |
| 1736 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/common.js" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/common.js"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1737 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1738 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1739 | </test> | |
| 1740 | ||
| 1741 | <test id="http-basic-auth-cleartext" key="/cgi-bin/style/elegant/lang_pack/english.js" status="vulnerable-exploited"> | |
| 1742 | ||
| 1743 | <Paragraph> | |
| 1744 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1745 | <Paragraph> | |
| 1746 | <ContainerBlockElement> | |
| 1747 | <Paragraph>HTTP request to | |
| 1748 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/lang_pack/english.js" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/lang_pack/english.js"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1749 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1750 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1751 | </test> | |
| 1752 | ||
| 1753 | <test id="http-basic-auth-cleartext" key="/cgi-bin/lang_pack/Management.asp" status="vulnerable-exploited"> | |
| 1754 | ||
| 1755 | <Paragraph> | |
| 1756 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1757 | <Paragraph> | |
| 1758 | <ContainerBlockElement> | |
| 1759 | <Paragraph>HTTP request to | |
| 1760 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/lang_pack/Management.asp" LinkTitle="http://192.168.1.18/cgi-bin/lang_pack/Management.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1761 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1762 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1763 | </test> | |
| 1764 | ||
| 1765 | <test id="http-basic-auth-cleartext" key="/cgi-bin/lang_pack/Services.asp" status="vulnerable-exploited"> | |
| 1766 | ||
| 1767 | <Paragraph> | |
| 1768 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1769 | <Paragraph> | |
| 1770 | <ContainerBlockElement> | |
| 1771 | <Paragraph>HTTP request to | |
| 1772 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/lang_pack/Services.asp" LinkTitle="http://192.168.1.18/cgi-bin/lang_pack/Services.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1773 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1774 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1775 | </test> | |
| 1776 | ||
| 1777 | <test id="http-basic-auth-cleartext" key="/cgi-bin/lang_pack/Status_Router.asp" status="vulnerable-exploited"> | |
| 1778 | ||
| 1779 | <Paragraph> | |
| 1780 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1781 | <Paragraph> | |
| 1782 | <ContainerBlockElement> | |
| 1783 | <Paragraph>HTTP request to | |
| 1784 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/lang_pack/Status_Router.asp" LinkTitle="http://192.168.1.18/cgi-bin/lang_pack/Status_Router.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1785 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1786 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1787 | </test> | |
| 1788 | ||
| 1789 | <test id="http-basic-auth-cleartext" key="/cgi-bin/lang_pack/Wireless_Basic.asp" status="vulnerable-exploited"> | |
| 1790 | ||
| 1791 | <Paragraph> | |
| 1792 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1793 | <Paragraph> | |
| 1794 | <ContainerBlockElement> | |
| 1795 | <Paragraph>HTTP request to | |
| 1796 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/lang_pack/Wireless_Basic.asp" LinkTitle="http://192.168.1.18/cgi-bin/lang_pack/Wireless_Basic.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1797 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1798 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1799 | </test> | |
| 1800 | ||
| 1801 | <test id="http-basic-auth-cleartext" key="/cgi-bin/lang_pack/index.asp" status="vulnerable-exploited"> | |
| 1802 | ||
| 1803 | <Paragraph> | |
| 1804 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1805 | <Paragraph> | |
| 1806 | <ContainerBlockElement> | |
| 1807 | <Paragraph>HTTP request to | |
| 1808 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/lang_pack/index.asp" LinkTitle="http://192.168.1.18/cgi-bin/lang_pack/index.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1809 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1810 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1811 | </test> | |
| 1812 | ||
| 1813 | <test id="http-basic-auth-cleartext" key="/cgi-bin/style/elegant/Filters.asp" status="vulnerable-exploited"> | |
| 1814 | ||
| 1815 | <Paragraph> | |
| 1816 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1817 | <Paragraph> | |
| 1818 | <ContainerBlockElement> | |
| 1819 | <Paragraph>HTTP request to | |
| 1820 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/Filters.asp" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/Filters.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1821 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1822 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1823 | </test> | |
| 1824 | ||
| 1825 | <test id="http-basic-auth-cleartext" key="/cgi-bin/style/elegant/Firewall.asp" status="vulnerable-exploited"> | |
| 1826 | ||
| 1827 | <Paragraph> | |
| 1828 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1829 | <Paragraph> | |
| 1830 | <ContainerBlockElement> | |
| 1831 | <Paragraph>HTTP request to | |
| 1832 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/Firewall.asp" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/Firewall.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1833 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1834 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1835 | </test> | |
| 1836 | ||
| 1837 | <test id="http-basic-auth-cleartext" key="/cgi-bin/style/elegant/ForwardSpec.asp" status="vulnerable-exploited"> | |
| 1838 | ||
| 1839 | <Paragraph> | |
| 1840 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1841 | <Paragraph> | |
| 1842 | <ContainerBlockElement> | |
| 1843 | <Paragraph>HTTP request to | |
| 1844 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/ForwardSpec.asp" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/ForwardSpec.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1845 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1846 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1847 | </test> | |
| 1848 | ||
| 1849 | <test id="http-basic-auth-cleartext" key="/cgi-bin/style/elegant/Management.asp" status="vulnerable-exploited"> | |
| 1850 | ||
| 1851 | <Paragraph> | |
| 1852 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1853 | <Paragraph> | |
| 1854 | <ContainerBlockElement> | |
| 1855 | <Paragraph>HTTP request to | |
| 1856 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/Management.asp" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/Management.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1857 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1858 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1859 | </test> | |
| 1860 | ||
| 1861 | <test id="http-basic-auth-cleartext" key="/cgi-bin/style/elegant/Services.asp" status="vulnerable-exploited"> | |
| 1862 | ||
| 1863 | <Paragraph> | |
| 1864 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1865 | <Paragraph> | |
| 1866 | <ContainerBlockElement> | |
| 1867 | <Paragraph>HTTP request to | |
| 1868 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/Services.asp" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/Services.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1869 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1870 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1871 | </test> | |
| 1872 | ||
| 1873 | <test id="http-basic-auth-cleartext" key="/cgi-bin/style/elegant/Status_Router.asp" status="vulnerable-exploited"> | |
| 1874 | ||
| 1875 | <Paragraph> | |
| 1876 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1877 | <Paragraph> | |
| 1878 | <ContainerBlockElement> | |
| 1879 | <Paragraph>HTTP request to | |
| 1880 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/Status_Router.asp" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/Status_Router.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1881 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1882 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1883 | </test> | |
| 1884 | ||
| 1885 | <test id="http-basic-auth-cleartext" key="/cgi-bin/style/elegant/Wireless_Basic.asp" status="vulnerable-exploited"> | |
| 1886 | ||
| 1887 | <Paragraph> | |
| 1888 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1889 | <Paragraph> | |
| 1890 | <ContainerBlockElement> | |
| 1891 | <Paragraph>HTTP request to | |
| 1892 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/Wireless_Basic.asp" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/Wireless_Basic.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1893 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1894 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1895 | </test> | |
| 1896 | ||
| 1897 | <test id="http-basic-auth-cleartext" key="/cgi-bin/style/elegant/index.asp" status="vulnerable-exploited"> | |
| 1898 | ||
| 1899 | <Paragraph> | |
| 1900 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1901 | <Paragraph> | |
| 1902 | <ContainerBlockElement> | |
| 1903 | <Paragraph>HTTP request to | |
| 1904 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/index.asp" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/index.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1905 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1906 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1907 | </test> | |
| 1908 | ||
| 1909 | <test id="http-basic-auth-cleartext" key="/cgi-bin/lang_pack/apply.cgi" status="vulnerable-exploited"> | |
| 1910 | ||
| 1911 | <Paragraph> | |
| 1912 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1913 | <Paragraph> | |
| 1914 | <ContainerBlockElement> | |
| 1915 | <Paragraph>HTTP request to | |
| 1916 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/lang_pack/apply.cgi" LinkTitle="http://192.168.1.18/cgi-bin/lang_pack/apply.cgi"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1917 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1918 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1919 | </test> | |
| 1920 | ||
| 1921 | <test id="http-basic-auth-cleartext" key="/cgi-bin/style/elegant/apply.cgi" status="vulnerable-exploited"> | |
| 1922 | ||
| 1923 | <Paragraph> | |
| 1924 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1925 | <Paragraph> | |
| 1926 | <ContainerBlockElement> | |
| 1927 | <Paragraph>HTTP request to | |
| 1928 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/apply.cgi" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/apply.cgi"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1929 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1930 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1931 | </test> | |
| 1932 | ||
| 1933 | <test id="http-basic-auth-cleartext" key="/cgi-bin/lang_pack/Info.live.htm" status="vulnerable-exploited"> | |
| 1934 | ||
| 1935 | <Paragraph> | |
| 1936 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1937 | <Paragraph> | |
| 1938 | <ContainerBlockElement> | |
| 1939 | <Paragraph>HTTP request to | |
| 1940 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/lang_pack/Info.live.htm" LinkTitle="http://192.168.1.18/cgi-bin/lang_pack/Info.live.htm"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1941 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1942 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1943 | </test> | |
| 1944 | ||
| 1945 | <test id="http-basic-auth-cleartext" key="/cgi-bin/lang_pack/style/elegant/style.css" status="vulnerable-exploited"> | |
| 1946 | ||
| 1947 | <Paragraph> | |
| 1948 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1949 | <Paragraph> | |
| 1950 | <ContainerBlockElement> | |
| 1951 | <Paragraph>HTTP request to | |
| 1952 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/lang_pack/style/elegant/style.css" LinkTitle="http://192.168.1.18/cgi-bin/lang_pack/style/elegant/style.css"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1953 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1954 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1955 | </test> | |
| 1956 | ||
| 1957 | <test id="http-basic-auth-cleartext" key="/cgi-bin/style/elegant/Info.live.htm" status="vulnerable-exploited"> | |
| 1958 | ||
| 1959 | <Paragraph> | |
| 1960 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1961 | <Paragraph> | |
| 1962 | <ContainerBlockElement> | |
| 1963 | <Paragraph>HTTP request to | |
| 1964 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/Info.live.htm" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/Info.live.htm"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1965 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1966 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1967 | </test> | |
| 1968 | ||
| 1969 | <test id="http-basic-auth-cleartext" key="/cgi-bin/style/elegant/style/elegant/style.css" status="vulnerable-exploited"> | |
| 1970 | ||
| 1971 | <Paragraph> | |
| 1972 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1973 | <Paragraph> | |
| 1974 | <ContainerBlockElement> | |
| 1975 | <Paragraph>HTTP request to | |
| 1976 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/style/elegant/style.css" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/style/elegant/style.css"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1977 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1978 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1979 | </test> | |
| 1980 | ||
| 1981 | <test id="http-basic-auth-cleartext" key="/cgi-bin/style/elegant/style_ie.css" status="vulnerable-exploited"> | |
| 1982 | ||
| 1983 | <Paragraph> | |
| 1984 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1985 | <Paragraph> | |
| 1986 | <ContainerBlockElement> | |
| 1987 | <Paragraph>HTTP request to | |
| 1988 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/style_ie.css" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/style_ie.css"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 1989 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 1990 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 1991 | </test> | |
| 1992 | ||
| 1993 | <test id="http-basic-auth-cleartext" key="/cgi-bin/web.config" status="vulnerable-exploited"> | |
| 1994 | ||
| 1995 | <Paragraph> | |
| 1996 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 1997 | <Paragraph> | |
| 1998 | <ContainerBlockElement> | |
| 1999 | <Paragraph>HTTP request to | |
| 2000 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/web.config" LinkTitle="http://192.168.1.18/cgi-bin/web.config"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2001 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2002 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2003 | </test> | |
| 2004 | ||
| 2005 | <test id="http-basic-auth-cleartext" key="/exchange/default.asp" status="vulnerable-exploited"> | |
| 2006 | ||
| 2007 | <Paragraph> | |
| 2008 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2009 | <Paragraph> | |
| 2010 | <ContainerBlockElement> | |
| 2011 | <Paragraph>HTTP request to | |
| 2012 | <URLLink LinkURL="http://192.168.1.18/exchange/default.asp" LinkTitle="http://192.168.1.18/exchange/default.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2013 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2014 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2015 | </test> | |
| 2016 | ||
| 2017 | <test id="http-basic-auth-cleartext" key="/exchange/logon.asp" status="vulnerable-exploited"> | |
| 2018 | ||
| 2019 | <Paragraph> | |
| 2020 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2021 | <Paragraph> | |
| 2022 | <ContainerBlockElement> | |
| 2023 | <Paragraph>HTTP request to | |
| 2024 | <URLLink LinkURL="http://192.168.1.18/exchange/logon.asp" LinkTitle="http://192.168.1.18/exchange/logon.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2025 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2026 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2027 | </test> | |
| 2028 | ||
| 2029 | <test id="http-basic-auth-cleartext" key="/exchweb/bin/auth/owalogon.asp" status="vulnerable-exploited"> | |
| 2030 | ||
| 2031 | <Paragraph> | |
| 2032 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2033 | <Paragraph> | |
| 2034 | <ContainerBlockElement> | |
| 2035 | <Paragraph>HTTP request to | |
| 2036 | <URLLink LinkURL="http://192.168.1.18/exchweb/bin/auth/owalogon.asp" LinkTitle="http://192.168.1.18/exchweb/bin/auth/owalogon.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2037 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2038 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2039 | </test> | |
| 2040 | ||
| 2041 | <test id="http-basic-auth-cleartext" key="/iisstart.asp" status="vulnerable-exploited"> | |
| 2042 | ||
| 2043 | <Paragraph> | |
| 2044 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2045 | <Paragraph> | |
| 2046 | <ContainerBlockElement> | |
| 2047 | <Paragraph>HTTP request to | |
| 2048 | <URLLink LinkURL="http://192.168.1.18/iisstart.asp" LinkTitle="http://192.168.1.18/iisstart.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2049 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2050 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2051 | </test> | |
| 2052 | ||
| 2053 | <test id="http-basic-auth-cleartext" key="/localstart.asp" status="vulnerable-exploited"> | |
| 2054 | ||
| 2055 | <Paragraph> | |
| 2056 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2057 | <Paragraph> | |
| 2058 | <ContainerBlockElement> | |
| 2059 | <Paragraph>HTTP request to | |
| 2060 | <URLLink LinkURL="http://192.168.1.18/localstart.asp" LinkTitle="http://192.168.1.18/localstart.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2061 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2062 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2063 | </test> | |
| 2064 | ||
| 2065 | <test id="http-basic-auth-cleartext" key="/login.asp" status="vulnerable-exploited"> | |
| 2066 | ||
| 2067 | <Paragraph> | |
| 2068 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2069 | <Paragraph> | |
| 2070 | <ContainerBlockElement> | |
| 2071 | <Paragraph>HTTP request to | |
| 2072 | <URLLink LinkURL="http://192.168.1.18/login.asp" LinkTitle="http://192.168.1.18/login.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2073 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2074 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2075 | </test> | |
| 2076 | ||
| 2077 | <test id="http-basic-auth-cleartext" key="/test.asp" status="vulnerable-exploited"> | |
| 2078 | ||
| 2079 | <Paragraph> | |
| 2080 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2081 | <Paragraph> | |
| 2082 | <ContainerBlockElement> | |
| 2083 | <Paragraph>HTTP request to | |
| 2084 | <URLLink LinkURL="http://192.168.1.18/test.asp" LinkTitle="http://192.168.1.18/test.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2085 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2086 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2087 | </test> | |
| 2088 | ||
| 2089 | <test id="http-basic-auth-cleartext" key="/.cobalt/default.asp" status="vulnerable-exploited"> | |
| 2090 | ||
| 2091 | <Paragraph> | |
| 2092 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2093 | <Paragraph> | |
| 2094 | <ContainerBlockElement> | |
| 2095 | <Paragraph>HTTP request to | |
| 2096 | <URLLink LinkURL="http://192.168.1.18/.cobalt/default.asp" LinkTitle="http://192.168.1.18/.cobalt/default.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2097 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2098 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2099 | </test> | |
| 2100 | ||
| 2101 | <test id="http-basic-auth-cleartext" key="/.cobalt/index.asp" status="vulnerable-exploited"> | |
| 2102 | ||
| 2103 | <Paragraph> | |
| 2104 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2105 | <Paragraph> | |
| 2106 | <ContainerBlockElement> | |
| 2107 | <Paragraph>HTTP request to | |
| 2108 | <URLLink LinkURL="http://192.168.1.18/.cobalt/index.asp" LinkTitle="http://192.168.1.18/.cobalt/index.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2109 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2110 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2111 | </test> | |
| 2112 | ||
| 2113 | <test id="http-basic-auth-cleartext" key="/<script>xss</script>.asp" status="vulnerable-exploited"> | |
| 2114 | ||
| 2115 | <Paragraph> | |
| 2116 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2117 | <Paragraph> | |
| 2118 | <ContainerBlockElement> | |
| 2119 | <Paragraph>HTTP request to | |
| 2120 | <URLLink LinkURL="http://192.168.1.18/<script>xss</script>.asp" LinkTitle="http://192.168.1.18/<script>xss</script>.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2121 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2122 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2123 | </test> | |
| 2124 | ||
| 2125 | <test id="http-basic-auth-cleartext" key="/AdminScripts/Filters.asp" status="vulnerable-exploited"> | |
| 2126 | ||
| 2127 | <Paragraph> | |
| 2128 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2129 | <Paragraph> | |
| 2130 | <ContainerBlockElement> | |
| 2131 | <Paragraph>HTTP request to | |
| 2132 | <URLLink LinkURL="http://192.168.1.18/AdminScripts/Filters.asp" LinkTitle="http://192.168.1.18/AdminScripts/Filters.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2133 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2134 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2135 | </test> | |
| 2136 | ||
| 2137 | <test id="http-basic-auth-cleartext" key="/AdminScripts/Firewall.asp" status="vulnerable-exploited"> | |
| 2138 | ||
| 2139 | <Paragraph> | |
| 2140 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2141 | <Paragraph> | |
| 2142 | <ContainerBlockElement> | |
| 2143 | <Paragraph>HTTP request to | |
| 2144 | <URLLink LinkURL="http://192.168.1.18/AdminScripts/Firewall.asp" LinkTitle="http://192.168.1.18/AdminScripts/Firewall.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2145 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2146 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2147 | </test> | |
| 2148 | ||
| 2149 | <test id="http-basic-auth-cleartext" key="/AdminScripts/ForwardSpec.asp" status="vulnerable-exploited"> | |
| 2150 | ||
| 2151 | <Paragraph> | |
| 2152 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2153 | <Paragraph> | |
| 2154 | <ContainerBlockElement> | |
| 2155 | <Paragraph>HTTP request to | |
| 2156 | <URLLink LinkURL="http://192.168.1.18/AdminScripts/ForwardSpec.asp" LinkTitle="http://192.168.1.18/AdminScripts/ForwardSpec.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2157 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2158 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2159 | </test> | |
| 2160 | ||
| 2161 | <test id="http-basic-auth-cleartext" key="/AdminScripts/Management.asp" status="vulnerable-exploited"> | |
| 2162 | ||
| 2163 | <Paragraph> | |
| 2164 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2165 | <Paragraph> | |
| 2166 | <ContainerBlockElement> | |
| 2167 | <Paragraph>HTTP request to | |
| 2168 | <URLLink LinkURL="http://192.168.1.18/AdminScripts/Management.asp" LinkTitle="http://192.168.1.18/AdminScripts/Management.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2169 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2170 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2171 | </test> | |
| 2172 | ||
| 2173 | <test id="http-basic-auth-cleartext" key="/AdminScripts/Services.asp" status="vulnerable-exploited"> | |
| 2174 | ||
| 2175 | <Paragraph> | |
| 2176 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2177 | <Paragraph> | |
| 2178 | <ContainerBlockElement> | |
| 2179 | <Paragraph>HTTP request to | |
| 2180 | <URLLink LinkURL="http://192.168.1.18/AdminScripts/Services.asp" LinkTitle="http://192.168.1.18/AdminScripts/Services.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2181 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2182 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2183 | </test> | |
| 2184 | ||
| 2185 | <test id="http-basic-auth-cleartext" key="/AdminScripts/Status_Router.asp" status="vulnerable-exploited"> | |
| 2186 | ||
| 2187 | <Paragraph> | |
| 2188 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2189 | <Paragraph> | |
| 2190 | <ContainerBlockElement> | |
| 2191 | <Paragraph>HTTP request to | |
| 2192 | <URLLink LinkURL="http://192.168.1.18/AdminScripts/Status_Router.asp" LinkTitle="http://192.168.1.18/AdminScripts/Status_Router.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2193 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2194 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2195 | </test> | |
| 2196 | ||
| 2197 | <test id="http-basic-auth-cleartext" key="/AdminScripts/Wireless_Basic.asp" status="vulnerable-exploited"> | |
| 2198 | ||
| 2199 | <Paragraph> | |
| 2200 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2201 | <Paragraph> | |
| 2202 | <ContainerBlockElement> | |
| 2203 | <Paragraph>HTTP request to | |
| 2204 | <URLLink LinkURL="http://192.168.1.18/AdminScripts/Wireless_Basic.asp" LinkTitle="http://192.168.1.18/AdminScripts/Wireless_Basic.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2205 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2206 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2207 | </test> | |
| 2208 | ||
| 2209 | <test id="http-basic-auth-cleartext" key="/AdminScripts/default.asp" status="vulnerable-exploited"> | |
| 2210 | ||
| 2211 | <Paragraph> | |
| 2212 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2213 | <Paragraph> | |
| 2214 | <ContainerBlockElement> | |
| 2215 | <Paragraph>HTTP request to | |
| 2216 | <URLLink LinkURL="http://192.168.1.18/AdminScripts/default.asp" LinkTitle="http://192.168.1.18/AdminScripts/default.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2217 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2218 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2219 | </test> | |
| 2220 | ||
| 2221 | <test id="http-basic-auth-cleartext" key="/AdminScripts/index.asp" status="vulnerable-exploited"> | |
| 2222 | ||
| 2223 | <Paragraph> | |
| 2224 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2225 | <Paragraph> | |
| 2226 | <ContainerBlockElement> | |
| 2227 | <Paragraph>HTTP request to | |
| 2228 | <URLLink LinkURL="http://192.168.1.18/AdminScripts/index.asp" LinkTitle="http://192.168.1.18/AdminScripts/index.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2229 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2230 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2231 | </test> | |
| 2232 | ||
| 2233 | <test id="http-basic-auth-cleartext" key="/Filters.asp" status="vulnerable-exploited"> | |
| 2234 | ||
| 2235 | <Paragraph> | |
| 2236 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2237 | <Paragraph> | |
| 2238 | <ContainerBlockElement> | |
| 2239 | <Paragraph>HTTP request to | |
| 2240 | <URLLink LinkURL="http://192.168.1.18/Filters.asp" LinkTitle="http://192.168.1.18/Filters.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2241 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2242 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2243 | </test> | |
| 2244 | ||
| 2245 | <test id="http-basic-auth-cleartext" key="/Firewall.asp" status="vulnerable-exploited"> | |
| 2246 | ||
| 2247 | <Paragraph> | |
| 2248 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2249 | <Paragraph> | |
| 2250 | <ContainerBlockElement> | |
| 2251 | <Paragraph>HTTP request to | |
| 2252 | <URLLink LinkURL="http://192.168.1.18/Firewall.asp" LinkTitle="http://192.168.1.18/Firewall.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2253 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2254 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2255 | </test> | |
| 2256 | ||
| 2257 | <test id="http-basic-auth-cleartext" key="/ForwardSpec.asp" status="vulnerable-exploited"> | |
| 2258 | ||
| 2259 | <Paragraph> | |
| 2260 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2261 | <Paragraph> | |
| 2262 | <ContainerBlockElement> | |
| 2263 | <Paragraph>HTTP request to | |
| 2264 | <URLLink LinkURL="http://192.168.1.18/ForwardSpec.asp" LinkTitle="http://192.168.1.18/ForwardSpec.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2265 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2266 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2267 | </test> | |
| 2268 | ||
| 2269 | <test id="http-basic-auth-cleartext" key="/Management.asp" status="vulnerable-exploited"> | |
| 2270 | ||
| 2271 | <Paragraph> | |
| 2272 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2273 | <Paragraph> | |
| 2274 | <ContainerBlockElement> | |
| 2275 | <Paragraph>HTTP request to | |
| 2276 | <URLLink LinkURL="http://192.168.1.18/Management.asp" LinkTitle="http://192.168.1.18/Management.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2277 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2278 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2279 | </test> | |
| 2280 | ||
| 2281 | <test id="http-basic-auth-cleartext" key="/Services.asp" status="vulnerable-exploited"> | |
| 2282 | ||
| 2283 | <Paragraph> | |
| 2284 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2285 | <Paragraph> | |
| 2286 | <ContainerBlockElement> | |
| 2287 | <Paragraph>HTTP request to | |
| 2288 | <URLLink LinkURL="http://192.168.1.18/Services.asp" LinkTitle="http://192.168.1.18/Services.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2289 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2290 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2291 | </test> | |
| 2292 | ||
| 2293 | <test id="http-basic-auth-cleartext" key="/Status_Router.asp" status="vulnerable-exploited"> | |
| 2294 | ||
| 2295 | <Paragraph> | |
| 2296 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2297 | <Paragraph> | |
| 2298 | <ContainerBlockElement> | |
| 2299 | <Paragraph>HTTP request to | |
| 2300 | <URLLink LinkURL="http://192.168.1.18/Status_Router.asp" LinkTitle="http://192.168.1.18/Status_Router.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2301 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2302 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2303 | </test> | |
| 2304 | ||
| 2305 | <test id="http-basic-auth-cleartext" key="/Statusinfo.live.asp" status="vulnerable-exploited"> | |
| 2306 | ||
| 2307 | <Paragraph> | |
| 2308 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2309 | <Paragraph> | |
| 2310 | <ContainerBlockElement> | |
| 2311 | <Paragraph>HTTP request to | |
| 2312 | <URLLink LinkURL="http://192.168.1.18/Statusinfo.live.asp" LinkTitle="http://192.168.1.18/Statusinfo.live.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2313 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2314 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2315 | </test> | |
| 2316 | ||
| 2317 | <test id="http-basic-auth-cleartext" key="/Wireless_Basic.asp" status="vulnerable-exploited"> | |
| 2318 | ||
| 2319 | <Paragraph> | |
| 2320 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2321 | <Paragraph> | |
| 2322 | <ContainerBlockElement> | |
| 2323 | <Paragraph>HTTP request to | |
| 2324 | <URLLink LinkURL="http://192.168.1.18/Wireless_Basic.asp" LinkTitle="http://192.168.1.18/Wireless_Basic.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2325 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2326 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2327 | </test> | |
| 2328 | ||
| 2329 | <test id="http-basic-auth-cleartext" key="/default.asp" status="vulnerable-exploited"> | |
| 2330 | ||
| 2331 | <Paragraph> | |
| 2332 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2333 | <Paragraph> | |
| 2334 | <ContainerBlockElement> | |
| 2335 | <Paragraph>HTTP request to | |
| 2336 | <URLLink LinkURL="http://192.168.1.18/default.asp" LinkTitle="http://192.168.1.18/default.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2337 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2338 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2339 | </test> | |
| 2340 | ||
| 2341 | <test id="http-basic-auth-cleartext" key="/index.asp" status="vulnerable-exploited"> | |
| 2342 | ||
| 2343 | <Paragraph> | |
| 2344 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2345 | <Paragraph> | |
| 2346 | <ContainerBlockElement> | |
| 2347 | <Paragraph>HTTP request to | |
| 2348 | <URLLink LinkURL="http://192.168.1.18/index.asp" LinkTitle="http://192.168.1.18/index.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2349 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2350 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2351 | </test> | |
| 2352 | ||
| 2353 | <test id="http-basic-auth-cleartext" key="/apply.cgi" status="vulnerable-exploited"> | |
| 2354 | ||
| 2355 | <Paragraph> | |
| 2356 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2357 | <Paragraph> | |
| 2358 | <ContainerBlockElement> | |
| 2359 | <Paragraph>HTTP request to | |
| 2360 | <URLLink LinkURL="http://192.168.1.18/apply.cgi" LinkTitle="http://192.168.1.18/apply.cgi"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2361 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2362 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2363 | </test> | |
| 2364 | ||
| 2365 | <test id="http-basic-auth-cleartext" key="/cgi-bin/printenv" status="vulnerable-exploited"> | |
| 2366 | ||
| 2367 | <Paragraph> | |
| 2368 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2369 | <Paragraph> | |
| 2370 | <ContainerBlockElement> | |
| 2371 | <Paragraph>HTTP request to | |
| 2372 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/printenv" LinkTitle="http://192.168.1.18/cgi-bin/printenv"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2373 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2374 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2375 | </test> | |
| 2376 | ||
| 2377 | <test id="http-basic-auth-cleartext" key="/cgi-bin/test-cgi" status="vulnerable-exploited"> | |
| 2378 | ||
| 2379 | <Paragraph> | |
| 2380 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2381 | <Paragraph> | |
| 2382 | <ContainerBlockElement> | |
| 2383 | <Paragraph>HTTP request to | |
| 2384 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/test-cgi" LinkTitle="http://192.168.1.18/cgi-bin/test-cgi"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2385 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2386 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2387 | </test> | |
| 2388 | ||
| 2389 | <test id="http-basic-auth-cleartext" key="/cgi-bin/common.js" status="vulnerable-exploited"> | |
| 2390 | ||
| 2391 | <Paragraph> | |
| 2392 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2393 | <Paragraph> | |
| 2394 | <ContainerBlockElement> | |
| 2395 | <Paragraph>HTTP request to | |
| 2396 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/common.js" LinkTitle="http://192.168.1.18/cgi-bin/common.js"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2397 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2398 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2399 | </test> | |
| 2400 | ||
| 2401 | <test id="http-basic-auth-cleartext" key="/cgi-bin/lang_pack/english.js" status="vulnerable-exploited"> | |
| 2402 | ||
| 2403 | <Paragraph> | |
| 2404 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2405 | <Paragraph> | |
| 2406 | <ContainerBlockElement> | |
| 2407 | <Paragraph>HTTP request to | |
| 2408 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/lang_pack/english.js" LinkTitle="http://192.168.1.18/cgi-bin/lang_pack/english.js"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2409 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2410 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2411 | </test> | |
| 2412 | ||
| 2413 | <test id="http-basic-auth-cleartext" key="/cgi-bin/%3f.jsp" status="vulnerable-exploited"> | |
| 2414 | ||
| 2415 | <Paragraph> | |
| 2416 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2417 | <Paragraph> | |
| 2418 | <ContainerBlockElement> | |
| 2419 | <Paragraph>HTTP request to | |
| 2420 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/%3f.jsp" LinkTitle="http://192.168.1.18/cgi-bin/%3f.jsp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2421 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2422 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2423 | </test> | |
| 2424 | ||
| 2425 | <test id="http-basic-auth-cleartext" key="/cgi-bin/default.jsp" status="vulnerable-exploited"> | |
| 2426 | ||
| 2427 | <Paragraph> | |
| 2428 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2429 | <Paragraph> | |
| 2430 | <ContainerBlockElement> | |
| 2431 | <Paragraph>HTTP request to | |
| 2432 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/default.jsp" LinkTitle="http://192.168.1.18/cgi-bin/default.jsp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2433 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2434 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2435 | </test> | |
| 2436 | ||
| 2437 | <test id="http-basic-auth-cleartext" key="/cgi-bin/index.jsp" status="vulnerable-exploited"> | |
| 2438 | ||
| 2439 | <Paragraph> | |
| 2440 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2441 | <Paragraph> | |
| 2442 | <ContainerBlockElement> | |
| 2443 | <Paragraph>HTTP request to | |
| 2444 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.jsp" LinkTitle="http://192.168.1.18/cgi-bin/index.jsp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2445 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2446 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2447 | </test> | |
| 2448 | ||
| 2449 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Filters.asp" status="vulnerable-exploited"> | |
| 2450 | ||
| 2451 | <Paragraph> | |
| 2452 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2453 | <Paragraph> | |
| 2454 | <ContainerBlockElement> | |
| 2455 | <Paragraph>HTTP request to | |
| 2456 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Filters.asp" LinkTitle="http://192.168.1.18/cgi-bin/Filters.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2457 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2458 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2459 | </test> | |
| 2460 | ||
| 2461 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Firewall.asp" status="vulnerable-exploited"> | |
| 2462 | ||
| 2463 | <Paragraph> | |
| 2464 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2465 | <Paragraph> | |
| 2466 | <ContainerBlockElement> | |
| 2467 | <Paragraph>HTTP request to | |
| 2468 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Firewall.asp" LinkTitle="http://192.168.1.18/cgi-bin/Firewall.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2469 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2470 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2471 | </test> | |
| 2472 | ||
| 2473 | <test id="http-basic-auth-cleartext" key="/cgi-bin/ForwardSpec.asp" status="vulnerable-exploited"> | |
| 2474 | ||
| 2475 | <Paragraph> | |
| 2476 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2477 | <Paragraph> | |
| 2478 | <ContainerBlockElement> | |
| 2479 | <Paragraph>HTTP request to | |
| 2480 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/ForwardSpec.asp" LinkTitle="http://192.168.1.18/cgi-bin/ForwardSpec.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2481 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2482 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2483 | </test> | |
| 2484 | ||
| 2485 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Services.asp" status="vulnerable-exploited"> | |
| 2486 | ||
| 2487 | <Paragraph> | |
| 2488 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2489 | <Paragraph> | |
| 2490 | <ContainerBlockElement> | |
| 2491 | <Paragraph>HTTP request to | |
| 2492 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Services.asp" LinkTitle="http://192.168.1.18/cgi-bin/Services.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2493 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2494 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2495 | </test> | |
| 2496 | ||
| 2497 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Wireless_Basic.asp" status="vulnerable-exploited"> | |
| 2498 | ||
| 2499 | <Paragraph> | |
| 2500 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2501 | <Paragraph> | |
| 2502 | <ContainerBlockElement> | |
| 2503 | <Paragraph>HTTP request to | |
| 2504 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Wireless_Basic.asp" LinkTitle="http://192.168.1.18/cgi-bin/Wireless_Basic.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2505 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2506 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2507 | </test> | |
| 2508 | ||
| 2509 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Status_Router.asp" status="vulnerable-exploited"> | |
| 2510 | ||
| 2511 | <Paragraph> | |
| 2512 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2513 | <Paragraph> | |
| 2514 | <ContainerBlockElement> | |
| 2515 | <Paragraph>HTTP request to | |
| 2516 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Status_Router.asp" LinkTitle="http://192.168.1.18/cgi-bin/Status_Router.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2517 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2518 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2519 | </test> | |
| 2520 | ||
| 2521 | <test id="http-basic-auth-cleartext" key="/cgi-bin/default.asp" status="vulnerable-exploited"> | |
| 2522 | ||
| 2523 | <Paragraph> | |
| 2524 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2525 | <Paragraph> | |
| 2526 | <ContainerBlockElement> | |
| 2527 | <Paragraph>HTTP request to | |
| 2528 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/default.asp" LinkTitle="http://192.168.1.18/cgi-bin/default.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2529 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2530 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2531 | </test> | |
| 2532 | ||
| 2533 | <test id="http-basic-auth-cleartext" key="/cgi-bin/index.asp" status="vulnerable-exploited"> | |
| 2534 | ||
| 2535 | <Paragraph> | |
| 2536 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2537 | <Paragraph> | |
| 2538 | <ContainerBlockElement> | |
| 2539 | <Paragraph>HTTP request to | |
| 2540 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.asp" LinkTitle="http://192.168.1.18/cgi-bin/index.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2541 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2542 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2543 | </test> | |
| 2544 | ||
| 2545 | <test id="http-basic-auth-cleartext" key="/cgi-bin/default.aspx" status="vulnerable-exploited"> | |
| 2546 | ||
| 2547 | <Paragraph> | |
| 2548 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2549 | <Paragraph> | |
| 2550 | <ContainerBlockElement> | |
| 2551 | <Paragraph>HTTP request to | |
| 2552 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/default.aspx" LinkTitle="http://192.168.1.18/cgi-bin/default.aspx"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2553 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2554 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2555 | </test> | |
| 2556 | ||
| 2557 | <test id="http-basic-auth-cleartext" key="/cgi-bin/index.aspx" status="vulnerable-exploited"> | |
| 2558 | ||
| 2559 | <Paragraph> | |
| 2560 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2561 | <Paragraph> | |
| 2562 | <ContainerBlockElement> | |
| 2563 | <Paragraph>HTTP request to | |
| 2564 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.aspx" LinkTitle="http://192.168.1.18/cgi-bin/index.aspx"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2565 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2566 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2567 | </test> | |
| 2568 | ||
| 2569 | <test id="http-basic-auth-cleartext" key="/cgi-bin/index.cfm" status="vulnerable-exploited"> | |
| 2570 | ||
| 2571 | <Paragraph> | |
| 2572 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2573 | <Paragraph> | |
| 2574 | <ContainerBlockElement> | |
| 2575 | <Paragraph>HTTP request to | |
| 2576 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.cfm" LinkTitle="http://192.168.1.18/cgi-bin/index.cfm"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2577 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2578 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2579 | </test> | |
| 2580 | ||
| 2581 | <test id="http-basic-auth-cleartext" key="/cgi-bin/apply.cgi" status="vulnerable-exploited"> | |
| 2582 | ||
| 2583 | <Paragraph> | |
| 2584 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2585 | <Paragraph> | |
| 2586 | <ContainerBlockElement> | |
| 2587 | <Paragraph>HTTP request to | |
| 2588 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/apply.cgi" LinkTitle="http://192.168.1.18/cgi-bin/apply.cgi"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2589 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2590 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2591 | </test> | |
| 2592 | ||
| 2593 | <test id="http-basic-auth-cleartext" key="/cgi-bin/index.cgi" status="vulnerable-exploited"> | |
| 2594 | ||
| 2595 | <Paragraph> | |
| 2596 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2597 | <Paragraph> | |
| 2598 | <ContainerBlockElement> | |
| 2599 | <Paragraph>HTTP request to | |
| 2600 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.cgi" LinkTitle="http://192.168.1.18/cgi-bin/index.cgi"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2601 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2602 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2603 | </test> | |
| 2604 | ||
| 2605 | <test id="http-basic-auth-cleartext" key="/cgi-bin/default.php" status="vulnerable-exploited"> | |
| 2606 | ||
| 2607 | <Paragraph> | |
| 2608 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2609 | <Paragraph> | |
| 2610 | <ContainerBlockElement> | |
| 2611 | <Paragraph>HTTP request to | |
| 2612 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/default.php" LinkTitle="http://192.168.1.18/cgi-bin/default.php"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2613 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2614 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2615 | </test> | |
| 2616 | ||
| 2617 | <test id="http-basic-auth-cleartext" key="/cgi-bin/index.php" status="vulnerable-exploited"> | |
| 2618 | ||
| 2619 | <Paragraph> | |
| 2620 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2621 | <Paragraph> | |
| 2622 | <ContainerBlockElement> | |
| 2623 | <Paragraph>HTTP request to | |
| 2624 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.php" LinkTitle="http://192.168.1.18/cgi-bin/index.php"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2625 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2626 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2627 | </test> | |
| 2628 | ||
| 2629 | <test id="http-basic-auth-cleartext" key="/cgi-bin/wp-login.php" status="vulnerable-exploited"> | |
| 2630 | ||
| 2631 | <Paragraph> | |
| 2632 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2633 | <Paragraph> | |
| 2634 | <ContainerBlockElement> | |
| 2635 | <Paragraph>HTTP request to | |
| 2636 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/wp-login.php" LinkTitle="http://192.168.1.18/cgi-bin/wp-login.php"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2637 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2638 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2639 | </test> | |
| 2640 | ||
| 2641 | <test id="http-basic-auth-cleartext" key="/cgi-bin/index.php3" status="vulnerable-exploited"> | |
| 2642 | ||
| 2643 | <Paragraph> | |
| 2644 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2645 | <Paragraph> | |
| 2646 | <ContainerBlockElement> | |
| 2647 | <Paragraph>HTTP request to | |
| 2648 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.php3" LinkTitle="http://192.168.1.18/cgi-bin/index.php3"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2649 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2650 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2651 | </test> | |
| 2652 | ||
| 2653 | <test id="http-basic-auth-cleartext" key="/cgi-bin/default.shtml" status="vulnerable-exploited"> | |
| 2654 | ||
| 2655 | <Paragraph> | |
| 2656 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2657 | <Paragraph> | |
| 2658 | <ContainerBlockElement> | |
| 2659 | <Paragraph>HTTP request to | |
| 2660 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/default.shtml" LinkTitle="http://192.168.1.18/cgi-bin/default.shtml"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2661 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2662 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2663 | </test> | |
| 2664 | ||
| 2665 | <test id="http-basic-auth-cleartext" key="/cgi-bin/index.shtml" status="vulnerable-exploited"> | |
| 2666 | ||
| 2667 | <Paragraph> | |
| 2668 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2669 | <Paragraph> | |
| 2670 | <ContainerBlockElement> | |
| 2671 | <Paragraph>HTTP request to | |
| 2672 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.shtml" LinkTitle="http://192.168.1.18/cgi-bin/index.shtml"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2673 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2674 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2675 | </test> | |
| 2676 | ||
| 2677 | <test id="http-basic-auth-cleartext" key="/cgi-bin/" status="vulnerable-exploited"> | |
| 2678 | ||
| 2679 | <Paragraph> | |
| 2680 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2681 | <Paragraph> | |
| 2682 | <ContainerBlockElement> | |
| 2683 | <Paragraph>HTTP request to | |
| 2684 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/?P=+ADw-script+AD4-alert(42)+ADw-/script+AD4-" LinkTitle="http://192.168.1.18/cgi-bin/?P=+ADw-script+AD4-alert(42)+ADw-/script+AD4-"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2685 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2686 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2687 | </test> | |
| 2688 | ||
| 2689 | <test id="http-basic-auth-cleartext" key="/cgi-bin/ADw-script AD4-alert(42) ADw-/script AD4-" status="vulnerable-exploited"> | |
| 2690 | ||
| 2691 | <Paragraph> | |
| 2692 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2693 | <Paragraph> | |
| 2694 | <ContainerBlockElement> | |
| 2695 | <Paragraph>HTTP request to | |
| 2696 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/ADw-script AD4-alert(42) ADw-/script AD4-" LinkTitle="http://192.168.1.18/cgi-bin/ADw-script AD4-alert(42) ADw-/script AD4-"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2697 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2698 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2699 | </test> | |
| 2700 | ||
| 2701 | <test id="http-basic-auth-cleartext" key="/cgi-bin/CVS/Root" status="vulnerable-exploited"> | |
| 2702 | ||
| 2703 | <Paragraph> | |
| 2704 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2705 | <Paragraph> | |
| 2706 | <ContainerBlockElement> | |
| 2707 | <Paragraph>HTTP request to | |
| 2708 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/CVS/Root" LinkTitle="http://192.168.1.18/cgi-bin/CVS/Root"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2709 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2710 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2711 | </test> | |
| 2712 | ||
| 2713 | <test id="http-basic-auth-cleartext" key="/cgi-bin/DEADJOE" status="vulnerable-exploited"> | |
| 2714 | ||
| 2715 | <Paragraph> | |
| 2716 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2717 | <Paragraph> | |
| 2718 | <ContainerBlockElement> | |
| 2719 | <Paragraph>HTTP request to | |
| 2720 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/DEADJOE" LinkTitle="http://192.168.1.18/cgi-bin/DEADJOE"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2721 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2722 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2723 | </test> | |
| 2724 | ||
| 2725 | <test id="http-basic-auth-cleartext" key="/cgi-bin/CVS/Entries" status="vulnerable-exploited"> | |
| 2726 | ||
| 2727 | <Paragraph> | |
| 2728 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2729 | <Paragraph> | |
| 2730 | <ContainerBlockElement> | |
| 2731 | <Paragraph>HTTP request to | |
| 2732 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/CVS/Entries" LinkTitle="http://192.168.1.18/cgi-bin/CVS/Entries"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2733 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2734 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2735 | </test> | |
| 2736 | ||
| 2737 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Filters.asp/<script>xss</script>" status="vulnerable-exploited"> | |
| 2738 | ||
| 2739 | <Paragraph> | |
| 2740 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2741 | <Paragraph> | |
| 2742 | <ContainerBlockElement> | |
| 2743 | <Paragraph>HTTP request to | |
| 2744 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Filters.asp/<script>xss</script>" LinkTitle="http://192.168.1.18/cgi-bin/Filters.asp/<script>xss</script>"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2745 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2746 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2747 | </test> | |
| 2748 | ||
| 2749 | <test id="http-basic-auth-cleartext" key="/cgi-bin/.svn/entries" status="vulnerable-exploited"> | |
| 2750 | ||
| 2751 | <Paragraph> | |
| 2752 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2753 | <Paragraph> | |
| 2754 | <ContainerBlockElement> | |
| 2755 | <Paragraph>HTTP request to | |
| 2756 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/.svn/entries" LinkTitle="http://192.168.1.18/cgi-bin/.svn/entries"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2757 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2758 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2759 | </test> | |
| 2760 | ||
| 2761 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Firewall.asp/<script>xss</script>" status="vulnerable-exploited"> | |
| 2762 | ||
| 2763 | <Paragraph> | |
| 2764 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2765 | <Paragraph> | |
| 2766 | <ContainerBlockElement> | |
| 2767 | <Paragraph>HTTP request to | |
| 2768 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Firewall.asp/<script>xss</script>" LinkTitle="http://192.168.1.18/cgi-bin/Firewall.asp/<script>xss</script>"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2769 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2770 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2771 | </test> | |
| 2772 | ||
| 2773 | <test id="http-basic-auth-cleartext" key="/cgi-bin/ForwardSpec.asp/<script>xss</script>" status="vulnerable-exploited"> | |
| 2774 | ||
| 2775 | <Paragraph> | |
| 2776 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2777 | <Paragraph> | |
| 2778 | <ContainerBlockElement> | |
| 2779 | <Paragraph>HTTP request to | |
| 2780 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/ForwardSpec.asp/<script>xss</script>" LinkTitle="http://192.168.1.18/cgi-bin/ForwardSpec.asp/<script>xss</script>"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2781 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2782 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2783 | </test> | |
| 2784 | ||
| 2785 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Info.htm" status="vulnerable-exploited"> | |
| 2786 | ||
| 2787 | <Paragraph> | |
| 2788 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2789 | <Paragraph> | |
| 2790 | <ContainerBlockElement> | |
| 2791 | <Paragraph>HTTP request to | |
| 2792 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Info.htm" LinkTitle="http://192.168.1.18/cgi-bin/Info.htm"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2793 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2794 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2795 | </test> | |
| 2796 | ||
| 2797 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Info.live.htm" status="vulnerable-exploited"> | |
| 2798 | ||
| 2799 | <Paragraph> | |
| 2800 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2801 | <Paragraph> | |
| 2802 | <ContainerBlockElement> | |
| 2803 | <Paragraph>HTTP request to | |
| 2804 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Info.live.htm" LinkTitle="http://192.168.1.18/cgi-bin/Info.live.htm"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2805 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2806 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2807 | </test> | |
| 2808 | ||
| 2809 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Info.live.htm/<script>xss</script>" status="vulnerable-exploited"> | |
| 2810 | ||
| 2811 | <Paragraph> | |
| 2812 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2813 | <Paragraph> | |
| 2814 | <ContainerBlockElement> | |
| 2815 | <Paragraph>HTTP request to | |
| 2816 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Info.live.htm/<script>xss</script>" LinkTitle="http://192.168.1.18/cgi-bin/Info.live.htm/<script>xss</script>"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2817 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2818 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2819 | </test> | |
| 2820 | ||
| 2821 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Management.asp/<script>xss</script>" status="vulnerable-exploited"> | |
| 2822 | ||
| 2823 | <Paragraph> | |
| 2824 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2825 | <Paragraph> | |
| 2826 | <ContainerBlockElement> | |
| 2827 | <Paragraph>HTTP request to | |
| 2828 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Management.asp/<script>xss</script>" LinkTitle="http://192.168.1.18/cgi-bin/Management.asp/<script>xss</script>"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2829 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2830 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2831 | </test> | |
| 2832 | ||
| 2833 | <test id="http-basic-auth-cleartext" key="/cgi-bin/README" status="vulnerable-exploited"> | |
| 2834 | ||
| 2835 | <Paragraph> | |
| 2836 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2837 | <Paragraph> | |
| 2838 | <ContainerBlockElement> | |
| 2839 | <Paragraph>HTTP request to | |
| 2840 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/README" LinkTitle="http://192.168.1.18/cgi-bin/README"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2841 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2842 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2843 | </test> | |
| 2844 | ||
| 2845 | <test id="http-basic-auth-cleartext" key="/cgi-bin/README.TXT" status="vulnerable-exploited"> | |
| 2846 | ||
| 2847 | <Paragraph> | |
| 2848 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2849 | <Paragraph> | |
| 2850 | <ContainerBlockElement> | |
| 2851 | <Paragraph>HTTP request to | |
| 2852 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/README.TXT" LinkTitle="http://192.168.1.18/cgi-bin/README.TXT"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2853 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2854 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2855 | </test> | |
| 2856 | ||
| 2857 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Status_Router.asp/<script>xss</script>" status="vulnerable-exploited"> | |
| 2858 | ||
| 2859 | <Paragraph> | |
| 2860 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2861 | <Paragraph> | |
| 2862 | <ContainerBlockElement> | |
| 2863 | <Paragraph>HTTP request to | |
| 2864 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Status_Router.asp/<script>xss</script>" LinkTitle="http://192.168.1.18/cgi-bin/Status_Router.asp/<script>xss</script>"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2865 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2866 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2867 | </test> | |
| 2868 | ||
| 2869 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Trace.axd" status="vulnerable-exploited"> | |
| 2870 | ||
| 2871 | <Paragraph> | |
| 2872 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2873 | <Paragraph> | |
| 2874 | <ContainerBlockElement> | |
| 2875 | <Paragraph>HTTP request to | |
| 2876 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Trace.axd" LinkTitle="http://192.168.1.18/cgi-bin/Trace.axd"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2877 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2878 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2879 | </test> | |
| 2880 | ||
| 2881 | <test id="http-basic-auth-cleartext" key="/cgi-bin/WS_FTP.LOG" status="vulnerable-exploited"> | |
| 2882 | ||
| 2883 | <Paragraph> | |
| 2884 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2885 | <Paragraph> | |
| 2886 | <ContainerBlockElement> | |
| 2887 | <Paragraph>HTTP request to | |
| 2888 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/WS_FTP.LOG" LinkTitle="http://192.168.1.18/cgi-bin/WS_FTP.LOG"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2889 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2890 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2891 | </test> | |
| 2892 | ||
| 2893 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Web.sitemap" status="vulnerable-exploited"> | |
| 2894 | ||
| 2895 | <Paragraph> | |
| 2896 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2897 | <Paragraph> | |
| 2898 | <ContainerBlockElement> | |
| 2899 | <Paragraph>HTTP request to | |
| 2900 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Web.sitemap" LinkTitle="http://192.168.1.18/cgi-bin/Web.sitemap"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2901 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2902 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2903 | </test> | |
| 2904 | ||
| 2905 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Wireless_Basic.asp/<script>xss</script>" status="vulnerable-exploited"> | |
| 2906 | ||
| 2907 | <Paragraph> | |
| 2908 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2909 | <Paragraph> | |
| 2910 | <ContainerBlockElement> | |
| 2911 | <Paragraph>HTTP request to | |
| 2912 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Wireless_Basic.asp/<script>xss</script>" LinkTitle="http://192.168.1.18/cgi-bin/Wireless_Basic.asp/<script>xss</script>"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2913 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2914 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2915 | </test> | |
| 2916 | ||
| 2917 | <test id="http-basic-auth-cleartext" key="/cgi-bin/adojavas.inc" status="vulnerable-exploited"> | |
| 2918 | ||
| 2919 | <Paragraph> | |
| 2920 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2921 | <Paragraph> | |
| 2922 | <ContainerBlockElement> | |
| 2923 | <Paragraph>HTTP request to | |
| 2924 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/adojavas.inc" LinkTitle="http://192.168.1.18/cgi-bin/adojavas.inc"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2925 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2926 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2927 | </test> | |
| 2928 | ||
| 2929 | <test id="http-basic-auth-cleartext" key="/cgi-bin/adovbs.inc" status="vulnerable-exploited"> | |
| 2930 | ||
| 2931 | <Paragraph> | |
| 2932 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2933 | <Paragraph> | |
| 2934 | <ContainerBlockElement> | |
| 2935 | <Paragraph>HTTP request to | |
| 2936 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/adovbs.inc" LinkTitle="http://192.168.1.18/cgi-bin/adovbs.inc"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2937 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2938 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2939 | </test> | |
| 2940 | ||
| 2941 | <test id="http-basic-auth-cleartext" key="/cgi-bin/default.htm" status="vulnerable-exploited"> | |
| 2942 | ||
| 2943 | <Paragraph> | |
| 2944 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2945 | <Paragraph> | |
| 2946 | <ContainerBlockElement> | |
| 2947 | <Paragraph>HTTP request to | |
| 2948 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/default.htm" LinkTitle="http://192.168.1.18/cgi-bin/default.htm"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2949 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2950 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2951 | </test> | |
| 2952 | ||
| 2953 | <test id="http-basic-auth-cleartext" key="/cgi-bin/default.html" status="vulnerable-exploited"> | |
| 2954 | ||
| 2955 | <Paragraph> | |
| 2956 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2957 | <Paragraph> | |
| 2958 | <ContainerBlockElement> | |
| 2959 | <Paragraph>HTTP request to | |
| 2960 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/default.html" LinkTitle="http://192.168.1.18/cgi-bin/default.html"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2961 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2962 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2963 | </test> | |
| 2964 | ||
| 2965 | <test id="http-basic-auth-cleartext" key="/cgi-bin/default.wml" status="vulnerable-exploited"> | |
| 2966 | ||
| 2967 | <Paragraph> | |
| 2968 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2969 | <Paragraph> | |
| 2970 | <ContainerBlockElement> | |
| 2971 | <Paragraph>HTTP request to | |
| 2972 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/default.wml" LinkTitle="http://192.168.1.18/cgi-bin/default.wml"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2973 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2974 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2975 | </test> | |
| 2976 | ||
| 2977 | <test id="http-basic-auth-cleartext" key="/cgi-bin/images/common.js" status="vulnerable-exploited"> | |
| 2978 | ||
| 2979 | <Paragraph> | |
| 2980 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2981 | <Paragraph> | |
| 2982 | <ContainerBlockElement> | |
| 2983 | <Paragraph>HTTP request to | |
| 2984 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/images/common.js" LinkTitle="http://192.168.1.18/cgi-bin/images/common.js"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2985 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2986 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2987 | </test> | |
| 2988 | ||
| 2989 | <test id="http-basic-auth-cleartext" key="/cgi-bin/images/lang_pack/english.js" status="vulnerable-exploited"> | |
| 2990 | ||
| 2991 | <Paragraph> | |
| 2992 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 2993 | <Paragraph> | |
| 2994 | <ContainerBlockElement> | |
| 2995 | <Paragraph>HTTP request to | |
| 2996 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/images/lang_pack/english.js" LinkTitle="http://192.168.1.18/cgi-bin/images/lang_pack/english.js"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 2997 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 2998 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 2999 | </test> | |
| 3000 | ||
| 3001 | <test id="http-basic-auth-cleartext" key="/cgi-bin/images/Filters.asp" status="vulnerable-exploited"> | |
| 3002 | ||
| 3003 | <Paragraph> | |
| 3004 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3005 | <Paragraph> | |
| 3006 | <ContainerBlockElement> | |
| 3007 | <Paragraph>HTTP request to | |
| 3008 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/images/Filters.asp" LinkTitle="http://192.168.1.18/cgi-bin/images/Filters.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 3009 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 3010 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 3011 | </test> | |
| 3012 | ||
| 3013 | <test id="http-basic-auth-cleartext" key="/cgi-bin/images/Firewall.asp" status="vulnerable-exploited"> | |
| 3014 | ||
| 3015 | <Paragraph> | |
| 3016 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3017 | <Paragraph> | |
| 3018 | <ContainerBlockElement> | |
| 3019 | <Paragraph>HTTP request to | |
| 3020 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/images/Firewall.asp" LinkTitle="http://192.168.1.18/cgi-bin/images/Firewall.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 3021 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 3022 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 3023 | </test> | |
| 3024 | ||
| 3025 | <test id="http-basic-auth-cleartext" key="/cgi-bin/images/ForwardSpec.asp" status="vulnerable-exploited"> | |
| 3026 | ||
| 3027 | <Paragraph> | |
| 3028 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3029 | <Paragraph> | |
| 3030 | <ContainerBlockElement> | |
| 3031 | <Paragraph>HTTP request to | |
| 3032 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/images/ForwardSpec.asp" LinkTitle="http://192.168.1.18/cgi-bin/images/ForwardSpec.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 3033 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 3034 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 3035 | </test> | |
| 3036 | ||
| 3037 | <test id="http-basic-auth-cleartext" key="/cgi-bin/images/Management.asp" status="vulnerable-exploited"> | |
| 3038 | ||
| 3039 | <Paragraph> | |
| 3040 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3041 | <Paragraph> | |
| 3042 | <ContainerBlockElement> | |
| 3043 | <Paragraph>HTTP request to | |
| 3044 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/images/Management.asp" LinkTitle="http://192.168.1.18/cgi-bin/images/Management.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 3045 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 3046 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 3047 | </test> | |
| 3048 | ||
| 3049 | <test id="http-basic-auth-cleartext" key="/cgi-bin/images/Services.asp" status="vulnerable-exploited"> | |
| 3050 | ||
| 3051 | <Paragraph> | |
| 3052 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3053 | <Paragraph> | |
| 3054 | <ContainerBlockElement> | |
| 3055 | <Paragraph>HTTP request to | |
| 3056 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/images/Services.asp" LinkTitle="http://192.168.1.18/cgi-bin/images/Services.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 3057 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 3058 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 3059 | </test> | |
| 3060 | ||
| 3061 | <test id="http-basic-auth-cleartext" key="/cgi-bin/Services.asp/<script>xss</script>" status="vulnerable-exploited"> | |
| 3062 | ||
| 3063 | <Paragraph> | |
| 3064 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3065 | <Paragraph> | |
| 3066 | <ContainerBlockElement> | |
| 3067 | <Paragraph>HTTP request to | |
| 3068 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/Services.asp/<script>xss</script>" LinkTitle="http://192.168.1.18/cgi-bin/Services.asp/<script>xss</script>"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 3069 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 3070 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 3071 | </test> | |
| 3072 | ||
| 3073 | <test id="http-basic-auth-cleartext" key="/cgi-bin/images/Status_Router.asp" status="vulnerable-exploited"> | |
| 3074 | ||
| 3075 | <Paragraph> | |
| 3076 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3077 | <Paragraph> | |
| 3078 | <ContainerBlockElement> | |
| 3079 | <Paragraph>HTTP request to | |
| 3080 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/images/Status_Router.asp" LinkTitle="http://192.168.1.18/cgi-bin/images/Status_Router.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 3081 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 3082 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 3083 | </test> | |
| 3084 | ||
| 3085 | <test id="http-basic-auth-cleartext" key="/cgi-bin/images/Wireless_Basic.asp" status="vulnerable-exploited"> | |
| 3086 | ||
| 3087 | <Paragraph> | |
| 3088 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3089 | <Paragraph> | |
| 3090 | <ContainerBlockElement> | |
| 3091 | <Paragraph>HTTP request to | |
| 3092 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/images/Wireless_Basic.asp" LinkTitle="http://192.168.1.18/cgi-bin/images/Wireless_Basic.asp"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 3093 | <Paragraph preformat="true">1: Basic realm="DD-WRT"</Paragraph> | |
| 3094 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 3095 | </test> | |
| 3096 | ||
| 3097 | <test id="http-iis-0014" status="not-vulnerable"> | |
| 3098 | ||
| 3099 | <Paragraph> | |
| 3100 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3101 | <Paragraph>Based on the following 3 results: | |
| 3102 | <OrderedList> | |
| 3103 | <ListItem> | |
| 3104 | <Paragraph> | |
| 3105 | <ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem> | |
| 3106 | <ListItem> | |
| 3107 | <Paragraph> | |
| 3108 | <ContainerBlockElement> | |
| 3109 | <ContainerBlockElement> | |
| 3110 | <Paragraph>HTTP GET request to | |
| 3111 | <URLLink LinkURL="http://192.168.1.18/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|" LinkTitle="http://192.168.1.18/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|"></URLLink></Paragraph>HTTP response code was 401 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem> | |
| 3112 | <ListItem> | |
| 3113 | <Paragraph> | |
| 3114 | <ContainerBlockElement> | |
| 3115 | <ContainerBlockElement> | |
| 3116 | <Paragraph>HTTP GET request to | |
| 3117 | <URLLink LinkURL="http://192.168.1.18/ASPSamp/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|" LinkTitle="http://192.168.1.18/ASPSamp/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|"></URLLink></Paragraph>HTTP response code was 401 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem></OrderedList></Paragraph></Paragraph> | |
| 3118 | </test> | |
| 3119 | ||
| 3120 | <test id="http-cgi-viewsource-arbitrary-file-access" key="/cgi-bin/view-source?../../../../../../../etc/passwd" status="not-vulnerable"> | |
| 3121 | ||
| 3122 | <Paragraph> | |
| 3123 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3124 | <Paragraph> | |
| 3125 | <ContainerBlockElement> | |
| 3126 | <ContainerBlockElement> | |
| 3127 | <Paragraph>HTTP GET request to | |
| 3128 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/view-source?../../../../../../../etc/passwd" LinkTitle="http://192.168.1.18/cgi-bin/view-source?../../../../../../../etc/passwd"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3129 | </test> | |
| 3130 | ||
| 3131 | <test id="http-trace-method-enabled" key="/" status="not-vulnerable"> | |
| 3132 | ||
| 3133 | <Paragraph> | |
| 3134 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3135 | <Paragraph> | |
| 3136 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3137 | </test> | |
| 3138 | ||
| 3139 | <test id="http-track-method-enabled" key="/" status="not-vulnerable"> | |
| 3140 | ||
| 3141 | <Paragraph> | |
| 3142 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3143 | <Paragraph> | |
| 3144 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3145 | </test> | |
| 3146 | ||
| 3147 | <test id="spider-adobe-flash-permissive-crossdomain-xml" key="/crossdomain.xml" status="not-vulnerable"> | |
| 3148 | ||
| 3149 | <Paragraph> | |
| 3150 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3151 | <Paragraph> | |
| 3152 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3153 | </test> | |
| 3154 | ||
| 3155 | <test id="adobe-apsb13-03-cve-2013-0631" key="/CFIDE/adminapi/customtags/fusebox.cfm" status="not-vulnerable"> | |
| 3156 | ||
| 3157 | <Paragraph> | |
| 3158 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3159 | <Paragraph> | |
| 3160 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3161 | </test> | |
| 3162 | ||
| 3163 | <test id="adobe-apsb13-13-cve-2013-3336" key="/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=U" status="not-vulnerable"> | |
| 3164 | ||
| 3165 | <Paragraph> | |
| 3166 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3167 | <Paragraph> | |
| 3168 | <ContainerBlockElement> | |
| 3169 | <ContainerBlockElement> | |
| 3170 | <Paragraph>HTTP GET request to | |
| 3171 | <URLLink LinkURL="http://192.168.1.18/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test" LinkTitle="http://192.168.1.18/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test"></URLLink></Paragraph>HTTP response code was 400 but expected 200HTTP response code was 400 but expected 200HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 3172 | <ContainerBlockElement> | |
| 3173 | <Paragraph>HTTP GET request to | |
| 3174 | <URLLink LinkURL="http://192.168.1.18/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test" LinkTitle="http://192.168.1.18/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test"></URLLink></Paragraph>HTTP response code was 400 but expected 200HTTP response code was 400 but expected 200HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3175 | </test> | |
| 3176 | ||
| 3177 | <test id="http-asp-dot-net-debug-enabled" key="/cgi-bin/default.aspx" status="error"> | |
| 3178 | ||
| 3179 | <Paragraph> | |
| 3180 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3181 | <Paragraph> | |
| 3182 | <ContainerBlockElement> | |
| 3183 | <Paragraph>HTTP request to | |
| 3184 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/default.aspx" LinkTitle="http://192.168.1.18/cgi-bin/default.aspx"></URLLink></Paragraph></ContainerBlockElement></Paragraph> | |
| 3185 | <Paragraph>java.io.EOFException: Peer closed connection before first line could be read</Paragraph></Paragraph> | |
| 3186 | </test> | |
| 3187 | ||
| 3188 | <test id="http-asp-dot-net-debug-enabled" key="/cgi-bin/index.aspx" status="error"> | |
| 3189 | ||
| 3190 | <Paragraph> | |
| 3191 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3192 | <Paragraph> | |
| 3193 | <ContainerBlockElement> | |
| 3194 | <Paragraph>HTTP request to | |
| 3195 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/index.aspx" LinkTitle="http://192.168.1.18/cgi-bin/index.aspx"></URLLink></Paragraph></ContainerBlockElement></Paragraph> | |
| 3196 | <Paragraph>java.io.EOFException: Peer closed connection before first line could be read</Paragraph></Paragraph> | |
| 3197 | </test> | |
| 3198 | ||
| 3199 | <test id="http-awstats-debug-information-disclosure" key="/cgi-bin/awstats/awstats.pl?debug=1" status="not-vulnerable"> | |
| 3200 | ||
| 3201 | <Paragraph> | |
| 3202 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3203 | <Paragraph> | |
| 3204 | <ContainerBlockElement> | |
| 3205 | <ContainerBlockElement> | |
| 3206 | <Paragraph>HTTP GET request to | |
| 3207 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/awstats.pl?debug=1" LinkTitle="http://192.168.1.18/cgi-bin/awstats.pl?debug=1"></URLLink></Paragraph>HTTP response code was 401 but expected 200</ContainerBlockElement> | |
| 3208 | <ContainerBlockElement> | |
| 3209 | <Paragraph>HTTP GET request to | |
| 3210 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/awstats/awstats.pl?debug=1" LinkTitle="http://192.168.1.18/cgi-bin/awstats/awstats.pl?debug=1"></URLLink></Paragraph>HTTP response code was 401 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3211 | </test> | |
| 3212 | ||
| 3213 | <test id="http-bigbrother-accessible" key="/bb/" status="not-vulnerable"> | |
| 3214 | ||
| 3215 | <Paragraph> | |
| 3216 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3217 | <Paragraph> | |
| 3218 | <ContainerBlockElement> | |
| 3219 | <ContainerBlockElement> | |
| 3220 | <Paragraph>HTTP GET request to | |
| 3221 | <URLLink LinkURL="http://192.168.1.18/bb/" LinkTitle="http://192.168.1.18/bb/"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3222 | </test> | |
| 3223 | ||
| 3224 | <test id="http-cgi-htdig-arbitrary-file-access" key="/cgi-bin/htsearch?Exclude=%60/etc/passwd%60" status="not-vulnerable"> | |
| 3225 | ||
| 3226 | <Paragraph> | |
| 3227 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3228 | <Paragraph> | |
| 3229 | <ContainerBlockElement> | |
| 3230 | <ContainerBlockElement> | |
| 3231 | <Paragraph>HTTP GET request to | |
| 3232 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/htsearch?Exclude=%60/etc/passwd%60" LinkTitle="http://192.168.1.18/cgi-bin/htsearch?Exclude=%60/etc/passwd%60"></URLLink></Paragraph>HTTP response code was 401 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3233 | </test> | |
| 3234 | ||
| 3235 | <test id="http-cgi-htgrep-arbitrary-file-access" key="/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd" status="not-vulnerable"> | |
| 3236 | ||
| 3237 | <Paragraph> | |
| 3238 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3239 | <Paragraph> | |
| 3240 | <ContainerBlockElement> | |
| 3241 | <ContainerBlockElement> | |
| 3242 | <Paragraph>HTTP GET request to | |
| 3243 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd" LinkTitle="http://192.168.1.18/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd"></URLLink></Paragraph>HTTP response code was 401 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3244 | </test> | |
| 3245 | ||
| 3246 | <test id="http-cgi-htmlscript-arbitrary-file-access" key="/cgi-bin/htmlscript?../../../../../../../etc/passwd" status="not-vulnerable"> | |
| 3247 | ||
| 3248 | <Paragraph> | |
| 3249 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3250 | <Paragraph> | |
| 3251 | <ContainerBlockElement> | |
| 3252 | <ContainerBlockElement> | |
| 3253 | <Paragraph>HTTP GET request to | |
| 3254 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/htmlscript?../../../../../../../etc/passwd" LinkTitle="http://192.168.1.18/cgi-bin/htmlscript?../../../../../../../etc/passwd"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3255 | </test> | |
| 3256 | ||
| 3257 | <test id="http-cgi-testcgi-file-listing" key="/cgi-bin/test-cgi" status="not-vulnerable"> | |
| 3258 | ||
| 3259 | <Paragraph> | |
| 3260 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3261 | <Paragraph> | |
| 3262 | <ContainerBlockElement> | |
| 3263 | <ContainerBlockElement> | |
| 3264 | <Paragraph>HTTP POST request to | |
| 3265 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/test-cgi" LinkTitle="http://192.168.1.18/cgi-bin/test-cgi"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3266 | </test> | |
| 3267 | ||
| 3268 | <test id="http-generic-propfind-dir-browsing" status="skipped-version"> | |
| 3269 | ||
| 3270 | <Paragraph> | |
| 3271 | <Paragraph> | |
| 3272 | <ContainerBlockElement> | |
| 3273 | <Paragraph>HTTP request to | |
| 3274 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/lang_pack/" LinkTitle="http://192.168.1.18/cgi-bin/lang_pack/"></URLLink></Paragraph></ContainerBlockElement></Paragraph> | |
| 3275 | <Paragraph>Server did not respond to PROPFIND request on: /cgi-bin/lang_pack/</Paragraph> | |
| 3276 | <Paragraph>Based on the result of the "WebDAV Extensions are Enabled" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 3277 | </test> | |
| 3278 | ||
| 3279 | <test id="http-generic-propfind-dir-browsing" status="skipped-version"> | |
| 3280 | ||
| 3281 | <Paragraph> | |
| 3282 | <Paragraph> | |
| 3283 | <ContainerBlockElement> | |
| 3284 | <Paragraph>HTTP request to | |
| 3285 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/style/elegant/" LinkTitle="http://192.168.1.18/cgi-bin/style/elegant/"></URLLink></Paragraph></ContainerBlockElement></Paragraph> | |
| 3286 | <Paragraph>Server did not respond to PROPFIND request on: /cgi-bin/style/elegant/</Paragraph> | |
| 3287 | <Paragraph>Based on the result of the "WebDAV Extensions are Enabled" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 3288 | </test> | |
| 3289 | ||
| 3290 | <test id="http-generic-propfind-dir-browsing" status="skipped-version"> | |
| 3291 | ||
| 3292 | <Paragraph> | |
| 3293 | <Paragraph> | |
| 3294 | <ContainerBlockElement> | |
| 3295 | <Paragraph>HTTP request to | |
| 3296 | <URLLink LinkURL="http://192.168.1.18/.cobalt/" LinkTitle="http://192.168.1.18/.cobalt/"></URLLink></Paragraph></ContainerBlockElement></Paragraph> | |
| 3297 | <Paragraph>Server did not respond to PROPFIND request on: /.cobalt/</Paragraph> | |
| 3298 | <Paragraph>Based on the result of the "WebDAV Extensions are Enabled" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 3299 | </test> | |
| 3300 | ||
| 3301 | <test id="http-generic-propfind-dir-browsing" status="skipped-version"> | |
| 3302 | ||
| 3303 | <Paragraph> | |
| 3304 | <Paragraph> | |
| 3305 | <ContainerBlockElement> | |
| 3306 | <Paragraph>HTTP request to | |
| 3307 | <URLLink LinkURL="http://192.168.1.18/AdminScripts/" LinkTitle="http://192.168.1.18/AdminScripts/"></URLLink></Paragraph></ContainerBlockElement></Paragraph> | |
| 3308 | <Paragraph>Server did not respond to PROPFIND request on: /AdminScripts/</Paragraph> | |
| 3309 | <Paragraph>Based on the result of the "WebDAV Extensions are Enabled" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 3310 | </test> | |
| 3311 | ||
| 3312 | <test id="http-generic-propfind-dir-browsing" status="skipped-version"> | |
| 3313 | ||
| 3314 | <Paragraph> | |
| 3315 | <Paragraph> | |
| 3316 | <ContainerBlockElement> | |
| 3317 | <Paragraph>HTTP request to | |
| 3318 | <URLLink LinkURL="http://192.168.1.18/" LinkTitle="http://192.168.1.18/"></URLLink></Paragraph></ContainerBlockElement></Paragraph> | |
| 3319 | <Paragraph>Server did not respond to PROPFIND request on: /</Paragraph> | |
| 3320 | <Paragraph>Based on the result of the "WebDAV Extensions are Enabled" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 3321 | </test> | |
| 3322 | ||
| 3323 | <test id="http-generic-propfind-dir-browsing" status="skipped-version"> | |
| 3324 | ||
| 3325 | <Paragraph> | |
| 3326 | <Paragraph> | |
| 3327 | <ContainerBlockElement> | |
| 3328 | <Paragraph>HTTP request to | |
| 3329 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/" LinkTitle="http://192.168.1.18/cgi-bin/"></URLLink></Paragraph></ContainerBlockElement></Paragraph> | |
| 3330 | <Paragraph>Server did not respond to PROPFIND request on: /cgi-bin/</Paragraph> | |
| 3331 | <Paragraph>Based on the result of the "WebDAV Extensions are Enabled" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 3332 | </test> | |
| 3333 | ||
| 3334 | <test id="http-generic-propfind-dir-browsing" status="skipped-version"> | |
| 3335 | ||
| 3336 | <Paragraph> | |
| 3337 | <Paragraph> | |
| 3338 | <ContainerBlockElement> | |
| 3339 | <Paragraph>HTTP request to | |
| 3340 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/?P=+ADw-script+AD4-alert(42)+ADw-/script+AD4-" LinkTitle="http://192.168.1.18/cgi-bin/?P=+ADw-script+AD4-alert(42)+ADw-/script+AD4-"></URLLink></Paragraph></ContainerBlockElement></Paragraph> | |
| 3341 | <Paragraph>Server did not respond to PROPFIND request on: /cgi-bin/</Paragraph> | |
| 3342 | <Paragraph>Based on the result of the "WebDAV Extensions are Enabled" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 3343 | </test> | |
| 3344 | ||
| 3345 | <test id="http-generic-propfind-dir-browsing" status="skipped-version"> | |
| 3346 | ||
| 3347 | <Paragraph> | |
| 3348 | <Paragraph> | |
| 3349 | <ContainerBlockElement> | |
| 3350 | <Paragraph>HTTP request to | |
| 3351 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/images/" LinkTitle="http://192.168.1.18/cgi-bin/images/"></URLLink></Paragraph></ContainerBlockElement></Paragraph> | |
| 3352 | <Paragraph>Server did not respond to PROPFIND request on: /cgi-bin/images/</Paragraph> | |
| 3353 | <Paragraph>Based on the result of the "WebDAV Extensions are Enabled" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 3354 | </test> | |
| 3355 | ||
| 3356 | <test id="http-lighttpd-mod_userdir-info-discl" key="/~bin/true" status="not-vulnerable"> | |
| 3357 | ||
| 3358 | <Paragraph> | |
| 3359 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3360 | <Paragraph> | |
| 3361 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3362 | </test> | |
| 3363 | ||
| 3364 | <test id="http-open-proxy" key="http://www.google.com:80/" status="not-vulnerable"> | |
| 3365 | ||
| 3366 | <Paragraph> | |
| 3367 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3368 | <Paragraph> | |
| 3369 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3370 | </test> | |
| 3371 | ||
| 3372 | <test id="http-php-ini-file-exposed" key="/cgi-bin/php.ini" status="not-vulnerable"> | |
| 3373 | ||
| 3374 | <Paragraph> | |
| 3375 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3376 | <Paragraph> | |
| 3377 | <ContainerBlockElement> | |
| 3378 | <ContainerBlockElement> | |
| 3379 | <Paragraph>HTTP GET request to | |
| 3380 | <URLLink LinkURL="http://192.168.1.18/cgi-bin/php.ini" LinkTitle="http://192.168.1.18/cgi-bin/php.ini"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3381 | </test> | |
| 3382 | ||
| 3383 | <test id="http-symantec-scan-engine-file-disclosure" key="/README.txt" status="not-vulnerable"> | |
| 3384 | ||
| 3385 | <Paragraph> | |
| 3386 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3387 | <Paragraph> | |
| 3388 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3389 | </test> | |
| 3390 | ||
| 3391 | <test id="http-tomcat-jkstatus-accessible" key="/jkstatus/" status="not-vulnerable"> | |
| 3392 | ||
| 3393 | <Paragraph> | |
| 3394 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3395 | <Paragraph> | |
| 3396 | <ContainerBlockElement> | |
| 3397 | <ContainerBlockElement> | |
| 3398 | <Paragraph>HTTP GET request to | |
| 3399 | <URLLink LinkURL="http://192.168.1.18/jkstatus/" LinkTitle="http://192.168.1.18/jkstatus/"></URLLink></Paragraph>HTTP response code was an expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3400 | </test> | |
| 3401 | ||
| 3402 | <test id="http-vignette-app-portal-diag" status="not-vulnerable"> | |
| 3403 | ||
| 3404 | <Paragraph> | |
| 3405 | <Paragraph>No response returned to diagnostics request</Paragraph></Paragraph> | |
| 3406 | </test> | |
| 3407 | ||
| 3408 | <test id="adobe-apsb13-03-cve-2013-0629" key="/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../../license.html" status="not-vulnerable"> | |
| 3409 | ||
| 3410 | <Paragraph> | |
| 3411 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3412 | <Paragraph> | |
| 3413 | <ContainerBlockElement> | |
| 3414 | <ContainerBlockElement> | |
| 3415 | <Paragraph>HTTP GET request to | |
| 3416 | <URLLink LinkURL="http://192.168.1.18/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../license.txt" LinkTitle="http://192.168.1.18/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../license.txt"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 3417 | <ContainerBlockElement> | |
| 3418 | <Paragraph>HTTP GET request to | |
| 3419 | <URLLink LinkURL="http://192.168.1.18/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../../license.html" LinkTitle="http://192.168.1.18/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../../license.html"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3420 | </test> | |
| 3421 | ||
| 3422 | <test id="apache-httpd-cve-2008-0005" key="ftp://ftp.kernel.org/;utf7xss" status="not-vulnerable"> | |
| 3423 | ||
| 3424 | <Paragraph> | |
| 3425 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3426 | <Paragraph> | |
| 3427 | <ContainerBlockElement> | |
| 3428 | <ContainerBlockElement> | |
| 3429 | <Paragraph>HTTP GET request to | |
| 3430 | <URLLink LinkURL="ftp://ftp.kernel.org/;utf7xss" LinkTitle="ftp://ftp.kernel.org/;utf7xss"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3431 | </test> | |
| 3432 | ||
| 3433 | <test id="apache-httpd-cve-2008-0005" key="ftp://ftp.kernel.org/;utf7xss" status="not-vulnerable"> | |
| 3434 | ||
| 3435 | <Paragraph> | |
| 3436 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3437 | <Paragraph> | |
| 3438 | <ContainerBlockElement> | |
| 3439 | <ContainerBlockElement> | |
| 3440 | <Paragraph>HTTP GET request to | |
| 3441 | <URLLink LinkURL="ftp://ftp.kernel.org/;utf7xss" LinkTitle="ftp://ftp.kernel.org/;utf7xss"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3442 | </test> | |
| 3443 | ||
| 3444 | <test id="apache-httpd-cve-2008-2939" key="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" status="not-vulnerable"> | |
| 3445 | ||
| 3446 | <Paragraph> | |
| 3447 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3448 | <Paragraph> | |
| 3449 | <ContainerBlockElement> | |
| 3450 | <ContainerBlockElement> | |
| 3451 | <Paragraph>HTTP GET request to | |
| 3452 | <URLLink LinkURL="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" LinkTitle="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3453 | </test> | |
| 3454 | ||
| 3455 | <test id="apache-httpd-cve-2008-2939" key="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" status="not-vulnerable"> | |
| 3456 | ||
| 3457 | <Paragraph> | |
| 3458 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3459 | <Paragraph> | |
| 3460 | <ContainerBlockElement> | |
| 3461 | <ContainerBlockElement> | |
| 3462 | <Paragraph>HTTP GET request to | |
| 3463 | <URLLink LinkURL="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" LinkTitle="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3464 | </test> | |
| 3465 | ||
| 3466 | <test id="http-adobe-amf-gateway-xxe-cve-2009-3960" key="/flex2gateway/http" status="not-vulnerable"> | |
| 3467 | ||
| 3468 | <Paragraph> | |
| 3469 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3470 | <Paragraph> | |
| 3471 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3472 | </test> | |
| 3473 | </tests> | |
| 3474 | </service> | |
| 3475 | </services> | |
| 3476 | </endpoint> | |
| 3477 | </endpoints> | |
| 3478 | </node> | |
| 3479 | ||
| 3480 | <node address="192.168.1.33" status="alive" device-id="5"> | |
| 3481 | <fingerprints> | |
| 3482 | <os certainty="0.80" vendor="Linux" family="Linux" product="Linux" version="2.6.18_pro500-davinci_IPNC_1.00" arch="armv5tejl"/> | |
| 3483 | <os certainty="0.70" device-class="General" vendor="Linux" family="Linux" product="Linux" version="2.6.9"/> | |
| 3484 | <os certainty="0.60" vendor="Linux" family="Linux" product="Linux"/> | |
| 3485 | </fingerprints> | |
| 3486 | <tests> | |
| 3487 | <test id="tcp-seq-num-approximation" status="vulnerable-exploited"> | |
| 3488 | ||
| 3489 | <Paragraph> | |
| 3490 | <Paragraph>TCP reset with incorrect sequence number triggered this fault on 192.168.1.33:443: Connection reset by peer</Paragraph></Paragraph> | |
| 3491 | </test> | |
| 3492 | ||
| 3493 | <test id="generic-icmp-netmask" status="not-vulnerable"> | |
| 3494 | ||
| 3495 | <Paragraph> | |
| 3496 | <Paragraph>No response</Paragraph></Paragraph> | |
| 3497 | </test> | |
| 3498 | ||
| 3499 | <test id="generic-icmp-timestamp" status="vulnerable-exploited"> | |
| 3500 | ||
| 3501 | <Paragraph> | |
| 3502 | <Paragraph>Remote system time: 05:15:22.694 UTC</Paragraph></Paragraph> | |
| 3503 | </test> | |
| 3504 | ||
| 3505 | <test id="generic-tcp-timestamp" status="vulnerable-exploited"> | |
| 3506 | ||
| 3507 | <Paragraph> | |
| 3508 | <Paragraph>Apparent system boot time: Sat Nov 23 20:27:00 UTC 2013</Paragraph></Paragraph> | |
| 3509 | </test> | |
| 3510 | ||
| 3511 | <test id="udp-ipid-zero" status="vulnerable-version"> | |
| 3512 | ||
| 3513 | <Paragraph> | |
| 3514 | <Paragraph>Received UDP packet with IP ID of zero: | |
| 3515 | <UnorderedList> | |
| 3516 | <ListItem> | |
| 3517 | <Paragraph preformat="true">IPv4 SRC[192.168.1.33] TGT[192.168.1.39] | |
| 3518 | TOS[0] TTL[64] Flags[40] Proto[17] ID[0] FragOff[0] | |
| 3519 | HDR-LENGTH[20] TOTAL-LENGTH[76] CKSUM[46856] | |
| 3520 | UDP SRC-PORT[123] TGT-PORT[3037] CKSUM[59938] | |
| 3521 | RAW DATA [48]: | |
| 3522 | 1A050AEF0000A7FF00003A4B3D43D2F1 ...�..��..:K=C�� | |
| 3523 | D63FFC67709A9973C6F15EDB78000000 �?�gp��s��^�x... | |
| 3524 | D63FFE5FA76C15D2D63FFE5FA77AE579 �?�_�l.��?�_�z�y | |
| 3525 | </Paragraph></ListItem></UnorderedList></Paragraph></Paragraph> | |
| 3526 | </test> | |
| 3527 | </tests> | |
| 3528 | <endpoints> | |
| 3529 | <endpoint protocol="tcp" port="80" status="open"> | |
| 3530 | <services> | |
| 3531 | <service name="HTTP"> | |
| 3532 | <tests> | |
| 3533 | <test id="adobe-apsb13-03-cve-2013-0632" key="/CFIDE/adminapi/administrator.cfc?" status="not-vulnerable"> | |
| 3534 | ||
| 3535 | <Paragraph> | |
| 3536 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3537 | <Paragraph> | |
| 3538 | <ContainerBlockElement> | |
| 3539 | <ContainerBlockElement> | |
| 3540 | <Paragraph>HTTP POST request to | |
| 3541 | <URLLink LinkURL="http://192.168.1.33/CFIDE/adminapi/administrator.cfc" LinkTitle="http://192.168.1.33/CFIDE/adminapi/administrator.cfc"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3542 | </test> | |
| 3543 | ||
| 3544 | <test id="adobe-apsb13-13-cve-2013-1389" status="skipped-version"> | |
| 3545 | ||
| 3546 | <Paragraph> | |
| 3547 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3548 | <Paragraph>Based on the result of the "APSB13-13: Security updates available for Adobe ColdFusion (CVE-2013-3336)" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 3549 | </test> | |
| 3550 | ||
| 3551 | <test id="http-3com-wap-default-admin-password" key="/index.htm" status="not-vulnerable"> | |
| 3552 | ||
| 3553 | <Paragraph> | |
| 3554 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3555 | <Paragraph> | |
| 3556 | <ContainerBlockElement> | |
| 3557 | <ContainerBlockElement> | |
| 3558 | <Paragraph>HTTP POST request to | |
| 3559 | <URLLink LinkURL="http://192.168.1.33/index.htm" LinkTitle="http://192.168.1.33/index.htm"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3560 | </test> | |
| 3561 | ||
| 3562 | <test id="http-drac-default-login" key="/data/login" status="not-vulnerable"> | |
| 3563 | ||
| 3564 | <Paragraph> | |
| 3565 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3566 | <Paragraph> | |
| 3567 | <ContainerBlockElement> | |
| 3568 | <ContainerBlockElement> | |
| 3569 | <Paragraph>HTTP POST request to | |
| 3570 | <URLLink LinkURL="http://192.168.1.33/data/login" LinkTitle="http://192.168.1.33/data/login"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3571 | </test> | |
| 3572 | ||
| 3573 | <test id="http-drac-default-login" key="/cgi/login" status="not-vulnerable"> | |
| 3574 | ||
| 3575 | <Paragraph> | |
| 3576 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3577 | <Paragraph> | |
| 3578 | <ContainerBlockElement> | |
| 3579 | <ContainerBlockElement> | |
| 3580 | <Paragraph>HTTP POST request to | |
| 3581 | <URLLink LinkURL="http://192.168.1.33/cgi/login" LinkTitle="http://192.168.1.33/cgi/login"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3582 | </test> | |
| 3583 | ||
| 3584 | <test id="http-glassfish-default-admin-password" key="/common/index.jsf" status="not-vulnerable"> | |
| 3585 | ||
| 3586 | <Paragraph> | |
| 3587 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3588 | <Paragraph> | |
| 3589 | <ContainerBlockElement> | |
| 3590 | <ContainerBlockElement> | |
| 3591 | <Paragraph>HTTP GET request to | |
| 3592 | <URLLink LinkURL="http://192.168.1.33/common/index.jsf" LinkTitle="http://192.168.1.33/common/index.jsf"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3593 | </test> | |
| 3594 | ||
| 3595 | <test id="http-nokia-firewall-default-admin-password" key="/cgi-bin/home.tcl" status="not-vulnerable"> | |
| 3596 | ||
| 3597 | <Paragraph> | |
| 3598 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3599 | <Paragraph> | |
| 3600 | <ContainerBlockElement> | |
| 3601 | <ContainerBlockElement> | |
| 3602 | <Paragraph>HTTP POST request to | |
| 3603 | <URLLink LinkURL="http://192.168.1.33/cgi-bin/home.tcl" LinkTitle="http://192.168.1.33/cgi-bin/home.tcl"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3604 | </test> | |
| 3605 | ||
| 3606 | <test id="http-phpmyadmin-account-pma-password-empty" key="/phpmyadmin/" status="not-vulnerable"> | |
| 3607 | ||
| 3608 | <Paragraph> | |
| 3609 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3610 | <Paragraph> | |
| 3611 | <ContainerBlockElement> | |
| 3612 | <ContainerBlockElement> | |
| 3613 | <Paragraph>HTTP GET request to | |
| 3614 | <URLLink LinkURL="http://192.168.1.33/phpmyadmin/" LinkTitle="http://192.168.1.33/phpmyadmin/"></URLLink></Paragraph>HTTP response code was 404 but expected 401</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3615 | </test> | |
| 3616 | ||
| 3617 | <test id="apache-struts-cve-2013-2251" key="/struts2-blank/example/HelloWorld.action" status="not-vulnerable"> | |
| 3618 | ||
| 3619 | <Paragraph> | |
| 3620 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3621 | <Paragraph> | |
| 3622 | <ContainerBlockElement> | |
| 3623 | <ContainerBlockElement> | |
| 3624 | <Paragraph>HTTP GET request to | |
| 3625 | <URLLink LinkURL="http://192.168.1.33/struts2-blank/example/HelloWorld.action" LinkTitle="http://192.168.1.33/struts2-blank/example/HelloWorld.action"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3626 | </test> | |
| 3627 | ||
| 3628 | <test id="apache-struts-cve-2013-2251" key="/struts2-showcase/employee/save.action" status="not-vulnerable"> | |
| 3629 | ||
| 3630 | <Paragraph> | |
| 3631 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3632 | <Paragraph> | |
| 3633 | <ContainerBlockElement> | |
| 3634 | <ContainerBlockElement> | |
| 3635 | <Paragraph>HTTP GET request to | |
| 3636 | <URLLink LinkURL="http://192.168.1.33/struts2-showcase/employee/save.action" LinkTitle="http://192.168.1.33/struts2-showcase/employee/save.action"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3637 | </test> | |
| 3638 | ||
| 3639 | <test id="checkpoint-ess-info-disclosure-sk57881" key="/conf/ssl/apache/integrity-smartcenter.key" status="not-vulnerable"> | |
| 3640 | ||
| 3641 | <Paragraph> | |
| 3642 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3643 | <Paragraph> | |
| 3644 | <ContainerBlockElement> | |
| 3645 | <ContainerBlockElement> | |
| 3646 | <Paragraph>HTTP GET request to | |
| 3647 | <URLLink LinkURL="http://192.168.1.33/conf/ssl/apache/integrity.key" LinkTitle="http://192.168.1.33/conf/ssl/apache/integrity.key"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 3648 | <ContainerBlockElement> | |
| 3649 | <Paragraph>HTTP GET request to | |
| 3650 | <URLLink LinkURL="http://192.168.1.33/conf/ssl/apache/integrity-smartcenter.key" LinkTitle="http://192.168.1.33/conf/ssl/apache/integrity-smartcenter.key"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3651 | </test> | |
| 3652 | ||
| 3653 | <test id="adobe-apsb10-18-cve-2010-2861" key="/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en" status="not-vulnerable"> | |
| 3654 | ||
| 3655 | <Paragraph> | |
| 3656 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3657 | <Paragraph> | |
| 3658 | <ContainerBlockElement> | |
| 3659 | <ContainerBlockElement> | |
| 3660 | <Paragraph>HTTP GET request to | |
| 3661 | <URLLink LinkURL="http://192.168.1.33/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en" LinkTitle="http://192.168.1.33/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en"></URLLink></Paragraph>HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3662 | </test> | |
| 3663 | ||
| 3664 | <test id="http-awstats-remote-code-execution" key="/cgi-bin/awstats/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" status="not-vulnerable"> | |
| 3665 | ||
| 3666 | <Paragraph> | |
| 3667 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3668 | <Paragraph> | |
| 3669 | <ContainerBlockElement> | |
| 3670 | <ContainerBlockElement> | |
| 3671 | <Paragraph>HTTP GET request to | |
| 3672 | <URLLink LinkURL="http://192.168.1.33/cgi-bin/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" LinkTitle="http://192.168.1.33/cgi-bin/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 3673 | <ContainerBlockElement> | |
| 3674 | <Paragraph>HTTP GET request to | |
| 3675 | <URLLink LinkURL="http://192.168.1.33/cgi-bin/awstats/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" LinkTitle="http://192.168.1.33/cgi-bin/awstats/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3676 | </test> | |
| 3677 | ||
| 3678 | <test id="http-cgi-faxsurvey-command-execution" key="/cgi-bin/faxquery?/bin/cat%20/etc/passwd" status="not-vulnerable"> | |
| 3679 | ||
| 3680 | <Paragraph> | |
| 3681 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3682 | <Paragraph> | |
| 3683 | <ContainerBlockElement> | |
| 3684 | <ContainerBlockElement> | |
| 3685 | <Paragraph>HTTP GET request to | |
| 3686 | <URLLink LinkURL="http://192.168.1.33/cgi-bin/faxsurvey?/bin/cat%20/etc/passwd" LinkTitle="http://192.168.1.33/cgi-bin/faxsurvey?/bin/cat%20/etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 3687 | <ContainerBlockElement> | |
| 3688 | <Paragraph>HTTP GET request to | |
| 3689 | <URLLink LinkURL="http://192.168.1.33/cgi-bin/faxquery?/bin/cat%20/etc/passwd" LinkTitle="http://192.168.1.33/cgi-bin/faxquery?/bin/cat%20/etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3690 | </test> | |
| 3691 | ||
| 3692 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/orm/" status="not-vulnerable"> | |
| 3693 | ||
| 3694 | <Paragraph> | |
| 3695 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3696 | <Paragraph> | |
| 3697 | <ContainerBlockElement> | |
| 3698 | <ContainerBlockElement> | |
| 3699 | <Paragraph>HTTP GET request to | |
| 3700 | <URLLink LinkURL="http://192.168.1.33/CFIDE/orm/" LinkTitle="http://192.168.1.33/CFIDE/orm/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3701 | </test> | |
| 3702 | ||
| 3703 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/administrator/enter.cfm" status="not-vulnerable"> | |
| 3704 | ||
| 3705 | <Paragraph> | |
| 3706 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3707 | <Paragraph> | |
| 3708 | <ContainerBlockElement> | |
| 3709 | <ContainerBlockElement> | |
| 3710 | <Paragraph>HTTP GET request to | |
| 3711 | <URLLink LinkURL="http://192.168.1.33/CFIDE/administrator/" LinkTitle="http://192.168.1.33/CFIDE/administrator/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 3712 | <ContainerBlockElement> | |
| 3713 | <Paragraph>HTTP GET request to | |
| 3714 | <URLLink LinkURL="http://192.168.1.33/CFIDE/administrator/enter.cfm" LinkTitle="http://192.168.1.33/CFIDE/administrator/enter.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3715 | </test> | |
| 3716 | ||
| 3717 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/AIR/" status="not-vulnerable"> | |
| 3718 | ||
| 3719 | <Paragraph> | |
| 3720 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3721 | <Paragraph> | |
| 3722 | <ContainerBlockElement> | |
| 3723 | <ContainerBlockElement> | |
| 3724 | <Paragraph>HTTP GET request to | |
| 3725 | <URLLink LinkURL="http://192.168.1.33/CFIDE/AIR/" LinkTitle="http://192.168.1.33/CFIDE/AIR/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3726 | </test> | |
| 3727 | ||
| 3728 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/appdeployment/" status="not-vulnerable"> | |
| 3729 | ||
| 3730 | <Paragraph> | |
| 3731 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3732 | <Paragraph> | |
| 3733 | <ContainerBlockElement> | |
| 3734 | <ContainerBlockElement> | |
| 3735 | <Paragraph>HTTP GET request to | |
| 3736 | <URLLink LinkURL="http://192.168.1.33/CFIDE/appdeployment/" LinkTitle="http://192.168.1.33/CFIDE/appdeployment/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3737 | </test> | |
| 3738 | ||
| 3739 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/componentutils/" status="not-vulnerable"> | |
| 3740 | ||
| 3741 | <Paragraph> | |
| 3742 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3743 | <Paragraph> | |
| 3744 | <ContainerBlockElement> | |
| 3745 | <ContainerBlockElement> | |
| 3746 | <Paragraph>HTTP GET request to | |
| 3747 | <URLLink LinkURL="http://192.168.1.33/CFIDE/componentutils/" LinkTitle="http://192.168.1.33/CFIDE/componentutils/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3748 | </test> | |
| 3749 | ||
| 3750 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/scheduler/" status="not-vulnerable"> | |
| 3751 | ||
| 3752 | <Paragraph> | |
| 3753 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3754 | <Paragraph> | |
| 3755 | <ContainerBlockElement> | |
| 3756 | <ContainerBlockElement> | |
| 3757 | <Paragraph>HTTP GET request to | |
| 3758 | <URLLink LinkURL="http://192.168.1.33/CFIDE/scheduler/" LinkTitle="http://192.168.1.33/CFIDE/scheduler/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3759 | </test> | |
| 3760 | ||
| 3761 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/servermanager/" status="not-vulnerable"> | |
| 3762 | ||
| 3763 | <Paragraph> | |
| 3764 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3765 | <Paragraph> | |
| 3766 | <ContainerBlockElement> | |
| 3767 | <ContainerBlockElement> | |
| 3768 | <Paragraph>HTTP GET request to | |
| 3769 | <URLLink LinkURL="http://192.168.1.33/CFIDE/servermanager/" LinkTitle="http://192.168.1.33/CFIDE/servermanager/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3770 | </test> | |
| 3771 | ||
| 3772 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/services/" status="not-vulnerable"> | |
| 3773 | ||
| 3774 | <Paragraph> | |
| 3775 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3776 | <Paragraph> | |
| 3777 | <ContainerBlockElement> | |
| 3778 | <ContainerBlockElement> | |
| 3779 | <Paragraph>HTTP GET request to | |
| 3780 | <URLLink LinkURL="http://192.168.1.33/CFIDE/services/" LinkTitle="http://192.168.1.33/CFIDE/services/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3781 | </test> | |
| 3782 | ||
| 3783 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/adminapi/base.cfc?wsdl" status="not-vulnerable"> | |
| 3784 | ||
| 3785 | <Paragraph> | |
| 3786 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3787 | <Paragraph> | |
| 3788 | <ContainerBlockElement> | |
| 3789 | <ContainerBlockElement> | |
| 3790 | <Paragraph>HTTP GET request to | |
| 3791 | <URLLink LinkURL="http://192.168.1.33/CFIDE/adminapi/base.cfc?wsdl" LinkTitle="http://192.168.1.33/CFIDE/adminapi/base.cfc?wsdl"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3792 | </test> | |
| 3793 | ||
| 3794 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/wizards/common/" status="not-vulnerable"> | |
| 3795 | ||
| 3796 | <Paragraph> | |
| 3797 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3798 | <Paragraph> | |
| 3799 | <ContainerBlockElement> | |
| 3800 | <ContainerBlockElement> | |
| 3801 | <Paragraph>HTTP GET request to | |
| 3802 | <URLLink LinkURL="http://192.168.1.33/CFIDE/wizards/common/" LinkTitle="http://192.168.1.33/CFIDE/wizards/common/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3803 | </test> | |
| 3804 | ||
| 3805 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/adminiapi/" status="not-vulnerable"> | |
| 3806 | ||
| 3807 | <Paragraph> | |
| 3808 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3809 | <Paragraph> | |
| 3810 | <ContainerBlockElement> | |
| 3811 | <ContainerBlockElement> | |
| 3812 | <Paragraph>HTTP GET request to | |
| 3813 | <URLLink LinkURL="http://192.168.1.33/CFIDE/adminiapi/" LinkTitle="http://192.168.1.33/CFIDE/adminiapi/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3814 | </test> | |
| 3815 | ||
| 3816 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=localhost&vport=22&vstart=&vusername=&vpassword=&returnformat=json" status="not-vulnerable"> | |
| 3817 | ||
| 3818 | <Paragraph> | |
| 3819 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3820 | <Paragraph> | |
| 3821 | <ContainerBlockElement> | |
| 3822 | <ContainerBlockElement> | |
| 3823 | <Paragraph>HTTP GET request to | |
| 3824 | <URLLink LinkURL="http://192.168.1.33/CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=localhost&vport=22&vstart=&vusername=&vpassword=&returnformat=json" LinkTitle="http://192.168.1.33/CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=localhost&vport=22&vstart=&vusername=&vpassword=&returnformat=json"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3825 | </test> | |
| 3826 | ||
| 3827 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/websocket/" status="not-vulnerable"> | |
| 3828 | ||
| 3829 | <Paragraph> | |
| 3830 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3831 | <Paragraph> | |
| 3832 | <ContainerBlockElement> | |
| 3833 | <ContainerBlockElement> | |
| 3834 | <Paragraph>HTTP GET request to | |
| 3835 | <URLLink LinkURL="http://192.168.1.33/CFIDE/websocket/" LinkTitle="http://192.168.1.33/CFIDE/websocket/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3836 | </test> | |
| 3837 | ||
| 3838 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/portlets/" status="not-vulnerable"> | |
| 3839 | ||
| 3840 | <Paragraph> | |
| 3841 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3842 | <Paragraph> | |
| 3843 | <ContainerBlockElement> | |
| 3844 | <ContainerBlockElement> | |
| 3845 | <Paragraph>HTTP GET request to | |
| 3846 | <URLLink LinkURL="http://192.168.1.33/CFIDE/portlets/" LinkTitle="http://192.168.1.33/CFIDE/portlets/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3847 | </test> | |
| 3848 | ||
| 3849 | <test id="http-frontpage-unprotected" key="/_vti_bin/_vti_aut/author.dll" status="not-vulnerable"> | |
| 3850 | ||
| 3851 | <Paragraph> | |
| 3852 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3853 | <Paragraph> | |
| 3854 | <ContainerBlockElement> | |
| 3855 | <ContainerBlockElement> | |
| 3856 | <Paragraph>HTTP GET request to | |
| 3857 | <URLLink LinkURL="http://192.168.1.33/_vti_bin/_vti_aut/author.dll" LinkTitle="http://192.168.1.33/_vti_bin/_vti_aut/author.dll"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3858 | </test> | |
| 3859 | ||
| 3860 | <test id="http-php-xmlrpc-code-injection" key="/script/xmlrpc.php" status="not-vulnerable"> | |
| 3861 | ||
| 3862 | <Paragraph> | |
| 3863 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3864 | <Paragraph> | |
| 3865 | <ContainerBlockElement> | |
| 3866 | <ContainerBlockElement> | |
| 3867 | <Paragraph>HTTP POST request to | |
| 3868 | <URLLink LinkURL="http://192.168.1.33/xmlrpc.php" LinkTitle="http://192.168.1.33/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 3869 | <ContainerBlockElement> | |
| 3870 | <Paragraph>HTTP POST request to | |
| 3871 | <URLLink LinkURL="http://192.168.1.33/serendipity/serendipity_xmlrpc.php" LinkTitle="http://192.168.1.33/serendipity/serendipity_xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 3872 | <ContainerBlockElement> | |
| 3873 | <Paragraph>HTTP POST request to | |
| 3874 | <URLLink LinkURL="http://192.168.1.33/serendipity/xmlrpc.php" LinkTitle="http://192.168.1.33/serendipity/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 3875 | <ContainerBlockElement> | |
| 3876 | <Paragraph>HTTP POST request to | |
| 3877 | <URLLink LinkURL="http://192.168.1.33/drupal/xmlrpc.php" LinkTitle="http://192.168.1.33/drupal/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 3878 | <ContainerBlockElement> | |
| 3879 | <Paragraph>HTTP POST request to | |
| 3880 | <URLLink LinkURL="http://192.168.1.33/bblog/xmlrpc.php" LinkTitle="http://192.168.1.33/bblog/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 3881 | <ContainerBlockElement> | |
| 3882 | <Paragraph>HTTP POST request to | |
| 3883 | <URLLink LinkURL="http://192.168.1.33/blogs/xmlsrv/xmlrpc.php" LinkTitle="http://192.168.1.33/blogs/xmlsrv/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 3884 | <ContainerBlockElement> | |
| 3885 | <Paragraph>HTTP POST request to | |
| 3886 | <URLLink LinkURL="http://192.168.1.33/xmlsrv/xmlrpc.php" LinkTitle="http://192.168.1.33/xmlsrv/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 3887 | <ContainerBlockElement> | |
| 3888 | <Paragraph>HTTP POST request to | |
| 3889 | <URLLink LinkURL="http://192.168.1.33/xmlrpc/xmlrpc.php" LinkTitle="http://192.168.1.33/xmlrpc/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 3890 | <ContainerBlockElement> | |
| 3891 | <Paragraph>HTTP POST request to | |
| 3892 | <URLLink LinkURL="http://192.168.1.33/script/xmlrpc.php" LinkTitle="http://192.168.1.33/script/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3893 | </test> | |
| 3894 | ||
| 3895 | <test id="adobe-apsb13-03-cve-2013-0625" status="skipped-version"> | |
| 3896 | ||
| 3897 | <Paragraph> | |
| 3898 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3899 | <Paragraph>Based on the result of the "APSB13-03: Security updates available for Adobe ColdFusion (CVE-2013-0629)" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 3900 | </test> | |
| 3901 | ||
| 3902 | <test id="http-basic-auth-cleartext" key="/" status="vulnerable-exploited"> | |
| 3903 | ||
| 3904 | <Paragraph> | |
| 3905 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3906 | <Paragraph> | |
| 3907 | <ContainerBlockElement> | |
| 3908 | <Paragraph>HTTP request to | |
| 3909 | <URLLink LinkURL="http://192.168.1.33/" LinkTitle="http://192.168.1.33/"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 3910 | <Paragraph preformat="true">1: Basic realm="DCS-2132L"</Paragraph> | |
| 3911 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></Paragraph></Paragraph> | |
| 3912 | </test> | |
| 3913 | ||
| 3914 | <test id="http-basic-auth-cleartext" key="/" status="vulnerable-exploited"> | |
| 3915 | ||
| 3916 | <Paragraph> | |
| 3917 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3918 | <Paragraph> | |
| 3919 | <ContainerBlockElement> | |
| 3920 | <ContainerBlockElement> | |
| 3921 | <Paragraph>HTTP GET request to | |
| 3922 | <URLLink LinkURL="http://192.168.1.33/" LinkTitle="http://192.168.1.33/"></URLLink></Paragraph>HTTP response code was an expected 401 | |
| 3923 | <Paragraph preformat="true">1: Basic realm="DCS-2132L"</Paragraph> | |
| 3924 | <Paragraph>HTTP header 'WWW-Authenticate' was present and matched expectation</Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3925 | </test> | |
| 3926 | ||
| 3927 | <test id="http-iis-0014" status="not-vulnerable"> | |
| 3928 | ||
| 3929 | <Paragraph> | |
| 3930 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3931 | <Paragraph>Based on the following 3 results: | |
| 3932 | <OrderedList> | |
| 3933 | <ListItem> | |
| 3934 | <Paragraph> | |
| 3935 | <ContainerBlockElement> | |
| 3936 | <ContainerBlockElement> | |
| 3937 | <Paragraph>HTTP GET request to | |
| 3938 | <URLLink LinkURL="http://192.168.1.33/scripts/tools/newdsn.exe?driver=Microsoft%2BAccess%2BDriver%2B%28*.mdb%29&dsn=Web%20SQL&dbq=c:\temp\xyz.mdb&newdb=CREATE_DB&attr=" LinkTitle="http://192.168.1.33/scripts/tools/newdsn.exe?driver=Microsoft%2BAccess%2BDriver%2B%28*.mdb%29&dsn=Web%20SQL&dbq=c:\temp\xyz.mdb&newdb=CREATE_DB&attr="></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem> | |
| 3939 | <ListItem> | |
| 3940 | <Paragraph> | |
| 3941 | <ContainerBlockElement> | |
| 3942 | <ContainerBlockElement> | |
| 3943 | <Paragraph>HTTP GET request to | |
| 3944 | <URLLink LinkURL="http://192.168.1.33/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|" LinkTitle="http://192.168.1.33/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem> | |
| 3945 | <ListItem> | |
| 3946 | <Paragraph> | |
| 3947 | <ContainerBlockElement> | |
| 3948 | <ContainerBlockElement> | |
| 3949 | <Paragraph>HTTP GET request to | |
| 3950 | <URLLink LinkURL="http://192.168.1.33/ASPSamp/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|" LinkTitle="http://192.168.1.33/ASPSamp/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem></OrderedList></Paragraph></Paragraph> | |
| 3951 | </test> | |
| 3952 | ||
| 3953 | <test id="http-cgi-viewsource-arbitrary-file-access" key="/cgi-bin/view-source?../../../../../../../etc/passwd" status="not-vulnerable"> | |
| 3954 | ||
| 3955 | <Paragraph> | |
| 3956 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3957 | <Paragraph> | |
| 3958 | <ContainerBlockElement> | |
| 3959 | <ContainerBlockElement> | |
| 3960 | <Paragraph>HTTP GET request to | |
| 3961 | <URLLink LinkURL="http://192.168.1.33/cgi-bin/view-source?../../../../../../../etc/passwd" LinkTitle="http://192.168.1.33/cgi-bin/view-source?../../../../../../../etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3962 | </test> | |
| 3963 | ||
| 3964 | <test id="http-trace-method-enabled" key="/" status="not-vulnerable"> | |
| 3965 | ||
| 3966 | <Paragraph> | |
| 3967 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3968 | <Paragraph> | |
| 3969 | <ContainerBlockElement> | |
| 3970 | <ContainerBlockElement> | |
| 3971 | <Paragraph>HTTP TRACE request to | |
| 3972 | <URLLink LinkURL="http://192.168.1.33/" LinkTitle="http://192.168.1.33/"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3973 | </test> | |
| 3974 | ||
| 3975 | <test id="http-track-method-enabled" key="/" status="not-vulnerable"> | |
| 3976 | ||
| 3977 | <Paragraph> | |
| 3978 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3979 | <Paragraph> | |
| 3980 | <ContainerBlockElement> | |
| 3981 | <ContainerBlockElement> | |
| 3982 | <Paragraph>HTTP TRACK request to | |
| 3983 | <URLLink LinkURL="http://192.168.1.33/" LinkTitle="http://192.168.1.33/"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3984 | </test> | |
| 3985 | ||
| 3986 | <test id="spider-adobe-flash-permissive-crossdomain-xml" key="/crossdomain.xml" status="not-vulnerable"> | |
| 3987 | ||
| 3988 | <Paragraph> | |
| 3989 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 3990 | <Paragraph> | |
| 3991 | <ContainerBlockElement> | |
| 3992 | <ContainerBlockElement> | |
| 3993 | <Paragraph>HTTP GET request to | |
| 3994 | <URLLink LinkURL="http://192.168.1.33/crossdomain.xml" LinkTitle="http://192.168.1.33/crossdomain.xml"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 3995 | </test> | |
| 3996 | ||
| 3997 | <test id="adobe-apsb13-03-cve-2013-0631" key="/CFIDE/r.cfm" status="not-vulnerable"> | |
| 3998 | ||
| 3999 | <Paragraph> | |
| 4000 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4001 | <Paragraph> | |
| 4002 | <ContainerBlockElement> | |
| 4003 | <ContainerBlockElement> | |
| 4004 | <Paragraph>HTTP GET request to | |
| 4005 | <URLLink LinkURL="http://192.168.1.33/CFIDE/adminapi/customtags/fusebox.cfm" LinkTitle="http://192.168.1.33/CFIDE/adminapi/customtags/fusebox.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4006 | <ContainerBlockElement> | |
| 4007 | <Paragraph>HTTP GET request to | |
| 4008 | <URLLink LinkURL="http://192.168.1.33/CFIDE/adminapi/customtags/adss.cfm" LinkTitle="http://192.168.1.33/CFIDE/adminapi/customtags/adss.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4009 | <ContainerBlockElement> | |
| 4010 | <Paragraph>HTTP GET request to | |
| 4011 | <URLLink LinkURL="http://192.168.1.33/CFIDE/h.cfm" LinkTitle="http://192.168.1.33/CFIDE/h.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4012 | <ContainerBlockElement> | |
| 4013 | <Paragraph>HTTP GET request to | |
| 4014 | <URLLink LinkURL="http://192.168.1.33/CFIDE/h9.cfm" LinkTitle="http://192.168.1.33/CFIDE/h9.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4015 | <ContainerBlockElement> | |
| 4016 | <Paragraph>HTTP GET request to | |
| 4017 | <URLLink LinkURL="http://192.168.1.33/CFIDE/help.cfm" LinkTitle="http://192.168.1.33/CFIDE/help.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4018 | <ContainerBlockElement> | |
| 4019 | <Paragraph>HTTP GET request to | |
| 4020 | <URLLink LinkURL="http://192.168.1.33/CFIDE/i.cfm" LinkTitle="http://192.168.1.33/CFIDE/i.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4021 | <ContainerBlockElement> | |
| 4022 | <Paragraph>HTTP GET request to | |
| 4023 | <URLLink LinkURL="http://192.168.1.33/CFIDE/r.cfm" LinkTitle="http://192.168.1.33/CFIDE/r.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4024 | </test> | |
| 4025 | ||
| 4026 | <test id="adobe-apsb13-13-cve-2013-3336" key="/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=U" status="not-vulnerable"> | |
| 4027 | ||
| 4028 | <Paragraph> | |
| 4029 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4030 | <Paragraph> | |
| 4031 | <ContainerBlockElement> | |
| 4032 | <ContainerBlockElement> | |
| 4033 | <Paragraph>HTTP GET request to | |
| 4034 | <URLLink LinkURL="http://192.168.1.33/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test" LinkTitle="http://192.168.1.33/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test"></URLLink></Paragraph>HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4035 | <ContainerBlockElement> | |
| 4036 | <Paragraph>HTTP GET request to | |
| 4037 | <URLLink LinkURL="http://192.168.1.33/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test" LinkTitle="http://192.168.1.33/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test"></URLLink></Paragraph>HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4038 | </test> | |
| 4039 | ||
| 4040 | <test id="http-awstats-debug-information-disclosure" key="/cgi-bin/awstats/awstats.pl?debug=1" status="not-vulnerable"> | |
| 4041 | ||
| 4042 | <Paragraph> | |
| 4043 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4044 | <Paragraph> | |
| 4045 | <ContainerBlockElement> | |
| 4046 | <ContainerBlockElement> | |
| 4047 | <Paragraph>HTTP GET request to | |
| 4048 | <URLLink LinkURL="http://192.168.1.33/cgi-bin/awstats.pl?debug=1" LinkTitle="http://192.168.1.33/cgi-bin/awstats.pl?debug=1"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4049 | <ContainerBlockElement> | |
| 4050 | <Paragraph>HTTP GET request to | |
| 4051 | <URLLink LinkURL="http://192.168.1.33/cgi-bin/awstats/awstats.pl?debug=1" LinkTitle="http://192.168.1.33/cgi-bin/awstats/awstats.pl?debug=1"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4052 | </test> | |
| 4053 | ||
| 4054 | <test id="http-bigbrother-accessible" key="/bb/" status="not-vulnerable"> | |
| 4055 | ||
| 4056 | <Paragraph> | |
| 4057 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4058 | <Paragraph> | |
| 4059 | <ContainerBlockElement> | |
| 4060 | <ContainerBlockElement> | |
| 4061 | <Paragraph>HTTP GET request to | |
| 4062 | <URLLink LinkURL="http://192.168.1.33/bb/" LinkTitle="http://192.168.1.33/bb/"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4063 | </test> | |
| 4064 | ||
| 4065 | <test id="http-cgi-htdig-arbitrary-file-access" key="/cgi-bin/htsearch?Exclude=%60/etc/passwd%60" status="not-vulnerable"> | |
| 4066 | ||
| 4067 | <Paragraph> | |
| 4068 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4069 | <Paragraph> | |
| 4070 | <ContainerBlockElement> | |
| 4071 | <ContainerBlockElement> | |
| 4072 | <Paragraph>HTTP GET request to | |
| 4073 | <URLLink LinkURL="http://192.168.1.33/cgi-bin/htsearch?Exclude=%60/etc/passwd%60" LinkTitle="http://192.168.1.33/cgi-bin/htsearch?Exclude=%60/etc/passwd%60"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4074 | </test> | |
| 4075 | ||
| 4076 | <test id="http-cgi-htgrep-arbitrary-file-access" key="/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd" status="not-vulnerable"> | |
| 4077 | ||
| 4078 | <Paragraph> | |
| 4079 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4080 | <Paragraph> | |
| 4081 | <ContainerBlockElement> | |
| 4082 | <ContainerBlockElement> | |
| 4083 | <Paragraph>HTTP GET request to | |
| 4084 | <URLLink LinkURL="http://192.168.1.33/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd" LinkTitle="http://192.168.1.33/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4085 | </test> | |
| 4086 | ||
| 4087 | <test id="http-cgi-htmlscript-arbitrary-file-access" key="/cgi-bin/htmlscript?../../../../../../../etc/passwd" status="not-vulnerable"> | |
| 4088 | ||
| 4089 | <Paragraph> | |
| 4090 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4091 | <Paragraph> | |
| 4092 | <ContainerBlockElement> | |
| 4093 | <ContainerBlockElement> | |
| 4094 | <Paragraph>HTTP GET request to | |
| 4095 | <URLLink LinkURL="http://192.168.1.33/cgi-bin/htmlscript?../../../../../../../etc/passwd" LinkTitle="http://192.168.1.33/cgi-bin/htmlscript?../../../../../../../etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4096 | </test> | |
| 4097 | ||
| 4098 | <test id="http-cgi-testcgi-file-listing" key="/cgi-bin/test-cgi" status="not-vulnerable"> | |
| 4099 | ||
| 4100 | <Paragraph> | |
| 4101 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4102 | <Paragraph> | |
| 4103 | <ContainerBlockElement> | |
| 4104 | <ContainerBlockElement> | |
| 4105 | <Paragraph>HTTP POST request to | |
| 4106 | <URLLink LinkURL="http://192.168.1.33/cgi-bin/test-cgi" LinkTitle="http://192.168.1.33/cgi-bin/test-cgi"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4107 | </test> | |
| 4108 | ||
| 4109 | <test id="http-lighttpd-mod_userdir-info-discl" key="/~bin/true" status="not-vulnerable"> | |
| 4110 | ||
| 4111 | <Paragraph> | |
| 4112 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4113 | <Paragraph> | |
| 4114 | <ContainerBlockElement> | |
| 4115 | <ContainerBlockElement> | |
| 4116 | <Paragraph>HTTP GET request to | |
| 4117 | <URLLink LinkURL="http://192.168.1.33/~bin/true" LinkTitle="http://192.168.1.33/~bin/true"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4118 | </test> | |
| 4119 | ||
| 4120 | <test id="http-open-proxy" key="http://www.google.com:80/" status="not-vulnerable"> | |
| 4121 | ||
| 4122 | <Paragraph> | |
| 4123 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4124 | <Paragraph> | |
| 4125 | <ContainerBlockElement> | |
| 4126 | <ContainerBlockElement> | |
| 4127 | <Paragraph>HTTP HEAD request to | |
| 4128 | <URLLink LinkURL="http://www.google.com/" LinkTitle="http://www.google.com/"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4129 | </test> | |
| 4130 | ||
| 4131 | <test id="http-php-ini-file-exposed" key="/cgi-bin/php.ini" status="not-vulnerable"> | |
| 4132 | ||
| 4133 | <Paragraph> | |
| 4134 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4135 | <Paragraph> | |
| 4136 | <ContainerBlockElement> | |
| 4137 | <ContainerBlockElement> | |
| 4138 | <Paragraph>HTTP GET request to | |
| 4139 | <URLLink LinkURL="http://192.168.1.33/cgi-bin/php.ini" LinkTitle="http://192.168.1.33/cgi-bin/php.ini"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4140 | </test> | |
| 4141 | ||
| 4142 | <test id="http-symantec-scan-engine-file-disclosure" key="/README.txt" status="not-vulnerable"> | |
| 4143 | ||
| 4144 | <Paragraph> | |
| 4145 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4146 | <Paragraph> | |
| 4147 | <ContainerBlockElement> | |
| 4148 | <ContainerBlockElement> | |
| 4149 | <Paragraph>HTTP GET request to | |
| 4150 | <URLLink LinkURL="http://192.168.1.33/README.txt" LinkTitle="http://192.168.1.33/README.txt"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4151 | </test> | |
| 4152 | ||
| 4153 | <test id="http-tomcat-jkstatus-accessible" key="/jkstatus/" status="not-vulnerable"> | |
| 4154 | ||
| 4155 | <Paragraph> | |
| 4156 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4157 | <Paragraph> | |
| 4158 | <ContainerBlockElement> | |
| 4159 | <ContainerBlockElement> | |
| 4160 | <Paragraph>HTTP GET request to | |
| 4161 | <URLLink LinkURL="http://192.168.1.33/jkstatus/" LinkTitle="http://192.168.1.33/jkstatus/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4162 | </test> | |
| 4163 | ||
| 4164 | <test id="adobe-apsb13-03-cve-2013-0629" key="/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../../license.html" status="not-vulnerable"> | |
| 4165 | ||
| 4166 | <Paragraph> | |
| 4167 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4168 | <Paragraph> | |
| 4169 | <ContainerBlockElement> | |
| 4170 | <ContainerBlockElement> | |
| 4171 | <Paragraph>HTTP GET request to | |
| 4172 | <URLLink LinkURL="http://192.168.1.33/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../license.txt" LinkTitle="http://192.168.1.33/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../license.txt"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4173 | <ContainerBlockElement> | |
| 4174 | <Paragraph>HTTP GET request to | |
| 4175 | <URLLink LinkURL="http://192.168.1.33/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../../license.html" LinkTitle="http://192.168.1.33/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../../license.html"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4176 | </test> | |
| 4177 | ||
| 4178 | <test id="apache-httpd-cve-2008-0005" key="ftp://ftp.kernel.org/;utf7xss" status="not-vulnerable"> | |
| 4179 | ||
| 4180 | <Paragraph> | |
| 4181 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4182 | <Paragraph> | |
| 4183 | <ContainerBlockElement> | |
| 4184 | <ContainerBlockElement> | |
| 4185 | <Paragraph>HTTP GET request to | |
| 4186 | <URLLink LinkURL="ftp://ftp.kernel.org/;utf7xss" LinkTitle="ftp://ftp.kernel.org/;utf7xss"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4187 | </test> | |
| 4188 | ||
| 4189 | <test id="apache-httpd-cve-2008-0005" key="ftp://ftp.kernel.org/;utf7xss" status="not-vulnerable"> | |
| 4190 | ||
| 4191 | <Paragraph> | |
| 4192 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4193 | <Paragraph> | |
| 4194 | <ContainerBlockElement> | |
| 4195 | <ContainerBlockElement> | |
| 4196 | <Paragraph>HTTP GET request to | |
| 4197 | <URLLink LinkURL="ftp://ftp.kernel.org/;utf7xss" LinkTitle="ftp://ftp.kernel.org/;utf7xss"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4198 | </test> | |
| 4199 | ||
| 4200 | <test id="apache-httpd-cve-2008-2939" key="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" status="not-vulnerable"> | |
| 4201 | ||
| 4202 | <Paragraph> | |
| 4203 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4204 | <Paragraph> | |
| 4205 | <ContainerBlockElement> | |
| 4206 | <ContainerBlockElement> | |
| 4207 | <Paragraph>HTTP GET request to | |
| 4208 | <URLLink LinkURL="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" LinkTitle="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4209 | </test> | |
| 4210 | ||
| 4211 | <test id="apache-httpd-cve-2008-2939" key="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" status="not-vulnerable"> | |
| 4212 | ||
| 4213 | <Paragraph> | |
| 4214 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4215 | <Paragraph> | |
| 4216 | <ContainerBlockElement> | |
| 4217 | <ContainerBlockElement> | |
| 4218 | <Paragraph>HTTP GET request to | |
| 4219 | <URLLink LinkURL="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" LinkTitle="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4220 | </test> | |
| 4221 | ||
| 4222 | <test id="http-adobe-amf-gateway-xxe-cve-2009-3960" key="/lcds-samples/messagebroker/httpsecure" status="not-vulnerable"> | |
| 4223 | ||
| 4224 | <Paragraph> | |
| 4225 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 4226 | <Paragraph> | |
| 4227 | <ContainerBlockElement> | |
| 4228 | <ContainerBlockElement> | |
| 4229 | <Paragraph>HTTP POST request to | |
| 4230 | <URLLink LinkURL="http://192.168.1.33/flex2gateway/http" LinkTitle="http://192.168.1.33/flex2gateway/http"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4231 | <ContainerBlockElement> | |
| 4232 | <Paragraph>HTTP POST request to | |
| 4233 | <URLLink LinkURL="http://192.168.1.33/flex2gateway/httpsecure" LinkTitle="http://192.168.1.33/flex2gateway/httpsecure"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4234 | <ContainerBlockElement> | |
| 4235 | <Paragraph>HTTP POST request to | |
| 4236 | <URLLink LinkURL="http://192.168.1.33/messagebroker/http" LinkTitle="http://192.168.1.33/messagebroker/http"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4237 | <ContainerBlockElement> | |
| 4238 | <Paragraph>HTTP POST request to | |
| 4239 | <URLLink LinkURL="http://192.168.1.33/messagebroker/httpsecure" LinkTitle="http://192.168.1.33/messagebroker/httpsecure"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4240 | <ContainerBlockElement> | |
| 4241 | <Paragraph>HTTP POST request to | |
| 4242 | <URLLink LinkURL="http://192.168.1.33/blazeds/messagebroker/http" LinkTitle="http://192.168.1.33/blazeds/messagebroker/http"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4243 | <ContainerBlockElement> | |
| 4244 | <Paragraph>HTTP POST request to | |
| 4245 | <URLLink LinkURL="http://192.168.1.33/blazeds/messagebroker/httpsecure" LinkTitle="http://192.168.1.33/blazeds/messagebroker/httpsecure"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4246 | <ContainerBlockElement> | |
| 4247 | <Paragraph>HTTP POST request to | |
| 4248 | <URLLink LinkURL="http://192.168.1.33/samples/messagebroker/http" LinkTitle="http://192.168.1.33/samples/messagebroker/http"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4249 | <ContainerBlockElement> | |
| 4250 | <Paragraph>HTTP POST request to | |
| 4251 | <URLLink LinkURL="http://192.168.1.33/samples/messagebroker/httpsecure" LinkTitle="http://192.168.1.33/samples/messagebroker/httpsecure"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4252 | <ContainerBlockElement> | |
| 4253 | <Paragraph>HTTP POST request to | |
| 4254 | <URLLink LinkURL="http://192.168.1.33/lcds/messagebroker/http" LinkTitle="http://192.168.1.33/lcds/messagebroker/http"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4255 | <ContainerBlockElement> | |
| 4256 | <Paragraph>HTTP POST request to | |
| 4257 | <URLLink LinkURL="http://192.168.1.33/lcds/messagebroker/httpsecure" LinkTitle="http://192.168.1.33/lcds/messagebroker/httpsecure"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4258 | <ContainerBlockElement> | |
| 4259 | <Paragraph>HTTP POST request to | |
| 4260 | <URLLink LinkURL="http://192.168.1.33/lcds-samples/messagebroker/http" LinkTitle="http://192.168.1.33/lcds-samples/messagebroker/http"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4261 | <ContainerBlockElement> | |
| 4262 | <Paragraph>HTTP POST request to | |
| 4263 | <URLLink LinkURL="http://192.168.1.33/lcds-samples/messagebroker/httpsecure" LinkTitle="http://192.168.1.33/lcds-samples/messagebroker/httpsecure"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4264 | </test> | |
| 4265 | </tests> | |
| 4266 | </service> | |
| 4267 | </services> | |
| 4268 | </endpoint> | |
| 4269 | ||
| 4270 | <endpoint protocol="udp" port="123" status="open"> | |
| 4271 | <services> | |
| 4272 | <service name="NTP"> | |
| 4273 | <fingerprints> | |
| 4274 | <fingerprint certainty="0.90" family="NTP" product="NTP" version="4.2.0a@1:4.2.0a+stable-8-r"/> | |
| 4275 | </fingerprints> | |
| 4276 | <configuration> | |
| 4277 | <config name="ntp.variables">version="ntpd 4.2.0a@1:4.2.0a+stable-8-r Sat Aug 30 06:44:03 EDT 2008 (1)", | |
| 4278 | processor="armv5tejl", system="Linux/2.6.18_pro500-davinci_IPNC_1.00", | |
| 4279 | leap=0, stratum=5, precision=-17, rootdelay=663.555, | |
| 4280 | rootdispersion=223.836, peer=16948, refid=61.67.210.241, | |
| 4281 | reftime=0xd63ff867.7092ee84, poll=9, clock=0xd63ffb99.954b167e, state=4, | |
| 4282 | offset=-29.969, frequency=6.641, noise=9.203, jitter=5.336, | |
| 4283 | stability=21.220 | |
| 4284 | </config> | |
| 4285 | </configuration> | |
| 4286 | <tests> | |
| 4287 | <test id="ntpd-crypto-recv-buffer-overflow" status="vulnerable-version"> | |
| 4288 | ||
| 4289 | <Paragraph> | |
| 4290 | <Paragraph>Running vulnerable NTP service: NTP 4.2.0a@1:4.2.0a+stable-8-r.</Paragraph></Paragraph> | |
| 4291 | </test> | |
| 4292 | ||
| 4293 | <test id="ntp-clock-variables-disclosure" status="vulnerable-exploited"> | |
| 4294 | ||
| 4295 | <Paragraph> | |
| 4296 | <Paragraph>The following NTP variables were found from a readvar request: version="ntpd 4.2.0a@1:4.2.0a+stable-8-r Sat Aug 30 06:44:03 EDT 2008 (1)", | |
| 4297 | processor="armv5tejl", system="Linux/2.6.18_pro500-davinci_IPNC_1.00", | |
| 4298 | leap=0, stratum=5, precision=-17, rootdelay=663.555, | |
| 4299 | rootdispersion=223.836, peer=16948, refid=61.67.210.241, | |
| 4300 | reftime=0xd63ff867.7092ee84, poll=9, clock=0xd63ffb99.954b167e, state=4, | |
| 4301 | offset=-29.969, frequency=6.641, noise=9.203, jitter=5.336, | |
| 4302 | stability=21.220 | |
| 4303 | </Paragraph></Paragraph> | |
| 4304 | </test> | |
| 4305 | </tests> | |
| 4306 | </service> | |
| 4307 | </services> | |
| 4308 | </endpoint> | |
| 4309 | ||
| 4310 | <endpoint protocol="tcp" port="443" status="open"> | |
| 4311 | <services> | |
| 4312 | <service name="HTTPS"> | |
| 4313 | <configuration> | |
| 4314 | <config name="ssl">true</config> | |
| 4315 | <config name="ssl.cert.issuer.dn">CN=www.dlink.com.tw, OU=R&D Dept., O=D-Link Taiwan, L=Taipei, ST=Taiwan, C=TW</config> | |
| 4316 | <config name="ssl.cert.key.alg.name">RSA</config> | |
| 4317 | <config name="ssl.cert.key.rsa.modulusBits">1024</config> | |
| 4318 | <config name="ssl.cert.not.valid.after">Sat, 11 Mar 2023 10:43:06 UTC</config> | |
| 4319 | <config name="ssl.cert.not.valid.before">Wed, 13 Mar 2013 10:43:06 UTC</config> | |
| 4320 | <config name="ssl.cert.selfsigned">true</config> | |
| 4321 | <config name="ssl.cert.serial.number">11340214068356762790</config> | |
| 4322 | <config name="ssl.cert.sig.alg.name">SHA1withRSA</config> | |
| 4323 | <config name="ssl.cert.subject.dn">CN=www.dlink.com.tw, OU=R&D Dept., O=D-Link Taiwan, L=Taipei, ST=Taiwan, C=TW</config> | |
| 4324 | <config name="ssl.cert.validsignature">true</config> | |
| 4325 | <config name="ssl.version.ssl20">true</config> | |
| 4326 | </configuration> | |
| 4327 | <tests> | |
| 4328 | <test id="adobe-apsb13-03-cve-2013-0632" key="/CFIDE/adminapi/administrator.cfc?" status="not-vulnerable"> | |
| 4329 | ||
| 4330 | <Paragraph> | |
| 4331 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4332 | <Paragraph> | |
| 4333 | <ContainerBlockElement> | |
| 4334 | <ContainerBlockElement> | |
| 4335 | <Paragraph>HTTP POST request to | |
| 4336 | <URLLink LinkURL="https://192.168.1.33/CFIDE/adminapi/administrator.cfc" LinkTitle="https://192.168.1.33/CFIDE/adminapi/administrator.cfc"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4337 | </test> | |
| 4338 | ||
| 4339 | <test id="adobe-apsb13-13-cve-2013-1389" status="skipped-version"> | |
| 4340 | ||
| 4341 | <Paragraph> | |
| 4342 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4343 | <Paragraph>Based on the result of the "APSB13-13: Security updates available for Adobe ColdFusion (CVE-2013-3336)" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 4344 | </test> | |
| 4345 | ||
| 4346 | <test id="http-3com-wap-default-admin-password" key="/index.htm" status="not-vulnerable"> | |
| 4347 | ||
| 4348 | <Paragraph> | |
| 4349 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4350 | <Paragraph> | |
| 4351 | <ContainerBlockElement> | |
| 4352 | <ContainerBlockElement> | |
| 4353 | <Paragraph>HTTP POST request to | |
| 4354 | <URLLink LinkURL="https://192.168.1.33/index.htm" LinkTitle="https://192.168.1.33/index.htm"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4355 | </test> | |
| 4356 | ||
| 4357 | <test id="http-drac-default-login" key="/data/login" status="not-vulnerable"> | |
| 4358 | ||
| 4359 | <Paragraph> | |
| 4360 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4361 | <Paragraph> | |
| 4362 | <ContainerBlockElement> | |
| 4363 | <ContainerBlockElement> | |
| 4364 | <Paragraph>HTTP POST request to | |
| 4365 | <URLLink LinkURL="https://192.168.1.33/data/login" LinkTitle="https://192.168.1.33/data/login"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4366 | </test> | |
| 4367 | ||
| 4368 | <test id="http-drac-default-login" key="/cgi/login" status="not-vulnerable"> | |
| 4369 | ||
| 4370 | <Paragraph> | |
| 4371 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4372 | <Paragraph> | |
| 4373 | <ContainerBlockElement> | |
| 4374 | <ContainerBlockElement> | |
| 4375 | <Paragraph>HTTP POST request to | |
| 4376 | <URLLink LinkURL="https://192.168.1.33/cgi/login" LinkTitle="https://192.168.1.33/cgi/login"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4377 | </test> | |
| 4378 | ||
| 4379 | <test id="http-glassfish-default-admin-password" key="/common/index.jsf" status="not-vulnerable"> | |
| 4380 | ||
| 4381 | <Paragraph> | |
| 4382 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4383 | <Paragraph> | |
| 4384 | <ContainerBlockElement> | |
| 4385 | <ContainerBlockElement> | |
| 4386 | <Paragraph>HTTP GET request to | |
| 4387 | <URLLink LinkURL="https://192.168.1.33/common/index.jsf" LinkTitle="https://192.168.1.33/common/index.jsf"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4388 | </test> | |
| 4389 | ||
| 4390 | <test id="http-nokia-firewall-default-admin-password" key="/cgi-bin/home.tcl" status="not-vulnerable"> | |
| 4391 | ||
| 4392 | <Paragraph> | |
| 4393 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4394 | <Paragraph> | |
| 4395 | <ContainerBlockElement> | |
| 4396 | <ContainerBlockElement> | |
| 4397 | <Paragraph>HTTP POST request to | |
| 4398 | <URLLink LinkURL="https://192.168.1.33/cgi-bin/home.tcl" LinkTitle="https://192.168.1.33/cgi-bin/home.tcl"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4399 | </test> | |
| 4400 | ||
| 4401 | <test id="http-phpmyadmin-account-pma-password-empty" key="/phpmyadmin/" status="not-vulnerable"> | |
| 4402 | ||
| 4403 | <Paragraph> | |
| 4404 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4405 | <Paragraph> | |
| 4406 | <ContainerBlockElement> | |
| 4407 | <ContainerBlockElement> | |
| 4408 | <Paragraph>HTTP GET request to | |
| 4409 | <URLLink LinkURL="https://192.168.1.33/phpmyadmin/" LinkTitle="https://192.168.1.33/phpmyadmin/"></URLLink></Paragraph>HTTP response code was 404 but expected 401</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4410 | </test> | |
| 4411 | ||
| 4412 | <test id="apache-struts-cve-2013-2251" key="/struts2-showcase/employee/save.action" status="not-vulnerable"> | |
| 4413 | ||
| 4414 | <Paragraph> | |
| 4415 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4416 | <Paragraph> | |
| 4417 | <ContainerBlockElement> | |
| 4418 | <ContainerBlockElement> | |
| 4419 | <Paragraph>HTTP GET request to | |
| 4420 | <URLLink LinkURL="https://192.168.1.33/struts2-showcase/employee/save.action" LinkTitle="https://192.168.1.33/struts2-showcase/employee/save.action"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4421 | </test> | |
| 4422 | ||
| 4423 | <test id="apache-struts-cve-2013-2251" key="/struts2-blank/example/HelloWorld.action" status="not-vulnerable"> | |
| 4424 | ||
| 4425 | <Paragraph> | |
| 4426 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4427 | <Paragraph> | |
| 4428 | <ContainerBlockElement> | |
| 4429 | <ContainerBlockElement> | |
| 4430 | <Paragraph>HTTP GET request to | |
| 4431 | <URLLink LinkURL="https://192.168.1.33/struts2-blank/example/HelloWorld.action" LinkTitle="https://192.168.1.33/struts2-blank/example/HelloWorld.action"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4432 | </test> | |
| 4433 | ||
| 4434 | <test id="checkpoint-ess-info-disclosure-sk57881" key="/conf/ssl/apache/integrity-smartcenter.key" status="not-vulnerable"> | |
| 4435 | ||
| 4436 | <Paragraph> | |
| 4437 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4438 | <Paragraph> | |
| 4439 | <ContainerBlockElement> | |
| 4440 | <ContainerBlockElement> | |
| 4441 | <Paragraph>HTTP GET request to | |
| 4442 | <URLLink LinkURL="https://192.168.1.33/conf/ssl/apache/integrity.key" LinkTitle="https://192.168.1.33/conf/ssl/apache/integrity.key"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4443 | <ContainerBlockElement> | |
| 4444 | <Paragraph>HTTP GET request to | |
| 4445 | <URLLink LinkURL="https://192.168.1.33/conf/ssl/apache/integrity-smartcenter.key" LinkTitle="https://192.168.1.33/conf/ssl/apache/integrity-smartcenter.key"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4446 | </test> | |
| 4447 | ||
| 4448 | <test id="adobe-apsb10-18-cve-2010-2861" key="/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en" status="not-vulnerable"> | |
| 4449 | ||
| 4450 | <Paragraph> | |
| 4451 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4452 | <Paragraph> | |
| 4453 | <ContainerBlockElement> | |
| 4454 | <ContainerBlockElement> | |
| 4455 | <Paragraph>HTTP GET request to | |
| 4456 | <URLLink LinkURL="https://192.168.1.33/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en" LinkTitle="https://192.168.1.33/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en"></URLLink></Paragraph>HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4457 | </test> | |
| 4458 | ||
| 4459 | <test id="http-awstats-remote-code-execution" key="/cgi-bin/awstats/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" status="not-vulnerable"> | |
| 4460 | ||
| 4461 | <Paragraph> | |
| 4462 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4463 | <Paragraph> | |
| 4464 | <ContainerBlockElement> | |
| 4465 | <ContainerBlockElement> | |
| 4466 | <Paragraph>HTTP GET request to | |
| 4467 | <URLLink LinkURL="https://192.168.1.33/cgi-bin/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" LinkTitle="https://192.168.1.33/cgi-bin/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4468 | <ContainerBlockElement> | |
| 4469 | <Paragraph>HTTP GET request to | |
| 4470 | <URLLink LinkURL="https://192.168.1.33/cgi-bin/awstats/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" LinkTitle="https://192.168.1.33/cgi-bin/awstats/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4471 | </test> | |
| 4472 | ||
| 4473 | <test id="http-cgi-faxsurvey-command-execution" key="/cgi-bin/faxquery?/bin/cat%20/etc/passwd" status="not-vulnerable"> | |
| 4474 | ||
| 4475 | <Paragraph> | |
| 4476 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4477 | <Paragraph> | |
| 4478 | <ContainerBlockElement> | |
| 4479 | <ContainerBlockElement> | |
| 4480 | <Paragraph>HTTP GET request to | |
| 4481 | <URLLink LinkURL="https://192.168.1.33/cgi-bin/faxsurvey?/bin/cat%20/etc/passwd" LinkTitle="https://192.168.1.33/cgi-bin/faxsurvey?/bin/cat%20/etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4482 | <ContainerBlockElement> | |
| 4483 | <Paragraph>HTTP GET request to | |
| 4484 | <URLLink LinkURL="https://192.168.1.33/cgi-bin/faxquery?/bin/cat%20/etc/passwd" LinkTitle="https://192.168.1.33/cgi-bin/faxquery?/bin/cat%20/etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4485 | </test> | |
| 4486 | ||
| 4487 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/administrator/enter.cfm" status="not-vulnerable"> | |
| 4488 | ||
| 4489 | <Paragraph> | |
| 4490 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4491 | <Paragraph> | |
| 4492 | <ContainerBlockElement> | |
| 4493 | <ContainerBlockElement> | |
| 4494 | <Paragraph>HTTP GET request to | |
| 4495 | <URLLink LinkURL="https://192.168.1.33/CFIDE/administrator/" LinkTitle="https://192.168.1.33/CFIDE/administrator/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4496 | <ContainerBlockElement> | |
| 4497 | <Paragraph>HTTP GET request to | |
| 4498 | <URLLink LinkURL="https://192.168.1.33/CFIDE/administrator/enter.cfm" LinkTitle="https://192.168.1.33/CFIDE/administrator/enter.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4499 | </test> | |
| 4500 | ||
| 4501 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/appdeployment/" status="not-vulnerable"> | |
| 4502 | ||
| 4503 | <Paragraph> | |
| 4504 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4505 | <Paragraph> | |
| 4506 | <ContainerBlockElement> | |
| 4507 | <ContainerBlockElement> | |
| 4508 | <Paragraph>HTTP GET request to | |
| 4509 | <URLLink LinkURL="https://192.168.1.33/CFIDE/appdeployment/" LinkTitle="https://192.168.1.33/CFIDE/appdeployment/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4510 | </test> | |
| 4511 | ||
| 4512 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/adminiapi/" status="not-vulnerable"> | |
| 4513 | ||
| 4514 | <Paragraph> | |
| 4515 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4516 | <Paragraph> | |
| 4517 | <ContainerBlockElement> | |
| 4518 | <ContainerBlockElement> | |
| 4519 | <Paragraph>HTTP GET request to | |
| 4520 | <URLLink LinkURL="https://192.168.1.33/CFIDE/adminiapi/" LinkTitle="https://192.168.1.33/CFIDE/adminiapi/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4521 | </test> | |
| 4522 | ||
| 4523 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/componentutils/" status="not-vulnerable"> | |
| 4524 | ||
| 4525 | <Paragraph> | |
| 4526 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4527 | <Paragraph> | |
| 4528 | <ContainerBlockElement> | |
| 4529 | <ContainerBlockElement> | |
| 4530 | <Paragraph>HTTP GET request to | |
| 4531 | <URLLink LinkURL="https://192.168.1.33/CFIDE/componentutils/" LinkTitle="https://192.168.1.33/CFIDE/componentutils/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4532 | </test> | |
| 4533 | ||
| 4534 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/adminapi/base.cfc?wsdl" status="not-vulnerable"> | |
| 4535 | ||
| 4536 | <Paragraph> | |
| 4537 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4538 | <Paragraph> | |
| 4539 | <ContainerBlockElement> | |
| 4540 | <ContainerBlockElement> | |
| 4541 | <Paragraph>HTTP GET request to | |
| 4542 | <URLLink LinkURL="https://192.168.1.33/CFIDE/adminapi/base.cfc?wsdl" LinkTitle="https://192.168.1.33/CFIDE/adminapi/base.cfc?wsdl"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4543 | </test> | |
| 4544 | ||
| 4545 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/orm/" status="not-vulnerable"> | |
| 4546 | ||
| 4547 | <Paragraph> | |
| 4548 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4549 | <Paragraph> | |
| 4550 | <ContainerBlockElement> | |
| 4551 | <ContainerBlockElement> | |
| 4552 | <Paragraph>HTTP GET request to | |
| 4553 | <URLLink LinkURL="https://192.168.1.33/CFIDE/orm/" LinkTitle="https://192.168.1.33/CFIDE/orm/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4554 | </test> | |
| 4555 | ||
| 4556 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/AIR/" status="not-vulnerable"> | |
| 4557 | ||
| 4558 | <Paragraph> | |
| 4559 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4560 | <Paragraph> | |
| 4561 | <ContainerBlockElement> | |
| 4562 | <ContainerBlockElement> | |
| 4563 | <Paragraph>HTTP GET request to | |
| 4564 | <URLLink LinkURL="https://192.168.1.33/CFIDE/AIR/" LinkTitle="https://192.168.1.33/CFIDE/AIR/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4565 | </test> | |
| 4566 | ||
| 4567 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/scheduler/" status="not-vulnerable"> | |
| 4568 | ||
| 4569 | <Paragraph> | |
| 4570 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4571 | <Paragraph> | |
| 4572 | <ContainerBlockElement> | |
| 4573 | <ContainerBlockElement> | |
| 4574 | <Paragraph>HTTP GET request to | |
| 4575 | <URLLink LinkURL="https://192.168.1.33/CFIDE/scheduler/" LinkTitle="https://192.168.1.33/CFIDE/scheduler/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4576 | </test> | |
| 4577 | ||
| 4578 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/servermanager/" status="not-vulnerable"> | |
| 4579 | ||
| 4580 | <Paragraph> | |
| 4581 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4582 | <Paragraph> | |
| 4583 | <ContainerBlockElement> | |
| 4584 | <ContainerBlockElement> | |
| 4585 | <Paragraph>HTTP GET request to | |
| 4586 | <URLLink LinkURL="https://192.168.1.33/CFIDE/servermanager/" LinkTitle="https://192.168.1.33/CFIDE/servermanager/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4587 | </test> | |
| 4588 | ||
| 4589 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/services/" status="not-vulnerable"> | |
| 4590 | ||
| 4591 | <Paragraph> | |
| 4592 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4593 | <Paragraph> | |
| 4594 | <ContainerBlockElement> | |
| 4595 | <ContainerBlockElement> | |
| 4596 | <Paragraph>HTTP GET request to | |
| 4597 | <URLLink LinkURL="https://192.168.1.33/CFIDE/services/" LinkTitle="https://192.168.1.33/CFIDE/services/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4598 | </test> | |
| 4599 | ||
| 4600 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/websocket/" status="not-vulnerable"> | |
| 4601 | ||
| 4602 | <Paragraph> | |
| 4603 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4604 | <Paragraph> | |
| 4605 | <ContainerBlockElement> | |
| 4606 | <ContainerBlockElement> | |
| 4607 | <Paragraph>HTTP GET request to | |
| 4608 | <URLLink LinkURL="https://192.168.1.33/CFIDE/websocket/" LinkTitle="https://192.168.1.33/CFIDE/websocket/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4609 | </test> | |
| 4610 | ||
| 4611 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/wizards/common/" status="not-vulnerable"> | |
| 4612 | ||
| 4613 | <Paragraph> | |
| 4614 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4615 | <Paragraph> | |
| 4616 | <ContainerBlockElement> | |
| 4617 | <ContainerBlockElement> | |
| 4618 | <Paragraph>HTTP GET request to | |
| 4619 | <URLLink LinkURL="https://192.168.1.33/CFIDE/wizards/common/" LinkTitle="https://192.168.1.33/CFIDE/wizards/common/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4620 | </test> | |
| 4621 | ||
| 4622 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=localhost&vport=22&vstart=&vusername=&vpassword=&returnformat=json" status="not-vulnerable"> | |
| 4623 | ||
| 4624 | <Paragraph> | |
| 4625 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4626 | <Paragraph> | |
| 4627 | <ContainerBlockElement> | |
| 4628 | <ContainerBlockElement> | |
| 4629 | <Paragraph>HTTP GET request to | |
| 4630 | <URLLink LinkURL="https://192.168.1.33/CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=localhost&vport=22&vstart=&vusername=&vpassword=&returnformat=json" LinkTitle="https://192.168.1.33/CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=localhost&vport=22&vstart=&vusername=&vpassword=&returnformat=json"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4631 | </test> | |
| 4632 | ||
| 4633 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/portlets/" status="not-vulnerable"> | |
| 4634 | ||
| 4635 | <Paragraph> | |
| 4636 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4637 | <Paragraph> | |
| 4638 | <ContainerBlockElement> | |
| 4639 | <ContainerBlockElement> | |
| 4640 | <Paragraph>HTTP GET request to | |
| 4641 | <URLLink LinkURL="https://192.168.1.33/CFIDE/portlets/" LinkTitle="https://192.168.1.33/CFIDE/portlets/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4642 | </test> | |
| 4643 | ||
| 4644 | <test id="http-frontpage-unprotected" key="/_vti_bin/_vti_aut/author.dll" status="not-vulnerable"> | |
| 4645 | ||
| 4646 | <Paragraph> | |
| 4647 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4648 | <Paragraph> | |
| 4649 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4650 | </test> | |
| 4651 | ||
| 4652 | <test id="http-php-xmlrpc-code-injection" key="/script/xmlrpc.php" status="not-vulnerable"> | |
| 4653 | ||
| 4654 | <Paragraph> | |
| 4655 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4656 | <Paragraph> | |
| 4657 | <ContainerBlockElement> | |
| 4658 | <ContainerBlockElement> | |
| 4659 | <Paragraph>HTTP POST request to | |
| 4660 | <URLLink LinkURL="https://192.168.1.33/xmlrpc.php" LinkTitle="https://192.168.1.33/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4661 | <ContainerBlockElement> | |
| 4662 | <Paragraph>HTTP POST request to | |
| 4663 | <URLLink LinkURL="https://192.168.1.33/serendipity/serendipity_xmlrpc.php" LinkTitle="https://192.168.1.33/serendipity/serendipity_xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4664 | <ContainerBlockElement> | |
| 4665 | <Paragraph>HTTP POST request to | |
| 4666 | <URLLink LinkURL="https://192.168.1.33/serendipity/xmlrpc.php" LinkTitle="https://192.168.1.33/serendipity/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4667 | <ContainerBlockElement> | |
| 4668 | <Paragraph>HTTP POST request to | |
| 4669 | <URLLink LinkURL="https://192.168.1.33/drupal/xmlrpc.php" LinkTitle="https://192.168.1.33/drupal/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4670 | <ContainerBlockElement> | |
| 4671 | <Paragraph>HTTP POST request to | |
| 4672 | <URLLink LinkURL="https://192.168.1.33/bblog/xmlrpc.php" LinkTitle="https://192.168.1.33/bblog/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4673 | <ContainerBlockElement> | |
| 4674 | <Paragraph>HTTP POST request to | |
| 4675 | <URLLink LinkURL="https://192.168.1.33/blogs/xmlsrv/xmlrpc.php" LinkTitle="https://192.168.1.33/blogs/xmlsrv/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4676 | <ContainerBlockElement> | |
| 4677 | <Paragraph>HTTP POST request to | |
| 4678 | <URLLink LinkURL="https://192.168.1.33/xmlsrv/xmlrpc.php" LinkTitle="https://192.168.1.33/xmlsrv/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4679 | <ContainerBlockElement> | |
| 4680 | <Paragraph>HTTP POST request to | |
| 4681 | <URLLink LinkURL="https://192.168.1.33/xmlrpc/xmlrpc.php" LinkTitle="https://192.168.1.33/xmlrpc/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 4682 | <ContainerBlockElement> | |
| 4683 | <Paragraph>HTTP POST request to | |
| 4684 | <URLLink LinkURL="https://192.168.1.33/script/xmlrpc.php" LinkTitle="https://192.168.1.33/script/xmlrpc.php"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4685 | </test> | |
| 4686 | ||
| 4687 | <test id="adobe-apsb13-03-cve-2013-0625" status="skipped-version"> | |
| 4688 | ||
| 4689 | <Paragraph> | |
| 4690 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4691 | <Paragraph>Based on the result of the "APSB13-03: Security updates available for Adobe ColdFusion (CVE-2013-0629)" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 4692 | </test> | |
| 4693 | ||
| 4694 | <test id="certificate-common-name-mismatch" status="vulnerable-exploited"> | |
| 4695 | ||
| 4696 | <Paragraph> | |
| 4697 | <Paragraph>The subject common name found in the X.509 certificate ('CN=www.dlink.com.tw') does not seem to match the scan target '192.168.1.33': | |
| 4698 | <UnorderedList> | |
| 4699 | <ListItem>Subject CN 'www.dlink.com.tw' does not match node name '192.168.1.33'</ListItem> | |
| 4700 | <ListItem>Subject CN's resolved IP address 'www.dlink.com.tw/58.86.33.135' differs from node IP address '/192.168.1.33'</ListItem></UnorderedList></Paragraph></Paragraph> | |
| 4701 | </test> | |
| 4702 | ||
| 4703 | <test id="http-iis-0014" status="not-vulnerable"> | |
| 4704 | ||
| 4705 | <Paragraph> | |
| 4706 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4707 | <Paragraph>Based on the following 3 results: | |
| 4708 | <OrderedList> | |
| 4709 | <ListItem> | |
| 4710 | <Paragraph> | |
| 4711 | <ContainerBlockElement> | |
| 4712 | <ContainerBlockElement> | |
| 4713 | <Paragraph>HTTP GET request to | |
| 4714 | <URLLink LinkURL="https://192.168.1.33/scripts/tools/newdsn.exe?driver=Microsoft%2BAccess%2BDriver%2B%28*.mdb%29&dsn=Web%20SQL&dbq=c:\temp\xyz.mdb&newdb=CREATE_DB&attr=" LinkTitle="https://192.168.1.33/scripts/tools/newdsn.exe?driver=Microsoft%2BAccess%2BDriver%2B%28*.mdb%29&dsn=Web%20SQL&dbq=c:\temp\xyz.mdb&newdb=CREATE_DB&attr="></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem> | |
| 4715 | <ListItem> | |
| 4716 | <Paragraph> | |
| 4717 | <ContainerBlockElement> | |
| 4718 | <ContainerBlockElement> | |
| 4719 | <Paragraph>HTTP GET request to | |
| 4720 | <URLLink LinkURL="https://192.168.1.33/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|" LinkTitle="https://192.168.1.33/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem> | |
| 4721 | <ListItem> | |
| 4722 | <Paragraph> | |
| 4723 | <ContainerBlockElement> | |
| 4724 | <ContainerBlockElement> | |
| 4725 | <Paragraph>HTTP GET request to | |
| 4726 | <URLLink LinkURL="https://192.168.1.33/ASPSamp/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|" LinkTitle="https://192.168.1.33/ASPSamp/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem></OrderedList></Paragraph></Paragraph> | |
| 4727 | </test> | |
| 4728 | ||
| 4729 | <test id="tls-server-cert-expired" status="not-vulnerable"> | |
| 4730 | ||
| 4731 | <Paragraph> | |
| 4732 | <Paragraph>Certificate valid from Wed, 13 Mar 2013 10:43:06 UTC to Sat, 11 Mar 2023 10:43:06 UTC</Paragraph></Paragraph> | |
| 4733 | </test> | |
| 4734 | ||
| 4735 | <test id="http-cgi-viewsource-arbitrary-file-access" key="/cgi-bin/view-source?../../../../../../../etc/passwd" status="not-vulnerable"> | |
| 4736 | ||
| 4737 | <Paragraph> | |
| 4738 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4739 | <Paragraph> | |
| 4740 | <ContainerBlockElement> | |
| 4741 | <ContainerBlockElement> | |
| 4742 | <Paragraph>HTTP GET request to | |
| 4743 | <URLLink LinkURL="https://192.168.1.33/cgi-bin/view-source?../../../../../../../etc/passwd" LinkTitle="https://192.168.1.33/cgi-bin/view-source?../../../../../../../etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4744 | </test> | |
| 4745 | ||
| 4746 | <test id="http-trace-method-enabled" key="/" status="not-vulnerable"> | |
| 4747 | ||
| 4748 | <Paragraph> | |
| 4749 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4750 | <Paragraph> | |
| 4751 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4752 | </test> | |
| 4753 | ||
| 4754 | <test id="http-track-method-enabled" key="/" status="not-vulnerable"> | |
| 4755 | ||
| 4756 | <Paragraph> | |
| 4757 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4758 | <Paragraph> | |
| 4759 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4760 | </test> | |
| 4761 | ||
| 4762 | <test id="spider-adobe-flash-permissive-crossdomain-xml" key="/crossdomain.xml" status="not-vulnerable"> | |
| 4763 | ||
| 4764 | <Paragraph> | |
| 4765 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4766 | <Paragraph> | |
| 4767 | <ContainerBlockElement> | |
| 4768 | <ContainerBlockElement> | |
| 4769 | <Paragraph>HTTP GET request to | |
| 4770 | <URLLink LinkURL="https://192.168.1.33/crossdomain.xml" LinkTitle="https://192.168.1.33/crossdomain.xml"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4771 | </test> | |
| 4772 | ||
| 4773 | <test id="ssl-weak-ciphers" status="vulnerable-exploited"> | |
| 4774 | ||
| 4775 | <Paragraph> | |
| 4776 | <Paragraph>Negotiated with the following insecure cipher suites. SSLv2 ciphers: | |
| 4777 | <UnorderedList> | |
| 4778 | <ListItem>SSL_CK_RC4_128_WITH_MD5</ListItem> | |
| 4779 | <ListItem>SSL_CK_RC4_128_EXPORT40_WITH_MD5</ListItem> | |
| 4780 | <ListItem>SSL_CK_RC2_128_CBC_WITH_MD5</ListItem> | |
| 4781 | <ListItem>SSL_CK_RC2_128_CBC_EXPORT40_WITH_MD5</ListItem> | |
| 4782 | <ListItem>SSL_CK_DES_64_CBC_WITH_MD5</ListItem> | |
| 4783 | <ListItem>SSL_CK_DES_192_EDE3_CBC_WITH_MD5</ListItem></UnorderedList>SSLv3 ciphers: | |
| 4784 | <UnorderedList> | |
| 4785 | <ListItem>SSL_RSA_WITH_DES_CBC_SHA</ListItem></UnorderedList></Paragraph></Paragraph> | |
| 4786 | </test> | |
| 4787 | ||
| 4788 | <test id="sslv2-and-up-enabled" status="vulnerable-exploited"> | |
| 4789 | ||
| 4790 | <Paragraph> | |
| 4791 | <Paragraph>SSLv2 is supported</Paragraph></Paragraph> | |
| 4792 | </test> | |
| 4793 | ||
| 4794 | <test id="adobe-apsb13-03-cve-2013-0631" key="/CFIDE/r.cfm" status="not-vulnerable"> | |
| 4795 | ||
| 4796 | <Paragraph> | |
| 4797 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4798 | <Paragraph> | |
| 4799 | <ContainerBlockElement> | |
| 4800 | <ContainerBlockElement> | |
| 4801 | <Paragraph>HTTP GET request to | |
| 4802 | <URLLink LinkURL="https://192.168.1.33/CFIDE/adminapi/customtags/fusebox.cfm" LinkTitle="https://192.168.1.33/CFIDE/adminapi/customtags/fusebox.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4803 | <ContainerBlockElement> | |
| 4804 | <Paragraph>HTTP GET request to | |
| 4805 | <URLLink LinkURL="https://192.168.1.33/CFIDE/adminapi/customtags/adss.cfm" LinkTitle="https://192.168.1.33/CFIDE/adminapi/customtags/adss.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4806 | <ContainerBlockElement> | |
| 4807 | <Paragraph>HTTP GET request to | |
| 4808 | <URLLink LinkURL="https://192.168.1.33/CFIDE/h.cfm" LinkTitle="https://192.168.1.33/CFIDE/h.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4809 | <ContainerBlockElement> | |
| 4810 | <Paragraph>HTTP GET request to | |
| 4811 | <URLLink LinkURL="https://192.168.1.33/CFIDE/h9.cfm" LinkTitle="https://192.168.1.33/CFIDE/h9.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4812 | <ContainerBlockElement> | |
| 4813 | <Paragraph>HTTP GET request to | |
| 4814 | <URLLink LinkURL="https://192.168.1.33/CFIDE/help.cfm" LinkTitle="https://192.168.1.33/CFIDE/help.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4815 | <ContainerBlockElement> | |
| 4816 | <Paragraph>HTTP GET request to | |
| 4817 | <URLLink LinkURL="https://192.168.1.33/CFIDE/i.cfm" LinkTitle="https://192.168.1.33/CFIDE/i.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4818 | <ContainerBlockElement> | |
| 4819 | <Paragraph>HTTP GET request to | |
| 4820 | <URLLink LinkURL="https://192.168.1.33/CFIDE/r.cfm" LinkTitle="https://192.168.1.33/CFIDE/r.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4821 | </test> | |
| 4822 | ||
| 4823 | <test id="adobe-apsb13-13-cve-2013-3336" key="/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=U" status="not-vulnerable"> | |
| 4824 | ||
| 4825 | <Paragraph> | |
| 4826 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4827 | <Paragraph> | |
| 4828 | <ContainerBlockElement> | |
| 4829 | <ContainerBlockElement> | |
| 4830 | <Paragraph>HTTP GET request to | |
| 4831 | <URLLink LinkURL="https://192.168.1.33/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test" LinkTitle="https://192.168.1.33/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test"></URLLink></Paragraph>HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4832 | <ContainerBlockElement> | |
| 4833 | <Paragraph>HTTP GET request to | |
| 4834 | <URLLink LinkURL="https://192.168.1.33/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test" LinkTitle="https://192.168.1.33/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test"></URLLink></Paragraph>HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4835 | </test> | |
| 4836 | ||
| 4837 | <test id="http-awstats-debug-information-disclosure" key="/cgi-bin/awstats/awstats.pl?debug=1" status="not-vulnerable"> | |
| 4838 | ||
| 4839 | <Paragraph> | |
| 4840 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4841 | <Paragraph> | |
| 4842 | <ContainerBlockElement> | |
| 4843 | <ContainerBlockElement> | |
| 4844 | <Paragraph>HTTP GET request to | |
| 4845 | <URLLink LinkURL="https://192.168.1.33/cgi-bin/awstats.pl?debug=1" LinkTitle="https://192.168.1.33/cgi-bin/awstats.pl?debug=1"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4846 | <ContainerBlockElement> | |
| 4847 | <Paragraph>HTTP GET request to | |
| 4848 | <URLLink LinkURL="https://192.168.1.33/cgi-bin/awstats/awstats.pl?debug=1" LinkTitle="https://192.168.1.33/cgi-bin/awstats/awstats.pl?debug=1"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4849 | </test> | |
| 4850 | ||
| 4851 | <test id="http-bigbrother-accessible" key="/bb/" status="not-vulnerable"> | |
| 4852 | ||
| 4853 | <Paragraph> | |
| 4854 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4855 | <Paragraph> | |
| 4856 | <ContainerBlockElement> | |
| 4857 | <ContainerBlockElement> | |
| 4858 | <Paragraph>HTTP GET request to | |
| 4859 | <URLLink LinkURL="https://192.168.1.33/bb/" LinkTitle="https://192.168.1.33/bb/"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4860 | </test> | |
| 4861 | ||
| 4862 | <test id="http-cgi-htdig-arbitrary-file-access" key="/cgi-bin/htsearch?Exclude=%60/etc/passwd%60" status="not-vulnerable"> | |
| 4863 | ||
| 4864 | <Paragraph> | |
| 4865 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4866 | <Paragraph> | |
| 4867 | <ContainerBlockElement> | |
| 4868 | <ContainerBlockElement> | |
| 4869 | <Paragraph>HTTP GET request to | |
| 4870 | <URLLink LinkURL="https://192.168.1.33/cgi-bin/htsearch?Exclude=%60/etc/passwd%60" LinkTitle="https://192.168.1.33/cgi-bin/htsearch?Exclude=%60/etc/passwd%60"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4871 | </test> | |
| 4872 | ||
| 4873 | <test id="http-cgi-htgrep-arbitrary-file-access" key="/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd" status="not-vulnerable"> | |
| 4874 | ||
| 4875 | <Paragraph> | |
| 4876 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4877 | <Paragraph> | |
| 4878 | <ContainerBlockElement> | |
| 4879 | <ContainerBlockElement> | |
| 4880 | <Paragraph>HTTP GET request to | |
| 4881 | <URLLink LinkURL="https://192.168.1.33/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd" LinkTitle="https://192.168.1.33/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4882 | </test> | |
| 4883 | ||
| 4884 | <test id="http-cgi-htmlscript-arbitrary-file-access" key="/cgi-bin/htmlscript?../../../../../../../etc/passwd" status="not-vulnerable"> | |
| 4885 | ||
| 4886 | <Paragraph> | |
| 4887 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4888 | <Paragraph> | |
| 4889 | <ContainerBlockElement> | |
| 4890 | <ContainerBlockElement> | |
| 4891 | <Paragraph>HTTP GET request to | |
| 4892 | <URLLink LinkURL="https://192.168.1.33/cgi-bin/htmlscript?../../../../../../../etc/passwd" LinkTitle="https://192.168.1.33/cgi-bin/htmlscript?../../../../../../../etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4893 | </test> | |
| 4894 | ||
| 4895 | <test id="http-cgi-testcgi-file-listing" key="/cgi-bin/test-cgi" status="not-vulnerable"> | |
| 4896 | ||
| 4897 | <Paragraph> | |
| 4898 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4899 | <Paragraph> | |
| 4900 | <ContainerBlockElement> | |
| 4901 | <ContainerBlockElement> | |
| 4902 | <Paragraph>HTTP POST request to | |
| 4903 | <URLLink LinkURL="https://192.168.1.33/cgi-bin/test-cgi" LinkTitle="https://192.168.1.33/cgi-bin/test-cgi"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4904 | </test> | |
| 4905 | ||
| 4906 | <test id="http-lighttpd-mod_userdir-info-discl" key="/~bin/true" status="not-vulnerable"> | |
| 4907 | ||
| 4908 | <Paragraph> | |
| 4909 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4910 | <Paragraph> | |
| 4911 | <ContainerBlockElement> | |
| 4912 | <ContainerBlockElement> | |
| 4913 | <Paragraph>HTTP GET request to | |
| 4914 | <URLLink LinkURL="https://192.168.1.33/~bin/true" LinkTitle="https://192.168.1.33/~bin/true"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4915 | </test> | |
| 4916 | ||
| 4917 | <test id="http-open-proxy" key="http://www.google.com:80/" status="not-vulnerable"> | |
| 4918 | ||
| 4919 | <Paragraph> | |
| 4920 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4921 | <Paragraph> | |
| 4922 | <ContainerBlockElement> | |
| 4923 | <ContainerBlockElement> | |
| 4924 | <Paragraph>HTTP HEAD request to | |
| 4925 | <URLLink LinkURL="http://www.google.com/" LinkTitle="http://www.google.com/"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4926 | </test> | |
| 4927 | ||
| 4928 | <test id="http-php-ini-file-exposed" key="/cgi-bin/php.ini" status="not-vulnerable"> | |
| 4929 | ||
| 4930 | <Paragraph> | |
| 4931 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4932 | <Paragraph> | |
| 4933 | <ContainerBlockElement> | |
| 4934 | <ContainerBlockElement> | |
| 4935 | <Paragraph>HTTP GET request to | |
| 4936 | <URLLink LinkURL="https://192.168.1.33/cgi-bin/php.ini" LinkTitle="https://192.168.1.33/cgi-bin/php.ini"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4937 | </test> | |
| 4938 | ||
| 4939 | <test id="http-symantec-scan-engine-file-disclosure" key="/README.txt" status="not-vulnerable"> | |
| 4940 | ||
| 4941 | <Paragraph> | |
| 4942 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4943 | <Paragraph> | |
| 4944 | <ContainerBlockElement> | |
| 4945 | <ContainerBlockElement> | |
| 4946 | <Paragraph>HTTP GET request to | |
| 4947 | <URLLink LinkURL="https://192.168.1.33/README.txt" LinkTitle="https://192.168.1.33/README.txt"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4948 | </test> | |
| 4949 | ||
| 4950 | <test id="http-tomcat-jkstatus-accessible" key="/jkstatus/" status="not-vulnerable"> | |
| 4951 | ||
| 4952 | <Paragraph> | |
| 4953 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4954 | <Paragraph> | |
| 4955 | <ContainerBlockElement> | |
| 4956 | <ContainerBlockElement> | |
| 4957 | <Paragraph>HTTP GET request to | |
| 4958 | <URLLink LinkURL="https://192.168.1.33/jkstatus/" LinkTitle="https://192.168.1.33/jkstatus/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4959 | </test> | |
| 4960 | ||
| 4961 | <test id="tls-server-cert-sig-alg-md5" status="not-vulnerable"> | |
| 4962 | ||
| 4963 | <Paragraph> | |
| 4964 | <Paragraph>SSL certificate is signed with SHA1withRSA</Paragraph></Paragraph> | |
| 4965 | </test> | |
| 4966 | ||
| 4967 | <test id="adobe-apsb13-03-cve-2013-0629" key="/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../../license.html" status="not-vulnerable"> | |
| 4968 | ||
| 4969 | <Paragraph> | |
| 4970 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4971 | <Paragraph> | |
| 4972 | <ContainerBlockElement> | |
| 4973 | <ContainerBlockElement> | |
| 4974 | <Paragraph>HTTP GET request to | |
| 4975 | <URLLink LinkURL="https://192.168.1.33/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../license.txt" LinkTitle="https://192.168.1.33/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../license.txt"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 4976 | <ContainerBlockElement> | |
| 4977 | <Paragraph>HTTP GET request to | |
| 4978 | <URLLink LinkURL="https://192.168.1.33/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../../license.html" LinkTitle="https://192.168.1.33/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../../license.html"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4979 | </test> | |
| 4980 | ||
| 4981 | <test id="apache-httpd-cve-2008-0005" key="ftp://ftp.kernel.org/;utf7xss" status="not-vulnerable"> | |
| 4982 | ||
| 4983 | <Paragraph> | |
| 4984 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4985 | <Paragraph> | |
| 4986 | <ContainerBlockElement> | |
| 4987 | <ContainerBlockElement> | |
| 4988 | <Paragraph>HTTP GET request to | |
| 4989 | <URLLink LinkURL="ftp://ftp.kernel.org/;utf7xss" LinkTitle="ftp://ftp.kernel.org/;utf7xss"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 4990 | </test> | |
| 4991 | ||
| 4992 | <test id="apache-httpd-cve-2008-0005" key="ftp://ftp.kernel.org/;utf7xss" status="not-vulnerable"> | |
| 4993 | ||
| 4994 | <Paragraph> | |
| 4995 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 4996 | <Paragraph> | |
| 4997 | <ContainerBlockElement> | |
| 4998 | <ContainerBlockElement> | |
| 4999 | <Paragraph>HTTP GET request to | |
| 5000 | <URLLink LinkURL="ftp://ftp.kernel.org/;utf7xss" LinkTitle="ftp://ftp.kernel.org/;utf7xss"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5001 | </test> | |
| 5002 | ||
| 5003 | <test id="apache-httpd-cve-2008-2939" key="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" status="not-vulnerable"> | |
| 5004 | ||
| 5005 | <Paragraph> | |
| 5006 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 5007 | <Paragraph> | |
| 5008 | <ContainerBlockElement> | |
| 5009 | <ContainerBlockElement> | |
| 5010 | <Paragraph>HTTP GET request to | |
| 5011 | <URLLink LinkURL="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" LinkTitle="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5012 | </test> | |
| 5013 | ||
| 5014 | <test id="apache-httpd-cve-2008-2939" key="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" status="not-vulnerable"> | |
| 5015 | ||
| 5016 | <Paragraph> | |
| 5017 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 5018 | <Paragraph> | |
| 5019 | <ContainerBlockElement> | |
| 5020 | <ContainerBlockElement> | |
| 5021 | <Paragraph>HTTP GET request to | |
| 5022 | <URLLink LinkURL="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" LinkTitle="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5023 | </test> | |
| 5024 | ||
| 5025 | <test id="http-adobe-amf-gateway-xxe-cve-2009-3960" key="/lcds-samples/messagebroker/httpsecure" status="not-vulnerable"> | |
| 5026 | ||
| 5027 | <Paragraph> | |
| 5028 | <Paragraph>Running vulnerable HTTPS service.</Paragraph> | |
| 5029 | <Paragraph> | |
| 5030 | <ContainerBlockElement> | |
| 5031 | <ContainerBlockElement> | |
| 5032 | <Paragraph>HTTP POST request to | |
| 5033 | <URLLink LinkURL="https://192.168.1.33/flex2gateway/http" LinkTitle="https://192.168.1.33/flex2gateway/http"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 5034 | <ContainerBlockElement> | |
| 5035 | <Paragraph>HTTP POST request to | |
| 5036 | <URLLink LinkURL="https://192.168.1.33/flex2gateway/httpsecure" LinkTitle="https://192.168.1.33/flex2gateway/httpsecure"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 5037 | <ContainerBlockElement> | |
| 5038 | <Paragraph>HTTP POST request to | |
| 5039 | <URLLink LinkURL="https://192.168.1.33/messagebroker/http" LinkTitle="https://192.168.1.33/messagebroker/http"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 5040 | <ContainerBlockElement> | |
| 5041 | <Paragraph>HTTP POST request to | |
| 5042 | <URLLink LinkURL="https://192.168.1.33/messagebroker/httpsecure" LinkTitle="https://192.168.1.33/messagebroker/httpsecure"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 5043 | <ContainerBlockElement> | |
| 5044 | <Paragraph>HTTP POST request to | |
| 5045 | <URLLink LinkURL="https://192.168.1.33/blazeds/messagebroker/http" LinkTitle="https://192.168.1.33/blazeds/messagebroker/http"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 5046 | <ContainerBlockElement> | |
| 5047 | <Paragraph>HTTP POST request to | |
| 5048 | <URLLink LinkURL="https://192.168.1.33/blazeds/messagebroker/httpsecure" LinkTitle="https://192.168.1.33/blazeds/messagebroker/httpsecure"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 5049 | <ContainerBlockElement> | |
| 5050 | <Paragraph>HTTP POST request to | |
| 5051 | <URLLink LinkURL="https://192.168.1.33/samples/messagebroker/http" LinkTitle="https://192.168.1.33/samples/messagebroker/http"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 5052 | <ContainerBlockElement> | |
| 5053 | <Paragraph>HTTP POST request to | |
| 5054 | <URLLink LinkURL="https://192.168.1.33/samples/messagebroker/httpsecure" LinkTitle="https://192.168.1.33/samples/messagebroker/httpsecure"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 5055 | <ContainerBlockElement> | |
| 5056 | <Paragraph>HTTP POST request to | |
| 5057 | <URLLink LinkURL="https://192.168.1.33/lcds/messagebroker/http" LinkTitle="https://192.168.1.33/lcds/messagebroker/http"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 5058 | <ContainerBlockElement> | |
| 5059 | <Paragraph>HTTP POST request to | |
| 5060 | <URLLink LinkURL="https://192.168.1.33/lcds/messagebroker/httpsecure" LinkTitle="https://192.168.1.33/lcds/messagebroker/httpsecure"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 5061 | <ContainerBlockElement> | |
| 5062 | <Paragraph>HTTP POST request to | |
| 5063 | <URLLink LinkURL="https://192.168.1.33/lcds-samples/messagebroker/http" LinkTitle="https://192.168.1.33/lcds-samples/messagebroker/http"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement> | |
| 5064 | <ContainerBlockElement> | |
| 5065 | <Paragraph>HTTP POST request to | |
| 5066 | <URLLink LinkURL="https://192.168.1.33/lcds-samples/messagebroker/httpsecure" LinkTitle="https://192.168.1.33/lcds-samples/messagebroker/httpsecure"></URLLink></Paragraph>HTTP response code was 400 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5067 | </test> | |
| 5068 | ||
| 5069 | <test id="ssl-self-signed-certificate" status="vulnerable-exploited"> | |
| 5070 | ||
| 5071 | <Paragraph> | |
| 5072 | <Paragraph>TLS/SSL certificate is self-signed.</Paragraph></Paragraph> | |
| 5073 | </test> | |
| 5074 | ||
| 5075 | <test id="weak-crypto-key" status="vulnerable-exploited"> | |
| 5076 | ||
| 5077 | <Paragraph> | |
| 5078 | <Paragraph>Length of RSA modulus in X.509 certificate: 1024 bits (less than 2047 bits)</Paragraph></Paragraph> | |
| 5079 | </test> | |
| 5080 | ||
| 5081 | <test id="tls-server-cert-to-expire" status="not-vulnerable"> | |
| 5082 | ||
| 5083 | <Paragraph> | |
| 5084 | <Paragraph>Certificate valid from Wed, 13 Mar 2013 10:43:06 UTC to Sat, 11 Mar 2023 10:43:06 UTC</Paragraph></Paragraph> | |
| 5085 | </test> | |
| 5086 | </tests> | |
| 5087 | </service> | |
| 5088 | </services> | |
| 5089 | </endpoint> | |
| 5090 | ||
| 5091 | <endpoint protocol="tcp" port="554" status="open"> | |
| 5092 | <services> | |
| 5093 | <service name="RTSP"> | |
| 5094 | <configuration> | |
| 5095 | <config name="verbs-1">DESCRIBE</config> | |
| 5096 | <config name="verbs-2">GET_PARAMETER</config> | |
| 5097 | <config name="verbs-3">OPTIONS</config> | |
| 5098 | <config name="verbs-4">PAUSE</config> | |
| 5099 | <config name="verbs-5">PLAY</config> | |
| 5100 | <config name="verbs-6">SETUP</config> | |
| 5101 | <config name="verbs-7">SET_PARAMETER</config> | |
| 5102 | <config name="verbs-8">TEARDOWN</config> | |
| 5103 | <config name="verbs-count">8</config> | |
| 5104 | </configuration> | |
| 5105 | <tests> | |
| 5106 | </tests> | |
| 5107 | </service> | |
| 5108 | </services> | |
| 5109 | </endpoint> | |
| 5110 | ||
| 5111 | <endpoint protocol="tcp" port="1010" status="open"> | |
| 5112 | <services> | |
| 5113 | <service name="<unknown>"> | |
| 5114 | <tests> | |
| 5115 | </tests> | |
| 5116 | </service> | |
| 5117 | </services> | |
| 5118 | </endpoint> | |
| 5119 | ||
| 5120 | <endpoint protocol="tcp" port="7777" status="open"> | |
| 5121 | <services> | |
| 5122 | <service name="<unknown>"> | |
| 5123 | <tests> | |
| 5124 | </tests> | |
| 5125 | </service> | |
| 5126 | </services> | |
| 5127 | </endpoint> | |
| 5128 | </endpoints> | |
| 5129 | </node> | |
| 5130 | ||
| 5131 | <node address="192.168.1.34" status="alive" device-id="4"> | |
| 5132 | <fingerprints> | |
| 5133 | <os certainty="0.70" device-class="Specialized" vendor="Apple" family="Mac OS X" product="Mac OS X" version="10.8.0" cpe="cpe:/o:apple:mac_os_x:10.0"/> | |
| 5134 | <os certainty="0.70" device-class="VoIP" vendor="Apple" family="Mac OS X" product="Mac OS X" version="10.8.0" cpe="cpe:/o:apple:mac_os_x:10.0"/> | |
| 5135 | </fingerprints> | |
| 5136 | <tests> | |
| 5137 | <test id="http-upnp-0001" status="skipped-version"> | |
| 5138 | ||
| 5139 | <Paragraph> | |
| 5140 | <Paragraph>Based on the result of the "Windows XP UPnP NOTIFY LOCATION Denial of Service" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 5141 | </test> | |
| 5142 | ||
| 5143 | <test id="tcp-seq-num-approximation" status="not-vulnerable"> | |
| 5144 | ||
| 5145 | <Paragraph> | |
| 5146 | <Paragraph>TCP reset with incorrect sequence number did not trigger fault on 192.168.1.34:5000 (TCP read returned no data)</Paragraph></Paragraph> | |
| 5147 | </test> | |
| 5148 | ||
| 5149 | <test id="generic-icmp-netmask" status="not-vulnerable"> | |
| 5150 | ||
| 5151 | <Paragraph> | |
| 5152 | <Paragraph>No response</Paragraph></Paragraph> | |
| 5153 | </test> | |
| 5154 | ||
| 5155 | <test id="generic-icmp-timestamp" status="not-vulnerable"> | |
| 5156 | ||
| 5157 | <Paragraph> | |
| 5158 | <Paragraph>No response</Paragraph></Paragraph> | |
| 5159 | </test> | |
| 5160 | ||
| 5161 | <test id="generic-tcp-timestamp" status="vulnerable-exploited"> | |
| 5162 | ||
| 5163 | <Paragraph> | |
| 5164 | <Paragraph>Apparent system boot time: Thu Nov 14 01:50:04 UTC 2013</Paragraph></Paragraph> | |
| 5165 | </test> | |
| 5166 | ||
| 5167 | <test id="udp-ipid-zero" status="unknown"/> | |
| 5168 | </tests> | |
| 5169 | <endpoints> | |
| 5170 | <endpoint protocol="tcp" port="5000" status="open"> | |
| 5171 | <services> | |
| 5172 | <service name="UPnP-HTTPU"> | |
| 5173 | <configuration> | |
| 5174 | <config name="upnp.headers.server">AirTunes/190.9</config> | |
| 5175 | </configuration> | |
| 5176 | <tests> | |
| 5177 | <test id="http-upnp-0002" status="not-vulnerable"> | |
| 5178 | ||
| 5179 | <Paragraph> | |
| 5180 | <Paragraph>DoS attacks are not possible, server closes the connection</Paragraph></Paragraph> | |
| 5181 | </test> | |
| 5182 | </tests> | |
| 5183 | </service> | |
| 5184 | </services> | |
| 5185 | </endpoint> | |
| 5186 | ||
| 5187 | <endpoint protocol="udp" port="5353" status="open"> | |
| 5188 | <services> | |
| 5189 | <service name="zeroconf (Rendezvous)"> | |
| 5190 | <tests> | |
| 5191 | </tests> | |
| 5192 | </service> | |
| 5193 | </services> | |
| 5194 | </endpoint> | |
| 5195 | ||
| 5196 | <endpoint protocol="tcp" port="7100" status="open"> | |
| 5197 | <services> | |
| 5198 | <service name="XFS"> | |
| 5199 | <tests> | |
| 5200 | </tests> | |
| 5201 | </service> | |
| 5202 | </services> | |
| 5203 | </endpoint> | |
| 5204 | </endpoints> | |
| 5205 | </node> | |
| 5206 | ||
| 5207 | <node address="192.168.1.35" status="alive" device-id="8"> | |
| 5208 | <fingerprints> | |
| 5209 | <os certainty="0.68" device-class="General" vendor="Apple" family="Mac OS X" product="Mac OS X" version="10.5.6" cpe="cpe:/o:apple:mac_os_x:10.0"/> | |
| 5210 | <os certainty="0.66" device-class="General" vendor="FreeBSD" family="FreeBSD" product="FreeBSD" version="5.5-STABLE"/> | |
| 5211 | <os certainty="0.65" device-class="General" vendor="FreeBSD" family="FreeBSD" product="FreeBSD" version="6.1-RELEASE"/> | |
| 5212 | <os certainty="0.65" device-class="General" vendor="FreeBSD" family="FreeBSD" product="FreeBSD" version="8.0-STABLE"/> | |
| 5213 | <os certainty="0.64" device-class="General" vendor="Caldera" family="Open Unix" product="UNIX" version="7.1.0"/> | |
| 5214 | <os certainty="0.64" device-class="General" vendor="HP" family="VMS" product="VMS" version="5.1B"/> | |
| 5215 | <os certainty="0.64" device-class="General" vendor="HP" family="VMS" product="VMS" version="8.2"/> | |
| 5216 | <os certainty="0.64" device-class="General" vendor="HP" family="VMS" product="VMS" version="8.3" cpe="cpe:/o:hp:openvms:8.3"/> | |
| 5217 | <os certainty="0.64" device-class="Printer" vendor="Lexmark" family="embedded" product="embedded"/> | |
| 5218 | <os certainty="0.64" device-class="General" vendor="OpenBSD" family="OpenBSD" product="OpenBSD" version="4.3"/> | |
| 5219 | </fingerprints> | |
| 5220 | <tests> | |
| 5221 | <test id="generic-icmp-netmask" status="not-vulnerable"> | |
| 5222 | ||
| 5223 | <Paragraph> | |
| 5224 | <Paragraph>No response</Paragraph></Paragraph> | |
| 5225 | </test> | |
| 5226 | ||
| 5227 | <test id="generic-icmp-timestamp" status="not-vulnerable"> | |
| 5228 | ||
| 5229 | <Paragraph> | |
| 5230 | <Paragraph>No response</Paragraph></Paragraph> | |
| 5231 | </test> | |
| 5232 | </tests> | |
| 5233 | </node> | |
| 5234 | ||
| 5235 | <node address="192.168.1.37" status="alive" hardware-address="E4CE8F490D7C" device-id="2"> | |
| 5236 | <names> | |
| 5237 | <name>MACBOOKPRO-C9A7</name> | |
| 5238 | </names> | |
| 5239 | <tests> | |
| 5240 | <test id="generic-icmp-netmask" status="not-vulnerable"> | |
| 5241 | ||
| 5242 | <Paragraph> | |
| 5243 | <Paragraph>No response</Paragraph></Paragraph> | |
| 5244 | </test> | |
| 5245 | ||
| 5246 | <test id="generic-icmp-timestamp" status="not-vulnerable"> | |
| 5247 | ||
| 5248 | <Paragraph> | |
| 5249 | <Paragraph>No response</Paragraph></Paragraph> | |
| 5250 | </test> | |
| 5251 | ||
| 5252 | <test id="udp-ipid-zero" status="not-vulnerable"> | |
| 5253 | ||
| 5254 | <Paragraph> | |
| 5255 | <Paragraph>No UDP replies had an IP ID of zero</Paragraph></Paragraph> | |
| 5256 | </test> | |
| 5257 | </tests> | |
| 5258 | <endpoints> | |
| 5259 | <endpoint protocol="udp" port="123" status="open"> | |
| 5260 | <services> | |
| 5261 | <service name="NTP"> | |
| 5262 | <tests> | |
| 5263 | <test id="ntp-clock-variables-disclosure" status="not-vulnerable"> | |
| 5264 | ||
| 5265 | <Paragraph> | |
| 5266 | <Paragraph>No NTP variables were found from a readvar request</Paragraph></Paragraph> | |
| 5267 | </test> | |
| 5268 | </tests> | |
| 5269 | </service> | |
| 5270 | </services> | |
| 5271 | </endpoint> | |
| 5272 | ||
| 5273 | <endpoint protocol="udp" port="137" status="open"> | |
| 5274 | <services> | |
| 5275 | <service name="CIFS Name Service"> | |
| 5276 | <configuration> | |
| 5277 | <config name="advertised-name-1">MACBOOKPRO-C9A7 (Computer Name)</config> | |
| 5278 | <config name="advertised-name-count">1</config> | |
| 5279 | <config name="mac-address">E4CE8F490D7C</config> | |
| 5280 | </configuration> | |
| 5281 | <tests> | |
| 5282 | </tests> | |
| 5283 | </service> | |
| 5284 | </services> | |
| 5285 | </endpoint> | |
| 5286 | </endpoints> | |
| 5287 | </node> | |
| 5288 | ||
| 5289 | <node address="192.168.1.38" status="alive" device-id="9"> | |
| 5290 | <tests> | |
| 5291 | <test id="generic-icmp-netmask" status="not-vulnerable"> | |
| 5292 | ||
| 5293 | <Paragraph> | |
| 5294 | <Paragraph>No response</Paragraph></Paragraph> | |
| 5295 | </test> | |
| 5296 | ||
| 5297 | <test id="generic-icmp-timestamp" status="vulnerable-exploited"> | |
| 5298 | ||
| 5299 | <Paragraph> | |
| 5300 | <Paragraph>Remote system time: 05:03:21.216 UTC</Paragraph></Paragraph> | |
| 5301 | </test> | |
| 5302 | </tests> | |
| 5303 | </node> | |
| 5304 | ||
| 5305 | <node address="192.168.1.40" status="alive" device-id="3"> | |
| 5306 | <fingerprints> | |
| 5307 | <os certainty="0.70" device-class="VoIP" vendor="Microsoft" family="Windows" product="Windows" version="7.5"/> | |
| 5308 | <os certainty="0.70" device-class="General" vendor="Microsoft" family="Windows" product="Windows Server 2008" version="3"/> | |
| 5309 | <os certainty="0.70" device-class="General" vendor="Microsoft" family="Windows" product="Windows Server 2008" version="7"/> | |
| 5310 | </fingerprints> | |
| 5311 | <tests> | |
| 5312 | <test id="cifs-insecure-acct-lockout-limit" key="Microsoft Windows Phone 7.5" status="skipped-version"> | |
| 5313 | ||
| 5314 | <Paragraph> | |
| 5315 | <Paragraph>Skipped OS: Microsoft Windows Phone 7.5 | |
| 5316 | <Paragraph> | |
| 5317 | <UnorderedList> | |
| 5318 | <ListItem>The property "account-lockout-failure-threshold is empty.</ListItem></UnorderedList></Paragraph></Paragraph></Paragraph> | |
| 5319 | </test> | |
| 5320 | ||
| 5321 | <test id="cifs-insecure-password-length-min" key="Microsoft Windows Phone 7.5" status="skipped-version"> | |
| 5322 | ||
| 5323 | <Paragraph> | |
| 5324 | <Paragraph>Skipped OS: Microsoft Windows Phone 7.5 | |
| 5325 | <Paragraph> | |
| 5326 | <UnorderedList> | |
| 5327 | <ListItem>The property "password-minimum-length is empty.</ListItem></UnorderedList></Paragraph></Paragraph></Paragraph> | |
| 5328 | </test> | |
| 5329 | ||
| 5330 | <test id="cifs-no-acct-lockout-limit" key="Microsoft Windows Phone 7.5" status="skipped-version"> | |
| 5331 | ||
| 5332 | <Paragraph> | |
| 5333 | <Paragraph>Skipped OS: Microsoft Windows Phone 7.5 | |
| 5334 | <Paragraph> | |
| 5335 | <UnorderedList> | |
| 5336 | <ListItem>The property "account-lockout-failure-threshold is empty.</ListItem></UnorderedList></Paragraph></Paragraph></Paragraph> | |
| 5337 | </test> | |
| 5338 | ||
| 5339 | <test id="cifs-no-password-length-min" key="Microsoft Windows Phone 7.5" status="skipped-version"> | |
| 5340 | ||
| 5341 | <Paragraph> | |
| 5342 | <Paragraph>Skipped OS: Microsoft Windows Phone 7.5 | |
| 5343 | <Paragraph> | |
| 5344 | <UnorderedList> | |
| 5345 | <ListItem>The property "password-minimum-length is empty.</ListItem></UnorderedList></Paragraph></Paragraph></Paragraph> | |
| 5346 | </test> | |
| 5347 | ||
| 5348 | <test id="tcp-seq-num-approximation" status="not-vulnerable"> | |
| 5349 | ||
| 5350 | <Paragraph> | |
| 5351 | <Paragraph>TCP reset with incorrect sequence number did not trigger fault on 192.168.1.40:80 (TCP read returned no data)</Paragraph></Paragraph> | |
| 5352 | </test> | |
| 5353 | ||
| 5354 | <test id="generic-icmp-netmask" status="not-vulnerable"> | |
| 5355 | ||
| 5356 | <Paragraph> | |
| 5357 | <Paragraph>No response</Paragraph></Paragraph> | |
| 5358 | </test> | |
| 5359 | ||
| 5360 | <test id="generic-icmp-timestamp" status="not-vulnerable"> | |
| 5361 | ||
| 5362 | <Paragraph> | |
| 5363 | <Paragraph>No response</Paragraph></Paragraph> | |
| 5364 | </test> | |
| 5365 | ||
| 5366 | <test id="generic-tcp-timestamp" status="vulnerable-exploited"> | |
| 5367 | ||
| 5368 | <Paragraph> | |
| 5369 | <Paragraph>Apparent system boot time: Wed Nov 27 04:31:19 UTC 2013</Paragraph></Paragraph> | |
| 5370 | </test> | |
| 5371 | </tests> | |
| 5372 | <endpoints> | |
| 5373 | <endpoint protocol="tcp" port="80" status="open"> | |
| 5374 | <services> | |
| 5375 | <service name="HTTP"> | |
| 5376 | <tests> | |
| 5377 | <test id="adobe-apsb13-03-cve-2013-0632" key="/CFIDE/adminapi/administrator.cfc?" status="not-vulnerable"> | |
| 5378 | ||
| 5379 | <Paragraph> | |
| 5380 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5381 | <Paragraph> | |
| 5382 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5383 | </test> | |
| 5384 | ||
| 5385 | <test id="adobe-apsb13-13-cve-2013-1389" status="skipped-version"> | |
| 5386 | ||
| 5387 | <Paragraph> | |
| 5388 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5389 | <Paragraph>Based on the result of the "APSB13-13: Security updates available for Adobe ColdFusion (CVE-2013-3336)" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 5390 | </test> | |
| 5391 | ||
| 5392 | <test id="http-3com-wap-default-admin-password" key="/index.htm" status="not-vulnerable"> | |
| 5393 | ||
| 5394 | <Paragraph> | |
| 5395 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5396 | <Paragraph> | |
| 5397 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5398 | </test> | |
| 5399 | ||
| 5400 | <test id="http-drac-default-login" key="/cgi/login" status="not-vulnerable"> | |
| 5401 | ||
| 5402 | <Paragraph> | |
| 5403 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5404 | <Paragraph> | |
| 5405 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5406 | </test> | |
| 5407 | ||
| 5408 | <test id="http-drac-default-login" status="error"> | |
| 5409 | ||
| 5410 | <Paragraph> | |
| 5411 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5412 | <Paragraph>java.lang.StringIndexOutOfBoundsException: String index out of range: 55 | |
| 5413 | at java.lang.String.substring(String.java:1907) | |
| 5414 | at com.rapid7.net.http.HTTPResponseParser.parseFirstLine(Unknown Source) | |
| 5415 | at com.rapid7.net.http.HTTPMessageParser.parse(Unknown Source) | |
| 5416 | at com.rapid7.net.http.HTTPResponseParser.parseResponse(Unknown Source) | |
| 5417 | at com.rapid7.net.http.HTTPSession.parseResponse(Unknown Source) | |
| 5418 | at com.rapid7.net.http.HTTPSession.doReceiveResponse(Unknown Source) | |
| 5419 | at com.rapid7.net.http.HTTPSession.getResponseFor(Unknown Source) | |
| 5420 | at com.rapid7.net.http.HTTPSession.sendRequest(Unknown Source) | |
| 5421 | at com.rapid7.net.http.HTTPClient.request(Unknown Source) | |
| 5422 | at com.rapid7.net.http.HTTPClient.request(Unknown Source) | |
| 5423 | at com.rapid7.net.http.HTTPClient.request(Unknown Source) | |
| 5424 | at com.rapid7.nexpose.plugin.http.HTTPCheckHandler$HTTPReqRespTest.isMatch(Unknown Source) | |
| 5425 | at com.rapid7.nexpose.plugin.http.HTTPCheckHandler$HTTPCheckTest.performCheck(Unknown Source) | |
| 5426 | at com.rapid7.nexpose.plugin.http.HTTPCheckHandler.handle(Unknown Source) | |
| 5427 | at com.rapid7.nexpose.plugin.BaseCheckContext.invokeTest(Unknown Source) | |
| 5428 | at com.rapid7.nexpose.nse.VulnerabilityCheckContext.performTests(Unknown Source) | |
| 5429 | at sun.reflect.GeneratedMethodAccessor252.invoke(Unknown Source) | |
| 5430 | at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) | |
| 5431 | at java.lang.reflect.Method.invoke(Method.java:606) | |
| 5432 | at com.rapid7.thread.ThreadedCall.invokeCall(Unknown Source) | |
| 5433 | at com.rapid7.thread.ThreadedCall.execute(Unknown Source) | |
| 5434 | at com.rapid7.thread.ThreadedCallRunner.executeCall(Unknown Source) | |
| 5435 | at com.rapid7.thread.ThreadedCallRunner.run(Unknown Source) | |
| 5436 | </Paragraph></Paragraph> | |
| 5437 | </test> | |
| 5438 | ||
| 5439 | <test id="http-glassfish-default-admin-password" key="/common/index.jsf" status="not-vulnerable"> | |
| 5440 | ||
| 5441 | <Paragraph> | |
| 5442 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5443 | <Paragraph> | |
| 5444 | <ContainerBlockElement> | |
| 5445 | <ContainerBlockElement> | |
| 5446 | <Paragraph>HTTP GET request to | |
| 5447 | <URLLink LinkURL="http://192.168.1.40/common/index.jsf" LinkTitle="http://192.168.1.40/common/index.jsf"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5448 | </test> | |
| 5449 | ||
| 5450 | <test id="http-nokia-firewall-default-admin-password" key="/cgi-bin/home.tcl" status="not-vulnerable"> | |
| 5451 | ||
| 5452 | <Paragraph> | |
| 5453 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5454 | <Paragraph> | |
| 5455 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5456 | </test> | |
| 5457 | ||
| 5458 | <test id="http-phpmyadmin-account-pma-password-empty" key="/phpmyadmin/" status="not-vulnerable"> | |
| 5459 | ||
| 5460 | <Paragraph> | |
| 5461 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5462 | <Paragraph> | |
| 5463 | <ContainerBlockElement> | |
| 5464 | <ContainerBlockElement> | |
| 5465 | <Paragraph>HTTP GET request to | |
| 5466 | <URLLink LinkURL="http://192.168.1.40/phpmyadmin/" LinkTitle="http://192.168.1.40/phpmyadmin/"></URLLink></Paragraph>HTTP response code was 404 but expected 401</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5467 | </test> | |
| 5468 | ||
| 5469 | <test id="apache-struts-cve-2013-2251" key="/struts2-blank/example/HelloWorld.action" status="not-vulnerable"> | |
| 5470 | ||
| 5471 | <Paragraph> | |
| 5472 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5473 | <Paragraph> | |
| 5474 | <ContainerBlockElement> | |
| 5475 | <ContainerBlockElement> | |
| 5476 | <Paragraph>HTTP GET request to | |
| 5477 | <URLLink LinkURL="http://192.168.1.40/struts2-blank/example/HelloWorld.action" LinkTitle="http://192.168.1.40/struts2-blank/example/HelloWorld.action"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5478 | </test> | |
| 5479 | ||
| 5480 | <test id="apache-struts-cve-2013-2251" key="/struts2-showcase/employee/save.action" status="not-vulnerable"> | |
| 5481 | ||
| 5482 | <Paragraph> | |
| 5483 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5484 | <Paragraph> | |
| 5485 | <ContainerBlockElement> | |
| 5486 | <ContainerBlockElement> | |
| 5487 | <Paragraph>HTTP GET request to | |
| 5488 | <URLLink LinkURL="http://192.168.1.40/struts2-showcase/employee/save.action" LinkTitle="http://192.168.1.40/struts2-showcase/employee/save.action"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5489 | </test> | |
| 5490 | ||
| 5491 | <test id="checkpoint-ess-info-disclosure-sk57881" key="/conf/ssl/apache/integrity-smartcenter.key" status="not-vulnerable"> | |
| 5492 | ||
| 5493 | <Paragraph> | |
| 5494 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5495 | <Paragraph> | |
| 5496 | <ContainerBlockElement> | |
| 5497 | <ContainerBlockElement> | |
| 5498 | <Paragraph>HTTP GET request to | |
| 5499 | <URLLink LinkURL="http://192.168.1.40/conf/ssl/apache/integrity.key" LinkTitle="http://192.168.1.40/conf/ssl/apache/integrity.key"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 5500 | <ContainerBlockElement> | |
| 5501 | <Paragraph>HTTP GET request to | |
| 5502 | <URLLink LinkURL="http://192.168.1.40/conf/ssl/apache/integrity-smartcenter.key" LinkTitle="http://192.168.1.40/conf/ssl/apache/integrity-smartcenter.key"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5503 | </test> | |
| 5504 | ||
| 5505 | <test id="adobe-apsb10-18-cve-2010-2861" key="/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en" status="not-vulnerable"> | |
| 5506 | ||
| 5507 | <Paragraph> | |
| 5508 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5509 | <Paragraph> | |
| 5510 | <ContainerBlockElement> | |
| 5511 | <ContainerBlockElement> | |
| 5512 | <Paragraph>HTTP GET request to | |
| 5513 | <URLLink LinkURL="http://192.168.1.40/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en" LinkTitle="http://192.168.1.40/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en"></URLLink></Paragraph>HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5514 | </test> | |
| 5515 | ||
| 5516 | <test id="http-awstats-remote-code-execution" key="/cgi-bin/awstats/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" status="not-vulnerable"> | |
| 5517 | ||
| 5518 | <Paragraph> | |
| 5519 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5520 | <Paragraph> | |
| 5521 | <ContainerBlockElement> | |
| 5522 | <ContainerBlockElement> | |
| 5523 | <Paragraph>HTTP GET request to | |
| 5524 | <URLLink LinkURL="http://192.168.1.40/cgi-bin/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" LinkTitle="http://192.168.1.40/cgi-bin/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 5525 | <ContainerBlockElement> | |
| 5526 | <Paragraph>HTTP GET request to | |
| 5527 | <URLLink LinkURL="http://192.168.1.40/cgi-bin/awstats/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" LinkTitle="http://192.168.1.40/cgi-bin/awstats/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5528 | </test> | |
| 5529 | ||
| 5530 | <test id="http-cgi-faxsurvey-command-execution" key="/cgi-bin/faxquery?/bin/cat%20/etc/passwd" status="not-vulnerable"> | |
| 5531 | ||
| 5532 | <Paragraph> | |
| 5533 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5534 | <Paragraph> | |
| 5535 | <ContainerBlockElement> | |
| 5536 | <ContainerBlockElement> | |
| 5537 | <Paragraph>HTTP GET request to | |
| 5538 | <URLLink LinkURL="http://192.168.1.40/cgi-bin/faxsurvey?/bin/cat%20/etc/passwd" LinkTitle="http://192.168.1.40/cgi-bin/faxsurvey?/bin/cat%20/etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 5539 | <ContainerBlockElement> | |
| 5540 | <Paragraph>HTTP GET request to | |
| 5541 | <URLLink LinkURL="http://192.168.1.40/cgi-bin/faxquery?/bin/cat%20/etc/passwd" LinkTitle="http://192.168.1.40/cgi-bin/faxquery?/bin/cat%20/etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5542 | </test> | |
| 5543 | ||
| 5544 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/servermanager/" status="not-vulnerable"> | |
| 5545 | ||
| 5546 | <Paragraph> | |
| 5547 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5548 | <Paragraph> | |
| 5549 | <ContainerBlockElement> | |
| 5550 | <ContainerBlockElement> | |
| 5551 | <Paragraph>HTTP GET request to | |
| 5552 | <URLLink LinkURL="http://192.168.1.40/CFIDE/servermanager/" LinkTitle="http://192.168.1.40/CFIDE/servermanager/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5553 | </test> | |
| 5554 | ||
| 5555 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/AIR/" status="not-vulnerable"> | |
| 5556 | ||
| 5557 | <Paragraph> | |
| 5558 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5559 | <Paragraph> | |
| 5560 | <ContainerBlockElement> | |
| 5561 | <ContainerBlockElement> | |
| 5562 | <Paragraph>HTTP GET request to | |
| 5563 | <URLLink LinkURL="http://192.168.1.40/CFIDE/AIR/" LinkTitle="http://192.168.1.40/CFIDE/AIR/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5564 | </test> | |
| 5565 | ||
| 5566 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/administrator/enter.cfm" status="not-vulnerable"> | |
| 5567 | ||
| 5568 | <Paragraph> | |
| 5569 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5570 | <Paragraph> | |
| 5571 | <ContainerBlockElement> | |
| 5572 | <ContainerBlockElement> | |
| 5573 | <Paragraph>HTTP GET request to | |
| 5574 | <URLLink LinkURL="http://192.168.1.40/CFIDE/administrator/" LinkTitle="http://192.168.1.40/CFIDE/administrator/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 5575 | <ContainerBlockElement> | |
| 5576 | <Paragraph>HTTP GET request to | |
| 5577 | <URLLink LinkURL="http://192.168.1.40/CFIDE/administrator/enter.cfm" LinkTitle="http://192.168.1.40/CFIDE/administrator/enter.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5578 | </test> | |
| 5579 | ||
| 5580 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/adminiapi/" status="not-vulnerable"> | |
| 5581 | ||
| 5582 | <Paragraph> | |
| 5583 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5584 | <Paragraph> | |
| 5585 | <ContainerBlockElement> | |
| 5586 | <ContainerBlockElement> | |
| 5587 | <Paragraph>HTTP GET request to | |
| 5588 | <URLLink LinkURL="http://192.168.1.40/CFIDE/adminiapi/" LinkTitle="http://192.168.1.40/CFIDE/adminiapi/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5589 | </test> | |
| 5590 | ||
| 5591 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/adminapi/base.cfc?wsdl" status="not-vulnerable"> | |
| 5592 | ||
| 5593 | <Paragraph> | |
| 5594 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5595 | <Paragraph> | |
| 5596 | <ContainerBlockElement> | |
| 5597 | <ContainerBlockElement> | |
| 5598 | <Paragraph>HTTP GET request to | |
| 5599 | <URLLink LinkURL="http://192.168.1.40/CFIDE/adminapi/base.cfc?wsdl" LinkTitle="http://192.168.1.40/CFIDE/adminapi/base.cfc?wsdl"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5600 | </test> | |
| 5601 | ||
| 5602 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=localhost&vport=22&vstart=&vusername=&vpassword=&returnformat=json" status="not-vulnerable"> | |
| 5603 | ||
| 5604 | <Paragraph> | |
| 5605 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5606 | <Paragraph> | |
| 5607 | <ContainerBlockElement> | |
| 5608 | <ContainerBlockElement> | |
| 5609 | <Paragraph>HTTP GET request to | |
| 5610 | <URLLink LinkURL="http://192.168.1.40/CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=localhost&vport=22&vstart=&vusername=&vpassword=&returnformat=json" LinkTitle="http://192.168.1.40/CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=localhost&vport=22&vstart=&vusername=&vpassword=&returnformat=json"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5611 | </test> | |
| 5612 | ||
| 5613 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/scheduler/" status="not-vulnerable"> | |
| 5614 | ||
| 5615 | <Paragraph> | |
| 5616 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5617 | <Paragraph> | |
| 5618 | <ContainerBlockElement> | |
| 5619 | <ContainerBlockElement> | |
| 5620 | <Paragraph>HTTP GET request to | |
| 5621 | <URLLink LinkURL="http://192.168.1.40/CFIDE/scheduler/" LinkTitle="http://192.168.1.40/CFIDE/scheduler/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5622 | </test> | |
| 5623 | ||
| 5624 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/wizards/common/" status="not-vulnerable"> | |
| 5625 | ||
| 5626 | <Paragraph> | |
| 5627 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5628 | <Paragraph> | |
| 5629 | <ContainerBlockElement> | |
| 5630 | <ContainerBlockElement> | |
| 5631 | <Paragraph>HTTP GET request to | |
| 5632 | <URLLink LinkURL="http://192.168.1.40/CFIDE/wizards/common/" LinkTitle="http://192.168.1.40/CFIDE/wizards/common/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5633 | </test> | |
| 5634 | ||
| 5635 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/appdeployment/" status="not-vulnerable"> | |
| 5636 | ||
| 5637 | <Paragraph> | |
| 5638 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5639 | <Paragraph> | |
| 5640 | <ContainerBlockElement> | |
| 5641 | <ContainerBlockElement> | |
| 5642 | <Paragraph>HTTP GET request to | |
| 5643 | <URLLink LinkURL="http://192.168.1.40/CFIDE/appdeployment/" LinkTitle="http://192.168.1.40/CFIDE/appdeployment/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5644 | </test> | |
| 5645 | ||
| 5646 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/componentutils/" status="not-vulnerable"> | |
| 5647 | ||
| 5648 | <Paragraph> | |
| 5649 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5650 | <Paragraph> | |
| 5651 | <ContainerBlockElement> | |
| 5652 | <ContainerBlockElement> | |
| 5653 | <Paragraph>HTTP GET request to | |
| 5654 | <URLLink LinkURL="http://192.168.1.40/CFIDE/componentutils/" LinkTitle="http://192.168.1.40/CFIDE/componentutils/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5655 | </test> | |
| 5656 | ||
| 5657 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/websocket/" status="not-vulnerable"> | |
| 5658 | ||
| 5659 | <Paragraph> | |
| 5660 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5661 | <Paragraph> | |
| 5662 | <ContainerBlockElement> | |
| 5663 | <ContainerBlockElement> | |
| 5664 | <Paragraph>HTTP GET request to | |
| 5665 | <URLLink LinkURL="http://192.168.1.40/CFIDE/websocket/" LinkTitle="http://192.168.1.40/CFIDE/websocket/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5666 | </test> | |
| 5667 | ||
| 5668 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/services/" status="not-vulnerable"> | |
| 5669 | ||
| 5670 | <Paragraph> | |
| 5671 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5672 | <Paragraph> | |
| 5673 | <ContainerBlockElement> | |
| 5674 | <ContainerBlockElement> | |
| 5675 | <Paragraph>HTTP GET request to | |
| 5676 | <URLLink LinkURL="http://192.168.1.40/CFIDE/services/" LinkTitle="http://192.168.1.40/CFIDE/services/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5677 | </test> | |
| 5678 | ||
| 5679 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/orm/" status="not-vulnerable"> | |
| 5680 | ||
| 5681 | <Paragraph> | |
| 5682 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5683 | <Paragraph> | |
| 5684 | <ContainerBlockElement> | |
| 5685 | <ContainerBlockElement> | |
| 5686 | <Paragraph>HTTP GET request to | |
| 5687 | <URLLink LinkURL="http://192.168.1.40/CFIDE/orm/" LinkTitle="http://192.168.1.40/CFIDE/orm/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5688 | </test> | |
| 5689 | ||
| 5690 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/portlets/" status="not-vulnerable"> | |
| 5691 | ||
| 5692 | <Paragraph> | |
| 5693 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5694 | <Paragraph> | |
| 5695 | <ContainerBlockElement> | |
| 5696 | <ContainerBlockElement> | |
| 5697 | <Paragraph>HTTP GET request to | |
| 5698 | <URLLink LinkURL="http://192.168.1.40/CFIDE/portlets/" LinkTitle="http://192.168.1.40/CFIDE/portlets/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5699 | </test> | |
| 5700 | ||
| 5701 | <test id="http-frontpage-unprotected" key="/_vti_bin/_vti_aut/author.dll" status="not-vulnerable"> | |
| 5702 | ||
| 5703 | <Paragraph> | |
| 5704 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5705 | <Paragraph> | |
| 5706 | <ContainerBlockElement> | |
| 5707 | <ContainerBlockElement> | |
| 5708 | <Paragraph>HTTP GET request to | |
| 5709 | <URLLink LinkURL="http://192.168.1.40/_vti_bin/_vti_aut/author.dll" LinkTitle="http://192.168.1.40/_vti_bin/_vti_aut/author.dll"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5710 | </test> | |
| 5711 | ||
| 5712 | <test id="http-php-xmlrpc-code-injection" key="/xmlrpc.php" status="not-vulnerable"> | |
| 5713 | ||
| 5714 | <Paragraph> | |
| 5715 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5716 | <Paragraph> | |
| 5717 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5718 | </test> | |
| 5719 | ||
| 5720 | <test id="adobe-apsb13-03-cve-2013-0625" status="skipped-version"> | |
| 5721 | ||
| 5722 | <Paragraph> | |
| 5723 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5724 | <Paragraph>Based on the result of the "APSB13-03: Security updates available for Adobe ColdFusion (CVE-2013-0629)" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 5725 | </test> | |
| 5726 | ||
| 5727 | <test id="http-basic-auth-cleartext" key="/" status="not-vulnerable"> | |
| 5728 | ||
| 5729 | <Paragraph> | |
| 5730 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5731 | <Paragraph> | |
| 5732 | <ContainerBlockElement> | |
| 5733 | <ContainerBlockElement> | |
| 5734 | <Paragraph>HTTP GET request to | |
| 5735 | <URLLink LinkURL="http://192.168.1.40/" LinkTitle="http://192.168.1.40/"></URLLink></Paragraph>HTTP response code was 404 but expected 401</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5736 | </test> | |
| 5737 | ||
| 5738 | <test id="http-iis-0014" status="not-vulnerable"> | |
| 5739 | ||
| 5740 | <Paragraph> | |
| 5741 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5742 | <Paragraph>Based on the following 3 results: | |
| 5743 | <OrderedList> | |
| 5744 | <ListItem> | |
| 5745 | <Paragraph> | |
| 5746 | <ContainerBlockElement> | |
| 5747 | <ContainerBlockElement> | |
| 5748 | <Paragraph>HTTP GET request to | |
| 5749 | <URLLink LinkURL="http://192.168.1.40/scripts/tools/newdsn.exe?driver=Microsoft%2BAccess%2BDriver%2B%28*.mdb%29&dsn=Web%20SQL&dbq=c:\temp\xyz.mdb&newdb=CREATE_DB&attr=" LinkTitle="http://192.168.1.40/scripts/tools/newdsn.exe?driver=Microsoft%2BAccess%2BDriver%2B%28*.mdb%29&dsn=Web%20SQL&dbq=c:\temp\xyz.mdb&newdb=CREATE_DB&attr="></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem> | |
| 5750 | <ListItem> | |
| 5751 | <Paragraph> | |
| 5752 | <ContainerBlockElement> | |
| 5753 | <ContainerBlockElement> | |
| 5754 | <Paragraph>HTTP GET request to | |
| 5755 | <URLLink LinkURL="http://192.168.1.40/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|" LinkTitle="http://192.168.1.40/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem> | |
| 5756 | <ListItem> | |
| 5757 | <Paragraph> | |
| 5758 | <ContainerBlockElement> | |
| 5759 | <ContainerBlockElement> | |
| 5760 | <Paragraph>HTTP GET request to | |
| 5761 | <URLLink LinkURL="http://192.168.1.40/ASPSamp/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|" LinkTitle="http://192.168.1.40/ASPSamp/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem></OrderedList></Paragraph></Paragraph> | |
| 5762 | </test> | |
| 5763 | ||
| 5764 | <test id="http-cgi-viewsource-arbitrary-file-access" key="/cgi-bin/view-source?../../../../../../../etc/passwd" status="not-vulnerable"> | |
| 5765 | ||
| 5766 | <Paragraph> | |
| 5767 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5768 | <Paragraph> | |
| 5769 | <ContainerBlockElement> | |
| 5770 | <ContainerBlockElement> | |
| 5771 | <Paragraph>HTTP GET request to | |
| 5772 | <URLLink LinkURL="http://192.168.1.40/cgi-bin/view-source?../../../../../../../etc/passwd" LinkTitle="http://192.168.1.40/cgi-bin/view-source?../../../../../../../etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5773 | </test> | |
| 5774 | ||
| 5775 | <test id="http-trace-method-enabled" key="/" status="not-vulnerable"> | |
| 5776 | ||
| 5777 | <Paragraph> | |
| 5778 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5779 | <Paragraph> | |
| 5780 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5781 | </test> | |
| 5782 | ||
| 5783 | <test id="http-track-method-enabled" key="/" status="not-vulnerable"> | |
| 5784 | ||
| 5785 | <Paragraph> | |
| 5786 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5787 | <Paragraph> | |
| 5788 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5789 | </test> | |
| 5790 | ||
| 5791 | <test id="spider-adobe-flash-permissive-crossdomain-xml" key="/crossdomain.xml" status="not-vulnerable"> | |
| 5792 | ||
| 5793 | <Paragraph> | |
| 5794 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5795 | <Paragraph> | |
| 5796 | <ContainerBlockElement> | |
| 5797 | <ContainerBlockElement> | |
| 5798 | <Paragraph>HTTP GET request to | |
| 5799 | <URLLink LinkURL="http://192.168.1.40/crossdomain.xml" LinkTitle="http://192.168.1.40/crossdomain.xml"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5800 | </test> | |
| 5801 | ||
| 5802 | <test id="adobe-apsb13-03-cve-2013-0631" key="/CFIDE/r.cfm" status="not-vulnerable"> | |
| 5803 | ||
| 5804 | <Paragraph> | |
| 5805 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5806 | <Paragraph> | |
| 5807 | <ContainerBlockElement> | |
| 5808 | <ContainerBlockElement> | |
| 5809 | <Paragraph>HTTP GET request to | |
| 5810 | <URLLink LinkURL="http://192.168.1.40/CFIDE/adminapi/customtags/fusebox.cfm" LinkTitle="http://192.168.1.40/CFIDE/adminapi/customtags/fusebox.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 5811 | <ContainerBlockElement> | |
| 5812 | <Paragraph>HTTP GET request to | |
| 5813 | <URLLink LinkURL="http://192.168.1.40/CFIDE/adminapi/customtags/adss.cfm" LinkTitle="http://192.168.1.40/CFIDE/adminapi/customtags/adss.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 5814 | <ContainerBlockElement> | |
| 5815 | <Paragraph>HTTP GET request to | |
| 5816 | <URLLink LinkURL="http://192.168.1.40/CFIDE/h.cfm" LinkTitle="http://192.168.1.40/CFIDE/h.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 5817 | <ContainerBlockElement> | |
| 5818 | <Paragraph>HTTP GET request to | |
| 5819 | <URLLink LinkURL="http://192.168.1.40/CFIDE/h9.cfm" LinkTitle="http://192.168.1.40/CFIDE/h9.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 5820 | <ContainerBlockElement> | |
| 5821 | <Paragraph>HTTP GET request to | |
| 5822 | <URLLink LinkURL="http://192.168.1.40/CFIDE/help.cfm" LinkTitle="http://192.168.1.40/CFIDE/help.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 5823 | <ContainerBlockElement> | |
| 5824 | <Paragraph>HTTP GET request to | |
| 5825 | <URLLink LinkURL="http://192.168.1.40/CFIDE/i.cfm" LinkTitle="http://192.168.1.40/CFIDE/i.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 5826 | <ContainerBlockElement> | |
| 5827 | <Paragraph>HTTP GET request to | |
| 5828 | <URLLink LinkURL="http://192.168.1.40/CFIDE/r.cfm" LinkTitle="http://192.168.1.40/CFIDE/r.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5829 | </test> | |
| 5830 | ||
| 5831 | <test id="adobe-apsb13-13-cve-2013-3336" key="/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=U" status="not-vulnerable"> | |
| 5832 | ||
| 5833 | <Paragraph> | |
| 5834 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5835 | <Paragraph> | |
| 5836 | <ContainerBlockElement> | |
| 5837 | <ContainerBlockElement> | |
| 5838 | <Paragraph>HTTP GET request to | |
| 5839 | <URLLink LinkURL="http://192.168.1.40/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test" LinkTitle="http://192.168.1.40/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test"></URLLink></Paragraph>HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 5840 | <ContainerBlockElement> | |
| 5841 | <Paragraph>HTTP GET request to | |
| 5842 | <URLLink LinkURL="http://192.168.1.40/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test" LinkTitle="http://192.168.1.40/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test"></URLLink></Paragraph>HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5843 | </test> | |
| 5844 | ||
| 5845 | <test id="http-awstats-debug-information-disclosure" key="/cgi-bin/awstats/awstats.pl?debug=1" status="not-vulnerable"> | |
| 5846 | ||
| 5847 | <Paragraph> | |
| 5848 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5849 | <Paragraph> | |
| 5850 | <ContainerBlockElement> | |
| 5851 | <ContainerBlockElement> | |
| 5852 | <Paragraph>HTTP GET request to | |
| 5853 | <URLLink LinkURL="http://192.168.1.40/cgi-bin/awstats.pl?debug=1" LinkTitle="http://192.168.1.40/cgi-bin/awstats.pl?debug=1"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 5854 | <ContainerBlockElement> | |
| 5855 | <Paragraph>HTTP GET request to | |
| 5856 | <URLLink LinkURL="http://192.168.1.40/cgi-bin/awstats/awstats.pl?debug=1" LinkTitle="http://192.168.1.40/cgi-bin/awstats/awstats.pl?debug=1"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5857 | </test> | |
| 5858 | ||
| 5859 | <test id="http-bigbrother-accessible" key="/bb/" status="not-vulnerable"> | |
| 5860 | ||
| 5861 | <Paragraph> | |
| 5862 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5863 | <Paragraph> | |
| 5864 | <ContainerBlockElement> | |
| 5865 | <ContainerBlockElement> | |
| 5866 | <Paragraph>HTTP GET request to | |
| 5867 | <URLLink LinkURL="http://192.168.1.40/bb/" LinkTitle="http://192.168.1.40/bb/"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5868 | </test> | |
| 5869 | ||
| 5870 | <test id="http-cgi-htdig-arbitrary-file-access" key="/cgi-bin/htsearch?Exclude=%60/etc/passwd%60" status="not-vulnerable"> | |
| 5871 | ||
| 5872 | <Paragraph> | |
| 5873 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5874 | <Paragraph> | |
| 5875 | <ContainerBlockElement> | |
| 5876 | <ContainerBlockElement> | |
| 5877 | <Paragraph>HTTP GET request to | |
| 5878 | <URLLink LinkURL="http://192.168.1.40/cgi-bin/htsearch?Exclude=%60/etc/passwd%60" LinkTitle="http://192.168.1.40/cgi-bin/htsearch?Exclude=%60/etc/passwd%60"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5879 | </test> | |
| 5880 | ||
| 5881 | <test id="http-cgi-htgrep-arbitrary-file-access" key="/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd" status="not-vulnerable"> | |
| 5882 | ||
| 5883 | <Paragraph> | |
| 5884 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5885 | <Paragraph> | |
| 5886 | <ContainerBlockElement> | |
| 5887 | <ContainerBlockElement> | |
| 5888 | <Paragraph>HTTP GET request to | |
| 5889 | <URLLink LinkURL="http://192.168.1.40/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd" LinkTitle="http://192.168.1.40/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5890 | </test> | |
| 5891 | ||
| 5892 | <test id="http-cgi-htmlscript-arbitrary-file-access" key="/cgi-bin/htmlscript?../../../../../../../etc/passwd" status="not-vulnerable"> | |
| 5893 | ||
| 5894 | <Paragraph> | |
| 5895 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5896 | <Paragraph> | |
| 5897 | <ContainerBlockElement> | |
| 5898 | <ContainerBlockElement> | |
| 5899 | <Paragraph>HTTP GET request to | |
| 5900 | <URLLink LinkURL="http://192.168.1.40/cgi-bin/htmlscript?../../../../../../../etc/passwd" LinkTitle="http://192.168.1.40/cgi-bin/htmlscript?../../../../../../../etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5901 | </test> | |
| 5902 | ||
| 5903 | <test id="http-cgi-testcgi-file-listing" key="/cgi-bin/test-cgi" status="not-vulnerable"> | |
| 5904 | ||
| 5905 | <Paragraph> | |
| 5906 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5907 | <Paragraph> | |
| 5908 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5909 | </test> | |
| 5910 | ||
| 5911 | <test id="http-lighttpd-mod_userdir-info-discl" key="/~bin/true" status="not-vulnerable"> | |
| 5912 | ||
| 5913 | <Paragraph> | |
| 5914 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5915 | <Paragraph> | |
| 5916 | <ContainerBlockElement> | |
| 5917 | <ContainerBlockElement> | |
| 5918 | <Paragraph>HTTP GET request to | |
| 5919 | <URLLink LinkURL="http://192.168.1.40/~bin/true" LinkTitle="http://192.168.1.40/~bin/true"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5920 | </test> | |
| 5921 | ||
| 5922 | <test id="http-open-proxy" key="http://www.google.com:80/" status="not-vulnerable"> | |
| 5923 | ||
| 5924 | <Paragraph> | |
| 5925 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5926 | <Paragraph> | |
| 5927 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5928 | </test> | |
| 5929 | ||
| 5930 | <test id="http-php-ini-file-exposed" key="/cgi-bin/php.ini" status="not-vulnerable"> | |
| 5931 | ||
| 5932 | <Paragraph> | |
| 5933 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5934 | <Paragraph> | |
| 5935 | <ContainerBlockElement> | |
| 5936 | <ContainerBlockElement> | |
| 5937 | <Paragraph>HTTP GET request to | |
| 5938 | <URLLink LinkURL="http://192.168.1.40/cgi-bin/php.ini" LinkTitle="http://192.168.1.40/cgi-bin/php.ini"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5939 | </test> | |
| 5940 | ||
| 5941 | <test id="http-symantec-scan-engine-file-disclosure" key="/README.txt" status="not-vulnerable"> | |
| 5942 | ||
| 5943 | <Paragraph> | |
| 5944 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5945 | <Paragraph> | |
| 5946 | <ContainerBlockElement> | |
| 5947 | <ContainerBlockElement> | |
| 5948 | <Paragraph>HTTP GET request to | |
| 5949 | <URLLink LinkURL="http://192.168.1.40/README.txt" LinkTitle="http://192.168.1.40/README.txt"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5950 | </test> | |
| 5951 | ||
| 5952 | <test id="http-tomcat-jkstatus-accessible" key="/jkstatus/" status="not-vulnerable"> | |
| 5953 | ||
| 5954 | <Paragraph> | |
| 5955 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5956 | <Paragraph> | |
| 5957 | <ContainerBlockElement> | |
| 5958 | <ContainerBlockElement> | |
| 5959 | <Paragraph>HTTP GET request to | |
| 5960 | <URLLink LinkURL="http://192.168.1.40/jkstatus/" LinkTitle="http://192.168.1.40/jkstatus/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5961 | </test> | |
| 5962 | ||
| 5963 | <test id="adobe-apsb13-03-cve-2013-0629" key="/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../../license.html" status="not-vulnerable"> | |
| 5964 | ||
| 5965 | <Paragraph> | |
| 5966 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5967 | <Paragraph> | |
| 5968 | <ContainerBlockElement> | |
| 5969 | <ContainerBlockElement> | |
| 5970 | <Paragraph>HTTP GET request to | |
| 5971 | <URLLink LinkURL="http://192.168.1.40/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../license.txt" LinkTitle="http://192.168.1.40/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../license.txt"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 5972 | <ContainerBlockElement> | |
| 5973 | <Paragraph>HTTP GET request to | |
| 5974 | <URLLink LinkURL="http://192.168.1.40/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../../license.html" LinkTitle="http://192.168.1.40/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../../license.html"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5975 | </test> | |
| 5976 | ||
| 5977 | <test id="apache-httpd-cve-2008-0005" key="ftp://ftp.kernel.org/;utf7xss" status="not-vulnerable"> | |
| 5978 | ||
| 5979 | <Paragraph> | |
| 5980 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5981 | <Paragraph> | |
| 5982 | <ContainerBlockElement> | |
| 5983 | <ContainerBlockElement> | |
| 5984 | <Paragraph>HTTP GET request to | |
| 5985 | <URLLink LinkURL="ftp://ftp.kernel.org/;utf7xss" LinkTitle="ftp://ftp.kernel.org/;utf7xss"></URLLink></Paragraph>HTTP response code was 501 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5986 | </test> | |
| 5987 | ||
| 5988 | <test id="apache-httpd-cve-2008-0005" key="ftp://ftp.kernel.org/;utf7xss" status="not-vulnerable"> | |
| 5989 | ||
| 5990 | <Paragraph> | |
| 5991 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 5992 | <Paragraph> | |
| 5993 | <ContainerBlockElement> | |
| 5994 | <ContainerBlockElement> | |
| 5995 | <Paragraph>HTTP GET request to | |
| 5996 | <URLLink LinkURL="ftp://ftp.kernel.org/;utf7xss" LinkTitle="ftp://ftp.kernel.org/;utf7xss"></URLLink></Paragraph>HTTP response code was 501 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 5997 | </test> | |
| 5998 | ||
| 5999 | <test id="apache-httpd-cve-2008-2939" key="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" status="not-vulnerable"> | |
| 6000 | ||
| 6001 | <Paragraph> | |
| 6002 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6003 | <Paragraph> | |
| 6004 | <ContainerBlockElement> | |
| 6005 | <ContainerBlockElement> | |
| 6006 | <Paragraph>HTTP GET request to | |
| 6007 | <URLLink LinkURL="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" LinkTitle="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">"></URLLink></Paragraph>HTTP response code was 501 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6008 | </test> | |
| 6009 | ||
| 6010 | <test id="apache-httpd-cve-2008-2939" key="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" status="not-vulnerable"> | |
| 6011 | ||
| 6012 | <Paragraph> | |
| 6013 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6014 | <Paragraph> | |
| 6015 | <ContainerBlockElement> | |
| 6016 | <ContainerBlockElement> | |
| 6017 | <Paragraph>HTTP GET request to | |
| 6018 | <URLLink LinkURL="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" LinkTitle="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">"></URLLink></Paragraph>HTTP response code was 501 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6019 | </test> | |
| 6020 | ||
| 6021 | <test id="http-adobe-amf-gateway-xxe-cve-2009-3960" key="/flex2gateway/http" status="not-vulnerable"> | |
| 6022 | ||
| 6023 | <Paragraph> | |
| 6024 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6025 | <Paragraph> | |
| 6026 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6027 | </test> | |
| 6028 | </tests> | |
| 6029 | </service> | |
| 6030 | </services> | |
| 6031 | </endpoint> | |
| 6032 | ||
| 6033 | <endpoint protocol="tcp" port="443" status="open"> | |
| 6034 | <services> | |
| 6035 | <service name="HTTP"> | |
| 6036 | <tests> | |
| 6037 | <test id="adobe-apsb13-03-cve-2013-0632" key="/CFIDE/adminapi/administrator.cfc?" status="not-vulnerable"> | |
| 6038 | ||
| 6039 | <Paragraph> | |
| 6040 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6041 | <Paragraph> | |
| 6042 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6043 | </test> | |
| 6044 | ||
| 6045 | <test id="adobe-apsb13-13-cve-2013-1389" status="skipped-version"> | |
| 6046 | ||
| 6047 | <Paragraph> | |
| 6048 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6049 | <Paragraph>Based on the result of the "APSB13-13: Security updates available for Adobe ColdFusion (CVE-2013-3336)" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 6050 | </test> | |
| 6051 | ||
| 6052 | <test id="http-3com-wap-default-admin-password" key="/index.htm" status="not-vulnerable"> | |
| 6053 | ||
| 6054 | <Paragraph> | |
| 6055 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6056 | <Paragraph> | |
| 6057 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6058 | </test> | |
| 6059 | ||
| 6060 | <test id="http-drac-default-login" key="/cgi/login" status="not-vulnerable"> | |
| 6061 | ||
| 6062 | <Paragraph> | |
| 6063 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6064 | <Paragraph> | |
| 6065 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6066 | </test> | |
| 6067 | ||
| 6068 | <test id="http-drac-default-login" key="/data/login" status="not-vulnerable"> | |
| 6069 | ||
| 6070 | <Paragraph> | |
| 6071 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6072 | <Paragraph> | |
| 6073 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6074 | </test> | |
| 6075 | ||
| 6076 | <test id="http-glassfish-default-admin-password" key="/common/index.jsf" status="not-vulnerable"> | |
| 6077 | ||
| 6078 | <Paragraph> | |
| 6079 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6080 | <Paragraph> | |
| 6081 | <ContainerBlockElement> | |
| 6082 | <ContainerBlockElement> | |
| 6083 | <Paragraph>HTTP GET request to | |
| 6084 | <URLLink LinkURL="http://192.168.1.40:443/common/index.jsf" LinkTitle="http://192.168.1.40:443/common/index.jsf"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6085 | </test> | |
| 6086 | ||
| 6087 | <test id="http-nokia-firewall-default-admin-password" key="/cgi-bin/home.tcl" status="not-vulnerable"> | |
| 6088 | ||
| 6089 | <Paragraph> | |
| 6090 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6091 | <Paragraph> | |
| 6092 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6093 | </test> | |
| 6094 | ||
| 6095 | <test id="http-phpmyadmin-account-pma-password-empty" key="/phpmyadmin/" status="not-vulnerable"> | |
| 6096 | ||
| 6097 | <Paragraph> | |
| 6098 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6099 | <Paragraph> | |
| 6100 | <ContainerBlockElement> | |
| 6101 | <ContainerBlockElement> | |
| 6102 | <Paragraph>HTTP GET request to | |
| 6103 | <URLLink LinkURL="http://192.168.1.40:443/phpmyadmin/" LinkTitle="http://192.168.1.40:443/phpmyadmin/"></URLLink></Paragraph>HTTP response code was 404 but expected 401</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6104 | </test> | |
| 6105 | ||
| 6106 | <test id="apache-struts-cve-2013-2251" key="/struts2-showcase/employee/save.action" status="not-vulnerable"> | |
| 6107 | ||
| 6108 | <Paragraph> | |
| 6109 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6110 | <Paragraph> | |
| 6111 | <ContainerBlockElement> | |
| 6112 | <ContainerBlockElement> | |
| 6113 | <Paragraph>HTTP GET request to | |
| 6114 | <URLLink LinkURL="http://192.168.1.40:443/struts2-showcase/employee/save.action" LinkTitle="http://192.168.1.40:443/struts2-showcase/employee/save.action"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6115 | </test> | |
| 6116 | ||
| 6117 | <test id="apache-struts-cve-2013-2251" key="/struts2-blank/example/HelloWorld.action" status="not-vulnerable"> | |
| 6118 | ||
| 6119 | <Paragraph> | |
| 6120 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6121 | <Paragraph> | |
| 6122 | <ContainerBlockElement> | |
| 6123 | <ContainerBlockElement> | |
| 6124 | <Paragraph>HTTP GET request to | |
| 6125 | <URLLink LinkURL="http://192.168.1.40:443/struts2-blank/example/HelloWorld.action" LinkTitle="http://192.168.1.40:443/struts2-blank/example/HelloWorld.action"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6126 | </test> | |
| 6127 | ||
| 6128 | <test id="checkpoint-ess-info-disclosure-sk57881" key="/conf/ssl/apache/integrity-smartcenter.key" status="not-vulnerable"> | |
| 6129 | ||
| 6130 | <Paragraph> | |
| 6131 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6132 | <Paragraph> | |
| 6133 | <ContainerBlockElement> | |
| 6134 | <ContainerBlockElement> | |
| 6135 | <Paragraph>HTTP GET request to | |
| 6136 | <URLLink LinkURL="http://192.168.1.40:443/conf/ssl/apache/integrity.key" LinkTitle="http://192.168.1.40:443/conf/ssl/apache/integrity.key"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 6137 | <ContainerBlockElement> | |
| 6138 | <Paragraph>HTTP GET request to | |
| 6139 | <URLLink LinkURL="http://192.168.1.40:443/conf/ssl/apache/integrity-smartcenter.key" LinkTitle="http://192.168.1.40:443/conf/ssl/apache/integrity-smartcenter.key"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6140 | </test> | |
| 6141 | ||
| 6142 | <test id="adobe-apsb10-18-cve-2010-2861" key="/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en" status="not-vulnerable"> | |
| 6143 | ||
| 6144 | <Paragraph> | |
| 6145 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6146 | <Paragraph> | |
| 6147 | <ContainerBlockElement> | |
| 6148 | <ContainerBlockElement> | |
| 6149 | <Paragraph>HTTP GET request to | |
| 6150 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en" LinkTitle="http://192.168.1.40:443/CFIDE/administrator/enter.cfm?locale=../../../../../../../lib/password.properties%00en"></URLLink></Paragraph>HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6151 | </test> | |
| 6152 | ||
| 6153 | <test id="http-awstats-remote-code-execution" key="/cgi-bin/awstats/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" status="not-vulnerable"> | |
| 6154 | ||
| 6155 | <Paragraph> | |
| 6156 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6157 | <Paragraph> | |
| 6158 | <ContainerBlockElement> | |
| 6159 | <ContainerBlockElement> | |
| 6160 | <Paragraph>HTTP GET request to | |
| 6161 | <URLLink LinkURL="http://192.168.1.40:443/cgi-bin/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" LinkTitle="http://192.168.1.40:443/cgi-bin/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 6162 | <ContainerBlockElement> | |
| 6163 | <Paragraph>HTTP GET request to | |
| 6164 | <URLLink LinkURL="http://192.168.1.40:443/cgi-bin/awstats/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;" LinkTitle="http://192.168.1.40:443/cgi-bin/awstats/awstats.pl?PluginMode=:print+%22x%22%2e(1042+%2b+1099)%2e%22x%22;"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6165 | </test> | |
| 6166 | ||
| 6167 | <test id="http-cgi-faxsurvey-command-execution" key="/cgi-bin/faxquery?/bin/cat%20/etc/passwd" status="not-vulnerable"> | |
| 6168 | ||
| 6169 | <Paragraph> | |
| 6170 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6171 | <Paragraph> | |
| 6172 | <ContainerBlockElement> | |
| 6173 | <ContainerBlockElement> | |
| 6174 | <Paragraph>HTTP GET request to | |
| 6175 | <URLLink LinkURL="http://192.168.1.40:443/cgi-bin/faxsurvey?/bin/cat%20/etc/passwd" LinkTitle="http://192.168.1.40:443/cgi-bin/faxsurvey?/bin/cat%20/etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 6176 | <ContainerBlockElement> | |
| 6177 | <Paragraph>HTTP GET request to | |
| 6178 | <URLLink LinkURL="http://192.168.1.40:443/cgi-bin/faxquery?/bin/cat%20/etc/passwd" LinkTitle="http://192.168.1.40:443/cgi-bin/faxquery?/bin/cat%20/etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6179 | </test> | |
| 6180 | ||
| 6181 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/componentutils/" status="not-vulnerable"> | |
| 6182 | ||
| 6183 | <Paragraph> | |
| 6184 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6185 | <Paragraph> | |
| 6186 | <ContainerBlockElement> | |
| 6187 | <ContainerBlockElement> | |
| 6188 | <Paragraph>HTTP GET request to | |
| 6189 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/componentutils/" LinkTitle="http://192.168.1.40:443/CFIDE/componentutils/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6190 | </test> | |
| 6191 | ||
| 6192 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=localhost&vport=22&vstart=&vusername=&vpassword=&returnformat=json" status="not-vulnerable"> | |
| 6193 | ||
| 6194 | <Paragraph> | |
| 6195 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6196 | <Paragraph> | |
| 6197 | <ContainerBlockElement> | |
| 6198 | <ContainerBlockElement> | |
| 6199 | <Paragraph>HTTP GET request to | |
| 6200 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=localhost&vport=22&vstart=&vusername=&vpassword=&returnformat=json" LinkTitle="http://192.168.1.40:443/CFIDE/wizards/common/utils.cfc?method=verifyldapserver&vserver=localhost&vport=22&vstart=&vusername=&vpassword=&returnformat=json"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6201 | </test> | |
| 6202 | ||
| 6203 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/wizards/common/" status="not-vulnerable"> | |
| 6204 | ||
| 6205 | <Paragraph> | |
| 6206 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6207 | <Paragraph> | |
| 6208 | <ContainerBlockElement> | |
| 6209 | <ContainerBlockElement> | |
| 6210 | <Paragraph>HTTP GET request to | |
| 6211 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/wizards/common/" LinkTitle="http://192.168.1.40:443/CFIDE/wizards/common/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6212 | </test> | |
| 6213 | ||
| 6214 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/websocket/" status="not-vulnerable"> | |
| 6215 | ||
| 6216 | <Paragraph> | |
| 6217 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6218 | <Paragraph> | |
| 6219 | <ContainerBlockElement> | |
| 6220 | <ContainerBlockElement> | |
| 6221 | <Paragraph>HTTP GET request to | |
| 6222 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/websocket/" LinkTitle="http://192.168.1.40:443/CFIDE/websocket/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6223 | </test> | |
| 6224 | ||
| 6225 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/services/" status="not-vulnerable"> | |
| 6226 | ||
| 6227 | <Paragraph> | |
| 6228 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6229 | <Paragraph> | |
| 6230 | <ContainerBlockElement> | |
| 6231 | <ContainerBlockElement> | |
| 6232 | <Paragraph>HTTP GET request to | |
| 6233 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/services/" LinkTitle="http://192.168.1.40:443/CFIDE/services/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6234 | </test> | |
| 6235 | ||
| 6236 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/servermanager/" status="not-vulnerable"> | |
| 6237 | ||
| 6238 | <Paragraph> | |
| 6239 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6240 | <Paragraph> | |
| 6241 | <ContainerBlockElement> | |
| 6242 | <ContainerBlockElement> | |
| 6243 | <Paragraph>HTTP GET request to | |
| 6244 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/servermanager/" LinkTitle="http://192.168.1.40:443/CFIDE/servermanager/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6245 | </test> | |
| 6246 | ||
| 6247 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/scheduler/" status="not-vulnerable"> | |
| 6248 | ||
| 6249 | <Paragraph> | |
| 6250 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6251 | <Paragraph> | |
| 6252 | <ContainerBlockElement> | |
| 6253 | <ContainerBlockElement> | |
| 6254 | <Paragraph>HTTP GET request to | |
| 6255 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/scheduler/" LinkTitle="http://192.168.1.40:443/CFIDE/scheduler/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6256 | </test> | |
| 6257 | ||
| 6258 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/portlets/" status="not-vulnerable"> | |
| 6259 | ||
| 6260 | <Paragraph> | |
| 6261 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6262 | <Paragraph> | |
| 6263 | <ContainerBlockElement> | |
| 6264 | <ContainerBlockElement> | |
| 6265 | <Paragraph>HTTP GET request to | |
| 6266 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/portlets/" LinkTitle="http://192.168.1.40:443/CFIDE/portlets/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6267 | </test> | |
| 6268 | ||
| 6269 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/orm/" status="not-vulnerable"> | |
| 6270 | ||
| 6271 | <Paragraph> | |
| 6272 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6273 | <Paragraph> | |
| 6274 | <ContainerBlockElement> | |
| 6275 | <ContainerBlockElement> | |
| 6276 | <Paragraph>HTTP GET request to | |
| 6277 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/orm/" LinkTitle="http://192.168.1.40:443/CFIDE/orm/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6278 | </test> | |
| 6279 | ||
| 6280 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/appdeployment/" status="not-vulnerable"> | |
| 6281 | ||
| 6282 | <Paragraph> | |
| 6283 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6284 | <Paragraph> | |
| 6285 | <ContainerBlockElement> | |
| 6286 | <ContainerBlockElement> | |
| 6287 | <Paragraph>HTTP GET request to | |
| 6288 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/appdeployment/" LinkTitle="http://192.168.1.40:443/CFIDE/appdeployment/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6289 | </test> | |
| 6290 | ||
| 6291 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/AIR/" status="not-vulnerable"> | |
| 6292 | ||
| 6293 | <Paragraph> | |
| 6294 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6295 | <Paragraph> | |
| 6296 | <ContainerBlockElement> | |
| 6297 | <ContainerBlockElement> | |
| 6298 | <Paragraph>HTTP GET request to | |
| 6299 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/AIR/" LinkTitle="http://192.168.1.40:443/CFIDE/AIR/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6300 | </test> | |
| 6301 | ||
| 6302 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/administrator/enter.cfm" status="not-vulnerable"> | |
| 6303 | ||
| 6304 | <Paragraph> | |
| 6305 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6306 | <Paragraph> | |
| 6307 | <ContainerBlockElement> | |
| 6308 | <ContainerBlockElement> | |
| 6309 | <Paragraph>HTTP GET request to | |
| 6310 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/administrator/" LinkTitle="http://192.168.1.40:443/CFIDE/administrator/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 6311 | <ContainerBlockElement> | |
| 6312 | <Paragraph>HTTP GET request to | |
| 6313 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/administrator/enter.cfm" LinkTitle="http://192.168.1.40:443/CFIDE/administrator/enter.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6314 | </test> | |
| 6315 | ||
| 6316 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/adminiapi/" status="not-vulnerable"> | |
| 6317 | ||
| 6318 | <Paragraph> | |
| 6319 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6320 | <Paragraph> | |
| 6321 | <ContainerBlockElement> | |
| 6322 | <ContainerBlockElement> | |
| 6323 | <Paragraph>HTTP GET request to | |
| 6324 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/adminiapi/" LinkTitle="http://192.168.1.40:443/CFIDE/adminiapi/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6325 | </test> | |
| 6326 | ||
| 6327 | <test id="http-coldfusion-cfide-unprotected" key="/CFIDE/adminapi/base.cfc?wsdl" status="not-vulnerable"> | |
| 6328 | ||
| 6329 | <Paragraph> | |
| 6330 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6331 | <Paragraph> | |
| 6332 | <ContainerBlockElement> | |
| 6333 | <ContainerBlockElement> | |
| 6334 | <Paragraph>HTTP GET request to | |
| 6335 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/adminapi/base.cfc?wsdl" LinkTitle="http://192.168.1.40:443/CFIDE/adminapi/base.cfc?wsdl"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6336 | </test> | |
| 6337 | ||
| 6338 | <test id="http-frontpage-unprotected" key="/_vti_bin/_vti_aut/author.dll" status="not-vulnerable"> | |
| 6339 | ||
| 6340 | <Paragraph> | |
| 6341 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6342 | <Paragraph> | |
| 6343 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6344 | </test> | |
| 6345 | ||
| 6346 | <test id="http-php-xmlrpc-code-injection" key="/xmlrpc.php" status="not-vulnerable"> | |
| 6347 | ||
| 6348 | <Paragraph> | |
| 6349 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6350 | <Paragraph> | |
| 6351 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6352 | </test> | |
| 6353 | ||
| 6354 | <test id="adobe-apsb13-03-cve-2013-0625" status="skipped-version"> | |
| 6355 | ||
| 6356 | <Paragraph> | |
| 6357 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6358 | <Paragraph>Based on the result of the "APSB13-03: Security updates available for Adobe ColdFusion (CVE-2013-0629)" test, this node is not vulnerable to this issue.</Paragraph></Paragraph> | |
| 6359 | </test> | |
| 6360 | ||
| 6361 | <test id="http-basic-auth-cleartext" key="/" status="not-vulnerable"> | |
| 6362 | ||
| 6363 | <Paragraph> | |
| 6364 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6365 | <Paragraph> | |
| 6366 | <ContainerBlockElement> | |
| 6367 | <ContainerBlockElement> | |
| 6368 | <Paragraph>HTTP GET request to | |
| 6369 | <URLLink LinkURL="http://192.168.1.40:443/" LinkTitle="http://192.168.1.40:443/"></URLLink></Paragraph>HTTP response code was 404 but expected 401</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6370 | </test> | |
| 6371 | ||
| 6372 | <test id="http-iis-0014" status="not-vulnerable"> | |
| 6373 | ||
| 6374 | <Paragraph> | |
| 6375 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6376 | <Paragraph>Based on the following 3 results: | |
| 6377 | <OrderedList> | |
| 6378 | <ListItem> | |
| 6379 | <Paragraph> | |
| 6380 | <ContainerBlockElement> | |
| 6381 | <ContainerBlockElement> | |
| 6382 | <Paragraph>HTTP GET request to | |
| 6383 | <URLLink LinkURL="http://192.168.1.40:443/scripts/tools/newdsn.exe?driver=Microsoft%2BAccess%2BDriver%2B%28*.mdb%29&dsn=Web%20SQL&dbq=c:\temp\xyz.mdb&newdb=CREATE_DB&attr=" LinkTitle="http://192.168.1.40:443/scripts/tools/newdsn.exe?driver=Microsoft%2BAccess%2BDriver%2B%28*.mdb%29&dsn=Web%20SQL&dbq=c:\temp\xyz.mdb&newdb=CREATE_DB&attr="></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem> | |
| 6384 | <ListItem> | |
| 6385 | <Paragraph> | |
| 6386 | <ContainerBlockElement> | |
| 6387 | <ContainerBlockElement> | |
| 6388 | <Paragraph>HTTP GET request to | |
| 6389 | <URLLink LinkURL="http://192.168.1.40:443/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|" LinkTitle="http://192.168.1.40:443/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem> | |
| 6390 | <ListItem> | |
| 6391 | <Paragraph> | |
| 6392 | <ContainerBlockElement> | |
| 6393 | <ContainerBlockElement> | |
| 6394 | <Paragraph>HTTP GET request to | |
| 6395 | <URLLink LinkURL="http://192.168.1.40:443/ASPSamp/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|" LinkTitle="http://192.168.1.40:443/ASPSamp/AdvWorks/equipment/catalog_type.asp?ProductType=|shell("c:cmd.exe")|"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></ListItem></OrderedList></Paragraph></Paragraph> | |
| 6396 | </test> | |
| 6397 | ||
| 6398 | <test id="http-cgi-viewsource-arbitrary-file-access" key="/cgi-bin/view-source?../../../../../../../etc/passwd" status="not-vulnerable"> | |
| 6399 | ||
| 6400 | <Paragraph> | |
| 6401 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6402 | <Paragraph> | |
| 6403 | <ContainerBlockElement> | |
| 6404 | <ContainerBlockElement> | |
| 6405 | <Paragraph>HTTP GET request to | |
| 6406 | <URLLink LinkURL="http://192.168.1.40:443/cgi-bin/view-source?../../../../../../../etc/passwd" LinkTitle="http://192.168.1.40:443/cgi-bin/view-source?../../../../../../../etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6407 | </test> | |
| 6408 | ||
| 6409 | <test id="http-trace-method-enabled" key="/" status="not-vulnerable"> | |
| 6410 | ||
| 6411 | <Paragraph> | |
| 6412 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6413 | <Paragraph> | |
| 6414 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6415 | </test> | |
| 6416 | ||
| 6417 | <test id="http-track-method-enabled" key="/" status="not-vulnerable"> | |
| 6418 | ||
| 6419 | <Paragraph> | |
| 6420 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6421 | <Paragraph> | |
| 6422 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6423 | </test> | |
| 6424 | ||
| 6425 | <test id="spider-adobe-flash-permissive-crossdomain-xml" key="/crossdomain.xml" status="not-vulnerable"> | |
| 6426 | ||
| 6427 | <Paragraph> | |
| 6428 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6429 | <Paragraph> | |
| 6430 | <ContainerBlockElement> | |
| 6431 | <ContainerBlockElement> | |
| 6432 | <Paragraph>HTTP GET request to | |
| 6433 | <URLLink LinkURL="http://192.168.1.40:443/crossdomain.xml" LinkTitle="http://192.168.1.40:443/crossdomain.xml"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6434 | </test> | |
| 6435 | ||
| 6436 | <test id="adobe-apsb13-03-cve-2013-0631" key="/CFIDE/r.cfm" status="not-vulnerable"> | |
| 6437 | ||
| 6438 | <Paragraph> | |
| 6439 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6440 | <Paragraph> | |
| 6441 | <ContainerBlockElement> | |
| 6442 | <ContainerBlockElement> | |
| 6443 | <Paragraph>HTTP GET request to | |
| 6444 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/adminapi/customtags/fusebox.cfm" LinkTitle="http://192.168.1.40:443/CFIDE/adminapi/customtags/fusebox.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 6445 | <ContainerBlockElement> | |
| 6446 | <Paragraph>HTTP GET request to | |
| 6447 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/adminapi/customtags/adss.cfm" LinkTitle="http://192.168.1.40:443/CFIDE/adminapi/customtags/adss.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 6448 | <ContainerBlockElement> | |
| 6449 | <Paragraph>HTTP GET request to | |
| 6450 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/h.cfm" LinkTitle="http://192.168.1.40:443/CFIDE/h.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 6451 | <ContainerBlockElement> | |
| 6452 | <Paragraph>HTTP GET request to | |
| 6453 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/h9.cfm" LinkTitle="http://192.168.1.40:443/CFIDE/h9.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 6454 | <ContainerBlockElement> | |
| 6455 | <Paragraph>HTTP GET request to | |
| 6456 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/help.cfm" LinkTitle="http://192.168.1.40:443/CFIDE/help.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 6457 | <ContainerBlockElement> | |
| 6458 | <Paragraph>HTTP GET request to | |
| 6459 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/i.cfm" LinkTitle="http://192.168.1.40:443/CFIDE/i.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 6460 | <ContainerBlockElement> | |
| 6461 | <Paragraph>HTTP GET request to | |
| 6462 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/r.cfm" LinkTitle="http://192.168.1.40:443/CFIDE/r.cfm"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6463 | </test> | |
| 6464 | ||
| 6465 | <test id="adobe-apsb13-13-cve-2013-3336" key="/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=U" status="not-vulnerable"> | |
| 6466 | ||
| 6467 | <Paragraph> | |
| 6468 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6469 | <Paragraph> | |
| 6470 | <ContainerBlockElement> | |
| 6471 | <ContainerBlockElement> | |
| 6472 | <Paragraph>HTTP GET request to | |
| 6473 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test" LinkTitle="http://192.168.1.40:443/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test"></URLLink></Paragraph>HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 6474 | <ContainerBlockElement> | |
| 6475 | <Paragraph>HTTP GET request to | |
| 6476 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test" LinkTitle="http://192.168.1.40:443/CFIDE/adminapi/customtags/l10n.cfm?attributes.id=test&attributes.file=../../administrator/mail/download.cfm&filename=../lib/password.properties&attributes.locale=it&attributes.var=it&attributes.jscript=false&attributes.type=text/html&attributes.charset=UTF-8&thisTag.executionmode=end&thisTag.generatedContent=test"></URLLink></Paragraph>HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6477 | </test> | |
| 6478 | ||
| 6479 | <test id="http-awstats-debug-information-disclosure" key="/cgi-bin/awstats/awstats.pl?debug=1" status="not-vulnerable"> | |
| 6480 | ||
| 6481 | <Paragraph> | |
| 6482 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6483 | <Paragraph> | |
| 6484 | <ContainerBlockElement> | |
| 6485 | <ContainerBlockElement> | |
| 6486 | <Paragraph>HTTP GET request to | |
| 6487 | <URLLink LinkURL="http://192.168.1.40:443/cgi-bin/awstats.pl?debug=1" LinkTitle="http://192.168.1.40:443/cgi-bin/awstats.pl?debug=1"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 6488 | <ContainerBlockElement> | |
| 6489 | <Paragraph>HTTP GET request to | |
| 6490 | <URLLink LinkURL="http://192.168.1.40:443/cgi-bin/awstats/awstats.pl?debug=1" LinkTitle="http://192.168.1.40:443/cgi-bin/awstats/awstats.pl?debug=1"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6491 | </test> | |
| 6492 | ||
| 6493 | <test id="http-bigbrother-accessible" key="/bb/" status="not-vulnerable"> | |
| 6494 | ||
| 6495 | <Paragraph> | |
| 6496 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6497 | <Paragraph> | |
| 6498 | <ContainerBlockElement> | |
| 6499 | <ContainerBlockElement> | |
| 6500 | <Paragraph>HTTP GET request to | |
| 6501 | <URLLink LinkURL="http://192.168.1.40:443/bb/" LinkTitle="http://192.168.1.40:443/bb/"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6502 | </test> | |
| 6503 | ||
| 6504 | <test id="http-cgi-htdig-arbitrary-file-access" key="/cgi-bin/htsearch?Exclude=%60/etc/passwd%60" status="not-vulnerable"> | |
| 6505 | ||
| 6506 | <Paragraph> | |
| 6507 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6508 | <Paragraph> | |
| 6509 | <ContainerBlockElement> | |
| 6510 | <ContainerBlockElement> | |
| 6511 | <Paragraph>HTTP GET request to | |
| 6512 | <URLLink LinkURL="http://192.168.1.40:443/cgi-bin/htsearch?Exclude=%60/etc/passwd%60" LinkTitle="http://192.168.1.40:443/cgi-bin/htsearch?Exclude=%60/etc/passwd%60"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6513 | </test> | |
| 6514 | ||
| 6515 | <test id="http-cgi-htgrep-arbitrary-file-access" key="/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd" status="not-vulnerable"> | |
| 6516 | ||
| 6517 | <Paragraph> | |
| 6518 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6519 | <Paragraph> | |
| 6520 | <ContainerBlockElement> | |
| 6521 | <ContainerBlockElement> | |
| 6522 | <Paragraph>HTTP GET request to | |
| 6523 | <URLLink LinkURL="http://192.168.1.40:443/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd" LinkTitle="http://192.168.1.40:443/cgi-bin/htgrep/file=index.html&hdr=/etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6524 | </test> | |
| 6525 | ||
| 6526 | <test id="http-cgi-htmlscript-arbitrary-file-access" key="/cgi-bin/htmlscript?../../../../../../../etc/passwd" status="not-vulnerable"> | |
| 6527 | ||
| 6528 | <Paragraph> | |
| 6529 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6530 | <Paragraph> | |
| 6531 | <ContainerBlockElement> | |
| 6532 | <ContainerBlockElement> | |
| 6533 | <Paragraph>HTTP GET request to | |
| 6534 | <URLLink LinkURL="http://192.168.1.40:443/cgi-bin/htmlscript?../../../../../../../etc/passwd" LinkTitle="http://192.168.1.40:443/cgi-bin/htmlscript?../../../../../../../etc/passwd"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6535 | </test> | |
| 6536 | ||
| 6537 | <test id="http-cgi-testcgi-file-listing" key="/cgi-bin/test-cgi" status="not-vulnerable"> | |
| 6538 | ||
| 6539 | <Paragraph> | |
| 6540 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6541 | <Paragraph> | |
| 6542 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6543 | </test> | |
| 6544 | ||
| 6545 | <test id="http-lighttpd-mod_userdir-info-discl" key="/~bin/true" status="not-vulnerable"> | |
| 6546 | ||
| 6547 | <Paragraph> | |
| 6548 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6549 | <Paragraph> | |
| 6550 | <ContainerBlockElement> | |
| 6551 | <ContainerBlockElement> | |
| 6552 | <Paragraph>HTTP GET request to | |
| 6553 | <URLLink LinkURL="http://192.168.1.40:443/~bin/true" LinkTitle="http://192.168.1.40:443/~bin/true"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6554 | </test> | |
| 6555 | ||
| 6556 | <test id="http-open-proxy" key="http://www.google.com:80/" status="not-vulnerable"> | |
| 6557 | ||
| 6558 | <Paragraph> | |
| 6559 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6560 | <Paragraph> | |
| 6561 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6562 | </test> | |
| 6563 | ||
| 6564 | <test id="http-php-ini-file-exposed" key="/cgi-bin/php.ini" status="not-vulnerable"> | |
| 6565 | ||
| 6566 | <Paragraph> | |
| 6567 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6568 | <Paragraph> | |
| 6569 | <ContainerBlockElement> | |
| 6570 | <ContainerBlockElement> | |
| 6571 | <Paragraph>HTTP GET request to | |
| 6572 | <URLLink LinkURL="http://192.168.1.40:443/cgi-bin/php.ini" LinkTitle="http://192.168.1.40:443/cgi-bin/php.ini"></URLLink></Paragraph></ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6573 | </test> | |
| 6574 | ||
| 6575 | <test id="http-symantec-scan-engine-file-disclosure" key="/README.txt" status="not-vulnerable"> | |
| 6576 | ||
| 6577 | <Paragraph> | |
| 6578 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6579 | <Paragraph> | |
| 6580 | <ContainerBlockElement> | |
| 6581 | <ContainerBlockElement> | |
| 6582 | <Paragraph>HTTP GET request to | |
| 6583 | <URLLink LinkURL="http://192.168.1.40:443/README.txt" LinkTitle="http://192.168.1.40:443/README.txt"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6584 | </test> | |
| 6585 | ||
| 6586 | <test id="http-tomcat-jkstatus-accessible" key="/jkstatus/" status="not-vulnerable"> | |
| 6587 | ||
| 6588 | <Paragraph> | |
| 6589 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6590 | <Paragraph> | |
| 6591 | <ContainerBlockElement> | |
| 6592 | <ContainerBlockElement> | |
| 6593 | <Paragraph>HTTP GET request to | |
| 6594 | <URLLink LinkURL="http://192.168.1.40:443/jkstatus/" LinkTitle="http://192.168.1.40:443/jkstatus/"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6595 | </test> | |
| 6596 | ||
| 6597 | <test id="adobe-apsb13-03-cve-2013-0629" key="/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../../license.html" status="not-vulnerable"> | |
| 6598 | ||
| 6599 | <Paragraph> | |
| 6600 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6601 | <Paragraph> | |
| 6602 | <ContainerBlockElement> | |
| 6603 | <ContainerBlockElement> | |
| 6604 | <Paragraph>HTTP GET request to | |
| 6605 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../license.txt" LinkTitle="http://192.168.1.40:443/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../license.txt"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement> | |
| 6606 | <ContainerBlockElement> | |
| 6607 | <Paragraph>HTTP GET request to | |
| 6608 | <URLLink LinkURL="http://192.168.1.40:443/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../../license.html" LinkTitle="http://192.168.1.40:443/CFIDE/componentutils/cfcexplorer.cfc?method=getcfcinhtml&name=CFIDE.componentutils.cfcexplorer&path=../../../../license.html"></URLLink></Paragraph>HTTP response code was 404 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6609 | </test> | |
| 6610 | ||
| 6611 | <test id="apache-httpd-cve-2008-0005" key="ftp://ftp.kernel.org/;utf7xss" status="not-vulnerable"> | |
| 6612 | ||
| 6613 | <Paragraph> | |
| 6614 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6615 | <Paragraph> | |
| 6616 | <ContainerBlockElement> | |
| 6617 | <ContainerBlockElement> | |
| 6618 | <Paragraph>HTTP GET request to | |
| 6619 | <URLLink LinkURL="ftp://ftp.kernel.org/;utf7xss" LinkTitle="ftp://ftp.kernel.org/;utf7xss"></URLLink></Paragraph>HTTP response code was 501 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6620 | </test> | |
| 6621 | ||
| 6622 | <test id="apache-httpd-cve-2008-0005" key="ftp://ftp.kernel.org/;utf7xss" status="not-vulnerable"> | |
| 6623 | ||
| 6624 | <Paragraph> | |
| 6625 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6626 | <Paragraph> | |
| 6627 | <ContainerBlockElement> | |
| 6628 | <ContainerBlockElement> | |
| 6629 | <Paragraph>HTTP GET request to | |
| 6630 | <URLLink LinkURL="ftp://ftp.kernel.org/;utf7xss" LinkTitle="ftp://ftp.kernel.org/;utf7xss"></URLLink></Paragraph>HTTP response code was 501 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6631 | </test> | |
| 6632 | ||
| 6633 | <test id="apache-httpd-cve-2008-2939" key="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" status="not-vulnerable"> | |
| 6634 | ||
| 6635 | <Paragraph> | |
| 6636 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6637 | <Paragraph> | |
| 6638 | <ContainerBlockElement> | |
| 6639 | <ContainerBlockElement> | |
| 6640 | <Paragraph>HTTP GET request to | |
| 6641 | <URLLink LinkURL="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" LinkTitle="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">"></URLLink></Paragraph>HTTP response code was 501 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6642 | </test> | |
| 6643 | ||
| 6644 | <test id="apache-httpd-cve-2008-2939" key="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" status="not-vulnerable"> | |
| 6645 | ||
| 6646 | <Paragraph> | |
| 6647 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6648 | <Paragraph> | |
| 6649 | <ContainerBlockElement> | |
| 6650 | <ContainerBlockElement> | |
| 6651 | <Paragraph>HTTP GET request to | |
| 6652 | <URLLink LinkURL="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">" LinkTitle="ftp://ftp.kernel.org/*<img%20src=""%20onerror="alert(42)">"></URLLink></Paragraph>HTTP response code was 501 but expected 200</ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6653 | </test> | |
| 6654 | ||
| 6655 | <test id="http-adobe-amf-gateway-xxe-cve-2009-3960" key="/flex2gateway/http" status="not-vulnerable"> | |
| 6656 | ||
| 6657 | <Paragraph> | |
| 6658 | <Paragraph>Running vulnerable HTTP service.</Paragraph> | |
| 6659 | <Paragraph> | |
| 6660 | <ContainerBlockElement></ContainerBlockElement></Paragraph></Paragraph> | |
| 6661 | </test> | |
| 6662 | </tests> | |
| 6663 | </service> | |
| 6664 | </services> | |
| 6665 | </endpoint> | |
| 6666 | </endpoints> | |
| 6667 | </node> | |
| 6668 | </nodes><VulnerabilityDefinitions> | |
| 6669 | <vulnerability id="adobe-apsb10-18-CVE-2010-2861" title="APSB10-18: Security updates available for Adobe ColdFusion (CVE-2010-2861)" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20100811T000000000" added="20130414T000000000" modified="20131031T000000000"> | |
| 6670 | <description> | |
| 6671 | ||
| 6672 | <ContainerBlockElement> | |
| 6673 | ||
| 6674 | <Paragraph>Multiple directory traversal vulnerabilities in the administrator console in Adobe ColdFusion 9.0.1 and earlier allow remote attackers to read arbitrary files via the locale parameter to (1) CFIDE/administrator/settings/mappings.cfm, (2) logging/settings.cfm, (3) datasources/index.cfm, (4) j2eepackaging/editarchive.cfm, and (5) enter.cfm in CFIDE/administrator/.</Paragraph> | |
| 6675 | </ContainerBlockElement></description> | |
| 6676 | <references> | |
| 6677 | <reference source="CVE">CVE-2010-2861</reference> | |
| 6678 | <reference source="URL">http://www.adobe.com/support/security/bulletins/apsb10-18.html</reference> | |
| 6679 | </references><tags> | |
| 6680 | <tag>Adobe</tag> | |
| 6681 | <tag>Adobe ColdFusion</tag> | |
| 6682 | <tag>Directory Traversal</tag> | |
| 6683 | <tag>Web</tag> | |
| 6684 | <tag>IAVM</tag> | |
| 6685 | </tags> | |
| 6686 | <solution> | |
| 6687 | ||
| 6688 | <ContainerBlockElement> | |
| 6689 | <Paragraph> | |
| 6690 | <Paragraph>Adobe recommends affected ColdFusion customers update their installation using the instructions provided in the technote: http://kb2.adobe.com/cps/857/cpsid_85766.html.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 6691 | </vulnerability> | |
| 6692 | ||
| 6693 | <vulnerability id="adobe-apsb13-03-CVE-2013-0625" title="APSB13-03: Security updates available for Adobe ColdFusion (CVE-2013-0625)" severity="7" pciSeverity="4" cvssScore="6.8" cvssVector="(AV:N/AC:M/Au:N/C:P/I:P/A:P)" published="20130115T000000000" added="20130327T000000000" modified="20131031T000000000"> | |
| 6694 | <description> | |
| 6695 | ||
| 6696 | <ContainerBlockElement> | |
| 6697 | ||
| 6698 | <Paragraph>Adobe ColdFusion 9.0, 9.0.1, and 9.0.2, when a password is not configured, allows remote attackers to bypass authentication and possibly execute arbitrary code via unspecified vectors, as exploited in the wild in January 2013.</Paragraph> | |
| 6699 | </ContainerBlockElement></description> | |
| 6700 | <references> | |
| 6701 | <reference source="BID">57164</reference> | |
| 6702 | <reference source="CVE">CVE-2013-0625</reference> | |
| 6703 | <reference source="URL">http://www.adobe.com/support/security/bulletins/apsb13-03.html</reference> | |
| 6704 | </references><tags> | |
| 6705 | <tag>Adobe</tag> | |
| 6706 | <tag>Adobe ColdFusion</tag> | |
| 6707 | <tag>Remote Execution</tag> | |
| 6708 | <tag>Web</tag> | |
| 6709 | </tags> | |
| 6710 | <solution> | |
| 6711 | ||
| 6712 | <ContainerBlockElement> | |
| 6713 | <Paragraph> | |
| 6714 | <Paragraph> | |
| 6715 | Adobe recommends ColdFusion customers update their installation using the | |
| 6716 | instructions provided in the technote | |
| 6717 | ||
| 6718 | <URLLink LinkURL="http://helpx.adobe.com/coldfusion/kb/coldfusion-security-hotfix-apsb13-03.html" LinkTitle="http://helpx.adobe.com/coldfusion/kb/coldfusion-security-hotfix-apsb13-03.html" href="http://helpx.adobe.com/coldfusion/kb/coldfusion-security-hotfix-apsb13-03.html">APSB13-03 technote</URLLink>. | |
| 6719 | </Paragraph> | |
| 6720 | <Paragraph> | |
| 6721 | Customers should also inspect files and scheduled tasks of unknown origin | |
| 6722 | located in the CFIDE, CFIDE/adminapi or webroot directories, and remove | |
| 6723 | any suspicious files (some examples of malicious file names include | |
| 6724 | h.cfm, i.cfm, h9.cfm, r.cfm, adss.cfm or fusebox.cfm). | |
| 6725 | </Paragraph> | |
| 6726 | <Paragraph> | |
| 6727 | Additionally, Adobe recommends that customers follow security best | |
| 6728 | practices, which include the following steps to harden their ColdFusion | |
| 6729 | server: | |
| 6730 | ||
| 6731 | <UnorderedList> | |
| 6732 | <ListItem> | |
| 6733 | Configure a username and password for Remote Development Services (RDS) | |
| 6734 | that is different from the Administrator account. After configuring the | |
| 6735 | RDS account, users should disable RDS if not needed. | |
| 6736 | </ListItem> | |
| 6737 | <ListItem> | |
| 6738 | Disable external access to the following directories for all hosted | |
| 6739 | sites: | |
| 6740 | ||
| 6741 | <UnorderedList> | |
| 6742 | <ListItem>/CFIDE/administrator</ListItem> | |
| 6743 | <ListItem>/CFIDE/adminapi</ListItem> | |
| 6744 | <ListItem>/CFIDE/componentutils</ListItem></UnorderedList></ListItem> | |
| 6745 | <ListItem> | |
| 6746 | Implement access control restrictions for the Administrator interface and | |
| 6747 | internal applications via the Administrator Console (in ColdFusion | |
| 6748 | version 10) or within your web server's access control mechanisms for | |
| 6749 | versions 9.0.2 and below. | |
| 6750 | </ListItem> | |
| 6751 | <ListItem> | |
| 6752 | Ensure your ColdFusion product has the latest hotfix applied. | |
| 6753 | </ListItem> | |
| 6754 | <ListItem> | |
| 6755 | Refer to the ColdFusion 9 Lockdown Guide and ColdFusion 10 Lockdown Guide | |
| 6756 | for security best practices and further information on these hardening | |
| 6757 | techniques. | |
| 6758 | </ListItem></UnorderedList></Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 6759 | </vulnerability> | |
| 6760 | ||
| 6761 | <vulnerability id="adobe-apsb13-03-CVE-2013-0629" title="APSB13-03: Security updates available for Adobe ColdFusion (CVE-2013-0629)" severity="4" pciSeverity="3" cvssScore="4.3" cvssVector="(AV:N/AC:M/Au:N/C:P/I:N/A:N)" published="20130115T000000000" added="20130327T000000000" modified="20131031T000000000"> | |
| 6762 | <description> | |
| 6763 | ||
| 6764 | <ContainerBlockElement> | |
| 6765 | ||
| 6766 | <Paragraph>Adobe ColdFusion 9.0, 9.0.1, 9.0.2, and 10, when a password is not configured, allows attackers to access restricted directories via unspecified vectors, as exploited in the wild in January 2013.</Paragraph> | |
| 6767 | </ContainerBlockElement></description> | |
| 6768 | <references> | |
| 6769 | <reference source="BID">57165</reference> | |
| 6770 | <reference source="CVE">CVE-2013-0629</reference> | |
| 6771 | <reference source="URL">http://www.adobe.com/support/security/bulletins/apsb13-03.html</reference> | |
| 6772 | </references><tags> | |
| 6773 | <tag>Adobe</tag> | |
| 6774 | <tag>Adobe ColdFusion</tag> | |
| 6775 | <tag>Web</tag> | |
| 6776 | </tags> | |
| 6777 | <solution> | |
| 6778 | ||
| 6779 | <ContainerBlockElement> | |
| 6780 | <Paragraph> | |
| 6781 | <Paragraph> | |
| 6782 | Adobe recommends ColdFusion customers update their installation using the | |
| 6783 | instructions provided in the technote | |
| 6784 | ||
| 6785 | <URLLink LinkURL="http://helpx.adobe.com/coldfusion/kb/coldfusion-security-hotfix-apsb13-03.html" LinkTitle="http://helpx.adobe.com/coldfusion/kb/coldfusion-security-hotfix-apsb13-03.html" href="http://helpx.adobe.com/coldfusion/kb/coldfusion-security-hotfix-apsb13-03.html">APSB13-03 technote</URLLink>. | |
| 6786 | </Paragraph> | |
| 6787 | <Paragraph> | |
| 6788 | Customers should also inspect files and scheduled tasks of unknown origin | |
| 6789 | located in the CFIDE, CFIDE/adminapi or webroot directories, and remove | |
| 6790 | any suspicious files (some examples of malicious file names include | |
| 6791 | h.cfm, i.cfm, h9.cfm, r.cfm, adss.cfm or fusebox.cfm). | |
| 6792 | </Paragraph> | |
| 6793 | <Paragraph> | |
| 6794 | Additionally, Adobe recommends that customers follow security best | |
| 6795 | practices, which include the following steps to harden their ColdFusion | |
| 6796 | server: | |
| 6797 | ||
| 6798 | <UnorderedList> | |
| 6799 | <ListItem> | |
| 6800 | Configure a username and password for Remote Development Services (RDS) | |
| 6801 | that is different from the Administrator account. After configuring the | |
| 6802 | RDS account, users should disable RDS if not needed. | |
| 6803 | </ListItem> | |
| 6804 | <ListItem> | |
| 6805 | Disable external access to the following directories for all hosted | |
| 6806 | sites: | |
| 6807 | ||
| 6808 | <UnorderedList> | |
| 6809 | <ListItem>/CFIDE/administrator</ListItem> | |
| 6810 | <ListItem>/CFIDE/adminapi</ListItem> | |
| 6811 | <ListItem>/CFIDE/componentutils</ListItem></UnorderedList></ListItem> | |
| 6812 | <ListItem> | |
| 6813 | Implement access control restrictions for the Administrator interface and | |
| 6814 | internal applications via the Administrator Console (in ColdFusion | |
| 6815 | version 10) or within your web server's access control mechanisms for | |
| 6816 | versions 9.0.2 and below. | |
| 6817 | </ListItem> | |
| 6818 | <ListItem> | |
| 6819 | Ensure your ColdFusion product has the latest hotfix applied. | |
| 6820 | </ListItem> | |
| 6821 | <ListItem> | |
| 6822 | Refer to the ColdFusion 9 Lockdown Guide and ColdFusion 10 Lockdown Guide | |
| 6823 | for security best practices and further information on these hardening | |
| 6824 | techniques. | |
| 6825 | </ListItem></UnorderedList></Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 6826 | </vulnerability> | |
| 6827 | ||
| 6828 | <vulnerability id="adobe-apsb13-03-CVE-2013-0631" title="APSB13-03: Security updates available for Adobe ColdFusion (CVE-2013-0631)" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="20130115T000000000" added="20130327T000000000" modified="20131031T000000000"> | |
| 6829 | <description> | |
| 6830 | ||
| 6831 | <ContainerBlockElement> | |
| 6832 | ||
| 6833 | <Paragraph>Adobe ColdFusion 9.0, 9.0.1, and 9.0.2 allows attackers to obtain sensitive information via unspecified vectors, as exploited in the wild in January 2013.</Paragraph> | |
| 6834 | </ContainerBlockElement></description> | |
| 6835 | <references> | |
| 6836 | <reference source="CVE">CVE-2013-0631</reference> | |
| 6837 | <reference source="URL">http://www.adobe.com/support/security/bulletins/apsb13-03.html</reference> | |
| 6838 | </references><tags> | |
| 6839 | <tag>Adobe</tag> | |
| 6840 | <tag>Adobe ColdFusion</tag> | |
| 6841 | <tag>Web</tag> | |
| 6842 | </tags> | |
| 6843 | <solution> | |
| 6844 | ||
| 6845 | <ContainerBlockElement> | |
| 6846 | <Paragraph> | |
| 6847 | <Paragraph> | |
| 6848 | Adobe recommends ColdFusion customers update their installation using the | |
| 6849 | instructions provided in the technote | |
| 6850 | ||
| 6851 | <URLLink LinkURL="http://helpx.adobe.com/coldfusion/kb/coldfusion-security-hotfix-apsb13-03.html" LinkTitle="http://helpx.adobe.com/coldfusion/kb/coldfusion-security-hotfix-apsb13-03.html" href="http://helpx.adobe.com/coldfusion/kb/coldfusion-security-hotfix-apsb13-03.html">APSB13-03 technote</URLLink>. | |
| 6852 | </Paragraph> | |
| 6853 | <Paragraph> | |
| 6854 | Customers should also inspect files and scheduled tasks of unknown origin | |
| 6855 | located in the CFIDE, CFIDE/adminapi or webroot directories, and remove | |
| 6856 | any suspicious files (some examples of malicious file names include | |
| 6857 | h.cfm, i.cfm, h9.cfm, r.cfm, adss.cfm or fusebox.cfm). | |
| 6858 | </Paragraph> | |
| 6859 | <Paragraph> | |
| 6860 | Additionally, Adobe recommends that customers follow security best | |
| 6861 | practices, which include the following steps to harden their ColdFusion | |
| 6862 | server: | |
| 6863 | ||
| 6864 | <UnorderedList> | |
| 6865 | <ListItem> | |
| 6866 | Configure a username and password for Remote Development Services (RDS) | |
| 6867 | that is different from the Administrator account. After configuring the | |
| 6868 | RDS account, users should disable RDS if not needed. | |
| 6869 | </ListItem> | |
| 6870 | <ListItem> | |
| 6871 | Disable external access to the following directories for all hosted | |
| 6872 | sites: | |
| 6873 | ||
| 6874 | <UnorderedList> | |
| 6875 | <ListItem>/CFIDE/administrator</ListItem> | |
| 6876 | <ListItem>/CFIDE/adminapi</ListItem> | |
| 6877 | <ListItem>/CFIDE/componentutils</ListItem></UnorderedList></ListItem> | |
| 6878 | <ListItem> | |
| 6879 | Implement access control restrictions for the Administrator interface and | |
| 6880 | internal applications via the Administrator Console (in ColdFusion | |
| 6881 | version 10) or within your web server's access control mechanisms for | |
| 6882 | versions 9.0.2 and below. | |
| 6883 | </ListItem> | |
| 6884 | <ListItem> | |
| 6885 | Ensure your ColdFusion product has the latest hotfix applied. | |
| 6886 | </ListItem> | |
| 6887 | <ListItem> | |
| 6888 | Refer to the ColdFusion 9 Lockdown Guide and ColdFusion 10 Lockdown Guide | |
| 6889 | for security best practices and further information on these hardening | |
| 6890 | techniques. | |
| 6891 | </ListItem></UnorderedList></Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 6892 | </vulnerability> | |
| 6893 | ||
| 6894 | <vulnerability id="adobe-apsb13-03-CVE-2013-0632" title="APSB13-03: Security updates available for Adobe ColdFusion (CVE-2013-0632)" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20130115T000000000" added="20130327T000000000" modified="20131031T000000000"> | |
| 6895 | <description> | |
| 6896 | ||
| 6897 | <ContainerBlockElement> | |
| 6898 | ||
| 6899 | <Paragraph>Adobe ColdFusion 9.0, 9.0.1, 9.0.2, and 10 allows remote attackers to bypass authentication and possibly execute arbitrary code via unspecified vectors, as exploited in the wild in January 2013.</Paragraph> | |
| 6900 | </ContainerBlockElement></description> | |
| 6901 | <references> | |
| 6902 | <reference source="CVE">CVE-2013-0632</reference> | |
| 6903 | <reference source="URL">http://www.adobe.com/support/security/bulletins/apsb13-03.html</reference> | |
| 6904 | </references><tags> | |
| 6905 | <tag>Adobe</tag> | |
| 6906 | <tag>Adobe ColdFusion</tag> | |
| 6907 | <tag>Remote Execution</tag> | |
| 6908 | <tag>Web</tag> | |
| 6909 | </tags> | |
| 6910 | <solution> | |
| 6911 | ||
| 6912 | <ContainerBlockElement> | |
| 6913 | <Paragraph> | |
| 6914 | <Paragraph> | |
| 6915 | Adobe recommends ColdFusion customers update their installation using the | |
| 6916 | instructions provided in the technote | |
| 6917 | ||
| 6918 | <URLLink LinkURL="http://helpx.adobe.com/coldfusion/kb/coldfusion-security-hotfix-apsb13-03.html" LinkTitle="http://helpx.adobe.com/coldfusion/kb/coldfusion-security-hotfix-apsb13-03.html" href="http://helpx.adobe.com/coldfusion/kb/coldfusion-security-hotfix-apsb13-03.html">APSB13-03 technote</URLLink>. | |
| 6919 | </Paragraph> | |
| 6920 | <Paragraph> | |
| 6921 | Customers should also inspect files and scheduled tasks of unknown origin | |
| 6922 | located in the CFIDE, CFIDE/adminapi or webroot directories, and remove | |
| 6923 | any suspicious files (some examples of malicious file names include | |
| 6924 | h.cfm, i.cfm, h9.cfm, r.cfm, adss.cfm or fusebox.cfm). | |
| 6925 | </Paragraph> | |
| 6926 | <Paragraph> | |
| 6927 | Additionally, Adobe recommends that customers follow security best | |
| 6928 | practices, which include the following steps to harden their ColdFusion | |
| 6929 | server: | |
| 6930 | ||
| 6931 | <UnorderedList> | |
| 6932 | <ListItem> | |
| 6933 | Configure a username and password for Remote Development Services (RDS) | |
| 6934 | that is different from the Administrator account. After configuring the | |
| 6935 | RDS account, users should disable RDS if not needed. | |
| 6936 | </ListItem> | |
| 6937 | <ListItem> | |
| 6938 | Disable external access to the following directories for all hosted | |
| 6939 | sites: | |
| 6940 | ||
| 6941 | <UnorderedList> | |
| 6942 | <ListItem>/CFIDE/administrator</ListItem> | |
| 6943 | <ListItem>/CFIDE/adminapi</ListItem> | |
| 6944 | <ListItem>/CFIDE/componentutils</ListItem></UnorderedList></ListItem> | |
| 6945 | <ListItem> | |
| 6946 | Implement access control restrictions for the Administrator interface and | |
| 6947 | internal applications via the Administrator Console (in ColdFusion | |
| 6948 | version 10) or within your web server's access control mechanisms for | |
| 6949 | versions 9.0.2 and below. | |
| 6950 | </ListItem> | |
| 6951 | <ListItem> | |
| 6952 | Ensure your ColdFusion product has the latest hotfix applied. | |
| 6953 | </ListItem> | |
| 6954 | <ListItem> | |
| 6955 | Refer to the ColdFusion 9 Lockdown Guide and ColdFusion 10 Lockdown Guide | |
| 6956 | for security best practices and further information on these hardening | |
| 6957 | techniques. | |
| 6958 | </ListItem></UnorderedList></Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 6959 | </vulnerability> | |
| 6960 | ||
| 6961 | <vulnerability id="adobe-apsb13-13-CVE-2013-1389" title="APSB13-13: Security updates available for Adobe ColdFusion (CVE-2013-1389)" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20130514T000000000" added="20130516T000000000" modified="20131031T000000000"> | |
| 6962 | <description> | |
| 6963 | ||
| 6964 | <ContainerBlockElement> | |
| 6965 | ||
| 6966 | <Paragraph>Unspecified vulnerability in Adobe ColdFusion 9.0 before Update 11, 9.0.1 before Update 10, 9.0.2 before Update 5, and 10 before Update 10 allows remote attackers to execute arbitrary code via unknown vectors.</Paragraph> | |
| 6967 | </ContainerBlockElement></description> | |
| 6968 | <references> | |
| 6969 | <reference source="CVE">CVE-2013-1389</reference> | |
| 6970 | <reference source="URL">http://www.adobe.com/support/security/bulletins/apsb13-13.html</reference> | |
| 6971 | </references><tags> | |
| 6972 | <tag>Adobe</tag> | |
| 6973 | <tag>Adobe ColdFusion</tag> | |
| 6974 | <tag>Remote Execution</tag> | |
| 6975 | <tag>Web</tag> | |
| 6976 | </tags> | |
| 6977 | <solution> | |
| 6978 | ||
| 6979 | <ContainerBlockElement> | |
| 6980 | <Paragraph> | |
| 6981 | <Paragraph>Adobe recommends ColdFusion customers update their installation using the instructions provided in the technote located here: | |
| 6982 | http://helpx.adobe.com/coldfusion/kb/coldfusion-security-hotfix-apsb13-13.html | |
| 6983 | Customers should also apply the security configuration settings as outlined on the ColdFusion Security page, as well as review the ColdFusion 9 Lockdown Guide and ColdFusion 10 Lockdown Guide.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 6984 | </vulnerability> | |
| 6985 | ||
| 6986 | <vulnerability id="adobe-apsb13-13-CVE-2013-3336" title="APSB13-13: Security updates available for Adobe ColdFusion (CVE-2013-3336)" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="20100811T000000000" added="20130414T000000000" modified="20131031T000000000"> | |
| 6987 | <description> | |
| 6988 | ||
| 6989 | <ContainerBlockElement> | |
| 6990 | ||
| 6991 | <Paragraph>Unspecified vulnerability in Adobe ColdFusion 9.0, 9.0.1, 9.0.2, and 10 allows remote attackers to read arbitrary files via unknown vectors.</Paragraph> | |
| 6992 | </ContainerBlockElement></description> | |
| 6993 | <references> | |
| 6994 | <reference source="CVE">CVE-2013-3336</reference> | |
| 6995 | <reference source="URL">http://www.adobe.com/support/security/bulletins/apsb13-13.html</reference> | |
| 6996 | </references><tags> | |
| 6997 | <tag>Adobe</tag> | |
| 6998 | <tag>Adobe ColdFusion</tag> | |
| 6999 | <tag>Web</tag> | |
| 7000 | </tags> | |
| 7001 | <solution> | |
| 7002 | ||
| 7003 | <ContainerBlockElement> | |
| 7004 | <Paragraph> | |
| 7005 | <Paragraph>Adobe recommends ColdFusion customers update their installation using the instructions provided in the technote located here: | |
| 7006 | http://helpx.adobe.com/coldfusion/kb/coldfusion-security-hotfix-apsb13-13.html | |
| 7007 | Customers should also apply the security configuration settings as outlined on the ColdFusion Security page, as well as review the ColdFusion 9 Lockdown Guide and ColdFusion 10 Lockdown Guide.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 7008 | </vulnerability> | |
| 7009 | ||
| 7010 | <vulnerability id="apache-httpd-cve-2008-0005" title="Apache HTTPD: mod_proxy_ftp UTF-7 XSS (CVE-2008-0005)" severity="4" pciSeverity="3" cvssScore="4.3" cvssVector="(AV:N/AC:M/Au:N/C:N/I:P/A:N)" published="20080111T000000000" added="20120412T000000000" modified="20130822T000000000"> | |
| 7011 | <description> | |
| 7012 | ||
| 7013 | <ContainerBlockElement> | |
| 7014 | ||
| 7015 | <Paragraph>The affected asset is vulnerable to this vulnerability ONLY if it is running one of the following modules: mod_proxy_ftp. Review your web server configuration for validation. A workaround was added in the mod_proxy_ftp module. On sites where mod_proxy_ftp is enabled and a forward proxy is configured, a cross-site scripting attack is possible against Web browsers which do not correctly derive the response character set following the rules in RFC 2616.</Paragraph> | |
| 7016 | </ContainerBlockElement></description> | |
| 7017 | <references> | |
| 7018 | <reference source="APPLE">APPLE-SA-2008-03-18</reference> | |
| 7019 | <reference source="BID">27234</reference> | |
| 7020 | <reference source="CVE">CVE-2008-0005</reference> | |
| 7021 | <reference source="OVAL">OVAL10812</reference> | |
| 7022 | <reference source="REDHAT">RHSA-2008:0004</reference> | |
| 7023 | <reference source="REDHAT">RHSA-2008:0005</reference> | |
| 7024 | <reference source="REDHAT">RHSA-2008:0006</reference> | |
| 7025 | <reference source="REDHAT">RHSA-2008:0007</reference> | |
| 7026 | <reference source="REDHAT">RHSA-2008:0008</reference> | |
| 7027 | <reference source="REDHAT">RHSA-2008:0009</reference> | |
| 7028 | <reference source="SECUNIA">28467</reference> | |
| 7029 | <reference source="SECUNIA">28471</reference> | |
| 7030 | <reference source="SECUNIA">28526</reference> | |
| 7031 | <reference source="SECUNIA">28607</reference> | |
| 7032 | <reference source="SECUNIA">28749</reference> | |
| 7033 | <reference source="SECUNIA">28977</reference> | |
| 7034 | <reference source="SECUNIA">29348</reference> | |
| 7035 | <reference source="SECUNIA">29420</reference> | |
| 7036 | <reference source="SECUNIA">29640</reference> | |
| 7037 | <reference source="SECUNIA">30732</reference> | |
| 7038 | <reference source="SECUNIA">35650</reference> | |
| 7039 | <reference source="SUSE">SUSE-SA:2008:021</reference> | |
| 7040 | <reference source="URL">http://httpd.apache.org/security/vulnerabilities_20.html</reference> | |
| 7041 | <reference source="URL">http://httpd.apache.org/security/vulnerabilities_22.html</reference> | |
| 7042 | <reference source="XF">39615</reference> | |
| 7043 | </references><tags> | |
| 7044 | <tag>Apache</tag> | |
| 7045 | <tag>Apache HTTP Server</tag> | |
| 7046 | <tag>Web</tag> | |
| 7047 | <tag>XSS</tag> | |
| 7048 | </tags> | |
| 7049 | <solution> | |
| 7050 | ||
| 7051 | <ContainerBlockElement> | |
| 7052 | <UnorderedList> | |
| 7053 | <ListItem> | |
| 7054 | <Paragraph>Apache HTTPD >= 2.0 and < 2.0.63</Paragraph> | |
| 7055 | <Paragraph>Download and apply the upgrade from: | |
| 7056 | <URLLink LinkURL="http://archive.apache.org/dist/httpd/httpd-2.0.63.tar.gz" LinkTitle="http://archive.apache.org/dist/httpd/httpd-2.0.63.tar.gz"></URLLink></Paragraph> | |
| 7057 | <Paragraph> | |
| 7058 | <Paragraph>Many platforms and distributions provide pre-built binary packages for Apache HTTP server. These pre-built packages are usually customized and optimized for a particular distribution, therefore we recommend that you use the packages if they are available for your operating system.</Paragraph></Paragraph></ListItem> | |
| 7059 | <ListItem> | |
| 7060 | <Paragraph>Apache HTTPD >= 2.2 and < 2.2.8</Paragraph> | |
| 7061 | <Paragraph>Download and apply the upgrade from: | |
| 7062 | <URLLink LinkURL="http://archive.apache.org/dist/httpd/httpd-2.2.8.tar.gz" LinkTitle="http://archive.apache.org/dist/httpd/httpd-2.2.8.tar.gz"></URLLink></Paragraph> | |
| 7063 | <Paragraph> | |
| 7064 | <Paragraph>Many platforms and distributions provide pre-built binary packages for Apache HTTP server. These pre-built packages are usually customized and optimized for a particular distribution, therefore we recommend that you use the packages if they are available for your operating system.</Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 7065 | </vulnerability> | |
| 7066 | ||
| 7067 | <vulnerability id="apache-httpd-cve-2008-2939" title="Apache HTTPD: mod_proxy_ftp globbing XSS (CVE-2008-2939)" severity="4" pciSeverity="3" cvssScore="4.3" cvssVector="(AV:N/AC:M/Au:N/C:N/I:P/A:N)" published="20080806T000000000" added="20120412T000000000" modified="20130822T000000000"> | |
| 7068 | <description> | |
| 7069 | ||
| 7070 | <ContainerBlockElement> | |
| 7071 | ||
| 7072 | <Paragraph>The affected asset is vulnerable to this vulnerability ONLY if it is running one of the following modules: mod_proxy_ftp. Review your web server configuration for validation. A flaw was found in the handling of wildcards in the path of a FTP URL with mod_proxy_ftp. If mod_proxy_ftp is enabled to support FTP-over-HTTP, requests containing globbing characters could lead to cross-site scripting (XSS) attacks.</Paragraph> | |
| 7073 | </ContainerBlockElement></description> | |
| 7074 | <references> | |
| 7075 | <reference source="APPLE">APPLE-SA-2009-05-12</reference> | |
| 7076 | <reference source="BID">30560</reference> | |
| 7077 | <reference source="CERT">TA09-133A</reference> | |
| 7078 | <reference source="CERT-VN">663763</reference> | |
| 7079 | <reference source="CVE">CVE-2008-2939</reference> | |
| 7080 | <reference source="OVAL">OVAL11316</reference> | |
| 7081 | <reference source="OVAL">OVAL7716</reference> | |
| 7082 | <reference source="REDHAT">RHSA-2008:0966</reference> | |
| 7083 | <reference source="REDHAT">RHSA-2008:0967</reference> | |
| 7084 | <reference source="SECUNIA">31384</reference> | |
| 7085 | <reference source="SECUNIA">31673</reference> | |
| 7086 | <reference source="SECUNIA">32685</reference> | |
| 7087 | <reference source="SECUNIA">32838</reference> | |
| 7088 | <reference source="SECUNIA">33156</reference> | |
| 7089 | <reference source="SECUNIA">33797</reference> | |
| 7090 | <reference source="SECUNIA">34219</reference> | |
| 7091 | <reference source="SECUNIA">35074</reference> | |
| 7092 | <reference source="URL">http://httpd.apache.org/security/vulnerabilities_20.html</reference> | |
| 7093 | <reference source="URL">http://httpd.apache.org/security/vulnerabilities_22.html</reference> | |
| 7094 | <reference source="XF">44223</reference> | |
| 7095 | </references><tags> | |
| 7096 | <tag>Apache</tag> | |
| 7097 | <tag>Apache HTTP Server</tag> | |
| 7098 | <tag>FTP</tag> | |
| 7099 | <tag>Web</tag> | |
| 7100 | <tag>XSS</tag> | |
| 7101 | </tags> | |
| 7102 | <solution> | |
| 7103 | ||
| 7104 | <ContainerBlockElement> | |
| 7105 | <UnorderedList> | |
| 7106 | <ListItem> | |
| 7107 | <Paragraph>Apache HTTPD >= 2.0 and < 2.0.64</Paragraph> | |
| 7108 | <Paragraph>Download and apply the upgrade from: | |
| 7109 | <URLLink LinkURL="http://archive.apache.org/dist/httpd/httpd-2.0.64.tar.gz" LinkTitle="http://archive.apache.org/dist/httpd/httpd-2.0.64.tar.gz"></URLLink></Paragraph> | |
| 7110 | <Paragraph> | |
| 7111 | <Paragraph>Many platforms and distributions provide pre-built binary packages for Apache HTTP server. These pre-built packages are usually customized and optimized for a particular distribution, therefore we recommend that you use the packages if they are available for your operating system.</Paragraph></Paragraph></ListItem> | |
| 7112 | <ListItem> | |
| 7113 | <Paragraph>Apache HTTPD >= 2.2 and < 2.2.10</Paragraph> | |
| 7114 | <Paragraph>Download and apply the upgrade from: | |
| 7115 | <URLLink LinkURL="http://archive.apache.org/dist/httpd/httpd-2.2.10.tar.gz" LinkTitle="http://archive.apache.org/dist/httpd/httpd-2.2.10.tar.gz"></URLLink></Paragraph> | |
| 7116 | <Paragraph> | |
| 7117 | <Paragraph>Many platforms and distributions provide pre-built binary packages for Apache HTTP server. These pre-built packages are usually customized and optimized for a particular distribution, therefore we recommend that you use the packages if they are available for your operating system.</Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 7118 | </vulnerability> | |
| 7119 | ||
| 7120 | <vulnerability id="apache-struts-CVE-2013-2251" title="Apache Struts DefaultActionMapper OGNL arbitrary command execution (CVE-2013-2251)" severity="9" pciSeverity="5" cvssScore="9.3" cvssVector="(AV:N/AC:M/Au:N/C:C/I:C/A:C)" published="20130720T000000000" added="20130725T000000000" modified="20131105T000000000"> | |
| 7121 | <description> | |
| 7122 | ||
| 7123 | <ContainerBlockElement> | |
| 7124 | ||
| 7125 | <Paragraph>Apache Struts 2.0.0 through 2.3.15 allows remote attackers to execute arbitrary OGNL expressions via a parameter with a crafted (1) action:, (2) redirect:, or (3) redirectAction: prefix.</Paragraph> | |
| 7126 | </ContainerBlockElement></description> | |
| 7127 | <references> | |
| 7128 | <reference source="CVE">CVE-2013-2251</reference> | |
| 7129 | <reference source="OSVDB">98445</reference> | |
| 7130 | <reference source="URL">http://struts.apache.org/release/2.3.x/docs/s2-016.html</reference> | |
| 7131 | </references><tags> | |
| 7132 | <tag>Apache</tag> | |
| 7133 | <tag>Apache Struts</tag> | |
| 7134 | <tag>Remote Execution</tag> | |
| 7135 | <tag>Web</tag> | |
| 7136 | </tags> | |
| 7137 | <solution> | |
| 7138 | ||
| 7139 | <ContainerBlockElement></ContainerBlockElement></solution> | |
| 7140 | </vulnerability> | |
| 7141 | ||
| 7142 | <vulnerability id="certificate-common-name-mismatch" title="X.509 Certificate Subject CN Does Not Match the Entity Name" severity="7" pciSeverity="5" cvssScore="7.1" cvssVector="(AV:N/AC:H/Au:N/C:C/I:C/A:N)" published="20070803T000000000" added="20070803T000000000" modified="20120731T000000000"> | |
| 7143 | <description> | |
| 7144 | ||
| 7145 | <ContainerBlockElement> | |
| 7146 | ||
| 7147 | <Paragraph>The subject common name (CN) field in the X.509 certificate does not match | |
| 7148 | the name of the entity presenting the certificate.</Paragraph> | |
| 7149 | ||
| 7150 | ||
| 7151 | <Paragraph>Before issuing a certificate, a Certification Authority (CA) must check the | |
| 7152 | identity of the entity requesting the certificate, as specified in the CA's | |
| 7153 | Certification Practice Statement (CPS). Thus, standard certificate validation | |
| 7154 | procedures require the subject CN field of a certificate to match the actual | |
| 7155 | name of the entity presenting the certificate. For example, in a certificate | |
| 7156 | presented by "https://www.example.com/", the CN should be "www.example.com". | |
| 7157 | </Paragraph> | |
| 7158 | ||
| 7159 | ||
| 7160 | <Paragraph>In order to detect and prevent active eavesdropping attacks, the validity of | |
| 7161 | a certificate must be verified, or else an attacker could then launch a | |
| 7162 | man-in-the-middle attack and gain full control of the data stream. Of | |
| 7163 | particular importance is the validity of the subject's CN, that should match | |
| 7164 | the name of the entity (hostname).</Paragraph> | |
| 7165 | ||
| 7166 | ||
| 7167 | <Paragraph>A CN mismatch most often occurs due to a configuration error, though it can | |
| 7168 | also indicate that a man-in-the-middle attack is being conducted.</Paragraph> | |
| 7169 | </ContainerBlockElement></description> | |
| 7170 | <references> | |
| 7171 | </references><tags> | |
| 7172 | <tag>HTTP</tag> | |
| 7173 | <tag>Web</tag> | |
| 7174 | </tags> | |
| 7175 | <solution> | |
| 7176 | ||
| 7177 | <ContainerBlockElement> | |
| 7178 | <Paragraph> | |
| 7179 | The subject's common name (CN) field in the X.509 certificate should be fixed | |
| 7180 | to reflect the name of the entity presenting the certificate (e.g., the | |
| 7181 | hostname). This is done by generating a new certificate usually signed by a | |
| 7182 | Certification Authority (CA) trusted by both the client and server. | |
| 7183 | </Paragraph></ContainerBlockElement></solution> | |
| 7184 | </vulnerability> | |
| 7185 | ||
| 7186 | <vulnerability id="checkpoint-ess-info-disclosure-sk57881" title="CheckPoint Endpoint Security Server Information Disclosure" severity="9" pciSeverity="5" cvssScore="9.4" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:N)" published="20101215T000000000" added="20110117T000000000" modified="20120731T000000000"> | |
| 7187 | <description> | |
| 7188 | ||
| 7189 | <ContainerBlockElement> | |
| 7190 | ||
| 7191 | <Paragraph> | |
| 7192 | The web interface of CheckPoint Endpoint Security Server 7.x (R71, | |
| 7193 | R72 and R73) ships with an improperly protected configuration that | |
| 7194 | allows remote, unauthenticated users to access arbitrary files in the | |
| 7195 | 'bin', 'conf', 'templates', 'install' and 'logs' directories within | |
| 7196 | the Tomcat directory. While the full extent of this vulnerability is | |
| 7197 | not currently understood, at a minimum it allows attackers to obtain | |
| 7198 | the private keys used to encrypt communication with the Endpoint | |
| 7199 | Security Server management interface, making a man-in-the-middle | |
| 7200 | attack considerably easier. | |
| 7201 | </Paragraph> | |
| 7202 | </ContainerBlockElement></description> | |
| 7203 | <references> | |
| 7204 | <reference source="URL">http://www.rapid7.com/security-center/advisories/R7-0038.jsp</reference> | |
| 7205 | <reference source="URL">https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk57881</reference> | |
| 7206 | </references><tags> | |
| 7207 | <tag>HTTP</tag> | |
| 7208 | <tag>Information Gathering</tag> | |
| 7209 | <tag>Web</tag> | |
| 7210 | </tags> | |
| 7211 | <solution> | |
| 7212 | ||
| 7213 | <ContainerBlockElement> | |
| 7214 | <Paragraph> | |
| 7215 | Apply the hotfix as described in CheckPoint Solution ID | |
| 7216 | ||
| 7217 | <URLLink LinkURL="https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk57881" LinkTitle="https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk57881" href="https://supportcenter.checkpoint.com/supportcenter/portal?eventSubmit_doGoviewsolutiondetails=&solutionid=sk57881"> | |
| 7218 | SK57881</URLLink>, which will prevent the contents of these sensitive files | |
| 7219 | from being disclosed with an HTTP GET request, however this solution | |
| 7220 | does not prevent the size or presence of these files from being obtained | |
| 7221 | with an HTTP HEAD request, which is an information disclosure. | |
| 7222 | </Paragraph></ContainerBlockElement></solution> | |
| 7223 | </vulnerability> | |
| 7224 | ||
| 7225 | <vulnerability id="cifs-insecure-acct-lockout-limit" title="CIFS Account Lockout Policy Allows Password Brute Forcing" severity="7" pciSeverity="4" cvssScore="6.8" cvssVector="(AV:N/AC:M/Au:N/C:P/I:P/A:P)" published="20041101T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 7226 | <description> | |
| 7227 | ||
| 7228 | <ContainerBlockElement> | |
| 7229 | ||
| 7230 | <Paragraph>The account lockout threshold of the CIFS/Samba (SMB) server is | |
| 7231 | too high. This is a security risk. Having a high account | |
| 7232 | lockout threshold allows a hacker to launch an effective | |
| 7233 | brute force attack to guess users' passwords. Using | |
| 7234 | a lower account lockout threshold will greatly limit the | |
| 7235 | effectiveness of any brute forcing attempts.</Paragraph> | |
| 7236 | </ContainerBlockElement></description> | |
| 7237 | <references> | |
| 7238 | </references><tags> | |
| 7239 | <tag>CIFS</tag> | |
| 7240 | <tag>Policy Violation</tag> | |
| 7241 | </tags> | |
| 7242 | <solution> | |
| 7243 | ||
| 7244 | <ContainerBlockElement> | |
| 7245 | <UnorderedList> | |
| 7246 | <ListItem> | |
| 7247 | <Paragraph>Microsoft Windows Vista, Microsoft Windows Vista Home, Basic Edition, Microsoft Windows Vista Home, Basic N Edition, Microsoft Windows Vista Home, Premium Edition, Microsoft Windows Vista Ultimate Edition, Microsoft Windows Vista Enterprise Edition, Microsoft Windows Vista Business Edition, Microsoft Windows Vista Business N Edition, Microsoft Windows Vista Starter Edition, Microsoft Windows Server 2008, Microsoft Windows Server 2008 Standard Edition, Microsoft Windows Server 2008 Enterprise Edition, Microsoft Windows Server 2008 Datacenter Edition, Microsoft Windows Server 2008 HPC Edition, Microsoft Windows Server 2008 Web Edition, Microsoft Windows Server 2008 Storage Edition, Microsoft Windows Small Business Server 2008, Microsoft Windows Essential Business Server 2008, Microsoft Windows Server 2012, Microsoft Windows Server 2012 Essentials Edition, Microsoft Windows Server 2012 Standard Edition, Microsoft Windows Server 2012 Datacenter Edition, Microsoft Windows Server 2012 Foundation Edition, Microsoft Windows Storage Server 2012, Microsoft Windows 7, Microsoft Windows 7 Home, Basic Edition, Microsoft Windows 7 Home, Basic N Edition, Microsoft Windows 7 Home, Premium Edition, Microsoft Windows 7 Home, Premium N Edition, Microsoft Windows 7 Ultimate Edition, Microsoft Windows 7 Ultimate N Edition, Microsoft Windows 7 Enterprise Edition, Microsoft Windows 7 Enterprise N Edition, Microsoft Windows 7 Professional Edition, Microsoft Windows 7 Starter Edition, Microsoft Windows 7 Starter N Edition, Microsoft Windows Embedded Standard 7, Microsoft Windows Server 2008 R2, Microsoft Windows Server 2008 R2, Enterprise Edition, Microsoft Windows Server 2008 R2, Standard Edition, Microsoft Windows Server 2008 R2, Datacenter Edition, Microsoft Windows Server 2008 R2, Web Edition, Microsoft Windows 8, Microsoft Windows 8 Enterprise Edition, Microsoft Windows 8 Professional Edition, Microsoft Windows RT</Paragraph> | |
| 7248 | <Paragraph> | |
| 7249 | <OrderedList> | |
| 7250 | <ListItem>Open the Windows Control Panel.</ListItem> | |
| 7251 | <ListItem>Select "Administrative Tools".</ListItem> | |
| 7252 | <ListItem>To change the domain-wide lockout policy, select "Domain | |
| 7253 | Security Policy" (or "Domain Controller Security Policy" if | |
| 7254 | the computer is a Domain Controller). Otherwise, to change | |
| 7255 | the policy for this computer only, select "Local Security | |
| 7256 | Policy."</ListItem> | |
| 7257 | <ListItem>Expand the "Account Policies" folder and select | |
| 7258 | "Account Lockout Policy".</ListItem> | |
| 7259 | <ListItem>Set the Account Lockout Duration. This setting | |
| 7260 | controls the amount of time an account will remain | |
| 7261 | locked after repeated failed login attempts. To keep | |
| 7262 | accounts locked until the Administrator intervenes, | |
| 7263 | set the lockout duration to 0. Otherwise, be sure to | |
| 7264 | use a reasonable value, preferably 1440 minutes (1 day) | |
| 7265 | or greater.</ListItem> | |
| 7266 | <ListItem>Set the Account Lockout Threshold. This setting | |
| 7267 | determines the number of successive failed login attempts | |
| 7268 | that will cause the account to be locked. Set the | |
| 7269 | lockout threshold to 3 or fewer.</ListItem> | |
| 7270 | <ListItem>Restart the system for the changes to take effect.</ListItem></OrderedList></Paragraph></ListItem> | |
| 7271 | <ListItem> | |
| 7272 | <Paragraph>Microsoft Windows XP, Microsoft Windows XP Home, Microsoft Windows XP Professional, Microsoft Windows Server 2003, Microsoft Windows Server 2003, Standard Edition, Microsoft Windows Server 2003, Enterprise Edition, Microsoft Windows Server 2003, Datacenter Edition, Microsoft Windows Server 2003, Web Edition, Microsoft Windows Small Business Server 2003</Paragraph> | |
| 7273 | <Paragraph> | |
| 7274 | <OrderedList> | |
| 7275 | <ListItem>Open the "Performance and Maintenance" control panel.</ListItem> | |
| 7276 | <ListItem>Select "Administrative Tools".</ListItem> | |
| 7277 | <ListItem>To change the domain-wide lockout policy, select "Domain | |
| 7278 | Security Policy" (or "Domain Controller Security Policy" if | |
| 7279 | the computer is a Domain Controller). Otherwise, to change | |
| 7280 | the policy for this computer only, select "Local Security | |
| 7281 | Policy."</ListItem> | |
| 7282 | <ListItem>Expand the "Account Policies" folder and select | |
| 7283 | "Account Lockout Policy".</ListItem> | |
| 7284 | <ListItem>Set the Account Lockout Duration. This setting | |
| 7285 | controls the amount of time an account will remain | |
| 7286 | locked after repeated failed login attempts. To keep | |
| 7287 | accounts locked until the Administrator intervenes, | |
| 7288 | set the lockout duration to 0. Otherwise, be sure to | |
| 7289 | use a reasonable value, preferably 1440 minutes (1 day) | |
| 7290 | or greater.</ListItem> | |
| 7291 | <ListItem>Set the Account Lockout Threshold. This setting | |
| 7292 | determines the number of successive failed login attempts | |
| 7293 | that will cause the account to be locked. Set the | |
| 7294 | lockout threshold to 3 or fewer.</ListItem> | |
| 7295 | <ListItem>Restart the system for the changes to take effect.</ListItem></OrderedList></Paragraph></ListItem> | |
| 7296 | <ListItem> | |
| 7297 | <Paragraph>Microsoft Windows 2000, Microsoft Windows 2000 Professional, Microsoft Windows 2000 Server, Microsoft Windows 2000 Advanced Server, Microsoft Windows 2000 Datacenter Server</Paragraph> | |
| 7298 | <Paragraph> | |
| 7299 | <OrderedList> | |
| 7300 | <ListItem>Open the "Administrative Tools" control panel.</ListItem> | |
| 7301 | <ListItem>To change the domain-wide lockout policy, select "Domain | |
| 7302 | Security Policy" (or "Domain Controller Security Policy" if | |
| 7303 | the computer is a Domain Controller). Otherwise, to change | |
| 7304 | the policy for this computer only, select "Local Security | |
| 7305 | Policy."</ListItem> | |
| 7306 | <ListItem>Expand the "Account Policies" folder and select | |
| 7307 | "Account Lockout Policy".</ListItem> | |
| 7308 | <ListItem>Set the Account Lockout Duration. This setting | |
| 7309 | controls the amount of time an account will remain | |
| 7310 | locked after repeated failed login attempts. To keep | |
| 7311 | accounts locked until the Administrator intervenes, | |
| 7312 | set the lockout duration to 0. Otherwise, be sure to | |
| 7313 | use a reasonable value, preferably 1440 minutes (1 day) | |
| 7314 | or greater.</ListItem> | |
| 7315 | <ListItem>Set the Account Lockout Threshold. This setting | |
| 7316 | determines the number of successive failed login attempts | |
| 7317 | that will cause the account to be locked. Set the | |
| 7318 | lockout threshold to 3 or fewer.</ListItem> | |
| 7319 | <ListItem>Restart the system for the changes to take effect.</ListItem></OrderedList></Paragraph></ListItem> | |
| 7320 | <ListItem> | |
| 7321 | <Paragraph>Microsoft Windows NT, Microsoft Windows NT Workstation, Microsoft Windows NT Server, Microsoft Windows NT Advanced Server, Microsoft Windows NT Server, Enterprise Edition, Microsoft Windows NT Server, Terminal Server Edition</Paragraph> | |
| 7322 | <Paragraph> | |
| 7323 | <OrderedList> | |
| 7324 | <ListItem>Click on the "Start" button from the Task Bar</ListItem> | |
| 7325 | <ListItem>Select "Programs"</ListItem> | |
| 7326 | <ListItem>Select "Administrative Tools"</ListItem> | |
| 7327 | <ListItem>To change the domain-wide lockout policy, select | |
| 7328 | "User Manager for Domains". Otherwise, to change | |
| 7329 | the policy for this computer only, select "User Manager".</ListItem> | |
| 7330 | <ListItem>From the "Policies" menu, select "Account..."</ListItem> | |
| 7331 | <ListItem>Click on the "Account Lockout" radio button to enable | |
| 7332 | use of the account lockout policy feature.</ListItem> | |
| 7333 | <ListItem>"Lockout after [n] bad logon attempts" determines how many | |
| 7334 | successive failed logins attempts will trigger the lockout. | |
| 7335 | This should be set to a reasonably low value such as 3, which | |
| 7336 | would cause the account to get locked after 3 failed login | |
| 7337 | attempts.</ListItem> | |
| 7338 | <ListItem>"Reset count after [30] minutes" is the amount of time | |
| 7339 | to track failed logins for. This should be set to a reasonably | |
| 7340 | high value, such as 1440 minutes (1 day).</ListItem> | |
| 7341 | <ListItem>"Lockout Duration" is used to define how long the account | |
| 7342 | remains locked. To keep the account locked until the | |
| 7343 | administrator intervenes, select the "Forever (until admin | |
| 7344 | unlocks)" radio button. Otherwise, be sure to use a reasonably | |
| 7345 | high value, preferably 1440 minutes (1 day) or greater.</ListItem> | |
| 7346 | <ListItem>Restart the system for the changes to take effect</ListItem></OrderedList></Paragraph></ListItem> | |
| 7347 | <ListItem> | |
| 7348 | <Paragraph>IBM OS/400</Paragraph> | |
| 7349 | <Paragraph> | |
| 7350 | <Paragraph>OS/400 V4R2 and later include a feature called | |
| 7351 | ||
| 7352 | <URLLink LinkURL="http://www-1.ibm.com/servers/eserver/iseries/netserver/" LinkTitle="http://www-1.ibm.com/servers/eserver/iseries/netserver/" href="http://www-1.ibm.com/servers/eserver/iseries/netserver/">NetServer</URLLink> | |
| 7353 | which provides Windows compatible file and printer sharing. Early | |
| 7354 | versions of NetServer relied on the underlying OS/400 user authentication | |
| 7355 | system. However, starting with V5R1 and V5R2, NetServer can be integrated | |
| 7356 | into your Windows Domain or Active Directory via Kerberos, NetBIOS, or | |
| 7357 | LDAP. This integration allows the NetServer to inherit the domain's account | |
| 7358 | lockout policies. Refer to the NetServer documentation for more information.</Paragraph></Paragraph></ListItem> | |
| 7359 | <ListItem> | |
| 7360 | <Paragraph>Samba</Paragraph> | |
| 7361 | <Paragraph> | |
| 7362 | <Paragraph>The Samba server uses the host operating system's authentication | |
| 7363 | mechanism to control access. If you want to integrate | |
| 7364 | Samba into your NT4 domain or Win2k Active Directory, you can | |
| 7365 | use Samba 2.2.2 or later with winbind to achieve "single sign-on". | |
| 7366 | However, integrating Samba with LDAP/Kerberos/Active Directory is | |
| 7367 | not a trivial task and should only be undertaken with caution.</Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 7368 | </vulnerability> | |
| 7369 | ||
| 7370 | <vulnerability id="cifs-insecure-password-length-min" title="CIFS Minimum Password Length Policy Allows Password Brute Forcing" severity="7" pciSeverity="4" cvssScore="6.8" cvssVector="(AV:N/AC:M/Au:N/C:P/I:P/A:P)" published="20041101T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 7371 | <description> | |
| 7372 | ||
| 7373 | <ContainerBlockElement> | |
| 7374 | ||
| 7375 | <Paragraph>The minimum password length on the CIFS/Samba server is too low. | |
| 7376 | This is a security risk. If the account policy does not | |
| 7377 | enforce a reasonable minimum password length, an attacker | |
| 7378 | will stand a much better chance of guessing or brute forcing | |
| 7379 | users' passwords. Enforcing a higher minimum password length | |
| 7380 | will limit the effectiveness of any brute forcing attempts.</Paragraph> | |
| 7381 | ||
| 7382 | ||
| 7383 | <Paragraph>The default password length is typically set to 0, which | |
| 7384 | allows empty passwords. Most policies recommend setting the | |
| 7385 | minimum to 6 or more characters.</Paragraph> | |
| 7386 | </ContainerBlockElement></description> | |
| 7387 | <references> | |
| 7388 | </references><tags> | |
| 7389 | <tag>CIFS</tag> | |
| 7390 | <tag>Default Account</tag> | |
| 7391 | <tag>Policy Violation</tag> | |
| 7392 | </tags> | |
| 7393 | <solution> | |
| 7394 | ||
| 7395 | <ContainerBlockElement> | |
| 7396 | <UnorderedList> | |
| 7397 | <ListItem> | |
| 7398 | <Paragraph>Microsoft Windows Vista, Microsoft Windows Vista Home, Basic Edition, Microsoft Windows Vista Home, Basic N Edition, Microsoft Windows Vista Home, Premium Edition, Microsoft Windows Vista Ultimate Edition, Microsoft Windows Vista Enterprise Edition, Microsoft Windows Vista Business Edition, Microsoft Windows Vista Business N Edition, Microsoft Windows Vista Starter Edition, Microsoft Windows Server 2008, Microsoft Windows Server 2008 Standard Edition, Microsoft Windows Server 2008 Enterprise Edition, Microsoft Windows Server 2008 Datacenter Edition, Microsoft Windows Server 2008 HPC Edition, Microsoft Windows Server 2008 Web Edition, Microsoft Windows Server 2008 Storage Edition, Microsoft Windows Small Business Server 2008, Microsoft Windows Essential Business Server 2008, Microsoft Windows Server 2012, Microsoft Windows Server 2012 Essentials Edition, Microsoft Windows Server 2012 Standard Edition, Microsoft Windows Server 2012 Datacenter Edition, Microsoft Windows Server 2012 Foundation Edition, Microsoft Windows Storage Server 2012, Microsoft Windows 7, Microsoft Windows 7 Home, Basic Edition, Microsoft Windows 7 Home, Basic N Edition, Microsoft Windows 7 Home, Premium Edition, Microsoft Windows 7 Home, Premium N Edition, Microsoft Windows 7 Ultimate Edition, Microsoft Windows 7 Ultimate N Edition, Microsoft Windows 7 Enterprise Edition, Microsoft Windows 7 Enterprise N Edition, Microsoft Windows 7 Professional Edition, Microsoft Windows 7 Starter Edition, Microsoft Windows 7 Starter N Edition, Microsoft Windows Embedded Standard 7, Microsoft Windows Server 2008 R2, Microsoft Windows Server 2008 R2, Enterprise Edition, Microsoft Windows Server 2008 R2, Standard Edition, Microsoft Windows Server 2008 R2, Datacenter Edition, Microsoft Windows Server 2008 R2, Web Edition, Microsoft Windows 8, Microsoft Windows 8 Enterprise Edition, Microsoft Windows 8 Professional Edition, Microsoft Windows RT</Paragraph> | |
| 7399 | <Paragraph> | |
| 7400 | <OrderedList> | |
| 7401 | <ListItem>Open the Windows Control Panel.</ListItem> | |
| 7402 | <ListItem>Select "Administrative Tools".</ListItem> | |
| 7403 | <ListItem>To change the domain-wide lockout policy, select "Domain | |
| 7404 | Security Policy" (or "Domain Controller Security Policy" if | |
| 7405 | the computer is a Domain Controller). Otherwise, to change | |
| 7406 | the policy for this computer only, select "Local Security | |
| 7407 | Policy."</ListItem> | |
| 7408 | <ListItem>Expand the "Account Policies" folder and select | |
| 7409 | "Password Policy".</ListItem> | |
| 7410 | <ListItem>Set the Minimum Password Length. This setting | |
| 7411 | enforces a minimum length for new or changed passwords. | |
| 7412 | A value of 6 or higher is recommended.</ListItem> | |
| 7413 | <ListItem>Note that this policy does not affect existing | |
| 7414 | passwords. It will only take effect when an existing | |
| 7415 | user changes his password.</ListItem></OrderedList></Paragraph></ListItem> | |
| 7416 | <ListItem> | |
| 7417 | <Paragraph>Microsoft Windows XP, Microsoft Windows XP Home, Microsoft Windows XP Professional, Microsoft Windows Server 2003, Microsoft Windows Server 2003, Standard Edition, Microsoft Windows Server 2003, Enterprise Edition, Microsoft Windows Server 2003, Datacenter Edition, Microsoft Windows Server 2003, Web Edition, Microsoft Windows Small Business Server 2003</Paragraph> | |
| 7418 | <Paragraph> | |
| 7419 | <OrderedList> | |
| 7420 | <ListItem>Open the "Performance and Maintenance" control panel.</ListItem> | |
| 7421 | <ListItem>Select "Administrative Tools".</ListItem> | |
| 7422 | <ListItem>To change the domain-wide lockout policy, select "Domain | |
| 7423 | Security Policy" (or "Domain Controller Security Policy" if | |
| 7424 | the computer is a Domain Controller). Otherwise, to change | |
| 7425 | the policy for this computer only, select "Local Security | |
| 7426 | Policy."</ListItem> | |
| 7427 | <ListItem>Expand the "Account Policies" folder and select | |
| 7428 | "Password Policy".</ListItem> | |
| 7429 | <ListItem>Set the Minimum Password Length. This setting | |
| 7430 | enforces a minimum length for new or changed passwords. | |
| 7431 | A value of 6 or higher is recommended.</ListItem> | |
| 7432 | <ListItem>Note that this policy does not affect existing | |
| 7433 | passwords. It will only take effect when an existing | |
| 7434 | user changes his password.</ListItem></OrderedList></Paragraph></ListItem> | |
| 7435 | <ListItem> | |
| 7436 | <Paragraph>Microsoft Windows 2000, Microsoft Windows 2000 Professional, Microsoft Windows 2000 Server, Microsoft Windows 2000 Advanced Server, Microsoft Windows 2000 Datacenter Server</Paragraph> | |
| 7437 | <Paragraph> | |
| 7438 | <OrderedList> | |
| 7439 | <ListItem>Open the "Administrative Tools" control panel.</ListItem> | |
| 7440 | <ListItem>To change the domain-wide lockout policy, select "Domain | |
| 7441 | Security Policy" (or "Domain Controller Security Policy" if | |
| 7442 | the computer is a Domain Controller). Otherwise, to change | |
| 7443 | the policy for this computer only, select "Local Security | |
| 7444 | Policy."</ListItem> | |
| 7445 | <ListItem>Expand the "Account Policies" folder and select | |
| 7446 | "Password Policy".</ListItem> | |
| 7447 | <ListItem>Set the Minimum Password Length. This setting | |
| 7448 | enforces a minimum length for new or changed passwords. | |
| 7449 | A value of 6 or higher is recommended.</ListItem> | |
| 7450 | <ListItem>Note that this policy does not affect existing | |
| 7451 | passwords. It will only take effect when an existing | |
| 7452 | user changes his password.</ListItem></OrderedList></Paragraph></ListItem> | |
| 7453 | <ListItem> | |
| 7454 | <Paragraph>Microsoft Windows NT, Microsoft Windows NT Workstation, Microsoft Windows NT Server, Microsoft Windows NT Advanced Server, Microsoft Windows NT Server, Enterprise Edition, Microsoft Windows NT Server, Terminal Server Edition</Paragraph> | |
| 7455 | <Paragraph> | |
| 7456 | <OrderedList> | |
| 7457 | <ListItem>Click on the "Start" button from the Task Bar</ListItem> | |
| 7458 | <ListItem>Select "Programs"</ListItem> | |
| 7459 | <ListItem>Select "Administrative Tools"</ListItem> | |
| 7460 | <ListItem>To change the domain-wide lockout policy, select | |
| 7461 | "User Manager for Domains". Otherwise, to change | |
| 7462 | the policy for this computer only, select "User Manager".</ListItem> | |
| 7463 | <ListItem>From the "Policies" menu, select "Account..."</ListItem> | |
| 7464 | <ListItem>Set the Minimum Password Length. This setting | |
| 7465 | enforces a minimum length for new or changed passwords. | |
| 7466 | A value of 6 or higher is recommended.</ListItem> | |
| 7467 | <ListItem>Note that this policy does not affect existing | |
| 7468 | passwords. It will only take effect when an existing | |
| 7469 | user changes his password.</ListItem></OrderedList></Paragraph></ListItem> | |
| 7470 | <ListItem> | |
| 7471 | <Paragraph>IBM OS/400</Paragraph> | |
| 7472 | <Paragraph> | |
| 7473 | <Paragraph>OS/400 V4R2 and later include a feature called | |
| 7474 | ||
| 7475 | <URLLink LinkURL="http://www-1.ibm.com/servers/eserver/iseries/netserver/" LinkTitle="http://www-1.ibm.com/servers/eserver/iseries/netserver/" href="http://www-1.ibm.com/servers/eserver/iseries/netserver/">NetServer</URLLink> | |
| 7476 | which provides Windows compatible file and printer sharing. Early | |
| 7477 | versions of NetServer relied on the underlying OS/400 user authentication | |
| 7478 | system. However, starting with V5R1 and V5R2, NetServer can be integrated | |
| 7479 | into your Windows Domain or Active Directory via Kerberos, NetBIOS, or | |
| 7480 | LDAP. This integration allows the NetServer to inherit the domain's account | |
| 7481 | lockout policies. Refer to the NetServer documentation for more information.</Paragraph></Paragraph></ListItem> | |
| 7482 | <ListItem> | |
| 7483 | <Paragraph>Samba</Paragraph> | |
| 7484 | <Paragraph> | |
| 7485 | <Paragraph>The Samba server uses the host operating system's authentication | |
| 7486 | mechanism to control access. If you want to integrate | |
| 7487 | Samba into your NT4 domain or Win2k Active Directory, you can | |
| 7488 | use Samba 2.2.2 or later with winbind to achieve "single sign-on". | |
| 7489 | However, integrating Samba with LDAP/Kerberos/Active Directory is | |
| 7490 | not a trivial task and should only be undertaken with caution.</Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 7491 | </vulnerability> | |
| 7492 | ||
| 7493 | <vulnerability id="cifs-no-acct-lockout-limit" title="CIFS Account Lockout Policy Not Enforced" severity="7" pciSeverity="4" cvssScore="6.8" cvssVector="(AV:N/AC:M/Au:N/C:P/I:P/A:P)" published="20041101T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 7494 | <description> | |
| 7495 | ||
| 7496 | <ContainerBlockElement> | |
| 7497 | ||
| 7498 | <Paragraph>The CIFS server is not using an account lockout threshold. | |
| 7499 | This is a security risk. Having no lockout threshold | |
| 7500 | allows a hacker to launch a very effective brute force | |
| 7501 | attack to guess users' passwords. Using an account lockout | |
| 7502 | threshold of 3 or lower will greatly limit the effectiveness | |
| 7503 | of any brute forcing attempts.</Paragraph> | |
| 7504 | </ContainerBlockElement></description> | |
| 7505 | <references> | |
| 7506 | </references><tags> | |
| 7507 | <tag>CIFS</tag> | |
| 7508 | <tag>Policy Violation</tag> | |
| 7509 | </tags> | |
| 7510 | <solution> | |
| 7511 | ||
| 7512 | <ContainerBlockElement> | |
| 7513 | <UnorderedList> | |
| 7514 | <ListItem> | |
| 7515 | <Paragraph>Microsoft Windows Vista, Microsoft Windows Vista Home, Basic Edition, Microsoft Windows Vista Home, Basic N Edition, Microsoft Windows Vista Home, Premium Edition, Microsoft Windows Vista Ultimate Edition, Microsoft Windows Vista Enterprise Edition, Microsoft Windows Vista Business Edition, Microsoft Windows Vista Business N Edition, Microsoft Windows Vista Starter Edition, Microsoft Windows Server 2008, Microsoft Windows Server 2008 Standard Edition, Microsoft Windows Server 2008 Enterprise Edition, Microsoft Windows Server 2008 Datacenter Edition, Microsoft Windows Server 2008 HPC Edition, Microsoft Windows Server 2008 Web Edition, Microsoft Windows Server 2008 Storage Edition, Microsoft Windows Small Business Server 2008, Microsoft Windows Essential Business Server 2008, Microsoft Windows Server 2012, Microsoft Windows Server 2012 Essentials Edition, Microsoft Windows Server 2012 Standard Edition, Microsoft Windows Server 2012 Datacenter Edition, Microsoft Windows Server 2012 Foundation Edition, Microsoft Windows Storage Server 2012, Microsoft Windows 7, Microsoft Windows 7 Home, Basic Edition, Microsoft Windows 7 Home, Basic N Edition, Microsoft Windows 7 Home, Premium Edition, Microsoft Windows 7 Home, Premium N Edition, Microsoft Windows 7 Ultimate Edition, Microsoft Windows 7 Ultimate N Edition, Microsoft Windows 7 Enterprise Edition, Microsoft Windows 7 Enterprise N Edition, Microsoft Windows 7 Professional Edition, Microsoft Windows 7 Starter Edition, Microsoft Windows 7 Starter N Edition, Microsoft Windows Embedded Standard 7, Microsoft Windows Server 2008 R2, Microsoft Windows Server 2008 R2, Enterprise Edition, Microsoft Windows Server 2008 R2, Standard Edition, Microsoft Windows Server 2008 R2, Datacenter Edition, Microsoft Windows Server 2008 R2, Web Edition, Microsoft Windows 8, Microsoft Windows 8 Enterprise Edition, Microsoft Windows 8 Professional Edition, Microsoft Windows RT</Paragraph> | |
| 7516 | <Paragraph> | |
| 7517 | <OrderedList> | |
| 7518 | <ListItem>Open the Windows Control Panel.</ListItem> | |
| 7519 | <ListItem>Select "Administrative Tools".</ListItem> | |
| 7520 | <ListItem>To change the domain-wide lockout policy, select "Domain | |
| 7521 | Security Policy" (or "Domain Controller Security Policy" if | |
| 7522 | the computer is a Domain Controller). Otherwise, to change | |
| 7523 | the policy for this computer only, select "Local Security | |
| 7524 | Policy."</ListItem> | |
| 7525 | <ListItem>Expand the "Account Policies" folder and select | |
| 7526 | "Account Lockout Policy".</ListItem> | |
| 7527 | <ListItem>Set the Account Lockout Duration. This setting | |
| 7528 | controls the amount of time an account will remain | |
| 7529 | locked after repeated failed login attempts. To keep | |
| 7530 | accounts locked until the Administrator intervenes, | |
| 7531 | set the lockout duration to 0. Otherwise, be sure to | |
| 7532 | use a reasonable value, preferably 1440 minutes (1 day) | |
| 7533 | or greater.</ListItem> | |
| 7534 | <ListItem>Set the Account Lockout Threshold. This setting | |
| 7535 | determines the number of successive failed login attempts | |
| 7536 | that will cause the account to be locked. Set the | |
| 7537 | lockout threshold to 3 or fewer.</ListItem> | |
| 7538 | <ListItem>Restart the system for the changes to take effect.</ListItem></OrderedList></Paragraph></ListItem> | |
| 7539 | <ListItem> | |
| 7540 | <Paragraph>Microsoft Windows XP, Microsoft Windows XP Home, Microsoft Windows XP Professional, Microsoft Windows Server 2003, Microsoft Windows Server 2003, Standard Edition, Microsoft Windows Server 2003, Enterprise Edition, Microsoft Windows Server 2003, Datacenter Edition, Microsoft Windows Server 2003, Web Edition, Microsoft Windows Small Business Server 2003</Paragraph> | |
| 7541 | <Paragraph> | |
| 7542 | <OrderedList> | |
| 7543 | <ListItem>Open the "Performance and Maintenance" control panel.</ListItem> | |
| 7544 | <ListItem>Select "Administrative Tools".</ListItem> | |
| 7545 | <ListItem>To change the domain-wide lockout policy, select "Domain | |
| 7546 | Security Policy" (or "Domain Controller Security Policy" if | |
| 7547 | the computer is a Domain Controller). Otherwise, to change | |
| 7548 | the policy for this computer only, select "Local Security | |
| 7549 | Policy."</ListItem> | |
| 7550 | <ListItem>Expand the "Account Policies" folder and select | |
| 7551 | "Account Lockout Policy".</ListItem> | |
| 7552 | <ListItem>Set the Account Lockout Duration. This setting | |
| 7553 | controls the amount of time an account will remain | |
| 7554 | locked after repeated failed login attempts. To keep | |
| 7555 | accounts locked until the Administrator intervenes, | |
| 7556 | set the lockout duration to 0. Otherwise, be sure to | |
| 7557 | use a reasonable value, preferably 1440 minutes (1 day) | |
| 7558 | or greater.</ListItem> | |
| 7559 | <ListItem>Set the Account Lockout Threshold. This setting | |
| 7560 | determines the number of successive failed login attempts | |
| 7561 | that will cause the account to be locked. Set the | |
| 7562 | lockout threshold to 3 or fewer.</ListItem> | |
| 7563 | <ListItem>Restart the system for the changes to take effect.</ListItem></OrderedList></Paragraph></ListItem> | |
| 7564 | <ListItem> | |
| 7565 | <Paragraph>Microsoft Windows 2000, Microsoft Windows 2000 Professional, Microsoft Windows 2000 Server, Microsoft Windows 2000 Advanced Server, Microsoft Windows 2000 Datacenter Server</Paragraph> | |
| 7566 | <Paragraph> | |
| 7567 | <OrderedList> | |
| 7568 | <ListItem>Open the "Administrative Tools" control panel.</ListItem> | |
| 7569 | <ListItem>To change the domain-wide lockout policy, select "Domain | |
| 7570 | Security Policy" (or "Domain Controller Security Policy" if | |
| 7571 | the computer is a Domain Controller). Otherwise, to change | |
| 7572 | the policy for this computer only, select "Local Security | |
| 7573 | Policy."</ListItem> | |
| 7574 | <ListItem>Expand the "Account Policies" folder and select | |
| 7575 | "Account Lockout Policy".</ListItem> | |
| 7576 | <ListItem>Set the Account Lockout Duration. This setting | |
| 7577 | controls the amount of time an account will remain | |
| 7578 | locked after repeated failed login attempts. To keep | |
| 7579 | accounts locked until the Administrator intervenes, | |
| 7580 | set the lockout duration to 0. Otherwise, be sure to | |
| 7581 | use a reasonable value, preferably 1440 minutes (1 day) | |
| 7582 | or greater.</ListItem> | |
| 7583 | <ListItem>Set the Account Lockout Threshold. This setting | |
| 7584 | determines the number of successive failed login attempts | |
| 7585 | that will cause the account to be locked. Set the | |
| 7586 | lockout threshold to 3 or fewer.</ListItem> | |
| 7587 | <ListItem>Restart the system for the changes to take effect.</ListItem></OrderedList></Paragraph></ListItem> | |
| 7588 | <ListItem> | |
| 7589 | <Paragraph>Microsoft Windows NT, Microsoft Windows NT Workstation, Microsoft Windows NT Server, Microsoft Windows NT Advanced Server, Microsoft Windows NT Server, Enterprise Edition, Microsoft Windows NT Server, Terminal Server Edition</Paragraph> | |
| 7590 | <Paragraph> | |
| 7591 | <OrderedList> | |
| 7592 | <ListItem>Click on the "Start" button from the Task Bar</ListItem> | |
| 7593 | <ListItem>Select "Programs"</ListItem> | |
| 7594 | <ListItem>Select "Administrative Tools"</ListItem> | |
| 7595 | <ListItem>To change the domain-wide lockout policy, select | |
| 7596 | "User Manager for Domains". Otherwise, to change | |
| 7597 | the policy for this computer only, select "User Manager".</ListItem> | |
| 7598 | <ListItem>From the "Policies" menu, select "Account..."</ListItem> | |
| 7599 | <ListItem>Click on the "Account Lockout" radio button to enable | |
| 7600 | use of the account lockout policy feature.</ListItem> | |
| 7601 | <ListItem>"Lockout after [n] bad logon attempts" determines how many | |
| 7602 | successive failed logins attempts will trigger the lockout. | |
| 7603 | This should be set to a reasonably low value such as 3, which | |
| 7604 | would cause the account to get locked after 3 failed login | |
| 7605 | attempts.</ListItem> | |
| 7606 | <ListItem>"Reset count after [30] minutes" is the amount of time | |
| 7607 | to track failed logins for. This should be set to a reasonably | |
| 7608 | high value, such as 1440 minutes (1 day).</ListItem> | |
| 7609 | <ListItem>"Lockout Duration" is used to define how long the account | |
| 7610 | remains locked. To keep the account locked until the | |
| 7611 | administrator intervenes, select the "Forever (until admin | |
| 7612 | unlocks)" radio button. Otherwise, be sure to use a reasonably | |
| 7613 | high value, preferably 1440 minutes (1 day) or greater.</ListItem> | |
| 7614 | <ListItem>Restart the system for the changes to take effect</ListItem></OrderedList></Paragraph></ListItem> | |
| 7615 | <ListItem> | |
| 7616 | <Paragraph>IBM OS/400</Paragraph> | |
| 7617 | <Paragraph> | |
| 7618 | <Paragraph>OS/400 V4R2 and later include a feature called | |
| 7619 | ||
| 7620 | <URLLink LinkURL="http://www-1.ibm.com/servers/eserver/iseries/netserver/" LinkTitle="http://www-1.ibm.com/servers/eserver/iseries/netserver/" href="http://www-1.ibm.com/servers/eserver/iseries/netserver/">NetServer</URLLink> | |
| 7621 | which provides Windows compatible file and printer sharing. Early | |
| 7622 | versions of NetServer relied on the underlying OS/400 user authentication | |
| 7623 | system. However, starting with V5R1 and V5R2, NetServer can be integrated | |
| 7624 | into your Windows Domain or Active Directory via Kerberos, NetBIOS, or | |
| 7625 | LDAP. This integration allows the NetServer to inherit the domain's account | |
| 7626 | lockout policies. Refer to the NetServer documentation for more information.</Paragraph></Paragraph></ListItem> | |
| 7627 | <ListItem> | |
| 7628 | <Paragraph>Samba</Paragraph> | |
| 7629 | <Paragraph> | |
| 7630 | <Paragraph>The Samba server uses the host operating system's authentication | |
| 7631 | mechanism to control access. If you want to integrate | |
| 7632 | Samba into your NT4 domain or Win2k Active Directory, you can | |
| 7633 | use Samba 2.2.2 or later with winbind to achieve "single sign-on". | |
| 7634 | However, integrating Samba with LDAP/Kerberos/Active Directory is | |
| 7635 | not a trivial task and should only be undertaken with caution.</Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 7636 | </vulnerability> | |
| 7637 | ||
| 7638 | <vulnerability id="cifs-no-password-length-min" title="CIFS Minimum Password Length Policy Not Enforced" severity="7" pciSeverity="4" cvssScore="6.8" cvssVector="(AV:N/AC:M/Au:N/C:P/I:P/A:P)" published="20041101T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 7639 | <description> | |
| 7640 | ||
| 7641 | <ContainerBlockElement> | |
| 7642 | ||
| 7643 | <Paragraph>The minimum password length on the CIFS server is set | |
| 7644 | to 0, which allows accounts with no password and accounts | |
| 7645 | with very short passwords. This is a security risk. If the | |
| 7646 | account policy does not enforce a reasonable minimum password | |
| 7647 | length, an attacker will stand a much better chance of | |
| 7648 | guessing or brute forcing users' passwords. Enforcing a higher | |
| 7649 | minimum password length will limit the effectiveness of | |
| 7650 | any brute forcing attempts.</Paragraph> | |
| 7651 | ||
| 7652 | ||
| 7653 | <Paragraph>The default password length is typically set to 0, which | |
| 7654 | allows empty passwords. Most policies recommend setting the | |
| 7655 | minimum to 6 or more characters.</Paragraph> | |
| 7656 | </ContainerBlockElement></description> | |
| 7657 | <references> | |
| 7658 | </references><tags> | |
| 7659 | <tag>CIFS</tag> | |
| 7660 | <tag>Default Account</tag> | |
| 7661 | <tag>Policy Violation</tag> | |
| 7662 | </tags> | |
| 7663 | <solution> | |
| 7664 | ||
| 7665 | <ContainerBlockElement> | |
| 7666 | <UnorderedList> | |
| 7667 | <ListItem> | |
| 7668 | <Paragraph>Microsoft Windows Vista, Microsoft Windows Vista Home, Basic Edition, Microsoft Windows Vista Home, Basic N Edition, Microsoft Windows Vista Home, Premium Edition, Microsoft Windows Vista Ultimate Edition, Microsoft Windows Vista Enterprise Edition, Microsoft Windows Vista Business Edition, Microsoft Windows Vista Business N Edition, Microsoft Windows Vista Starter Edition, Microsoft Windows Server 2008, Microsoft Windows Server 2008 Standard Edition, Microsoft Windows Server 2008 Enterprise Edition, Microsoft Windows Server 2008 Datacenter Edition, Microsoft Windows Server 2008 HPC Edition, Microsoft Windows Server 2008 Web Edition, Microsoft Windows Server 2008 Storage Edition, Microsoft Windows Small Business Server 2008, Microsoft Windows Essential Business Server 2008, Microsoft Windows Server 2012, Microsoft Windows Server 2012 Essentials Edition, Microsoft Windows Server 2012 Standard Edition, Microsoft Windows Server 2012 Datacenter Edition, Microsoft Windows Server 2012 Foundation Edition, Microsoft Windows Storage Server 2012, Microsoft Windows 7, Microsoft Windows 7 Home, Basic Edition, Microsoft Windows 7 Home, Basic N Edition, Microsoft Windows 7 Home, Premium Edition, Microsoft Windows 7 Home, Premium N Edition, Microsoft Windows 7 Ultimate Edition, Microsoft Windows 7 Ultimate N Edition, Microsoft Windows 7 Enterprise Edition, Microsoft Windows 7 Enterprise N Edition, Microsoft Windows 7 Professional Edition, Microsoft Windows 7 Starter Edition, Microsoft Windows 7 Starter N Edition, Microsoft Windows Embedded Standard 7, Microsoft Windows Server 2008 R2, Microsoft Windows Server 2008 R2, Enterprise Edition, Microsoft Windows Server 2008 R2, Standard Edition, Microsoft Windows Server 2008 R2, Datacenter Edition, Microsoft Windows Server 2008 R2, Web Edition, Microsoft Windows 8, Microsoft Windows 8 Enterprise Edition, Microsoft Windows 8 Professional Edition, Microsoft Windows RT</Paragraph> | |
| 7669 | <Paragraph> | |
| 7670 | <OrderedList> | |
| 7671 | <ListItem>Open the Windows Control Panel.</ListItem> | |
| 7672 | <ListItem>Select "Administrative Tools".</ListItem> | |
| 7673 | <ListItem>To change the domain-wide lockout policy, select "Domain | |
| 7674 | Security Policy" (or "Domain Controller Security Policy" if | |
| 7675 | the computer is a Domain Controller). Otherwise, to change | |
| 7676 | the policy for this computer only, select "Local Security | |
| 7677 | Policy."</ListItem> | |
| 7678 | <ListItem>Expand the "Account Policies" folder and select | |
| 7679 | "Password Policy".</ListItem> | |
| 7680 | <ListItem>Set the Minimum Password Length. This setting | |
| 7681 | enforces a minimum length for new or changed passwords. | |
| 7682 | A value of 6 or higher is recommended.</ListItem> | |
| 7683 | <ListItem>Note that this policy does not affect existing | |
| 7684 | passwords. It will only take effect when an existing | |
| 7685 | user changes his password.</ListItem></OrderedList></Paragraph></ListItem> | |
| 7686 | <ListItem> | |
| 7687 | <Paragraph>Microsoft Windows XP, Microsoft Windows XP Home, Microsoft Windows XP Professional, Microsoft Windows Server 2003, Microsoft Windows Server 2003, Standard Edition, Microsoft Windows Server 2003, Enterprise Edition, Microsoft Windows Server 2003, Datacenter Edition, Microsoft Windows Server 2003, Web Edition, Microsoft Windows Small Business Server 2003</Paragraph> | |
| 7688 | <Paragraph> | |
| 7689 | <OrderedList> | |
| 7690 | <ListItem>Open the "Performance and Maintenance" control panel.</ListItem> | |
| 7691 | <ListItem>Select "Administrative Tools".</ListItem> | |
| 7692 | <ListItem>To change the domain-wide lockout policy, select "Domain | |
| 7693 | Security Policy" (or "Domain Controller Security Policy" if | |
| 7694 | the computer is a Domain Controller). Otherwise, to change | |
| 7695 | the policy for this computer only, select "Local Security | |
| 7696 | Policy."</ListItem> | |
| 7697 | <ListItem>Expand the "Account Policies" folder and select | |
| 7698 | "Password Policy".</ListItem> | |
| 7699 | <ListItem>Set the Minimum Password Length. This setting | |
| 7700 | enforces a minimum length for new or changed passwords. | |
| 7701 | A value of 6 or higher is recommended.</ListItem> | |
| 7702 | <ListItem>Note that this policy does not affect existing | |
| 7703 | passwords. It will only take effect when an existing | |
| 7704 | user changes his password.</ListItem></OrderedList></Paragraph></ListItem> | |
| 7705 | <ListItem> | |
| 7706 | <Paragraph>Microsoft Windows 2000, Microsoft Windows 2000 Professional, Microsoft Windows 2000 Server, Microsoft Windows 2000 Advanced Server, Microsoft Windows 2000 Datacenter Server</Paragraph> | |
| 7707 | <Paragraph> | |
| 7708 | <OrderedList> | |
| 7709 | <ListItem>Open the "Administrative Tools" control panel.</ListItem> | |
| 7710 | <ListItem>To change the domain-wide lockout policy, select "Domain | |
| 7711 | Security Policy" (or "Domain Controller Security Policy" if | |
| 7712 | the computer is a Domain Controller). Otherwise, to change | |
| 7713 | the policy for this computer only, select "Local Security | |
| 7714 | Policy."</ListItem> | |
| 7715 | <ListItem>Expand the "Account Policies" folder and select | |
| 7716 | "Password Policy".</ListItem> | |
| 7717 | <ListItem>Set the Minimum Password Length. This setting | |
| 7718 | enforces a minimum length for new or changed passwords. | |
| 7719 | A value of 6 or higher is recommended.</ListItem> | |
| 7720 | <ListItem>Note that this policy does not affect existing | |
| 7721 | passwords. It will only take effect when an existing | |
| 7722 | user changes his password.</ListItem></OrderedList></Paragraph></ListItem> | |
| 7723 | <ListItem> | |
| 7724 | <Paragraph>Microsoft Windows NT, Microsoft Windows NT Workstation, Microsoft Windows NT Server, Microsoft Windows NT Advanced Server, Microsoft Windows NT Server, Enterprise Edition, Microsoft Windows NT Server, Terminal Server Edition</Paragraph> | |
| 7725 | <Paragraph> | |
| 7726 | <OrderedList> | |
| 7727 | <ListItem>Click on the "Start" button from the Task Bar</ListItem> | |
| 7728 | <ListItem>Select "Programs"</ListItem> | |
| 7729 | <ListItem>Select "Administrative Tools"</ListItem> | |
| 7730 | <ListItem>To change the domain-wide lockout policy, select | |
| 7731 | "User Manager for Domains". Otherwise, to change | |
| 7732 | the policy for this computer only, select "User Manager".</ListItem> | |
| 7733 | <ListItem>From the "Policies" menu, select "Account..."</ListItem> | |
| 7734 | <ListItem>Set the Minimum Password Length. This setting | |
| 7735 | enforces a minimum length for new or changed passwords. | |
| 7736 | A value of 6 or higher is recommended.</ListItem> | |
| 7737 | <ListItem>Note that this policy does not affect existing | |
| 7738 | passwords. It will only take effect when an existing | |
| 7739 | user changes his password.</ListItem></OrderedList></Paragraph></ListItem> | |
| 7740 | <ListItem> | |
| 7741 | <Paragraph>IBM OS/400</Paragraph> | |
| 7742 | <Paragraph> | |
| 7743 | <Paragraph>OS/400 V4R2 and later include a feature called | |
| 7744 | ||
| 7745 | <URLLink LinkURL="http://www-1.ibm.com/servers/eserver/iseries/netserver/" LinkTitle="http://www-1.ibm.com/servers/eserver/iseries/netserver/" href="http://www-1.ibm.com/servers/eserver/iseries/netserver/">NetServer</URLLink> | |
| 7746 | which provides Windows compatible file and printer sharing. Early | |
| 7747 | versions of NetServer relied on the underlying OS/400 user authentication | |
| 7748 | system. However, starting with V5R1 and V5R2, NetServer can be integrated | |
| 7749 | into your Windows Domain or Active Directory via Kerberos, NetBIOS, or | |
| 7750 | LDAP. This integration allows the NetServer to inherit the domain's account | |
| 7751 | lockout policies. Refer to the NetServer documentation for more information.</Paragraph></Paragraph></ListItem> | |
| 7752 | <ListItem> | |
| 7753 | <Paragraph>Samba</Paragraph> | |
| 7754 | <Paragraph> | |
| 7755 | <Paragraph>The Samba server uses the host operating system's authentication | |
| 7756 | mechanism to control access. If you want to integrate | |
| 7757 | Samba into your NT4 domain or Win2k Active Directory, you can | |
| 7758 | use Samba 2.2.2 or later with winbind to achieve "single sign-on". | |
| 7759 | However, integrating Samba with LDAP/Kerberos/Active Directory is | |
| 7760 | not a trivial task and should only be undertaken with caution.</Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 7761 | </vulnerability> | |
| 7762 | ||
| 7763 | <vulnerability id="DNS-0004" title="Unrestricted DNS Zone Transfer (CVE-1999-0532)" severity="1" pciSeverity="3" cvssScore="0.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:N/A:N)" published="19970701T000000000" added="20041101T000000000" modified="20130718T000000000"> | |
| 7764 | <description> | |
| 7765 | ||
| 7766 | <ContainerBlockElement> | |
| 7767 | ||
| 7768 | <Paragraph>A DNS server allows zone transfers.</Paragraph> | |
| 7769 | </ContainerBlockElement></description> | |
| 7770 | <references> | |
| 7771 | <reference source="CVE">CVE-1999-0532</reference> | |
| 7772 | </references><tags> | |
| 7773 | <tag>DNS</tag> | |
| 7774 | <tag>ISC</tag> | |
| 7775 | <tag>ISC BIND</tag> | |
| 7776 | <tag>Zone Transfer</tag> | |
| 7777 | </tags> | |
| 7778 | <solution> | |
| 7779 | ||
| 7780 | <ContainerBlockElement> | |
| 7781 | <Paragraph> | |
| 7782 | Restrict zone transfers to slave servers only. | |
| 7783 | ||
| 7784 | ||
| 7785 | <UnorderedList> | |
| 7786 | <ListItem>For BIND, use the | |
| 7787 | ||
| 7788 | ||
| 7789 | <URLLink LinkURL="http://www.isc.org/products/BIND/docs/bog-4.9.4/bog-sh-5.html#sh-5.1.13" LinkTitle="http://www.isc.org/products/BIND/docs/bog-4.9.4/bog-sh-5.html#sh-5.1.13" href="http://www.isc.org/products/BIND/docs/bog-4.9.4/bog-sh-5.html#sh-5.1.13">"xfernets" directive</URLLink> | |
| 7790 | ( http://www.isc.org/products/BIND/docs/bog-4.9.4/bog-sh-5.html#sh-5.1.13 ) .</ListItem> | |
| 7791 | <ListItem>For djbdns/tinydns, see | |
| 7792 | ||
| 7793 | ||
| 7794 | <URLLink LinkURL="http://cr.yp.to/djbdns/faq/axfrdns.html" LinkTitle="http://cr.yp.to/djbdns/faq/axfrdns.html" href="http://cr.yp.to/djbdns/faq/axfrdns.html">http://cr.yp.to/djbdns/faq/axfrdns.html</URLLink> ( http://cr.yp.to/djbdns/faq/axfrdns.html ) .</ListItem> | |
| 7795 | <ListItem>For Microsoft DNS, make sure that your DNS services are integrated | |
| 7796 | with Active Directory, and then use Active Directory's built-in | |
| 7797 | object security mechanisms to place restrictions on the data. If you | |
| 7798 | are using Active Directory exclusively, you can disable zone transfer | |
| 7799 | in favor of Active Directory replication. This will only allow | |
| 7800 | designated domain controllers to obtain the Active Directory information.</ListItem></UnorderedList></Paragraph></ContainerBlockElement></solution> | |
| 7801 | </vulnerability> | |
| 7802 | ||
| 7803 | <vulnerability id="dns-allows-cache-snooping" title="DNS server allows cache snooping" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="19900101T000000000" added="20110401T000000000" modified="20121023T000000000"> | |
| 7804 | <description> | |
| 7805 | ||
| 7806 | <ContainerBlockElement> | |
| 7807 | ||
| 7808 | <Paragraph> | |
| 7809 | This DNS server is susceptible to DNS cache snooping, whereby an attacker | |
| 7810 | can make non-recursive queries to a DNS server, looking for records | |
| 7811 | potentially already resolved by this DNS server for other clients. | |
| 7812 | Depending on the response, an attacker can use this information to | |
| 7813 | potentially launch other attacks. | |
| 7814 | </Paragraph> | |
| 7815 | </ContainerBlockElement></description> | |
| 7816 | <references> | |
| 7817 | <reference source="URL">http://www.rootsecure.net/content/downloads/pdf/dns_cache_snooping.pdf</reference> | |
| 7818 | </references><tags> | |
| 7819 | <tag>DNS</tag> | |
| 7820 | <tag>ISC</tag> | |
| 7821 | <tag>ISC BIND</tag> | |
| 7822 | </tags> | |
| 7823 | <solution> | |
| 7824 | ||
| 7825 | <ContainerBlockElement> | |
| 7826 | <Paragraph> | |
| 7827 | <Paragraph> | |
| 7828 | Restrict the processing of DNS queries to only systems that should | |
| 7829 | be allowed to use this nameserver. | |
| 7830 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 7831 | </vulnerability> | |
| 7832 | ||
| 7833 | <vulnerability id="dns-processes-recursive-queries" title="Nameserver Processes Recursive Queries" severity="5" pciSeverity="2" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:N/A:P)" published="19900101T000000000" added="20100226T000000000" modified="20121023T000000000"> | |
| 7834 | <description> | |
| 7835 | ||
| 7836 | <ContainerBlockElement> | |
| 7837 | ||
| 7838 | <Paragraph> | |
| 7839 | Allowing nameservers to process recursive queries coming from any system | |
| 7840 | may, in certain situations, help attackers conduct denial of service or | |
| 7841 | cache poisoning attacks. | |
| 7842 | </Paragraph> | |
| 7843 | </ContainerBlockElement></description> | |
| 7844 | <references> | |
| 7845 | <reference source="URL">http://www.us-cert.gov/reading_room/DNS-recursion033006.pdf</reference> | |
| 7846 | </references><tags> | |
| 7847 | <tag>DNS</tag> | |
| 7848 | <tag>Denial of Service</tag> | |
| 7849 | <tag>ISC</tag> | |
| 7850 | <tag>ISC BIND</tag> | |
| 7851 | </tags> | |
| 7852 | <solution> | |
| 7853 | ||
| 7854 | <ContainerBlockElement> | |
| 7855 | <Paragraph> | |
| 7856 | <Paragraph> | |
| 7857 | Restrict the processing of recursive queries to only systems that | |
| 7858 | should be allowed to use this nameserver. | |
| 7859 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 7860 | </vulnerability> | |
| 7861 | ||
| 7862 | <vulnerability id="dns-unrestricted-reverse-zone-transfer" title="Unrestricted Reverse DNS Zone Transfer" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="20071126T000000000" added="20071126T000000000" modified="20121023T000000000"> | |
| 7863 | <description> | |
| 7864 | ||
| 7865 | <ContainerBlockElement> | |
| 7866 | Allowing unrestricted reverse zone transfers gives anonymous users access to information about | |
| 7867 | all hostnames defined in a particular domain. This information can aid further attacks on | |
| 7868 | vulnerable systems. | |
| 7869 | </ContainerBlockElement></description> | |
| 7870 | <references> | |
| 7871 | </references><tags> | |
| 7872 | <tag>DNS</tag> | |
| 7873 | <tag>ISC</tag> | |
| 7874 | <tag>ISC BIND</tag> | |
| 7875 | <tag>Zone Transfer</tag> | |
| 7876 | </tags> | |
| 7877 | <solution> | |
| 7878 | ||
| 7879 | <ContainerBlockElement> | |
| 7880 | <Paragraph> | |
| 7881 | <Paragraph> | |
| 7882 | See the documentation of your DNS server to disable or restrict reverse zone transfers. | |
| 7883 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 7884 | </vulnerability> | |
| 7885 | ||
| 7886 | <vulnerability id="ftp-anonymous-writeable-directories" title="Anonymous FTP Writeable Directories" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="19990101T000000000" added="20041101T000000000" modified="20120713T000000000"> | |
| 7887 | <description> | |
| 7888 | ||
| 7889 | <ContainerBlockElement> | |
| 7890 | ||
| 7891 | <Paragraph>Anonymous users can upload files to the FTP server. This can often be used | |
| 7892 | in combination with other services, such as HTTP, to compromise the server.</Paragraph> | |
| 7893 | </ContainerBlockElement></description> | |
| 7894 | <references> | |
| 7895 | <reference source="CVE">CVE-1999-0527</reference> | |
| 7896 | </references><tags> | |
| 7897 | <tag>FTP</tag> | |
| 7898 | <tag>Web</tag> | |
| 7899 | </tags> | |
| 7900 | <solution> | |
| 7901 | ||
| 7902 | <ContainerBlockElement> | |
| 7903 | <Paragraph> | |
| 7904 | <Paragraph>Disable write access (upload) for anonymous users. It is also best | |
| 7905 | to restrict world writeable permissions to any directory or file | |
| 7906 | accessible via FTP.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 7907 | </vulnerability> | |
| 7908 | ||
| 7909 | <vulnerability id="ftp-default-login-admin-null" title="FTP access with admin/null credentials" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="19990101T000000000" added="20100715T000000000" modified="20120927T000000000"> | |
| 7910 | <description> | |
| 7911 | ||
| 7912 | <ContainerBlockElement> | |
| 7913 | Access to the FTP server was gained using the user account "admin" and password "". | |
| 7914 | </ContainerBlockElement></description> | |
| 7915 | <references> | |
| 7916 | </references><tags> | |
| 7917 | <tag>Default Account</tag> | |
| 7918 | <tag>FTP</tag> | |
| 7919 | </tags> | |
| 7920 | <solution> | |
| 7921 | ||
| 7922 | <ContainerBlockElement> | |
| 7923 | <Paragraph> | |
| 7924 | <Paragraph>Remove or disable the account if it is not critical for the | |
| 7925 | system to function. Otherwise, the password should be changed | |
| 7926 | to a non-default value.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 7927 | </vulnerability> | |
| 7928 | ||
| 7929 | <vulnerability id="ftp-default-login-admin-passwd" title="FTP access with admin/passwd credentials" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="19990101T000000000" added="20100715T000000000" modified="20120927T000000000"> | |
| 7930 | <description> | |
| 7931 | ||
| 7932 | <ContainerBlockElement> | |
| 7933 | Access to the FTP server was gained using the user account "admin" and password "passwd". | |
| 7934 | </ContainerBlockElement></description> | |
| 7935 | <references> | |
| 7936 | </references><tags> | |
| 7937 | <tag>Default Account</tag> | |
| 7938 | <tag>FTP</tag> | |
| 7939 | </tags> | |
| 7940 | <solution> | |
| 7941 | ||
| 7942 | <ContainerBlockElement> | |
| 7943 | <Paragraph> | |
| 7944 | <Paragraph>Remove or disable the account if it is not critical for the | |
| 7945 | system to function. Otherwise, the password should be changed | |
| 7946 | to a non-default value.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 7947 | </vulnerability> | |
| 7948 | ||
| 7949 | <vulnerability id="ftp-default-login-admin-password" title="FTP access with admin/password credentials" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="19990101T000000000" added="20100715T000000000" modified="20120927T000000000"> | |
| 7950 | <description> | |
| 7951 | ||
| 7952 | <ContainerBlockElement> | |
| 7953 | Access to the FTP server was gained using the user account "admin" and password "password". | |
| 7954 | </ContainerBlockElement></description> | |
| 7955 | <references> | |
| 7956 | </references><tags> | |
| 7957 | <tag>Default Account</tag> | |
| 7958 | <tag>FTP</tag> | |
| 7959 | </tags> | |
| 7960 | <solution> | |
| 7961 | ||
| 7962 | <ContainerBlockElement> | |
| 7963 | <Paragraph> | |
| 7964 | <Paragraph>Remove or disable the account if it is not critical for the | |
| 7965 | system to function. Otherwise, the password should be changed | |
| 7966 | to a non-default value.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 7967 | </vulnerability> | |
| 7968 | ||
| 7969 | <vulnerability id="ftp-default-login-administrator-null" title="FTP access with administrator/null credentials" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="19990101T000000000" added="20100715T000000000" modified="20120927T000000000"> | |
| 7970 | <description> | |
| 7971 | ||
| 7972 | <ContainerBlockElement> | |
| 7973 | Access to the FTP server was gained using the user account "administrator" and password "". | |
| 7974 | </ContainerBlockElement></description> | |
| 7975 | <references> | |
| 7976 | </references><tags> | |
| 7977 | <tag>Default Account</tag> | |
| 7978 | <tag>FTP</tag> | |
| 7979 | </tags> | |
| 7980 | <solution> | |
| 7981 | ||
| 7982 | <ContainerBlockElement> | |
| 7983 | <Paragraph> | |
| 7984 | <Paragraph>Remove or disable the account if it is not critical for the | |
| 7985 | system to function. Otherwise, the password should be changed | |
| 7986 | to a non-default value.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 7987 | </vulnerability> | |
| 7988 | ||
| 7989 | <vulnerability id="ftp-default-login-administrator-passwd" title="FTP access with administrator/passwd credentials" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="19990101T000000000" added="20100715T000000000" modified="20120927T000000000"> | |
| 7990 | <description> | |
| 7991 | ||
| 7992 | <ContainerBlockElement> | |
| 7993 | Access to the FTP server was gained using the user account "administrator" and password "passwd". | |
| 7994 | </ContainerBlockElement></description> | |
| 7995 | <references> | |
| 7996 | </references><tags> | |
| 7997 | <tag>Default Account</tag> | |
| 7998 | <tag>FTP</tag> | |
| 7999 | </tags> | |
| 8000 | <solution> | |
| 8001 | ||
| 8002 | <ContainerBlockElement> | |
| 8003 | <Paragraph> | |
| 8004 | <Paragraph>Remove or disable the account if it is not critical for the | |
| 8005 | system to function. Otherwise, the password should be changed | |
| 8006 | to a non-default value.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8007 | </vulnerability> | |
| 8008 | ||
| 8009 | <vulnerability id="ftp-default-login-administrator-password" title="FTP access with administrator/password credentials" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="19990101T000000000" added="20100715T000000000" modified="20120927T000000000"> | |
| 8010 | <description> | |
| 8011 | ||
| 8012 | <ContainerBlockElement> | |
| 8013 | Access to the FTP server was gained using the user account "administrator" and password "password". | |
| 8014 | </ContainerBlockElement></description> | |
| 8015 | <references> | |
| 8016 | </references><tags> | |
| 8017 | <tag>Default Account</tag> | |
| 8018 | <tag>FTP</tag> | |
| 8019 | </tags> | |
| 8020 | <solution> | |
| 8021 | ||
| 8022 | <ContainerBlockElement> | |
| 8023 | <Paragraph> | |
| 8024 | <Paragraph>Remove or disable the account if it is not critical for the | |
| 8025 | system to function. Otherwise, the password should be changed | |
| 8026 | to a non-default value.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8027 | </vulnerability> | |
| 8028 | ||
| 8029 | <vulnerability id="FTP-GENERIC-0001" title="FTP access with ftp account" severity="1" pciSeverity="3" cvssScore="0.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:N/A:N)" published="19990101T000000000" added="20041101T000000000" modified="20130718T000000000"> | |
| 8030 | <description> | |
| 8031 | ||
| 8032 | <ContainerBlockElement> | |
| 8033 | Many FTP servers support a default account with the user ID "ftp" and password "ftp". It is best practice to remove default accounts, if possible. For accounts required by the system, the default password should be changed. | |
| 8034 | </ContainerBlockElement></description> | |
| 8035 | <references> | |
| 8036 | <reference source="CVE">CVE-1999-0497</reference> | |
| 8037 | </references><tags> | |
| 8038 | <tag>Default Account</tag> | |
| 8039 | <tag>FTP</tag> | |
| 8040 | </tags> | |
| 8041 | <solution> | |
| 8042 | ||
| 8043 | <ContainerBlockElement> | |
| 8044 | <Paragraph> | |
| 8045 | <Paragraph>Remove or disable the account if it is not critical for the | |
| 8046 | system to function. Otherwise, the password should be changed | |
| 8047 | to a non-default value.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8048 | </vulnerability> | |
| 8049 | ||
| 8050 | <vulnerability id="FTP-GENERIC-0002" title="FTP access with anonymous account" severity="1" pciSeverity="3" cvssScore="0.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:N/A:N)" published="19990101T000000000" added="20041101T000000000" modified="20130718T000000000"> | |
| 8051 | <description> | |
| 8052 | ||
| 8053 | <ContainerBlockElement> | |
| 8054 | Many FTP servers support a default account with the user ID "anonymous" and password "ftp@". It is best practice to remove default accounts, if possible. For accounts required by the system, the default password should be changed. | |
| 8055 | </ContainerBlockElement></description> | |
| 8056 | <references> | |
| 8057 | <reference source="CVE">CVE-1999-0497</reference> | |
| 8058 | </references><tags> | |
| 8059 | <tag>Default Account</tag> | |
| 8060 | <tag>FTP</tag> | |
| 8061 | </tags> | |
| 8062 | <solution> | |
| 8063 | ||
| 8064 | <ContainerBlockElement> | |
| 8065 | <Paragraph> | |
| 8066 | <Paragraph>Remove or disable the account if it is not critical for the | |
| 8067 | system to function. Otherwise, the password should be changed | |
| 8068 | to a non-default value.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8069 | </vulnerability> | |
| 8070 | ||
| 8071 | <vulnerability id="FTP-GENERIC-0003" title="FTP access with guest account" severity="1" pciSeverity="3" cvssScore="0.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:N/A:N)" published="19990101T000000000" added="20041101T000000000" modified="20130718T000000000"> | |
| 8072 | <description> | |
| 8073 | ||
| 8074 | <ContainerBlockElement> | |
| 8075 | Many FTP servers support a default account with the user ID "guest" and password "". It is best practice to remove default accounts, if possible. For accounts required by the system, the default password should be changed. | |
| 8076 | </ContainerBlockElement></description> | |
| 8077 | <references> | |
| 8078 | <reference source="CVE">CVE-1999-0497</reference> | |
| 8079 | </references><tags> | |
| 8080 | <tag>Default Account</tag> | |
| 8081 | <tag>FTP</tag> | |
| 8082 | </tags> | |
| 8083 | <solution> | |
| 8084 | ||
| 8085 | <ContainerBlockElement> | |
| 8086 | <Paragraph> | |
| 8087 | <Paragraph>Remove or disable the account if it is not critical for the | |
| 8088 | system to function. Otherwise, the password should be changed | |
| 8089 | to a non-default value.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8090 | </vulnerability> | |
| 8091 | ||
| 8092 | <vulnerability id="FTP-GENERIC-0004" title="FTP access without authentication" severity="1" pciSeverity="1" cvssScore="0.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:N/A:N)" published="19990101T000000000" added="20041101T000000000" modified="20120713T000000000"> | |
| 8093 | <description> | |
| 8094 | ||
| 8095 | <ContainerBlockElement> | |
| 8096 | Some FTP servers allow users to specify any user ID and password to gain access. | |
| 8097 | </ContainerBlockElement></description> | |
| 8098 | <references> | |
| 8099 | <reference source="CVE">CVE-1999-0497</reference> | |
| 8100 | </references><tags> | |
| 8101 | <tag>FTP</tag> | |
| 8102 | </tags> | |
| 8103 | <solution> | |
| 8104 | ||
| 8105 | <ContainerBlockElement> | |
| 8106 | <Paragraph> | |
| 8107 | <Paragraph>Password protected accounts should always be used | |
| 8108 | to protect file access.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8109 | </vulnerability> | |
| 8110 | ||
| 8111 | <vulnerability id="FTP-GENERIC-0005" title="FTP access with blank account and password" severity="1" pciSeverity="1" cvssScore="0.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:N/A:N)" published="19990101T000000000" added="20041101T000000000" modified="20120713T000000000"> | |
| 8112 | <description> | |
| 8113 | ||
| 8114 | <ContainerBlockElement> | |
| 8115 | Some FTP servers permit access with the user ID "" and password "". | |
| 8116 | </ContainerBlockElement></description> | |
| 8117 | <references> | |
| 8118 | <reference source="CVE">CVE-1999-0497</reference> | |
| 8119 | </references><tags> | |
| 8120 | <tag>FTP</tag> | |
| 8121 | </tags> | |
| 8122 | <solution> | |
| 8123 | ||
| 8124 | <ContainerBlockElement> | |
| 8125 | <Paragraph> | |
| 8126 | <Paragraph>Password protected accounts should always be used | |
| 8127 | to protect file access.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8128 | </vulnerability> | |
| 8129 | ||
| 8130 | <vulnerability id="FTP-GENERIC-0006" title="FTP access with no account and password" severity="1" pciSeverity="1" cvssScore="0.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:N/A:N)" published="19990101T000000000" added="20041101T000000000" modified="20120713T000000000"> | |
| 8131 | <description> | |
| 8132 | ||
| 8133 | <ContainerBlockElement> | |
| 8134 | Some FTP servers permit access with the user ID "" and password "". | |
| 8135 | </ContainerBlockElement></description> | |
| 8136 | <references> | |
| 8137 | <reference source="CVE">CVE-1999-0497</reference> | |
| 8138 | </references><tags> | |
| 8139 | <tag>FTP</tag> | |
| 8140 | </tags> | |
| 8141 | <solution> | |
| 8142 | ||
| 8143 | <ContainerBlockElement> | |
| 8144 | <Paragraph> | |
| 8145 | <Paragraph>Password protected accounts should always be used | |
| 8146 | to protect file access.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8147 | </vulnerability> | |
| 8148 | ||
| 8149 | <vulnerability id="FTP-GENERIC-0007" title="FTP server does not support AUTH command" severity="6" pciSeverity="3" cvssScore="5.8" cvssVector="(AV:N/AC:M/Au:N/C:P/I:P/A:N)" published="20041101T000000000" added="20041101T000000000" modified="20120709T000000000"> | |
| 8150 | <description> | |
| 8151 | ||
| 8152 | <ContainerBlockElement> | |
| 8153 | ||
| 8154 | <Paragraph> | |
| 8155 | FTP clients send credentials (user ID and password) in clear text to | |
| 8156 | the FTP server by default. This allows malicious users to intercept the | |
| 8157 | credentials if they can eavesdrop on the connection. | |
| 8158 | </Paragraph> | |
| 8159 | ||
| 8160 | <Paragraph> | |
| 8161 | Newer FTP servers support the AUTH command, which provides enhanced | |
| 8162 | authentication options such as TLS, Kerberos, GSSAPI, etc. This | |
| 8163 | should be used to prevent eavesdropping on FTP connections. | |
| 8164 | </Paragraph> | |
| 8165 | </ContainerBlockElement></description> | |
| 8166 | <references> | |
| 8167 | </references><tags> | |
| 8168 | <tag>FTP</tag> | |
| 8169 | </tags> | |
| 8170 | <solution> | |
| 8171 | ||
| 8172 | <ContainerBlockElement> | |
| 8173 | <Paragraph> | |
| 8174 | <Paragraph>Upgrade/migrate to a FTP server that supports the AUTH command.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8175 | </vulnerability> | |
| 8176 | ||
| 8177 | <vulnerability id="ftp-proftpd-1-3-3c-backdoor" title="ProFTPD 1.3.3c backdoor" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20101202T000000000" added="20101203T000000000" modified="20120713T000000000"> | |
| 8178 | <description> | |
| 8179 | ||
| 8180 | <ContainerBlockElement> | |
| 8181 | ||
| 8182 | <Paragraph> | |
| 8183 | Version 1.3.3c of ProFTPD, if downloaded and installed between | |
| 8184 | November 28, 2010 and December 2, 2010, contains a backdoor that | |
| 8185 | allows remote, unauthenticated attackers to execute arbitrary | |
| 8186 | code as the user running the ProFTPD service. | |
| 8187 | </Paragraph> | |
| 8188 | </ContainerBlockElement></description> | |
| 8189 | <references> | |
| 8190 | <reference source="URL">http://sourceforge.net/mailarchive/message.php?msg_name=alpine.DEB.2.00.1012011542220.12930%40familiar.castaglia.org</reference> | |
| 8191 | </references><tags> | |
| 8192 | <tag>Backdoor</tag> | |
| 8193 | <tag>FTP</tag> | |
| 8194 | <tag>Remote Execution</tag> | |
| 8195 | </tags> | |
| 8196 | <solution> | |
| 8197 | ||
| 8198 | <ContainerBlockElement> | |
| 8199 | <Paragraph> | |
| 8200 | <Paragraph> | |
| 8201 | All users who run versions of ProFTPD which have been downloaded and | |
| 8202 | compiled in this time window are strongly advised to check their | |
| 8203 | systems for security compromises and install unmodified versions of | |
| 8204 | ProFTPD. To verify the integrity of your source files, use the PGP | |
| 8205 | signatures which can be found here as well as on the FTP servers. | |
| 8206 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8207 | </vulnerability> | |
| 8208 | ||
| 8209 | <vulnerability id="generic-icmp-netmask" title="ICMP netmask response" severity="1" pciSeverity="1" cvssScore="0.0" cvssVector="(AV:L/AC:L/Au:N/C:N/I:N/A:N)" published="19970801T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 8210 | <description> | |
| 8211 | ||
| 8212 | <ContainerBlockElement> | |
| 8213 | The remote host responded to an ICMP netmask request. The ICMP netmask response contains the remote host's network mask (on the interface that processed the request). This information can be used by a hacker to accurately map your subnet structures, determining the broadcast addresses in use, and which routers are responsible for which subnets. This may make it easier for them to launch a "SMURF attack" using broadcast-directed ICMP ping packets. | |
| 8214 | </ContainerBlockElement></description> | |
| 8215 | <references> | |
| 8216 | <reference source="CVE">CVE-1999-0524</reference> | |
| 8217 | <reference source="OSVDB">95</reference> | |
| 8218 | <reference source="XF">icmp-netmask(306)</reference> | |
| 8219 | <reference source="XF">icmp-timestamp(322)</reference> | |
| 8220 | </references><tags> | |
| 8221 | <tag>Network</tag> | |
| 8222 | </tags> | |
| 8223 | <solution> | |
| 8224 | ||
| 8225 | <ContainerBlockElement> | |
| 8226 | <UnorderedList> | |
| 8227 | <ListItem> | |
| 8228 | <Paragraph>IBM AIX</Paragraph> | |
| 8229 | <Paragraph> | |
| 8230 | <Paragraph>Execute the following command:</Paragraph> | |
| 8231 | <Paragraph preFormat="true"> /usr/sbin/no -o icmpaddressmask=0</Paragraph> | |
| 8232 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8233 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8234 | types 17 (netmask request) and 18 (netmask response).</Paragraph></Paragraph></ListItem> | |
| 8235 | <ListItem> | |
| 8236 | <Paragraph>OpenBSD, FreeBSD, NetBSD</Paragraph> | |
| 8237 | <Paragraph> | |
| 8238 | <Paragraph>Set the "net.inet.icmp.maskrepl" sysctl variable to 0.</Paragraph> | |
| 8239 | <Paragraph preformat="true"> sysctl -w net.inet.icmp.maskrepl=0</Paragraph> | |
| 8240 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8241 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8242 | types 17 (netmask request) and 18 (netmask response).</Paragraph></Paragraph></ListItem> | |
| 8243 | <ListItem> | |
| 8244 | <Paragraph> | |
| 8245 | <Paragraph>Configure your firewall to block incoming and outgoing ICMP packets | |
| 8246 | with ICMP types 17 (netmask request) and 18 (netmask response), | |
| 8247 | respectively.</Paragraph></Paragraph></ListItem> | |
| 8248 | <ListItem> | |
| 8249 | <Paragraph>HP-UX</Paragraph> | |
| 8250 | <Paragraph> | |
| 8251 | <Paragraph>Execute the following command:</Paragraph> | |
| 8252 | <Paragraph preFormat="true"> ndd -set /dev/ip ip_respond_to_address_mask_broadcast 0</Paragraph> | |
| 8253 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8254 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8255 | types 17 (netmask request) and 18 (netmask response).</Paragraph></Paragraph></ListItem> | |
| 8256 | <ListItem> | |
| 8257 | <Paragraph>Cisco IOS</Paragraph> | |
| 8258 | <Paragraph> | |
| 8259 | <Paragraph>Issue the "no ip mask-reply" command for each affected | |
| 8260 | interface. For example:</Paragraph> | |
| 8261 | <Paragraph preformat="true"> config t</Paragraph> | |
| 8262 | <Paragraph preformat="true"> interface fastethernet0/0</Paragraph> | |
| 8263 | <Paragraph preformat="true"> no ip mask-reply</Paragraph> | |
| 8264 | <Paragraph preformat="true"> exit</Paragraph> | |
| 8265 | <Paragraph>Don't forget to save the configuration when you are finished.</Paragraph> | |
| 8266 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8267 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8268 | types 17 (netmask request) and 18 (netmask response).</Paragraph></Paragraph></ListItem> | |
| 8269 | <ListItem> | |
| 8270 | <Paragraph>SGI Irix</Paragraph> | |
| 8271 | <Paragraph> | |
| 8272 | <Paragraph>IRIX does not offer a way to disable ICMP netmask responses. | |
| 8273 | Therefore, you should block ICMP on the affected host using | |
| 8274 | ipfilterd, and/or block it at the firewall.</Paragraph> | |
| 8275 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8276 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8277 | types 17 (netmask request) and 18 (netmask response).</Paragraph></Paragraph></ListItem> | |
| 8278 | <ListItem> | |
| 8279 | <Paragraph>Linux</Paragraph> | |
| 8280 | <Paragraph> | |
| 8281 | <Paragraph>Linux offers neither a sysctl nor a /proc/sys/net/ipv4 interface to | |
| 8282 | disable ICMP netmask responses. Therefore, you should block ICMP on | |
| 8283 | the affected host using iptables, and/or block it at the firewall. | |
| 8284 | For example:</Paragraph> | |
| 8285 | <Paragraph preformat="true"> ipchains -A input -p icmp --icmp-type address-mask-request -j DROP</Paragraph> | |
| 8286 | <Paragraph preformat="true"> ipchains -A output -p icmp --icmp-type address-mask-reply -j DROP</Paragraph> | |
| 8287 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8288 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8289 | types 17 (netmask request) and 18 (netmask response).</Paragraph></Paragraph></ListItem> | |
| 8290 | <ListItem> | |
| 8291 | <Paragraph>Microsoft Windows NT, Microsoft Windows NT Workstation, Microsoft Windows NT Server, Microsoft Windows NT Advanced Server, Microsoft Windows NT Server, Enterprise Edition, Microsoft Windows NT Server, Terminal Server Edition</Paragraph> | |
| 8292 | <Paragraph> | |
| 8293 | <Paragraph>Windows NT 4 does not provide a way to block ICMP packets. | |
| 8294 | Therefore, you should block it at the firewall.</Paragraph> | |
| 8295 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8296 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8297 | types 17 (netmask request) and 18 (netmask response).</Paragraph></Paragraph></ListItem> | |
| 8298 | <ListItem> | |
| 8299 | <Paragraph>Cisco PIX</Paragraph> | |
| 8300 | <Paragraph> | |
| 8301 | <Paragraph>A properly configured PIX firewall should never respond to ICMP | |
| 8302 | packets on its external interface. In PIX Software versions 4.1(6) | |
| 8303 | until 5.2.1, ICMP traffic to the PIX's internal interface is | |
| 8304 | always permitted; the PIX cannot be configured to NOT respond. | |
| 8305 | Beginning in PIX Software version 5.2.1, ICMP is still permitted on | |
| 8306 | the internal interface by default, but ICMP netmask responses from | |
| 8307 | its internal interfaces can be disabled with the icmp command, as | |
| 8308 | follows, where <inside> is the name of the internal interface:</Paragraph> | |
| 8309 | <Paragraph preformat="true"> icmp deny any 17 <inside></Paragraph> | |
| 8310 | <Paragraph preformat="true"> icmp deny any 18 <inside></Paragraph> | |
| 8311 | <Paragraph>Don't forget to save the configuration when you are finished.</Paragraph> | |
| 8312 | <Paragraph>See Cisco's support document | |
| 8313 | ||
| 8314 | <URLLink LinkURL="http://www.cisco.com/warp/public/110/31.html" LinkTitle="http://www.cisco.com/warp/public/110/31.html" href="http://www.cisco.com/warp/public/110/31.html">Handling ICMP Pings with the PIX Firewall</URLLink> | |
| 8315 | for more information.</Paragraph> | |
| 8316 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8317 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8318 | types 17 (netmask request) and 18 (netmask response).</Paragraph></Paragraph></ListItem> | |
| 8319 | <ListItem> | |
| 8320 | <Paragraph>Sun Solaris</Paragraph> | |
| 8321 | <Paragraph> | |
| 8322 | <Paragraph>Solaris does not offer a way to disable responses to unicast ICMP | |
| 8323 | netmask requests. The following command will block responses to | |
| 8324 | broadcast ICMP netmask requests:</Paragraph> | |
| 8325 | <Paragraph preformat="true"> /usr/sbin/ndd -set /dev/ip ip_respond_to_address_mask_broadcast 0</Paragraph> | |
| 8326 | <Paragraph>However, the Solaris host will always respond to ICMP netmask | |
| 8327 | requests directed to the host. In order to completely disable ICMP | |
| 8328 | netmask responses, the ICMP requests and responses must be blocked at | |
| 8329 | the firewall. Alternately, firewall software could be installed on | |
| 8330 | the host itself. Sun's SunScreen firewall suite is available for | |
| 8331 | Solaris 9 and Trusted Solaris 8. Solaris 10 will offer a more tightly | |
| 8332 | integrated SunScreen firewall. Other open source firewall packages such as | |
| 8333 | ||
| 8334 | <URLLink LinkURL="http://coombs.anu.edu.au/~avalon/" LinkTitle="http://coombs.anu.edu.au/~avalon/" href="http://coombs.anu.edu.au/~avalon/">IPFilter</URLLink> | |
| 8335 | are available for Solaris.</Paragraph> | |
| 8336 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8337 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8338 | types 17 (netmask request) and 18 (netmask response).</Paragraph></Paragraph></ListItem> | |
| 8339 | <ListItem> | |
| 8340 | <Paragraph>Microsoft Windows 2000, Microsoft Windows 2000 Professional, Microsoft Windows 2000 Server, Microsoft Windows 2000 Advanced Server, Microsoft Windows 2000 Datacenter Server, Microsoft Windows XP, Microsoft Windows XP Home, Microsoft Windows XP Professional, Microsoft Windows Server 2003, Microsoft Windows Server 2003, Standard Edition, Microsoft Windows Server 2003, Enterprise Edition, Microsoft Windows Server 2003, Datacenter Edition, Microsoft Windows Server 2003, Web Edition, Microsoft Windows Small Business Server 2003</Paragraph> | |
| 8341 | <Paragraph> | |
| 8342 | <Paragraph>Use the IPSec filter feature to define and apply an IP filter list | |
| 8343 | that blocks ICMP types 17 and 18. Note that the standard TCP/IP | |
| 8344 | blocking capability under the "Networking and Dialup | |
| 8345 | Connections" control panel is NOT capable of blocking ICMP (only | |
| 8346 | TCP and UDP). The IPSec filter features, while they may seem strictly | |
| 8347 | related to the IPSec standards, will allow you to selectively block | |
| 8348 | these ICMP packets. See | |
| 8349 | ||
| 8350 | <URLLink LinkURL="http://www.microsoft.com/technet/treeview/default.asp?url=/technet/columns/security/askus/au091100.asp" LinkTitle="http://www.microsoft.com/technet/treeview/default.asp?url=/technet/columns/security/askus/au091100.asp" href="http://www.microsoft.com/technet/treeview/default.asp?url=/technet/columns/security/askus/au091100.asp"></URLLink> | |
| 8351 | for more information.</Paragraph> | |
| 8352 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8353 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8354 | types 17 (netmask request) and 18 (netmask response).</Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 8355 | </vulnerability> | |
| 8356 | ||
| 8357 | <vulnerability id="generic-icmp-timestamp" title="ICMP timestamp response" severity="1" pciSeverity="1" cvssScore="0.0" cvssVector="(AV:L/AC:L/Au:N/C:N/I:N/A:N)" published="19970801T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 8358 | <description> | |
| 8359 | ||
| 8360 | <ContainerBlockElement> | |
| 8361 | ||
| 8362 | <Paragraph>The remote host responded to an ICMP timestamp request. The ICMP timestamp response | |
| 8363 | contains the remote host's date and time. This information could theoretically be | |
| 8364 | used against some systems to exploit weak time-based random number generators in | |
| 8365 | other services.</Paragraph> | |
| 8366 | ||
| 8367 | ||
| 8368 | <Paragraph>In addition, the versions of some operating systems can be accurately fingerprinted | |
| 8369 | by analyzing their responses to invalid ICMP timestamp requests.</Paragraph> | |
| 8370 | </ContainerBlockElement></description> | |
| 8371 | <references> | |
| 8372 | <reference source="CVE">CVE-1999-0524</reference> | |
| 8373 | <reference source="OSVDB">95</reference> | |
| 8374 | <reference source="XF">icmp-netmask(306)</reference> | |
| 8375 | <reference source="XF">icmp-timestamp(322)</reference> | |
| 8376 | </references><tags> | |
| 8377 | <tag>Network</tag> | |
| 8378 | </tags> | |
| 8379 | <solution> | |
| 8380 | ||
| 8381 | <ContainerBlockElement> | |
| 8382 | <UnorderedList> | |
| 8383 | <ListItem> | |
| 8384 | <Paragraph>HP-UX</Paragraph> | |
| 8385 | <Paragraph> | |
| 8386 | <Paragraph>Execute the following command:</Paragraph> | |
| 8387 | <Paragraph preFormat="true"> ndd -set /dev/ip ip_respond_to_timestamp_broadcast 0</Paragraph> | |
| 8388 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8389 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8390 | types 13 (timestamp request) and 14 (timestamp response).</Paragraph></Paragraph></ListItem> | |
| 8391 | <ListItem> | |
| 8392 | <Paragraph>Cisco IOS</Paragraph> | |
| 8393 | <Paragraph> | |
| 8394 | <Paragraph>Use ACLs to block ICMP types 13 and 14. For example:</Paragraph> | |
| 8395 | <Paragraph preformat="true"> deny icmp any any 13</Paragraph> | |
| 8396 | <Paragraph preformat="true"> deny icmp any any 14</Paragraph> | |
| 8397 | <Paragraph>Note that it is generally preferable to use ACLs that block everything | |
| 8398 | by default and then selectively allow certain types of traffic in. For | |
| 8399 | example, block everything and then only allow ICMP unreachable, ICMP | |
| 8400 | echo reply, ICMP time exceeded, and ICMP source quench:</Paragraph> | |
| 8401 | <Paragraph preformat="true"> permit icmp any any unreachable</Paragraph> | |
| 8402 | <Paragraph preformat="true"> permit icmp any any echo-reply</Paragraph> | |
| 8403 | <Paragraph preformat="true"> permit icmp any any time-exceeded</Paragraph> | |
| 8404 | <Paragraph preformat="true"> permit icmp any any source-quench</Paragraph> | |
| 8405 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8406 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8407 | types 13 (timestamp request) and 14 (timestamp response).</Paragraph></Paragraph></ListItem> | |
| 8408 | <ListItem> | |
| 8409 | <Paragraph>SGI Irix</Paragraph> | |
| 8410 | <Paragraph> | |
| 8411 | <Paragraph>IRIX does not offer a way to disable ICMP timestamp responses. | |
| 8412 | Therefore, you should block ICMP on the affected host using ipfilterd, | |
| 8413 | and/or block it at any external firewalls.</Paragraph> | |
| 8414 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8415 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8416 | types 13 (timestamp request) and 14 (timestamp response).</Paragraph></Paragraph></ListItem> | |
| 8417 | <ListItem> | |
| 8418 | <Paragraph>Linux</Paragraph> | |
| 8419 | <Paragraph> | |
| 8420 | <Paragraph>Linux offers neither a sysctl nor a /proc/sys/net/ipv4 interface | |
| 8421 | to disable ICMP timestamp responses. Therefore, you should block | |
| 8422 | ICMP on the affected host using iptables, and/or block it at the | |
| 8423 | firewall. For example:</Paragraph> | |
| 8424 | <Paragraph preformat="true"> ipchains -A input -p icmp --icmp-type timestamp-request -j DROP</Paragraph> | |
| 8425 | <Paragraph preformat="true"> ipchains -A output -p icmp --icmp-type timestamp-reply -j DROP</Paragraph> | |
| 8426 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8427 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8428 | types 13 (timestamp request) and 14 (timestamp response).</Paragraph></Paragraph></ListItem> | |
| 8429 | <ListItem> | |
| 8430 | <Paragraph>Microsoft Windows NT, Microsoft Windows NT Workstation, Microsoft Windows NT Server, Microsoft Windows NT Advanced Server, Microsoft Windows NT Server, Enterprise Edition, Microsoft Windows NT Server, Terminal Server Edition</Paragraph> | |
| 8431 | <Paragraph> | |
| 8432 | <Paragraph>Windows NT 4 does not provide a way to block ICMP packets. | |
| 8433 | Therefore, you should block them at the firewall.</Paragraph> | |
| 8434 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8435 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8436 | types 13 (timestamp request) and 14 (timestamp response).</Paragraph></Paragraph></ListItem> | |
| 8437 | <ListItem> | |
| 8438 | <Paragraph>OpenBSD</Paragraph> | |
| 8439 | <Paragraph> | |
| 8440 | <Paragraph>Set the "net.inet.icmp.tstamprepl" sysctl variable to 0.</Paragraph> | |
| 8441 | <Paragraph preformat="true"> sysctl -w net.inet.icmp.tstamprepl=0</Paragraph> | |
| 8442 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8443 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8444 | types 13 (timestamp request) and 14 (timestamp response).</Paragraph></Paragraph></ListItem> | |
| 8445 | <ListItem> | |
| 8446 | <Paragraph>Cisco PIX</Paragraph> | |
| 8447 | <Paragraph> | |
| 8448 | <Paragraph>A properly configured PIX firewall should never respond to ICMP | |
| 8449 | packets on its external interface. In PIX Software versions 4.1(6) | |
| 8450 | until 5.2.1, ICMP traffic to the PIX's internal interface is | |
| 8451 | permitted; the PIX cannot be configured to NOT respond. Beginning in | |
| 8452 | PIX Software version 5.2.1, ICMP is still permitted on the internal | |
| 8453 | interface by default, but ICMP responses from its internal interfaces | |
| 8454 | can be disabled with the icmp command, as follows, where <inside> | |
| 8455 | is the name of the internal interface:</Paragraph> | |
| 8456 | <Paragraph preformat="true"> icmp deny any 13 <inside></Paragraph> | |
| 8457 | <Paragraph preformat="true"> icmp deny any 14 <inside></Paragraph> | |
| 8458 | <Paragraph>Don't forget to save the configuration when you are finished.</Paragraph> | |
| 8459 | <Paragraph>See Cisco's support document | |
| 8460 | ||
| 8461 | <URLLink LinkURL="http://www.cisco.com/warp/public/110/31.html" LinkTitle="http://www.cisco.com/warp/public/110/31.html" href="http://www.cisco.com/warp/public/110/31.html">Handling ICMP Pings with the PIX Firewall</URLLink> | |
| 8462 | for more information.</Paragraph> | |
| 8463 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8464 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8465 | types 13 (timestamp request) and 14 (timestamp response).</Paragraph></Paragraph></ListItem> | |
| 8466 | <ListItem> | |
| 8467 | <Paragraph>Sun Solaris</Paragraph> | |
| 8468 | <Paragraph> | |
| 8469 | <Paragraph>Execute the following commands:</Paragraph> | |
| 8470 | <Paragraph preformat="true"> /usr/sbin/ndd -set /dev/ip ip_respond_to_timestamp 0</Paragraph> | |
| 8471 | <Paragraph preformat="true"> /usr/sbin/ndd -set /dev/ip ip_respond_to_timestamp_broadcast 0</Paragraph> | |
| 8472 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8473 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8474 | types 13 (timestamp request) and 14 (timestamp response).</Paragraph></Paragraph></ListItem> | |
| 8475 | <ListItem> | |
| 8476 | <Paragraph>Microsoft Windows 2000, Microsoft Windows 2000 Professional, Microsoft Windows 2000 Server, Microsoft Windows 2000 Advanced Server, Microsoft Windows 2000 Datacenter Server</Paragraph> | |
| 8477 | <Paragraph> | |
| 8478 | <Paragraph>Use the IPSec filter feature to define and apply an IP filter list | |
| 8479 | that blocks ICMP types 13 and 14. Note that the standard TCP/IP | |
| 8480 | blocking capability under the "Networking and Dialup | |
| 8481 | Connections" control panel is NOT capable of blocking ICMP (only | |
| 8482 | TCP and UDP). The IPSec filter features, while they may seem strictly | |
| 8483 | related to the IPSec standards, will allow you to selectively block | |
| 8484 | these ICMP packets. See | |
| 8485 | ||
| 8486 | <URLLink LinkURL="http://support.microsoft.com/kb/313190" LinkTitle="http://support.microsoft.com/kb/313190" href="http://support.microsoft.com/kb/313190"></URLLink> | |
| 8487 | for more information.</Paragraph> | |
| 8488 | <Paragraph>The easiest and most effective solution is to configure your | |
| 8489 | firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8490 | types 13 (timestamp request) and 14 (timestamp response).</Paragraph></Paragraph></ListItem> | |
| 8491 | <ListItem> | |
| 8492 | <Paragraph>Microsoft Windows XP, Microsoft Windows XP Home, Microsoft Windows XP Professional, Microsoft Windows Server 2003, Microsoft Windows Server 2003, Standard Edition, Microsoft Windows Server 2003, Enterprise Edition, Microsoft Windows Server 2003, Datacenter Edition, Microsoft Windows Server 2003, Web Edition, Microsoft Windows Small Business Server 2003</Paragraph> | |
| 8493 | <Paragraph> | |
| 8494 | <Paragraph>ICMP timestamp responses can be disabled by deselecting the "allow incoming timestamp request" | |
| 8495 | option in the ICMP configuration panel of Windows Firewall.</Paragraph> | |
| 8496 | <OrderedList> | |
| 8497 | <ListItem>Go to the Network Connections control panel.</ListItem> | |
| 8498 | <ListItem>Right click on the network adapter and select "properties", or select the internet adapter and select File->Properties.</ListItem> | |
| 8499 | <ListItem>Select the "Advanced" tab.</ListItem> | |
| 8500 | <ListItem>In the Windows Firewall box, select "Settings".</ListItem> | |
| 8501 | <ListItem>Select the "General" tab.</ListItem> | |
| 8502 | <ListItem>Enable the firewall by selecting the "on (recommended)" option.</ListItem> | |
| 8503 | <ListItem>Select the "Advanced" tab.</ListItem> | |
| 8504 | <ListItem>In the ICMP box, select "Settings".</ListItem> | |
| 8505 | <ListItem>Deselect (uncheck) the "Allow incoming timestamp request" option.</ListItem> | |
| 8506 | <ListItem>Select "OK" to exit the ICMP Settings dialog and save the settings.</ListItem> | |
| 8507 | <ListItem>Select "OK" to exit the Windows Firewall dialog and save the settings.</ListItem> | |
| 8508 | <ListItem>Select "OK" to exit the internet adapter dialog.</ListItem></OrderedList> | |
| 8509 | <Paragraph>For more information, see: | |
| 8510 | ||
| 8511 | <URLLink LinkURL="http://www.microsoft.com/resources/documentation/windows/xp/all/proddocs/en-us/hnw_understanding_firewall.mspx?mfr=true" LinkTitle="http://www.microsoft.com/resources/documentation/windows/xp/all/proddocs/en-us/hnw_understanding_firewall.mspx?mfr=true" href="http://www.microsoft.com/resources/documentation/windows/xp/all/proddocs/en-us/hnw_understanding_firewall.mspx?mfr=true"></URLLink></Paragraph></Paragraph></ListItem> | |
| 8512 | <ListItem> | |
| 8513 | <Paragraph>Microsoft Windows Vista, Microsoft Windows Vista Home, Basic Edition, Microsoft Windows Vista Home, Basic N Edition, Microsoft Windows Vista Home, Premium Edition, Microsoft Windows Vista Ultimate Edition, Microsoft Windows Vista Enterprise Edition, Microsoft Windows Vista Business Edition, Microsoft Windows Vista Business N Edition, Microsoft Windows Vista Starter Edition, Microsoft Windows Server 2008, Microsoft Windows Server 2008 Standard Edition, Microsoft Windows Server 2008 Enterprise Edition, Microsoft Windows Server 2008 Datacenter Edition, Microsoft Windows Server 2008 HPC Edition, Microsoft Windows Server 2008 Web Edition, Microsoft Windows Server 2008 Storage Edition, Microsoft Windows Small Business Server 2008, Microsoft Windows Essential Business Server 2008</Paragraph> | |
| 8514 | <Paragraph> | |
| 8515 | <Paragraph>ICMP timestamp responses can be disabled via the netsh command line utility.</Paragraph> | |
| 8516 | <OrderedList> | |
| 8517 | <ListItem>Go to the Windows Control Panel.</ListItem> | |
| 8518 | <ListItem>Select "Windows Firewall".</ListItem> | |
| 8519 | <ListItem>In the Windows Firewall box, select "Change Settings".</ListItem> | |
| 8520 | <ListItem>Enable the firewall by selecting the "on (recommended)" option.</ListItem> | |
| 8521 | <ListItem>Open a Command Prompt.</ListItem> | |
| 8522 | <ListItem>Enter "netsh firewall set icmpsetting 13 disable"</ListItem></OrderedList> | |
| 8523 | <Paragraph>For more information, see: | |
| 8524 | ||
| 8525 | <URLLink LinkURL="http://www.microsoft.com/resources/documentation/windows/xp/all/proddocs/en-us/hnw_understanding_firewall.mspx?mfr=true" LinkTitle="http://www.microsoft.com/resources/documentation/windows/xp/all/proddocs/en-us/hnw_understanding_firewall.mspx?mfr=true" href="http://www.microsoft.com/resources/documentation/windows/xp/all/proddocs/en-us/hnw_understanding_firewall.mspx?mfr=true"></URLLink></Paragraph></Paragraph></ListItem> | |
| 8526 | <ListItem> | |
| 8527 | <Paragraph> | |
| 8528 | <Paragraph>Disable ICMP timestamp replies for the device. If the device does not support | |
| 8529 | this level of configuration, the easiest and most effective solution is to | |
| 8530 | configure your firewall to block incoming and outgoing ICMP packets with ICMP | |
| 8531 | types 13 (timestamp request) and 14 (timestamp response).</Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 8532 | </vulnerability> | |
| 8533 | ||
| 8534 | <vulnerability id="generic-tcp-timestamp" title="TCP timestamp response" severity="1" pciSeverity="1" cvssScore="0.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:N/A:N)" published="19970801T000000000" added="20110401T000000000" modified="20120712T000000000"> | |
| 8535 | <description> | |
| 8536 | ||
| 8537 | <ContainerBlockElement> | |
| 8538 | ||
| 8539 | <Paragraph> | |
| 8540 | The remote host responded with a TCP timestamp. The TCP timestamp response | |
| 8541 | can be used to approximate the remote host's uptime, potentially aiding in | |
| 8542 | further attacks. Additionally, some operating systems can be fingerprinted | |
| 8543 | based on the behavior of their TCP timestamps. | |
| 8544 | </Paragraph> | |
| 8545 | </ContainerBlockElement></description> | |
| 8546 | <references> | |
| 8547 | <reference source="URL">http://uptime.netcraft.com</reference> | |
| 8548 | <reference source="URL">http://www.forensicswiki.org/wiki/TCP_timestamps</reference> | |
| 8549 | <reference source="URL">http://www.ietf.org/rfc/rfc1323.txt</reference> | |
| 8550 | </references><tags> | |
| 8551 | <tag>Network</tag> | |
| 8552 | </tags> | |
| 8553 | <solution> | |
| 8554 | ||
| 8555 | <ContainerBlockElement> | |
| 8556 | <UnorderedList> | |
| 8557 | <ListItem> | |
| 8558 | <Paragraph>Cisco</Paragraph> | |
| 8559 | <Paragraph> | |
| 8560 | <Paragraph> | |
| 8561 | Run the following command to disable TCP timestamps: | |
| 8562 | </Paragraph> | |
| 8563 | <Paragraph preformat="true"> | |
| 8564 | no ip tcp timestamp | |
| 8565 | </Paragraph></Paragraph></ListItem> | |
| 8566 | <ListItem> | |
| 8567 | <Paragraph>FreeBSD</Paragraph> | |
| 8568 | <Paragraph> | |
| 8569 | <Paragraph> | |
| 8570 | Set the value of net.inet.tcp.rfc1323 to 0 by running the | |
| 8571 | following command: | |
| 8572 | </Paragraph> | |
| 8573 | <Paragraph preformat="true"> | |
| 8574 | sysctl -w net.inet.tcp.rfc1323=0 | |
| 8575 | </Paragraph> | |
| 8576 | <Paragraph> | |
| 8577 | Additionally, put the following value in the default sysctl | |
| 8578 | configuration file, generally sysctl.conf: | |
| 8579 | </Paragraph> | |
| 8580 | <Paragraph preformat="true"> | |
| 8581 | net.inet.tcp.rfc1323=0 | |
| 8582 | </Paragraph></Paragraph></ListItem> | |
| 8583 | <ListItem> | |
| 8584 | <Paragraph>Linux</Paragraph> | |
| 8585 | <Paragraph> | |
| 8586 | <Paragraph> | |
| 8587 | Set the value of net.ipv4.tcp_timestamps to 0 by running the | |
| 8588 | following command: | |
| 8589 | </Paragraph> | |
| 8590 | <Paragraph preformat="true"> | |
| 8591 | sysctl -w net.ipv4.tcp_timestamps=0 | |
| 8592 | </Paragraph> | |
| 8593 | <Paragraph> | |
| 8594 | Additionally, put the following value in the default sysctl | |
| 8595 | configuration file, generally sysctl.conf: | |
| 8596 | </Paragraph> | |
| 8597 | <Paragraph preformat="true"> | |
| 8598 | net.ipv4.tcp_timestamps=0 | |
| 8599 | </Paragraph></Paragraph></ListItem> | |
| 8600 | <ListItem> | |
| 8601 | <Paragraph>OpenBSD</Paragraph> | |
| 8602 | <Paragraph> | |
| 8603 | <Paragraph> | |
| 8604 | Set the value of net.inet.tcp.rfc1323 to 0 by running the | |
| 8605 | following command: | |
| 8606 | </Paragraph> | |
| 8607 | <Paragraph preformat="true"> | |
| 8608 | sysctl -w net.inet.tcp.rfc1323=0 | |
| 8609 | </Paragraph> | |
| 8610 | <Paragraph> | |
| 8611 | Additionally, put the following value in the default sysctl | |
| 8612 | configuration file, generally sysctl.conf: | |
| 8613 | </Paragraph> | |
| 8614 | <Paragraph preformat="true"> | |
| 8615 | net.inet.tcp.rfc1323=0 | |
| 8616 | </Paragraph></Paragraph></ListItem> | |
| 8617 | <ListItem> | |
| 8618 | <Paragraph>Microsoft Windows NT, Microsoft Windows NT Workstation, Microsoft Windows NT Server, Microsoft Windows NT Advanced Server, Microsoft Windows NT Server, Enterprise Edition, Microsoft Windows NT Server, Terminal Server Edition, Microsoft Windows 95, Microsoft Windows 98, Microsoft Windows 98SE, Microsoft Windows ME, Microsoft Windows 2000, Microsoft Windows 2000 Professional, Microsoft Windows 2000 Server, Microsoft Windows 2000 Advanced Server, Microsoft Windows 2000 Datacenter Server, Microsoft Windows XP, Microsoft Windows XP Home, Microsoft Windows XP Professional, Microsoft Windows XP Tablet PC Edition, Microsoft Windows CE, Microsoft Windows Server 2003, Microsoft Windows Server 2003, Standard Edition, Microsoft Windows Server 2003, Enterprise Edition, Microsoft Windows Server 2003, Datacenter Edition, Microsoft Windows Server 2003, Web Edition, Microsoft Windows Small Business Server 2003, Microsoft Windows Server 2003 R2, Microsoft Windows Server 2003 R2, Standard Edition, Microsoft Windows Server 2003 R2, Enterprise Edition, Microsoft Windows Server 2003 R2, Datacenter Edition, Microsoft Windows Server 2003 R2, Web Edition, Microsoft Windows Small Business Server 2003 R2, Microsoft Windows Server 2003 R2, Express Edition, Microsoft Windows Server 2003 R2, Workgroup Edition</Paragraph> | |
| 8619 | <Paragraph> | |
| 8620 | <Paragraph> | |
| 8621 | Set the Tcp1323Opts value in the following key to 1: | |
| 8622 | </Paragraph> | |
| 8623 | <Paragraph preformat="true"> | |
| 8624 | HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\Tcpip\Parameters | |
| 8625 | </Paragraph></Paragraph></ListItem> | |
| 8626 | <ListItem> | |
| 8627 | <Paragraph>Microsoft Windows Server 2008, Microsoft Windows Server 2008 Standard Edition, Microsoft Windows Server 2008 Enterprise Edition, Microsoft Windows Server 2008 Datacenter Edition, Microsoft Windows Server 2008 HPC Edition, Microsoft Windows Server 2008 Web Edition, Microsoft Windows Server 2008 Storage Edition, Microsoft Windows Small Business Server 2008, Microsoft Windows Essential Business Server 2008, Microsoft Windows Server 2008 R2, Microsoft Windows Server 2008 R2, Standard Edition, Microsoft Windows Server 2008 R2, Enterprise Edition, Microsoft Windows Server 2008 R2, Datacenter Edition, Microsoft Windows Server 2008 R2, Web Edition, Microsoft Windows Server 2012, Microsoft Windows Server 2012 Standard Edition, Microsoft Windows Server 2012 Foundation Edition, Microsoft Windows Server 2012 Essentials Edition, Microsoft Windows Server 2012 Datacenter Edition, Microsoft Windows Storage Server 2012, Microsoft Windows Vista, Microsoft Windows Vista Home, Basic Edition, Microsoft Windows Vista Home, Basic N Edition, Microsoft Windows Vista Home, Premium Edition, Microsoft Windows Vista Ultimate Edition, Microsoft Windows Vista Enterprise Edition, Microsoft Windows Vista Business Edition, Microsoft Windows Vista Business N Edition, Microsoft Windows Vista Starter Edition, Microsoft Windows 7, Microsoft Windows 7 Home, Basic Edition, Microsoft Windows 7 Home, Basic N Edition, Microsoft Windows 7 Home, Premium Edition, Microsoft Windows 7 Home, Premium N Edition, Microsoft Windows 7 Ultimate Edition, Microsoft Windows 7 Ultimate N Edition, Microsoft Windows 7 Enterprise Edition, Microsoft Windows 7 Enterprise N Edition, Microsoft Windows 7 Professional Edition, Microsoft Windows 7 Starter Edition, Microsoft Windows 7 Starter N Edition, Microsoft Windows 8, Microsoft Windows 8 Enterprise Edition, Microsoft Windows 8 Professional Edition, Microsoft Windows 8 RT, Microsoft Windows Longhorn Server Beta</Paragraph> | |
| 8628 | <Paragraph> | |
| 8629 | <Paragraph> | |
| 8630 | TCP timestamps cannot be reliably disabled on this OS. If TCP timestamps present enough of a risk, put a firewall capable of blocking TCP timestamp packets in front of the affected assets. | |
| 8631 | </Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 8632 | </vulnerability> | |
| 8633 | ||
| 8634 | <vulnerability id="http-3com-wap-default-admin-password" title="3Com WAP Default Administrator Password Vulnerability" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20080818T000000000" added="20080818T000000000" modified="20120731T000000000"> | |
| 8635 | <description> | |
| 8636 | ||
| 8637 | <ContainerBlockElement> | |
| 8638 | ||
| 8639 | <Paragraph> | |
| 8640 | The administrator password is unchanged from the default of 'password'. | |
| 8641 | As a result, anyone with access to the 3Com WAP can trivially gain full | |
| 8642 | access to the device. | |
| 8643 | </Paragraph> | |
| 8644 | </ContainerBlockElement></description> | |
| 8645 | <references> | |
| 8646 | </references><tags> | |
| 8647 | <tag>Default Account</tag> | |
| 8648 | <tag>HTTP</tag> | |
| 8649 | <tag>Web</tag> | |
| 8650 | <tag>Wireless</tag> | |
| 8651 | </tags> | |
| 8652 | <solution> | |
| 8653 | ||
| 8654 | <ContainerBlockElement> | |
| 8655 | <Paragraph> | |
| 8656 | Change the admin password using the Web interface. | |
| 8657 | </Paragraph></ContainerBlockElement></solution> | |
| 8658 | </vulnerability> | |
| 8659 | ||
| 8660 | <vulnerability id="http-adobe-amf-gateway-xxe-cve-2009-3960" title="Adobe products XML external entity injection vulnerability (CVE-2009-3960)" severity="4" pciSeverity="3" cvssScore="4.3" cvssVector="(AV:N/AC:M/Au:N/C:P/I:N/A:N)" published="20100215T000000000" added="20110105T000000000" modified="20120731T000000000"> | |
| 8661 | <description> | |
| 8662 | ||
| 8663 | <ContainerBlockElement> | |
| 8664 | ||
| 8665 | <Paragraph>Multiple Adobe server products are vulnerable to an XML external entity injection which allows remote, unauthenticated attackers | |
| 8666 | to read arbitrary files from the system. Affected software includes BlazeDS 3.2 and earlier versions, LiveCycle 9.0, 8.2.1, and 8.0.1, LiveCycle Data | |
| 8667 | Services 3.0, 2.6.1, and 2.5.1, Flex Data Services 2.0.1, ColdFusion 9.0, 8.0.1, 8.0, and 7.0.2.</Paragraph> | |
| 8668 | </ContainerBlockElement></description> | |
| 8669 | <references> | |
| 8670 | <reference source="BID">38197</reference> | |
| 8671 | <reference source="CVE">CVE-2009-3960</reference> | |
| 8672 | <reference source="OSVDB">62292</reference> | |
| 8673 | <reference source="SECUNIA">38543</reference> | |
| 8674 | <reference source="URL">http://www.adobe.com/support/security/bulletins/apsb10-05.html</reference> | |
| 8675 | </references><tags> | |
| 8676 | <tag>Adobe</tag> | |
| 8677 | <tag>HTTP</tag> | |
| 8678 | <tag>Web</tag> | |
| 8679 | <tag>IAVM</tag> | |
| 8680 | </tags> | |
| 8681 | <solution> | |
| 8682 | ||
| 8683 | <ContainerBlockElement> | |
| 8684 | <Paragraph> | |
| 8685 | Upgrade to the latest version of BlazeDS, LiveCycle, LCDS, or ColdFusion as documented | |
| 8686 | in Adobe security bulletin | |
| 8687 | <URLLink LinkURL="http://www.adobe.com/support/security/bulletins/apsb10-05.html" LinkTitle="http://www.adobe.com/support/security/bulletins/apsb10-05.html" href="http://www.adobe.com/support/security/bulletins/apsb10-05.html">APSB10-05</URLLink>. | |
| 8688 | </Paragraph></ContainerBlockElement></solution> | |
| 8689 | </vulnerability> | |
| 8690 | ||
| 8691 | <vulnerability id="http-asp-dot-net-debug-enabled" title="ASP.NET debug feature enabled" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="20071031T000000000" added="20071126T000000000" modified="20130620T000000000"> | |
| 8692 | <description> | |
| 8693 | ||
| 8694 | <ContainerBlockElement> | |
| 8695 | ||
| 8696 | <Paragraph>The ASP.NET application is running in debug mode which allows a remote user to glean | |
| 8697 | information about an application by using the DEBUG verb in an HTTP request. This can | |
| 8698 | leak information including source code, hidden filenames, and detailed error messages.</Paragraph> | |
| 8699 | </ContainerBlockElement></description> | |
| 8700 | <references> | |
| 8701 | </references><tags> | |
| 8702 | <tag>Microsoft</tag> | |
| 8703 | <tag>Microsoft ASP.NET</tag> | |
| 8704 | <tag>OWASP_2010</tag> | |
| 8705 | <tag>OWASP_2013</tag> | |
| 8706 | <tag>Web</tag> | |
| 8707 | <tag>Web Spider</tag> | |
| 8708 | </tags> | |
| 8709 | <solution> | |
| 8710 | ||
| 8711 | <ContainerBlockElement> | |
| 8712 | <Paragraph> | |
| 8713 | <Paragraph>Disable debug mode for this application by setting debug=false in | |
| 8714 | the Web.config file for each application on the server.</Paragraph> | |
| 8715 | <Paragraph>Also, follow Microsoft's detailed instructions in knowledgebase article | |
| 8716 | ||
| 8717 | <URLLink LinkURL="http://support.microsoft.com/kb/306355" LinkTitle="http://support.microsoft.com/kb/306355" href="http://support.microsoft.com/kb/306355">306355</URLLink> to disable | |
| 8718 | detailed ASP.NET error messages using either custom error pages | |
| 8719 | or the root-level Web.config file.</Paragraph> | |
| 8720 | <Paragraph>You may also consider using Microsoft's | |
| 8721 | <URLLink LinkURL="http://msdn2.microsoft.com/en-us/library/aa302368.aspx" LinkTitle="http://msdn2.microsoft.com/en-us/library/aa302368.aspx" href="http://msdn2.microsoft.com/en-us/library/aa302368.aspx">URLScan</URLLink> | |
| 8722 | tool to harden IIS servers. URLScan blocks the DEBUG verb by default.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8723 | </vulnerability> | |
| 8724 | ||
| 8725 | <vulnerability id="http-awstats-debug-information-disclosure" title="HTTP AWStats Debug Information Disclosure" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="20050502T000000000" added="20060320T000000000" modified="20120731T000000000"> | |
| 8726 | <description> | |
| 8727 | ||
| 8728 | <ContainerBlockElement> | |
| 8729 | ||
| 8730 | <Paragraph>AWStats is a tool that generates web, ftp or mail server statistics, | |
| 8731 | graphically. Written in perl, it works as a CGI or from command | |
| 8732 | line and shows all the possible information that the log file contains</Paragraph> | |
| 8733 | ||
| 8734 | ||
| 8735 | <Paragraph>awstats.pl in AWStats 6.3 and 6.4 allows remote attackers to | |
| 8736 | obtain sensitive information by setting the debug parameter.</Paragraph> | |
| 8737 | </ContainerBlockElement></description> | |
| 8738 | <references> | |
| 8739 | <reference source="CVE">CVE-2005-0438</reference> | |
| 8740 | <reference source="SECUNIA">14299</reference> | |
| 8741 | <reference source="URL">http://www.securityfocus.com/archive/1/390368</reference> | |
| 8742 | <reference source="XF">awstats-information-disclosure(19477)</reference> | |
| 8743 | </references><tags> | |
| 8744 | <tag>FTP</tag> | |
| 8745 | <tag>HTTP</tag> | |
| 8746 | <tag>Information Gathering</tag> | |
| 8747 | <tag>Web</tag> | |
| 8748 | </tags> | |
| 8749 | <solution> | |
| 8750 | ||
| 8751 | <ContainerBlockElement> | |
| 8752 | <Paragraph>Download and apply the upgrade from: | |
| 8753 | <URLLink LinkURL="http://awstats.sourceforge.net/#DOWNLOAD" LinkTitle="http://awstats.sourceforge.net/#DOWNLOAD"></URLLink></Paragraph></ContainerBlockElement></solution> | |
| 8754 | </vulnerability> | |
| 8755 | ||
| 8756 | <vulnerability id="http-awstats-remote-code-execution" title="HTTP AWStats Remote Code Execution" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20050502T000000000" added="20060320T000000000" modified="20120731T000000000"> | |
| 8757 | <description> | |
| 8758 | ||
| 8759 | <ContainerBlockElement> | |
| 8760 | ||
| 8761 | <Paragraph>AWStats is a tool that generates web, ftp or mail server statistics, | |
| 8762 | graphically. Written in perl, it works as a CGI or from command | |
| 8763 | line and shows all the possible information that the log file contains</Paragraph> | |
| 8764 | ||
| 8765 | ||
| 8766 | ||
| 8767 | <Paragraph>An input validation vulnerability exists in AWStats main script | |
| 8768 | awstats.pl using which a remote attacker may execute perl code | |
| 8769 | and call available perl modules with the priveleges of the web | |
| 8770 | server. An attacker can also use this vulnerability to get | |
| 8771 | sensitive information or launch a denial of service attack.</Paragraph> | |
| 8772 | </ContainerBlockElement></description> | |
| 8773 | <references> | |
| 8774 | <reference source="CVE">CVE-2005-0435</reference> | |
| 8775 | <reference source="CVE">CVE-2005-0436</reference> | |
| 8776 | <reference source="CVE">CVE-2005-0437</reference> | |
| 8777 | <reference source="OSVDB">13832</reference> | |
| 8778 | <reference source="SECUNIA">14299</reference> | |
| 8779 | <reference source="URL">http://www.securityfocus.com/archive/1/390368</reference> | |
| 8780 | <reference source="XF">awstats-awstatpl-obtain-information(19333)</reference> | |
| 8781 | <reference source="XF">awstats-function-code-execution(19336)</reference> | |
| 8782 | </references><tags> | |
| 8783 | <tag>Denial of Service</tag> | |
| 8784 | <tag>FTP</tag> | |
| 8785 | <tag>HTTP</tag> | |
| 8786 | <tag>Remote Execution</tag> | |
| 8787 | <tag>Web</tag> | |
| 8788 | </tags> | |
| 8789 | <solution> | |
| 8790 | ||
| 8791 | <ContainerBlockElement> | |
| 8792 | <Paragraph>Download and apply the upgrade from: | |
| 8793 | <URLLink LinkURL="http://awstats.sourceforge.net/#DOWNLOAD" LinkTitle="http://awstats.sourceforge.net/#DOWNLOAD"></URLLink></Paragraph></ContainerBlockElement></solution> | |
| 8794 | </vulnerability> | |
| 8795 | ||
| 8796 | <vulnerability id="http-basic-auth-cleartext" title="HTTP Basic Authentication Enabled" severity="7" pciSeverity="4" cvssScore="6.5" cvssVector="(AV:N/AC:L/Au:S/C:P/I:P/A:P)" published="19970101T000000000" added="20100226T000000000" modified="20130620T000000000"> | |
| 8797 | <description> | |
| 8798 | ||
| 8799 | <ContainerBlockElement> | |
| 8800 | ||
| 8801 | <Paragraph> | |
| 8802 | The HTTP Basic Authentication scheme is not considered to be a secure | |
| 8803 | method of user authentication (unless used in conjunction with some | |
| 8804 | external secure system such as TLS/SSL), as the user name and password | |
| 8805 | are passed over the network as cleartext. | |
| 8806 | </Paragraph> | |
| 8807 | </ContainerBlockElement></description> | |
| 8808 | <references> | |
| 8809 | <reference source="URL">http://tools.ietf.org/html/rfc2617</reference> | |
| 8810 | </references><tags> | |
| 8811 | <tag>HTTP</tag> | |
| 8812 | <tag>OWASP_2010</tag> | |
| 8813 | <tag>OWASP_2013</tag> | |
| 8814 | <tag>Web</tag> | |
| 8815 | <tag>Web Spider</tag> | |
| 8816 | </tags> | |
| 8817 | <solution> | |
| 8818 | ||
| 8819 | <ContainerBlockElement> | |
| 8820 | <UnorderedList> | |
| 8821 | <ListItem> | |
| 8822 | <Paragraph> | |
| 8823 | <Paragraph> | |
| 8824 | Enable HTTPS on the Web server. The TLS/SSL protocol will protect | |
| 8825 | cleartext Basic Authentication credentials. | |
| 8826 | </Paragraph></Paragraph></ListItem> | |
| 8827 | <ListItem> | |
| 8828 | <Paragraph> | |
| 8829 | <Paragraph> | |
| 8830 | Replace Basic Authentication with the alternative Digest | |
| 8831 | Authentication scheme. By modern cryptographic standards Digest | |
| 8832 | Authentication is weak. But for a large range of purposes it is | |
| 8833 | valuable as a replacement for Basic Authentication. It remedies | |
| 8834 | some, but not all, weaknesses of Basic Authentication. See RFC | |
| 8835 | 2617, section | |
| 8836 | ||
| 8837 | <URLLink LinkURL="http://tools.ietf.org/html/rfc2617#section-4" LinkTitle="http://tools.ietf.org/html/rfc2617#section-4" href="http://tools.ietf.org/html/rfc2617#section-4">4. Security Considerations</URLLink> | |
| 8838 | for more information. | |
| 8839 | </Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 8840 | </vulnerability> | |
| 8841 | ||
| 8842 | <vulnerability id="http-bigbrother-accessible" title="Big Brother Monitoring Suite Reports Page Accessible" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="20041101T000000000" added="20041101T000000000" modified="20120731T000000000"> | |
| 8843 | <description> | |
| 8844 | ||
| 8845 | <ContainerBlockElement> | |
| 8846 | ||
| 8847 | <Paragraph>The | |
| 8848 | ||
| 8849 | <URLLink LinkURL="http://www.bb4.com/" LinkTitle="http://www.bb4.com/" href="http://www.bb4.com/">Big Brother</URLLink> monitoring suite is a | |
| 8850 | collection of system monitoring scripts for UNIX based systems. The Big Brother | |
| 8851 | suite is capable of monitoring multiple remote systems and periodically outputting | |
| 8852 | reports to HTML (usually within the web root of a web server so that remote | |
| 8853 | administrators can view the reports from a web browser).</Paragraph> | |
| 8854 | ||
| 8855 | ||
| 8856 | <Paragraph>The Big Brother reports pages are a treasure trove for any attacker who | |
| 8857 | wants to learn about your network. Attackers can learn about other systems | |
| 8858 | on the network, what services they are running, what processes they are | |
| 8859 | running, usernames, exported directories, etc.</Paragraph> | |
| 8860 | </ContainerBlockElement></description> | |
| 8861 | <references> | |
| 8862 | </references><tags> | |
| 8863 | <tag>HTTP</tag> | |
| 8864 | <tag>Web</tag> | |
| 8865 | </tags> | |
| 8866 | <solution> | |
| 8867 | ||
| 8868 | <ContainerBlockElement> | |
| 8869 | <Paragraph> | |
| 8870 | <Paragraph>Either disable Big Brother or use your web server's access control mechanisms | |
| 8871 | to require user authentication via HTTP before viewing the reports.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8872 | </vulnerability> | |
| 8873 | ||
| 8874 | <vulnerability id="http-cgi-faxsurvey-command-execution" title="faxsurvey CGI Remote Command Execution" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="19980804T000000000" added="20050413T000000000" modified="20120731T000000000"> | |
| 8875 | <description> | |
| 8876 | ||
| 8877 | <ContainerBlockElement> | |
| 8878 | ||
| 8879 | <Paragraph>The faxsurvey cgi can be exploited by sending a GET request to execute shell code on the remote web server.</Paragraph> | |
| 8880 | </ContainerBlockElement></description> | |
| 8881 | <references> | |
| 8882 | <reference source="BID">2056</reference> | |
| 8883 | <reference source="CVE">CVE-1999-0262</reference> | |
| 8884 | <reference source="XF">http-cgi-faxsurvey(1532)</reference> | |
| 8885 | </references><tags> | |
| 8886 | <tag>CGI</tag> | |
| 8887 | <tag>HTTP</tag> | |
| 8888 | <tag>Remote Execution</tag> | |
| 8889 | <tag>Web</tag> | |
| 8890 | </tags> | |
| 8891 | <solution> | |
| 8892 | ||
| 8893 | <ContainerBlockElement> | |
| 8894 | <Paragraph> | |
| 8895 | <Paragraph>It is strongly recommended to disable this CGI by removing any copies of it from your web server.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8896 | </vulnerability> | |
| 8897 | ||
| 8898 | <vulnerability id="http-cgi-htdig-arbitrary-file-access" title="Ht://dig Arbitrary File Access" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="20000229T000000000" added="20050413T000000000" modified="20120731T000000000"> | |
| 8899 | <description> | |
| 8900 | ||
| 8901 | <ContainerBlockElement> | |
| 8902 | ||
| 8903 | <Paragraph>The htdig CGI can be used to access any file readable by the server process.</Paragraph> | |
| 8904 | </ContainerBlockElement></description> | |
| 8905 | <references> | |
| 8906 | <reference source="BID">1026</reference> | |
| 8907 | <reference source="CVE">CVE-2000-0208</reference> | |
| 8908 | <reference source="URL">http://www.securityfocus.com/templates/archive.pike?list=1&[email protected]</reference> | |
| 8909 | </references><tags> | |
| 8910 | <tag>CGI</tag> | |
| 8911 | <tag>HTTP</tag> | |
| 8912 | <tag>Web</tag> | |
| 8913 | </tags> | |
| 8914 | <solution> | |
| 8915 | ||
| 8916 | <ContainerBlockElement> | |
| 8917 | <Paragraph> | |
| 8918 | <Paragraph>It is strongly recommended to disable this CGI by removing any copies of it from your web server.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8919 | </vulnerability> | |
| 8920 | ||
| 8921 | <vulnerability id="http-cgi-htgrep-arbitrary-file-access" title="Htgrep Arbitrary File Access" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="20001114T000000000" added="20050413T000000000" modified="20120731T000000000"> | |
| 8922 | <description> | |
| 8923 | ||
| 8924 | <ContainerBlockElement> | |
| 8925 | ||
| 8926 | <Paragraph>The Htgrep CGI can be used to access any file readable by the server process.</Paragraph> | |
| 8927 | </ContainerBlockElement></description> | |
| 8928 | <references> | |
| 8929 | <reference source="CVE">CVE-2000-0832</reference> | |
| 8930 | <reference source="URL">http://archives.neohapsis.com/archives/bugtraq/2000-08/0208.html</reference> | |
| 8931 | <reference source="XF">htgrep-cgi-view-files(5476)</reference> | |
| 8932 | </references><tags> | |
| 8933 | <tag>CGI</tag> | |
| 8934 | <tag>HTTP</tag> | |
| 8935 | <tag>Web</tag> | |
| 8936 | </tags> | |
| 8937 | <solution> | |
| 8938 | ||
| 8939 | <ContainerBlockElement> | |
| 8940 | <Paragraph> | |
| 8941 | <Paragraph>It is strongly recommended to disable this CGI by removing any copies of it from your web server.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8942 | </vulnerability> | |
| 8943 | ||
| 8944 | <vulnerability id="http-cgi-htmlscript-arbitrary-file-access" title="Htmlscript Arbitrary File Access" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="19980127T000000000" added="20050413T000000000" modified="20120731T000000000"> | |
| 8945 | <description> | |
| 8946 | ||
| 8947 | <ContainerBlockElement> | |
| 8948 | ||
| 8949 | <Paragraph>The htmlscript CGI can be used to access any file readable by the server process.</Paragraph> | |
| 8950 | </ContainerBlockElement></description> | |
| 8951 | <references> | |
| 8952 | <reference source="CVE">CVE-1999-0264</reference> | |
| 8953 | </references><tags> | |
| 8954 | <tag>CGI</tag> | |
| 8955 | <tag>HTTP</tag> | |
| 8956 | <tag>Web</tag> | |
| 8957 | </tags> | |
| 8958 | <solution> | |
| 8959 | ||
| 8960 | <ContainerBlockElement> | |
| 8961 | <Paragraph> | |
| 8962 | <Paragraph>It is strongly recommended to disable this CGI by removing any copies of it from your web server.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8963 | </vulnerability> | |
| 8964 | ||
| 8965 | <vulnerability id="http-cgi-testcgi-file-listing" title="Test-cgi Remote File Listing" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:P/A:N)" published="19960401T000000000" added="20050407T000000000" modified="20120731T000000000"> | |
| 8966 | <description> | |
| 8967 | ||
| 8968 | <ContainerBlockElement> | |
| 8969 | ||
| 8970 | <Paragraph>The test-cgi script included in older distributions of NCSA | |
| 8971 | HTTPd and Apache HTTPd does not properly sanitize user-supplied | |
| 8972 | request parameters. It is possible to retrieve a file listing | |
| 8973 | of any directory readable by the web server process by sending a | |
| 8974 | POST request with the Content-type header set to a path on | |
| 8975 | the server.</Paragraph> | |
| 8976 | </ContainerBlockElement></description> | |
| 8977 | <references> | |
| 8978 | <reference source="CVE">CVE-1999-0070</reference> | |
| 8979 | </references><tags> | |
| 8980 | <tag>CGI</tag> | |
| 8981 | <tag>HTTP</tag> | |
| 8982 | <tag>Web</tag> | |
| 8983 | </tags> | |
| 8984 | <solution> | |
| 8985 | ||
| 8986 | <ContainerBlockElement> | |
| 8987 | <Paragraph> | |
| 8988 | <Paragraph>It is strongly recommended to disable this CGI by removing any copies of it from your web server.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 8989 | </vulnerability> | |
| 8990 | ||
| 8991 | <vulnerability id="http-cgi-viewsource-arbitrary-file-access" title="View-source Arbitrary File Access" severity="6" pciSeverity="4" cvssScore="6.4" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:N)" published="19970201T000000000" added="20050413T000000000" modified="20120731T000000000"> | |
| 8992 | <description> | |
| 8993 | ||
| 8994 | <ContainerBlockElement> | |
| 8995 | ||
| 8996 | <Paragraph>The view-source CGI can be used to access any file readable by the server process.</Paragraph> | |
| 8997 | </ContainerBlockElement></description> | |
| 8998 | <references> | |
| 8999 | <reference source="CVE">CVE-1999-0174</reference> | |
| 9000 | </references><tags> | |
| 9001 | <tag>CGI</tag> | |
| 9002 | <tag>HTTP</tag> | |
| 9003 | <tag>Web</tag> | |
| 9004 | </tags> | |
| 9005 | <solution> | |
| 9006 | ||
| 9007 | <ContainerBlockElement> | |
| 9008 | <Paragraph> | |
| 9009 | <Paragraph>It is strongly recommended to disable this CGI by removing any copies of it from your web server.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 9010 | </vulnerability> | |
| 9011 | ||
| 9012 | <vulnerability id="http-coldfusion-cfide-unprotected" title="Adobe ColdFusion not properly hardened" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20070606T000000000" added="20110630T000000000" modified="20130416T000000000"> | |
| 9013 | <description> | |
| 9014 | ||
| 9015 | <ContainerBlockElement> | |
| 9016 | ||
| 9017 | <Paragraph>Unprotected access is allowed to the scripts under the ColdFusion /CFIDE/ directory. These utility scripts | |
| 9018 | can expose information about the server and its configuration. Because of the history of vulnerabilities due to | |
| 9019 | scripts within the /CFIDE/ directory, ColdFusion hardening best practices recommend that access to most (if not | |
| 9020 | all) of the subdirectories under /CFIDE/ be protected with a password or completely disabled</Paragraph> | |
| 9021 | </ContainerBlockElement></description> | |
| 9022 | <references> | |
| 9023 | <reference source="URL">http://www.adobe.com/content/dam/Adobe/en/products/coldfusion/pdfs/91025512-cf9-lockdownguide-wp-ue.pdf</reference> | |
| 9024 | <reference source="URL">http://www.adobe.com/content/dam/Adobe/en/products/coldfusion-enterprise/pdf/CF10%20Lockdown%20Guide.pdf</reference> | |
| 9025 | </references><tags> | |
| 9026 | <tag>Adobe</tag> | |
| 9027 | <tag>Adobe ColdFusion</tag> | |
| 9028 | <tag>HTTP</tag> | |
| 9029 | <tag>Web</tag> | |
| 9030 | </tags> | |
| 9031 | <solution> | |
| 9032 | ||
| 9033 | <ContainerBlockElement> | |
| 9034 | <Paragraph> | |
| 9035 | <Paragraph>Consult the following two hardening guides and apply the relevant configuration changes to the server to secure your ColdFusion installation: | |
| 9036 | ||
| 9037 | <OrderedList> | |
| 9038 | <ListItem> | |
| 9039 | <URLLink LinkURL="http://www.adobe.com/content/dam/Adobe/en/products/coldfusion/pdfs/91025512-cf9-lockdownguide-wp-ue.pdf" LinkTitle="http://www.adobe.com/content/dam/Adobe/en/products/coldfusion/pdfs/91025512-cf9-lockdownguide-wp-ue.pdf" href="http://www.adobe.com/content/dam/Adobe/en/products/coldfusion/pdfs/91025512-cf9-lockdownguide-wp-ue.pdf">Adobe ColdFusion 9 Server Lockdown Guide</URLLink></ListItem> | |
| 9040 | <ListItem> | |
| 9041 | <URLLink LinkURL="http://www.adobe.com/content/dam/Adobe/en/products/coldfusion-enterprise/pdf/CF10%20Lockdown%20Guide.pdf" LinkTitle="http://www.adobe.com/content/dam/Adobe/en/products/coldfusion-enterprise/pdf/CF10%20Lockdown%20Guide.pdf" href="http://www.adobe.com/content/dam/Adobe/en/products/coldfusion-enterprise/pdf/CF10%20Lockdown%20Guide.pdf">Adobe ColdFusion 10 Server Lockdown Guide</URLLink></ListItem></OrderedList> | |
| 9042 | ||
| 9043 | For public-facing servers, you may also want to prevent search engines from indexing certain directories (such as /CFIDE/). This can be done with the use of | |
| 9044 | robots.txt, as described in the | |
| 9045 | <URLLink LinkURL="http://kb2.adobe.com/cps/175/tn_17511.html" LinkTitle="http://kb2.adobe.com/cps/175/tn_17511.html" href="http://kb2.adobe.com/cps/175/tn_17511.html">Adobe FAQ</URLLink> on the subject. | |
| 9046 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 9047 | </vulnerability> | |
| 9048 | ||
| 9049 | <vulnerability id="http-cookie-http-only-flag" title="Missing HttpOnly Flag From Cookie" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="20110531T000000000" added="20110817T000000000" modified="20131105T000000000"> | |
| 9050 | <description> | |
| 9051 | ||
| 9052 | <ContainerBlockElement> | |
| 9053 | ||
| 9054 | <Paragraph>HttpOnly is an additional flag included in a Set-Cookie HTTP response header. If supported by the browser, using | |
| 9055 | the HttpOnly flag when generating a cookie helps mitigate the risk of client side script accessing the protected | |
| 9056 | cookie. If a browser that supports HttpOnly detects a cookie containing the HttpOnly flag, and client side script | |
| 9057 | code attempts to read the cookie, the browser returns an empty string as the result. This causes the attack to fail | |
| 9058 | by preventing the malicious (usually XSS) code from sending the data to an attacker's website.</Paragraph> | |
| 9059 | </ContainerBlockElement></description> | |
| 9060 | <references> | |
| 9061 | <reference source="URL">http://msdn.microsoft.com/en-us/library/ms533046.aspx</reference> | |
| 9062 | <reference source="URL">https://www.owasp.org/index.php/HttpOnly</reference> | |
| 9063 | </references><tags> | |
| 9064 | <tag>OWASP_2010</tag> | |
| 9065 | <tag>OWASP_2013</tag> | |
| 9066 | <tag>Web</tag> | |
| 9067 | <tag>Web Spider</tag> | |
| 9068 | </tags> | |
| 9069 | <solution> | |
| 9070 | ||
| 9071 | <ContainerBlockElement> | |
| 9072 | <Paragraph> | |
| 9073 | <Paragraph>For each cookie generated by your web-site, add the "HttpOnly" flag to the cookie. | |
| 9074 | For example:</Paragraph> | |
| 9075 | <Paragraph preformat="true"> | |
| 9076 | <Paragraph preformat="true"> | |
| 9077 | Set-Cookie: <name>=<value>[; <Max-Age>=<age>] | |
| 9078 | [; expires=<date>][; domain=<domain_name>] | |
| 9079 | [; path=<some_path>][; secure][; HttpOnly] | |
| 9080 | </Paragraph></Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 9081 | </vulnerability> | |
| 9082 | ||
| 9083 | <vulnerability id="http-dd-wrt-remote-command-execution" title="DD-WRT Remote Command Execution as Root" severity="8" pciSeverity="5" cvssScore="8.3" cvssVector="(AV:A/AC:L/Au:N/C:C/I:C/A:C)" published="20090720T000000000" added="20090812T000000000" modified="20120731T000000000"> | |
| 9084 | <description> | |
| 9085 | ||
| 9086 | <ContainerBlockElement> | |
| 9087 | ||
| 9088 | <Paragraph> | |
| 9089 | There is a vulnerability in the DD-WRT firmware as recent as 2.4 SP1. A | |
| 9090 | remote attacker can execute commands as the root user by simply appending | |
| 9091 | a semi-colon to the URL of any string in the cgi-bin path, followed by | |
| 9092 | the command of their choice. Authentication is not required for the | |
| 9093 | command to run on the target access point. | |
| 9094 | </Paragraph> | |
| 9095 | </ContainerBlockElement></description> | |
| 9096 | <references> | |
| 9097 | <reference source="BID">35742</reference> | |
| 9098 | <reference source="CVE">CVE-2009-2765</reference> | |
| 9099 | <reference source="OSVDB">55990</reference> | |
| 9100 | <reference source="URL">http://milw0rm.com/exploits/9209</reference> | |
| 9101 | <reference source="URL">http://www.dd-wrt.com/dd-wrtv3/index.php?view=article&id=34</reference> | |
| 9102 | </references><tags> | |
| 9103 | <tag>HTTP</tag> | |
| 9104 | <tag>Remote Execution</tag> | |
| 9105 | <tag>Web</tag> | |
| 9106 | </tags> | |
| 9107 | <solution> | |
| 9108 | ||
| 9109 | <ContainerBlockElement> | |
| 9110 | <Paragraph>Download and apply the upgrade from: | |
| 9111 | <URLLink LinkURL="http://www.dd-wrt.com/dd-wrtv2/down.php?path=downloads%2Fothers%2Feko%2FBrainSlayer-V24-preSP2%2F07-21-09-r12533/" LinkTitle="http://www.dd-wrt.com/dd-wrtv2/down.php?path=downloads%2Fothers%2Feko%2FBrainSlayer-V24-preSP2%2F07-21-09-r12533/"></URLLink></Paragraph></ContainerBlockElement></solution> | |
| 9112 | </vulnerability> | |
| 9113 | ||
| 9114 | <vulnerability id="http-drac-default-login" title="Dell Remote Access Controller (DRAC) Default Login Credentials" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20070925T000000000" added="20070925T000000000" modified="20120731T000000000"> | |
| 9115 | <description> | |
| 9116 | ||
| 9117 | <ContainerBlockElement> | |
| 9118 | ||
| 9119 | <Paragraph> | |
| 9120 | Dell products that utilize Dell Remote Access Controllers (DRAC) are shipped | |
| 9121 | with the default username/password combination of root/calvin, respectively. | |
| 9122 | It is recommended that the password is changed in order to prevent unauthorized | |
| 9123 | access. Unauthorized users have access to view system information as well as | |
| 9124 | perform maintenance tasks such as firmware upgrades, system powerup, | |
| 9125 | powerdown, hardreset, powercycle and more. | |
| 9126 | Access to the system console is also possible. | |
| 9127 | </Paragraph> | |
| 9128 | </ContainerBlockElement></description> | |
| 9129 | <references> | |
| 9130 | <reference source="URL">http://support.dell.com/support/edocs/software/smdrac3/</reference> | |
| 9131 | </references><tags> | |
| 9132 | <tag>Default Account</tag> | |
| 9133 | <tag>HTTP</tag> | |
| 9134 | <tag>Web</tag> | |
| 9135 | </tags> | |
| 9136 | <solution> | |
| 9137 | ||
| 9138 | <ContainerBlockElement> | |
| 9139 | <Paragraph> | |
| 9140 | <Paragraph> | |
| 9141 | SSH to the DRAC interface using the default username: root and password: calvin. | |
| 9142 | At the RACADM command prompt (ie. $), issue the following command | |
| 9143 | (change "newpassword" to the new password of your choice): | |
| 9144 | </Paragraph> | |
| 9145 | <Paragraph preformat="true"> | |
| 9146 | racadm config -g cfgUserAdmin -o cfgUserAdminPassword -i 2 newpassword | |
| 9147 | </Paragraph> | |
| 9148 | <Paragraph> | |
| 9149 | Refer to the | |
| 9150 | ||
| 9151 | <URLLink LinkURL="http://support.dell.com/support/edocs/software/smdrac3/" LinkTitle="http://support.dell.com/support/edocs/software/smdrac3/" href="http://support.dell.com/support/edocs/software/smdrac3/">Dell</URLLink> | |
| 9152 | support page for more information. | |
| 9153 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 9154 | </vulnerability> | |
| 9155 | ||
| 9156 | <vulnerability id="http-frontpage-unprotected" title="Unprotected FrontPage Extensions" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20000602T000000000" added="20100804T000000000" modified="20120731T000000000"> | |
| 9157 | <description> | |
| 9158 | ||
| 9159 | <ContainerBlockElement> | |
| 9160 | Incorrect permissions were discovered on FrontPage extensions use for | |
| 9161 | controlling access and publishing content. By exploiting this | |
| 9162 | misconfiguration, attackers may be able to modify content served by | |
| 9163 | this web server. | |
| 9164 | </ContainerBlockElement></description> | |
| 9165 | <references> | |
| 9166 | <reference source="URL">http://www.auscert.org.au/render.html?it=828</reference> | |
| 9167 | </references><tags> | |
| 9168 | <tag>HTTP</tag> | |
| 9169 | <tag>Web</tag> | |
| 9170 | </tags> | |
| 9171 | <solution> | |
| 9172 | ||
| 9173 | <ContainerBlockElement> | |
| 9174 | <Paragraph> | |
| 9175 | <Paragraph> | |
| 9176 | Web site managers who are using FrontPage to administer their sites | |
| 9177 | should check these permissions to insure that only those who are allowed to | |
| 9178 | author or administer the site have access to the admin.dll and author.dll | |
| 9179 | extensions. Web site managers who are using IIS servers but not FrontPage | |
| 9180 | should check for the existence of the FrontPage extensions (check for the | |
| 9181 | _vti_* directories and for _vti_inf.html in the web root directory) and | |
| 9182 | remove them if FrontPage is not required. | |
| 9183 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 9184 | </vulnerability> | |
| 9185 | ||
| 9186 | <vulnerability id="http-generic-propfind-dir-browsing" title="WebDAV PROPFIND Method Allows Web Directory Browsing" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="20010101T000000000" added="20070730T000000000" modified="20130620T000000000"> | |
| 9187 | <description> | |
| 9188 | ||
| 9189 | <ContainerBlockElement> | |
| 9190 | ||
| 9191 | <Paragraph>It is possible to use the WebDAV PROPFIND method to browse web directories | |
| 9192 | on the server and discover content that would normally remain hidden. This | |
| 9193 | could potentially allow an attacker to obtain sensitive information, such as | |
| 9194 | data files and backup pages, or give them information about the directory | |
| 9195 | structure that could be useful in mounting a more sophisticated attack | |
| 9196 | later.</Paragraph> | |
| 9197 | </ContainerBlockElement></description> | |
| 9198 | <references> | |
| 9199 | </references><tags> | |
| 9200 | <tag>Backup</tag> | |
| 9201 | <tag>Directory Browsing</tag> | |
| 9202 | <tag>OWASP_2010</tag> | |
| 9203 | <tag>OWASP_2013</tag> | |
| 9204 | <tag>Web</tag> | |
| 9205 | <tag>Web Spider</tag> | |
| 9206 | </tags> | |
| 9207 | <solution> | |
| 9208 | ||
| 9209 | <ContainerBlockElement> | |
| 9210 | <UnorderedList> | |
| 9211 | <ListItem> | |
| 9212 | <Paragraph>IIS, PWS, Microsoft-IIS, Internet Information Services, Internet Information Services, Microsoft-PWS</Paragraph> | |
| 9213 | <Paragraph> | |
| 9214 | <Paragraph>For Microsoft Internet Information Services (IIS), you may | |
| 9215 | use the URLScan tool, freely available at | |
| 9216 | ||
| 9217 | <URLLink LinkURL="http://www.microsoft.com/technet/security/tools/urlscan.mspx" LinkTitle="http://www.microsoft.com/technet/security/tools/urlscan.mspx" href="http://www.microsoft.com/technet/security/tools/urlscan.mspx"></URLLink></Paragraph></Paragraph></ListItem> | |
| 9218 | <ListItem> | |
| 9219 | <Paragraph>Apache HTTPD</Paragraph> | |
| 9220 | <Paragraph> | |
| 9221 | <Paragraph>The PROPFIND method should be restricted from anonymous requests. | |
| 9222 | Enable authentication on the WebDAV directory so that only authorized users | |
| 9223 | can invoke the method to perform legitimate tasks, like so:</Paragraph> | |
| 9224 | <Paragraph preformat="true"><Location /webdav_dir/*> | |
| 9225 | <LimitExcept GET HEAD OPTIONS POST> | |
| 9226 | AuthType Basic | |
| 9227 | AuthName "WebDAV Authentication" | |
| 9228 | AuthUserFile /path/to/userfile | |
| 9229 | AuthGroupFile /path/to/groupfile | |
| 9230 | require group webdavusers | |
| 9231 | </LimitExcept> | |
| 9232 | </Location></Paragraph> | |
| 9233 | <Paragraph>Next, create the password file and group file:</Paragraph> | |
| 9234 | <Paragraph preformat="true">htpasswd -cs /path/to/userfile bob | |
| 9235 | echo "webdavusers: bob" > /path/to/groupfile</Paragraph></Paragraph></ListItem> | |
| 9236 | <ListItem> | |
| 9237 | <Paragraph>Java System Web Server, SunONE WebServer, Sun-ONE-Web-Server, iPlanet</Paragraph> | |
| 9238 | <Paragraph> | |
| 9239 | <Paragraph>In the server.xml configuration file, add the following lines to | |
| 9240 | restrict WebDAV methods to a particular user(s):</Paragraph> | |
| 9241 | <Paragraph preformat="true">acl "uri=/webdav_dir/*"; | |
| 9242 | deny(all) | |
| 9243 | user="anyone"; | |
| 9244 | ||
| 9245 | allow (read,list,execute,info,write,delete) | |
| 9246 | user = "username";</Paragraph></Paragraph></ListItem> | |
| 9247 | <ListItem> | |
| 9248 | <Paragraph>Apache Tomcat, Tomcat, Tomcat Web Server, Apache Coyote, Apache-Coyote</Paragraph> | |
| 9249 | <Paragraph> | |
| 9250 | <Paragraph>In the web.xml configuration file for the WebDAV-enabled directory, | |
| 9251 | add the following lines to restrict WebDAV functionality to a particular | |
| 9252 | user(s):</Paragraph> | |
| 9253 | <Paragraph preformat="true"> <security-constraint> | |
| 9254 | <web-resource-collection> | |
| 9255 | <web-resource-name>WebDav Directory</web-resource-name> | |
| 9256 | <url-pattern>/*</url-pattern> | |
| 9257 | </web-resource-collection> | |
| 9258 | <auth-constraint> | |
| 9259 | <role-name>webdav-user</role-name> | |
| 9260 | </auth-constraint> | |
| 9261 | </security-constraint> | |
| 9262 | ||
| 9263 | <login-config> | |
| 9264 | <auth-method>BASIC</auth-method> | |
| 9265 | <realm-name>WebDAV Realm</realm-name> | |
| 9266 | </login-config> | |
| 9267 | ||
| 9268 | <security-role> | |
| 9269 | <description> | |
| 9270 | Legitimate WebDAV users | |
| 9271 | </description> | |
| 9272 | <role-name>webdav-user</role-name> | |
| 9273 | </security-role></Paragraph> | |
| 9274 | <Paragraph>In the conf/tomcat-users.xml file, add a WebDAV user like so:</Paragraph> | |
| 9275 | <Paragraph preformat="true"><?xml version='1.0' encoding='utf-8'?> | |
| 9276 | <tomcat-users> | |
| 9277 | <role rolename="webdav-user"/> | |
| 9278 | <user username="bob" password="b0bsp455w0rdy0!" roles="webdav-user"/> | |
| 9279 | </tomcat-users></Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 9280 | </vulnerability> | |
| 9281 | ||
| 9282 | <vulnerability id="http-glassfish-default-admin-password" title="Glassfish Default Administrator Password Vulnerability" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20100615T000000000" added="20110718T000000000" modified="20120731T000000000"> | |
| 9283 | <description> | |
| 9284 | ||
| 9285 | <ContainerBlockElement> | |
| 9286 | ||
| 9287 | <Paragraph>The Glassfish administrator 'admin' has a password that is set to a | |
| 9288 | default blank value. As a result, anyone with access to the GlassFish | |
| 9289 | port can trivially gain full access to the machine via arbitrary remote | |
| 9290 | code execution. This requires the attacker to upload a malicious | |
| 9291 | webservice. | |
| 9292 | </Paragraph> | |
| 9293 | </ContainerBlockElement></description> | |
| 9294 | <references> | |
| 9295 | <reference source="URL">http://download.oracle.com/docs/cd/E18930_01/html/821-2435/ghgrp.html</reference> | |
| 9296 | </references><tags> | |
| 9297 | <tag>Default Account</tag> | |
| 9298 | <tag>HTTP</tag> | |
| 9299 | <tag>Remote Execution</tag> | |
| 9300 | <tag>Web</tag> | |
| 9301 | </tags> | |
| 9302 | <solution> | |
| 9303 | ||
| 9304 | <ContainerBlockElement> | |
| 9305 | <Paragraph> | |
| 9306 | <Paragraph>Change the admin password to a non-default value. This can be done by modifying the password through the | |
| 9307 | administrator interface. | |
| 9308 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 9309 | </vulnerability> | |
| 9310 | ||
| 9311 | <vulnerability id="HTTP-IIS-0014" title="Microsoft JET Database Engine VBA Vulnerability" severity="7" pciSeverity="5" cvssScore="7.2" cvssVector="(AV:L/AC:L/Au:N/C:C/I:C/A:C)" published="19990820T000000000" added="20041101T000000000" modified="20120731T000000000"> | |
| 9312 | <description> | |
| 9313 | ||
| 9314 | <ContainerBlockElement> | |
| 9315 | ||
| 9316 | <Paragraph>Microsoft's JET database engine feature allows the embedding of Visual Basic | |
| 9317 | for Application in SQL string expressions and the lack of metacharacter filtering | |
| 9318 | by many web applications may allow remote users to execute commands on the system.</Paragraph> | |
| 9319 | ||
| 9320 | <Paragraph>Microsoft's JET database engine (the core of Microsoft Access) allows the | |
| 9321 | embedding of Visual Basic for Application expressions in SQL strings. VBA expressions | |
| 9322 | withing two "|" characters within an SQL string will be executed and its result substituted | |
| 9323 | in the string. The VBA code is evaluated in an expression context. That means you cannot | |
| 9324 | make use of statements.</Paragraph> | |
| 9325 | ||
| 9326 | <Paragraph>The Microsoft JET database engine can be used via the ODBC API. It is commonly | |
| 9327 | used as a backend for web enabled applications. The fact that it uses the "|" character | |
| 9328 | to execute VBA code within SQL statements in JET is a largely unknown feature, meaning | |
| 9329 | that few applications escape user input for this metacharacter. Therefore any script | |
| 9330 | or application that uses Microsoft's JET ODBC DSN could potentially be exploited.</Paragraph> | |
| 9331 | ||
| 9332 | <Paragraph>Microsoft's IIS in particular executes ODBC commands in the context of the System | |
| 9333 | account. This may allow remote attackers to input VBA code in web enabled applications | |
| 9334 | that will be executed by IIS as the System user.</Paragraph> | |
| 9335 | ||
| 9336 | <Paragraph>The most dangerous VBA command available to an attacker is shell(), which enables | |
| 9337 | it to run any command in the system.</Paragraph> | |
| 9338 | ||
| 9339 | <Paragraph>Microsoft's IIS 4.0 ships with a number of sample scripts that are vulnerable | |
| 9340 | if used with the JET ODBC driver (e.g. details.idc). It also ships with MSADC which | |
| 9341 | allows remote uses to execute SQL queries on a DNS via HTTP.</Paragraph> | |
| 9342 | ||
| 9343 | <Paragraph>Tests seem to indicate JET 4.0 is not vulnerable to this issue.</Paragraph> | |
| 9344 | </ContainerBlockElement></description> | |
| 9345 | <references> | |
| 9346 | <reference source="BID">548</reference> | |
| 9347 | <reference source="CVE">CVE-2000-0325</reference> | |
| 9348 | <reference source="MS">MS99-030</reference> | |
| 9349 | <reference source="URL">http://marc.info/?l=bugtraq&m=92765973107637&w=2</reference> | |
| 9350 | <reference source="XF">jet-vba-shell(3155)</reference> | |
| 9351 | </references><tags> | |
| 9352 | <tag>DNS</tag> | |
| 9353 | <tag>HTTP</tag> | |
| 9354 | <tag>Microsoft</tag> | |
| 9355 | <tag>Microsoft IIS</tag> | |
| 9356 | <tag>Web</tag> | |
| 9357 | </tags> | |
| 9358 | <solution> | |
| 9359 | ||
| 9360 | <ContainerBlockElement> | |
| 9361 | <Paragraph>Download and apply the upgrade from: | |
| 9362 | <URLLink LinkURL="http://support.microsoft.com/default.aspx?scid=kb;en-us;Q239114" LinkTitle="http://support.microsoft.com/default.aspx?scid=kb;en-us;Q239114"></URLLink></Paragraph> | |
| 9363 | <Paragraph> | |
| 9364 | <Paragraph>Disable the JET ODBC drivers or | |
| 9365 | ||
| 9366 | ||
| 9367 | <URLLink LinkURL="http://support.microsoft.com/default.aspx?scid=kb;en-us;Q239114" LinkTitle="http://support.microsoft.com/default.aspx?scid=kb;en-us;Q239114" href="http://support.microsoft.com/default.aspx?scid=kb;en-us;Q239114">upgrade to JET 4.0 SP3</URLLink> | |
| 9368 | or later. The latest JET release is JET Service Pack 6, which is included with Windows 2000 | |
| 9369 | Service Pack 3. Please note that JET 4.0 may not be fully compatible with earlier versions | |
| 9370 | and some legacy applications may fail. JET 4.0 is part of Microsoft's Data Access (MDAC) 2.1.</Paragraph> | |
| 9371 | <Paragraph>The latest stable release of MDAC is | |
| 9372 | ||
| 9373 | ||
| 9374 | <URLLink LinkURL="http://msdn.microsoft.com/data/mdac/downloads/default.aspx" LinkTitle="http://msdn.microsoft.com/data/mdac/downloads/default.aspx" href="http://msdn.microsoft.com/data/mdac/downloads/default.aspx">MDAC v2.6 Service Pack 2</URLLink>. | |
| 9375 | Note that MDAC 2.6 and later | |
| 9376 | ||
| 9377 | ||
| 9378 | <URLLink LinkURL="http://support.microsoft.com/default.aspx?scid=kb;en-us;Q271908" LinkTitle="http://support.microsoft.com/default.aspx?scid=kb;en-us;Q271908" href="http://support.microsoft.com/default.aspx?scid=kb;en-us;Q271908">do not include</URLLink> | |
| 9379 | the JET ODBC drivers by default.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 9380 | </vulnerability> | |
| 9381 | ||
| 9382 | <vulnerability id="http-lighttpd-mod_userdir-info-discl" title="Lighttpd 'mod_userdir' Information Disclosure" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="20080305T000000000" added="20080811T000000000" modified="20120731T000000000"> | |
| 9383 | <description> | |
| 9384 | ||
| 9385 | <ContainerBlockElement> | |
| 9386 | ||
| 9387 | <Paragraph> | |
| 9388 | With certain versions of lighttpd, if mod_userdir is loaded but "userdir.path" | |
| 9389 | is not configured, the default directory for userdir requests is $HOME (instead | |
| 9390 | of $HOME/public_html for example). This could lead to information disclosure. | |
| 9391 | </Paragraph> | |
| 9392 | </ContainerBlockElement></description> | |
| 9393 | <references> | |
| 9394 | <reference source="BID">28226</reference> | |
| 9395 | <reference source="CVE">CVE-2008-1270</reference> | |
| 9396 | <reference source="DEBIAN">DSA-1521</reference> | |
| 9397 | <reference source="SECUNIA">29318</reference> | |
| 9398 | <reference source="SECUNIA">29403</reference> | |
| 9399 | <reference source="SECUNIA">29622</reference> | |
| 9400 | <reference source="SECUNIA">29636</reference> | |
| 9401 | <reference source="URL">http://trac.lighttpd.net/trac/ticket/1587</reference> | |
| 9402 | <reference source="URL">http://www.lighttpd.net/security/lighttpd_sa_2008_03.txt</reference> | |
| 9403 | <reference source="XF">lighttpd-moduserdir-information-disclosure(41173)</reference> | |
| 9404 | </references><tags> | |
| 9405 | <tag>HTTP</tag> | |
| 9406 | <tag>Information Gathering</tag> | |
| 9407 | <tag>Web</tag> | |
| 9408 | <tag>lighttpd</tag> | |
| 9409 | </tags> | |
| 9410 | <solution> | |
| 9411 | ||
| 9412 | <ContainerBlockElement> | |
| 9413 | <Paragraph>Download and apply the upgrade from: | |
| 9414 | <URLLink LinkURL="http://www.lighttpd.net/download/lighttpd-1.4.19.tar.gz" LinkTitle="http://www.lighttpd.net/download/lighttpd-1.4.19.tar.gz"></URLLink></Paragraph></ContainerBlockElement></solution> | |
| 9415 | </vulnerability> | |
| 9416 | ||
| 9417 | <vulnerability id="http-nokia-firewall-default-admin-password" title="Nokia Firewall Default Administrator Password Vulnerability" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20040101T000000000" added="20090716T000000000" modified="20120731T000000000"> | |
| 9418 | <description> | |
| 9419 | ||
| 9420 | <ContainerBlockElement> | |
| 9421 | ||
| 9422 | <Paragraph> | |
| 9423 | The administrator credentials are unchanged from the default of 'admin' and 'password'. | |
| 9424 | As a result, anyone with access to the Nokia Firewall can trivially gain full access | |
| 9425 | to the device. | |
| 9426 | </Paragraph> | |
| 9427 | </ContainerBlockElement></description> | |
| 9428 | <references> | |
| 9429 | </references><tags> | |
| 9430 | <tag>Default Account</tag> | |
| 9431 | <tag>HTTP</tag> | |
| 9432 | <tag>Web</tag> | |
| 9433 | </tags> | |
| 9434 | <solution> | |
| 9435 | ||
| 9436 | <ContainerBlockElement> | |
| 9437 | <Paragraph> | |
| 9438 | Change the admin password using the Web interface. | |
| 9439 | </Paragraph></ContainerBlockElement></solution> | |
| 9440 | </vulnerability> | |
| 9441 | ||
| 9442 | <vulnerability id="http-open-proxy" title="Open HTTP Proxy" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:P/A:N)" published="20070723T000000000" added="20070723T000000000" modified="20120731T000000000"> | |
| 9443 | <description> | |
| 9444 | ||
| 9445 | <ContainerBlockElement> | |
| 9446 | ||
| 9447 | <Paragraph> | |
| 9448 | Open proxies allow malicious clients to mount attacks which | |
| 9449 | originate from the IP of the proxy server, without requiring the | |
| 9450 | attacker to authenticate to the proxy first. | |
| 9451 | </Paragraph> | |
| 9452 | ||
| 9453 | <Paragraph> | |
| 9454 | Additionally, an open proxy may allow an attacker to access | |
| 9455 | an internal network which would be otherwise secure. | |
| 9456 | </Paragraph> | |
| 9457 | ||
| 9458 | <Paragraph> | |
| 9459 | Steps should be taken to correctly configure the proxy server | |
| 9460 | such that unauthorized connections are denied. | |
| 9461 | </Paragraph> | |
| 9462 | </ContainerBlockElement></description> | |
| 9463 | <references> | |
| 9464 | <reference source="CERT-VN">150227</reference> | |
| 9465 | <reference source="URL">http://spamlinks.net/prevent-secure-proxy-fix.htm</reference> | |
| 9466 | <reference source="URL">http://www.web-cache.com/Writings/Internet-Drafts/draft-luotonen-web-proxy-tunneling-01.txt</reference> | |
| 9467 | </references><tags> | |
| 9468 | <tag>HTTP</tag> | |
| 9469 | <tag>Web</tag> | |
| 9470 | </tags> | |
| 9471 | <solution> | |
| 9472 | ||
| 9473 | <ContainerBlockElement> | |
| 9474 | <UnorderedList> | |
| 9475 | <ListItem> | |
| 9476 | <Paragraph>squid</Paragraph> | |
| 9477 | <Paragraph> | |
| 9478 | <Paragraph> | |
| 9479 | An access control list (ACL) should be defined for the squid proxy server | |
| 9480 | in the file: | |
| 9481 | <Paragraph preformat="true">squid.conf</Paragraph></Paragraph> | |
| 9482 | <Paragraph> | |
| 9483 | Consult the Squid 3.0 configuration manual, located at the | |
| 9484 | ||
| 9485 | <URLLink LinkURL="http://www.visolve.com/squid/squid30/contents.php" LinkTitle="http://www.visolve.com/squid/squid30/contents.php" href="http://www.visolve.com/squid/squid30/contents.php">ViSolve</URLLink> website. | |
| 9486 | </Paragraph></Paragraph></ListItem> | |
| 9487 | <ListItem> | |
| 9488 | <Paragraph> | |
| 9489 | <Paragraph> | |
| 9490 | Consult the ISA server 2006 hardening guide below for steps on | |
| 9491 | how to securely configure the web proxy component: | |
| 9492 | </Paragraph> | |
| 9493 | <Paragraph> | |
| 9494 | <URLLink LinkURL="http://www.microsoft.com/technet/isa/2006/security_guide.mspx" LinkTitle="http://www.microsoft.com/technet/isa/2006/security_guide.mspx" href="http://www.microsoft.com/technet/isa/2006/security_guide.mspx"></URLLink></Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 9495 | </vulnerability> | |
| 9496 | ||
| 9497 | <vulnerability id="http-php-ini-file-exposed" title="PHP Exposed 'ini' File Vulnerability" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="20050119T000000000" added="20050119T000000000" modified="20130620T000000000"> | |
| 9498 | <description> | |
| 9499 | ||
| 9500 | <ContainerBlockElement> | |
| 9501 | ||
| 9502 | <Paragraph>PHP's 'ini' file is exposed inside the 'cgi-bin' directory. This allows any unauthenticated remote user to discover sensitive information about your server(s), including database logins and passwords.</Paragraph> | |
| 9503 | </ContainerBlockElement></description> | |
| 9504 | <references> | |
| 9505 | </references><tags> | |
| 9506 | <tag>HTTP</tag> | |
| 9507 | <tag>OWASP_2010</tag> | |
| 9508 | <tag>OWASP_2013</tag> | |
| 9509 | <tag>PHP</tag> | |
| 9510 | <tag>Web</tag> | |
| 9511 | </tags> | |
| 9512 | <solution> | |
| 9513 | ||
| 9514 | <ContainerBlockElement> | |
| 9515 | <Paragraph> | |
| 9516 | <Paragraph>Consult your HTTP daemon's documentation for instructions on restricting access to this file:</Paragraph> | |
| 9517 | <Paragraph> | |
| 9518 | <UnorderedList> | |
| 9519 | <ListItem> | |
| 9520 | <URLLink LinkURL="http://httpd.apache.org/docs/" LinkTitle="http://httpd.apache.org/docs/" href="http://httpd.apache.org/docs/">Apache v1.3.x Documentation</URLLink></ListItem> | |
| 9521 | <ListItem> | |
| 9522 | <URLLink LinkURL="http://httpd.apache.org/docs-2.0/" LinkTitle="http://httpd.apache.org/docs-2.0/" href="http://httpd.apache.org/docs-2.0/">Apache v2.0.x Documentation</URLLink></ListItem> | |
| 9523 | <ListItem> | |
| 9524 | <URLLink LinkURL="http://www.microsoft.com/technet/prodtechnol/windowsserver2003/technologies/webapp/iis/default.mspx" LinkTitle="http://www.microsoft.com/technet/prodtechnol/windowsserver2003/technologies/webapp/iis/default.mspx" href="http://www.microsoft.com/technet/prodtechnol/windowsserver2003/technologies/webapp/iis/default.mspx">Microsoft Internet Information Services Documentation</URLLink></ListItem> | |
| 9525 | <ListItem> | |
| 9526 | <URLLink LinkURL="http://docs.sun.com/db/coll/S1_websvr61_en" LinkTitle="http://docs.sun.com/db/coll/S1_websvr61_en" href="http://docs.sun.com/db/coll/S1_websvr61_en">Sun ONE v6.1 Documentation</URLLink></ListItem></UnorderedList></Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 9527 | </vulnerability> | |
| 9528 | ||
| 9529 | <vulnerability id="http-php-xmlrpc-code-injection" title="PHP XML-RPC Code Injection" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20050705T000000000" added="20060318T000000000" modified="20121025T000000000"> | |
| 9530 | <description> | |
| 9531 | ||
| 9532 | <ContainerBlockElement> | |
| 9533 | ||
| 9534 | <Paragraph>Eval injection vulnerability in PEAR XML_RPC 1.3.0 and earlier (aka XML-RPC or xmlrpc) and PHPXMLRPC (aka XML-RPC For PHP or php-xmlrpc) 1.1 and earlier, as used in products such as (1) WordPress, (2) Serendipity, (3) Drupal, (4) egroupware, (5) MailWatch, (6) TikiWiki, (7) phpWebSite, (8) Ampache, and others, allows remote attackers to execute arbitrary PHP code via an XML file, which is not properly sanitized before being used in an eval statement.</Paragraph> | |
| 9535 | </ContainerBlockElement></description> | |
| 9536 | <references> | |
| 9537 | <reference source="BID">14088</reference> | |
| 9538 | <reference source="CVE">CVE-2005-1921</reference> | |
| 9539 | <reference source="DEBIAN">DSA-745</reference> | |
| 9540 | <reference source="DEBIAN">DSA-746</reference> | |
| 9541 | <reference source="DEBIAN">DSA-747</reference> | |
| 9542 | <reference source="DEBIAN">DSA-789</reference> | |
| 9543 | <reference source="MANDRAKE">MDKSA-2005:109</reference> | |
| 9544 | <reference source="OVAL">OVAL11294</reference> | |
| 9545 | <reference source="OVAL">OVAL350</reference> | |
| 9546 | <reference source="REDHAT">RHSA-2005:564</reference> | |
| 9547 | <reference source="SECUNIA">15810</reference> | |
| 9548 | <reference source="SECUNIA">15852</reference> | |
| 9549 | <reference source="SECUNIA">15855</reference> | |
| 9550 | <reference source="SECUNIA">15861</reference> | |
| 9551 | <reference source="SECUNIA">15872</reference> | |
| 9552 | <reference source="SECUNIA">15883</reference> | |
| 9553 | <reference source="SECUNIA">15884</reference> | |
| 9554 | <reference source="SECUNIA">15895</reference> | |
| 9555 | <reference source="SECUNIA">15903</reference> | |
| 9556 | <reference source="SECUNIA">15904</reference> | |
| 9557 | <reference source="SECUNIA">15916</reference> | |
| 9558 | <reference source="SECUNIA">15917</reference> | |
| 9559 | <reference source="SECUNIA">15922</reference> | |
| 9560 | <reference source="SECUNIA">15944</reference> | |
| 9561 | <reference source="SECUNIA">15947</reference> | |
| 9562 | <reference source="SECUNIA">15957</reference> | |
| 9563 | <reference source="SECUNIA">16001</reference> | |
| 9564 | <reference source="SECUNIA">16339</reference> | |
| 9565 | <reference source="SECUNIA">16693</reference> | |
| 9566 | <reference source="SECUNIA">17440</reference> | |
| 9567 | <reference source="SECUNIA">17674</reference> | |
| 9568 | <reference source="SECUNIA">18003</reference> | |
| 9569 | <reference source="SUSE">SUSE-SA:2005:041</reference> | |
| 9570 | <reference source="SUSE">SUSE-SA:2005:049</reference> | |
| 9571 | <reference source="SUSE">SUSE-SA:2005:051</reference> | |
| 9572 | <reference source="URL">http://marc.theaimsgroup.com/?l=bugtraq&m=112008638320145&w=2</reference> | |
| 9573 | <reference source="URL">http://marc.theaimsgroup.com/?l=bugtraq&m=112015336720867&w=2</reference> | |
| 9574 | <reference source="URL">http://pear.php.net/package/XML_RPC/download/1.3.1</reference> | |
| 9575 | <reference source="URL">http://sourceforge.net/project/showfiles.php?group_id=87163</reference> | |
| 9576 | <reference source="URL">http://sourceforge.net/project/shownotes.php?release_id=338803</reference> | |
| 9577 | <reference source="URL">http://www.ampache.org/announce/3_3_1_2.php</reference> | |
| 9578 | <reference source="URL">http://www.drupal.org/security/drupal-sa-2005-003/advisory.txt</reference> | |
| 9579 | <reference source="URL">http://www.frsirt.com/english/advisories/2005/2827</reference> | |
| 9580 | <reference source="URL">http://www.gulftech.org/?node=research&article_id=00087-07012005</reference> | |
| 9581 | <reference source="URL">http://www.hardened-php.net/advisory-022005.php</reference> | |
| 9582 | <reference source="URL">http://www.securityfocus.com/archive/1/archive/1/419064/100/0/threaded</reference> | |
| 9583 | </references><tags> | |
| 9584 | <tag>HTTP</tag> | |
| 9585 | <tag>PHP</tag> | |
| 9586 | <tag>RPC</tag> | |
| 9587 | <tag>Remote Execution</tag> | |
| 9588 | <tag>Web</tag> | |
| 9589 | </tags> | |
| 9590 | <solution> | |
| 9591 | ||
| 9592 | <ContainerBlockElement> | |
| 9593 | <Paragraph> | |
| 9594 | <Paragraph>If XML-RPC functionality is not required, the xmlrpc.php file should be remove.</Paragraph> | |
| 9595 | <Paragraph>Otherwise, the software using the XML-RPC module should be upgraded accordingly.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 9596 | </vulnerability> | |
| 9597 | ||
| 9598 | <vulnerability id="http-phpmyadmin-account-pma-password-empty" title="phpMyAdmin Credentials: user 'pma' with empty password" severity="10" pciSeverity="5" cvssScore="9.7" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:P)" published="19990101T000000000" added="20100727T000000000" modified="20120717T000000000"> | |
| 9599 | <description> | |
| 9600 | ||
| 9601 | <ContainerBlockElement> | |
| 9602 | ||
| 9603 | <Paragraph> | |
| 9604 | The phpMyAdmin installation is vulnerable to password guessing attacks, | |
| 9605 | as it has an account with the username 'pma' and an empty password. | |
| 9606 | </Paragraph> | |
| 9607 | </ContainerBlockElement></description> | |
| 9608 | <references> | |
| 9609 | </references><tags> | |
| 9610 | <tag>HTTP</tag> | |
| 9611 | <tag>PHP</tag> | |
| 9612 | <tag>Web</tag> | |
| 9613 | </tags> | |
| 9614 | <solution> | |
| 9615 | ||
| 9616 | <ContainerBlockElement> | |
| 9617 | <Paragraph> | |
| 9618 | <Paragraph> | |
| 9619 | In the config.inc.php file, either remove the values for | |
| 9620 | $cfg['Servers'][$i]['user'] and $cfg['Servers'][$i]['password'] , | |
| 9621 | or set a strong password in the $cfg['Servers'][$i]['password'] | |
| 9622 | field. Please visit the | |
| 9623 | ||
| 9624 | <URLLink LinkURL="http://wiki.phpmyadmin.net/pma/Auth_types" LinkTitle="http://wiki.phpmyadmin.net/pma/Auth_types" href="http://wiki.phpmyadmin.net/pma/Auth_types">phpMyAdmin wiki</URLLink> | |
| 9625 | for more information. | |
| 9626 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 9627 | </vulnerability> | |
| 9628 | ||
| 9629 | <vulnerability id="http-symantec-scan-engine-file-disclosure" title="Symantec Scan Engine File Disclosure Vulnerability" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="20060421T000000000" added="20060421T000000000" modified="20120927T000000000"> | |
| 9630 | <description> | |
| 9631 | ||
| 9632 | <ContainerBlockElement> | |
| 9633 | ||
| 9634 | <Paragraph> | |
| 9635 | There is a vulnerability in Symantec Scan Engine which allows | |
| 9636 | unauthenticated remote users to download any file located | |
| 9637 | under the Symantec Scan Engine installation directory. For | |
| 9638 | instance the configuration file, the scanning logs, as well as | |
| 9639 | the current virus definitions can all be accessed by any | |
| 9640 | remote user using regular or specially crafted HTTP requests. | |
| 9641 | </Paragraph> | |
| 9642 | </ContainerBlockElement></description> | |
| 9643 | <references> | |
| 9644 | <reference source="BID">17637</reference> | |
| 9645 | <reference source="CVE">CVE-2006-0232</reference> | |
| 9646 | <reference source="SECUNIA">19734</reference> | |
| 9647 | <reference source="URL">http://archives.neohapsis.com/archives/vulnwatch/2006-q2/0012.html</reference> | |
| 9648 | <reference source="URL">http://www.frsirt.com/english/advisories/2006/1464</reference> | |
| 9649 | <reference source="URL">http://www.rapid7.com/advisories/R7-0023.html</reference> | |
| 9650 | <reference source="URL">http://www.securityfocus.com/archive/1/archive/1/431728/100/0/threaded</reference> | |
| 9651 | <reference source="URL">http://www.securityfocus.com/archive/1/archive/1/431734/100/0/threaded</reference> | |
| 9652 | <reference source="URL">http://www.symantec.com/avcenter/security/Content/2006.04.21.html</reference> | |
| 9653 | <reference source="XF">sse-unauth-file-access(25974)</reference> | |
| 9654 | </references><tags> | |
| 9655 | <tag>HTTP</tag> | |
| 9656 | <tag>Symantec</tag> | |
| 9657 | <tag>Symantec Scan Engine</tag> | |
| 9658 | <tag>Virus</tag> | |
| 9659 | <tag>Web</tag> | |
| 9660 | </tags> | |
| 9661 | <solution> | |
| 9662 | ||
| 9663 | <ContainerBlockElement> | |
| 9664 | <Paragraph>Download and apply the upgrade from: | |
| 9665 | <URLLink LinkURL="http://www.symantec.com/Products/enterprise?c=prodinfo&refId=836" LinkTitle="http://www.symantec.com/Products/enterprise?c=prodinfo&refId=836"></URLLink></Paragraph></ContainerBlockElement></solution> | |
| 9666 | </vulnerability> | |
| 9667 | ||
| 9668 | <vulnerability id="http-thttpd-obsolete" title="THTTPD Obsolete Version" severity="9" pciSeverity="5" cvssScore="9.3" cvssVector="(AV:N/AC:M/Au:N/C:C/I:C/A:C)" published="20070404T000000000" added="20070404T000000000" modified="20130503T000000000"> | |
| 9669 | <description> | |
| 9670 | ||
| 9671 | <ContainerBlockElement> | |
| 9672 | ||
| 9673 | <Paragraph> | |
| 9674 | Versions of THTTPD earlier than | |
| 9675 | 2.0.3 are considered obsolete. | |
| 9676 | Later versions contain critical security, | |
| 9677 | performance, and compatibility enhancements. | |
| 9678 | It is recommended that you | |
| 9679 | upgrade your THTTPD | |
| 9680 | installation to the latest release. | |
| 9681 | </Paragraph> | |
| 9682 | </ContainerBlockElement></description> | |
| 9683 | <references> | |
| 9684 | </references><tags> | |
| 9685 | <tag>HTTP</tag> | |
| 9686 | <tag>Obsolete Software</tag> | |
| 9687 | <tag>Web</tag> | |
| 9688 | </tags> | |
| 9689 | <solution> | |
| 9690 | ||
| 9691 | <ContainerBlockElement> | |
| 9692 | <Paragraph>Download and apply the upgrade from: | |
| 9693 | <URLLink LinkURL="http://www.acme.com/software/thttpd/thttpd-2.25b.tar.gz" LinkTitle="http://www.acme.com/software/thttpd/thttpd-2.25b.tar.gz"></URLLink></Paragraph> | |
| 9694 | <Paragraph> | |
| 9695 | <Paragraph>Upgrade to THTTP v2.25b or later. See the | |
| 9696 | ||
| 9697 | <URLLink LinkURL="http://www.acme.com/software/thttpd/" LinkTitle="http://www.acme.com/software/thttpd/" href="http://www.acme.com/software/thttpd/">Acme THTTPD</URLLink> | |
| 9698 | website for more information. | |
| 9699 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 9700 | </vulnerability> | |
| 9701 | ||
| 9702 | <vulnerability id="http-tomcat-jkstatus-accessible" title="Unprotected Tomcat JK jkstatus management and diagnostics page" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="20080512T000000000" added="20080512T000000000" modified="20130620T000000000"> | |
| 9703 | <description> | |
| 9704 | ||
| 9705 | <ContainerBlockElement> | |
| 9706 | ||
| 9707 | <Paragraph>JK is a technology which allows Apache Tomcat (or related servers like JBoss) to | |
| 9708 | run behind another web server such as Apache, IIS, or iPlanet. JK provides a management | |
| 9709 | and diagnostics web application called jkstatus that is often activated under the web | |
| 9710 | application path /jkstatus.</Paragraph> | |
| 9711 | ||
| 9712 | <Paragraph>The jkstatus application, in addition to allowing remote users to start, stop, and | |
| 9713 | reconfigure the JK connector, allows remote clients to view detailed configuration | |
| 9714 | information.</Paragraph> | |
| 9715 | ||
| 9716 | <Paragraph>The jkstatus application is rarely needed in production environments and should | |
| 9717 | be disabled in most cases. If access to jkstatus is required by remote administrators, | |
| 9718 | the jkstatus URL should be configured to require authentication.</Paragraph> | |
| 9719 | </ContainerBlockElement></description> | |
| 9720 | <references> | |
| 9721 | <reference source="URL">http://tomcat.apache.org/connectors-doc-archive/jk2/index.html</reference> | |
| 9722 | </references><tags> | |
| 9723 | <tag>HTTP</tag> | |
| 9724 | <tag>OWASP_2010</tag> | |
| 9725 | <tag>OWASP_2013</tag> | |
| 9726 | <tag>Web</tag> | |
| 9727 | </tags> | |
| 9728 | <solution> | |
| 9729 | ||
| 9730 | <ContainerBlockElement> | |
| 9731 | <Paragraph> | |
| 9732 | <Paragraph>Follow your web server documentation to require a username and password | |
| 9733 | to access the /jkstatus page. Note that this protection is usually done | |
| 9734 | at the front-end web server level rather than within Tomcat itself.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 9735 | </vulnerability> | |
| 9736 | ||
| 9737 | <vulnerability id="http-trace-method-enabled" title="HTTP TRACE Method Enabled" severity="6" pciSeverity="3" cvssScore="5.8" cvssVector="(AV:N/AC:M/Au:N/C:P/I:P/A:N)" published="20041101T000000000" added="20041101T000000000" modified="20120731T000000000"> | |
| 9738 | <description> | |
| 9739 | ||
| 9740 | <ContainerBlockElement> | |
| 9741 | ||
| 9742 | <Paragraph>The HTTP TRACE method is normally used to return the full HTTP request back to the requesting client for proxy-debugging purposes. An attacker can create a webpage using XMLHTTP, ActiveX, or XMLDOM to cause a client to issue a TRACE request and capture the client's cookies. This effectively results in a Cross-Site Scripting attack.</Paragraph> | |
| 9743 | </ContainerBlockElement></description> | |
| 9744 | <references> | |
| 9745 | <reference source="APPLE">APPLE-SA-2009-11-09-1</reference> | |
| 9746 | <reference source="BID">15222</reference> | |
| 9747 | <reference source="BID">19915</reference> | |
| 9748 | <reference source="BID">24456</reference> | |
| 9749 | <reference source="BID">36956</reference> | |
| 9750 | <reference source="BID">9506</reference> | |
| 9751 | <reference source="CERT-VN">867593</reference> | |
| 9752 | <reference source="CVE">CVE-2004-2320</reference> | |
| 9753 | <reference source="CVE">CVE-2004-2763</reference> | |
| 9754 | <reference source="CVE">CVE-2005-3398</reference> | |
| 9755 | <reference source="CVE">CVE-2006-4683</reference> | |
| 9756 | <reference source="CVE">CVE-2007-3008</reference> | |
| 9757 | <reference source="CVE">CVE-2008-7253</reference> | |
| 9758 | <reference source="CVE">CVE-2009-2823</reference> | |
| 9759 | <reference source="CVE">CVE-2010-0386</reference> | |
| 9760 | <reference source="OSVDB">35511</reference> | |
| 9761 | <reference source="OSVDB">3726</reference> | |
| 9762 | <reference source="OVAL">OVAL1445</reference> | |
| 9763 | <reference source="SECUNIA">10726</reference> | |
| 9764 | <reference source="SECUNIA">17334</reference> | |
| 9765 | <reference source="SECUNIA">21802</reference> | |
| 9766 | <reference source="SECUNIA">25636</reference> | |
| 9767 | <reference source="URL">http://www.apacheweek.com/issues/03-01-24#news</reference> | |
| 9768 | <reference source="URL">http://www.kb.cert.org/vuls/id/867593</reference> | |
| 9769 | <reference source="XF">mbedthis-httptrace-xss(34854)</reference> | |
| 9770 | <reference source="XF">weblogic-trace-xss(14959)</reference> | |
| 9771 | </references><tags> | |
| 9772 | <tag>HTTP</tag> | |
| 9773 | <tag>Web</tag> | |
| 9774 | <tag>XSS</tag> | |
| 9775 | </tags> | |
| 9776 | <solution> | |
| 9777 | ||
| 9778 | <ContainerBlockElement> | |
| 9779 | <UnorderedList> | |
| 9780 | <ListItem> | |
| 9781 | <Paragraph>Apache HTTPD</Paragraph> | |
| 9782 | <Paragraph> | |
| 9783 | <Paragraph>Newer versions of Apache (1.3.34 and 2.0.55 and later) provide a | |
| 9784 | configuration directive called TraceEnable. To deny TRACE requests, | |
| 9785 | add the following line to the server configuration:</Paragraph> | |
| 9786 | <Paragraph preformat="true">TraceEnable off</Paragraph> | |
| 9787 | <Paragraph>For older versions of the Apache webserver, use the mod_rewrite module to | |
| 9788 | deny the TRACE requests:</Paragraph> | |
| 9789 | <Paragraph preformat="true">RewriteEngine On | |
| 9790 | RewriteCond %{REQUEST_METHOD} ^TRACE | |
| 9791 | RewriteRule .* - [F]</Paragraph></Paragraph></ListItem> | |
| 9792 | <ListItem> | |
| 9793 | <Paragraph>IIS, PWS, Microsoft-IIS, Internet Information Services, Internet Information Services, Microsoft-PWS</Paragraph> | |
| 9794 | <Paragraph> | |
| 9795 | <Paragraph>For Microsoft Internet Information Services (IIS), you may | |
| 9796 | use the URLScan tool, freely available at | |
| 9797 | ||
| 9798 | <URLLink LinkURL="http://www.microsoft.com/technet/security/tools/urlscan.mspx" LinkTitle="http://www.microsoft.com/technet/security/tools/urlscan.mspx" href="http://www.microsoft.com/technet/security/tools/urlscan.mspx">http://www.microsoft.com/technet/security/tools/urlscan.mspx</URLLink></Paragraph></Paragraph></ListItem> | |
| 9799 | <ListItem> | |
| 9800 | <Paragraph>Java System Web Server, SunONE WebServer, Sun-ONE-Web-Server, iPlanet</Paragraph> | |
| 9801 | <Paragraph> | |
| 9802 | <UnorderedList> | |
| 9803 | <ListItem> | |
| 9804 | <Paragraph>For Sun ONE/iPlanet Web Server v6.0 SP2 and later, add the | |
| 9805 | following configuration to the top of the default object in the | |
| 9806 | 'obj.conf' file:</Paragraph> | |
| 9807 | <Paragraph preformat="true"><Client method="TRACE"> | |
| 9808 | AuthTrans fn="set-variable" | |
| 9809 | remove-headers="transfer-encoding" | |
| 9810 | set-headers="content-length: -1" | |
| 9811 | error="501" | |
| 9812 | </Client></Paragraph> | |
| 9813 | <Paragraph>You must then restart the server for the changes to take effect.</Paragraph></ListItem> | |
| 9814 | <ListItem> | |
| 9815 | <Paragraph>For Sun ONE/iPlanet Web Server prior to v6.0 SP2, follow the | |
| 9816 | instructions provided the 'Relief/Workaround' section of | |
| 9817 | Sun's official advisory: | |
| 9818 | ||
| 9819 | <URLLink LinkURL="http://sunsolve.sun.com/pub-cgi/retrieve.pl?doc=fsalert%2F50603" LinkTitle="http://sunsolve.sun.com/pub-cgi/retrieve.pl?doc=fsalert%2F50603" href="http://sunsolve.sun.com/pub-cgi/retrieve.pl?doc=fsalert%2F50603">http://sunsolve.sun.com/pub-cgi/retrieve.pl?doc=fsalert%2F50603</URLLink></Paragraph></ListItem></UnorderedList></Paragraph></ListItem> | |
| 9820 | <ListItem> | |
| 9821 | <Paragraph>Lotus Domino</Paragraph> | |
| 9822 | <Paragraph> | |
| 9823 | <Paragraph>Follow | |
| 9824 | <URLLink LinkURL="http://www-1.ibm.com/support/docview.wss?&uid=swg21201202" LinkTitle="http://www-1.ibm.com/support/docview.wss?&uid=swg21201202" href="http://www-1.ibm.com/support/docview.wss?&uid=swg21201202">IBM's instructions</URLLink> | |
| 9825 | for disabling HTTP methods on the Domino server by adding the following line to the | |
| 9826 | server's NOTES.INI file:</Paragraph> | |
| 9827 | <Paragraph preformat="true">HTTPDisableMethods=TRACE</Paragraph> | |
| 9828 | <Paragraph>After saving NOTES.INI, restart the Notes web server by issuing the console | |
| 9829 | command "tell http restart".</Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 9830 | </vulnerability> | |
| 9831 | ||
| 9832 | <vulnerability id="http-track-method-enabled" title="HTTP TRACK Method Enabled" severity="6" pciSeverity="3" cvssScore="5.8" cvssVector="(AV:N/AC:M/Au:N/C:P/I:P/A:N)" published="20031228T000000000" added="20050405T000000000" modified="20120731T000000000"> | |
| 9833 | <description> | |
| 9834 | ||
| 9835 | <ContainerBlockElement> | |
| 9836 | ||
| 9837 | <Paragraph>The HTTP TRACK method is normally used to return the full HTTP request back to the requesting client for proxy-debugging purposes. An attacker can create a webpage using XMLHTTP, ActiveX, or XMLDOM to cause a client to issue a TRACK request and capture the client's cookies. This effectively results in a Cross-Site Scripting attack.</Paragraph> | |
| 9838 | </ContainerBlockElement></description> | |
| 9839 | <references> | |
| 9840 | <reference source="CERT-VN">288308</reference> | |
| 9841 | <reference source="CVE">CVE-2003-1567</reference> | |
| 9842 | <reference source="OSVDB">5648</reference> | |
| 9843 | <reference source="URL">http://www.aqtronix.com/Advisories/AQ-2003-02.txt</reference> | |
| 9844 | </references><tags> | |
| 9845 | <tag>HTTP</tag> | |
| 9846 | <tag>Web</tag> | |
| 9847 | <tag>XSS</tag> | |
| 9848 | </tags> | |
| 9849 | <solution> | |
| 9850 | ||
| 9851 | <ContainerBlockElement> | |
| 9852 | <Paragraph>IIS, PWS, Microsoft-IIS, Internet Information Services, Internet Information Services, Microsoft-PWS</Paragraph> | |
| 9853 | <Paragraph> | |
| 9854 | <Paragraph>For Microsoft Internet Information Services (IIS), you may | |
| 9855 | use the URLScan tool, freely available at | |
| 9856 | ||
| 9857 | <URLLink LinkURL="http://www.microsoft.com/technet/security/tools/urlscan.mspx" LinkTitle="http://www.microsoft.com/technet/security/tools/urlscan.mspx" href="http://www.microsoft.com/technet/security/tools/urlscan.mspx">http://www.microsoft.com/technet/security/tools/urlscan.mspx</URLLink></Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 9858 | </vulnerability> | |
| 9859 | ||
| 9860 | <vulnerability id="http-unrestricted-webdav-put-delete" title="Unrestricted WebDAV PUT/DELETE Access" severity="9" pciSeverity="5" cvssScore="9.4" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:N)" published="20050120T000000000" added="20050120T000000000" modified="20130620T000000000"> | |
| 9861 | <description> | |
| 9862 | ||
| 9863 | <ContainerBlockElement> | |
| 9864 | ||
| 9865 | <Paragraph>Unrestricted WebDAV requests expose a server to defacements and denial of service attacks. If the PUT method can be used by any unauthenticated remote user, arbitrary web pages can be inserted into the web root, or the disk can be filled with meaningless data; if the DELETE method is unprotected, then any file in a DAV-enabled directory can be removed at will.</Paragraph> | |
| 9866 | </ContainerBlockElement></description> | |
| 9867 | <references> | |
| 9868 | </references><tags> | |
| 9869 | <tag>Denial of Service</tag> | |
| 9870 | <tag>HTTP</tag> | |
| 9871 | <tag>OWASP_2010</tag> | |
| 9872 | <tag>OWASP_2013</tag> | |
| 9873 | <tag>Web</tag> | |
| 9874 | </tags> | |
| 9875 | <solution> | |
| 9876 | ||
| 9877 | <ContainerBlockElement> | |
| 9878 | <Paragraph> | |
| 9879 | <Paragraph>For users of the Apache server, access can be restricted to the WebDAVdirectory like so:</Paragraph> | |
| 9880 | <Paragraph preformat="true"> | |
| 9881 | <Location /> | |
| 9882 | Dav On | |
| 9883 | AuthType Basic | |
| 9884 | AuthName DAV | |
| 9885 | AuthUserFile .htpasswd | |
| 9886 | <LimitExcept GET> | |
| 9887 | require user someuser | |
| 9888 | </LimitExcept> | |
| 9889 | </Location> | |
| 9890 | </Paragraph> | |
| 9891 | <Paragraph>Users of Microsoft IIS should use an authentication method other than Anonymous authentication, and should take | |
| 9892 | advantage of other security features of their version of IIS. For more information, refer to the following links | |
| 9893 | from Microsoft: | |
| 9894 | ||
| 9895 | <UnorderedList> | |
| 9896 | <ListItem>http://support.microsoft.com/kb/323470</ListItem> | |
| 9897 | <ListItem>http://technet.microsoft.com/en-us/library/cc778809%28v=ws.10%29.aspx</ListItem> | |
| 9898 | <ListItem>http://www.iis.net/configreference/system.webserver/security/requestfiltering</ListItem></UnorderedList></Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 9899 | </vulnerability> | |
| 9900 | ||
| 9901 | <vulnerability id="HTTP-UPNP-0001" title="Windows XP UPnP NOTIFY Method LOCATION Header Buffer Overflow" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20011220T000000000" added="20041101T000000000" modified="20120731T000000000"> | |
| 9902 | <description> | |
| 9903 | ||
| 9904 | <ContainerBlockElement> | |
| 9905 | ||
| 9906 | <Paragraph>Windows XP and some versions of Windows ME and 98 support UPnP | |
| 9907 | (Universal Plug and Play). UPnP follows the HTTP syntax, defining | |
| 9908 | some new request methods and headers. One of these request types is | |
| 9909 | NOTIFY. When a NOTIFY packet is received, the UPnP service can locate | |
| 9910 | detailed information about the advertising UPnP service by connecting | |
| 9911 | to the URL specified in the LOCATION header. Windows does not | |
| 9912 | validate this URL before connecting to it, allowing a buffer overflow | |
| 9913 | to occur.</Paragraph> | |
| 9914 | </ContainerBlockElement></description> | |
| 9915 | <references> | |
| 9916 | <reference source="BID">3723</reference> | |
| 9917 | <reference source="CERT">CA-2001-37</reference> | |
| 9918 | <reference source="CERT-VN">951555</reference> | |
| 9919 | <reference source="CIAC">M-030</reference> | |
| 9920 | <reference source="CVE">CVE-2001-0876</reference> | |
| 9921 | <reference source="MS">MS01-059</reference> | |
| 9922 | <reference source="URL">http://marc.theaimsgroup.com/?l=bugtraq&m=100887440810532&w=2</reference> | |
| 9923 | <reference source="XF">win-upnp-notify-bo(7721)</reference> | |
| 9924 | </references><tags> | |
| 9925 | <tag>HTTP</tag> | |
| 9926 | <tag>Web</tag> | |
| 9927 | </tags> | |
| 9928 | <solution> | |
| 9929 | ||
| 9930 | <ContainerBlockElement> | |
| 9931 | <Paragraph>Download and apply the patch from: | |
| 9932 | <URLLink LinkURL="http://www.microsoft.com/technet/security/bulletin/MS01-059.mspx" LinkTitle="http://www.microsoft.com/technet/security/bulletin/MS01-059.mspx"></URLLink></Paragraph> | |
| 9933 | <Paragraph> | |
| 9934 | <Paragraph>Microsoft has provided the following patches for this problem. | |
| 9935 | For more information, see the | |
| 9936 | ||
| 9937 | ||
| 9938 | ||
| 9939 | <URLLink LinkURL="http://www.microsoft.com/technet/security/bulletin/MS01-059.mspx" LinkTitle="http://www.microsoft.com/technet/security/bulletin/MS01-059.mspx" href="http://www.microsoft.com/technet/security/bulletin/MS01-059.mspx">Microsoft advisory</URLLink>.</Paragraph> | |
| 9940 | <UnorderedList> | |
| 9941 | <ListItem> | |
| 9942 | <URLLink LinkURL="http://www.microsoft.com/Downloads/details.aspx?displaylang=en&FamilyID=4F1C2546-9CF8-413D-866F-DD1E5A2D7454" LinkTitle="http://www.microsoft.com/Downloads/details.aspx?displaylang=en&FamilyID=4F1C2546-9CF8-413D-866F-DD1E5A2D7454" href="http://www.microsoft.com/Downloads/details.aspx?displaylang=en&FamilyID=4F1C2546-9CF8-413D-866F-DD1E5A2D7454">Microsoft Windows 98/98SE</URLLink></ListItem> | |
| 9943 | <ListItem> | |
| 9944 | <URLLink LinkURL="http://download.microsoft.com/download/winme/Update/22940/WinMe/EN-US/314757USAM.EXE" LinkTitle="http://download.microsoft.com/download/winme/Update/22940/WinMe/EN-US/314757USAM.EXE" href="http://download.microsoft.com/download/winme/Update/22940/WinMe/EN-US/314757USAM.EXE">Microsoft Windows ME</URLLink></ListItem> | |
| 9945 | <ListItem> | |
| 9946 | <URLLink LinkURL="http://www.microsoft.com/Downloads/details.aspx?displaylang=en&FamilyID=D17CBEB5-7478-4147-B4BA-E6CF686A352B" LinkTitle="http://www.microsoft.com/Downloads/details.aspx?displaylang=en&FamilyID=D17CBEB5-7478-4147-B4BA-E6CF686A352B" href="http://www.microsoft.com/Downloads/details.aspx?displaylang=en&FamilyID=D17CBEB5-7478-4147-B4BA-E6CF686A352B">Microsoft Windows XP</URLLink></ListItem></UnorderedList></Paragraph></ContainerBlockElement></solution> | |
| 9947 | </vulnerability> | |
| 9948 | ||
| 9949 | <vulnerability id="HTTP-UPNP-0002" title="Windows XP UPnP NOTIFY LOCATION Denial of Service" severity="5" pciSeverity="2" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:N/A:P)" published="20011220T000000000" added="20041101T000000000" modified="20120731T000000000"> | |
| 9950 | <description> | |
| 9951 | ||
| 9952 | <ContainerBlockElement> | |
| 9953 | Windows XP and some versions of Windows ME and 98 support UPnP (Universal Plug and Play). UPnP follows the HTTP syntax, defining some new request methods and headers. One of these request types is NOTIFY. When a NOTIFY packet is received, the UPnP service can locate detailed information about the advertising UPnP service by connecting to the URL specified in the LOCATION header. Windows does not validate this URL, nor the content received from it. By sending invalid data the Windows UPnP service will consume all resources while processing the data. | |
| 9954 | </ContainerBlockElement></description> | |
| 9955 | <references> | |
| 9956 | <reference source="BID">3724</reference> | |
| 9957 | <reference source="CERT">CA-2001-37</reference> | |
| 9958 | <reference source="CERT-VN">411059</reference> | |
| 9959 | <reference source="CIAC">M-030</reference> | |
| 9960 | <reference source="CVE">CVE-2001-0877</reference> | |
| 9961 | <reference source="MS">MS01-059</reference> | |
| 9962 | <reference source="URL">http://marc.theaimsgroup.com/?l=bugtraq</reference> | |
| 9963 | <reference source="XF">win-upnp-udp-dos(7722)</reference> | |
| 9964 | </references><tags> | |
| 9965 | <tag>Denial of Service</tag> | |
| 9966 | <tag>HTTP</tag> | |
| 9967 | <tag>Web</tag> | |
| 9968 | </tags> | |
| 9969 | <solution> | |
| 9970 | ||
| 9971 | <ContainerBlockElement> | |
| 9972 | <Paragraph>Download and apply the patch from: | |
| 9973 | <URLLink LinkURL="http://www.microsoft.com/technet/security/bulletin/MS01-059.mspx" LinkTitle="http://www.microsoft.com/technet/security/bulletin/MS01-059.mspx"></URLLink></Paragraph> | |
| 9974 | <Paragraph> | |
| 9975 | <Paragraph>Microsoft has provided the following patches for this problem. | |
| 9976 | For more information, see the | |
| 9977 | ||
| 9978 | ||
| 9979 | ||
| 9980 | <URLLink LinkURL="http://www.microsoft.com/technet/security/bulletin/MS01-059.mspx" LinkTitle="http://www.microsoft.com/technet/security/bulletin/MS01-059.mspx" href="http://www.microsoft.com/technet/security/bulletin/MS01-059.mspx">Microsoft advisory</URLLink>.</Paragraph> | |
| 9981 | <UnorderedList> | |
| 9982 | <ListItem> | |
| 9983 | <URLLink LinkURL="http://www.microsoft.com/Downloads/details.aspx?displaylang=en&FamilyID=4F1C2546-9CF8-413D-866F-DD1E5A2D7454" LinkTitle="http://www.microsoft.com/Downloads/details.aspx?displaylang=en&FamilyID=4F1C2546-9CF8-413D-866F-DD1E5A2D7454" href="http://www.microsoft.com/Downloads/details.aspx?displaylang=en&FamilyID=4F1C2546-9CF8-413D-866F-DD1E5A2D7454">Microsoft Windows 98/98SE</URLLink></ListItem> | |
| 9984 | <ListItem> | |
| 9985 | <URLLink LinkURL="http://download.microsoft.com/download/winme/Update/22940/WinMe/EN-US/314757USAM.EXE" LinkTitle="http://download.microsoft.com/download/winme/Update/22940/WinMe/EN-US/314757USAM.EXE" href="http://download.microsoft.com/download/winme/Update/22940/WinMe/EN-US/314757USAM.EXE">Microsoft Windows ME</URLLink></ListItem> | |
| 9986 | <ListItem> | |
| 9987 | <URLLink LinkURL="http://www.microsoft.com/Downloads/details.aspx?displaylang=en&FamilyID=D17CBEB5-7478-4147-B4BA-E6CF686A352B" LinkTitle="http://www.microsoft.com/Downloads/details.aspx?displaylang=en&FamilyID=D17CBEB5-7478-4147-B4BA-E6CF686A352B" href="http://www.microsoft.com/Downloads/details.aspx?displaylang=en&FamilyID=D17CBEB5-7478-4147-B4BA-E6CF686A352B">Microsoft Windows XP</URLLink></ListItem></UnorderedList></Paragraph></ContainerBlockElement></solution> | |
| 9988 | </vulnerability> | |
| 9989 | ||
| 9990 | <vulnerability id="http-vignette-app-portal-diag" title="Vignette Application Portal Unauthenticated Diagnostics" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:P/I:N/A:N)" published="20040928T000000000" added="20050120T000000000" modified="20120731T000000000"> | |
| 9991 | <description> | |
| 9992 | ||
| 9993 | <ContainerBlockElement> | |
| 9994 | ||
| 9995 | <Paragraph>The Vignette Application Portal allows anyone to retrieve the Vignette diagnostics script. This page contains sensitive information, including operating system version, database connection parameters, usernames, and possibly even authentication information. Besides information gathering, attackers could abuse the diagnostic script to cause CPU and network usage to spike.</Paragraph> | |
| 9996 | ||
| 9997 | ||
| 9998 | ||
| 9999 | <Paragraph>See Vignette knowledge base article KB 6947 for more information. Vignette support articles are available only to Vignette customers.</Paragraph> | |
| 10000 | </ContainerBlockElement></description> | |
| 10001 | <references> | |
| 10002 | <reference source="BID">11267</reference> | |
| 10003 | <reference source="CVE">CVE-2004-0917</reference> | |
| 10004 | <reference source="URL">http://www.atstake.com/research/advisories/2004/a092804-1.txt</reference> | |
| 10005 | <reference source="URL">http://xforce.iss.net/xforce/xfdb/17530</reference> | |
| 10006 | <reference source="XF">vignette-diagnostic-obtain-info(17530)</reference> | |
| 10007 | </references><tags> | |
| 10008 | <tag>HTTP</tag> | |
| 10009 | <tag>Web</tag> | |
| 10010 | </tags> | |
| 10011 | <solution> | |
| 10012 | ||
| 10013 | <ContainerBlockElement> | |
| 10014 | <Paragraph> | |
| 10015 | <Paragraph>Use the web server's access controls to deny anonymous access to the /portal/diag/ web directory and all pages and subdirectories under it. Review your log files for requests targeting this directory, which would indicate possible probing by attackers.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10016 | </vulnerability> | |
| 10017 | ||
| 10018 | <vulnerability id="ntp-clock-variables-disclosure" title="NTP clock variables information disclosure" severity="1" pciSeverity="1" cvssScore="0.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:N/A:N)" published="20090506T000000000" added="20110401T000000000" modified="20120712T000000000"> | |
| 10019 | <description> | |
| 10020 | ||
| 10021 | <ContainerBlockElement> | |
| 10022 | ||
| 10023 | <Paragraph> | |
| 10024 | This sytem allows the internal NTP variables to be queried. These | |
| 10025 | variables contain potentially sensitive information, such as the NTP | |
| 10026 | software version, operating system version, peers, and more. | |
| 10027 | </Paragraph> | |
| 10028 | </ContainerBlockElement></description> | |
| 10029 | <references> | |
| 10030 | </references><tags> | |
| 10031 | <tag>Information Gathering</tag> | |
| 10032 | <tag>Network</tag> | |
| 10033 | </tags> | |
| 10034 | <solution> | |
| 10035 | ||
| 10036 | <ContainerBlockElement> | |
| 10037 | <UnorderedList> | |
| 10038 | <ListItem> | |
| 10039 | <Paragraph> | |
| 10040 | <Paragraph> | |
| 10041 | Apply a restrict option to all hosts that are not authorized to perform | |
| 10042 | NTP readvar queries. For example, to deny readvar requests from all clients, | |
| 10043 | put the following in the NTP configuration file, typically /etc/ntp.conf, and | |
| 10044 | restart the NTP service: | |
| 10045 | </Paragraph> | |
| 10046 | <Paragraph preformat="true"> | |
| 10047 | restrict default mask 0.0.0.0 noquery | |
| 10048 | </Paragraph></Paragraph></ListItem> | |
| 10049 | <ListItem> | |
| 10050 | <Paragraph>Cisco</Paragraph> | |
| 10051 | <Paragraph> | |
| 10052 | <Paragraph> | |
| 10053 | Apply an ACL that restricts NTP readvar queries from unauthorized clients, | |
| 10054 | as described in the | |
| 10055 | <URLLink LinkURL="http://www.cisco.com/en/US/docs/ios/12_1/configfun/configuration/guide/fcd303.html#wp1001299" LinkTitle="http://www.cisco.com/en/US/docs/ios/12_1/configfun/configuration/guide/fcd303.html#wp1001299" href="http://www.cisco.com/en/US/docs/ios/12_1/configfun/configuration/guide/fcd303.html#wp1001299"> | |
| 10056 | 'Configuring NTP Access Restrictions' section of the Cisco IOS documentation</URLLink>. | |
| 10057 | </Paragraph> | |
| 10058 | <Paragraph> | |
| 10059 | Alternatively, if NTP is not required, disable it entirely by running the | |
| 10060 | following command: | |
| 10061 | </Paragraph> | |
| 10062 | <Paragraph preformat="true"> | |
| 10063 | ntp disable | |
| 10064 | </Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 10065 | </vulnerability> | |
| 10066 | ||
| 10067 | <vulnerability id="ntpd-crypto-recv-buffer-overflow" title="NTP 'ntpd' Autokey Stack Buffer Overflow Vulnerability" severity="7" pciSeverity="4" cvssScore="6.8" cvssVector="(AV:N/AC:M/Au:N/C:P/I:P/A:P)" published="20090506T000000000" added="20090716T000000000" modified="20120712T000000000"> | |
| 10068 | <description> | |
| 10069 | ||
| 10070 | <ContainerBlockElement> | |
| 10071 | ||
| 10072 | <Paragraph> | |
| 10073 | There exists a stack-based buffer overflow in the crypto_recv function | |
| 10074 | found in ntpd before 4.2.4p7 and 4.2.5 before 4.2.5p74. When OpenSSL | |
| 10075 | and autokey are enabled, the flaw allows remote attackers to execute | |
| 10076 | arbitrary code via a specially crafted packet containing an extension | |
| 10077 | field. | |
| 10078 | </Paragraph> | |
| 10079 | </ContainerBlockElement></description> | |
| 10080 | <references> | |
| 10081 | <reference source="BID">35017</reference> | |
| 10082 | <reference source="CERT-VN">853097</reference> | |
| 10083 | <reference source="CVE">CVE-2009-1252</reference> | |
| 10084 | <reference source="DEBIAN">DSA-1801</reference> | |
| 10085 | <reference source="NETBSD">NetBSD-SA2009-006</reference> | |
| 10086 | <reference source="OVAL">OVAL11231</reference> | |
| 10087 | <reference source="OVAL">OVAL6307</reference> | |
| 10088 | <reference source="REDHAT">RHSA-2009:1039</reference> | |
| 10089 | <reference source="REDHAT">RHSA-2009:1040</reference> | |
| 10090 | <reference source="SECUNIA">35137</reference> | |
| 10091 | <reference source="SECUNIA">35138</reference> | |
| 10092 | <reference source="SECUNIA">35166</reference> | |
| 10093 | <reference source="SECUNIA">35169</reference> | |
| 10094 | <reference source="SECUNIA">35243</reference> | |
| 10095 | <reference source="SECUNIA">35253</reference> | |
| 10096 | <reference source="SECUNIA">35308</reference> | |
| 10097 | <reference source="SECUNIA">35336</reference> | |
| 10098 | <reference source="SECUNIA">35388</reference> | |
| 10099 | <reference source="SECUNIA">35416</reference> | |
| 10100 | <reference source="SECUNIA">35630</reference> | |
| 10101 | <reference source="SECUNIA">37470</reference> | |
| 10102 | <reference source="SECUNIA">37471</reference> | |
| 10103 | <reference source="URL">http://bugs.ntp.org/1151</reference> | |
| 10104 | <reference source="URL">http://www.kb.cert.org/vuls/id/853097</reference> | |
| 10105 | <reference source="URL">https://lists.ntp.org/pipermail/announce/2009-May/000062.html</reference> | |
| 10106 | </references><tags> | |
| 10107 | <tag>Network</tag> | |
| 10108 | <tag>Remote Execution</tag> | |
| 10109 | </tags> | |
| 10110 | <solution> | |
| 10111 | ||
| 10112 | <ContainerBlockElement> | |
| 10113 | <UnorderedList> | |
| 10114 | <ListItem> | |
| 10115 | <Paragraph>Download and apply the upgrade from: | |
| 10116 | <URLLink LinkURL="http://www.eecis.udel.edu/~ntp/ntp_spool/ntp4/ntp-4.2/ntp-4.2.4p7.tar.gz" LinkTitle="http://www.eecis.udel.edu/~ntp/ntp_spool/ntp4/ntp-4.2/ntp-4.2.4p7.tar.gz"></URLLink></Paragraph></ListItem> | |
| 10117 | <ListItem> | |
| 10118 | <Paragraph>Download and apply the upgrade from: | |
| 10119 | <URLLink LinkURL="http://www.eecis.udel.edu/~ntp/ntp_spool/ntp4/ntp-dev/ntp-dev-4.2.5p74.tar.gz" LinkTitle="http://www.eecis.udel.edu/~ntp/ntp_spool/ntp4/ntp-dev/ntp-dev-4.2.5p74.tar.gz"></URLLink></Paragraph></ListItem> | |
| 10120 | <ListItem> | |
| 10121 | <Paragraph> | |
| 10122 | <Paragraph> | |
| 10123 | This vulnerability can be mitigated by removing the | |
| 10124 | `crypto pw password` line from the ntp.conf file. | |
| 10125 | </Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 10126 | </vulnerability> | |
| 10127 | ||
| 10128 | <vulnerability id="openssl-debian-weak-keys" title="Debian's OpenSSL Library Predictable Random Number Generator" severity="8" pciSeverity="5" cvssScore="7.8" cvssVector="(AV:N/AC:L/Au:N/C:C/I:N/A:N)" published="20080513T000000000" added="20080605T000000000" modified="20121003T000000000"> | |
| 10129 | <description> | |
| 10130 | ||
| 10131 | <ContainerBlockElement> | |
| 10132 | ||
| 10133 | <Paragraph>A weakness has been discovered in the random number generator used by OpenSSL on Debian and Ubuntu systems. As a result of this weakness, certain encryption keys are much more common than they should be, such that an attacker could guess the key through a brute-force attack given minimal knowledge of the system. This particularly affects the use of encryption keys in OpenSSH, OpenVPN and SSL certificates. This vulnerability only affects operating systems which are based on Debian. However, other systems can be indirectly affected if weak keys are imported into them.</Paragraph> | |
| 10134 | </ContainerBlockElement></description> | |
| 10135 | <references> | |
| 10136 | <reference source="BID">29179</reference> | |
| 10137 | <reference source="CERT">TA08-137A</reference> | |
| 10138 | <reference source="CERT-VN">925211</reference> | |
| 10139 | <reference source="CVE">CVE-2008-0166</reference> | |
| 10140 | <reference source="DEBIAN">DSA-1571</reference> | |
| 10141 | <reference source="DEBIAN">DSA-1576</reference> | |
| 10142 | <reference source="SECUNIA">30136</reference> | |
| 10143 | <reference source="SECUNIA">30220</reference> | |
| 10144 | <reference source="SECUNIA">30221</reference> | |
| 10145 | <reference source="SECUNIA">30231</reference> | |
| 10146 | <reference source="SECUNIA">30239</reference> | |
| 10147 | <reference source="SECUNIA">30249</reference> | |
| 10148 | <reference source="URL">http://metasploit.com/users/hdm/tools/debian-openssl/</reference> | |
| 10149 | <reference source="URL">http://wiki.debian.org/SSLkeys</reference> | |
| 10150 | <reference source="URL">http://www.debian.org/security/2008/dsa-1571</reference> | |
| 10151 | <reference source="URL">http://www.debian.org/security/2008/dsa-1576</reference> | |
| 10152 | <reference source="URL">http://www.debian.org/security/key-rollover/</reference> | |
| 10153 | <reference source="URL">http://www.ubuntu.com/usn/usn-612-1</reference> | |
| 10154 | <reference source="URL">http://www.ubuntu.com/usn/usn-612-2</reference> | |
| 10155 | <reference source="URL">http://www.ubuntu.com/usn/usn-612-3</reference> | |
| 10156 | <reference source="URL">http://www.ubuntu.com/usn/usn-612-4</reference> | |
| 10157 | <reference source="URL">http://www.ubuntu.com/usn/usn-612-5</reference> | |
| 10158 | <reference source="URL">http://www.ubuntu.com/usn/usn-612-6</reference> | |
| 10159 | <reference source="URL">http://www.ubuntu.com/usn/usn-612-7</reference> | |
| 10160 | <reference source="URL">http://www.ubuntu.com/usn/usn-612-8</reference> | |
| 10161 | <reference source="XF">openssl-rng-weak-security(42375)</reference> | |
| 10162 | </references><tags> | |
| 10163 | <tag>OpenSSL</tag> | |
| 10164 | <tag>SSH</tag> | |
| 10165 | <tag>VPN</tag> | |
| 10166 | </tags> | |
| 10167 | <solution> | |
| 10168 | ||
| 10169 | <ContainerBlockElement> | |
| 10170 | <Paragraph> | |
| 10171 | <Paragraph>Upgrade the OpenSSL package to the version recomended below to fix the random number generator and stop generating weak keys</Paragraph> | |
| 10172 | <UnorderedList> | |
| 10173 | <ListItem>For Debian 4.0 etch, upgrade to 0.9.8c-4etch3 </ListItem> | |
| 10174 | <ListItem>For Debian testing (lenny), upgrade to 0.9.8g-9</ListItem> | |
| 10175 | <ListItem>For Debian unstable (sid), upgrade to 0.9.8g-9</ListItem> | |
| 10176 | <ListItem>For Ubuntu 7.0.4 (feisty), upgrade to 0.9.8c-4ubuntu0.3 </ListItem> | |
| 10177 | <ListItem>For Ubuntu 7.10 (gusty), upgrade to 0.9.8e-5ubuntu3.2</ListItem> | |
| 10178 | <ListItem>For Ubuntu 8.0.4 (hardy), upgrade to 0.9.8g-4ubuntu3.1 </ListItem></UnorderedList> | |
| 10179 | <Paragraph>Then regenerate all cryptographic key material which has been created by vulnerable OpenSSL versions on Debian-based systems. Affected keys include SSH server and user keys, OpenVPN keys, DNSSEC keys, keys associated to X.509 certificates, etc.</Paragraph> | |
| 10180 | <Paragraph>Optionally, Debian and Ubuntu have released updated OpenSSH, OpenSSL and OpenVPN packages to automatically blacklist known weak keys. It is recomended to install these upgrades on all systems.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10181 | </vulnerability> | |
| 10182 | ||
| 10183 | <vulnerability id="spider-adobe-flash-permissive-crossdomain-xml" title="Adobe Flash permissive crossdomain.xml policy" severity="6" pciSeverity="3" cvssScore="5.8" cvssVector="(AV:N/AC:M/Au:N/C:P/I:P/A:N)" published="20070312T000000000" added="20101001T000000000" modified="20130620T000000000"> | |
| 10184 | <description> | |
| 10185 | ||
| 10186 | <ContainerBlockElement> | |
| 10187 | ||
| 10188 | <Paragraph>Permissive crossdomain.xml policy files allow external Adobe Flash (SWF) scripts to interact with your website.</Paragraph> | |
| 10189 | ||
| 10190 | <Paragraph>Depending on how authorization is restricted on your website, this could inadvertently expose data to other domains or allow invocation of functionality across domains. The cross-domain policy file should permit only domains that can be trusted to make requests that include the user's domain-specific cookies.</Paragraph> | |
| 10191 | ||
| 10192 | <Paragraph>See | |
| 10193 | <URLLink LinkURL="http://www.adobe.com/devnet/flashplayer/articles/cross_domain_policy.html" LinkTitle="http://www.adobe.com/devnet/flashplayer/articles/cross_domain_policy.html" href="http://www.adobe.com/devnet/flashplayer/articles/cross_domain_policy.html">Cross-domain policy file usage recommendations for Flash Player</URLLink></Paragraph> | |
| 10194 | </ContainerBlockElement></description> | |
| 10195 | <references> | |
| 10196 | <reference source="URL">http://www.adobe.com/devnet/flashplayer/articles/cross_domain_policy.html</reference> | |
| 10197 | </references><tags> | |
| 10198 | <tag>Adobe</tag> | |
| 10199 | <tag>Adobe Flash</tag> | |
| 10200 | <tag>OWASP_2010</tag> | |
| 10201 | <tag>OWASP_2013</tag> | |
| 10202 | <tag>Policy Violation</tag> | |
| 10203 | <tag>Web</tag> | |
| 10204 | <tag>Web Spider</tag> | |
| 10205 | </tags> | |
| 10206 | <solution> | |
| 10207 | ||
| 10208 | <ContainerBlockElement> | |
| 10209 | <Paragraph> | |
| 10210 | <Paragraph>Edit the crossdomain.xml file, ensuring:</Paragraph> | |
| 10211 | <UnorderedList> | |
| 10212 | <ListItem>No 'site-control' tags have the "permitted-cross-domain-policies" set to "all"</ListItem> | |
| 10213 | <ListItem>No 'allow-access-from' tags have the 'domain' attribute set to '*' or '*.TLD'</ListItem> | |
| 10214 | <ListItem>No 'allow-access-from' tags have the 'secure' attribute set to 'false'</ListItem> | |
| 10215 | <ListItem>No 'allow-http-headers-from' tags have the 'domain' attribute set to '*' or '*.TLD'</ListItem> | |
| 10216 | <ListItem>No 'allow-http-headers-from' tags have the 'secure' attribute set to 'false'</ListItem></UnorderedList></Paragraph></ContainerBlockElement></solution> | |
| 10217 | </vulnerability> | |
| 10218 | ||
| 10219 | <vulnerability id="ssh-default-account-admin-password-admin" title="Default SSH password: admin password "admin"" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="19700101T000000000" added="20130115T000000000" modified="20130115T000000000"> | |
| 10220 | <description> | |
| 10221 | ||
| 10222 | <ContainerBlockElement> | |
| 10223 | ||
| 10224 | <Paragraph>The admin account uses a password of "admin". This would allow | |
| 10225 | anyone to log into the machine via SSH and take complete | |
| 10226 | control.</Paragraph> | |
| 10227 | </ContainerBlockElement></description> | |
| 10228 | <references> | |
| 10229 | </references><tags> | |
| 10230 | <tag>Default Account</tag> | |
| 10231 | <tag>SSH</tag> | |
| 10232 | </tags> | |
| 10233 | <solution> | |
| 10234 | ||
| 10235 | <ContainerBlockElement> | |
| 10236 | <Paragraph> | |
| 10237 | <Paragraph> | |
| 10238 | Change the password to a non-default value. | |
| 10239 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10240 | </vulnerability> | |
| 10241 | ||
| 10242 | <vulnerability id="ssh-default-account-admin-password-password" title="Default SSH password: admin password "password"" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="19700101T000000000" added="20090512T000000000" modified="20090512T000000000"> | |
| 10243 | <description> | |
| 10244 | ||
| 10245 | <ContainerBlockElement> | |
| 10246 | ||
| 10247 | <Paragraph>The admin account uses a password of "password". This would allow | |
| 10248 | anyone to log into the machine via SSH and take complete | |
| 10249 | control.</Paragraph> | |
| 10250 | </ContainerBlockElement></description> | |
| 10251 | <references> | |
| 10252 | </references><tags> | |
| 10253 | <tag>Default Account</tag> | |
| 10254 | <tag>SSH</tag> | |
| 10255 | </tags> | |
| 10256 | <solution> | |
| 10257 | ||
| 10258 | <ContainerBlockElement> | |
| 10259 | <Paragraph> | |
| 10260 | <Paragraph> | |
| 10261 | Change the password to a non-default value. | |
| 10262 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10263 | </vulnerability> | |
| 10264 | ||
| 10265 | <vulnerability id="ssh-default-account-guest-password-guest" title="Default SSH password: guest password "guest"" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="19980101T000000000" added="20090318T000000000" modified="20100916T000000000"> | |
| 10266 | <description> | |
| 10267 | ||
| 10268 | <ContainerBlockElement> | |
| 10269 | ||
| 10270 | <Paragraph>A common configuration weakness is to create a | |
| 10271 | 'guest' user with a password of 'guest'. This is usually a user-level account | |
| 10272 | that can be used to SSH into the system.</Paragraph> | |
| 10273 | </ContainerBlockElement></description> | |
| 10274 | <references> | |
| 10275 | </references><tags> | |
| 10276 | <tag>Default Account</tag> | |
| 10277 | <tag>SSH</tag> | |
| 10278 | </tags> | |
| 10279 | <solution> | |
| 10280 | ||
| 10281 | <ContainerBlockElement> | |
| 10282 | <Paragraph> | |
| 10283 | <Paragraph>Use the "passwd" command to set a more secure login password. A good | |
| 10284 | password should consist of a mix of lower- and upper-case characters, | |
| 10285 | numbers, and punctuation and should be at least 8 characters long.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10286 | </vulnerability> | |
| 10287 | ||
| 10288 | <vulnerability id="ssh-default-account-root-no-password" title="Default SSH password: root with blank password" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20041101T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 10289 | <description> | |
| 10290 | ||
| 10291 | <ContainerBlockElement> | |
| 10292 | ||
| 10293 | <Paragraph>The root account uses a blank password. This would allow | |
| 10294 | anyone to log into the machine via SSH and take complete | |
| 10295 | control.</Paragraph> | |
| 10296 | </ContainerBlockElement></description> | |
| 10297 | <references> | |
| 10298 | </references><tags> | |
| 10299 | <tag>Default Account</tag> | |
| 10300 | <tag>SSH</tag> | |
| 10301 | </tags> | |
| 10302 | <solution> | |
| 10303 | ||
| 10304 | <ContainerBlockElement> | |
| 10305 | <Paragraph> | |
| 10306 | <Paragraph>Use the "passwd" command to set a more secure login password. A good | |
| 10307 | password should consist of a mix of lower- and upper-case characters, | |
| 10308 | numbers, and punctuation and should be at least 8 characters long. | |
| 10309 | You may also want to disable root login via SSH, which you can | |
| 10310 | do in OpenSSH by adding the following to sshd.conf:</Paragraph> | |
| 10311 | <Paragraph preformat="true">PermitRootLogin: no</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10312 | </vulnerability> | |
| 10313 | ||
| 10314 | <vulnerability id="ssh-default-account-root-password-password" title="Default SSH password: root password "password"" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20041101T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 10315 | <description> | |
| 10316 | ||
| 10317 | <ContainerBlockElement> | |
| 10318 | ||
| 10319 | <Paragraph>The root account uses a password of "password". This would allow | |
| 10320 | anyone to log into the machine via SSH and take complete | |
| 10321 | control.</Paragraph> | |
| 10322 | </ContainerBlockElement></description> | |
| 10323 | <references> | |
| 10324 | </references><tags> | |
| 10325 | <tag>Default Account</tag> | |
| 10326 | <tag>SSH</tag> | |
| 10327 | </tags> | |
| 10328 | <solution> | |
| 10329 | ||
| 10330 | <ContainerBlockElement> | |
| 10331 | <Paragraph> | |
| 10332 | <Paragraph>Use the "passwd" command to set a more secure login password. A good | |
| 10333 | password should consist of a mix of lower- and upper-case characters, | |
| 10334 | numbers, and punctuation and should be at least 8 characters long. | |
| 10335 | You may also want to disable root login via SSH, which you can | |
| 10336 | do in OpenSSH by adding the following to sshd.conf:</Paragraph> | |
| 10337 | <Paragraph preformat="true">PermitRootLogin: no</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10338 | </vulnerability> | |
| 10339 | ||
| 10340 | <vulnerability id="ssh-default-account-root-password-root" title="Default SSH password: root password "root"" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20100513T000000000" added="20100513T000000000" modified="20120712T000000000"> | |
| 10341 | <description> | |
| 10342 | ||
| 10343 | <ContainerBlockElement> | |
| 10344 | ||
| 10345 | <Paragraph>The root account uses a password of "root". | |
| 10346 | This would allow anyone to log into the machine via SSH and take complete control.</Paragraph> | |
| 10347 | </ContainerBlockElement></description> | |
| 10348 | <references> | |
| 10349 | </references><tags> | |
| 10350 | <tag>Default Account</tag> | |
| 10351 | <tag>SSH</tag> | |
| 10352 | </tags> | |
| 10353 | <solution> | |
| 10354 | ||
| 10355 | <ContainerBlockElement> | |
| 10356 | <Paragraph> | |
| 10357 | <Paragraph>Use the "passwd" command to set a more secure login password. A good | |
| 10358 | password should consist of a mix of lower- and upper-case characters, | |
| 10359 | numbers, and punctuation and should be at least 8 characters long. | |
| 10360 | You may also want to disable root login via SSH, which you can | |
| 10361 | do in OpenSSH by adding the following to sshd.conf:</Paragraph> | |
| 10362 | <Paragraph preformat="true">PermitRootLogin: no</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10363 | </vulnerability> | |
| 10364 | ||
| 10365 | <vulnerability id="ssh-default-account-root-password-toor" title="Default SSH password: root password "toor"" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20080624T000000000" added="20080624T000000000" modified="20120712T000000000"> | |
| 10366 | <description> | |
| 10367 | ||
| 10368 | <ContainerBlockElement> | |
| 10369 | ||
| 10370 | <Paragraph>The root account uses a password of "toor" (which is root spelled backwards). | |
| 10371 | This would allow anyone to log into the machine via SSH and take complete control.</Paragraph> | |
| 10372 | </ContainerBlockElement></description> | |
| 10373 | <references> | |
| 10374 | </references><tags> | |
| 10375 | <tag>Default Account</tag> | |
| 10376 | <tag>SSH</tag> | |
| 10377 | </tags> | |
| 10378 | <solution> | |
| 10379 | ||
| 10380 | <ContainerBlockElement> | |
| 10381 | <Paragraph> | |
| 10382 | <Paragraph>Use the "passwd" command to set a more secure login password. A good | |
| 10383 | password should consist of a mix of lower- and upper-case characters, | |
| 10384 | numbers, and punctuation and should be at least 8 characters long. | |
| 10385 | You may also want to disable root login via SSH, which you can | |
| 10386 | do in OpenSSH by adding the following to sshd.conf:</Paragraph> | |
| 10387 | <Paragraph preformat="true">PermitRootLogin: no</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10388 | </vulnerability> | |
| 10389 | ||
| 10390 | <vulnerability id="ssh-default-account-vmware-password-vmware" title="Default SSH password: vmware password "vmware"" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20080824T000000000" added="20080824T000000000" modified="20120712T000000000"> | |
| 10391 | <description> | |
| 10392 | ||
| 10393 | <ContainerBlockElement> | |
| 10394 | ||
| 10395 | <Paragraph>A common configuration weakness in VMWare host or guest systems is to create a | |
| 10396 | 'vmware' user with a password of 'vmware'. This is usually a user-level account | |
| 10397 | that can be used to SSH into the system.</Paragraph> | |
| 10398 | </ContainerBlockElement></description> | |
| 10399 | <references> | |
| 10400 | </references><tags> | |
| 10401 | <tag>Default Account</tag> | |
| 10402 | <tag>SSH</tag> | |
| 10403 | </tags> | |
| 10404 | <solution> | |
| 10405 | ||
| 10406 | <ContainerBlockElement> | |
| 10407 | <Paragraph> | |
| 10408 | <Paragraph>Use the "passwd" command to set a more secure login password. A good | |
| 10409 | password should consist of a mix of lower- and upper-case characters, | |
| 10410 | numbers, and punctuation and should be at least 8 characters long.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10411 | </vulnerability> | |
| 10412 | ||
| 10413 | <vulnerability id="SSH-GENERIC-0003" title="SSH Inc and OpenSSH CRC-32 Integer Overflow Vulnerability" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20010312T000000000" added="20041101T000000000" modified="20121204T000000000"> | |
| 10414 | <description> | |
| 10415 | ||
| 10416 | <ContainerBlockElement> | |
| 10417 | There exists an integer overflow bug in code shared between the ssh daemons of SSH Inc and OpenSSH, which can result in letting an attacker overwrite arbitrary locations in memory. This affects SSH Inc < 2.4.0 and OpenSSH < 2.3.0. Note that it has been reported that this vulnerability is being widely exploited "in the wild". | |
| 10418 | </ContainerBlockElement></description> | |
| 10419 | <references> | |
| 10420 | <reference source="BID">2347</reference> | |
| 10421 | <reference source="CERT">CA-2001-35</reference> | |
| 10422 | <reference source="CVE">CVE-2001-0144</reference> | |
| 10423 | <reference source="OSVDB">503</reference> | |
| 10424 | <reference source="OSVDB">795</reference> | |
| 10425 | <reference source="URL">http://marc.theaimsgroup.com/?l=bugtraq&m=98168366406903&w=2</reference> | |
| 10426 | <reference source="URL">http://razor.bindview.com/publish/advisories/adv_ssh1crc.html</reference> | |
| 10427 | <reference source="XF">ssh-deattack-overwrite-memory(6083)</reference> | |
| 10428 | </references><tags> | |
| 10429 | <tag>SSH</tag> | |
| 10430 | </tags> | |
| 10431 | <solution> | |
| 10432 | ||
| 10433 | <ContainerBlockElement> | |
| 10434 | <Paragraph>Download and apply the upgrade from: | |
| 10435 | <URLLink LinkURL="ftp://ftp.ssh.com/pub/ssh/old/ssh-2.4.0.tar.gz" LinkTitle="ftp://ftp.ssh.com/pub/ssh/old/ssh-2.4.0.tar.gz"></URLLink></Paragraph> | |
| 10436 | <Paragraph> | |
| 10437 | <Paragraph>Upgrade to SSH v2.4.0 or later. See the | |
| 10438 | ||
| 10439 | <URLLink LinkURL="http://www.ssh.com/support/downloads/" LinkTitle="http://www.ssh.com/support/downloads/" href="http://www.ssh.com/support/downloads/">SSH</URLLink> | |
| 10440 | website for download information. | |
| 10441 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10442 | </vulnerability> | |
| 10443 | ||
| 10444 | <vulnerability id="ssh-iphone-default-account-root-password-alpine" title="Default SSH password: root password "alpine"" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20070701T000000000" added="20091204T000000000" modified="20120712T000000000"> | |
| 10445 | <description> | |
| 10446 | ||
| 10447 | <ContainerBlockElement> | |
| 10448 | ||
| 10449 | <Paragraph> | |
| 10450 | The root account uses a password of "alpine". This would allow | |
| 10451 | anyone to log into the machine via SSH and take complete control. This | |
| 10452 | default account exists on some jailbroken iPhone and iPod Touch devices. | |
| 10453 | </Paragraph> | |
| 10454 | </ContainerBlockElement></description> | |
| 10455 | <references> | |
| 10456 | </references><tags> | |
| 10457 | <tag>Default Account</tag> | |
| 10458 | <tag>SSH</tag> | |
| 10459 | </tags> | |
| 10460 | <solution> | |
| 10461 | ||
| 10462 | <ContainerBlockElement> | |
| 10463 | <Paragraph> | |
| 10464 | <Paragraph>Use the "passwd" command to set a more secure login password. A good | |
| 10465 | password should consist of a mix of lower- and upper-case characters, | |
| 10466 | numbers, and punctuation and should be at least 8 characters long. | |
| 10467 | You may also want to disable root login via SSH, which you can | |
| 10468 | do in OpenSSH by adding the following to sshd.conf:</Paragraph> | |
| 10469 | <Paragraph preformat="true">PermitRootLogin: no</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10470 | </vulnerability> | |
| 10471 | ||
| 10472 | <vulnerability id="ssh-iphone-default-account-root-password-dottie" title="Default SSH password: root password "dottie"" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20070701T000000000" added="20091204T000000000" modified="20120712T000000000"> | |
| 10473 | <description> | |
| 10474 | ||
| 10475 | <ContainerBlockElement> | |
| 10476 | ||
| 10477 | <Paragraph> | |
| 10478 | The root account uses a password of "dottie". This would allow | |
| 10479 | anyone to log into the machine via SSH and take complete control. This | |
| 10480 | default account exists on some jailbroken iPhone and iPod Touch devices. | |
| 10481 | </Paragraph> | |
| 10482 | </ContainerBlockElement></description> | |
| 10483 | <references> | |
| 10484 | </references><tags> | |
| 10485 | <tag>Default Account</tag> | |
| 10486 | <tag>SSH</tag> | |
| 10487 | </tags> | |
| 10488 | <solution> | |
| 10489 | ||
| 10490 | <ContainerBlockElement> | |
| 10491 | <Paragraph> | |
| 10492 | <Paragraph>Use the "passwd" command to set a more secure login password. A good | |
| 10493 | password should consist of a mix of lower- and upper-case characters, | |
| 10494 | numbers, and punctuation and should be at least 8 characters long. | |
| 10495 | You may also want to disable root login via SSH, which you can | |
| 10496 | do in OpenSSH by adding the following to sshd.conf:</Paragraph> | |
| 10497 | <Paragraph preformat="true">PermitRootLogin: no</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10498 | </vulnerability> | |
| 10499 | ||
| 10500 | <vulnerability id="SSH-OPENSSH-0001" title="OpenSSH Channel Code Off By One Vulnerability" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20020315T000000000" added="20041101T000000000" modified="20130822T000000000"> | |
| 10501 | <description> | |
| 10502 | ||
| 10503 | <ContainerBlockElement> | |
| 10504 | ||
| 10505 | <Paragraph>Off-by-one error in the channel code of OpenSSH 2.0 through 3.0.2 allows local users or remote malicious servers to gain privileges.</Paragraph> | |
| 10506 | </ContainerBlockElement></description> | |
| 10507 | <references> | |
| 10508 | <reference source="BID">4241</reference> | |
| 10509 | <reference source="CALDERA">CSSA-2002-012.0</reference> | |
| 10510 | <reference source="CALDERA">CSSA-2002-SCO.10</reference> | |
| 10511 | <reference source="CALDERA">CSSA-2002-SCO.11</reference> | |
| 10512 | <reference source="CONECTIVA">CLA-2002:467</reference> | |
| 10513 | <reference source="CVE">CVE-2002-0083</reference> | |
| 10514 | <reference source="DEBIAN">DSA-119</reference> | |
| 10515 | <reference source="MANDRAKE">MDKSA-2002:019</reference> | |
| 10516 | <reference source="NETBSD">NetBSD-SA2002-004</reference> | |
| 10517 | <reference source="OSVDB">730</reference> | |
| 10518 | <reference source="REDHAT">RHSA-2002:043</reference> | |
| 10519 | <reference source="SUSE">SuSE-SA:2002:009</reference> | |
| 10520 | <reference source="XF">8383</reference> | |
| 10521 | </references><tags> | |
| 10522 | <tag>OpenSSH</tag> | |
| 10523 | <tag>SSH</tag> | |
| 10524 | </tags> | |
| 10525 | <solution> | |
| 10526 | ||
| 10527 | <ContainerBlockElement> | |
| 10528 | <Paragraph>Download and apply the upgrade from: | |
| 10529 | <URLLink LinkURL="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH" LinkTitle="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH"></URLLink></Paragraph> | |
| 10530 | <Paragraph> | |
| 10531 | <Paragraph>The latest version of OpenSSH is 6.4.</Paragraph> | |
| 10532 | <Paragraph> | |
| 10533 | While you can always | |
| 10534 | <URLLink LinkURL="http://www.openssh.com/portable.html" LinkTitle="http://www.openssh.com/portable.html" href="http://www.openssh.com/portable.html">build OpenSSH from source</URLLink>, | |
| 10535 | many platforms and distributions provide pre-built binary packages for OpenSSH. These pre-built | |
| 10536 | packages are usually customized and optimized for a particular distribution, therefore we | |
| 10537 | recommend that you use the packages if they are available for your operating system. | |
| 10538 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10539 | </vulnerability> | |
| 10540 | ||
| 10541 | <vulnerability id="SSH-OPENSSH-0002" title="OpenSSH UseLogin Vulnerability" severity="7" pciSeverity="5" cvssScore="7.2" cvssVector="(AV:L/AC:L/Au:N/C:C/I:C/A:C)" published="20011221T000000000" added="20041101T000000000" modified="20130822T000000000"> | |
| 10542 | <description> | |
| 10543 | ||
| 10544 | <ContainerBlockElement> | |
| 10545 | ||
| 10546 | <Paragraph>OpenSSH 3.0.1 and earlier with UseLogin enabled does not properly cleanse critical environment variables such as LD_PRELOAD, which allows local users to gain root privileges.</Paragraph> | |
| 10547 | </ContainerBlockElement></description> | |
| 10548 | <references> | |
| 10549 | <reference source="BID">3614</reference> | |
| 10550 | <reference source="CALDERA">CSSA-2001-042.1</reference> | |
| 10551 | <reference source="CERT-VN">157447</reference> | |
| 10552 | <reference source="CIAC">M-026</reference> | |
| 10553 | <reference source="CONECTIVA">CLA-2001:446</reference> | |
| 10554 | <reference source="CVE">CVE-2001-0872</reference> | |
| 10555 | <reference source="DEBIAN">DSA-091</reference> | |
| 10556 | <reference source="MANDRAKE">MDKSA-2001:092</reference> | |
| 10557 | <reference source="OSVDB">688</reference> | |
| 10558 | <reference source="REDHAT">RHSA-2001:161</reference> | |
| 10559 | <reference source="SUSE">SuSE-SA:2001:045</reference> | |
| 10560 | <reference source="XF">7647</reference> | |
| 10561 | </references><tags> | |
| 10562 | <tag>OpenSSH</tag> | |
| 10563 | <tag>Privilege Escalation</tag> | |
| 10564 | <tag>SSH</tag> | |
| 10565 | </tags> | |
| 10566 | <solution> | |
| 10567 | ||
| 10568 | <ContainerBlockElement> | |
| 10569 | <Paragraph>Download and apply the upgrade from: | |
| 10570 | <URLLink LinkURL="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH" LinkTitle="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH"></URLLink></Paragraph> | |
| 10571 | <Paragraph> | |
| 10572 | <Paragraph>The latest version of OpenSSH is 6.4.</Paragraph> | |
| 10573 | <Paragraph> | |
| 10574 | While you can always | |
| 10575 | <URLLink LinkURL="http://www.openssh.com/portable.html" LinkTitle="http://www.openssh.com/portable.html" href="http://www.openssh.com/portable.html">build OpenSSH from source</URLLink>, | |
| 10576 | many platforms and distributions provide pre-built binary packages for OpenSSH. These pre-built | |
| 10577 | packages are usually customized and optimized for a particular distribution, therefore we | |
| 10578 | recommend that you use the packages if they are available for your operating system. | |
| 10579 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10580 | </vulnerability> | |
| 10581 | ||
| 10582 | <vulnerability id="SSH-OPENSSH-0003" title="OpenSSH Kerberos Authentication Bypass Vulnerability" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20011231T000000000" added="20041101T000000000" modified="20130822T000000000"> | |
| 10583 | <description> | |
| 10584 | ||
| 10585 | <ContainerBlockElement> | |
| 10586 | ||
| 10587 | <Paragraph>OpenSSH before 3.0.1 with Kerberos V enabled does not properly authenticate users, which could allow remote attackers to login unchallenged.</Paragraph> | |
| 10588 | </ContainerBlockElement></description> | |
| 10589 | <references> | |
| 10590 | <reference source="BID">3560</reference> | |
| 10591 | <reference source="CVE">CVE-2001-1507</reference> | |
| 10592 | <reference source="XF">7598</reference> | |
| 10593 | </references><tags> | |
| 10594 | <tag>OpenSSH</tag> | |
| 10595 | <tag>SSH</tag> | |
| 10596 | </tags> | |
| 10597 | <solution> | |
| 10598 | ||
| 10599 | <ContainerBlockElement> | |
| 10600 | <Paragraph>OpenBSD OpenSSH < 3.0.1</Paragraph> | |
| 10601 | <Paragraph>Download and apply the upgrade from: | |
| 10602 | <URLLink LinkURL="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH" LinkTitle="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH"></URLLink></Paragraph> | |
| 10603 | <Paragraph> | |
| 10604 | <Paragraph> | |
| 10605 | While you can always | |
| 10606 | <URLLink LinkURL="http://www.openssh.com/portable.html" LinkTitle="http://www.openssh.com/portable.html" href="http://www.openssh.com/portable.html">build OpenSSH from source</URLLink>, | |
| 10607 | many platforms and distributions provide pre-built binary packages for OpenSSH. These pre-built | |
| 10608 | packages are usually customized and optimized for a particular distribution, therefore we | |
| 10609 | recommend that you use the packages if they are available for your operating system. | |
| 10610 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10611 | </vulnerability> | |
| 10612 | ||
| 10613 | <vulnerability id="SSH-OPENSSH-0004" title="OpenSSH IP Restriction Bypass Vulnerability" severity="7" pciSeverity="4" cvssScore="6.5" cvssVector="(AV:N/AC:L/Au:S/C:P/I:P/A:P)" published="20011018T000000000" added="20041101T000000000" modified="20121205T000000000"> | |
| 10614 | <description> | |
| 10615 | ||
| 10616 | <ContainerBlockElement> | |
| 10617 | ||
| 10618 | <Paragraph>OpenSSH versions previous to v2.9.9 contain a vulnerability which allows | |
| 10619 | a remote attacker to bypass the IP restrictions. Note that valid | |
| 10620 | credentials are still required to log in.</Paragraph> | |
| 10621 | </ContainerBlockElement></description> | |
| 10622 | <references> | |
| 10623 | </references><tags> | |
| 10624 | <tag>SSH</tag> | |
| 10625 | </tags> | |
| 10626 | <solution> | |
| 10627 | ||
| 10628 | <ContainerBlockElement> | |
| 10629 | <Paragraph>Download and apply the upgrade from: | |
| 10630 | <URLLink LinkURL="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH" LinkTitle="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH"></URLLink></Paragraph> | |
| 10631 | <Paragraph> | |
| 10632 | <Paragraph>The latest version of OpenSSH is 6.4.</Paragraph> | |
| 10633 | <Paragraph> | |
| 10634 | While you can always | |
| 10635 | <URLLink LinkURL="http://www.openssh.com/portable.html" LinkTitle="http://www.openssh.com/portable.html" href="http://www.openssh.com/portable.html">build OpenSSH from source</URLLink>, | |
| 10636 | many platforms and distributions provide pre-built binary packages for OpenSSH. These pre-built | |
| 10637 | packages are usually customized and optimized for a particular distribution, therefore we | |
| 10638 | recommend that you use the packages if they are available for your operating system. | |
| 10639 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10640 | </vulnerability> | |
| 10641 | ||
| 10642 | <vulnerability id="SSH-OPENSSH-0005" title="OpenSSH PAM Restriction Evasion Vulnerability" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20010619T000000000" added="20041101T000000000" modified="20130822T000000000"> | |
| 10643 | <description> | |
| 10644 | ||
| 10645 | <ContainerBlockElement> | |
| 10646 | ||
| 10647 | <Paragraph>OpenSSH 2.9 and earlier does not initiate a Pluggable Authentication Module (PAM) session if commands are executed with no pty, which allows local users to bypass resource limits (rlimits) set in pam.d.</Paragraph> | |
| 10648 | </ContainerBlockElement></description> | |
| 10649 | <references> | |
| 10650 | <reference source="BID">2917</reference> | |
| 10651 | <reference source="CERT-VN">797027</reference> | |
| 10652 | <reference source="CVE">CVE-2001-1459</reference> | |
| 10653 | <reference source="XF">6757</reference> | |
| 10654 | </references><tags> | |
| 10655 | <tag>OpenSSH</tag> | |
| 10656 | <tag>SSH</tag> | |
| 10657 | </tags> | |
| 10658 | <solution> | |
| 10659 | ||
| 10660 | <ContainerBlockElement> | |
| 10661 | <Paragraph>Download and apply the upgrade from: | |
| 10662 | <URLLink LinkURL="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH" LinkTitle="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH"></URLLink></Paragraph> | |
| 10663 | <Paragraph> | |
| 10664 | <Paragraph>The latest version of OpenSSH is 6.4.</Paragraph> | |
| 10665 | <Paragraph> | |
| 10666 | While you can always | |
| 10667 | <URLLink LinkURL="http://www.openssh.com/portable.html" LinkTitle="http://www.openssh.com/portable.html" href="http://www.openssh.com/portable.html">build OpenSSH from source</URLLink>, | |
| 10668 | many platforms and distributions provide pre-built binary packages for OpenSSH. These pre-built | |
| 10669 | packages are usually customized and optimized for a particular distribution, therefore we | |
| 10670 | recommend that you use the packages if they are available for your operating system. | |
| 10671 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10672 | </vulnerability> | |
| 10673 | ||
| 10674 | <vulnerability id="SSH-OPENSSH-0006" title="OpenSSH Public Key Authentication Vulnerability" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20011231T000000000" added="20041101T000000000" modified="20121205T000000000"> | |
| 10675 | <description> | |
| 10676 | ||
| 10677 | <ContainerBlockElement> | |
| 10678 | ||
| 10679 | <Paragraph>OpenSSH v2.3.1, if set up to only allow public-key based | |
| 10680 | authentication, allows a remote attacker to log in without a valid | |
| 10681 | corresponding private key. It is possible to attain any priviledge | |
| 10682 | level with this vulnerability, even root. Note that this vulnerability | |
| 10683 | exists only in v2.3.1.</Paragraph> | |
| 10684 | </ContainerBlockElement></description> | |
| 10685 | <references> | |
| 10686 | </references><tags> | |
| 10687 | <tag>SSH</tag> | |
| 10688 | </tags> | |
| 10689 | <solution> | |
| 10690 | ||
| 10691 | <ContainerBlockElement> | |
| 10692 | <Paragraph>Download and apply the upgrade from: | |
| 10693 | <URLLink LinkURL="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH" LinkTitle="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH"></URLLink></Paragraph> | |
| 10694 | <Paragraph> | |
| 10695 | <Paragraph>The latest version of OpenSSH is 6.4.</Paragraph> | |
| 10696 | <Paragraph> | |
| 10697 | While you can always | |
| 10698 | <URLLink LinkURL="http://www.openssh.com/portable.html" LinkTitle="http://www.openssh.com/portable.html" href="http://www.openssh.com/portable.html">build OpenSSH from source</URLLink>, | |
| 10699 | many platforms and distributions provide pre-built binary packages for OpenSSH. These pre-built | |
| 10700 | packages are usually customized and optimized for a particular distribution, therefore we | |
| 10701 | recommend that you use the packages if they are available for your operating system. | |
| 10702 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10703 | </vulnerability> | |
| 10704 | ||
| 10705 | <vulnerability id="SSH-OPENSSH-0007" title="OpenSSH UseLogin SetUID Vulnerability" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20000608T000000000" added="20041101T000000000" modified="20130822T000000000"> | |
| 10706 | <description> | |
| 10707 | ||
| 10708 | <ContainerBlockElement> | |
| 10709 | ||
| 10710 | <Paragraph>OpenSSH does not properly drop privileges when the UseLogin option is enabled, which allows local users to execute arbitrary commands by providing the command to the ssh daemon.</Paragraph> | |
| 10711 | </ContainerBlockElement></description> | |
| 10712 | <references> | |
| 10713 | <reference source="BID">1334</reference> | |
| 10714 | <reference source="CVE">CVE-2000-0525</reference> | |
| 10715 | <reference source="OSVDB">341</reference> | |
| 10716 | <reference source="XF">4646</reference> | |
| 10717 | </references><tags> | |
| 10718 | <tag>OpenSSH</tag> | |
| 10719 | <tag>Remote Execution</tag> | |
| 10720 | <tag>SSH</tag> | |
| 10721 | </tags> | |
| 10722 | <solution> | |
| 10723 | ||
| 10724 | <ContainerBlockElement> | |
| 10725 | <Paragraph>OpenBSD OpenSSH < 2.1.1</Paragraph> | |
| 10726 | <Paragraph>Download and apply the upgrade from: | |
| 10727 | <URLLink LinkURL="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH" LinkTitle="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH"></URLLink></Paragraph> | |
| 10728 | <Paragraph> | |
| 10729 | <Paragraph> | |
| 10730 | While you can always | |
| 10731 | <URLLink LinkURL="http://www.openssh.com/portable.html" LinkTitle="http://www.openssh.com/portable.html" href="http://www.openssh.com/portable.html">build OpenSSH from source</URLLink>, | |
| 10732 | many platforms and distributions provide pre-built binary packages for OpenSSH. These pre-built | |
| 10733 | packages are usually customized and optimized for a particular distribution, therefore we | |
| 10734 | recommend that you use the packages if they are available for your operating system. | |
| 10735 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10736 | </vulnerability> | |
| 10737 | ||
| 10738 | <vulnerability id="SSH-OPENSSH-0008" title="OpenSSH Kerberos AFS Buffer Overflow Vulnerability" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20020618T000000000" added="20041101T000000000" modified="20130822T000000000"> | |
| 10739 | <description> | |
| 10740 | ||
| 10741 | <ContainerBlockElement> | |
| 10742 | ||
| 10743 | <Paragraph> | |
| 10744 | OpenSSH < 3.2.2 contains a buffer overflow in the Kerberos/AFS | |
| 10745 | support code. In versions < 2.9.9, this can be used to gain a | |
| 10746 | root shell remotely. In versions < 3.2.2, only a local user can | |
| 10747 | gain a root shell. | |
| 10748 | </Paragraph> | |
| 10749 | ||
| 10750 | <Paragraph> | |
| 10751 | Note that Kerberos/AFS support is not enabled by default. Additionally, | |
| 10752 | vendor-supplied patches may have already been applied, even though this | |
| 10753 | test cannot discern their presence. | |
| 10754 | </Paragraph> | |
| 10755 | ||
| 10756 | </ContainerBlockElement></description> | |
| 10757 | <references> | |
| 10758 | <reference source="BID">4560</reference> | |
| 10759 | <reference source="CALDERA">CSSA-2002-022.2</reference> | |
| 10760 | <reference source="CVE">CVE-2002-0575</reference> | |
| 10761 | <reference source="OSVDB">781</reference> | |
| 10762 | <reference source="XF">8896</reference> | |
| 10763 | </references><tags> | |
| 10764 | <tag>OpenSSH</tag> | |
| 10765 | <tag>SSH</tag> | |
| 10766 | </tags> | |
| 10767 | <solution> | |
| 10768 | ||
| 10769 | <ContainerBlockElement> | |
| 10770 | <Paragraph>OpenBSD OpenSSH < 3.2.2</Paragraph> | |
| 10771 | <Paragraph>Download and apply the upgrade from: | |
| 10772 | <URLLink LinkURL="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH" LinkTitle="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH"></URLLink></Paragraph> | |
| 10773 | <Paragraph> | |
| 10774 | <Paragraph> | |
| 10775 | While you can always | |
| 10776 | <URLLink LinkURL="http://www.openssh.com/portable.html" LinkTitle="http://www.openssh.com/portable.html" href="http://www.openssh.com/portable.html">build OpenSSH from source</URLLink>, | |
| 10777 | many platforms and distributions provide pre-built binary packages for OpenSSH. These pre-built | |
| 10778 | packages are usually customized and optimized for a particular distribution, therefore we | |
| 10779 | recommend that you use the packages if they are available for your operating system. | |
| 10780 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10781 | </vulnerability> | |
| 10782 | ||
| 10783 | <vulnerability id="SSH-OPENSSH-0009" title="OpenSSH BSD_AUTH Authentication Confusion Vulnerability" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20020812T000000000" added="20041101T000000000" modified="20130822T000000000"> | |
| 10784 | <description> | |
| 10785 | ||
| 10786 | <ContainerBlockElement> | |
| 10787 | ||
| 10788 | <Paragraph>sshd in OpenSSH 3.2.2, when using YP with netgroups and under certain conditions, may allow users to successfully authenticate and log in with another user's password.</Paragraph> | |
| 10789 | </ContainerBlockElement></description> | |
| 10790 | <references> | |
| 10791 | <reference source="BID">4803</reference> | |
| 10792 | <reference source="CVE">CVE-2002-0765</reference> | |
| 10793 | <reference source="OSVDB">5113</reference> | |
| 10794 | <reference source="XF">9215</reference> | |
| 10795 | </references><tags> | |
| 10796 | <tag>OpenSSH</tag> | |
| 10797 | <tag>SSH</tag> | |
| 10798 | </tags> | |
| 10799 | <solution> | |
| 10800 | ||
| 10801 | <ContainerBlockElement> | |
| 10802 | <Paragraph>OpenBSD OpenSSH < 3.4</Paragraph> | |
| 10803 | <Paragraph>Download and apply the upgrade from: | |
| 10804 | <URLLink LinkURL="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH" LinkTitle="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH"></URLLink></Paragraph> | |
| 10805 | <Paragraph> | |
| 10806 | <Paragraph> | |
| 10807 | While you can always | |
| 10808 | <URLLink LinkURL="http://www.openssh.com/portable.html" LinkTitle="http://www.openssh.com/portable.html" href="http://www.openssh.com/portable.html">build OpenSSH from source</URLLink>, | |
| 10809 | many platforms and distributions provide pre-built binary packages for OpenSSH. These pre-built | |
| 10810 | packages are usually customized and optimized for a particular distribution, therefore we | |
| 10811 | recommend that you use the packages if they are available for your operating system. | |
| 10812 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10813 | </vulnerability> | |
| 10814 | ||
| 10815 | <vulnerability id="SSH-OPENSSH-0010" title="OpenSSH Challenge-Response Buffer Overflow" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20020703T000000000" added="20041101T000000000" modified="20121205T000000000"> | |
| 10816 | <description> | |
| 10817 | ||
| 10818 | <ContainerBlockElement> | |
| 10819 | ||
| 10820 | <Paragraph>There exist multiple buffer overflows in the OpenSSH daemon during the | |
| 10821 | challenge-response handshake when compiled with BSD_AUTH or SKEY support. | |
| 10822 | Authentication is not required, and successful exploitation of this | |
| 10823 | vulnerability yields root access.</Paragraph> | |
| 10824 | </ContainerBlockElement></description> | |
| 10825 | <references> | |
| 10826 | <reference source="BID">5093</reference> | |
| 10827 | <reference source="CALDERA">CSSA-2002-030.0</reference> | |
| 10828 | <reference source="CERT">CA-2002-18</reference> | |
| 10829 | <reference source="CERT-VN">369347</reference> | |
| 10830 | <reference source="CONECTIVA">CLA-2002:502</reference> | |
| 10831 | <reference source="CVE">CVE-2002-0639</reference> | |
| 10832 | <reference source="CVE">CVE-2002-0640</reference> | |
| 10833 | <reference source="DEBIAN">DSA-134</reference> | |
| 10834 | <reference source="MANDRAKE">MDKSA-2002:040</reference> | |
| 10835 | <reference source="OSVDB">6245</reference> | |
| 10836 | <reference source="OSVDB">839</reference> | |
| 10837 | <reference source="REDHAT">RHSA-2002:127</reference> | |
| 10838 | <reference source="REDHAT">RHSA-2002:131</reference> | |
| 10839 | <reference source="SUSE">SuSE-SA:2002:024</reference> | |
| 10840 | <reference source="XF">openssh-challenge-response-bo(9169)</reference> | |
| 10841 | </references><tags> | |
| 10842 | <tag>SSH</tag> | |
| 10843 | </tags> | |
| 10844 | <solution> | |
| 10845 | ||
| 10846 | <ContainerBlockElement> | |
| 10847 | <UnorderedList> | |
| 10848 | <ListItem> | |
| 10849 | <Paragraph>OpenBSD OpenSSH < 3.4</Paragraph> | |
| 10850 | <Paragraph>Download and apply the upgrade from: | |
| 10851 | <URLLink LinkURL="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH" LinkTitle="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH"></URLLink></Paragraph> | |
| 10852 | <Paragraph> | |
| 10853 | <Paragraph> | |
| 10854 | While you can always | |
| 10855 | <URLLink LinkURL="http://www.openssh.com/portable.html" LinkTitle="http://www.openssh.com/portable.html" href="http://www.openssh.com/portable.html">build OpenSSH from source</URLLink>, | |
| 10856 | many platforms and distributions provide pre-built binary packages for OpenSSH. These pre-built | |
| 10857 | packages are usually customized and optimized for a particular distribution, therefore we | |
| 10858 | recommend that you use the packages if they are available for your operating system. | |
| 10859 | </Paragraph></Paragraph></ListItem> | |
| 10860 | <ListItem> | |
| 10861 | <Paragraph>Download and apply the upgrade from: | |
| 10862 | <URLLink LinkURL="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH" LinkTitle="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH"></URLLink></Paragraph> | |
| 10863 | <Paragraph> | |
| 10864 | <Paragraph>The latest version of OpenSSH is 6.4.</Paragraph> | |
| 10865 | <Paragraph> | |
| 10866 | While you can always | |
| 10867 | <URLLink LinkURL="http://www.openssh.com/portable.html" LinkTitle="http://www.openssh.com/portable.html" href="http://www.openssh.com/portable.html">build OpenSSH from source</URLLink>, | |
| 10868 | many platforms and distributions provide pre-built binary packages for OpenSSH. These pre-built | |
| 10869 | packages are usually customized and optimized for a particular distribution, therefore we | |
| 10870 | recommend that you use the packages if they are available for your operating system. | |
| 10871 | </Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 10872 | </vulnerability> | |
| 10873 | ||
| 10874 | <vulnerability id="ssh-openssh-pam-multiple-vulns" title="OpenSSH Portable Branch Multiple Unspecified PAM Vulnerabilities" severity="9" pciSeverity="5" cvssScore="9.3" cvssVector="(AV:N/AC:M/Au:N/C:C/I:C/A:C)" published="20041101T000000000" added="20041101T000000000" modified="20121205T000000000"> | |
| 10875 | <description> | |
| 10876 | ||
| 10877 | <ContainerBlockElement> | |
| 10878 | ||
| 10879 | <Paragraph>Multiple unspecified PAM-related vulnerabilities were announced on September 23rd, 2003. These | |
| 10880 | vulnerabilities affect the portable branch of OpenSSH versions 3.7.1p1 and earlier, | |
| 10881 | if PAM is enabled.</Paragraph> | |
| 10882 | </ContainerBlockElement></description> | |
| 10883 | <references> | |
| 10884 | <reference source="URL">http://www.openssh.com/txt/sshpam.adv</reference> | |
| 10885 | </references><tags> | |
| 10886 | <tag>OpenSSH</tag> | |
| 10887 | <tag>SSH</tag> | |
| 10888 | </tags> | |
| 10889 | <solution> | |
| 10890 | ||
| 10891 | <ContainerBlockElement> | |
| 10892 | <Paragraph>Download and apply the upgrade from: | |
| 10893 | <URLLink LinkURL="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH" LinkTitle="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH"></URLLink></Paragraph> | |
| 10894 | <Paragraph> | |
| 10895 | <Paragraph>The latest version of OpenSSH is 6.4.</Paragraph> | |
| 10896 | <Paragraph> | |
| 10897 | While you can always | |
| 10898 | <URLLink LinkURL="http://www.openssh.com/portable.html" LinkTitle="http://www.openssh.com/portable.html" href="http://www.openssh.com/portable.html">build OpenSSH from source</URLLink>, | |
| 10899 | many platforms and distributions provide pre-built binary packages for OpenSSH. These pre-built | |
| 10900 | packages are usually customized and optimized for a particular distribution, therefore we | |
| 10901 | recommend that you use the packages if they are available for your operating system. | |
| 10902 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 10903 | </vulnerability> | |
| 10904 | ||
| 10905 | <vulnerability id="ssh-openssh-valid-username-info-leak" title="OpenSSH Valid Username Information Leak" severity="4" pciSeverity="3" cvssScore="4.3" cvssVector="(AV:N/AC:M/Au:N/C:P/I:N/A:N)" published="20041101T000000000" added="20041101T000000000" modified="20121205T000000000"> | |
| 10906 | <description> | |
| 10907 | ||
| 10908 | <ContainerBlockElement> | |
| 10909 | ||
| 10910 | <Paragraph>In certain situations, it is possible to determine if a username exists on the target system by analyzing differences in response timings from the OpenSSH server. While not a vulnerability in and of itself, this information may simplify more complex attacks against the system.</Paragraph> | |
| 10911 | </ContainerBlockElement></description> | |
| 10912 | <references> | |
| 10913 | </references><tags> | |
| 10914 | <tag>OpenSSH</tag> | |
| 10915 | <tag>SSH</tag> | |
| 10916 | </tags> | |
| 10917 | <solution> | |
| 10918 | ||
| 10919 | <ContainerBlockElement> | |
| 10920 | <UnorderedList> | |
| 10921 | <ListItem> | |
| 10922 | <Paragraph>OpenBSD OpenSSH < 3.1</Paragraph> | |
| 10923 | <Paragraph>Download and apply the upgrade from: | |
| 10924 | <URLLink LinkURL="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH" LinkTitle="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH"></URLLink></Paragraph> | |
| 10925 | <Paragraph> | |
| 10926 | <Paragraph> | |
| 10927 | While you can always | |
| 10928 | <URLLink LinkURL="http://www.openssh.com/portable.html" LinkTitle="http://www.openssh.com/portable.html" href="http://www.openssh.com/portable.html">build OpenSSH from source</URLLink>, | |
| 10929 | many platforms and distributions provide pre-built binary packages for OpenSSH. These pre-built | |
| 10930 | packages are usually customized and optimized for a particular distribution, therefore we | |
| 10931 | recommend that you use the packages if they are available for your operating system. | |
| 10932 | </Paragraph></Paragraph></ListItem> | |
| 10933 | <ListItem> | |
| 10934 | <Paragraph>Download and apply the upgrade from: | |
| 10935 | <URLLink LinkURL="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH" LinkTitle="ftp://ftp.openbsd.org/pub/OpenBSD/OpenSSH"></URLLink></Paragraph> | |
| 10936 | <Paragraph> | |
| 10937 | <Paragraph>The latest version of OpenSSH is 6.4.</Paragraph> | |
| 10938 | <Paragraph> | |
| 10939 | While you can always | |
| 10940 | <URLLink LinkURL="http://www.openssh.com/portable.html" LinkTitle="http://www.openssh.com/portable.html" href="http://www.openssh.com/portable.html">build OpenSSH from source</URLLink>, | |
| 10941 | many platforms and distributions provide pre-built binary packages for OpenSSH. These pre-built | |
| 10942 | packages are usually customized and optimized for a particular distribution, therefore we | |
| 10943 | recommend that you use the packages if they are available for your operating system. | |
| 10944 | </Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 10945 | </vulnerability> | |
| 10946 | ||
| 10947 | <vulnerability id="ssh-pragma-sshredder-overflow" title="Pragma SecureShell SSHredder buffer overflow" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20021223T000000000" added="20041101T000000000" modified="20120730T000000000"> | |
| 10948 | <description> | |
| 10949 | ||
| 10950 | <ContainerBlockElement> | |
| 10951 | Pragma SecureShell server v2.x and earlier are vulnerable to a buffer overflow attack that can potentially give an attacker full control over the remote system. This buffer overflow occurs before any authentication takes place, which means that an attacker does not need a password to be able to exploit it. | |
| 10952 | </ContainerBlockElement></description> | |
| 10953 | <references> | |
| 10954 | <reference source="BID">6407</reference> | |
| 10955 | <reference source="CERT">CA-2002-36</reference> | |
| 10956 | <reference source="CVE">CVE-2002-1359</reference> | |
| 10957 | <reference source="OVAL">OVAL5848</reference> | |
| 10958 | <reference source="URL">http://archives.neohapsis.com/archives/vulnwatch/2002-q4/0110.html</reference> | |
| 10959 | <reference source="URL">http://www.pragmasys.com/PressReleases/SSHVulnerabilityFixed.htm</reference> | |
| 10960 | <reference source="XF">ssh-transport-multiple-bo(10870)</reference> | |
| 10961 | </references><tags> | |
| 10962 | <tag>SSH</tag> | |
| 10963 | </tags> | |
| 10964 | <solution> | |
| 10965 | ||
| 10966 | <ContainerBlockElement> | |
| 10967 | <Paragraph>Download and apply the upgrade from: | |
| 10968 | <URLLink LinkURL="http://www.pragmasys.com/SecureShell/" LinkTitle="http://www.pragmasys.com/SecureShell/"></URLLink></Paragraph> | |
| 10969 | <Paragraph> | |
| 10970 | ||
| 10971 | ||
| 10972 | ||
| 10973 | ||
| 10974 | ||
| 10975 | ||
| 10976 | Upgrade to | |
| 10977 | ||
| 10978 | Pragma SecureShell v3.0 ( http://www.pragmasys.com/SecureShell/ ) | |
| 10979 | or later. | |
| 10980 | ||
| 10981 | ||
| 10982 | ||
| 10983 | ||
| 10984 | </Paragraph></ContainerBlockElement></solution> | |
| 10985 | </vulnerability> | |
| 10986 | ||
| 10987 | <vulnerability id="SSH-SSHINC-0001" title="SSH Inc Kerberos Credentials Exposure Vulnerability" severity="7" pciSeverity="5" cvssScore="7.2" cvssVector="(AV:L/AC:L/Au:N/C:C/I:C/A:C)" published="20000705T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 10988 | <description> | |
| 10989 | ||
| 10990 | <ContainerBlockElement> | |
| 10991 | ||
| 10992 | <Paragraph>If a user logs into an SSH 1.2.27 server, and uses Kerberos during | |
| 10993 | the session, a file called 'none' is created in the current | |
| 10994 | directory. This file contains the user's Kerberos credentials, and | |
| 10995 | if the current directory is publicly accessible (like an NFS volume), | |
| 10996 | then another user on the system may intercept the credentials.</Paragraph> | |
| 10997 | </ContainerBlockElement></description> | |
| 10998 | <references> | |
| 10999 | <reference source="BID">1426</reference> | |
| 11000 | <reference source="CVE">CVE-2000-0575</reference> | |
| 11001 | <reference source="URL">http://www.securityfocus.com/templates/archive.pike?list=1&[email protected]</reference> | |
| 11002 | <reference source="XF">ssh-kerberos-tickets-disclosure(4903)</reference> | |
| 11003 | </references><tags> | |
| 11004 | <tag>NFS</tag> | |
| 11005 | <tag>SSH</tag> | |
| 11006 | </tags> | |
| 11007 | <solution> | |
| 11008 | ||
| 11009 | <ContainerBlockElement> | |
| 11010 | <Paragraph>Download and apply the upgrade from: | |
| 11011 | <URLLink LinkURL="ftp://ftp.ssh.com/pub/ssh/ssh-1.2.33.tar.gz" LinkTitle="ftp://ftp.ssh.com/pub/ssh/ssh-1.2.33.tar.gz"></URLLink></Paragraph> | |
| 11012 | <Paragraph> | |
| 11013 | <Paragraph>Upgrade to | |
| 11014 | ||
| 11015 | <URLLink LinkURL="ftp://ftp.ssh.com/pub/ssh/ssh-1.2.33.tar.gz" LinkTitle="ftp://ftp.ssh.com/pub/ssh/ssh-1.2.33.tar.gz" href="ftp://ftp.ssh.com/pub/ssh/ssh-1.2.33.tar.gz">v1.2.33</URLLink> | |
| 11016 | or later.</Paragraph> | |
| 11017 | <Paragraph>See the | |
| 11018 | <URLLink LinkURL="http://www.ssh.com/support/downloads/" LinkTitle="http://www.ssh.com/support/downloads/" href="http://www.ssh.com/support/downloads/">SSH</URLLink> | |
| 11019 | website for more information.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11020 | </vulnerability> | |
| 11021 | ||
| 11022 | <vulnerability id="SSH-SSHINC-0002" title="SSH Inc Logging Failure Vulnerability" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20010627T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 11023 | <description> | |
| 11024 | ||
| 11025 | <ContainerBlockElement> | |
| 11026 | ||
| 11027 | <Paragraph>SSH Inc < 1.2.31 ceases to log authentication failures after | |
| 11028 | four successive attempts. This allows a remote attacker to | |
| 11029 | brute-force login IDs without risk of detection. This vulnerability | |
| 11030 | is exacerbated by the fact that root logins are enabled by default.</Paragraph> | |
| 11031 | </ContainerBlockElement></description> | |
| 11032 | <references> | |
| 11033 | <reference source="BID">2345</reference> | |
| 11034 | <reference source="CVE">CVE-2001-0471</reference> | |
| 11035 | <reference source="URL">http://www.securityfocus.com/archive/1/160648</reference> | |
| 11036 | </references><tags> | |
| 11037 | <tag>SSH</tag> | |
| 11038 | </tags> | |
| 11039 | <solution> | |
| 11040 | ||
| 11041 | <ContainerBlockElement> | |
| 11042 | <Paragraph>Download and apply the upgrade from: | |
| 11043 | <URLLink LinkURL="ftp://ftp.ssh.com/pub/ssh/ssh-1.2.33.tar.gz" LinkTitle="ftp://ftp.ssh.com/pub/ssh/ssh-1.2.33.tar.gz"></URLLink></Paragraph> | |
| 11044 | <Paragraph> | |
| 11045 | <Paragraph>Upgrade to | |
| 11046 | ||
| 11047 | <URLLink LinkURL="ftp://ftp.ssh.com/pub/ssh/ssh-1.2.33.tar.gz" LinkTitle="ftp://ftp.ssh.com/pub/ssh/ssh-1.2.33.tar.gz" href="ftp://ftp.ssh.com/pub/ssh/ssh-1.2.33.tar.gz">v1.2.33</URLLink> | |
| 11048 | or later.</Paragraph> | |
| 11049 | <Paragraph>See the | |
| 11050 | <URLLink LinkURL="http://www.ssh.com/support/downloads/" LinkTitle="http://www.ssh.com/support/downloads/" href="http://www.ssh.com/support/downloads/">SSH</URLLink> | |
| 11051 | website for more information.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11052 | </vulnerability> | |
| 11053 | ||
| 11054 | <vulnerability id="SSH-SSHINC-0004" title="SSH Secure-RPC Weak Encryption Vulnerability" severity="4" pciSeverity="2" cvssScore="3.6" cvssVector="(AV:L/AC:L/Au:N/C:P/I:P/A:N)" published="20010602T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 11055 | <description> | |
| 11056 | ||
| 11057 | <ContainerBlockElement> | |
| 11058 | ||
| 11059 | <Paragraph>SSH Inc < 1.2.31 uses a weak authentication mechanism whereby | |
| 11060 | which a local attacker can recover another user's SUN-DES-1 magic | |
| 11061 | phrase, and decrypt that user's private key.</Paragraph> | |
| 11062 | </ContainerBlockElement></description> | |
| 11063 | <references> | |
| 11064 | <reference source="BID">2222</reference> | |
| 11065 | <reference source="CVE">CVE-2001-0259</reference> | |
| 11066 | <reference source="URL">http://archives.neohapsis.com/archives/bugtraq/2001-01/0262.html</reference> | |
| 11067 | <reference source="URL">http://www.ssh.com/products/ssh/patches/secureRPCvulnerability.html</reference> | |
| 11068 | <reference source="XF">ssh-rpc-private-key(5963)</reference> | |
| 11069 | </references><tags> | |
| 11070 | <tag>RPC</tag> | |
| 11071 | <tag>SSH</tag> | |
| 11072 | </tags> | |
| 11073 | <solution> | |
| 11074 | ||
| 11075 | <ContainerBlockElement> | |
| 11076 | <Paragraph>Download and apply the upgrade from: | |
| 11077 | <URLLink LinkURL="ftp://ftp.ssh.com/pub/ssh/ssh-1.2.33.tar.gz" LinkTitle="ftp://ftp.ssh.com/pub/ssh/ssh-1.2.33.tar.gz"></URLLink></Paragraph> | |
| 11078 | <Paragraph> | |
| 11079 | <Paragraph>Upgrade to | |
| 11080 | ||
| 11081 | <URLLink LinkURL="ftp://ftp.ssh.com/pub/ssh/ssh-1.2.33.tar.gz" LinkTitle="ftp://ftp.ssh.com/pub/ssh/ssh-1.2.33.tar.gz" href="ftp://ftp.ssh.com/pub/ssh/ssh-1.2.33.tar.gz">v1.2.33</URLLink> | |
| 11082 | or later.</Paragraph> | |
| 11083 | <Paragraph>See the | |
| 11084 | <URLLink LinkURL="http://www.ssh.com/support/downloads/" LinkTitle="http://www.ssh.com/support/downloads/" href="http://www.ssh.com/support/downloads/">SSH</URLLink> | |
| 11085 | website for more information.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11086 | </vulnerability> | |
| 11087 | ||
| 11088 | <vulnerability id="SSH-SSHINC-0005" title="SSH Inc Short Password Authentication Failure Vulnerability" severity="7" pciSeverity="5" cvssScore="7.2" cvssVector="(AV:L/AC:L/Au:N/C:C/I:C/A:C)" published="20010814T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 11089 | <description> | |
| 11090 | ||
| 11091 | <ContainerBlockElement> | |
| 11092 | ||
| 11093 | <Paragraph>Under SSH Inc < 3.0.1, if there exists a user whose password | |
| 11094 | in the system password file is two characters or less, it is possible | |
| 11095 | for an attacker to log in under that user ID with an arbitrary | |
| 11096 | password.</Paragraph> | |
| 11097 | </ContainerBlockElement></description> | |
| 11098 | <references> | |
| 11099 | <reference source="BID">3078</reference> | |
| 11100 | <reference source="CERT-VN">737451</reference> | |
| 11101 | <reference source="CIAC">L-121</reference> | |
| 11102 | <reference source="CVE">CVE-2001-0553</reference> | |
| 11103 | <reference source="OSVDB">586</reference> | |
| 11104 | <reference source="URL">http://archives.neohapsis.com/archives/bugtraq/2001-07/0486.html</reference> | |
| 11105 | <reference source="URL">http://www.ssh.com/products/ssh/exploit.cfm</reference> | |
| 11106 | <reference source="XF">ssh-password-length-unauth-access(6868)</reference> | |
| 11107 | </references><tags> | |
| 11108 | <tag>SSH</tag> | |
| 11109 | </tags> | |
| 11110 | <solution> | |
| 11111 | ||
| 11112 | <ContainerBlockElement> | |
| 11113 | <Paragraph>Download and apply the upgrade from: | |
| 11114 | <URLLink LinkURL="ftp://ftp.ssh.com/pub/ssh/ssh-3.0.1.tar.gz" LinkTitle="ftp://ftp.ssh.com/pub/ssh/ssh-3.0.1.tar.gz"></URLLink></Paragraph> | |
| 11115 | <Paragraph> | |
| 11116 | <Paragraph>Upgrade SSH v3.0.1 or later. | |
| 11117 | See the following | |
| 11118 | <URLLink LinkURL="http://www.ssh.com/support/downloads/" LinkTitle="http://www.ssh.com/support/downloads/" href="http://www.ssh.com/support/downloads/">link</URLLink> | |
| 11119 | for download information. | |
| 11120 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11121 | </vulnerability> | |
| 11122 | ||
| 11123 | <vulnerability id="SSH-SSHINC-0006" title="SSH Inc Restricted Shell Bypass Vulnerability" severity="7" pciSeverity="5" cvssScore="7.2" cvssVector="(AV:L/AC:L/Au:N/C:C/I:C/A:C)" published="20021231T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 11124 | <description> | |
| 11125 | ||
| 11126 | <ContainerBlockElement> | |
| 11127 | ||
| 11128 | <Paragraph>Under SSH < 3.1.1, it is possible for a user with a restricted | |
| 11129 | shell upload scripts to a world-writable directory, then execute it. | |
| 11130 | This allows the user to gain a regular, unrestricted shell to the | |
| 11131 | system.</Paragraph> | |
| 11132 | </ContainerBlockElement></description> | |
| 11133 | <references> | |
| 11134 | <reference source="BID">4547</reference> | |
| 11135 | <reference source="CVE">CVE-2002-1715</reference> | |
| 11136 | <reference source="XF">ssh-bypass-restricted-shells(8908)</reference> | |
| 11137 | </references><tags> | |
| 11138 | <tag>SSH</tag> | |
| 11139 | </tags> | |
| 11140 | <solution> | |
| 11141 | ||
| 11142 | <ContainerBlockElement> | |
| 11143 | <Paragraph>Download and apply the upgrade from: | |
| 11144 | <URLLink LinkURL="ftp://ftp.ssh.com/pub/ssh/ssh-3.1.1.tar.gz" LinkTitle="ftp://ftp.ssh.com/pub/ssh/ssh-3.1.1.tar.gz"></URLLink></Paragraph> | |
| 11145 | <Paragraph> | |
| 11146 | <Paragraph>Upgrade to v3.1.1 or later. To correct other security issues, | |
| 11147 | we recommend upgrading to the latest 3.1 release, currently | |
| 11148 | ||
| 11149 | <URLLink LinkURL="ftp://ftp.ssh.com/pub/ssh/ssh-3.1.1.tar.gz" LinkTitle="ftp://ftp.ssh.com/pub/ssh/ssh-3.1.1.tar.gz" href="ftp://ftp.ssh.com/pub/ssh/ssh-3.1.1.tar.gz">v3.1.1</URLLink></Paragraph> | |
| 11150 | <Paragraph> | |
| 11151 | See the | |
| 11152 | <URLLink LinkURL="http://www.ssh.com/support/downloads/" LinkTitle="http://www.ssh.com/support/downloads/" href="http://www.ssh.com/support/downloads/">SSH</URLLink> | |
| 11153 | website for download information. | |
| 11154 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11155 | </vulnerability> | |
| 11156 | ||
| 11157 | <vulnerability id="SSH-SSHINC-0007" title="SSH Inc AllowedAuthentications Override Vulnerability" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20021231T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 11158 | <description> | |
| 11159 | ||
| 11160 | <ContainerBlockElement> | |
| 11161 | ||
| 11162 | <Paragraph>It is sometimes possible for a remote user to circumvent the | |
| 11163 | server's "AllowedAuthentications" directive. This could allow | |
| 11164 | authentication via a weaker mechanism (such as a password) where | |
| 11165 | users would otherwise be required to log in using a stronger | |
| 11166 | method (such as public keys).</Paragraph> | |
| 11167 | </ContainerBlockElement></description> | |
| 11168 | <references> | |
| 11169 | <reference source="BID">4810</reference> | |
| 11170 | <reference source="CERT-VN">341187</reference> | |
| 11171 | <reference source="CIAC">M-081</reference> | |
| 11172 | <reference source="CVE">CVE-2002-1646</reference> | |
| 11173 | <reference source="URL">http://archives.neohapsis.com/archives/bugtraq/2002-05/0204.html</reference> | |
| 11174 | <reference source="URL">http://www.ssh.com/products/ssh/advisories/authentication.cfm</reference> | |
| 11175 | <reference source="XF">ssh-allowedauthentications-bypass-auth(9163)</reference> | |
| 11176 | </references><tags> | |
| 11177 | <tag>SSH</tag> | |
| 11178 | </tags> | |
| 11179 | <solution> | |
| 11180 | ||
| 11181 | <ContainerBlockElement> | |
| 11182 | <Paragraph> | |
| 11183 | <Paragraph> | |
| 11184 | Upgrade to SSH v3.1.2 or later. See the following | |
| 11185 | ||
| 11186 | <URLLink LinkURL="http://www.ssh.com/support/downloads/" LinkTitle="http://www.ssh.com/support/downloads/" href="http://www.ssh.com/support/downloads/">link</URLLink> | |
| 11187 | for download information. | |
| 11188 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11189 | </vulnerability> | |
| 11190 | ||
| 11191 | <vulnerability id="ssh-sshinc-getlogin-spoof-privilege-escalation" title="SSH Inc. getlogin() Spoofing Privilege Escalation Vulnerability" severity="7" pciSeverity="5" cvssScore="7.2" cvssVector="(AV:L/AC:L/Au:N/C:C/I:C/A:C)" published="20021125T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 11192 | <description> | |
| 11193 | ||
| 11194 | <ContainerBlockElement> | |
| 11195 | ||
| 11196 | <Paragraph>Due to a flaw in the process grouping logic, certain versions of SSH Inc. Secure Shell may allow a local attacker to spoof the result of the 'getlogin()' system call. This vulnerability allows the insertion of SSH syslog entries to be logged as coming from the root account; local attackers may also be able to elevate privileges as well.</Paragraph> | |
| 11197 | </ContainerBlockElement></description> | |
| 11198 | <references> | |
| 11199 | <reference source="BID">6247</reference> | |
| 11200 | <reference source="CERT-VN">740619</reference> | |
| 11201 | <reference source="CVE">CVE-2002-1644</reference> | |
| 11202 | <reference source="URL">http://www.ssh.com/company/newsroom/article/286/</reference> | |
| 11203 | <reference source="XF">ssh-setsid-privilege-elevation(10710)</reference> | |
| 11204 | </references><tags> | |
| 11205 | <tag>Privilege Escalation</tag> | |
| 11206 | <tag>SSH</tag> | |
| 11207 | </tags> | |
| 11208 | <solution> | |
| 11209 | ||
| 11210 | <ContainerBlockElement> | |
| 11211 | <Paragraph>Download and apply the upgrade from: | |
| 11212 | <URLLink LinkURL="ftp://ftp.ssh.com/pub/ssh/old/ssh-3.2.2.tar.gz" LinkTitle="ftp://ftp.ssh.com/pub/ssh/old/ssh-3.2.2.tar.gz"></URLLink></Paragraph> | |
| 11213 | <Paragraph> | |
| 11214 | <Paragraph>Upgrade to SSH v3.2.2 or later. See the | |
| 11215 | ||
| 11216 | <URLLink LinkURL="http://www.ssh.com/support/downloads/" LinkTitle="http://www.ssh.com/support/downloads/" href="http://www.ssh.com/support/downloads/">SSH</URLLink> | |
| 11217 | website for download information. | |
| 11218 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11219 | </vulnerability> | |
| 11220 | ||
| 11221 | <vulnerability id="ssh-sshinc-rsa-signature-forging" title="SSH Inc. RSA Signature Forging Vulnerability" severity="5" pciSeverity="3" cvssScore="5.1" cvssVector="(AV:N/AC:H/Au:N/C:P/I:P/A:P)" published="20041101T000000000" added="20041101T000000000" modified="20120712T000000000"> | |
| 11222 | <description> | |
| 11223 | ||
| 11224 | <ContainerBlockElement> | |
| 11225 | ||
| 11226 | <Paragraph>Certain versions of SSH Communications Secure Shell incorrectly verify invalid RSA signatures. As a result, a remote attacker could authenticate with the server and gain shell access. However, this attack is largely theoretical since the attacker must make (2 ^ 67) computations in order to generate a forged signature.</Paragraph> | |
| 11227 | </ContainerBlockElement></description> | |
| 11228 | <references> | |
| 11229 | </references><tags> | |
| 11230 | <tag>SSH</tag> | |
| 11231 | </tags> | |
| 11232 | <solution> | |
| 11233 | ||
| 11234 | <ContainerBlockElement> | |
| 11235 | <UnorderedList> | |
| 11236 | <ListItem> | |
| 11237 | <Paragraph> | |
| 11238 | <Paragraph> | |
| 11239 | Upgrade to SSH v3.1.8 or later. See the | |
| 11240 | ||
| 11241 | <URLLink LinkURL="http://www.ssh.com/support/downloads/" LinkTitle="http://www.ssh.com/support/downloads/" href="http://www.ssh.com/support/downloads/">SSH</URLLink> | |
| 11242 | website for download information. | |
| 11243 | </Paragraph></Paragraph></ListItem> | |
| 11244 | <ListItem> | |
| 11245 | <Paragraph> | |
| 11246 | <Paragraph> | |
| 11247 | <URLLink LinkURL="http://www.ssh.com/support/downloads/" LinkTitle="http://www.ssh.com/support/downloads/" href="http://www.ssh.com/support/downloads/"></URLLink></Paragraph></Paragraph></ListItem> | |
| 11248 | <ListItem> | |
| 11249 | <Paragraph> | |
| 11250 | <Paragraph>As of July, 2003, the latest version of SSH Secure Shell is v3.2.5. | |
| 11251 | ||
| 11252 | ||
| 11253 | <URLLink LinkURL="http://www.ssh.com/support/downloads/" LinkTitle="http://www.ssh.com/support/downloads/" href="http://www.ssh.com/support/downloads/"></URLLink></Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 11254 | </vulnerability> | |
| 11255 | ||
| 11256 | <vulnerability id="ssh-suse-default-account-suse-gm-password-123456" title="Default SSH password: suse-gm password "123456"" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20091104T000000000" added="20091104T000000000" modified="20120712T000000000"> | |
| 11257 | <description> | |
| 11258 | ||
| 11259 | <ContainerBlockElement> | |
| 11260 | ||
| 11261 | <Paragraph>The suse-gm account has the password "123456", which is one of the most | |
| 11262 | common passwords in use.</Paragraph> | |
| 11263 | </ContainerBlockElement></description> | |
| 11264 | <references> | |
| 11265 | </references><tags> | |
| 11266 | <tag>Default Account</tag> | |
| 11267 | <tag>SSH</tag> | |
| 11268 | </tags> | |
| 11269 | <solution> | |
| 11270 | ||
| 11271 | <ContainerBlockElement> | |
| 11272 | <Paragraph> | |
| 11273 | <Paragraph>Use the "passwd" command to set a more secure login | |
| 11274 | password. A good password should consist of a mix of lower- and | |
| 11275 | upper-case characters, numbers, and punctuation and should be at least | |
| 11276 | 8 characters long.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11277 | </vulnerability> | |
| 11278 | ||
| 11279 | <vulnerability id="ssh-v1-supported" title="SSH server supports SSH protocol v1 clients" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20050421T000000000" added="20061121T000000000" modified="20130703T000000000"> | |
| 11280 | <description> | |
| 11281 | ||
| 11282 | <ContainerBlockElement> | |
| 11283 | ||
| 11284 | <Paragraph>The SSH server support SSH version 1 clients. Version 1 of the SSH protocol | |
| 11285 | contains fundamental weaknesses which make sessions vulnerable to man-in-the-middle | |
| 11286 | attacks. Since all modern SSH clients have supported SSH v2 for at least 5 years, | |
| 11287 | there is no reason to support SSHv1. | |
| 11288 | </Paragraph> | |
| 11289 | </ContainerBlockElement></description> | |
| 11290 | <references> | |
| 11291 | <reference source="CERT-VN">684820</reference> | |
| 11292 | <reference source="CVE">CVE-2001-1473</reference> | |
| 11293 | <reference source="XF">ssh-authentication-forwarding(6603)</reference> | |
| 11294 | </references><tags> | |
| 11295 | <tag>Insecure Remote Access</tag> | |
| 11296 | <tag>SSH</tag> | |
| 11297 | </tags> | |
| 11298 | <solution> | |
| 11299 | ||
| 11300 | <ContainerBlockElement> | |
| 11301 | <Paragraph> | |
| 11302 | <Paragraph> | |
| 11303 | Configure the SSH server to support protocol version 2 only. For OpenSSH-based | |
| 11304 | servers, change the "Protocol" line in the sshd_config file to read: | |
| 11305 | </Paragraph> | |
| 11306 | <Paragraph preformat="true">Protocol 2</Paragraph> | |
| 11307 | <Paragraph> | |
| 11308 | For systems not based on OpenSSH, you may need | |
| 11309 | to upgrade the operating system version to enable SSHv2 support. | |
| 11310 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11311 | </vulnerability> | |
| 11312 | ||
| 11313 | <vulnerability id="ssl-self-signed-certificate" title="Self-signed TLS/SSL certificate" severity="4" pciSeverity="3" cvssScore="4.3" cvssVector="(AV:N/AC:M/Au:N/C:N/I:P/A:N)" published="19950101T000000000" added="20090716T000000000" modified="20120712T000000000"> | |
| 11314 | <description> | |
| 11315 | ||
| 11316 | <ContainerBlockElement> | |
| 11317 | ||
| 11318 | <Paragraph> | |
| 11319 | The server's TLS/SSL certificate is self-signed. Self-signed certificates cannot be | |
| 11320 | trusted by default, especially because TLS/SSL man-in-the-middle attacks typically use | |
| 11321 | self-signed certificates to eavesdrop on TLS/SSL connections. | |
| 11322 | </Paragraph> | |
| 11323 | </ContainerBlockElement></description> | |
| 11324 | <references> | |
| 11325 | </references><tags> | |
| 11326 | <tag>Network</tag> | |
| 11327 | </tags> | |
| 11328 | <solution> | |
| 11329 | ||
| 11330 | <ContainerBlockElement> | |
| 11331 | <Paragraph> | |
| 11332 | <Paragraph>Obtain a new TLS/SSL server certificate that is NOT self-signed and install it on the server. | |
| 11333 | The exact instructions for obtaining a new certificate depend on your organization's requirements. | |
| 11334 | Generally, you will need to generate a certificate request and save the request as a file. This | |
| 11335 | file is then sent to a Certificate Authority (CA) for processing. Your organization may have its | |
| 11336 | own internal Certificate Authority. If not, you may have to pay for a certificate from a trusted | |
| 11337 | external Certificate Authority, such as | |
| 11338 | <URLLink LinkURL="http://www.thawte.com" LinkTitle="http://www.thawte.com" href="http://www.thawte.com">Thawte</URLLink> or | |
| 11339 | ||
| 11340 | <URLLink LinkURL="http://www.verisign.com" LinkTitle="http://www.verisign.com" href="http://www.verisign.com">Verisign</URLLink>.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11341 | </vulnerability> | |
| 11342 | ||
| 11343 | <vulnerability id="ssl-weak-ciphers" title="TLS/SSL Server Supports Weak Cipher Algorithms" severity="6" pciSeverity="3" cvssScore="5.8" cvssVector="(AV:N/AC:M/Au:N/C:P/I:P/A:N)" published="19960101T000000000" added="20090212T000000000" modified="20130515T000000000"> | |
| 11344 | <description> | |
| 11345 | ||
| 11346 | <ContainerBlockElement> | |
| 11347 | ||
| 11348 | <Paragraph> | |
| 11349 | The TLS/SSL server supports cipher suites based on weak algorithms. This may | |
| 11350 | enable an attacker to launch man-in-the-middle attacks and monitor or | |
| 11351 | tamper with sensitive data. In general, the following ciphers are | |
| 11352 | considered weak: | |
| 11353 | </Paragraph> | |
| 11354 | ||
| 11355 | <UnorderedList> | |
| 11356 | <ListItem>So called "null" ciphers, because they do not encrypt data.</ListItem> | |
| 11357 | <ListItem>Export ciphers using secret key lengths restricted to 40 bits. | |
| 11358 | This is usually indicated by the word EXP/EXPORT in the name of the cipher suite.</ListItem> | |
| 11359 | <ListItem>Obsolete encryption algorithms with secret key lengths considered short by | |
| 11360 | today's standards, eg. DES or RC4 with 56-bit keys.</ListItem></UnorderedList> | |
| 11361 | </ContainerBlockElement></description> | |
| 11362 | <references> | |
| 11363 | </references><tags> | |
| 11364 | <tag>Network</tag> | |
| 11365 | </tags> | |
| 11366 | <solution> | |
| 11367 | ||
| 11368 | <ContainerBlockElement> | |
| 11369 | <Paragraph> | |
| 11370 | <Paragraph>Configure the server to disable support for weak ciphers.</Paragraph> | |
| 11371 | <Paragraph>For Microsoft IIS web servers, see Microsoft Knowledgebase article | |
| 11372 | <URLLink LinkURL="http://support.microsoft.com/kb/245030/" LinkTitle="http://support.microsoft.com/kb/245030/" href="http://support.microsoft.com/kb/245030/">245030</URLLink> | |
| 11373 | for instructions on disabling weak ciphers.</Paragraph> | |
| 11374 | <Paragraph>For Apache web servers with mod_ssl, edit the Apache configuration file and change the SSLCipherSuite line to read:</Paragraph> | |
| 11375 | <Paragraph preformat="true">SSLCipherSuite ALL:!aNULL:!eNULL:!LOW:!EXP:RC4+RSA:+HIGH:+MEDIUM</Paragraph> | |
| 11376 | <Paragraph>For other servers, refer to the respective vendor documentation to disable the weak ciphers</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11377 | </vulnerability> | |
| 11378 | ||
| 11379 | <vulnerability id="sslv2-and-up-enabled" title="TLS/SSL Server Supports SSLv2" severity="6" pciSeverity="3" cvssScore="5.8" cvssVector="(AV:N/AC:M/Au:N/C:P/I:P/A:N)" published="19960101T000000000" added="20090209T000000000" modified="20131011T000000000"> | |
| 11380 | <description> | |
| 11381 | ||
| 11382 | <ContainerBlockElement> | |
| 11383 | ||
| 11384 | <Paragraph>Although the server accepts clients using TLS or SSLv3, it also accepts clients using SSLv2. | |
| 11385 | SSLv2 is an older implementation of the Secure Sockets Layer protocol. | |
| 11386 | It suffers from a number of security flaws allowing attackers to | |
| 11387 | capture and alter information passed between a client and the server, | |
| 11388 | including the following weaknesses:</Paragraph> | |
| 11389 | ||
| 11390 | ||
| 11391 | <UnorderedList> | |
| 11392 | <ListItem>No protection from against man-in-the-middle attacks during the handshake.</ListItem> | |
| 11393 | <ListItem>Weak MAC construction and MAC relying solely on the MD5 hash function.</ListItem> | |
| 11394 | <ListItem>Exportable cipher suites unnecessarily weaken the MACs</ListItem> | |
| 11395 | <ListItem>Same cryptographic keys used for message authentication and encryption.</ListItem> | |
| 11396 | <ListItem>Vulnerable to truncation attacks by forged TCP FIN packets</ListItem></UnorderedList> | |
| 11397 | ||
| 11398 | ||
| 11399 | <Paragraph>SSLv2 has been deprecated and is no longer recommended. Note that neither | |
| 11400 | SSLv2 nor SSLv3 meet the U.S. FIPS 140-2 standard, which governs cryptographic | |
| 11401 | modules for use in federal information systems. Only the newer TLS (Transport | |
| 11402 | Layer Security) protocol meets FIPS 140-2 requirements. In addition, the | |
| 11403 | presence of an SSLv2-only service on a host is deemed a failure by the PCI | |
| 11404 | (Payment Card Industry) Data Security Standard.</Paragraph> | |
| 11405 | ||
| 11406 | ||
| 11407 | <Paragraph>Note that this vulnerability will be reported when the remote server | |
| 11408 | supports SSLv2 regardless of whether TLS or SSLv3 are also supported.</Paragraph> | |
| 11409 | </ContainerBlockElement></description> | |
| 11410 | <references> | |
| 11411 | <reference source="URL">http://www.eucybervote.org/Reports/MSI-WP2-D7V1-V1.0-02.htm</reference> | |
| 11412 | <reference source="URL">https://www.pcisecuritystandards.org/pdfs/pcissc_assessors_nl_2008-11.pdf</reference> | |
| 11413 | </references><tags> | |
| 11414 | <tag>Network</tag> | |
| 11415 | </tags> | |
| 11416 | <solution> | |
| 11417 | ||
| 11418 | <ContainerBlockElement> | |
| 11419 | <UnorderedList> | |
| 11420 | <ListItem> | |
| 11421 | <Paragraph>Apache HTTPD</Paragraph> | |
| 11422 | <Paragraph> | |
| 11423 | <Paragraph>For Apache web servers with mod_ssl, edit the Apache configuration file and change the SSLCipherSuite line to read:</Paragraph> | |
| 11424 | <Paragraph preformat="true">SSLCipherSuite ALL:!ADH:RC4+RSA:+HIGH:!SSLv2</Paragraph> | |
| 11425 | <Paragraph>The ! (exclamation point) before SSLv2 is what disables this protocol.</Paragraph></Paragraph></ListItem> | |
| 11426 | <ListItem> | |
| 11427 | <Paragraph>Windows</Paragraph> | |
| 11428 | <Paragraph> | |
| 11429 | <Paragraph>Configure the server to require clients to use at least SSLv3 or TLS.</Paragraph> | |
| 11430 | <Paragraph> | |
| 11431 | For Microsoft Windows before Windows 2003, see | |
| 11432 | <URLLink LinkURL="http://support.microsoft.com/kb/187498" LinkTitle="http://support.microsoft.com/kb/187498" href="http://support.microsoft.com/kb/187498">KB187498</URLLink>. | |
| 11433 | For newer versions of Microsoft Windows, see | |
| 11434 | <URLLink LinkURL="http://support.microsoft.com/kb/245030" LinkTitle="http://support.microsoft.com/kb/245030" href="http://support.microsoft.com/kb/245030">KB245030</URLLink>. | |
| 11435 | </Paragraph></Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 11436 | </vulnerability> | |
| 11437 | ||
| 11438 | <vulnerability id="tcp-seq-num-approximation" title="TCP Sequence Number Approximation Vulnerability" severity="5" pciSeverity="2" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:N/A:P)" published="20040421T000000000" added="20100125T000000000" modified="20120712T000000000"> | |
| 11439 | <description> | |
| 11440 | ||
| 11441 | <ContainerBlockElement> | |
| 11442 | ||
| 11443 | <Paragraph> | |
| 11444 | TCP, when using a large Window Size, makes it easier for remote | |
| 11445 | attackers to guess sequence numbers and cause a denial of service | |
| 11446 | (connection loss) to persistent TCP connections by repeatedly | |
| 11447 | injecting a TCP RST packet, especially in protocols that use | |
| 11448 | long-lived connections, such as BGP. | |
| 11449 | </Paragraph> | |
| 11450 | </ContainerBlockElement></description> | |
| 11451 | <references> | |
| 11452 | <reference source="BID">10183</reference> | |
| 11453 | <reference source="CERT">TA04-111A</reference> | |
| 11454 | <reference source="CERT-VN">415294</reference> | |
| 11455 | <reference source="CVE">CVE-2004-0230</reference> | |
| 11456 | <reference source="MS">MS05-019</reference> | |
| 11457 | <reference source="MS">MS06-064</reference> | |
| 11458 | <reference source="NETBSD">NetBSD-SA2004-006</reference> | |
| 11459 | <reference source="OSVDB">4030</reference> | |
| 11460 | <reference source="OVAL">OVAL2689</reference> | |
| 11461 | <reference source="OVAL">OVAL270</reference> | |
| 11462 | <reference source="OVAL">OVAL3508</reference> | |
| 11463 | <reference source="OVAL">OVAL4791</reference> | |
| 11464 | <reference source="OVAL">OVAL5711</reference> | |
| 11465 | <reference source="SECUNIA">11440</reference> | |
| 11466 | <reference source="SECUNIA">11458</reference> | |
| 11467 | <reference source="SECUNIA">22341</reference> | |
| 11468 | <reference source="SGI">20040403-01-A</reference> | |
| 11469 | <reference source="URL">ftp://ftp.netbsd.org/pub/NetBSD/security/advisories/NetBSD-SA2004-006.txt.asc</reference> | |
| 11470 | <reference source="URL">http://tools.ietf.org/html/draft-ietf-tcpm-tcpsecure-12</reference> | |
| 11471 | <reference source="URL">http://www.uniras.gov.uk/vuls/2004/236929/index.htm</reference> | |
| 11472 | <reference source="XF">tcp-rst-dos(15886)</reference> | |
| 11473 | </references><tags> | |
| 11474 | <tag>Denial of Service</tag> | |
| 11475 | <tag>Network</tag> | |
| 11476 | </tags> | |
| 11477 | <solution> | |
| 11478 | ||
| 11479 | <ContainerBlockElement> | |
| 11480 | <UnorderedList> | |
| 11481 | <ListItem> | |
| 11482 | <Paragraph>Microsoft Windows Server 2003 < SP1 (x86), Microsoft Windows Server 2003, Standard Edition < SP1 (x86), Microsoft Windows Server 2003, Enterprise Edition < SP1 (x86), Microsoft Windows Server 2003, Datacenter Edition < SP1 (x86), Microsoft Windows Server 2003, Web Edition < SP1 (x86), Microsoft Windows Small Business Server 2003 < SP1 (x86)</Paragraph> | |
| 11483 | <Paragraph>Download and apply the patch from: | |
| 11484 | <URLLink LinkURL="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windowsserver2003-kb893066-v2-x86-enu_ed6adba942906756fec6fea17347ba1a526c594b.exe" LinkTitle="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windowsserver2003-kb893066-v2-x86-enu_ed6adba942906756fec6fea17347ba1a526c594b.exe"></URLLink></Paragraph></ListItem> | |
| 11485 | <ListItem> | |
| 11486 | <Paragraph>Microsoft Windows 2000 SP4 OR SP3 (x86), Microsoft Windows 2000 Professional SP4 OR SP3 (x86), Microsoft Windows 2000 Server SP4 OR SP3 (x86), Microsoft Windows 2000 Advanced Server SP4 OR SP3 (x86), Microsoft Windows 2000 Datacenter Server SP4 OR SP3 (x86)</Paragraph> | |
| 11487 | <Paragraph>Download and apply the patch from: | |
| 11488 | <URLLink LinkURL="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windows2000-kb893066-v2-x86-enu_a5b95ec14e70e531e784ea83e633d24a0ea83795.exe" LinkTitle="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windows2000-kb893066-v2-x86-enu_a5b95ec14e70e531e784ea83e633d24a0ea83795.exe"></URLLink></Paragraph></ListItem> | |
| 11489 | <ListItem> | |
| 11490 | <Paragraph>Microsoft Windows XP Professional SP2 OR SP1 (x86), Microsoft Windows XP Home SP2 OR SP1 (x86)</Paragraph> | |
| 11491 | <Paragraph>Download and apply the patch from: | |
| 11492 | <URLLink LinkURL="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windowsxp-kb893066-v2-x86-enu_3d2029a4300c0b7943b20c1287c8143087045d52.exe" LinkTitle="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windowsxp-kb893066-v2-x86-enu_3d2029a4300c0b7943b20c1287c8143087045d52.exe"></URLLink></Paragraph></ListItem> | |
| 11493 | <ListItem> | |
| 11494 | <Paragraph>Microsoft Windows Server 2003 SP1 OR < SP1 (x86), Microsoft Windows Server 2003, Standard Edition SP1 OR < SP1 (x86), Microsoft Windows Server 2003, Enterprise Edition SP1 OR < SP1 (x86), Microsoft Windows Server 2003, Datacenter Edition SP1 OR < SP1 (x86), Microsoft Windows Server 2003, Web Edition SP1 OR < SP1 (x86), Microsoft Windows Small Business Server 2003 SP1 OR < SP1 (x86)</Paragraph> | |
| 11495 | <Paragraph>Download and apply the patch from: | |
| 11496 | <URLLink LinkURL="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windowsserver2003-kb922819-x86-enu_22c5d80f99afb4a79b6245a4b5db1e8c95cb03fa.exe" LinkTitle="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windowsserver2003-kb922819-x86-enu_22c5d80f99afb4a79b6245a4b5db1e8c95cb03fa.exe"></URLLink></Paragraph></ListItem> | |
| 11497 | <ListItem> | |
| 11498 | <Paragraph>Microsoft Windows Server 2003 SP1 (x86_64), Microsoft Windows Server 2003, Standard Edition SP1 (x86_64), Microsoft Windows Server 2003, Enterprise Edition SP1 (x86_64), Microsoft Windows Server 2003, Datacenter Edition SP1 (x86_64), Microsoft Windows Server 2003, Web Edition SP1 (x86_64), Microsoft Windows Small Business Server 2003 SP1 (x86_64)</Paragraph> | |
| 11499 | <Paragraph>Download and apply the patch from: | |
| 11500 | <URLLink LinkURL="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windowsserver2003.windowsxp-kb922819-x64-enu_4c34629b0664f2d2cd78c0276e4bd6b5e72ede61.exe" LinkTitle="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windowsserver2003.windowsxp-kb922819-x64-enu_4c34629b0664f2d2cd78c0276e4bd6b5e72ede61.exe"></URLLink></Paragraph></ListItem> | |
| 11501 | <ListItem> | |
| 11502 | <Paragraph>Microsoft Windows XP Professional SP1 OR SP2 (x86), Microsoft Windows XP Home SP1 OR SP2 (x86)</Paragraph> | |
| 11503 | <Paragraph>Download and apply the patch from: | |
| 11504 | <URLLink LinkURL="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windowsxp-kb922819-x86-enu_e4dceecdd4a72e5ad91cc78fe5f4572f91ee5db0.exe" LinkTitle="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windowsxp-kb922819-x86-enu_e4dceecdd4a72e5ad91cc78fe5f4572f91ee5db0.exe"></URLLink></Paragraph></ListItem> | |
| 11505 | <ListItem> | |
| 11506 | <Paragraph>Microsoft Windows Server 2003 SP1 OR < SP1 (ia64), Microsoft Windows Server 2003, Standard Edition SP1 OR < SP1 (ia64), Microsoft Windows Server 2003, Enterprise Edition SP1 OR < SP1 (ia64), Microsoft Windows Server 2003, Datacenter Edition SP1 OR < SP1 (ia64), Microsoft Windows Server 2003, Web Edition SP1 OR < SP1 (ia64), Microsoft Windows Small Business Server 2003 SP1 OR < SP1 (ia64)</Paragraph> | |
| 11507 | <Paragraph>Download and apply the patch from: | |
| 11508 | <URLLink LinkURL="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windowsserver2003-kb922819-ia64-enu_34ecda284c6fc7b6fbbbfd6e2c823525ab9c838a.exe" LinkTitle="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windowsserver2003-kb922819-ia64-enu_34ecda284c6fc7b6fbbbfd6e2c823525ab9c838a.exe"></URLLink></Paragraph></ListItem> | |
| 11509 | <ListItem> | |
| 11510 | <Paragraph>Microsoft Windows XP Professional SP1 (x86_64)</Paragraph> | |
| 11511 | <Paragraph>Download and apply the patch from: | |
| 11512 | <URLLink LinkURL="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windowsserver2003.windowsxp-kb922819-x64-enu_4c34629b0664f2d2cd78c0276e4bd6b5e72ede61.exe" LinkTitle="http://www.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windowsserver2003.windowsxp-kb922819-x64-enu_4c34629b0664f2d2cd78c0276e4bd6b5e72ede61.exe"></URLLink></Paragraph></ListItem> | |
| 11513 | <ListItem> | |
| 11514 | <Paragraph> | |
| 11515 | <Paragraph> | |
| 11516 | Enable the TCP MD5 signature option as documented in | |
| 11517 | ||
| 11518 | <URLLink LinkURL="http://www.ietf.org/rfc/rfc2385.txt" LinkTitle="http://www.ietf.org/rfc/rfc2385.txt" href="http://www.ietf.org/rfc/rfc2385.txt">RFC 2385</URLLink>. It was | |
| 11519 | designed to reduce the danger from certain security attacks on BGP, | |
| 11520 | such as TCP resets. | |
| 11521 | </Paragraph></Paragraph></ListItem> | |
| 11522 | <ListItem> | |
| 11523 | <Paragraph> | |
| 11524 | In many situations, target systems are, by themselves, patched or | |
| 11525 | otherwise unaffected by this vulnerability. In certain | |
| 11526 | configurations, however, unaffected systems can be made vulnerable if | |
| 11527 | the path between an attacker and the target system contains an | |
| 11528 | affected and unpatched network device such as a firewall or router | |
| 11529 | and that device is responsible for handling TCP connections for the | |
| 11530 | target. In this case, locate and apply remediation steps for network | |
| 11531 | devices along the route that are affected. | |
| 11532 | </Paragraph></ListItem></UnorderedList></ContainerBlockElement></solution> | |
| 11533 | </vulnerability> | |
| 11534 | ||
| 11535 | <vulnerability id="telnet-avaya-default-login-diag" title="Undocumented Default Account: diag" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20041101T000000000" added="20041101T000000000" modified="20120716T000000000"> | |
| 11536 | <description> | |
| 11537 | ||
| 11538 | <ContainerBlockElement> | |
| 11539 | ||
| 11540 | <Paragraph>Certain software versions for Avaya switches come with a default account, 'diag', which has read-write access. This account is completely undocumented and cannot be removed unless the firmware is upgraded.</Paragraph> | |
| 11541 | </ContainerBlockElement></description> | |
| 11542 | <references> | |
| 11543 | </references><tags> | |
| 11544 | <tag>Default Account</tag> | |
| 11545 | <tag>Telnet</tag> | |
| 11546 | </tags> | |
| 11547 | <solution> | |
| 11548 | ||
| 11549 | <ContainerBlockElement> | |
| 11550 | <Paragraph>Download and apply the upgrade from: | |
| 11551 | <URLLink LinkURL="http://support.avaya.com" LinkTitle="http://support.avaya.com"></URLLink></Paragraph> | |
| 11552 | <Paragraph> | |
| 11553 | <Paragraph>Upgrade to firmware v5.3.0 or later, and disable the accounts: | |
| 11554 | ||
| 11555 | ||
| 11556 | ||
| 11557 | <URLLink LinkURL="http://support.avaya.com" LinkTitle="http://support.avaya.com" href="http://support.avaya.com">http://support.avaya.com</URLLink> ( http://support.avaya.com ) </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11558 | </vulnerability> | |
| 11559 | ||
| 11560 | <vulnerability id="telnet-avaya-default-login-manuf" title="Undocumented Default Account: manuf" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20041101T000000000" added="20041101T000000000" modified="20120716T000000000"> | |
| 11561 | <description> | |
| 11562 | ||
| 11563 | <ContainerBlockElement> | |
| 11564 | ||
| 11565 | <Paragraph>Certain software versions for Avaya switches come with a default account, 'manuf', which has read-write access. This account is completely undocumented and cannot be removed unless the firmware is upgraded.</Paragraph> | |
| 11566 | </ContainerBlockElement></description> | |
| 11567 | <references> | |
| 11568 | </references><tags> | |
| 11569 | <tag>Default Account</tag> | |
| 11570 | <tag>Telnet</tag> | |
| 11571 | </tags> | |
| 11572 | <solution> | |
| 11573 | ||
| 11574 | <ContainerBlockElement> | |
| 11575 | <Paragraph>Download and apply the upgrade from: | |
| 11576 | <URLLink LinkURL="http://support.avaya.com" LinkTitle="http://support.avaya.com"></URLLink></Paragraph> | |
| 11577 | <Paragraph> | |
| 11578 | <Paragraph>Upgrade to firmware v5.3.0 or later, and disable the accounts: | |
| 11579 | ||
| 11580 | ||
| 11581 | ||
| 11582 | <URLLink LinkURL="http://support.avaya.com" LinkTitle="http://support.avaya.com" href="http://support.avaya.com">http://support.avaya.com</URLLink> ( http://support.avaya.com ) </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11583 | </vulnerability> | |
| 11584 | ||
| 11585 | <vulnerability id="telnet-db2-default-login-db2as" title="Telnet DB2 Default Login: db2as" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20010216T000000000" added="20041101T000000000" modified="20120716T000000000"> | |
| 11586 | <description> | |
| 11587 | ||
| 11588 | <ContainerBlockElement> | |
| 11589 | ||
| 11590 | <Paragraph>After installing certain versions of IBM's DB2 server, a system account named 'db2as' is automatically created with a default password of 'ibmdb2'. This default password should be changed immediately to prevent database and system exploitation.</Paragraph> | |
| 11591 | </ContainerBlockElement></description> | |
| 11592 | <references> | |
| 11593 | <reference source="BID">2068</reference> | |
| 11594 | <reference source="CVE">CVE-2001-0051</reference> | |
| 11595 | <reference source="URL">http://www.securityfocus.com/archive/1/149222</reference> | |
| 11596 | <reference source="XF">ibm-db2-gain-access(5662)</reference> | |
| 11597 | </references><tags> | |
| 11598 | <tag>Default Account</tag> | |
| 11599 | <tag>IBM</tag> | |
| 11600 | <tag>IBM DB2</tag> | |
| 11601 | <tag>Telnet</tag> | |
| 11602 | </tags> | |
| 11603 | <solution> | |
| 11604 | ||
| 11605 | <ContainerBlockElement> | |
| 11606 | <Paragraph> | |
| 11607 | <Paragraph>Change the password to a non-default value.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11608 | </vulnerability> | |
| 11609 | ||
| 11610 | <vulnerability id="telnet-db2-default-login-db2fenc1" title="Telnet DB2 Default Login: db2fenc1" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20010216T000000000" added="20041101T000000000" modified="20120716T000000000"> | |
| 11611 | <description> | |
| 11612 | ||
| 11613 | <ContainerBlockElement> | |
| 11614 | ||
| 11615 | <Paragraph>After installing certain versions of IBM's DB2 server, a system account named 'db2fenc1' is automatically created with a default password of 'ibmdb2'. This default password should be changed immediately to prevent database and system exploitation.</Paragraph> | |
| 11616 | </ContainerBlockElement></description> | |
| 11617 | <references> | |
| 11618 | <reference source="BID">2068</reference> | |
| 11619 | <reference source="CVE">CVE-2001-0051</reference> | |
| 11620 | <reference source="URL">http://www.securityfocus.com/archive/1/149222</reference> | |
| 11621 | <reference source="XF">ibm-db2-gain-access(5662)</reference> | |
| 11622 | </references><tags> | |
| 11623 | <tag>Default Account</tag> | |
| 11624 | <tag>IBM</tag> | |
| 11625 | <tag>IBM DB2</tag> | |
| 11626 | <tag>Telnet</tag> | |
| 11627 | </tags> | |
| 11628 | <solution> | |
| 11629 | ||
| 11630 | <ContainerBlockElement> | |
| 11631 | <Paragraph> | |
| 11632 | <Paragraph>Change the password to a non-default value.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11633 | </vulnerability> | |
| 11634 | ||
| 11635 | <vulnerability id="telnet-db2-default-login-db2inst1" title="Telnet DB2 Default Login: db2inst1" severity="8" pciSeverity="5" cvssScore="7.5" cvssVector="(AV:N/AC:L/Au:N/C:P/I:P/A:P)" published="20010216T000000000" added="20041101T000000000" modified="20120716T000000000"> | |
| 11636 | <description> | |
| 11637 | ||
| 11638 | <ContainerBlockElement> | |
| 11639 | ||
| 11640 | <Paragraph>After installing certain versions of IBM's DB2 server, a system account named 'db2inst1' is automatically created with a default password of 'ibmdb2'. This default password should be changed immediately to prevent database and system exploitation.</Paragraph> | |
| 11641 | </ContainerBlockElement></description> | |
| 11642 | <references> | |
| 11643 | <reference source="BID">2068</reference> | |
| 11644 | <reference source="CVE">CVE-2001-0051</reference> | |
| 11645 | <reference source="URL">http://www.securityfocus.com/archive/1/149222</reference> | |
| 11646 | <reference source="XF">ibm-db2-gain-access(5662)</reference> | |
| 11647 | </references><tags> | |
| 11648 | <tag>Default Account</tag> | |
| 11649 | <tag>IBM</tag> | |
| 11650 | <tag>IBM DB2</tag> | |
| 11651 | <tag>Telnet</tag> | |
| 11652 | </tags> | |
| 11653 | <solution> | |
| 11654 | ||
| 11655 | <ContainerBlockElement> | |
| 11656 | <Paragraph> | |
| 11657 | <Paragraph>Change the password to a non-default value.</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11658 | </vulnerability> | |
| 11659 | ||
| 11660 | <vulnerability id="telnet-default-account-admin-password-password" title="Default Telnet password: admin password "password"" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="19700101T000000000" added="20090512T000000000" modified="20120716T000000000"> | |
| 11661 | <description> | |
| 11662 | ||
| 11663 | <ContainerBlockElement> | |
| 11664 | ||
| 11665 | <Paragraph>The admin account uses a password of "password". This would allow | |
| 11666 | anyone to log into the machine via telnet and take complete | |
| 11667 | control.</Paragraph> | |
| 11668 | </ContainerBlockElement></description> | |
| 11669 | <references> | |
| 11670 | </references><tags> | |
| 11671 | <tag>Default Account</tag> | |
| 11672 | <tag>Telnet</tag> | |
| 11673 | </tags> | |
| 11674 | <solution> | |
| 11675 | ||
| 11676 | <ContainerBlockElement> | |
| 11677 | <Paragraph> | |
| 11678 | <Paragraph> | |
| 11679 | Change the password to a non-default value. | |
| 11680 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11681 | </vulnerability> | |
| 11682 | ||
| 11683 | <vulnerability id="telnet-default-account-root-password-password" title="Default Telnet password: root password "password"" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20050125T000000000" added="20050125T000000000" modified="20120716T000000000"> | |
| 11684 | <description> | |
| 11685 | ||
| 11686 | <ContainerBlockElement> | |
| 11687 | ||
| 11688 | <Paragraph>The root account uses a password of "password". This would allow | |
| 11689 | anyone to log into the machine via Telnet and take complete control.</Paragraph> | |
| 11690 | </ContainerBlockElement></description> | |
| 11691 | <references> | |
| 11692 | </references><tags> | |
| 11693 | <tag>Default Account</tag> | |
| 11694 | <tag>Telnet</tag> | |
| 11695 | </tags> | |
| 11696 | <solution> | |
| 11697 | ||
| 11698 | <ContainerBlockElement> | |
| 11699 | <Paragraph> | |
| 11700 | <Paragraph>Use the "passwd" command to set a more secure login password. A good | |
| 11701 | password should consist of a mix of lower- and upper-case characters, | |
| 11702 | numbers, and punctuation and should be at least 8 characters long. | |
| 11703 | You may also want to disable the Telnet service altogether and switch | |
| 11704 | to something like SSH. If you switch to SSH, consider disabling root | |
| 11705 | login via SSH, which you can do in OpenSSH by adding the following to | |
| 11706 | sshd.conf:</Paragraph> | |
| 11707 | <Paragraph preformat="true">PermitRootLogin: no</Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11708 | </vulnerability> | |
| 11709 | ||
| 11710 | <vulnerability id="TELNET-GENERIC-0001" title="TELNET access with no account and password admin" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20041101T000000000" added="20041101T000000000" modified="20120716T000000000"> | |
| 11711 | <description> | |
| 11712 | ||
| 11713 | <ContainerBlockElement> | |
| 11714 | Many systems, such as routers, do not require an account name. This system appears to use the password "admin". It is best practice to remove default accounts, if possible. For accounts required by the system, the default password should be changed. | |
| 11715 | </ContainerBlockElement></description> | |
| 11716 | <references> | |
| 11717 | </references><tags> | |
| 11718 | <tag>Default Account</tag> | |
| 11719 | <tag>Telnet</tag> | |
| 11720 | </tags> | |
| 11721 | <solution> | |
| 11722 | ||
| 11723 | <ContainerBlockElement> | |
| 11724 | <Paragraph> | |
| 11725 | Remove or disable the account if it is not critical for the system to function. Otherwise, the password should be changed to a non-default value. | |
| 11726 | </Paragraph></ContainerBlockElement></solution> | |
| 11727 | </vulnerability> | |
| 11728 | ||
| 11729 | <vulnerability id="TELNET-GENERIC-0002" title="TELNET access with account admin and password admin" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20041101T000000000" added="20041101T000000000" modified="20120716T000000000"> | |
| 11730 | <description> | |
| 11731 | ||
| 11732 | <ContainerBlockElement> | |
| 11733 | Many systems, such as routers, use an administrative account "admin" with the password "admin". It is best practice to remove default accounts, if possible. For accounts required by the system, the default password should be changed. | |
| 11734 | </ContainerBlockElement></description> | |
| 11735 | <references> | |
| 11736 | </references><tags> | |
| 11737 | <tag>Default Account</tag> | |
| 11738 | <tag>Telnet</tag> | |
| 11739 | </tags> | |
| 11740 | <solution> | |
| 11741 | ||
| 11742 | <ContainerBlockElement> | |
| 11743 | <Paragraph> | |
| 11744 | Remove or disable the account if it is not critical for the system to function. Otherwise, the password should be changed to a non-default value. | |
| 11745 | </Paragraph></ContainerBlockElement></solution> | |
| 11746 | </vulnerability> | |
| 11747 | ||
| 11748 | <vulnerability id="TELNET-GENERIC-0003" title="TELNET access with no account and password password" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20041101T000000000" added="20041101T000000000" modified="20120716T000000000"> | |
| 11749 | <description> | |
| 11750 | ||
| 11751 | <ContainerBlockElement> | |
| 11752 | Many systems, such as routers, do not require an account name. This system appears to use the password "password". It is best practice to remove default accounts, if possible. For accounts required by the system, the default password should be changed. | |
| 11753 | </ContainerBlockElement></description> | |
| 11754 | <references> | |
| 11755 | </references><tags> | |
| 11756 | <tag>Default Account</tag> | |
| 11757 | <tag>Telnet</tag> | |
| 11758 | </tags> | |
| 11759 | <solution> | |
| 11760 | ||
| 11761 | <ContainerBlockElement> | |
| 11762 | <Paragraph> | |
| 11763 | Remove or disable the account if it is not critical for the system to function. Otherwise, the password should be changed to a non-default value. | |
| 11764 | </Paragraph></ContainerBlockElement></solution> | |
| 11765 | </vulnerability> | |
| 11766 | ||
| 11767 | <vulnerability id="TELNET-GENERIC-0004" title="TELNET access with root and password root" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20041101T000000000" added="20041101T000000000" modified="20120716T000000000"> | |
| 11768 | <description> | |
| 11769 | ||
| 11770 | <ContainerBlockElement> | |
| 11771 | Many systems, such as Unix systems, have an administrative account with the user ID "root" and password "root". It is best practice to remove default accounts, if possible. For accounts required by the system, the default password should be changed. This account often grants full access to the system. | |
| 11772 | </ContainerBlockElement></description> | |
| 11773 | <references> | |
| 11774 | </references><tags> | |
| 11775 | <tag>Default Account</tag> | |
| 11776 | <tag>Telnet</tag> | |
| 11777 | </tags> | |
| 11778 | <solution> | |
| 11779 | ||
| 11780 | <ContainerBlockElement> | |
| 11781 | <Paragraph> | |
| 11782 | Remove or disable the account if it is not critical for the system to function. Otherwise, the password should be changed to a non-default value. | |
| 11783 | </Paragraph></ContainerBlockElement></solution> | |
| 11784 | </vulnerability> | |
| 11785 | ||
| 11786 | <vulnerability id="TELNET-GENERIC-0005" title="TELNET access with root and no password" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="20041101T000000000" added="20041101T000000000" modified="20120716T000000000"> | |
| 11787 | <description> | |
| 11788 | ||
| 11789 | <ContainerBlockElement> | |
| 11790 | Many systems, such as Unix systems, have an administrative account with the user ID "root" and password "". It is best practice to remove default accounts, if possible. For accounts required by the system, the default password should be changed. This account often grants full access to the system. | |
| 11791 | </ContainerBlockElement></description> | |
| 11792 | <references> | |
| 11793 | </references><tags> | |
| 11794 | <tag>Default Account</tag> | |
| 11795 | <tag>Telnet</tag> | |
| 11796 | </tags> | |
| 11797 | <solution> | |
| 11798 | ||
| 11799 | <ContainerBlockElement> | |
| 11800 | <Paragraph> | |
| 11801 | Remove or disable the account if it is not critical for the system to function. Otherwise, the password should be changed to a non-default value. | |
| 11802 | </Paragraph></ContainerBlockElement></solution> | |
| 11803 | </vulnerability> | |
| 11804 | ||
| 11805 | <vulnerability id="telnet-netscreen-default-netscreen-netscreen" title="Netscreen device default password: netscreen" severity="10" pciSeverity="5" cvssScore="10.0" cvssVector="(AV:N/AC:L/Au:N/C:C/I:C/A:C)" published="19980101T000000000" added="20090212T000000000" modified="20120716T000000000"> | |
| 11806 | <description> | |
| 11807 | ||
| 11808 | <ContainerBlockElement> | |
| 11809 | ||
| 11810 | <Paragraph> | |
| 11811 | Many Netscreen devices use the default password "netscreen". | |
| 11812 | It is best practice to change the default password on all devices. | |
| 11813 | </Paragraph> | |
| 11814 | </ContainerBlockElement></description> | |
| 11815 | <references> | |
| 11816 | </references><tags> | |
| 11817 | <tag>Default Account</tag> | |
| 11818 | <tag>Telnet</tag> | |
| 11819 | </tags> | |
| 11820 | <solution> | |
| 11821 | ||
| 11822 | <ContainerBlockElement> | |
| 11823 | <Paragraph> | |
| 11824 | <Paragraph> | |
| 11825 | Change the password to a non-default value. | |
| 11826 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11827 | </vulnerability> | |
| 11828 | ||
| 11829 | <vulnerability id="telnet-open-port" title="Unencrypted Telnet Service Available" severity="3" pciSeverity="3" cvssScore="2.9" cvssVector="(AV:A/AC:M/Au:N/C:P/I:N/A:N)" published="20100101T000000000" added="20100930T000000000" modified="20130703T000000000"> | |
| 11830 | <description> | |
| 11831 | ||
| 11832 | <ContainerBlockElement> | |
| 11833 | ||
| 11834 | <Paragraph> | |
| 11835 | Telnet is an unencrypted protocol, as such it sends sensitive data | |
| 11836 | (usernames and passwords) in clear text. For this reason, it is a | |
| 11837 | violation of PCI DSS section 2.3 to have telnet enabled, unless a | |
| 11838 | business case can be made for why it is required. | |
| 11839 | </Paragraph> | |
| 11840 | </ContainerBlockElement></description> | |
| 11841 | <references> | |
| 11842 | <reference source="URL">https://www.pcisecuritystandards.org/security_standards/download.html?id=pci_dss_v1-2.pdf</reference> | |
| 11843 | </references><tags> | |
| 11844 | <tag>Insecure Remote Access</tag> | |
| 11845 | <tag>Telnet</tag> | |
| 11846 | </tags> | |
| 11847 | <solution> | |
| 11848 | ||
| 11849 | <ContainerBlockElement> | |
| 11850 | <Paragraph> | |
| 11851 | <Paragraph> | |
| 11852 | Disable the telnet service. Replace it with technologies | |
| 11853 | such as SSH, VPN, or TLS. | |
| 11854 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11855 | </vulnerability> | |
| 11856 | ||
| 11857 | <vulnerability id="tls-server-cert-expired" title="X.509 Server Certificate Is Invalid/Expired" severity="7" pciSeverity="4" cvssScore="6.8" cvssVector="(AV:N/AC:M/Au:N/C:P/I:P/A:P)" published="19950101T000000000" added="20090716T000000000" modified="20121019T000000000"> | |
| 11858 | <description> | |
| 11859 | ||
| 11860 | <ContainerBlockElement> | |
| 11861 | ||
| 11862 | <Paragraph> | |
| 11863 | The TLS/SSL server's X.509 certificate either contains a start date | |
| 11864 | in the future or is expired. Please refer to the proof for more details. | |
| 11865 | </Paragraph> | |
| 11866 | </ContainerBlockElement></description> | |
| 11867 | <references> | |
| 11868 | </references><tags> | |
| 11869 | <tag>Network</tag> | |
| 11870 | </tags> | |
| 11871 | <solution> | |
| 11872 | ||
| 11873 | <ContainerBlockElement> | |
| 11874 | <Paragraph> | |
| 11875 | <Paragraph> | |
| 11876 | Obtain a new certificate and install it on the server. The exact | |
| 11877 | instructions for obtaining a new certificate depend on your | |
| 11878 | organization's requirements. Generally, you will need to generate a | |
| 11879 | certificate request and save the request as a file. This file is then | |
| 11880 | sent to a Certificate Authority (CA) for processing. Please ensure that | |
| 11881 | the start date and the end date on the new certificate are valid. | |
| 11882 | </Paragraph> | |
| 11883 | <Paragraph> | |
| 11884 | Your organization may have its own internal Certificate Authority. If not, you | |
| 11885 | may have to pay for a certificate from a trusted external Certificate Authority. | |
| 11886 | </Paragraph> | |
| 11887 | <Paragraph> | |
| 11888 | After you have received a new certificate file from the Certificate | |
| 11889 | Authority, you will have to install it on the TLS/SSL server. The | |
| 11890 | exact instructions for installing a certificate differ for each product. | |
| 11891 | Please follow their documentation. | |
| 11892 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11893 | </vulnerability> | |
| 11894 | ||
| 11895 | <vulnerability id="tls-server-cert-sig-alg-md5" title="MD5-based Signature in TLS/SSL Server X.509 Certificate" severity="5" pciSeverity="3" cvssScore="5.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:P/A:N)" published="20040817T000000000" added="20090105T000000000" modified="20120712T000000000"> | |
| 11896 | <description> | |
| 11897 | ||
| 11898 | <ContainerBlockElement> | |
| 11899 | ||
| 11900 | <Paragraph> | |
| 11901 | Multiple weaknesses exist in the MD5 cryptographic hash function, which make | |
| 11902 | it insecure when used to sign X.509 certificates. Namely: | |
| 11903 | </Paragraph> | |
| 11904 | ||
| 11905 | <UnorderedList> | |
| 11906 | <ListItem> | |
| 11907 | In August 2004, Xiaoyun Wang, Dengguo Feng, Xuejia Lai, and Hongbo Yu | |
| 11908 | published the results of a | |
| 11909 | ||
| 11910 | <URLLink LinkURL="http://eprint.iacr.org/2004/199" LinkTitle="http://eprint.iacr.org/2004/199" href="http://eprint.iacr.org/2004/199">collision attack</URLLink>. | |
| 11911 | </ListItem> | |
| 11912 | <ListItem> | |
| 11913 | In October 2006, Marc Stevens, Arjen K. Lenstra, and Benne de Weger | |
| 11914 | produced a | |
| 11915 | ||
| 11916 | <URLLink LinkURL="http://www.win.tue.nl/hashclash/TargetCollidingCertificates/" LinkTitle="http://www.win.tue.nl/hashclash/TargetCollidingCertificates/" href="http://www.win.tue.nl/hashclash/TargetCollidingCertificates/">pair | |
| 11917 | of colliding X.509 certificates for different identities</URLLink>. The | |
| 11918 | method used to produce them was later published in the EuroCrypt 2007 Proceedings, | |
| 11919 | and described as one practical application of | |
| 11920 | ||
| 11921 | <URLLink LinkURL="http://www.win.tue.nl/hashclash/ChosenPrefixCollisions/" LinkTitle="http://www.win.tue.nl/hashclash/ChosenPrefixCollisions/" href="http://www.win.tue.nl/hashclash/ChosenPrefixCollisions/">chosen-prefix | |
| 11922 | collision attacks</URLLink>. | |
| 11923 | </ListItem> | |
| 11924 | <ListItem> | |
| 11925 | In December 2008, a larger team of security researchers used this attack to create a | |
| 11926 | ||
| 11927 | <URLLink LinkURL="http://www.win.tue.nl/hashclash/rogue-ca/" LinkTitle="http://www.win.tue.nl/hashclash/rogue-ca/" href="http://www.win.tue.nl/hashclash/rogue-ca/">rogue CA certificate</URLLink>, | |
| 11928 | allowing them to impersonate any website on the Internet, including banking and | |
| 11929 | e-commerce sites secured using the HTTPS protocol. | |
| 11930 | </ListItem></UnorderedList> | |
| 11931 | </ContainerBlockElement></description> | |
| 11932 | <references> | |
| 11933 | <reference source="BID">33065</reference> | |
| 11934 | <reference source="CERT-VN">836068</reference> | |
| 11935 | <reference source="CVE">CVE-2004-2761</reference> | |
| 11936 | <reference source="REDHAT">RHSA-2010:0837</reference> | |
| 11937 | <reference source="REDHAT">RHSA-2010:0838</reference> | |
| 11938 | <reference source="SECUNIA">33826</reference> | |
| 11939 | <reference source="SECUNIA">34281</reference> | |
| 11940 | <reference source="SECUNIA">42181</reference> | |
| 11941 | <reference source="URL">http://blogs.technet.com/swi/archive/2008/12/30/information-regarding-md5-collisions-problem.aspx</reference> | |
| 11942 | <reference source="URL">http://www.microsoft.com/technet/security/advisory/961509.mspx</reference> | |
| 11943 | </references><tags> | |
| 11944 | <tag>Network</tag> | |
| 11945 | <tag>Web</tag> | |
| 11946 | </tags> | |
| 11947 | <solution> | |
| 11948 | ||
| 11949 | <ContainerBlockElement> | |
| 11950 | <Paragraph> | |
| 11951 | <Paragraph> | |
| 11952 | Stop using signature algorithms relying on MD5, such as "MD5withRSA", | |
| 11953 | when signing X.509 certificates. Instead, use SHA-1, or preferably the | |
| 11954 | SHA-2 family (SHA-224, SHA-256, SHA-384, and SHA-512). | |
| 11955 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11956 | </vulnerability> | |
| 11957 | ||
| 11958 | <vulnerability id="tls-server-cert-to-expire" title="X.509 Server Certificate Will Expire Within 30 Days" severity="1" pciSeverity="1" cvssScore="-0.0" cvssVector="(AV:L/AC:H/Au:N/C:N/I:N/A:N)" published="19950101T000000000" added="20121018T000000000" modified="20121018T000000000"> | |
| 11959 | <description> | |
| 11960 | ||
| 11961 | <ContainerBlockElement> | |
| 11962 | ||
| 11963 | <Paragraph> | |
| 11964 | The TLS/SSL server's X.509 certificate will expire within 30 days. | |
| 11965 | Please refer to the proof for more details. | |
| 11966 | </Paragraph> | |
| 11967 | </ContainerBlockElement></description> | |
| 11968 | <references> | |
| 11969 | </references><tags> | |
| 11970 | <tag>Network</tag> | |
| 11971 | </tags> | |
| 11972 | <solution> | |
| 11973 | ||
| 11974 | <ContainerBlockElement> | |
| 11975 | <Paragraph> | |
| 11976 | <Paragraph> | |
| 11977 | Obtain a new certificate and install it on the server. The exact | |
| 11978 | instructions for obtaining a new certificate depend on your | |
| 11979 | organization's requirements. Generally, you will need to generate a | |
| 11980 | certificate request and save the request as a file. This file is then | |
| 11981 | sent to a Certificate Authority (CA) for processing. Please ensure that | |
| 11982 | the start date and the end date on the new certificate are valid. | |
| 11983 | </Paragraph> | |
| 11984 | <Paragraph> | |
| 11985 | Your organization may have its own internal Certificate Authority. If not, you | |
| 11986 | may have to pay for a certificate from a trusted external Certificate Authority. | |
| 11987 | </Paragraph> | |
| 11988 | <Paragraph> | |
| 11989 | After you have received a new certificate file from the Certificate | |
| 11990 | Authority, you will have to install it on the TLS/SSL server. The | |
| 11991 | exact instructions for installing a certificate differ for each product. | |
| 11992 | Please follow their documentation. | |
| 11993 | </Paragraph></Paragraph></ContainerBlockElement></solution> | |
| 11994 | </vulnerability> | |
| 11995 | ||
| 11996 | <vulnerability id="udp-ipid-zero" title="UDP IP ID Zero" severity="1" pciSeverity="1" cvssScore="0.0" cvssVector="(AV:N/AC:L/Au:N/C:N/I:N/A:N)" published="20020812T000000000" added="20110523T000000000" modified="20120712T000000000"> | |
| 11997 | <description> | |
| 11998 | ||
| 11999 | <ContainerBlockElement> | |
| 12000 | ||
| 12001 | <Paragraph> | |
| 12002 | The remote host responded with a UDP packet whose IP ID was zero. | |
| 12003 | Normally the IP ID should be set to a unique value and is used in the | |
| 12004 | reconstruction of fragmented packets. Generally this behavior is only | |
| 12005 | seen with systems derived from a Linux kernel, which may allow an | |
| 12006 | attacker to fingerprint the target's operating system. | |
| 12007 | </Paragraph> | |
| 12008 | </ContainerBlockElement></description> | |
| 12009 | <references> | |
| 12010 | </references><tags> | |
| 12011 | <tag>Network</tag> | |
| 12012 | </tags> | |
| 12013 | <solution> | |
| 12014 | ||
| 12015 | <ContainerBlockElement> | |
| 12016 | <Paragraph> | |
| 12017 | Many vendors do not consider this to be a vulnerability, | |
| 12018 | or a vulnerability worth fixing, so there are no vendor-provided | |
| 12019 | solutions aside from putting a firewall or other filtering device | |
| 12020 | between the target and hostile attackers that is capable of | |
| 12021 | randomizing IP IDs. | |
| 12022 | </Paragraph></ContainerBlockElement></solution> | |
| 12023 | </vulnerability> | |
| 12024 | ||
| 12025 | <vulnerability id="weak-crypto-key" title="Weak Cryptographic Key" severity="3" pciSeverity="3" cvssScore="3.2" cvssVector="(AV:A/AC:H/Au:N/C:P/I:P/A:N)" published="20050101T000000000" added="20111024T000000000" modified="20130718T000000000"> | |
| 12026 | <description> | |
| 12027 | ||
| 12028 | <ContainerBlockElement> | |
| 12029 | ||
| 12030 | <Paragraph> | |
| 12031 | The key length used by a cryptographic algorithm determines the highest | |
| 12032 | security it can offer. Newly discovered theoretical attacks and hardware | |
| 12033 | advances constantly erode this security level over time. Taking this | |
| 12034 | into account, as of 2011, governmental, academic, and private | |
| 12035 | organizations providing guidance on cryptographic security, such as | |
| 12036 | the | |
| 12037 | <URLLink LinkURL="http://www.nist.gov" LinkTitle="http://www.nist.gov" href="http://www.nist.gov">National Institute of Standards and Technology</URLLink> (NIST), | |
| 12038 | the | |
| 12039 | <URLLink LinkURL="http://www.ecrypt.eu.org" LinkTitle="http://www.ecrypt.eu.org" href="http://www.ecrypt.eu.org">European Network of Excellence in Cryptology II</URLLink> (ECRYPT II), | |
| 12040 | make the following general recommendations to provide short to medium term | |
| 12041 | security against even the most well-funded attackers (eg. intelligence agencies): | |
| 12042 | ||
| 12043 | <UnorderedList> | |
| 12044 | <ListItem>Symmetric key lengths of at least 80-112 bits.</ListItem> | |
| 12045 | <ListItem>Elliptic curve key lengths of at least 160-224 bits.</ListItem> | |
| 12046 | <ListItem>RSA key lengths of at least 1248-2048 bits. | |
| 12047 | In particular, the CA/Browser Forum | |
| 12048 | ||
| 12049 | <URLLink LinkURL="http://www.cabforum.org/EV_Certificate_Guidelines.pdf" LinkTitle="http://www.cabforum.org/EV_Certificate_Guidelines.pdf" href="http://www.cabforum.org/EV_Certificate_Guidelines.pdf">Extended Validation (EV) Guidelines</URLLink> | |
| 12050 | require a minimum key length of 2048 bits. | |
| 12051 | Also, current research shows that factoring a 1024-bit RSA modulus | |
| 12052 | ||
| 12053 | <URLLink LinkURL="http://people.csail.mit.edu/tromer/papers/tromer-phd-dissertation-11pt.pdf" LinkTitle="http://people.csail.mit.edu/tromer/papers/tromer-phd-dissertation-11pt.pdf" href="http://people.csail.mit.edu/tromer/papers/tromer-phd-dissertation-11pt.pdf">is within practical reach.</URLLink> | |
| 12054 | </ListItem> | |
| 12055 | <ListItem>DSA key lengths of at least 2048 bits.</ListItem></UnorderedList> | |
| 12056 | </Paragraph> | |
| 12057 | ||
| 12058 | <Paragraph> | |
| 12059 | Additionally, starting in 2014, the Certificate Authority/Browser Forum has mandated that 1024-bit RSA keys no | |
| 12060 | longer be supported for SSL certificates or code signing. | |
| 12061 | </Paragraph> | |
| 12062 | </ContainerBlockElement></description> | |
| 12063 | <references> | |
| 12064 | <reference source="URL">http://www.symantec.com/page.jsp?id=1024-bit-certificate-support</reference> | |
| 12065 | <reference source="URL">http://csrc.nist.gov/publications/nistpubs/800-131A/sp800-131A.pdf</reference> | |
| 12066 | <reference source="URL">http://csrc.nist.gov/groups/ST/toolkit/key_management.html</reference> | |
| 12067 | <reference source="URL">http://www.bundesnetzagentur.de/SharedDocs/Downloads/DE/BNetzA/Sachgebiete/QES/Veroeffentlichungen/Algorithmen/2011_2_AlgoKatpdf.pdf</reference> | |
| 12068 | <reference source="URL">http://www.ecrypt.eu.org/documents/D.SPA.17.pdf</reference> | |
| 12069 | <reference source="URL">http://www.keylength.com</reference> | |
| 12070 | <reference source="URL">http://www.ssi.gouv.fr/IMG/pdf/RGS_B_1.pdf</reference> | |
| 12071 | </references><tags> | |
| 12072 | <tag>Network</tag> | |
| 12073 | <tag>Web</tag> | |
| 12074 | </tags> | |
| 12075 | <solution> | |
| 12076 | ||
| 12077 | <ContainerBlockElement> | |
| 12078 | <Paragraph> | |
| 12079 | <Paragraph> | |
| 12080 | If the weak key is used in an X.509 certificate (for example for an HTTPS server), | |
| 12081 | generate a longer key and recreate the certificate. | |
| 12082 | </Paragraph></Paragraph> | |
| 12083 | <Paragraph> | |
| 12084 | Please also refer to | |
| 12085 | <URLLink LinkURL="http://csrc.nist.gov/publications/nistpubs/800-131A/sp800-131A.pdf" LinkTitle="http://csrc.nist.gov/publications/nistpubs/800-131A/sp800-131A.pdf" href="http://csrc.nist.gov/publications/nistpubs/800-131A/sp800-131A.pdf">NIST's | |
| 12086 | recommendations on cryptographic algorithms and key lengths</URLLink>. | |
| 12087 | </Paragraph></ContainerBlockElement></solution> | |
| 12088 | </vulnerability> | |
| 12089 | </VulnerabilityDefinitions> | |
| 12090 | </NexposeReport>⏎ |
| 0 | <?xml version="1.0" encoding="UTF-8"?> | |
| 1 | <!DOCTYPE nmaprun> | |
| 2 | <?xml-stylesheet href="file:///usr/bin/../share/nmap/nmap.xsl" type="text/xsl"?> | |
| 3 | <!-- Nmap 7.12 scan initiated Mon May 16 14:56:59 2016 as: nmap -oX /home/joaquin/.faraday/data/test-test-nmap_Nmap_output-9.17673265273.xml joaquinlp.me --> | |
| 4 | <nmaprun scanner="nmap" args="nmap -oX /home/joaquin/.faraday/data/test-test-nmap_Nmap_output-9.17673265273.xml joaquinlp.me" start="1463421419" startstr="Mon May 16 14:56:59 2016" version="7.12" xmloutputversion="1.04"> | |
| 5 | <scaninfo type="connect" protocol="tcp" numservices="1000" services="1,3-4,6-7,9,13,17,19-26,30,32-33,37,42-43,49,53,70,79-85,88-90,99-100,106,109-111,113,119,125,135,139,143-144,146,161,163,179,199,211-212,222,254-256,259,264,280,301,306,311,340,366,389,406-407,416-417,425,427,443-445,458,464-465,481,497,500,512-515,524,541,543-545,548,554-555,563,587,593,616-617,625,631,636,646,648,666-668,683,687,691,700,705,711,714,720,722,726,749,765,777,783,787,800-801,808,843,873,880,888,898,900-903,911-912,981,987,990,992-993,995,999-1002,1007,1009-1011,1021-1100,1102,1104-1108,1110-1114,1117,1119,1121-1124,1126,1130-1132,1137-1138,1141,1145,1147-1149,1151-1152,1154,1163-1166,1169,1174-1175,1183,1185-1187,1192,1198-1199,1201,1213,1216-1218,1233-1234,1236,1244,1247-1248,1259,1271-1272,1277,1287,1296,1300-1301,1309-1311,1322,1328,1334,1352,1417,1433-1434,1443,1455,1461,1494,1500-1501,1503,1521,1524,1533,1556,1580,1583,1594,1600,1641,1658,1666,1687-1688,1700,1717-1721,1723,1755,1761,1782-1783,1801,1805,1812,1839-1840,1862-1864,1875,1900,1914,1935,1947,1971-1972,1974,1984,1998-2010,2013,2020-2022,2030,2033-2035,2038,2040-2043,2045-2049,2065,2068,2099-2100,2103,2105-2107,2111,2119,2121,2126,2135,2144,2160-2161,2170,2179,2190-2191,2196,2200,2222,2251,2260,2288,2301,2323,2366,2381-2383,2393-2394,2399,2401,2492,2500,2522,2525,2557,2601-2602,2604-2605,2607-2608,2638,2701-2702,2710,2717-2718,2725,2800,2809,2811,2869,2875,2909-2910,2920,2967-2968,2998,3000-3001,3003,3005-3007,3011,3013,3017,3030-3031,3052,3071,3077,3128,3168,3211,3221,3260-3261,3268-3269,3283,3300-3301,3306,3322-3325,3333,3351,3367,3369-3372,3389-3390,3404,3476,3493,3517,3527,3546,3551,3580,3659,3689-3690,3703,3737,3766,3784,3800-3801,3809,3814,3826-3828,3851,3869,3871,3878,3880,3889,3905,3914,3918,3920,3945,3971,3986,3995,3998,4000-4006,4045,4111,4125-4126,4129,4224,4242,4279,4321,4343,4443-4446,4449,4550,4567,4662,4848,4899-4900,4998,5000-5004,5009,5030,5033,5050-5051,5054,5060-5061,5080,5087,5100-5102,5120,5190,5200,5214,5221-5222,5225-5226,5269,5280,5298,5357,5405,5414,5431-5432,5440,5500,5510,5544,5550,5555,5560,5566,5631,5633,5666,5678-5679,5718,5730,5800-5802,5810-5811,5815,5822,5825,5850,5859,5862,5877,5900-5904,5906-5907,5910-5911,5915,5922,5925,5950,5952,5959-5963,5987-5989,5998-6007,6009,6025,6059,6100-6101,6106,6112,6123,6129,6156,6346,6389,6502,6510,6543,6547,6565-6567,6580,6646,6666-6669,6689,6692,6699,6779,6788-6789,6792,6839,6881,6901,6969,7000-7002,7004,7007,7019,7025,7070,7100,7103,7106,7200-7201,7402,7435,7443,7496,7512,7625,7627,7676,7741,7777-7778,7800,7911,7920-7921,7937-7938,7999-8002,8007-8011,8021-8022,8031,8042,8045,8080-8090,8093,8099-8100,8180-8181,8192-8194,8200,8222,8254,8290-8292,8300,8333,8383,8400,8402,8443,8500,8600,8649,8651-8652,8654,8701,8800,8873,8888,8899,8994,9000-9003,9009-9011,9040,9050,9071,9080-9081,9090-9091,9099-9103,9110-9111,9200,9207,9220,9290,9415,9418,9485,9500,9502-9503,9535,9575,9593-9595,9618,9666,9876-9878,9898,9900,9917,9929,9943-9944,9968,9998-10004,10009-10010,10012,10024-10025,10082,10180,10215,10243,10566,10616-10617,10621,10626,10628-10629,10778,11110-11111,11967,12000,12174,12265,12345,13456,13722,13782-13783,14000,14238,14441-14442,15000,15002-15004,15660,15742,16000-16001,16012,16016,16018,16080,16113,16992-16993,17877,17988,18040,18101,18988,19101,19283,19315,19350,19780,19801,19842,20000,20005,20031,20221-20222,20828,21571,22939,23502,24444,24800,25734-25735,26214,27000,27352-27353,27355-27356,27715,28201,30000,30718,30951,31038,31337,32768-32785,33354,33899,34571-34573,35500,38292,40193,40911,41511,42510,44176,44442-44443,44501,45100,48080,49152-49161,49163,49165,49167,49175-49176,49400,49999-50003,50006,50300,50389,50500,50636,50800,51103,51493,52673,52822,52848,52869,54045,54328,55055-55056,55555,55600,56737-56738,57294,57797,58080,60020,60443,61532,61900,62078,63331,64623,64680,65000,65129,65389"/> | |
| 6 | <verbose level="0"/> | |
| 7 | <debugging level="0"/> | |
| 8 | <host starttime="1463421419" endtime="1463421451"><status state="up" reason="syn-ack" reason_ttl="0"/> | |
| 9 | <address addr="198.38.82.159" addrtype="ipv4"/> | |
| 10 | <hostnames> | |
| 11 | <hostname name="joaquinlp.me" type="user"/> | |
| 12 | <hostname name="mocha2005.mochahost.com" type="PTR"/> | |
| 13 | </hostnames> | |
| 14 | <ports><extraports state="filtered" count="956"> | |
| 15 | <extrareasons reason="no-responses" count="956"/> | |
| 16 | </extraports> | |
| 17 | <extraports state="closed" count="31"> | |
| 18 | <extrareasons reason="conn-refused" count="31"/> | |
| 19 | </extraports> | |
| 20 | <port protocol="tcp" portid="21"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="ftp" method="table" conf="3"/></port> | |
| 21 | <port protocol="tcp" portid="25"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="smtp" method="table" conf="3"/></port> | |
| 22 | <port protocol="tcp" portid="53"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="domain" method="table" conf="3"/></port> | |
| 23 | <port protocol="tcp" portid="80"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="http" method="table" conf="3"/></port> | |
| 24 | <port protocol="tcp" portid="110"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="pop3" method="table" conf="3"/></port> | |
| 25 | <port protocol="tcp" portid="143"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="imap" method="table" conf="3"/></port> | |
| 26 | <port protocol="tcp" portid="443"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="https" method="table" conf="3"/></port> | |
| 27 | <port protocol="tcp" portid="465"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="smtps" method="table" conf="3"/></port> | |
| 28 | <port protocol="tcp" portid="587"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="submission" method="table" conf="3"/></port> | |
| 29 | <port protocol="tcp" portid="993"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="imaps" method="table" conf="3"/></port> | |
| 30 | <port protocol="tcp" portid="995"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="pop3s" method="table" conf="3"/></port> | |
| 31 | <port protocol="tcp" portid="2525"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="ms-v-worlds" method="table" conf="3"/></port> | |
| 32 | <port protocol="tcp" portid="3306"><state state="open" reason="syn-ack" reason_ttl="0"/><service name="mysql" method="table" conf="3"/></port> | |
| 33 | </ports> | |
| 34 | <times srtt="193191" rttvar="22985" to="285131"/> | |
| 35 | </host> | |
| 36 | <runstats><finished time="1463421451" timestr="Mon May 16 14:57:31 2016" elapsed="32.05" summary="Nmap done at Mon May 16 14:57:31 2016; 1 IP address (1 host up) scanned in 32.05 seconds" exit="success"/><hosts up="1" down="0" total="1"/> | |
| 37 | </runstats> | |
| 38 | </nmaprun> |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | ''' | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | ''' | |
| 9 | from __future__ import absolute_import | |
| 10 | import unittest | |
| 11 | import sys | |
| 12 | from queue import Queue | |
| 13 | from collections import defaultdict | |
| 14 | ||
| 15 | import os | |
| 16 | import pytest | |
| 17 | ||
| 18 | sys.path.append(os.path.abspath(os.getcwd())) | |
| 19 | from faraday.client.plugins.repo.acunetix.plugin import AcunetixPlugin | |
| 20 | from faraday.client.model.common import factory | |
| 21 | from faraday.client.persistence.server.models import ( | |
| 22 | Vuln, | |
| 23 | Credential, | |
| 24 | VulnWeb, | |
| 25 | Note, | |
| 26 | Host, | |
| 27 | Service, | |
| 28 | ModelBase) | |
| 29 | ||
| 30 | ||
| 31 | class TestAcunetixParser: | |
| 32 | ||
| 33 | cd = os.path.dirname(os.path.realpath(__file__)) | |
| 34 | ||
| 35 | ||
| 36 | ||
| 37 | def test_Plugin_creates_apropiate_objects(self, monkeypatch): | |
| 38 | self.plugin = AcunetixPlugin() | |
| 39 | factory.register(Host) | |
| 40 | factory.register(Service) | |
| 41 | factory.register(Vuln) | |
| 42 | factory.register(VulnWeb) | |
| 43 | factory.register(Note) | |
| 44 | factory.register(Credential) | |
| 45 | ||
| 46 | pending_actions = Queue() | |
| 47 | # getID will wait for faraday-server api response. | |
| 48 | # Since the thread model controller is not running | |
| 49 | # no object will be persisted. | |
| 50 | # The mock is to simulated the api response | |
| 51 | monkeypatch.setattr(ModelBase, 'getID', lambda _: 1) | |
| 52 | self.plugin.set_actions_queue(pending_actions) | |
| 53 | self.plugin.processReport(self.cd + '/acunetix_xml') | |
| 54 | actions = defaultdict(list) | |
| 55 | while not pending_actions.empty(): | |
| 56 | action = self.plugin._pending_actions.get(block=True) | |
| 57 | actions[action[0]].append(action[1]) | |
| 58 | ||
| 59 | assert list(actions.keys()) == [2000, 20008, 2038] | |
| 60 | assert len(actions[2000]) == 1 | |
| 61 | assert actions[2000][0].name == "5.175.17.140" | |
| 62 | assert len(actions[20008]) == 1 | |
| 63 | assert len(actions[2038]) == 52 | |
| 64 | ||
| 65 | assert actions[20008][0].ports == [80] | |
| 66 | assert actions[20008][0].name == 'http' | |
| 67 | assert actions[20008][0].protocol == 'tcp' | |
| 68 | ||
| 69 | assert "ASP.NET error message" in map(lambda vuln_web: vuln_web.name, actions[2038]) | |
| 70 | ||
| 71 | ||
| 72 | if __name__ == '__main__': | |
| 73 | unittest.main() | |
| 74 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | ''' | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | ''' | |
| 9 | ||
| 10 | from __future__ import absolute_import | |
| 11 | import unittest | |
| 12 | import sys | |
| 13 | from queue import Queue | |
| 14 | from collections import defaultdict | |
| 15 | ||
| 16 | import os | |
| 17 | sys.path.append(os.path.abspath(os.getcwd())) | |
| 18 | from faraday.client.plugins.repo.burp.plugin import BurpPlugin | |
| 19 | from faraday.client.model.common import factory | |
| 20 | from faraday.client.persistence.server.models import ( | |
| 21 | Vuln, | |
| 22 | VulnWeb, | |
| 23 | Credential, | |
| 24 | Note, | |
| 25 | Host, | |
| 26 | Service, | |
| 27 | ModelBase) | |
| 28 | ||
| 29 | ||
| 30 | class TestBurp: | |
| 31 | ||
| 32 | cd = os.path.dirname(os.path.realpath(__file__)) | |
| 33 | ||
| 34 | ||
| 35 | def test_Plugin_creates_adecuate_objects(self, monkeypatch): | |
| 36 | # Disable deprecation warnings | |
| 37 | import deprecation | |
| 38 | monkeypatch.setattr( | |
| 39 | deprecation.warnings, 'warn', lambda *a, **kw: None) | |
| 40 | ||
| 41 | self.plugin = BurpPlugin() | |
| 42 | factory.register(Host) | |
| 43 | factory.register(Service) | |
| 44 | factory.register(Vuln) | |
| 45 | factory.register(VulnWeb) | |
| 46 | factory.register(Note) | |
| 47 | factory.register(Credential) | |
| 48 | pending_actions = Queue() | |
| 49 | self.plugin.set_actions_queue(pending_actions) | |
| 50 | monkeypatch.setattr(ModelBase, 'getID', lambda _: 1) | |
| 51 | self.plugin.processReport(self.cd + '/burp_xml') | |
| 52 | actions = defaultdict(list) | |
| 53 | while not pending_actions.empty(): | |
| 54 | action = self.plugin._pending_actions.get(block=True) | |
| 55 | actions[action[0]].append(action[1]) | |
| 56 | ||
| 57 | assert actions[2000][0].name == "200.20.20.201" | |
| 58 | assert list(actions.keys()) == [2000, 20008, 2038] | |
| 59 | assert len(actions[20008]) == 14 | |
| 60 | assert len(actions[2038]) == 14 | |
| 61 | ||
| 62 | assert all('http' == name for name in map(lambda service: service.name, actions[20008])) | |
| 63 | assert all([80] == ports for ports in map(lambda service: service.getPorts(), actions[20008])) | |
| 64 | assert all('tcp' == protocol for protocol in map(lambda service: service.protocol, actions[20008])) | |
| 65 | assert all('open' for status in map(lambda service: service.status, actions[20008])) | |
| 66 | ||
| 67 | # self.assertEqual(action[3], 'Cleartext submission of password') | |
| 68 | ||
| 69 | if __name__ == '__main__': | |
| 70 | unittest.main() | |
| 71 | # I'm Py3⏎ |
| 0 | ''' | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | ''' | |
| 6 | def skip(self, n): | |
| 7 | for x in range(n): | |
| 8 | action = self.plugin._pending_actions.get(block=True) | |
| 9 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | ''' | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | ''' | |
| 9 | from __future__ import absolute_import | |
| 10 | import sys | |
| 11 | import unittest | |
| 12 | from queue import Queue | |
| 13 | from collections import defaultdict | |
| 14 | ||
| 15 | import os | |
| 16 | sys.path.append(os.path.abspath(os.getcwd())) | |
| 17 | from faraday.client.plugins.repo.nessus.plugin import NessusPlugin | |
| 18 | from faraday.client.model.common import factory | |
| 19 | from faraday.client.persistence.server.models import ( | |
| 20 | Vuln, | |
| 21 | Credential, | |
| 22 | VulnWeb, | |
| 23 | Note, | |
| 24 | Host, | |
| 25 | Service, | |
| 26 | ModelBase) | |
| 27 | ||
| 28 | ||
| 29 | class TestNessusParser: | |
| 30 | cd = os.path.dirname(os.path.realpath(__file__)) | |
| 31 | ||
| 32 | def test_Plugin_Calls_createAndAddHost(self, monkeypatch): | |
| 33 | self.plugin = NessusPlugin() | |
| 34 | factory.register(Host) | |
| 35 | factory.register(Service) | |
| 36 | factory.register(Vuln) | |
| 37 | factory.register(VulnWeb) | |
| 38 | factory.register(Note) | |
| 39 | factory.register(Credential) | |
| 40 | ||
| 41 | pending_actions = Queue() | |
| 42 | self.plugin.set_actions_queue(pending_actions) | |
| 43 | monkeypatch.setattr(ModelBase, 'getID', lambda _: 1) | |
| 44 | self.plugin.processReport(self.cd + '/nessus_xml') | |
| 45 | actions = defaultdict(list) | |
| 46 | while not pending_actions.empty(): | |
| 47 | action = self.plugin._pending_actions.get(block=True) | |
| 48 | actions[action[0]].append(action[1]) | |
| 49 | ||
| 50 | assert actions[2000][0].name == "12.233.108.201" | |
| 51 | assert set(actions.keys()) == {2000, 2017, 2038, 20008} | |
| 52 | assert len(actions[20008]) == 1 | |
| 53 | assert len(actions[2038]) == 1 | |
| 54 | ||
| 55 | assert actions[2038][0].name == "Nessus SYN scanner" | |
| 56 | ||
| 57 | assert actions[20008][0].ports == [443] | |
| 58 | assert actions[20008][0].name == 'https?' | |
| 59 | assert actions[20008][0].protocol == 'tcp' | |
| 60 | ||
| 61 | ||
| 62 | ||
| 63 | if __name__ == '__main__': | |
| 64 | unittest.main() | |
| 65 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | ''' | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | ''' | |
| 9 | ||
| 10 | from __future__ import absolute_import | |
| 11 | import unittest | |
| 12 | import sys | |
| 13 | from queue import Queue | |
| 14 | from collections import defaultdict | |
| 15 | ||
| 16 | import os | |
| 17 | sys.path.append(os.path.abspath(os.getcwd())) | |
| 18 | # module's path has a dash (-) in it, so we need to do this... | |
| 19 | import importlib | |
| 20 | plugin = importlib.import_module('faraday.client.plugins.repo.nexpose-full.plugin') | |
| 21 | NexposeFullPlugin = plugin.NexposeFullPlugin | |
| 22 | from faraday.client.model.common import factory | |
| 23 | from faraday.client.persistence.server.models import ( | |
| 24 | Vuln, | |
| 25 | Credential, | |
| 26 | VulnWeb, | |
| 27 | Note, | |
| 28 | Host, | |
| 29 | Service, | |
| 30 | ModelBase) | |
| 31 | ||
| 32 | ||
| 33 | class TestNexpose: | |
| 34 | cd = os.path.dirname(os.path.realpath(__file__)) | |
| 35 | ||
| 36 | def test_Plugin_creates_apropiate_objects(self, monkeypatch): | |
| 37 | self.plugin = NexposeFullPlugin() | |
| 38 | factory.register(Host) | |
| 39 | factory.register(Service) | |
| 40 | factory.register(Vuln) | |
| 41 | factory.register(VulnWeb) | |
| 42 | factory.register(Note) | |
| 43 | factory.register(Credential) | |
| 44 | pending_actions = Queue() | |
| 45 | self.plugin.set_actions_queue(pending_actions) | |
| 46 | monkeypatch.setattr(ModelBase, 'getID', lambda _: 1) | |
| 47 | self.plugin.processReport(self.cd + '/nexpose_full_xml') | |
| 48 | ||
| 49 | actions = defaultdict(list) | |
| 50 | while not pending_actions.empty(): | |
| 51 | action = self.plugin._pending_actions.get(block=True) | |
| 52 | actions[action[0]].append(action[1]) | |
| 53 | ||
| 54 | assert actions[2000][0].name == "192.168.1.1" | |
| 55 | assert set(actions.keys()) == {2000, 2017, 2019, 2038, 20008} | |
| 56 | ||
| 57 | assert len(actions[2000]) == 8 | |
| 58 | assert len(actions[20008]) == 20 | |
| 59 | assert len(actions[2027]) == 0 | |
| 60 | assert len(actions[2038]) == 403 | |
| 61 | assert len(actions[2039]) == 0 | |
| 62 | ||
| 63 | ||
| 64 | ||
| 65 | if __name__ == '__main__': | |
| 66 | unittest.main() | |
| 67 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | ''' | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | ''' | |
| 9 | from __future__ import absolute_import | |
| 10 | ||
| 11 | import os | |
| 12 | import sys | |
| 13 | from queue import Queue | |
| 14 | from collections import defaultdict | |
| 15 | ||
| 16 | sys.path.append(os.path.abspath(os.getcwd())) | |
| 17 | from faraday.client.plugins.repo.nmap.plugin import NmapPlugin | |
| 18 | from faraday.client.model.common import factory | |
| 19 | from faraday.client.persistence.server.models import ( | |
| 20 | Vuln, | |
| 21 | Credential, | |
| 22 | VulnWeb, | |
| 23 | Note, | |
| 24 | Host, | |
| 25 | Service, | |
| 26 | ModelBase) | |
| 27 | ||
| 28 | ||
| 29 | class TestNmapXMLParserTest: | |
| 30 | plugin = NmapPlugin() | |
| 31 | outputNmapBlog = ("Starting Nmap 7.12 ( https://nmap.org ) at 2016-05-16 14:56 ART\n" | |
| 32 | "Nmap scan report for joaquinlp.me (198.38.82.159)\n" | |
| 33 | "Host is up (0.19s latency).\n" | |
| 34 | "rDNS record for 198.38.82.159: mocha2005.mochahost.com\n" | |
| 35 | "Not shown: 956 filtered ports, 31 closed ports\n" | |
| 36 | "PORT STATE SERVICE\n" | |
| 37 | "21/tcp open ftp\n" | |
| 38 | "25/tcp open smtp\n" | |
| 39 | "53/tcp open domain\n" | |
| 40 | "80/tcp open http\n" | |
| 41 | "110/tcp open pop3\n" | |
| 42 | "143/tcp open imap\n" | |
| 43 | "443/tcp open https\n" | |
| 44 | "465/tcp open smtps\n" | |
| 45 | "587/tcp open submission\n" | |
| 46 | "993/tcp open imaps\n" | |
| 47 | "995/tcp open pop3s\n" | |
| 48 | "2525/tcp open ms-v-worlds\n" | |
| 49 | "3306/tcp open mysql\n" | |
| 50 | "\n" | |
| 51 | "Nmap done: 1 IP address (1 host up) scanned in 32.05 seconds\n") | |
| 52 | ||
| 53 | cd = os.path.dirname(os.path.realpath(__file__)) | |
| 54 | with open(cd + '/nmap_output_xml', 'r') as output: | |
| 55 | xml_output = output.read() | |
| 56 | ||
| 57 | def register_factorties(self, monkeypatch): | |
| 58 | factory.register(Host) | |
| 59 | factory.register(Service) | |
| 60 | factory.register(Vuln) | |
| 61 | factory.register(VulnWeb) | |
| 62 | factory.register(Note) | |
| 63 | factory.register(Credential) | |
| 64 | self.pending_actions = Queue() | |
| 65 | self.plugin.set_actions_queue(self.pending_actions) | |
| 66 | monkeypatch.setattr(ModelBase, 'getID', lambda _: 1) | |
| 67 | ||
| 68 | def test_Plugin_Calls_createAndAddHost(self, monkeypatch): | |
| 69 | self.register_factorties(monkeypatch) | |
| 70 | ||
| 71 | self.plugin.parseOutputString(self.xml_output) | |
| 72 | actions = defaultdict(list) | |
| 73 | while not self.pending_actions.empty(): | |
| 74 | action = self.plugin._pending_actions.get(block=True) | |
| 75 | actions[action[0]].append(action[1]) | |
| 76 | ||
| 77 | assert actions[2000][0].name == "198.38.82.159" | |
| 78 | assert list(actions.keys()) == [2000, 20008] | |
| 79 | ||
| 80 | assert len(actions[2000]) == 1 | |
| 81 | assert len(actions[20008]) == 13 | |
| 82 | ||
| 83 | assert list(map(lambda service: service.name, actions[20008])) == [ | |
| 84 | 'ftp', | |
| 85 | 'smtp', | |
| 86 | 'domain', | |
| 87 | 'http', | |
| 88 | 'pop3', | |
| 89 | 'imap', | |
| 90 | 'https', | |
| 91 | 'smtps', | |
| 92 | 'submission', | |
| 93 | 'imaps', | |
| 94 | 'pop3s', | |
| 95 | 'ms-v-worlds', | |
| 96 | 'mysql' | |
| 97 | ] | |
| 98 | ||
| 99 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | ''' | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | ''' | |
| 9 | ||
| 10 | from __future__ import absolute_import | |
| 11 | import unittest | |
| 12 | import sys | |
| 13 | from queue import Queue | |
| 14 | from collections import defaultdict | |
| 15 | ||
| 16 | import os | |
| 17 | sys.path.append(os.path.abspath(os.getcwd())) | |
| 18 | from faraday.client.plugins.repo.ping.plugin import CmdPingPlugin | |
| 19 | from faraday.client.model.common import factory | |
| 20 | from faraday.client.persistence.server.models import ( | |
| 21 | Vuln, | |
| 22 | Credential, | |
| 23 | VulnWeb, | |
| 24 | Note, | |
| 25 | Host, | |
| 26 | Service, | |
| 27 | ModelBase) | |
| 28 | ||
| 29 | ||
| 30 | class TestCmdPingPlugin: | |
| 31 | plugin = CmdPingPlugin() | |
| 32 | outputPingGoogle = ("PING google.com (216.58.222.142) 56(84) bytes of" | |
| 33 | "data.\n64 bytes from scl03s11-in-f14.1e100.net" | |
| 34 | "(216.58.222.142): icmp_seq=1 ttl=53 time=28.9 ms") | |
| 35 | ||
| 36 | def test_Plugin_Calls_createAndAddHost(self, monkeypatch): | |
| 37 | factory.register(Host) | |
| 38 | factory.register(Service) | |
| 39 | factory.register(Vuln) | |
| 40 | factory.register(VulnWeb) | |
| 41 | factory.register(Note) | |
| 42 | factory.register(Credential) | |
| 43 | pending_actions = Queue() | |
| 44 | self.plugin.set_actions_queue(pending_actions) | |
| 45 | monkeypatch.setattr(ModelBase, 'getID', lambda _: 1) | |
| 46 | self.plugin.parseOutputString(self.outputPingGoogle) | |
| 47 | ||
| 48 | actions = defaultdict(list) | |
| 49 | while not pending_actions.empty(): | |
| 50 | action = self.plugin._pending_actions.get(block=True) | |
| 51 | actions[action[0]].append(action[1]) | |
| 52 | ||
| 53 | assert actions[2000][0].name == "216.58.222.142" | |
| 54 | assert list(actions.keys()) == [2000] | |
| 55 | ||
| 56 | assert len(actions[2000]) == 1 | |
| 57 | ||
| 58 | ||
| 59 | ||
| 60 | if __name__ == '__main__': | |
| 61 | unittest.main() | |
| 62 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | ''' | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | ''' | |
| 9 | from __future__ import absolute_import | |
| 10 | from queue import Queue | |
| 11 | from collections import defaultdict | |
| 12 | ||
| 13 | import os | |
| 14 | import sys | |
| 15 | import unittest | |
| 16 | ||
| 17 | sys.path.append(os.path.abspath(os.getcwd())) | |
| 18 | from faraday.client.plugins.repo.telnet.plugin import TelnetRouterPlugin | |
| 19 | from faraday.client.model.common import factory | |
| 20 | from faraday.client.persistence.server.models import ( | |
| 21 | Vuln, | |
| 22 | Credential, | |
| 23 | VulnWeb, | |
| 24 | Note, | |
| 25 | Host, | |
| 26 | Service, | |
| 27 | ModelBase) | |
| 28 | ||
| 29 | ||
| 30 | class TestCmdPingPlugin: | |
| 31 | plugin = TelnetRouterPlugin() | |
| 32 | outputTelnetLocalhost = ("Connection failed: Connection refused\n" | |
| 33 | "Trying ::1%1...\n" | |
| 34 | "Trying 127.0.0.1...\n" | |
| 35 | "Connected to localhost.\n" | |
| 36 | "Escape character is '^]'.\n" | |
| 37 | "a\n" | |
| 38 | "HTTP/1.1 400 Bad Request\n" | |
| 39 | "Server: MochiWeb/1.0 (Any of you quaids got a smint?)\n" | |
| 40 | "Date: Mon, 16 May 2016 17:42:18 GMT\n" | |
| 41 | "Content-Length: 0\n\n" | |
| 42 | "Connection closed by foreign host.\n") | |
| 43 | ||
| 44 | def test_Plugin_Calls_createAndAddHost(self, monkeypatch): | |
| 45 | factory.register(Host) | |
| 46 | factory.register(Service) | |
| 47 | factory.register(Vuln) | |
| 48 | factory.register(VulnWeb) | |
| 49 | factory.register(Note) | |
| 50 | factory.register(Credential) | |
| 51 | pending_actions = Queue() | |
| 52 | self.plugin.set_actions_queue(pending_actions) | |
| 53 | monkeypatch.setattr(ModelBase, 'getID', lambda _: 1) | |
| 54 | ||
| 55 | self.plugin.parseOutputString(self.outputTelnetLocalhost) | |
| 56 | ||
| 57 | actions = defaultdict(list) | |
| 58 | while not pending_actions.empty(): | |
| 59 | action = self.plugin._pending_actions.get(block=True) | |
| 60 | actions[action[0]].append(action[1]) | |
| 61 | ||
| 62 | assert actions[2000][0].name == "127.0.0.1" | |
| 63 | assert list(actions.keys()) == [2000, 20008] | |
| 64 | ||
| 65 | assert len(actions[2000]) == 1 | |
| 66 | assert len(actions[20008]) == 1 | |
| 67 | ||
| 68 | ||
| 69 | if __name__ == '__main__': | |
| 70 | unittest.main() | |
| 71 | # I'm Py3⏎ |
| 0 | #!/usr/bin/env python3 | |
| 1 | # -*- coding: utf-8 -*- | |
| 2 | ||
| 3 | ''' | |
| 4 | Faraday Penetration Test IDE | |
| 5 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 6 | See the file 'doc/LICENSE' for the license information | |
| 7 | ||
| 8 | ''' | |
| 9 | ||
| 10 | from __future__ import absolute_import | |
| 11 | import unittest | |
| 12 | import sys | |
| 13 | from queue import Queue | |
| 14 | from collections import defaultdict | |
| 15 | ||
| 16 | import os | |
| 17 | from faraday.client.plugins.repo.whois.plugin import CmdWhoisPlugin | |
| 18 | from faraday.client.model.common import factory | |
| 19 | from faraday.client.persistence.server.models import ( | |
| 20 | Vuln, | |
| 21 | Credential, | |
| 22 | VulnWeb, | |
| 23 | Note, | |
| 24 | Host, | |
| 25 | Service, | |
| 26 | ModelBase) | |
| 27 | ||
| 28 | ||
| 29 | class TestCmdPingPlugin: | |
| 30 | plugin = CmdWhoisPlugin() | |
| 31 | cd = os.path.dirname(os.path.realpath(__file__)) | |
| 32 | with open(cd + '/whois_output', 'r') as output: | |
| 33 | outputWhoisInfobyte = output.read() | |
| 34 | ||
| 35 | ||
| 36 | def test_Plugin_Calls_createAndAddHost(self, monkeypatch): | |
| 37 | factory.register(Host) | |
| 38 | factory.register(Service) | |
| 39 | factory.register(Vuln) | |
| 40 | factory.register(VulnWeb) | |
| 41 | factory.register(Note) | |
| 42 | factory.register(Credential) | |
| 43 | pending_actions = Queue() | |
| 44 | self.plugin.set_actions_queue(pending_actions) | |
| 45 | monkeypatch.setattr(ModelBase, 'getID', lambda _: 1) | |
| 46 | ||
| 47 | # Disable deprecation warnings | |
| 48 | import deprecation | |
| 49 | monkeypatch.setattr( | |
| 50 | deprecation.warnings, 'warn', lambda *a, **kw: None) | |
| 51 | ||
| 52 | self.plugin.parseOutputString(self.outputWhoisInfobyte) | |
| 53 | ||
| 54 | actions = defaultdict(list) | |
| 55 | while not pending_actions.empty(): | |
| 56 | action = self.plugin._pending_actions.get(block=True) | |
| 57 | actions[action[0]].append(action[1]) | |
| 58 | ||
| 59 | assert actions[2000][0].name == "205.251.196.172" | |
| 60 | assert list(actions.keys()) == [2000] | |
| 61 | ||
| 62 | assert len(actions[2000]) == 8 | |
| 63 | # I'm Py3⏎ |
| 0 | Whois Server Version 2.0 | |
| 1 | ||
| 2 | Domain names in the .com and .net domains can now be registered | |
| 3 | with many different competing registrars. Go to http://www.internic.net | |
| 4 | for detailed information. | |
| 5 | ||
| 6 | Domain Name: INFOBYTESEC.COM | |
| 7 | Registrar: GODADDY.COM, LLC | |
| 8 | Sponsoring Registrar IANA ID: 146 | |
| 9 | Whois Server: whois.godaddy.com | |
| 10 | Referral URL: http://www.godaddy.com | |
| 11 | Name Server: NS-1196.AWSDNS-21.ORG | |
| 12 | Name Server: NS-121.AWSDNS-15.COM | |
| 13 | Name Server: NS-1959.AWSDNS-52.CO.UK | |
| 14 | Name Server: NS-869.AWSDNS-44.NET | |
| 15 | Status: clientDeleteProhibited https://icann.org/epp#clientDeleteProhibited | |
| 16 | Status: clientRenewProhibited https://icann.org/epp#clientRenewProhibited | |
| 17 | Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited | |
| 18 | Status: clientUpdateProhibited https://icann.org/epp#clientUpdateProhibited | |
| 19 | Updated Date: 08-may-2016 | |
| 20 | Creation Date: 07-may-2009 | |
| 21 | Expiration Date: 07-may-2021 | |
| 22 | ||
| 23 | >>> Last update of whois database: Mon, 16 May 2016 16:00:55 GMT <<< | |
| 24 | ||
| 25 | For more information on Whois status codes, please visit https://icann.org/epp | |
| 26 | ||
| 27 | NOTICE: The expiration date displayed in this record is the date the | |
| 28 | registrar's sponsorship of the domain name registration in the registry is | |
| 29 | currently set to expire. This date does not necessarily reflect the expiration | |
| 30 | date of the domain name registrant's agreement with the sponsoring | |
| 31 | registrar. Users may consult the sponsoring registrar's Whois database to | |
| 32 | view the registrar's reported date of expiration for this registration. | |
| 33 | ||
| 34 | TERMS OF USE: You are not authorized to access or query our Whois | |
| 35 | database through the use of electronic processes that are high-volume and | |
| 36 | automated except as reasonably necessary to register domain names or | |
| 37 | modify existing registrations; the Data in VeriSign Global Registry | |
| 38 | Services' ("VeriSign") Whois database is provided by VeriSign for | |
| 39 | information purposes only, and to assist persons in obtaining information | |
| 40 | about or related to a domain name registration record. VeriSign does not | |
| 41 | guarantee its accuracy. By submitting a Whois query, you agree to abide | |
| 42 | by the following terms of use: You agree that you may use this Data only | |
| 43 | for lawful purposes and that under no circumstances will you use this Data | |
| 44 | to: (1) allow, enable, or otherwise support the transmission of mass | |
| 45 | unsolicited, commercial advertising or solicitations via e-mail, telephone, | |
| 46 | or facsimile; or (2) enable high volume, automated, electronic processes | |
| 47 | that apply to VeriSign (or its computer systems). The compilation, | |
| 48 | repackaging, dissemination or other use of this Data is expressly | |
| 49 | prohibited without the prior written consent of VeriSign. You agree not to | |
| 50 | use electronic processes that are automated and high-volume to access or | |
| 51 | query the Whois database except as reasonably necessary to register | |
| 52 | domain names or modify existing registrations. VeriSign reserves the right | |
| 53 | to restrict your access to the Whois database in its sole discretion to ensure | |
| 54 | operational stability. VeriSign may restrict or terminate your access to the | |
| 55 | Whois database for failure to abide by these terms of use. VeriSign | |
| 56 | reserves the right to modify these terms at any time. | |
| 57 | ||
| 58 | The Registry database contains ONLY .COM, .NET, .EDU domains and | |
| 59 | Registrars. | |
| 60 | Domain Name: INFOBYTESEC.COM | |
| 61 | Registry Domain ID: 1554772171_DOMAIN_COM-VRSN | |
| 62 | Registrar WHOIS Server: whois.godaddy.com | |
| 63 | Registrar URL: http://www.godaddy.com | |
| 64 | Update Date: 2016-05-08T13:33:14Z | |
| 65 | Creation Date: 2009-05-07T15:10:17Z | |
| 66 | Registrar Registration Expiration Date: 2021-05-07T15:10:17Z | |
| 67 | Registrar: GoDaddy.com, LLC | |
| 68 | Registrar IANA ID: 146 | |
| 69 | Registrar Abuse Contact Email: [email protected] | |
| 70 | Registrar Abuse Contact Phone: +1.4806242505 | |
| 71 | Domain Status: clientTransferProhibited http://www.icann.org/epp#clientTransferProhibited | |
| 72 | Domain Status: clientUpdateProhibited http://www.icann.org/epp#clientUpdateProhibited | |
| 73 | Domain Status: clientRenewProhibited http://www.icann.org/epp#clientRenewProhibited | |
| 74 | Domain Status: clientDeleteProhibited http://www.icann.org/epp#clientDeleteProhibited | |
| 75 | Registry Registrant ID: Not Available From Registry | |
| 76 | Registrant Name: Francisco Amato | |
| 77 | Registrant Organization: Infobyte LLC | |
| 78 | Registrant Street: 2699 S. Bayshore Dr #300 | |
| 79 | Registrant City: Miami | |
| 80 | Registrant State/Province: Florida | |
| 81 | Registrant Postal Code: 33133 | |
| 82 | Registrant Country: US | |
| 83 | Registrant Phone: +1.3058513373 | |
| 84 | Registrant Phone Ext: | |
| 85 | Registrant Fax: | |
| 86 | Registrant Fax Ext: | |
| 87 | Registrant Email: [email protected] | |
| 88 | Registry Admin ID: Not Available From Registry | |
| 89 | Admin Name: Francisco Amato | |
| 90 | Admin Organization: Infobyte LLC | |
| 91 | Admin Street: 2699 S. Bayshore Dr #300 | |
| 92 | Admin City: Miami | |
| 93 | Admin State/Province: Florida | |
| 94 | Admin Postal Code: 33133 | |
| 95 | Admin Country: US | |
| 96 | Admin Phone: +1.3058513373 | |
| 97 | Admin Phone Ext: | |
| 98 | Admin Fax: | |
| 99 | Admin Fax Ext: | |
| 100 | Admin Email: [email protected] | |
| 101 | Registry Tech ID: Not Available From Registry | |
| 102 | Tech Name: Francisco Amato | |
| 103 | Tech Organization: Infobyte LLC | |
| 104 | Tech Street: 2699 S. Bayshore Dr #300 | |
| 105 | Tech City: Miami | |
| 106 | Tech State/Province: Florida | |
| 107 | Tech Postal Code: 33133 | |
| 108 | Tech Country: US | |
| 109 | Tech Phone: +1.3058513373 | |
| 110 | Tech Phone Ext: | |
| 111 | Tech Fax: | |
| 112 | Tech Fax Ext: | |
| 113 | Tech Email: [email protected] | |
| 114 | Name Server: NS-1959.AWSDNS-52.CO.UK | |
| 115 | Name Server: NS-869.AWSDNS-44.NET | |
| 116 | Name Server: NS-121.AWSDNS-15.COM | |
| 117 | Name Server: NS-1196.AWSDNS-21.ORG | |
| 118 | DNSSEC: unsigned | |
| 119 | URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/ | |
| 120 | >>> Last update of WHOIS database: 2016-05-16T16:00:00Z <<< | |
| 121 | ||
| 122 | For more information on Whois status codes, please visit https://www.icann.org/resources/pages/epp-status-codes-2014-06-16-en | |
| 123 | ||
| 124 | The data contained in GoDaddy.com, LLC's WhoIs database, | |
| 125 | while believed by the company to be reliable, is provided "as is" | |
| 126 | with no guarantee or warranties regarding its accuracy. This | |
| 127 | information is provided for the sole purpose of assisting you | |
| 128 | in obtaining information about domain name registration records. | |
| 129 | Any use of this data for any other purpose is expressly forbidden without the prior written | |
| 130 | permission of GoDaddy.com, LLC. By submitting an inquiry, | |
| 131 | you agree to these terms of usage and limitations of warranty. In particular, | |
| 132 | you agree not to use this data to allow, enable, or otherwise make possible, | |
| 133 | dissemination or collection of this data, in part or in its entirety, for any | |
| 134 | purpose, such as the transmission of unsolicited advertising and | |
| 135 | and solicitations of any kind, including spam. You further agree | |
| 136 | not to use this data to enable high volume, automated or robotic electronic | |
| 137 | processes designed to collect or compile this data for any purpose, | |
| 138 | including mining this data for your own personal or commercial purposes. | |
| 139 | ||
| 140 | Please note: the registrant of the domain name is specified | |
| 141 | in the "registrant" section. In most cases, GoDaddy.com, LLC | |
| 142 | is not the registrant of domain names listed in this database. | |
| 143 |
| 9 | 9 | |
| 10 | 10 | from faraday.server.api.modules.agent import AgentView |
| 11 | 11 | from faraday.server.models import Agent |
| 12 | from tests.factories import AgentFactory, WorkspaceFactory | |
| 12 | from tests.factories import AgentFactory, WorkspaceFactory, ExecutorFactory | |
| 13 | 13 | from tests.test_api_workspaced_base import ReadOnlyAPITests |
| 14 | 14 | from tests import factories |
| 15 | 15 | |
| 215 | 215 | headers=headers) |
| 216 | 216 | assert res.status_code == 400 |
| 217 | 217 | |
| 218 | def test_happy_path_valid_json(self, test_client, session, csrf_token): | |
| 218 | def test_invalid_executor(self, test_client, session, csrf_token): | |
| 219 | 219 | agent = AgentFactory.create(workspace=self.workspace) |
| 220 | 220 | session.add(agent) |
| 221 | 221 | session.commit() |
| 228 | 228 | "executor": "executor_name" |
| 229 | 229 | }, |
| 230 | 230 | } |
| 231 | res = test_client.post(self.url() + f'{agent.id}/run/',json=payload) | |
| 232 | assert res.status_code == 400 | |
| 233 | ||
| 234 | def test_happy_path_valid_json(self, test_client, session, csrf_token): | |
| 235 | agent = AgentFactory.create(workspace=self.workspace) | |
| 236 | executor = ExecutorFactory.create(agent=agent) | |
| 237 | ||
| 238 | session.add(executor) | |
| 239 | session.commit() | |
| 240 | payload = { | |
| 241 | 'csrf_token': csrf_token, | |
| 242 | 'executorData': { | |
| 243 | "args": { | |
| 244 | "param1": True | |
| 245 | }, | |
| 246 | "executor": executor.name | |
| 247 | }, | |
| 248 | } | |
| 231 | 249 | res = test_client.post(self.url() + f'{agent.id}/run/', json=payload) |
| 232 | 250 | assert res.status_code == 200 |
| 233 | 251 | |
| 0 | 0 | from __future__ import absolute_import |
| 1 | from builtins import bytes | |
| 1 | from datetime import datetime, timedelta, timezone | |
| 2 | 2 | |
| 3 | 3 | import pytest |
| 4 | 4 | from marshmallow import ValidationError |
| 36 | 36 | 'accountability': True, |
| 37 | 37 | 'availability': False, |
| 38 | 38 | }, |
| 39 | 'refs': ['CVE-1234'] | |
| 39 | 'refs': ['CVE-1234'], | |
| 40 | 'tool': 'some_tool' | |
| 40 | 41 | } |
| 41 | 42 | |
| 42 | 43 | vuln_web_data = { |
| 112 | 113 | |
| 113 | 114 | |
| 114 | 115 | def test_create_service(session, host): |
| 115 | data = bc.ServiceSchema(strict=True).load(service_data).data | |
| 116 | data = bc.BulkServiceSchema(strict=True).load(service_data).data | |
| 116 | 117 | bc._create_service(host.workspace, host, data) |
| 117 | 118 | assert count(Service, host.workspace) == 1 |
| 118 | 119 | service = Service.query.filter(Service.workspace == host.workspace).one() |
| 128 | 129 | "port": service.port, |
| 129 | 130 | "protocol": service.protocol, |
| 130 | 131 | } |
| 131 | data = bc.ServiceSchema(strict=True).load(data).data | |
| 132 | data = bc.BulkServiceSchema(strict=True).load(data).data | |
| 132 | 133 | bc._create_service(service.workspace, service.host, data) |
| 133 | 134 | assert count(Service, service.host.workspace) == 1 |
| 134 | 135 | |
| 145 | 146 | assert not vuln.impact_availability |
| 146 | 147 | assert not vuln.impact_confidentiality |
| 147 | 148 | assert vuln.references == {u'CVE-1234'} |
| 149 | assert vuln.tool == "some_tool" | |
| 148 | 150 | |
| 149 | 151 | |
| 150 | 152 | def test_create_service_vuln(session, service): |
| 161 | 163 | assert not vuln.impact_availability |
| 162 | 164 | assert not vuln.impact_confidentiality |
| 163 | 165 | assert vuln.references == {u'CVE-1234'} |
| 164 | ||
| 166 | assert vuln.tool == "some_tool" | |
| 167 | ||
| 168 | ||
| 169 | def test_create_host_vuln_without_tool(session, host): | |
| 170 | no_tool_data = vuln_data.copy() | |
| 171 | no_tool_data.pop('tool') | |
| 172 | data = bc.VulnerabilitySchema(strict=True).load(no_tool_data).data | |
| 173 | bc._create_hostvuln(host.workspace, host, data) | |
| 174 | vuln = host.workspace.vulnerabilities[0] | |
| 175 | assert vuln.tool == "Web UI" | |
| 176 | ||
| 177 | ||
| 178 | def test_creates_vuln_with_command_object_with_tool(session, service): | |
| 179 | host_data_ = host_data.copy() | |
| 180 | service_data_ = service_data.copy() | |
| 181 | vuln_web_data_ = vuln_data.copy() | |
| 182 | service_data_['vulnerabilities'] = [vuln_web_data_] | |
| 183 | host_data_['services'] = [service_data_] | |
| 184 | bc.bulk_create(service.workspace, dict(command=command_data, hosts=[host_data_])) | |
| 185 | assert count(Vulnerability, service.workspace) == 1 | |
| 186 | vuln = service.workspace.vulnerabilities[0] | |
| 187 | assert vuln.tool == vuln_data['tool'] | |
| 188 | ||
| 189 | ||
| 190 | def test_creates_vuln_with_command_object_without_tool(session, service): | |
| 191 | host_data_ = host_data.copy() | |
| 192 | service_data_ = service_data.copy() | |
| 193 | vuln_web_data_ = vuln_data.copy() | |
| 194 | vuln_web_data_.pop('tool') | |
| 195 | service_data_['vulnerabilities'] = [vuln_web_data_] | |
| 196 | host_data_['services'] = [service_data_] | |
| 197 | bc.bulk_create(service.workspace, dict(command=command_data, hosts=[host_data_])) | |
| 198 | assert count(Vulnerability, service.workspace) == 1 | |
| 199 | vuln = service.workspace.vulnerabilities[0] | |
| 200 | assert vuln.tool == command_data['tool'] | |
| 165 | 201 | |
| 166 | 202 | def test_cannot_create_host_vulnweb(session, host): |
| 167 | 203 | data = vuln_data.copy() |
| 240 | 276 | def test_create_service_with_vuln(session, host): |
| 241 | 277 | service_data_ = service_data.copy() |
| 242 | 278 | service_data_['vulnerabilities'] = [vuln_data] |
| 243 | data = bc.ServiceSchema(strict=True).load(service_data_).data | |
| 279 | data = bc.BulkServiceSchema(strict=True).load(service_data_).data | |
| 244 | 280 | bc._create_service(host.workspace, host, data) |
| 245 | 281 | assert count(Service, host.workspace) == 1 |
| 246 | 282 | service = host.workspace.services[0] |
| 254 | 290 | def test_create_service_with_cred(session, host): |
| 255 | 291 | service_data_ = service_data.copy() |
| 256 | 292 | service_data_['credentials'] = [credential_data] |
| 257 | data = bc.ServiceSchema(strict=True).load(service_data_).data | |
| 293 | data = bc.BulkServiceSchema(strict=True).load(service_data_).data | |
| 258 | 294 | bc._create_service(host.workspace, host, data) |
| 259 | 295 | assert count(Service, host.workspace) == 1 |
| 260 | 296 | service = host.workspace.services[0] |
| 273 | 309 | del vuln_data_['name'] |
| 274 | 310 | service_data_['vulnerabilities'] = [vuln_data_] |
| 275 | 311 | with pytest.raises(ValidationError): |
| 276 | data = bc.ServiceSchema(strict=True).load(service_data_).data | |
| 312 | data = bc.BulkServiceSchema(strict=True).load(service_data_).data | |
| 277 | 313 | bc._create_service(host.workspace, host, data) |
| 278 | 314 | assert count(Service, host.workspace) == 0 |
| 279 | 315 | assert count(Vulnerability, host.workspace) == 0 |
| 285 | 321 | del vuln_data_['name'] |
| 286 | 322 | service_data_['vulnerabilities'] = [1, 2, 3] |
| 287 | 323 | with pytest.raises(ValidationError): |
| 288 | data = bc.ServiceSchema(strict=True).load(service_data_).data | |
| 324 | data = bc.BulkServiceSchema(strict=True).load(service_data_).data | |
| 289 | 325 | bc._create_service(host.workspace, host, data) |
| 290 | 326 | assert count(Service, host.workspace) == 0 |
| 291 | 327 | assert count(Vulnerability, host.workspace) == 0 |
| 296 | 332 | vuln_data_ = vuln_data.copy() |
| 297 | 333 | vuln_data_.update(vuln_web_data) |
| 298 | 334 | service_data_['vulnerabilities'] = [vuln_data_] |
| 299 | data = bc.ServiceSchema(strict=True).load(service_data_).data | |
| 335 | data = bc.BulkServiceSchema(strict=True).load(service_data_).data | |
| 300 | 336 | bc._create_service(host.workspace, host, data) |
| 301 | 337 | assert count(Service, host.workspace) == 1 |
| 302 | 338 | service = host.workspace.services[0] |
| 480 | 516 | |
| 481 | 517 | |
| 482 | 518 | @pytest.mark.usefixtures('logged_user') |
| 483 | def test_bulk_create_endpoint(session, workspace, test_client): | |
| 519 | def test_bulk_create_endpoint(session, workspace, test_client, logged_user): | |
| 484 | 520 | assert count(Host, workspace) == 0 |
| 485 | 521 | assert count(VulnerabilityGeneric, workspace) == 0 |
| 486 | 522 | url = 'v2/ws/{}/bulk_create/'.format(workspace.name) |
| 487 | 523 | host_data_ = host_data.copy() |
| 524 | host_data_['services'] = [service_data] | |
| 525 | host_data_['credentials'] = [credential_data] | |
| 488 | 526 | host_data_['vulnerabilities'] = [vuln_data] |
| 489 | 527 | res = test_client.post(url, data=dict(hosts=[host_data_])) |
| 490 | 528 | assert res.status_code == 201, res.json |
| 492 | 530 | assert count(Vulnerability, workspace) == 1 |
| 493 | 531 | host = Host.query.filter(Host.workspace == workspace).one() |
| 494 | 532 | assert host.ip == "127.0.0.1" |
| 533 | assert host.creator_id == logged_user.id | |
| 495 | 534 | assert set({hn.name for hn in host.hostnames}) == {"test.com", "test2.org"} |
| 535 | service = Service.query.filter(Service.workspace == workspace).one() | |
| 536 | assert service.creator_id == logged_user.id | |
| 537 | credential = Credential.query.filter(Credential.workspace == workspace).one() | |
| 538 | assert credential.creator_id == logged_user.id | |
| 496 | 539 | |
| 497 | 540 | |
| 498 | 541 | @pytest.mark.usefixtures('logged_user') |
| 580 | 623 | assert count(Host, second_workspace) == 0 |
| 581 | 624 | |
| 582 | 625 | |
| 583 | def test_bulk_create_endpoint_with_agent_token(session, agent, test_client): | |
| 626 | def test_bulk_create_with_not_existent_workspace_fails( | |
| 627 | session, agent, test_client): | |
| 628 | assert agent.workspace | |
| 629 | session.add(agent) | |
| 630 | session.commit() | |
| 631 | assert agent.token | |
| 632 | url = 'v2/ws/{}/bulk_create/'.format("im_a_incorrect_ws") | |
| 633 | res = test_client.post( | |
| 634 | url, | |
| 635 | data=dict(hosts=[host_data]), | |
| 636 | headers=[("authorization", "agent {}".format(agent.token))] | |
| 637 | ) | |
| 638 | assert res.status_code == 404 | |
| 639 | assert b'No such workspace' in res.data | |
| 640 | assert count(Host, agent.workspace) == 0 | |
| 641 | ||
| 642 | ||
| 643 | def test_bulk_create_endpoint_with_agent_token_without_execution_id(session, agent, test_client): | |
| 584 | 644 | session.add(agent) |
| 585 | 645 | session.commit() |
| 586 | 646 | assert count(Host, agent.workspace) == 0 |
| 590 | 650 | data=dict(hosts=[host_data]), |
| 591 | 651 | headers=[("authorization", "agent {}".format(agent.token))] |
| 592 | 652 | ) |
| 653 | assert res.status_code == 400 | |
| 654 | assert b"\'execution_id\' argument expected" in res.data | |
| 655 | assert count(Host, agent.workspace) == 0 | |
| 656 | assert count(Command, agent.workspace) == 0 | |
| 657 | ||
| 658 | ||
| 659 | def test_bulk_create_endpoint_with_agent_token(session, agent_execution, test_client, workspace_factory, | |
| 660 | agent_execution_factory): | |
| 661 | agent = agent_execution.executor.agent | |
| 662 | agent_execution.executor.parameters_metadata = {} | |
| 663 | agent_execution.parameters_data = {} | |
| 664 | extra_agent_execution = agent_execution_factory.create() | |
| 665 | session.add(agent_execution) | |
| 666 | session.add(extra_agent_execution) | |
| 667 | session.commit() | |
| 668 | assert count(Host, agent.workspace) == 0 | |
| 669 | url = 'v2/ws/{}/bulk_create/'.format(agent.workspace.name) | |
| 670 | res = test_client.post( | |
| 671 | url, | |
| 672 | data=dict(hosts=[host_data], execution_id=-1), | |
| 673 | headers=[("authorization", "agent {}".format(agent.token))] | |
| 674 | ) | |
| 675 | assert res.status_code == 400 | |
| 676 | ||
| 677 | assert count(Host, agent.workspace) == 0 | |
| 678 | assert count(Command, agent.workspace) == 0 | |
| 679 | res = test_client.post( | |
| 680 | url, | |
| 681 | data=dict(hosts=[host_data], execution_id=extra_agent_execution.id), | |
| 682 | headers=[("authorization", "agent {}".format(agent.token))] | |
| 683 | ) | |
| 684 | assert res.status_code == 400 | |
| 685 | assert count(Host, agent.workspace) == 0 | |
| 686 | assert count(Command, agent.workspace) == 0 | |
| 687 | res = test_client.post( | |
| 688 | url, | |
| 689 | data=dict(hosts=[host_data], execution_id=agent_execution.id), | |
| 690 | headers=[("authorization", "agent {}".format(agent.token))] | |
| 691 | ) | |
| 593 | 692 | assert res.status_code == 201 |
| 594 | 693 | assert count(Host, agent.workspace) == 1 |
| 694 | host = Host.query.filter(Host.workspace == agent.workspace).one() | |
| 695 | assert host.creator_id is None | |
| 696 | assert count(Command, agent.workspace) == 1 | |
| 697 | command = Command.query.filter(Command.workspace == agent.workspace).one() | |
| 698 | assert command.tool == agent.name | |
| 699 | assert command.command == agent_execution.executor.name | |
| 700 | assert command.params == "" | |
| 701 | assert command.import_source == 'agent' | |
| 702 | ||
| 703 | ||
| 704 | def test_bulk_create_endpoint_with_agent_token_with_param(session, agent_execution, test_client): | |
| 705 | agent = agent_execution.executor.agent | |
| 706 | session.add(agent_execution) | |
| 707 | session.commit() | |
| 708 | assert count(Host, agent.workspace) == 0 | |
| 709 | url = 'v2/ws/{}/bulk_create/'.format(agent.workspace.name) | |
| 710 | res = test_client.post( | |
| 711 | url, | |
| 712 | data=dict(hosts=[host_data], execution_id=agent_execution.id), | |
| 713 | headers=[("authorization", "agent {}".format(agent.token))] | |
| 714 | ) | |
| 715 | assert res.status_code == 201 | |
| 716 | assert count(Host, agent.workspace) == 1 | |
| 717 | host = Host.query.filter(Host.workspace == agent.workspace).one() | |
| 718 | assert host.creator_id is None | |
| 719 | assert count(Command, agent.workspace) == 1 | |
| 720 | command = Command.query.filter(Command.workspace == agent.workspace).one() | |
| 721 | assert command.tool == agent.name | |
| 722 | assert command.command == agent_execution.executor.name | |
| 723 | params = ', '.join([f'{key}={value}' for (key, value) in agent_execution.parameters_data.items()]) | |
| 724 | assert command.params == str(params) | |
| 725 | assert command.import_source == 'agent' | |
| 595 | 726 | |
| 596 | 727 | |
| 597 | 728 | def test_bulk_create_endpoint_with_agent_token_readonly_workspace( |
| 635 | 766 | ) |
| 636 | 767 | assert res.status_code == 400 |
| 637 | 768 | |
| 638 | ||
| 639 | # I'm Py3 | |
| 769 | @pytest.mark.usefixtures('logged_user') | |
| 770 | def test_bulk_create_endpoint_with_vuln_run_date(session, workspace, test_client): | |
| 771 | assert count(Host, workspace) == 0 | |
| 772 | assert count(VulnerabilityGeneric, workspace) == 0 | |
| 773 | url = 'v2/ws/{}/bulk_create/'.format(workspace.name) | |
| 774 | run_date = datetime.now(timezone.utc) - timedelta(days=30) | |
| 775 | host_data_copy = host_data.copy() | |
| 776 | vuln_data_copy = vuln_data.copy() | |
| 777 | vuln_data_copy['run_date'] = run_date.timestamp() | |
| 778 | host_data_copy['vulnerabilities'] = [vuln_data_copy] | |
| 779 | res = test_client.post(url, data=dict(hosts=[host_data_copy])) | |
| 780 | assert res.status_code == 201, res.json | |
| 781 | assert count(Host, workspace) == 1 | |
| 782 | assert count(VulnerabilityGeneric, workspace) == 1 | |
| 783 | vuln = Vulnerability.query.filter(Vulnerability.workspace == workspace).one() | |
| 784 | assert vuln.create_date.date() == run_date.date() | |
| 785 | ||
| 786 | @pytest.mark.usefixtures('logged_user') | |
| 787 | def test_bulk_create_endpoint_with_vuln_future_run_date(session, workspace, test_client): | |
| 788 | assert count(Host, workspace) == 0 | |
| 789 | assert count(VulnerabilityGeneric, workspace) == 0 | |
| 790 | url = 'v2/ws/{}/bulk_create/'.format(workspace.name) | |
| 791 | run_date = datetime.now(timezone.utc) + timedelta(days=10) | |
| 792 | host_data_copy = host_data.copy() | |
| 793 | vuln_data_copy = vuln_data.copy() | |
| 794 | vuln_data_copy['run_date'] = run_date.timestamp() | |
| 795 | host_data_copy['vulnerabilities'] = [vuln_data_copy] | |
| 796 | res = test_client.post(url, data=dict(hosts=[host_data_copy])) | |
| 797 | assert res.status_code == 201, res.json | |
| 798 | assert count(Host, workspace) == 1 | |
| 799 | assert count(VulnerabilityGeneric, workspace) == 1 | |
| 800 | vuln = Vulnerability.query.filter(Vulnerability.workspace == workspace).one() | |
| 801 | print(vuln.create_date) | |
| 802 | assert vuln.create_date.date() < run_date.date() | |
| 803 | ||
| 804 | @pytest.mark.usefixtures('logged_user') | |
| 805 | def test_bulk_create_endpoint_with_invalid_vuln_run_date(session, workspace, test_client): | |
| 806 | assert count(Host, workspace) == 0 | |
| 807 | assert count(VulnerabilityGeneric, workspace) == 0 | |
| 808 | url = 'v2/ws/{}/bulk_create/'.format(workspace.name) | |
| 809 | host_data_copy = host_data.copy() | |
| 810 | vuln_data_copy = vuln_data.copy() | |
| 811 | vuln_data_copy['run_date'] = "INVALID_VALUE" | |
| 812 | host_data_copy['vulnerabilities'] = [vuln_data_copy] | |
| 813 | res = test_client.post(url, data=dict(hosts=[host_data_copy])) | |
| 814 | assert res.status_code == 400, res.json | |
| 815 | assert count(VulnerabilityGeneric, workspace) == 0 | |
| 816 | ||
| 817 | ||
| 818 | ||
| 819 | ||
| 820 | @pytest.mark.usefixtures('logged_user') | |
| 821 | def test_bulk_create_endpoint_fails_with_list_in_NullToBlankString(session, workspace, test_client, logged_user): | |
| 822 | assert count(Host, workspace) == 0 | |
| 823 | assert count(VulnerabilityGeneric, workspace) == 0 | |
| 824 | url = 'v2/ws/{}/bulk_create/'.format(workspace.name) | |
| 825 | host_data_ = host_data.copy() | |
| 826 | host_data_['services'] = [service_data] | |
| 827 | host_data_['credentials'] = [credential_data] | |
| 828 | host_data_['vulnerabilities'] = [vuln_data] | |
| 829 | host_data_['default_gateway'] = ["localhost"] # Can not be a list | |
| 830 | res = test_client.post(url, data=dict(hosts=[host_data_])) | |
| 831 | assert res.status_code == 400, res.json | |
| 832 | assert count(Host, workspace) == 0 | |
| 833 | assert count(Service, workspace) == 0 | |
| 834 | assert count(Credential, workspace) == 0 | |
| 835 | assert count(Vulnerability, workspace) == 0 | |
| 836 | ||
| 25 | 25 | |
| 26 | 26 | def test_get_list_backwards_compatibility(self, test_client, session, second_workspace): |
| 27 | 27 | cred = self.factory.create(workspace=second_workspace) |
| 28 | session.add(cred) | |
| 28 | 29 | session.commit() |
| 29 | 30 | res = test_client.get(self.url()) |
| 30 | 31 | assert res.status_code == 200 |
| 235 | 236 | assert b'Parent id not found' in res.data |
| 236 | 237 | |
| 237 | 238 | |
| 239 | def test_sort_credentials_target(self, test_client, second_workspace): | |
| 240 | host = HostFactory(workspace=second_workspace, ip="192.168.1.1") | |
| 241 | service = ServiceFactory(name="http", workspace=second_workspace, host=host) | |
| 242 | ||
| 243 | host2 = HostFactory(workspace=second_workspace, ip="192.168.1.2") | |
| 244 | service2 = ServiceFactory(name="ssh", workspace=second_workspace, host=host2) | |
| 245 | ||
| 246 | credential = self.factory.create(service=service, host=None, workspace=second_workspace) | |
| 247 | credential2 = self.factory.create(service=None, host=host2, workspace=second_workspace) | |
| 248 | credential3 = self.factory.create(service=None, host=host, workspace=second_workspace) | |
| 249 | credential4 = self.factory.create(service=service2, host=None, workspace=second_workspace) | |
| 250 | ||
| 251 | credentials_target = [ | |
| 252 | "{}/{}".format(credential.service.host.ip, credential.service.name), | |
| 253 | "{}".format(credential2.host.ip), | |
| 254 | "{}".format(credential3.host.ip), | |
| 255 | "{}/{}".format(credential4.service.host.ip, credential4.service.name), | |
| 256 | ] | |
| 257 | ||
| 258 | # Desc order | |
| 259 | response = test_client.get(self.url(workspace=second_workspace) + "?sort=target&sort_dir=desc") | |
| 260 | assert response.status_code == 200 | |
| 261 | assert sorted(credentials_target, reverse=True) == [ v['value']['target'] for v in response.json['rows']] | |
| 262 | ||
| 263 | # Asc order | |
| 264 | response = test_client.get(self.url(workspace=second_workspace) + "?sort=target&sort_dir=asc") | |
| 265 | assert response.status_code == 200 | |
| 266 | assert sorted(credentials_target) == [v['value']['target'] for v in response.json['rows']] | |
| 238 | 267 | # I'm Py3 |
| 0 | ''' | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | ''' | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | import os | |
| 9 | import pytest | |
| 10 | from lxml.etree import fromstring, tostring | |
| 11 | ||
| 12 | from tests.factories import ( | |
| 13 | WorkspaceFactory, | |
| 14 | HostFactory, | |
| 15 | ServiceFactory, | |
| 16 | VulnerabilityFactory, | |
| 17 | VulnerabilityWebFactory | |
| 18 | ) | |
| 19 | ||
| 20 | ||
| 21 | @pytest.mark.usefixtures('logged_user') | |
| 22 | class TestExportData(): | |
| 23 | def test_export_data_without_format(self, test_client): | |
| 24 | workspace = WorkspaceFactory.create() | |
| 25 | url = '/v2/ws/{ws_name}/export_data'.format(ws_name=workspace.name) | |
| 26 | response = test_client.get(url) | |
| 27 | assert response.status_code == 400 | |
| 28 | ||
| 29 | def test_export_data_xml_metasploit_format(self, test_client, session): | |
| 30 | workspace = WorkspaceFactory.create() | |
| 31 | host = HostFactory.create( | |
| 32 | workspace=workspace, | |
| 33 | ip='127.0.0.1', | |
| 34 | os='Linux', | |
| 35 | mac='30-65-EC-6F-C4-58', | |
| 36 | description='Host for test purposes' | |
| 37 | ) | |
| 38 | host.set_hostnames(['localhost', 'test']) | |
| 39 | session.add(host) | |
| 40 | session.commit() | |
| 41 | ||
| 42 | # Hardcode create_date and update_date for tests purposes | |
| 43 | host.create_date = host.create_date.replace(2020, 4, 1, 20, 49, 31) | |
| 44 | host.update_date = host.update_date.replace(2020, 4, 1, 20, 49, 31) | |
| 45 | ||
| 46 | service = ServiceFactory.create( | |
| 47 | workspace=workspace, | |
| 48 | host=host, | |
| 49 | port=8080, | |
| 50 | protocol='tcp', | |
| 51 | status='open', | |
| 52 | name='Test service', | |
| 53 | version='5.0', | |
| 54 | description='Description for service' | |
| 55 | ) | |
| 56 | session.add(service) | |
| 57 | session.commit() | |
| 58 | ||
| 59 | # Hardcode create_date and update_date for tests purposes | |
| 60 | service.create_date = service.create_date.replace(2020, 4, 1, 20, 49, 49) | |
| 61 | service.update_date = service.update_date.replace(2020, 4, 1, 20, 49, 49) | |
| 62 | ||
| 63 | vuln = VulnerabilityFactory.create( | |
| 64 | workspace=workspace, | |
| 65 | host=host, | |
| 66 | service=None, | |
| 67 | name='Vulnerability test', | |
| 68 | description='Desc for testing' | |
| 69 | ) | |
| 70 | session.add(vuln) | |
| 71 | ||
| 72 | vuln_web = VulnerabilityWebFactory.create( | |
| 73 | workspace=workspace, | |
| 74 | service=service, | |
| 75 | name='Vulnerability Web test', | |
| 76 | description='Desc for testing web vuln', | |
| 77 | severity="high", | |
| 78 | path='faraday.com', | |
| 79 | method="GET", | |
| 80 | parameters="ABCDEF", | |
| 81 | parameter_name="qwerty", | |
| 82 | query_string="query for vuln", | |
| 83 | request="GET for vuln" | |
| 84 | ) | |
| 85 | session.add(vuln_web) | |
| 86 | session.commit() | |
| 87 | ||
| 88 | url = '/v2/ws/{ws_name}/export_data?format=xml_metasploit'.format(ws_name=workspace.name) | |
| 89 | response = test_client.get(url) | |
| 90 | assert response.status_code == 200 | |
| 91 | response_xml = response.data | |
| 92 | ||
| 93 | xml_file_path = os.path.join( | |
| 94 | os.path.dirname(os.path.realpath(__file__)), | |
| 95 | 'data', | |
| 96 | 'faraday_export_data_xml_metasploit.xml') | |
| 97 | with open(xml_file_path, 'rb') as output: | |
| 98 | xml_file = output.read() | |
| 99 | ||
| 100 | response_tree = fromstring(response_xml) | |
| 101 | xml_file_tree = fromstring(xml_file) | |
| 102 | ||
| 103 | xpaths_list = [ | |
| 104 | { | |
| 105 | '//host': ['address', 'mac', 'name', 'comments'] | |
| 106 | }, | |
| 107 | { | |
| 108 | '//host/services/service': ['port', 'proto', 'state', 'name', 'info'] | |
| 109 | }, | |
| 110 | { | |
| 111 | '//MetasploitV4/services/service': ['port', 'proto', 'state', 'name', 'info'] | |
| 112 | }, | |
| 113 | { | |
| 114 | '//MetasploitV4/web_sites/web_site': ['vhost', 'host', 'port', 'comments', 'ssl'] | |
| 115 | }, | |
| 116 | { | |
| 117 | '//host/vulns/vuln': ['name', 'info'] | |
| 118 | }, | |
| 119 | { | |
| 120 | '//MetasploitV4/web_vulns/web_vuln': ['name', 'description', 'risk', 'path', | |
| 121 | 'method', 'params', 'pname', 'query', | |
| 122 | 'request', 'vhost', 'host', 'port', 'ssl'] | |
| 123 | } | |
| 124 | ] | |
| 125 | ||
| 126 | for xpath_data in xpaths_list: | |
| 127 | for xpath, tags_list in xpath_data.items(): | |
| 128 | for tag in tags_list: | |
| 129 | full_xpath = xpath + '/' + tag | |
| 130 | if full_xpath == '//host/name': | |
| 131 | # Check hostnames list order | |
| 132 | # Sometimes host.set_hostnames() switch the order of the hostnames list sent. | |
| 133 | response_hostnames = response_tree.xpath(full_xpath)[0].text | |
| 134 | xml_file_hostnames = xml_file_tree.xpath(full_xpath)[0].text | |
| 135 | if response_hostnames != xml_file_hostnames: | |
| 136 | # For testing purposes, response_hostnames list will be reordered. | |
| 137 | response_hostnames = response_hostnames.split(',') | |
| 138 | response_hostnames[0], response_hostnames[1] = response_hostnames[1], response_hostnames[0] | |
| 139 | response_tree.xpath(full_xpath)[0].text = ','.join(response_hostnames) | |
| 140 | assert response_tree.xpath(full_xpath)[0].text == xml_file_hostnames | |
| 141 | else: | |
| 142 | assert response_tree.xpath(full_xpath)[0].text == xml_file_tree.xpath(full_xpath)[0].text |
| 122 | 122 | assert host.os == '' |
| 123 | 123 | assert host.workspace == self.workspace |
| 124 | 124 | |
| 125 | def test_create_a_host_with_rev_succeeds(self, test_client): | |
| 126 | res = test_client.post(self.url(), data={ | |
| 127 | "ip": "127.0.0.1", | |
| 128 | "description": "aaaaa", | |
| 129 | "_rev":"saraza" | |
| 130 | # os is not required | |
| 131 | }) | |
| 132 | assert res.status_code == 201 | |
| 133 | assert Host.query.count() == HOSTS_COUNT + 1 | |
| 134 | host_id = res.json['id'] | |
| 135 | host = Host.query.get(host_id) | |
| 136 | assert host.ip == "127.0.0.1" | |
| 137 | assert host.description == "aaaaa" | |
| 138 | assert host.os == '' | |
| 139 | assert host.workspace == self.workspace | |
| 140 | ||
| 125 | 141 | def test_create_a_host_fails_with_missing_desc(self, test_client): |
| 126 | 142 | res = test_client.post(self.url(), data={ |
| 127 | 143 | "ip": "127.0.0.1", |
| 536 | 552 | assert res.json['hosts_with_errors'] == 0 |
| 537 | 553 | assert session.query(Host).filter_by(description="test_host").count() == expected_created_hosts |
| 538 | 554 | |
| 555 | def test_bulk_delete_hosts(self, test_client, session): | |
| 556 | ws = WorkspaceFactory.create(name="abc") | |
| 557 | host_1 = HostFactory.create(workspace=ws) | |
| 558 | host_2 = HostFactory.create(workspace=ws) | |
| 559 | session.commit() | |
| 560 | hosts_ids = [host_1.id, host_2.id] | |
| 561 | request_data = {'hosts_ids': hosts_ids} | |
| 562 | ||
| 563 | delete_response = test_client.delete('/v2/ws/{0}/hosts/bulk_delete/'.format(ws.name), data=request_data) | |
| 564 | ||
| 565 | deleted_hosts = delete_response.json['deleted_hosts'] | |
| 566 | host_count_after_delete = db.session.query(Host).filter( | |
| 567 | Host.id.in_(hosts_ids), | |
| 568 | Host.workspace_id == ws.id).count() | |
| 569 | ||
| 570 | assert delete_response.status_code == 200 | |
| 571 | assert deleted_hosts == len(hosts_ids) | |
| 572 | assert host_count_after_delete == 0 | |
| 573 | ||
| 574 | def test_bulk_delete_hosts_without_hosts_ids(self, test_client): | |
| 575 | ws = WorkspaceFactory.create(name="abc") | |
| 576 | request_data = {'hosts_ids': []} | |
| 577 | ||
| 578 | delete_response = test_client.delete('/v2/ws/{0}/hosts/bulk_delete/'.format(ws.name), data=request_data) | |
| 579 | ||
| 580 | assert delete_response.status_code == 400 | |
| 581 | ||
| 582 | def test_bulk_delete_hosts_from_another_workspace(self, test_client, session): | |
| 583 | workspace_1 = WorkspaceFactory.create(name='workspace_1') | |
| 584 | host_of_ws_1 = HostFactory.create(workspace=workspace_1) | |
| 585 | workspace_2 = WorkspaceFactory.create(name='workspace_2') | |
| 586 | host_of_ws_2 = HostFactory.create(workspace=workspace_2) | |
| 587 | session.commit() | |
| 588 | ||
| 589 | # Try to delete workspace_2's host from workspace_1 | |
| 590 | request_data = {'hosts_ids': [host_of_ws_2.id]} | |
| 591 | url = '/v2/ws/{0}/hosts/bulk_delete/'.format(workspace_1.name) | |
| 592 | delete_response = test_client.delete(url, data=request_data) | |
| 593 | ||
| 594 | assert delete_response.json['deleted_hosts'] == 0 | |
| 595 | ||
| 596 | def test_bulk_delete_hosts_invalid_characters_in_request(self, test_client): | |
| 597 | ws = WorkspaceFactory.create(name="abc") | |
| 598 | request_data = {'hosts_ids': [-1, 'test']} | |
| 599 | delete_response = test_client.delete('/v2/ws/{0}/hosts/bulk_delete/'.format(ws.name), data=request_data) | |
| 600 | ||
| 601 | assert delete_response.json['deleted_hosts'] == 0 | |
| 602 | ||
| 603 | def test_bulk_delete_hosts_wrong_content_type(self, test_client, session): | |
| 604 | ws = WorkspaceFactory.create(name="abc") | |
| 605 | host_1 = HostFactory.create(workspace=ws) | |
| 606 | host_2 = HostFactory.create(workspace=ws) | |
| 607 | session.commit() | |
| 608 | hosts_ids = [host_1.id, host_2.id] | |
| 609 | ||
| 610 | request_data = {'hosts_ids': hosts_ids} | |
| 611 | headers = [('content-type', 'text/xml')] | |
| 612 | ||
| 613 | delete_response = test_client.delete( | |
| 614 | '/v2/ws/{0}/hosts/bulk_delete/'.format(ws.name), | |
| 615 | data=request_data, | |
| 616 | headers=headers) | |
| 617 | ||
| 618 | assert delete_response.status_code == 400 | |
| 539 | 619 | |
| 540 | 620 | |
| 541 | 621 | class TestHostAPIGeneric(ReadWriteAPITests, PaginationTestsMixin): |
| 773 | 853 | assert res.status_code in [201, 400, 409] |
| 774 | 854 | |
| 775 | 855 | send_api_request() |
| 776 | ||
| 777 | ||
| 778 | # I'm Py3 | |
| 31 | 31 | res = test_client.get('/config') |
| 32 | 32 | assert res.status_code == 200 |
| 33 | 33 | assert res.json['lic_db'] == 'faraday_licenses' |
| 34 | ||
| 35 | ||
| 36 | # I'm Py3 |
| 0 | import pytest | |
| 1 | ||
| 2 | from tests.test_api_non_workspaced_base import GenericAPITest | |
| 3 | from tests.factories import UserFactory | |
| 4 | from faraday.server.models import User | |
| 5 | from faraday.server.api.modules.preferences import PreferencesView | |
| 6 | ||
| 7 | pytest.fixture('logged_user') | |
| 8 | class TestPreferences(GenericAPITest): | |
| 9 | model = User | |
| 10 | factory = UserFactory | |
| 11 | api_endpoint = 'preferences' | |
| 12 | view_class = PreferencesView | |
| 13 | ||
| 14 | def test_add_preference(self, test_client): | |
| 15 | preferences = {'field1': 1, 'field2': 'str1'} | |
| 16 | data = {'preferences': preferences} | |
| 17 | response = test_client.post(self.url(), data=data) | |
| 18 | ||
| 19 | assert response.status_code == 200 | |
| 20 | ||
| 21 | response = test_client.get(self.url()) | |
| 22 | ||
| 23 | assert response.status_code == 200 | |
| 24 | assert response.json['preferences'] == preferences | |
| 25 | ||
| 26 | def test_list_preferences_from_session(self, test_client): | |
| 27 | preferences = {'field1': 1, 'field2': 'str1'} | |
| 28 | data = {'preferences': preferences} | |
| 29 | response = test_client.post(self.url(), data=data) | |
| 30 | ||
| 31 | assert response.status_code == 200 | |
| 32 | ||
| 33 | response = test_client.get('/session') | |
| 34 | ||
| 35 | assert response.status_code == 200 | |
| 36 | assert response.json['preferences'] == preferences | |
| 37 | ||
| 38 | ||
| 39 | def test_add_invalid_preference(self, test_client): | |
| 40 | preferences = {'field1': 1, 'field2': 'str1'} | |
| 41 | data = {'p': preferences} | |
| 42 | response = test_client.post(self.url(), data=data) | |
| 43 | ||
| 44 | assert response.status_code == 400 |
| 11 | 11 | |
| 12 | 12 | from tests.factories import WorkspaceFactory |
| 13 | 13 | |
| 14 | from faraday.server.threads.reports_processor import REPORTS_QUEUE | |
| 15 | ||
| 16 | from faraday.server.models import Host, Vulnerability, Service, Command | |
| 17 | ||
| 18 | ||
| 14 | 19 | @pytest.mark.usefixtures('logged_user') |
| 15 | 20 | class TestFileUpload(): |
| 16 | 21 | |
| 17 | def test_file_upload(self, test_client, session, csrf_token): | |
| 22 | def test_file_upload(self, test_client, session, csrf_token, logged_user): | |
| 18 | 23 | ws = WorkspaceFactory.create(name="abc") |
| 19 | 24 | session.add(ws) |
| 20 | 25 | session.commit() |
| 36 | 41 | use_json_data=False) |
| 37 | 42 | |
| 38 | 43 | assert res.status_code == 200 |
| 44 | assert len(REPORTS_QUEUE.queue) == 1 | |
| 45 | queue_elem = REPORTS_QUEUE.queue[0] | |
| 46 | assert queue_elem[0] == ws.name | |
| 47 | assert queue_elem[2].id == logged_user.id | |
| 48 | ||
| 49 | # I'm testing a method which lost referene of workspace and logged_user within the test | |
| 50 | ws_id = ws.id | |
| 51 | logged_user_id = logged_user.id | |
| 52 | ||
| 53 | from faraday.server.threads.reports_processor import ReportsManager | |
| 54 | false_thread = ReportsManager(None) | |
| 55 | false_thread.process_report(queue_elem[0], queue_elem[1], queue_elem[2]) | |
| 56 | command = Command.query.filter(Command.workspace_id == ws_id).one() | |
| 57 | assert command | |
| 58 | assert command.creator_id == logged_user_id | |
| 59 | host = Host.query.filter(Host.workspace_id == ws_id).first() | |
| 60 | assert host | |
| 61 | assert host.creator_id == logged_user_id | |
| 62 | service = Service.query.filter(Service.workspace_id == ws_id).first() | |
| 63 | assert service | |
| 64 | assert service.creator_id == logged_user_id | |
| 39 | 65 | |
| 40 | 66 | |
| 41 | 67 | def test_no_file_in_request(self, test_client, session): |
| 96 | 122 | use_json_data=False) |
| 97 | 123 | |
| 98 | 124 | assert res.status_code == 404 |
| 99 | ||
| 100 | ||
| 101 | # I'm Py3 | |
| 51 | 51 | Reference, |
| 52 | 52 | PolicyViolation, |
| 53 | 53 | CommandObject, |
| 54 | File | |
| 54 | File, | |
| 55 | Host, | |
| 56 | Service | |
| 55 | 57 | ) |
| 56 | 58 | from tests.factories import ( |
| 57 | 59 | ServiceFactory, |
| 84 | 86 | severity='critical', |
| 85 | 87 | update_controller_action='UI Web', |
| 86 | 88 | service_id=None, |
| 89 | tool="" | |
| 87 | 90 | ): |
| 88 | 91 | if not impact: |
| 89 | 92 | impact = {'accountability': False, 'availability': False, |
| 119 | 122 | '_attachments': {}, |
| 120 | 123 | 'description': '', |
| 121 | 124 | 'protocol': '', |
| 122 | 'version': ''} | |
| 125 | 'version': '', | |
| 126 | 'tool': tool | |
| 127 | } | |
| 123 | 128 | |
| 124 | 129 | if vuln_type == 'VulnerabilityWeb': |
| 125 | 130 | data.update({ |
| 161 | 166 | view_class = VulnerabilityView |
| 162 | 167 | |
| 163 | 168 | def test_backward_json_compatibility(self, test_client, second_workspace, session): |
| 164 | self.factory.create(workspace=second_workspace) | |
| 169 | new_obj = self.factory.create(workspace=second_workspace) | |
| 170 | session.add(new_obj) | |
| 165 | 171 | session.commit() |
| 166 | 172 | res = test_client.get(self.url()) |
| 167 | 173 | assert res.status_code == 200 |
| 702 | 708 | vulnerability_web_factory): |
| 703 | 709 | |
| 704 | 710 | # Vulns that shouldn't be shown |
| 705 | vulnerability_factory.create_batch(5, workspace=second_workspace) | |
| 706 | vulnerability_web_factory.create_batch(5, workspace=second_workspace, | |
| 711 | vuln_second_workspace = vulnerability_factory.create_batch(5, workspace=second_workspace) | |
| 712 | more_vuln_second_workspace = vulnerability_web_factory.create_batch(5, workspace=second_workspace, | |
| 707 | 713 | method='POSTT') |
| 708 | 714 | |
| 709 | 715 | # Vulns that must be shown |
| 710 | 716 | expected_vulns = vulnerability_web_factory.create_batch( |
| 711 | 717 | 5, workspace=second_workspace, method='POST') |
| 712 | 718 | |
| 719 | session.add_all(vuln_second_workspace) | |
| 720 | session.add_all(more_vuln_second_workspace) | |
| 721 | session.add_all(expected_vulns) | |
| 713 | 722 | session.commit() |
| 714 | 723 | expected_ids = {vuln.id for vuln in expected_vulns} |
| 715 | 724 | |
| 735 | 744 | ): |
| 736 | 745 | |
| 737 | 746 | # Vulns that shouldn't be shown |
| 738 | vulnerability_factory.create_batch(5, workspace=second_workspace) | |
| 739 | vulnerability_web_factory.create_batch( | |
| 747 | second_workspace_vulns = vulnerability_factory.create_batch(5, workspace=second_workspace) | |
| 748 | second_workspace_more_vulns = vulnerability_web_factory.create_batch( | |
| 740 | 749 | 5, workspace=second_workspace, website='other.com') |
| 741 | 750 | |
| 742 | 751 | # Vulns that must be shown |
| 743 | 752 | expected_vulns = vulnerability_web_factory.create_batch( |
| 744 | 753 | 5, workspace=second_workspace, website='faradaysec.com') |
| 754 | session.add_all(second_workspace_vulns) | |
| 755 | session.add_all(second_workspace_more_vulns) | |
| 756 | session.add_all(expected_vulns) | |
| 745 | 757 | session.commit() |
| 746 | 758 | expected_ids = {vuln.id for vuln in expected_vulns} |
| 747 | 759 | |
| 1034 | 1046 | created_vuln = Vulnerability.query.get(res.json['_id']) |
| 1035 | 1047 | assert created_vuln.ease_of_resolution is None |
| 1036 | 1048 | |
| 1049 | ||
| 1050 | def test_count_order_by_incorrect_keyword(self, test_client, session): | |
| 1051 | for i, vuln in enumerate(self.objects[:3]): | |
| 1052 | vuln.confirmed = True | |
| 1053 | # Set critical severity to first vuln, high to the others | |
| 1054 | if i == 0: | |
| 1055 | vuln.severity = 'critical' | |
| 1056 | else: | |
| 1057 | vuln.severity = 'high' | |
| 1058 | ||
| 1059 | session.add(vuln) | |
| 1060 | session.commit() | |
| 1061 | ||
| 1062 | #Desc | |
| 1063 | res = test_client.get(self.url() + | |
| 1064 | "count/?confirmed=1&group_by=severity&order=sc") | |
| 1065 | assert res.status_code == 400 | |
| 1066 | ||
| 1067 | #Asc | |
| 1068 | res = test_client.get(self.url() + | |
| 1069 | "count/?confirmed=1&group_by=severity&order=name,asc") | |
| 1070 | assert res.status_code == 400 | |
| 1071 | ||
| 1072 | ||
| 1073 | def test_count_order_by(self, test_client, session): | |
| 1074 | for i, vuln in enumerate(self.objects[:3]): | |
| 1075 | vuln.confirmed = True | |
| 1076 | # Set critical severity to first vuln, high to the others | |
| 1077 | if i == 0: | |
| 1078 | vuln.severity = 'critical' | |
| 1079 | else: | |
| 1080 | vuln.severity = 'high' | |
| 1081 | ||
| 1082 | session.add(vuln) | |
| 1083 | session.commit() | |
| 1084 | ||
| 1085 | #Desc | |
| 1086 | res = test_client.get(self.url() + | |
| 1087 | "count/?confirmed=1&group_by=severity&order=desc") | |
| 1088 | assert res.status_code == 200 | |
| 1089 | assert res.json['total_count'] == 3 | |
| 1090 | assert sorted(res.json['groups'], key=lambda i: (i['name'],i['count'],i['severity'])) == sorted([ | |
| 1091 | {"name": "high", "severity": "high", "count": 2}, | |
| 1092 | {"name": "critical", "severity": "critical", "count": 1}, | |
| 1093 | ], key=lambda i: (i['name'],i['count'],i['severity'])) | |
| 1094 | ||
| 1095 | #Asc | |
| 1096 | res = test_client.get(self.url() + | |
| 1097 | "count/?confirmed=1&group_by=severity&order=asc") | |
| 1098 | assert res.status_code == 200 | |
| 1099 | assert res.json['total_count'] == 3 | |
| 1100 | assert sorted(res.json['groups'], key=lambda i: (i['name'],i['count'],i['severity']), reverse=True) == sorted([ | |
| 1101 | {"name": "critical", "severity": "critical", "count": 1}, | |
| 1102 | {"name": "high", "severity": "high", "count": 2}, | |
| 1103 | ], key=lambda i: (i['name'],i['count'],i['severity']), reverse=True) | |
| 1104 | ||
| 1105 | ||
| 1106 | def test_count_group_by_incorrect_vuln_column(self, test_client, session): | |
| 1107 | for i, vuln in enumerate(self.objects[:3]): | |
| 1108 | vuln.confirmed = True | |
| 1109 | # Set critical severity to first vuln, high to the others | |
| 1110 | if i == 0: | |
| 1111 | vuln.severity = 'critical' | |
| 1112 | else: | |
| 1113 | vuln.severity = 'high' | |
| 1114 | ||
| 1115 | session.add(vuln) | |
| 1116 | session.commit() | |
| 1117 | ||
| 1118 | res = test_client.get(self.url() + | |
| 1119 | "count/?confirmed=1&group_by=username") | |
| 1120 | assert res.status_code == 400 | |
| 1121 | ||
| 1122 | res = test_client.get(self.url() + | |
| 1123 | "count/?confirmed=1&group_by=") | |
| 1124 | assert res.status_code == 400 | |
| 1125 | ||
| 1126 | ||
| 1127 | ||
| 1037 | 1128 | def test_count_confirmed(self, test_client, session): |
| 1038 | 1129 | for i, vuln in enumerate(self.objects[:3]): |
| 1039 | 1130 | vuln.confirmed = True |
| 1075 | 1166 | {"name": "low", "severity": "low", "count": 2}, |
| 1076 | 1167 | {"name": "info", "severity": "info", "count": 4}, |
| 1077 | 1168 | ], key=lambda i: (i['count'],i['name'],i['severity'])) |
| 1169 | ||
| 1170 | def test_count_multiworkspace_one_workspace(self, test_client, session): | |
| 1171 | for i, vuln in enumerate(self.objects): | |
| 1172 | vuln.confirmed = True | |
| 1173 | # Set critical severity to first vuln, high to the others | |
| 1174 | if i == 0: | |
| 1175 | vuln.severity = 'critical' | |
| 1176 | else: | |
| 1177 | vuln.severity = 'high' | |
| 1178 | ||
| 1179 | session.add(vuln) | |
| 1180 | session.commit() | |
| 1181 | ||
| 1182 | res = test_client.get(f'{self.url()}' | |
| 1183 | f'count_multi_workspace/?workspaces=' | |
| 1184 | f'{self.workspace.name}' | |
| 1185 | f'&confirmed=1&group_by=severity&order=desc') | |
| 1186 | ||
| 1187 | assert res.status_code == 200 | |
| 1188 | assert len(res.json['groups']) == 1 | |
| 1189 | assert res.json['total_count'] == 5 | |
| 1190 | ||
| 1191 | ||
| 1192 | def test_count_multiworkspace_two_public_workspaces(self, test_client, session, second_workspace): | |
| 1193 | vulns = self.factory.create_batch(1, severity='informational', | |
| 1194 | workspace=second_workspace) | |
| 1195 | vulns += self.factory.create_batch(3, severity='medium', | |
| 1196 | workspace=second_workspace) | |
| 1197 | vulns += self.factory.create_batch(1, severity='low', | |
| 1198 | workspace=second_workspace) | |
| 1199 | session.add_all(vulns) | |
| 1200 | session.commit() | |
| 1201 | ||
| 1202 | for i, vuln in enumerate(self.objects): | |
| 1203 | vuln.confirmed = True | |
| 1204 | # Set critical severity to first vuln, high to the others | |
| 1205 | if i == 0: | |
| 1206 | vuln.severity = 'critical' | |
| 1207 | else: | |
| 1208 | vuln.severity = 'high' | |
| 1209 | ||
| 1210 | session.add(vuln) | |
| 1211 | session.commit() | |
| 1212 | ||
| 1213 | res = test_client.get(f'{self.url()}' | |
| 1214 | f'count_multi_workspace/?workspaces=' | |
| 1215 | f'{self.workspace.name}' | |
| 1216 | f',' | |
| 1217 | f'{second_workspace.name}' | |
| 1218 | f'&confirmed=1&group_by=severity&order=desc') | |
| 1219 | ||
| 1220 | assert res.status_code == 200 | |
| 1221 | assert len(res.json['groups']) == 2 | |
| 1222 | assert res.json['total_count'] == 10 | |
| 1223 | ||
| 1224 | def test_count_multiworkspace_no_workspace_param(self, test_client): | |
| 1225 | res = test_client.get(f'{self.url()}count_multi_workspace/?confirmed=1&group_by=severity&order=desc') | |
| 1226 | assert res.status_code == 400 | |
| 1227 | ||
| 1228 | def test_count_multiworkspace_no_groupby_param(self, test_client): | |
| 1229 | res = test_client.get(f'{self.url()}count_multi_workspace/?workspaces={self.workspace.name}&confirmed=1&order=desc') | |
| 1230 | assert res.status_code == 400 | |
| 1231 | ||
| 1232 | def test_count_multiworkspace_nonexistent_ws(self, test_client): | |
| 1233 | res = test_client.get(f'{self.url()}count_multi_workspace/?workspaces=asdf,{self.workspace.name}&confirmed=1&group_by=severity&order=desc') | |
| 1234 | assert res.status_code == 404 | |
| 1235 | ||
| 1078 | 1236 | |
| 1079 | 1237 | @pytest.mark.usefixtures('mock_envelope_list') |
| 1080 | 1238 | def test_target(self, test_client, session, second_workspace, |
| 1217 | 1375 | vuln = VulnerabilityWebFactory.create( |
| 1218 | 1376 | service=service, |
| 1219 | 1377 | creator=owner, |
| 1220 | workspace=workspace | |
| 1378 | workspace=workspace, | |
| 1221 | 1379 | ) |
| 1222 | 1380 | session.flush() |
| 1223 | 1381 | CommandObjectFactory.create( |
| 1250 | 1408 | u'update_time': pytz.UTC.localize(vuln.update_date).isoformat(), |
| 1251 | 1409 | u'update_user': None |
| 1252 | 1410 | } |
| 1253 | ||
| 1254 | 1411 | assert expected_metadata == from_json_vuln[0]['value']['metadata'] |
| 1255 | 1412 | |
| 1256 | 1413 | @pytest.mark.parametrize("parent_type, parent_factory", [ |
| 1432 | 1589 | res = test_client.put('/v2/ws/{0}/vulns/{1}/?command_id={2}'.format(ws_name, res.json['_id'], command.id), |
| 1433 | 1590 | data=raw_data) |
| 1434 | 1591 | assert res.status_code == 200 |
| 1592 | ||
| 1435 | 1593 | |
| 1436 | 1594 | def test_create_vuln_from_command(self, test_client, session): |
| 1437 | 1595 | command = EmptyCommandFactory.create(workspace=self.workspace) |
| 1895 | 2053 | .format(ws_name=workspace.name,vuln_id=vuln.id, name="random_name")) |
| 1896 | 2054 | assert res.status_code == 404 |
| 1897 | 2055 | |
| 1898 | def test_export_vuln_csv_empty_workspace(self, test_client): | |
| 1899 | Vulnerability.query.delete() | |
| 1900 | res = test_client.get(self.url() + 'export_csv/') | |
| 2056 | def test_export_vuln_csv_empty_workspace(self, test_client, session): | |
| 2057 | ws = WorkspaceFactory(name='abc') | |
| 2058 | res = test_client.get('/v2/ws/{ws_name}/vulns/export_csv/'.format(ws_name=ws.name)) | |
| 1901 | 2059 | expected_headers = [ |
| 1902 | "confirmed", "id", "date", "name", "severity", "service", | |
| 1903 | "target", "desc", "status", "hostnames", "comments", "owner", "os", "resolution", "easeofresolution", "web_vulnerability", | |
| 1904 | "data", "website", "path", "status_code", "request", "method", "params", "pname", "query", | |
| 1905 | "policyviolations", "external_id", "impact_confidentiality", "impact_integrity", "impact_availability", | |
| 1906 | "impact_accountability", "update_date" | |
| 2060 | "confirmed", "id", "date", "name", "severity", "service", | |
| 2061 | "target", "desc", "status", "hostnames", "comments", "owner", | |
| 2062 | "os", "resolution", "refs", "easeofresolution", "web_vulnerability", | |
| 2063 | "data", "website", "path", "status_code", "request", "response", "method", | |
| 2064 | "params", "pname", "query", "policyviolations", "external_id", "impact_confidentiality", | |
| 2065 | "impact_integrity", "impact_availability", "impact_accountability", "update_date", | |
| 2066 | "host_id", "host_description", "mac", | |
| 2067 | "host_owned", "host_creator_id", "host_date", "host_update_date", | |
| 2068 | "service_id", "service_name", "service_description", "service_owned", | |
| 2069 | "port", "protocol", "summary", "version", "service_status", | |
| 2070 | "service_creator_id", "service_date", "service_update_date", "service_parent_id" | |
| 1907 | 2071 | ] |
| 1908 | 2072 | assert res.status_code == 200 |
| 1909 | assert res.data.decode('utf-8').strip('\r\n').split(',') == expected_headers | |
| 2073 | assert expected_headers == res.data.decode('utf-8').strip('\r\n').split(',') | |
| 1910 | 2074 | |
| 1911 | 2075 | @pytest.mark.usefixtures('ignore_nplusone') |
| 1912 | 2076 | def test_export_vuln_csv_filters_confirmed_using_filters_query(self, test_client, session): |
| 1953 | 2117 | |
| 1954 | 2118 | @pytest.mark.usefixtures('ignore_nplusone') |
| 1955 | 2119 | def test_export_vulns_check_update_time(self, session, test_client): |
| 1956 | self.first_object.confirm =True | |
| 1957 | session.add(self.first_object) | |
| 1958 | session.commit() | |
| 1959 | res = test_client.get(self.url() + 'export_csv/') | |
| 1960 | assert res.status_code == 200 | |
| 2120 | workspace = WorkspaceFactory.create() | |
| 2121 | host = HostFactory.create(workspace=workspace) | |
| 2122 | session.add(host) | |
| 2123 | service = ServiceFactory.create(workspace=workspace, host=host) | |
| 2124 | session.add(service) | |
| 2125 | vuln = VulnerabilityFactory.create(workspace=workspace, host=host) | |
| 2126 | vuln.service = service | |
| 2127 | session.add(vuln) | |
| 2128 | session.commit() | |
| 2129 | ||
| 2130 | host.owned = True | |
| 2131 | service.owned = True | |
| 2132 | vuln.confirmed = True | |
| 2133 | session.add(host) | |
| 2134 | session.add(service) | |
| 2135 | session.add(vuln) | |
| 2136 | session.commit() | |
| 2137 | ||
| 2138 | res = test_client.get('v2/ws/{}/vulns/export_csv/'.format(workspace.name)) | |
| 2139 | assert res.status_code == 200 | |
| 2140 | ||
| 1961 | 2141 | csv_data = csv.DictReader(StringIO(res.data.decode('utf-8')), delimiter=',') |
| 2142 | ||
| 1962 | 2143 | for index, line in enumerate(csv_data): |
| 1963 | if self.first_object.id == int(line['id']): | |
| 1964 | create_date = parser.parse(line['date']) | |
| 1965 | update_date = parser.parse(line['update_date']) | |
| 1966 | delta = update_date - create_date | |
| 1967 | assert create_date < update_date | |
| 1968 | ||
| 2144 | create_date = parser.parse(line['date']) | |
| 2145 | update_date = parser.parse(line['update_date']) | |
| 2146 | assert create_date < update_date | |
| 2147 | ||
| 2148 | create_date = parser.parse(line['host_date']) | |
| 2149 | update_date = parser.parse(line['host_update_date']) | |
| 2150 | assert create_date < update_date | |
| 2151 | ||
| 2152 | create_date = parser.parse(line['service_date']) | |
| 2153 | update_date = parser.parse(line['service_update_date']) | |
| 2154 | assert create_date < update_date | |
| 1969 | 2155 | |
| 1970 | 2156 | @pytest.mark.usefixtures('ignore_nplusone') |
| 1971 | 2157 | def test_export_vulns_csv_with_custom_fields(self, session, test_client): |
| 1990 | 2176 | session.commit() |
| 1991 | 2177 | |
| 1992 | 2178 | res = test_client.get(self.url() + 'export_csv/') |
| 1993 | ||
| 1994 | 2179 | assert self._verify_csv(res.data) |
| 1995 | 2180 | |
| 1996 | 2181 | def _verify_csv(self, raw_csv_data, confirmed=False, severity=None): |
| 1997 | 2182 | custom_fields = [custom_field.field_name for custom_field in CustomFieldsSchema.query.all()] |
| 1998 | expected_headers = [ | |
| 1999 | "confirmed", "id", "date", "name", "severity", "service", | |
| 2000 | "target", "desc", "status", "hostnames", "comments", "owner", "os", "resolution", "easeofresolution", "web_vulnerability", | |
| 2001 | "data", "website", "path", "status_code", "request", "method", "params", "pname", "query", | |
| 2002 | "policyviolations", "external_id", "impact_confidentiality", "impact_integrity", "impact_availability", | |
| 2003 | "impact_accountability", "update_date" | |
| 2183 | vuln_headers = [ | |
| 2184 | "confirmed", "id", "date", "name", "severity", "service", | |
| 2185 | "target", "desc", "status", "hostnames", "comments", "owner", | |
| 2186 | "os", "resolution", "refs", "easeofresolution", "web_vulnerability", | |
| 2187 | "data", "website", "path", "status_code", "request", "response", "method", | |
| 2188 | "params", "pname", "query", "policyviolations", "external_id", "impact_confidentiality", | |
| 2189 | "impact_integrity", "impact_availability", "impact_accountability", "update_date" | |
| 2004 | 2190 | ] |
| 2005 | final_expected_headers = expected_headers + custom_fields | |
| 2006 | csv_data = csv.reader(StringIO(raw_csv_data.decode('utf-8')), delimiter=',') | |
| 2191 | host_and_service_headers = [ | |
| 2192 | "host_id", "host_description", "mac", | |
| 2193 | "host_owned", "host_creator_id", "host_date", "host_update_date", | |
| 2194 | "service_id", "service_name", "service_description", "service_owned", | |
| 2195 | "port", "protocol", "summary", "version", "service_status", | |
| 2196 | "service_creator_id", "service_date", "service_update_date", "service_parent_id" | |
| 2197 | ] | |
| 2198 | ||
| 2199 | final_headers = vuln_headers + custom_fields + host_and_service_headers | |
| 2200 | ||
| 2201 | csv_data = csv.DictReader(StringIO(raw_csv_data.decode('utf-8')), delimiter=',') | |
| 2202 | ||
| 2007 | 2203 | for index, line in enumerate(csv_data): |
| 2008 | ||
| 2009 | 2204 | if index == 0: |
| 2010 | if line != final_expected_headers: | |
| 2205 | csv_headers = list(line.keys()) | |
| 2206 | if csv_headers != final_headers: | |
| 2011 | 2207 | return False |
| 2012 | 2208 | else: |
| 2013 | vuln = Vulnerability.query.filter_by(id=line[1], confirmed=confirmed) | |
| 2209 | # test vulns | |
| 2210 | vuln = Vulnerability.query.filter_by(id=line['id'], confirmed=confirmed) | |
| 2014 | 2211 | if severity: |
| 2015 | 2212 | vuln.filter_by(severity=severity) |
| 2016 | 2213 | |
| 2017 | 2214 | vuln = vuln.first() |
| 2018 | if vuln.name != line[3]: | |
| 2215 | if vuln.name != line['name']: | |
| 2019 | 2216 | return False |
| 2020 | 2217 | # test custom fields |
| 2021 | 2218 | for c_index, custom_field in enumerate(custom_fields): |
| 2022 | if vuln.custom_fields[custom_field] != line[len(expected_headers) + c_index]: | |
| 2219 | if vuln.custom_fields[custom_field] != line[custom_field]: | |
| 2023 | 2220 | return False |
| 2024 | 2221 | |
| 2222 | #test hosts | |
| 2223 | host = Host.query.filter(Host.id == line['host_id']).first() | |
| 2224 | if host.ip != line['target']: | |
| 2225 | return False | |
| 2226 | ||
| 2227 | # test services | |
| 2228 | if line['service_id']: | |
| 2229 | service = Service.query.filter(Service.id == line['service_id']).first() | |
| 2230 | if service.summary != line['summary']: | |
| 2231 | return False | |
| 2232 | ||
| 2025 | 2233 | return True |
| 2234 | ||
| 2235 | @pytest.mark.usefixtures('ignore_nplusone') | |
| 2236 | def test_update_vuln_cant_change_tool(self, test_client, session): | |
| 2237 | host = HostFactory.create(workspace=self.workspace) | |
| 2238 | tool = "tool_name" | |
| 2239 | updated_tool = "new_tool" | |
| 2240 | vuln = VulnerabilityFactory.create(workspace=self.workspace, host_id=host.id, tool=tool) | |
| 2241 | session.add(vuln) | |
| 2242 | session.commit() # flush host_with_hostnames | |
| 2243 | raw_data = self._create_put_data( | |
| 2244 | 'Updated vuln Name', | |
| 2245 | 'Updated vuln', | |
| 2246 | 'open', | |
| 2247 | host.id, | |
| 2248 | 'Host', | |
| 2249 | ) | |
| 2250 | raw_data.update({'tool': updated_tool}) | |
| 2251 | res = test_client.put(self.url(obj=vuln, workspace=self.workspace), data=raw_data) | |
| 2252 | assert res.status_code == 200 | |
| 2253 | assert res.json['tool'] == tool | |
| 2026 | 2254 | |
| 2027 | 2255 | |
| 2028 | 2256 | |
| 2283 | 2511 | assert vuln_count_previous == vuln_count_after |
| 2284 | 2512 | assert deleted_vulns == len(vulns_to_delete) |
| 2285 | 2513 | |
| 2514 | def test_create_vuln_with_tool(self, host_with_hostnames, test_client, session): | |
| 2515 | """ | |
| 2516 | This one should only check basic vuln properties | |
| 2517 | :param host_with_hostnames: | |
| 2518 | :param test_client: | |
| 2519 | :param session: | |
| 2520 | :return: | |
| 2521 | """ | |
| 2522 | session.commit() # flush host_with_hostnames | |
| 2523 | tool_name = "tool_name" | |
| 2524 | raw_data = _create_post_data_vulnerability( | |
| 2525 | name='New vulns', | |
| 2526 | vuln_type='Vulnerability', | |
| 2527 | parent_id=host_with_hostnames.id, | |
| 2528 | parent_type='Host', | |
| 2529 | refs=[], | |
| 2530 | policyviolations=[], | |
| 2531 | description='helloworld', | |
| 2532 | severity='low', | |
| 2533 | tool=tool_name | |
| 2534 | ) | |
| 2535 | ws_name = host_with_hostnames.workspace.name | |
| 2536 | vuln_count_previous = session.query(Vulnerability).count() | |
| 2537 | res = test_client.post('/v2/ws/{0}/vulns/'.format(ws_name), data=raw_data) | |
| 2538 | assert res.status_code == 201 | |
| 2539 | assert vuln_count_previous + 1 == session.query(Vulnerability).count() | |
| 2540 | assert res.json['tool'] == tool_name | |
| 2541 | ||
| 2542 | def test_create_vuln_without_tool(self, host_with_hostnames, test_client, session): | |
| 2543 | """ | |
| 2544 | This one should only check basic vuln properties | |
| 2545 | :param host_with_hostnames: | |
| 2546 | :param test_client: | |
| 2547 | :param session: | |
| 2548 | :return: | |
| 2549 | """ | |
| 2550 | session.commit() # flush host_with_hostnames | |
| 2551 | raw_data = _create_post_data_vulnerability( | |
| 2552 | name='New vulns', | |
| 2553 | vuln_type='Vulnerability', | |
| 2554 | parent_id=host_with_hostnames.id, | |
| 2555 | parent_type='Host', | |
| 2556 | refs=[], | |
| 2557 | policyviolations=[], | |
| 2558 | description='helloworld', | |
| 2559 | severity='low', | |
| 2560 | ) | |
| 2561 | ws_name = host_with_hostnames.workspace.name | |
| 2562 | vuln_count_previous = session.query(Vulnerability).count() | |
| 2563 | res = test_client.post('/v2/ws/{0}/vulns/'.format(ws_name), data=raw_data) | |
| 2564 | assert res.status_code == 201 | |
| 2565 | assert vuln_count_previous + 1 == session.query(Vulnerability).count() | |
| 2566 | assert res.json['tool'] == "Web UI" | |
| 2567 | ||
| 2568 | def test_create_vuln_from_command_with_tool(self, test_client, session): | |
| 2569 | command = EmptyCommandFactory.create(workspace=self.workspace) | |
| 2570 | service = ServiceFactory.create(workspace=self.workspace) | |
| 2571 | session.commit() | |
| 2572 | tool = "tool_name" | |
| 2573 | url = self.url(workspace=command.workspace) + '?' + urlencode({'command_id': command.id}) | |
| 2574 | raw_data = _create_post_data_vulnerability( | |
| 2575 | name='Update vulnsweb', | |
| 2576 | vuln_type='VulnerabilityWeb', | |
| 2577 | parent_id=service.id, | |
| 2578 | parent_type='Service', | |
| 2579 | refs=[], | |
| 2580 | policyviolations=[], | |
| 2581 | description='helloworld', | |
| 2582 | severity='high', | |
| 2583 | tool=tool | |
| 2584 | ) | |
| 2585 | res = test_client.post(url, data=raw_data) | |
| 2586 | assert res.status_code == 201 | |
| 2587 | assert len(command.command_objects) == 1 | |
| 2588 | cmd_obj = command.command_objects[0] | |
| 2589 | assert cmd_obj.object_type == 'vulnerability' | |
| 2590 | assert cmd_obj.object_id == res.json['_id'] | |
| 2591 | assert res.json['tool'] == tool | |
| 2592 | ||
| 2593 | def test_create_vuln_from_command_without_tool(self, test_client, session): | |
| 2594 | command = EmptyCommandFactory.create(workspace=self.workspace) | |
| 2595 | service = ServiceFactory.create(workspace=self.workspace) | |
| 2596 | session.commit() | |
| 2597 | url = self.url(workspace=command.workspace) + '?' + urlencode({'command_id': command.id}) | |
| 2598 | raw_data = _create_post_data_vulnerability( | |
| 2599 | name='Update vulnsweb', | |
| 2600 | vuln_type='VulnerabilityWeb', | |
| 2601 | parent_id=service.id, | |
| 2602 | parent_type='Service', | |
| 2603 | refs=[], | |
| 2604 | policyviolations=[], | |
| 2605 | description='helloworld', | |
| 2606 | severity='high', | |
| 2607 | ) | |
| 2608 | res = test_client.post(url, data=raw_data) | |
| 2609 | assert res.status_code == 201 | |
| 2610 | assert len(command.command_objects) == 1 | |
| 2611 | cmd_obj = command.command_objects[0] | |
| 2612 | assert cmd_obj.object_type == 'vulnerability' | |
| 2613 | assert cmd_obj.object_id == res.json['_id'] | |
| 2614 | assert res.json['tool'] == command.tool | |
| 2615 | ||
| 2616 | ||
| 2617 | ||
| 2286 | 2618 | @pytest.mark.usefixtures('logged_user') |
| 2287 | 2619 | class TestVulnerabilityCustomFields(ReadOnlyAPITests): |
| 2288 | 2620 | model = Vulnerability |
| 2446 | 2778 | filter_ = VulnerabilityFilterSet().filters['creator'] |
| 2447 | 2779 | std_vulns = vulnerability_factory.create_batch(10, |
| 2448 | 2780 | workspace=workspace)[:5] |
| 2781 | session.add(workspace) | |
| 2449 | 2782 | web_vulns = vulnerability_web_factory.create_batch(10, |
| 2450 | 2783 | workspace=workspace)[:5] |
| 2451 | 2784 | command = empty_command_factory.create(workspace=workspace, |
| 2452 | 2785 | tool="metasploit") |
| 2453 | 2786 | |
| 2454 | 2787 | vulns = std_vulns + web_vulns |
| 2788 | session.add(command) | |
| 2455 | 2789 | session.add_all(vulns) |
| 2456 | 2790 | session.commit() |
| 2457 | session.flush() | |
| 2458 | 2791 | for vuln in vulns: |
| 2459 | 2792 | command_object_factory.create(command=command, |
| 2460 | 2793 | object_type='vulnerability', |
| 2504 | 2837 | vulnerability_factory.create_batch(5, host=host, workspace=workspace) |
| 2505 | 2838 | expected_vulns = vulnerability_factory.create_batch( |
| 2506 | 2839 | 5, host=host, workspace=workspace, name="Old OpenSSL version") |
| 2507 | for vuln in expected_vulns: | |
| 2508 | session.add(vuln) | |
| 2840 | session.add_all(expected_vulns) | |
| 2841 | session.add(workspace) | |
| 2509 | 2842 | session.commit() |
| 2510 | 2843 | filtered = filter_.filter(VulnerabilityGeneric.query, |
| 2511 | 2844 | VulnerabilityGeneric, |
| 227 | 227 | |
| 228 | 228 | |
| 229 | 229 | class CountTestsMixin: |
| 230 | pass | |
| 230 | def test_count(self, test_client, session, user_factory): | |
| 231 | ||
| 232 | session.add(self.factory.create(creator=self.first_object.creator, | |
| 233 | workspace=self.first_object.workspace)) | |
| 234 | ||
| 235 | session.commit() | |
| 236 | res = test_client.get(self.url() + "count/?group_by=creator_id").get_json() | |
| 237 | ||
| 238 | creators = [] | |
| 239 | grouped = 0 | |
| 240 | for obj in res['groups']: | |
| 241 | if obj['count'] == 2: | |
| 242 | grouped += 1 | |
| 243 | creators.append(obj['creator_id']) | |
| 244 | ||
| 245 | assert grouped == 1 | |
| 246 | assert creators == sorted(creators) | |
| 247 | ||
| 248 | def test_count_descending(self, test_client, session, user_factory): | |
| 249 | ||
| 250 | session.add(self.factory.create(creator=self.first_object.creator, | |
| 251 | workspace=self.first_object.workspace)) | |
| 252 | ||
| 253 | session.commit() | |
| 254 | res = test_client.get(self.url() + "count/?group_by=creator_id&order=desc").get_json() | |
| 255 | ||
| 256 | creators = [] | |
| 257 | grouped = 0 | |
| 258 | for obj in res['groups']: | |
| 259 | if obj['count'] == 2: | |
| 260 | grouped += 1 | |
| 261 | creators.append(obj['creator_id']) | |
| 262 | ||
| 263 | assert grouped == 1 | |
| 264 | assert creators == sorted(creators, reverse=True) | |
| 265 | ||
| 231 | 266 | |
| 232 | 267 | |
| 233 | 268 | class DeleteTestsMixin: |
| 0 | ''' | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | ''' | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | try: | |
| 9 | from lxml import etree as ET | |
| 10 | except ImportError: | |
| 11 | import xml.etree.ElementTree as ET | |
| 12 | ||
| 13 | import os | |
| 14 | ||
| 15 | from faraday import __version__ as faraday_version | |
| 16 | from faraday.server.config import FARADAY_BASE | |
| 17 | ||
| 18 | ||
| 19 | def test_matching_versions(): | |
| 20 | version_default = parse_element_from_xml('version') | |
| 21 | ||
| 22 | assert faraday_version == version_default | |
| 23 | ||
| 24 | ||
| 25 | def parse_element_from_xml(tag_name): | |
| 26 | with open(os.path.join(FARADAY_BASE, 'config/default.xml'), 'r') as output: | |
| 27 | default_data = output.read() | |
| 28 | tree = ET.fromstring(default_data) | |
| 29 | default_element = tree.find(tag_name).text | |
| 30 | ||
| 31 | return default_element | |
| 32 | ||
| 33 | ||
| 34 | # I'm Py3 |
| 71 | 71 | with open(log_path, 'r') as log_file: |
| 72 | 72 | print(log_file.read()) |
| 73 | 73 | assert subproc.returncode == 0, (out, err, command) |
| 74 | ||
| 75 | ||
| 76 | # I'm Py3 |
| 0 | ''' | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | ''' | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | from functools import partial | |
| 9 | ||
| 10 | import pytest | |
| 11 | ||
| 12 | from faraday.client.managers.mapper_manager import MapperManager | |
| 13 | from faraday.client.persistence.server.server import _create_server_api_url | |
| 14 | from faraday.client.persistence.server.models import ( | |
| 15 | Host, | |
| 16 | Service, | |
| 17 | Vuln, | |
| 18 | Credential, | |
| 19 | VulnWeb, | |
| 20 | Note, | |
| 21 | Command, | |
| 22 | ) | |
| 23 | import faraday.client.persistence.server.server | |
| 24 | from faraday.client.persistence.server.utils import ( | |
| 25 | get_host_properties, | |
| 26 | get_service_properties, | |
| 27 | get_vuln_properties, | |
| 28 | get_vuln_web_properties, | |
| 29 | get_credential_properties, get_command_properties) | |
| 30 | from tests.factories import ( | |
| 31 | WorkspaceFactory, | |
| 32 | CommandFactory, | |
| 33 | HostFactory, | |
| 34 | ServiceFactory, | |
| 35 | VulnerabilityFactory, | |
| 36 | CredentialFactory, | |
| 37 | VulnerabilityWebFactory, | |
| 38 | CommentFactory, | |
| 39 | EmptyCommandFactory) | |
| 40 | ||
| 41 | # OBJ_DATA is used to parametrize tests (https://docs.pytest.org/en/latest/parametrize.html) | |
| 42 | # We use it to test all model classes. | |
| 43 | # to add more tests you need to add items in the list or more objects in the dict. | |
| 44 | ||
| 45 | OBJ_DATA = [ | |
| 46 | # the key is the object being tested | |
| 47 | { | |
| 48 | 'class': Host, | |
| 49 | 'factory': HostFactory, | |
| 50 | # api_end_point is used to assert the generated url. | |
| 51 | 'api_end_point': 'hosts', | |
| 52 | # parent is used to assert parent information is correcly generated. | |
| 53 | 'parent': {}, | |
| 54 | # data is used to instanciate a persistence.server.models class. | |
| 55 | 'data': { | |
| 56 | '_id': 1, | |
| 57 | 'name': '192.168.0.20', | |
| 58 | 'description': 'My computer', | |
| 59 | 'default_gateway': '192.168.0.1', | |
| 60 | 'hostnames': [], | |
| 61 | 'os': 'Debian', | |
| 62 | 'owned': False, | |
| 63 | 'owner': 'leo' | |
| 64 | }, | |
| 65 | # expected_payload is asserted with the generated payload that will be sent to the API of faraday-server | |
| 66 | 'expected_payload': { | |
| 67 | 'command_id': None, | |
| 68 | 'default_gateway': '192.168.0.1', | |
| 69 | 'description': 'My computer', | |
| 70 | 'ip': '192.168.0.20', | |
| 71 | 'hostnames': [], | |
| 72 | 'os': 'Debian', | |
| 73 | 'owned': False, | |
| 74 | 'owner': 'leo', | |
| 75 | 'parent': None, | |
| 76 | 'type': 'Host', | |
| 77 | 'mac': '' | |
| 78 | }, | |
| 79 | }, | |
| 80 | { | |
| 81 | 'class': Service, | |
| 82 | 'factory': ServiceFactory, | |
| 83 | 'api_end_point': 'services', | |
| 84 | 'parent': { | |
| 85 | 'parent_type': 'Host', | |
| 86 | 'parent_factory': HostFactory | |
| 87 | }, | |
| 88 | 'data': { | |
| 89 | '_id': 1, | |
| 90 | 'name': 'Service port 60', | |
| 91 | 'description': 'My service', | |
| 92 | 'owned': False, | |
| 93 | 'owner': 'leo', | |
| 94 | 'protocol': 'tcp', | |
| 95 | 'ports': 60, | |
| 96 | 'version': '2', | |
| 97 | 'status': 'open', | |
| 98 | 'vulns': 0, | |
| 99 | }, | |
| 100 | 'expected_payload': { | |
| 101 | 'command_id': None, | |
| 102 | 'name': 'Service port 60', | |
| 103 | 'description': 'My service', | |
| 104 | 'protocol': 'tcp', | |
| 105 | 'ports': [60], | |
| 106 | 'version': '2', | |
| 107 | 'status': 'open', | |
| 108 | 'owned': False, | |
| 109 | 'owner': 'leo', | |
| 110 | 'type': 'Service' | |
| 111 | }, | |
| 112 | }, | |
| 113 | { | |
| 114 | 'class': Vuln, | |
| 115 | 'factory': VulnerabilityFactory, | |
| 116 | 'api_end_point': 'vulns', | |
| 117 | 'parent': { | |
| 118 | 'parent_type': 'Service', | |
| 119 | 'parent_factory': ServiceFactory | |
| 120 | }, | |
| 121 | 'data': { | |
| 122 | '_id': 1, | |
| 123 | 'name': 'Service vulnerable', | |
| 124 | 'desc': 'My vuln', | |
| 125 | 'owned': False, | |
| 126 | 'owner': 'leo', | |
| 127 | 'severity': 'critical', | |
| 128 | 'data': '', | |
| 129 | 'external_id': '1.30.9988.20.asdf.x20.vuln' | |
| 130 | }, | |
| 131 | 'expected_payload': { | |
| 132 | 'command_id': None, | |
| 133 | 'name': 'Service vulnerable', | |
| 134 | 'desc': 'My vuln', | |
| 135 | 'description': 'My vuln', | |
| 136 | 'owner': 'leo', | |
| 137 | 'owned': False, | |
| 138 | 'confirmed': False, | |
| 139 | 'severity': 'critical', | |
| 140 | 'data': '', | |
| 141 | 'type': 'Vulnerability', | |
| 142 | 'parent_type': 'Service', | |
| 143 | 'policyviolations': [], | |
| 144 | 'refs': [], | |
| 145 | 'status': 'opened', | |
| 146 | 'resolution': None, | |
| 147 | 'external_id': '1.30.9988.20.asdf.x20.vuln' | |
| 148 | }, | |
| 149 | }, | |
| 150 | { | |
| 151 | 'class': VulnWeb, | |
| 152 | 'factory': VulnerabilityWebFactory, | |
| 153 | 'api_end_point': 'vulns', | |
| 154 | 'parent': { | |
| 155 | 'parent_type': 'Service', | |
| 156 | 'parent_factory': ServiceFactory | |
| 157 | }, | |
| 158 | 'data': { | |
| 159 | '_id': 1, | |
| 160 | 'name': 'Service vulnerable', | |
| 161 | 'desc': 'My vuln', | |
| 162 | 'owned': False, | |
| 163 | 'owner': 'leo', | |
| 164 | 'severity': 'critical', | |
| 165 | 'data': '', | |
| 166 | 'website': 'www.faradaysec.com', | |
| 167 | 'method': 'GET', | |
| 168 | 'pname': 'param_name', | |
| 169 | 'params': 'params', | |
| 170 | 'path': 'path', | |
| 171 | 'request': 'test', | |
| 172 | 'query': 'query test', | |
| 173 | 'response': 'repsonse data', | |
| 174 | 'external_id': '1.30.9988.20.asdf.x20.vuln' | |
| 175 | }, | |
| 176 | 'expected_payload': { | |
| 177 | 'category': '', | |
| 178 | 'command_id': None, | |
| 179 | 'name': 'Service vulnerable', | |
| 180 | 'desc': 'My vuln', | |
| 181 | 'description': 'My vuln', | |
| 182 | 'owner': 'leo', | |
| 183 | 'owned': False, | |
| 184 | 'confirmed': False, | |
| 185 | 'severity': 'critical', | |
| 186 | 'data': '', | |
| 187 | 'type': 'VulnerabilityWeb', | |
| 188 | 'parent_type': 'Service', | |
| 189 | 'policyviolations': [], | |
| 190 | 'refs': [], | |
| 191 | 'status': 'opened', | |
| 192 | 'resolution': None, | |
| 193 | 'website': 'www.faradaysec.com', | |
| 194 | 'method': 'GET', | |
| 195 | 'pname': 'param_name', | |
| 196 | 'params': 'params', | |
| 197 | 'path': 'path', | |
| 198 | 'request': 'test', | |
| 199 | 'query': 'query test', | |
| 200 | 'response': 'repsonse data', | |
| 201 | 'external_id': '1.30.9988.20.asdf.x20.vuln' | |
| 202 | }, | |
| 203 | }, | |
| 204 | { | |
| 205 | 'class': Credential, | |
| 206 | 'factory': CredentialFactory, | |
| 207 | 'api_end_point': 'credential', | |
| 208 | 'parent': { | |
| 209 | 'parent_type': 'Host', | |
| 210 | 'parent_factory': HostFactory | |
| 211 | }, | |
| 212 | 'data': { | |
| 213 | '_id': 1, | |
| 214 | 'name': 'New credential', | |
| 215 | 'description': 'Test credential', | |
| 216 | 'owned': False, | |
| 217 | 'owner': 'leo', | |
| 218 | 'password': 'testpass', | |
| 219 | 'username': 'username1' | |
| 220 | }, | |
| 221 | 'expected_payload': { | |
| 222 | 'command_id': None, | |
| 223 | 'name': 'New credential', | |
| 224 | 'description': 'Test credential', | |
| 225 | 'owner': 'leo', | |
| 226 | 'owned': False, | |
| 227 | 'password': 'testpass', | |
| 228 | 'username': 'username1', | |
| 229 | 'type': 'Cred', | |
| 230 | }, | |
| 231 | }, | |
| 232 | { | |
| 233 | 'class': Note, | |
| 234 | 'factory': CommentFactory, | |
| 235 | 'api_end_point': 'comment', | |
| 236 | # parent not used | |
| 237 | 'parent': { | |
| 238 | 'parent_type': 'Host', | |
| 239 | 'parent_factory': HostFactory | |
| 240 | }, | |
| 241 | 'data': { | |
| 242 | '_id': 1, | |
| 243 | 'text': 'Text from Note', | |
| 244 | 'object_id': 10, | |
| 245 | 'object_type': 'Host', | |
| 246 | 'owned': False, | |
| 247 | 'owner': 'leo', | |
| 248 | 'password': 'testpass', | |
| 249 | 'username': 'username1' | |
| 250 | }, | |
| 251 | 'expected_payload': { | |
| 252 | 'command_id': None, | |
| 253 | 'description': '', | |
| 254 | 'name': None, | |
| 255 | 'object_id': 10, | |
| 256 | 'object_type': 'Host', | |
| 257 | 'owned': False, | |
| 258 | 'owner': 'leo', | |
| 259 | 'text': 'Text from Note', | |
| 260 | 'type': 'Note'}, | |
| 261 | }, | |
| 262 | { | |
| 263 | 'class': Command, | |
| 264 | 'factory': EmptyCommandFactory, | |
| 265 | 'api_end_point': 'commands', | |
| 266 | # parent not used | |
| 267 | 'parent': { | |
| 268 | 'parent_type': 'Host', | |
| 269 | 'parent_factory': HostFactory | |
| 270 | }, | |
| 271 | 'data': { | |
| 272 | 'itime': 1513959206, | |
| 273 | 'ip': "192.168.124.1", | |
| 274 | 'hostname': "mandarina", | |
| 275 | 'command': "Import Nexpose:", | |
| 276 | 'tool': "Import Nexpose:", | |
| 277 | 'import_source': "report", | |
| 278 | 'user': "leonardo", | |
| 279 | 'workspace': "airbnb", | |
| 280 | 'duration': 0.164561, | |
| 281 | 'params': "/home/lcubo/.faraday/report/airbnb/nexpose_5.7.19_Website_PT.xml", | |
| 282 | '_id': 280 | |
| 283 | }, | |
| 284 | 'expected_payload':{ | |
| 285 | 'command': 'Import Nexpose:', | |
| 286 | 'tool': "Import Nexpose:", | |
| 287 | 'import_source': "report", | |
| 288 | 'duration': 0.164561, | |
| 289 | 'hostname': 'mandarina', | |
| 290 | 'ip': '192.168.124.1', | |
| 291 | 'itime': 1513959206, | |
| 292 | 'params': '/home/lcubo/.faraday/report/airbnb/nexpose_5.7.19_Website_PT.xml', | |
| 293 | 'type': 'CommandRunInformation', | |
| 294 | 'user': 'leonardo', | |
| 295 | 'workspace': u'test' | |
| 296 | } | |
| 297 | } | |
| 298 | ] | |
| 299 | ||
| 300 | ||
| 301 | # the following dict is used to parametrize find (GET) tests | |
| 302 | # mocked_response is the json returned by the api | |
| 303 | # serialized_expected_results the expected serialized result. | |
| 304 | GET_OBJ_DATA = [ | |
| 305 | { | |
| 306 | 'class': VulnWeb, | |
| 307 | 'factory': VulnerabilityWebFactory, | |
| 308 | 'api_end_point': 'vulns', | |
| 309 | 'get_properties_function': get_vuln_web_properties, | |
| 310 | 'mocked_response': { | |
| 311 | "website": "www.faradaysec.com", | |
| 312 | "_rev": "", | |
| 313 | "parent_type": "Service", | |
| 314 | "owned": False, | |
| 315 | "owner": "leonardo", | |
| 316 | "query": "query", | |
| 317 | "refs": [ | |
| 318 | "ref" | |
| 319 | ], | |
| 320 | "impact": { | |
| 321 | "accountability": False, | |
| 322 | "integrity": False, | |
| 323 | "confidentiality": False, | |
| 324 | "availability": False | |
| 325 | }, | |
| 326 | "confirmed": True, | |
| 327 | "severity": "high", | |
| 328 | "service": { | |
| 329 | "status": "open", | |
| 330 | "protocol": "fdsf", | |
| 331 | "name": "gfdgfd", | |
| 332 | "summary": "(32/fdsf) gfdgfd", | |
| 333 | "version": "", | |
| 334 | "_id": 299, | |
| 335 | "ports": "32" | |
| 336 | }, | |
| 337 | "policyviolations": [], | |
| 338 | "params": "parameters", | |
| 339 | "type": "VulnerabilityWeb", | |
| 340 | "method": "GET", | |
| 341 | "metadata": { | |
| 342 | "update_time": 1513982385000, | |
| 343 | "update_user": "", | |
| 344 | "update_action": 0, | |
| 345 | "creator": "", | |
| 346 | "create_time": 1513982385000, | |
| 347 | "update_controller_action": "", | |
| 348 | "owner": "leonardo", | |
| 349 | "command_id": None | |
| 350 | }, | |
| 351 | "status": "opened", | |
| 352 | "issuetracker": {}, | |
| 353 | "description": "Description", | |
| 354 | "parent": 299, | |
| 355 | "tags": [ ], | |
| 356 | "easeofresolution": "simple", | |
| 357 | "hostnames": [ | |
| 358 | "macbookpro-c9a7" | |
| 359 | ], | |
| 360 | "pname": "pname", | |
| 361 | "date": "2017-12-22T19:39:45.014203+00:00", | |
| 362 | "path": "path", | |
| 363 | "data": "data", | |
| 364 | "response": "response", | |
| 365 | "desc": "Description", | |
| 366 | "name": "Vuln web", | |
| 367 | "obj_id": "348", | |
| 368 | "request": "request", | |
| 369 | "_attachments": [], | |
| 370 | "target": "172.16.138.1", | |
| 371 | "_id": 348, | |
| 372 | "resolution": "resolution", | |
| 373 | "external_id": "1.30.9988.20.asdf.x20.vuln" | |
| 374 | }, | |
| 375 | 'serialized_expected_results': { | |
| 376 | 'confirmed': True, | |
| 377 | 'data': 'data', | |
| 378 | 'desc': 'Description', | |
| 379 | 'description': 'Description', | |
| 380 | 'name': 'Vuln web', | |
| 381 | 'owned': False, | |
| 382 | 'owner': 'leonardo', | |
| 383 | 'parent': 299, | |
| 384 | 'parent_type': 'Service', | |
| 385 | 'params': 'parameters', | |
| 386 | 'path': 'path', | |
| 387 | 'policyviolations': [], | |
| 388 | 'response': 'response', | |
| 389 | 'method': 'GET', | |
| 390 | 'refs': ['ref'], | |
| 391 | 'request': 'request', | |
| 392 | 'resolution': 'resolution', | |
| 393 | 'severity': 'high', | |
| 394 | 'status': 'opened', | |
| 395 | 'website': 'www.faradaysec.com', | |
| 396 | "query": "query", | |
| 397 | 'external_id': '1.30.9988.20.asdf.x20.vuln', | |
| 398 | "pname": "pname" | |
| 399 | } | |
| 400 | ||
| 401 | }, | |
| 402 | { | |
| 403 | 'class': Vuln, | |
| 404 | 'factory': VulnerabilityFactory, | |
| 405 | 'api_end_point': 'vulns', | |
| 406 | 'get_properties_function': get_vuln_properties, | |
| 407 | 'mocked_response': { | |
| 408 | "website": "", | |
| 409 | "_rev": "", | |
| 410 | "parent_type": "Service", | |
| 411 | "owned": False, | |
| 412 | "owner": "leonardo", | |
| 413 | "query": "", | |
| 414 | "refs": [], | |
| 415 | "impact": { | |
| 416 | "accountability": False, | |
| 417 | "integrity": False, | |
| 418 | "confidentiality": False, | |
| 419 | "availability": False | |
| 420 | }, | |
| 421 | "confirmed": True, | |
| 422 | "severity": "med", | |
| 423 | "service": { | |
| 424 | "status": "open", | |
| 425 | "protocol": "tcp", | |
| 426 | "name": "ssh", | |
| 427 | "summary": "(21/tcp) ssh", | |
| 428 | "version": "", | |
| 429 | "_id": 1, | |
| 430 | "ports": "21" | |
| 431 | }, | |
| 432 | "policyviolations": [], | |
| 433 | "params": "", | |
| 434 | "type": "Vulnerability", | |
| 435 | "method": "", | |
| 436 | "metadata": { | |
| 437 | "update_time": 1513290499000, | |
| 438 | "update_user": "", | |
| 439 | "update_action": 0, | |
| 440 | "creator": "", | |
| 441 | "create_time": 1513290499000, | |
| 442 | "update_controller_action": "", | |
| 443 | "owner": "leonardo", | |
| 444 | "command_id": None | |
| 445 | }, | |
| 446 | "status": "opened", | |
| 447 | "issuetracker": {}, | |
| 448 | "description": "description", | |
| 449 | "parent": 1, | |
| 450 | "tags": [], | |
| 451 | "easeofresolution": "trivial", | |
| 452 | "hostnames": [], | |
| 453 | "pname": "", | |
| 454 | "date": "2017-12-14T19:28:19.427274+00:00", | |
| 455 | "path": "", | |
| 456 | "data": "data", | |
| 457 | "response": "", | |
| 458 | "desc": "description", | |
| 459 | "name": "Vuln test", | |
| 460 | "obj_id": "1", | |
| 461 | "request": "", | |
| 462 | "_attachments": [], | |
| 463 | "target": "192.168.0.1", | |
| 464 | "_id": 1, | |
| 465 | "resolution": "", | |
| 466 | "external_id": "1.30.9988.20.asdf.x20.vuln" | |
| 467 | }, | |
| 468 | 'serialized_expected_results': { | |
| 469 | 'confirmed': True, | |
| 470 | 'data': 'data', | |
| 471 | 'desc': 'description', | |
| 472 | 'description': 'description', | |
| 473 | 'name': 'Vuln test', | |
| 474 | 'owned': False, | |
| 475 | 'owner': 'leonardo', | |
| 476 | 'parent': 1, | |
| 477 | 'parent_type': 'Service', | |
| 478 | 'policyviolations': [], | |
| 479 | 'refs': [], | |
| 480 | 'resolution': '', | |
| 481 | 'severity': 'med', | |
| 482 | 'external_id': '1.30.9988.20.asdf.x20.vuln', | |
| 483 | 'status': 'opened' | |
| 484 | } | |
| 485 | ||
| 486 | }, | |
| 487 | { | |
| 488 | 'class': Host, | |
| 489 | 'factory': HostFactory, | |
| 490 | 'api_end_point': 'hosts', | |
| 491 | 'get_properties_function': get_host_properties, | |
| 492 | 'mocked_response': { | |
| 493 | 'name': "192.168.1.1", 'default_gateway': None, | |
| 494 | 'ip': "192.168.1.1", '_rev': "", | |
| 495 | 'description': "Test description", 'owned': False, | |
| 496 | 'services': 7, 'hostnames': [], | |
| 497 | 'vulns': 45, 'owner': "leonardo", | |
| 498 | 'credentials': 1, '_id': 16, | |
| 499 | 'os': "Linux 2.6.9", 'id': 16, | |
| 500 | 'metadata': { | |
| 501 | 'update_time': 1513381792000, 'update_user': "", | |
| 502 | 'update_action': 0, 'creator': "", | |
| 503 | 'create_time': 1513381792000, 'update_controller_action': "", | |
| 504 | 'owner': "leonardo", 'command_id': None | |
| 505 | } | |
| 506 | }, | |
| 507 | 'serialized_expected_results': { | |
| 508 | 'description': 'Test description', | |
| 509 | 'ip': '192.168.1.1', | |
| 510 | 'os': 'Linux 2.6.9', | |
| 511 | 'hostnames': [], | |
| 512 | 'owned': False, | |
| 513 | 'owner': 'leonardo', | |
| 514 | 'mac': ''} | |
| 515 | ||
| 516 | }, | |
| 517 | { | |
| 518 | 'class': Service, | |
| 519 | 'factory': ServiceFactory, | |
| 520 | 'api_end_point': 'services', | |
| 521 | 'parent': { | |
| 522 | 'parent_type': 'Host', | |
| 523 | 'parent_factory': HostFactory | |
| 524 | }, | |
| 525 | 'get_properties_function': get_service_properties, | |
| 526 | 'mocked_response': { | |
| 527 | "status": "open", | |
| 528 | "protocol": "tcp", | |
| 529 | "description": "Test description", | |
| 530 | "vulns": 2, | |
| 531 | "_rev": "", | |
| 532 | "metadata": { | |
| 533 | "update_time": 1513290473000, | |
| 534 | "update_user": "", | |
| 535 | "update_action": 0, | |
| 536 | "creator": "", | |
| 537 | "create_time": 1513290473000, | |
| 538 | "update_controller_action": "", | |
| 539 | "owner": "leonardo", | |
| 540 | "command_id": None | |
| 541 | }, | |
| 542 | "owned": False, | |
| 543 | "summary": "(21/tcp) ssh", | |
| 544 | "port": 21, | |
| 545 | "owner": "leonardo", | |
| 546 | "version": "", | |
| 547 | "host_id": 1, | |
| 548 | "parent": 1, | |
| 549 | "id": 1, | |
| 550 | "credentials": 0, | |
| 551 | "_id": 1, | |
| 552 | "ports": 21, | |
| 553 | "name": "ssh" | |
| 554 | }, | |
| 555 | 'serialized_expected_results': { | |
| 556 | 'name': 'ssh', | |
| 557 | 'description': 'Test description', | |
| 558 | 'ports': [21], | |
| 559 | 'protocol': 'tcp', | |
| 560 | 'status': 'open', | |
| 561 | 'parent': 1, | |
| 562 | 'version': '', | |
| 563 | 'owned': False, | |
| 564 | 'owner': 'leonardo' | |
| 565 | } | |
| 566 | ||
| 567 | }, | |
| 568 | { | |
| 569 | 'class': Credential, | |
| 570 | 'factory': ServiceFactory, | |
| 571 | 'api_end_point': 'credential', | |
| 572 | 'parent': { | |
| 573 | 'parent_type': 'Host', | |
| 574 | 'parent_factory': HostFactory | |
| 575 | }, | |
| 576 | 'get_properties_function': get_credential_properties, | |
| 577 | 'mocked_response': { | |
| 578 | "username": "user1", | |
| 579 | "password": "secretpassword", | |
| 580 | "description": "Credential obtained using hashcat", | |
| 581 | "couchdbid": "", | |
| 582 | 'parent': 64, | |
| 583 | 'parent_type': 'Host', | |
| 584 | "_rev": "", | |
| 585 | "metadata": { | |
| 586 | "update_time": 1514312337000, | |
| 587 | "update_user": "", | |
| 588 | "update_action": 0, | |
| 589 | "creator": "", | |
| 590 | "create_time": 1514312336000, | |
| 591 | "update_controller_action": "", | |
| 592 | "owner": "leonardo", | |
| 593 | "command_id": None | |
| 594 | }, | |
| 595 | "owned": False, | |
| 596 | "owner": "leonardo", | |
| 597 | "_id": 2, | |
| 598 | "id": 2, | |
| 599 | "name": "dsds" | |
| 600 | }, | |
| 601 | 'serialized_expected_results': { | |
| 602 | 'description': 'Credential obtained using hashcat', | |
| 603 | 'name': 'dsds', | |
| 604 | 'owned': False, | |
| 605 | 'owner': 'leonardo', | |
| 606 | 'parent': 64, | |
| 607 | 'parent_type': 'Host', | |
| 608 | 'password': 'secretpassword', | |
| 609 | 'username': 'user1' | |
| 610 | } | |
| 611 | }, | |
| 612 | { | |
| 613 | 'class': Credential, | |
| 614 | 'factory': ServiceFactory, | |
| 615 | 'api_end_point': 'credential', | |
| 616 | 'parent': { | |
| 617 | 'parent_type': 'Host', | |
| 618 | 'parent_factory': HostFactory | |
| 619 | }, | |
| 620 | 'get_properties_function': get_credential_properties, | |
| 621 | 'mocked_response': { | |
| 622 | "username": "user1", | |
| 623 | "password": "secretpassword", | |
| 624 | "description": "Credential obtained using hashcat", | |
| 625 | "couchdbid": "", | |
| 626 | 'parent': 64, | |
| 627 | 'parent_type': 'Host', | |
| 628 | "_rev": "", | |
| 629 | "metadata": { | |
| 630 | "update_time": 1514312337000, | |
| 631 | "update_user": "", | |
| 632 | "update_action": 0, | |
| 633 | "creator": "", | |
| 634 | "create_time": 1514312336000, | |
| 635 | "update_controller_action": "", | |
| 636 | "owner": "leonardo", | |
| 637 | "command_id": None | |
| 638 | }, | |
| 639 | "owned": False, | |
| 640 | "owner": "leonardo", | |
| 641 | "_id": 2, | |
| 642 | "id": 2, | |
| 643 | "name": "dsds" | |
| 644 | }, | |
| 645 | 'serialized_expected_results': { | |
| 646 | 'description': 'Credential obtained using hashcat', | |
| 647 | 'name': 'dsds', | |
| 648 | 'owned': False, | |
| 649 | 'owner': 'leonardo', | |
| 650 | 'parent': 64, | |
| 651 | 'parent_type': 'Host', | |
| 652 | 'password': 'secretpassword', | |
| 653 | 'username': 'user1' | |
| 654 | } | |
| 655 | }, | |
| 656 | { | |
| 657 | 'class': Command, | |
| 658 | 'factory': ServiceFactory, | |
| 659 | 'api_end_point': 'commands', | |
| 660 | 'parent': { | |
| 661 | 'parent_type': 'Host', | |
| 662 | 'parent_factory': HostFactory | |
| 663 | }, | |
| 664 | 'get_properties_function': get_command_properties, | |
| 665 | 'mocked_response': { | |
| 666 | "itime": 1513365824, | |
| 667 | "ip": "192.168.20.53", | |
| 668 | "hostname": "mandarina", | |
| 669 | "command": "Import Nessus:", | |
| 670 | "tool": "Import Nessus:", | |
| 671 | "import_source": "report", | |
| 672 | "user": "lcubo", | |
| 673 | "workspace": "dsadsa", | |
| 674 | "duration": "In progress", | |
| 675 | "params": "/home/lcubo/.faraday/report/dsadsa/nessus_report_Remote.nessus", | |
| 676 | "_id": 1 | |
| 677 | }, | |
| 678 | 'serialized_expected_results': { | |
| 679 | 'command': 'Import Nessus:', | |
| 680 | "tool": "Import Nessus:", | |
| 681 | 'duration': 'In progress', | |
| 682 | "import_source": "report", | |
| 683 | 'hostname': 'mandarina', | |
| 684 | 'ip': '192.168.20.53', | |
| 685 | 'itime': 1513365824, | |
| 686 | 'params': '/home/lcubo/.faraday/report/dsadsa/nessus_report_Remote.nessus', | |
| 687 | 'user': 'lcubo'} | |
| 688 | } | |
| 689 | ] | |
| 690 | ||
| 691 | class MockResponse: | |
| 692 | def __init__(self, json_data, status_code): | |
| 693 | self.json_data = json_data | |
| 694 | self.status_code = status_code | |
| 695 | ||
| 696 | def json(self): | |
| 697 | return self.json_data | |
| 698 | ||
| 699 | ||
| 700 | @pytest.mark.usefixtures('logged_user') | |
| 701 | class TestMapperManager(): | |
| 702 | ||
| 703 | @pytest.mark.parametrize("many_test_data", OBJ_DATA) | |
| 704 | def test_save_without_command(self, many_test_data, monkeypatch, session): | |
| 705 | """ | |
| 706 | This test verifies that the request made to the api are the expected ones | |
| 707 | """ | |
| 708 | obj_class = many_test_data['class'] | |
| 709 | workspace = WorkspaceFactory.create(name='test') | |
| 710 | session.commit() | |
| 711 | mapper_manager = MapperManager() | |
| 712 | mapper_manager.createMappers(workspace.name) | |
| 713 | test_data = many_test_data | |
| 714 | raw_data = test_data['data'] | |
| 715 | if test_data['parent']: | |
| 716 | parent = test_data['parent']['parent_factory'].create() | |
| 717 | session.commit() | |
| 718 | test_data['data']['parent'] = parent.id | |
| 719 | test_data['data']['parent_type'] = test_data['parent']['parent_type'] | |
| 720 | if obj_class not in [Note, Command]: | |
| 721 | test_data['expected_payload']['parent'] = parent.id | |
| 722 | if obj_class in [Vuln, Credential]: | |
| 723 | test_data['expected_payload']['parent_type'] = test_data['parent']['parent_type'] | |
| 724 | def mock_server_post(test_data, post_url, update=False, expected_response=201, **params): | |
| 725 | assert post_url == '{0}/ws/test/{1}/'.format( | |
| 726 | _create_server_api_url(), test_data['api_end_point']) | |
| 727 | assert expected_response == 201 | |
| 728 | assert update == False | |
| 729 | if obj_class not in [Command]: | |
| 730 | metadata = params.pop('metadata') | |
| 731 | assert metadata['owner'] == test_data['expected_payload']['owner'] | |
| 732 | assert params == test_data['expected_payload'] | |
| 733 | return { | |
| 734 | 'id': 1, | |
| 735 | 'ok': True, | |
| 736 | 'rev': '' | |
| 737 | } | |
| 738 | ||
| 739 | monkeypatch.setattr(faraday.client.persistence.server.server, '_post', partial(mock_server_post, test_data)) | |
| 740 | obj = obj_class(raw_data, workspace.name) | |
| 741 | mapper_manager.save(obj) | |
| 742 | ||
| 743 | @pytest.mark.parametrize("many_test_data", OBJ_DATA) | |
| 744 | def test_save_with_command(self, many_test_data, monkeypatch, session): | |
| 745 | obj_class = many_test_data['class'] | |
| 746 | if obj_class == Command: | |
| 747 | return | |
| 748 | workspace = WorkspaceFactory.create(name='test') | |
| 749 | command = CommandFactory.create(workspace=workspace) | |
| 750 | session.commit() | |
| 751 | mapper_manager = MapperManager() | |
| 752 | mapper_manager.createMappers(workspace.name) | |
| 753 | test_data = many_test_data | |
| 754 | raw_data = test_data['data'] | |
| 755 | if test_data['parent']: | |
| 756 | parent = test_data['parent']['parent_factory'].create() | |
| 757 | session.commit() | |
| 758 | ||
| 759 | test_data['data']['parent'] = parent.id | |
| 760 | test_data['data']['parent_type'] = test_data['parent']['parent_type'] | |
| 761 | if obj_class not in [Note]: | |
| 762 | test_data['expected_payload']['parent'] = parent.id | |
| 763 | if obj_class in [Vuln, Credential]: | |
| 764 | test_data['expected_payload']['parent_type'] = test_data['parent']['parent_type'] | |
| 765 | def mock_server_post(test_data, post_url, update=False, expected_response=201, **params): | |
| 766 | assert post_url == '{0}/ws/test/{1}/?command_id={2}'.format(_create_server_api_url(), test_data['api_end_point'], params['command_id']) | |
| 767 | assert expected_response == 201 | |
| 768 | assert update == False | |
| 769 | metadata = params.pop('metadata') | |
| 770 | assert metadata['owner'] == test_data['expected_payload']['owner'] | |
| 771 | params.pop('command_id') | |
| 772 | test_data['expected_payload'].pop('command_id') | |
| 773 | assert params == test_data['expected_payload'] | |
| 774 | return { | |
| 775 | 'id': 1, | |
| 776 | 'ok': True, | |
| 777 | 'rev': '' | |
| 778 | } | |
| 779 | ||
| 780 | monkeypatch.setattr(faraday.client.persistence.server.server, '_post', partial(mock_server_post, test_data)) | |
| 781 | obj = obj_class(raw_data, workspace.name) | |
| 782 | mapper_manager.save(obj, command.id) | |
| 783 | ||
| 784 | @pytest.mark.parametrize("many_test_data", OBJ_DATA) | |
| 785 | def test_update_without_command(self, many_test_data, monkeypatch, session): | |
| 786 | obj_class = many_test_data['class'] | |
| 787 | workspace = WorkspaceFactory.create(name='test') | |
| 788 | mapper_manager = MapperManager() | |
| 789 | mapper_manager.createMappers(workspace.name) | |
| 790 | test_data = many_test_data | |
| 791 | relational_model = test_data['factory'].create() | |
| 792 | session.add(relational_model) | |
| 793 | session.commit() | |
| 794 | raw_data = test_data['data'] | |
| 795 | if test_data['parent']: | |
| 796 | parent = test_data['parent']['parent_factory'].create() | |
| 797 | session.add(parent) | |
| 798 | session.commit() | |
| 799 | ||
| 800 | test_data['data']['parent'] = parent.id | |
| 801 | test_data['data']['parent_type'] = test_data['parent']['parent_type'] | |
| 802 | if obj_class not in [Note, Command]: | |
| 803 | test_data['expected_payload']['parent'] = parent.id | |
| 804 | if obj_class in [Vuln, Credential]: | |
| 805 | test_data['expected_payload']['parent_type'] = test_data['parent']['parent_type'] | |
| 806 | def mock_server_put(test_data, put_url, update=False, expected_response=201, **params): | |
| 807 | assert put_url == '{0}/ws/test/{1}/{2}/'.format(_create_server_api_url(), test_data['api_end_point'], test_data['id']) | |
| 808 | assert expected_response == 200 | |
| 809 | assert update == False | |
| 810 | if obj_class not in [Command]: | |
| 811 | metadata = params.pop('metadata') | |
| 812 | assert metadata['owner'] == test_data['expected_payload']['owner'] | |
| 813 | params.pop('command_id', None) | |
| 814 | test_data['expected_payload'].pop('command_id', None) | |
| 815 | assert params == test_data['expected_payload'] | |
| 816 | ||
| 817 | return { | |
| 818 | 'id': 1, | |
| 819 | 'ok': True, | |
| 820 | 'rev': '' | |
| 821 | } | |
| 822 | ||
| 823 | raw_data['id'] = relational_model.id | |
| 824 | test_data['id'] = relational_model.id | |
| 825 | monkeypatch.setattr(faraday.client.persistence.server.server, '_put', partial(mock_server_put, test_data)) | |
| 826 | ||
| 827 | obj = obj_class(raw_data, workspace.name) | |
| 828 | mapper_manager.update(obj) | |
| 829 | ||
| 830 | @pytest.mark.parametrize("many_test_data", OBJ_DATA) | |
| 831 | def test_update_with_command(self, many_test_data, monkeypatch, session): | |
| 832 | obj_class = many_test_data['class'] | |
| 833 | if obj_class in [Command]: | |
| 834 | return | |
| 835 | workspace = WorkspaceFactory.create(name='test') | |
| 836 | command = CommandFactory.create(workspace=workspace) | |
| 837 | session.add(command) | |
| 838 | session.commit() | |
| 839 | mapper_manager = MapperManager() | |
| 840 | mapper_manager.createMappers(workspace.name) | |
| 841 | ||
| 842 | test_data = many_test_data | |
| 843 | raw_data = test_data['data'] | |
| 844 | if test_data['parent']: | |
| 845 | parent = test_data['parent']['parent_factory'].create() | |
| 846 | session.add(parent) | |
| 847 | session.commit() | |
| 848 | test_data['data']['parent'] = parent.id | |
| 849 | test_data['data']['parent_type'] = test_data['parent']['parent_type'] | |
| 850 | test_data['expected_payload']['parent'] = parent.id | |
| 851 | if obj_class in [Vuln, Credential]: | |
| 852 | test_data['expected_payload']['parent_type'] = test_data['parent']['parent_type'] | |
| 853 | relational_model = test_data['factory'].create() | |
| 854 | session.add(relational_model) | |
| 855 | session.commit() | |
| 856 | def mock_server_put(put_url, update=False, expected_response=201, **params): | |
| 857 | assert put_url == '{0}/ws/test/{1}/{2}/?command_id={3}'.format( | |
| 858 | _create_server_api_url(), | |
| 859 | test_data['api_end_point'], | |
| 860 | test_data['id'], | |
| 861 | params['command_id']) | |
| 862 | assert expected_response == 200 | |
| 863 | assert update == False | |
| 864 | return { | |
| 865 | 'id': 1, | |
| 866 | 'ok': True, | |
| 867 | 'rev': '' | |
| 868 | } | |
| 869 | ||
| 870 | raw_data['id'] = relational_model.id | |
| 871 | test_data['id'] = relational_model.id | |
| 872 | monkeypatch.setattr(faraday.client.persistence.server.server, '_put', mock_server_put) | |
| 873 | obj = obj_class(raw_data, workspace.name) | |
| 874 | mapper_manager.update(obj, command.id) | |
| 875 | ||
| 876 | @pytest.mark.parametrize("many_test_data", GET_OBJ_DATA) | |
| 877 | def test_find_obj_by_id(self, many_test_data, session, monkeypatch): | |
| 878 | obj_class = many_test_data['class'] | |
| 879 | test_data = many_test_data | |
| 880 | persisted_obj = test_data['factory'].create() | |
| 881 | session.add(persisted_obj) | |
| 882 | session.commit() | |
| 883 | mapper_manager = MapperManager() | |
| 884 | mapper_manager.createMappers(persisted_obj.workspace.name) | |
| 885 | ||
| 886 | def mock_unsafe_io_with_server(host, test_data, server_io_function, server_expected_response, server_url, **payload): | |
| 887 | mocked_response = test_data['mocked_response'] | |
| 888 | assert '{0}/ws/{1}/{2}/{3}/'.format( | |
| 889 | _create_server_api_url(), | |
| 890 | persisted_obj.workspace.name, | |
| 891 | test_data['api_end_point'], | |
| 892 | persisted_obj.id) == server_url | |
| 893 | return MockResponse(mocked_response, 200) | |
| 894 | ||
| 895 | monkeypatch.setattr(faraday.client.persistence.server.server, '_unsafe_io_with_server', partial(mock_unsafe_io_with_server, persisted_obj, test_data)) | |
| 896 | found_obj = mapper_manager.find(obj_class.class_signature, persisted_obj.id) | |
| 897 | serialized_obj = test_data['get_properties_function'](found_obj) | |
| 898 | if obj_class not in [Command]: | |
| 899 | metadata = serialized_obj.pop('metadata') | |
| 900 | assert serialized_obj == test_data['serialized_expected_results'] | |
| 901 | ||
| 902 | ||
| 903 | # I'm Py3 |
| 0 | ''' | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | ''' | |
| 6 | from __future__ import absolute_import | |
| 7 | from __future__ import print_function | |
| 8 | ||
| 9 | from queue import Queue | |
| 10 | ||
| 11 | import time | |
| 12 | ||
| 13 | from unittest import mock | |
| 14 | import pytest | |
| 15 | ||
| 16 | from faraday.client.managers.mapper_manager import MapperManager | |
| 17 | from faraday.client.model import Modelactions | |
| 18 | from faraday.client.model.controller import ModelController | |
| 19 | from tests.factories import ( | |
| 20 | WorkspaceFactory, | |
| 21 | VulnerabilityFactory, | |
| 22 | HostFactory, | |
| 23 | VulnerabilityWebFactory, | |
| 24 | CredentialFactory, | |
| 25 | ServiceFactory | |
| 26 | ) | |
| 27 | ||
| 28 | TEST_CASES = { | |
| 29 | 'hosts': { | |
| 30 | 'factory': HostFactory, | |
| 31 | 'class_signature': 'Host', | |
| 32 | 'expected_result': {} | |
| 33 | }, | |
| 34 | 'vulns': { | |
| 35 | 'factory':VulnerabilityFactory, | |
| 36 | 'class_signature': 'Vulnerability', | |
| 37 | 'api_result': { | |
| 38 | 'name': 'Vuln 1', | |
| 39 | 'desc': 'Description', | |
| 40 | 'data': 'Data', | |
| 41 | 'severity': 'critical', | |
| 42 | 'confirmed': True, | |
| 43 | }, | |
| 44 | }, | |
| 45 | 'vulns': { | |
| 46 | 'factory': VulnerabilityWebFactory, | |
| 47 | 'class_signature': 'VulnerabilityWeb', | |
| 48 | 'api_result': { | |
| 49 | 'name': 'Vuln 1', | |
| 50 | 'desc': 'Description', | |
| 51 | 'data': 'Data', | |
| 52 | 'severity': 'critical', | |
| 53 | 'confirmed': True, | |
| 54 | }, | |
| 55 | }, | |
| 56 | 'credential': { | |
| 57 | 'factory': CredentialFactory, | |
| 58 | 'class_signature': 'Cred', | |
| 59 | 'api_result': { | |
| 60 | 'name': 'test', | |
| 61 | 'username': 'test', | |
| 62 | 'password': 'test' | |
| 63 | }, | |
| 64 | }, | |
| 65 | 'services': { | |
| 66 | 'factory': ServiceFactory, | |
| 67 | 'class_signature': 'Service', | |
| 68 | 'api_result': { | |
| 69 | 'name': 'SSH', | |
| 70 | 'protocol': 'tcp', | |
| 71 | 'ports': [22], | |
| 72 | 'version': '2.1', | |
| 73 | 'status': 'open' | |
| 74 | } | |
| 75 | } | |
| 76 | } | |
| 77 | ||
| 78 | def test_controller_stop_when_is_not_processing(): | |
| 79 | mappers_manager = MapperManager() | |
| 80 | pending_actions = Queue() | |
| 81 | controller = ModelController(mappers_manager, pending_actions) | |
| 82 | assert controller.processing is False | |
| 83 | assert controller._must_stop is False | |
| 84 | controller.start() | |
| 85 | assert controller.is_alive() | |
| 86 | controller.stop() | |
| 87 | controller.join() | |
| 88 | assert controller._must_stop is True | |
| 89 | assert controller.is_alive() is False | |
| 90 | ||
| 91 | ||
| 92 | def test_controller_cant_be_stopped_when_is_processing(): | |
| 93 | """ | |
| 94 | If someone tells the controller to stop and it is processing then it | |
| 95 | will stop when the processing finishes | |
| 96 | """ | |
| 97 | ||
| 98 | mappers_manager = MapperManager() | |
| 99 | pending_actions = Queue() | |
| 100 | controller = ModelController(mappers_manager, pending_actions) | |
| 101 | assert controller.processing is False | |
| 102 | assert controller._must_stop is False | |
| 103 | controller.start() | |
| 104 | controller.processing = True | |
| 105 | controller.active_plugins_count = 1 | |
| 106 | assert controller.is_alive() | |
| 107 | controller.stop() | |
| 108 | assert controller._must_stop is True | |
| 109 | assert controller.processing | |
| 110 | controller.join(timeout=2) | |
| 111 | assert controller.is_alive() | |
| 112 | controller.processing = False | |
| 113 | controller.join() | |
| 114 | assert controller.is_alive() is False | |
| 115 | ||
| 116 | ||
| 117 | def test_controller_plugin_start_action_updates_internal_state(): | |
| 118 | mappers_manager = MapperManager() | |
| 119 | pending_actions = Queue() | |
| 120 | controller = ModelController(mappers_manager, pending_actions) | |
| 121 | controller.start() | |
| 122 | controller.add_action((Modelactions.PLUGINSTART, "test", None)) | |
| 123 | time.sleep(1) | |
| 124 | assert controller.active_plugins_count == 1 | |
| 125 | assert controller.processing | |
| 126 | controller.add_action((Modelactions.PLUGINEND, "test", None)) | |
| 127 | time.sleep(1) | |
| 128 | assert controller.active_plugins_count == 0 | |
| 129 | assert controller.processing is False | |
| 130 | controller.stop() | |
| 131 | controller.join() | |
| 132 | assert controller.is_alive() is False | |
| 133 | ||
| 134 | def test_only_start_plugin(): | |
| 135 | mappers_manager = MapperManager() | |
| 136 | pending_actions = Queue() | |
| 137 | controller = ModelController(mappers_manager, pending_actions) | |
| 138 | controller._pluginStart('test', None) | |
| 139 | assert controller.active_plugins_count == 1 | |
| 140 | assert controller.processing | |
| 141 | controller._pluginStart('test', None) | |
| 142 | assert controller.active_plugins_count == 2 | |
| 143 | ||
| 144 | def test_only_end_pluging(): | |
| 145 | mappers_manager = MapperManager() | |
| 146 | pending_actions = Queue() | |
| 147 | controller = ModelController(mappers_manager, pending_actions) | |
| 148 | controller._pluginStart('test', None) | |
| 149 | controller._pluginEnd('test', None) | |
| 150 | assert controller.active_plugins_count == 0 | |
| 151 | assert controller.processing is False | |
| 152 | ||
| 153 | def test_end_pluging_multiple_times(): | |
| 154 | mappers_manager = MapperManager() | |
| 155 | pending_actions = Queue() | |
| 156 | controller = ModelController(mappers_manager, pending_actions) | |
| 157 | controller._pluginEnd('test', None) | |
| 158 | controller._pluginEnd('test', None) | |
| 159 | assert controller.active_plugins_count == 0 | |
| 160 | assert controller.processing is False | |
| 161 | ||
| 162 | ||
| 163 | ||
| 164 | @pytest.mark.parametrize("url_endpoint, test_data", list(TEST_CASES.items())) | |
| 165 | @mock.patch('faraday.client.persistence.server.server._get') | |
| 166 | def test_find(get, url_endpoint, test_data, session): | |
| 167 | if 'api_result' in test_data: | |
| 168 | get.return_value = test_data['api_result'] | |
| 169 | mappers_manager = MapperManager() | |
| 170 | pending_actions = Queue() | |
| 171 | controller = ModelController(mappers_manager, pending_actions) | |
| 172 | workspace = WorkspaceFactory.create() | |
| 173 | mappers_manager.createMappers(workspace.name) | |
| 174 | obj = test_data['factory'].create(workspace=workspace) | |
| 175 | session.add(obj) | |
| 176 | session.commit() | |
| 177 | result = controller.find(test_data['class_signature'], obj.id) | |
| 178 | assert get.called | |
| 179 | print(get.mock_calls[0][1][0]) | |
| 180 | assert get.mock_calls[0][1][0].endswith( | |
| 181 | '/_api/v2/ws/{0}/{1}/{2}/'.format(workspace.name, url_endpoint, obj.id)) | |
| 182 | ||
| 183 | ||
| 184 | # I'm Py3 |
| 0 | ''' | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | ''' | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | import unittest | |
| 9 | import json | |
| 10 | from faraday.client.persistence.server import models | |
| 11 | from unittest.mock import patch | |
| 12 | ||
| 13 | HOST_JSON_STRING = '{"_id":1,"id":"08d3b6545ec70897daf05cd471f4166a8e605c00","key":"08d3b6545ec70897daf05cd471f4166a8e605c00","value":{"_id":"08d3b6545ec70897daf05cd471f4166a8e605c00","_rev":"1-a12368dc03d557c337e833f8090db568","default_gateway":["192.168.20.1","00:1d:aa:c9:83:e8"],"description":"","metadata":{"create_time":1475852074.455225,"creator":"","owner":"","update_action":0,"update_controller_action":"ModelControler._processAction ModelControler.newHost","update_time":1475852074.455226,"update_user":""},"name":"10.31.112.29","os":"Microsoft Windows Server 2008 R2 Standard Service Pack 1","owned":"false","owner":"","services":12,"vulns":43}}' | |
| 14 | ||
| 15 | INTERFACE_JSON_STRING = '{"_id":1,"id":"08d3b6545ec70897daf05cd471f4166a8e605c00.02946afc59c50a4d76c1adbb082c2d5439baf50a","key":"08d3b6545ec70897daf05cd471f4166a8e605c00.02946afc59c50a4d76c1adbb082c2d5439baf50a","value":{"_id":"08d3b6545ec70897daf05cd471f4166a8e605c00.02946afc59c50a4d76c1adbb082c2d5439baf50a","_rev":"1-c279e0906d2b1f02b832a99d5f58f99c","description":"","host_id":1,"hostnames":["qa3app09"],"ipv4":{"DNS":[],"address":"10.31.112.29","gateway":"0.0.0.0","mask":"0.0.0.0"},"ipv6":{"DNS":[],"address":"0000:0000:0000:0000:0000:0000:0000:0000","gateway":"0000:0000:0000:0000:0000:0000:0000:0000","prefix":"00"},"mac":"00:50:56:81:01:e3","metadata":{"create_time":1475852074.456803,"creator":"","owner":"","update_action":0,"update_controller_action":"ModelControler._processAction ModelControler.newInterface","update_time":1475852074.456803,"update_user":""},"name":"10.31.112.29","network_segment":"","owned":false,"owner":"","ports":{"closed":null,"filtered":null,"opened":null}}}' | |
| 16 | ||
| 17 | SERVICE_JSON_STRING = '{"_id":1,"id":"08d3b6545ec70897daf05cd471f4166a8e605c00.02946afc59c50a4d76c1adbb082c2d5439baf50a.029384202ef91fff5892042392875595fb0b41ed","key":"08d3b6545ec70897daf05cd471f4166a8e605c00.02946afc59c50a4d76c1adbb082c2d5439baf50a.029384202ef91fff5892042392875595fb0b41ed","value":{"_id":"08d3b6545ec70897daf05cd471f4166a8e605c00.02946afc59c50a4d76c1adbb082c2d5439baf50a.029384202ef91fff5892042392875595fb0b41ed","_rev":"1-73ef6b9e6488fd05823b89e36bbbb626","description":"","metadata":{"create_time":1475852074.457551,"creator":"","owner":"","update_action":0,"update_controller_action":"ModelControler._processAction ModelControler.newService","update_time":1475852074.457551,"update_user":""},"name":"msrdp","owned":false,"owner":"","ports":[3389],"protocol":"tcp","status":"open","version":"unknown", "host_id": 1},"vulns":8}' | |
| 18 | ||
| 19 | VULN_JSON_STRING = '{"_id":8,"id":"08d3b6545ec70897daf05cd471f4166a8e605c00.2a21f3916b8c9a40e70b2fc6b7ea8f7a3a498558","key":"08d3b6545ec70897daf05cd471f4166a8e605c00.2a21f3916b8c9a40e70b2fc6b7ea8f7a3a498558","value":{"_attachments":{},"_id":"08d3b6545ec70897daf05cd471f4166a8e605c00.2a21f3916b8c9a40e70b2fc6b7ea8f7a3a498558","_rev":"1-28cb6b1372f4712dbbf7b8e1e23699e4","confirmed":false,"data":"","desc":"Each ethernet MAC address starts with a 24-bit Organizationally Unique Identifier.\\nThese OUI are registered by IEEE.\\nOutput: The following card manufacturers were identified :\\n\\n00:50:56:81:01:e3 : VMware, Inc.","description":"Each ethernet MAC address starts with a 24-bit Organizationally Unique Identifier.\\nThese OUI are registered by IEEE.\\nOutput: The following card manufacturers were identified :\\n\\n00:50:56:81:01:e3 : VMware, Inc.","easeofresolution":null,"hostnames":["qa3app09"],"impact":{"accountability":null,"availability":null,"confidentiality":null,"integrity":null},"issuetracker":{},"metadata":{"create_time":1475852074.459108,"creator":"","owner":"","update_action":0,"update_controller_action":"ModelControler._processAction ModelControler.newVuln","update_time":1475852074.459108,"update_user":""},"method":null,"name":"Ethernet Card Manufacturer Detection","obj_id":"2a21f3916b8c9a40e70b2fc6b7ea8f7a3a498558","owned":"false","owner":"","params":"","parent":"08d3b6545ec70897daf05cd471f4166a8e605c00","path":null,"pname":null,"query":null,"refs":[],"request":null,"resolution":"n/a","response":null,"service":"","severity":"info","status":"","tags":[],"target":"10.31.112.29","type":"Vulnerability","website":null}}' | |
| 20 | ||
| 21 | VULN_WEB_JSON_STRING = '{"_id":20,"id":"08d3b6545ec70897daf05cd471f4166a8e605c00.02946afc59c50a4d76c1adbb082c2d5439baf50a.790670b8824bf95588c1a00e4e65cb3c681e94d6.f0390f7e450cb71a4ff31e3bd38c2049c5f189f8","key":"08d3b6545ec70897daf05cd471f4166a8e605c00.02946afc59c50a4d76c1adbb082c2d5439baf50a.790670b8824bf95588c1a00e4e65cb3c681e94d6.f0390f7e450cb71a4ff31e3bd38c2049c5f189f8","value":{"_attachments":{},"_id":"08d3b6545ec70897daf05cd471f4166a8e605c00.02946afc59c50a4d76c1adbb082c2d5439baf50a.790670b8824bf95588c1a00e4e65cb3c681e94d6.f0390f7e450cb71a4ff31e3bd38c2049c5f189f8","_rev":"1-aeee90afddaa938dff756baf8d2cebda","confirmed":false,"data":"","desc":"It was possible to identify the remote service by its banner or by looking at the error message it sends when it receives an HTTP request.\\nOutput: A web server is running on this port.","description":"It was possible to identify the remote service by its banner or by looking at the error message it sends when it receives an HTTP request.\\nOutput: A web server is running on this port.","easeofresolution":null,"hostnames":["qa3app09"],"impact":{"accountability":null,"availability":null,"confidentiality":null,"integrity":null},"issuetracker":{},"metadata":{"create_time":1475852074.464117,"creator":"","owner":"","update_action":0,"update_controller_action":"ModelControler.newVulnWeb","update_time":1475852074.464117,"update_user":""},"method":"","name":"Service Detection","obj_id":"f0390f7e450cb71a4ff31e3bd38c2049c5f189f8","owned":"false","owner":"","params":"","parent":"08d3b6545ec70897daf05cd471f4166a8e605c00.02946afc59c50a4d76c1adbb082c2d5439baf50a.790670b8824bf95588c1a00e4e65cb3c681e94d6","path":"","pname":"","query":"","refs":[],"request":"","resolution":"n/a","response":"","service":"(80/tcp) www","severity":"info","status":"","tags":[],"target":"10.31.112.29","type":"VulnerabilityWeb","website":"qa3app09"}}' | |
| 22 | ||
| 23 | NOTE_JSON_STRING = '{"_id":1,"id":"08d3b6545ec70897daf05cd471f4166a8e605c00.02946afc59c50a4d76c1adbb082c2d5439baf50a.790670b8824bf95588c1a00e4e65cb3c681e94d6.83b3a120d6928b3c1f04a41cfccc59a55c627cf2","key":"08d3b6545ec70897daf05cd471f4166a8e605c00.02946afc59c50a4d76c1adbb082c2d5439baf50a.790670b8824bf95588c1a00e4e65cb3c681e94d6.83b3a120d6928b3c1f04a41cfccc59a55c627cf2","value":{"_id":"08d3b6545ec70897daf05cd471f4166a8e605c00.02946afc59c50a4d76c1adbb082c2d5439baf50a.790670b8824bf95588c1a00e4e65cb3c681e94d6.83b3a120d6928b3c1f04a41cfccc59a55c627cf2","couchid":"08d3b6545ec70897daf05cd471f4166a8e605c00.02946afc59c50a4d76c1adbb082c2d5439baf50a.790670b8824bf95588c1a00e4e65cb3c681e94d6.83b3a120d6928b3c1f04a41cfccc59a55c627cf2","description":"","metadata":{"create_time":1475852074.461232,"creator":"","owner":"","update_action":0,"update_controller_action":"ModelControler._processAction ModelControler.newNote","update_time":1475852074.461232,"update_user":""},"name":"website","owned":false,"owner":"","text":""}}' | |
| 24 | ||
| 25 | models.FARADAY_UP = False | |
| 26 | models.MERGE_STRATEGY = None # this is the default :) | |
| 27 | ||
| 28 | class ModelsTest(unittest.TestCase): | |
| 29 | ||
| 30 | def setUp(self): | |
| 31 | self.ws = 'a_workspace_name' | |
| 32 | self.a_host_dictionary = json.loads(HOST_JSON_STRING) | |
| 33 | self.an_interface_dictionary = json.loads(INTERFACE_JSON_STRING) | |
| 34 | self.a_service_dictionary = json.loads(SERVICE_JSON_STRING) | |
| 35 | self.a_vuln_dictionary = json.loads(VULN_JSON_STRING) | |
| 36 | self.a_vuln_web_dictionary = json.loads(VULN_WEB_JSON_STRING) | |
| 37 | self.a_note_dictionary = json.loads(NOTE_JSON_STRING) | |
| 38 | ||
| 39 | self.maxDiff = None # show the diff when test run no matter how big | |
| 40 | ||
| 41 | def test_ignore_in_changes(self): | |
| 42 | def server_io(): return {'ok': True, 'rev': 1, 'id': 2} | |
| 43 | decorated = models._ignore_in_changes(server_io) | |
| 44 | with patch.dict(models._LOCAL_CHANGES_ID_TO_REV, clear=True): | |
| 45 | json = decorated() | |
| 46 | self.assertEqual(models._LOCAL_CHANGES_ID_TO_REV[json['id']], json['rev']) | |
| 47 | ||
| 48 | def test_flatten_dictionary(self): | |
| 49 | flattened_host_dictionary = models._flatten_dictionary(self.a_host_dictionary) | |
| 50 | what_the_flattened_dict_should_look_like = { | |
| 51 | u"_id":1, | |
| 52 | u"id":u"08d3b6545ec70897daf05cd471f4166a8e605c00", | |
| 53 | u"_rev":u"1-a12368dc03d557c337e833f8090db568", | |
| 54 | u"default_gateway":[u"192.168.20.1",u"00:1d:aa:c9:83:e8"], | |
| 55 | u"description":u"", | |
| 56 | u"metadata":{u"create_time":1475852074.455225, | |
| 57 | u"creator":u"", | |
| 58 | u"owner":u"", | |
| 59 | u"update_action":0, | |
| 60 | u"update_controller_action":u"ModelControler._processAction ModelControler.newHost", | |
| 61 | u"update_time":1475852074.455226, | |
| 62 | u"update_user":u""}, | |
| 63 | u"name":u"10.31.112.29", | |
| 64 | u"os":u"Microsoft Windows Server 2008 R2 Standard Service Pack 1", | |
| 65 | u"owned": u'false', | |
| 66 | u"owner":u"", | |
| 67 | u"services":12, | |
| 68 | u"vulns":43} | |
| 69 | ||
| 70 | self.assertDictEqual(flattened_host_dictionary, what_the_flattened_dict_should_look_like) | |
| 71 | ||
| 72 | def test_faraday_ready_objects_getter(self): | |
| 73 | hosts = models._get_faraday_ready_objects(self.ws, [self.a_host_dictionary], 'hosts') | |
| 74 | services = models._get_faraday_ready_objects(self.ws, [self.a_service_dictionary], 'services') | |
| 75 | vulns = models._get_faraday_ready_objects(self.ws, [self.a_vuln_dictionary], 'vulns') | |
| 76 | vulns_web = models._get_faraday_ready_objects(self.ws, [self.a_vuln_dictionary], 'vulns_web') | |
| 77 | ||
| 78 | self.assertTrue(all([isinstance(h, models.Host) for h in hosts])) | |
| 79 | self.assertTrue(all([isinstance(s, models.Service) for s in services])) | |
| 80 | self.assertTrue(all([isinstance(v, models.Vuln) for v in vulns])) | |
| 81 | self.assertTrue(all([isinstance(v, models.VulnWeb) for v in vulns_web])) | |
| 82 | ||
| 83 | ||
| 84 | # I'm Py3 |
| 0 | ''' | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | ''' | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | import faraday.client.persistence.server.models as models | |
| 9 | import pytest | |
| 10 | import responses | |
| 11 | import requests | |
| 12 | from unittest.mock import Mock, patch | |
| 13 | ||
| 14 | ||
| 15 | from tests.test_api_workspaced_base import GenericAPITest | |
| 16 | ||
| 17 | from tests.factories import VulnerabilityWebFactory, VulnerabilityFactory | |
| 18 | ||
| 19 | ||
| 20 | @pytest.mark.usefixtures('logged_user') | |
| 21 | class TestVulnPersistanceModelsFuncions(GenericAPITest): | |
| 22 | factory = VulnerabilityFactory | |
| 23 | ||
| 24 | @responses.activate | |
| 25 | @patch('faraday.config.configuration.getInstanceConfiguration') | |
| 26 | @patch('faraday.client.persistence.server.server.SERVER_URL', 'http://localhost:5985') | |
| 27 | def test_persistence_server_update_vuln(self, getInstanceConfigurationMock): | |
| 28 | fo = self.first_object | |
| 29 | conf_mock = Mock() | |
| 30 | getInstanceConfigurationMock.return_value = conf_mock | |
| 31 | port = 5985 | |
| 32 | conf_mock.getDBSessionCookies.return_value = None | |
| 33 | conf_mock.getAPIUrl.return_value = 'http://localhost:{0}'.format(port) | |
| 34 | conf_mock.getServerURI.return_value = 'http://localhost:{0}'.format(port) | |
| 35 | conf_mock.getAPIUsername.return_value = 'faraday' | |
| 36 | conf_mock.getAPIPassword.return_value = 'mocked_password' | |
| 37 | ||
| 38 | vuln = {'desc': fo.description, 'data': fo.data, 'severity': fo.severity, 'refs': list(fo.references), | |
| 39 | 'confirmed': fo.confirmed, 'resolution': fo.resolution, 'status': fo.status, | |
| 40 | 'policyviolations': list(fo.policy_violations)} | |
| 41 | ||
| 42 | v = models.Vuln(vuln, self.workspace.name) | |
| 43 | v.id = fo.id | |
| 44 | ||
| 45 | resp = {u'status': u'closed', | |
| 46 | u'_rev': u'', | |
| 47 | u'parent_type': v.getParentType(), | |
| 48 | u'owned': v.isOwned(), | |
| 49 | u'owner': v.getParent(), | |
| 50 | u'query': u'', | |
| 51 | u'refs': v.getRefs(), | |
| 52 | u'impact': {u'integrity': False, u'confidentiality': False, u'availability': False, | |
| 53 | u'accountability': False}, | |
| 54 | u'confirmed': v.getConfirmed(), | |
| 55 | u'severity': v.getSeverity(), | |
| 56 | u'service': None, | |
| 57 | u'policyviolations': v.getPolicyViolations(), | |
| 58 | u'params': u'', | |
| 59 | u'type': u'Vulnerability', | |
| 60 | u'method': u'', | |
| 61 | u'metadata': {u'update_time': u'2018-05-23T17:03:27.880196+00:00', u'update_user': u'<User: faraday>', | |
| 62 | u'update_action': 0, u'creator': u'Nmap', | |
| 63 | u'create_time': u'2018-05-18T16:30:26.011851+00:00', | |
| 64 | u'update_controller_action': u'', u'owner': u'faraday', u'command_id': 22}, | |
| 65 | u'website': u'', | |
| 66 | u'issuetracker': {}, | |
| 67 | u'description': v.getDesc(), | |
| 68 | u'tags': [], | |
| 69 | u'easeofresolution': None, | |
| 70 | u'hostnames': [], | |
| 71 | u'pname': u'', | |
| 72 | u'date': u'2018-05-18T16:30:26.011851+00:00', | |
| 73 | u'path': u'', | |
| 74 | u'data': v.getData(), | |
| 75 | u'response': u'', | |
| 76 | u'desc': v.getDesc(), | |
| 77 | u'name': v.getName(), | |
| 78 | u'obj_id': str(v.getID()), | |
| 79 | u'request': u'', | |
| 80 | u'_attachments': {}, | |
| 81 | u'target': u'192.168.10.103', | |
| 82 | u'_id': v.getID(), | |
| 83 | u'resolution': v.getResolution() | |
| 84 | } | |
| 85 | ||
| 86 | responses.add(responses.PUT, | |
| 87 | 'http://localhost:{0}/_api/v2/ws/{1}/vulns/{2}/'.format(port,self.workspace.name, v.id), | |
| 88 | json=resp, status=200) | |
| 89 | ||
| 90 | a = requests.put('http://localhost:{0}/_api/v2/ws/{1}/vulns/{2}/'.format(port,self.workspace.name, v.id)) | |
| 91 | ||
| 92 | models.update_vuln(self.workspace.name, v) | |
| 93 | ||
| 94 | ||
| 95 | @pytest.mark.usefixtures('logged_user') | |
| 96 | class TestVulnWebPersistanceModelsFuncions(GenericAPITest): | |
| 97 | factory = VulnerabilityWebFactory | |
| 98 | ||
| 99 | @responses.activate | |
| 100 | @patch('faraday.config.configuration.getInstanceConfiguration') | |
| 101 | @patch('faraday.client.persistence.server.server.SERVER_URL', 'http://localhost:5985') | |
| 102 | def test_persistence_server_update_vuln_web(self, getInstanceConfigurationMock): | |
| 103 | fo = self.first_object | |
| 104 | ||
| 105 | conf_mock = Mock() | |
| 106 | getInstanceConfigurationMock.return_value = conf_mock | |
| 107 | port = 5985 | |
| 108 | conf_mock.getDBSessionCookies.return_value = None | |
| 109 | conf_mock.getAPIUrl.return_value = 'http://localhost:{0}'.format(port) | |
| 110 | conf_mock.getServerURI.return_value = 'http://localhost:{0}'.format(port) | |
| 111 | conf_mock.getAPIUsername.return_value = 'faraday' | |
| 112 | conf_mock.getAPIPassword.return_value = 'mocked_password' | |
| 113 | ||
| 114 | vuln_web = {'desc': fo.description, 'data': fo.data, 'severity': fo.severity, 'refs': list(fo.references), | |
| 115 | 'confirmed': fo.confirmed, 'resolution': fo.resolution, 'status': fo.status, | |
| 116 | 'policyviolations': list(fo.policy_violations), 'path': fo.path, 'website': fo.website, | |
| 117 | 'request': fo.request, 'response': fo.response, 'method': fo.method, 'params': fo.parameters, | |
| 118 | 'pname': fo.parameter_name, 'query': str(fo.query), '_attachments': fo.attachments, | |
| 119 | 'hostnames': list(fo.hostnames), | |
| 120 | 'impact': {'accountability': fo.impact_accountability, 'availability': fo.impact_availability, | |
| 121 | 'confidentiality': fo.impact_confidentiality, 'integrity': fo.impact_integrity}, | |
| 122 | 'service': fo.service_id, 'tags': list(fo.tags), 'target': fo.target_host_ip} | |
| 123 | ||
| 124 | v = models.VulnWeb(vuln_web, self.workspace.name) | |
| 125 | v.id = fo.id | |
| 126 | ||
| 127 | resp = {u'status': u'closed', | |
| 128 | u'_rev': u'', | |
| 129 | u'parent_type': v.getParentType(), | |
| 130 | u'owned': v.isOwned(), | |
| 131 | u'owner': v.getParent(), | |
| 132 | u'query': str(v.getQuery()), | |
| 133 | u'refs': v.getRefs(), | |
| 134 | u'impact': v.getImpact(), | |
| 135 | u'confirmed': v.getConfirmed(), | |
| 136 | u'severity': v.getSeverity(), | |
| 137 | u'service': v.getService(), | |
| 138 | u'policyviolations': v.getPolicyViolations(), | |
| 139 | u'params': v.getParams(), | |
| 140 | u'type': u'VulnerabilityWeb', | |
| 141 | u'method': v.getMethod(), | |
| 142 | u'metadata': {u'update_time': u'2018-05-23T17:03:27.880196+00:00', u'update_user': u'<User: faraday>', | |
| 143 | u'update_action': 0, u'creator': u'Nmap', | |
| 144 | u'create_time': u'2018-05-18T16:30:26.011851+00:00', | |
| 145 | u'update_controller_action': u'', u'owner': u'faraday', u'command_id': 22}, | |
| 146 | u'website': v.getWebsite(), | |
| 147 | u'issuetracker': {}, | |
| 148 | u'description': v.getDesc(), | |
| 149 | u'tags': v.getTags(), | |
| 150 | u'easeofresolution': None, | |
| 151 | u'hostnames': v.getHostnames(), | |
| 152 | u'pname': v.getPname(), | |
| 153 | u'date': u'2018-05-18T16:30:26.011851+00:00', | |
| 154 | u'path': v.getPath(), | |
| 155 | u'data': v.getData(), | |
| 156 | u'response': v.getResponse(), | |
| 157 | u'desc': v.getDesc(), | |
| 158 | u'name': v.getName(), | |
| 159 | u'obj_id': str(v.getID()), | |
| 160 | u'request': v.getRequest(), | |
| 161 | u'_attachments': str(v.getAttachments()), | |
| 162 | u'target': v.getTarget(), | |
| 163 | u'_id': v.getID(), | |
| 164 | u'resolution': v.getResolution() | |
| 165 | } | |
| 166 | ||
| 167 | responses.add(responses.PUT, | |
| 168 | 'http://localhost:{0}/_api/v2/ws/{1}/vulns/{2}/'.format(port,self.workspace.name, v.id), | |
| 169 | json=resp, status=200) | |
| 170 | ||
| 171 | a = requests.put('http://localhost:{0}/_api/v2/ws/{1}/vulns/{2}/'.format(port,self.workspace.name, v.id)) | |
| 172 | ||
| 173 | models.update_vuln_web(self.workspace.name, v) | |
| 174 | ||
| 175 | ||
| 176 | # I'm Py3 |
| 0 | ''' | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | ''' | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | import sys | |
| 9 | sys.path.append('.') | |
| 10 | import unittest | |
| 11 | from queue import Queue | |
| 12 | from unittest.mock import MagicMock as mock | |
| 13 | ||
| 14 | import faraday.client.plugins.controller | |
| 15 | ||
| 16 | ||
| 17 | class PluginControllerUnitTest(unittest.TestCase): | |
| 18 | ||
| 19 | def setUp(self): | |
| 20 | ||
| 21 | def create_not_plugin(name, can_parse_command_string): | |
| 22 | plugin = mock() | |
| 23 | plugin.canParseCommandString = mock(return_value=can_parse_command_string) | |
| 24 | plugin.updateSettings = mock() | |
| 25 | plugin.name = name | |
| 26 | plugin.processCommandString = mock(return_value='modified cmd string') | |
| 27 | return plugin | |
| 28 | ||
| 29 | def create_not_plugin_manager(): | |
| 30 | not_plugin_manager = mock() | |
| 31 | self.plugin1 = create_not_plugin('plugin1', True) | |
| 32 | self.plugin2 = create_not_plugin('plugin2', False) | |
| 33 | self.plugin3 = create_not_plugin('plugin3', False) | |
| 34 | self.plugin4 = create_not_plugin('plugin4', False) | |
| 35 | not_plugin_manager.getPlugins = mock(return_value={'plugin1': self.plugin1, | |
| 36 | 'plugin2': self.plugin2, | |
| 37 | 'plugin3': self.plugin3, | |
| 38 | 'plugin4': self.plugin4}) | |
| 39 | return not_plugin_manager | |
| 40 | ||
| 41 | def create_not_mappers_manager(): | |
| 42 | not_mappers_manager = mock() | |
| 43 | ||
| 44 | self.pending_actions = Queue() | |
| 45 | self.not_plugin_manager = create_not_plugin_manager() | |
| 46 | self.not_mappers_manager = create_not_mappers_manager() | |
| 47 | self.controller = faraday.client.plugins.controller.PluginController('PluginController', | |
| 48 | self.not_plugin_manager, | |
| 49 | self.not_mappers_manager, | |
| 50 | self.pending_actions) | |
| 51 | ||
| 52 | def test_find_plugin_that_exists(self): | |
| 53 | plugin = self.controller._find_plugin('plugin1') | |
| 54 | self.assertEqual(plugin.name, 'plugin1') | |
| 55 | ||
| 56 | def test_find_plugin_that_doesnt_exist(self): | |
| 57 | plugin = self.controller._find_plugin('key_non_existant') | |
| 58 | self.assertIs(plugin, None) | |
| 59 | ||
| 60 | def test_command_malformed(self): | |
| 61 | blocked_with_pipe = self.controller._is_command_malformed("test --command", "test --command | tee test") | |
| 62 | blocked_with_dollar = self.controller._is_command_malformed("test --command", "test --command $HOLA") | |
| 63 | blocked_with_hash = self.controller._is_command_malformed("test --command", "test # --command ") | |
| 64 | self.assertEqual(blocked_with_pipe, True) | |
| 65 | self.assertEqual(blocked_with_dollar, True) | |
| 66 | self.assertEqual(blocked_with_hash, True) | |
| 67 | ||
| 68 | def test_command_not_malformed(self): | |
| 69 | nice_command_blocked = self.controller._is_command_malformed("test --command", "test --command wush") | |
| 70 | self.assertEqual(nice_command_blocked, False) | |
| 71 | ||
| 72 | def test_getting_plugins_by_input_that_can_parse_cmd(self): | |
| 73 | plugin_set = { | |
| 74 | '1': self.plugin1, | |
| 75 | '2': self.plugin2, | |
| 76 | '3': self.plugin3, | |
| 77 | '4': self.plugin4} | |
| 78 | should_be_plugin_1 = self.controller._get_plugins_by_input('ping', plugin_set) | |
| 79 | self.assertIs(should_be_plugin_1, self.plugin1) | |
| 80 | ||
| 81 | def test_return_none_when_cant_find_plugin_that_can_parse_cmd(self): | |
| 82 | plugin_set = { | |
| 83 | '2': self.plugin2, | |
| 84 | '3': self.plugin3, | |
| 85 | '4': self.plugin4} | |
| 86 | should_be_none = self.controller._get_plugins_by_input('ping', plugin_set) | |
| 87 | self.assertIs(should_be_none, None) | |
| 88 | ||
| 89 | def test_update_plugin_settings(self): | |
| 90 | plugin_id = 'plugin1' | |
| 91 | new_settings = {'setting1': 'value1', 'setting2': 'value2'} | |
| 92 | self.controller.updatePluginSettings(plugin_id, new_settings) | |
| 93 | self.plugin1.updateSettings.assert_called_once_with(new_settings) | |
| 94 | ||
| 95 | def test_update_plugin_settings_with_no_settings(self): | |
| 96 | plugin_id = 'plugin1' | |
| 97 | new_settings = {} | |
| 98 | self.controller.updatePluginSettings(plugin_id, new_settings) | |
| 99 | self.plugin1.updateSettings.assert_called_once_with(new_settings) | |
| 100 | ||
| 101 | ||
| 102 | # I'm Py3 |
| 3 | 3 | |
| 4 | 4 | |
| 5 | 5 | class ImportTests(unittest.TestCase): |
| 6 | ||
| 7 | def test_couchdb(self): | |
| 8 | from faraday.server.config import couchdb | |
| 9 | self.host = couchdb.host | |
| 10 | self.password = couchdb.password | |
| 11 | self.protocol = couchdb.protocol | |
| 12 | self.port = couchdb.port | |
| 13 | self.ssl_port = couchdb.ssl_port | |
| 14 | self.user = couchdb.user | |
| 15 | 6 | |
| 16 | 7 | def test_database(self): |
| 17 | 8 | from faraday.server.config import database |
| 0 | 0 | from __future__ import absolute_import |
| 1 | ||
| 2 | import json | |
| 1 | 3 | |
| 2 | 4 | import pytest |
| 3 | 5 | |
| 4 | 6 | from faraday.searcher.api import Api |
| 5 | 7 | from faraday.searcher.searcher import Searcher, MailNotification |
| 6 | 8 | from faraday.searcher.sqlapi import SqlApi |
| 7 | from faraday.server.models import Service, Host | |
| 8 | 9 | from faraday.server.models import Service, Host, VulnerabilityWeb |
| 9 | 10 | from faraday.server.models import Vulnerability, CommandObject |
| 10 | from tests.factories import VulnerabilityTemplateFactory, ServiceFactory, \ | |
| 11 | HostFactory, CustomFieldsSchemaFactory, VulnerabilityWebFactory | |
| 11 | from faraday.server.schemas import WorkerRuleSchema | |
| 12 | from tests.factories import ( | |
| 13 | VulnerabilityTemplateFactory, | |
| 14 | ServiceFactory, | |
| 15 | HostFactory, | |
| 16 | CustomFieldsSchemaFactory, | |
| 17 | VulnerabilityWebFactory, | |
| 18 | RuleFactory, | |
| 19 | ActionFactory, | |
| 20 | RuleActionFactory, | |
| 21 | UserFactory, | |
| 22 | ) | |
| 12 | 23 | from tests.factories import WorkspaceFactory, VulnerabilityFactory |
| 13 | 24 | |
| 14 | 25 | |
| 414 | 425 | |
| 415 | 426 | assert vuln1.severity == 'informational' |
| 416 | 427 | assert vuln2.severity == 'informational' |
| 428 | ||
| 429 | @pytest.mark.parametrize("api", [ | |
| 430 | lambda workspace, test_client, session: Api(workspace.name, test_client, session, username='test', | |
| 431 | password='test', base=''), | |
| 432 | lambda workspace, test_client, session: SqlApi(workspace.name, test_client, session), | |
| 433 | ]) | |
| 434 | @pytest.mark.usefixtures('ignore_nplusone') | |
| 435 | def test_update_severity_by_tool(self, api, session, test_client): | |
| 436 | workspace = WorkspaceFactory.create() | |
| 437 | host = HostFactory.create(workspace=workspace) | |
| 438 | vuln = VulnerabilityFactory.create( | |
| 439 | workspace=workspace, | |
| 440 | tool='Nessus', | |
| 441 | severity='low', | |
| 442 | host=host, | |
| 443 | service=None) | |
| 444 | session.add(workspace) | |
| 445 | session.add(vuln) | |
| 446 | ||
| 447 | session.add(host) | |
| 448 | session.commit() | |
| 449 | ||
| 450 | vuln_id = vuln.id | |
| 451 | assert vuln.severity == 'low' | |
| 452 | searcher = Searcher(api(workspace, test_client, session)) | |
| 453 | rules = [{ | |
| 454 | 'id': 'CHANGE_SEVERITY_INSIDE_HOST', | |
| 455 | 'model': 'Vulnerability', | |
| 456 | 'object': "tool=Nessus", # Without --old param Searcher deletes all duplicated objects | |
| 457 | 'conditions': ['tool=Nessus'], | |
| 458 | 'actions': ["--UPDATE:severity=info"] | |
| 459 | }] | |
| 460 | ||
| 461 | searcher.process(rules) | |
| 462 | vuln = session.query(Vulnerability).get(vuln_id) | |
| 463 | assert vuln.severity == 'informational' | |
| 464 | ||
| 465 | @pytest.mark.parametrize("api", [ | |
| 466 | lambda workspace, test_client, session: Api(workspace.name, test_client, session, username='test', | |
| 467 | password='test', base=''), | |
| 468 | lambda workspace, test_client, session: SqlApi(workspace.name, test_client, session), | |
| 469 | ]) | |
| 470 | @pytest.mark.usefixtures('ignore_nplusone') | |
| 471 | def test_update_severity_by_values_with_space(self, api, session, test_client): | |
| 472 | workspace = WorkspaceFactory.create() | |
| 473 | vuln = VulnerabilityFactory.create( | |
| 474 | workspace=workspace, | |
| 475 | tool='Nessus Tool', | |
| 476 | severity='low', | |
| 477 | service=None) | |
| 478 | ||
| 479 | session.add(workspace) | |
| 480 | session.add(vuln) | |
| 481 | session.commit() | |
| 482 | ||
| 483 | vuln_id = vuln.id | |
| 484 | assert vuln.severity == 'low' | |
| 485 | searcher = Searcher(api(workspace, test_client, session)) | |
| 486 | rules = [{ | |
| 487 | 'id': 'CHANGE_SEVERITY', | |
| 488 | 'model': 'Vulnerability', | |
| 489 | 'object': "tool=Nessus%Tool", # Without --old param Searcher deletes all duplicated objects | |
| 490 | 'conditions': ['severity=low'], | |
| 491 | 'actions': ["--UPDATE:severity=info"] | |
| 492 | }] | |
| 493 | ||
| 494 | searcher.process(rules) | |
| 495 | vuln = session.query(Vulnerability).get(vuln_id) | |
| 496 | assert vuln.severity == 'informational' | |
| 497 | ||
| 498 | @pytest.mark.parametrize("api", [ | |
| 499 | lambda workspace, test_client, session: Api(workspace.name, test_client, session, username='test', | |
| 500 | password='test', base=''), | |
| 501 | lambda workspace, test_client, session: SqlApi(workspace.name, test_client, session), | |
| 502 | ]) | |
| 503 | @pytest.mark.usefixtures('ignore_nplusone') | |
| 504 | def test_update_severity_by_values_with_space_2(self, api, session, test_client): | |
| 505 | workspace = WorkspaceFactory.create() | |
| 506 | vuln = VulnerabilityFactory.create( | |
| 507 | workspace=workspace, | |
| 508 | name='Cross-domain Referer leakage', | |
| 509 | severity='low', | |
| 510 | service=None) | |
| 511 | ||
| 512 | session.add(workspace) | |
| 513 | session.add(vuln) | |
| 514 | session.commit() | |
| 515 | ||
| 516 | vuln_id = vuln.id | |
| 517 | assert vuln.severity == 'low' | |
| 518 | searcher = Searcher(api(workspace, test_client, session)) | |
| 519 | rules = [{ | |
| 520 | 'id': 'CHANGE_SEVERITY', | |
| 521 | 'model': 'Vulnerability', | |
| 522 | 'object': "name=Cross-domain%Referer%leakage", # Without --old param Searcher deletes all duplicated objects | |
| 523 | 'conditions': ['name=Cross-domain%Referer%leakage'], | |
| 524 | 'actions': ["--UPDATE:severity=info"] | |
| 525 | }] | |
| 526 | ||
| 527 | searcher.process(rules) | |
| 528 | vuln = session.query(Vulnerability).get(vuln_id) | |
| 529 | assert vuln.severity == 'informational' | |
| 530 | ||
| 531 | ||
| 532 | @pytest.mark.parametrize("api", [ | |
| 533 | lambda workspace, test_client, session: Api(workspace.name, test_client, session, username='test', | |
| 534 | password='test', base=''), | |
| 535 | lambda workspace, test_client, session: SqlApi(workspace.name, test_client, session), | |
| 536 | ]) | |
| 537 | @pytest.mark.usefixtures('ignore_nplusone') | |
| 538 | def test_update_severity_by_creator(self, api, session, test_client): | |
| 539 | workspace = WorkspaceFactory.create() | |
| 540 | host = HostFactory.create(workspace=workspace) | |
| 541 | user = UserFactory.create() | |
| 542 | vuln = VulnerabilityFactory.create( | |
| 543 | workspace=workspace, | |
| 544 | tool='Nessus', | |
| 545 | severity='low', | |
| 546 | host=host, | |
| 547 | creator=user, | |
| 548 | service=None) | |
| 549 | session.add(workspace) | |
| 550 | session.add(vuln) | |
| 551 | ||
| 552 | session.add(host) | |
| 553 | session.commit() | |
| 554 | ||
| 555 | vuln_id = vuln.id | |
| 556 | assert vuln.severity == 'low' | |
| 557 | searcher = Searcher(api(workspace, test_client, session)) | |
| 558 | rules = [{ | |
| 559 | 'id': 'CHANGE_SEVERITY_INSIDE_HOST', | |
| 560 | 'model': 'Vulnerability', | |
| 561 | 'object': f'creator={user.username}', # Without --old param Searcher deletes all duplicated objects | |
| 562 | 'conditions': ['tool=Nessus'], | |
| 563 | 'actions': ["--UPDATE:severity=info"] | |
| 564 | }] | |
| 565 | ||
| 566 | searcher.process(rules) | |
| 567 | vuln = session.query(Vulnerability).get(vuln_id) | |
| 568 | assert vuln.severity == 'informational' | |
| 417 | 569 | |
| 418 | 570 | @pytest.mark.parametrize("api", [ |
| 419 | 571 | lambda workspace, test_client, session: Api(workspace.name, test_client, session, username='test', |
| 681 | 833 | assert host.ip == '10.25.50.47' |
| 682 | 834 | assert host.os == 'Windows' |
| 683 | 835 | assert host.owned is True |
| 836 | ||
| 837 | @pytest.mark.parametrize("api", [ | |
| 838 | lambda workspace, test_client, session: Api(workspace.name, test_client, session, username='test', | |
| 839 | password='test', base=''), | |
| 840 | lambda workspace, test_client, session: SqlApi(workspace.name, test_client, session), | |
| 841 | ]) | |
| 842 | @pytest.mark.usefixtures('ignore_nplusone') | |
| 843 | def test_disable_rule(self, api, session, test_client, vulnerability_factory): | |
| 844 | workspace = WorkspaceFactory.create() | |
| 845 | vulns = vulnerability_factory.create_batch(5, workspace=workspace, severity='low') | |
| 846 | vulns2 = vulnerability_factory.create_batch(5, workspace=workspace, severity='medium') | |
| 847 | session.add(workspace) | |
| 848 | session.add_all(vulns) | |
| 849 | session.add_all(vulns2) | |
| 850 | session.commit() | |
| 851 | ||
| 852 | vulns_count = session.query(Vulnerability).filter_by(workspace=workspace).count() | |
| 853 | assert vulns_count == 10 | |
| 854 | ||
| 855 | searcher = Searcher(api(workspace, test_client, session)) | |
| 856 | rule_disabled = RuleFactory.create(object="severity=low", disabled=True, workspace=workspace) | |
| 857 | rule_enabled = RuleFactory.create(object="severity=medium", disabled=False, workspace=workspace) | |
| 858 | ||
| 859 | action = ActionFactory.create(command='DELETE') | |
| 860 | session.add(action) | |
| 861 | ||
| 862 | session.add(rule_disabled) | |
| 863 | session.add(rule_enabled) | |
| 864 | ||
| 865 | rules = [rule_disabled, rule_enabled] | |
| 866 | ||
| 867 | for rule in rules: | |
| 868 | rule_action = RuleActionFactory.create(action=action, rule=rule) | |
| 869 | session.add(rule_action) | |
| 870 | ||
| 871 | session.commit() | |
| 872 | rules_data = [] | |
| 873 | for rule in rules: | |
| 874 | rule_data = WorkerRuleSchema().dumps(rule).data | |
| 875 | rules_data.append(json.loads(rule_data)) | |
| 876 | searcher.process(rules_data) | |
| 877 | vulns_count = session.query(Vulnerability).filter_by(workspace=workspace).count() | |
| 878 | assert vulns_count == 5 | |
| 879 | ||
| 880 | ||
| 0 | ''' | |
| 1 | Faraday Penetration Test IDE | |
| 2 | Copyright (C) 2013 Infobyte LLC (http://www.infobytesec.com/) | |
| 3 | See the file 'doc/LICENSE' for the license information | |
| 4 | ||
| 5 | ''' | |
| 6 | from __future__ import absolute_import | |
| 7 | ||
| 8 | import os | |
| 9 | import sys | |
| 10 | import unittest | |
| 11 | ||
| 12 | import responses | |
| 13 | import requests | |
| 14 | sys.path.append(os.path.abspath(os.getcwd())) | |
| 15 | from faraday.client.persistence.server import server | |
| 16 | from faraday.client.persistence.server import server_io_exceptions | |
| 17 | from unittest.mock import MagicMock, patch | |
| 18 | ||
| 19 | server.FARADAY_UP = False | |
| 20 | server.SERVER_URL = "http://localhost:5985" | |
| 21 | example_url = "http://just_some_url" | |
| 22 | ||
| 23 | ||
| 24 | class ClientServerAPITests(unittest.TestCase): | |
| 25 | ||
| 26 | def setUp(self): | |
| 27 | self.ws_name = "a_ws" | |
| 28 | self.server_api_url = "http://localhost:5985/_api" | |
| 29 | ||
| 30 | def test_get_base_server_url(self): | |
| 31 | s = server._get_base_server_url() | |
| 32 | self.assertEqual(server.SERVER_URL, s) | |
| 33 | ||
| 34 | def test_create_server_api_url(self): | |
| 35 | s = server._create_server_api_url() | |
| 36 | self.assertEqual("{0}/_api/v2".format(server.SERVER_URL), s) | |
| 37 | ||
| 38 | def test_create_server_get_url(self): | |
| 39 | obj_name = "hosts" | |
| 40 | s = server._create_server_get_url(self.ws_name, obj_name) | |
| 41 | self.assertEqual("{0}/_api/v2/ws/{1}/{2}".format(server.SERVER_URL, self.ws_name, obj_name), s) | |
| 42 | ||
| 43 | def test_create_serve_post_url(self): | |
| 44 | server_post_url = server._create_server_post_url(self.ws_name, 'Service', 1) | |
| 45 | self.assertEqual(self.server_api_url + '/v2/ws/a_ws/services/?command_id=1', server_post_url) | |
| 46 | ||
| 47 | def test_create_server_get_ws_names_url(self): | |
| 48 | s = server._create_server_get_url(self.ws_name) | |
| 49 | self.assertEqual("{0}/_api/v2/ws/{1}".format(server.SERVER_URL, self.ws_name), s) | |
| 50 | ||
| 51 | @responses.activate | |
| 52 | def test_raise_conflict_in_database(self): | |
| 53 | url = "http://just_raise_conflict.com" | |
| 54 | responses.add(responses.PUT, url, status=409, | |
| 55 | content_type="application/json", json={'error': 'conflict'}) | |
| 56 | with self.assertRaises(server_io_exceptions.ConflictInDatabase): | |
| 57 | server._unsafe_io_with_server(requests.put, [200], url, json={"name": "betcha"}) | |
| 58 | ||
| 59 | @responses.activate | |
| 60 | def test_raise_resource_does_not_exist(self): | |
| 61 | url = "http://dont_exist.com" | |
| 62 | responses.add(responses.GET, url, body='{"name": "betcha"}', status=404) | |
| 63 | with self.assertRaises(server_io_exceptions.ResourceDoesNotExist): | |
| 64 | server._unsafe_io_with_server(requests.get, [200], url, json={"name": "betcha"}) | |
| 65 | ||
| 66 | @responses.activate | |
| 67 | def test_raise_unauthorized(self): | |
| 68 | url = "http://nope.com" | |
| 69 | responses.add(responses.GET, url, body='{"name": "betcha"}', status=403) | |
| 70 | with self.assertRaises(server_io_exceptions.Unauthorized): | |
| 71 | server._unsafe_io_with_server(requests.get, [200], url, json={"name": "betcha"}) | |
| 72 | url2 = "http://nope2.com" | |
| 73 | responses.add(responses.GET, url2, body='{"name": "betcha"}', status=401) | |
| 74 | with self.assertRaises(server_io_exceptions.Unauthorized): | |
| 75 | server._unsafe_io_with_server(requests.get, [200], url, json={"name": "betcha"}) | |
| 76 | ||
| 77 | @responses.activate | |
| 78 | def test_raise_cant_comm_with_server_on_wrong_response_code(self): | |
| 79 | url = "http://yes.com" | |
| 80 | responses.add(responses.GET, url, status=204) | |
| 81 | with self.assertRaises(server_io_exceptions.CantCommunicateWithServerError): | |
| 82 | server._unsafe_io_with_server(requests.get, [200], url) | |
| 83 | ||
| 84 | @responses.activate | |
| 85 | def test_server_with_okey_request(self): | |
| 86 | url = "http://this-is-ok.com" | |
| 87 | responses.add(responses.GET, url, body='{"name": "betcha"}', status=200) | |
| 88 | responses.add(responses.PUT, url, body='{"ok": "true"}', status=200) | |
| 89 | response_get = server._unsafe_io_with_server(requests.get, [200], url) | |
| 90 | response_put = server._unsafe_io_with_server(requests.put, [200], url) | |
| 91 | self.assertEqual(response_get.text, requests.get(url).text) | |
| 92 | self.assertEqual(response_put.text, requests.put(url).text) | |
| 93 | ||
| 94 | @responses.activate | |
| 95 | def test_json_parsing(self): | |
| 96 | url = "http://give_me_json.com" | |
| 97 | responses.add(responses.GET, url, body='{"some": "valid", "json": "string"}') | |
| 98 | url2 = "http://give_me_invalid_json.com" | |
| 99 | responses.add(responses.GET, url2, body='{"this is not", "valid": "json"}') | |
| 100 | json_as_dict = server._parse_json(requests.get(url)) | |
| 101 | json_as_empty_dict = server._parse_json(requests.get(url2)) | |
| 102 | self.assertEqual({'some': 'valid', 'json': 'string'}, json_as_dict) | |
| 103 | self.assertEqual({}, json_as_empty_dict) | |
| 104 | ||
| 105 | @responses.activate | |
| 106 | def test_get(self): | |
| 107 | url = "http://get_url" | |
| 108 | responses.add(responses.GET, url, body='{"some": "object"}') | |
| 109 | expected_json = server._get(url) | |
| 110 | self.assertEqual(expected_json, {"some": "object"}) | |
| 111 | ||
| 112 | @responses.activate | |
| 113 | def test_put_with_no_update(self): | |
| 114 | responses.add(responses.PUT, example_url, body='{"ok": "true"}', status=200) | |
| 115 | self.assertEqual(server._put(example_url, expected_response=200), {"ok": "true"}) | |
| 116 | ||
| 117 | def test_faraday_dictionary_dispatcher_result(self): | |
| 118 | mock_raw_hosts = MagicMock() | |
| 119 | mock_raw_hosts.return_value = {'rows': [{'a': 'host', 'value': {'stuff': 'other_stuff'}}], 'total_rows': 4} | |
| 120 | with patch('faraday.client.persistence.server.server._get_raw_hosts', mock_raw_hosts): | |
| 121 | list_of_dicts = server._get_faraday_ready_dictionaries('some_workspace', 'hosts', 'rows', full_table=False) | |
| 122 | with patch('faraday.client.persistence.server.server._get_raw_hosts', mock_raw_hosts): | |
| 123 | full_list_of_dicts = server._get_faraday_ready_dictionaries('some_workspace', 'hosts', | |
| 124 | 'rows', full_table=True) | |
| 125 | self.assertTrue(len(list_of_dicts) == 1 == len(full_list_of_dicts)) | |
| 126 | self.assertEqual(list_of_dicts, [mock_raw_hosts.return_value['rows'][0]['value']]) | |
| 127 | self.assertEqual(full_list_of_dicts, mock_raw_hosts.return_value['rows']) | |
| 128 | ||
| 129 | @patch('faraday.client.persistence.server.server._get_raw_hosts') | |
| 130 | @patch('faraday.client.persistence.server.server._get_raw_vulns') | |
| 131 | @patch('faraday.client.persistence.server.server._get_raw_services') | |
| 132 | @patch('faraday.client.persistence.server.server._get_raw_notes') | |
| 133 | @patch('faraday.client.persistence.server.server._get_raw_credentials') | |
| 134 | @patch('faraday.client.persistence.server.server._get_raw_commands') | |
| 135 | def test_faraday_dictionary_dispatcher_calls(self, mock_hosts, mock_vulns, | |
| 136 | mock_services, mock_notes, | |
| 137 | mock_credentials, mock_commands): | |
| 138 | # NOTE: if you finds any bugs here, i have the suspipcion that mock_host is actually mock_commands | |
| 139 | # i mean that the parameters names are wrong. I'd check for that. Good luck. | |
| 140 | server._get_faraday_ready_dictionaries('a', 'hosts', 'whatever') | |
| 141 | server._get_faraday_ready_dictionaries('a', 'vulns', 'whatever') | |
| 142 | server._get_faraday_ready_dictionaries('a', 'services', 'whatever') | |
| 143 | server._get_faraday_ready_dictionaries('a', 'notes', 'whatever') | |
| 144 | server._get_faraday_ready_dictionaries('a', 'credentials', 'whatever') | |
| 145 | server._get_faraday_ready_dictionaries('a', 'commands', 'whatever') | |
| 146 | mock_hosts.assert_called_once_with('a') | |
| 147 | mock_vulns.assert_called_once_with('a') | |
| 148 | mock_services.assert_called_once_with('a') | |
| 149 | mock_notes.assert_called_once_with('a') | |
| 150 | mock_credentials.assert_called_once_with('a') | |
| 151 | mock_commands.assert_called_once_with('a') | |
| 152 | ||
| 153 | @patch('faraday.client.persistence.server.server.get_hosts', return_value='hosts') | |
| 154 | @patch('faraday.client.persistence.server.server.get_vulns', return_value='vulns') | |
| 155 | @patch('faraday.client.persistence.server.server.get_services', return_value='services') | |
| 156 | @patch('faraday.client.persistence.server.server.get_credentials', return_value='CREDENTIAL') | |
| 157 | @patch('faraday.client.persistence.server.server.get_notes', return_value='NOTE') | |
| 158 | @patch('faraday.client.persistence.server.server.get_commands', return_value='COMMAND') | |
| 159 | def test_get_objects(self, not_command, not_note, | |
| 160 | not_credential, not_service, not_vuln, not_host): | |
| 161 | obj_sign_to_mock = {'hosts': not_host, 'vulns': not_vuln, | |
| 162 | 'services': not_service, 'credentials': not_credential, | |
| 163 | 'notes': not_note, 'commands': not_command} | |
| 164 | for obj_sign in obj_sign_to_mock.keys(): | |
| 165 | server.get_objects('a', obj_sign) | |
| 166 | obj_sign_to_mock[obj_sign].assert_called_once_with('a') | |
| 167 | with self.assertRaises(server_io_exceptions.WrongObjectSignature): | |
| 168 | server.get_objects('a', 'not a signature') | |
| 169 | ||
| 170 | ||
| 171 | # I'm Py3 |